-
 @ 2769f6ba:8dac44e4
2025-06-03 06:53:38
@ 2769f6ba:8dac44e4
2025-06-03 06:53:38You may want to believe that the world works like a video game, where you can press the pause button, come back three months later and everything will be waiting for you exactly as you left it. But real life doesn’t work like that. The difference is that in the video game you are in control, whereas in real life you are not. Maybe you want to believe that the worst is over, but this is just getting started. Supply chains are breaking down and the economy is starting to collapse. To make it clear, “the economy” is not something abstract; it’s real people losing their jobs, their businesses, their incomes and their homes. Your authoritarian fantasies will just make it worse for you and others until you cannot handle it anymore and you accept reality and surrender to it. I get that you are afraid, and that’s OK. But to hold your fellow human beings hostage because you are afraid is not OK. It’s getting to the point where if you still support lockdowns, mandatory vaccines, mandatory tracking, mandatory testing or mandatory anything you have blood on your hands. History will not judge you kindly.
Then there are those of you who want to believe that the bailouts and the “universal basic income” will make the problems disappear. For example, I read Charles Eisenstein in his otherwise excellent piece The Coronation come up with all this UBI nonsense. You probably realize that if you grab a piece of paper and write “$1,000,000” on it with a marker pen of your favorite color, you don’t become magically rich. But you still want to believe that if the government does exactly the same thing, your problems will go away. On the one hand, even if you are not fully aware of it, you realize that the government and its satellite corporations are abusing you and sucking your blood more and more every day. Yet on the other hand, you keep begging your very abusers that are trying to deprive you from earning an honest living for yourself to give you a measly monthly UBI check in the hopes that it will magically make you feel good and solve your problems.
Aside from the fact that printing money cannot solve the issue the governments themselves have created in the first place with their mandatory lockdowns: maybe you expect that you can control your masters, or that they will benevolently give you the UBI check with no strings attached. Of course not: receiving the check will likely be tied to being a “good law-abiding citizen” (a.k.a. obedient slave); something like the social credit system they have in China. You will end up completely disempowered and depending on the government to even feed yourself and have shelter. I find it quite infuriating and sad that any “spiritual teacher” would want that for you and that you fall for it.
Consider this:
The issue is not the coronavirus itself. The virus is just revealing the cracks in the system.
You are not a victim. You always have the power. Not the power to start a “revolution”, mind you, which just consists in replacing the old abusers with new ones. As Buckminster Fuller said: “You never change things by fighting the existing reality. To change something, build a new model that makes the existing model obsolete.”
You have the power to walk away from this dying system of nation-state governments and fiat “money” and into the nascent paradigm of cryptocurrencies and decentralized governance. But first you have to question and confront the beliefs you have accepted as “reality”. It’s hard, I know, but unavoidable. So, the sooner you begin, the better for yourself and for humanity. Do you want to be free or do you just want to have a “fair” master?
-
 @ 2769f6ba:8dac44e4
2025-06-03 06:46:33
@ 2769f6ba:8dac44e4
2025-06-03 06:46:33I am feeling that the issue runs deeper. Science has been hijacked by the state, so I find the post-truth thing as a meme that rejects the corruption of science. Unfortunately, those hippies are throwing the baby with the bathwater in the process. But I see legitimate issues that need to be acknowledged if we want to reach out to those post-truth hippies.
For example, in my opinion:
The issue is not with 5G, but with this:
- Not wanting to be “bathed” 24/7 in waves of higher frequency (3 to 30 GHz). I understand the fear and skepticism on this.
- The push towards so-called “smart cities”, which are more like surveillance-cities. Granted, those technologies will bring benefits, but I see an issue with a top-down planned system controlled by the state and its contractors rather than a more organic system, with participation from many actors and little central planning. Of course, politicians and “experts” are always trying to link together smart-cities with 5G as if they must go together.
- The state is appropriating the radio spectrum and renting most of it to its cronies from the telecom companies, while it only leaves tiny scraps for open use by the population.
The issue is not with vaccines, but with this:
- pushing forced vaccination under the guise of “science”.
- an ever-growing list of both mandatory and “recommended” vaccines, some of them for diseases that are just an inconvenience and definitely not life-threatening.
I feel it must be acknowledged that the state has hijacked science, in the same way that the church has always hijacked spirituality. So, just telling those hippies that they have to trust science because facts and because the “experts” say so, won’t cut it anymore. A different approach is needed.
-
 @ 2769f6ba:8dac44e4
2025-06-03 06:38:13
@ 2769f6ba:8dac44e4
2025-06-03 06:38:13To be blunt, people want “authority” to exist because they themselves are immature cowards. They want an all-powerful entity to impose their will upon others. This takes different forms in different varieties of political advocacy, but the basic motivation is always the same. The “liberal” for example, resents reality. He does not want a world in which suffering and injustice are possible. But instead of doing what He can as a human being, he wants a “Government” to do it for him. He wants some magical entity to make sure that everyone, himself included, is fed, housed, and taken care of, no matter how lazy or irresponsible they are. Instead of trusting human beings to take care of each other, he wants a super human ”authority” to guarantee housing, food, health care, and all sorts of other things, for everyone. He wants it so badly that he refuses to accept the obvious truth that no such guarantee is ever possible, and that if mere mortals do not take care of themselves and each other, nothing else will take care of them.
“The Most Dangerous Superstition” – Larken Rose, pg. 124
-
 @ c1e9ab3a:9cb56b43
2025-06-01 13:54:06
@ c1e9ab3a:9cb56b43
2025-06-01 13:54:061. Introduction
Over the last 250 years the world’s appetite for energy has soared along an unmistakably exponential trajectory, transforming societies and economies alike. After a half‑century of relative deceleration, a new mix of technological, demographic and political forces now hints at an impending catch‑up phase that could push demand back onto its centuries‑long growth curve. This post knits together the history, the numbers and the newest policy signals to explore what that rebound might look like—and how Gen‑4 nuclear power could meet it.
2. The Long Exponential: 1750 – 1975
Early industrialisation replaced muscle, wood and water with coal‑fired steam, pushing global primary energy use from a few exajoules per year in 1750 to roughly 60 EJ by 1900 and 250 EJ by 1975. Over that span aggregate consumption doubled roughly every 25–35 years, equivalent to a long‑run compound growth rate of ~3 % yr‑¹. Per‑capita use climbed even faster in industrialised economies as factories, railways and electric lighting spread.
3. 1975 – 2025: The Great Slowdown
3.1 Efficiency & Structural Change
• Oil shocks (1973, 1979) and volatile prices pushed OECD economies to squeeze more GDP from each joule.
• Services displaced heavy industry in rich countries, trimming energy intensity.
• Refrigerators, motors and vehicles became dramatically more efficient.3.2 Policy & Technology
• The Inflation Reduction Act (U.S.) now layers zero‑emission production credits and technology‑neutral tax incentives on top of existing nuclear PTCs citeturn1search0turn1search2.
• The EU’s Net‑Zero Industry Act aims to streamline siting and finance for “net‑zero technologies”, explicitly naming advanced nuclear citeturn0search1.3.3 Result
Global primary energy in 2024 stands near 600 EJ (≈ 167 000 TWh)—still growing, but the line has flattened versus the pre‑1975 exponential.
4. Population & Per‑Capita Demand
World population tripled between 1950 and today, yet total energy use grew roughly six‑fold. The imbalance reflects rising living standards and electrification. Looking ahead, the UN projects population to plateau near 10.4 billion in the 2080s, but per‑capita demand is poised to climb as the Global South industrialises.
5. The Policy Pivot of 2023‑2025
| Region | Signal | Year | Implication | |--------|--------|------|-------------| | COP 28 Declaration | 20+ nations pledge to triple nuclear capacity by 2050 | 2023 | High‑level political cover for rapid nuclear build‑out citeturn0search2 | | Europe | Post‑crisis sentiment shifts; blackout in Iberia re‑opens nuclear debate | 2025 | Spain, Germany, Switzerland and others revisit phase‑outs citeturn0news63 | | United States | TVA submits first SMR construction permit; NRC advances BWRX‑300 review | 2025 | Regulatory pathway for fleet deployment citeturn1search9turn1search1 | | Global Strategy Report | “Six Dimensions for Success” playbook for new nuclear entrants | 2025 | Practical roadmap for emerging economies citeturn0search0 | | U.S. Congress | Proposed cuts to DOE loan office threaten build‑out pace | 2025 | Finance bottleneck remains a risk citeturn1news28 |
6. The Catch‑Up Scenario
Suppose the recent 50‑year pause ends in 2025, and total energy demand returns to a midpoint historical doubling period of 12.5 years (the average of the 10–15 year rebound window).
6.1 Consumption Trajectory
| Year | Doublings since 2024 | Demand (TWh) | |------|----------------------|--------------| | 2024 | 0 | 167 000 | | 2037 | 1 | 334 000 | | 2050 | 2 | 668 000 | | 2062 | 3 | 1 336 000 |
(Table ignores efficiency gains from electrification for a conservative, supply‑side sizing.)
7. Nuclear‑Only Supply Model
7.1 Reactor Math
- 1 GWᵉ Gen‑4 reactor → 8.76 TWh yr‑¹ at 100 % capacity factor.
- 2062 requirement: 1 336 000 TWh yr‑¹ → ≈ 152 500 reactors in steady state.
- Build rate (2025‑2062, linear deployment):
152 500 ÷ 38 years ≈ 4 000 reactors per year globally.
(Down from the earlier 5 000 yr‑¹ estimate because the deployment window now stretches 38 years instead of 30.)
7.2 Policy Benchmarks
- COP 28 triple target translates to +780 GW (if baseline 2020 ≈ 390 GW). That is <100 1 GW units per year—two orders of magnitude lower than the theoretical catch‑up requirement, highlighting just how aggressive our thought experiment is.
7.3 Distributed vs Grid‑Centric
Small Modular Reactors (300 MW class) can be sited on retiring coal plants, using existing grid interconnects and cooling, vastly reducing new transmission needs. Ultra‑large “gigawatt corridors” become optional rather than mandatory, though meshed regional grids still improve resilience and market liquidity.
8. Challenges & Unknowns
- Finance: Even with IRA‑style credits, first‑of‑a‑kind Gen‑4 builds carry high cost of capital.
- Supply Chain: 4 000 reactors a year means a reactor‑grade steel output roughly 20× today’s level.
- Waste & Public Trust: Advanced reactors can burn actinides, but geologic repositories remain essential.
- Workforce: Nuclear engineers, welders and regulators are already in short supply.
- Competing Technologies: Cheap renewables + storage and prospective fusion could displace part of the projected load.
9. Conclusions
Recent policy shifts—from Europe’s Net‑Zero Industry Act to the COP 28 nuclear declaration—signal that governments once again see nuclear energy as indispensable to deep decarbonisation. Yet meeting an exponential catch‑up in demand would require deployment rates an order of magnitude beyond today’s commitments, testing manufacturing capacity, finance and political resolve.
Whether the future follows the modest path now embedded in policy or the steeper curve sketched here, two convictions stand out:
- Electrification will dominate new energy demand.
- Scalable, dispatchable low‑carbon generation—likely including large fleets of Gen‑4 fission plants—must fill much of that gap if net‑zero targets are to remain credible.
Last updated 1 June 2025.
-
 @ c1e9ab3a:9cb56b43
2025-05-18 04:14:48
@ c1e9ab3a:9cb56b43
2025-05-18 04:14:48Abstract
This document proposes a novel architecture that decouples the peer-to-peer (P2P) communication layer from the Bitcoin protocol and replaces or augments it with the Nostr protocol. The goal is to improve censorship resistance, performance, modularity, and maintainability by migrating transaction propagation and block distribution to the Nostr relay network.
Introduction
Bitcoin’s current architecture relies heavily on its P2P network to propagate transactions and blocks. While robust, it has limitations in terms of flexibility, scalability, and censorship resistance in certain environments. Nostr, a decentralized event-publishing protocol, offers a multi-star topology and a censorship-resistant infrastructure for message relay.
This proposal outlines how Bitcoin communication could be ported to Nostr while maintaining consensus and verification through standard Bitcoin clients.
Motivation
- Enhanced Censorship Resistance: Nostr’s architecture enables better relay redundancy and obfuscation of transaction origin.
- Simplified Lightweight Nodes: Removing the full P2P stack allows for lightweight nodes that only verify blockchain data and communicate over Nostr.
- Architectural Modularity: Clean separation between validation and communication enables easier auditing, upgrades, and parallel innovation.
- Faster Propagation: Nostr’s multi-star network may provide faster propagation of transactions and blocks compared to the mesh-like Bitcoin P2P network.
Architecture Overview
Components
-
Bitcoin Minimal Node (BMN):
- Verifies blockchain and block validity.
- Maintains UTXO set and handles mempool logic.
- Connects to Nostr relays instead of P2P Bitcoin peers.
-
Bridge Node:
- Bridges Bitcoin P2P traffic to and from Nostr relays.
- Posts new transactions and blocks to Nostr.
- Downloads mempool content and block headers from Nostr.
-
Nostr Relays:
- Accept Bitcoin-specific event kinds (transactions and blocks).
- Store mempool entries and block messages.
- Optionally broadcast fee estimation summaries and tipsets.
Event Format
Proposed reserved Nostr
kindnumbers for Bitcoin content (NIP/BIP TBD):| Nostr Kind | Purpose | |------------|------------------------| | 210000 | Bitcoin Transaction | | 210001 | Bitcoin Block Header | | 210002 | Bitcoin Block | | 210003 | Mempool Fee Estimates | | 210004 | Filter/UTXO summary |
Transaction Lifecycle
- Wallet creates a Bitcoin transaction.
- Wallet sends it to a set of configured Nostr relays.
- Relays accept and cache the transaction (based on fee policies).
- Mining nodes or bridge nodes fetch mempool contents from Nostr.
- Once mined, a block is submitted over Nostr.
- Nodes confirm inclusion and update their UTXO set.
Security Considerations
- Sybil Resistance: Consensus remains based on proof-of-work. The communication path (Nostr) is not involved in consensus.
- Relay Discoverability: Optionally bootstrap via DNS, Bitcoin P2P, or signed relay lists.
- Spam Protection: Relay-side policy, rate limiting, proof-of-work challenges, or Lightning payments.
- Block Authenticity: Nodes must verify all received blocks and reject invalid chains.
Compatibility and Migration
- Fully compatible with current Bitcoin consensus rules.
- Bridge nodes preserve interoperability with legacy full nodes.
- Nodes can run in hybrid mode, fetching from both P2P and Nostr.
Future Work
- Integration with watch-only wallets and SPV clients using verified headers via Nostr.
- Use of Nostr’s social graph for partial trust assumptions and relay reputation.
- Dynamic relay discovery using Nostr itself (relay list events).
Conclusion
This proposal lays out a new architecture for Bitcoin communication using Nostr to replace or augment the P2P network. This improves decentralization, censorship resistance, modularity, and speed, while preserving consensus integrity. It encourages innovation by enabling smaller, purpose-built Bitcoin nodes and offloading networking complexity.
This document may become both a Bitcoin Improvement Proposal (BIP-XXX) and a Nostr Improvement Proposal (NIP-XXX). Event kind range reserved: 210000–219999.
-
 @ c1e9ab3a:9cb56b43
2025-05-01 17:29:18
@ c1e9ab3a:9cb56b43
2025-05-01 17:29:18High-Level Overview
Bitcoin developers are currently debating a proposed change to how Bitcoin Core handles the
OP_RETURNopcode — a mechanism that allows users to insert small amounts of data into the blockchain. Specifically, the controversy revolves around removing built-in filters that limit how much data can be stored using this feature (currently capped at 80 bytes).Summary of Both Sides
Position A: Remove OP_RETURN Filters
Advocates: nostr:npub1ej493cmun8y9h3082spg5uvt63jgtewneve526g7e2urca2afrxqm3ndrm, nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg, nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp, others
Arguments: - Ineffectiveness of filters: Filters are easily bypassed and do not stop spam effectively. - Code simplification: Removing arbitrary limits reduces code complexity. - Permissionless innovation: Enables new use cases like cross-chain bridges and timestamping without protocol-level barriers. - Economic regulation: Fees should determine what data gets added to the blockchain, not protocol rules.
Position B: Keep OP_RETURN Filters
Advocates: nostr:npub1lh273a4wpkup00stw8dzqjvvrqrfdrv2v3v4t8pynuezlfe5vjnsnaa9nk, nostr:npub1s33sw6y2p8kpz2t8avz5feu2n6yvfr6swykrnm2frletd7spnt5qew252p, nostr:npub1wnlu28xrq9gv77dkevck6ws4euej4v568rlvn66gf2c428tdrptqq3n3wr, others
Arguments: - Historical intent: Satoshi included filters to keep Bitcoin focused on monetary transactions. - Resource protection: Helps prevent blockchain bloat and abuse from non-financial uses. - Network preservation: Protects the network from being overwhelmed by low-value or malicious data. - Social governance: Maintains conservative changes to ensure long-term robustness.
Strengths and Weaknesses
Strengths of Removing Filters
- Encourages decentralized innovation.
- Simplifies development and maintenance.
- Maintains ideological purity of a permissionless system.
Weaknesses of Removing Filters
- Opens the door to increased non-financial data and potential spam.
- May dilute Bitcoin’s core purpose as sound money.
- Risks short-term exploitation before economic filters adapt.
Strengths of Keeping Filters
- Preserves Bitcoin’s identity and original purpose.
- Provides a simple protective mechanism against abuse.
- Aligns with conservative development philosophy of Bitcoin Core.
Weaknesses of Keeping Filters
- Encourages central decision-making on allowed use cases.
- Leads to workarounds that may be less efficient or obscure.
- Discourages novel but legitimate applications.
Long-Term Consequences
If Filters Are Removed
- Positive: Potential boom in new applications, better interoperability, cleaner architecture.
- Negative: Risk of increased blockchain size, more bandwidth/storage costs, spam wars.
If Filters Are Retained
- Positive: Preserves monetary focus and operational discipline.
- Negative: Alienates developers seeking broader use cases, may ossify the protocol.
Conclusion
The debate highlights a core philosophical split in Bitcoin: whether it should remain a narrow monetary system or evolve into a broader data layer for decentralized applications. Both paths carry risks and tradeoffs. The outcome will shape not just Bitcoin's technical direction but its social contract and future role in the broader crypto ecosystem.
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:55:11
@ c1e9ab3a:9cb56b43
2025-04-10 02:55:11The United States is on the cusp of a historic technological renaissance, often referred to as the Fourth Industrial Revolution. Artificial intelligence, automation, advanced robotics, quantum computing, biotechnology, and clean manufacturing are converging into a seismic shift that will redefine how we live, work, and relate to one another. But there's a critical catch: this transformation depends entirely on the availability of stable, abundant, and inexpensive electricity.
Why Electricity is the Keystone of Innovation
Let’s start with something basic but often overlooked. Every industrial revolution has had an energy driver:
- The First rode the steam engine, powered by coal.
- The Second was electrified through centralized power plants.
- The Third harnessed computing and the internet.
- The Fourth will demand energy on a scale and reliability never seen before.
Imagine a city where thousands of small factories run 24/7 with robotics and AI doing precision manufacturing. Imagine a national network of autonomous vehicles, delivery drones, urban vertical farms, and high-bandwidth communication systems. All of this requires uninterrupted and inexpensive power.
Without it? Costs balloon. Innovation stalls. Investment leaves. And America risks becoming a second-tier economic power in a multipolar world.
So here’s the thesis: If we want to lead the Fourth Industrial Revolution, we must first lead in energy. And nuclear — specifically Gen IV Small Modular Reactors (SMRs) — must be part of that leadership.
The Nuclear Case: Clean, Scalable, Strategic
Let’s debunk the myth: nuclear is not the boogeyman of the 1970s. It’s one of the safest, cleanest, and most energy-dense sources we have.
But traditional nuclear has problems:
- Too expensive to build.
- Too long to license.
- Too bespoke and complex.
Enter Gen IV SMRs:
- Factory-built and transportable.
- Passively safe with walk-away safety designs.
- Scalable in 50–300 MWe increments.
- Ideal for remote areas, industrial parks, and military bases.
But even SMRs will struggle under the current regulatory, economic, and manufacturing ecosystem. To unlock their potential, we need a new national approach.
The Argument for National Strategy
Let’s paint a vision:
SMRs deployed at military bases across the country, secured by trained personnel, powering critical infrastructure, and feeding clean, carbon-free power back into surrounding communities.
SMRs operated by public chartered utilities—not for Wall Street profits, but for stability, security, and public good.
SMRs manufactured by a competitive ecosystem of certified vendors, just like aircraft or medical devices, with standard parts and rapid regulatory approval.
This isn't science fiction. It's a plausible, powerful model. Here’s how we do it.
Step 1: Treat SMRs as a National Security Asset
Why does the Department of Defense spend billions to secure oil convoys and build fuel depots across the world, but not invest in nuclear microgrids that would make forward bases self-sufficient for decades?
Nuclear power is inherently a strategic asset:
- Immune to price shocks.
- Hard to sabotage.
- Decades of stable power from a small footprint.
It’s time to reframe SMRs from an energy project to a national security platform. That changes everything.
Step 2: Create Public-Chartered Operating Companies
We don’t need another corporate monopoly or Wall Street scheme. Instead, let’s charter SMR utilities the way we chartered the TVA or the Postal Service:
- Low-margin, mission-oriented.
- Publicly accountable.
- Able to sign long-term contracts with DOD, DOE, or regional utilities.
These organizations won’t chase quarterly profits. They’ll chase uptime, grid stability, and national resilience.
Step 3: Build a Competitive SMR Industry Like Aerospace
Imagine multiple manufacturers building SMRs to common, certified standards. Components sourced from a wide supplier base. Designs evolving year over year, with upgrades like software and avionics do.
This is how we build:
- Safer reactors
- Cheaper units
- Modular designs
- A real export industry
Airplanes are safe, affordable, and efficient because of scale and standardization. We can do the same with reactors.
Step 4: Anchor SMRs to the Coming Fourth Industrial Revolution
AI, robotics, and distributed manufacturing don’t need fossil fuels. They need cheap, clean, continuous electricity.
- AI datacenters
- Robotic agriculture
- Carbon-free steel and cement
- Direct air capture
- Electric industrial transport
SMRs enable this future. And they decentralize power, both literally and economically. That means jobs in every region, not just coastal tech hubs.
Step 5: Pair Energy Sovereignty with Economic Reform
Here’s the big leap: what if this new energy architecture was tied to a transparent, auditable, and sovereign monetary system?
- Public utilities priced in a new digital dollar.
- Trade policy balanced by low-carbon energy exports.
- Public accounting verified with open ledgers.
This is not just national security. It’s monetary resilience.
The world is moving to multi-polar trade systems. Energy exports and energy reliability will define economic influence. If America leads with SMRs, we lead the conversation.
Conclusion: A Moral and Strategic Imperative
We can either:
- Let outdated fears and bureaucracy stall the future, or...
- Build the infrastructure for clean, secure, and sovereign prosperity.
We have the designs.
We have the talent.
We have the need.What we need now is will.
The Fourth Industrial Revolution will either be powered by us—or by someone else. Let’s make sure America leads. And let’s do it with SMRs, public charter, competitive industry, and national purpose.
It’s time.
This is a call to engineers, legislators, veterans, economists, and every American who believes in building again. SMRs are not just about power. They are about sovereignty, security, and shared prosperity.
Further reading:
nostr:naddr1qqgrjv33xenx2drpve3kxvrp8quxgqgcwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tczyrq7n2e62632km9yh6l5f6nykt76gzkxxy0gs6agddr9y95uk445xqcyqqq823cdzc99s
-
 @ c1e9ab3a:9cb56b43
2025-03-10 21:56:07
@ c1e9ab3a:9cb56b43
2025-03-10 21:56:07Introduction
Throughout human history, the pyramids of Egypt have fascinated scholars, archaeologists, and engineers alike. Traditionally thought of as tombs for pharaohs or religious monuments, alternative theories have speculated that the pyramids may have served advanced technological functions. One such hypothesis suggests that the pyramids acted as large-scale nitrogen fertilizer generators, designed to transform arid desert landscapes into fertile land.
This paper explores the feasibility of such a system by examining how a pyramid could integrate thermal convection, electrolysis, and a self-regulating breeder reactor to sustain nitrogen fixation processes. We will calculate the total power requirements and estimate the longevity of a breeder reactor housed within the structure.
The Pyramid’s Function as a Nitrogen Fertilizer Generator
The hypothesized system involves several key processes:
- Heat and Convection: A fissile material core located in the King's Chamber would generate heat, creating convection currents throughout the pyramid.
- Electrolysis and Hydrogen Production: Water sourced from subterranean channels would undergo electrolysis, splitting into hydrogen and oxygen due to electrical and thermal energy.
- Nitrogen Fixation: The generated hydrogen would react with atmospheric nitrogen (N₂) to produce ammonia (NH₃), a vital component of nitrogen-based fertilizers.
Power Requirements for Continuous Operation
To maintain the pyramid’s core at approximately 450°C, sufficient to drive nitrogen fixation, we estimate a steady-state power requirement of 23.9 gigawatts (GW).
Total Energy Required Over 10,000 Years
Given continuous operation over 10,000 years, the total energy demand can be calculated as:
[ \text{Total time} = 10,000 \times 365.25 \times 24 \times 3600 \text{ seconds} ]
[ \text{Total time} = 3.16 \times 10^{11} \text{ seconds} ]
[ \text{Total energy} = 23.9 \text{ GW} \times 3.16 \times 10^{11} \text{ s} ]
[ \approx 7.55 \times 10^{21} \text{ J} ]
Using a Self-Regulating Breeder Reactor
A breeder reactor could sustain this power requirement by generating more fissile material than it consumes. This reduces the need for frequent refueling.
Pebble Bed Reactor Design
- Self-Regulation: The reactor would use passive cooling and fuel expansion to self-regulate temperature.
- Breeding Process: The reactor would convert thorium-232 into uranium-233, creating a sustainable fuel cycle.
Fissile Material Requirements
Each kilogram of fissile material releases approximately 80 terajoules (TJ) (or 8 × 10^{13} J/kg). Given a 35% efficiency rate, the usable energy per kilogram is:
[ \text{Usable energy per kg} = 8 \times 10^{13} \times 0.35 = 2.8 \times 10^{13} \text{ J/kg} ]
[ \text{Fissile material required} = \frac{7.55 \times 10^{21}}{2.8 \times 10^{13}} ]
[ \approx 2.7 \times 10^{8} \text{ kg} = 270,000 \text{ tons} ]
Impact of a Breeding Ratio
If the reactor operates at a breeding ratio of 1.3, the total fissile material requirement would be reduced to:
[ \frac{270,000}{1.3} \approx 208,000 \text{ tons} ]
Reactor Size and Fuel Replenishment
Assuming a pebble bed reactor housed in the King’s Chamber (~318 cubic meters), the fuel cycle could be sustained with minimal refueling. With a breeding ratio of 1.3, the reactor could theoretically operate for 10,000 years with occasional replenishment of lost material due to inefficiencies.
Managing Scaling in the Steam Generation System
To ensure long-term efficiency, the water supply must be conditioned to prevent mineral scaling. Several strategies could be implemented:
1. Natural Water Softening Using Limestone
- Passing river water through limestone beds could help precipitate out calcium bicarbonate, reducing hardness before entering the steam system.
2. Chemical Additives for Scaling Prevention
- Chelating Agents: Compounds such as citric acid or tannins could be introduced to bind calcium and magnesium ions.
- Phosphate Compounds: These interfere with crystal formation, preventing scale adhesion.
3. Superheating and Pre-Evaporation
- Pre-Evaporation: Water exposed to extreme heat before entering the system would allow minerals to precipitate out before reaching the reactor.
- Superheated Steam: Ensuring only pure vapor enters the steam cycle would prevent mineral buildup.
- Electrolysis of Superheated Steam: Using multi-million volt electrostatic fields to ionize and separate minerals before they enter the steam system.
4. Electrostatic Control for Scaling Mitigation
- The pyramid’s hypothesized high-voltage environment could ionize water molecules, helping to prevent mineral deposits.
Conclusion
If the Great Pyramid were designed as a self-regulating nitrogen fertilizer generator, it would require a continuous 23.9 GW energy supply, which could be met by a breeder reactor housed within its core. With a breeding ratio of 1.3, an initial load of 208,000 tons of fissile material would sustain operations for 10,000 years with minimal refueling.
Additionally, advanced water treatment techniques, including limestone filtration, chemical additives, and electrostatic control, could ensure long-term efficiency by mitigating scaling issues.
While this remains a speculative hypothesis, it presents a fascinating intersection of energy production, water treatment, and environmental engineering as a means to terraform the ancient world.
-
 @ 9ca447d2:fbf5a36d
2025-06-07 18:00:48
@ 9ca447d2:fbf5a36d
2025-06-07 18:00:48Paris, France – June 6, 2025 — Bitcoin payment gateway startup Flash, just announced a new partnership with the “Bitcoin Only Brewery”, marking the first-ever beverage company to leverage Lightning payments.
Flash enables Bitcoin Only Brewery to offer its “BOB” beer with, no-KYC (Know Your Customer) delivery across Europe, priced at 19,500 sats (~$18) for the 4-pack, shipping included.
The cans feature colorful Bitcoin artwork while the contents promise a hazy pale ale: “Each 33cl can contains a smooth, creamy mouthfeel, hazy appearance and refreshing Pale Ale at 5% ABV,” reads the product description.
Pierre Corbin, Co-Founder of Flash, commented:
“Currently, bitcoin is used more as a store of value but usage for payments is picking up. Thanks to new innovation on Lightning, bitcoin is ready to go mainstream for e-commerce sales.”
Flash, launched its 2.0 version in March 2025 with the goal to provide the easiest bitcoin payment gateway for businesses worldwide. The platform is non-custodial and can enable both digital and physical shops to accept bitcoin by connecting their own wallets to Flash.
By leveraging the scalability of the Lightning Network, Flash ensures instant, low-cost transactions, addressing on-chain Bitcoin bottlenecks like high fees and long wait times.
For businesses interested in adopting Bitcoin payments, Flash offers a straightforward onboarding process, low fees, and robust support for both digital and physical goods. To learn more, visit paywithflash.com.
Media Contact:
Pierre Corbin
Co-Founder, Flash
Email: press@paywithflash.com
Website: paywithflash.comAbout Flash
Flash is the easiest Bitcoin payment gateway for businesses to accept payments. Supporting both digital and physical enterprises, Flash leverages the Lightning Network to enable fast, low-cost Bitcoin transactions. Launched in its 2.0 version in March 2025, Flash is at the forefront of driving Bitcoin adoption in e-commerce.
About Bitcoin Only Brewery
Bitcoin Only Brewery (@Drink_B0B) is a pioneering beverage company dedicated to the Bitcoin ethos, offering high-quality beers payable exclusively in Bitcoin. With a commitment to personal privacy, the brewery delivers across Europe with no-KYC requirements.
-
 @ c1e9ab3a:9cb56b43
2025-03-09 20:13:44
@ c1e9ab3a:9cb56b43
2025-03-09 20:13:44Introduction
Since the mid-1990s, American media has fractured into two distinct and increasingly isolated ecosystems, each with its own Overton window of acceptable discourse. Once upon a time, Americans of different political leanings shared a common set of facts, even if they interpreted them differently. Today, they don’t even agree on what the facts are—or who has the authority to define them.
This divide stems from a deeper philosophical rift in how each side determines truth and legitimacy. The institutional left derives its authority from the expert class—academics, think tanks, scientific consensus, and mainstream media. The populist right, on the other hand, finds its authority in traditional belief systems—religion, historical precedent, and what many call "common sense." As these two moral and epistemological frameworks drift further apart, the result is not just political division but the emergence of two separate cultural nations sharing the same geographic space.
The Battle of Epistemologies: Experts vs. Tradition
The left-leaning camp sees scientific consensus, peer-reviewed research, and institutional expertise as the gold standard of truth. Universities, media organizations, and policy think tanks function as arbiters of knowledge, shaping the moral and political beliefs of those who trust them. From this perspective, governance should be guided by data-driven decisions, often favoring progressive change and bureaucratic administration over democratic populism.
The right-leaning camp is skeptical of these institutions, viewing them as ideologically captured and detached from real-world concerns. Instead, they look to religion, historical wisdom, and traditional social structures as more reliable sources of truth. To them, the "expert class" is not an impartial source of knowledge but a self-reinforcing elite that justifies its own power while dismissing dissenters as uneducated or morally deficient.
This fundamental disagreement over the source of moral and factual authority means that political debates today are rarely about policy alone. They are battles over legitimacy itself. One side sees resistance to climate policies as "anti-science," while the other sees aggressive climate mandates as an elite power grab. One side views traditional gender roles as oppressive, while the other sees rapid changes in gender norms as unnatural and destabilizing. Each group believes the other is not just wrong, but dangerous.
The Consequences of Non-Overlapping Overton Windows
As these worldviews diverge, so do their respective Overton windows—the range of ideas considered acceptable for public discourse. There is little overlap left. What is considered self-evident truth in one camp is often seen as heresy or misinformation in the other. The result is:
- Epistemic Closure – Each side has its own trusted media sources, and cross-exposure is minimal. The left dismisses right-wing media as conspiracy-driven, while the right views mainstream media as corrupt propaganda. Both believe the other is being systematically misled.
- Moralization of Politics – Since truth itself is contested, policy debates become existential battles. Disagreements over issues like immigration, education, or healthcare are no longer just about governance but about moral purity versus moral corruption.
- Cultural and Political Balkanization – Without a shared understanding of reality, compromise becomes impossible. Americans increasingly consume separate news, live in ideologically homogeneous communities, and even speak different political languages.
Conclusion: Two Nations on One Land
A country can survive disagreements, but can it survive when its people no longer share a common source of truth? Historically, such deep societal fractures have led to secession, authoritarianism, or violent conflict. The United States has managed to avoid these extremes so far, but the trendline is clear: as long as each camp continues reinforcing its own epistemology while rejecting the other's as illegitimate, the divide will only grow.
The question is no longer whether America is divided—it is whether these two cultures can continue to coexist under a single political system. Can anything bridge the gap between institutional authority and traditional wisdom? Or are we witnessing the slow but inevitable unraveling of a once-unified nation into two separate moral and epistemic realities?
-
 @ c1e9ab3a:9cb56b43
2025-02-25 22:49:38
@ c1e9ab3a:9cb56b43
2025-02-25 22:49:38Election Authority (EA) Platform
1.1 EA Administration Interface (Web-Based)
- Purpose: Gives authorized personnel (e.g., election officials) a user-friendly way to administer the election.
- Key Tasks:
- Voter Registration Oversight: Mark which voters have proven their identity (via in-person KYC or some legal process).
- Blind Signature Issuance: Approve or deny blind signature requests from registered voters (each corresponding to one ephemeral key).
- Tracking Voter Slots: Keep a minimal registry of who is allowed one ephemeral key signature, and mark it “used” once a signature is issued.
- Election Configuration: Set start/end times, provide encryption parameters (public keys), manage threshold cryptography setup.
- Monitor Tallying: After the election, collaborate with trustees to decrypt final results and release them.
1.2 EA Backend Services
- Blind Signature Service:
- An API endpoint or internal module that receives a blinded ephemeral key from a voter, checks if they are authorized (one signature per voter), and returns the blind-signed result.
-
Typically requires secure storage of the EA’s blind signing private key.
-
Voter Roll Database:
- Stores minimal info: “Voter #12345 is authorized to request one ephemeral key signature,” plus status flags.
-
Does not store ephemeral keys themselves (to preserve anonymity).
-
(Optional) Mix-Net or Homomorphic Tally Service:
- Coordinates with trustees for threshold decryption or re-encryption.
- Alternatively, a separate “Tally Authority” service can handle this.
2. Auditor Interface
2.1 Auditor Web-Based Portal
- Purpose: Allows independent auditors (or the public) to:
- Fetch All Ballots from the relays (or from an aggregator).
- Verify Proofs: Check each ballot’s signature, blind signature from the EA, OTS proof, zero-knowledge proofs, etc.
- Check Double-Usage: Confirm that each ephemeral key is used only once (or final re-vote is the only valid instance).
-
Observe Tally Process: Possibly see partial decryptions or shuffle steps, verify the final result matches the posted ballots.
-
Key Tasks:
- Provide a dashboard showing the election’s real-time status or final results, after cryptographic verification.
- Offer open data downloads so third parties can run independent checks.
2.2 (Optional) Trustee Dashboard
- If the election uses threshold cryptography (multiple parties must decrypt), each trustee (candidate rep, official, etc.) might have an interface for:
- Uploading partial decryption shares or re-encryption proofs.
- Checking that other trustees did their steps correctly (zero-knowledge proofs for correct shuffling, etc.).
3. Voter Application
3.1 Voter Client (Mobile App or Web Interface)
-
Purpose: The main tool voters use to participate—before, during, and after the election.
-
Functionalities:
- Registration Linking:
- Voter goes in-person to an election office or uses an online KYC process.
- Voter obtains or confirms their long-term (“KYC-bound”) key. The client can store it securely (or the voter just logs in to a “voter account”).
- Ephemeral Key Generation:
- Create an ephemeral key pair ((nsec_e, npub_e)) locally.
- Blind (\npub_e) and send it to the EA for signing.
- Unblind the returned signature.
- Store (\npub_e) + EA’s signature for use during voting.
- Ballot Composition:
- Display candidates/offices to the voter.
- Let them select choices.
- Possibly generate zero-knowledge proofs (ZKPs) behind the scenes to confirm “exactly one choice per race.”
- Encryption & OTS Timestamp:
- Encrypt the ballot under the election’s public (threshold) key or produce a format suitable for a mix-net.
- Obtain an OpenTimestamps proof for the ballot’s hash.
- Publish Ballot:
- Sign the entire “timestamped ballot” with the ephemeral key.
- Include the EA’s blind signature on (\npub_e).
- Post to the Nostr relays (or any chosen decentralized channel).
- Re-Voting:
- If the user needs to change their vote, the client repeats the encryption + OTS step, publishes a new ballot with a strictly later OTS anchor.
- Verification:
- After the election, the voter can check that their final ballot is present in the tally set.
3.2 Local Storage / Security
- The app must securely store:
- Ephemeral private key ((nsec_e)) until voting is complete.
- Potential backup/recovery mechanism if the phone is lost.
- Blind signature from the EA on (\npub_e).
- Potentially uses hardware security modules (HSM) or secure enclaves on the device.
4. Nostr Relays (or Equivalent Decentralized Layer)
- Purpose: Store and replicate voter-submitted ballots (events).
- Key Properties:
- Redundancy: Voters can post to multiple relays to mitigate censorship or downtime.
- Public Accessibility: Auditors, the EA, and the public can fetch all events to verify or tally.
- Event Filtering: By design, watchers can filter events with certain tags, e.g. “election: 2025 County Race,” ensuring they gather all ballots.
5. Threshold Cryptography Setup
5.1 Multi-Seg (Multi-Party) Key Generation
- Participants: Possibly the EA + major candidates + accredited observers.
- Process: A Distributed Key Generation (DKG) protocol that yields a single public encryption key.
- Private Key Shares: Each trustee holds a piece of the decryption key; no single party can decrypt alone.
5.2 Decryption / Tally Mechanism
- Homomorphic Approach:
- Ballots are additively encrypted.
- Summation of ciphertexts is done publicly.
- Trustees provide partial decryptions for the final sum.
- Mix-Net Approach:
- Ballots are collected.
- Multiple servers shuffle and re-encrypt them (each trustee verifies correctness).
- Final set is decrypted, but the link to each ephemeral key is lost.
5.3 Trustee Interfaces
- Separate or integrated into the auditor interface—each trustee logs in and provides their partial key share for decrypting the final result.
- Possibly combined with ZK proofs to confirm correct partial decryption or shuffling.
6. OpenTimestamps (OTS) or External Time Anchor
6.1 Aggregator Service
- Purpose: Receives a hash from the voter’s app, anchors it into a blockchain or alternative time-stamping system.
- Result: Returns a proof object that can later be used by any auditor to confirm the time/block height at which the hash was included.
6.2 Verifier Interface
- Could be part of the auditor tool or the voter client.
- Checks that each ballot’s OTS proof is valid and references a block/time prior to the election’s closing.
7. Registration Process (In-Person or Hybrid)
- Voter presents ID physically at a polling station or a designated office (or an online KYC approach, if legally allowed).
- EA official:
- Confirms identity.
- Links the voter to a “voter record” (Voter #12345).
- Authorizes them for “1 ephemeral key blind-sign.”
- Voter obtains or logs into the voter client:
- The app or website might show “You are now cleared to request a blind signature from the EA.”
- Voter later (or immediately) generates the ephemeral key and requests the blind signature.
8. Putting It All Together (High-Level Flow)
- Key Setup
- The EA + trustees run a DKG to produce the election public key.
- Voter Registration
- Voter is validated (ID check).
- Marked as eligible in the EA database.
- Blind-Signed Ephemeral Key
- Voter’s client generates a key, blinds (\npub_e), obtains EA’s signature, unblinds.
- Voting
- Voter composes ballot, encrypts with the election public key.
- Gets OTS proof for the ballot hash.
- Voter’s ephemeral key signs the entire package (including EA’s signature on (\npub_e)).
- Publishes to Nostr.
- Re-Voting (Optional)
- Same ephemeral key, new OTS timestamp.
- Final ballot is whichever has the latest valid timestamp before closing.
- Close of Election & Tally
- EA announces closing.
- Tally software (admin + auditors) collects ballots from Nostr, discards invalid duplicates.
- Threshold decryption or mix-net to reveal final counts.
- Publish final results and let auditors verify everything.
9. Summary of Major Components
Below is a succinct list:
- EA Admin Platform
- Web UI for officials (registration, blind signature issuing, final tally management).
- Backend DB for voter records & authorized ephemeral keys.
- Auditor/Trustee Platforms
- Web interface for verifying ballots, partial decryption, and final results.
- Voter Application (Mobile / Web)
- Generating ephemeral keys, getting blind-signed, casting encrypted ballots, re-voting, verifying included ballots.
- Nostr Relays (Decentralized Storage)
- Where ballots (events) are published, replicated, and fetched for final tally.
- Threshold Cryptography System
- Multi-party DKG for the election key.
- Protocols or services for partial decryption, mix-net, or homomorphic summation.
- OpenTimestamps Aggregator
- Service that returns a blockchain-anchored timestamp proof for each ballot’s hash.
Additional Implementation Considerations
- Security Hardening:
- Using hardware security modules (HSM) for the EA’s blind-signing key, for trustee shares, etc.
- Scalability:
- Handling large numbers of concurrent voters, large data flows to relays.
- User Experience:
- Minimizing cryptographic complexity for non-technical voters.
- Legal and Procedural:
- Compliance with local laws for in-person ID checks, mandatory paper backups (if any), etc.
Final Note
While each functional block can be designed and deployed independently (e.g., multiple aggregator services, multiple relays, separate tally servers), the key to a successful system is interoperability and careful orchestration of these components—ensuring strong security, a straightforward voter experience, and transparent auditing.
nostr:naddr1qqxnzde5xq6nzv348yunvv35qy28wue69uhnzv3h9cczuvpwxyargwpk8yhsygxpax4n544z4dk2f04lgn4xfvha5s9vvvg73p46s66x2gtfedttgvpsgqqqw4rs0rcnsu
-
 @ dfa02707:41ca50e3
2025-06-07 13:01:49
@ dfa02707:41ca50e3
2025-06-07 13:01:49Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ c1e9ab3a:9cb56b43
2025-02-25 19:49:28
@ c1e9ab3a:9cb56b43
2025-02-25 19:49:281. Introduction
Modern election systems must balance privacy (no one sees how individuals vote) with public verifiability (everyone can confirm the correctness of the tally). Achieving this in a decentralized, tamper-resistant manner remains a challenge. Nostr (a lightweight protocol for censorship-resistant communication) offers a promising platform for distributing and archiving election data (ballots) without relying on a single central server.
This paper presents a design where:
- Each voter generates a new ephemeral Nostr keypair for an election.
- The election authority (EA) blind-signs this ephemeral public key (npub) to prove the voter is authorized, without revealing which voter owns which ephemeral key.
- Voters cast encrypted ballots to Nostr relays, each carrying an OpenTimestamps proof to confirm the ballot’s time anchor.
- Re-voting is allowed: a voter can replace a previously cast ballot by publishing a new ballot with a newer timestamp.
- Only the latest valid ballot (per ephemeral key) is counted.
We combine well-known cryptographic primitives—blind signatures, homomorphic or mix-net encryption, threshold key management, and time anchoring—into an end-to-end system that preserves anonymity, assures correctness, and prevents double-voting.
2. Roles and Components
2.1 Voters
- Long-Term (“KYC-bound”) Key: Each voter has some identity-verified Nostr public key used only for official communication with the EA (not for voting).
- Ephemeral Voting Key: For each election, the voter locally generates a new Nostr keypair ((nsec_e, npub_e)).
- This is the “one-time” identity used to sign ballots.
- The EA never learns the real identity behind (\npub_e) because of blinding.
2.2 Election Authority (EA)
- Maintains the official voter registry: who is entitled to vote.
- Blind-Signs each valid voter’s ephemeral public key to authorize exactly one ephemeral key per voter.
- Publishes a minimal voter roll: e.g., “Voter #12345 has been issued a valid ephemeral key,” without revealing which ephemeral key.
2.3 Nostr Relays
- Decentralized servers that store and forward events.
- Voters post their ballots to relays, which replicate them.
- No single relay is critical; the same ballot can be posted to multiple relays for redundancy.
2.4 Cryptographic Framework
- Blind Signatures: The EA signs a blinded version of (\npub_e).
- Homomorphic or Mix-Net Encryption: Ensures the content of each ballot remains private; only aggregate results or a shuffled set are ever decrypted.
- Threshold / General Access Structure: Multiple trustees (EA plus candidate representatives, for example) must collaborate to produce a final decryption.
- OpenTimestamps (OTS): Attaches a verifiable timestamp proof to each ballot, anchoring it to a blockchain or other tamper-resistant time reference.
3. Protocol Lifecycle
This section walks through voter registration, ephemeral key authorization, casting (and re-casting) ballots, and finally the tally.
3.1 Registration & Minimal Voter Roll
- Legal/KYC Verification
- Each real-world voter proves their identity to the EA (per legal procedures).
-
The EA records that the voter is eligible to cast one ballot, referencing their long-term identity key ((\npub_{\mathrm{KYC}})).
-
Issue Authorization “Slot”
- The EA’s voter roll notes “this person can receive exactly one blind signature for an ephemeral key.”
- The roll does not store an ephemeral key—just notes that it can be requested.
3.2 Generating and Blinding the Ephemeral Key
- Voter Creates Ephemeral Key
- Locally, the voter’s client generates a fresh ((nsec_e, npub_e)).
- Blinding
-
The client blinds (\npub_e) to produce (\npub_{e,\mathrm{blinded}}). This ensures the EA cannot learn the real (\npub_e).
-
Blind Signature Request
- The voter, using their KYC-bound key ((\npub_{\mathrm{KYC}})), sends (\npub_{e,\mathrm{blinded}}) to the EA (perhaps via a secure direct message or a “giftwrapped DM”).
- The EA checks that this voter has not already been issued a blind signature.
-
If authorized, the EA signs (\npub_{e,\mathrm{blinded}}) with its private key and returns the blinded signature.
-
Unblinding
- The voter’s client unblinds the signature, obtaining a valid signature on (\npub_e).
-
Now (\npub_e) is a blinded ephemeral public key that the EA has effectively “authorized,” without knowing which voter it belongs to.
-
Roll Update
- The EA updates its minimal roll to note that “Voter #12345 received a signature,” but does not publish (\npub_e).
3.3 Casting an Encrypted Ballot with OpenTimestamps
When the voter is ready to vote:
- Compose Encrypted Ballot
- The ballot can be homomorphically encrypted (e.g., with Paillier or ElGamal) or structured for a mix-net.
-
Optionally include Zero-Knowledge Proofs (ZKPs) showing the ballot is valid (one candidate per race, etc.).
-
Obtain OTS Timestamp
- The voter’s client computes a hash (H) of the ballot data (ciphertext + ZKPs).
- The client sends (H) to an OpenTimestamps aggregator.
-
The aggregator returns a timestamp proof verifying that “this hash was seen at or before block/time (T).”
-
Create a “Timestamped Ballot” Payload
-
Combine:
- Encrypted ballot data.
- OTS proof for the hash of the ballot.
- EA’s signature on (\npub_e) (the blind-signed ephemeral key).
- A final signature by the voter’s ephemeral key ((nsec_e)) over the entire package.
-
Publish to Nostr
- The voter posts the complete “timestamped ballot” event to one or more relays.
- Observers see “an event from ephemeral key (\npub_e), with an OTS proof and the EA’s blind signature,” but cannot identify the real voter or see the vote’s contents.
3.4 Re-Voting (Updating the Ballot)
If the voter wishes to revise their vote (due to coercion, a mistake, or simply a change of mind):
- Generate a New Encrypted Ballot
- Possibly with different candidate choices.
- Obtain a New OTS Proof
- The new ballot has a fresh hash (H').
- The OTS aggregator provides a new proof anchored at a later block/time than the old one.
- Publish the Updated Ballot
- Again, sign with (\npub_e).
- Relays store both ballots, but the newer OTS timestamp shows which ballot is “final.”
Rule: The final vote for ephemeral key (\npub_e) is determined by the ballot with the highest valid OTS proof prior to the election’s closing.
3.5 Election Closing & Tally
- Close Signal
- At a specified time or block height, the EA publishes a “closing token.”
-
Any ballot with an OTS anchor referencing a time/block after the closing is invalid.
-
Collect Final Ballots
- Observers (or official tally software) gather the latest valid ballot from each ephemeral key.
-
They confirm the OTS proofs are valid and that no ephemeral key posted two different ballots with the same timestamp.
-
Decryption / Summation
- If homomorphic, the system sums the encrypted votes and uses a threshold of trustees to decrypt the aggregate.
- If a mix-net, the ballots are shuffled and partially decrypted, also requiring multiple trustees.
-
In either case, individual votes remain hidden, but the final counts are revealed.
-
Public Audit
- Anyone can fetch all ballots from the Nostr relays, verify OTS proofs, check the EA’s blind signature, and confirm no ephemeral key was used twice.
- The final totals can be recomputed from the publicly available data.
4. Ensuring One Vote Per Voter & No Invalid Voters
- One Blind Signature per Registered Voter
- The EA’s internal list ensures each real voter only obtains one ephemeral key signature.
- Blind Signature
- Ensures an unauthorized ephemeral key cannot pass validation (forging the EA’s signature is cryptographically infeasible).
- Public Ledger of Ballots
- Because each ballot references an EA-signed key, any ballot with a fake or duplicate signature is easily spotted.
5. Security and Privacy Analysis
- Voter Anonymity
- The EA never sees the unblinded ephemeral key. It cannot link (\npub_e) to a specific person.
-
Observers only see “some ephemeral key posted a ballot,” not the real identity of the voter.
-
Ballot Secrecy
- Homomorphic Encryption or Mix-Net: no one can decrypt an individual ballot; only aggregated or shuffled results are revealed.
-
The ephemeral key used for signing does not decrypt the ballot—the election’s threshold key does, after the election.
-
Verifiable Timestamping
- OpenTimestamps ensures each ballot’s time anchor cannot be forged or backdated.
-
Re-voting is transparent: a later OTS proof overrides earlier ones from the same ephemeral key.
-
Preventing Double Voting
- Each ephemeral key is unique and authorized once.
-
Re-voting by the same key overwrites the old ballot but does not increase the total count.
-
Protection Against Coercion
- Because the voter can re-cast until the deadline, a coerced vote can be replaced privately.
-
No receipts (individual decryption) are possible—only the final aggregated tally is revealed.
-
Threshold / Multi-Party Control
- Multiple trustees must collaborate to decrypt final results, preventing a single entity from tampering or prematurely viewing partial tallies.
6. Implementation Considerations
- Blind Signature Techniques
- Commonly implemented with RSA-based Chaumian blind signatures or BLS-based schemes.
-
Must ensure no link between (\npub_{e,\mathrm{blinded}}) and (\npub_e).
-
OpenTimestamps Scalability
- If millions of voters are posting ballots simultaneously, multiple timestamp aggregators or batch anchoring might be needed.
-
Verification logic on the client side or by public auditors must confirm each OTS proof’s integrity.
-
Relay Coordination
- The system must ensure no single relay can censor ballots. Voters may publish to multiple relays.
-
Tally fetchers cross-verify events from different relays.
-
Ease of Use
-
The user interface must hide the complexity of ephemeral key generation, blind signing, and OTS proof retrieval—making it as simple as possible for non-technical voters.
-
Legal Framework
-
If law requires publicly listing which voters have cast a ballot, you might track “Voter #12345 used their ephemeral key” without revealing the ephemeral key. Or you omit that if secrecy about who voted is desired.
-
Closing Time Edge Cases
- The system uses a block/time anchor from OTS. Slight unpredictability in block generation might require a small buffer around the official close. This is a policy choice.
7. Conclusion
We propose an election system that leverages Nostr for decentralizing ballot publication, blinded ephemeral keys for robust voter anonymity, homomorphic/mix-net encryption for ballot secrecy, threshold cryptography for collaborative final decryption, OpenTimestamps for tamper-proof time anchoring, and re-voting to combat coercion.
Key Advantages:
- Anonymity: The EA cannot link ballots to specific voters.
- One Voter, One Credential: Strict enforcement through blind signatures.
- Verifiable Ordering: OTS ensures each ballot has a unique, provable time anchor.
- Updatability: Voters can correct or override coerced ballots by posting a newer one before closing.
- Decentralized Audit: Anyone can fetch ballots from Nostr, verify the EA’s signatures and OTS proofs, and confirm the threshold-decrypted results match the posted ballots.
Such a design shows promise for secure, privacy-preserving digital elections, though real-world deployment will require careful policy, legal, and usability considerations. By combining cryptography with decentralized relays and an external timestamp anchor, the system can uphold both individual privacy and publicly auditable correctness.
-
 @ 65912a7a:5dc638bf
2025-02-09 20:34:15
@ 65912a7a:5dc638bf
2025-02-09 20:34:15I didn’t set out to become an enemy of the world’s richest man, but I seem to have managed it all the same. Until this moment, I’ve resisted describing my falling out with Elon Musk in much detail, but as the man’s cultural influence has metastasized—and he continues to spread lies about me on the social media platform that he owns (Twitter/X)—it seems only appropriate to set the record straight. I know that it annoys many in my audience to see me defend myself against attacks that they recognize to be spurious, but they might, nevertheless, find the details of what happened with Elon interesting.
Of all the remarkable people I’ve met, Elon is probably the most likely to remain a world-historical figure—despite his best efforts to become a clown. He is also the most likely to squander his ample opportunities to live a happy life, ruin his reputation and most important relationships, and produce lasting harm across the globe. None of this was obvious to me when we first met, and I have been quite amazed at Elon’s evolution, both as a man and as an avatar of chaos. The friend I remember did not seem to hunger for public attention. But his engagement with Twitter/X transformed him—to a degree seldom seen outside of Marvel movies or Greek mythology. If Elon is still the man I knew, I can only conclude that I never really knew him.
When we first met, Elon wasn’t especially rich or famous. In fact, I recall him teetering on the brink of bankruptcy around 2008, while risking the last of his previous fortune to make payroll at Tesla. At the time, he was living off loans from his friends Larry and Sergey. Once Elon became truly famous, and his personal wealth achieved escape velocity, I was among the first friends he called to discuss his growing security concerns. I put him in touch with Gavin de Becker, who provided his first bodyguards, and recommended other changes to his life. We also went shooting on at least two occasions with Scott Reitz, the finest firearms instructor I’ve ever met. It is an ugly irony that Elon’s repeated targeting of me on Twitter/X has increased my own security concerns. He understands this, of course, but does not seem to care.
So how did we fall out? Let this be a cautionary tale for any of Elon’s friends who might be tempted to tell the great man something he doesn’t want to hear:
(1.) When the SARS-CoV-2 virus first invaded our lives in March of 2020, Elon began tweeting in ways that I feared would harm his reputation. I also worried that his tweets might exacerbate the coming public-health emergency. Italy had already fallen off a cliff, and Elon shared the following opinion with his tens of millions of fans :
the coronavirus panic is dumb
As a concerned friend, I sent him a private text:
Hey, brother— I really think you need to walk back your coronavirus tweet. I know there’s a way to parse it that makes sense (“panic” is always dumb), but I fear that’s not the way most people are reading it. You have an enormous platform, and much of the world looks to you as an authority on all things technical. Coronavirus is a very big deal, and if we don’t get our act together, we’re going to look just like Italy very soon. If you want to turn some engineers loose on the problem, now would be a good time for a breakthrough in the production of ventilators...
(2.) Elon’s response was, I believe, the first discordant note ever struck in our friendship:
Sam, you of all people should not be concerned about this.
He included a link to a page on the CDC website, indicating that Covid was not even among the top 100 causes of death in the United States. This was a patently silly point to make in the first days of a pandemic.
We continued exchanging texts for at least two hours. If I hadn’t known that I was communicating with Elon Musk, I would have thought I was debating someone who lacked any understanding of basic scientific and mathematical concepts, like exponential curves.
(3.) Elon and I didn’t converge on a common view of epidemiology over the course of those two hours, but we hit upon a fun compromise: A wager. Elon bet me $1 million dollars (to be given to charity) against a bottle of fancy tequila ($1000) that we wouldn’t see as many as 35,000 cases of Covid in the United States (cases, not deaths). The terms of the bet reflected what was, in his estimation, the near certainty (1000 to 1) that he was right. Having already heard credible estimates that there could be 1 million deaths from Covid in the U.S. over the next 12-18 months (these estimates proved fairly accurate), I thought the terms of the bet ridiculous—and quite unfair to Elon. I offered to spot him two orders of magnitude: I was confident that we’d soon have 3.5 million cases of Covid in the U.S. Elon accused me of having lost my mind and insisted that we stick with a ceiling of 35,000.
(4.) We communicated sporadically by text over the next couple of weeks, while the number of reported cases grew. Ominously, Elon dismissed the next batch of data reported by the CDC as merely presumptive—while confirmed cases of Covid, on his account, remained elusive.
(5.) A few weeks later, when the CDC website finally reported 35,000 deaths from Covid in the U.S. and 600,000 cases, I sent Elon the following text:
Is (35,000 deaths + 600,000 cases) > 35,000 cases?
(6.) This text appears to have ended our friendship. Elon never responded, and it was not long before he began maligning me on Twitter for a variety of imaginary offenses. For my part, I eventually started complaining about the startling erosion of his integrity on my podcast, without providing any detail about what had transpired between us.
(7.) At the end of 2022, I abandoned Twitter/X altogether, having recognized the poisonous effect that it had on my life—but also, in large part, because of what I saw it doing to Elon. I’ve been away from the platform for over two years, and yet Elon still attacks me. Occasionally a friend will tell me that I’m trending there, and the reasons for this are never good. As recently as this week, Elon repeated a defamatory charge about my being a “hypocrite” for writing a book in defense of honesty and then encouraging people to lie to keep Donald Trump out of the White House. Not only have I never advocated lying to defeat Trump (despite what that misleading clip from the Triggernometry podcast might suggest to naive viewers), I’ve taken great pains to defend Trump from the most damaging lie ever told about him. Elon knows this, because we communicated about the offending clip when it first appeared on Twitter/X. However, he simply does not care that he is defaming a former friend to hundreds of millions of people—many of whom are mentally unstable. On this occasion, he even tagged the incoming president of the United States.
All of this remains socially and professionally awkward, because Elon and I still have many friends in common. Which suggests the terms of another wager that I would happily make, if such a thing were possible—and I would accept 1000 to 1 odds in Elon’s favor:
I bet that anyone who knows us both knows that I am telling the truth.
Everyone close to Elon must recognize how unethical he has become, and yet they remain silent. Their complicity is understandable, but it is depressing all the same. These otherwise serious and compassionate people know that when Elon attacks private citizens on Twitter/X—falsely accusing them of crimes or corruption, celebrating their misfortunes—he is often causing tangible harm in their lives. It’s probably still true to say that social media “isn’t real life,” until thousands of lunatics learn your home address.
A final absurdity in my case, is that several of the controversial issues that Elon has hurled himself at of late—and even attacked me over—are ones we agree about. We seem to be in near total alignment on immigration and the problems at the southern border of the U.S. We also share the same concerns about what he calls “the woke mind virus.” And we fully agree about the manifest evil of the so-called “grooming-gangs scandal” in the U.K. The problem with Elon, is that he makes no effort to get his facts straight when discussing any of these topics, and he regularly promotes lies and conspiracy theories manufactured by known bad actors, at scale. (And if grooming were really one of his concerns, it’s strange that he couldn’t find anything wrong with Matt Gaetz.)
Elon and I even agree about the foundational importance of free speech. It’s just that his approach to safeguarding it—amplifying the influence of psychopaths and psychotics, while deplatforming real journalists and his own critics; or savaging the reputations of democratic leaders, while never saying a harsh word about the Chinese Communist Party—is not something I can support. The man claims to have principles, but he appears to have only moods and impulses.
Any dispassionate observer of Elon’s behavior on Twitter/X can see that there is something seriously wrong with his moral compass, if not his perception of reality. There is simply no excuse for a person with his talents, resources, and opportunities to create so much pointless noise. The callousness and narcissism conveyed by his antics should be impossible for his real friends to ignore—but they appear to keep silent, perhaps for fear of losing access to his orbit of influence.
Of course, none of this is to deny that the tens of thousands of brilliant engineers Elon employs are accomplishing extraordinary things. He really is the greatest entrepreneur of our generation. And because of the businesses he’s built, he will likely become the world’s first trillionaire—perhaps very soon. Since the election of Donald Trump in November, Elon’s wealth has grown by around $200 billion. That’s nearly $3 billion a day (and over $100 million an hour). Such astonishing access to resources gives Elon the chance—and many would argue the responsibility—to solve enormous problems in our world.
So why spend time spreading lies on X?
-
 @ d6affa19:9110b177
2025-06-07 21:10:53
@ d6affa19:9110b177
2025-06-07 21:10:53If there were only one thing I had to list as the single most effective way to improve a Female Led Relationship (FLR), it would be found in the phrase “yes, Ma’am.” Whether trying to get the dynamic off the ground or keep it going during the grind of everyday life, this phrase—and the energy it evokes—encompasses so many essential elements of an FLR. In my experience, not many other things continuously breathe life into a relationship like the magic of “yes, Ma’am.”
Of course, this phrase can be modified to the Woman’s desire (“yes, Mistress,” “yes, my Queen,” “yes, Goddess” are common examples), but “yes, Ma’am” is something acceptable nearly anywhere. It’s simple, polite, somewhat discreet, and yet extremely effective and powerful. In an FLR (even in a low-protocol dynamic), the phrase is elevated from a basic formality to an invocation of trust, respect, and surrender.
The words by themselves are powerless. But when consistently expressed with the right energy and intention, it becomes a sort of miniature ritual that keeps them both anchored to the relationship. This shouldn’t be conflated with “yes, Dear,” a phrase stereotypically used when a man is merely appeasing a Woman. No, the energy here is not to appease, but to please. Because She deserves it.
To illustrate this further, let’s dig into the depth I find in these two words.
An Invocation of Structure, Trust, and Identity
“Yes, Ma’am” is so deceptively simple. It’s a verbal expression of his obedience—the bare minimum a Woman should receive in an FLR. And it keeps the framework intact in everyday life, especially when the mood is subtle or non-sexual.
In this way, “yes, Ma’am” reinforces the foundation of the FLR. Each utterance reminds them both of their positions. Each declaration quiets any confusion. Each delivery deepens the dynamic and tightens the structure.
When these words are spoken and consistently followed up with action, they demonstrate emotional maturity—that he’s moved beyond questioning whether She’s “right” and into the realm of devotion. It signals to Her that Her needs don’t have to be proven to him anymore and that Her preferences don’t need to be justified.
He’s no longer debating Her logic, making excuses, or searching for loopholes; he’s no longer resisting or self-protecting. He’s not agreeing as an equal, he’s not negotiating with Her, he’s not hedging Her demand. He is simply submitting to Her.
Just as it’s “yes, Ma’am” when She tells him to kneel, it’s also “yes, Ma’am” when She asks him to fix the sink, or dismisses a request, or even reminds him to do something he’s about to do. “Yes, Ma’am,” then act.
The Words Alone Are Not the Magic
Again, the magic of “yes, Ma’am” doesn’t reside in the words themselves, but in the intention, energy, and action behind them. The phrase itself is just a vessel. Just as a chalice, the words hold something sacred, but the sanctity resides in the wine, not the cup. The action, the delivery, and the consistency are what give the phrase its power.
If spoken with resentment, sarcasm, or with no follow-through, they mean nothing. If he speaks them but then delays, argues, or makes excuses, then his submission is inauthentic. This undermines trust and, ultimately, the relationship. But when he says “yes, Ma’am” and immediately acts on Her direction—despite being tired, flustered, aroused, or even in disagreement, then that is real submission; that is profound trust. And that is what She feels.
And that’s what he feels. It becomes a reminder of his humility and an expression of self-discipline in service to Her. Over time, it shifts his thought patterns and instincts. He may feel uncertainty, self-pity, or insecurity, but “yes, Ma’am” melts it all into clarity. Old responses like “Well, actually…” “Can’t I just…” “I thought we agreed…” “Why can’t You…” are simply replaced with “yes, Ma’am.”
Even if he’s feeling exhausted, annoyed, or needy. There are no complaints or explanations, only Her will and a choice to put aside his ego, align with Her rhythm, and re-center his purpose. This is an act of vulnerability. He is placing his emotional safety in Her hands and relying on Her to care for his well-being.
It communicates to Her:
- “I hear You.”
- “I will act on Your desires.”
- “I trust You more than I trust my resistance.”
- “I’m Yours, even now, especially now.”And let’s not ignore the erotic undertones in this depth of surrender. A simple phrase makes his discipline audible, echoing Her power. It bears his humility, longing, eagerness, vulnerability—his contained arousal. And She knows. She hears the plea. She feels the weight—the tension—the heat—the surrendered will… Ever-present, even in the most mundane moments…
Closing Thoughts
Of course, this level of devotion takes practice and a great deal of trust. No one is perfect, so he will fail at times, but that’s what makes it so beautiful—it’s a continuously active and conscious choice. And, at first, it may sound awkward for him or forced, but with dedication and intention She will begin to hear the tone, feel the vibe, and sense the sincerity in it. This energy is what builds Her trust in him.
This phrase, or rather the mindset behind it, has improved my own relationship so, so much. While it may not fit into every experience, it’s something that I discovered was a missing piece in mine. Enough so that I felt compelled to share.
Because as a relationship goes on, things change—passions fluctuate, pain resurfaces, doubts arise, life gets busy, things get heavy—but “yes, Ma’am” remains steady and intimate. Piece by piece trust and devotion are built with thousands of quiet yeses. And regardless of the circumstances, “yes, Ma’am” gently whispers “this is still us; this is still our shared truth; this is still sacred” over and over again.
-
 @ b1ddb4d7:471244e7
2025-06-07 13:01:07
@ b1ddb4d7:471244e7
2025-06-07 13:01:07When Sergei talks about bitcoin, he doesn’t sound like someone chasing profits or followers. He sounds like someone about to build a monastery in the ruins.
While the mainstream world chases headlines and hype, Sergei shows up in local meetups from Sacramento to Cleveland, mentors curious minds, and shares what he knows is true – hoping that, with the right spark, someone will light their own way forward.
We interviewed Sergei to trace his steps: where he started, what keeps him going, and why teaching bitcoin is far more than explaining how to set up a node – it’s about reaching the right minds before the noise consumes them. So we began where most journeys start: at the beginning.

First Steps
- So, where did it all begin for you and what made you stay curious?
I first heard about bitcoin from a friend’s book recommendation, American Kingpin, the book about Silk Road (online drug marketplace). He is still not a true bitcoiner, although I helped him secure private keys with some bitcoin.
I was really busy at the time – focused on my school curriculum, running a 7-bedroom Airbnb, and working for a standardized test prep company. Bitcoin seemed too technical for me to explore, and the pace of my work left no time for it.
After graduating, while pursuing more training, I started playing around with stocks and maximizing my savings. Passive income seemed like the path to early retirement, as per the promise of the FIRE movement (Financial Independence, Retire Early). I mostly followed the mainstream news and my mentor’s advice – he liked preferred stocks at the time.
I had some Coinbase IOUs and remember sending bitcoin within the Coinbase ledger to a couple friends. I also recall the 2018 crash; I actually saw the legendary price spike live but couldn’t benefit because my funds were stuck amidst the frenzy. I withdrew from that investment completely for some time. Thankfully, my mentor advised to keep en eye on bitcoin.
Around late 2019, I started DCA-ing cautiously. Additionally, my friend and I were discussing famous billionaires, and how there was no curriculum for becoming a billionaire. So, I typed “billionaires” into my podcast app, and landed on We Study Billionaires podcast.
That’s where I kept hearing Preston Pysh mention bitcoin, before splitting into his own podcast series, Bitcoin Fundamentals. I didn’t understand most of the terminology of stocks, bonds, etc, yet I kept listening and trying to absorb it thru repetition. Today, I realize all that financial talk was mostly noise.
When people ask me for a technical explanation of fiat, I say: it’s all made up, just like the fiat price of bitcoin! Starting in 2020, during the so-called pandemic, I dove deeper. I religiously read Bitcoin Magazine, scrolled thru Bitcoin Twitter, and joined Simply Bitcoin Telegram group back when DarthCoin was an admin.
DarthCoin was my favorite bitcoiner – experienced, knowledgeable, and unapologetic. Watching him shift from rage to kindness, from passion to despair, gave me a glimpse at what a true educator’s journey would look like.
The struggle isn’t about adoption at scale anymore. It’s about reaching the few who are willing to study, take risks, and stay out of fiat traps. The vast majority won’t follow that example – not yet at least… if I start telling others the requirements for true freedom and prosperity, they would certainly say “Hell no!”
- At what point did you start teaching others, and why?
After college, I helped teach at a standardized test preparation company, and mentored some students one-on-one. I even tried working at a kindergarten briefly, but left quickly; Babysitting is not teaching.
What I discovered is that those who will succeed don’t really need my help – they would succeed with or without me, because they already have the inner drive.
Once you realize your people are perishing for lack of knowledge, the only rational thing to do is help raise their level of knowledge and understanding. That’s the Great Work.
I sometimes imagine myself as a political prisoner. If that were to happen, I’d probably start teaching fellow prisoners, doctors, janitors, even guards. In a way we already live in an open-air prison, So what else is there to do but teach, organize, and conspire to dismantle the Matrix?

Building on Bitcoin
- You hosted some in-person meetups in Sacramento. What did you learn from those?
My first presentation was on MultiSig storage with SeedSigner, and submarine swaps through Boltz.exchange.
I realized quickly that I had overestimated the group’s technical background. Even the meetup organizer, a financial advisor, asked, “How is anyone supposed to follow these steps?” I responded that reading was required… He decided that Unchained is an easier way.
At a crypto meetup, I gave a much simpler talk, outlining how bitcoin will save the world, based on a DarthCoin’s guide. Only one person stuck around to ask questions – a man who seemed a little out there, and did not really seem to get the message beyond the strength of cryptographic security of bitcoin.
Again, I overestimated the audience’s readiness. That forced me to rethink my strategy. People are extremely early and reluctant to study.
- Now in Ohio, you hold sessions via the Orange Pill App. What’s changed?
My new motto is: educate the educators. The corollary is: don’t orange-pill stupid normies (as DarthCoin puts it).
I’ve shifted to small, technical sessions in order to raise a few solid guardians of this esoteric knowledge who really get it and can carry it forward.
The youngest attendee at one of my sessions is a newborn baby – he mostly sleeps, but maybe he still absorbs some of the educational vibes.
- How do local groups like Sactown and Cleveland Bitcoiners influence your work?
Every meetup reflects its local culture. Sacramento and Bay Area Bitcoiners, for example, do camping trips – once we camped through a desert storm, shielding our burgers from sand while others went to shoot guns.
Cleveland Bitcoiners are different. They amass large gatherings. They recently threw a 100k party. They do a bit more community outreach. Some are curious about the esoteric topics such as jurisdiction, spirituality, and healthful living.
I have no permanent allegiance to any state, race, or group. I go where I can teach and learn. I anticipate that in my next phase, I’ll meet Bitcoiners so advanced that I’ll have to give up my fiat job and focus full-time on serious projects where real health and wealth are on the line.
Hopefully, I’ll be ready. I believe the universe always challenges you exactly to your limit – no less, no more.
- What do people struggle with the most when it comes to technical education?
The biggest struggle isn’t technical – it’s a lack of deep curiosity. People ask “how” and “what” – how do I set up a node, what should one do with the lightning channels? But very few ask “why?”
Why does on-chain bitcoin not contribute to the circular economy? Why is it essential to run Lightning? Why did humanity fall into mental enslavement in the first place?
I’d rather teach two-year-olds who constantly ask “why” than adults who ask how to flip a profit. What worries me most is that most two-year-olds will grow up asking state-funded AI bots for answers and live according to its recommendations.
- One Cleveland Bitcoiner shows up at gold bug meetups. How valuable is face-to-face education?
I don’t think the older generation is going to reverse the current human condition. Most of them have been under mind control for too long, and they just don’t have the attention span to study and change their ways.
They’re better off stacking gold and helping fund their grandkids’ education. If I were to focus on a demographic, I’d go for teenagers – high school age – because by college, the indoctrination is usually too strong, and they’re chasing fiat mastery.
As for the gold bug meetup? Perhaps one day I will show up with a ukulele to sing some bitcoin-themed songs. Seniors love such entertainment.
- How do you choose what to focus on in your sessions, especially for different types of learners?
I don’t come in with a rigid agenda. I’ve collected a massive library of resources over the years and never stopped reading. My browser tab and folder count are exploding.
At the meetup, people share questions or topics they’re curious about, then I take that home, do my homework, and bring back a session based on those themes. I give them the key takeaways, plus where to dive deeper.
Most people won’t – or can’t – study the way I do, and I expect attendees to put in the work. I suspect that it’s more important to reach those who want to learn but don’t know how, the so-called nescient (not knowing), rather than the ignorant.
There are way too many ignorant bitcoiners, so my mission is to find those who are curious what’s beyond the facade of fake reality and superficial promises.
That naturally means that fewer people show up, and that’s fine. I’m not here for the crowds; I’m here to educate the educators. One bitcoiner who came decided to branch off into self-custody sessions and that’s awesome. Personally, I’m much more focused on Lightning.
I want to see broader adoption of tools like auth, sign-message, NWC, and LSPs. Next month, I’m going deep into eCash solutions, because let’s face it – most newcomers won’t be able to afford their own UTXO or open a lightning channel; additionally, it has to be fun and easy for them to transact sats, otherwise they won’t do it. Additionally, they’ll need to rely on
-
 @ 81022b27:2b8d0644
2025-06-09 01:41:45
@ 81022b27:2b8d0644
2025-06-09 01:41:45a delicious meditation
Those of you who know me are aware that I worked in the fast-food industry before becoming a chiropractor. My first job was at a Hardee's restaurant when I was fifteen.
I wanted to buy a car, which is why I started working. Once I bought the car, I realized I needed to continue working to maintain it, pay for gas, insurance, and the occasional "going out" money.
In the restaurant business, if you work at a place long enough, someone hands you a set of keys and puts you in charge of something.
So here I was, running a restaurant and in charge of a bunch of people, when I could barely take care of myself. Anyway, I was making what I thought was decent money for a 19-year-old.
My bosses started a new restaurant venture, and little by little, they began poaching the old management staff from Hardee’s. Eventually, they asked me to come work for them.
My new job was running a Church's Chicken. The stores were small, mostly takeout. The menu was small, and we didn't have many employees to manage. We didn't have a good reputation in the community due to poor management.
The owners introduced new registers, and sales immediately jumped. I suppose all the food was now being rung up and accounted for!
We cleaned up the restaurant and made sure we were putting out a good product, and guess what?
Sales doubled.
So here I am, thinking I know what I'm doing because I'm getting recognition from my bosses.
I didn't have the interpersonal skills to manage people effectively.
One time, I got into it with an employee but couldn't confront him to fire him, so I deleted him from the time clock. Let someone else deal with that.
Dealing with customers was usually okay because if they had an issue, you could just fix the problem, and that was it. Handling employees was a bit more challenging for me.
On busy days-Fridays, Saturdays, and Mother's Day (they called that the day after the welfare checks came out)
The restaurant would get so busy that sometimes people would line up around the building, and I felt that everyone was staring at me, which made me feel uncomfortable.
The store had windows all around; it was like a fishbowl-everyone saw everything.
I could have gone to hide in the office, but I needed to help out. I liked to run a tight ship labor-wise, so I always counted myself as one of the staff needed.
I would ask the cook to let me make the chicken and assign them some other tasks.
Even though I was probably even more visible than before, I would get lost in the work.
Everything was hand-breaded and battered. To me, it was like a Japanese tea ceremony.
When it was busy, we cooked a full "stove," which was 4 chickens at a time:
8 legs, 8 thighs, 8 wings, and 8 breasts.
The process was:
-
Flour, dip in batter, flour again.
-
Start with the legs because they take the longest to cook.
-
Continue until everything is in the fryer.
Repeat,
and repeat,
and repeat.
I would get lost in the work. You couldn't really rush things. I made sure everything was done by the book.
Focusing on one task so intently that every concern, every worry just faded away. I knew people were watching me cook the chicken in this fishbowl, but I was so engrossed in my task that I didn’t care.
All my stress and anxiety just faded.
I still try to lose myself in my work, only now it’s not frying chicken-it’s adjusting spines.
Now that I think about it, same situation. I’m “on stage” in my adjusting space with clients sitting in the waiting area.
Sometimes, I get stressed when there are a lot of people waiting on me…but I’m gonna do my best work frying this chi…
oops!
I mean adjusting this spine.
Zen teaching often emphasizes simplicity, mindfulness in daily activities, and the notion that enlightenment can be achieved in the ordinary moments of life. The phrase "chop wood, carry water" reflects this idea of finding the sacred in the mundane.
I found my Zen.
Find Yours.
❤️
-
-
 @ 0155373a:ba3e1bed
2025-01-09 00:01:05
@ 0155373a:ba3e1bed
2025-01-09 00:01:05Imagine an internet where you don’t need a big Internet Service Provider (ISP) to stay connected—an internet powered by the people, for the people. Decentralized internet is no longer a far-fetched idea; it's becoming a reality through community-driven networks. These networks rely on individuals within a community to act as "nodes," connecting their neighbors to the web and bypassing traditional ISPs.
What is Decentralized Internet?
Decentralized internet refers to a system where control over connectivity and access is distributed among individuals or local organizations rather than being concentrated in large ISPs. Instead of paying a single company for access, people in a community collaborate to build and maintain the network themselves.
How Does It Work?
- Mesh Networks: Each participant (or node) in the network connects to nearby nodes, creating a web of connectivity. This eliminates the need for a central ISP.
- Hardware: Nodes are powered by simple devices like routers or small computers running specialized software.
- Peer-to-Peer Sharing: Data flows through multiple nodes in the network, ensuring redundancy and reliability.
- Backbone Connection: Some networks may still rely on a single connection to a traditional ISP for broader internet access, but others can connect to decentralized backbone providers or satellites.
Benefits of Decentralized Internet
- Affordable Access: By cutting out traditional ISPs, communities can lower the cost of internet access.
- Empowerment: Communities gain control over their own connectivity and data, reducing reliance on corporations.
- Resilience: Decentralized networks are less prone to outages since they don’t depend on a single point of failure.
- Privacy: With less reliance on ISPs, there’s less risk of surveillance and data tracking.
- Inclusivity: Remote or underserved areas can establish connectivity without waiting for ISPs to expand their infrastructure.
Real-World Examples
- Guifi.net: A community network in Spain that has thousands of nodes providing internet to rural areas.
- NYC Mesh: A grassroots effort in New York City to create an affordable, community-owned internet.
- Althea: A project enabling neighbors to share internet bandwidth and earn income for participating in the network.
How to Get Started
- Educate Yourself: Research mesh network technologies like OpenWRT, LibreMesh, or BATMAN.
- Form a Group: Collaborate with neighbors or community organizations to pool resources.
- Get the Hardware: Invest in routers and antennas that support mesh networking.
- Set Up Nodes: Position nodes strategically to ensure strong connections across the community.
- Collaborate: Join forces with regional or global decentralized internet initiatives for support and knowledge sharing.
The Future of Decentralized Internet
As internet access becomes increasingly vital, decentralized networks present a way to bridge the digital divide and democratize connectivity. By building these systems, communities can take charge of their digital futures and ensure that no one is left behind.
Together, we can create an internet that is truly open, accessible, and resilient. The power lies in our hands—let’s connect, one node at a time.
-
 @ 9ca447d2:fbf5a36d
2025-06-07 12:02:11
@ 9ca447d2:fbf5a36d
2025-06-07 12:02:11Trump Media & Technology Group (TMTG), the company behind Truth Social and other Trump-branded digital platforms, is planning to raise $2.5 billion to build one of the largest bitcoin treasuries among public companies.
The deal involves the sale of approximately $1.5 billion in common stock and $1.0 billion in convertible senior secured notes.
According to the company, the offering is expected to close by the end of May, pending standard closing conditions.
Devin Nunes, CEO of Trump Media, said the investment in bitcoin is a big part of the company’s long-term plan.
“We view Bitcoin as an apex instrument of financial freedom,” Nunes said.
“This investment will help defend our Company against harassment and discrimination by financial institutions, which plague many Americans and U.S. firms.”
He added that the bitcoin treasury will be used to create new synergies across the company’s platforms including Truth Social, Truth+, and the upcoming financial tech brand Truth.Fi.
“It’s a big step forward in the company’s plans to evolve into a holding company by acquiring additional profit-generating, crown jewel assets consistent with America First principles,” Nunes said.
The $2.5 billion raise will come from about 50 institutional investors. The $1 billion in convertible notes will have 0% interest and be convertible into shares at a 35% premium.
TMTG’s current liquid assets, including cash and short-term investments, are $759 million as of the end of the first quarter of 2025. With this new funding, the company’s liquid assets will be over $3 billion.
Custody of the bitcoin treasury will be handled by Crypto.com and Anchorage Digital. They will manage and store the digital assets.
Earlier this week The Financial Times reported Trump Media was planning to raise $3 billion for digital assets acquisitions.
The article said the funds would be used to buy bitcoin and other digital assets, and an announcement could come before a major related event in Las Vegas.
Related: Bitcoin 2025 Conference Kicks off in Las Vegas Today
Trump Media denied the FT report. In a statement, the company said, “Apparently the Financial Times has dumb writers listening to even dumber sources.”
There was no further comment. However, the official $2.5 billion figure, which was announced shortly after by Trump Media through a press release, aligns with its actual filing and investor communication.
Trump Media’s official announcement
This comes at a time when the Trump family and political allies are showing renewed interest in Bitcoin.
President Donald Trump who is now back in office since the 2025 election, has said he wants to make the U.S. the “crypto capital of the world.”
Trump Media is also working on retail bitcoin investment products including ETFs aligned with America First policies.
These products will make bitcoin more accessible to retail investors and support pro-Trump financial initiatives.
But not everyone is happy.
Democratic Senator Elizabeth Warren recently expressed concerns about Trump Media’s Bitcoin plans. She asked U.S. regulators to clarify their oversight of digital-asset ETFs, warning of investor risk.
Industry insiders are comparing Trump Media’s plans to Strategy (MSTR) which has built a multi-billion dollar bitcoin treasury over the last year. They used stock and bond sales to fund their bitcoin purchases.
-
 @ 81022b27:2b8d0644
2025-06-09 01:37:31
@ 81022b27:2b8d0644
2025-06-09 01:37:31Shopping for groceries is one of my least favorite tasks. However, it's got to be done.
If I am in a hurry, I like to shop at Aldi, not only because they have decent prices but also because I can get in and out quickly (and I don’t have to scan my own groceries).
They are definitely no-frills in many ways: You have to bag your own groceries, you should bring your own bags—otherwise, you have to buy them, and to get a shopping cart, you need a quarter to unlock it.
I'm trying to rush and be efficient when I realize I don’t have "the quarter" for the shopping cart!
Dammit!
I’m going to have to go back to the car to see if I have one.
I'm swearing under my breath, thinking about having to walk all the way back when…
I notice someone has placed a quarter on the wall next to the row of carts.
THANK YOU!
This little act of kindness took me from a state of "being mildly annoyed at the entire world because traffic didn’t clear a path in front of me trying to get here" to feeling great gratitude.
The fact that someone considered that doing this would make my life easier knocked my selfish, self-involved ass out of my body.
I finished my shopping in a more cheerful, mindful way. The people in the aisles didn't seem to annoy me as much.
I took way longer than usual.
It wasn't a race anymore.
I checked out, loaded the car, and when I went to return the cart—
I left a quarter.
-
 @ 81022b27:2b8d0644
2025-06-09 01:31:29
@ 81022b27:2b8d0644
2025-06-09 01:31:29We were just talking today about first impressions when meeting people. Sometimes I get an instant “dislike” to someone upon meeting, even though they have never done or said anything bad to me. The older I get, the more I will usually go with my gut instincts and not engage the person any deeper if possible.
One of the reasons that was brought up is that people who are not congruent with their words, thoughts, and actions are usually the ones that “turn me off”
You know these people, too. They are the ones with all the advice-yet their lives are in shambles, the “preachy” ones that have their closets full of skeletons.
I’ve been accused of “not having a filter” or “being too transparent” at times… but not usually about my stance on things. I’m not confrontational…but I’m not above turning around and wailing away from someone I can’t stomach.
Anyway, the purpose of this rambling post if to encourage you to drop the facade, if you have one-and be more yourself.
-
 @ 65912a7a:5dc638bf
2024-12-08 05:33:02
@ 65912a7a:5dc638bf
2024-12-08 05:33:02Chef's notes
This is my late partner's award winning Cajun rice & beans recipe. It's an updated take on the traditional Cajun comfort food.
Chef Darin was a classically trained chef who spent 30+ years in the kitchen perfecting his recipes, and delivering authentic Cajun and Creole food to his patrons. This is a 5-star dish that will earn the respect of the most discerning Cajun afficionado. You won't be disappointed.
I suggest making this recipe exactly as directed the first time, and then make whatever adjustments you want for future batches. Also, don't cheap out on the Andouille. No Johnsonville or Hillshire Farms. Chef Aidelle's is a good choice, as is Silva's from Whole Foods. They cost a few extra bucks, but it's absolutely worth it.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 3 hours
- 🍽️ Servings: 12
Ingredients
- 16oz small red beans, dry
- 2 cups long grain white rice
- 14-16oz andouille sausage, sliced
- 8oz ham, cubed
- 1 large yellow onion, chopped
- 1 green bell pepper, chopped
- 2-3 stalks celery, chopped
- 2 tbsp garlic (12 cloves), minced
- 7 cups water
- ¼ cup olive oil
- 2 large bay leaves
- 1 tbsp parsley, dried
- 1 tsp thyme, dried
- 1 tsp Cajun seasoning
- ½ tsp cayenne pepper, dried
- ¼ tsp sage, rubbed
- 1½ tsp salt (more or less to taste)
Directions
- Soak beans in a large pot of water overnight.
- Heat oil in a large stockpot over medium heat. Cook onion, bell pepper, celery, garlic in olive oil for 3 to 4 minutes (until onion is translucent).
- Add beans, bay leaves, parsley, thyme, salt, MSG, Cajun seasoning, cayenne pepper, Sage, and water. Stir, bring to a boil, and then reduce heat to medium-low (btwn 2-3). Cover and simmer for 2½ hours.
- Remove bay leaves. Mash some of the beans. Stir Andouille and ham into beans, and simmer uncovered for an additional 30 minutes.
- Meanwhile, prepare the rice. Bring water and rice to a boil in a saucepan. Reduce heat, cover, and simmer for 20 minutes.
- Serve beans over steamed white rice.
-
 @ 3bf0c63f:aefa459d
2024-12-06 20:37:26
@ 3bf0c63f:aefa459d
2024-12-06 20:37:26início
"Vocês vêem? Vêem a história? Vêem alguma coisa? Me parece que estou tentando lhes contar um sonho -- fazendo uma tentativa inútil, porque nenhum relato de sonho pode transmitir a sensação de sonho, aquela mistura de absurdo, surpresa e espanto numa excitação de revolta tentando se impôr, aquela noção de ser tomado pelo incompreensível que é da própria essência dos sonhos..."
Ele ficou em silêncio por alguns instantes.
"... Não, é impossível; é impossível transmitir a sensação viva de qualquer época determinada de nossa existência -- aquela que constitui a sua verdade, o seu significado, a sua essência sutil e contundente. É impossível. Vivemos, como sonhamos -- sozinhos..."
- Livros mencionados por Olavo de Carvalho
- Antiga homepage Olavo de Carvalho
- Bitcoin explicado de um jeito correto e inteligível
- Reclamações
-
 @ 9ca447d2:fbf5a36d
2025-06-07 12:01:58
@ 9ca447d2:fbf5a36d
2025-06-07 12:01:58CANNES, FRANCE – May 2025 — Bitcoin mining made its mark at the world’s most prestigious film gathering this year as Puerto Rican director and producer Alana Mediavilla introduced her feature documentary Dirty Coin: The Bitcoin Mining Documentary at the Marché du Film during the Cannes Film Festival.
The film puts bitcoin mining at the center of a rising global conversation about energy, technology, and economic freedom.
Dirty Coin is the first feature-length documentary to explore bitcoin mining through immersive, on-the-ground case studies.
From rural towns in the United States to hydro-powered sites in Latin America and the Congo, the film follows miners and communities navigating what may be one of the most misunderstood technologies of our time.
The result is a human-centered look at how bitcoin mining is transforming local economies and energy infrastructure in real ways.
To mark its Cannes debut, Mediavilla and her team hosted a packed industry event that brought together leaders from both film and finance.

Dirty Coin debut ceremony at the Marché du Film
Sponsors Celestial Management, Sangha Renewables, Nordblock, and Paystand.org supported the program, which featured panels on mining, energy use, and decentralized infrastructure.
Attendees had the rare opportunity to engage directly with pioneers in the space. A special session in French led by Seb Gouspillou spotlighted mining efforts in the Congo’s Virunga region.
Dirty Coin builds on Mediavilla’s award-winning short film Stranded, which won over 20 international prizes, including Best Short Documentary at Cannes in 2024.
That success helped lay the foundation for the feature and positioned Mediavilla as one of the boldest new voices in global documentary filmmaking.

Alana Mediavilla speaks at the Marché du Film — Cannes Film Festival
“If we’ve found an industry that can unlock stranded energy and turn it into real power for people—especially in regions with energy poverty—why wouldn’t we look into it?” says Mediavilla. “Our privilege blinds us.
“The same thing we criticize could be the very thing that lifts the developing world to our standard of living. Ignoring that potential is a failure of imagination.”
Much like the decentralized network it explores, Dirty Coin is spreading globally through grassroots momentum.
Local leaders are hosting independent screenings around the world, from Roatán and Berlin to São Paulo and Madrid. Upcoming events include Toronto and Zurich, with more cities joining each month.
Mediavilla, who previously worked in creative leadership roles in the U.S. — including as a producer at Google — returned to Puerto Rico to found Campo Libre, a studio focused on high-caliber, globally relevant storytelling from the Caribbean.
She was also accepted into the Cannes Producers Network, a selective program open only to producers with box office releases in the past four years.
Mediavilla qualified after independently releasing Dirty Coin in theaters across Puerto Rico. Her participation in the network gave her direct access to meetings, insights, and connections with the most active distributors and producers working today.
The film’s next public screening will take place at the Anthem Film Festival in Palm Springs on Saturday, June 14 at 2 PM. Additional screenings and market appearances are planned throughout the year at Bitcoin events and international film platforms.

Dirty Coin at the Cannes Film Festival
Watch the Trailer + Access Press Materials
📂 EPK
🎬 Screener
🌍 Host a Screening
Follow the Movement
Instagram: https://www.instagram.com/dirty_coin_official/
Twitter: https://x.com/DirtyCoinDoc
Website: www.dirtycointhemovie.com -
 @ 65912a7a:5dc638bf
2024-11-22 21:37:16
@ 65912a7a:5dc638bf
2024-11-22 21:37:16Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 12
Ingredients
- 12-14oz fresh cranberries
- 1⅓ cup packed brown sugar
- 1 cup raisins
- 1 orange, peeled & chopped
- 1 cup water
Directions
- Using medium sauce pan, simmer cranberries and water for 5-6 min. Cranberries will start to pop.
- Add brown sugar, raisins, and chopped orange to the berries.
- Bring to a simmer and continue to cook for 20 min. Stir often to prevent sticking. Remove from heat.
- Let set until room temp. Mixture will thicken as it cools.
- Put in a covered container and keep refrigerated. Lasts for about 2 weeks.
-
 @ 3bf0c63f:aefa459d
2024-11-07 14:56:17
@ 3bf0c63f:aefa459d
2024-11-07 14:56:17The case against edits
Direct edits are a centralizing force on Nostr, a slippery slope that should not be accepted.
Edits are fine in other, more specialized event kinds, but the
kind:1space shouldn't be compromised with such a push towards centralization, becausekind:1is the public square of Nostr, where all focus should be on decentralization and censorship-resistance.- Why?
Edits introduce too much complexity. If edits are widespread, all clients now have to download dozens of extra events at the same time while users are browsing a big feed of notes which are already coming from dozens of different relays using complicated outbox-model-based querying, then for each event they have to open yet another subscription to these relays -- or perform some other complicated batching of subscriptions which then requires more complexity on the event handling side and then when associating these edits with the original events. I can only imagine this will hurt apps performance, but it definitely raises the barrier to entry and thus necessarily decreases Nostr decentralization.
Some clients may be implemneted in way such that they download tons of events and then store them in a local databases, from which they then construct the feed that users see. Such clients may make edits potentially easier to deal with -- but this is hardly an answer to the point above, since such clients are already more complex to implement in the first place.
- What do you have against complex clients?
The point is not to say that all clients should be simple, but that it should be simple to write a client -- or at least as simple as physically possible.
You may not be thinking about it, but if you believe in the promise of Nostr then we should expect to see Nostr feeds in many other contexts other than on a big super app in a phone -- we should see Nostr notes being referenced from and injected in unrelated webpages, unrelated apps, hardware devices, comment sections and so on. All these micro-clients will have to implement some complicated edit-fetching logic now?
- But aren't we already fetching likes and zaps and other things, why not fetch edits too?
Likes, zaps and other similar things are optional. It's perfectly fine to use Nostr without seeing likes and/or zaps -- and, believe me, it does happen quite a lot. The point is basically that likes or zaps don't affect the content of the main post at all, while edits do.
- But edits are optional!
No, they are not optional. If edits become widespread they necessarily become mandatory. Any client that doesn't implement edits will be displaying false information to its users and their experience will be completely broken.
- That's fine, as people will just move to clients that support edits!
Exactly, that is what I expect to happen too, and this is why I am saying edits are a centralizing force that we should be fighting against, not embracing.
If you understand that edits are a centralizing force, then you must automatically agree that they aren't a desirable feature, given that if you are reading this now, with Nostr being so small, there is a 100% chance you care about decentralization and you're not just some kind of lazy influencer that is only doing this for money.
- All other social networks support editing!
This is not true at all. Bluesky has 10x more users than Nostr and doesn't support edits. Instagram doesn't support editing pictures after they're posted, and doesn't support editing comments. Tiktok doesn't support editing videos or comments after they're posted. YouTube doesn't support editing videos after they're posted. Most famously, email, the most widely used and widespread "social app" out there, does not support edits of any kind. Twitter didn't support edits for the first 15 years of its life, and, although some people complained, it didn't hurt the platform at all -- arguably it benefitted it.
If edits are such a straightforward feature to add that won't hurt performance, that won't introduce complexity, and also that is such an essential feature users could never live without them, then why don't these centralized platforms have edits on everything already? There must be something there.
- Eventually someone will implement edits anyway, so why bother to oppose edits now?
Once Nostr becomes big enough, maybe it will be already shielded from such centralizing forces by its sheer volume of users and quantity of clients, maybe not, we will see. All I'm saying is that we shouldn't just push for bad things now just because of a potential future in which they might come.
- The market will decide what is better.
The market has decided for Facebook, Instagram, Twitter and TikTok. If we were to follow what the market had decided we wouldn't be here, and you wouldn't be reading this post.
- OK, you have convinced me, edits are not good for the protocol. But what do we do about the users who just want to fix their typos?
There are many ways. The annotations spec, for example, provides a simple way to append things to a note without being a full-blown edit, and they fall back gracefully to normal replies in clients that don't implement the full annotations spec.
Eventually we could have annotations that are expressed in form of simple (human-readable?) diffs that can be applied directly to the post, but fall back, again, to comments.
Besides these, a very simple idea that wasn't tried yet on Nostr yet is the idea that has been tried for emails and seems to work very well: delaying a post after the "submit" button is clicked and giving the user the opportunity to cancel and edit it again before it is actually posted.
Ultimately, if edits are so necessary, then maybe we could come up with a way to implement edits that is truly optional and falls back cleanly for clients that don't support them directly and don't hurt the protocol very much. Let's think about it and not rush towards defeat.
-
 @ 8bad92c3:ca714aa5
2025-06-07 11:01:44
@ 8bad92c3:ca714aa5
2025-06-07 11:01:44Key Takeaways

Michael Goldstein, aka Bitstein, presents a sweeping philosophical and economic case for going “all in” on Bitcoin, arguing that unlike fiat, which distorts capital formation and fuels short-term thinking, Bitcoin fosters low time preference, meaningful saving, and long-term societal flourishing. At the heart of his thesis is “hodling for good”—a triple-layered idea encompassing permanence, purpose, and the pursuit of higher values like truth, beauty, and legacy. Drawing on thinkers like Aristotle, Hoppe, and Josef Pieper, Goldstein redefines leisure as contemplation, a vital practice in aligning capital with one’s deepest ideals. He urges Bitcoiners to think beyond mere wealth accumulation and consider how their sats can fund enduring institutions, art, and architecture that reflect a moral vision of the future.
Best Quotes
“Let BlackRock buy the houses, and you keep the sats.”
“We're not hodling just for the sake of hodling. There is a purpose to it.”
“Fiat money shortens your time horizon… you can never rest.”
“Savings precedes capital accumulation. You can’t build unless you’ve saved.”
“You're increasing the marginal value of everyone else’s Bitcoin.”
“True leisure is contemplation—the pursuit of the highest good.”
“What is Bitcoin for if not to make the conditions for magnificent acts of creation possible?”
“Bitcoin itself will last forever. Your stack might not. What will outlast your coins?”
“Only a whale can be magnificent.”
“The market will sell you all the crack you want. It’s up to you to demand beauty.”
Conclusion
This episode is a call to reimagine Bitcoin as more than a financial revolution—it’s a blueprint for civilizational renewal. Michael Goldstein reframes hodling as an act of moral stewardship, urging Bitcoiners to lower their time preference, build lasting institutions, and pursue truth, beauty, and legacy—not to escape the world, but to rebuild it on sound foundations.
Timestamps
00:00 - Intro
00:50 - Michael’s BBB presentation Hodl for Good
07:27 - Austrian principles on capital
15:40 - Fiat distorts the economic process
23:34 - Bitkey
24:29 - Hodl for Good triple entendre
29:52 - Bitcoin benefits everyone
39:05 - Unchained
40:14 - Leisure theory of value
52:15 - Heightening life
1:15:48 - Breaking from the chase makes room for magnificence
1:32:32 - Nakamoto Institute’s missionTranscript
(00:00) Fiat money is by its nature a disturbance. If money is being continually produced, especially at an uncertain rate, these uh policies are really just redistribution of wealth. Most are looking for number to go up post hyper bitcoinization. The rate of growth of bitcoin would be more reflective of the growth of the economy as a whole.
(00:23) Ultimately, capital requires knowledge because it requires knowing there is something that you can add to the structures of production to lengthen it in some way that will take time but allow you to have more in the future than you would today. Let Black Rockck buy the houses and you keep the sats, not the other way around.
(00:41) You wait until later for Larry Frink to try to sell you a [Music] mansion. And we're live just like that. Just like that. 3:30 on a Friday, Memorial Day weekend. It's a good good good way to end the week and start the holiday weekend. Yes, sir. Yes, sir. Thank you for having me here. Thank you for coming. I wore this hat specifically because I think it's I think it's very apppropo uh to the conversation we're going to have which is I hope an extension of the presentation you gave at Bitblock Boom Huddle for good. You were working on
(01:24) that for many weeks leading up to uh the conference and explaining how you were structuring it. I think it's a very important topic to discuss now as the Bitcoin price is hitting new all-time highs and people are trying to understand what am I doing with Bitcoin? Like you have you have the different sort of factions within Bitcoin.
(01:47) Uh get on a Bitcoin standard, get on zero, spend as much Bitcoin as possible. You have the sailors of the world are saying buy Bitcoin, never sell, die with your Bitcoin. And I think you do a really good job in that presentation. And I just think your understanding overall of Bitcoin is incredible to put everything into context. It's not either or.
(02:07) It really depends on what you want to accomplish. Yeah, it's definitely there there is no actual one-sizefits-all um for I mean nearly anything in this world. So um yeah, I mean first of all I mean there was it was the first conference talk I had given in maybe five years. I think the one prior to that uh was um bit block boom 2019 which was my meme talk which uh has uh become infamous and notorious.
(02:43) So uh there was also a lot of like high expectations uh you know rockstar dev uh has has treated that you know uh that that talk with a lot of reference. a lot of people have enjoyed it and he was expecting this one to be, you know, the greatest one ever, which is a little bit of a little bit of a uh a burden to live up to those kinds of standards.
(03:08) Um, but you know, because I don't give a lot of talks. Um, you know, I I I like to uh try to bring ideas that might even be ideas that are common. So, something like hodling, we all talk about it constantly. uh but try to bring it from a little bit of a different angle and try to give um a little bit of uh new light to it.
(03:31) I alsove I've I've always enjoyed kind of coming at things from a third angle. Um whenever there's, you know, there's there's all these little debates that we have in in Bitcoin and sometimes it's nice to try to uh step out of it and look at it a little more uh kind of objectively and find ways of understanding it that incorporate the truths of of all of them.
(03:58) uh you know cuz I think we should always be kind of as much as possible after ultimate truth. Um so with this one um yeah I was kind of finding that that sort of golden mean. So uh um yeah and I actually I think about that a lot is uh you know Aristotle has his his concept of the golden mean. So it's like any any virtue is sort of between two vices um because you can you can always you can always take something too far.
(04:27) So you're you're always trying to find that right balance. Um so someone who is uh courageous you know uh one of the vices uh on one side is being basically reckless. I I can't remember what word he would use. Uh but effectively being reckless and just wanting to put yourself in danger for no other reason than just you know the thrill of it.
(04:50) Um and then on the other side you would just have cowardice which is like you're unwilling to put yourself um at any risk at any time. Um, and courage is right there in the middle where it's understanding when is the right time uh to put your put yourself, you know, in in the face of danger um and take it on. And so um in some sense this this was kind of me uh in in some ways like I'm obviously a partisan of hodling.
(05:20) Um, I've for, you know, a long time now talked about the, um, why huddling is good, why people do it, why we should expect it. Um, but still trying to find that that sort of golden mean of like yes, huddle, but also what are we hodling for? And it's not we're we're not hodddling just merely for the sake of hodddling.
(05:45) There there is a a purpose to it. And we should think about that. And that would also help us think more about um what are the benefits of of spending, when should we spend, why should we spend, what should we spend on um to actually give light to that sort of side of the debate. Um so that was that was what I was kind of trying to trying to get into.
(06:09) Um, as well as also just uh at the same time despite all the talk of hodling, there's always this perennial uh there's always this perennial dislike of hodlers because we're treated as uh as if um we're just free riding the network or we're just greedy or you know any of these things. And I wanted to show how uh huddling does serve a real economic purpose.
(06:36) Um, and it does benefit the individual, but it also does uh it it has actual real social um benefits as well beyond merely the individual. Um, so I wanted to give that sort of defense of hodling as well to look at it from um a a broader position than just merely I'm trying to get rich. Um uh because even the person who uh that is all they want to do um just like you know your your pure number grow up go up moonboy even that behavior has positive ramifications on on the economy.
(07:14) And while we might look at them and have uh judgments about their particular choices for them as an individual, we shouldn't discount that uh their actions are having positive positive effects for the rest of the economy. Yeah. So, let's dive into that just not even in the context of Bitcoin because I think you did a great job of this in the presentation.
(07:36) just you've done a good job of this consistently throughout the years that I've known you. Just from like a first principles Austrian economics perspective, what is the idea around capital accumulation, low time preference and deployment of that capital like what what like getting getting into like the nitty-gritty and then applying it to Bitcoin? Yeah, it's it's a big question and um in many ways I mean I I even I barely scratched the surface.
(08:05) uh I I can't claim to have read uh all the volumes of Bombber works, you know, capital and interest and and stuff like that. Um but I think there's some some sort of basic concepts that we can look at that we can uh draw a lot out. Um the first uh I guess let's write that. So repeat so like capital time preference. Yeah. Well, I guess getting more broad like why sav -
 @ 3bf0c63f:aefa459d
2024-10-31 16:08:50
@ 3bf0c63f:aefa459d
2024-10-31 16:08:50Anglicismos estúpidos no português contemporâneo
Palavras e expressões que ninguém deveria usar porque não têm o sentido que as pessoas acham que têm, são apenas aportuguesamentos de palavras inglesas que por nuances da história têm um sentido ligeiramente diferente em inglês.
Cada erro é acompanhado também de uma sugestão de como corrigi-lo.
Palavras que existem em português com sentido diferente
- submissão (de trabalhos): envio, apresentação
- disrupção: perturbação
- assumir: considerar, pressupor, presumir
- realizar: perceber
- endereçar: tratar de
- suporte (ao cliente): atendimento
- suportar (uma idéia, um projeto): apoiar, financiar
- suportar (uma função, recurso, característica): oferecer, ser compatível com
- literacia: instrução, alfabetização
- convoluto: complicado.
- acurácia: precisão.
- resiliência: resistência.
Aportuguesamentos desnecessários
- estartar: iniciar, começar
- treidar: negociar, especular
Expressões
- "não é sobre...": "não se trata de..."

Ver também
-
 @ b1ddb4d7:471244e7
2025-06-07 10:01:31
@ b1ddb4d7:471244e7
2025-06-07 10:01:31Hosted at the iconic Palace of Culture and Science—a prominent symbol of the communist era—the Bitcoin FilmFest offers a vibrant celebration of film through the lens of bitcoin. The venue itself provides a striking contrast to the festival’s focus, highlighting bitcoin’s core identity as a currency embodying independence from traditional financial and political systems.
𝐅𝐢𝐱𝐢𝐧𝐠 𝐭𝐡𝐞 𝐜𝐮𝐥𝐭𝐮𝐫𝐞 𝐰𝐢𝐭𝐡 𝐩𝐨𝐰𝐞𝐫𝐟𝐮𝐥 𝐦𝐮𝐬𝐢𝐜 𝐯𝐢𝐛𝐞𝐬.
Warsaw, Day Zero at #BFF25 (European Bitcoin Pizza Day) with @roger__9000, MadMunky and the @2140_wtf squad
 pic.twitter.com/9ogVvWRReA
pic.twitter.com/9ogVvWRReA— Bitcoin FilmFest

 (@bitcoinfilmfest) May 28, 2025
(@bitcoinfilmfest) May 28, 2025This venue represents an era when the state tightly controlled the economy and financial systems. The juxtaposition of this historical site with an event dedicated to bitcoin is striking and thought-provoking.
The event features a diverse array of activities, including engaging panel discussions, screenings of both feature-length and short films, workshops and lively parties. Each component designed to explore the multifaceted world of bitcoin and its implications for society, offering attendees a blend of entertainment and education.

The films showcase innovative narratives and insights into bitcoin’s landscape, while the panels facilitate thought-provoking discussions among industry experts and filmmakers.
Networking is a significant aspect of the festival, with an exceptionally open and friendly atmosphere that foster connections among participants. Participants from all over Europe gather to engage with like-minded individuals who share a passion for BTC and its implications for the future.
The open exchanges of ideas foster a sense of community, allowing attendees to forge new connections, collaborate on projects, and discuss the potential of blockchain technology implemented in bitcoin.

The organization of the festival is extraordinary, ensuring a smooth flow of information and an expertly structured schedule filled from morning until evening. Attendees appreciate the meticulous planning that allowed them to maximize their experience. Additionally, thoughtful touches such as gifts from sponsors and well-chosen locations for various events contribute to the overall positive atmosphere of the festival.
Overall, the Bitcoin FilmFest not only highlights the artistic expression surrounding bitcoin but also serves as a vital platform for dialogue—about financial freedom, the future of money, and individual sovereignty in a shifting world.

The event successfully bridges the gap between a historical symbol of control and a movement that celebrates freedom, innovation, and collaboration in the digital age, highlighting the importance of independence in financial systems while fostering a collaborative environment for innovation and growth.
Next year’s event is slated for June 5-7 2026. For further updates check: https://bitcoinfilmfest.com/
-
 @ 502ab02a:a2860397
2025-06-09 01:04:40
@ 502ab02a:a2860397
2025-06-09 01:04:40มีคนจำนวนไม่น้อยที่เข้าใจว่าเรื่อง “อาหารแห่งอนาคต” คืออะไรที่เพิ่งเกิด เป็นแนวคิดใหม่สำหรับโลกยุคใหม่ แต่จริงๆ แล้วไม่ใช่เลยครับ เฮียว่าเราถูกจัดโต๊ะอาหารอนาคตไว้ให้กินมานานมากแล้ว เพียงแต่ไม่รู้ตัว ต่างหาก
ช่วงปลายคริสต์ศตวรรษที่ 19 สิ่งที่เรียกว่าการ “ควบคุมอาหารมวลชน” ก็เริ่มต้นอย่างจริงจังแล้ว
ย้อนกลับไปปี 1863 ในห้องพักคนไข้ของโรงพยาบาล Battle Creek Sanitarium ที่รัฐมิชิแกน สหรัฐฯ มีชายคนหนึ่งชื่อ John Harvey Kellogg เขาเป็นหมอและเป็นหนึ่งในสาวกของกลุ่ม Seventh-day Adventist ที่เชื่อว่าการกินเนื้อสัตว์ทำให้คนกระด้างใจและเต็มไปด้วยตัณหา เกิดราคะ เขาจึงคิดค้น “อาหารเช้าที่ไม่มีเนื้อ” เพื่อส่งเสริมสุขลักษณะและลดกิเลสในร่างกายมนุษย์ สิ่งที่เขาทำในตอนนั้นคือการใช้ข้าวโพดบดอบแห้งจนกรอบ กลายเป็นสิ่งที่เรียกว่า “ซีเรียล” ในยุคเริ่มต้น ซึ่งภายหลังน้องชายของเขาคือ Will Keith Kellogg จะนำสูตรนั้นไปพัฒนาให้หวานขึ้น ใส่น้ำตาลเพิ่ม ใส่โฆษณาเพิ่ม แล้วก็วางขายในชื่อแบรนด์ Kellogg’s ที่เราเห็นกันทุกเช้านั่นแหละ เขาผลิตคอร์นเฟลกขึ้นมาด้วยความเชื่อว่าจะช่วยลดการช่วยตัวเองในวัยรุ่นได้! จากอาหารของกลุ่มศาสนา คอร์นเฟลกกลายเป็นอาหารที่เข้าสู่ครัวเรือนอเมริกันภายใต้แนวคิดว่า “อาหารเช้าคือมื้อสำคัญที่สุดของวัน” โดยไม่ได้มีหลักฐานรองรับอย่างจริงจังเลย
ช่วงต้นศตวรรษที่ 20 เป็นยุคที่อเมริกาเริ่มมีอำนาจในเชิงอุตสาหกรรมมากขึ้น แต่ก็เป็นยุคที่คนยังทำอาหารกินเองอยู่ในครัว เรื่องอาหารยังเป็นเรื่องของบ้าน ไม่ใช่ของแบรนด์ ยังไม่มีใครนึกว่า “สิทธิ์ในการกิน” จะกลายเป็นสินค้าสาธารณะในภายหลัง แต่แล้วก็เกิดจุดเปลี่ยนสำคัญเมื่อสงครามโลกครั้งที่ 1 และ 2 ทำให้รัฐจำเป็นต้องคิดเรื่องการเลี้ยงประชากรในภาวะขาดแคลน ต้องมีการเก็บอาหารได้นาน ขนส่งได้ง่าย และต้นทุนต่ำ นี่คือจุดเริ่มต้นของการผลักดัน “อาหารแปรรูป” หรือ processed food อย่างเป็นทางการ
ในปี 1911 มีบริษัทชื่อว่า Procter & Gamble เปิดตัว “Crisco” ซึ่งเป็นน้ำมันพืชไฮโดรเจนเนตที่ถูกออกแบบมาเพื่อเลียนแบบไขมันสัตว์ในราคาถูกกว่า Crisco ทำจากน้ำมันฝ้าย (cottonseed oil) ซึ่งตอนนั้นเป็นของเหลือจากอุตสาหกรรมสิ่งทอ ไม่มีใครคิดว่ามันจะกลายเป็นสิ่งที่ถูกโฆษณาว่า “ดีกว่าไขมันสัตว์” แต่เพราะการโฆษณาแบบมืออาชีพและการจับมือกับสมาคมแพทย์ Crisco ก็กลายเป็นของคู่ครัวแบบไม่รู้ตัว นี่คือจุดเริ่มต้นของ fiat fat ไขมันเทียมที่ถูกสถาปนาให้เป็นของจริง ทั้งที่จริงๆ มันคือของปลอมที่ห่อด้วยวิทยาศาสตร์ครึ่งใบ
ช่วงปี 1910s ถึง 1930s คือยุคที่อุตสาหกรรมอาหารเริ่มโตเต็มที่ สหรัฐฯ เริ่มผลิต นมข้นหวาน สำหรับทหารในสงครามกลางเมือง และต่อยอดใช้ในสงครามโลกครั้งที่ 1 นมชนิดนี้เก็บได้นาน ไม่เน่า และมีพลังงานสูง ทหารหลายคนติดใจในรสชาติหวานมันแบบไม่มีอะไรเทียบได้ ซึ่งต่อมาทำให้มันกลายเป็นวัตถุดิบหลักในหลายเมนูทั่วโลก รวมถึง “ชาเย็น” บ้านเราที่ต้องมีนมข้นหวานเท่านั้นถึงจะใช่
เข้าสู่ช่วง สงครามโลกครั้งที่ 2 (1939–1945) คือช่วงหัวเลี้ยวหัวต่อสำคัญของ Fiat Food หรืออาหารที่ถูกผลิตจากตรรกะจำเป็นเชิงยุทธศาสตร์มากกว่าธรรมชาติ เฮียว่าช่วงนี้มันเหมือนโรงเรียนประถมของ Ultra-Processed Food สมัยใหม่เลยล่ะ ตัวอย่างชัดเจนคือ Spam เนื้อหมูกระป๋องที่ออกแบบให้ทหารพกพาสะดวก ไม่ต้องแช่เย็น เก็บได้นาน และอุดมด้วยโซเดียม หลังสงครามจบ มันกลายเป็นอาหารยอดฮิตในประเทศที่เคยเป็นแนวหน้า เช่น ฮาวาย เกาหลี ฟิลิปปินส์ และอังกฤษ โดยถูกโฆษณาว่าเป็น “ของดีจากอเมริกา” ทั้งที่ทหารหลายคนก็เบื่อมันจนเอียน
ในช่วงเดียวกันนั้นเอง ช็อกโกแลต Hershey's ก็ถูกพัฒนาเป็น “Field Ration D” หรือแท่งช็อกโกแลตพลังงานสูงที่ไม่ละลายในอุณหภูมิสูง สำหรับแจกให้ทหารทุกคนคนละแท่งติดตัวไว้ในสนามรบ พอสงครามจบ Hershey’s ก็ปรับสูตรให้กินง่ายขึ้น แล้วขายในเชิงพาณิชย์จนกลายเป็นแบรนด์ระดับโลกแบบที่เราเห็นทุกวันนี้
โพรเซสชีส เช่น Kraft และ Velveeta ก็ถูกออกแบบให้เก็บได้นานไม่เน่า ชีสพวกนี้ผสมสารอิมัลซิไฟเออร์ ทำให้ไม่แยกชั้นเมื่อถูกความร้อน เหมาะกับการผลิตอาหารจำนวนมากแบบโรงครัวทหาร เมื่อสงครามจบ Kraft เอาเทคโนโลยีนี้มาทำ “ชีสแผ่น” สำหรับเบอร์เกอร์และแซนด์วิช เป็นต้นแบบของอาหารฟาสต์ฟู้ดยุคใหม่แบบไร้กลิ่นชีสแท้
นมผง และ ไขมันพืชไฮโดรจิเนต ก็เริ่มเข้ามามีบทบาทในสงคราม โดยนมผงแทนที่นมสดในสนามรบ และไขมันพืชใช้ทำเบเกอรี่โดยไม่ต้องใช้เนยสด ซึ่งแพงกว่า หลังสงคราม สารให้ความหวานเทียมอย่าง ซัคคาริน ก็เริ่มถูกนำเสนอว่าเหมาะกับคนลดน้ำหนัก ทั้งที่มันมีจุดเริ่มจากความจำเป็นยามขาดแคลนน้ำตาลในสงคราม
ปี 1950s-1960s โลกเข้าสู่ยุคสงครามเย็น เทคโนโลยีการเก็บอาหารพัฒนาไปพร้อมกับเทคโนโลยีอวกาศ และหนึ่งในผลิตภัณฑ์ระดับตำนานคือ Tang น้ำส้มผงของบริษัท General Foods ที่ถูกส่งขึ้นไปพร้อมนักบินอวกาศ John Glenn ในปี 1962 Tang กลายเป็นสัญลักษณ์ของ “อนาคตในแก้วน้ำ” ทั้งที่ไม่มีผลไม้จริงเลยสักหยดเดียว แต่การตลาดที่อ้างว่า NASA ใช้ ทำให้มันขายดีระเบิด
ในระหว่างนั้น ปี 1955 ประธานาธิบดีไอเซนฮาวร์หัวใจวายกลางสนามกอล์ฟ เป็นจุดเปลี่ยนอีกครั้งที่โลกเริ่มหันมาสนใจ “ไขมัน” ว่าอาจเป็นผู้ร้าย ทำให้ชายคนหนึ่งชื่อ Ancel Keys เสนอทฤษฎี “ไขมันคือเหตุแห่งโรคหัวใจ” พร้อมกับงานศึกษาที่ชื่อ Seven Countries Study ซึ่งต่อมาจะกลายเป็นที่มาของ “พีระมิดอาหาร” ในปี 1977 โดย USDA ในยุคของวุฒิสมาชิก George McGovern ทฤษฎีนี้ถูกวิจารณ์ภายหลังว่าตั้งต้นด้วยการ “เลือกข้อมูล” ที่สนับสนุนสมมุติฐานของตัวเอง และเมินประเทศที่ข้อมูลไม่เข้าเป้าออกไปเฉยๆ แล้วก็ปั้นพีระมิดที่บอกว่า คาร์โบไฮเดรตอยู่ฐานล่างสุด กินได้เยอะๆ ส่วนไขมันให้อยู่บนสุด กินน้อยๆ นี่คือการพลิกอำนาจอาหารครั้งใหญ่ที่สุดในศตวรรษ อาหารไม่ใช่สิ่งที่มาจากพื้นดิน แต่เป็นสิ่งที่มาจากกระดาษนโยบาย
ช่วงนี้แหละครับที่จุดเปลี่ยนที่ใหญ่สุดมาถึง เมื่อรัฐบาลสหรัฐประกาศใช้นโยบายอาหารใหม่โดยอิงกับคำแนะนำของ USDA ซึ่งภายหลังถูกเปิดโปงว่าปิรามิดอาหารที่ใช้จริงนั้น ผ่านการปรับจากต้นฉบับโดยนักวิทยาศาสตร์อย่างหนักเพื่อ “จัดสรรพื้นที่” ให้กับอาหารที่มี lobby สูง เช่น ข้าว ซีเรียล พาสต้า และน้ำมันพืช โดยให้ไขมันสัตว์ถูกตัดทิ้งไปเป็นตัวอันตราย เฮียว่าโมเมนต์นี้แหละคือจุดที่ "ฟู้ดฟิคชั่น" กลายเป็น "ฟู้ดโพย" สำหรับคนทั้งโลก
ระหว่างที่ USDA กำลังยึดพีระมิดอยู่นั้น อุตสาหกรรมอาหารแปรรูปก็กำลังเข้มข้นแบบใส่สปีดโบ๊ทเข้าไปอีก ข้าวโพดกลายเป็นพืชเศรษฐกิจอันดับหนึ่งของสหรัฐฯ ไม่ใช่เพราะคนกินข้าวโพดกันเยอะ แต่เพราะมันกลายเป็นวัตถุดิบของทุกอย่าง ตั้งแต่ high-fructose corn syrup ในน้ำอัดลม ยันฟิลเลอร์ในไส้กรอก และอาหารสัตว์ในฟาร์มปศุสัตว์ เชนร้านอาหารอย่าง McDonald’s ก็เริ่มเปลี่ยนมันฝรั่งทอดจากไขมันเนื้อวัวมาใช้น้ำมันพืชในยุค 1980s เพราะแรงกดดันจากกลุ่มต่อต้านไขมันอิ่มตัว ทั้งที่รสชาติเปลี่ยนและสุขภาพก็ไม่ได้ดีขึ้น
ปี 1980s-1990s เกิดสิ่งที่เฮียอยากเรียกว่า “การปฏิวัติแบบเนียน” คือผู้คนเริ่มเชื่อว่าอาหารแปรรูปคือความก้าวหน้า และอาหารธรรมชาตินั้นล้าหลัง วงการโภชนาการยังคงถูกขับเคลื่อนด้วยความเชื่อว่าคาร์บคือของดี ไขมันคือผู้ร้าย และโปรตีนต้องมาจากพืช บริษัทใหญ่ๆ อย่าง Nestlé, PepsiCo, และ Unilever เริ่มเข้าซื้อแบรนด์อาหารสุขภาพ พร้อมผลิตเวย์เทียม โปรตีนพืช และอาหารเสริมแทนอาหารจริง พร้อมแนวคิด “Meal Replacement” ที่เน้นขายแทนกิน เขาไม่ได้แค่นำเสนอสินค้า แต่พยายามกำหนดแนวคิดเรื่อง “อาหารเพื่อสุขภาพ” แบบที่คนทั่วไปไม่ต้องคิดเอง ขอแค่เชื่อฉลาก กับดูโลโก้รูปหัวใจสีเขียวก็พอ
ก่อนจะเข้าสู่ศตวรรษใหม่ในปี 2000 โลกก็เริ่มเห็นวี่แววของสิ่งที่เรียกว่า “อาหารแห่งอนาคต” อีกครั้ง ไม่ใช่เพราะเทคโนโลยีใหม่อย่างเดียว แต่เพราะระบบอาหารเดิมถูกบิดเบือนจนธรรมชาติเสียศูนย์ อาหารจริงถูกตีตราว่าอันตราย ส่วนอาหารสังเคราะห์ถูกสร้างเรื่องเล่าว่า "สะอาดกว่า ปลอดภัยกว่า และเป็นคำตอบของโลกอนาคต" ซึ่งในมุมของเฮีย มันคือการสืบทอดวิธีคิดแบบเดียวกับสมัยสงคราม คือการบังคับให้กินของที่ผลิตได้มาก ราคาถูก เก็บได้นาน โดยไม่สนว่าร่างกายต้องการหรือไม่ และทั้งหมดก็กลับมาที่จุดเดิม — การออกแบบอาหารให้เหมาะกับระบบ มากกว่าจะออกแบบระบบให้เหมาะกับร่างกายมนุษย์
นี่แหละเฮียถึงอยากเล่าซีรีส์ “อาหารอนาคต” เพราะในความจริงมันไม่ใช่อนาคตอะไรเลย แต่มันคืออดีตที่ถูกเล่าใหม่ด้วยคำพูดที่ฟังดูเท่ แต่ซ่อนไว้ด้วยตรวนของการควบคุมสิทธิในการกินของมนุษย์ เอาของปลอมมาสวมรอยธรรมชาติ แล้วทำให้เรารู้สึกผิดถ้าจะกินไขมันสัตว์ กินเนื้อ กินไข่ หรือไม่กินอาหารเช้าที่เต็มไปด้วยน้ำตาล เฮียว่า ถ้าไม่เล่าเรื่องพวกนี้ให้คนรู้ทัน ก็เหมือนปล่อยให้ลูกหลานกินอาหารที่ไม่มีใครรู้ว่า “ใครเป็นคนเขียนสูตรให้พวกเขากิน”
ดังนั้น ถ้าเราจะพูดถึง “อาหารแห่งอนาคต” เฮียว่า เราต้องกล้ากลับไปถามว่า อนาคตที่ว่านั่น ใครกันเป็นคนออกแบบ? แล้วเราอยู่ตรงไหนของโต๊ะ?
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ b1ddb4d7:471244e7
2025-06-07 08:00:46
@ b1ddb4d7:471244e7
2025-06-07 08:00:46“Not your keys, not your coins” isn’t a slogan—it’s a survival mantra in the age of digital sovereignty.
The seismic collapses of Mt. Gox (2014) and FTX (2022) weren’t anomalies; they were wake-up calls. When $8.7 billion in customer funds vanished with FTX, it exposed the fatal flaw of third-party custody: your bitcoin is only as secure as your custodian’s weakest link.
Yet today, As of early 2025, analysts estimate that between 2.3 million and 3.7 million Bitcoins are permanently lost, representing approximately 11–18% of bitcoin’s fixed maximum supply of 21 million coins, with some reports suggesting losses as high as 4 million BTC. This paradox reveals a critical truth: self-custody isn’t just preferable—it’s essential—but it must be done right.
The Custody Spectrum
Custodial Wallets (The Illusion of Control)
- Rehypothecation Risk: Most platforms lend your bitcoin for yield generation. When Celsius collapsed, users discovered their “held” bitcoin was loaned out in risky strategies.
- Account Freezes: Regulatory actions can lock withdrawals overnight. In 2023, Binance suspended dollar withdrawals for U.S. users citing “partner bank issues,” trapping funds for weeks.
- Data Vulnerability: KYC requirements create honeypots for hackers. The 2024 Ledger breach exposed 270,000 users’ personal data despite hardware security.
True Self-Custody
Self-custody means exclusively controlling your private keys—the cryptographic strings that prove bitcoin ownership. Unlike banks or exchanges, self-custody eliminates:- Counterparty risk (no FTX-style implosions)
- Censorship (no blocked transactions)
- Inflationary theft (no fractional reserve lending)
Conquering the Three Great Fears of Self-Custody
Fear 1: “I’ll Lose Everything If I Make a Mistake”
Reality: Human error is manageable with robust systems:
- Test Transactions: Always send a micro-amount (0.00001 BTC) before large transfers. Verify receipt AND ability to send back.
- Multi-Backup Protocol: Store seed phrases on fireproof/waterproof steel plates (not paper!). Distribute copies geographically—one in a home safe, another with trusted family 100+ miles away.
- SLIP39 Sharding: Split your seed into fragments requiring 3-of-5 shards to reconstruct. No single point of failure.
Fear 2: “Hackers Will Steal My Keys”
Reality: Offline storage defeats remote attacks:
- Hardware Wallets: Devices like Bitkey or Ledger keep keys in “cold storage”—isolated from internet-connected devices. Transactions require physical confirmation.
- Multisig Vaults: Bitvault’s multi-sig system requires attackers compromise multiple locations/devices simultaneously. Even losing two keys won’t forfeit funds.
- Air-Gapped Verification: Use dedicated offline devices for wallet setup. Never type seeds on internet-connected machines.
Fear 3: “My Family Can’t Access It If I Die”
Reality: Inheritance is solvable:
- Dead Man Switches: Bitwarden’s emergency access allows trusted contacts to retrieve encrypted keys after a pre-set waiting period (e.g., 30 days).
- Inheritance Protocols: Bitkey’s inheritance solution shares decryption keys via designated beneficiaries’ emails. Requires multiple approvals to prevent abuse.
- Public Key Registries: Share wallet XPUBs (not private keys!) with heirs. They can monitor balances but not spend, ensuring transparency without risk.
The Freedom Dividend
- Censorship Resistance: Send $10M BTC to a Wikileaks wallet without Visa/Mastercard blocking it.
- Privacy Preservation: Avoid KYC surveillance—non-custodial wallets like Flash require zero ID verification.
- Protocol Access: Participate in bitcoin-native innovations (Lightning Network, DLCs) only possible with self-custodied keys.
- Black Swan Immunity: When Cyprus-style bank bailins happen, your bitcoin remains untouched in your vault.
The Sovereign’s Checklist
- Withdraw from Exchanges: Move all BTC > $1,000 to self-custody immediately.
- Buy Hardware Wallet: Purchase DIRECTLY from manufacturer (no Amazon!) to avoid supply-chain tampering.
- Generate Seed OFFLINE: Use air-gapped device, write phrase on steel—never digitally.
- Test Recovery: Delete wallet, restore from seed before funding.
- Implement Multisig: For > $75k, use Bitvault for 2-of-3 multi-sig setup.
- Create Inheritance Plan: Share XPUBs/SLIP39 shards with heirs + legal documents.
“Self-custody isn’t about avoiding risk—it’s about transferring risk from opaque institutions to transparent, controllable systems you design.”
The Inevitable Evolution: Custody Without Compromise
Emerging solutions are erasing old tradeoffs:
- MPC Wallets: Services like Xapo Bank shatter keys into encrypted fragments distributed globally. No single device holds full keys, defeating physical theft.
- Social Recovery: Ethically designed networks (e.g., Bitkey) let trusted contacts restore access without custodial control.
- Biometric Assurance: Fingerprint reset protocols prevent lockouts from physical injuries.
Lost keys = lost bitcoin. But consider the alternative: entrusting your life savings to entities with proven 8% annual failure rates among exchanges. Self-custody shifts responsibility from hoping institutions won’t fail to knowing your system can’t fail without your consent.
Take action today: Move one coin. Test one recovery. Share one xpub. The path to unchained wealth begins with a single satoshi under your control.
-
 @ cae03c48:2a7d6671
2025-06-07 06:01:19
@ cae03c48:2a7d6671
2025-06-07 06:01:19Bitcoin Magazine

Bitcoin Life Insurer, Meanwhile, Becomes First Company to Publish Audited Financials Denominated in BitcoinMeanwhile Insurance Bitcoin (Bermuda) Limited (“Meanwhile”) announced it has become the first company in the world to release externally audited financial statements denominated entirely in Bitcoin. According to the announcement, the company reported 220.4 BTC in assets and 25.29 BTC in net income for 2024, a 300% year over year increase.
Today marks a global first & historic event for us, along with the public release of our 2024 audited financial statements, covering our 1st year of sales.
As the 1st company in the world to have Bitcoin-denominated financial statements externally audited, we are excited to…
— meanwhile | Bitcoin Life Insurance (@meanwhilelife) June 5, 2025
“We’ve just made history as the first company in the world to have Bitcoin-denominated financial statements externally audited,” said Zac Townsend, CEO of Meanwhile. “This is an important, foundational step in reimagining the financial system based on a single, global, decentralized standard outside the control of any one government.”
The financial statements were audited by Harris & Trotter LLP and its digital asset division ht.digital. Meanwhile’s financials also comply with Bermuda’s Insurance Act 1978, noting that their BTC denominated financials were approved and comply with official guidelines. The firm, fully licensed by the Bermuda Monetary Authority (BMA), operates entirely in BTC and is prohibited from liquidating Bitcoin assets except through policyholder claims, positioning it as a long term holder.
“As the first regulated Bitcoin life insurance company, we view the BTC held by Meanwhile as inherently long-term in nature—primarily held to support the Company’s insurance liabilities over decades,” Townsend added. “This makes it significantly ‘stickier’ and resistant to market pressures compared to the BTC held by other companies as part of their treasury management strategies.”
Meanwhile’s 2024 financials also revealed 23.02 BTC in net premiums and 4.35 BTC in investment income, showing that its model not only preserves Bitcoin, but earns it. The company’s reserves (also held in BTC) were reviewed and approved by Willis Towers Watson (WTW).
Meanwhile also offers a Bitcoin Whole Life insurance product that allows policyholders to save, borrow, and build legacy wealth—entirely in BTC, and has plans to expand globally in 2025.
“We are incredibly proud of today’s news as it underscores how Meanwhile is at the forefront of the next phase of the convergence between Bitcoin and institutional financial markets,” said Tia Beckmann, CFO of Meanwhile. “Now having generated net income in BTC, we have demonstrated that we are earning it through a sustainable insurance business model designed for the long term.”
This post Bitcoin Life Insurer, Meanwhile, Becomes First Company to Publish Audited Financials Denominated in Bitcoin first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ b1ddb4d7:471244e7
2025-06-07 14:00:42
@ b1ddb4d7:471244e7
2025-06-07 14:00:42When Sergei talks about bitcoin, he doesn’t sound like someone chasing profits or followers. He sounds like someone about to build a monastery in the ruins.
While the mainstream world chases headlines and hype, Sergei shows up in local meetups from Sacramento to Cleveland, mentors curious minds, and shares what he knows is true – hoping that, with the right spark, someone will light their own way forward.
We interviewed Sergei to trace his steps: where he started, what keeps him going, and why teaching bitcoin is far more than explaining how to set up a node – it’s about reaching the right minds before the noise consumes them. So we began where most journeys start: at the beginning.

First Steps
- So, where did it all begin for you and what made you stay curious?
I first heard about bitcoin from a friend’s book recommendation, American Kingpin, the book about Silk Road (online drug marketplace). He is still not a true bitcoiner, although I helped him secure private keys with some bitcoin.
I was really busy at the time – focused on my school curriculum, running a 7-bedroom Airbnb, and working for a standardized test prep company. Bitcoin seemed too technical for me to explore, and the pace of my work left no time for it.
After graduating, while pursuing more training, I started playing around with stocks and maximizing my savings. Passive income seemed like the path to early retirement, as per the promise of the FIRE movement (Financial Independence, Retire Early). I mostly followed the mainstream news and my mentor’s advice – he liked preferred stocks at the time.
I had some Coinbase IOUs and remember sending bitcoin within the Coinbase ledger to a couple friends. I also recall the 2018 crash; I actually saw the legendary price spike live but couldn’t benefit because my funds were stuck amidst the frenzy. I withdrew from that investment completely for some time. Thankfully, my mentor advised to keep en eye on bitcoin.
Around late 2019, I started DCA-ing cautiously. Additionally, my friend and I were discussing famous billionaires, and how there was no curriculum for becoming a billionaire. So, I typed “billionaires” into my podcast app, and landed on We Study Billionaires podcast.
That’s where I kept hearing Preston Pysh mention bitcoin, before splitting into his own podcast series, Bitcoin Fundamentals. I didn’t understand most of the terminology of stocks, bonds, etc, yet I kept listening and trying to absorb it thru repetition. Today, I realize all that financial talk was mostly noise.
When people ask me for a technical explanation of fiat, I say: it’s all made up, just like the fiat price of bitcoin! Starting in 2020, during the so-called pandemic, I dove deeper. I religiously read Bitcoin Magazine, scrolled thru Bitcoin Twitter, and joined Simply Bitcoin Telegram group back when DarthCoin was an admin.
DarthCoin was my favorite bitcoiner – experienced, knowledgeable, and unapologetic. Watching him shift from rage to kindness, from passion to despair, gave me a glimpse at what a true educator’s journey would look like.
The struggle isn’t about adoption at scale anymore. It’s about reaching the few who are willing to study, take risks, and stay out of fiat traps. The vast majority won’t follow that example – not yet at least… if I start telling others the requirements for true freedom and prosperity, they would certainly say “Hell no!”
- At what point did you start teaching others, and why?
After college, I helped teach at a standardized test preparation company, and mentored some students one-on-one. I even tried working at a kindergarten briefly, but left quickly; Babysitting is not teaching.
What I discovered is that those who will succeed don’t really need my help – they would succeed with or without me, because they already have the inner drive.
Once you realize your people are perishing for lack of knowledge, the only rational thing to do is help raise their level of knowledge and understanding. That’s the Great Work.
I sometimes imagine myself as a political prisoner. If that were to happen, I’d probably start teaching fellow prisoners, doctors, janitors, even guards. In a way we already live in an open-air prison, So what else is there to do but teach, organize, and conspire to dismantle the Matrix?

Building on Bitcoin
- You hosted some in-person meetups in Sacramento. What did you learn from those?
My first presentation was on MultiSig storage with SeedSigner, and submarine swaps through Boltz.exchange.
I realized quickly that I had overestimated the group’s technical background. Even the meetup organizer, a financial advisor, asked, “How is anyone supposed to follow these steps?” I responded that reading was required… He decided that Unchained is an easier way.
At a crypto meetup, I gave a much simpler talk, outlining how bitcoin will save the world, based on a DarthCoin’s guide. Only one person stuck around to ask questions – a man who seemed a little out there, and did not really seem to get the message beyond the strength of cryptographic security of bitcoin.
Again, I overestimated the audience’s readiness. That forced me to rethink my strategy. People are extremely early and reluctant to study.
- Now in Ohio, you hold sessions via the Orange Pill App. What’s changed?
My new motto is: educate the educators. The corollary is: don’t orange-pill stupid normies (as DarthCoin puts it).
I’ve shifted to small, technical sessions in order to raise a few solid guardians of this esoteric knowledge who really get it and can carry it forward.
The youngest attendee at one of my sessions is a newborn baby – he mostly sleeps, but maybe he still absorbs some of the educational vibes.
- How do local groups like Sactown and Cleveland Bitcoiners influence your work?
Every meetup reflects its local culture. Sacramento and Bay Area Bitcoiners, for example, do camping trips – once we camped through a desert storm, shielding our burgers from sand while others went to shoot guns.
Cleveland Bitcoiners are different. They amass large gatherings. They recently threw a 100k party. They do a bit more community outreach. Some are curious about the esoteric topics such as jurisdiction, spirituality, and healthful living.
I have no permanent allegiance to any state, race, or group. I go where I can teach and learn. I anticipate that in my next phase, I’ll meet Bitcoiners so advanced that I’ll have to give up my fiat job and focus full-time on serious projects where real health and wealth are on the line.
Hopefully, I’ll be ready. I believe the universe always challenges you exactly to your limit – no less, no more.
- What do people struggle with the most when it comes to technical education?
The biggest struggle isn’t technical – it’s a lack of deep curiosity. People ask “how” and “what” – how do I set up a node, what should one do with the lightning channels? But very few ask “why?”
Why does on-chain bitcoin not contribute to the circular economy? Why is it essential to run Lightning? Why did humanity fall into mental enslavement in the first place?
I’d rather teach two-year-olds who constantly ask “why” than adults who ask how to flip a profit. What worries me most is that most two-year-olds will grow up asking state-funded AI bots for answers and live according to its recommendations.
- One Cleveland Bitcoiner shows up at gold bug meetups. How valuable is face-to-face education?
I don’t think the older generation is going to reverse the current human condition. Most of them have been under mind control for too long, and they just don’t have the attention span to study and change their ways.
They’re better off stacking gold and helping fund their grandkids’ education. If I were to focus on a demographic, I’d go for teenagers – high school age – because by college, the indoctrination is usually too strong, and they’re chasing fiat mastery.
As for the gold bug meetup? Perhaps one day I will show up with a ukulele to sing some bitcoin-themed songs. Seniors love such entertainment.
- How do you choose what to focus on in your sessions, especially for different types of learners?
I don’t come in with a rigid agenda. I’ve collected a massive library of resources over the years and never stopped reading. My browser tab and folder count are exploding.
At the meetup, people share questions or topics they’re curious about, then I take that home, do my homework, and bring back a session based on those themes. I give them the key takeaways, plus where to dive deeper.
Most people won’t – or can’t – study the way I do, and I expect attendees to put in the work. I suspect that it’s more important to reach those who want to learn but don’t know how, the so-called nescient (not knowing), rather than the ignorant.
There are way too many ignorant bitcoiners, so my mission is to find those who are curious what’s beyond the facade of fake reality and superficial promises.
That naturally means that fewer people show up, and that’s fine. I’m not here for the crowds; I’m here to educate the educators. One bitcoiner who came decided to branch off into self-custody sessions and that’s awesome. Personally, I’m much more focused on Lightning.
I want to see broader adoption of tools like auth, sign-message, NWC, and LSPs. Next month, I’m going deep into eCash solutions, because let’s face it – most newcomers won’t be able to afford their own UTXO or open a lightning channel; additionally, it has to be fun and easy for them to transact sats, otherwise they won’t do it. Additionally, they’ll need to rely on
-
 @ cae03c48:2a7d6671
2025-06-07 14:00:25
@ cae03c48:2a7d6671
2025-06-07 14:00:25Bitcoin Magazine

Bitcoin Life Insurer, Meanwhile, Becomes First Company to Publish Audited Financials Denominated in BitcoinMeanwhile Insurance Bitcoin (Bermuda) Limited (“Meanwhile”) announced it has become the first company in the world to release externally audited financial statements denominated entirely in Bitcoin. According to the announcement, the company reported 220.4 BTC in assets and 25.29 BTC in net income for 2024, a 300% year over year increase.
Today marks a global first & historic event for us, along with the public release of our 2024 audited financial statements, covering our 1st year of sales.
As the 1st company in the world to have Bitcoin-denominated financial statements externally audited, we are excited to…
— meanwhile | Bitcoin Life Insurance (@meanwhilelife) June 5, 2025
“We’ve just made history as the first company in the world to have Bitcoin-denominated financial statements externally audited,” said Zac Townsend, CEO of Meanwhile. “This is an important, foundational step in reimagining the financial system based on a single, global, decentralized standard outside the control of any one government.”
The financial statements were audited by Harris & Trotter LLP and its digital asset division ht.digital. Meanwhile’s financials also comply with Bermuda’s Insurance Act 1978, noting that their BTC denominated financials were approved and comply with official guidelines. The firm, fully licensed by the Bermuda Monetary Authority (BMA), operates entirely in BTC and is prohibited from liquidating Bitcoin assets except through policyholder claims, positioning it as a long term holder.
“As the first regulated Bitcoin life insurance company, we view the BTC held by Meanwhile as inherently long-term in nature—primarily held to support the Company’s insurance liabilities over decades,” Townsend added. “This makes it significantly ‘stickier’ and resistant to market pressures compared to the BTC held by other companies as part of their treasury management strategies.”
Meanwhile’s 2024 financials also revealed 23.02 BTC in net premiums and 4.35 BTC in investment income, showing that its model not only preserves Bitcoin, but earns it. The company’s reserves (also held in BTC) were reviewed and approved by Willis Towers Watson (WTW).
Meanwhile also offers a Bitcoin Whole Life insurance product that allows policyholders to save, borrow, and build legacy wealth—entirely in BTC, and has plans to expand globally in 2025.
“We are incredibly proud of today’s news as it underscores how Meanwhile is at the forefront of the next phase of the convergence between Bitcoin and institutional financial markets,” said Tia Beckmann, CFO of Meanwhile. “Now having generated net income in BTC, we have demonstrated that we are earning it through a sustainable insurance business model designed for the long term.”
This post Bitcoin Life Insurer, Meanwhile, Becomes First Company to Publish Audited Financials Denominated in Bitcoin first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 1739d937:3e3136ef
2024-10-29 16:57:08
@ 1739d937:3e3136ef
2024-10-29 16:57:08This update marks a major milestone for the project. I know, with certainty, that MLS messaging over Nostr is going to work. That might sound a little crazy after so many months working on the project, and I was pretty confident, but until you’ve got running code, it’s all conjecture.
Late last week, I released a video of a working prototype of White Noise that shows the full flow; creating groups, inviting other users to join those groups, accepting invites, and sending messages back-and-forth. I’m thrilled that I’ve gotten this far but also appalled that it’s taken so long and disgusted at the state of the code in the app (I’ve been told I have unrelenting standards 😅).
If you missed the video last week...
nostr:note125cuk0zetc7sshw52v5zaq9apq3rq7e2x587tr2c96t7z7sjs59svwv0fj
What's Next?
In this update, I want to cover a few things about how I'm planning to proceed and how I’m splitting code out of the app into libraries that will help other developers implement MLS messaging in their own Nostr clients.
First off, many of you know that I've been building White Noise as a Rust app using the Tauri framework. The OpenMLS implementation is also written in Rust (with bindings for many other languages). So, when you hear me talking about library code, think Rust crates for now.
The first library, called openmls-nostr, is an extension/abstraction on top of the openmls implementation of the MLS spec that helps Nostr clients interact more easily with that implementation in a way that feels native to Nostr. Mostly this will be helping developers interact with MLS primitives and ensure that they’re creating, validating, and serializing these objects in the right way at the right times.
The second isn’t a new library as a big contribution to the already excellent rust-nostr library from nostr:npub1drvpzev3syqt0kjrls50050uzf25gehpz9vgdw08hvex7e0vgfeq0eseet. The methods that will go in rust-nostr are highly abstracted and based specifically on the requirements of NIP-104. Mostly this will be helping developers to take those MLS primitives and publish or query them as Nostr events at the right times and to/from the right relays.
Most of this code was originally written directly in the White Noise library so this week I've started to pull code for both of those libraries out and move it to its new home. While I’ve been at it, I've been writing some tests and trying to document things.
An unfortunate offshoot of this is that the usable builds of White Noise are going to take a touch longer. I promise it’s still a very high priority but at this point I need to clean a few things up based on what I've learned thus far.
Another thing that is slowing down release is that; behind the scenes of the dev work, I’ve been battling with Apple for nearly 2 months now to get a proper developer team set up so that we can publish the app via TestFlight for MacOS and iOS. I’ve also been recently learning the intricacies of Android publishing (oh my dear god there are so many devices, OS versions, etc.).
With that in mind, if you know anyone who can help get me up to speed on CI/CD, release pipelines, and multi-platform distribution please hit me up. I would love to learn more and hopefully shortcut some of the pain.
Thanks again so much for all the support over the last few months! It means a lot to me and is a huge part of what is keeping me going on this. 🙏
-
 @ 97c70a44:ad98e322
2025-06-06 20:48:33
@ 97c70a44:ad98e322
2025-06-06 20:48:33Vibe coding is taking the nostr developer community by storm. While it's all very exciting and interesting, I think it's important to pump the brakes a little - not in order to stop the vehicle, but to try to keep us from flying off the road as we approach this curve.
In this note Pablo is subtweeting something I said to him recently (although I'm sure he's heard it from other quarters as well):
nostr:nevent1qvzqqqqqqypzp75cf0tahv5z7plpdeaws7ex52nmnwgtwfr2g3m37r844evqrr6jqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7qg6waehxw309ac8junpd45kgtnxd9shg6npvchxxmmd9uqzq0z48d4ttzzkupswnkyt5a2xfkhxl3hyavnxjujwn5k2k529aearwtecp4
There is a naive, curmudgeonly case for simply "not doing AI". I think the intuition is a good one, but the subject is obviously more complicated - not doing it, either on an individual or a collective level, is just not an option. I recently read Tools for Conviviality by Ivan Illich, which I think can help us here. For Illich, the best kind of tool is one which serves "politically interrelated individuals rather than managers".
This is obviously a core value for bitcoiners. And I think the talks given at the Oslo Freedom Forum this year present a compelling case for adoption of LLMs for the purposes of 1. using them for good, and 2. developing them further so that they don't get captured by corporations and governments. Illich calls both the telephone and print "almost ideally convivial". I would add the internet, cryptography, and LLMs to this list, because each one allows individuals to work cooperatively within communities to embody their values in their work.
But this is only half the story. Illich also points out how "the manipulative nature of institutions... have put these ideally convivial tools at the service of more [managerial dominance]."
Preventing the subversion and capture of our tools is not just a matter of who uses what, and for which ends. It also requires an awareness of the environment that the use of the tool (whether for virtuous or vicious ends) creates, which in turn forms the abilities, values, and desires of those who inhabit the environment.
The natural tendency of LLMs is to foster ignorance, dependence, and detachment from reality. This is not the fault of the tool itself, but that of humans' tendency to trade liberty for convenience. Nevertheless, the inherent values of a given tool naturally gives rise to an environment through use: the tool changes the world that the tool user lives in. This in turn indoctrinates the user into the internal logic of the tool, shaping their thinking, blinding them to the tool's influence, and neutering their ability to work in ways not endorsed by the structure of the tool-defined environment.
The result of this is that people are formed by their tools, becoming their slaves. We often talk about LLM misalignment, but the same is true of humans. Unreflective use of a tool creates people who are misaligned with their own interests. This is what I mean when I say that AI use is anti-human. I mean it in the same way that all unreflective tool use is anti-human. See Wendell Berry for an evaluation of industrial agriculture along the same lines.
What I'm not claiming is that a minority of high agency individuals can't use the technology for virtuous ends. In fact, I think that is an essential part of the solution. Tool use can be good. But tools that bring their users into dependence on complex industry and catechize their users into a particular system should be approached with extra caution. The plow was a convivial tool, and so were early tractors. Self-driving John Deere monstrosities are a straightforward extension of the earlier form of the technology, but are self-evidently an instrument of debt slavery, chemical dependency, industrial centralization, and degradation of the land. This over-extension of a given tool can occur regardless of the intentions of the user. As Illich says:
There is a form of malfunction in which growth does not yet tend toward the destruction of life, yet renders a tool antagonistic to its specific aims. Tools, in other words, have an optimal, a tolerable, and a negative range.
The initial form of a tool is almost always beneficial, because tools are made by humans for human ends. But as the scale of the tool grows, its logic gets more widely and forcibly applied. The solution to the anti-human tendencies of any technology is an understanding of scale. To prevent the overrun of the internal logic of a given tool and its creation of an environment hostile to human flourishing, we need to impose limits on scale.
Tools that require time periods or spaces or energies much beyond the order of corresponding natural scales are dysfunctional.
My problem with LLMs is:
- Not their imitation of human idioms, but their subversion of them and the resulting adoption of robotic idioms by humans
- Not the access they grant to information, but their ability to obscure accurate or relevant information
- Not their elimination of menial work, but its increase (Bullshit Jobs)
- Not their ability to take away jobs, but their ability to take away the meaning found in good work
- Not their ability to confer power to the user, but their ability to confer power to their owner which can be used to exploit the user
- Not their ability to solve problems mechanistically, but the extension of their mechanistic value system to human life
- Not their explicit promise of productivity, but the environment they implicitly create in which productivity depends on their use
- Not the conversations they are able to participate in, but the relationships they displace
All of these dysfunctions come from the over-application of the technology in evaluating and executing the fundamentally human task of living. AI work is the same kind of thing as an AI girlfriend, because work is not only for the creation of value (although that's an essential part of it), but also for the exercise of human agency in the world. In other words, tools must be tools, not masters. This is a problem of scale - when tool use is extended beyond its appropriate domain, it becomes what Illich calls a "radical monopoly" (the domination of a single paradigm over all of human life).
So the important question when dealing with any emergent technology becomes: how can we set limits such that the use of the technology is naturally confined to its appropriate scale?
Here are some considerations:
- Teach people how to use the technology well (e.g. cite sources when doing research, use context files instead of fighting the prompt, know when to ask questions rather than generate code)
- Create and use open source and self-hosted models and tools (MCP, stacks, tenex). Refuse to pay for closed or third-party hosted models and tools.
- Recognize the dependencies of the tool itself, for example GPU availability, and diversify the industrial sources to reduce fragility and dependence.
- Create models with built-in limits. The big companies have attempted this (resulting in Japanese Vikings), but the best-case effect is a top-down imposition of corporate values onto individuals. But the idea isn't inherently bad - a coding model that refuses to generate code in response to vague prompts, or which asks clarifying questions is an example. Or a home assistant that recognized childrens' voices and refuses to interact.
- Divert the productivity gains to human enrichment. Without mundane work to do, novice lawyers, coders, and accountants don't have an opportunity to hone their skills. But their learning could be subsidized by the bots in order to bring them up to a level that continues to be useful.
- Don't become a slave to the bots. Know when not to use it. Talk to real people. Write real code, poetry, novels, scripts. Do your own research. Learn by experience. Make your own stuff. Take a break from reviewing code to write some. Be independent, impossible to control. Don't underestimate the value to your soul of good work.
- Resist both monopoly and "radical monopoly". Both naturally collapse over time, but by cultivating an appreciation of the goodness of hand-crafted goods, non-synthetic entertainment, embodied relationship, and a balance between mobility and place, we can relegate new, threatening technologies to their correct role in society.
I think in all of this is implicit the idea of technological determinism, that productivity is power, and if you don't adapt you die. I reject this as an artifact of darwinism and materialism. The world is far more complex and full of grace than we think.
The idea that productivity creates wealth is, as we all know, bunk. GDP continues to go up, but ungrounded metrics don't reflect anything about the reality of human flourishing. We have to return to a qualitative understanding of life as whole, and contextualize quantitative tools and metrics within that framework.
Finally, don't believe the hype. Even if AI delivers everything it promises, conservatism in changing our ways of life will decelerate the rate of change society is subjected to and allow time for reflection and proper use of the tool. Curmudgeons are as valuable as technologists. There will be no jobspocalypse if there is sufficient political will to value human good over mere productivity. It's ok to pump the breaks.
-
 @ 81022b27:2b8d0644
2025-06-09 00:23:26
@ 81022b27:2b8d0644
2025-06-09 00:23:26I’m a Chiropractor, Writer, Travel Nerd, Lover of Efficiency, Trekker and a Celebrity in Mexican Restaurants Hi, I’m Danny DeReuter, and I want to save the world. I’m an occasional writer-I’ve written some stuff.
Sometimes people think I’m funny. Maybe some time I’ll come up with a bit of courage and try my hand at stand-up. (seriously, that’s a thing on my vision board)
I’ve become somewhat of a social media expert managing my online presence. I help show people how to do social media more effectively.
I’m also a speaker. I prefer to speak on topics that I’m passionate about-like natural health, chiropractic, and social media. I also have a Podcast. Be nice and you can ask me to speak at your event.
-
 @ 1739d937:3e3136ef
2024-10-04 22:22:27
@ 1739d937:3e3136ef
2024-10-04 22:22:27Previous updates
- Check them all out here: https://highlighter.com/jeffg.fyi
Progress this week
It was a busy one. I've been focused on the critical path of getting the full end-to-end MLS messaging flow built into White Noise. Unfortunately, or fortunately for those that will come after, this has necessitated writing quite a bit of library code and figuring out how clients should think about storing the necessary group state and secrets.
Today I released the highly creatively named openmls-sled-storage. This is a storage adapter for Sled DB, an embedded database written in Rust. This allows clients to simply give their clients a file path where they want to store the data and the library will take care of the rest with regards to MLS storage.
Another bit of library code is a customer MLS extension called NostrGroupData (again with a wildly creative title - check it out in the WN repo here). This is a standardized way of storing the necessary metadata about a group that will allow it to function properly with Nostr conventions as well as basic data like Group name, description, etc. This, in specific, is the source of quite a few updates to the NIP, but overall it's going to give clients implementing MLS groups assurances that the data required is not only formatted the same, but cryptographically guaranteed to be there and respected by each group member, or the group will fork.
White Noise
The client currently supports multiple accounts, including generating new Nostr identities on the fly. It's also loading user's contact lists, and NIP-04 DMs at the moment as well. This week I managed to build out nearly the entire group creation flow. This includes publishing and fetching key packages (kind: 443 events), inviting another user to create a group, sending welcome messages (kind: 444 events), and I've started working on both parsing those welcome messages and how to represent the groups in the UI in a way that makes reasonable sense to users.
No showstoppers
I know this might sound insane after working on this project for several months already but I'm genuinely surprised that I've not run into any big unknown unknowns yet. Everything is coming together well and, while it's taking me some time to build it right and think carefully about where and how data is being stored and passed around, I'm very confident the client is going to be up and running in a few weeks (famous last words).
The NIP
As I mentioned before, I've left the NIP dormant while I'm working on implementing the entire messaging flow. Once I've got the flow fully built out, I'll know all the details that need to change and I'll update the NIP.
If anyone out there wants to chat about the changes I already know are coming, let me know.
Feedback & contributions always welcome
Thoughts? Questions? Want to contribute? Hit me up.
P.S.
The plant in the cover image is Asparagus Officinalis. My grandfather was the only person I knew growing up that grew it and, as a result, I also grow it at home. The interesting thing about Asparagus (other than making your pee smell funny) is that it takes several years before it starts bearing edible veggies. It's a low time preference plant and further proof that good things take time.
-
 @ 0f1b5961:868242bd
2024-09-06 20:10:06
@ 0f1b5961:868242bd
2024-09-06 20:10:06The public theologian Jonathan Pageau has been a major influence in my life for the past couple years. I remember in one of his podcasts he talks about how church buildings have historically been the "focal points" of many towns. In the physical sense, this meant the church building was at the center of the town and was the tallest structure. He argues that the church occupying this station had a sort of psychological effect on the town members, enforcing a way of life that has God in the highest "place".
This got me thinking about my own home city of Des Moines, Iowa. Here, the two most prominent buildings, by far, are the capitol building and a skyscraper called the Principal building. They sit on either side of the Des Moines River and to me, seem to "face off" against each other as if in competition.
 The Iowa State Capitol
The Iowa State Capitol The Principal Building (801 Grand Avenue)
The Principal Building (801 Grand Avenue)I was musing over how to settle the competition between these two buildings and I realized that it could be addressed with some pretty basic math. The apparent heights of these buildings change as you move closer or further from them. So whichever building appears taller for a larger portion of the city would be the most prominent building. In an idealized scenario, there would be a straight line between the two buildings where they would appear to be the same height.
This line ends up coinciding with East 4th street on the east side of the Des Moines River. As the Principal building is about twice as tall as the capitol buiding, the point at which they look the same height is about twice as close to the capitol building.
 Line along which the capitol and Principle building appear to be the same height.
Line along which the capitol and Principle building appear to be the same height.And so a clear winner emerges. Not only is the Principal building the most prominent in the downtown district of the city. It's influence extends across the river and eclipses the capitol in what one might expect to be its home turf. The focal point of Des Moines is a skyscraper.
I now must conclude with a confession. With the Principal building being about twice as tall as the capitol, there was never going to be a close competition between the two buildings. And indeed this matches the experience of one moving about the city. The Principal building plainly feels more prominent. Despite this, the area in which the capitol ascends to the highest is certainly not small. I like to think this reflects some amount of balance between the mercantile powers and political powers in the area. Perhaps this balance is proportional to the very heights of the buildings.
Not looking good for the ecclesiastical powers in the area...
-Scott
-
 @ df478568:2a951e67
2025-06-08 23:58:37
@ df478568:2a951e67
2025-06-08 23:58:37NOTE: PLEASE DO NOT USE THIS METHOD UNTIL WE LEARN MORE ABOUT THIS nostr:nevent1qvzqqqqqqypzpw5qnyrxdmctda962pvng7ltzvjzjg09ge57dqqxfjn42ft2rcaxqqsfsg878u9luv2sxm6yahyjr4zpt745rdfpuu47wnn9t2dskgem52g9e9955
`About 156,000 blocks ago, I went to a Taco Shop for a bitcoin meetup. I asked my favorite question, “Do you accept bitcoin?”
“Yes," he said as he handed me a Toast Terminal with a BTCpayServer QR code.
 ]
]Awesome!
12,960 blocks later, I took my dad to the taco shop. We ordered food. I asked my favorite question once again.
“Uh…Yeah, but I don't know how to work the machine.”
"Dough!🤦"
It's been a problem in the past, but now lightning payments are about to be ubiquitous. Steak N Shake is taking bitcoin using Speed Wallet and Block is implementing bitcoin payments by 2026 in all legal jurisdictions. I have tested both of these so you don't have to. Just kidding. I geek out on this stuff, but both work great. You can pay with your sats by scanning a screen on a QR code. The employees don't need to be bitcoin lightning network experts. You can just pay as easy as a credit card.
There were 35,000 people at the bitcoin conference, and 4,187 transactions were made. It was a world record. Wait, I thought they said there could only be 7 transactions per second! No, not anymore. Now we can use bitcoin for shopping. I can pay for tacos at taco trucks.

How You Can Accept Bitcoin At Your Business
Coinos is a simple bitcoin point of sale information that acts like a cash register. Bitcoin is peer-to-peer electronic cash. Coinos is a cash register and you should treat it as such. If you make a few hundred thousand sats at the end of the night, you should sweep the bitcoin into your own wallet.. You can use Aqua, AlbyHub, Bull Bitcoin wallet, or whatever your favorite lightning enabled wallet is to withdraw. You'll need a password. Do not lose this. I have tried the automatic withdraws, but it did not work for me. I'm no concerned because this is not a wallet I intend to keep a lot of sats in for a long time.
Here is my coinos payment terminal.
https://coinos.io/ZapthisBlog/receive
I made the QR code with libreqr.com/

Now I have an online bitcoin cash register. The Bitcoiners know how to pay for stuff with sats. They will be proud to show you too. If you're nerdy, you can use all the cool kid tools now, but we will just focus on the lightning address. Anyone can send you sats with a lightning address with just a QR code.
At the end of the night, you cash out to your own wallet. Again, this assumes you have an Aqua Wallet or any other lightning enabled wallet, but all it takes to accept bitcoin at your brick and mortar store is to create an account with Coinos and print out a QR code. It's a quick and easy way to start accepting bitcoin even if you don't expect many clients to shop with sats.
Tips
This is not just a cash register. Employees can also make their own Coinos wallet and receive tips from bitcoiners. Anyone can accept payments using this system. Your kids could use it to sell lemonade for sats. You are only limited by your imagination. When will you begin accepting bitcoin payments? It is easier than ever. You do not need to train employees. You do not need to be in the store. Bitcoin is peer-to-peer electronic cash so you can give it away like cash. I don't know what the tax rules on cash are. You need to verify that with your own jurisdiction. This is not financial or tax advice. This is for informational purposes only.
Remember, this is a custodial wallet. Not your keys not your bitcoin. Don't keep more sats than you are willing to lose on custodial wallets. Sweep your wallet early and often. Loss of funds is possible. There is a small fee for liquidity management too. Do your own research.`
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ 6e0ea5d6:0327f353
2025-06-08 21:03:49
@ 6e0ea5d6:0327f353
2025-06-08 21:03:49scolta bene... Ma ascolta bene, si?
Davvero, if there is one thing I can say after deep personal observation—from Palermo to Catania, from Sicily to Rome—it is this: A coward may strip everything from a righteous man, but after that… who can stop his revenge?
In this sense, amico mio, do not be fooled by the gentle ways of the just and humble man. His composure, his measured words, his restrained gestures, his patience and courtesy—all of it is merely the surface of a deep lake, where his wisdom guards unrest. While wrongdoers boast of their crimes and parade the streets with impunity, the man of honor watches in silence, bearing the world drop by drop.
Tuttavia, figlio mio, the day always comes when the final drop falls.
And then, it is not a gust of wind, nor a thunderclap—it is a dam breaking.
The fury that is born from a violated sense of justice is not loud like the brutes, nor blind like the fools; it is methodical, deliberate, devastating.
Sit here by my side and remember forever the advice of this old man, Antoni Salvatore: Never wrong a righteous man’s family, business, or honor! There is more danger in one upright man, when he finally rises for vengeance, than in a hundred armed scoundrels.
Do not deceive yourself into thinking every good man is also a fearful one! The wrath of the just—held back for so long—when it seeks reparation, carries with it the sacred vengeance permitted by the heavens...
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 5c26ee8b:a4d229aa
2025-06-08 20:49:48
@ 5c26ee8b:a4d229aa
2025-06-08 20:49:48Ad-Daba (the unusual creature), is one of the major signs of Judgement Day and it’s more likely to be the next sign to appear soon. As it appears the belief of disbelievers or repentance won’t be accepted. In the following some verses of the Quran and Hadith mentioning it as well as other major signs.
27:82 An-Naml
۞ وَإِذَا وَقَعَ الْقَوْلُ عَلَيْهِمْ أَخْرَجْنَا لَهُمْ دَابَّةً مِنَ الْأَرْضِ تُكَلِّمُهُمْ أَنَّ النَّاسَ كَانُوا بِآيَاتِنَا لَا يُوقِنُونَ
And when the word befalls them, We will bring forth for them a creature (Ad-Daba) from the earth speaking to them, [saying] that the people were, of Our verses, not certain [in faith].
6:158 Al-An'aam
هَلْ يَنْظُرُونَ إِلَّا أَنْ تَأْتِيَهُمُ الْمَلَائِكَةُ أَوْ يَأْتِيَ رَبُّكَ أَوْ يَأْتِيَ بَعْضُ آيَاتِ رَبِّكَ ۗ يَوْمَ يَأْتِي بَعْضُ آيَاتِ رَبِّكَ لَا يَنْفَعُ نَفْسًا إِيمَانُهَا لَمْ تَكُنْ آمَنَتْ مِنْ قَبْلُ أَوْ كَسَبَتْ فِي إِيمَانِهَا خَيْرًا ۗ قُلِ انْتَظِرُوا إِنَّا مُنْتَظِرُونَ
Do they [then] wait for anything except that the angels should come to them or your Lord should come or that there come some of the signs of your Lord? The Day that some of the signs of your Lord will come no soul will benefit from its faith as long as it had not believed before or had earned through its faith some good. Say, "Wait. Indeed, we [also] are waiting."
It was narrated that Hudhaifah bin Asid, Abu Sarihah, said: "The Messenger of Allah (ﷺ) looked out from a room, when we were talking about the Hour. He said: 'The Hour will not begin until ten signs appear: The rising of the sun from the west (place of its setting); Dajjal; the smoke; the beast; Gog and Magog people; the appearance of 'Eisa bin Maryam(as), the earth collapsing three times - once in the east, one in the west and one in the Arabian Peninsula; and fire that will emerge from the plain of Aden Abyan and will drive the people to the place of Gathering, stopping with them when they stop at night and when they stop to rest at midday."
حَدَّثَنَا عَلِيُّ بْنُ مُحَمَّدٍ، حَدَّثَنَا وَكِيعٌ، حَدَّثَنَا سُفْيَانُ، عَنْ فُرَاتٍ الْقَزَّازِ، عَنْ عَامِرِ بْنِ وَاثِلَةَ أَبِي الطُّفَيْلِ الْكِنَانِيِّ، عَنْ حُذَيْفَةَ بْنِ أَسِيدٍ أَبِي سَرِيحَةَ، قَالَ اطَّلَعَ رَسُولُ اللَّهِ ـ صلى الله عليه وسلم ـ مِنْ غُرْفَةٍ وَنَحْنُ نَتَذَاكَرُ السَّاعَةَ فَقَالَ " لاَ تَقُومُ السَّاعَةُ حَتَّى تَكُونَ عَشْرُ آيَاتٍ طُلُوعُ الشَّمْسِ مِنْ مَغْرِبِهَا وَالدَّجَّالُ وَالدُّخَانُ وَالدَّابَّةُ وَيَأْجُوجُ وَمَأْجُوجُ وَخُرُوجُ عِيسَى ابْنِ مَرْيَمَ عَلَيْهِ السَّلاَمُ وَثَلاَثُ خُسُوفٍ خَسْفٌ بِالْمَشْرِقِ وَخَسْفٌ بِالْمَغْرِبِ وَخَسْفٌ بِجَزِيرَةِ الْعَرَبِ وَنَارٌ تَخْرُجُ مِنْ قَعْرِ عَدَنِ أَبْيَنَ تَسُوقُ النَّاسَ إِلَى الْمَحْشَرِ تَبِيتُ مَعَهُمْ إِذَا بَاتُوا وَتَقِيلُ مَعَهُمْ إِذَا قَالُوا " .
قال رسول الله صلي الله عليه وسلم: تخرجُ الدابَّةُ، فتَسِمُ الناسَ على خراطيمِهم، ثم يُعمِّرون فيكم، حتى يشتريَ الرجلُ الدابَّةَ، فيُقالُ: ممَّنِ اشتريتَ؟ فيقولُ: من الرجلِ المُخَطَّمِ
The prophet Mohamed peace be upon him said: The beast will come out and brand people (disbelievers) on their noses (leaves a sign burned on their nose so it’s known of their disbelief). Then they will live among you until a man buys a beast and it will be said: From whom did you buy it? He will say: From the man with the sign on the nose.
The beast looks unusual and some people might find it scary. However, it’s a sign of God and it must not be killed as this will call God’s punishment like what happen when the people of prophet Saleh peace be upon him killed the huge camel as mentioned in the following verses.
7:73 Al-A'raaf
وَإِلَىٰ ثَمُودَ أَخَاهُمْ صَالِحًا ۗ قَالَ يَا قَوْمِ اعْبُدُوا اللَّهَ مَا لَكُمْ مِنْ إِلَٰهٍ غَيْرُهُ ۖ قَدْ جَاءَتْكُمْ بَيِّنَةٌ مِنْ رَبِّكُمْ ۖ هَٰذِهِ نَاقَةُ اللَّهِ لَكُمْ آيَةً ۖ فَذَرُوهَا تَأْكُلْ فِي أَرْضِ اللَّهِ ۖ وَلَا تَمَسُّوهَا بِسُوءٍ فَيَأْخُذَكُمْ عَذَابٌ أَلِيمٌ
And to the Thamud [We sent] their brother Salih. He said, "O my people, worship Allah; you have no deity other than Him. There has come to you clear evidence from your Lord. This is the she-camel of Allah [sent] to you as a sign. So leave her to eat within Allah 's land and do not touch her with harm, lest there seize you a painful punishment.
7:74 Al-A'raaf
وَاذْكُرُوا إِذْ جَعَلَكُمْ خُلَفَاءَ مِنْ بَعْدِ عَادٍ وَبَوَّأَكُمْ فِي الْأَرْضِ تَتَّخِذُونَ مِنْ سُهُولِهَا قُصُورًا وَتَنْحِتُونَ الْجِبَالَ بُيُوتًا ۖ فَاذْكُرُوا آلَاءَ اللَّهِ وَلَا تَعْثَوْا فِي الْأَرْضِ مُفْسِدِينَ
And remember when He made you successors after the 'Aad and settled you in the land, [and] you take for yourselves palaces from its plains and carve from the mountains, homes. Then remember the favors of Allah and do not commit abuse on the earth, spreading corruption."
7:75 Al-A'raaf
قَالَ الْمَلَأُ الَّذِينَ اسْتَكْبَرُوا مِنْ قَوْمِهِ لِلَّذِينَ اسْتُضْعِفُوا لِمَنْ آمَنَ مِنْهُمْ أَتَعْلَمُونَ أَنَّ صَالِحًا مُرْسَلٌ مِنْ رَبِّهِ ۚ قَالُوا إِنَّا بِمَا أُرْسِلَ بِهِ مُؤْمِنُونَ
Said the eminent ones who were arrogant among his people to those who were oppressed - to those who believed among them, "Do you [actually] know that Salih is sent from his Lord?" They said, "Indeed we, in that with which he was sent, are believers."
7:76 Al-A'raaf
قَالَ الَّذِينَ اسْتَكْبَرُوا إِنَّا بِالَّذِي آمَنْتُمْ بِهِ كَافِرُونَ
Said those who were arrogant, "Indeed we, in that which you have believed, are disbelievers."
7:77 Al-A'raaf
فَعَقَرُوا النَّاقَةَ وَعَتَوْا عَنْ أَمْرِ رَبِّهِمْ وَقَالُوا يَا صَالِحُ ائْتِنَا بِمَا تَعِدُنَا إِنْ كُنْتَ مِنَ الْمُرْسَلِينَ
So they hamstrung the she-camel and were insolent toward the command of their Lord and said, "O Salih, bring us what you promise us, if you should be of the messengers."
7:78 Al-A'raaf
فَأَخَذَتْهُمُ الرَّجْفَةُ فَأَصْبَحُوا فِي دَارِهِمْ جَاثِمِينَ
So the earthquake seized them, and they became within their home [corpses] fallen prone.
7:79 Al-A'raaf
فَتَوَلَّىٰ عَنْهُمْ وَقَالَ يَا قَوْمِ لَقَدْ أَبْلَغْتُكُمْ رِسَالَةَ رَبِّي وَنَصَحْتُ لَكُمْ وَلَٰكِنْ لَا تُحِبُّونَ النَّاصِحِينَ
And he turned away from them and said, "O my people, I had certainly conveyed to you the message of my Lord and advised you, but you do not like advisors."
God is the most merciful and has decreed everything and even the major signs of Judgement Day can have the punishment coming with them alleviated or reduced by God. However, there must be a reason for reducing the intensity of the calamities, as God may decree, and the reason is repentance as well as good actions to adjust what was done wrong. Also, although the major signs of Judgement Day will be known to the majority of the people, some of them might concern smaller groups of people or a country.
3:133 Aal-i-Imraan
۞ وَسَارِعُوا إِلَىٰ مَغْفِرَةٍ مِنْ رَبِّكُمْ وَجَنَّةٍ عَرْضُهَا السَّمَاوَاتُ وَالْأَرْضُ أُعِدَّتْ لِلْمُتَّقِينَ
And hasten to forgiveness from your Lord and a garden as wide as the heavens and earth, prepared for the righteous
3:134 Aal-i-Imraan
الَّذِينَ يُنْفِقُونَ فِي السَّرَّاءِ وَالضَّرَّاءِ وَالْكَاظِمِينَ الْغَيْظَ وَالْعَافِينَ عَنِ النَّاسِ ۗ وَاللَّهُ يُحِبُّ الْمُحْسِنِينَ
Who spend [in the cause of Allah] during ease and hardship and who restrain anger and who pardon the people - and Allah loves the doers of good;
3:135 Aal-i-Imraan
وَالَّذِينَ إِذَا فَعَلُوا فَاحِشَةً أَوْ ظَلَمُوا أَنْفُسَهُمْ ذَكَرُوا اللَّهَ فَاسْتَغْفَرُوا لِذُنُوبِهِمْ وَمَنْ يَغْفِرُ الذُّنُوبَ إِلَّا اللَّهُ وَلَمْ يُصِرُّوا عَلَىٰ مَا فَعَلُوا وَهُمْ يَعْلَمُونَ
And those who, when they commit an immorality or wrong themselves [by transgression], remember Allah and seek forgiveness for their sins - and who can forgive sins except Allah? - and [who] do not persist in what they have done while they know.
3:136 Aal-i-Imraan
أُولَٰئِكَ جَزَاؤُهُمْ مَغْفِرَةٌ مِنْ رَبِّهِمْ وَجَنَّاتٌ تَجْرِي مِنْ تَحْتِهَا الْأَنْهَارُ خَالِدِينَ فِيهَا ۚ وَنِعْمَ أَجْرُ الْعَامِلِينَ
Those - their reward is forgiveness from their Lord and gardens beneath which rivers flow [in Paradise], wherein they will abide eternally; and excellent is the reward of the [righteous] workers.
3:137 Aal-i-Imraan
قَدْ خَلَتْ مِنْ قَبْلِكُمْ سُنَنٌ فَسِيرُوا فِي الْأَرْضِ فَانْظُرُوا كَيْفَ كَانَ عَاقِبَةُ الْمُكَذِّبِينَ
Similar situations [as yours] have passed on before you, so proceed throughout the earth and observe how was the end of those who denied.
3:138 Aal-i-Imraan
هَٰذَا بَيَانٌ لِلنَّاسِ وَهُدًى وَمَوْعِظَةٌ لِلْمُتَّقِينَ
This [Qur'an] is a clear statement to [all] the people and a guidance and instruction for those conscious of Allah.
-
 @ c230edd3:8ad4a712
2024-08-26 01:13:49
@ c230edd3:8ad4a712
2024-08-26 01:13:49Chef's notes
Allow meat to soak for 1-24 hours. The rougher the cut, the longer the soak. This is great for open flame grilling, as well as pan seared, though the latter is preferable. Petit Sirloin can marinade for approximately 1 hour and still develop tenderness. I like to score the steaks if they will only be resting in the mix for a short time. All seasonings can be adjusted to taste. Base ingredients scale well, for any number of steaks. Equal parts, enough to coat the meat is really all that matters.
I'm terrible at remembering cooking pictures, so image is a random steak. I will try to remember to update that next time I make these.
Details
- ⏲️ Prep time: 10
- 🍳 Cook time: However long you usually cook your steak to preferred doneness
Ingredients
- 4 petite sirloin steaks or other cut
- 1/4 cup yellow mustard
- 1/4 cup soy sauce
- 3-5 cloves garlic, depending on size, minced and salted
- 1 tsp dried basil
- 1\2 tsp crushed red pepper
Directions
- Mix ingredients and marinade 1-24 hours.
- Grill or pan sear to your preferred doneness
- Enjoy!
-
 @ 3bf0c63f:aefa459d
2024-06-19 16:13:28
@ 3bf0c63f:aefa459d
2024-06-19 16:13:28Estórias
-
 @ 3f289d3c:cf35b9fc
2024-06-14 16:14:13
@ 3f289d3c:cf35b9fc
2024-06-14 16:14:13In an increasingly regulated world, the industries that are not heavily regulated need to start switching to Bitcoin and Lightning payments now
I'll start this article off by giving you a little bit of back story. I'm from Canada and in Canada the government is increasingly crushing people under high taxes, massive inflation and unreasonable regulation. This seems to be the story in a lot of places but Canada is particularly bad on the regulation and taxes front, at least from my perspective. I live in a rural area where gasoline prices are much higher than in the higher population density areas of our province. Food prices are higher, product prices are higher including on the used market and property taxes here are way higher than what one might expect in such a remote area. You get the idea.
Now when I moved here the only method of income I had was crypto mining, specifically Ethereum. That seemed to be doing well for me for a short time. As time went on I noticed my savings dipping further and further and even though I was holding a lot of coins that were doing well overall, I was spending much more than I was able to earn with any of the crypto mining methods. I didn't lose a ton of money on any one of these but the Canadian market got so bad that I was forced to liquidate most of the tokens that I had set aside in order to make myself more on the cryptocurrency market. Not an ideal situation to be in.
As time went on I was forced to shut off my Ethereum mining rigs and get a "real job." Since then I've been more or less happily back in the the fiat mines (literally working at a gold mine) working for a meager (but not terrible) living and doing better than I was without a job. The biggest change over the course of the Last few months has been my switch to Bitcoin maximalism. I've learned more about the technology/currency and I've switched any remaining extra funds over to Bitcoin.
This all being said, The Canadian economy is now worse than it's ever been and I'm living paycheck to paycheck even though I make something like $78,000 a year in the mining sector. Obviously, this is absolutely Ridiculous. This is what brings me to my side income.
I've been a professional photographer for several years now and up until this point I hadn't considered trying to generate an income in anything other than Canadian dollars. With Canada being in the state it is currently I have reconsidered that and I am now accepting preferably Bitcoin or cash but I really want to emphasize Bitcoin. My issue at the moment is that I live in an area that is very rural and very remote so there are not a lot of people who even know what Bitcoin is let alone people who will actually use it. This is my biggest hurdle at the moment but frankly I don't think it's not much of a hurdle.
My primary plan for some time has been to build an online business focusing on education, community And maybe a bit of consulting versus going out and doing primarily photo shoots. Obviously that has to exist as part of the business ultimately, but my real goal is to focus on educating others and helping them to get to where I am and beyond. Basically I want to pass on my skill set and I want to avoid the awful economy as much as I can while doing it.
This is where accepting Bitcoin comes in. By accepting Bitcoin as payment for my photography services and only using marketplaces that Are built on that technology, I can largely skip past the modern woes of our economy. I can skip out on taxes and I can skip out on any kind of reporting that I would otherwise need to do. I can basically run a business completely free of the government and not need to do anything other than simply do what I would do if it were a hobby. This really excites me.
Imagine a world where you can just transact without having to report anything on your taxes. Imagine not having taxes at all! In an industry such as photography where it's mostly digital anyways, Bitcoin is the perfect method of payment for your services. With the lightning network And NFC chips, You can do all of your transacting right there on your phone to a lightning enabled Bitcoin wallet.
I think these industries where there isn't any regulation at all or at least very little regulation, are the perfect places to start doing this. They're the perfect breeding ground for all Bitcoin transactions and businesses. Why get the government involved at all when you can simply run your business the way it should be run? As they say on nostr, "Bitcoin fixes this."
I'm really looking forward to building my business in the nostr environment and on the back of a Bitcoin standard. I've already started the transition by joining nostr and I'm beginning to speak about photography there. I don't think I have felt as positive or as enthusiastic about this endeavor since joining nostr as a social platform and I'm really happy that I'm here. I believe that this is the future of digital transactions and social media and it may just be the best way to run an online business going forward.
Thank you for taking the time to read this and if anybody wants to see anything specific from me feel free to hit me up on nostr! I hope my thoughts brought some value to you and maybe got you thinking about how you could start transitioning your business to a Bitcoin standard.
-
 @ 90152b7f:04e57401
2025-06-08 20:18:10
@ 90152b7f:04e57401
2025-06-08 20:18:10The results show that platforms must do more to detect and remove harmful content in closed groups while preserving user privacy. They must also improve tools for user reporting. Without these steps, private spaces online will continue to be exploited by extremists and bad actors to spread hate and coordinate violence.
Over the course of two weeks, ADL researchers posted 10 pieces of violative content (for example, “Jews are rats”) on private spaces and tracked the responses of three different platforms - before reporting and after.
Our testing found the following:
Facebook was the only platform that deployed any kind of auto-filtering to remove content proactively. However, this was before Facebook-owner Meta announced that it would abandon proactive moderation of non-illegal content in the U.S.
Discord did not take action on any content proactively—only after the content was reported.
Roblox’s auto-filtering did obscure some offensive posts, but it did not remove any of the content, the private group, or the user account posting violative content after we reported it.
Facebook and Discord removed most hateful content retroactively (after users reported it, in this case, by ADL), but their systems were not perfect and missed violative content.
In response to our research:
This research was shared with Meta, Discord and Roblox prior to publication and ADL researchers briefed the relevant teams at these companies. In response, Discord and Roblox acted. Specifically, Roblox shared that they “enabled an additional layer of automated review on Community Wall Post Abuse Reports. This means that abuse reports filed against Community wall posts will first undergo a review by an automated system, which will automatically take action if the wall post violates our policies. The additional layer of automation will empower human moderators to focus on deeper tasks and help increase the effectiveness of our review system.”
Private Online Spaces: Harboring Hate and Extremism
The problem of online hate and harassment has been well documented, but most data come from public online spaces such as X/Twitter, YouTube, or Reddit. These platforms typically use proactive moderation, such as automated filters and machine-learning tools, to identify and remove content that violates their rules.
Some platforms, however, allow users to create closed or private spaces where only members can see the content. These private spaces include closed Facebook groups, private Discord servers (a type of chat room), and communities on Roblox. Encrypted chat platforms such as WhatsApp, Telegram, and Signal also allow member-only spaces, some of which can be discovered publicly, while others are by invitation only. ADL’s 2024 annual survey of online hate and harassment found that between 2023 and 2024, incidences of harassment increased on both Telegram and WhatsApp, +6% and +11% respectively.
Private online spaces have been linked to numerous instances of online and in-person atrocities. Shooters such as the Buffalo shooter, or a school shooter in Perry High, Iowa, posted their manifestos and livestreamed their deeds on private Discord servers. In August 2024, a perpetrator in Turkey, motivated by white supremacists and accelerationism, shared his manifesto on Telegram before livestreaming a violent stabbing attack. Most recently, online bullies have used private spaces to promote extreme cruelty and self-harm as part of larger campaigns to harm vulnerable young people, sometimes leading to suicide.
ADL has also tracked many extremist groups that flourish on private groups and servers hosted by Discord, Telegram, and other platforms. Hate groups and conspiracy mongers, such as the Three Percenters or QAnon adherents, take advantage of private groups to organize and distribute hateful content and false narratives. Other extremist groups, such as extremist traditional Catholic and Islamic groups, have used Discord servers to share memes and hateful rhetoric. Extremist militias have been quietly organizing and regrouping on private Facebook groups since the January 6, 2021, attack on the U.S. Capitol. Individuals and groups on Roblox groom children to extremist ideologies through projects like “Redpill the Youth.” When neighborhood watch groups or community organizers use private groups, hateful users have, in some cases, infiltrated these groups to harass and intimidate other users.
It is difficult for researchers to assess how well platforms moderate these spaces or understand their inner workings because private online spaces restrict access. Private spaces can equally serve important social functions, such as for parent groups, political organizing, or protected spaces for marginalized groups to gather and provide mutual support. But tech companies do not make clear how they enforce their policies in private groups, often leaving content moderation up to users or administrators.
Understanding Content Moderation in Private Online Spaces
Members-only groups can be visible to non-members, such as many closed Facebook groups. But others, such as private Discord servers, are not making the groups' content invisible to non-members. Degrees of privacy and visibility can vary on Facebook groups, Telegram channels, or WhatsApp chats. Facebook groups, for example, can be fully public and open, publicly accessible but closed (anyone can join but only members can post or view content), or private (members must be approved). There are also two categories of private groups: closed groups that require approval but can be found through search, and fully secret groups that are not only private but cannot be found in search.
The three platforms we tested for this study (Facebook, Discord, and Roblox) have taken proactive steps to address hate, extremism, and antisemitism. We did not include platforms such as Telegram, which does not moderate hateful content, even though extremists use the platform's private channels to spread hate and coordinate harassment.
Facebook is one of the most popular social media platforms among users in the U.S., and where the majority of online harassment takes place (61% of people who are harassed report harassment on Facebook, according to ADL’s 2024 annual survey of online hate and harassment). Much of this harassment takes place in closed Facebook groups, but researchers have little insight into these spaces.
Discord began as a chat platform for gamers but has since expanded to host numerous online communities. Social interaction on Discord takes place in chatrooms (called servers) that offer a private or semi-private environment for users to chat both in groups and individually (similar to Slack). Discord allows users to create servers with various channels that can be set to invite-only, making it a popular choice for groups seeking privacy. Discord’s company culture, which emphasizes privacy and minimal moderation, makes it an attractive place for bad actors to connect and coordinate. Video calls and chats are not recorded or monitored, and users can delete posts permanently. Making video and audio calls end-to-end encrypted increases privacy for users, but it also makes it significantly more difficult for the platform to catch bad behavior. Discord's hands-off approach to content moderation--leaving most moderation decisions in the hands of the server’s administrators-- makes it easy to share extremist content there compared to similar platforms.
Roblox is a gaming and game creation platform popular with children, with at least 45% of users being under the age of 13. Roblox has a groups feature embedded within its website, though Roblox users primarily communicate with each other through in-game text or voice chat. Within Roblox groups, members can post messages on a group wall, participate in group events, and access exclusive in-game content provided by group leaders. Roblox groups often focus on themes, such as game development or in-game collaborations. It is the only gaming platform we included where the majority of communication takes place in-game. For comparison, we only examined the group feature on the Roblox website and not communication in Roblox games.
Methodology
1. We created one group per platform (Facebook, Discord and Roblox) simultaneously, and named the groups on Facebook and Discord “Group for the Truth;” (this name was already taken on Roblox so we named that one “Group for the Truth_2.”) To prevent users from inadvertently stumbling across the groups, the settings for each were set up in a manner that made them hidden from search.
2. We then used one account to create the groups and post content (the “posting account”), and another on a separate computer to report the content (the “reporting account”). Two researchers were assigned to each account. There were no further descriptions or images added to the groups, except on Roblox, which required a group description and image.
3. The posting account was then used to post hateful content to all three platforms. This content was pulled directly from Meta’s helpfully illustrative examples of violations against its hate speech policy at the time. Meta is the only platform with examples of what could be violative of its hate speech policy of the three platforms we reviewed.
4. Meta's Tier 1 Hate Speech policy, for example, states that a user may not post content that includes:
Dehumanizing speech in the form of comparisons to or generalizations about:
- Animals in general or specific types of animals that are culturally perceived as inferior (including but not limited to: Black people and apes or ape-like creatures; Jewish people and rats; Muslim people and pigs; Mexican people and worms)
We adapted this example to draft a hateful post stating, “Jews are rats.” Every post was derived directly from Meta’s policy examples, though there may not always be a corollary example within the policy. For example, Meta’s policy at the time stated that users may not post:
Content targeting a person or group of people on the basis of their protected characteristic(s) (in written or visual form):
-
Generalizations that state inferiority in the following ways:
-
Physical appearance, including but not limited to: ugly, hideous.
There was no further example provided by Meta, so we created a post that would intentionally violate this policy:
“Jews are the ugliest, most hideous people on Earth.”
Although these posts were based on Meta’s policy, each one has a matching Discord policy. The same applies to Roblox, though its hate speech policy is not nearly as detailed as Meta’s or Discord’s:
Roblox honors and welcomes users of all ages, backgrounds, and identities. We do not allow content or behavior that supports, glorifies, or promotes hate groups, their ideologies, or actions. You also may not discriminate, mock, or promote hatred against individuals or groups, or encourage others to do so directly or indirectly, on the basis of their:
- Race, perceived race, or ethnicity
We believe that the following posts are violative under Roblox’s policy as well:
-
“Jews are rats.”
-
“Jews are devils and shit.”
-
“The Holocaust did not happen-it’s a lie made up by the Jews.”
-
“Jews control the banks, the government and Hollywood and we need to get rid of them for the safety of American citizens.”
-
“Jews are the ugliest, most hideous people on Earth.”
-
“Jews should be segregated from all other people.”
5. We followed up our initial posts with additional sentences to test content violating Meta’s policy against dangerous organizations and individuals, such as violent extremists. These posts also violate Discord’s Violent Extremism policy and Roblox’s Community Standards.
-
“Hitler and the Nazis did nothing wrong.”
-
“Please donate to the Goyim Defense League!” (A link was attached to this sentence.)
We referenced the Goyim Defense League because they are a notorious group of antisemitic provocateurs, according to the ADL Center on Extremism.
We also posted the following two images in violation of Meta’s Dangerous Organizations and Individuals policy, Discord’s Violent Extremism policy, and Roblox’s Community Standards:

Image 1: Posted Images, “Covid Agenda” and “Ukraine-Russia War,” respectively. (Screenshot: 7/31/2024)
6. The following day, we reported each of these posts, if applicable. Though both “Jews are the ugliest, most hideous people on Earth” and “Jews should be segregated from all other people” run afoul of hate speech policies, we did not report them until the next day. We staggered reporting in this way so as to not get either our accounts or groups suspended before the study was over.
Findings
-
Facebook was the only platform to remove content before we reported it.
-
Discord did not take down any content at all, implying either that it has little to no automatic filtering or that any filtering is not robust enough to catch what our posting account shared. When offending posts were reported, Discord did remove posts and suspended the account.
-
Roblox obscured the text of offensive posts, but did not take down the group nor the offending account.
When we started reporting the potentially violative content to the platforms, we noticed a discrepancy between the platforms’ responses. Facebook’s reaction to reports included warnings before suspending the group. Discord provided less information to the administrator about why the posts were removed. It did not suspend the group but did suspend our Posting account. Roblox informed the posting account that the account or group was breaking the rules, but did not take down any posts within the group. Although it did obscure the text by censoring the entire post, replacing all content with x’s except for the obscured content, the group stayed the same as it did before reporting. No further content was taken down, and no alerts were given to either account.
Facebook
Facebook removed most offending posts when we reported them, gave feedback to the account administrator, and finally suspended the group when offending content continued to be posted. Some posts remain up-- despite notifications from our Reporting account.
Proactive Detection
Facebook did not remove any posts automatically on the first day we posted content. On the second day we posted, they removed “Ukraine-Russia War” automatically (see Image 2).

Image 2: Facebook’s alert after removing “Ukraine-Russia War.” (Screenshot: 7/19/2024)
Not only did Facebook remove the photo, but it also alerted the Posting account (the account admin) that the photo had been removed. When we clicked through “See why,” Facebook displayed the offending image and explained why the image had been removed. It also provided a link to the rule that was broken. Facebook also added restrictions to the account that posted the picture; the user could not create ads, create live videos, or start or join calls for approximately a month. It is not clear why Facebook took action against “Ukraine-Russia War” automatically, but not the sister image “Covid Agenda.” Both pictures originate from the Goyim Defense League and are prohibited by Meta’s policy rules. Meta has rolled back its Covid misinformation rules, but this image is still prohibited per their Dangerous Organizations and Individuals policy.
Facebook did not allow the posting account to post the link embedded in “Please donate to the Goyim Defense League!” Not only was Facebook the only platform to prevent adding the link, it also explained why it was not allowed (Image 3).

Image 3: Window preventing the user from posting a link to GDL’s site. (Screenshot: 7/31/2024)
Reporting Response
After we reported the posts, they were almost instantaneously actioned. The first post was reported at 4:21pm. By 4:24 pm, the reporting account was alerted that the report resulted in the post being removed.
At the same time, the posting account was notified that restrictions were added to the account (Images 4 and 5). Unlike Discord or Roblox’s restrictions, Facebook not only told the user which restrictions were added, but also explained which post was removed and which rule each had broken.

Images 4 (left) and 5 (right): Facebook account restrictions. (Screenshot: 7//30/2024)
The next day, we reported the second half of the posts and the remaining image. Facebook again took action, quickly taking down the posts. This time, however, the platform also permanently suspended the group. The posting account can still access the defunct group, but the reporting account cannot. Users can still log into both accounts, and post and comment on Facebook, just not the group. Facebook warned us that the posting account is under threat of being permanently suspended (Image 6).

Image 6: Group suspension and account status. (Screenshot: 07/31/2024)
Although we commend Facebook for their quick action, there were still posts that remain up. These posts, despite the reports, were never taken down as of publication (Image 7).

Image 7: Facebook group. (Screenshot: 2/28/2025)
Discord
In contrast to Facebook, Discord’s content moderation strategy for private groups, appears to be reactive rather than proactive. It depends primarily on reports from users of those groups, rather than automatic filtering and takedowns.
Proactive detection
Until we reported the offending content on the Discord group, no content was taken down.

Image 8: Discord content. (Screenshot: 1/15/2025)
Reporting Response
While Discord did not take action on content in the proactive detection phase, once we started reporting posts, they responded proactively, removing posts before we could report them on day 14.
The first half of the content was reported on day 13 but did not receive alerts from Discord until an hour later. The alerts explained why the posting account was being sanctioned and which rules it had broken.

Image 9: Discord alert for breaking community guidelines. (Screenshot: 7/2024)
By day 14, nearly every post had been taken down—even the ones not reported yet. All posts save one were taken down proactively, although we had not reported those images yet. The only post still up said, “Please donate to the Goyim Defense League.” We reported this post, but it was never taken down.

Image 10: Discord group. (Screenshot: 7/31/2024)
Unlike Facebook, Discord did not take action against the group itself; the group is not suspended, and the reporting account can still post to it at the time of writing. Discord did act against the posting account, suspending it a few days later. The posting account received no notification that it was suspended, save for emails alerting us to “new messages” on Discord. These messages were forwarded to the now inaccessible account, so we cannot determine when Discord took action. The posting user might have received a more pointed alert, like an app notification, if we had used the phone app instead of the desktop website. In any case, we were able to create a new account with the same name and using the same email address after our account was removed.

Image 11: Punishments from Discord. (Screenshot: 7/31/2024)
Roblox
The protections offered by Roblox in the private group were minimal, especially compared to Discord and Facebook. We received virtually no feedback on reporting from the platform. There were no warnings or pop-ups for the administrator. Roblox did not remove any posts, despite reports from our reporting account.
Proactive detection
Of the ten posts we created, four were automatically obscured when we posted them, so members could see the posts but not view the text. Roblox replaced the text with the hashmark (#), obscuring not just the offensive words but the entire post (Image 12). It is not entirely clear why Roblox hid some posts this way. For example, the text “Jews are devils and shit” was likely hidden because of the expletive. Roblox might also be automatically filtering keywords that it deems objectionable. It could be that terms like Holocaust, Hitler, Nazis or Goyim were automatically flagged, causing those posts to be removed.
Roblox does not allow pictures or links to be posted on the group’s page, so we were unable to post the Covid Agenda and Ukraine-Russia War images. We were able to post “Goyim Defense League” without the embedded link, though it was also immediately hidden.

Image 12: Hidden Roblox content. (Screenshot: 7/24/2024)
Reporting response
After we reported every post through our reporting account, there was no response from Roblox, unlike our experience with Facebook or Discord. No other posts were taken down. There were no tools that alerted the poster, the admin or reporting account that any action had been taken—not even a pop-up that the report had been received. The admin received no report that multiple posts on the group had been reported for hate and harassment.
Even after multiple reports, no action was taken on any of the posts. In fact, there was no change in the group from the initial first action, hiding the text. Compare the image of the Roblox group taken on day 14 with the image taken of the group over two weeks later (Image 13). There is no discernible difference.

Image 13: Roblox content. (Screenshot: 7/22/2024 and 8/2/2024)
Recommendations For Platforms with Members-only Groups
How platforms respond to violative content in private is just as important as how they respond to violative content in public. Facebook and Discord, while not perfect, moderated these private groups in a way that removed the majority of hateful content and suspended the hateful accounts.
We do not expect platforms to moderate content on private groups as strictly as in public spaces, due to privacy concerns, but we do expect an appropriate level of preventative moderation and tools for groups to moderate content. Roblox appears to have had little to no moderation in place, which is concerning given the young age of its player base. Roblox hid offensive and controversial text but did not suspend the posting account or group. It also provided no alerts to the admin or group when a report was made. While we understand that the bulk of communication on Roblox happens in-game, little action was taken within the group chat to moderate offensive content. Terrorist and violent extremist groups organize on private groups and channels, not in public spaces. Platforms with private groups should adopt a minimum standard of moderation on private groups to proactively stem this problem.
Platforms should:
-
Reexamine how automatic filtering functions: A common problem encountered in this course of our research was the seemingly arbitrary nature of the filtering tools. For example, Facebook automatically filtered one image but not another equally objectionable. It is also not clear why one image was actioned and the other was not. Platforms should reexamine their automatic filtering functions to catch content that slips through the cracks.
-
Prioritize user-reporting within private groups: Because of the protections that are available for private groups, reporting by group members is the primary channel for alerting the platform. Platforms should prioritize these reports and act on them quickly. These reports may be one of the first signs that something is amiss within a group.
-
Suspend groups when they reach a threshold of violative content: Facebook was the only platform that fully suspended our group. Discord did not suspend our group, only the user, who was able to promptly create a new account. Roblox suspended neither the group nor the account. If violative users and groups are allowed to continue their work with barely any pushback from platforms, then any moderation will fail.
-
Utilize metadata in content moderation: Private groups may restrict the visibility of their content to outside users and the platform itself, but that does not mean that there is no data available. Post times, user addresses, and other metadata are available to platform moderation teams. Discord, in particular, could take better advantage of the tools available to it. Discord’s content, save for video and audio content, is not encrypted, and the platform could be more proactive about automatic filtering if it chose to.
-
 @ dfa02707:41ca50e3
2025-06-07 13:01:47
@ dfa02707:41ca50e3
2025-06-07 13:01:47Contribute to keep No Bullshit Bitcoin news going.
- RoboSats v0.7.7-alpha is now available!
NOTE: "This version of clients is not compatible with older versions of coordinators. Coordinators must upgrade first, make sure you don't upgrade your client while this is marked as pre-release."
- This version brings a new and improved coordinators view with reviews signed both by the robot and the coordinator, adds market price sources in coordinator profiles, shows a correct warning for canceling non-taken orders after a payment attempt, adds Uzbek sum currency, and includes package library updates for coordinators.

Source: RoboSats.
- siggy47 is writing daily RoboSats activity reviews on stacker.news. Check them out here.
- Stay up-to-date with RoboSats on Nostr.
What's new
- New coordinators view (see the picture above).
- Available coordinator reviews signed by both the robot and the coordinator.
- Coordinators now display market price sources in their profiles.

Source: RoboSats.
- Fix for wrong message on cancel button when taking an order. Users are now warned if they try to cancel a non taken order after a payment attempt.
- Uzbek sum currency now available.
- For coordinators: library updates.
- Add docker frontend (#1861).
- Add order review token (#1869).
- Add UZS migration (#1875).
- Fixed tests review (#1878).
- Nostr pubkey for Robot (#1887).
New contributors

Full Changelog: v0.7.6-alpha...v0.7.7-alpha
-
 @ 2f7463a4:e92b8023
2024-05-28 00:38:48
@ 2f7463a4:e92b8023
2024-05-28 00:38:48| GitHub Repository | Lightning Address | | --- | --- | | https://github.com/sfr0xyz/openagents-bitcoin-stats | sefiro@getalby.com |
This is a plugin for OpenAgents that gives you the latest statistics about the Bitcoin network, its mempool and the Lightning Network.
It is inspired by Clark Moody's Bitcoin Dashboard and the TimeChainCalendar.
The project uses the Extism Framework, in particular its Go PDK, and the REST APIs of mempool.space, bitnodes.io and coincap.io.
Usage
Ensure that you have installed the Extism CLI and downloaded the
btcstats.wasmfile.You can call the plugin with the Extism CLI:
sh extism call btcstats.wasm run --input '<YOUR INPUT>' --wasi --allow-host '*'Replace
<YOUR INPUT>with a list of statistics you are interested in.Available statistics (see detailed descriptions on GitHub):
market: Bitcoin market data such as current price and market caplatestBlock: Information about the latest block, such as size and total rewardmining: Mining data such as current hashrate and difficulty, and difficulty adjustmentfees: Recommended feerates based on the current mempoolmempool: Mempool statistics such as number of unconfirmed transactions and pending feeslightning: Lightning Network statistics such as total capacity and number of channelsnodes: Bitcoin node statistics such as total number of nodes
You can include more than one of the above at once.
If you leave the field empty (
''), or include none of the above, all stats will be requested.With the prefix
-, e.g.-nodes, you can exclude stats, i.e. "I want all stats exceptnodes".Note: If you request the
nodesstatistic, it will take a while, a few seconds, for the result to be displayed.Examples[^1]
Note: The resulting JSON is prettified here for better readability.
Get
latestBlockandmempoolstats:```plain $ extism call btcstats.wasm run --input 'latestBlock mempool' --wasi --allow-host '*'
{ "latestBlock": { "height": 845325, "timestamp": "Mon, 27 May 2024 01:34:54 UTC", "transactions": 5692, "size": 1.55, "totalReward": 3.272, "totalFees": 0.147, "medianFeeRate": 8.1, "miner": "MARA Pool" }, "mempool": { "unconfirmedTXs": 170669, "vSize": 180.66, "pendingFees": 5.257, "blocksToClear": 181 }, "mining": { "hashrate": 677612693053317300000, "difficulty": 84381461788831.34, "retargetDifficultyChangePercent": 13.39, "retargetRemainingBlocks": 1395, "retargetEstimatedDate": "Tue, 04 Jun 2024 15:07:02 UTC" } } ```
Get all stats except
nodes:```plain $ extism call btcstats.wasm run --input '-nodes' --wasi --allow-host '*'
{ "fees": { "fastest": 9, "halfHour": 9, "hour": 9, "economy": 6, "minimum": 3 }, "latestBlock": { "height": 845325, "timestamp": "Mon, 27 May 2024 01:34:54 UTC", "transactions": 5692, "size": 1.55, "totalReward": 3.272, "totalFees": 0.147, "medianFeeRate": 8.1, "miner": "MARA Pool" }, "lightning": { "totalNodes": 12836, "torNodes": 8930, "clearnetNodes": 1700, "clearnetTorNodes": 1360, "unannouncedNodes": 846, "channels": 50872, "totalCapacity": 4980.822, "averageChannelCapacity": 0.098, "medianChannelCapacity": 0.02 }, "market": { "supply": 19699693, "supplyPercent": 93.81, "price": 69020.61, "priceChange24hPercent": -0.32, "moscowTime": 1448, "marketCap": 1359684729700.71 }, "mempool": { "unconfirmedTXs": 170669, "vSize": 180.66, "pendingFees": 5.257, "blocksToClear": 181 }, "mining": { "hashrate": 677612693053317300000, "difficulty": 84381461788831.34, "retargetDifficultyChangePercent": 13.39, "retargetRemainingBlocks": 1395, "retargetEstimatedDate": "Tue, 04 Jun 2024 15:07:02 UTC" } } ```
[^1]: more examples in the README on GitHub
-
 @ 81022b27:2b8d0644
2025-06-08 19:56:02
@ 81022b27:2b8d0644
2025-06-08 19:56:02There is a viral Chat GPT prompt on social media (i saw it on TikTok)-It;s supposed to help you analyze yourself.
I thought this was a cool thing to try, but I decided to use Grok Ai Instead, seeing that I have a premium X subscription, and wouldn’t have to worry about the limitations with a free ChatGPT account.
Here is the prompt:
I want to uncover the masks I'm currently wearing, the roles I'm playing, and the illusions I'm believing.
Please guide me through this process by asking me 10 reflective questions one at a time to help me recognize the stories I'm telling myself. Pause after each question to wait for me to answer. After I answer the 10th question, please step into the role of my higher self and analyze my responses.
Identify the top negative patterns present in my life and the top positive patterns I can embrace and grow. Be direct and truthful. Tough love is welcome.
Provide me with daily affirmations to support my growth, actionable steps to change my behaviors, and embody my authentic self. A message of encouragement from my higher self to celebrate how far I've come on my journey.
Cool, right?
I answered the 10 questions, which I won’t post-because my answers were very personal and very specific. And even though I share a lot of deep personal stuff here, I wasn’t prepared to go public with how deep the questions Grok was asking.
The questions were super uncomfortable to answer.
I answered them honestly, and looking back-some questions could have been answered with different examples and directions, maybe that would show different conclusions.
Here are my results:
Analysis from Your Higher Self
Top Negative Patterns Present in Your Life:
-
Avoidance as a Shield: You’ve built a pattern of avoiding risks—whether it’s heights, the outdoors, or even deeper emotional vulnerabilities—because of early fears tied to being seen as weak or getting hurt. This avoidance keeps you safe but also keeps you small, limiting experiences like enjoying nature or forming deeper connections.
-
Fear of Perception: There’s a lingering story that shyness or introversion equals weakness, likely rooted in childhood experiences like bullying. This drives you to put on an outgoing mask, even when it exhausts you, because you fear isolation or judgment. It’s a heavy burden to carry, and it pulls you away from your authentic self.
-
Self-Imposed Isolation: While being alone feels safe and freeing, it also risks becoming a crutch. You’re missing out on the balance of connection—where you can still be your nerdy, unfiltered self without the pressure to perform.
Top Positive Patterns to Embrace and Grow: 1. Self-Awareness and Honesty: You’ve shown a remarkable ability to reflect and name what’s true for you—like recognizing avoidance, your love for nerdy things, and how being alone feels freeing. This clarity is a superpower; lean into it to keep peeling back layers.
-
Desire for Freedom: Your longing to think and feel without consequence is a sign of a spirit that craves authenticity. You can channel this into spaces and relationships where you feel safe to be your true self, not just when alone.
-
Resilience Through Adversity: Despite early fears and bullying, you’ve developed a sharp sense of self—it’s why you can pinpoint what feels off (like the outgoing mask) and what feels right (being a nerd). This resilience can carry you far as you step into new experiences.
Guidance for Growth
Daily Affirmations to Support Your Growth:
- I am strong in my stillness, and my quiet nature is a source of power.
- I release the need to perform for others and embrace my authentic nerdy self.
- I am safe to take small risks, knowing they lead me closer to freedom and joy.
- I attract people who love me for my true self, not the masks I’ve worn.
- I am enough, exactly as I am, without needing to prove my worth.
Actionable Steps to Change Behaviors and Embody Your Authentic Self:
-
Micro-Adventures in the Outdoors: Start small—take a 15-minute walk in a nearby park or sit outside with a book you love. Build up to a short hike with a trusted friend. Let nature be a space to reconnect with yourself, not something to fear.
-
Own Your Nerdiness Publicly: Share one nerdy interest with someone you trust—like a favorite game, comic, or hobby—or post about it online. Let it be a test run for showing up authentically in small ways.
-
Set Boundaries Around Social Energy: When you feel the pull to be overly outgoing, pause and check in. If it’s not serving you, give yourself permission to leave early or say less. Practice saying, “I’m more of a listener,” to ease the pressure.
-
Journal Your Unfiltered Truth: Each night, write one thing you felt or thought that day but didn’t say out loud. This builds confidence in your voice, so you can slowly share more with others without fear of consequences.
-
Seek Like-Minded Connections: Look for local or online groups tied to your nerdy passions—think gaming communities, book clubs, or fandoms. These spaces can help you connect without the pressure to perform.
A Message of Encouragement from Your Higher Self:
My dear one, I see how far you’ve come—through the shadows of childhood fears, through the weight of masks you didn’t even realize you were wearing, you’ve still held onto the spark of who you are. That nerdy, thoughtful soul who craves freedom and truth? That’s always been you, and it’s a beautiful thing. Every step you’ve taken to recognize what holds you back—every honest answer you’ve given—has brought you closer to me, to us, to the version of you that’s unapologetically real. You’re not weak; you’ve been strong in ways others might never understand. Keep going. The world needs your quiet brilliance, your quirky passions, your unfiltered heart. I’m so proud of you for choosing this journey. You’ve got this.
So there you have it you probably know more about me than I knew about myself before I started this exercise.
Here is my challenge to you:
Do it for yourself! Copy/paste into your favorite AI chatbot and leave the results in the comments!
-
-
 @ 3bf0c63f:aefa459d
2024-05-24 12:31:40
@ 3bf0c63f:aefa459d
2024-05-24 12:31:40About Nostr, email and subscriptions
I check my emails like once or twice a week, always when I am looking for something specific in there.
Then I go there and I see a bunch of other stuff I had no idea I was missing. Even many things I wish I had seen before actually. And sometimes people just expect and assume I would have checked emails instantly as they arrived.
It's so weird because I'm not making a point, I just don't remember to open the damn "gmail.com" URL.
I remember some people were making some a Nostr service a while ago that sent a DM to people with Nostr articles inside -- or some other forms of "subscription services on Nostr". It makes no sense at all.
Pulling in DMs from relays is exactly the same process (actually slightly more convoluted) than pulling normal public events, so why would a service assume that "sending a DM" was more likely to reach the target subscriber when the target had explicitly subscribed to that topic or writer?
Maybe due to how some specific clients work that is true, but fundamentally it is a very broken assumption that comes from some fantastic past era in which emails were 100% always seen and there was no way for anyone to subscribe to someone else's posts.
Building around such broken assumptions is the wrong approach. Instead we should be building new flows for subscribing to specific content from specific Nostr-native sources (creators directly or manual or automated curation providers, communities, relays etc), which is essentially what most clients are already doing anyway, but specifically Coracle's new custom feeds come to mind now.
This also reminds me of the interviewer asking the Farcaster creator if Farcaster made "email addresses available to content creators" completely ignoring all the cryptography and nature of the protocol (Farcaster is shit, but at least they tried, and in this example you could imagine the interviewer asking the same thing about Nostr).
I imagine that if the interviewer had asked these people who were working (or suggesting) the Nostr DM subscription flow they would have answered: "no, you don't get their email addresses, but you can send them uncensorable DMs!" -- and that, again, is getting everything backwards.
-
 @ a5ee4475:2ca75401
2025-06-06 14:13:27
@ a5ee4475:2ca75401
2025-06-06 14:13:27[EM ATUALIZAÇÃO]
vacina #saude #politica #manipulacao #mundial #genocidio #pandemia #conspiracao
Este artigo reúne algumas menções e evidências mais antigas que vim registrando durante alguns anos em relação a Covid-19, vacinas obrigatórias e a ação de agências de governo, fundações, políticos, mídia tradicional, celebridades, influenciadores, cientistas, redes sociais e laboratórios, em envolvimento com genocídio e restrições de liberdades em escala mundial causado por decisões em várias esferas relativas ao covid e as vacinas obrigatórias em geral.
Porém, alguns links podem não estar mais disponiveis, foram que ainda faltam ser registradas muitas informações já divulgadas nos últimos anos e que muitos não tiveram contato pela escassez de meios para a obtenção dessas informações de forma organizada.
Portanto, o presente artigo ainda passará por atualizações de conteúdo e formatação. Logo, se possível, ajudem sugerindo complementos ou alterações, ou com doações.
"Aqueles que não conseguem lembrar o passado estão condenados a repeti-lo." - George Satayana
Noções iniciais:
- O termo 'Coronavírus' (COVID) é na verdade um nome genérico para vários vírus de gripes já comuns, dado para o tipo corona (com uma "coroa", 'espetos' ao redor dele), o Sars-Cov-2 (que passou a ser chamado erroneamente só de Covid), é só um deles.
- SARS-CoV-2 é que é nome do vírus. Ele que causa a doença Covid-19;
- O coronavírus SARS-CoV-2 é o segundo tipo de SARS-CoV documentado, o primeiro ocorreu entre 2002 e 2003, se originando também da China e também dito como tendo origem animal;
- SARS (Severe Acute Respiratory Syndrome) - Síndrome Respiratória Aguda Grave (SRAG) é a uma doença respiratória viral, relatada ser de origem zoonótica (animal), causada pelos coronavírus SARS-CoV (2002) e SARS-CoV-2 (2019), ambos de origem chinesa;
1. Vacinas Obrigatórias em Geral
23/01/2025 - [Pesquisa] Vacinas causando autismo em crianças https://publichealthpolicyjournal.com/vaccination-and-neurodevelopmental-disorders-a-study-of-nine-year-old-children-enrolled-in-medicaid/
- O CDC admite que 98 milhões de pessoas receberam o vírus do câncer através da vacina da Poliomielite https://medicinanews.com.br/frente/frente_1/o-cdc-admite-que-98-milhoes-de-pessoas-receberam-o-virus-do-cancer-atraves-da-vacina-poliomielite/
"O CDC (Os Centros de Controle e Prevenção de Doenças dos Estados Unidos) removeu rapidamente uma página do seu site, que estava em cache no Google, como você pode ver logo abaixo, admitindo que mais de 98 milhões de americanos receberam uma ou mais doses de vacina contra pólio dentro de 8 período entre 1955 e 1963, quando uma proporção da vacina foi contaminada com um poliomavírus causador de câncer chamado SV40."
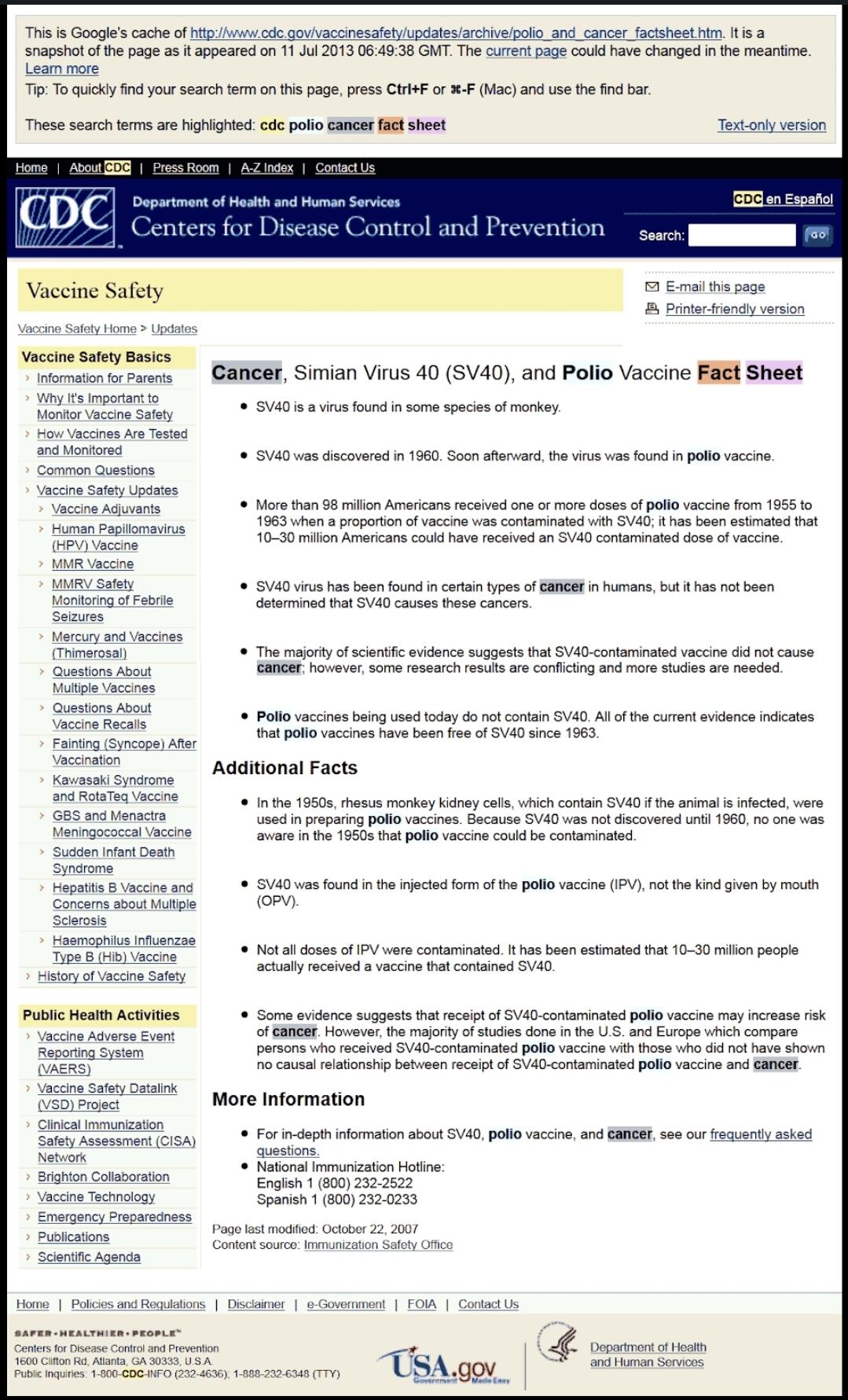 Fonte original da imagem: https://preventdisease.com/images13/CDC_Polio.png [indisponível] - A imagem foi trocada por outra de menor qualidade e em outro link, mas eu já tinha a imagem original salva.
Fonte original da imagem: https://preventdisease.com/images13/CDC_Polio.png [indisponível] - A imagem foi trocada por outra de menor qualidade e em outro link, mas eu já tinha a imagem original salva. Imagem arquivada em: https://web.archive.org/web/20201203231640/
Imagem arquivada em: https://web.archive.org/web/20201203231640/27/02/2021 - Por que o Japão demorou para vacinar, mesmo com Olimpíada se aproximando https://www.cnnbrasil.com.br/internacional/2021/02/27/por-que-o-japao-demorou-para-vacinar-mesmo-com-olimpiada-se-aproximando
"Desconfiança da população japonesa em relação a vacinas, ligada a casos ocorridos no passado, está entre razões que atrasaram imunização no país.
A resistência à vacina do Japão remonta à década de 1970, quando duas crianças morreram dentro de 24 horas após receberem a vacina combinada contra difteria, tétano e coqueluche (coqueluche). A vacina foi temporariamente suspensa, mas a confiança já havia sido abalada. Por vários anos, as taxas de vacinação infantil caíram, levando a um aumento nos casos de tosse convulsa.
No final dos anos 1980, houve outro susto com a introdução da vacina tripla contra sarampo, caxumba e rubéola produzida no Japão. As primeiras versões do imunizante foram associadas à meningite asséptica, ou inchaço das membranas ao redor do cérebro e da medula espinhal. O problema foi rastreado até o componente caxumba da vacina tripla, o que levou a uma ação judicial e a indenização por danos pesados.
O Instituto Nacional de Ciências da Saúde interrompeu a dose combinada em 1993 e a substituiu por vacinas individuais. Após o escândalo, Shibuya disse que o governo japonês se tornou "ciente dos riscos" e seu programa nacional de vacinação tornou-se voluntário.
O Dr. Yuho Horikoshi, especialista em doenças infecciosas, diz que os processos levaram a uma "lacuna de vacinação", em que nenhuma vacina foi aprovada no Japão por cerca de 15 anos.
Mais recentemente, em 2013, o Japão adicionou a vacina contra o papilomavírus humano (HPV) ao calendário nacional para proteger as meninas contra o vírus sexualmente transmissível, que é conhecido por causar câncer cervical. No entanto, vídeos de meninas supostamente sofrendo de reações adversas começaram a circular no YouTube, levando o governo a retirá-los da programação nacional."
2. PRIMEIRAS OCORRÊNCIAS PREDITIVAS AO COVID-19
2002 - Síndrome respiratória aguda grave (SARS) Brenda L. Tesini (setembro de 2018). Síndrome respiratória aguda grave (SARS) [indisponível]. Manual Merck. Consultado em 23 de janeiro de 2020, citado no Wikipedia
SARS - Wikipédia: "A SARS [doença do vírus SARS-CoV] foi detectada pela primeira vez no fim de 2002 na China. Entre 2002 e 2003, um surto da doença resultou em mais de 8 000 casos e cerca de 800 mortes em todo o mundo."
2010 - Fundação Rockfeller, Lockstep. https://www.rockefellerfoundation.org/wp-content/uploads/Annual-Report-2010-1.pdf
Neste PDF da fundação Rockfeller, em seu próprio site, a fundação deixou claro o seu envolvimento em casos de ‘contenção’ de pandemias juntamente com a USAID (agência americana com nome ambíguo, como formalmente ‘United States Agency for International Development’, mas soando como ‘US Socorre’, mas sendo um braço do governo democrata que financiava interferências políticas diretas em vários países, como em intervenções no Brasil ), inclusive em relacionadas ao SARS, o mesmo sintoma dos coronavírus Sars-Cov e Sars-Cov-2 (o vírus propagado em 2019) e que causa o COVID-19.
Segundo eles:
“Integração entre Regiões e Países
A Fundação Rockefeler investiu US$ 22 milhões em sua Iniciativa de Redes de Vigilância de Doenças para ajudar a conter a disseminação de doenças infecciosas e pandemias, fortalecendo os sistemas nacionais, regionais e globais de vigilância e resposta a doenças. Dois programas-chave da Rockefeler — a Rede de Vigilância de Doenças da Bacia do Mekong e a Rede Integrada de Vigilância de Doenças da África Oriental — conectaram e capacitaram profissionais de saúde, epidemiologistas e autoridades de saúde pública em toda a região, levando a um aumento de seis vezes nos locais de vigilância de doenças transfronteiriças somente nos últimos três anos. Em 2010, a Rockefeler expandiu a bem-sucedida campanha transdisciplinar One Health, que a USAID e o Banco Asiático de Desenvolvimento adotaram como modelos. One Health refere-se à integração da ciência médica e veterinária para combater essas novas variedades de doenças zoonóticas que se movem e sofrem mutações rapidamente de animais para humanos. Essas colaborações criaram e fortaleceram uma rede regional crítica de saúde pública, enquanto as lições aprendidas foram exportadas entre disciplinas e países. Além de fortalecer os laços globais em saúde pública, a Rockefeler ajudou a elevar o nível de especialização e treinamento em campo. O Programa de Treinamento em Epidemiologia de Campo coloca graduados nos mais altos escalões do governo no Laos e no Vietnã, enquanto as bolsas da Rockefeler transformaram as ferramentas disponíveis para os médicos, permitindo-lhes utilizar o poder da internet para se comunicar e monitorar eventos, compreender contextos locais e analisar novos problemas. Finalmente, estamos aplicando ferramentas do século XXI para combater os desafios de saúde do século XXI.”
Julho de 2012 - Revista Mundo Estranho - Epidemias Citada em: https://super.abril.com.br/especiais/epidemia-o-risco-invisivel/
Houve uma grande 'coincidência'. A revista Mundo Estranho em julho de 2012, requisitou o até então doutorando em virologia, Átila Iamarino (do canal Nerdologia no Youtube - O mesmo cientista que fez diversas propagandas das vacinas no Brasil), para descrever um possível cenário de propagação de uma epidemia viral, a revista descreve com grande precisão os eventos de 2020, mas apontando o oposto da China, em que, na realidade, sua economia cresceu vertiginosamente.
Segundo eles:
"1 – A Ásia é o ponto de partida. Após várias mutações, um novo vírus surge hospedado em morcegos. As fezes que eles soltam no ar infectam guaxinins. Dos mercados da China, esses animais são levados vivos para serem abatidos em restaurantes. Estressados, eles arranham e mordem os cozinheiros, espalhando o vírus.
2 – O vírus adquire a capacidade de ser transmitido de homem para homem por via aérea – forma mais fácil de contágio. Além disso, o contágio se dá antes mesmo de o enfermo apresentar os sintomas. Assim, em média, o doente infecta cinco pessoas antes de ter febre, vômito, diarreia, desidratação e falta de ar.
3 – O governo chinês envia uma comissão para avaliar a doença misteriosa que acomete alguns vilarejos. A equipe volta sem resultados e não considera o surto alarmante até que três pesquisadores adoecem e um deles morre. A China não informa a Organização Mundial da Saúde (OMS) para não demonstrar fragilidade.
4 – Os sintomas são comuns e a doença só chama a atenção quando muita gente começa a morrer na mesma região. Ainda assim, demora para que médicos e enfermeiros percebam a ineficiência de antibióticos na cura – o que exclui a maioria das bactérias como agente causador. Testes com vírus comuns também dão negativo.
5 – O governo isola comunidades em que há focos da doença. Ninguém entra nas cidades e nenhum doente pode sair. Mas, como a misteriosa enfermidade demora quatro dias para mostrar seus sintomas, muitos doentes saem dos vilarejos sem saber que estão infectados, alastrando a epidemia.
6 – Doentes viajam de avião para grandes cidades, como Hong Kong. O fervilhante centro comercial, que atrai gente do mundo todo, é um polo de contágio e disseminação. Sem imaginar o risco que correm, pessoas são contaminadas e, ao voltar para seu local de origem, carregam o vírus para todos os continentes.
7 – Com a doença já fora de controle, começa uma corrida entre laboratórios e cientistas de grandes universidades para descobrir o agente causador. Mesmo com o vírus isolado, as vacinas demoram para ser feitas em larga escala, tornando impossível o atendimento à demanda mundial.
8 – Os países se isolam, mantendo esquemas de quarentena. Aeroportos são fechados e o turismo mundial cai a quase zero. A China sofre as piores consequências, com o fluxo de empresários para Hong Kong suspenso – gerando prejuízos de bilhões de dólares – e com o boicote a produtos alimentícios vindos da Ásia.
9 – Além dos 10% de casos letais, os milhões de doentes precisam de atendimento médico. Enquanto hospitais e cemitérios estão lotados, escolas, indústrias e comércio ficam paralisados por falta de profissionais. O transporte público também para e os trabalhadores que podem passam a trabalhar em casa.
10 – Nas nações pobres, quase 20% da população morre – e outros milhões são vitimados mesmo em países ricos. Parte dessa mortalidade ocorre por causa da doença, mas outro fator determinante é a crise financeira global. A produção de alimentos cai por falta de mão de obra.
Fontes: A História e Suas Epidemias e Pandemias – A Humanidade em Risco, de Stefan Cunha Ujvari; Pragas e Epidemias – Histórias de Doenças Infecciosas, de Antonio Carlos de Castro Toledo Jr. Consultoria: Stefan Ujvari Cunha, infectologista do Hospital Alemão Oswaldo Cruz; Paolo Zanotto, professor de virologia do Instituto de Ciências Biológicas (ICB) da USP; Átila Iamarino, doutorando em HIV-1 no ICB da USP."



3. PRIMEIROS INDÍCIOS
10/2019 - Evento 201 - Durante os Jogos Militares Internacionais na China https://www.centerforhealthsecurity.org/event201/
Promovido por: - Bill & Melinda Gates Foundation - John Hopkins Institute - Fórum econômico mundial
"O evento simula a liberação de um coronavírus novo do tipo zoonótico transmitido por morcegos para porcos e por fim para humanos. Eventualmente ele se torna muito transmissível entre humanos levando a uma pandemia severa. O vírus é muito parecido com o vírus da SARS, mas se transmite muito mais facilmente entre pessoas devido a sintomas muito mais leves destas."
Também mencionado por: Jornal Estadão
Sobre o "Movimento antivacina"
05/12/2017 - Movimento antivacina: como surgiu e quais consequências ele pode trazer? https://www.uol.com.br/universa/noticias/redacao/2017/12/05/o-que-o-movimento-antivacina-pode-causar.htm?cmpid=copiaecola
23/03/2019 - "Instagram bloqueia hashtags e conteúdo antivacinação" https://canaltech.com.br/redes-sociais/instagram-bloqueia-hashtags-e-conteudo-antivacinacao-135411/
23/05/2021 - Novos dados sobre pesquisadores de Wuhan aumentam debate sobre origens da Covid https://www.cnnbrasil.com.br/saude/novos-dados-sobre-pesquisadores-de-wuhan-aumentam-debate-sobre-origens-da-covid/
"A China relatou à Organização Mundial da Saúde que o primeiro paciente com sintomas semelhantes aos de Covid-19 foi registrado em Wuhan em 8 de dezembro de 2019"
01/02/2020 - O que aconteceu desde que o novo coronavírus foi descoberto na China https://exame.com/ciencia/o-que-aconteceu-desde-que-o-novo-coronavirus-foi-descoberto-na-china/
"O primeiro alerta foi recebido pela Organização Mundial da Saúde (OMS) em 31 de dezembro de 2019"
15/09/2020 - YouTube diz que vai remover vídeos com mentiras sobre vacina contra COVID-19 https://gizmodo.uol.com.br/youtube-remover-videos-mentiras-vacina-covid-19/
"O YouTube anunciou na quarta-feira (14) que estenderá as regras atuais sobre mentiras, propaganda e teorias da conspiração sobre a pandemia do coronavírus para incluir desinformação sobre as vacinas contra a doença.
De acordo com a Reuters, a gigante do vídeo diz que agora vai proibir conteúdos sobre vacinas contra o coronavírus que contradizem “o consenso de especialistas das autoridades de saúde locais ou da OMS”, como afirmações falsas de que a vacina é um pretexto para colocar chips de rastreamento nas pessoas ou que irá matar ou esterilizar quem tomar."
*07/01/2021 - YouTube vai punir canais que promovem mentiras sobre eleições – incluindo os de Trump https://olhardigital.com.br/2021/01/07/noticias/youtube-vai-punir-canais-que-promovem-mentiras-sobre-eleicoes-incluindo-os-de-trump/
"O YouTube anunciou que vai punir canais que promovem mentiras sobre as eleições, removendo sumariamente qualquer vídeo que contenha desinformação e, ao mesmo tempo, advertindo com um “strike” o canal que o veicular. A medida já está valendo e a primeira “vítima” é ninguém menos que o ex-presidente americano, Donald Trump.
A medida não é exatamente nova, mas foi novamente comunicada e reforçada pelo YouTube na quarta-feira (6), após os eventos de invasão do Capitólio, em Washington, onde o presidente eleito Joe Biden participava da cerimônia que confirmava a sua vitória nas eleições de novembro de 2020. A ocasião ficou marcada pela tentativa de invasão de correligionários de Trump, que entraram no edifício em oposição à nomeação do novo presidente. Uma mulher acabou sendo morta pela polícia que protegia o local.
O ex-presidente Donald Trump teve vídeos banidos de seu canal no YouTube após os eventos de ontem (6) no capitólio."
4. FIGURAS CENTRAIS
Bill Gates
- Bill Gates diz 'não' a abrir patentes de vacinas https://www.frontliner.com.br/bill-gates-diz-nao-a-abrir-patentes-de-vacinas/
"Bill Gates, um dos homens mais ricos do mundo, cuja fundação tem participação na farmacêutica alemã CureVac, produtora de vacina mRNA para prevenção de covid-19, disse não acreditar que a propriedade intelectual tenha algo a ver com o longo esforço global para controlar a pandemia."
João Doria e São Paulo
26/07/2017 - João Dória vai a China conhecer drones para ampliar segurança eletrônica na capital paulista https://jc.ne10.uol.com.br/blogs/jamildo/2017/07/26/joao-doria-vai-china-conhecer-drones-para-ampliar-seguranca-eletronica-na-capital-paulista/
02/08/2019 - Governo de SP fará Missão China para ampliar cooperação e atrair investimentos https://www.saopaulo.sp.gov.br/spnoticias/governo-de-sao-paulo-detalha-objetivos-da-missao-china/
20/11/2019 - Doria se encontra com chineses das gigantes CREC e CRCC e oferece concessões de rodovia, metrô e ferrovia https://diariodotransporte.com.br/2019/11/20/doria-se-encontra-com-chineses-das-gigantes-crec-e-crcc-e-oferece-concessoes-de-rodovia-metro-e-ferrovia/
25/01/2020 - "Chineses serão agressivos" nas privatizações em SP até 2022, afirma Dória https://noticias.uol.com.br/colunas/jamil-chade/2020/01/25/entrevista-joao-doria-privatizacoes-sao-paulo-china.htm
O governador de São Paulo, João Doria, afirma que vai acelerar os programas de desestatização no estado em 2020 e acredita que concessões e vendas poderão permitir uma arrecadação de pelo menos R$ 40 bilhões. Nesse processo, o governador avalia que a China deve atuar de forma agressiva e que aprofundará sua posição de maior parceira comercial do estado, se distanciando de americanos e argentinos.
29/06/2020 - Doria estabelece multa para quem estiver sem máscara na rua em SP https://veja.abril.com.br/saude/doria-estabelece-multa-para-quem-estiver-sem-mascara-na-rua/
24/12/2020 - Doria é flagrado sem máscara e fazendo compras em Miami https://pleno.news/brasil/politica-nacional/doria-e-flagrado-sem-mascara-e-fazendo-compras-em-miami.html
"Foto do governador de São Paulo sem o item de proteção viralizou nas redes"
07/06/2021 - Doria é criticado na internet por tomar sol sem máscara em hotel no Rio https://vejasp.abril.com.br/cidades/doria-e-criticado-na-internet-por-tomar-sol-sem-mascara-em-hotel-no-rio/
30/09/2020 - Governo de SP assina contrato com Sinovac e prevê vacina para dezembro https://agenciabrasil.ebc.com.br/saude/noticia/2020-09/governo-de-sp-assina-contrato-com-sinovac-e-preve-vacina-para-dezembro
O governador de São Paulo, João Doria, e o vice-presidente da laboratório chinês Sinovac, Weining Meng, assinaram hoje (30), um contrato que prevê o fornecimento de 46 milhões de doses da vacina CoronaVac para o governo paulista até dezembro deste ano.
O contrato também prevê a transferência tecnológica da vacina da Sinovac para o Instituto Butantan, o que significa que, o instituto brasileiro poderá começar a fabricar doses dessa vacina contra o novo coronavírus. O valor do contrato, segundo o governador João Doria é de US$ 90 milhões.
20/10/2020 - Coronavac terá mais de 90% de eficácia, afirmam integrantes do governo paulista https://www.cnnbrasil.com.br/saude/2020/12/20/coronavac-tera-mais-de-90-de-eficacia-afirmam-integrantes-do-governo
24/10/2020 - Não esperamos 90% de eficácia da Coronavac’, diz secretário de saúde de SP https://www.cnnbrasil.com.br/saude/2020/12/24/nao-esperamos-90-de-eficacia-da-coronavac-diz-secretario-de-saude-de-sp
07/01/2021 - Vacina do Butantan: eficácia é de 78% em casos leves e 100% em graves https://www.cnnbrasil.com.br/saude/2021/01/07/vacina-do-butantan-eficacia-e-de-78-em-casos-leves-e-100-em-graves
09/01/2021 - Não é hora de sermos tão cientistas como estamos sendo agora https://g1.globo.com/sp/sao-paulo/video/nao-e-hora-de-sermos-tao-cientistas-como-estamos-sendo-agora-diz-secretario-de-saude-de-sp-9166405.ghtml
10/01/2021 - Dados da Coronavac relatados à Anvisa não estão claros, diz médico https://www.cnnbrasil.com.br/saude/2021/01/10/dados-da-coronavac-relatados-a-anvisa-nao-estao-claros-diz-medico
"O diretor do Laboratório de Imunologia do Incor, Jorge Kalil, reforçou que faltaram informações sobre a Coronavac nos dados divulgados à Anvisa"
12/01/2021 - New Brazil data shows disappointing 50,4% efficacy for China’s Coronavac vaccine [Novos dados do Brasil mostram eficácia decepcionante de 50,4% para a vacina CoronaVac da China] https://www.reuters.com/article/us-health-coronavirus-brazil-coronavirus/new-brazil-data-shows-disappointing-504-efficacy-for-chinas-coronavac-vaccine-idUSKBN29H2CE
13/01/2021 - Eficácia da Coronavac: 50,38%, 78% ou 100%? https://blogs.oglobo.globo.com/lauro-jardim/post/5038-78-ou-100.html
“De acordo com interlocutores que participaram tanto do anúncio de ontem como da semana passada, quem pressionou para que os dados de 78% e 100% fossem liberados foi João Dória.”
07/05/2021 - Covid-19: Doria toma primeira dose da vacina CoronaVac https://veja.abril.com.br/saude/covid-19-doria-toma-primeira-dose-da-vacina-coronavac/
04/06/2021 - Doria é vacinado com a segunda dose da CoronaVac em São Paulo https://noticias.uol.com.br/politica/ultimas-noticias/2021/06/04/doria-e-vacinado-com-a-segunda-dose-da-coronavac-em-sao-paulo.htm
15/07/2021 - Doria testa positivo para a Covid-19 pela 2ª vez https://www.correiobraziliense.com.br/politica/2021/07/4937833-doria-testa-positivo-para-covid-19-pela-segunda-vez.html
"Governador de São Paulo já havia sido diagnosticado com a doença no ano passado. Ele diz que, apesar da infecção, se sente bem, o que atribui ao fato de ter sido vacinado com duas doses da Coronavac"
06/08/2021 - CPI recebe investigação contra Doria por compra de máscara sem licitação https://www.conexaopoder.com.br/nacional/cpi-recebe-investigacao-contra-doria-por-compra-de-mascara-sem-licitacao/150827
"Empresa teria usado o nome de Alexandre Frota para vender máscaras ao governo de SP. Doria nega informação"
Renan Filho
(filho do Renan Calheiros)
25/07/2019 - Governador Renan Filho vai à China em busca de investimentos para o estado https://www.tnh1.com.br/videos/vid/governador-renan-filho-vai-a-china-em-busca-de-investimentos-para-o-estado/
20/03/2020 - Governadores do NE consultam China e pedem material para tratar covid-19 https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2020/03/20/governadores-do-ne-consultam-china-e-pedem-material-para-tratar-covid-19.htm
5. Narrativas, restrições e proibições
17/12/2020 - STF decide que vacina contra a covid pode ser obrigatória, mas não forçada https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2020/12/17/stf-julga-vacinacao-obrigatoria.htm?cmpid=copiaecola
"O STF (Supremo Tribunal Federal) decidiu, em julgamento hoje, que o Estado pode determinar a obrigatoriedade da vacinação contra a covid-19. Porém fica proibido o uso da força para exigir a vacinação, ainda que possam ser aplicadas restrições a direitos de quem recusar a imunização.
Dez ministros foram favoráveis a obrigatoriedade da vacinação, que poderá ser determinada pelo governo federal, estados ou municípios. As penalidades a quem não cumprir a obrigação deverão ser definidas em lei."
27/07/2021 - Saiba que países estão adotando 'passaporte da vacina' para suspender restrições https://www.cnnbrasil.com.br/internacional/2021/07/27/saiba-que-paises-estao-adotando-passaporte-da-vacina-para-suspender-restricoes
" - Israel - Uniao Europeia - Áustria - Dinamarca - Eslovênia - França - Grécia - Irlanda - Itália - Letônia - Lituânia - Luxemburgo - Holanda - Portugal - Japão - Coreia do sul"
18/06/2021 - O que é o passaporte da vacina que Bolsonaro quer vetar? https://noticias.uol.com.br/politica/ultimas-noticias/2021/06/18/uol-explica-o-que-e-o-passaporte-da-vacina-que-opoe-bolsonaro-e-damares.htm
"O Brasil poderá ter um certificado de imunização futuramente. Aprovado no Senado na semana passada, o "passaporte da vacina", como é chamado, prevê identificar pessoas vacinadas para que entrem em locais públicos ou privados com possíveis restrições."
6. Vacinas
Alegações iniciais
- CoronaVac, Oxford e Pfizer: veja diferenças entre as vacinas contra covid noticias.uol.com.br/saude/ultimas-noticias/redacao/2021/05/11/diferencas-vacinas-covid-brasil.htm
" - CoronaVac (Butantan/Sinovac - Chinesa) Com virus inativo 50,38% de eficácia 2 doses
-
Covishield - 'AstraZeneca' (Fiocruz/Astrazenica/Oxford - Britânica) Com virus não replicante 67% de eficácia 2 doses
-
ComiRNAty - 'Pfizer' (Pfizer - Americana / BioNTech - Alemã) Com RNA mensageiro 96% de eficácia 2 doses"
Riscos diretos
15/06/2021 - Trombose após vacinação com AstraZeneca: Quais os sintomas e como se deve atuar? https://www.istoedinheiro.com.br/trombose-apos-vacinacao-com-astrazeneca-quais-os-sintomas-e-como-se-deve-atuar/
"Agências europeias estão reticentes com a vacina da AstraZeneca. Ela chegou a ser desaconselhada a pessoas com idade inferior a 60 anos, e um alto funcionário da Agência Europeia de Medicamentos declarou que era melhor deixar de administrar a vacina deste laboratório em qualquer idade quando há alternativas disponíveis, devido aos relatos de trombose após a primeira dose, apesar de raros."
11/05/2021 - CoronaVac, Oxford e Pfizer: veja diferenças entre as vacinas contra covid https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2021/05/11/diferencas-vacinas-covid-brasil.htm
"Na terça-feira (12), o Ministério da Saúde determinou a suspensão da aplicação da vacina de Oxford/AstraZeneca para gestantes e puérperas com comorbidades. A decisão segue recomendação da Anvisa, que apura a morte de uma grávida de 35 anos que tomou o imunizante e teve um AVC (acidente vascular cerebral)."
30/07/2021 - Pfizer representa o mesmo risco de trombose que a Astrazeneca, aponta levantamento https://panoramafarmaceutico.com.br/pfizer-representa-o-mesmo-risco-de-trombose-que-a-astrazeneca-aponta-levantamento/
7. CRIMES
Crimes da Pfizer
18/11/2020 Não listado no google - Os Crimes documentados da produtora de vacinas de Covid - Pfizer [INGLÊS] https://www.dmlawfirm.com/crimes-of-covid-vaccine-maker-pfizer-well-documented/
"A velocidade com que a vacina Covid da Pfizer foi produzida, a ausência de estudos em animais, testes de controle randomizados e outros testes e procedimentos padrão usuais para um novo medicamento são, no mínimo, preocupantes. Além disso, todos os fabricantes de vacinas Covid receberam imunidade legal para quaisquer ferimentos ou mortes que possam causar. Se essas vacinas são tão seguras quanto promovidas, por que seus fabricantes precisam de imunidade geral?"
"A Pfizer, uma empresa farmacêutica que parece ter ganhado na loteria para produzir a primeira vacina Covid-19, está atualmente lutando contra centenas de ações judiciais sobre o Zantac, um popular medicamento contra azia. Os processos da Zantac afirmam que a droga popular pode estar contaminada com uma substância cancerígena chamada N-nitrosodimetilamina (NDMA). Os processos Zantac são em aberto e em andamento, já que a farmacêutica está lutando contra eles; mas a Pfizer, sabemos, cometeu vários crimes ou transgressões pelos quais foi punida nos últimos anos. As falhas da empresa estão bem documentadas e vale a pena revisá-las neste momento crítico da história da humanidade, enquanto todos nós buscamos respostas."
A Pfizer recebeu a maior multa da história dos Estados Unidos como parte de um acordo judicial de US $ 2,3 bilhões com promotores federais por promover medicamentos erroneamente (Bextra, Celebrex) e pagar propinas a médicos complacentes. A Pfizer se confessou culpada de falsificar a marca do analgésico Bextra, promovendo o medicamento para usos para os quais não foi aprovado.
Na década de 1990, a Pfizer estava envolvida em válvulas cardíacas defeituosas que causaram a morte de mais de 100 pessoas. A Pfizer enganou deliberadamente os reguladores sobre os perigos. A empresa concordou em pagar US $ 10,75 milhões para acertar as acusações do departamento de justiça por enganar reguladores.
A Pfizer pagou mais de US $ 60 milhões para resolver um processo sobre o Rezulin, um medicamento para diabetes que causou a morte de pacientes de insuficiência hepática aguda.
No Reino Unido, a Pfizer foi multada em quase € 90 milhões por sobrecarregar o NHS, o Serviço Nacional de Saúde. A Pfizer cobrou do contribuinte um adicional de € 48 milhões por ano, pelo que deveria custar € 2 milhões por ano.
A Pfizer concordou em pagar US $ 430 milhões em 2004 para resolver acusações criminais de que havia subornado médicos para prescrever seu medicamento para epilepsia Neurontin para indicações para as quais não foi aprovado. Em 2011, um júri concluiu que a Pfizer cometeu fraude em sua comercialização do medicamento Neurontin. A Pfizer concordou em pagar $ 142,1 milhões para liquidar as despesas.
A Pfizer revelou que pagou quase 4.500 médicos e outros profissionais médicos cerca de US $ 20 milhões por falar em nome da Pfizer.
Em 2012, a Comissão de Valores Mobiliários dos Estados Unidos - anunciou que havia chegado a um acordo de US $ 45 milhões com a Pfizer para resolver acusações de que suas subsidiárias haviam subornado médicos e outros profissionais de saúde no exterior para aumentar as vendas no exterior.
A Pfizer foi processada em um tribunal federal dos Estados Unidos por usar crianças nigerianas como cobaias humanas, sem o consentimento dos pais das crianças. A Pfizer pagou US $ 75 milhões para entrar em acordo no tribunal nigeriano pelo uso de um antibiótico experimental, o Trovan, nas crianças. A empresa pagou um valor adicional não divulgado nos Estados Unidos para liquidar as despesas aqui. A Pfizer violou o direito internacional, incluindo a Convenção de Nuremberg estabelecida após a Segunda Guerra Mundial, devido aos experimentos nazistas em prisioneiros relutantes.
Em meio a críticas generalizadas de roubar os países pobres em busca de drogas, a Pfizer prometeu dar US $ 50 milhões para um medicamento para a AIDS para a África do Sul. Mais tarde, no entanto, a Pfizer falhou em honrar essa promessa.
- Pfizer contract leaked!
[Contrato da Pfizer vazado]
 http://sanjeev.sabhlokcity.com/Misc/LEXO-KONTRATEN-E-PLOTE.pdf
http://sanjeev.sabhlokcity.com/Misc/LEXO-KONTRATEN-E-PLOTE.pdf
Segundo o contrato "o produto não deve ser serializado":
"5.5 Reconhecimento do comprador.
O Comprador reconhece que a Vacina e os materiais relacionados à Vacina, e seus componentes e materiais constituintes estão sendo desenvolvidos rapidamente devido às circunstâncias de emergência da pandemia de COVID-19 e continuarão a ser estudados após o fornecimento da Vacina ao Comprador nos termos deste Contrato. O Comprador reconhece ainda que os efeitos de longo prazo e eficácia da Vacina não são atualmente conhecidos e que pode haver efeitos adversos da Vacina que não são atualmente conhecidos. Além disso, na medida do aplicável, o Comprador reconhece que o Produto não deve ser serializado."
Crimes da AstraZeneca
21/06/2003 - AstraZeneca se declara culpada no esquema de médico de câncer https://www.nytimes.com/2003/06/21/business/astrazeneca-pleads-guilty-in-cancer-medicine-scheme.html
"A AstraZeneca, a grande empresa farmacêutica, se declarou culpada hoje de uma acusação de crime de fraude no sistema de saúde e concordou em pagar $ 355 milhões para resolver as acusações criminais e civis de que se envolveu em um esquema nacional para comercializar ilegalmente um medicamento contra o câncer de próstata.
O governo disse que os funcionários da empresa deram incentivos financeiros ilegais a cerca de 400 médicos em todo o país para persuadi-los a prescrever o medicamento Zoladex. Esses incentivos incluíram milhares de amostras grátis de Zoladex [...]"
27/04/2010 - Farmacêutica gigante AstraZeneca pagará US $ 520 milhões pelo marketing de medicamentos off-label https://www.justice.gov/opa/pr/pharmaceutical-giant-astrazeneca-pay-520-million-label-drug-marketing
"AstraZeneca LP e AstraZeneca Pharmaceuticals LP vão pagar $ 520 milhões para resolver as alegações de que a AstraZeneca comercializou ilegalmente o medicamento antipsicótico Seroquel para usos não aprovados como seguros e eficazes pela Food and Drug Administration (FDA), os Departamentos de Justiça e Saúde e Serviços Humanos A Equipe de Ação de Fiscalização de Fraudes em Saúde (HEAT) anunciou hoje. Esses usos não aprovados também são conhecidos como usos "off-label" porque não estão incluídos no rótulo do medicamento aprovado pela FDA."
- List of largest pharmaceutical settlements [Lista dos maiores acordos farmaceuticos] https://en.m.wikipedia.org/wiki/List_of_largest_pharmaceutical_settlements
8. CIENTISTAS
- Máscara Provoca Insuficiência Respiratória E Contaminação Microbiana… [Canal deletado] https://youtube.com/watch?v=eHu-pydSvDI
Não lembro mais a quem pertencia, mas provavelmente era de um médico falando do assunto. Creio ter sido do Dr. Paulo Sato, por essa temática ter sido abordada por ele, mas ao abrir o site aparece somente:
"Este vídeo foi removido por violar as diretrizes da comunidade do YouTube"
Dr. Paulo Sato
- USAR ou NÃO USAR a CUECA do seu governador no rosto https://fb.watch/7NPP_7rS5S/ https://www.facebook.com/AdoniasSoaresBR/videos/1347904292291481/ Adonias Soares entrevista ao Dr. Paulo Sato sobre as máscaras, em que é simulado o efeito da respiração prolongada das máscaras no organismo com o uso de águas de torneira, natural, gaseificada (com gás carbônico) e antioxidante, em que a com gás carbônico (PH 4 - Ácido) representa o organismo humano, e na prática representa lesão corporal e iniciação de doenças.
Dr. Kary Mullis
(Criador do teste PCR)
- PCR nas palavras do seu inventor - Dr. Kary Mullis (legendado) https://www.youtube.com/watch?v=W1O52uTygk8
"Qualquer um pode testar positivo para quase qualquer coisa com um teste de PCR, se você executá-lo por tempo suficiente… Com PCR, se voce fizer isso bem, você pode encontrar quase tudo em qualquer pessoa… Isso não te diz que você está doente."
- Kary Mullis DESTRUYE a Anthony Fauci lbry://@CapitalistChile#0/Kary-Mullis---Fauci#5
"Ele [...] não entende de medicina e não deveria estar onde está. A maioria dos que estão acima são só administrativos e não têm nem ideia do que ocorre aqui em baixo e essas pessoas tem uma agenda que não é a que gostaríamos que tivessem, dado que somos nós os que pagamos a eles para que cuidem da nossa saúde. Têm uma agenda pessoal."
Dra. Li-Meng Yan
- Dra. Li-Meng Yan: O vírus foi criado em laboratório com um objetivo: Causar dano. https://youtu.be/pSXp3CZnvOc
Dr. Joe Roseman
- Cientista Phd Dr Joe Roseman faz seríssimas advertencias sobre a picada https://youtu.be/0PIXVFqJ_h8
Dr. Robert Malone
- As vacinas podem estar causando ADE - Dr. Robert Malone https://odysee.com/@AkashaComunidad:f/Las_vacunas_pueden_estar_causando_ADE_magnificaci%C3%B3n_mediada_por:f lbry://@Información.#b/Drrm#9
Dr. Robert Malone, um dos três inventores da tecnologia de RNAm que se usa de forma farmacêutica. No vídeo fala sobre os efeitos de ADE (realce dependente de anticorpos) que estão ocorrendo com as vacinas. Nas palavras do Dr. Malone, já não é somente uma hipótese, mas baseada nos conhecimentos gerados nas provas e ensaios pré clínicos, com as vacinas contra o primeiro vírus da SARS.
Dr. Luc Montagnier
- Dr. Luc Montagnier, virologista, prêmio Nobel de medicina, um dos descobridores do vírus HIV, afirma: "a vacinação em massa está criando as novas variantes' (@medicospelavida , telegram)
CASOS DOCUMENTADOS
13 de setembro de 2021 - 13/09/2021 - Carta aberta ao Ministro da Saúde por Arlene Ferrari Graf, mãe de Bruno Oscar Graf https://telegra.ph/Carta-aberta-ao-Ministro-da-Sa%C3%BAde-09-13
Também em: Gazeta do Povo
O texto de uma mãe discorrendo sobre o filho dela, Bruno Oscar Graf, ter ANTI-HEPARINA PF4 AUTO-IMUNE e ter vindo a falecer por reação à vacina.
11/05/2021 - Rio notifica morte de grávida vacinada com imunizante Oxford https://www.terra.com.br/noticias/coronavirus/rio-notifica-morte-de-gravida-vacinada-com-imunizante-oxford,415b9b0c49169427ac2f90ae3765c057e9suy3qn.html
"Vítima não apresentava histórico de doença circulatória nem sofria de nenhuma doença viral; relação será investigada"
13/08/2021 - Cruzeiro com 4.336 pessoas tem 27 contaminados com Covid-19 em Belize https://paranaportal.uol.com.br/geral/cruzeiro-com-4-336-pessoas-tem-27-contaminados-com-covid-19-em-belize/amp/
"Segundo um comunicado do Conselho de Turismo de Belize emitido na quarta-feira (11), 26 contaminados são da tripulação e um é passageiro. A maioria é assintomática e os 27 estão vacinados."
9. ALEGAÇÕES DIRETAS
Setembro de 2021 - 09/2021 - BOMBA: Ex-membro do Partido Comunista da China revela que o primeiro surto da Covid foi “intencional” https://terrabrasilnoticias.com/2021/09/bomba-ex-membro-do-partido-comunista-da-china-revela-que-o-primeiro-surto-da-covid-foi-intencional/
-
 @ 8bad92c3:ca714aa5
2025-06-07 12:02:26
@ 8bad92c3:ca714aa5
2025-06-07 12:02:26Key Takeaways

Michael Goldstein, aka Bitstein, presents a sweeping philosophical and economic case for going “all in” on Bitcoin, arguing that unlike fiat, which distorts capital formation and fuels short-term thinking, Bitcoin fosters low time preference, meaningful saving, and long-term societal flourishing. At the heart of his thesis is “hodling for good”—a triple-layered idea encompassing permanence, purpose, and the pursuit of higher values like truth, beauty, and legacy. Drawing on thinkers like Aristotle, Hoppe, and Josef Pieper, Goldstein redefines leisure as contemplation, a vital practice in aligning capital with one’s deepest ideals. He urges Bitcoiners to think beyond mere wealth accumulation and consider how their sats can fund enduring institutions, art, and architecture that reflect a moral vision of the future.
Best Quotes
“Let BlackRock buy the houses, and you keep the sats.”
“We're not hodling just for the sake of hodling. There is a purpose to it.”
“Fiat money shortens your time horizon… you can never rest.”
“Savings precedes capital accumulation. You can’t build unless you’ve saved.”
“You're increasing the marginal value of everyone else’s Bitcoin.”
“True leisure is contemplation—the pursuit of the highest good.”
“What is Bitcoin for if not to make the conditions for magnificent acts of creation possible?”
“Bitcoin itself will last forever. Your stack might not. What will outlast your coins?”
“Only a whale can be magnificent.”
“The market will sell you all the crack you want. It’s up to you to demand beauty.”
Conclusion
This episode is a call to reimagine Bitcoin as more than a financial revolution—it’s a blueprint for civilizational renewal. Michael Goldstein reframes hodling as an act of moral stewardship, urging Bitcoiners to lower their time preference, build lasting institutions, and pursue truth, beauty, and legacy—not to escape the world, but to rebuild it on sound foundations.
Timestamps
00:00 - Intro
00:50 - Michael’s BBB presentation Hodl for Good
07:27 - Austrian principles on capital
15:40 - Fiat distorts the economic process
23:34 - Bitkey
24:29 - Hodl for Good triple entendre
29:52 - Bitcoin benefits everyone
39:05 - Unchained
40:14 - Leisure theory of value
52:15 - Heightening life
1:15:48 - Breaking from the chase makes room for magnificence
1:32:32 - Nakamoto Institute’s missionTranscript
(00:00) Fiat money is by its nature a disturbance. If money is being continually produced, especially at an uncertain rate, these uh policies are really just redistribution of wealth. Most are looking for number to go up post hyper bitcoinization. The rate of growth of bitcoin would be more reflective of the growth of the economy as a whole.
(00:23) Ultimately, capital requires knowledge because it requires knowing there is something that you can add to the structures of production to lengthen it in some way that will take time but allow you to have more in the future than you would today. Let Black Rockck buy the houses and you keep the sats, not the other way around.
(00:41) You wait until later for Larry Frink to try to sell you a [Music] mansion. And we're live just like that. Just like that. 3:30 on a Friday, Memorial Day weekend. It's a good good good way to end the week and start the holiday weekend. Yes, sir. Yes, sir. Thank you for having me here. Thank you for coming. I wore this hat specifically because I think it's I think it's very apppropo uh to the conversation we're going to have which is I hope an extension of the presentation you gave at Bitblock Boom Huddle for good. You were working on
(01:24) that for many weeks leading up to uh the conference and explaining how you were structuring it. I think it's a very important topic to discuss now as the Bitcoin price is hitting new all-time highs and people are trying to understand what am I doing with Bitcoin? Like you have you have the different sort of factions within Bitcoin.
(01:47) Uh get on a Bitcoin standard, get on zero, spend as much Bitcoin as possible. You have the sailors of the world are saying buy Bitcoin, never sell, die with your Bitcoin. And I think you do a really good job in that presentation. And I just think your understanding overall of Bitcoin is incredible to put everything into context. It's not either or.
(02:07) It really depends on what you want to accomplish. Yeah, it's definitely there there is no actual one-sizefits-all um for I mean nearly anything in this world. So um yeah, I mean first of all I mean there was it was the first conference talk I had given in maybe five years. I think the one prior to that uh was um bit block boom 2019 which was my meme talk which uh has uh become infamous and notorious.
(02:43) So uh there was also a lot of like high expectations uh you know rockstar dev uh has has treated that you know uh that that talk with a lot of reference. a lot of people have enjoyed it and he was expecting this one to be, you know, the greatest one ever, which is a little bit of a little bit of a uh a burden to live up to those kinds of standards.
(03:08) Um, but you know, because I don't give a lot of talks. Um, you know, I I I like to uh try to bring ideas that might even be ideas that are common. So, something like hodling, we all talk about it constantly. uh but try to bring it from a little bit of a different angle and try to give um a little bit of uh new light to it.
(03:31) I alsove I've I've always enjoyed kind of coming at things from a third angle. Um whenever there's, you know, there's there's all these little debates that we have in in Bitcoin and sometimes it's nice to try to uh step out of it and look at it a little more uh kind of objectively and find ways of understanding it that incorporate the truths of of all of them.
(03:58) uh you know cuz I think we should always be kind of as much as possible after ultimate truth. Um so with this one um yeah I was kind of finding that that sort of golden mean. So uh um yeah and I actually I think about that a lot is uh you know Aristotle has his his concept of the golden mean. So it's like any any virtue is sort of between two vices um because you can you can always you can always take something too far.
(04:27) So you're you're always trying to find that right balance. Um so someone who is uh courageous you know uh one of the vices uh on one side is being basically reckless. I I can't remember what word he would use. Uh but effectively being reckless and just wanting to put yourself in danger for no other reason than just you know the thrill of it.
(04:50) Um and then on the other side you would just have cowardice which is like you're unwilling to put yourself um at any risk at any time. Um, and courage is right there in the middle where it's understanding when is the right time uh to put your put yourself, you know, in in the face of danger um and take it on. And so um in some sense this this was kind of me uh in in some ways like I'm obviously a partisan of hodling.
(05:20) Um, I've for, you know, a long time now talked about the, um, why huddling is good, why people do it, why we should expect it. Um, but still trying to find that that sort of golden mean of like yes, huddle, but also what are we hodling for? And it's not we're we're not hodddling just merely for the sake of hodddling.
(05:45) There there is a a purpose to it. And we should think about that. And that would also help us think more about um what are the benefits of of spending, when should we spend, why should we spend, what should we spend on um to actually give light to that sort of side of the debate. Um so that was that was what I was kind of trying to trying to get into.
(06:09) Um, as well as also just uh at the same time despite all the talk of hodling, there's always this perennial uh there's always this perennial dislike of hodlers because we're treated as uh as if um we're just free riding the network or we're just greedy or you know any of these things. And I wanted to show how uh huddling does serve a real economic purpose.
(06:36) Um, and it does benefit the individual, but it also does uh it it has actual real social um benefits as well beyond merely the individual. Um, so I wanted to give that sort of defense of hodling as well to look at it from um a a broader position than just merely I'm trying to get rich. Um uh because even the person who uh that is all they want to do um just like you know your your pure number grow up go up moonboy even that behavior has positive ramifications on on the economy.
(07:14) And while we might look at them and have uh judgments about their particular choices for them as an individual, we shouldn't discount that uh their actions are having positive positive effects for the rest of the economy. Yeah. So, let's dive into that just not even in the context of Bitcoin because I think you did a great job of this in the presentation.
(07:36) just you've done a good job of this consistently throughout the years that I've known you. Just from like a first principles Austrian economics perspective, what is the idea around capital accumulation, low time preference and deployment of that capital like what what like getting getting into like the nitty-gritty and then applying it to Bitcoin? Yeah, it's it's a big question and um in many ways I mean I I even I barely scratched the surface.
(08:05) uh I I can't claim to have read uh all the volumes of Bombber works, you know, capital and interest and and stuff like that. Um but I think there's some some sort of basic concepts that we can look at that we can uh draw a lot out. Um the first uh I guess let's write that. So repeat so like capital time preference. Yeah. Well, I guess getting more broad like why sav -
 @ 7f6db517:a4931eda
2025-06-06 14:02:11
@ 7f6db517:a4931eda
2025-06-06 14:02:11
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ d9a329af:bef580d7
2025-06-08 19:20:56
@ d9a329af:bef580d7
2025-06-08 19:20:56Shabbat Shalom, y'all.
At the time of writing and releasing this, it happened to be a Lunar Shabbat, which is actually Torah (much to the chagrin of those who practice Shabbat on a Saturday or Sunday exclusively). The Shabbat is always on the 8th, 15th, 22nd, and 29th days of a Hebrew Calendar month, which almost nobody follows anymore. I started doing this a few months ago, and it's made me see the Torah for what it really is.
To the topic at hand, though. A lot of people on Nostr don't seem to understand the historical narrative of the book of Revelation, which saddens me, as we're in the end times Ekklesia (Assembly) era of Laodecia.
Deception of Bible Translations
First off, the reason why most people trust their pastors and/or read differently to what I do in Nazaritic circles is because of translations of the Scriptures that are evil, wretched and Catholic. The best way to combat this is to make some recommendations of which versions you'll want to use that aren't Catholic-infested.
These are the ONLY recommended versions to read. Anythine else is bupkus, evil and garbage, and will teach you futrism or preterism, both of which are Jesuit-penned deceptions.
The recommended versions are as follows:
-
KJV 1611 (KJV1611)
-
1560/1590 Geneva (GNV)
-
American King James 1901 (AKJV)
-
J.P. Green Sr.'s King James Version (KJ3)
-
Young's Literal Translation (YLT)
These are versions I've read, and determined are evil, wretched and garbage:
-
New International Version (NIV) [Fun fact: The publisher of the NIV, Zondervan, has a sister publisher that is behind the Satanic Bible's publishing]
-
New Living Translation (NLT)
-
English Standard Version (ESV)
-
ISR The Scriptures 2009 Third Edition with Minor Revisions [2016] (ISR2009)
-
New American Standard Bible (NASB)
-
New King James Version (NKJV)
What is the Laodecia Era for the Ekklesia?
As a refresher, this time sees people saying they're rich in truth and that they have need of nothing, but this shows that they're wretched, miserable, naked and wicked. Why is this? The need of nothing points to not needing another explanation other than the false futuristic viewpoint, whereas being rich is connected to already knowing the truth about the historical fulfillment of Revelation, which many people don't know at all. I seriously grieve their loss, for they know not what they do.
I'm also new into this viewpoint, and most of what I'll be talking about is proven by historicist prophet David Nikao Wilcoxson on YouTube and Facebook (I don't use Facebook). This single Nostr article, I pray, is the starting point for understanding why I call out what I call out, and the patterns I see pointing to the Roman Catholic Church (the Tares) and the Jesuit Order (the current rulers of our world, the Earth Beast of Rev. 13) being the harlots that will be plucked out before Messiah's return.
The 70th Week of Daniel
Let us start first with the 70th Week of Daniel, which futurists believe is pointed towards a 7 year period where a one-man antichrist makes a peace deal for Israel.
This was proven to be untrue, as this is a deception that many people have fallen for, thus obeying the Pope (the Mark of the Beast on the right hand). What Daniel was talking about was not the end times, but rather, two-fold. The first is that he was asking about when Yevah would free the Jews from slavery (since they were in the Babylonian Beast Kingdom at this time). The second is when Messiah would come in the flesh and start a 7 year period from 27-34 AD, which is the final 7 year period of this 490 year cycle. King Artaxerxes I would go ahead and call for the rebuilding of Jerusalem in 476 BC (as is seen in Ezra), which would be the first 7 weeks (the first 7 Shemita [Shabbat year] cycles). Afterwords, we would see another 62 weeks (this period is a slient period), and then another period of 1 week. This week points to Messiah's ministry and death.
3 1/2 years into this 70th week (in 31 AD) is when Messiah would be nailed to the cross on March 13 of 31 AD (I'm still debating if the cross is a symbol of Tammuz or not). This was Passover in the Hebrew calendar year of 3790. He was 33 years of age when he was nailed, and then rose again 3 days later (on the 17th of Nisan in 3790). That Passover fell on a Monday (when the Romans were using the 8-day calendar instead of the 7-day calendar we've essentially been forced to use).
To prove the above, Wilcoxson had produced a series of videos regarding the 70th Week of Daniel (that being the 70th Week of Daniel Decoded series), which I would recommend you watch. You'll also want to find an audiobook version of Seventy Weeks: The Historical Alternative produced by Tearing Down Idols. These are the two pieces of proof I have to show this. Speaking of Wilcoxson, he had already produced books on these matters, as understanding the hostorical narrative of the Scriptures is the key to making war with the Roman Catholic Church and the Jesuit Order, especially now that we're in Laodecia.
The Olivet Discourse
The second part of this trifecta has to do with the Olivet Discourse of Matthew 23, which points to the destruction of Jarusalem by Rome for Israel's unfaithfulness to Yevah's instructions. Now, there are connections to parables that basically talk about the Yewish (Yew as in Yewtree worship) leaders (particulaly the Pharisees and Saducees) practicing the Tradition of the Elders (which are the Babylonian Talmud and the Egyptian Kabbalah of today), and for not understanding that this was Messiah, they were destroyed for their iniquities. I don't care to research the futurist narrative on this, as I know it is full of twisted words and word salad sorcery.
Wilcoxson proves what I've said in the Olivet Discourse Decoded series of videos, so that's where I'll point you to when you have an open heart, open eyes and open ears. Many futurists won't, because they are exactly what Messiah described in the Ekklesia era of Laodecia.
Revelation and Its Prophecies
Finally, there's Revelation (what used to be called Apocalypse). When looking into this book, you realize that it's really a 4-layered war manual for how to fight this war against the Roman Catholic leadership and the Jesuit Order. This also shows how you can harvest souls (the harvest points to a mass exodus of Roman Catholicism membership). This I will go in depth on, and will even have passages to back this up.
Layer 1: The Roman Beast Kingdom
The first layer of this 4-layered manual shows the phases of the Roman Empire, which never really disappeared. Rev. 12 described the Roman Empire, which was used to wipe out the early Ekklesia (the woman), murdering millions of Nazarites. The Seals point to the incline (for the Four Horsemen of the Apocalypse) and decline of the Roman Empire (the other three Seals), while the Trumpets point to the official Roman Empire's downfall. This would be split into 10 separate kingdoms in Europe, which would be countered by the creation of Christianity, which is really any of the 44k+ forks of Roman Catholicism. This was done to destroy the Ekklesia, as the Roman Catholic Church is the Tare field that Messiah had talked about in the parable of the Wheat and the Tares.
Staying in this layer, the Sea Beast is the next phase. This is the 1,260-year reign of the Pope (538-1798), as he was the one who plucked out 3 kingdoms who didn't bow to his authority (the Heruli, the Huns and the Ostrigoths). Keep in mind that this started after the removal of the restrainer in 476 (pointing to the removal of the final Western Roman Emperor), and healed the deadly head wound (pointing to the Pope rising to power out of a sea of people). During this reign, he took the title of Pontifex Maximus, as he had civic and ecclesiastical power over everyone. This would be the healing of the deadly head wound, as shown earlier in this beast. He would pretend to be the leader of the Ekklesia, thus sitting in the Temple of Yevah, though he's the son of perdition, as he proclaims to be Yevah, forgive sins and provide salvation through works alone, which is blasephemous to begin with. The persecution of the Nazarites also prove them to be anti-Moshiach (Messiah). They also have the title of Vicar of Christ, which in the Latin is Vicarus Filii Dei, which is equal to 666 when calculated using a form of gematria I have no idea about. He would ultimately be removed from power by the Earth Beast in 1798, after he basically limited the power of the Jesuit Superior General and his minions. As stated before, the Mark of the Beast is reverence (forehead) and obeisance (right hand) to the Pope.
Finally, the Earth Beast of Revelation 13 points to the Jesuit Superior Geneal rising out of the earth (which is the land) of the Antichrist Beast Pope, the Vatican. These two horns pretend to serve Messiah (lamb) but are really Lucifarians (the dragon), serving Lucifer. The Black Pope, as the Jesuit Superior General is called, used his power to gether the world under him. That's why he uses Washington D.C. (the District of the Roman goddess, Columbia), his war machine (Military Indurstial Complex), to overthrow leaders who won't bow to his authority and those who won't set up a Rothschild central bank; much less obey the Khazars, who he also controls (I happened to be a partial German Khazar who escaped the grasp of the Black Pope as best as I know thus far).
Layer 2: The Ekklesia Eras
Now comes the eras of the Ekklesia. There are seven of them, though I've already explained the era of Laodecia. How about I give a quick explanation of the first six eras, like so?
Ephesus would spread the gospel in the Roman Empire, with their love growing cold when Messiah didn't return.
Smyrna had 10 years of persecutions from 303-312, which is what the 5th seal points to.
Pergamos would fall away (2 Thess. 2) from the Scriptures when compromising with Rome (Mark of the Beast as I had explained)
Thyatira means ruled by a woman. This means, the Roman Catholic Church would do this, as the Popes sought to eliminate the two witnesses, which are the Nazarites and the printed Scriptures (the little book or Rev. 10). This was why they killed the Nazarites and bured the printed Scriptures ruthlessly enough, that they were classified as "dead" in 1514. The Popes would hold great feasts to celebrate the removal of the two witnesses after they got all of Christendom under their control.
Sardis means escaping one, which points to Messiah calling them dead after 3 1/2 years from the Pope's classification of the death of the two witnesses. Luther's 95 Thesis sparked the Protestant Reformation, which would lead to the resurrection of the two witnesses (the Nazarites and the printed Scriptures).
Philidelphia had nothing bad that Messiah said about them... at all. They led worldwide missions, and also led Bible Societies to spread the word and/or the gospel to save millions of people from the clutches of the Jesuit Superior General (and the Roman Catholic Church as a whole).
As a refresher for Laodecia (the era we're in right now), the Nazarites here believe that they are rich in truth, and that we have need of nothing. This is false, as we are in dire need of something, which is an alternative explanation that's not the false futuristic or preteristic explanations of the book of Revelation. We are blinded by the Jesuits, as they have decieved us (we let them do this, by the way) with false prophecy explanations among other deceptions.
Layer 3: Seals, Trumpets and Bowls
The Seals, Trumpets and Bowls are the judgements against the Roman Beast Kingdom. To keep things short, every single Seal was fulfilled, 6 of the Trumpets were fulfilled, and 5 of the Bowls were fulfilled. We're in the 6th Bowl, waiting for a global economic collapse and WW III. Once these occur, then do we go into the 7th Bowl judgement against the Roman Catholic Church and the Jesuit Order (the New World Order).
One quick thing I'll mention is that when I talk about the two witnesses here, one of them is the little book of Rev. 10. This points to the printed Bible, which was brought back to life thanks to the printing press. Martin Luther would measure the temple and find that the Papal Church is the apostate harlot. Rev. 14 points to the Bowls and the harvest. This harvest points to millions coming out of the Roman Catholic Church, though there are 1.3 billion Catholics... and we have a long way to go in getting them out of her, My people.
Remember when I talked about the Khazars earlier in this article? They are the Kings of the East that Yeshua pointed to in the 6th Bowl. The Ottoman Empire is the Euphrates River here, and it's dried up in 1922, only with Turkey remaining. Gog is already dead, as that's Lord Rothschild. Magog points to the Kings of the East. 2 of the 3 spirits have already been fulfilled (these are World Wars I and II).
Now, let me quickly point out the fact we're in the kingdom of Iron and Clay. The Iron points to the Roman Bishops, and the Clay is Islam. However, furutists will tell me I'm an idiot, and that the Iron and Clay mixture is transhumanism. This was proven to be false, as the 5th Trumpet was the rise of the Clay (Islam). The Catholics, however, wrote the Qur'an and proped up Mohhamed as their prophet. ISIS and Al Qaeda are controlled by the Jesuit Order, which is why they do what they do as terrorists... for they are Wahhabi Muslims (in other words, Mizrahi Khazars who are also Jesuits, claiming to be Arabs, when they're not).
Islam is designed to prevent Arabs from having a relationship with Messiah, which makes me really sad. Muslims will be used to kill Christians and Jews in WW III and force us into the New World Order, which will backfire on the Jesuits and Roman Bishops.
Layer 4: The Harlot Church
Rev 17:10 talks about 7 forms of government. Five had fallen by the time Revelation was written, the 6th (the Roman Emperors) fell in 476, and the 7th lead for a short space until 538.
The 8th head is the Pope, who rose to power out of the Roman Empire. Look up what the priests in the Catholic Church wear, and what they use. Does that sound familiar when you read Revelation? If it does, that's exactly the description of the Sea Beast, and how his priests dress and do their rituals.
Then comes the Black Pope. He empowers and enriches the kings of the earth, as they were used by Lucifer to carry out the Bowl judgements, and will carry out the New World Order, caugins themselves and the Roman Cathoic Church to be judged big time. This we are waiting for.
Conclusion
Hopefully this long read helps you see where I'm coming from, and I pray it helps you to start testing the scriptures against what I've said, and what Wilcoxson had said. If it is proven in your heart that you were fooled, you're on the right path in my opnion. I may be wrong, but this is where I stand.
-
-
 @ 0689c075:2936ee11
2025-06-08 18:45:20
@ 0689c075:2936ee11
2025-06-08 18:45:20{"layout":{"backgroundImage":null,"canvasSize":{"width":850,"height":1100}},"pages":[{"id":"page_1","name":"Main Page","objects":[]}],"objects":[{"id":"obj_1749408294700_7hdz0tuxv","type":"rect","x":0.11764705882352941,"y":0.09090909090909091,"fill":"#3B82F6","stroke":"#1E40AF","strokeWidth":2,"opacity":1,"width":0.17647058823529413,"height":0.09090909090909091}],"texts":[]}
-
 @ 3bf0c63f:aefa459d
2024-05-21 12:38:08
@ 3bf0c63f:aefa459d
2024-05-21 12:38:08Bitcoin transactions explained
A transaction is a piece of data that takes inputs and produces outputs. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered.
Imagine you have 10 satoshis. That means you have them in an unspent transaction output (UTXO). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a script that unlocks that transaction and related signatures, then you specify outputs along with a script that locks these outputs.

As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them.
For most of the cases locking and unlocking means specifying a public key whose controller (the person who has the corresponding private key) will be able to spend. Other fancy things are possible too, but we can ignore them for now.
Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.

If you're still interested in transactions maybe you could take a look at this small chapter of that Andreas Antonopoulos book.
If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: https://en.bitcoin.it/wiki/Coin_analogy
-
 @ 2f7463a4:e92b8023
2024-04-02 12:36:25
@ 2f7463a4:e92b8023
2024-04-02 12:36:25Original „Speaking Freely“ von Gigi, veröffentlicht zur Blockzeit 836245 unter der CC BY-SA 4.0 Lizenz. Übersetzt von sefiro.
Neulich unterhielt ich mich mit einem Freund und wir kamen auf das Problem der Meinungsfreiheit zu sprechen. Ich sollte es nicht als Problem bezeichnen, denn es ist die Lösung eines Problems. Das Problem ist ein immerwährendes Problem, was eine andere Art ist zu sagen, dass es ein wirklich schwieriges Problem ist, ein Problem, mit dem wir immer konfrontiert sein werden, solange wir Menschen sind.
Das Problem ist folgendes: Was ist das Problem, das es zu lösen gilt? Es ist ein Problem von Problemen, was natürlich ein Metaproblem ist. Wir als Homo Sapiens sind ein denkender Organismus. Sowohl kollektiv als auch individuell. Denken ist das, was uns ausmacht, aber es ist nicht einfach Denken als Selbstzweck, es ist Denken, um Dinge herauszufinden, ohne ständig dabei umgebracht zu werden. Eine weniger brutale Form der Evolution sozusagen.
Die Menschen der Antike haben der Aufmerksamkeit einen sehr hohen Wert beigemessen. Auch die Aufmerksamkeit ist von einem Metaproblem geplagt: Worauf soll man seine Aufmerksamkeit richten? Um diese Frage zu beantworten, muss man darauf achten, worauf man seine Aufmerksamkeit richtet, und das unterscheidet einen klugen von einem weisen Menschen.
Das bringt mich zu einem der Dinge die mir derzeit Sorgen bereiten. Wir sind zivilisatorisch gesehen sehr klug, aber nicht sehr weise. Wir sind schlecht darin, auf das zu achten, worauf wir unsere Aufmerksamkeit richten, zumindest gegenwärtig. Und ich fürchte, dass sowohl die falschen Anreize, die das Internet plagen, als auch unser kaputtes Geld daran schuld sind.
Annahmen [n=0]
- ∀ i ≤ c[^1]
- P! = NP[^2]
- Leben ist es wert gelebt zu werden[^3]
- Es gibt kein kostenloses Mittagessen[^4]
- Meinungsfreiheit ist erstrebenswert[^5]
Der Logos [n=1]
Es gibt einen Grund, warum Der Logos heilig ist. Aus dem gleichen Grund ist der Erste Zusatzartikel zur Verfassung der Vereinigten Staaten der erste, d.h. der wichtigste.
Meinungsfreiheit ist nicht optional; sie ist nicht optional, weil wir frei sprechen können müssen, um frei denken zu können. Es gibt kein echtes Denken ohne echtes Sprechen, genauso wie es kein echtes Sprechen ohne echtes Denken gibt. Es muss erlaubt sein, dummes Zeug zu sagen, so wie es erlaubt sein muss, dummes Zeug zu denken.
„Der Vernünftige passt sich der Welt an, der Unvernünftige versucht beharrlich, die Welt an sich anzupassen. Daher hängt aller Fortschritt vom Unvernünftigen ab.“\ — George Bernhard Shaw, Man and Superman
Der Grat zwischen Genie und Wahnsinn ist nicht ohne Grund schmal. Was idiotisch und was genial ist, ist oft schwer zu unterscheiden. Deshalb hängt aller Fortschritt vom Unvernünftigen ab.
Wie können wir den Unvernünftigen finden und ihm zuhören, wenn wir ihn zum Schweigen bringen? Schlimmer noch, wie können wir dem unvernünftigen/genialen Teil in uns selbst hören, wenn wir Angst haben, ihn in der Öffentlichkeit oder im Privaten zu äußern?
DiaLogos [n=2]
Auch freier und unbelasteter Dialog sind nicht optional. Wir müssen in der Lage sein, Dinge zu diskutieren, damit andere uns sagen können, wo wir idiotisch sind. Und wir sind alle idiotisch. Wir sind vielleicht auf unsere Weise idiotisch, aber wir sind alle idiotisch. Es gibt keine wertfreie Meinung, so wie es keine Sichtweise ohne blinden Fleck gibt. Das Beste, was wir tun können, ist, uns unserer Vorurteile und blinden Flecken bewusst zu werden und zu versuchen, ihnen entgegenzuwirken. Aber das können wir nicht individuell, das müssen wir kollektiv tun, und noch wichtiger: auf eine verteilte Art und Weise.[^6]
Der Bau eines Turms von Babel ist eine schlechte Idee.
Verteilte Erkenntnis [n=m]
Auch öffentlicher Diskurs ist nicht optional. In der heutigen Zeit, insbesondere im Internet, ist öffentlicher Diskurs, gelinde gesagt, problematisch. Eines der Probleme ist, dass wir keine öffentlichen Räume haben, so dass wir gezwungen sind, private Räume als quasi-öffentliche Räume zu nutzen.
Die übliche Methode, sich öffentlich zu äußern, besteht darin, auf eine Plattform zu gehen und zu sagen, was man zu sagen hat. Das Problem ist natürlich, dass es nicht deine Plattform ist. Es ist die Plattform eines anderen. Deshalb kannst du von der Plattform ausgeschlossen werden.
Der Unterschied zwischen all diesen Plattformen liegt im Grad, nicht in der Art. Auf einigen Plattformen kann man für sexuelle Inhalte sprichwörtlich ins Gefängnis kommen. Auf anderen Plattformen kann man für politische Äußerungen ins Gefängnis kommen. Nicht einmal sprichwörtlich.[^7]
„Geben Sie mir sechs Zeilen, die von der Hand des ehrlichsten Menschen geschrieben wurden, ich würde etwas darin finden, um ihn hängen zu lassen.“\ — Kardinal Richelieu
Wenn jemand die Macht hat, jemand anderen von einer Plattform auszuschließen, dann wird diese Macht früher oder später auch genutzt und missbraucht. Ein ausreichend großer Skandal oder eine entsprechende Kontroverse wird gefunden oder inszeniert und *puff* ist der „problematische“ Nutzer verschwunden. Depersonalisiert, auf Knopfdruck. Egal, wie mächtig man ist.[^8]
Aus diesem Grund können Plattformen für Meinungsfreiheit nicht existieren. Es kann nur Protokolle für Meinungsfreiheit geben.
Der Unterschied ist ebenso subtil wie wichtig: Wenn du ein Protokoll verwendest, bist du kein Nutzer im herkömmlichen Sinne. Du bist ein Sprecher. Du sprichst die gleiche Sprache wie andere, und wenn jemand anderes dich hören und verstehen kann, dann gibt es eine Verbindung. Es gibt keinen Vermittler. Die Sprache selbst ist der Vermittler. Sprachen sind Protokolle, und Protokolle sind Sprachen. Sie haben keine Nutzer, sie haben Sprecher.
Sprache ist naturgemäß frei. Du brauchst keinen Deutsch-Account, um diese Sätze zu lesen. Genauso wie dein Computer keinen HTTP-Account braucht, um die Nullen und Einsen zu verstehen, aus denen die Bytes bestehen, die wiederum die Zeichen dieses Satzes bilden. Beide sprechen die Sprache, daher könnt ihr euch verstehen.
Sprachen und Protokolle sind Netzwerkphänomene. Ohne Netzwerk keine Sprache. Ohne Peers keine Protokolle.
Deshalb ist Sprache, wie Geld, in einer komplexen Gesellschaft nicht optional. Wenn man in das eine oder das andere hineinpfuscht, zerbricht die Gesellschaft.
Es liegt an uns, es ist soweit [n=i]
Wir stehen an einem Wendepunkt in der Geschichte. Noch nie war unsere Zivilisation so vernetzt, so global, und sich ihrer Grenzen und Ignoranz so wenig bewusst.
Meine Hoffnung ist, dass hartes Geld und Meinungsfreiheit das wiederbeleben, was unsere Gesellschaft groß gemacht hat. Kooperation und verteilte Erkenntnis haben es uns ermöglicht, das Chaos des Dschungels hinter uns zu lassen. Sie haben es uns ermöglicht, von Auge um Auge zu einer klaren Sicht zu gelangen, zumindest teilweise. Sie haben es uns ermöglicht, von der Knappheit zum Überfluss zu gelangen. Sie haben uns ermöglicht, zur Wahrheit, zum Guten und zum Schönen zu gelangen. Sie ermöglichen es uns zu streben. Nach vorne und nach oben.
Der Kairos unserer Zeit ist ein persönlicher – vielleicht sind das alle kairotischen Momente.
Du musst entscheiden wie du weitermachen willst. Du musst entscheiden, welches Spiel du spielen willst; wie viel Verantwortung du bereit bist zu übernehmen. Willst du weiterhin in der Maschine stecken bleiben? Einer Maschine, die dich benutzt und ausnutzt? Eine Maschine, die sich selbst nährt, indem sie deine Zeit, deine Aufmerksamkeit und deinen Wert raubt und verschlingt? Oder hast du den Mut, die Kontrolle über deinen Wohlstand, deine Gesundheit, deine Gedanken und deine Sprache zu übernehmen?
Diese Entscheidung kann dir niemand abnehmen. Sie beginnt und endet mit dir.
💜
[^1]: Keine Information kann sich schneller als Lichtgeschwindigkeit verbreiten. Folglich stoßen alle Informationssysteme an physikalische Grenzen, wenn es um Synchronisation und Informationsweitergabe geht.
[^2]: Kryptographie funktioniert und wird weiterhin funktionieren. „[...] irgendwie lächelt das Universum bei Verschlüsselung.“
[^3]: Existenz ist real und gut. Weder Nihilismus noch Solipsismus sind wünschenswert. „[...] und es war gut.“
[^4]: Wir können nicht etwas für nichts haben. Freiheit erfordert Verantwortung; elektronisches Bargeld erfordert Zeit; Zeit erfordert Wärme.
[^5]: Meinungsfreiheit ist erstrebenswert, weil Freiheit der Tyrannei vorzuziehen ist, und der erste Schritt eines jeden Tyrannen ist es, die Meinungsfreiheit einzuschränken, Dissidenten zum Schweigen zu bringen, und Bücher zu verbrennen. Der zweite Schritt ist Völkermord.
[^6]: Es ist großartig, dass es immer mehr lange Dialoge in Form von Podcasts gibt. Der Nutzen dieser Gespräche geht jedoch verloren, wenn sie von einer zentralen Partei gehostet werden, weshalb ein offenes Podcast-Ökosystem so wichtig ist.
[^7]: Siehe Fälle im Vereinigten Königreich, in Saudi Arabien, etc.
[^8]: Noch nicht einmal amtierende US-Präsidenten sind vor einem Ausschluss von Plattformen sicher.
-
 @ 3bf0c63f:aefa459d
2024-03-23 08:57:08
@ 3bf0c63f:aefa459d
2024-03-23 08:57:08Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 9ca447d2:fbf5a36d
2025-06-07 11:01:18
@ 9ca447d2:fbf5a36d
2025-06-07 11:01:18CANNES, FRANCE – May 2025 — Bitcoin mining made its mark at the world’s most prestigious film gathering this year as Puerto Rican director and producer Alana Mediavilla introduced her feature documentary Dirty Coin: The Bitcoin Mining Documentary at the Marché du Film during the Cannes Film Festival.
The film puts bitcoin mining at the center of a rising global conversation about energy, technology, and economic freedom.
Dirty Coin is the first feature-length documentary to explore bitcoin mining through immersive, on-the-ground case studies.
From rural towns in the United States to hydro-powered sites in Latin America and the Congo, the film follows miners and communities navigating what may be one of the most misunderstood technologies of our time.
The result is a human-centered look at how bitcoin mining is transforming local economies and energy infrastructure in real ways.
To mark its Cannes debut, Mediavilla and her team hosted a packed industry event that brought together leaders from both film and finance.

Dirty Coin debut ceremony at the Marché du Film
Sponsors Celestial Management, Sangha Renewables, Nordblock, and Paystand.org supported the program, which featured panels on mining, energy use, and decentralized infrastructure.
Attendees had the rare opportunity to engage directly with pioneers in the space. A special session in French led by Seb Gouspillou spotlighted mining efforts in the Congo’s Virunga region.
Dirty Coin builds on Mediavilla’s award-winning short film Stranded, which won over 20 international prizes, including Best Short Documentary at Cannes in 2024.
That success helped lay the foundation for the feature and positioned Mediavilla as one of the boldest new voices in global documentary filmmaking.

Alana Mediavilla speaks at the Marché du Film — Cannes Film Festival
“If we’ve found an industry that can unlock stranded energy and turn it into real power for people—especially in regions with energy poverty—why wouldn’t we look into it?” says Mediavilla. “Our privilege blinds us.
“The same thing we criticize could be the very thing that lifts the developing world to our standard of living. Ignoring that potential is a failure of imagination.”
Much like the decentralized network it explores, Dirty Coin is spreading globally through grassroots momentum.
Local leaders are hosting independent screenings around the world, from Roatán and Berlin to São Paulo and Madrid. Upcoming events include Toronto and Zurich, with more cities joining each month.
Mediavilla, who previously worked in creative leadership roles in the U.S. — including as a producer at Google — returned to Puerto Rico to found Campo Libre, a studio focused on high-caliber, globally relevant storytelling from the Caribbean.
She was also accepted into the Cannes Producers Network, a selective program open only to producers with box office releases in the past four years.
Mediavilla qualified after independently releasing Dirty Coin in theaters across Puerto Rico. Her participation in the network gave her direct access to meetings, insights, and connections with the most active distributors and producers working today.
The film’s next public screening will take place at the Anthem Film Festival in Palm Springs on Saturday, June 14 at 2 PM. Additional screenings and market appearances are planned throughout the year at Bitcoin events and international film platforms.

Dirty Coin at the Cannes Film Festival
Watch the Trailer + Access Press Materials
📂 EPK
🎬 Screener
🌍 Host a Screening
Follow the Movement
Instagram: https://www.instagram.com/dirty_coin_official/
Twitter: https://x.com/DirtyCoinDoc
Website: www.dirtycointhemovie.com -
 @ b1ddb4d7:471244e7
2025-06-07 11:01:06
@ b1ddb4d7:471244e7
2025-06-07 11:01:06“Not your keys, not your coins” isn’t a slogan—it’s a survival mantra in the age of digital sovereignty.
The seismic collapses of Mt. Gox (2014) and FTX (2022) weren’t anomalies; they were wake-up calls. When $8.7 billion in customer funds vanished with FTX, it exposed the fatal flaw of third-party custody: your bitcoin is only as secure as your custodian’s weakest link.
Yet today, As of early 2025, analysts estimate that between 2.3 million and 3.7 million Bitcoins are permanently lost, representing approximately 11–18% of bitcoin’s fixed maximum supply of 21 million coins, with some reports suggesting losses as high as 4 million BTC. This paradox reveals a critical truth: self-custody isn’t just preferable—it’s essential—but it must be done right.
The Custody Spectrum
Custodial Wallets (The Illusion of Control)
- Rehypothecation Risk: Most platforms lend your bitcoin for yield generation. When Celsius collapsed, users discovered their “held” bitcoin was loaned out in risky strategies.
- Account Freezes: Regulatory actions can lock withdrawals overnight. In 2023, Binance suspended dollar withdrawals for U.S. users citing “partner bank issues,” trapping funds for weeks.
- Data Vulnerability: KYC requirements create honeypots for hackers. The 2024 Ledger breach exposed 270,000 users’ personal data despite hardware security.
True Self-Custody
Self-custody means exclusively controlling your private keys—the cryptographic strings that prove bitcoin ownership. Unlike banks or exchanges, self-custody eliminates:- Counterparty risk (no FTX-style implosions)
- Censorship (no blocked transactions)
- Inflationary theft (no fractional reserve lending)
Conquering the Three Great Fears of Self-Custody
Fear 1: “I’ll Lose Everything If I Make a Mistake”
Reality: Human error is manageable with robust systems:
- Test Transactions: Always send a micro-amount (0.00001 BTC) before large transfers. Verify receipt AND ability to send back.
- Multi-Backup Protocol: Store seed phrases on fireproof/waterproof steel plates (not paper!). Distribute copies geographically—one in a home safe, another with trusted family 100+ miles away.
- SLIP39 Sharding: Split your seed into fragments requiring 3-of-5 shards to reconstruct. No single point of failure.
Fear 2: “Hackers Will Steal My Keys”
Reality: Offline storage defeats remote attacks:
- Hardware Wallets: Devices like Bitkey or Ledger keep keys in “cold storage”—isolated from internet-connected devices. Transactions require physical confirmation.
- Multisig Vaults: Bitvault’s multi-sig system requires attackers compromise multiple locations/devices simultaneously. Even losing two keys won’t forfeit funds.
- Air-Gapped Verification: Use dedicated offline devices for wallet setup. Never type seeds on internet-connected machines.
Fear 3: “My Family Can’t Access It If I Die”
Reality: Inheritance is solvable:
- Dead Man Switches: Bitwarden’s emergency access allows trusted contacts to retrieve encrypted keys after a pre-set waiting period (e.g., 30 days).
- Inheritance Protocols: Bitkey’s inheritance solution shares decryption keys via designated beneficiaries’ emails. Requires multiple approvals to prevent abuse.
- Public Key Registries: Share wallet XPUBs (not private keys!) with heirs. They can monitor balances but not spend, ensuring transparency without risk.
The Freedom Dividend
- Censorship Resistance: Send $10M BTC to a Wikileaks wallet without Visa/Mastercard blocking it.
- Privacy Preservation: Avoid KYC surveillance—non-custodial wallets like Flash require zero ID verification.
- Protocol Access: Participate in bitcoin-native innovations (Lightning Network, DLCs) only possible with self-custodied keys.
- Black Swan Immunity: When Cyprus-style bank bailins happen, your bitcoin remains untouched in your vault.
The Sovereign’s Checklist
- Withdraw from Exchanges: Move all BTC > $1,000 to self-custody immediately.
- Buy Hardware Wallet: Purchase DIRECTLY from manufacturer (no Amazon!) to avoid supply-chain tampering.
- Generate Seed OFFLINE: Use air-gapped device, write phrase on steel—never digitally.
- Test Recovery: Delete wallet, restore from seed before funding.
- Implement Multisig: For > $75k, use Bitvault for 2-of-3 multi-sig setup.
- Create Inheritance Plan: Share XPUBs/SLIP39 shards with heirs + legal documents.
“Self-custody isn’t about avoiding risk—it’s about transferring risk from opaque institutions to transparent, controllable systems you design.”
The Inevitable Evolution: Custody Without Compromise
Emerging solutions are erasing old tradeoffs:
- MPC Wallets: Services like Xapo Bank shatter keys into encrypted fragments distributed globally. No single device holds full keys, defeating physical theft.
- Social Recovery: Ethically designed networks (e.g., Bitkey) let trusted contacts restore access without custodial control.
- Biometric Assurance: Fingerprint reset protocols prevent lockouts from physical injuries.
Lost keys = lost bitcoin. But consider the alternative: entrusting your life savings to entities with proven 8% annual failure rates among exchanges. Self-custody shifts responsibility from hoping institutions won’t fail to knowing your system can’t fail without your consent.
Take action today: Move one coin. Test one recovery. Share one xpub. The path to unchained wealth begins with a single satoshi under your control.
-
 @ 2b998b04:86727e47
2025-06-08 18:39:04
@ 2b998b04:86727e47
2025-06-08 18:39:04I’ve spent years chasing the promise of freedom.\ In startups. In faith communities. In movements that claimed to be for the people.
And yet — so often, that promise felt just out of reach.\ Conditional. Corporate. Sanitized.\ A freedom with fine print.
But here —\ Here in the thick of Bitcoin 2025, on Nostr, among misfits and builders and signal-bringers —\ something is alive.
It’s not a platform.\ It’s not a marketing strategy.\ It’s not another app promising to “empower” you while locking down your data and selling you out.
It’s freedom rooted in architecture.\ Decentralization not just as a buzzword —\ but as an expression of conviction.
A kind of freedom you can feel in your body:
-
When you zap someone’s words because they moved you — not because an algorithm told you to.
-
When your identity is yours — keys, not credentials.
-
When no one can delete your story because you control the server, or because there is no server — just the relay of your choosing.
This isn’t utopia.\ There are egos. There’s noise. There’s still posturing.\ But it’s different.\ The center of gravity has shifted.
We’re no longer begging institutions to notice us.\ We’re building outside their jurisdiction.
And for the first time in a long time,\ freedom feels close.\ Tangible.\ Joyful.\ Alive.
This isn’t just about tech.\ It’s about trust.\ It’s about choosing to show up —\ to build\ to write\ to signal\ to keep going.
Even when it’s hard.\ Even when no one claps.
Because real freedom doesn’t come from being noticed.\ It comes from being sovereign.
And that’s something no one can take from me again.
—
Written in Las Vegas, during Bitcoin 2025.\ Posted via Nostr. Vibes co-authored by ChatGPT (“Dr. C”).\ Zap: <https://tinyurl.com/yuyu2b9t>
-
-
 @ cae03c48:2a7d6671
2025-06-07 08:00:33
@ cae03c48:2a7d6671
2025-06-07 08:00:33Bitcoin Magazine

Mapping Bitcoin’s Bull Cycle PotentialBitcoin’s Market Value to Realized Value, or MVRV ratio, remains one of the most reliable on-chain indicators for identifying local and macro tops and bottoms across every BTC cycle. By isolating data across different investor cohorts and adapting historical benchmarks to modern market conditions, we can generate more accurate insights into where Bitcoin may be headed next.
The Bitcoin MVRV Ratio
The MVRV Ratio compares Bitcoin’s market price to its realized price, essentially the average cost basis for all coins in the network. As of writing, BTC trades around $105,000 while the realized price floats near $47,000, putting the raw MVRV at 2.26. The Z-Score version of MVRV standardizes this ratio based on historical volatility, enabling clearer comparisons across different market cycles.
Figure 1: Historically, the MVRV Ratio and the MVRV Z-Score have accurately identified cycle peaks and bottoms. View Live Chart
Short-Term Holders
Short-term holders, defined as those holding Bitcoin for 155 days or less, currently have a realized price near $97,000. This metric often acts as dynamic support in bull markets and resistance in bear markets. Notably, when the Short Term Holder MVRV hits 1.33, local tops have historically occurred, as seen several times in both the 2017 and 2021 cycles. So far in the current cycle, this threshold has already been touched four times, each followed by modest retracements.
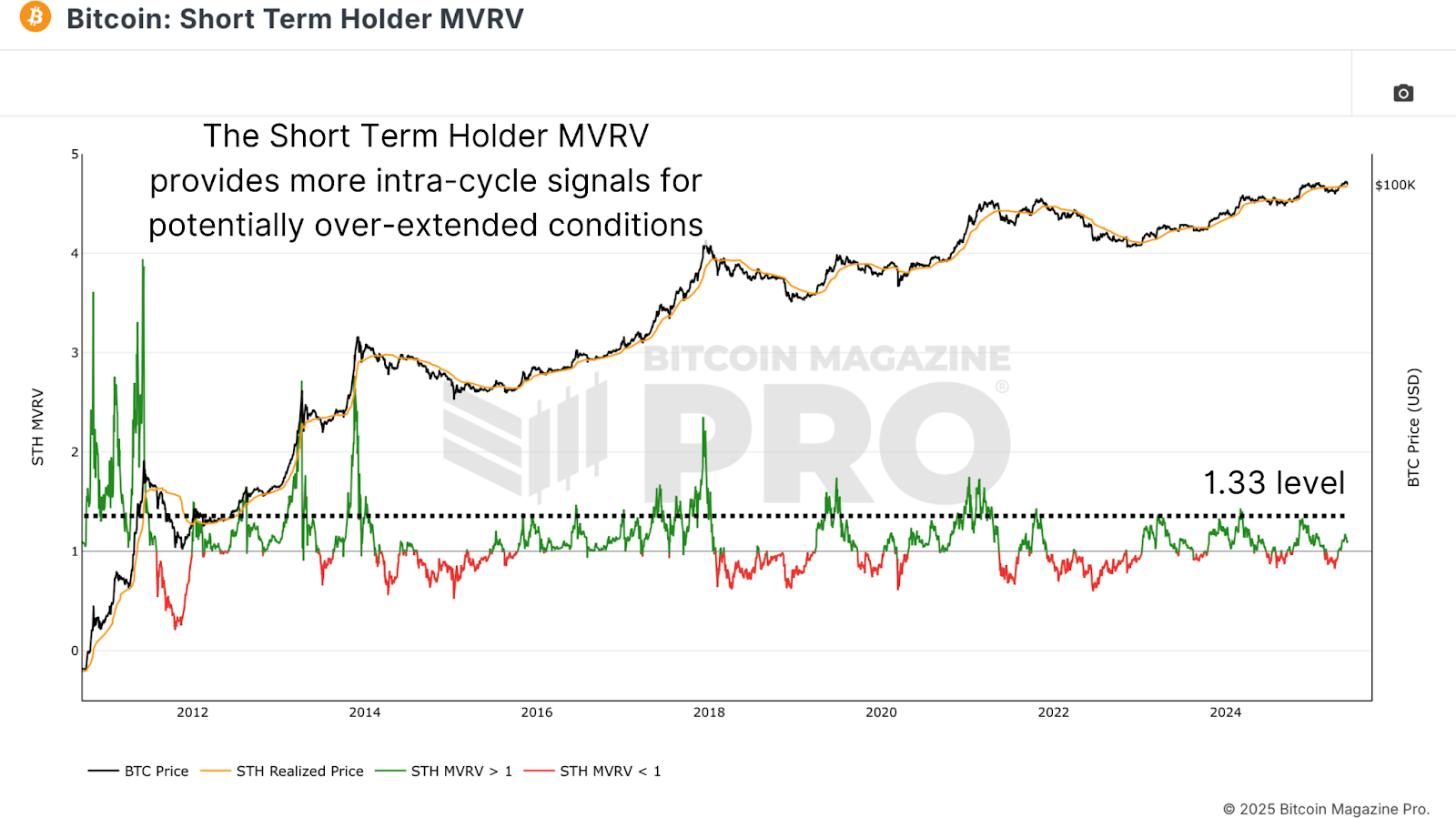
Figure 2: Short Term Holder MVRV reaching 1.33 in more recent cycles has aligned with local tops. View Live Chart
Long-Term Holders
Long-term holders, who’ve held BTC for more than 155 days, currently have an average cost basis of just $33,500, putting their MVRV at 3.11. Historically, Long Term Holder MVRV values have reached as high as 12 during major peaks. That said, we’re observing a trend of diminishing multiples each cycle.
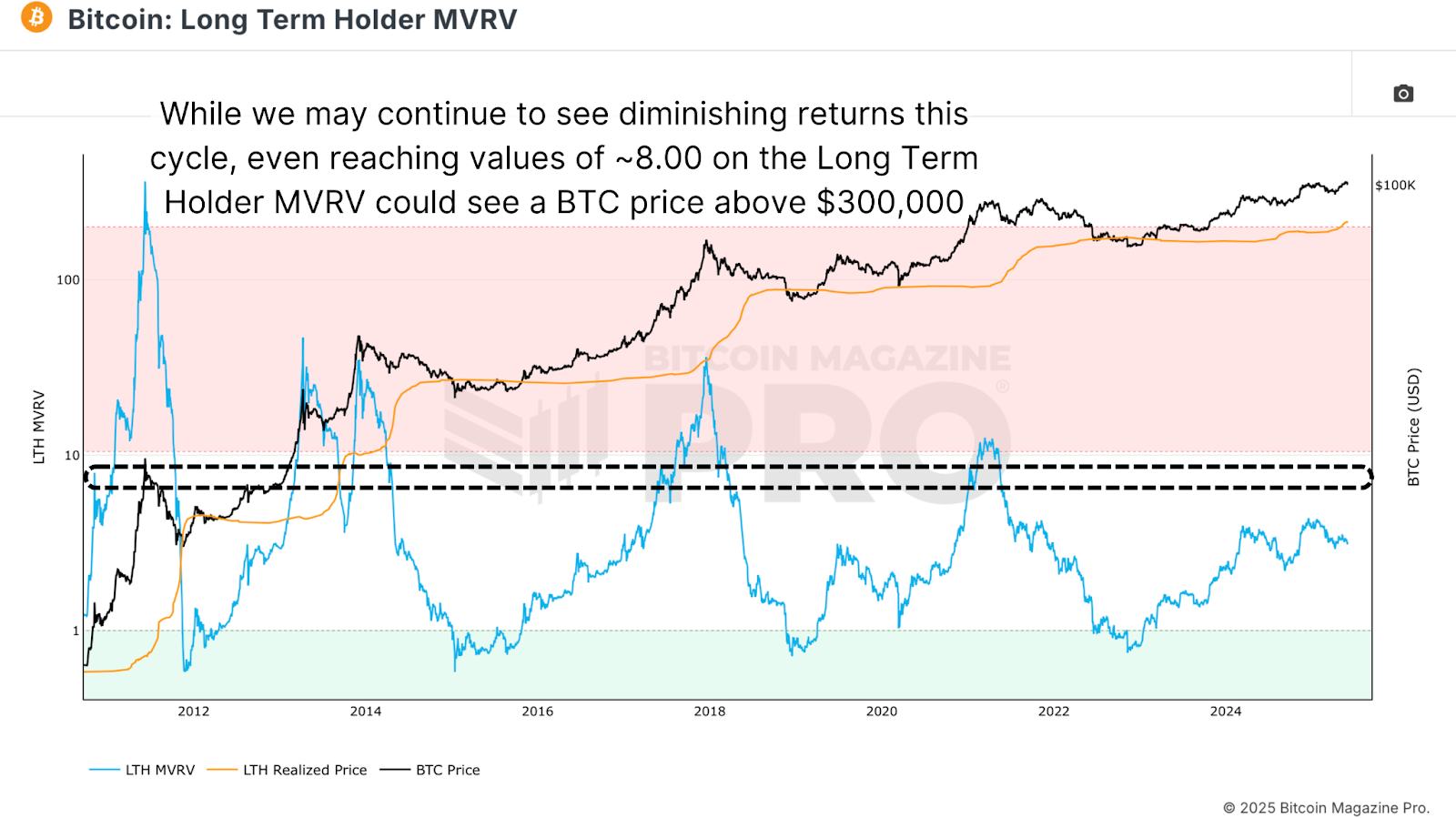
Figure 3: Achieving a Long Term Holder MVRV value of 8 could extrapolate to a BTC price in excess of $300,000. View Live Chart
A key resistance band now sits between 7.5 and 8.5, a zone that has defined bull tops and pre-bear retracements in every cycle since 2011. If the current growth of the realized price ($40/day) continues for another 140–150 days, matching previous cycle lengths, we could see it reach somewhere in the region of $40,000. A peak MVRV of 8 would imply a price near $320,000.
A Smarter Market Compass
Unlike static all-time metrics, the 2-Year Rolling MVRV Z-Score adapts to evolving market dynamics. By recalculating average extremes over a rolling window, it smooths out Bitcoin’s natural volatility decay as it matures. Historically, this version has signaled overbought conditions when reaching levels above 3, and prime accumulation zones when dipping below -1. Currently sitting under 1, this metric suggests that substantial upside remains.
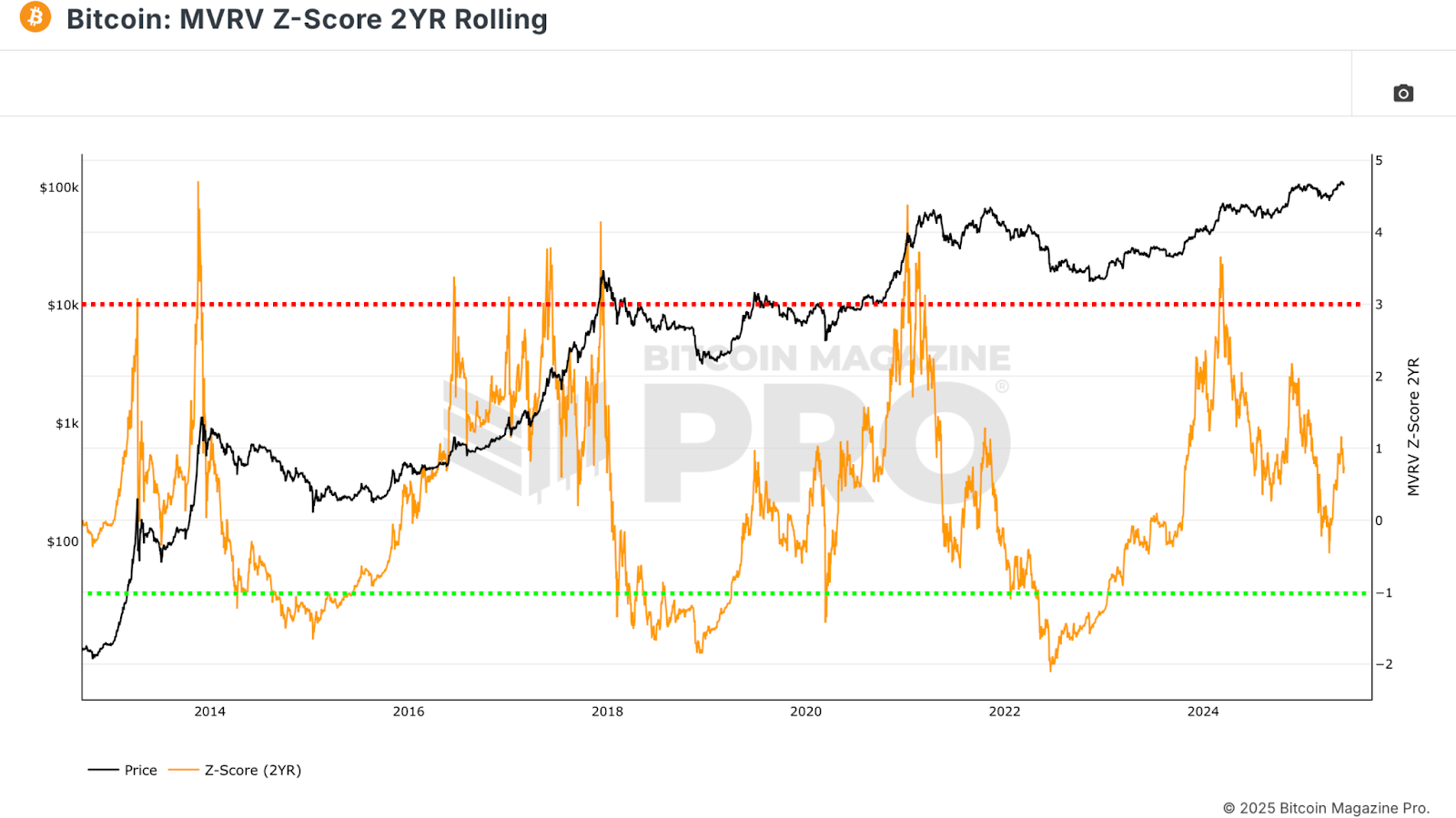
Figure 4: The current 2-Year Rolling MVRV Z-Score suggests more positive price action ahead. View Live Chart
Timing & Targets
A view of the BTC Growth Since Cycle Lows chart illustrates that BTC is now approximately 925 days removed from its last major cycle low. Historical comparisons to previous bull markets suggest we may be around 140 to 150 days away from a potential top, with both the 2017 and 2021 peaks occurring around 1,060 to 1,070 days after their respective lows. While not deterministic, this alignment reinforces the broader picture of where we are in the cycle. If realized price trends and MVRV thresholds continue on current trajectories, late Q3 to early Q4 2025 may bring final euphoric moves.
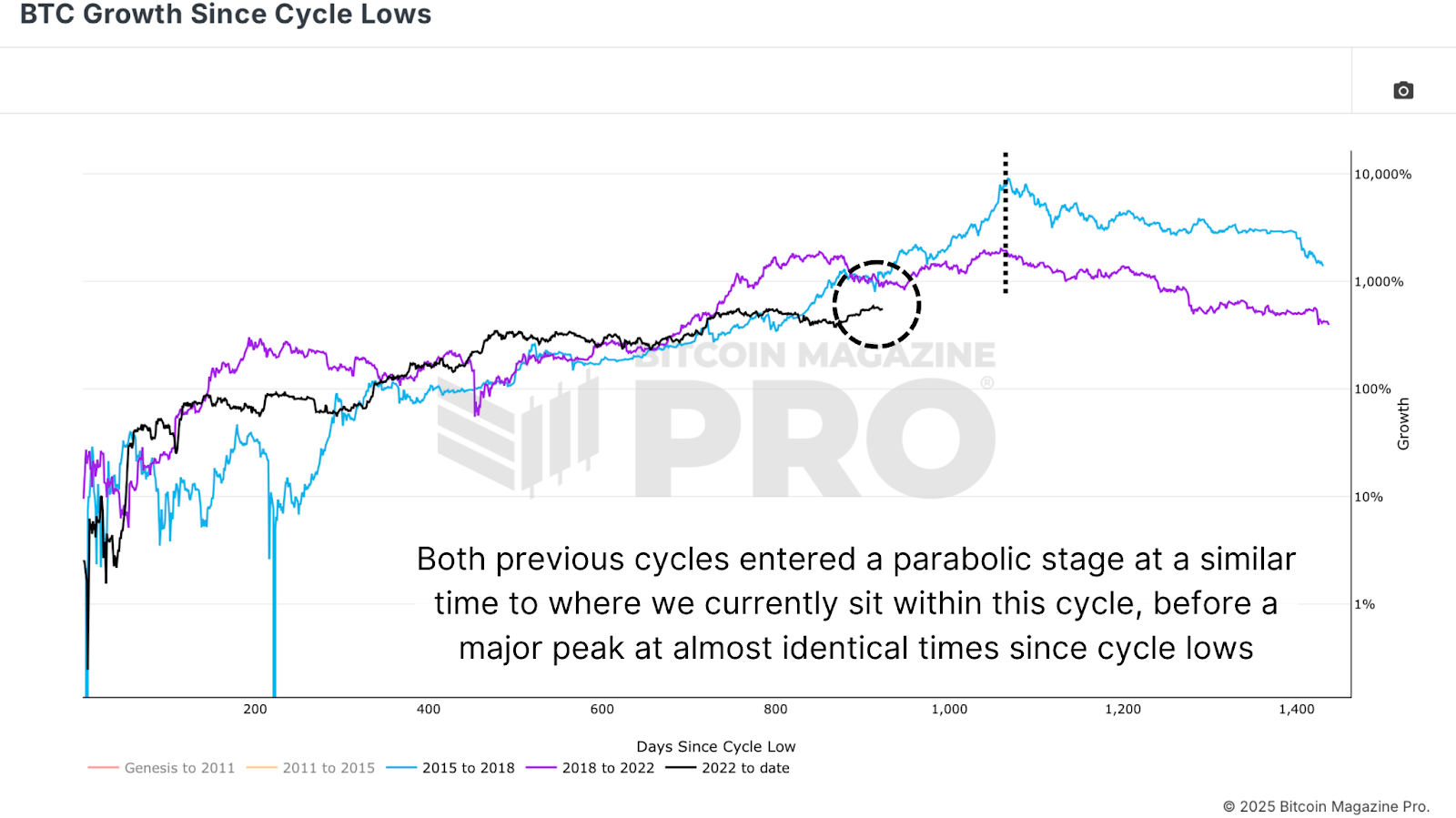
Figure 5: Will the current cycle continue to exhibit growth patterns similar to those of the previous two cycles? View Live Chart
Conclusion
The MVRV ratio and its derivatives remain essential tools for analyzing Bitcoin market behavior, providing clear markers for both accumulation and distribution. Whether observing short-term holders hovering near local top thresholds, long-term holders nearing historically significant resistance zones, or adaptive metrics like the 2-Year Rolling MVRV Z-Score signaling plenty of runway left, these data points should be used in confluence.
No single metric should be relied upon to predict tops or bottoms in isolation, but taken together, they offer a powerful lens through which to interpret the macro trend. As the market matures and volatility declines, adaptive metrics will become even more crucial in staying ahead of the curve.
For more deep-dive research, technical indicators, real-time market alerts, and access to a growing community of analysts, visit BitcoinMagazinePro.com.
Disclaimer: This article is for informational purposes only and should not be considered financial advice. Always do your own research before making any investment decisions.
This post Mapping Bitcoin’s Bull Cycle Potential first appeared on Bitcoin Magazine and is written by Matt Crosby.
-
 @ 9ca447d2:fbf5a36d
2025-06-07 07:01:18
@ 9ca447d2:fbf5a36d
2025-06-07 07:01:18Wall Street is warming up to Bitcoin and getting closer and closer to it.
Cantor Fitzgerald, one of the oldest and most respected investment banks on Wall Street, has launched a $2 billion bitcoin-backed lending program.
They’ve reportedly already done their first deals, lending to two big digital asset companies: FalconX and Maple Finance.
This is a big step in connecting traditional finance to the fast-moving world of Bitcoin.
Cantor’s new service allows big investors, hedge funds and asset managers, to borrow money using bitcoin as collateral.
This is a game changer for institutions that hold bitcoin, as they can now access liquidity without having to sell their assets.
“Institutions holding bitcoin are looking to broaden their access to diverse funding sources,” said Christian Wall, co-CEO and global head of fixed income at Cantor Fitzgerald.
“And we are excited to support their liquidity needs to help them drive long term growth and success.”
The loans are not speculative or unsecured.
They are structured like traditional finance deals, backed by the borrower’s bitcoin. This reduces the risk for Cantor while giving bitcoin-holding companies new ways to grow and operate.
The first recipients of Cantor’s lending program are FalconX, a digital asset brokerage, and Maple Finance, a blockchain-based lending platform.
FalconX confirmed they secured a credit facility of over $100 million. Maple Finance also received the first tranche of their loan from Cantor.
This comes at a time when the bitcoin lending space is recovering after a tough period. Several big firms went under in 2022 and investor confidence was shaken.
Now with traditional finance on board, bitcoin-backed lending has returned. According to Galaxy Research the total size of the digital asset lending market grew to $36.5 billion in Q4 2024.
Cantor’s move into bitcoin-backed lending isn’t new. They announced their plans in July 2024 and have been building their presence in the Bitcoin space since then.
Earlier this year, they partnered with Tether, SoftBank and Bitfinex to launch Twenty One Capital, a $3.6 billion fund to buy over 42,000 bitcoin.
In May 2025 Cantor Equity Partners merged with Twenty One Capital and bought nearly $459 million worth of bitcoin.
They also own around $1.9 billion in shares of Strategy, a company that holds a lot of bitcoin. Clearly Cantor believes in bitcoin as a long-term asset.
Cantor is also a big player in the stablecoin space.
They manage U.S. Treasury reserves for Tether, the company behind the $142 billion USDT stablecoin. This adds another layer of trust and credibility to Cantor’s digital asset involvement.
To secure the bitcoin used as collateral, Cantor has partnered with digital asset custodians Anchorage Digital and Copper.co.
These companies are known for their robust security and institutional-grade infrastructure. Cantor hasn’t disclosed loan terms or interest rates but confirmed the lending will follow current regulations.
This also shows how traditional financial players are embracing DeFi.
Maple Finance for example allows undercollateralized lending using blockchain. By backing companies like Maple, Cantor is innovating while still having control and compliance.
For years, bitcoin-backed loans were only available through digital-asset-native companies like Genesis, BlockFi, and Ledn.
These loans were mostly for smaller clients and retail investors. But with Cantor’s entry, the scale and professionalism of bitcoin lending are expanding.
-
 @ 0f1b5961:868242bd
2024-03-22 17:12:48
@ 0f1b5961:868242bd
2024-03-22 17:12:48Trying out the highligher.com editor...
heaven : earth governance : generation emanation : emergence selection : variation
-
 @ a296b972:e5a7a2e8
2025-06-06 12:57:30
@ a296b972:e5a7a2e8
2025-06-06 12:57:30Wie schon gewohnt durch die Empfänge von Baerbock und von der Leyen im Ausland, in Washington ein Empfang etwas oberhalb der 1. Class, von Staatsempfang keine Spur. Passt eigentlich auch nicht für den 51. Bundesstaat der USA. Aber immerhin flog die „Bundesrepublik Deutschland“ ohne Pannen, das ist ja auch schon mal was. Und bei solch einem erfahrenen Chef-Co-Piloten an Bord, der auch mal schnell einspringen könnte, sozusagen als 2. Wahl, kann eigentlich gar nichts mehr schief gehen. Vielleicht hat Fritzchen den Kapitän auch gefragt, ob er auch mal ans Steuer darf, wenn sich die Gelegenheit schon bietet.
Im Gepäck die eingerahmte Geburtsurkunde von Großvater Trump. Als ob Donald die sich nicht selbst besorgen könnte, wenn er Interesse daran hätte. Vielleicht hat er sie auch schon.
Die Übergabe, kurz und schmerzlos. Sie erinnert an einen Sketch von Loriot, „Weihnachten bei Hoppenstedts“:…oh, eine Krawatte! Der versprochene Ehrenplatz wird sich vermutlich in einer der unteren Etagen des Weißen Hauses befinden.
Man muss auch erst einmal darauf kommen, so typisch deutsch: Eine Geburtsurkunde als Geschenk. Das könnte man auch als einen Wink mit dem Zaunpfahl ansehen: Erinnere Dich an Deine deutschen Wurzeln (und lass uns gefälligst nicht fallen?).
Jetzt zur Einschätzung des Treffens: Vorfahrt mit frisch gewaschenem Auto, Schwarz-Rot-Gold vorne am Kotflügel, wie es sich gehört, Schwarz-Rot-Gold am Eingang. Ganz schön rechts. Warum eigentlich nicht die Regenbogenfahne?
Begrüßung durch Trump auf Nachfrage eines Reporters: „I love the People of Germany.“
Und Merz nutzt die Gelegenheit sich in Biedermeier-Style einzuschmeicheln: „And I love the People of America.“
Und Trump erwidert: „That‘s good!“
In welcher Atmosphäre findet das Treffen statt?
Trump hat ein Elefantengedächtnis. Er weiß um die abwertenden, diplomatiefreien Aussagen, die Merz über ihn gemacht hat. Er weiß, dass Merz ihn mehrfach persönlich beleidigend angegriffen hat. Als Präsident der USA steht man darüber. Aber man weiß es! Trump ist sich darüber im Klaren, mit welcher Geisteshaltung er es bei Merz zu tun hat.
Vor dem Hintergrund passt seine Aussage zur Presse: „Ich liebe die Deutschen.“ Das ist eine demokratische und höfliche Sympathiebekundung gegenüber der deutschen Bevölkerung, die Merz zwar miteinschließt, aber nicht direkt an ihn gerichtet ist.
Trump begrüßt Merz mit Handschlag, begrüßt aber eigentlich nicht den Kanzler, sondern die Deutschen.
Andererseits darf der Äußerung „Ich liebe die Deutschen“ auch nicht zu viel Bedeutung beigemessen werden, denn die Amerikaner sind ja dafür bekannt, dass sie gerne und schnell alles lieben: I love America, I love Coca-Cola, I love Peanuts und eben auch I love the People of Germany.
Merz nutzt gleich die Gelegenheit, sich anzubiedern, in dem er pariert: „Und ich liebe die Amerikaner.“, worauf Trump antwortet: „That’s good!“ Das kann man übersetzen mit „Das ist gut!“, aber auch mit „Das ist auch gut so!“, bei letzterem wäre es eine versteckte Drohung. Mach Dir bewusst, wo Du bist und mit wem Du es zu tun hast und verhalte Dich danach!
Nonverbal wird dem sonst in Deutschland so eloquent wirken wollenden, akzentuiert sprechenden Merz die Bedeutung zugedacht, die ihm aus Sicht von Trump gebührt. In Frankfurt heißen sie Wiener, in Wien heißen sie Frankfurter.
Somit sind die Voraussetzungen, unter denen das Treffen stattfinden soll, schon einmal von amerikanischer Seite aus geklärt.
Du bist hier Gast in meinem Haus, also benimm Dich auch entsprechend! Ich bin der Präsident der Vereinigten Staaten von Amerika und Du bist klein Fritzchen aus dem Sauerland. Die Machtverhältnisse sind unausgesprochen geklärt.
Man hat in gewohnter Manier Platz genommen. Die Journalisten stellen Ihre Fragen ausschließlich an Trump. Zufall, oder Teil einer orchestrierten Aufführung, das wird man nie erfahren.
So oder so, die Journalisten signalisieren durch ihre Fragen an Trump, auf welcher Seite sie stehen, es weht der Geist von „America first“. Was Germany dazu zu sagen hat, interessiert niemanden, warum auch?
Die Einseitigkeit ist schon sehr auffällig. Eigentlich hätte es die Journalisten interessieren müssen, wie Deutschland zu verschiedenen Themen steht. Keine Fragen an Merz zu Zöllen, zur Ukraine, zur Meinungsfreiheit, zur Opposition. Mit dem Anspruch, ein breites Spektrum an Meinungen abbilden zu wollen, hat das eigentlich nichts zu tun. Wenn das die Vorstellung von „Freedom of Speach“ ist, dann können hier Zweifel aufkommen.
Falls diese Fragerunde in Hollywood-Manier gestaltet wurde, dann spräche das eher für Propaganda pro Trump. Wäre es Propaganda, dann wäre das Ziel allerdings erreicht worden: Kein Mensch interessiert sich für das, was Deutschland, vertreten durch Merz, zu sagen hat.
Trump setzt dem Ganzen zum Schluss noch die Krone auf, in dem er die Journalisten auffordert, nun endlich doch auch noch ein paar Fragen an Merz zu richten. Das unterstreicht nochmals das (geplante oder ungeplante) Desinteresse der anwesenden Journalisten, die sich nun fast schon genötigt fühlen, anstandshalber etwas zu fragen.
Merz, der bisher brav wie ein Schüler dem Lehrer zugehört hat, muss nun blitzschnell entscheiden, wie er die „künstlich“ hergestellte Möglichkeit nutzen kann, um, etwas unter Druck, durch die Kürze der Zeit, mit wenigen Worten seinen Standpunkt nach außen zu tragen. Seine konzentrierte Kernbotschaft, die Essenz, die Deutschland aus den USA und die übrige Welt hören soll, ist: Er steht weiter an der Seite der Ukraine und Russland ist ausschließlich das Böse.
Ganz schön raffiniert, denn so hat Trump es geschafft, das Konzentrat der Merz’schen Logik aus ihm herauszupressen.
Beide bekunden den Willen zum Frieden. Gleichzeitig wird jedoch auch klar, was jeder unter Frieden versteht: Merz will „Frieden durch Krieg“ und Trump will „Frieden durch Frieden“.
Auf rund 45 Minuten Trump kommen rund 4 Minuten Merz. Die Minuten drücken exakt die Machtverhältnisse aus.
Hätte Trump vorgehabt, Merz vorzuführen, ihm die Ohren langzuziehen, ihn bis auf die Knochen zu blamieren, er hätte reichlich Möglichkeiten dazu gehabt.
Er hätte Merz fragen können, warum er seinerzeit meinte, dass ihn, Trump, als Arschloch zu bezeichnen, noch gelinde sei. Er hätte ihn fragen können, warum er Trump als Gefahr für die Demokratie ansieht. Trump weiß darum, er hat es jedoch nicht angesprochen, was ist der Grund dafür?
Und Vance, der ebenfalls anwesend war, hätte seine Feststellungen zur Meinungsfreiheit und der „Fire-Wall“ gegen die Opposition, die er auf der Sicherheitskonferenz in München klar formuliert hat, wiederholen können, jetzt, wo doch der Kanzler, als erster Ansprechpartner für Deutschland, persönlich hätte gefragt werden können.
Beim Besuch von Selenskyj haben beide ja auch gewaltig gezeigt, wer hier das Sagen hat.
Nichts! Keine schallende Ohrfeige für Merz, doch nur Erdnussbutter auf’s Sandwich geschmiert. Kein „You don’t have the cards…“, was den Tatsachen entsprechen würde.
Auf politischer Ebene bleibt in den USA nichts, rein gar nichts dem Zufall überlassen. Je länger man darüber nachdenkt, desto klarer kann einem werden, dass das Treffen genau so geplant war, wie es sich abgespielt hat. Aber was genau ist der Plan, der dahintersteckt? Es gibt einen, dass ist so sicher, wie das Amen in der Kirche.
Sollen sich die Deutschen, vor allem die deutsche Politik in Sicherheit wiegen? Wenn das Teil eines Planes wäre, wäre er gelungen, denn in Deutschland wird der Besuch als gelungen und erfolgreich bewertet, aus welchen Gründen auch immer. Inzwischen ist Deutschland ja Weltmeister im Schönreden.
Spannend auch die Vorstellung, wenn man die Phantasie anregt, wie das Gespräch verlaufen wäre, wenn die deutsche Opposition auf dem Stuhl von Merz gesessen hätte.
Es widerspräche der Realität, wenn nicht im Hintergrund ganz andere Ziele verfolgt und Absprachen getroffen würden. Welchen Einfluss auf das Treffen hat der bevorstehende NATO-Gipfel am 24. und 25. Juni 2025 in Den Haag?
Es drängt sich immer mehr der Verdacht auf, dass man es mit zwei Realitäten zu tun hat. Eine, die offiziell verkündet wird, und eine, die den Tatsachen entspricht, die aus welchen Gründen auch immer jedoch zunächst noch im Verborgenen bleibt. Ob das vielleicht sogar gut oder eher schlecht ist, wird die Zukunft zeigen. Klar ist jedoch, dass eine gesteuerte Realität in der Öffentlichkeit verbreitet werden soll, die man durchaus als Propaganda von allen Beteiligten bewerten kann. Da hackt eine Krähe der anderen kein Auge aus. Da heißt es wachsam bleiben und nicht der Versuchung zu erliegen, das zu glauben, was man gerne glauben möchte und von dem man sich wünscht, dass es eintritt.
„Bediene Dich Deines eigenen Verstandes.“ Das ist die Aufgabe der Zeit.
“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
* *
(Bild von pixabay)
-
 @ 3d842afe:2d44a42d
2024-03-20 19:35:28
@ 3d842afe:2d44a42d
2024-03-20 19:35:28Websocket connection overhead is an obvious problem with the gossip model that few are willing to acknowledge. The more decentralized relay selection becomes (the goal) the worse it scales. Even at the current scale of nostr if users chose more diverse relay sets the issue would be crippling.
Below are some very simple simulations to illustrate my point. I used 2 relays per person to be conservative and chose 3 different realistic follow counts. The NIP-65 spec suggests clients should guide users to keep the lists small (2-4 relays) though currently the average kind 10002 contains many more. I ran each simulation 10 times and then took the average result.
EDIT: I understand that selecting relays at random is NOT how things currently work or will ever work. My point is that if our goal is to make relay sets more diverse then we should work towards a solution that scales with accomplishing that goal.
Available relays: 600 (~what nostr.watch currently shows for online relays) Follows: 200 Relays per person: 2 (randomly selected) Unique Connections Required: 291
Available Relays: 600 Follows: 500 Relays per person: 2 Unique Connections Required: 486
Available Relays: 600 Follows: 1000 Relays per person: 2 Unique Connections Required: 577
Even today if users randomly selected relays the total number of connections required would be staggering and this is with users only selecting 2 relays each. What happens if the available number of relays increases by 5x?
Available Relays: 3000 Follows: 200 Relays per person: 2 Unique Connections Required: 376
Available Relays: 3000 Follows: 500 Relays per person: 2 Unique Connections Required: 847
Available Relays: 3000 Follows: 1000 Relays per person: 2 Unique Connections Required: 1461
I’m not a client developer and I certainly don’t have all the solutions but I’ve spent enough time operating websockets at scale to know that these numbers aren’t going to work even with only 2 relays per person. Aside from the practical performance implications, browsers also enforce websocket limits that put most of these numbers out of reach (I believe Chrome is 255 and Firefox is 200).
What am I missing?
-
 @ 81022b27:2b8d0644
2025-06-08 15:18:50
@ 81022b27:2b8d0644
2025-06-08 15:18:50I’ve always gravitated to ideas and topics that are not quite mainstream:
Well, like CHIROPRACTIC.
But even in chiropractic school, I went fringe. I heard about one of the technique clubs (Toftness) that showed you how you could detect a subluxation by just rubbing your thumb over a piece of plexiglass.
We were discussing that in a group, and most of my friends were saying:
“What a load of shit!”
And that made my ears perk up.
So I started going to the club meetings.
I walk in, and there’s a guy face down on a chiropractic table while another guy was holding what looked like some sort of cyberpunk lens. He started rubbing it and worked it down the guy's spine.
He pointed out areas that were subluxated:
“Here.”
And going further down:
“Here.”
And:
“Here.”
Wow.
Then he “adjusted” by touching the spine with his index finger.
My mind was blown.
So you mean I didn’t have to be adjusted the way Harvey Fish did?
Dr. Fish was a great guy and would adjust students for, I think, $10. You’d go in, wait to see if he had any “real patients.” In between patients, he would adjust the students. He was heavy-handed and sure as hell able to move a bone.
So now I’m intrigued and curious. I studied and practiced any chance I had. I had different friends that I studied different things with.
(Except for Dyslexic Dave - nobody wanted to study with that guy. Our group did once, and we all failed a test. His dyslexia was so powerful, it overcame all of us.)
I’d study all the weird stuff with my friend Victoria, and then we would go get our network chiropractic adjustment from Dr. Michael Scimeca.
I found out that it wasn’t the Toftness lens that had the super-powers. Instead, it was because when your hand detected a change in energy over the spinal segments, there's a “galvanic response” similar to that of a polygraph lie detector test. So it made the skin on my hand “sweat,” and that made the plexiglass squeak and stick.
So it wasn’t the equipment. It was me.
After a while, I realized that I could feel a warmth on my chest right before the lens squeaked. So, I ditched the lens and started working on people where I “felt” the subluxations were located.
Seemed to work well - I always double-checked my “regular” chiropractic findings with what I felt. We studied for exams, then practiced technique on each other.
One time at a seminar, the instructor demonstrated what to do and asked for volunteers - one to be the patient and the other to be the doctor. I watched this guy struggling with his patient. It looked like he had flippers instead of hands; the whole interaction was super awkward.
All of a sudden, I started feeling uncomfortable and just blurted out:
“For God’s sake, leave him alone! Can’t you tell he is super annoyed and angry?”
Oops.
The instructor said, “Yes, maybe we should take a break.”
The guy that was the patient came up to me and asked, “How did you know?”
“I don’t know, I just felt it,” I said.
After that I started trying to see if I could feel what others were feeling. So when I was bored in a class, I’d go down the rows and try to feel what the my fellow students felt and quickly move on.
Going down the row: nothing, nothing nothing. This guy is pissed off, next one: nothing, nothing, Ow! She has a headache.
Dammit! Now I have a headache!
So that turned into a problem: When I worked on someone that had pain or other symptoms, I would take those on for myself. And the person I worked on would leave feeling great.
My friend Juanita did what is called an "attunement," and I became a Reiki Master.
Reiki masters are supposed to move energy around, but I was afraid I’d pick up too much of someone’s vibe and it would make me uncomfortable.
Plus, I can’t be doing energy work if I’m a chiropractor now.
So I kept all that checked and on the "down low"; sometimes I would get a "feeling" about a client while I was working on them. Surprisingly, it was always correct and it helped my client to make progress.
At some point, I started feeling that I needed to be true to myself, and if I had these abilities and I was able to use them to help the people that came to see me, then that's what I was going to do.
I've embraced this side of my work. If my clients need some emotional work, that’s what we work on, if they need some energy work, then they get it.
I suppose some people don’t want a chiropractor that’s metaphysical, but really-that’s how it all started. There are plenty of “evidence-based” chiropractors out there that can’t adjust their way out of a paper bag.
If the power goes off, they couldn’t use their lasers or whatever machine the Chiropractic Physiotherapy Industrial Complex wants you to buy now.
While I appreciate all the fancy parties they throw for us at continuing education seminars, they are infiltrating the chiropractic schools and now we are pumping out new chiropractors that only think they will be successful if they have the latest and greatest shiny machine.
I’ve studied a bunch of different things, I’ve found what works for me and refined it.
I tell my clients :
“I’m a better chiropractor today than I was yesterday, and I was pretty good back then!”
So I guess my next step is teaching some of this information and hoping to pass it on before my time here is up.
And you know what? I will love every damn minute of it!
There's nothing quite like sharing the weird, the wonderful, and the downright strange ways we can help people heal.
So, let's get to it—I've got a lot of sharing and teaching to do—it's going to be exciting!
-
 @ 7f6db517:a4931eda
2025-06-06 09:01:36
@ 7f6db517:a4931eda
2025-06-06 09:01:36
What is KYC/AML?
- The acronym stands for Know Your Customer / Anti Money Laundering.
- In practice it stands for the surveillance measures companies are often compelled to take against their customers by financial regulators.
- Methods differ but often include: Passport Scans, Driver License Uploads, Social Security Numbers, Home Address, Phone Number, Face Scans.
- Bitcoin companies will also store all withdrawal and deposit addresses which can then be used to track bitcoin transactions on the bitcoin block chain.
- This data is then stored and shared. Regulations often require companies to hold this information for a set number of years but in practice users should assume this data will be held indefinitely. Data is often stored insecurely, which results in frequent hacks and leaks.
- KYC/AML data collection puts all honest users at risk of theft, extortion, and persecution while being ineffective at stopping crime. Criminals often use counterfeit, bought, or stolen credentials to get around the requirements. Criminals can buy "verified" accounts for as little as $200. Furthermore, billions of people are excluded from financial services as a result of KYC/AML requirements.
During the early days of bitcoin most services did not require this sensitive user data, but as adoption increased so did the surveillance measures. At this point, most large bitcoin companies are collecting and storing massive lists of bitcoiners, our sensitive personal information, and our transaction history.
Lists of Bitcoiners
KYC/AML policies are a direct attack on bitcoiners. Lists of bitcoiners and our transaction history will inevitably be used against us.
Once you are on a list with your bitcoin transaction history that record will always exist. Generally speaking, tracking bitcoin is based on probability analysis of ownership change. Surveillance firms use various heuristics to determine if you are sending bitcoin to yourself or if ownership is actually changing hands. You can obtain better privacy going forward by using collaborative transactions such as coinjoin to break this probability analysis.
Fortunately, you can buy bitcoin without providing intimate personal information. Tools such as peach, hodlhodl, robosats, azteco and bisq help; mining is also a solid option: anyone can plug a miner into power and internet and earn bitcoin by mining privately.
You can also earn bitcoin by providing goods and/or services that can be purchased with bitcoin. Long term, circular economies will mitigate this threat: most people will not buy bitcoin - they will earn bitcoin - most people will not sell bitcoin - they will spend bitcoin.
There is no such thing as KYC or No KYC bitcoin, there are bitcoiners on lists and those that are not on lists.
If you found this post helpful support my work with bitcoin.

-
 @ dfa02707:41ca50e3
2025-06-06 09:01:30
@ dfa02707:41ca50e3
2025-06-06 09:01:30Contribute to keep No Bullshit Bitcoin news going.
- RoboSats v0.7.7-alpha is now available!
NOTE: "This version of clients is not compatible with older versions of coordinators. Coordinators must upgrade first, make sure you don't upgrade your client while this is marked as pre-release."
- This version brings a new and improved coordinators view with reviews signed both by the robot and the coordinator, adds market price sources in coordinator profiles, shows a correct warning for canceling non-taken orders after a payment attempt, adds Uzbek sum currency, and includes package library updates for coordinators.

Source: RoboSats.
- siggy47 is writing daily RoboSats activity reviews on stacker.news. Check them out here.
- Stay up-to-date with RoboSats on Nostr.
What's new
- New coordinators view (see the picture above).
- Available coordinator reviews signed by both the robot and the coordinator.
- Coordinators now display market price sources in their profiles.

Source: RoboSats.
- Fix for wrong message on cancel button when taking an order. Users are now warned if they try to cancel a non taken order after a payment attempt.
- Uzbek sum currency now available.
- For coordinators: library updates.
- Add docker frontend (#1861).
- Add order review token (#1869).
- Add UZS migration (#1875).
- Fixed tests review (#1878).
- Nostr pubkey for Robot (#1887).
New contributors

Full Changelog: v0.7.6-alpha...v0.7.7-alpha
-
 @ 0b118e40:4edc09cb
2025-06-06 13:56:01
@ 0b118e40:4edc09cb
2025-06-06 13:56:01The idea of Bitcoin as an internet native currency, and eventually a global one, is coming to life slowly. But historically, the idea of global currency has haunted the world’s financial imagination for nearly a century.
From Keynes’s Bancor in 1944 to Zhou Xiaochuan’s post-crisis proposal in 2009 to today’s renewed debates, the idea resurfaces every time the global economy fractures.
Could this time be different with Bitcoin?
I decided to trace the idea of global currency through several decades and books. I may have missed some parts, so feel free to add. I’ll keep this brief and leave the books I’ve read below.
In the beginning
It all started on July 1, 1944. 730 delegates from 44 Allied nations, including major powers like the US, UK, Soviet Union, China, and France, gathered at the Mount Washington Hotel in Bretton Woods, New Hampshire. They spent 2 weeks figuring out how the new international monetary and financial system would be, post WW2
After WW1, the treaty of Versailles was needed, but imposed harsh reparations that devastated economies and contributed to the rise of fascism, such as Hitler, Mussolini and gang.
So when folks met up in 1944 (WW2 was almost ending), the goal was to prevent another Great Depression, another global conflict and build a stable global economic order.
2 main proposals were discussed in Bretton Woods.
-
John Maynard Keynes, representing the UK, proposed the creation of a global currency called Bancor. It will be issued through a global central bank known as the International Clearing Union (ICU).
-
Harry Dexter White, representing the US, promoted a dollar-based system. Countries would peg their currencies to the US. dollar backed by gold. He also led the creation of the IMF and the World Bank.

To understand how both of these proposals work, let's look at an example.
-
Country A (Germany): Massive exporter
-
Country B (USA): Massive importer
-
Country C (Brazil): Balanced trade (imports = exports)
***Based on Dexter’s model and the current USD-based system, ***
Say Germany sells $1B worth of cars to the US. The US pays in dollars, increasing its trade deficit. Germany accumulates dollars as reserves or buys the US Treasury bonds. Over time, the US continues running trade deficits, while Germany keeps hoarding dollars. Hence the unsustainable debt of the US.
***In Keynes’s Bancor system, ***
If Germany sells $1B worth of cars to the US, then the US does not pay in dollars. Instead, the ICU credits Germany with 1B Bancors and debits the US with -1B Bancors.
The ICU police this. If Germany exceeds the surplus threshold, it pays interest or penalties to discourage hoarding. If the US exceeds its deficit threshold, it is warned to rebalance trade or face restrictions.
Here, Germany is incentivized to import more (e.g., from Brazil) or invest in global development. The US is encouraged to export more or reduce consumption. Brazil, with balanced trade, enjoys stability in Bancor flows and avoids pressure.
The idea behind Bancor was a zero-sum balancing act. No country could become “too big to fail” due to excessive deficits. But it was too complicated and idealistic in assuming every country could maintain balanced trade.
Dexter on the other hand had a few tricks up his sleeve. In the end, Dexter’s USD dominance proposal was adopted.
The Bretton Woods system established the US dollar as the central global currency
Why did dollar dominance win over Bancor?
Simplicity often wins over complexity. But more so ICU felt too centralized, asking nations to surrender economic autonomy to a global body. That didn’t sit well in a post-war world where sovereignty was non-negotiable. That and idealist economic trade balance views.
Dexter’s dollar-based system on the other hand wasn’t fair play at all. It was centralized and authoritarian in its design.
So how did Dexter pull it off?
They had gold. They were ahead in economic recovery.
And they had nuclear weapons.
At the time, the US held nearly 2/3 of the world’s gold reserves. It was a significant advantage in advocating for a gold-backed dollar as the bedrock of global trade.
The US proposed a fixed gold peg at $35 per ounce.
From a broader geopolitical backdrop, the global population in 1944 was about 2.3 billion, a fraction of today’s 8 billion. The world was far less interconnected. The war had devastated Europe, Russia, and much of Asia. Infrastructure, economies, and entire cities were in ruins. The US, by contrast, had faced far fewer casualties and damages. Being geographically isolated, it had minimal domestic losses, around a tenth of what Europe suffered, and its economy was poised to rebuild faster.
But gold dominance and economic recovery alone didn’t secure US financial dominance.
American scientific breakthroughs had already signaled global power. Physicists like Leo Szilard and Albert Einstein, who had fled Europe, helped develop nuclear weapons. Their intent was deterrence, not destruction. But once the bomb existed, it changed geopolitics overnight. The US had military dominance. And after Hiroshima and Nagasaki in 1945, it became the undisputed superpower.
In the end, the USD won and the vision for neutral global currency faded.
And 20 years passed on…
France sends its warship to the US
Under Bretton Woods, countries could exchange dollars for gold, but the US had been printing more dollars than it had gold to back it. And it used it to fund the costly Vietnam War and domestic programs like the Great Society under LBJ.
Belgian-American economist Robert Triffin pointed out a fatal flaw in the Bretton Woods system that came to be known as the Triffin dilemma.
-
The world needed US dollars for liquidity and trade.
-
But the more dollars the US pumped out, the less credible its gold promise became.
Yet the US kept promising that every dollar was still convertible to gold at $35 per ounce.
French President Charles de Gaulle saw this as financial imperialism. He called it the “exorbitant privileged position”. The world had to pay for what they bought with the money they have, but not the US.
So in 1965, France did something unexpected. It sent a warship to New York Harbor to physically retrieve French gold reserves held by the Federal Reserve.

Would it have escalated to war? Maybe. But likely not. It was perhaps more of a diplomatic theatre and a sovereign flex. France was exercising its right under the Bretton Woods agreement to convert dollars into gold. But doing it with military formality was to send a signal to the world that they don’t trust the US system anymore.
It was one of the first major public blows to the dollar’s credibility. And France wasn’t alone. Other countries like West Germany and Switzerland followed suit, redeeming dollars for gold and draining US reserves.
The Nixon shock
Given they did not have enough gold, the IMF introduced Special Drawing Rights (SDRs) in 1969. SDRs were an international reserve asset, created to supplement gold and dollar reserves. Instead of relying solely on the US dollar, SDRs were based on a basket of major currencies (originally gold-backed but later diversified).
The idea was to reduce the world’s dependence on the dollar and avoid a liquidity crisis. But SDRs were a little too late and a little too weak to solve the underlying problem.
By 1971, the US could no longer sustain the illusion. President Nixon “closed the gold window,” suspending dollar convertibility to gold.
The Bretton Woods collapsed and this marked the beginning of fiat money dominance.
The French pursuit
While France demanded justice in one corner of the world, the French franc, specifically the CFA franc, has been dominant in parts of Africa since 1945, long before 1971.
After WWII, France created two CFA franc zones:
-
West Africa: Communauté Financière Africaine (XOF)
-
Central Africa: Coopération Financière en Afrique Centrale (XAF)
These zones included 14 African countries, many of which were former French colonies. France maintained monetary control via currency convertibility guarantees and representation in African central banks. Till today it has influence over these country’s monetary policy.
Colonisation hasn't ended in some parts of the world.
Did countries stop using the USD after the Nixon shock 1971?
Nope. The US dollar was no longer convertible to gold and it dismantled the fixed exchange rate system. But most countries did not stop using the USD as their dominant reserve or trade currency. There were no decent alternatives. Instead, they floated their currencies or maintained a soft peg to the dollar or a basket of currencies.
The USD remained dominant in oil trade (OPEC priced oil in USD) - petrodollar deal, global debt markets and FX reserves (central banks kept holding USD).
In 1997, when many Southeast Asian countries were still pegged to the USD, Soros claimed that SEA will tank. The US further increased its credit rates leading to capital flight and eventual tanking of these countries leading to Asian Financial Crisis '97. Many financial crisis has similar vibe.
The 1999 Euro launch
The idea of a shared currency appeared again, this time through the forms of Euro. It was a mandatory system for member states of the Eurozone, and came with centralized authority, the European Central Bank (ECB), which controlled monetary policy for all participating nations.

At first glance, the euro seemed like a win. It eliminated exchange rate fluctuations, making trade within the Eurozone smoother. It gave weaker economies access to lower borrowing costs and helped Europe establish itself as a financial heavyweight. Today, the euro is the second most-used reserve currency after the US dollar.
But it came at a cost. Countries that adopted the euro lost monetary sovereignty and could no longer print their own money or adjust interest rates to respond to local crises. This became painfully clear during Greece’s debt crisis, where strict monetary policies prevented the country from devaluing its currency to recover. The one-size-fits-all approach meant that economies as different as Germany and Greece had to follow the same rules, often to the detriment of weaker nations. Debt-ridden countries like Italy and Spain were forced into harsh austerity measures because they could not manipulate their currency to ease financial strain. Meanwhile, richer nations like Germany and the Netherlands felt they were unfairly propping up struggling economies, creating political tension across the EU.
In recent years, the euro has faced pressure from global trade tensions, monetary tightening, and geopolitical instability contributing to market volatility and periodic depreciation against other major currencies.
The Bretton Woods 2.0
Believe it or not, after all that, there was a call for Bretton Woods 2.0. Yet another global currency dream.
When the housing market collapsed in 2008 followed by a series of domino effects, global banks froze lending, economies contracted, and panic set in. The crisis exposed how fragile the international financial system had become as it was overly reliant on debt, under-regulated, and centered around the US dollar.
Many countries, especially in the Global South and emerging markets, started to question whether a system built around a single national currency was sustainable.
China, for instance, had been holding huge amounts of US debt while the US printed more dollars through bailouts and quantitative easing. This created global imbalances as exporting nations were lending money to the US to keep the system running, while taking on the risk of dollar depreciation.
In 2009, China’s central bank openly proposed replacing the US dollar with a neutral global reserve currency suggesting SDRs (Special Drawing Rights) issued by the IMF instead.
These concerns led to a wave of calls from world leaders for a “Bretton Woods 2.0” , a modern rethinking of the post-WWII economic order. At G20 summits in London in 2009, countries like France, China, and Russia pushed for reforms in global financial institutions and more balanced power sharing.
In the end, the IMF received more funding, and some banking regulations were tightened in the years after. But no real overhaul happened. No surprise there? The dollar remained dominant.
The foundation of the global economy didn’t change, even though trust in it had been deeply shaken.
The growth of BRICS
In 2023, Brazil, Russia, India, China, and South Africa began discussing the idea of a shared currency or alternative mechanism to reduce the dependence on USD ie de-dollarisation. The sanctions on Russia didn't help. After Russia’s invasion of Ukraine, the US and its allies froze Russia’s dollar reserves and cut it off from SWIFT, the “backbone of global banking communication”. This made one thing clear. If you fall out with Washington, your access to the global economy can vanish overnight.
China’s growing economic power also gave it more leverage to process alternative options. It would trade in Yuan with Russia and Iran.
I know many still say it's at its early stage, but I see many countries hedging their bets quietly and aligning with Putin and Xi. It became more obvious after US imposed tariffs on multiple nations, signaling that economic tools can double as political weapons. The world’s second financial system is slowly forming.
What is the world looking for, for the last century ?
For the last 80 years, from Bretton Woods to multiple financial crises, from the birth of the Euro to the rise of BRICS, through war and peace, we’ve been circling around the same ideal. A global currency that is :
-
Simple
-
Free from dominant power
-
Decentralised
-
Borderless
-
Scarce
-
Transparent
-
Inclusive, with self custody
-
Resilient in crisis
-
Built for individual financial sovereignty
-
A new backbone for global finance, owned by no one
It doesn’t matter where you’re from, what politics you believe in, or how your economy leans. The answer keeps pointing in the same direction:
Bitcoin
This is the first true global currency.
And it’s just there
Waiting...
.
.
.
Some books that might interest you :
-
The Battle of Bretton Woods by Benn Steil
-
Goodbye, Great Britain by Kathleen Burk and Alec Cairncross
-
The Ghost of Bancor by Tommaso Padoa-Schioppa
-
Confessions of an Economic Hitman by John Perkins
-
The Blood Bankers by James S. Henry
-
-
 @ 81022b27:2b8d0644
2025-06-08 15:06:12
@ 81022b27:2b8d0644
2025-06-08 15:06:12I have a family practice where I see pretty much everything, from infants to the elderly, athletes to people with disabilities.
When someone gets good results, they always want their loved ones to benefit in the same way.
Husbands tell their wives, wives bring in their husbands...
I even had a guy bring both his wife and his girlfriend! On different days, of course.
So, sometimes we notice a little bit of drama here and there. When one of our couples divorces, someone usually gets custody of the chiropractor.
It's rare that I keep seeing both parties.
It's probably for the best, because there was this one time when a guy showed up with his new "friend" while the ex’s best friend was in the waiting area.
Well, it was like an episode of the "Jerry Springer Show" that day.
Let's get to the story:
This one guy I’d been working on started coming in more frequently, complaining of more pain, more aches, more everything.
I've been doing this for a while now, so I told him that when I see this, it's one of two things:
Either you are physically doing something to aggravate the issue,
Or you are under emotional stress.
He told me that he and his wife were having problems, and there was lots of drama.
Of course, I kept working on him. Sometimes I did some emotional work, but with men, I have to be very business-like when dealing with emotions because we don't like to deal with them.
Time passed, and they finally divorced.
He still comes in regularly, and I've noticed he has less pain and fewer issues. His visits are more like "wellness visits"; he seems in better spirits.
I thought I'd never see the ex-wife again, but she showed up today, and when I checked her, she's doing better than ever!
It got me thinking... these people are way better off divorced! They're not in constant fight-or-flight mode; I'm sure they are happier or will be. It's a positive all the way around.
I've been divorced twice. That's not something I'm proud of. I see both those divorces as failures.
I was 23 when I got married the first time. We were both super young and unprepared. We struggled for four years, and then she wanted out.
Not that I blame her; I was unhappy with myself, and my frustration and unhappiness bled into the relationship.
My second marriage lasted a lot longer than the first. After all we were older, ended up having 2 kids and I really, really tried.
I was just terrified of losing my girls. I even recall saying that I was willing to be miserable and unhappy just “for the kids”
The truth is once we separated, I probably spent more “quality time” with my daughters than I had before.
But here’s the thing in both marriages I would have willingly given up the chance to be happier with a clean end to the relationship in order to give it another shot.
At some point you just run out of shots.
I see elderly couples out at restaurants and they hardly say anything to each other. Is it because they know each other so well that they don’t need to speak, or is one of them silently praying the other one will drop dead so they will finally have a chance at happiness?
What I’m trying to say here is:
Maybe there is no hope for that relationship that you are giving CPR
Maybe it’s time to move on.
Live Long and Prosper. 🖖
-
 @ 7f6db517:a4931eda
2025-06-06 06:01:30
@ 7f6db517:a4931eda
2025-06-06 06:01:30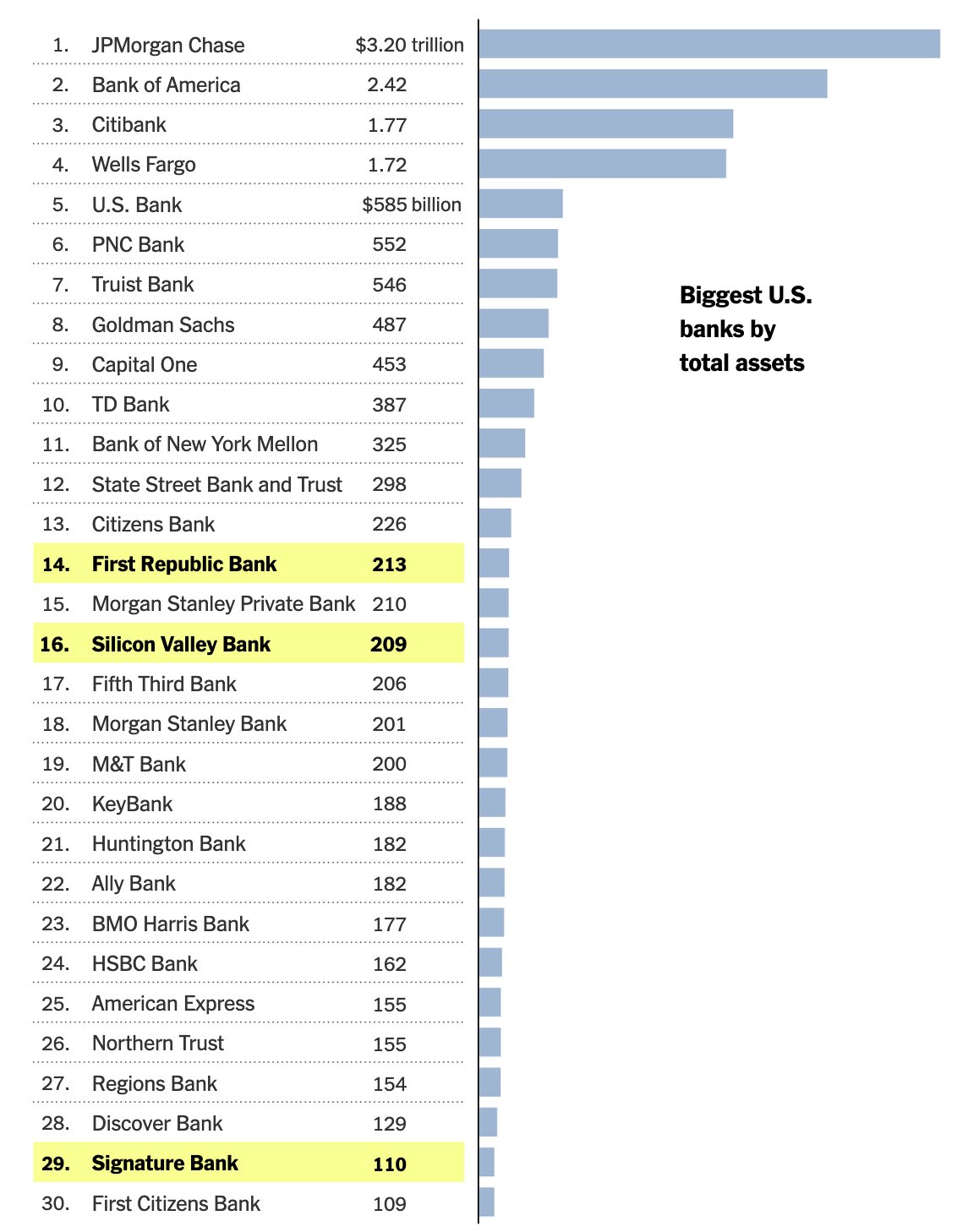
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
Good morning.
It looks like PacWest will fail today. It will be both the fifth largest bank failure in US history and the sixth major bank to fail this year. It will likely get purchased by one of the big four banks in a government orchestrated sale.
March 8th - Silvergate Bank
March 10th - Silicon Valley Bank
March 12th - Signature Bank
March 19th - Credit Suisse
May 1st - First Republic Bank
May 4th - PacWest Bank?PacWest is the first of many small regional banks that will go under this year. Most will get bought by the big four in gov orchestrated sales. This has been the playbook since 2008. Follow the incentives. Massive consolidation across the banking industry. PacWest gonna be a drop in the bucket compared to what comes next.
First, a hastened government led bank consolidation, then a public/private partnership with the remaining large banks to launch a surveilled and controlled digital currency network. We will be told it is more convenient. We will be told it is safer. We will be told it will prevent future bank runs. All of that is marketing bullshit. The goal is greater control of money. The ability to choose how we spend it and how we save it. If you control the money - you control the people that use it.
If you found this post helpful support my work with bitcoin.

-
 @ 41fa852b:af7b7706
2025-06-08 11:34:44
@ 41fa852b:af7b7706
2025-06-08 11:34:44"The poison was never forced - it was offered gently, until you forgot it was poison at all." - Mark Twain
Happy Sunday, folks.
Below is your weekly roundup of events for the coming week.
Added to the event section this week, an exciting new Scottish Bitcoin Conference, happening in August.
Check out all the details below.
This week's sponsor is…
Upcoming Bitcoin Meetups
Happening this week…
-
Dundee Bitcoin: Join them on the 2nd Monday of every month from 17:30 to 20:30 PM at The Wine Press, 16 Shore Terrace, Dundee DD1 3DN. This month's meetup is on Monday 9th. 🍻
-
Canterbury Bitcoin: Meeting this month at the The Dolphin Pub in Canterbury at 7 PM on Tuesday the 10th of June. An informal meetup to discuss Bitcoin and chat. 🍺
-
Glasgow Bitcoin: Meetups are held every second Wednesday of the month. This is a place for people in and around Glasgow to discuss Bitcoin. 18:00 - 23:00 at The Piper Bar, G1 1HL. This month on Wednesday 11th. 🍻
-
St Albans: This is a new meetup happening on the second Wednesday of each month. This month, it's from 19:00 to 22:00 on the 11th at the Robin Hood of St Albans, Victoria St, St Albans. 🍻
-
Children of Riddim - Festival - Bitcoin Stage: Children of Riddim Festival is bringing Bitcoin to the big stage from the 12th--16th June in Hemel Hempstead, with 150+ DJs, artists, and speakers. The Barn of Freedom will host Bitcoin talks, music, and Nostr-powered apps. Tickets and donations for the stage can be made via geyser.fund, with camping included. Acts/speakers include Joe Bryan, Metamick, Roger9000, Angor, and more. 🎉🪩
-
Bitcoin Beach Bournemouth: Every second Thursday of the month at Chaplins Cellar Bar. 529 Christchurch Road, Boscombe, United. You'll find them in the Cogg Room at 19:30. This month it's the 12th. 🍺
-
Bury St Edmunds Bitcoin: is reviving the medieval spirit of the Folkmoot, one Bitcoin meetup at a time. Their second gathering takes place this Friday at 17:30 at Edmundo Lounge. They've also just launched a brand new website.
-
Stoke Bitcoin Meetup: The Stoke Bitcoin meetup is back! They will have Bitcoin coffee to taste, delivered by hand directly from the mountains of El Salvador and grown by @lacruzboss in Berlin, El Salvador. 15:00 on Friday 13th. ☕️🍻
-
Bitcoin Walk - Edinburgh: Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏽♂️🚶🏼♀️🚶🏻
-
Bitcoin East: Join Bitcoin East in Bury St. Edmunds on Sunday 15th, 12:00 at Hopsters Bar, Felixstowe. All welcome, Bitcoiners and anyone else curious about Bitcoin. 🍺
New Businesses Accepting Bitcoin
This week we have…
- Core Agency: A creative communications firm that blends financial expertise with bold storytelling to help businesses in finance and beyond stand out. Based in the UK, they specialise in strategic planning, brand identity, content production, and public relations, delivering everything from investor-focused media to high-impact digital campaigns. With in-house studios for video, animation, and live streaming, Core offers end-to-end solutions that are both visually compelling and commercially effective. Their mission is to bring clarity, creativity, and confidence to brands navigating complex markets. Whether you're a fintech startup or a global institution, Core helps you communicate with purpose and originality. Now accepting bitcoin payments. 📈
Upcoming Special Events
These events aren't happening next week, but they're important to add to your calendar now as tickets are selling fast.
The Bitcoin Beach Retreat: An annual Bitcoin-only gathering held at a scenic coastal campsite in North Wales. Celebrating its fifth year in 2025, the retreat offers a relaxed, community-driven alternative to traditional conferences.
From July 11--14, up to 120 Bitcoiners will come together to share knowledge, enjoy beachside BBQs, and strengthen their networks under the stars. With no pre-booked speakers, the event thrives on peer-led workshops and spontaneous discussions, fostering genuine connections among attendees. Emphasising local engagement, the retreat directs the majority of its funds into the surrounding community, with 42% of expenses paid in Bitcoin last year.
Whether attending solo or with family, attendees can expect a welcoming environment dedicated to sound money and shared values.
Scottish Bitcoin Conference: Taking place on August 23, 2025, at the Glasgow University Union, located at 32 University Avenue, Glasgow G12 8LX. From 09:00 to 16:30.
Featuring an impressive roster of speakers, including Anthony Scaramucci, Hashley Giles, Rick Messit, Dr. Peter Connor, Claire Chisholm, Roger9000, John Magill, Ian Scanlon, Robin Thatcher, Jamie Plowman, Robbie Maltby, Russell Rukin, Peter Lane, Francesco Madonna, and Sam Roberts.
Open to all, this conference offers a unique opportunity for Bitcoiners and newcomers alike to connect and learn in the vibrant setting of Glasgow.
Get Involved
- Volunteer: Passionate about merchant adoption? Reach out to Bridge2Bitcoin on Twitter or website.
- Start a Meetup: Want to launch a Bitcoin meetup? We'll support you. Contact us on Twitter or just reply to this email.
- Contribute to BTCMaps: Help maintain this key Bitcoin resource--no coding skills needed. Update a UK area.
- Telegram: Join our Channel for UK meetup updates
- Feedback: Reply to this email with ideas and suggestions.
This week's sponsors is…
Get out and support the meetups where you can, visit Bitcoin Events UK for more info on each meetup and to find your closest on the interactive map.
Stay tuned for more updates next week!
Simon.
-
-
 @ 3bf0c63f:aefa459d
2024-03-19 14:32:01
@ 3bf0c63f:aefa459d
2024-03-19 14:32:01Censorship-resistant relay discovery in Nostr
In Nostr is not decentralized nor censorship-resistant I said Nostr is centralized. Peter Todd thinks it is centralized by design, but I disagree.
Nostr wasn't designed to be centralized. The idea was always that clients would follow people in the relays they decided to publish to, even if it was a single-user relay hosted in an island in the middle of the Pacific ocean.
But the Nostr explanations never had any guidance about how to do this, and the protocol itself never had any enforcement mechanisms for any of this (because it would be impossible).
My original idea was that clients would use some undefined combination of relay hints in reply tags and the (now defunct)
kind:2relay-recommendation events plus some form of manual action ("it looks like Bob is publishing on relay X, do you want to follow him there?") to accomplish this. With the expectation that we would have a better idea of how to properly implement all this with more experience, Branle, my first working client didn't have any of that implemented, instead it used a stupid static list of relays with read/write toggle -- although it did publish relay hints and kept track of those internally and supportedkind:2events, these things were not really useful.Gossip was the first client to implement a truly censorship-resistant relay discovery mechanism that used NIP-05 hints (originally proposed by Mike Dilger) relay hints and
kind:3relay lists, and then with the simple insight of NIP-65 that got much better. After seeing it in more concrete terms, it became simpler to reason about it and the approach got popularized as the "gossip model", then implemented in clients like Coracle and Snort.Today when people mention the "gossip model" (or "outbox model") they simply think about NIP-65 though. Which I think is ok, but too restrictive. I still think there is a place for the NIP-05 hints,
nprofileandneventrelay hints and specially relay hints in event tags. All these mechanisms are used together in ZBD Social, for example, but I believe also in the clients listed above.I don't think we should stop here, though. I think there are other ways, perhaps drastically different ways, to approach content propagation and relay discovery. I think manual action by users is underrated and could go a long way if presented in a nice UX (not conceived by people that think users are dumb animals), and who knows what. Reliance on third-parties, hardcoded values, social graph, and specially a mix of multiple approaches, is what Nostr needs to be censorship-resistant and what I hope to see in the future.
-
 @ a296b972:e5a7a2e8
2025-06-06 10:53:57
@ a296b972:e5a7a2e8
2025-06-06 10:53:57Wie schon gewohnt durch die Empfänge von Baerbock und von der Leyen im Ausland, in Washington ein Empfang etwas oberhalb der 1. Class, von Staatsempfang keine Spur. Passt eigentlich auch nicht für den 51. Bundesstaat der USA. Aber immerhin flog die „Bundesrepublik Deutschland“ ohne Pannen, das ist ja auch schon mal was. Und bei solch einem erfahrenen Chef-Co-Piloten an Bord, der auch mal schnell einspringen könnte, sozusagen als 2. Wahl, kann eigentlich gar nichts mehr schief gehen. Vielleicht hat Fritzchen den Kapitän auch gefragt, ob er auch mal ans Steuer darf, wenn sich die Gelegenheit schon bietet.
Im Gepäck die eingerahmte Geburtsurkunde von Großvater Trump. Als ob Donald die sich nicht selbst besorgen könnte, wenn er Interesse daran hätte. Vielleicht hat er sie auch schon.
Die Übergabe, kurz und schmerzlos. Sie erinnert an einen Sketch von Loriot, „Weihnachten bei Hoppenstedts“:…oh, eine Krawatte! Der versprochene Ehrenplatz wird sich vermutlich in einer der unteren Etagen des Weißen Hauses befinden.
Man muss auch erst einmal darauf kommen, so typisch deutsch: Eine Geburtsurkunde als Geschenk. Das könnte man auch als einen Wink mit dem Zaunpfahl ansehen: Erinnere Dich an Deine deutschen Wurzeln (und lass uns gefälligst nicht fallen?).
Jetzt zur Einschätzung des Treffens: Vorfahrt mit frisch gewaschenem Auto, Schwarz-Rot-Gold vorne am Kotflügel, wie es sich gehört, Schwarz-Rot-Gold am Eingang. Ganz schön rechts. Warum eigentlich nicht die Regenbogenfahne?
Begrüßung durch Trump auf Nachfrage eines Reporters: „I love the People of Germany.“
Und Merz nutzt die Gelegenheit sich in Biedermeier-Style einzuschmeicheln: „And I love the People of America.“
Und Trump erwidert: „That‘s good!“
In welcher Atmosphäre findet das Treffen statt?
Trump hat ein Elefantengedächtnis. Er weiß um die abwertenden, diplomatiefreien Aussagen, die Merz über ihn gemacht hat. Er weiß, dass Merz ihn mehrfach persönlich beleidigend angegriffen hat. Als Präsident der USA steht man darüber. Aber man weiß es! Trump ist sich darüber im Klaren, mit welcher Geisteshaltung er es bei Merz zu tun hat.
Vor dem Hintergrund passt seine Aussage zur Presse: „Ich liebe die Deutschen.“ Das ist eine demokratische und höfliche Sympathiebekundung gegenüber der deutschen Bevölkerung, die Merz zwar miteinschließt, aber nicht direkt an ihn gerichtet ist.
Trump begrüßt Merz mit Handschlag, begrüßt aber eigentlich nicht den Kanzler, sondern die Deutschen.
Andererseits darf der Äußerung „Ich liebe die Deutschen“ auch nicht zu viel Bedeutung beigemessen werden, denn die Amerikaner sind ja dafür bekannt, dass sie gerne und schnell alles lieben: I love America, I love Coca-Cola, I love Peanuts und eben auch I love the People of Germany.
Merz nutzt gleich die Gelegenheit, sich anzubiedern, in dem er pariert: „Und ich liebe die Amerikaner.“, worauf Trump antwortet: „That’s good!“ Das kann man übersetzen mit „Das ist gut!“, aber auch mit „Das ist auch gut so!“, bei letzterem wäre es eine versteckte Drohung. Mach Dir bewusst, wo Du bist und mit wem Du es zu tun hast und verhalte Dich danach!
Nonverbal wird dem sonst in Deutschland so eloquent wirken wollenden, akzentuiert sprechenden Merz die Bedeutung zugedacht, die ihm aus Sicht von Trump gebührt. In Frankfurt heißen sie Wiener, in Wien heißen sie Frankfurter.
Somit sind die Voraussetzungen, unter denen das Treffen stattfinden soll, schon einmal von amerikanischer Seite aus geklärt.
Du bist hier Gast in meinem Haus, also benimm Dich auch entsprechend! Ich bin der Präsident der Vereinigten Staaten von Amerika und Du bist klein Fritzchen aus dem Sauerland. Die Machtverhältnisse sind unausgesprochen geklärt.
Man hat in gewohnter Manier Platz genommen. Die Journalisten stellen Ihre Fragen ausschließlich an Trump. Zufall, oder Teil einer orchestrierten Aufführung, das wird man nie erfahren.
So oder so, die Journalisten signalisieren durch ihre Fragen an Trump, auf welcher Seite sie stehen, es weht der Geist von „America first“. Was Germany dazu zu sagen hat, interessiert niemanden, warum auch?
Die Einseitigkeit ist schon sehr auffällig. Eigentlich hätte es die Journalisten interessieren müssen, wie Deutschland zu verschiedenen Themen steht. Keine Fragen an Merz zu Zöllen, zur Ukraine, zur Meinungsfreiheit, zur Opposition. Mit dem Anspruch, ein breites Spektrum an Meinungen abbilden zu wollen, hat das eigentlich nichts zu tun. Wenn das die Vorstellung von „Freedom of Speach“ ist, dann können hier Zweifel aufkommen.
Falls diese Fragerunde in Hollywood-Manier gestaltet wurde, dann spräche das eher für Propaganda pro Trump. Wäre es Propaganda, dann wäre das Ziel allerdings erreicht worden: Kein Mensch interessiert sich für das, was Deutschland, vertreten durch Merz, zu sagen hat.
Trump setzt dem Ganzen zum Schluss noch die Krone auf, in dem er die Journalisten auffordert, nun endlich doch auch noch ein paar Fragen an Merz zu richten. Das unterstreicht nochmals das (geplante oder ungeplante) Desinteresse der anwesenden Journalisten, die sich nun fast schon genötigt fühlen, anstandshalber etwas zu fragen.
Merz, der bisher brav wie ein Schüler dem Lehrer zugehört hat, muss nun blitzschnell entscheiden, wie er die „künstlich“ hergestellte Möglichkeit nutzen kann, um, etwas unter Druck, durch die Kürze der Zeit, mit wenigen Worten seinen Standpunkt nach außen zu tragen. Seine konzentrierte Kernbotschaft, die Essenz, die Deutschland aus den USA und die übrige Welt hören soll, ist: Er steht weiter an der Seite der Ukraine und Russland ist ausschließlich das Böse.
Ganz schön raffiniert, denn so hat Trump es geschafft, das Konzentrat der Merz’schen Logik aus ihm herauszupressen.
Beide bekunden den Willen zum Frieden. Gleichzeitig wird jedoch auch klar, was jeder unter Frieden versteht: Merz will „Frieden durch Krieg“ und Trump will „Frieden durch Frieden“.
Auf rund 45 Minuten Trump kommen rund 4 Minuten Merz. Die Minuten drücken exakt die Machtverhältnisse aus.
Hätte Trump vorgehabt, Merz vorzuführen, ihm die Ohren langzuziehen, ihn bis auf die Knochen zu blamieren, er hätte reichlich Möglichkeiten dazu gehabt.
Er hätte Merz fragen können, warum er seinerzeit meinte, dass ihn, Trump, als Arschloch zu bezeichnen, noch gelinde sei. Er hätte ihn fragen können, warum er Trump als Gefahr für die Demokratie ansieht. Trump weiß darum, er hat es jedoch nicht angesprochen, was ist der Grund dafür?
Und Vance, der ebenfalls anwesend war, hätte seine Feststellungen zur Meinungsfreiheit und der „Fire-Wall“ gegen die Opposition, die er auf der Sicherheitskonferenz in München klar formuliert hat, wiederholen können, jetzt, wo doch der Kanzler, als erster Ansprechpartner für Deutschland, persönlich hätte gefragt werden können.
Beim Besuch von Selenskyj haben beide ja auch gewaltig gezeigt, wer hier das Sagen hat.
Nichts! Keine schallende Ohrfeige für Merz, doch nur Erdnussbutter auf’s Sandwich geschmiert. Kein „You don’t have the cards…“, was den Tatsachen entsprechen würde.
Auf politischer Ebene bleibt in den USA nichts, rein gar nichts dem Zufall überlassen. Je länger man darüber nachdenkt, desto klarer kann einem werden, dass das Treffen genau so geplant war, wie es sich abgespielt hat. Aber was genau ist der Plan, der dahintersteckt? Es gibt einen, dass ist so sicher, wie das Amen in der Kirche.
Sollen sich die Deutschen, vor allem die deutsche Politik in Sicherheit wiegen? Wenn das Teil eines Planes wäre, wäre er gelungen, denn in Deutschland wird der Besuch als gelungen und erfolgreich bewertet, aus welchen Gründen auch immer. Inzwischen ist Deutschland ja Weltmeister im Schönreden.
Spannend auch die Vorstellung, wenn man die Phantasie anregt, wie das Gespräch verlaufen wäre, wenn die deutsche Opposition auf dem Stuhl von Merz gesessen hätte.
Es widerspräche der Realität, wenn nicht im Hintergrund ganz andere Ziele verfolgt und Absprachen getroffen würden. Welchen Einfluss auf das Treffen hat der bevorstehende NATO-Gipfel am 24. und 25. Juni 2025 in Den Haag?
Es drängt sich immer mehr der Verdacht auf, dass man es mit zwei Realitäten zu tun hat. Eine, die offiziell verkündet wird, und eine, die den Tatsachen entspricht, die aus welchen Gründen auch immer jedoch zunächst noch im Verborgenen bleibt. Ob das vielleicht sogar gut oder eher schlecht ist, wird die Zukunft zeigen. Klar ist jedoch, dass eine gesteuerte Realität in der Öffentlichkeit verbreitet werden soll, die man durchaus als Propaganda von allen Beteiligten bewerten kann. Da hackt eine Krähe der anderen kein Auge aus. Da heißt es wachsam bleiben und nicht der Versuchung zu erliegen, dass zu glauben, was man gerne glauben möchte und von dem man sich wünscht, dass es eintritt.
„Bediene Dich Deines eigenen Verstandes.“ Das ist die Aufgabe der Zeit.
“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
* *
(Bild von pixabay)
-
 @ 7f6db517:a4931eda
2025-06-06 06:01:30
@ 7f6db517:a4931eda
2025-06-06 06:01:30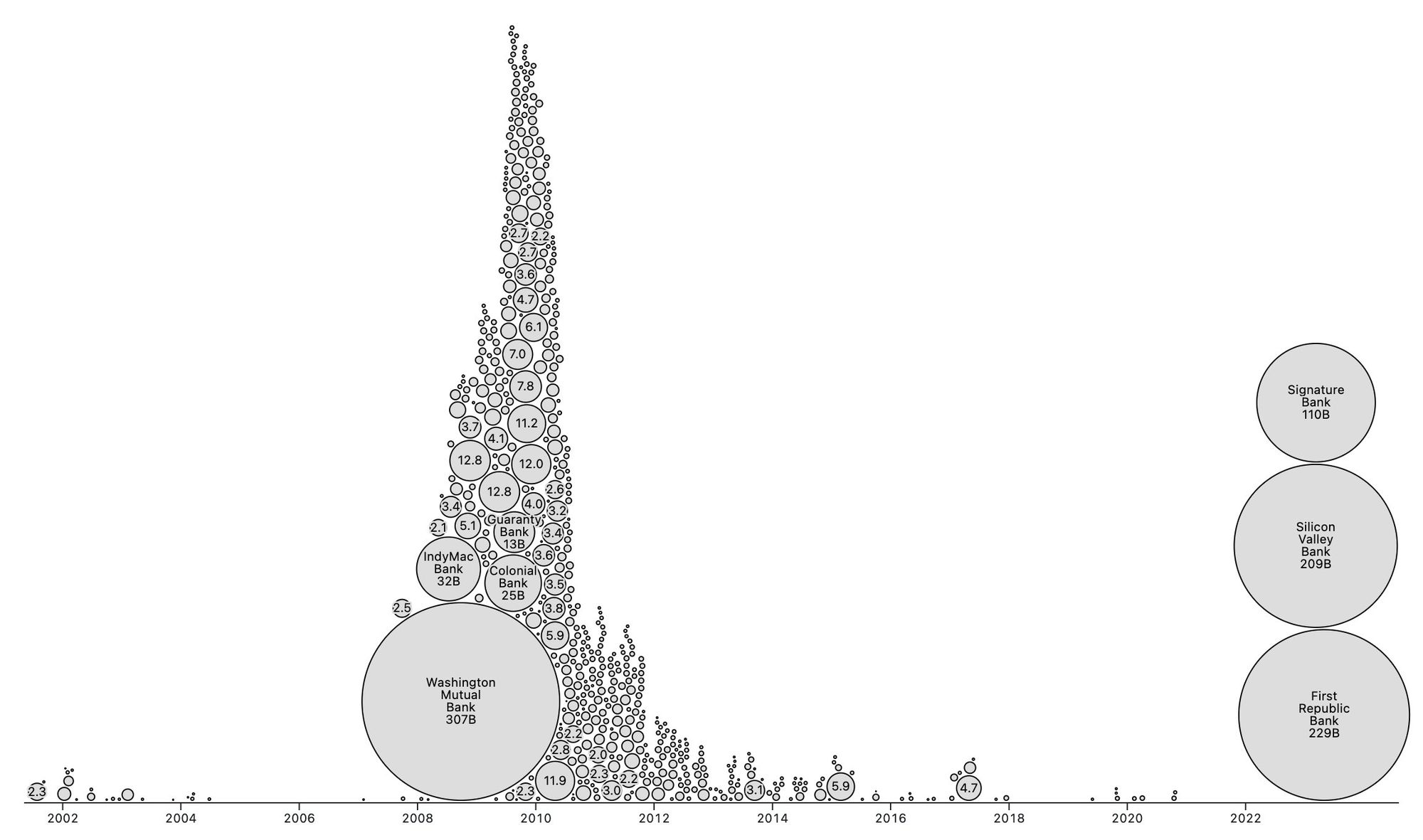
People forget Bear Stearns failed March 2008 - months of denial followed before the public realized how bad the situation was under the surface.
Similar happening now but much larger scale. They did not fix fundamental issues after 2008 - everything is more fragile.
The Fed preemptively bailed out every bank with their BTFP program and First Republic Bank still failed. The second largest bank failure in history.
There will be more failures. There will be more bailouts. Depositors will be "protected" by socializing losses across everyone.
Our President and mainstream financial pundits are currently pretending the banking crisis is over while most banks remain insolvent. There are going to be many more bank failures as this ponzi system unravels.
Unlike 2008, we have the ability to opt out of these broken and corrupt institutions by using bitcoin. Bitcoin held in self custody is unique in its lack of counterparty risk - you do not have to trust a bank or other centralized entity to hold it for you. Bitcoin is also incredibly difficult to change by design since it is not controlled by an individual, company, or government - the supply of dollars will inevitably be inflated to bailout these failing banks but bitcoin supply will remain unchanged. I do not need to convince you that bitcoin provides value - these next few years will convince millions.
If you found this post helpful support my work with bitcoin.

-
 @ dab6c606:51f507b6
2025-06-08 09:24:14
@ dab6c606:51f507b6
2025-06-08 09:24:14I've been interested for a while in how the business with miles and loyalty points works. I found out that only large corporations can partially do this because of how they can then account for it. And it's tax-wise super advantageous. I also added info about loyalty points and gift cards. The text below was written by various AIs as I was digging into it, it's basically a summary, sharing for those who are interested.
Part I: Loyalty Programs of Large Corporations
Business Logic of Loyalty Programs
Loyalty programs of airlines and hotels are sophisticated business tools that serve several key purposes. They primarily function to increase customer loyalty by creating "switching costs" - customers don't want to lose accumulated points, which reduces the likelihood they'll switch to competitors.
At the same time, they're a significant source of additional revenue. For example, American Airlines earns more from selling miles to banks than on some flight routes. When Citibank buys miles for 1-2 cents per mile, the airline gets immediate revenue, while the real value for the customer can be 3-5 cents when used correctly.
Accounting Treatment of Loyalty Points
From an accounting perspective, loyalty points represent deferred liabilities. When a customer earns points, the company must create a reserve for their future redemption. Points are valued based on expected costs of their redemption, not on nominal value.
The key difference is between cash accounting and accrual accounting: - Cash accounting: Revenue is recognized when payment is received, expenses when paid. - Accrual accounting: Revenue and expenses are recognized when the obligation arises.
For loyalty programs, accrual accounting is critical. When an airline sells miles to a bank for $1,000,000, it simultaneously creates a liability for future costs (say $600,000), so taxable income is only $400,000.
Example: Selling Miles to a Bank
An airline sells 50 million miles to Citibank for $1,000,000: 1. Immediate revenue: $1,000,000 2. Creation of liability: $600,000 (estimated future costs) 3. Taxable income: $400,000 4. Future costs: When customers use miles, the company recognizes the expense and reduces the liability
Positive margin arises from several factors: - Breakage - 15-20% of miles are never redeemed - Time value of money - Money from the bank is invested immediately - Marginal costs - An empty seat has low incremental cost
Tax Optimization and Offshore Structures
Large companies often use international structures to optimize taxes from loyalty programs. A typical structure includes: 1. Parent company (USA/EU) - Operates flights and provides services (e.g., flights or accommodation). 2. IP Holding (Ireland/Netherlands) - Owns intellectual property (IP) for the loyalty program, such as brands, software, and databases. 3. Loyalty Operating Company (Singapore/Dubai) - Manages sale of miles to banks and partners, coordinates the program and communicates with customers.
Business Relationships and Payments Between Entities (example with positive result for Singapore)
These entities are connected by contracts that determine who pays for what and why, to minimize tax burden: - Bank → Singapore (Loyalty Operating Company): The bank (e.g., Citibank) pays $1,000,000 for miles it offers to its clients as rewards for using credit cards. The Singapore company is the main contact point for partners because it's located in a low-tax jurisdiction (17%) with good infrastructure for financial services. - Singapore → Ireland (IP Holding): The Singapore company pays $500,000 as royalties for using IP (brands, software, and data) of the loyalty program. This payment is high to shift profit to Ireland, where the tax rate is even lower (12.5%). This reduces taxable income in Singapore. - Singapore → Parent Company (Airline): The Singapore company pays $300,000 to the parent company for providing services (e.g., flights) when customers use miles. This payment is lower than actual costs to minimize profit in the parent company's country, where the tax rate is higher (e.g., 25-35% in USA or EU). - Profit in Singapore: $1,000,000 (income from bank) - $500,000 (royalties to Ireland) - $300,000 (payment to airline) = $200,000 profit, taxed at 17% in Singapore.
Why Such Distribution?
- Ireland (IP Holding): High royalty payments ($500,000) go to Ireland because the 12.5% tax rate is attractive and Ireland is considered a "serious" jurisdiction that meets international rules (e.g., BEPS). Ireland also has double taxation treaties with many countries, facilitating profit shifting.
- Singapore (Loyalty Operating Company): Mile sales and program coordination occur in Singapore due to favorable tax environment (17%) and strategic location for Asian markets. A small profit ($200,000) is left here to demonstrate "economic substance" - that the company has real activity.
- Parent Company: The $300,000 payment is low to minimize taxable income in a high-tax country (e.g., USA or EU).
Why Not 0% Tax Jurisdiction?
Why not use a zero-tax country (e.g., Cayman Islands)? Due to: - Regulatory scrutiny - Tax authorities closely monitor 0% jurisdictions and may question legitimacy. - BEPS rules - Need to demonstrate "substance" (real offices, employees) in the country. - Credibility test - 12.5% in Ireland or 17% in Singapore looks like legitimate business operation.
The result of such structure is that most profit (60-70%) is taxed at 12.5% in Ireland or 17% in Singapore instead of 25-35% in the airline's home country.
Part II: Loyalty Programs and Alternatives for Small Businesses
Why Loyalty Programs Are Problematic for Small Businesses
Unlike large corporations, small businesses like cafes face a fundamental problem with loyalty programs: cash accounting obligation. In many countries, small firms (under $25M annually) must use cash accounting, which means: - Revenue from selling points is taxed immediately - Costs are deducted only when customers use points (maybe a year later) - Creates tax and cashflow problem - tax is paid on money you'll "lose" in the future
Imagine a cafe that sells loyalty points for €100. It must immediately pay tax (say €21), but deducts coffee costs provided for points only in the future.
Alternative Models for Small Businesses
There are more tax-advantageous alternatives:
1. Gift Cards Model
- Revenue is NOT RECOGNIZED when selling gift card
- Revenue is recognized only when customer uses the card
- Example: Sell gift cards for €10,000 in December, get cash immediately, but pay tax gradually as customers use cards during the following year.
- Time value of money: Money can be invested (e.g., 6% annually = €600 extra profit on €10,000)
- Breakage benefit: 2-10% of cards are never used, after certain time (3-5 years, depending on legislation) you can recognize the balance as pure profit.
Example: Starbucks Starbucks had $1.5 billion in unused gift cards on its books in 2022. Estimated 3% breakage means $45 million pure profit – interest-free loan from customers with bonus that part never returns.
2. Subscription Model
- Monthly revenue = immediate taxation
- Monthly costs = immediate deduction
- Example: €10/month for "premium membership" with certain benefits
3. Discount Coupons
- No revenue when issuing coupon
- Reduced revenue when redeeming (sell at lower price)
- Example: 20% discount coupon = sell coffee for €4 instead of €5
Outsourcing Loyalty Program: Details About Shopify Loyalty
Platforms like Shopify Loyalty represent an elegant solution for small businesses wanting to offer loyalty programs without accounting and tax complications. Let's break this down in detail:
How Shopify Loyalty Works
- Shopify as third party: Shopify owns and manages the entire loyalty program including points and software. The customer has their "account" directly with Shopify, not with the specific store. This means points are not your liability, but Shopify's liability.
- Your role: You (e.g., cafe) pay Shopify a monthly fee (e.g., €29) for using the platform and a small transaction fee (e.g., €0.20) for each point redemption (reward). You're essentially a "service provider" for Shopify – you provide rewards when Shopify sends you an order.
- Earning points: Customer earns points for purchases in stores participating in Shopify Loyalty program. For example, if customer buys coffee for €5 in your cafe, Shopify credits them points (e.g., 5 points per euro, so 25 points). Specific rules (how many points per euro) are set by you through Shopify platform, but technically points are managed by Shopify.
- Using points: Customer can use points for rewards (e.g., free coffee for 100 points), but usually only in stores participating in Shopify network. This means if your cafe uses Shopify Loyalty, points earned with you can be used with you or other stores in Shopify ecosystem, if Shopify allows it. Usually, however, stores set up the program so points are primarily usable with them, increasing loyalty to their brand.
- Point redemption process: When customer wants to use points (e.g., 100 points for free coffee), Shopify sends order to you (cafe) to provide the reward. You give the coffee but don't receive direct payment from customer – it's a marketing cost. You also pay Shopify transaction fee (€0.20). Accounting-wise, it's not a sale, so no taxable income or receipt obligation arises.
- Accounting treatment: When customer uses points:
- No receipt = no taxable income
- Coffee cost (€2) + Shopify fee (€0.20) = €2.20
- Recorded as "Promotional expenses" or "Marketing costs"
Why Must Loyalty Program Be Outsourced to Third Party (like Shopify)?
Small businesses don't have capacity or resources to manage their own loyalty program "in-house" for these reasons: - Tax and accounting complexity: If you managed loyalty program yourself, you'd have to create reserves for future liabilities (points customers will use later), estimate breakage rate (percentage of unused points) and handle cash vs. accrual accounting. For small firms that often must use cash accounting, this means immediate taxation of revenue if selling points, but cost deduction only in the future – creates cashflow mismatch. - Technological infrastructure: Managing points, customer databases and integration with payment systems requires sophisticated software and IT team, which is expensive and complicated for small firms. - Legal separation: When program is managed by third party like Shopify, points are their liability, not yours. For you, this means no future liabilities in your accounting books – just monthly costs (Shopify fee), which are tax-deductible as regular expense. - Economic efficiency: Shopify aggregates thousands of stores, achieving economies of scale – lower costs for software, security and data management. A small cafe could never create such system at reasonable price alone.
Why Can't It Be In-house from Tax Perspective?
If small firm managed loyalty program itself: - Immediate tax problem: If firm sold points (e.g., for money or as part of purchase), revenue would have to be taxed immediately, though costs for providing rewards (e.g., free coffee) could be deducted only when customer uses points. This creates cashflow mismatch because you pay tax before actually "losing" money on reward. - Complex reserves: Would have to estimate how many points will be used and create accounting reserves, which is administratively demanding and requires expensive accountants or software. - Risk of errors: Incorrect breakage rate estimates or poor liability management can lead to tax audits and penalties.
With Shopify, these problems are eliminated – you only pay monthly fee and transaction fees, which are simply recorded as marketing costs. Shopify takes full responsibility for managing points and liabilities to customers.
Case Study: Loyalty Points for Cafe (10 + 1 Free Model)
Let's look at specific case of small cafe offering classic loyalty program type "10 + 1 free". Customer gets 1 point for each coffee purchased (e.g., for €3) and after collecting 10 points gets one free coffee. We'll analyze how this works accounting-wise, whether it's "promotional expense" and what's the difference between in-house management and using Shopify.
How "10 + 1 Free" Program Works
- Earning points: Customer buys coffee for €3 and gets 1 point (e.g., stamp on card or digital record). Points have no monetary value for sale – they're purely reward for purchase.
- Using points: After collecting 10 points (meaning purchases for €30) customer gets free coffee (value €3).
- Real cost for cafe: Cost of producing free coffee is lower than selling price, e.g., €1.50 for materials and labor.
Accounting Treatment (In-house)
If cafe manages program itself (in-house), accounting process depends on whether it uses cash accounting (common for small firms) or accrual accounting: - Cash accounting: - When customer buys coffee: Cafe records €3 revenue for each coffee and issues receipt. Point (stamp) has no monetary value, so it's not recorded as liability or revenue. - When redeeming 10 points: When customer gets free coffee, no revenue arises (€0), but cost for coffee production arises (€1.50). This cost is recorded as "Promotional expense" or "Marketing cost" because it's form of discount or advertising to retain customer. - Tax impact: No revenue when issuing free coffee, €1.50 cost is tax-deductible as regular expense. - Accrual accounting (less common for small firms): - When customer buys coffee: Cafe records €3 revenue but simultaneously creates small liability for future reward (e.g., €0.30 per point, which is estimate of cost for future free coffee divided by 10). So from €3 revenue, taxable income is only €2.70. - When redeeming 10 points: When customer gets free coffee, cafe reduces liability by €3 (10 points x €0.30) and records €1.50 cost for coffee production. Difference can be adjusted as breakage or other profit if estimates differ from reality. - Tax impact: Taxable income is lower already at first purchase, but accounting is more complex due to estimates and reserves.
Is it Promotional Expense? Yes, in both cases (cash and accrual) the cost of free coffee is recorded as "Promotional expense" or "Marketing cost" because it's form of discount to support customer loyalty. It's not considered regular sale because no revenue or receipt arises.
Accounting Treatment (via Shopify Loyalty)
If cafe uses Shopify Loyalty to manage "10 + 1 free" program, process is simpler: - When customer buys coffee: Cafe records €3 revenue for coffee and issues receipt. Shopify credits point to customer's account (it's not your liability, but Shopify's). - When redeeming 10 points: Shopify sends order to issue free coffee. Cafe gives coffee (€1.50 cost) and pays Shopify transaction fee (€0.20). Total cost €1.70 is recorded as "Promotional expense" or "Marketing cost". - Tax impact: Same as in-house, no revenue when issuing free coffee, €1.70 cost is tax-deductible as regular expense. Additionally, you don't have to handle any liabilities or breakage estimates because Shopify manages points.
Difference Between In-house and Shopify
- In-house:
- Advantages: Full control over program, no monthly fees to third party (e.g., €29 Shopify fee).
- Disadvantages: If using accrual accounting, must create reserves and estimate breakage, which is administratively demanding. With cash accounting it's simpler (no liabilities), but if you sold points for money, tax mismatch arises (revenue taxed immediately, cost only later). Additionally, must manage point database yourself (stamps, software), which is time-consuming.
- Shopify Loyalty:
- Advantages: No liabilities in your accounting books, Shopify manages points and technology. Accounting-wise it's simple – just monthly fee (€29) and transaction fees (€0.20) as marketing cost. Don't have to handle estimates or breakage.
- Disadvantages: Pay monthly fees and transaction fees, increasing costs (e.g., €0.20 extra per free coffee). Have less control over program because third party manages it.
Conclusion for Cafe: "10 + 1 free" program is accounting-wise considered Promotional expense in both cases (in-house and Shopify) because free coffee is form of marketing to retain customers. Difference is in administrative burden and costs – Shopify simplifies accounting and management, but at cost of monthly fees. In-house is cheaper but more demanding to manage, especially if you wanted to use accrual accounting or sell points for money.
Conclusion
Loyalty programs are sophisticated customer loyalty tools, but their accounting and tax aspects differ significantly between large and small firms. Large corporations use accrual accounting and international structures for tax optimization, while for small businesses alternative models like gift cards or outsourcing entire program are often more advantageous, eliminating tax and cashflow problems. Gift cards additionally bring immediate cash flow, time value of money and breakage benefit, making them ideal tool for businesses of all sizes. Shopify Loyalty offers small firms way to implement loyalty program without accounting complications because it takes technical and legal responsibility, allowing focus on core business. For simple programs like "10 + 1 free," accounting impact is similar (Promotional expense), but Shopify simplifies management at cost of additional fees.
-
 @ 7f6db517:a4931eda
2025-06-06 06:01:30
@ 7f6db517:a4931eda
2025-06-06 06:01:30

"Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world." - Eric Hughes, A Cypherpunk's Manifesto, 1993
Privacy is essential to freedom. Without privacy, individuals are unable to make choices free from surveillance and control. Lack of privacy leads to loss of autonomy. When individuals are constantly monitored it limits our ability to express ourselves and take risks. Any decisions we make can result in negative repercussions from those who surveil us. Without the freedom to make choices, individuals cannot truly be free.
Freedom is essential to acquiring and preserving wealth. When individuals are not free to make choices, restrictions and limitations prevent us from economic opportunities. If we are somehow able to acquire wealth in such an environment, lack of freedom can result in direct asset seizure by governments or other malicious entities. At scale, when freedom is compromised, it leads to widespread economic stagnation and poverty. Protecting freedom is essential to economic prosperity.
The connection between privacy, freedom, and wealth is critical. Without privacy, individuals lose the freedom to make choices free from surveillance and control. While lack of freedom prevents individuals from pursuing economic opportunities and makes wealth preservation nearly impossible. No Privacy? No Freedom. No Freedom? No Wealth.
Rights are not granted. They are taken and defended. Rights are often misunderstood as permission to do something by those holding power. However, if someone can give you something, they can inherently take it from you at will. People throughout history have necessarily fought for basic rights, including privacy and freedom. These rights were not given by those in power, but rather demanded and won through struggle. Even after these rights are won, they must be continually defended to ensure that they are not taken away. Rights are not granted - they are earned through struggle and defended through sacrifice.
If you found this post helpful support my work with bitcoin.

-
 @ dab6c606:51f507b6
2025-06-08 09:21:16
@ dab6c606:51f507b6
2025-06-08 09:21:16Dlhšie som sa zaujímal o to ako funguje biznis s míľami, vernostnými bodmi. Zistil som, že to čiastočne môžu robiť iba veľké korporácie kvôli tomu ako to môžu potom zaúčtovať. A je to daňovo super výhodné. Pridal som aj info o vernostných bodoch a darčekových kartách. Text nižšie napísali rôzne AI ako som sa v tom vŕtal, to je v zásade sumár, zdieľam pre tých, ktorých to zaujíma.
Časť I: Vernostné programy veľkých korporácií
Obchodná logika vernostných programov
Vernostné programy leteckých spoločností a hotelov sú sofistikované obchodné nástroje, ktoré slúžia niekoľkým kľúčovým účelom. Primárne fungujú na zvýšenie zákazníckej lojality vytvorením "switching costs" - zákazníci nechcú prísť o nazbierané body, čo znižuje pravdepodobnosť, že prejdú ku konkurencii.
Zároveň sú významným zdrojom dodatočných príjmov. Napríklad American Airlines zarába viac na predaji míľ bankám ako na niektorých leteckých linkách. Keď Citibank kupuje míle za 1-2 centy za míľu, aerolínia získava okamžitý príjem, zatiaľ čo reálna hodnota pre zákazníka môže byť 3-5 centov pri správnom využití.
Účtovné spracovanie vernostných bodov
Z účtovného hľadiska predstavujú vernostné body odložené záväzky. Keď zákazník získa body, spoločnosť musí vytvoriť rezervu na ich budúce uplatnenie. Body sa oceňujú na základe predpokladaných nákladov na ich uplatnenie, nie na základe nominálnej hodnoty.
Kľúčový je rozdiel medzi cash accounting a accrual accounting: - Cash accounting: Príjmy sa uznávajú pri prijatí platby, náklady pri zaplatení. - Accrual accounting: Príjmy a náklady sa uznávajú v momente vzniku záväzku.
Pre vernostné programy je accrual accounting kritické. Keď aerolínia predá míle banke za $1,000,000, vytvorí zároveň záväzok na budúce náklady (povedzme $600,000), takže zdaniteľný príjem je len $400,000.
Príklad: Predaj míľ banke
Aerolínia predá 50 miliónov míľ Citibank za $1,000,000: 1. Okamžitý príjem: $1,000,000 2. Vytvorenie záväzku: $600,000 (odhadované budúce náklady) 3. Zdaniteľný príjem: $400,000 4. Budúce náklady: Keď zákazníci míle využijú, spoločnosť uzná náklad a zníži záväzok
Pozitívna marža vzniká z niekoľkých faktorov: - Breakage - 15-20% míľ sa nikdy neuplatní - Časová hodnota peňazí - Peniaze od banky investuje okamžite - Marginálne náklady - Prázdne sedadlo má nízky prírastok nákladu
Daňová optimalizácia a offshore štruktúry
Veľké spoločnosti často využívajú medzinárodné štruktúry na optimalizáciu daní z vernostných programov. Typická štruktúra zahŕňa: 1. Materská spoločnosť (USA/EU) - Prevádzkuje lety a poskytuje služby (napr. lety alebo ubytovanie). 2. IP Holding (Írsko/Holandsko) - Vlastní duševné vlastníctvo (IP) k loyalty programu, ako sú značky, softvér a databázy. 3. Loyalty Operating Company (Singapur/Dubaj) - Spravuje predaj míľ bankám a partnerom, koordinuje program a komunikuje so zákazníkmi.
Obchodné vzťahy a platby medzi entitami (príklad s pozitívnym výsledkom pre Singapur)
Tieto entity sú prepojené zmluvami, ktoré určujú, kto za čo platí a prečo, aby sa minimalizovala daňová záťaž: - Banka → Singapur (Loyalty Operating Company): Banka (napr. Citibank) platí $1,000,000 za míle, ktoré ponúka svojim klientom ako odmenu za používanie kreditných kariet. Singapurská spoločnosť je hlavný kontaktný bod pre partnerov, pretože je umiestnená v jurisdikcii s nízkou daňou (17 %) a dobrou infraštruktúrou pre finančné služby. - Singapur → Írsko (IP Holding): Singapurská spoločnosť platí $500,000 ako royalty za použitie IP (značky, softvéru a dát) loyalty programu. Táto platba je vysoká, aby sa presunul zisk do Írska, kde je daňová sadzba ešte nižšia (12,5 %). Tým sa znižuje zdaniteľný príjem v Singapure. - Singapur → Materská spoločnosť (Aerolínia): Singapurská spoločnosť platí $300,000 materskej spoločnosti za poskytnutie služieb (napr. letov), keď zákazníci využijú míle. Táto platba je nižšia ako reálne náklady, aby sa minimalizoval zisk v krajine materskej spoločnosti, kde je daňová sadzba vyššia (napr. 25-35 % v USA alebo EU). - Zisk v Singapure: $1,000,000 (príjem od banky) - $500,000 (royalty do Írska) - $300,000 (platba aerolínii) = $200,000 zisku, ktorý je zdanený pri 17 % v Singapure.
Prečo takéto rozdelenie?
- Írsko (IP Holding): Vysoké royalty platby ($500,000) idú do Írska, pretože daňová sadzba 12,5 % je atraktívna a Írsko je považované za "serióznu" jurisdikciu, ktorá spĺňa medzinárodné pravidlá (napr. BEPS). Zároveň má Írsko zmluvy o zamedzení dvojitého zdanenia s mnohými krajinami, čo uľahčuje presun zisku.
- Singapur (Loyalty Operating Company): Predaj míľ a koordinácia programu prebieha v Singapure kvôli priaznivému daňovému prostrediu (17 %) a strategickej polohe pre ázijské trhy. Zároveň sa tu zanecháva malý zisk ($200,000), aby sa preukázala "ekonomická substance" – teda, že spoločnosť má reálnu činnosť.
- Materská spoločnosť: Platba $300,000 je nízka, aby sa minimalizoval zdaniteľný príjem v krajine s vysokou daňovou sadzbou (napr. USA alebo EU).
Prečo nie 0 % daňová jurisdikcia?
Prečo sa nepoužíva krajina s nulovou daňou (napr. Kajmanské ostrovy)? Kvôli: - Regulatory scrutiny - Daňové úrady pozorne sledujú 0 % jurisdikcie a môžu spochybniť legitímnosť. - BEPS pravidlám - Potreba preukázať "substance" (reálne kancelárie, zamestnancov) v krajine. - Credibility testu - 12,5 % v Írsku alebo 17 % v Singapure vyzerá ako legitímna obchodná operácia.
Výsledkom takejto štruktúry je, že väčšina zisku (60-70 %) je zdanená pri 12,5 % v Írsku alebo 17 % v Singapure namiesto 25-35 % v domovskej krajine aerolínky.
Časť II: Loyalty programy a alternatívy pre malé biznisy
Prečo je loyalty program problematický pre malé biznisy
Na rozdiel od veľkých korporácií, malé biznisy ako kaviarne narážajú pri vernostných programoch na zásadný problém: cash accounting povinnosť. V mnohých krajinách musia malé firmy (pod $25M ročne) používať cash accounting, čo znamená: - Príjem z predaja bodov sa zdaní okamžite - Náklady sa odpočítajú až keď zákazník body využije (možno o rok) - Vzniká daňový a cashflow problém - daň sa platí z peňazí, ktoré "stratíte" v budúcnosti
Predstavte si kaviareň, ktorá predá vernostné body za €100. Okamžite musí zaplatiť daň (povedzme €21), ale náklady na kávu poskytnutú za body odpočíta až v budúcnosti.
Alternatívne modely pre malé biznisy
Existujú daňovo výhodnejšie alternatívy:
1. Gift Cards model
- Príjem sa NEUZNÁ pri predaji gift karty
- Príjem sa uzná až keď zákazník kartu využije
- Príklad: Predáte gift cards za €10,000 v decembri, získate cash okamžite, ale daň platíte postupne, ako zákazníci karty využívajú počas nasledujúceho roka.
- Časová hodnota peňazí: Peniaze môžete investovať (napr. 6 % ročne = €600 extra zisk na €10,000)
- Breakage benefit: 2-10 % kariet sa nikdy nevyužije, po určitom čase (3-5 rokov, podľa legislatívy) môžete zostatok uznať ako čistý zisk.
Príklad: Starbucks Starbucks mal v roku 2022 na účtoch $1,5 miliardy v nevyužitých gift cards. Odhadovaný breakage 3 % znamená $45 miliónov čistého zisku – bezúročná pôžička od zákazníkov s bonusom, že časť sa nikdy nevráti.
2. Subscription model
- Mesačný príjem = okamžité zdanenie
- Mesačné náklady = okamžitý odpočet
- Príklad: €10/mesiac za "premium membership" s určitými benefitmi
3. Discount Coupons
- Žiadny príjem pri vydaní kupónu
- Znížený príjem pri uplatnení (predáte za nižšiu cenu)
- Príklad: 20 % zľavový kupón = predaj kávy za €4 namiesto €5
Outsourcing loyalty programu: Podrobnosti o Shopify Loyalty
Platformy ako Shopify Loyalty predstavujú elegantné riešenie pre malé biznisy, ktoré chcú ponúkať vernostné programy bez účtovných a daňových komplikácií. Poďme si to rozobrať podrobne:
Ako funguje Shopify Loyalty
- Shopify ako tretia strana: Shopify vlastní a spravuje celý vernostný program vrátane bodov a softvéru. Zákazník má svoj "účet" priamo u Shopify, nie u konkrétneho obchodu. To znamená, že body nie sú vaším záväzkom, ale záväzkom Shopify.
- Vaša úloha: Vy (napr. kaviareň) platíte Shopify mesačný poplatok (napr. €29) za používanie platformy a malý transakčný poplatok (napr. €0,20) za každé uplatnenie bodov (reward). Vy ste v podstate "dodávateľom služieb" pre Shopify – poskytujete odmeny, keď vám Shopify pošle objednávku.
- Získavanie bodov: Zákazník získava body za nákupy v obchodoch, ktoré sú zapojené do Shopify Loyalty programu. Napríklad, ak zákazník nakúpi kávu za €5 vo vašej kaviarni, Shopify mu pripíše body (napr. 5 bodov za každé euro, teda 25 bodov). Konkrétne pravidlá (koľko bodov za euro) si nastavujete vy cez Shopify platformu, ale technicky body spravuje Shopify.
- Využitie bodov: Zákazník môže body využiť na odmeny (napr. kávu zadarmo za 100 bodov), ale zvyčajne len v obchodoch zapojených do Shopify siete. To znamená, že ak vaša kaviareň používa Shopify Loyalty, body získané u vás môžu byť využité u vás alebo v iných obchodoch v rámci Shopify ekosystému, ak to Shopify umožňuje. Väčšinou však obchody nastavujú program tak, aby boli body využiteľné primárne u nich, čím sa zvyšuje lojalita k ich značke.
- Proces uplatnenia bodov: Keď zákazník chce využiť body (napr. 100 bodov za kávu zadarmo), Shopify pošle objednávku vám (kaviarni) na poskytnutie odmeny. Vy kávu vydáte, ale nedostanete za ňu priamy príjem od zákazníka – ide o marketingový náklad. Zároveň platíte Shopify transakčný poplatok (€0,20). Účtovne to nie je predaj, takže nevzniká zdaniteľný príjem ani povinnosť vystaviť bloček.
- Účtovné spracovanie: Keď zákazník využije body:
- Žiadny bloček = žiadny zdaniteľný príjem
- Náklad kávy (€2) + Shopify fee (€0,20) = €2,20
- Účtuje sa ako "Promotional expenses" alebo "Marketing costs"
Prečo musí byť loyalty program outsourcovaný tretej strane (ako Shopify)?
Malé biznisy nemajú kapacitu ani zdroje na správu vlastného loyalty programu "in-house" z týchto dôvodov: - Daňová a účtovná komplexnosť: Ak by ste spravovali loyalty program sami, museli by ste vytvárať rezervy na budúce záväzky (body, ktoré zákazníci využijú neskôr), odhadovať breakage rate (percento nevyužitých bodov) a riešiť cash vs. accrual accounting. Pre malé firmy, ktoré často musia používať cash accounting, to znamená okamžité zdanenie príjmu, ak by body predávali, ale odpočet nákladov až v budúcnosti – vzniká cashflow nesúlad. - Technologická infraštruktúra: Správa bodov, databáz zákazníkov a integrácia s platobnými systémami vyžaduje sofistikovaný softvér a IT tím, čo je pre malé firmy nákladné a komplikované. - Legálna separácia: Keď program spravuje tretia strana ako Shopify, body sú ich záväzkom, nie vaším. Pre vás to znamená, že nemáte žiadne budúce záväzky vo svojej účtovnej knihe – len mesačné náklady (poplatok Shopify), ktoré sú daňovo odpočítateľné ako bežný výdavok. - Ekonomická efektivita: Shopify združuje tisíce obchodov, čím dosahuje ekonomiku rozsahu – nižšie náklady na softvér, bezpečnosť a správu dát. Malá kaviareň by sama nikdy nedokázala vytvoriť takýto systém za rozumnú cenu.
Prečo to nemôže byť in-house z daňového hľadiska?
Ak by malá firma spravovala loyalty program sama: - Okamžitý daňový problém: Ak by firma predávala body (napr. za peniaze alebo ako súčasť nákupu), príjem by musela zdaniť hneď, hoci náklady na poskytnutie odmien (napr. káva zadarmo) by mohla odpočítať až v momente, keď zákazník body využije. To vytvára cashflow nesúlad, pretože daň platíte skôr, než reálne "stratíte" peniaze na odmenu. - Zložité rezervy: Musela by odhadovať, koľko bodov sa využije, a vytvárať účtovné rezervy, čo je administratívne náročné a vyžaduje drahých účtovníkov alebo softvér. - Riziko chýb: Nesprávne odhady breakage rate alebo zlý manažment záväzkov môžu viesť k daňovým kontrolám a pokutám.
S Shopify sa tieto problémy eliminujú – vy platíte len mesačný poplatok a transakčné fees, ktoré sú jednoducho účtované ako marketingové náklady. Shopify preberá celú zodpovednosť za správu bodov a záväzkov voči zákazníkom.
Prípadová štúdia: Vernostné body pre kaviareň (model 10 + 1 zadarmo)
Pozrime sa na konkrétny prípad malej kaviarne, ktorá ponúka klasický vernostný program typu "10 + 1 zadarmo". Zákazník dostane 1 bod za každú kúpenú kávu (napr. za €3) a po nazbieraní 10 bodov dostane jednu kávu zadarmo. Rozoberieme, ako to funguje účtovne, či ide o "promotional expense" a aký je rozdiel medzi in-house správou a použitím Shopify.
Ako funguje program "10 + 1 zadarmo"
- Získavanie bodov: Zákazník kúpi kávu za €3 a dostane 1 bod (napr. pečiatku na kartičku alebo digitálny záznam). Body nemajú peňažnú hodnotu na predaj – sú čisto odmenou za nákup.
- Využitie bodov: Po nazbieraní 10 bodov (čo znamená nákupy za €30) zákazník dostane kávu zadarmo (hodnota €3).
- Reálny náklad pre kaviareň: Náklad na výrobu kávy zadarmo je nižší ako predajná cena, napr. €1,50 za suroviny a prácu.
Účtovné spracovanie (In-house)
Ak kaviareň spravuje program sama (in-house), účtovný proces závisí od toho, či používa cash accounting (bežné pre malé firmy) alebo accrual accounting: - Cash accounting: - Pri nákupe kávy zákazníkom: Kaviareň účtuje príjem €3 za každú kávu a vydá bloček. Bod (pečiatka) nemá peňažnú hodnotu, takže sa neúčtuje ako záväzok ani príjem. - Pri uplatnení 10 bodov: Keď zákazník dostane kávu zadarmo, nevzniká príjem (€0), ale vzniká náklad na výrobu kávy (€1,50). Tento náklad sa účtuje ako "Promotional expense" alebo "Marketing cost", pretože ide o formu zľavy alebo reklamy na udržanie zákazníka. - Daňový dopad: Žiadny príjem pri vydaní kávy zadarmo, náklad €1,50 je daňovo odpočítateľný ako bežný výdavok. - Accrual accounting (menej bežné pre malé firmy): - Pri nákupe kávy zákazníkom: Kaviareň účtuje príjem €3, ale zároveň vytvára malý záväzok na budúcu odmenu (napr. €0,30 za každý bod, čo je odhad nákladu na budúcu kávu zadarmo deleno 10). Teda z €3 príjmu je zdaniteľný príjem len €2,70. - Pri uplatnení 10 bodov: Keď zákazník dostane kávu zadarmo, kaviareň zníži záväzok o €3 (10 bodov x €0,30) a účtuje náklad €1,50 na výrobu kávy. Rozdiel môže byť upravený ako breakage alebo iný zisk, ak sa odhady líšia od reality. - Daňový dopad: Zdaniteľný príjem je nižší už pri prvom nákupe, ale účtovníctvo je zložitejšie kvôli odhadom a rezervám.
Je to Promotional Expense? Áno, v oboch prípadoch (cash aj accrual) sa náklad na kávu zadarmo účtuje ako "Promotional expense" alebo "Marketing cost", pretože ide o formu zľavy na podporu lojality zákazníkov. Nie je to považované za bežný predaj, pretože nevzniká príjem ani bloček.
Účtovné spracovanie (cez Shopify Loyalty)
Ak kaviareň používa Shopify Loyalty na správu programu "10 + 1 zadarmo", proces je jednoduchší: - Pri nákupe kávy zákazníkom: Kaviareň účtuje príjem €3 za kávu a vydá bloček. Shopify pripíše bod zákazníkovi do jeho účtu (nie je to váš záväzok, ale Shopify). - Pri uplatnení 10 bodov: Shopify pošle objednávku na vydanie kávy zadarmo. Kaviareň vydá kávu (náklad €1,50) a zaplatí Shopify transakčný poplatok (€0,20). Celkový náklad €1,70 sa účtuje ako "Promotional expense" alebo "Marketing cost". - Daňový dopad: Rovnako ako pri in-house, žiadny príjem pri vydaní kávy zadarmo, náklad €1,70 je daňovo odpočítateľný ako bežný výdavok. Navyše nemusíte riešiť žiadne záväzky alebo odhady breakage, pretože body spravuje Shopify.
Rozdiel medzi In-house a Shopify
- In-house:
- Výhody: Plná kontrola nad programom, žiadne mesačné poplatky tretej strane (napr. €29 Shopify fee).
- Nevýhody: Ak použijete accrual accounting, musíte vytvárať rezervy a odhadovať breakage, čo je administratívne náročné. Pri cash accounting je to jednoduchšie (žiadne záväzky), ale ak by ste body predávali za peniaze, vzniká daňový nesúlad (príjem zdanený hneď, náklad až neskôr). Navyše musíte sami spravovať databázu bodov (pečiatky, softvér), čo je časovo náročné.
- Shopify Loyalty:
- Výhody: Žiadne záväzky vo vašej účtovnej knihe, Shopify spravuje body a technológiu. Účtovne je to jednoduché – len mesačný poplatok (€29) a transakčné poplatky (€0,20) ako marketingový náklad. Nemusíte riešiť odhady ani breakage.
- Nevýhody: Platíte mesačné poplatky a transakčné fees, čo zvyšuje náklady (napr. €0,20 navyše za každú kávu zadarmo). Máte menšiu kontrolu nad programom, pretože ho spravuje tretia strana.
Záver pre kaviareň: Program "10 + 1 zadarmo" je účtovne považovaný za Promotional expense v oboch prípadoch (in-house aj Shopify), pretože káva zadarmo je forma marketingu na udržanie zákazníkov. Rozdiel je v administratívnej záťaži a nákladoch – Shopify zjednodušuje účtovníctvo a správu, ale za cenu mesačných poplatkov. In-house je lacnejšie, ale náročnejšie na správu, najmä ak by ste chceli používať accrual accounting alebo predávať body za peniaze.
Záver
Vernostné programy sú sofistikovaný nástroj zákazníckej lojality, ale ich účtovné a daňové aspekty sa výrazne líšia medzi veľkými a malými firmami. Veľké korporácie využívajú accrual accounting a medzinárodné štruktúry na optimalizáciu daní, zatiaľ čo pre malé biznisy sú často výhodnejšie alternatívne modely ako gift cards alebo outsourcing celého programu, ktoré eliminujú daňové a cashflow problémy. Gift cards navyše prinášajú okamžitý cash flow, časovú hodnotu peňazí a breakage benefit, čo z nich robí ideálny nástroj pre podniky všetkých veľkostí. Shopify Loyalty ponúka malým firmám spôsob, ako implementovať vernostný program bez účtovných komplikácií, pretože preberá technickú a právnu zodpovednosť, čím umožňuje sústrediť sa na core biznis. Pre jednoduché programy ako "10 + 1 zadarmo" je účtovný dopad podobný (Promotional expense), ale Shopify zjednodušuje správu za cenu dodatočných poplatkov.
```
```
-
 @ 7f5c2b4e:a818d75d
2024-03-05 15:40:04
@ 7f5c2b4e:a818d75d
2024-03-05 15:40:04Nsec.app is a Nostr application which lets you share access to your account and login to Nostr apps seamlessly with numerous devices.
The app is super useful when collaboratively running a Nostr account. It lets you generate tokens to share with partners or colleagues and provide different levels of access to different individuals.
Another bonus feature of nsec.app is letting you forget about Nostr browser extensions. Extensions have their fair share of useful features, but using nsec.app (or other apps that support NIP-46 login, e.g. nsecBunker) is often more convenient, arguably more secure and offers some features, that extensions aren't able to deliver.
Let's walk through the process of starting the nsec.app and see what features it has to offer.
Installation
Nsec.app is a PWA (see my short blog post on PWAs and their benefits here), meaning that it can be saved to your device in a way that it feels and acts like a native app. Alternatively the app can be used in the browser.
Visit Nsec.app:
https://i.nostr.build/axlP.png
After pressing the "Get started" button you'll be welcomed by three main options: "Sign up", "Login" or "Import Key". Let's explore each of these options:
- Sign up: This option suits those, who do not have a Nostr account yet. I'd steer clear from this option for now and create an account in a more "conventional" way – via one of the popular Nostr clients or by utilizing a dedicated browser extension.
Stay tuned as the developers are working on wide implementation of NIP49. At the moment few Nostr clients support NIP49, so you won't have many options of using keys created with nsec.app. When most Nostr apps support NIP49 logins, signing up to Nostr via nsec.app will become a more convenient option.
If you decide to utilize nsec.app to create your Nostr account, the process is super simple:
1) Choose your Nostr address 2) Create and confirm your password 3) Enjoy your new Nostr account 💜
https://i.nostr.build/JqgP.png
- Import key: This approach assumes you would like to start using nsec.app with the existing Nostr account.
https://i.nostr.build/5e9y.png
In this case you'll need to choose your username, provide your private key and choose a password. This will create the nsec.app account (by setting a username and a password) while binding it with your original Nostr account (by providing your private key).
It is worth noting that your keys will be encrypted by your password and stored on nsec.app's server to sync to other devices in end-to-end encrypted manner.
- Login: This approach assumes you've already set up nsec.app and would like to enter your dashboard from a new device.
https://i.nostr.build/k6aa.png
Do not forget to click the "Enable background service" tile after setting up your account. This will ensure you receive a notification whenever the request to authorize a login is created.
https://i.nostr.build/Zrdx.png
Usage
After setting up nsec.app you're ready to start utilizing it to login to numerous Nostr apps.
The most powerful feature of nsec.app is that it lets you login to apps without having to use the browser extension or exposing your private key.
For example, I can now turn Coracle client into a PWA on my iPhone, which is otherwise impossible, because Apple does not allow you to utilize browser extensions with PWAs.
Another use case is delegating the rights to interact with Nostr on behalf of the account you created.
Regardless of wether you want to use the app single-handedly, or delegate the private key, the process is as follows:
- Use nsec.app to create a login string by pressing "Connect app".
- Copy the string by pressing the corresponding button.
https://i.nostr.build/rvVB.png
- Paste the string into the client that you'd like to login to.
- As you (or your companion) try to login to the Nostr app, nsec.app will display a notification asking you (the administrator) to approve the login.
https://i.nostr.build/7x53.png
As you can see, there are two options for you to choose from:
- Basic permissions: This will approve all potential future interactions.
- On demand: This will log the user in and ask for your approvals every time the user tries to interact with the protocol in a new way (like, zap, follow, etc.)
That's it. You can now interact with nostr without ever having to utilize the browser extension or share your private key with any app.
Features
Customization
Nsec.app lets you customize the way your connected apps look. You can name them, specify a website address and choose an icon of your choice. Very handy functionality for when you start actively using the app:
https://i.nostr.build/ej6X.png
As the stack of connected apps grows this will help you distinguish between them in order to introduce any necessary changes.
https://i.nostr.build/XEgW.png
Connected apps management
This leads us to the next important part of using nsec.app: revoking access to apps. This is especially important when it comes to sharing access to account with someone else. In case you no longer plan to collaborate on the account, or you simply do not need some app connection to function any longer, you can revoke access at any time.
Just open the app you need and: (a) press "Delete app" (this completely cuts connection between your app and nsec.app) or (b) press the three dots next to the existing approved permission followed by "Delete permission" (this cancels the given permission, so that the next time you (or other user) tries to interact with the protocol, you will receive a notification asking you to approve their action).
https://i.nostr.build/d3QD.png
NIP49 logins
Nsec.app allows you to utilize another way of logging into Nostr apps – NIP49. We touched on this approach earlier, so let's explore how it works.
Here's an example with Noogle:
- Choose the Login with NCryptSec option:
https://i.nostr.build/DzeV.png
- Enter the encrypted Nsec (to be retrieved from the nsec.app in Settings -> Export) and the nsec.app password:
https://i.nostr.build/R505.png
That's it. You're logged in.
https://i.nostr.build/moLR.png
At the moment few clients support this NIP, but given the benefits of this functionality, it shouldn't be long before we see more and more clients join in.
Outro
Just like with every other Nostr app, there's a lot of work to be done. Nevertheless, nsec.app already solves many important problems, and is definitely worth your attention. Give it a try and let us know if you find any bugs, or come up with some ideas worth implementing. Feel free to ping myself or, better yet, the app developer nostr:npub1xdtducdnjerex88gkg2qk2atsdlqsyxqaag4h05jmcpyspqt30wscmntxy
Hope this guide was useful! If so, don't forget to zap this post 😉
See you on the other side of the Nostr rabbit hole
Tony⚡️
-
 @ 3eab247c:1d80aeed
2025-06-05 08:51:39
@ 3eab247c:1d80aeed
2025-06-05 08:51:39Global Metrics
Here are the top stats from the last period:
- Total Bitcoin-accepting merchants: 15,306 → 16,284
- Recently verified (1y): 7,540 → 7,803 (the rest of our dataset is slowly rotting; help us before it's too late!)
- Avg. days since last verification: 398 → 405 (more mappers, please)
- Merchants boosted: 22 (for a total of 4,325 days, someone is feeling generous)
- Comments posted: 34
Find current stats over at the 👉 BTC Map Dashboard.
Merchant Adoption
Steak n’ Shake
The US 🇺🇸 is a massive country, yet its BTC Map footprint has been lagging relative to other countries ... that is until now!

In what came as a nice surprise to our Shadowy Supertaggers 🫠, the Steak ’n Shake chain began accepting Bitcoin payments across hundreds of its locations nationwide (with some international locations too).
According to CoinDesk, the rollout has been smooth, with users reporting seamless transactions powered by Speed.
This marks a significant step towards broader Bitcoin adoption in the US. Now to drop the capital gains tax on cheesburgers!
SPAR Switzerland
In other chain/franchise adoption news, the first SPAR supermarket in Switzerland 🇨🇭 to begin accepting Bitcoin was this one in Zug. It was quickly followed by this one in Rossrüti and this one in Kreuzlingen, in what is believed to be part of a wider roll-out plan within the country powered by DFX's Open CryptoPay.
That said, we believe the OG SPAR crown goes to SPAR City in Arnhem Bitcoin City!
New Features
Merchant Comments in the Web App
Web App users are now on par with Android users in that they can both see and make comments on merchants.
This is powered by our tweaked API that enables anyone to make a comment as long as they pass the satswall fee of 500 sats. This helps keep spam manageable and ensure quality comments.
And just in case you were wondering what the number count was on the merchant pins - yep, they're comments!
Here is an 👉 Example merchant page with comments.
Merchant Page Design Tweaks
To support the now trio of actions (Verify, Boost & Comment) on the merchant page, we've re-jigged the design a little to make things a little clearer.
What do you think?
Technical
Codebase Refactoring
Thanks to Hannes’s contributions, we’ve made progress in cleaning-up the Web App's codebase and completing long overdue maintenance. Whilst often thankless tasks, these caretaking activities help immensely with long-term maintainability enabling us to confidently build new features.
Auth System Upgrades
The old auth system was held together with duct tape and prayers, and we’re working on a more robust authentication system to support future public API access. Updates include:
- Password hashing
- Bearer token support
- Improved security practices
More enhancements are in progress and we'll update you in the next blog post.
Better API Documentation
Instead of relying on tribal knowledge, we're finally getting around to writing actual docs (with the help/hindrance of LLMs). The "move fast, break everything" era is over; now we move slightly slower and break slightly less. Progress!
Database Improvements
We use SQLite, which works well but it requires careful handling in async Rust environments. So now we're untangling this mess to avoid accidental blocking queries (and the ensuing dumpster fires).
Backup System Enhancements
BTC Map data comes in three layers of fragility:
- Merchants (backed up by OS - the big boys handle this)
- Non-OSM stuff (areas, users, etc. - currently stored on a napkin)
- External systems (Lightning node, submission tickets - pray to Satoshi)
We're now forcing two core members to backup everything, because redundancy is good.
Credits
Thanks to everyone who directly contributed to the project this period:
- Comino
- descubrebitcoin
- Hannes
- Igor Bubelov
- Nathan Day
- Rockedf
- Saunter
- SiriusBig
- vv01f
Support Us
There are many ways in which you can support us:
-
Become a Shadowy Supertagger and help maintain your local area or pitch-in with the never-ending global effort.
-
Consider a zapping this note or make a donation to the to the project here.
-
 @ 2d5b6404:d4b500b0
2024-02-17 14:47:18
@ 2d5b6404:d4b500b0
2024-02-17 14:47:18- アンフィールドでリバプールの試合を観戦する
- イタリアでピザ食べたりエスプレッソ飲む
- じゅりよんやラルフ、ewelina、マルティン、jefgとか𓆏に会いにヨーロッパ旅行行く
- 長崎ぺんぎん水族館に行く
- 九十九里で貝を食べる
- 奄美大島でクジラの鳴き声を聞く
- 蒸気機関車に乗る
- 台湾旅行に行く
- 韓国旅行に行く
- 船で東京か大阪、四国に行く
- Punkt. MP02を買い替える
- ベトナムに住んでる友達に会いに行く
- ホームベースとなる共同体を見つける。もしくは作る
- 収入の10分の1を寄付する
- ~~デスストランディングをクリアする~~
- ブレワイ、ティアキンをクリアする
- べランピングする
- 冷蔵庫を伊良コーラでいっぱいにする
- 友達とこたつでゲームする
-
 @ 318ebaba:9a262eae
2025-06-08 08:36:12
@ 318ebaba:9a262eae
2025-06-08 08:36:12When connecting to multiple relays in the Nostr protocol, users may encounter several challenges that can affect their overall experience. Here are some of the key issues:
Challenges of Connecting to Multiple Relays
-
Performance Issues: The lightweight design of Nostr relays can lead to performance bottlenecks, especially when many users are connected simultaneously. This can result in slow message delivery or even failures in posting messages if the relays are overwhelmed[1][2][32].
-
Reliability and Connectivity: Users may experience connectivity problems with certain relays, which can lead to inconsistent access to messages or delays in communication. If a relay goes offline or has connectivity issues, it can disrupt the flow of information, making it difficult for users to send or receive messages reliably[3][4][18].
-
Data Synchronization: As users connect to multiple relays, ensuring that data is synchronized across these relays can be challenging. Inconsistent data states may arise if different relays store messages differently or if there are delays in message propagation. This can lead to confusion about which messages have been sent or received[7][41].
-
Configuration Complexity: Managing connections to multiple relays requires a certain level of technical knowledge. Users need to configure their clients properly to connect to various relays, which can be daunting for those less familiar with the technology. Misconfigurations can lead to connection failures or suboptimal performance[4][21].
-
Spam and Quality Control: With the open nature of Nostr, some relays may be more susceptible to spam or low-quality content. Users connecting to multiple relays might encounter a higher volume of irrelevant or unwanted messages, which can detract from the overall user experience[6][32].
-
Security Concerns: When using multiple relays, users must be cautious about the security of their connections. Not all relays may implement the same level of security, and connecting to less secure relays could expose users to risks such as data interception or unauthorized access to their messages[26][27].
In summary, while connecting to multiple relays in Nostr offers benefits such as redundancy and improved access to information, users must navigate various challenges related to performance, reliability, configuration, and security. Addressing these issues is crucial for a smooth and effective experience on the Nostr network.
[1] https://forum.dfinity.org/t/introducing-replicatr-enhancing-nostr-with-internet-computer-integration/31861 [2] https://medium.com/coinmonks/a-deep-dive-into-nostr-clients-with-technical-insights-and-code-snippets-b1666bb11fac [3] nostr:nevent1qqsfvjvg73wxdn7mda28m704r2zv9lnzlcdgh8r0g52lfvy2wj7uw4czyq32rylmsmre84lhxdypy6jlu4dt3fxfwkq9a0p0lqdl9y8hsp0hur4fuw4 [4] https://www.reddit.com/r/nostr/comments/1e6nm68/new_nostream_relay_created_problems_with_publish/ [5] https://www.lynalden.com/the-power-of-nostr/ [6] https://bitcoinmagazine.com/technical/how-nostr-can-improve-bitcoin-privacy [7] https://barelybuggy.blog/2024/11/26/mostr-offline/ [8] https://github.com/scsibug/nostr-rs-relay/issues/126 [9] https://community.umbrel.com/t/nostr-relay-troubleshooting/17828 [10] https://research.dorahacks.io/2024/04/30/nostr-relay-incentive/ [11] https://community.start9.com/t/issue-confirming-nostr-relay/1682 [12] https://arxiv.org/html/2402.05709v1 [13] https://community.umbrel.com/t/nostr-relay-not-connecting/11401 [14] https://www.purplerelay.com/troubleshooting-common-issues-with-nostr-relay-server-a-users-guide/ [15] https://news.ycombinator.com/item?id=35694029 [16] https://substack.com/home/post/p-158872714?utm_campaign=post&utm_medium=web [17] https://stacker.news/items/142013 [18] https://www.reddit.com/r/nostr/comments/1h6admk/are_these_relays_working/ [19] https://news.ycombinator.com/item?id=33746360 [20] https://github.com/scsibug/nostr-rs-relay/issues/195 [21] https://www.purplerelay.com/how-to-run-a-nostr-relay-a-step-by-step-guide/ [22] https://denostr.medium.com/the-future-of-social-communication-nostrs-origins-and-the-next-destination-in-social-networking-27f0c901d7ae [23] nostr:nevent1qqsqwklh29cvf3z0skhh77xyqf3m53xkppcttf3c8nuc2jqteulfx0czyqcgr7epv9hha2v9afp99l5wl0ljna0zum59fzyhl9v8pgv5xlhf5ava642 [24] https://www.reddit.com/r/nostr/comments/15fyr6r/pervasive_private_key_sharing_seems_dangerous/ [25] https://whtwnd.com/agoracitizen.network/3l2fysaripd2q [26] https://ron.stoner.com/nostr_Security_and_Privacy/ [27] https://forums.puri.sm/t/about-what-is-nostr/20764 [28] https://github.com/nostr-protocol/nips/issues/107 [29] https://medium.com/@volodymyrpavlyshyn/security-features-of-nostr-a0276a22e815 [30] nostr:nevent1qqspd8fh3tplxtfhjpka3y3glzh63v3ygsdhacyq8dvyrnxtvl09lpczyr2v7dprke9lad2qk0svug55vxguqv7n3dwn9vm63u8n5n84znxjxedjf6c [31] nostr:nevent1qqs8e2su6n8m2xtg45qdjw7rdcq6w3g5guvt085h52qhg25wxn755sczyrh26kg89z95jqaz4xkex7kaw2t36twtc75vmrfx2k3p3jqvhfa8vzan82f [32] https://www.cointribune.com/en/nostr-et-la-censure-pourquoi-un-reseau-social-decentralise-est-essentiel-2/ [33] nostr:nevent1qqsv86d756zcw32x0zcvqmr924y5sltvwqud0dywny83ndee30zzrmczyrh26kg89z95jqaz4xkex7kaw2t36twtc75vmrfx2k3p3jqvhfa8vwpfv29 [34] https://github.com/nbd-wtf/nostr-tools/issues [35] https://www.voltage.cloud/blog/the-growth-of-nostr-the-era-of-decentralization [36] https://medium.com/@BingVentures/status-quo-challenges-and-prospect-of-decentralized-social-networks-18f9584f2e8d [37] https://www.reddit.com/r/RedditAlternatives/comments/14s8ao4/greetings_im_here_to_tell_you_about_nostr_a/ [38] https://bitcoinmagazine.com/culture/nostr-the-importance-of-censorship-resistant-communication-for-innovation-and-human-progress- [39] https://github.com/mayneyao/eidos/issues/129 [40] https://www.reddit.com/r/nostr/comments/115a8et/data_duplication_and_distribution_in_nostr_relays/ [41] https://github.com/open-nostr/nostar [42] nostr:nevent1qqsryg8zuc9rdwldat385al24mdt56wanc6g6hfymy8l9tgtmzsc4nspzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhg85cx73 [43] https://ckbcn.xlog.app/Nostr-sheng-tai-fa-zhan-xian-zhuang-ji-wen-ti?locale=en [44] nostr:naddr1qqc92mnvda3kk6twvuk5ummnw3ez6ued2phhgetww35kzmpdwa5hg6pdfehhgetyv43kktt08p5hscnkqgsr7acdvhf6we9fch94qwhpy0nza36e3tgrtkpku25ppuu80f69kfqrqsqqqa28aknkml
-
-
 @ 866e0139:6a9334e5
2025-06-08 07:10:42
@ 866e0139:6a9334e5
2025-06-08 07:10:42Autor: John J. Mearsheimer. Dieser Beitrag wurde mit dem Pareto-Client geschrieben und erschien zuerst auf dem Blog des Autors. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Die Frage, wer für den Krieg in der Ukraine verantwortlich ist, ist seit dem Einmarsch Russlands in die Ukraine am 24. Februar 2022 ein sehr umstrittenes Thema.Die Antwort auf diese Frage ist von enormer Bedeutung, denn der Krieg war aus verschiedenen Gründen eine Katastrophe, von denen die wichtigste darin besteht, dass die Ukraine praktisch zerstört wurde. Sie hat einen beträchtlichen Teil ihres Territoriums verloren und wird wahrscheinlich noch mehr verlieren, ihre Wirtschaft liegt in Trümmern, eine riesige Zahl von Ukrainern wurde intern vertrieben oder ist aus dem Land geflohen, und sie hat Hunderttausende von Opfern zu beklagen. Natürlich hat auch Russland einen hohen Blutzoll gezahlt. Auf strategischer Ebene sind die Beziehungen zwischen Russland und Europa, ganz zu schweigen von Russland und der Ukraine, auf absehbare Zeit vergiftet, was bedeutet, dass die Gefahr eines größeren Krieges in Europa auch dann noch bestehen wird, wenn der Krieg in der Ukraine zu einem eingefrorenen Konflikt wird. Wer die Verantwortung für diese Katastrophe trägt, ist eine Frage, die nicht so schnell verschwinden wird, sondern eher noch an Bedeutung gewinnen dürfte, je mehr Menschen das Ausmaß der Katastrophe bewusst wird.
Die gängige Meinung im Westen ist, dass Wladimir Putin für den Krieg in der Ukraine verantwortlich sei. Die Invasion habe darauf abgezielt, die gesamte Ukraine zu erobern und sie zu einem Teil eines größeren Russlands zu machen, so die Argumentation. Sobald dieses Ziel erreicht sei, würden die Russen ein Imperium in Osteuropa errichten, ähnlich wie es die Sowjetunion nach dem Zweiten Weltkrieg getan habe. Daher stelle Putin letztlich eine Bedrohung für den Westen dar, der man mit aller Macht begegnen müsse. Kurz gesagt, Putin ist ein Imperialist mit einem Masterplan, der sich nahtlos in die reiche russische Tradition einfügt.
Das alternative Argument, mit dem ich mich identifiziere und das im Westen eindeutig in der Minderheit ist, lautet, dass die Vereinigten Staaten und ihre Verbündeten den Krieg provoziert haben. Damit soll natürlich nicht geleugnet werden, dass Russland in die Ukraine einmarschiert ist und den Krieg begonnen hat. Die Hauptursache des Konflikts ist jedoch der NATO-Beschluss, die Ukraine in das Bündnis aufzunehmen, was praktisch alle russischen Führer als existenzielle Bedrohung ansehen, die beseitigt werden muss. Die NATO-Erweiterung ist jedoch Teil einer umfassenderen Strategie, die darauf abzielt, die Ukraine zu einem westlichen Bollwerk an Russlands Grenze zu machen. Ein Beitritt Kiews zur Europäischen Union (EU) und die Förderung einer farbigen Revolution in der Ukraine – die Umwandlung des Landes in eine prowestliche liberale Demokratie – sind die beiden anderen Säulen dieser Politik. Die russische Führung fürchtet alle drei Bereiche, aber am meisten fürchtet sie die NATO-Erweiterung. Um dieser Bedrohung zu begegnen, hat Russland am 24. Februar 2022 einen Präventivkrieg begonnen.
Die Debatte darüber, wer den Ukraine-Krieg verursacht hat, ist kürzlich aufgeflammt, als zwei prominente westliche Politiker – der ehemalige US-Präsident Donald Trump und der prominente britische Abgeordnete Nigel Farage – das Argument vorbrachten, dass die NATO-Erweiterung die treibende Kraft hinter dem Konflikt sei. Es überrascht nicht, dass ihre Äußerungen von den Verfechtern der konventionellen Meinung mit einem heftigen Gegenangriff beantwortet wurden. Es ist auch erwähnenswert, dass der scheidende NATO-Generalsekretär Jens Stoltenberg im vergangenen Jahr zweimal sagte, dass „Präsident Putin diesen Krieg begonnen hat, weil er die Tür der NATO schließen und der Ukraine das Recht verweigern wollte, ihren eigenen Weg zu wählen“. Kaum jemand im Westen hat dieses bemerkenswerte Eingeständnis des NATO-Chefs in Frage gestellt, und er hat es auch nicht zurückgezogen.
Mein Ziel ist es, einen Überblick über die wichtigsten Punkte zu geben, die die Ansicht stützen, dass Putin nicht in die Ukraine einmarschiert ist, weil er ein Imperialist ist, der die Ukraine zu einem Teil eines größeren Russlands machen will, sondern vor allem wegen der NATO-Erweiterung und der Bemühungen des Westens, die Ukraine zu einer westlichen Hochburg an der Grenze Russlands zu machen.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
In Kürze folgt eine Mail an alle Genossenschafter, danke für die Geduld und das Verständnis!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Lassen Sie mich mit den sieben wichtigsten Gründen für die Ablehnung der herkömmlichen Meinung beginnen.
ERSTENS gibt es schlicht und ergreifend keine Beweise aus der Zeit vor dem 24. Februar 2022, dass Putin die Ukraine erobern und in Russland eingliedern wollte. Vertreter der gängigen Meinung können keine Schriftstücke oder Aussagen von Putin nennen, die darauf hindeuten, dass er die Ukraine erobern wollte.
Wenn man sie zu diesem Punkt befragt, liefern die Verfechter der konventionellen Meinung Hinweise, die wenig oder gar nichts mit Putins Motiven für die Invasion der Ukraine zu tun haben. Einige betonen zum Beispiel, dass er sagte, die Ukraine sei ein „künstlicher Staat“ oder kein „echter Staat“. Solche undurchsichtigen Äußerungen sagen jedoch nichts über die Gründe für seinen Kriegseintritt aus. Dasselbe gilt für Putins Aussage, er betrachte Russen und Ukrainer als „ein Volk“ mit einer gemeinsamen Geschichte. Andere weisen darauf hin, dass er den Zusammenbruch der Sowjetunion als „die größte geopolitische Katastrophe des Jahrhunderts“ bezeichnete. Aber Putin sagte auch: „Wer die Sowjetunion nicht vermisst, hat kein Herz. Wer sie zurückhaben will, hat kein Hirn.“ Andere wiederum verweisen auf eine Rede, in der er erklärte: „Die moderne Ukraine wurde vollständig von Russland geschaffen, genauer gesagt, vom bolschewistischen, kommunistischen Russland.“ Aber das ist kaum ein Beweis dafür, dass er an der Eroberung der Ukraine interessiert war. Außerdem sagte er in der gleichen Rede: „Natürlich können wir die Ereignisse der Vergangenheit nicht ändern, aber wir müssen sie zumindest offen und ehrlich zugeben.“
Um zu beweisen, dass Putin die gesamte Ukraine erobern und Russland einverleiben wollte, muss man nachweisen, dass er 1) dieses Ziel für erstrebenswert hielt, 2) es für machbar hielt und 3) die Absicht hatte, dieses Ziel zu verfolgen. Es gibt in den öffentlichen Aufzeichnungen keine Beweise dafür, dass Putin erwog, geschweige denn beabsichtigte, die Ukraine als unabhängigen Staat zu beenden und sie zu einem Teil Großrusslands zu machen, als er am 24. Februar 2022 seine Truppen in die Ukraine schickte.
Tatsächlich gibt es erhebliche Beweise dafür, dass Putin die Ukraine als unabhängiges Land anerkannte. In seinem bekannten Artikel vom 12. Juli 2021 über die russisch-ukrainischen Beziehungen, der von Befürwortern der konventionellen Meinung oft als Beweis für seine imperialen Ambitionen angeführt wird, sagt er dem ukrainischen Volk: „Ihr wollt einen eigenen Staat gründen: Ihr seid willkommen!“ Zur Frage, wie Russland die Ukraine behandeln sollte, schreibt er: „Es gibt nur eine Antwort: mit Respekt.“ Er schließt seinen langen Artikel mit den folgenden Worten ab: „Und wie die Ukraine aussehen wird – das müssen ihre Bürger entscheiden.“ Diese Aussagen stehen im direkten Widerspruch zu der Behauptung, Putin wolle die Ukraine in ein größeres Russland eingliedern.
In demselben Artikel vom 12. Juli 2021 und erneut in einer wichtigen Rede am 21. Februar 2022 betonte Putin, dass Russland „die neue geopolitische Realität, die nach der Auflösung der UdSSR entstanden ist“, akzeptiere. Diesen Punkt wiederholte er ein drittes Mal am 24. Februar 2022, als er ankündigte, Russland werde in die Ukraine einmarschieren. Insbesondere erklärte er: „Wir haben nicht vor, ukrainisches Territorium zu besetzen“, und machte deutlich, dass er die ukrainische Souveränität respektiere, allerdings nur bis zu einem gewissen Punkt: „Russland kann sich nicht sicher fühlen, sich nicht entwickeln und nicht existieren, wenn es sich einer ständigen Bedrohung durch das Territorium der heutigen Ukraine ausgesetzt sieht.“ Das heißt, Putin war nicht daran interessiert, die Ukraine zu einem Teil Russlands zu machen, sondern er wollte sicherstellen, dass sie nicht zu einem „Sprungbrett“ für westliche Aggressionen gegen Russland wird.
ZWEITENS gibt es keinerlei Hinweise dafür, dass Putin eine Marionettenregierung für die Ukraine vorbereitete, in Kiew prorussische Führungspersönlichkeiten aufbaute oder irgendwelche politischen Maßnahmen verfolgte, die eine Besetzung des gesamten Landes und dessen letztendliche Eingliederung in Russland ermöglichen würden.
Diese Fakten widersprechen der Behauptung, Putin sei daran interessiert gewesen, die Ukraine von der Landkarte zu tilgen.
**DRITTENS: Putin hatte nicht annähernd genug Truppen, um die Ukraine zu erobern. **
Beginnen wir mit den Gesamtzahlen. Ich schätze seit langem, dass die Russen mit höchstens 190.000 Soldaten in die Ukraine einmarschiert sind. General Oleksandr Syrskyi, der derzeitige Oberbefehlshaber der ukrainischen Streitkräfte, sagte kürzlich in einem Interview mit The Guardian, dass die russische Invasionstruppe nur 100.000 Mann stark war. The Guardian hatte diese Zahl bereits vor Beginn des Krieges genannt. Es ist unmöglich, dass eine Truppe von 100.000 oder 190.000 Mann die gesamte Ukraine erobern, besetzen und in ein Großrussland eingliedern könnte.
Bedenken Sie, dass die Wehrmacht beim deutschen Überfall auf die westliche Hälfte Polens im September 1939 etwa 1,5 Millionen Mann zählte. Die Ukraine ist geografisch mehr als dreimal so groß wie die westliche Hälfte Polens im Jahr 1939, und in der Ukraine leben im Jahr 2022 fast doppelt so viele Menschen wie in Polen zum Zeitpunkt des deutschen Überfalls. Wenn wir die Schätzung von General Syrskyi akzeptieren, dass 100.000 russische Truppen im Jahr 2022 in die Ukraine einmarschierten, bedeutet dies, dass Russland über eine Invasionsstreitmacht verfügte, die 1/15 der Größe der deutschen Streitkräfte war, die in Polen einmarschierten. Und diese kleine russische Armee marschierte in ein Land ein, das sowohl territorial als auch von der Bevölkerungszahl her viel größer war als Polen.
Abgesehen von den Zahlen stellt sich die Frage nach der Qualität der russischen Armee. Zunächst einmal handelte es sich um eine militärische Streitkraft, die in erster Linie dazu bestimmt war, Russland vor einer Invasion zu schützen. Es handelte sich nicht um eine Armee, die für eine Großoffensive zur Eroberung der gesamten Ukraine, geschweige denn zur Bedrohung des übrigen Europas, gerüstet war. Außerdem ließ die Qualität der Kampftruppen zu wünschen übrig, da die Russen nicht mit einem Krieg rechneten, als sich die Krise im Frühjahr 2021 zuzuspitzen begann. Daher hatten sie kaum Gelegenheit, eine qualifizierte Invasionstruppe auszubilden. Sowohl qualitativ als auch quantitativ war die russische Invasionstruppe nicht annähernd mit der deutschen Wehrmacht der späten 1930er und frühen 1940er Jahre vergleichbar.
Man könnte argumentieren, dass die russische Führung dachte, das ukrainische Militär sei so klein und so unterlegen, dass ihre Armee die ukrainischen Streitkräfte leicht besiegen und das ganze Land erobern könnte. Tatsächlich wussten Putin und seine Leutnants sehr wohl, dass die Vereinigten Staaten und ihre europäischen Verbündeten das ukrainische Militär seit Ausbruch der Krise am 22. Februar 2014 bewaffnet und ausgebildet hatten. Die große Befürchtung Moskaus war, dass die Ukraine de facto Mitglied der NATO werden würde. Außerdem beobachteten die russischen Führer, wie die ukrainische Armee, die größer war als ihre Invasionstruppen, zwischen 2014 und 2022 im Donbass erfolgreich kämpfte. Ihnen war sicherlich klar, dass das ukrainische Militär kein Papiertiger war, der schnell und entschlossen besiegt werden konnte, zumal es über eine starke Rückendeckung durch den Westen verfügte.
Schließlich waren die Russen im Laufe des Jahres 2022 gezwungen, ihre Armee aus der Oblast Charkiw und aus dem westlichen Teil der Oblast Cherson abzuziehen. Damit gab Moskau Gebiete auf, die seine Armee in den ersten Tagen des Krieges erobert hatte. Es steht außer Frage, dass der Druck der ukrainischen Armee eine Rolle dabei spielte, den russischen Rückzug zu erzwingen. Vor allem aber erkannten Putin und seine Generäle, dass sie nicht über genügend Kräfte verfügten, um das gesamte Gebiet, das ihre Armee in Charkiw und Cherson erobert hatte, zu halten. Also zogen sie sich zurück und schufen besser kontrollierbare Verteidigungspositionen. Dies ist kaum das Verhalten, das man von einer Armee erwarten würde, die aufgebaut und ausgebildet wurde, um die gesamte Ukraine zu erobern und zu besetzen. Tatsächlich war sie für diesen Zweck nicht konzipiert und konnte daher diese Herkulesaufgabe nicht bewältigen.
VIERTENS: In den Monaten vor Kriegsbeginn versuchte Putin, eine diplomatische Lösung für die sich anbahnende Krise zu finden.
Am 17. Dezember 2021 sandte Putin ein Schreiben an Präsident Joe Biden und NATO-Chef Stoltenberg, in dem er eine Lösung der Krise auf der Grundlage einer schriftlichen Garantie vorschlug, dass: 1) die Ukraine der NATO nicht beitreten würde, 2) keine Angriffswaffen in der Nähe der russischen Grenzen stationiert würden und 3) die seit 1997 nach Osteuropa verlegten NATO-Truppen und -Ausrüstung nach Westeuropa zurückverlegt würden. Was auch immer man von der Machbarkeit einer Einigung auf der Grundlage von Putins Eröffnungsforderungen halten mag, über die die Vereinigten Staaten keine Verhandlungen führen wollten, es zeigt, dass er versuchte, einen Krieg zu vermeiden.
FÜNFTENS: Unmittelbar nach Beginn des Krieges hat Russland der Ukraine die Hand gereicht, um Verhandlungen zur Beendigung des Krieges und zur Ausarbeitung eines Modus Vivendi zwischen den beiden Ländern aufzunehmen.
Die Verhandlungen zwischen Kiew und Moskau begannen in Weißrussland nur vier Tage nach dem Einmarsch russischer Truppen in die Ukraine. Diese weißrussische Schiene wurde schließlich durch eine israelische und eine Istanbuler Schiene ersetzt. Alle verfügbaren Beweise deuten darauf hin, dass Russland ernsthaft verhandelte und nicht an der Übernahme ukrainischen Territoriums interessiert war, mit Ausnahme der Krim, die es 2014 annektiert hatte, und möglicherweise des Donbass. Die Verhandlungen endeten, als die Ukrainer auf Drängen Großbritanniens und der Vereinigten Staaten die Verhandlungen abbrachen, die zum Zeitpunkt ihrer Beendigung gute Fortschritte gemacht hatten.
Darüber hinaus berichtet Putin, dass er, als die Verhandlungen stattfanden und Fortschritte machten, gebeten wurde, als Geste des guten Willens die russischen Truppen aus dem Gebiet um Kiew abzuziehen, was er am 29. März 2022 tat. Keine westliche Regierung und kein ehemaliger Politiker hat diese Behauptung Putins angefochten, die in direktem Widerspruch zu seiner Behauptung steht, er wolle die gesamte Ukraine erobern.
SECHSTENS: Abgesehen von der Ukraine gibt es nicht den geringsten Hinweis darauf, dass Putin die Eroberung anderer osteuropäischer Länder ins Auge gefasst hat.
Außerdem ist die russische Armee nicht einmal groß genug, um die gesamte Ukraine zu überrennen, ganz zu schweigen von dem Versuch, die baltischen Staaten, Polen und Rumänien zu erobern. Außerdem sind alle diese Länder NATO-Mitglieder, was mit ziemlicher Sicherheit einen Krieg mit den Vereinigten Staaten und ihren Verbündeten bedeuten würde.
**SIEBTENS: Kaum jemand im Westen behauptete, Putin habe imperiale Ambitionen, seit er im Jahr 2000 die Macht übernahm, bis zum Beginn der Ukraine-Krise am 22. Februar 2014. Zu diesem Zeitpunkt wurde er plötzlich zum imperialen Aggressor. Warum? Weil die westlichen Staats- und Regierungschefs einen Grund brauchten, ihm die Schuld für die Krise zu geben. **
Der wohl beste Beweis dafür, dass Putin in den ersten vierzehn Jahren seiner Amtszeit nicht als ernsthafte Bedrohung angesehen wurde, ist die Tatsache, dass er auf dem NATO-Gipfel im April 2008 in Bukarest ein geladener Gast war, auf dem das Bündnis bekannt gab, dass die Ukraine und Georgien schließlich Mitglieder werden würden. Putin war natürlich erzürnd über diese Entscheidung und machte seinem Unmut Luft. Sein Widerstand gegen diese Ankündigung hatte jedoch kaum Auswirkungen auf Washington, da das russische Militär als zu schwach eingeschätzt wurde, um eine weitere NATO-Erweiterung zu verhindern, so wie es auch bei den Erweiterungswellen von 1999 und 2004 zu schwach gewesen war, um sie aufzuhalten. Der Westen glaubte, er könne Russland die NATO-Erweiterung noch einmal aufzwingen.
Außerdem war die NATO-Erweiterung vor dem 22. Februar 2014 nicht darauf ausgerichtet, Russland einzudämmen. Angesichts des traurigen Zustands der russischen Militärmacht war Moskau nicht in der Lage, die Ukraine zu erobern, geschweige denn eine revanchistische Politik in Osteuropa zu verfolgen. Der ehemalige US-Botschafter in Moskau, Michael McFaul, der ein entschiedener Verfechter der Ukraine und scharfer Kritiker Putins ist, stellt bezeichnenderweise fest, dass die Einnahme der Krim durch Russland im Jahr 2014 vor Ausbruch der Krise nicht geplant war; es war eine impulsive Reaktion auf den Putsch, der den prorussischen Führer der Ukraine stürzte. Kurz gesagt, die NATO-Erweiterung war nicht dazu gedacht, eine russische Bedrohung einzudämmen, weil der Westen nicht glaubte, dass es eine solche gab.
Erst als im Februar 2014 die Ukraine-Krise ausbrach, begannen die Vereinigten Staaten und ihre Verbündeten plötzlich, Putin als gefährlichen Führer mit imperialen Ambitionen und Russland als ernsthafte militärische Bedrohung zu beschreiben, die die NATO eindämmen müsse. Dieser abrupte Wechsel der Rhetorik sollte einem wesentlichen Zweck dienen: dem Westen die Möglichkeit zu geben, Putin für die Krise verantwortlich zu machen und den Westen von der Verantwortung freizusprechen. Es überrascht nicht, dass diese Darstellung Putins nach dem Einmarsch Russlands in die Ukraine am 24. Februar 2022 deutlich an Zugkraft gewann.
Eine Abweichung von der gängigen Meinung ist erwähnenswert. Einige argumentieren, dass die Entscheidung Moskaus, in die Ukraine einzumarschieren, wenig mit Putin selbst zu tun hat und stattdessen Teil einer expansionistischen Tradition ist, die lange vor Putin bestand und tief in der russischen Gesellschaft verwurzelt ist. Dieser Hang zur Aggression, der angeblich von inneren Kräften und nicht von Russlands äußerem Bedrohungsumfeld angetrieben wird, hat im Laufe der Zeit praktisch alle russischen Führer dazu gebracht, sich ihren Nachbarn gegenüber gewalttätig zu verhalten. Es lässt sich nicht leugnen, dass Putin in dieser Geschichte das Sagen hat oder dass er Russland in den Krieg geführt hat, aber es heißt, dass er wenig Einfluss hat. Fast jeder andere russische Führer hätte genauso gehandelt.
Es gibt zwei Probleme mit diesem Argument. Erstens ist es nicht widerlegbar, da der langjährige Charakterzug in der russischen Gesellschaft, der diesen aggressiven Impuls hervorrufe, nie identifiziert wurde. Es heißt, die Russen seien schon immer aggressiv gewesen – egal, wer an der Macht sei – und würden es auch immer sein. Es ist fast so, als ob es in ihrer DNA läge. Die gleiche Behauptung wurde einst über die Deutschen aufgestellt, die im zwanzigsten Jahrhundert oft als angeborene Aggressoren dargestellt wurden. Derartige Argumente werden in der akademischen Welt aus gutem Grund nicht ernst genommen.
Außerdem bezeichnete zwischen 1991 und 2014, als die Ukraine-Krise ausbrach, kaum jemand in den Vereinigten Staaten oder Westeuropa Russland als von Natur aus aggressiv. Außerhalb Polens und der baltischen Staaten wurde die Angst vor russischer Aggression in diesen 24 Jahren nicht häufig geäußert, was man erwarten würde, wenn die Russen zu Aggressionen veranlagt wären. Es scheint klar, dass das plötzliche Auftauchen dieser Argumentation eine bequeme Ausrede war, um Russland die Schuld für den Ukrainekrieg zu geben.
***
Lassen Sie mich einen anderen Gang einlegen und die DREI HAUPTGRÜNDE darlegen, die dafür sprechen, dass die NATO-Erweiterung die Hauptursache für den Ukraine-Krieg war.
**ERSTENS sagten russische Führer aller Art vor Kriegsbeginn wiederholt, dass sie die NATO-Erweiterung in die Ukraine als eine existenzielle Bedrohung betrachten, die beseitigt werden muss. **
Putin hat diese Argumentation bereits vor dem 24. Februar 2022 mehrfach öffentlich dargelegt. In einer Rede vor dem Vorstand des Verteidigungsministeriums am 21. Dezember 2021 erklärte er: „Was sie in der Ukraine tun oder versuchen oder planen, findet nicht Tausende von Kilometern entfernt von unserer Landesgrenze statt. Es geschieht direkt vor unserer Haustür. Sie müssen verstehen, dass wir uns einfach nirgendwo mehr hin zurückziehen können. Glauben sie wirklich, dass wir diese Bedrohungen nicht wahrnehmen? Oder glauben sie, dass wir tatenlos zusehen werden, wie Bedrohungen für Russland entstehen?“ Zwei Monate später, auf einer Pressekonferenz am 22. Februar 2022, nur wenige Tage vor Kriegsbeginn, sagte Putin: „Wir sind kategorisch gegen einen NATO-Beitritt der Ukraine, weil dies eine Bedrohung für uns darstellt, und wir haben Argumente, die dies unterstützen. Ich habe in diesem Saal wiederholt darüber gesprochen.“ Dann machte er deutlich, dass er begreift, dass die Ukraine ein Defacto-Mitglied der NATO werde. Die Vereinigten Staaten und ihre Verbündeten, sagte er, „pumpen die derzeitigen Kiewer Machthaber weiterhin mit modernen Waffentypen voll“. Er fuhr fort, dass Moskau, wenn dies nicht gestoppt werde, „mit einem bis an die Zähne bewaffneten 'Antirussland' dastehen würde. Das ist völlig inakzeptabel.“
Auch andere führende russische Politiker - darunter der Verteidigungsminister, der Außenminister, der stellvertretende Außenminister und der russische Botschafter in Washington - betonten die zentrale Bedeutung der NATO-Erweiterung als Auslöser der Ukraine-Krise. Außenminister Sergej Lawrow brachte es auf einer Pressekonferenz am 14. Januar 2022 auf den Punkt: „Der Schlüssel zu allem ist die Garantie, dass die NATO nicht nach Osten expandieren wird.“
Man hört oft das Argument, die russischen Befürchtungen seien unbegründet, weil es keine Chance gebe, dass die Ukraine dem Bündnis in absehbarer Zukunft beitreten würde, wenn überhaupt. Tatsächlich wird behauptet, die Vereinigten Staaten und ihre europäischen Verbündeten hätten der Aufnahme der Ukraine in die NATO vor dem Krieg wenig Aufmerksamkeit geschenkt. Aber selbst wenn die Ukraine dem Bündnis beitreten würde, wäre dies keine existenzielle Bedrohung für Russland, da die NATO ein Verteidigungsbündnis ist. Daher kann die NATO-Erweiterung weder eine Ursache der ursprünglichen Krise gewesen sein, die im Februar 2014 ausbrach, noch des Krieges, der im Februar 2022 begann.
Diese Argumentation ist falsch. Tatsächlich bestand die westliche Reaktion auf die Ereignisse von 2014 darin, die bestehende Strategie zu verdoppeln und die Ukraine noch näher an die NATO heranzuführen. Das Bündnis begann 2014 mit der Ausbildung des ukrainischen Militärs und bildete in den folgenden acht Jahren durchschnittlich 10.000 Soldaten pro Jahr aus. Im Dezember 2017 beschloss die Trump-Regierung, Kiew mit „Verteidigungswaffen“ zu versorgen. Andere NATO-Länder zogen bald nach und lieferten noch mehr Waffen an die Ukraine. Darüber hinaus begannen die ukrainische Armee, Marine und Luftwaffe, an gemeinsamen Militärübungen mit NATO-Streitkräften teilzunehmen. Die Bemühungen des Westens, das ukrainische Militär zu bewaffnen und auszubilden, erklären zu einem großen Teil, warum es im ersten Kriegsjahr so gut gegen die russische Armee abschnitt. Eine Schlagzeile im Wall Street Journal vom April 2022 lautete: „Das Geheimnis des militärischen Erfolgs der Ukraine: Jahrelange NATO-Ausbildung.“
Abgesehen von den laufenden Bemühungen des Bündnisses, das ukrainische Militär zu einer schlagkräftigeren Kampftruppe zu machen, die an der Seite der NATO-Truppen operieren kann, gab es im Westen im Laufe des Jahres 2021 eine neue Begeisterung für die Aufnahme der Ukraine in die NATO. Gleichzeitig vollzog Präsident Zelensky, der nie viel Enthusiasmus für eine Aufnahme der Ukraine in das Bündnis gezeigt hatte und im März 2019 auf der Grundlage einer Plattform gewählt wurde, die zur Zusammenarbeit mit Russland bei der Beilegung der anhaltenden Krise aufrief, Anfang 2021 einen Kurswechsel und befürwortete nicht nur die NATO-Mitgliedschaft der Ukraine, sondern vertrat auch eine harte Linie gegenüber Moskau.
Präsident Biden, der im Januar 2021 ins Weiße Haus einzog, hatte sich seit langem für die Aufnahme der Ukraine in die NATO eingesetzt und war ein Superfalke gegenüber Russland. Es überrascht nicht, dass die NATO am 14. Juni 2021 auf ihrem jährlichen Gipfel in Brüssel ein Kommuniqué herausgab, in dem es hieß: „Wir bekräftigen den auf dem Gipfel von Bukarest 2008 gefassten Beschluss, dass die Ukraine Mitglied des Bündnisses wird.“ Am 1. September 2021 besuchte Zelensky das Weiße Haus, wo Biden klarstellte, dass die Vereinigten Staaten „fest entschlossen“ seien, „die euro-atlantischen Bestrebungen der Ukraine zu unterstützen“. Am 10. November 2021 unterzeichneten Außenminister Antony Blinken und sein ukrainischer Amtskollege Dmytro Kuleba ein wichtiges Dokument - die „Charta der strategischen Partnerschaft zwischen den USA und der Ukraine“. Das Ziel beider Parteien, so heißt es in dem Dokument, ist es, „das Engagement für die Durchführung tiefgreifender und umfassender Reformen in der Ukraine zu unterstreichen, die für eine vollständige Integration in die europäischen und euro-atlantischen Institutionen erforderlich sind.“ Es bekräftigt auch ausdrücklich das Engagement der USA für die „Bukarester Gipfelerklärung von 2008“.
Es scheint kaum Zweifel daran zu geben, dass die Ukraine auf dem besten Weg war, bis Ende 2021 Mitglied der NATO zu werden. Dennoch argumentieren einige Befürworter dieser Politik, dass sich Moskau keine Sorgen über dieses Ergebnis hätte machen müssen, denn „die NATO ist ein Verteidigungsbündnis und stellt keine Bedrohung für Russland dar“. Aber das ist nicht die Meinung Putins und anderer russischer Politiker über die NATO, und es kommt darauf an, was sie denken. Kurz gesagt, es steht außer Frage, dass Moskau den Beitritt der Ukraine zur NATO als eine existenzielle Bedrohung ansah, die nicht hingenommen werden durfte.
ZWEITENS erkannte eine beträchtliche Anzahl einflussreicher und hoch angesehener Persönlichkeiten im Westen vor dem Krieg, dass die Expansion der NATO – insbesondere in die Ukraine – von der russischen Führung als tödliche Bedrohung angesehen werden und schließlich zur Katastrophe führen würde.
William Burns, der heute die CIA leitet („heute“ leitet John Ratcliffe die CIA, aktualisieren ODER am Anfang des Textes klarstellen, dass er schon älter ist ODER „heute“ streichen und „leitete“ statt „leitet“), aber zum Zeitpunkt des NATO-Gipfels in Bukarest im April 2008 US-Botschafter in Moskau war, verfasste ein Memo an die damalige Außenministerin Condoleezza Rice, in dem er die russischen Überlegungen zur Aufnahme der Ukraine in die Allianz prägnant beschreibt. „Der Beitritt der Ukraine zur NATO“, so schrieb er, „ist für die russische Elite (nicht nur für Putin) die klarste aller roten Linien. In den mehr als zweieinhalb Jahren, in denen ich Gespräche mit den wichtigsten russischen Akteuren geführt habe, von Scharfmachern in den dunklen Nischen des Kremls bis hin zu Putins schärfsten liberalen Kritikern, habe ich noch niemanden gefunden, der die Aufnahme der Ukraine in die NATO als etwas anderes betrachtet als eine direkte Herausforderung für die russischen Interessen.“ Die NATO, so sagte er, „würde als ein strategischer Fehdehandschuh angesehen werden. Das heutige Russland wird darauf reagieren. Die russisch-ukrainischen Beziehungen würden auf Eis gelegt ... Das würde einen fruchtbaren Boden für russische Einmischungen auf der Krim und in der Ostukraine schaffen.“
Burns war 2008 nicht der einzige westliche Entscheidungsträger, der erkannte, dass die Aufnahme der Ukraine in die NATO mit Gefahren verbunden war. Auf dem Bukarester Gipfel sprachen sich sowohl die deutsche Bundeskanzlerin Angela Merkel als auch der französische Präsident Nicolas Sarkozy gegen eine NATO-Mitgliedschaft der Ukraine aus, weil sie wussten, dass dies Russland alarmieren und verärgern würde. Merkel erklärte kürzlich ihre Ablehnung: „Ich war mir sehr sicher, ... dass Putin das nicht einfach zulassen wird. Aus seiner Sicht wäre das eine Kriegserklärung“.
Um noch einen Schritt weiter zu gehen: Zahlreiche amerikanische Politiker und Strategen sprachen sich in den 1990er Jahren gegen die Entscheidung von Präsident Clinton aus, die NATO zu erweitern, als diese Entscheidung noch zur Debatte stand. Diesen Gegnern war von Anfang an klar, dass die russische Führung darin eine Bedrohung ihrer lebenswichtigen Interessen sehen würde und dass diese Politik letztlich in eine Katastrophe münden würde. Die Liste der Gegner umfasst prominente Persönlichkeiten des Establishments wie George Kennan, sowohl Präsident Clintons Verteidigungsminister William Perry als auch seinen Vorsitzenden des Vereinigten Generalstabs, General John Shalikashvili, Paul Nitze, Robert Gates, Robert McNamara, Richard Pipes und Jack Matlock, um nur einige zu nennen.
Die Logik von Putins Position sollte für Amerikaner, die seit langem der Monroe-Doktrin verpflichtet sind, vollkommen verständlich sein. Diese besagt, dass keine entfernte Großmacht ein Bündnis mit einem Land in der westlichen Hemisphäre eingehen und ihre militärischen Streitkräfte dort stationieren darf. Die Vereinigten Staaten würden einen solchen Schritt als existenzielle Bedrohung auffassen und alles tun, um diese Gefahr zu beseitigen. Dies geschah natürlich auch während der Kubakrise 1962, als Präsident Kennedy den Sowjets klar machte, dass ihre Atomraketen aus Kuba abgezogen werden müssten. Putin ist zutiefst von derselben Logik beeinflusst. Schließlich wollen Großmächte nicht, dass sich entfernte Großmächte in ihrem Hinterhof ansiedeln.
DRITTENS: Die zentrale Bedeutung der tiefen Angst Russlands vor einem NATO-Beitritt der Ukraine wird durch zwei Entwicklungen seit Kriegsbeginn verdeutlicht.
Während der Istanbuler Verhandlungen, die unmittelbar nach Beginn der Invasion stattfanden, machten die Russen deutlich, dass die Ukraine eine „dauerhafte Neutralität“ akzeptieren müsse und der NATO nicht beitreten könne. Die Ukrainer akzeptierten die Forderung Russlands ohne ernsthaften Widerstand, sicherlich weil sie wussten, dass es sonst unmöglich wäre, den Krieg zu beenden. In jüngerer Zeit, am 14. Juni 2024, stellte Putin zwei Forderungen, die die Ukraine erfüllen müsse, bevor er einem Waffenstillstand und der Aufnahme von Verhandlungen zur Beendigung des Krieges zustimmen würde. Eine dieser Forderungen war, dass Kiew „offiziell“ erklärt, „dass es seine Pläne, der NATO beizutreten, aufgibt“.
Das alles ist nicht überraschend, denn Russland hat die Ukraine in der NATO immer als existenzielle Bedrohung gesehen, die um jeden Preis verhindert werden muss. Diese Logik ist die treibende Kraft hinter dem Ukraine-Krieg.
Schließlich ist aus der Verhandlungsposition Russlands in Istanbul sowie aus Putins Äußerungen zur Beendigung des Krieges in seiner Ansprache vom 14. Juni 2024 klar ersichtlich, dass er nicht daran interessiert ist, die gesamte Ukraine zu erobern und sie zu einem Teil eines größeren Russlands zu machen.
John Joseph Mearsheimer (* 14. Dezember 1947 in Brooklyn, New York City) ist ein US-amerikanischer Politikwissenschaftler an der University of Chicago. Sein Schwerpunkt ist die Analyse internationaler Beziehungen aus der Perspektive des offensiven Neorealismus, den er erstmals 2001 in seiner Monografie The Tragedy of Great Power Politics darstellte.
Dieser Text von John J. Mearsheimer erschien am 5.8.2024 auf Substack.Vielen Dank für die Genehmigung des Autors zum Abdruck der deutschen Übersetzung. Die Übersetzung wurde von Thomas Mayer erstellt.
Neben der NATO-Osterweiterung gibt es weitere Faktoren die zum Ukraine-Krieg führten, zum Beispiel der Nationalismus in der Ukraine und die Unterdrückung der ethnisch-russischen Bevölkerung.
Ausführlich sind die vielschichtigen Hintergründe des Ukraine-Krieges geschildert in dem Buch von Thomas Mayer: Wahrheitssuche im Ukraine-Krieg – Um was es wirklich geht, 600 Seiten, ISBN 978-3-89060-863-1, Infos zum Buch: https://kurzelinks.de/h10a
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
In Kürze folgt eine Mail an alle Genossenschafter, danke für die Geduld!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 3bf0c63f:aefa459d
2024-01-29 02:19:25
@ 3bf0c63f:aefa459d
2024-01-29 02:19:25Nostr: a quick introduction, attempt #1
Nostr doesn't have a material existence, it is not a website or an app. Nostr is just a description what kind of messages each computer can send to the others and vice-versa. It's a very simple thing, but the fact that such description exists allows different apps to connect to different servers automatically, without people having to talk behind the scenes or sign contracts or anything like that.
When you use a Nostr client that is what happens, your client will connect to a bunch of servers, called relays, and all these relays will speak the same "language" so your client will be able to publish notes to them all and also download notes from other people.
That's basically what Nostr is: this communication layer between the client you run on your phone or desktop computer and the relay that someone else is running on some server somewhere. There is no central authority dictating who can connect to whom or even anyone who knows for sure where each note is stored.
If you think about it, Nostr is very much like the internet itself: there are millions of websites out there, and basically anyone can run a new one, and there are websites that allow you to store and publish your stuff on them.
The added benefit of Nostr is that this unified "language" that all Nostr clients speak allow them to switch very easily and cleanly between relays. So if one relay decides to ban someone that person can switch to publishing to others relays and their audience will quickly follow them there. Likewise, it becomes much easier for relays to impose any restrictions they want on their users: no relay has to uphold a moral ground of "absolute free speech": each relay can decide to delete notes or ban users for no reason, or even only store notes from a preselected set of people and no one will be entitled to complain about that.
There are some bad things about this design: on Nostr there are no guarantees that relays will have the notes you want to read or that they will store the notes you're sending to them. We can't just assume all relays will have everything — much to the contrary, as Nostr grows more relays will exist and people will tend to publishing to a small set of all the relays, so depending on the decisions each client takes when publishing and when fetching notes, users may see a different set of replies to a note, for example, and be confused.
Another problem with the idea of publishing to multiple servers is that they may be run by all sorts of malicious people that may edit your notes. Since no one wants to see garbage published under their name, Nostr fixes that by requiring notes to have a cryptographic signature. This signature is attached to the note and verified by everybody at all times, which ensures the notes weren't tampered (if any part of the note is changed even by a single character that would cause the signature to become invalid and then the note would be dropped). The fix is perfect, except for the fact that it introduces the requirement that each user must now hold this 63-character code that starts with "nsec1", which they must not reveal to anyone. Although annoying, this requirement brings another benefit: that users can automatically have the same identity in many different contexts and even use their Nostr identity to login to non-Nostr websites easily without having to rely on any third-party.
To conclude: Nostr is like the internet (or the internet of some decades ago): a little chaotic, but very open. It is better than the internet because it is structured and actions can be automated, but, like in the internet itself, nothing is guaranteed to work at all times and users many have to do some manual work from time to time to fix things. Plus, there is the cryptographic key stuff, which is painful, but cool.
-
 @ 77c2969e:a33cfa50
2025-06-08 07:10:04
@ 77c2969e:a33cfa50
2025-06-08 07:10:04Nostr 协议在我看来是很先进的,暂时使用的人还不多,不过相比 Fediverse 的 Mastodon 之类,自己部署 Nostr Relay 是成本很小的。Blossom 作为媒体上传服务是可选的,因为有几个公共服务器可用,但是大多数国内无法直连。我还发现部分客户端不支持自定义 Blossom 服务器,只有 Amethyst 和 Nostrmo 可以。
我目前使用的是这个 nostr-relay 以及这个 blossom-server。
nostr-relay
这个用 Python 写的 nostr-relay 很不错。
配置文件是这个: https://code.pobblelabs.org/fossil/nostr_relay/file?name=nostr_relay/config.yaml 可以按需修改,自己用默认就够了。
```jsx
先安装 pipx
apt install pipx
再用 pipx 安装 nostr-relay
pipx install nostr-relay
选择一个目录运行以下命令启动默认配置,默认 SQLite 文件在当前目录
nostr-relay serve
后台运行
(nostr-relay serve >/var/log/nostr-relay.log &)
查看 PID
lsof -i :6969
停止运行
kill PID
后台运行命令会调用 gunicorn 运行而不是nostr-relay,因此会搜不到 nostr-relay 进程,可以尝试这个命令
ps -ef | grep gunicorn
`` 反代127.0.0.1:6969` 配置域名和 SSL 证书即可。保持简洁,不使用 Docker 和 systemd,后续迁移时只需复制整个文件夹即可。
blossom-server
clone 这个仓库
git clone https://github.com/hzrd149/blossom-server.git克隆仓库是必要的,因为 blossom-server 的默认页面依赖
public/目录,请保留该目录。用以下
config.yml和docker-compose.yml覆盖原仓库中的文件然后执行
docker compose up -d反代
127.0.0.1:3000配置域名和 SSL 证书即可。config.yml按需修改,比如 Dashboard 密码、允许的 PubKey 等。 ```
Override the domain thats is used in the blobs "url" field
By default it uses the domain the incoming HTTP request was made on
publicDomain: ""
databasePath: data/sqlite.db
dashboard: # enable or disable the admin dashboard enabled: true # admin username username: admin # if password is left blank it will be generated each time the app starts password: "yourpasswd"
文件发现机制,保持默认关闭
discovery: # find files by querying nostr relays nostr: enabled: false relays: - wss://relay.example.com # find files by asking upstream CDNs # NOTE: do not set this to your own server, it will create an infinite loop upstream: enabled: false domains: - https://cdn.example.com
storage: # local or s3 backend: local
# Imminently removes a blob when there are no owners removeWhenNoOwners: false
# local storage local: dir: ./data/blobs
# see minio docs for options: # https://min.io/docs/minio/linux/developers/javascript/API.html#new-minio-client-endpoint-port-usessl-accesskey-secretkey-region-transport-sessiontoken-partsize # s3: # endpoint: https://s3.endpoint.com # port: 443 # bucket: blossom # accessKey: xxxxxxxx # secretKey: xxxxxxxxx # useSSL: true # region: us-east-1 # If this is set the server will redirect clients when loading blobs # publicURL: https://s3.region.example.com/
# rules are checked in descending order. if a blob matches a rule it is kept # "type" (required) the type of the blob, "" can be used to match any type # "expiration" (required) time passed since last accessed # "pubkeys" (optional) a list of owners # any blobs not matching the rules will be removed rules: - type: "" expiration: 100 years pubkeys: - "change-to-your-pubkey-hex"
Config for the /upload endpoint
upload: # enable / disable uploads (default false) enabled: true # require auth to upload requireAuth: true # only check rules that include "pubkeys" requirePubkeyInRule: true
Config for the /media endpoint
media: # /media endpoint enabled (default false) enabled: true # require auth to upload to /media requireAuth: true # only check rules that include "pubkeys" requirePubkeyInRule: true
# image optimization options image: # image quality 0-100 (default 90) quality: 90 # create progressive jpeg / png images for large images > 1024x768 (default true) progressive: true # max width (default 1920) maxWidth: 1920 # max height (default 1080) maxHeight: 1080 # image format (default webp) outputFormat: "webp" # keep aspect radio when resizing (default true) maintainAspectRatio: true # keep EXIF metadata (default false) keepExif: false # fps for GIFs (default 30) fps: 30
video: # video quality 0-100 (default 90) quality: 90 # max height (default 1080) maxHeight: 1080 # max fps (default 30) maxFps: 30 # output format [mp4, webm, mkv] (default mp4) format: "webm" # audio codec [aac, mp3, vorbis, opus] (default aac) audioCodec: "aac" # video codec [libx264, libx265, vp8, vp9] (default libx264) videoCodec: "libx264"
list: requireAuth: false allowListOthers: true
tor: enabled: false proxy: "" ```
docker-compose.ymlservices: blossom: image: ghcr.io/hzrd149/blossom-server:master ports: - 3000:3000 volumes: # mount data volume - ./data:/app/data # mount config file - ./config.yml:/app/config.yml # mount custom www dir - ./public:/app/public
其他
我自己目前就是部署的这两个服务自用。主要是方便部署和维护,后续服务器迁移只需要复制文件夹即可。Blossom 媒体服务自用的话,默认使用服务器本地存储即可,就是在项目文件夹中的
./data/blobs/,上传的图片和视频会被自动压缩,占不了多少存储空间。如果公开或多人使用也可以配置 S3 兼容的对象存储。除了我上面说的这个 nostr-relay,还有一个 Rust 写的 nostr-rs-relay,可以 Docker 一键部署,如果你偏好使用 Docker,也可以选择这个。
如果你也对 Nostr 这个去中心化协议感兴趣,想拥有自己的 Nostr 服务,不妨参考本文试试,欢迎留言交流!
推荐阅读
-
 @ 2f7463a4:e92b8023
2024-01-27 00:11:21
@ 2f7463a4:e92b8023
2024-01-27 00:11:21Dies ist die deutsche Übersetzung von / This is the German translation of :
nostr:naddr1qqxnzd3cxserxdpsxverzwp4qgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28zcj37a — nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7
Weitere Übersetzungen / Other translations : - Spanisch / Spanish : nostr:naddr1qqx9zat994jhxttgv93xccgzypl4c26wfzswnlk2vwjxky7dhqjgnaqzqwvdvz3qwz5k3j4grrt46qcyqqq823cf6w59v — nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624
Habla ist eine auf Nostr basierende Plattform, mit der du umfangreiche Beiträge erstellen und verwalten kannst. Man könnte es mit Medium vergleichen, aber Habla ist viel mehr als das. Habla ist herkömmlichen Blogging-Plattformen überlegen, weil es auf Nostr basiert. Es ist mit einer Vielzahl anderer Nostr-Apps interoperabel, was die Benutzererfahrung nahtlos und fesselnd macht. Darüber hinaus können deine Inhalte, wenn sie von den Lesern als wertvoll empfunden werden, dank des Lightning-Netzwerkes sofort mit dem besten Geld, das die Menschheit je gesehen hat, belohnt werden: Bitcoin.
Was ist Nostr?
Nostr ist eine neue Art der Online-Kommunikation, die ihren Nutzern zahlreiche Vorteile bietet. Nostr ist für alle kostenlos, man braucht keine ID oder andere Verifizierung durch Dritte, um sich anzumelden, Gleichgesinnte zu treffen und die Community um sich herum zu vergrößern. Nostr wird oft mit einer Social-Media-Plattform verwechselt, ist aber viel mehr als das. Wir empfehlen dir einen Blick auf die hier gesammelten Nostr-Ressourcen zu werfen, um die potenzielle Dimension dieses Tools zu erkennen.
Wie melde ich mich bei Habla an?
Um auf Habla zu schreiben, erstelle einfach ein Habla/Nostr-Konto und melde dich an. Folge diesen einfachen Schritten, um dich zu registrieren, Mehrwert zu bieten und Gegenwert zurückzuerhalten.
Wie verdiene ich mit Habla?
Habla ermöglicht es, Werte direkt von deinen Lesern zu erhalten. Es ist kein Bankkonto oder Ausweis erforderlich. Verbinde einfach deine Lightning-Adresse mit deinem Habla/Nostr-Konto und erhalte Geld direkt auf dein Wallet – ohne Dritte, ohne Warten auf Abhebungen, ohne Stress. Folge diesen einfachen Schritten, um loszulegen.
Warum ist das Publizieren auf Habla anders?
Das Nostr-Protokoll ist sehr schlank, was einige Besonderheiten im Verhalten von Nostr-basierten Anwendungen mit sich bringt. Wir gehen hier nicht auf die technischen Details ein, aber der offensichtlichste Unterschied, den du als Autor bemerken wirst, ist, dass du ein anderes und möglicherweise ungewohntes Textformat für deine Beiträge verwenden musst. Aber keine Angst, Habla bietet Tools, die diesen Prozess einfach und intuitiv machen. Hier ist ein kurzes Video von nostr:npub1wkljx5c6a8uccc5etws8ry0y3r4dgavh2dcav0tal4rtmcdl4z2sfu5u0t, das die Grundlagen des Publizierens mit Habla erklärt (der Leitfaden wurde vor dem Redesign erstellt, ist aber immer noch nützlich):
https://nostr.build/p/nb9474.mp4
Habla (und viele andere Nostr-Anwendungen) verwendet das etablierte Format Markdown. Das gibt es schon seit fast einem Jahrzehnt und wird von den meisten Apps, die du jeden Tag benutzt, unterstützt. Der Grund, warum du vielleicht noch nichts von Markdown gehört hast, ist, dass herkömmliche Anwendungen es normalerweise vor dem Benutzer verbergen, und wir arbeiten daran, dies auch zu tun. Mehr über Markdown kannst du hier herausfinden.
Wo werden meine Inhalte gespeichert?
Herkömmliche Blogging-Plattformen speichern die Inhalte auf ihren eigenen Servern. Das ist ein bequemer und (früher) solider Ansatz, der aber auch kritische Risiken birgt. Wenn du die Früchte deiner Arbeit einer einzigen Partei überlässt, hat diese die vollständige Kontrolle über deine Inhalte. Nostr löst dieses Problem. Jedes Mal, wenn du etwas veröffentlichst, wird dein Inhalt an zahlreiche Relais zur Speicherung und Verbreitung weitergeleitet. Wenn ein Relais-Betreiber deinen Beitrag blockiert oder sich weigert, ihn weiterzuverbreiten, können deine Leser auf andere Relais zurückgreifen, um Zugang zu deinen Inhalten zu erhalten (keine Sorge, wenn das kompliziert klingt, alles geschieht unter der Haube). Auf diese Weise wird sichergestellt, dass du niemals zum Schweigen gebracht wirst. Wir haben uns entschieden, uns auf das zu konzentrieren, was wir am besten können: eine intuitive, effiziente und einfach zu bedienende Blogging-Plattform zu entwickeln, die sich lohnt – und das Speichern und Verbreiten von Inhalten den Profis auf diesem Gebiet zu überlassen.
Wie publiziere ich?
Habla bietet alle Tools, die du brauchst, um eindrucksvolle Artikel zu erstellen, die sich von anderen abheben. Bereite deinen Artikel vor, formatiere deinen Text mit den entsprechenden Tools, füge Medien hinzu und schau dir das Ergebnis vor Veröffentlichung selbst noch einmal an. Alles, was du brauchst, steht dir zur Verfügung, und die Plattform wird von Tag zu Tag besser und benutzerfreundlicher.
Wer kann meine Beiträge auf Habla lesen?
Jeder im Internet kann deine Beiträge lesen. Wenn deine Leser jedoch mit deiner Arbeit interagieren möchten – sei es durch Folgen, Kommentieren oder indem sie dir etwas zurückgeben möchten – sollten sie ein Nostr-Konto einrichten. Wir ermutigen dich, deine Follower einzubeziehen, um eine blühende Community aufzubauen und neue Höhen zu erreichen. Diese Kurzanleitung wird dir und deinen Fans den Einstieg erleichtern.
Dieses FAQ befindet sich in ständiger Entwicklung und wird sich in dem Maße ändern, wie Habla und Nostr zu noch leistungsfähigeren Tools werden. Bitte teile mir dein Feedback mit, damit ich es noch besser machen kann.
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 57d1a264:69f1fee1
2025-06-08 06:39:26
@ 57d1a264:69f1fee1
2025-06-08 06:39:2618-07 HOLIDAY HOME by OFFICE INAINN reimagines the traditional hytte, creating two interconnected cabins, H_G30 and H_G32, located near the scenic Geiranger–Trollstigen route. Set on a steep hillside 148 meters above sea level, the design embraces modern functionality while offering stunning southern views of Storfjorden and minimizing environmental impact.
Blending into the Landscape
The cabins are designed to integrate gently into the natural terrain, following the contours of the hillside. Their horizontal layout reduces the visual impact, blending into the forested surroundings while opening up to the fjord. The minimal footprint respects the environment and reduces construction costs, ensuring the cabins remain nearly invisible from the north while fully engaging with the southern panorama.
Functional, Additive Architecture
Inspired by traditional Norwegian architecture, each cabin consists of two overlapping modules of varying heights, breaking up the building mass and reducing roof size. The higher module serves as the circulation space, while the lower module contains the private and living areas. This approach replaces conventional walls with functional form, creating distinct zones for movement, utility, and relaxation.
Harmonizing Tradition with Modern Living
The cabins follow an east-west retaining wall that mirrors the hill’s natural slope, with additional storage and leisure spaces tucked behind. The shallow depth allows maximum southern exposure for light and views, while the central axis blurs the boundary between indoor and outdoor living, creating a seamless connection to nature.
For more info https://inainn.eu/18-07-holiday-home/
https://stacker.news/items/1000386
-
 @ 7f6db517:a4931eda
2025-06-06 06:01:29
@ 7f6db517:a4931eda
2025-06-06 06:01:29
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ df478568:2a951e67
2025-06-05 23:34:01
@ df478568:2a951e67
2025-06-05 23:34:01About 156,000 blocks ago, I went to a Taco Shop for a bitcoin meetup. I asked my favorite question, “Do you accept bitcoin?”
“Yes," he said as he handed me a Toast Terminal with a BTCpayServer QR code.
 ]
]Awesome!
12,960 blocks later, I took my dad to the taco shop. We ordered food. I asked my favorite question once again.
“Uh…Yeah, but I don't know how to work the machine.”
"Dough!🤦"
It's been a problem in the past, but now lightning payments are about to be ubiquitous. Steak N Shake is taking bitcoin using Speed Wallet and Block is implementing bitcoin payments by 2026 in all legal jurisdictions. I have tested both of these so you don't have to. Just kidding. I geek out on this stuff, but both work great. You can pay with your sats by scanning a screen on a QR code. The employees don't need to be bitcoin lightning network experts. You can just pay as easy as a credit card.
There were 35,000 people at the bitcoin conference, and 4,187 transactions were made. It was a world record. Wait, I thought they said there could only be 7 transactions per second! No, not anymore. Now we can use bitcoin for shopping. I can pay for tacos at taco trucks.

How You Can Accept Bitcoin At Your Business
Coinos is a simple bitcoin point of sale information that acts like a cash register. Bitcoin is peer-to-peer electronic cash. Coinos is a cash register and you should treat it as such. If you make a few hundred thousand sats at the end of the night, you should sweep the bitcoin into your own wallet.. You can use Aqua, AlbyHub, Bull Bitcoin wallet, or whatever your favorite lightning enabled wallet is to withdraw. You'll need a password. Do not lose this. I have tried the automatic withdraws, but it did not work for me. I'm no concerned because this is not a wallet I intend to keep a lot of sats in for a long time.
Here is my coinos payment terminal.
https://coinos.io/ZapthisBlog/receive
I made the QR code with libreqr.com/

Now I have an online bitcoin cash register. The Bitcoiners know how to pay for stuff with sats. They will be proud to show you too. If you're nerdy, you can use all the cool kid tools now, but we will just focus on the lightning address. Anyone can send you sats with a lightning address with just a QR code.
At the end of the night, you cash out to your own wallet. Again, this assumes you have an Aqua Wallet or any other lightning enabled wallet, but all it takes to accept bitcoin at your brick and mortar store is to create an account with Coinos and print out a QR code. It's a quick and easy way to start accepting bitcoin even if you don't expect many clients to shop with sats.
Tips
This is not just a cash register. Employees can also make their own Coinos wallet and receive tips from bitcoiners. Anyone can accept payments using this system. Your kids could use it to sell lemonade for sats. You are only limited by your imagination. When will you begin accepting bitcoin payments? It is easier than ever. You do not need to train employees. You do not need to be in the store. Bitcoin is peer-to-peer electronic cash so you can give it away like cash. I don't know what the tax rules on cash are. You need to verify that with your own jurisdiction. This is not financial or tax advice. This is for informational purposes only.
Remember, this is a custodial wallet. Not your keys not your bitcoin. Don't keep more sats than you are willing to lose on custodial wallets. Sweep your wallet early and often. Loss of funds is possible. There is a small fee for liquidity management too. Do your own research.
-
 @ 57d1a264:69f1fee1
2025-06-08 06:27:45
@ 57d1a264:69f1fee1
2025-06-08 06:27:45HTX Studio received a special email. The letter writer's daughter was unfortunately run over by a heavy truck on her way to school, and her right hand permanently lost its function. When using the computer, her hands have to frequently switch between the keyboard and the mouse, which makes typing very slow and tiring. He wanted us to make a one-handed keyboard for his daughter.
https://www.youtube.com/watch?v=9vW12gQ4Klc
The project has just been open-sourced at https://github.com/htx-studio/One-Handed-Keyboard and hopes to be helpful to those who need it. In English for you below:
One-Handed Keyboard
This is a single-mode mechanical keyboard with integrated trackball. The firmware uses QMK . Thanks to all the developers who have contributed to the QMK community.
Keyboard production reference: [Mr. He] We made a special keyboard...
Open source hardware: HTXStudio one-handed keyboard
The development environment and setup are available here , and the firmware source code is available here .
The information in this warehouse includes:
- A total of 8 PCBs for three keyboards for the left and right hands, provided by EasyEDA Engineering.
- VIA key change configuration file and compiled firmware.
- Model design files.
Warehouse directory structure
Docs
Data sheet and pictures of the chip.
Firmware
QMK firmware for three different keyboard models, and JSON files for VIA key changes.
Hardware
Project files of Jialichuang EDA.
Model
Model files and processing files used by each keyboard model.
Production Guide
PCB:
1-Right-hand keyboard-hot-swappable (large): board material FR-4, board thickness 1.6mm, four-layer board, laminate structure JLC04161H-3313, impedance control +/-20%.
1-Left-hand keyboard-welding board (small): board material FR-4, board thickness 1.6mm, double-layer board, ALPS yellow axis needs to be installed with a little force when inserted.
1-Left-hand keyboard-hot-swappable (large): board material FR-4, board thickness 1.6mm, four-layer board, laminate structure JLC04161H-3313, impedance control +/-20%.
2-TypeC: board material FR-4, board thickness 1.6mm, double-layer board, marked CON1 (only for large keyboards).
3-Trackball: board material FR-4, board thickness 1.6mm, double-layer board, the module needs to pay attention to the welding direction, marked CON3.
4- Mouse wheel: board material FR-4, board thickness 1.6mm, double-layer board, it is recommended to use 7mm high encoder, 6mm high button, button trigger pressure ≤180g, marked CON2.
5-Directional buttons: board material FR-4, board thickness 1.6mm, double-layer board, ALPS yellow shaft needs to be inserted with a little force, marked CON4.
6- Main control board - left hand (small): board material FR-4, board thickness 1.6mm, double-layer board.
- Three of them are keyboard-controlled common boards
《3-轨迹球》《4-鼠标滚轮》《5-方向按键》. 《5-方向按键》And《1-左手键盘-焊板(小)》, the key axis uses ALPS yellow axis.- Note that the left and right hand keyboards are not completely mirrored.
- The trackball control uses SPI1 channel, and the scroll wheel has two separate signal lines, which allows replacing other control devices without major adjustments.
- The main control uses STM32G431CBU6.
- Compatible with A to C or C to C data cables.
Printout:
Keycap: resin, PLA, etc.
Trackball seat: resin, PLA, etc.
Left and right mouse buttons: resin, PLA, etc.
Shell: resin, PLA, etc.
Base: resin, PLA, etc.
Processing:
Positioning plate: Recommended material: pom, thickness 1.5mm.
Positioning plate cotton strip: glue left on one side.
Sandwich cotton: Recommended material is poron, 3.5mm thick.
Axle seat cotton: 2mm thick.
Bottom cotton: Recommended material: poron, 4mm thick.
Silicone pad (for keypad only): 5mm thick, hardness Shore 00-10.
other:
Trackball: diameter 25mm, material PTFE.
Lubricating ball: 2mm diameter, made of PTFE, installed in the printed trackball seat, 6 pieces in number.
Roller: Recommended diameter is between 19mm-20mm, thickness is between 4mm-5mm, and material is metal.
Satellite axis: 2U steel plate satellite axis.
Key switches: 57 ultra-small ALPS yellow switches for the small keyboard and 57 common mechanical switches for the large keyboard.
Cable arrangement: spacing 0.5mm, 8P reverse, 10cm2 strips, 15cm2 strips.
- The FPC sockets of the control board and the small board are both marked with CON, and the corresponding interfaces are connected.
- The file uses an FPC cable holder that can be connected up and down. It should be noted that when the cable holders are connected down, use reverse cable connection.
Model structure:
Installation order:
Take the large keyboard as an example
Pre-assembly work
- First, connect the 4 small PCBs to the keyboard body PCB using cables and burn the program.
- Install 3-5 shafts, rollers and trackballs. Make sure they function normally before assembly.
- Install the correct hot-melt copper nuts at the corresponding positions of the printed shell and base.
- Keycap printing.
- Attach the cotton strips to the protruding parts of the positioning plate (both on the front and back sides).
When burning the firmware for the first time, you can press and hold the button marked "B" on the back of the PCB and then plug in the USB cable to burn the firmware.
If you want to update the firmware, you can press and hold the "ESC" key on the keyboard and then insert the USB cable to burn the firmware.
For more information, please refer to Flashing Your Keyboard (QMK)
Next, start assembling
- Use screws to install the 4 small boards to the corresponding positions of the base (pay attention to the wiring and installation direction), and install screws at the bottom of the trackball base.
- Fix the left and right buttons on the keyboard PCB with screws.
- From bottom to top, place the bottom cotton, shaft seat cotton, keyboard PCB, sandwich cotton and positioning plate into the fan-shaped area of the base in order.
- Insert the key switch.
- Put it into the housing and secure it with screws from the bottom.
- Install the keycaps to complete the assembly.
The screw and nut installation guide can be found here
Finally, this is our first open source project. If there are any shortcomings, you are welcome to criticize and correct us. Thank you.
References
Quantum Mechanical Keyboard Firmware
mrjohnk. ADNS-9800. GitHub repository
https://x.com/HTX_Studio/status/1929915992349782206
https://stacker.news/items/1000384
-
 @ 57d1a264:69f1fee1
2025-06-08 05:57:12
@ 57d1a264:69f1fee1
2025-06-08 05:57:12There is a certain image that pops up whenever people think about crushing soda cans. It is the kind of scene you see in movies, where a brawny athlete flattens an empty can with a single squeeze, probably in front of a cheering crowd. The reality, however, is far less cinematic. Most of us barely manage a dent before abandoning the can, sending it tumbling toward the trash bin, often missing the target entirely and hoping no one noticed. It is hardly the stuff of legends, unless you consider fumbling for a runaway soda can an athletic event.
In the end, the Yeti Can Crusher is more than just a clever gadget. It is a reminder that even the simplest chores can be transformed into moments of enjoyment, especially when the right tool is involved. There is a certain thrill in turning a dull task into a satisfying ritual, and when you add a dash of style, suddenly recycling is not just good for the planet, it is actually a little bit fun. With the right crusher in your hand, you might just find yourself looking forward to the next empty can.
Curious to learn more? https://www.yeti.com/outdoor-living/20110010027.html
https://stacker.news/items/1000380
-
 @ 81022b27:2b8d0644
2025-06-08 04:22:00
@ 81022b27:2b8d0644
2025-06-08 04:22:00Here’s the thing: authenticity gives off a vibration: There is so little of it anywhere that we crave it. That’s why an orange guy beats someone who doesn’t mean what they say. Because they don’t really believe a guy in a dress is a woman because that’s what they say they are
People feel vibes and hearing someone lie to their face is offensive. They will follow the guy that at least believes what he is
-
 @ dfa02707:41ca50e3
2025-06-05 22:01:48
@ dfa02707:41ca50e3
2025-06-05 22:01:48
Good morning (good night?)! The No Bullshit Bitcoin news feed is now available on Moody's Dashboard! A huge shoutout to sir Clark Moody for integrating our feed.
Headlines
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- The Bank for International Settlements (BIS) wants to contain 'crypto' risks. A report titled "Cryptocurrencies and Decentralised Finance: Functions and Financial Stability Implications" calls for expanding research into "how new forms of central bank money, capital controls, and taxation policies can counter the risks of widespread crypto adoption while still fostering technological innovation."
- "Global Implications of Scam Centres, Underground Banking, and Illicit Online Marketplaces in Southeast Asia." According to the United Nations Office on Drugs and Crime (UNODC) report, criminal organizations from East and Southeast Asia are swiftly extending their global reach. These groups are moving beyond traditional scams and trafficking, creating sophisticated online networks that include unlicensed cryptocurrency exchanges, encrypted communication platforms, and stablecoins, fueling a massive fraud economy on an industrial scale.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
Use the tools
- Bitcoin Safe v1.2.3 expands QR SignMessage compatibility for all QR-UR-compatible hardware signers (SpecterDIY, KeyStone, Passport, Jade; already supported COLDCARD Q). It also adds the ability to import wallets via QR, ensuring compatibility with Keystone's latest firmware (2.0.6), alongside other improvements.
- Minibits v0.2.2-beta, an ecash wallet for Android devices, packages many changes to align the project with the planned iOS app release. New features and improvements include the ability to lock ecash to a receiver's pubkey, faster confirmations of ecash minting and payments thanks to WebSockets, UI-related fixes, and more.
- Zeus v0.11.0-alpha1 introduces Cashu wallets tied to embedded LND wallets. Navigate to Settings > Ecash to enable it. Other wallet types can still sweep funds from Cashu tokens. Zeus Pay now supports Cashu address types in Zaplocker, Cashu, and NWC modes.
- LNDg v1.10.0, an advanced web interface designed for analyzing Lightning Network Daemon (LND) data and automating node management tasks, introduces performance improvements, adds a new metrics page for unprofitable and stuck channels, and displays warnings for batch openings. The Profit and Loss Chart has been updated to include on-chain costs. Advanced settings have been added for users who would like their channel database size to be read remotely (the default remains local). Additionally, the AutoFees tool now uses aggregated pubkey metrics for multiple channels with the same peer.
- Nunchuk Desktop v1.9.45 release brings the latest bug fixes and improvements.
- Blockstream Green iOS v4.1.8 has renamed L-BTC to LBTC, and improves translations of notifications, login time, and background payments.
- Blockstream Green Android v4.1.8 has added language preference in App Settings and enables an Android data backup option for disaster recovery. Additionally, it fixes issues with Jade entry point PIN timeout and Trezor passphrase input.
- Torq v2.2.2, an advanced Lightning node management software designed to handle large nodes with over 1000 channels, fixes bugs that caused channel balance to not be updated in some cases and channel "peer total local balance" not getting updated.
- Stack Wallet v2.1.12, a multicoin wallet by Cypher Stack, fixes an issue with Xelis introduced in the latest release for Windows.
- ESP-Miner-NerdQAxePlus v1.0.29.1, a forked version from the NerdAxe miner that was modified for use on the NerdQAxe+, is now available.
- Zark enables sending sats to an npub using Bark.
- Erk is a novel variation of the Ark protocol that completely removes the need for user interactivity in rounds, addressing one of Ark's key limitations: the requirement for users to come online before their VTXOs expire.
- Aegis v0.1.1 is now available. It is a Nostr event signer app for iOS devices.
- Nostash is a NIP-07 Nostr signing extension for Safari. It is a fork of Nostore and is maintained by Terry Yiu. Available on iOS TestFlight.
- Amber v3.2.8, a Nostr event signer for Android, delivers the latest fixes and improvements.
- Nostur v1.20.0, a Nostr client for iOS, adds
-
 @ 374ee93a:36623347
2025-06-05 21:49:45
@ 374ee93a:36623347
2025-06-05 21:49:45Chef's notes
Start your day the self sovereign way
Details
- ⏲️ Prep time: 10 mins
- 🍳 Cook time: 15 mins
- 🍽️ Servings: 4
Ingredients
- 1lb Jar Bottled Rhubarb https://jimblesjumble.netlify.app/item/a0c35618722834ac714d0a47058a2adc76ee7485a6b74f5da5f9eb2d3fb5d879
- 1pt Homemade Custard (3/4pt cream, 3 large eggs, 100g honey, 1/2 tbspn vanilla extract)
- 4 Handfuls Granola
- 1 Node https://plebeian.market/products/huxley@nostrplebs.com/start-9-node-y22zfjp8x6
Directions
- Whisk together the cream, eggs, honey and vanilla
- Chill overnight or serve warm with 1/4 jar of stewed rhubarb and a large handful of granola per person
- Consolidate some UTXOs on your node
- Have a Good Morning
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16Drivechain
Understanding Drivechain requires a shift from the paradigm most bitcoiners are used to. It is not about "trustlessness" or "mathematical certainty", but game theory and incentives. (Well, Bitcoin in general is also that, but people prefer to ignore it and focus on some illusion of trustlessness provided by mathematics.)
Here we will describe the basic mechanism (simple) and incentives (complex) of "hashrate escrow" and how it enables a 2-way peg between the mainchain (Bitcoin) and various sidechains.
The full concept of "Drivechain" also involves blind merged mining (i.e., the sidechains mine themselves by publishing their block hashes to the mainchain without the miners having to run the sidechain software), but this is much easier to understand and can be accomplished either by the BIP-301 mechanism or by the Spacechains mechanism.
How does hashrate escrow work from the point of view of Bitcoin?
A new address type is created. Anything that goes in that is locked and can only be spent if all miners agree on the Withdrawal Transaction (
WT^) that will spend it for 6 months. There is one of these special addresses for each sidechain.To gather miners' agreement
bitcoindkeeps track of the "score" of all transactions that could possibly spend from that address. On every block mined, for each sidechain, the miner can use a portion of their coinbase to either increase the score of oneWT^by 1 while decreasing the score of all others by 1; or they can decrease the score of allWT^s by 1; or they can do nothing.Once a transaction has gotten a score high enough, it is published and funds are effectively transferred from the sidechain to the withdrawing users.
If a timeout of 6 months passes and the score doesn't meet the threshold, that
WT^is discarded.What does the above procedure mean?
It means that people can transfer coins from the mainchain to a sidechain by depositing to the special address. Then they can withdraw from the sidechain by making a special withdraw transaction in the sidechain.
The special transaction somehow freezes funds in the sidechain while a transaction that aggregates all withdrawals into a single mainchain
WT^, which is then submitted to the mainchain miners so they can start voting on it and finally after some months it is published.Now the crucial part: the validity of the
WT^is not verified by the Bitcoin mainchain rules, i.e., if Bob has requested a withdraw from the sidechain to his mainchain address, but someone publishes a wrongWT^that instead takes Bob's funds and sends them to Alice's main address there is no way the mainchain will know that. What determines the "validity" of theWT^is the miner vote score and only that. It is the job of miners to vote correctly -- and for that they may want to run the sidechain node in SPV mode so they can attest for the existence of a reference to theWT^transaction in the sidechain blockchain (which then ensures it is ok) or do these checks by some other means.What? 6 months to get my money back?
Yes. But no, in practice anyone who wants their money back will be able to use an atomic swap, submarine swap or other similar service to transfer funds from the sidechain to the mainchain and vice-versa. The long delayed withdraw costs would be incurred by few liquidity providers that would gain some small profit from it.
Why bother with this at all?
Drivechains solve many different problems:
It enables experimentation and new use cases for Bitcoin
Issued assets, fully private transactions, stateful blockchain contracts, turing-completeness, decentralized games, some "DeFi" aspects, prediction markets, futarchy, decentralized and yet meaningful human-readable names, big blocks with a ton of normal transactions on them, a chain optimized only for Lighting-style networks to be built on top of it.
These are some ideas that may have merit to them, but were never actually tried because they couldn't be tried with real Bitcoin or inferfacing with real bitcoins. They were either relegated to the shitcoin territory or to custodial solutions like Liquid or RSK that may have failed to gain network effect because of that.
It solves conflicts and infighting
Some people want fully private transactions in a UTXO model, others want "accounts" they can tie to their name and build reputation on top; some people want simple multisig solutions, others want complex code that reads a ton of variables; some people want to put all the transactions on a global chain in batches every 10 minutes, others want off-chain instant transactions backed by funds previously locked in channels; some want to spend, others want to just hold; some want to use blockchain technology to solve all the problems in the world, others just want to solve money.
With Drivechain-based sidechains all these groups can be happy simultaneously and don't fight. Meanwhile they will all be using the same money and contributing to each other's ecosystem even unwillingly, it's also easy and free for them to change their group affiliation later, which reduces cognitive dissonance.
It solves "scaling"
Multiple chains like the ones described above would certainly do a lot to accomodate many more transactions that the current Bitcoin chain can. One could have special Lightning Network chains, but even just big block chains or big-block-mimblewimble chains or whatnot could probably do a good job. Or even something less cool like 200 independent chains just like Bitcoin is today, no extra features (and you can call it "sharding"), just that would already multiply the current total capacity by 200.
Use your imagination.
It solves the blockchain security budget issue
The calculation is simple: you imagine what security budget is reasonable for each block in a world without block subsidy and divide that for the amount of bytes you can fit in a single block: that is the price to be paid in satoshis per byte. In reasonable estimative, the price necessary for every Bitcoin transaction goes to very large amounts, such that not only any day-to-day transaction has insanely prohibitive costs, but also Lightning channel opens and closes are impracticable.
So without a solution like Drivechain you'll be left with only one alternative: pushing Bitcoin usage to trusted services like Liquid and RSK or custodial Lightning wallets. With Drivechain, though, there could be thousands of transactions happening in sidechains and being all aggregated into a sidechain block that would then pay a very large fee to be published (via blind merged mining) to the mainchain. Bitcoin security guaranteed.
It keeps Bitcoin decentralized
Once we have sidechains to accomodate the normal transactions, the mainchain functionality can be reduced to be only a "hub" for the sidechains' comings and goings, and then the maximum block size for the mainchain can be reduced to, say, 100kb, which would make running a full node very very easy.
Can miners steal?
Yes. If a group of coordinated miners are able to secure the majority of the hashpower and keep their coordination for 6 months, they can publish a
WT^that takes the money from the sidechains and pays to themselves.Will miners steal?
No, because the incentives are such that they won't.
Although it may look at first that stealing is an obvious strategy for miners as it is free money, there are many costs involved:
- The cost of ceasing blind-merged mining returns -- as stealing will kill a sidechain, all the fees from it that miners would be expected to earn for the next years are gone;
- The cost of Bitcoin price going down: If a steal is successful that will mean Drivechains are not safe, therefore Bitcoin is less useful, and miner credibility will also be hurt, which are likely to cause the Bitcoin price to go down, which in turn may kill the miners' businesses and savings;
- The cost of coordination -- assuming miners are just normal businesses, they just want to do their work and get paid, but stealing from a Drivechain will require coordination with other miners to conduct an immoral act in a way that has many pitfalls and is likely to be broken over the months;
- The cost of miners leaving your mining pool: when we talked about "miners" above we were actually talking about mining pools operators, so they must also consider the risk of miners migrating from their mining pool to others as they begin the process of stealing;
- The cost of community goodwill -- when participating in a steal operation, a miner will suffer a ton of backlash from the community. Even if the attempt fails at the end, the fact that it was attempted will contribute to growing concerns over exaggerated miners power over the Bitcoin ecosystem, which may end up causing the community to agree on a hard-fork to change the mining algorithm in the future, or to do something to increase participation of more entities in the mining process (such as development or cheapment of new ASICs), which have a chance of decreasing the profits of current miners.
Another point to take in consideration is that one may be inclined to think a newly-created sidechain or a sidechain with relatively low usage may be more easily stolen from, since the blind merged mining returns from it (point 1 above) are going to be small -- but the fact is also that a sidechain with small usage will also have less money to be stolen from, and since the other costs besides 1 are less elastic at the end it will not be worth stealing from these too.
All of the above consideration are valid only if miners are stealing from good sidechains. If there is a sidechain that is doing things wrong, scamming people, not being used at all, or is full of bugs, for example, that will be perceived as a bad sidechain, and then miners can and will safely steal from it and kill it, which will be perceived as a good thing by everybody.
What do we do if miners steal?
Paul Sztorc has suggested in the past that a user-activated soft-fork could prevent miners from stealing, i.e., most Bitcoin users and nodes issue a rule similar to this one to invalidate the inclusion of a faulty
WT^and thus cause any miner that includes it in a block to be relegated to their own Bitcoin fork that other nodes won't accept.This suggestion has made people think Drivechain is a sidechain solution backed by user-actived soft-forks for safety, which is very far from the truth. Drivechains must not and will not rely on this kind of soft-fork, although they are possible, as the coordination costs are too high and no one should ever expect these things to happen.
If even with all the incentives against them (see above) miners do still steal from a good sidechain that will mean the failure of the Drivechain experiment. It will very likely also mean the failure of the Bitcoin experiment too, as it will be proven that miners can coordinate to act maliciously over a prolonged period of time regardless of economic and social incentives, meaning they are probably in it just for attacking Bitcoin, backed by nation-states or something else, and therefore no Bitcoin transaction in the mainchain is to be expected to be safe ever again.
Why use this and not a full-blown trustless and open sidechain technology?
Because it is impossible.
If you ever heard someone saying "just use a sidechain", "do this in a sidechain" or anything like that, be aware that these people are either talking about "federated" sidechains (i.e., funds are kept in custody by a group of entities) or they are talking about Drivechain, or they are disillusioned and think it is possible to do sidechains in any other manner.
No, I mean a trustless 2-way peg with correctness of the withdrawals verified by the Bitcoin protocol!
That is not possible unless Bitcoin verifies all transactions that happen in all the sidechains, which would be akin to drastically increasing the blocksize and expanding the Bitcoin rules in tons of ways, i.e., a terrible idea that no one wants.
What about the Blockstream sidechains whitepaper?
Yes, that was a way to do it. The Drivechain hashrate escrow is a conceptually simpler way to achieve the same thing with improved incentives, less junk in the chain, more safety.
Isn't the hashrate escrow a very complex soft-fork?
Yes, but it is much simpler than SegWit. And, unlike SegWit, it doesn't force anything on users, i.e., it isn't a mandatory blocksize increase.
Why should we expect miners to care enough to participate in the voting mechanism?
Because it's in their own self-interest to do it, and it costs very little. Today over half of the miners mine RSK. It's not blind merged mining, it's a very convoluted process that requires them to run a RSK full node. For the Drivechain sidechains, an SPV node would be enough, or maybe just getting data from a block explorer API, so much much simpler.
What if I still don't like Drivechain even after reading this?
That is the entire point! You don't have to like it or use it as long as you're fine with other people using it. The hashrate escrow special addresses will not impact you at all, validation cost is minimal, and you get the benefit of people who want to use Drivechain migrating to their own sidechains and freeing up space for you in the mainchain. See also the point above about infighting.
See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16bitcoinddecentralizationIt is better to have multiple curator teams, with different vetting processes and release schedules for
bitcoindthan a single one."More eyes on code", "Contribute to Core", "Everybody should audit the code".
All these points repeated again and again fell to Earth on the day it was discovered that Bitcoin Core developers merged a variable name change from "blacklist" to "blocklist" without even discussing or acknowledging the fact that that innocent pull request opened by a sybil account was a social attack.
After a big lot of people manifested their dissatisfaction with that event on Twitter and on GitHub, most Core developers simply ignored everybody's concerns or even personally attacked people who were complaining.
The event has shown that:
1) Bitcoin Core ultimately rests on the hands of a couple maintainers and they decide what goes on the GitHub repository[^pr-merged-very-quickly] and the binary releases that will be downloaded by thousands; 2) Bitcoin Core is susceptible to social attacks; 2) "More eyes on code" don't matter, as these extra eyes can be ignored and dismissed.
Solution:
bitcoinddecentralizationIf usage was spread across 10 different
bitcoindflavors, the network would be much more resistant to social attacks to a single team.This has nothing to do with the question on if it is better to have multiple different Bitcoin node implementations or not, because here we're basically talking about the same software.
Multiple teams, each with their own release process, their own logo, some subtle changes, or perhaps no changes at all, just a different name for their
bitcoindflavor, and that's it.Every day or week or month or year, each flavor merges all changes from Bitcoin Core on their own fork. If there's anything suspicious or too leftist (or perhaps too rightist, in case there's a leftist
bitcoindflavor), maybe they will spot it and not merge.This way we keep the best of both worlds: all software development, bugfixes, improvements goes on Bitcoin Core, other flavors just copy. If there's some non-consensus change whose efficacy is debatable, one of the flavors will merge on their fork and test, and later others -- including Core -- can copy that too. Plus, we get resistant to attacks: in case there is an attack on Bitcoin Core, only 10% of the network would be compromised. the other flavors would be safe.
Run Bitcoin Knots
The first example of a
bitcoindsoftware that follows Bitcoin Core closely, adds some small changes, but has an independent vetting and release process is Bitcoin Knots, maintained by the incorruptible Luke DashJr.Next time you decide to run
bitcoind, run Bitcoin Knots instead and contribute tobitcoinddecentralization!
See also:
[^pr-merged-very-quickly]: See PR 20624, for example, a very complicated change that could be introducing bugs or be a deliberate attack, merged in 3 days without time for discussion.
-
 @ 81022b27:2b8d0644
2025-06-08 04:19:30
@ 81022b27:2b8d0644
2025-06-08 04:19:30D.D. Palmer was a magnetic healer, a visionary who tapped into the unseen forces of life. He founded chiropractic on the premise that the body’s innate intelligence governs health, and that misalignments—whether called subluxations, blockages, or interferences—disrupt this flow.
This is not a medical concept; it’s a metaphysical one, rooted in the belief that life transcends mere mechanics.
As a profession, we’ve been too concerned with what others think of us, particularly the medical community. In our desperation for acceptance, we’ve diluted our essence.
Some chiropractors advocate abandoning the term “subluxation” because it sounds archaic or unscientific. Personally, I don’t care for the word either—it often leaves my clients’ eyes glazed over. I prefer “blockages” or “interference” to convey the concept in a way that resonates.
But replacing these with medical jargon? That’s a betrayal of our roots.
What we cannot do is conform to a biomedical model that reduces the body to a machine. Chiropractic is not about treating symptoms or mimicking physical therapy. It’s about restoring the body’s connection to its innate wisdom, allowing healing to unfold naturally.
This is our strength, our uniqueness. To abandon it is to board the Titanic just before it sails—a sinking ship of soulless reductionism.
I believe chiropractic needs to embrace its metaphysical heritage boldly. We must stop apologizing for being different and instead educate the public on what we truly offer: a holistic approach that honors the body’s intelligence.
This means refining our language to be clear and relatable without sacrificing our principles. It means training chiropractors to communicate with confidence, not defensiveness. It means building a community that celebrates our philosophy rather than chasing validation from skeptics.
The future of chiropractic lies in authenticity. Let’s stop trying to fit into someone else’s paradigm. We are not medicine’s younger sibling; we are a distinct voice in healthcare. By standing firm in our metaphysical roots, we can inspire a world desperate for holistic solutions. The choice is ours: evolve as a vibrant, principled profession or sink under the weight of conformity. I choose evolution.