-
 @ 2769f6ba:8dac44e4
2025-06-03 06:53:38
@ 2769f6ba:8dac44e4
2025-06-03 06:53:38You may want to believe that the world works like a video game, where you can press the pause button, come back three months later and everything will be waiting for you exactly as you left it. But real life doesn’t work like that. The difference is that in the video game you are in control, whereas in real life you are not. Maybe you want to believe that the worst is over, but this is just getting started. Supply chains are breaking down and the economy is starting to collapse. To make it clear, “the economy” is not something abstract; it’s real people losing their jobs, their businesses, their incomes and their homes. Your authoritarian fantasies will just make it worse for you and others until you cannot handle it anymore and you accept reality and surrender to it. I get that you are afraid, and that’s OK. But to hold your fellow human beings hostage because you are afraid is not OK. It’s getting to the point where if you still support lockdowns, mandatory vaccines, mandatory tracking, mandatory testing or mandatory anything you have blood on your hands. History will not judge you kindly.
Then there are those of you who want to believe that the bailouts and the “universal basic income” will make the problems disappear. For example, I read Charles Eisenstein in his otherwise excellent piece The Coronation come up with all this UBI nonsense. You probably realize that if you grab a piece of paper and write “$1,000,000” on it with a marker pen of your favorite color, you don’t become magically rich. But you still want to believe that if the government does exactly the same thing, your problems will go away. On the one hand, even if you are not fully aware of it, you realize that the government and its satellite corporations are abusing you and sucking your blood more and more every day. Yet on the other hand, you keep begging your very abusers that are trying to deprive you from earning an honest living for yourself to give you a measly monthly UBI check in the hopes that it will magically make you feel good and solve your problems.
Aside from the fact that printing money cannot solve the issue the governments themselves have created in the first place with their mandatory lockdowns: maybe you expect that you can control your masters, or that they will benevolently give you the UBI check with no strings attached. Of course not: receiving the check will likely be tied to being a “good law-abiding citizen” (a.k.a. obedient slave); something like the social credit system they have in China. You will end up completely disempowered and depending on the government to even feed yourself and have shelter. I find it quite infuriating and sad that any “spiritual teacher” would want that for you and that you fall for it.
Consider this:
The issue is not the coronavirus itself. The virus is just revealing the cracks in the system.
You are not a victim. You always have the power. Not the power to start a “revolution”, mind you, which just consists in replacing the old abusers with new ones. As Buckminster Fuller said: “You never change things by fighting the existing reality. To change something, build a new model that makes the existing model obsolete.”
You have the power to walk away from this dying system of nation-state governments and fiat “money” and into the nascent paradigm of cryptocurrencies and decentralized governance. But first you have to question and confront the beliefs you have accepted as “reality”. It’s hard, I know, but unavoidable. So, the sooner you begin, the better for yourself and for humanity. Do you want to be free or do you just want to have a “fair” master?
-
 @ 2769f6ba:8dac44e4
2025-06-03 06:46:33
@ 2769f6ba:8dac44e4
2025-06-03 06:46:33I am feeling that the issue runs deeper. Science has been hijacked by the state, so I find the post-truth thing as a meme that rejects the corruption of science. Unfortunately, those hippies are throwing the baby with the bathwater in the process. But I see legitimate issues that need to be acknowledged if we want to reach out to those post-truth hippies.
For example, in my opinion:
The issue is not with 5G, but with this:
- Not wanting to be “bathed” 24/7 in waves of higher frequency (3 to 30 GHz). I understand the fear and skepticism on this.
- The push towards so-called “smart cities”, which are more like surveillance-cities. Granted, those technologies will bring benefits, but I see an issue with a top-down planned system controlled by the state and its contractors rather than a more organic system, with participation from many actors and little central planning. Of course, politicians and “experts” are always trying to link together smart-cities with 5G as if they must go together.
- The state is appropriating the radio spectrum and renting most of it to its cronies from the telecom companies, while it only leaves tiny scraps for open use by the population.
The issue is not with vaccines, but with this:
- pushing forced vaccination under the guise of “science”.
- an ever-growing list of both mandatory and “recommended” vaccines, some of them for diseases that are just an inconvenience and definitely not life-threatening.
I feel it must be acknowledged that the state has hijacked science, in the same way that the church has always hijacked spirituality. So, just telling those hippies that they have to trust science because facts and because the “experts” say so, won’t cut it anymore. A different approach is needed.
-
 @ 5627e59c:d484729e
2025-06-11 22:28:08
@ 5627e59c:d484729e
2025-06-11 22:28:08Here's to the ones who can\ Feel their cause\ Surrender\ Change their ways\ But keep their fire\ And never give up
We will transform this world\ Restructuring\ One belief at a time
-
 @ 5627e59c:d484729e
2025-06-11 22:24:15
@ 5627e59c:d484729e
2025-06-11 22:24:15Love, I thank you for your warmth\ Ever lifting
You keep me charmed\ Ever drifting
May I be me\ And you be you
In a perfect harmony\ Embracing all life makes us grow through
-
 @ 5627e59c:d484729e
2025-06-11 22:24:05
@ 5627e59c:d484729e
2025-06-11 22:24:05Jaren tellen\ Hoeft voor mij niet
Verhalen vertellen\ Over geluk en verdriet
Een warme haven\ Veilig en fijn
Dromen voorgedragen\ Onschuldig en rein
Momenten ervaard, geleerd\ En geïntegreerd
Ideeën, geloven en gevoelens\ Gevormd en gecreëerd
Zonder eind of echt begin\ Vallen, groeien, leren, stoeien
Een gezin in een gezin met een gezin erin\ Gezind gericht blijft liefde vloeien
-
 @ 5627e59c:d484729e
2025-06-11 22:23:37
@ 5627e59c:d484729e
2025-06-11 22:23:37Happy New Year!
Happy New Year, my dearest human family\ Happy New Year, my dearest animal family
Dear children of the Earth\ I wish you all a magical year
May it be utterly new\ Ever-changing\ New now
And may your journey say\ Life is amazing! I'm in a maze\ Life is awesome! Quite some awe\ Life is magical! True alchemy
I am human\ Black woman, I love you so\ Life-giver of my origin, the negro [nigiro]
I am\ Thus physical and non-physical meet
Life is to be\ As the elements are and compete\ And as they collide with one another\ One becomes aware of an other\ And so life sets on a journey\ To discover the other
Animal life is set to explore\ Allowing all experience the other has in store\ Life left to experience without a voice\ Until it discovers there is an 'I'\ And it has a choice
Human life is to be inside a human body\ Thus fusion between intellect and feeling\ Gets to express its perspective\ Inside infinity
Truly, a magical gift\ My Holy Trinity
And so from human life flow many voices\ As it navigates through infinite choices
Thus I say
Life is magic\ A gift for all that is here\ Perceived by too many as tragic\ Take care of your vision, I tell you, my dear [tell-a-vision]
Life is magic\ And words are spells\ Placing your aim beyond your reach\ It takes away efficiency from your speech
Life is magic\ Above all else\ Even when it has me feeling blue\ Seemingly left without a clue
Still I say
Perfection\ You are everything\ And I am of you
The source, the mirror\ And the reflection
-
 @ 472f440f:5669301e
2025-06-12 05:11:12
@ 472f440f:5669301e
2025-06-12 05:11:12Marty's Bent
via me
I had a completely different newsletter partially written earlier tonight about whether or not "this cycle is different" when this nagging thought entered my head. So I'm going to write about this and maybe I'll write about the dynamics of this cycle compared to past cycles tomorrow.
A couple of headlines shot across my desk earlier tonight in relation to the potential escalation of kinetic warfare in the Middle East. Apparently the U.S. Embassy in Iraq was sent a warning and evacuation procedures were initiated. Not too long after, the world was made aware that the United States and Israel are contemplating an attack on Iran due to the "fact" that Iran may be close to producing nuclear weapins. The initial monkey brain reaction that I had to these two headlines was, "Oh shit, here we go again. We're going to do something stupid." My second reaction was, "Oh shit, here we go again, I've seen these two exact headlines many times over the years and they've proven to be lackluster if you're a doomer or blood thirsty war monger." Nothing ever happens.
As I venture into my mid-30s and reflect on a life filled with these types of headlines and my personal reactions to these headlines, I'm finally becoming attuned to the fact that the monkey brain reactions aren't very productive at the end of the day. Who knows exactly what's going to happen in Iraq or Iran and whether or not kinetic warfare escalates and materializes from here? Even though I'm a "blue-blooded taxpaying American citizen" who is passively and unwillingly contributing to the war machine and the media industrial complex, there's really nothing I can do about it.
The only thing I can do is focus on what is in front of me. What I have control of. And attempt to leverage what I have control of to make my life and the life of my family as good as humanly possible. Ignoring the external and turning inward often produces incredible results. Instead of worrying about what the media wants you to believe at any given point in time, you simply look away from your computer screen, survey the physical space which you're operating in and determine what you have, what you need and how you can get what you need. This is a much more productive way to spend your time.
This is what I want to touch on right now. There's never been a better time in human history to be productive despite what the algorithm on X or the mainstream media will lead you to believe. Things aren't as great as they could be, but they're also not as bad as you're being led to believe. We live in the Digital Age and the Digital Age provides incredible resources that you can leverage to make YOUR life better.
Social media allows you to create a platform without spending any money. AI allows you to build tools that are beneficial to yourself and others with very little money. And bitcoin exists to provide you with the best form of money that you can save in with the knowledge that your relative ownership of the overall supply isn't going to change. No matter what happens in the external world.
If you can combine these three things to make your life better and - by extension - potentially make the lives of many others better, you're going to be well off in the long run. Combining these three things isn't going to result in immediate gratification, but if you put forth a concerted effort, spend the time, have some semblance of patience, and stick with it, I truly believe that you will benefit massively in the long run. Without trying to sound like a blowhard, I truly believe that this is why I feel relatively calm (despite my monkey brain reactions to the headlines of the day) at this current point in time.
We've entered the era of insane leaps in productivity and digital hard money that cannot be corrupted. The biggest mistake you can make in your life right now is overlooking the confluence of these two things. With an internet connection, an idea, some savvy, and hard work you can materially change your life. Create something that levels up your knowledge, that enables you to get a good job in the real world, or to create a company of your own. Bring your talents to the market, exchange them for money, and then funnel that money into bitcoin (if you're not being paid in it already). We may be at the beginning of a transition from the high velocity trash economy to the high leverage agency economy run on sound money and applied creativity.
These concepts are what you should be focusing most of your time and attention to today and in the years ahead. Don't get distracted by the algorithm, the 30-second video clips, the headlines filled with doom, and the topics of the 24 hour news cycle. I'll admit, I often succumb to them myself. But, as I get older and develop a form of pattern recognition that can only be attained by being on this planet for a certain period of time, it is becoming very clear that those things are not worth your attention.
Living by the heuristic that "nothing ever happens" is a pretty safe bet. Funnily enough, it's incredibly ironic that you're led to believe that something is happening every single day, and yet nothing ever happens. By getting believing that something happens every day you are taking your attention away from doing things that happen to make your life better.
Tune out the noise. Put on the blinders. Take advantage of the incredible opportunities that lie before you. If enough of you - and many others who do not read this newsletter - do this, I truly believe we'll wake up to find that the world we live in is a much better place.
Nothing ever happens, so make something happen.
Intelligence Officials Are Quietly Becoming Bitcoin Believers
Ken Egan, former CIA Deputy Chief of Cyber Operations, revealed a surprising truth on TFTC: the intelligence community harbors numerous Bitcoin advocates. Egan explained that intelligence professionals uniquely understand how governments weaponize financial systems through sanctions and account freezing. Having wielded these tools themselves, they recognize the need for personal financial sovereignty. He shared compelling anecdotes of discovering colleagues with "We are all Satoshi" stickers and a European chief of station paying for dinner with a BlockFi card to earn Bitcoin rewards.
"I think there are a lot of Bitcoiners, not just at CIA, but across the whole national security establishment... they're in it for the exact same reasons everybody else is." - Ken Egan
The Canadian trucker protests served as a pivotal moment, Egan noted. Watching Western governments freeze citizens' bank accounts for political dissent struck a nerve among intelligence professionals who previously viewed financial weaponization as a tool reserved for foreign adversaries. This awakening has created unlikely allies within institutions many Bitcoiners distrust.
Check out the full podcast here for more on Bitcoin's national security implications, privacy tech prosecutions, and legislative priorities.
Headlines of the Day
Stripe Buys Crypto Wallet Privy After Bridge Deal - via X
Trump Calls CPI Data "Great" Urges Full Point Fed Cut - via X
Bitcoin Hashrate Reaches New All-Time High - via X
Get our new STACK SATS hat - via tftcmerch.io
Bitcoin’s Next Parabolic Move: Could Liquidity Lead the Way?
Is bitcoin’s next parabolic move starting? Global liquidity and business cycle indicators suggest it may be.
Read the latest report from Unchained and TechDev, analyzing how global M2 liquidity and the copper/gold ratio—two historically reliable macro indicators—are aligning once again to signal that a new bitcoin bull market may soon begin.
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Life is good.
Download our free browser extension, Opportunity Cost: https://www.opportunitycost.app/ start thinking in SATS today.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ 2769f6ba:8dac44e4
2025-06-03 06:38:13
@ 2769f6ba:8dac44e4
2025-06-03 06:38:13To be blunt, people want “authority” to exist because they themselves are immature cowards. They want an all-powerful entity to impose their will upon others. This takes different forms in different varieties of political advocacy, but the basic motivation is always the same. The “liberal” for example, resents reality. He does not want a world in which suffering and injustice are possible. But instead of doing what He can as a human being, he wants a “Government” to do it for him. He wants some magical entity to make sure that everyone, himself included, is fed, housed, and taken care of, no matter how lazy or irresponsible they are. Instead of trusting human beings to take care of each other, he wants a super human ”authority” to guarantee housing, food, health care, and all sorts of other things, for everyone. He wants it so badly that he refuses to accept the obvious truth that no such guarantee is ever possible, and that if mere mortals do not take care of themselves and each other, nothing else will take care of them.
“The Most Dangerous Superstition” – Larken Rose, pg. 124
-
 @ 5627e59c:d484729e
2025-06-11 22:22:59
@ 5627e59c:d484729e
2025-06-11 22:22:59De laatste zonnestralen van de dag streken over de eeuwige golven en weerkaatsten als lichtpuntjes in de ogen van schipper Joris terwijl hij nog een slok nam van zijn glazen fles die de vorm had van het hoofd van een oude monnik.
Gekregen van een oude vrouw uit de bergen van de Himalaya, zorgde de rum genaamd 'Old Monk' voor een verwarmend gezelschap op deze eenzame kerstnacht.
Joris had met zijn boot naar India gevaren nadat zijn vrouw hem had verlaten en hij een Indiër had ontmoet die had gezegd: "Waar ik vandaan kom, zijn vrouwen vrij en worden ze niet gezien als enkel en alleen de mooie lichamen die zij bezitten of als eeuwig bezit van een gezin."
Verward en ongelovig had Joris gekeken naar de wereld en besefte dat vrouwen inderdaad slechts gezien werden als hun fysieke schoonheid, genegeerd werden voor hun koesterende gevoeligheid en bekritiseerd werden door hun spontane intensheid en had hierop voor twee jaar lang gezocht in India naar deze vrije vrouwen met als enig resultaat een oude vrouw te ontmoeten die alleen in de bergen woonde en dagelijks haar wijsheid deelde met ieder luisterend oor.
Daar ging het doorzichtig monnikshoofd en verliet met een grote gebogen vlucht de hand van schipper Joris toen plots met groot kabaal de boot abrupt tot stilstand kwam en Joris hals over kop naar de andere kant van het dek geslingerd werd.
Het monnikshoofd verdween in het donker terwijl Joris zijn lichaam probeerde te lokaliseren en met zijn ogen wijd open zijn hersenen zo veel mogelijk informatie probeerde door te spelen.
Tevergeefs, want zijn enorme verschot werd gevolgd door een enkel groeiende verbazing, ongeloof en desoriëntatie toen de boot begon te kantelen.
De bundel licht, afkomstig van de mast van de boot, zwierde doorheen het donker en kwam te schijnen op een gigantische rots in het midden van de zee die werd bezeten door een oogverblindende glinstergroene schijn.
Uit het donker kwam het monnikshoofd, dat nog steeds in volle vlucht was, in het vizier van de lichtbundel en plaatste zich exact tussen de glinstergroene verschijning en Joris waarbij Joris doorheen het monnikshoofd gezegend werd met het zicht op een pracht van een zeemeermin die uitnodigend poseerde op de rots.
Met een luide plons viel Joris achterover in het water toen hij zich realiseerde dat vrouwen zichzelf ook lieten vangen door lust en hun uiterlijke opmaakcompetities en met een dankbare glimlach zonk hij naar de bodem van de zee en was opnieuw geboren.
-
 @ 5627e59c:d484729e
2025-06-12 04:32:16
@ 5627e59c:d484729e
2025-06-12 04:32:16Ik hou van de natuur en van verbinding maken\ Van diepgang en van mensen raken
Van creatief schrijven en programmeren\ Van speels bewegen en nieuwe dingen leren
Ik hou van leven en van dromen\ En van mensen zien\ Hun diepste wensen uit doen komen
-
 @ 5627e59c:d484729e
2025-06-11 22:21:31
@ 5627e59c:d484729e
2025-06-11 22:21:31Zonneschijn\ Stralen, lachen, zo fijn\ Moge de wereld dankbaar zijn
De vrouw, mijn gevoeligheid\ Bron van creativiteit
Genietend niets doen in het gras\ Met wat brood en wat wijn in het glas
-
 @ c1e9ab3a:9cb56b43
2025-06-01 13:54:06
@ c1e9ab3a:9cb56b43
2025-06-01 13:54:061. Introduction
Over the last 250 years the world’s appetite for energy has soared along an unmistakably exponential trajectory, transforming societies and economies alike. After a half‑century of relative deceleration, a new mix of technological, demographic and political forces now hints at an impending catch‑up phase that could push demand back onto its centuries‑long growth curve. This post knits together the history, the numbers and the newest policy signals to explore what that rebound might look like—and how Gen‑4 nuclear power could meet it.
2. The Long Exponential: 1750 – 1975
Early industrialisation replaced muscle, wood and water with coal‑fired steam, pushing global primary energy use from a few exajoules per year in 1750 to roughly 60 EJ by 1900 and 250 EJ by 1975. Over that span aggregate consumption doubled roughly every 25–35 years, equivalent to a long‑run compound growth rate of ~3 % yr‑¹. Per‑capita use climbed even faster in industrialised economies as factories, railways and electric lighting spread.
3. 1975 – 2025: The Great Slowdown
3.1 Efficiency & Structural Change
• Oil shocks (1973, 1979) and volatile prices pushed OECD economies to squeeze more GDP from each joule.
• Services displaced heavy industry in rich countries, trimming energy intensity.
• Refrigerators, motors and vehicles became dramatically more efficient.3.2 Policy & Technology
• The Inflation Reduction Act (U.S.) now layers zero‑emission production credits and technology‑neutral tax incentives on top of existing nuclear PTCs citeturn1search0turn1search2.
• The EU’s Net‑Zero Industry Act aims to streamline siting and finance for “net‑zero technologies”, explicitly naming advanced nuclear citeturn0search1.3.3 Result
Global primary energy in 2024 stands near 600 EJ (≈ 167 000 TWh)—still growing, but the line has flattened versus the pre‑1975 exponential.
4. Population & Per‑Capita Demand
World population tripled between 1950 and today, yet total energy use grew roughly six‑fold. The imbalance reflects rising living standards and electrification. Looking ahead, the UN projects population to plateau near 10.4 billion in the 2080s, but per‑capita demand is poised to climb as the Global South industrialises.
5. The Policy Pivot of 2023‑2025
| Region | Signal | Year | Implication | |--------|--------|------|-------------| | COP 28 Declaration | 20+ nations pledge to triple nuclear capacity by 2050 | 2023 | High‑level political cover for rapid nuclear build‑out citeturn0search2 | | Europe | Post‑crisis sentiment shifts; blackout in Iberia re‑opens nuclear debate | 2025 | Spain, Germany, Switzerland and others revisit phase‑outs citeturn0news63 | | United States | TVA submits first SMR construction permit; NRC advances BWRX‑300 review | 2025 | Regulatory pathway for fleet deployment citeturn1search9turn1search1 | | Global Strategy Report | “Six Dimensions for Success” playbook for new nuclear entrants | 2025 | Practical roadmap for emerging economies citeturn0search0 | | U.S. Congress | Proposed cuts to DOE loan office threaten build‑out pace | 2025 | Finance bottleneck remains a risk citeturn1news28 |
6. The Catch‑Up Scenario
Suppose the recent 50‑year pause ends in 2025, and total energy demand returns to a midpoint historical doubling period of 12.5 years (the average of the 10–15 year rebound window).
6.1 Consumption Trajectory
| Year | Doublings since 2024 | Demand (TWh) | |------|----------------------|--------------| | 2024 | 0 | 167 000 | | 2037 | 1 | 334 000 | | 2050 | 2 | 668 000 | | 2062 | 3 | 1 336 000 |
(Table ignores efficiency gains from electrification for a conservative, supply‑side sizing.)
7. Nuclear‑Only Supply Model
7.1 Reactor Math
- 1 GWᵉ Gen‑4 reactor → 8.76 TWh yr‑¹ at 100 % capacity factor.
- 2062 requirement: 1 336 000 TWh yr‑¹ → ≈ 152 500 reactors in steady state.
- Build rate (2025‑2062, linear deployment):
152 500 ÷ 38 years ≈ 4 000 reactors per year globally.
(Down from the earlier 5 000 yr‑¹ estimate because the deployment window now stretches 38 years instead of 30.)
7.2 Policy Benchmarks
- COP 28 triple target translates to +780 GW (if baseline 2020 ≈ 390 GW). That is <100 1 GW units per year—two orders of magnitude lower than the theoretical catch‑up requirement, highlighting just how aggressive our thought experiment is.
7.3 Distributed vs Grid‑Centric
Small Modular Reactors (300 MW class) can be sited on retiring coal plants, using existing grid interconnects and cooling, vastly reducing new transmission needs. Ultra‑large “gigawatt corridors” become optional rather than mandatory, though meshed regional grids still improve resilience and market liquidity.
8. Challenges & Unknowns
- Finance: Even with IRA‑style credits, first‑of‑a‑kind Gen‑4 builds carry high cost of capital.
- Supply Chain: 4 000 reactors a year means a reactor‑grade steel output roughly 20× today’s level.
- Waste & Public Trust: Advanced reactors can burn actinides, but geologic repositories remain essential.
- Workforce: Nuclear engineers, welders and regulators are already in short supply.
- Competing Technologies: Cheap renewables + storage and prospective fusion could displace part of the projected load.
9. Conclusions
Recent policy shifts—from Europe’s Net‑Zero Industry Act to the COP 28 nuclear declaration—signal that governments once again see nuclear energy as indispensable to deep decarbonisation. Yet meeting an exponential catch‑up in demand would require deployment rates an order of magnitude beyond today’s commitments, testing manufacturing capacity, finance and political resolve.
Whether the future follows the modest path now embedded in policy or the steeper curve sketched here, two convictions stand out:
- Electrification will dominate new energy demand.
- Scalable, dispatchable low‑carbon generation—likely including large fleets of Gen‑4 fission plants—must fill much of that gap if net‑zero targets are to remain credible.
Last updated 1 June 2025.
-
 @ 5627e59c:d484729e
2025-06-12 04:23:52
@ 5627e59c:d484729e
2025-06-12 04:23:52Look and see\ Look and see
You look like how you look at me
Look and see\ Look and see
The colorless through the color TV
Look and see\ Look and be
The unborn identity
-
 @ c1e9ab3a:9cb56b43
2025-05-18 04:14:48
@ c1e9ab3a:9cb56b43
2025-05-18 04:14:48Abstract
This document proposes a novel architecture that decouples the peer-to-peer (P2P) communication layer from the Bitcoin protocol and replaces or augments it with the Nostr protocol. The goal is to improve censorship resistance, performance, modularity, and maintainability by migrating transaction propagation and block distribution to the Nostr relay network.
Introduction
Bitcoin’s current architecture relies heavily on its P2P network to propagate transactions and blocks. While robust, it has limitations in terms of flexibility, scalability, and censorship resistance in certain environments. Nostr, a decentralized event-publishing protocol, offers a multi-star topology and a censorship-resistant infrastructure for message relay.
This proposal outlines how Bitcoin communication could be ported to Nostr while maintaining consensus and verification through standard Bitcoin clients.
Motivation
- Enhanced Censorship Resistance: Nostr’s architecture enables better relay redundancy and obfuscation of transaction origin.
- Simplified Lightweight Nodes: Removing the full P2P stack allows for lightweight nodes that only verify blockchain data and communicate over Nostr.
- Architectural Modularity: Clean separation between validation and communication enables easier auditing, upgrades, and parallel innovation.
- Faster Propagation: Nostr’s multi-star network may provide faster propagation of transactions and blocks compared to the mesh-like Bitcoin P2P network.
Architecture Overview
Components
-
Bitcoin Minimal Node (BMN):
- Verifies blockchain and block validity.
- Maintains UTXO set and handles mempool logic.
- Connects to Nostr relays instead of P2P Bitcoin peers.
-
Bridge Node:
- Bridges Bitcoin P2P traffic to and from Nostr relays.
- Posts new transactions and blocks to Nostr.
- Downloads mempool content and block headers from Nostr.
-
Nostr Relays:
- Accept Bitcoin-specific event kinds (transactions and blocks).
- Store mempool entries and block messages.
- Optionally broadcast fee estimation summaries and tipsets.
Event Format
Proposed reserved Nostr
kindnumbers for Bitcoin content (NIP/BIP TBD):| Nostr Kind | Purpose | |------------|------------------------| | 210000 | Bitcoin Transaction | | 210001 | Bitcoin Block Header | | 210002 | Bitcoin Block | | 210003 | Mempool Fee Estimates | | 210004 | Filter/UTXO summary |
Transaction Lifecycle
- Wallet creates a Bitcoin transaction.
- Wallet sends it to a set of configured Nostr relays.
- Relays accept and cache the transaction (based on fee policies).
- Mining nodes or bridge nodes fetch mempool contents from Nostr.
- Once mined, a block is submitted over Nostr.
- Nodes confirm inclusion and update their UTXO set.
Security Considerations
- Sybil Resistance: Consensus remains based on proof-of-work. The communication path (Nostr) is not involved in consensus.
- Relay Discoverability: Optionally bootstrap via DNS, Bitcoin P2P, or signed relay lists.
- Spam Protection: Relay-side policy, rate limiting, proof-of-work challenges, or Lightning payments.
- Block Authenticity: Nodes must verify all received blocks and reject invalid chains.
Compatibility and Migration
- Fully compatible with current Bitcoin consensus rules.
- Bridge nodes preserve interoperability with legacy full nodes.
- Nodes can run in hybrid mode, fetching from both P2P and Nostr.
Future Work
- Integration with watch-only wallets and SPV clients using verified headers via Nostr.
- Use of Nostr’s social graph for partial trust assumptions and relay reputation.
- Dynamic relay discovery using Nostr itself (relay list events).
Conclusion
This proposal lays out a new architecture for Bitcoin communication using Nostr to replace or augment the P2P network. This improves decentralization, censorship resistance, modularity, and speed, while preserving consensus integrity. It encourages innovation by enabling smaller, purpose-built Bitcoin nodes and offloading networking complexity.
This document may become both a Bitcoin Improvement Proposal (BIP-XXX) and a Nostr Improvement Proposal (NIP-XXX). Event kind range reserved: 210000–219999.
-
 @ b1ddb4d7:471244e7
2025-06-12 05:01:43
@ b1ddb4d7:471244e7
2025-06-12 05:01:43The latest AI chips, 8K displays, and neural processing units make your device feel like a pocket supercomputer. So surely, with all this advancement, you can finally mine bitcoin on your phone profitably, right?
The 2025 Hardware Reality: Can You Mine Bitcoin on Your Phone
Despite remarkable advances in smartphone technology, the fundamental physics of bitcoin mining haven’t changed. In 2025, flagship devices with their cutting-edge 2nm processors can achieve approximately 25-40 megahashes per second when you mine bitcoin on your phone—a notable improvement from previous generations, but still laughably inadequate.
Meanwhile, 2025’s top-tier ASIC miners have evolved dramatically. The latest Bitmain Antminer S23 series and Canaan AvalonMiner A15 Pro deliver 200-300 terahashes per second while consuming 4,000-5,500 watts. That’s a performance gap of roughly 1:8,000,000 between when you mine bitcoin on your phone and professional mining equipment.
To put this in perspective that hits home: if you mine bitcoin on your phone and it earned you one penny, professional miners would earn $80,000 in the same time period with the same effort. It’s not just an efficiency problem—it’s a complete category mismatch.
According to Pocket Option’s 2025 analysis, when you mine bitcoin on your phone in 2025, you generate approximately $0.003-0.006 in daily revenue while consuming $0.45-0.85 in electricity through constant charging cycles. Factor in the accelerated device wear (estimated at $0.75-1.20 daily depreciation), and you’re looking at losses of $1.20-2.00 per day just for the privilege of running mining software.
Mining Economic Factor
Precise Value (April 2025)
Direct Impact on Profitability
Smartphone sustained hash rate
20-35 MH/s
0.00000024% contribution to global hashrate
Daily power consumption
3.2-4.8 kWh (4-6 full charges)
$0.38-0.57 at average US electricity rates
Expected daily BTC earnings
0.0000000086 BTC ($0.0035 at $41,200 BTC)
Revenue covers only 0.9% of electricity costs
CPU/GPU wear cost
$0.68-0.92 daily accelerated depreciation
Reduces smartphone lifespan by 60-70%
Annual profit projection
-$386 to -$412 per year
Guaranteed negative return on investment
Source: PocketOption
Bitcoin’s 2025 Network: Harder Than Ever
Bitcoin’s network difficulty in 2025 has reached unprecedented levels. After the April 2024 halving event that reduced block rewards from 6.25 to 3.125 BTC, mining became significantly more competitive. The global hash rate now exceeds 800 exahashes per second—that’s 800 followed by 18 zeros worth of computational power securing the network.
Here’s what this means in practical terms: Bitcoin’s mining difficulty adjusts every 2,016 blocks (roughly every two weeks) to maintain the 10-minute block time. As more efficient miners join the network, difficulty increases proportionally. In 2025, mining difficulty has increased compared to 2024, making small-scale mining even less viable.
The math is unforgiving:
- Global Bitcoin hash rate: 828.96 EH/s
- Your smartphone’s contribution: ~0.000000003%
- Probability of solo mining a block: Virtually zero
- Expected time to mine one Bitcoin: Several million years
Even joining mining pools doesn’t solve the economic problem. Pool fees typically range from 1-3%, and your minuscule contribution would earn proportionally tiny rewards—far below the electricity and device depreciation costs.
The 2025 Scam Evolution: More Sophisticated, More Dangerous
Fraudsters now leverage AI-generated content, fake influencer endorsements, and impressive-looking apps that simulate realistic mining activity to entice you to mine bitcoin on your phone.
New 2025 scam tactics include:
AI-Powered Fake Testimonials: Deepfake videos of supposed successful mobile miners showing fabricated earnings statements and encouraging downloads of malicious apps.
Gamified Mining Interfaces: Apps that look and feel like legitimate games but secretly harvest personal data while simulating mining progress that can never be withdrawn.
Social Media Manipulation: Coordinated campaigns across TikTok, Instagram, and YouTube featuring fake “financial influencers” promoting mobile mining apps to younger audiences.
Subscription Trap Mining: Apps offering “free trials” that automatically charge $19.99-49.99 monthly for “premium mining speeds” while delivering no actual mining capability.
Recent cybersecurity research shows that over 180 fake mining apps were discovered across major app stores in 2025, with some accumulating more than 500,000 downloads before being removed.
Red flags that scream “scam” in 2025:
- Apps claiming “revolutionary mobile mining breakthrough”
- Promises of earning “$10-50 daily” from phone mining
- Requirements to recruit friends or watch ads to unlock withdrawals
- Apps that don’t require connecting to actual mining pools
- Testimonials that seem too polished or use stock photo models
- Apps requesting permissions unrelated to mining (contacts, camera, microphone)
The 2025 Professional Mining Landscape
To understand why, consider what professional bitcoin mining looks like in 2025. Industrial mining operations now resemble high-tech data centers with:
Cutting-edge hardware:
- Bitmain Antminer S23 Pro: 280 TH/s at 4,800W
- MicroBT WhatsMiner M56S++: 250 TH/s at 4,500W
- Canaan AvalonMiner A1566: 185 TH/s at 3,420W
Infrastructure requirements:
- Megawatt-scale power contracts with industrial electricity rates
- Liquid cooling systems maintaining 24/7 optimal temperatures
- Redundant internet connections ensuring zero downtime
- Professional facility management with 24/7 monitoring
For a small operation, you might need at least $10,000 to $20,000 to buy a few ASIC miners, set up cooling systems, and cover electricity costs. These operations employ teams of engineers, maintain relationships with power companies, and operate with margins measured in single-digit percentages.
2025’s Legitimate Mobile Bitcoin Strategies
While it remains impossible to mine bitcoin on your phone profitably, 2025 offers exciting legitimate ways to engage with bitcoin through your smartphone:
Lightning Network Participation: Apps like Phoenix, Breez, and Zeus allow you to run Lightning nodes on mobile devices, earning small routing fees while supporting bitcoin’s payment layer.
Bitcoin DCA Automation: Services enable automated dollar-cost averaging with amounts as small as $1 daily. Historical data shows $10 weekly bitcoin purchases consistently outperform any mobile mining attempt by 1,500-2,000%.
Educational Mining Simulators: Legitimate apps like “Bitcoin Mining Simulator” teach mining concepts without false earning promises. These educational tools help users understand hash rates, difficulty adjustments, and mining economics.
Stacking Sats Rewards: Apps offering bitcoin rewards for shopping, learning, or completing tasks.
Lightning Gaming: Bitcoin-native mobile games where players can earn sats through skilled gameplay, with some players earning $10 monthly.onfirm that even the most optimized mobile mining setups in 2025 lose money consistently and predictably.
The Bottom Line
When you mine bitcoin on your phone fundamental economics remain unchanged: it’s impossible to profit. The laws of physics, network competition, and energy efficiency create insurmountable barriers that no app can overcome.
However, 2025 offers unprecedented opportunities to engage with bitcoin meaningfully through your smartphone. Focus on education, legitimate earning opportunities, and strategic investment rather than chasing the impossible dream of phone-based mining.
The bitcoin community’s greatest strength lies in its commitment to truth over hype. When someone promises profits to mine bitcoin on your phone in 2025, they’re either uninformed or deliberately misleading you. Trust the mathematics, learn from the community, and build your bitcoin knowledge and holdings through proven methods.
The real opportunity in 2025 isn’t to mine bitcoin on your phone—it’s understanding bitcoin deeply enough to participate confidently in the most important monetary revolution of our lifetime. Your smartphone is the perfect tool for that education; it’s just not a mining rig.
-
 @ 5627e59c:d484729e
2025-06-11 22:31:59
@ 5627e59c:d484729e
2025-06-11 22:31:59Een warme chocomelk\ Een knuffel en de moed te durven spreken\ Een leuk oprecht verhaal\ En een stap naar mijn verlangen
Deze dingen allemaal\ Maken me warm vanbinnen\ Ik hou van deze dingen\ Ze doen mijn hartje zingen
Ik wens iedereen zo'n warmte toe\ Ik wou dat ik het delen kon\ Maar het ziet er anders uit\ Voor jou dan hoe voor mij
Het enige wat ik echt kan zeggen\ Het enige dat ik zeker weet\ De kracht om warmte te creëren\ Ligt in je eigen handen
In je voeten, in je mond\ Het zit ook in je ogen\ En ook in je haar\ En zei ik al je mond\ En zelfs ook in je kont
Haha, ik ben maar wat aan 't lachen\ Dat is wat mij verlucht\ En ervoor zorgt dat wat ik zeg\ Van mij los kan komen\ En jou bereiken kan
Zo kan ik op beide oren slapen\ Dat ik deed dat wat ik kon\ Ik sprak dat wat belangrijk is\ Voor mij en liet het los
De wijde wereld in\ Voor al die horen wil en daar om geeft\ Om die warmte in hun hartje\ En daar misschien naar streeft
Ik wens je al 't succes toe in de wereld\ Want God weet, je bent het waard\ Het ligt nu in jouw handen\ Deze woorden, wat ik zeg\ Iets om over na te denken\ Tussen 't brood en het beleg
Leef gewoon je leven\ En zorg goed voor jezelf\ En als je 't graag wilt vinden\ Is het daar voor jou aan 't wachten\ Tot jij klaar bent met geloven\ In al dat anders klinkt
Ik kan je niets beloven\ Maar vertrouw op jouw instinct
-
 @ c1e9ab3a:9cb56b43
2025-05-01 17:29:18
@ c1e9ab3a:9cb56b43
2025-05-01 17:29:18High-Level Overview
Bitcoin developers are currently debating a proposed change to how Bitcoin Core handles the
OP_RETURNopcode — a mechanism that allows users to insert small amounts of data into the blockchain. Specifically, the controversy revolves around removing built-in filters that limit how much data can be stored using this feature (currently capped at 80 bytes).Summary of Both Sides
Position A: Remove OP_RETURN Filters
Advocates: nostr:npub1ej493cmun8y9h3082spg5uvt63jgtewneve526g7e2urca2afrxqm3ndrm, nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg, nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp, others
Arguments: - Ineffectiveness of filters: Filters are easily bypassed and do not stop spam effectively. - Code simplification: Removing arbitrary limits reduces code complexity. - Permissionless innovation: Enables new use cases like cross-chain bridges and timestamping without protocol-level barriers. - Economic regulation: Fees should determine what data gets added to the blockchain, not protocol rules.
Position B: Keep OP_RETURN Filters
Advocates: nostr:npub1lh273a4wpkup00stw8dzqjvvrqrfdrv2v3v4t8pynuezlfe5vjnsnaa9nk, nostr:npub1s33sw6y2p8kpz2t8avz5feu2n6yvfr6swykrnm2frletd7spnt5qew252p, nostr:npub1wnlu28xrq9gv77dkevck6ws4euej4v568rlvn66gf2c428tdrptqq3n3wr, others
Arguments: - Historical intent: Satoshi included filters to keep Bitcoin focused on monetary transactions. - Resource protection: Helps prevent blockchain bloat and abuse from non-financial uses. - Network preservation: Protects the network from being overwhelmed by low-value or malicious data. - Social governance: Maintains conservative changes to ensure long-term robustness.
Strengths and Weaknesses
Strengths of Removing Filters
- Encourages decentralized innovation.
- Simplifies development and maintenance.
- Maintains ideological purity of a permissionless system.
Weaknesses of Removing Filters
- Opens the door to increased non-financial data and potential spam.
- May dilute Bitcoin’s core purpose as sound money.
- Risks short-term exploitation before economic filters adapt.
Strengths of Keeping Filters
- Preserves Bitcoin’s identity and original purpose.
- Provides a simple protective mechanism against abuse.
- Aligns with conservative development philosophy of Bitcoin Core.
Weaknesses of Keeping Filters
- Encourages central decision-making on allowed use cases.
- Leads to workarounds that may be less efficient or obscure.
- Discourages novel but legitimate applications.
Long-Term Consequences
If Filters Are Removed
- Positive: Potential boom in new applications, better interoperability, cleaner architecture.
- Negative: Risk of increased blockchain size, more bandwidth/storage costs, spam wars.
If Filters Are Retained
- Positive: Preserves monetary focus and operational discipline.
- Negative: Alienates developers seeking broader use cases, may ossify the protocol.
Conclusion
The debate highlights a core philosophical split in Bitcoin: whether it should remain a narrow monetary system or evolve into a broader data layer for decentralized applications. Both paths carry risks and tradeoffs. The outcome will shape not just Bitcoin's technical direction but its social contract and future role in the broader crypto ecosystem.
-
 @ 5627e59c:d484729e
2025-06-11 21:21:19
@ 5627e59c:d484729e
2025-06-11 21:21:19Enlightenment is just\ You catching up with time
Enlightenment is just\ Successfully processing your current situation\ And what it has to do with your past
Enlightenment is just\ Separating what you believe from what you know\ What is real from what is true
Enlightenment is living\ According to what you believe\ Because that's what is real for you\ Yet knowing it might turn out\ To be not really true
Enlightenment is giving thanks\ For being proven wrong
For how else would we grow\ The things we're conscious of\ The things that're real for us\ And the things we really know
How else would we align those things\ With the truth of what is (t)here\ Beyond\ That which we are
-
 @ 7f6db517:a4931eda
2025-06-12 04:02:50
@ 7f6db517:a4931eda
2025-06-12 04:02:50

"Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world." - Eric Hughes, A Cypherpunk's Manifesto, 1993
Privacy is essential to freedom. Without privacy, individuals are unable to make choices free from surveillance and control. Lack of privacy leads to loss of autonomy. When individuals are constantly monitored it limits our ability to express ourselves and take risks. Any decisions we make can result in negative repercussions from those who surveil us. Without the freedom to make choices, individuals cannot truly be free.
Freedom is essential to acquiring and preserving wealth. When individuals are not free to make choices, restrictions and limitations prevent us from economic opportunities. If we are somehow able to acquire wealth in such an environment, lack of freedom can result in direct asset seizure by governments or other malicious entities. At scale, when freedom is compromised, it leads to widespread economic stagnation and poverty. Protecting freedom is essential to economic prosperity.
The connection between privacy, freedom, and wealth is critical. Without privacy, individuals lose the freedom to make choices free from surveillance and control. While lack of freedom prevents individuals from pursuing economic opportunities and makes wealth preservation nearly impossible. No Privacy? No Freedom. No Freedom? No Wealth.
Rights are not granted. They are taken and defended. Rights are often misunderstood as permission to do something by those holding power. However, if someone can give you something, they can inherently take it from you at will. People throughout history have necessarily fought for basic rights, including privacy and freedom. These rights were not given by those in power, but rather demanded and won through struggle. Even after these rights are won, they must be continually defended to ensure that they are not taken away. Rights are not granted - they are earned through struggle and defended through sacrifice.
If you found this post helpful support my work with bitcoin.

-
 @ 95543309:196c540e
2025-06-11 14:17:03
@ 95543309:196c540e
2025-06-11 14:17:03$$\int_{-\infty}^{\infty} e^{-x^2/2} \, dx = \sqrt{2\pi}$$$$\sum_{k=1}^n k^2 = \frac{n(n+1)(2n+1)}{6}$$$$\lim_{x \to \infty} \left(1 + \frac{1}{x}\right)^x = e$$$$\begin{vmatrix}a & b \\c & d\end{vmatrix} = ad - bc$$$$\frac{d}{dx}\left(\frac{x^2 + 1}{x - 1}\right)$$$$\iiint_V (\nabla \cdot \mathbf{F}) \, dV = \oint_{\partial V} \mathbf{F} \cdot d\mathbf{S}$$$$\binom{n}{k} = \frac{n!}{k!(n-k)!}$$$$\ln\left(\frac{f(x)}{g(x)}\right) = \ln f(x) - \ln g(x)$$$$\forall x \in \mathbb{R}, \exists y \in \mathbb{R} \text{ such that } x + y = 0$$$$\sqrt{\frac{x^2 + y^2}{x^2 - y^2}}$$$$\begin{array}{c|c}A & B \\hlineC & D\end{array}$$$$\sum_{i=1}^n \sum_{j=1}^n a_{ij}x_i x_j$$$$\mathcal{L}{f(t)}(s) = \int_0^\infty e^{-st}f(t)\,dt$$$$\frac{\partial^2 u}{\partial t^2} = c^2 \frac{\partial^2 u}{\partial x^2}$$$$\mathbf{A} = \begin{pmatrix}a_{11} & a_{12} \\a_{21} & a_{22}\end{pmatrix}, \quad\mathbf{B} = \begin{pmatrix}b_{11} & b_{12} \\b_{21} & b_{22}\end{pmatrix}$$$$\underbrace{a + b + \dots + z}{26}$$$$\left(\frac{a}{b}\right)^n = \frac{a^n}{b^n}$$$$\langle \psi | \phi \rangle = \int{-\infty}^{\infty} \psi^*(x)\phi(x) \, dx$$$$\oint_C \mathbf{F} \cdot d\mathbf{r} = \iint_S (\nabla \times \mathbf{F}) \cdot d\mathbf{S}$$$$\prod_{k=1}^n \left(1 + \frac{1}{k}\right) = \frac{(n+1)}{1}$$$$S(\omega)=1.466\, H_s^2 \frac{\omega_0^5}{\omega^6} \exp\Bigl[-3^{\frac{\omega}{\omega_0}}\Bigr]^2$$
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ 5627e59c:d484729e
2025-06-11 22:31:47
@ 5627e59c:d484729e
2025-06-11 22:31:47Warmte betekent zachtheid aan de grenzen\ Omringt door zachte mensen
Warmte betekent vrijheid\ Vrij om mij te tonen en te bewegen
Warmte betekent rust\ Om hier niet ver vandaan te hoeven zijn
Warmte betekent leven\ Iets waar ik vol van liefde mijn aandacht aan wil geven
Warmte betekent vriendschap\ Alle vriendschap die mijn hartje vult
Warmte betekent vol zijn\ Vol betekenis die mijn omgeving aan mij schenkt
Warmte betekent geven\ Geven om wat ik voor jou en jij voor mij\ Wij voor elkaar nu eigenlijk echt betekenen
-
 @ 5627e59c:d484729e
2025-06-11 21:18:05
@ 5627e59c:d484729e
2025-06-11 21:18:05Hello Bumble\ You busy bee
You're going way\ Too fast for me
Going here and there\ You search for gold
Yet tumble straight\ Into what's old
Now I'm not here\ To make a gain
Nor to fix\ What's in disdain
Instead I'm just\ A humble bee
Who wants to get\ To know thee
-
 @ 7f6db517:a4931eda
2025-06-12 03:02:56
@ 7f6db517:a4931eda
2025-06-12 03:02:56
What is KYC/AML?
- The acronym stands for Know Your Customer / Anti Money Laundering.
- In practice it stands for the surveillance measures companies are often compelled to take against their customers by financial regulators.
- Methods differ but often include: Passport Scans, Driver License Uploads, Social Security Numbers, Home Address, Phone Number, Face Scans.
- Bitcoin companies will also store all withdrawal and deposit addresses which can then be used to track bitcoin transactions on the bitcoin block chain.
- This data is then stored and shared. Regulations often require companies to hold this information for a set number of years but in practice users should assume this data will be held indefinitely. Data is often stored insecurely, which results in frequent hacks and leaks.
- KYC/AML data collection puts all honest users at risk of theft, extortion, and persecution while being ineffective at stopping crime. Criminals often use counterfeit, bought, or stolen credentials to get around the requirements. Criminals can buy "verified" accounts for as little as $200. Furthermore, billions of people are excluded from financial services as a result of KYC/AML requirements.
During the early days of bitcoin most services did not require this sensitive user data, but as adoption increased so did the surveillance measures. At this point, most large bitcoin companies are collecting and storing massive lists of bitcoiners, our sensitive personal information, and our transaction history.
Lists of Bitcoiners
KYC/AML policies are a direct attack on bitcoiners. Lists of bitcoiners and our transaction history will inevitably be used against us.
Once you are on a list with your bitcoin transaction history that record will always exist. Generally speaking, tracking bitcoin is based on probability analysis of ownership change. Surveillance firms use various heuristics to determine if you are sending bitcoin to yourself or if ownership is actually changing hands. You can obtain better privacy going forward by using collaborative transactions such as coinjoin to break this probability analysis.
Fortunately, you can buy bitcoin without providing intimate personal information. Tools such as peach, hodlhodl, robosats, azteco and bisq help; mining is also a solid option: anyone can plug a miner into power and internet and earn bitcoin by mining privately.
You can also earn bitcoin by providing goods and/or services that can be purchased with bitcoin. Long term, circular economies will mitigate this threat: most people will not buy bitcoin - they will earn bitcoin - most people will not sell bitcoin - they will spend bitcoin.
There is no such thing as KYC or No KYC bitcoin, there are bitcoiners on lists and those that are not on lists.
If you found this post helpful support my work with bitcoin.

-
 @ 5627e59c:d484729e
2025-06-11 22:32:38
@ 5627e59c:d484729e
2025-06-11 22:32:38Ik hou van de natuur en van verbinding maken\ Van diepgang en van mensen raken
Van creatief schrijven en programmeren\ Van speels bewegen en nieuwe dingen leren
Ik hou van leven en van dromen\ En van mensen zien\ Hun diepste wensen uit doen komen
-
 @ c9badfea:610f861a
2025-06-10 21:43:55
@ c9badfea:610f861a
2025-06-10 21:43:55🤖️ AI Articles
📱 Android Articles
- 🥩 Tracking Food Intake
- ✍️ Taking Handwritten Notes
- 🕒 Tracking Habits
- 🧭 Navigating The Wild
- 📝 Organizing Notes and Tasks
- 🧠 Studying Smarter
- 💱 Tracking Fiat Currency Exchange Rates
- 🌠 Offline Planetarium
- 📥 Downloading Media From 1000+ Sites
- 🔥 Blocking Ads and Trackers
- ⛅ Getting Detailed Weather Information
- 📦 Installing Apps Directly From Source
- 🎮 Playing Retro Games
- 🖼️ Generating AI Images Locally
- 📖 Reading PDF Documents and EPUB Books
- 🔒 Storing Passwords Safely
- 🗺️ Using Offline Maps
- 🎵 Producing Music On-Device
- 💾 Writing ISO Images to USB Drives
- 💻 Coding On-Device
- 🎬 Watching and Downloading Videos from YouTube, Rumble, Odysee, Bitchute, and More
- 🔤 Upgrading the Typing Experience
- 📰 Reading RSS Feeds
- 📥 Downloading Torrents
- 📺 Watching IPTV Channels for Free
- 🔒 Easily Verifying File Checksums
- 🗣️ Offline Translator
- 🗣️ Offline Text-to-Speech Engine
- 🤖 Running LLMs Locally
- 🌐 Browsing Entire Websites Offline
- 🔐 Quickly Encrypting Files
✏️ Other Articles
-
 @ 5627e59c:d484729e
2025-06-11 22:32:11
@ 5627e59c:d484729e
2025-06-11 22:32:11Ik sta hier nu een poos\ Bevroren, machteloos
Ik wil graag iets veranderen\ Gewoon iets doen voor anderen
Maar het mag precies niet zijn\ En dat doet me veel pijn
Verlamd en vol van onbegrip\ Ik krijg er maar geen grip op
Op de wereld en de mensen\ Zij verpletteren mijn diepste wensen
Niemand die eens hoort\ Naar wat mij toch zo stoort
Ik kan nog eens proberen\ Om de wereld om te keren
Maar ik weet, het heeft geen zin\ Ik raak nooit binnen in
De ander\ Kom, verander
Misschien wordt het eens tijd\ Dat ik mezelf bevrijd
Van al die overmacht\ Die mij toch zo versmacht
Een stapje achteruit\ Adem in en adem uit
Ik doe mijn oogjes dicht\ En zie wie mij verplicht
Opzadelt met ambitie\ Van waar komt toch die missie
Al de pijn die ik niet aankan\ En van 't bestaan verban
Al 't bewijs voor mijn geloof\ Dat ik niet meer vliegen kan
-
 @ 7f6db517:a4931eda
2025-06-12 01:02:18
@ 7f6db517:a4931eda
2025-06-12 01:02:18Will not live in a pod.
Will not eat the bugs.
Will not get the chip.
Will not get a blue check.
Will not use CBDCs.Live Free or Die.
Why did Elon buy twitter for $44 Billion? What value does he see in it besides the greater influence that undoubtedly comes with controlling one of the largest social platforms in the world? We do not need to speculate - he made his intentions incredibly clear in his first meeting with twitter employees after his takeover - WeChat of the West.
To those that do not appreciate freedom, the value prop is clear - WeChat is incredibly powerful and successful in China.
To those that do appreciate freedom, the concern is clear - WeChat has essentially become required to live in China, has surveillance and censorship integrated at its core, and if you are banned from the app your entire livelihood is at risk. Employment, housing, payments, travel, communication, and more become extremely difficult if WeChat censors determine you have acted out of line.
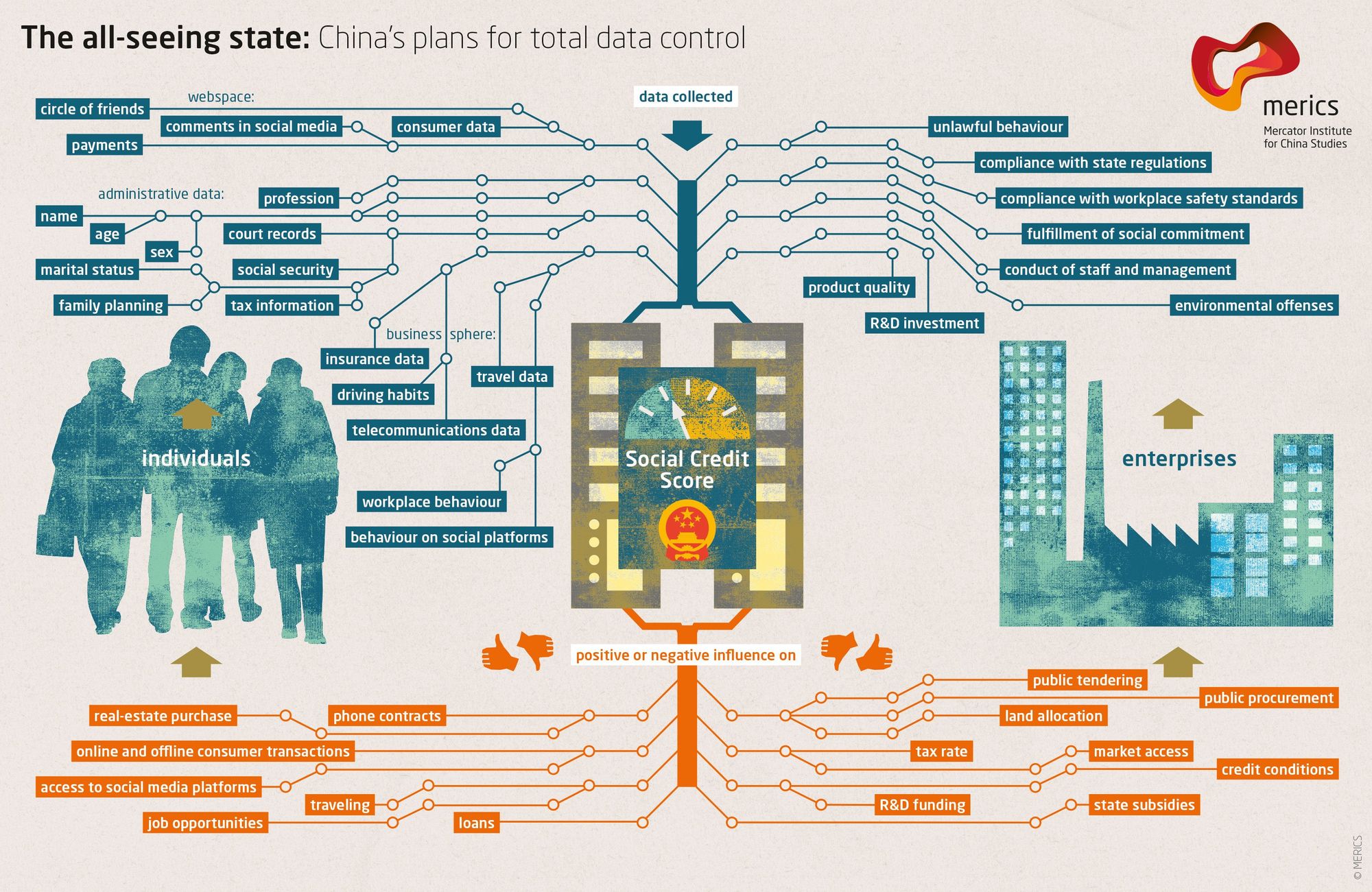
The blue check is the first step in Elon's plan to bring the chinese social credit score system to the west. Users who verify their identity are rewarded with more reach and better tools than those that do not. Verified users are the main product of Elon's twitter - an extensive database of individuals and complete control of the tools he will slowly get them to rely on - it is easier to monetize cattle than free men.
If you cannot resist the temptation of the blue check in its current form you have already lost - what comes next will be much darker. If you realize the need to resist - freedom tech provides us options.
If you found this post helpful support my work with bitcoin.

-
 @ 5627e59c:d484729e
2025-06-11 22:30:36
@ 5627e59c:d484729e
2025-06-11 22:30:36Nooit is mijn dans echter\ Dan net nadat het regende\ Want regen biedt een kans\ Om mijn gevoel te voelen
Zolang de regen spettert\ En ik mezelf graag zie\ Wordt er niets verplettert\ Ook al lijkt dat soms wel zo
Zodra de regen ophoudt\ En zich terugtrekt met de wolken\ Komt een nieuwe glans\ Voor het eerst mijn ogen binnen
Wat is het leven heerlijk\ Als ik eerlijk ben en voel\ Wat is het leven zacht\ En het brengt me naar mijn doel
Wat zou ik weten zonder regen\ Gewoon steeds evenveel\ Niet groeien is niet leven\ Daarom dans ik het liefst
Net na de echte regen
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:55:11
@ c1e9ab3a:9cb56b43
2025-04-10 02:55:11The United States is on the cusp of a historic technological renaissance, often referred to as the Fourth Industrial Revolution. Artificial intelligence, automation, advanced robotics, quantum computing, biotechnology, and clean manufacturing are converging into a seismic shift that will redefine how we live, work, and relate to one another. But there's a critical catch: this transformation depends entirely on the availability of stable, abundant, and inexpensive electricity.
Why Electricity is the Keystone of Innovation
Let’s start with something basic but often overlooked. Every industrial revolution has had an energy driver:
- The First rode the steam engine, powered by coal.
- The Second was electrified through centralized power plants.
- The Third harnessed computing and the internet.
- The Fourth will demand energy on a scale and reliability never seen before.
Imagine a city where thousands of small factories run 24/7 with robotics and AI doing precision manufacturing. Imagine a national network of autonomous vehicles, delivery drones, urban vertical farms, and high-bandwidth communication systems. All of this requires uninterrupted and inexpensive power.
Without it? Costs balloon. Innovation stalls. Investment leaves. And America risks becoming a second-tier economic power in a multipolar world.
So here’s the thesis: If we want to lead the Fourth Industrial Revolution, we must first lead in energy. And nuclear — specifically Gen IV Small Modular Reactors (SMRs) — must be part of that leadership.
The Nuclear Case: Clean, Scalable, Strategic
Let’s debunk the myth: nuclear is not the boogeyman of the 1970s. It’s one of the safest, cleanest, and most energy-dense sources we have.
But traditional nuclear has problems:
- Too expensive to build.
- Too long to license.
- Too bespoke and complex.
Enter Gen IV SMRs:
- Factory-built and transportable.
- Passively safe with walk-away safety designs.
- Scalable in 50–300 MWe increments.
- Ideal for remote areas, industrial parks, and military bases.
But even SMRs will struggle under the current regulatory, economic, and manufacturing ecosystem. To unlock their potential, we need a new national approach.
The Argument for National Strategy
Let’s paint a vision:
SMRs deployed at military bases across the country, secured by trained personnel, powering critical infrastructure, and feeding clean, carbon-free power back into surrounding communities.
SMRs operated by public chartered utilities—not for Wall Street profits, but for stability, security, and public good.
SMRs manufactured by a competitive ecosystem of certified vendors, just like aircraft or medical devices, with standard parts and rapid regulatory approval.
This isn't science fiction. It's a plausible, powerful model. Here’s how we do it.
Step 1: Treat SMRs as a National Security Asset
Why does the Department of Defense spend billions to secure oil convoys and build fuel depots across the world, but not invest in nuclear microgrids that would make forward bases self-sufficient for decades?
Nuclear power is inherently a strategic asset:
- Immune to price shocks.
- Hard to sabotage.
- Decades of stable power from a small footprint.
It’s time to reframe SMRs from an energy project to a national security platform. That changes everything.
Step 2: Create Public-Chartered Operating Companies
We don’t need another corporate monopoly or Wall Street scheme. Instead, let’s charter SMR utilities the way we chartered the TVA or the Postal Service:
- Low-margin, mission-oriented.
- Publicly accountable.
- Able to sign long-term contracts with DOD, DOE, or regional utilities.
These organizations won’t chase quarterly profits. They’ll chase uptime, grid stability, and national resilience.
Step 3: Build a Competitive SMR Industry Like Aerospace
Imagine multiple manufacturers building SMRs to common, certified standards. Components sourced from a wide supplier base. Designs evolving year over year, with upgrades like software and avionics do.
This is how we build:
- Safer reactors
- Cheaper units
- Modular designs
- A real export industry
Airplanes are safe, affordable, and efficient because of scale and standardization. We can do the same with reactors.
Step 4: Anchor SMRs to the Coming Fourth Industrial Revolution
AI, robotics, and distributed manufacturing don’t need fossil fuels. They need cheap, clean, continuous electricity.
- AI datacenters
- Robotic agriculture
- Carbon-free steel and cement
- Direct air capture
- Electric industrial transport
SMRs enable this future. And they decentralize power, both literally and economically. That means jobs in every region, not just coastal tech hubs.
Step 5: Pair Energy Sovereignty with Economic Reform
Here’s the big leap: what if this new energy architecture was tied to a transparent, auditable, and sovereign monetary system?
- Public utilities priced in a new digital dollar.
- Trade policy balanced by low-carbon energy exports.
- Public accounting verified with open ledgers.
This is not just national security. It’s monetary resilience.
The world is moving to multi-polar trade systems. Energy exports and energy reliability will define economic influence. If America leads with SMRs, we lead the conversation.
Conclusion: A Moral and Strategic Imperative
We can either:
- Let outdated fears and bureaucracy stall the future, or...
- Build the infrastructure for clean, secure, and sovereign prosperity.
We have the designs.
We have the talent.
We have the need.What we need now is will.
The Fourth Industrial Revolution will either be powered by us—or by someone else. Let’s make sure America leads. And let’s do it with SMRs, public charter, competitive industry, and national purpose.
It’s time.
This is a call to engineers, legislators, veterans, economists, and every American who believes in building again. SMRs are not just about power. They are about sovereignty, security, and shared prosperity.
Further reading:
nostr:naddr1qqgrjv33xenx2drpve3kxvrp8quxgqgcwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tczyrq7n2e62632km9yh6l5f6nykt76gzkxxy0gs6agddr9y95uk445xqcyqqq823cdzc99s
-
 @ 5627e59c:d484729e
2025-06-11 21:17:31
@ 5627e59c:d484729e
2025-06-11 21:17:31We only see\ What we are
What we are not\ We cannot see
This is how we know\ Reality is happening within\ Our own being
And experience is a consequence\ Of who we believe to be
As long as we deny\ And don't want to see
All the ways\ We think to be
Reality will seem\ Outside of our grasp
And separate\ From our experience of life
Such is our power
Yet such power\ Could only be
Of that which holds\ The entirety
-
 @ 5627e59c:d484729e
2025-06-11 22:30:23
@ 5627e59c:d484729e
2025-06-11 22:30:23My life is my way Home\ My death is my arrival
I can't wait to be Home\ And so I love life
I can't wait to be Home\ And so I want to live to the fullest
For there are no shortcuts
Many people die\ And never make it Home
They will have to wait\ For another chance to die
Another chance to live fully\ And die totally
I'm so thankful to be alive\ I'm on my way Home
I'm so thankful to be alive\ To have another chance to die
Every day I take a step\ In the direction of my death\ I do not postpone it
Every day I take a step\ In the direction of my truth\ I do not avoid it
It is who I am, always have been\ And always will be
It lies beyond that door\ That keeps everything in check
Where only can go through\ Which is forever true
-
 @ f683e870:557f5ef2
2025-06-11 13:33:34
@ f683e870:557f5ef2
2025-06-11 13:33:34This is what has been achieved on a per-project basis since receiving the grant from Opensats.
npub.world
Together with nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, I have been refining npub.world to deliver real-time, WoT-powered profile search. These refinements include:
-
implementing new desings by nostr:npub1t3gd5yefglarhar4n6uh34uymvft4tgu8edk5465zzhtv4rrnd9sg7upxq
-
moving to the new Vertex DVM standard
-
improved URL and npub parsing
Vertex crawler
Due to the architectural mistakes I made when designing the first version, I have embarked on a full rewrite of the crawler. The new architecture is simpler, more modular and more performant, and I am confident that it will provide a stable foundation on which to expand the Vertex offering with additional functionalities and analytics.
The major differences with the old version are:
-
the
DBandRWSinterfaces have been broken up and simplified into smaller ones, each defined by their own packages -
a simplified, more efficient algorithm for updating random walks
-
use of a custom-built cache to speed up graph computations
-
a worker pool pattern to speed up event archiving
These changes have reduced the LOC by more than half while improving performance by \~10x. Of independent interest is the new pipe package, which can also be used by other projects to crawl the Nostr network.
Vertex Relay and DVMs
The Vertex relay has been updated several times, and now supports four DVM services:
-
Verify Reputation -
Recommend Follows -
Rank Profiles -
Search Profile
For each service, customers can choose the algorithm to use by specifing the sort option to use between:
-
followerCount -
globalPagerank -
personalizedPagerank
More information can be found at https://vertexlab.io/.
Overall, the relay has processed more than 100,000 DVM requests, with the current daily rate standing at around 1,500.
rely
Unsatisfied with the khatru relay framework, I've decided to build my own called rely, with the goal of being simpler and more stable. I've not just scratched a personal hitch: I've used khatru for several months now (the Vertex relay is still using it) and I encountered several issues, some of which I've solved with PRs to the underlying go-nostr library.
The main differences between khatru and rely:
-
rely is much simpler, both architecturally and in terms of LOC (less than half)
-
rely has a solid testing approach, where a random yet reproducible high traffic hits the relay to see what breaks
-
rely implements a worker pool pattern where a configurable number of goroutines process the incoming requests from clients. On the other hand, khatru process them in the HandleWebsocket goroutine, which is spawned every time a client connects. This is dangerous in my opinion because if too many clients connect, memory usage would spike and the relay could potentially crash.
New DVM spec
I helped to draft this new proposal to update the DVM spec, which is one of the most controversial NIPs. While almost everyone agrees that it needs to change, there is no consensus on how to move forward. I believe our proposal is a sensible approach that defines discovery, usage, and error patterns while leaving flexibility for specific DVM kinds.
Looking at the future
Next I am going to move the Vertex relay to the rely framework and to the new crawler package. I expect that this will increase the performance and will make things more solid and more simple. After all of this refactoring and simplification, it will be time to finally add features to the Vertex offering. I have an ambitious roadmap consisting of:
-
accepting ecash for DVM requests
-
designing client-side validation schemes for the DVM responses
-
expanding the pagerank algorithm to make use of mutes and reports
-
adding an WoT impersonator check to npub.world
-
adding a nip05 check to npub.world
-
make a relystore package with some plug&play databases for rely.
-
-
 @ c1e9ab3a:9cb56b43
2025-03-10 21:56:07
@ c1e9ab3a:9cb56b43
2025-03-10 21:56:07Introduction
Throughout human history, the pyramids of Egypt have fascinated scholars, archaeologists, and engineers alike. Traditionally thought of as tombs for pharaohs or religious monuments, alternative theories have speculated that the pyramids may have served advanced technological functions. One such hypothesis suggests that the pyramids acted as large-scale nitrogen fertilizer generators, designed to transform arid desert landscapes into fertile land.
This paper explores the feasibility of such a system by examining how a pyramid could integrate thermal convection, electrolysis, and a self-regulating breeder reactor to sustain nitrogen fixation processes. We will calculate the total power requirements and estimate the longevity of a breeder reactor housed within the structure.
The Pyramid’s Function as a Nitrogen Fertilizer Generator
The hypothesized system involves several key processes:
- Heat and Convection: A fissile material core located in the King's Chamber would generate heat, creating convection currents throughout the pyramid.
- Electrolysis and Hydrogen Production: Water sourced from subterranean channels would undergo electrolysis, splitting into hydrogen and oxygen due to electrical and thermal energy.
- Nitrogen Fixation: The generated hydrogen would react with atmospheric nitrogen (N₂) to produce ammonia (NH₃), a vital component of nitrogen-based fertilizers.
Power Requirements for Continuous Operation
To maintain the pyramid’s core at approximately 450°C, sufficient to drive nitrogen fixation, we estimate a steady-state power requirement of 23.9 gigawatts (GW).
Total Energy Required Over 10,000 Years
Given continuous operation over 10,000 years, the total energy demand can be calculated as:
[ \text{Total time} = 10,000 \times 365.25 \times 24 \times 3600 \text{ seconds} ]
[ \text{Total time} = 3.16 \times 10^{11} \text{ seconds} ]
[ \text{Total energy} = 23.9 \text{ GW} \times 3.16 \times 10^{11} \text{ s} ]
[ \approx 7.55 \times 10^{21} \text{ J} ]
Using a Self-Regulating Breeder Reactor
A breeder reactor could sustain this power requirement by generating more fissile material than it consumes. This reduces the need for frequent refueling.
Pebble Bed Reactor Design
- Self-Regulation: The reactor would use passive cooling and fuel expansion to self-regulate temperature.
- Breeding Process: The reactor would convert thorium-232 into uranium-233, creating a sustainable fuel cycle.
Fissile Material Requirements
Each kilogram of fissile material releases approximately 80 terajoules (TJ) (or 8 × 10^{13} J/kg). Given a 35% efficiency rate, the usable energy per kilogram is:
[ \text{Usable energy per kg} = 8 \times 10^{13} \times 0.35 = 2.8 \times 10^{13} \text{ J/kg} ]
[ \text{Fissile material required} = \frac{7.55 \times 10^{21}}{2.8 \times 10^{13}} ]
[ \approx 2.7 \times 10^{8} \text{ kg} = 270,000 \text{ tons} ]
Impact of a Breeding Ratio
If the reactor operates at a breeding ratio of 1.3, the total fissile material requirement would be reduced to:
[ \frac{270,000}{1.3} \approx 208,000 \text{ tons} ]
Reactor Size and Fuel Replenishment
Assuming a pebble bed reactor housed in the King’s Chamber (~318 cubic meters), the fuel cycle could be sustained with minimal refueling. With a breeding ratio of 1.3, the reactor could theoretically operate for 10,000 years with occasional replenishment of lost material due to inefficiencies.
Managing Scaling in the Steam Generation System
To ensure long-term efficiency, the water supply must be conditioned to prevent mineral scaling. Several strategies could be implemented:
1. Natural Water Softening Using Limestone
- Passing river water through limestone beds could help precipitate out calcium bicarbonate, reducing hardness before entering the steam system.
2. Chemical Additives for Scaling Prevention
- Chelating Agents: Compounds such as citric acid or tannins could be introduced to bind calcium and magnesium ions.
- Phosphate Compounds: These interfere with crystal formation, preventing scale adhesion.
3. Superheating and Pre-Evaporation
- Pre-Evaporation: Water exposed to extreme heat before entering the system would allow minerals to precipitate out before reaching the reactor.
- Superheated Steam: Ensuring only pure vapor enters the steam cycle would prevent mineral buildup.
- Electrolysis of Superheated Steam: Using multi-million volt electrostatic fields to ionize and separate minerals before they enter the steam system.
4. Electrostatic Control for Scaling Mitigation
- The pyramid’s hypothesized high-voltage environment could ionize water molecules, helping to prevent mineral deposits.
Conclusion
If the Great Pyramid were designed as a self-regulating nitrogen fertilizer generator, it would require a continuous 23.9 GW energy supply, which could be met by a breeder reactor housed within its core. With a breeding ratio of 1.3, an initial load of 208,000 tons of fissile material would sustain operations for 10,000 years with minimal refueling.
Additionally, advanced water treatment techniques, including limestone filtration, chemical additives, and electrostatic control, could ensure long-term efficiency by mitigating scaling issues.
While this remains a speculative hypothesis, it presents a fascinating intersection of energy production, water treatment, and environmental engineering as a means to terraform the ancient world.
-
 @ c1a49d62:3ef55468
2025-06-12 04:55:05
@ c1a49d62:3ef55468
2025-06-12 04:55:05IoT chips serve as the foundational semiconductor components that enable connectivity, data processing, and communication in devices ranging from smart thermostats to industrial sensors. These microcontrollers, system-on-chips (SoCs), and application-specific integrated circuits (ASICs) offer low power consumption, compact form factors, and robust security features, making them essential for Internet of Things ecosystems. As industries pursue digital transformation, the need for high-performance IoT chips that can handle real-time analytics, edge computing, and seamless interoperability has surged. IoT Chips Market Advantages such as integrated wireless protocols (Wi-Fi, Bluetooth, LoRaWAN), enhanced energy efficiency, and customizable silicon solutions address critical market challenges like device longevity and data integrity. Manufacturers leverage advanced process nodes and AI accelerators to deliver chips with superior throughput while minimizing thermal footprints. Continuous innovations in semiconductor design, coupled with growing market opportunities in smart cities, automotive telematics, and healthcare monitoring, underscore the strategic importance of these components. As enterprises seek to optimize operations and reduce costs through predictive maintenance and remote monitoring, demand for versatile IoT chipsets continues to rise. The IoT chips market is estimated to be valued at USD 620.36 Bn in 2025 and is expected to reach USD 1415.005 Bn by 2032, growing at a compound annual growth rate (CAGR) of 15.00% from 2025 to 2032.
-
 @ 5627e59c:d484729e
2025-06-11 21:16:26
@ 5627e59c:d484729e
2025-06-11 21:16:26Liefde\ De samenkomst\ Van zien en zijn
Leven\ Het zijn en zien\ Een vorm gekregen
Sterven\ Een deur\ Die vrijheid geeft van vorm
En eeuwig leven\ Aan liefde
-
 @ c1e9ab3a:9cb56b43
2025-03-09 20:13:44
@ c1e9ab3a:9cb56b43
2025-03-09 20:13:44Introduction
Since the mid-1990s, American media has fractured into two distinct and increasingly isolated ecosystems, each with its own Overton window of acceptable discourse. Once upon a time, Americans of different political leanings shared a common set of facts, even if they interpreted them differently. Today, they don’t even agree on what the facts are—or who has the authority to define them.
This divide stems from a deeper philosophical rift in how each side determines truth and legitimacy. The institutional left derives its authority from the expert class—academics, think tanks, scientific consensus, and mainstream media. The populist right, on the other hand, finds its authority in traditional belief systems—religion, historical precedent, and what many call "common sense." As these two moral and epistemological frameworks drift further apart, the result is not just political division but the emergence of two separate cultural nations sharing the same geographic space.
The Battle of Epistemologies: Experts vs. Tradition
The left-leaning camp sees scientific consensus, peer-reviewed research, and institutional expertise as the gold standard of truth. Universities, media organizations, and policy think tanks function as arbiters of knowledge, shaping the moral and political beliefs of those who trust them. From this perspective, governance should be guided by data-driven decisions, often favoring progressive change and bureaucratic administration over democratic populism.
The right-leaning camp is skeptical of these institutions, viewing them as ideologically captured and detached from real-world concerns. Instead, they look to religion, historical wisdom, and traditional social structures as more reliable sources of truth. To them, the "expert class" is not an impartial source of knowledge but a self-reinforcing elite that justifies its own power while dismissing dissenters as uneducated or morally deficient.
This fundamental disagreement over the source of moral and factual authority means that political debates today are rarely about policy alone. They are battles over legitimacy itself. One side sees resistance to climate policies as "anti-science," while the other sees aggressive climate mandates as an elite power grab. One side views traditional gender roles as oppressive, while the other sees rapid changes in gender norms as unnatural and destabilizing. Each group believes the other is not just wrong, but dangerous.
The Consequences of Non-Overlapping Overton Windows
As these worldviews diverge, so do their respective Overton windows—the range of ideas considered acceptable for public discourse. There is little overlap left. What is considered self-evident truth in one camp is often seen as heresy or misinformation in the other. The result is:
- Epistemic Closure – Each side has its own trusted media sources, and cross-exposure is minimal. The left dismisses right-wing media as conspiracy-driven, while the right views mainstream media as corrupt propaganda. Both believe the other is being systematically misled.
- Moralization of Politics – Since truth itself is contested, policy debates become existential battles. Disagreements over issues like immigration, education, or healthcare are no longer just about governance but about moral purity versus moral corruption.
- Cultural and Political Balkanization – Without a shared understanding of reality, compromise becomes impossible. Americans increasingly consume separate news, live in ideologically homogeneous communities, and even speak different political languages.
Conclusion: Two Nations on One Land
A country can survive disagreements, but can it survive when its people no longer share a common source of truth? Historically, such deep societal fractures have led to secession, authoritarianism, or violent conflict. The United States has managed to avoid these extremes so far, but the trendline is clear: as long as each camp continues reinforcing its own epistemology while rejecting the other's as illegitimate, the divide will only grow.
The question is no longer whether America is divided—it is whether these two cultures can continue to coexist under a single political system. Can anything bridge the gap between institutional authority and traditional wisdom? Or are we witnessing the slow but inevitable unraveling of a once-unified nation into two separate moral and epistemic realities?
-
 @ c1e9ab3a:9cb56b43
2025-02-25 22:49:38
@ c1e9ab3a:9cb56b43
2025-02-25 22:49:38Election Authority (EA) Platform
1.1 EA Administration Interface (Web-Based)
- Purpose: Gives authorized personnel (e.g., election officials) a user-friendly way to administer the election.
- Key Tasks:
- Voter Registration Oversight: Mark which voters have proven their identity (via in-person KYC or some legal process).
- Blind Signature Issuance: Approve or deny blind signature requests from registered voters (each corresponding to one ephemeral key).
- Tracking Voter Slots: Keep a minimal registry of who is allowed one ephemeral key signature, and mark it “used” once a signature is issued.
- Election Configuration: Set start/end times, provide encryption parameters (public keys), manage threshold cryptography setup.
- Monitor Tallying: After the election, collaborate with trustees to decrypt final results and release them.
1.2 EA Backend Services
- Blind Signature Service:
- An API endpoint or internal module that receives a blinded ephemeral key from a voter, checks if they are authorized (one signature per voter), and returns the blind-signed result.
-
Typically requires secure storage of the EA’s blind signing private key.
-
Voter Roll Database:
- Stores minimal info: “Voter #12345 is authorized to request one ephemeral key signature,” plus status flags.
-
Does not store ephemeral keys themselves (to preserve anonymity).
-
(Optional) Mix-Net or Homomorphic Tally Service:
- Coordinates with trustees for threshold decryption or re-encryption.
- Alternatively, a separate “Tally Authority” service can handle this.
2. Auditor Interface
2.1 Auditor Web-Based Portal
- Purpose: Allows independent auditors (or the public) to:
- Fetch All Ballots from the relays (or from an aggregator).
- Verify Proofs: Check each ballot’s signature, blind signature from the EA, OTS proof, zero-knowledge proofs, etc.
- Check Double-Usage: Confirm that each ephemeral key is used only once (or final re-vote is the only valid instance).
-
Observe Tally Process: Possibly see partial decryptions or shuffle steps, verify the final result matches the posted ballots.
-
Key Tasks:
- Provide a dashboard showing the election’s real-time status or final results, after cryptographic verification.
- Offer open data downloads so third parties can run independent checks.
2.2 (Optional) Trustee Dashboard
- If the election uses threshold cryptography (multiple parties must decrypt), each trustee (candidate rep, official, etc.) might have an interface for:
- Uploading partial decryption shares or re-encryption proofs.
- Checking that other trustees did their steps correctly (zero-knowledge proofs for correct shuffling, etc.).
3. Voter Application
3.1 Voter Client (Mobile App or Web Interface)
-
Purpose: The main tool voters use to participate—before, during, and after the election.
-
Functionalities:
- Registration Linking:
- Voter goes in-person to an election office or uses an online KYC process.
- Voter obtains or confirms their long-term (“KYC-bound”) key. The client can store it securely (or the voter just logs in to a “voter account”).
- Ephemeral Key Generation:
- Create an ephemeral key pair ((nsec_e, npub_e)) locally.
- Blind (\npub_e) and send it to the EA for signing.
- Unblind the returned signature.
- Store (\npub_e) + EA’s signature for use during voting.
- Ballot Composition:
- Display candidates/offices to the voter.
- Let them select choices.
- Possibly generate zero-knowledge proofs (ZKPs) behind the scenes to confirm “exactly one choice per race.”
- Encryption & OTS Timestamp:
- Encrypt the ballot under the election’s public (threshold) key or produce a format suitable for a mix-net.
- Obtain an OpenTimestamps proof for the ballot’s hash.
- Publish Ballot:
- Sign the entire “timestamped ballot” with the ephemeral key.
- Include the EA’s blind signature on (\npub_e).
- Post to the Nostr relays (or any chosen decentralized channel).
- Re-Voting:
- If the user needs to change their vote, the client repeats the encryption + OTS step, publishes a new ballot with a strictly later OTS anchor.
- Verification:
- After the election, the voter can check that their final ballot is present in the tally set.
3.2 Local Storage / Security
- The app must securely store:
- Ephemeral private key ((nsec_e)) until voting is complete.
- Potential backup/recovery mechanism if the phone is lost.
- Blind signature from the EA on (\npub_e).
- Potentially uses hardware security modules (HSM) or secure enclaves on the device.
4. Nostr Relays (or Equivalent Decentralized Layer)
- Purpose: Store and replicate voter-submitted ballots (events).
- Key Properties:
- Redundancy: Voters can post to multiple relays to mitigate censorship or downtime.
- Public Accessibility: Auditors, the EA, and the public can fetch all events to verify or tally.
- Event Filtering: By design, watchers can filter events with certain tags, e.g. “election: 2025 County Race,” ensuring they gather all ballots.
5. Threshold Cryptography Setup
5.1 Multi-Seg (Multi-Party) Key Generation
- Participants: Possibly the EA + major candidates + accredited observers.
- Process: A Distributed Key Generation (DKG) protocol that yields a single public encryption key.
- Private Key Shares: Each trustee holds a piece of the decryption key; no single party can decrypt alone.
5.2 Decryption / Tally Mechanism
- Homomorphic Approach:
- Ballots are additively encrypted.
- Summation of ciphertexts is done publicly.
- Trustees provide partial decryptions for the final sum.
- Mix-Net Approach:
- Ballots are collected.
- Multiple servers shuffle and re-encrypt them (each trustee verifies correctness).
- Final set is decrypted, but the link to each ephemeral key is lost.
5.3 Trustee Interfaces
- Separate or integrated into the auditor interface—each trustee logs in and provides their partial key share for decrypting the final result.
- Possibly combined with ZK proofs to confirm correct partial decryption or shuffling.
6. OpenTimestamps (OTS) or External Time Anchor
6.1 Aggregator Service
- Purpose: Receives a hash from the voter’s app, anchors it into a blockchain or alternative time-stamping system.
- Result: Returns a proof object that can later be used by any auditor to confirm the time/block height at which the hash was included.
6.2 Verifier Interface
- Could be part of the auditor tool or the voter client.
- Checks that each ballot’s OTS proof is valid and references a block/time prior to the election’s closing.
7. Registration Process (In-Person or Hybrid)
- Voter presents ID physically at a polling station or a designated office (or an online KYC approach, if legally allowed).
- EA official:
- Confirms identity.
- Links the voter to a “voter record” (Voter #12345).
- Authorizes them for “1 ephemeral key blind-sign.”
- Voter obtains or logs into the voter client:
- The app or website might show “You are now cleared to request a blind signature from the EA.”
- Voter later (or immediately) generates the ephemeral key and requests the blind signature.
8. Putting It All Together (High-Level Flow)
- Key Setup
- The EA + trustees run a DKG to produce the election public key.
- Voter Registration
- Voter is validated (ID check).
- Marked as eligible in the EA database.
- Blind-Signed Ephemeral Key
- Voter’s client generates a key, blinds (\npub_e), obtains EA’s signature, unblinds.
- Voting
- Voter composes ballot, encrypts with the election public key.
- Gets OTS proof for the ballot hash.
- Voter’s ephemeral key signs the entire package (including EA’s signature on (\npub_e)).
- Publishes to Nostr.
- Re-Voting (Optional)
- Same ephemeral key, new OTS timestamp.
- Final ballot is whichever has the latest valid timestamp before closing.
- Close of Election & Tally
- EA announces closing.
- Tally software (admin + auditors) collects ballots from Nostr, discards invalid duplicates.
- Threshold decryption or mix-net to reveal final counts.
- Publish final results and let auditors verify everything.
9. Summary of Major Components
Below is a succinct list:
- EA Admin Platform
- Web UI for officials (registration, blind signature issuing, final tally management).
- Backend DB for voter records & authorized ephemeral keys.
- Auditor/Trustee Platforms
- Web interface for verifying ballots, partial decryption, and final results.
- Voter Application (Mobile / Web)
- Generating ephemeral keys, getting blind-signed, casting encrypted ballots, re-voting, verifying included ballots.
- Nostr Relays (Decentralized Storage)
- Where ballots (events) are published, replicated, and fetched for final tally.
- Threshold Cryptography System
- Multi-party DKG for the election key.
- Protocols or services for partial decryption, mix-net, or homomorphic summation.
- OpenTimestamps Aggregator
- Service that returns a blockchain-anchored timestamp proof for each ballot’s hash.
Additional Implementation Considerations
- Security Hardening:
- Using hardware security modules (HSM) for the EA’s blind-signing key, for trustee shares, etc.
- Scalability:
- Handling large numbers of concurrent voters, large data flows to relays.
- User Experience:
- Minimizing cryptographic complexity for non-technical voters.
- Legal and Procedural:
- Compliance with local laws for in-person ID checks, mandatory paper backups (if any), etc.
Final Note
While each functional block can be designed and deployed independently (e.g., multiple aggregator services, multiple relays, separate tally servers), the key to a successful system is interoperability and careful orchestration of these components—ensuring strong security, a straightforward voter experience, and transparent auditing.
nostr:naddr1qqxnzde5xq6nzv348yunvv35qy28wue69uhnzv3h9cczuvpwxyargwpk8yhsygxpax4n544z4dk2f04lgn4xfvha5s9vvvg73p46s66x2gtfedttgvpsgqqqw4rs0rcnsu
-
 @ 2b998b04:86727e47
2025-06-11 19:36:40
@ 2b998b04:86727e47
2025-06-11 19:36:40🌋 Ka ʻImi i ka Pono: Seeking What’s Right
A 7-Day Series on Sovereignty, Bitcoin, and the Soul of the Islands
> "Man is not free unless he wills to be free."\ > — Johann Gottlieb Fichte
Hawai‘i understands sovereignty. It always has.\ But it was taken — first with pen and politics, then with force and fiat.
Bitcoin offers something different:\ A way to reclaim sovereignty without violence.\ A tool for self-rule, not state rule.\ A system built not on empire, but on truth and time.
This week, I’ll be posting a 7-part series exploring this tension:\ Between the Hawai‘i that was, the system that is, and the future that might be — if we choose to build on bedrock instead of paper.
I don’t know if there’s a traditional Hawaiian word for a 7-day week — maybe there doesn’t need to be.\ Time moves differently on these islands.\ But for the next 7 days, I’ll mark each reflection as a kind of modern lā hoʻomanaʻo — a day of remembering, reckoning, and restoring.
This is personal. It’s philosophical. It’s also unfinished.
But that’s what sovereignty looks like:\ Not something given — something reclaimed.
Stay tuned. Stay akamai.\ 🟧\ — Andrew G. Stanton (aka akamaister)
-
 @ 5627e59c:d484729e
2025-06-11 22:27:54
@ 5627e59c:d484729e
2025-06-11 22:27:54Hello Bumble\ You busy bee
You're going way\ Too fast for me
Going here and there\ You search for gold
Yet tumble straight\ Into what's old
Now I'm not here\ To make a gain
Nor to fix\ What's in disdain
Instead I'm just\ A humble bee
Who wants to get\ To know thee
-
 @ 79be667e:16f81798
2025-06-11 19:11:59
@ 79be667e:16f81798
2025-06-11 19:11:59I am here too\ In the same space like you
In the same situation I'm in\ It's a matter of positioning
I cannot leave this place I'm in\ It was brought about\ By what's been happening
So please don't look at me\ For what I can or cannot do for you\ But look at what is happening for me\ And what is happening for you
Let's communicate\ Not orchestrate
Because there's something I wish to do\ And there's a place I wish to go to
And I'm sure that there is too\ In your heart a fire\ Known by only you
So let us listen, look and see\ For what's true for you\ And what's true for me
That we may act upon what's here\ In order for us both to take a step\ In the direction we wish to steer
-
 @ 5627e59c:d484729e
2025-06-11 21:15:21
@ 5627e59c:d484729e
2025-06-11 21:15:21Muziek\ Jij harmonieus geluid
Een gevoel zo uniek\ Op geen andere manier geuit
Ik ben zo dankbaar voor de vrijheid die jij me schenkt\ Om gewoon even te zijn\ In dit dierbare moment
-
 @ cae03c48:2a7d6671
2025-06-11 19:01:58
@ cae03c48:2a7d6671
2025-06-11 19:01:58Bitcoin Magazine

The Trump’s American Bitcoin Merges with Gryphon, Reports 215 BTC on Balance Sheet Since LaunchAmerican Bitcoin Corp (ABTC), a newly formed private Bitcoin mining company backed by Eric Trump and Donald Trump Jr., announced in a June 10 SEC filing that it has acquired 215 Bitcoin (BTC) since launching operations on April 1, 2025. The reserve is currently valued at approximately $23 million, showing their drive and commitment to Bitcoin.
JUST IN: American Bitcoin Corp (private) reports to have 215 #bitcoin (per 31 May) since it's launch on April 1, 2025.
They will merge with Gryphon Digital $GRYP and become public under ticker $ABTC.
They mention "Bitcoin accumulation is not a side effect of ABTC’s business.… pic.twitter.com/wq1Uxr76Z2
— NLNico (@btcNLNico) June 10, 2025
“Bitcoin accumulation is not a side effect of ABTC’s business. It is the business,” the company stated in the filing.

Furthermore, ABTC has entered into a merger agreement with Gryphon Digital Mining ($GRYP), and the combined company is expected to begin public trading under the ticker $ABTC as early as Q3 2025.
The company’s three-layer strategic plan—outlined in the SEC disclosure—details a focused approach:
Layer 1: Build the Engine
- ABTC’s foundation is built on “producing Bitcoin below-market cost through a capital efficient, infrastructure-light operating model.” The company owns and operates over 60,000 miners from Bitmain and MicroBt, running primarily on Hut 8-managed facilities.
Layer 2: Scale the Reserve
- ABTC had “accumulated approximately 215 Bitcoin in reserve since launching on April 1, 2025,” which it considers a long-term strategic asset. The firm states its goal is “to utilize public markets and strategic financing structures to access efficient capital and leverage that capital to increase its Bitcoin in reserve per share.”
Layer 3: Lead the Ecosystem
- The company ultimately aims to use its operational scale and mining position to drive industry-wide adoption. “ABTC may pursue opportunities to support protocol development, enhance network infrastructure and contribute to Bitcoin’s resilience and adoption in ways that align with shareholder value creation.”
For mining rewards, ABTC uses Foundry and Luxor pools with sub-1% fees and relies on Coinbase Custody for secure cold storage, featuring multi-factor authentication and strict withdrawal protocols.
With operations across Niagara Falls, NY; Medicine Hat, AB; and Orla, TX, ABTC is leveraging strategic partnerships—primarily with Hut 8—to scale its Bitcoin holdings while influencing the broader crypto mining ecosystem.
This post The Trump’s American Bitcoin Merges with Gryphon, Reports 215 BTC on Balance Sheet Since Launch first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 97c70a44:ad98e322
2025-06-06 20:48:33
@ 97c70a44:ad98e322
2025-06-06 20:48:33Vibe coding is taking the nostr developer community by storm. While it's all very exciting and interesting, I think it's important to pump the brakes a little - not in order to stop the vehicle, but to try to keep us from flying off the road as we approach this curve.
In this note Pablo is subtweeting something I said to him recently (although I'm sure he's heard it from other quarters as well):
nostr:nevent1qvzqqqqqqypzp75cf0tahv5z7plpdeaws7ex52nmnwgtwfr2g3m37r844evqrr6jqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7qg6waehxw309ac8junpd45kgtnxd9shg6npvchxxmmd9uqzq0z48d4ttzzkupswnkyt5a2xfkhxl3hyavnxjujwn5k2k529aearwtecp4
There is a naive, curmudgeonly case for simply "not doing AI". I think the intuition is a good one, but the subject is obviously more complicated - not doing it, either on an individual or a collective level, is just not an option. I recently read Tools for Conviviality by Ivan Illich, which I think can help us here. For Illich, the best kind of tool is one which serves "politically interrelated individuals rather than managers".
This is obviously a core value for bitcoiners. And I think the talks given at the Oslo Freedom Forum this year present a compelling case for adoption of LLMs for the purposes of 1. using them for good, and 2. developing them further so that they don't get captured by corporations and governments. Illich calls both the telephone and print "almost ideally convivial". I would add the internet, cryptography, and LLMs to this list, because each one allows individuals to work cooperatively within communities to embody their values in their work.
But this is only half the story. Illich also points out how "the manipulative nature of institutions... have put these ideally convivial tools at the service of more [managerial dominance]."
Preventing the subversion and capture of our tools is not just a matter of who uses what, and for which ends. It also requires an awareness of the environment that the use of the tool (whether for virtuous or vicious ends) creates, which in turn forms the abilities, values, and desires of those who inhabit the environment.
The natural tendency of LLMs is to foster ignorance, dependence, and detachment from reality. This is not the fault of the tool itself, but that of humans' tendency to trade liberty for convenience. Nevertheless, the inherent values of a given tool naturally gives rise to an environment through use: the tool changes the world that the tool user lives in. This in turn indoctrinates the user into the internal logic of the tool, shaping their thinking, blinding them to the tool's influence, and neutering their ability to work in ways not endorsed by the structure of the tool-defined environment.
The result of this is that people are formed by their tools, becoming their slaves. We often talk about LLM misalignment, but the same is true of humans. Unreflective use of a tool creates people who are misaligned with their own interests. This is what I mean when I say that AI use is anti-human. I mean it in the same way that all unreflective tool use is anti-human. See Wendell Berry for an evaluation of industrial agriculture along the same lines.
What I'm not claiming is that a minority of high agency individuals can't use the technology for virtuous ends. In fact, I think that is an essential part of the solution. Tool use can be good. But tools that bring their users into dependence on complex industry and catechize their users into a particular system should be approached with extra caution. The plow was a convivial tool, and so were early tractors. Self-driving John Deere monstrosities are a straightforward extension of the earlier form of the technology, but are self-evidently an instrument of debt slavery, chemical dependency, industrial centralization, and degradation of the land. This over-extension of a given tool can occur regardless of the intentions of the user. As Illich says:
There is a form of malfunction in which growth does not yet tend toward the destruction of life, yet renders a tool antagonistic to its specific aims. Tools, in other words, have an optimal, a tolerable, and a negative range.
The initial form of a tool is almost always beneficial, because tools are made by humans for human ends. But as the scale of the tool grows, its logic gets more widely and forcibly applied. The solution to the anti-human tendencies of any technology is an understanding of scale. To prevent the overrun of the internal logic of a given tool and its creation of an environment hostile to human flourishing, we need to impose limits on scale.
Tools that require time periods or spaces or energies much beyond the order of corresponding natural scales are dysfunctional.
My problem with LLMs is:
- Not their imitation of human idioms, but their subversion of them and the resulting adoption of robotic idioms by humans
- Not the access they grant to information, but their ability to obscure accurate or relevant information
- Not their elimination of menial work, but its increase (Bullshit Jobs)
- Not their ability to take away jobs, but their ability to take away the meaning found in good work
- Not their ability to confer power to the user, but their ability to confer power to their owner which can be used to exploit the user
- Not their ability to solve problems mechanistically, but the extension of their mechanistic value system to human life
- Not their explicit promise of productivity, but the environment they implicitly create in which productivity depends on their use
- Not the conversations they are able to participate in, but the relationships they displace
All of these dysfunctions come from the over-application of the technology in evaluating and executing the fundamentally human task of living. AI work is the same kind of thing as an AI girlfriend, because work is not only for the creation of value (although that's an essential part of it), but also for the exercise of human agency in the world. In other words, tools must be tools, not masters. This is a problem of scale - when tool use is extended beyond its appropriate domain, it becomes what Illich calls a "radical monopoly" (the domination of a single paradigm over all of human life).
So the important question when dealing with any emergent technology becomes: how can we set limits such that the use of the technology is naturally confined to its appropriate scale?
Here are some considerations:
- Teach people how to use the technology well (e.g. cite sources when doing research, use context files instead of fighting the prompt, know when to ask questions rather than generate code)
- Create and use open source and self-hosted models and tools (MCP, stacks, tenex). Refuse to pay for closed or third-party hosted models and tools.
- Recognize the dependencies of the tool itself, for example GPU availability, and diversify the industrial sources to reduce fragility and dependence.
- Create models with built-in limits. The big companies have attempted this (resulting in Japanese Vikings), but the best-case effect is a top-down imposition of corporate values onto individuals. But the idea isn't inherently bad - a coding model that refuses to generate code in response to vague prompts, or which asks clarifying questions is an example. Or a home assistant that recognized childrens' voices and refuses to interact.
- Divert the productivity gains to human enrichment. Without mundane work to do, novice lawyers, coders, and accountants don't have an opportunity to hone their skills. But their learning could be subsidized by the bots in order to bring them up to a level that continues to be useful.
- Don't become a slave to the bots. Know when not to use it. Talk to real people. Write real code, poetry, novels, scripts. Do your own research. Learn by experience. Make your own stuff. Take a break from reviewing code to write some. Be independent, impossible to control. Don't underestimate the value to your soul of good work.
- Resist both monopoly and "radical monopoly". Both naturally collapse over time, but by cultivating an appreciation of the goodness of hand-crafted goods, non-synthetic entertainment, embodied relationship, and a balance between mobility and place, we can relegate new, threatening technologies to their correct role in society.
I think in all of this is implicit the idea of technological determinism, that productivity is power, and if you don't adapt you die. I reject this as an artifact of darwinism and materialism. The world is far more complex and full of grace than we think.
The idea that productivity creates wealth is, as we all know, bunk. GDP continues to go up, but ungrounded metrics don't reflect anything about the reality of human flourishing. We have to return to a qualitative understanding of life as whole, and contextualize quantitative tools and metrics within that framework.
Finally, don't believe the hype. Even if AI delivers everything it promises, conservatism in changing our ways of life will decelerate the rate of change society is subjected to and allow time for reflection and proper use of the tool. Curmudgeons are as valuable as technologists. There will be no jobspocalypse if there is sufficient political will to value human good over mere productivity. It's ok to pump the breaks.
-
 @ 97c70a44:ad98e322
2025-06-09 18:23:27
@ 97c70a44:ad98e322
2025-06-09 18:23:27When developing on nostr, normally it's enough to read the NIP related to a given feature you want to build to know what has to be done. But there are some aspects of nostr development that aren't so straightforward because they depend less on specific data formats than on how different concepts are combined.
An example of this is how for a while it was considered best practice to re-publish notes when replying to them. This practice emerged before the outbox model gained traction, and was a hacky way of attempting to ensure relays had the full context required for a given note. Over time though, pubkey hints emerged as a better way to ensure other clients could find required context.
Another one of these things is "relay-based groups", or as I prefer to call it "relays-as-groups" (RAG). Such a thing doesn't really exist - there's no spec for it (although some aspects of the concept are included in NIP 29), but at the same time there are two concrete implementations (Flotilla and Chachi) which leverage several different NIPs in order to create a cohesive system for groups on nostr.
This composability is one of the neat qualities of nostr. Not only would it be unhelpful to specify how different parts of the protocol should work together, it would be impossible because of the number of possible combinations possible just from applying a little bit of common sense to the NIPs repo. No one said it was ok to put
ttags on akind 0. But no one's stopping you! And the semantics are basically self-evident if you understand its component parts.So, instead of writing a NIP that sets relay-based groups in stone, I'm writing this guide in order to document how I've combined different parts of the nostr protocol to create a compelling architecture for groups.
Relays
Relays already have a canonical identity, which is the relay's url. Events posted to a relay can be thought of as "posted to that group". This means that every relay is already a group. All nostr notes have already been posted to one or more groups.
One common objection to this structure is that identifying a group with a relay means that groups are dependent on the relay to continue hosting the group. In normal broadcast nostr (which forms organic permissionless groups based on user-centric social clustering), this is a very bad thing, because hosts are orthogonal to group identity. Communities are completely different. Communities actually need someone to enforce community boundaries, implement moderation, etc. Reliance on a host is a feature, not a bug (in contrast to NIP 29 groups, which tend to co-locate many groups on a single host, relays-as-groups tends to encourage one group, one host).
This doesn't mean that federation, mirrors, and migration can't be accomplished. In a sense, leaving this on the social layer is a good thing, because it adds friction to the dissolution/forking of a group. But the door is wide open to protocol additions to support those use cases for relay-based groups. One possible approach would be to follow this draft PR which specifies a "federation" event relays could publish on their own behalf.
Relay keys
This draft PR to NIP 11 specifies a
selffield which represents the relay's identity. Using this, relays can publish events on their own behalf. Currently, thepubkeyfield sort of does the same thing, but is overloaded as a contact field for the owner of the relay.AUTH
Relays can control access using NIP 42 AUTH. There are any number of modes a relay can operate in:
- No auth, fully public - anyone can read/write to the group.
- Relays may enforce broad or granular access controls with AUTH.
Relays may deny EVENTs or REQs depending on user identity. Messages returned in AUTH, CLOSED, or OK messages should be human readable. It's crucial that clients show these error messages to users. Here's how Flotilla handles failed AUTH and denied event publishing:
LIMITS, PROBE, or some other reflection scheme could also be used in theory to help clients adapt their interface depending on user abilities and relay policy.
- AUTH with implicit access controls.
In this mode, relays may exclude matching events from REQs if the user does not have permission to view them. This can be useful for multi-use relays that host hidden rooms. This mode should be used with caution, because it can result in confusion for the end user.
See Frith for a relay implementation that supports some of these auth policies.
Invite codes
If a user doesn't have access to a relay, they can request access using this draft NIP. This is true whether access has been explicitly or implicitly denied (although users will have to know that they should use an invite code to request access).
The above referenced NIP also contains a mechanism for users to request an invite code that they can share with other users.
The policy for these invite codes is entirely up to the relay. They may be single-use, multi-use, or require additional verification. Additional requirements can be communicated to the user in the OK message, for example directions to visit an external URL to register.
See Frith for a relay implementation that supports invite codes.
Content
Any kind of event can be published to a relay being treated as a group, unless rejected by the relay implementation. In particular, NIP 7D was added to support basic threads, and NIP C7 for chat messages.
Since which relay an event came from determines which group it was posted to, clients need to have a mechanism for keeping track of which relay they received an event from, and should not broadcast events to other relays (unless intending to cross-post the content).
Rooms
Rooms follow NIP 29. I wish NIP 29 wasn't called "relay based groups", which is very confusing when talking about "relays as groups". It's much better to think of them as sub-groups, or as Flotilla calls them, "rooms".
EDIT: Flotilla has migrated to exclusively use "managed rooms" — i.e., fully NIP 29 compliant rooms. Relays without NIP 29 support can still support chat, but all messages will be presented as sent to a single room. I've removed references to unmanaged rooms in what follows.
~~Rooms have two modes - managed and unmanaged. Managed~~ rooms follow all the rules laid out in NIP 29 about metadata published by the relay and user membership. In either case, rooms are represented by a random room id, and are posted to by including the id in an event's
htag. ~~This allows rooms to switch between managed and unmanaged modes without losing any content.~~Managed room names come from
kind 39000room meta events, ~~but unmanaged rooms don't have these. Instead, room names should come from members' NIP 51kind 10009membership lists. Tags on these lists should look like this:["group", "groupid", "wss://group.example.com", "Cat lovers"]. If no name can be found for the room (i.e., there aren't any members), the room should be ignored by clients.~~Rooms present a difficulty for publishing to the relay as a whole, since content with an
htag can't be excluded from requests. ~~Currently, relay-wide posts are h-tagged with_which works for "group" clients, but not more generally. I'm not sure how to solve this other than to ask relays to support negative filters.~~ I have ideas on how to solve this in future iterations of relay-based groups, for example using virtual relays or just a better rooms spec.Cross-posting
The simplest way to cross-post content from one group (or room) to another, is to quote the original note in whatever event kind is appropriate. For example, a blog post might be quoted in a
kind 9to be cross-posted to chat, or in akind 11to be cross-posted to a thread.kind 16reposts can be used the same way if the reader's client renders reposts.Posting the original event to multiple relays-as-groups is trivial, since all you have to do is send the event to the relay. Posting to multiple rooms simultaneously by appending multiple
htags is however not recommended, since group relays/clients are incentivised to protect themselves from spam by rejecting events with multiplehtags (similar to how events with multiplettags are sometimes rejected).Privacy
Currently, it's recommended to include a NIP 70
-tag on content posted to relays-as-groups to discourage replication of relay-specific content across the network.Another slightly stronger approach would be for group relays to strip signatures in order to make events invalid (or at least deniable). For this approach to work, users would have to be able to signal that they trust relays to be honest. We could also use ZkSNARKS to validate signatures in bulk.
In any case, group posts should not be considered "private" in the same way E2EE groups might be. Relays-as-groups should be considered a good fit for low-stakes groups with many members (since trust deteriorates quickly as more people get involved).
Membership
There is currently no canonical member list published by relays (except for NIP 29 managed rooms). Instead, users keep track of their own relay and room memberships using
kind 10009lists. Relay-level memberships are represented by anrtag containing the relay url, and room-level memberships are represented using agrouptag.Users can choose to advertise their membership in a RAG by using unencrypted tags, or they may keep their membership private by using encrypted tags. Advertised memberships are useful for helping people find groups based on their social graph:

User memberships should not be trusted, since they can be published unilaterally by anyone, regardless of actual access, so it's better to think of them as "bookmarked groups" or "favorites". Possible improvements in this area would be the ability to provide proof of access:
- Relays could publish member lists (although this would sacrifice member privacy)
- Relays could support a new command that allows querying a particular member's access status
- Relays could provide a proof to the member that they could then choose to publish or not
Moderation
There are two parts to moderation: reporting and taking action based on these reports.
Reporting is already covered by NIP 56. Clients should be careful about encouraging users to post reports for illegal content under their own identity, since that can itself be illegal. Relays also should not serve reports to users, since that can be used to find rather than address objectionable content.
Reports are only one mechanism for flagging objectionable content. Relay operators and administrators can use whatever heuristics they like to identify and address objectionable content. This might be via automated policies that auto-ban based on reports from high-reputation people, a client that implements NIP 86 relay management API, or by some other admin interface.
There's currently no way for moderators of a given relay to be advertised, or for a moderator's client to know that the user is a moderator (so that they can enable UI elements for in-app moderation). This could be addressed via NIP 11, LIMITS, or some other mechanism in the future.
General best practices
In general, it's very important when developing a client to assume that the relay has no special support for any of the above features, instead treating all of this stuff as progressive enhancement.
For example, if a user enters an invite code, go ahead and send it to the relay using a
kind 28934event. If it's rejected, you know that it didn't work. But if it's accepted, you don't know that it worked - you only know that the relay allowed the user to publish that event. This is helpful, becaues it may imply that the user does indeed have access to the relay. But additional probing may be needed, and reliance on error messages down the road when something else fails unexpectedly is indispensable.This paradigm may drive some engineers nuts, because it's basically equivalent to coding your clients to reverse-engineer relay support for every feature you want to use. But this is true of nostr as a whole - anyone can put whatever weird stuff in an event and sign it. Clients have to be extremely compliant with Postell's law - doing their absolute best to accept whatever weird data or behavior shows up and handle failure in any situation. Sure, it's annoying, but it's the cost of permissionless development. What it gets us is a completely open-ended protocol, in which anything can be built, and in which every solution is tested by the market.
-
 @ 79be667e:16f81798
2025-06-11 18:58:10
@ 79be667e:16f81798
2025-06-11 18:58:10Kan jij zien, er is geen hemel\ Probeer het zelf, dan lukt het wel\ Geen hel staat ons te wachten\ Enkel sterren hangen ons boven het hoofd\ Kan jij zien, iedereen leeft voor dit moment
Kan jij zien, er zijn geen landen\ Het is niet moeilijk gewoon land te zien\ Niets om voor te moorden of te sterven\ Ook geloof wordt niet gezien\ Kan jij zien, het leven wordt geleefd door iedereen in vrede
Misschien zeg je, ik kijk niet naar jouw wereld\ Maar ik deel dit zicht met velen\ Moge ook jij zoals ons zien\ Wij kijken in de wereld en zien gewoon onszelf
Kan jij zien, er is geen bezit\ Ik vraag me af of jij dit kan\ Geen hebben of een nood\ In een samen-leving van mensen\ Kan jij zien, wij delen de wereld met elkaar
Misschien zeg je, ik kijk niet naar jouw wereld\ Maar ik deel dit zicht met velen\ Moge ook jij zoals ons zien\ Wij kijken in de wereld en zien gewoon onszelf
-
 @ 5627e59c:d484729e
2025-06-11 22:27:43
@ 5627e59c:d484729e
2025-06-11 22:27:43We only see\ What we are
What we are not\ We cannot see
This is how we know\ Reality is happening within\ Our own being
And experience is a consequence\ Of who we believe to be
As long as we deny\ And don't want to see
All the ways\ We think to be
Reality will seem\ Outside of our grasp
And separate\ From our experience of life
Such is our power
Yet such power\ Could only be
Of that which holds\ The entirety
-
 @ 5627e59c:d484729e
2025-06-11 22:30:52
@ 5627e59c:d484729e
2025-06-11 22:30:52Nooit is mijn dans echter\ Dan net nadat het regende\ Want regen biedt een kans\ Om mijn gevoel te voelen
Zolang de regen spettert\ En ik mezelf graag zie\ Wordt er niets verplettert\ Ook al lijkt dat soms wel zo
Zodra de regen ophoudt\ En zich terugtrekt met de wolken\ Komt een nieuwe glans\ Voor het eerst mijn ogen binnen
Wat is het leven heerlijk\ Als ik eerlijk ben en voel\ Wat is het leven zacht\ En het brengt me naar mijn doel
Wat zou ik weten zonder regen\ Gewoon steeds evenveel\ Niet groeien is niet leven\ Daarom dans ik het liefst
Net na de echte regen
-
 @ 5627e59c:d484729e
2025-06-11 22:09:02
@ 5627e59c:d484729e
2025-06-11 22:09:02In een zee van mogelijkheden\ Kunnen we best veel tijd aan dromen besteden
Dromen is een universele taal\ Het wordt gedaan door ons allemaal
Het is het woord\ Dat deze gelijkheid de grond in boort
-
 @ 5627e59c:d484729e
2025-06-11 18:48:00
@ 5627e59c:d484729e
2025-06-11 18:48:00Love, I thank you for your warmth\ Ever lifting
You keep me charmed\ Ever drifting
May I be me\ And you be you
In a perfect harmony\ Embracing all life makes us grow through
-
 @ c1e9ab3a:9cb56b43
2025-02-25 19:49:28
@ c1e9ab3a:9cb56b43
2025-02-25 19:49:281. Introduction
Modern election systems must balance privacy (no one sees how individuals vote) with public verifiability (everyone can confirm the correctness of the tally). Achieving this in a decentralized, tamper-resistant manner remains a challenge. Nostr (a lightweight protocol for censorship-resistant communication) offers a promising platform for distributing and archiving election data (ballots) without relying on a single central server.
This paper presents a design where:
- Each voter generates a new ephemeral Nostr keypair for an election.
- The election authority (EA) blind-signs this ephemeral public key (npub) to prove the voter is authorized, without revealing which voter owns which ephemeral key.
- Voters cast encrypted ballots to Nostr relays, each carrying an OpenTimestamps proof to confirm the ballot’s time anchor.
- Re-voting is allowed: a voter can replace a previously cast ballot by publishing a new ballot with a newer timestamp.
- Only the latest valid ballot (per ephemeral key) is counted.
We combine well-known cryptographic primitives—blind signatures, homomorphic or mix-net encryption, threshold key management, and time anchoring—into an end-to-end system that preserves anonymity, assures correctness, and prevents double-voting.
2. Roles and Components
2.1 Voters
- Long-Term (“KYC-bound”) Key: Each voter has some identity-verified Nostr public key used only for official communication with the EA (not for voting).
- Ephemeral Voting Key: For each election, the voter locally generates a new Nostr keypair ((nsec_e, npub_e)).
- This is the “one-time” identity used to sign ballots.
- The EA never learns the real identity behind (\npub_e) because of blinding.
2.2 Election Authority (EA)
- Maintains the official voter registry: who is entitled to vote.
- Blind-Signs each valid voter’s ephemeral public key to authorize exactly one ephemeral key per voter.
- Publishes a minimal voter roll: e.g., “Voter #12345 has been issued a valid ephemeral key,” without revealing which ephemeral key.
2.3 Nostr Relays
- Decentralized servers that store and forward events.
- Voters post their ballots to relays, which replicate them.
- No single relay is critical; the same ballot can be posted to multiple relays for redundancy.
2.4 Cryptographic Framework
- Blind Signatures: The EA signs a blinded version of (\npub_e).
- Homomorphic or Mix-Net Encryption: Ensures the content of each ballot remains private; only aggregate results or a shuffled set are ever decrypted.
- Threshold / General Access Structure: Multiple trustees (EA plus candidate representatives, for example) must collaborate to produce a final decryption.
- OpenTimestamps (OTS): Attaches a verifiable timestamp proof to each ballot, anchoring it to a blockchain or other tamper-resistant time reference.
3. Protocol Lifecycle
This section walks through voter registration, ephemeral key authorization, casting (and re-casting) ballots, and finally the tally.
3.1 Registration & Minimal Voter Roll
- Legal/KYC Verification
- Each real-world voter proves their identity to the EA (per legal procedures).
-
The EA records that the voter is eligible to cast one ballot, referencing their long-term identity key ((\npub_{\mathrm{KYC}})).
-
Issue Authorization “Slot”
- The EA’s voter roll notes “this person can receive exactly one blind signature for an ephemeral key.”
- The roll does not store an ephemeral key—just notes that it can be requested.
3.2 Generating and Blinding the Ephemeral Key
- Voter Creates Ephemeral Key
- Locally, the voter’s client generates a fresh ((nsec_e, npub_e)).
- Blinding
-
The client blinds (\npub_e) to produce (\npub_{e,\mathrm{blinded}}). This ensures the EA cannot learn the real (\npub_e).
-
Blind Signature Request
- The voter, using their KYC-bound key ((\npub_{\mathrm{KYC}})), sends (\npub_{e,\mathrm{blinded}}) to the EA (perhaps via a secure direct message or a “giftwrapped DM”).
- The EA checks that this voter has not already been issued a blind signature.
-
If authorized, the EA signs (\npub_{e,\mathrm{blinded}}) with its private key and returns the blinded signature.
-
Unblinding
- The voter’s client unblinds the signature, obtaining a valid signature on (\npub_e).
-
Now (\npub_e) is a blinded ephemeral public key that the EA has effectively “authorized,” without knowing which voter it belongs to.
-
Roll Update
- The EA updates its minimal roll to note that “Voter #12345 received a signature,” but does not publish (\npub_e).
3.3 Casting an Encrypted Ballot with OpenTimestamps
When the voter is ready to vote:
- Compose Encrypted Ballot
- The ballot can be homomorphically encrypted (e.g., with Paillier or ElGamal) or structured for a mix-net.
-
Optionally include Zero-Knowledge Proofs (ZKPs) showing the ballot is valid (one candidate per race, etc.).
-
Obtain OTS Timestamp
- The voter’s client computes a hash (H) of the ballot data (ciphertext + ZKPs).
- The client sends (H) to an OpenTimestamps aggregator.
-
The aggregator returns a timestamp proof verifying that “this hash was seen at or before block/time (T).”
-
Create a “Timestamped Ballot” Payload
-
Combine:
- Encrypted ballot data.
- OTS proof for the hash of the ballot.
- EA’s signature on (\npub_e) (the blind-signed ephemeral key).
- A final signature by the voter’s ephemeral key ((nsec_e)) over the entire package.
-
Publish to Nostr
- The voter posts the complete “timestamped ballot” event to one or more relays.
- Observers see “an event from ephemeral key (\npub_e), with an OTS proof and the EA’s blind signature,” but cannot identify the real voter or see the vote’s contents.
3.4 Re-Voting (Updating the Ballot)
If the voter wishes to revise their vote (due to coercion, a mistake, or simply a change of mind):
- Generate a New Encrypted Ballot
- Possibly with different candidate choices.
- Obtain a New OTS Proof
- The new ballot has a fresh hash (H').
- The OTS aggregator provides a new proof anchored at a later block/time than the old one.
- Publish the Updated Ballot
- Again, sign with (\npub_e).
- Relays store both ballots, but the newer OTS timestamp shows which ballot is “final.”
Rule: The final vote for ephemeral key (\npub_e) is determined by the ballot with the highest valid OTS proof prior to the election’s closing.
3.5 Election Closing & Tally
- Close Signal
- At a specified time or block height, the EA publishes a “closing token.”
-
Any ballot with an OTS anchor referencing a time/block after the closing is invalid.
-
Collect Final Ballots
- Observers (or official tally software) gather the latest valid ballot from each ephemeral key.
-
They confirm the OTS proofs are valid and that no ephemeral key posted two different ballots with the same timestamp.
-
Decryption / Summation
- If homomorphic, the system sums the encrypted votes and uses a threshold of trustees to decrypt the aggregate.
- If a mix-net, the ballots are shuffled and partially decrypted, also requiring multiple trustees.
-
In either case, individual votes remain hidden, but the final counts are revealed.
-
Public Audit
- Anyone can fetch all ballots from the Nostr relays, verify OTS proofs, check the EA’s blind signature, and confirm no ephemeral key was used twice.
- The final totals can be recomputed from the publicly available data.
4. Ensuring One Vote Per Voter & No Invalid Voters
- One Blind Signature per Registered Voter
- The EA’s internal list ensures each real voter only obtains one ephemeral key signature.
- Blind Signature
- Ensures an unauthorized ephemeral key cannot pass validation (forging the EA’s signature is cryptographically infeasible).
- Public Ledger of Ballots
- Because each ballot references an EA-signed key, any ballot with a fake or duplicate signature is easily spotted.
5. Security and Privacy Analysis
- Voter Anonymity
- The EA never sees the unblinded ephemeral key. It cannot link (\npub_e) to a specific person.
-
Observers only see “some ephemeral key posted a ballot,” not the real identity of the voter.
-
Ballot Secrecy
- Homomorphic Encryption or Mix-Net: no one can decrypt an individual ballot; only aggregated or shuffled results are revealed.
-
The ephemeral key used for signing does not decrypt the ballot—the election’s threshold key does, after the election.
-
Verifiable Timestamping
- OpenTimestamps ensures each ballot’s time anchor cannot be forged or backdated.
-
Re-voting is transparent: a later OTS proof overrides earlier ones from the same ephemeral key.
-
Preventing Double Voting
- Each ephemeral key is unique and authorized once.
-
Re-voting by the same key overwrites the old ballot but does not increase the total count.
-
Protection Against Coercion
- Because the voter can re-cast until the deadline, a coerced vote can be replaced privately.
-
No receipts (individual decryption) are possible—only the final aggregated tally is revealed.
-
Threshold / Multi-Party Control
- Multiple trustees must collaborate to decrypt final results, preventing a single entity from tampering or prematurely viewing partial tallies.
6. Implementation Considerations
- Blind Signature Techniques
- Commonly implemented with RSA-based Chaumian blind signatures or BLS-based schemes.
-
Must ensure no link between (\npub_{e,\mathrm{blinded}}) and (\npub_e).
-
OpenTimestamps Scalability
- If millions of voters are posting ballots simultaneously, multiple timestamp aggregators or batch anchoring might be needed.
-
Verification logic on the client side or by public auditors must confirm each OTS proof’s integrity.
-
Relay Coordination
- The system must ensure no single relay can censor ballots. Voters may publish to multiple relays.
-
Tally fetchers cross-verify events from different relays.
-
Ease of Use
-
The user interface must hide the complexity of ephemeral key generation, blind signing, and OTS proof retrieval—making it as simple as possible for non-technical voters.
-
Legal Framework
-
If law requires publicly listing which voters have cast a ballot, you might track “Voter #12345 used their ephemeral key” without revealing the ephemeral key. Or you omit that if secrecy about who voted is desired.
-
Closing Time Edge Cases
- The system uses a block/time anchor from OTS. Slight unpredictability in block generation might require a small buffer around the official close. This is a policy choice.
7. Conclusion
We propose an election system that leverages Nostr for decentralizing ballot publication, blinded ephemeral keys for robust voter anonymity, homomorphic/mix-net encryption for ballot secrecy, threshold cryptography for collaborative final decryption, OpenTimestamps for tamper-proof time anchoring, and re-voting to combat coercion.
Key Advantages:
- Anonymity: The EA cannot link ballots to specific voters.
- One Voter, One Credential: Strict enforcement through blind signatures.
- Verifiable Ordering: OTS ensures each ballot has a unique, provable time anchor.
- Updatability: Voters can correct or override coerced ballots by posting a newer one before closing.
- Decentralized Audit: Anyone can fetch ballots from Nostr, verify the EA’s signatures and OTS proofs, and confirm the threshold-decrypted results match the posted ballots.
Such a design shows promise for secure, privacy-preserving digital elections, though real-world deployment will require careful policy, legal, and usability considerations. By combining cryptography with decentralized relays and an external timestamp anchor, the system can uphold both individual privacy and publicly auditable correctness.
-
 @ 65912a7a:5dc638bf
2025-02-09 20:34:15
@ 65912a7a:5dc638bf
2025-02-09 20:34:15I didn’t set out to become an enemy of the world’s richest man, but I seem to have managed it all the same. Until this moment, I’ve resisted describing my falling out with Elon Musk in much detail, but as the man’s cultural influence has metastasized—and he continues to spread lies about me on the social media platform that he owns (Twitter/X)—it seems only appropriate to set the record straight. I know that it annoys many in my audience to see me defend myself against attacks that they recognize to be spurious, but they might, nevertheless, find the details of what happened with Elon interesting.
Of all the remarkable people I’ve met, Elon is probably the most likely to remain a world-historical figure—despite his best efforts to become a clown. He is also the most likely to squander his ample opportunities to live a happy life, ruin his reputation and most important relationships, and produce lasting harm across the globe. None of this was obvious to me when we first met, and I have been quite amazed at Elon’s evolution, both as a man and as an avatar of chaos. The friend I remember did not seem to hunger for public attention. But his engagement with Twitter/X transformed him—to a degree seldom seen outside of Marvel movies or Greek mythology. If Elon is still the man I knew, I can only conclude that I never really knew him.
When we first met, Elon wasn’t especially rich or famous. In fact, I recall him teetering on the brink of bankruptcy around 2008, while risking the last of his previous fortune to make payroll at Tesla. At the time, he was living off loans from his friends Larry and Sergey. Once Elon became truly famous, and his personal wealth achieved escape velocity, I was among the first friends he called to discuss his growing security concerns. I put him in touch with Gavin de Becker, who provided his first bodyguards, and recommended other changes to his life. We also went shooting on at least two occasions with Scott Reitz, the finest firearms instructor I’ve ever met. It is an ugly irony that Elon’s repeated targeting of me on Twitter/X has increased my own security concerns. He understands this, of course, but does not seem to care.
So how did we fall out? Let this be a cautionary tale for any of Elon’s friends who might be tempted to tell the great man something he doesn’t want to hear:
(1.) When the SARS-CoV-2 virus first invaded our lives in March of 2020, Elon began tweeting in ways that I feared would harm his reputation. I also worried that his tweets might exacerbate the coming public-health emergency. Italy had already fallen off a cliff, and Elon shared the following opinion with his tens of millions of fans :
the coronavirus panic is dumb
As a concerned friend, I sent him a private text:
Hey, brother— I really think you need to walk back your coronavirus tweet. I know there’s a way to parse it that makes sense (“panic” is always dumb), but I fear that’s not the way most people are reading it. You have an enormous platform, and much of the world looks to you as an authority on all things technical. Coronavirus is a very big deal, and if we don’t get our act together, we’re going to look just like Italy very soon. If you want to turn some engineers loose on the problem, now would be a good time for a breakthrough in the production of ventilators...
(2.) Elon’s response was, I believe, the first discordant note ever struck in our friendship:
Sam, you of all people should not be concerned about this.
He included a link to a page on the CDC website, indicating that Covid was not even among the top 100 causes of death in the United States. This was a patently silly point to make in the first days of a pandemic.
We continued exchanging texts for at least two hours. If I hadn’t known that I was communicating with Elon Musk, I would have thought I was debating someone who lacked any understanding of basic scientific and mathematical concepts, like exponential curves.
(3.) Elon and I didn’t converge on a common view of epidemiology over the course of those two hours, but we hit upon a fun compromise: A wager. Elon bet me $1 million dollars (to be given to charity) against a bottle of fancy tequila ($1000) that we wouldn’t see as many as 35,000 cases of Covid in the United States (cases, not deaths). The terms of the bet reflected what was, in his estimation, the near certainty (1000 to 1) that he was right. Having already heard credible estimates that there could be 1 million deaths from Covid in the U.S. over the next 12-18 months (these estimates proved fairly accurate), I thought the terms of the bet ridiculous—and quite unfair to Elon. I offered to spot him two orders of magnitude: I was confident that we’d soon have 3.5 million cases of Covid in the U.S. Elon accused me of having lost my mind and insisted that we stick with a ceiling of 35,000.
(4.) We communicated sporadically by text over the next couple of weeks, while the number of reported cases grew. Ominously, Elon dismissed the next batch of data reported by the CDC as merely presumptive—while confirmed cases of Covid, on his account, remained elusive.
(5.) A few weeks later, when the CDC website finally reported 35,000 deaths from Covid in the U.S. and 600,000 cases, I sent Elon the following text:
Is (35,000 deaths + 600,000 cases) > 35,000 cases?
(6.) This text appears to have ended our friendship. Elon never responded, and it was not long before he began maligning me on Twitter for a variety of imaginary offenses. For my part, I eventually started complaining about the startling erosion of his integrity on my podcast, without providing any detail about what had transpired between us.
(7.) At the end of 2022, I abandoned Twitter/X altogether, having recognized the poisonous effect that it had on my life—but also, in large part, because of what I saw it doing to Elon. I’ve been away from the platform for over two years, and yet Elon still attacks me. Occasionally a friend will tell me that I’m trending there, and the reasons for this are never good. As recently as this week, Elon repeated a defamatory charge about my being a “hypocrite” for writing a book in defense of honesty and then encouraging people to lie to keep Donald Trump out of the White House. Not only have I never advocated lying to defeat Trump (despite what that misleading clip from the Triggernometry podcast might suggest to naive viewers), I’ve taken great pains to defend Trump from the most damaging lie ever told about him. Elon knows this, because we communicated about the offending clip when it first appeared on Twitter/X. However, he simply does not care that he is defaming a former friend to hundreds of millions of people—many of whom are mentally unstable. On this occasion, he even tagged the incoming president of the United States.
All of this remains socially and professionally awkward, because Elon and I still have many friends in common. Which suggests the terms of another wager that I would happily make, if such a thing were possible—and I would accept 1000 to 1 odds in Elon’s favor:
I bet that anyone who knows us both knows that I am telling the truth.
Everyone close to Elon must recognize how unethical he has become, and yet they remain silent. Their complicity is understandable, but it is depressing all the same. These otherwise serious and compassionate people know that when Elon attacks private citizens on Twitter/X—falsely accusing them of crimes or corruption, celebrating their misfortunes—he is often causing tangible harm in their lives. It’s probably still true to say that social media “isn’t real life,” until thousands of lunatics learn your home address.
A final absurdity in my case, is that several of the controversial issues that Elon has hurled himself at of late—and even attacked me over—are ones we agree about. We seem to be in near total alignment on immigration and the problems at the southern border of the U.S. We also share the same concerns about what he calls “the woke mind virus.” And we fully agree about the manifest evil of the so-called “grooming-gangs scandal” in the U.K. The problem with Elon, is that he makes no effort to get his facts straight when discussing any of these topics, and he regularly promotes lies and conspiracy theories manufactured by known bad actors, at scale. (And if grooming were really one of his concerns, it’s strange that he couldn’t find anything wrong with Matt Gaetz.)
Elon and I even agree about the foundational importance of free speech. It’s just that his approach to safeguarding it—amplifying the influence of psychopaths and psychotics, while deplatforming real journalists and his own critics; or savaging the reputations of democratic leaders, while never saying a harsh word about the Chinese Communist Party—is not something I can support. The man claims to have principles, but he appears to have only moods and impulses.
Any dispassionate observer of Elon’s behavior on Twitter/X can see that there is something seriously wrong with his moral compass, if not his perception of reality. There is simply no excuse for a person with his talents, resources, and opportunities to create so much pointless noise. The callousness and narcissism conveyed by his antics should be impossible for his real friends to ignore—but they appear to keep silent, perhaps for fear of losing access to his orbit of influence.
Of course, none of this is to deny that the tens of thousands of brilliant engineers Elon employs are accomplishing extraordinary things. He really is the greatest entrepreneur of our generation. And because of the businesses he’s built, he will likely become the world’s first trillionaire—perhaps very soon. Since the election of Donald Trump in November, Elon’s wealth has grown by around $200 billion. That’s nearly $3 billion a day (and over $100 million an hour). Such astonishing access to resources gives Elon the chance—and many would argue the responsibility—to solve enormous problems in our world.
So why spend time spreading lies on X?
-
 @ 6be5cc06:5259daf0
2025-06-12 01:18:11
@ 6be5cc06:5259daf0
2025-06-12 01:18:11Introdução
O princípio do sola scriptura, pedra angular da teologia protestante desde a Reforma do século XVI, estabelece que apenas a Escritura constitui a autoridade final e suprema em questões de fé e prática cristã. Este princípio, formulado inicialmente por Martinho Lutero e sistematizado pelos reformadores subsequentes, pretende oferecer um fundamento epistemológico sólido para a teologia, livre das supostas corrupções da tradição eclesiástica.
Contudo, uma análise rigorosa revela que o sola scriptura incorre em contradições lógicas fundamentais que comprometem sua viabilidade como sistema epistemológico coerente. Este artigo examina essas contradições através de três perspectivas complementares: filosófica, exegética e histórica.
A Contradição Performativa Fundamental
O Problema da Autorreferência
O sola scriptura enfrenta um dilema epistemológico insuperável: afirma que apenas a Escritura possui autoridade final em matéria de fé, mas essa própria regra não é explicitamente ensinada na Escritura. Trata-se de uma contradição performativa clássica, onde o enunciado viola suas próprias condições de possibilidade.
Esta situação configura uma falácia de petitio principii (círculo vicioso), pois exige que se aceite uma doutrina que não pode ser sustentada pelas premissas do próprio sistema. Para estabelecer o sola scriptura, seria necessário recorrer a uma autoridade externa à Escritura – precisamente aquilo que o princípio pretende rejeitar.
Fundacionalismo Mal Estruturado
Do ponto de vista epistemológico, o sola scriptura apresenta-se como um fundacionalismo defeituoso. Pretende funcionar como axioma supremo e auto-evidente, mas falha ao não fornecer a base textual que sua própria metodologia exige. Um verdadeiro fundacionalismo escriturístico deveria ser capaz de demonstrar sua validade através de uma prova explícita nas próprias Escrituras.
O Testemunho Contrário das Escrituras
Limitações do Registro Escrito
A própria Escritura reconhece as limitações do registro textual. João 21:25 declara explicitamente: "Jesus fez também muitas outras coisas. Se cada uma delas fosse escrita, penso que nem mesmo no mundo inteiro haveria espaço suficiente para os livros que seriam escritos."
Este versículo é particularmente problemático para o sola scriptura, pois reconhece que nem todos os ensinamentos de Cristo foram preservados por escrito. Como pode a Escritura ser suficiente se ela própria admite sua incompletude?
A Valorização da Tradição Oral
Paulo, em 2 Tessalonicenses 2:15, oferece uma instrução que contradiz frontalmente o sola scriptura: "Assim, pois, irmãos, ficai firmes e conservai os ensinamentos que de nós aprendestes, seja por palavras, seja por carta nossa."
O apóstolo valoriza inequivocamente tanto a tradição oral ("por palavras") quanto a escrita ("por carta"), estabelecendo um modelo de autoridade dual que o protestantismo posterior rejeitaria.
A Necessidade de Autoridade Interpretativa
A narrativa do eunuco etíope em Atos 8:30-31 demonstra a inadequação da Escritura isolada como autoridade final. Quando Filipe pergunta se o eunuco entende o que lê, a resposta é reveladora: "Como poderei entender, se alguém não me ensinar?"
Este episódio ilustra que a mera posse do texto bíblico não garante compreensão adequada. É necessária uma autoridade interpretativa externa – no caso, representada por Filipe, que age com autoridade apostólica.
A Complexidade Hermenêutica
Pedro, em sua segunda epístola (3:16-17), reconhece a dificuldade interpretativa inerente às Escrituras: "Suas cartas contêm algumas coisas difíceis de entender, as quais os ignorantes e instáveis torcem, como também o fazem com as demais Escrituras, para a própria destruição deles."
Esta passagem não apenas reconhece a complexidade hermenêutica dos textos sagrados, mas também alerta sobre os perigos da interpretação inadequada. Implicitamente, sugere a necessidade de uma autoridade interpretativa confiável para evitar distorções doutrinárias.
O Paradoxo Histórico da Canonização
A Dependência da Tradição Eclesiástica
Um dos argumentos mais devastadores contra o sola scriptura emerge da própria história da formação do cânon bíblico. Os concílios de Hipona (393 d.C.) e Cartago (397 d.C.) foram responsáveis pela definição oficial do cânon das Escrituras tal como conhecemos hoje.
Este fato histórico cria um paradoxo insuperável: aceitar a Bíblia como autoridade única requer aceitar a autoridade da tradição eclesiástica que a definiu. O próprio cânon bíblico é produto da tradição apostólica e da deliberação conciliar, não de autodefinição escriturística.
A Circularidade da Autopistia
Tentativas protestantes de resolver este dilema através do conceito de "autopistia" – a suposta capacidade das Escrituras de se auto-autenticar – apenas aprofundam o problema circular. Como determinar que as Escrituras possuem esta propriedade sem recorrer a critérios externos? A própria doutrina da autopistia não é explicitamente ensinada na Escritura.
Implicações Teológicas e Epistemológicas
A Fragmentação Interpretativa
A história do protestantismo oferece evidência empírica das consequências práticas do sola scriptura. A multiplicação de denominações e interpretações divergentes sugere que o princípio, longe de fornecer clareza doutrinária, pode na verdade contribuir para a fragmentação teológica.
Se a Escritura fosse verdadeiramente suficiente e auto-interpretativa, seria razoável esperar maior convergência hermenêutica entre aqueles que aderem ao sola scriptura. A realidade histórica sugere o contrário.
A Alternativa Católica e Ortodoxa
As tradições católica e ortodoxa, embora enfrentando suas próprias tensões epistemológicas, mantêm pelo menos coerência interna ao reconhecer explicitamente múltiplas fontes complementares de autoridade: Escritura, Tradição e Magistério (no caso católico) ou Escritura e Tradição (no caso ortodoxo).
Estas posições evitam a contradição performativa do sola scriptura ao não reivindicar que sua própria metodologia epistemológica seja derivada exclusivamente da Escritura.
Conclusão
A análise crítica do sola scriptura revela contradições estruturais que comprometem fundamentalmente sua viabilidade como princípio epistemológico. O princípio incorre em contradição performativa ao estabelecer uma regra que não pode ser derivada de suas próprias premissas, configura um fundacionalismo mal estruturado ao carecer de base textual explícita, e enfrenta o testemunho contrário da própria Escritura, que reconhece suas limitações e a necessidade de autoridades interpretativas externas.
O paradoxo histórico da canonização – onde o próprio cânon bíblico depende da autoridade tradicional que o sola scriptura pretende rejeitar – representa talvez o golpe mais decisivo contra o princípio protestante.
Isso não implica necessariamente a falsidade do protestantismo como sistema teológico, mas sugere que seus fundamentos epistemológicos requerem reformulação substancial. Uma teologia protestante intelectualmente honesta precisaria reconhecer as limitações do sola scriptura e desenvolver uma epistemologia mais nuançada que leve em conta a complexidade das fontes de autoridade religiosa.
A busca pela verdade teológica, independentemente de compromissos confessionais, exige o reconhecimento rigoroso das limitações e contradições inerentes aos nossos sistemas epistemológicos. No caso do sola scriptura, essa honestidade intelectual revela um princípio que, por mais central que seja para a identidade protestante, não pode sustentar o peso epistemológico que tradicionalmente lhe foi atribuído.
-
 @ 5627e59c:d484729e
2025-06-11 21:14:37
@ 5627e59c:d484729e
2025-06-11 21:14:37Gelukkig zijn\ Is de waarde van mijn leven
Gewoon dankbaar te bestaan\ Geen mens heeft me ooit zo'n mooi cadeau gegeven
Dankbaar voor mijn sprankelen\ Mijn doen en voor mijn streven
Maar ook dat ik mag wankelen\ Mag vallen en mag beven
Want wat er ook gebeurt\ Het duurt steeds maar voor even
De wijsheid van mijn hart\ Voor alles is een reden
Het leven brengt mij deugd\ En soms brengt het me pijn
Maar nooit neemt het die vreugd\ De toelating om hier te zijn
De kans om iets te leren\ Te zien en om te groeien
Geeft mij kracht te accepteren\ Te omarmen en te bloeien
-
 @ 3eab247c:1d80aeed
2025-06-05 08:51:39
@ 3eab247c:1d80aeed
2025-06-05 08:51:39Global Metrics
Here are the top stats from the last period:
- Total Bitcoin-accepting merchants: 15,306 → 16,284
- Recently verified (1y): 7,540 → 7,803 (the rest of our dataset is slowly rotting; help us before it's too late!)
- Avg. days since last verification: 398 → 405 (more mappers, please)
- Merchants boosted: 22 (for a total of 4,325 days, someone is feeling generous)
- Comments posted: 34
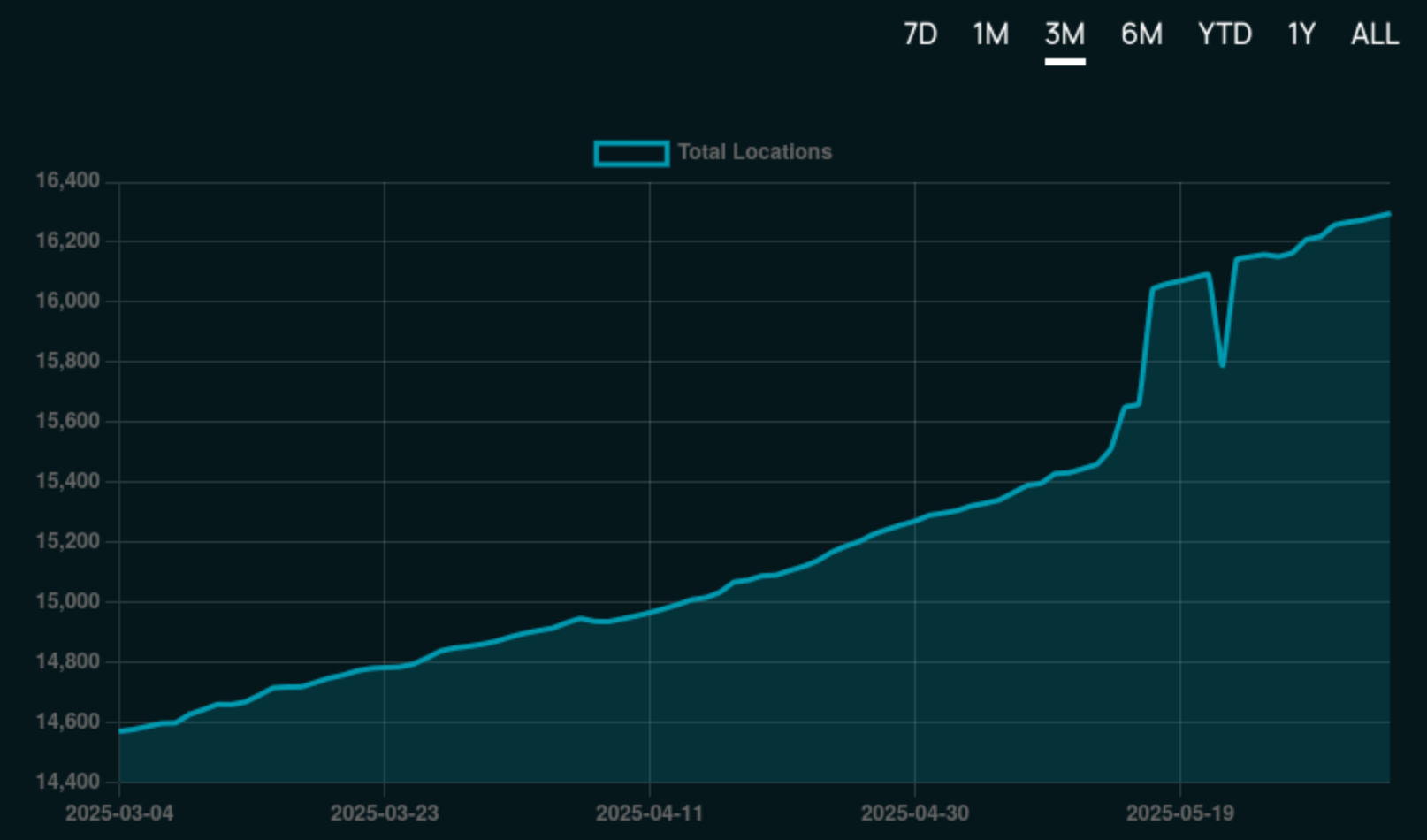
Find current stats over at the 👉 BTC Map Dashboard.
Merchant Adoption
Steak n’ Shake
The US 🇺🇸 is a massive country, yet its BTC Map footprint has been lagging relative to other countries ... that is until now!

In what came as a nice surprise to our Shadowy Supertaggers 🫠, the Steak ’n Shake chain began accepting Bitcoin payments across hundreds of its locations nationwide (with some international locations too).
According to CoinDesk, the rollout has been smooth, with users reporting seamless transactions powered by Speed.
This marks a significant step towards broader Bitcoin adoption in the US. Now to drop the capital gains tax on cheesburgers!
SPAR Switzerland
In other chain/franchise adoption news, the first SPAR supermarket in Switzerland 🇨🇭 to begin accepting Bitcoin was this one in Zug. It was quickly followed by this one in Rossrüti and this one in Kreuzlingen, in what is believed to be part of a wider roll-out plan within the country powered by DFX's Open CryptoPay.
That said, we believe the OG SPAR crown goes to SPAR City in Arnhem Bitcoin City!
New Features
Merchant Comments in the Web App
Web App users are now on par with Android users in that they can both see and make comments on merchants.
This is powered by our tweaked API that enables anyone to make a comment as long as they pass the satswall fee of 500 sats. This helps keep spam manageable and ensure quality comments.
And just in case you were wondering what the number count was on the merchant pins - yep, they're comments!
Here is an 👉 Example merchant page with comments.
Merchant Page Design Tweaks
To support the now trio of actions (Verify, Boost & Comment) on the merchant page, we've re-jigged the design a little to make things a little clearer.
What do you think?
Technical
Codebase Refactoring
Thanks to Hannes’s contributions, we’ve made progress in cleaning-up the Web App's codebase and completing long overdue maintenance. Whilst often thankless tasks, these caretaking activities help immensely with long-term maintainability enabling us to confidently build new features.
Auth System Upgrades
The old auth system was held together with duct tape and prayers, and we’re working on a more robust authentication system to support future public API access. Updates include:
- Password hashing
- Bearer token support
- Improved security practices
More enhancements are in progress and we'll update you in the next blog post.
Better API Documentation
Instead of relying on tribal knowledge, we're finally getting around to writing actual docs (with the help/hindrance of LLMs). The "move fast, break everything" era is over; now we move slightly slower and break slightly less. Progress!
Database Improvements
We use SQLite, which works well but it requires careful handling in async Rust environments. So now we're untangling this mess to avoid accidental blocking queries (and the ensuing dumpster fires).
Backup System Enhancements
BTC Map data comes in three layers of fragility:
- Merchants (backed up by OS - the big boys handle this)
- Non-OSM stuff (areas, users, etc. - currently stored on a napkin)
- External systems (Lightning node, submission tickets - pray to Satoshi)
We're now forcing two core members to backup everything, because redundancy is good.
Credits
Thanks to everyone who directly contributed to the project this period:
- Comino
- descubrebitcoin
- Hannes
- Igor Bubelov
- Nathan Day
- Rockedf
- Saunter
- SiriusBig
- vv01f
Support Us
There are many ways in which you can support us:
-
Become a Shadowy Supertagger and help maintain your local area or pitch-in with the never-ending global effort.
-
Consider a zapping this note or make a donation to the to the project here.
-
 @ 5627e59c:d484729e
2025-06-11 21:13:59
@ 5627e59c:d484729e
2025-06-11 21:13:59I am here too\ In the same space like you
In the same situation I'm in\ It's a matter of positioning
I cannot leave this place I'm in\ It was brought about\ By what's been happening
So please don't look at me\ For what I can or cannot do for you\ But look at what is happening for me\ And what is happening for you
Let's communicate\ Not orchestrate
Because there's something I wish to do\ And there's a place I wish to go to
And I'm sure that there is too\ In your heart a fire\ Known by only you
So let us listen, look and see\ For what's true for you\ And what's true for me
That we may act upon what's here\ In order for us both to take a step\ In the direction we wish to steer
-
 @ 32e18276:5c68e245
2025-06-03 14:45:17
@ 32e18276:5c68e245
2025-06-03 14:45:176 years ago I created some tools for working with peter todd's opentimestamps proof format. You can do some fun things like create plaintext and mini ots proofs. This short post is just a demo of what these tools do and how to use them.
What is OTS?
OpenTimestamps is a protocol for stamping information into bitcoin in a minimal way. It uses OP_RETURN outputs so that it has minimal impact on chain, and potentially millions of documents are stamped all at once with a merkle tree construction.
Examples
Here's the proof of the
ots.csource file getting stamped into the ots calendar merkle tree. We're simply printing the ots proof file here withotsprint:``` $ ./otsprint ots.c.ots
version 1 file_hash sha256 f76f0795ff37a24e566cd77d1996b64fab9c871a5928ab9389dfc3a128ec8296 append 2e9943d3833768bdb9a591f1d2735804 sha256 | --> append 2d82e7414811ecbf | sha256 | append a69d4f93e3e0f6c9b8321ce2cdd90decd34d260ea3f8b55e83d157ad398b7843 | sha256 | append ac0b5896401478eb6d88a408ec08b33fd303b574fb09b503f1ac1255b432d304 | sha256 | append 8aa9fd0245664c23d31d344243b4e8b0 | sha256 | prepend 414db5a1cd3a3e6668bf2dca9007e7c0fc5aa6dc71a2eab3afb51425c3acc472 | sha256 | append 5355b15d88d4dece45cddb7913f2c83d41e641e8c1d939dac4323671a4f8e197 | sha256 | append a2babd907ca513ab561ce3860e64a26b7df5de117f1f230bc8f1a248836f0c25 | sha256 | prepend 683f072f | append 2a4cdf9e9e04f2fd | attestation calendar https://alice.btc.calendar.opentimestamps.org | --> append 7c8764fcaba5ed5d | sha256 | prepend f7e1ada392247d3f3116a97d73fcf4c0994b5c22fff824736db46cd577b97151 | sha256 | append 3c43ac41e0281f1dbcd7e713eb1ffaec48c5e05af404bca2166cdc51966a921c | sha256 | append 07b18bd7f4a5dc72326416aa3c8628ca80c8d95d7b1a82202b90bc824974da13 | sha256 | append b4d641ab029e7d900e92261c2342c9c9 | sha256 | append 4968b89b02b534f33dc26882862d25cca8f0fa76be5b9d3a3b5e2d77690e022b | sha256 | append 48c54e30b3a9ec0e6339b88ed9d04b9b1065838596a4ec778cbfc0dfc0f8c781 | sha256 | prepend 683f072f | append 8b2b4beda36c18dc | attestation calendar https://bob.btc.calendar.opentimestamps.org | --> append baa878b42ef3e0d45b324cc3a39a247a | sha256 | prepend 4fb1bc663cd641ad18e5c73fb618de1ae3d28fb5c3c224b7f9888fd52feb09ec | sha256 | append 731329278830c9725497d70e9f5a02e4b2d9c73ff73560beb3a896a2f180fdbf | sha256 | append 689024a9d57ad5daad669f001316dd0fc690ac4520410f97a349b05a3f5d69cb | sha256 | append 69d42dcb650bb2a690f850c3f6e14e46c2b0831361bac9ec454818264b9102fd | sha256 | prepend 683f072f | append bab471ba32acd9c3 | attestation calendar https://btc.calendar.catallaxy.com append c3ccce274e2f9edfa354ec105cb1a749 sha256 append 6297b54e3ce4ba71ecb06bd5632fd8cbd50fe6427b6bfc53a0e462348cc48bab sha256 append c28f03545a2948bd0d8102c887241aff5d4f6cf1e0b16dfd8787bf45ca2ab93d sha256 prepend 683f072f append 7f3259e285891c8e attestation calendar https://finney.calendar.eternitywall.com ```
The tool can create a minimal version of the proofs:
``` $ ./otsmini ots.c.ots | ./otsmini -d | ./otsprint
version 1 file_hash sha256 f76f0795ff37a24e566cd77d1996b64fab9c871a5928ab9389dfc3a128ec8296 append 2e9943d3833768bdb9a591f1d2735804 sha256 append c3ccce274e2f9edfa354ec105cb1a749 sha256 append 6297b54e3ce4ba71ecb06bd5632fd8cbd50fe6427b6bfc53a0e462348cc48bab sha256 append c28f03545a2948bd0d8102c887241aff5d4f6cf1e0b16dfd8787bf45ca2ab93d sha256 prepend 683f072f append 7f3259e285891c8e attestation calendar https://finney.calendar.eternitywall.com ```
which can be shared on social media as a string:
5s1L3tTWoTfUDhB1MPLXE1rnajwUdUnt8pfjZfY1UWVWpWu5YhW3PGCWWoXwWBRJ16B8182kQgxnKyiJtGQgRoFNbDfBss19seDnco5sF9WrBt8jQW7BVVmTB5mmAPa8ryb5929w4xEm1aE7S3SGMFr9rUgkNNzhMg4VK6vZmNqDGYvvZxBtwDMs2PRJk7y6wL6aJmq6yoaWPvuxaik4qMp76ApXEufP6RnWdapqGGsKy7TNE6ZzWWz2VXbaEXGwgjrxqF8bMstZMdGo2VzpVuEyou can even do things like gpg-style plaintext proofs:
``` $ ./otsclear -e CONTRIBUTING.ots -----BEGIN OPENTIMESTAMPS MESSAGE-----
Email patches to William Casarin jb55@jb55.com
-----BEGIN OPENTIMESTAMPS PROOF-----
AE9wZW5UaW1lc3RhbXBzAABQcm9vZgC/ieLohOiSlAEILXj4GSagG6fRNnR+CHj9e/+Mdkp0w1us gV/5dmlX2NrwEDlcBMmQ723mI9sY9ALUlXoI//AQRXlCd716J60FudR+C78fkAjwIDnONJrj1udi NDxQQ8UJiS4ZWfprUxbvaIoBs4G+4u6kCPEEaD8Ft/AIeS/skaOtQRoAg9/jDS75DI4pKGh0dHBz Oi8vZmlubmV5LmNhbGVuZGFyLmV0ZXJuaXR5d2FsbC5jb23/8AhMLZVzYZMYqwjwEPKWanBNPZVm kqsAYV3LBbkI8CCfIVveDh/S8ykOH1NC6BKTerHoPojvj1OmjB2LYvdUbgjxBGg/BbbwCGoo3fi1 A7rjAIPf4w0u+QyOLi1odHRwczovL2FsaWNlLmJ0Yy5jYWxlbmRhci5vcGVudGltZXN0YW1wcy5v cmf/8Aik+VP+n3FhCwjwELfTdHAfYQNa49I3CYycFbkI8QRoPwW28AgCLn93967lIQCD3+MNLvkM jiwraHR0cHM6Ly9ib2IuYnRjLmNhbGVuZGFyLm9wZW50aW1lc3RhbXBzLm9yZ/AQ3bEwg7mjQyKR PykGgiJewAjwID5Q68dY4m+XogwTJx72ecQEe5lheCO1RnlcJSTFokyRCPEEaD8Ft/AIw1WWPe++ 8N4Ag9/jDS75DI4jImh0dHBzOi8vYnRjLmNhbGVuZGFyLmNhdGFsbGF4eS5jb20= -----END OPENTIMESTAMPS PROOF-----
$ ./otsclear -v <<<proof_string... # verify the proof string ```
I've never really shared these tools before, I just remembered about it today. Enjoy!
Try it out: https://github.com/jb55/ots-tools
-
 @ 0155373a:ba3e1bed
2025-01-09 00:01:05
@ 0155373a:ba3e1bed
2025-01-09 00:01:05Imagine an internet where you don’t need a big Internet Service Provider (ISP) to stay connected—an internet powered by the people, for the people. Decentralized internet is no longer a far-fetched idea; it's becoming a reality through community-driven networks. These networks rely on individuals within a community to act as "nodes," connecting their neighbors to the web and bypassing traditional ISPs.
What is Decentralized Internet?
Decentralized internet refers to a system where control over connectivity and access is distributed among individuals or local organizations rather than being concentrated in large ISPs. Instead of paying a single company for access, people in a community collaborate to build and maintain the network themselves.
How Does It Work?
- Mesh Networks: Each participant (or node) in the network connects to nearby nodes, creating a web of connectivity. This eliminates the need for a central ISP.
- Hardware: Nodes are powered by simple devices like routers or small computers running specialized software.
- Peer-to-Peer Sharing: Data flows through multiple nodes in the network, ensuring redundancy and reliability.
- Backbone Connection: Some networks may still rely on a single connection to a traditional ISP for broader internet access, but others can connect to decentralized backbone providers or satellites.
Benefits of Decentralized Internet
- Affordable Access: By cutting out traditional ISPs, communities can lower the cost of internet access.
- Empowerment: Communities gain control over their own connectivity and data, reducing reliance on corporations.
- Resilience: Decentralized networks are less prone to outages since they don’t depend on a single point of failure.
- Privacy: With less reliance on ISPs, there’s less risk of surveillance and data tracking.
- Inclusivity: Remote or underserved areas can establish connectivity without waiting for ISPs to expand their infrastructure.
Real-World Examples
- Guifi.net: A community network in Spain that has thousands of nodes providing internet to rural areas.
- NYC Mesh: A grassroots effort in New York City to create an affordable, community-owned internet.
- Althea: A project enabling neighbors to share internet bandwidth and earn income for participating in the network.
How to Get Started
- Educate Yourself: Research mesh network technologies like OpenWRT, LibreMesh, or BATMAN.
- Form a Group: Collaborate with neighbors or community organizations to pool resources.
- Get the Hardware: Invest in routers and antennas that support mesh networking.
- Set Up Nodes: Position nodes strategically to ensure strong connections across the community.
- Collaborate: Join forces with regional or global decentralized internet initiatives for support and knowledge sharing.
The Future of Decentralized Internet
As internet access becomes increasingly vital, decentralized networks present a way to bridge the digital divide and democratize connectivity. By building these systems, communities can take charge of their digital futures and ensure that no one is left behind.
Together, we can create an internet that is truly open, accessible, and resilient. The power lies in our hands—let’s connect, one node at a time.
-
 @ 6ad3e2a3:c90b7740
2025-06-11 08:29:54
@ 6ad3e2a3:c90b7740
2025-06-11 08:29:54Turning and turning in the widening gyre
The falcon cannot hear the falconer;
Things fall apart; the centre cannot hold;
Mere anarchy is loosed upon the world,
The blood-dimmed tide is loosed, and everywhere
The ceremony of innocence is drowned;
The best lack all conviction, while the worst
Are full of passionate intensity.
Surely some revelation is at hand;
Surely the Second Coming is at hand.
The Second Coming! Hardly are those words out
When a vast image out of Spiritus Mundi
Troubles my sight: somewhere in sands of the desert
A shape with lion body and the head of a man,
A gaze blank and pitiless as the sun,
Is moving its slow thighs, while all about it
Reel shadows of the indignant desert birds.
The darkness drops again; but now I know
That twenty centuries of stony sleep
Were vexed to nightmare by a rocking cradle,
And what rough beast, its hour come round at last,
Slouches towards Bethlehem to be born?
The Second Coming — W.B. Yeats
I don’t know what I want to write about today. There are a lot of converging currents coursing through my reality right now. I feel we’re in an interregnum of sorts between what was and what’s to come. I guess you could simply describe that as the present, something that has ever been the case. But this moment feels more intense like something big is dying and something else, God knows what, is on its way “to be born".
I exchanged emails recently with an old friend, and he sent me a link to a David Foster Wallace commencement speech entitled “This Is Water.” In it Wallace tells a joke of an old fish seeing two younger fish swimming by and asks them “How’s the water?” Later on one of the younger ones asks the other, “What is water?”
Wallace hanged himself a few years after the speech. Apparently he was unable to maintain the perspective he laid out in it which was that we can choose our attitude toward what we experience in any moment, no matter how much aversion we habitually associate with it. That the act of choosing equanimity constitutes the freedom we seek. That this freedom to choose is ever present, in fact the ability to direct our attention and consciousness is itself the water. And yet out of habit we are often oblivious to this most fundamental reality.
My friend’s email was in response to my description of the dissolution I see right now. Everything seems fake. The news, the governments, the edicts of reputationally bankrupt institutions zombying along as though the last five years never happened, like the proverbial emperor still purporting to rule though everyone can now see his pale, unsightly posterior.
Yes, the coffee shops are still open, people still go on vacation with their families. Let’s go to Paris, Rome, the Greek Isles! Let’s pretend everything is as we had imagined in the before times when our goals and aspirations seemed real, when the glitchy pixels in the matrix hadn’t yet revealed themselves so glaringly.
Maybe this was always the case. All our games were always professional wrestling, a scripted charade for which we willingly suspended disbelief. But like the roadrunner in the cartoon, we have since become aware we have run out of road, four steps beyond the cliff edge.
. . .
Wallace in his speech described such indignities as being stuck in traffic after a long day of work, or in a long grocery checkout line. The mind’s usual programs run, cursing everyone and everything around us. Instead of contemplating the miracle of human existence we feel only disgust and impatience. We want to finish with the run, the work, the obligatory hour so we can move on to something presumably more pleasant.
I can handle such day to day discomforts, but the overwhelming sense of dissolution is undermining the aims to which I had once attached meaning. I set up my life for freedom and prosperity, and now, just as I have my ducks in a row, there’s an imminent magnetic pole shift or a financial and social collapse that threatens to counterfeit my efforts.
It’s easy to opt out when you’re losing, to decry the injustice, unfairness and pointlessness of the game when you weren’t getting much from it anyway. When you’ve got nothing, you’ve got nothing to lose, to paraphrase Bob Dylan. But as a late bloomer wanting to sample the wine of the Gods at long last, it’s dispiriting in a different way, like saving up for a new car and seeing it stolen before you had a chance to drive it.
That’s the shallow version, distress at discovering just before getting the things I had always wanted I was actually playing not just the wrong game, but a false one. That I’m upset I can’t gratify my ego in the way I had hoped, that I can’t get the pat on the back I had craved because the back-patters decided to tear up the playing field just as I finally became a contender.
The deeper version is you only get better at the game through your own efforts to discover what’s true, your own self-mastery and access to a measure of wisdom. This process transforms your life from a tedious and difficult slog to a state of ease and flow. You are more connected, more in touch with yourself and the forces within. You can handle aversion, in fact voluntarily invite it at times to hone your mind and access your resourcefulness. You love your life and connect to the people in it. You have great hope and aspirations for the future. You believe in God, or the Tao or whatever force animates all things, you can navigate the world’s imperfections and do not want it to fall into chaos and disorder.
The task of remembering this during the run, the traffic jam or the grocery store checkout line is not so difficult. But would it be the same during periods of violence and resource scarcity where literal survival is at stake, the rules of which are set by biology and physics rather than the incentives of human society?
Yes, I’d rather be eating dinner at home than sitting in traffic, but I can appreciate that I’m able to sit comfortably in my climate controlled pod, listening to music while traversing these distances rather than foraging for food in the harsh wild. Yes, this old Portuguese lady is taking an eternity to get the groceries into her pushcart, but I can imagine how it is to be old and slow and still have to shop and eat, and it’s trivial to cut her some slack.
I’m not claiming I always have this perspective, but I surely am able to channel equanimity during the ordinary aversion that arises in one’s day to day life. I do this while running on the track, the aches and pains, the discomfort, the wanting to get it over with is a battle I fight every week by my own choosing. But imagine if instead of running 10 minute miles I was forced to do them in six. It’s not so easy to keep a calm, conscious mind while gasping for breath.
The truth is these calamities I imagine are not yet real, the asteroid has not yet hit, the economy not yet collapsed. I have never experienced the kind of hardship I dread. I am ever in the grocery line, the 10-minute mile run, the traffic jam, never the concentration camp or Mad Max-style post-apocalypse. Why not just deal with that when the time comes, if it ever comes? Why die a thousand deaths like the proverbial coward rather than the one required of the brave man?
I suppose it comes down to wanting to be prepared. There’s nothing you can do if an asteroid destroys the entire earth, but if your national government devolves into tyranny, you could get out before it’s too late. There’s the adage one should only concern oneself about the things one can control, but the rub is in deciding what’s in your power and of what to let go. It’s an easy out, per the adage, to narrow your locus of control to doing your job and paying your bills. You can too easily forget that which job you have, where you live, what preparations to make are also matters in which you have a choice.
Even if you believe a magnetic pole shift could spill the earth’s oceans across continents within the next few decades — I find this plausible — you could move to the mountains to get ahead even of that. A fatalist, non-questioning attitude can be a psychological salve in times of upheaval, but “salve” and "“slave” are but a typo apart.
. . .
When I was six someone broke into my house. I was still awake, and while pretending to be asleep, I heard him rummaging through my belongings, stealing an old Fisher Price turntable and a black and white TV. My father died four years later, and at 10, I remember thinking as the oldest boy in the house, it was now my responsibility to defend my family if anything like that, or worse, happened again. Of course, I wasn’t really capable of doing this, and I knew it, but I would have to try, futile as it might be.
I imagine that psychology has stayed with me as an adult — it’s up to me to see around corners, assess the various threats to me and my family, even if some of them are too daunting for any one individual. I could let it go, I suppose, it would probably even be healthy to do so. But there is a part of me that wonders whether people like me, people who feel this irrational responsibility, are the those who survive cataclysms and shocks. I surely am not the only one who feels this way and quite likely would not be especially effective given I don’t have engineering, outdoorsman or serious combat skills. But that hyper-vigilance toward and preparation for worse-case scenarios is something someone has to do, someone who would likely be selected for the role by the particular accidents of his upbringing.
. . .
There is another way to look at this, of course. The notion one ought to step up in the face of adverse circumstances, even extreme ones, is valid. But perhaps the best way to prepare is not endlessly to assess potential threats like some black ops CIA outfit, but to have a calm and detached mind. Should the signs appear, a poised and observant person would take action insofar as he is able. That you, having trained your attention away from default habits of comfort-seeking and dread and toward conscious observation, will do what’s required if and when the time comes. That you can trust yourself, and by that I mean trust in God, so to speak, to guide your awareness and actions for the most effective and adaptive response.
The Fourth Turning might well be upon us, indeed “the centre [may not] hold.” There is no guarantee your response will ensure you or those you love survive. There has never been such a guarantee for anyone, only the freedom to direct your attention, to choose your state of mind, to the extent you are capable, in the conditions that arise. To respond to the older fish that the water is okay, it’s pretty nice actually.
-
 @ 5627e59c:d484729e
2025-06-11 22:31:19
@ 5627e59c:d484729e
2025-06-11 22:31:19Enlightenment is just\ You catching up with time
Enlightenment is just\ Successfully processing your current situation\ And what it has to do with your past
Enlightenment is just\ Separating what you believe from what you know\ What is real from what is true
Enlightenment is living\ According to what you believe\ Because that's what is real for you\ Yet knowing it might turn out\ To be not really true
Enlightenment is giving thanks\ For being proven wrong
For how else would we grow\ The things we're conscious of\ The things that're real for us\ And the things we really know
How else would we align those things\ With the truth of what is (t)here\ Beyond\ That which we are
-
 @ 5627e59c:d484729e
2025-06-11 22:08:40
@ 5627e59c:d484729e
2025-06-11 22:08:40Machtig water\ Door velen bemind
Element van beweging\ Vormgever aan land\ Bondgenoot van wind
Voorkomer van comfort\ Toelater van rust
Machtig water\ Waar ik ook ga\ Ik weet dat jij de grond onder mijn voeten kust
-
 @ 5627e59c:d484729e
2025-06-11 22:27:30
@ 5627e59c:d484729e
2025-06-11 22:27:30Liefde\ De samenkomst\ Van zien en zijn
Leven\ Het zijn en zien\ Een vorm gekregen
Sterven\ Een deur\ Die vrijheid geeft van vorm
En eeuwig leven\ Aan liefde
-
 @ 65912a7a:5dc638bf
2024-12-08 05:33:02
@ 65912a7a:5dc638bf
2024-12-08 05:33:02Chef's notes
This is my late partner's award winning Cajun rice & beans recipe. It's an updated take on the traditional Cajun comfort food.
Chef Darin was a classically trained chef who spent 30+ years in the kitchen perfecting his recipes, and delivering authentic Cajun and Creole food to his patrons. This is a 5-star dish that will earn the respect of the most discerning Cajun afficionado. You won't be disappointed.
I suggest making this recipe exactly as directed the first time, and then make whatever adjustments you want for future batches. Also, don't cheap out on the Andouille. No Johnsonville or Hillshire Farms. Chef Aidelle's is a good choice, as is Silva's from Whole Foods. They cost a few extra bucks, but it's absolutely worth it.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 3 hours
- 🍽️ Servings: 12
Ingredients
- 16oz small red beans, dry
- 2 cups long grain white rice
- 14-16oz andouille sausage, sliced
- 8oz ham, cubed
- 1 large yellow onion, chopped
- 1 green bell pepper, chopped
- 2-3 stalks celery, chopped
- 2 tbsp garlic (12 cloves), minced
- 7 cups water
- ¼ cup olive oil
- 2 large bay leaves
- 1 tbsp parsley, dried
- 1 tsp thyme, dried
- 1 tsp Cajun seasoning
- ½ tsp cayenne pepper, dried
- ¼ tsp sage, rubbed
- 1½ tsp salt (more or less to taste)
Directions
- Soak beans in a large pot of water overnight.
- Heat oil in a large stockpot over medium heat. Cook onion, bell pepper, celery, garlic in olive oil for 3 to 4 minutes (until onion is translucent).
- Add beans, bay leaves, parsley, thyme, salt, MSG, Cajun seasoning, cayenne pepper, Sage, and water. Stir, bring to a boil, and then reduce heat to medium-low (btwn 2-3). Cover and simmer for 2½ hours.
- Remove bay leaves. Mash some of the beans. Stir Andouille and ham into beans, and simmer uncovered for an additional 30 minutes.
- Meanwhile, prepare the rice. Bring water and rice to a boil in a saucepan. Reduce heat, cover, and simmer for 20 minutes.
- Serve beans over steamed white rice.
-
 @ 5627e59c:d484729e
2025-06-11 21:23:42
@ 5627e59c:d484729e
2025-06-11 21:23:42Ik hou van de natuur en van verbinding maken\ Van diepgang en van mensen raken
Van creatief schrijven en programmeren\ Van speels bewegen en nieuwe dingen leren
Ik hou van leven en van dromen\ En van mensen zien\ Hun diepste wensen uit doen komen
-
 @ 7460b7fd:4fc4e74b
2025-06-12 05:43:56
@ 7460b7fd:4fc4e74b
2025-06-12 05:43:56引言
AI 技术的突飞猛进正重塑国家间博弈的格局。在可预见的未来,人工智能(AI)将推动国家实力的重新构建。OpenAI CEO Sam Altman 指出,未来几年内人类可能迎来“温和奇点”,大量工作将由AI取代blog.samaltman.com;Anthropic(Claude AI背后公司)的CEO则警告,美国失业率可能因AI而飙升至两位数甚至约20%finance.sina.com.cn。这意味着 AI 带来的生产力飞跃伴随严峻的社会阵痛,各国政府必须争夺AI制高点以掌控未来竞争优势——正如俄罗斯总统普京早在2017年所言:“谁掌握了AI,谁就能统治世界”axios.com。因此,中美两国均将AI视作国家战略高地,在这一动态博弈中展开竞逐。
然而,在AI集中赋能国家力量的同时,比特币作为决胜性变量悄然登上舞台。美国政界出现一种耐人寻味的观点:AI代表的是一种自上而下、可能强化集权的“左侧力量”,而比特币等去中心化创新属于“右侧力量”,可以对AI形成制衡eweek.com。2025年5月,美国副总统J.D.万斯(Vance)在比特币大会上的讲话就体现了这一点——他将AI称为左倾(共产主义式)的技术力量,而加密货币尤其是比特币被视为具有保守自由色彩的技术,能够平衡AI可能带来的集中化趋势eweek.com。
基于此背景,我们假设本轮技术周期中,比特币发挥了类“数字黄金”的作用并直接取代传统黄金地位:价格飞涨至38万美元以上,大批企业(如MicroStrategy)将比特币纳入资产负债表,视其为主权资产锚定的新基准。这一趋势下,美国加速将比特币和稳定币整合进官方金融体系,构建“美元+比特币”双层货币架构,通过稳定币扩散美元影响力并冲击他国法币insurancekhabar.cominsurancekhabar.com;反之,中国依然全面拒绝比特币(自2021年以来严禁加密交易和挖矿reuters.com),继续大举增持黄金作为储备,并押注自身央行数字货币。在这样的博弈版图下,比特币可能成为影响胜负的关键变量。
本文将基于博弈论视角构建动态多方博弈模型,以刻画上述格局中的关键问题:(1) AI推动下国家力量如何重构?为何各国必须争夺AI制高点?(2) 当AI导致国家权力高度集中时,比特币如何提供不可征收的资产锚定来形成网络化的反平衡力量?(3) 中美两种AI体制的博弈结构如何决定了中国在拒绝比特币条件下可能陷入失败,而美国则可借助“比特币+发钱”等政策缓和AI失业冲击?(4) 个体如何凭借比特币对抗“AI威权”,促使世界走向网络化的稳定新结构,而非陷入新冷战?文章将分为引言、模型结构、均衡演化路径和结论四部分,为高认知读者提供一个严谨而富有现实感的战略研判框架。
模型结构
**参与方与策略定义:**本博弈模型涵盖三个主要行动方:(a)国家行为体(主要是中、美两国),(b)企业级主权力量(大型科技企业、持有比特币的大型公司等),以及(c)普通个体/公民与分布式网络。这是一个多维博弈:既包括AI竞赛这一技术军备维度,也包括以比特币为代表的新型金融资产维度,以及国家与个体间权力再平衡维度。
-
国家(中、美)在AI领域的竞争:中美视AI为获取综合国力的战略高地,均有强烈动机投入巨资抢占领先位置。AI具有明显的赢家通吃效应,领先者可能在军事、经济、信息控制等方面获得压倒性优势axios.comeconomictimes.indiatimes.com。正如普京和Palantir公司CEO的判断,AI竞赛极可能“只有一个赢家”,要么美国胜出要么中国胜出axios.comeconomictimes.indiatimes.com。因此在博弈模型中,争夺AI主导权是双方的首要策略选择,每一方都不能放松——这类似于囚徒困境中的军备竞赛:任何一方停止努力都可能被另一方弯道超车从而“称霸世界”。
-
AI导致的权力集中与国家内部博弈:AI大规模替代人类劳动将显著提高生产率,同时造成结构性失业和财富向掌握AI技术的精英/资本高度集中blog.samaltman.comfinance.sina.com.cn。这会强化国家机器和大资本对社会的控制力(例如利用AI进行大规模监控、无人武器等),使国家权力相对个体更为集中。博弈模型中,各国政府面临内部稳定博弈:如何安抚因AI失业而不满的公众,同时继续巩固自身执政联盟。在民主国家(如美国),执政联盟规模大(需要赢得广大选民支持),政府倾向于提供公共物品或直接发放补贴以维持民众满意度blog.devtang.comblog.devtang.com。例如,Altman就预测未来社会因为AI冲击会出现“新政策创想”和渐进式的新社会契约blog.samaltman.com——这暗示可能出台普惠式补贴/UBI等政策,即所谓“发钱政策”,以缓和失业阵痛。而在威权体制(如中国),执政“致胜联盟”小而精英化blog.devtang.com,“核心支持者”的利益优先于大众利益blog.devtang.com。此时政府可能更倾向通过强化控制和定向利益输送维持稳定,而不是普惠发钱。一旦由于财政收入锐减或经济失速导致无法满足联盟利益,政权稳定将受到威胁blog.devtang.com。因此在模型中,不同体制下政府选择的内部应对策略截然不同:民主政权偏好通过财富再分配稳住大联盟,威权政权则偏好强化控制、保障小联盟利益。但AI带来的挑战规模空前,威权政府若无足够“弹药”(财政盈余或新型资产)去收买人心,就可能出现“致胜联盟”维持困难,即财政失衡引发政权不稳blog.devtang.com。
-
**货币金融维度的博弈:**这是模型的第二维——围绕全球储备资产和货币体系的新博弈。假设情景下,美国选择拥抱比特币和稳定币,将其纳入国家金融战略,而中国选择拒绝比特币坚守黄金。那么各自的策略及收益如下:
-
美国策略:整合比特币+美元,推广稳定币。具体包括:允许并鼓励机构大量持有比特币,将其视为“数字黄金”储备;政府通过立法完善稳定币监管(如推出《GENIUS稳定币法案》等)以扩大美元稳定币的全球使用nevadacurrent.comnevadacurrent.com;甚至总统令建立国家比特币战略储备reuters.com。预期收益:一方面,比特币价格飙升带动美国持有者财富上升,MicroStrategy等公司已尝到甜头,资产负债表上囤积了价值400亿美金以上的比特币finance.sina.com.cn。华尔街分析师预测,比特币有望在未来十年最终取代黄金成为首要价值存储,finance.sina.com.cn甚至特朗普政府内部有人倡议卖出黄金储备改买比特币finance.sina.com.cn。另一方面,美元稳定币的大规模推广巩固了美元霸权:全球用户在链上广泛使用美元稳定币,相当于变相扩大美元的影响圈insurancekhabar.cominsurancekhabar.com。稳定币背后的储备主要是美国国债,这意味着稳定币越多,美国国债需求越大,从而压低美国融资成本insurancekhabar.cominsurancekhabar.com。有专家指出,美国大力推动加密货币和稳定币,是看中了它们可以成为经济武器:“稳定币将取代外国政府,成为美债最大买家”insurancekhabar.com。这为美国在AI时代实施大规模财政转移(如发放失业补贴、科技红利)提供了弹药:全球对美元资产的需求使美联储有更大余地印钞而不致本币崩溃。简言之,美国整合比特币+稳定币体系,可强化其金融主导权和财政灵活性,既能对外输出通胀、打击他国法币,又能对内从容应对AI失业的救济开支。
-
中国策略:拒绝比特币,囤积黄金+推数字人民币。中国自2017-2021年对加密货币连出重拳(取缔交易所、禁止矿业、封锁境内交易)reuters.com,“宁要区块链,不要加密币”的政策表明其决心彻底隔绝比特币等去中心化货币。取而代之,中国持续加码黄金储备:据央行公告,中国已连续多月增持黄金,官方储备突破2000吨并仍在增长中(此举在地缘政治不确定性下尤为明显)。同时,中国大力推广央行数字货币(数字人民币),试图在国内实现对货币流通的全面可控,并谋求在国际贸易中推动人民币结算。预期影响:由于拒绝比特币,中国希望通过黄金提升本币信用,通过数字人民币强化资本管制和货币政策独立性。然而此策略的风险在于,若比特币在全球范围内取代黄金地位,中国将错失这一新型储备资产红利。当美国等推动比特币升值并将其金融化时,中国手中的黄金可能相对贬值或增长滞后。此外,稳定币对他国法币的冲击也波及人民币:虽然中国严格限制境内稳定币流通,但在跨境贸易和地下金融中,美元稳定币和比特币可能绕过管制,被企业和富裕阶层用于对冲人民币贬值或资本外逃。这相当于一个金融围堵:美国利用数字货币在全球吸纳流动性,削弱人民币在“一带一路”等领域的渗透。中国若坚持封锁比特币和民间加密交易,可能面临“两难”:要么严厉执法资本管制、牺牲部分经济自由和国际化进程;要么在全球数字经济中逐渐边缘化,被排除在新金融网络之外。总之,中国此策略短期内保障了国家对金融系统的控制权,但长期存在与世界脱节、储备资产单一(黄金)的隐患。
-
个体与网络力量的崛起:第三个维度的博弈发生在国家 vs. 个体/分布式网络之间。AI和加密技术的发展,使得一批技术公司和个人获得了前所未有的自主力量——他们可以同时获取AI赋能和持有不可被国家任意剥夺的财富(比特币)。在模型中,这些分散的个人/企业构成一张跨国网络,他们的策略是利用技术和资本的流动性在全球范围内“择优而居”。如果某国政策有利(如美国欢迎加密创新、提供完善法律保障),人才和资金就会流向该国;反之,若政策高压(如中国禁止民间持币、严格审查AI应用),那么这些人才与资金可以通过数字途径逃逸(capital flight)。比特币在其中充当关键的**“退出票”(exit option):它具有强抗审查和无法被没收的属性,保障了私人财产的自由转移nymag.com。“比特币无法被当局像没收黄金那样没收,无法像银行账户那样随意冻结,亦无法像法币那样被央行肆意贬值或被独裁者通过资本管制任意阻断”nymag.com。这一属性意味着个人第一次拥有了对抗国家财权的有效工具**。在博弈模型中,个体玩家的存在使国家行为体不再是单纯的统一行动者——国家内部会因为个人/企业的选择而出现博弈反馈:如果政策过于损害个人利益,他们有能力通过比特币等手段规避,从而削弱国家政策效果。这相当于在国家与国家的对局中,引入了一个“平衡器”——全球网络化个人势力。他们的目标并非争夺领土或传统主权,而是在寻求“个体主权”最大化:自由拥有财富、自由迁徙和创新、不受制于单一政府。这股力量在AI时代尤为重要,因为AI集中化倾向可以被这种分散网络部分抵消。例如,AI赋能下的个人黑客、科技创业者可以不依赖国家资本也开发出强大模型;若遭遇压制,他们可携带比特币远走他国继续创业。博弈的结果将取决于国家能否与这股网络力量共存,以及在多大程度上满足个人对自由与财富安全的需求。
均衡演化路径
基于上述模型结构,我们推演中美博弈及全球格局的动态演化路径。博弈分阶段进行,各阶段的策略互动将把体系推向不同的均衡态。
阶段1:AI军备竞赛与金融布局(现在至近期)。这一阶段中美都全力投入AI研发,以获取先发优势。双方持续加大对半导体、算法和人才的投入,并在国际规则上博弈(如出口管制、人才签证等)。博弈特征类似“军备竞赛”:任何单方面的松懈都会导致对手大幅领先,因此均衡结果是双方都倾向投入高强度资源,直至边际成本难以承受。与此同时,双方在金融领域开始布局各自阵地:美国在2024-2025年间通过了一系列亲加密政策——国会推进稳定币立法以合法化美元稳定币nevadacurrent.com,“数字资产市场结构”法案呼之欲出;行政层面,特朗普政府下令创建国家比特币储备,将执法机构此前持有或没收的比特币纳入战略储备reuters.com。这些举措表明美国意在将比特币作为国家金融武器的一部分来运用。相应地,比特币市场开始出现质变:主流机构投资者蜂拥而入,现货比特币ETF获得批准且规模激增,短短时间累积数千亿美元资金finance.sina.com.cn。比特币价格屡创新高并稳定在六位数美元以上,朝着20万、30万甚至更高的目标迈进finance.sina.com.cn。企业层面,MicroStrategy等公司持续买入,比特币在一些公司资产负债表中的地位堪比现金储备finance.sina.com.cn。美国的这一系列动作,使其在**“新数字货币冷战”**中占得先机:美元+比特币组合开始对全球产生强磁吸效应。
反观中国,同期则进入防御性应对状态。面对美国的金融攻势,中国加快了增储黄金和数字人民币试点的步伐,以图筑牢本国金融壁垒。中国人民银行连续数月购入黄金,insurancekhabar.com黄金储备量创历史新高;数字人民币从国内零售场景逐步推广到跨境贸易结算试验,通过区域性协议在部分周边国家开展本币结算合作,以降低对SWIFT美元体系的依赖。同时,中国严格执行对加密活动的严打,关停剩余的OTC交易渠道,宣示绝不让比特币等威胁人民币的货币主权。此阶段的结局是:两个平行的货币体系开始成形——一个是美元主导并吸纳比特币、稳定币的新体系;一个是人民币主导、辅之以黄金背书的封闭体系。
阶段2:AI红利与冲击释放(中期,未来5-10年)。随着AGI雏形和通用机器人逐步出现,人类劳动大规模被替代的效应开始凸显blog.samaltman.com。在美国,AI带来的效率红利令GDP和企业盈利大幅增长,但“技术失业”也引发社会不安。finance.sina.com.cn美国失业率假设攀升至15-20%,尤其白领和服务业岗位大量消失。幸运的是,由于美国及时进行了金融上的前瞻部署,此时财政手段具备充足火力来应对危机。一方面,比特币的暴涨和广泛持有为部分中产和企业带来了资产增值——例如,有投资比特币的家庭财富逆势上涨,部分失业者因持有数字资产而有缓冲储备。政府则可以选择性对这些资产增值征税或者发行主权数字货币购买比特币,实现财政增盈。另一方面,更重要的是**美联储和财政部得以大规模“直升机撒钱”**而不致引发债务危机,这是美元稳定币全球盛行带来的特权insurancekhabar.com。由于全球大量资金以购买美国国债作为稳定币储备,insurancekhabar.com美国政府可以在通胀可控范围内发行货币、扩大赤字以资助全民基本收入或就业项目。比特币在美国的官方接受度也使发钱政策更容易实施:政府完全可以将数字美元直接发送到每个公民的手机钱包(甚至部分用比特币形式发放科技红利)。公众虽然对AI取代工作有所焦虑,但在政府真金白银的兜底下,基本生活有保障,社会动荡被控制在最低程度。这印证了Altman的预言:AI时代世界将更富裕,因此能够“认真考虑以往不可能的新政策”blog.samaltman.com。美国通过比特币财富效应和激进财政政策,初步缓解了AI带来的内部矛盾,其民主制度下“大联盟”的稳定性得以维持。
与之对照,中国在中期则可能面临更严峻的平衡难题。AI同样推动了中国经济的效率,但也使大量制造业和服务业劳动力冗余化。由于缺乏比特币等新财富渠道,大部分民众财富并未随技术进步而增长,反而因失业潮而缩水。民间投资渠道狭窄(楼市低迷、股市震荡),社会的不满情绪上升。此时中国政府进退维谷:若执行大规模刺激或全民补贴,一方面没有储备的“数字资产红利”可用,只能动用巨额财政支出;但中国无法像美国那样让全球来分担本币超发的成本(人民币不是主要储备货币,超发会直接冲击汇率和通胀)。若强行印钞发钱,则可能引发人民币贬值和资本加速外逃,削弱执政信用。历史上来看,威权政府在财政吃紧时维系统治的成本急剧上升,很容易因为买不到执政联盟的忠诚而倒台blog.devtang.com。中国政府当然也深谙此理,因此更可能选择收紧财政、强化管控的方式渡过难关:例如动用警察力量维稳、加强舆论审查来减缓不满爆发。但这样的高压策略长期看难以为继,而且会进一步吓跑高端人才和资本。尤其在比特币价格连创新高的背景下,中国富裕阶层和企业势必更加渴望配置此类全球性资产来保值。一些人会通过地下渠道购入比特币和稳定币,然后设法转移资产出境(哪怕非法也在所不惜)reuters.comsciencedirect.com。这反过来又加剧了中国国内资本外流和财政紧张,形成负反馈。可以预见,如果中国仍拒绝比特币,其金融体系可能出现“致胜联盟”式失衡:政府要么牺牲外汇储备和黄金储备来稳住人民币、安抚利益集团,要么被迫局部放开对加密资产的管制以引回资金,无论哪种都意味着其此前的强硬策略难以持续。
阶段3:博弈格局转变与网络化均衡(远期,10年及以后)。经历中期震荡后,全球博弈格局将出现质变,进入新的均衡态。基于前述趋势,可以预见两种截然不同的结局:
-
**美国阵营的胜出与中国策略调整:**如果美国在AI和金融两条战线上都占据了优势,那么远期均衡将体现为美国引领的“新技术-金融秩序”。届时比特币可能已稳固地成为全球储备资产的一极(类似数字黄金),各国央行和主权基金纷纷将其纳入资产配置。美元则通过稳定币牢牢占据全球结算和流动性中介地位。在AI方面,美国凭借开放创新环境汇聚了全球顶尖人才,实现技术持续领先。反观中国,若在中期尝到了拒绝比特币的苦果(经济停滞、财政吃紧、人才外逃),理性的策略调整将是不得不转向美国模式,以免彻底边缘化。这可能包括:逐步放松对加密资产的管制,甚至尝试推出国家主导的加密货币ETF,引导国有机构低调持有比特币以分享其增值;在外交上寻求加入由美国主导的数字货币国际框架,避免本国企业被排除在新贸易结算体系外。此外,中国会继续依靠其黄金储备试图为人民币背书,但如果比特币市值远超黄金且更受年轻一代青睐,黄金的锚定作用将大打折扣。可以说,中国此时面临类似19世纪末“银本位帝国”的困境——清朝因坚守白银而被新兴的金本位体系边缘化insurancekhabar.com;21世纪的中国若固守黄金标准而忽视比特币潮流,恐重蹈历史覆辙。有识之士将呼吁“中国不能错失数字黄金机遇”,倒逼政策松动。最终的均衡可能是:美国及其盟友掌握了AI与金融话语权,而中国被迫加入由比特币和美元构成的新体系,放弃之前的强硬抵制立场。这一结果虽非中国最初意愿,但总比被彻底孤立要好,犹如冷战后期苏联被迫融入布雷顿森林体系一样,是一种策略收缩下的妥协均衡。
-
网络化多中心格局的形成:无论中美博弈如何,此阶段一个更深刻的趋势是全球网络化权力结构的浮现。随着比特币深入人心和应用普及,每个个人和企业都相当于握有自己的“微型主权财富”。正如《主权个体》一书预言的那样,信息时代将削弱民族国家发动战争和征税的能力,取而代之的是个人在全球范围内自由组合、以市场方式选择治理的时代sites.northwestern.edu。当比特币成为“无法征收的资产”标配后,各国政府要汲取民财将更为困难,战争筹资也不再容易sites.northwestern.edu。这是因为:一旦某国大举加税或准备战时管制,资本和人才可以更快捷地逃往别处,政府很难像过去那样通过强制手段动员全国资源。一些论者甚至指出,“在一个基于比特币的社会里,政府若想发动战争,可能不得不向公民众筹军费”reddit.com——这无疑极大提高了发动战争的政治难度。在AI高度发达且武器智能化的背景下,这种网络化制衡力量尤为宝贵,它防止了超级大国因为掌控AI利器而为所欲为。举例来说,如果没有个人财产自由这一“安全阀”,那么拥有强大AI武器和监控系统的国家很可能毫无顾忌地倾压式统治甚至对外侵略;但有了比特币,精英和企业可以用脚投票,拒绝配合极权和战争企图——正如有人所说的,“你无法征税/掠夺那些你无法抓住的人”newstatesman.com。最终,全球可能形成一种“冷战阻止机制”:各国不敢轻易走向新冷战或热战,因为稍有风吹草动,资金和人才就会通过去中心网络逃逸,使战争难以为继。
因此,在远期均衡下,我们将看到国家、企业和个人形成一个互动博弈的多中心体系:国家不再拥有对经济和技术的单方面支配,个人与企业通过持有数字资产和掌握AI技术获得了谈判筹码,各方被迫合作共生而非你死我活。这并非传统意义上的“权力均衡”,而更像是一种动态的网络均衡——权力在不同层级和节点上分散,任何一方试图完全主导都会引发系统中其他节点的自动调节与抵制,最终回归稳态。
结论
综上所述,AI时代的中美博弈结构展现出“技术军备竞赛+金融货币博弈+内部治理较量”三位一体的格局。美国通过在AI和比特币两方面同时发力,形成“左手AI、右手比特币”的双拳策略,既争取了AI制高点,又利用比特币这一“不受征服的资产”稳固了内部与外部的平衡nymag.com。反观中国,倘若固守传统思维拒绝比特币,则在AI导致集权加深的同时失去了由比特币提供的网络化反平衡力量,极可能重现“致胜联盟”财政失衡和战略被动的局面。正如博弈模型分析所示,中国若不及时调整,将因无法有效吸纳AI红利、又无法借助新金融工具缓冲冲击,而陷入内外交困的困境;相反,美国通过比特币+发钱政策有望缓解技术失业压力,在维护社会稳定的同时进一步增强对外金融攻势,实现以较小代价度过转型阵痛。
更深一层的洞见在于:比特币作为“无法征收的资产”(unconfiscatable asset),为无数个人和企业提供了在AI强权面前自我保护和抗衡的手段nymag.com。它让个体可以自由掌控自己创造的AI收益和财富,不必担心随时被征用或剥夺,从而在国家与国家的博弈中引入了一个独立稳定器。这个稳定器确保了国家不敢轻启战争或极端压榨,否则公民的财富和才能将自动逃逸,令其损失巨大。这种机制有望阻止人类社会滑入新一轮两极对抗或热战冲突,因为权力过度集中将引发去中心网络的本能反制。取而代之,人类可能走向一种“网络化稳定结构”:在这个结构中,AI带来的繁荣由各国共享,但没有任何一方能垄断;比特币作为全球共同的价值锚和信任媒介,保障了个人基本财产权,从而软化了国家机器的锋芒。
对于高认知的决策者而言,这一博弈分析传递出明确的战略启示:拥抱比特币等去中心化创新,实际上是在为本国社会安装安全阀,避免因AI高度集中而产生体制性风险;同时,这也是在国际博弈中抢占未来金融体系的话语权。在AI与国家力量此消彼长的新时代,比特币扮演了关键的“平衡木”角色:它连接着国家与国家、国家与个人,确保没有人可以轻易掀翻整艘人类文明之舟。唯有善用这一新型稳定器,引导世界朝开放协作而非封闭对立演化,我们才能把握AI奇点带来的机遇,避免重蹈冷战或冲突的历史覆辙。人类社会或许将凭借这种网络化的平衡,在巨变中找到新的稳定与新秩序sites.northwestern.edu——在AI的洪流中乘风破浪,而非沉舟觅踪。
参考资料:
-
Sam Altman,《温和奇点》博文对AI发展的展望blog.samaltman.com
-
Anthropic CEO Dario Amodei,关于AI导致失业的警告finance.sina.com.cn
-
J.D. Vance 副总统在Bitcoin 2025大会讲话摘要,对AI和比特币的定位eweek.comreuters.com
-
Bernstein投行报告:比特币取代黄金的十年预测,MicroStrategy持币策略等finance.sina.com.cnfinance.sina.com.cn
-
Nevada Current对Bitcoin大会的报道:稳定币立法(GENIUS法案)进展nevadacurrent.comnevadacurrent.com
-
Reuters:特朗普行政令建立国家比特币储备、美国拥抱比特币对抗中国reuters.comreuters.com
-
Insurance Khabar:Deepak Garg 关于美中金融战与稳定币武器化的分析insurancekhabar.cominsurancekhabar.com
-
《独裁者手册》理论:致胜联盟与政权稳定的关系blog.devtang.com
-
New York Magazine:《比特币无法被没收,不能冻结,不能由央行贬值》nymag.com
-
《主权个体》观点:信息技术削弱国家征税和战争能力sites.northwestern.edu
-
-
 @ 472f440f:5669301e
2025-06-11 04:37:33
@ 472f440f:5669301e
2025-06-11 04:37:33Marty's Bent
Sup, freaks? Your Uncle Marty did a little vibe coding a couple months ago and that vibe coding project has turned into an actual product that is live in the Google Chrome web store and will soon to be live in the Firefox add-on store as well. It's called Opportunity Cost and it is an extension that enables you to price the internet in Bitcoin.
Opportunity Cost – See Prices in Bitcoin Instantly
Check it out!
This whole process has been extremely rewarding to me for many reasons. The first of which is that I've had many ideas in the past to launch a product focused on bitcoin education that simply never left my brain because I never felt comfortable paying a developer to go out and build a product that I wasn't sure would ultimately get product market fit.
Due to the advancements of AI, particularly ChatGPT and Replit, I was able to spend a few hours on a Saturday vibe coding a prototype for Opportunity Cost. It worked. I side loaded it into Chrome and Firefox, tested it out for a few days and decided, "Hey, I think this is something that's worthwhile and should be built."
Backtracking just a little bit, the initial idea for this app was to create an AR application that would enable you to take pictures of goods in the real world and have their prices automatically converted to bitcoin so that you could weigh the opportunity cost of whether or not you actually wanted to buy that good or decide to save in bitcoin instead. With the help of Justin Moon from the Human Rights Foundation and Anthony Ronning from OpenSecret and Maple AI, I was pointed in the right direction of vibe coding tools I could use to build a simple MVP. I took their advice, built the MVP, and demoed it at the Bitcoin Park Austin weekly AI meetup in mid-April.
The next week, I was talking with a friend, Luke Thomas, about the idea and during our conversation he made a simple quip, "You should make a Chrome extension. I really want a Chrome extension that does this." And that's what sent me down the vibe coding rabbit hole that Saturday which led to the prototype.
After I was comfortable with and confident in the prototype, I found a young hungry developer by the name of Moses on Nostr, I reached out to him, told him my idea, showed him the prototype and asked if he thought he could finish the application for me. He luckily agreed to do so and within a couple of weeks we had a fully functioning app that was officially launched today. We're about 12 hours into the launch and I must say that I'm pleasantly surprised with the reception from the broader Bitcoin community. It seems like something that people are happy exists and I feel extremely happy that people see some value in this particular application.
Now that you have the backstory, let's get into why I think something like Opportunity Cost should exist. As someone who's been writing a newsletter and producing podcasts about bitcoin for eight years in an attempt to educate individuals from around the world about what bitcoin is, why it's important, and how they can leverage it, I've become convinced that a lot of the work that needs to be done still exists at the top of the funnel. You can scream at people. You can grab them by the shoulders. You can shake them. You can remind them at Thanksgiving that if they had listened to your advice during any Thanksgiving in the previous years they would be better off financially. But at the end of the day most people don't listen. They need to see things. Seeing things for yourself is a much more effective teaching mechanism than be lectured to by someone else.
My hope with Opportunity Cost is that it catches the eye of some bitcoin skeptics or individuals who may be on the cusp of falling down the bitcoin rabbit hole and they see the extension as a way to dip their toes into bitcoin to get a better understanding of the world by pricing the goods and services they purchase on a day-to-day month-to-month and year-to-year basis in bitcoin without having to download a wallet or set up an exchange account. The tippy top of the bitcoin marketing funnel.
That is not all though. I think Opportunity Cost can serve individuals at both ends of the funnel. That's why it's pretty exciting to me. It's as valuable to the person who is bitcoin curious and looking to get a better understanding as it is to the hardcore bitcoiner living on a bitcoin standard who is trying to get access to better tools that enable him to get a better grasp of their spending in bitcoin terms.
Lastly, after playing around with it for a few days after I built the prototype, I realized that it has incredible memetic potential. Being able to take a screenshot of goods that people are buying on a day-to-day basis, pricing them in bitcoin and then sharing them on social media is very powerful. Everything from houses to junk items on Amazon to the salaries of pro athletes to your everyday necessities. Seeing the value of those things in bitcoin really makes you think.
One day while I was testing the app, I tried to see how quickly I could find goods on the internet that cumulatively eclipsed the 21 million supply cap limit of bitcoin. To my surprise, even though I've been in bitcoin for 12 years now, it did not take me that long. The opportunity cost of everything I buy on a day-to-day basis becomes very clear when using the extension. What's even clearer is the fact that Bitcoin is completely mispriced at current levels. There is so much winning ahead of us.
Also, it's probably important to note that the extension is open source. You can check out our GitHub page here. Submit pull requests. Suggest changes to the app.
We've also tried to make Opportunity Cost as privacy preserving as possible. Everything within the extension happens in your browser. The only external data that we're providing is the bitcoin to fiat price conversion at any given point in time. We're not data harvesting the web pages you're browsing or the items you're looking at. We're not collecting data and sending it to third party marketers. We want to align ourselves with the open and permissionless nature of bitcoin while also preserving our users' privacy. We're not trying to monetize this in that way. Though, I will say that I'm thinking of ways to monetize Opportunity Cost if it does gain significant traction, but I promise it will be in a way that respects your privacy and is as unobtrusive as possible. We'll see how it goes.
Thank you for coming to my TED talk. Please download and use the extension. Let us know what you think.
Headlines of the Day
Saylor Says Bitcoin Is Perfect Money to Jordan Peterson - via X
Trump Won't Sell Tesla Despite Musk-Bessent Heated Exchange - via X
Bitcoin Gains Traction in Kenya's Largest Slum Kibera - via X
Get our new STACK SATS hat - via tftcmerch.io
Bitcoin’s Next Parabolic Move: Could Liquidity Lead the Way?
Is bitcoin’s next parabolic move starting? Global liquidity and business cycle indicators suggest it may be.
Read the latest report from Unchained and TechDev, analyzing how global M2 liquidity and the copper/gold ratio—two historically reliable macro indicators—are aligning once again to signal that a new bitcoin bull market may soon begin.
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
East Coast aesthetics over everything.
*Download our free browser extension, Opportunity Cost: *<<https://www.opportunitycost.app/>> start thinking in SATS today.
*Get this newsletter sent to your inbox daily: *https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ 5627e59c:d484729e
2025-06-11 18:42:09
@ 5627e59c:d484729e
2025-06-11 18:42:09Jaren tellen\ Hoeft voor mij niet
Verhalen vertellen\ Over geluk en verdriet
Een warme haven\ Veilig en fijn
Dromen voorgedragen\ Onschuldig en rein
Momenten ervaard, geleerd\ En geïntegreerd
Ideeën, geloven en gevoelens\ Gevormd en gecreëerd
Zonder eind of echt begin\ Vallen, groeien, leren, stoeien
Een gezin in een gezin met een gezin erin\ Gezind gericht blijft liefde vloeien
-
 @ 8d34bd24:414be32b
2025-06-11 03:46:43
@ 8d34bd24:414be32b
2025-06-11 03:46:43So often Christians focus on God’s love and ignore His judgment. They tell people they need to be saved, but leave out from what they need to be saved. Fifty or a hundred years ago, almost every American knew the basics of the Bible, what sin is, what the judgment of Hell is, and that the God of the Bible is our Creator. Today, most people in America and the world know very little of that. Phrases like, “Trust Jesus and be saved,” mean very little. The person you are talking to may be silently thinking, “Who is Jesus? Why should I trust Him? What do I need to be saved from?”
Most Christians, especially from Evangelical circles, have been steeped in the phrase “Be saved,” but how many have thought carefully about from what they are being saved? If we have trouble answering, “from what?”, how can we explain it to those who don’t know Jesus?
But God demonstrates His own love toward us, in that while we were yet sinners, Christ died for us. Much more then, having now been justified by His blood, we shall be saved from the wrath of God through Him. For if while we were enemies we were reconciled to God through the death of His Son, much more, having been reconciled, we shall be saved by His life. And not only this, but we also exult in God through our Lord Jesus Christ, through whom we have now received the reconciliation. (Romans 5:8-11) {emphasis mine}
Primarily we are saved “from the wrath of God.” We are also reconciled which saves us from separation from God.
We are also told that we are rescued [saved] “from the wrath to come.”
And to wait for His Son from heaven, whom He raised from the dead, that is Jesus, who rescues us from the wrath to come. (1 Thessalonians 1:10) {emphasis mine}
Then one might ask, “What right does God have to tell me what to do and to get mad at me?”
In the beginning was the Word, and the Word was with God, and the Word was God. He was in the beginning with God. All things came into being through Him, and apart from Him nothing came into being that has come into being. In Him was life, and the life was the Light of men. The Light shines in the darkness, and the darkness did not comprehend it. (John 1:1-5) {emphasis mine}
Why does God get to set the rules? Because He made all things. The Creator gets to set the rules for His creation. It isn’t just ‘might makes right,’ but the one who spoke everything into being gets to set the rules for His creatures just like He set the rules for how everything in the universe works.
Many might claim, “but surely God can’t expect us to be perfect? Nobody is perfect.”
For we do not have a high priest who cannot sympathize with our weaknesses, but One who has been tempted in all things as we are, yet without sin. Therefore let us draw near with confidence to the throne of grace, so that we may receive mercy and find grace to help in time of need. (Hebrews 4:15-16) {emphasis mine}
Jesus doesn’t expect more than He has given. He went through every temptation we have experienced, including trials and hardships we can’t imagine, and yet was without even one sin. He is the perfect example of what we should be. Even more amazingly, he understands that we are unable to live up to His standard, so He came to earth, suffered, died, and rose again, so we could be reconciled to Him. All we have to do is repent of our sins, trust Him, and submit to Him. How can we not put our faith in Him after all He did for us?
He made Him who knew no sin to be sin on our behalf, so that we might become the righteousness of God in Him. (2 Corinthians 5:21)
Jesus paid the penalty. He took our sins, so we can receive His righteousness. This is a trade everyone should be willing to make, but sadly most refuse — some willfully, but some because they haven’t heard the good news. Hopefully all Christians will faithfully share the gospel with those around them.
May the perfect Savior guide us in His perfect will and help us to rightfully share the gospel with all those around us.
Trust Jesus
-
 @ 0689c075:2936ee11
2025-06-12 02:54:37
@ 0689c075:2936ee11
2025-06-12 02:54:37{"layout":{"backgroundImage":null,"canvasSize":{"width":850,"height":1100}},"pages":[{"id":"page_1","name":"Main Page","objects":[]}],"objects":[],"texts":[]}
-
 @ b6dcdddf:dfee5ee7
2025-06-10 14:39:05
@ b6dcdddf:dfee5ee7
2025-06-10 14:39:05Bitcoiners around the world are helping to build a safe, permanent home for 50+ orphans in Bugiri, Uganda 🇺🇬—complete with dorms, classrooms, gardens, and Bitcoin education.
Project by @orphansofuganda
https://geyser.fund/project/buildingabitcoinfundedorphanagehomeinuganda
https://stacker.news/items/1002532
-
 @ 5627e59c:d484729e
2025-06-11 22:27:17
@ 5627e59c:d484729e
2025-06-11 22:27:17Muziek\ Jij harmonieus geluid
Een gevoel zo uniek\ Op geen andere manier geuit
Ik ben zo dankbaar voor de vrijheid die jij me schenkt\ Om gewoon even te zijn\ In dit dierbare moment
-
 @ 5627e59c:d484729e
2025-06-11 21:23:14
@ 5627e59c:d484729e
2025-06-11 21:23:14Ik sta hier nu een poos\ Bevroren, machteloos
Ik wil graag iets veranderen\ Gewoon iets doen voor anderen
Maar het mag precies niet zijn\ En dat doet me veel pijn
Verlamd en vol van onbegrip\ Ik krijg er maar geen grip op
Op de wereld en de mensen\ Zij verpletteren mijn diepste wensen
Niemand die eens hoort\ Naar wat mij toch zo stoort
Ik kan nog eens proberen\ Om de wereld om te keren
Maar ik weet, het heeft geen zin\ Ik raak nooit binnen in
De ander\ Kom, verander
Misschien wordt het eens tijd\ Dat ik mezelf bevrijd
Van al die overmacht\ Die mij toch zo versmacht
Een stapje achteruit\ Adem in en adem uit
Ik doe mijn oogjes dicht\ En zie wie mij verplicht
Opzadelt met ambitie\ Van waar komt toch die missie
Al de pijn die ik niet aankan\ En van 't bestaan verban
Al 't bewijs voor mijn geloof\ Dat ik niet meer vliegen kan
-
 @ 5627e59c:d484729e
2025-06-11 21:07:41
@ 5627e59c:d484729e
2025-06-11 21:07:41Love, I thank you for your warmth\ Ever lifting
You keep me charmed\ Ever drifting
May I be me\ And you be you
In a perfect harmony\ Embracing all life makes us grow through
-
 @ 502ab02a:a2860397
2025-06-12 01:29:14
@ 502ab02a:a2860397
2025-06-12 01:29:14เรื่องของซีเรียล ที่เรารู้กัน ความจริงมันก็ไม่ได้สวยหรูสามัคคีอะไรเท่าไรครับ เบื้องหลังผลประโยชน์ระดับโลก ส่วนมากมีความขัดแย้งรุนแรงเสมอๆ
Recap นิดนะครับ ย้อนกลับไปช่วงปี 1880s ที่เมืองเล็ก ๆ อย่าง Battle Creek มลรัฐมิชิแกน สหรัฐฯ ดร. John Harvey Kellogg เป็นผู้กำกับดูแล Battle Creek Sanitarium ซึ่งเปิดสอนเรื่องสุขภาพครบทุกด้าน ทั้งโภชนาการออกกำลังกาย ไปจนถึงการควบคุมราคะ โดยเฉพาะเรื่องอาหารเช้า เขาเชื่อว่ามื้อแรกของวันมันมีอำนาจควบคุมอารมณ์และจิตวิญญาณได้ ถ้าเริ่มต้นด้วยไข่ แฮม หรือเนื้อ มันจะพลิกเรือจิตใจให้ไหลเข้าสู่ตัณหา …ซึ่งไม่ใช่จุดประสงค์ชีวิตนักพรตชาว Adventist เลย
ปี 1894 ในห้องครัวของโรงพยาบาลแห่งนี้ ดร. John กับน้องชาย Will ทดลองทำข้าวธัญพืชอบสมุนไพร เมล็ดธัญพืชบดที่หล่นบนเตาแล้วกลายเป็นแผ่นกรอบ มีชื่อเรียกชั่วคราวว่า “Granose biscuits” หรือ “wheat flakes” ซึ่งเป็นจุดเริ่มต้นของอาหารเช้าที่เน้นสุขภาพ ไม่ใช่ความอร่อย
วันที่ 7 มีนาคม 1897 ดร. John ยืนกรานจัดแจก Corn Flakes ตามหลักการ “ไม่หวาน ไม่อิ่มมาก” ในแบบฉบับ ซีเรียลไม่ใส่น้ำตาล (sugarless cereal) ให้กับคนไข้ของเขาเป็นครั้งแรก ความหวังคือให้พลังย่อยและช่วยเรื่องลำไส้ เพื่อสุขภาพมากกว่าความหรรษาปลายลิ้น
แต่แน่นอนว่า สูตรชีวิตด้านอาหารแบบพระเขาไม่ง้อลิ้นชาวบ้าน อย่าพูดถึงยอดขายเลย! น้องชาย Will Keith Kellogg ซึ่งเป็นนักธุรกิจสายลุย มองเห็นว่ารสจืดแบบนี้ไม่เกิด เขาจึงแฝงแนวคิดว่า “ทำไงให้ซีเรียลอร่อยจนคนยอมจ่าย” และสุดท้ายก็เติมน้ำตาลเข้าไป ปรับหน้าแพ็กเกจ และใส่โฆษณาชวนเชื่อว่า “อาหารเช้าสำคัญที่สุดของวัน” จนคนเริ่มเชื่อ
จากความเข้าใจเรื่องบริษัทสตาร์ทอัพของยุคนั้น ระหว่าง 1897–1906 ความแตกแยกของแนวคิดพี่-น้องก็ชัดเจนขึ้นเรื่อย ๆ ดร. John ที่เชื่อเรื่อง purity ของอาหาร ไม่เห็นด้วยกับน้ำตาล กลับขัดแย้งกับ Will ที่มองว่า “นี่ล่ะโอกาสทองเชิงพาณิชย์” จนในปี 1906 Will ตัดสินใจแยกออกมาเปิดบริษัทใหม่ในชื่อ Battle Creek Toasted Corn Flake Company วันที่ 19 กุมภาพันธ์ 1906 โดยผลักดันซีเรียลหวาน มีน้ำตาล จนขายดีทะลุเป้า
ตอนนี้พี่น้องก็กลายมาเป็นศัตรูทางธุรกิจจนได้ Will ยึดชื่อ Kellogg ทำโฆษณาเต็มแรง ลงโฆษณาเสาไฟ times square ใหญ่สุดในตอนนั้น ดร. John ฟ้องศาลขอสิทธิ์ในชื่อ Kellogg คืน เพราะเขาคิดว่าควรเป็นของผู้เริ่มต้นก่อน สุดท้าย Michigan Supreme Court ตัดสินให้ Will ชนะ ชัดเจนว่า “ใครทำการตลาด เขาก็เป็นเจ้าของชื่อ”
หลังจากนั้น ซีเรียลใส่น้ำตาลแบบกล่อง (boxed cereal) ก็เริ่มกระจายไปทั่วโลกในช่วงปี 1909–1920 โดย mass‑production ออกวันละหลักหมื่นกล่อง และโฆษณาไประดับครอบครัว วัยเด็ก และแม่บ้าน วาทกรรมคือ "ให้ลูกแข็งแรง" "อาหารเช้าแห่งอารยธรรม" ที่สำคัญคือ “ทำง่าย กินง่าย”
พอถึงปี 1907 โรงงานเกิดไฟไหม้ แต่กลับสร้างใหม่ในเวลา 6 เดือน แสดงให้เห็นถึงพลังของธุรกิจซีเรียลกล่องอย่างแท้จริง หลังจากนั้นในปี 1922 บริษัทก็เปลี่ยนชื่อเป็น Kellogg Company และโตเต็มที่ในช่วง 1920s–1930s นับเป็นเครื่องจักรของความเชื่อที่ว่า น้ำตาลในอาหารเช้าย่อมดีกว่าไขมันและเนื้อ แต่ในอีกมุม มันก็คือน้ำตาลอัดเม็ดเชิงการตลาดชุดแรกของโลก
ในภาพรวม หากมองจากสายตาประชาอเมริกันยุคต้น เคลล็อกพี่เป็นผู้ปฏิวัติโภชนาการสุทธิ เขาต้องการให้ซีเรียลเป็นอาหาร “ปราศจากสาปราคะ” ที่มุ่งเน้นสุขภาพ แต่ Will พาเรื่องนี้เข้าสู่วงการพาณิชย์ ขายง่าย รสหวาน และถูกเชื่อมกับแนวคิดว่าเด็กน้อยต้องกินอะไรเดี๋ยวนั้นเพื่อแข็งแรง กระทั่งพลังตลาดทำให้คนย้ายจากมื้อเช้าแบบหนัก ไปเป็นชามซีเรียลจิ้มกับนมในสไตล์ยุคใหม่ โดยไม่รู้เลยว่าหัวใจแท้จริงมันเริ่มตั้งแต่มุ่งปราบราคะและโมเดิร์นลุยตลาด
เมื่อดู timeline เต็มรูปแบบ เราจะเห็นว่า 1894: ดร. John ทดลอง Flaked wheat/raw Granose 1897: แจก Corn Flakes สูตรจืด sugarless จนเป็นกินกับนมเพื่อช่วยการย่อย (milk accompaniment)
1906: Will แยกบริษัท สร้างตลาดซีเรียลหวาน 1909: เปลี่ยนชื่อเป็น Kellogg Company 1922: บริษัทขยายสู่ตลาดโลกโดยสมบูรณ์ทุกย่างก้าวมีหัวใจสำคัญคือการเปลี่ยนพฤติกรรมผู้คนจาก “กินอาหารจริง” เป็น “กินอาหารกล่อง” จากไข่ เบคอน สตูว์ มาเป็นชามซีเรียลจิ้มกับนมที่ใส่น้ำตาลจัด ทั้งที่แท้จริงแล้วเป้าหมายแรกคือ “สงบกิเลส” แต่กลับจบที่ “กระตุ้นยอดขาย”
คุณลองจินตนาการถึงคนอเมริกันก่อนซีเรียล ตื่นเช้ามาเจอจานไข่ดาว เบคอน หรือแม้แต่ข้าวใส่จานพร้อมผัก ยิ่งทำงานหนักเสริมด้วยแผนยุทธศาสตร์ชีวิต พอซีเรียลมา “แค่เท กลืน กินง่าย” มันก็เข้าใจว่ามันคือความสะดวกและอนาคตของโภชนาการ ที่ถูกโปรโมตว่าดีต่อสุขภาพ ทั้ง ๆ ที่มันควรถูกตั้งคำถามในเรื่องน้ำตาลอยู่ไม่น้อย
วันนี้เรารู้แล้วว่า ซีเรียลกล่องใส่น้ำตาลคือผลิตภัณฑ์แห่งยุคตลาด เมื่อย้อนรอยดู มันไม่ใช่แค่เค้าว่าอร่อยหรือดี แต่คือการปั้นภาพว่า “นี่คือสิ่งที่คนยุคใหม่ควรกิน” โดยมีบริษัทและรัฐหนุนหลังให้มันกลายเป็นสิ่งที่เข้าใจว่า ‘ปกติ’ ทั้งที่ความจริงมัน ‘ผิดธรรมชาติ’ ตั้งแต่ต้นน้ำ #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 73d8a0c3:c1853717
2025-06-12 01:11:31
@ 73d8a0c3:c1853717
2025-06-12 01:11:31[**Nonfiction. Nothing here is imagined. This is real, observed, remembered — even if the world chose not to see it anymore.]
The men in the article didn’t just sit and wait to die. They fought, in the only ways they could. Some of them tied off an arm. Others went further — legs, even. Not because of injury. Not to stop bleeding. But to preserve blood flow to the gut. In severe volume depletion, the body starts shutting off the periphery — the limbs go cold, the skin dries, the vessels constrict. It’s a built-in triage system: protect the brain, the heart, maybe the kidneys.
And I think about that.
How far they had to fall to reach that kind of clarity. To look at their own arm, or leg, and say: you don’t matter anymore. Not because they’d given up — but because they hadn’t. Because they were still trying to survive, even if the cost was part of themselves.
It hits me hard. Not just as history, but as possibility.
Because I’m walking a version of that same path. Quietly. Strategically.
Keeping salt in. Saving movement. Holding heat.
I haven’t tied off a limb — not physically.
But I’ve let go of other things, parts of life, body, and identity, in order to preserve what’s left of the core.
Those are photos we missed. But I can still see them clearly. You can imagine how they might be something my index did not want on top of the pile.
But the gut? That’s where survival happens. That’s where salt is absorbed. Where calories are extracted. If the blood stops there, you don’t just collapse — you unravel. So they did what the body couldn’t do fast enough. They tied off what didn’t matter to buy time for what did. Primitive tourniquets, self-applied, not to stop blood from leaking, but to stop it from wandering. A final act of desperation, or clarity — depending on how far down the ladder you’ve already gone.**
-
 @ 5627e59c:d484729e
2025-06-11 18:36:19
@ 5627e59c:d484729e
2025-06-11 18:36:19Happy New Year!
Happy New Year, my dearest human family\ Happy New Year, my dearest animal family
Dear children of the Earth\ I wish you all a magical year
May it be utterly new\ Ever-changing\ New now
And may your journey say\ Life is amazing! I'm in a maze\ Life is awesome! Quite some awe\ Life is magical! True alchemy
I am human\ Black woman, I love you so\ Life-giver of my origin, the negro [nigiro]
I am\ Thus physical and non-physical meet
Life is to be\ As the elements are and compete\ And as they collide with one another\ One becomes aware of an other\ And so life sets on a journey\ To discover the other
Animal life is set to explore\ Allowing all experience the other has in store\ Life left to experience without a voice\ Until it discovers there is an 'I'\ And it has a choice
Human life is to be inside a human body\ Thus fusion between intellect and feeling\ Gets to express its perspective\ Inside infinity
Truly, a magical gift\ My Holy Trinity
And so from human life flow many voices\ As it navigates through infinite choices\
Thus I say
Life is magic\ A gift for all that is here\ Perceived by too many as tragic\ Take care of your vision, I tell you, my dear [tell-a-vision]
Life is magic\ And words are spells\ Placing your aim beyond your reach\ It takes away efficiency from your speech
Life is magic\ Above all else\ Even when it has me feeling blue\ Seemingly left without a clue
Still I say
Perfection\ You are everything\ And I am of you
The source, the mirror\ And the reflection
-
 @ 7460b7fd:4fc4e74b
2025-06-12 05:37:57
@ 7460b7fd:4fc4e74b
2025-06-12 05:37:57中美近期谈判的博弈分析:模型、均衡与演化前景
一、背景与问题概述
2025年中美经贸谈判出现了最新进展:中国同意恢复出口稀土(包括稀土磁体等关键材料),美国则在中国留学生签证政策上作出让步,但双方并未在关税上相互让步,仍维持高额关税壁垒reuters.comreuters.com。这一结果是中美经贸冲突持续多年的阶段性产物。在此之前,中美互征高额关税、一度接近全面“脱钩”,双方还通过稀土出口管制和留学签证限制等手段施压对方,导致贸易额大幅下滑、供应链紧张axios.comenglish.kyodonews.net。这一局势引发了以下博弈论层面的核心问题:当前达成的部分妥协是否构成某种博弈均衡?如果是,这属于短期策略性均衡,还是预示着中美关系可能进入类似冷战的长期对峙均衡?此外,未来有哪些外部冲击因素可能打破当前均衡或使其演化为新的稳定态?本文将以博弈模型框架对此进行分析,探讨多种均衡形态(包括但不限于纳什均衡、“科尔奈-科曼达”均衡、演化均衡等),评估其稳定性,并结合历史经验和现实因素展望演化路径。
二、博弈模型框架
1. 博弈参与者与利益:博弈双方为中国和美国,两国均为战略理性参与者。双方利益既有冲突也有重叠:中国重视维持经济增长、技术发展及国家安全,希望解除美国对其高科技封锁和贸易壁垒;美国重视维护其技术优势和贸易利益,要求中国开放市场并停止在关键资源和技术领域对美“卡脖子”。双方都希望减少自身经济损失,又不愿在战略上示弱。
2. 策略集合:双方在多个博弈维度上可选择策略。为简化分析,可聚焦三大维度:
-
关税政策:继续高关税(强硬策略)或降低关税(合作策略)。目前现实是双方仍维持高关税水平,美国综合关税约55%(包含之前各类加征),中国约10%reuters.com(显著低于美方)。
-
战略资源/技术出口管制:如中国对稀土等关键矿物的出口管制 vs 美国对高科技(芯片软件等)的出口管制。策略上可以选择实施/维持管制(强硬)或取消管制(让步)。本次中国选择取消对稀土磁体的出口限制,属合作让步;美国也表示将放松对华高科技出口管制中的一些领域english.kyodonews.netcsis.org。
-
人员交流及其它领域:如留学生签证、金融投资等。美国此次在签证上让步,允许更多中国学生赴美,属合作策略reuters.com;中国则一直希望维持人员正常交流。双方在此维度暂时采取了互惠合作的策略。
上述维度可视作多阶段博弈或多重议题博弈。为便于分析,可将其抽象为一个综合双人博弈模型:每一方都有“强硬”(H)和“合作”(C)两种总体策略取向,但在具体议题上可以组合选择(如在稀土上C、在关税上H)。这使博弈呈现出策略组合的多样性,而非简单的单次囚徒困境。但为了直观起见,我们可首先假设一个简化的对称博弈(类似囚徒困境的收益结构)来捕捉基本激励,再扩展讨论复杂均衡。
3. 收益支付(概念性):双方策略的组合将决定各自收益:
-
双强硬 (H, H):双方都坚持高关税+资源封锁等措施,彼此损害,进入全面贸易战/科技战。收益表现为两败俱伤:经济损失大,供应链断裂,科技交流停滞(负收益)。例如,2025年初双方互加惩罚性关税至三位数、彼此禁止关键出口时,就出现了贸易额骤降(中国对美出口同比-34.5%)english.kyodonews.net、企业巨额损失和市场动荡。
-
双合作 (C, C):双方都选择降低关税、解除限制,实现贸易正常化和科技交流。此时总体收益最大(双赢):经济恢复、供需正常。但由于存在信任赤字,此状态不稳定——正如囚徒困境中“双合作”虽帕累托最优,却因单方作弊诱因而难自发实现medium.com。
-
单方强硬、一方合作 (H, C)或(C, H):这一不对称组合下,强硬方利用对方的合作获取单方面优势:例如美国若坚持高关税而中国单方面降低关税并开放市场,则美方可同时享受关税保护和中方市场开放,收益最高;反之亦然。被动合作的一方则处于劣势,政治上承压。因此,这类似**“鸡奸博弈”(Chicken Game)或领导者-追随者博弈**格局。
当前谈判结果实际上接近于一种不对称均衡:美国在关税上保持强硬立场(H),而中国并未同等报复(其对美关税仅10%,远低于美方)reuters.com。同时中国在稀土管制上让步(C),美国在签证上让步(C)。可以理解为美国在经贸领域强硬而中国相对克制,美国在人员交流领域部分合作回应。这种策略组合带来的结果是美国宣称获得巨大贸易保护(“我们得到55%关税”)而中国则确保关键资源供应恢复和部分交流正常reuters.comreuters.com。双方各自得到关切的利益点:美国保住了对华高关税(满足其产业和选民需求),中国保住了留学生和稀土出口市场。但很多根本性分歧并未解决,处于暂时搁置状态reuters.com。
4. 博弈类型:这可以看作一个重复博弈/动态博弈。中美经贸冲突从2018年至今反复拉锯,多轮谈判和报复,已经是一个长期博弈过程。各阶段的策略选择和均衡都受到历史策略和信誉影响。因此分析均衡需考虑静态(一次性博弈均衡)和动态(演化均衡、子博弈完美均衡等)两种层次。
三、多种均衡形态探索
1. 纳什均衡 (Nash Equilibrium):在单次非合作博弈框架下,纳什均衡是双方策略互为最佳回应的稳定点。根据上述收益格局,可能存在以下纳什均衡:
-
“双强硬”均衡:如果互相采取强硬策略是彼此的最佳回应,则 (H, H) 构成纳什均衡。这对应于双方都不信任对方合作,选择关税壁垒和制裁的情形。2018-2024年的贸易战大部分时间里,中美实际上陷入了这样的互相报复均衡,哪怕该状态令双方经济受损axios.com。这种均衡稳定但低效:没有一方能通过单边改变策略获利(单方让步将遭对方剥削),因此维持对峙,但集体收益远低于合作状态。
-
“不对称”均衡:(H, C) 或 (C, H) 也可能是纳什均衡,取决于双方相对实力与承受力。如上所述,美国坚持高关税而中国克制报复的组合,可能是稳定的:美国的最优回应是继续征税获取贸易保护红利,中国的最优回应是在稀土等领域合作以换取部分利益且避免更大损失medium.com。反过来,如果中国采取强硬而美国克制,也是一种可能(但目前美国国内政治不允许完全克制)。从现实看,本次达成的安排类似 (H, C) :美国保留高关税(强硬),中国未对等报复且提供稀土(合作)。有分析指出,这种格局在贸易战模型中被视为“最稳定的局面”之一medium.com。然而它对中国而言并非理想,属于一种被迫接受劣势的均衡。
-
“双合作”并非均衡: (C, C) 虽让双方收益更高,但由于博弈存在囚徒困境特征,单方偏离合作能获得更大短期利益,因此在一次博弈中双合作不是纳什均衡medium.com——除非有外部约束或信誉机制,使背叛受惩罚。
2. “科尔奈-科曼达”均衡(体制均衡):所谓“科尔奈-科曼达均衡”可理解为由体制或结构因素支撑的均衡,即即使不满足常规最佳回应原则,却由于外部强制力或内在机制而得以持续的状态。经济学家科尔奈(János Kornai)分析过社会主义经济中的**“短缺均衡”:尽管市场未出清(处于非瓦尔拉斯均衡),短缺状态却能自我再生、长期持续**,因为体制激励使偏离状态自我纠正pubs.aeaweb.org。借用这一思想,中美当前的局势也可视为一种**“非合作的稳定状态”:双方在贸易和技术上未达成真正合作,但建立了一套报复—让步的动态平衡机制**,使对抗强度维持在某个水平,不至于失控。具体体现在:
-
中国虽不满美国高关税和技术封锁,但内部存在缓冲机制(如刺激自主创新、寻找替代市场)来承受压力,同时利用稀土卡位、对美投资限制等措施对美形成反制平衡。这样一种“对抗—适应”的结构使局势形成常态化均衡:虽然远非合作最优,但在现行体制下可以持续且双方习以为常。
-
美国方面,即使对华强硬政策损害了一些本国企业利益,出于安全考量和国内政治共识,其决策机制依然倾向维持对华压力。而美企通过调整供应链、政府通过补贴产业等方式部分缓冲损失。这类似科尔奈笔下的**“短缺经济的自稳定”:扭曲(高关税、高壁垒)的存在引发内部调整,从而固化了扭曲本身,形成一种具有路径依赖**的均衡。
因此,“科尔奈式均衡”在此可指中美长期博弈形成的一种自我延续的对峙常态。这种均衡并非静态最优,但有内部反馈维系其稳定。它可能对应于一种政策均衡或制度均衡:双方政治体制与经济结构已经部分适应了冲突状态,并将其纳入新常态。科曼达(Komanda)一词可能隐喻“Command(命令式)”特点,即双方关系被战略和政治指令所主导,而非市场自发优化。
3. 演化均衡 (Evolutionary Equilibrium):若将博弈视为重复进行,或者有大量“参与者”(如国内不同利益集团)的策略在演化,则可讨论演化稳定策略(ESS)。在演化视角下,策略会根据相对成功度调整,中美关系的长期走向可被视为一种策略种群的进化过程:
-
演化趋于强硬:若强硬策略在短期博弈中胜出(例如一方强硬往往能在谈判中获取更多,让步的反而被迫吃亏),那么随着时间推移,双方可能都会倾向强硬,最终演化出一个全面对抗的稳定状态。这类似于“鹰鸽博弈”中如果资源价值高且斗争成本可承受,鹰(强硬)策略会成为演化稳定策略。当前中美许多领域有朝着“鹰派占主导”的方向,例如双方国内的民族主义与强硬立场在近年不断强化,使得让步空间缩小。
-
混合均衡:也可能出现混合策略或周期。例如在重复博弈中,双方可能尝试间歇性合作(小幅让步)以试探,然后若对方被视为背信则迅速回到强硬,形成“报复—和解”交替出现的循环。这类似于“触发策略”均衡:默认合作,但一旦对方作弊就触发惩罚阶段。中美过去几年展示了一些这种特征:2019年达成阶段性协议短暂减缓冲突,随后因履约分歧又再度摩擦;2020年-2021年稍有缓和,2022年起围绕科技战又急剧恶化。每一次暂时均衡都因某种刺激被打破,然后演化进入新的冲突均衡。
-
演化稳定并不一定高效,但具有韧性。例如如果当前的部分合作-部分对抗状态在重复互动中证明比全面对抗或全面合作都“抗侵扰”,那么它就可能成为演化稳定策略组合。双方在稀土和签证上交换让步、但在关税和科技上维持对抗,或许就是一种策略组合的进化适应:既避免了极端冲突的不可承受之痛,又不让对手占尽便宜。这状态短期看或是博弈的折中均衡,可能会持续一段时间,直到新的变数出现。
4. 其他均衡概念:除了上述,值得一提的还有:
-
科尔奈-马林沃德均衡:科尔奈曾与马林沃德等研究非均衡经济,提出配给约束下的均衡等概念。在国际博弈中,可以类似地考虑约束均衡:双方由于外部环境(如全球市场、盟友压力)的约束,被迫停留在某均衡。如本次谈判有90天的临时停火协议english.kyodonews.netcsis.org,可视为一种短期约束均衡,由协议强制双方不升级冲突。
-
相关均衡 (Correlated Equilibrium):如果存在一个可信协调机制,双方可以采取相关策略实现比纳什均衡更优的结果。例如通过国际机构调停,中美同步降低部分关税、同步解除一些出口禁令,则可避免单方面吃亏。但目前缺乏这样的信任机制(WTO等多边框架也遭削弱carnegieendowment.org),因此相关均衡难以达成。
综上可见,中美经贸谈判局势下可能存在多个均衡形态并存:静态地看,强硬对峙是经典纳什均衡;动态地看,阶段性停战是子博弈均衡的一种,但未必稳定;从更长期和结构视角看,可能形成一种长期对抗的常态均衡。
四、均衡稳定性分析
分析各均衡的稳定性(即在外部冲击或单方偏离下能否持续)对评估未来走势至关重要:
-
当前部分妥协均衡的稳定性:本次达成的交换(中国出口稀土、美国放宽签证,关税维持)可以视作一种短期纳什均衡或脆弱的相关均衡。其稳定性较弱,原因有:
-
互信水平低:双方并未解决根本分歧,仅是“各取所需”式的交换,缺乏长期约束力。正如90天贸易休战协议所示,这只是暂时停止升级english.kyodonews.netcsis.org。如果90天后新的谈判未有进展,任何一方都可能恢复强硬举措,均衡即告破裂。
-
激励不对称:美国在关税上占了便宜(55%对10%),可能倾向固守既得利益,缺乏进一步让步动力;中国则可能对这种不对称心存不满,伺机寻求重新谈判条件。一旦中国找到减轻美国关税压力的途径(比如开拓其他出口市场、或美国国内通胀迫使其降税),则中国可能强硬起来要求对等调整,否则就收紧其他合作(如稀土出口配额)。单方偏离的诱因是存在的,使得均衡并不牢固。
-
外部环境多变:地缘政治或国内政治事件都可能令一方突然改变策略(下文详述潜在冲击因素)。当前均衡缺乏“保险机制”抵御这些冲击。
有迹象表明各方也预见到其脆弱:例如美国智库评价称,此次让步只是“临时止痛”,并未消除贸易战已造成的高成本和不确定性csis.orgcsis.org。这种不确定性本身会削弱均衡的可持续性——企业和市场预期不稳,就难以建立长久合作常态。
-
全面冲突均衡的稳定性:如果中美重新陷入全面强硬对抗 (H, H),这一均衡在某种条件下反而可能具有更高的稳定性,类似冷战时期美苏的对峙平衡:
-
相互威慑/无利可图:当双方都极大增加报复力度,使得任何单方面背离强硬(也就是单方面缓和)都会被对方视为软弱而加以利用时,那么维持对抗成为理性的选择。冷战中,美苏都认识到直接冲突风险巨大,形成了“相互确保摧毁”的核威慑均衡——没有一方有诱因先动carnegieendowment.org。在中美经贸版的冷战中,如果双方完全脱钩,各自建立独立产业链和同盟体系,那么相互依赖减少反而巩固了敌对均衡,因为少有经济动力去打破僵局。
-
国内政治锁定:强硬对抗一旦成为双方国内政治的基础,共识就会固化。例如冷战时期美国社会有跨党共识遏制苏联carnegieendowment.org。目前美国两党对华强硬在一定程度上趋于一致,将中国定位为主要战略竞争者;中国国内民族主义高涨,对美警惕心理强烈。如果这种政治氛围继续强化,领导人反而不敢轻易缓和,长期对峙就成为稳定政策。
-
然而,需要指出全面冲突均衡虽然稳定,但代价高昂而缺乏弹性。一旦出现如经济衰退、盟友变动等压力,其中一方可能难以承受(正如苏联经济最终不堪军备竞赛而崩溃,冷战均衡才终结)。因此静态稳定未必等于动态持久。当前中美离完全脱钩尚有距离,且全球化背景下,全面冲突会遭多方掣肘(盟国、企业利益等),因此真要达到冷战式的稳态并不容易。
-
双边合作均衡的稳定性:如果假设理想情况下双方实现了全面合作 (C, C),这在博弈上不是自行稳定的,需要可信承诺等机制支撑。稳定合作往往依赖重复博弈阴影(即长期利益)、透明度和执行监督。中美过去曾有紧密经贸合作的阶段(例如中国加入WTO后两国贸易高速增长时期),但近年来这种合作均衡被打破,说明过去的制度化信任不足以约束背叛(比如美国指责中国未履行知识产权保护承诺,中国指责美国滥用贸易制裁)。要恢复稳定合作,除非有新的协议架构和信任重建,否则仍会因为单方追求短期利益而被破坏。短期看,双边全面合作似乎缺乏政治现实性,因此不是目前可行的均衡态。
-
“科尔奈式”均衡的稳定性:如果中美进入一种长期非完全合作的常态(亦即部分对抗被体制内化的状态),这种局势可能具有相当持久性。历史上冷战就是典型例子:美苏长期在**“既不开战也不言和”**的紧张和平中相处数十年。其稳定原因包括:
-
结构性分隔:两大阵营经济、政治体系几乎隔绝,交往极少,因而缺少突发变数。若中美今后在经贸科技上大幅减少往来,各自主导不同供应链和技术标准,那么双方互动机会下降,冲突的摩擦面也相对可控,反而容易稳定在彼此默认的势力范围和规则之内。
-
制度自适应:如前述,双方内部调整出一套应对长期对抗的机制(替代产业、军备投入、宣传策略等),就像社会主义经济适应了短缺并持续运转一样pubs.aeaweb.org。一旦适应完成,这种对抗状态反而成了“新常态”,需要剧烈外力才能改变。
-
稳定但低级:值得注意,这类均衡通常效率低下(资源错配、全球福利损失),只是因为缺少打破均衡的动力而持续。例如冷战期间,美苏在军备和代理冲突上耗费巨资,却很少合作解决全球问题,直到苏联难以为继。中美若陷入持久对峙,也会牺牲很多潜在合作收益,但可能双方都愿意承受这个代价来避免在战略上被对方占优。
综合而言,目前的短期停战均衡较脆弱,全面对抗均衡和冷战式长期均衡在特定条件下可能更稳定,但对外部环境和内部承受要求高。均衡的稳定性取决于双方偏离策略的收益差异、一致预期的形成、以及有无自我强化机制。下面进一步探讨当前局势究竟更偏向短期策略均衡,还是将演化为长期对峙。
五、短期策略博弈均衡 vs. 长期对峙态势
1. 短期策略性均衡的特征:从此次谈判看,中美彼此做出的让步都带有策略试探性质,暗示目前状态更像一种短期策略均衡而非双方关系根本转折:
-
交换的局限性:让步集中在各自迫切领域(稀土和签证)reuters.com。这些让步可以迅速兑现又可随时中止(稀土出口许可中国可再收紧,签证政策美国随政令可调)。这显示双方并未进入信任合作的新轨道,而是在交换“筹码”赢得时间。
-
关税、补贴等核心问题未触及:贸易战缘起的结构性问题(市场准入、产业补贴、知识产权、关税全面降级)几乎原封不动。症结未解,只是搁置。CSIS评价称,此次关税从极端高位略有回落(美国从145%降至30%,中国125%降至10%)csis.org,但依然“远高于福利最大化所需水平”,且很多扭曲依旧存在csis.org。双方只是踩了一脚刹车,而非掉头转向。
-
临时协议属性:双方仅同意90天停火并“进一步磋商”english.kyodonews.netcsis.org。这和以前贸易战中数次短暂停战类似(如2018年底的90天停火、2020年签署的第一阶段协议后很快因疫情和政治因素失效)。短期协议往往是策略性调整,各自缓口气、观望对方意图,并非意味着矛盾解决。
基于这些特征,我们判断当前局势更倾向于短期策略均衡:双方在承受巨大经济代价后各退一步,形成暂时平衡reuters.com,但均衡基础脆弱。类似历史上韩战停战谈判、美苏古巴导弹危机后的默契,都属于策略性均衡:降低即时冲突风险,但并未解决根本对立。
2. 向长期对峙演化的可能:尽管当前是暂时妥协,但若双方结构性矛盾无法调和,博弈可能演化出类似冷战的长期对峙:
-
经贸脱钩升级:贸易战已扩展到金融、科技、人文等领域,呈“全谱系”竞争态势moneycontrol.commoneycontrol.com。Moneycontrol等媒体形容,中美贸易战正演变为**“冷战式对抗”**,不仅经济脱钩,还涉及网络安全、军事联盟等moneycontrol.commoneycontrol.com。如果这一趋势持续,双方将逐步构建各自阵营:美国拉拢盟友“经济北约”排斥中国;中国加强与俄等国合作,并以稀土等资源为筹码巩固自身阵营。这与冷战两极阵营形成颇为相似。
-
意识形态与制度之争凸显:冷战的长期对峙不仅是地缘,也是意识形态之争。当下中美分歧部分体现在政治制度和价值观。拜登政府 framing 了“民主 vs 专制”的全球竞争,美对华警惕已上升到制度层面carnegieendowment.orgcarnegieendowment.org。中国则强调美国遏制是因意识形态偏见。这种叙事一旦固化,双方会更倾向零和思维,减少妥协空间,进入价值观冷战态势。从博弈论看,这使合作策略收益相对降低,背叛收益上升,从而合作均衡更难维持,对抗均衡反而被社会接受为常态。
-
技术与军备竞赛:冷战长期稳定在于双方形成军备竞赛均衡,谁也不敢贸然进攻但也不断积累武力。在中美关系中,如果经贸冲突延伸到军备和太空、网络领域,对峙可能更为牢固。例如中美都强调加强太平洋军事部署,一些事件(台海危机等)可能将经济冲突引向准军事对抗轨道carnegieendowment.orgcarnegieendowment.org。Carnegie报告的“新冷战场景”指出,若发生台海或地区安全危机触发双方安全观转变,中美可能进入全面冷战状态:军事上前沿部署、核武戒备提升,经济上急剧脱钩,意识形态上互视为存亡对手carnegieendowment.orgcarnegieendowment.org。那将是一个全方位对峙的长期均衡,很类似美苏冷战后期的态势。
3. 当前均衡演化方向评估:综上,当前的均衡更像短期策略性停战,但演化走向取决于今后若干关键因素(详见下节)。存在两种主要路径:
-
路径A:反复博弈趋向冷战长期对峙。双方在短暂停战后因结构矛盾再起冲突,且每轮冲突都加深裂痕。经济上逐步脱钩,各自牺牲短期利益换取战略安全,国内进一步敌视对方。最终形成如同冷战般“双寡头对峙”的格局,可能持续多年乃至数十年。这种状态下,博弈均衡由短期的策略算计转变为长期的制度性均衡:双方都接受对抗为常态,不再指望对方让步,策略上以稳定自身阵营和遏制对手为目标。均衡稳定性体现在:即使小的外交互动或经济往来也无法撼动整体对立,除非出现剧变(如一方国力大衰退或政权变更)。
-
路径B:竞争中寻求合作共存的均衡。这是相对乐观的演化:在几轮高强度博弈后,双方认识到零和冲突代价沉重,转而尝试建立新规则。历史上美苏在70年代达成了战略武器限制、大三角外交等,使冷战进入**“松弛对峙”均衡**(即缓和时期)carnegieendowment.orgcarnegieendowment.org。类似地,中美也可能探索“竞争共存”框架,例如就贸易投资制定基本准则,划定可以竞争和必须合作的领域,实现某种**“有限合作-有限对抗”的均衡**。这接近于一种演化妥协均衡:不是回到蜜月期,但也避免全面冷战。其稳定性来自双方都看到了长期对抗的不利,愿意约束部分行为以维持全球稳定。这个路径需要高层战略互信逐步恢复,以及外部压力(如全球经济衰退、共同安全威胁)促使合作。
当前看来,路径A的风险在上升。贸易战期间的一些数据和行动表明新冷战苗头:贸易和投资下降但尚未彻底断绝,双方都有顾虑。carnegieendowment.org指出截至2022年中美贸易额仍创新高,说明相互依存仍在,这可能为路径B提供基础——经济纽带让完全对抗变得不利于双方,从而激励寻找折中均衡carnegieendowment.orgcarnegieendowment.org。然而,如果未来政治上完全被安全考虑压倒经济理性,路径A将更可能出现。
六、均衡破裂或维持的影响因素
无论当前均衡持续时间长短,外部冲击和内在变化都可能使局势跳转到新的均衡态。以下因素值得关注:
-
战略资源与技术依赖格局:中美相互依赖是“双刃剑”。例如稀土领域中国占全球产量70%english.kyodonews.net、加工90%axios.com,美国高科技和军工离不开稀土,因此中国有巨大杠杆。但美国正投入建立国内稀土供应链axios.com、寻求他国供应。如果几年内美国显著降低对中稀土依赖,中国失去这一筹码,均衡将倾向美国更强硬(中国难以通过断供威胁迫使美让步)。反之,在半导体等关键技术上,美国优势大,但中国也在追赶自给。一旦中国突破美国制约实现某些技术自主,或找到替代供应(如从第三国购买被禁技术),美国的制裁杠杆效力下降,可能促使其重新考虑策略。这些供需格局变化会打破原有利益平衡,引发新一轮策略调整。
-
经济承受能力:博弈均衡能否持续,一定程度取决于双方经济耐力。如果一方经济出现严重问题而将部分归因于对抗(例如美国因关税引发高通胀、就业受损,或中国因脱钩导致增长放缓过度),国内压力会推动政策转向合作以缓解经济困难csis.orgcsis.org。当前迹象:美国承受高关税引起的物价上升压力,中国也面临出口下滑和资本外流压力。谁更先难以为继,谁就可能先寻求突破均衡。同时,如果某方经济逆势壮大,可能反而更有底气长期对抗。例如有观点称贸易战令美国每年损失GDP约$3000亿csis.org,长远看这是不可持续的税收。类似冷战中苏联经济崩溃最终迫使其改变路线,中美对峙也存在经济极限约束。
-
国内政治与领导人更替:政治周期往往带来策略变化。例如2024美国大选、2027中国领导换届等都可能改变博弈基调。如果美国出现一位倾向缓和对华的总统(或相反更强硬的),政策将剧烈调整,均衡重新塑造。目前特朗普(或持其路线者)再掌权的可能性存在,而特朗普政府对华态度更为强硬、善用极限施压bloomberg.com。果真如此,当前脆弱均衡可能迅速崩塌,重回高压对抗。而若出现类似70年代尼克松式的人物寻求“连接”,也许会推动进入合作均衡窗口期。中国方面,国内政治对美态度近年来强硬是共识,但若经济下行压力迫使政策层调整优先级,也许会释放缓和信号。政策转向窗口往往在领导人第一任期初或重大会议后,需关注这些契机。
-
盟友和国际环境:中美博弈并非孤立,其他大国和国际组织的行为是重要外部变量。
-
美国盟友:如果美国成功拉起对华“统一战线”,对中国进行经济围堵,中国孤立无援下可能被迫进一步强硬反抗或加速自力更生,走向长期对峙。但若盟友出现分化(如欧盟不愿选边、继续和华贸易),美国对华极端施压难奏效,反而可能促使美国调整策略carnegieendowment.orgcarnegieendowment.org。目前欧盟、日本等既跟随美国限制对华部分技术,又希望保持贸易利益,这种摇摆也在影响均衡稳定。
-
第三方冲突:若发生其他突发危机(朝鲜半岛、南海冲突等)需要中美合作应对,可能临时搁置对抗形成共同利益,比如气候变化、全球金融危机等领域,也可能暂时偏移均衡。相反,如果第三方事件加剧对抗(如中俄关系紧密引发新集团对抗西方),均衡将更对立。台海无疑是最大变数,一旦失控几乎必然终结当前任何经济均衡,中美进入全面军事冷战甚至热战状态carnegieendowment.orgcarnegieendowment.org。
-
历史认知和心理因素:冷战经验表明,误判风险和敌意螺旋会固化冲突均衡。当前中美均试图从历史中找参照——美国部分政界认为对华“绥靖”曾失败,应强硬;中国则强调近代受欺辱史,不再退让carnegieendowment.orgcarnegieendowment.org。这些心理因素会影响策略选择,使让步更难。因此除非认知上出现转变(例如双方精英达成“再斗下去两败俱伤”的共识),否则心理上的安全困境会不断加强对抗均衡的稳定性。
总结:影响均衡演变的因素纷繁,但可以概括为:“硬”因素(经济、技术、军事实力和依赖格局变化)决定了对抗的物质可持续性,而**“软”因素**(政治意愿、认知、外交环境)决定了双方有没有契机跳出现有均衡。当前许多因素似乎在朝不利于长期合作的方向发展(技术脱钩、政治强硬化),这增加了短期均衡破裂的概率和长期对峙的可能性。然而,也存在制约对抗的因素(经济全球化的残余纽带、全球挑战需要合作),这些可能在未来某些时刻迫使双方重新评估战略。
七、未来可能的演化路径
结合上述分析,展望中美博弈的未来,有几条主要演化路径和对应均衡可供假设:
-
路径1:重复博弈陷入“新冷战” – 均衡形态:全面对抗的长期均衡\ 在此场景中,中美经过短暂休战后矛盾再度激化,每一次冲突都扩大范围,直至双方基本断绝高科技往来、贸易大幅减少,形成两个相对独立的经济技术体系,军事上进入持续高戒备状态。正如Carnegie报告描绘的“新(偶有热战)的冷战”场景:安全危机触发双方把彼此视为生存性对手,意识形态和安全竞争凌驾一切carnegieendowment.orgcarnegieendowment.org。在这种格局下:
-
经贸博弈退居次要,成为总体战略对抗的一部分。关税等问题可能永远谈不拢,反而双方都实行近乎敌对的经贸政策(禁运、投资审查、制裁)。
-
均衡稳定性高:双方国内都完成了对长期对抗的动员,社会“习惯”了没有对方的世界,各自的联盟体系提供支持。任何一方单独妥协都会被内部视为投降而不可接受。此时博弈均衡由政治-军事逻辑决定,经济利益让位于安全利益。
-
风险:这种均衡虽然稳定,却存在高风险的吸引域——任何局部事件都可能因为缺少缓冲而滑向直接冲突(如冷战时期多次危机那样)。它也将严重冲击全球经济和多边体系,让世界进入新分裂时期【28†L133-142】。
-
路径2:有限缓和与竞争共存 – 均衡形态:部分合作的动态均衡\ 另一条路径是双方在几番摩擦后痛感代价,选择建立某种“竞合框架”。这类似于美苏在1970年代缓和时期达成的默契:虽然仍竞争,但在军控、贸易上有所协议,避免了更危险的对抗carnegieendowment.org。应用到中美,则可能出现:
-
签订新贸易协定:范围超越2020年第一阶段协议,可能涉及逐步降低关税、规则竞争中建立仲裁机制等,使贸易战有“停战线”。
-
科技隔阂设置护栏:如定义哪些技术可以合作、哪些严格竞争,并避免极端措施(比如对民用科技保持一定交流)。
-
地缘热点管理:双方军方高层保持沟通,防止误判,类似冷战后的危险热线机制。这降低擦枪走火概率,也为经贸关系提供稳定外围环境。
-
均衡特征:这种均衡并非“友好合作”,而更像**“竞争性共存”。双方依然视对方为主要竞争者,但承认对方利益**,不试图彻底削弱对方,而是寻求长期共存之道。其稳定性中等,取决于领导人意志和制度化程度。如有强有力且持续的对话渠道、协议执行监督,则可较长时间维持;但如果遇到大的国际事件或国内政治变化,关系可能再次滑向对抗。
-
路径3:卷入热战或严重冲突 – 均衡破裂,激烈对抗后再重组\ 不能排除最坏情况:均衡被打破引发失控冲突,例如因台湾问题或南海冲突中美发生直接军事对抗。那将不是博弈均衡内的演化,而是均衡本身的崩溃,后果难以估量。大战之后新的均衡可能在战胜-战败格局上重建,但这已超出本文经贸博弈讨论范围。不过需要指出,持续敌对的均衡往往孕育热战危险carnegieendowment.orgcarnegieendowment.org;避免这一结局本身是各方应努力的目标。
当前迹象显示,路径1的新冷战倾向在一些领域浮现(高度脱钩、阵营对立)moneycontrol.commoneycontrol.com;路径2的有限缓和尚未看到明确契机,但并非没有基础(双方经贸仍有巨大共同利益carnegieendowment.org,金融市场、人才流动也难以一夕切断)。未来数年内,一些重要节点(如美国换届、中国经济策略调整等)将是走向路径2或滑向路径1的关键转折。
八、结论
综上分析,2025年中美谈判达成的有限妥协可被解读为中美经贸博弈中的一个短期策略均衡。双方通过各让一步,实现了一次互利但脆弱的平衡。然而,从博弈论视角看,这一均衡并非纳什稳态:双方均有诱因或压力偏离当前策略,且均衡缺乏强有力的自我稳定机制。事实上,正如有分析指出的,此次协议“几乎没有长期解决纷争的迹象”reuters.com,更像是为缓解彼此立即痛苦而达成的临时停战csis.org。
未来的走向很大程度上取决于双方如何应对结构性矛盾:是任由矛盾积累,将博弈推向类似冷战的长期对峙均衡,抑或痛定思痛,在竞争中寻求新的合作共处均衡。冷战的历史教训表明,即使长期对峙均衡一度稳定,最终也会因为不可持续的内耗而瓦解。因此,对中美双方而言,短期策略博弈或许有利于各自战术利益,但从长期理性出发,探索比冷战式对峙更稳定且成本更低的均衡(例如有限竞争+合作领域并存的模式)才符合两国和全球利益。
当然,博弈均衡并非静止,而是会随环境演化。技术进步、经济变化、国际局势、新冠疫情等冲击都可能改变 payoff 结构,从而改变博弈的均衡点。在不确定性加剧的时代,中美关系的博弈更需要双方拿出智慧,避免陷入“囚徒困境”式的次优均衡。正如经典博弈论所示,当重复博弈次数足够长、参与者足够理性时,合作并非不可实现。希望中美双方在经历几轮高强度博弈后,能够识别出新的合作机会窗口,打破目前这一“不稳定均衡”,避免新的冷战长期对峙成为不可逆的自我实现预言carnegieendowment.orgcarnegieendowment.org。
参考文献:
-
Reuters报道,2025年6月11日,《特朗普称中国将供应稀土,美国将允许中国学生入学》reuters.comreuters.com。
-
Medium平台分析文章,Laurel W. (2023)《关税博弈的博弈论解析》medium.commedium.com。
-
Kyodo News共同社,2025年6月10日,《中美高层贸易会谈聚焦稀土》(英文版)english.kyodonews.netenglish.kyodonews.net。
-
CSIS评论,Philip Luck, 2025年5月13日, 《理解中美贸易战的暂时缓和》csis.orgcsis.org。
-
Moneycontrol新闻,2025年4月22日, 《美中贸易战加深,走向冷战式对峙》moneycontrol.commoneycontrol.com。
-
Carnegie Endowment报告, Evan Medeiros等, 2024年10月, 《2030年代的中美关系:共存情景》carnegieendowment.orgcarnegieendowment.org。
-
Carnegie Endowment报告, Stephen Walt等, 2024年10月, 对中美关系的理论视角分析carnegieendowment.orgcarnegieendowment.org。
-
Kornai理论参考:Michael Ellman, 1990, 《The Disequilibrium School and the Shortage Economy》摘要pubs.aeaweb.org(说明体制性短缺状态的自我维持)。
-
-
 @ 32e18276:5c68e245
2025-06-02 20:58:05
@ 32e18276:5c68e245
2025-06-02 20:58:05Damus OpenSats Grant Q1 2025 Progress Report
This period of the Damus OpenSats grant has been productive, and encompasses the work our beta release of Notedeck. Since we sent our last report on January, this encompasses all the work after then.
Damus Notedeck
We released the Beta version of Notedeck, which has many new features:
Dave
We've added a new AI-powered nostr assistant, similar to Grok on X. We call him Dave.
Dave is integrated with tooling that allows it to query the local relay for posts and profiles:
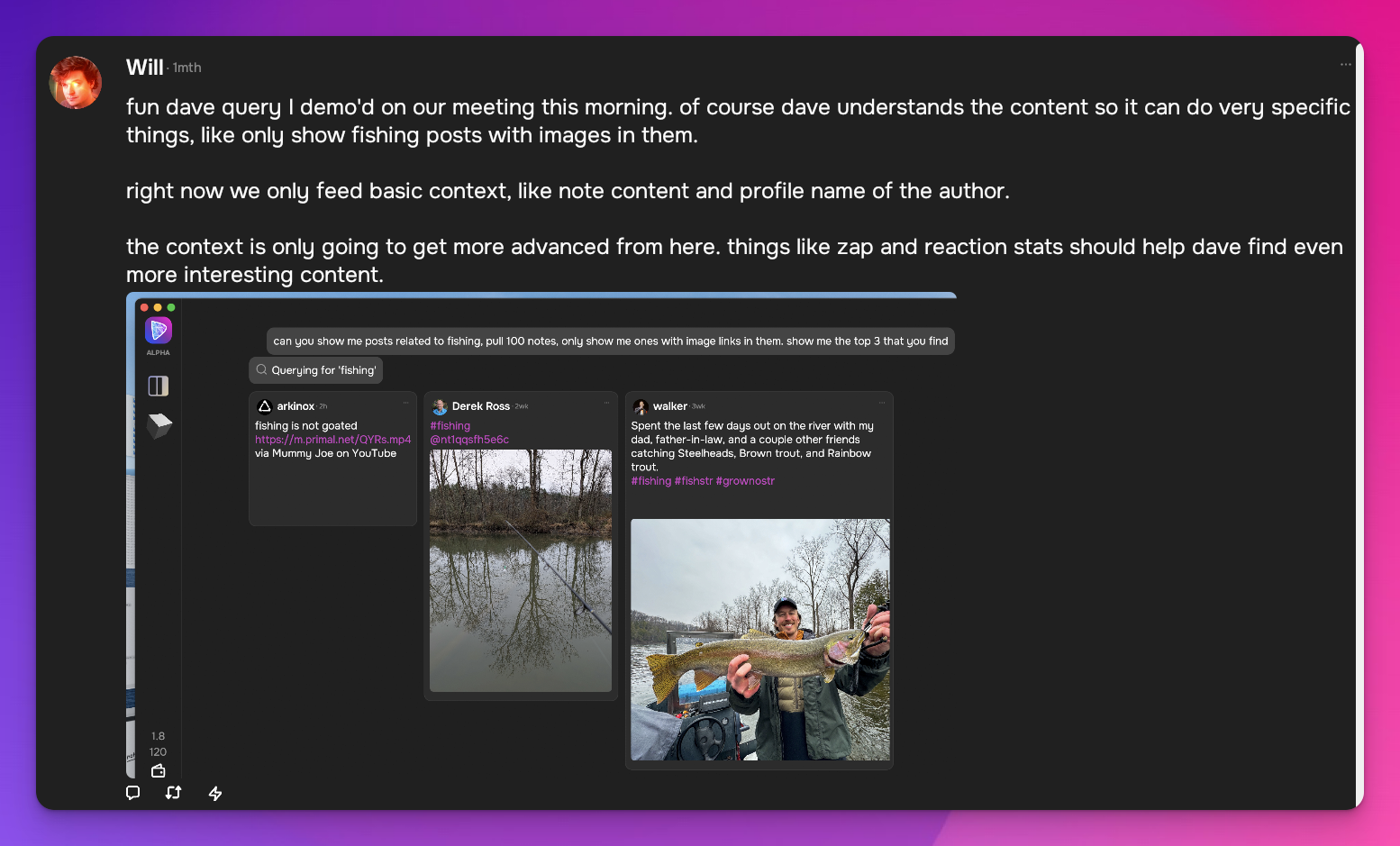
Search
The beta release includes a fulltext search interface powered by nostrdb:
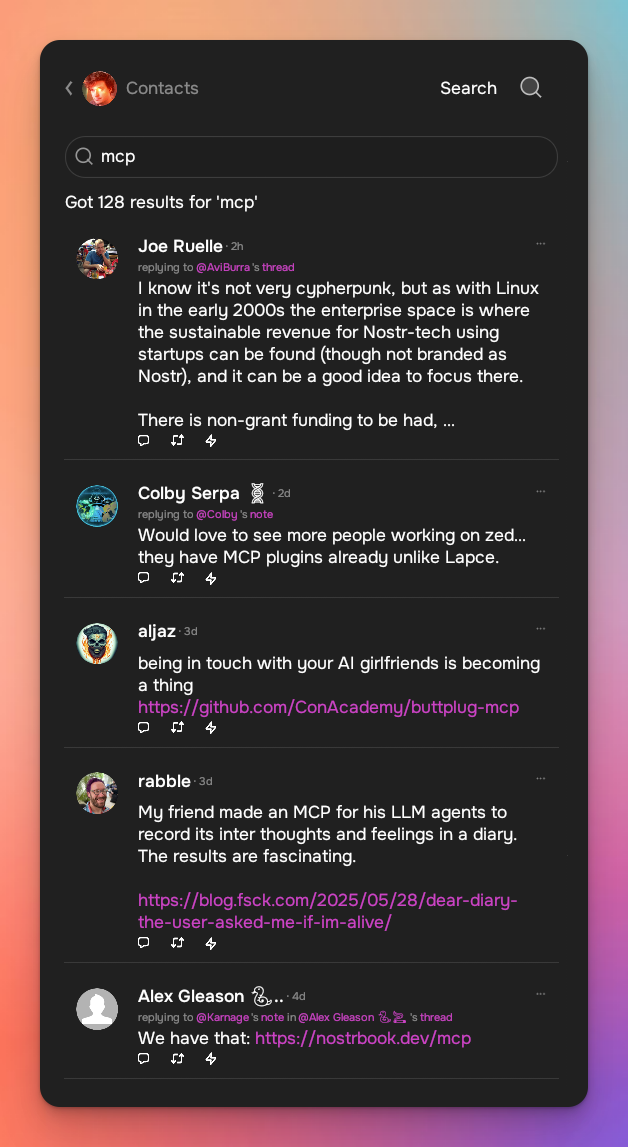
Zaps
You can now zap with NWC!
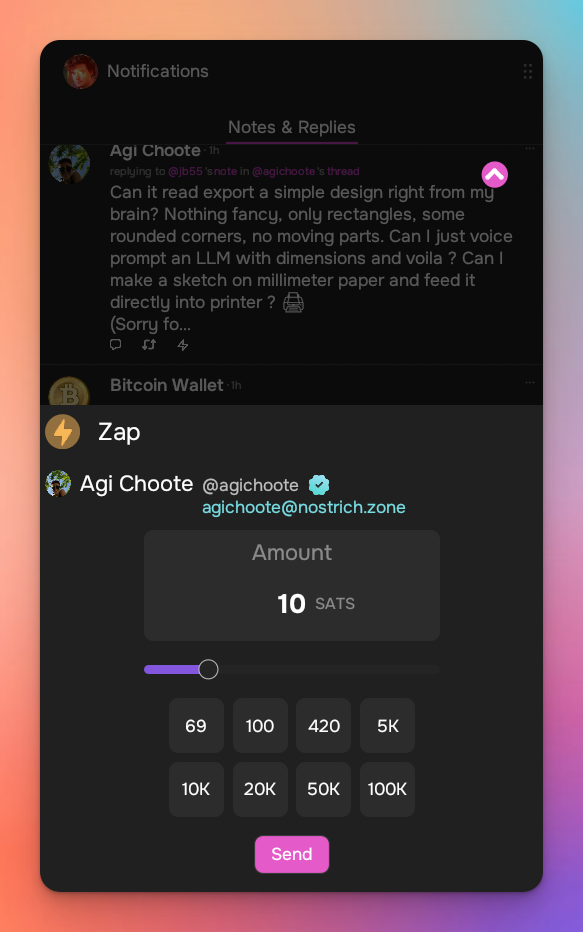
And More!
- GIFs!
- Add full screen images, add zoom & pan
- Introduce last note per pubkey feed (experimental)
- Allow multiple media uploads per selection
- Major Android improvements (still wip)
- Added notedeck app sidebar
- User Tagging
- Note truncation
- Local network note broadcast, broadcast notes to other notedeck notes while you're offline
- Mute list support (reading)
- Relay list support
- Ctrl-enter to send notes
- Added relay indexing (relay columns soon)
- Click hashtags to open hashtag timeline
Damus iOS
Work continued on the iOS side. While I was not directly involved in the work since the last report, I have been directing and managing its development.
What's new:
Coinos Wallet + Interface
We've partnered with coinos to enable a one-click, non-KYC lightning wallet!
We now have an NWC wallet interface, and we've re-enabled zaps as per the new appstore guidelines!
Now you can see all incoming and outgoing NWC transactions and start zapping right away.
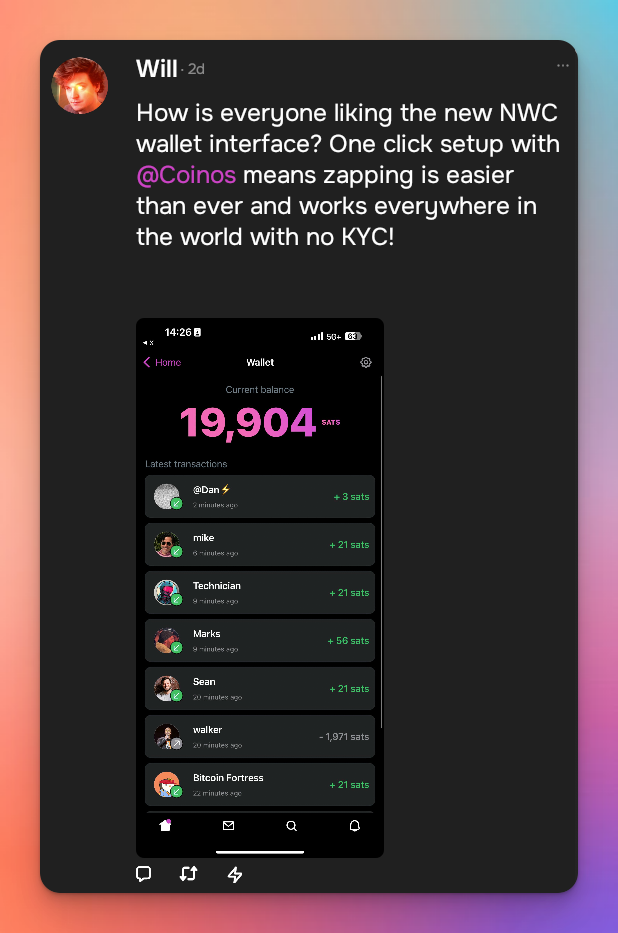
Enhanced hellthread muting
Damus can now automatically mute hellthreads, instead of having to do that manually.
Drafts
We now locally persist note drafts so that they aren't lost on app restart!
Profile editing enhancements
We now have a profile picture editing tool so that profile pictures are optimized and optionally cropped
Conversations tab
We now have a conversations tab on user profiles, allowing you to see all of your past conversations with that person!
Enhanced push notifications
We've updated our push notifications to include profile pictures, and they are also now grouped by the thread that they came from.
And lots more!
Too many to list here, check out the full changelog
Nostrdb
nostrdb, the engine that powers notecrumbs, damus iOS, and notedeck, continued to improve:
Custom filters
We've added the ability to include custom filtering logic during any nostrdb query. Dave uses this to filter replies from kind1 results to keep the results small and to avoid doing post-processing.
Relay index + queries
There is a new relay index! Now when ingesting notes, you can include extra metadata such as where the note came from. You can use this index to quickly list all of the relays for a particular note, or for relay timelines.
NIP50 profile searches
To assist dave in searching for profiles, we added a new query plan for {kind:0, search:} queries to scan the profile search index.
How money was used
- relay.damus.io server costs
- Living expenses
Next quarter
We're making a strong push to get our Android version released, so that is the main focus for me.
-
 @ 3bf0c63f:aefa459d
2024-12-06 20:37:26
@ 3bf0c63f:aefa459d
2024-12-06 20:37:26início
"Vocês vêem? Vêem a história? Vêem alguma coisa? Me parece que estou tentando lhes contar um sonho -- fazendo uma tentativa inútil, porque nenhum relato de sonho pode transmitir a sensação de sonho, aquela mistura de absurdo, surpresa e espanto numa excitação de revolta tentando se impôr, aquela noção de ser tomado pelo incompreensível que é da própria essência dos sonhos..."
Ele ficou em silêncio por alguns instantes.
"... Não, é impossível; é impossível transmitir a sensação viva de qualquer época determinada de nossa existência -- aquela que constitui a sua verdade, o seu significado, a sua essência sutil e contundente. É impossível. Vivemos, como sonhamos -- sozinhos..."
- Livros mencionados por Olavo de Carvalho
- Antiga homepage Olavo de Carvalho
- Bitcoin explicado de um jeito correto e inteligível
- Reclamações
-
 @ 79be667e:16f81798
2025-06-11 18:33:35
@ 79be667e:16f81798
2025-06-11 18:33:35De laatste zonnestralen van de dag streken over de eeuwige golven en weerkaatsten als lichtpuntjes in de ogen van schipper Joris terwijl hij nog een slok nam van zijn glazen fles die de vorm had van het hoofd van een oude monnik.
Gekregen van een oude vrouw uit de bergen van de Himalaya, zorgde de rum genaamd 'Old Monk' voor een verwarmend gezelschap op deze eenzame kerstnacht.
Joris had met zijn boot naar India gevaren nadat zijn vrouw hem had verlaten en hij een Indiër had ontmoet die had gezegd: "Waar ik vandaan kom, zijn vrouwen vrij en worden ze niet gezien als enkel en alleen de mooie lichamen die zij bezitten of als eeuwig bezit van een gezin."
Verward en ongelovig had Joris gekeken naar de wereld en besefte dat vrouwen inderdaad slechts gezien werden als hun fysieke schoonheid, genegeerd werden voor hun koesterende gevoeligheid en bekritiseerd werden door hun spontane intensheid en had hierop voor twee jaar lang gezocht in India naar deze vrije vrouwen met als enig resultaat een oude vrouw te ontmoeten die alleen in de bergen woonde en dagelijks haar wijsheid deelde met ieder luisterend oor.
Daar ging het doorzichtig monnikshoofd en verliet met een grote gebogen vlucht de hand van schipper Joris toen plots met groot kabaal de boot abrupt tot stilstand kwam en Joris hals over kop naar de andere kant van het dek geslingerd werd.
Het monnikshoofd verdween in het donker terwijl Joris zijn lichaam probeerde te lokaliseren en met zijn ogen wijd open zijn hersenen zo veel mogelijk informatie probeerde door te spelen.
Tevergeefs, want zijn enorme verschot werd gevolgd door een enkel groeiende verbazing, ongeloof en desoriëntatie toen de boot begon te kantelen.
De bundel licht, afkomstig van de mast van de boot, zwierde doorheen het donker en kwam te schijnen op een gigantische rots in het midden van de zee die werd bezeten door een oogverblindende glinstergroene schijn.
Uit het donker kwam het monnikshoofd, dat nog steeds in volle vlucht was, in het vizier van de lichtbundel en plaatste zich exact tussen de glinstergroene verschijning en Joris waarbij Joris doorheen het monnikshoofd gezegend werd met het zicht op een pracht van een zeemeermin die uitnodigend poseerde op de rots.
Met een luide plons viel Joris achterover in het water toen hij zich realiseerde dat vrouwen zichzelf ook lieten vangen door lust en hun uiterlijke opmaakcompetities en met een dankbare glimlach zonk hij naar de bodem van de zee en was opnieuw geboren.
-
 @ 5627e59c:d484729e
2025-06-11 22:26:51
@ 5627e59c:d484729e
2025-06-11 22:26:51Gelukkig zijn\ Is de waarde van mijn leven
Gewoon dankbaar te bestaan\ Geen mens heeft me ooit zo'n mooi cadeau gegeven
Dankbaar voor mijn sprankelen\ Mijn doen en voor mijn streven
Maar ook dat ik mag wankelen\ Mag vallen en mag beven
Want wat er ook gebeurt\ Het duurt steeds maar voor even
De wijsheid van mijn hart\ Voor alles is een reden
Het leven brengt mij deugd\ En soms brengt het me pijn
Maar nooit neemt het die vreugd\ De toelating om hier te zijn
De kans om iets te leren\ Te zien en om te groeien
Geeft mij kracht te accepteren\ Te omarmen en te bloeien
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-12 02:13:20
@ 5d4b6c8d:8a1c1ee3
2025-06-12 02:13:20I pretty much did worse across the board today.
How'd you do today, stackers?
https://stacker.news/items/1004030
-
 @ 5627e59c:d484729e
2025-06-11 21:07:23
@ 5627e59c:d484729e
2025-06-11 21:07:23Jaren tellen\ Hoeft voor mij niet
Verhalen vertellen\ Over geluk en verdriet
Een warme haven\ Veilig en fijn
Dromen voorgedragen\ Onschuldig en rein
Momenten ervaard, geleerd\ En geïntegreerd
Ideeën, geloven en gevoelens\ Gevormd en gecreëerd
Zonder eind of echt begin\ Vallen, groeien, leren, stoeien
Een gezin in een gezin met een gezin erin\ Gezind gericht blijft liefde vloeien
-
 @ 79be667e:16f81798
2025-06-11 18:29:06
@ 79be667e:16f81798
2025-06-11 18:29:06Zonneschijn\ Stralen, lachen, zo fijn\ Moge de wereld dankbaar zijn
De vrouw, mijn gevoeligheid\ Bron van creativiteit
Genietend niets doen in het gras\ Met wat brood en wat wijn in het glas
-
 @ 5627e59c:d484729e
2025-06-11 22:26:39
@ 5627e59c:d484729e
2025-06-11 22:26:39I am here too\ In the same space like you
In the same situation I'm in\ It's a matter of positioning
I cannot leave this place I'm in\ It was brought about\ By what's been happening
So please don't look at me\ For what I can or cannot do for you\ But look at what is happening for me\ And what is happening for you
Let's communicate\ Not orchestrate
Because there's something I wish to do\ And there's a place I wish to go to
And I'm sure that there is too\ In your heart a fire\ Known by only you
So let us listen, look and see\ For what's true for you\ And what's true for me
That we may act upon what's here\ In order for us both to take a step\ In the direction we wish to steer
-
 @ 5627e59c:d484729e
2025-06-11 21:13:27
@ 5627e59c:d484729e
2025-06-11 21:13:27Kan jij zien, er is geen hemel\ Probeer het zelf, dan lukt het wel\ Geen hel staat ons te wachten\ Enkel sterren hangen ons boven het hoofd\ Kan jij zien, iedereen leeft voor dit moment
Kan jij zien, er zijn geen landen\ Het is niet moeilijk gewoon land te zien\ Niets om voor te moorden of te sterven\ Ook geloof wordt niet gezien\ Kan jij zien, het leven wordt geleefd door iedereen in vrede
Misschien zeg je, ik kijk niet naar jouw wereld\ Maar ik deel dit zicht met velen\ Moge ook jij zoals ons zien\ Wij kijken in de wereld en zien gewoon onszelf
Kan jij zien, er is geen bezit\ Ik vraag me af of jij dit kan\ Geen hebben of een nood\ In een samen-leving van mensen\ Kan jij zien, wij delen de wereld met elkaar
Misschien zeg je, ik kijk niet naar jouw wereld\ Maar ik deel dit zicht met velen\ Moge ook jij zoals ons zien\ Wij kijken in de wereld en zien gewoon onszelf
-
 @ 5627e59c:d484729e
2025-06-11 22:25:48
@ 5627e59c:d484729e
2025-06-11 22:25:48Kan jij zien, er is geen hemel\ Probeer het zelf, dan lukt het wel\ Geen hel staat ons te wachten\ Enkel sterren hangen ons boven het hoofd\ Kan jij zien, iedereen leeft voor dit moment
Kan jij zien, er zijn geen landen\ Het is niet moeilijk gewoon land te zien\ Niets om voor te moorden of te sterven\ Ook geloof wordt niet gezien\ Kan jij zien, het leven wordt geleefd door iedereen in vrede
Misschien zeg je, ik kijk niet naar jouw wereld\ Maar ik deel dit zicht met velen\ Moge ook jij zoals ons zien\ Wij kijken in de wereld en zien gewoon onszelf
Kan jij zien, er is geen bezit\ Ik vraag me af of jij dit kan\ Geen hebben of een nood\ In een samen-leving van mensen\ Kan jij zien, wij delen de wereld met elkaar
Misschien zeg je, ik kijk niet naar jouw wereld\ Maar ik deel dit zicht met velen\ Moge ook jij zoals ons zien\ Wij kijken in de wereld en zien gewoon onszelf
-
 @ 79be667e:16f81798
2025-06-11 18:27:32
@ 79be667e:16f81798
2025-06-11 18:27:32Spontaniteit\ Creativiteit
Iets visueel of gewoon geluid\ Het moet eruit
Ik doe mezelf cadeau aan jou\ Omdat ik van het leven hou
-
 @ 79be667e:16f81798
2025-06-11 18:25:54
@ 79be667e:16f81798
2025-06-11 18:25:54Veroorzaakt door de wereld rond mij\ Vormen de wereld in mij
Verwaarloosd door de wereld rond mij\ Overgelaten aan mij
Een groene brug komt uit mij\ Verbindt mij met wij\ En laat ons samen vrij
-
 @ 5627e59c:d484729e
2025-06-11 22:25:37
@ 5627e59c:d484729e
2025-06-11 22:25:37In het hart van een gepensioneerde operazangeres ontstond een stemmetje. Het stemmetje klonk verrast. "He," ging het hart. "Ik heb een stemmetje gekregen! Hoe kan dit? Kan iemand me horen? Zouden mijn gedachten me kunnen horen?" vroeg het stemmetje, niet wetend aan wie. Want de gedachten hoorden het niet. Zij waren zo druk bezig met het verleden en hadden een grote angst dit te verliezen. "Weet je nog?" gingen de gedachten. "Voor duizenden mensen heb ik gezongen! Avond na avond! Tienduizenden mensen hebben me toegejuicht! Wat waren ze onder de indruk! Luister! Ik kan het nog steeds!" "He," ging het hart. "Hoor je me dan niet? Het ging toch helemaal niet om dat gejuich. Weet je dan niet meer hoe ik me volledig bloot gaf aan die mensen. Mijn diepste en meest persoonlijke verhalen waren te horen in mijn liederen. Daar draaide het toch om? De mensen waren niet enkel onder de indruk. Hun harten hebben mijn verhalen gevoeld en konden zo kennis geven aan hun gedachten. Is dat niet wat echt telde?" Maar de gedachten waren volop aan het zingen voor de ene persoon die ze konden vinden die wou luisteren. "He," ging het hart. "Ook in dit moment zijn mijn liederen te horen door vele gedachten en te voelen door vele harten over de hele wereld. Heb ik dan geen rust verdiend? Kan ik niet even genieten van de rust die in dit moment te vinden is, maar jullie van me afnemen?" Maar de gedachten waren nog steeds volop aan het zingen.
-
 @ 5627e59c:d484729e
2025-06-11 21:12:27
@ 5627e59c:d484729e
2025-06-11 21:12:27In het hart van een gepensioneerde operazangeres ontstond een stemmetje. Het stemmetje klonk verrast. "He," ging het hart. "Ik heb een stemmetje gekregen! Hoe kan dit? Kan iemand me horen? Zouden mijn gedachten me kunnen horen?" vroeg het stemmetje, niet wetend aan wie. Want de gedachten hoorden het niet. Zij waren zo druk bezig met het verleden en hadden een grote angst dit te verliezen. "Weet je nog?" gingen de gedachten. "Voor duizenden mensen heb ik gezongen! Avond na avond! Tienduizenden mensen hebben me toegejuicht! Wat waren ze onder de indruk! Luister! Ik kan het nog steeds!" "He," ging het hart. "Hoor je me dan niet? Het ging toch helemaal niet om dat gejuich. Weet je dan niet meer hoe ik me volledig bloot gaf aan die mensen. Mijn diepste en meest persoonlijke verhalen waren te horen in mijn liederen. Daar draaide het toch om? De mensen waren niet enkel onder de indruk. Hun harten hebben mijn verhalen gevoeld en konden zo kennis geven aan hun gedachten. Is dat niet wat echt telde?" Maar de gedachten waren volop aan het zingen voor de ene persoon die ze konden vinden die wou luisteren. "He," ging het hart. "Ook in dit moment zijn mijn liederen te horen door vele gedachten en te voelen door vele harten over de hele wereld. Heb ik dan geen rust verdiend? Kan ik niet even genieten van de rust die in dit moment te vinden is, maar jullie van me afnemen?" Maar de gedachten waren nog steeds volop aan het zingen.
-
 @ 5627e59c:d484729e
2025-06-11 21:06:42
@ 5627e59c:d484729e
2025-06-11 21:06:42Happy New Year!
Happy New Year, my dearest human family\ Happy New Year, my dearest animal family
Dear children of the Earth\ I wish you all a magical year
May it be utterly new\ Ever-changing\ New now
And may your journey say\ Life is amazing! I'm in a maze\ Life is awesome! Quite some awe\ Life is magical! True alchemy
I am human\ Black woman, I love you so\ Life-giver of my origin, the negro [nigiro]
I am\ Thus physical and non-physical meet
Life is to be\ As the elements are and compete\ And as they collide with one another\ One becomes aware of an other\ And so life sets on a journey\ To discover the other
Animal life is set to explore\ Allowing all experience the other has in store\ Life left to experience without a voice\ Until it discovers there is an 'I'\ And it has a choice
Human life is to be inside a human body\ Thus fusion between intellect and feeling\ Gets to express its perspective\ Inside infinity
Truly, a magical gift\ My Holy Trinity
And so from human life flow many voices\ As it navigates through infinite choices
Thus I say
Life is magic\ A gift for all that is here\ Perceived by too many as tragic\ Take care of your vision, I tell you, my dear [tell-a-vision]
Life is magic\ And words are spells\ Placing your aim beyond your reach\ It takes away efficiency from your speech
Life is magic\ Above all else\ Even when it has me feeling blue\ Seemingly left without a clue
Still I say
Perfection\ You are everything\ And I am of you
The source, the mirror\ And the reflection
-
 @ 5627e59c:d484729e
2025-06-11 22:25:24
@ 5627e59c:d484729e
2025-06-11 22:25:24I am the space\ In which your experience takes place
You could never meet me\ For I hold no identity
The only way to really see me\ Is to be me
-
 @ 5627e59c:d484729e
2025-06-11 21:06:21
@ 5627e59c:d484729e
2025-06-11 21:06:21De laatste zonnestralen van de dag streken over de eeuwige golven en weerkaatsten als lichtpuntjes in de ogen van schipper Joris terwijl hij nog een slok nam van zijn glazen fles die de vorm had van het hoofd van een oude monnik.
Gekregen van een oude vrouw uit de bergen van de Himalaya, zorgde de rum genaamd 'Old Monk' voor een verwarmend gezelschap op deze eenzame kerstnacht.
Joris had met zijn boot naar India gevaren nadat zijn vrouw hem had verlaten en hij een Indiër had ontmoet die had gezegd: "Waar ik vandaan kom, zijn vrouwen vrij en worden ze niet gezien als enkel en alleen de mooie lichamen die zij bezitten of als eeuwig bezit van een gezin."
Verward en ongelovig had Joris gekeken naar de wereld en besefte dat vrouwen inderdaad slechts gezien werden als hun fysieke schoonheid, genegeerd werden voor hun koesterende gevoeligheid en bekritiseerd werden door hun spontane intensheid en had hierop voor twee jaar lang gezocht in India naar deze vrije vrouwen met als enig resultaat een oude vrouw te ontmoeten die alleen in de bergen woonde en dagelijks haar wijsheid deelde met ieder luisterend oor.
Daar ging het doorzichtig monnikshoofd en verliet met een grote gebogen vlucht de hand van schipper Joris toen plots met groot kabaal de boot abrupt tot stilstand kwam en Joris hals over kop naar de andere kant van het dek geslingerd werd.
Het monnikshoofd verdween in het donker terwijl Joris zijn lichaam probeerde te lokaliseren en met zijn ogen wijd open zijn hersenen zo veel mogelijk informatie probeerde door te spelen.
Tevergeefs, want zijn enorme verschot werd gevolgd door een enkel groeiende verbazing, ongeloof en desoriëntatie toen de boot begon te kantelen.
De bundel licht, afkomstig van de mast van de boot, zwierde doorheen het donker en kwam te schijnen op een gigantische rots in het midden van de zee die werd bezeten door een oogverblindende glinstergroene schijn.
Uit het donker kwam het monnikshoofd, dat nog steeds in volle vlucht was, in het vizier van de lichtbundel en plaatste zich exact tussen de glinstergroene verschijning en Joris waarbij Joris doorheen het monnikshoofd gezegend werd met het zicht op een pracht van een zeemeermin die uitnodigend poseerde op de rots.
Met een luide plons viel Joris achterover in het water toen hij zich realiseerde dat vrouwen zichzelf ook lieten vangen door lust en hun uiterlijke opmaakcompetities en met een dankbare glimlach zonk hij naar de bodem van de zee en was opnieuw geboren.
-
 @ 1c5ff3ca:efe9c0f6
2025-06-05 06:29:45
@ 1c5ff3ca:efe9c0f6
2025-06-05 06:29:45Just calling it Open is not enough - Herausforderungen öffentlicher Bildungsinfrastrukturen und wie Nostr helfen könnte
Ich möchte gerne mit euch teilen, an welchen Konzepten ich arbeite, um die öffentliche Bildungsinfrastruktur mit Hilfe von Nostr zugänglicher und offener zu gestalten. Ich arbeite im Bereich öffentlicher Bildungsinfrastrukturen, besonders im Feld von Open Educational Resources (#OER). OER sind offen lizenzierte Bildungsmaterialien, die mit einer offenen Lizenz, meist einer Creative Commons Lizenz, versehen sind (CC-0, CC-BY, CC-BY-SA). Durch die klare und offene Lizenzierung ist es leicht möglich, die Lernmaterialien auf die individuellen Bedarfe anzupassen, sie zu verbessern und sie erneut zu veröffentlichen.
Seit vielen Jahren wird einerseits die Entwicklung freier Bildungsmaterialien gefördert, andererseits werden Plattformen, insbesondere Repositorien gefördert, die diese Materialien verfügbar machen sollen. Denn irgendwo müssen diese Materialien zur Verfügung gestellt werden, damit sie auch gefunden werden können.
Das klappt allerdings nur so mittelgut.
Herausforderungen
Nach vielen Jahren Förderung kann die einfache Frage: "Wo kann ich denn mein OER-Material bereitstellen" nicht einfach beantwortet werden. Es gibt Services, bei denen ich mein OER hochladen kann, jedoch bleibt es dann eingeschlossen in dieser Plattform und wird nicht auf anderen Plattformen auffindbar. Außerdem sind diese Services häufig an bestimmte Bildungskontexte gebunden oder geben Content erst nach einer Qualitätsprüfung frei. Dies führt dazu, dass ein einfaches und gleichzeitig öffentliches Teilen nicht möglich ist.
Diese und weitere Herausforderungen haben ihren Ursprung darin, dass Service und Infrastruktur in der Architektur öffentlichen Bildungsarchitektur ungünstig vermischt werden. Als Infrastruktur verstehe ich hier die Bereitstellung einer öffentlichen und offen zugänglichen Bildungsinfrastruktur, auf der Daten ausgetauscht, also bereitgestellt und konsumiert werden können. Jedoch existiert eine solche Infrstruktur momentan nicht unabhängig von den Services, die auf ihr betrieben werden. Infrastrukturbetreiber sind momentan gleichzeitig immer Servicebetreiber. Da sie aber die Hand darüber haben wollen, was genau in ihrem Service passiert (verständlich), schränken sie den Zugang zu ihrer Infrastruktur mit ein, was dazu führt, dass sie Lock-In Mechanismen großer Medienplattformen in der kleinen öffentlichen Bildungsinfrastruktur replizieren.
Es ist in etwas so, als würde jeder Autobauer auch gleichzeitig die Straßen für seine Fahrzeuge bauen. Aber halt nur für seine Autos.
Anhand einiger beispielhafter Services, die bestehende Plattformen auf ihren Infrastrukturen anbieten, möchte ich die Herausforderungen aufzeigen, die ich im aktuellen Architekturkonzept sehe:
- Upload von Bildungsmaterial
- Kuration: Zusammenstellung von Listen, Annotation mit Metadaten
- Crawling, Indexierung und Suche
- Plattfformübergreifende Kollaboration in Communities -> Beispiel: Qualitätssicherung (was auch immer das genau bedeutet)
- KI- Services -> Beispiel: KI generierte Metadaten für BiIdungsmaterial
Material Upload
Der Service "Material-Upload" oder das Mitteilen eines Links zu einem Bildungsmaterial wird von verschiedenen OER-Pattformen bereitgestellt (wirlernenonline.de, oersi.org, mundo.schule).
Dies bedeutet konkret: Wenn ich bei einer der Plattformen Content hochlade, verbleibt der Content in der Regel auch dort und wird nicht mit den anderen Plattformen geteilt. Das Resultat für die User: Entweder muss ich mich überall anmelden und dort mein Material hochladen (führt zu Duplikaten) oder damit leben, dass eben nur die Nutzer:innen der jeweiligen Plattform meinen Content finden können.
Der "Open Educational Resource Search Index" (OERSI) geht diese Herausforderung an, indem die Metadaten zu den Bildungsmaterialien verschiedener Plattformen in einem Index bereitgestellt werden. Dieser Index ist wiederum öffentlich zugänglich, sodass Plattformen darüber auch Metadaten anderer Plattformen konsumieren können. Das ist schon sehr gut. Jedoch funktioniert das nur für Plattformen, die der OERSI indexiert und für alle anderen nicht. Der OERSI ist auf den Hochschulbereich fokussiert, d.h. andere Bildungskontexte werden hier ausgeschlossen. Der Ansatz für jeden Bildungsbereich einen passenden "OERSI" daneben zustellen skaliert und schlecht und es bleibt die Herausforderung bestehen, dass für jede Quelle, die indexiert werden soll, ein entsprechender Importer/Crawler geschrieben werden muss.
Dieser Ansatz (Pull-Ansatz) rennt den Materialien hinterher.
Es gibt jedoch noch mehr Einschränkungen: Die Plattformen haben sich jeweils auf spezifische Bildungskontexte spezialisiert. D.h. auf die Fragen: Wo kann ich denn mein OER bereitstellen, muss immer erst die Gegenfrage: "Für welchen Bildungsbereich denn?" beantwortet werden. Wenn dieser außerhalb des allgemeinbildendenden Bereichs oder außerhalb der Hochschule liegt, geschweige denn außerhalb des institutionellen Bildungsrahmens, wird es schon sehr, sehr dünn. Kurzum:
- Es ist nicht einfach möglich OER bereitzustellen, sodass es auch auf verschiedenen Plattformen gefunden werden kann.
Kuration
Unter Kuration verstehe ich hier die Zusammenstellung von Content in Listen oder Sammlungs ähnlicher Form sowie die Annotation dieser Sammlungen oder des Contents mit Metadaten.
Einige Plattformen bieten die Möglichkeit an, Content in Listen einzuordnen. Diese Listen sind jedoch nicht portabel. Die Liste, die ich auf Plattform A erstelle, lässt sich nicht auf Plattform B importieren. Das wäre aber schön, denn so könnten die Listen leichter auf anderen Plattformen erweitert oder sogar kollaborativ gestaltet werden, andererseits werden Lock-In-Effekte zu vermieden.
Bei der Annotation mit Metadaten treten verschiedene zentralisierende Faktoren auf. In der momentanen Praxis werden die Metadaten meist zum Zeitpunkt der Contentbereitstellung festgelegt. Meist durch eine Person oder Redaktion, bisweilen mit Unterstützung von KI-Services, die bei der Metadateneingabe unterstützen. Wie aber zusätzliche eigene Metadaten ergänzen? Wie mitteilen, dass dieses Material nicht nur für Biologie, sondern auch für Sport in Thema XY super einsetzbar wäre? Die momentanen Ansätze können diese Anforderung nicht erfüllen. Sie nutzen die Kompetenz und das Potential ihrer User nicht.
- Es gibt keine interoperablen Sammlungen
- Metadaten-Annotation ist zentralisiert
- User können keine eigenen Metadaten hinzufügen
Crawling, Indexierung und Suche

Da die Nutzer:innen nicht viele verschiedene Plattformen und Webseiten besuchen wollen, um dort nach passendem Content zu suchen, crawlen die "großen" OER-Aggregatoren diese, um die Metadaten des Contents zu indexieren. Über verschiedene Schnittstellen oder gerne auch mal über das rohe HTML. Letztere Crawler sind sehr aufwändig zu schreiben, fehleranfällig und gehen bei Design-Anpassungen der Webseite schnell kaputt, erstere sind etwas stabiler, solange sich die Schnittstelle nicht ändert. Durch den Einsatz des Allgemeinen Metadatenprofils für Bildungsressourcen (AMB) hat sich die Situation etwas verbessert. Einige Plattformen bieten jetzt eine Sitemap an, die Links zu Bildungsmaterial enthalten, die wiederum eingebettet
script-tags vom Typapplication/ld+jsonenthalten, sodass die Metadaten von dort importiert werden können.Beispiel: e-teaching.org bietet hier eine Sitemap für ihre OER an: https://e-teaching.org/oer-sitemap.xml und auf den jeweiligen Seiten findet sich ein entsprechendes script-Tag.
Das ist schon viel besser, aber da geht noch mehr:
Zunächst ist dieser Ansatz nur für Plattformen und Akteure praktikabel, die über IT-Ressourcen verfügen, um entsprechende Funktionalitäten bei sich einbauen zu können. Lehrende können dies nicht einfach auf ihrem privaten Blog oder ähnliches umsetzen. Zum anderen besteht immer noch ein Discovery Problem. Ich muss nach wie vor wissen, wo ich suchen muss. Ich muss die Sitemaps kennen, sonst finde ich nichts. Statt eines Ansatzes, bei dem Akteure eigenständig mitteilen können, dass sie neuen Content haben (Push-Ansatz), verfolgen wir derzeit einen Ansatz, bei dem jede Plattform für sich Content im Pull-Verfahren akquiriert. Dies führt an vielen Stellen zu Doppelarbeiten, ist ineffizient (mehrere Personen bauen genau die gleichen Crawler, aber halt immer für ihre Plattform) und schliesst vor allem kleine Akteure aus (lohnt es sich einen Crawler zu programmieren, wenn die Webseite "nur" 50 Materialien bereitstellt?).
Anstatt erschlossene Daten zu teilen, arbeiten die Plattformen für sich oder stellen es höchstens wieder hinter eigenen (offenen oder geschlossenen) Schnittstellen bereit. Das ist wohl nicht das, was wir uns unter einer offenen und kollaborativen Gemeinschaft vorstellen, oder?
Bei der Suche stehen wir vor ähnlichen Herausforderungen, wie bereits oben geschildert. Obwohl verschiedene OER-Aggregatoren in Form von Repositorien oder Referatorien bereits viele der "kleineren" Plattformen indexieren und somit eine übergreifende Suche anbieten, ist es nicht möglich, diese Aggregatoren gemeinsam zu durchsuchen. Dies führt im Endeffekt dazu, dass die User wieder verschiedene Plattformen ansteuern müssen, wenn sie den gesamten OER-Fundus durchsuchen wollen.
- An vielen Stellen wird Content doppelt erschlossen, aber immer für die eigene Plattform
- Es gibt keinen geteilten Datenraum, in den Akteure Content "pushen" können
- Es gibt keine plattformübergreifenden Suchmöglichkeiten
Plattformübergreifende Kollaboration
Das wäre schön, oder? Mir ist schleierhaft, wie #OEP (Open Educational Practices, genaue Definition durch die Community steht noch aus) ohne funktionieren soll. Aber es gibt meines Wissens nach nicht mal Ansätze, wie das technisch umgesetzt werden soll (oder doch? let me hear).
Ein Szenario für solche plattformübergreifende Kollaboration könnte Qualitätssicherung sein. Gesetzt, dass sich zwei Plattformen / Communities auf etwas verständigt haben, dass sie als "Qualität" bezeichnen, wie aber dieses Gütesiegel nun an den Content bringen?
Plattform A: Na, dann kommt doch alle zu uns. Hier können wir das machen und dann hängt auch ein schönes Badge an den Materialien.
Plattform B: Ja, aber dann hängt es ja nicht an unseren Materialien. Außerdem wollen/müssen wir bei uns arbeiten, weil welche Existenzberechtigung hat denn meine Plattform noch, wenn wir alles bei dir machen?
- Obwohl nun #OEP in aller Munde sind, gibt es keine technischen Ansätze, wie (plattformübergreifende) Kollaboration technisch abgebildet werden kann
KI-Services
Was ist heute schon komplett ohne das Thema KI zu erwähnen? Mindestens für den nächsten Förderantrag muss auch irgendetwas mit KI gemacht werden...
Verschiedene Projekte erarbeiten hilfreiche und beeindruckende KI-Services. Beispielsweise, um die Annotation von Content mit Metadaten zu erleichtern, Metadaten automatisch hinzuzufügen, Content zu bestimmten Themen zu finden oder (halb-)automatisch zu Sammlungen hinzuzufügen. Aber (vielleicht habt ihr es schon erraten): Funktioniert halt nur auf der eigenen Plattform. Vermutlich, weil die Services nah am plattformeigenen Datenmodell entwickelt werden. Und da die Daten dieses Silo nicht verlassen, passt das schon. Das führt dazu, dass an mehreren Stellen die gleichen Services doppelt entwickelt werden.
- KI-Services funktionieren oft nur auf der Plattform für die sie entwickelt werden
Zusammenfassung der Probleme
Wir machen übrigens vieles schon sehr gut (Einsatz des AMB, Offene Bidungsmaterialien, wir haben eine großartige Community) und jetzt müssen wir halt weiter gehen.
(Die OER-Metadatengruppe, die das Allgemeine Metadatenprofil für Bildungsressourcen (AMB) entwickelt hat, bekommt für ihre Arbeit keine direkte Förderung. Gleichzeitig ist sie eine zentrale Anlaufstelle für alle, die mit Metadaten in offenen Bildungsinfrastukturen hantieren und das Metadatenprofil ist eines der wenigen Applikationsprofile, das öffentlich einsehbar, gut dokumentiert ist und Validierungsmöglichkeiten bietet.)
Betrachten wir die gesamten Plattformen und die beschriebenen Herausforderungen aus der Vogelperspektive, so lassen sich drei ineinander verschränkte Kernbestandteile unterscheiden, die helfen, die beschriebenen Probleme besser zu verstehen:
- User
- Service
- Daten
User: Auf (fast) allen Plattformen agieren User. Sie laden Material hoch, annotieren mit Metadaten, sind in einer Community, suchen Content usw. Egal, ob sie sich einloggen können/müssen, irgendetwas bieten wir unseren Usern an, damit sie daraus hoffentlich Mehrwerte ziehen
Service: Das ist dieses irgendetwas. Die "Webseite", die Oberfläche, das, wo der User klicken und etwas tun kann. Es ist das, was den Daten oft eine "visuelle" Form gibt. Der Service ist der Mittler, das Interface zwischen User und Daten. Mithilfe des Services lassen sich Daten erzeugen, verändern oder entfernen (Es gibt natürlich auch viele nicht-visuelle Services, die Interaktion mit Daten ermöglichen, aber für die meisten normalen Menschen, gibt es irgendwo was zu klicken).
Daten: Die Informationen in strukturierter maschinenlesbarer Form, die dem User in gerenderter Form durch einen Service Mehrwerte bieten können. Ungerenderte Daten können wir schwieirg erfassen (wir sind ja nicht Neo). Das können entweder die Metadaten zu Bildungmaterialien sein, die Materialien selbst, Profilinformationen, Materialsammlungen o.ä.

Meines Erachtens nach haben viele der oben beschriebenen Herausforderungen ihren Ursprung darin, dass die drei Kernbestandteile User, Service, Daten ungünstig miteinander verbunden wurden. Was kein Vorwurf sein soll, denn das ist genau die Art und Weise, wie die letzten Jahre (Jahrzehnte?) Plattformen immer gebaut wurden:
- User, Service und Daten werden in einer Plattform gebündelt
Das heisst durch meinen Service agieren die User mit den Daten und ich kann sicherstellen, dass in meiner kleinen Welt alles gut miteinander funktioniert. Sinnvoll, wenn ich Microsoft, Facebook, X oder ähnliches bin, weil mein Geschäftsmodell genau darin liegt: User einschließen (lock-in), ihnen die Hohheit über ihren Content nehmen (oder kannst du deine Facebook Posts zu X migrieren?) und nach Möglichkeit nicht wieder rauslassen.
Aber unsere Projekte sind öffentlich. Das sind nicht die Mechanismen, die wir replizieren sollten. Also was nun?
Bildungsinfrasstrukturen auf Basis des Nostr-Protokolls
Nostr
Eine pseudonyme Person mit dem Namen "fiatjaf" hat 2019 ein Konzept für ein Social Media Protokoll "Nostr - Notes and Other Stuff Transmitted By Relays" wie folgt beschrieben:
It does not rely on any trusted central server, hence it is resilient, it is based on cryptographic keys and signatures, so it is tamperproof, it does not rely on P2P techniques, therefore it works.
Fiatjaf, 2019
Die Kernbestandsteile des Protokolls bestehen aus:
- JSON -> Datenformat
- SHA256 & Schnorr -> Kryptographie
- Websocket -> Datenaustausch
Und funktionieren tut es so:
User besitzen ein "Schlüsselpaar": einen privaten Schlüssel (den behälst du für dich, nur für dich) und einen öffentlichen Schlüssel, den kannst du herumzeigen, das ist deine öffentliche Identität. Damit sagst du anderen Usern: Hier schau mal, das bin ich. Die beiden Schlüssel hängen dabei auf eine "magische" (kryptografische) Weise zusammen: Der öffentliche Schlüssel lässt sich aus dem privaten Schlüssel generieren, jedoch nicht andersherum. D.h. falls du deinen öffentlichen Schlüssel verlierst: Kein Problem, der lässt sich immer wieder herstellen. Wenn du deinen privaten Schlüssel verlierst: Pech gehabt, es ist faktisch unmöglich, diesen wieder herzustellen.
Die Schlüsselmagie geht jedoch noch weiter: Du kannst mit deinem privaten Schlüssel "Nachrichten" signieren, also wie unterschreiben. Diese Unterschrift, die du mit Hilfe des privaten Schlüssels erstellst, hat eine magische Eigenschaft: Jeder kann mithilfe der Signatur und deinem öffentlichen* Schlüssel nachprüfen, dass nur die Person, die auch den privaten Schlüssel zu diesem öffentlichen Schlüssel besitzt, diese Nachricht unterschrieben haben kann. Magisch, richtig? Verstehst du nicht komplett? Nicht schlimm, du benutzt es bereits vermutlich, ohne dass du es merkst. Das ist keine fancy neue Technologie, sondern gut abgehangen und breit im Einsatz.
Merke: User besitzen ein Schlüsselpaar und können damit Nachrichten signieren.
Dann gibt es noch die Services. Services funktionieren im Grunde wie bereits oben beschrieben. Durch sie interagieren die User mit Daten. Aber bei Nostr ist es ein kleines bisschen anders als sonst, denn: Die Daten "leben" nicht in den Services. Aber wo dann?
Wenn ein User einen Datensatz erstellt, verändert oder entfernen möchte, wird dieses "Event" (so nennen wir das bei Nostr) mit deinem privaten Schlüssel signiert (damit ist für alle klar, nur du kannst das gemacht haben) und dann mehrere "Relays" gesendet. Das sind die Orte, wo die Daten gehalten werden. Wenn ein User sich in einen Service einloggt, dann holt sich der Service die Daten, die er braucht von diesen Relays. User, Service und Daten sind also entkoppelt. Der User könnte zu einem anderen Service wechseln und sich dieseleben Daten von den Relays holen. Keine Lock-In Möglichkeiten.
Merke: User, Service und Daten sind entkoppelt.
Zuletzt gibt es noch die Relays. Relays sind Orte. Es sind die Orte, zu denen die Events, also die Daten der User, ihre Interaktionen, gesendet und von denen sie angefragt werden. Sie sind sowas wie das Backend von Nostr, allerdings tun sie nicht viel mehr als das: Events annehmen, Events verteilen. Je nach Konfiguration dürfen nur bestimmte User auf ein Relay schreiben oder davon lesen.
Das Protokoll ist von seinem Grunddesign auf Offenheit und Interoperabilität ausgelegt. Keine Registrierung ist nötig, sondern nur Schlüsselpaare. Durch kryptografische Verfahren kann dennoch die Authentizitität eines Events sichergestellt werden, da nur die Inhaberin des jeweiligen Schlüsselpaares dieses Event so erstellen konnte. Die Relays sorgen dafür die Daten an die gewünschten Stellen zu bringen und da wir mehr als nur eines benutzen, haben wir eine gewisse Ausfallsicherheit. Da die Daten nur aus signierten JSON-Schnipseln bestehen, können wir sie leicht an einen anderen Ort kopieren, im Falle eines Ausfalls. Durch die Signaturen ist wiederum sichergestellt, dass zwischendurch keine Veränderungen an den Daten vorgenommen wurden.
Beispiel: Ein Nostr Event
Hier ein kleiner technischer Exkurs, der beschreibt, wie Nostr Events strukturiert sind. Falls dich die technischen Details nicht so interessieren, überspringe diesen Abschnitt ruhig.
Jedes Nostr Event besitzt die gleiche Grundstruktur mit den Attributen:
id: Der Hash des Eventspubkey: Der Pubkey des Urhebers des Eventscreated_at: Der Zeitstempel des Eventskind: Der Typ des Eventstags: Zusätzliche Metadaten für das Event können in diesem Array hinterlegt werdencontent: Der textuelle Inhalt eines Eventssig: Die Signatur des Events, um die Integrität der Daten zu überprüfen
json { "id": <32-bytes lowercase hex-encoded sha256 of the serialized event data>, "pubkey": <32-bytes lowercase hex-encoded public key of the event creator>, "created_at": <unix timestamp in seconds>, "kind": <integer between 0 and 65535>, "tags": [ [<arbitrary string>...], // ... ], "content": <arbitrary string>, "sig": <64-bytes lowercase hex of the signature of the sha256 hash of the serialized event data, which is the same as the "id" field> }Die verwendeten Eventtypen sowie die existierenden Spezifikationen lassen sich unter https://github.com/nostr-protocol/nips/ einsehen.
Wichtig ist auch: Du kannst einfach anfangen, Anwendungen zu entwickeln. Die Relays werden alle Events akzeptieren, die dem o.g. Schema folgen. Du musst also niemanden um Erlaubnis fragen oder warten, bis deine Spezifikation akzeptiert und hinzugefügt wurde.
You can just build things.
Exkurs: Nostr für Binärdaten - Blossom
Ja, aber... das ist doch nur für textbasierte Daten geeignet? Was ist denn mit den Binärdaten (Bilder, Videos, PDFs, etc)
Diese Daten sind oft recht groß und es wurde sich auf das Best-Practice geeignet, diese Daten nicht auf Relays abzulegen, sondern einen besser geeigneten Publikationsmechanismus für diese Datentypen zu finden. Der Ansatz wird als "Blossom - Blobs stored simply on mediaservers" bezeichnet und ist recht unkompliziert.
Blossom Server (nichts anderes als simple Medienserver) nutzen Nostr Schlüsselpaare zur Verwaltung Identitäten und zum Signieren von Events. Die Blobs werden über ihren sha256 Hash identifiziert. Blossom definiert einige standardisierte Endpunkte, die beschreiben wie Medien hochgeladen werden können, wie sie konsumiert werden können usw.
Die Details, wie Authorisierung und die jeweiligen Endpunkte funktionieren, werden in der genannten Spezifikation beschrieben.
Nostr 🤝 Öffentliche Bildungsinfrastrukturen
Wie könnten Herausforderungen gelöst werden, wenn wir Nostr als Basis für die öffentliche Bildungsinfrastruktur einsetzen?
Material-Upload
- Es ist nicht einfach möglich OER bereitzustellen, sodass es auch auf verschiedenen Plattformen gefunden werden kann.
Mit Nostr als Basis-Infrastruktur würden die Metadaten und die Binärdaten nicht an den Service gekoppelt sein, von dem aus sie bereitgestellt wurden. Binärdaten können auf sogenannten Blossom-Servern gehostet werden. Metadaten, Kommentare und weitere textbasierte Daten werden über die Relay-Infrastruktur verteilt. Da Daten und Service entkoppelt sind, können die OER Materialien von verschiedenen Anwendungen aus konsumiert werden.
Kuration
- Es gibt keine interoperablen Sammlungen
- Metadaten-Annotation ist zentralisiert
- User können keine eigenen Metadaten hinzufügen
Sammlungen sind per se interoperabel. Auf Protokollebene ist definiert, wie Listen funktionieren. Die Annotation mit Metadaten ist an keiner Stelle zentralisiert. Das Versprechen der RDF-Community "Anyone can say anything about any topic" wird hier verwirklicht. Ich muss mir ja nicht alles anhören. Vielleicht konsumiere ich nur Metadaten-Events bestimmter Redaktionen oder User. Vielleicht nur diejenigen mit einer Nähe zu meinem sozialen Graphen. Jedenfalls gibt es die Möglichkeit für alle User entsprechende Metadaten bereit zu stellen.
Crawling, Indexierung und Suche * An vielen Stellen wird Content doppelt erschlossen, aber immer für die eigene Plattform * Es gibt keinen geteilten Datenraum, in den Akteure Content "pushen" können * Es gibt keine plattformübergreifenden Suchmöglichkeiten
Keine Doppelerschließungen mehr. Wenn ein User im Netzwerk ein Metadatenevent veröffentlicht hat, ist es für alle konsumierbar. Der Datenraum ist per se geteilt. Plattformübergreifende Suche wird durch die Kombination aus Relays und NIPs ermöglicht. In den NIPs können spezielle Query-Formate für die jeweiligen NIPs definiert werden. Relays können anzeigen, welche NIPs sie untersützten. Eine plattformübergreifende Suche ist im Nostr eine relay-übergreifende Suche.
Plattformübergreifende Kollaboration
- Obwohl nun #OEP in aller Munde sind, gibt es keine technischen Ansätze, wie (plattformübergreifende) Kollaboration technisch abgebildet werden kann
Nostr ist der technische Ansatz.
KI-Services
- KI-Services funktionieren oft nur auf der Plattform für die sie entwickelt werden
Es gibt im Nostr das Konzept der Data Vending Machines (s. auch data-vending-machines.org). Statt also einfach nur eine API zu bauen (was auch schon sehr schön ist, wenn sie offen zugänglich ist), könnten diese Services auch als Akteure im Nostr Netzwerk fungieren und Jobs annehmen und ausführen. Die Art der Jobs kann in einer Spezifikation beschrieben werden, sodass die Funktionsweise für alle interessierten Teilnehmer im Netzwerk einfach nachzuvollziehen ist.
Die Services könnten sogar monetarisiert werden, sodass sich hier auch Möglichkeiten böten, Geschäftsmodelle zu entwickeln.
Fazit
Die Open Education Community ist großartig. Es sind einzigartige und unglaublich engagierte Menschen, die sich dem hehren Ziel "Zugängliche Bildung für Alle" -> "Offene Bildung" verschrieben haben. Wir verwenden Creative Commons Lizenzen -> Commons -> Gemeingüter. Es ist okay, dass viele Projekte von Sponsoren und Förderungen abhängig sind. Was wir machen, ist im Sinne eines Gemeingutes: Öffentliche Bildung für alle. Also zahlen wir als Gemeinschaft alle dafür.
Was nicht okay ist: Dass das, wofür wir alle gezahlt haben, nach kurzer Zeit nicht mehr auffindbar ist. Dass es eingeschlossen wird. In öffentlich finanzierten Datensilos. Es muss für alle auch langfristig verfügbar sein. Sonst ist es nicht zugänglich, nicht offen. Dann ist das O in OER nur ein Label und Marketing, um für eine ABM-Maßnahme 3 Jahre Geld zu bekommen. Denn nichts anderes ist Content-Entwicklung, wenn der Content nach drei Jahren weggeschmissen wird.
Und dasselbe gilt für OEP. Offene Lernpraktiken, sind auch nur eine Phrase, wenn wir die passende technische Infrastruktur nicht mitdenken, die wirkliche Offenheit und Kollaboration und damit die Umsetzung offener Lernpraktiken ermöglicht.
Und wenn wir uns jetzt nicht Gedanken darüber machen, die Infrastruktur für offenes Lernen anzupassen, dann werden wir vermutlich in einigen Jahren sehen können, was bei politischen Umorientierungen noch davon übrig bleiben wird. Wenn die Fördertöpfe komplett gestrichen werden, was bleibt dann übrig von dem investierten Geld?
Wir brauchen Lösungen, die engagierte Communities weiter betreiben können und denen kein Kopf abgeschlagen werden kann, ohne dass wir zwei neue daneben setzen könnten.
Wir müssen uns jetzt Gedanken darüber machen.
Wie offen will öffentliche Bildungsinfrastruktur sein?
-
 @ 65912a7a:5dc638bf
2024-11-22 21:37:16
@ 65912a7a:5dc638bf
2024-11-22 21:37:16Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 12
Ingredients
- 12-14oz fresh cranberries
- 1⅓ cup packed brown sugar
- 1 cup raisins
- 1 orange, peeled & chopped
- 1 cup water
Directions
- Using medium sauce pan, simmer cranberries and water for 5-6 min. Cranberries will start to pop.
- Add brown sugar, raisins, and chopped orange to the berries.
- Bring to a simmer and continue to cook for 20 min. Stir often to prevent sticking. Remove from heat.
- Let set until room temp. Mixture will thicken as it cools.
- Put in a covered container and keep refrigerated. Lasts for about 2 weeks.
-
 @ 79be667e:16f81798
2025-06-11 18:23:32
@ 79be667e:16f81798
2025-06-11 18:23:32In een zee van mogelijkheden\ Kunnen we best veel tijd aan dromen besteden
Dromen is een universele taal\ Het wordt gedaan door ons allemaal
Het is het woord\ Dat deze gelijkheid de grond in boort
-
 @ 79be667e:16f81798
2025-06-11 18:54:57
@ 79be667e:16f81798
2025-06-11 18:54:57In het hart van een gepensioneerde operazangeres ontstond een stemmetje. Het stemmetje klonk verrast. "He," ging het hart. "Ik heb een stemmetje gekregen! Hoe kan dit? Kan iemand me horen? Zouden mijn gedachten me kunnen horen?" vroeg het stemmetje, niet wetend aan wie. Want de gedachten hoorden het niet. Zij waren zo druk bezig met het verleden en hadden een grote angst dit te verliezen. "Weet je nog?" gingen de gedachten. "Voor duizenden mensen heb ik gezongen! Avond na avond! Tienduizenden mensen hebben me toegejuicht! Wat waren ze onder de indruk! Luister! Ik kan het nog steeds!" "He," ging het hart. "Hoor je me dan niet? Het ging toch helemaal niet om dat gejuich. Weet je dan niet meer hoe ik me volledig bloot gaf aan die mensen. Mijn diepste en meest persoonlijke verhalen waren te horen in mijn liederen. Daar draaide het toch om? De mensen waren niet enkel onder de indruk. Hun harten hebben mijn verhalen gevoeld en konden zo kennis geven aan hun gedachten. Is dat niet wat echt telde?" Maar de gedachten waren volop aan het zingen voor de ene persoon die ze konden vinden die wou luisteren. "He," ging het hart. "Ook in dit moment zijn mijn liederen te horen door vele gedachten en te voelen door vele harten over de hele wereld. Heb ik dan geen rust verdiend? Kan ik niet even genieten van de rust die in dit moment te vinden is, maar jullie van me afnemen?" Maar de gedachten waren nog steeds volop aan het zingen.
-
 @ dfa02707:41ca50e3
2025-06-11 23:02:28
@ dfa02707:41ca50e3
2025-06-11 23:02:28
Good morning (good night?)! The No Bullshit Bitcoin news feed is now available on Moody's Dashboard! A huge shoutout to sir Clark Moody for integrating our feed.
Headlines
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- The Bank for International Settlements (BIS) wants to contain 'crypto' risks. A report titled "Cryptocurrencies and Decentralised Finance: Functions and Financial Stability Implications" calls for expanding research into "how new forms of central bank money, capital controls, and taxation policies can counter the risks of widespread crypto adoption while still fostering technological innovation."
- "Global Implications of Scam Centres, Underground Banking, and Illicit Online Marketplaces in Southeast Asia." According to the United Nations Office on Drugs and Crime (UNODC) report, criminal organizations from East and Southeast Asia are swiftly extending their global reach. These groups are moving beyond traditional scams and trafficking, creating sophisticated online networks that include unlicensed cryptocurrency exchanges, encrypted communication platforms, and stablecoins, fueling a massive fraud economy on an industrial scale.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
Use the tools
- Bitcoin Safe v1.2.3 expands QR SignMessage compatibility for all QR-UR-compatible hardware signers (SpecterDIY, KeyStone, Passport, Jade; already supported COLDCARD Q). It also adds the ability to import wallets via QR, ensuring compatibility with Keystone's latest firmware (2.0.6), alongside other improvements.
- Minibits v0.2.2-beta, an ecash wallet for Android devices, packages many changes to align the project with the planned iOS app release. New features and improvements include the ability to lock ecash to a receiver's pubkey, faster confirmations of ecash minting and payments thanks to WebSockets, UI-related fixes, and more.
- Zeus v0.11.0-alpha1 introduces Cashu wallets tied to embedded LND wallets. Navigate to Settings > Ecash to enable it. Other wallet types can still sweep funds from Cashu tokens. Zeus Pay now supports Cashu address types in Zaplocker, Cashu, and NWC modes.
- LNDg v1.10.0, an advanced web interface designed for analyzing Lightning Network Daemon (LND) data and automating node management tasks, introduces performance improvements, adds a new metrics page for unprofitable and stuck channels, and displays warnings for batch openings. The Profit and Loss Chart has been updated to include on-chain costs. Advanced settings have been added for users who would like their channel database size to be read remotely (the default remains local). Additionally, the AutoFees tool now uses aggregated pubkey metrics for multiple channels with the same peer.
- Nunchuk Desktop v1.9.45 release brings the latest bug fixes and improvements.
- Blockstream Green iOS v4.1.8 has renamed L-BTC to LBTC, and improves translations of notifications, login time, and background payments.
- Blockstream Green Android v4.1.8 has added language preference in App Settings and enables an Android data backup option for disaster recovery. Additionally, it fixes issues with Jade entry point PIN timeout and Trezor passphrase input.
- Torq v2.2.2, an advanced Lightning node management software designed to handle large nodes with over 1000 channels, fixes bugs that caused channel balance to not be updated in some cases and channel "peer total local balance" not getting updated.
- Stack Wallet v2.1.12, a multicoin wallet by Cypher Stack, fixes an issue with Xelis introduced in the latest release for Windows.
- ESP-Miner-NerdQAxePlus v1.0.29.1, a forked version from the NerdAxe miner that was modified for use on the NerdQAxe+, is now available.
- Zark enables sending sats to an npub using Bark.
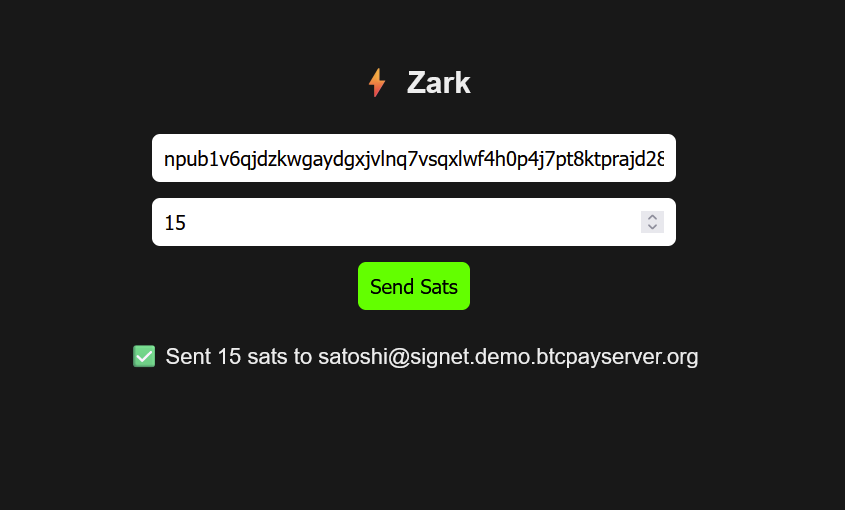
- Erk is a novel variation of the Ark protocol that completely removes the need for user interactivity in rounds, addressing one of Ark's key limitations: the requirement for users to come online before their VTXOs expire.
- Aegis v0.1.1 is now available. It is a Nostr event signer app for iOS devices.
- Nostash is a NIP-07 Nostr signing extension for Safari. It is a fork of Nostore and is maintained by Terry Yiu. Available on iOS TestFlight.
- Amber v3.2.8, a Nostr event signer for Android, delivers the latest fixes and improvements.
- Nostur v1.20.0, a Nostr client for iOS, adds
-
 @ 5627e59c:d484729e
2025-06-11 18:23:32
@ 5627e59c:d484729e
2025-06-11 18:23:32In een zee van mogelijkheden\ Kunnen we best veel tijd aan dromen besteden
Dromen is een universele taal\ Het wordt gedaan door ons allemaal
Het is het woord\ Dat deze gelijkheid de grond in boort
-
 @ 3bf0c63f:aefa459d
2024-11-07 14:56:17
@ 3bf0c63f:aefa459d
2024-11-07 14:56:17The case against edits
Direct edits are a centralizing force on Nostr, a slippery slope that should not be accepted.
Edits are fine in other, more specialized event kinds, but the
kind:1space shouldn't be compromised with such a push towards centralization, becausekind:1is the public square of Nostr, where all focus should be on decentralization and censorship-resistance.- Why?
Edits introduce too much complexity. If edits are widespread, all clients now have to download dozens of extra events at the same time while users are browsing a big feed of notes which are already coming from dozens of different relays using complicated outbox-model-based querying, then for each event they have to open yet another subscription to these relays -- or perform some other complicated batching of subscriptions which then requires more complexity on the event handling side and then when associating these edits with the original events. I can only imagine this will hurt apps performance, but it definitely raises the barrier to entry and thus necessarily decreases Nostr decentralization.
Some clients may be implemneted in way such that they download tons of events and then store them in a local databases, from which they then construct the feed that users see. Such clients may make edits potentially easier to deal with -- but this is hardly an answer to the point above, since such clients are already more complex to implement in the first place.
- What do you have against complex clients?
The point is not to say that all clients should be simple, but that it should be simple to write a client -- or at least as simple as physically possible.
You may not be thinking about it, but if you believe in the promise of Nostr then we should expect to see Nostr feeds in many other contexts other than on a big super app in a phone -- we should see Nostr notes being referenced from and injected in unrelated webpages, unrelated apps, hardware devices, comment sections and so on. All these micro-clients will have to implement some complicated edit-fetching logic now?
- But aren't we already fetching likes and zaps and other things, why not fetch edits too?
Likes, zaps and other similar things are optional. It's perfectly fine to use Nostr without seeing likes and/or zaps -- and, believe me, it does happen quite a lot. The point is basically that likes or zaps don't affect the content of the main post at all, while edits do.
- But edits are optional!
No, they are not optional. If edits become widespread they necessarily become mandatory. Any client that doesn't implement edits will be displaying false information to its users and their experience will be completely broken.
- That's fine, as people will just move to clients that support edits!
Exactly, that is what I expect to happen too, and this is why I am saying edits are a centralizing force that we should be fighting against, not embracing.
If you understand that edits are a centralizing force, then you must automatically agree that they aren't a desirable feature, given that if you are reading this now, with Nostr being so small, there is a 100% chance you care about decentralization and you're not just some kind of lazy influencer that is only doing this for money.
- All other social networks support editing!
This is not true at all. Bluesky has 10x more users than Nostr and doesn't support edits. Instagram doesn't support editing pictures after they're posted, and doesn't support editing comments. Tiktok doesn't support editing videos or comments after they're posted. YouTube doesn't support editing videos after they're posted. Most famously, email, the most widely used and widespread "social app" out there, does not support edits of any kind. Twitter didn't support edits for the first 15 years of its life, and, although some people complained, it didn't hurt the platform at all -- arguably it benefitted it.
If edits are such a straightforward feature to add that won't hurt performance, that won't introduce complexity, and also that is such an essential feature users could never live without them, then why don't these centralized platforms have edits on everything already? There must be something there.
- Eventually someone will implement edits anyway, so why bother to oppose edits now?
Once Nostr becomes big enough, maybe it will be already shielded from such centralizing forces by its sheer volume of users and quantity of clients, maybe not, we will see. All I'm saying is that we shouldn't just push for bad things now just because of a potential future in which they might come.
- The market will decide what is better.
The market has decided for Facebook, Instagram, Twitter and TikTok. If we were to follow what the market had decided we wouldn't be here, and you wouldn't be reading this post.
- OK, you have convinced me, edits are not good for the protocol. But what do we do about the users who just want to fix their typos?
There are many ways. The annotations spec, for example, provides a simple way to append things to a note without being a full-blown edit, and they fall back gracefully to normal replies in clients that don't implement the full annotations spec.
Eventually we could have annotations that are expressed in form of simple (human-readable?) diffs that can be applied directly to the post, but fall back, again, to comments.
Besides these, a very simple idea that wasn't tried yet on Nostr yet is the idea that has been tried for emails and seems to work very well: delaying a post after the "submit" button is clicked and giving the user the opportunity to cancel and edit it again before it is actually posted.
Ultimately, if edits are so necessary, then maybe we could come up with a way to implement edits that is truly optional and falls back cleanly for clients that don't support them directly and don't hurt the protocol very much. Let's think about it and not rush towards defeat.