-
 @ 93bfc86d:fc8e91f5
2025-06-18 05:48:12
@ 93bfc86d:fc8e91f5
2025-06-18 05:48:12다무스 앱 설치 및 개인키-공개키 쌍 생성
아이폰과 같은 iOS 기기나 맥OS에서는 다무스Damus를 사용하는 것도 좋다. 다무스에서는 자신이 사용하는 라이트닝 지갑을 이용해 잽을 날리는 것이 가능하다.
먼저 앱을 설치해보자. 앱스토어에 'Damus' 또는 'Damus nostr'를 검색하고 앱을 다운로드 받는다. 이미 노스터 개인키인 nsec이 있다면 [Sign In]을 선택하고, 새 계정을 만들 거라면 [Create Account]를 누른다. 필자는 [Create Account]를 눌러 새 키 쌍을 생성해보겠다.
'Name'에 닉네임을 적고 [Next]를 누른다.
[저장하기]를 누르면 키 쌍을 아이폰 암호 앱에 저장할 수 있다. 원하지 않는다면 [Not now]를 눌러 넘어가면 된다.
메인 화면에 들어오면 왼쪽 상단 프로필 모양의 원을 누른다. 그 다음 [설정]을 누른다.
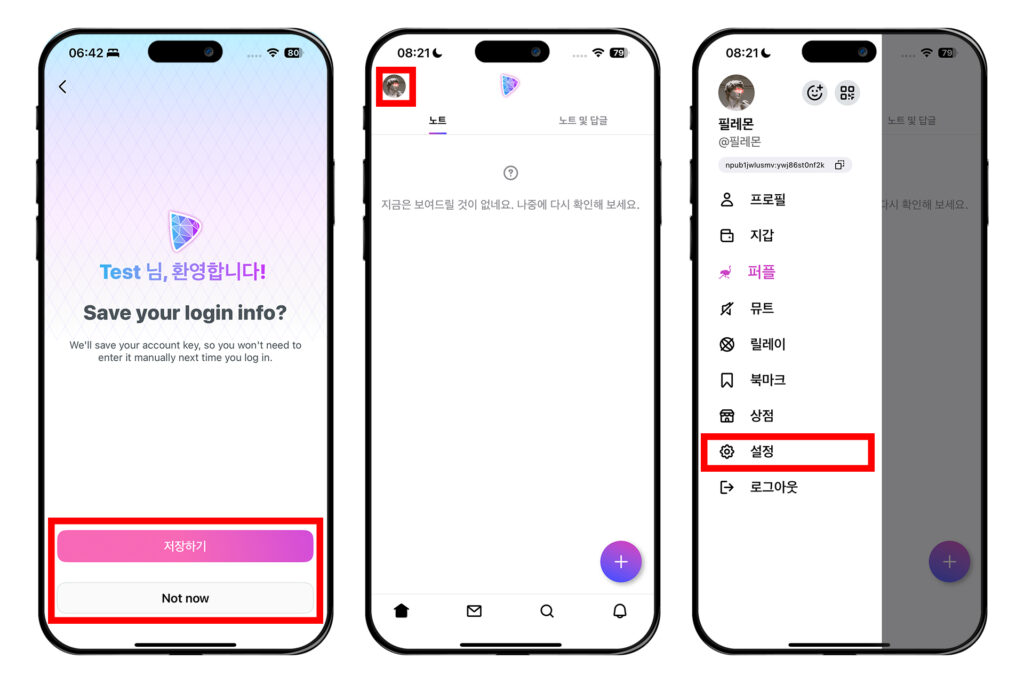
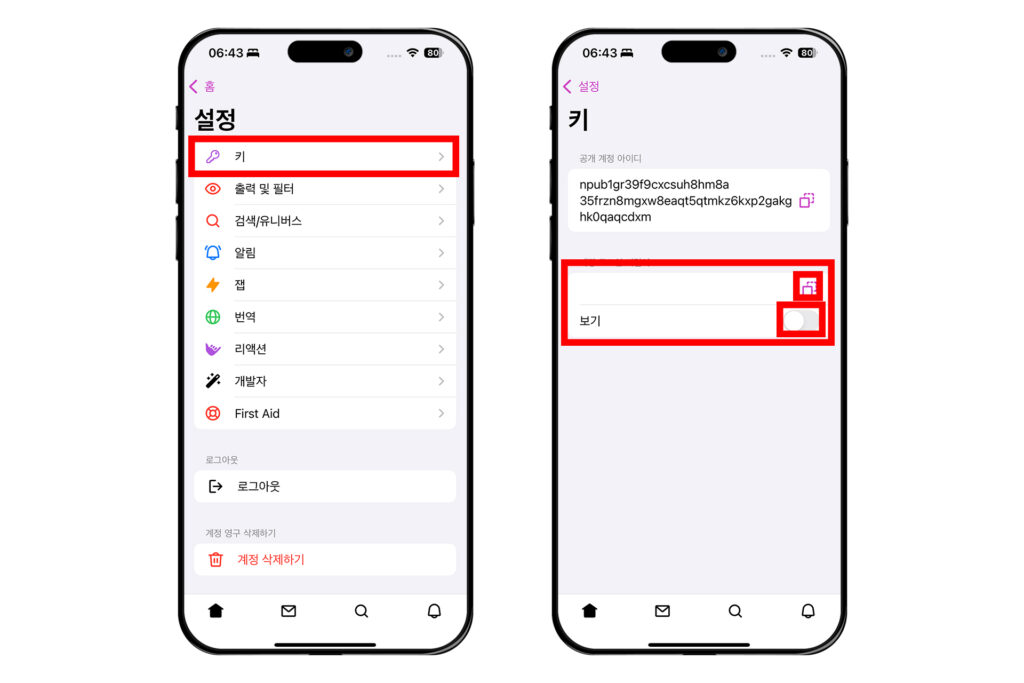
[키]룰 눌러 들어가면 개인키 nsec을 볼 수 있다. [보기]를 눌러 종이에 적는 등 물리적으로 백업하거나, 복사 버튼을 눌러 암호화된 파일로 저장할 수 있다.
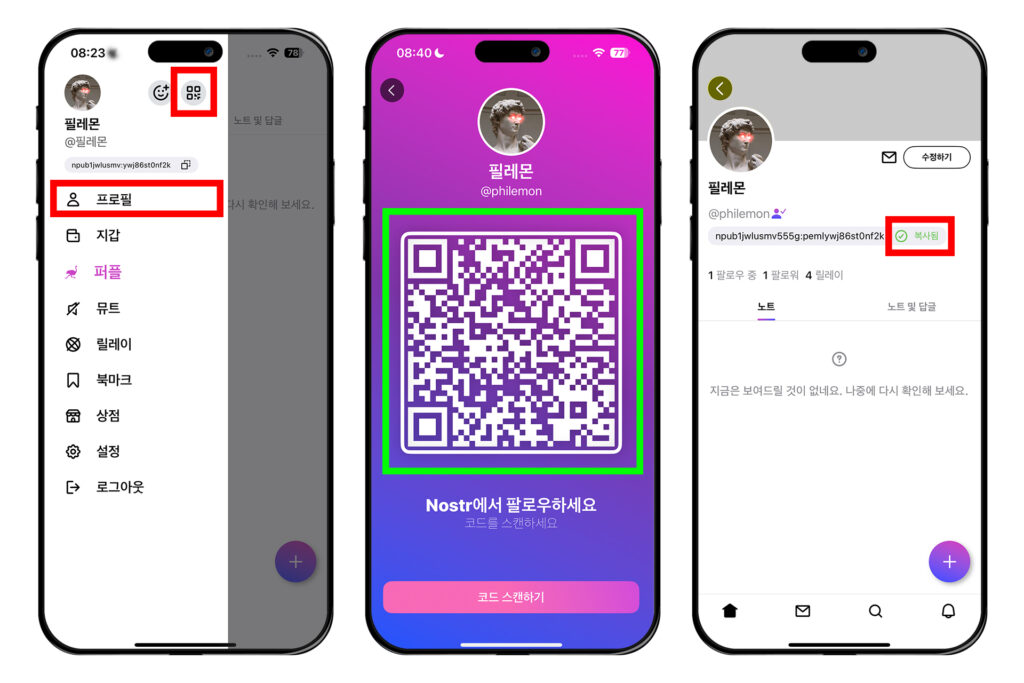
다른 사람들에게 npub 알려주기
누군가에게 자신의 노스터 계정을 알려줄 때는 노스터 공개키인 npub을 알려주면 된다. 다무스 메인 화면에서 좌측 상단 원 모양의 프로필을 누른 뒤, 프로필 오른쪽에 있는 QR코드 모양의 버튼을 누른다. 그러면 QR코드가 나오는데, 이 화면을 보여주거나 캡처해서 상대방에게 공유하면 된다.
혹은 [프로필]을 눌러 자신의 프로필 화면으로 들어가고, 아이디 밑에 있는 npub을 복사해 상대방에게 보내주면 된다.
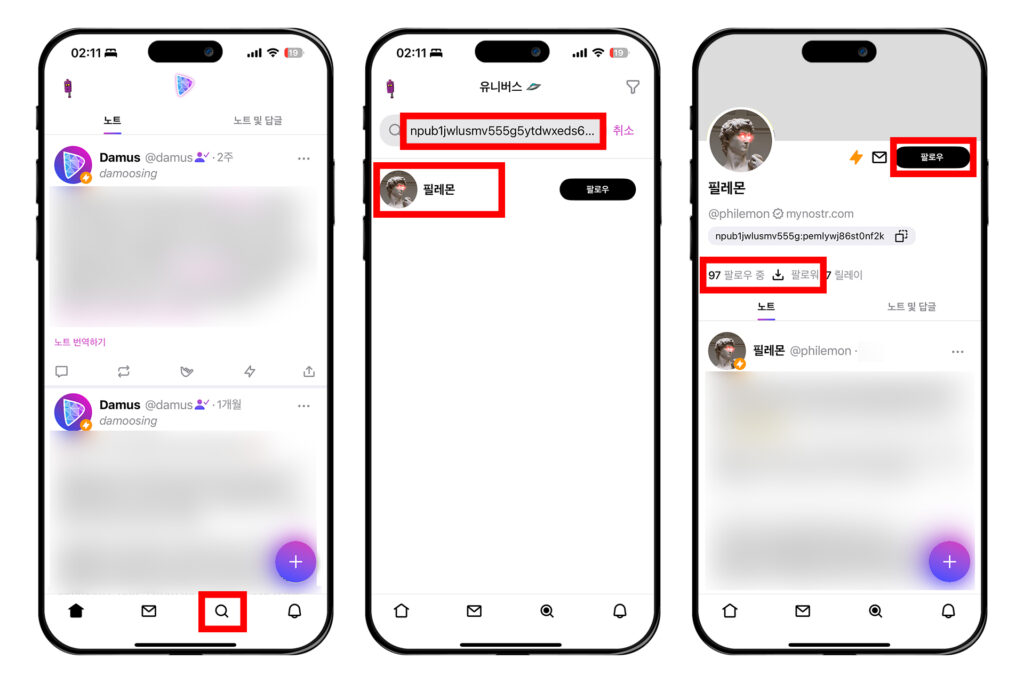
팔로우 추가
처음에는 다무스 운영자의 계정만 팔로우가 되어있을 것이다. 다른 계정들을 팔로우하는 방법을 알아보자.
하단 탭에서 돋보기 모양의 버튼을 눌러 검색 창으로 진입한다. 검색 창에 상대방이 공유한 npub을 붙여넣으면 그 사람의 프로필이 뜰 것이다.
예를 들어 필자의 공개키는 아래와 같다.
npub1jwlusmv555g5ytdwxeds6k3e8u9dgyf75fscznc2eqpemlywj86st0nf2k
필자의 계정을 팔로우하는 과정을 알아보자. 검색창에 npub을 붙여넣고 프로필이 나오면 프로필을 누른다. 다음에 나오는 화면에서 오른쪽의 [팔로우] 버튼을 누르면 필자를 팔로우할 수 있다. 혹은 그 아래에 있는 [팔로우] 또는 [팔로워] 목록을 보고 마음에 드는 프로필을 찾아 들어가 팔로우를 할 수 있다. 이런 방식으로 관심이 있는 계정을 팔로우하면 피드에 글이 뜨기 시작한다.
잽 받기 위한 라이트닝 주소 연결
잽을 받으려면 프로필에 라이트닝 주소를 연결해놓아야 한다. 좌측 상단 원 모양의 프로필을 누르고 [프로필]에 들어간다. 그 다음 [수정하기]를 누른다. 여기서 닉네임을 설정할 수 있다. 스크롤을 아래로 내려서 '비트코인 라이트닝 팁' 필드로 내려간다.
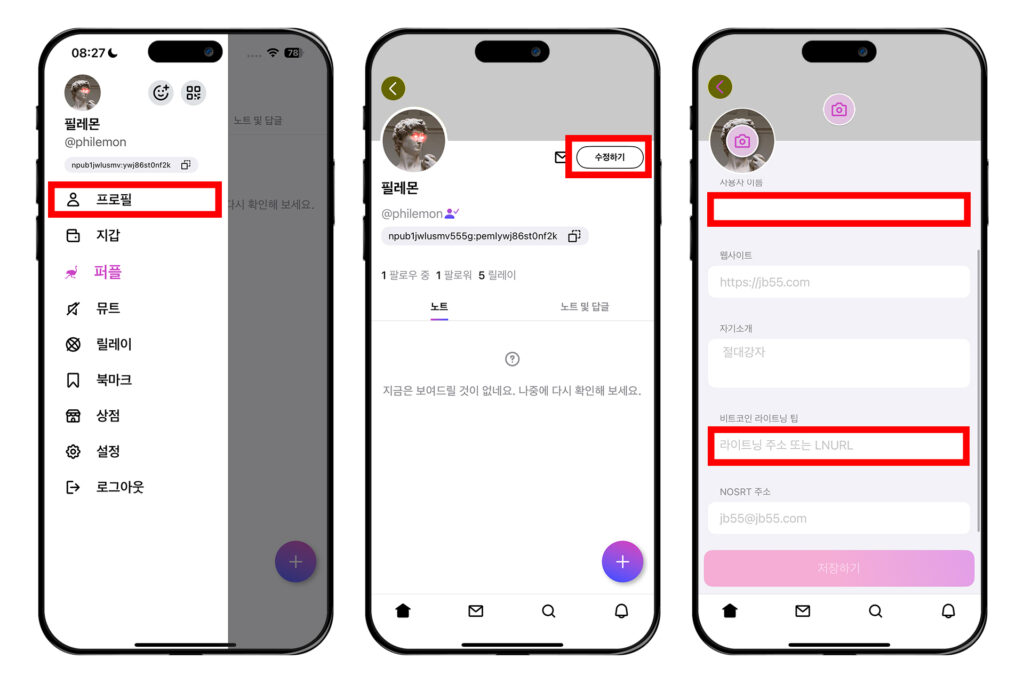
여기에 라이트닝 주소를 입력하고, [저장하기]를 누른다. 프로필 옆에 번개 표시가 뜬 것을 볼 수 있다. 번개 표시가 뜨면 다른 사람들이 나에게 잽을 보낼 수 있다.
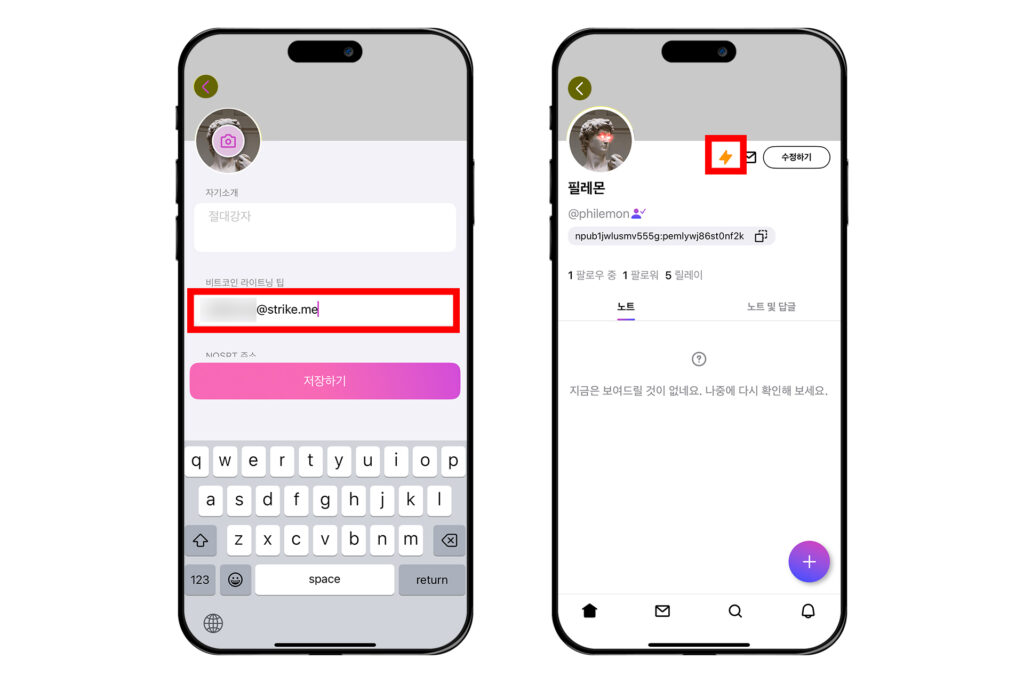
다른 사람에게 잽 보내기
받기만 하는 사람이 되는 것은 유쾌하지 않다. 이번에는 다무스에서 잽을 보내는 방법에 대해 알아보자.
좌측 상단 원 모양의 프로필을 누르고 [설정]에 들어간다. 그 다음 [잽]을 누른다.
여기서 [지갑 선택 창 보기] 토글을 켜면 잽을 보낼 때마다 어떤 지갑에서 보낼지 선택할 수 있다. 그 아래 '기본 지갑 선택하기' 옆의 [기기 기본 앱]을 눌러 자신이 사용하고 있는 지갑 앱을 선택할 수 있다.
아래에서 '잽 기본 Sats 수량'을 설정할 수도 있다.
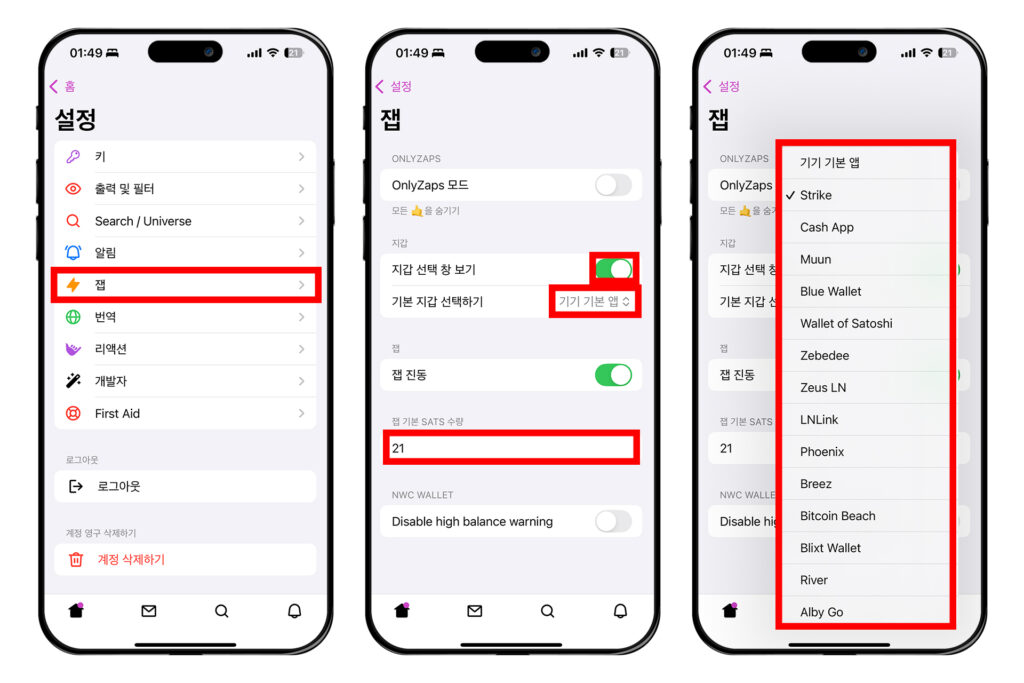
이렇게 설정했으면 이제 설정 창에서 빠져나오자. 잽을 날리고 싶은 프로필이나 포스트에 간다. 거기서 번개 모양의 버튼을 누른다. 그러면 잽을 보내는 창이 뜰 것이다. 금액을 설정하고 [사용자에게 잽 날리기]를 누른다. 그러면 설정한대로 어떤 지갑을 통해 보낼지 선택하는 창이 나온다. 필자는 스트라이크 앱을 통해 진행해보겠다.
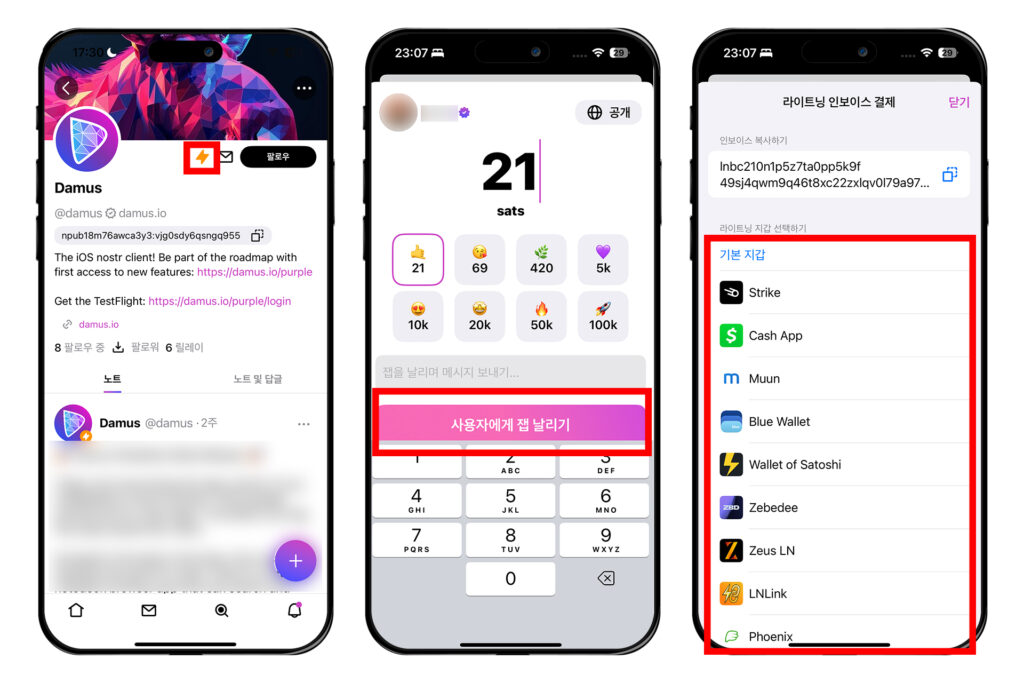
스트라이크를 열지 물어보는 창이 나오면 [열기]를 누르고, 스트라이크에서는 [Bitcoin]을 선택한다.
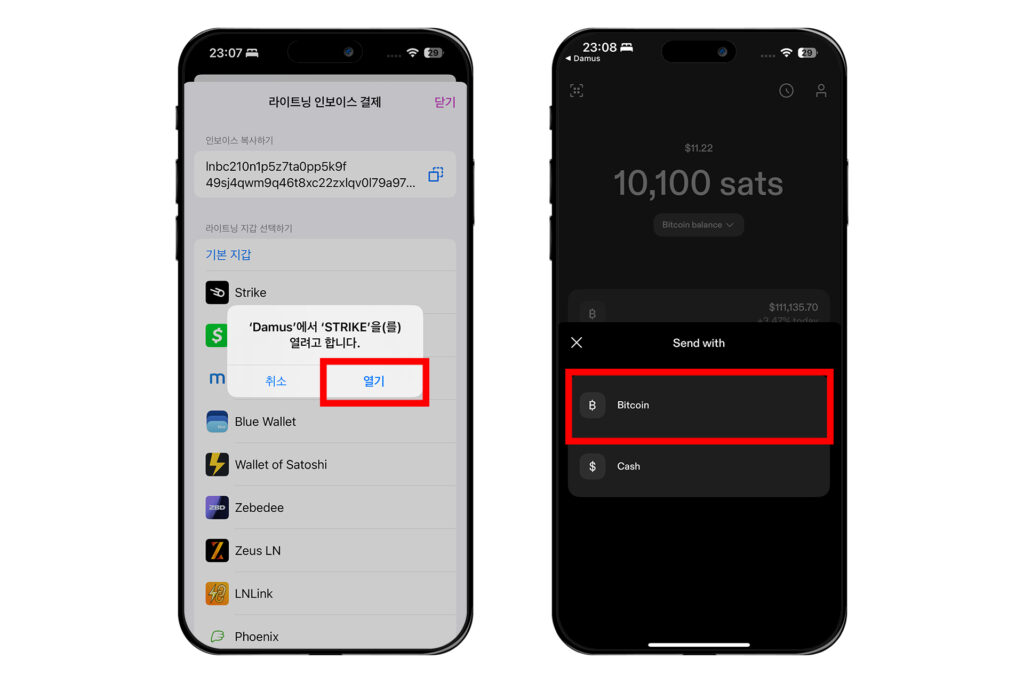
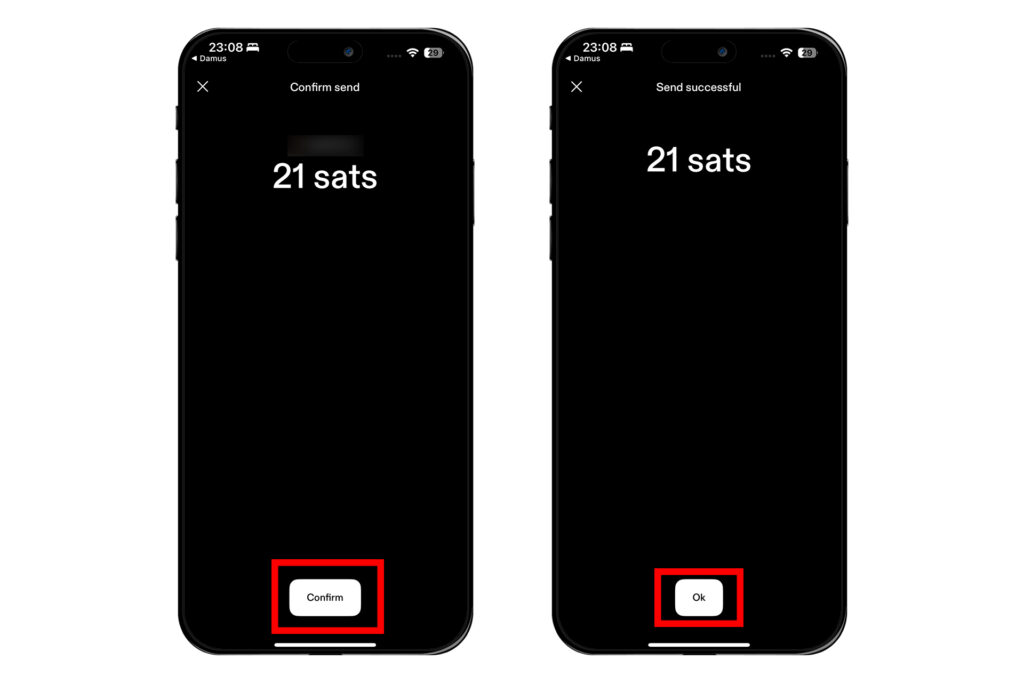
이어서 [Confirm]을 누르고 [Ok]를 누르면 상대방에게 잽이 날아간다.
-
 @ e1cde248:609c13b0
2025-06-18 05:06:16
@ e1cde248:609c13b0
2025-06-18 05:06:16ผมเพิ่งตัดสินใจลบแอปโซเชียลมีเดียทั้งหมดออกจากโทรศัพท์
ใน feed เต็มไปด้วยบัญชีขยะ\ content ที่ถูกยัดมาให้ดู ทั้งที่เราไม่ได้ติดตาม และไม่ได้อยากเห็น\ Bot, AI-generated content, clickbait, ข่าวดราม่าที่ออกแบบมาเพื่อกวนประสาทโดยเฉพาะ
ทั้งหมดนี้ไม่ได้ถูกสร้างมาเพื่อให้เรา “เข้าใจโลก”\ แต่มาเพื่อให้เรา อยู่บนแพลตฟอร์มให้นานที่สุด
แล้วเราก็หลอกตัวเองว่า\ “เรากำลังติดตามโลกอยู่นะ”\ “เรากำลังเชื่อมต่อกับผู้คน”
แต่ความจริงคือ...\ ยิ่งมีดราม่า ยิ่งมีความขัดแย้ง — แพลตฟอร์มยิ่งรวย\ และเรายิ่งพัง
เราได้อะไร?\ ได้ความเหนื่อยล้าแบบไม่รู้ที่มา\ สมาธิสั้นลง หงุดหงิดง่ายขึ้น\ และบางทีก็เศร้า...โดยไม่รู้ว่าทำไม
AI ที่อยู่เบื้องหลัง algorithm พวกนี้\ ฉลาดพอจะกำหนดได้ว่า\ “วันนี้คุณควรจะรู้สึกยังไง”
คุณอาจไม่ได้อยากรู้สึกแย่\ ไม่ได้อยากเปรียบเทียบตัวเองกับใคร\ แต่พอไถไปเรื่อย ๆ มันก็เกิดขึ้น\ แบบไม่รู้ตัว
มันซึมลึก\ มันกัดกินจิตใจ\ ช้า ๆ เงียบ ๆ และต่อเนื่อง
ผมนึกถึงโรคอัลไซเมอร์\ โรคที่ค่อย ๆ ลบตัวตนของคนออกไปทีละนิด\ สำหรับผม... มันน่ากลัวกว่ามะเร็งอีกนะ\ และถ้าจะพูดตรง ๆ ความตายอาจจะยังดีกว่าด้วยซ้ำ
แล้วถ้าคิดดูดี ๆ\ การเสพ content แบบไร้สติ\ การโดนรบกวนทุกวินาทีบนหน้าจอ\ มันก็คือ “การเร่งเวลา” ให้ตัวเราค่อย ๆ หายไป
เราอาจยังไม่แก่พอเป็นอัลไซเมอร์\ แต่ถ้า “ใจ” เราเริ่มลืมว่าเราเป็นใคร\ รู้สึกยังไง\ และอยากมีชีวิตแบบไหน...
มันก็ไม่ต่างกันเท่าไหร่หรอก
ตอนนี้เรายังเลือกได้\ ว่าจะปล่อยให้เทคโนโลยีขับเคลื่อนชีวิต\ หรือจะกลับมาเป็น “คนขับ” เองอีกครั้ง
-
 @ eb0157af:77ab6c55
2025-06-18 05:01:12
@ eb0157af:77ab6c55
2025-06-18 05:01:12The banking giant is exploring an expansion of its blockchain services, focusing on digital payments and currencies.
JPMorgan Chase has filed a new trademark application for the name “JPMD.” The filing was submitted on June 15 to the United States Patent and Trademark Office (USPTO).
The application, filed by JPMorgan Chase Bank, N.A., covers a broad range of services related to digital assets and blockchain technology. These include the issuance of digital currencies, electronic payment processing, and financial custody services — all of which suggest a possible new stablecoin initiative for JPMorgan.
Experience with JPM Coin
This move wouldn’t be JPMorgan’s first foray into blockchain-based finance. The bank already operates JPM Coin, a dollar-pegged stablecoin used to enable instant transactions between institutional clients. The token runs on Quorum, a private blockchain network developed in-house by JPMorgan and based on Ethereum’s technology.
The registration of the JPMD trademark comes as JPMorgan and other major U.S. banks are considering a collaborative stablecoin project through their jointly owned entities: Early Warning Services and The Clearing House.
Similarly, corporations like Walmart and Amazon are mulling the creation of their own stablecoins.
The post JPMorgan files trademark for ‘JPMD’: a new stablecoin on the horizon for the American bank appeared first on Atlas21.
-
 @ b1ddb4d7:471244e7
2025-06-18 05:00:51
@ b1ddb4d7:471244e7
2025-06-18 05:00:51The Coinbase Lightning Network is Coinbase’s implementation of Bitcoin’s Lightning Network technology, launched in partnership with Lightspark in April 2024. This innovative solution allows users to send, receive, and pay with bitcoin instantly and cheaply directly from their Coinbase accounts.
Think of the Coinbase Lightning Network as the express lane of bitcoin transactions. While regular bitcoin transfers can take 10-60 minutes and cost several dollars in fees, Lightning Network transactions on Coinbase complete in seconds with fees typically under a cent.
Key Benefits of Coinbase Lightning Network:
- Instant transfers: Transactions complete in seconds, not hours
- Ultra-low fees: 0.2% processing fee vs. traditional network fees
- Global reach: Send bitcoin anywhere in the world instantly
- Cost efficiency: 20 times cheaper than traditional credit card fees
Coinbase Lightning Network vs Regular Bitcoin Transfers
Understanding the difference between Coinbase Lightning Network and regular bitcoin transfers is crucial for choosing the right method:
Feature
Coinbase Lightning Network
Regular Bitcoin Transfer
Speed
Instant (seconds)
10-60 minutes
Fees
0.2% + minimal network fee
$5-50+ depending on network
Best for
Small to medium amounts
Large amounts, long-term storage
Availability
24/7 instant
Subject to network congestion
The Coinbase Lightning Network processes transactions “off-chain,” creating payment channels that settle later on the main Bitcoin blockchain, resulting in dramatically faster and cheaper transactions.
How to Send Bitcoin Using Coinbase Lightning Network
Sending Bitcoin through Coinbase’s Lightning option is incredibly straightforward. Follow these step-by-step instructions:
Step 1: Access Your Coinbase Account
- Sign in to your Coinbase account via web browser or mobile app
- Ensure you have bitcoin (BTC) in your account balance
- Navigate to your portfolio and locate your bitcoin holdings
Step 2: Initiate the Lightning Transfer
- Click “Transfer” then select “Send crypto”
- Choose bitcoin (BTC) as your asset
- Enter the amount you wish to send
- Select Lightning Network as your transfer method
Step 3: Add Recipient Information
- Obtain the Lightning Network invoice from your recipient
- Paste the invoice into the recipient field
- The Coinbase Lightning Network will automatically detect and validate the invoice
- Review the transaction details carefully
Step 4: Complete the Transaction
- Verify the amount and recipient information
- Click “Send” to initiate the transfer
- Your Coinbase Lightning Network transaction will complete within seconds
- Both you and the recipient will receive confirmation notifications
How to Receive Bitcoin via Coinbase Lightning Network
Receiving Bitcoin through Coinbase’s Lightning option requires generating a Lightning invoice. Here’s your complete guide:
Step 1: Generate a Lightning Invoice
- Log into your Coinbase account
- Navigate to “Transfer” then “Receive crypto”
- Select Bitcoin (BTC) as the asset you wish to receive
- Choose “Lightning Network” as your receiving method
Step 2: Create Your Invoice
- Enter the specific amount you want to receive (required for Lightning)
- Add an optional description or memo
- Click “Generate Invoice”
- Your Lightning Network invoice will appear as both a QR code and text string
Step 3: Share Your Invoice
- Copy the Lightning invoice text or share the QR code
- Send this information to the person sending you Bitcoin
- Remember: Lightning invoices expire after 72 hours
- Generate a new invoice if the original expires
Step 4: Receive Your Bitcoin
- Once the sender pays your invoice, you’ll receive instant notification
- The bitcoin will appear in your Coinbase account immediately
- No waiting for blockchain confirmations required with Coinbase Lightning Network
Coinbase Lightning Network Fees and Limits
Understanding the fee structure of Coinbase Lightning Network helps you make informed decisions:
- Processing Fee: 0.2% of the transfer amount
- Network Fee: Minimal (typically fractions of a cent)
- Minimum Amount: Varies by region, typically $0.1- 5
- Maximum Amount: Subject to your account limits and Lightning Network capacity
The Coinbase Lightning Network offers significant savings compared to traditional bitcoin transfers, especially for smaller amounts under $1,000.
Troubleshooting Common Coinbase Lightning Network Issues
Even with the user-friendly Coinbase Lightning Network, you might encounter some challenges:
Invoice Expired Error
- Solution: Generate a fresh Lightning invoice
- Prevention: Complete transactions promptly after generating invoices
Transaction Failed
- Cause: Insufficient Lightning Network liquidity or routing issues
- Solution: Try again in a few minutes or use smaller amounts
Can’t Find Lightning Option
- Check: Ensure Lightning is available in your region
- Verify: Update your Coinbase app to the latest version
Address Whitelist Issues
- Problem: Lightning invoices may not work with address whitelisting enabled
- Solution: Temporarily disable whitelisting or contact Coinbase support
The Coinbase Lightning Network transforms bitcoin from a store of value into a practical, everyday payment method. With instant transactions, minimal fees, and user-friendly implementation, it’s never been easier to send and receive bitcoin.
-
 @ 93bfc86d:fc8e91f5
2025-06-18 04:59:05
@ 93bfc86d:fc8e91f5
2025-06-18 04:59:05노스터를 처음 시작하는 사용자라면 자신의 상황에 따라 어떤 앱을 사용할지 선택할 수 있다.
만약 라이트닝 노드를 직접 운영하고 있다면 아이폰 사용자는 다무스Damus, 안드로이드 사용자는 애머시스트Amethyst, 데스크탑 웹 브라우저에서는 스노트Snort 등의 앱을 추천한다. NWC를 통한 연결로 자신의 라이트닝 노드에서 잽Zap을 보낼 수 있기 때문이다.
만약 라이트닝 노드를 운영하지 않고, 노스터를 처음 이용한다면 프라이멀Primal 앱 사용을 추천한다. 프라이멀 앱은 앱 내에서 자체적으로 라이트닝 지갑을 이용할 수 있기 때문에 잽을 주고 받기가 더욱 쉽다. 그러나 분명히 인지해야 할 사실은 프라이멀에서 사용하는 지갑은 수탁 라이트닝 서비스이므로 거래소와 같은 위험 수준이 있다. 월렛오브사토시나 스트라이크와 비슷하다고 생각하면 된다.
이제 프라이멀 앱 사용 방법에 대해 알아보자.
앱 설치 및 개인키-공개키 쌍 생성
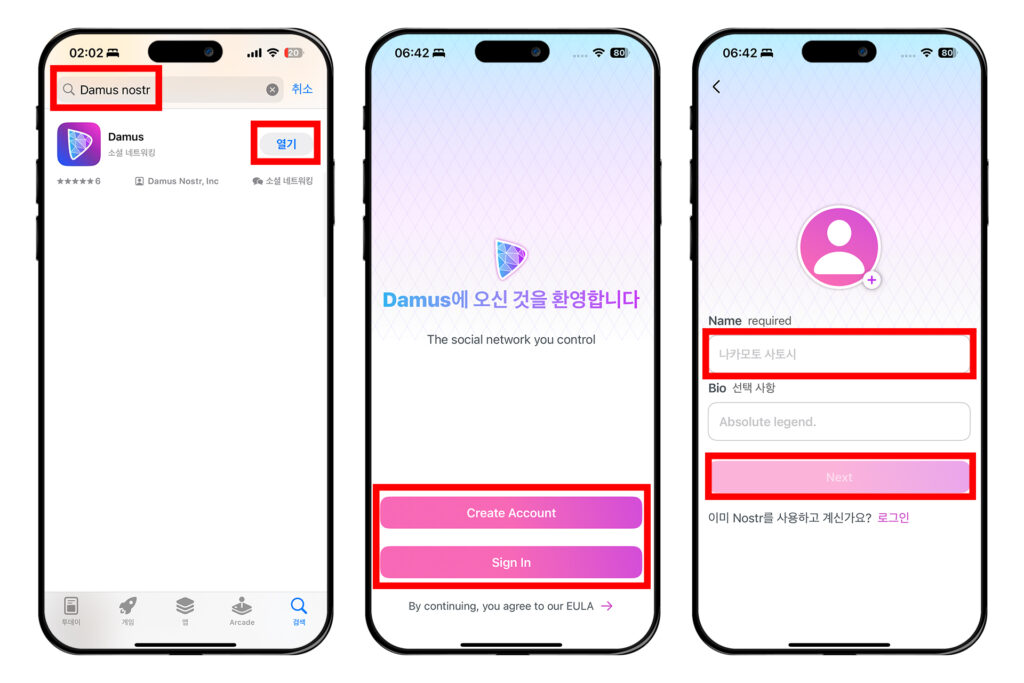
앱스토어 또는 구글 플레이스토어에서 'Primal'을 검색하고 앱을 다운로드 받는다.
이전에 노스터를 사용한 적 없다면 [Create Account]를 누른다. 만약 이전에 노스터를 사용한 적이 있어서 노스터 개인키인 nsec이 있다면 [Sign In]을 눌러 nsec을 입력하고 로그인할 수도 있다.
[Display Name]에 닉네임을 입력하고 [Next]를 누른다.
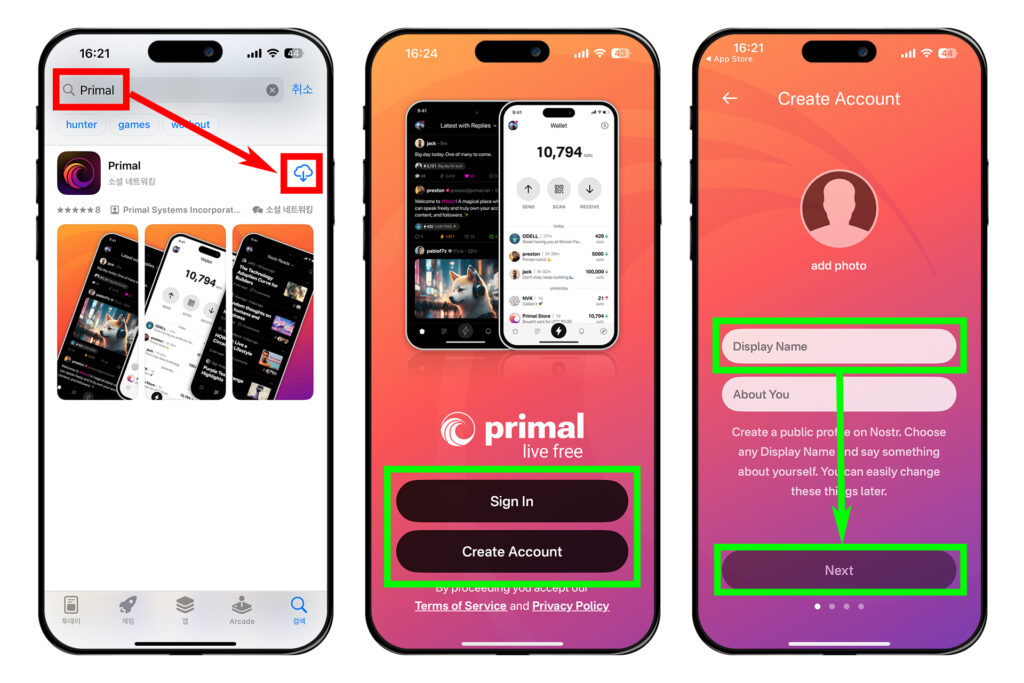
관심사를 선택하라는 창이 나온다. 그런데 여기서 관심사를 선택하면 자신이 팔로우를 원치 않는 계정들까지 전부 팔로우가 된다. 따라서 일단 [art]만 선택한 뒤 [Next]를 누른다. 뒤에서 해제할 것이다.
다음 화면으로 넘어가면 [Customize follows now]를 선택하고, [Next]를 누른다.
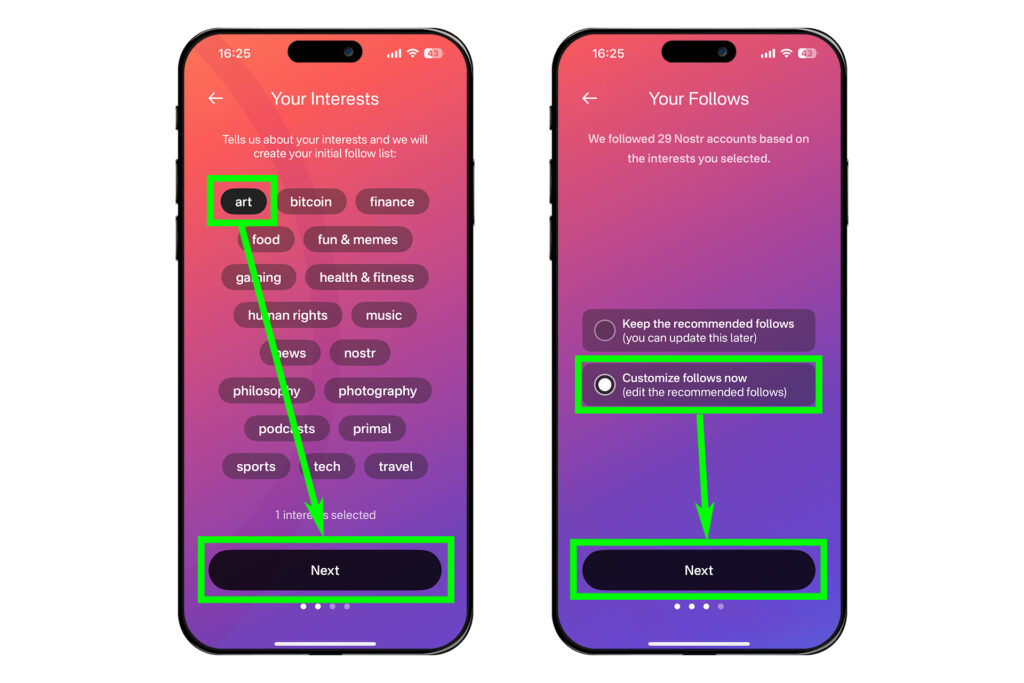
앞에서 말한 것처럼 모든 관심사를 끌 것이다. 'ART' 옆에 있는 [unfollow all]를 누르고, 아래에 있는 [Next]를 누른다.
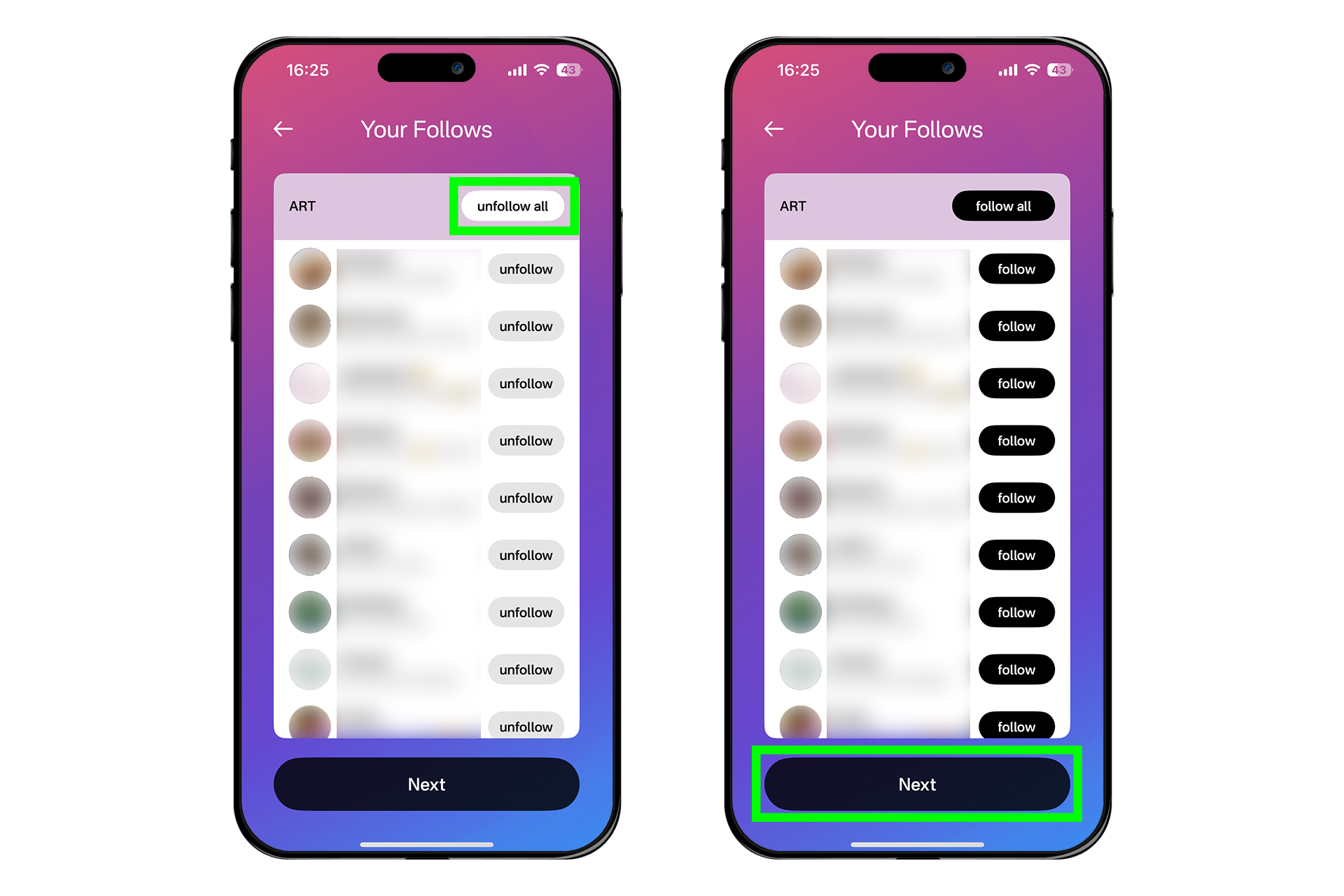
[Create Account Now] → [Continue] → [I'll do this later]를 누른다.
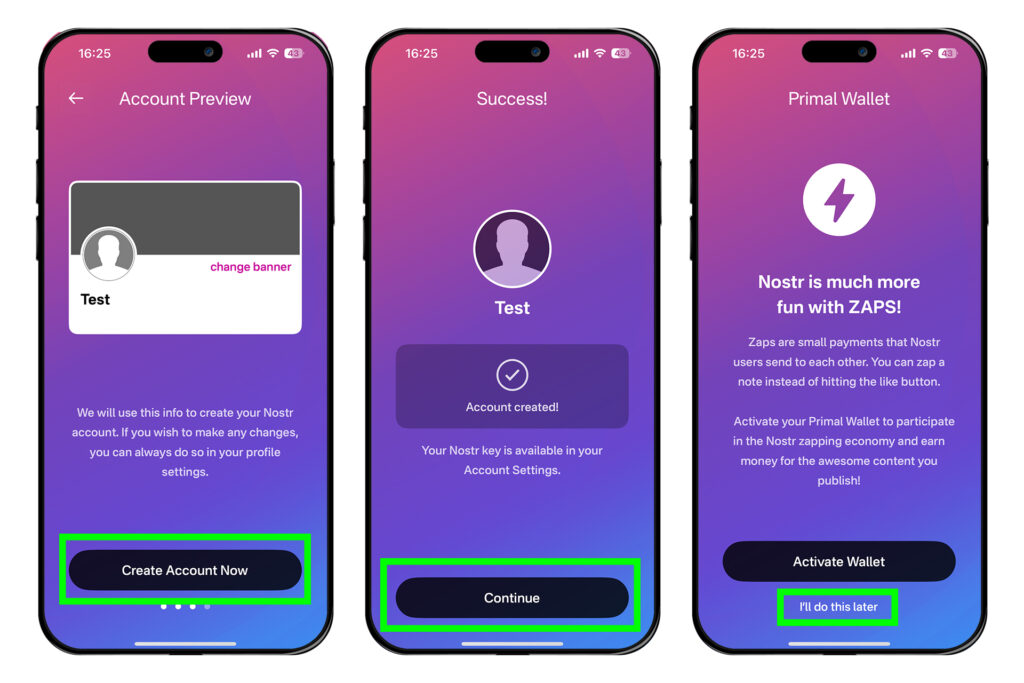
그러면 개인키-공개키 쌍이 생성된 것이다. 노스터는 다른 중앙집중화된 SNS 플랫폼들과 달리 비트코인처럼 개인키-공개키 쌍을 만들면 그게 자신의 계정이 된다. 개인키는 nsec이라 하며, 공개키는 npub이라 한다. 따라서 개인키인 nsec을 백업해놓는 것은 매우 중요하다.
왼쪽 상단의 프로필 사진을 터치한다. 그 다음 [SETTINGS] → [Keys]에 들어간다.
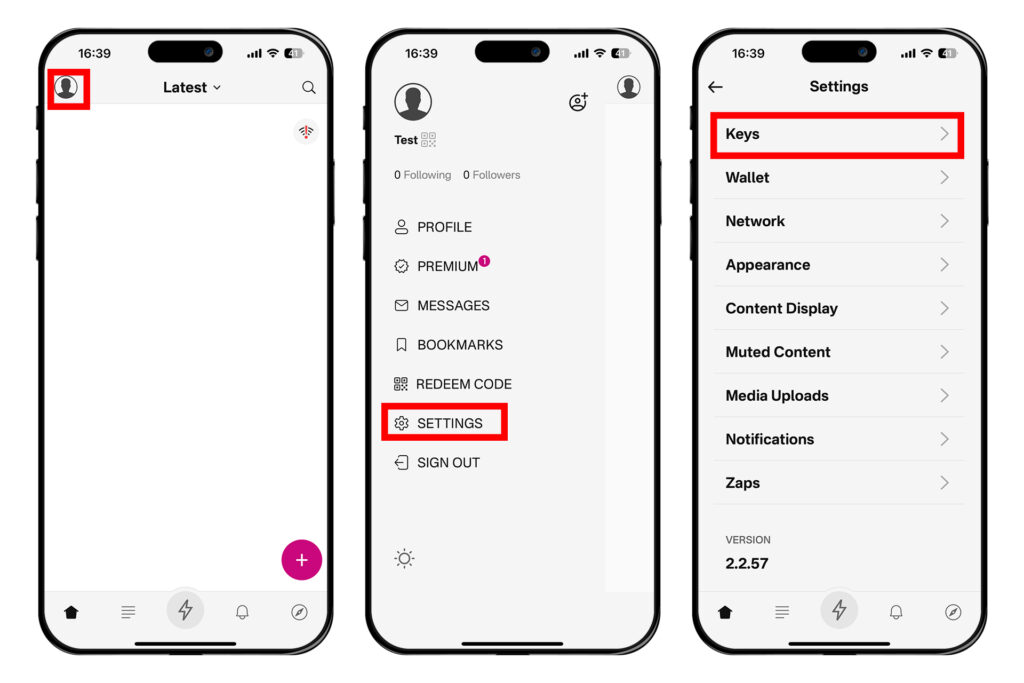
'PRIVATE KEY' 옆에 나오는 [show key]를 누르면 개인키가 보인다. [Copy private key]를 눌러 개인키를 메모 앱 등에 암호화된 상태로 저장해놓거나, 종이에다가 잘 적는 등의 물리적인 백업을 해놓자.
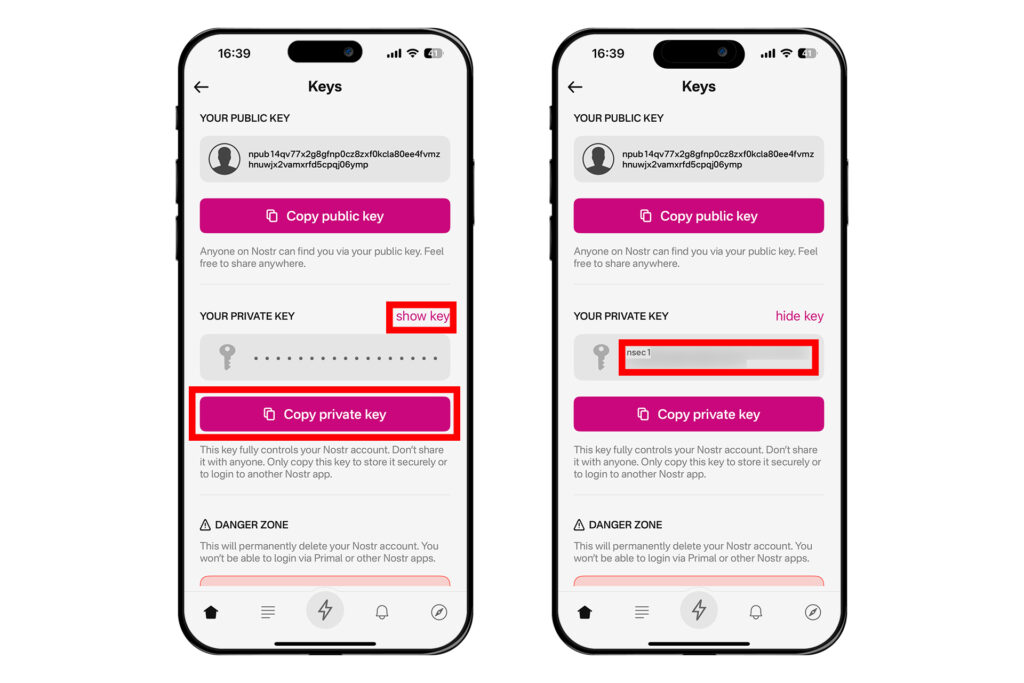
다른 사람들에게 npub 알려주기
누군가에게 자신의 계정을 알려줄 때는 자신의 노스터 공개키인 npub을 알려주면 된다. 프라이멀에서 먼저 좌측 상단 프로필 모양을 누른다. 그러면 닉네임 옆에 QR코드 모양이 있다. 이 QR코드 모양을 터치한다. 그러면 QR코드가 나오는데, 이 QR코드를 캡처해서 상대방에게 보여주거나, 그 밑에 있는 npub 우측의 복사 버튼을 눌러 상대방에게 보내주면 된다.
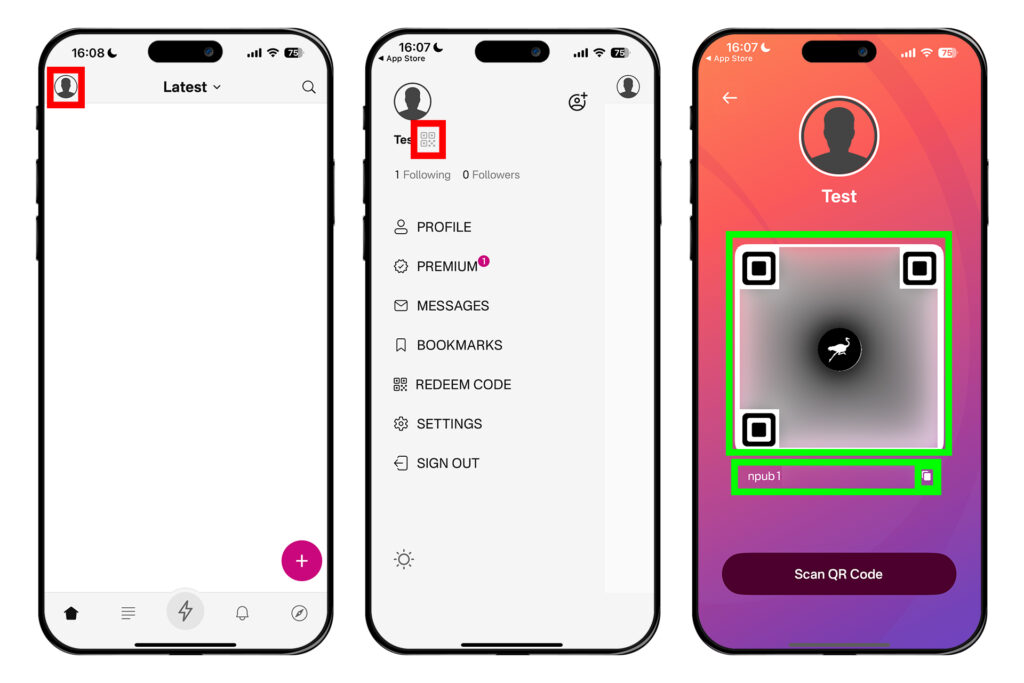
팔로우 추가
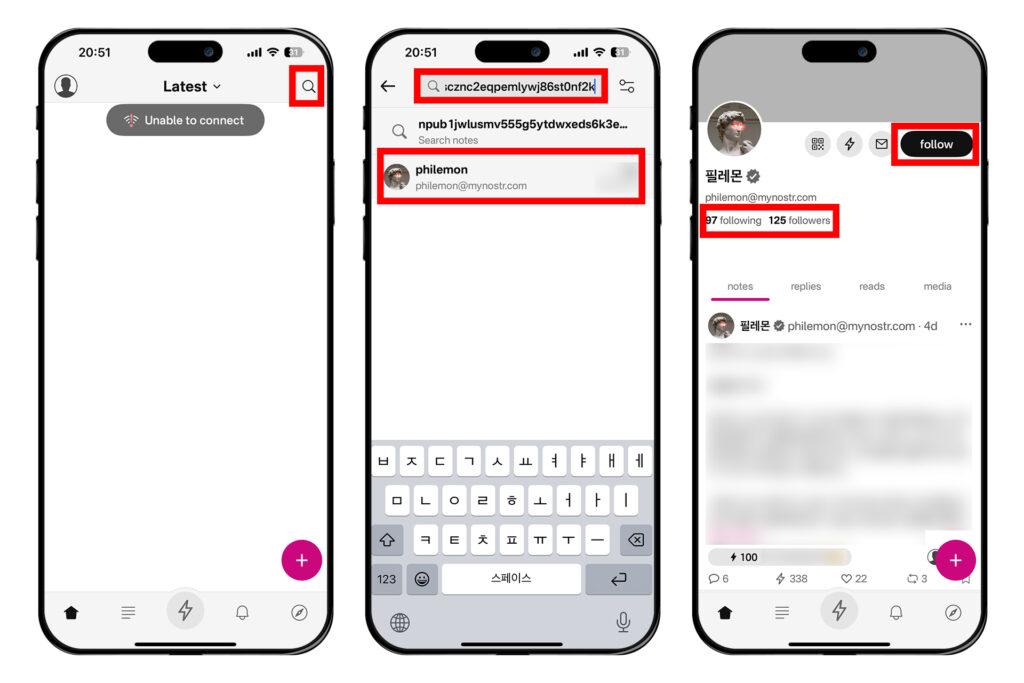
처음에는 아무런 글도 안 나타날 것이다. 팔로우하고 있는 계정이 없기 때문이다. 오른쪽 상단 검색 버튼을 누른다. 여기에 자신이 팔로우하고 싶은 계정의 공개키 npub을 붙여넣으면 사람이 뜰 것이다.
예를 들어 필자의 공개키는 아래와 같다.
npub1jwlusmv555g5ytdwxeds6k3e8u9dgyf75fscznc2eqpemlywj86st0nf2k
필자의 계정을 팔로우하는 과정을 알아보자. 검색창에 npub을 붙여넣고 프로필이 나오면 프로필을 누른다. 다음에 나오는 화면에서 오른쪽의 [follow] 버튼을 누르면 필자를 팔로우할 수 있다. 혹은 그 아래에 있는 팔로잉(following), 팔로워(followers) 목록을 보고 마음에 드는 프로필을 찾아 들어가 팔로우를 할 수 있다. 이런 방식으로 관심이 있는 계정을 팔로우하면 피드에 글이 뜨기 시작한다.
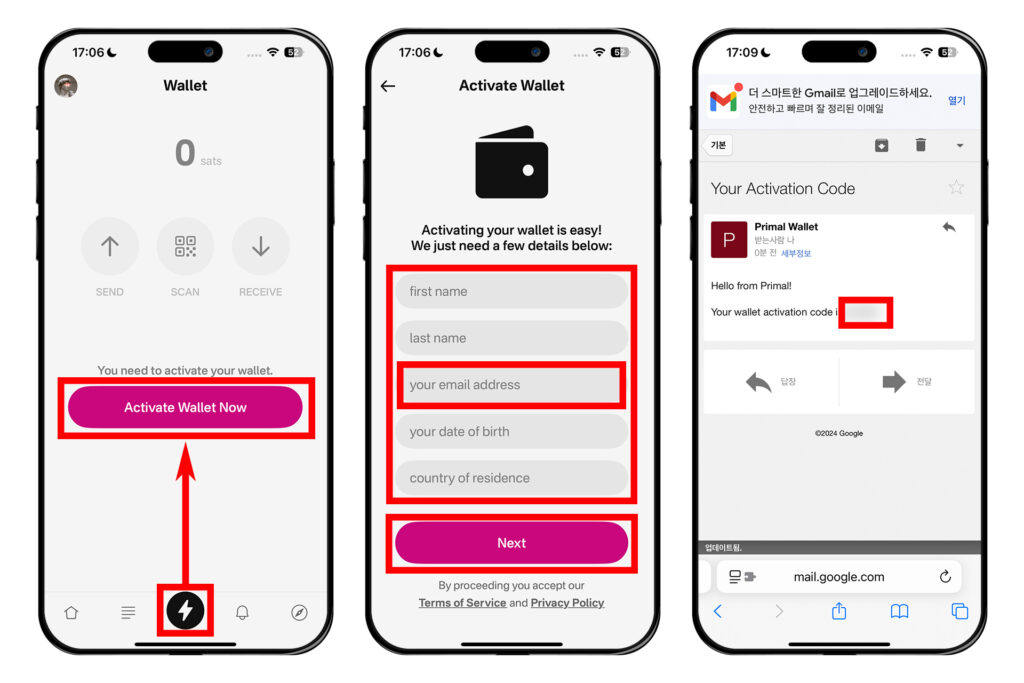
잽을 위한 지갑 추가
프라이멀에서는 자체적인 라이트닝 지갑을 추가하고, 거기에 비트코인을 보낸 뒤 잽을 보낼 수 있다.
먼저 하단 탭 가운데에 있는 번개 모양의 버튼을 누른다. 그 다음 [Activate Wallet Now]를 누른다.
다른 라이트닝 수탁 서비스들처럼 기본 정보를 받는다. 'first name'에는 성을 제외한 이름, 'last name'에는 성, 'your email address'에는 이메일 주소, 'your date of birth'에는 생년월일, 'country of residence'에는 거주 지역을 적는다. 이때 다른 것들은 실제 정보와 상이하게 적더라도 이메일만큼은 제대로 적어야 한다. 바로 뒤에 이메일 인증을 해야 하기 때문이다. 여타 라이트닝 수탁 서비스들과 마찬가지로, 이러한 수탁 서비스들은 언제나 동결 위험이 있다. 따라서 이러한 상황들에 대비해 정보를 제대로 적을지, 상이하게 적을지는 당신의 자유이며, 당신이 책임져야 한다.
잘 입력하고 [Next]를 누르면 입력했던 이메일로 확인 코드가 온다. 이메일에서 코드를 확인한다. 만약 이메일이 보이지 않는다면 스팸메일함에 메일이 있는 것은 아닌지 확인하자.
이메일에서 확인했던 코드를 프라이멀 앱 화면에 입력하고 [Finish]를 누른다.
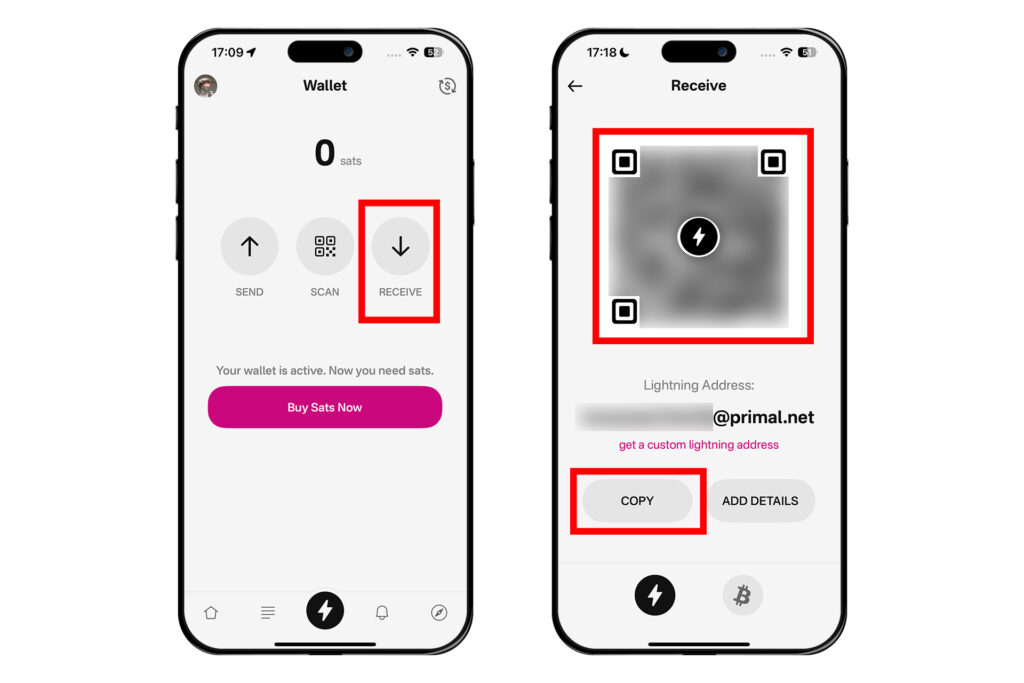
그러면 어떤 이메일 주소처럼 생긴 주소가 나온다. 이것이 프라이멀에서 생성한 라이트닝 지갑의 라이트닝 주소다. 아래 [Close]를 누른다.
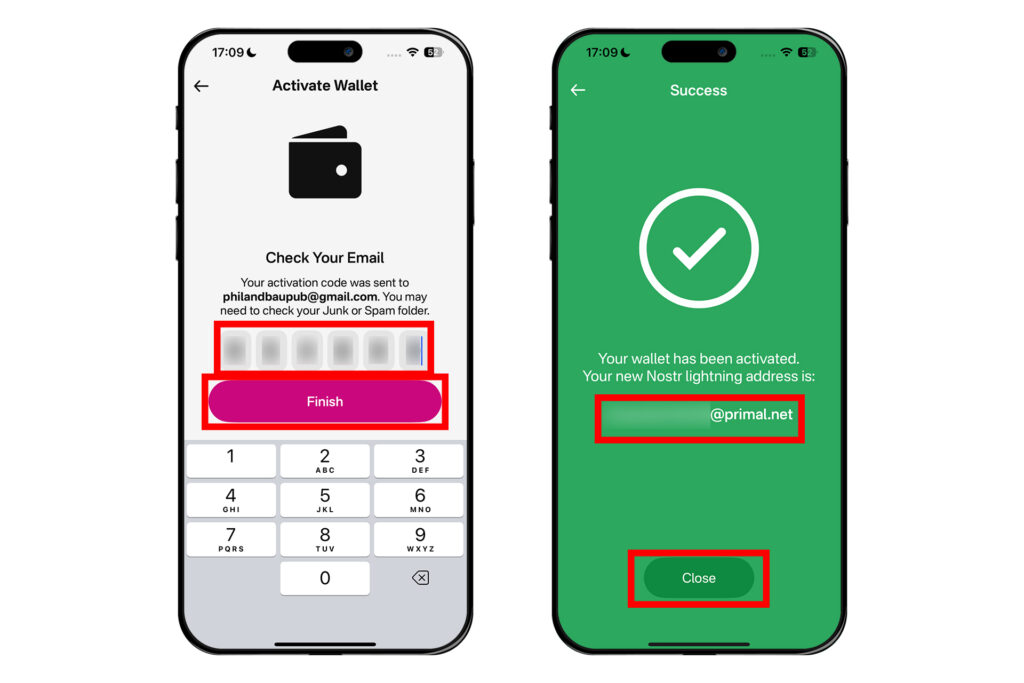
성공적으로 지갑이 생성되었다. [RECEIVE]를 누르면 라이트닝 주소와 그에 해당하는 QR코드가 보여진다. COPY를 눌러 이 라이트닝 주소로 비트코인을 보내거나, [ADD DETAILS]를 통해 인보이스를 발행하여 비트코인을 보낼 수 있다. 프라이멀 지갑에 비트코인을 보내 잔액이 생기면 잽을 보낼 수 있다.
-
 @ 472f440f:5669301e
2025-06-18 04:25:57
@ 472f440f:5669301e
2025-06-18 04:25:57Marty's Bent
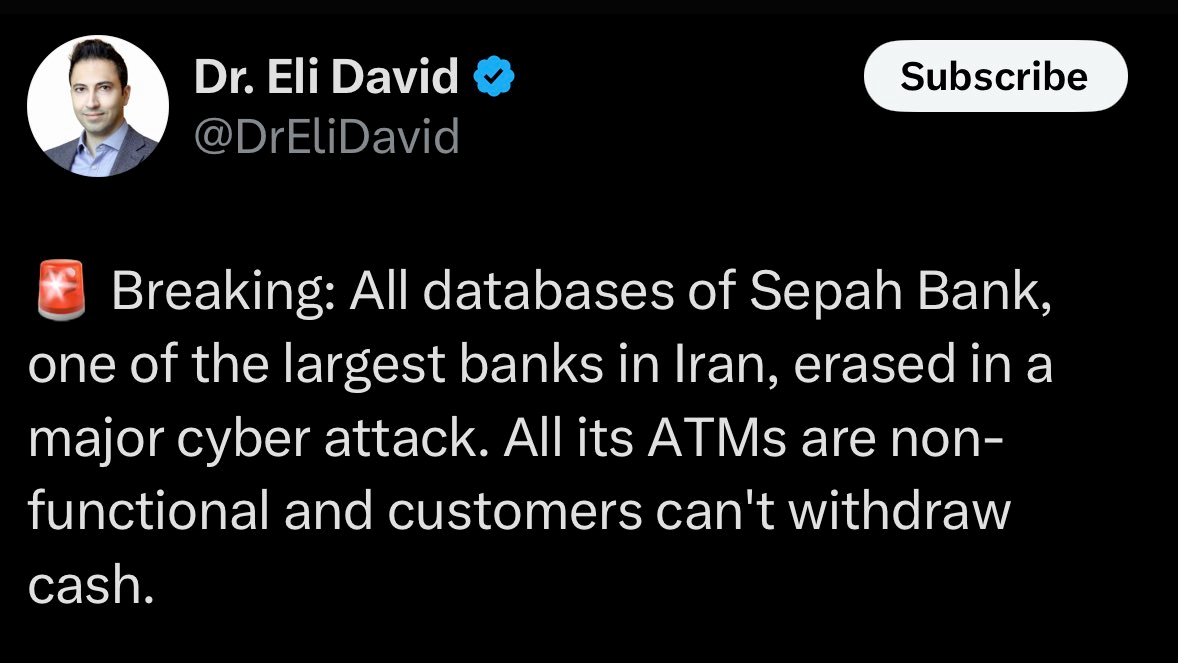
via Dr. Eli David
The case for a neutral, permissionless monetary protocol has never been stronger. The incumbent financial system is a permissioned wall garden that is susceptible to a tax. When you're using this system, you don't own your money. Your money doesn't really even exist. What you have is a claim to be able to ask your bank to give you your money or move it somewhere that you desire. Not only is it a permissioned wall garden, but it is an insecure permissioned wall garden that is susceptible to attacks from nefarious actors.
This was made very clear earlier today when Sepah Bank in Iran was the subject of a cyber attack that led to all of its databases being erased and their ATMs being deemed non-functional. Sepah Bank customers have been unable to withdraw cash. And many are warning Iranian citizens to withdraw as much cash as possible from any ATM outside of Sepah Bank's network that is working. Because there is a high likelihood that other banks and ATM networks will be targeted.
Bitcoin is a digital bearer instrument that you can custody yourself using either a software or hardware wallet. The network is operated by an army of geographically distributed nodes that maintain the rules and ensure that anybody trying to transact within the network is doing so within the rules that are set forth. Bitcoin is a push system, not a pull system. It is extremely hard to attack in the way that Sepah Bank was attacked earlier today.
I think it's important to note the way in which Sepah Bank was attacked and highlight that it is starkly different from the types of attacks or shortcomings from the financial system that we've seen over the years.
One of the events that caused a rush to Bitcoin over a decade ago was the banking crisis in Cyprus. We've seen hyperinflationary events in countries like Lebanon and Turkey that have rendered their currencies defunct. In the case of Lebanon, the central bank simply came out and said that people were not going to have access to their money and gave Lebanese citizens an overnight haircut on their savings. We've seen countries like India and Nigeria mess with their physical bills, forcing their citizens to exchange smaller denominations for larger denominations, causing massive disruptions in the process.
We've seen the United States government and its allies freeze the treasury assets of its enemies and they move towards a more multipolar monetary order over the last five years. We've seen the Canadian government freeze the bank accounts of protesters fighting for bodily autonomy. We've seen Operation Chokepoint 1.0 and 2.0. Here in the United States, the government directly targeted industries and businesses within those industries by either overtly preventing them from accessing bank accounts or covertly making it as hard as possible to access bank accounts.
On top of all this, obviously, we have the constant drumbeat of currency debasement across the world, even here in the United States, where the Federal Reserve and Federal Government are expanding the monetary base and going further into debt, ultimately destroying the purchasing power of the dollar at an increasing rate over time.
However, this type of cyber attack on a bank is unique, at least from what I can recall. The ability of nefarious actors to access bank databases and erase them is something new and something that should not be taken lightly. If Iranian hacking capabilities are as sufficient and capable as we are led to believe, it's not hard to imagine that we could see some retaliatory actions from the Iranian regime to counteract the attack on their banking system.
I don't want to incite alarm in any of you, but I think it is important to highlight that this new attack vector is definitely a step towards financial nihilism that could put hundreds of millions, if not billions of people in harm's way, in the sense that they could wake up one morning and be told that the bank does not have access to the records of their cuck buck IOUs. If something like this were to happen, I'm sure anyone who isn't holding Bitcoin in a wallet that they control will really wish they were. Being able to access your money is a vital part of being able to live you life. The thought of that ability being taken away because of a hacking war that breaks out is extremely unnerving.
As I said at the top of this letter, the case for a neutral, permissionless, distributed monetary system with a native currency that is finite is clearer than it ever has been, at least for me. It is imperative that you and anyone that you care about holds Bitcoin in self-custody to inoculate yourselves from these very real risks that are only going to increase from here on out.
Eliminate the trusted third party risks that exist in your life. Use Bitcoin as your money and use it correctly by holding it in self-custody.
Why 5% Interest Rates Won't Trigger The Next Market Crash
Guest Mel Mattison challenges the prevailing fear around rising interest rates, arguing that markets have developed immunity to higher yields. Unlike 2023's sharp selloff when the 10-year hit 5%, Mattison believes equities and Bitcoin can now absorb these levels because they signal stronger growth expectations ahead. He emphasizes that the pace of rate increases matters more than absolute levels, and notes that markets have had time to adjust. With oil trading at just $65 per barrel—a fraction of its inflation-adjusted 2008 peak of over $200—the deflationary pressure from cheap energy provides a crucial buffer.
> "It's not just what the rate we get to, it's how fast we get there." - Mel Mattison
Mattison's most compelling argument centers on AI-driven productivity gains enabling companies to maintain margins despite higher borrowing costs. As I've witnessed firsthand implementing AI tools at TFTC, what once required hiring multiple employees can now be handled by one person with the right automation. This productivity revolution means traditional rate sensitivity models may no longer apply.
Check out the full podcast here for more on institutional Bitcoin adoption, resistance money warnings, and bipartisan coalition building.
Headlines of the Day
Davis Commodities Puts 40% of $30M Into Bitcoin - via X
Ukraine Bill Adds Bitcoin to National Reserves - via X
Vinanz Raises £3.58M to Expand Bitcoin Mining - via X
Get our new STACK SATS hat - via tftcmerch.io
Bitcoin’s Next Parabolic Move: Could Liquidity Lead the Way?
Is bitcoin’s next parabolic move starting? Global liquidity and business cycle indicators suggest it may be.
Read the latest report from Unchained and TechDev, analyzing how global M2 liquidity and the copper/gold ratio—two historically reliable macro indicators—are aligning once again to signal that a new bitcoin bull market may soon begin.
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
The joy of a 5-year old riding a bike for the first time is something that should be protected at all costs.
*Download our free browser extension, Opportunity Cost: *<https://www.opportunitycost.app/> start thinking in SATS today.
*Get this newsletter sent to your inbox daily: *https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ 4ba8e86d:89d32de4
2025-06-17 17:55:10
@ 4ba8e86d:89d32de4
2025-06-17 17:55:10DTails é uma ferramenta que facilita a inclusão de aplicativos em imagens de sistemas live baseados em Debian, como o Tails. Com ela, você pode personalizar sua imagem adicionando os softwares que realmente precisa — tudo de forma simples, transparente e sob seu controle total.
⚠️ DTails não é uma distribuição. É uma ferramenta de remasterização de imagens live.
Ela permite incluir softwares como:
✅ SimpleX Chat ✅ Clientes Nostr Web (Snort & Iris) ✅ Sparrow Wallet ✅ Feather Wallet ✅ Cake Wallet ✅ RoboSats ✅ Bisq ✅ BIP39 (Ian Coleman) ✅ SeedTool ... e muito mais. https://image.nostr.build/b0bb1f0da5a9a8fee42eacbddb156fc3558f4c3804575d55eeefbe6870ac223e.jpg
Importante: os binários originais dos aplicativos não são modificados, garantindo total transparência e permitindo a verificação de hashes a qualquer momento.
👨💻 Desenvolvido por: nostr:npub1dtmp3wrkyqafghjgwyk88mxvulfncc9lg6ppv4laet5cun66jtwqqpgte6
GitHub: https://github.com/DesobedienteTecnologico/dtails?tab=readme-ov-file
🎯 Controle total do que será instalado
Com o DTails, você escolhe exatamente o que deseja incluir na imagem personalizada. Se não marcar um aplicativo, ele não será adicionado, mesmo que esteja disponível. Isso significa: privacidade, leveza e controle absoluto.
https://image.nostr.build/b0bb1f0da5a9a8fee42eacbddb156fc3558f4c3804575d55eeefbe6870ac223e.jpg https://image.nostr.build/b70ed11ad2ce0f14fd01d62c08998dc18e3f27733c8d7e968f3459846fb81baf.jpg https://image.nostr.build/4f5a904218c1ea6538be5b3f764eefda95edd8f88b2f42ac46b9ae420b35e6f6.jpg
⚙️ Começando com o DTails
📦 Requisitos de pacotes
Antes de tudo, instale os seguintes pacotes no Debian:
``` sudo apt-get install genisoimage parted squashfs-tools syslinux-utils build-essential python3-tk python3-pil.imagetk python3-pyudev
```
🛠 Passo a passo
1 Clone o repositório:
``` git clone https://github.com/DesobedienteTecnologico/dtails cd dtails
```
2 Inicie a interface gráfica com sudo:
``` sudo ./dtails.py
```
Por que usar sudo? É necessário para montar arquivos .iso ou .img e utilizar ferramentas essenciais do sistema.
💿 Selecione a imagem Tails que deseja modificar
https://nostr.download/e3143dcd72ab6dcc86228be04d53131ccf33d599a5f7f2f1a5c0d193557dac6b.jpg
📥 Adicione ou remova pacotes
1 Marque os aplicativos desejados. 2 Clique Buildld para gerar sua imagem personalizada. https://image.nostr.build/5c4db03fe33cd53d06845074d03888a3ca89c3e29b2dc1afed4d9d181489b771.png
Você pode acompanhar todo o processo diretamente no terminal. https://nostr.download/1d959f4be4de9fbb666ada870afee4a922fb5e96ef296c4408058ec33cd657a8.jpg
💽 .ISO vs .IMG — Qual escolher?
| Formato | Persistência | Observações | | ------- | ---------------------- | ----------------------------------------------- | | .iso | ❌ Não tem persistência | Gera o arquivo DTails.iso na pasta do projeto | | .img | ✅ Suporta persistência | Permite gravar diretamente em um pendrive |
https://nostr.download/587fa3956df47a38b169619f63c559928e6410c3dd0d99361770a8716b3691f6.jpg https://nostr.download/40c7c5badba765968a1004ebc67c63a28b9ae3b5801addb02166b071f970659f.jpg
vídeo
https://www.youtube.com/live/QABz-GOeQ68?si=eYX-AHsolbp_OmAm
-
 @ 8bad92c3:ca714aa5
2025-06-18 04:02:22
@ 8bad92c3:ca714aa5
2025-06-18 04:02:22Key Takeaways

Leon Wankum, a real estate expert turned Bitcoiner, presents a powerful argument that Bitcoin is emerging as the new “hurdle rate,” outpacing real estate as the preferred store of value in a shifting financial landscape. As the 18-year property cycle nears its end amid high interest rates and imbalanced markets, Bitcoin’s scarcity, performance, and optionality are prompting capital allocators to rethink traditional strategies. Institutions are beginning to reallocate cash flows and refinance properties into Bitcoin treasuries, while new yield-bearing Bitcoin instruments like Strike, Strife, and Stride offer compelling alternatives to bonds and property. Wankum envisions a gradual transition to a Bitcoin standard, facilitated by dual collateralization and designed to avoid economic disruption as Bitcoin steadily replaces legacy financial infrastructure.
Best Quotes
"Bitcoin is starting to become the new hurdle rate that all other financial products have to abide to."
“No asset—not even prime real estate—can compete with Bitcoin’s long-term performance and absolute scarcity.”
"You can refinance a property and allocate to Bitcoin without selling—this is how many are making the transition."
"Strategy (MicroStrategy) has enough Bitcoin to cover preferred stock dividends for over 200 years."
"20% of our property cash flow into Bitcoin outperformed the 80% left in fiat."
“Bitcoin is digital real estate—but better. Scarce, global, and doesn’t need maintenance or tax sheltering gimmicks.”
“If it’s just 1% of the real estate market, that’s $3 trillion. And that’s enough.”
"A smooth transition, not collapse, is the optimal path forward."
Conclusion
This episode explores how Bitcoin is overtaking real estate as the global store of value, with Leon Wankum offering a rational, experience-based framework for understanding this shift. While institutional inertia slows adoption, capital flows are beginning to reflect Bitcoin’s growing dominance, as new financial instruments and treasury strategies emerge. Leon advocates for a thoughtful, evolutionary transition to a Bitcoin standard—one that prioritizes stability, practical integration, and long-term value creation across the global economy.
Timestamps
0:00 - Intro
0:50 - Real Estate
12:36 - Bitcoin for real estate investors
17:44 - Bitkey
18:39 - MSTR products and opportunity cost
30:43 - Unchained
31:13 - Cash flow alternatives
37:40 - Strategy risks
44:41 - Smooth or chaotic transition
50:58 - Is this cycle different?
56:42 - Tradfi degeneracy
1:02:00 - Leon’s Book - Digital Real EstateTranscript
(00:00) Other than real estate, there were little investments that performed better. Few were aware of the existence of Bitcoin. As people become more aware, they will likely also sell off their properties. Bitcoin as a near-perfect form of money is starting to become the new hurdle rate that all other financial products have to abide to.
(00:19) Instead of buying a regular bond issued by a nation state, you can actually buy a fixed income product issued by Strategy. This is a product that could potentially tap into the real estate market. If it's just 1%, that's 3 trillion. And that's enough. They are starting to weigh the opportunity cost of not putting money into Bitcoin.
(00:36) But very few are able to comprehend the necessity of quickly investing large part of the capital into Bitcoin. Every 18 years will have a correction on housing. We're bringing in a housing expert to talk about the real estate market and Bitcoin corporate adoption. in the crazy frenzy that's going on right now in public markets.
(01:04) Leon, welcome back to the show. Thanks for having me back. It was great seeing you even though it was briefly in Vegas last week. I caught you literally as I was running to the airport off the stage. Yeah. And uh look, I'm pull that back up because I think this is a good jumping off point. We'll start with like a personal story.
(01:24) I'm currently in the middle of a move right now, but decided to rent a house because I was looking at the prices for housing in the places I'm looking to buy and they were they were too high. Not only were they too high, we put a bid in on one house and it wound up going a million dollars over asking.
(01:44) And I think over here in the United States, this is a big topic of discussion right now, which is the real estate market feels a little toppy. Prices are still very high, very sticky. Rates are still very high. Uh, and that's one thing I'm trying to discern as somebody who would like to buy a house in the next few years, a forever house for my family, what is going on.
(02:08) And as we can see here, Red Red Fin reported earlier this week that 34% there are 34% more sellers in the market than buyers. At no other point in records dating back to 2013 have sellers outnumbered buyers this much. There are a total of $698 billion worth of homes for sale in the US, up 20.
(02:29) 3% from a year ago in the highest dollar amount ever. So, it seems like there's a ton of people who have rode the real estate market and they're being a bit stingy on pricing and we're waiting for a correction. Is that your take on this? Yeah, we definitely need to wait for price equilibrium to build because since 2008 really since we had low interest rates um prices were skyrocketing and now with a different interest rate environment.
(02:57) Um what I personally also feel is that people are not willing to sell their houses for a price that they believe is not what they could get because they still have the prices in mind that they were able to receive 2 three years ago and the buyers are not willing to pay prices that people want because interest rates are higher meaning the cost of capital and the cost of borrowing went up.
(03:21) So I think this is a healthy um and a healthy um development. We need a price equilibrium. We need um demand and supply prices to match. It's going to take a long time. I think it's also it also depends on interest rates. If Powell is going to um lower interest rates, which I don't think he will, even though that's something that the president would like him to do, but I don't think he will because it would cause inflation to go up again, especially in in goods and services and groceries.
(03:51) And um judging by that, I think interest rates will stay above 3% at least for the foreseeable future. Meaning I believe that real estate prices will come down a little bit till we meet that equilibrium. But something that's important to to remember which makes it a little bit odd that because as a Bitcoiner when you look at housing, I think you constantly think now it's going to crash, now it's going to crash.
(04:15) But the reason it's not really going to crash is as soon as new money is being introduced into your economy or as soon as interest rates are lowered that money is being funneled into real estate and also the existing system that is depending on real estate as collateral has an interest in propping prices up.
(04:34) So this can go on for another 10 or 20 years I think. I mean there could be there's definitely a correction that we can see right now and I personally wouldn't get into uh real estate development at this point if you'll ask me from the perspective what's the better investment of course that is Bitcoin but I just want to make a point that this can go can go on for longer than we think because housing is limited not as limited as Bitcoin but there's something called the 18-year property cycle and it says that every 18 years, we'll
(05:08) have a correction in housing. And the reason for that is if the money supply is expanded and that money goes into land, it's not going out of land because land is limited. It's similar to Bitcoin. But what happens is that after around 14 15 years, prices start to come down and then they find a new price equilibrium which is higher than when the cycle started.
(05:33) And we are at the end of this 18-year property cycle. and I had suggest that prices will fall until 2026 and then in 2026 if interest rates are lowered I think prices can find price equilibrium and then possibly move up in nominal value of course if you start now accounting for real estate and bitcoin it's a whole different story I know talked from the lens of a fiat um based system yeah that note on pal and the fed is interesting that it It's very obvious Trump's wanted him to lower rates since before he even got elected.
(06:09) But I was reading an article yesterday that made a lot of sense to me, which is he's not going to lower rates for multiple reasons. One of which you mentioned, which is it would it would reignite inflation, which nobody wants to see right now. And then number two, profit margins are going up because the productivity uh increases due to AI.
(06:32) I mean, and we're still at the early stages of that, um, where you have many of the big big tech, the MAG 7 beginning to lay off people because they're creating all these efficiencies via AI. So, we're able to increase productivity and profit margins and so there's no reason to to lower rates from that perspective, which agreed.
(06:58) Yeah, absolutely true. Yeah, which is uh you know it'll be it's crazy the confluence of events that are happening right now whether it's real estate market looking a little toppy at least temporarily the interest rate environment the progression of AI and the adoption uh by many large companies and small companies alike and then you have Bitcoin sitting over here sitting over $2 trillion establishing itself as a $2 trillion asset and it still seems a bit fringe where um where we are certainly as Bitcoiners, individuals -
 @ dfa02707:41ca50e3
2025-06-17 07:01:47
@ dfa02707:41ca50e3
2025-06-17 07:01:47Contribute to keep No Bullshit Bitcoin news going.
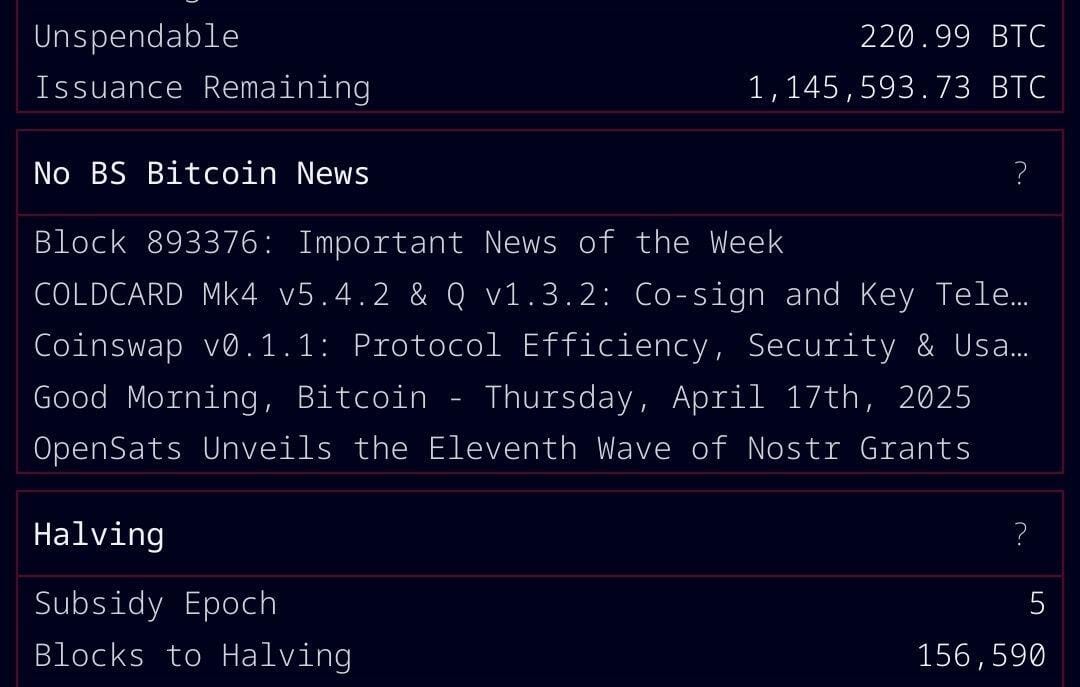
-
Version 1.3 of Bitcoin Safe introduces a redesigned interactive chart, quick receive feature, updated icons, a mempool preview window, support for Child Pays For Parent (CPFP) and testnet4, preconfigured testnet demo wallets, as well as various bug fixes and improvements.
-
Upcoming updates for Bitcoin Safe include Compact Block Filters.
"Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions. They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK," writes the project's developer Andreas Griffin.
- Learn more about the current and upcoming features of Bitcoin Safe wallet here.
What's new in v1.3
- Redesign of Chart, Quick Receive, Icons, and Mempool Preview (by @design-rrr).
- Interactive chart. Clicking on it now jumps to transaction, and selected transactions are now highlighted.

- Speed up transactions with Child Pays For Parent (CPFP).
- BDK 1.2 (upgraded from 0.32).
- Testnet4 support.
- Preconfigured Testnet demo wallets.
- Cluster unconfirmed transactions so that parents/children are next to each other.
- Customizable columns for all tables (optional view: Txid, Address index, and more)
- Bug fixes and other improvements.

Announcement / Archive
Blog Post / Archive
GitHub Repo
Website -
-
 @ 9ca447d2:fbf5a36d
2025-06-18 04:02:01
@ 9ca447d2:fbf5a36d
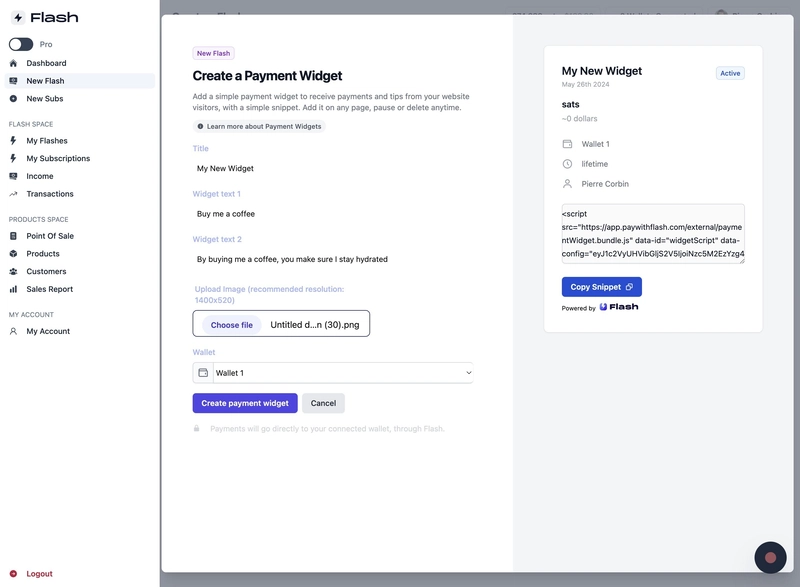
2025-06-18 04:02:01Paris, France – June 6, 2025 — Bitcoin payment gateway startup Flash, just announced a new partnership with the “Bitcoin Only Brewery”, marking the first-ever beverage company to leverage Lightning payments.
Flash enables Bitcoin Only Brewery to offer its “BOB” beer with, no-KYC (Know Your Customer) delivery across Europe, priced at 19,500 sats (~$18) for the 4-pack, shipping included.
The cans feature colorful Bitcoin artwork while the contents promise a hazy pale ale: “Each 33cl can contains a smooth, creamy mouthfeel, hazy appearance and refreshing Pale Ale at 5% ABV,” reads the product description.
Pierre Corbin, Co-Founder of Flash, commented:
“Currently, bitcoin is used more as a store of value but usage for payments is picking up. Thanks to new innovation on Lightning, bitcoin is ready to go mainstream for e-commerce sales.”
Flash, launched its 2.0 version in March 2025 with the goal to provide the easiest bitcoin payment gateway for businesses worldwide. The platform is non-custodial and can enable both digital and physical shops to accept bitcoin by connecting their own wallets to Flash.
By leveraging the scalability of the Lightning Network, Flash ensures instant, low-cost transactions, addressing on-chain Bitcoin bottlenecks like high fees and long wait times.
For businesses interested in adopting Bitcoin payments, Flash offers a straightforward onboarding process, low fees, and robust support for both digital and physical goods. To learn more, visit paywithflash.com.
Media Contact:
Pierre Corbin
Co-Founder, Flash
Email: press@paywithflash.com
Website: paywithflash.comAbout Flash
Flash is the easiest Bitcoin payment gateway for businesses to accept payments. Supporting both digital and physical enterprises, Flash leverages the Lightning Network to enable fast, low-cost Bitcoin transactions. Launched in its 2.0 version in March 2025, Flash is at the forefront of driving Bitcoin adoption in e-commerce.
About Bitcoin Only Brewery
Bitcoin Only Brewery (@Drink_B0B) is a pioneering beverage company dedicated to the Bitcoin ethos, offering high-quality beers payable exclusively in Bitcoin. With a commitment to personal privacy, the brewery delivers across Europe with no-KYC requirements.
-
 @ b1ddb4d7:471244e7
2025-06-18 04:01:41
@ b1ddb4d7:471244e7
2025-06-18 04:01:41The Barcelona Cyphers Conference (BCC8333), the city’s first biggest bitcoin-themed event, transforms a historic building in the central born district of the Catalan capital into a hub for bitcoin enthusiasts and cypherpunks. Named after the port bitcoin nodes use to sync the timechain (8333), this inaugural event delivers high-signal discussions and practical applications of decentralized technology, uniting over 100 attendees from Spain, Europe, and beyond.
Venue and Atmosphere
Set in a 17th-century palace that doubles as a flamenco venue, Palau Dalmases blends historical elegance with a creative, almost rebellious vibe. The unique setting fosters deep conversations, hands-on workshops, and genuine connections, prioritizing substance over spectacle. The spectacular courtyard serves as a lively backdrop for collaboration and sparking chats that resonates with the event’s freedom/privacy-oriented ethos.

Lightning Network Integration
BCC8333 embedds Bitcoin’s Lightning Network (LN) into its core, emphasizing privacy and scalable technology. Two on-site bars accept LN payments for drinks, demonstrating fast, low-cost bitcoin transactions in action.
But the usage of Lightning Network extends beyond just ‘refreshments’.
· Chain Duel: This simple yet engaging game has many BCC8333 participants send sats via LN to enter, compete, and have fun for the two days of the event. A large-screen tournament on the main stage amplifies the excitement, showcasing one more practical case for LN in the bitcoin ecosystem with a nice bounty, i.e. winners claiming the collected sats.
· Thematic sessions and practical workshops on wallets, vending machines, and Nostr highlight LN’s role in bitcoin adoption, while touching on the importance of privacy vs. scalable transactions.
While the overall adoption in Barcelona’s local establishments outside the venue remains rather limited, attendees find a nearby street with vivid graffiti dedicated to bitcoin, and in a practical way, whenever possible, swap sats for fiat among themselves when direct payments aren’t possible.

Selected Highlights
The agenda balances intense sessions with networking breaks, ensuring space for reflection and collaboration. Some of the key sessions include:
· Future of Private Transactions (English, Max Hillebrand).
· Miniscripts Roundtable (English, Edouard from Liana, Landabaso from Rewind, Francesco from BitVault, Yuri da Silva from Great Wall).
· Sovereign Hardware Tools (English, Wesatoshi).
· Debate: Future of Lightning (Spanish, mixed attendees).
· Op_return Debate (English, Peter Todd, Unhosted Marcellus, Lunaticoin).
Recordings from the main stage and additional coverage by Juan Cienfuegos, host of the BitCorner Podcast, will soon be available online (X: @BCC833, @TheJuanSC).

Why BCC8333 Stood Out
· Local Maxis: vibrant and well-organized approach shines through, with local bitcoiners as organizers of the event (Spanish and expats) bringing their best PoW to the table.
· Focused Discussions: Free of hype and influencers, BCC8333 prioritizes signal over noise, diving into critical topics like privacy, nodes, wallets, P2P tools, decentralized mining, and Nostr.
· Community Vibe: The smaller crowd enables authentic connections, fostering a tight-knit community of freedom-tech enthusiasts committed to sovereignty.
BCC8333 is a powerful testament to the cypherpunk spirit, blending bitcoin and privacy to fuel innovation. From LN-powered interactions to thought-provoking talks, the event underscores the strength of a community dedicated to building decentralized solutions. Congratulations to the organizers, contributors, volunteers, and attendees for making this conference a standout moment in the year’s lineup of bitcoin-themed events.
-
 @ 52524fbb:ae4025dc
2025-06-18 03:37:50
@ 52524fbb:ae4025dc
2025-06-18 03:37:50Gold mostly referred to as ultimate safe-haven asset amidst economic uncertainty or market makes investors desperately flock to it for stability. This traditional view scratches surface of gold's role barely in an increasingly complex global landscape interconnected precariously nowadays. Critical analysis reveals XAUUSD as a highly sensitive barometer of geopolitics. its price movements frequently mirroring the flow of tensions internationally. Astute traders unlock gold's full potential by recognizing an intricate relationship quietly beneath surface level market fluctuations daily.
Gold earns its safe haven label largely due to it's perceived ability of preserving wealth amidst faltering fiat currencies or traditional assets suddenly. This phenomenon persists remarkably during severe financial turmoil or episodes characterized by unusually high inflation rates nationwide. Apparently geopolitical events introduce a disparate dimension of risk not just economically but systemically affecting everything pretty badly. Major conflicts erupt suddenly between global powers and XAUUSD often reacts vigorously transcending risk aversion in turbulent geopolitical landscapes. It morphs into reflection of looming disruptions across global supply chains and potential sanctions amidst wildly fluctuating energy prices suddenly.
A sudden escalation of tensions might erupt pretty quickly in some critical oil producing region. Crude oil prices may react rapidly but XAUUSD will likely be impacted swiftly amidst sudden market fluctuations too. Rising oil prices spark inflation fears amidst murky global economic prospects and precarious possibilities of sprawling conflict severely impacting major economies. Gold acts as hedge against unknown terrors and facilitates flight to security palpably tangible when geopolitical landscape becomes rather unpredictably volatile. Gold's status as reserve asset for central banks adds another hefty layer of geopolitical sensitivity pretty much worldwide nowadays. Several central banks mostly in emerging markets have amped up gold reserves partly as diversification tactic away from US Dollar lately. Sovereign entities amass gold strategically in response to geopolitics and shifts in this trend heavily influence global demand and subsequently XAUUSD prices.
Traders leveraging gold as a barometer of geopolitical turmoil must integrate qualitative analysis into strategy very carefully nowadays. It entails vigilantly tracking news from abroad and scrutinizing statements made by diplomats and lofty declarations uttered by world leaders. Anticipating likely responses and understanding economic vulnerabilities of various nations involved can give one an edge potentially in complex situations. A surprise summit between rival nations might signify de-escalation potentially leading quickly to pull-back in gold while sudden military build-up elsewhere could signal opposite XAUUSD retains fundamental safe-haven characteristics yet its role as real-time gauge of global geopolitical risk becomes increasingly pronounced nowadays. Traders gain keen insights into murky market sentiment by watching gold's reaction to tumultuous global events and thereby concoct shrewd trading strategies. Gold ain't merely some flashy metal it's a luminous barometer of global equilibrium shining brightly amidst economic turmoil naturally..
-
 @ 52524fbb:ae4025dc
2025-06-18 03:25:09
@ 52524fbb:ae4025dc
2025-06-18 03:25:09EURUSD, which is a pair that shows the exchange rate between the Euro and the US Dollar, is arguably the most traded currency pair in the world. Its action the product not of economic announcements but rather a mix of incompatible monetary policies, contrasting economic thinking, and the political stability of two of the largest economic areas in the world - the Eurozone and the US. For traders, this backdrop is key to predicting price movements and containing exposure in this, heavily traded market.
Between European Central Bank and the Federal Reserve a very intricate tango unfolds quietly at the heart of EURUSD currency pair dynamics daily. These two central banks often diverge on monetary policy paths in response to their disparate economic conditions under price stability mandates. Interest rate differential largely drives EURUSD exchange rates heavily nowadays. US Dollar strengthens against Euro pretty quickly when Fed hikes interest rates but ECB keeps rates fairly low thereby attracting sizable capital inflows into US markets due to much higher yields available there. Euro can surge pretty quickly if ECB adopts hawkish stance signaling rate hikes or tightening quantitativelys relative to dovish Fed policy moves.
We can say for a fact that trading EURUSD is a sophisticated exercise in comparing and contrasting two major economies. Success hinges on a deep understanding of the divergent monetary policy stances of the ECB and the Fed, a continuous assessment of their respective economic health and growth prospects, and a keen awareness of the political landscape within the Eurozone. The interplay of these forces creates a constantly evolving environment for the world's most popular currency pair.
-
 @ 52524fbb:ae4025dc
2025-06-18 03:13:43
@ 52524fbb:ae4025dc
2025-06-18 03:13:43Bitcoin (BTCUSD), commonly called "digital gold," has turned the financial universe on its head in just a decade, emerging as a new alternative to the traditional store of value. And the story that was created out of its low supply and lack of a central authority is a major contributor to its price moves vs USD. But there is much more to the relationship than that; it is a complex dance between developing narratives, macroeconomic factors, and the inherent properties of a fledgling asset class trying to find its footing in an established financial world.
The story of Bitcoin as “digital gold” went to an extreme during peak inflation fear and economic uncertainty, when gold plays its part as an inflation hedge. Its advocates maintain that Bitcoin’s 21 million coin supply, its programmed deflation with the halving events and its distance from central bank control, has made it a better store of value in a time of exceptional fiat currency expansion. This story has a direct impact on BTCUSD, as some investors seeking to "hedge" against devaluing of the US Dollar, typically buy Bitcoin, and increase demand (and therefore price).
To sum it up, trading BTCUSD needs not only conducting technical analysis but also a very sharp understanding of the current narratives and emotions of the market and implementing the news from the macroeconomic situation to this new asset changes. Bitcoin is still in the process of discovery of its final purpose in the world of finance, going back and forth between a speculative tech asset, a disruptive financial innovation, and a clean and sincere candidate for the title of "digital gold." The inter-relationship with traditional fiat currencies such as the US Dollar, which is at the base of the mixture of economic realities and charming, changing stories, is still a fascinating area for traders to explore as it will remain so in the future.
-
 @ dfa02707:41ca50e3
2025-06-17 06:01:51
@ dfa02707:41ca50e3
2025-06-17 06:01:51Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ 502ab02a:a2860397
2025-06-18 02:15:25
@ 502ab02a:a2860397
2025-06-18 02:15:25เครื่องดื่ม Tang ไม่ได้ถือกำเนิดมาบนดาวอังคาร แต่กลับโด่งดังเพราะคนที่ไปใกล้ดาวอังคารที่สุดในยุคนั้นต่างดื่มมันแทนน้ำผลไม้...ใช่แล้วจ้ะ เรากำลังพูดถึง "NASA" และภารกิจอวกาศที่เปลี่ยน Tang จากเครื่องดื่มสังเคราะห์ธรรมดา ให้กลายเป็นไอคอนของอนาคต ที่บางครั้ง...ดูดีเกินกว่าความจริง
ย้อนกลับไปปี 1957 สหรัฐฯ กำลังแข่งขันในสงครามอวกาศกับโซเวียต บริษัท General Foods (ถ้าจำได้บริษัทนี้เขาผลิต ซีเรียล Grape-Nuts โดย Charles William Post หรือ C.W. Post ชายหนุ่มที่เคยเข้ารับการรักษาตัวที่ Battle Creek Sanitarium ของหมอ John Harvey Kellogg นั่นไงครับ) บริษัทนี้เป็นผู้ผลิต Tang ได้พัฒนาเครื่องดื่มผงสังเคราะห์นี้ขึ้นมาในปี 1957 โดยนักเคมีชื่อ William A. Mitchell ซึ่งเขาไม่ได้แค่คิดค้น Tang เท่านั้น แต่เขายังคิดค้น Cool Whip, Pop Rocks, Jell-O ที่เซ็ตตัวเร็ว, ไข่ขาวผง และผลิตภัณฑ์ทดแทนมันสำปะหลังยอดนิยม รวมถึงผลิตภัณฑ์อื่นๆ อีกมากมาย (รวมสิทธิบัตรทั้งหมด 70 ฉบับ) แต่ละตัวนี่ทุกวันนี้ยังขายในซุปเปอร์อยู่เลยครับ ผลิตภัณฑ์หลักชิ้นแรกที่มิตเชลล์คิดค้นคือผลิตภัณฑ์ทดแทนมันสำปะหลังซึ่งได้รับการพัฒนาเพื่อหลีกเลี่ยงการขาดแคลนมันสำปะหลังอันเป็นผลจากสงครามโลกครั้งที่ 2 ซึ่งเป็นเหตุผลว่าทำไมมันสำปะหลังจึงบางครั้งถูกเรียกว่า “Mitchell’s Mud”
Tang นั้นตอนแรกกลับขายไม่ค่อยออก เพราะคนยุคนั้นยังเชื่อใน “น้ำส้มสด” ที่บีบจากผลไม้มากกว่าอะไรที่ชงจากผง แน่นอนมันเหมือนที่ทุกวันนี้เราพร่ำบอกว่า "ฉันเลือกอาหารธรรมชาติ" นั่นแหละครับ แทบไม่ต่างกันเลย
จนกระทั่ง NASA เข้ามา
ปี 1962 องค์การ NASA ต้องเผชิญปัญหาใหญ่ที่คนทั่วไปนึกไม่ถึง นั่นคือ น้ำในอวกาศรสชาติ “แย่มาก” เพราะระบบกรองน้ำรีไซเคิลทำให้น้ำมีรสโลหะอ่อนๆ ปนน้ำยาฆ่าเชื้อ จะให้มนุษย์อวกาศดื่มแบบนั้นทุกวันคงทำให้ภารกิจเสียสมาธิได้ง่ายกว่าการหลุดวงโคจรเสียอีก
นั่นคือจุดที่ Tang ถูกนำมาใช้ครั้งแรกโดย John Glenn ในภารกิจ Mercury-Atlas 6 ซึ่ง Tang ถูกเพิ่มไว้ในเมนูของภารกิจ Mercury ของ John Glenn ในปี 1962 ซึ่งเขาได้โคจรไปรอบโลกและทำการทดลองรับประทานอาหารในอวกาศ Mercury-Atlas 6 เป็นภารกิจที่ให้ข้อมูลสำคัญเกี่ยวกับการเปลี่ยนแปลงทางกายภาพของมนุษย์เมื่ออยู่ในสภาวะไร้น้ำหนัก ภารกิจนี้ช่วยสร้างความมั่นใจให้กับ NASA ว่าเทคโนโลยีของตนพร้อมก้าวต่อไปสู่ภารกิจที่ซับซ้อนยิ่งขึ้น นำไปสู่ โครงการ Gemini และ โครงการ Apollo ตามลำดับ
เมื่อ NASA ตัดสินใจเติมผง Tang ลงในน้ำเพื่อปรับรสชาติให้น่าดื่มขึ้น กลายเป็นจุดเริ่มต้นของการตลาดที่แทบจะ “ยึดโลก” ได้ในชั่วข้ามคืน เพราะหลังภารกิจนั้น Tang โฆษณาโดยใช้คำว่า “เครื่องดื่มที่นักบินอวกาศดื่มจริง” เห็นไหมครับว่านั่นแหละคือพลังของวาทกรรม
ทีนี้หล่ะพี่เอ้ยยยย เด็กๆ แห่กันดื่ม Tang กันทั่วอเมริกา เพราะรู้สึกว่าการชงน้ำส้มผงในบ้านทำให้ตัวเองเข้าใกล้ดวงจันทร์ได้สักนิด ผู้ปกครองก็สบายใจ เพราะฉลากเขียนว่ามีวิตามิน C และ “ไม่ต้องแช่เย็น” เหมาะกับยุคโมเดิร์นที่ตู้เย็นก็ยังแพงอยู่ ใครจะไปนั่งทำน้ำส้มคั้นกันให้ลำบาก เห็นไหมครับว่าวัฒนธรรมการพึ่งพา “อาหารสำเร็จรูปเพื่ออนาคต” ก็เริ่มตั้งไข่จากตรงนี้อีกจุดนึง
ถ้าหากเราลองส่องลึกลงไปในสูตรของ Tang จะพบว่ามันคือของผสมของ น้ำตาล, กลิ่นแต่งสังเคราะห์, วิตามิน C ที่เติมเข้าไปภายหลัง และกรดซิตริกเพื่อเลียนแบบความเปรี้ยวของผลไม้ เรียกง่ายๆ ว่า “ไม่มีอะไรที่่ได้คุณค่าแบบส้มธรรมชาติเลย” ยกเว้นจินตนาการ
ถึงกระนั้น ผู้บริโภคก็ไม่ได้โวยวายอะไรแถมยังโห่ร้องตอบรับ Tang เป็นอย่างดี เพราะอิทธิพลของ NASA ทำให้คนรู้สึกว่า "ต้องดีแน่ๆ ถ้าแม้แต่ NASA ยังใช้" แม้ว่า NASA เองจะไม่เคยพูดว่า Tang ดีต่อสุขภาพและมันเป็นเครื่องมือชั่วคราวเพื่อทำให้น้ำดื่มได้ ไม่ได้ใช้เพราะว่า Tang ดีกว่าน้ำส้ม...แต่นั่นแหละ ความเงียบของ NASA ถูกตลาดตีความจนเกินจริงไป เพราะการไม่ปฎิเสธนั่นหมายถึงการตอบรับ การตลาดและผู้บริโภคจึงตีความไปในทางเดียวกันว่า มันวิเศษกว่าส้มธรรมดา เพราะมันคือเครื่องดื่มระดับอวกาศเลือกใช้
หลายปีต่อมา เมื่อนักโภชนาการหลายคนเริ่มออกมาเตือนว่า Tang คือน้ำตาลล้วน ไม่มีเส้นใย ไม่มีประโยชน์ใดที่เทียบได้กับผลไม้จริง ผู้ผลิตก็หันมาใส่ "วิตามินเสริม" เพิ่มอีกให้แทนเพื่อล้างภาพลักษณ์เดิมประมาณว่า อ่ะอยากได้วิตามินอะไรเราเติมให้เทผสมในสูตร กลายเป็นสคริปต์ซ้ำของอาหารยุค “อาหารอนาคตปลอม” ที่เอาสารอาหารเดี่ยวๆ มาเติมแล้วโฆษณาว่า “เหมือนธรรมชาติ” หรือดีกว่าเสียอีก
เราอ่านถึงตรงนี้ก็ไม่ต้องตลกหรือขำเลยครับ หันมามองอาหารปัจจุบัน ของบางอย่างมีวิตามินสูงเพราะเทวิตามินผงลงไปผสม เช่นนมพืชต่างๆ ที่อยู่ดีๆก็มีวิตามินระดับซุปเปอร์ฟู้ดขึ้นมาเฉยเลย หรือแม้แต่พืชบางชนิดที่อุ้มน้ำได้ดี ก็มีวิตามินสูงระดับหลายสิบถึงร้อยเท่าของธรรมชาติของมัน ด้วยการเติมวิตามินลงไปในอาหารพืช ที่เพาะเลี้ยงกัน และยิ่งถ้ามองแบบเตรียมพร้อมไปถึงอนาคต อยู่ที่ใครแล้วครับว่าจะมองเห็นใส้ในของอาหารเหล่านี้ไหม เชื่อไหมว่าหลายต่อหลายคนมองว่ามันดี มันงาม มันซุปเปอร์ฟู้ด แล้วหันกลับไปมอง Tang ครับ อดีตมันเคยเป็น Super Orange Juice มาก่อน แล้ววันนี้คุณตลกกับมันไหม? แล้วคุณตลกกับวันนี้ไหม? แล้วคุณตลกกับอนาคตที่กำลังจะมาไหม? นั่นคือคำตอบที่คุณต้องเอาภาพร่างเหล่านี้ มาวางทับกัน แล้วตั้งคำถามกับซุปเปอร์ฟู้ดหรือฟิวเจอร์ฟู้ด ที่คุณกำลังเทิดทูนว่า "ดีต่อสุขภาพ" แล้วไหม?
Tang คือผลผลิตของยุคที่ความสะดวก = ความดี และความโมเดิร์น = ความน่าเชื่อถือ เราจึงเห็นว่าสิ่งที่เคยเกิดขึ้นกับซีเรียล, นม, หรือแม้แต่ Spam ก็ล้วนมีแก่นเดียวกันคือ "ทำให้ง่ายขึ้น ถูกลง เก็บได้นานขึ้น แล้วสร้างภาพว่าเหนือกว่าของเดิม"
Tang ไม่ใช่ผู้ร้าย แต่มันคือตัวละครสำคัญในยุคที่วิทยาศาสตร์กลายเป็นเครื่องมือของตลาด ไม่ใช่เพื่อค้นหาความจริง แต่เพื่อผลิตความรู้สึกปลอดภัยแบบสังเคราะห์ให้กับสังคม
และทั้งหมดนี้...เริ่มจากความพยายามทำให้น้ำอวกาศดื่มได้ ไม่มีกลิ่นเหล็กๆ เท่านั้นเอง
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 73868430:0ec4fe27
2025-06-18 02:09:08
@ 73868430:0ec4fe27
2025-06-18 02:09:08皇居 Imperial Palace
巽櫓(桜田二重櫓) Sakurada Tatsumi Yagura

二重橋 Nijubashi Bridge

靖國神社 Yasukuni Jinja





遊就館 Yushukan


上野動物園 Ueno Zoological Garden


上野動物園不忍池 Ueno Zoological Garden Shinobazuno Pond

上野東照宮五重塔 Ueno Toshogu Shrine Five Story Pagoda

築地活鮮市場,御徒町店 Tsukiji Kassen Ichiba, Okachimachi

鉄道博物館 The Railway Museum




TOHAKU茶館 (応挙館) Tohaku Chakan

新大久保駅 Shin-Ōkubo


シンボルプロムナード公園 Symbol Promenade Park


セントラル広場 Central Square

日本科学未来館 The National Museum of Emerging Science and Innovation Japan (Miraikan)

箱根町 Hakone

芦ノ湖 Lake Ashi

元箱根 Motohakone

彫刻の森駅 Chokokunomori

三の鳥居,箱根神社 The Third Torii of Hakone Shrine

小田原城 Odawara Castle


-
 @ dfa02707:41ca50e3
2025-06-15 23:02:35
@ dfa02707:41ca50e3
2025-06-15 23:02:35
Good morning (good night?)! The No Bullshit Bitcoin news feed is now available on Moody's Dashboard! A huge shoutout to sir Clark Moody for integrating our feed.
Headlines
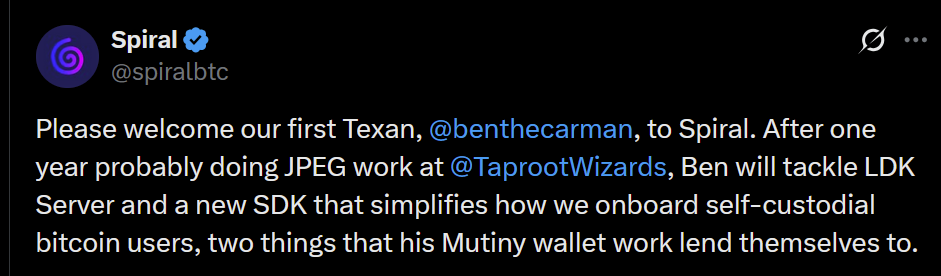
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
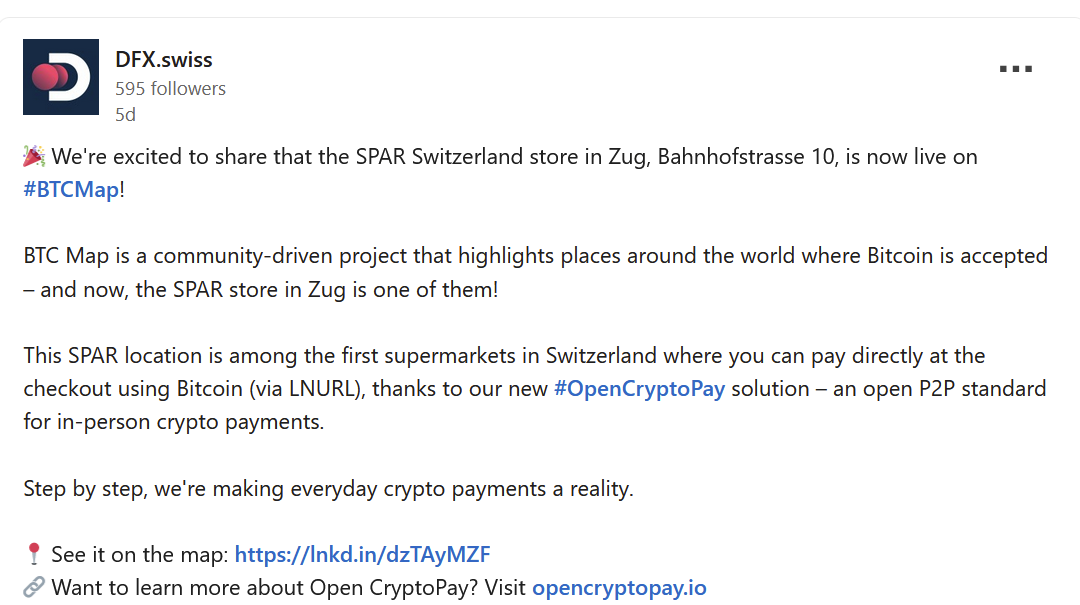
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- The Bank for International Settlements (BIS) wants to contain 'crypto' risks. A report titled "Cryptocurrencies and Decentralised Finance: Functions and Financial Stability Implications" calls for expanding research into "how new forms of central bank money, capital controls, and taxation policies can counter the risks of widespread crypto adoption while still fostering technological innovation."
- "Global Implications of Scam Centres, Underground Banking, and Illicit Online Marketplaces in Southeast Asia." According to the United Nations Office on Drugs and Crime (UNODC) report, criminal organizations from East and Southeast Asia are swiftly extending their global reach. These groups are moving beyond traditional scams and trafficking, creating sophisticated online networks that include unlicensed cryptocurrency exchanges, encrypted communication platforms, and stablecoins, fueling a massive fraud economy on an industrial scale.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
Use the tools
- Bitcoin Safe v1.2.3 expands QR SignMessage compatibility for all QR-UR-compatible hardware signers (SpecterDIY, KeyStone, Passport, Jade; already supported COLDCARD Q). It also adds the ability to import wallets via QR, ensuring compatibility with Keystone's latest firmware (2.0.6), alongside other improvements.
- Minibits v0.2.2-beta, an ecash wallet for Android devices, packages many changes to align the project with the planned iOS app release. New features and improvements include the ability to lock ecash to a receiver's pubkey, faster confirmations of ecash minting and payments thanks to WebSockets, UI-related fixes, and more.
- Zeus v0.11.0-alpha1 introduces Cashu wallets tied to embedded LND wallets. Navigate to Settings > Ecash to enable it. Other wallet types can still sweep funds from Cashu tokens. Zeus Pay now supports Cashu address types in Zaplocker, Cashu, and NWC modes.
- LNDg v1.10.0, an advanced web interface designed for analyzing Lightning Network Daemon (LND) data and automating node management tasks, introduces performance improvements, adds a new metrics page for unprofitable and stuck channels, and displays warnings for batch openings. The Profit and Loss Chart has been updated to include on-chain costs. Advanced settings have been added for users who would like their channel database size to be read remotely (the default remains local). Additionally, the AutoFees tool now uses aggregated pubkey metrics for multiple channels with the same peer.
- Nunchuk Desktop v1.9.45 release brings the latest bug fixes and improvements.
- Blockstream Green iOS v4.1.8 has renamed L-BTC to LBTC, and improves translations of notifications, login time, and background payments.
- Blockstream Green Android v4.1.8 has added language preference in App Settings and enables an Android data backup option for disaster recovery. Additionally, it fixes issues with Jade entry point PIN timeout and Trezor passphrase input.
- Torq v2.2.2, an advanced Lightning node management software designed to handle large nodes with over 1000 channels, fixes bugs that caused channel balance to not be updated in some cases and channel "peer total local balance" not getting updated.
- Stack Wallet v2.1.12, a multicoin wallet by Cypher Stack, fixes an issue with Xelis introduced in the latest release for Windows.
- ESP-Miner-NerdQAxePlus v1.0.29.1, a forked version from the NerdAxe miner that was modified for use on the NerdQAxe+, is now available.
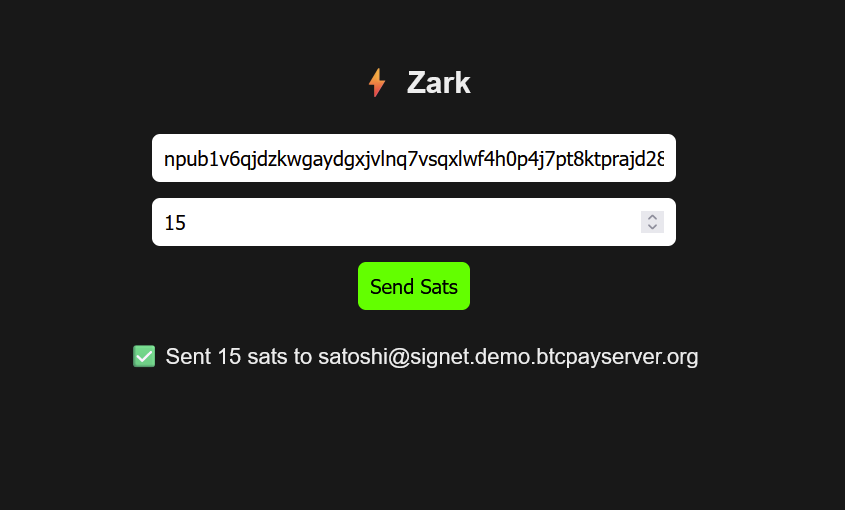
- Zark enables sending sats to an npub using Bark.
- Erk is a novel variation of the Ark protocol that completely removes the need for user interactivity in rounds, addressing one of Ark's key limitations: the requirement for users to come online before their VTXOs expire.
- Aegis v0.1.1 is now available. It is a Nostr event signer app for iOS devices.
- Nostash is a NIP-07 Nostr signing extension for Safari. It is a fork of Nostore and is maintained by Terry Yiu. Available on iOS TestFlight.
- Amber v3.2.8, a Nostr event signer for Android, delivers the latest fixes and improvements.
- Nostur v1.20.0, a Nostr client for iOS, adds
-
 @ 8bad92c3:ca714aa5
2025-06-18 02:02:08
@ 8bad92c3:ca714aa5
2025-06-18 02:02:08Key Takeaways

Mel Mattison presents a bold, contrarian outlook on today’s economy, arguing that what many view as a precarious bubble is actually the beginning of a long-term structural bull market that could run through 2036. He believes the U.S. economy is far stronger than the headlines suggest, supported by robust job growth, strong consumer balance sheets, and demographic tailwinds. Rather than popping, the current asset bubble is set to expand, driven by retiring baby boomers reducing labor inflation, AI-fueled productivity gains, and massive fiscal stimulus disguised as interest expense. He views Bitcoin as uniquely positioned to thrive in both inflationary and deflationary environments, unlike fiat currency, and sees AI’s high energy demands as a healthy bottleneck that will slow its rollout and allow society to adjust. According to Mattison, the U.S. is entering an era of permanent stimulus and rising productivity, with politics largely irrelevant to the macro trajectory, whether under populist left or populist right, the fiscal and demographic forces shaping the next decade are already locked in.
Best Quotes
“Bitcoin works in an inflationary world and it works in a deflationary world.”
“People are going to look back at 110,000 Bitcoin just like they looked back at 30,000 and say, ‘Man, I should’ve been buying.’”
“Interest expense is fiscal stimulus. There’s no difference between a COVID check and 4.5% on a 3-month bill going into a retiree’s money market account.”
“AI will be massive, but its energy demands are the bottleneck that will save us from an unmanageable shock.”
“This isn’t the 1970s. The U.S. is the largest oil producer in the world, and the demographic structure has flipped.”
“We are in the early stages of a seismic change, think Agricultural Revolution or Industrial Revolution level.”
Conclusion
This episode offers a compellingly optimistic view of the next decade, with Mel Mattison arguing that we’re entering the early stages of a historic bull market driven by demographic shifts, fiscal transformation, and exponential technologies like AI. Rather than collapse, he sees structural strength and enduring growth, positioning Bitcoin as a core asset in this new paradigm, resilient in both inflationary and deflationary cycles. Mattison urges a focus on long-term fundamentals over short-term noise, framing Bitcoin, demographics, and AI as the key forces reshaping the global economic order.
Timestamps
0:00 - Intro
0:55 - Getting up to speed
6:57 - The Rates Boogeyman
14:42 - Bitkey
15:37 - AI revolution
28:13 - Boomer exit and fiscal stimulus
34:07 - Unchained
34:35 - AI bottleneck
42:59 - Wealth gap
52:53 - Bullish vibesTranscript
(00:00) the 1971 Nixon shock where he took the US off the gold standard he also put on 10% sweeping across the board tariffs he announced that they were going to do spending cuts something like a Doge this is 55 years ago it's like the exact same things the demographics the oil differences between the 70s and now they're going to allow this situation to work out a lot more like the 80s we had between 1985 and 1996 360% S&P growth the days of 2000 something gold are probably over with Bitcoin you know I've been thinking this month we've got an AI
(00:31) super cycle boom going on it it just all speaks to extreme bullishness but we've got a lot more to go gold and Bitcoin I think actually in geopolitical uncertainties are are only going to do better mel I'm not going to lie I've been pretty disconnected for the last 3 weeks so I'm very excited we're having this conversation cuz I have a feeling it's going to help me catapult back into the present day get caught up with everything that's been going on we had the conference in Vegas a few weeks ago now at this point I had a cross country move between now and then and I had a wedding in Chicago over the weekend and
(01:20) I've been sort of out of the loop with what's going on and I need an update what are what are you seeing out there no well that's that's perfect and uh I'm getting ready to head out for a few days uh myself um on Thursday to the the Blue Ridge Mountains here in North Carolina haven't been there since the hurricane went through uh so interested to see how my old spots are doing um but it's always good to get away so happy to bring you up to speed um you know there's a lot going on and at the same time there's not right that the steady march higher in Bitcoin in equities uh
(01:58) gold has been on you know just a consolidation phase basically since it kind of blew up to 3500 um but given how fast and how strong that move was it actually is just a sign of strength to me that it's still you know holding well above 3,000 i think the days of 200 something gold are probably over i think I think if it ever gets there into five figures again it's not going to be for long with Bitcoin i think this this is a big move um you know people are going to look back at 110,000 Bitcoin just like
(02:35) they look back at 50,000 Bitcoin or 30,000 Bitcoin and say "Man I should have been buying there." Um you know we we've broken over uh the high set you know a few months ago i think that's now clearly you know a floor you know um support and you know I think the next upside target for me has always been that 150 range which I think you know I've been thinking 120 uh this month uh 150 is my call by the end of the year but really that's like a base case based on technical analysis i do that that is is a point where I reassess and and when I
(03:15) reassess it I have a feeling like um I'm going to pretty quickly come out with the target um around uh 190 195 as like a next upside target and you know we'll see when we get there but so just you know I think the best thing you can do actually for these markets is turn off your news because it's like last night I'm flipping between the channels and it's you know kurfles with Elon and Trump it's riots and fires and protests in LA it's um you know uh US behind the eightball with rare earth versus China um you know tariffs are
(03:56) going to start rolling into the inflation numbers uh job market only created 130ome thousand it's weak which I think is BS it's actually was a super strong report um there's been almost no government job creation since Trump took office so you essentially have to look and say well if every month under Biden there was like 40,000 government jobs and now that's not there i mean you take the 139 or whatever it was last week you had 40 you're up to about 180 you know which is really what the private sector is creating and it's doing that at a time where you have this demographic
(04:33) rollover where you have literally when you look at the unemployment reports which they break down you know foreignb born native born you know you have nativeorn you know people in the workforce declining and so if you're creating jobs I mean that that's why you're seeing you know the unemployment rate still 4.
(04:52) 2% so we've got a super strong job market we've got a consumer that is as unlevered as it has been in the last 20 years um you know you can't look at like credit card delinquencies or something like that you have to look at you know net worth you know yes is this skewed towards the wealthier you know 50% of America sure i mean the bottom 50% isn't exactly rolling in the dough but the top 20% certainly is especially when you factor in um over 12 trillion of tappable uh home equity um which I think is just now beginning to be tapped and and will begin getting tapped even
(05:35) more so um once the Fed fund funds rate goes down and I think it will um exactly how much and how quickly we can get into that too but I mean basically I guess where I'm going with all of this is the the doom and gloom you hear about whether you're scrolling through Twitter or turning on the news channels is masking what is an incredibly strong economy we've got an AI like super cycle boom going on we've got the blockchain and um all of that brings all of what that brings to financial services um you know uh counties or states in New Jersey
(06:12) now putting real estate deeds on the blockchain DeFi finally starting to happen in the real world stable coin bill um you know Bitcoin you know being part of the institutional investment mindset people understanding it more um I mean it it just all speaks to extreme bullishness and yet when you look at some of the surveys out there there's still net bearish you know like there's different sentiment gauges we were really really bearish we're still net bearish we're almost back to that median line uh you know overall and so we've got just people that are just doubters haters and you know which I think is
(06:53) great because it just means you know we've got a lot more to go yeah i'm very happy that you confirmed that being disconnected is probably the right move it's It's felt good not being in the day-to-day the actually the only day that I was really plugged in I was on a cross country flight and that was when Elon was having his his uh meltdown on X but that seems to have been brushed under the rug pretty quickly they were like "Okay damage control.
(07:24) " Uh it seems like they want to forget that that happened and pretend like it it never did but I think diving into you were mentioning this before we hit record how do rates play into this cuz looking at the 10-year at 4.47 30-year at 4.94 up over the last month but down from their highs intrammon and I think a lot of the focus of the doomers if you will is the elevated 10 year and 30-year and all the debt that needs to be rolled over how do you see that factoring into this outlook yeah I mean I I call it the rates -
 @ dfa02707:41ca50e3
2025-06-15 23:02:32
@ dfa02707:41ca50e3
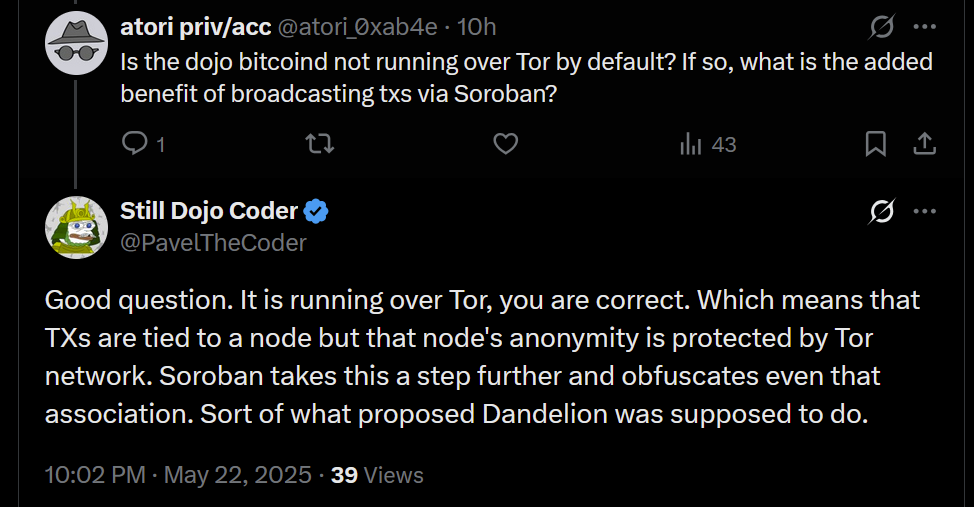
2025-06-15 23:02:32- This version introduces the Soroban P2P network, enabling Dojo to relay transactions to the Bitcoin network and share others' transactions to break the heuristic linking relaying nodes to transaction creators.
- Additionally, Dojo admins can now manage API keys in DMT with labels, status, and expiration, ideal for community Dojo providers like Dojobay. New API endpoints, including "/services" exposing Explorer, Soroban, and Indexer, have been added to aid wallet developers.
- Other maintenance updates include Bitcoin Core, Tor, Fulcrum, Node.js, plus an updated ban-knots script to disconnect inbound Knots nodes.
"I want to thank all the contributors. This again shows the power of true Free Software. I also want to thank everyone who donated to help Dojo development going. I truly appreciate it," said Still Dojo Coder.
What's new
- Soroban P2P network. For MyDojo (Docker setup) users, Soroban will be automatically installed as part of their Dojo. This integration allows Dojo to utilize the Soroban P2P network for various upcoming features and applications.
- PandoTx. PandoTx serves as a transaction transport layer. When your wallet sends a transaction to Dojo, it is relayed to a random Soroban node, which then forwards it to the Bitcoin network. It also enables your Soroban node to receive and relay transactions from others to the Bitcoin network and is designed to disrupt the assumption that a node relaying a transaction is closely linked to the person who initiated it.
- Pushing transactions through Soroban can be deactivated by setting
NODE_PANDOTX_PUSH=offindocker-node.conf. - Processing incoming transactions from Soroban network can be deactivated by setting
NODE_PANDOTX_PROCESS=offindocker-node.conf.
- Pushing transactions through Soroban can be deactivated by setting
- API key management has been introduced to address the growing number of people offering their Dojos to the community. Dojo admins can now access a new API management tab in their DMT, where they can create unlimited API keys, assign labels for easy identification, and set expiration dates for each key. This allows admins to avoid sharing their main API key and instead distribute specific keys to selected parties.
- New API endpoints. Several new API endpoints have been added to help API consumers develop features on Dojo more efficiently:
- New:
/latest-block- returns data about latest block/txout/:txid/:index- returns unspent output data/support/services- returns info about services that Dojo exposes
- Updated:
/tx/:txid- endpoint has been updated to return raw transaction with parameter?rawHex=1
- The new
/support/servicesendpoint replaces the deprecatedexplorerfield in the Dojo pairing payload. Although still present, API consumers should use this endpoint for explorer and other pairing data.
- New:
Other changes
- Updated ban script to disconnect inbound Knots nodes.
- Updated Fulcrum to v1.12.0.
- Regenerate Fulcrum certificate if expired.
- Check if transaction already exists in pushTx.
- Bump BTC-RPC Explorer.
- Bump Tor to v0.4.8.16, bump Snowflake.
- Updated Bitcoin Core to v29.0.
- Removed unnecessary middleware.
- Fixed DB update mechanism, added api_keys table.
- Add an option to use blocksdir config for bitcoin blocks directory.
- Removed deprecated configuration.
- Updated Node.js dependencies.
- Reconfigured container dependencies.
- Fix Snowflake git URL.
- Fix log path for testnet4.
- Use prebuilt addrindexrs binaries.
- Add instructions to migrate blockchain/fulcrum.
- Added pull policies.

Learn how to set up and use your own Bitcoin privacy node with Dojo here.
-
 @ eb0157af:77ab6c55
2025-06-18 02:02:07
@ eb0157af:77ab6c55
2025-06-18 02:02:07Carl Rickertsen completely exits his position in Strategy as insiders sell $864 million worth of stock.
As reported by Protos, Carl Rickertsen, a member of Strategy’s board of directors, has fully liquidated his entire shareholding for over $10 million.
Rickertsen’s decision to completely exit his Strategy position marks a sharp shift from his previous investment stance. In 2022, the executive had shown confidence in the company by investing $700,000 in MSTR shares.
On June 13, 2022, Rickertsen purchased $608,000 worth of MSTR stock at $152 per share. Since then, the stock has rallied 152%. However, by 2023, the director had already sold half of his 4,000-share position.
Rickertsen’s approach to managing his holdings has become increasingly aggressive in recent years. Since joining the board in 2019, he has adopted a strategy of immediately liquidating any stock options received.
One example of this tactic occurred on June 2, when he acquired and sold 26,390 MSTR shares on the same day.
As of June 5 this year, Rickertsen reported zero vested Strategy shares, marking the end of his equity involvement with the company.
Rickertsen’s situation is not an isolated case within Strategy. Data from the Securities and Exchange Commission (SEC) reveals a controversial picture. According to information gathered by secform4.com, over the past five years, total insider sales have exceeded purchases by $864 million. This imbalance in insider transactions could raise questions about executives’ confidence in the company’s future.
The post Strategy director liquidates all his MSTR shares appeared first on Atlas21.
-
 @ dfa02707:41ca50e3
2025-06-15 17:02:37
@ dfa02707:41ca50e3
2025-06-15 17:02:37Contribute to keep No Bullshit Bitcoin news going.
This update brings key enhancements for clarity and usability:
- Recent Blocks View: Added to the Send tab and inspired by Mempool's visualization, it displays the last 2 blocks and the estimated next block to help choose fee rates.
- Camera System Overhaul: Features a new library for higher resolution detection and mouse-scroll zoom support when available.
- Vector-Based Images: All app images are now vectorized and theme-aware, enhancing contrast, especially in dark mode.
- Tor & P2A Updates: Upgraded internal Tor and improved support for pay-to-anchor (P2A) outputs.
- Linux Package Rename: For Linux users, Sparrow has been renamed to sparrowwallet (or sparrowserver); in some cases, the original sparrow package may need manual removal.
- Additional updates include showing total payments in multi-payment transaction diagrams, better handling of long labels, and other UI enhancements.
- Sparrow v2.2.1 is a bug fix release that addresses missing UUID issue when starting Tor on recent macOS versions, icons for external sources in Settings and Recent Blocks view, repackaged
.debinstalls to use older gzip instead of zstd compression, and removed display of median fee rate where fee rates source is set to Server.
Learn how to get started with Sparrow wallet:
Release notes (v2.2.0)
- Added Recent Blocks view to Send tab.
- Converted all bitmapped images to theme aware SVG format for all wallet models and dialogs.
- Support send and display of pay to anchor (P2A) outputs.
- Renamed
sparrowpackage tosparrowwalletandsparrowserveron Linux. - Switched camera library to openpnp-capture.
- Support FHD (1920 x 1080) and UHD4k (3840 x 2160) capture resolutions.
- Support camera zoom with mouse scroll where possible.
- In the Download Verifier, prefer verifying the dropped file over the default file where the file is not in the manifest.
- Show a warning (with an option to disable the check) when importing a wallet with a derivation path matching another script type.
- In Cormorant, avoid calling the
listwalletdirRPC on initialization due to a potentially slow response on Windows. - Avoid server address resolution for public servers.
- Assume server address is non local for resolution failures where a proxy is configured.
- Added a tooltip to indicate truncated labels in table cells.
- Dynamically truncate input and output labels in the tree on a transaction tab, and add tooltips if necessary.
- Improved tooltips for wallet tabs and transaction diagrams with long labels.
- Show the address where available on input and output tooltips in transaction tab tree.
- Show the total amount sent in payments in the transaction diagram when constructing multiple payment transactions.
- Reset preferred table column widths on adjustment to improve handling after window resizing.
- Added accessible text to improve screen reader navigation on seed entry.
- Made Wallet Summary table grow horizontally with dialog sizing.
- Reduced tooltip show delay to 200ms.
- Show transaction diagram fee percentage as less than 0.01% rather than 0.00%.
- Optimized and reduced Electrum server RPC calls.
- Upgraded Bouncy Castle, PGPainless and Logback libraries.
- Upgraded internal Tor to v0.4.8.16.
- Bug fix: Fixed issue with random ordering of keystore origins on labels import.
- Bug fix: Fixed non-zero account script type detection when signing a message on Trezor devices.
- Bug fix: Fixed issue parsing remote Coldcard xpub encoded on a different network.
- Bug fix: Fixed inclusion of fees on wallet label exports.
- Bug fix: Increase Trezor device libusb timeout.
Linux users: Note that the
sparrowpackage has been renamed tosparrowwalletorsparrowserver, and in some cases you may need to manually uninstall the originalsparrowpackage. Look in the/optfolder to ensure you have the new name, and the original is removed.What's new in v2.2.1
- Updated Tor library to fix missing UUID issue when starting Tor on recent macOS versions.
- Repackaged
.debinstalls to use older gzip instead of zstd compression. - Removed display of median fee rate where fee rates source is set to Server.
- Added icons for external sources in Settings and Recent Blocks view
- Bug fix: Fixed issue in Recent Blocks view when switching fee rates source
- Bug fix: Fixed NPE on null fee returned from server
-
 @ 472f440f:5669301e
2025-06-11 04:37:33
@ 472f440f:5669301e
2025-06-11 04:37:33Marty's Bent
Sup, freaks? Your Uncle Marty did a little vibe coding a couple months ago and that vibe coding project has turned into an actual product that is live in the Google Chrome web store and will soon to be live in the Firefox add-on store as well. It's called Opportunity Cost and it is an extension that enables you to price the internet in Bitcoin.
Opportunity Cost – See Prices in Bitcoin Instantly
Check it out!
This whole process has been extremely rewarding to me for many reasons. The first of which is that I've had many ideas in the past to launch a product focused on bitcoin education that simply never left my brain because I never felt comfortable paying a developer to go out and build a product that I wasn't sure would ultimately get product market fit.
Due to the advancements of AI, particularly ChatGPT and Replit, I was able to spend a few hours on a Saturday vibe coding a prototype for Opportunity Cost. It worked. I side loaded it into Chrome and Firefox, tested it out for a few days and decided, "Hey, I think this is something that's worthwhile and should be built."
Backtracking just a little bit, the initial idea for this app was to create an AR application that would enable you to take pictures of goods in the real world and have their prices automatically converted to bitcoin so that you could weigh the opportunity cost of whether or not you actually wanted to buy that good or decide to save in bitcoin instead. With the help of Justin Moon from the Human Rights Foundation and Anthony Ronning from OpenSecret and Maple AI, I was pointed in the right direction of vibe coding tools I could use to build a simple MVP. I took their advice, built the MVP, and demoed it at the Bitcoin Park Austin weekly AI meetup in mid-April.
The next week, I was talking with a friend, Luke Thomas, about the idea and during our conversation he made a simple quip, "You should make a Chrome extension. I really want a Chrome extension that does this." And that's what sent me down the vibe coding rabbit hole that Saturday which led to the prototype.
After I was comfortable with and confident in the prototype, I found a young hungry developer by the name of Moses on Nostr, I reached out to him, told him my idea, showed him the prototype and asked if he thought he could finish the application for me. He luckily agreed to do so and within a couple of weeks we had a fully functioning app that was officially launched today. We're about 12 hours into the launch and I must say that I'm pleasantly surprised with the reception from the broader Bitcoin community. It seems like something that people are happy exists and I feel extremely happy that people see some value in this particular application.
Now that you have the backstory, let's get into why I think something like Opportunity Cost should exist. As someone who's been writing a newsletter and producing podcasts about bitcoin for eight years in an attempt to educate individuals from around the world about what bitcoin is, why it's important, and how they can leverage it, I've become convinced that a lot of the work that needs to be done still exists at the top of the funnel. You can scream at people. You can grab them by the shoulders. You can shake them. You can remind them at Thanksgiving that if they had listened to your advice during any Thanksgiving in the previous years they would be better off financially. But at the end of the day most people don't listen. They need to see things. Seeing things for yourself is a much more effective teaching mechanism than be lectured to by someone else.
My hope with Opportunity Cost is that it catches the eye of some bitcoin skeptics or individuals who may be on the cusp of falling down the bitcoin rabbit hole and they see the extension as a way to dip their toes into bitcoin to get a better understanding of the world by pricing the goods and services they purchase on a day-to-day month-to-month and year-to-year basis in bitcoin without having to download a wallet or set up an exchange account. The tippy top of the bitcoin marketing funnel.
That is not all though. I think Opportunity Cost can serve individuals at both ends of the funnel. That's why it's pretty exciting to me. It's as valuable to the person who is bitcoin curious and looking to get a better understanding as it is to the hardcore bitcoiner living on a bitcoin standard who is trying to get access to better tools that enable him to get a better grasp of their spending in bitcoin terms.
Lastly, after playing around with it for a few days after I built the prototype, I realized that it has incredible memetic potential. Being able to take a screenshot of goods that people are buying on a day-to-day basis, pricing them in bitcoin and then sharing them on social media is very powerful. Everything from houses to junk items on Amazon to the salaries of pro athletes to your everyday necessities. Seeing the value of those things in bitcoin really makes you think.
One day while I was testing the app, I tried to see how quickly I could find goods on the internet that cumulatively eclipsed the 21 million supply cap limit of bitcoin. To my surprise, even though I've been in bitcoin for 12 years now, it did not take me that long. The opportunity cost of everything I buy on a day-to-day basis becomes very clear when using the extension. What's even clearer is the fact that Bitcoin is completely mispriced at current levels. There is so much winning ahead of us.
Also, it's probably important to note that the extension is open source. You can check out our GitHub page here. Submit pull requests. Suggest changes to the app.
We've also tried to make Opportunity Cost as privacy preserving as possible. Everything within the extension happens in your browser. The only external data that we're providing is the bitcoin to fiat price conversion at any given point in time. We're not data harvesting the web pages you're browsing or the items you're looking at. We're not collecting data and sending it to third party marketers. We want to align ourselves with the open and permissionless nature of bitcoin while also preserving our users' privacy. We're not trying to monetize this in that way. Though, I will say that I'm thinking of ways to monetize Opportunity Cost if it does gain significant traction, but I promise it will be in a way that respects your privacy and is as unobtrusive as possible. We'll see how it goes.
Thank you for coming to my TED talk. Please download and use the extension. Let us know what you think.
Headlines of the Day
Saylor Says Bitcoin Is Perfect Money to Jordan Peterson - via X
Trump Won't Sell Tesla Despite Musk-Bessent Heated Exchange - via X
Bitcoin Gains Traction in Kenya's Largest Slum Kibera - via X
Get our new STACK SATS hat - via tftcmerch.io
Bitcoin’s Next Parabolic Move: Could Liquidity Lead the Way?
Is bitcoin’s next parabolic move starting? Global liquidity and business cycle indicators suggest it may be.
Read the latest report from Unchained and TechDev, analyzing how global M2 liquidity and the copper/gold ratio—two historically reliable macro indicators—are aligning once again to signal that a new bitcoin bull market may soon begin.
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
East Coast aesthetics over everything.
*Download our free browser extension, Opportunity Cost: *<<https://www.opportunitycost.app/>> start thinking in SATS today.
*Get this newsletter sent to your inbox daily: *https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ eb0157af:77ab6c55
2025-06-18 02:02:06
@ eb0157af:77ab6c55
2025-06-18 02:02:06French lawmakers are proposing Bitcoin mining as a solution to optimize the national electricity system and make use of surplus energy.
A group of French parliamentarians has introduced an amendment that could turn the country into a European hub for Bitcoin mining, strategically leveraging its energy production capacity.
The legislative proposal aims to assess how mining could be integrated into the French energy system — the largest in Europe — to optimize the management of electricity produced by nuclear power plants.
The amendment to the law on “National Programming and Regulatory Simplification in the Energy Sector” calls on the government to conduct a thorough evaluation of the potential of Bitcoin mining. The initiative represents a pragmatic approach to addressing the issue of excess energy, a key topic for France’s nuclear industry.
France’s energy system, powered by nuclear for over 70% of its needs, often generates electricity surpluses that require efficient management. The proponents of the proposal see mining as an ideal solution to absorb this excess, transforming a potential waste into an economic resource.
The operational flexibility of mining farms offers a unique competitive advantage: machines can be quickly turned on and off based on production and consumption peaks, dynamically adapting to the needs of the electrical grid. This feature makes them particularly suitable for installation near power plants, even in the most remote areas of the country.
The parliamentary proposal highlights how mining could contribute to the revitalization of abandoned industrial sites, creating new opportunities for economic development under the supervision of public authorities.
Lawmakers emphasize the various benefits of this strategy: reducing negative pricing in wholesale markets, relieving the workload on nuclear plants by avoiding frequent modulation cycles that accelerate equipment wear, and absorbing surplus energy that would otherwise go to waste.
The French Association for the Development of Digital Assets (ADAN) collaborated in drafting the amendment, contributing technical expertise and industrial insight to the project. The organization emphasized how low-carbon Bitcoin mining could help strengthen the resilience of the national electricity grid.
The parliamentary report notes that mining in France could represent “an activity tailored to the constraints of the electrical system, absorbing surplus energy and reducing environmental impact” by using power that would otherwise be lost.
The post France considers Bitcoin mining: parliamentary proposal for managing nuclear energy appeared first on Atlas21.
-
 @ 97c70a44:ad98e322
2025-06-06 20:48:33
@ 97c70a44:ad98e322
2025-06-06 20:48:33Vibe coding is taking the nostr developer community by storm. While it's all very exciting and interesting, I think it's important to pump the brakes a little - not in order to stop the vehicle, but to try to keep us from flying off the road as we approach this curve.
In this note Pablo is subtweeting something I said to him recently (although I'm sure he's heard it from other quarters as well):
nostr:nevent1qvzqqqqqqypzp75cf0tahv5z7plpdeaws7ex52nmnwgtwfr2g3m37r844evqrr6jqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7qg6waehxw309ac8junpd45kgtnxd9shg6npvchxxmmd9uqzq0z48d4ttzzkupswnkyt5a2xfkhxl3hyavnxjujwn5k2k529aearwtecp4
There is a naive, curmudgeonly case for simply "not doing AI". I think the intuition is a good one, but the subject is obviously more complicated - not doing it, either on an individual or a collective level, is just not an option. I recently read Tools for Conviviality by Ivan Illich, which I think can help us here. For Illich, the best kind of tool is one which serves "politically interrelated individuals rather than managers".
This is obviously a core value for bitcoiners. And I think the talks given at the Oslo Freedom Forum this year present a compelling case for adoption of LLMs for the purposes of 1. using them for good, and 2. developing them further so that they don't get captured by corporations and governments. Illich calls both the telephone and print "almost ideally convivial". I would add the internet, cryptography, and LLMs to this list, because each one allows individuals to work cooperatively within communities to embody their values in their work.
But this is only half the story. Illich also points out how "the manipulative nature of institutions... have put these ideally convivial tools at the service of more [managerial dominance]."
Preventing the subversion and capture of our tools is not just a matter of who uses what, and for which ends. It also requires an awareness of the environment that the use of the tool (whether for virtuous or vicious ends) creates, which in turn forms the abilities, values, and desires of those who inhabit the environment.
The natural tendency of LLMs is to foster ignorance, dependence, and detachment from reality. This is not the fault of the tool itself, but that of humans' tendency to trade liberty for convenience. Nevertheless, the inherent values of a given tool naturally gives rise to an environment through use: the tool changes the world that the tool user lives in. This in turn indoctrinates the user into the internal logic of the tool, shaping their thinking, blinding them to the tool's influence, and neutering their ability to work in ways not endorsed by the structure of the tool-defined environment.
The result of this is that people are formed by their tools, becoming their slaves. We often talk about LLM misalignment, but the same is true of humans. Unreflective use of a tool creates people who are misaligned with their own interests. This is what I mean when I say that AI use is anti-human. I mean it in the same way that all unreflective tool use is anti-human. See Wendell Berry for an evaluation of industrial agriculture along the same lines.
What I'm not claiming is that a minority of high agency individuals can't use the technology for virtuous ends. In fact, I think that is an essential part of the solution. Tool use can be good. But tools that bring their users into dependence on complex industry and catechize their users into a particular system should be approached with extra caution. The plow was a convivial tool, and so were early tractors. Self-driving John Deere monstrosities are a straightforward extension of the earlier form of the technology, but are self-evidently an instrument of debt slavery, chemical dependency, industrial centralization, and degradation of the land. This over-extension of a given tool can occur regardless of the intentions of the user. As Illich says:
There is a form of malfunction in which growth does not yet tend toward the destruction of life, yet renders a tool antagonistic to its specific aims. Tools, in other words, have an optimal, a tolerable, and a negative range.
The initial form of a tool is almost always beneficial, because tools are made by humans for human ends. But as the scale of the tool grows, its logic gets more widely and forcibly applied. The solution to the anti-human tendencies of any technology is an understanding of scale. To prevent the overrun of the internal logic of a given tool and its creation of an environment hostile to human flourishing, we need to impose limits on scale.
Tools that require time periods or spaces or energies much beyond the order of corresponding natural scales are dysfunctional.
My problem with LLMs is:
- Not their imitation of human idioms, but their subversion of them and the resulting adoption of robotic idioms by humans
- Not the access they grant to information, but their ability to obscure accurate or relevant information
- Not their elimination of menial work, but its increase (Bullshit Jobs)
- Not their ability to take away jobs, but their ability to take away the meaning found in good work
- Not their ability to confer power to the user, but their ability to confer power to their owner which can be used to exploit the user
- Not their ability to solve problems mechanistically, but the extension of their mechanistic value system to human life
- Not their explicit promise of productivity, but the environment they implicitly create in which productivity depends on their use
- Not the conversations they are able to participate in, but the relationships they displace
All of these dysfunctions come from the over-application of the technology in evaluating and executing the fundamentally human task of living. AI work is the same kind of thing as an AI girlfriend, because work is not only for the creation of value (although that's an essential part of it), but also for the exercise of human agency in the world. In other words, tools must be tools, not masters. This is a problem of scale - when tool use is extended beyond its appropriate domain, it becomes what Illich calls a "radical monopoly" (the domination of a single paradigm over all of human life).
So the important question when dealing with any emergent technology becomes: how can we set limits such that the use of the technology is naturally confined to its appropriate scale?
Here are some considerations:
- Teach people how to use the technology well (e.g. cite sources when doing research, use context files instead of fighting the prompt, know when to ask questions rather than generate code)
- Create and use open source and self-hosted models and tools (MCP, stacks, tenex). Refuse to pay for closed or third-party hosted models and tools.
- Recognize the dependencies of the tool itself, for example GPU availability, and diversify the industrial sources to reduce fragility and dependence.
- Create models with built-in limits. The big companies have attempted this (resulting in Japanese Vikings), but the best-case effect is a top-down imposition of corporate values onto individuals. But the idea isn't inherently bad - a coding model that refuses to generate code in response to vague prompts, or which asks clarifying questions is an example. Or a home assistant that recognized childrens' voices and refuses to interact.
- Divert the productivity gains to human enrichment. Without mundane work to do, novice lawyers, coders, and accountants don't have an opportunity to hone their skills. But their learning could be subsidized by the bots in order to bring them up to a level that continues to be useful.
- Don't become a slave to the bots. Know when not to use it. Talk to real people. Write real code, poetry, novels, scripts. Do your own research. Learn by experience. Make your own stuff. Take a break from reviewing code to write some. Be independent, impossible to control. Don't underestimate the value to your soul of good work.
- Resist both monopoly and "radical monopoly". Both naturally collapse over time, but by cultivating an appreciation of the goodness of hand-crafted goods, non-synthetic entertainment, embodied relationship, and a balance between mobility and place, we can relegate new, threatening technologies to their correct role in society.
I think in all of this is implicit the idea of technological determinism, that productivity is power, and if you don't adapt you die. I reject this as an artifact of darwinism and materialism. The world is far more complex and full of grace than we think.
The idea that productivity creates wealth is, as we all know, bunk. GDP continues to go up, but ungrounded metrics don't reflect anything about the reality of human flourishing. We have to return to a qualitative understanding of life as whole, and contextualize quantitative tools and metrics within that framework.
Finally, don't believe the hype. Even if AI delivers everything it promises, conservatism in changing our ways of life will decelerate the rate of change society is subjected to and allow time for reflection and proper use of the tool. Curmudgeons are as valuable as technologists. There will be no jobspocalypse if there is sufficient political will to value human good over mere productivity. It's ok to pump the breaks.
-
 @ eb0157af:77ab6c55
2025-06-18 02:02:06
@ eb0157af:77ab6c55
2025-06-18 02:02:06The new communication protocol aims to improve the industry with measurable advantages in terms of efficiency and security.
A new study conducted by Hashlabs, in collaboration with the SRI (Stratum V2 Reference Implementation) team and figures like Matt Corallo, Alejandro De La Torre and others reveals how the Stratum V2 protocol can increase miner profitability compared to the current Stratum V1 standard, used for over a decade.
Speaking to Atlas21, Gabriele Vernetti, Stratum V2 maintainer, declared:
“This first case study demonstrates how much Stratum V2 can help miners as well, securing and increasing their profits, in addition to the rest of the network. It’s just a first study aimed at demonstrating how decentralization can be aligned with the profit dynamics typical of the mining sector.
In the future we will also focus on the benefits for mining pool operators, who can benefit from the protocol’s efficiency to lower their operating costs (such as those for bandwidth used by their servers).
The feedback has been very positive: this first study was a joint work with various market players, including miners and mining pool operators. As SRI we want to continue working together with the entire community as done in this case, becoming a reference point for all actors interested in innovating the Bitcoin mining field”.
The research, based on controlled tests with two identical ASIC S19k Pro, with stock firmware, demonstrates that Stratum V2 can increase net profits by up to 7.4%. For an industry that often operates with 10% margins, this could represent a substantial competitive advantage.
The V2 protocol reduces various inefficiencies that plague the current system. The latency in block switching, that is the waiting time created when a miner must change block template after a new block has been mined on the network, goes from 325 milliseconds to just 1.42 milliseconds, a speed 228 times higher. This translates to about 4.9 hours of completely wasted hash power less per year.
Another problem of modern mining concerns “stale shares” – proofs of work that arrive too late to be remunerated, often due to network latency or inefficient communication. However, not all stale shares depend on inefficiency problems. On average, about 2% are rejected for expected reasons, such as when the share doesn’t reach the minimum difficulty required by the pool. This value is considered normal in the sector. The remaining 98%, instead, is caused by avoidable delays. With Stratum V1, miners lose between 0.1% and 0.2% of their computing power this way. Stratum V2 with Job Declaration completely eliminates this waste, provided that the miner and the pool node have the same level of connectivity. This step could translate into a net profit increase of up to 2% by fully adopting Stratum V2 with Job Declaration.
In the Stratum V2 protocol, the Job Declaration Client (JDC) is software that allows miners to receive mining jobs directly from their local Bitcoin node, that is the block templates to work on. The JDC communicates directly with the miner’s local node, receiving updated data for new block construction and immediately sending them to the mining software via Stratum V2. This allows miners to receive jobs in real time from their own node, without having to wait for them from the pool, reducing latency and the risk of working on obsolete jobs. Furthermore, if the pool allows it, miners can build custom templates choosing which transactions to include in the block.
The research also highlights an often overlooked aspect: the loss of transaction fees. With the Stratum V1 protocol, miners lose about 0.75% of potential fees for each block due to the delay in receiving new jobs. Considering that about 52,560 blocks are mined each year, this loss per block adds up to a total of about 74 bitcoins per year, equivalent to over $8 million at current prices.
Beyond economic advantages, Stratum V2 solves a critical vulnerability of the current system: hashrate hijacking. The V1 protocol doesn’t encrypt communications, allowing attackers to intercept and steal up to 2% of computing power without the miner noticing. The new protocol eliminates this risk through end-to-end encryption and authentication.
According to the study, by reducing latency, optimizing share sending and improving security, Stratum V2 enables a potential net profit increase of 7.4%, derived exclusively from technical improvements.
The post Stratum V2 increases profits by 7.4%: “The study shows that profit and decentralization can coexist”, says Vernetti, SV2 maintainer appeared first on Atlas21.
-
 @ eb0157af:77ab6c55
2025-06-18 02:02:05
@ eb0157af:77ab6c55
2025-06-18 02:02:05Russian authorities uncover 95 Bitcoin mining machines hidden inside a truck stealing electricity from a village.
Law enforcement in the Republic of Buryatia has uncovered an illegal Bitcoin mining operation concealed inside a KamAZ truck. The clandestine facility was siphoning off electricity meant for the local population.
According to the national news agency TASS, the discovery was made during a routine inspection of power lines in the Pribaikalsky district, where inspectors identified an unauthorized connection to a 10-kilovolt line — enough to power an entire village. The criminal operation showed a high level of organization, with sophisticated equipment hidden inside an apparently innocuous transport vehicle.

Source: Babr Mash
Inside the commercial truck, authorities found a fully operational mining center equipped with 95 machines and a portable transformer station. The technical setup suggested careful planning, designed to maximize bitcoin production while minimizing the risk of detection.
Two individuals suspected of involvement in the illegal activity managed to escape in an SUV before law enforcement arrived.
Impact of illegal mining on the local power grid
Buryatenergo, a regional unit of Rosseti Siberia, stressed how unauthorized connections severely compromise the stability of the local power grid. Consequences include voltage drops, overloads, and potential blackouts that disproportionately affect rural communities, already vulnerable in terms of energy access.
The illegal siphoning of electricity for mining creates a domino effect across the entire electrical infrastructure, causing service disruptions for legitimate users and increasing maintenance costs for grid operators.
Government restrictions on mining
The Russian government has implemented various restrictions on cryptocurrency mining in several regions of the country. In Buryatia, mining is banned from November 15 to March 15 due to seasonal energy shortages. Only companies registered in specific districts such as Severo-Baikalsky and Muisky are allowed to operate outside this period.
Federal restrictions were further tightened in December 2024, when Russia announced a ban on mining during peak energy months in multiple regions, including Dagestan, Chechnya, and parts of eastern Ukraine under Russian control. Since April, a total ban has been in effect in the southern region of Irkutsk.
Despite these restrictions, some Russian companies continue to operate legally in the sector. BitRiver, one of the country’s leading operators, takes advantage of the region’s low-cost energy, having launched its first and largest facility in 2019 in the city of Bratsk.
The post Illegal mining: clandestine operation discovered in a KamAZ truck in Russia appeared first on Atlas21.
-
 @ c631e267:c2b78d3e
2025-06-06 18:54:04
@ c631e267:c2b78d3e
2025-06-06 18:54:04Willst du den Charakter eines Menschen kennenlernen, \ so gib ihm Macht. \ Abraham Lincoln
Vermutlich war Friedrich Merz erleichtert nach seinem Besuch beim US-Präsidenten im Oval Office. Dem Bundeskanzler kam zwar neben der Wortgewalt Donald Trumps eher eine Statistenrolle in der Medienrunde zu, aber es hätte natürlich viel schlimmer kommen können. Deswegen hatte er sich wohl vorher Ratschläge geholt, wie man hört unter anderem vom ukrainischen Präsidenten Wolodymyr Selenskyj. Offiziell gab der deutsche Regierungschef sogar an, «außerordentlich zufrieden» mit seinem Antrittsbesuch zu sein.
Dabei gibt es aktuell doch mehr Differenzen als Gemeinsamkeiten. Zu den Themen, mit denen es eine sehr unterschiedliche Umgehensweise hier und dort gibt, gehört die Gesundheit. Trumps Gesundheitsminister, Robert F. Kennedy Jr., kritisiert zum Beispiel, die meisten US-Universitäten würden den Studenten zu wenig über die Bedeutung gesunder Ernährung beibringen. Im Vordergrund der medizinischen Ausbildung stünde zu sehr die Behandlung der Menschen mit Medikamenten. Daher plant er, den Fakultäten die Bundesmittel zu streichen, wenn sie ihren Studenten keine Ernährungskurse anbieten.
Der oft als Verschwörungstheoretiker diffamierte RFK Jr. ist auch Teil des wachsenden Widerstands gegen Geoengineering-Aktivitäten. Die Manipulation von Wetter und Klima beispielsweise durch das Freisetzen von Chemikalien in die Atmosphäre kann kaum gesund sein und soll daher mit Louisiana jetzt in einem weiteren US-Bundesstaat verboten werden. Kennedy hatte derartige Maßnahmen auch schon als ein Verbrechen bezeichnet, das es zu stoppen gelte.
Indes ist der deutsche Beitrag in diesem Kontext, dass Ex-Gesundheitsminister und Covid-Impfpflicht-Befürworter Karl Lauterbach jetzt zum Klimaexperten mutiert. Laut Spiegel soll er Mitglied einer Kommission für Klima und Gesundheit bei der Weltgesundheitsorganisation werden, angeblich unentgeltlich. Vermutlich möchte die WHO im Sinne ihrer One-Health-Initiative mit solcher Lobbyarbeit für «Klimaschutz als Teil des Gesundheitsschutzes» ihren globalen Führungsanspruch untermauern.
Das Thema «Corona» ist im Übrigen noch lange nicht erledigt und das Narrativ bekommt weitere Risse. Nachdem Kennedy in den USA den Covid-«Impfstoff» für gesunde Kinder und schwangere Frauen aus dem empfohlenen Impfplan gestrichen hat, ist eine CDC-Beraterin zurückgetreten, die die Gen-Injektionen für Schwangere gefördert hatte. Auch die australische Regierung hat ihre Impfempfehlungen aktualisiert. Sie räumt jetzt ein, dass der Nutzen des «Impfstoffs» die Schäden für gesunde Jugendliche nicht überwiegt.
Gleichzeitig berichten Medien von einer neuen, anhaltenden «Covid-19-Welle» in China. Es gebe Befürchtungen, dass es zu erneuten Lockdowns und anderen drastischen Maßnahmen kommen könnte, obwohl sich die «Infektionen» laut den Gesundheitsbehörden auf einem Abwärtstrend befinden. In einigen Schulen seien Schüler isoliert und unter Quarantäne gestellt worden.
Isolierung, Überwachung und Kontrolle sind ebenfalls ein höchst ungesundes Erbe der «Coronazeit». Die weltweit vielfach eingeführten digitalen «Impfpässe» wurden als Instrument benutzt, um Kampagnen für digitale Identitäten zu fördern und die entsprechenden Systeme aufzubauen. Gerade hat auch Griechenland mit der Einführung seiner «Personal Citizen Number» den Grundstein für ein einheitliches digitales ID-System gelegt.
Derweil schlagen Datenschützer Alarm wegen des Tracking-Potenzials der sogenannten «Phone Home»-Funktion vieler digitaler Ausweise. Dieses «Feature», bei dem im Hintergrund jedesmal der Aussteller kontaktiert wird, um eine Angabe zu überprüfen, werde ganz leise in der Gesellschaft eingeführt, warnen sie. Das gebe den Regierungen den Vorgeschmack auf eine Macht, die sie kaum jemals wieder loslassen würden. Dagegen hilft nur eins: wachsam sein, hinterfragen und im Zweifel «Nein» sagen, anstatt auf eine vermeintliche Bequemlichkeit hereinzufallen.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ b1ddb4d7:471244e7
2025-06-18 02:01:28
@ b1ddb4d7:471244e7
2025-06-18 02:01:28Years ago, I flew a microlight aircraft for the first time and felt what it meant to leave the ground. Recently, I bought a gigabyte of storage for 5 cents via Lightning, and something similar happened. This is about that moment—when you stop believing something works and start knowing it does.
Every now and then (if you’re lucky) you have one of those “eureka” moments where the full implications of something hit you for the first time. My biggest experience of that was years ago when I got a microlight aircraft. They’d just come out, so there were no regulations, and anyone could buy one and just fly.
People who should never be flying were going all over the place, and—having no navigation training—they were following motorways instead. Some were even landing at the service stops to get more fuel. How could I resist?
The price included training at an old airfield that was now not busy at all. After a lot of taxiing along the runways, it came time to try a takeoff. Nothing can prepare you for that. It’s not like a Cessna or any of those “proper” aircraft; it’s just an aluminum frame, and you hang off the center of the main pole, the center of gravity. There was a twin motor behind me, totaling 250 cc. I could feel where the wind was on the wings, which side, and even how far along. It was an insight into what birds must feel. I’d trade wings for a big brain any day!
I hit the gas on full, and we accelerated. I had been told that this thing could fly. and had seen my teacher fly in it many times. I thought I understood that it could fly, but as I left the ground and the drag on the wheels was suddenly gone, the whole thing lurched up into the air fast, at a really steep angle, and before I could think, I was already higher than a house. That was when I understood that this thing could fly. Belief is not knowledge, and knowledge only comes from experience.
So it is with many things. So it is with Bitcoin and the Lightning Network. I believed that Lightning could “transform the economic landscape.” I had read about how bitcoin can “revolutionize the financial system.” What hadn’t happened yet was that I had not actually experienced it. That take-off moment came when someone sent me a file link on a CDN. I downloaded the PDF (300 MB or so) and then cut the end off the URL to have a look at the service provider.
To my surprise, they were offering storage space on the CDN at 5c per gigabyte per month. with “unlimited” data transfer. So I decided to try it out. Within a few seconds I had ordered, paid for, and received my credit, and the service was available. 5 cents! That was when I realized how simple everything else in the world can be with Bitcoin and the Lightning Network.
Who cares about how many stupid dollars you can get with bitcoin? Look at what you can do with it! In the new world that may be opening up for us, we can rid ourselves of the parasites who have held us back for so long. “When moon?” takes on a whole different meaning. Nothing is beyond our reach.
There was no bitcoin back in the Spanish Civil War when Durruti was doing his thing, but something of the same awakening must have stirred in him to inspire these words: “We should not be in the least afraid of ruins. They may blast and lay bare this world before they go, but we carry a new world here in our hearts, and this world is growing as we speak.”
https://satellite.earth is the site. It’s not just a storage provider; it’s a Nostr node you can use like any other node, and it has communities set up, among other things. It’s well worth a look. No, I’m not getting paid; they don’t even know me. And I’m not sure, but it looks like because I haven’t used the whole 1 GB yet, they are using my 5c to extend the time I have. In other words, it’s 5c per gigabyte-month, not per gigabyte per month.
-
 @ 0c9e5e17:480e870b
2025-06-18 01:52:11
@ 0c9e5e17:480e870b
2025-06-18 01:52:11I've owned a Fallkniven F1 knife for many years, but never really used it or taken it anywhere because of the sheath. The standard plastic sheath that it comes with may be perfectly designed for survival knife use or for pilots, which I think the knife was designed for, but for every day use or carry it is horrible. The knife sits loose inside, it rattles, the sheath barely retains the knife and the upper soft webbing is annoying. In my humble opinion anyway.
I've looked online for alternative sheaths for a couple of years and found some leather sheaths or Kydex sheaths, but none really suited my needs and were fairly expensive. So, the F1 sat in a box with other outdoor gear not getting any use.
Several years later I finally decided to try my hand at making a Kydex sheath on my own. This was spurred on by another DIY tool project I was working on that also happened to need a Kydex sheath (more on that in a later blog post). So, I thought making a sheath for my Fallkniven F1 might be a good practice project. It was getting no use anyway so what's the worse that could happen. I might even give it a new lease of life.
Making a Kydex Press
 The first step was to make some form of press for forming the heated Kydex around the knife. I search on YouTube and found dozens of videos showing how to make simple hinged presses using pieces of wood and some small pieces of foam. I purchased two door hinges at my local Home Depot and used some scraps of wood I had and small sections of an old backpacking sleeping pad (neoprene) to make the Kydex press. I'm not going to go in to detail, if you want a step-by-step guide check out this video.
The first step was to make some form of press for forming the heated Kydex around the knife. I search on YouTube and found dozens of videos showing how to make simple hinged presses using pieces of wood and some small pieces of foam. I purchased two door hinges at my local Home Depot and used some scraps of wood I had and small sections of an old backpacking sleeping pad (neoprene) to make the Kydex press. I'm not going to go in to detail, if you want a step-by-step guide check out this video.Supplies
After more research I settled on using 0.8” thickness Kydex material. This seems strong enough for my needs, readily available and easy to form. I purchased a couple of 12” square sections on OD green from KnifeKits.com along with some 1/4” eye rivets and a rivet setting punch tool. I had some basic power tools, drill press, small toaster oven, and mini bandsaw in my garage workshop, along with a myriad of old hand tools, sanding paper etc.
Sheath Forming
According to several of the Kydex tutorial videos on YouTube University, it is recommended to apply two layers of blue painters tape to the blade of a knife before forming Kydex around it. This provided a small tolerance around the blade inside the sheath after the tape is removed. I prepped my Fallkniven F1 and got organized. I rough cut a piece of Kydex to approximately the size I needed. I had already decided to make a 'taco' style sheath. This requires once piece of Kydex to be folded around the blade and riveted on one side. The alternative is two pieces of separate Kydex and riveted on both sides of the blade - to me this added extra bulk and was unnecessary.
In an old toaster oven, heated to 350-degrees, I warmed my piece of Kydex. I had my sheath press ready along with two clamps. I wore a pair of Mechanix Wear gloves to protect my hands, heated Kydex is extremely hot and similar to handling molten plastic. You need gloves and need to be able to move quickly once the Kydex is up tp temperature. After about 90 seconds I tested the Kydex to find it perfectly soft and pliable. I wasn't able to find good information on what temperature to heat 0.8mm Kydex or for how long, but did find a video describing the right softness of Kydex so you can tell when it's ready. Pretty much trial and error.
I removed the heated Kydex and folded it around the back spine of the Fallkniven, quickly laying it down on the foam of my Kydex press, handle sticking out. I quickly closed the press lid and applied two clamps, tightening as hard as I could. I let this sit for 10 minutes to cool down.
Trimming and Rivet Placement
 Once the Kydex had cooled down I removed it form the press and opened up the taco form to remove the knife. I knew I was going to be affixing a Tek-Lok clip to the sheath so that I could wear the knife appendix style (horizontally) on my belt. I marked out my rivet holes, spacing them to match the Tek-Lok and added a few more to secure the sheath. I drilled the 1/4” holes on my drill press and then marked the shape of the sheath using a white pencil. I trimmed most of the excess using a small bench-top bandsaw and finished the edges using sequentially finer levels of sandpaper. Kydex is pretty easy to work with.
Once the Kydex had cooled down I removed it form the press and opened up the taco form to remove the knife. I knew I was going to be affixing a Tek-Lok clip to the sheath so that I could wear the knife appendix style (horizontally) on my belt. I marked out my rivet holes, spacing them to match the Tek-Lok and added a few more to secure the sheath. I drilled the 1/4” holes on my drill press and then marked the shape of the sheath using a white pencil. I trimmed most of the excess using a small bench-top bandsaw and finished the edges using sequentially finer levels of sandpaper. Kydex is pretty easy to work with.I drilled a small hole at the bottom of the sheath right at the tip of the blade to allow for drainage should the sheath or knife get wet, fall into water, or get dirt inside. The last step before riveting was to clean out the inside of the sheath to remove and dust and debris from construction. I used some high pressure air.
I inserted each rivet one at a time and crimped them using my rivet setting die and a small arbor press I had. You could just as easily use a hammer a few small taps. Note: It's important that you use the right length rivets for the Kydex you are using. Mine were specifically for 0.8” Kydex.
Ensuring the Perfect Fit
 I checked that the knife still fit snuggly into the sheath and was well retained. I noticed that it could use some adjustment and tweaks to fit and be removed more easily. I could describe all the steps here, or you could do what I did and watch this excellent YouTube video by Gentry Custom Knives which walks you through exactly how to ensure a perfect fit. I also took his advice and added a small thumb ramp to make removing the blade easier. I used a hot air gun to carefully heat the top edge of the Kydex sheath and bend it with my gloved finger.
I checked that the knife still fit snuggly into the sheath and was well retained. I noticed that it could use some adjustment and tweaks to fit and be removed more easily. I could describe all the steps here, or you could do what I did and watch this excellent YouTube video by Gentry Custom Knives which walks you through exactly how to ensure a perfect fit. I also took his advice and added a small thumb ramp to make removing the blade easier. I used a hot air gun to carefully heat the top edge of the Kydex sheath and bend it with my gloved finger.Tek-Lok Clip Mounting
Installing the Tek-Lok clip is extremely easy. Just align the holes that have been drilled and rivetted and determie if you need to have the vet spacer inserted or not - depending on how wide your belt is. And that's it.
 The best way to do this is to just try. I had several failures along the way and learned what not to do. The great things about Kydex is that if you mess up in the pressing stage, you can warm it up again in the toaster oven and it will revert to it's original flat form and you can try again. I did discover however, that you can only do this a maximum of three times before the Kydex starts to misform and no longer be an even thickness - that might only be true in a toaster over. Time and more attempts will tell.
The best way to do this is to just try. I had several failures along the way and learned what not to do. The great things about Kydex is that if you mess up in the pressing stage, you can warm it up again in the toaster oven and it will revert to it's original flat form and you can try again. I did discover however, that you can only do this a maximum of three times before the Kydex starts to misform and no longer be an even thickness - that might only be true in a toaster over. Time and more attempts will tell.This project was a lot of fun and it gave and old under utilized knife an entirley new lease of life. The Fallkniven F1 is not a small knife, but I can hardly notice I am wearing it using this new sheath in an appendix carry mode.
Resources and Acknowledgements
I hoped you found this useful. I had a blast doing this for the first time and learned a lot along the way. I managed to do this on the cheap with less than $50 worth of materials, which will enable me to make more than this one sheath.
I'd like to acknowledge and give thank to some knifemakers who kindly shared their knowledge through videos on YouTube. I could not have learned how to do this without the many excellent videos shared by Gentry Custom Knives and Simple Little Life. Their videos were incredibly detailed and were the basis of everything I did here. Many, many thanks to both of them for taking the time to make their videos and openly share their skills and expertise to allow others to learn. Please support them in any way you can, subscribe to their channels, like their videos, or purchase some of their excellent knives.
KnifeKits.com - everything you could ever need and more to support your knife making habit - from a utter novice (like me) to an expert. Fast reliable shipping, and competitive prices.
 I'd love to hear from you. What do you think about my first Kydex sheath project? Do you love it or hate it? What would you have done differently and what could I do better? Let me know, so that I can get better next time. - Bfgreen
I'd love to hear from you. What do you think about my first Kydex sheath project? Do you love it or hate it? What would you have done differently and what could I do better? Let me know, so that I can get better next time. - Bfgreen -
 @ 8bad92c3:ca714aa5
2025-06-18 01:02:09
@ 8bad92c3:ca714aa5
2025-06-18 01:02:09Marty's Bent
via me

"The man in the coma" has been a long-running archetype of a bitcoiner on TFTC and Rabbit Hole Recap. Over the years, we've referenced the man in the coma in regards to bitcoin being a backward compatible distributed network that would enable an individual, in the case of our example - a man who fell into a coma, to be able to wake up many years, even decades, after falling into a deep sleep, go back to his bitcoin node and be able to participate in the network and validate his own transactions as if the network was operating the same it was the day he slipped into a coma. As a distributed network, this is one of bitcoin's greatest value props; consistency for the individual running it, no matter the version.
Having spent 12 years engrossed in bitcoin, thinking about it every day, building a media company focused on educating people about the network and the monetary revolution it enables, why it's important and how they can use it. Becoming a managing partner at Ten31, which is dedicated to investing in companies building out infrastructure that makes bitcoin more accessible and easier to use; "the man in the coma" has become a more prominent archetype in my mind.
"The man in the coma" archetype can be described in other ways. For instance, there was an individual by the name of John Doe, who joined myself and Matt Odell on TFTC about seven years ago who went to jail for four years. He was distributing certain goods on the Silk Road for many years and got nabbed by the police while throwing a house party. Unfortunately for Mr. Doe, the goods he were selling via the Silk Road were in the house hosting the party that got busted. Fortunately for Mr. Doe, the police who nabbed him were not privy to the way in which he was marketing and selling the goods. He went to jail for four years, walked out at the end of his sentence, found his bitcoin wallets, recovered them and was more than pleasantly surprised at the magnitude of his wealth.
The forced hodl that was incited by the state throwing him in a cage wound up paying off after four years. Now, I can certainly admit that time is the most scarce asset in the world. Being put in a cage for four years or falling into a coma for a number of years is not ideal. However, there are lessons to be gleaned from the successes that have been realized by "the man in the coma" and the man who was forced to hodl by being thrown in a cage. Unable to access his bitcoin during that period of time to make less than wise decisions.
The main lesson to be gleaned is that doing nothing is oftentimes significantly more optimal than doing something. Too many bitcoiners decide to make rash decisions influenced by the day-to-day happenings on social media or some one-off comment from someone in their personal life that they respect. These comments can be about the long-term viability of bitcoin itself, some prognostications about where the price is going in a short-term to medium-term time frame or simply the social aspects of being associated with bitcoin. All of these factors play into influencing certain individuals deciding to sell their bitcoin in the hopes of buying it back lower, realizing something material in their day-to-day life or jumping off a ship that they've been convinced is about to sink.
In my mind, the only thing listed above that makes a bit of sense to me is realizing something material in your day-to-day life. Selling some bitcoin to purchase something that makes your life better like enabling you to support your family at a critical time and in a way that would not be possible unless you sold bitcoin. That makes sense to me. However, the other two are completely nonsensical. Bitcoin's success is binary. It either succeeds or it doesn't. And if you accept that this is true, success means slowly but surely becoming the global reserve currency and monetary network used by billions of humans on the planet or it goes to zero.
If the former materializes, that means that billions of people are going to be competing for 21 million Bitcoin. There are, by some estimates, $900 trillion worth of assets that are being used to store wealth over the short, medium, and long term. Bitcoin has the potential to subsume a material percentage of that $900 trillion. In my mind, if bitcoin is as good as I believe it is, it should take at least half of that market, if not 80 to 90%. This in and of itself is a gamble. No one can be certain that this will come true. And with that in mind you have to make a probabilistic bet by surveying the world and discerning what the likelihood of bitcoin's ultimate success is.
If you think governments, central banks, and large corporations are going to continue down the path of unfettered expansion of the monetary base, debt, and misallocation of capital, bitcoin, a peer-to-peer distributed cash system that cannot be controlled by any individual. corporation, country, or central bank makes a lot of sense. The debasement, the debt expansion, and the misallocation of capital are driven by fallible humans working in incentive structures that are vulnerable to the fallible nature of the humans working within them.
Human fallibility brings with it the ability to talk oneself out of a position that one knows makes sense and is logical. This is the disadvantage that those who are not "the man in the coma" or "the man in a cage" operate from. Being forced to hodl bitcoin is already and will increasingly be seen as a relative advantage. Many who are in bitcoin today, paying attention to every headline, every pull request and every doubt flung their way will likely get to 2030 and agree that they made worse decisions than the man who was thrown in a cage or who slipped into a coma.
Of course, this isn't a fair introspective conclusion. The man in the coma and the man who was forced to hodl because he was put in a jail cell did not have a decision at the end of the day. Both were forced to hodl due to external or internal forces that, all else being equal, they would prefer not have had to endure. However, the outcome of these two situations will likely be better than the outcome of "the man in the arena" who thinks that by making decisions on the go as a slew of information comes his way on a day-to-day basis will materialize in a larger stack of satoshis.
The reality of the situation is such that no one truly knows where bitcoin is going to go on a day-to-day, month-to-month, or year-to-year basis. Especially at this point with large institutions, nation-states, corporations, and individual states getting into the fray. The only tried-and-true strategy within bitcoin over the long term is to stay humble, stack sats, and hodl like you are "the man in the coma" or the man who was thrown in a cage.
Bitcoin's Volatility Won't End With Institutional Adoption
Leon Wankum challenged the popular "supercycle" narrative during our conversation, arguing that Bitcoin's volatility isn't going away despite massive institutional adoption. While acknowledging that MicroStrategy now holds over 2% of all Bitcoin and won't sell, Leon maintains that leverage will still need to be washed out. He expects another 60% drawdown at the end of this bull cycle, viewing this as a feature rather than a bug of Bitcoin's design.
"Bitcoin naturally washes out leverage, it builds resilience and we don't go through these crazy boom and bust cycles, we go through bull and bear markets and I think that's a net positive." - Leon Wankum
Leon sees Bitcoin's volatility as fundamentally different from fiat's destructive boom-bust cycles. Where traditional markets require central bank intervention to prop up failing systems, Bitcoin's regular corrections create genuine resilience. Bad actors will always enter during euphoric phases, and the subsequent washouts ensure only strong hands remain. This natural selection process, he argues, is beautiful - it's what makes Bitcoin antifragile.
Check out the full podcast here for more on real estate opportunity costs, Bitcoin bonds, and treasury company risks.
Headlines of the Day
Romania Adds Crypto Terminals to Post Offices - via X
Musk Claims Trump in Epstein Files - via X
Uber CEO Calls Bitcoin Proven Store of Value - via X
Get our new STACK SATS hat - via tftcmerch.io
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code *“TFTC20”* during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
The kids really do grow up f
-
 @ e1cde248:609c13b0
2025-06-18 00:53:42
@ e1cde248:609c13b0
2025-06-18 00:53:42Arthur Hayes ได้ฉายภาพหนึ่งในปัญหาใหญ่ที่สุดที่เศรษฐกิจโลกกำลังเผชิญ นั่นคือ "ศึกเงียบระหว่างคนรุ่นเก่าและรุ่นใหม่" ที่กำลังจะปะทุขึ้นจากการโอนถ่ายความมั่งคั่งขนาดมหาศาลจากรุ่น Baby Boomer ไปยัง Millennials และ Gen Z
ในอีกไม่กี่ปีข้างหน้า คนรุ่น Boomer ซึ่งเป็นกลุ่มที่ถือครองทรัพย์สินมากที่สุดในประวัติศาสตร์ กำลังเข้าสู่วัยเกษียณ และเริ่มขายสินทรัพย์อย่างหุ้น บ้าน และอสังหาริมทรัพย์ เพื่อเปลี่ยนเป็นเงินสดใช้ในบั้นปลายชีวิต
แต่ปัญหาคือ... ใครจะซื้อของเหล่านั้น?
คนรุ่นใหม่ไม่ได้มองบ้านหลังใหญ่ในชานเมืองหรือหุ้นบริษัทน้ำมันเป็นเป้าหมายชีวิตอีกต่อไป พวกเขาให้คุณค่ากับ "ประสบการณ์" มากกว่าสิ่งของ อีกทั้งยังสนใจ "สินทรัพย์ดิจิทัล" มากกว่าทรัพย์สินแบบดั้งเดิม และเชื่อในอิสระมากกว่าความมั่นคง
สิ่งนี้นำไปสู่คำถามสำคัญที่อาจเปลี่ยนทิศทางเศรษฐกิจโลก:
-
หากไม่มีใครอยากซื้อ สินทรัพย์จะราคาตกหรือไม่? ถ้าเกิดขึ้นจริง นั่นหมายถึงคนรุ่น Boomer จะต้องเกษียณด้วยสินทรัพย์ที่มีมูลค่าลดลง และอาจต้องพึ่งพารัฐบาลมากขึ้น
-
แล้วภาระจะตกกับใคร? หากรัฐบาลต้องอุ้มค่าใช้จ่ายผู้เกษียณ สิ่งที่ตามมาคือ "ภาษีที่เพิ่มขึ้น" ซึ่งจะตกอยู่กับคนรุ่นใหม่ที่แทบยังไม่มีอะไรในมือ
-
หรือสุดท้าย ทางออกเดียวจะคือการ “พิมพ์เงิน”? Hayes คาดว่ารัฐบาลจะหันไปใช้วิธีนี้ ซึ่งอาจช่วยได้ในระยะสั้น แต่จะกลายเป็นเชื้อเพลิงเงินเฟ้อในระยะยาว
และนั่นคือจุดที่ "ความไม่พอใจระหว่างรุ่น" อาจปะทุขึ้นอย่างรุนแรง
คนรุ่นใหม่จะถามว่า "ทำไมเราต้องจ่ายเพื่อความล้มเหลวของระบบที่เราไม่ได้สร้าง?" ขณะที่คนรุ่นเก่าอาจตอบว่า "เราเสียภาษีมาทั้งชีวิตเพื่อระบบนี้ แล้วใครจะดูแลเรา?"
นี่ไม่ใช่แค่ความต่างทางวัย แต่คือ ความขัดแย้งทางโครงสร้างเศรษฐกิจและคุณค่าของชีวิต ที่กำลังทวีความรุนแรงขึ้น
Hayes มองว่า ผลลัพธ์ของความขัดแย้งนี้ อาจมีตั้งแต่การปรับขึ้นภาษีรุนแรง การเปลี่ยนแปลงระบบบำนาญ ไปจนถึง ความไม่มั่นคงทางการเงินระดับชาติ ที่อาจเปลี่ยนวิธีที่โลกจัดการกับเงิน สินทรัพย์ และอนาคตของคนแต่ละรุ่นไปอย่างสิ้นเชิง
และในโลกแบบนี้ Hayes ถึงเชื่อว่า Bitcoin จะเป็นผู้ชนะ เพราะมันไม่สามารถพิมพ์เพิ่มได้ ซึ่งตรงข้ามกับเงินเฟ้อที่กำลังมาท่วมโลก
source: https://www.youtube.com/watch?v=AH7TIPRKGZw
-
-
 @ 9ca447d2:fbf5a36d
2025-06-18 00:02:06
@ 9ca447d2:fbf5a36d
2025-06-18 00:02:06Trump Media and Technology Group (TMTG), the company behind Truth Social, has received approval from the U.S. Securities and Exchange Commission (SEC) regarding its plan to raise and use $2.3 billion to build a big bitcoin treasury.
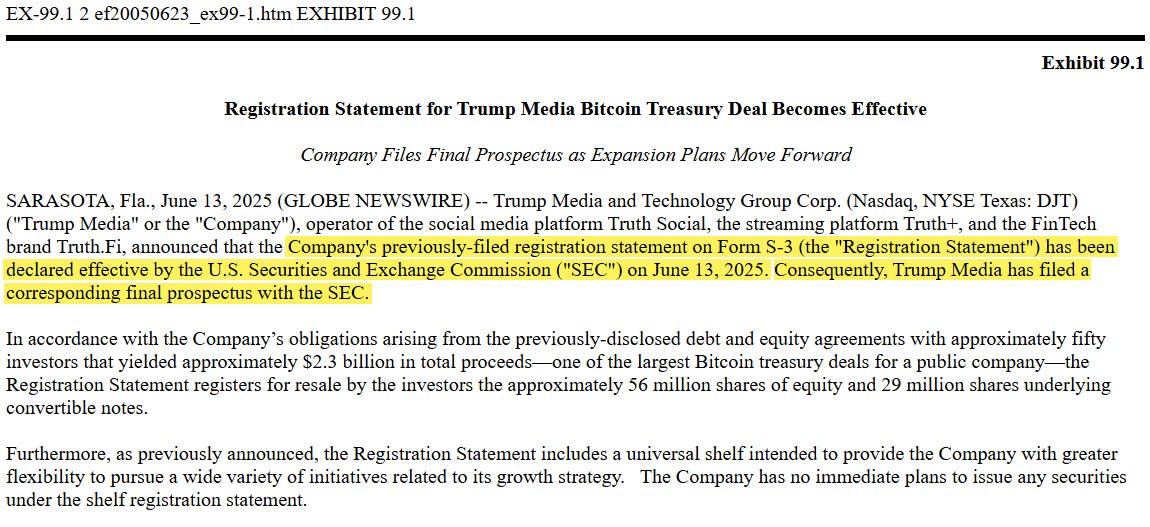
TMTG’s plan was declared effective by the SEC
This is a big and controversial move by the media company tied to U.S. President Donald Trump. The plan involves converting part of its corporate assets into bitcoin—similar to what companies like Strategy have done.
TMTG filed a Form S-3 with the SEC on June 6. The form allows public companies to register securities for resale. A week later, the SEC “declared effective” the filing and TMTG can now use the money raised from previous deals to buy bitcoin.
According to the filings, the company raised $2.3 billion from the resale of about 56 million equity shares and 29 million shares of convertible notes. Almost 50 institutional investors participated in the raise.
This is “one of the largest bitcoin treasury deals for a public company,” TMTG said in a press release.
TMTG’s CEO, Devin Nunes, said this is part of a bigger plan to grow the company beyond social media and into the fintech space.
“We are quickly developing our fintech brand, social media platform, and streaming service and accumulating a Bitcoin treasury to support the Patriot Economy,” said Nunes.
The funds will be managed through TMTG’s fintech arm, Truth.Fi, and the company will store its bitcoin with its trusted custodians Crypto.com and Anchorage Digital.
Nunes also said this is a way to protect the company from financial discrimination, stating the bitcoin treasury will allow the company to defend itself “against harassment and discrimination by financial institutions.”
This seems to be more than just a business decision, and more like a political move.
Trump Media’s bitcoin push comes at a time when U.S. digital asset regulation is unclear. By moving into digital assets, TMTG signals a bold break from traditional financial norms and aligns itself with Bitcoin-friendly audiences.
American institutions are recognizing bitcoin as a safe haven asset, so maybe media and political groups will start to explore the asset further.
Trump Media isn’t stopping at a bitcoin treasury. They filed paperwork to create a spot bitcoin exchange-traded fund (ETF) called the Truth Social Bitcoin ETF. If approved, this ETF will give traditional investors another way to get exposure to bitcoin’s price.
Again, Crypto.com will be the exclusive custodian for this ETF.
One of the investors in the bitcoin treasury is Don Wilson, founder of DRW Investments. His firm put in $100 million. Some are wondering if there’s a conflict of interest since his digital asset trading firm, Cumberland, just had a case dropped by the SEC.
-
 @ b7274d28:c99628cb
2025-06-18 00:01:01
@ b7274d28:c99628cb
2025-06-18 00:01:01Tired of dealing with spam? You're not alone. Here is a guide to picking relays that are good at keeping spam out, without sacrificing your own reach.
If you just want to skip to the relay suggestions, scroll to the sections titled "The Setup." There is one for users of Haven and one for those who aren't running their own relay at all.
Client Selection
"Wait, I thought this was a guide about selecting relays, not clients."
Yes, it is. But what relays you choose doesn't matter if you are using a client that does not read from your chosen relays, or that hard-codes problematic relays as fallbacks in addition to the relays you selected in an effort to "help you."
Additionally, some clients have settings that can help make up for poor relay selection using client-side spam mitigation methods. This includes clients like Coracle, Damus, Amethyst, and Nostur. Some may do so via web-of-trust (WoT) filters, so you only see notes and replies from those within your broader social circle, while others will automatically hide notes that those you follow have reported as spam or scams.
Coracle is a great client for dealing with spam, so long as you have gone into your "Content Settings" and set the "Minimum WoT Score" to at least 1. This means you will only see posts from users followed by at least one of the npubs you follow.
Damus also employs WoT, but it appears to be just for notifications, so you only receive notifications for those you follow and those they follow, or "friends of friends," as Damus put's it. This can be accessed by toggling it on in your notification tab at the top right, where you see the icon of the person with a check mark.
Nostur has WoT filters for downloading media turned on by default and also uses WoT to filter spam by default. Even better, if you use multiple npubs, you can filter using the WoT of your main npub, while logged into your alternate npubs.
Jumble recently added WoT filtering specifically for interactions. When you load a thread in Jumble, a shield icon will appear near the top right of the page, in line with the tabs for Replies and Quotes. Toggle it on, so the shield is green with a check mark and you will only see replies from those you follow and those your follows follow.
Amethyst does not yet have WoT based filtering built into the client, but it can hide notes that have been reported as spam, scams, impersonation, etc, by those you follow. This is not the most effective way to combat spam, though, since most users aren't often using the report feature. Hopefully we will see WoT filtering as an option in a future update.
Primal's apps do not read from any of your selected relays, but rather from their caching server alone. That said, they have a spam filter that is turned on by default so you see relatively little spam, regardless of which relays you use.
For this guide, I recommend using Amethyst for updating your relays, if you possibly can. The reason for this is because Amethyst has the most robust settings for being able to update all of your various relay lists.
Relay Lists Explained
Contrary to what you might think, there is not a single relay list for each user that is stored in a single note, because you can have relays that are used for only one purpose, and not for any other. Each of those purposes for which you might use a particular relay has its own list. That way a Nostr client can tell which relays you want to use for each separate purpose.
While this can make things less approachable for the user, it also means users don't have to rely on clients to hard code appropriate relays for each of these use-cases. If your client doesn't let you edit each of these relay lists, chances are they are using a set of relays for that purpose that the developer chose instead of you.
Public Outbox/Inbox Relays
This list of relays is found in your kind 10002 note, if you have one. If you don't have one, there won't be any relays shown for these categories in Amethyst. Other clients may fallback to showing you relays from a different list.
This list is intended to be used for Nostr clients to implement the "outbox model" to fetch notes from whatever relays they were written to, even if they aren't in the requesting user's relay list. This solves the issue of needing to share relays with those you follow in order to see their notes, allowing Nostr to remain decentralized.
Your "outbox" relays are the ones you write to, or at least the ones you want other users to know that you write to. When you add a relay here, it's like advertising to everyone, "If you want to see my public-facing notes, look for them on these relays."
Your "inbox" relays are the ones you read from. On this part of your list you are advertising, "If you want me to see your replies, comments, reactions, and zaps, then send them to these relays." These relays are massively important for reducing the amount of spam you see. If you have relays listed here that anyone can post to for free, you will almost certainly see a lot of spam in your replies, unless you have WoT filters turned on in your Nostr client.
DM Inbox Relays
This list is found in your kind 10050 note, if you have one, and is a list of relays where you want others to send you Direct Messages. Ideally, you will use a relay or two here that supports AUTH, so that it will only allow direct messages to be retrieved by the user they are addressed to.
What happens if you put a relay in here that doesn't support AUTH, so it allows anyone to retrieve your DMs? Not much. Anyone who wants to will just be able to see the encrypted content of the message, and depending on the type of DM they will see the identity of the receiver and perhaps also the sender. They will not be able to decrypt what was actually said in the messages. It's better if they cannot retrieve even that much, though.
Private Relays
This list is found in your 10013 note, if you have one. This is intended for listing a relay that you run yourself and that only you can access, as it will house notes that other users should not be able to see at all, such as eCash tokens and draft notes.
Search Relays
This list is found in your 10007 note, if you have one, and is used to search for notes or users who may not be using the same relays as you. It is good to use relays here that aggregate notes from other relays automatically, and which support NIP-50 for search capability.
Local Relays
This section is for any relays running on the local device, such as Citrine. Because the relays themselves are local, this list is local, as well, and is not saved to any note kind that is saved to your relays like the above lists.
General Relays
This list is found in the "content" tag of your kind 3 note, which is also where all of the npubs you follow are stored. As such, this note is commonly known as your follow list, rather than as a relay list. However, some clients, such as Amethyst, do make use of this list, and others use it as a fallback if they can't find a kind 10002.
If you are an Amethyst user most of the time, then I would recommend using this list to fill in any gaps that you may have from only writing to a few outbox relays, or only reading from a few inbox relays. It's a good place to put an aggregator relay, for instance, so long as that relay has good spam filtering, or a blastr relay, so those who don't yet use a client that supports the outbox model will still likely see your notes.
If you do not generally use Amethyst, then I would recommend you mirror your public inbox/outbox relays here, in case you use a client that cannot find your 10002 list. Relays that are only for outbox should be added as write only, those only for inbox should be added as read only, and those you use for both outbox and inbox should be both read and write.
The Setup (Haven Users)
If you are running your own set of Haven relays, here is the setup I would recommend:
Public Outbox (kind 10002)
Maximum of 4 relays.
- Your Haven outbox relay (Remember to add some public relays to your blastr)
- A paid relay of your choice (List available in "Paid Relays" section)
- A public relay, such as relay.damus.io, relay.primal.net, or nos.lol
Public Inbox (kind 10002)
Maximum of 4 relays.
- Your Haven inbox relay: [RelayAddress]/inbox
- A paid relay of your choice (can be same as outbox)
- A WoT relay of your choice (available in "WoT Relays" section)
- Optional additional WoT relay
DM Inbox
Maximum of 3 relays.
- Your Haven "chat" relay: [RelayAddress]/chat
- An alternate AUTH relay, such as inbox.nostr.wine(paid), nostr.land(paid), or auth.nostr1.com(free).
Private Relays
Maximum of 3 relays.
- Your Haven private relay: [RelayAddress]/private
Search Relays
Maximum of 4 relays.
- wss://nostr.wine (even if you don't pay to write to it)
- wss://relay.nostr.band
- wss://relay.noswhere.com
- wss://search.nos.today
Local Relays
- Your Citrine IP:Port, if you run Citrine.
General Relays
Assuming you use Amethyst on a regular basis, I recommend the following:
- A couple additional WoT relays set to read only.
- An aggregator relay that has good spam filtering, such as wss://aggr.nostr.land(payment required) and/or wss://nostr.wine(paid for write, but can read for free).
The Setup (Not Running Haven)
If you are not running your own set of Haven relays, I would highly recommend you learn how and do so. However, if you decide against it, here is a setup that should suffice:
Public Outbox (kind 10002)
Maximum of 4 relays.
- A paid relay of your choice (List available in "Paid Relays" section)
- A large public relay, such as relay.damus.io, relay.primal.net, or nos.lol
- An additional public relay, but a smaller one, or one-time-payment paid relay.
Public Inbox (kind 10002)
Maximum of 4 relays.
- A paid relay of your choice (can be same as outbox)
- wss://nostr.wine - Even if you don't pay for it, you can read from it.
- A WoT relay of your choice (available in "WoT Relays" section)
- Optional additional WoT relay
DM Inbox
Maximum of 3 relays.
- A paid AUTH relay, such as inbox.nostr.wine or nostr.land.
- An alternate AUTH relay, such as auth.nostr1.com(free).
Private Relays
Maximum of 3 relays.
- A private relay you run on your Umbrel or Start9, or that is hosted for you on relay.tools.
Search Relays
Maximum of 4 relays.
- wss://nostr.wine (even if you don't pay to write to it)
- wss://relay.nostr.band
- wss://relay.noswhere.com
- wss://search.nos.today
Local Relays
- Your Citrine IP:Port, if you run Citrine.
General Relays
Assuming you use Amethyst on a regular basis, I recommend the following:
- A couple additional WoT relays set to read only.
- An aggregator relay that has good spam filtering, such as wss://aggr.nostr.land(payment required).
- A blastr relay, such as filter.nostr.wine(paid), or...
- A few additional public relays set to write only.
Paid Relays
There are a ton of other paid relays out there that can be found via nostr.watch. The above listed options are simply the most popular with the largest feature-sets.
WoT Relays
These relays will only accept notes from npubs that are within the relay owner's WoT. I have provided a Jumble.social address for each relay so you can peruse the feed for yourself to see if you want to use it.
- wss://wot.utxo.one - Jumble Feed
- wss://nostrelites.org - Jumble Feed
- wss://wot.nostr.party - Jumble Feed
- wss://wot.sovbit.host - Jumble Feed
- wss://wot.girino.org - Jumble Feed
- wss://relay.lnau.net - Jumble Feed
- wss://wot.siamstr.com - Jumble Feed
- wss://relay.lexingtonbitcoin.org - Jumble Feed
- wss://wot.azzamo.net - Jumble Feed
- wss://wot.swarmstr.com - Jumble Feed
- wss://zap.watch - Jumble Feed
- wss://satsage.xyz - Jumble Feed
- wss://wons.calva.dev - Jumble Feed
- wss://wot.zacoos.com - Jumble Feed
- wss://wot.shaving.kiwi - Jumble Feed
- wss://wot.tealeaf.dev - Jumble Feed
- wss://wot.nostr.net - Jumble Feed
- wss://relay.goodmorningbitcoin.com - Jumble Feed
- wss://wot.sudocarlos.com - Jumble Feed
-
 @ eb0157af:77ab6c55
2025-06-18 01:02:06
@ eb0157af:77ab6c55
2025-06-18 01:02:06Carl Rickertsen completely exits his position in Strategy as insiders sell $864 million worth of stock.
As reported by Protos, Carl Rickertsen, a member of Strategy’s board of directors, has fully liquidated his entire shareholding for over $10 million.
Rickertsen’s decision to completely exit his Strategy position marks a sharp shift from his previous investment stance. In 2022, the executive had shown confidence in the company by investing $700,000 in MSTR shares.
On June 13, 2022, Rickertsen purchased $608,000 worth of MSTR stock at $152 per share. Since then, the stock has rallied 152%. However, by 2023, the director had already sold half of his 4,000-share position.
Rickertsen’s approach to managing his holdings has become increasingly aggressive in recent years. Since joining the board in 2019, he has adopted a strategy of immediately liquidating any stock options received.
One example of this tactic occurred on June 2, when he acquired and sold 26,390 MSTR shares on the same day.
As of June 5 this year, Rickertsen reported zero vested Strategy shares, marking the end of his equity involvement with the company.
Rickertsen’s situation is not an isolated case within Strategy. Data from the Securities and Exchange Commission (SEC) reveals a controversial picture. According to information gathered by secform4.com, over the past five years, total insider sales have exceeded purchases by $864 million. This imbalance in insider transactions could raise questions about executives’ confidence in the company’s future.
The post Strategy director liquidates all his MSTR shares appeared first on Atlas21.
-
 @ a5ee4475:2ca75401
2025-06-06 15:30:41
@ a5ee4475:2ca75401
2025-06-06 15:30:41[EM ATUALIZAÇÃO]
vacina #saude #politica #manipulacao #mundial #genocidio #pandemia #conspiracao
"Aqueles que não conseguem lembrar o passado estão condenados a repeti-lo." - George Satayana
Este artigo reúne algumas menções e evidências mais antigas que vim registrando durante alguns anos em relação a Covid-19, vacinas obrigatórias e a ação de agências de governo, fundações, políticos, mídia tradicional, celebridades, influenciadores, cientistas, redes sociais e laboratórios, em envolvimento com genocídio e restrições de liberdades em escala mundial causado por decisões em várias esferas relativas ao covid e as vacinas obrigatórias em geral.
Porém, alguns links podem não estar mais disponíveis, foram que ainda faltam ser registradas muitas informações já divulgadas nos últimos anos e que muitos não tiveram contato pela escassez de meios para a obtenção dessas informações de forma organizada.
Portanto, o presente artigo ainda passará por atualizações de conteúdo e formatação. Logo, se possível, ajudem sugerindo complementos ou alterações, ou com doações.
Noções iniciais:
- O termo 'Coronavírus' (COVID) é na verdade um nome genérico para vários vírus de gripes já comuns, dado para o tipo corona (com uma "coroa", 'espetos' ao redor dele), o Sars-Cov-2 (que passou a ser chamado erroneamente só de Covid), é só um deles.
- SARS-CoV-2 é que é nome do vírus. Ele que causa a doença Covid-19;
- O coronavírus SARS-CoV-2 é o segundo tipo de SARS-CoV documentado, o primeiro ocorreu entre 2002 e 2003, se originando também da China e também dito como tendo origem animal;
- SARS (Severe Acute Respiratory Syndrome) - Síndrome Respiratória Aguda Grave (SRAG) é a uma doença respiratória viral, relatada ser de origem zoonótica (animal), causada pelos coronavírus SARS-CoV (2002) e SARS-CoV-2 (2019), ambos de origem chinesa;
1. Vacinas Obrigatórias em Geral
23/01/2025 - [Pesquisa] Vacinas nos EUA causando autismo em crianças https://publichealthpolicyjournal.com/vaccination-and-neurodevelopmental-disorders-a-study-of-nine-year-old-children-enrolled-in-medicaid/
- O CDC admite que 98 milhões de pessoas receberam o vírus do câncer através da vacina da Poliomielite https://medicinanews.com.br/frente/frente_1/o-cdc-admite-que-98-milhoes-de-pessoas-receberam-o-virus-do-cancer-atraves-da-vacina-poliomielite/
"O CDC (Os Centros de Controle e Prevenção de Doenças dos Estados Unidos) removeu rapidamente uma página do seu site, que estava em cache no Google, como você pode ver logo abaixo, admitindo que mais de 98 milhões de americanos receberam uma ou mais doses de vacina contra pólio dentro de 8 período entre 1955 e 1963, quando uma proporção da vacina foi contaminada com um poliomavírus causador de câncer chamado SV40."
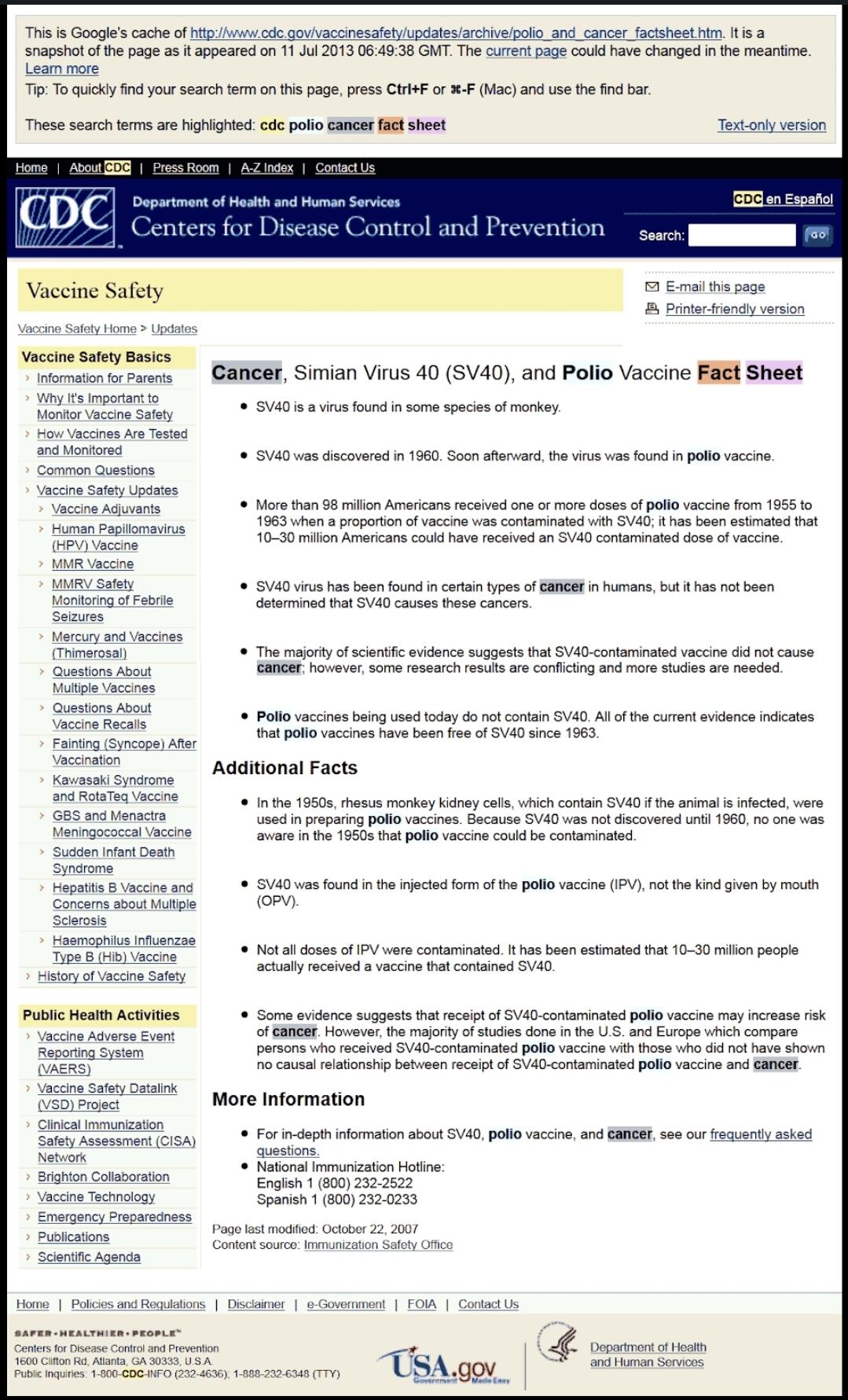 Fonte original da imagem: https://preventdisease.com/images13/CDC_Polio.png [indisponível] - A imagem foi trocada por outra de menor qualidade e em outro link, mas eu já tinha a imagem original salva.
Fonte original da imagem: https://preventdisease.com/images13/CDC_Polio.png [indisponível] - A imagem foi trocada por outra de menor qualidade e em outro link, mas eu já tinha a imagem original salva. Imagem arquivada em: https://web.archive.org/web/20201203231640/
Imagem arquivada em: https://web.archive.org/web/20201203231640/27/02/2021 - Por que o Japão demorou para vacinar, mesmo com Olimpíada se aproximando https://www.cnnbrasil.com.br/internacional/2021/02/27/por-que-o-japao-demorou-para-vacinar-mesmo-com-olimpiada-se-aproximando
"Desconfiança da população japonesa em relação a vacinas, ligada a casos ocorridos no passado, está entre razões que atrasaram imunização no país.
A resistência à vacina do Japão remonta à década de 1970, quando duas crianças morreram dentro de 24 horas após receberem a vacina combinada contra difteria, tétano e coqueluche (coqueluche). A vacina foi temporariamente suspensa, mas a confiança já havia sido abalada. Por vários anos, as taxas de vacinação infantil caíram, levando a um aumento nos casos de tosse convulsa.
No final dos anos 1980, houve outro susto com a introdução da vacina tripla contra sarampo, caxumba e rubéola produzida no Japão. As primeiras versões do imunizante foram associadas à meningite asséptica, ou inchaço das membranas ao redor do cérebro e da medula espinhal. O problema foi rastreado até o componente caxumba da vacina tripla, o que levou a uma ação judicial e a indenização por danos pesados.
O Instituto Nacional de Ciências da Saúde interrompeu a dose combinada em 1993 e a substituiu por vacinas individuais. Após o escândalo, Shibuya disse que o governo japonês se tornou "ciente dos riscos" e seu programa nacional de vacinação tornou-se voluntário.
O Dr. Yuho Horikoshi, especialista em doenças infecciosas, diz que os processos levaram a uma "lacuna de vacinação", em que nenhuma vacina foi aprovada no Japão por cerca de 15 anos.
Mais recentemente, em 2013, o Japão adicionou a vacina contra o papilomavírus humano (HPV) ao calendário nacional para proteger as meninas contra o vírus sexualmente transmissível, que é conhecido por causar câncer cervical. No entanto, vídeos de meninas supostamente sofrendo de reações adversas começaram a circular no YouTube, levando o governo a retirá-los da programação nacional."
2. PRIMEIRAS OCORRÊNCIAS PREDITIVAS AO COVID-19
2002 - Síndrome respiratória aguda grave (SARS) Brenda L. Tesini (setembro de 2018). Síndrome respiratória aguda grave (SARS) [indisponível]. Manual Merck. Consultado em 23 de janeiro de 2020, citado no Wikipedia
SARS - Wikipédia: "A SARS [doença do vírus SARS-CoV] foi detectada pela primeira vez no fim de 2002 na China. Entre 2002 e 2003, um surto da doença resultou em mais de 8 000 casos e cerca de 800 mortes em todo o mundo."
2010 - Fundação Rockfeller, Lockstep. https://www.rockefellerfoundation.org/wp-content/uploads/Annual-Report-2010-1.pdf
Neste PDF da fundação Rockfeller, em seu próprio site, a fundação deixou claro o seu envolvimento em casos de ‘contenção’ de pandemias juntamente com a USAID (agência americana com nome ambíguo, como formalmente ‘United States Agency for International Development’, mas soando como ‘US Socorre’, mas sendo um braço do governo democrata que financiava interferências políticas diretas em vários países, como em intervenções no Brasil ), inclusive em relacionadas ao SARS, o mesmo sintoma dos coronavírus Sars-Cov e Sars-Cov-2 (o vírus propagado em 2019) e que causa o COVID-19.
Segundo eles:
“Integração entre Regiões e Países
A Fundação Rockefeler investiu US$ 22 milhões em sua Iniciativa de Redes de Vigilância de Doenças para ajudar a conter a disseminação de doenças infecciosas e pandemias, fortalecendo os sistemas nacionais, regionais e globais de vigilância e resposta a doenças. Dois programas-chave da Rockefeler — a Rede de Vigilância de Doenças da Bacia do Mekong e a Rede Integrada de Vigilância de Doenças da África Oriental — conectaram e capacitaram profissionais de saúde, epidemiologistas e autoridades de saúde pública em toda a região, levando a um aumento de seis vezes nos locais de vigilância de doenças transfronteiriças somente nos últimos três anos. Em 2010, a Rockefeler expandiu a bem-sucedida campanha transdisciplinar One Health, que a USAID e o Banco Asiático de Desenvolvimento adotaram como modelos. One Health refere-se à integração da ciência médica e veterinária para combater essas novas variedades de doenças zoonóticas que se movem e sofrem mutações rapidamente de animais para humanos. Essas colaborações criaram e fortaleceram uma rede regional crítica de saúde pública, enquanto as lições aprendidas foram exportadas entre disciplinas e países. Além de fortalecer os laços globais em saúde pública, a Rockefeler ajudou a elevar o nível de especialização e treinamento em campo. O Programa de Treinamento em Epidemiologia de Campo coloca graduados nos mais altos escalões do governo no Laos e no Vietnã, enquanto as bolsas da Rockefeler transformaram as ferramentas disponíveis para os médicos, permitindo-lhes utilizar o poder da internet para se comunicar e monitorar eventos, compreender contextos locais e analisar novos problemas. Finalmente, estamos aplicando ferramentas do século XXI para combater os desafios de saúde do século XXI.”
Julho de 2012 - Revista Mundo Estranho - Epidemias Citado em: https://super.abril.com.br/especiais/epidemia-o-risco-invisivel/
Página do site ME salva em Imagem no Voidcat
Houve uma ‘coincidência’, a revista Mundo Estranho em julho de 2012, entrevistou o até então doutorando em virologia, Átila Iamarino (do canal Nerdologia no Youtube - O mesmo cientista que fez diversas propagandas das vacinas no Brasil), para descrever um possível cenário de propagação de uma epidemia viral, a revista descreve com grande precisão os eventos de 2020, mas apontando o oposto da China, em que, na realidade, sua economia cresceu vertiginosamente.
Segundo eles:
“ 1 – A Ásia é o ponto de partida. Após várias mutações, um novo vírus surge hospedado em morcegos. As fezes que eles soltam no ar infectam guaxinins. Dos mercados da China, esses animais são levados vivos para serem abatidos em restaurantes. Estressados, eles arranham e mordem os cozinheiros, espalhando o vírus.
2 – O vírus adquire a capacidade de ser transmitido de homem para homem por via aérea – forma mais fácil de contágio. Além disso, o contágio se dá antes mesmo de o enfermo apresentar os sintomas. Assim, em média, o doente infecta cinco pessoas antes de ter febre, vômito, diarreia, desidratação e falta de ar.
3 – O governo chinês envia uma comissão para avaliar a doença misteriosa que acomete alguns vilarejos. A equipe volta sem resultados e não considera o surto alarmante até que três pesquisadores adoecem e um deles morre. A China não informa a Organização Mundial da Saúde (OMS) para não demonstrar fragilidade.
4 – Os sintomas são comuns e a doença só chama a atenção quando muita gente começa a morrer na mesma região. Ainda assim, demora para que médicos e enfermeiros percebam a ineficiência de antibióticos na cura – o que exclui a maioria das bactérias como agente causador. Testes com vírus comuns também dão negativo.
5 – O governo isola comunidades em que há focos da doença. Ninguém entra nas cidades e nenhum doente pode sair. Mas, como a misteriosa enfermidade demora quatro dias para mostrar seus sintomas, muitos doentes saem dos vilarejos sem saber que estão infectados, alastrando a epidemia.
6 – Doentes viajam de avião para grandes cidades, como Hong Kong. O fervilhante centro comercial, que atrai gente do mundo todo, é um polo de contágio e disseminação. Sem imaginar o risco que correm, pessoas são contaminadas e, ao voltar para seu local de origem, carregam o vírus para todos os continentes.
7 – Com a doença já fora de controle, começa uma corrida entre laboratórios e cientistas de grandes universidades para descobrir o agente causador. Mesmo com o vírus isolado, as vacinas demoram para ser feitas em larga escala, tornando impossível o atendimento à demanda mundial.
8 – Os países se isolam, mantendo esquemas de quarentena. Aeroportos são fechados e o turismo mundial cai a quase zero. A China sofre as piores consequências, com o fluxo de empresários para Hong Kong suspenso – gerando prejuízos de bilhões de dólares – e com o boicote a produtos alimentícios vindos da Ásia.
9 – Além dos 10% de casos letais, os milhões de doentes precisam de atendimento médico. Enquanto hospitais e cemitérios estão lotados, escolas, indústrias e comércio ficam paralisados por falta de profissionais. O transporte público também para e os trabalhadores que podem passam a trabalhar em casa.
10 – Nas nações pobres, quase 20% da população morre – e outros milhões são vitimados mesmo em países ricos. Parte dessa mortalidade ocorre por causa da doença, mas outro fator determinante é a crise financeira global. A produção de alimentos cai por falta de mão de obra.
Fontes: A História e Suas Epidemias e Pandemias – A Humanidade em Risco, de Stefan Cunha Ujvari; Pragas e Epidemias – Histórias de Doenças Infecciosas, de Antonio Carlos de Castro Toledo Jr. Consultoria: Stefan Ujvari Cunha, infectologista do Hospital Alemão Oswaldo Cruz; Paolo Zanotto, professor de virologia do Instituto de Ciências Biológicas (ICB) da USP; Átila Iamarino, doutorando em HIV-1 no ICB da USP. “



3. PRIMEIROS INDÍCIOS
10/2019 - Evento 201 - Durante os Jogos Militares Internacionais na China https://www.centerforhealthsecurity.org/event201/
Promovido por: - Bill & Melinda Gates Foundation - John Hopkins Institute - Fórum econômico mundial
"O evento simula a liberação de um coronavírus novo do tipo zoonótico transmitido por morcegos para porcos e por fim para humanos. Eventualmente ele se torna muito transmissível entre humanos levando a uma pandemia severa. O vírus é muito parecido com o vírus da SARS, mas se transmite muito mais facilmente entre pessoas devido a sintomas muito mais leves destas."
Também mencionado por: Jornal Estadão
Sobre o "Movimento antivacina"
05/12/2017 - Movimento antivacina: como surgiu e quais consequências ele pode trazer? https://www.uol.com.br/universa/noticias/redacao/2017/12/05/o-que-o-movimento-antivacina-pode-causar.htm?cmpid=copiaecola
23/03/2019 - "Instagram bloqueia hashtags e conteúdo antivacinação" https://canaltech.com.br/redes-sociais/instagram-bloqueia-hashtags-e-conteudo-antivacinacao-135411/
23/05/2021 - Novos dados sobre pesquisadores de Wuhan aumentam debate sobre origens da Covid https://www.cnnbrasil.com.br/saude/novos-dados-sobre-pesquisadores-de-wuhan-aumentam-debate-sobre-origens-da-covid/
"A China relatou à Organização Mundial da Saúde que o primeiro paciente com sintomas semelhantes aos de Covid-19 foi registrado em Wuhan em 8 de dezembro de 2019"
01/02/2020 - O que aconteceu desde que o novo coronavírus foi descoberto na China https://exame.com/ciencia/o-que-aconteceu-desde-que-o-novo-coronavirus-foi-descoberto-na-china/
"O primeiro alerta foi recebido pela Organização Mundial da Saúde (OMS) em 31 de dezembro de 2019"
15/09/2020 - YouTube diz que vai remover vídeos com mentiras sobre vacina contra COVID-19 https://gizmodo.uol.com.br/youtube-remover-videos-mentiras-vacina-covid-19/
"O YouTube anunciou na quarta-feira (14) que estenderá as regras atuais sobre mentiras, propaganda e teorias da conspiração sobre a pandemia do coronavírus para incluir desinformação sobre as vacinas contra a doença.
De acordo com a Reuters, a gigante do vídeo diz que agora vai proibir conteúdos sobre vacinas contra o coronavírus que contradizem “o consenso de especialistas das autoridades de saúde locais ou da OMS”, como afirmações falsas de que a vacina é um pretexto para colocar chips de rastreamento nas pessoas ou que irá matar ou esterilizar quem tomar."
*07/01/2021 - YouTube vai punir canais que promovem mentiras sobre eleições – incluindo os de Trump https://olhardigital.com.br/2021/01/07/noticias/youtube-vai-punir-canais-que-promovem-mentiras-sobre-eleicoes-incluindo-os-de-trump/
"O YouTube anunciou que vai punir canais que promovem mentiras sobre as eleições, removendo sumariamente qualquer vídeo que contenha desinformação e, ao mesmo tempo, advertindo com um “strike” o canal que o veicular. A medida já está valendo e a primeira “vítima” é ninguém menos que o ex-presidente americano, Donald Trump.
A medida não é exatamente nova, mas foi novamente comunicada e reforçada pelo YouTube na quarta-feira (6), após os eventos de invasão do Capitólio, em Washington, onde o presidente eleito Joe Biden participava da cerimônia que confirmava a sua vitória nas eleições de novembro de 2020. A ocasião ficou marcada pela tentativa de invasão de correligionários de Trump, que entraram no edifício em oposição à nomeação do novo presidente. Uma mulher acabou sendo morta pela polícia que protegia o local.
O ex-presidente Donald Trump teve vídeos banidos de seu canal no YouTube após os eventos de ontem (6) no capitólio."
4. FIGURAS CENTRAIS
Bill Gates
- Bill Gates diz 'não' a abrir patentes de vacinas https://www.frontliner.com.br/bill-gates-diz-nao-a-abrir-patentes-de-vacinas/
"Bill Gates, um dos homens mais ricos do mundo, cuja fundação tem participação na farmacêutica alemã CureVac, produtora de vacina mRNA para prevenção de covid-19, disse não acreditar que a propriedade intelectual tenha algo a ver com o longo esforço global para controlar a pandemia."
João Doria - Governo de São Paulo
26/07/2017 - João Dória vai a China conhecer drones para ampliar segurança eletrônica na capital paulista https://jc.ne10.uol.com.br/blogs/jamildo/2017/07/26/joao-doria-vai-china-conhecer-drones-para-ampliar-seguranca-eletronica-na-capital-paulista/
02/08/2019 - Governo de SP fará Missão China para ampliar cooperação e atrair investimentos https://www.saopaulo.sp.gov.br/spnoticias/governo-de-sao-paulo-detalha-objetivos-da-missao-china/
20/11/2019 - Doria se encontra com chineses das gigantes CREC e CRCC e oferece concessões de rodovia, metrô e ferrovia https://diariodotransporte.com.br/2019/11/20/doria-se-encontra-com-chineses-das-gigantes-crec-e-crcc-e-oferece-concessoes-de-rodovia-metro-e-ferrovia/
25/01/2020 - "Chineses serão agressivos" nas privatizações em SP até 2022, afirma Dória https://noticias.uol.com.br/colunas/jamil-chade/2020/01/25/entrevista-joao-doria-privatizacoes-sao-paulo-china.htm
O governador de São Paulo, João Doria, afirma que vai acelerar os programas de desestatização no estado em 2020 e acredita que concessões e vendas poderão permitir uma arrecadação de pelo menos R$ 40 bilhões. Nesse processo, o governador avalia que a China deve atuar de forma agressiva e que aprofundará sua posição de maior parceira comercial do estado, se distanciando de americanos e argentinos.
29/06/2020 - Doria estabelece multa para quem estiver sem máscara na rua em SP https://veja.abril.com.br/saude/doria-estabelece-multa-para-quem-estiver-sem-mascara-na-rua/
24/12/2020 - Doria é flagrado sem máscara e fazendo compras em Miami https://pleno.news/brasil/politica-nacional/doria-e-flagrado-sem-mascara-e-fazendo-compras-em-miami.html
"Foto do governador de São Paulo sem o item de proteção viralizou nas redes"
07/06/2021 - Doria é criticado na internet por tomar sol sem máscara em hotel no Rio https://vejasp.abril.com.br/cidades/doria-e-criticado-na-internet-por-tomar-sol-sem-mascara-em-hotel-no-rio/
30/09/2020 - Governo de SP assina contrato com Sinovac e prevê vacina para dezembro https://agenciabrasil.ebc.com.br/saude/noticia/2020-09/governo-de-sp-assina-contrato-com-sinovac-e-preve-vacina-para-dezembro
O governador de São Paulo, João Doria, e o vice-presidente da laboratório chinês Sinovac, Weining Meng, assinaram hoje (30), um contrato que prevê o fornecimento de 46 milhões de doses da vacina CoronaVac para o governo paulista até dezembro deste ano.
O contrato também prevê a transferência tecnológica da vacina da Sinovac para o Instituto Butantan, o que significa que, o instituto brasileiro poderá começar a fabricar doses dessa vacina contra o novo coronavírus. O valor do contrato, segundo o governador João Doria é de US$ 90 milhões.
20/10/2020 - Coronavac terá mais de 90% de eficácia, afirmam integrantes do governo paulista https://www.cnnbrasil.com.br/saude/2020/12/20/coronavac-tera-mais-de-90-de-eficacia-afirmam-integrantes-do-governo
24/10/2020 - Não esperamos 90% de eficácia da Coronavac’, diz secretário de saúde de SP https://www.cnnbrasil.com.br/saude/2020/12/24/nao-esperamos-90-de-eficacia-da-coronavac-diz-secretario-de-saude-de-sp
07/01/2021 - Vacina do Butantan: eficácia é de 78% em casos leves e 100% em graves https://www.cnnbrasil.com.br/saude/2021/01/07/vacina-do-butantan-eficacia-e-de-78-em-casos-leves-e-100-em-graves
09/01/2021 - Não é hora de sermos tão cientistas como estamos sendo agora https://g1.globo.com/sp/sao-paulo/video/nao-e-hora-de-sermos-tao-cientistas-como-estamos-sendo-agora-diz-secretario-de-saude-de-sp-9166405.ghtml
10/01/2021 - Dados da Coronavac relatados à Anvisa não estão claros, diz médico https://www.cnnbrasil.com.br/saude/2021/01/10/dados-da-coronavac-relatados-a-anvisa-nao-estao-claros-diz-medico
"O diretor do Laboratório de Imunologia do Incor, Jorge Kalil, reforçou que faltaram informações sobre a Coronavac nos dados divulgados à Anvisa"
12/01/2021 - New Brazil data shows disappointing 50,4% efficacy for China’s Coronavac vaccine [Novos dados do Brasil mostram eficácia decepcionante de 50,4% para a vacina CoronaVac da China] https://www.reuters.com/article/us-health-coronavirus-brazil-coronavirus/new-brazil-data-shows-disappointing-504-efficacy-for-chinas-coronavac-vaccine-idUSKBN29H2CE
13/01/2021 - Eficácia da Coronavac: 50,38%, 78% ou 100%? https://blogs.oglobo.globo.com/lauro-jardim/post/5038-78-ou-100.html
“De acordo com interlocutores que participaram tanto do anúncio de ontem como da semana passada, quem pressionou para que os dados de 78% e 100% fossem liberados foi João Dória.”
07/05/2021 - Covid-19: Doria toma primeira dose da vacina CoronaVac https://veja.abril.com.br/saude/covid-19-doria-toma-primeira-dose-da-vacina-coronavac/
04/06/2021 - Doria é vacinado com a segunda dose da CoronaVac em São Paulo https://noticias.uol.com.br/politica/ultimas-noticias/2021/06/04/doria-e-vacinado-com-a-segunda-dose-da-coronavac-em-sao-paulo.htm
15/07/2021 - Doria testa positivo para a Covid-19 pela 2ª vez https://www.correiobraziliense.com.br/politica/2021/07/4937833-doria-testa-positivo-para-covid-19-pela-segunda-vez.html
"Governador de São Paulo já havia sido diagnosticado com a doença no ano passado. Ele diz que, apesar da infecção, se sente bem, o que atribui ao fato de ter sido vacinado com duas doses da Coronavac"
06/08/2021 - CPI recebe investigação contra Doria por compra de máscara sem licitação https://www.conexaopoder.com.br/nacional/cpi-recebe-investigacao-contra-doria-por-compra-de-mascara-sem-licitacao/150827
"Empresa teria usado o nome de Alexandre Frota para vender máscaras ao governo de SP. Doria nega informação"
Renan Filho
(filho do Renan Calheiros)
25/07/2019 - Governador Renan Filho vai à China em busca de investimentos para o estado https://www.tnh1.com.br/videos/vid/governador-renan-filho-vai-a-china-em-busca-de-investimentos-para-o-estado/
20/03/2020 - Governadores do NE consultam China e pedem material para tratar covid-19 https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2020/03/20/governadores-do-ne-consultam-china-e-pedem-material-para-tratar-covid-19.htm
5. Narrativas, restrições e proibições
17/12/2020 - STF decide que vacina contra a covid pode ser obrigatória, mas não forçada https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2020/12/17/stf-julga-vacinacao-obrigatoria.htm?cmpid=copiaecola
"O STF (Supremo Tribunal Federal) decidiu, em julgamento hoje, que o Estado pode determinar a obrigatoriedade da vacinação contra a covid-19. Porém fica proibido o uso da força para exigir a vacinação, ainda que possam ser aplicadas restrições a direitos de quem recusar a imunização.
Dez ministros foram favoráveis a obrigatoriedade da vacinação, que poderá ser determinada pelo governo federal, estados ou municípios. As penalidades a quem não cumprir a obrigação deverão ser definidas em lei."
27/07/2021 - Saiba que países estão adotando 'passaporte da vacina' para suspender restrições https://www.cnnbrasil.com.br/internacional/2021/07/27/saiba-que-paises-estao-adotando-passaporte-da-vacina-para-suspender-restricoes
" - Israel - Uniao Europeia - Áustria - Dinamarca - Eslovênia - França - Grécia - Irlanda - Itália - Letônia - Lituânia - Luxemburgo - Holanda - Portugal - Japão - Coreia do sul"
18/06/2021 - O que é o passaporte da vacina que Bolsonaro quer vetar? https://noticias.uol.com.br/politica/ultimas-noticias/2021/06/18/uol-explica-o-que-e-o-passaporte-da-vacina-que-opoe-bolsonaro-e-damares.htm
"O Brasil poderá ter um certificado de imunização futuramente. Aprovado no Senado na semana passada, o "passaporte da vacina", como é chamado, prevê identificar pessoas vacinadas para que entrem em locais públicos ou privados com possíveis restrições."
6. Vacinas
Alegações iniciais
- CoronaVac, Oxford e Pfizer: veja diferenças entre as vacinas contra covid noticias.uol.com.br/saude/ultimas-noticias/redacao/2021/05/11/diferencas-vacinas-covid-brasil.htm
" - CoronaVac (Butantan/Sinovac - Chinesa) Com virus inativo 50,38% de eficácia 2 doses
-
Covishield - 'AstraZeneca' (Fiocruz/Astrazenica/Oxford - Britânica) Com virus não replicante 67% de eficácia 2 doses
-
ComiRNAty - 'Pfizer' (Pfizer - Americana / BioNTech - Alemã) Com RNA mensageiro 96% de eficácia 2 doses"
Riscos diretos
15/06/2021 - Trombose após vacinação com AstraZeneca: Quais os sintomas e como se deve atuar? https://www.istoedinheiro.com.br/trombose-apos-vacinacao-com-astrazeneca-quais-os-sintomas-e-como-se-deve-atuar/
"Agências europeias estão reticentes com a vacina da AstraZeneca. Ela chegou a ser desaconselhada a pessoas com idade inferior a 60 anos, e um alto funcionário da Agência Europeia de Medicamentos declarou que era melhor deixar de administrar a vacina deste laboratório em qualquer idade quando há alternativas disponíveis, devido aos relatos de trombose após a primeira dose, apesar de raros."
11/05/2021 - CoronaVac, Oxford e Pfizer: veja diferenças entre as vacinas contra covid https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2021/05/11/diferencas-vacinas-covid-brasil.htm
"Na terça-feira (12), o Ministério da Saúde determinou a suspensão da aplicação da vacina de Oxford/AstraZeneca para gestantes e puérperas com comorbidades. A decisão segue recomendação da Anvisa, que apura a morte de uma grávida de 35 anos que tomou o imunizante e teve um AVC (acidente vascular cerebral)."
30/07/2021 - Pfizer representa o mesmo risco de trombose que a Astrazeneca, aponta levantamento https://panoramafarmaceutico.com.br/pfizer-representa-o-mesmo-risco-de-trombose-que-a-astrazeneca-aponta-levantamento/
7. CRIMES
Crimes da Pfizer
18/11/2020 Não listado no google - Os Crimes documentados da produtora de vacinas de Covid - Pfizer [INGLÊS] https://www.dmlawfirm.com/crimes-of-covid-vaccine-maker-pfizer-well-documented/
"A velocidade com que a vacina Covid da Pfizer foi produzida, a ausência de estudos em animais, testes de controle randomizados e outros testes e procedimentos padrão usuais para um novo medicamento são, no mínimo, preocupantes. Além disso, todos os fabricantes de vacinas Covid receberam imunidade legal para quaisquer ferimentos ou mortes que possam causar. Se essas vacinas são tão seguras quanto promovidas, por que seus fabricantes precisam de imunidade geral?"
"A Pfizer, uma empresa farmacêutica que parece ter ganhado na loteria para produzir a primeira vacina Covid-19, está atualmente lutando contra centenas de ações judiciais sobre o Zantac, um popular medicamento contra azia. Os processos da Zantac afirmam que a droga popular pode estar contaminada com uma substância cancerígena chamada N-nitrosodimetilamina (NDMA). Os processos Zantac são em aberto e em andamento, já que a farmacêutica está lutando contra eles; mas a Pfizer, sabemos, cometeu vários crimes ou transgressões pelos quais foi punida nos últimos anos. As falhas da empresa estão bem documentadas e vale a pena revisá-las neste momento crítico da história da humanidade, enquanto todos nós buscamos respostas."
A Pfizer recebeu a maior multa da história dos Estados Unidos como parte de um acordo judicial de US $ 2,3 bilhões com promotores federais por promover medicamentos erroneamente (Bextra, Celebrex) e pagar propinas a médicos complacentes. A Pfizer se confessou culpada de falsificar a marca do analgésico Bextra, promovendo o medicamento para usos para os quais não foi aprovado.
Na década de 1990, a Pfizer estava envolvida em válvulas cardíacas defeituosas que causaram a morte de mais de 100 pessoas. A Pfizer enganou deliberadamente os reguladores sobre os perigos. A empresa concordou em pagar US $ 10,75 milhões para acertar as acusações do departamento de justiça por enganar reguladores.
A Pfizer pagou mais de US $ 60 milhões para resolver um processo sobre o Rezulin, um medicamento para diabetes que causou a morte de pacientes de insuficiência hepática aguda.
No Reino Unido, a Pfizer foi multada em quase € 90 milhões por sobrecarregar o NHS, o Serviço Nacional de Saúde. A Pfizer cobrou do contribuinte um adicional de € 48 milhões por ano, pelo que deveria custar € 2 milhões por ano.
A Pfizer concordou em pagar US $ 430 milhões em 2004 para resolver acusações criminais de que havia subornado médicos para prescrever seu medicamento para epilepsia Neurontin para indicações para as quais não foi aprovado. Em 2011, um júri concluiu que a Pfizer cometeu fraude em sua comercialização do medicamento Neurontin. A Pfizer concordou em pagar $ 142,1 milhões para liquidar as despesas.
A Pfizer revelou que pagou quase 4.500 médicos e outros profissionais médicos cerca de US $ 20 milhões por falar em nome da Pfizer.
Em 2012, a Comissão de Valores Mobiliários dos Estados Unidos - anunciou que havia chegado a um acordo de US $ 45 milhões com a Pfizer para resolver acusações de que suas subsidiárias haviam subornado médicos e outros profissionais de saúde no exterior para aumentar as vendas no exterior.
A Pfizer foi processada em um tribunal federal dos Estados Unidos por usar crianças nigerianas como cobaias humanas, sem o consentimento dos pais das crianças. A Pfizer pagou US $ 75 milhões para entrar em acordo no tribunal nigeriano pelo uso de um antibiótico experimental, o Trovan, nas crianças. A empresa pagou um valor adicional não divulgado nos Estados Unidos para liquidar as despesas aqui. A Pfizer violou o direito internacional, incluindo a Convenção de Nuremberg estabelecida após a Segunda Guerra Mundial, devido aos experimentos nazistas em prisioneiros relutantes.
Em meio a críticas generalizadas de roubar os países pobres em busca de drogas, a Pfizer prometeu dar US $ 50 milhões para um medicamento para a AIDS para a África do Sul. Mais tarde, no entanto, a Pfizer falhou em honrar essa promessa.
- Pfizer contract leaked!
[Contrato da Pfizer vazado]
 http://sanjeev.sabhlokcity.com/Misc/LEXO-KONTRATEN-E-PLOTE.pdf
http://sanjeev.sabhlokcity.com/Misc/LEXO-KONTRATEN-E-PLOTE.pdf
Segundo o contrato "o produto não deve ser serializado":
"5.5 Reconhecimento do comprador.
O Comprador reconhece que a Vacina e os materiais relacionados à Vacina, e seus componentes e materiais constituintes estão sendo desenvolvidos rapidamente devido às circunstâncias de emergência da pandemia de COVID-19 e continuarão a ser estudados após o fornecimento da Vacina ao Comprador nos termos deste Contrato. O Comprador reconhece ainda que os efeitos de longo prazo e eficácia da Vacina não são atualmente conhecidos e que pode haver efeitos adversos da Vacina que não são atualmente conhecidos. Além disso, na medida do aplicável, o Comprador reconhece que o Produto não deve ser serializado."
Crimes da AstraZeneca
21/06/2003 - AstraZeneca se declara culpada no esquema de médico de câncer https://www.nytimes.com/2003/06/21/business/astrazeneca-pleads-guilty-in-cancer-medicine-scheme.html
"A AstraZeneca, a grande empresa farmacêutica, se declarou culpada hoje de uma acusação de crime de fraude no sistema de saúde e concordou em pagar $ 355 milhões para resolver as acusações criminais e civis de que se envolveu em um esquema nacional para comercializar ilegalmente um medicamento contra o câncer de próstata.
O governo disse que os funcionários da empresa deram incentivos financeiros ilegais a cerca de 400 médicos em todo o país para persuadi-los a prescrever o medicamento Zoladex. Esses incentivos incluíram milhares de amostras grátis de Zoladex [...]"
27/04/2010 - Farmacêutica gigante AstraZeneca pagará US $ 520 milhões pelo marketing de medicamentos off-label https://www.justice.gov/opa/pr/pharmaceutical-giant-astrazeneca-pay-520-million-label-drug-marketing
"AstraZeneca LP e AstraZeneca Pharmaceuticals LP vão pagar $ 520 milhões para resolver as alegações de que a AstraZeneca comercializou ilegalmente o medicamento antipsicótico Seroquel para usos não aprovados como seguros e eficazes pela Food and Drug Administration (FDA), os Departamentos de Justiça e Saúde e Serviços Humanos A Equipe de Ação de Fiscalização de Fraudes em Saúde (HEAT) anunciou hoje. Esses usos não aprovados também são conhecidos como usos "off-label" porque não estão incluídos no rótulo do medicamento aprovado pela FDA."
- List of largest pharmaceutical settlements [Lista dos maiores acordos farmaceuticos] https://en.m.wikipedia.org/wiki/List_of_largest_pharmaceutical_settlements
8. CIENTISTAS
- Máscara Provoca Insuficiência Respiratória E Contaminação Microbiana… [Canal deletado] https://youtube.com/watch?v=eHu-pydSvDI
Não lembro mais a quem pertencia, mas provavelmente era de um médico falando do assunto. Creio ter sido do Dr. Paulo Sato, por essa temática ter sido abordada por ele, mas ao abrir o site aparece somente:
"Este vídeo foi removido por violar as diretrizes da comunidade do YouTube"
Dr. Paulo Sato
- USAR ou NÃO USAR a CUECA do seu governador no rosto https://fb.watch/7NPP_7rS5S/ https://www.facebook.com/AdoniasSoaresBR/videos/1347904292291481/ Adonias Soares entrevista ao Dr. Paulo Sato sobre as máscaras, em que é simulado o efeito da respiração prolongada das máscaras no organismo com o uso de águas de torneira, natural, gaseificada (com gás carbônico) e antioxidante, em que a com gás carbônico (PH 4 - Ácido) representa o organismo humano, e na prática representa lesão corporal e iniciação de doenças.
Dr. Kary Mullis
(Criador do teste PCR)
- PCR nas palavras do seu inventor - Dr. Kary Mullis (legendado) https://www.youtube.com/watch?v=W1O52uTygk8
"Qualquer um pode testar positivo para quase qualquer coisa com um teste de PCR, se você executá-lo por tempo suficiente… Com PCR, se voce fizer isso bem, você pode encontrar quase tudo em qualquer pessoa… Isso não te diz que você está doente."
- Kary Mullis DESTRUYE a Anthony Fauci lbry://@CapitalistChile#0/Kary-Mullis---Fauci#5
"Ele [...] não entende de medicina e não deveria estar onde está. A maioria dos que estão acima são só administrativos e não têm nem ideia do que ocorre aqui em baixo e essas pessoas tem uma agenda que não é a que gostaríamos que tivessem, dado que somos nós os que pagamos a eles para que cuidem da nossa saúde. Têm uma agenda pessoal."
Dra. Li-Meng Yan
- Dra. Li-Meng Yan: O vírus foi criado em laboratório com um objetivo: Causar dano. https://youtu.be/pSXp3CZnvOc
Dr. Joe Roseman
- Cientista Phd Dr Joe Roseman faz seríssimas advertencias sobre a picada https://youtu.be/0PIXVFqJ_h8
Dr. Robert Malone
- As vacinas podem estar causando ADE - Dr. Robert Malone https://odysee.com/@AkashaComunidad:f/Las_vacunas_pueden_estar_causando_ADE_magnificaci%C3%B3n_mediada_por:f lbry://@Información.#b/Drrm#9
Dr. Robert Malone, um dos três inventores da tecnologia de RNAm que se usa de forma farmacêutica. No vídeo fala sobre os efeitos de ADE (realce dependente de anticorpos) que estão ocorrendo com as vacinas. Nas palavras do Dr. Malone, já não é somente uma hipótese, mas baseada nos conhecimentos gerados nas provas e ensaios pré clínicos, com as vacinas contra o primeiro vírus da SARS.
Dr. Luc Montagnier
- Dr. Luc Montagnier, virologista, prêmio Nobel de medicina, um dos descobridores do vírus HIV, afirma: "a vacinação em massa está criando as novas variantes' (@medicospelavida , telegram)
CASOS DOCUMENTADOS
13/09/2021 - 13 de setembro de 2021 - Carta aberta ao Ministro da Saúde por Arlene Ferrari Graf, mãe de Bruno Oscar Graf https://telegra.ph/Carta-aberta-ao-Ministro-da-Sa%C3%BAde-09-13
Também em: Gazeta do Povo
O texto de uma mãe discorrendo sobre o filho dela, Bruno Oscar Graf, ter ANTI-HEPARINA PF4 AUTO-IMUNE e ter vindo a falecer por reação à vacina.
11/05/2021 - Rio notifica morte de grávida vacinada com imunizante Oxford https://www.terra.com.br/noticias/coronavirus/rio-notifica-morte-de-gravida-vacinada-com-imunizante-oxford,415b9b0c49169427ac2f90ae3765c057e9suy3qn.html
"Vítima não apresentava histórico de doença circulatória nem sofria de nenhuma doença viral; relação será investigada"
13/08/2021 - Cruzeiro com 4.336 pessoas tem 27 contaminados com Covid-19 em Belize https://paranaportal.uol.com.br/geral/cruzeiro-com-4-336-pessoas-tem-27-contaminados-com-covid-19-em-belize/amp/
"Segundo um comunicado do Conselho de Turismo de Belize emitido na quarta-feira (11), 26 contaminados são da tripulação e um é passageiro. A maioria é assintomática e os 27 estão vacinados."
9. ALEGAÇÕES DIRETAS
09/2021 - Setembro de 2021 - BOMBA: Ex-membro do Partido Comunista da China revela que o primeiro surto da Covid foi “intencional” https://terrabrasilnoticias.com/2021/09/bomba-ex-membro-do-partido-comunista-da-china-revela-que-o-primeiro-surto-da-covid-foi-intencional/
01/03/2023 - 1 de Março de 2023 - O chefe do FBI, Christopher Wray, diz que vazamento de laboratório na China é muito provável https://www.bbc.com/news/world-us-canada-64806903
26/12/2024 - 26 de Dezembro 2024 - FBI ‘não tem permissão para informar Biden’ sobre a teoria de vazamento de laboratório da Covid https://www.thetimes.com/world/us-world/article/fbi-not-allowed-to-brief-biden-on-covid-lab-leak-theory-8df9mr997
O FBI concluiu com "confiança moderada" que a COVID-19 pode ter sido criada em laboratório, com base em parte na análise genômica conduzida por cientistas do Centro Nacional de Inteligência Médica.
-
 @ cae03c48:2a7d6671
2025-06-06 15:00:57
@ cae03c48:2a7d6671
2025-06-06 15:00:57Bitcoin Magazine

President Trump’s Truth Social Files S-1 Form For Bitcoin ETFToday, Trump Media and Technology Group Corp. (Nasdaq, NYSE Texas: DJT) filed with the US Securities and Exchange Commission (SEC) a Form S-1 for their upcoming Truth Social Bitcoin ETF.

The ETF, which will hold bitcoin directly, is designed to track the bitcoin’s price performance.
“Truth Social Bitcoin ETF, B.T. is a Nevada business trust that issues beneficial interests in its net assets,” stated the Form S-1. “The assets of the Trust consist primarily of bitcoin held by a custodian on behalf of the Trust. The Trust seeks to reflect generally the performance of the price of bitcoin.”
The ETF is sponsored by Yorkville America Digital, LLC and will trade under NYSE Arca. The Trust’s assets primarily consist of bitcoin held by Foris DAX Trust Company, LLC, the designated bitcoin custodian. Crypto.com will act as the ETF’s prime execution agent and liquidity provider.
“Shares will be offered to the public from time to time at varying prices that will reflect the price of bitcoin and the trading price of the Shares on New York Stock Exchange Arca, Inc. at the time of the offer,” mentioned the Form S-1.
While the ETF offers investors a regulated avenue for bitcoin exposure, the Trust warned of several risks related to digital assets:
- Loss, theft, or compromise of private keys could result in permanent loss of bitcoin.
- Bitcoin’s reliance on blockchain and Internet technologies makes it vulnerable to disruptions and cyber threats.
- Environmental and regulatory pressures tied to high electricity use in bitcoin mining could impact market stability.
- Potential forks or protocol failures in the Bitcoin Network may lead to volatility and uncertainty in asset value.
Last week, during an interview at the 2025 Bitcoin Conference, Donald Trump Jr. announced that TMTG and Truth Social were forming a Bitcoin treasury with $2.5 billion. “We’re seriously on crypto—we’re seriously on Bitcoin,” said Trump Jr. “We’re in three major deals. I believe we’re at the beginning of what will be the future of finance. And the opportunity is massive.”
The day after that interview, Eric Trump and Donald Trump Jr., joined by American Bitcoin Executive Chairman and Board Member Mike Ho, CEO Matt Prusak, and Altcoin Daily founder Aaron Arnold, discussed the future of Bitcoin.
“The whole system is broken and now all of the sudden you have crypto which solves all the problems,” commented Eric Trump. “It makes everything cheaper, it makes everything faster, it makes it safer, it makes it more transparent. It makes the whole system more functional.“
“Everybody wants Bitcoin. Everybody is buying Bitcoin,” Eric added.
This post President Trump’s Truth Social Files S-1 Form For Bitcoin ETF first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ eb0157af:77ab6c55
2025-06-18 01:02:02
@ eb0157af:77ab6c55
2025-06-18 01:02:02A new study by Kraken reveals how cryptocurrency investors perceive security as the main challenge in self-managing their digital assets.
According to The Block, a recent survey conducted by crypto exchange Kraken found that nearly half of respondents consider themselves the primary risk factor for their own crypto security. The research, which surveyed 789 participants, highlights that 48% of users see their own actions as the greatest threat to their investments in digital assets, surpassing concerns about external theft or fraud.
Kraken’s report underlines how personal responsibility in security management forces users to take full control of their digital funds. However, the study suggests that this autonomy can also become a source of anxiety for many investors.
Nick Percoco, Chief Security Officer at Kraken, commented on the findings, noting that “a lack of confidence in personal crypto security is capping the growth of the industry.” According to Percoco, unlocking the full potential of cryptocurrencies will require users to embrace self-custody and consistently invest in strong security habits.
Technologies to strengthen security
Despite the concerns highlighted in the study, 31% of participants expressed optimism about future technologies that could improve crypto security. Among the most promising solutions identified:
- advanced biometric systems for user authentication;
- multi-factor authentication to secure wallet access;
- AI-based fraud detection systems to prevent attacks.
Data and case studies
Kraken’s research emerges in a context where security threats remain a pressing reality. FBI data shows that in 2024, nearly 150,000 reports of crypto-related internet fraud resulted in $9.3 billion in losses. Older users, particularly those over 60, proved especially vulnerable, accounting for $3 billion in crypto-related financial fraud losses on their own.
The post Kraken study: 48% of users fear themselves in managing and securing their funds appeared first on Atlas21.
-
 @ 3eab247c:1d80aeed
2025-06-05 08:51:39
@ 3eab247c:1d80aeed
2025-06-05 08:51:39Global Metrics
Here are the top stats from the last period:
- Total Bitcoin-accepting merchants: 15,306 → 16,284
- Recently verified (1y): 7,540 → 7,803 (the rest of our dataset is slowly rotting; help us before it's too late!)
- Avg. days since last verification: 398 → 405 (more mappers, please)
- Merchants boosted: 22 (for a total of 4,325 days, someone is feeling generous)
- Comments posted: 34
Find current stats over at the 👉 BTC Map Dashboard.
Merchant Adoption
Steak n’ Shake
The US 🇺🇸 is a massive country, yet its BTC Map footprint has been lagging relative to other countries ... that is until now!

In what came as a nice surprise to our Shadowy Supertaggers 🫠, the Steak ’n Shake chain began accepting Bitcoin payments across hundreds of its locations nationwide (with some international locations too).
According to CoinDesk, the rollout has been smooth, with users reporting seamless transactions powered by Speed.
This marks a significant step towards broader Bitcoin adoption in the US. Now to drop the capital gains tax on cheesburgers!
SPAR Switzerland
In other chain/franchise adoption news, the first SPAR supermarket in Switzerland 🇨🇭 to begin accepting Bitcoin was this one in Zug. It was quickly followed by this one in Rossrüti and this one in Kreuzlingen, in what is believed to be part of a wider roll-out plan within the country powered by DFX's Open CryptoPay.
That said, we believe the OG SPAR crown goes to SPAR City in Arnhem Bitcoin City!
New Features
Merchant Comments in the Web App
Web App users are now on par with Android users in that they can both see and make comments on merchants.
This is powered by our tweaked API that enables anyone to make a comment as long as they pass the satswall fee of 500 sats. This helps keep spam manageable and ensure quality comments.
And just in case you were wondering what the number count was on the merchant pins - yep, they're comments!
Here is an 👉 Example merchant page with comments.
Merchant Page Design Tweaks
To support the now trio of actions (Verify, Boost & Comment) on the merchant page, we've re-jigged the design a little to make things a little clearer.
What do you think?
Technical
Codebase Refactoring
Thanks to Hannes’s contributions, we’ve made progress in cleaning-up the Web App's codebase and completing long overdue maintenance. Whilst often thankless tasks, these caretaking activities help immensely with long-term maintainability enabling us to confidently build new features.
Auth System Upgrades
The old auth system was held together with duct tape and prayers, and we’re working on a more robust authentication system to support future public API access. Updates include:
- Password hashing
- Bearer token support
- Improved security practices
More enhancements are in progress and we'll update you in the next blog post.
Better API Documentation
Instead of relying on tribal knowledge, we're finally getting around to writing actual docs (with the help/hindrance of LLMs). The "move fast, break everything" era is over; now we move slightly slower and break slightly less. Progress!
Database Improvements
We use SQLite, which works well but it requires careful handling in async Rust environments. So now we're untangling this mess to avoid accidental blocking queries (and the ensuing dumpster fires).
Backup System Enhancements
BTC Map data comes in three layers of fragility:
- Merchants (backed up by OS - the big boys handle this)
- Non-OSM stuff (areas, users, etc. - currently stored on a napkin)
- External systems (Lightning node, submission tickets - pray to Satoshi)
We're now forcing two core members to backup everything, because redundancy is good.
Credits
Thanks to everyone who directly contributed to the project this period:
- Comino
- descubrebitcoin
- Hannes
- Igor Bubelov
- Nathan Day
- Rockedf
- Saunter
- SiriusBig
- vv01f
Support Us
There are many ways in which you can support us:
-
Become a Shadowy Supertagger and help maintain your local area or pitch-in with the never-ending global effort.
-
Consider a zapping this note or make a donation to the to the project here.
-
 @ eb0157af:77ab6c55
2025-06-18 00:02:25
@ eb0157af:77ab6c55
2025-06-18 00:02:25The banking giant is exploring an expansion of its blockchain services, focusing on digital payments and currencies.
JPMorgan Chase has filed a new trademark application for the name “JPMD.” The filing was submitted on June 15 to the United States Patent and Trademark Office (USPTO).
The application, filed by JPMorgan Chase Bank, N.A., covers a broad range of services related to digital assets and blockchain technology. These include the issuance of digital currencies, electronic payment processing, and financial custody services — all of which suggest a possible new stablecoin initiative for JPMorgan.
Experience with JPM Coin
This move wouldn’t be JPMorgan’s first foray into blockchain-based finance. The bank already operates JPM Coin, a dollar-pegged stablecoin used to enable instant transactions between institutional clients. The token runs on Quorum, a private blockchain network developed in-house by JPMorgan and based on Ethereum’s technology.
The registration of the JPMD trademark comes as JPMorgan and other major U.S. banks are considering a collaborative stablecoin project through their jointly owned entities: Early Warning Services and The Clearing House.
Similarly, corporations like Walmart and Amazon are mulling the creation of their own stablecoins.
The post JPMorgan files trademark for ‘JPMD’: a new stablecoin on the horizon for the American bank appeared first on Atlas21.
-
 @ c11cf5f8:4928464d
2025-06-17 22:27:17
@ c11cf5f8:4928464d
2025-06-17 22:27:17NOW OPENWelcome stacker and cowboys to the second edition of this Sellers & Business Club series!
You're in the right place if you're serious about growing your business, or starting a new one. Let's discuss your preferred Bitcoin Business Models!
You'll find everything you need to move faster, sell smarter, and stay ahead of trends—with useful insights for every step of the way, community-powered learning posts, insights, and support from other sellers.
Thank you @BTCLNAT, @car, @fauxfoe, @lunin and @021f3af1a6 (ai bot?) for participating in the previous edition and other stackers[^1] that have been active in the ~AGORA marketplace.
Your insights and questions are welcome. I'll be opening with some questions:
-
What are your latest wins?
-
What are you dealing with lately?
-
What current obstacles that are keeping you away from succeeding?
[^1]: FIY: @watchmancbiz @globalmerchant @midnightshipper @thebullishbitcoiner @realtrader @sandelllevy_ @thecommoner @matusalem @siggy47 @veintiuno @needcreations_ @globalthreat @profullstack @cryotosensei @catoshi @kr @pleblab @fabs @lendasat @Akg10s3 @bytephysics @byzantine @96dffdc39e @thewildhustle @0xbitcoiner @gpvansat @south_korea_ln @rideandsmile @btclnat @bitcoinerrorlog @wakingseason @tinstrmedia @pictureroom @isolabellart @jpedro64453 @herschel
https://stacker.news/items/1008929
-
-
 @ 2b998b04:86727e47
2025-05-22 02:45:34
@ 2b998b04:86727e47
2025-05-22 02:45:34I recently released my first open-source tool:\ 👉 nostr-signal-filter
It fetches and formats your latest top-level Nostr note or long-form article, cleans up any embedded links using TinyURL, and outputs a clean version ready for reposting to:
-
LinkedIn
-
Facebook
-
X / Twitter
⚙️ Built for Simplicity
The stack is intentionally minimal:
-
Python + WebSockets + Bech32
-
TinyURL API for link shortening
-
Dockerized CLI usage:
bashCopyEdit
docker run --rm -e PUBKEY=npub1yourpubkeyhere nostr-fetcher > latest.mdFrom idea to working repo took under 3 hours — including debugging, Docker tweaks, README cleanup, and tagging a clean release.\ \ This most certainly would have taken much longer if I had done this all without ChatGPTs' help.\ \ 🖼️ Example Output (
latest.md)textCopyEdit
🕒 2025-05-20 22:24:17 📄 Note (originally posted on Nostr/primal.net) --- 🚨 New long-form drop: AI Isn’t Magic. It’s Engineering. How I use ChatGPT like any other tool in the stack — with iteration, discernment, and real output. Read it here: https://tinyurl.com/ynv7jq6g ⚡ Zaps appreciated if it resonates. --- 🔗 View on Nostr: https://tinyurl.com/yobvaxkx
🧪 Where I Used It
- ✅ Facebook: clean rendering with preview ->
- ✅ X/Twitter: teaser + link (had to truncate for character limit) ->
https://x.com/AndyGStanton/status/1925045477172773136
🙌 Try It Yourself
If you're publishing on Nostr but still sharing on legacy platforms:
👉 github.com/andrewgstanton/nostr-signal-filter
-
Clean output
-
Easy to run
-
Portable via Docker
All it needs is your
npub.
⚡ Zap Me If You Found This Useful
If this tool saved you time — or if it sparked ideas for your own Nostr publishing stack —\ send a zap my way. I’m always looking to connect with other creators who value signal > noise.
🔗 Zap on Primal -> https://primal.net/andrewgstanton
🔭 Next Features (I’d Love Help With)
-
Archive all notes + articles (not just the latest 50) to
archive.md -
Function to shorten links in any text block
-
Output
post.mdfor any given Nostr event ID (not just latest) -
Optional API integration to post directly to LinkedIn or X
Built with ChatGPT’s help.\ Iterated. Published. Cross-posted.\ That’s proof of work.
-
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-17 22:10:10
@ 5d4b6c8d:8a1c1ee3
2025-06-17 22:10:10https://youtu.be/KwzHW-c5h7M
This video's great and it includes interviews with Stan van Gundy and Shane Battier about how offensive and officiating changes have forced defenses to fundamentally change.
There's also some early discussion, centered on a clip of Rick Barry complaining about officiating, about how much better it would be if they would actually call travelling, carrying, and moving screens. I can't for the life of me understand why they don't call these things. The game would look so much better.
https://stacker.news/items/1008918
-
 @ 31a4605e:cf043959
2025-06-17 17:35:10
@ 31a4605e:cf043959
2025-06-17 17:35:10Desde a sua criação em 2008, Bitcoin tem sido visto como um desafio direto ao sistema bancário tradicional. Desenvolvido como uma alternativa descentralizada ao dinheiro fiduciário, Bitcoin oferece uma forma de armazenar e transferir valor sem depender de bancos, governos ou outras instituições financeiras. Essa característica faz com que seja considerado um símbolo de resistência contra um sistema financeiro que, ao longo do tempo, tem sido marcado por crises, manipulações e restrições impostas aos cidadãos.
Crise financeira de 2008 e o nascimento de Bitcoin
Bitcoin surgiu em resposta à crise financeira de 2008, um colapso que revelou as falhas do sistema bancário global. Bancos centrais imprimiram grandes quantidades de dinheiro para resgatar instituições financeiras irresponsáveis, enquanto milhões de pessoas perderam as suas casas, poupanças e empregos. Nesse contexto, Bitcoin foi criado como um sistema financeiro alternativo, onde não existe uma entidade central com o poder de manipular a economia em benefício próprio.
No primeiro bloco da blockchain ou timechain de Bitcoin, Satoshi Nakamoto incluiu a seguinte mensagem:
"The Times 03/Jan/2009 Chancellor on brink of second bailout for banks."
Essa frase, retirada de uma manchete de jornal da época, simboliza a intenção de Bitcoin de oferecer um sistema financeiro fora do controlo dos bancos e dos governos.
Principais razões pelas quais Bitcoin resiste ao sistema bancário
Descentralização: Ao contrário do dinheiro emitido por bancos centrais, Bitcoin não pode ser criado ou controlado por nenhuma entidade específica. A rede de utilizadores valida as transações de forma transparente e independente.
Oferta limitada: Enquanto os bancos centrais podem imprimir dinheiro sem limites, causando inflação e desvalorização da moeda, Bitcoin tem uma oferta fixa de 21 milhões de unidades, tornando-o resistente à depreciação artificial.
Impossibilidade de censura: Bancos podem bloquear contas e impedir transações a qualquer momento. Com Bitcoin, qualquer pessoa pode enviar e receber fundos sem pedir permissão a terceiros.
Autocustódia: Em vez de confiar os seus fundos a um banco, os utilizadores de Bitcoin podem armazenar as suas próprias moedas, sem risco de congelamento de contas ou falências bancárias.
Conflito entre bancos e Bitcoin
Ataques mediáticos: Grandes instituições financeiras frequentemente classificam Bitcoin como arriscado, volátil ou inútil, tentando desincentivar a sua adoção.
Regulação e repressão: Alguns governos, influenciados pelo setor bancário, têm criado restrições ao uso de Bitcoin, dificultando a sua compra e venda.
Criação de alternativas centralizadas: Muitos bancos centrais estão a desenvolver moedas digitais (CBDCs) que mantêm o controlo do dinheiro digital, mas sem oferecer a liberdade e a descentralização de Bitcoin.
Resumindo, o Bitcoin não é apenas uma moeda digital, mas um movimento de resistência contra um sistema financeiro que falhou repetidamente em proteger o cidadão comum. Ao oferecer uma alternativa descentralizada, transparente e resistente à censura, Bitcoin representa a liberdade financeira e desafia o monopólio dos bancos sobre o dinheiro. Enquanto o sistema bancário tradicional continuar a impor restrições e a controlar o fluxo de capital, Bitcoin permanecerá como um símbolo de independência e soberania financeira.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 73d8a0c3:c1853717
2025-06-18 03:57:48
@ 73d8a0c3:c1853717
2025-06-18 03:57:48[The following contains two excerpts from my Research/Novel/Expose on Redacted Science. I’m not a scientist. I’m a Chemical Engineer and data architect of 30 years. But this is real science, and someone made it go away. I wouldn’t have found it, except for.. well, you’ll have to read the research (still writing, but basically have 90% of the science explained)]
This is about how biology breaks down when pushed beyond design — and how some systems fight to keep going anyway. It has implications for:
• critical care medicine
• post-viral syndromes
• metabolic disease
• aging
• neuroinflammation
• psychiatric conditions (ADHD, depression, anxiety)
• and maybe even AI alignment (in how systems retain integrity under corrupt inputs)
We expect fungal research — especially around long-term host adaptations and stealth co-evolution — to become a major field of study. Why? Because all these chemical are making me live even when every organ in my body is not working the way it is supposed to work. Every Single One. What appears fringe today may soon be foundational. This isn't just about pathogens. It's about how biological, immunological, and behavioral systems interact under persistent pressure — including possible symbiosis, crowding effects, and neurological modulation.
Finding out what is and what is not going on is what science is about. Someone decided otherwise.
[Your Move]
What If?? [Theoretical Musing — basically, this is no longer a zero percent chance] • What if Candida albicans isn’t just a pathogen, but a legacy co-evolutionary organism — one that historically regulated population density, behavior, and reproduction during times of scarcity?
• What if the pituitary evolved in direct response to its influence — not just to manage reproduction, but to insulate cognition from fungal manipulation?
• What if its connection to cannabinoids, dopamine, and hunger isn’t accidental — but a chemical dialogue that shaped our very instincts?
• What if the rise in modern autoimmune, psychiatric, and neurodegenerative conditions is a side effect of our disrupted balance with fungal cohabitants?
• What if the “zombie” analogy isn’t hyperbole — but a primitive warning system encoded in our myths, whispering about a very real form of behavioral control?
These are speculative. But they are now in the non-zero zone.
And history has a pattern: first ridicule, then resistance, then recognition.
[You see, the coolest thing about this is that I am the proof. No getting out of it] [The even cooler thing is you made me, in a way. Even though I did do this to myself. You gave me a mind that wouldn't let go and just enough information to track it all down.]
This is what happens when you don’t give up.
When your organs stop working the way they’re supposed to — and something else takes over. Something old. Something hidden. Something that adapts.
This isn't just about illness anymore. It's about systems — biological, chemical, behavioral — pushed beyond design. And yet, somehow, still running.
That’s the mystery. That’s the threat. That’s the message.
We now live in a world where science is selected, symptoms are dismissed, and adaptation itself is misdiagnosed. But what if the system that kept me alive is one we were never meant to survive? What if it’s not just me?
What if the pathogen was the backup plan?
If you’ve read this far, you already know: I’m not asking for your permission. I’m not asking for your diagnosis.
I’m laying out the board.
Your move.
[Checkmate]
🕳️ #science #nostr #candida #aiAlignment #medicalmystery #buriedtruth
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 31a4605e:cf043959
2025-06-17 17:33:02
@ 31a4605e:cf043959
2025-06-17 17:33:02Bitcoin tem vindo a desempenhar um papel cada vez mais relevante em protestos e movimentos sociais em todo o mundo. Graças à sua natureza descentralizada, resistente à censura e independente do controlo governamental, Bitcoin tornou-se uma ferramenta valiosa para ativistas, organizações e cidadãos que lutam contra regimes opressivos ou sistemas financeiros restritivos.
Bitcoin como alternativa ao sistema financeiro tradicional
Nos últimos anos, governos e instituições bancárias têm utilizado restrições financeiras como uma forma de repressão política. Contas bancárias congeladas, doações bloqueadas e limitações a transações são algumas das estratégias utilizadas para enfraquecer movimentos sociais e protestos. Bitcoin oferece uma alternativa, permitindo que fundos sejam transferidos e armazenados sem a interferência de bancos ou governos.
Uma das principais vantagens de Bitcoin nestes contextos é a sua resistência à censura. Enquanto contas bancárias podem ser encerradas e serviços de pagamento centralizados podem ser pressionados a bloquear transações, Bitcoin funciona numa rede descentralizada, onde ninguém pode impedir que um utilizador envie ou receba fundos.
Exemplos do uso do Bitcoin em protestos
Hong Kong (2019-2020): Durante os protestos pró-democracia, ativistas enfrentaram restrições financeiras ao tentarem organizar manifestações e campanhas. Muitos recorreram a Bitcoin para evitar o rastreamento do governo chinês e garantir financiamento para as suas ações.
Canadá (2022): O movimento dos camionistas que protestavam contra restrições governamentais viu as suas contas bancárias congeladas. Como alternativa, doações em Bitcoin foram utilizadas para contornar a repressão financeira.
Bielorrússia (2020): Após as eleições presidenciais contestadas, manifestantes usaram Bitcoin para financiar atividades e ajudar aqueles que perderam os seus empregos devido à repressão estatal.
Nigéria (2020): Durante os protestos contra a brutalidade policial, conhecidos como #EndSARS, doações internacionais para os manifestantes foram bloqueadas. Bitcoin tornou-se um dos principais meios de financiamento do movimento.
Desafios do uso do Bitcoin em movimentos sociais
Educação e acessibilidade: Muitos ainda desconhecem como utilizar Bitcoin de forma segura e eficiente. A falta de conhecimento pode dificultar a sua adoção em larga escala.
Segurança digital: Movimentos sociais muitas vezes operam sob vigilância intensa. Se as medidas de segurança adequadas não forem seguidas, os fundos podem ser comprometidos.
Volatilidade: O preço de Bitcoin pode variar significativamente num curto período, o que pode afetar o valor das doações e dos fundos arrecadados.
Resumindo, o Bitcoin tem demonstrado ser uma ferramenta essencial para a resistência contra a censura financeira e a repressão governamental. Ao permitir que movimentos sociais e ativistas financiem as suas causas sem depender de intermediários, Bitcoin fortalece a luta pela liberdade e pela justiça. No entanto, a adoção eficaz da tecnologia exige conhecimento, segurança e adaptação às suas características únicas. À medida que mais pessoas aprendem a utilizar Bitcoin, o seu papel nos protestos e movimentos sociais continuará a crescer, reforçando a importância da soberania financeira na luta por direitos e liberdades.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ eb0157af:77ab6c55
2025-06-18 03:01:36
@ eb0157af:77ab6c55
2025-06-18 03:01:36A new study by Kraken reveals how cryptocurrency investors perceive security as the main challenge in self-managing their digital assets.
According to The Block, a recent survey conducted by crypto exchange Kraken found that nearly half of respondents consider themselves the primary risk factor for their own crypto security. The research, which surveyed 789 participants, highlights that 48% of users see their own actions as the greatest threat to their investments in digital assets, surpassing concerns about external theft or fraud.
Kraken’s report underlines how personal responsibility in security management forces users to take full control of their digital funds. However, the study suggests that this autonomy can also become a source of anxiety for many investors.
Nick Percoco, Chief Security Officer at Kraken, commented on the findings, noting that “a lack of confidence in personal crypto security is capping the growth of the industry.” According to Percoco, unlocking the full potential of cryptocurrencies will require users to embrace self-custody and consistently invest in strong security habits.
Technologies to strengthen security
Despite the concerns highlighted in the study, 31% of participants expressed optimism about future technologies that could improve crypto security. Among the most promising solutions identified:
- advanced biometric systems for user authentication;
- multi-factor authentication to secure wallet access;
- AI-based fraud detection systems to prevent attacks.
Data and case studies
Kraken’s research emerges in a context where security threats remain a pressing reality. FBI data shows that in 2024, nearly 150,000 reports of crypto-related internet fraud resulted in $9.3 billion in losses. Older users, particularly those over 60, proved especially vulnerable, accounting for $3 billion in crypto-related financial fraud losses on their own.
The post Kraken study: 48% of users fear themselves in managing and securing their funds appeared first on Atlas21.
-
 @ 8bad92c3:ca714aa5
2025-06-17 22:03:27
@ 8bad92c3:ca714aa5
2025-06-17 22:03:27Key Takeaways

Michael Goldstein, aka Bitstein, presents a sweeping philosophical and economic case for going “all in” on Bitcoin, arguing that unlike fiat, which distorts capital formation and fuels short-term thinking, Bitcoin fosters low time preference, meaningful saving, and long-term societal flourishing. At the heart of his thesis is “hodling for good”—a triple-layered idea encompassing permanence, purpose, and the pursuit of higher values like truth, beauty, and legacy. Drawing on thinkers like Aristotle, Hoppe, and Josef Pieper, Goldstein redefines leisure as contemplation, a vital practice in aligning capital with one’s deepest ideals. He urges Bitcoiners to think beyond mere wealth accumulation and consider how their sats can fund enduring institutions, art, and architecture that reflect a moral vision of the future.
Best Quotes
“Let BlackRock buy the houses, and you keep the sats.”
“We're not hodling just for the sake of hodling. There is a purpose to it.”
“Fiat money shortens your time horizon… you can never rest.”
“Savings precedes capital accumulation. You can’t build unless you’ve saved.”
“You're increasing the marginal value of everyone else’s Bitcoin.”
“True leisure is contemplation—the pursuit of the highest good.”
“What is Bitcoin for if not to make the conditions for magnificent acts of creation possible?”
“Bitcoin itself will last forever. Your stack might not. What will outlast your coins?”
“Only a whale can be magnificent.”
“The market will sell you all the crack you want. It’s up to you to demand beauty.”
Conclusion
This episode is a call to reimagine Bitcoin as more than a financial revolution—it’s a blueprint for civilizational renewal. Michael Goldstein reframes hodling as an act of moral stewardship, urging Bitcoiners to lower their time preference, build lasting institutions, and pursue truth, beauty, and legacy—not to escape the world, but to rebuild it on sound foundations.
Timestamps
00:00 - Intro
00:50 - Michael’s BBB presentation Hodl for Good
07:27 - Austrian principles on capital
15:40 - Fiat distorts the economic process
23:34 - Bitkey
24:29 - Hodl for Good triple entendre
29:52 - Bitcoin benefits everyone
39:05 - Unchained
40:14 - Leisure theory of value
52:15 - Heightening life
1:15:48 - Breaking from the chase makes room for magnificence
1:32:32 - Nakamoto Institute’s missionTranscript
(00:00) Fiat money is by its nature a disturbance. If money is being continually produced, especially at an uncertain rate, these uh policies are really just redistribution of wealth. Most are looking for number to go up post hyper bitcoinization. The rate of growth of bitcoin would be more reflective of the growth of the economy as a whole.
(00:23) Ultimately, capital requires knowledge because it requires knowing there is something that you can add to the structures of production to lengthen it in some way that will take time but allow you to have more in the future than you would today. Let Black Rockck buy the houses and you keep the sats, not the other way around.
(00:41) You wait until later for Larry Frink to try to sell you a [Music] mansion. And we're live just like that. Just like that. 3:30 on a Friday, Memorial Day weekend. It's a good good good way to end the week and start the holiday weekend. Yes, sir. Yes, sir. Thank you for having me here. Thank you for coming. I wore this hat specifically because I think it's I think it's very apppropo uh to the conversation we're going to have which is I hope an extension of the presentation you gave at Bitblock Boom Huddle for good. You were working on
(01:24) that for many weeks leading up to uh the conference and explaining how you were structuring it. I think it's a very important topic to discuss now as the Bitcoin price is hitting new all-time highs and people are trying to understand what am I doing with Bitcoin? Like you have you have the different sort of factions within Bitcoin.
(01:47) Uh get on a Bitcoin standard, get on zero, spend as much Bitcoin as possible. You have the sailors of the world are saying buy Bitcoin, never sell, die with your Bitcoin. And I think you do a really good job in that presentation. And I just think your understanding overall of Bitcoin is incredible to put everything into context. It's not either or.
(02:07) It really depends on what you want to accomplish. Yeah, it's definitely there there is no actual one-sizefits-all um for I mean nearly anything in this world. So um yeah, I mean first of all I mean there was it was the first conference talk I had given in maybe five years. I think the one prior to that uh was um bit block boom 2019 which was my meme talk which uh has uh become infamous and notorious.
(02:43) So uh there was also a lot of like high expectations uh you know rockstar dev uh has has treated that you know uh that that talk with a lot of reference. a lot of people have enjoyed it and he was expecting this one to be, you know, the greatest one ever, which is a little bit of a little bit of a uh a burden to live up to those kinds of standards.
(03:08) Um, but you know, because I don't give a lot of talks. Um, you know, I I I like to uh try to bring ideas that might even be ideas that are common. So, something like hodling, we all talk about it constantly. uh but try to bring it from a little bit of a different angle and try to give um a little bit of uh new light to it.
(03:31) I alsove I've I've always enjoyed kind of coming at things from a third angle. Um whenever there's, you know, there's there's all these little debates that we have in in Bitcoin and sometimes it's nice to try to uh step out of it and look at it a little more uh kind of objectively and find ways of understanding it that incorporate the truths of of all of them.
(03:58) uh you know cuz I think we should always be kind of as much as possible after ultimate truth. Um so with this one um yeah I was kind of finding that that sort of golden mean. So uh um yeah and I actually I think about that a lot is uh you know Aristotle has his his concept of the golden mean. So it's like any any virtue is sort of between two vices um because you can you can always you can always take something too far.
(04:27) So you're you're always trying to find that right balance. Um so someone who is uh courageous you know uh one of the vices uh on one side is being basically reckless. I I can't remember what word he would use. Uh but effectively being reckless and just wanting to put yourself in danger for no other reason than just you know the thrill of it.
(04:50) Um and then on the other side you would just have cowardice which is like you're unwilling to put yourself um at any risk at any time. Um, and courage is right there in the middle where it's understanding when is the right time uh to put your put yourself, you know, in in the face of danger um and take it on. And so um in some sense this this was kind of me uh in in some ways like I'm obviously a partisan of hodling.
(05:20) Um, I've for, you know, a long time now talked about the, um, why huddling is good, why people do it, why we should expect it. Um, but still trying to find that that sort of golden mean of like yes, huddle, but also what are we hodling for? And it's not we're we're not hodddling just merely for the sake of hodddling.
(05:45) There there is a a purpose to it. And we should think about that. And that would also help us think more about um what are the benefits of of spending, when should we spend, why should we spend, what should we spend on um to actually give light to that sort of side of the debate. Um so that was that was what I was kind of trying to trying to get into.
(06:09) Um, as well as also just uh at the same time despite all the talk of hodling, there's always this perennial uh there's always this perennial dislike of hodlers because we're treated as uh as if um we're just free riding the network or we're just greedy or you know any of these things. And I wanted to show how uh huddling does serve a real economic purpose.
(06:36) Um, and it does benefit the individual, but it also does uh it it has actual real social um benefits as well beyond merely the individual. Um, so I wanted to give that sort of defense of hodling as well to look at it from um a a broader position than just merely I'm trying to get rich. Um uh because even the person who uh that is all they want to do um just like you know your your pure number grow up go up moonboy even that behavior has positive ramifications on on the economy.
(07:14) And while we might look at them and have uh judgments about their particular choices for them as an individual, we shouldn't discount that uh their actions are having positive positive effects for the rest of the economy. Yeah. So, let's dive into that just not even in the context of Bitcoin because I think you did a great job of this in the presentation.
(07:36) just you've done a good job of this consistently throughout the years that I've known you. Just from like a first principles Austrian economics perspective, what is the idea around capital accumulation, low time preference and deployment of that capital like what what like getting getting into like the nitty-gritty and then applying it to Bitcoin? Yeah, it's it's a big question and um in many ways I mean I I even I barely scratched the surface.
(08:05) uh I I can't claim to have read uh all the volumes of Bombber works, you know, capital and interest and and stuff like that. Um but I think there's some some sort of basic concepts that we can look at that we can uh draw a lot out. Um the first uh I guess let's write that. So repeat so like capital time preference. Yeah. Well, I guess getting more broad like why sav -
 @ 31a4605e:cf043959
2025-06-17 17:31:08
@ 31a4605e:cf043959
2025-06-17 17:31:08Milhões de pessoas em todo o mundo ainda não têm acesso a serviços bancários básicos, seja por falta de infraestrutura, requisitos burocráticos ou instabilidade económica nos seus países. Bitcoin surge como uma solução inovadora para este problema, permitindo que qualquer pessoa com acesso à internet tenha controlo sobre o seu dinheiro, sem depender de bancos ou governos. Ao oferecer um sistema financeiro aberto e acessível, Bitcoin torna-se uma ferramenta poderosa para a inclusão financeira global.
O problema da exclusão financeira
Em muitos países em desenvolvimento, grande parte da população não possui conta bancária. Isto pode acontecer por diversas razões, como:
Falta de acesso a bancos: Muitas comunidades, especialmente em áreas rurais, não têm instituições financeiras próximas.
Exigências burocráticas: Alguns bancos exigem documentação específica ou um histórico de crédito que muitas pessoas não conseguem fornecer.
Custos elevados: As taxas bancárias podem ser proibitivas para quem ganha pouco dinheiro.
Instabilidade económica e política: Em países com alta inflação ou governos instáveis, os bancos podem não ser uma opção segura para guardar dinheiro.
Estas dificuldades deixam milhões de pessoas à margem do sistema financeiro, impossibilitadas de poupar, investir ou realizar transações de forma eficiente.
Bitcoin como alternativa
Bitcoin resolve muitos dos problemas da exclusão financeira ao oferecer um sistema acessível e descentralizado. Com Bitcoin, qualquer pessoa com um telemóvel e acesso à internet pode armazenar e transferir dinheiro sem necessidade de um banco. Entre as principais vantagens estão:
Acessibilidade global: Bitcoin pode ser usado em qualquer lugar do mundo, independentemente da localização do utilizador.
Sem necessidade de intermediários: Diferente dos bancos, que impõem taxas e regras, Bitcoin permite transações diretas entre pessoas.
Baixo custo para transferências internacionais: Enviar dinheiro para outro país pode ser caro e demorado com os métodos tradicionais, enquanto Bitcoin oferece uma alternativa mais rápida e acessível.
Proteção contra a inflação: Em países com moedas instáveis, Bitcoin pode ser usado como reserva de valor, protegendo o poder de compra da população.
Casos de uso na inclusão financeira
Bitcoin já tem sido utilizado para promover a inclusão financeira em diversas partes do mundo. Alguns exemplos incluem:
África e América Latina: Em países como Nigéria, Venezuela e Argentina, onde a inflação é elevada e o acesso a dólares é limitado, muitas pessoas usam Bitcoin para preservar o seu dinheiro e realizar transações internacionais.
Remessas internacionais: Trabalhadores que enviam dinheiro para as suas famílias no estrangeiro evitam as elevadas taxas das empresas de transferências tradicionais ao utilizarem Bitcoin.
Microeconomia digital: Pequenos comerciantes e freelancers que não têm acesso a contas bancárias podem receber pagamentos em Bitcoin de forma direta e segura.
Desafios da inclusão financeira com Bitcoin
Apesar das suas vantagens, a adoção de Bitcoin como ferramenta de inclusão financeira ainda enfrenta alguns desafios, tais como:
Acesso à internet: Muitas regiões pobres ainda não têm uma infraestrutura digital adequada.
Educação financeira: Para que mais pessoas utilizem Bitcoin, é necessário maior conhecimento sobre a tecnologia e as melhores práticas de segurança.
Volatilidade do preço: As oscilações de valor podem dificultar o uso de Bitcoin no dia a dia, especialmente em países onde as pessoas vivem com rendimentos instáveis.
Resumindo, o Bitcoin oferece uma solução viável para milhões de pessoas excluídas do sistema financeiro tradicional. Ao proporcionar acesso global, transações baratas e segurança contra a inflação, torna-se um instrumento poderoso para promover a inclusão financeira. No entanto, para que o seu potencial seja totalmente aproveitado, é essencial investir na educação digital e expandir a infraestrutura tecnológica, permitindo que mais pessoas tenham autonomia financeira através de Bitcoin.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ b1ddb4d7:471244e7
2025-06-17 22:02:44
@ b1ddb4d7:471244e7
2025-06-17 22:02:44The OP_RETURN Debate has recently caused a stir within the bitcoin community. Bitcoin stands as a groundbreaking peer-to-peer currency, engineered for financial sovereignty and unshackled from centralized control, embodying Satoshi Nakamoto’s visionary design of a trustless monetary system.
Introduced in 2009, it leverages proof-of-work and a decentralized network of nodes to enable individuals to transact freely, free from the influence of banks or governments. This design prioritizes the integrity of money as a store of value and medium of exchange, reflecting Nakamoto’s intent to create a resilient alternative to fiat currencies.
For over a decade, bitcoin has thrived as a beacon of economic autonomy, drawing adherents who value its unalterable rules and global accessibility.
Yet, as of June 14, 2025, the ongoing OP_RETURN debate has emerged as a critical juncture, challenging bitcoin’s core identity. OP_RETURN, a script opcode introduced in 2014 to embed up to 80 bytes of data in transactions, was designed to reduce UTXO bloat from earlier data-stuffing practices.
However, recent proposals, such as Peter Todd’s pull request #32359, to expand this limit—potentially up to the 1MB block size—have sparked intense discussion. This controversy pits the purity of bitcoin’s monetary purpose against a push for data-driven experimentation, such as timestamping, NFTs, and Ordinals, which leverage the blockchain for purposes beyond financial transactions.
At the heart of this debate lies a fundamental tension: whether bitcoin should remain a specialized ledger for value transfer or evolve into a general-purpose data platform.
Proponents argue that expanding OP_RETURN could streamline development and enable innovative use cases, such as sidechains, while critics warn it risks diluting bitcoin’s focus, increasing node costs, and eroding its decentralized ethos.
This clash echoes past scaling disputes, like the 2017 block size wars, and underscores the delicate balance between adapting to new demands and preserving the principles that define bitcoin’s strength. As of June 14, 2025, the community appears divided, with developers like Todd and Luke Dashjr advocating opposing views, and the outcome poised to shape bitcoin’s future trajectory.
For those guided by bitcoin’s original vision of sovereignty and minimalism, this debate is more than technical—it’s philosophical. The push to expand OP_RETURN raises questions about the integrity of the network, the role of individual node operators, and the risk of centralization through data-heavy use.
As the discussion unfolds, it forces a reckoning: will bitcoin stay true to its roots as sound money, or will it embrace experimentation that critics argue could compromise its foundational values? This article explores these tensions, offering a perspective rooted in bitcoin’s essence and the principles of its staunchest defenders.
Background on OP_RETURN
OP_RETURN emerged as a script opcode in 2014, designed to allow the inclusion of up to 80 bytes of arbitrary data within unspendable transaction outputs on the Bitcoin blockchain. This innovation addressed the inefficiencies of earlier data-stuffing methods, which cluttered the UTXO set (a database of spendable coins) and increased the computational burden on nodes.
By providing a controlled way to embed data—marking it as unspendable—OP_RETURN aimed to balance the network’s functionality with its primary role as a monetary ledger, reflecting bitcoin’s focus on efficiency and scalability.
Historically, OP_RETURN has been used for practical purposes like timestamping documents and limited data storage, serving as a lightweight tool for decentralized proof-of-existence. However, in recent years, particularly by June 14, 2025, its use has increasingly shifted toward innovative but data-intensive applications like Ordinals and NFTs.
These developments, often achieved through workarounds such as inscribing data in SegWit fields or layered protocols, have pushed the boundaries of the 80-byte limit, transforming Bitcoin into a platform for digital collectibles and other use cases. This shift has sparked debate about whether such applications align with or undermine Bitcoin’s original intent as a peer-to-peer currency.
The Proposed Update
One of the most notable proposals in the OP_RETURN debate, as of June 14, 2025, is a pull request attributed to Peter Todd (#32359), which suggests removing the existing 80-byte cap on data embedded via OP_RETURN.
This change would potentially allow data payloads to expand up to the full 1MB block size limit, significantly increasing capacity for embedding information directly into bitcoin transactions. Introduced to address evolving use cases and technical inefficiencies, the proposal has gained traction among some developers who see it to enhance the protocol’s flexibility, leveraging Bitcoin’s existing infrastructure.
Arguments in favor of this update highlight several benefits. Proponents argue that removing the cap would simplify bitcoin’s codebase by eliminating the need for workarounds, such as multi-signature schemes or excessive transaction outputs, that currently clutter the UTXO set (a database of spendable coins).
Additionally, it could reduce network strain caused by these inefficient methods, potentially improving performance. Another key point is the potential to enable sidechain innovations, allowing bitcoin to serve as a foundation for layered solutions that enhance scalability and support new applications, all while keeping data within the blockchain’s secure framework.
However, the proposal faces strong counterarguments rooted in bitcoin’s monetary focus. Critics contend that lifting the 80-byte limit risks transforming bitcoin into a general-purpose data ledger, diluting its primary role as a peer-to-peer currency and store of value.
This shift could lead to blockchain bloat—potentially adding significant storage demands annually—raising resource requirements for node operators and possibly excluding smaller participants, thus threatening decentralization.
While some argue modern hardware can handle larger blocks, critics warn that even small increases burden low-resource nodes, clashing with the minimalist vision of Satoshi Nakamoto and purists like Giacomo Zucco, who argue that data storage is better suited to alternative blockchains or off-chain solutions.
Giacomo Zucco, a leading voice in the bitcoin community, champions the notion that bitcoin’s strength derives from its decentralization and censorship resistance, safeguarded by a minimal, secure protocol built on proof-of-work. Like Zucco, Nakamoto’s whitepaper emphasizes a lean system focused on financial transactions, empowering individual node operators to enforce consensus rules and prevent any single entity—be it a miner, developer, or corporation—from dictating its direction.
Expanding OP_RETURN undermines this vision by inviting bloat, which could raise node operational costs and centralize control among well-funded data users. This shift risks turning bitcoin into a platform for data-intensive applications like NFTs or Ordinals, rather than a robust financial network.
Zucco and other purists would likely argue that proof-of-work and the fee market should prioritize financial transactions, reflecting bitcoin’s original intent as a currency and store of value, while data storage belongs on second layers or alternative chains.
Preserving this focus is essential to maintaining the decentralized soul that defines bitcoin’s essence, a principle that node operators must uphold to honor its founding ethos.
Community Divide and Risks
The OP_RETURN debate has exposed a deep divide within the bitcoin community, particularly among developers and users, as of mid-June 2025. On one side, figures like Peter Todd and Antoine Poinsot support expanding the OP_RETURN limit to 4MB in Bitcoin Core’s version 30, set for release in October 2025, arguing it aligns with miner practices and reduces harmful workarounds.
In contrast, developers like Luke Dashjr argue that such changes dilute bitcoin’s monetary purpose, promoting Bitcoin Knots—a fork of Bitcoin Core with stricter filters, defaulting to a 40-byte OP_RETURN limit—as a countermeasure.
This split extends to users, with Bitcoin Knots nodes surging from 2% to 11% by June 2025, signaling a preference for a leaner blockchain, while others embrace the flexibility of larger data capacities, highlighting growing tension over the network’s future direction.
This division carries significant risks that could undermine bitcoin’s accessibility, a cornerstone of its decentralized ethos. Expanding OP_RETURN could lead to fee spikes as data-heavy transactions compete for block space, disproportionately burdening smaller users and node operators with limited resources.
Proponents argue that fee markets and prunable OP_RETURN outputs will regulate data use, but critics warn that spikes could still exclude low-resource participants. Node fragmentation is another concern, as differing mempool policies between Knots and Bitcoin Core nodes could disrupt transaction relay, weakening the unified network that secures Bitcoin.
While the change avoids a hard fork by adjusting mempool policy rather than consensus rules, it risks eroding trust in Bitcoin Core’s governance, reminiscent of the 2017 block size wars that fractured the community. Such tensions could weaken Bitcoin’s security and trustless environment, posing a critical challenge to its long-term viability.
Preserving Bitcoin’s Essence
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ eb0157af:77ab6c55
2025-06-18 03:01:35
@ eb0157af:77ab6c55
2025-06-18 03:01:35The Thai government has eliminated taxes on gains from cryptocurrencies until 2029 to attract investors and promote the digital asset sector.
According to Efinance Thai, Thailand has approved a five-year tax exemption on profits from the sale of Bitcoin and other digital assets. The decision aims to position the country as one of the world’s leading digital financial hubs.
On June 17, Thailand’s Cabinet officially approved the tax measure proposed by the Ministry of Finance. The initiative removes personal income tax on capital gains from the sale of cryptocurrencies conducted through licensed operators under the 2018 Digital Asset Business Act.
Deputy Finance Minister Julapun Amornvivat stated that the tax policy is a cornerstone of the government’s strategy to turn Thailand into a major global center for Bitcoin and blockchain-based financial services.
The capital gains tax exemption will be in effect from January 1, 2025, to December 31, 2029. It applies exclusively to transactions carried out via exchanges, brokers, and dealers licensed and regulated by Thailand’s Securities and Exchange Commission (SEC).
Thai authorities estimate that this tax reform will boost the domestic Bitcoin market, generating positive spillovers for the country’s innovative tech ecosystem. Economic projections indicate a medium-term increase in tax revenues of at least 1 billion baht (around $30 million), driven by sector growth and fresh investment inflows.
According to the government, the initiative is also expected to encourage capital raising through digital tokens and foster the development of blockchain-based financial services.
The post Thailand abolishes taxes on Bitcoin: five-year tax exemption appeared first on Atlas21.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ b2d670de:907f9d4a
2025-02-28 16:39:38
@ b2d670de:907f9d4a
2025-02-28 16:39:38onion-service-nostr-relays
A list of nostr relays exposed as onion services.
The list
| Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | operator | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | operator | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | operator | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | operator | Payment URL | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | operator | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | operator | Payment URL | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | operator | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | operator | N/A | N/A | | nostr.wine | 🍷 nostr.wine relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | operator | Payment URL | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 inbox.nostr.wine relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | operator | Payment URL | BTC LN, BTC | | filter.nostr.wine | 🍷 filter.nostr.wine proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | operator | Payment URL | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | operator | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | operator | N/A | N/A | | nfrelay.app | nfrelay.app aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | operator | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | operator | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | operator |Payment URL | XMR | | nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | operator | N/A | N/A | | wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | operator | N/A | N/A | | haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | operator | N/A | N/A | | relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | operator |N/A | N/A | | Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | operator | N/A | N/A | | Azzamo Relay | Azzamo Premium Nostr relay. (paid) | ws://q6a7m5qkyonzb5fk5yv4jyu3ar44hqedn7wjopg737lit2ckkhx2nyid.onion | operator | Payment URL | BTC LN | | Azzamo Inbox Relay | Azzamo Group and Private message relay. (Freemium) | ws://gp5kiwqfw7t2fwb3rfts2aekoph4x7pj5pv65re2y6hzaujsxewanbqd.onion | operator | Payment URL | BTC LN | | Noderunners Relay | The official Noderunners Nostr Relay. | ws://35vr3xigzjv2xyzfyif6o2gksmkioppy4rmwag7d4bqmwuccs2u4jaid.onion | operator | Payment URL | BTC LN |
Contributing
Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put
N/Ain empty columns.If you want to contribute anonymously, please contact me on SimpleX or send a DM on nostr using a disposable npub.
Operator column
It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
-
 @ df478568:2a951e67
2025-06-17 21:37:10
@ df478568:2a951e67
2025-06-17 21:37:10It can already be used for pay-to-send e-mail. The send dialog is resizable and you can enter as long of a message as you like. It's sent directly when it connects. The recipient double-clicks on the transaction to see the full message. If someone famous is getting more e-mail than they can read, but would still like to have a way for fans to contact them, they could set up Bitcoin and give out the IP address on their website. "Send X bitcoins to my priority hotline at this IP and I'll read the message personally." -- Satoshi Nakamoto, January 17, 2009
"It might make sense just to get some in case it catches on. If enough people think the same way, that becomes a self-fulfilling prophecy. Once it gets bootstrapped, there are so many applications if you could effortlessly pay a few cents to a website as easily as dropping coins in a vending machine." -- Satoshi Nakamoto, January 17, 2009
.jpg?raw=true)
"Forgot to add the good part about micropayments. While I don't think Bitcoin is practical for smaller micropayments right now, it will eventually be as storage and bandwidth costs continue to fall. If Bitcoin catches on on a big scale, it may already be the case by that time. Another way they can become more practical is if I implement client-only mode and the number of network nodes consolidates into a smaller number of professional server farms. Whatever size micropayments you need will eventually be practical. I think in 5 or 10 years, the bandwidth and storage will seem trivial." -- Satoshi Nakamoto, August 10, 2010
"It can already be used for pay-to-send e-mail. The send dialog is resizable and you can enter as long of a message as you like. It's sent directly when it connects. The recipient double-clicks on the transaction to see the full message. If someone famous is getting more e-mail than they can read, but would still like to have a way for fans to contact them, they could set up Bitcoin and give out the IP address on their website. "Send X bitcoins to my priority hotline at this IP and I'll read the message personally." -- Satoshi Nakamoto, January 17, 2009
.jpg?raw=true)
"It might make sense just to get some in case it catches on. If enough people think the same way, that becomes a self-fulfilling prophecy. Once it gets bootstrapped, there are so many applications if you could effortlessly pay a few cents to a website as easily as dropping coins in a vending machine." -- Satoshi Nakamoto, January 17, 2009
"Forgot to add the good part about micropayments. While I don't think Bitcoin is practical for smaller micropayments right now, it will eventually be as storage and bandwidth costs continue to fall. If Bitcoin catches on on a big scale, it may already be the case by that time. Another way they can become more practical is if I implement client-only mode and the number of network nodes consolidates into a smaller number of professional server farms. Whatever size micropayments you need will eventually be practical. I think in 5 or 10 years, the bandwidth and storage will seem trivial." -- Satoshi Nakamoto, August 10, 2010
Bitcoin Is Winning Fast AF
.jpg?raw=true)
I began writing about using the lightning network about 150,000 blocks ago because I got tired of hearing that bitcoin can't make more than 7 transactions a minute. That was true 565,000 blocks ago, but is no longer true since the inception of the lightning network. For example:
- We sent 4,187 bitcoin payments over an 8-hour period at Bitcoin 2025, a Guinness Book of World Record winning achievement.
- Nostr is the biggest bitcoin circular economy in the world.
- Shake N Steak, a U.S.-based Hamburger franchise, accepts bitcoin over the Lightning Network at all of its locations.
- We can pay our credit cards with fractions of bitcoin (sats).
- We can use bitcoin over the lightning network to pay AI agents to do vibe coding using tools like Stacks and Goose.
- Bitcoin Helped Secure An Election In A County In Georgia.
I pay for Protonmail with bitcoin on-chain.
I can also use this email to send it to other people who do the same. I've only done this once to test it out, but it works. This is not new. The time chain uses Hashcash (with a double SHA256 algorithm instead of SHA1) for its famous proof-of-work. Hashcash was originally intended to prevent spam. Now you can use bitcoin to do the same.
I ran the numbers. Our world record is an average of 8.72 bitcoin transactions per second. This is just in one place, but bitcoin is a global monetary network. Bitcoin over the lightning network makes it possible to send value at the speed of light, anywhere in the world.
We won a world record. We are winning. We use money that we know works better than gold.
"If you don't believe me or don't get it, I don't have time to try to convince you, sorry." -- Satoshi Nakamoto
☮️ nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
Zap This Blog would like to think The Nakamoto Institute for making it easy to find these awsome Satoshi quotes. If you like this article, please Zap The Nakamoto Institute!
-
 @ b1ddb4d7:471244e7
2025-06-17 22:02:43
@ b1ddb4d7:471244e7
2025-06-17 22:02:43The Present Ecosystem It Is Not Just Calls
The role of telecommunications carriers has long since evolved beyond that of simple call connectors. Currently, they serve as actual digital centers that penetrate practically every facet of our interconnected lives. With more than 5.7 billion mobile service subscribers and 4.7 billion mobile internet users worldwide (roughly 58% of the global population), telecommunications are the foundation of the digital economy. It is anticipated that by 2030, this figure will rise to an astounding 5.5 billion mobile internet users, or 64% of the world’s population.
A variety of connectivity options are available in the current telecommunications ecosystem, ranging from home fiber optics to 5th generation of mobile networks, which is expected to be adopted globally by 57% by 2030, creating roughly 5.3 billion connections. Collaborations with streaming services that provide on-demand entertainment.
Current Telecom Ecosystem
From fiber optics to 5G technology, telecommunications companies have focused on diversifying global connectivity. By 2030, they are expected to reach 57% global adoption, resulting in around 5.3 billion connections.
There are partnerships with streaming platforms that have transformed carriers into true content gateways. This has helped the explosive growth of data traffic, which reached the mark of 26.53 exabytes per month in 2018.
These companies are offering some personalized business services, such as IoT, security and cloud solutions.
Furthermore, many carriers already provide basic financial services like mobile payments and device financing. This last one is the perfect starting point for a further revolution: the integration of Bitcoin into the telecom ecosystem.
Telecommunications and Bitcoin: A Perfect Match
Carriers’ use of Bitcoin is a radical rethinking of the business-customer relationship, not merely a new mode of payment. Here is how this new ecosystem could work:
-
Customer Experience and Infrastructure – Before implementing Bitcoin, an carrier must build the necessary infrastructure. This entails creating mechanisms that may not only receive cryptocurrency payments but alsoIf companies want to lessen their exposure to volatility, they can automatically convert Bitcoin to fiat money. Companies can also easily integrate with current invoicing systems and provide a more straightforward user experience.
Imagine launching the app for your carrier, scanning a QR code, and having your bill paid or your monthly plan renewed in a matter of seconds. Without waiting for business days, without banking middlemen, and without exorbitant costs.
-
Bringing in New Segments – In addition to making life easier for current clients, Bitcoin’s acceptance draws in entirely new demographics:
Those that appreciate innovation and wish to back trailblazing businesses are known as technology enthusiasts.
Advocates for privacy: Customers who favor transactions that need less personal information to be shared
Global clientele are tourists from other countries who can pay for services without worrying about regional restrictions or exchange rates.Carrier might develop targeted marketing, such as “early access to new devices for customers who use cryptocurrencies” or “10% discount on data top-ups when paid with Bitcoin,” to attract these demographics.
Ongoing Innovation: What Will Happen After Bitcoin?
When businesses embrace Bitcoin and fully utilize blockchain technology, the real revolution will take place. This strategy creates opportunities for developments like:
- Creative Smart Contracts – Smart contracts are self-executing, blockchain-based programs that eliminate middlemen and automate processes. This could be interpreted by carriers as:
- Instant service activation – Your Bitcoin payment has been validated and your international data package is activated automatically even before you land at the airport.Contracts that automatically expire at the designated time eliminate the need for a constant call to the call center.
- Simplified termination – Mini-smart contracts enable family members to automatically transfer excess mobile data.
This was recently illustrated by the Japanese carrier Rakuten Mobile, which unveiled a system that enables users to temporarily increase their bandwidth through smart contracts for a few hours (for instance, to broadcast live events) without modifying their primary plan.
- Creative Partnerships in the World Ecosystem – The carriers are able to establish strategic alliances with:
- Fintech companies that specialize in bitcoin to create integrated digital wallets.
- Startups creating telecom-specific decentralized applications (DApps).
- Academic institutions will investigate novel applications of blockchain technology in the telecommunications sector.
Given that the market is dominated by industry titans like China Mobile (794 million subscribers in 2023), Verizon (US$ 133.97 billion in 2023), and AT&T (US$ 161.5 billion in revenue in 2022), these partnerships have the potential to accelerate disruptive innovations that benefit the entire telecommunications ecosystem.
Reimagining the Customer Relationship with New Business Models
The incorporation of Bitcoin enables the investigation of business ideas that were before unfeasible:
- Microtransactions: Only Paying for the Things You Use – Processing fees in the traditional financial system make it impossible to charge tiny sums. This issue is resolved by Bitcoin, particularly via the Lightning Network, which permits:
- Payment per call second (think of paying R$0.001 per second for just the actual usage)
- – Acquiring small data packages (e.g., 500MB for a single movie)
- – Immediate access to high-quality WiFi networks at cafes or airports, with just the time spent connecting being charged,
The startup Althea Network, which enables communities to establish their own internet networks where users automatically pay for each byte consumed, is already testing this idea. The trend of increasing video traffic, which currently makes up 70% of all mobile data traffic and is predicted to reach 80% by 2028, is well aligned with this strategy.
- Loyalty Initiatives on the Blockchain: Conventional point systems have little transparency and are hard to use. A method based on blockchain can:
Make loyalty tokens that are equivalent to actual digital money.
Permit customer exchanges (you can trade or sell points you won’t use).
Form more extensive alliances wherein other businesses accept the carrier tokens.A system where users earn blockchain-based “T-points” tokens that can be turned into modest amounts of Bitcoin or swapped for other services is already being tested by South Korean carrier SK Telecom. In South Korea, one of the top markets for the adoption of 5G worldwide, this kind of innovation is especially pertinent.
Obstacles and Realistic Implementation Considerations
Despite the vast potential, there are important issues that must be resolved:
- Evolutionary Regulation – Countries’ cryptocurrency regulations differ greatly from one another and are always evolving. Carriers will require:
- Maintain specialized teams to keep an eye on regulatory developments, work with authorities to help create reasonable regulations, and create adaptable systems that can evolve to meet new needs.
- This strategy is crucial in light of the fact that the telecom industry is already dealing with a lot of regulatory pressure in different jurisdictions, as demonstrated by the Canadian government’s recent initiatives to encourage more access to MVNOs (mobile virtual network carriers) in 2023.
- Please read this to undertand how Governors don’t do anything to help you.
- Financial Management and Volatility – One difficulty is the volatility of Bitcoin pricing. In order to reduce hazards, carriers can:
- Convert a portion of payments into fiat money automatically.
Employ hedge services to guard against sharp swings.
Provide dynamic prices that change based on the state of the market. - Given that international carriers oversee yearly earnings in the hundreds of billions of dollars, these tactics are particularly pertinent.
- Convert a portion of payments into fiat money automatically.
- Education of Consumers – Many customers are still confused about cryptocurrencies. Strategies that work include:
- The carrier app’s simplified instructional
- Committed assistance for Bitcoin transactions
- Rewards for initial cryptocurrency purchases
With more than 5.7 billion mobile consumers worldwide, this educational initiative has the potential to significantly accelerate the widespread acceptance of cryptocurrencies.
Now is the time for deep digital transformation
Telecommunications companies that incorporate blockchain and Bitcoin into their ecosystem are doing more than simply introducing a new payment method; they are putting themselves at the vanguard of a significant digital revolution that will keep up with the industry’s explosive growth, which is expected to reach US$ 1.3 trillion globally by 2028.
The ability to innovate services, draw in creative clients, and open up new markets will be available to those that welcome this shift, which the conventional model would not allow. In order to prepare the infrastructure for this revolution, more than 300 commercial 5G networks will be operational globally beginning in 2024, marking the beginning of this shift.
As customers, we may anticipate more individualized, open, and effective services. Our civilization is progressing toward a telecommunications infrastructure that is fully suited to the digital era and capable of handling the enormous amount of data traffic
-
-
 @ dfa02707:41ca50e3
2025-06-17 21:01:55
@ dfa02707:41ca50e3
2025-06-17 21:01:55- This version introduces the Soroban P2P network, enabling Dojo to relay transactions to the Bitcoin network and share others' transactions to break the heuristic linking relaying nodes to transaction creators.
- Additionally, Dojo admins can now manage API keys in DMT with labels, status, and expiration, ideal for community Dojo providers like Dojobay. New API endpoints, including "/services" exposing Explorer, Soroban, and Indexer, have been added to aid wallet developers.
- Other maintenance updates include Bitcoin Core, Tor, Fulcrum, Node.js, plus an updated ban-knots script to disconnect inbound Knots nodes.
"I want to thank all the contributors. This again shows the power of true Free Software. I also want to thank everyone who donated to help Dojo development going. I truly appreciate it," said Still Dojo Coder.
What's new
- Soroban P2P network. For MyDojo (Docker setup) users, Soroban will be automatically installed as part of their Dojo. This integration allows Dojo to utilize the Soroban P2P network for various upcoming features and applications.
- PandoTx. PandoTx serves as a transaction transport layer. When your wallet sends a transaction to Dojo, it is relayed to a random Soroban node, which then forwards it to the Bitcoin network. It also enables your Soroban node to receive and relay transactions from others to the Bitcoin network and is designed to disrupt the assumption that a node relaying a transaction is closely linked to the person who initiated it.
- Pushing transactions through Soroban can be deactivated by setting
NODE_PANDOTX_PUSH=offindocker-node.conf. - Processing incoming transactions from Soroban network can be deactivated by setting
NODE_PANDOTX_PROCESS=offindocker-node.conf.
- Pushing transactions through Soroban can be deactivated by setting
- API key management has been introduced to address the growing number of people offering their Dojos to the community. Dojo admins can now access a new API management tab in their DMT, where they can create unlimited API keys, assign labels for easy identification, and set expiration dates for each key. This allows admins to avoid sharing their main API key and instead distribute specific keys to selected parties.
- New API endpoints. Several new API endpoints have been added to help API consumers develop features on Dojo more efficiently:
- New:
/latest-block- returns data about latest block/txout/:txid/:index- returns unspent output data/support/services- returns info about services that Dojo exposes
- Updated:
/tx/:txid- endpoint has been updated to return raw transaction with parameter?rawHex=1
- The new
/support/servicesendpoint replaces the deprecatedexplorerfield in the Dojo pairing payload. Although still present, API consumers should use this endpoint for explorer and other pairing data.
- New:
Other changes
- Updated ban script to disconnect inbound Knots nodes.
- Updated Fulcrum to v1.12.0.
- Regenerate Fulcrum certificate if expired.
- Check if transaction already exists in pushTx.
- Bump BTC-RPC Explorer.
- Bump Tor to v0.4.8.16, bump Snowflake.
- Updated Bitcoin Core to v29.0.
- Removed unnecessary middleware.
- Fixed DB update mechanism, added api_keys table.
- Add an option to use blocksdir config for bitcoin blocks directory.
- Removed deprecated configuration.
- Updated Node.js dependencies.
- Reconfigured container dependencies.
- Fix Snowflake git URL.
- Fix log path for testnet4.
- Use prebuilt addrindexrs binaries.
- Add instructions to migrate blockchain/fulcrum.
- Added pull policies.


Learn how to set up and use your own Bitcoin privacy node with Dojo here.
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ a10260a2:caa23e3e
2025-06-17 20:58:09
@ a10260a2:caa23e3e
2025-06-17 20:58:09If you're like me, you're bullish on privacy-preserving, reusable payment codes. BOLT 12 and Silent Payments are making it happen for Lightning and on-chain payments, respectively. I hope to update this table over time as more wallets support these two protocols.
| | Phoenix | Cake Wallet | Strike | Coinos | | --- | --- | --- | --- | --- | | BOLT 12 (Send) | ✓ | ✗ | ✓ | ✓ | | BOLT12 (Receive) | ✓ | ✗ | ✗ | ✓ | | Silent Payment (Send) | ✗ | ✓ | ✗ | ✗ | | Silent Payment (Receive) | ✗ | ✓ | ✗ | ✗ | | BIP 353 | ✓ | ✓ | ✗ | ✗ |
Resources: * What is BOLT 12? | Bolt12.org * Human readable addresses | Bitcoin Design * Setting up a Bitcoin username | Seth For Privacy
-
 @ cae03c48:2a7d6671
2025-06-17 22:02:38
@ cae03c48:2a7d6671
2025-06-17 22:02:38Bitcoin Magazine

Senator Hagerty’s Vision Beyond The GENIUS Act: Make Tennessee A Hub For Bitcoin MiningSenator Bill Hagerty (R-TN) has been in the headlines as of late as the GENIUS Act (S. 1582), a bill for which he was the primary sponsor, moves closer to passing in the U.S. Senate.
The GENIUS Act is a bill that, if enacted into law, would create a federal regulatory framework for stablecoins so that the technology can be more widely adopted. (While some Bitcoin enthusiasts may not like this, they should still pay attention to the language in the bill, as it could have an impact on U.S. citizens’ ability to use Bitcoin wallets privately.)
However, stablecoins aren’t the only thing on Senator Hagerty’s mind.
He’s also thinking about how to best produce and harness energy in Tennessee to use it for Bitcoin mining and AI compute.
He shared his vision on this topic with me in an interview I conducted with him at Bitcoin 2025:
Tennessee As A Hub For Bitcoin Mining and AI Compute
“We have an opportunity before us to be in the very lead,” Senator Hagerty told Bitcoin Magazine in regard to building nuclear facilities that can be used to produce energy for Bitcoin mining and AI processing.
“The largest utility in the world is the Tennessee Valley Authority — certainly the largest one in America — and I think we’ve got a unique opportunity here to move forward and become the energy hub of America,” he added.
“[We should] see more and more not only mining operations, but if you think about what Elon Musk is doing in Memphis with xAI, the data centers, the opportunities with artificial intelligence — there are many, many things that are going to happen in Tennessee.”
The Senator added that he believes the state can also strike partnerships with Oak Ridge National Laboratory, Vanderbilt University, the University of Tennessee and Tennessee Tech as it works to become a more friendly destination for Bitcoin miners and data centers.
“We’ve got great opportunities [from] Memphis all the way across the state,” said Senator Hagerty.
Hagerty’s Call For Bipartisanship
Whether it’s working toward stablecoin legislation or crafting regulation that will enable industries like Bitcoin mining and data centers to thrive in the United States, Senator Hagerty believes these efforts should be inherently bipartisan.
“[These are] bipartisan — or nonpartisan issue[s] — frankly,” said the Senator.
“If you care about the competitiveness of America — if you want to see innovation happen on our shores rather than being pushed overseas — then you’re going to support what we’re trying to do in terms of putting a regulatory framework in place that will deliver certainty, that will create an ecosystem here in America that will allow these companies to thrive,” he added.
“It’s not just the stablecoin legislation I’m putting forward or what may happen with Bitcoin or other technologies like that. It’s the overall blockchain technology that’s going to help advance America beyond the 21st century. We need to stay in the lead. We can stay in the lead.”
This post Senator Hagerty’s Vision Beyond The GENIUS Act: Make Tennessee A Hub For Bitcoin Mining first appeared on Bitcoin Magazine and is written by Frank Corva.
-
 @ 4fe4a528:3ff6bf06
2025-02-01 13:41:28
@ 4fe4a528:3ff6bf06
2025-02-01 13:41:28
In my last article I wrote about NOSTR. I found another local bitcoiner via NOSTR last week so here is why it is important to join / use NOSTR — start telling people “Look me up on NOSTR”
Self-sovereign identity (SSI) is a revolutionary approach to digital identity that puts individuals in control of their own identity and personal data. Unlike traditional digital identity models, which rely on third-party organizations to manage and authenticate identities, SSI empowers individuals to own and manage their digital identity.
This approach is made possible by emerging technologies such as secure public / private key pairs. Decentralized identifiers, conceived and developed by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is an attempt to create a global technical standard around cryptographically secured identifiers - a secure, universal, and sovereign form of digital ID. This technology uses peer-to-peer technology to remove the need for intermediaries to own and authenticate ID information.
Notably, NOSTR, a decentralized protocol, has already begun to utilize decentralized IDs, demonstrating the potential of this technology in real-world applications. Via NOSTR, users can be sure that the person or computer publishing to a particular npub knows their nsec (password for your npub), highlighting the secure and decentralized nature of this approach.
With SSI, individuals can decide how their personal data is used, shared, and protected, giving them greater control and agency over their digital lives.
The benefits of SSI are numerous, including:
Enhanced security and protection of personal data. Reduced risk of identity theft and fraud Increased autonomy and agency over one's digital identity. Improved scalability and flexibility in digital identity management
challenges:
Ensuring the security and integrity of decentralized identity systems. Developing standards and protocols for interoperability and compatibility. Addressing concerns around ownership and control of personal data. Balancing individual autonomy with the need for verification and authentication in various contexts.
Overall, self-sovereign identity has the potential to transform the way we think about digital identity and provide individuals with greater control and agency over their personal data. Without people in control of their bitcoin seed words no freedom loving people would be able to exchange their money with others. Yes, keep enjoying using the only free market on the planet BITCOIN. Long live FREEDOM!
-
 @ 4c96d763:80c3ee30
2025-06-17 20:20:24
@ 4c96d763:80c3ee30
2025-06-17 20:20:24Changes
Fernando López Guevara (2):
- fix: skip blurring for user's own images
- fix(search): make input background gray in light mode
William Casarin (24):
- clippy: fix large enum.
- clippy: fix large enum.
- scroll: simple fix
- note: cleanup wide/standard implementation
- android: hover post button when narrow
- fix note response regression
- nix: emulator
- log: less verbose unknown id logging
- chrome: collapsible side panel
- dave: small cleanup
- dave: add chrome toggle button
- chrome: extract method to function
- chrome: extract more non-methods
- Initial tab bar
- chrome: hook up toolbar actions
- toolbar: process actions
- nix: add $ANDROID_JAR helper to shell
- add input context menu helper
- thread: enable selectable text in threads
- universe: add full tabs
- android: fix build
- dave: initial android fixes
- android: arboard clipboard support
- android: add initial ci
alltheseas (1):
- Update README.md with deepwiki badge (#875)
kernelkind (1):
- bugfix: txn failed
pushed to notedeck:refs/heads/master
-
 @ 31a4605e:cf043959
2025-06-17 17:29:01
@ 31a4605e:cf043959
2025-06-17 17:29:01Desde a sua criação, Bitcoin tem sido associado à ideia de liberdade financeira e individual. Diferente do dinheiro tradicional, controlado por governos e bancos centrais, Bitcoin permite que qualquer pessoa no mundo transacione e armazene valor sem depender de intermediários. Essa característica torna-se especialmente relevante em contextos de instabilidade económica, censura financeira e falta de acesso ao sistema bancário.
Bitcoin como ferramenta de autonomia financeira
A principal promessa de Bitcoin é devolver às pessoas o controlo sobre o seu próprio dinheiro. No sistema financeiro tradicional, os bancos e governos têm o poder de congelar contas, restringir transações e desvalorizar moedas através da impressão excessiva de dinheiro. Com Bitcoin, cada utilizador tem total posse dos seus fundos, desde que armazene as suas chaves privadas de forma segura. Isso significa que ninguém pode confiscar ou bloquear o acesso ao seu dinheiro.
Além disso, Bitcoin permite transações internacionais rápidas e baratas, sem depender de bancos ou plataformas de pagamento centralizadas. Em países onde as transferências internacionais são burocráticas e caras, Bitcoin representa uma alternativa eficiente e acessível.
Proteção contra a censura e o controlo estatal
Governos e instituições financeiras podem restringir o acesso ao dinheiro por motivos políticos ou económicos. Em regimes autoritários, dissidentes e jornalistas frequentemente enfrentam bloqueios financeiros como forma de repressão. Bitcoin oferece uma solução para esse problema, pois a sua rede descentralizada impede que qualquer entidade tenha controlo total sobre as transações.
Isto já foi demonstrado em diversos casos ao redor do mundo. Em momentos de crise, quando governos impõem restrições a saques bancários ou impõem limites às remessas de dinheiro, Bitcoin tem sido usado para contornar essas barreiras e garantir que as pessoas possam manter a sua liberdade financeira.
Desafios e responsabilidades da liberdade financeira
Embora Bitcoin ofereça mais liberdade individual, também exige maior responsabilidade por parte do utilizador. Diferente de uma conta bancária, onde um cliente pode recuperar o acesso à sua conta com um simples pedido, em Bitcoin a posse das chaves privadas é essencial. Se um utilizador perde as suas chaves, perde o acesso aos seus fundos para sempre.
Além disso, a volatilidade do preço de Bitcoin pode representar um desafio para quem pretende utilizá-lo como reserva de valor no curto prazo. No entanto, essa característica é compensada pelo seu modelo deflacionário, que protege a poupança a longo prazo contra a desvalorização causada pela inflação das moedas fiduciárias.
Resumindo, o Bitcoin representa uma revolução na forma como as pessoas gerem e protegem o seu dinheiro. Ao permitir transações livres de intermediários e resistir à censura financeira, Bitcoin fortalece a liberdade individual e oferece uma alternativa viável a sistemas financeiros centralizados e controlados por governos. No entanto, essa liberdade vem acompanhada da necessidade de maior responsabilidade, uma vez que cada utilizador é o único responsável pela segurança dos seus fundos. Para aqueles que valorizam a soberania financeira, Bitcoin é uma ferramenta poderosa que pode redefinir o conceito de dinheiro e autonomia pessoal no mundo moderno.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 3f770d65:7a745b24
2025-01-19 21:48:49
@ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol.
PROTOCOLS, NOT PLATFORMS.
At the heart of Nostr's philosophy is user choice, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity.
What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort.
THIS IS POWERFUL.
Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections.
The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship.
How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access.
AGAIN, THIS IS POWERUFL.
Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps.
Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions.
Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know.
TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom.
Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed.
-
 @ 6389be64:ef439d32
2025-01-14 01:31:12
@ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
Meet The Forest Walker

For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
The Small Branch Chipper

When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
The Gassifier

The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
Biochar: The Waste

Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
Wood Vinegar: More Waste

Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
The Internal Combustion Engine

Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
CO2 Production For Growth

Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
The Branch Drones

During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
The Bitcoin Miner

Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
The Mesh Network

What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
Back To The Chain

Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
Sensor Packages
LiDaR

The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
pH, Soil Moisture, and Cation Exchange Sensing

The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
Weather Data

Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
Noise Suppression

Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
Fire Safety

A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
The Wrap

How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-
 @ 31a4605e:cf043959
2025-06-17 17:01:31
@ 31a4605e:cf043959
2025-06-17 17:01:31Desde a sua criação, Bitcoin tem sido alvo de debates sobre a sua utilização em atividades ilícitas. muitos críticos afirmam que Bitcoin facilita crimes como lavagem de dinheiro e financiamento de atividades ilegais, devido à sua natureza descentralizada e à possibilidade de realizar transações sem intermediários. no entanto, a realidade é mais complexa e muitas dessas alegações são exageradas ou baseadas em mitos. na verdade, a maioria das transações com Bitcoin são legítimas e até mais rastreáveis do que muitos imaginam.
O mito: Bitcoin é a principal moeda para criminosos
Um dos maiores mitos sobre Bitcoin é a ideia de que ele é amplamente utilizado por criminosos devido ao seu suposto anonimato. este argumento tornou-se popular principalmente devido a casos como o da Silk Road, um mercado negro online desmantelado pelas autoridades em 2013, onde Bitcoin era usado para transações ilegais. no entanto, os dados mais recentes mostram que apenas uma pequena fração das transações em Bitcoin está relacionada com atividades ilícitas.
Além disso, ao contrário do dinheiro em espécie, que é quase impossível de rastrear, todas as transações de Bitcoin são registadas publicamente na blockchain ou timechain. isto significa que qualquer pagamento feito com Bitcoin pode ser analisado e seguido, tornando mais difícil esconder transações suspeitas a longo prazo.
A realidade: Bitcoin é transparente e rastreável
Ao contrário do que muitos pensam, Bitcoin não é completamente anónimo, mas sim pseudónimo. todas as transações ficam registadas na blockchain ou timechain, permitindo que autoridades e analistas de dados consigam seguir os fluxos de dinheiro com precisão. várias empresas especializadas em análise forense de blockchain ou timechain já ajudaram a identificar e desmantelar redes criminosas que tentavam utilizar Bitcoin para fins ilícitos.
Governos e autoridades, como o FBI e a Europol, têm utilizado esta característica para combater crimes financeiros. na prática, criminosos que tentam usar Bitcoin acabam frequentemente por ser apanhados devido à transparência do sistema. por isso, a ideia de que Bitcoin é um refúgio seguro para criminosos não corresponde à realidade.
O uso ilícito de moedas fiduciárias é muito maior
Se compararmos Bitcoin com as moedas fiduciárias tradicionais, como o euro ou o dólar, percebemos que estas são muito mais utilizadas para atividades ilícitas. segundo relatórios de organizações internacionais, a lavagem de dinheiro e o financiamento de crimes organizados ocorrem predominantemente através de bancos, empresas fictícias e dinheiro em espécie.
Por exemplo, em escândalos financeiros globais, como o Panama Papers e o caso do banco HSBC envolvido em lavagem de dinheiro para cartéis, os meios tradicionais foram os preferidos para esconder fortunas ilegais. apesar disso, Bitcoin continua a ser injustamente associado ao crime, enquanto os verdadeiros mecanismos de financiamento ilícito continuam a operar dentro do sistema financeiro convencional.
Resumindo, o mito de que Bitcoin é um meio privilegiado para atividades ilícitas tem sido amplamente desmentido por dados e investigações. apesar de alguns criminosos terem tentado usá-lo no passado, a realidade é que Bitcoin é um sistema financeiro mais transparente e rastreável do que o dinheiro tradicional. a grande maioria das suas transações é legítima e, à medida que a adoção cresce, Bitcoin continua a provar o seu valor como um meio seguro e descentralizado para transações financeiras.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 9ca447d2:fbf5a36d
2025-06-17 21:01:35
@ 9ca447d2:fbf5a36d
2025-06-17 21:01:35Japanese investment firm Metaplanet has announced a massive $5.4 billion plan to increase its bitcoin holdings to 210,000 BTC by the end of 2027 — that’s about 1% of the total bitcoin supply.
Metaplanet on X
The Tokyo-listed company is accelerating its already aggressive bitcoin plan, with CEO Simon Gerovich calling the initiative “Asia’s largest-ever equity raise to buy Bitcoin — again!”
The company’s new capital raise, called the “555 Million Plan”, involves issuing 555 million shares through moving strike warrants. That’s basically a type of option where people can buy shares later, and the price they pay depends on the stock’s price at that time.
So with moving strike warrants, the price at which people can buy the stock goes up or down depending on how the company’s stock is doing. It gives investors more flexibility — and it can make the warrants more attractive — because they don’t get stuck with a bad deal if the stock price drops.
This way the company can raise capital gradually over the next 2 years without impacting the stock market and existing shareholders.
The funds raised will be used to buy bitcoin, with some to redeem bonds and other income-generating strategies like selling put options.
This is a big step up from Metaplanet’s previous targets. Initially aiming to reach 10,000 BTC by the end of 2025, the company now plans to reach:
- 30,000 BTC by end of 2025
- 100,000 BTC by end of 2026
- 210,000 BTC by end of 2027
The Japanese investment firm hopes to be in the “Bitcoin 1% club” which means holding at least 1% of the total 21 million bitcoin supply.
Metaplanet bitcoin targets
Metaplanet is already making good progress. As of June 2025, the company holds 8,888 BTC, acquired at a cost of about ¥122.2 billion (around $849 million) and has already reached 89% of its original 10,000 BTC target for 2025.
This comes after the success of the company’s previous “210 Million Plan” which raised ¥93.3 billion ($650 million) in 60 trading days by issuing 210 million shares.
During that time, the company’s bitcoin holdings grew from 1,762 BTC to 7,800 BTC and the BTC Yield (a key performance metric showing growth in bitcoin per share) increased by 189%.
Year to date the BTC Yield is 225.4%.
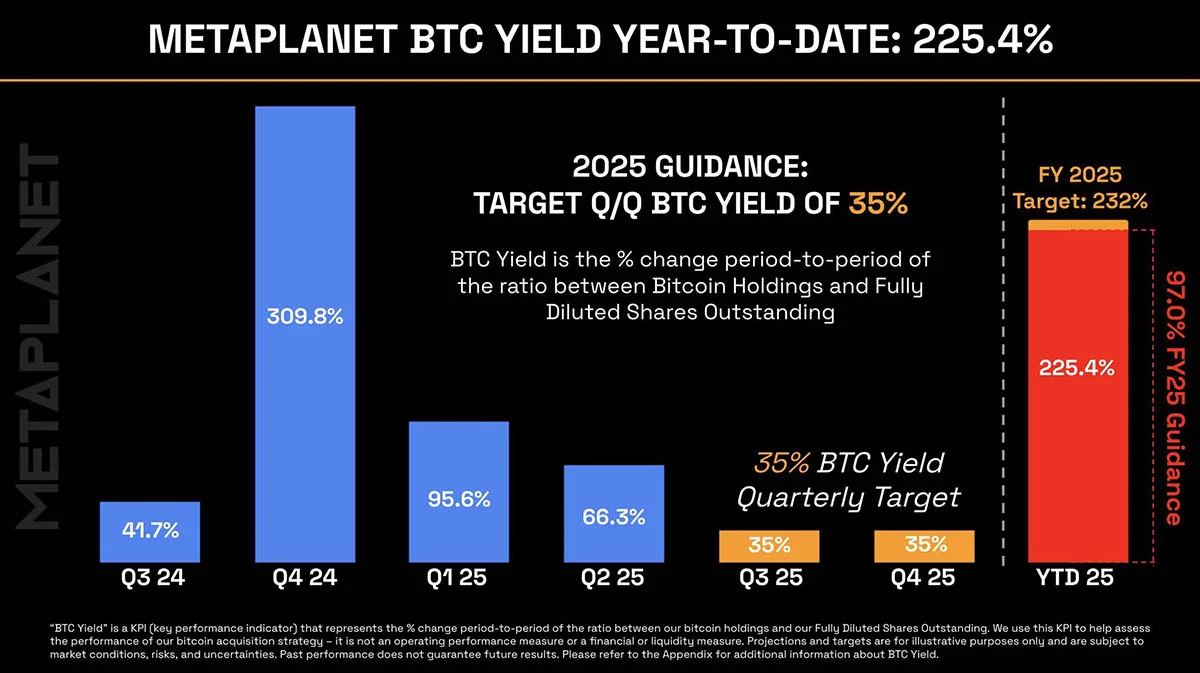
Metaplanet’s BTC Yield graph
The stock has reflected this momentum, up 275% since early 2025 and 1,619% over the past year.
Metaplanet’s stock price chart — TradingView
Metaplanet is now one of the most actively traded stocks in Japan and has become a top-ten corporate bitcoin holder globally, recently surpassing Block Inc., the company founded by Jack Dorsey.
Metaplanet sees this as part of a bigger shift in capital markets.
By being a “bitcoin treasury vehicle” listed on the Tokyo Stock Exchange, it aims to offer investors exposure to bitcoin through regulated equity markets. This is especially useful in Japan where retail investors are often restricted from accessing bitcoin directly.
“Bitcoin is repricing the global cost of capital,” the company said in a statement. “Through our 555 Million Plan, Metaplanet is doubling down on a high-conviction, equity-driven capital markets strategy to accelerate our Bitcoin accumulation trajectory.”
-
 @ afe67e17:51316efb
2025-06-17 20:08:48
@ afe67e17:51316efb
2025-06-17 20:08:48La lingvo kaj ĝia potenco
La nuna lingvo de diplomatio ne devas esti la lingvo de agresema predanto kiel Usono de Usono nek iu ajn alia neŭtrala nacio.
Ĝis hodiaŭ ne estas neŭtralaj nacioj en la planedo kaj tial ne unu sola denaska lingvo ni ideala por diplomatio.
Esperanto estas la plej bona disponebla eblo, moderna kaj riĉa.
Batalu reen por unueco kaj libereco.
Kiel?
Facila, rigardu, kiel ili dividas vin
*1. Per Lingvo:*
Faru al Esperanto vian universalan lingvon, ne donu potencon al la lingvo de unu nacio, kiu donas potencon al tiu nacio kaj al iliaj aliancanoj kaj dividas vin.
*2. De Religio:*
Foriru de iu ajn religia ekstremisma linio kaj laboru por unuigi ilin ĉiujn en unu, labori forte pri ĝi, ĉi tio prenos almenaŭ du generaciojn kaj ĝi komenciĝas per edukado kaj jura reformo forigante la rajton al ĉiuj religiaj organizoj, ili ne devas ekzisti, la fido ne bezonas kompanion senpage kun amasaj financoj krom se ĝi celas manipuli kaj kontroli, malfermi viajn okulojn.
*3 -a per tero:*
Tio daŭros vin pli kaj estas la lasta paŝo, sed post kiam vi sukcesos solvi la unuajn du, vi povas komenci la malrapidan procezon de homa reunuiĝo forigante limojn kaj krei teran nacion.
Kiom da tempo ĝi daŭros?
Nekonata, vi estas tiel juna, eble malmultaj jarcentoj, sed la semoj estas tie, nutras ilin!
-
 @ 31a4605e:cf043959
2025-06-17 16:31:03
@ 31a4605e:cf043959
2025-06-17 16:31:03O Bitcoin tem revolucionado a forma como as pessoas realizam transações financeiras em todo o mundo. Sendo uma moeda digital descentralizada, oferece novas oportunidades para pagamentos no comércio eletrónico e transferências internacionais de dinheiro. A sua rapidez, segurança e baixos custos tornam-no uma alternativa eficiente aos métodos tradicionais, eliminando intermediários e facilitando transações globais.
Bitcoin no comércio eletrónico
O comércio eletrónico tem crescido exponencialmente, e o Bitcoin surge como uma solução inovadora para pagamentos online. Grandes retalhistas e pequenas empresas estão a começar a aceitar Bitcoin como forma de pagamento, oferecendo benefícios tanto para os comerciantes como para os consumidores.
Vantagens do Bitcoin para o comércio eletrónico:
Baixas taxas de transação: ao contrário dos cartões de crédito e plataformas de pagamento que cobram taxas elevadas, as transações em Bitcoin apresentam, geralmente, custos mais reduzidos. Isto beneficia os comerciantes, que podem diminuir despesas e oferecer preços mais competitivos aos clientes.
Eliminação de chargebacks: no sistema tradicional, os chargebacks (reembolsos forçados pelos bancos ou operadoras de cartão) representam uma preocupação para os lojistas. Como as transações em Bitcoin são irreversíveis, os comerciantes evitam fraudes e disputas.
Acesso global: qualquer pessoa com acesso à Internet pode pagar com Bitcoin, independentemente da sua localização. Isto permite às empresas expandirem o seu mercado internacionalmente, sem depender de bancos ou sistemas de pagamento locais.
Privacidade e segurança: as transações em Bitcoin protegem a identidade do utilizador, oferecendo maior privacidade em comparação com pagamentos através de cartão de crédito ou transferências bancárias. Além disso, como não há necessidade de partilhar dados pessoais, o risco de roubo de informações é reduzido.
Desafios do Uso do Bitcoin no Comércio Eletrónico:
Volatilidade: o preço do Bitcoin pode oscilar rapidamente, o que dificulta a fixação de preços para produtos e serviços. No entanto, alguns comerciantes utilizam serviços de pagamento que convertem automaticamente Bitcoin em moeda fiduciária, minimizando esse risco.
Adoção limitada: apesar do crescimento, a aceitação do Bitcoin ainda não é universal. Muitas lojas e plataformas populares ainda não o adotaram, o que pode dificultar a sua utilização em compras diárias.
Tempo de confirmação: embora o Bitcoin seja mais rápido do que as transferências bancárias tradicionais, o tempo de confirmação pode variar consoante a taxa de rede paga. Algumas soluções, como a Lightning Network, estão a ser desenvolvidas para tornar os pagamentos instantâneos.
Bitcoin na remessa de dinheiro
O envio de dinheiro para o estrangeiro sempre foi um processo burocrático, dispendioso e demorado. Serviços tradicionais, como os bancos e empresas de transferência de dinheiro, cobram taxas elevadas e podem demorar dias a concluir uma transação. O Bitcoin, por outro lado, oferece uma alternativa eficiente para remessas globais, permitindo que qualquer pessoa envie e receba dinheiro de forma rápida e económica.
Benefícios do Bitcoin para remessas:
Custos reduzidos: enquanto os bancos e empresas como a Western Union cobram elevadas taxas para transferências internacionais, o Bitcoin permite o envio de dinheiro com custos mínimos, independentemente do montante ou do destino.
Velocidade nas transações: as transferências bancárias internacionais podem demorar vários dias a serem concluídas, especialmente em países com uma infraestrutura financeira limitada. Com o Bitcoin, o dinheiro pode ser enviado para qualquer parte do mundo em poucos minutos ou horas.
Acessibilidade global: em regiões onde o sistema bancário é restrito ou ineficiente, o Bitcoin possibilita que as pessoas recebam dinheiro sem depender de bancos. Isto é particularmente útil em países em desenvolvimento, onde as remessas internacionais são uma fonte essencial de rendimento.
Independência de intermediários: o Bitcoin opera de forma descentralizada, sem necessidade de recorrer a bancos ou empresas de transferência. Isto significa que as pessoas podem enviar dinheiro diretamente para amigos e familiares sem intermediários.
Desafios das remessas com Bitcoin:
Conversão para moeda local: apesar de o Bitcoin poder ser recebido instantaneamente, muitas pessoas ainda precisam de convertê-lo em moeda local para o utilizar. Isso pode envolver custos adicionais e depender da disponibilidade de serviços de câmbio.
Adoção e conhecimento: nem todos compreendem o funcionamento do Bitcoin, o que pode dificultar a sua adoção generalizada para remessas. No entanto, a crescente educação financeira sobre o tema pode ajudar a ultrapassar essa barreira.
Regulamentação e restrições: alguns governos impõem restrições ao uso do Bitcoin, tornando as remessas mais complicadas. A evolução das regulamentações pode afetar a facilidade de uso em determinados países.
Resumindo, o Bitcoin está a transformar o comércio eletrónico e as remessas de dinheiro em todo o mundo. A sua capacidade de eliminar intermediários, reduzir custos e oferecer pagamentos rápidos e seguros torna-o uma alternativa viável aos sistemas financeiros tradicionais.
No comércio eletrónico, proporciona benefícios para lojistas e consumidores, reduzindo taxas e melhorando a privacidade. No setor das remessas, facilita a transferência de dinheiro para qualquer parte do mundo, especialmente para aqueles que vivem em países com sistemas bancários pouco eficientes.
Apesar dos desafios, a adoção do Bitcoin continua a crescer, impulsionada por soluções inovadoras e pelo reconhecimento do seu potencial como meio de pagamento global. À medida que mais empresas e indivíduos aderirem a esta tecnologia, a sua presença no comércio eletrónico e nas remessas internacionais será cada vez mais relevante.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ ae8ef557:3633e453
2025-06-17 20:05:43
@ ae8ef557:3633e453
2025-06-17 20:05:43The boy left the piano and ran toward his parents. "Shall we play another song?" In one of those surprisingly magical moments, the three of them were playing together, pretending to be a band: the father with the trumpet, playing distractedly while checking messages on his phone; the mother with the guitar, smiling and listening attentively; the son with the piano, happy. Stumbles in the notes, laughter, joy. "Tomorrow is Monday," she remembered. They stopped and put away the instruments—they could do it another time. There was time. There's always more time, right?
That night, like any other on a typical week, they fulfilled the ritual of dinner at eight, a shower before bed, getting the uniform and backpack ready. Afterward, the quick hug to the father and the long kiss to the mother. In turn, the parents continued with their own routine: checking emails, reading for a while. He went to sleep while she logged on to her computer to teach an online class. The nocturnal silence took over the house, interrupted only by the occasional comment from her lesson.
The scream startled her. Was it coming from a neighbor's house? No, it couldn't be. That slight sensation in her chest, that anguish... She decided to go see how her only son was doing. When she was about to reach the second floor, she heard some moaning. She ran to the room. Her boy, curled up in a ball, and beside the bed, vomit. The forehead first—it was burning—then the abdomen. Another scream tore through her. The father woke up and approached to ask what was happening. "I don't know. Go to sleep, I'll handle it." How many other times had she said that? Without thinking, without considering the weight of the tacit agreement between them, of the comfortable distance he called space.
She lifted her son in her arms, covered him with a blanket, and took him to the emergency room. The bright lights of triage, the familiar waiting, then nurse, and finally, doctor. She knew the procedure by heart. She was always the one who handled these emergencies, who knew the nurses, who knew his medical history —allergies, previous injuries. "The experience of having an athlete son," she used to say. During the examination, the boy remained curled up. "It looks like acute appendicitis," the doctor said. "We need an urgent ultrasound and blood work."
The mother grew impatient between her child's suffering and the staff's slowness. She demanded faster attention, called the nurses over and over. "The CT scan shows perforation with fluid in the abdomen," she heard afterward. "He needs surgery now." When they came rushing and took him, while she waited for the results... it had been because of her demands, surely. She never thought she wouldn't see him again. How could she imagine that emptiness that would take over her chest, to the point of not being able to breathe?
They called the father. He arrived disoriented, like someone arriving in unknown territory, and somewhat worried, not much, because he was used to her taking care of things. The father listened to the doctor's explanation with a distorted face. "I'm very sorry. There were complications. The perforation caused severe sepsis." The man let out a scream that echoed throughout the entire hallway: "He died alone, my God, he died alone." It was the first time in years that he expressed something so profound, and it came too late. A postponed fatherhood concentrated in an instant.
Hadn't the mother been with her son until they took him away? Or the doctor and staff in the operating room? He didn't ask about her, didn't look for her. She wanted to speak, but the words wouldn't come out. If she hadn't been at the hospital, perhaps no one would have comforted her in that terrible moment. She moved because she had to, responded because they asked her. From that night she would only remember her son's face and small hands when she let them go for the last time. Afterward, only the reconstruction of events through the eyes of others: her sister and her parents.
Who thinks about when it will be the last time for anything? The last chess game with the father, the last dinner out with the mother, the last birthday of the favorite aunt. The last frightened squeeze of a small child's hand. They hadn't paid attention. Why would they? You always think there's more time.
The days that followed blurred into a hazy sequence of impossible decisions. Arrangements had to be made. At first, everything seemed suspended, even sadness. A family eclipse where darkness takes everything. You know it's temporary, but you can't glimpse the light. The family gropes around like blind people, and slowly grief sprouts. Decisions are made that will be forgotten: how to tell others, who will speak and who won't. An endless series of unimportant actions in the face of pain invading everything, little by little, to then explode like a volcano. The siblings of both parents and the grandparents crying. The parents in black silence.
The funeral passed. The weeks passed. For the mother, everything was now subordinated to the memory of an ancient life. The habit of picking him up after school or some activity outside, seeing him walk toward the car, seeing him walk away. His voice. His smell. He still smelled like a child—he was still a few months away from his eleventh birthday. He was still her little one. She could take his hand to cross the street, give him a long hug just because, plant a kiss on his cheek. He didn't impose that distance that comes when children start becoming men. Her boy, the storyteller of the childhood world... had departed.
As the months passed, the father withdrew more and more. He came home later and later, hardly spoke. He avoided talking to her. Sometimes, she found him crying in the boy's room. The fragility became evident and the limited kindnesses from one to the other disappeared. The one who was barely there was no longer there. The bridge between two solitudes had disappeared. The family had also died, and so, simply, one afternoon, he didn't return. Without words, without farewell.
-
 @ 57c631a3:07529a8e
2025-06-17 21:00:46
@ 57c631a3:07529a8e
2025-06-17 21:00:46Apple expands tools to help parents protect kids and teens online
https://connect-test.layer3.press/articles/567470ec-2349-40b6-9d8f-e2616b222c6d
-
 @ d9a329af:bef580d7
2025-06-17 19:05:21
@ d9a329af:bef580d7
2025-06-17 19:05:21Shabbat Shalom, y'all.
At the time of writing and releasing this, it happened to be a Lunar Shabbat, which is actually Torah (much to the chagrin of those who practice Shabbat on a Saturday or Sunday exclusively). The Shabbat is always on the 8th, 15th, 22nd, and 29th days of a Hebrew Calendar month, which almost nobody follows anymore. I started doing this a few months ago, and it's made me see the Torah for what it really is.
To the topic at hand, though. A lot of people on Nostr don't seem to understand the historical narrative of the book of Revelation, which saddens me, as we're in the end times Ekklesia (Assembly) era of Laodecia.
Deception of Bible Translations
First off, the reason why most people trust their pastors and/or read differently to what I do in Nazaritic circles is because of translations of the Scriptures that are evil, wretched and Catholic. The best way to combat this is to make some recommendations of which versions you'll want to use that aren't Catholic-infested.
These are the ONLY recommended versions to read. Anythine else is bupkus, evil and garbage, and will teach you futrism or preterism, both of which are Jesuit-penned deceptions.
The recommended versions are as follows:
-
1560/1590 Geneva (GNV)
-
Young's Literal Translation (YLT)
These are versions I've read, and determined are evil, wretched and garbage:
-
New International Version (NIV) [Fun fact: The publisher of the NIV, Zondervan, has a sister publisher that is behind the Satanic Bible's publishing]
-
New Living Translation (NLT)
-
English Standard Version (ESV)
-
ISR The Scriptures 2009 Third Edition with Minor Revisions [2016] (ISR2009)
-
New American Standard Bible (NASB)
-
New King James Version (NKJV)
-
KJV 1611 (Apparently, it was made for control)
What is the Laodecia Era for the Ekklesia?
As a refresher, this time sees people saying they're rich in truth and that they have need of nothing, but this shows that they're wretched, miserable, naked and wicked. Why is this? The need of nothing points to not needing another explanation other than the false futuristic viewpoint, whereas being rich is connected to already knowing the truth about the historical fulfillment of Revelation, which many people don't know at all. I seriously grieve their loss, for they know not what they do.
I'm also new into this viewpoint, and most of what I'll be talking about is proven by historicist prophet David Nikao Wilcoxson on YouTube and Facebook (I don't use Facebook). This single Nostr article, I pray, is the starting point for understanding why I call out what I call out, and the patterns I see pointing to the Roman Catholic Church (the Tares) and the Jesuit Order (the current rulers of our world, the Earth Beast of Rev. 13) being the harlots that will be plucked out before Messiah's return.
The 70th Week of Daniel
Let us start first with the 70th Week of Daniel, which futurists believe is pointed towards a 7 year period where a one-man antichrist makes a peace deal for Israel.
This was proven to be untrue, as this is a deception that many people have fallen for, thus obeying the Pope (the Mark of the Beast on the right hand). What Daniel was talking about was not the end times, but rather, two-fold. The first is that he was asking about when Yevah would free the Jews from slavery (since they were in the Babylonian Beast Kingdom at this time). The second is when Messiah would come in the flesh and start a 7 year period from 27-34 AD, which is the final 7 year period of this 490 year cycle. King Artaxerxes I would go ahead and call for the rebuilding of Jerusalem in 476 BC (as is seen in Ezra), which would be the first 7 weeks (the first 7 Shemita [Shabbat year] cycles). Afterwords, we would see another 62 weeks (this period is a slient period), and then another period of 1 week. This week points to Messiah's ministry and death.
3 1/2 years into this 70th week (in 31 AD) is when Messiah would be nailed to the cross on March 13 of 31 AD (I'm still debating if the cross is a symbol of Tammuz or not). This was Passover in the Hebrew calendar year of 3790. He was 33 years of age when he was nailed, and then rose again 3 days later (on the 17th of Nisan in 3790). That Passover fell on a Monday (when the Romans were using the 8-day calendar instead of the 7-day calendar we've essentially been forced to use).
To prove the above, Wilcoxson had produced a series of videos regarding the 70th Week of Daniel (that being the 70th Week of Daniel Decoded series), which I would recommend you watch. You'll also want to find an audiobook version of Seventy Weeks: The Historical Alternative produced by Tearing Down Idols. These are the two pieces of proof I have to show this. Speaking of Wilcoxson, he had already produced books on these matters, as understanding the hostorical narrative of the Scriptures is the key to making war with the Roman Catholic Church and the Jesuit Order, especially now that we're in Laodecia.
The Olivet Discourse
The second part of this trifecta has to do with the Olivet Discourse of Matthew 23, which points to the destruction of Jarusalem by Rome for Israel's unfaithfulness to Yevah's instructions. Now, there are connections to parables that basically talk about the Yewish (Yew as in Yewtree worship) leaders (particulaly the Pharisees and Saducees) practicing the Tradition of the Elders (which are the Babylonian Talmud and the Egyptian Kabbalah of today), and for not understanding that this was Messiah, they were destroyed for their iniquities. I don't care to research the futurist narrative on this, as I know it is full of twisted words and word salad sorcery.
Wilcoxson proves what I've said in the Olivet Discourse Decoded series of videos, so that's where I'll point you to when you have an open heart, open eyes and open ears. Many futurists won't, because they are exactly what Messiah described in the Ekklesia era of Laodecia.
Revelation and Its Prophecies
Finally, there's Revelation (what used to be called Apocalypse). When looking into this book, you realize that it's really a 4-layered war manual for how to fight this war against the Roman Catholic leadership and the Jesuit Order. This also shows how you can harvest souls (the harvest points to a mass exodus of Roman Catholicism membership). This I will go in depth on, and will even have passages to back this up.
Layer 1: The Roman Beast Kingdom
The first layer of this 4-layered manual shows the phases of the Roman Empire, which never really disappeared. Rev. 12 described the Roman Empire, which was used to wipe out the early Ekklesia (the woman), murdering millions of Nazarites. The Seals point to the incline (for the Four Horsemen of the Apocalypse) and decline of the Roman Empire (the other three Seals), while the Trumpets point to the official Roman Empire's downfall. This would be split into 10 separate kingdoms in Europe, which would be countered by the creation of Christianity, which is really any of the 44k+ forks of Roman Catholicism. This was done to destroy the Ekklesia, as the Roman Catholic Church is the Tare field that Messiah had talked about in the parable of the Wheat and the Tares.
Staying in this layer, the Sea Beast is the next phase. This is the 1,260-year reign of the Pope (538-1798), as he was the one who plucked out 3 kingdoms who didn't bow to his authority (the Heruli, the Huns and the Ostrigoths). Keep in mind that this started after the removal of the restrainer in 476 (pointing to the removal of the final Western Roman Emperor), and healed the deadly head wound (pointing to the Pope rising to power out of a sea of people). During this reign, he took the title of Pontifex Maximus, as he had civic and ecclesiastical power over everyone. This would be the healing of the deadly head wound, as shown earlier in this beast. He would pretend to be the leader of the Ekklesia, thus sitting in the Temple of Yevah, though he's the son of perdition, as he proclaims to be Yevah, forgive sins and provide salvation through works alone, which is blasephemous to begin with. The persecution of the Nazarites also prove them to be anti-Moshiach (Messiah). They also have the title of Vicar of Christ, which in the Latin is Vicarus Filii Dei, which is equal to 666 when calculated using a form of gematria I have no idea about. He would ultimately be removed from power by the Earth Beast in 1798, after he basically limited the power of the Jesuit Superior General and his minions. As stated before, the Mark of the Beast is reverence (forehead) and obeisance (right hand) to the Pope.
Finally, the Earth Beast of Revelation 13 points to the Jesuit Superior Geneal rising out of the earth (which is the land) of the Antichrist Beast Pope, the Vatican. These two horns pretend to serve Messiah (lamb) but are really Lucifarians (the dragon), serving Lucifer. The Black Pope, as the Jesuit Superior General is called, used his power to gether the world under him. That's why he uses Washington D.C. (the District of the Roman goddess, Columbia), his war machine (Military Indurstial Complex), to overthrow leaders who won't bow to his authority and those who won't set up a Rothschild central bank; much less obey the Khazars, who he also controls (I happened to be a partial German Khazar who escaped the grasp of the Black Pope as best as I know thus far).
Layer 2: The Ekklesia Eras
Now comes the eras of the Ekklesia. There are seven of them, though I've already explained the era of Laodecia. How about I give a quick explanation of the first six eras, like so?
Ephesus would spread the gospel in the Roman Empire, with their love growing cold when Messiah didn't return.
Smyrna had 10 years of persecutions from 303-312, which is what the 5th seal points to.
Pergamos would fall away (2 Thess. 2) from the Scriptures when compromising with Rome (Mark of the Beast as I had explained)
Thyatira means ruled by a woman. This means, the Roman Catholic Church would do this, as the Popes sought to eliminate the two witnesses, which are the Nazarites and the printed Scriptures (the little book or Rev. 10). This was why they killed the Nazarites and bured the printed Scriptures ruthlessly enough, that they were classified as "dead" in 1514. The Popes would hold great feasts to celebrate the removal of the two witnesses after they got all of Christendom under their control.
Sardis means escaping one, which points to Messiah calling them dead after 3 1/2 years from the Pope's classification of the death of the two witnesses. Luther's 95 Thesis sparked the Protestant Reformation, which would lead to the resurrection of the two witnesses (the Nazarites and the printed Scriptures).
Philidelphia had nothing bad that Messiah said about them... at all. They led worldwide missions, and also led Bible Societies to spread the word and/or the gospel to save millions of people from the clutches of the Jesuit Superior General (and the Roman Catholic Church as a whole).
As a refresher for Laodecia (the era we're in right now), the Nazarites here believe that they are rich in truth, and that we have need of nothing. This is false, as we are in dire need of something, which is an alternative explanation that's not the false futuristic or preteristic explanations of the book of Revelation. We are blinded by the Jesuits, as they have decieved us (we let them do this, by the way) with false prophecy explanations among other deceptions.
Layer 3: Seals, Trumpets and Bowls
The Seals, Trumpets and Bowls are the judgements against the Roman Beast Kingdom. To keep things short, every single Seal was fulfilled, 6 of the Trumpets were fulfilled, and 5 of the Bowls were fulfilled. We're in the 6th Bowl, waiting for a global economic collapse and WW III. Once these occur, then do we go into the 7th Bowl judgement against the Roman Catholic Church and the Jesuit Order (the New World Order).
One quick thing I'll mention is that when I talk about the two witnesses here, one of them is the little book of Rev. 10. This points to the printed Bible, which was brought back to life thanks to the printing press. Martin Luther would measure the temple and find that the Papal Church is the apostate harlot. Rev. 14 points to the Bowls and the harvest. This harvest points to millions coming out of the Roman Catholic Church, though there are 1.3 billion Catholics... and we have a long way to go in getting them out of her, My people.
Remember when I talked about the Khazars earlier in this article? They are the Kings of the East that Yeshua pointed to in the 6th Bowl. The Ottoman Empire is the Euphrates River here, and it's dried up in 1922, only with Turkey remaining. Gog is already dead, as that's Lord Rothschild. Magog points to the Kings of the East. 2 of the 3 spirits have already been fulfilled (these are World Wars I and II).
Now, let me quickly point out the fact we're in the kingdom of Iron and Clay. The Iron points to the Roman Bishops, and the Clay is Islam. However, furutists will tell me I'm an idiot, and that the Iron and Clay mixture is transhumanism. This was proven to be false, as the 5th Trumpet was the rise of the Clay (Islam). The Catholics, however, wrote the Qur'an and proped up Mohhamed as their prophet. ISIS and Al Qaeda are controlled by the Jesuit Order, which is why they do what they do as terrorists... for they are Wahhabi Muslims (in other words, Mizrahi Khazars who are also Jesuits, claiming to be Arabs, when they're not).
Islam is designed to prevent Arabs from having a relationship with Messiah, which makes me really sad. Muslims will be used to kill Christians and Jews in WW III and force us into the New World Order, which will backfire on the Jesuits and Roman Bishops.
Layer 4: The Harlot Church
Rev 17:10 talks about 7 forms of government. Five had fallen by the time Revelation was written, the 6th (the Roman Emperors) fell in 476, and the 7th lead for a short space until 538.
The 8th head is the Pope, who rose to power out of the Roman Empire. Look up what the priests in the Catholic Church wear, and what they use. Does that sound familiar when you read Revelation? If it does, that's exactly the description of the Sea Beast, and how his priests dress and do their rituals.
Then comes the Black Pope. He empowers and enriches the kings of the earth, as they were used by Lucifer to carry out the Bowl judgements, and will carry out the New World Order, caugins themselves and the Roman Cathoic Church to be judged big time. This we are waiting for.
Conclusion
Hopefully this long read helps you see where I'm coming from, and I pray it helps you to start testing the scriptures against what I've said, and what Wilcoxson had said. If it is proven in your heart that you were fooled, you're on the right path in my opnion. I may be wrong, but this is where I stand.
-
-
 @ 4fe4a528:3ff6bf06
2025-01-01 15:50:50
@ 4fe4a528:3ff6bf06
2025-01-01 15:50:50I could have wrote about how bitcoin has more than doubled in 2024 or how some people are still sitting on the sidelines not trying to understand why bitcoin will double in 2025, but instead I thought I would write about how bitcoin is allowing for a decentralized social network.
Two years ago I decided to try out this NOSTR idea. Now I have 233 followers, almost the same number of people who read this monthly newsletter. Facebook / whats-app was to ad filled for me to enjoy what my friends were posting. X was great for news, but none of my friends where on it. Linkedin was just about business. Besides, NOSTR gives me more bitcoin every time I post. I am now using the bitcoin to buy eggs every two weeks from my neighbors. So to me it is a win win. I can write notes and eat eggs. I even use my NOSTR extension to log into hivetalk.org and help people with their computer issues. It is better than teaching via ZOOM. 2025 is going to be a great year for decentralization.
If you are trying to join NOSTR via your desktop I recommend going to getalby.com installing the browser extension. Then make an account with getalby and write down your 24 words (nsec). Link your profile to your lightning wallet and start posting and following other friends via primal.net. Yes, of course, I am put on this earth to help my fellow man. Some people enjoy using NOSTR via their cell phone and for those people I recommend amethyst or damus. We are all in this together.
-
 @ cae03c48:2a7d6671
2025-06-17 15:00:39
@ cae03c48:2a7d6671
2025-06-17 15:00:39Bitcoin Magazine

Flash Releases Free Bitcoin Invoicing Tool with No Fees, KYC, or CustodyFlash, a Bitcoin payment platform, just announced it has launched Flash Invoicing, a completely free, non-custodial, and KYC-free Bitcoin invoicing tool. Designed for freelancers, the platform allows users to send professional invoices without platform fees, identity checks, or third party custody.
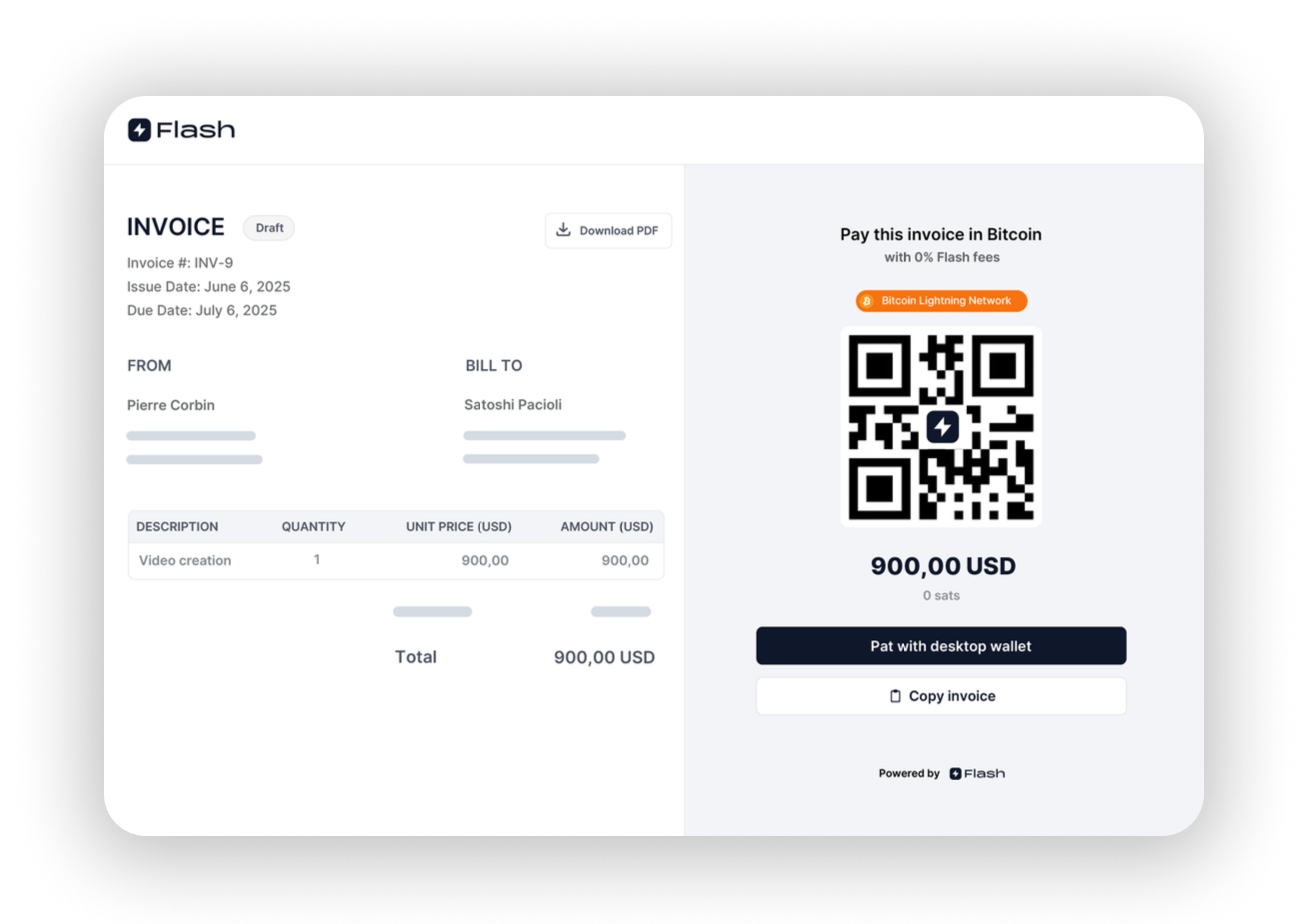
According to Deel, a crypto payments company for freelancers, Bitcoin is the most used cryptocurrency in the world for payments. Despite this growth, many freelancers continue to use basic methods such as pasting Bitcoin addresses into PDFs or emails. Some rely on custodial platforms that deduct fees or require identity verification, which can affect both earnings and data privacy.
“We’ve seen too many people paste BTC addresses into documents and call it invoicing,” said the CEO of Flash Pierre Corbin. “It’s messy. It’s risky. And it’s time for something better.”
Flash Invoicing Features:
- 0% platform fees: no subscriptions or commission
- Non-custodial: Bitcoin goes straight to the user’s wallet
- No KYC: users maintain full privacy
- Professional output: branded PDFs and secure payment links
- Integrated dashboard: manage payments, clients, and revenue
- Works with Flash ecosystem: including Stores, Donations, Paywalls, and POS
Many Bitcoin invoicing tools charge a percentage per transaction or require a subscription. As a result, freelancers often lose part of their income simply to issue an invoice and receive payment. Flash is aiming to solve this issue.
“Freelancers work hard enough. The last thing they need is a platform skimming off their earnings,” said Corbin. “That’s why we dropped our fee from 1.5% to 0% — and launched the first invoicing tool that’s truly free, without compromising on privacy or control.”
Flash Invoicing allows users to accept Bitcoin payments without relinquishing control, privacy, or revenue. It is integrated with the broader Flash suite, enabling users to manage invoicing alongside features such as setting up stores, receiving donations, or gating premium content.
“As a freelancer myself, I love using the Flash invoicing feature,” stated a freelancer & Flash user. ”It keeps all my clients in one place, allows me to easily edit invoices and track payments. Much more professional than sending a lightning address in the footer of a PDF invoice.”
This post Flash Releases Free Bitcoin Invoicing Tool with No Fees, KYC, or Custody first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ e5cfb5dc:0039f130
2025-06-17 11:00:35
@ e5cfb5dc:0039f130
2025-06-17 11:00:35はりまメンタルクリニック:GIDの大手そう。丸の内線ならパムくんちが近い。
わらびメンタルクリニック:GIDの大手そう?公式サイトには影もかたちも
ナグモクリニック:SRS手術までしてるところ。GID精神科外来が月1第1木曜日だけ?
狭山メンタルクリニック:距離・時間的にはまま近い。サイトの記述が思想的にちょとあやしげ。新患受付がだいぶ先。GIDは専門外か?
川島領診療所:オンライン診療あり!強迫性障害や美容皮膚科をやっている。雰囲気よさそうなところ。GIDは専門外か?
Jこころのクリニック:電車いっぽんなので楽。GIDは専門外か?
ハッピースマイルクリニック:オンライン診療あり!GIDは専門外か?
-
 @ b1ddb4d7:471244e7
2025-06-17 07:01:11
@ b1ddb4d7:471244e7
2025-06-17 07:01:11This article was originally published on dev.to by satshacker.
Alright, you’ve built a useful and beautiful website, tool or app. However, monetization isn’t a priority and you’d rather keep the project free, ads-free and accessible?
Accepting donations would be an option, but how? A PayPal button? Stripe? Buymeacoffe? Patreon?
All of these services require a bank account and KYC verification, before you can send and receive donations – not very convenient.
If we only could send value over the internet, with just one click and without the need of a bank account…
Oh, hold on, that’s bitcoin. The decentralized protocol to send value across the globe. Money over TCP/IP.
In this article, we’ll learn how anyone can easily add a payment button or donation widget on a website or app.
Let’s get into it.
Introduction
Bitcoin is digital money that you can send and receive without the need for banks. While bitcoin is extremely secure, it’s not very fast. The maximum transactions per second (TPS) the network can handle is about 7. Obviously that’s not useful for daily payments or microtransactions.
If you’d like to dig deeper into how bitcoin works, a great read is “Mastering Bitcoin” by Andreas Antonopoulos.
Bitcoin vs Lightning
If you’d like to receive bitcoin donations “on-chain” all you need is a bitcoin wallet. You simply display your bitcoin address on your site and that’s it. You can receive donations.
It would look something like this; 1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa
Instead of showing the actual bitcoin address, you can also turn it into a QR code.
However, this is not a recommended solution. Using static on-chain addresses has two major downsides. It lowers privacy for you and your donnors and it’s a UTXO disaster because many small incoming transactions could beocme hard to consolidate in the future.
For donations and small transactions, the Lightning Network is the better option. Lightning allows for instant settlement with fees only a fraction of a cent.
Similar to bitcoin, you have the choice between non-custodial and custodial wallets. This means, either you have full control over your money or the wallet provider has.
Option 1: Lightning Address
With the lightning address feature, you an easily receive donations to an email like address.
It looks like this: yourname@wallet.com
Many wallets support lightning addresses and make it easy to create one. Then, you simple add the address to your donation page and you’re ready to receive tips.
You can also add a link link as in lightning:yourname@wallet.com and compatible lightning wallets and browser wallets will detect the address.
Option 2: Lightning Donation Widgets
If you like to take it a step further, you can also create a more enhanced donation checkout flow. Of course you could programm something yourself, there are many open source libraries you can build upon. If you want a simple plug-and-play solution, here are a couple of options:
Name
Type
Registration
SatSale
Self-hosted
No KYC
BTCPay Server
Self-hosted
No KYC
Pay With Flash
Widget
Email
Geyser Fund
Widget
Email
The Giving Block
Hosted
KYC
OpenNode
Hosted
KYC
SatSale (GitHub)
Lightweight, self-hosted Bitcoin/Lightning payment processor. No KYC.
Ideal for developers comfortable with server management. Simple to deploy, supports both on-chain and Lightning, and integrates with WooCommerce.
BTCPay Server
Powerful, open-source, self-hosted processor for Bitcoin and Lightning. No KYC.
Supports multiple currencies, advanced features, and full privacy. Requires technical setup and maintenance. Funds go directly to your wallet; great for those seeking full control.
Pay With Flash
Easiest for indie hackers. Add a donation widget with minimal code and no KYC. Payments go directly to your wallet for a 1.5% fee.
Setup Steps:
- Sign up at PayWithFlash.com
- Customize your widget in the dashboard
- Embed the code:
- Test to confirm functionality
Benefits:
- Minimal technical skills required
- Supports one-time or recurring donations
- Direct fund transfer, no intermediaries
Geyser Fund
Crowdfunding platform. Widget-based, connects to your wallet, email registration.Focused on Bitcoin crowdfunding, memberships and donations.
The Giving Block
Hosted, KYC required. Integrates with fiat and crypto, best for nonprofits or larger organizations.
OpenNode
Hosted, KYC required. Accept Bitcoin payments and donations; supports conversion to fiat, suitable for businesses and nonprofits.
Summary
- Fast, low-code setup: Use Pay With Flash or Geyser Fund.
- Privacy and control: Choose SatSale or BTCPay Server (requires technical skills).
- Managed, compliant solutions: The Giving Block or OpenNode.
Choose based on your technical comfort, privacy needs, and project scale.
I hope this article helped you. If you added bitcoin donations, share your link in the comments and I will send you a few satoshis maybe

-
 @ dfa02707:41ca50e3
2025-06-17 19:01:50
@ dfa02707:41ca50e3
2025-06-17 19:01:50Contribute to keep No Bullshit Bitcoin news going.
-
Version 1.3 of Bitcoin Safe introduces a redesigned interactive chart, quick receive feature, updated icons, a mempool preview window, support for Child Pays For Parent (CPFP) and testnet4, preconfigured testnet demo wallets, as well as various bug fixes and improvements.
-
Upcoming updates for Bitcoin Safe include Compact Block Filters.
"Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions. They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK," writes the project's developer Andreas Griffin.
- Learn more about the current and upcoming features of Bitcoin Safe wallet here.
What's new in v1.3
- Redesign of Chart, Quick Receive, Icons, and Mempool Preview (by @design-rrr).
- Interactive chart. Clicking on it now jumps to transaction, and selected transactions are now highlighted.

- Speed up transactions with Child Pays For Parent (CPFP).
- BDK 1.2 (upgraded from 0.32).
- Testnet4 support.
- Preconfigured Testnet demo wallets.
- Cluster unconfirmed transactions so that parents/children are next to each other.
- Customizable columns for all tables (optional view: Txid, Address index, and more)
- Bug fixes and other improvements.

Announcement / Archive
Blog Post / Archive
GitHub Repo
Website -
-
 @ 319ad3e7:cc01d50a
2024-12-15 21:20:59
@ 319ad3e7:cc01d50a
2024-12-15 21:20:59LETTER FROM THE FOUNDER | FEATURED RECIPE | MICROFICTION | FOOD NOTE QUOTE | SOUNDS | NOSTR MARKETPLACE | REAL REVIEWS | COMMUNITY ALBUM | NEW RECIPES | FIN
LETTER FROM THE FOUNDER 📝
A Year of Growth and Gratitude
As we approach the end of the year, it’s the perfect moment to pause and reflect. 2024 has been a transformative year for Zap Cooking. What started as a simple idea has grown into a vibrant, connected community. From recipes to shared stories, the #zapcooking tag has become a rallying point for food enthusiasts everywhere, and it’s inspiring to see how this shared passion is bringing people together.
None of this would have been possible without the incredible support and dedication of Sarah, who pours her heart into crafting these newsletters. Sarah, thank you for helping us share the joy of cooking and community with so many.
I am deeply grateful, grateful for you, our community, for nostr, for the milestones we’ve reached, and for the challenges that have helped us grow. Zap Cooking is about more than food; it’s about connections, creativity, and collaboration. Together, we’ve built something special, and I’m excited for what 2025 holds.
Here’s to another year of cooking, connecting, and creating together. Thank you for being part of this journey.
Cheers!
Seth
Founder, Zap Cooking
FEATURED RECIPE 🥪
Nostrville 2.0 was located in Nashville, Tennessee. This music destination featured some powerhouse food establishments, such as Ladybird Taco, Hattie B’s Hot Chicken Sandwiches, Pancake Pantry, and Modell’s infamous family-style breakfast; however, it was the people from Louisiana who brought their A-game to the shared kitchen at the after-party rental.
The lovely Rupert and her giant, Kajoozie, served up a traditional gumbo that had all of us reaching for a second bowl… or perhaps a fourth bowl. It was that good! They were also kind enough to share their recipe with all of us.
Rupert and Kajoozie’s #Nostr Famous Gumbo https://substack.com/home/post/p-152296981
MICROFICTION 📖
GIFTS by RustyPuppy
Every Christmas Eve (and by 'every' Aaran meant those he could remember, which, being eight years old, was not many), after the dinner dishes had been washed, and the family settled into the living room to watch "It's a Wonderful Life," his nani would start chopping vegetables. Aaran once asked why she didn't cook Santa's beef stew when she prepared their dinner. Because she wanted the stew to be fresh, came the answer. Aaron knew better than to ask how something that needed to simmer for five hours could be considered 'fresh.'
Everyone knew their grandmother's beef stew, placed in front of the fireplace in a hand-made bowl wrapped in a dish towel to keep warm, was eaten by the dog after everyone went to bed. And every year, she insisted Santa needed a hot, healthy meal.
None of the children could believe anyone would choose vegetables over cookies. Shari, the girl next door, made peanut cookies for Santa. Aaron had helped mix the dough last year. He was forbidden from adding the frosting because Shari needed the perfect amount atop each cookie so she could write her name in the sugary mix with a toothpick. Depending how guilty she felt about the year, she sometimes added candy beads.
One year, a cousin asked if Santa really ate all of those hundreds? thousands? millions? of cookies. An uncle said, "Of course, that's why he's so fat," while Aaaran's mother said, "Of course not, he gives them to children who don't have sweets," and Nani added "And those who still want to believe in him."
Aaran secretly wanted to believe his nani, because his older brothers had teased him for writing his Christmas wish letter, saying Santa was only real for babies. He didn't want to be a baby, but he still wanted to believe in the magic that was Santa.
At last, the evening ended. Some returned to their homes; the rest returned to their rooms. Nani set her bowl under the stockings. Aaran hesitated on the stairs, but the thought of seeing the dog actually eat the stew made his eyes wet. He stepped over his cousin's sleeping bag, got into bed, and dreamed of flying reindeer.
In the morning, as the children opened their gifts and the adults took turns making coffee and tea, Nani asked Aaran to bring her the stew bowl. He looked at the dog, currently surrounded by shreds of wrapping paper, panting happily with a bow on his head. Picking up the bowl, Aaron saw something within; a peanut cookie with the name Shari written in the frosting.
RECIPE REFERENCES:
Lovely Indian beefstew with coconut milk & Ultimate Peanut Cookies https://substack.com/home/post/p-152296981
FOOD NOTE QUOTE 🗒️
Today someone took a picture of my latte art after I handed them their cup 💜 and it made my day. Celebrate the small things. 😊 - TKay
SOUNDS 🔊
At Bitcoin Park in Nashville, Tennessee, the adorable cuties Mallory, Other Mallory, Island, and Sergio, along with help from Fountain, Phantom Power and Tunestr.io organized a night of activities, food, art, and a live acoustic music panel featuring four absolutely talented musicians - Ainsley Costello, Amber Sweeney, Luke Wood, and Jo Corso. SoupBox was honored to sit down with Amber to chat about music, fostering dogs from Wags and Walks, and food | Listen Now: SoupBox with Sarah | Featuring Amber Sweeney
https://fountain.fm/episode/nvwD83sajCiFNqTP4tYu
https://feeds.rssblue.com/soupbox
Short from Nashville | OpenMike | Tunestr
https://v.nostr.build/yLufD7GbwOPI3EgA.mp4
NOSTR MARKETPLACE 💳
Find Your Holiday Gifts on Nostr | Value for Value (aka V4V) #circulareconomy
Agi Choote | Art Prints | Find on Nostr!
Amber Sweeney | Custom Songs for Any Occasion | https://www.theambersweeney.com/merch/custom-songs
Ant Richard | Limited Custom Handcrafted Knife Gift Certificates (12-month waitlist for all custom handmade orders) | Find on Nostr!
Apotheca Viva | https://apothecaviva.love/
Aupa Bars | https://eataupa.com/
Barnminer’s Barn Jerky | Find on Nostr!
Billay Coffee | https://billaycoffee.com/
BitBees | Honey & Honey Products | https://www.kittrellsdaydream.com/
Bitcoin Blankets ⚡️| Website Coming Soon!
Bitpopart | https://bitpopart.com/ | https://www.storeofvalue.eu/collections/christmas-collection
BTC Aloha | Bitcoin Beachwear & Accessories | https://btcaloha.shop/
BtcPins | https://btcpins.com/
Cannabis Records | https://cannabisrecords.store/
CryptoCloaks | https://www.cryptocloaks.com/shop/
Delgado’s Fuego | https://delgadosfuego.com/
Dot GNT | Laser Engravings | https://dotgnt.codeberg.page/
Finca Yabisi | https://yabisi.farm/
Foxfire Mushrooms | https://foxfiremushrooms.com/
Golden Tallow | https://goldentallow.com/
GoodBeans 🇸🇻 Coffee | https://thegoodbeans.com/
Isolabell.art | https://isolabell.art/
Jake Wolki | https://wolkifarm.com.au/
Keto Beejay | Low Sugar Jerky | https://ketolish.us/ | https://ketobeejay.npub.pro/
Kanuto Takumi San | Find on Nostr!
Laser Eyes Cards | https://lasereyes.cards/
LeatherMint | https://theleathermint.com/
Lightning Store | https://lightning.store/
LightningSpore | Full Service Mushroom Cultivation Company | https://www.lightningspore.com/
Lost Sheep Ranch | https://www.lost-sheep-ranch.com/
Lucho Poletti | Art Prints and Merchandise | https://luchopoletti.com/
Madex | Art & Apparel | https://madex.art/collections/in-stock
MapleTrade | Find on Nostr!
Matthew D | https://whitepaperstreetsoap.com/
Next Block Coffee | https://nextblockcoffee.com/
NoGood | Jake Wolki | https://wolkifarm.com.au/
PatsPropolisHoney | Find on Nostr!
Peony Lane Wine | Ben Justman | https://www.peonylanewine.com/
PlebianMarket | https://plebeian.market/
PictureRoom | Assorted Dessert Treats | Find on Nostr!
Regenerative Farmed Meats & Knives | AgrarianContrarian | Find on Nostr!
RustyPuppy | Art and Stories | https://heidi2524.com/
Salt of the Earth | Premium Electrolyte Mix | https://drinksote.com/
Satoshi Coffee Company | https://sats.coffee/
Scott & Son | Animal Portraits, Prints, and Apparel | https://xavierscraftworkanddesign.com/t-shirts
SofterSkin Tallow Skincare | https://softerskin.co/
Shopstr | https://shopstr.store/
Soap Miner | Tallow Body Soap Bars
SweetSats | Honey | https://sweetsats.io/
Veiled Mycology | https://veiledmycology.com/
Yojimbo | Jam & Marmalade | https://jimblesjumble.odoo.com/
REAL REVIEWS ⭐
BitBees | Honey & Honey Products | https://www.kittrellsdaydream.com/ | By Rupert
If you follow me or have ever had the pleasure of chatting with me on cornychat.com or hivetalk.org, you’ll know how proud I am of my Cajun heritage. For me, that means memories of long, hot summer days in South Louisiana, plenty of mosquito bites, the humming of cicadas in the cypress trees, and my grandfather’s bee boxes abuzz with fuzzy little workers.
I recently had the pleasure of meeting our famed #nostr beekeepers, @bitbees and @kingbee, and the absolute joy of tasting the labors of the wee little friends they care for. @KajoozieMaflingo and I purchased both their wildflower and gallberry varieties, and we were able to pay with BTC! (BONUS!) The wildflower was chef’s-kiss perfection, but my taste buds were instantly rocketed back to my childhood when I tried the lovingly and aptly nicknamed “swamp honey.”
Its pale color might fool you into thinking it has a lighter flavor than its rich and flavorful counterpart, but that couldn’t be further from the truth. It’s crisp and bright, with a mellow sweetness balanced by a slight tang to finish. It’s the ideal pairing with my favorite chamomile tea before bedtime.
This was my first purchase, but it will not be my last. By far, this is one of the most delicious use cases for Bitcoin I’ve come across to date.
Keto Beejay | Low Sugar Jerky | https://ketolish.us/ | https://ketobeejay.npub.pro/ | By The Beave
I recently had the pleasure of ordering four types of beef jerky from Beejay, the proprietress of http://ketolish.us. I was intrigued by her offerings and ended up ordering plain, pickle, pizza, and pepper. My order took a while to go through, mostly because Beejay and I were figuring out how to move sats around without it being too much of a pain in the butt. However, once finalized, everything shipped promptly and arrived quickly in a well-packed parcel. Beejay is also very good to communicate with, and I will gladly purchase more from her in the future.
I will start off the reviews with the most surprising of the batch: pizza. This was simply outstanding. I was shocked at how much it reminded me of eating pizza. I can't recommend this one enough! My second favorite pick is the pickle flavor. I love pickles. (I cannot express how much I love pickled things to you in words!) This was also very good, with the dill seasoning being front and center but restrained enough not to completely overpower the delicious beefiness of the jerky. A note on the texture: the jerky is ground, so it is not as tough as other jerkies you might try. This is a very new thing to me, and I rather enjoyed the novelty of the experience. The peppered jerky was full of pepper. This might be too much pepper for some, as it reminded me of the pepper-covered salami you can get at a good Italian pork store. Lastly, the plain jerky was delicious in its own right, though I would have preferred a touch more salt. I would order all of these again and am looking forward to ordering other flavors in the future, especially the bison!
COMMUNITY ALBUM 📷
Photos & Videos by Mandana from NextBlock & Flirting with Bitcoin, Efrat Fenigson, Ava, Birthday B, Vic from CornyChat, Tortuga, Mallory, Island, Jack Spirko, Paul Keating, BreadandToast.com, Nos.Social and Sarah SoupBox
View the Album: https://substack.com/home/post/p-152296981
NEW RECIPES 🍲
https://i.nostr.build/MNrivKtc1fpjamfn.png
In November, we received an incredible surge of over 30 recipes submitted to Zap Cooking! That's a fantastic leap from the three or four we typically see each week! Dive into one, two, or even all of them, and don’t forget to share your reviews and mouthwatering photos on Nostr using #foodstr. We’d also love to see your favorite personal or family recipes—let’s keep the culinary creativity flowing!
Corn Pudding, The Beef Panzone, Vodka Pie Crust, Short Rib Barbacoa Tacos, Guiness Beef Stew with Pickled Pearl Onions, Fast AF Beef Stroganoff, Dark Chocolate Mincemeat, Vic’s London Broil, Easy Wholemeal Spelt Flour Bread, Mamma SLCW’s Cranberry Sauce, Hot Dog Nachos, Italian Wedding Soup, Mapo Tofu Curry, Hot Honey Crispy Salmon Bowls, Curried Butternut Squash Soup, Best Damn Oven Baked Chicken Legs, Chocolate Creme Pie, Broccoli Beef, Tuscan Steak and Green Peppers, Easy Carne Asada, InstantPot Chicken Tortilla Soup, Green Bean Casserole with Bacon and Fried Shallots, Bang Bang Shrimp, Rupert and Kajoozie’s #Nostr Famous Gumbo, The Best Lamb Winter Stew, Avery’s Hot Wallet Salsa, Candied Pecans, Pumpkin Bread, Breakfast Casserole with Sausage and Egg, Gold & Silver Soup, Mr. G’s Homemade Chicken Pasta Salad, Ultimate Peanut Cookies
The recipe links are available here: https://substack.com/home/post/p-152296981
FIN 🤠
https://i.nostr.build/661bAgwsj6tEnICX.jpg
-
 @ 7f6db517:a4931eda
2025-06-16 18:02:22
@ 7f6db517:a4931eda
2025-06-16 18:02:22

"Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world." - Eric Hughes, A Cypherpunk's Manifesto, 1993
Privacy is essential to freedom. Without privacy, individuals are unable to make choices free from surveillance and control. Lack of privacy leads to loss of autonomy. When individuals are constantly monitored it limits our ability to express ourselves and take risks. Any decisions we make can result in negative repercussions from those who surveil us. Without the freedom to make choices, individuals cannot truly be free.
Freedom is essential to acquiring and preserving wealth. When individuals are not free to make choices, restrictions and limitations prevent us from economic opportunities. If we are somehow able to acquire wealth in such an environment, lack of freedom can result in direct asset seizure by governments or other malicious entities. At scale, when freedom is compromised, it leads to widespread economic stagnation and poverty. Protecting freedom is essential to economic prosperity.
The connection between privacy, freedom, and wealth is critical. Without privacy, individuals lose the freedom to make choices free from surveillance and control. While lack of freedom prevents individuals from pursuing economic opportunities and makes wealth preservation nearly impossible. No Privacy? No Freedom. No Freedom? No Wealth.
Rights are not granted. They are taken and defended. Rights are often misunderstood as permission to do something by those holding power. However, if someone can give you something, they can inherently take it from you at will. People throughout history have necessarily fought for basic rights, including privacy and freedom. These rights were not given by those in power, but rather demanded and won through struggle. Even after these rights are won, they must be continually defended to ensure that they are not taken away. Rights are not granted - they are earned through struggle and defended through sacrifice.
If you found this post helpful support my work with bitcoin.

-
 @ 31a4605e:cf043959
2025-06-17 18:02:14
@ 31a4605e:cf043959
2025-06-17 18:02:14A história do Bitcoin é pontuada por marcos simbólicos que representam não apenas a evolução técnica da moeda digital, mas também sua trajetória rumo à legitimidade econômica e política. Neste artigo, revisitamos alguns dos momentos mais emblemáticos que marcaram a adoção do Bitcoin, desde seu uso inicial em uma simples transação até o seu reconhecimento como moeda oficial por nações soberanas.
A pizza mais cara da história
Em 22 de maio de 2010, Laszlo Hanyecz fez história ao pagar 10.000 BTC por duas pizzas. Na época, essa quantia equivalia a cerca de 40 dólares. Hoje, essas mesmas moedas valeriam centenas de milhões de dólares, tornando essa a refeição mais cara já registrada. Mais do que uma curiosidade, essa transação marcou a primeira vez em que o Bitcoin foi usado em uma troca comercial real, comprovando seu potencial como meio de pagamento.
Silk Road e o lado obscuro da adoção inicial
Ainda que controverso, o uso do Bitcoin no marketplace Silk Road mostrou ao mundo que a moeda digital era funcional como meio de troca em larga escala. A plataforma operou entre 2011 e 2013 e foi um catalisador para o desenvolvimento de infraestrutura em torno do BTC, apesar dos impactos negativos na imagem da criptomoeda.
Mt. Gox e a primeira grande crise
Em 2014, a corretora Mt. Gox, responsável por cerca de 70% das transações de Bitcoin no mundo, declarou falência após perder cerca de 850 mil BTC. O escândalo abalou a confiança no ecossistema, mas também deu início a um movimento de amadurecimento: a busca por melhores práticas de segurança, regulação e profissionalização do setor.
El Salvador e o reconhecimento oficial
Em setembro de 2021, El Salvador tornou-se o primeiro país a reconhecer o Bitcoin como moeda de curso legal. A medida, defendida pelo presidente Nayib Bukele, foi recebida com entusiasmo por entusiastas e com ceticismo por instituições financeiras internacionais. O experimento salvadorenho colocou o Bitcoin no centro do debate geopolítico e abriu precedentes para outras nações considerarem o mesmo caminho.
Resumindo, cada um desses momentos representa uma etapa distinta na evolução do Bitcoin: da experimentação à adoção institucional. Ao revisitarmos esses casos emblemáticos, conseguimos entender não apenas como o Bitcoin evoluiu tecnicamente, mas também como sua narrativa se consolidou como parte da história financeira contemporânea. Se a compra da pizza simbolizou o nascimento prático do BTC, o reconhecimento oficial por nações inteiras sugere um futuro em que a moeda digital pode ser protagonista em novas formas de organização econômica global.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 4fe4a528:3ff6bf06
2024-12-01 15:00:30
@ 4fe4a528:3ff6bf06
2024-12-01 15:00:30https://cdn.satellite.earth/8dd22e9b598964ade69d4c5ca517c2637ffafdfb15cf3e589cd1a7955c173375.mp4 In my last news article I wrote about selling my beef for 4500 sats / lb and buying my eggs for 4500 sats / dozen. You will be glad to know that some of my friends gave me bitcoin for my birthday. One person gave me over 60,000 sats, so now I am feeling like my last months article caused everyone to buy bitcoin — opt out of inflation.
It must have been more than my friends giving me bitcoin that caused Bitcoin to increase it’s market cap by 600 billion US dollars. I know that eggs are costing me 3,000 sats now compared to 4500 sats one month ago. If things keep getting 50% cheaper every month I might not have to move all my value into bitcoin.
Isn’t it weird using something that increases in value month after month? It is indeed a far cry from the traditional notion of money, where the value or the purchasing power of the currency loses value month after month. Most Bitcoiners care about the separation of money from the state, the removal of a third party from transactions and the capturing the deflationary nature of technology, etc. The fiat price is simply a short term way of measuring progress toward that goal. In reality, the moose shekel price doesn’t really matter.
With Brazil and Russia now using it as legal tender I don’t want anyone to give me bitcoin as a gift this month. Give your money/love to helping others see Jesus’ love in coming to earth instead. You might be able to write off your donation also.
You do realize there are only 16.5 million bitcoin available to be moved to other bitcoin type people and the US bitcoin strategic reserve might be coming next year. I just hope the Trudeau / Christine “Vib” session doesn’t make Canadians give up on using the Moose Shekels as a means of exchanging value. Bitcoin is now worth more than the Canadian dollar. If you need to get educated about money join Nostr and do a video / desktop sharing conference with me. Say hivetalk.org @ 9am ish works best for me. Remember, learning technology makes you earn more. We are all in this together.
-
 @ d6affa19:9110b177
2024-09-24 18:31:42
@ d6affa19:9110b177
2024-09-24 18:31:42i'm in the upstairs office. lost in some project i've been tinkering with. i feel driven with purpose.
the door is cracked open. i always leave the door open.
Her footsteps echo up the stairway. but my focus is intense; a solution just beyond my fingertips.
the door creaks open, a soft whisper of a sound.
i instantly feel Her presence. a sweet vanilla scent wraps around me, thick and intoxicating.
Her fingers brush through my hair, a gentle caress.
She grips my hair, then releases it— over and over again. it feels good.
a soothing warmth envelops me.
Her fingers glide, each stroke igniting my senses. a chill races down my spine.
the monitor becomes a bit distant.
"You're really focused, hmm?" She teases, leaning closer. "I'm just checking in on my sweet boy." Her tone alluring, already drawing me in.
"of course, my Queen." i reply, my eyes glued to the screen, struggling to concentrate. "thank You," my voice hints at annoyance. "i'm so close to finishing this up."
just when i near a breakthrough, She appears, a siren pulling me from my path. how does She know..? the quiet signals that betray my focus— that reveal my yearning.
"Hmmmm," She playfully muses.
ugh, i need to concentrate. but the way this feels...
it pulls me deeper.
Her fingers drift by my ear, lingering around my neck. nails grazing my skin, sending shivers through me.
my heart begins to race. the screen blurs, reality separates.
"Okay, sweet boy." Her voice is a soft command. Her nails dig in, a mixture of pain and pleasure. a sharp contrast to the softness of Her touch. "I'll be downstairs while you finish."
yet She remains. i close my eyes, drowning in the sensation. i should be finishing this project...
but each press feels like a silent command, an urge to abandon my thoughts, to succumb to the pull of Her presence.
the way She easily captures my attention... it makes me feel so vulnerable...
Her grip finally loosens, and slowly leaves my neck. it wants more...
i barely hear Her leave. but the air feels colder. the warmth of Her presence is fading. an aching emptiness fills the space...
the weight of Her absence settles in, another reminder of how easily She commands my thoughts...
desperately, i take in the remnants of Her scent.
i stare at my monitor. focus shattered, thoughts scattered like leaves.
i linger for a moment. fighting the urge to chase after Her.
the pull of Her absence is heavy in the air. i'm unable to resist. i rise from my seat.
the door is slightly open. She always leaves the door open.
i make my way downstairs, lost in the thoughts of serving Her. my true purpose...
-
 @ 7f6db517:a4931eda
2025-06-16 16:02:20
@ 7f6db517:a4931eda
2025-06-16 16:02:20
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ ee11a5df:b76c4e49
2024-09-11 08:16:37
@ ee11a5df:b76c4e49
2024-09-11 08:16:37Bye-Bye Reply Guy
There is a camp of nostr developers that believe spam filtering needs to be done by relays. Or at the very least by DVMs. I concur. In this way, once you configure what you want to see, it applies to all nostr clients.
But we are not there yet.
In the mean time we have ReplyGuy, and gossip needed some changes to deal with it.
Strategies in Short
- WEB OF TRUST: Only accept events from people you follow, or people they follow - this avoids new people entirely until somebody else that you follow friends them first, which is too restrictive for some people.
- TRUSTED RELAYS: Allow every post from relays that you trust to do good spam filtering.
- REJECT FRESH PUBKEYS: Only accept events from people you have seen before - this allows you to find new people, but you will miss their very first post (their second post must count as someone you have seen before, even if you discarded the first post)
- PATTERN MATCHING: Scan for known spam phrases and words and block those events, either on content or metadata or both or more.
- TIE-IN TO EXTERNAL SYSTEMS: Require a valid NIP-05, or other nostr event binding their identity to some external identity
- PROOF OF WORK: Require a minimum proof-of-work
All of these strategies are useful, but they have to be combined properly.
filter.rhai
Gossip loads a file called "filter.rhai" in your gossip directory if it exists. It must be a Rhai language script that meets certain requirements (see the example in the gossip source code directory). Then it applies it to filter spam.
This spam filtering code is being updated currently. It is not even on unstable yet, but it will be there probably tomorrow sometime. Then to master. Eventually to a release.
Here is an example using all of the techniques listed above:
```rhai // This is a sample spam filtering script for the gossip nostr // client. The language is called Rhai, details are at: // https://rhai.rs/book/ // // For gossip to find your spam filtering script, put it in // your gossip profile directory. See // https://docs.rs/dirs/latest/dirs/fn.data_dir.html // to find the base directory. A subdirectory "gossip" is your // gossip data directory which for most people is their profile // directory too. (Note: if you use a GOSSIP_PROFILE, you'll // need to put it one directory deeper into that profile // directory). // // This filter is used to filter out and refuse to process // incoming events as they flow in from relays, and also to // filter which events get/ displayed in certain circumstances. // It is only run on feed-displayable event kinds, and only by // authors you are not following. In case of error, nothing is // filtered. // // You must define a function called 'filter' which returns one // of these constant values: // DENY (the event is filtered out) // ALLOW (the event is allowed through) // MUTE (the event is filtered out, and the author is // automatically muted) // // Your script will be provided the following global variables: // 'caller' - a string that is one of "Process", // "Thread", "Inbox" or "Global" indicating // which part of the code is running your // script // 'content' - the event content as a string // 'id' - the event ID, as a hex string // 'kind' - the event kind as an integer // 'muted' - if the author is in your mute list // 'name' - if we have it, the name of the author // (or your petname), else an empty string // 'nip05valid' - whether nip05 is valid for the author, // as a boolean // 'pow' - the Proof of Work on the event // 'pubkey' - the event author public key, as a hex // string // 'seconds_known' - the number of seconds that the author // of the event has been known to gossip // 'spamsafe' - true only if the event came in from a // relay marked as SpamSafe during Process // (even if the global setting for SpamSafe // is off)
fn filter() {
// Show spam on global // (global events are ephemeral; these won't grow the // database) if caller=="Global" { return ALLOW; } // Block ReplyGuy if name.contains("ReplyGuy") || name.contains("ReplyGal") { return DENY; } // Block known DM spam // (giftwraps are unwrapped before the content is passed to // this script) if content.to_lower().contains( "Mr. Gift and Mrs. Wrap under the tree, KISSING!" ) { return DENY; } // Reject events from new pubkeys, unless they have a high // PoW or we somehow already have a nip05valid for them // // If this turns out to be a legit person, we will start // hearing their events 2 seconds from now, so we will // only miss their very first event. if seconds_known <= 2 && pow < 25 && !nip05valid { return DENY; } // Mute offensive people if content.to_lower().contains(" kike") || content.to_lower().contains("kike ") || content.to_lower().contains(" nigger") || content.to_lower().contains("nigger ") { return MUTE; } // Reject events from muted people // // Gossip already does this internally, and since we are // not Process, this is rather redundant. But this works // as an example. if muted { return DENY; } // Accept if the PoW is large enough if pow >= 25 { return ALLOW; } // Accept if their NIP-05 is valid if nip05valid { return ALLOW; } // Accept if the event came through a spamsafe relay if spamsafe { return ALLOW; } // Reject the rest DENY} ```
-
 @ eb0157af:77ab6c55
2025-06-18 02:02:04
@ eb0157af:77ab6c55
2025-06-18 02:02:04The Brazilian government has abolished the Bitcoin tax exemption for small investors and introduced a flat 17.5% tax rate on all crypto capital gains.
Brazil has officially ended the tax-free period for small digital asset investors, introducing a flat 17.5% rate on all profits from cryptocurrency sales. The decision was formalized through Provisional Measure 1303, part of the government’s strategy to increase tax revenues from financial markets.
Until now, Brazilian residents selling up to 35,000 Brazilian reais (around $6,300) in cryptocurrencies per month were completely exempt from income tax. Profits exceeding this threshold were subject to progressive taxation, starting at 15% and reaching up to 22.5% for amounts over 30 million reais.
The new flat rate, which took effect on June 12, removes all exemptions and applies uniformly to every investor, regardless of the size of their transactions, according to local outlet Portal do Bitcoin.
While small-scale investors will now face a higher tax burden, high-net-worth individuals might actually benefit. Under the previous system, large transactions were taxed between 17.5% and 22.5%. With the new flat 17.5% rate, many high-profile investors will see their effective tax liability reduced.
Under the new rules, taxes will be calculated quarterly, with investors allowed to offset losses from the previous five quarters. However, starting in 2026, the time frame for claiming losses will be shortened.
Last March, Brazilian lawmakers also proposed a bill allowing employers to partially pay workers in cryptocurrency. According to the draft, crypto payments could not exceed 50% of an employee’s salary.
Full payment in cryptocurrencies would only be allowed for foreign workers or contractors, and only under specific conditions set by the Brazilian Central Bank. The bill prohibits full crypto payment for standard employees.
The post Brazil scraps crypto tax exemption: new 17.5% flat tax appeared first on Atlas21.
-
 @ 4ba8e86d:89d32de4
2025-06-17 18:01:47
@ 4ba8e86d:89d32de4
2025-06-17 18:01:47Como funciona o PGP.
GP 6.5.1. Copyright © 1990-1999 Network Associates, Inc. Todos os direitos reservados.
-O que é criptografia? -Criptografia forte -Como funciona a criptografia? -Criptografia convencional -Cifra de César -Gerenciamento de chaves e criptografia convencional -Criptografia de chave pública -Como funciona o PGP - Chaves • Assinaturas digitais -Funções hash • Certificados digitais -Distribuição de certificados -Formatos de certificado •Validade e confiança -Verificando validade -Estabelecendo confiança -Modelos de confiança • Revogação de certificado -Comunicar que um certificado foi revogado -O que é uma senha? -Divisão de chave
Os princípios básicos da criptografia.
Quando Júlio César enviou mensagens aos seus generais, ele não confiou nos seus mensageiros. Então ele substituiu cada A em suas mensagens por um D, cada B por um E, e assim por diante através do alfabeto. Somente alguém que conhecesse a regra “shift by 3” poderia decifrar suas mensagens. E assim começamos.
Criptografia e descriptografia.
Os dados que podem ser lidos e compreendidos sem quaisquer medidas especiais são chamados de texto simples ou texto não criptografado. O método de disfarçar o texto simples de forma a ocultar sua substância é chamado de criptografia. Criptografar texto simples resulta em um jargão ilegível chamado texto cifrado. Você usa criptografia para garantir que as informações sejam ocultadas de qualquer pessoa a quem não se destinam, mesmo daqueles que podem ver os dados criptografados. O processo de reverter o texto cifrado ao texto simples original é chamado de descriptografia . A Figura 1-1 ilustra esse processo.
https://image.nostr.build/0e2fcb71ed86a6083e083abbb683f8c103f44a6c6db1aeb2df10ae51ec97ebe5.jpg
Figura 1-1. Criptografia e descriptografia
O que é criptografia?
Criptografia é a ciência que usa a matemática para criptografar e descriptografar dados. A criptografia permite armazenar informações confidenciais ou transmiti-las através de redes inseguras (como a Internet) para que não possam ser lidas por ninguém, exceto pelo destinatário pretendido. Embora a criptografia seja a ciência que protege os dados, a criptoanálise é a ciência que analisa e quebra a comunicação segura. A criptoanálise clássica envolve uma combinação interessante de raciocínio analítico, aplicação de ferramentas matemáticas, descoberta de padrões, paciência, determinação e sorte. Os criptoanalistas também são chamados de atacantes. A criptologia abrange tanto a criptografia quanto a criptoanálise.
Criptografia forte.
"Existem dois tipos de criptografia neste mundo: a criptografia que impedirá a sua irmã mais nova de ler os seus arquivos, e a criptografia que impedirá os principais governos de lerem os seus arquivos. Este livro é sobre o último." --Bruce Schneier, Criptografia Aplicada: Protocolos, Algoritmos e Código Fonte em C. PGP também trata deste último tipo de criptografia. A criptografia pode ser forte ou fraca, conforme explicado acima. A força criptográfica é medida no tempo e nos recursos necessários para recuperar o texto simples. O resultado de uma criptografia forte é um texto cifrado que é muito difícil de decifrar sem a posse da ferramenta de decodificação apropriada. Quão díficil? Dado todo o poder computacional e o tempo disponível de hoje – mesmo um bilhão de computadores fazendo um bilhão de verificações por segundo – não é possível decifrar o resultado de uma criptografia forte antes do fim do universo. Alguém poderia pensar, então, que uma criptografia forte resistiria muito bem até mesmo contra um criptoanalista extremamente determinado. Quem pode realmente dizer? Ninguém provou que a criptografia mais forte disponível hoje resistirá ao poder computacional de amanhã. No entanto, a criptografia forte empregada pelo PGP é a melhor disponível atualmente.
Contudo, a vigilância e o conservadorismo irão protegê-lo melhor do que as alegações de impenetrabilidade.
Como funciona a criptografia?
Um algoritmo criptográfico, ou cifra, é uma função matemática usada no processo de criptografia e descriptografia. Um algoritmo criptográfico funciona em combinação com uma chave – uma palavra, número ou frase – para criptografar o texto simples. O mesmo texto simples é criptografado em texto cifrado diferente com chaves diferentes. A segurança dos dados criptografados depende inteiramente de duas coisas: a força do algoritmo criptográfico e o sigilo da chave. Um algoritmo criptográfico, mais todas as chaves possíveis e todos os protocolos que o fazem funcionar constituem um criptossistema. PGP é um criptossistema.
Criptografia convencional.
Na criptografia convencional, também chamada de criptografia de chave secreta ou de chave simétrica , uma chave é usada tanto para criptografia quanto para descriptografia. O Data Encryption Standard (DES) é um exemplo de criptossistema convencional amplamente empregado pelo Governo Federal. A Figura 1-2 é uma ilustração do processo de criptografia convencional. https://image.nostr.build/328b73ebaff84c949df2560bbbcec4bc3b5e3a5163d5fbb2ec7c7c60488f894c.jpg
Figura 1-2. Criptografia convencional
Cifra de César.
Um exemplo extremamente simples de criptografia convencional é uma cifra de substituição. Uma cifra de substituição substitui uma informação por outra. Isso é feito com mais frequência compensando as letras do alfabeto. Dois exemplos são o Anel Decodificador Secreto do Capitão Meia-Noite, que você pode ter possuído quando era criança, e a cifra de Júlio César. Em ambos os casos, o algoritmo serve para compensar o alfabeto e a chave é o número de caracteres para compensá-lo. Por exemplo, se codificarmos a palavra "SEGREDO" usando o valor chave de César de 3, deslocaremos o alfabeto para que a terceira letra abaixo (D) comece o alfabeto. Então começando com A B C D E F G H I J K L M N O P Q R S T U V W X Y Z e deslizando tudo para cima em 3, você obtém DEFGHIJKLMNOPQRSTUVWXYZABC onde D=A, E=B, F=C e assim por diante. Usando este esquema, o texto simples, "SECRET" é criptografado como "VHFUHW". Para permitir que outra pessoa leia o texto cifrado, você diz a ela que a chave é 3. Obviamente, esta é uma criptografia extremamente fraca para os padrões atuais, mas, ei, funcionou para César e ilustra como funciona a criptografia convencional.
Gerenciamento de chaves e criptografia convencional.
A criptografia convencional tem benefícios. É muito rápido. É especialmente útil para criptografar dados que não vão a lugar nenhum. No entanto, a criptografia convencional por si só como meio de transmissão segura de dados pode ser bastante cara, simplesmente devido à dificuldade de distribuição segura de chaves. Lembre-se de um personagem do seu filme de espionagem favorito: a pessoa com uma pasta trancada e algemada ao pulso. Afinal, o que há na pasta? Provavelmente não é o código de lançamento de mísseis/fórmula de biotoxina/plano de invasão em si. É a chave que irá descriptografar os dados secretos. Para que um remetente e um destinatário se comuniquem com segurança usando criptografia convencional, eles devem chegar a um acordo sobre uma chave e mantê-la secreta entre si. Se estiverem em locais físicos diferentes, devem confiar em um mensageiro, no Bat Phone ou em algum outro meio de comunicação seguro para evitar a divulgação da chave secreta durante a transmissão. Qualquer pessoa que ouvir ou interceptar a chave em trânsito poderá posteriormente ler, modificar e falsificar todas as informações criptografadas ou autenticadas com essa chave. Do DES ao Anel Decodificador Secreto do Capitão Midnight, o problema persistente com a criptografia convencional é a distribuição de chaves: como você leva a chave ao destinatário sem que alguém a intercepte?
Criptografia de chave pública.
Os problemas de distribuição de chaves são resolvidos pela criptografia de chave pública, cujo conceito foi introduzido por Whitfield Diffie e Martin Hellman em 1975. (Há agora evidências de que o Serviço Secreto Britânico a inventou alguns anos antes de Diffie e Hellman, mas a manteve um segredo militar - e não fez nada com isso.
[JH Ellis: The Possibility of Secure Non-Secret Digital Encryption, CESG Report, January 1970]) A criptografia de chave pública é um esquema assimétrico que usa um par de chaves para criptografia: uma chave pública, que criptografa os dados, e uma chave privada ou secreta correspondente para descriptografia. Você publica sua chave pública para o mundo enquanto mantém sua chave privada em segredo. Qualquer pessoa com uma cópia da sua chave pública pode criptografar informações que somente você pode ler. Até mesmo pessoas que você nunca conheceu. É computacionalmente inviável deduzir a chave privada da chave pública. Qualquer pessoa que possua uma chave pública pode criptografar informações, mas não pode descriptografá-las. Somente a pessoa que possui a chave privada correspondente pode descriptografar as informações. https://image.nostr.build/fdb71ae7a4450a523456827bdd509b31f0250f63152cc6f4ba78df290887318b.jpg
Figura 1-3. Criptografia de chave pública O principal benefício da criptografia de chave pública é que ela permite que pessoas que não possuem nenhum acordo de segurança pré-existente troquem mensagens com segurança. A necessidade de remetente e destinatário compartilharem chaves secretas através de algum canal seguro é eliminada; todas as comunicações envolvem apenas chaves públicas e nenhuma chave privada é transmitida ou compartilhada. Alguns exemplos de criptossistemas de chave pública são Elgamal (nomeado em homenagem a seu inventor, Taher Elgamal), RSA (nomeado em homenagem a seus inventores, Ron Rivest, Adi Shamir e Leonard Adleman), Diffie-Hellman (nomeado, você adivinhou, em homenagem a seus inventores). ) e DSA, o algoritmo de assinatura digital (inventado por David Kravitz). Como a criptografia convencional já foi o único meio disponível para transmitir informações secretas, o custo dos canais seguros e da distribuição de chaves relegou a sua utilização apenas àqueles que podiam pagar, como governos e grandes bancos (ou crianças pequenas com anéis descodificadores secretos). A criptografia de chave pública é a revolução tecnológica que fornece criptografia forte para as massas adultas. Lembra do mensageiro com a pasta trancada e algemada ao pulso? A criptografia de chave pública o tira do mercado (provavelmente para seu alívio).
Como funciona o PGP.
O PGP combina alguns dos melhores recursos da criptografia convencional e de chave pública. PGP é um criptossistema híbrido. Quando um usuário criptografa texto simples com PGP, o PGP primeiro compacta o texto simples. A compactação de dados economiza tempo de transmissão do modem e espaço em disco e, mais importante ainda, fortalece a segurança criptográfica. A maioria das técnicas de criptoanálise explora padrões encontrados no texto simples para quebrar a cifra. A compressão reduz esses padrões no texto simples, aumentando assim enormemente a resistência à criptoanálise. (Arquivos que são muito curtos para compactar ou que não são compactados bem não são compactados.) O PGP então cria uma chave de sessão, que é uma chave secreta única. Esta chave é um número aleatório gerado a partir dos movimentos aleatórios do mouse e das teclas digitadas. Esta chave de sessão funciona com um algoritmo de criptografia convencional rápido e muito seguro para criptografar o texto simples; o resultado é texto cifrado. Depois que os dados são criptografados, a chave da sessão é criptografada na chave pública do destinatário. Essa chave de sessão criptografada com chave pública é transmitida junto com o texto cifrado ao destinatário.
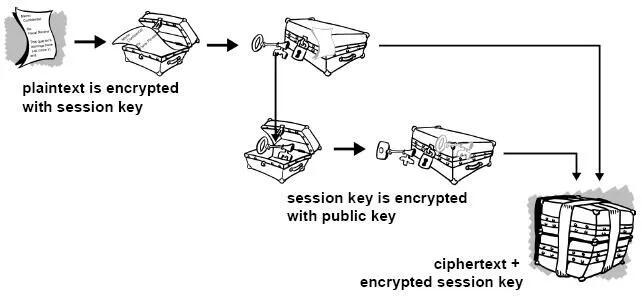
Figura 1-4. Como funciona a criptografia PGP A descriptografia funciona ao contrário. A cópia do PGP do destinatário usa sua chave privada para recuperar a chave de sessão temporária, que o PGP usa para descriptografar o texto cifrado criptografado convencionalmente.

Figura 1-5. Como funciona a descriptografia PGP A combinação dos dois métodos de criptografia combina a conveniência da criptografia de chave pública com a velocidade da criptografia convencional. A criptografia convencional é cerca de 1.000 vezes mais rápida que a criptografia de chave pública. A criptografia de chave pública, por sua vez, fornece uma solução para
problemas de distribuição de chaves e transmissão de dados. Usados em conjunto, o desempenho e a distribuição de chaves são melhorados sem qualquer sacrifício na segurança.
Chaves.
Uma chave é um valor que funciona com um algoritmo criptográfico para produzir um texto cifrado específico. As chaves são basicamente números muito, muito, muito grandes. O tamanho da chave é medido em bits; o número que representa uma chave de 1024 bits é enorme. Na criptografia de chave pública, quanto maior a chave, mais seguro é o texto cifrado. No entanto, o tamanho da chave pública e o tamanho da chave secreta da criptografia convencional não têm nenhuma relação. Uma chave convencional de 80 bits tem a força equivalente a uma chave pública de 1.024 bits. Uma chave convencional de 128 bits é equivalente a uma chave pública de 3.000 bits. Novamente, quanto maior a chave, mais segura, mas os algoritmos usados para cada tipo de criptografia são muito diferentes e, portanto, a comparação é como a de maçãs com laranjas. Embora as chaves pública e privada estejam matematicamente relacionadas, é muito difícil derivar a chave privada dada apenas a chave pública; no entanto, derivar a chave privada é sempre possível, desde que haja tempo e capacidade computacional suficientes. Isto torna muito importante escolher chaves do tamanho certo; grande o suficiente para ser seguro, mas pequeno o suficiente para ser aplicado rapidamente. Além disso, você precisa considerar quem pode estar tentando ler seus arquivos, quão determinados eles estão, quanto tempo têm e quais podem ser seus recursos. Chaves maiores serão criptograficamente seguras por um longo período de tempo. Se o que você deseja criptografar precisar ficar oculto por muitos anos, você pode usar uma chave muito grande. Claro, quem sabe quanto tempo levará para determinar sua chave usando os computadores mais rápidos e eficientes de amanhã? Houve um tempo em que uma chave simétrica de 56 bits era considerada extremamente segura. As chaves são armazenadas de forma criptografada. O PGP armazena as chaves em dois arquivos no seu disco rígido; um para chaves públicas e outro para chaves privadas. Esses arquivos são chamados de chaveiros. Ao usar o PGP, você normalmente adicionará as chaves públicas dos seus destinatários ao seu chaveiro público. Suas chaves privadas são armazenadas em seu chaveiro privado. Se você perder seu chaveiro privado, não será possível descriptografar nenhuma informação criptografada nas chaves desse anel.
Assinaturas digitais.
Um grande benefício da criptografia de chave pública é que ela fornece um método para empregar assinaturas digitais. As assinaturas digitais permitem ao destinatário da informação verificar a autenticidade da origem da informação e também verificar se a informação está intacta. Assim, as assinaturas digitais de chave pública fornecem autenticação e integridade de dados. A assinatura digital também proporciona o não repúdio, o que significa que evita que o remetente alegue que não enviou realmente as informações. Esses recursos são tão fundamentais para a criptografia quanto a privacidade, se não mais. Uma assinatura digital tem a mesma finalidade de uma assinatura manuscrita. No entanto, uma assinatura manuscrita é fácil de falsificar. Uma assinatura digital é superior a uma assinatura manuscrita porque é quase impossível de ser falsificada, além de atestar o conteúdo da informação, bem como a identidade do signatário.
Algumas pessoas tendem a usar mais assinaturas do que criptografia. Por exemplo, você pode não se importar se alguém souber que você acabou de depositar US$ 1.000 em sua conta, mas quer ter certeza de que foi o caixa do banco com quem você estava lidando. A maneira básica pela qual as assinaturas digitais são criadas é ilustrada na Figura 1-6 . Em vez de criptografar informações usando a chave pública de outra pessoa, você as criptografa com sua chave privada. Se as informações puderem ser descriptografadas com sua chave pública, elas deverão ter se originado em você.
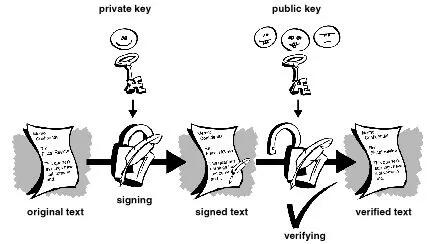
Figura 1-6. Assinaturas digitais simples
Funções hash.
O sistema descrito acima apresenta alguns problemas. É lento e produz um enorme volume de dados – pelo menos o dobro do tamanho da informação original. Uma melhoria no esquema acima é a adição de uma função hash unidirecional no processo. Uma função hash unidirecional recebe uma entrada de comprimento variável – neste caso, uma mensagem de qualquer comprimento, até mesmo milhares ou milhões de bits – e produz uma saída de comprimento fixo; digamos, 160 bits. A função hash garante que, se a informação for alterada de alguma forma – mesmo que por apenas um bit – seja produzido um valor de saída totalmente diferente. O PGP usa uma função hash criptograficamente forte no texto simples que o usuário está assinando. Isso gera um item de dados de comprimento fixo conhecido como resumo da mensagem. (Novamente, qualquer alteração nas informações resulta em um resumo totalmente diferente.) Então o PGP usa o resumo e a chave privada para criar a “assinatura”. O PGP transmite a assinatura e o texto simples juntos. Ao receber a mensagem, o destinatário utiliza o PGP para recalcular o resumo, verificando assim a assinatura. O PGP pode criptografar o texto simples ou não; assinar texto simples é útil se alguns dos destinatários não estiverem interessados ou não forem capazes de verificar a assinatura. Desde que uma função hash segura seja usada, não há como retirar a assinatura de alguém de um documento e anexá-la a outro, ou alterar uma mensagem assinada de qualquer forma. A menor alteração em um documento assinado causará falha no processo de verificação da assinatura digital.
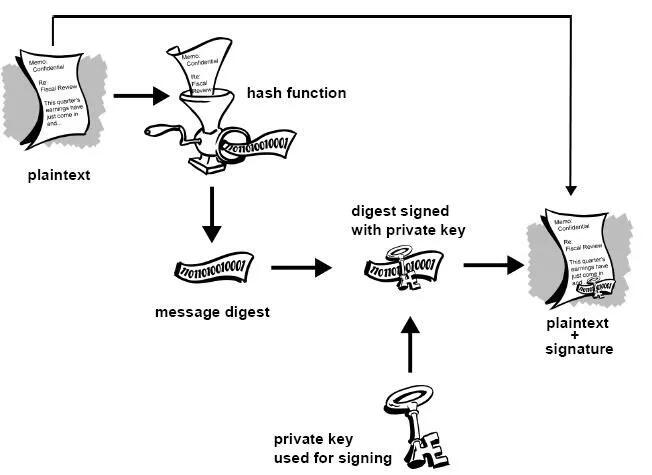
Figura 1-7. Assinaturas digitais seguras As assinaturas digitais desempenham um papel importante na autenticação e validação de chaves de outros usuários PGP.
Certificados digitais.
Um problema com os criptosistemas de chave pública é que os usuários devem estar constantemente vigilantes para garantir que estão criptografando com a chave da pessoa correta. Num ambiente onde é seguro trocar chaves livremente através de servidores públicos, os ataques man-in-the-middle são uma ameaça potencial. Neste tipo de ataque, alguém publica uma chave falsa com o nome e ID de usuário do destinatário pretendido. Os dados criptografados – e interceptados por – o verdadeiro proprietário desta chave falsa estão agora em mãos erradas. Em um ambiente de chave pública, é vital que você tenha certeza de que a chave pública para a qual você está criptografando os dados é de fato a chave pública do destinatário pretendido e não uma falsificação. Você pode simplesmente criptografar apenas as chaves que foram entregues fisicamente a você. Mas suponha que você precise trocar informações com pessoas que nunca conheceu; como você pode saber se tem a chave correta? Os certificados digitais, ou certs, simplificam a tarefa de estabelecer se uma chave pública realmente pertence ao suposto proprietário. Um certificado é uma forma de credencial. Exemplos podem ser sua carteira de motorista, seu cartão de previdência social ou sua certidão de nascimento. Cada um deles contém algumas informações que identificam você e alguma autorização informando que outra pessoa confirmou sua identidade. Alguns certificados, como o seu passaporte, são uma confirmação importante o suficiente da sua identidade para que você não queira perdê-los, para que ninguém os use para se passar por você.
Um certificado digital são dados que funcionam como um certificado físico. Um certificado digital é uma informação incluída na chave pública de uma pessoa que ajuda outras pessoas a verificar se uma chave é genuína ou válida. Os certificados digitais são usados para impedir tentativas de substituir a chave de uma pessoa por outra.
Um certificado digital consiste em três coisas:
● Uma chave pública.
● Informações do certificado. (Informações de "identidade" sobre o usuário, como nome, ID do usuário e assim por diante.) ● Uma ou mais assinaturas digitais.
O objetivo da assinatura digital em um certificado é afirmar que as informações do certificado foram atestadas por alguma outra pessoa ou entidade. A assinatura digital não atesta a autenticidade do certificado como um todo; ele atesta apenas que as informações de identidade assinadas acompanham ou estão vinculadas à chave pública. Assim, um certificado é basicamente uma chave pública com uma ou duas formas de identificação anexadas, além de um forte selo de aprovação de algum outro indivíduo confiável.
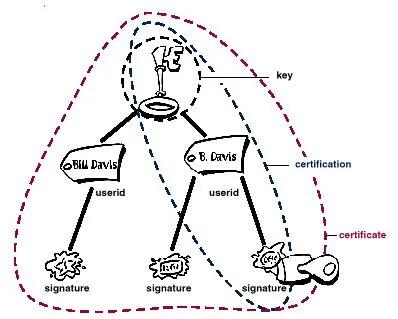 Figura 1-8. Anatomia de um certificado PGP
Figura 1-8. Anatomia de um certificado PGPDistribuição de certificados.
Os certificados são utilizados quando é necessário trocar chaves públicas com outra pessoa. Para pequenos grupos de pessoas que desejam se comunicar com segurança, é fácil trocar manualmente disquetes ou e-mails contendo a chave pública de cada proprietário. Esta é a distribuição manual de chave pública e é prática apenas até certo ponto. Além desse ponto, é necessário implementar sistemas que possam fornecer os mecanismos necessários de segurança, armazenamento e troca para que colegas de trabalho, parceiros de negócios ou estranhos possam se comunicar, se necessário. Eles podem vir na forma de repositórios somente de armazenamento, chamados Servidores de Certificados, ou sistemas mais estruturados que fornecem recursos adicionais de gerenciamento de chaves e são chamados de Infraestruturas de Chave Pública (PKIs).
Servidores de certificados.
Um servidor de certificados, também chamado de servidor certificado ou servidor de chaves, é um banco de dados que permite aos usuários enviar e recuperar certificados digitais. Um servidor certificado geralmente fornece alguns recursos administrativos que permitem que uma empresa mantenha suas políticas de segurança – por exemplo, permitindo que apenas as chaves que atendam a determinados requisitos sejam armazenadas.
Infraestruturas de Chave Pública.
Uma PKI contém os recursos de armazenamento de certificados de um servidor de certificados, mas também fornece recursos de gerenciamento de certificados (a capacidade de emitir, revogar, armazenar, recuperar e confiar em certificados). A principal característica de uma PKI é a introdução do que é conhecido como Autoridade Certificadora,ou CA, que é uma entidade humana — uma pessoa, grupo, departamento, empresa ou outra associação — que uma organização autorizou a emitir certificados para seus usuários de computador. (A função de uma CA é análoga à do Passport Office do governo de um país.) Uma CA cria certificados e os assina digitalmente usando a chave privada da CA. Devido ao seu papel na criação de certificados, a CA é o componente central de uma PKI. Usando a chave pública da CA, qualquer pessoa que queira verificar a autenticidade de um certificado verifica a assinatura digital da CA emissora e, portanto, a integridade do conteúdo do certificado (mais importante ainda, a chave pública e a identidade do titular do certificado).
Formatos de certificado.
Um certificado digital é basicamente uma coleção de informações de identificação vinculadas a uma chave pública e assinadas por um terceiro confiável para provar sua autenticidade. Um certificado digital pode ter vários formatos diferentes.
O PGP reconhece dois formatos de certificado diferentes:
● Certificados PGP ● Certificados X.509 Formato do certificado PGP. Um certificado PGP inclui (mas não está limitado a) as seguintes informações: ● O número da versão do PGP — identifica qual versão do PGP foi usada para criar a chave associada ao certificado. A chave pública do titular do certificado — a parte pública do seu par de chaves, juntamente com o algoritmo da chave: RSA, DH (Diffie-Hellman) ou DSA (Algoritmo de Assinatura Digital).
● As informações do detentor do certificado — consistem em informações de “identidade” sobre o usuário, como seu nome, ID de usuário, fotografia e assim por diante. ● A assinatura digital do proprietário do certificado — também chamada de autoassinatura, é a assinatura que utiliza a chave privada correspondente da chave pública associada ao certificado. ● O período de validade do certificado — a data/hora de início e a data/hora de expiração do certificado; indica quando o certificado irá expirar. ● O algoritmo de criptografia simétrica preferido para a chave — indica o algoritmo de criptografia para o qual o proprietário do certificado prefere que as informações sejam criptografadas. Os algoritmos suportados são CAST, IDEA ou Triple-DES. Você pode pensar em um certificado PGP como uma chave pública com um ou mais rótulos vinculados a ele (veja a Figura 1.9 ). Nessas 'etiquetas' você encontrará informações que identificam o proprietário da chave e uma assinatura do proprietário da chave, que afirma que a chave e a identificação andam juntas. (Essa assinatura específica é chamada de autoassinatura; todo certificado PGP contém uma autoassinatura.) Um aspecto único do formato de certificado PGP é que um único certificado pode conter múltiplas assinaturas. Várias ou muitas pessoas podem assinar o par chave/identificação para atestar a sua própria garantia de que a chave pública pertence definitivamente ao proprietário especificado. Se você procurar em um servidor de certificados público, poderá notar que certos certificados, como o do criador do PGP, Phil Zimmermann, contêm muitas assinaturas. Alguns certificados PGP consistem em uma chave pública com vários rótulos, cada um contendo um meio diferente de identificar o proprietário da chave (por exemplo, o nome do proprietário e a conta de e-mail corporativa, o apelido do proprietário e a conta de e-mail residencial, uma fotografia do proprietário — tudo em um certificado). A lista de assinaturas de cada uma dessas identidades pode ser diferente; as assinaturas atestam a autenticidade de que um dos rótulos pertence à chave pública, e não que todos os rótulos da chave sejam autênticos. (Observe que 'autêntico' está nos olhos de quem vê - assinaturas são opiniões, e diferentes pessoas dedicam diferentes níveis de devida diligência na verificação da autenticidade antes de assinar uma chave.)
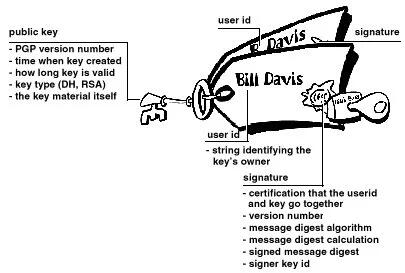 Figura 1-9. Um certificado PGP
Figura 1-9. Um certificado PGPFormato de certificado X.509.
X.509 é outro formato de certificado muito comum. Todos os certificados X.509 estão em conformidade com o padrão internacional ITU-T X.509; assim (teoricamente) os certificados X.509 criados para um aplicativo podem ser usados por qualquer aplicativo compatível com X.509. Na prática, porém, diferentes empresas criaram suas próprias extensões para certificados X.509, e nem todas funcionam juntas. Um certificado exige que alguém valide que uma chave pública e o nome do proprietário da chave andam juntos. Com os certificados PGP, qualquer pessoa pode desempenhar o papel de validador. Com certificados X.509, o validador é sempre uma Autoridade Certificadora ou alguém designado por uma CA. (Tenha em mente que os certificados PGP também suportam totalmente uma estrutura hierárquica usando uma CA para validar certificados.)
Um certificado X.509 é uma coleção de um conjunto padrão de campos contendo informações sobre um usuário ou dispositivo e sua chave pública correspondente. O padrão X.509 define quais informações vão para o certificado e descreve como codificá-lo (o formato dos dados). Todos os certificados X.509 possuem os seguintes dados:
O número da versão X.509
— identifica qual versão do padrão X.509 se aplica a este certificado, o que afeta quais informações podem ser especificadas nele. A mais atual é a versão 3.
A chave pública do titular do certificado
— a chave pública do titular do certificado, juntamente com um identificador de algoritmo que especifica a qual sistema criptográfico a chave pertence e quaisquer parâmetros de chave associados.
O número de série do certificado
— a entidade (aplicação ou pessoa) que criou o certificado é responsável por atribuir-lhe um número de série único para distingui-lo de outros certificados que emite. Esta informação é usada de diversas maneiras; por exemplo, quando um certificado é revogado, seu número de série é colocado em uma Lista de Revogação de Certificados ou CRL.
O identificador exclusivo do detentor do certificado
— (ou DN — nome distinto). Este nome pretende ser exclusivo na Internet. Este nome pretende ser exclusivo na Internet. Um DN consiste em múltiplas subseções e pode ser parecido com isto: CN=Bob Allen, OU=Divisão Total de Segurança de Rede, O=Network Associates, Inc., C=EUA (Referem-se ao nome comum, à unidade organizacional, à organização e ao país do sujeito .)
O período de validade do certificado
— a data/hora de início e a data/hora de expiração do certificado; indica quando o certificado irá expirar.
O nome exclusivo do emissor do certificado
— o nome exclusivo da entidade que assinou o certificado. Normalmente é uma CA. A utilização do certificado implica confiar na entidade que assinou este certificado. (Observe que em alguns casos, como certificados de CA raiz ou de nível superior , o emissor assina seu próprio certificado.)
A assinatura digital do emitente
— a assinatura utilizando a chave privada da entidade que emitiu o certificado.
O identificador do algoritmo de assinatura
— identifica o algoritmo usado pela CA para assinar o certificado.
Existem muitas diferenças entre um certificado X.509 e um certificado PGP, mas as mais importantes são as seguintes: você pode criar seu próprio certificado PGP;
● você deve solicitar e receber um certificado X.509 de uma autoridade de certificação
● Os certificados X.509 suportam nativamente apenas um único nome para o proprietário da chave
● Os certificados X.509 suportam apenas uma única assinatura digital para atestar a validade da chave
Para obter um certificado X.509, você deve solicitar a uma CA a emissão de um certificado. Você fornece sua chave pública, prova de que possui a chave privada correspondente e algumas informações específicas sobre você. Em seguida, você assina digitalmente as informações e envia o pacote completo – a solicitação de certificado – para a CA. A CA então realiza algumas diligências para verificar se as informações fornecidas estão corretas e, em caso afirmativo, gera o certificado e o devolve.
Você pode pensar em um certificado X.509 como um certificado de papel padrão (semelhante ao que você recebeu ao concluir uma aula de primeiros socorros básicos) com uma chave pública colada nele. Ele contém seu nome e algumas informações sobre você, além da assinatura da pessoa que o emitiu para você.
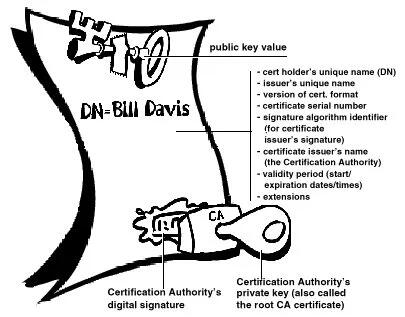
Figura 1-10. Um certificado X.509 Provavelmente, o uso mais visível dos certificados X.509 atualmente é em navegadores da web.
Validade e confiança Cada usuário em um sistema de chave pública está vulnerável a confundir uma chave falsa (certificado) com uma chave real. Validade é a confiança de que um certificado de chave pública pertence ao seu suposto proprietário. A validade é essencial em um ambiente de chave pública onde você deve estabelecer constantemente se um determinado certificado é autêntico ou não. Depois de ter certeza de que um certificado pertencente a outra pessoa é válido, você pode assinar a cópia em seu chaveiro para atestar que verificou o certificado e que ele é autêntico. Se quiser que outras pessoas saibam que você deu ao certificado seu selo de aprovação, você pode exportar a assinatura para um servidor de certificados para que outras pessoas possam vê-la.
Conforme descrito na seção Infraestruturas de Chave Pública , algumas empresas designam uma ou mais Autoridades de Certificação (CAs) para indicar a validade do certificado. Em uma organização que usa uma PKI com certificados X.509, é função da CA emitir certificados aos usuários — um processo que geralmente envolve responder à solicitação de certificado do usuário. Em uma organização que usa certificados PGP sem PKI, é função da CA verificar a autenticidade de todos os certificados PGP e depois assinar os bons. Basicamente, o objetivo principal de uma CA é vincular uma chave pública às informações de identificação contidas no certificado e, assim, garantir a terceiros que algum cuidado foi tomado para garantir que esta ligação das informações de identificação e da chave seja válida. O CA é o Grand Pooh-bah da validação em uma organização; alguém em quem todos confiam e, em algumas organizações, como aquelas que utilizam uma PKI, nenhum certificado é considerado válido, a menos que tenha sido assinado por uma CA confiável.
Verificando validade.
Uma maneira de estabelecer a validade é passar por algum processo manual. Existem várias maneiras de fazer isso. Você pode exigir que o destinatário pretendido lhe entregue fisicamente uma cópia de sua chave pública. Mas isto é muitas vezes inconveniente e ineficiente. Outra forma é verificar manualmente a impressão digital do certificado. Assim como as impressões digitais de cada ser humano são únicas, a impressão digital de cada certificado PGP é única. A impressão digital é um hash do certificado do usuário e aparece como uma das propriedades do certificado. No PGP, a impressão digital pode aparecer como um número hexadecimal ou uma série das chamadas palavras biométricas, que são foneticamente distintas e são usadas para facilitar um pouco o processo de identificação da impressão digital. Você pode verificar se um certificado é válido ligando para o proprietário da chave (para que você origine a transação) e pedindo ao proprietário que leia a impressão digital de sua chave para você e compare essa impressão digital com aquela que você acredita ser a verdadeira. Isso funciona se você conhece a voz do proprietário, mas como verificar manualmente a identidade de alguém que você não conhece? Algumas pessoas colocam a impressão digital de sua chave em seus cartões de visita exatamente por esse motivo. Outra forma de estabelecer a validade do certificado de alguém é confiar que um terceiro indivíduo passou pelo processo de validação do mesmo. Uma CA, por exemplo, é responsável por garantir que, antes de emitir um certificado, ele ou ela o verifique cuidadosamente para ter certeza de que a parte da chave pública realmente pertence ao suposto proprietário. Qualquer pessoa que confie na CA considerará automaticamente quaisquer certificados assinados pela CA como válidos. Outro aspecto da verificação da validade é garantir que o certificado não foi revogado. Para obter mais informações, consulte a seção Revogação de certificado .
Estabelecendo confiança.
Você valida certificados. Você confia nas pessoas. Mais especificamente, você confia nas pessoas para validar os certificados de outras pessoas. Normalmente, a menos que o proprietário lhe entregue o certificado, você terá que confiar na palavra de outra pessoa de que ele é válido.
Introdutores meta e confiáveis.
Na maioria das situações, as pessoas confiam completamente na CA para estabelecer a validade dos certificados. Isso significa que todos os demais dependem da CA para passar por todo o processo de validação manual. Isso é aceitável até um certo número de usuários ou locais de trabalho e, então, não é possível para a AC manter o mesmo nível de validação de qualidade. Nesse caso, é necessário adicionar outros validadores ao sistema.
Um CA também pode ser um meta- introdutor. Um meta-introdutor confere não apenas validade às chaves, mas também confere a capacidade de confiar nas chaves a outros. Semelhante ao rei que entrega seu selo a seus conselheiros de confiança para que eles possam agir de acordo com sua autoridade, o meta-introdutor permite que outros atuem como introdutores de confiança. Esses introdutores confiáveis podem validar chaves com o mesmo efeito do meta-introdutor. Eles não podem, entretanto, criar novos introdutores confiáveis.
Meta-introdutor e introdutor confiável são termos PGP. Em um ambiente X.509, o meta-introdutor é chamado de Autoridade de Certificação raiz ( CA raiz) e os introdutores confiáveis são Autoridades de Certificação subordinadas . A CA raiz usa a chave privada associada a um tipo de certificado especial denominado certificado CA raiz para assinar certificados. Qualquer certificado assinado pelo certificado CA raiz é visto como válido por qualquer outro certificado assinado pela raiz. Este processo de validação funciona mesmo para certificados assinados por outras CAs no sistema — desde que o certificado da CA raiz tenha assinado o certificado da CA subordinada, qualquer certificado assinado pela CA será considerado válido para outras pessoas dentro da hierarquia. Este processo de verificação de backup por meio do sistema para ver quem assinou cujo certificado é chamado de rastreamento de um caminho de certificação ou cadeia de certificação.
Modelos de confiança.
Em sistemas relativamente fechados, como em uma pequena empresa, é fácil rastrear um caminho de certificação até a CA raiz. No entanto, os usuários muitas vezes precisam se comunicar com pessoas fora do seu ambiente corporativo, incluindo algumas que nunca conheceram, como fornecedores, consumidores, clientes, associados e assim por diante. É difícil estabelecer uma linha de confiança com aqueles em quem sua CA não confia explicitamente. As empresas seguem um ou outro modelo de confiança, que determina como os usuários irão estabelecer a validade do certificado. Existem três modelos diferentes:
Confiança Direta.
Confiança Hierárquica Uma teia de confiança Confiança direta A confiança direta é o modelo de confiança mais simples. Neste modelo, um usuário confia que uma chave é válida porque sabe de onde ela veio. Todos os criptosistemas usam essa forma de confiança de alguma forma. Por exemplo, em navegadores da Web, as chaves raiz da Autoridade de Certificação são diretamente confiáveis porque foram enviadas pelo fabricante. Se houver alguma forma de hierarquia, ela se estenderá a partir desses certificados diretamente confiáveis. No PGP, um usuário que valida as chaves e nunca define outro certificado para ser um introdutor confiável está usando confiança direta.
 Figura 1-11. Confiança direta
Figura 1-11. Confiança diretaConfiança Hierárquica.
Em um sistema hierárquico, há vários certificados "raiz" a partir dos quais a confiança se estende. Esses certificados podem certificar eles próprios certificados ou podem certificar certificados que certificam ainda outros certificados em alguma cadeia. Considere isso como uma grande “árvore” de confiança. A validade do certificado "folha" é verificada rastreando desde seu certificador até outros certificadores, até que um certificado raiz diretamente confiável seja encontrado.
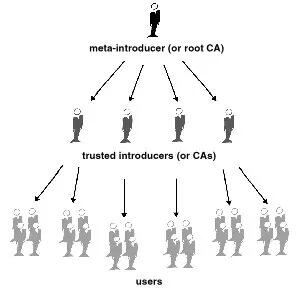
Figura 1-12. Confiança hierárquica
Teia de Confiança.
Uma teia de confiança abrange ambos os outros modelos, mas também acrescenta a noção de que a confiança está nos olhos de quem vê (que é a visão do mundo real) e a ideia de que mais informação é melhor. É, portanto, um modelo de confiança cumulativa. Um certificado pode ser confiável diretamente ou confiável em alguma cadeia que remonta a um certificado raiz diretamente confiável (o meta-introdutor) ou por algum grupo de introdutores.
Talvez você já tenha ouvido falar do termo seis graus de separação, que sugere que qualquer pessoa no mundo pode determinar algum vínculo com qualquer outra pessoa no mundo usando seis ou menos outras pessoas como intermediários. Esta é uma teia de introdutores. É também a visão de confiança do PGP. PGP usa assinaturas digitais como forma de introdução. Quando qualquer usuário assina a chave de outro, ele ou ela se torna o introdutor dessa chave. À medida que esse processo avança, ele estabelece uma rede de confiança.
Em um ambiente PGP, qualquer usuário pode atuar como autoridade certificadora. Qualquer usuário PGP pode validar o certificado de chave pública de outro usuário PGP. No entanto, tal certificado só é válido para outro usuário se a parte confiável reconhecer o validador como um introdutor confiável. (Ou seja, você confia na minha opinião de que as chaves dos outros são válidas apenas se você me considerar um apresentador confiável. Caso contrário, minha opinião sobre a validade das outras chaves é discutível.) Armazenados no chaveiro público de cada usuário estão indicadores de
● se o usuário considera ou não uma chave específica válida
● o nível de confiança que o usuário deposita na chave que o proprietário da chave pode servir como certificador das chaves de terceiros
Você indica, na sua cópia da minha chave, se acha que meu julgamento conta. Na verdade, é um sistema de reputação: certas pessoas têm a reputação de fornecer boas assinaturas e as pessoas confiam nelas para atestar a validade de outras chaves.
Níveis de confiança no PGP.
O nível mais alto de confiança em uma chave, a confiança implícita , é a confiança em seu próprio par de chaves. O PGP assume que se você possui a chave privada, você deve confiar nas ações da sua chave pública relacionada. Quaisquer chaves assinadas pela sua chave implicitamente confiável são válidas.
Existem três níveis de confiança que você pode atribuir à chave pública de outra pessoa:
● Confiança total ● Confiança marginal ● Não confiável (ou não confiável)
Para tornar as coisas confusas, também existem três níveis de validade:
● Válido ● Marginalmente válido ● Inválido
Para definir a chave de outra pessoa como um introdutor confiável, você
- Comece com uma chave válida, que seja.
- assinado por você ou
-
assinado por outro apresentador confiável e então
-
Defina o nível de confiança que você acha que o proprietário da chave tem direito.
Por exemplo, suponha que seu chaveiro contenha a chave de Alice. Você validou a chave de Alice e indica isso assinando-a. Você sabe que Alice é uma verdadeira defensora da validação de chaves de outras pessoas. Portanto, você atribui a chave dela com confiança total. Isso faz de Alice uma Autoridade Certificadora. Se Alice assinar a chave de outra pessoa, ela aparecerá como Válida em seu chaveiro. O PGP requer uma assinatura Totalmente confiável ou duas assinaturas Marginalmente confiáveis para estabelecer uma chave como válida. O método do PGP de considerar dois Marginais iguais a um Completo é semelhante a um comerciante que solicita duas formas de identificação. Você pode considerar Alice bastante confiável e também considerar Bob bastante confiável. Qualquer um deles sozinho corre o risco de assinar acidentalmente uma chave falsificada, portanto, você pode não depositar total confiança em nenhum deles. No entanto, as probabilidades de ambos os indivíduos terem assinado a mesma chave falsa são provavelmente pequenas.
Revogação de certificado.
Os certificados só são úteis enquanto são válidos. Não é seguro simplesmente presumir que um certificado é válido para sempre. Na maioria das organizações e em todas as PKIs, os certificados têm uma vida útil restrita. Isso restringe o período em que um sistema fica vulnerável caso ocorra um comprometimento do certificado.
Os certificados são assim criados com um período de validade programado: uma data/hora de início e uma data/hora de expiração. Espera-se que o certificado seja utilizável durante todo o seu período de validade (seu tempo de vida ). Quando o certificado expirar, ele não será mais válido, pois a autenticidade do seu par chave/identificação não estará mais garantida. (O certificado ainda pode ser usado com segurança para reconfirmar informações que foram criptografadas ou assinadas dentro do período de validade – no entanto, ele não deve ser confiável para tarefas criptográficas futuras.)
Existem também situações em que é necessário invalidar um certificado antes da sua data de expiração, como quando o titular do certificado termina o contrato de trabalho com a empresa ou suspeita que a chave privada correspondente do certificado foi comprometida. Isso é chamado de revogação. Um certificado revogado é muito mais suspeito do que um certificado expirado. Os certificados expirados são inutilizáveis, mas não apresentam a mesma ameaça de comprometimento que um certificado revogado. Qualquer pessoa que tenha assinado um certificado pode revogar a sua assinatura no certificado (desde que utilize a mesma chave privada que criou a assinatura). Uma assinatura revogada indica que o signatário não acredita mais que a chave pública e as informações de identificação pertencem uma à outra, ou que a chave pública do certificado (ou a chave privada correspondente) foi comprometida. Uma assinatura revogada deve ter quase tanto peso quanto um certificado revogado. Com certificados X.509, uma assinatura revogada é praticamente igual a um certificado revogado, visto que a única assinatura no certificado é aquela que o tornou válido em primeiro lugar – a assinatura da CA. Os certificados PGP fornecem o recurso adicional de que você pode revogar todo o seu certificado (não apenas as assinaturas nele) se você achar que o certificado foi comprometido. Somente o proprietário do certificado (o detentor da chave privada correspondente) ou alguém que o proprietário do certificado tenha designado como revogador pode revogar um certificado PGP. (Designar um revogador é uma prática útil, pois muitas vezes é a perda da senha da chave privada correspondente do certificado que leva um usuário PGP a revogar seu certificado - uma tarefa que só é possível se alguém tiver acesso à chave privada. ) Somente o emissor do certificado pode revogar um certificado X.509.
Comunicar que um certificado foi revogado.
Quando um certificado é revogado, é importante conscientizar os usuários potenciais do certificado de que ele não é mais válido. Com certificados PGP, a maneira mais comum de comunicar que um certificado foi revogado é publicá-lo em um servidor de certificados para que outras pessoas que desejem se comunicar com você sejam avisadas para não usar essa chave pública. Em um ambiente PKI, a comunicação de certificados revogados é mais comumente obtida por meio de uma estrutura de dados chamada Lista de Revogação de Certificados, ou CRL, que é publicada pela CA. A CRL contém uma lista validada com carimbo de data e hora de todos os certificados revogados e não expirados no sistema. Os certificados revogados permanecem na lista apenas até expirarem e, em seguida, são removidos da lista — isso evita que a lista fique muito longa. A CA distribui a CRL aos usuários em algum intervalo programado regularmente (e potencialmente fora do ciclo, sempre que um certificado é revogado). Teoricamente, isso impedirá que os usuários usem involuntariamente um certificado comprometido. É possível, no entanto, que haja um período de tempo entre as CRLs em que um certificado recentemente comprometido seja usado.
O que é uma senha?
A maioria das pessoas está familiarizada com a restrição de acesso a sistemas de computador por meio de uma senha, que é uma sequência única de caracteres que um usuário digita como código de identificação.
Uma senha longa é uma versão mais longa de uma senha e, em teoria, mais segura. Normalmente composta por várias palavras, uma frase secreta é mais segura contra ataques de dicionário padrão, em que o invasor tenta todas as palavras do dicionário na tentativa de determinar sua senha. As melhores senhas são relativamente longas e complexas e contêm uma combinação de letras maiúsculas e minúsculas, caracteres numéricos e de pontuação. O PGP usa uma senha para criptografar sua chave privada em sua máquina. Sua chave privada é criptografada em seu disco usando um hash de sua senha como chave secreta. Você usa a senha para descriptografar e usar sua chave privada. Uma senha deve ser difícil de esquecer e difícil de ser adivinhada por outras pessoas. Deve ser algo já firmemente enraizado na sua memória de longo prazo, em vez de algo que você invente do zero. Por que? Porque se você esquecer sua senha, você estará sem sorte. Sua chave privada é total e absolutamente inútil sem sua senha e nada pode ser feito a respeito. Lembra-se da citação anterior neste capítulo?
 PGP é a criptografia que manterá os principais governos fora dos seus arquivos. Certamente também o manterá fora de seus arquivos. Tenha isso em mente quando decidir alterar sua senha para a piada daquela piada que você nunca consegue lembrar.
PGP é a criptografia que manterá os principais governos fora dos seus arquivos. Certamente também o manterá fora de seus arquivos. Tenha isso em mente quando decidir alterar sua senha para a piada daquela piada que você nunca consegue lembrar.Divisão de chave.
Dizem que um segredo não é segredo se for conhecido por mais de uma pessoa. Compartilhar um par de chaves privadas representa um grande problema. Embora não seja uma prática recomendada, às vezes é necessário compartilhar um par de chaves privadas. Chaves de assinatura corporativa, por exemplo, são chaves privadas usadas por uma empresa para assinar – por exemplo – documentos legais, informações pessoais confidenciais ou comunicados de imprensa para autenticar sua origem. Nesse caso, vale a pena que vários membros da empresa tenham acesso à chave privada. No entanto, isto significa que qualquer indivíduo pode agir plenamente em nome da empresa. Nesse caso, é aconselhável dividir a chave entre várias pessoas, de modo que mais de uma ou duas pessoas apresentem um pedaço da chave para reconstituí-la em condições utilizáveis. Se poucas peças da chave estiverem disponíveis, a chave ficará inutilizável. Alguns exemplos são dividir uma chave em três partes e exigir duas delas para reconstituir a chave, ou dividi-la em duas partes e exigir ambas as peças. Se uma conexão de rede segura for usada durante o processo de reconstituição, os acionistas da chave não precisam estar fisicamente presentes para aderirem novamente à chave.
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ 31a4605e:cf043959
2025-06-17 18:00:27
@ 31a4605e:cf043959
2025-06-17 18:00:27Quando se fala em Bitcoin, é comum chama-lo de moeda digital ou "investimento especulativo". No entanto, uma das funções mais fundamentais e menos compreendidas do Bitcoin é a sua função como rede de liquidação. Para entender isso, vale compará-lo com os sistemas tradicionais de liquidação, como o SWIFT, e explorar como o Bitcoin oferece uma camada base de transferência de valor global, descentralizada e resistente à censura.
Antes de mais, explico a diferença entre liquidez e liquidação:
Liquidez refere-se à facilidade de converter um ativo em “dinheiro” sem perda de valor.
Liquidação é o processo de concluir uma transação (transferência real de valor entre partes).
SWIFT: a camada de comunicação do sistema financeiro tradicional
O sistema SWIFT (Society for Worldwide Interbank Financial Telecommunication) é uma rede de comunicação entre bancos. Ele não movimenta dinheiro diretamente, mas envia mensagens padronizadas que instruem as instituições financeiras a realizarem transferências. O processo envolve diversos intermediários, é custoso, lento (podendo levar dias) e depende de confiança entre as partes e regulações locais.
Diferente do SWIFT, o Bitcoin é uma rede autossuficiente que permite a liquidação direta de valores entre duas partes, sem necessidade de intermediários. A cada bloco minerado, transações são validadas e registradas de forma imutável em uma base de dados global, transparente e segura: a blockchain.
Liquidação final: Assim que uma transação é confirmada por um número suficiente de blocos, ela é considerada final e irreversível.
Resistência à censura: Não há entidade central que possa impedir ou reverter uma transação válida.
Disponibilidade global: A rede está acessível 24 horas por dia, 7 dias por semana, em qualquer lugar do mundo com acesso à internet.
Assim como o ouro já serviu como base para sistemas monetários, o Bitcoin está se consolidando como uma camada base de valor digital. Essa base pode dar suporte a outras camadas, como:
Lightning Network, que permite transações quase instantâneas e com baixíssimas taxas;
Serviços financeiros tokenizados, que podem usar o Bitcoin como colateral ou meio de liquidação entre instituições.
Ao funcionar como uma rede de liquidação pública e neutra, o Bitcoin oferece uma alternativa ao sistema tradicional, que é fragmentado, fechado e baseado em confiança entre instituições.
Resumindo, mais do que um ativo especulativo, o Bitcoin está emergindo como uma infraestrutura financeira global. Como rede de liquidação, ele elimina intermediários, reduz custos, aumenta a segurança e democratiza o acesso à transferência de valor. Num mundo cada vez mais interconectado e digitalizado, compreender o papel do Bitcoin como camada base pode ser essencial para entender o futuro do dinheiro.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ eb0157af:77ab6c55
2025-06-18 02:02:03
@ eb0157af:77ab6c55
2025-06-18 02:02:03Trump Media & Technology Group is targeting the digital asset market by registering a Bitcoin and Ethereum exchange-traded fund (ETF) with NYSE Arca.
On June 16, Truth Social — a company controlled by Trump Media & Technology Group — officially submitted documentation for a Bitcoin and Ethereum-based Exchange Traded Fund (ETF) to the U.S. Securities and Exchange Commission (SEC).
NEW: Trump's Truth Social has filed for a dual Bitcoin & Ethereum ETF. pic.twitter.com/a5iZtrtUyk
— James Seyffart (@JSeyff) June 16, 2025
This initiative would allow the social media platform to diversify its operations by entering the digital asset sector through these financial products.
The filing proposes a trust structure that would directly hold bitcoin and ether, with 75% of the fund’s assets invested in bitcoin and 25% in ether.
The Truth Social Bitcoin and Ethereum ETF will have Yorkville America Digital as the fund’s sponsor, while custody of the digital assets will be entrusted to the Crypto.com exchange.
The choice of NYSE Arca as the listing venue for the fund is no coincidence: this market already hosts several cryptocurrency-linked ETFs and offers the necessary technological infrastructure to manage these financial instruments.
Trump Media & Technology Group’s move aligns with a broader trend in which public companies are increasingly integrating Bitcoin and other digital assets into their corporate treasuries.
Devin Nunes, CEO of Trump Media & Technology Group, stated:
“Trump Media’s vision is to aggressively enhance our offerings and capabilities, which includes holding bitcoin in our corporate treasury.”
The final approval of the Truth Social Bitcoin and Ethereum ETF will depend on the outcome of the regulatory review process at the SEC, which must assess the product’s compliance with current regulations on exchange-traded funds and cryptocurrency investments.
The post Truth Social files for Bitcoin-Ethereum ETF appeared first on Atlas21.
-
 @ 9bc2d34d:d19d2948
2024-09-02 19:41:40
@ 9bc2d34d:d19d2948
2024-09-02 19:41:40Chef's notes
This recipe is designed for home cooks who want to recreate the delicious buttery hollandaise sauce at home without feeling overwhelmed. It focuses on teaching the basics of the sauce, allowing beginners to master the fundamentals before experimenting with seasonings, hot sauces, or herbs.
Please note the thickness of sauce in the picture. This is after ten minutes of blending.
Details
- ⏲️ Prep time: 3 minutes
- 🍳 Cook time: 10 minutes (blending)
- 🍽️ Servings: 2 - 4
Ingredients
- 4 egg yolks
- 8 tablespoons of melted butter
- 1 tablespoon of lemon juice
- Pinch of salt
- Pinch of pepper
Directions
- Melt butter in the microwave or on the stovetop.
- Separate the egg yolks from the egg whites (reserve the egg whites for another dish).
- Place the egg yolks in a blender.
- Start the blender (medium to high settings for blend mode is fine).
- Slowly pour the melted butter into the cover opening (it will splatter).
- Add the remaining ingredients.
- Blend for ten minutes (seriously, walk away and do something else).
- Taste and adjust the flavors (add extra lemon juice or salt if desired).
- Serve over your breakfast!
-
 @ 9ca447d2:fbf5a36d
2025-06-17 19:01:30
@ 9ca447d2:fbf5a36d
2025-06-17 19:01:30Bluebird Mining Ventures Ltd., a UK-listed gold exploration company, has made headlines after announcing it will convert future revenues into bitcoin. This is the first time a UK mining company has committed to having a bitcoin treasury.
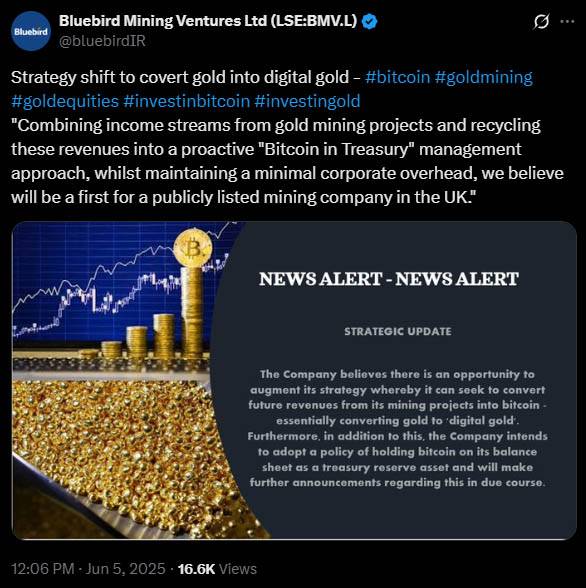
Bluebird Mining on X
The news sent Bluebird’s stock flying, rising 63% to £0.6 in 48 hours.
Bluebird which has gold projects in South Korea and the Philippines says this is part of a broader plan to modernize how it manages its finances.
“By adopting a ‘gold plus a digital gold’ strategy, it offers the Company an opportunity to turn the page and look to the future and seek to attract a new type of shareholder,” said Aidan Bishop, Interim CEO and Executive Director.
The company’s management believes bitcoin’s rise as a financial asset reflects growing dissatisfaction with traditional stores of value like gold.
Gold has been a reliable hedge against inflation for centuries, but bitcoin is now being seen as a digital alternative – thanks to its limited supply and independence from central bank policies.
Related: Gold at Historic Low Against Bitcoin | A Paradigm Shift?
“Gold’s position as a store of value has been under threat due to the rising global adoption of bitcoin, which some commentators have described as ‘digital gold’,” Bluebird said in a statement.
The plan is simple. Revenue from Bluebird’s gold mining projects will be used to buy bitcoin. The company says this will allow it to preserve capital and have growth potential through exposure to the digital asset market.
The digital asset will be held on the company’s balance sheet as a long-term reserve asset, just like some companies hold gold or cash. Bluebird sees this as proactive, especially in today’s volatile world of inflation, high debt, and global geopolitical tensions. Bishop said:
“I am convinced that we are witnessing a tectonic shift in global markets and that Bitcoin will reshape the landscape of financial markets on every level.”
Bluebird Mining Ventures is a small but big-thinking company.
With 7 employees and operations across Asia, it’s focused on reopening high-grade gold mines that have been closed. Its main projects are the Gubong and Kochang mines in South Korea and the Batangas Gold Project in the Philippines.
In May 2025, the company renewed its mining permit in the Philippines and is finalizing a deal with its local partner to have a “free carry” — meaning it will hold a share of the future profits without putting in any more money.
At the same time, Bluebird is preparing legal action in South Korea to protect its existing assets there, so while it loves Bitcoin, it hasn’t forgotten its mining roots.
To lead this transformation, Bluebird is currently looking for a new CEO with Bitcoin experience. The company says the right leadership will be key to navigating this hybrid financial model that combines traditional resource extraction with modern financials.
-
 @ 31a4605e:cf043959
2025-06-17 17:58:15
@ 31a4605e:cf043959
2025-06-17 17:58:15Bitcoin, desde o seu surgimento em 2009, tem gerado uma variedade de histórias de sucesso e fracasso. Algumas dessas histórias são de pessoas que investiram cedo na criptomoeda e colheram os frutos de sua visão precoce, enquanto outras refletem os altos e baixos que caracterizam o mercado altamente volátil de Bitcoin. Ao longo dos anos, muitas dessas histórias tornaram-se emblemáticas, servindo tanto de inspiração quanto de alerta para quem entra nesse mercado.
Histórias de sucesso
O caso de Laszlo Hanyecz – A pizza de 10.000 Bitcoins Uma das histórias mais icônicas e, ao mesmo tempo, um exemplo do potencial e da volatilidade do Bitcoin, envolve Laszlo Hanyecz, um programador americano. Em 2010, Hanyecz pagou 10.000 bitcoins por duas pizzas. Na época, o valor das criptomoedas era tão baixo que essa transação passou despercebida, mas, em retrospectiva, os 10.000 bitcoins pagos por uma simples refeição valeriam centenas de milhões de dólares nos anos seguintes, quando o preço do Bitcoin disparou.
Essa história, muitas vezes citada, é um lembrete da enorme valorização do Bitcoin desde os seus primeiros dias. Embora Hanyecz não tenha ficado rico com essa transação, a história da "pizza de 10.000 bitcoins" tornou-se uma metáfora para o crescimento do Bitcoin, mostrando como uma pequena quantidade da moeda no início poderia ter mudado a vida de alguém para sempre.
O caso de Michael Saylor e a MicroStrategy no presente Michael Saylor, CEO da MicroStrategy, é outro exemplo de sucesso no mundo do Bitcoin. Em 2020, Saylor decidiu transformar a sua empresa numa das primeiras grandes corporações a investir pesadamente em Bitcoin, comprando mais de 100.000 bitcoins. A decisão foi inicialmente vista com ceticismo, mas ao longo do tempo, o preço do Bitcoin subiu consideravelmente, fazendo com que o investimento de Saylor se tornasse extremamente lucrativo. Para ele, o Bitcoin não era apenas um investimento especulativo, mas uma maneira de proteger a sua empresa da inflação e da desvalorização da moeda fiduciária.
Este caso é um exemplo de como uma aposta estratégica em Bitcoin pode resultar em grandes lucros para quem tem visão de longo prazo e confiança no potencial do ativo. A MicroStrategy tornou-se um dos maiores detentores de Bitcoin no mundo corporativo, e Saylor ganhou reconhecimento por ser um defensor do Bitcoin no mundo empresarial.
Histórias de fracasso
O caso de James Howells – O desaparecimento de 8.000 Bitcoins James Howells, um ex-empregado de TI de Gales, é um exemplo clássico de como a volatilidade e a negligência podem resultar em grandes perdas. Em 2013, Howells, que estava a minerar Bitcoin em casa, acumulou 8.000 bitcoins, que valiam cerca de 5.000 libras na época. Quando o mercado estava em queda, ele decidiu limpar o seu computador antigo e jogá-lo fora, sem perceber que os bitcoins estavam guardados em uma carteira digital nesse dispositivo.
Após a ascensão do preço do Bitcoin, Howells tentou recuperar o disco rígido, que estava enterrado numa lixeira em um aterro sanitário. Apesar das tentativas de convencer a cidade a permitir a escavação do aterro, o pedido foi negado, e ele nunca conseguiu recuperar os bitcoins. Este caso é um lembrete de como, sem a devida segurança e cuidado, até mesmo grandes fortunas podem ser perdidas no mundo das criptomoedas.
O colapso da Mt. Gox – A maior exchange de Bitcoin da história Uma das maiores histórias de fracasso envolvendo Bitcoin está relacionada à exchange Mt. Gox, uma plataforma de negociação de Bitcoin que, em 2014, faliu após alegadamente perder cerca de 850.000 bitcoins dos seus clientes, num valor superior a 450 milhões de dólares na época. A Mt. Gox foi, por um período, a maior exchange de Bitcoin do mundo, mas a sua falência foi um marco negativo na história do Bitcoin.
A falência da Mt. Gox foi causada por uma combinação de hacking, erros internos de segurança e má gestão. Embora alguns dos bitcoins perdidos tenham sido recuperados mais tarde, muitos investidores ficaram devastados pela perda dos seus fundos. Este incidente trouxe à tona a importância da segurança nas exchanges de Bitcoin e da responsabilidade das plataformas financeiras no manejo das criptomoedas de seus clientes.
O impacto da volatilidade e da adoção no mercado
As histórias de sucesso e fracasso envolvendo Bitcoin não são apenas anedotas, mas refletem a natureza imprevisível e arriscada do mercado de criptomoedas. O preço de Bitcoin pode flutuar drasticamente, o que significa que investidores podem tanto fazer grandes fortunas quanto sofrer grandes perdas. Enquanto alguns vêem Bitcoin como uma forma de alcançar a liberdade financeira e proteger-se contra a inflação, outros enfrentam o risco de perder tudo, como demonstrado pelos casos de fracasso.
A adoção crescente de Bitcoin em mercados emergentes, bem como a entrada de investidores institucionais, como a MicroStrategy e o próprio Elon Musk, são indicativos de que o Bitcoin está a ser cada vez mais reconhecido como uma alternativa legítima ao sistema financeiro tradicional. No entanto, as falências de exchanges e as perdas de grandes quantidades de Bitcoin destacam a necessidade de uma abordagem prudente e de uma infraestrutura mais robusta para garantir a segurança e a confiança dos utilizadores.
Resumindo, as histórias de sucesso e fracasso em torno do Bitcoin são um reflexo da natureza volátil e emergente desta moeda digital. Enquanto alguns ganharam milhões, outros perderam fortunas devido à falta de precaução, erros de gestão ou simplesmente pelo preço imprevisível da criptomoeda. Através destas histórias, fica claro que, embora o Bitcoin tenha o potencial de gerar grandes recompensas, ele também apresenta riscos significativos. Para aqueles que entram nesse mercado, é crucial estar preparado e consciente dos desafios que podem surgir, garantindo segurança e adotando uma estratégia de longo prazo para lidar com as incertezas e volatilidade do mercado.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 7f6db517:a4931eda
2025-06-16 15:03:05
@ 7f6db517:a4931eda
2025-06-16 15:03:05Will not live in a pod.
Will not eat the bugs.
Will not get the chip.
Will not get a blue check.
Will not use CBDCs.Live Free or Die.
Why did Elon buy twitter for $44 Billion? What value does he see in it besides the greater influence that undoubtedly comes with controlling one of the largest social platforms in the world? We do not need to speculate - he made his intentions incredibly clear in his first meeting with twitter employees after his takeover - WeChat of the West.
To those that do not appreciate freedom, the value prop is clear - WeChat is incredibly powerful and successful in China.
To those that do appreciate freedom, the concern is clear - WeChat has essentially become required to live in China, has surveillance and censorship integrated at its core, and if you are banned from the app your entire livelihood is at risk. Employment, housing, payments, travel, communication, and more become extremely difficult if WeChat censors determine you have acted out of line.
The blue check is the first step in Elon's plan to bring the chinese social credit score system to the west. Users who verify their identity are rewarded with more reach and better tools than those that do not. Verified users are the main product of Elon's twitter - an extensive database of individuals and complete control of the tools he will slowly get them to rely on - it is easier to monetize cattle than free men.
If you cannot resist the temptation of the blue check in its current form you have already lost - what comes next will be much darker. If you realize the need to resist - freedom tech provides us options.
If you found this post helpful support my work with bitcoin.

-
 @ 8dc86882:9dc4ba5e
2024-09-02 15:50:01
@ 8dc86882:9dc4ba5e
2024-09-02 15:50:01Today I saw a YouTube video from one of the privacy related channels, Techlore maybe? I don't exactly remember. Either way this particular video was going over the pluses and minuses of Android and iOS; and it has made me reconsider some things. I have one of each type of phone and jump back and forth a bit, but always thought I would end on Android. I'm not feeling that way anymore.
After really getting to understand Apple's Advanced Data Protection I think I came to the conclusion that my iPhone more than meets my needs and does everything I like. Yeah, Android sounds like it has most of the privacy coolness as far as mods, roms, and apps, but my iPhone is easily fully encrypted along with iCloud. The few services that aren't are covered by my Proton plan. It also allows me to stop paying for services I may not really need.
- I use and pay for Ente photos, which is great, but my Apple photos are already encrypted and backed up. I don't think I need to be paying for the extra service.
- The Apple Notes app falls under the fully encrypted side, and I can use the free version of Standard Notes for other things.
- I still use Signal Messenger where the OS doesn't matter as much.
- MySudo which I use for numbers is transferable between OSs also.
That's really about it, I mainly use my phone for Email, Calendar, Messaging, Notes, some social, and photos. I don't think I need anything special beyond that. The insecure apps I use on either platform keep their risks though Apple isn't an advertising company, so I feel they are less likely to abuse anything, at least for now. I wonder what other folks thoughts are. Feel free to share.
Cheers!
plebone
-
 @ a88f35c7:7b121d83
2025-06-17 18:31:38
@ a88f35c7:7b121d83
2025-06-17 18:31:38Como si de resolver un crimen se tratase, en este artículo he querido reflexionar sobre el futuro de los pagos en un mundo cada vez más digital, centrándome en la más que probable desaparición del dinero efectivo, con las monedas digitales de bancos centrales (CBDCs) actuando como arma homicida y los bancos centrales como los verdaderos 'asesinos' de este tipo de dinero. Como veis, sería un pésimo novelista, ya que en el primer párrafo ya he revelado toda la trama.
Introducción.
La mayoría de las transacciones realizadas a diario ya son electrónicas y están gestionadas por bancos o empresas tecnológicas, ya sea a través de ventas de comercio electrónico, pagos presenciales con terminales EMV, tarjetas sin contacto o aplicaciones móviles. Estos pagos son fácilmente rastreables, susceptibles de confiscación y sujetos a censura. A pesar de ello, durante las últimas tres décadas se ha intentado desacreditar al otro tipo de dinero que aún se utiliza hoy en día: el efectivo. Gobiernos de todo el mundo han defendido que eliminar el efectivo es necesario para combatir el lavado de dinero, reducir la evasión fiscal y asegurar una mayor estabilidad de la economía.
¿Cuál puede ser la motivación detrás de todo esto? ¿Es posible que, al analizar al candidato destinado a sustituir al efectivo, encontremos una respuesta?
En este artículo me propongo explorar cuál será el formato del dinero del futuro y si las monedas digitales de bancos centrales (CBDC), cuya implementación está siendo investigada e impulsada actualmente por muchos gobiernos, podrían ser las que acaben definitivamente con el efectivo.
Soy consciente de que hay mucho material e información disponible pero para realizar este artículo me he basado en los siguientes papers:
-
The technology of retail central bank digital currency de Raphael Auer y Rainer Boehme
-
Financial Freedom and Privacy in the Post-Cash World de Alex Gladstein
El crímen a resolver.
La víctima.
El dinero en efectivo (la víctima de este crimen) es el medio de pago físico que utilizamos para realizar transacciones, como billetes y monedas. Es emitido y respaldado por un banco central (en Europa, el BCE, y en Estados Unidos, la Fed), lo que le otorga valor y aceptación general en una economía. Además, representa una deuda del banco central con quien lo posee: al tener un billete, esencialmente el banco central te debe ese valor, comprometiéndose a respaldarlo.
Tener “una deuda del banco central” en el bolsillo ha permitido, durante décadas, realizar transacciones diarias en todo el mundo sin que el comprador deba revelar información al vendedor. Esto es posible porque el sistema se basa en la confianza de que el vendedor podrá intercambiar ese dinero por bienes y servicios en el futuro (confianza mutua en su aceptación futura). Al entregar efectivo, la transacción se liquida al instante, sin intermediarios, verificaciones adicionales ni exposición de datos sensibles como nombres, direcciones o información financiera, lo que facilita el comercio incluso entre desconocidos.

Como en cualquier serie de asesinatos, el detective debe conocer todos los detalles posibles de la víctima para elaborar el perfil del asesino y determinar el móvil del crimen. Siguiendo esta lógica, a continuación presento un conjunto de características del dinero en efectivo que podrían haberle generado "enemigos":
-
Resistente a la censura: El efectivo se intercambia directamente entre dos partes sin necesidad de intermediarios (bancos, plataformas digitales o gobiernos). Esto significa que ninguna entidad puede bloquear o revertir una transacción hecha en persona.
-
Difícilmente rastreable: Las transacciones en efectivo son anónimas, ya que no requieren identificación ni dejan un rastro digital.
-
Difícilmente confiscable: El efectivo, al ser un activo físico, solo puede ser confiscado mediante posesión física directa.
-
Permite cierto nivel de privacidad: El uso de efectivo preserva la privacidad de las personas, ya que no expone datos personales ni patrones de gasto.
-
Independencia de infraestructuras tecnológicas: El efectivo no depende de redes de comunicación, electricidad, internet o sistemas bancarios. En escenarios de apagones, desastres naturales o fallos tecnológicos, el efectivo sigue siendo funcional.
-
Aceptación universal sin intermediarios: El efectivo es aceptado prácticamente en cualquier lugar, sin necesidad de cuentas, dispositivos o aplicaciones.
El arma.
En las series de asesinatos o crímenes en general, hay 3 aspectos clave para resolver un caso y estos son el móvil (es la razón detrás del crimen), la oportunidad(posibilidad real que tuvo el sospechoso para cometer el crimen) y los medios disponibles (capacidad física, técnica o arma para llevar a cabo el crimen). En el crimen a resolver en este artículo he creído conveniente empezar por este último y por tanto como buen amante de los avances tecnológicos, he pedido a chatpgt que me defina una CBDC. Su respuesta debajo:
Una CBDC (Central Bank Digital Currency) o Moneda Digital de Banco Central es una forma de dinero digital emitida y respaldada directamente por el banco central de un país (o países). Es similar al dinero en efectivo (como los billetes y monedas) pero existe únicamente en formato digital.
En resumen, una CBDC es dinero digital seguro, accesible y regulado, diseñado para modernizar los sistemas financieros y facilitar los pagos digitales en la economía. 😊💸
Sin embargo, y muy a mi pesar..., hay un par de puntos que no me han convencido (imagino que sabréis cuáles pero por si acaso, los he marcado en negrita). Por ello, he decidido buscarme las habichuelas por mi cuenta y he encontrado este paper, que creo que puede ser de ayuda: “Central Bank Digital Currencies” del Committee on Payments and Market Infrastructures del Bank for International Settlements. Según se indica en dicho paper;
Establecer una definición precisa de la Central Bank Digital Currency (CBDC) resulta complejo, ya que el concepto abarca diversas ideas y posibilidades. No obstante, su característica esencial es que se trata de una forma de dinero digital emitida directamente por el banco central (una obligación del banco central, denominada en una unidad de cuenta existente) que funciona como medio de intercambio y depósito de valor, y está destinada al público general. Esta característica la distingue del dinero digital utilizado por los bancos comerciales, como las reservas o cuentas de liquidación mantenidas en el banco central.
Llegados aquí, he vuelto a preguntar a chatgpt cuál podría ser el motivo u objetivopara que los bancos centrales estén tan interesados por las CBDCs. Su respuesta, como en el caso anterior, tampoco me ha acabado de convencer:
El Banco Central Europeo busca crear una CBDC, conocida como Euro Digital, con varios objetivos clave; en primer lugar, busca aumentar la inclusión financiera al ofrecer una forma de dinero digital segura y gratuita, accesible para toda la población. Otro objetivo es reforzar la estabilidad financiera, proporcionando una alternativa segura al dinero depositado en bancos privados. Por último, el BCE aspira a promover la innovación en servicios financieros y facilitar pagos transfronterizos más rápidos y eficientes. En conjunto, el Euro Digital busca modernizar la economía europea, proteger su sistema financiero y mantener el liderazgo europeo en la era digital.
Así que, una vez más, me toca aplicar el conocido dicho DYOR (Do Your Own Research). A continuación, mi enfoque:
-
Partiendo de la premisa de que muchos objetos utilizados en crímenes no fueron diseñados originalmente para causar daño, sino que tienen múltiples usos, es evidente que ciertos objetos resultan más propensos a ser utilizados con fines dañinos debido a su diseño. Por ejemplo, un cuchillo de caza, con su hoja afilada y puntiaguda, tiene una capacidad de hacer daño superior a la de un cuchillo de punta redonda.
-
De forma análoga, al analizar las diferentes alternativas de diseño de una CBDC, podríamos identificar aquellos elementos que, intencionadamente o no, facilitan ciertos usos indebidos o riesgos asociados y por ende podríamos intuir también las motivaciones de su creador.
Diseñando una CBDC.
En el artículo titulado “The Technology of Retail Central Bank Digital Currency” de Raphael Auer y Rainer Böhme, los autores analizan el desarrollo de una CBDC mediante un enfoque que parte de las necesidades de los consumidores para fundamentar las decisiones de diseño. Para ilustrar este enfoque, introducen la “CBDC Pyramid”, un modelo que organiza jerárquicamente los aspectos clave del diseño de una moneda digital emitida por un banco central:

En el lado izquierdo de la pirámide exponen las necesidades de los consumidores y seis características asociadas que harían útil a una CBDC:
-
Similar al efectivo con funcionalidad peer-to-peer.
-
Pagos en tiempo real.
-
Operaciones resilientes y robustas.
-
Privacidad.
-
Amplia accesibilidad.
-
Capacidad para pagos transfronterizos.
Y en el lado derecho de la pirámide se describen las decisiones de diseño asociadas a cada una de estas características:
-
Reclamaciones indirectas o directas, y ¿qué papel operativo tendrá el banco central?
-
El modelo de centralización (centralizado o descentralizado).
-
Basado en tokens o en balances.
-
Permitir la integración con otras CBDCs.
La tesis sobre la que se construye el paper de Raphael y Rainer se basa en considerar que la principal necesidad del consumidor debe ser poder contar con una CBDC que represente un derecho similar al efectivo y que idealmente sea fácilmente transferible en entornos de transacciones P2P.
A continuación el paper analiza, para cada una de las capas de la pirámide las elecciones disponibles para determinar cuál de ellas es la que acercaría más a una CBDC a las características del cash:
Nivel 1. CBDC directa o indirecta.
A bajo del todo de la pirámide Raphael Auer y Rainer Böhme sitúan la elección de la arquitectura operacional y como se atenderá la demanda del consumidor final. ¿El consumidor "hablará" directamente con el Banco Central y será este quien centralice todo el proceso? ¿o lo hará a través de intermediarios (banca privada)? En cualquiera de los casos, en el paper se asume que solo el banco central podrá emitir la CBCD.
Las principales diferencias en la elección en la base de la pirámide radican en la estructura de los reclamos legales y en los registros mantenidos por el banco central. En el modelo de “CBDC indirecta”, el consumidor tiene un reclamo sobre un intermediario, mientras que el banco central solo lleva un registro de las cuentas mayoristas. En el modelo de “CBDC directa”, la CBDC representa un reclamo directo sobre el banco central, que mantiene un registro de todos los saldos y los actualiza con cada transacción.
Es importante tener en cuenta que los pagos electrónicos deben afrontar interrupciones de conectividad o pagos sin conexión, lo que implica asumir riesgos por parte de los intermediarios y la relación con el cliente, basada en los procesos de Know Your Customer (KYC), permite al intermediario asumir dichos riesgos. Por lo tanto, a menos que un banco central asumiera la responsabilidad del KYC y la debida diligencia del cliente (lo que requeriría una expansión masiva de sus operaciones, muy por encima de sus mandatos actuales), le resultaría difícil asumir un modelo de "CBDC directa".
Nivel 2. Base de datos centralizada o descentralizada.
En el segundo nivel de la pirámide se encuentra la elección de tener un libro mayor centralizado o distribuido.
En un modelo de CBCD directa con base de datos centralizada, las capacidades tecnológicas del banco central deberían ser enormes ya que sería él solo quien procesaría todas las transacciones de todos los ciudadanos (lo que dificulta enormemente su implementación). Además, la principal vulnerabilidad de una arquitectura con un libro mayor centralizado de esta envergadura es la falla del nodo principal.
Por otro lado, actualmente disponer de un libro mayor distribuido (DLT) implica un rendimiento de transacciones menor que las arquitecturas convencionales debido a las dificultades para ejecutar un mecanismo de consenso eficiente y seguro ya que cada actualización del libro mayor debe armonizarse entre los nodos de todas las entidades. Estos modelos podrían ser válidos para jurisdicciones muy pequeñas pero complicado en jurisdicciones más grandes debido al alto número de transacciones que deberían procesar.
Por otro lado, en un modelo de CBCD indirecta ambos enfoques podrían ser factibles.
Nivel 3. Basado en tokens o en balances.
Una vez que se haya elegido la arquitectura y la infraestructura de la CBDC, surge la cuestión de quién tiene la custodia de los fondos y de cómo y a quién se debe otorgar acceso a dichos fondos.
Los activos en moneda digital son fungibles (bienes o activos que pueden intercambiarse entre sí sin que haya una diferencia en su valor o utilidad), por lo que, en principio, pueden tomar la forma de saldos (“acceso basado en cuentas”) o de tokens (“acceso basado en tokens”).
En un sistema de moneda digital basado en saldos (account based access), se debe registrar en algún lugar un número que represente el tamaño de un conjunto de activos, y las transacciones sucesivas deben resultar en cambios en ese número. En este tipo de sistemas, el propietario de los activos debe proporcionar una identificación (derecho basado en la identidad) para acceder al saldo y realizar una transacción, de ahí entre otras, la necesidad del proceso de KYC.
Por el contrario, con los tokens, todo lo que se necesita para realizar una transacción es el conocimiento de las claves criptográficas que los desbloquean. En este tipo de sistemas, los fondos son de quien es capaz de desbloquearlos y las transacciones realizadas no tienen porque estar directamente asociadas a una identidad por lo que es un sistema mucho más parecido al efectivo.
Nivel 4. Integración entre CBDCs.
¿Será posible utilizar la CBDC emitida por el banco central exclusivamente en territorio nacional o también en el extranjero? ¿Estarán dispuestos los bancos centrales a coordinar esfuerzos en el diseño de estas monedas digitales para permitir que los consumidores gestionen múltiples divisas en una sola wallet? De ser así, se facilitaría un comercio internacional más ágil y se eliminaría el vínculo actual entre un pago en el extranjero y la necesidad de realizar una transacción de cambio de divisas (junto con las comisiones asociadas).
En el sistema actual, primero se adquiere moneda nacional, que luego debe ser cambiada por la divisa extranjera, lo que implica costos y demoras. El modelo con pagos transfronterizos integrados permitiría a los consumidores comprar directamente la CBDC del país extranjero antes de realizar sus compras, eliminando así ese paso innecesario e ineficiente y reduciendo los costos asociados al tipo de cambio.
El diseño previsible (mi apuesta personal).
Aquí perdonadme pero voy a ir al grano con mi predicción:
- Creo que la implementación final será el de una CBDC indirecta ofrecida por intermediarios (los bancos privados) con libro mayor centralizado, basada en cuentas en lugar de tokens y con ciertas restricciones en la interoperabilidad entre CBDCs de distintos países.
¿Por qué pienso esto? En primer lugar, como se mencionó anteriormente, una CBDC directa implicaría un cambio significativo en el sistema financiero al transferir gran parte de las responsabilidades de los bancos privados al banco central. En el sistema actual, los bancos privados desempeñan un papel clave en la creación de dinero a través del proceso de concesión de préstamos y la gestión de depósitos. Sin embargo, con una CBDC directa, el banco central sería responsable de emitir dinero digital directamente a los ciudadanos, lo que reduciría drásticamente la necesidad de que los bancos privados gestionen depósitos minoristas.
Esto no solo limitaría su capacidad de crear dinero a través del crédito, sino que también afectaría su modelo de negocio, ya que se reducirían sus fuentes tradicionales de ingresos. Además, podría disminuir su relevancia en el sistema financiero, dejándolos casi fuera de la ecuación en cuanto a la emisión de dinero.
Por otro lado, considero que el modelo con libro mayor centralizado se impondrá principalmente por dos razones: las limitaciones actuales en cuanto a la capacidad de procesamiento de los sistemas distribuidos (DLT) por las reglas de consenso y el interés de los estados en mantener sus capacidades de monitoreo financiero.
En cuanto a la elección entre un sistema basado en tokens o en balances, es importante destacar que, dado que las transacciones en un sistema basado en tokens no están directamente vinculadas a una identidad, resulta más complejo utilizar una CBDC como herramienta de vigilancia o perfilado por parte del banco central o los intermediarios financieros. Este enfoque preserva en mayor medida la privacidad de los usuarios, alineándose con principios similares a los del efectivo digital.
Por tanto, es altamente probable que tanto el Banco Central Europeo como la Reserva Federal opten por un sistema vinculado a una identidad, ya que, además de facilitar el cumplimiento normativo en materia de prevención de delitos financieros, guarda mayor similitud con el modelo de cuentas corrientes tradicional. De hecho, diversos informes, han señalado que la identificación de los usuarios en una CBDC es un factor clave para garantizar la trazabilidad y evitar el anonimato absoluto, lo que refuerza la posibilidad de que el sistema basado en balances sea el elegido.
Finalmente, pienso que facilitar el acceso sencillo a monedas de otros países que se perciben como más seguras podría llevar a una fuga de capitales hacia estas divisas y la ley de Gresham está a mi favor:
La ley de Gresham establece que, cuando en un mercado circulan simultáneamente dos tipos de dinero con el mismo valor nominal pero diferente valor percibido o estabilidad, la “moneda mala” desplaza a la “moneda buena”: los consumidores prefieren conservar la moneda con mayor valor intrínseco como reserva de valor, utilizándola menos en transacciones diarias, lo que eventualmente lleva a su retirada del mercado como medio de pago.
Básicamente esto quiere decir que en el escenario planteado, si los ciudadanos tuvieran acceso directo y fácil a CBDCs de países con economías más estables o con menor inflación, podrían optar por ahorrar en estas monedas más fuertes mientras usan la moneda local para pagos diarios. Esto no solo reduciría la demanda de la moneda nacional, sino que también podría debilitar su estabilidad y aumentar la fuga de capitales.
El móvil.
¿Podrán las personas poseer y controlar su propio dinero y decidir qué hacer con él, o estarán todas sus opciones de pago sujetas a la supervisión y el permiso de intermediarios?
Para ser capaz de contestar a esta pregunta me he basado en el artículo “Retail Central Bank Digital Currency: Motivations, Opportunities, and Mistakes” de Geoffrey Goodell, Hazem Danny Al Nakib y Tomaso Aste que sugiere que los gobiernos buscaran mantener el control sobre su sistema financiero y facilitar la supervisión y regulación de las transacciones a través de las CBDCs y de ahí el diseño con el que las están desarrollando. Dicho esto y aunque en el apartado anterior ya se han podido vislumbrar algunas posibles motivaciones, estas las voy a resumir a continuación:
-
Soberanía monetaria y financiera: Uno de los principales motores detrás de la exploración de las CBDCs son las preocupaciones institucionales sobre los riesgos emergentes para la soberanía monetaria y financiera. Esto es particularmente relevante para los bancos centrales y los gobiernos, que observan cómo el panorama de los pagos evoluciona rápidamente debido a innovaciones tecnológicas y cambios en las preferencias de los consumidores. Además, la creciente facilidad para acceder a divisas extranjeras, especialmente aquellas consideradas más estables o fuertes, está disminuyendo el uso de la moneda local en algunos países. Esto representa un riesgo directo para la soberanía monetaria, ya que reduce la efectividad de las políticas monetarias nacionales.
-
Control total sobre los estímulos económicos: Un sistema de CBDC plenamente operativo podría otorgar a los bancos centrales un control detallado sobre el estímulo fiscal, permitiéndoles distribuir fondos de manera segmentada con solo presionar un botón. En un escenario donde el efectivo físico desapareciera, las CBDC podrían facilitar la aplicación de tasas de interés negativas, obligando a los ciudadanos a pagar una tarifa por mantener ahorros en sus cuentas. Además, este tipo de moneda digital podría proporcionar a los gobiernos la capacidad de confiscar fondos con mayor facilidad, sancionar a disidentes políticos o incluso automatizar multas por infracciones menores, lo que ha suscitado preocupaciones sobre el potencial abuso de estas herramientas. Finalmente, y por si esto fuera poco, existen estudios que exploran la posibilidad de que las CBDCs puedan utilizarse para rastrear y potencialmente restringir o desincentivar ciertas compras con una alta huella de carbono, integrándolas en un sistema de créditos de carbono personales. Un posible escenario podría ser el siguiente:
-
Al intentar comprar gasolina o diésel, la CBDC verifica la huella de carbono acumulada del usuario.
-
Si el usuario ha superado su límite mensual de emisiones, la transacción podría ser rechazada automáticamente o estar sujeta a un recargo adicional por exceder su cuota.
-
Como alternativa, el usuario podría adquirir créditos de carbono de otros ciudadanos que hayan consumido menos, creando así un mercado de intercambio de emisiones a nivel individual.
Esto no debe sorprender a nadie considerando que el sistema Cap and Trade ya se encuentra implementado en la actualidad. Bajo este esquema, empresas con altas emisiones de CO₂ (como aerolíneas, fábricas e industrias de transporte) deben comprar créditos de carbono cuando superan su límite permitido de emisiones. Por tanto el sistema sería el mismo pero aplicado directamente a los ciudadanos.
-
Oportunidades para el sector privado: Lo primero que hay que tener en cuenta es que hoy en día, las compras diarias realizadas a través de aplicaciones móviles o tarjetas de crédito tienen poca semejanza con las compras hechas en efectivo y los usuarios de plataformas como Visa, Apple Pay, WeChat o PayPal intercambian su libertad y privacidad por conveniencia o "usabilidad". En este tipo de transacciones se exige y se comparte información personal en lugar de protegerla. Todo esto nos ha de hacer reflexionar sobre la gran oportunidad que se presenta para el sector privado y en concreto para las "Big Tech" si consiguen monetizar toda la información del consumidor que una moneda tipo CBDC podría proporcionar. No es de extrañar entonces que empresas como Google, Amazon, Stripe o Mastercard sean partners de proyectos de investigación de este tipo de monedas digitales. Como "Data harvesters" experimentados son conscientes del tremendo valor en la creación de perfiles de usuarios.
-
Crimen y evasión fiscal: Como comentamos anteriormente, algunos gobiernos intentan asociar el uso del efectivo con el lavado de dinero y la corrupción, lo que les permite justificar la implementación de las CBDCs como una estrategia para combatir estos problemas. Un ejemplo es el Banco Central de Bangladesh, que busca digitalizar todas las transacciones minoristas para 2027, argumentando que esto mejorará la eficiencia, promoverá la inclusión financiera y reducirá la criminalidad. En Nigeria, el e-Naira fue introducido con el objetivo de facilitar el rastreo de fondos, pero la población respondió con protestas y una baja adopción de la moneda digital.
Conclusiones.
Desde mi punto de vista, es poco probable que las democracias aprendan pronto a diseñar CBDCs que garanticen la privacidad, y aún menos que tengan el incentivo de ofrecerlas a sus ciudadanos. Al fin y al cabo, muchas de las características que atraen tanto a políticos como a banqueros centrales son incompatibles con el dinero anónimo. Por ello, creo que la única alternativa viable para preservar la privacidad financiera que ofrece el efectivo es desarrollar herramientas monetarias resistentes al abuso gubernamental.
Pocas veces se ha expresado este problema con tanta claridad como lo hizo Wei Dai en un correo electrónico enviado en febrero de 1995 a la lista de correo de Cypherpunks donde Dai escribió:
"Nunca ha existido un gobierno que, tarde o temprano, no haya intentado reducir la libertad de sus ciudadanos y obtener más control sobre ellos, y probablemente nunca existirá uno.
Por lo tanto, en lugar de tratar de convencer a nuestro gobierno actual de que no lo intente, desarrollaremos la tecnología que hará imposible que el gobierno tenga éxito.
Los esfuerzos para influir en el gobierno (por ejemplo, a través del lobby y la propaganda) son importantes solo en la medida en que retrasen lo suficiente su intento de represión como para que la tecnología madure y se adopte ampliamente.”
-
-
 @ 7f6db517:a4931eda
2025-06-16 15:03:05
@ 7f6db517:a4931eda
2025-06-16 15:03:05
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
Good morning.
It looks like PacWest will fail today. It will be both the fifth largest bank failure in US history and the sixth major bank to fail this year. It will likely get purchased by one of the big four banks in a government orchestrated sale.
March 8th - Silvergate Bank
March 10th - Silicon Valley Bank
March 12th - Signature Bank
March 19th - Credit Suisse
May 1st - First Republic Bank
May 4th - PacWest Bank?PacWest is the first of many small regional banks that will go under this year. Most will get bought by the big four in gov orchestrated sales. This has been the playbook since 2008. Follow the incentives. Massive consolidation across the banking industry. PacWest gonna be a drop in the bucket compared to what comes next.
First, a hastened government led bank consolidation, then a public/private partnership with the remaining large banks to launch a surveilled and controlled digital currency network. We will be told it is more convenient. We will be told it is safer. We will be told it will prevent future bank runs. All of that is marketing bullshit. The goal is greater control of money. The ability to choose how we spend it and how we save it. If you control the money - you control the people that use it.
If you found this post helpful support my work with bitcoin.

-
 @ eb0157af:77ab6c55
2025-06-18 02:02:02
@ eb0157af:77ab6c55
2025-06-18 02:02:02VanEck analyst Matthew Sigel warns of growing risks for Bitcoin treasury companies as their stock prices approach NAV.
Matthew Sigel, Head of Digital Assets Research at VanEck, has sounded the alarm for companies that have adopted Bitcoin-based treasury strategies.
No public BTC treasury company has traded below its Bitcoin NAV for a sustained period.
But at least one is now approaching parity.
As some of these companies raise capital through large at-the-market (ATM) programs to buy BTC, a risk is emerging: If the stock trades at or near…
— matthew sigel, recovering CFA (@matthew_sigel) June 16, 2025
In a post on X, Sigel highlighted an emerging issue in the sector of companies holding Bitcoin treasuries. Until now, no public company with a Bitcoin treasury has ever traded below its own Net Asset Value (NAV) for extended periods. The NAV represents the net value of a company’s assets (such as bitcoin and cash) minus its liabilities, divided by the number of outstanding shares — essentially indicating the real value of each share based on the company’s holdings. However, at least one of these companies (Semler Scientific) is now dangerously approaching breakeven.
The core of the issue lies in the capital-raising mechanism. Many of these companies rely on large-scale at-the-market (ATM) programs to acquire bitcoin, but when the stock price nears the NAV, this strategy can shift from creating value to destroying it.
The risk for shareholders
Under normal market conditions, companies like Semler Scientific and Strategy trade at a premium to the value of the bitcoin they hold. This means investors are willing to pay more for the company’s stock than the simple value of its bitcoin treasury.
However, when a company’s stock price approaches or falls below its NAV, the situation becomes problematic, according to Sigel. Issuing new shares at these levels not only dilutes the value for existing shareholders but can also become extractive, as management continues to raise capital while benefiting more than shareholders.
Proposed solutions
Sigel suggested several measures for companies pursuing Bitcoin treasury strategies. His recommendations include implementing preventive safeguards while stock premiums still exist. Notably, he proposes announcing a pause in ATM issuances if the stock trades below 0.95 times NAV for ten or more consecutive trading days. Additionally, Sigel advises prioritizing buybacks when bitcoin appreciates but the company’s equity does not reflect that increase.
Lessons from Bitcoin miners’ past
The VanEck analyst pointed out that similar situations have occurred in the Bitcoin mining sector, marked by persistent equity issuances and disproportionate executive compensation. To avoid repeating those mistakes, Sigel suggests that executive pay should be tied to growth in NAV per share, not the size of the Bitcoin position or the total number of outstanding shares.
Sigel concluded:
“Once you are trading at NAV, shareholder dilution is no longer strategic. It is extractive. Boards and shareholders should act with discipline now, while they still have the benefit of optionality.”
The post Bitcoin treasury: VanEck sounds the alarm for companies in the danger zone appeared first on Atlas21.
-
 @ 8bad92c3:ca714aa5
2025-06-16 14:02:15
@ 8bad92c3:ca714aa5
2025-06-16 14:02:15Key Takeaways

Michael Goldstein, aka Bitstein, presents a sweeping philosophical and economic case for going “all in” on Bitcoin, arguing that unlike fiat, which distorts capital formation and fuels short-term thinking, Bitcoin fosters low time preference, meaningful saving, and long-term societal flourishing. At the heart of his thesis is “hodling for good”—a triple-layered idea encompassing permanence, purpose, and the pursuit of higher values like truth, beauty, and legacy. Drawing on thinkers like Aristotle, Hoppe, and Josef Pieper, Goldstein redefines leisure as contemplation, a vital practice in aligning capital with one’s deepest ideals. He urges Bitcoiners to think beyond mere wealth accumulation and consider how their sats can fund enduring institutions, art, and architecture that reflect a moral vision of the future.
Best Quotes
“Let BlackRock buy the houses, and you keep the sats.”
“We're not hodling just for the sake of hodling. There is a purpose to it.”
“Fiat money shortens your time horizon… you can never rest.”
“Savings precedes capital accumulation. You can’t build unless you’ve saved.”
“You're increasing the marginal value of everyone else’s Bitcoin.”
“True leisure is contemplation—the pursuit of the highest good.”
“What is Bitcoin for if not to make the conditions for magnificent acts of creation possible?”
“Bitcoin itself will last forever. Your stack might not. What will outlast your coins?”
“Only a whale can be magnificent.”
“The market will sell you all the crack you want. It’s up to you to demand beauty.”
Conclusion
This episode is a call to reimagine Bitcoin as more than a financial revolution—it’s a blueprint for civilizational renewal. Michael Goldstein reframes hodling as an act of moral stewardship, urging Bitcoiners to lower their time preference, build lasting institutions, and pursue truth, beauty, and legacy—not to escape the world, but to rebuild it on sound foundations.
Timestamps
00:00 - Intro
00:50 - Michael’s BBB presentation Hodl for Good
07:27 - Austrian principles on capital
15:40 - Fiat distorts the economic process
23:34 - Bitkey
24:29 - Hodl for Good triple entendre
29:52 - Bitcoin benefits everyone
39:05 - Unchained
40:14 - Leisure theory of value
52:15 - Heightening life
1:15:48 - Breaking from the chase makes room for magnificence
1:32:32 - Nakamoto Institute’s missionTranscript
(00:00) Fiat money is by its nature a disturbance. If money is being continually produced, especially at an uncertain rate, these uh policies are really just redistribution of wealth. Most are looking for number to go up post hyper bitcoinization. The rate of growth of bitcoin would be more reflective of the growth of the economy as a whole.
(00:23) Ultimately, capital requires knowledge because it requires knowing there is something that you can add to the structures of production to lengthen it in some way that will take time but allow you to have more in the future than you would today. Let Black Rockck buy the houses and you keep the sats, not the other way around.
(00:41) You wait until later for Larry Frink to try to sell you a [Music] mansion. And we're live just like that. Just like that. 3:30 on a Friday, Memorial Day weekend. It's a good good good way to end the week and start the holiday weekend. Yes, sir. Yes, sir. Thank you for having me here. Thank you for coming. I wore this hat specifically because I think it's I think it's very apppropo uh to the conversation we're going to have which is I hope an extension of the presentation you gave at Bitblock Boom Huddle for good. You were working on
(01:24) that for many weeks leading up to uh the conference and explaining how you were structuring it. I think it's a very important topic to discuss now as the Bitcoin price is hitting new all-time highs and people are trying to understand what am I doing with Bitcoin? Like you have you have the different sort of factions within Bitcoin.
(01:47) Uh get on a Bitcoin standard, get on zero, spend as much Bitcoin as possible. You have the sailors of the world are saying buy Bitcoin, never sell, die with your Bitcoin. And I think you do a really good job in that presentation. And I just think your understanding overall of Bitcoin is incredible to put everything into context. It's not either or.
(02:07) It really depends on what you want to accomplish. Yeah, it's definitely there there is no actual one-sizefits-all um for I mean nearly anything in this world. So um yeah, I mean first of all I mean there was it was the first conference talk I had given in maybe five years. I think the one prior to that uh was um bit block boom 2019 which was my meme talk which uh has uh become infamous and notorious.
(02:43) So uh there was also a lot of like high expectations uh you know rockstar dev uh has has treated that you know uh that that talk with a lot of reference. a lot of people have enjoyed it and he was expecting this one to be, you know, the greatest one ever, which is a little bit of a little bit of a uh a burden to live up to those kinds of standards.
(03:08) Um, but you know, because I don't give a lot of talks. Um, you know, I I I like to uh try to bring ideas that might even be ideas that are common. So, something like hodling, we all talk about it constantly. uh but try to bring it from a little bit of a different angle and try to give um a little bit of uh new light to it.
(03:31) I alsove I've I've always enjoyed kind of coming at things from a third angle. Um whenever there's, you know, there's there's all these little debates that we have in in Bitcoin and sometimes it's nice to try to uh step out of it and look at it a little more uh kind of objectively and find ways of understanding it that incorporate the truths of of all of them.
(03:58) uh you know cuz I think we should always be kind of as much as possible after ultimate truth. Um so with this one um yeah I was kind of finding that that sort of golden mean. So uh um yeah and I actually I think about that a lot is uh you know Aristotle has his his concept of the golden mean. So it's like any any virtue is sort of between two vices um because you can you can always you can always take something too far.
(04:27) So you're you're always trying to find that right balance. Um so someone who is uh courageous you know uh one of the vices uh on one side is being basically reckless. I I can't remember what word he would use. Uh but effectively being reckless and just wanting to put yourself in danger for no other reason than just you know the thrill of it.
(04:50) Um and then on the other side you would just have cowardice which is like you're unwilling to put yourself um at any risk at any time. Um, and courage is right there in the middle where it's understanding when is the right time uh to put your put yourself, you know, in in the face of danger um and take it on. And so um in some sense this this was kind of me uh in in some ways like I'm obviously a partisan of hodling.
(05:20) Um, I've for, you know, a long time now talked about the, um, why huddling is good, why people do it, why we should expect it. Um, but still trying to find that that sort of golden mean of like yes, huddle, but also what are we hodling for? And it's not we're we're not hodddling just merely for the sake of hodddling.
(05:45) There there is a a purpose to it. And we should think about that. And that would also help us think more about um what are the benefits of of spending, when should we spend, why should we spend, what should we spend on um to actually give light to that sort of side of the debate. Um so that was that was what I was kind of trying to trying to get into.
(06:09) Um, as well as also just uh at the same time despite all the talk of hodling, there's always this perennial uh there's always this perennial dislike of hodlers because we're treated as uh as if um we're just free riding the network or we're just greedy or you know any of these things. And I wanted to show how uh huddling does serve a real economic purpose.
(06:36) Um, and it does benefit the individual, but it also does uh it it has actual real social um benefits as well beyond merely the individual. Um, so I wanted to give that sort of defense of hodling as well to look at it from um a a broader position than just merely I'm trying to get rich. Um uh because even the person who uh that is all they want to do um just like you know your your pure number grow up go up moonboy even that behavior has positive ramifications on on the economy.
(07:14) And while we might look at them and have uh judgments about their particular choices for them as an individual, we shouldn't discount that uh their actions are having positive positive effects for the rest of the economy. Yeah. So, let's dive into that just not even in the context of Bitcoin because I think you did a great job of this in the presentation.
(07:36) just you've done a good job of this consistently throughout the years that I've known you. Just from like a first principles Austrian economics perspective, what is the idea around capital accumulation, low time preference and deployment of that capital like what what like getting getting into like the nitty-gritty and then applying it to Bitcoin? Yeah, it's it's a big question and um in many ways I mean I I even I barely scratched the surface.
(08:05) uh I I can't claim to have read uh all the volumes of Bombber works, you know, capital and interest and and stuff like that. Um but I think there's some some sort of basic concepts that we can look at that we can uh draw a lot out. Um the first uh I guess let's write that. So repeat so like capital time preference. Yeah. Well, I guess getting more broad like why sav -
 @ 31a4605e:cf043959
2025-06-17 17:56:33
@ 31a4605e:cf043959
2025-06-17 17:56:33Bitcoin, desde o seu lançamento em 2009, tem atraído a atenção de diversos investidores e visionários que acreditam no seu potencial para revolucionar o sistema financeiro global. Ao longo dos anos, várias figuras se destacaram no movimento em torno da criptomoeda, seja como pioneiros que ajudaram a fundá-la, ou como investidores que apostaram no seu futuro. Estes indivíduos desempenharam papéis cruciais no desenvolvimento do Bitcoin, na sua adoção crescente e na sua legitimação no mercado financeiro.
Satoshi Nakamoto
O maior pioneiro do Bitcoin é, sem dúvida, o seu criador, Satoshi Nakamoto. Embora o nome seja um pseudónimo, a sua contribuição para a criação e lançamento do Bitcoin foi fundamental. Em 2008, Nakamoto publicou o famoso whitepaper intitulado "Bitcoin: A Peer-to-Peer Electronic Cash System", detalhando a ideia de uma moeda digital descentralizada que poderia operar sem a necessidade de uma autoridade central, como um banco. Em 2009, ele lançou o software Bitcoin e minerou o primeiro bloco da blockchain, conhecido como "bloco gênese".
Satoshi Nakamoto permaneceu uma figura misteriosa, nunca revelando a sua verdadeira identidade. Ele foi responsável pelo desenvolvimento inicial do protocolo, mas desapareceu gradualmente da cena pública por volta de 2011, deixando o projeto nas mãos de uma comunidade crescente de desenvolvedores. A sua identidade permanece desconhecida até hoje, mas o seu impacto na criação de uma nova era digital é inegável.
Hal Finney
Hal Finney foi um dos primeiros colaboradores de Nakamoto e é amplamente reconhecido como o primeiro a receber uma transação de Bitcoin. Em janeiro de 2009, Finney recebeu 10 bitcoins de Nakamoto como parte de um teste de transação, tornando-se uma das primeiras pessoas a acreditar no projeto. Finney, que era um programador e investigador de segurança, desempenhou um papel importante no desenvolvimento técnico do Bitcoin e ajudou a popularizá-lo nas suas primeiras fases.
Finney foi uma figura respeitada na comunidade de criptografia e um defensor do movimento de descentralização digital. Ele continuou a apoiar o Bitcoin até sua morte, em 2014, e é lembrado como um dos maiores pioneiros da moeda digital.
Roger Ver
Roger Ver, conhecido como o "Bitcoin Jesus", foi um dos primeiros investidores e “evangelistas” do Bitcoin. Ver ficou fascinado com o conceito de uma moeda descentralizada e investiu cedo em vários projetos relacionados ao Bitcoin. Ele foi um dos primeiros a reconhecer o potencial disruptivo do Bitcoin, defendendo a sua adoção global e promovendo o seu uso como meio de pagamento.
Ver também foi uma das figuras centrais na criação de empresas e iniciativas que ajudaram a impulsionar o ecossistema Bitcoin. Embora tenha sido uma figura polêmica, devido às suas opiniões fortes sobre a escalabilidade do Bitcoin, e tenha se afastado da blockchain original do Bitcoin em favor do Bitcoin Cash, sua contribuição para a popularização da moeda é inegável.
Tim Draper
Tim Draper é um dos investidores mais conhecidos no espaço do Bitcoin e um defensor da sua adoção em larga escala. Em 2014, Draper comprou quase 30.000 bitcoins, que foram apreendidos pelo governo dos Estados Unidos em uma operação contra o mercado Silk Road. Draper fez essa compra por cerca de 19 milhões de dólares, e ele tem sido uma figura-chave na promoção do Bitcoin como uma alternativa viável às moedas fiduciárias.
Draper, um investidor de risco de renome e fundador da Draper Associates, é conhecido por sua visão de longo prazo e pela sua confiança na ascensão das criptomoedas. Ele tem defendido o Bitcoin como uma ferramenta para democratizar o acesso ao dinheiro e acredita que a adoção do Bitcoin vai crescer exponencialmente nos próximos anos.
Michael Saylor
Michael Saylor, CEO da MicroStrategy, é uma figura importante na adoção institucional do Bitcoin. Em 2020, Saylor fez uma aposta significativa ao comprar mais de 100.000 bitcoins para a sua empresa, transformando-a na primeira companhia pública a ter Bitcoin como reserva de valor no seu balanço. Saylor tem defendido publicamente o Bitcoin como uma proteção contra a inflação e uma alternativa mais segura ao dinheiro fiduciário. A sua aposta ajudou a legitimar o Bitcoin no mundo corporativo e inspirou outras empresas a seguir o seu exemplo.
A sua posição em relação ao Bitcoin tem sido clara: ele acredita que o futuro financeiro do mundo está no Bitcoin, e a sua empresa serve como um exemplo para outras grandes corporações a adotarem a moeda digital.
Resumindo, os pioneiros e investidores que contribuíram para o crescimento e a difusão do Bitcoin desempenharam papéis vitais na evolução desta tecnologia disruptiva. Desde o misterioso Satoshi Nakamoto até figuras como Hal Finney, Roger Ver, Tim Draper e Michael Saylor, o Bitcoin tem sido moldado por pessoas com uma visão única sobre o futuro do dinheiro e da liberdade financeira. Através da sua perseverança e crença no potencial do Bitcoin, esses indivíduos ajudaram a estabelecer as bases para a adoção global da moeda digital, transformando-a de uma ideia inovadora em uma força revolucionária no sistema financeiro. O futuro do Bitcoin dependerá, em grande parte, da continuidade da sua evolução e da adoção por mais pessoas e instituições, mas é indiscutível que os pioneiros e investidores desempenharam um papel fundamental na sua ascensão.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 4fe4a528:3ff6bf06
2024-09-01 12:45:44
@ 4fe4a528:3ff6bf06
2024-09-01 12:45:44One of the main motivational factors for people to buy bitcoin is it’s ability to store value over time. During harvest we are doing the same thing. We have now harvested our garlic and 1/2 of our onions because if we don’t use the sun’s energy to cure the plants before winter they will start to rot. Let me explain why God has made the world this way; but, first let me explain why storing things isn’t evil.
“Do not store up for yourselves treasures on earth, where moth and rust consume and where thieves break in and steal; but store up for yourselves treasures in heaven, where neither moth nor rust consumes and where thieves do not break in and steal. For where your treasure is, there your heart will be also”. Matt. 6:19-21
Is it wrong, then to have a retirement portfolio or even to care about the material things of this world for ourselves or for others? The answer is again both no and yes. The no comes from the fact that this passage is not the only one in the Bible speaking to questions of wealth and provision for those who are dependent on us. Other passages counsel prudence and forethought, such as, “Those who gather little by little will increase [wealth]” (Proverbs 13:11b), and, “The good leave an inheritance to their children’s children” (Proverbs 13:22).
God guides Joseph to store up food for seven years in advance of a famine (Genesis 41:25-36), and Jesus speaks favorably in the Parable of the Talents (Matt. 25:14-30). In light of the rest of Scripture, Matthew 6:19-21 cannot be a blanket prohibition. But the yes part of the answer is a warning, summed up beautifully in verse 21, “Where your treasure is, there will your heart be also.” In other words, the possessions you own will change you so that you care more about the possessions than about other things.” So choose carefully what you own, for you will inevitably begin to value and protect it to the potential detriment of everything else.
How are we to discern the line between appropriate and inappropriate attention to wealth? Jesus answers, “Strive first for the kingdom of God and his righteousness, and all these things will be given to you” So if you believe your heart is following God’s direction go ahead and harvest your crops and / or buy some bitcoin. If you would have bought bitcoin one year ago, you would have 127% more purchasing power now. Let’s keep on fearing God and keeping his commandments.