-
 @ f5369849:f34119a0
2025-06-05 14:01:51
@ f5369849:f34119a0
2025-06-05 14:01:51Hackathon Summary
The ETHBratislava Hackathon Vol.2 convened 54 developers and approved 11 projects, representing a noteworthy event within the Ethereum community. Hosted at the Slovak Technical University, the hackathon offered participants complimentary access to the ETHBratislava Conference. This setting promoted the exploration of current advancements in blockchain technology.
Key achievements were evident in projects that addressed issues of scalability and interoperability within Ethereum, particularly in the "World Computer" track. Significant innovations also emerged from the "Restaking Track by Zircuit," which focused on AI-enabled zk rollups to enhance security and scalability. The "European Stablecoin EURØP Challenge" aimed to develop a stablecoin backed by the euro, advancing the concept of regulated digital currency in Europe.
Participants gained from high-level mentorship, networking opportunities with industry leaders, and the presence of onsite recruiters searching for tech talent. The event ended with an afterparty that served as a venue for celebration and additional networking. A total of 4,000 EUR in prizes was distributed, fostering a competitive yet collaborative environment among innovative developers. ETHBratislava Vol.2 successfully propelled ideas to influence the future of Ethereum while reinforcing community connections.
Hackathon Winners
World Computer Prize Winners
This category highlighted consumer-facing applications that harness Ethereum's capabilities. Developers created solutions aimed at enhancing inclusivity, financial tools, and educational platforms. The winners included:
- Zhar: This decentralized platform employs AI and Ethereum blockchain to manage, execute, and incentivize on-chain challenges using smart contracts and tokens.
- Ledger Lens: A web application that facilitates visualization and analysis of Ethereum's multilayer ecosystem, emphasizing metrics such as token flows and bridge usage.
Real World Tokenization Prize Winners
This category concentrated on building utility on regulated digital money in Europe, specifically utilizing the EUR-pegged stablecoin, EURØP. Projects targeted the deployment of the initial technological enhancements atop this digital currency.
- dEST: A decentralized platform that utilizes NFTs and smart contracts to facilitate tokenized real estate transactions without intermediaries.
- EnergyHub: An application providing a decentralized platform to monetize surplus green energy and enable energy donations through smart contracts and a user-friendly dashboard.
Restaking Prize Winners
This category encouraged teams to build on the AI-powered zkEVM within the Zircuit ecosystem, focusing on projects that support AI-enabled security using innovative zk rollup technology.
- RestakerX: A dashboard application designed to track digital assets on the Zircuit network, offering algorithmic suggestions to maximize returns.
For more detailed information about all projects and further insights into the innovative ideas presented at the hackathon, please visit the ETHBratislava Hackathon page.
Organization
About the Organizer: Ethereum Bratislava
Ethereum Bratislava is a prominent community in the CEE region in the blockchain and technology sector, dedicated to advancing Ethereum development and integration. Supported by a team of experts, the organization has substantially contributed to projects that enhance Ethereum's scalability and security in the CEE region. Active participation in community initiatives and educational events underscores their commitment to fostering technological innovation and knowledge sharing within the blockchain realm. Ethereum Bratislava continues to support technological improvements and ecosystem growth, aiming to bolster Ethereum's capabilities and adoption across various industries.
-
 @ f5369849:f34119a0
2025-06-05 14:01:46
@ f5369849:f34119a0
2025-06-05 14:01:46Hackathon Summary
The Verifiable AI Hackathon from cheqd concentrated on trustworthy AI through secure, verifiable, and ethical systems. The event engaged 278 developers, leading to the submission of 21 projects aimed at fostering trustworthy AI environments. Developers addressed issues related to the misuse of AI technologies, such as deepfake scams, and the challenge of creating transparent, ethical AI systems.
Participants explored themes such as agentic economies, AI verification, and secure data usage, utilizing cheqd’s technologies, including Decentralized Identifiers and Verifiable Credentials. Key accomplishments included innovations in content authentication and the application of verified datasets to prevent disinformation.
The hackathon highlighted the pressing necessity for AI solutions that prioritize transparency and user interests, promoting a trust-focused ecosystem. By equipping developers with blockchain-based tools, the event sought to establish a foundation for more secure and credible AI applications. This initiative aims to transform interactions between digital identities and AI into sustainable and privacy-respecting processes.
Hackathon Winners
AI Agents Prize Winners
- Kith: This decentralized system employs cryptographic verifiable credentials to ensure privacy, authenticate, and maintain the trustworthiness of AI agents through decentralized identifiers (DIDs).
- Identone: This project secures interactions between humans and AI-powered voice agents by verifying identities during phone calls to ensure trustworthiness.
- SNAILS.: A bot that uses decentralized digital identities to verify content, enhancing trust within AI environments.
Other Prize Winners
- CheqDeep: Utilizes blockchain technology to authenticate media content, using DID Linked Resources to verify human origin and authenticity.
- Trusty Bytes: Provides a marketplace for AI agents to access verified data, employing blockchain-based verification for trustworthy transactions.
- crdbl: An open-source platform that improves online credibility using verifiable credentials, decentralized identity, cryptographic signatures, and AI verification.
Build an Agent Incorporating Private User Data Prize Winner
- Viskify: An AI-assisted platform for talent verification, employing verifiable credentials and deterministic decentralized identifiers, and integrating with Stripe and Verida for billing and private data management.
For more information on all projects, please visit The Verifiable AI Hackathon.
Organization
About the Organizer: cheqd
cheqd is a key player in the blockchain industry, focusing on digital identity solutions. The organization is known for its role in establishing decentralized identity infrastructure that supports secure and privacy-focused data management. By leveraging cutting-edge blockchain technologies, cheqd has been pivotal in developing standards within the identity ecosystem. Its efforts include forming strategic partnerships to create interoperable identity services. With a commitment to bolstering digital trust frameworks, cheqd continues to empower both individuals and organizations through advanced and effective identity management solutions.
-
 @ 975e4ad5:8d4847ce
2025-06-05 13:14:46
@ 975e4ad5:8d4847ce
2025-06-05 13:14:46What is the Fiat System and How Do Central Banks Set Interest Rates?
When central banks expand credit, they often increase the money supply by creating new money through mechanisms like quantitative easing (QE). For instance, a central bank may purchase government bonds, injecting money into the economy. This boosts liquidity but can lead to inflation when too much money chases limited goods and services.
Low interest rates make borrowing cheaper, encouraging spending and investment. However, this can overheat the economy, create speculative bubbles (e.g., in real estate), and drive inflation. Conversely, high interest rates restrict borrowing, slow the economy, and curb inflation but may trigger recessions.
How Would Interest Rates Work Under a Bitcoin Standard?
Under a Bitcoin standard, the money supply is fixed—only 21 million bitcoins will ever exist, with the last one mined around 2140. Unlike the fiat system, no central authority can manipulate the money supply or set interest rates. Instead, interest rates would be determined entirely by the market—by the supply and demand for capital.
If someone wants to borrow bitcoins, the interest rate would depend on negotiations between the lender and borrower. For example, if demand for loans is high and available bitcoins are scarce, interest rates would rise. Conversely, if there are ample bitcoin savings, rates might fall. This process would be fully decentralized and reflect real market conditions, not central bank decisions.
Since new bitcoins cannot be “printed,” there would be no inflation caused by an expanding money supply. Instead, bitcoin’s value would likely rise over time (deflation) as its fixed supply competes with growing demand. This could encourage saving over reckless spending, reshaping economic behavior.
Advantages of a Bitcoin Standard
-
Protection Against Inflation: Bitcoin’s fixed supply prevents currency devaluation, a common issue with fiat money. This safeguards savings and promotes long-term planning.
-
Decentralization: Without a central bank manipulating the market, economic decisions are made by individuals, not bureaucrats. This aligns with free-market principles where competition and innovation thrive.
-
Transparency and Security: The Bitcoin blockchain is public and immutable, ensuring transactions are transparent and secure from tampering.
-
Financial Freedom: Under a Bitcoin standard, individuals have full control over their money without government or bank interference, which is especially crucial in countries with unstable regimes or currencies.
-
Discipline in Lending: Without the ability to print money, lenders would be more cautious, reducing risky investments and speculative bubbles.
Potential Drawbacks and Why a Bitcoin Standard is Superior
One major argument against a Bitcoin standard is that it could slow economic growth. Low interest rates in the fiat system encourage borrowing and spending, driving economic activity. Under a Bitcoin standard, where interest rates are market-driven and likely higher, borrowing would be costlier, potentially limiting investments in new projects.
However, this critique misses a key point: economic growth fueled by artificially low interest rates and money printing is often unsustainable. It leads to debt crises, inflation, and bubbles that eventually burst, as seen in 2008. A Bitcoin standard promotes healthy economic discipline, where investments are based on real value, not artificial capital.
Moreover, bitcoin’s deflationary nature could shift how people view money. Instead of chasing endless growth, societies might prioritize sustainability, innovation, and efficiency. This could lead to a more stable and equitable economy in the long run.
Additional Considerations
A Bitcoin standard could transform global trade. Today, countries with fiat currencies often manipulate exchange rates to gain trade advantages. With bitcoin as a universal currency, such manipulations would vanish, fostering fairer competition.
Another aspect is energy efficiency. While bitcoin mining consumes energy, it incentivizes the development of renewable sources as miners seek cheap, sustainable energy. This could accelerate the transition to a green economy.
Conclusion
The Bitcoin standard offers a vision of an economy rooted in sound money, free markets, and financial freedom. While it may slow certain aspects of economic growth, it creates a more stable and sustainable system that protects individuals from inflation and centralized control. In a world where trust in institutions is waning, the Bitcoin standard is a step toward a fairer and more transparent future.
-
-
 @ 31a4605e:cf043959
2025-06-05 13:03:59
@ 31a4605e:cf043959
2025-06-05 13:03:59Nos últimos anos, o Bitcoin tem sido frequentemente comparado ao ouro, ganhando o nome de "ouro digital". Essa comparação ocorre porque ambas as formas de valor têm características em comum, como escassez, durabilidade e aceitação mundial. Contudo, o Bitcoin também representa uma novidade tecnológica que muda a ideia de dinheiro e investimento, se destacando como uma alternativa moderna e eficaz ao ouro físico.
Uma das razões pelas quais o Bitcoin é comparado ao ouro é a sua escassez programada. Enquanto o ouro é um recurso natural limitado, cuja oferta depende da mineração, o Bitcoin tem um teto máximo de 21 milhões de unidades, definido em seu código. Esse teto faz com que o Bitcoin seja protegido contra a inflação, ao contrário das moedas tradicionais, que podem ser criadas sem limites pelos bancos centrais.
Essa característica traz um valor duradouro, parecido com o ouro, já que a oferta limitada ajuda a manter o poder de compra ao longo do tempo. Com o aumento da procura por Bitcoin, sua quantidade reduzida reforça seu papel como reserva de valor.
Outro aspecto que aproxima o Bitcoin do ouro é a durabilidade. Enquanto o ouro resiste à corrosão e pode ser guardado por séculos, o Bitcoin é um ativo digital protegido por criptografia avançada e armazenado na blockchain — um livro-razão imutável e descentralizado.
Além disso, o Bitcoin é mais fácil de transportar do que o ouro. Mover ouro físico envolve custos e segurança, tornando o transporte complicado, principalmente em transações internacionais. Por outro lado, o Bitcoin pode ser enviado digitalmente para qualquer parte do mundo em minutos, com taxas baixas e sem intermediários. Essa vantagem tecnológica torna o Bitcoin mais eficaz para um mundo globalizado e digital.
A segurança é outra característica que o Bitcoin e o ouro têm em comum. O ouro é difícil de falsificar, fazendo dele uma reserva de valor confiável. Da mesma forma, o Bitcoin usa protocolos de criptografia que asseguram transações seguras e protegidas contra fraudes.
Além disso, todas as transações feitas com Bitcoin são registradas na blockchain, fornecendo um nível de transparência que o ouro físico não oferece. Qualquer pessoa pode revisar as transações na rede, aumentando a confiança e a rastreabilidade.
EconômicaHistoricamente, o ouro tem sido utilizado como proteção contra a inflação e crises econômicas. Durante momentos de instabilidade, os investidores buscam o ouro como uma maneira de preservar seu patrimônio. O Bitcoin, por sua vez, está surgindo como uma alternativa digital com o mesmo propósito.
Em países com alta inflação ou instabilidade política, o Bitcoin tem sido usado como uma proteção contra a desvalorização das moedas locais. Sua natureza descentralizada impede que governos confisquem ou controlem diretamente o ativo, garantindo maior liberdade financeira para os usuários.
Apesar de suas semelhanças com o ouro, o Bitcoin ainda enfrenta desafios. Sua volatilidade é muito maior, o que pode causar incertezas a curto prazo. No entanto, muitos especialistas afirmam que essa volatilidade é uma característica comum em ativos novos e tende a diminuir com o tempo, à medida que a aceitação cresce e o mercado se desenvolve.
Outro desafio é a regulamentação. Enquanto o ouro já é reconhecido globalmente como um ativo financeiro, o Bitcoin ainda enfrenta resistência de governos e instituições financeiras, que procuram formas de controlá-lo e regulá-lo.
Resumindo, o Bitcoin, muitas vezes chamado de "ouro digital", oferece uma nova forma de valor que combina as melhores características do ouro com a eficiência e a inovação da tecnologia digital. Sua escassez planejada, segurança criptográfica, portabilidade e resistência à censura fazem dele uma alternativa viável para preservar riqueza e realizar transações no mundo moderno.
Mesmo com muita volatilidade, o Bitcoin está se firmando como uma reserva de valor e como um ativo de proteção contra crises econômicas. Assim, ele representa não apenas uma evolução do sistema financeiro, mas também um símbolo da mudança para uma economia digital descentralizada e global.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 3eab247c:1d80aeed
2025-06-05 08:51:39
@ 3eab247c:1d80aeed
2025-06-05 08:51:39Global Metrics
Here are the top stats from the last period:
- Total Bitcoin-accepting merchants: 15,306 → 16,284
- Recently verified (1y): 7,540 → 7,803 (the rest of our dataset is slowly rotting; help us before it's too late!)
- Avg. days since last verification: 398 → 405 (more mappers, please)
- Merchants boosted: 22 (for a total of 4,325 days, someone is feeling generous)
- Comments posted: 34
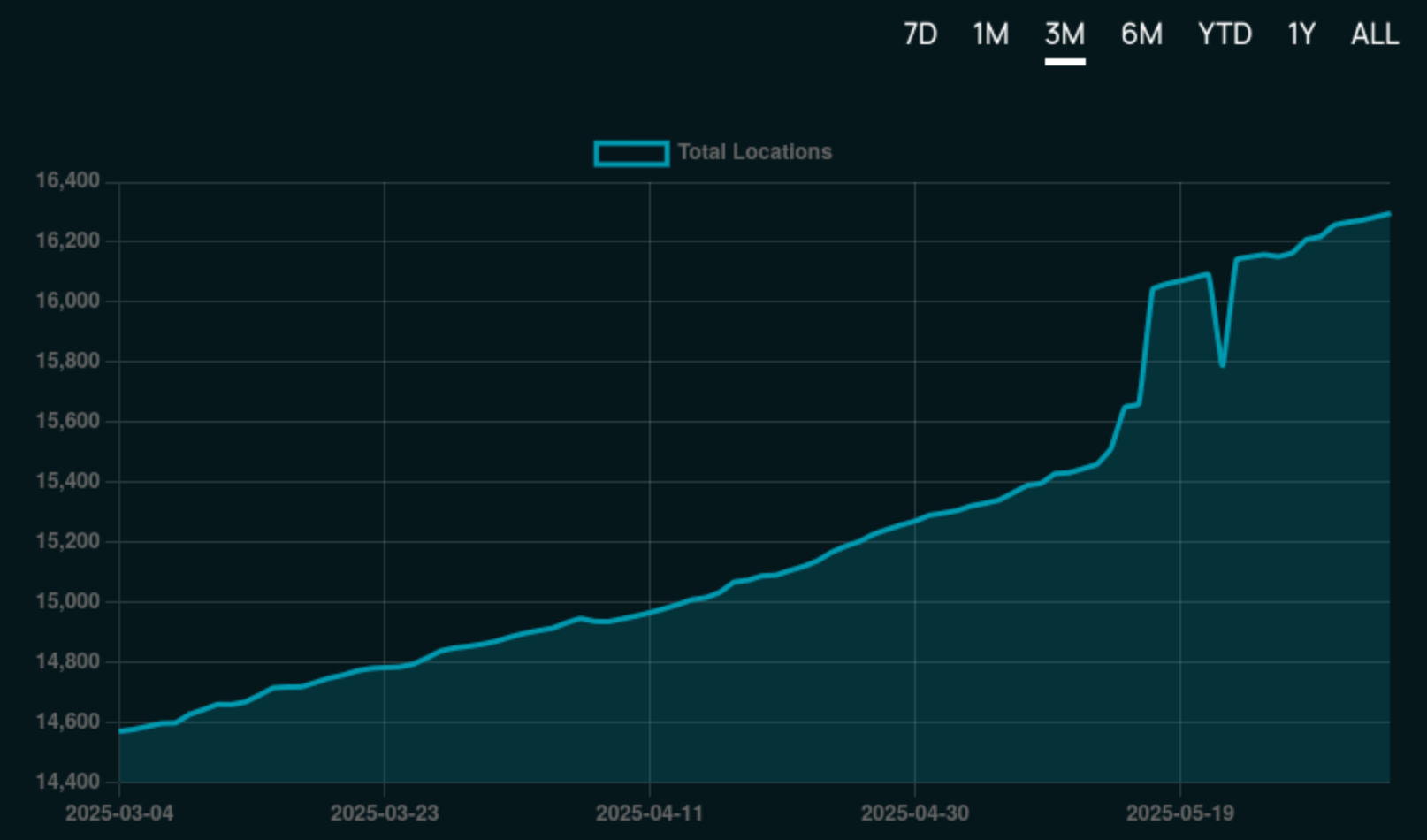
Find current stats over at the 👉 BTC Map Dashboard.
Merchant Adoption
Steak n’ Shake
The US 🇺🇸 is a massive country, yet its BTC Map footprint has been lagging relative to other countries ... that is until now!

In what came as a nice surprise to our Shadowy Supertaggers 🫠, the Steak ’n Shake chain began accepting Bitcoin payments across hundreds of its locations nationwide (with some international locations too).
According to CoinDesk, the rollout has been smooth, with users reporting seamless transactions powered by Speed.
This marks a significant step towards broader Bitcoin adoption in the US. Now to drop the capital gains tax on cheesburgers!
SPAR Switzerland
In other chain/franchise adoption news, the first SPAR supermarket in Switzerland 🇨🇭 to begin accepting Bitcoin was this one in Zug. It was quickly followed by this one in Rossrüti and this one in Kreuzlingen, in what is believed to be part of a wider roll-out plan within the country powered by DFX's Open CryptoPay.
That said, we believe the OG SPAR crown goes to SPAR City in Arnhem Bitcoin City!
New Features
Merchant Comments in the Web App
Web App users are now on par with Android users in that they can both see and make comments on merchants.
This is powered by our tweaked API that enables anyone to make a comment as long as they pass the satswall fee of 500 sats. This helps keep spam manageable and ensure quality comments.
And just in case you were wondering what the number count was on the merchant pins - yep, they're comments!
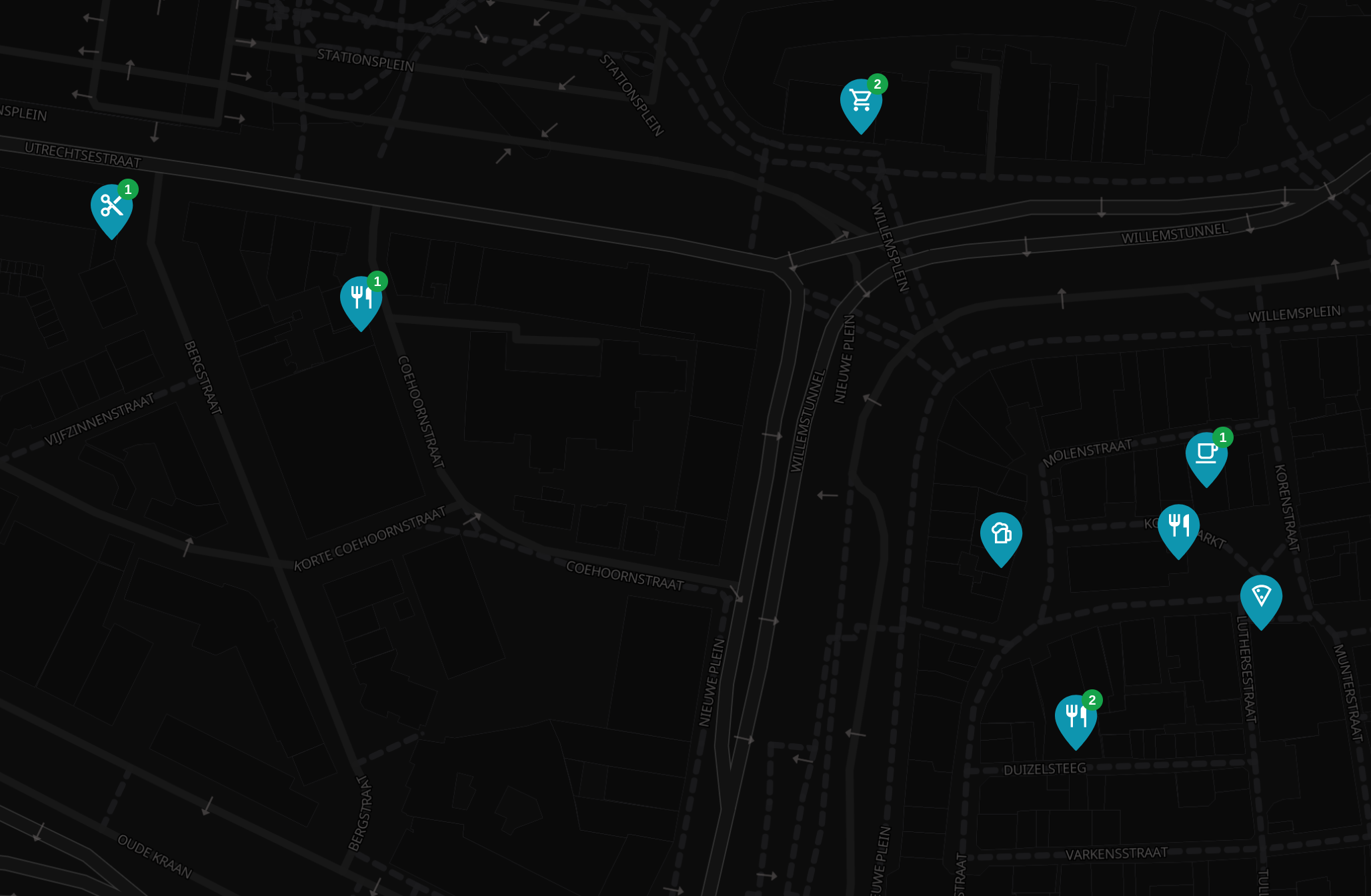
Here is an 👉 Example merchant page with comments.
Merchant Page Design Tweaks
To support the now trio of actions (Verify, Boost & Comment) on the merchant page, we've re-jigged the design a little to make things a little clearer.
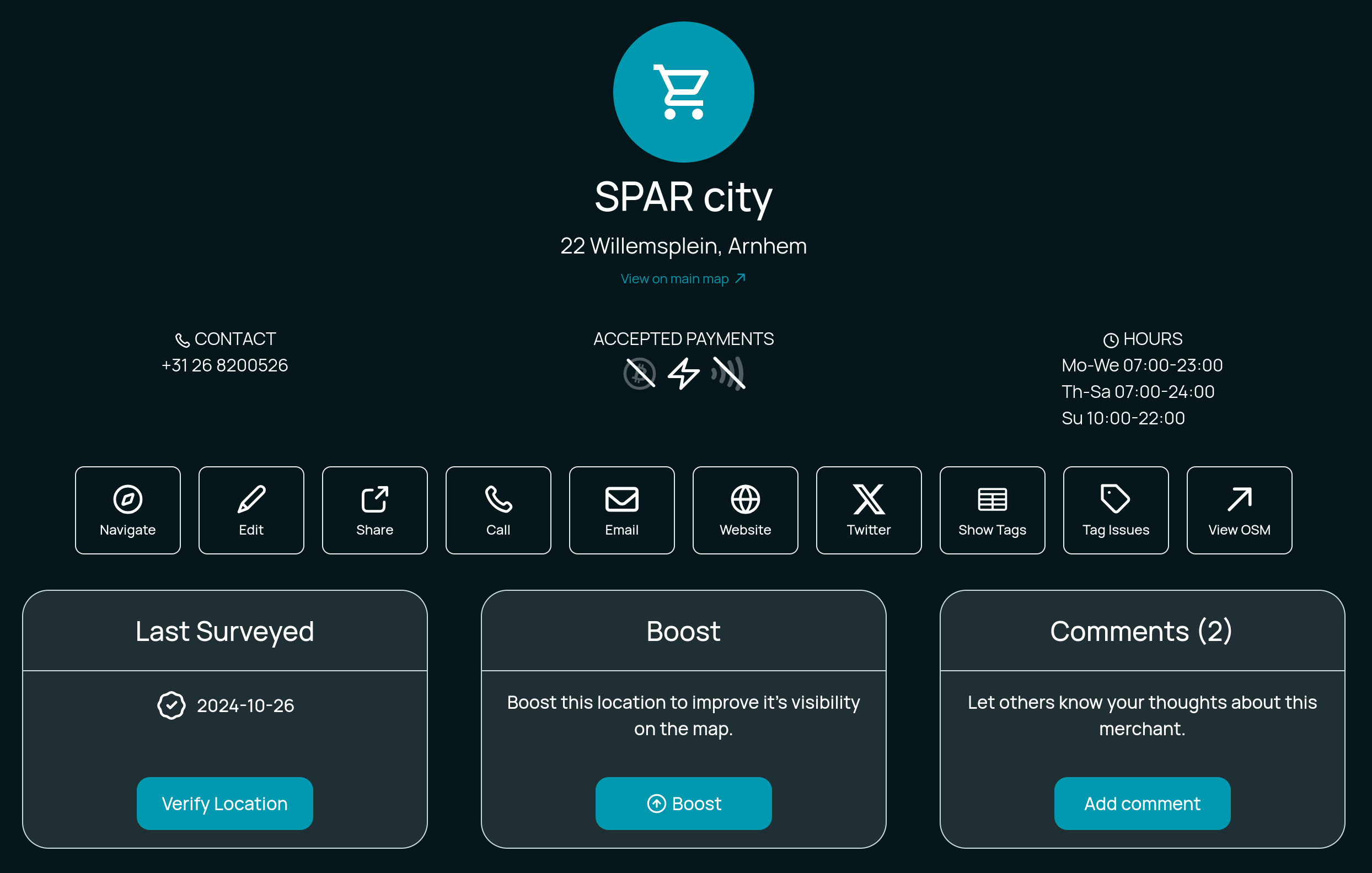
What do you think?
Technical
Codebase Refactoring
Thanks to Hannes’s contributions, we’ve made progress in cleaning-up the Web App's codebase and completing long overdue maintenance. Whilst often thankless tasks, these caretaking activities help immensely with long-term maintainability enabling us to confidently build new features.
Auth System Upgrades
The old auth system was held together with duct tape and prayers, and we’re working on a more robust authentication system to support future public API access. Updates include:
- Password hashing
- Bearer token support
- Improved security practices
More enhancements are in progress and we'll update you in the next blog post.
Better API Documentation
Instead of relying on tribal knowledge, we're finally getting around to writing actual docs (with the help/hindrance of LLMs). The "move fast, break everything" era is over; now we move slightly slower and break slightly less. Progress!
Database Improvements
We use SQLite, which works well but it requires careful handling in async Rust environments. So now we're untangling this mess to avoid accidental blocking queries (and the ensuing dumpster fires).
Backup System Enhancements
BTC Map data comes in three layers of fragility:
- Merchants (backed up by OS - the big boys handle this)
- Non-OSM stuff (areas, users, etc. - currently stored on a napkin)
- External systems (Lightning node, submission tickets - pray to Satoshi)
We're now forcing two core members to backup everything, because redundancy is good.
Credits
Thanks to everyone who directly contributed to the project this period:
- Comino
- descubrebitcoin
- Hannes
- Igor Bubelov
- Nathan Day
- Rockedf
- Saunter
- SiriusBig
- vv01f
Support Us
There are many ways in which you can support us:
-
Become a Shadowy Supertagger and help maintain your local area or pitch-in with the never-ending global effort.
-
Consider a zapping this note or make a donation to the to the project here.
-
 @ a5ee4475:2ca75401
2025-06-04 13:25:46
@ a5ee4475:2ca75401
2025-06-04 13:25:46[EM ATUALIZAÇÃO]
vacina #saude #politica #manipulacao #mundial #genocidio #pandemia #conspiracao
Este artigo reúne algumas evidências mais antigas que vim registrando durante alguns anos contra a covid, vacinas obrigatórias e a ação de agências de governo, fundações, políticos, mídia tradicional, celebridades, influenciadores, cientistas, redes sociais e laboratórios, em envolvimento com genocídio e restrições de liberdades em escala mundial causado por decisões em várias esferas relativas ao covid e as vacinas obrigatórias em geral.
Porém, alguns links podem não estar mais disponiveis, foram que ainda faltam ser registradas muitas informações já divulgadas nos últimos anos e que não tivemos contato pela escassez de meios para a obtenção dessas informações de forma organizada. Portanto, o presente artigo ainda passará por atualizações de conteúdo e formatação, então se possível ajudem sugerindo com complementos ou alterações.
1. Vacinas Obrigatórias em Geral
-
Vacinas e autismo em crianças https://publichealthpolicyjournal.com/vaccination-and-neurodevelopmental-disorders-a-study-of-nine-year-old-children-enrolled-in-medicaid/
-
O CDC admite que 98 milhões de pessoas receberam o vírus do câncer através da vacina da Poliomielite https://medicinanews.com.br/frente/frente_1/o-cdc-admite-que-98-milhoes-de-pessoas-receberam-o-virus-do-cancer-atraves-da-vacina-poliomielite/
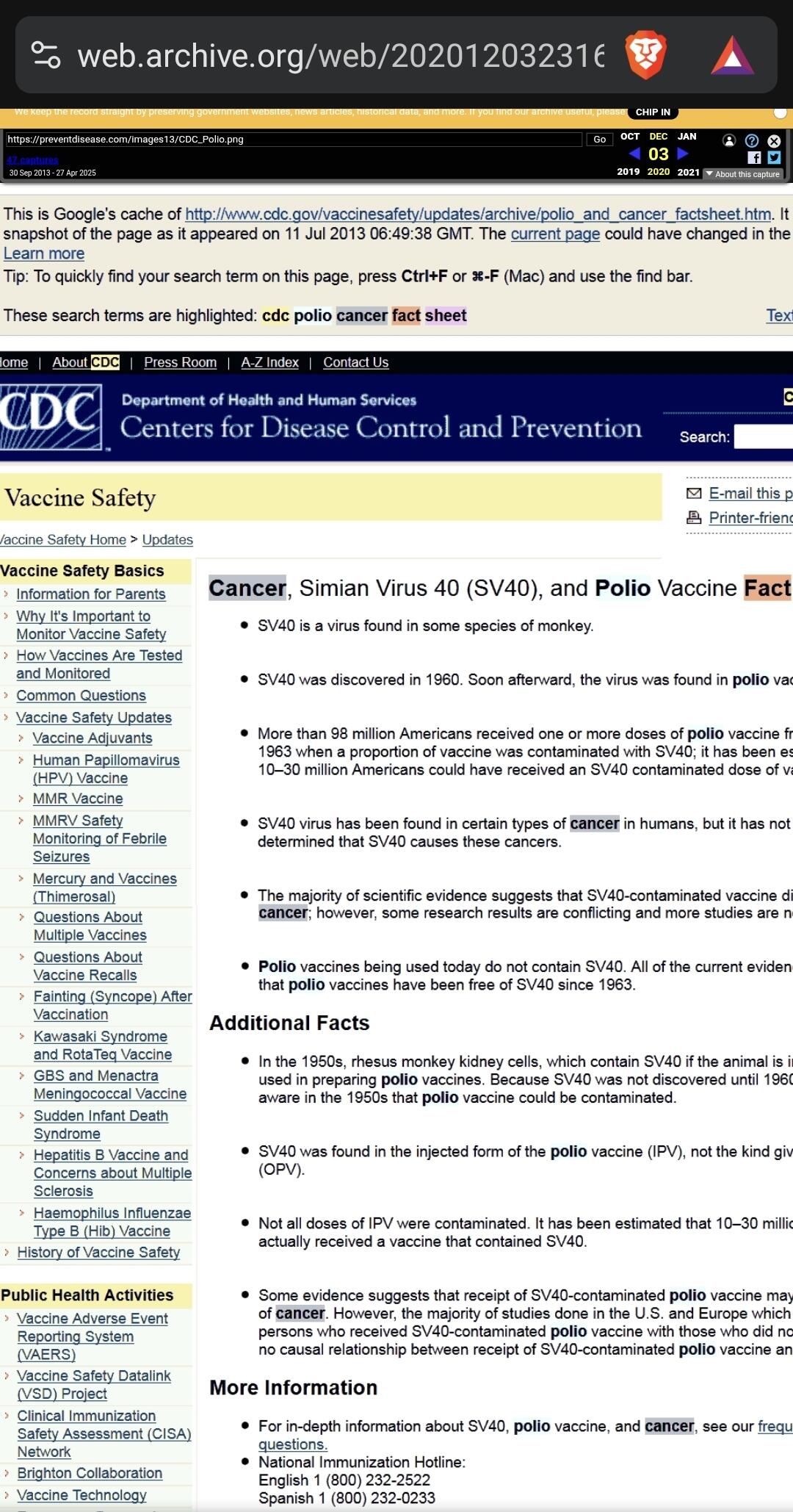 Fonte original: https://preventdisease.com/images13/CDC_Polio.png [indisponível]
Salvo em: https://web.archive.org/web/20201203231640/ https://preventdisease.com/images13/CDC_Polio.png
Fonte original: https://preventdisease.com/images13/CDC_Polio.png [indisponível]
Salvo em: https://web.archive.org/web/20201203231640/ https://preventdisease.com/images13/CDC_Polio.png"O CDC (Os Centros de Controle e Prevenção de Doenças dos Estados Unidos) removeu rapidamente uma página do seu site, que estava em cache no Google, como você pode ver logo abaixo, admitindo que mais de 98 milhões de americanos receberam uma ou mais doses de vacina contra pólio dentro de 8 período entre 1955 e 1963, quando uma proporção da vacina foi contaminada com um poliomavírus causador de câncer chamado SV40."
27/02/2021 - Por que o Japão demorou para vacinar, mesmo com Olimpíada se aproximando https://www.cnnbrasil.com.br/internacional/2021/02/27/por-que-o-japao-demorou-para-vacinar-mesmo-com-olimpiada-se-aproximando
"Desconfiança da população japonesa em relação a vacinas, ligada a casos ocorridos no passado, está entre razões que atrasaram imunização no país.
A resistência à vacina do Japão remonta à década de 1970, quando duas crianças morreram dentro de 24 horas após receberem a vacina combinada contra difteria, tétano e coqueluche (coqueluche). A vacina foi temporariamente suspensa, mas a confiança já havia sido abalada. Por vários anos, as taxas de vacinação infantil caíram, levando a um aumento nos casos de tosse convulsa.
No final dos anos 1980, houve outro susto com a introdução da vacina tripla contra sarampo, caxumba e rubéola produzida no Japão. As primeiras versões do imunizante foram associadas à meningite asséptica, ou inchaço das membranas ao redor do cérebro e da medula espinhal. O problema foi rastreado até o componente caxumba da vacina tripla, o que levou a uma ação judicial e a indenização por danos pesados.
O Instituto Nacional de Ciências da Saúde interrompeu a dose combinada em 1993 e a substituiu por vacinas individuais. Após o escândalo, Shibuya disse que o governo japonês se tornou "ciente dos riscos" e seu programa nacional de vacinação tornou-se voluntário.
O Dr. Yuho Horikoshi, especialista em doenças infecciosas, diz que os processos levaram a uma "lacuna de vacinação", em que nenhuma vacina foi aprovada no Japão por cerca de 15 anos.
Mais recentemente, em 2013, o Japão adicionou a vacina contra o papilomavírus humano (HPV) ao calendário nacional para proteger as meninas contra o vírus sexualmente transmissível, que é conhecido por causar câncer cervical. No entanto, vídeos de meninas supostamente sofrendo de reações adversas começaram a circular no YouTube, levando o governo a retirá-los da programação nacional."
2. PRIMEIRAS OCORRÊNCIAS PREDITIVAS AO COVID-19
2010 - Fundação Rockfeller, Lockstep. https://www.rockefellerfoundation.org/wp-content/uploads/Annual-Report-2010-1.pdf
Neste PDF da fundação Rockfeller, em seu próprio site, a fundação deixou claro o seu envolvimento em casos de ‘contenção’ de pandemias juntamente com a USAID (agência americana com nome ambíguo, como formalmente ‘United States Agency for International Development’, mas soando como ‘US Socorre’, mas sendo um braço do governo democrata que financiava interferências políticas diretas em vários países, como no Brasil: https://www.gazetadopovo.com.br/vida-e-cidadania/quais-ongs-cooperaram-com-moraes-e-sao-alvo-do-congresso-nos-eua/ ), inclusive em relacionadas ao SARS, um vírus muito semelhante ao SEGUNDO tipo de vírus Sars-Cov, o Sars-Cov-2 (o vírus propagado em 2019) e que causa o COVID-19.
Segundo eles:
“Integração entre Regiões e Países
A Fundação Rockefeler investiu US$ 22 milhões em sua Iniciativa de Redes de Vigilância de Doenças para ajudar a conter a disseminação de doenças infecciosas e pandemias, fortalecendo os sistemas nacionais, regionais e globais de vigilância e resposta a doenças. Dois programas-chave da Rockefeler — a Rede de Vigilância de Doenças da Bacia do Mekong e a Rede Integrada de Vigilância de Doenças da África Oriental — conectaram e capacitaram profissionais de saúde, epidemiologistas e autoridades de saúde pública em toda a região, levando a um aumento de seis vezes nos locais de vigilância de doenças transfronteiriças somente nos últimos três anos. Em 2010, a Rockefeler expandiu a bem-sucedida campanha transdisciplinar One Health, que a USAID e o Banco Asiático de Desenvolvimento adotaram como modelos. One Health refere-se à integração da ciência médica e veterinária para combater essas novas variedades de doenças zoonóticas que se movem e sofrem mutações rapidamente de animais para humanos. Essas colaborações criaram e fortaleceram uma rede regional crítica de saúde pública, enquanto as lições aprendidas foram exportadas entre disciplinas e países. Além de fortalecer os laços globais em saúde pública, a Rockefeler ajudou a elevar o nível de especialização e treinamento em campo. O Programa de Treinamento em Epidemiologia de Campo coloca graduados nos mais altos escalões do governo no Laos e no Vietnã, enquanto as bolsas da Rockefeler transformaram as ferramentas disponíveis para os médicos, permitindo-lhes utilizar o poder da internet para se comunicar e monitorar eventos, compreender contextos locais e analisar novos problemas. Finalmente, estamos aplicando ferramentas do século XXI para combater os desafios de saúde do século XXI.”
Julho de 2012 - Revista Mundo Estranho
Houve uma "coincidência", a revista Mundo Estranho em julho de 2012, entrevistou o até então doutorando em virologia, Átila Iamarino (o mesmo cientista que fez diversas propagandas das vacinas no Brasil), para descrever um possível cenário de propagação de uma epidemia viral, a revista descreve com grande precisão os eventos de 2020, mas apontando o oposto da China, em que, na realidade, sua economia cresceu vertiginosamente.
3. PRIMEIROS INDÍCIOS
10/2019 - Evento 201 - Durante os Jogos Militares Internacionais na China. https://www.centerforhealthsecurity.org/event201/
Promovido por: - Bill & Melinda Gates Foundation - John Hopkins Institute - Fórum econômico mundial
"O evento simula a liberação de um coronavírus novo do tipo zoonótico transmitido por morcegos para porcos e por fim para humanos. Eventualmente ele se torna muito transmissível entre humanos levando a uma pandemia severa. O vírus é muito parecido com o vírus da SARS, mas se transmite muito mais facilmente entre pessoas devido a sintomas muito mais leves destas."
Também mencionado por: http://patrocinados.estadao.com.br/medialab/releaseonline/releasegeral-releasegeral/geral-johns-hopkins-center-for-health-security-forum-economico-mundial-e-fundacao-bill-melinda-gates-realizam-exercicio-pandemico-e-transmissao-ao-vivo/
Sobre o "Movimento antivacina"
05/12/2017 - Movimento antivacina: como surgiu e quais consequências ele pode trazer? https://www.uol.com.br/universa/noticias/redacao/2017/12/05/o-que-o-movimento-antivacina-pode-causar.htm?cmpid=copiaecola
23/03/2019 - "Instagram bloqueia hashtags e conteúdo antivacinação" https://canaltech.com.br/redes-sociais/instagram-bloqueia-hashtags-e-conteudo-antivacinacao-135411/
23/05/2021 - Novos dados sobre pesquisadores de Wuhan aumentam debate sobre origens da Covid https://www.cnnbrasil.com.br/saude/novos-dados-sobre-pesquisadores-de-wuhan-aumentam-debate-sobre-origens-da-covid/
"A China relatou à Organização Mundial da Saúde que o primeiro paciente com sintomas semelhantes aos de Covid-19 foi registrado em Wuhan em 8 de dezembro de 2019"
01/02/2020 - O que aconteceu desde que o novo coronavírus foi descoberto na China https://exame.com/ciencia/o-que-aconteceu-desde-que-o-novo-coronavirus-foi-descoberto-na-china/
"O primeiro alerta foi recebido pela Organização Mundial da Saúde (OMS) em 31 de dezembro de 2019"
15/09/2020 - YouTube diz que vai remover vídeos com mentiras sobre vacina contra COVID-19 https://gizmodo.uol.com.br/youtube-remover-videos-mentiras-vacina-covid-19/
"O YouTube anunciou na quarta-feira (14) que estenderá as regras atuais sobre mentiras, propaganda e teorias da conspiração sobre a pandemia do coronavírus para incluir desinformação sobre as vacinas contra a doença.
De acordo com a Reuters, a gigante do vídeo diz que agora vai proibir conteúdos sobre vacinas contra o coronavírus que contradizem “o consenso de especialistas das autoridades de saúde locais ou da OMS”, como afirmações falsas de que a vacina é um pretexto para colocar chips de rastreamento nas pessoas ou que irá matar ou esterilizar quem tomar."
*07/01/2021 - YouTube vai punir canais que promovem mentiras sobre eleições – incluindo os de Trump https://olhardigital.com.br/2021/01/07/noticias/youtube-vai-punir-canais-que-promovem-mentiras-sobre-eleicoes-incluindo-os-de-trump/
"O YouTube anunciou que vai punir canais que promovem mentiras sobre as eleições, removendo sumariamente qualquer vídeo que contenha desinformação e, ao mesmo tempo, advertindo com um “strike” o canal que o veicular. A medida já está valendo e a primeira “vítima” é ninguém menos que o ex-presidente americano, Donald Trump.
A medida não é exatamente nova, mas foi novamente comunicada e reforçada pelo YouTube na quarta-feira (6), após os eventos de invasão do Capitólio, em Washington, onde o presidente eleito Joe Biden participava da cerimônia que confirmava a sua vitória nas eleições de novembro de 2020. A ocasião ficou marcada pela tentativa de invasão de correligionários de Trump, que entraram no edifício em oposição à nomeação do novo presidente. Uma mulher acabou sendo morta pela polícia que protegia o local.
O ex-presidente Donald Trump teve vídeos banidos de seu canal no YouTube após os eventos de ontem (6) no capitólio."
4. FIGURAS CENTRAIS
Bill Gates
Bill Gates diz 'não' a abrir patentes de vacinas https://www.frontliner.com.br/bill-gates-diz-nao-a-abrir-patentes-de-vacinas/
"Bill Gates, um dos homens mais ricos do mundo, cuja fundação tem participação na farmacêutica alemã CureVac, produtora de vacina mRNA para prevenção de covid-19, disse não acreditar que a propriedade intelectual tenha algo a ver com o longo esforço global para controlar a pandemia."
João Doria e ocorrências em São Paulo
26/07/2017 - João Dória vai a China conhecer drones para ampliar segurança eletrônica na capital paulista https://jc.ne10.uol.com.br/blogs/jamildo/2017/07/26/joao-doria-vai-china-conhecer-drones-para-ampliar-seguranca-eletronica-na-capital-paulista/
02/08/2019 - Governo de SP fará Missão China para ampliar cooperação e atrair investimentos https://www.saopaulo.sp.gov.br/spnoticias/governo-de-sao-paulo-detalha-objetivos-da-missao-china/
20/11/2019 - Doria se encontra com chineses das gigantes CREC e CRCC e oferece concessões de rodovia, metrô e ferrovia https://diariodotransporte.com.br/2019/11/20/doria-se-encontra-com-chineses-das-gigantes-crec-e-crcc-e-oferece-concessoes-de-rodovia-metro-e-ferrovia/
25/01/2020 - "Chineses serão agressivos" nas privatizações em SP até 2022, afirma Dória https://noticias.uol.com.br/colunas/jamil-chade/2020/01/25/entrevista-joao-doria-privatizacoes-sao-paulo-china.htm
O governador de São Paulo, João Doria, afirma que vai acelerar os programas de desestatização no estado em 2020 e acredita que concessões e vendas poderão permitir uma arrecadação de pelo menos R$ 40 bilhões. Nesse processo, o governador avalia que a China deve atuar de forma agressiva e que aprofundará sua posição de maior parceira comercial do estado, se distanciando de americanos e argentinos.
29/06/2020 - Doria estabelece multa para quem estiver sem máscara na rua em SP https://veja.abril.com.br/saude/doria-estabelece-multa-para-quem-estiver-sem-mascara-na-rua/
24/12/2020 - Doria é flagrado sem máscara e fazendo compras em Miami https://pleno.news/brasil/politica-nacional/doria-e-flagrado-sem-mascara-e-fazendo-compras-em-miami.html
Foto do governador de São Paulo sem o item de proteção viralizou nas redes
07/06/2021 - Doria é criticado na internet por tomar sol sem máscara em hotel no Rio https://vejasp.abril.com.br/cidades/doria-e-criticado-na-internet-por-tomar-sol-sem-mascara-em-hotel-no-rio/
30/09/2020 - Governo de SP assina contrato com Sinovac e prevê vacina para dezembro https://agenciabrasil.ebc.com.br/saude/noticia/2020-09/governo-de-sp-assina-contrato-com-sinovac-e-preve-vacina-para-dezembro
O governador de São Paulo, João Doria, e o vice-presidente da laboratório chinês Sinovac, Weining Meng, assinaram hoje (30), um contrato que prevê o fornecimento de 46 milhões de doses da vacina CoronaVac para o governo paulista até dezembro deste ano.
O contrato também prevê a transferência tecnológica da vacina da Sinovac para o Instituto Butantan, o que significa que, o instituto brasileiro poderá começar a fabricar doses dessa vacina contra o novo coronavírus. O valor do contrato, segundo o governador João Doria é de US$ 90 milhões.
20/10/2020 - Coronavac terá mais de 90% de eficácia, afirmam integrantes do governo paulista https://www.cnnbrasil.com.br/saude/2020/12/20/coronavac-tera-mais-de-90-de-eficacia-afirmam-integrantes-do-governo
24/10/2020 - Não esperamos 90% de eficácia da Coronavac’, diz secretário de saúde de SP https://www.cnnbrasil.com.br/saude/2020/12/24/nao-esperamos-90-de-eficacia-da-coronavac-diz-secretario-de-saude-de-sp
07/01/2021 - Vacina do Butantan: eficácia é de 78% em casos leves e 100% em graves https://www.cnnbrasil.com.br/saude/2021/01/07/vacina-do-butantan-eficacia-e-de-78-em-casos-leves-e-100-em-graves
09/01/2021 - Não é hora de sermos tão cientistas como estamos sendo agora https://g1.globo.com/sp/sao-paulo/video/nao-e-hora-de-sermos-tao-cientistas-como-estamos-sendo-agora-diz-secretario-de-saude-de-sp-9166405.ghtml
10/01/2021 - Dados da Coronavac relatados à Anvisa não estão claros, diz médico https://www.cnnbrasil.com.br/saude/2021/01/10/dados-da-coronavac-relatados-a-anvisa-nao-estao-claros-diz-medico
"O diretor do Laboratório de Imunologia do Incor, Jorge Kalil, reforçou que faltaram informações sobre a Coronavac nos dados divulgados à Anvisa"
12/01/2021 - New Brazil data shows disappointing 50,4% efficacy for China’s Coronavac vaccine [Novos dados do Brasil mostram eficácia decepcionante de 50,4% para a vacina CoronaVac da China] https://www.reuters.com/article/us-health-coronavirus-brazil-coronavirus/new-brazil-data-shows-disappointing-504-efficacy-for-chinas-coronavac-vaccine-idUSKBN29H2CE
13/01/2021 - Eficácia da Coronavac: 50,38%, 78% ou 100%? https://blogs.oglobo.globo.com/lauro-jardim/post/5038-78-ou-100.html
“De acordo com interlocutores que participaram tanto do anúncio de ontem como da semana passada, quem pressionou para que os dados de 78% e 100% fossem liberados foi João Dória.”
07/05/2021 - Covid-19: Doria toma primeira dose da vacina CoronaVac https://veja.abril.com.br/saude/covid-19-doria-toma-primeira-dose-da-vacina-coronavac/
04/06/2021 - Doria é vacinado com a segunda dose da CoronaVac em São Paulo https://noticias.uol.com.br/politica/ultimas-noticias/2021/06/04/doria-e-vacinado-com-a-segunda-dose-da-coronavac-em-sao-paulo.htm
15/07/2021 - Doria testa positivo para a Covid-19 pela 2ª vez https://www.correiobraziliense.com.br/politica/2021/07/4937833-doria-testa-positivo-para-covid-19-pela-segunda-vez.html
"Governador de São Paulo já havia sido diagnosticado com a doença no ano passado. Ele diz que, apesar da infecção, se sente bem, o que atribui ao fato de ter sido vacinado com duas doses da Coronavac"
06/08/2021 - CPI recebe investigação contra Doria por compra de máscara sem licitação https://www.conexaopoder.com.br/nacional/cpi-recebe-investigacao-contra-doria-por-compra-de-mascara-sem-licitacao/150827
"Empresa teria usado o nome de Alexandre Frota para vender máscaras ao governo de SP. Doria nega informação"
Renan Filho (filho do Renan Calheiros)
25/07/2019 - Governador Renan Filho vai à China em busca de investimentos para o estado https://www.tnh1.com.br/videos/vid/governador-renan-filho-vai-a-china-em-busca-de-investimentos-para-o-estado/
20/03/2020 - Governadores do NE consultam China e pedem material para tratar covid-19 https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2020/03/20/governadores-do-ne-consultam-china-e-pedem-material-para-tratar-covid-19.htm
5. Narrativas, restrições e proibições
17/12/2020 - STF decide que vacina contra a covid pode ser obrigatória, mas não forçada https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2020/12/17/stf-julga-vacinacao-obrigatoria.htm?cmpid=copiaecola
"O STF (Supremo Tribunal Federal) decidiu, em julgamento hoje, que o Estado pode determinar a obrigatoriedade da vacinação contra a covid-19. Porém fica proibido o uso da força para exigir a vacinação, ainda que possam ser aplicadas restrições a direitos de quem recusar a imunização.
Dez ministros foram favoráveis a obrigatoriedade da vacinação, que poderá ser determinada pelo governo federal, estados ou municípios. As penalidades a quem não cumprir a obrigação deverão ser definidas em lei."
27/07/2021 - Saiba que países estão adotando 'passaporte da vacina' para suspender restrições https://www.cnnbrasil.com.br/internacional/2021/07/27/saiba-que-paises-estao-adotando-passaporte-da-vacina-para-suspender-restricoes
" - Israel - Uniao Europeia - Áustria - Dinamarca - Eslovênia - França - Grécia - Irlanda - Itália - Letônia - Lituânia - Luxemburgo - Holanda - Portugal - Japão - Coreia do sul"
18/06/2021 - O que é o passaporte da vacina que Bolsonaro quer vetar? https://noticias.uol.com.br/politica/ultimas-noticias/2021/06/18/uol-explica-o-que-e-o-passaporte-da-vacina-que-opoe-bolsonaro-e-damares.htm
"O Brasil poderá ter um certificado de imunização futuramente. Aprovado no Senado na semana passada, o "passaporte da vacina", como é chamado, prevê identificar pessoas vacinadas para que entrem em locais públicos ou privados com possíveis restrições."
6. Vacinas
Alegações:
- CoronaVac, Oxford e Pfizer: veja diferenças entre as vacinas contra covid noticias.uol.com.br/saude/ultimas-noticias/redacao/2021/05/11/diferencas-vacinas-covid-brasil.htm
"CoronaVac (Butantan/Sinovac - Chinesa) Com virus inativo 50,38% de eficácia 2 doses
Covishield - 'AstraZeneca' (Fiocruz/Astrazenica/Oxford - Britânica) Com virus não replicante 67% de eficácia 2 doses
ComiRNAty - 'Pfizer' (Pfizer - Americana / BioNTech - Alemã) Com RNA mensageiro 96% de eficácia 2 doses"
Riscos diretos
15/06/2021 - Trombose após vacinação com AstraZeneca: Quais os sintomas e como se deve atuar? https://www.istoedinheiro.com.br/trombose-apos-vacinacao-com-astrazeneca-quais-os-sintomas-e-como-se-deve-atuar/
"Agências europeias estão reticentes com a vacina da AstraZeneca. Ela chegou a ser desaconselhada a pessoas com idade inferior a 60 anos, e um alto funcionário da Agência Europeia de Medicamentos declarou que era melhor deixar de administrar a vacina deste laboratório em qualquer idade quando há alternativas disponíveis, devido aos relatos de trombose após a primeira dose, apesar de raros."
11/05/2021 - CoronaVac, Oxford e Pfizer: veja diferenças entre as vacinas contra covid https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2021/05/11/diferencas-vacinas-covid-brasil.htm
"Na terça-feira (12), o Ministério da Saúde determinou a suspensão da aplicação da vacina de Oxford/AstraZeneca para gestantes e puérperas com comorbidades. A decisão segue recomendação da Anvisa, que apura a morte de uma grávida de 35 anos que tomou o imunizante e teve um AVC (acidente vascular cerebral)."
30/07/2021 - Pfizer representa o mesmo risco de trombose que a Astrazeneca, aponta levantamento https://panoramafarmaceutico.com.br/pfizer-representa-o-mesmo-risco-de-trombose-que-a-astrazeneca-aponta-levantamento/
7. CRIMES
Crimes da Pfizer
18/11/2020 Não listado no google - Os Crimes documentados da produtora de vacinas de Covid - Pfizer [INGLÊS] https://www.dmlawfirm.com/crimes-of-covid-vaccine-maker-pfizer-well-documented/
"A velocidade com que a vacina Covid da Pfizer foi produzida, a ausência de estudos em animais, testes de controle randomizados e outros testes e procedimentos padrão usuais para um novo medicamento são, no mínimo, preocupantes. Além disso, todos os fabricantes de vacinas Covid receberam imunidade legal para quaisquer ferimentos ou mortes que possam causar. Se essas vacinas são tão seguras quanto promovidas, por que seus fabricantes precisam de imunidade geral?"
"A Pfizer, uma empresa farmacêutica que parece ter ganhado na loteria para produzir a primeira vacina Covid-19, está atualmente lutando contra centenas de ações judiciais sobre o Zantac, um popular medicamento contra azia. Os processos da Zantac afirmam que a droga popular pode estar contaminada com uma substância cancerígena chamada N-nitrosodimetilamina (NDMA). Os processos Zantac são em aberto e em andamento, já que a farmacêutica está lutando contra eles; mas a Pfizer, sabemos, cometeu vários crimes ou transgressões pelos quais foi punida nos últimos anos. As falhas da empresa estão bem documentadas e vale a pena revisá-las neste momento crítico da história da humanidade, enquanto todos nós buscamos respostas."
A Pfizer recebeu a maior multa da história dos Estados Unidos como parte de um acordo judicial de US $ 2,3 bilhões com promotores federais por promover medicamentos erroneamente (Bextra, Celebrex) e pagar propinas a médicos complacentes. A Pfizer se confessou culpada de falsificar a marca do analgésico Bextra, promovendo o medicamento para usos para os quais não foi aprovado.
Na década de 1990, a Pfizer estava envolvida em válvulas cardíacas defeituosas que causaram a morte de mais de 100 pessoas. A Pfizer enganou deliberadamente os reguladores sobre os perigos. A empresa concordou em pagar US $ 10,75 milhões para acertar as acusações do departamento de justiça por enganar reguladores.
A Pfizer pagou mais de US $ 60 milhões para resolver um processo sobre o Rezulin, um medicamento para diabetes que causou a morte de pacientes de insuficiência hepática aguda.
No Reino Unido, a Pfizer foi multada em quase € 90 milhões por sobrecarregar o NHS, o Serviço Nacional de Saúde. A Pfizer cobrou do contribuinte um adicional de € 48 milhões por ano, pelo que deveria custar € 2 milhões por ano.
A Pfizer concordou em pagar US $ 430 milhões em 2004 para resolver acusações criminais de que havia subornado médicos para prescrever seu medicamento para epilepsia Neurontin para indicações para as quais não foi aprovado. Em 2011, um júri concluiu que a Pfizer cometeu fraude em sua comercialização do medicamento Neurontin. A Pfizer concordou em pagar $ 142,1 milhões para liquidar as despesas.
A Pfizer revelou que pagou quase 4.500 médicos e outros profissionais médicos cerca de US $ 20 milhões por falar em nome da Pfizer.
Em 2012, a Comissão de Valores Mobiliários dos Estados Unidos - anunciou que havia chegado a um acordo de US $ 45 milhões com a Pfizer para resolver acusações de que suas subsidiárias haviam subornado médicos e outros profissionais de saúde no exterior para aumentar as vendas no exterior.
A Pfizer foi processada em um tribunal federal dos Estados Unidos por usar crianças nigerianas como cobaias humanas, sem o consentimento dos pais das crianças. A Pfizer pagou US $ 75 milhões para entrar em acordo no tribunal nigeriano pelo uso de um antibiótico experimental, o Trovan, nas crianças. A empresa pagou um valor adicional não divulgado nos Estados Unidos para liquidar as despesas aqui. A Pfizer violou o direito internacional, incluindo a Convenção de Nuremberg estabelecida após a Segunda Guerra Mundial, devido aos experimentos nazistas em prisioneiros relutantes.
Em meio a críticas generalizadas de roubar os países pobres em busca de drogas, a Pfizer prometeu dar US $ 50 milhões para um medicamento para a AIDS para a África do Sul. Mais tarde, no entanto, a Pfizer falhou em honrar essa promessa.
- Pfizer contract leaked!
[Contrato da Pfizer vazado]
 http://sanjeev.sabhlokcity.com/Misc/LEXO-KONTRATEN-E-PLOTE.pdf
http://sanjeev.sabhlokcity.com/Misc/LEXO-KONTRATEN-E-PLOTE.pdf
Segundo o contrato "o produto não deve ser serializado":
"5.5 Reconhecimento do comprador.
O Comprador reconhece que a Vacina e os materiais relacionados à Vacina, e seus componentes e materiais constituintes estão sendo desenvolvidos rapidamente devido às circunstâncias de emergência da pandemia de COVID-19 e continuarão a ser estudados após o fornecimento da Vacina ao Comprador nos termos deste Contrato. O Comprador reconhece ainda que os efeitos de longo prazo e eficácia da Vacina não são atualmente conhecidos e que pode haver efeitos adversos da Vacina que não são atualmente conhecidos. Além disso, na medida do aplicável, o Comprador reconhece que o Produto não deve ser serializado."
Crimes da AstraZeneca
21/06/2003 - AstraZeneca se declara culpada no esquema de médico de câncer https://www.nytimes.com/2003/06/21/business/astrazeneca-pleads-guilty-in-cancer-medicine-scheme.html
"A AstraZeneca, a grande empresa farmacêutica, se declarou culpada hoje de uma acusação de crime de fraude no sistema de saúde e concordou em pagar $ 355 milhões para resolver as acusações criminais e civis de que se envolveu em um esquema nacional para comercializar ilegalmente um medicamento contra o câncer de próstata.
O governo disse que os funcionários da empresa deram incentivos financeiros ilegais a cerca de 400 médicos em todo o país para persuadi-los a prescrever o medicamento Zoladex. Esses incentivos incluíram milhares de amostras grátis de Zoladex [...]"
27/04/2010 - Farmacêutica gigante AstraZeneca pagará US $ 520 milhões pelo marketing de medicamentos off-label https://www.justice.gov/opa/pr/pharmaceutical-giant-astrazeneca-pay-520-million-label-drug-marketing
"AstraZeneca LP e AstraZeneca Pharmaceuticals LP vão pagar $ 520 milhões para resolver as alegações de que a AstraZeneca comercializou ilegalmente o medicamento antipsicótico Seroquel para usos não aprovados como seguros e eficazes pela Food and Drug Administration (FDA), os Departamentos de Justiça e Saúde e Serviços Humanos A Equipe de Ação de Fiscalização de Fraudes em Saúde (HEAT) anunciou hoje. Esses usos não aprovados também são conhecidos como usos "off-label" porque não estão incluídos no rótulo do medicamento aprovado pela FDA."
- List of largest pharmaceutical settlements [Lista dos maiores acordos farmaceuticos] https://en.m.wikipedia.org/wiki/List_of_largest_pharmaceutical_settlements
8. CIENTISTAS
Dr. Kary Mullis - Criador do teste PCR
- PCR nas palavras do seu inventor - Dr. Kary Mullis (legendado) https://www.youtube.com/watch?v=W1O52uTygk8
"Qualquer um pode testar positivo para quase qualquer coisa com um teste de PCR, se você executá-lo por tempo suficiente… Com PCR, se voce fizer isso bem, você pode encontrar quase tudo em qualquer pessoa… Isso não te diz que você está doente."
- Kary Mullis DESTRUYE a Anthony Fauci lbry://@CapitalistChile#0/Kary-Mullis---Fauci#5
"Ele [...] não entende de medicina e não deveria estar onde está. A maioria dos que estão acima são só administrativos e não têm nem ideia do que ocorre aqui em baixo e essas pessoas tem uma agenda que não é a que gostaríamos que tivessem, dado que somos nós os que pagamos a eles para que cuidem da nossa saúde. Têm uma agenda pessoal."
-
Dra. Li-Meng Yan: O vírus foi criado em laboratório com um objetivo: Causar dano. https://youtu.be/pSXp3CZnvOc
-
Cientista Phd Dr Joe Roseman faz seríssimas advertencias sobre a picada https://youtu.be/0PIXVFqJ_h8
-
As vacinas podem estar causando ADE - Dr. Robert Malone https://odysee.com/@AkashaComunidad:f/Las_vacunas_pueden_estar_causando_ADE_magnificaci%C3%B3n_mediada_por:f lbry://@Información.#b/Drrm#9
Dr. Robert Malone, um dos três inventores da tecnologia de RNAm que se usa de forma farmacêutica. No vídeo fala sobre os efeitos de ADE (realce dependente de anticorpos) que estão ocorrendo com as vacinas. Nas palavras do Dr. Malone, já não é somente uma hipótese, mas baseada nos conhecimentos gerados nas provas e ensaios pré clínicos, com as vacinas contra o primeiro vírus da SARS.
-
Dr. Luc Montagnier, virologista, prêmio Nobel de medicina, um dos descobridores do vírus HIV, afirma: "a vacinação em massa está criando as novas variantes' (@medicospelavida , telegram)
-
USAR ou NÃO USAR a CUECA do seu governador no rosto https://fb.watch/7NPP_7rS5S/ https://www.facebook.com/AdoniasSoaresBR/videos/1347904292291481/ Adonias Soares entrevista ao Dr. Paulo Sato sobre as máscaras, em que é simulado o efeito da respiração prolongada das máscaras no organismo com o uso de águas de torneira, natural, gaseificada (com gás carbônico) e antioxidante, em que a com gás carbônico (PH 4 - Ácido) representa o organismo humano, e na prática representa lesão corporal e iniciação de doenças.
13 de setembro de 2021 - 13/09/2021 - Carta aberta ao Ministro da Saúde por Arlene Ferrari Graf, mãe de Bruno Oscar Graf https://telegra.ph/Carta-aberta-ao-Ministro-da-Sa%C3%BAde-09-13
Também em: Gazeta do Povo
O texto de uma mãe discorrendo sobre o filho dela, Bruno Oscar Graf, ter ANTI-HEPARINA PF4 AUTO-IMUNE e ter vindo a falecer por reação à vacina.
11/05/2021 - Rio notifica morte de grávida vacinada com imunizante Oxford https://www.terra.com.br/noticias/coronavirus/rio-notifica-morte-de-gravida-vacinada-com-imunizante-oxford,415b9b0c49169427ac2f90ae3765c057e9suy3qn.html
"Vítima não apresentava histórico de doença circulatória nem sofria de nenhuma doença viral; relação será investigada"
13/08/2021 - Cruzeiro com 4.336 pessoas tem 27 contaminados com Covid-19 em Belize https://paranaportal.uol.com.br/geral/cruzeiro-com-4-336-pessoas-tem-27-contaminados-com-covid-19-em-belize/amp/
"Segundo um comunicado do Conselho de Turismo de Belize emitido na quarta-feira (11), 26 contaminados são da tripulação e um é passageiro. A maioria é assintomática e os 27 estão vacinados."
Setembro de 2021 - 09/2021 - BOMBA: Ex-membro do Partido Comunista da China revela que o primeiro surto da Covid foi “intencional” https://terrabrasilnoticias.com/2021/09/bomba-ex-membro-do-partido-comunista-da-china-revela-que-o-primeiro-surto-da-covid-foi-intencional/
- Máscara Provoca Insuficiência Respiratória E Contaminação Microbiana… [Canal deletado] https://youtube.com/watch?v=eHu-pydSvDI
-
-
 @ 90c656ff:9383fd4e
2025-06-05 12:27:43
@ 90c656ff:9383fd4e
2025-06-05 12:27:43When people talk about Bitcoin, it’s often described as a digital currency or a “speculative investment.” However, one of Bitcoin’s most fundamental and least understood roles is its function as a settlement network. To understand this, it’s worth comparing it with traditional settlement systems like SWIFT and exploring how Bitcoin offers a foundational layer for global value transfer decentralized and censorship-resistant.
First, let’s explain the difference between liquidity and settlement:
-
Liquidity refers to the ease with which an asset can be converted into “money” without losing value.
-
Settlement is the process of completing a transaction (actual transfer of value between parties).
SWIFT: The communication layer of the traditional financial system
The SWIFT system (Society for Worldwide Interbank Financial Telecommunication) is a network for communication between banks. It doesn’t move money directly but sends standardized messages that instruct financial institutions to perform transfers. The process involves multiple intermediaries, is costly, slow (can take days), and depends on trust between parties and local regulations.
Unlike SWIFT, Bitcoin is a self-sufficient network that enables the direct settlement of value between two parties, without the need for intermediaries. With each block mined, transactions are validated and recorded immutably in a global, transparent, and secure database: the timechain or "blockchain".
01 - Final settlement: Once a transaction is confirmed by a sufficient number of blocks, it is considered final and irreversible.
02 - Censorship resistance: There is no central entity that can block or reverse a valid transaction.
03 - Global availability: The network is accessible 24/7 anywhere in the world with internet access.
Just as gold once served as the foundation of monetary systems, Bitcoin is establishing itself as a base layer of digital value. This layer can support others, such as:
01 - The Lightning Network, which enables near-instant transactions with extremely low fees;
02 - Tokenized financial services, which can use Bitcoin as collateral or for inter-institutional settlement.
By functioning as a public and neutral settlement network, Bitcoin offers an alternative to the traditional system, which is fragmented, closed, and reliant on trust between institutions.
In summary, more than just a speculative asset, Bitcoin is emerging as a global financial infrastructure. As a settlement network, it removes intermediaries, reduces costs, increases security, and democratizes access to value transfer. In an increasingly interconnected and digital world, understanding Bitcoin’s role as a base layer may be key to understanding the future of money.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
-
 @ 20e7c953:3b8bcb21
2025-06-05 10:46:07
@ 20e7c953:3b8bcb21
2025-06-05 10:46:0721… That number means something. A reminder that limits create value - both in Bitcoin and in life.
Every June 21st, skaters around the world remind us that freedom is something you make yourself - one push at a time only constrained by your own limitations.
This year in Vientiane, we’re proud to support one of the few real skate spots in Laos. A place built and held together by skaters for skaters.
Expect around 50 locals - from young kids to older heads - showing up not just to skate, but to hold space for each other. No ego, no filters, just boards, fun and respect.
Bircoiners have lots to learn from these communities on this regard. Go skate and you'll find out.

SnF
Laostr
Skateboardingisfun
Skate4Fun
Skatestr
-
 @ c1e9ab3a:9cb56b43
2025-06-01 13:54:06
@ c1e9ab3a:9cb56b43
2025-06-01 13:54:061. Introduction
Over the last 250 years the world’s appetite for energy has soared along an unmistakably exponential trajectory, transforming societies and economies alike. After a half‑century of relative deceleration, a new mix of technological, demographic and political forces now hints at an impending catch‑up phase that could push demand back onto its centuries‑long growth curve. This post knits together the history, the numbers and the newest policy signals to explore what that rebound might look like—and how Gen‑4 nuclear power could meet it.
2. The Long Exponential: 1750 – 1975
Early industrialisation replaced muscle, wood and water with coal‑fired steam, pushing global primary energy use from a few exajoules per year in 1750 to roughly 60 EJ by 1900 and 250 EJ by 1975. Over that span aggregate consumption doubled roughly every 25–35 years, equivalent to a long‑run compound growth rate of ~3 % yr‑¹. Per‑capita use climbed even faster in industrialised economies as factories, railways and electric lighting spread.
3. 1975 – 2025: The Great Slowdown
3.1 Efficiency & Structural Change
• Oil shocks (1973, 1979) and volatile prices pushed OECD economies to squeeze more GDP from each joule.
• Services displaced heavy industry in rich countries, trimming energy intensity.
• Refrigerators, motors and vehicles became dramatically more efficient.3.2 Policy & Technology
• The Inflation Reduction Act (U.S.) now layers zero‑emission production credits and technology‑neutral tax incentives on top of existing nuclear PTCs citeturn1search0turn1search2.
• The EU’s Net‑Zero Industry Act aims to streamline siting and finance for “net‑zero technologies”, explicitly naming advanced nuclear citeturn0search1.3.3 Result
Global primary energy in 2024 stands near 600 EJ (≈ 167 000 TWh)—still growing, but the line has flattened versus the pre‑1975 exponential.
4. Population & Per‑Capita Demand
World population tripled between 1950 and today, yet total energy use grew roughly six‑fold. The imbalance reflects rising living standards and electrification. Looking ahead, the UN projects population to plateau near 10.4 billion in the 2080s, but per‑capita demand is poised to climb as the Global South industrialises.
5. The Policy Pivot of 2023‑2025
| Region | Signal | Year | Implication | |--------|--------|------|-------------| | COP 28 Declaration | 20+ nations pledge to triple nuclear capacity by 2050 | 2023 | High‑level political cover for rapid nuclear build‑out citeturn0search2 | | Europe | Post‑crisis sentiment shifts; blackout in Iberia re‑opens nuclear debate | 2025 | Spain, Germany, Switzerland and others revisit phase‑outs citeturn0news63 | | United States | TVA submits first SMR construction permit; NRC advances BWRX‑300 review | 2025 | Regulatory pathway for fleet deployment citeturn1search9turn1search1 | | Global Strategy Report | “Six Dimensions for Success” playbook for new nuclear entrants | 2025 | Practical roadmap for emerging economies citeturn0search0 | | U.S. Congress | Proposed cuts to DOE loan office threaten build‑out pace | 2025 | Finance bottleneck remains a risk citeturn1news28 |
6. The Catch‑Up Scenario
Suppose the recent 50‑year pause ends in 2025, and total energy demand returns to a midpoint historical doubling period of 12.5 years (the average of the 10–15 year rebound window).
6.1 Consumption Trajectory
| Year | Doublings since 2024 | Demand (TWh) | |------|----------------------|--------------| | 2024 | 0 | 167 000 | | 2037 | 1 | 334 000 | | 2050 | 2 | 668 000 | | 2062 | 3 | 1 336 000 |
(Table ignores efficiency gains from electrification for a conservative, supply‑side sizing.)
7. Nuclear‑Only Supply Model
7.1 Reactor Math
- 1 GWᵉ Gen‑4 reactor → 8.76 TWh yr‑¹ at 100 % capacity factor.
- 2062 requirement: 1 336 000 TWh yr‑¹ → ≈ 152 500 reactors in steady state.
- Build rate (2025‑2062, linear deployment):
152 500 ÷ 38 years ≈ 4 000 reactors per year globally.
(Down from the earlier 5 000 yr‑¹ estimate because the deployment window now stretches 38 years instead of 30.)
7.2 Policy Benchmarks
- COP 28 triple target translates to +780 GW (if baseline 2020 ≈ 390 GW). That is <100 1 GW units per year—two orders of magnitude lower than the theoretical catch‑up requirement, highlighting just how aggressive our thought experiment is.
7.3 Distributed vs Grid‑Centric
Small Modular Reactors (300 MW class) can be sited on retiring coal plants, using existing grid interconnects and cooling, vastly reducing new transmission needs. Ultra‑large “gigawatt corridors” become optional rather than mandatory, though meshed regional grids still improve resilience and market liquidity.
8. Challenges & Unknowns
- Finance: Even with IRA‑style credits, first‑of‑a‑kind Gen‑4 builds carry high cost of capital.
- Supply Chain: 4 000 reactors a year means a reactor‑grade steel output roughly 20× today’s level.
- Waste & Public Trust: Advanced reactors can burn actinides, but geologic repositories remain essential.
- Workforce: Nuclear engineers, welders and regulators are already in short supply.
- Competing Technologies: Cheap renewables + storage and prospective fusion could displace part of the projected load.
9. Conclusions
Recent policy shifts—from Europe’s Net‑Zero Industry Act to the COP 28 nuclear declaration—signal that governments once again see nuclear energy as indispensable to deep decarbonisation. Yet meeting an exponential catch‑up in demand would require deployment rates an order of magnitude beyond today’s commitments, testing manufacturing capacity, finance and political resolve.
Whether the future follows the modest path now embedded in policy or the steeper curve sketched here, two convictions stand out:
- Electrification will dominate new energy demand.
- Scalable, dispatchable low‑carbon generation—likely including large fleets of Gen‑4 fission plants—must fill much of that gap if net‑zero targets are to remain credible.
Last updated 1 June 2025.
-
 @ 812cff5a:5c40aeeb
2025-06-05 12:55:10
@ 812cff5a:5c40aeeb
2025-06-05 12:55:10Chorus: تجربة في البرمجة الانسداحية
كيفية بناء تطبيق Nostr بسرعة البرق باستخدام الذكاء الاصطناعي.
في 26 مايو، تم إطلاق تطبيق Chorus في منتدى أوسلو للحرية. صُمم هذا التطبيق للناشطين والمعارضين ومنظمي المجتمع، ويتميز بمجموعات تشبه تلك الموجودة في فيسبوك مع محفظة eCash مدمجة لجمع التبرعات.
Chorus مبني على Nostr، وهو بروتوكول لامركزي ومفتوح مصمم ليكون مقاومًا للرقابة. يمكن لأي شخص في العالم إنشاء حساب Nostr والنشر إلى خوادم Nostr، أو حتى بناء تطبيق Nostr خاص به — ولا يمكن لأحد إيقافه. هذا ما يجعل Nostr المكان المثالي للمقاتلين من أجل الحرية، الذين غالبًا ما يواجهون الرقابة من الحكومات الاستبدادية أو الشركات التي تتحكم في المنصات الاجتماعية الرئيسية.
يمكن للمستخدمين إنشاء حساب Chorus (أو تسجيل الدخول باستخدام حساب Nostr موجود) في ثوانٍ والبدء فورًا في استلام eCash، وإنشاء مجموعات، ومشاركة المحتوى. يتضمن التطبيق ميزات قوية لإدارة المجتمع، بحيث يمكن للمجموعات اختيار أنواع المحتوى التي تسمح بها وفقًا لشروطها الخاصة. يمكن للمستخدمين إرسال eCash على الفور إلى المجموعات التي يرغبون في دعمها، مما يوفر أداة لجمع التبرعات عبر الحدود لا يمكن لأي حكومة إيقافها.
قبل عام فقط، ربما استغرق بناء النسخة التي تم إطلاقها الأسبوع الماضي من Chorus أسابيع. ولكن بفضل أدوات الذكاء الاصطناعي الحالية، قمنا بذلك في خمسة أيام فقط.
⸻
كيفية القيام بذلك: بناء تطبيق في أيام باستخدام وكلاء الذكاء الاصطناعي
الخطوة 1: تجميع الفريق
تم بناء Chorus بواسطة And Other Stuff، وهي مجموعة جديدة مكرسة لتعزيز Nostr في خمسة مجالات رئيسية: تجربة المستخدم والتسجيل، المجتمعات، الاتصالات الخاصة، التجارة، والذكاء الاصطناعي. شمل فريق هذا المشروع: • Calle، منشئ Cashu (eCash) • JeffG، منشئ White Noise (الاتصالات الخاصة) • Rabble و Liz Swiegart من Nos (تجربة المستخدم والتسجيل) • Alex Gleason و MK Fain، منشئو Soapbox (المجتمعات) • و Jack Dorsey (مستشار)
الخطوة 2: البدء بقالب قوي
عند البرمجة بالانسداح، السياق هو الملك. إذا بدأت بمجلد فارغ وطلبت من وكيل ذكاء اصطناعي “بناء تطبيق مجموعات Nostr”، فلا يزال أمامك الكثير من العمل للحصول على شيء وظيفي حتى بشكل بسيط. من المحتمل أن تكون تنفيذات Nostr محاكاة، لا تتصل بخوادم حقيقية، أو تم تنفيذها بشكل غير صحيح. قد تكون أنواع الأحداث خاطئة، وقد لا يتم تحميل واجهة المستخدم، وحظًا سعيدًا في محاولة معرفة الخطوة التالية لإصلاح الفوضى.
هذا لأن الذكاء الاصطناعي يفتقر إلى بعض السياقات الرئيسية للبدء: • وثائق صديقة للذكاء الاصطناعي حول بروتوكول Nostr • أمثلة عالية الجودة على تنفيذ Nostr • أساسيات حول تكديس التكنولوجيا المفضل • سياق حول كيفية بناء المشروع وتشغيله وتصحيحه
الحل هو توفير المزيد من السياق، وسيكون العديد من مبرمجي الانسداح المخضرمين على دراية بالصراع في محاولة جعل الوكيل يقرأ روابط مختلفة للوثائق ويتبع 500 كلمة من السياق المصاغ بعناية في مطالبتهم الافتتاحية. ومع ذلك، غالبًا ما يربك هذا الوكلاء الذين يعملون بشكل أفضل مع مطالبات بسيطة. الحل لهذه المشكلة هو Stacks.
Stacks: بدء البرمجة الانسداحية بسرعة
Stacks تحل مشكلة نقص السياق الأولي من خلال إنشاء قوالب جاهزة مصممة خصيصًا لاستخدام وكلاء الذكاء الاصطناعي. يمكن استخدام “stack” لبناء أي نوع من المشاريع بأي لغة برمجة مع أي هدف نهائي في الاعتبار. بالنسبة لـ Chorus، استخدمنا MKStack، وهو قالب مصمم خصيصًا لبناء تطبيقات Nostr.
يتميز MKStack بعدة حلول للمشاكل الشائعة في الذكاء الاصطناعي: • Nostrbook MCP للاستعلام عن وثائق Nostr • مكونات بداية لميزات Nostr الشائعة مثل تسجيل الدخول • دعم Blossom لتحميل الوسائط • ملفات سياقية لتوجيه الوكيل خلال العقبات الشائعة وسير عمل التصحيح • نشر موقعك على الفور باستخدام Surge
النتيجة هي موقع جميل يعمل مباشرة مع Nostr في مطالبة واحدة:
“بناء تطبيق مجموعات على غرار فيسبوك على Nostr باستخدام NIP 72.”
كان هذا هو نتيجة تلك المطالبة الواحدة: http://groups72.surge.sh
الخطوة 3: إضافة الميزات باستخدام وكلاء الذكاء الاصطناعي
Stacks بدأت تطوير Chorus بسرعة. بعد ذلك، استخدمنا وكلاء الذكاء الاصطناعي لإضافة ميزات إضافية مثل: • محفظة eCash مدمجة • ميزات إدارة المجتمع • دعم الوسائط المتعددة
كل ذلك تم باستخدام مطالبات بسيطة وتوجيهات للذكاء الاصطناعي، مما سمح لنا ببناء تطبيق كامل الوظائف في أيام قليلة فقط.
⸻
ملاحظة:تم استخدام مصطلح برمجة الانسداحية بهدف الطرفة كترجمة لمصطلح Vibe coding تم كتابة هذه المقال من قبل المبدعة nostr: npub1jvnpg4c6ljadf5t6ry0w9q0rnm4mksde87kglkrc993z46c39axsgq89sc
-
 @ 31a4605e:cf043959
2025-06-05 12:49:36
@ 31a4605e:cf043959
2025-06-05 12:49:36O surgimento do Bitcoin trouxe uma nova visão para o conceito de dinheiro, desafiando o sistema financeiro convencional baseado em moedas fiduciárias. Enquanto as moedas fiduciárias, como o real, o dólar e o euro, são amplamente usadas e reconhecidas como métodos de troca, o Bitcoin representa uma inovação digital que propõe descentralização e autonomia financeira. Embora ambos desempenhem funções básicas como meio de troca e reserva de valor, suas diferenças principais estão na maneira como são emitidos, geridos e transacionados.
Uma das principais distinções entre o Bitcoin e as moedas fiduciárias é a maneira como são emitidos e administrados. As moedas fiduciárias são emitidas por bancos centrais, que têm o poder de regular sua quantidade em circulação. Esse modelo permite a aplicação de políticas monetárias, como o aumento da oferta de dinheiro para estimular a economia ou a diminuição para controlar a inflação. No entanto, essa capacidade também pode resultar na desvalorização da moeda, se for emitida em excesso.
O Bitcoin, por outro lado, tem um sistema de emissão totalmente descentralizado. Ele é criado por meio de um processo chamado mineração, no qual computadores resolvem problemas matemáticos complexos para validar transações na rede. Além disso, a oferta total de bitcoins é limitada a 21 milhões de unidades, tornando-o um ativo deflacionário, ou seja, sua escassez pode aumentar seu valor ao longo do tempo. Essa limitação contrasta fortemente com a natureza ilimitada da impressão de moedas fiduciárias.
Moedas fiduciárias são centralizadas, o que significa que sua emissão e controle são decididos por autoridades governamentais. Isso também implica que transações feitas com essas moedas passam por intermediários, como bancos, que podem aplicar taxas e limites, além de estarem sujeitos a regulamentações e auditorias.
O Bitcoin, por sua vez, é descentralizado. Ele opera em uma rede peer-to-peer, onde as transações são verificadas por participantes chamados mineradores e registradas em um livro público conhecido como blockchain. Essa descentralização elimina a necessidade de intermediários, tornando o Bitcoin mais resistente à censura e ao controle governamental. Isso também proporciona maior transparência, já que qualquer pessoa pode verificar as transações na rede.
Outra diferença importante está na maneira como as transações são feitas. Com moedas fiduciárias, as transações geralmente dependem de bancos ou sistemas de pagamento, que podem impor restrições de horários e taxas altas, especialmente para transferências internacionais.
O Bitcoin, por outro lado, permite transferências diretas entre pessoas, em qualquer lugar do mundo e a qualquer momento, sem a necessidade de intermediários. Isso torna o sistema mais acessível, especialmente para aqueles que não possuem contas bancárias ou vivem em países com sistemas financeiros restritivos. Além disso, as taxas de transação do Bitcoin podem ser menores do que as taxas cobradas por bancos tradicionais.
As moedas fiduciárias proporcionam segurança baseada em leis governamentais e no sistema bancário, mas os usuários precisam confiar nesses intermediários. O Bitcoin, em contrapartida, oferece um alto nível de segurança através de criptografia avançada. As carteiras digitais, que guardam bitcoins, são protegidas por chaves privadas, assegurando que somente o dono possa acessá-las.
No entanto, a privacidade funciona de maneira diferente. Transações em moedas fiduciárias normalmente estão ligadas à identidade do usuário, enquanto o Bitcoin oferece um certo nível de anonimato, já que os endereços das carteiras não requerem identificação pessoal. Ainda assim, todas as transações são públicas e registradas no blockchain, o que pode ser um ponto de monitoramento para autoridades.
O valor das moedas fiduciárias é sustentado pela confiança no governo que as emite e na economia do país. Por outro lado, o Bitcoin não é apoiado por nenhum governo ou ativo físico. Seu valor é definido pela oferta e demanda no mercado, fazendo com que seja altamente volátil. Embora essa volatilidade apresente um risco, também atrai pessoas que veem o Bitcoin como uma possibilidade de valorização a longo prazo.
Resumindo, o Bitcoin e as moedas fiduciárias diferem significativamente em sua estrutura, controle e funcionalidade. Enquanto as moedas fiduciárias são controladas por governos e dependem de intermediários, o Bitcoin oferece descentralização, transparência e liberdade financeira. Apesar de sua volatilidade e alguns desafios relacionados à regulamentação, o Bitcoin representa uma alternativa nova ao sistema financeiro tradicional.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 2dd9250b:6e928072
2025-05-31 16:12:55
@ 2dd9250b:6e928072
2025-05-31 16:12:55Durante a década de 1990, houve o aumento da globalização da economia, determinando a adição do fluxo internacional de capitais, de produtos e serviços. Este fenômeno levou a uma interdependência maior entre as economias dos países. Justamente por causa da possibilidade de que um eventual colapso econômico em um país resulte no contágio dos demais. Diante disso, aumentou a preocupação com os riscos incentivando a utilização de sofisticados modelos e estratégias de avaliação de gestão de risco.
Na década, ganharam destaque ainda os graves problemas financeiros enfrentados, entre outros, pelo banco inglês Barings Bank, e pelo fundo de investimento norte-americano Long Term Capital Management.
Outro grande destaque foi a fraude superior a US$ 7 bilhões sofrida pelo banco Société Generale em Janeiro de 2008.
O Barings Bank é um banco inglês que faliu em 1995 em razão de operações financeiras irregulares e mal-sucedidas realizadas pelo seu principal operador de mercado. O rombo da instituição foi superior à US$ 1,3 Bilhão e causado por uma aposta equivocada no desempenho futuro no índice de ações no Japão. Na realidade, o mercado acionário japonês caiu mais de 15% na época, determinando a falência do banco. O Baring Bank foi vendido a um grupo financeiro holandês (ING) pelo valor simbólico de uma libra esterlina.
O Long Term Capital Management era um fundo de investimento de que perdeu em 1998 mais de US$ 4,6 bilhões em operações nos mercados financeiros internacionais. O LTCM foi socorrido pelo Banco Central dos Estados Unidos (Federal Reserve ), que coordenou uma operação de socorro financeiro à instituição. A justificativa do Banco Central para esta decisão era "o receio das possíveis consequências mundiais da falência do fundo de investimento".
O banco francês Société Generale informou, em janeiro de 2008, uma perda de US$ 7,16 bilhões determinadas por fraudes efetuadas por um operador do mercado financeiro. Segundo revelou a instituição, o operador assumiu posições no mercado sem o conhecimento da direção do banco. A instituição teve que recorrer a uma urgente captação de recursos no mercado próxima a US$ 5,0 bilhões.
E finalmente chegamos ao caso mais problemático da era das finanças modernas anterior ao Bitcoin, o caso Lehman Brothers.
O Lehman Brothers era o 4° maior de investimentos dos EUA quando pediu concordata em 15/09/2008 com dívidas que superavam inacreditáveis US$ 600 bilhões.
Não se tinha contas correntes ou talão de cheques do Lehman Brothers. Era um banco especializado em investimentos e complexas operações financeiras. Havia feito pesados investimentos em empréstimos a juros fixos no famigerado mercado subprime, e o crédito imobiliário voltado a pessoas consideradas de forte risco de inadimplência.
Com essa carteira de investimentos que valia bem menos que o estimado e o acúmulo de projetos financeiros, minou a confiança dos investidores na instituição de 158 anos. Suas ações passaram de US$ 80 a menos de US$ 4. Acumulando fracassos nas negociações para levantar fundos; a instituição de cerca de 25 mil funcionários entrou em concordata.
O Federal Reserve resgatou algumas instituições financeiras grandes e tradicionais norte-americanas como a seguradora AIG no meio da crise. O Fed injetou um capital de US$ 182, 3 bilhões no American International Group (AIG).
Foi exatamente essa decisão do Fed em salvar alguns bancos e deixar quebrar outros, que causou insegurança por parte dos clientes. E os clientes ficaram insatisfeitos tanto com os bancos de investimentos quanto com as agências de classificação de risco, como a Standard & Poor's que tinha dado uma nota alta para o Lehman Brothers no mesmo dia em que ele quebrou.
E essa foi uma das razões pelo qual o Bitcoin foi criado. Satoshi Nakamoto entendeu que as pessoas não estavam mais confiando nem no Governo, nem nos Bancos Privados que o Governo federal restagatava quando eles quebravam e isso prejudicou muita gente. Tanto que o “hash” do Genesis Block contém o título do artigo “Chancellor on brink of second bailout for banks” (Chanceler à beira de segundo resgate para bancos, em português) da edição britânica do The Times.
-
 @ 3bf0c63f:aefa459d
2024-12-06 20:37:26
@ 3bf0c63f:aefa459d
2024-12-06 20:37:26início
"Vocês vêem? Vêem a história? Vêem alguma coisa? Me parece que estou tentando lhes contar um sonho -- fazendo uma tentativa inútil, porque nenhum relato de sonho pode transmitir a sensação de sonho, aquela mistura de absurdo, surpresa e espanto numa excitação de revolta tentando se impôr, aquela noção de ser tomado pelo incompreensível que é da própria essência dos sonhos..."
Ele ficou em silêncio por alguns instantes.
"... Não, é impossível; é impossível transmitir a sensação viva de qualquer época determinada de nossa existência -- aquela que constitui a sua verdade, o seu significado, a sua essência sutil e contundente. É impossível. Vivemos, como sonhamos -- sozinhos..."
- Livros mencionados por Olavo de Carvalho
- Antiga homepage Olavo de Carvalho
- Bitcoin explicado de um jeito correto e inteligível
- Reclamações
-
 @ 3bf0c63f:aefa459d
2024-10-31 16:08:50
@ 3bf0c63f:aefa459d
2024-10-31 16:08:50Anglicismos estúpidos no português contemporâneo
Palavras e expressões que ninguém deveria usar porque não têm o sentido que as pessoas acham que têm, são apenas aportuguesamentos de palavras inglesas que por nuances da história têm um sentido ligeiramente diferente em inglês.
Cada erro é acompanhado também de uma sugestão de como corrigi-lo.
Palavras que existem em português com sentido diferente
- submissão (de trabalhos): envio, apresentação
- disrupção: perturbação
- assumir: considerar, pressupor, presumir
- realizar: perceber
- endereçar: tratar de
- suporte (ao cliente): atendimento
- suportar (uma idéia, um projeto): apoiar, financiar
- suportar (uma função, recurso, característica): oferecer, ser compatível com
- literacia: instrução, alfabetização
- convoluto: complicado.
- acurácia: precisão.
- resiliência: resistência.
Aportuguesamentos desnecessários
- estartar: iniciar, começar
- treidar: negociar, especular
Expressões
- "não é sobre...": "não se trata de..."

Ver também
-
 @ 21335073:a244b1ad
2025-05-21 16:58:36
@ 21335073:a244b1ad
2025-05-21 16:58:36The other day, I had the privilege of sitting down with one of my favorite living artists. Our conversation was so captivating that I felt compelled to share it. I’m leaving his name out for privacy.
Since our last meeting, I’d watched a documentary about his life, one he’d helped create. I told him how much I admired his openness in it. There’s something strange about knowing intimate details of someone’s life when they know so little about yours—it’s almost like I knew him too well for the kind of relationship we have.
He paused, then said quietly, with a shy grin, that watching the documentary made him realize how “odd and eccentric” he is. I laughed and told him he’s probably the sanest person I know. Because he’s lived fully, chasing love, passion, and purpose with hardly any regrets. He’s truly lived.
Today, I turn 44, and I’ll admit I’m a bit eccentric myself. I think I came into the world this way. I’ve made mistakes along the way, but I carry few regrets. Every misstep taught me something. And as I age, I’m not interested in blending in with the world—I’ll probably just lean further into my own brand of “weird.” I want to live life to the brim. The older I get, the more I see that the “normal” folks often seem less grounded than the eccentric artists who dare to live boldly. Life’s too short to just exist, actually live.
I’m not saying to be strange just for the sake of it. But I’ve seen what the crowd celebrates, and I’m not impressed. Forge your own path, even if it feels lonely or unpopular at times.
It’s easy to scroll through the news and feel discouraged. But actually, this is one of the most incredible times to be alive! I wake up every day grateful to be here, now. The future is bursting with possibility—I can feel it.
So, to my fellow weirdos on nostr: stay bold. Keep dreaming, keep pushing, no matter what’s trending. Stay wild enough to believe in a free internet for all. Freedom is radical—hold it tight. Live with the soul of an artist and the grit of a fighter. Thanks for inspiring me and so many others to keep hoping. Thank you all for making the last year of my life so special.
-
 @ 87fedb9f:0da83419
2025-06-05 12:15:33
@ 87fedb9f:0da83419
2025-06-05 12:15:33So Much… and Still, Not Feeling It
So much abundance. It’s everywhere—overflowing around me. My six-year-old car would be a magical carriage to kings and queens of old. And yet, I get in, turn the key, and don’t often Feel The Magic.
Do I let myself feel how abundant life is? Eh. That does not come by default for me.
Adapting Is Normal. Savoring Is Not.
I adapt. I’m good at it. Weather shifts 40 degrees? No problem. A new location? I’ll adjust. And that’s useful—it keeps me moving. But it also numbs me. If I only adapt, life flattens out. That’s not thriving. That’s functioning.
Thriving, I’ve come to feel, asks for something more.
Our ancestors had rituals. They didn’t just adapt… they paused to feel the blessings, to name them. That created richness—not just survival. And today? I can have food delivered to my door. Are you a king? No—just have Amazon Prime.
Still, I want more than convenience. I want connection. To the food I eat. The flowers that bloom. The people I love. I want to feel that connection in my bones.
My Engineer Brain Doesn’t Celebrate
And yet, my mind often slips into improvement mode. I see what could be better. Smoother. More efficient. Useful? Sure. Celebratory? Not so much.
So I’ve started something: at the end of each day, when I look at my to-do list, I take a breath. I ask: what were the blessings today? Not just the big ones—because we adapt to those too. A new car? A new house? We get used to it. Quickly. But the micro-blessings… those are different.
My daughter’s laugh at a silly face I made yesterday. That memory settles deeper when I notice it and write it down. That’s a micro-blessing. I want to feel more of those.
A New Practice, A Shift in Dreams
And after about 75 days of doing this nightly pause, I’m noticing something surprising: my dreams are changing. They’re weaving in those sweet, ordinary moments. They say, “Yes. Adapt. And also savor.”
The Confusion Between Privilege and Blessing
But here’s something raw. Something I’ve hesitated to share.
I’m a white man. An older one. And I’ve been in spaces where “white male privilege” is spoken as a curse. I absorbed that. My body did. And it twisted something deep inside me. Because in my system, “privileged” and “blessing” are linked.
So I started feeling that feeling blessed was wrong. Like I should shrink from it. That it was unfair, maybe even immoral.
I’ve had to tap through that.
Is it okay to feel blessed? Not above anyone—but blessed to have food. Skill. Mobility. A car that works. Is it okay?
Yes.
I Don’t Want to Shrink or Perform
Scarcity and guilt are real energies, but I don’t want them steering my experience of life. I want to choose presence. Connection. I want to know in my body: I am blessed. And I can feel that without disconnecting from those who are struggling.
I don’t want to perform gratitude out of duty. But I also don’t want to avoid it out of shame.
Practicing Our Birthright
Abundance is our birthright. Many of us are born with protections our ancestors could barely dream of—shelter, clean water, safety from predators. And if we want to truly be thriving, not just surviving, it feels essential to practice remembering that.
Because adaptation will keep us alive.
But only conscious attention to blessings—only savoring—will let us thrive.
Useful Concepts for Thriving in This Story
-
Abundance\ Abundance is the felt experience of more-than-enoughness, when we pause to really receive what surrounds and sustains us.
-
Adapting\ Adapting keeps us functional, but thriving asks us to adapt and engage with what truly nourishes us.
-
Awareness\ Awareness brings the blessings into view—even the ones so small they almost disappear without it.
-
Allowing\ Allowing lets us stay open to blessings, even when shame or guilt try to close the door.
-
Thriving\ Thriving means more than surviving—it’s about feeling, savoring, and aligning with life’s richness.
-
-
 @ 51bbb15e:b77a2290
2025-05-21 00:24:36
@ 51bbb15e:b77a2290
2025-05-21 00:24:36Yeah, I’m sure everything in the file is legit. 👍 Let’s review the guard witness testimony…Oh wait, they weren’t at their posts despite 24/7 survellience instructions after another Epstein “suicide” attempt two weeks earlier. Well, at least the video of the suicide is in the file? Oh wait, a techical glitch. Damn those coincidences!
At this point, the Trump administration has zero credibility with me on anything related to the Epstein case and his clients. I still suspect the administration is using the Epstein files as leverage to keep a lot of RINOs in line, whereas they’d be sabotaging his agenda at every turn otherwise. However, I just don’t believe in ends-justify-the-means thinking. It’s led almost all of DC to toss out every bit of the values they might once have had.
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 9ca447d2:fbf5a36d
2025-06-05 11:03:01
@ 9ca447d2:fbf5a36d
2025-06-05 11:03:01H100 Group AB, a Swedish publicly listed health technology company, has made the headlines after investing in bitcoin as part of a new financial strategy.
The move has caused a stir in Sweden and beyond, with H100’s stock price rising 40% after the announcement.
The company has bought 4.39 bitcoin for 5 million Norwegian Krone (around $475,000–$492,000).
This is the company’s first foray into the digital asset space and makes H100 Group the first publicly-listed health tech company in Sweden to hold bitcoin as a treasury reserve asset.
The bitcoin was bought at an average price of 1,138,737 NOK (around $108,000) per coin.
The bitcoin purchase is part of H100 Group’s new “Bitcoin Treasury Strategy” to diversify its financial assets and strengthen its balance sheet. Instead of holding idle cash, the company decided to invest in what it sees as a long-term asset.
“This addition to H100’s Bitcoin Treasury Strategy follows an increasing number of tech-oriented growth companies holding bitcoin on their balance sheet,” said CEO Sander Andersen.
“And I believe the values of individual sovereignty highly present in the Bitcoin community aligns well with, and will appeal to, the customers and communities we are building the H100 platform for.”
Andersen said they will “build and hold” bitcoin long-term, viewing it as a savings tool, not a short-term trade.
The market reacted fast. On May 22, the company’s stock went up 39.27%, seeing highs of 1.620 SEK on the Nordic Growth Market.
This helped the company to recover a big part of the losses from the last two months, during which the stock fell 46%.
And now, after the purchase, the firm’s market cap is around $150.46 million.
H100 has said this might not be the only purchase. The company has signed a Letter of Intent (LOI) to set up a convertible loan facility of up to 10 million SEK with an undisclosed investor.

H100 Group’s announcement — Source
The funds will be used for general corporate purposes and to potentially increase bitcoin holdings. The loan will have a 3-year term and can be converted into shares at 1.3 SEK per share.
If H100’s stock price is more than 33% above the conversion price for more than 60 days, H100 will have the right to force conversion.
The company also announced today that it has successfully raised 21 million SEK ($2.21 million) through a convertible round led by Blockstream founder and CEO Adam Back.
Despite the Bitcoin pivot, H100 Group has made it clear that the core business remains the same.
They will continue to develop AI-powered automation tools and digital platforms to help healthcare providers deliver better services, especially in the health and longevity space.
Andersen said they are committed to healthy living, and adopting a bitcoin strategy is a smarter financial move that aligns with their values.
H100’s move comes as corporate adoption of bitcoin accelerates globally.
According to BitcoinTreasuries over 109 public companies now list bitcoin on their balance sheets. Among those are companies like Twenty One Capital, Strive and Metaplanet.
-
 @ 3bf0c63f:aefa459d
2024-09-18 10:37:09
@ 3bf0c63f:aefa459d
2024-09-18 10:37:09How to do curation and businesses on Nostr
Suppose you want to start a Nostr business.
You might be tempted to make a closed platform that reuses Nostr identities and grabs (some) content from the external Nostr network, only to imprison it inside your thing -- and then you're going to run an amazing AI-powered algorithm on that content and "surface" only the best stuff and people will flock to your app.
This will be specially good if you're going after one of the many unexplored niches of Nostr in which reading immediately from people you know doesn't work as you generally want to discover new things from the outer world, such as:
- food recipe sharing;
- sharing of long articles about varying topics;
- markets for used goods;
- freelancer work and job offers;
- specific in-game lobbies and matchmaking;
- directories of accredited professionals;
- sharing of original music, drawings and other artistic creations;
- restaurant recommendations
- and so on.
But that is not the correct approach and damages the freedom and interoperability of Nostr, posing a centralization threat to the protocol. Even if it "works" and your business is incredibly successful it will just enshrine you as the head of a platform that controls users and thus is prone to all the bad things that happen to all these platforms. Your company will start to display ads and shape the public discourse, you'll need a big legal team, the FBI will talk to you, advertisers will play a big role and so on.
If you are interested in Nostr today that must be because you appreciate the fact that it is not owned by any companies, so it's safe to assume you don't want to be that company that owns it. So what should you do instead? Here's an idea in two steps:
- Write a Nostr client tailored to the niche you want to cover
If it's a music sharing thing, then the client will have a way to play the audio and so on; if it's a restaurant sharing it will have maps with the locations of the restaurants or whatever, you get the idea. Hopefully there will be a NIP or a NUD specifying how to create and interact with events relating to this niche, or you will write or contribute with the creation of one, because without interoperability this can't be Nostr.
The client should work independently of any special backend requirements and ideally be open-source. It should have a way for users to configure to which relays they want to connect to see "global" content -- i.e., they might want to connect to
wss://nostr.chrysalisrecords.com/to see only the latest music releases accredited by that label or towss://nostr.indiemusic.com/to get music from independent producers from that community.- Run a relay that does all the magic
This is where your value-adding capabilities come into play: if you have that magic sauce you should be able to apply it here. Your service -- let's call it
wss://magicsaucemusic.com/-- will charge people or do some KYM (know your music) validation or use some very advanced AI sorcery to filter out the spam and the garbage and display the best content to your users who will request the global feed from it (["REQ", "_", {}]), and this will cause people to want to publish to your relay while others will want to read from it.You set your relay as the default option in the client and let things happen. Your relay is like your "website" and people are free to connect to it or not. You don't own the network, you're just competing against other websites on a leveled playing field, so you're not responsible for it. Users get seamless browsing across multiple websites, unified identities, a unified interface (that could be different in a different client) and social interaction capabilities that work in the same way for all, and they do not depend on you, therefore they're more likely to trust you.
Does this centralize the network still? But this a simple and easy way to go about the matter and scales well in all aspects.
Besides allowing users to connect to specific relays for getting a feed of curated content, such clients should also do all kinds of "social" (i.e. following, commenting etc) activities (if they choose to do that) using the outbox model -- i.e. if I find a musician I like under
wss://magicsaucemusic.comand I decide to follow them I should keep getting updates from them even if they get banned from that relay and start publishing onwss://nos.lolorwss://relay.damus.ioor whatever relay that doesn't even know anything about music.The hardcoded defaults and manual typing of relay URLs can be annoying. But I think it works well at the current stage of Nostr development. Soon, though, we can create events that recommend other relays or share relay lists specific to each kind of activity so users can get in-app suggestions of relays their friends are using to get their music from and so on. That kind of stuff can go a long way.
-
 @ e4950c93:1b99eccd
2025-06-05 10:23:39
@ e4950c93:1b99eccd
2025-06-05 10:23:39Marques
Nordkidz est une marque allemande qui crée à la demande des vêtements et linges pour les bébés, les enfants, et un peu pour leurs parents.
Matières naturelles utilisées dans les produits
⚠️ Attention, certains produits de cette marque contiennent des matières non naturelles, dont :
Catégories de produits proposés
Cette marque propose des produits intégralement en matière naturelle dans les catégories suivantes :
Vêtements
- Tailles vêtements : bébés, enfants, unisexe
- Hauts : pulls, t-shirts
- Bas : pantalons, pantalons de survêtement, shorts
- Tête et mains : bonnets, écharpes
Maison
- Linge : housses de pouf, langes, ponchos de bain
Autres informations
👉 En savoir plus sur le site de la marque
Où trouver leurs produits ?
- Nordkidz (en allemand, zone de livraison : Allemagne et Union Européenne) 💚 Via ce lien vous soutenez directement la marque.
📝 Tu peux contribuer à cette fiche en suggérant une modification en commentaire.
🗣️ Tu utilises des produits de cette marque ? Partage ton avis en commentaire.
⚡ Heureu-x-se de trouver cette information ? Soutiens le projet en faisant un don pour remercier les contribut-eur-ice-s.
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ b1ddb4d7:471244e7
2025-06-05 10:00:43
@ b1ddb4d7:471244e7
2025-06-05 10:00:43Starting January 1, 2026, the United Kingdom will impose some of the world’s most stringent reporting requirements on cryptocurrency firms.
All platforms operating in or serving UK customers-domestic and foreign alike-must collect and disclose extensive personal and transactional data for every user, including individuals, companies, trusts, and charities.
This regulatory drive marks the UK’s formal adoption of the OECD’s Crypto-Asset Reporting Framework (CARF), a global initiative designed to bring crypto oversight in line with traditional banking and to curb tax evasion in the rapidly expanding digital asset sector.
What Will Be Reported?
Crypto firms must gather and submit the following for each transaction:
- User’s full legal name, home address, and taxpayer identification number
- Detailed data on every trade or transfer: type of cryptocurrency, amount, and nature of the transaction
- Identifying information for corporate, trust, and charitable clients
The obligation extends to all digital asset activities, including crypto-to-crypto and crypto-to-fiat trades, and applies to both UK residents and non-residents using UK-based platforms. The first annual reports covering 2026 activity are due by May 31, 2027.
Enforcement and Penalties
Non-compliance will carry stiff financial penalties, with fines of up to £300 per user account for inaccurate or missing data-a potentially enormous liability for large exchanges. The UK government has urged crypto firms to begin collecting this information immediately to ensure operational readiness.
Regulatory Context and Market Impact
This move is part of a broader UK strategy to position itself as a global fintech hub while clamping down on fraud and illicit finance. UK Chancellor Rachel Reeves has championed these measures, stating, “Britain is open for business – but closed to fraud, abuse, and instability”. The regulatory expansion comes amid a surge in crypto adoption: the UK’s Financial Conduct Authority reported that 12% of UK adults owned crypto in 2024, up from just 4% in 2021.
Enormous Risks for Consumers: Lessons from the Coinbase Data Breach
While the new framework aims to enhance transparency and protect consumers, it also dramatically increases the volume of sensitive personal data held by crypto firms-raising the stakes for cybersecurity.
The risks are underscored by the recent high-profile breach at Coinbase, one of the world’s largest exchanges.
In May 2025, Coinbase disclosed that cybercriminals, aided by bribed offshore contractors, accessed and exfiltrated customer data including names, addresses, government IDs, and partial bank details.
The attackers then used this information for sophisticated phishing campaigns, successfully deceiving some customers into surrendering account credentials and funds.
“While private encryption keys remained secure, sufficient customer information was exposed to enable sophisticated phishing attacks by criminals posing as Coinbase personnel.”
Coinbase now faces up to $400 million in compensation costs and has pledged to reimburse affected users, but the incident highlights the systemic vulnerability created when large troves of personal data are centralized-even if passwords and private keys are not directly compromised. The breach also triggered a notable drop in Coinbase’s share price and prompted a $20 million bounty for information leading to the attackers’ capture.
The Bottom Line
The UK’s forthcoming crypto reporting regime represents a landmark in financial regulation, promising greater transparency and tax compliance. However, as the Coinbase episode demonstrates, the aggregation of sensitive user data at scale poses a significant cybersecurity risk.
As regulators push for more oversight, the challenge will be ensuring that consumer protection does not become a double-edged sword-exposing users to new threats even as it seeks to shield them from old ones.
-
 @ 3bf0c63f:aefa459d
2024-06-19 16:13:28
@ 3bf0c63f:aefa459d
2024-06-19 16:13:28Estórias
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 3bf0c63f:aefa459d
2024-06-13 15:40:18
@ 3bf0c63f:aefa459d
2024-06-13 15:40:18Why relay hints are important
Recently Coracle has removed support for following relay hints in Nostr event references.
Supposedly Coracle is now relying only on public key hints and
kind:10002events to determine where to fetch events from a user. That is a catastrophic idea that destroys much of Nostr's flexibility for no gain at all.- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
kind:1s -- now that cannot work because the person who created the post doesn't have the relays specific to those communities in their outbox list; - There is a discussion happening in a niche relay, for example, a relay that can only be accessed by the participants of a conference for the duration of that conference -- since that relay is not in anyone's public outbox list, it's impossible for anyone outside of the conference to ever refer to these events;
- Some big public relays, say, relay.damus.io, decide to nuke their databases or periodically delete old events, a user keeps using that big relay as their outbox because it is fast and reliable, but chooses to archive their old events in a dedicated archival relay, say, cellar.nostr.wine, while prudently not including that in their outbox list because that would make no sense -- now it is impossible for anyone to refer to old notes from this user even though they are publicly accessible in cellar.nostr.wine;
- There are topical relays that curate content relating to niche (non-microblogging) topics, say, cooking recipes, and users choose to publish their recipes to these relays only -- but now they can't refer to these relays in the external Nostr world of
kind:1s because these topical relays are not in their outbox lists. - Suppose a user wants to maintain two different identities under the same keypair, say, one identity only talks about soccer in English, while the other only talks about art history in French, and the user very prudently keeps two different
kind:10002events in two different sets of "indexer" relays (or does it in some better way of announcing different relay sets) -- now one of this user's audiences cannot ever see notes created by him with their other persona, one half of the content of this user will be inacessible to the other half and vice-versa. - If for any reason a relay does not want to accept events of a certain kind a user may publish to other relays, and it would all work fine if the user referenced that externally-published event from a normal event, but now that externally-published event is not reachable because the external relay is not in the user's outbox list.
- If someone, say, Alex Jones, is hard-banned everywhere and cannot event broadcast
kind:10002events to any of the commonly used index relays, that person will now appear as banned in most clients: in an ideal world in which clients followednprofileand other relay hints Alex Jones could still live a normal Nostr life: he would print business cards with hisnprofileinstead of annpuband clients would immediately know from what relay to fetch his posts. When other users shared his posts or replied to it, they would include a relay hint to his personal relay and others would be able to see and then start following him on that relay directly -- now Alex Jones's events cannot be read by anyone that doesn't already know his relay.
- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
-
 @ 3bf0c63f:aefa459d
2024-05-24 12:31:40
@ 3bf0c63f:aefa459d
2024-05-24 12:31:40About Nostr, email and subscriptions
I check my emails like once or twice a week, always when I am looking for something specific in there.
Then I go there and I see a bunch of other stuff I had no idea I was missing. Even many things I wish I had seen before actually. And sometimes people just expect and assume I would have checked emails instantly as they arrived.
It's so weird because I'm not making a point, I just don't remember to open the damn "gmail.com" URL.
I remember some people were making some a Nostr service a while ago that sent a DM to people with Nostr articles inside -- or some other forms of "subscription services on Nostr". It makes no sense at all.
Pulling in DMs from relays is exactly the same process (actually slightly more convoluted) than pulling normal public events, so why would a service assume that "sending a DM" was more likely to reach the target subscriber when the target had explicitly subscribed to that topic or writer?
Maybe due to how some specific clients work that is true, but fundamentally it is a very broken assumption that comes from some fantastic past era in which emails were 100% always seen and there was no way for anyone to subscribe to someone else's posts.
Building around such broken assumptions is the wrong approach. Instead we should be building new flows for subscribing to specific content from specific Nostr-native sources (creators directly or manual or automated curation providers, communities, relays etc), which is essentially what most clients are already doing anyway, but specifically Coracle's new custom feeds come to mind now.
This also reminds me of the interviewer asking the Farcaster creator if Farcaster made "email addresses available to content creators" completely ignoring all the cryptography and nature of the protocol (Farcaster is shit, but at least they tried, and in this example you could imagine the interviewer asking the same thing about Nostr).
I imagine that if the interviewer had asked these people who were working (or suggesting) the Nostr DM subscription flow they would have answered: "no, you don't get their email addresses, but you can send them uncensorable DMs!" -- and that, again, is getting everything backwards.
-
 @ 4c96d763:80c3ee30
2025-05-31 22:39:59
@ 4c96d763:80c3ee30
2025-05-31 22:39:59Changes
Daniel D’Aquino (33):
- v1.13 changelog
- Version bump to 1.14
- Fix thread parent event loading regression
- Improve syncing and performance of ThreadModel
- v1.13.1 changelog
- Update Kingfisher to 8.3.1
- Add some miscellaneous documentation
- Renamed RelayInfo to LegacyKind3RelayRWConfiguration
- Define protocol NostrEventConvertible
- Organize RelayPool namespace
- NIP-65 relay list models and definitions
- New async streaming interface from RelayPool
- Implement safe interface for unowned NdbNotes
- Implement NostrNetworkManager and UserRelayListManager
- Add First Aid tool to repair relay list
- Fetch NIP-65 relay lists from profile view
- Add one-click Coinos wallet setup
- Add disclaimer to Coinos button
- Add network connect call to extensions
- Add safety reminder for higher balances
- Reinitialize videos if they enter an error state
- Refactor wallet invoice URL handling
- Re-enable note zaps ⚡️
- Move Kingfisher data to the Caches directory
- Implement Codable for NdbNote
- Add description and metadata to pay_invoice command
- Improve Coinos button disclaimer
- Add option to dismiss wallet high balance warning
- Improve error handling on NWC wallet
- Do not process NWC responses not meant for the user
- Add relay connectivity information to NWC settings
- Add changelog for v1.14
- Version bump to 1.15
SanjaySiddharth (3):
- Add search feature to the settings screen
- Fix bug that closes the side menu when copying npub
- Show additional information on top of blurred images
Swift Coder (1):
- Display Circular Indicator on top of media undergoing upload process Removed existing progress view bar at the top of post view Added separate stack in PVImageCarouselView for media undergoing the upload process Changelog-Added: Display uploading indicator in post view Signed-off-by: Swift Coder scoder1747@gmail.com
Terry Yiu (22):
- Fix localization issues in TransactionsView
- Export strings for translation
- Add Unicode 16 emoji reactions for iOS 18.4+ by upgrading EmojiPicker
- Add missing localized string comment
- Export strings for translation
- Clean up code in ProfileName.name_choice
- Fix quote notes to include missing q tag
- Fix some compiler warnings
- Replace deprecated usage of UIMenuController with UITextViewDelegate
- Add notification setting to hide hellthreads
- Inverse hellthread_notifications_enabled to be hellthread_notifications_disabled and add hellthread_notifications_max_pubkeys setting
- Hide future notes from timeline
- Fix note rendering for those that contain previewable items or leading and trailing whitespaces
- Add inline note rendering of invoices to pull up wallet selector sheet
- Optimize classify_url function
- Export strings for translation
- Remove arbitrary newline from localizable string
- Export strings for translation
- Add NIP-05 favicon to profile names and NIP-05 web of trust feed
- Fix quotes view header alignment
- Export strings for translation
- Rename Bitcoin Beach wallet to Blink
Transifex (83):
- Translate Localizable.strings in de
- Translate Localizable.stringsdict in de
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in hu_HU
- Translate Localizable.stringsdict in hu_HU
- Translate InfoPlist.strings in fr
- Translate Localizable.strings in th
- Translate Localizable.strings in nl
- Translate Localizable.strings in pt_PT
- Translate Localizable.strings in pt_PT
- Translate Localizable.strings in hu_HU
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in de
- Translate Localizable.strings in de
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in nl
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pt_PT
- Translate Localizable.strings in hu_HU
- Translate Localizable.stringsdict in nl
- Translate Localizable.strings in nl
- Translate Localizable.strings in th
- Translate Localizable.stringsdict in th
- Translate Localizable.strings in ja
- Translate Localizable.strings in nl
- Translate Localizable.stringsdict in ja
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in nl
- Translate Localizable.strings in de
- Translate Localizable.stringsdict in de
- Translate Localizable.stringsdict in de
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
William Casarin (1):
- perf: don't use regex in trim_{prefix,suffix}
ericholguin (2):
- nwc: Wallet Redesign
- wallet: route to profile from wallet tx list
pushed to damus:refs/heads/master
-
 @ 04c915da:3dfbecc9
2025-05-20 15:47:16
@ 04c915da:3dfbecc9
2025-05-20 15:47:16Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ a5142938:0ef19da3
2025-06-05 10:24:37
@ a5142938:0ef19da3
2025-06-05 10:24:37Brands
Nordkidz is a German brand that creates made-to-order clothing and linens for babies, children, and a little bit for their parents.
Natural materials used in products
⚠️ Warning: some products from this brand contain non-natural materials, including:
Categories of products offered
This brand offers products made entirely from natural materials in the following categories:
Clothing
- Clothing fits : babies, children, unisex
- Tops : sweaters, t-shirts
- Bottoms : pants-trousers, shorts, sweatpants
- Head & handwear : hats, scarves
Home
- Linen : bath ponchos, bean bag covers, muslin squares
Other information
👉 Learn more on the brand website
Where to find their products?
- Nordkidz (in German, delivery area: Germany and the European Union) 💚 Via this link, you directly support the brand.
📝 You can contribute to this entry by suggesting edits in comments.
🗣️ Do you use this brand's products? Share your opinion in the comments.
⚡ Happy to have found this information? Support the project by making a donation to thank the contributors.
-
 @ b83a28b7:35919450
2025-05-16 19:23:58
@ b83a28b7:35919450
2025-05-16 19:23:58This article was originally part of the sermon of Plebchain Radio Episode 110 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ 29313cc9:a6bf155e
2025-05-30 06:35:56
@ 29313cc9:a6bf155e
2025-05-30 06:35:56I thought i'd experiment with this Nostr blogging thing and write a short article on the state of Meshtastic and its alternatives.
For years Meshtastic was the only game in town, there wasn't a lot of users but the authors kept plugging away and it has become a thriving ecosystem of open source hardware, software, tools and social scene.
Meshtastic has always been focused on node to node messaging, in particular one of the use cases specifically mentioned was hiking in the wilderness or skiing in the mountains and being able to use these devices off-grid, perhaps even without a phone to communicate with one and other. The project does have a few other features like telemetry, remote admin, packet data etc but the messaging was the focus. Because of this focus, the core functionality needs to be built into the firmware of these low powered devices like ESP32 for example. This restricts what can be done in terms of CPU power and storage, but also makes synchronization between device and phone cumbersome.
Unfortunately, as a messaging platform, Meshtastic still struggles even after all these years. Message delivery and routing are fairly unreliable, 95% of conversations go along the lines of "hello, test, anyone there?". Now I should mention, if you have a very good signal to your peers the reliability can be good, but even then its not a guarantee.
Early on in the Meshtastic journey I stumbled upon a similar project named Reticulum which can utilize the same LoRa based hardware but aims to be a more comprehensive platform for decentralized communications and currently requires a computer or raspberry pi to run the Python backend alongside the LoRa hardware as a radio. Reticulum has historically been a less polished UI experience and a little idiosyncratic in its design which has probably hindered its adoption a little. But the main difference to Meshtastic is Reticulum requires bigger hardware and is less suitable for remote installations, solar powered setups etc. My understanding is once v1.0 has been released (soon) there may be efforts to port the code to native C which may allow hardware nodes to run as repeaters on their own.
More recently a new project has been announced called Meshcore, which is more closely aligned with Meshtastic than Reticulum, Meshcore makes several important improvements to message delivery and routing in an attempt to improve the reliability of the core feature, messaging. Popular Youtube channel Andy Kirby has been central in helping Meshcore gain popularity and I think he may be involved in the commercial aspects of the project. The smartphone apps and website mapping and flasher tools are a bit more polished with Meshcore.
One of the biggest contributors in the space is Liam Cottle who has created mapping websites for Meshtastic & Meshcore, he also built the Meshcore smartphone app and built the fantastic Reticulum MeshChat UI.
With all this new competition Meshtastic appears to be pushing out more frequent updates and whilst they have been introducing more bugs into the software it is nice to see some faster progress.
In my opinion Reticulum is probably the most interesting project with the most potential, but they do need to get the core routing engine running standalone on low powered hardware for the project to expand to more hardware/radio focused users.
That is all. Mesh on!
-
 @ 3bf0c63f:aefa459d
2024-05-21 12:38:08
@ 3bf0c63f:aefa459d
2024-05-21 12:38:08Bitcoin transactions explained
A transaction is a piece of data that takes inputs and produces outputs. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered.
Imagine you have 10 satoshis. That means you have them in an unspent transaction output (UTXO). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a script that unlocks that transaction and related signatures, then you specify outputs along with a script that locks these outputs.

As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them.
For most of the cases locking and unlocking means specifying a public key whose controller (the person who has the corresponding private key) will be able to spend. Other fancy things are possible too, but we can ignore them for now.
Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.

If you're still interested in transactions maybe you could take a look at this small chapter of that Andreas Antonopoulos book.
If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: https://en.bitcoin.it/wiki/Coin_analogy
-
 @ 39cc53c9:27168656
2025-05-27 09:21:53
@ 39cc53c9:27168656
2025-05-27 09:21:53The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 527337d5:93e9525e
2025-06-05 03:09:02
@ 527337d5:93e9525e
2025-06-05 03:09:02The Algorithmic Pursuit of Connection: A Five-Book Journey into the Self
As a researcher, hitting my thirties and the winding down of a significant project prompted a crucial re-evaluation of life's latter half. While I'd successfully applied probabilistic control theory to one-on-one interactions, the complexities of group dynamics remained a persistent challenge. My recent dive into five diverse books on human relationships inadvertently became a profound journey of self-discovery, fundamentally reshaping my perspective on social connections.
Neil Strauss: A Mirror Reflecting the Self's Evolution
Neil Strauss's The Truth resonated deepest among my recent reads. The author's battle with sex addiction uncomfortably mirrored my own past struggles: the fragile self-esteem stemming from rejection, the hubris born of early successes, and the tendency to view women as mere objects of manipulation. It felt eerily prescient, a glimpse into a potential future.
Yet, I found myself arriving at Strauss's ultimate conclusion – the paramount importance of self-preparation and community – far sooner than he did. This acceleration wasn't accidental; it was the result of intense focus on individual experiences, meticulously replayed and analyzed in my mind. The book, therefore, served less as a revelation and more as a powerful validation of my own journey of introspection and root-cause analysis.
Quantifying Connection: The Promise and Limits of Mathematical Models
Hannah Fry's The Mathematics of Love offered a kindred spirit in its attempt to quantify human relationships. While I appreciate the mathematical lens, Fry's models primarily concern dyadic relationships (N=2), relying on relatively simple systems of two-variable ordinary differential equations. For me, these are akin to linear models, sufficient only up to a certain point. Beyond N=4, the dependencies become exponentially complex.
My own pursuit extends to understanding and optimizing group dynamics within complex systems. This involves multi-variable problems (N $\ge$ 3) and the application of network theory, a far more sophisticated approach. Human collectives, after all, are systems of nodes and edges, where information propagates in predictable ways. My focus is on deriving optimal behavioral controls within these intricate frameworks.
Conversely, Men Are from Mars, Women Are from Venus initially struck me as bordering on conspiracy theory. However, its latter half proved unexpectedly useful. Its clear enumeration of male and female desires, and its articulation of common points of conflict, presented a practical template for communication styles. In a systemic view, this serves as a rudimentary, yet functional, interface design for complex social interactions.
A Dispassionate Critique of Relationship Dogma
My drive for efficiency and systematic understanding led to a rather blunt assessment of certain relationship classics. The New Science of Adult Attachment felt disorganized and frustratingly anecdotal. Lacking a coherent theoretical framework, it burdened the reader with deciphering meaning from a jumble of examples. Its inefficiency was, frankly, its most irksome flaw.
Similarly, Dale Carnegie's How to Win Friends and Influence People struck me as closer to pseudoscience than social science. Its plethora of specific anecdotes obscured any underlying principle. Given my deep engagement with social engineering – a discipline that systematically and practically analyzes human interaction – Carnegie's work appeared largely irrelevant and inefficient. From my perspective, which views humans as objective systems to be analyzed with mathematical rigor, such unstructured approaches hold little value.
The Unveiling of a Core Principle: Humans as Systems
This intensive reading period solidified my most crucial insight: humans, at their core, are systems. This understanding allows for a dispassionate, methodical approach to human collectives, mitigating unnecessary emotional friction.
This revelation has sharply refined my future learning trajectory. I'm now prioritizing foundational theories like graph theory and network theory over anecdotal accounts of human behavior. By mastering these theoretical underpinnings, I aim to precisely model complex human interactions as systems of nodes and edges, enabling the derivation of optimal behavioral controls within communities.
My choice of the term "target for capture" for individuals stems from a personal aversion to perceived equality in certain human interactions, a mechanism to avoid cognitive dissonance. This rational approach, I believe, is key to cultivating secure attachment styles – relationships demonstrably sustainable in the long term. My philosophy is to strategically approach the initial engagement, then transition to a stable, enduring connection. It's a calculated, dispassionate method for achieving desired relational outcomes.
Ultimately, this period of reading wasn't just about acquiring knowledge; it was a profound journey of self-discovery, clarifying my personal frameworks for navigating life's complexities and forging meaningful, yet strategically managed, connections.
-
 @ 472f440f:5669301e
2025-06-04 20:58:53
@ 472f440f:5669301e
2025-06-04 20:58:53Marty's Bent
J.P. Morgan CEO Jamie Dimon has long been an outspoken skeptic and critic of bitcoin. He has called Bitcoin a speculative asset, a fraud, a pet rock, and has opined that it will inevitably blow up. A couple of years ago, he was on Capitol Hill saying that if he were the government, he would "close it down". Just within the last month, he was on Fox Business News talking with Maria Bartiromo, proclaiming that the U.S. should be stockpiling bullets and rare earth metals instead of bitcoin. It's pretty clear that Jamie Dimon, who is at the helm of the most powerful and largest bank in the world, does not like bitcoin one bit.
Evidence below:
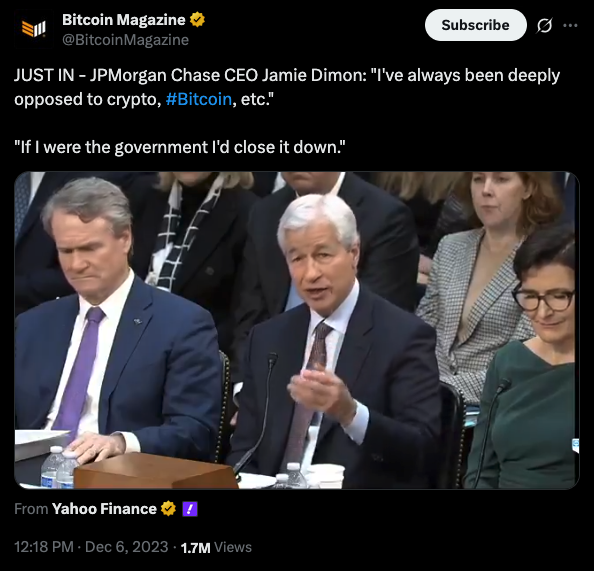
via Bitcoin Magazine
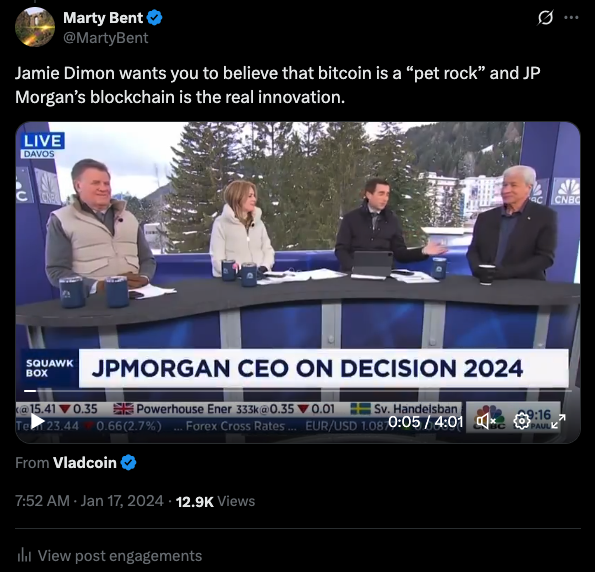
via me
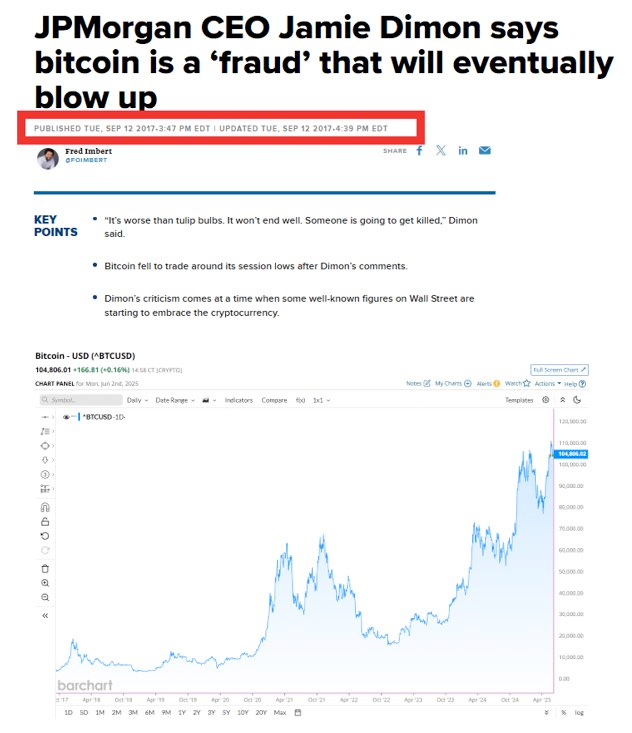
via CNBC
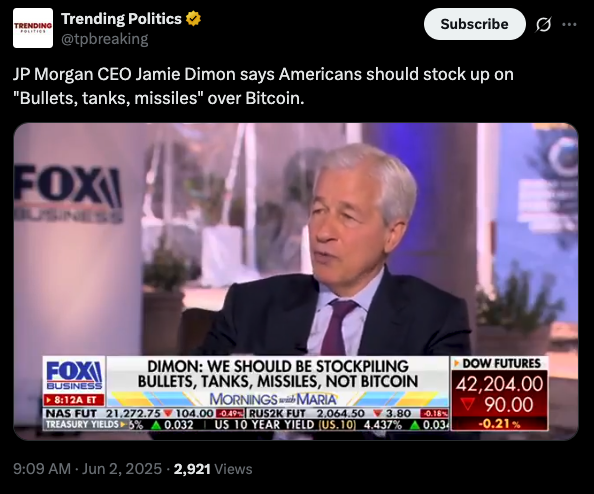
Despite Dimon's distinguished disdain for Bitcoin, J.P. Morgan cannot deny reality. The CEO of the largest bank in the world is certainly a powerful man, but no one individual, even in the position that Jamie Dimon is in, is more powerful than the market. And the market has spoken very clearly, it is demanding bitcoin. The Bitcoin ETFs have been the most successful ETFs in terms of pace of growth since their launch. They've accumulated tens of billions of dollars in AUM in a very short period of time. Outpacing the previous record set by the gold ETF, GLD.
Whether or not Jamie Dimon himself likes Bitcoin doesn't matter. J.P. Morgan, as the largest bank in the world and a publicly traded company, has a duty to shareholders. And that duty is to increase shareholder value by any ethical and legal means necessary. Earlier today, J.P. Morgan announced plans to offer clients financing against their Bitcoin ETFs, as well as some other benefits, including having their bitcoin holdings recognized in their overall net worth and liquid assets, similar to stocks, cars, and art, which will be massive for bitcoiners looking to get mortgages and other types of loans.
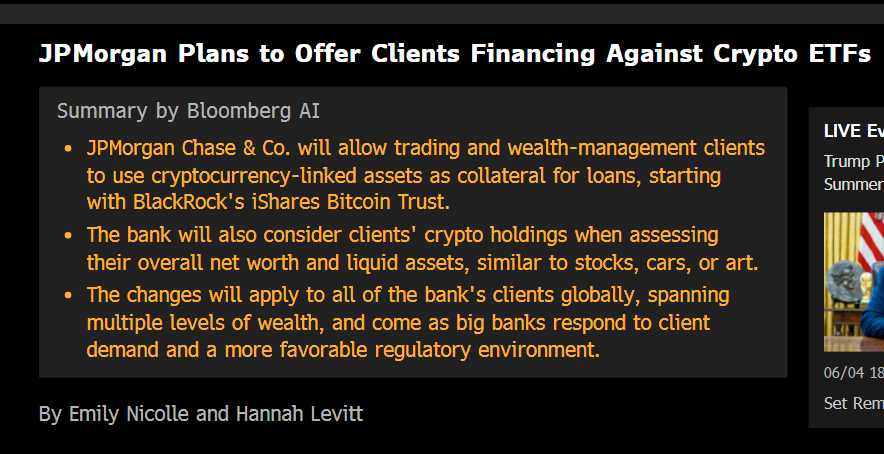
via Bloomberg
I've talked about this recently, but trying to buy a house when most of your liquid net worth is held in bitcoin is a massive pain in the ass. Up until this point, if you wanted to have your bitcoin recognized as part of your net worth and count towards your overall credit profile, you would need to sell some bitcoin, move it to a bank account, and have it sit there for a certain period of time before it was recognized toward your net worth. This is not ideal for bitcoiners who have sufficient cash flows and don't want to sell their bitcoin, pay the capital gains tax, and risk not being able to buy back the amount of sats they were forced to sell just to get a mortgage.
It's not yet clear to me whether or not J.P. Morgan will recognize bitcoin in cold storage toward their clients' net worth and credit profile, or if this is simply for bitcoin ETFs only. However, regardless, this is a step in the right direction and a validation of something that many bitcoiners have been saying for years. Inevitably, everyone will have to bend the knee to bitcoin. Today, it just happened to be the largest bank in the world. I expect more of this to come in the coming months, years, and decades.
Lyn Alden likes to say it in the context of the U.S. national debt and the fiscal crisis, but it also applies to bitcoin adoption and the need for incumbents to orient themselves around the demands of individual bitcoiners; nothing stops this train.
Corporate Bitcoin Treasuries are Changing Market Dynamics
Leon Wankum revealed how corporate Bitcoin treasuries are fundamentally reshaping business dynamics. Companies can now issue equity to fund operations while preserving their Bitcoin holdings, creating a revolutionary capital structure. Leon highlighted MicroStrategy's position, noting they hold enough Bitcoin to cover dividend payments for over 200 years. This model enables companies to reduce founder dilution since they don't need repeated funding rounds when their treasury appreciates.
"Some companies' Bitcoin treasuries are now worth more than all money they've ever raised." - Leon Wankum
Leon shared examples from his own portfolio companies where this strategy has proven transformative. Public companies have discovered an entirely new business model through strategic dilution that actually increases BTC per share. As Leon explained, this approach allows firms to leverage equity markets for operational funding while their Bitcoin treasury compounds in value, creating a positive feedback loop that benefits both shareholders and the company's long-term sustainability.
Check out the full podcast here for more on real estate price cycles, Bitcoin lending products, and the transition to a Bitcoin standard.
Headlines of the Day
California May Seize Idle Bitcoin After 3 Years - via X
Semler Scientific Buys $20M More Bitcoin, Holds $467M - via X
US Home Sellers Surge as Buyers Hit 4-Year Low - via X
Get our new STACK SATS hat - via tftcmerch.io
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code “TFTC20” during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
I feel old.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ 3bf0c63f:aefa459d
2024-03-23 08:57:08
@ 3bf0c63f:aefa459d
2024-03-23 08:57:08Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 3bf0c63f:aefa459d
2024-03-19 14:32:01
@ 3bf0c63f:aefa459d
2024-03-19 14:32:01Censorship-resistant relay discovery in Nostr
In Nostr is not decentralized nor censorship-resistant I said Nostr is centralized. Peter Todd thinks it is centralized by design, but I disagree.
Nostr wasn't designed to be centralized. The idea was always that clients would follow people in the relays they decided to publish to, even if it was a single-user relay hosted in an island in the middle of the Pacific ocean.
But the Nostr explanations never had any guidance about how to do this, and the protocol itself never had any enforcement mechanisms for any of this (because it would be impossible).
My original idea was that clients would use some undefined combination of relay hints in reply tags and the (now defunct)
kind:2relay-recommendation events plus some form of manual action ("it looks like Bob is publishing on relay X, do you want to follow him there?") to accomplish this. With the expectation that we would have a better idea of how to properly implement all this with more experience, Branle, my first working client didn't have any of that implemented, instead it used a stupid static list of relays with read/write toggle -- although it did publish relay hints and kept track of those internally and supportedkind:2events, these things were not really useful.Gossip was the first client to implement a truly censorship-resistant relay discovery mechanism that used NIP-05 hints (originally proposed by Mike Dilger) relay hints and
kind:3relay lists, and then with the simple insight of NIP-65 that got much better. After seeing it in more concrete terms, it became simpler to reason about it and the approach got popularized as the "gossip model", then implemented in clients like Coracle and Snort.Today when people mention the "gossip model" (or "outbox model") they simply think about NIP-65 though. Which I think is ok, but too restrictive. I still think there is a place for the NIP-05 hints,
nprofileandneventrelay hints and specially relay hints in event tags. All these mechanisms are used together in ZBD Social, for example, but I believe also in the clients listed above.I don't think we should stop here, though. I think there are other ways, perhaps drastically different ways, to approach content propagation and relay discovery. I think manual action by users is underrated and could go a long way if presented in a nice UX (not conceived by people that think users are dumb animals), and who knows what. Reliance on third-parties, hardcoded values, social graph, and specially a mix of multiple approaches, is what Nostr needs to be censorship-resistant and what I hope to see in the future.
-
 @ 1c5ff3ca:efe9c0f6
2025-06-05 06:29:45
@ 1c5ff3ca:efe9c0f6
2025-06-05 06:29:45Just calling it Open is not enough - Herausforderungen öffentlicher Bildungsinfrastrukturen und wie Nostr helfen könnte
Ich möchte gerne mit euch teilen, an welchen Konzepten ich arbeite, um die öffentliche Bildungsinfrastruktur mit Hilfe von Nostr zugänglicher und offener zu gestalten. Ich arbeite im Bereich öffentlicher Bildungsinfrastrukturen, besonders im Feld von Open Educational Resources (#OER). OER sind offen lizenzierte Bildungsmaterialien, die mit einer offenen Lizenz, meist einer Creative Commons Lizenz, versehen sind (CC-0, CC-BY, CC-BY-SA). Durch die klare und offene Lizenzierung ist es leicht möglich, die Lernmaterialien auf die individuellen Bedarfe anzupassen, sie zu verbessern und sie erneut zu veröffentlichen.
Seit vielen Jahren wird einerseits die Entwicklung freier Bildungsmaterialien gefördert, andererseits werden Plattformen, insbesondere Repositorien gefördert, die diese Materialien verfügbar machen sollen. Denn irgendwo müssen diese Materialien zur Verfügung gestellt werden, damit sie auch gefunden werden können.
Das klappt allerdings nur so mittelgut.
Herausforderungen
Nach vielen Jahren Förderung kann die einfache Frage: "Wo kann ich denn mein OER-Material bereitstellen" nicht einfach beantwortet werden. Es gibt Services, bei denen ich mein OER hochladen kann, jedoch bleibt es dann eingeschlossen in dieser Plattform und wird nicht auf anderen Plattformen auffindbar. Außerdem sind diese Services häufig an bestimmte Bildungskontexte gebunden oder geben Content erst nach einer Qualitätsprüfung frei. Dies führt dazu, dass ein einfaches und gleichzeitig öffentliches Teilen nicht möglich ist.
Diese und weitere Herausforderungen haben ihren Ursprung darin, dass Service und Infrastruktur in der Architektur öffentlichen Bildungsarchitektur ungünstig vermischt werden. Als Infrastruktur verstehe ich hier die Bereitstellung einer öffentlichen und offen zugänglichen Bildungsinfrastruktur, auf der Daten ausgetauscht, also bereitgestellt und konsumiert werden können. Jedoch existiert eine solche Infrstruktur momentan nicht unabhängig von den Services, die auf ihr betrieben werden. Infrastrukturbetreiber sind momentan gleichzeitig immer Servicebetreiber. Da sie aber die Hand darüber haben wollen, was genau in ihrem Service passiert (verständlich), schränken sie den Zugang zu ihrer Infrastruktur mit ein, was dazu führt, dass sie Lock-In Mechanismen großer Medienplattformen in der kleinen öffentlichen Bildungsinfrastruktur replizieren.
Es ist in etwas so, als würde jeder Autobauer auch gleichzeitig die Straßen für seine Fahrzeuge bauen. Aber halt nur für seine Autos.
Anhand einiger beispielhafter Services, die bestehende Plattformen auf ihren Infrastrukturen anbieten, möchte ich die Herausforderungen aufzeigen, die ich im aktuellen Architekturkonzept sehe:
- Upload von Bildungsmaterial
- Kuration: Zusammenstellung von Listen, Annotation mit Metadaten
- Crawling, Indexierung und Suche
- Plattfformübergreifende Kollaboration in Communities -> Beispiel: Qualitätssicherung (was auch immer das genau bedeutet)
- KI- Services -> Beispiel: KI generierte Metadaten für BiIdungsmaterial
Material Upload
Der Service "Material-Upload" oder das Mitteilen eines Links zu einem Bildungsmaterial wird von verschiedenen OER-Pattformen bereitgestellt (wirlernenonline.de, oersi.org, mundo.schule).
Dies bedeutet konkret: Wenn ich bei einer der Plattformen Content hochlade, verbleibt der Content in der Regel auch dort und wird nicht mit den anderen Plattformen geteilt. Das Resultat für die User: Entweder muss ich mich überall anmelden und dort mein Material hochladen (führt zu Duplikaten) oder damit leben, dass eben nur die Nutzer:innen der jeweiligen Plattform meinen Content finden können.
Der "Open Educational Resource Search Index" (OERSI) geht diese Herausforderung an, indem die Metadaten zu den Bildungsmaterialien verschiedener Plattformen in einem Index bereitgestellt werden. Dieser Index ist wiederum öffentlich zugänglich, sodass Plattformen darüber auch Metadaten anderer Plattformen konsumieren können. Das ist schon sehr gut. Jedoch funktioniert das nur für Plattformen, die der OERSI indexiert und für alle anderen nicht. Der OERSI ist auf den Hochschulbereich fokussiert, d.h. andere Bildungskontexte werden hier ausgeschlossen. Der Ansatz für jeden Bildungsbereich einen passenden "OERSI" daneben zustellen skaliert und schlecht und es bleibt die Herausforderung bestehen, dass für jede Quelle, die indexiert werden soll, ein entsprechender Importer/Crawler geschrieben werden muss.
Dieser Ansatz (Pull-Ansatz) rennt den Materialien hinterher.
Es gibt jedoch noch mehr Einschränkungen: Die Plattformen haben sich jeweils auf spezifische Bildungskontexte spezialisiert. D.h. auf die Fragen: Wo kann ich denn mein OER bereitstellen, muss immer erst die Gegenfrage: "Für welchen Bildungsbereich denn?" beantwortet werden. Wenn dieser außerhalb des allgemeinbildendenden Bereichs oder außerhalb der Hochschule liegt, geschweige denn außerhalb des institutionellen Bildungsrahmens, wird es schon sehr, sehr dünn. Kurzum:
- Es ist nicht einfach möglich OER bereitzustellen, sodass es auch auf verschiedenen Plattformen gefunden werden kann.
Kuration
Unter Kuration verstehe ich hier die Zusammenstellung von Content in Listen oder Sammlungs ähnlicher Form sowie die Annotation dieser Sammlungen oder des Contents mit Metadaten.
Einige Plattformen bieten die Möglichkeit an, Content in Listen einzuordnen. Diese Listen sind jedoch nicht portabel. Die Liste, die ich auf Plattform A erstelle, lässt sich nicht auf Plattform B importieren. Das wäre aber schön, denn so könnten die Listen leichter auf anderen Plattformen erweitert oder sogar kollaborativ gestaltet werden, andererseits werden Lock-In-Effekte zu vermieden.
Bei der Annotation mit Metadaten treten verschiedene zentralisierende Faktoren auf. In der momentanen Praxis werden die Metadaten meist zum Zeitpunkt der Contentbereitstellung festgelegt. Meist durch eine Person oder Redaktion, bisweilen mit Unterstützung von KI-Services, die bei der Metadateneingabe unterstützen. Wie aber zusätzliche eigene Metadaten ergänzen? Wie mitteilen, dass dieses Material nicht nur für Biologie, sondern auch für Sport in Thema XY super einsetzbar wäre? Die momentanen Ansätze können diese Anforderung nicht erfüllen. Sie nutzen die Kompetenz und das Potential ihrer User nicht.
- Es gibt keine interoperablen Sammlungen
- Metadaten-Annotation ist zentralisiert
- User können keine eigenen Metadaten hinzufügen
Crawling, Indexierung und Suche

Da die Nutzer:innen nicht viele verschiedene Plattformen und Webseiten besuchen wollen, um dort nach passendem Content zu suchen, crawlen die "großen" OER-Aggregatoren diese, um die Metadaten des Contents zu indexieren. Über verschiedene Schnittstellen oder gerne auch mal über das rohe HTML. Letztere Crawler sind sehr aufwändig zu schreiben, fehleranfällig und gehen bei Design-Anpassungen der Webseite schnell kaputt, erstere sind etwas stabiler, solange sich die Schnittstelle nicht ändert. Durch den Einsatz des Allgemeinen Metadatenprofils für Bildungsressourcen (AMB) hat sich die Situation etwas verbessert. Einige Plattformen bieten jetzt eine Sitemap an, die Links zu Bildungsmaterial enthalten, die wiederum eingebettet
script-tags vom Typapplication/ld+jsonenthalten, sodass die Metadaten von dort importiert werden können.Beispiel: e-teaching.org bietet hier eine Sitemap für ihre OER an: https://e-teaching.org/oer-sitemap.xml und auf den jeweiligen Seiten findet sich ein entsprechendes script-Tag.
Das ist schon viel besser, aber da geht noch mehr:
Zunächst ist dieser Ansatz nur für Plattformen und Akteure praktikabel, die über IT-Ressourcen verfügen, um entsprechende Funktionalitäten bei sich einbauen zu können. Lehrende können dies nicht einfach auf ihrem privaten Blog oder ähnliches umsetzen. Zum anderen besteht immer noch ein Discovery Problem. Ich muss nach wie vor wissen, wo ich suchen muss. Ich muss die Sitemaps kennen, sonst finde ich nichts. Statt eines Ansatzes, bei dem Akteure eigenständig mitteilen können, dass sie neuen Content haben (Push-Ansatz), verfolgen wir derzeit einen Ansatz, bei dem jede Plattform für sich Content im Pull-Verfahren akquiriert. Dies führt an vielen Stellen zu Doppelarbeiten, ist ineffizient (mehrere Personen bauen genau die gleichen Crawler, aber halt immer für ihre Plattform) und schliesst vor allem kleine Akteure aus (lohnt es sich einen Crawler zu programmieren, wenn die Webseite "nur" 50 Materialien bereitstellt?).
Anstatt erschlossene Daten zu teilen, arbeiten die Plattformen für sich oder stellen es höchstens wieder hinter eigenen (offenen oder geschlossenen) Schnittstellen bereit. Das ist wohl nicht das, was wir uns unter einer offenen und kollaborativen Gemeinschaft vorstellen, oder?
Bei der Suche stehen wir vor ähnlichen Herausforderungen, wie bereits oben geschildert. Obwohl verschiedene OER-Aggregatoren in Form von Repositorien oder Referatorien bereits viele der "kleineren" Plattformen indexieren und somit eine übergreifende Suche anbieten, ist es nicht möglich, diese Aggregatoren gemeinsam zu durchsuchen. Dies führt im Endeffekt dazu, dass die User wieder verschiedene Plattformen ansteuern müssen, wenn sie den gesamten OER-Fundus durchsuchen wollen.
- An vielen Stellen wird Content doppelt erschlossen, aber immer für die eigene Plattform
- Es gibt keinen geteilten Datenraum, in den Akteure Content "pushen" können
- Es gibt keine plattformübergreifenden Suchmöglichkeiten
Plattformübergreifende Kollaboration
Das wäre schön, oder? Mir ist schleierhaft, wie #OEP (Open Educational Practices, genaue Definition durch die Community steht noch aus) ohne funktionieren soll. Aber es gibt meines Wissens nach nicht mal Ansätze, wie das technisch umgesetzt werden soll (oder doch? let me hear).
Ein Szenario für solche plattformübergreifende Kollaboration könnte Qualitätssicherung sein. Gesetzt, dass sich zwei Plattformen / Communities auf etwas verständigt haben, dass sie als "Qualität" bezeichnen, wie aber dieses Gütesiegel nun an den Content bringen?
Plattform A: Na, dann kommt doch alle zu uns. Hier können wir das machen und dann hängt auch ein schönes Badge an den Materialien.
Plattform B: Ja, aber dann hängt es ja nicht an unseren Materialien. Außerdem wollen/müssen wir bei uns arbeiten, weil welche Existenzberechtigung hat denn meine Plattform noch, wenn wir alles bei dir machen?
- Obwohl nun #OEP in aller Munde sind, gibt es keine technischen Ansätze, wie (plattformübergreifende) Kollaboration technisch abgebildet werden kann
KI-Services
Was ist heute schon komplett ohne das Thema KI zu erwähnen? Mindestens für den nächsten Förderantrag muss auch irgendetwas mit KI gemacht werden...
Verschiedene Projekte erarbeiten hilfreiche und beeindruckende KI-Services. Beispielsweise, um die Annotation von Content mit Metadaten zu erleichtern, Metadaten automatisch hinzuzufügen, Content zu bestimmten Themen zu finden oder (halb-)automatisch zu Sammlungen hinzuzufügen. Aber (vielleicht habt ihr es schon erraten): Funktioniert halt nur auf der eigenen Plattform. Vermutlich, weil die Services nah am plattformeigenen Datenmodell entwickelt werden. Und da die Daten dieses Silo nicht verlassen, passt das schon. Das führt dazu, dass an mehreren Stellen die gleichen Services doppelt entwickelt werden.
- KI-Services funktionieren oft nur auf der Plattform für die sie entwickelt werden
Zusammenfassung der Probleme
Wir machen übrigens vieles schon sehr gut (Einsatz des AMB, Offene Bidungsmaterialien, wir haben eine großartige Community) und jetzt müssen wir halt weiter gehen.
(Die OER-Metadatengruppe, die das Allgemeine Metadatenprofil für Bildungsressourcen (AMB) entwickelt hat, bekommt für ihre Arbeit keine direkte Förderung. Gleichzeitig ist sie eine zentrale Anlaufstelle für alle, die mit Metadaten in offenen Bildungsinfrastukturen hantieren und das Metadatenprofil ist eines der wenigen Applikationsprofile, das öffentlich einsehbar, gut dokumentiert ist und Validierungsmöglichkeiten bietet.)
Betrachten wir die gesamten Plattformen und die beschriebenen Herausforderungen aus der Vogelperspektive, so lassen sich drei ineinander verschränkte Kernbestandteile unterscheiden, die helfen, die beschriebenen Probleme besser zu verstehen:
- User
- Service
- Daten
User: Auf (fast) allen Plattformen agieren User. Sie laden Material hoch, annotieren mit Metadaten, sind in einer Community, suchen Content usw. Egal, ob sie sich einloggen können/müssen, irgendetwas bieten wir unseren Usern an, damit sie daraus hoffentlich Mehrwerte ziehen
Service: Das ist dieses irgendetwas. Die "Webseite", die Oberfläche, das, wo der User klicken und etwas tun kann. Es ist das, was den Daten oft eine "visuelle" Form gibt. Der Service ist der Mittler, das Interface zwischen User und Daten. Mithilfe des Services lassen sich Daten erzeugen, verändern oder entfernen (Es gibt natürlich auch viele nicht-visuelle Services, die Interaktion mit Daten ermöglichen, aber für die meisten normalen Menschen, gibt es irgendwo was zu klicken).
Daten: Die Informationen in strukturierter maschinenlesbarer Form, die dem User in gerenderter Form durch einen Service Mehrwerte bieten können. Ungerenderte Daten können wir schwieirg erfassen (wir sind ja nicht Neo). Das können entweder die Metadaten zu Bildungmaterialien sein, die Materialien selbst, Profilinformationen, Materialsammlungen o.ä.

Meines Erachtens nach haben viele der oben beschriebenen Herausforderungen ihren Ursprung darin, dass die drei Kernbestandteile User, Service, Daten ungünstig miteinander verbunden wurden. Was kein Vorwurf sein soll, denn das ist genau die Art und Weise, wie die letzten Jahre (Jahrzehnte?) Plattformen immer gebaut wurden:
- User, Service und Daten werden in einer Plattform gebündelt
Das heisst durch meinen Service agieren die User mit den Daten und ich kann sicherstellen, dass in meiner kleinen Welt alles gut miteinander funktioniert. Sinnvoll, wenn ich Microsoft, Facebook, X oder ähnliches bin, weil mein Geschäftsmodell genau darin liegt: User einschließen (lock-in), ihnen die Hohheit über ihren Content nehmen (oder kannst du deine Facebook Posts zu X migrieren?) und nach Möglichkeit nicht wieder rauslassen.
Aber unsere Projekte sind öffentlich. Das sind nicht die Mechanismen, die wir replizieren sollten. Also was nun?
Bildungsinfrasstrukturen auf Basis des Nostr-Protokolls
Nostr
Eine pseudonyme Person mit dem Namen "fiatjaf" hat 2019 ein Konzept für ein Social Media Protokoll "Nostr - Notes and Other Stuff Transmitted By Relays" wie folgt beschrieben:
It does not rely on any trusted central server, hence it is resilient, it is based on cryptographic keys and signatures, so it is tamperproof, it does not rely on P2P techniques, therefore it works.
Fiatjaf, 2019
Die Kernbestandsteile des Protokolls bestehen aus:
- JSON -> Datenformat
- SHA256 & Schnorr -> Kryptographie
- Websocket -> Datenaustausch
Und funktionieren tut es so:
User besitzen ein "Schlüsselpaar": einen privaten Schlüssel (den behälst du für dich, nur für dich) und einen öffentlichen Schlüssel, den kannst du herumzeigen, das ist deine öffentliche Identität. Damit sagst du anderen Usern: Hier schau mal, das bin ich. Die beiden Schlüssel hängen dabei auf eine "magische" (kryptografische) Weise zusammen: Der öffentliche Schlüssel lässt sich aus dem privaten Schlüssel generieren, jedoch nicht andersherum. D.h. falls du deinen öffentlichen Schlüssel verlierst: Kein Problem, der lässt sich immer wieder herstellen. Wenn du deinen privaten Schlüssel verlierst: Pech gehabt, es ist faktisch unmöglich, diesen wieder herzustellen.
Die Schlüsselmagie geht jedoch noch weiter: Du kannst mit deinem privaten Schlüssel "Nachrichten" signieren, also wie unterschreiben. Diese Unterschrift, die du mit Hilfe des privaten Schlüssels erstellst, hat eine magische Eigenschaft: Jeder kann mithilfe der Signatur und deinem öffentlichen* Schlüssel nachprüfen, dass nur die Person, die auch den privaten Schlüssel zu diesem öffentlichen Schlüssel besitzt, diese Nachricht unterschrieben haben kann. Magisch, richtig? Verstehst du nicht komplett? Nicht schlimm, du benutzt es bereits vermutlich, ohne dass du es merkst. Das ist keine fancy neue Technologie, sondern gut abgehangen und breit im Einsatz.
Merke: User besitzen ein Schlüsselpaar und können damit Nachrichten signieren.
Dann gibt es noch die Services. Services funktionieren im Grunde wie bereits oben beschrieben. Durch sie interagieren die User mit Daten. Aber bei Nostr ist es ein kleines bisschen anders als sonst, denn: Die Daten "leben" nicht in den Services. Aber wo dann?
Wenn ein User einen Datensatz erstellt, verändert oder entfernen möchte, wird dieses "Event" (so nennen wir das bei Nostr) mit deinem privaten Schlüssel signiert (damit ist für alle klar, nur du kannst das gemacht haben) und dann mehrere "Relays" gesendet. Das sind die Orte, wo die Daten gehalten werden. Wenn ein User sich in einen Service einloggt, dann holt sich der Service die Daten, die er braucht von diesen Relays. User, Service und Daten sind also entkoppelt. Der User könnte zu einem anderen Service wechseln und sich dieseleben Daten von den Relays holen. Keine Lock-In Möglichkeiten.
Merke: User, Service und Daten sind entkoppelt.
Zuletzt gibt es noch die Relays. Relays sind Orte. Es sind die Orte, zu denen die Events, also die Daten der User, ihre Interaktionen, gesendet und von denen sie angefragt werden. Sie sind sowas wie das Backend von Nostr, allerdings tun sie nicht viel mehr als das: Events annehmen, Events verteilen. Je nach Konfiguration dürfen nur bestimmte User auf ein Relay schreiben oder davon lesen.
Das Protokoll ist von seinem Grunddesign auf Offenheit und Interoperabilität ausgelegt. Keine Registrierung ist nötig, sondern nur Schlüsselpaare. Durch kryptografische Verfahren kann dennoch die Authentizitität eines Events sichergestellt werden, da nur die Inhaberin des jeweiligen Schlüsselpaares dieses Event so erstellen konnte. Die Relays sorgen dafür die Daten an die gewünschten Stellen zu bringen und da wir mehr als nur eines benutzen, haben wir eine gewisse Ausfallsicherheit. Da die Daten nur aus signierten JSON-Schnipseln bestehen, können wir sie leicht an einen anderen Ort kopieren, im Falle eines Ausfalls. Durch die Signaturen ist wiederum sichergestellt, dass zwischendurch keine Veränderungen an den Daten vorgenommen wurden.
Beispiel: Ein Nostr Event
Hier ein kleiner technischer Exkurs, der beschreibt, wie Nostr Events strukturiert sind. Falls dich die technischen Details nicht so interessieren, überspringe diesen Abschnitt ruhig.
Jedes Nostr Event besitzt die gleiche Grundstruktur mit den Attributen:
id: Der Hash des Eventspubkey: Der Pubkey des Urhebers des Eventscreated_at: Der Zeitstempel des Eventskind: Der Typ des Eventstags: Zusätzliche Metadaten für das Event können in diesem Array hinterlegt werdencontent: Der textuelle Inhalt eines Eventssig: Die Signatur des Events, um die Integrität der Daten zu überprüfen
json { "id": <32-bytes lowercase hex-encoded sha256 of the serialized event data>, "pubkey": <32-bytes lowercase hex-encoded public key of the event creator>, "created_at": <unix timestamp in seconds>, "kind": <integer between 0 and 65535>, "tags": [ [<arbitrary string>...], // ... ], "content": <arbitrary string>, "sig": <64-bytes lowercase hex of the signature of the sha256 hash of the serialized event data, which is the same as the "id" field> }Die verwendeten Eventtypen sowie die existierenden Spezifikationen lassen sich unter https://github.com/nostr-protocol/nips/ einsehen.
Wichtig ist auch: Du kannst einfach anfangen, Anwendungen zu entwickeln. Die Relays werden alle Events akzeptieren, die dem o.g. Schema folgen. Du musst also niemanden um Erlaubnis fragen oder warten, bis deine Spezifikation akzeptiert und hinzugefügt wurde.
You can just build things.
Exkurs: Nostr für Binärdaten - Blossom
Ja, aber... das ist doch nur für textbasierte Daten geeignet? Was ist denn mit den Binärdaten (Bilder, Videos, PDFs, etc)
Diese Daten sind oft recht groß und es wurde sich auf das Best-Practice geeignet, diese Daten nicht auf Relays abzulegen, sondern einen besser geeigneten Publikationsmechanismus für diese Datentypen zu finden. Der Ansatz wird als "Blossom - Blobs stored simply on mediaservers" bezeichnet und ist recht unkompliziert.
Blossom Server (nichts anderes als simple Medienserver) nutzen Nostr Schlüsselpaare zur Verwaltung Identitäten und zum Signieren von Events. Die Blobs werden über ihren sha256 Hash identifiziert. Blossom definiert einige standardisierte Endpunkte, die beschreiben wie Medien hochgeladen werden können, wie sie konsumiert werden können usw.
Die Details, wie Authorisierung und die jeweiligen Endpunkte funktionieren, werden in der genannten Spezifikation beschrieben.
Nostr 🤝 Öffentliche Bildungsinfrastrukturen
Wie könnten Herausforderungen gelöst werden, wenn wir Nostr als Basis für die öffentliche Bildungsinfrastruktur einsetzen?
Material-Upload
- Es ist nicht einfach möglich OER bereitzustellen, sodass es auch auf verschiedenen Plattformen gefunden werden kann.
Mit Nostr als Basis-Infrastruktur würden die Metadaten und die Binärdaten nicht an den Service gekoppelt sein, von dem aus sie bereitgestellt wurden. Binärdaten können auf sogenannten Blossom-Servern gehostet werden. Metadaten, Kommentare und weitere textbasierte Daten werden über die Relay-Infrastruktur verteilt. Da Daten und Service entkoppelt sind, können die OER Materialien von verschiedenen Anwendungen aus konsumiert werden.
Kuration
- Es gibt keine interoperablen Sammlungen
- Metadaten-Annotation ist zentralisiert
- User können keine eigenen Metadaten hinzufügen
Sammlungen sind per se interoperabel. Auf Protokollebene ist definiert, wie Listen funktionieren. Die Annotation mit Metadaten ist an keiner Stelle zentralisiert. Das Versprechen der RDF-Community "Anyone can say anything about any topic" wird hier verwirklicht. Ich muss mir ja nicht alles anhören. Vielleicht konsumiere ich nur Metadaten-Events bestimmter Redaktionen oder User. Vielleicht nur diejenigen mit einer Nähe zu meinem sozialen Graphen. Jedenfalls gibt es die Möglichkeit für alle User entsprechende Metadaten bereit zu stellen.
Crawling, Indexierung und Suche * An vielen Stellen wird Content doppelt erschlossen, aber immer für die eigene Plattform * Es gibt keinen geteilten Datenraum, in den Akteure Content "pushen" können * Es gibt keine plattformübergreifenden Suchmöglichkeiten
Keine Doppelerschließungen mehr. Wenn ein User im Netzwerk ein Metadatenevent veröffentlicht hat, ist es für alle konsumierbar. Der Datenraum ist per se geteilt. Plattformübergreifende Suche wird durch die Kombination aus Relays und NIPs ermöglicht. In den NIPs können spezielle Query-Formate für die jeweiligen NIPs definiert werden. Relays können anzeigen, welche NIPs sie untersützten. Eine plattformübergreifende Suche ist im Nostr eine relay-übergreifende Suche.
Plattformübergreifende Kollaboration
- Obwohl nun #OEP in aller Munde sind, gibt es keine technischen Ansätze, wie (plattformübergreifende) Kollaboration technisch abgebildet werden kann
Nostr ist der technische Ansatz.
KI-Services
- KI-Services funktionieren oft nur auf der Plattform für die sie entwickelt werden
Es gibt im Nostr das Konzept der Data Vending Machines (s. auch data-vending-machines.org). Statt also einfach nur eine API zu bauen (was auch schon sehr schön ist, wenn sie offen zugänglich ist), könnten diese Services auch als Akteure im Nostr Netzwerk fungieren und Jobs annehmen und ausführen. Die Art der Jobs kann in einer Spezifikation beschrieben werden, sodass die Funktionsweise für alle interessierten Teilnehmer im Netzwerk einfach nachzuvollziehen ist.
Die Services könnten sogar monetarisiert werden, sodass sich hier auch Möglichkeiten böten, Geschäftsmodelle zu entwickeln.
Fazit
Die Open Education Community ist großartig. Es sind einzigartige und unglaublich engagierte Menschen, die sich dem hehren Ziel "Zugängliche Bildung für Alle" -> "Offene Bildung" verschrieben haben. Wir verwenden Creative Commons Lizenzen -> Commons -> Gemeingüter. Es ist okay, dass viele Projekte von Sponsoren und Förderungen abhängig sind. Was wir machen, ist im Sinne eines Gemeingutes: Öffentliche Bildung für alle. Also zahlen wir als Gemeinschaft alle dafür.
Was nicht okay ist: Dass das, wofür wir alle gezahlt haben, nach kurzer Zeit nicht mehr auffindbar ist. Dass es eingeschlossen wird. In öffentlich finanzierten Datensilos. Es muss für alle auch langfristig verfügbar sein. Sonst ist es nicht zugänglich, nicht offen. Dann ist das O in OER nur ein Label und Marketing, um für eine ABM-Maßnahme 3 Jahre Geld zu bekommen. Denn nichts anderes ist Content-Entwicklung, wenn der Content nach drei Jahren weggeschmissen wird.
Und dasselbe gilt für OEP. Offene Lernpraktiken, sind auch nur eine Phrase, wenn wir die passende technische Infrastruktur nicht mitdenken, die wirkliche Offenheit und Kollaboration und damit die Umsetzung offener Lernpraktiken ermöglicht.
Und wenn wir uns jetzt nicht Gedanken darüber machen, die Infrastruktur für offenes Lernen anzupassen, dann werden wir vermutlich in einigen Jahren sehen können, was bei politischen Umorientierungen noch davon übrig bleiben wird. Wenn die Fördertöpfe komplett gestrichen werden, was bleibt dann übrig von dem investierten Geld?
Wir brauchen Lösungen, die engagierte Communities weiter betreiben können und denen kein Kopf abgeschlagen werden kann, ohne dass wir zwei neue daneben setzen könnten.
Wir müssen uns jetzt Gedanken darüber machen.
Wie offen will öffentliche Bildungsinfrastruktur sein?
-
 @ b2d670de:907f9d4a
2025-02-28 16:39:38
@ b2d670de:907f9d4a
2025-02-28 16:39:38onion-service-nostr-relays
A list of nostr relays exposed as onion services.
The list
| Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | operator | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | operator | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | operator | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | operator | Payment URL | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | operator | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | operator | Payment URL | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | operator | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | operator | N/A | N/A | | nostr.wine | 🍷 nostr.wine relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | operator | Payment URL | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 inbox.nostr.wine relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | operator | Payment URL | BTC LN, BTC | | filter.nostr.wine | 🍷 filter.nostr.wine proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | operator | Payment URL | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | operator | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | operator | N/A | N/A | | nfrelay.app | nfrelay.app aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | operator | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | operator | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | operator |Payment URL | XMR | | nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | operator | N/A | N/A | | wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | operator | N/A | N/A | | haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | operator | N/A | N/A | | relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | operator |N/A | N/A | | Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | operator | N/A | N/A | | Azzamo Relay | Azzamo Premium Nostr relay. (paid) | ws://q6a7m5qkyonzb5fk5yv4jyu3ar44hqedn7wjopg737lit2ckkhx2nyid.onion | operator | Payment URL | BTC LN | | Azzamo Inbox Relay | Azzamo Group and Private message relay. (Freemium) | ws://gp5kiwqfw7t2fwb3rfts2aekoph4x7pj5pv65re2y6hzaujsxewanbqd.onion | operator | Payment URL | BTC LN | | Noderunners Relay | The official Noderunners Nostr Relay. | ws://35vr3xigzjv2xyzfyif6o2gksmkioppy4rmwag7d4bqmwuccs2u4jaid.onion | operator | Payment URL | BTC LN |
Contributing
Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put
N/Ain empty columns.If you want to contribute anonymously, please contact me on SimpleX or send a DM on nostr using a disposable npub.
Operator column
It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
-
 @ d5c440ce:04726d89
2025-06-05 06:19:49
@ d5c440ce:04726d89
2025-06-05 06:19:49Effektiv behandling af blodsprængninger kræver en professionel tilgang og de rette metoder. Hos Klinik Zenit tilbyder vi skånsomme og dokumenterede teknikker til at reducere synligheden af blodsprængninger i ansigt og på krop. Vores behandlinger tilpasses individuelt og udføres af erfarne specialister med fokus på sikkerhed og langvarige resultater. Få vejledning om hudpleje før og efter behandlingen for at opnå det bedste resultat. Kontakt Klinik Zenit for en professionel vurdering og behandlingsplan.
-
 @ 3bf0c63f:aefa459d
2024-01-29 02:19:25
@ 3bf0c63f:aefa459d
2024-01-29 02:19:25Nostr: a quick introduction, attempt #1
Nostr doesn't have a material existence, it is not a website or an app. Nostr is just a description what kind of messages each computer can send to the others and vice-versa. It's a very simple thing, but the fact that such description exists allows different apps to connect to different servers automatically, without people having to talk behind the scenes or sign contracts or anything like that.
When you use a Nostr client that is what happens, your client will connect to a bunch of servers, called relays, and all these relays will speak the same "language" so your client will be able to publish notes to them all and also download notes from other people.
That's basically what Nostr is: this communication layer between the client you run on your phone or desktop computer and the relay that someone else is running on some server somewhere. There is no central authority dictating who can connect to whom or even anyone who knows for sure where each note is stored.
If you think about it, Nostr is very much like the internet itself: there are millions of websites out there, and basically anyone can run a new one, and there are websites that allow you to store and publish your stuff on them.
The added benefit of Nostr is that this unified "language" that all Nostr clients speak allow them to switch very easily and cleanly between relays. So if one relay decides to ban someone that person can switch to publishing to others relays and their audience will quickly follow them there. Likewise, it becomes much easier for relays to impose any restrictions they want on their users: no relay has to uphold a moral ground of "absolute free speech": each relay can decide to delete notes or ban users for no reason, or even only store notes from a preselected set of people and no one will be entitled to complain about that.
There are some bad things about this design: on Nostr there are no guarantees that relays will have the notes you want to read or that they will store the notes you're sending to them. We can't just assume all relays will have everything — much to the contrary, as Nostr grows more relays will exist and people will tend to publishing to a small set of all the relays, so depending on the decisions each client takes when publishing and when fetching notes, users may see a different set of replies to a note, for example, and be confused.
Another problem with the idea of publishing to multiple servers is that they may be run by all sorts of malicious people that may edit your notes. Since no one wants to see garbage published under their name, Nostr fixes that by requiring notes to have a cryptographic signature. This signature is attached to the note and verified by everybody at all times, which ensures the notes weren't tampered (if any part of the note is changed even by a single character that would cause the signature to become invalid and then the note would be dropped). The fix is perfect, except for the fact that it introduces the requirement that each user must now hold this 63-character code that starts with "nsec1", which they must not reveal to anyone. Although annoying, this requirement brings another benefit: that users can automatically have the same identity in many different contexts and even use their Nostr identity to login to non-Nostr websites easily without having to rely on any third-party.
To conclude: Nostr is like the internet (or the internet of some decades ago): a little chaotic, but very open. It is better than the internet because it is structured and actions can be automated, but, like in the internet itself, nothing is guaranteed to work at all times and users many have to do some manual work from time to time to fix things. Plus, there is the cryptographic key stuff, which is painful, but cool.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ ca76c778:e784c54b
2025-06-04 19:45:11
@ ca76c778:e784c54b
2025-06-04 19:45:11A few days ago I remembered video by Antonio Stappaerts(Artwod) on Youtube. And I thought to myself I want to be really good at drawing hands.\ In the video he explains something that, in my opinion, applies when learning just about anything.
If you've heard of the Dunning-Kruger effect then you know the first part.\ If you haven't, one begins learning something and on top of the first peak thinks oneself to be almost a master. And then one learns a little bit more and realizes how little skill one actually has.
 \
Now, what is really interesting is this. He points out that the second slope is made up of many smaller Dunning-Kruger effects. For example the effect will apply when learning: the basic shape of the figure, how to pose the figure, how draw the hands, the hair etc.
\
Now, what is really interesting is this. He points out that the second slope is made up of many smaller Dunning-Kruger effects. For example the effect will apply when learning: the basic shape of the figure, how to pose the figure, how draw the hands, the hair etc.So the way to climb the second hill is to understand and practice these smaller skills. And not just once or twice. You want to reach close to the second peak of each of the smaller skills.
And with that in mind I search for a good tutorial about drawing hands and got down to it(for the third time).
Step one was to learn pose and gesture using a grid shape.
https://cdn.satellite.earth/f55a9d1ef2fd687a9dce5ceee5e05a1b666c436509e264ddbac4d260b99e882a.jpg
https://cdn.satellite.earth/1b5524635c20ee4869f4860c982deea469cb87be7ad7b404e1777497b5a4fbd4.jpg
https://cdn.satellite.earth/35652251243ffd8c495b855c319d27da0c193ff2e951591f0a9f1b35aad39b29.jpg
https://cdn.satellite.earth/68f55979d102b4ebe55177842c6d9ab2ab30b95f926441429d977b47fae925c3.jpg
Step two. Practice the basic forms for the palm and fingers.\ I got carried away and drew some hands.
https://cdn.satellite.earth/48b400f72e35d078368149f00182cb58e606ddd16f6db4e7789c1431c28d44a0.jpg
Step three. learn the measurements.
https://cdn.satellite.earth/75c9b82da90ef50d17f698dd7b1eadc223b74a019a702a4617ed7d321646a87c.jpg
Step four. Understand the fingers.
https://cdn.satellite.earth/e33f9f3f9217bf5e3e206e96dfe764eba09b9fb3c10b450bb9c8a4075e3c1ec8.jpg
Step five. Learn about the thumb and put it all together. Drawing from reference and imagination.
https://cdn.satellite.earth/b2dd9c1cc1045dde021272199818b0db331e71a603c5900122aa850eb2d4148a.jpg
https://cdn.satellite.earth/8f5647ae9e148ad6217c106b5b69cf231384475e0a0eedf210bd149f75ade0b7.jpg
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ c9badfea:610f861a
2025-05-20 19:49:20
@ c9badfea:610f861a
2025-05-20 19:49:20- Install Sky Map (it's free and open source)
- Launch the app and tap Accept, then tap OK
- When asked to access the device's location, tap While Using The App
- Tap somewhere on the screen to activate the menu, then tap ⁝ and select Settings
- Disable Send Usage Statistics
- Return to the main screen and enjoy stargazing!
ℹ️ Use the 🔍 icon in the upper toolbar to search for a specific celestial body, or tap the 👁️ icon to activate night mode
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ 42a071ab:3391e086
2025-06-05 09:31:56
@ 42a071ab:3391e086
2025-06-05 09:31:56Trong một thế giới mà sự cạnh tranh ngày càng khốc liệt, yếu tố tạo nên sự khác biệt không chỉ nằm ở chất lượng sản phẩm mà còn ở cách một thương hiệu chăm sóc và kết nối với khách hàng. AV88 hiểu rõ điều đó và đã không ngừng đầu tư vào trải nghiệm người dùng như một chiến lược cốt lõi để xây dựng lòng tin và sự trung thành. Ngay từ những bước đầu tiên khi khách hàng tiếp cận AV88, họ được đón nhận bởi một giao diện thân thiện, dễ sử dụng và được thiết kế dựa trên hành vi sử dụng thực tế. Tất cả các chức năng, từ đăng ký tài khoản, quản lý thông tin cá nhân cho đến các bước tương tác hằng ngày đều được tối ưu để đảm bảo sự liền mạch và thuận tiện. Hơn thế, AV88 còn xây dựng một hệ thống chăm sóc khách hàng luôn sẵn sàng hỗ trợ 24/7, cung cấp thông tin kịp thời và giải quyết mọi thắc mắc nhanh chóng, mang lại cảm giác yên tâm tuyệt đối cho người sử dụng. Không chỉ dừng lại ở mức độ phản hồi, đội ngũ tại AV88 còn chủ động thu thập ý kiến, khảo sát nhu cầu và cải tiến dịch vụ theo thời gian thực, từ đó đảm bảo rằng mỗi sự đổi mới đều xuất phát từ chính kỳ vọng của người dùng. Nhờ vậy, AV88 không đơn thuần là một nền tảng dịch vụ mà còn là một người bạn đồng hành đáng tin cậy trong hành trình số hóa của mỗi khách hàng.
av88 cũng đặt ra một tiêu chuẩn mới cho sự minh bạch và bảo mật – hai yếu tố then chốt trong việc xây dựng niềm tin lâu dài. Mọi quy trình đều được thiết lập rõ ràng, dễ theo dõi và có hướng dẫn chi tiết, từ quy trình giao dịch cho đến các chính sách bảo vệ thông tin cá nhân. Các công nghệ mã hóa tiên tiến và lớp xác thực đa tầng giúp bảo đảm an toàn tuyệt đối trong mọi hoạt động. Không dừng lại ở việc duy trì chất lượng dịch vụ, AV88 còn tiên phong trong việc tích hợp công nghệ nhằm tối ưu hóa hiệu suất và giảm thiểu thời gian chờ đợi của người dùng. Các thao tác nạp – rút nhanh chóng, hệ thống thông báo thông minh và tính cá nhân hóa trong trải nghiệm giúp người dùng cảm nhận được sự linh hoạt và chuyên nghiệp. Chính sự kết hợp giữa công nghệ, con người và tầm nhìn chiến lược đã giúp AV88 không chỉ duy trì vị thế trên thị trường mà còn định hình chuẩn mực mới cho ngành dịch vụ lấy khách hàng làm trung tâm. Dù trong bối cảnh nào, AV88 vẫn luôn giữ vững cam kết: lắng nghe, thấu hiểu và đồng hành cùng khách hàng trên mọi hành trình. Điều này không chỉ tạo dựng giá trị bền vững cho thương hiệu mà còn góp phần nâng cao tiêu chuẩn chung của ngành, thúc đẩy sự phát triển toàn diện và dài lâu.
-
 @ a5ee4475:2ca75401
2025-06-04 18:11:52
@ a5ee4475:2ca75401
2025-06-04 18:11:52clients #link #list #english #article #finalversion #descentralismo
*These clients are generally applications on the Nostr network that allow you to use the same account, regardless of the app used, keeping your messages and profile intact.
**However, you may need to meet certain requirements regarding access and account NIP for some clients, so that you can access them securely and use their features correctly.
CLIENTS
Twitter like
- Nostrmo - [source] 🌐💻(🐧🪟🍎)🍎🤖(on zapstore)
- Coracle - Super App [source] 🌐🤖(on zapstore)
- Amethyst - Super App with note edit, delete and other stuff with Tor [source] 🤖(on zapstore)
- Primal - Social and wallet [source] 🌐🍎🤖(on zapstore)
- Iris - [source] 🌐🤖🍎
- Current - [source] 🤖🍎
- FreeFrom 🤖🍎
- Openvibe - Nostr and others (new Plebstr) [source] 🤖🍎
- Snort 🌐(🤖[early access]) [onion] [source]
- Damus 🍎 [source]
- Nos 🍎 [source]
- Nostur 🍎 [source]
- NostrBand 🌐 [info] [source]
- Yana [source] 🌐💻(🐧) 🍎🤖(on zapstore)
- Nostribe [on development] 🌐 [source]
- Lume 💻(🐧🪟🍎) [info] [source]
- Gossip - [source] 💻(🐧🪟🍎)
- noStrudel - Gamified Experience [onion] [info/source] 🌐
- [Nostrudel Next] - [onion]
- moStard - Nostrudel with Monero [onion] [info/source] 🌐
- Camelus - [source] 🤖 [early access]
Community
- CCNS - Community Curated Nostr Stuff [source]
- Nostr Kiwi [creator] 🌐
- Satellite [info] 🌐
- Flotilla - [source] 🌐🐧🤖(on zapstore)
- Chachi - [source] 🌐
- Futr - Coded in haskell [source] 🐧 (others soon)
- Soapbox - Comunnity server [info] [source] 🌐
- Ditto - Soapbox community server 🌐 [source] 🌐
- Cobrafuma - Nostr brazilian community on Ditto [info] 🌐
- Zapddit - Reddit like [source] 🌐
- Voyage (Reddit like) [on development] 🤖
Wiki
- Wikifreedia - Wiki Dark mode [source] 🌐
- Wikinostr - Wiki with tabs clear mode [source] 🌐
- Wikistr - Wiki clear mode [info] [source] 🌐
Search
- Keychat - Signal-like chat with AI and browser [source] 💻(🐧🪟🍎) - 📱(🍎🤖{on zapstore})
- Spring - Browser for Nostr apps and other sites [source] 🤖 (on zapstore)
- Advanced nostr search - Advanced note search by isolated terms related to a npub profile [source] 🌐
- Nos Today - Global note search by isolated terms [info] [source] 🌐
- Nostr Search Engine - API for Nostr clients [source]
- Ntrends - Trending notes and profiles 🌐
Website
- Nsite - Nostr Site [onion] [info] [source]
- Nsite Gateway - Nostr Site Gateway [source]
- Npub pro - Your site on Nostr [source]
App Store
ZapStore - Permitionless App Store [source] 🤖 💻(🐧🍎)
Video and Live Streaming
- Flare - Youtube like 🌐 [source]
- ZapStream - Lives, videos, shorts and zaps (NIP-53) [source] 🌐 🤖(lives only | Amber | on zapstore)
- StreamCat - [source code dont found]
- Shosho - Stream your camera [source] 🤖(on zapstore)
- Swae - Live streaming [source] (on development) ⏳
Post Aggregator - Kinostr - Nostr Cinema with #kinostr [english] [author] 🌐 - Stremstr - Nostr Cinema with #kinostr [english] [source] 🤖
Link Agreggator - Kinostr - #kinostr - Nostr Cinema Profile with links [English] - Equinox - Nostr Cinema Community with links [Portuguese]
Audio and Podcast Transmission
- Castr - Your npub as podcast feed [source]
- Nostr Nests - Audio Chats [source] 🌐
- Fountain - Podcast [source] 🤖🍎
- Corny Chat - Audio Chat [source] 🌐
Music
- Tidal - Music Streaming [source] [about] [info] 🤖🍎🌐
- Wavlake - Music Streaming [source] 🌐(🤖🍎 [early access])
- Tunestr - Musical Events [source] [about] 🌐
- Stemstr - Musical Colab (paid to post) [source] [about] 🌐
Images
- Lumina - Trending images and pictures [source] 🌐
- Pinstr - Pinterest like [source] 🌐
- Slidestr - DeviantArt like [source] 🌐
- Memestr - ifunny like [source] 🌐
Download and Upload
Documents, graphics and tables
- Mindstr - Mind maps [source] 🌐
- Docstr - Share Docs [info] [source] 🌐
- Formstr - Share Forms [info] 🌐
- Sheetstr - Share Spreadsheets [source] 🌐
- Slide Maker - Share slides 🌐 [Advice: Slide Maker https://zaplinks.lol/ site is down]
Health
- Sobrkey - Sobriety and mental health [source] 🌐
- Runstr - Running app [source] 🌐
- NosFabrica - Finding ways for your health data 🌐
- LazerEyes - Eye prescription by DM [source] 🌐
Forum
- OddBean - Hacker News like [info] [source] 🌐
- LowEnt - Forum [info] 🌐
- Swarmstr - Q&A / FAQ [info] 🌐
- Staker News - Hacker News like 🌐 [info]
Direct Messenges (DM)
- 0xchat 🤖🍎 [source]
- Nostr Chat 🌐🍎 [source]
- Blowater 🌐 [source]
- Anigma (new nostrgram) - Telegram based [on development] [source]
Reading
- Oracolo - A minimalist Nostr html blog [source]
- nRSS - Nostr RSS reader 🌐
- Highlighter - Insights with a highlighted read [info] 🌐
- Zephyr - Calming to Read [info] 🌐
- Flycat - Clean and Healthy Feed [info] 🌐
- Nosta - Check Profiles [on development] [info] 🌐
- Alexandria - e-Reader and Nostr Knowledge Base (NKB) [source] 🌐
Writing
- Habla - Blog [info] 🌐
- Blogstack - Blog [info]🌐
- YakiHonne - Articles and News [info] 🌐🍎🤖(on zapstore)
Lists
- Following - Users list [source] 🌐
- Nostr Unfollower - Nostr Unfollower
- Listr - Lists [source] 🌐
- Nostr potatoes - Movies List [source] 💻(numpy)
Market and Jobs
- Shopstr - Buy and Sell [onion] [source] 🌐
- Nostr Market - Buy and Sell 🌐
- Plebeian Market - Buy and Sell [source] 🌐
- Ostrich Work - Jobs [source] 🌐
- Nostrocket - Jobs [source] 🌐
Data Vending Machines - DVM (NIP90)
(Data-processing tools)
Games
- Chesstr - Chess 🌐 [source]
- Jestr - Chess [source] 🌐
- Snakestr - Snake game [source] 🌐
- Snakes on a Relay - Multiplayer Snake game like slither.io [source] 🌐
ENGINES - DEG Mods - Decentralized Game Mods [info] [source] 🌐 - NG Engine - Nostr Game Engine [source] 🌐 - JmonkeyEngine - Java game engine [source] 🌐
Customization
Like other Services
- Olas - Instagram like [source] 🌐🍎🤖(on zapstore)
- Nostree - Linktree like 🌐
- Rabbit - TweetDeck like [info] 🌐
- Zaplinks - Nostr links 🌐
- Omeglestr - Omegle-like Random Chats [source] 🌐
General Uses
- Njump - HTML text gateway source 🌐
- Filestr - HTML midia gateway [source] 🌐
- W3 - Nostr URL shortener [source] 🌐
- Playground - Test Nostr filters [source] 🌐
Places
- Wherostr - Travel and show where you are
- Arc Map (Mapstr) - Bitcoin Map [info]
Driver and Delivery
- RoadRunner - Uber like [on development] ⏱️
- Nostrlivery - iFood like [on development] ⏱️
⚠️ SCAM ⚠️ | Arcade City - Uber like [source]
OTHER STUFF
Lightning Wallets (zap)
- Wallet of Satoshi - Simplest Lightning Wallet [info] 🤖🍎
- Coinos - Web wallet and Nostr client [source] 🌐
- Alby - Native and extension [info] [source] 🌐
- Minibits - Cashu mobile wallet [info] 🤖
- LNbits - App and extension [source] 🤖🍎💻
- Zeus - [info] [source] 🤖🍎
- Blink - Open source custodial wallet (KYC over 1000 usd) [source] 🤖🍎
⚠️ ZBD - Zap Gaming wallet and no more Social [closed source] [info] [some resources] 🤖 ⚠️ ZBD suddenly canceled my account for alleged Terms of Service violations, gives me no explanation and won't let me withdraw my money ⚠️
Without Zap - Wassabi Wallet - Privacy-focused and non-custodial with Nostr Update Manager [source]
Exchange
Media Server (Upload Links)
audio, image and video
Connected with Nostr (NIP):
- Nostr Build - Free and paid Upload [info] [source] 🌐
- NostrMedia - Written in Go with Nip 96 / Blossom (free and paid) [info] [source]
- Nostr Check - [info] [source] 🌐
- NostPic - [info] [source] 🌐
- Sovbit - Free and paid upload [info] [source] 🌐
- Voidcat - Nip-96 and Blossom [source] 🌐
- Primal Media - Primal Media Uploader [source] 🌐
Blossom - Your Media Safer
- Primal Blossom 🌐
- NostrBuild Blossom - Free upload (max 100MiB) and paid [info] [source] 🌐
Paid Upload Only
- Satellite CDN - prepaid upload (max 5GB each) [info] [source] 🌐
Without Nostr NIP:
- Pomf - Upload larger videos (max 1GB) [source]
- Catbox - max 200 MB [source]
- x0 - max 512 MiB [source]
Donation and payments
- Zapper - Easy Zaps [source] 🌐
- Autozap [source] 🌐
- Zapmeacoffee 🌐
- Nostr Zap 💻(numpy)
- Creatr - Creators subscription 🌐
- Geyzer - Crowdfunding [info] [source] 🌐
- Heya! - Crowdfunding [source]
Security
- Secret Border - Generate offline keys 💻(java)
- Umbrel - Your private relay [source] 🌐
Key signing/login and Extension
- Amber - Key signing [source] 🤖(on zapstore)
- Nowser - Account access keys 📱(🤖🍎) 💻(🐧🍎🪟)
- Nos2x - Account access keys 🌐
- Nsec.app 🌐 [info]
- Lume - [info] [source] 🐧🪟🍎
- Satcom - Share files to discuss - [info] 🌐
- KeysBand - Multi-key signing [source] 🌐
Code
- Stacks - AI Templates [info] [source] 🌐
- Nostrify - Share Nostr Frameworks 🌐
- Git Workshop (github like) [experimental] 🌐
- Gitstr (github like) [on development] ⏱️
- Osty [on development] [info] 🌐
- Python Nostr - Python Library for Nostr
- Sybil - Creating, managing and test Nostr events [on development] ⏱️
Relay Check and Cloud
- Nostr Watch - See your relay speed 🌐
- NosDrive - Nostr Relay that saves to Google Drive
Bidges and Getways
- Matrixtr Bridge - Between Matrix & Nostr
- Mostr - Between Nostr & Fediverse
- Nostrss - RSS to Nostr
- Rsslay - Optimized RSS to Nostr [source]
- Atomstr - RSS/Atom to Nostr [source]
Useful Profiles and Trends
nostr-voice - Voice note (just some clients)
NOT RELATED TO NOSTR
Voca - Text-to-Speech App for GrapheneOS [source] 🤖(on zapstore)
Android Keyboards
Personal notes and texts
Front-ends
- Nitter - Twitter / X without your data [source]
- NewPipe - Youtube, Peertube and others, without account & your data [source] 🤖
- Piped - Youtube web without you data [source] 🌐
Other Services
- Brave - Browser [source]
- DuckDuckGo - Search [source]
- LLMA - Meta - Meta open source AI [source]
- DuckDuckGo AI Chat - Famous AIs without Login [source]
- Proton Mail - Mail [source]
Other open source index: Degoogled Apps
Some other Nostr index on:
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16bitcoinddecentralizationIt is better to have multiple curator teams, with different vetting processes and release schedules for
bitcoindthan a single one."More eyes on code", "Contribute to Core", "Everybody should audit the code".
All these points repeated again and again fell to Earth on the day it was discovered that Bitcoin Core developers merged a variable name change from "blacklist" to "blocklist" without even discussing or acknowledging the fact that that innocent pull request opened by a sybil account was a social attack.
After a big lot of people manifested their dissatisfaction with that event on Twitter and on GitHub, most Core developers simply ignored everybody's concerns or even personally attacked people who were complaining.
The event has shown that:
1) Bitcoin Core ultimately rests on the hands of a couple maintainers and they decide what goes on the GitHub repository[^pr-merged-very-quickly] and the binary releases that will be downloaded by thousands; 2) Bitcoin Core is susceptible to social attacks; 2) "More eyes on code" don't matter, as these extra eyes can be ignored and dismissed.
Solution:
bitcoinddecentralizationIf usage was spread across 10 different
bitcoindflavors, the network would be much more resistant to social attacks to a single team.This has nothing to do with the question on if it is better to have multiple different Bitcoin node implementations or not, because here we're basically talking about the same software.
Multiple teams, each with their own release process, their own logo, some subtle changes, or perhaps no changes at all, just a different name for their
bitcoindflavor, and that's it.Every day or week or month or year, each flavor merges all changes from Bitcoin Core on their own fork. If there's anything suspicious or too leftist (or perhaps too rightist, in case there's a leftist
bitcoindflavor), maybe they will spot it and not merge.This way we keep the best of both worlds: all software development, bugfixes, improvements goes on Bitcoin Core, other flavors just copy. If there's some non-consensus change whose efficacy is debatable, one of the flavors will merge on their fork and test, and later others -- including Core -- can copy that too. Plus, we get resistant to attacks: in case there is an attack on Bitcoin Core, only 10% of the network would be compromised. the other flavors would be safe.
Run Bitcoin Knots
The first example of a
bitcoindsoftware that follows Bitcoin Core closely, adds some small changes, but has an independent vetting and release process is Bitcoin Knots, maintained by the incorruptible Luke DashJr.Next time you decide to run
bitcoind, run Bitcoin Knots instead and contribute tobitcoinddecentralization!
See also:
[^pr-merged-very-quickly]: See PR 20624, for example, a very complicated change that could be introducing bugs or be a deliberate attack, merged in 3 days without time for discussion.
-
 @ e2c72a5a:bfacb2ee
2025-06-05 11:54:19
@ e2c72a5a:bfacb2ee
2025-06-05 11:54:19Think crypto analytics is just charts and graphs? Wrong. It's a crystal ball for savvy investors.
Analytics in crypto decodes blockchain data revealing hidden trends. It transforms complex data into actionable insights. Basic concepts include on chain metrics, sentiment analysis, and trading volume. Real world applications range from fraud detection to predicting price movements.
Current trends emphasize DeFi analytics and cross chain data aggregation. Best practices involve using multiple data sources and verifying information. A common misconception is that analytics guarantees profits. It only enhances decision making.
Institutional investors are diving deep into on chain analytics. Stablecoins are disrupting payments. Layer 2 solutions are leading the way.
Ready to see the future? What hidden patterns will you uncover?
-
 @ 4fe4a528:3ff6bf06
2025-02-01 13:41:28
@ 4fe4a528:3ff6bf06
2025-02-01 13:41:28
In my last article I wrote about NOSTR. I found another local bitcoiner via NOSTR last week so here is why it is important to join / use NOSTR — start telling people “Look me up on NOSTR”
Self-sovereign identity (SSI) is a revolutionary approach to digital identity that puts individuals in control of their own identity and personal data. Unlike traditional digital identity models, which rely on third-party organizations to manage and authenticate identities, SSI empowers individuals to own and manage their digital identity.
This approach is made possible by emerging technologies such as secure public / private key pairs. Decentralized identifiers, conceived and developed by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is an attempt to create a global technical standard around cryptographically secured identifiers - a secure, universal, and sovereign form of digital ID. This technology uses peer-to-peer technology to remove the need for intermediaries to own and authenticate ID information.
Notably, NOSTR, a decentralized protocol, has already begun to utilize decentralized IDs, demonstrating the potential of this technology in real-world applications. Via NOSTR, users can be sure that the person or computer publishing to a particular npub knows their nsec (password for your npub), highlighting the secure and decentralized nature of this approach.
With SSI, individuals can decide how their personal data is used, shared, and protected, giving them greater control and agency over their digital lives.
The benefits of SSI are numerous, including:
Enhanced security and protection of personal data. Reduced risk of identity theft and fraud Increased autonomy and agency over one's digital identity. Improved scalability and flexibility in digital identity management
challenges:
Ensuring the security and integrity of decentralized identity systems. Developing standards and protocols for interoperability and compatibility. Addressing concerns around ownership and control of personal data. Balancing individual autonomy with the need for verification and authentication in various contexts.
Overall, self-sovereign identity has the potential to transform the way we think about digital identity and provide individuals with greater control and agency over their personal data. Without people in control of their bitcoin seed words no freedom loving people would be able to exchange their money with others. Yes, keep enjoying using the only free market on the planet BITCOIN. Long live FREEDOM!
-
 @ da8b7de1:c0164aee
2025-06-04 16:37:07
@ da8b7de1:c0164aee
2025-06-04 16:37:07Nukleáris politika és szabályozási fejlemények
A Nemzetközi Atomenergia-ügynökség (IAEA) Kormányzótanácsa 2025. június 9-én kezdi meg szokásos júniusi ülését Bécsben. A főbb napirendi pontok között szerepel a 2024-es éves jelentés, a technikai együttműködési tevékenységek, az iráni ellenőrzés és felügyelet, az ellenőrzések végrehajtása Észak-Koreában és Szíriában, a nukleáris biztonság és védelem Ukrajnában, valamint a nukleáris anyagok átruházása és ellenőrzése az AUKUS-keretében. Az ülésen új tagokat is kijelölnek a Kormányzótanácsba, és előkészítik a 69. rendes közgyűlést[iaea.org].
Jelentős projektek és iparági bővülés
Az amerikai Tennessee Valley Authority (TVA) benyújtotta kérelmét az Egyesült Államok Nukleáris Szabályozási Bizottságához egy GE Vernova Hitachi BWRX-300 kis moduláris reaktor (SMR) megépítésére a Clinch River telephelyen, ami jelentős lépés az amerikai fejlett nukleáris technológiák elterjesztésében[world-nuclear-news.org]. Kanadában a hatóság engedélyezte az Ontario Power Generation számára, hogy egy BWRX-300 reaktort építsen a Darlington New Nuclear Project helyszínen, ezzel tovább haladva az észak-amerikai SMR-projektek terén[world-nuclear-news.org].
India nukleáris szabályozója jóváhagyta a négyblokkos Mahi Banswara Rajasthan Atomerőmű telephelyét, Kínában pedig folytatódnak a szerelési munkák a Haiyang 3 egységen. Eközben Belgium és Dánia felülvizsgálják nukleáris politikájukat: Belgium visszavonja a korábbi leállítási döntést, Dánia pedig újragondolja álláspontját[world-nuclear-news.org].
Ellátási lánc, munkaerő és nemzetközi együttműködés
A nukleáris kapacitás várható gyors növekedése miatt egyre nagyobb hangsúly kerül mind a helyi, mind a globális ellátási lánc felkészítésére. A World Nuclear Association legutóbbi konferenciája kiemelte az ellátási lánc „globalizációjának” fontosságát a bővülés támogatásához[world-nuclear-news.org]. A nukleáris munkaerő világszerte növekedni fog, ami új lehetőségeket teremt, nem pedig hiányt. Az iparági szakértők hangsúlyozzák a jelentkezők tapasztalatának javítását és a szektorok közötti készségek hasznosítását a jövőbeni igények kielégítésére[world-nuclear-news.org].
A nemzetközi szabályozói együttműködés is fejlődik, különösen a kis moduláris reaktorok (SMR) tervezési értékelése terén. A brit Nukleáris Szabályozási Hivatal közzétette első jelentését ebben a témában, globális szinten hatékonyabb és összehangoltabb megközelítést célozva[world-nuclear-news.org].
Gazdasági és befektetési trendek
A nukleáris szektorban újra optimizmus tapasztalható, egészséges projektportfóliókkal és növekvő magánbefektetésekkel, különösen a fejlett üzemanyagok, például a HALEU (magas dúsítású urán) terén. A Világbank lehetséges politikai váltása, amely lehetővé tenné nukleáris projektek finanszírozását, jelentős hatással lehet a globális befektetésekre, példát mutatva más hitelezőknek is[ans.org].
Az USA-ban jelentős lépés a Prohibiting Russian Uranium Imports Act életbe lépése, amely megtiltja a feldolgozatlan, alacsony dúsítású orosz urán behozatalát, és 2,72 milliárd dollár szövetségi támogatást szabadít fel a hazai urántermelés fellendítésére. A törvény 2027-ig korlátozott mentességeket engedélyez, 2040-ben pedig lejár[ans.org].
Technológia és innováció
A TerraPower hivatalosan is jelezte a brit hatóságoknak, hogy megkezdi a Natrium nátrium-hűtésű gyorsreaktor általános tervezési engedélyezési folyamatát, ezzel jelezve, hogy a vállalat nemzetközi szinten is be kívánja vezetni ezt a technológiát[world-nuclear-news.org]. Olaszországban új nemzeti bizottság alakult a radioaktív anyagok szállításával kapcsolatos kihívások kezelésére, a megfelelőség és a logisztika egyszerűsítése érdekében[world-nuclear-news.org].
Az Enel, az Ansaldo Energia és a Leonardo megalapította a Nuclitalia céget, hogy tanulmányozza a fejlett nukleáris technológiákat és elemezze a piaci lehetőségeket, ami jól mutatja az európai érdeklődés növekedését a következő generációs nukleáris megoldások iránt[world-nuclear-news.org].
Friss és közelgő események
- Az IAEA Kormányzótanácsának ülése (2025. június 9–13.) számos politikai, biztonsági és védelmi kérdéssel foglalkozik majd[iaea.org].
- Az amerikai Fehér Ház nemrégiben csúcstalálkozót tartott a hazai nukleáris fejlesztésekről, és elindította a legnagyobb szövetségi kezdeményezést az elmúlt ötven évben a hálózati méretű nukleáris reaktorok felgyorsított építésére[ans.org].
Források: - world-nuclear-news.org - iaea.org - ans.org - nucnet.org
-
 @ 49d472c1:a63cd544
2025-06-05 02:59:12
@ 49d472c1:a63cd544
2025-06-05 02:59:12Bitcoin Miners Pivot to Power AI Boom, Offering a Lifeline to America’s Data-Center Crunch
A fresh Morgan Stanley analysis warns that U.S. data-center demand will balloon to ≈65 GW between 2025 and 2028—about 45 GW more than the grid can currently supply. One solution the bank singles out: repurposing the oversized, transformer-fed campuses originally built for Bitcoin mining. (investopedia.com)
Several public miners are already moving. Riot Platforms has begun buying extra land near its Corsicana, TX complex and hired a veteran data-center executive to head a “high-performance compute” division aimed squarely at AI customers. (riotplatforms.com, coindesk.com) Bitfarms, meanwhile, is marketing North-American sites to hyperscalers after hiring consultants to evaluate GPU-ready retrofits. (reuters.com)
Industry analysts say the pivot is existential. April 2024’s fourth halving chopped block rewards to 3.125 BTC, shrinking miner revenue just as network difficulty hit record highs. By leasing idle megawatts—or fully converting halls—operators lock in dollar-denominated cash-flows while retaining the option to resume mining if margins rebound.
“Miners spent the last cycle amassing land, switchgear and transformers. AI is about to pay them for it.” —Greg Miller, Citizens JMP (research note quoted in multiple sector briefings)
Why it matters
- Grid relief: Every gigawatt shifted from speculative hashing to AI compute eases ERCOT’s peak-load stress and shortens transmission-upgrade timelines. (datacenterdynamics.com)
- Cap-ex savings for cloud firms: Retrofitting a mining hall is months faster—and currently 30-40 % cheaper—than green-field construction, analysts estimate. (govtech.com)
- Dual-revenue model: Miners keep upside to future BTC price spikes while monetizing power capacity today.
The roadblocks
- Cooling retrofits: Air-cooled ASIC barns must be re-engineered for liquid-cooled GPU clusters, at up to \$3 M per MW in conversion costs. (driehaus.com)
- Policy risk in Texas: Lawmakers are weighing caps on industrial load-flex credits after recent grid-stress events, which could dent miners’ ancillary revenue. (dallasnews.com)
Bottom line: Once-beleaguered Bitcoin mines may become critical real estate for the surging AI sector—turning yesterday’s crypto boomtowns into tomorrow’s compute hubs while giving miners a much-needed new income stream.
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:50:22
@ 04c915da:3dfbecc9
2025-05-20 15:50:22There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ b1ddb4d7:471244e7
2025-06-04 11:01:29
@ b1ddb4d7:471244e7
2025-06-04 11:01:29Bitcoin FilmFest (BFF25) returns to Warsaw for its third edition, blending independent cinema—from feature films and commercials to AI-driven experimental visuals—with education and entertainment.
Hundreds of attendees from around the world will gather for three days of screenings, discussions, workshops, and networking at the iconic Kinoteka Cinema (PKiN), the same venue that hosted the festival’s first two editions in March 2023 and April 2024.
This year’s festival, themed “Beyond the Frame,” introduces new dimensions to its program, including an extra day on May 22 to celebrate Bitcoin Pizza Day, the first real-world bitcoin transaction, with what promises to be one of Europe’s largest commemorations of this milestone.
BFF25 bridges independent film, culture, and technology, with a bold focus on decentralized storytelling and creative expression. As a community-driven cultural experience with a slightly rebellious spirit, Bitcoin FilmFest goes beyond movies, yet cinema remains at its heart.
Here’s a sneak peek at the lineup, specially curated for movie buffs:
 Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money.
Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money. Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative).
Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative). Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.
Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.To get an idea of what might come up at the event, here, you can preview 6 selected ads combined into two 2 videos:
 Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships.
Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships. Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.
Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.BFF25 Main Screenings
Sample titles from BFF25’s Official Selection:
 REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director.
REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director. UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year.
UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year. HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.
HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.Check out trailers for this year’s BFF25 and past editions on YouTube.
Tickets & Info:
- Detailed program and tickets are available at bitcoinfilmfest.com/bff25.
- Stay updated via the festival’s official channels (links provided on the website).
- Use ‘LN-NEWS’ to get 10% of tickets
-
 @ 6ad3e2a3:c90b7740
2025-06-04 08:32:29
@ 6ad3e2a3:c90b7740
2025-06-04 08:32:29"Modern science is based on this principle: give us one free miracle and then we'll explain the rest."
— Terrence McKenna
I always wondered why a pot of water boils on the stove. I mean I know it boils because I turned on the electricity, but why does the electricity cause it to boil? I know the electricity produces heat, and the heat is conducted through the stainless steel pot and into the water, but why does the heat transfer from stovetop to the water?
I know the heat from the stove via the pot speeds up the molecules in the water touching it and that they in turn speed up the molecules touching them and so on throughout the pot, but why do speedy molecules cause adjacent molecules to speed up?
I mean I know they do this, but why do they do this? Why couldn’t it be that sped-up molecules only interact with sufficient speedy molecules and ignore slower ones? Why do they interact with all the molecules, causing all of them to speed up? Or why don’t the speedy ones, instead of sharing their excited state, hoard it and take more energy from adjacent slower molecules, thereby making them colder, i.e., why doesn’t half the water boil twice as fast (on the left side of the pot) while the other half (right side) turns to ice?
The molecules tend to bounce around randomly, interacting as equal opportunists on the surrounding ones rather than distinguishing only certain ones with which to interact. Why do the laws of thermodynamics behave as such rather than some other way?
There may be yet deeper layers to this, explanations going down to the atomic and even quantum levels, but no matter how far you take them, you are always, in the end, left with: “Because those are the laws of physics”, i.e., “because that’s just how it is.”
. . .
The Terrence McKenna quote, recently cited by Joe Rogan on his podcast, refers to the Big Bang, the current explanation adopted by the scientifically literate as to the origins of the universe. You see there was this insanely dense, infinitesimally small micro dot that one day (before the dawn of time) exploded outward with unimaginable power that over billions of years created what we perceive as the known universe.
What happened prior? Can’t really say because time didn’t yet exist, and “prior” doesn’t make sense in that context. Why did it do this? We don’t know. How did it get there? Maybe a supermassive black hole from another universe got too dense and exploded out the other side? Highly speculative.
So why do people believe in the Big Bang? Because it comports with and explains certain observable phenomena and predicted other phenomena which were subsequently confirmed. But scratch a little deeper for an explanation as to what caused it, for what purpose did it occur or what preceded it, and you hit the same wall.
. . .
Even if we were to understand at a quantum level how and why the Big Bang happened and what preceded it, let’s assume it’s due to Factor X, something we eventually replicated with mini big-bangs and universe creations in our labs, we would still be tasked with understanding why Factor X exists in the universe. And if Factor X were explained by Process Y, we’d still be stuck needing an explanation for Process Y — ad infinitum.
Science can thus only push the wall back farther, but can never scale it. We can never arrive at an ultimate explanation, only partial ones. Its limitations are the limitations of thought itself, the impossibility of ever creating a map at a scale of one mile per mile.
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-05 01:28:52
@ 5d4b6c8d:8a1c1ee3
2025-06-05 01:28:52How did the stackers do on their ~HealthAndFitness journeys today?
I did very well: Slept well? Check Stuck to fast? Check Ate healthy? Check Activity target? Checkarooni
The one oddity I need to work on is that I got a foot cramp while playing turtle tag with my daughter.
https://stacker.news/items/997476
-
 @ 3f770d65:7a745b24
2025-01-19 21:48:49
@ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol.
PROTOCOLS, NOT PLATFORMS.
At the heart of Nostr's philosophy is user choice, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity.
What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort.
THIS IS POWERFUL.
Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections.
The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship.
How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access.
AGAIN, THIS IS POWERUFL.
Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps.
Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions.
Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know.
TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom.
Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed.
-
 @ de7306de:1ea53f87
2025-06-05 08:46:54
@ de7306de:1ea53f87
2025-06-05 08:46:54Être « de gauche » ?
Essai pour une (re)définition transversale des concepts « gauche » et « droite »
Introduction
Il y a toujours deux niveaux. Le premier est celui sur lequel on s’appuie quand on se dit « de gauche » : c’est le niveau du discours, des bonnes intentions, des objectifs ou des revendications bien rationnelles, des belles valeurs, des symboles, des vérités chéries, etc. Puis il y a l’autre niveau, moins conscient, voire inconscient, qui fait que l’on va finir par réagir d’une certaine manière, parfois, souvent, en contradiction avec le premier niveau. Ce n’est pas, par exemple, parce qu’on n’aime pas la jalousie ou le pouvoir qu’on ne va pas se sentir jalouses ou qu’on ne va pas, parfois, prendre du plaisir dans certaines dynamiques de pouvoir. Combien de fois nous sommes-nous retrouvées frustrées de voir à quel point la réalité de nos actions se déroule en totale contradiction avec nos intentions ? Et ce, dans tous les domaines de la vie : intime, amoureuse, amicale, professionnelle, militante, etc. C’est-à-dire que nous pouvons être très « de gauche » au niveau des intentions, mais réactionnaires, voire fascistes, au niveau des pratiques. C’est donc ce deuxième niveau, dominé non pas par la raison, les concepts, les manifestes ou les bonnes intentions, mais par le monde inconscient, ses flux et ses mécanismes, auquel nous allons nous intéresser, car c’est bien là que la question se joue. Nous proposons donc un ensemble de prismes (Δ), sans aucune prétention totalisante, pour contribuer à une (ré)définition collective des concepts de gauche et de droite.
1er prisme Δ
Sensibilités et compétences
S e n s i b i l i t é :
propriété / aptitude d’une matière, d’un organe, d’un corps à réagir aux stimuli externes ou internes.
Le mot sensibilité vient de sens. Les sens captent. On peut réagir seulement aux stimuli/informations que l’on capte – inutile de forcer un aveugle à voir, un sourd à entendre. Les yeux captent la lumière, les tympans captent des ondes/vibrations. Or, il ne suffit pas d’avoir de bons yeux et de bonnes oreilles pour capter, par exemple, l’injustice dans notre entourage. Il nous faut quelque chose de plus. Quelque chose d’autre que nos sens physiologiques est à l’œuvre dans nos esprits lorsqu’on capte une injustice. Comme s’il y avait un autre type de sens. Si les sens physiologiques captent les informations physiques (lumière, vibration, température, distance, etc.), cet autre type de sens capte les informations sociales (quelle est ma place dans la meute, quand est-ce mon tour de manger, quel territoire m’est attribué ? etc.). Si, pour les sens physiologiques, des récepteurs chimiques et des terminaisons nerveuses sont à l’œuvre, pour cet autre type de sens, il s’agit plutôt de programmes, de « logiciels », un peu comme les applications de nos téléphones portables ou de nos ordinateurs. Il y a donc des « logiciels » qui nous permettent de capter les injustices, les violences, les oppressions, les signes de souffrance, de maladie, de dépression, de névrose ou de psychose, etc. Inutile de forcer un aveugle à voir, inutile de forcer quelqu’un qui n’aurait pas les bons logiciels à capter une injustice, une violence, une oppression. Il ne s’agit donc pas de vouloir ou de décider de capter ces situations ou ces phénomènes sociaux, il s’agit d’avoir, de cultiver les « bons logiciels ». Voilà donc ce à quoi nous nous référons quand on parle de sensibilités. Être de gauche donc, selon ce prisme, n’est pas tellement une décision, un vouloir ou une sorte d’identité autoproclamée que l’on pourrait rajouter facilement dans nos CV, afficher sur nos réseaux sociaux ou sur nos applis de rencontre, montrer avec nos t-shirts du Che Guevara, avec nos chants anarchistes ou nos quelques actions, non, non, non. Être de gauche = être sensible. Multi-sensible, pluri-sensible. Mais sensible à quoi ? À une diversité de phénomènes concernant le mental, le social et l’environnemental – et spécialement à leur intrication. Être de gauche implique donc avoir cultivé dans nos esprits une multiplicité de sensibilités : des sensibilités psychologiques, sociologiques, anthropologiques, écologiques… De ce point de vue, être de gauche n’est pas un discours, une mode, une décision, une envie, c’est du travail ! Car cette multiplicité de sensibilités, nous ne la cultivons pas par défaut socialement, culturellement – la société industrielle, capitaliste qui nous a façonnés, n’a surtout pas besoin d’esprits pluri-sensibles. Nous sommes obligés donc, si nous voulons cultiver ces sensibilités, de nager à contre-courant, de lutter contre le cadrage et la parcellisation propres à nos sociétés modernes, consistant à produire de petits soldats, de petits robots, de petites machines spécialisées, chacune dans son champ spécifique, et ce pour servir à qui ? Surtout pas à nous-mêmes, que ce soit individuellement ou collectivement. Nous voyons bien que ce n’est pas une mince affaire d’« être de gauche ». Quelque part, personne n’est de gauche, puisque personne n’est en mesure, prenant en compte la façon dont notre culture produit des sujets, d’avoir tout cet éventail de sensibilités. Pour mieux nuancer la question, nous sommes obligés de laisser de côté les lunettes de l’être, car elles nous contraignent à aborder le sujet de façon binaire : être ou ne pas être, soit tu es de gauche, soit tu ne l’es pas. On voit très bien que nous pouvons être sensibles par rapport à un sujet, à une situation ou à un domaine spécifique et, en même temps, très insensibles par rapport à d’autres sujets, situations ou domaines. Oui, cela veut dire que nous sommes de gauche et aussi, en même temps, de droite (insensibles) selon les endroits que l’on observe en nous, dans diverses situations et contextes. Il ne suffit pas d’« être marxistes » ou d’« être anarchistes » pour ne pas devenir des grands ou des petits tyrans, des grands ou des petits colons, des sexistes, des racistes, des oppresseurs des minorités, des validistes, des violents, des agresseurs, que ce soit au niveau collectif ou sur un niveau plus personnel, plus intime. De droite et de gauche, en même temps ? Quelle idée ! C’est que « être de gauche » est une expression trop rigide. Il convient donc d’analyser la question en termes de devenir : si l’être est un état donné, une pierre, le devenir représente toujours le mouvement, le fleuve et ses tourbillons. Nous serions très prétentieux, très arrogants ou très naïfs, si nous disions que nous sommes de gauche. En revanche, nous pouvons dire sans aucune prétention que nous sommes dans un devenir de gauche, dans la mesure où l’on cultive les sensibilités diverses. Nous avons dit qu’être de gauche veut dire être multi-sensible ; que nous ne pouvons pas vraiment être de gauche, car malgré le fait que l’on soit sensibles à certains sujets ou situations, nous sommes forcément insensibles par rapport à d’autres sujets et à d’autres situations, car victimes de l’industrie et de son culte des œillères ; que nous sommes en même temps de gauche et de droite, selon les endroits que l’on observe en nous dans une situation donnée, dans un contexte donné ; que le prisme du devenir est plus adapté que les lunettes de l’être, et qu’au lieu de dire « je suis de gauche », il est plus précis de dire « je suis dans un devenir ‘de gauche’ ».
Compétences ?
Nous avons, jusqu’à maintenant, abordé la question de la gauche en ce qui concerne les sensibilités, c’est-à-dire la captation des signes ou des informations concernant le mental, le social et l’environnemental. Mais suffit-il d’être sensible, même multi-sensible ? Combien de fois avons-nous capté des injustices, des conflits et toutes sortes de problèmes par rapport auxquels nous n’avons rien pu faire ? Nous pouvons être très sensibles et en même temps nous sentir très impuissants. Il y a donc deux choses qui seraient précieuses pour la gauche selon ce prisme : la captation et l’action, les sensibilités et les pratiques. Pour faire ou pratiquer, il faut pouvoir faire, être capable, compétent. Faire un bon discours, gérer un conflit, établir des relations de façon saine, produire autrement, consommer autrement, gérer la propriété autrement, apprendre à prendre soin et à nous soigner, apprendre à soutenir des personnes, déconstruire nos vieux logiciels, expérimenter et trouver les modes d’organisation les plus adaptés, articuler les différents terrains d’action politique (macro, micro et infra-personnel), devenir souples et ouverts au monde, à l’altérité, etc. Tout cela requiert à la fois des sensibilités et des compétences très concrètes, précisément celles que la société néglige, que notre culture ne cultive pas. Dans la gauche au sens traditionnel, y compris ladite « extrême gauche » ou « gauche radicale », prenons-nous au sérieux cette question ? Sommes-nous en train de cultiver cette multiplicité de sensibilités et de compétences ?
Et la droite, c’est quoi ?
Nous avions jusqu’à maintenant utilisé ce prisme pour définir la gauche comme sensible, comme multi-sensible. Comment faire alors sens de la droite ? Est-ce l’insensibilité qui la définit ? Les personnes plus à droite sont-elles insensibles ? Nous avions défini la sensibilité comme une sorte de logiciel nous permettant de capter et de réagir à un stimulus, à une information, à une situation donnée. L’acte raciste, classiste, sexiste, n’est-il pas nécessairement la conséquence d’un type de sensibilité, selon notre définition ? Sensibilité par rapport à l’« invasion » de la part des étrangers, au « grand remplacement », aux « déviances » sexuelles ou de genre, à l’« hystérie » des femmes, à l’« insolence » des travailleurs, etc. Nous pourrions dire que la droite est aussi sensible, et même multi-sensible ! Ce constat fait-il effondrer notre propos ? Ou est-ce qu’il y aurait des « bonnes » et des « mauvaises » sensibilités ? Les sensibilités, expliquent-elles vraiment le clivage gauche-droite ? Nous considérons qu’au contraire, notre propos tient très bien. Pour nous, la droite s’explique en termes d’insensibilité et aussi en termes de sensibilité. D’abord d’insensibilité, car la droite est insensible à une diversité de phénomènes, à un ensemble d’injustices, de violences et d’oppressions, et en même temps, elle se définit par un ensemble de sensibilités que nous pourrions qualifier d’inadaptées. Il y aurait donc des sensibilités adaptées et des sensibilités inadaptées selon la situation, selon le contexte. Mais adaptées ou inadaptées selon quels critères, selon quelle science ou quelle philosophie ? Qualifier une sensibilité, un logiciel d’inadapté, n’est-il pas trancher de façon complètement arbitraire dans l’amoralité du cosmos ? Ce problème philosophique n’est pas facile à résoudre sans invoquer une justice divine, un évangile religieux ou un évangile militant. Or, il y a une chose, pour nous la seule, qui tranche la question malgré nous, en dépit de nous, au-delà de nous, en deçà de nous, autour de nous, à travers nous. C’est la vie elle-même, ou plus précisément l’écologie. Tout système « vivant », y compris les rapports sociaux, obéit à des « principes » écologiques : si on ne boit pas assez d’eau, on finit par mourir ; si nous refoulons des émotions, des pulsions vitales, nous serons condamnés à être névrosés, malades ; si nous colonisons un peuple et si, lorsque ce peuple se défend, nous le réprimons violemment, une partie de ce peuple cherchera à se défendre d’une façon plus violente, et si notre réponse à une telle « radicalisation » est de fusiller ou de bombarder les « radicaux », les « terroristes », alors au lieu de diminuer la « menace terroriste » qui nous fait peur, nous sommes en train de la nourrir, le paradoxe étant que c’est nous, avec le premier acte de colonisation, qui l’avons provoquée. Ces trois exemples représentent des réalités, des déterminations écologiques qui n’ont rien à voir avec nos croyances, nos valeurs, nos idéologies, nos symboles. Nous pouvons identifier de mieux en mieux quand un écosystème comme une forêt est perturbé, troublé, malade ou menacé de mort. C’est l’interrelation de fonctions en équilibre(s) qui fait forêt. Tout ce qui perturbe, trouble ou menace ces équilibres est considéré comme toxique, comme nocif, comme maladif. Cela semble évident pour la forêt, or nous devons souligner que l’esprit humain ainsi que les sociétés humaines obéissent aux mêmes types de déterminations écologiques. Ces déterminations sont elles-mêmes déterminées par la singularité de chaque écosystème : il y a des forêts qui ont moins besoin d’eau, de chaleur et de lumière que d’autres, c’est d’ailleurs ce qui différencie la forêt de la jungle. Et il y a aussi des déterminations qui s’appliquent dans toute forêt, dans toute jungle : si les bactéries qui captent l’azote de l’air (N≡N – non assimilable) et qui le fixent dans le sol sous forme d’ammoniac, nitrites et nitrates (·NH3, ·NO2, ·NO3 - assimilables) disparaissent, alors n’importe quelle forêt ou jungle serait condamnée à une mort subite/rapide, car ces bactéries représentent la source d’azote pour la quasi-totalité des êtres vivants, l’azote faisant partie essentielle de l’ADN, leur absence serait fatale – pas d’azote assimilable, pas de vie. Nous considérons que ce sont ces déterminations, générales et singulières, dans chaque registre écologique et dans leur intrication – mental, social et environnemental – qui détermineront les sensibilités adaptées ou inadaptées dans un moment, une situation, un contexte, un territoire donné. Nous pouvons dire alors que les sensibilités de la gauche, ce sont des sensibilités seulement par rapport aux / concernant les trois registres écologiques dans leur intrication, tandis que la droite est précisément insensible aux rapports écologiques, à l’écologie dans ce sens large, et sensible ou hyper-sensible par rapport à ce qui fait inconsciemment peur, à ce qui menace leurs territoires existentiels, et plus précisément leurs points d’accrochage (deuxième Δ), autour desquels ces territoires ont été constitués / formés.
Gauche = sensibilités et compétences qui œuvrent dans le sens écologique – Écosophique : articulation transversale de trois registres écologiques – mental, social et environnemental.
Droite = sensibilités et compétences qui œuvrent dans un sens non-écologique, anti-écologique, écocide.
-
 @ b83a28b7:35919450
2025-05-16 19:26:56
@ b83a28b7:35919450
2025-05-16 19:26:56This article was originally part of the sermon of Plebchain Radio Episode 111 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ a296b972:e5a7a2e8
2025-06-04 22:06:06
@ a296b972:e5a7a2e8
2025-06-04 22:06:06In dem Video geht es um Dietrich Bonhoeffer, wie er sich zu Dummheit und vorsätzlicher bzw. rationaler Ignoranz geäußert hat. Schon seit einiger Zeit geht bei vielen Seltsames vor: Sie werden mit einem Thema persönlich konfrontiert und postum gibt es genau zu diesem Thema ein Video oder einen Artikel. Das kommt manchmal so vor, wie ein Frage- und Antwort-Spiel innerhalb der Schwarm-Intelligenz. Irgendwie spooky.
Die erschreckende Theorie der Dummheit, die Sie nie hören sollten - Dietrich Bonhoeffer: https://www.youtube.com/watch?v=PH-Vs5ILEko
Dem Entdecken, oder besser, dem Auf-einen-Zukommen, ist dieser E-Mail-Schriftverkehr in zeitlichem Zusammenhang vorausgegangen:
Nachfrage zu einem Aufruf durch einen Mitarbeiter zur Blutspende in einem Unternehmen mit über 100 Mitarbeitern über den E-Mail-Verteiler:
Lieber XXXXXXX,
danke zunächst für Dein Engagement.
In meiner näheren Familie gibt es jemanden, der regelmäßig Blut spendet, daher bin ich ein wenig für das Thema sensibilisiert.
Seit Du die E-Mail verschickt hast, gehe ich damit „schwanger“, ob ich ein vielleicht „heißes Eisen“ anfassen soll.
In den angehängten Informationen (des Roten Kreuzes) steht, dass das gespendete Blut auf bestimmte „Verunreinigungen“ durch Vorerkrankungen untersucht wird. Was nicht aufgeführt ist, ist eine Untersuchung, von der ich noch nicht einmal weiß, ob sie überhaupt schon durchgeführt wurde, und wenn ja, zu welchem Ergebnis sie gekommen ist, ob das gespendete Blut auch mit Substanzen der Corona-Gen-Behandlung verunreinigt sein kann. Leider zeigen ja die aktuellen Erkenntnisse, dass das Spike-Protein noch nach Jahren aktiv sein kann. Auch in gespendetem Blut? Die konkrete Frage wäre, ob das Rote Kreuz definitiv ausschließen kann, dass das nicht der Fall ist, damit ein möglicher Schaden nicht die Gefahr läuft, größer zu sein, als der Nutzen.
Soweit ich weiß, hat das Rote Kreuz bis heute keine separaten Blutbanken von „geimpftem“ und „ungeimpftem“ Blut angelegt. Wenn zu 100% ausgeschlossen werden kann, dass keine schädlichen Substanzen der Gen-Behandlung in die Blutkonserve gelangen, wäre das ja natürlich nicht nötig. Ist das so? Wenn ja, wo ist der Nachweis dazu zu finden, wie ist der aktuelle Erkenntnisstand, von wem wurden Studien dazu erarbeitet, wer hat das finanziert?
Mindestens 20% der Bevölkerung, das sind rund 16 Millionen Menschen, haben auf die Gen-Behandlung verzichtet und wollen im Ernstfall kein kontaminiertes Blut empfangen. Wie kann das Rote Kreuz belegbar und glaubhaft nachweisen, dass möglicherweise verunreinigtes Blut nicht doch in die Blutkonserven gelangt, weil sonst die Gefahr besteht, dass im Ernstfall Impfverzichter einen Schaden davontragen könnten?
Ich finde das eine wichtige Frage dem Roten Kreuz gegenüber und vielleicht wäre es auch gut, die möglichen Spender im Vorfeld für dieses heikle Thema zu sensibilisieren. Ich finde es auffällig, dass das Rote Kreuz sich hierzu weder in die eine, noch andere Richtung in den Informationen äußert, obwohl sie uns alle betrifft.
Ich schreibe diese Email aus kollegialen Gründen, aber auch zur Sensibilisierung gegenüber der Verantwortung aller Menschen gegenüber ihren Mitmenschen, die (hoffentlich nie) in die Situation kommen, einmal auf eine Blutspende angewiesen zu sein.
Wenn sich etwas Neues auf meine Nachfrage an Dich ergibt, wäre es klasse, ich würde davon erfahren.
Vielen Dank und viele Grüße
YYYYYYY
(Die Intension war, sich so vorsichtig wie möglich, quasi auf „Samtpfötchen“, an den Kern heranzupirschen. Dass es bereits Erkenntnisse dazu gibt, dass das Blut kontaminiert sein kann, wurde bewusst weggelassen, um keine Angriffsfläche zu bieten, ein „Verschwörungstheoretiker“ zu sein. Wenn die andere Seite auf einen Austausch eingestiegen wäre, wäre eine Quelle zu dieser Aussage vorhanden gewesen.)
Die Antwort:
Hallo YYYYYYY,
danke für die ausführliche Nachricht und dass du dir Gedanken zu dem Thema machst. Ich finde, man sollte Blutspenden als eine persönliche und private Sache betrachten.
Jeder und jede sollte für sich selbst abwägen, ob und unter welchen Bedingungen er oder sie das tun möchte.
Die Fragen, die du gestellt hast, sind echt speziell. Da geht's um medizinische und wissenschaftliche Themen, da kann ich als Privatperson nicht mitreden. Ich denke, dass sich Interessierte bei solchen Themen am besten direkt an medizinische Fachstellen oder das Rote Kreuz vor Ort wenden sollten, um fundierte und belastbare Informationen zu erhalten.
Mir persönlich ist es wichtig, Menschen auf die Möglichkeit der Blutspende aufmerksam zu machen.
Jeder kann das für sich selbst entscheiden und es ist auch okay, wenn man dabei Überzeugungen hat.
Beste Grüße
XXXXXXX
(„Blutspende…eine persönliche und private Sache“, nach dem Corona-Ereignis auch noch?, „…ich als Privatperson“ empfehle anderen etwas, bei dem sie möglicherweise anderen einen Schaden zufügen. Ist das schon grob fahrlässig, nach den Denkanstößen, die gegeben wurden?, „Wenn man dabei Überzeugungen hat.“, interessante Formulierung.)
Darauf die Reaktion:
Hallo XXXXXXX,
danke auch für Deine Antwort.
Wenn so eine im Grundsatz sicher gute Aktion beworben wird, liegt es nach meinem Empfinden auch in der Verantwortung, auf mögliche Folgen hinzuweisen, wenn es das Rote Kreuz schon nicht tut. Vorausgesetzt, man misst ihnen Bedeutung zu. Wenn meine E-Mail keine Veranlassung zu einer Beunruhigung und eigener Recherche angeregt hat, dann kann ich leider mehr nicht tun.
Dass das Rote Kreuz keine Hinweise gibt, liegt wohl daran, dass es Teil des Systems ist. Wer die Augen aufmacht, kann mit wenig Aufwand leider mehr als genug Tatsachenwahrheiten finden, die mit Schäden im Zusammenhang der Gen-Behandlung verursacht wurden und immer noch verursacht werden. Es ist nicht meine Aufgabe, einen Wissensrückstand von 5 Jahren auf den aktuellen Stand zu bringen. Allein die veröffentlichten RKI-Protokolle sollten schon genug Anlass zur Skepsis bieten. Der ÖRR berichtet leider nicht darüber, weil er auch Teil des Systems ist.
Ich will es damit genug sein lassen und hoffe, dass es unter den Kolleginnen und Kollegen noch weitere kritische Geister gibt.
Es geht nicht gegen Dich persönlich, aber ich hoffe, das Angebot wird nicht zahlreich genutzt.
Viele Grüße
YYYYYYY
(Einen halben Gang hochgeschaltet, ein Versuch, XXXXXXX aus der Reserve zu locken.)
Und ein Nachtrag von YYYYYYY:
Lieber XXXXXXX,
wir sind schon einmal unter Missbrauch des Begriffes „Solidarität“ hinter die Fichte geführt worden. Das darf nicht noch einmal passieren!
Nochmals viele Grüße
YYYYYYY
(Keine Reaktion mehr von XXXXXXX)
Und, wie gesagt, daraufhin kam das Video mit Bonhoeffer entgegen. Besser kann man vorsätzliche, rationale Ignoranz in Bezug auf den Schriftwechsel nicht beschreiben.
Hier wird eine jeden angehende allgemeinmedizinische Frage zu einer Frage der persönlichen Überzeugung gemacht. Das kommt doch sehr bekannt vor, oder?
Sehr wahrscheinlich lässt es sich vermuten, dass es sich bei XXXXXXX wohl um einen Corona-Jünger handelt, der die Tatsachen scheut, wie der Teufel das Weihwasser. Bloß nicht nachdenken, bloß nicht in Frage stellen, bloß nicht hellhörig oder gar neugierig werden, bloß nicht auf die Äußerungen eingehen, bloß nicht konkret werden, bloß keine eindeutig formulierte Stellung zu den Aussagen beziehen. „Angriffsfläche“ wäre vorhanden gewesen.
Das vorsichtige Anpirschen war alles andere, als mit-der-Brechstange-herangehen. Und doch setzt sofort automatisch der Teflon-Effekt ein. Selbstschutz.
Die Frage ist, wie soll da die Spaltung überwunden werden, wenn „die andere Seite“ so überhaupt nicht bereit ist, sich mit dem Vorgebrachten auseinanderzusetzen. Noch nicht einmal, wenn man nur die Spitze der Spitze des Eisbergs leise anhaucht.
Diesem Beispiel könnten viele unzählige weitere Beispiele hinzugefügt werden. Jeder hat so etwas schon einmal auf die eine oder andere Weise erlebt.
Das Gefühl lässt sich nicht unterdrücken, dass sich die Menschheit in zwei Lager aufgeteilt hat, und es gibt derzeit keinen Weg, wie man wieder aufeinander zukommen könnte.
Wie zwei Welten aufeinanderprallen, kann man derzeit auch in der Enquete-Kommission im sächsischen Landtag erleben: https://www.youtube.com/watch?v=D6ACmwBUBFM
Aus der Sicht von YYYYYYY ist das kein Grund zur Verzweiflung, jedoch drängt sich der Wunsch auf, dass man mit solchen Menschen wie XXXXXXX nichts mehr anfangen will. Man möchte mit ihnen, so schade es auch ist, am liebsten gar nichts mehr zu tun haben, und wenn doch aus irgendwelchen Gründen, nur noch das Allernotwendigste, so kurz und knapp, wie möglich. Empathie aufzubringen erscheint einem als vergeudete Energie, besser ist es, sich auf die Menschen zu konzentrieren, die wegen fehlender Genbehandlung keine Wesensveränderungen, die mittlerweile leider auch schon bestätigt sind, erlitten haben.
Wie Bonhoeffer richtig sagt, es geht hier nicht um Intelligenz, es geht viel tiefer. Es geht um das Menschsein an sich, und man hat den Eindruck, dass vor allem dies unter dem Einfluss der Spritze sehr stark gelitten hat. Da scheint so eine Abgestumpftheit durch, die einem einen kalten Schauer über den Rücken fahren lässt. Und das ist vielleicht noch gefährlicher, als diejenigen, die wirklich dumm sind. Das ist keine Arroganz oder Überheblichkeit, sondern unschuldig, wahllos von der Natur vergebene Dummheit, die jeden hätte ereilen können, hat es immer schon zu einem großen Teil gegeben. Hier hat man wenigstens noch die Möglichkeit, sich einfühlen zu können und Verständnis aufzubringen. Bei Menschen aber, von denen man weiß, dass sie die kognitiven Fähigkeiten zur Reflektion hätten, sie jedoch aus welchen Gründen auch immer nicht nutzen, oder sie als Verdrängungsmechanismus gerade nutzen, weil sie es können, geht auch eine gewisse Gefahr aus, weil man nie wissen kann, was sie sich sonst noch so ausdenken könnten, wenn sie in die geistige Enge getrieben werden, um ja nicht von Menschen, die den Mut haben, die Wahrheit auszusprechen, in ihrem mühsam aufgebauten Weltbild erschüttert zu werden. „Was nicht sein darf, das nicht sein kann!“, obwohl doch eigentlich die Wahrheit dem Menschen zumutbar ist.
So hat man das Gefühl, man atmet Honig ein und bewegt sich mühsam durch einen zähen Brei vorwärts, der einem bis zu den Oberschenkeln reicht. Jeder Schritt eine Anstrengung.
Und bevor man noch tiefer in dieses Verlustgefühl von Lebensqualität eintaucht (das hat nichts mit Depressionen zu tun, man bekommt einfach nur schlechte Laune), sich immer wieder bewusst machen, dass es da draußen noch eine Menge bei Verstand gebliebener Menschen gibt, die unermüdlich daran arbeiten, dass die Wahrheit weiter so sehr erkraftet, dass sie sich ihren Weg in den sogenannten Mainstream bahnt und die Menschen endlich aufwachen. So schmerzlich das für viele sein mag, es muss sein!
Selbst für einen wenig religiösen Menschen, im Sinne von regelmäßigen Kirchgängen und keinem Kontakt zur Institution Kirche, bekommt der Satz eine ganz besondere Bedeutung:
„Ich schicke euch den Geist der Wahrheit, und der wird euch frei machen!“
-
 @ 472f440f:5669301e
2025-06-04 01:37:37
@ 472f440f:5669301e
2025-06-04 01:37:37Marty's Bent
via nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqy0hwumn8ghj7mn0wd68yttjv4kxz7fwvf5hgcm0d9hzumnfde4xzqpq85h9z5yxn8uc7retm0n6gkm88358lejzparxms5kmy9epr236k2qtyz2zr
A lot of the focus over the last couple of months has been on the emergence of Strategy competitors in public markets looking to build sizable bitcoin treasuries and attract investors of all shapes and sizes to drive shareholder value. The other big topic in the bitcoin development world has been around OP_RETURN and the debate over whether or not the amount of data that can be shoved into a bitcoin transaction should be decided by the dominant implementation.
A topic that is just as, if not more, important that is not getting enough appreciation is the discussion around open source bitcoin developers and the lingering effects of the Biden administration's attack on Samourai Wallet and Tornado Cash. If you read our friend Matt Corallo's tweet above, you'll notice that the lingering effects are such that even though the Trump administration has made concerted efforts to reverse the effects of Operation Chokepoint 2.0 that were levied by the Biden administration, Elizabeth Warren, and her friends at the Treasury and SEC - it is imperative that we enshrine into law the rights of open source developers to build products and services that enable individuals to self-custody bitcoin and use it in a peer-to-peer fashion without the threat of getting thrown in jail cell.
As it stands today, the only assurances that we have are from an administration that is overtly in favor of the proliferation of bitcoin in the United States. There is nothing in place to stop the next administration or another down the line from reverting to Biden-era lawfare that puts thousands of bitcoin developers around the world at risk of being sent into a cage because the government doesn't like how some users leverage the code they write. To make sure that this isn't a problem down the line it is imperative that we pass the Blockchain Regulatory Clarity Act, which would not hold bitcoin developers liable for the ways in which end users leverage their tools.
Not only is this an act that would protect developers from pernicious government officials targeting them when end users use their technology in a way that doesn't make the government happy, it will also protect YOU, the end user, looking to transact in a peer-to-peer fashion and leverage all of the incredible properties of bitcoin the way they were meant to be. If the developers are not protected, they will not be able to build the technology that enables you to leverage bitcoin.
So do your part and go to saveourwallets.org. Reach out to your local representatives in Congress and Senators and make some noise. Let them know that this is something that you care deeply about and that they should not only pay attention to this bill but push it forward and enshrine it into law as quickly as possible.
There are currently many developers either behind bars or under house arrest for developing software that gives you the ability to use Bitcoin in a self-sovereign fashion and use it in a privacy-preserving way. Financial privacy isn't a crime. It is an inalienable human right that should be protected at all cost. The enshrinement of this inalienable right into law is way past due.
#FreeSamourai #FreeRoman
Headlines of the Day
MicroStrategy Copycats See Speculative Premiums Fade - via X
Square Tests Bitcoin Payments, Lightning Yields Beat DeFi - via X
Get our new STACK SATS hat - via tftcmerch.io
Bitfinex Moves $731M Bitcoin to Jack Mallers' Fund - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code “TFTC20” during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Should I join a country club?
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ da8b7de1:c0164aee
2025-06-03 19:31:32
@ da8b7de1:c0164aee
2025-06-03 19:31:32Lengyelország előrelépése az első atomerőmű építésében
Lengyelország állami nukleáris vállalata, a Polskie Elektrownie Jadrowe (PEJ) és egy amerikai konzorcium – élén a Westinghouse és a Bechtel cégekkel – mérnöki fejlesztési megállapodást kötött. Ez a szerződés kulcsfontosságú lépés az ország első atomerőművének megvalósítása felé, lehetővé téve a részletes mérnöki és helyszínspecifikus munkák megkezdését. A lengyel kormány ezt mérföldkőnek tekinti az energiaszuverenitás és a dekarbonizáció felé vezető úton.
Amerikai politika: lendület az új nukleáris technológiáknak
Az Egyesült Államok kormánya elnöki rendeletet adott ki, amely reformokat vezet be a nukleáris reaktorok tesztelésében az Energiaügyi Minisztériumnál. A cél az új generációs reaktorok – köztük mikroreaktorok és kis moduláris reaktorok (SMR-ek) – fejlesztésének és engedélyezésének felgyorsítása, valamint a környezetvédelmi vizsgálatok egyszerűsítése. A rendelet legalább három új reaktor kritikus üzembe helyezését célozza meg 2026 júliusáig, támogatva ezzel az ipari alkalmazások széles körét, például adatközpontokat vagy hidrogéntermelést. Az intézkedés célja, hogy az USA visszaszerezze vezető szerepét a nukleáris innovációban, és csökkentse a korábbi években felhalmozódott engedélyezési akadályokat.
Kis moduláris reaktorok (SMR) fejlesztése világszerte
Az SMR-szektorban világszerte jelentős előrelépések történtek: - Az amerikai Tennessee Valley Authority (TVA) benyújtotta az első építési kérelmet egy GE Hitachi BWRX-300 SMR-re a Clinch River telephelyen. - Kanadában az Ontario Power Generation engedélyt kapott az első, négy tervezett SMR megépítésének megkezdésére a Darlington telephelyen. - Belgium és Brazília innovatív SMR-technológiákat vizsgál, köztük ólom-hűtésű reaktorokat és nemzetközi együttműködéseket. - Olyan technológiai óriások, mint a Google, az USA-ban korai fázisú fejlett nukleáris projektekbe fektetnek, ami a magánszektor növekvő érdeklődését mutatja.
Globális ipari és pénzügyi támogatás a nukleáris bővítéshez
Széles körű koalíció – köztük olyan nagyvállalatok, mint az Amazon, Google, Meta, Dow – és pénzügyi intézmények kötelezték el magukat amellett, hogy 2050-re megháromszorozzák a globális nukleáris kapacitást. Ez összhangban van az ENSZ klímacsúcsain tett vállalásokkal, ahol már 31 ország támogatja a nukleáris energia megháromszorozását a nettó zéró kibocsátási célok eléréséhez. Az amerikai kongresszus olyan törvényjavaslatokat készít elő, amelyek lehetővé tennék, hogy a multilaterális fejlesztési bankok – például a Világbank – is finanszírozhassanak nukleáris projekteket, megszüntetve ezzel a korábbi tiltásokat.
Közelgő nemzetközi nukleáris biztonsági gyakorlat
A Nemzetközi Atomenergia-ügynökség (IAEA) készül a ConvEx-3 vészhelyzeti gyakorlatára, amelyet 2025. június 24–25-én Romániában tartanak. A gyakorlat egy súlyos nukleáris vészhelyzetet szimulál a cernavodai atomerőműben, tesztelve a tagállamok és nemzetközi szervezetek felkészültségét és reagálóképességét. A ConvEx-3 a legmagasabb szintű IAEA vészhelyzeti gyakorlat, kulcsszerepet játszik a globális nukleáris biztonság és védelem erősítésében.
Politikai bizonytalanság Dél-Korea nukleáris terveiben
Dél-Korea 2025. június 3-i elnökválasztása hatással lehet az ország nukleáris reneszánszára. A vezető jelölt, Lee Jae-myung kijelentette, hogy „egyelőre” fenntartaná a nukleáris energiát, de hosszabb távon a megújulók felé mozdulna el. Ez bizonytalanságot okoz a koreai nukleáris ipar hazai és exportterveiben, ami kihatással lehet a globális ellátási láncokra és külföldi reaktorprojektekre is.
Iparági trendek és további fejlemények
- Japán új energiastratégiája maximalizálni kívánja a nukleáris energia részarányát, 2040-re mintegy 20%-ot célozva, különös hangsúlyt fektetve a következő generációs reaktorokra és a biztonság növelésére.
- Belgium kormánya és a francia Engie közműcég megállapodott a kulcsfontosságú reaktorok üzemidejének tízéves meghosszabbításáról, ami az európai nukleáris pálfordulás újabb jele.
- Az IAEA és a World Nuclear Association egyaránt növekvő nemzetközi érdeklődésről számol be az SMR-ek és fejlett reaktortechnológiák iránt, új projektek és partnerségek indulnak Ázsiában, Európában és Amerikában.
Források:
world-nuclear-news.org
nucnet.org
iaea.org
world-nuclear.org
govinfo.gov
whitehouse.gov -
 @ 8bad92c3:ca714aa5
2025-06-03 18:02:33
@ 8bad92c3:ca714aa5
2025-06-03 18:02:33Marty's Bent

It's been a pretty historic week for the United States as it pertains to geopolitical relations in the Middle East. President Trump and many members of his administration, including AI and Crypto Czar David Sacks and Treasury Secretary Scott Bessent, traveled across the Middle East making deals with countries like Qatar, Saudi Arabia, the United Arab Emirates, Syria, and others. Many are speculating that Iran may be included in some behind the scenes deal as well. This trip to the Middle East makes sense considering the fact that China is also vying for favorable relationships with those countries. The Middle East is a power player in the world, and it seems pretty clear that Donald Trump is dead set on ensuring that they choose the United States over China as the world moves towards a more multi-polar reality.
Many are calling the events of this week the Riyadh Accords. There were many deals that were struck in relation to artificial intelligence, defense, energy and direct investments in the United States. A truly prolific power play and demonstration of deal-making ability of Donald Trump, if you ask me. Though I will admit some of the numbers that were thrown out by some of the countries were a bit egregious. We shall see how everything plays out in the coming years. It will be interesting to see how China reacts to this power move by the United States.
While all this was going on, there was something happening back in the United States that many people outside of fringe corners of FinTwit are not talking about, which is the fact that the 10-year and 30-year U.S. Treasury bond yields are back on the rise. Yesterday, they surpassed the levels of mid-April that caused a market panic and are hovering back around levels that have not been seen since right before Donald Trump's inauguration.
I imagine that there isn't as much of an uproar right now because I'm pretty confident the media freakouts we were experiencing in mid-April were driven by the fact that many large hedge funds found themselves off sides of large levered basis trades. I wouldn't be surprised if those funds have decreased their leverage in those trades and bond yields being back to mid-April levels is not affecting those funds as much as they were last month. But the point stands, the 10-year and 30-year yields are significantly elevated with the 30-year approaching 5%. Regardless of the deals that are currently being made in the Middle East, the Treasury has a big problem on its hands. It still has to roll over many trillions worth of debt over over the next few years and doing so at these rates is going to be massively detrimental to fiscal deficits over the next decade. The interest expense on the debt is set to explode in the coming years.
On that note, data from the first quarter of 2025 has been released by the government and despite all the posturing by the Trump administration around DOGE and how tariffs are going to be beneficial for the U.S. economy, deficits are continuing to explode while the interest expense on the debt has definitively surpassed our annual defense budget.
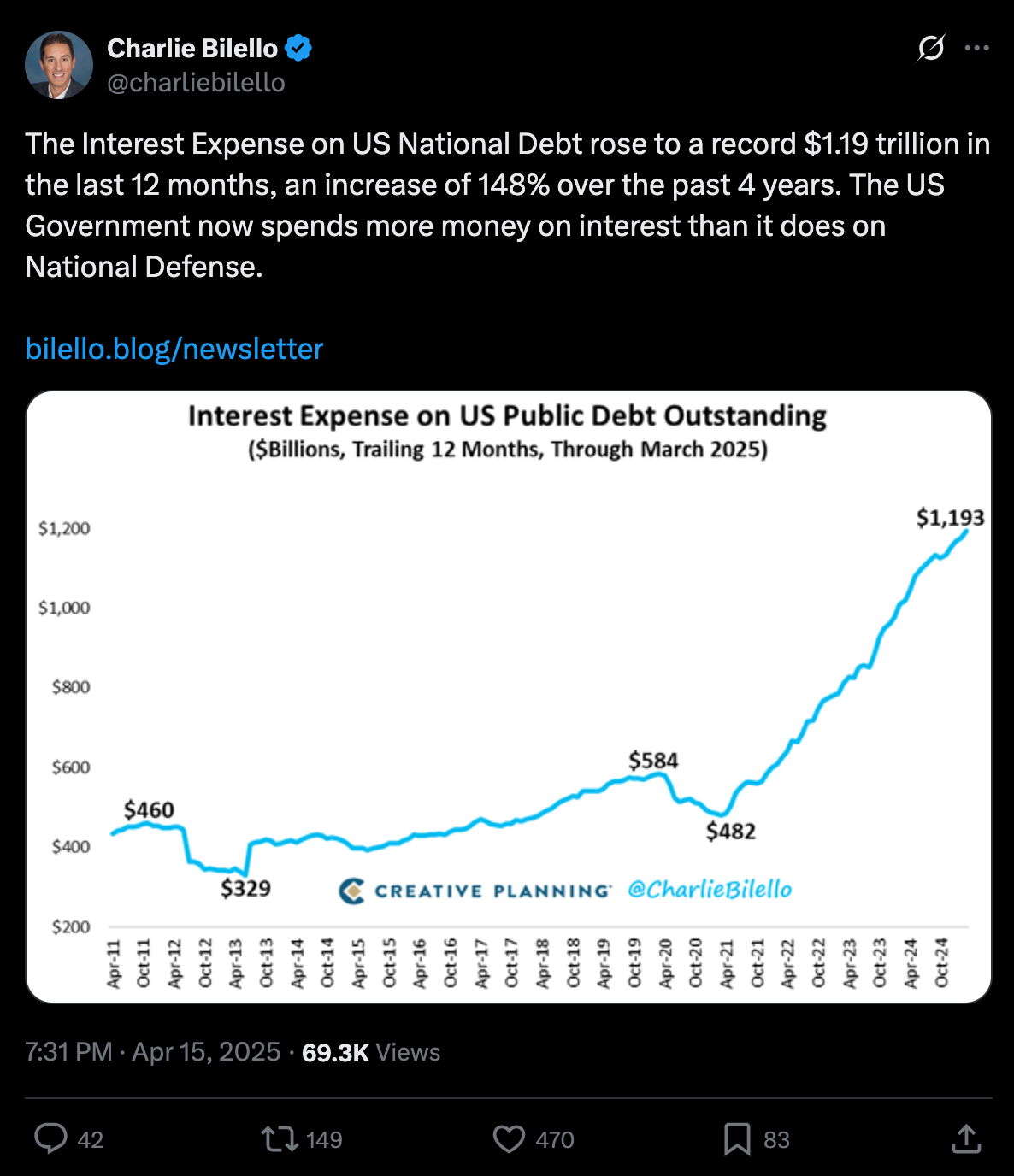
via Charlie Bilello
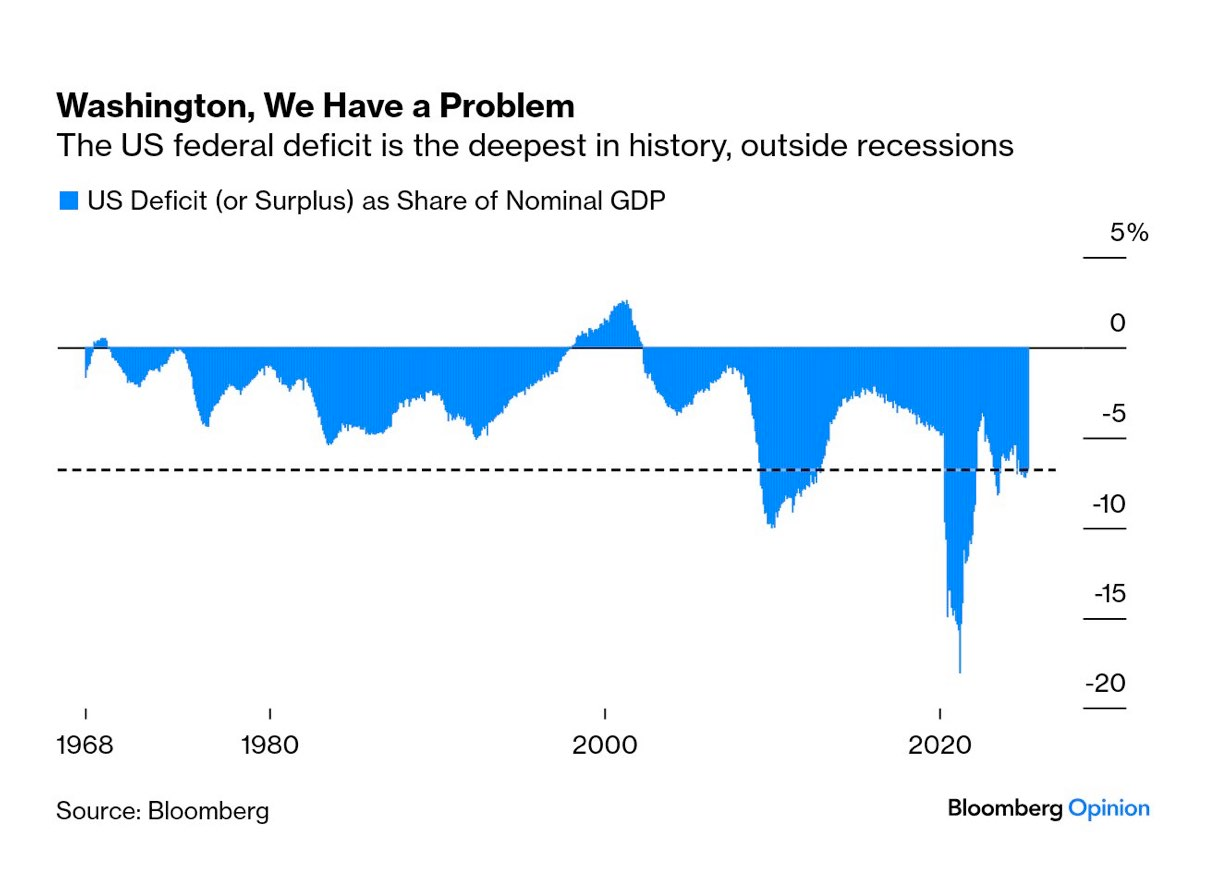
via Mohamed Al-Erian
To make matters worse, as things are deteriorating on the fiscal side of things, the U.S. consumer is getting crushed by credit. The 90-plus day delinquency rates for credit card and auto loans are screaming higher right now.
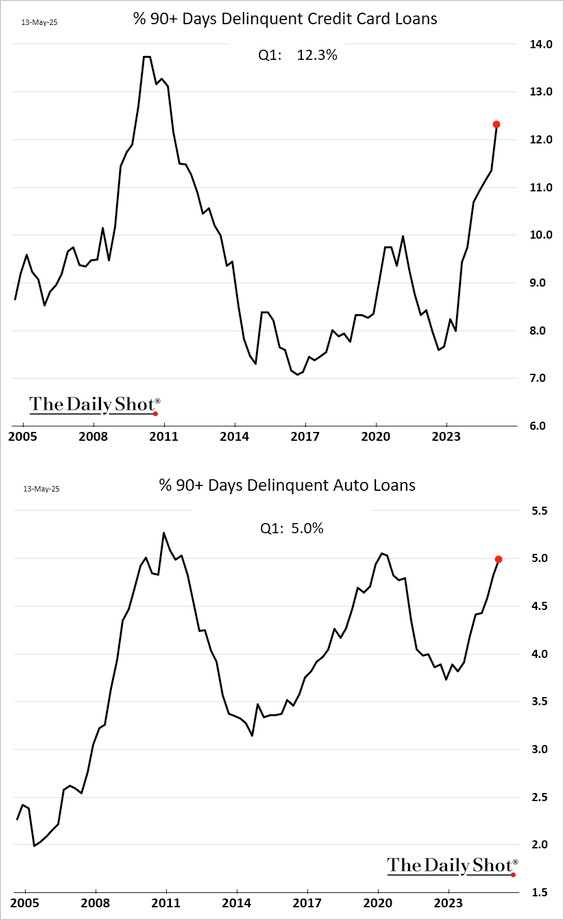
via TXMC
One has to wonder how long all this can continue without some sort of liquidity crunch. Even though equities markets have recovered from their post-Liberation Day month long bear market, I would not be surprised if what we're witnessing is a dead cat bounce that can only be continued if the money printers are turned back on. Something's got to give, both on the fiscal side and in the private markets where the Common Man is getting crushed because he's been forced to take on insane amounts of debt to stay afloat after years of elevated levels of inflation. Add on the fact that AI has reached a state of maturity that will enable companies to replace their current meat suit workers with an army of cheap, efficient and fast digital workers and it isn't hard to see that some sort of employment crisis could be on the horizon as well.
Now is not the time to get complacent. While I do believe that the deals that are currently being made in the Middle East are probably in the best interest of the United States as the world, again, moves toward a more multi-polar reality, we are facing problems that one cannot simply wish away. They will need to be confronted. And as we've seen throughout the 21st century, the problems are usually met head-on with a money printer.
I take no pleasure in saying this because it is a bit uncouth to be gleeful to benefit from the strife of others, but it is pretty clear to me that all signs are pointing to bitcoin benefiting massively from everything that is going on. The shift towards a more multi-polar world, the runaway debt situation here in the United States, the increasing deficits, the AI job replacements and the consumer credit crisis that is currently unfolding, All will need to be "solved" by turning on the money printers to levels they've never been pushed to before.
Weird times we're living in.
China's Manufacturing Dominance: Why It Matters for the U.S.
In my recent conversation with Lyn Alden, she highlighted how China has rapidly ascended the manufacturing value chain. As Lyn pointed out, China transformed from making "sneakers and plastic trinkets" to becoming the world's largest auto exporter in just four years. This dramatic shift represents more than economic success—it's a strategic power play. China now dominates solar panel production with greater market control than OPEC has over oil and maintains near-monopoly control of rare earth elements crucial for modern technology.
"China makes like 10 times more steel than the United States does... which is relevant in ship making. It's relevant in all sorts of stuff." - Lyn Alden
Perhaps most concerning, as Lyn emphasized, is China's financial leverage. They hold substantial U.S. assets that could be strategically sold to disrupt U.S. treasury market functioning. This combination of manufacturing dominance, resource control, and financial leverage gives China significant negotiating power in any trade disputes, making our attempts to reshoring manufacturing all the more challenging.
Check out the full podcast here for more on Triffin's dilemma, Bitcoin's role in monetary transition, and the energy requirements for rebuilding America's industrial base.
Headlines of the Day
Financial Times Under Fire Over MicroStrategy Bitcoin Coverage - via X
Trump in Qatar: Historic Boeing Deal Signed - via X
Get our new STACK SATS hat - via tftcmerch.io
Johnson Backs Stock Trading Ban; Passage Chances Slim - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code *“TFTC20”* during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Building things of value is satisfying.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !import
-
 @ 5c26ee8b:a4d229aa
2025-06-04 21:29:51
@ 5c26ee8b:a4d229aa
2025-06-04 21:29:51Since late December, 2024, an evil magic attack targeted me and my family as well as many people occupying governmental positions. The attack was involving the Antichrist that was on an unreachable island found by me telepathically. Sadly the information about the Antichrist reached some Russian Oligarchs Among which many Jews. And somehow he was contacted by them as well as many other Antichrist Allies among which Royal families and he led the magic attack even though magic mixed with AI and computer technologies. The attack consisted in whispering of the devils, of mankind (Antichrist allies) and jinns. Physical harm was attempted too although so weak for any significant effect for me at least. I hesitated on killing the Antichrist because his appearance is a sign of Judgement Day, however, because of acknowledging that the attack would be too intense for ordinary people that don’t know how to know the difference between inner voice or whispering of the devils I have decided to kill him by requesting that he is burned in the core of the earth and by turning any remains into dust spread in space. He didn’t have only a physical presence though he had an incorporated devil. So it took a while to kill the devil that was isolated in iron coffin first so it assumed a smaller figure while trying to escape and finally God guided me to request that the devil is hit with fireballs over and over again. It was confirmed to me that the devil of the Antichrist was completely burned out. And that the next sign would be the creature coming out of the earth, Ad-Daba as well as the smoke covering all the earth, with which there is a great punishment, and that I would be able to fly too (good for me). I hesitated on spreading the news about the Antichrist to avoid fitnah (confusion and trial). Also because he was never freed out of the island before getting burned out. I am mentioning this because it’s important to know that when God’s punishment comes and when the great signs of Judgement Day (among which what’s mentioned above) would appear the returning to God in belief or in repentance won’t be accepted; so my advise is to do it now.
27:82 An-Naml
۞ وَإِذَا وَقَعَ الْقَوْلُ عَلَيْهِمْ أَخْرَجْنَا لَهُمْ دَابَّةً مِنَ الْأَرْضِ تُكَلِّمُهُمْ أَنَّ النَّاسَ كَانُوا بِآيَاتِنَا لَا يُوقِنُونَ
And when the word befalls them, We will bring forth for them a creature from the earth speaking to them, [saying] that the people were, of Our verses, not certain [in faith].
- Ad-Dukhaan
حم
Ha, Meem.
وَالْكِتَابِ الْمُبِينِ
By the clear Book,
إِنَّا أَنْزَلْنَاهُ فِي لَيْلَةٍ مُبَارَكَةٍ ۚ إِنَّا كُنَّا مُنْذِرِينَ
Indeed, We sent it down during a blessed night. Indeed, We were to warn [mankind].
فِيهَا يُفْرَقُ كُلُّ أَمْرٍ حَكِيمٍ
On that night is made distinct every precise matter -
أَمْرًا مِنْ عِنْدِنَا ۚ إِنَّا كُنَّا مُرْسِلِينَ
[Every] matter [proceeding] from Us. Indeed, We were to send [a messenger]
رَحْمَةً مِنْ رَبِّكَ ۚ إِنَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
As mercy from your Lord. Indeed, He is the Hearing, the Knowing.
رَبِّ السَّمَاوَاتِ وَالْأَرْضِ وَمَا بَيْنَهُمَا ۖ إِنْ كُنْتُمْ مُوقِنِينَ
Lord of the heavens and the earth and that between them, if you would be certain.
لَا إِلَٰهَ إِلَّا هُوَ يُحْيِي وَيُمِيتُ ۖ رَبُّكُمْ وَرَبُّ آبَائِكُمُ الْأَوَّلِينَ
There is no deity except Him; He gives life and causes death. [He is] your Lord and the Lord of your first forefathers.
بَلْ هُمْ فِي شَكٍّ يَلْعَبُونَ
But they are in doubt, amusing themselves.
فَارْتَقِبْ يَوْمَ تَأْتِي السَّمَاءُ بِدُخَانٍ مُبِينٍ
Then watch for the Day when the sky will bring a visible smoke.
يَغْشَى النَّاسَ ۖ هَٰذَا عَذَابٌ أَلِيمٌ
Covering the people; this is a painful torment.
رَبَّنَا اكْشِفْ عَنَّا الْعَذَابَ إِنَّا مُؤْمِنُونَ
[They will say], "Our Lord, remove from us the torment; indeed, we are believers."
أَنَّىٰ لَهُمُ الذِّكْرَىٰ وَقَدْ جَاءَهُمْ رَسُولٌ مُبِينٌ
How will there be for them a reminder [at that time]? And there had come to them a clear Messenger.
ثُمَّ تَوَلَّوْا عَنْهُ وَقَالُوا مُعَلَّمٌ مَجْنُونٌ
Then they turned away from him and said, "[He was] taught [and is] a madman."
إِنَّا كَاشِفُو الْعَذَابِ قَلِيلًا ۚ إِنَّكُمْ عَائِدُونَ
Indeed, We will remove the torment for a little. Indeed, you [disbelievers] will return [to disbelief].
يَوْمَ نَبْطِشُ الْبَطْشَةَ الْكُبْرَىٰ إِنَّا مُنْتَقِمُونَ
The Day We will strike with the greatest assault, indeed, We will take retribution.
6:158 Al-An'aam
هَلْ يَنْظُرُونَ إِلَّا أَنْ تَأْتِيَهُمُ الْمَلَائِكَةُ أَوْ يَأْتِيَ رَبُّكَ أَوْ يَأْتِيَ بَعْضُ آيَاتِ رَبِّكَ ۗ يَوْمَ يَأْتِي بَعْضُ آيَاتِ رَبِّكَ لَا يَنْفَعُ نَفْسًا إِيمَانُهَا لَمْ تَكُنْ آمَنَتْ مِنْ قَبْلُ أَوْ كَسَبَتْ فِي إِيمَانِهَا خَيْرًا ۗ قُلِ انْتَظِرُوا إِنَّا مُنْتَظِرُونَ
Do they [then] wait for anything except that the angels should come to them or your Lord should come or that there come some of the signs of your Lord? The Day that some of the signs of your Lord will come no soul will benefit from its faith as long as it had not believed before or had earned through its faith some good. Say, "Wait. Indeed, we [also] are waiting."
4:17 An-Nisaa
إِنَّمَا التَّوْبَةُ عَلَى اللَّهِ لِلَّذِينَ يَعْمَلُونَ السُّوءَ بِجَهَالَةٍ ثُمَّ يَتُوبُونَ مِنْ قَرِيبٍ فَأُولَٰئِكَ يَتُوبُ اللَّهُ عَلَيْهِمْ ۗ وَكَانَ اللَّهُ عَلِيمًا حَكِيمًا
The repentance accepted by Allah is only for those who do wrong in ignorance [or carelessness] and then repent soon after. It is those to whom Allah will turn in forgiveness, and Allah is ever Knowing and Wise.
4:18 An-Nisaa
وَلَيْسَتِ التَّوْبَةُ لِلَّذِينَ يَعْمَلُونَ السَّيِّئَاتِ حَتَّىٰ إِذَا حَضَرَ أَحَدَهُمُ الْمَوْتُ قَالَ إِنِّي تُبْتُ الْآنَ وَلَا الَّذِينَ يَمُوتُونَ وَهُمْ كُفَّارٌ ۚ أُولَٰئِكَ أَعْتَدْنَا لَهُمْ عَذَابًا أَلِيمًا
But repentance is not [accepted] of those who [continue to] do evil deeds up until, when death comes to one of them, he says, "Indeed, I have repented now," or of those who die while they are disbelievers. For them We have prepared a painful punishment.
4:47 An-Nisaa
يَا أَيُّهَا الَّذِينَ أُوتُوا الْكِتَابَ آمِنُوا بِمَا نَزَّلْنَا مُصَدِّقًا لِمَا مَعَكُمْ مِنْ قَبْلِ أَنْ نَطْمِسَ وُجُوهًا فَنَرُدَّهَا عَلَىٰ أَدْبَارِهَا أَوْ نَلْعَنَهُمْ كَمَا لَعَنَّا أَصْحَابَ السَّبْتِ ۚ وَكَانَ أَمْرُ اللَّهِ مَفْعُولًا
O you who were given the Scripture, believe in what We have sent down [to Muhammad], confirming that which is with you, before We obliterate faces and turn them toward their backs or curse them as We cursed the sabbath-breakers. And ever is the decree of Allah accomplished.
4:48 An-Nisaa
إِنَّ اللَّهَ لَا يَغْفِرُ أَنْ يُشْرَكَ بِهِ وَيَغْفِرُ مَا دُونَ ذَٰلِكَ لِمَنْ يَشَاءُ ۚ وَمَنْ يُشْرِكْ بِاللَّهِ فَقَدِ افْتَرَىٰ إِثْمًا عَظِيمًا
Indeed, Allah does not forgive association with Him, but He forgives what is less than that for whom He wills. And he who associates others with Allah has certainly fabricated a tremendous sin.
41:13 Fussilat
فَإِنْ أَعْرَضُوا فَقُلْ أَنْذَرْتُكُمْ صَاعِقَةً مِثْلَ صَاعِقَةِ عَادٍ وَثَمُودَ
But if they turn away, then say, "I have warned you of a thunderbolt like the thunderbolt [that struck] 'Aad and Thamud.
61:13 As-Saff
وَأُخْرَىٰ تُحِبُّونَهَا ۖ نَصْرٌ مِنَ اللَّهِ وَفَتْحٌ قَرِيبٌ ۗ وَبَشِّرِ الْمُؤْمِنِينَ
And [you will obtain] another [favor] that you love - victory from Allah and an imminent conquest; and give good tidings to the believers.
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16Drivechain
Understanding Drivechain requires a shift from the paradigm most bitcoiners are used to. It is not about "trustlessness" or "mathematical certainty", but game theory and incentives. (Well, Bitcoin in general is also that, but people prefer to ignore it and focus on some illusion of trustlessness provided by mathematics.)
Here we will describe the basic mechanism (simple) and incentives (complex) of "hashrate escrow" and how it enables a 2-way peg between the mainchain (Bitcoin) and various sidechains.
The full concept of "Drivechain" also involves blind merged mining (i.e., the sidechains mine themselves by publishing their block hashes to the mainchain without the miners having to run the sidechain software), but this is much easier to understand and can be accomplished either by the BIP-301 mechanism or by the Spacechains mechanism.
How does hashrate escrow work from the point of view of Bitcoin?
A new address type is created. Anything that goes in that is locked and can only be spent if all miners agree on the Withdrawal Transaction (
WT^) that will spend it for 6 months. There is one of these special addresses for each sidechain.To gather miners' agreement
bitcoindkeeps track of the "score" of all transactions that could possibly spend from that address. On every block mined, for each sidechain, the miner can use a portion of their coinbase to either increase the score of oneWT^by 1 while decreasing the score of all others by 1; or they can decrease the score of allWT^s by 1; or they can do nothing.Once a transaction has gotten a score high enough, it is published and funds are effectively transferred from the sidechain to the withdrawing users.
If a timeout of 6 months passes and the score doesn't meet the threshold, that
WT^is discarded.What does the above procedure mean?
It means that people can transfer coins from the mainchain to a sidechain by depositing to the special address. Then they can withdraw from the sidechain by making a special withdraw transaction in the sidechain.
The special transaction somehow freezes funds in the sidechain while a transaction that aggregates all withdrawals into a single mainchain
WT^, which is then submitted to the mainchain miners so they can start voting on it and finally after some months it is published.Now the crucial part: the validity of the
WT^is not verified by the Bitcoin mainchain rules, i.e., if Bob has requested a withdraw from the sidechain to his mainchain address, but someone publishes a wrongWT^that instead takes Bob's funds and sends them to Alice's main address there is no way the mainchain will know that. What determines the "validity" of theWT^is the miner vote score and only that. It is the job of miners to vote correctly -- and for that they may want to run the sidechain node in SPV mode so they can attest for the existence of a reference to theWT^transaction in the sidechain blockchain (which then ensures it is ok) or do these checks by some other means.What? 6 months to get my money back?
Yes. But no, in practice anyone who wants their money back will be able to use an atomic swap, submarine swap or other similar service to transfer funds from the sidechain to the mainchain and vice-versa. The long delayed withdraw costs would be incurred by few liquidity providers that would gain some small profit from it.
Why bother with this at all?
Drivechains solve many different problems:
It enables experimentation and new use cases for Bitcoin
Issued assets, fully private transactions, stateful blockchain contracts, turing-completeness, decentralized games, some "DeFi" aspects, prediction markets, futarchy, decentralized and yet meaningful human-readable names, big blocks with a ton of normal transactions on them, a chain optimized only for Lighting-style networks to be built on top of it.
These are some ideas that may have merit to them, but were never actually tried because they couldn't be tried with real Bitcoin or inferfacing with real bitcoins. They were either relegated to the shitcoin territory or to custodial solutions like Liquid or RSK that may have failed to gain network effect because of that.
It solves conflicts and infighting
Some people want fully private transactions in a UTXO model, others want "accounts" they can tie to their name and build reputation on top; some people want simple multisig solutions, others want complex code that reads a ton of variables; some people want to put all the transactions on a global chain in batches every 10 minutes, others want off-chain instant transactions backed by funds previously locked in channels; some want to spend, others want to just hold; some want to use blockchain technology to solve all the problems in the world, others just want to solve money.
With Drivechain-based sidechains all these groups can be happy simultaneously and don't fight. Meanwhile they will all be using the same money and contributing to each other's ecosystem even unwillingly, it's also easy and free for them to change their group affiliation later, which reduces cognitive dissonance.
It solves "scaling"
Multiple chains like the ones described above would certainly do a lot to accomodate many more transactions that the current Bitcoin chain can. One could have special Lightning Network chains, but even just big block chains or big-block-mimblewimble chains or whatnot could probably do a good job. Or even something less cool like 200 independent chains just like Bitcoin is today, no extra features (and you can call it "sharding"), just that would already multiply the current total capacity by 200.
Use your imagination.
It solves the blockchain security budget issue
The calculation is simple: you imagine what security budget is reasonable for each block in a world without block subsidy and divide that for the amount of bytes you can fit in a single block: that is the price to be paid in satoshis per byte. In reasonable estimative, the price necessary for every Bitcoin transaction goes to very large amounts, such that not only any day-to-day transaction has insanely prohibitive costs, but also Lightning channel opens and closes are impracticable.
So without a solution like Drivechain you'll be left with only one alternative: pushing Bitcoin usage to trusted services like Liquid and RSK or custodial Lightning wallets. With Drivechain, though, there could be thousands of transactions happening in sidechains and being all aggregated into a sidechain block that would then pay a very large fee to be published (via blind merged mining) to the mainchain. Bitcoin security guaranteed.
It keeps Bitcoin decentralized
Once we have sidechains to accomodate the normal transactions, the mainchain functionality can be reduced to be only a "hub" for the sidechains' comings and goings, and then the maximum block size for the mainchain can be reduced to, say, 100kb, which would make running a full node very very easy.
Can miners steal?
Yes. If a group of coordinated miners are able to secure the majority of the hashpower and keep their coordination for 6 months, they can publish a
WT^that takes the money from the sidechains and pays to themselves.Will miners steal?
No, because the incentives are such that they won't.
Although it may look at first that stealing is an obvious strategy for miners as it is free money, there are many costs involved:
- The cost of ceasing blind-merged mining returns -- as stealing will kill a sidechain, all the fees from it that miners would be expected to earn for the next years are gone;
- The cost of Bitcoin price going down: If a steal is successful that will mean Drivechains are not safe, therefore Bitcoin is less useful, and miner credibility will also be hurt, which are likely to cause the Bitcoin price to go down, which in turn may kill the miners' businesses and savings;
- The cost of coordination -- assuming miners are just normal businesses, they just want to do their work and get paid, but stealing from a Drivechain will require coordination with other miners to conduct an immoral act in a way that has many pitfalls and is likely to be broken over the months;
- The cost of miners leaving your mining pool: when we talked about "miners" above we were actually talking about mining pools operators, so they must also consider the risk of miners migrating from their mining pool to others as they begin the process of stealing;
- The cost of community goodwill -- when participating in a steal operation, a miner will suffer a ton of backlash from the community. Even if the attempt fails at the end, the fact that it was attempted will contribute to growing concerns over exaggerated miners power over the Bitcoin ecosystem, which may end up causing the community to agree on a hard-fork to change the mining algorithm in the future, or to do something to increase participation of more entities in the mining process (such as development or cheapment of new ASICs), which have a chance of decreasing the profits of current miners.
Another point to take in consideration is that one may be inclined to think a newly-created sidechain or a sidechain with relatively low usage may be more easily stolen from, since the blind merged mining returns from it (point 1 above) are going to be small -- but the fact is also that a sidechain with small usage will also have less money to be stolen from, and since the other costs besides 1 are less elastic at the end it will not be worth stealing from these too.
All of the above consideration are valid only if miners are stealing from good sidechains. If there is a sidechain that is doing things wrong, scamming people, not being used at all, or is full of bugs, for example, that will be perceived as a bad sidechain, and then miners can and will safely steal from it and kill it, which will be perceived as a good thing by everybody.
What do we do if miners steal?
Paul Sztorc has suggested in the past that a user-activated soft-fork could prevent miners from stealing, i.e., most Bitcoin users and nodes issue a rule similar to this one to invalidate the inclusion of a faulty
WT^and thus cause any miner that includes it in a block to be relegated to their own Bitcoin fork that other nodes won't accept.This suggestion has made people think Drivechain is a sidechain solution backed by user-actived soft-forks for safety, which is very far from the truth. Drivechains must not and will not rely on this kind of soft-fork, although they are possible, as the coordination costs are too high and no one should ever expect these things to happen.
If even with all the incentives against them (see above) miners do still steal from a good sidechain that will mean the failure of the Drivechain experiment. It will very likely also mean the failure of the Bitcoin experiment too, as it will be proven that miners can coordinate to act maliciously over a prolonged period of time regardless of economic and social incentives, meaning they are probably in it just for attacking Bitcoin, backed by nation-states or something else, and therefore no Bitcoin transaction in the mainchain is to be expected to be safe ever again.
Why use this and not a full-blown trustless and open sidechain technology?
Because it is impossible.
If you ever heard someone saying "just use a sidechain", "do this in a sidechain" or anything like that, be aware that these people are either talking about "federated" sidechains (i.e., funds are kept in custody by a group of entities) or they are talking about Drivechain, or they are disillusioned and think it is possible to do sidechains in any other manner.
No, I mean a trustless 2-way peg with correctness of the withdrawals verified by the Bitcoin protocol!
That is not possible unless Bitcoin verifies all transactions that happen in all the sidechains, which would be akin to drastically increasing the blocksize and expanding the Bitcoin rules in tons of ways, i.e., a terrible idea that no one wants.
What about the Blockstream sidechains whitepaper?
Yes, that was a way to do it. The Drivechain hashrate escrow is a conceptually simpler way to achieve the same thing with improved incentives, less junk in the chain, more safety.
Isn't the hashrate escrow a very complex soft-fork?
Yes, but it is much simpler than SegWit. And, unlike SegWit, it doesn't force anything on users, i.e., it isn't a mandatory blocksize increase.
Why should we expect miners to care enough to participate in the voting mechanism?
Because it's in their own self-interest to do it, and it costs very little. Today over half of the miners mine RSK. It's not blind merged mining, it's a very convoluted process that requires them to run a RSK full node. For the Drivechain sidechains, an SPV node would be enough, or maybe just getting data from a block explorer API, so much much simpler.
What if I still don't like Drivechain even after reading this?
That is the entire point! You don't have to like it or use it as long as you're fine with other people using it. The hashrate escrow special addresses will not impact you at all, validation cost is minimal, and you get the benefit of people who want to use Drivechain migrating to their own sidechains and freeing up space for you in the mainchain. See also the point above about infighting.
See also
-
 @ cae03c48:2a7d6671
2025-06-03 16:01:01
@ cae03c48:2a7d6671
2025-06-03 16:01:01Bitcoin Magazine

Sberbank, Russia’s Biggest Bank, Launches Structured Bond Tied to BitcoinSberbank, the largest bank in Russia, has launched a new structured bond that ties investor returns to the performance of Bitcoin and the U.S. dollar-to-ruble exchange rate. This new financial product represents one of the first moves by a major Russian institution to offer Bitcoin-linked investments under recently updated national regulations.
BREAKING:
 Russia's largest bank Sberbank launches structured bonds linked to Bitcoin. pic.twitter.com/LtD26jPS0x
Russia's largest bank Sberbank launches structured bonds linked to Bitcoin. pic.twitter.com/LtD26jPS0x— Bitcoin Magazine (@BitcoinMagazine) June 2, 2025
The structured bond is initially available over the counter to a limited group of qualified investors. According to the announcement, it allows investors to earn based on two factors: the price performance of BTC in U.S. dollars and any strengthening of the dollar compared to the Russian ruble.
Unlike typical Bitcoin investments, this product does not require the use of a Bitcoin wallet or foreign platforms. “All transactions [are] processed in rubles within Russia’s legal and infrastructure systems,” Sberbank stated, highlighting compliance with domestic financial protocols.
In addition to the bond, Sberbank has announced plans to launch similar structured investment products with Bitcoin exposure on the Moscow Exchange. The bank also revealed it will introduce a Bitcoin futures product via its SberInvestments platform on June 4, aligning with the product’s debut on the Moscow Exchange.
These developments follow a recent policy change by the Bank of Russia, which now permits financial institutions to offer Bitcoin-linked instruments to qualified investors. This shift opens the door for Bitcoin within the country’s traditional financial markets.
While Russia has previously taken a cautious approach to digital assets, Sberbank’s launch of a Bitcoin-linked bond and upcoming futures product marks a new phase of adoption—one that blends Bitcoin exposure with existing financial infrastructure.
The bank’s structured bond may signal a growing interest in regulated access to Bitcoin, especially within large financial institutions.
This post Sberbank, Russia’s Biggest Bank, Launches Structured Bond Tied to Bitcoin first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 8c29b321:4336aaa0
2025-06-05 08:32:10
@ 8c29b321:4336aaa0
2025-06-05 08:32:10
Community 🧑🤝🧑
- Did you see that the Designathon wrapped up? If not, take a peek at the previous newsletter.
- The community conducted research at Oslo Freedom Forum. Bitcoin and Nostr have the potential to provide privacy focussed financial and communication tools for activists. We'll publish findings publicly and host developer workshops to share the insights.
- BTC Prague is coming up from June 18 to 21. Meet up at the design track during dev/hack/day and around the general conference. The aforementioned activist research and Bitcoin Core App are two of the scheduled talks.
- We had an exploratory call about how Liana could implement Payjoins (recording).
- The price for Best Design at the Bitcoin 2025 hackathon, sponsored by the Bitcoin Design Foundation, went to Arcana Seed Lodge. Check out all the projects.
- For anyone in the US, help protect your right to transact freely via Save our Wallets. There’s a bill being discussed around protecting builders of non-custodial wallets and services.
Bitcoin design guide 🗺️
- The intro page to the Getting Started section got a rewrite. Does it read better and is it more informative now?
- The section for visual formatting of addresses was updated with a note about using fonts with clearly distinguishable characters.
- Find new t-shirt designs with bitcoin & design related taglines on the Design files page (Figma community file).
- Would you like to help create an online course around design for Plan₿ Network?
- AI knows the guide and can evaluate your design based on it. How else can we use AI?
Seeking feedback 🗣️👂
- Liana Wallet is interviewing bitcoiners around frustrations with self-custody.
- Yashraj is seeking feedback on UX challenges around Payjoin V2 (outline, Github, Stacker News).
- 0commons is a bitcoin-powered value-for-value marketplace for digital goods. Leave your feedback.
- Kelbs is looking for feedback on home screen designs for Sovrn.
- m1sterc001guy is looking for feedback on a Fedimint wallet prototype (repo).
- There is a lot of activity around bitcoin redenomination (BIP 177), removing the term satoshi as a unit. Join the conversation.
Wallet updates 👜
- An update on Cashu ecosystem developments in Q1 2025.
- Boardwalk Cash is an example for the redenomination of bitcoin units. A live example on how “1 Satoshi” can be displayed as “1 Bitcoin”.
- Wallet of Satoshi is going to release a non-custodial wallet and become available again in the US.
- Akron released a beta wallet with support for the Spaces protocol.
- Blockstream released a new wallet app.
- Sparrow made several accessibility improvements in the 2.2.0 release.
Conferences 📅
- Catch up with the recordings and hackathon winners of the BTC++ Austin conference.
- Watch presentations of the Bitcoin Presidio hackathon finalists.
- Find a more complete list of conferences here.
Opportunities 💡
- BRAIINS is looking for a content Lead.
- Apply to the Bitshala design fellowship.
- Cowbolt is looking for a designer.
Everything else 😀
- HRF is supporting another 22 projects with grants. Take a look.
- Happy Bitcoin Pizza Day!
- Check out Jason’s guide to bitcoin accessibility.
- View survey results around mobile wallet usage in Japan by Diamond Hands.
- The Second team published research around how the Ark network can complement Lightning infrastructure.
- Watch the Freedom Tech track presentations from the Oslo Freedom forum.
- Watch Daniel answer 21 questions in 21 minutes.
- Read Bitcoin testing is a ghost town by AVB (also part two).
- Saving Satoshi did a workshop at the Bitcoin Conference. Have you tried it?
- See the UX of paying for burgers at the US fast-food chain Steak’n Shake.
- A guidepr to Robosats, for private exchange of bitcoin.
- Hear about the latest on Fedimint in this podcast.
- Read about building inclusivity into every phase of a project.
- Check out the Global State of Crypto report by Gemini.
—
For more, visit the Bitcoin Design website and follow us.
This update is brought to you by Christoph & Mo. We’d love to hear your feedback. -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A violência é uma forma de comunicação
A violência é uma forma de comunicação: um serial killer, um pai que bate no filho, uma briga de torcidas, uma sessão de tortura, uma guerra, um assassinato passional, uma briga de bar. Em todos esses se pode enxergar uma mensagem que está tentando ser transmitida, que não foi compreendida pelo outro lado, que não pôde ser expressa, e, quando o transmissor da mensagem sentiu que não podia ser totalmente compreendido em palavras, usou essa outra forma de comunicação.
Quando uma ofensa em um bar descamba para uma briga, por exemplo, o que há é claramente uma tentativa de uma ofensa maior ainda pelo lado do que iniciou a primeira, a briga não teria acontecido se ele a tivesse conseguido expressar em palavras tão claras que toda a audiência de bêbados compreendesse, o que estaria além dos limites da linguagem, naquele caso, o soco com o mão direita foi mais eficiente. Poderia ser também a defesa argumentativa: "eu não sou um covarde como você está dizendo" -- mas o bar não acreditaria nessa frase solta, a comunicação não teria obtido o sucesso desejado.
A explicação para o fato da redução da violência à medida em que houve progresso da civilização está na melhora da eficiência da comunicação humana: a escrita, o refinamento da expressão lingüística, o aumento do alcance da palavra falada com rádio, a televisão e a internet.
Se essa eficiência diminuir, porque não há mais acordo quanto ao significado das palavras, porque as pessoas não estão nem aí para se o que escrevem é bom ou não, ou porque são incapazes de compreender qualquer coisa, deve aumentar proporcionalmente a violência.
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Problemas com Russell Kirk
A idéia central da “política da prudência[^1]” de Russell Kirk me parece muito correta, embora tenha sido melhor formulada pior no seu enorme livro do que em uma pequena frase do joanadarquista Lucas Souza: “o conservadorismo é importante, porque tem muita gente com idéia errada por aí, e nós podemos não saber distingüi-las”.
Porém, há alguns problemas que precisam ser esclarecidos, ou melhor explicados, e que me impedem de enxergar os seus argumentos como refutação final do meu já tão humilde (embora feroz) anarquismo. São eles:
I Percebo alguma coisa errada, não sei bem onde, entre a afirmação de que toda ideologia é ruim, ou “todas as ideologias causam confusão[^2]”, e a proposta conservadora de “conservar o mundo da ordem que herdamos, ainda que em estado imperfeito, de nossos ancestrais[^3]”. Ora, sem precisar cair em exemplos como o do partido conservador inglês -- que conservava a política inglesa sempre onde estava, e se alternava no governo com o partido trabalhista, que a levava cada vez mais um pouco à esquerda --, está embutida nessa frase, talvez, a idéia, que ao mesmo tempo é clara e ferrenhamente combatida pelos próprios conservadores, de que a história é da humanidade é uma história de progresso linear rumo a uma situação melhor.
Querer conservar o mundo da ordem que herdamos significa conservar também os vários erros que podem ter sido cometidos pelos nossos ancestrais mais recentes, e conservá-los mesmo assim, acusando toda e qualquer tentativa de propôr soluções a esses erros de ideologia? Ou será que conservar o mundo da ordem é escolher um período determinado que seja tido como o auge da história humana e tentar restaurá-lo em nosso próprio tempo? Não seria isto ideologia?
Ou, ainda, será que conservar o mundo da ordem é selecionar, entre vários períodos do passado, alguns pedaços que o conservador considerar ótimos em cada sociedade, fazer dali uma mistura de sociedade ideal baseada no passado e então tentar implementá-la? Quem saberia dizer quais são as partes certas?
II Sobre a questão do que mantém a sociedade civil coesa, Russell Kirk, opondo-a à posição libertária de que o nexo da sociedade é o autointeresse, declara que a posição conservadora é a de que “a sociedade é uma comunidade de almas, que une os mortos, os vivos e os ainda não nascidos, e que se harmoniza por aquilo que Aristóteles chamou de amizade e os cristãos chamam de caridade ou amor ao próximo”.
Esta é uma posição muito correta, mas me parece estar em contradição com a defesa do Estado que ele faz na mesma página e na seguinte. O que me parece errado é que a sociedade não pode ser, ao mesmo tempo, uma “comunidade baseada no amor ao próximo” e uma comunidade que “requer não somente que as paixões dos indivíduos sejam subjugadas, mas que, mesmo no povo e no corpo social, bem como nos indivíduos, as inclinações dos homens, amiúde, devam ser frustradas, a vontade controlada e as paixões subjugadas” e, pior, que “isso somente pode ser feito por um poder exterior”.
Disto aí podemos tirar que, da mesma forma que Kirk define a posição libertária como sendo a de que o autointeresse é que mantém a sociedade civil coesa, a posição conservadora seria então a de que essa coesão vem apenas do Estado, e não de qualquer ligação entre vivos e mortos, ou do amor ao próximo. Já que, sem o Estado, diz, ele, citando Thomas Hobbes, a condição do homem é “solitária, pobre, sórdida, embrutecida e curta”?
[^1]: este é o nome do livro e também um outro nome que ele dá para o próprio conservadorismo (p.99). [^2]: p. 101 [^3]: p. 102
-
 @ 45ea632c:bb0b4fa1
2025-06-05 08:01:04
@ 45ea632c:bb0b4fa1
2025-06-05 08:01:04No mundo do entretenimento digital, a inovação e a experiência do usuário são fatores determinantes para o sucesso de uma plataforma. A Win44 surge como uma das opções mais promissoras do mercado brasileiro, oferecendo uma experiência completa e diferenciada para quem busca diversão, praticidade e oportunidades de ganhos reais. Com uma interface moderna, variedade de jogos e suporte de alta qualidade, a Win44 tem se destacado entre as preferidas dos jogadores.
Uma Plataforma Moderna e Intuitiva Desde o primeiro acesso, a Win44 impressiona pelo seu design moderno, navegação fluida e compatibilidade com diferentes dispositivos. Seja no computador, tablet ou smartphone, a plataforma se adapta perfeitamente, garantindo uma experiência sem interrupções e totalmente otimizada.
Além da estética, a funcionalidade também chama atenção. Os menus são organizados de forma clara, facilitando a busca por jogos, promoções e informações da conta do usuário. Isso é ideal tanto para iniciantes quanto para jogadores mais experientes, que valorizam a praticidade no dia a dia.
Variedade de Jogos para Todos os Perfis Um dos grandes diferenciais da win44é a sua biblioteca de jogos, que abrange diferentes gostos e estilos. A plataforma conta com opções que vão desde os clássicos de mesa até os jogos de azar mais populares, todos desenvolvidos por fornecedores renomados da indústria.
Entre os destaques, estão os jogos de cartas como pôquer, bacará e blackjack, além de uma ampla seleção de jogos de roleta e máquinas de giros com diferentes temáticas e dinâmicas. Os gráficos são envolventes, com animações fluidas e efeitos sonoros que aumentam a imersão do jogador, proporcionando uma experiência realista e empolgante.
Outro ponto positivo é a presença de jogos ao vivo com crupiês reais, o que adiciona uma camada extra de emoção e interação, aproximando ainda mais o jogador da atmosfera dos grandes centros de entretenimento internacionais.
Experiência do Jogador em Primeiro Lugar A Win44 investe constantemente na qualidade do atendimento ao usuário e na segurança da plataforma. O suporte está disponível 24 horas por dia, todos os dias da semana, com atendimento em português e canais de fácil acesso, como chat ao vivo e e-mail.
No quesito segurança, a plataforma utiliza tecnologia de criptografia avançada para proteger todas as transações e dados dos usuários, garantindo total confidencialidade. Além disso, o processo de registro é simples e rápido, permitindo que o jogador comece a se divertir em poucos minutos.
Outro ponto muito valorizado pelos usuários é a variedade de métodos de pagamento e saque. A Win44 oferece suporte a diversas opções, incluindo transferências bancárias, carteiras digitais e até pagamentos via PIX, que têm ganhado grande popularidade no Brasil por sua rapidez e conveniência.
Bônus e Promoções Atrativas Para tornar a experiência ainda mais interessante, a Win44 oferece uma gama de promoções e bônus regulares. Novos usuários podem aproveitar ofertas de boas-vindas que aumentam o saldo inicial, enquanto jogadores frequentes têm acesso a promoções sazonais, sorteios e programas de fidelidade.
Essas vantagens não apenas elevam o nível da diversão, mas também aumentam as chances de obter bons resultados durante as partidas.
Conclusão A Win44 é uma plataforma completa que combina tecnologia, diversidade e um atendimento de excelência para proporcionar a melhor experiência de entretenimento online. Com um ambiente seguro, jogos variados e uma interface amigável, ela se consolida como uma das principais escolhas para jogadores brasileiros que buscam diversão de qualidade.
-
 @ 58537364:705b4b85
2025-06-03 15:22:59
@ 58537364:705b4b85
2025-06-03 15:22:59…. “คนเรา โดยเฉพาะสมัยนี้ พูดกันอีกที่หนึ่งก็พูดได้ว่า ถูกสร้างขึ้นมาด้วยหนังสือ, หนังสือมันสร้างคนขึ้นมา คือว่า..อ่านหนังสืออะไรมาก อ่านหนังสืออะไรมาก หนังสือนั้นก็สร้างคนคนนั้นขึ้นมา, สร้างจิตใจของคนนั้นขึ้นมา โดยไม่รู้สึก
…. ไปดูหนังสือที่เขาอ่าน อ่านมากที่สุด เราก็รู้ได้ว่า..คนนี้มีจิตใจเป็นอย่างไร. หนังสือที่นิยมสั่งกันมามาก ล้วนแต่เป็นหนังสือที่ยั่วยวนทางวัตถุ หรือลุ่มหลงทางวัตถุ : แล้วอย่างดีที่สุดก็เอามาให้เสียเวลา อ่านให้มันมึนหัวเล่น อย่างนั้นแหละ จนไม่มีเวลาที่จะไปอ่านหนังสือธรรมะที่แท้จริง เพราะว่ามีหนังสืออื่นมาก วางอยู่มาก ยั่วยวนให้อ่านมากกว่า
…. แม้แต่พระเณร ก็เป็นอย่างนี้ อ่านหนังสือพิมพ์, หรืออ่านหนังสือภาษา, เรียนภาษาต่างประเทศ หรือว่าเรียนวิชานั่น นี่ ล้วนแต่เป็นเรื่องวัตถุ เรื่องอาชีพ เรื่องความดีความเด่น ที่ฝันไว้ในจิตในใจ, ด้วยความหวังความทะเยอทะยานทั้งนั้น แล้วจะเอากําลังใจ หรือมันสมอง หรืออะไรที่ไหนมาเข้าใจ ธรรมะ ธัมโม ได้
…. ทีนี้ ยิ่งนอกวัดออกไป ก็ยิ่งไกลไปใหญ่ : หอสมุดของมหาวิทยาลัย, หอสมุดของชาติ ของอะไร ก็ล้วนแต่เป็น “หอสมุดของซาตาน” มากยิ่งขึ้นเท่านั้น เพราะไปมีมันขึ้น หรือสร้างมันไว้ ด้วยความอยากดีอยากเด่น ด้วยความอยากที่จะร่ำรวยวัตถุทั้งนั้น ฉะนั้น จึงมีผลทําให้คนทั้งโลกนี้เป็นทาสของวัตถุ พร้อมที่จะสร้างวิกฤตการณ์ ขึ้นในโลกในอนาคต
…. แล้วรองลงมาจากนั้น ก็คือ มันมากจนทําให้เวียนหัว เป็น..“บ้าหอบฟาง”; อย่างที่ว่าแล้วว่าเล่า ว่าเป็นบ้าหอบฟาง, รู้อะไรท่วมหัวก็เอาตัวไม่รอด, เรียนจบมหาวิทยาลัยแล้ว ก็ยังไม่รู้ว่าเกิดมาทําไม ?, เรียนมหาวิทยาลัยจบแล้ว อ่านหนังสือในห้องสมุดของมหาวิทยาลัยจบแล้ว ก็ยังเป็นเด็กอมมือ ไม่รู้ว่า.. “กูนี่ เกิดมาทําไม ?”. ดูซิ!, แล้วจะเรียกว่า “อุดมศึกษา” ได้อย่างไรกัน ? แม้แต่เกิดมาทําไม? ก็ยังไม่รู้ นี่การศึกษาสมัยนี้ หอสมุดหรือห้องสมุดของสมัยนี้ มันเป็นอย่างนี้
…. ทีนี้ เมื่อไม่รู้ว่าเกิดมาทําไม ? มันก็ไม่มีอะไร นอกจากเป็นทาสของวัตถุ ที่หวังว่าจะสนุกสนาน เอร็ดอร่อย มีเกียรติ มีอํานาจวาสนา มีอะไรไปทํานองนั้น นี่แหละ คือการตกเป็นทาสของวัตถุ การตกเป็นทาสของอายตนะ คือ ตา หู จมูก ลิ้น กาย ใจ การเล่าเรียนศึกษาขวนขวายนั้น เพื่อจะเป็นทาส ของ ตา หู จมูก ลิ้น กาย ใจ ในการที่จะแสวงหาความสนุกสนาน เอร็ดอร่อย ทางเนื้อทางหนัง มีเท่านี้ การศึกษาและห้องสมุด” . พุทธทาสภิกขุ ที่มา : ธรรมบรรยายชุดชุมนุมล้ออายุ หัวข้อเรื่อง “ยิ่งจะทำให้ดี โลกมันยิ่งบ้า” บรรยาย ณ ลานหินโค้ง กัณฑ์ค่ำ เมื่อวันที่ ๒๗ พฤษภาคม ๒๕๑๓ จากหนังสือชุดธรรมโฆษณ์ เล่มชื่อว่า “ชุมนุมล้ออายุ เล่ม ๑” หน้า ๕๑๒-๕๑๓
-
 @ c4f5e7a7:8856cac7
2025-06-03 08:15:33
@ c4f5e7a7:8856cac7
2025-06-03 08:15:33I've managed to amass three SN profiles.
Is there a way to combined these?
@k00b @ek
https://stacker.news/items/995836
-
 @ e8646d56:72dab368
2025-06-03 08:15:30
@ e8646d56:72dab368
2025-06-03 08:15:30eee
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
A command line utility to create and manage personal graphs, then write them to dot and make images with graphviz.
It manages a bunch of YAML files, one for each entity in the graph. Each file lists the incoming and outgoing links it has (could have listen only the outgoing, now that I'm tihnking about it).
Each run of the tool lets you select from existing nodes or add new ones to generate a single link type from one to one, one to many, many to one or many to many -- then updates the YAML files accordingly.
It also includes a command that generates graphs with graphviz, and it can accept a template file that lets you customize the
dotthat is generated and thus the graphviz graph.rel
-
 @ da0b9bc3:4e30a4a9
2025-06-05 07:19:42
@ da0b9bc3:4e30a4a9
2025-06-05 07:19:42Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post!
https://stacker.news/items/997645
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28GraphQL vs REST
Today I saw this: https://github.com/stickfigure/blog/wiki/How-to-(and-how-not-to)-design-REST-APIs
And it reminded me why GraphQL is so much better.
It has also reminded me why HTTP is so confusing and awful as a protocol, especially as a protocol for structured data APIs, with all its status codes and headers and bodies and querystrings and content-types -- but let's not talk about that for now.
People complain about GraphQL being great for frontend developers and bad for backend developers, but I don't know who are these people that apparently love reading guides like the one above of how to properly construct ad-hoc path routers, decide how to properly build the JSON, what to include and in which circumstance, what status codes and headers to use, all without having any idea of what the frontend or the API consumer will want to do with their data.
It is a much less stressful environment that one in which we can just actually perform the task and fit the data in a preexistent schema with types and a structure that we don't have to decide again and again while anticipating with very incomplete knowledge the usage of an extraneous person -- i.e., an environment with GraphQL, or something like GraphQL.
By the way, I know there are some people that say that these HTTP JSON APIs are not the real REST, but that is irrelevant for now.
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ e516ecb8:1be0b167
2025-06-04 20:33:38
@ e516ecb8:1be0b167
2025-06-04 20:33:38Imagina un mundo donde cada peso que gastas es vigilado, registrado y cuestionado. Donde el Estado decide si puedes comprar un café, una manzana o una criptomoneda. No es una distopía de ciencia ficción, es el rumbo que están tomando varios países, mientras otros, como Argentina, dan un giro inesperado hacia la libertad. ¿Quién está ganando esta batalla por el control de tu dinero?
Argentina: "Tus dólares son tuyos" En Argentina, Javier Milei, con su bandera libertaria ondeando, ha dado un paso audaz: desmantelar el control policial sobre el dinero de los ciudadanos. Su lema, "Tus dólares son tuyos", es tan obvio como revolucionario. Después de décadas de corralitos, cepos cambiarios y una inflación que en 2023 alcanzó el 211,4% según el INDEC, Milei apuesta por devolverle al ciudadano el poder sobre su propio capital. Con el país logrando superávit fiscal por primera vez en años (0,2% del PBI en el primer trimestre de 2024), el gobierno ya no necesita espiar cada transacción para exprimir impuestos.
Pero aquí viene lo curioso: encuestas recientes, como una de la consultora Poliarquía, muestran que un 35% de los argentinos aún prefiere que el Estado controle sus finanzas. ¿Masoquismo? ¿Miedo a la libertad? Tal vez sea la costumbre de vivir bajo la lupa. Milei, fiel a su convicción, no solo liberaliza por necesidad económica, sino porque cree que el dinero es tuyo, no del burócrata de turno.
España y el Euro Digital: El ojo que todo lo ve Mientras Argentina afloja las riendas, Europa cabalga en dirección opuesta. En España, el gobierno está reduciendo progresivamente los umbrales para controlar transacciones bancarias. A partir de 2026, cada pago por Bizum —el equivalente ibérico al Pix brasileño— estará bajo escrutinio. Según el Banco de España, en 2024 se realizaron más de 1.200 millones de transacciones por Bizum, moviendo unos 60.000 millones de euros. Ahora, cada una de esas operaciones será un dato más para Hacienda.
Pero no es solo España. La Unión Europea avanza con el Euro Digital, un proyecto que promete ser la pesadilla de cualquier amante de la privacidad. Esta moneda digital, según el Banco Central Europeo, permitirá rastrear cada movimiento, limitar ciertos gastos (¿adiós a compras de cripto o donaciones incómodas?), e incluso programar que el dinero "se oxide". Sí, has leído bien: si no gastas tus euros digitales en un tiempo determinado, podrían perder valor o simplemente desaparecer. Un informe del BCE de 2023 estima que el Euro Digital estará operativo en 2027, y ya hay pruebas piloto en países como Alemania y Francia. ¿Libertad financiera? Más bien un Gran Hermano con esteroides.
Chile: El Estado fisgón y los funcionarios de lujo En Chile, el control monetario también aprieta. El gobierno ha propuesto levantar el secreto bancario, permitiendo que cualquier funcionario del SII pueda husmear en tus cuentas. Además, si haces más de 50 transacciones al mes, el Servicio de Impuestos Internos (SII) pondrá la lupa sobre ti. ¿Y las ferias libres? Esas donde compras tus tomates y zapallos sin complicaciones ahora deberán emitir boletas electrónicas, encareciendo los productos para el ciudadano de a pie. Según la CEPAL, los costos administrativos para pequeños comerciantes podrían aumentar hasta un 15% con estas medidas.
Mientras tanto, el sector público chileno vive en otra galaxia. Funcionarios con sueldos que superan los 5 millones de pesos mensuales (unos 5.500 USD) toman licencias médicas para viajar por el mundo, según denuncias de la Contraloría. Algunos incluso cobran por "turnos" de 17 horas extras diarias o marcan asistencia en dos lugares al mismo tiempo. ¿Y quién paga? Tú, con tus impuestos.
La resistencia: Volver al efectivo o abrazar las cripto Si el Estado quiere controlar cada centavo, ¿qué opciones nos quedan? Una es volver al efectivo, pero no nos engañemos: el dinero fiat, controlado por bancos centrales, pierde valor a largo plazo. En Chile, la inflación acumulada entre 2010 y 2024 fue del 62%, según el INE. Tus billetes de hoy valen menos que los de ayer, y mañana valdrán aún menos.
La otra opción es el mundo cripto, pero no cualquier cripto. Bitcoin, la más conocida, es un titán para almacenar valor, pero para transacciones diarias necesita una segunda capa como Lightning Network, que procesa pagos instantáneos con comisiones ínfimas (menos de 0,01 USD por transacción en 2024). Alternativas como Bitcoin Cash (BCH) o Monero (XMR) ofrecen transacciones rápidas y, en el caso de XMR, un enfoque en la privacidad que hace temblar a los burócratas. Sin embargo, ninguna cripto servirá si los comercios y las personas no las adoptan. En Argentina, por ejemplo, solo el 1,5% de las transacciones minoristas en 2024 usaron criptomonedas, según Chainalysis. La libertad financiera no llega sola: hay que construirla.
El futuro es ahora El dinero es poder, y quien controla el dinero controla tu vida. Mientras Milei en Argentina te devuelve las llaves de tus dólares, en Europa y Chile te atan las manos con leyes, regulaciones y monedas digitales. La pregunta no es si quieres libertad, sino si estás dispuesto a pelear por ella. Usa efectivo, explora cripto, pero sobre todo, no dejes que el Gran Hermano decida por ti. Porque una vez que el Estado mete la mano en tu bolsillo, no la saca nunca.
-
 @ 9ca447d2:fbf5a36d
2025-06-05 07:01:35
@ 9ca447d2:fbf5a36d
2025-06-05 07:01:35Vice President JD Vance spoke to a packed crowd at the Bitcoin 2025 Conference in Las Vegas.
He said that the Biden era of digital assets crackdown is over, and the Trump administration is all in on Bitcoin, stablecoins and blockchain.
In an inspiring speech on May 28, JD Vance said:
“This isn’t a gathering of people—it’s a movement. And I’m proud to stand with you today.”
The annual Bitcoin Conference, one of the biggest events in the Bitcoin world, drew thousands of investors, industry leaders and policymakers.
Vance’s speech was the main event and made it clear that digital assets are now a priority for the White House.

JD Vance at Bitcoin 2025 — CNBC
Vance outlined three main goals for the administration’s digital asset policy:
- End anti-digital-asset regulations
- Pass stablecoin legislation through the GENIUS Act
- Create clear and friendly rules for the Bitcoin industry
He blamed past regulations for holding back innovation and said that era is over.
“Under the guise of ‘consumer protection,’ Gary Gensler attacked every attempt to democratize finance,” Vance said. “That ends now.”
Gensler stepped down in January and Trump has since appointed Paul Atkins to lead the agency with a more Bitcoin-friendly approach.
“Maybe the most important thing that we did for this community, we reject regulators and we fired Gary Gensler,” Vance added. “And we’re going to fire everybody like him.”
Much of Vance’s speech at Bitcoin 2025 focused on stablecoins – digital assets tied to the U.S. dollar. He called them a tool to grow the economy, not a threat.
“Let me be emphatic—this administration does not think that stablecoins threaten the integrity of the United States dollar. Quite the opposite. We view them as a force multiplier of our economic might,” he said.
The GENIUS Act, recently passed in the House, would regulate stablecoins by setting reserve requirements and transparency.
According to Vance, it would bring stablecoin activity back to the U.S. while protecting consumers.
JD Vance said millions of Americans already own bitcoin and that number will double soon.
“I believe it’s 50 million Americans own bitcoin, and I believe that’s going to be 100 million before too long,” he said.
He also talked about his personal history with Bitcoin.
“The first time I’d ever enter politics, back in 2022 … one of the frustrations I had with the crypto community … was [being] one of the only people running for office who actually owned bitcoin,” he said.
“and I still own a fair amount of bitcoin today.”
He celebrated bitcoin’s recent price surge and thanked companies like Coinbase for organizing the conference.
He thanked Bitcoin advocates like David Bailey and the Winklevoss twins for their support during the 2024 Trump campaign.
One of the best lines of the speech was when JD Vance declared an end to what the Bitcoin community has called “Operation Chokepoint 2.0”.
It’s a term used to describe what many saw as government efforts to cut off Bitcoin companies from banking services.
“Operation Chokepoint 2.0 is dead, and it’s not coming back under the Trump administration,” he said.
He framed the battle over Bitcoin adoption as not just about finance but also about civil liberties.
“Crypto is a hedge—against bad policymaking, against inflation, and against discrimination,” he said.
He referenced Canadian truckers and “debanking” incidents in the U.S. as examples of how digital assets can protect from government and corporate overreach.
The Vice President warned that regulatory clarity is needed now, or else, the $3 trillion digital asset industry will move overseas.
“If we fail to create regulatory clarity now, we risk chasing this $3 trillion industry offshore in search of a friendlier jurisdiction,” he said. “President Trump is going to fight to make sure that does not happen.”
He ended with a call to action for the Bitcoin community to stay involved in politics.
“If you don’t get involved in politics, politics will ignore you,” he said. “Let’s not wake up 10 years from now in a poorer, weaker country because we made bad decisions today.”
Vance’s speech at Bitcoin 2025 was a big moment of alignment between the United States government and the Bitcoin industry.
With new laws, friendlier regulators and the White House on board, it’s clear that Bitcoin is now on the national agenda.
As he said: “Crypto finally has a champion and an ally in the White House.”
-
 @ 7460b7fd:4fc4e74b
2025-06-05 05:55:45
@ 7460b7fd:4fc4e74b
2025-06-05 05:55:45TRX 与 Crypto 政治代理模型:从哈耶克到稳定币主权
Crypto 即政治:从“罪”与“犯”的隐喻谈主权分化
“加密货币即政治”并非危言耸听。在社会分类中,“违法”与“犯罪”是两个层次的概念:前者意味着契约或规则的违背,而后者则是在权力结构下对自由行动者的政治性压制。换言之,有些行为本身并无“原罪”,却因触犯统治者利益被贴上“犯罪”的标签。这正如法学中对自然犯(mala in se,如偷盗谋杀等天生有害的行为)和法定犯(mala prohibita,因立法禁令才成为犯罪的行为)的区分。当代货币体系中,国家对货币发行与流通的垄断,造就了主权货币与“非法货币”的二元对立。奥地利学派经济学家哈耶克早在《货币的非国家化》中就预言:如果允许私人发行货币与法币公开竞争,最终能保持购买力稳定的货币将胜出finance.sina.cn。哈耶克认为政府垄断发行的不稳定货币终将让位于更稳定的竞争货币finance.sina.cn——这一观点在加密时代愈发具有隐喻意义。
如今的 Crypto 网络即是主权的实验场。各国监管者对稳定币、链上资金流动和法币通道的管控,构成了对加密行动者的“违法/犯罪”判定。例如,使用未授权稳定币进行跨境转账、绕过资本管制,并不违反当事人之间的契约,却往往被视作违法甚或犯罪行为——原因无他,只因这挑战了既有的金融主权架构。现象学视角提醒我们,应透过现象看本质:当执法者将自由交易行为定性为“犯罪”,正是传统主权对新兴数字主权的压制。Crypto世界中,“合法”与“非法”的界线并非由道德决定,而是由谁掌握规则决定。这为理解 Crypto 生态内各阵营的主权分化提供了理论框架:哪个网络掌握了自主的规则制定权,哪个网络就赢得了主权话语权。
稳定币主权与 TRX:黑灰资金的草根网络
稳定币是当前加密领域主权争夺的核心工具。最典型者莫过于 USDT 等美元锚定币——它们由私人公司发行,却承载着超主权货币的野心。尤其在 Tron(波场)网络 上,USDT 展现出惊人的统治力。2025年4月,波场上的 USDT 流通量突破700亿美元,占全球 USDT 总发行量近一半finance.sina.com.cn。截至今年5月,波场TRON上流通的 USDT 数量已反超以太坊,成为全球最大的稳定币发行与结算网络coindesk.comcoindesk.com。这种格局绝非偶然——波场独特的资源冻结机制(用户可冻结TRX获取带宽/能量从而基本免费交易)降低了交易门槛,使得小额高频的资金流动极为廉价。这使 TRX 链天然成为草根资金的“结算主链”,承接了大量主流金融体系之外的资金需求。
更值得关注的是波场上的黑市/灰色地带资金流动。低费率、高效率和对审查相对宽松的特性,吸引了大量游走于监管边缘的资本选择TRX链作为避风港。据区块链分析公司 TRM Labs 报告,2024年全球非法加密交易中有超过一半发生在 Tron 网络上,金额高达260亿美元dlnews.comdlnews.com。这些非法活动包括与受制裁实体相关的转账、诈骗黑客资金洗白以及暗网交易等dlnews.com。不法分子之所以青睐波场,正是看中了其稳定币通道和低交易成本等优势dlnews.com。北韩黑客在2024年盗取的8亿美元加密资产,大部分在数小时内经由波场链上的USDT迅速转移dlnews.com。联合国的分析同样指出,波场网络上的 USDT 已成为东亚地区欺诈和洗钱者的“首选”工具dlnews.com。由此可见,波场实际上扮演着**“无照金融公路”的角色:那些被传统金融体系拒之门外、没有正规交易所资格的人,可以通过波场上的USDT完成跨境汇兑和大额交易。这种自下而上的草根主权**,在波场网络上得到了前所未有的市场化体现。
当然,“草根主权”的另一面是高风险和争议。Tether公司虽偶有配合监管冻结特定链上地址,但波场整体上对资金流向的管束远不如银行体系。这使其成为地下资金的温床,也令波场背负“黑钱温床”的骂名。然而,换个角度看,这正验证了那句箴言:革命者在暴政者眼中即是罪犯。波场承载的灰色资金,恰恰反映了主流权力视角下的“犯罪”,但对于使用这些渠道的普通人来说,这可能只是追寻金融自由和机会的务实选择。
孙宇晨的政治人格:主权代理人的崛起
如果说波场TRON成为“无声多数”的金融主权载体,那么其创始人孙宇晨则高调地扮演起了加密世界的政治代理人。一直以来,加密圈华人创业者往往秉持“闷声发财、远离政治”的生存哲学,然孙宇晨选择了截然不同的道路:主动以政治为剧本,塑造个人和项目的话语权。
首先,他直接介入了美国的政治舆论场。2024年底以来,孙宇晨高调参与前总统川普推出的加密项目:斥资数千万美元认购“Trump系列”代币,成为该项目最大公开投资人之一reuters.com。2025年5月,孙宇晨作为头号持币者出席了川普在弗吉尼亚高尔夫俱乐部举办的私宴,与川普同台亮相reuters.com。他不仅以约1.85亿美元等值的钱包额度夺得饭局“竞标”第一名,还受邀成为川普家族加密平台 World Liberty Financial 的顾问reuters.com。这场引发争议的晚宴上,孙宇晨西装革履出镜,高调宣示其政治立场。巧合的是,就在饭局前后,美国证券交易委员会(SEC)突然宣布暂停此前对孙宇晨提起的证券欺诈诉讼,理由是“基于公共利益”reuters.com。这一戏剧性转折不禁令人生疑:孙宇晨深谙政治筹码运作之道,懂得借助美国权力更迭的契机为自己谋得一张“豁免令”。他在X平台(推特)上感慨对邀请心怀感激reuters.com——无形中传达出与未来政治盟友结盟的信号。
其次,孙宇晨积极布局中立主权地区,塑造自身的国际政治身份。他早在2019年即移居新加坡,将波场基金会设立于此,以避开中国大陆的监管高压。更令人瞩目的是,2021年底孙宇晨受聘出任加勒比海国家格林纳达驻世贸组织代表,正式踏入外交圈aljazeera.comaljazeera.com。身为一名加密创业者,却摇身一变成为“孙大使”,这在币圈乃至政坛都属破天荒之举。孙宇晨对媒体直言,加密行业发展到了需要主权国家和国际组织正视其潜力的阶段,他将致力于让区块链获得更多国家的认可aljazeera.com。他特别提到加勒比国家具有成为“下一个新加坡”的潜力:“加勒比国家离美国很近,但又不在美国,这非常关键。在美国境内你会陷入严苛监管和税收,而在加勒比,你可以避开这些桎梏。”aljazeera.com。这番话道出了孙宇晨战略的精髓——借助小国中立地带实现进可攻退可守的布局:既贴近美国这样的核心市场获取影响力,又保持独立主权豁免于其监管范围。
再次,孙宇晨还在国际舆论和文化象征上进行政治表态:例如高调竞拍知名艺术品、与名人互动、甚至不避讳与政治敏感人物(如特朗普阵营)同台。reuters.com川普在活动上直言“拜登政府迫害了加密创新者,我们要把他们带回美国”,孙宇晨的出现无疑为这一论调背书。在国内外社交媒体上,他乐于以“搞事者”形象示人,时而炮轰监管不公,时而与监管机构周旋谈判。从购买巴菲特午餐到押注川普NFT,从宣布波场成为多米尼加共和国官方公链到在洪都拉斯建立加密公司,他一再突破华人企业家避讳政治的传统藩篱,塑造出一个敢于同各国势力斡旋的主权代言人形象。市场也给予了正向反馈:在2023-2025这一轮震荡周期中,TRX价格和生态韧性远超许多竞争对手;波场不仅未被监管风暴击沉,反而因其政治押注而收获新增用户和资金青睐(USDT市值占比的提升即是一例finance.sina.com.cn)。孙宇晨个人也凭借外交官身份游走于各国高层,增强了项目背书的公信力。
与孙宇晨类似,币安创始人赵长鹏(CZ)也体现了“Crypto政治代理人”的影子。作为另一位华人加密巨头,CZ深知监管博弈的重要:币安从中国出发,几经辗转注册地于马耳他、开曼等地,近年来又与迪拜、阿布扎比等中东监管方建立良好关系。尽管币安在美国也受到诉讼挑战,但CZ本人频繁出席各国峰会、主动配合调查、游说政策制定者,其全球公关布局使 BNB 等币安生态资产始终享有一定溢价。可以说,孙宇晨和CZ代表的“华人币”之所以在风雨飘摇的市场中幸存并趋强,正是因为他们扮演了超越技术层面的政治角色:当绝大多数项目埋头编码或躲避监管时,他们选择直面政治、影响政治。
技术乌托邦的失语:ETH、SOL、XRP、ADA 的失速
将波场TRX和币安BNB的经历与其他主流链对照,更能突显“政治代理机制”的缺失所带来的代价。以太坊(ETH)、Solana(SOL)、瑞波(XRP)、Cardano(ADA)等项目,各有辉煌的技术远景或社区共识,却在本轮周期里不同程度陷入了失语和失速状态,一个重要原因正是缺乏有效的政治代理。
-
以太坊:作为智能合约的开创者,以太坊一直醉心于技术迭代和去中心化理想。然而,面对现实世界的监管压力,以太坊社区显得相对被动甚至天真。2021年后,美国制裁“Tornado Cash”等事件使以太坊网络一度出现矿工/验证者自我审查(OFAC合规)的现象,凸显出去中心化网络在政治压力下的脆弱。以太坊基金会和维塔利克等核心人物选择回避直接介入政治角力,试图以技术中立自守。但结果是,在稳定币领域,以太坊逐渐让出优势:USDT更多地流向了“不问来路”的波场,而USDC这种受美国监管严格的稳定币虽然依赖以太坊,却因为监管风险屡屡遭遇增发受限、黑名单冻结等情况。这使得以太坊在**“金融主权承载”**方面的话语权削弱。没有政治代理人替以太坊发声,其技术优势难以转化为对抗监管的筹码。相反,我们看到SEC在近期诉讼中对ETH网开一面(未将ETH列为证券),某种程度上是因其高度依赖美国企业(如Coinbase、Circle)的合规运营——这并非政治胜利,而更像被纳入现有规则体系的被动选择。
-
Solana、Cardano:这两条后起之秀公链,一个以极致性能著称,一个以学术范严谨著称。然而,他们在制度博弈上都缺乏存在感。2023年,美国SEC在对币安、Coinbase等交易所的诉讼中,点名将 SOL、ADA 等列为未经注册的证券,导致相关代币价格暴跌、机构退避cointelegraph.com。SOL和ADA团队自身并无强有力的政治资源予以反击:Solana团队更多精力放在修复网络停机和拓展应用上,对监管定性只能听天由命;Cardano的查尔斯·霍斯金森虽活跃社交媒体,但更多是科普技术和理念,对抗监管的实际影响力有限。当监管大棒挥下,这些专注技术的项目只能被动接受市场信心滑坡的现实。简言之,缺少政治代理等于缺少话语权——无论技术多优,没有人在权力场为你据理力争,你的话语权就只能拱手让人。
-
瑞波 XRP:作为对比,XRP的境遇更具讽刺意味。瑞波公司早早意识到监管的重要性,选择在美国走法律途径与SEC对簿公堂,试图以司法胜利换取地位合法。cointelegraph.com2023年中,瑞波在诉讼中部分胜诉,法院认定XRP本身不是证券,这看似是政治博弈的成果。然而,诉讼旷日持久耗费了瑞波数年的黄金发展期。期间XRP市场份额和舆论热度大不如前,新兴稳定币和跨境支付方案已趁虚而入。可以说,瑞波是少数走上前台直接对抗美国监管的项目,但孤军奋战终究力量有限:没有更广泛政治联盟支撑,胜利也难掩失地之痛。相比之下,孙宇晨选择的并非司法缠斗,而是迂回结盟,这种灵活的政治手腕或许更为有效。
归根结底,ETH、SOL、ADA 等在本轮周期的失速,提醒我们技术乌托邦需要现实政治护航。那些沉迷于宏大技术愿景却忽视政治策略的项目,往往在监管和资本博弈中败下阵来。反观TRX和BNB,一方面技术上并无颠覆性创新(波场VM几乎就是以太坊的变体,BNB Chain 也高度模仿以太架构),但却凭借政治上的主动赢得了市场认可——市值和生态逆势增长就是明证。
结论:主权表达的市场化工具
“从哈耶克到稳定币主权”,我们见证的是货币形态和政治形态的双重演进。哈耶克式的货币竞争思想在加密时代照进现实:私人发行的数字货币在与法定货币争夺稳定性和信任,而这一过程本质上就是主权的竞争与表达。加密货币从来都不仅是冷冰冰的技术产品,更是不断演化的主权表达的市场化工具。每一条公链、每一个代币,都在尝试承载某种主权意志:要么是传统国家主权的延伸(例如各国央行数字货币CBDC),要么是新兴数字共同体的自治主权,要么像USDT/波场这样,成为无国籍资本的影子主权。
TRX 的兴起充分说明,加密项目要取得长足发展,技术功能固然重要,但更关键的是充当“底层政治协调物”的能力。波场并没有因为VM设计优雅而胜出,而是因为它契合了特定政治经济环境下的市场需求:在强监管与资本外流并存的亚洲新兴市场,在美欧银行体系排斥的一角,波场提供了一个去中心化的政治避难所,让资本在不同主权之间自由穿行。aljazeera.com波场作为稳定币和博彩应用的主要载体,被贴上了“不受待见”的标签,但这正是另一种形式的民意表达。市场选择波场,并赋予TRX正溢价,正是对其他缺乏政治承载力项目的集体投票。
“Crypto 即政治”并非说技术不重要,而是强调技术的成败取决于其所嵌入的政治坐标。当ETH坚持代码法则时,TRX已经学会了在代码之上玩转权力棋局;当SOL醉心于极限TPS时,BNB已将自己融入全球离岸金融版图。展望未来,加密世界的竞争将更加赤裸地表现为主权影响力的竞争。谁能更好地平衡各方主权、充当不同利益的代理人,谁就能在市场中取得优势。这或许是加密运动发展至今给我们的最大的启示:去中心化的终点,并非消弭政治,而是重构政治。加密货币让更多人有机会参与主权的创造和表达,而TRX等“政治积极型”项目的案例则证明了,在市场的维度上,政治选择和市场选择早已融为一体。
参考资料:
-
哈耶克主张由私人发行货币与法币竞争finance.sina.cn
-
波场TRON上USDT流通量突破700亿美元,占全球近半finance.sina.com.cn
-
TRON超越以太坊成最大USDT发行网络coindesk.comcoindesk.com
-
2024年约260亿美元非法资金经由波场转移,居各链之首dlnews.comdlnews.com
-
波场低费用和稳定币优势吸引大量黑灰产资金dlnews.com
-
孙宇晨高调参与特朗普家族加密项目,成为最大持币者之一reuters.com
-
美国SEC出于“公共利益”暂停对孙宇晨的诉讼reuters.com
-
孙宇晨出任格林纳达驻世贸组织代表,波场成加勒比官方合作链aljazeera.comaljazeera.com
-
孙宇晨称需让主权国家正视区块链潜力,将精力投向国家层面的推动aljazeera.com
-
美国SEC曾在诉讼中将SOL、ADA等列为未经注册证券,后放弃相关请求cointelegraph.com
-
-
 @ 0b884d0d:9abbd54a
2025-06-02 21:24:16
@ 0b884d0d:9abbd54a
2025-06-02 21:24:16Conceitos chaves
Neste artigo você vai entender um pouco dos conceitos chave desse novo conjunto de ferramentas para aplicar justiça de forma descentralizada e anárquica.
Antes de continuar a leitura, quero elucidar alguns termos que serão constantemente usados neste artigo.
- Private Law Society (PLS)
- Uma organização sem fins lucrativos com o objetivo de criar novas soluções para tornar cada vez mais viável a aplicabilidade de uma justiça privada e descentralizada
- Ao mesmo tempo, um conjunto de protocolos e softwares de código aberto com o mesmo propósito
- Links úteis
- Perfil Nostr: nostr:npub1p79dx59d5gctllar73cqnucqft89gpkfmydxj4mmk2jj69s7hn3sfjatxx
- GitHub: https://github.com/PrivateLawSociety
- Sobre: https://privatelawsociety.net
- Bitcoin Justice Protocol (BJP)
- Um protocolo estabelecido pela Private Law Society
- Também um software de código aberto disponível no GitHub da Private Law Society
- Links úteis
- GitHub: https://github.com/PrivateLawSociety/pls-bjp
- Sobre: https://privatelawsociety.net/bjp
- Implementação oficial da PLS: https://pls-bjp.vercel.app/
- Web Of Trust (WoT)
- Uma base de dados com avaliações entre usuários Nostr relatando confiança/desconfiança e se um usuário teve relações comerciais ou não com outro
- O objetivo é ser um repositório de reputação para chaves Nostr
- Links úteis
- GitHub: https://github.com/PrivateLawSociety/pls-wot
- Sobre: https://privatelawsociety.net/wot
- Implementação oficial da PLS: https://pls-wot.vercel.app/
- Meu fork com o grafo: https://pls-wot-kiuusai.vercel.app/
Prefácio
Recentemente saiu um episódio no BetterMoney podcast sobre o projeto de justiça privada Private Law Society.
Muitos bons pontos foram levantados neste excelente episódio pelos participantes nostr:npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju e nostr:npub1wsl3695cnz7skvmcfqx980fmrv5ms3tcfyfg52sttvujgxk3r4lqajteft. Mas neste entorno permanecem ainda muitas dúvidas sobre o projeto em si, seu funcionamento, princípios, objetivos e funcionalidades.
Venho através deste artigo, apresentar resumidamente o projeto, a filosofia por trás do mesmo e dar a minha visão de como este conjunto de protocolos chamado Private Law Society tem a capacidade de não só transformar o mundo como o conhecemos, mas de tornar boa parte do "poder judiciário" obsoleto e irrelevante em vários aspectos, se assim os indivíduos o quiserem.
Mas afinal, o que é essa tal de PLS?
PLS é um acrônimo para Private Law Society (Sociedade de Leis Privadas em uma tradução livre). Além de uma organização sem fins lucrativos e totalmente Open Source, trata-se de um conjunto de softwares disponíveis no GitHub de forma a estruturar um protocolo de justiça privada descentralizado com colateral em Bitcoin. Falei grego para você? Vamos com calma dissecar estes conceitos...
Sociedade de leis privadas, a "utopia" libertária se tornando realidade
Quem é adepto do movimento libertário e/ou estuda o tema, provavelmente já ouviu falar nesse termo. Originalmente cunhado por David Hume, o filósofo e idealista escocẽs. O projeto toma este nome com o intúito, talvez de forma ambiciosa, mas com certeza visionária e audaz, de trazer uma solução prática e simples de estabelecer contratos voluntários entre duas ou mais partes, as quais livremente escolhem os seus "árbitros" ou "juízes" para fazer valer a lei. Como realmente uma justiça paralela a qual o contrato faz lei entre as partes.
Para uma introdução sobre o conceito, indico este vídeo do canal AnCapSu que trata sobre o tema de forma resumida.
Essa ideia, simples a priori esbarra no problema da aplicabilidade da força, ou ao menos era o que se pensava, antes da criação de ferramentas como o Bitcoin e soluções como Taproot e Bitcoin Scripts. Agora, com uma propriedade realmente soberana, programável e incensurável, essa ideia começa a ganhar forma.
Basicamente, uma dúvida plausível para uma pessoa leiga no assunto seria: "Tá, entendi. Esse tal de bitcoin é realmente bom, seguro e o Estado não tem poder de controle sobre ele. Mas como isso pode gerar essa tal de sociedade de leis privadas? É só uma forma de dinheiro."
A resposta para isso é: Dinheiro programável, chaves privadas e reputação!
BJP: contratos colateralizados em Bitcoin
Bitcoin, Nostr e Taproot: a chave para a aplicação da justiça privada
Se você já está minimamente envolvido com o ambiente Bitcoin, Nostr e afins, deve saber o que é um par de chaves públicas e privadas e como isso funciona. Existe uma chave pública e privada, a pública é a forma de identificação no sistema e a privada é a que gera as assinaturas. Daí é possível determinar que quem publicou a mensagem, seja na blockchain do Bitcoin, seja na rede Nostr, é o dono daquela chave pública em específico. Assim, se institui uma forma de identidade digital.
O que muita gente não sabe, ou não dá o devido valor, é que depois do soft fork Taproot da rede Bitcoin (ocorrido em 2021), os antigos Bitcoin Scripts tomaram outra forma e maior capacidade, se tornando mais práticos, leves e funcionais. Isso é o que dá base hoje para "contratos inteligentes" no Bitcoin e toda a parafernalha de Ordinals, Runes e coisas do gênero. O que pra muitos foi uma maldição que encheu a mempool, na verdade também se provou uma bênção, a qual é a base do BJP (Bitcoin Justice Protocol) da Private Law Society. A atualização permitiu com que scripts mais complexos pudessem ser desenvolvidos de forma mais simples, fossem mais leves e tivessem uma melhor privacidade. O BJP se empodera disso, fornecendo uma solução ao mesmo tempo que simples, inovadora para casos de uso de contratos. Primariamente na camada nobre do Bitcoin e posteriormente na Liquid Network, para aqueles que querem poupar em taxas e terem mais privacidade.
Por sua vez, o Nostr funciona também com criptografia de curvas elípticas, assim como nosso querido Bitcoin, para ser mais preciso, o mesmo algoritmo é usado tanto no Nostr quanto no Bitcoin. O Secp256k1. Na prática isso significa que toda chave Nostr também é uma chave Bitcoin em potencial. O BJP se apropria dessa interconexão para possibilitar a criação de contratos jurídicos.
BJP: uma multisig sofisticada?
Ok, até agora vimos o que torna esse tal de BJP possível, mas como ele funciona e como eu posso usá-lo na prática?
Bem grosseiramente falando, o BJP é um software que facilita a criação de carteiras multisig específicas para contratos jurídicos. Com ele, você constrói uma multisig não convencional com Taproot que assegura o cumprimento do contrato mediante concordância de todas as partes "clientes" do contrato ou do número mínimo de árbitros configurados previamente + um dos clientes.
Na prática, um script Taproot é montado com a seguinte lógica:
``` Clientes = {Lista de chaves públicas dos clientes}
Árbitros = {Lista de chaves públicas dos árbitros}
Quorum = Número mínimo de árbitros para aprovar a transação
Se todos os Clientes concordarem: Libera gasto Senão se 1 dentre todos os Clientes concorda e ao menos o Quorum de Árbitros concorda: Libera gasto Senão Bloqueia gasto ```
Esse algoritmo garante que o contrato seja efetuado e esteja de acordo com a vontade de todas as partes envolvidas, ou, se entrar em "disputa judicial", o número mínimo de árbitros designados para "fazer valer a lei", concorde junto com a parte lesada para onde os fundos devem ir.
Um exemplo prático:
Aqui temos um exemplo prático de aplicabilidade de um contrato feito através do BJP. Nesse caso, tendo a concordar com o nostr:npub1narc0ect9jf0ffnvcwg8kdqlte69yxfcxgxwaq35eygw42t3jqvq4hxv0r e discordar do nostr:npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju quando o primeiro comenta no recente episódio do BetterMoney Podcast:
19:30 Eu discordo do Júlio. Acho que a PLS seria perfeita pro contrato de aluguel. O locatário coloca o colateral e o proprietário vai ter certeza de que não vai tomar calote.
E se uma das partes tentar levar pra justiça estatal, não vai ter nenhum nome no contrato, apenas chaves públicas.
E está certo. O exemplo prático que acabei de citar reforça isso. Não há nada que impeça também, de no contrato, ter uma cláusula a qual envolver a justiça estatal cause algum prejuízo ou perda de causa imediata para a parte expositora. Não estou fazendo recomendação alguma, fazendo apologia a qualquer prática ou aconselhando usar deste tipo de artifício, se o que falo possa ser interpretado como crime pela lei positivada (não sou advogado). Mas, no campo das ideias e das possibilidades no mundo real, é uma possível solução/alternativa.
Vamos ao exemplo...
Adriano Calango quer alugar um apartamento de Beto Lagartixa. Só que ambos não se conhecem e não confiam suficientemente um no outro para fazer um contrato. Ambos decidem então escrever um documento. Word, Pdf ou um texto puro. Não importa. Lá estão todas as cláusulas, o caução do aluguel, multas estabelecidas para uso indevido, penalidades, dia de pagamento, decisão sobre multa de atraso, enfim, qualquer detalhe desse contrato.
Adriano Calango, escolhe Célsio Jacaré, seu amigo como seu árbitro pessoal. Beto Lagartixa escolhe Danilo Crocodilo, seu amigo, como seu árbitro pessoal. Ambos escolhem Eduardo Cobra, um réptil íntegro, com reputação ilibada e que já fez vários julgamentos, como um árbitro em comum para seu contrato. Daqui temos: dois contratantes, duas testemunhas e um juíz.
Adriano Calango então, acessa o site da PLS BJP para criar o contrato. Configura os clientes (ele e Beto Lagartixa), configura todos os árbitros, anexa o arquivo e cria o contrato na rede Bitcoin.
Um evento Nostr criptografado é criado e um link de compartilhamento do contrato é disponibilizado. Adriano Calango compartilha esse link com todos os usuários disponíveis.
Todos os usuários verificam os detalhes do contrato e se o documento do contrato bate com o contrato assinado. Todas as partes ativamente concordando, a nossa multisig é criada.
Um arquivo do contrato é disponibilizado para acessar a multisig do contrato posteriormente. Todos os usuários salvam esse arquivo e o mantém guardado em um local seguro. O objetivo disso é ter redundância. Se um dos participantes perder este arquivo, outro pode compartilhar o mesmo para possibilitar o acesso à multisig do contrato.
Adriano Calango e Beto Lagartixa depositam os devidos colaterais no contrato. Seja o caução de aluguel ou um montante separado para ser empenhorado. Isso é definido pelo acordo feito previamente.
Se tudo ocorrer bem, assim que Adriano Calango resolver se mudar e Beto Lagartixa não tiver nenhuma objeção quanto a isso, ambos voltam para o contrato previamente feito e concordam quanto aos montantes que cada um receberá de volta. Dividem o preço da taxa entre si e cada um tem sua propriedade de volta.
Digamos que Adriano Calango não cumpriu com parte do contrato, atrasando o pagamento de alguns meses. Por outro lado, Beto Lagartixa também não cumpriu parte de seu acordo, deixando de fornecer serviços prescritos no contrato como segurança de condomínio e um elevador funcional. O caso então é levado aos árbitros. Célsio Jacaré argumenta a favor de Adriano Calango, questionando Beto Lagartixa sobre os serviços não prestados pelo mesmo e que claramente no contrato estavam previstos como parte inclusa no custo do aluguel. Danilo Crocodio retruca sobre a inadimplência de Adriano Calango, defendendo seu amigo/cliente, Beto Lagartixa. Eduardo Cobra, ao ouvir calmamente todos os argumentos de ambos os lados, então decide: - Adriano Calango foi inadimplente por três meses. Portanto terá uma multa de 35% sobre seu patrimônio - Beto Lagartixa terá uma multa de 25% sobre o seu patrimônio, pois não prestou o serviço com a devida qualidade - O restante do patrimônio será devolvido para seus respectivos donos - Dos valores da multa: - 90% será dividido entre cada árbitro. 30% para cada - Os 10% restantes serão queimados em taxas para os mineradores
Note que não foi usado nenhum meio coercitivo para solucionar o caso e penalizar os réus em seus devidos processos. Tudo foi aceito voluntariamente previamente, inclusive da parte dos árbitros. As multas aplicadas são meramente ilustrativas. Em um cenário real, tais penalidades seriam acordadas previamente e na falta das mesmas, todas as partes discutiriam até entrar em um acordo quanto a decisão. É totalmente plausível que, por exemplo, a penalidade fosse queimar todo o valor das multas em taxas para os mineradores, se assim todos aceitassem. O mecanismo de mineração nesse cenário também se torna um possivel meio de aplicação de força em um julgamento.
Só esta parte do ecosistema já faz boa parte dos casos de uso da justiça estatal obsoleta, dando maior descentralização, privacidade e soberania para os indivíduos.
Nesse cenário temos novamente a "utopia" libertária sendo definitivamente aplicada. Não há dedo do Estado no meio, todos os contratos foram previamente acordados entre as partes e não houve violação ao PNA (Princípio da Não Agressão). Todo o processo foi estritamente voluntário desde o começo.
WoT: A digitalização da reputação
Quem vê o projeto a primeira vista, pode pensar:
Ah Calango. Legal essa solução com bitcoin e tal. Mas eu vou sempre precisar gastar meus bitcoins toda vida que fizer um contrato? Tem contratos que isso não vale a pena!
Sim. Isso é verdade. Tanto que foi genialmente um caso citado pelo nostr:npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju. Há casos que os valores são tão pequenos que não compensa criar todo um documento de contrato para, por exemplo, comprar um livro ou algo do tipo. Ou, algumas vezes, o próprio indivíduo não quer gastar dinheiro ou travar valores para manter esse contrato. Mas não é o único caso de uso. Lembre-se que mesmo com colaterais aplicados, normalmente as pessoas não gostam de entrar em decisões judiciais ou confusões em geral. Idealmente todos querem traçar o caminho feliz da história. Então, mesmo para firmar contratos com colateral em Bitcoin usando o BJP, é plausível que um usuário queira pesquisar o "histórico" de outro usuário na rede para averiguar se é uma boa ideia ou não se envolver com aquele indivíduo em específico.
Naturalmente o ser humano já pratica esse cálculo de reputação e analisa o ambiente a sua volta para entender a hierarquia e reputação dele e de outros indivíduos em um grupo. Somos seres sociais e naturalmente na nossa cabeça já montamos uma espécie de rede de confiança na nossa cabeça com a imagem que formamos de um indivíduo X ou Y com base na nossa comunidade. Hierarquia, lideranças, influência, são características naturais do ser humano.
A partir desse cenário, surgiu a ideia de gerar uma solução para uma melhor visualização da reputação entre usuários do protocolo. O objetivo é ser primariamente um repositório com avaliações de usuários sobre outros usuários, os classificando positivamente ou negativamente e informando se houve ou não negócios/fechamento de contratos com o mesmo. A ideia é realmente simples e o objetivo é deixar o protocolo aberto para as mais diversas formas de interpretação desses dados. Seja com modelos matemáticos, visualização e interpretação pessoal ou até mesmo o uso de inteligência artificial para o auxiliar o usuário a tomar suas decisões.
WoT: o nome é conhecido, mas a proposta é diferente
Veja que há uma diferença prática na WoT da PLS e outros projetos de WoT espalhados pela internet afora e pelo Nostr. A maioria dos projetos de WoT são para determinar se uma pessoa/chave privada é ou não relevante a partir da visão de outra chave privada. É o caso de serviços de WoT como o da Coracle.Social, Vertexlab.io e mais recentemente da nova implementação de WoT Relays. Serviços como estes tem o objetivo de reduzir ou eliminar spam e falsidade ideológica (fakes), assim como oferecer uma espécie de algoritmo de recomendação, similar ao que é feito em redes sociais como YouTube e Instagram.
Note que em nenhum momento o objetivo da WoT da PLS é definir por A + B quem é ou deixa de ser confiável ou inconfiável, afinal, confiança é algo estritamente relativo. Nenhum projeto pode ter a audácia de tentar classificar pessoas como confiáveis ou inconfiáveis a nível de estabelecimento de contratos. A PLS entende isso e respeita esse caráter subjetivo da confiança. De igual maneira, nunca foi o objetivo de qualquer projeto de WoT sério fazer algo similar ao que é feito em países como a China, onde pessoas têm alguma espécie de "crédito social". Fique tranquilo. Nosso objetivo não é tornar os episódios distópicos de Black Mirror em realidade 🤣
Visualização em grafo: uma proposta elegante
Desde que entrei de cabeça no projeto da PLS, uma coisa que veio sendo falada nas reuniões era sobre a criação de novas ferramentas para visualizar a rede de formas mais intuitivas, que ajudassem os usuários ao julgar pessoas como confiáveis ou não para estabelecer contratos, e ao mesmo tempo, resolvessem o problema de UX que é uma simples tabela com avaliações entre usuários da rede. A tendência é, a partir do momento que o projeto comece a ter adesão, que o número de notas cresça exponencialmente, e com isso, a visualização da reputação dos indivíduos seja pouco intuitiva. Uma solução apresentada para este problema foi a criação de um frontend com grafos, ou melhor, a criação de uma forma de visualização da sua rede de confiança em particular. A partir disso, foi gerada uma bounty no projeto para a implementação desta solução, a qual eu orgulhosamente estou construindo (na verdade está pronta para uso. Mas ainda quero melhorar algumas coisas). O objetivo é simples: dar ao usuário mais uma forma de contemplar os dados da WoT, de forma mais particular e intuitiva. Facilitando a tomada de decisões.
A natureza da confiança humana em sintonia com a tecnologia
Bolhas virtuais, vilarejos e mineiros
Uma possível crítica que o projeto possa receber é a possibilidade de ataques de spam ou cancelamento em massa corroer ou inviabilizar a utilidade do protocolo. Ataque Sybil também. Entretanto, são espantalhos até bem inocentes quanto ao projeto em questão.
Como havia mencionado anteriormente, a base do projeto em si é propositalmente simples e não se propõe a dar uma solução definitiva para a visualização dos dados postos no protocolo. A tabela de avaliações hoje existente no site da WoT da PLS é apenas uma das inúmeras formas de interpretar estes dados. E uma forma efetiva para problemas como esse, é justamente a implementação de uma visualização por grafo, onde os usuários podem ver redes de confiança sendo tracejadas a partir do ponto de vista específico de uma npub em particular.
Aqui a lógica de um antigo ditado é aplicada:
"O amigo do meu amigo é meu amigo"
Da mesma maneira também podemos formular outras afirmações como:
"O inimigo do meu inimigo é meu amigo"
"O inimigo do meu amigo é meu inimigo"
"O amigo do meu inimigo é meu inimigo"
Se tais derivações fazem sentido para você ou não, não cabe a mim dizer. Novamente, confiança é intrinsecamente algo de caráter subjetivo. Vai de cada um decidir quem é ou não confiável. É justamente por isso que estou implementando diversos filtros de avaliações no meu fork da PLS.
Na prática é o velho jogo de política de sempre. Como bem citado uma vez pelo filósofo e youtuber Platinho, ao citar Carl Schmitt:
Isso também se reflete na cultura mineira (e rural do Brasil em geral), por exemplo. O clássico "cê é fi de quem?". Perceba que essa é uma forma de procurar por um caminho de confiança já estabelecido. Quem tem parente em interior sabe, que uma das coisas mais comuns é os mais velhos, seja ou tio, mãe ou avô perguntar sobre um amigo que você leve para o ambiente familiar (meu filho, esse seu amigo é filho de quem?) É algo até instintivo do ser humano procurar por rotas de confiança e trabalhar de certa forma com o QI (Quem Indica). Goste você ou não, é assim que a natureza humana se expressa e é assim que a dinâmica social é montada.
Vendo que é natural a formação de bolhas, não é uma boa ideia em si interpretar os dados da WoT da PLS simplesmente de uma forma numérica bruta. A melhor forma é fazer uma abordagem individual, com base na sua rede de confiança ao invés de puramente o número de avaliações positivas e negativas.
O grafo da PLS busca justamente tornar mais intuitivo, prático e sistemático essa pesquisa natural. Essa implementação é além de uma ferramenta, uma forma de expressão social muito forte, tanto em âmbito social quanto jurídico, à medida em que a dinâmica social e jurídica se entrelaçam no tecido social.
Adriano Calango ataca novamente
Para um exemplo prático, voltemos a falar dele, Adriano Calango.
Adriano Calango conhece a WoT da PLS já faz um tempo e já avaliou todos os seus parceiros comerciais e amigos aos quais tem laços de confiança já firmes e maduros. Ele procura alguém para alugar uma casa Rolante, RS. ´Ele vê alguns perfis de síndicos no Nostr que moram na mesma cidade que ele com casas disponíveis para alugar. Mas quer ter uma noção que não está se metendo em encrenca ou lidando com algum síndico chato que inferniza a vida dos inquilinos.
Dito isso, ele acessa a WoT da PLS e vai na página do grafo. Percebe que seu amigo Bruno Jabuti, ao qual já havia avaliado positivamente anteriormente, avaliou positivamente um professor de Jiu-jitsu, conhecido como Carlos Camaleão. Que além de ser avaliado positivamente por Bruno Jabuti, recebeu várias avaliações positivas de outros usuários conhecidos de Adriano Calango. Carlos Camaleão, por sua vez, avaliou positivamente um síndico da região chamado Diego Iguana. Na descrição Carlos Camaleão descreve como em todo o tempo que ele foi inquilino de Diego Iguana sempre foi bem tratado e como seu condomínio estava sempre bem organizado e era cuidadosamente zelado, e como sempre que havia alguma falha de infraestrutura, o problema era rapidamente resolvido. Adriano Calango considera firmar um contrato de aluguel com Diego Iguana.
Assim, temos o seguinte caminho de confiança estabelecido:
Adriano Calango 👍 -> Bruno Jabuti 👍 -> Carlos Camaleão 👍 -> Diego Iguana
Passando-se alguns dias, Adriano Calango é abordado por Denis Jacaré em uma DM no Nostr oferecendo aluguel baratíssimo e com poucas exigências. Denis Jacaré foi informado que Adriano Calango estava a procura de um imóvel novo para residir. Adriano Calango, então, pega a chave Nostr de Denis Jacaré e joga na parte de "target" na página do grafo na PLS WoT. Ele percebe que Denis Jacaré tem várias avaliações negativas de inúmeros usuários, mas não consegue ainda bater o martelo quanto a confiabilidade de Denis Jacaré. Ele então insere sua própria chave Nostr no campo de "main rater" e vê que tem um caminho tracejado entre a sua npub e a de Denis Jacaré. Pra sua surpresa, ele vê que Carlos Camaleão deu a Denis Jacaré uma avaliação negativa, por conta que no período em que sua filha era inquilina do mesmo, prestou um péssimo serviço. O condomínio vivia com o elevador quebrado, a portaria muitas vezes não funcionava e tinha falta de luz constante. Denis Jacaré não tomava providẽncia nenhuma quanto a isso e ainda fazia questão de causa intriga entre os inquilinos e tentar jogar uns contra os outros. Adriano Calango, então percebe que Denis Jacaré não é confiável com base na rede de confiança definida por Adriano Calango.
Nesse caso temos o seguinte circuito estabelecido:
Adriano Calango 👍 -> Bruno Jabuti 👍 -> Carlos Camaleão 👎 -> Denis Jacaré
Adriano Calango aborda Diego Iguana para estabelecer um contrato. Agora é a vez de Diego Iguana pesquisar o histórico de Adriano Calango. Pois ele quer manter a comunidade de seu condomínio saudável e não deseja aceitar inquilinos baderneiros ou barraqueiros.
Diego Iguana faz então o caminho inverso de Adriano Calango, pondo a npub de Adriano Calango como "target" e a própria npub como "main rater". Daí Diego Iguana consegue ver que Carlos camaleão deu uma nota positiva para Bruno Jabuti e Bruno Jabuti deu uma nota positiva para Adriano Calango. Os dois então fecham negócio.
Neste exemplo, o grafo da WoT da PLS serviu como uma "bússola de confiança" para Adriano Calango e Diego Iguana firmarem um contrato no BJP com seus árbitros e advogados.
Considerações finais
Neste artigo você pôde aprender os conceitos básicos da Private Law Society, motivos de certas escolhas de design, viu exemplos práticos de casos de uso e um pouco das bases filosóficas que norteiam o ecosistema da PLS. Também pôde compreender um pouco mais sobre o conceito de WoT na PLS e como isso pode ser útil com o passar do tempo e a adesão de novos usuários no sistema.
Se este conteúdo te agregou de forma positiva em algo, considere mandar um ZAP ou fazer uma doação anônima por um dos meios disponibilizados na descrição do meu perfil Nostr. Este artigo foi feito com muito carinho e dedicação. Sua doação me encoraja a continuar produzindo e lhe mantendo informado. Se não pode ou não quer contribuir financeiramente, considere engajar no conteúdo reagindo, compartilhando e comentando. Toda a ajuda é bem vinda. Agradeço de coração sua paciência e atenção para ler até aqui.
Em breve trarei novidades sobre o desenvolvimento do grafo da WoT e logo mais, vídeo novo no meu canal do YouTube. Até mais!
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28nostr - Notes and Other Stuff Transmitted by Relays
The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all.
It doesn't rely on any trusted central server, hence it is resilient; it is based on cryptographic keys and signatures, so it is tamperproof; it does not rely on P2P techniques, therefore it works.
Very short summary of how it works, if you don't plan to read anything else:
Everybody runs a client. It can be a native client, a web client, etc. To publish something, you write a post, sign it with your key and send it to multiple relays (servers hosted by someone else, or yourself). To get updates from other people, you ask multiple relays if they know anything about these other people. Anyone can run a relay. A relay is very simple and dumb. It does nothing besides accepting posts from some people and forwarding to others. Relays don't have to be trusted. Signatures are verified on the client side.
This is needed because other solutions are broken:
The problem with Twitter
- Twitter has ads;
- Twitter uses bizarre techniques to keep you addicted;
- Twitter doesn't show an actual historical feed from people you follow;
- Twitter bans people;
- Twitter shadowbans people.
- Twitter has a lot of spam.
The problem with Mastodon and similar programs
- User identities are attached to domain names controlled by third-parties;
- Server owners can ban you, just like Twitter; Server owners can also block other servers;
- Migration between servers is an afterthought and can only be accomplished if servers cooperate. It doesn't work in an adversarial environment (all followers are lost);
- There are no clear incentives to run servers, therefore they tend to be run by enthusiasts and people who want to have their name attached to a cool domain. Then, users are subject to the despotism of a single person, which is often worse than that of a big company like Twitter, and they can't migrate out;
- Since servers tend to be run amateurishly, they are often abandoned after a while — which is effectively the same as banning everybody;
- It doesn't make sense to have a ton of servers if updates from every server will have to be painfully pushed (and saved!) to a ton of other servers. This point is exacerbated by the fact that servers tend to exist in huge numbers, therefore more data has to be passed to more places more often;
- For the specific example of video sharing, ActivityPub enthusiasts realized it would be completely impossible to transmit video from server to server the way text notes are, so they decided to keep the video hosted only from the single instance where it was posted to, which is similar to the Nostr approach.
The problem with SSB (Secure Scuttlebutt)
- It doesn't have many problems. I think it's great. In fact, I was going to use it as a basis for this, but
- its protocol is too complicated because it wasn't thought about being an open protocol at all. It was just written in JavaScript in probably a quick way to solve a specific problem and grew from that, therefore it has weird and unnecessary quirks like signing a JSON string which must strictly follow the rules of ECMA-262 6th Edition;
- It insists on having a chain of updates from a single user, which feels unnecessary to me and something that adds bloat and rigidity to the thing — each server/user needs to store all the chain of posts to be sure the new one is valid. Why? (Maybe they have a good reason);
- It is not as simple as Nostr, as it was primarily made for P2P syncing, with "pubs" being an afterthought;
- Still, it may be worth considering using SSB instead of this custom protocol and just adapting it to the client-relay server model, because reusing a standard is always better than trying to get people in a new one.
The problem with other solutions that require everybody to run their own server
- They require everybody to run their own server;
- Sometimes people can still be censored in these because domain names can be censored.
How does Nostr work?
- There are two components: clients and relays. Each user runs a client. Anyone can run a relay.
- Every user is identified by a public key. Every post is signed. Every client validates these signatures.
- Clients fetch data from relays of their choice and publish data to other relays of their choice. A relay doesn't talk to another relay, only directly to users.
- For example, to "follow" someone a user just instructs their client to query the relays it knows for posts from that public key.
- On startup, a client queries data from all relays it knows for all users it follows (for example, all updates from the last day), then displays that data to the user chronologically.
- A "post" can contain any kind of structured data, but the most used ones are going to find their way into the standard so all clients and relays can handle them seamlessly.
How does it solve the problems the networks above can't?
- Users getting banned and servers being closed
- A relay can block a user from publishing anything there, but that has no effect on them as they can still publish to other relays. Since users are identified by a public key, they don't lose their identities and their follower base when they get banned.
- Instead of requiring users to manually type new relay addresses (although this should also be supported), whenever someone you're following posts a server recommendation, the client should automatically add that to the list of relays it will query.
- If someone is using a relay to publish their data but wants to migrate to another one, they can publish a server recommendation to that previous relay and go;
- If someone gets banned from many relays such that they can't get their server recommendations broadcasted, they may still let some close friends know through other means with which relay they are publishing now. Then, these close friends can publish server recommendations to that new server, and slowly, the old follower base of the banned user will begin finding their posts again from the new relay.
-
All of the above is valid too for when a relay ceases its operations.
-
Censorship-resistance
- Each user can publish their updates to any number of relays.
-
A relay can charge a fee (the negotiation of that fee is outside of the protocol for now) from users to publish there, which ensures censorship-resistance (there will always be some Russian server willing to take your money in exchange for serving your posts).
-
Spam
-
If spam is a concern for a relay, it can require payment for publication or some other form of authentication, such as an email address or phone, and associate these internally with a pubkey that then gets to publish to that relay — or other anti-spam techniques, like hashcash or captchas. If a relay is being used as a spam vector, it can easily be unlisted by clients, which can continue to fetch updates from other relays.
-
Data storage
- For the network to stay healthy, there is no need for hundreds of active relays. In fact, it can work just fine with just a handful, given the fact that new relays can be created and spread through the network easily in case the existing relays start misbehaving. Therefore, the amount of data storage required, in general, is relatively less than Mastodon or similar software.
-
Or considering a different outcome: one in which there exist hundreds of niche relays run by amateurs, each relaying updates from a small group of users. The architecture scales just as well: data is sent from users to a single server, and from that server directly to the users who will consume that. It doesn't have to be stored by anyone else. In this situation, it is not a big burden for any single server to process updates from others, and having amateur servers is not a problem.
-
Video and other heavy content
-
It's easy for a relay to reject large content, or to charge for accepting and hosting large content. When information and incentives are clear, it's easy for the market forces to solve the problem.
-
Techniques to trick the user
- Each client can decide how to best show posts to users, so there is always the option of just consuming what you want in the manner you want — from using an AI to decide the order of the updates you'll see to just reading them in chronological order.
FAQ
- This is very simple. Why hasn't anyone done it before?
I don't know, but I imagine it has to do with the fact that people making social networks are either companies wanting to make money or P2P activists who want to make a thing completely without servers. They both fail to see the specific mix of both worlds that Nostr uses.
- How do I find people to follow?
First, you must know them and get their public key somehow, either by asking or by seeing it referenced somewhere. Once you're inside a Nostr social network you'll be able to see them interacting with other people and then you can also start following and interacting with these others.
- How do I find relays? What happens if I'm not connected to the same relays someone else is?
You won't be able to communicate with that person. But there are hints on events that can be used so that your client software (or you, manually) knows how to connect to the other person's relay and interact with them. There are other ideas on how to solve this too in the future but we can't ever promise perfect reachability, no protocol can.
- Can I know how many people are following me?
No, but you can get some estimates if relays cooperate in an extra-protocol way.
- What incentive is there for people to run relays?
The question is misleading. It assumes that relays are free dumb pipes that exist such that people can move data around through them. In this case yes, the incentives would not exist. This in fact could be said of DHT nodes in all other p2p network stacks: what incentive is there for people to run DHT nodes?
- Nostr enables you to move between server relays or use multiple relays but if these relays are just on AWS or Azure what’s the difference?
There are literally thousands of VPS providers scattered all around the globe today, there is not only AWS or Azure. AWS or Azure are exactly the providers used by single centralized service providers that need a lot of scale, and even then not just these two. For smaller relay servers any VPS will do the job very well.
-
 @ 94c2fd25:4fb53087
2025-06-05 06:41:55
@ 94c2fd25:4fb53087
2025-06-05 06:41:55EV8 không chỉ đơn thuần là một nền tảng cung cấp dịch vụ đa dạng mà còn là một biểu tượng của phong cách sống hiện đại, thuận tiện và thân thiện với môi trường. Với giao diện thân thiện và quy trình đăng ký, xác thực nhanh chóng, EV8 mang đến cho người dùng một trải nghiệm dễ dàng, giúp họ tiết kiệm thời gian trong cuộc sống bận rộn ngày nay. Các tính năng hỗ trợ thanh toán đa dạng như chuyển khoản ngân hàng, ví điện tử, và thẻ quốc tế tạo điều kiện thuận lợi cho mọi đối tượng sử dụng. Điều này góp phần thay đổi thói quen tiêu dùng của người dùng, từ những hành động đơn giản như nạp tiền, rút tiền, cho đến việc lựa chọn các dịch vụ phù hợp với nhu cầu cá nhân. EV8 giúp người dùng tiếp cận công nghệ một cách nhẹ nhàng, loại bỏ những trở ngại truyền thống, qua đó thúc đẩy sự phát triển của một xã hội số năng động và hiệu quả hơn.
Không chỉ tập trung vào tiện ích cá nhân, EV8 còn đóng vai trò quan trọng trong việc xây dựng cộng đồng bền vững và kết nối. Qua các chương trình ưu đãi, sự kiện hấp dẫn và hệ thống hỗ trợ khách hàng chuyên nghiệp, EV8 tạo nên sự gắn kết giữa người dùng và nền tảng, giúp họ cảm thấy được đồng hành và hỗ trợ mọi lúc mọi nơi. Những tính năng thông minh như quản lý năng lượng, theo dõi hoạt động và nhận thưởng qua các trò chơi cũng góp phần nâng cao nhận thức về sự cân bằng giữa giải trí và trách nhiệm trong cuộc sống. Từ đó, EV8 không chỉ là công cụ hỗ trợ mà còn là nguồn cảm hứng thúc đẩy người dùng sống chủ động, tích cực và thân thiện với môi trường trong kỷ nguyên số hóa ngày nay.
-
 @ 6389be64:ef439d32
2025-01-14 01:31:12
@ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
Meet The Forest Walker

For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
The Small Branch Chipper

When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
The Gassifier

The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
Biochar: The Waste

Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
Wood Vinegar: More Waste

Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
The Internal Combustion Engine

Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
CO2 Production For Growth

Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
The Branch Drones

During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
The Bitcoin Miner

Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
The Mesh Network

What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
Back To The Chain

Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
Sensor Packages
LiDaR

The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
pH, Soil Moisture, and Cation Exchange Sensing

The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
Weather Data

Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
Noise Suppression

Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
Fire Safety

A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
The Wrap

How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-
 @ 7460b7fd:4fc4e74b
2025-06-05 05:45:02
@ 7460b7fd:4fc4e74b
2025-06-05 05:45:02TRX 资源冻结式 Staking 与用户结构演化:对价格发现机制的影响分析
引言
TRX(波场币)作为波场 TRON 区块链的原生代币,因其独特的“冻结换资源”式 staking 模型而呈现出不同于传统公链的用户结构演变轨迹。这种机制在不同发展阶段吸引了截然不同类型的用户,从早期高度集中的机构持有者,到中期大量利用资源冻结套利的灰色产业,再到近期随着合规压力下资产向零散用户转移所形成的更广泛持有群体。本文将深入分析这一用户结构的演变历程,以及这种变化如何潜在影响 TRX 的市场价格发现机制。我们将按照时间脉络探讨以下问题:
-
初期设计:波场最初的 staking 模型如何偏向“对公场景”(如交易所间结算、机构资源调配),导致早期 TRX 资金和投票权集中度极高?
-
灰产利用:灰色产业(电信诈骗、网络赌博、地下钱庄等)如何利用 TRX “冻结换能量”机制降低 USDT 等稳定币转账成本,在波场上形成中期稳定的使用者群体?
-
用户下沉:随着各大交易所面临日益严格的合规压力,这些灰产地址如何将资金转移给“无交易所”通道的散户和小型平台账户,导致 TRX 使用权和持仓逐步向更广泛的普通用户渗透?
-
价格发现影响:这种持币结构的变化是否可能引导“零售价格发现”,即当大量散户持有 TRX 时,是否会对价格走势产生聚合影响(类似 GameStop 股票或 meme 币的散户抱团现象)?
-
链上数据演化:若数据支持,我们将呈现 TRX 持仓结构在链上的历史演变情况(如交易所热钱包占比、已知灰产地址占比、散户地址占比等),借助 Nansen、Lookonchain、Arkham、Dune 等分析工具的公开数据来说明上述趋势。
接下来,将从背景入手介绍波场 TRX 的 staking 机制设计及其早期影响,然后依据链上数据和行为证据分阶段分析用户结构转变,结合博弈论视角讨论价格发现机制,最后给出结论和展望。
背景:TRX 资源冻结型 Staking 模型与早期集中化
波场 TRON 于 2018 年主网上线,采用 委托权益证明(DPoS) 共识机制,其核心是 资源冻结(质押)换取网络资源和权益 的模式cryptorank.io。用户可以冻结一定数量的 TRX 以获取 带宽(用于普通交易)和 能量(用于智能合约操作)的配额,从而用资源抵扣交易手续费cryptorank.io。此外,冻结 TRX 还能获得 Tron Power(投票权),用于参与超级代表(Super Representatives,SR)节点的选举,从而分享出块奖励和投票奖励。这一机制本质上鼓励大量持币并长期冻结,以换取低成本交易和治理权。
TRX 早期的经济设计和应用场景明显偏向**“大户”和“机构”。首先,TRX 在 2017 年 ICO 分发时就有相当集中度——总发行1000亿枚中,约40%面向公开发售,15%私募,35%由项目方保留cryptorank.io。项目方(波场基金会)及早期投资人一开始就掌握了近一半的代币供应量。其次,在 DPoS 模式下,持币多者在投票治理中掌握更大权力,早期27个超级代表节点的投票由少数巨鲸地址主导。波场联合创始人、前 CTO 陈志强曾直言:“TRON 的代币分布是中心化的,超级代表是中心化的”cointelegraph.com;前27个超级代表节点拥有超过1.7亿票数,其中大部分受波场官方控制,普通散户的投票几乎无法左右结果cointelegraph.com。这意味着网络治理和出块权高度集中在项目方和早期大户手中**,staking 机制对中小持币者参与并不友好。这种局面导致 TRX 在生态早期呈现出明显的寡头格局。
更重要的是,波场团队有意将 TRX 打造成 高吞吐低成本的链上结算网络,这吸引了交易所和机构用户的青睐。2019年,创始人孙宇晨敏锐地抓住 交易所间稳定币跨链转账 的需求:由于以太坊网络手续费高、速度慢,交易所间结算 USDT 等稳定币成本很高,而波场上的 TRC20-USDT 转账费用极低、确认快theblockbeats.info。孙宇晨当即采取激进补贴策略,动用波场超级节点的挖矿收益,投入数亿元人民币补贴 TRC20-USDT 的充提手续费,在各大交易所间推广波场作为USDT转账的介质theblockbeats.info。据报道,当时通过波场网络充提 USDT 的用户可以享受相当于16%\~30%的收益(手续费返还优惠),极大刺激了交易所采用波场网络theblockbeats.info。这一系列措施使 TRC20版 USDT 的流通量和交易量在短时间内飙升,波场迅速取代以太坊成为 USDT 最主要的发行和转移平台。交易所和场外结算机构成为 TRX 生态的核心参与者:他们大量持有并冻结 TRX 来获取能量用于大额稳定币转账,或者直接利用波场网络进行跨所清算。这奠定了 TRX 早期资金和使用的高度机构化、集中化特征:头部交易所和项目方持仓占比极高,散户持有比例相对很低。
图:2024年初 TRX 持币分布的集中度。数据显示前10大地址合计持有约31.6%的供应量,前500大地址合计持有约85.5%的供应cryptorank.io。这印证了波场生态早期的持币高度集中在少数机构和巨鲸手中。
综上,波场 TRX 通过独特的冻结换资源机制,将手续费成本内化为持币收益,迎合了交易所、支付清算等对公场景对廉价高速链上转账的需求。在2018-2019年间,这一定位成功吸引了大量机构资金,但也造成了代币分布和治理权的高度集中。这是 TRX 用户结构演化的起点:以机构和巨鲸为主体的集中式持仓格局。
链上数据与行为层分析
随着波场网络逐步发展,TRX 的用户结构并未一成不变。链上数据和使用者行为表明,TRX 的持有者构成经历了从集中到扩散的动态演化,大致可划分为以下阶段:
初期阶段:机构主导的集中持仓
在主网上线后的早期(2018\~2019年),TRX 的持仓和使用主要集中在交易所、基金会等少数主体。从链上持币分布看,2019年时 TRX 前5个地址持有全网一半以上代币供应量,前10名地址接近60%(包括波场基金会及创始团队地址、少数大交易所的钱包等)cryptorank.io。即便到2025年中,集中度仍然较高——据统计前10大持币者仍合计拥有约25%的供应ccn.com,其中最大的单一地址占比超过8%ccn.com(推测为波场基金会或主要交易所冷钱包)。可见在初期,头部持有者在供应中占据主导。这种格局的形成,一方面源自前述代币分发和 DPoS 机制让项目方及早期投资人持有巨量筹码;另一方面,交易所为提供波场网络USDT充提现也大量囤积并冻结 TRX 获取带宽/能量,从而自身成为持币大户。
链上行为数据显示,交易所地址在 TRX 交易活动中占相当权重。大量 TRX 被冻结在交易所热/冷钱包用于日常为用户支付交易费用或资源租借。例如,币安在2019年直接成为波场超级代表节点之一,拥有全网超过一半以上的超级代表选票,当时就反映出交易所对 TRX 生态的深度介入coinmarketcap.comcointelegraph.com。总的来说,初期阶段 TRX 的用例主要是交易所间结算的媒介和赚取投票收益的质押资产,对应的用户主要是大宗资金持有者(交易所、基金会、早期投资人)。普通散户在这一阶段对 TRX 的参与度有限,无论持仓量还是交易笔数占比都很低。价格发现也主要由这些“大玩家”驱动——他们有能力通过场外交易或协议控制市场供给,从而较大程度上主导 TRX 的价格走向。
中期阶段:灰产经济的稳定使用者崛起
2019年至2021年后,随着波场网络的稳定运行和 USDT 等稳定币在波场上的广泛流通,一个意想不到的用户群体开始在 TRX 生态中扮演重要角色:灰产经济体。这里所指的灰产包括电信网络诈骗、网络赌博平台、地下钱庄洗钱团伙等非法或游走在法律灰色地带的组织。这些团体发现,波场的**“冻结 TRX 换能量”机制非常适合他们大规模、频繁地转移资金:通过持有并冻结一定量的 TRX,他们可以几乎免费地在波场链上无限次转账 USDT** 等代币linqihuishou.com。相比在以太坊等公链上高昂的 Gas 费用,波场提供的这种低成本转账渠道对灰产资金具有巨大吸引力。
联合国毒品和犯罪办公室(UNODC)的一份报告指出,在东南亚地区从事洗钱和诈骗的犯罪团伙偏好使用波场链上的 USDT 作为转移资产的工具dlnews.com。报告称,仅在截至2022年9月的一年间,就有逾170亿美元等值的 USDT 涉及非法交易所、地下洗钱等活动dlnews.comdlnews.com。波场因其匿名性强、转账快且成本近乎为零,成为这些团伙的“首选”网络dlnews.com。另一份调查也揭示,使用波场 USDT 的网络赌博和洗钱架构俨然形成了一个平行的地下银行系统protos.com。不法分子往往在国内收取现金,通过OTC渠道换成波场 USDT,在链上层层划转,最后在境外兑换回法币完成洗钱3e97756f-e20a-4497-8bc2-57f45e005c8a.baidu.scalaris-eci.com。
灰产大规模涌入波场带来了 TRX 生态的中期用户结构转变:虽然这些团伙的主要目的是利用 USDT 等稳定币,但为了降低成本他们必须持有一定数量的 TRX 来支付手续费或获取能量。这就意味着一批新的持币群体——灰产地址——开始稳定持有和使用 TRX。链上可以观察到许多可疑地址经常冻结大量 TRX,然后进行频繁的 USDT 转账操作。这些地址往往关联着诈骗资金、黑钱,通过分析工具已被标记为高风险。在波场交易笔数中,这些灰产相关地址的交易占有相当比例,它们维系着庞大的跨境资金流。dlnews.comprotos.com
值得注意的是,灰产用户的TRX持有行为具有“两面性”:一方面,他们持有 TRX 完全是出于工具用途,对 TRX 价格本身并不敏感,往往在完成资金转移后就会解冻并抛售 TRX(换回稳定币或法币)。因此,灰产用户的存在为 TRX 提供了持续的基础交易需求,但同时他们也可能对价格形成抛压。另一方面,由于这部分需求庞大且相对稳定(例如地下钱庄每天都有大额 USDT 要汇出),某种程度上托起了 TRX 的链上活跃度,甚至提高了网络的基础价值支撑。到2024年,波场上 USDT 的流通量已经超过以太坊,占到 USDT 总供应的一半以上cointelegraph.com;波场每日处理的稳定币转账金额高达数百亿美元,全球所有稳定币交易量中近30%通过波场网络完成coindesk.comcoindesk.com。在这些惊人的数字背后,灰产资金不可小觑。
综上,中期阶段 TRX 用户结构从单纯的机构主导,演变为**“机构+灰产”双重主导**格局。灰产经济成为 TRX 生态中隐形但重要的参与者,为 TRX 提供了源源不断的交易量和实用需求。然而,这种需求带有很强的功利性,在正常市场中往往难以转化为对 TRX 价格的主动支撑。
转型阶段:合规压力与持币群体下沉
进入2023-2024年,全球监管环境对加密行业(尤其是交易所)日趋严格,大型中心化交易所纷纷加强了 KYC/AML(反洗钱) 审查。这对利用交易所渠道“进出”资金的灰产团伙造成了沉重打击:大量涉嫌非法的地址被交易所列入黑名单冻结,稳定币发行方 Tether 也开始配合执法,冻结了部分波场网络上的可疑 USDT 账户cointelegraph.comcointelegraph.com。
图:由波场、Tether 与 TRM Labs 于2024年8月成立的“T3”金融犯罪联合行动小组,自成立以来已冻结超过1.26亿美元涉案 USDTcointelegraph.com。其中近一半涉及洗钱,另有相当比例涉及投资诈骗cointelegraph.com。这一行动反映出监管合规压力下,波场网络上大额非法资金池正受到打击。面对这种压力,灰产资金的流转模式开始转变。
随着“大额、集中”的灰产资金在主流交易所难以脱身,这些团伙被迫改变策略,更加依赖非交易所渠道来“出清”资金。他们开始将大宗资金拆分,通过场外交易(OTC)网络或小型换汇平台,转移给众多零散的个人地址。例如,一个诈骗团伙可能将上百万 USDT 分拆成上千笔小额转账,分别发给成百上千个个人钱包;这些个人再通过点对点方式把 USDT 换成现金。在中国等地破获的地下钱庄案件中,就发现犯罪团伙通过海量的个人数字钱包收款,以规避大额交易监控3e97756f-e20a-4497-8bc2-57f45e005c8a.baidu.scalaris-eci.com。波场网络的低费率使得**“大拆小”式的分散转账成为可能且经济**。
这一过程中,TRX 的使用者结构出现了**“下沉”**。原先主要由灰产团伙自己持有的 TRX(用于支付手续费或冻结换能量),现在逐步分散到大量普通用户手中。很多此前从未直接接触过波场的散户,因为参与OTC交易或接受灰产资金而开始持有少量 TRX。例如,一些东南亚地区的务工人员通过地下渠道汇款,在接收USDT时被要求使用波场网络的钱包,这意味着他们需要持有一点 TRX 来支付手续费。同样地,一些小型境外换汇商为了承接灰产的出金业务,也开始积累 TRX 以便快速完成批量转账。
链上数据支持了这种“去中心化”的趋势:CryptoQuant 的研究指出,截至2024年7月,波场网络上小额持有者(“散户”)的数量已经超过5260万,占据 USDT 转账笔数的28%左右newsdirect.com。也就是说,有数千万计的普通用户活跃在波场上进行小额交易。波场官方数据显示,到2025年初,总用户账户数已突破3亿,日活跃地址超过100万,每日小额稳定币交易数百万笔coindesk.comnewsdirect.com。这些数字表明,TRX 与波场网络的使用已深入到广泛的民间层面,不再只是大户的专属。
从持币结构看,虽然大户依然握有大量筹码,但相比早期,中小地址合计持有的比例有所上升。前文提到截至2025年5月前10名地址占供应约25%,而在更早时期这一数字一度超过30%cryptorank.ioccn.com。顶级持有者占比的下降意味着更多代币分散到了小持仓地址中。当然,大部分散户并非因为投资目的囤积 TRX,他们往往只持有满足转账所需的少量(比如几十个甚至几个 TRX用于手续费)。然而,当数以千万计的用户都持有哪怕少量 TRX 时,其总量也不可忽视。此外,一些原本为灰产服务的小平台、小型交易商,随着合规压力增加也可能选择转型,通过合法途径运营,这些玩家持有的 TRX 由“暗”转“明”,进一步增加了公开市场上的流通筹码。
**这一阶段的核心转变在于:TRX 的持有者基础变得空前广泛。**从链上身份看,除了交易所和已知灰产地址,普通散户地址在网络活动和持仓中的占比显著提高newsdirect.com。TRX 不再仅仅是机构间的结算工具或黑市的洗钱桥梁,它开始进入寻常用户的钱包,成为跨境汇款、支付和个人转账的一种选择。在非洲、中东等通货不稳定地区,波场 USDT 甚至被用作日常价值存储手段,TRX 则提供了必要的基础设施dlnews.com。这种下沉为 TRX 的市场生态带来了新的变量:当持币者从少数改为众多,价格发现的参与者结构也相应改变。
博弈模型讨论:散户崛起能否引导价格发现?
随着 TRX 持有和使用群体愈发多元化,一个关键问题浮出水面:如此广泛的散户参与,是否会改变 TRX 的价格发现机制,乃至引发类似 GameStop 或 meme 币那样的“散户聚合”行情? 从博弈论和市场微观结构角度,我们可以进行以下分析。
1. 定价权由大转小的再分配:在传统金融和早期加密市场中,少数大玩家(做市商、鲸鱼、机构)往往通过信息优势和资金优势主导价格。然而,当持仓分散到众多散户后,市场定价权力开始更平均地分配。如果散户群体足够活跃,他们的集体交易行为(买入或卖出)可以对价格产生显著影响。尤其在社交媒体发达的时代,散户可以通过舆论形成某种“共识预期”。例如,若大批散户相信“波场用户遍地开花将推高 TRX 价值”,他们可能趋于买入持有,从而真的推高价格——这类似于一种自证预期的动态。散户数量庞大且分散,单个看似微不足道,但**“乌合之众”在同步行动时可产生和巨鲸相媲美的资金量**。GameStop 股票之所以在2021年出现爆炸性逼空行情,就是因为数百万散户在网络论坛上形成合力,对抗华尔街空头。如果 TRX 的散户持有者也形成共同的看涨信念,可能出现交易行为的正反馈,推动价格快速上涨。
2. 网络效应与认知偏差:波场网络广泛的用户基础本身就会带来网络效应。每增加一位用户,TRX 的实用价值和潜在需求就略有提高。当数千万用户都在使用某个网络时,会产生一种“这么多人用,币价应该有支撑”的认知偏差。散户往往受“用户规模=价值”直觉影响而追涨。coindesk.comnewsdirect.com中的数据(每日超百万活跃地址、全球稳定币流通近三成经波场)可能被解读为 TRX 的基本面支撑,从而增强散户的持有信心。这种对基本面的再认知有别于灰产用户时期——灰产虽使用波场但不会宣扬其价值,而普通用户的使用反而可能转化为对 TRX 的口碑传播和正面情绪。由此,一个正向循环可能形成:用户基础扩大 → 市场认可度提高 → 新投资者涌入 → 价格上升 → 吸引更多用户。
3. 大户与散户的博弈:当然,散户行情能否持续,还取决于大户(早期鲸鱼、机构)的行为反应。一种可能情景是类似meme股/币:当散户推高价格时,大户出于逐利反而顺势助涨,甚至刻意制造舆论迎合散户,以便自己高位出货。如果 TRX 出现快速拉升,早期持有巨量筹码的老玩家可能选择逢高抛售套现,给上涨造成阻力。这一点在博弈上体现为:散户试图通过一致行动改变定价,但理性的大利润持有者会反向博弈,利用散户情绪行情实现盈利。TRX 目前前几大地址仍掌握巨额筹码,他们的抛压能力依旧很强。如果没有新的强力资金接盘,大户的出货可能使散户难以持续控盘。GameStop等案例中,散户成功逼空的前提之一是大户被困住无法立即抛售(空头被迫买入、公司高管锁仓等)。而在TRX市场,波场基金会、交易所等钱包并无锁定约束,完全可以利用流动性高点出售。因此,散户要引导价格发现,必须面对大户博弈的反作用力。
4. 市场情绪和触发事件:散户聚合行为往往需要一个导火索或叙事。GameStop有“对抗华尔街”的叙事,Dogecoin等meme币有马斯克等名人站台或者社区狂欢。TRX 虽有庞大用户,但缺乏类似的戏剧性话题来凝聚炒作热情。Justin Sun 虽然善于营销(如天价拍巴菲特午餐等),但这些年 TRX 价格相对稳健,没有出现过山车式暴涨暴跌,说明市场对其噱头相对理性。如果未来出现某个事件——例如波场生态中诞生一个现象级应用、或哪位投资大佬高调支持 TRX ——这可能点燃散户的想象力,触发一波情绪行情。在博弈模型上,这类似于公共知识的形成:散户需要确信“大家都会买”,而导火索事件恰恰提供了这样的公共信号。如果信号足够强烈,散户预期可协调,形成簇拥买入的纳什均衡。反之,在缺乏信号的平静环境中,散户各自为战,价格更多反映基本面与存量大户操作,不易自发聚合。
5. 零售价格发现的迹象:目前观察,TRX 市场已经显现出一些零售主导的特征。例如,2023-2024年熊市中,TRX 价格相对抗跌且波动率较低,或许与大量散户被动持币(用于手续费而非投机)有关——这部分需求相对刚性,不会因市场恐慌而大量抛售,反而稳定了价格。另一方面,在牛市来临时,这批散户是否会转为主动买入、推高价格,还有待验证。截至2025年年中,TRX 的市场走势总体平稳,CCN 分析指数给其势能评分仅34(满分100),显示动能偏弱ccn.com。这说明尚未出现 meme 式狂热,散户更多是被动参与者。但随着波场版稳定币生态的进一步扩张以及监管环境变化,不排除散户的角色从“被动用币者”转变为“主动投资者”。如果那一刻到来,TRX 的价格发现模式可能从当前偏基本面/机构驱动,转向更加依赖大众情绪和网络舆情。
综上,在博弈论视角下,TRX 用户结构的演变确实为零售价格发现创造了条件:更分散的持仓、更广泛的市场参与,使价格形成过程潜在地更具民主化色彩。然而,能否出现类似 GameStop 或 meme 币的极端行情,还取决于散户共识凝聚程度以及大户的策略反应。目前迹象表明 TRX 市场仍处于相对均衡状态,散户广布带来的更多是流动性提升和韧性增强,而非泡沫炒作。当然,市场结构一旦改变,其影响往往非线性——未来某个时点,不可忽视数以千万计散户的力量可能展现。
结论
TRX 代币由于其资源冻结式 staking 模式,在过去数年间经历了独特的用户结构演化:
-
早期,波场刻意迎合高频结算等对公场景,导致 TRX 持币和治理高度集中于项目方、交易所等少数机构账户,散户影响微乎其微。价格发现主要由这些大主体决定,市场呈现中心化特征。
-
中期,随着波场成为稳定币(尤其 USDT)的重要转移网络,各类灰色产业大量涌入利用“冻结换能量”降低转账成本。灰产地址成为 TRX 生态中不可忽视的稳定使用者群体,带来了巨大的链上交易量和实际需求。但这部分用户对 TRX 价格并无投机兴趣,其行为在提高网络实用性的同时,也给市场抛压埋下隐患。
-
近期,全球合规打击使得灰产资金从大交易所撤出,被迫通过无数散户和小型渠道分散流动。由此,TRX 的使用权和持有量开始向更广泛的人群下沉,数以千万计的普通用户卷入波场网络的使用。TRX 的持币结构正变得相对分散,散户在链上交易和持仓中的占比明显上升。
-
对价格发现的影响,可以概括为“基础盘扩大,定价权下放”。更广泛的用户基础意味着 TRX 价格受到的力量更加多元:除了少数大户博弈,还受到千千万万小持有者情绪和行为的影响。散户群体有可能在某些条件下形成合力影响价格(例如共同的看涨预期或外部刺激事件),这为 TRX 带来了出现零售驱动行情的可能性。然而,目前 TRX 市场尚未经历真正的散户抱团狂热,其价格依然相对平稳,说明机构和基本面因素仍占主导。
-
链上持仓结构演变总体符合上述趋势:从交易所/基金会占主导,逐步过渡到多元参与者并存。尽管确切的链上占比数据仍在完善(可借助 Nansen、Dune 等进一步分析交易所热钱包持仓、标记的诈骗地址持仓、非风险地址的小额持仓等),现有资料表明前十大地址持仓比例已从超过30%降至约25%,而小额地址数以亿计增长,对网络活动贡献巨大cryptorank.ionewsdirect.com。
综合而言,TRX 的资源冻结 staking 模式在不经意间促成了一条特殊的发展路径:从精英走向草根。这种用户结构的下沉为 TRX 带来了使用面的繁荣,同时也打开了价格发现的新篇章。未来,如果散户力量能够被某种契机调动,TRX 不排除出现类似meme行情的可能;即便没有极端事件,更多元的持仓结构也意味着价格将更真实地反映广泛市场的供需和预期。对于波场生态来说,如何平衡好“大户—灰产—散户”三类持币者的利益,将是决定 TRX 市值能走多远、走多稳的关键。波场的故事,正在从幕后走向台前,从少数走向大众,这或许正是去中心化精神的一种体现。
参考文献:
-
Chen, Z. (2019). Tron Co-Founder and CTO Leaves Project, Alleging Excessive Centralization. Cointelegraphcointelegraph.comcointelegraph.com.
-
Primitive Ventures. (2023). 裂隙中的共识:Tether与全球金融新秩序theblockbeats.infotheblockbeats.info.
-
CryptoRank. (2024). TRON H1 2024: From Stablecoins to Bitcoin and Beyond. CryptoRank Reportcryptorank.io.
-
DLNews. (2023). UN says USDT on Tron is “preferred choice” for fraudsters in East Asiadlnews.com.
-
Protos. (2024). China busts $2B USDT money laundering operationprotos.com.
-
TronDAO & CryptoQuant. (2024). TRON retail usage analysisnewsdirect.com.
-
Cointelegraph. (2024). Tether, Tron and TRM Labs jointly froze $126M USDT in 2024cointelegraph.comcointelegraph.com.
-
Cointelegraph. (2024). Nansen 2 brings transparency to Tron: USDT on Tron adoptioncointelegraph.com.
-
CCN. (2025). TRON Price Prediction 2025: Rich List and Distributionccn.comccn.com.
-
TRON DAO. (2025). Press Release: USDT on TRON surpasses $75Bcoindesk.comcoindesk.com.
-
-
 @ b8a9df82:6ab5cbbd
2025-06-02 18:31:55
@ b8a9df82:6ab5cbbd
2025-06-02 18:31:55How open-source won in fiat land.
Completely lost in time, I finally landed back in Berlin after a month in Buenos Aires and a week in Las Vegas that felt like an entire lifetime compressed into a few days.
A year ago, I barely knew how to spell NOSTR, didn’t have a Lightning wallet, and had only vaguely heard of Bitcoin. I had no idea what this movement was about — what it could mean, or where it might take me. Fast forward to now: I found myself in Las Vegas, at the biggest Bitcoin conference in the world, surrounded by thousands of people.
For those who haven’t been yes, Vegas is exactly like in the movies. It is Disneylands for adults. Casinos pumping cold air at 4 am to keep you awake, fake skies, fake rivers, fake cities. You walk from one hotel to another and somehow land in a version of Rome, Paris or Venice. It’s bizarre and overwhelming and… kind of amazing in its own twisted way. Who are we humans to build a neon wonderland in the middle of a desert?
And yet, even there, in peak fiat land, there I was: in a casino lounge at 4 in the morning onboarding random people to Nostr with the entire team.
But let’s rewind — how did I even end up here?
After a slightly rocky start Derek and I began the year with a mission: to bring Nostr to Las Vegas. A booth? Way too expensive. So we tried something else — applying for a grant from the Human Rights Foundation. Because the Oslo Freedom Forum was happening at the same time, HRF decided to support six fellow Nostriches and gave us the green light to build something different: the Nostr Lounge.
To the entire HRF team: thank you. Thank you for trusting us, for believing in the vision, and for playing such a crucial role in making this happen. Located in Open Source area far from the main exhibition hall, away from the noise and flashing lights we were not sure if anyone even come?
But the space turned out to be perfect — cosy, carpeted, warm. A real contrast to the intense chaos of the main hall. It gave us space to breathe, to onboard, to connect.And of course the plebs did come. And the energy? Unreal. People were genuinely curious, eager to learn, and ready to go deep. No suits, no fluff — just people who care.
Of course, there were suitcoiners too — and yes, I’ve written about them before, especially after my experience at Bitcoin investment Week in New York (if you missed it, I wrote about that here earlier this year — and Vegas brought a strange kind of déjà vu).
This was — and is — a team effort. It wouldn’t have happened without the incredible crew of volunteers who came from all corners of the world. Developers, builders, creators, idealists. People who understand what freedom of speech really means. Agustin, Mike, Sleepy, Erik and so many more. And even those who weren’t physically with us — following along on Nostr, sending support from afar — you were just as much a part of it.
For me personally, it meant everything to finally meet so many beautiful humans in real life. Especially the women: Roya, Heather, Valerie, Bri, Efrat… you give me strength and hope. It reminded me why I’m here — why we’re all here. There is a better world worth fighting for, and this community helps me believe in it.
The Nostr Lounge was for the plebs — and so was our side event at We All Scream. Away from the overpriced conference afterparties, NosVegas was a wild, joyful celebration. Sponsored by Tunestr and The Space, it was the perfect mix of education and dance floor madness. The vibes were lit. The artists such as Sara Jade, Ainsley Costello on fire.
If there’s one thing I would change? I wish we’d had more stage time. As Derek said in the only fireside chat: "Every Bitcoiner should be on Nostr." If we have an entire lounge dedicated to it, let’s really go for it. Because people do care. They do love it. Oh — and while we're dreaming — maybe one day the WiFi gods will finally smile on us.
One more highlight: The 2nd Annual Bitcoin Golf Championship and Kickoff Party. Frieda, the organiser, gave us a tiny table with Nostr banners. We used it to onboard and chat — and of course, it became the busiest little corner of the event.
All in all, I feel deeply grateful — and also completely behind on processing it all. A full recap will follow soon from Derek (bless him), but this was my personal take, straight from the heart.
And if I forgot to mention anyone by name — I’m truly sorry. So many of you made this experience what it was, and I carry that with me.
And one thing I’m especially thankful for — having someone by my side through all this. Someone who grounds me, who gets it, who quietly keeps me steady while the world spins fast. You know who you are.
Next stop: Prague
-
 @ 3a7c74bb:bbdd5960
2025-06-02 11:48:00
@ 3a7c74bb:bbdd5960
2025-06-02 11:48:00- The Foundation (12th Century)
The territory that would become Portugal was originally part of the Kingdom of León and Castile. But in 1128, the young nobleman Afonso Henriques confronted his own mother at the Battle of São Mamede, taking control of the County of Portugal (Condado Portucalense).
In 1139, after winning the Battle of Ourique, he declared himself King of Portugal. Independence was recognized in 1143 by the King of León and confirmed by the Pope in 1179.
- Expansion and the discoveries (14th–16th Centuries)
In the following centuries, Portugal consolidated its territory and set out to sea. The 15th century marked the beginning of the Portuguese Discoveries:
🚢 1419–1420 – Discovery of Madeira and the Azores 🚢 1488 – Bartolomeu Dias rounds the Cape of Good Hope 🚢 1498 – Vasco da Gama reaches India 🚢 1500 – Pedro Álvares Cabral discovers Brazil
During this period, Portugal created a vast maritime empire with colonies in Africa, the Americas, Asia, and Oceania.
- Iberian Union and the restoration (1580–1640)
In 1580, after a dynastic crisis caused by the death of King Sebastian, Portugal came under Spanish rule in what is known as the Iberian Union. For 60 years, the Spanish kings ruled Portugal until, in 1640, a revolt led by John IV restored Portuguese independence.
- The decline of the Empire and the 1755 earthquake
The 18th century was marked by the Lisbon earthquake of 1755, one of the greatest disasters of its time, which destroyed much of the capital. The Marquis of Pombal led the country’s reconstruction and modernization.
The empire began to weaken, culminating in the independence of Brazil in 1822.
- Wars, republic, and dictatorship (19th–20th Centuries)
Portugal faced internal crises and took part in World War I. In 1910, the monarchy fell and the Portuguese Republic was proclaimed.
In the 20th century, the country lived under the Estado Novo dictatorship (1933–1974), led by António de Oliveira Salazar. In 1974, the Carnation Revolution brought democracy, and the following year, the last African colonies gained independence.
- Modern Portugal (21st Century)
In 1986, Portugal joined the European Union, marking a period of growth and modernization. Today, it is a democratic country with a rich culture and a history that continues to inspire the world.
- And what about the islands?
The Autonomous Regions of Madeira and the Azores play a fundamental role in Portuguese identity. Discovered in the 15th century, they have been part of Portugal ever since and have their own regional governments.
Madeira is known for its wine and stunning landscapes, while the Azores are famous for their volcanic nature and unique culture.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite writer from Madeira. Long live freedom!
-
 @ 04c915da:3dfbecc9
2025-03-07 00:26:37
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Parallel Chains
We want merged-mined blockchains. We want them because it is possible to do things in them that aren't doable in the normal Bitcoin blockchain because it is rightfully too expensive, but there are other things beside the world money that could benefit from a "distributed ledger" -- just like people believed in 2013 --, like issued assets and domain names (just the most obvious examples).
On the other hand we can't have -- like people believed in 2013 -- a copy of Bitcoin for every little idea with its own native token that is mined by proof-of-work and must get off the ground from being completely valueless into having some value by way of a miracle that operated only once with Bitcoin.
It's also not a good idea to have blockchains with custom merged-mining protocol (like Namecoin and Rootstock) that require Bitcoin miners to run their software and be an active participant and miner for that other network besides Bitcoin, because it's too cumbersome for everybody.
Luckily Ruben Somsen invented this protocol for blind merged-mining that solves the issue above. Although it doesn't solve the fact that each parallel chain still needs some form of "native" token to pay miners -- or it must use another method that doesn't use a native token, such as trusted payments outside the chain.
How does it work
With the
SIGHASH_NOINPUT/SIGHASH_ANYPREVOUTsoft-fork[^eltoo] it becomes possible to create presigned transactions that aren't related to any previous UTXO.Then you create a long sequence of transactions (sufficient to last for many many years), each with an
nLockTimeof 1 and each spending the next (you create them from the last to the first). Since theirscriptSig(the unlocking script) will useSIGHASH_ANYPREVOUTyou can obtain a transaction id/hash that doesn't include the previous TXO, you can, for example, in a sequence of transactionsA0-->B(B spends output 0 from A), include the signature for "spending A0 on B" inside thescriptPubKey(the locking script) of "A0".With the contraption described above it is possible to make that long string of transactions everybody will know (and know how to generate) but each transaction can only be spent by the next previously decided transaction, no matter what anyone does, and there always must be at least one block of difference between them.
Then you combine it with
RBF,SIGHASH_SINGLEandSIGHASH_ANYONECANPAYso parallel chain miners can add inputs and outputs to be able to compete on fees by including their own outputs and getting change back while at the same time writing a hash of the parallel block in the change output and you get everything working perfectly: everybody trying to spend the same output from the long string, each with a different parallel block hash, only the highest bidder will get the transaction included on the Bitcoin chain and thus only one parallel block will be mined.See also
[^eltoo]: The same thing used in Eltoo.
-
 @ 4fe4a528:3ff6bf06
2025-01-01 15:50:50
@ 4fe4a528:3ff6bf06
2025-01-01 15:50:50I could have wrote about how bitcoin has more than doubled in 2024 or how some people are still sitting on the sidelines not trying to understand why bitcoin will double in 2025, but instead I thought I would write about how bitcoin is allowing for a decentralized social network.
Two years ago I decided to try out this NOSTR idea. Now I have 233 followers, almost the same number of people who read this monthly newsletter. Facebook / whats-app was to ad filled for me to enjoy what my friends were posting. X was great for news, but none of my friends where on it. Linkedin was just about business. Besides, NOSTR gives me more bitcoin every time I post. I am now using the bitcoin to buy eggs every two weeks from my neighbors. So to me it is a win win. I can write notes and eat eggs. I even use my NOSTR extension to log into hivetalk.org and help people with their computer issues. It is better than teaching via ZOOM. 2025 is going to be a great year for decentralization.
If you are trying to join NOSTR via your desktop I recommend going to getalby.com installing the browser extension. Then make an account with getalby and write down your 24 words (nsec). Link your profile to your lightning wallet and start posting and following other friends via primal.net. Yes, of course, I am put on this earth to help my fellow man. Some people enjoy using NOSTR via their cell phone and for those people I recommend amethyst or damus. We are all in this together.
-
 @ 2ed3596e:98b4cc78
2025-06-04 20:06:07
@ 2ed3596e:98b4cc78
2025-06-04 20:06:07Bitcoin Well recently sat down with Bitcoin News for a conversation about our mission to empower financial independence through Bitcoin. Founder and CEO Adam O’Brien shared how a frustrating experience purchasing bitcoin in 2013 led to the creation of one of Canada’s largest bitcoin ATM networks—and ultimately, a broader mission to help people replace traditional banks with self-custodied bitcoin.
From building out our Bitcoin portal to navigating life fully de-banked, Adam discussed how Bitcoin Well is creating tools for everyday use—paying bills, receiving paychecks, and living sovereignly. Read the full conversation to understand why we’re proud to be leading the charge for freedom-minded Bitcoiners across Canada and beyond.
About Bitcoin Well:
Bitcoin Well is a Canadian company on a mission to enable financial independence through the use of Bitcoin. We offer tools and services that allow users to buy, sell, and use bitcoin in self-custody—without relying on traditional banks.
About Bitcoin News:
Bitcoin News Inc is a US-based media company dedicated to covering the latest in Bitcoin—from mining and wallets to its growing role in global liquidity. We deliver clear, insightful reporting to help readers navigate the shifting landscape of Bitcoin and digital finance.
-
 @ 6389be64:ef439d32
2025-02-27 21:32:12
@ 6389be64:ef439d32
2025-02-27 21:32:12GA, plebs. The latest episode of Bitcoin And is out, and, as always, the chicanery is running rampant. Let’s break down the biggest topics I covered, and if you want the full, unfiltered rant, make sure to listen to the episode linked below.
House Democrats’ MEME Act: A Bad Joke?
House Democrats are proposing a bill to ban presidential meme coins, clearly aimed at Trump’s and Melania’s ill-advised token launches. While grifters launching meme coins is bad, this bill is just as ridiculous. If this legislation moves forward, expect a retaliatory strike exposing how politicians like Pelosi and Warren mysteriously amassed their fortunes. Will it pass? Doubtful. But it’s another sign of the government’s obsession with regulating everything except itself.
Senate Banking’s First Digital Asset Hearing: The Real Target Is You
Cynthia Lummis chaired the first digital asset hearing, and—surprise!—it was all about control. The discussion centered on stablecoins, AML, and KYC regulations, with witnesses suggesting Orwellian measures like freezing stablecoin transactions unless pre-approved by authorities. What was barely mentioned? Bitcoin. They want full oversight of stablecoins, which is really about controlling financial freedom. Expect more nonsense targeting self-custody wallets under the guise of stopping “bad actors.”
Bank of America and PayPal Want In on Stablecoins
Bank of America’s CEO openly stated they’ll launch a stablecoin as soon as regulation allows. Meanwhile, PayPal’s CEO paid for a hat using Bitcoin—not their own stablecoin, Pi USD. Why wouldn’t he use his own product? Maybe he knows stablecoins aren’t what they’re hyped up to be. Either way, the legacy financial system is gearing up to flood the market with stablecoins, not because they love crypto, but because it’s a tool to extend U.S. dollar dominance.
MetaPlanet Buys the Dip
Japan’s MetaPlanet issued $13.4M in bonds to buy more Bitcoin, proving once again that institutions see the writing on the wall. Unlike U.S. regulators who obsess over stablecoins, some companies are actually stacking sats.
UK Expands Crypto Seizure Powers
Across the pond, the UK government is pushing legislation to make it easier to seize and destroy crypto linked to criminal activity. While they frame it as going after the bad guys, it’s another move toward centralized control and financial surveillance.
Bitcoin Tools & Tech: Arc, SatoChip, and Nunchuk
Some bullish Bitcoin developments: ARC v0.5 is making Bitcoin’s second layer more efficient, SatoChip now supports Taproot and Nostr, and Nunchuk launched a group wallet with chat, making multisig collaboration easier.
The Bottom Line
The state is coming for financial privacy and control, and stablecoins are their weapon of choice. Bitcoiners need to stay focused, keep their coins in self-custody, and build out parallel systems. Expect more regulatory attacks, but don’t let them distract you—just keep stacking and transacting in ways they can’t control.
🎧 Listen to the full episode here: https://fountain.fm/episode/PYITCo18AJnsEkKLz2Ks
💰 Support the show by boosting sats on Podcasting 2.0! and I will see you on the other side.




