-
 @ eb0157af:77ab6c55
2025-06-05 03:02:03
@ eb0157af:77ab6c55
2025-06-05 03:02:03The Russian banking giant introduces financial instruments linked to Bitcoin for qualified investors.
Russia’s largest commercial banking institution, Sber, has made its entry into the Bitcoin space by unveiling a bond product tied to the asset.
Sber has officially launched its structured financial instrument that mirrors the price performance of Bitcoin alongside fluctuations in the dollar-ruble exchange rate. The product is already available to qualified investors through the over-the-counter (OTC) market, with plans to list it on the Moscow Exchange in the near future.
Formerly known as Sberbank, the institution stated in a May 30 announcement that the listing would provide transparency, liquidity, and convenience for a wide range of professional investors. This structured approach will allow investors to benefit both from Bitcoin’s appreciation in dollars and from the strengthening of the US dollar against the Russian ruble, the bank suggests.
The lender also announced plans to expand its crypto offering through the SberInvestments platform, introducing exchange-traded products that provide exposure to digital assets. The first product will be a Bitcoin futures instrument, scheduled for listing on June 4, coinciding with its official launch by the Moscow Exchange.
Sber’s initiative follows the authorization granted by Russia’s Central Bank on May 28, which permitted financial institutions to offer specific crypto-related financial instruments to accredited investors. However, the direct offering of cryptocurrencies remains prohibited.
Meanwhile, T-Bank (formerly Tinkoff Bank) launched an investment product linked to Bitcoin’s price, branding it a “smart asset” issued through Russia’s state-backed tokenization platform Atomyze.
According to the Russian Central Bank’s report for the first quarter of 2025, Russian residents hold approximately 827 billion rubles ($9.2 billion) in cryptocurrencies on centralized exchanges. Inflows into Russian crypto platforms surged by 51%, reaching 7.3 trillion rubles ($81.5 billion) over the same period.
The post Sber, Russia’s largest bank, launches Bitcoin bonds appeared first on Atlas21.
-
 @ 49d472c1:a63cd544
2025-06-05 02:59:12
@ 49d472c1:a63cd544
2025-06-05 02:59:12Bitcoin Miners Pivot to Power AI Boom, Offering a Lifeline to America’s Data-Center Crunch
A fresh Morgan Stanley analysis warns that U.S. data-center demand will balloon to ≈65 GW between 2025 and 2028—about 45 GW more than the grid can currently supply. One solution the bank singles out: repurposing the oversized, transformer-fed campuses originally built for Bitcoin mining. (investopedia.com)
Several public miners are already moving. Riot Platforms has begun buying extra land near its Corsicana, TX complex and hired a veteran data-center executive to head a “high-performance compute” division aimed squarely at AI customers. (riotplatforms.com, coindesk.com) Bitfarms, meanwhile, is marketing North-American sites to hyperscalers after hiring consultants to evaluate GPU-ready retrofits. (reuters.com)
Industry analysts say the pivot is existential. April 2024’s fourth halving chopped block rewards to 3.125 BTC, shrinking miner revenue just as network difficulty hit record highs. By leasing idle megawatts—or fully converting halls—operators lock in dollar-denominated cash-flows while retaining the option to resume mining if margins rebound.
“Miners spent the last cycle amassing land, switchgear and transformers. AI is about to pay them for it.” —Greg Miller, Citizens JMP (research note quoted in multiple sector briefings)
Why it matters
- Grid relief: Every gigawatt shifted from speculative hashing to AI compute eases ERCOT’s peak-load stress and shortens transmission-upgrade timelines. (datacenterdynamics.com)
- Cap-ex savings for cloud firms: Retrofitting a mining hall is months faster—and currently 30-40 % cheaper—than green-field construction, analysts estimate. (govtech.com)
- Dual-revenue model: Miners keep upside to future BTC price spikes while monetizing power capacity today.
The roadblocks
- Cooling retrofits: Air-cooled ASIC barns must be re-engineered for liquid-cooled GPU clusters, at up to \$3 M per MW in conversion costs. (driehaus.com)
- Policy risk in Texas: Lawmakers are weighing caps on industrial load-flex credits after recent grid-stress events, which could dent miners’ ancillary revenue. (dallasnews.com)
Bottom line: Once-beleaguered Bitcoin mines may become critical real estate for the surging AI sector—turning yesterday’s crypto boomtowns into tomorrow’s compute hubs while giving miners a much-needed new income stream.
-
 @ 502ab02a:a2860397
2025-06-05 02:42:04
@ 502ab02a:a2860397
2025-06-05 02:42:04ย้อนกลับไปเมื่อไม่กี่ปีที่ผ่านมา… มีบริษัทหน้าใหม่จากสหรัฐอเมริกาที่ชื่อไม่คุ้นหู แต่เสียงเงียบๆ ของมันดังไปถึงหูนักลงทุนรายใหญ่ระดับโลก ชื่อของมันคือ Motif FoodWorks
มันไม่ได้มาพร้อมคำสัญญาว่าจะเลี้ยงวัวด้วยดนตรีบำบัด แต่มาพร้อม “ความทะเยอทะยานทางวิทยาศาสตร์” ที่จะเปลี่ยนวิธีที่โลกกินไปตลอดกาล ไม่ใช่ด้วยรสมือคุณยาย แต่ด้วยสารเคมี วิศวกรรมชีวภาพ และเงินลงทุนที่แทบมองไม่เห็นก้นถุง
Motif FoodWorks ก่อตั้งในปี 2019 ในฐานะบริษัทลูกของ Ginkgo Bioworks ซึ่งเป็นบริษัทไบโอเทคชื่อดังจากบอสตัน วิสัยทัศน์ของ Motif คือการ “ออกแบบอาหารใหม่จากศูนย์” โดยไม่ต้องพึ่งพิงวัตถุดิบจากสัตว์เลย พวกเขาใช้เครื่องมือระดับห้องแล็บสร้างส่วนผสมใหม่ๆ เช่น… HEMAMI™ สารรส “อูมามิ” ที่ผลิตจากยีสต์ที่ถูกดัดแปลงพันธุกรรมให้สร้างโมเลกุล heme (แบบเดียวกับในเลือดสัตว์) APPETEX™ โปรตีนจากพืชที่ถูก “ทำให้เด้ง” เหมือนเนื้อสัตว์ ด้วยเทคนิคทางชีววิทยาโมเลกุล
มันคือการพยายามตอบคำถามว่า “จะทำอย่างไรให้ของที่ไม่ใช่เนื้อ…มีรสชาติเหมือนเนื้อ?”
เงินลงทุนรอบ Series A ของ Motif ทะลุ 200 ล้านดอลลาร์ภายในเวลาไม่กี่ปี ลงทุนโดยกองทุนสายเทคโนโลยีและ VC รายใหญ่ รวมถึงบริษัทผลิตอาหารรายใหญ่ระดับโลกที่เฮียคุ้นชื่อ แต่ที่น่าสนใจว่า ลูกค้ารายใหญ่ของ Motif กลับไม่ใช่ผู้บริโภคโดยตรง แต่เป็น บริษัทผลิตอาหาร “ทางเลือก” รายอื่นๆ ที่ต้องการสารปรุงแต่งใหม่ๆ เพื่อให้ผลิตภัณฑ์ให้ดูน่ากินขึ้น
ถ้า Impossible Foods คือร้านอาหาร Motif FoodWorks คือโรงงานผลิต “เครื่องปรุง” ที่จะทำให้ร้านอื่นๆ ทำอาหารเลียนแบบเนื้อได้อร่อยขึ้น มันคือ “เคมีแห่งความอร่อย” ที่ขายเป็น B2B ไม่ใช่ B2C ฟังดูแล้วเหมือนจะดีกับโลกไม่ต้องฆ่าสัตว์แต่ยังได้รสเนื้อ แต่คำถามคือ…
“ถ้าเราสร้างรสชาติที่เหมือนเนื้อจากยีสต์ดัดแปลงพันธุกรรม แล้วให้คนกินมันคือความก้าวหน้าทางวิทยาศาสตร์ หรือการทดลองที่ไม่มี IRB?”
Motif FoodWorks ใช้เทคโนโลยีเดียวกับหลายบริษัทในสาย Bioengineered Food เช่น CRISPR, precision fermentation, synthetic biology โดยเฉพาะ HEMAMI™ ที่หลายคนในวงการตั้งคำถามเรื่องความปลอดภัยระยะยาว และผลกระทบต่อ gut microbiome แม้จะผ่านการรับรอง GRAS (Generally Recognized As Safe) จาก FDA แต่ “ความปลอดภัย” กับ “ความเหมาะสม” มันเป็นคนละเรื่อง
การเปลี่ยนเนื้อให้เป็นสารสกัดการออกแบบรสชาติด้วยโมเลกุลมันคือแนวคิดเดียวกับที่ Ultra-Processed Food ใช้ในการสร้างน้ำอัดลมที่มี “กลิ่นมะนาว” โดยไม่มีมะนาวเลยแม้แต่นิด
Motif จึงไม่ต่างอะไรกับการ “รีแบรนด์ของให้ดูไฮเทค” หรืออีกนัยหนึ่งคือการเอาวิทยาศาสตร์ไปสร้างรสชาติ เพื่อให้ “ของที่ไม่ใช่” ดูเหมือน “ของที่ใช่”
และสิ่งนี้อาจเป็นอาวุธที่ทำให้มนุษย์ยิ่งห่างจาก real food แบบไม่รู้ตัว
การเกิดขึ้นของ Motif ไม่ใช่ความบังเอิญแต่มันคือชิ้นส่วนหนึ่งในเกมของ Big Food ที่กำลังพยายามออกแบบ “อาหารแห่งอนาคต” ไม่ใช่เพื่อสุขภาพ แต่เพื่อ ต้นทุน ความควบคุม และการขยายสิทธิ์ในทรัพย์สินทางปัญญา เพราะเมื่ออาหารถูกออกแบบด้วยสูตรที่จดสิทธิบัตร บริษัทจะสามารถเก็บค่าลิขสิทธิ์ได้ เหมือนที่ Microsoft เก็บเงินจากทุกเครื่องคอมพิวเตอร์ที่ลง Windows
แต่นั่นก็ไม่ใช่เรื่องแปลกใหม่อะไร เพราะเราก็ทำความรู้จัก future food มาด้วยกันพอสมควรแล้ว ประเด็นของ Motif นั้นมันทำให้เรารู้ว่า ในฝูงของนักล่า เขาไม่ได้แบ่งชิ้นเนื้อกันครับ การเป็นจ่าฝูงของนักล่า มันห้ำหั่นกันแบบเจ้าหมาป่ากันในแบบที่ สมันเหยื่อแบบพวกเรา รอวันโดนขย้ำเท่านั้น แล้วจะมาเล่าให้พรุ่งนี้ครับ
สำหรับวันนี้ ถ้าอยากเห็นสิ่งที่ Motif ทำไว้สามารถดูได้คลิปนี้ https://youtu.be/zZeRIVK6dDI?si=PYliM0v-9kj_sRE4 #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-05 01:28:52
@ 5d4b6c8d:8a1c1ee3
2025-06-05 01:28:52How did the stackers do on their ~HealthAndFitness journeys today?
I did very well: Slept well? Check Stuck to fast? Check Ate healthy? Check Activity target? Checkarooni
The one oddity I need to work on is that I got a foot cramp while playing turtle tag with my daughter.
https://stacker.news/items/997476
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ a296b972:e5a7a2e8
2025-06-04 22:06:06
@ a296b972:e5a7a2e8
2025-06-04 22:06:06In dem Video geht es um Dietrich Bonhoeffer, wie er sich zu Dummheit und vorsätzlicher bzw. rationaler Ignoranz geäußert hat. Schon seit einiger Zeit geht bei vielen Seltsames vor: Sie werden mit einem Thema persönlich konfrontiert und postum gibt es genau zu diesem Thema ein Video oder einen Artikel. Das kommt manchmal so vor, wie ein Frage- und Antwort-Spiel innerhalb der Schwarm-Intelligenz. Irgendwie spooky.
Die erschreckende Theorie der Dummheit, die Sie nie hören sollten - Dietrich Bonhoeffer: https://www.youtube.com/watch?v=PH-Vs5ILEko
Dem Entdecken, oder besser, dem Auf-einen-Zukommen, ist dieser E-Mail-Schriftverkehr in zeitlichem Zusammenhang vorausgegangen:
Nachfrage zu einem Aufruf durch einen Mitarbeiter zur Blutspende in einem Unternehmen mit über 100 Mitarbeitern über den E-Mail-Verteiler:
Lieber XXXXXXX,
danke zunächst für Dein Engagement.
In meiner näheren Familie gibt es jemanden, der regelmäßig Blut spendet, daher bin ich ein wenig für das Thema sensibilisiert.
Seit Du die E-Mail verschickt hast, gehe ich damit „schwanger“, ob ich ein vielleicht „heißes Eisen“ anfassen soll.
In den angehängten Informationen (des Roten Kreuzes) steht, dass das gespendete Blut auf bestimmte „Verunreinigungen“ durch Vorerkrankungen untersucht wird. Was nicht aufgeführt ist, ist eine Untersuchung, von der ich noch nicht einmal weiß, ob sie überhaupt schon durchgeführt wurde, und wenn ja, zu welchem Ergebnis sie gekommen ist, ob das gespendete Blut auch mit Substanzen der Corona-Gen-Behandlung verunreinigt sein kann. Leider zeigen ja die aktuellen Erkenntnisse, dass das Spike-Protein noch nach Jahren aktiv sein kann. Auch in gespendetem Blut? Die konkrete Frage wäre, ob das Rote Kreuz definitiv ausschließen kann, dass das nicht der Fall ist, damit ein möglicher Schaden nicht die Gefahr läuft, größer zu sein, als der Nutzen.
Soweit ich weiß, hat das Rote Kreuz bis heute keine separaten Blutbanken von „geimpftem“ und „ungeimpftem“ Blut angelegt. Wenn zu 100% ausgeschlossen werden kann, dass keine schädlichen Substanzen der Gen-Behandlung in die Blutkonserve gelangen, wäre das ja natürlich nicht nötig. Ist das so? Wenn ja, wo ist der Nachweis dazu zu finden, wie ist der aktuelle Erkenntnisstand, von wem wurden Studien dazu erarbeitet, wer hat das finanziert?
Mindestens 20% der Bevölkerung, das sind rund 16 Millionen Menschen, haben auf die Gen-Behandlung verzichtet und wollen im Ernstfall kein kontaminiertes Blut empfangen. Wie kann das Rote Kreuz belegbar und glaubhaft nachweisen, dass möglicherweise verunreinigtes Blut nicht doch in die Blutkonserven gelangt, weil sonst die Gefahr besteht, dass im Ernstfall Impfverzichter einen Schaden davontragen könnten?
Ich finde das eine wichtige Frage dem Roten Kreuz gegenüber und vielleicht wäre es auch gut, die möglichen Spender im Vorfeld für dieses heikle Thema zu sensibilisieren. Ich finde es auffällig, dass das Rote Kreuz sich hierzu weder in die eine, noch andere Richtung in den Informationen äußert, obwohl sie uns alle betrifft.
Ich schreibe diese Email aus kollegialen Gründen, aber auch zur Sensibilisierung gegenüber der Verantwortung aller Menschen gegenüber ihren Mitmenschen, die (hoffentlich nie) in die Situation kommen, einmal auf eine Blutspende angewiesen zu sein.
Wenn sich etwas Neues auf meine Nachfrage an Dich ergibt, wäre es klasse, ich würde davon erfahren.
Vielen Dank und viele Grüße
YYYYYYY
(Die Intension war, sich so vorsichtig wie möglich, quasi auf „Samtpfötchen“, an den Kern heranzupirschen. Dass es bereits Erkenntnisse dazu gibt, dass das Blut kontaminiert sein kann, wurde bewusst weggelassen, um keine Angriffsfläche zu bieten, ein „Verschwörungstheoretiker“ zu sein. Wenn die andere Seite auf einen Austausch eingestiegen wäre, wäre eine Quelle zu dieser Aussage vorhanden gewesen.)
Die Antwort:
Hallo YYYYYYY,
danke für die ausführliche Nachricht und dass du dir Gedanken zu dem Thema machst. Ich finde, man sollte Blutspenden als eine persönliche und private Sache betrachten.
Jeder und jede sollte für sich selbst abwägen, ob und unter welchen Bedingungen er oder sie das tun möchte.
Die Fragen, die du gestellt hast, sind echt speziell. Da geht's um medizinische und wissenschaftliche Themen, da kann ich als Privatperson nicht mitreden. Ich denke, dass sich Interessierte bei solchen Themen am besten direkt an medizinische Fachstellen oder das Rote Kreuz vor Ort wenden sollten, um fundierte und belastbare Informationen zu erhalten.
Mir persönlich ist es wichtig, Menschen auf die Möglichkeit der Blutspende aufmerksam zu machen.
Jeder kann das für sich selbst entscheiden und es ist auch okay, wenn man dabei Überzeugungen hat.
Beste Grüße
XXXXXXX
(„Blutspende…eine persönliche und private Sache“, nach dem Corona-Ereignis auch noch?, „…ich als Privatperson“ empfehle anderen etwas, bei dem sie möglicherweise anderen einen Schaden zufügen. Ist das schon grob fahrlässig, nach den Denkanstößen, die gegeben wurden?, „Wenn man dabei Überzeugungen hat.“, interessante Formulierung.)
Darauf die Reaktion:
Hallo XXXXXXX,
danke auch für Deine Antwort.
Wenn so eine im Grundsatz sicher gute Aktion beworben wird, liegt es nach meinem Empfinden auch in der Verantwortung, auf mögliche Folgen hinzuweisen, wenn es das Rote Kreuz schon nicht tut. Vorausgesetzt, man misst ihnen Bedeutung zu. Wenn meine E-Mail keine Veranlassung zu einer Beunruhigung und eigener Recherche angeregt hat, dann kann ich leider mehr nicht tun.
Dass das Rote Kreuz keine Hinweise gibt, liegt wohl daran, dass es Teil des Systems ist. Wer die Augen aufmacht, kann mit wenig Aufwand leider mehr als genug Tatsachenwahrheiten finden, die mit Schäden im Zusammenhang der Gen-Behandlung verursacht wurden und immer noch verursacht werden. Es ist nicht meine Aufgabe, einen Wissensrückstand von 5 Jahren auf den aktuellen Stand zu bringen. Allein die veröffentlichten RKI-Protokolle sollten schon genug Anlass zur Skepsis bieten. Der ÖRR berichtet leider nicht darüber, weil er auch Teil des Systems ist.
Ich will es damit genug sein lassen und hoffe, dass es unter den Kolleginnen und Kollegen noch weitere kritische Geister gibt.
Es geht nicht gegen Dich persönlich, aber ich hoffe, das Angebot wird nicht zahlreich genutzt.
Viele Grüße
YYYYYYY
(Einen halben Gang hochgeschaltet, ein Versuch, XXXXXXX aus der Reserve zu locken.)
Und ein Nachtrag von YYYYYYY:
Lieber XXXXXXX,
wir sind schon einmal unter Missbrauch des Begriffes „Solidarität“ hinter die Fichte geführt worden. Das darf nicht noch einmal passieren!
Nochmals viele Grüße
YYYYYYY
(Keine Reaktion mehr von XXXXXXX)
Und, wie gesagt, daraufhin kam das Video mit Bonhoeffer entgegen. Besser kann man vorsätzliche, rationale Ignoranz in Bezug auf den Schriftwechsel nicht beschreiben.
Hier wird eine jeden angehende allgemeinmedizinische Frage zu einer Frage der persönlichen Überzeugung gemacht. Das kommt doch sehr bekannt vor, oder?
Sehr wahrscheinlich lässt es sich vermuten, dass es sich bei XXXXXXX wohl um einen Corona-Jünger handelt, der die Tatsachen scheut, wie der Teufel das Weihwasser. Bloß nicht nachdenken, bloß nicht in Frage stellen, bloß nicht hellhörig oder gar neugierig werden, bloß nicht auf die Äußerungen eingehen, bloß nicht konkret werden, bloß keine eindeutig formulierte Stellung zu den Aussagen beziehen. „Angriffsfläche“ wäre vorhanden gewesen.
Das vorsichtige Anpirschen war alles andere, als mit-der-Brechstange-herangehen. Und doch setzt sofort automatisch der Teflon-Effekt ein. Selbstschutz.
Die Frage ist, wie soll da die Spaltung überwunden werden, wenn „die andere Seite“ so überhaupt nicht bereit ist, sich mit dem Vorgebrachten auseinanderzusetzen. Noch nicht einmal, wenn man nur die Spitze der Spitze des Eisbergs leise anhaucht.
Diesem Beispiel könnten viele unzählige weitere Beispiele hinzugefügt werden. Jeder hat so etwas schon einmal auf die eine oder andere Weise erlebt.
Das Gefühl lässt sich nicht unterdrücken, dass sich die Menschheit in zwei Lager aufgeteilt hat, und es gibt derzeit keinen Weg, wie man wieder aufeinander zukommen könnte.
Wie zwei Welten aufeinanderprallen, kann man derzeit auch in der Enquete-Kommission im sächsischen Landtag erleben: https://www.youtube.com/watch?v=D6ACmwBUBFM
Aus der Sicht von YYYYYYY ist das kein Grund zur Verzweiflung, jedoch drängt sich der Wunsch auf, dass man mit solchen Menschen wie XXXXXXX nichts mehr anfangen will. Man möchte mit ihnen, so schade es auch ist, am liebsten gar nichts mehr zu tun haben, und wenn doch aus irgendwelchen Gründen, nur noch das Allernotwendigste, so kurz und knapp, wie möglich. Empathie aufzubringen erscheint einem als vergeudete Energie, besser ist es, sich auf die Menschen zu konzentrieren, die wegen fehlender Genbehandlung keine Wesensveränderungen, die mittlerweile leider auch schon bestätigt sind, erlitten haben.
Wie Bonhoeffer richtig sagt, es geht hier nicht um Intelligenz, es geht viel tiefer. Es geht um das Menschsein an sich, und man hat den Eindruck, dass vor allem dies unter dem Einfluss der Spritze sehr stark gelitten hat. Da scheint so eine Abgestumpftheit durch, die einem einen kalten Schauer über den Rücken fahren lässt. Und das ist vielleicht noch gefährlicher, als diejenigen, die wirklich dumm sind. Das ist keine Arroganz oder Überheblichkeit, sondern unschuldig, wahllos von der Natur vergebene Dummheit, die jeden hätte ereilen können, hat es immer schon zu einem großen Teil gegeben. Hier hat man wenigstens noch die Möglichkeit, sich einfühlen zu können und Verständnis aufzubringen. Bei Menschen aber, von denen man weiß, dass sie die kognitiven Fähigkeiten zur Reflektion hätten, sie jedoch aus welchen Gründen auch immer nicht nutzen, oder sie als Verdrängungsmechanismus gerade nutzen, weil sie es können, geht auch eine gewisse Gefahr aus, weil man nie wissen kann, was sie sich sonst noch so ausdenken könnten, wenn sie in die geistige Enge getrieben werden, um ja nicht von Menschen, die den Mut haben, die Wahrheit auszusprechen, in ihrem mühsam aufgebauten Weltbild erschüttert zu werden. „Was nicht sein darf, das nicht sein kann!“, obwohl doch eigentlich die Wahrheit dem Menschen zumutbar ist.
So hat man das Gefühl, man atmet Honig ein und bewegt sich mühsam durch einen zähen Brei vorwärts, der einem bis zu den Oberschenkeln reicht. Jeder Schritt eine Anstrengung.
Und bevor man noch tiefer in dieses Verlustgefühl von Lebensqualität eintaucht (das hat nichts mit Depressionen zu tun, man bekommt einfach nur schlechte Laune), sich immer wieder bewusst machen, dass es da draußen noch eine Menge bei Verstand gebliebener Menschen gibt, die unermüdlich daran arbeiten, dass die Wahrheit weiter so sehr erkraftet, dass sie sich ihren Weg in den sogenannten Mainstream bahnt und die Menschen endlich aufwachen. So schmerzlich das für viele sein mag, es muss sein!
Selbst für einen wenig religiösen Menschen, im Sinne von regelmäßigen Kirchgängen und keinem Kontakt zur Institution Kirche, bekommt der Satz eine ganz besondere Bedeutung:
„Ich schicke euch den Geist der Wahrheit, und der wird euch frei machen!“
-
 @ e2c72a5a:bfacb2ee
2025-06-05 00:20:03
@ e2c72a5a:bfacb2ee
2025-06-05 00:20:03Think AI in crypto is just hype? It's secretly battling blockchain's biggest threat: cybercrime.
AI is revolutionizing crypto security. It learns attack patterns faster than any human, predicting threats before they strike. Imagine AI as your crypto bodyguard, constantly evolving to outsmart hackers.
Basic concepts? AI analyzes data to spot anomalies, like unusual transaction patterns. Real world? AI flags suspicious wallets and prevents fraud. Trends? AI is getting better at detecting sophisticated phishing scams and malware. Best practices? Use multi factor authentication and stay informed about the latest threats. Misconceptions? AI isn't a magic bullet; it needs human oversight.
Ready to level up your crypto security game? Explore AI powered security tools today.
-
 @ 4d41a7cb:7d3633cc
2025-06-04 23:21:10
@ 4d41a7cb:7d3633cc
2025-06-04 23:21:10Abstract. A purely digital version of a constitutional republic allows individuals worldwide to protect and exchange their private property without the need for state intervention or banks. Cryptography, proof of work, and difficulty adjustment provide part of the solution, but the main benefits come from the division of power and a worldwide network of nodes. Bitcoin solves the problem of trusting legislators and judges that can corrupt the law by letting anyone in the world be a judge and make sure the rules of the constitution are being followed. As long as there are honest nodes somewhere, the integrity of the network will be maintained; there’s no chance of buying or shutting down the judges. The requirements to be part of this republic are minimal: an internet connection, the capacity to keep a secret, and a device to make transactions.
Republic vs democracy
Numerous books elucidate the history and evolution of money, enabling a broader understanding of this ancient technology than ever before, including why Bitcoin is the ideal money. Bitcoin is revolutionary because it provides a new way of protecting and exchanging private property without the need of governments or banks, and I will make the case for why it is also the perfect constitutional republic.
A constitutional republic is a system of government in which the people hold sovereign power over the government and elect representatives who exercise that power. The sovereignty is held by the people, and the laws are written in the constitution to limit the actions of the elected officials running the government.
In contrast to a pure democracy, where a ‘collective’ community wields the sovereign power of the government to rule, and with a 51% agreement they can modify the constitution and slave the other 49%.
Some people still have the view that the Bitcoin protocol is like a democracy and miners are some kind of voters and if they have 51% of the hashing power they can change the rules of the network. But if the blocksize wars (2015-2017) taught us something is that this is not the case. Bitcoin is like a republic that needs total consensus from the nodes to change its constitution.
The only article I found making this case for Bitcoin was: The Republic of Bitcoin by Adam Ierymenko published on July 18, 2014. https://medium.com/@adamierymenko/the-republic-of-bitcoin-624f7639b2a5
Here’s my highlight from it:
I would argue that Bitcoin is a de-facto and unofficial republic, not a pure democracy* and not completely decentralized. The largest miners, most active members of the various Bitcoin forums, and the maintainers of the main Bitcoin code tree constitute a set of representative governors that can wield tremendous power over the network. Yet this power is checked by Bitcoin’s overall user base. *
Why do democracies fail?
A democracy cannot exist as a permanent form of Government. It can exist only until the voters discover that they can vote themselves largess out of the public treasury. From that moment on the majority always votes for the candidate promising the most benefits from the public treasury with the results that Democracy always collapses over a loose fiscal policy, always to be followed by a Dictatorship. (Written by Professor Alexander Fraser Tytler, nearly two centuries ago while our thirteen original states were still colonies of Great Britain. At the time he was writing of the decline and fall of the Athenian Republic over two thousands years before).
Did I say “republic”? By God, yes, I said “republic”! Long live the glorious Republic of the United States of America. Damn democracy. It is a fraudulent term used, often by ignorant persons but no less often by intellectual fakers, to describe an infamous mixture of socialism, miscegenation, graft, confiscation of property and denial of personal rights to individuals whose virtuous principles make them offensive. (Westbrook Pegler: New York Journal American, January 25th and 26th, 1951, under the titles- Upholds Republic of U.S Against Phony Democracy, Democracy in the U.S. Branded Meaningless)
The fall of great Republics follows a pattern, and the root cause is the abandoning of the original rules upon which the republic was founded to adopt a democracy. Once democracy is adopted, it gradually adopts socialism, dictatorships, and communism until it collapses under its own weight. This cycle takes many generations.
Unfortunately, we have abandoned our Republican forms of government by gradually modifying our constitution and by adopting unconstitutional central banks and fiat currencies: a legal fiction of money, a.k.a fake money designed to lose value over time.
It’s our responsibility to understand how our government’s have failed us, why and what we can do about it. This is an ancient problem but we have before our eyes a window of opportunity to be part of history, thanks to Bitcoin. Because **where our republics failed Bitcoin is winning! **
"The price good men pay for indifference to public affairs is to be ruled by evil men." said Plato in The Republic more than two and a half millennia ago and this is exactly where we are now. We can complain on the internet and point our fingers outside or we can take personal responsibility and do something about it.
From a young age we we are taught to be proud of our democratic systems and the equality it brings, but even the most enlightened and genius men of the past warned us of how dangerous this system of government is: "Dictatorship naturally arises out of democracy*, and the most aggravated form of tyranny and oppression comes from that source." Plato, The Republic. “Democracy is when the indigent and not the men of property are the rulers” Aristotele . *
In the last century our constitutions were modified and our republican governments were replaced by mob rule democracies. This system was used to turn the government into tax farm corporations for and by their creditors: the international banks. This parasitic group extracts economic value without providing equal compensation for our labor the same way it did before the colonies won their independence. Our republics were returned to their colonial status thanks to democratic governments. While the system works for a few, it is failing for the majority.
Before Bitcoin, we had to play within this system to improve our economic situation; a complete opt-out was not possible. The minimum interaction with the public infrastructure and banks comes with contractual liabilities, obligations, and hidden costs. These hidden costs range from artificial inflation to fees, colonial taxes, time delays, banking holidays, increasing bureaucracy, and the need to obtain permissions, approvals, and licenses.
In republics like the United States of America (1788) and Argentina (1853), our constitutions were explicitly written to avoid all of these evils. With some differences in their foundational laws and distribution of central and regional authorities but with the same goals; escape the colonial tax farm and unfair rules, protecting the individual rights such as: freedom over commerce, private property and equality under the law.
The American Revolution
The revolutionary war was fought to free the American colonies from the rule of the British monarchy, their oppressive and restrictive laws, colonial taxes and corrupt monetary system. The Constitutional Republic form of government was chosen to self govern the new Nation.
Other’s colonies like Argentina, ruled by the Spanish monarchy in this case, followed this same path and chose the same form of government to reclaim the power to be self-governed and protect economic freedom, because they understood there’s no human rights if you cannot freely enjoy the fruits of your labour and protect individual property.
The American colonies declared their independence from the tyrannical British monarchy in 1776 because they were done with the abuses of power, the intervention in commerce, the taxation without representation, their unfair monetary system of the Bank Of England, and the deprivation of trial by jury.
They wrote the document and declared their autonomy as independent states:
We hold these truths to be self-evident, that all men are created equal, that they are endowed by their Creator with certain unalienable rights, that among these are life, liberty, and the pursuit of happiness. That to secure these rights, governments are instituted among men, deriving their just powers from the consent of the governed—that whenever any form of government becomes destructive of these ends, it is the right of the people to alter or to abolish it and to institute new government, laying its foundation on such principles and organizing its powers in such form as to them shall seem most likely to effect their safety and happiness. Declaration of Independence July 4, 1776
The founding fathers were brave and smart; they pledged their lives, fortunes, and sacred honor, believing that Providence wanted men to be free. Many of them lost their lives to give us the best form of government known by men: a constitutional republic.
Autocracy declares the divine right of kings; its superiority cannot be questioned; its powers are arbitrarily or unjustly administered. Democracy is the “direct” rule of the people and has been repeatedly tried without success. Our constitutional fathers, familiar with the strength and weakness of both autocracy and democracy, with fixed principles definitely in mind, defined a representative republican form of government. They made a very marked distinction between a republic and a democracy and said repeatedly and emphatically they had funded a republic.
Training manual War Department Washington D.C,1928.
Under this form of government the constitution is the supreme law of the land. This document established the principles upon which the nation is funded and provides a structure of government to ensure and protect these principles. It defines its roles and responsibilities in order to protect individual’s rights and justice, dividing the power into: executive, legislative and judiciary bodies to prevent the centralization and abuses of power.
Under a constitutional Republic no men rule over other men, we are all equal under the law. The main goals of these constitutional republics is to ensure that no single person or group can hold absolute power over the rest of the population. Our ancestors inherit this form of government, but it takes vigilance and responsibility to maintain it.
2. The problem: Democracy, central banks and fiat currencies
Unfortunately, all of these protections given by our constitutions were lost or heavily degraded, especially private property because of popular democracy, central banks and fiat currencies, all of them contrary to the original principles of our republican governments.
Our constitutional republics were replaced by mob rule democracies during the first third of the XX century, inverting the role of the government from being a ‘protector of rights’ to a ‘violator of rights’ pushing for socialist, communist, and tyrannical laws. The government transitioned from safeguarding individual liberties to imposing the "will of the majority" and **substituting rights with privileges and licenses. **
*Central banks and income taxes are parasitic communist devices specifically designed to extract wealth from the majority and to prevent economic freedom. *
What was needed was alternative rails to commerce freely adapted to the times we are living in: completely digital and protected with military-grade cryptography, to trade without the need to go through archaic and corrupt financial institutions or governments. Bitcoin is a system of government that prioritizes minimal governance. The system is secure as long as participants are using the original protocol or participating in the original constitution and not weak and insecure copies.
From being a government controlled by people that do not ask for permission to a government that controls the people who have to ask for permission. This was, of course, thanks to the many wars, panics, and artificial chaos generated by those willing to expand their already enormous power: international bankers. This group is actively working to push tyranny on a global scale through mass surveillance, digital IDs, and a cashless society. Democracies are facilitating this agenda. Plato said in The Republic that "Tyranny naturally arises out of democracy”.
The strength of the Republic comes from its constitution, this document is worthless if legislators and citizens do not enforce and follow the original principles, letting new laws invalidate the original ones.
In less than two generations since the Argentine Republic adopted the libertarian constitution of 1853 it became one of the wealthiest nations in the world surpassing many Western European countries like Italy, Spain and Portugal.
Juan Bautista Alberdi (1810-1884) was a lawyer, politician, economist and the intellectual author of the Argentine Constitution of 1853. The main goals of this constitution were:
-
Abolish slavery
-
Protect private property rights
-
Provide equality under the law (no licences or nobility titles)
-
Get rid of colonial taxes
-
Free the markets from state intervention
“Simple taxpayers or colonists, for three centuries, we are to this day the work of this antecedent, which has more power than our written constitutions. After being machines of the Spanish taxman, we have become machines of the national taxman: that is the difference. After being colonists of Spain, we have become colonists of our national governments: always fiscal states, always servile revenue machines, which never arrive, because misery and backwardness can never yield anything” (...)
But in economics, more than in any other field, it is nothing to enshrine the principle; what matters most, what is most difficult, is to put it into practice. A regime is not annihilated by a decree, even if it is constitutional, but by the slow action of a new one, whose creation costs the same time it took to form the bad one, and many times more, because to destroy and forget is another previous work.
The modern regime is in our hearts, but the colonial one is in our habits, which are usually more powerful than the abstract desire for the best.
That is precisely why the Argentine Constitution has made its economic system the faction that distinguishes it and places it above all the republican constitutions of South America.
Indeed, all the economic liberties of the Constitution may be annulled and reduced to gilded disappointments, by merely leaving standing a large part of our old economic laws, and enacting new ones which, instead of being in conformity with the new principles, are in conformity with our old rent-seeking and fiscal habits, ordinarily stronger than our principles.
Outside the Constitution there does not exist, nor can there be, nor should there be, any law that in any way is not regulatory of the private and public principles, rights and guarantees that the Constitution establishes as the fundamental basis of all law in the Republic.
There is, therefore, a stumbling block to which the beautiful system of the Argentine Constitution may succumb, if it is not taken into account by the legislator who must regulate the execution of the new system in its relations with the production of national wealth.
Up to this point, the worst enemy of the country's wealth has been the wealth of the tax collector. We owe to the old colonial regime the legacy of this fundamental error of its Spanish economy. ***We are countries of fiscal complexion, peoples organized to produce real incomes. ***
I repeat that I speak of economic liberty; and as much as of my country of all South America on this point, - It matters, above all, to keep always in view the danger of annulling each and every economic liberty in the Constitution by laws regulating its exercise.
In republics like the United States of America and Argentina, the constitutional systems were designed to promote fairness, accountability, and the protection of individual rights by dividing power among multiple branches of government (legislative, executive, and judicial) and levels of governance (federal, state, and municipal).
This division of powers establishes a balance between centralization and decentralization to ensure that no single entity can hold absolute power over the rest of the population.
Benjamin Franklin told us, "We have given you a republic—if you can keep it." History is proof that we haven’t kept it; in fact, we have replaced it with democracy, the worst form of government. Such blame primarily falls on the shoulders of the "elected officials," who are typically lawyers acting as legislators and judges. However, 'We The People' also bear responsibility for our lack of vigilance. “The price of freedom is eternal vigilance” said Thomas Jefferson, the principal author of the Declaration of Independence and the third president of the United States of America from 1801 to 1809.
“If you do not take interest in the affairs of your government, then you are doomed to live under the rule of fools,” said Socrates more than two thousands years ago. And "The price good men pay for indifference to public affairs is to be ruled by evil men." said Plato in The Republic.
**The time lawyers start manipulating the laws, ignoring the constitutional principles, the spirit of the constitution is abandoned, and all the evils reappear: infiltration, inflation, and corruption. **
Unfortunately, we have abandoned our republican forms of government by gradually modifying our constitution and by adopting parasitic central banks. Money was replaced by worthless currency, and common law was replaced by codified law, increasing bureaucracy, state intervention, costs, and the opposite of justice.
In the U.S., these events happened between 1913, when the Federal Reserve was created, and 1933, when the gold standard, common law, and the republican form of government were totally abandoned.
By 1913 Argentina was the 4th wealthiest nation on earth, and it owed its success to its libertarian constitution that guaranteed economic freedom. Unfortunately Argentina stopped using gold in 1929, the central bank was installed in 1935, and the constitution was heavily modified in 1949, introducing universal suffrage and adopting socialism. This was the beginning of the end of the “Argentine Republic”.
We have freedom written down in our constitutions but we are again living under a colonial system in economic terms because of **central banks, fiat currencies and taxes. **
Routine and hereditary ignorance in economic matters are the cause of this transmigration of the colonial system into the republican system. Inherited customs, beliefs and concerns are more powerful than written laws and accepted opinions. Juan Bautista Alberdi.
The sixth president of the United States, John Quincy Adams (1825-1829), warned: "The central bank is an institution of the most deadly hostility existing against the principles and form of our Constitution." And also “There are two ways to conquer and enslave a nation. One is by the sword. The other is by debt."
**3. The reaction: debt slavery **
Since our liberators won their freedoms with the sword, we lost them by contracting fraudulent debt publicly and privately. The tool used to enslave our nations: central banks and fiat currencies.
This institution have the monopoly over the national fiat currency that they print to buy government debt. This system was possible thanks to codified law and the widespread ignorance of the public on monetary and banking issues. The problem with traditional currencies is that they are subject to inflation, regulations and we have to trust those in control of them. Since fiat currencies are a creation of the state they are subject to their authority and arbitrary changes. It’s a contract and when we use them we fall under the government’s jurisdiction: this comes with ‘privileges’ and tax liabilities.
Private companies that manage these currencies and process payments such as banks can arbitrarily freeze, confiscate and steal our money at every moment without any real evidence of a crime. They can do this to bail out banks who give risky loans that cannot be repaid. This creates a cycle of currency debasement, increasing cost of living, economic stagnation, demoralization of the markets, market distortions and many other evils. This has us in a loop of: more inflation, more taxes, less savings, more crisis. And there’s no remedy ‘inside’ the system.
This currency that central banks print is not based on substance (gold, silver, or other commodities) but on faith over the government credit. A faith that is crumbling. This currency is not real money; in fact, it is the opposite: debt.
Every unit of currency represents a government debt obligation, which must be repaid to the central bank that holds the corresponding asset: government bonds. If the government has the ability to create bonds, it could also create currency without the need to borrow from the central bank. But the reality is that international bankers control the government, and they want the government to be in debt.
Those with control of the currency printer can buy any legislator, any university, any business, or any influential media channel to manipulate the mechanism of democracy and to use the government as a mask to advance their agenda of expanding their monopolistic and parasitic power. They can get legal immunity, modify the laws to their advantage, and control the education and the information we get.
We are led to believe the system is “broken” and it needs to be fixed, when the reality is that this monetary system that took over our governments is designed to enslave us and our future generations with hopeless debts. This parasitic system sucks the wealth of nations with inflation, deflation, and taxation while they don't give us equal value. The mechanism is literally engineered to transfer wealth from the citizens to the banks: THIS IS BY DESIGN.
Thomas Jefferson also warned us when he said, "I believe that banking institutions are more dangerous to our liberties than standing armies. If the American people ever allow private banks to control the issue of their currency, first by inflation, then by deflation, the banks and corporations that will grow up around [the banks] will deprive the people of all property until their children wake up homeless on the continent their fathers conquered."
By inflating the currency and credit supply, they create an artificial boom in the economy, incentivizing the public to collateralize real wealth and borrow worthless bank promissory notes that these institutions can create out of thin air because of "licenses’ and legal privileges. When the banks consider it time to turn the wheel, they raise interest rates and start deflating the currency and credit supply, triggering liquidations of collateral, business bankruptcies, and economic depression. We are told this process is a natural phenomenon from the “economic cycle,” but the truth is that this process is artificially designed to transfer the wealth from the citizens and businesses to the banks and their corporations.
We have become enslaved to the banks, who control our economic success or downfall due to our adoption of their worthless promissory notes as the primary means of exchange for commerce. They introduced this fake money in our legislation as ‘legal tender’ for all debts, public and private. This currency is not money; it is fake money based on a debt designed to enslave us.
In order to have more currency, we have to pledge real wealth as collateral, risking losing it in a game of chance where the bank controls the odds. This is the real reason why the Great Depression of 1929-1933 happened; this is how the banks stole all the gold and infiltrated every big business board of directors by turning themselves into majority stockholders using a network of private trusts and corporations.
Nations of the world and citizens are being enslaved by the international bankers and their debt-based currencies, lending air and stealing the resources of the nations. **This creates artificial scarcity, misery, and economic stagnation. **
This system creates two types of citizens: those who have to exchange time, energy, and work to obtain currency and are heavily taxed on the process and those who can print it out of thin air or loan against their assets tax-free. This is the root of inequality under the law and the equivalent of reestablishing nobility titles in the form of “banking licenses.”
These contracted debts are mathematically impossible to repay since there’s more debt than currency due to the interest that compound every year. This creates the need to pay the old debts with new emission of debts creating more inflation of the currency while devaluing its purchasing power and increasing the cost of living.
Government deficits only grow while the public services decline and its cost to the public increase in the form of higher taxes and inflation. As the situation gets worse, direct confiscation of wealth happens.. Authority abuses, surveillance and violation of rights from governments are common things, especially during the big debt crisis.
This system created a big debt spiral. When the government “prints currency” it is getting itself deeper in debt issuing bonds that generate interest that grows the size of the debt every year. This death spiral debases the currency faster and faster accelerating all the evils from the economic crisis that cannot be fixed.
This monetary system is what killed our constitutional republics and the root of most of the evils our modern society faces. But not everything is lost; we have reason to be positive, we have hope! We have Bitcoin!
**4. The solution: going back to our roots **
On February 8, 1996, John Perry Barlow published The Declaration of Independence in Cyberspace in response to the increasing government control and surveillance over the internet, which raised concerns about privacy, free speech, and other human rights. He called cyberspace the “new home of the mind,” where the sovereignty of the governments has no jurisdiction.
Now more than ever, mental privacy and freedom of thought are key elements for self-determination.
I declare the global social space we are building to be naturally independent of the tyrannies you seek to impose on us. You have no moral right to rule us, nor do you possess any methods of enforcement we have true reason to fear. (...) Governments derive their just powers from the consent of the governed. *You have neither solicited nor received ours. We did not invite you. (...) *
The declaration continues saying that many of the problems that governments affirm they need to solve are nonexistent, and if there are problems to solve, the people will fix them by their own means without the government. It says that they were creating a world where everyone is equal in terms of having the same possibility to express their minds and beliefs without the fear of being coerced into silence or conformity. Adding that the only law that all our constituent cultures would generally recognize is the Golden Rule. Inviting freedom lovers and self-determination supporters to bring back the dreams of Jefferson, Washington, Mill, Madison, De Tocqueville, and Brandeis.
*We must declare our virtual selves immune to your sovereignty, even as we continue to consent to your rule over our bodies. We will spread ourselves across the planet so that no one can arrest our thoughts. *
We will create a civilization of the mind in cyberspace. May it be more humane and fair than the world your governments have made before.
Satoshi Nakamoto published his white paper on the cyberpunk mailing list on October 31, 2008, twelve years after the publication of this new declaration of independence. He did so during the great financial crisis created by the banks as a revolutionary yet silent act. This list was a place where computer scientists, hackers, and developers from all around the world shared ideas, debated technical issues, and pushed for digital security and anonymity.
The idea was solid but still needed some collaboration and help to make it a reality: the mailing list was the key. As prophesied in the new declaration, a new idea started flowing freely on the internet with the intention of fixing a problem (created by banks) by people’s means without asking for ‘authorities’ permission. A group of individuals started voluntarily working on this new idea because they knew the importance of it and the impact of its promise.
**During these seventeen years, this idea has transformed into a more viable alternative system for those who uphold the principles of human freedom, self-determination, and self-government. **
Bitcoin was designed for individuals who have opted to assume personal responsibility, rather than relying on external powers to enhance their lives. This is a choice for individuals who are courageous, inquisitive, and truth-seekers, fed up with the constant bombardment of falsehoods and manipulation. This is a choice for individuals who have reached the point of no longer accepting lies and manipulation.
We have to recognize the libertarian and Austrian economic spirit of Bitcoin because this was THE SAME SPIRIT UPON WHICH OUR CONSTITUTIONS WERE WRITTEN CENTURIES AGO. I refer mainly to the constitutions of the United States of America (1788) and the Argentine Republic (1853). These are our roots, and we should never forget them if we want to be free and protect our individual freedoms.
First of all, libertarians defend individual freedoms and small governments with limited intervention in people’s lives. The golden rule of “Do unto others as you would have them do unto you,” or, reversed, “Do not do unto others what you would not want done to yourself,” is **the moral code of the libertarians, as it was the moral code of the Lord Jesus Christ. **
The libertarian philosophy embraces autonomy, entrepreneurship, and voluntary cooperation while it opposes coercion, authoritarianism, and bureaucracy. It encourages a society where individuals are responsible for their actions and decisions while fostering cooperation and mutual respect among them.
The Austrian school of economics shares the same values, opposing central planning, government intervention in the economy, socialism, and communism and advocating for free market systems based on voluntary exchanges and private property.
It also points to the central bank's fiat currency manipulation as the root cause of great financial crises such as the 2008 one, when Satoshi published his white-paper as a way of saying: WE NEED AN ALTERNATIVE TO THIS MADNESS, AND WE NEED TO DO IT BY OUR OWN MEANS BECAUSE THE GOVERNMENT WAS PART OF THE PROBLEM, NOT PART OF THE SOLUTION. HE LEFT THIS CLEAR IN THE GENESIS BLOCK.
“The Federal Reserve is an organized cartel of bankers, who are creating inflation, ripping off the public, destroying the savings of the average American”
Murray Rothbard (1926-1995), founder and leading theoretician of anarcho-capitalism.
The Austrian school of economics points to central banks and their fiat currencies as the responsible parties for every type of distortion in the markets leading to recessions and financial crises, opposing both of them and advocating for hard money that governments cannot manipulate, especially gold.
Following the golden rule and the Austrian teachings, Satoshi gave humanity the ideal monetary system ever engineered and with the cyberpunks they made it real.
And Bitcoin is not just money, but also a new form of protecting private property, monetizing energy, distributing governance, connecting individuals worldwide and expanding commerce rails.
Bitcoin is a social network, a perfect republic, by bitcoiners and for bitcoiners. Bitcoin is so far the best REAL option we have to opt out of this rigged game and reclaim our sovereignty and self-respect. Bitcoin is the remedy that cannot be found under the law, and if we did, we have no guarantees it will not be taken away.
The adoption of Bitcoin is voluntary; no one is going to force it upon you with ‘legal tender’ laws or arbitrary regulations. Bitcoin is de facto lawful money that does not require permission or licenses, following the spirit of our original constitutions.
It provides a new way of doing commerce, with a global network of individuals organized around a consensus of rules. Today, commerce operates on a global scale, unencumbered by state intervention, and the boundaries exist only in our imaginations due to the limitless possibilities. Free enterprise is again possible even under the cashless society that banks are actively pushing on us.
Bitcoin is not just honest and hard money; Bitcoin is a set of rules without rulers. Bitcoin is money backed by math and energy that cannot be manipulated. Our property rights are protected by code, computing power, and energy.
Bitcoin is the perfect republic. The division of power of the Bitcoin network replicates those of the Republic, guaranteeing a balance between centralization and decentralization that is capable of providing equality under the code.
Bitcoin is the re-evolution of money, governance, and banking, and it has the potential to replace them all at once or at least force them to adapt and improve their services if they don't want to become obsolete in the next decades.
5. The perfect Republic
The organized power of a Republic is divided in Legislative, executive and judicial systems, in the case of Bitcoin is the protocol, the miners and the nodes. Bitcoin is not only money, but the perfect Republic: a distributed power with no kings, no central banks and no ballot boxes full of lies. It is a network where power is divided, distributed, audited and encrypted.
No bank and no government control Bitcoin. Just math, incentives, cryptography and a worldwide web of individuals who want bitcoin to succeed.
The code is the legislative power
The rules of the protocol are its constitutions: 21 million, halving every 210,000 blocks, difficulty adjustment, blocksize. Instead of being a set of traditional laws it’s a set of modern computer codes. Similar to the written constitutions the Bitcoin protocol established a set of rules that ensure the integrity, fairness and stability of the network.
These rules are written and are visible and audible. You need a total consensus in order to change them, something that is very difficult, almost impossible. There’s no such thing as emergency powers or govern by a majority, decree or executive orders.
The best government is the one who governs the less, and the bitcoin monetary policy can be reduced to this simple geometric regression:
The Bitcoin fixed supply and predictable monetary policy are key rules of the protocol. They incentivice savings and eliminate inflation forever. It also eliminates currency supply manipulation forever, giving clarity to the individuals and facilitating economic planification based on strong principles: certainty and predictability.
This not only preserves and grows the value of the bitcoins but it also serves as a check on the power of governments and central banks that manipulate the money supply for their benefit.
Miners are the executive power
They execute transactions, validate blocks and maintain the network flowing. But they cannot manipulate the code, they execute, they do not govern. The process of mining employs cryptography to secure transactions and prevent fraud, ensuring the system remains trustworthy and reliable for its users.
Miners have skin in the game, they invest in hardware and energy to mine the bitcoins, so they have an incentive to act honestly to get the rewards, cheating is against their interest and if they do their blocks get rejected by the network of nodes and they waste valuable energy.
In fact miners are incentivized to find the cheapest source of energy, usually wasted energy to mine bitcoin. In this process they not only maintain the network alive and secure with the transactions flowing but also monetize energy: they turn energy into bitcoin!
The nodes are the judicial power
They are the guardians of the protocol, they make sure the rules are being followed and if someone is trying to cheat they can invalidate the transaction.
Nodes have a complete copy of the bitcoin transactions history (blockchain) as a publicly-accessible record of all transactions that have ever taken place within the system. Nodes verify that every new transaction is following the rules of the protocol. This feature ensures that the record cannot be altered or hidden, promoting transparency and accountability in its operations.
They act like the supreme court, they don't produce laws, they don't process transactions, but they can say “this is not valid”. **This is the equivalent of having thousands of judges all around the world that nobody can buy or shut down. **
Like citizens can vote in a constitutional republic, users of the Bitcoin network can do it by running nodes. Changes in the protocol require total agreement among nodes to ensure that no single entity or group can modify the rules. This maintains the integrity of the network. This system of governance ensures that decisions are made transparently and with input from all nodes runners.
**Users: Citizens of the Bitcoin Republic a.k.a bitcoiners **
With no central authority or supreme power all bitcoiners are equal under the code. Bitcoin is a global system, it works 24/7, totally accessible for everyone, it cannot be manipulated by bankers or by governments and everyone is free to build a business around Bitcoin.
There’s no need for IDs, licenses or approvals, the network is open to everyone and functions in a permission-less way. Bitcoin is a parallel system and does not depend on the state or banks infrastructures, in fact it serves to ***protect private property and make payments in a more secure, easiest and cheaper way. ***
Bitcoiners can earn, save and spend bitcoin, they are the human part of the network, some of them are behind the nodes and the miners, others contribute to the improvements of the network and some are just ‘regular’ users.
Even do they are not ‘regular’ in any sense, in fact they are sovereign individuals who can control their own wealth in the form of private keys, they do not depend from the state, they can operate with freedom, they don't have to ask for permission in order to convert their value and protect it against the parasites.
**This is real freedom and bitcoiners are the citizens of a worldwide perfect republic funded on cyberspace but not limited to the metaverse. ** The system has been operating without interruption for more than a decade. An idea that in less than two decades became a worldwide giant network with trillions in value. If this is not winning I don't know what it is.
So Bitcoin is working as a libertarian Republic, based on voluntarism, nobody is forced to join the network but if they want they can, enjoying the benefits of: equality under the code (law), accountability, and the protection of individual rights by limiting the power of central authorities and ensuring that the decision-making processes are transparent and accessible to all participants requiring a total consensus to be implemented.
One of the biggest differences with traditional Republics is that you don't have to be lucky to born in its territory, in fact you can live in a communist country and still be part of a global libertarian digital and perfect Republic; where your property rights are respected, where you can save and protect the fruits of your labour in a ultra-secure way with military level cryptography, where you can provide your services or sell your goods to the world; monetizing your work directly without state intervention or unnecessary intermediaries.
Earning freely and keeping the totality of what you earn is proof that the torch of freedom is still on, even with a system that continuously conspires to turn it off.
**5. This time is different **
As republics usually do, Bitcoin had its own civil war. This kind of war is generally between those who want to centralize control and power and those who want to distribute control and power. In the case of the Bitcoin civil war this was no different.
The Block-size war lasted from August 2015 to November 2017 and it was the biggest challenge and the most turbulent moments that bitcoin has faced so far.
The fight was around the following: Bitcoin doesn't scale, we have to do something.
From February 2015 to 2018 the intellectual debate around the Lightning Network developed. But it wasn't until 2019 that started to get traction among users and proved to be a good form of scaling Bitcoin without sacrificing decentralization if you are running a node.
I personally believe that 2020 was a turning point. There was an explosion of companies working on the lighting network and they have been building nonstop since then improving many aspects and lowering the barriers for new users.
From that year Bitcoin had enough time proof and had survived enough difficulties to get the credibility and trust needed to scale to the next level.
6. Conclusión
Bitcoin has no competition and everything else is a distraction. There’s no second best, there’s no such thing as a “crypto currency / blockchain revolution” there is only a Bitcoin re-evolution. **The United States government is bankrupt, on the verge of economic disaster, we are witnessing the death of the dollar and nobody is going to save us but ourselves. **
The solution is here, its adoption is optional, the incentive creates an honest consensus that is almost impossible to destroy thanks to the decentralized network of nodes. The block-size war demonstrated this fact, it was literally the civil war for Bitcoin and proof that where our constitutional republics failed, Bitcoin is succeeding. BUT WE NEED TO STAY VIGILANT. VICTORY IS NOT GUARANTEED.
Nation-States, corporations and individuals can interact in some way with this worldwide distributed perfect republic to enjoy the benefits it provides, but the individual is the one who can gain the most out of it.
Bitcoin is a sovereignty-increasing tool that liberates the individual from the tyrannical forms of government and many of the corporate products that extract its wealth in a parasitic way. **Bitcoin makes legislators, accountants and financial advisors obsolete. But it requires the individual to embody self-determination and responsibility. **
Let’s not repeat the mistakes of the past, we have to embody the spirit of our constitution and put these freedoms into practice, because information and freedom are worthless if they are not applied in the real world. Let’s keep building on the wisdom we inherit from our founding fathers and let’s not forget where we came from.
**Final quotes **
"A well-instructed people alone can be permanently a free people." - James Madison
"A primary object should be the education of our youth in the science of government. In a republic, what species of knowledge can be equally important? And what duty is more pressing than communicating it to those who are to be the future guardians of the liberties of the country?" - George Washington.
A primary object should be the education of our youth in the science of Bitcoin. In the information age, what species of knowledge can be equally important? And what duty is more pressing than communicating it to those who are to be future developers guardians of the protocol? -Micael
"The education of a nation instead of being confined to the studies of youth during school-time, should be extended to all its stages of life, to all its pursuits, to all its duties; and the principles of knowledge should be in constant application." - Thomas Jefferson
"The Republic owes its existence to the wisdom, the courage and the devotion of its citizens." - Calvin Coolidge.
“Bitcoin owes its existence the the wisdom, the courage and the devotion of its developers, enthusiasts and supporters” Micael
"A strong constitution is the foundation of a stable and prosperous nation." Juan Bautista Alberdi (JBA)
“A strong protocol is the foundation of a stable and prosperous Bitcoin network”
"A nation's success depends on its ability to adapt to changing circumstances and embrace new ideas." JBA
"The most effective way to prevent corruption is to create a transparent and accountable government system." JBA
"A nation's progress is measured by its ability to invest in infrastructure, education, and technology." JBA
"The most effective way to promote economic growth is to create an environment that encourages entrepreneurship, innovation, and investment." JBA
"Education is the most powerful weapon which you can use to change the world." JBA
A nation's prosperity depends on its ability to attract and retain talented individuals." JBA
BITCOIN IS ALBERDI'S IDEAS IMMORTALIZED IN CODE.
IF OUR FOUNDING FATHERS WERE ALIVE, THEY WOULD UNDOUBTEDLY BE BITCOINERS.
THANK YOU SATOSHI! THANK YOU BITCOINERS!
-
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ fd06f542:8d6d54cd
2025-04-15 02:38:14
@ fd06f542:8d6d54cd
2025-04-15 02:38:14排名随机, 列表正在增加中。
Cody Tseng
jumble.social 的作者
https://jumble.social/users/npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wl
- Running [ wss://nostr-relay.app ] (free & WoT) 💜⚡️
- Building 👨💻:
- https://github.com/CodyTseng/jumble
- https://github.com/CodyTseng/nostr-relay-tray
- https://github.com/CodyTseng/danmakustr
- https://github.com/CodyTseng/nostr-relay-nestjs
- https://github.com/CodyTseng/nostr-relay
- https://github.com/CodyTseng
阿甘
- @agan0
- 0xchat.com
- canidae40@coinos.io
- https://jumble.social/users/npub13zyg3zysfylqc6nwfgj2uvce5rtlck2u50vwtjhpn92wzyusprfsdl2rce
joomaen
- Follows you
- joomaen.com
-
95aebd@wallet.yakihonne.com
-
nobot
- https://joomaen.filegear-sg.me/
- https://jumble.social/users/npub1wlpfd84ymdx2rpvnqht7h2lkq5lazvkaejywrvtchlvn3geulfgqp74qq0
颜值精选官
- wasp@ok0.org
- 专注分享 各类 图片与视频,每日为你带来颜值盛宴,心动不止一点点。欢迎关注,一起发现更多美好!
- https://jumble.social/users/npub1d5ygkef6r0l7w29ek9l9c7hulsvdshms2qh74jp5qpfyad4g6h5s4ap6lz
6svjszwk
- 6svjszwk@ok0.org
- 83vEfErLivtS9to39i73ETeaPkCF5ejQFbExoM5Vc2FDLqSE5Ah6NbqN6JaWPQbMeJh2muDiHPEDjboCVFYkHk4dHitivVi
-
low-time-preference
-
anarcho-capitalism
-
libertarianism
-
bitcoin #monero
- https://jumble.social/users/npub1sxgnpqfyd5vjexj4j5tsgfc826ezyz2ywze3w8jchd0rcshw3k6svjszwk
𝘌𝘷𝘦𝘳𝘺𝘥𝘢𝘺 𝘔𝘰𝘳𝘯𝘪𝘯𝘨 𝘚𝘵𝘢𝘳
- everyday@iris.to
- 虽然现在对某些事情下结论还为时尚早,但是从趋势来看,邪恶抬头已经不可避免。
- 我们要做的就是坚持内心的那一份良知,与邪恶战斗到底。
- 黑暗森林时代,当好小透明。
- bc1q7tuckqhkwf4vgc64rsy3rxy5qy6pmdrgxewcww
- https://jumble.social/users/npub1j2pha2chpr0qsmj2f6w783200upa7dvqnnard7vn9l8tv86m7twqszmnke
nostr_cn_dev
npub1l5r02s4udsr28xypsyx7j9lxchf80ha4z6y6269d0da9frtd2nxsvum9jm@npub.cash
Developed the following products: - NostrBridge, 网桥转发 - TaskQ5, 分布式多任务 - NostrHTTP, nostr to http - Postr, 匿名交友,匿名邮局 - nostrclient (Python client) . -nostrbook, (nostrbook.com) 用nostr在线写书 * https://www.duozhutuan.com nostrhttp demo * https://github.com/duozhutuan/NostrBridge * * https://jumble.social/users/npub1l5r02s4udsr28xypsyx7j9lxchf80ha4z6y6269d0da9frtd2nxsvum9jm *
CXPLAY
- lightning@cxplay.org
- 😉很高兴遇到你, 你可以叫我 CX 或 CXPLAY, 这个名字没有特殊含义, 无需在意.
- ©本账号下所有内容如未经特殊声明均使用 CC BY-NC-SA 4.0 许可协议授权.
- 🌐如果您在 Fediverse 收到本账号的内容则说明您的实例已与 Mostr.pub 或 Momostr.pink Bridge 互联, 您所看到的账号为镜像, 所有账号内容正在跨网传递. 如有必要请检查原始页面.
- 🧑💻正在提供中文本地化(i10n): #Amethyst #Amber #Citrine #Soapbox #Ditto #Alby
- https://cx.ms/
https://jumble.social/users/npub1gd8e0xfkylc7v8c5a6hkpj4gelwwcy99jt90lqjseqjj2t253s2s6ch58h
w
- 0xchat的作者
- 0xchat@getalby.com
- Building for 0xchat
- https://www.0xchat.com/
- https://jumble.social/users/npub10td4yrp6cl9kmjp9x5yd7r8pm96a5j07lk5mtj2kw39qf8frpt8qm9x2wl
Michael
- highman@blink.sv
- Composer Artist | Musician
- 🎹🎼🎤🏸🏝️🐕❤️
- 在這裡可以看到「我看世界」的樣子
- 他是光良
- https://jumble.social/users/npub1kr5vqlelt8l47s2z0l47z4myqg897m04vrnaqks3emwryca3al7sv83ry3
-
 @ 5c26ee8b:a4d229aa
2025-06-04 21:29:51
@ 5c26ee8b:a4d229aa
2025-06-04 21:29:51Since late December, 2024, an evil magic attack targeted me and my family as well as many people occupying governmental positions. The attack was involving the Antichrist that was on an unreachable island found by me telepathically. Sadly the information about the Antichrist reached some Russian Oligarchs Among which many Jews. And somehow he was contacted by them as well as many other Antichrist Allies among which Royal families and he led the magic attack even though magic mixed with AI and computer technologies. The attack consisted in whispering of the devils, of mankind (Antichrist allies) and jinns. Physical harm was attempted too although so weak for any significant effect for me at least. I hesitated on killing the Antichrist because his appearance is a sign of Judgement Day, however, because of acknowledging that the attack would be too intense for ordinary people that don’t know how to know the difference between inner voice or whispering of the devils I have decided to kill him by requesting that he is burned in the core of the earth and by turning any remains into dust spread in space. He didn’t have only a physical presence though he had an incorporated devil. So it took a while to kill the devil that was isolated in iron coffin first so it assumed a smaller figure while trying to escape and finally God guided me to request that the devil is hit with fireballs over and over again. It was confirmed to me that the devil of the Antichrist was completely burned out. And that the next sign would be the creature coming out of the earth, Ad-Daba as well as the smoke covering all the earth, with which there is a great punishment, and that I would be able to fly too (good for me). I hesitated on spreading the news about the Antichrist to avoid fitnah (confusion and trial). Also because he was never freed out of the island before getting burned out. I am mentioning this because it’s important to know that when God’s punishment comes and when the great signs of Judgement Day (among which what’s mentioned above) would appear the returning to God in belief or in repentance won’t be accepted; so my advise is to do it now.
27:82 An-Naml
۞ وَإِذَا وَقَعَ الْقَوْلُ عَلَيْهِمْ أَخْرَجْنَا لَهُمْ دَابَّةً مِنَ الْأَرْضِ تُكَلِّمُهُمْ أَنَّ النَّاسَ كَانُوا بِآيَاتِنَا لَا يُوقِنُونَ
And when the word befalls them, We will bring forth for them a creature from the earth speaking to them, [saying] that the people were, of Our verses, not certain [in faith].
- Ad-Dukhaan
حم
Ha, Meem.
وَالْكِتَابِ الْمُبِينِ
By the clear Book,
إِنَّا أَنْزَلْنَاهُ فِي لَيْلَةٍ مُبَارَكَةٍ ۚ إِنَّا كُنَّا مُنْذِرِينَ
Indeed, We sent it down during a blessed night. Indeed, We were to warn [mankind].
فِيهَا يُفْرَقُ كُلُّ أَمْرٍ حَكِيمٍ
On that night is made distinct every precise matter -
أَمْرًا مِنْ عِنْدِنَا ۚ إِنَّا كُنَّا مُرْسِلِينَ
[Every] matter [proceeding] from Us. Indeed, We were to send [a messenger]
رَحْمَةً مِنْ رَبِّكَ ۚ إِنَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
As mercy from your Lord. Indeed, He is the Hearing, the Knowing.
رَبِّ السَّمَاوَاتِ وَالْأَرْضِ وَمَا بَيْنَهُمَا ۖ إِنْ كُنْتُمْ مُوقِنِينَ
Lord of the heavens and the earth and that between them, if you would be certain.
لَا إِلَٰهَ إِلَّا هُوَ يُحْيِي وَيُمِيتُ ۖ رَبُّكُمْ وَرَبُّ آبَائِكُمُ الْأَوَّلِينَ
There is no deity except Him; He gives life and causes death. [He is] your Lord and the Lord of your first forefathers.
بَلْ هُمْ فِي شَكٍّ يَلْعَبُونَ
But they are in doubt, amusing themselves.
فَارْتَقِبْ يَوْمَ تَأْتِي السَّمَاءُ بِدُخَانٍ مُبِينٍ
Then watch for the Day when the sky will bring a visible smoke.
يَغْشَى النَّاسَ ۖ هَٰذَا عَذَابٌ أَلِيمٌ
Covering the people; this is a painful torment.
رَبَّنَا اكْشِفْ عَنَّا الْعَذَابَ إِنَّا مُؤْمِنُونَ
[They will say], "Our Lord, remove from us the torment; indeed, we are believers."
أَنَّىٰ لَهُمُ الذِّكْرَىٰ وَقَدْ جَاءَهُمْ رَسُولٌ مُبِينٌ
How will there be for them a reminder [at that time]? And there had come to them a clear Messenger.
ثُمَّ تَوَلَّوْا عَنْهُ وَقَالُوا مُعَلَّمٌ مَجْنُونٌ
Then they turned away from him and said, "[He was] taught [and is] a madman."
إِنَّا كَاشِفُو الْعَذَابِ قَلِيلًا ۚ إِنَّكُمْ عَائِدُونَ
Indeed, We will remove the torment for a little. Indeed, you [disbelievers] will return [to disbelief].
يَوْمَ نَبْطِشُ الْبَطْشَةَ الْكُبْرَىٰ إِنَّا مُنْتَقِمُونَ
The Day We will strike with the greatest assault, indeed, We will take retribution.
6:158 Al-An'aam
هَلْ يَنْظُرُونَ إِلَّا أَنْ تَأْتِيَهُمُ الْمَلَائِكَةُ أَوْ يَأْتِيَ رَبُّكَ أَوْ يَأْتِيَ بَعْضُ آيَاتِ رَبِّكَ ۗ يَوْمَ يَأْتِي بَعْضُ آيَاتِ رَبِّكَ لَا يَنْفَعُ نَفْسًا إِيمَانُهَا لَمْ تَكُنْ آمَنَتْ مِنْ قَبْلُ أَوْ كَسَبَتْ فِي إِيمَانِهَا خَيْرًا ۗ قُلِ انْتَظِرُوا إِنَّا مُنْتَظِرُونَ
Do they [then] wait for anything except that the angels should come to them or your Lord should come or that there come some of the signs of your Lord? The Day that some of the signs of your Lord will come no soul will benefit from its faith as long as it had not believed before or had earned through its faith some good. Say, "Wait. Indeed, we [also] are waiting."
4:17 An-Nisaa
إِنَّمَا التَّوْبَةُ عَلَى اللَّهِ لِلَّذِينَ يَعْمَلُونَ السُّوءَ بِجَهَالَةٍ ثُمَّ يَتُوبُونَ مِنْ قَرِيبٍ فَأُولَٰئِكَ يَتُوبُ اللَّهُ عَلَيْهِمْ ۗ وَكَانَ اللَّهُ عَلِيمًا حَكِيمًا
The repentance accepted by Allah is only for those who do wrong in ignorance [or carelessness] and then repent soon after. It is those to whom Allah will turn in forgiveness, and Allah is ever Knowing and Wise.
4:18 An-Nisaa
وَلَيْسَتِ التَّوْبَةُ لِلَّذِينَ يَعْمَلُونَ السَّيِّئَاتِ حَتَّىٰ إِذَا حَضَرَ أَحَدَهُمُ الْمَوْتُ قَالَ إِنِّي تُبْتُ الْآنَ وَلَا الَّذِينَ يَمُوتُونَ وَهُمْ كُفَّارٌ ۚ أُولَٰئِكَ أَعْتَدْنَا لَهُمْ عَذَابًا أَلِيمًا
But repentance is not [accepted] of those who [continue to] do evil deeds up until, when death comes to one of them, he says, "Indeed, I have repented now," or of those who die while they are disbelievers. For them We have prepared a painful punishment.
4:47 An-Nisaa
يَا أَيُّهَا الَّذِينَ أُوتُوا الْكِتَابَ آمِنُوا بِمَا نَزَّلْنَا مُصَدِّقًا لِمَا مَعَكُمْ مِنْ قَبْلِ أَنْ نَطْمِسَ وُجُوهًا فَنَرُدَّهَا عَلَىٰ أَدْبَارِهَا أَوْ نَلْعَنَهُمْ كَمَا لَعَنَّا أَصْحَابَ السَّبْتِ ۚ وَكَانَ أَمْرُ اللَّهِ مَفْعُولًا
O you who were given the Scripture, believe in what We have sent down [to Muhammad], confirming that which is with you, before We obliterate faces and turn them toward their backs or curse them as We cursed the sabbath-breakers. And ever is the decree of Allah accomplished.
4:48 An-Nisaa
إِنَّ اللَّهَ لَا يَغْفِرُ أَنْ يُشْرَكَ بِهِ وَيَغْفِرُ مَا دُونَ ذَٰلِكَ لِمَنْ يَشَاءُ ۚ وَمَنْ يُشْرِكْ بِاللَّهِ فَقَدِ افْتَرَىٰ إِثْمًا عَظِيمًا
Indeed, Allah does not forgive association with Him, but He forgives what is less than that for whom He wills. And he who associates others with Allah has certainly fabricated a tremendous sin.
41:13 Fussilat
فَإِنْ أَعْرَضُوا فَقُلْ أَنْذَرْتُكُمْ صَاعِقَةً مِثْلَ صَاعِقَةِ عَادٍ وَثَمُودَ
But if they turn away, then say, "I have warned you of a thunderbolt like the thunderbolt [that struck] 'Aad and Thamud.
61:13 As-Saff
وَأُخْرَىٰ تُحِبُّونَهَا ۖ نَصْرٌ مِنَ اللَّهِ وَفَتْحٌ قَرِيبٌ ۗ وَبَشِّرِ الْمُؤْمِنِينَ
And [you will obtain] another [favor] that you love - victory from Allah and an imminent conquest; and give good tidings to the believers.
-
 @ 73868430:0ec4fe27
2025-06-04 21:18:22
@ 73868430:0ec4fe27
2025-06-04 21:18:22皇居 Imperial Palace
巽櫓(桜田二重櫓) Sakurada Tatsumi Yagura

二重橋 Nijubashi Bridge

靖國神社 Yasukuni Jinja





遊就館 Yushukan


上野動物園 Ueno Zoological Garden


上野動物園不忍池 Ueno Zoological Garden Shinobazuno Pond

上野東照宮五重塔 Ueno Toshogu Shrine Five Story Pagoda

築地活鮮市場,御徒町店 Tsukiji Kassen Ichiba, Okachimachi

鉄道博物館 The Railway Museum




TOHAKU茶館 (応挙館) Tohaku Chakan

新大久保駅 Shin-Ōkubo


シンボルプロムナード公園 Symbol Promenade Park


セントラル広場 Central Square

日本科学未来館 The National Museum of Emerging Science and Innovation Japan (Miraikan)

箱根町 Hakone

芦ノ湖 Lake Ashi

元箱根 Motohakone

彫刻の森駅 Chokokunomori

三の鳥居,箱根神社 The Third Torii of Hakone Shrine

小田原城 Odawara Castle


-
 @ 472f440f:5669301e
2025-06-04 20:58:53
@ 472f440f:5669301e
2025-06-04 20:58:53Marty's Bent
J.P. Morgan CEO Jamie Dimon has long been an outspoken skeptic and critic of bitcoin. He has called Bitcoin a speculative asset, a fraud, a pet rock, and has opined that it will inevitably blow up. A couple of years ago, he was on Capitol Hill saying that if he were the government, he would "close it down". Just within the last month, he was on Fox Business News talking with Maria Bartiromo, proclaiming that the U.S. should be stockpiling bullets and rare earth metals instead of bitcoin. It's pretty clear that Jamie Dimon, who is at the helm of the most powerful and largest bank in the world, does not like bitcoin one bit.
Evidence below:
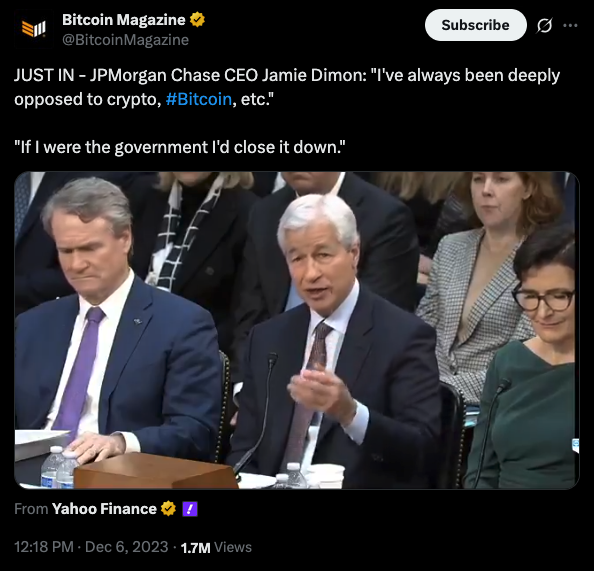
via Bitcoin Magazine
via me
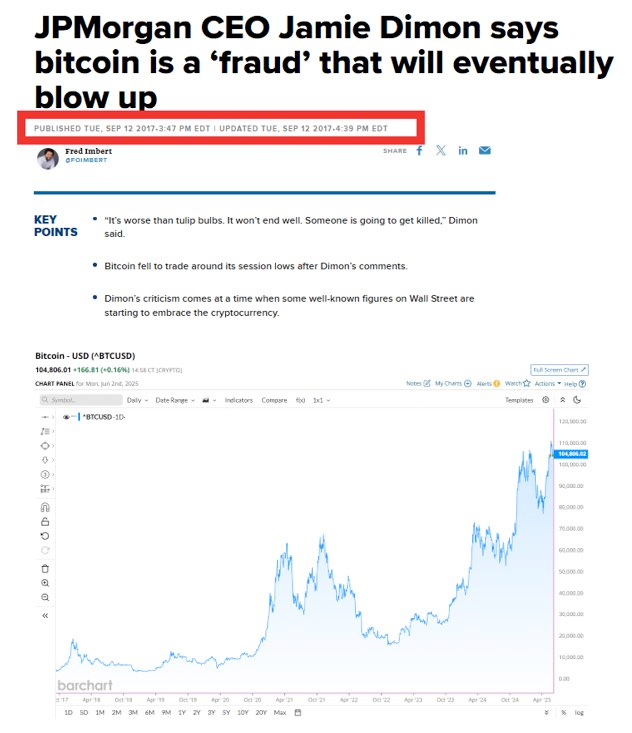
via CNBC
Despite Dimon's distinguished disdain for Bitcoin, J.P. Morgan cannot deny reality. The CEO of the largest bank in the world is certainly a powerful man, but no one individual, even in the position that Jamie Dimon is in, is more powerful than the market. And the market has spoken very clearly, it is demanding bitcoin. The Bitcoin ETFs have been the most successful ETFs in terms of pace of growth since their launch. They've accumulated tens of billions of dollars in AUM in a very short period of time. Outpacing the previous record set by the gold ETF, GLD.
Whether or not Jamie Dimon himself likes Bitcoin doesn't matter. J.P. Morgan, as the largest bank in the world and a publicly traded company, has a duty to shareholders. And that duty is to increase shareholder value by any ethical and legal means necessary. Earlier today, J.P. Morgan announced plans to offer clients financing against their Bitcoin ETFs, as well as some other benefits, including having their bitcoin holdings recognized in their overall net worth and liquid assets, similar to stocks, cars, and art, which will be massive for bitcoiners looking to get mortgages and other types of loans.
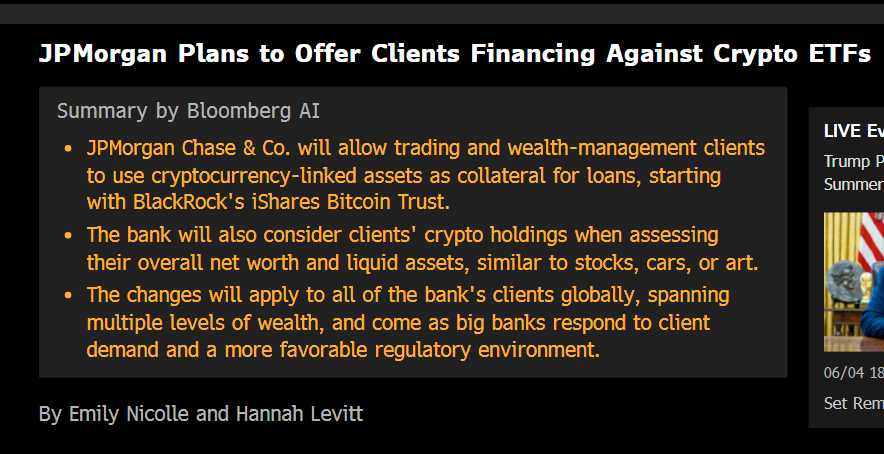
via Bloomberg
I've talked about this recently, but trying to buy a house when most of your liquid net worth is held in bitcoin is a massive pain in the ass. Up until this point, if you wanted to have your bitcoin recognized as part of your net worth and count towards your overall credit profile, you would need to sell some bitcoin, move it to a bank account, and have it sit there for a certain period of time before it was recognized toward your net worth. This is not ideal for bitcoiners who have sufficient cash flows and don't want to sell their bitcoin, pay the capital gains tax, and risk not being able to buy back the amount of sats they were forced to sell just to get a mortgage.
It's not yet clear to me whether or not J.P. Morgan will recognize bitcoin in cold storage toward their clients' net worth and credit profile, or if this is simply for bitcoin ETFs only. However, regardless, this is a step in the right direction and a validation of something that many bitcoiners have been saying for years. Inevitably, everyone will have to bend the knee to bitcoin. Today, it just happened to be the largest bank in the world. I expect more of this to come in the coming months, years, and decades.
Lyn Alden likes to say it in the context of the U.S. national debt and the fiscal crisis, but it also applies to bitcoin adoption and the need for incumbents to orient themselves around the demands of individual bitcoiners; nothing stops this train.
Corporate Bitcoin Treasuries are Changing Market Dynamics
Leon Wankum revealed how corporate Bitcoin treasuries are fundamentally reshaping business dynamics. Companies can now issue equity to fund operations while preserving their Bitcoin holdings, creating a revolutionary capital structure. Leon highlighted MicroStrategy's position, noting they hold enough Bitcoin to cover dividend payments for over 200 years. This model enables companies to reduce founder dilution since they don't need repeated funding rounds when their treasury appreciates.
"Some companies' Bitcoin treasuries are now worth more than all money they've ever raised." - Leon Wankum
Leon shared examples from his own portfolio companies where this strategy has proven transformative. Public companies have discovered an entirely new business model through strategic dilution that actually increases BTC per share. As Leon explained, this approach allows firms to leverage equity markets for operational funding while their Bitcoin treasury compounds in value, creating a positive feedback loop that benefits both shareholders and the company's long-term sustainability.
Check out the full podcast here for more on real estate price cycles, Bitcoin lending products, and the transition to a Bitcoin standard.
Headlines of the Day
California May Seize Idle Bitcoin After 3 Years - via X
Semler Scientific Buys $20M More Bitcoin, Holds $467M - via X
US Home Sellers Surge as Buyers Hit 4-Year Low - via X
Get our new STACK SATS hat - via tftcmerch.io
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code “TFTC20” during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
I feel old.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ e516ecb8:1be0b167
2025-06-04 20:33:38
@ e516ecb8:1be0b167
2025-06-04 20:33:38Imagina un mundo donde cada peso que gastas es vigilado, registrado y cuestionado. Donde el Estado decide si puedes comprar un café, una manzana o una criptomoneda. No es una distopía de ciencia ficción, es el rumbo que están tomando varios países, mientras otros, como Argentina, dan un giro inesperado hacia la libertad. ¿Quién está ganando esta batalla por el control de tu dinero?
Argentina: "Tus dólares son tuyos" En Argentina, Javier Milei, con su bandera libertaria ondeando, ha dado un paso audaz: desmantelar el control policial sobre el dinero de los ciudadanos. Su lema, "Tus dólares son tuyos", es tan obvio como revolucionario. Después de décadas de corralitos, cepos cambiarios y una inflación que en 2023 alcanzó el 211,4% según el INDEC, Milei apuesta por devolverle al ciudadano el poder sobre su propio capital. Con el país logrando superávit fiscal por primera vez en años (0,2% del PBI en el primer trimestre de 2024), el gobierno ya no necesita espiar cada transacción para exprimir impuestos.
Pero aquí viene lo curioso: encuestas recientes, como una de la consultora Poliarquía, muestran que un 35% de los argentinos aún prefiere que el Estado controle sus finanzas. ¿Masoquismo? ¿Miedo a la libertad? Tal vez sea la costumbre de vivir bajo la lupa. Milei, fiel a su convicción, no solo liberaliza por necesidad económica, sino porque cree que el dinero es tuyo, no del burócrata de turno.
España y el Euro Digital: El ojo que todo lo ve Mientras Argentina afloja las riendas, Europa cabalga en dirección opuesta. En España, el gobierno está reduciendo progresivamente los umbrales para controlar transacciones bancarias. A partir de 2026, cada pago por Bizum —el equivalente ibérico al Pix brasileño— estará bajo escrutinio. Según el Banco de España, en 2024 se realizaron más de 1.200 millones de transacciones por Bizum, moviendo unos 60.000 millones de euros. Ahora, cada una de esas operaciones será un dato más para Hacienda.
Pero no es solo España. La Unión Europea avanza con el Euro Digital, un proyecto que promete ser la pesadilla de cualquier amante de la privacidad. Esta moneda digital, según el Banco Central Europeo, permitirá rastrear cada movimiento, limitar ciertos gastos (¿adiós a compras de cripto o donaciones incómodas?), e incluso programar que el dinero "se oxide". Sí, has leído bien: si no gastas tus euros digitales en un tiempo determinado, podrían perder valor o simplemente desaparecer. Un informe del BCE de 2023 estima que el Euro Digital estará operativo en 2027, y ya hay pruebas piloto en países como Alemania y Francia. ¿Libertad financiera? Más bien un Gran Hermano con esteroides.
Chile: El Estado fisgón y los funcionarios de lujo En Chile, el control monetario también aprieta. El gobierno ha propuesto levantar el secreto bancario, permitiendo que cualquier funcionario del SII pueda husmear en tus cuentas. Además, si haces más de 50 transacciones al mes, el Servicio de Impuestos Internos (SII) pondrá la lupa sobre ti. ¿Y las ferias libres? Esas donde compras tus tomates y zapallos sin complicaciones ahora deberán emitir boletas electrónicas, encareciendo los productos para el ciudadano de a pie. Según la CEPAL, los costos administrativos para pequeños comerciantes podrían aumentar hasta un 15% con estas medidas.
Mientras tanto, el sector público chileno vive en otra galaxia. Funcionarios con sueldos que superan los 5 millones de pesos mensuales (unos 5.500 USD) toman licencias médicas para viajar por el mundo, según denuncias de la Contraloría. Algunos incluso cobran por "turnos" de 17 horas extras diarias o marcan asistencia en dos lugares al mismo tiempo. ¿Y quién paga? Tú, con tus impuestos.
La resistencia: Volver al efectivo o abrazar las cripto Si el Estado quiere controlar cada centavo, ¿qué opciones nos quedan? Una es volver al efectivo, pero no nos engañemos: el dinero fiat, controlado por bancos centrales, pierde valor a largo plazo. En Chile, la inflación acumulada entre 2010 y 2024 fue del 62%, según el INE. Tus billetes de hoy valen menos que los de ayer, y mañana valdrán aún menos.
La otra opción es el mundo cripto, pero no cualquier cripto. Bitcoin, la más conocida, es un titán para almacenar valor, pero para transacciones diarias necesita una segunda capa como Lightning Network, que procesa pagos instantáneos con comisiones ínfimas (menos de 0,01 USD por transacción en 2024). Alternativas como Bitcoin Cash (BCH) o Monero (XMR) ofrecen transacciones rápidas y, en el caso de XMR, un enfoque en la privacidad que hace temblar a los burócratas. Sin embargo, ninguna cripto servirá si los comercios y las personas no las adoptan. En Argentina, por ejemplo, solo el 1,5% de las transacciones minoristas en 2024 usaron criptomonedas, según Chainalysis. La libertad financiera no llega sola: hay que construirla.
El futuro es ahora El dinero es poder, y quien controla el dinero controla tu vida. Mientras Milei en Argentina te devuelve las llaves de tus dólares, en Europa y Chile te atan las manos con leyes, regulaciones y monedas digitales. La pregunta no es si quieres libertad, sino si estás dispuesto a pelear por ella. Usa efectivo, explora cripto, pero sobre todo, no dejes que el Gran Hermano decida por ti. Porque una vez que el Estado mete la mano en tu bolsillo, no la saca nunca.
-
 @ 2ed3596e:98b4cc78
2025-06-04 20:06:07
@ 2ed3596e:98b4cc78
2025-06-04 20:06:07Bitcoin Well recently sat down with Bitcoin News for a conversation about our mission to empower financial independence through Bitcoin. Founder and CEO Adam O’Brien shared how a frustrating experience purchasing bitcoin in 2013 led to the creation of one of Canada’s largest bitcoin ATM networks—and ultimately, a broader mission to help people replace traditional banks with self-custodied bitcoin.
From building out our Bitcoin portal to navigating life fully de-banked, Adam discussed how Bitcoin Well is creating tools for everyday use—paying bills, receiving paychecks, and living sovereignly. Read the full conversation to understand why we’re proud to be leading the charge for freedom-minded Bitcoiners across Canada and beyond.
About Bitcoin Well:
Bitcoin Well is a Canadian company on a mission to enable financial independence through the use of Bitcoin. We offer tools and services that allow users to buy, sell, and use bitcoin in self-custody—without relying on traditional banks.
About Bitcoin News:
Bitcoin News Inc is a US-based media company dedicated to covering the latest in Bitcoin—from mining and wallets to its growing role in global liquidity. We deliver clear, insightful reporting to help readers navigate the shifting landscape of Bitcoin and digital finance.
-
 @ b2caa9b3:9eab0fb5
2025-06-04 19:50:29
@ b2caa9b3:9eab0fb5
2025-06-04 19:50:29If you'd like to connect with me on XMPP, you're very welcome! I first used it many years ago, and now I've returned to it — and I'm really glad I did.
XMPP is a secure and privacy-friendly way to communicate. It's spam-resistant: messages only go through once you've accepted a contact request. To request a connection, just send me a message.
One of the great things about XMPP is that you have control over encryption. You can choose to use strong encryption like PGP or OMEMO, or even no encryption at all — it's entirely up to you. Your messages aren’t tied to any one company or service.
There are many apps (called clients) you can use with XMPP, and you’re not locked into a single one that monitors or sells your data. XMPP is an open protocol, which means freedom of choice and better privacy.
My XMPP username is: rubenstorm@c0nnect.de
I’ve also been much less active on Facebook, Instagram, and other social media. That’s because I’ve shifted from platforms to protocols — more decentralized, censorship-resistant tools that put users in control. I started exploring these about two years ago and haven’t looked back.
If you’re interested in learning more or want help getting started, feel free to reach out. Just message me using any XMPP client — I’ll be happy to connect!
-
 @ ca76c778:e784c54b
2025-06-04 19:45:11
@ ca76c778:e784c54b
2025-06-04 19:45:11A few days ago I remembered video by Antonio Stappaerts(Artwod) on Youtube. And I thought to myself I want to be really good at drawing hands.\ In the video he explains something that, in my opinion, applies when learning just about anything.
If you've heard of the Dunning-Kruger effect then you know the first part.\ If you haven't, one begins learning something and on top of the first peak thinks oneself to be almost a master. And then one learns a little bit more and realizes how little skill one actually has.
 \
Now, what is really interesting is this. He points out that the second slope is made up of many smaller Dunning-Kruger effects. For example the effect will apply when learning: the basic shape of the figure, how to pose the figure, how draw the hands, the hair etc.
\
Now, what is really interesting is this. He points out that the second slope is made up of many smaller Dunning-Kruger effects. For example the effect will apply when learning: the basic shape of the figure, how to pose the figure, how draw the hands, the hair etc.So the way to climb the second hill is to understand and practice these smaller skills. And not just once or twice. You want to reach close to the second peak of each of the smaller skills.
And with that in mind I search for a good tutorial about drawing hands and got down to it(for the third time).
Step one was to learn pose and gesture using a grid shape.
https://cdn.satellite.earth/f55a9d1ef2fd687a9dce5ceee5e05a1b666c436509e264ddbac4d260b99e882a.jpg
https://cdn.satellite.earth/1b5524635c20ee4869f4860c982deea469cb87be7ad7b404e1777497b5a4fbd4.jpg
https://cdn.satellite.earth/35652251243ffd8c495b855c319d27da0c193ff2e951591f0a9f1b35aad39b29.jpg
https://cdn.satellite.earth/68f55979d102b4ebe55177842c6d9ab2ab30b95f926441429d977b47fae925c3.jpg
Step two. Practice the basic forms for the palm and fingers.\ I got carried away and drew some hands.
https://cdn.satellite.earth/48b400f72e35d078368149f00182cb58e606ddd16f6db4e7789c1431c28d44a0.jpg
Step three. learn the measurements.
https://cdn.satellite.earth/75c9b82da90ef50d17f698dd7b1eadc223b74a019a702a4617ed7d321646a87c.jpg
Step four. Understand the fingers.
https://cdn.satellite.earth/e33f9f3f9217bf5e3e206e96dfe764eba09b9fb3c10b450bb9c8a4075e3c1ec8.jpg
Step five. Learn about the thumb and put it all together. Drawing from reference and imagination.
https://cdn.satellite.earth/b2dd9c1cc1045dde021272199818b0db331e71a603c5900122aa850eb2d4148a.jpg
https://cdn.satellite.earth/8f5647ae9e148ad6217c106b5b69cf231384475e0a0eedf210bd149f75ade0b7.jpg
-
 @ e2c72a5a:bfacb2ee
2025-06-04 18:18:32
@ e2c72a5a:bfacb2ee
2025-06-04 18:18:32Forget Lambos, Bitcoin's going corporate.
Sixty one publicly listed companies now hold over 3% of Bitcoin's total supply, doubling their holdings in just two months. That's faster than even Michael Saylor's MicroStrategy. K Wave Media, a South Korean firm, is raising $500M for a Bitcoin treasury, aiming to be the "Metaplanet of Korea." Even Pakistan is discussing Bitcoin reserve plans with Trump's crypto team.
Is your portfolio ready for the corporate Bitcoin takeover?
-
 @ 57c631a3:07529a8e
2025-04-07 13:17:50
@ 57c631a3:07529a8e
2025-04-07 13:17:50What is Growth Engineering? Before we start: if you’ve already filled out the What is your tech stack? survey: thank you! If you’ve not done so, your help will be greatly appreciated. It takes 5-15 minutes to complete. Those filling out will receive results before anyone else, and additional analysis from myself and Elin. Fill out this survey here.**
npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m
Growth engineering was barely known a decade ago, but today, most scaleups and many publicly traded tech companies have dedicated growth teams staffed by growth engineers. However, some software engineers are still suspicious of this new area because of its reputation for hacky code with little to no code coverage.
For this reason and others, I thought it would be interesting to learn more from an expert who can tell us all about the practicalities of this controversial domain. So I turned to Alexey Komissarouk, who’s been in growth engineering since 2016, and was in charge of it at online education platform, MasterClass. These days, Alexey lives in Tokyo, Japan, where he advises on growth engineering and teaches the Growth Engineering course at Reforge.
In today’s deep dive, Alexey covers:
- What is Growth Engineering? In the simplest terms: writing code to help a company make more money. But there are details to consider: like the company size where it makes sense to have a dedicated team do this.
- What do Growth Engineers work on? Business-facing work, empowerment and platform work are the main areas.
- Why Growth Engineers move faster than Product Engineers. Product Engineers ship to build: Growth Engineers ship to learn. Growth Engineers do take shortcuts that would make no sense when building for longevity – doing this on purpose.
- Tech stack. Common programming languages, monitoring and oncall, feature flags and experimentation, product analytics, review apps, and more.
- What makes a good Growth Engineer? Curiosity, “build to learn” mindset and a “Jack of all trades” approach.
- Where do Growth Engineers fit in? Usually part of the engineering department, either operating as with an “owner” or a “hitchiker” model.
- Becoming a Growth Engineer. A great area if you want to eventually become a founder or product manager – but even if not, it can accelerate your career growth. Working in Growth forces you to learn more about the business.
With that, it’s over to Alexey:
I’ll never forget the first time I made my employer a million dollars.
I was running a push notification A/B test for meal delivery startup Sprig, trying to boost repeat orders.
A push notification similar to what we tested to boost repeat orders
Initial results were unpromising; the push notification was not receiving many opens. Still, I wanted to be thorough: before concluding the idea was a failure, I wrote a SQL query to compare order volume for subsequent weeks between customers in test vs control.
The SQL used to figure out the push notification’s efficiency
As it turned out, our test group “beat” the control group by around 10%:
‘review_5_push’ was the new type of push notification. Roughly the same amount of users clicked it, but they placed 10% more in orders
I plugged the numbers into a significance calculator, which showed it was statistically significant – or “stat-sig” – and therefore highly unlikely to be a coincidence. This meant we had a winner on our hands! But how meaningful was it, really, and what would adding the push notification mean for revenue, if rolled out to 100% of users?
It turned out this experiment created an additional $1.5 million dollars, annually, with just one push notification. Wow!
I was hooked. Since that day, I've shipped hundreds of experimental “winners” which generated hundreds of millions of incremental revenue for my employers. But you never forget the first one. Moments like this is what growth engineering is all about.
1. What is Growth Engineering?
Essentially, growth engineering is the writing of code to make a company money. Of course, all code produced by a business on some level serves this purpose, but while Product Engineers focus on creating a Product worth paying for, Growth Engineers instead focus on making that good product have a good business. To this end, they focus on optimizing and refining key parts of the customer journey, such as:
- Getting more people to consider the product
- Converting them into paying customers
- Keeping them as customers for longer, and spending more
What kinds of companies employ Growth Engineers? Places you’ve heard of, like Meta, LinkedIn, DoorDash, Coinbase, and Dropbox, are some of the ones I’ve had students from. There’s also OpenAI, Uber, Tiktok, Tinder, Airbnb, Pinterest… the list of high-profile companies goes on. Most newer public consumer companies you’ve heard have a growth engineering org, too.
Typically, growth engineering orgs are started by companies at Series B stage and beyond, so long as they are selling to either consumers or businesses via SaaS. These are often places trying to grow extremely fast, and have enough software engineers that some can focus purely on growth. Before the Series B stage, a team is unlikely to be ready for growth for various reasons; likely that it hasn’t found product-market fit, or has no available headcount, or lacks the visitor traffic required to run A/B tests.
Cost is a consideration. A fully-loaded growth team consisting of a handful of engineers, a PM, and a designer costs approximately 1 million dollars annually. To justify this, a rule of thumb is to have at least $5 million dollars in recurring revenue – a milestone often achieved at around the Series B stage.
Despite the presence of growth engineering at many public consumer tech companies, the field itself is still quite new, as a discipline and as a proper title.
Brief history of growth engineering
When I joined Opendoor in 2016, there was a head of growth but no dedicated growth engineers, but there were by the time I left in 2020. At MasterClass soon after, there was a growth org and a dozen dedicated growth engineers. So when did growth engineering originate?
The story is that its origins lie at Facebook in 2007. The team was created by then-VP of platform and monetization Chamath Palihapitiya. Reforce founder and CEO Brian Balfour shares:
“Growth (the kind found on an org chart) began at Facebook under the direction of Chamath Palihapitiya. In 2007, he joined the early team in a nebulous role that fell somewhere between Product, Marketing, and Operations. According to his retelling of the story on Recode Decode, after struggling to accomplish anything meaningful in his first year on the job, he was on the verge of being fired.Sheryl Sandberg joined soon after him, and in a hail mary move he pitched her the game-changing idea that led to the creation of the first-ever growth team. This idea not only saved his job, but earned him the lion’s share of the credit for Facebook’s unprecedented growth.At the time, Sheryl and Mark asked him, “What do you call this thing where you help change the product, do some SEO and SEM, and algorithmically do this or that?”His response: “I don’t know, I just call that, like, Growth, you know, we’re going to try to grow. I’ll be the head of growing stuff."And just like that, Growth became a thing.”
Rather than focus on a particular product or feature, the growth team at Facebook focused on moving the needle, and figuring out which features to work on. These days, Meta employs hundreds if not thousands of growth engineers.
2. What do Growth Engineers work on?
Before we jump into concrete examples, let’s identify three primary focus areas that a growth engineer’s work usually involves.
- Business-facing work – improving the business directly
- Empowerment work – enabling other teams to improve the business
- Platform work – improving the velocity of the above activities
Let’s go through all three:
Business-facing work
This is the bread and butter of growth engineering, and follows a common pattern:
- Implement an idea. Try something big or small to try and move a key business metric, which differs by team but is typically related to conversion rate or retention.
- Quantify impact. Usually via A/B testing.
- Analyze impact. Await results, analyze impact, ship or roll back – then go back to the first step.
Experiments can lead to sweeping or barely noticeable changes. A famous “I can’t believe they needed to test this” was when Google figured out which shade of blue generates the most clicks. At MasterClass, we tested things across the spectrum:
- Small: should we show the price right on the homepage, was that a winner? Yes, but we framed it in monthly terms of $15/month, not $180/year.
- Medium: when browsing a course page, should we include related courses, or more details about the course itself? Was it a winner? After lengthy experimentation, it was hard to tell: both are valuable and we needed to strike the right balance.
- Large: when a potential customer is interested, do we take them straight to checkout, or encourage them to learn more? Counterintuitively, adding steps boosted conversion!
Empowerment
One of the best ways an engineer can move a target metric is by removing themselves as a bottleneck, so colleagues from marketing can iterate and optimize freely. To this end, growth engineers can either build internal tools or integrate self-serve MarTech (Marketing Technology) vendors.
With the right tool, there’s a lot that marketers can do without engineering’s involvement:
- Build and iterate on landing pages (Unbounce, Instapage, etc)
- Draft and send email, SMS and Push Notifications (Iterable, Braze, Customer.io, etc)
- Connect new advertising partners (Google Tag Manager, Segment, etc)
We go more into detail about benefits and applications in the MarTech section of Tech Stack, below.
Platform work
As a business scales, dedicated platform teams help improve stability and velocity for the teams they support. Within growth, this often includes initiatives like:
- Experiment Platform. Many parts of running an experiment can be standardized, from filtering the audience, to bucketing users properly, to observing statistical methodology. Historically, companies built reusable Experiment Platforms in-house, but more recently, vendors such as Eppo and Statsig have grown in popularity with fancy statistical methodologies like “Controlled Using Pre-Experiment Data” (CUPED) that give more signal with less data.
- Reusable components. Companies with standard front-end components for things like headlines, buttons, and images, dramatically reduce the time required to spin up a new page. No more "did you want 5 or 6 pixels here" with a designer; instead growth engineers rely on tools like Storybook to standardize and share reusable React components.
- Monitoring. Growth engineering benefits greatly from leveraging monitoring to compensate for reduced code coverage. High-quality business metric monitoring tools can detect bugs before they cause damage.
When I worked at MasterClass, having monitoring at the ad layer prevented at least one six-figure incident. One Friday, a marketer accidentally broadened the audience for a particular ad from US-only, to worldwide. In response, the Facebook Ad algorithm went on a spending spree, bringing in plenty of visitors from places like Brazil and India, whom we knew from past experience were unlikely to purchase the product. Fortunately, our monitoring noticed the low-performing campaign within minutes, and an alert was sent to the growth engineer on-call, who immediately reached out to the marketer and confirmed the change was unintentional, and then shut down the campaign.
Without this monitoring, a subtle targeting error like this could have gone unnoticed all weekend and would have eaten up $100,000+ of marketing budget. This episode shows that platform investment can benefit everyone; and since growth needs them most, it’s often the growth platform engineering team which implements them.
As the day-to-day work of a Growth Engineer shows, A/B tests are a critical tool to both measure success and learn. It’s a numbers game: the more A/B tests a team can run in a given quarter, the more of them will end up winners, making the team successful. It’s no wonder, then, that Growth Engineering will pull out all the stops to improve velocity.
3. Why Growth Engineers move faster than Product Engineers
On the surface, growth engineering teams look like product engineering ones; writing code, shipping pull requests, monitoring on-call, etc. So how do they move so much faster? The big reason lies in philosophy and focus, not technology. To quote Elena Verna, head of growth at Dropbox:
“Product Engineering teams ship to build; Growth Engineering teams ship to learn.”
Real-world case: price changes at Masterclass
A few years ago at MasterClass, the growth team wanted to see if changing our pricing model to multiple tiers would improve revenue.
Inspired in part by multiple pricing tiers for competitors such as Netflix (above), Disney Plus, and Hulu.
The “multiple pricing tier” proposal for MasterClass.
From a software engineering perspective, this was a highly complex project because:
- Backend engineering work: the backend did not yet support multiple pricing options, requiring a decent amount of engineering, and rigorous testing to make sure existing customers weren’t affected.
- Client app changes: on the device side, multiple platforms (iOS, iPad, Android, Roku, Apple TV, etc) would each need to be updated, including each relevant app store.
The software engineering team estimated that becoming a “multi-pricing-tier” company would take months across numerous engineering teams, and engineering leadership was unwilling to greenlight that significant investment.
We in growth engineering took this as a challenge. As usual, our goal was not just to add the new pricing model, but to learn how much money it might bring in. The approach we ended up proposing was a Fake Door test, which involves offering a not-yet-available option to customers to gauge interest level. This was risky, as taking a customer who’s ready to pay and telling them to join some kind of waiting list is a colossal waste, and risks making them feel like the target of a “bait and switch” trick.
We found a way. The key insight was that people are only offended about a “bait and switch”, if the “switch” is worse than the “bait.” Telling customers they would pay $100 and then switching to $150 would cause a riot, but starting at $150 and then saying “just kidding, it’s only $100” is a pleasant surprise.
The good kind of surprise.
So long as every test “pricing tier” is less appealing – higher prices, fewer features – than the current offering, we could “upgrade” customers after their initial selection. A customer choosing the cheapest tier gets extra features at no extra cost, while a customer choosing a more expensive tier is offered a discount.
We created three new tiers, at different prices. The new “premium” tier would describe the existing, original offering. Regardless of what potential customers selected, they got this “original offering,” during the experiment.
The best thing about this was that no backend changes were required. There were no real, new, back-end pricing plans; everybody ended up purchasing the same version of MasterClass for the same price, with the same features. The entirety of the engineering work was on building a new pricing page, and the “congratulations, you’ve been upgraded” popup. This took just a few days.
Within a couple of weeks, we had enough data to be confident the financial upside of moving to a multi-pricing-tier model would be significant. With this, we’re able to convince the rest of engineering’s leadership to invest in building the feature properly. In the end, launching multiple pricing tiers turned out to be one of the biggest revenue wins of the year.
Building a skyscraper vs building a tent
The MasterClass example demonstrates the spirit of growth engineering; focusing on building to learn, instead of building to last. Consider building skyscrapers versus tents.
Building a tent optimizes for speed of set-up and tear-down over longevity. You don’t think of a tent as one that is shoddy or low-quality compared to skyscrapers: it’s not even the same category of buildings! Growth engineers maximize use of lightweight materials. To stick with the tents vs skyscraper metaphor: we prioritize lightweight fabric materials over steel and concrete whenever possible. We only resort to traditional building materials when there’s no other choice, or when a direction is confirmed as correct. Quality is important – after all, a tent must keep out rain and mosquitoes. However, the speed-vs-durability tradeoff decision results in very different approaches and outcomes.
4. Tech stack
At first glance, growth and product engineers use the same tooling, and contribute to the same codebases. But growth engineering tends to be high-velocity, experiment-heavy, and with limited test coverage. This means that certain “nice to have” tools for product engineering are mission-critical for growth engineers.
Read more https://connect-test.layer3.press/articles/ea02c1a1-7cfa-42b4-8722-0165abcae8bb
-
 @ a5ee4475:2ca75401
2025-06-04 18:11:52
@ a5ee4475:2ca75401
2025-06-04 18:11:52clients #link #list #english #article #finalversion #descentralismo
*These clients are generally applications on the Nostr network that allow you to use the same account, regardless of the app used, keeping your messages and profile intact.
**However, you may need to meet certain requirements regarding access and account NIP for some clients, so that you can access them securely and use their features correctly.
CLIENTS
Twitter like
- Nostrmo - [source] 🌐💻(🐧🪟🍎)🍎🤖(on zapstore)
- Coracle - Super App [source] 🌐🤖(on zapstore)
- Amethyst - Super App with note edit, delete and other stuff with Tor [source] 🤖(on zapstore)
- Primal - Social and wallet [source] 🌐🍎🤖(on zapstore)
- Iris - [source] 🌐🤖🍎
- Current - [source] 🤖🍎
- FreeFrom 🤖🍎
- Openvibe - Nostr and others (new Plebstr) [source] 🤖🍎
- Snort 🌐(🤖[early access]) [onion] [source]
- Damus 🍎 [source]
- Nos 🍎 [source]
- Nostur 🍎 [source]
- NostrBand 🌐 [info] [source]
- Yana [source] 🌐💻(🐧) 🍎🤖(on zapstore)
- Nostribe [on development] 🌐 [source]
- Lume 💻(🐧🪟🍎) [info] [source]
- Gossip - [source] 💻(🐧🪟🍎)
- noStrudel - Gamified Experience [onion] [info/source] 🌐
- [Nostrudel Next] - [onion]
- moStard - Nostrudel with Monero [onion] [info/source] 🌐
- Camelus - [source] 🤖 [early access]
Community
- CCNS - Community Curated Nostr Stuff [source]
- Nostr Kiwi [creator] 🌐
- Satellite [info] 🌐
- Flotilla - [source] 🌐🐧🤖(on zapstore)
- Chachi - [source] 🌐
- Futr - Coded in haskell [source] 🐧 (others soon)
- Soapbox - Comunnity server [info] [source] 🌐
- Ditto - Soapbox community server 🌐 [source] 🌐
- Cobrafuma - Nostr brazilian community on Ditto [info] 🌐
- Zapddit - Reddit like [source] 🌐
- Voyage (Reddit like) [on development] 🤖
Wiki
- Wikifreedia - Wiki Dark mode [source] 🌐
- Wikinostr - Wiki with tabs clear mode [source] 🌐
- Wikistr - Wiki clear mode [info] [source] 🌐
Search
- Keychat - Signal-like chat with AI and browser [source] 💻(🐧🪟🍎) - 📱(🍎🤖{on zapstore})
- Spring - Browser for Nostr apps and other sites [source] 🤖 (on zapstore)
- Advanced nostr search - Advanced note search by isolated terms related to a npub profile [source] 🌐
- Nos Today - Global note search by isolated terms [info] [source] 🌐
- Nostr Search Engine - API for Nostr clients [source]
- Ntrends - Trending notes and profiles 🌐
Website
- Nsite - Nostr Site [onion] [info] [source]
- Nsite Gateway - Nostr Site Gateway [source]
- Npub pro - Your site on Nostr [source]
App Store
ZapStore - Permitionless App Store [source] 🤖 💻(🐧🍎)
Video and Live Streaming
- Flare - Youtube like 🌐 [source]
- ZapStream - Lives, videos, shorts and zaps (NIP-53) [source] 🌐 🤖(lives only | Amber | on zapstore)
- StreamCat - [source code dont found]
- Shosho - Stream your camera [source] 🤖(on zapstore)
- Swae - Live streaming [source] (on development) ⏳
Post Aggregator - Kinostr - Nostr Cinema with #kinostr [english] [author] 🌐 - Stremstr - Nostr Cinema with #kinostr [english] [source] 🤖
Link Agreggator - Kinostr - #kinostr - Nostr Cinema Profile with links [English] - Equinox - Nostr Cinema Community with links [Portuguese]
Audio and Podcast Transmission
- Castr - Your npub as podcast feed [source]
- Nostr Nests - Audio Chats [source] 🌐
- Fountain - Podcast [source] 🤖🍎
- Corny Chat - Audio Chat [source] 🌐
Music
- Tidal - Music Streaming [source] [about] [info] 🤖🍎🌐
- Wavlake - Music Streaming [source] 🌐(🤖🍎 [early access])
- Tunestr - Musical Events [source] [about] 🌐
- Stemstr - Musical Colab (paid to post) [source] [about] 🌐
Images
- Lumina - Trending images and pictures [source] 🌐
- Pinstr - Pinterest like [source] 🌐
- Slidestr - DeviantArt like [source] 🌐
- Memestr - ifunny like [source] 🌐
Download and Upload
Documents, graphics and tables
- Mindstr - Mind maps [source] 🌐
- Docstr - Share Docs [info] [source] 🌐
- Formstr - Share Forms [info] 🌐
- Sheetstr - Share Spreadsheets [source] 🌐
- Slide Maker - Share slides 🌐 [Advice: Slide Maker https://zaplinks.lol/ site is down]
Health
- Sobrkey - Sobriety and mental health [source] 🌐
- Runstr - Running app [source] 🌐
- NosFabrica - Finding ways for your health data 🌐
- LazerEyes - Eye prescription by DM [source] 🌐
Forum
- OddBean - Hacker News like [info] [source] 🌐
- LowEnt - Forum [info] 🌐
- Swarmstr - Q&A / FAQ [info] 🌐
- Staker News - Hacker News like 🌐 [info]
Direct Messenges (DM)
- 0xchat 🤖🍎 [source]
- Nostr Chat 🌐🍎 [source]
- Blowater 🌐 [source]
- Anigma (new nostrgram) - Telegram based [on development] [source]
Reading
- Oracolo - A minimalist Nostr html blog [source]
- nRSS - Nostr RSS reader 🌐
- Highlighter - Insights with a highlighted read [info] 🌐
- Zephyr - Calming to Read [info] 🌐
- Flycat - Clean and Healthy Feed [info] 🌐
- Nosta - Check Profiles [on development] [info] 🌐
- Alexandria - e-Reader and Nostr Knowledge Base (NKB) [source] 🌐
Writing
- Habla - Blog [info] 🌐
- Blogstack - Blog [info]🌐
- YakiHonne - Articles and News [info] 🌐🍎🤖(on zapstore)
Lists
- Following - Users list [source] 🌐
- Nostr Unfollower - Nostr Unfollower
- Listr - Lists [source] 🌐
- Nostr potatoes - Movies List [source] 💻(numpy)
Market and Jobs
- Shopstr - Buy and Sell [onion] [source] 🌐
- Nostr Market - Buy and Sell 🌐
- Plebeian Market - Buy and Sell [source] 🌐
- Ostrich Work - Jobs [source] 🌐
- Nostrocket - Jobs [source] 🌐
Data Vending Machines - DVM (NIP90)
(Data-processing tools)
Games
- Chesstr - Chess 🌐 [source]
- Jestr - Chess [source] 🌐
- Snakestr - Snake game [source] 🌐
- Snakes on a Relay - Multiplayer Snake game like slither.io [source] 🌐
ENGINES - DEG Mods - Decentralized Game Mods [info] [source] 🌐 - NG Engine - Nostr Game Engine [source] 🌐 - JmonkeyEngine - Java game engine [source] 🌐
Customization
Like other Services
- Olas - Instagram like [source] 🌐🍎🤖(on zapstore)
- Nostree - Linktree like 🌐
- Rabbit - TweetDeck like [info] 🌐
- Zaplinks - Nostr links 🌐
- Omeglestr - Omegle-like Random Chats [source] 🌐
General Uses
- Njump - HTML text gateway source 🌐
- Filestr - HTML midia gateway [source] 🌐
- W3 - Nostr URL shortener [source] 🌐
- Playground - Test Nostr filters [source] 🌐
Places
- Wherostr - Travel and show where you are
- Arc Map (Mapstr) - Bitcoin Map [info]
Driver and Delivery
- RoadRunner - Uber like [on development] ⏱️
- Nostrlivery - iFood like [on development] ⏱️
⚠️ SCAM ⚠️ | Arcade City - Uber like [source]
OTHER STUFF
Lightning Wallets (zap)
- Wallet of Satoshi - Simplest Lightning Wallet [info] 🤖🍎
- Coinos - Web wallet and Nostr client [source] 🌐
- Alby - Native and extension [info] [source] 🌐
- Minibits - Cashu mobile wallet [info] 🤖
- LNbits - App and extension [source] 🤖🍎💻
- Zeus - [info] [source] 🤖🍎
- Blink - Open source custodial wallet (KYC over 1000 usd) [source] 🤖🍎
⚠️ ZBD - Zap Gaming wallet and no more Social [closed source] [info] [some resources] 🤖 ⚠️ ZBD suddenly canceled my account for alleged Terms of Service violations, gives me no explanation and won't let me withdraw my money ⚠️
Without Zap - Wassabi Wallet - Privacy-focused and non-custodial with Nostr Update Manager [source]
Exchange
Media Server (Upload Links)
audio, image and video
Connected with Nostr (NIP):
- Nostr Build - Free and paid Upload [info] [source] 🌐
- NostrMedia - Written in Go with Nip 96 / Blossom (free and paid) [info] [source]
- Nostr Check - [info] [source] 🌐
- NostPic - [info] [source] 🌐
- Sovbit - Free and paid upload [info] [source] 🌐
- Voidcat - Nip-96 and Blossom [source] 🌐
- Primal Media - Primal Media Uploader [source] 🌐
Blossom - Your Media Safer
- Primal Blossom 🌐
- NostrBuild Blossom - Free upload (max 100MiB) and paid [info] [source] 🌐
Paid Upload Only
- Satellite CDN - prepaid upload (max 5GB each) [info] [source] 🌐
Without Nostr NIP:
- Pomf - Upload larger videos (max 1GB) [source]
- Catbox - max 200 MB [source]
- x0 - max 512 MiB [source]
Donation and payments
- Zapper - Easy Zaps [source] 🌐
- Autozap [source] 🌐
- Zapmeacoffee 🌐
- Nostr Zap 💻(numpy)
- Creatr - Creators subscription 🌐
- Geyzer - Crowdfunding [info] [source] 🌐
- Heya! - Crowdfunding [source]
Security
- Secret Border - Generate offline keys 💻(java)
- Umbrel - Your private relay [source] 🌐
Key signing/login and Extension
- Amber - Key signing [source] 🤖(on zapstore)
- Nowser - Account access keys 📱(🤖🍎) 💻(🐧🍎🪟)
- Nos2x - Account access keys 🌐
- Nsec.app 🌐 [info]
- Lume - [info] [source] 🐧🪟🍎
- Satcom - Share files to discuss - [info] 🌐
- KeysBand - Multi-key signing [source] 🌐
Code
- Stacks - AI Templates [info] [source] 🌐
- Nostrify - Share Nostr Frameworks 🌐
- Git Workshop (github like) [experimental] 🌐
- Gitstr (github like) [on development] ⏱️
- Osty [on development] [info] 🌐
- Python Nostr - Python Library for Nostr
- Sybil - Creating, managing and test Nostr events [on development] ⏱️
Relay Check and Cloud
- Nostr Watch - See your relay speed 🌐
- NosDrive - Nostr Relay that saves to Google Drive
Bidges and Getways
- Matrixtr Bridge - Between Matrix & Nostr
- Mostr - Between Nostr & Fediverse
- Nostrss - RSS to Nostr
- Rsslay - Optimized RSS to Nostr [source]
- Atomstr - RSS/Atom to Nostr [source]
Useful Profiles and Trends
nostr-voice - Voice note (just some clients)
NOT RELATED TO NOSTR
Voca - Text-to-Speech App for GrapheneOS [source] 🤖(on zapstore)
Android Keyboards
Personal notes and texts
Front-ends
- Nitter - Twitter / X without your data [source]
- NewPipe - Youtube, Peertube and others, without account & your data [source] 🤖
- Piped - Youtube web without you data [source] 🌐
Other Services
- Brave - Browser [source]
- DuckDuckGo - Search [source]
- LLMA - Meta - Meta open source AI [source]
- DuckDuckGo AI Chat - Famous AIs without Login [source]
- Proton Mail - Mail [source]
Other open source index: Degoogled Apps
Some other Nostr index on:
-
 @ cae03c48:2a7d6671
2025-06-04 20:02:18
@ cae03c48:2a7d6671
2025-06-04 20:02:18Bitcoin Magazine

Vegas Comedown, or Was Bitcoin 2025 Too Noisy?
“Shitcoin Magazine,” tweeted Bitcoin educator and author Knut Svanholm about the event that BTC Inc, the parent company of Bitcoin Magazine, organized in Las Vegas last week. Dancing cows dashed across my feed. “It’s a political convention now,” I overheard two attendees saying as they exited the Nakamoto stage, heads shaking. Nigel Farage, the inflammatory British politician and leader of Reform UK, was shouting on stage about becoming prime minister. A somewhat calmer personality, Vice President JD Vance spoke about “crypto” and thanked Coinbase.
Word on the (online) street is that Bitcoin 2025 was captured by political and shitcoin-y interests. Our own technical editor, Shinobi, opted out of mass surveillance and bailed for freer pastures at the Oslo Freedom Forum. Erik Cason was uncharacteristically polite (“shitcoin adjacent”), though he was there in person, happily signing the Cryptosovereignty book that Bitcoin Magazine Books published in 2023.
“None of my Bitcoiner friends come here anymore,” said Ben, an entrepreneur who runs a Bitcoin business, on the fence about coming back next year.
Whenever I mention that I work for Bitcoin Magazine, I usually have to field questions about shitcoinery and political shilling (Are you a MAGA dude now?!). Coming to Vegas was inspection time for me — or at least a chance to see what it is that troubles so many people.
With the glamor of the Strip itself and its sensory overload, it’d be easy to be dazzled — plus, it was the first time I had left Fort Europa for the land of the free in years, first time in Vegas, and first time at an American Bitcoin event. It’d be easy for me to simply dismiss the haters by paraphrasing Taylor (“haters gonna hate, hate, hate, hate…”).
While sitting down in the whale pass area the Deep, a hipster-looking gentleman started talking to me about how Bitcoin is fundamentally broken and that I should investigate his energy-based shitcoin instead. Waiting for Vance’s speech in the main hall, I was introduced to three young dudes dressed up to perfection and barely out of college, at the conference “to land a job in the industry” — i.e., grifters. A mid-60s technology dude interjected himself into the conversation, bragged about how he worked on tech for Microsoft in the ’90s, and explained how blockchain (not Bitcoin) is the future — only to have us scan the NFC card he had implanted in his left hand. Ugh.
Thus, it wasn’t difficult to see the things all these people online had objected to: Our conference was a party, or “an elaborate Bitcoin extraction scheme,” a “circus, shitcoin fest,” or stablecoin mania. Plus:
— Daniel Prince (@Princey21M) May 30, 2025
They’re not wrong. But honestly, you don’t have to look.
Here’s an underappreciated order to the known universe: To each successful movement or phenomenon, parasites and fraudsters are drawn. It’s why the shitcoin guys are around Bitcoin events and why the politicians are pandering to our cause. Vegas itself is the center of gravity for that sort of thing — gambling, nudity, alcohol, prostitution, and other dopamine-inducing stimulants. I first titled this tak_e_ What Hookers in Vegas Can Teach Us About Politicians at Bitcoin 2025; the simple observation is that fraudsters, grifters, and scammers go to where the value is. Parasites feed off healthy, growing, flourishing organisms.
“Scammers flooding in,” as Tomer Strolight post-conference tweeted, is thus the least surprising thing ever.
We’re succeeding, growing, and becoming if not respectable then at least a household name. The FT and WSJ covering us feel somewhere between “…then they laugh at you“ and “…then they fight you” stages.
Running around meeting people — hardcore Bitcoiners I’ve only ever met online, authors and writers and editors I’ve worked with (they were all in Vegas, since that was the place to be…) — and attending the sum total of three presentations, I felt what Wayne Vaughan of Bitcoin First described:
The Bitcoin Conference 2025 was different and in many ways disappointing.
Good:
The private events were excellent opportunities to reconnect with old friends and meet new people.Bitcoin has grown up. We’re finally legit.
Neutral:
The conference was dominated by politics and…— Wayne Vaughan (@WayneVaughan) May 30, 2025
You can just meet people, just do things.
To make an obvious analogy: The internet is littered with porn, gambling, and cat videos, and it’s the most successful technology in a generation. You don’t have to look; you can just work and provide value instead of wasting away your life talking to shitcoiners or being annoyed at politicians and other fraudsters doing their things.
“Cozying up to any government is a bad idea,” concluded the WSJ piece, citing a “wing” of purist Bitcoin that we all feel. Yes, agreed. But the puritism that its opposite requires condemns us to irrelevancy — belittles and betrays the broader mission.
So yeah: the grifters, the parasites, the politicians, and the financial engineers are here. Good for them. That they’re here is a sign of victory.
Knock me over with a feather, haters.
Come join us for Bitcoin 2026 and see for yourself.
This post Vegas Comedown, or Was Bitcoin 2025 Too Noisy? first appeared on Bitcoin Magazine and is written by Joakim Book.
-
 @ fd78c37f:a0ec0833
2025-04-01 11:49:06
@ fd78c37f:a0ec0833
2025-04-01 11:49:06In this edition, we invited Keypleb, the founder of Bitcoin Indonesia, to share how he built the Bitcoin community in Indonesia, overcoming challenges like member turnover and venue selection, while driving the adoption and growth of Bitcoin.
YakiHonne: Welcome, Keypleb. Before we begin, let me briefly introduce YakiHonne. YakiHonne is a decentralized media client built on Nostr—a protocol designed to empower freedom of speech through technology. It enables creators to own their voices and assets while offering innovative tools like smart widgets, verified notes, and support for long-form content. We focus on free speech and free media by user privacy and data to be protected. So before starting the interview, I'd like to hear about yourself and your community.
Keypleb:My name is Keypleb, though it’s a pseudonym—a name I use to respect privacy. I'm a co-founder of Bitcoin Indonesia, Bitcoin House Bali, and Code Orange, a new developer school we launched at a conference just a few days ago. We focus on driving adoption through meetups, hackathons, and technical workshops. I'll dive into more details later, but that's a brief overview. I'm based in Bali now, though I travel a lot and consider myself quite nomadic. Great to be here.
YakiHonne: What sparked your interest in Bitcoin and what motivated you to create a community on Bitcoin?
Keypleb:I first got interested in Bitcoin because it solved a specific problem. At the time, I didn’t know exactly what the solution was, but the problem was that I couldn’t afford a home. Back in 2019, I was living in London, and a two-bedroom apartment was £600,000, which was insanely expensive. First-time buyers like myself simply couldn’t afford it. Why was it so expensive? Why was buying a house so hard? During the COVID lockdown, I had more time on my hands and started listening to Michael Saylor on a Bitcoin podcast, where he talked about how the system is rigged, and that’s why people work hard but still can’t afford a house. That really resonated with me. So I started looking for a community, but unfortunately, there wasn’t one.. Keypleb:After moving to Bali, I attended a lot of crypto meetups, especially scammy altcoin ones, thinking, “There has to be a solution.” But none of them resonated with me. There was no sense of freedom, and no real discussion about inflation resistance. I remembered a podcast from Dea Reskita, an Indonesian host who’s pretty well-known online. I reached out to her and said, “ you’ve got to help me. I’m surrounded by all these shitcoiners, and I can’t take it anymore. I need a real community. Is anything happening?” She replied, “Yes, something is happening. We should restart these meetups next month.” And that’s how it all began. Keypleb:There’s also another story about how we started Bitcoin House and how Bitcoin in Asia came to be, but maybe I’ll save that for later. Anyway, the spark of interest came from Bitcoin solving a real problem, and my drive to keep going came from the lack of quality meetups. Now, we’ve hosted 31 meetups, launched Bitcoin House and Code Orange, and the movement is growing rapidly.

YakiHonne: That’s such an amazing story—going from being on the brink of homelessness to creating something so impactful, and keeping it running every day, bringing new people into the journey. It’s truly inspiring. I’m curious about how the community started. How did you manage to attract members and build a strong community? What challenges did you face along the way?
Keypleb:It all started with our first meetup at the end of 2022, which was two and a half years ago now. At that time, we sent out an email to a group from a previous database, and the first meetup had around 20 people, which was a good start. However, problems quickly arose as people started dropping off, and the community lacked retention. In Bali, people come and go, usually staying for no more than two months, leading to a lack of long-term participation. This became one of our challenges: how to attract more people and, more importantly, get the same people to keep coming back. While I've been coming back for two and a half years, not everyone is able to return as often, and that has been a real challenge. Keypleb:Actually, I should also mention how I met my co-founders—Marius, Diana, and Dimas. We met at the 2023 Indonesia Bitcoin Conference. As time went on, we kept hosting meetups and had a lot of fun each time, though the locations kept changing. One of the initial challenges was that we didn't realize the importance of having a fixed meetup location. We changed venues several times before we realized that having a consistent location is crucial. If anyone wants to run a meetup, it's best to always choose a fixed location. We learned this through trial and error, but now it's no longer an issue. Keypleb:Since the conference, my co-founders and I have been working together, consistently putting in the effort. This is why our community has grown so large—so far, we are hosting 31 monthly meetups, 6 of which are in Bali. This means there is a bitcoin meetup almost every day on a regular basis. We've also established Bitcoin House Bali, a physical space, and the movement is growing rapidly. Without this movement, the region would face many challenges, including inflation and heavy censorship. It all started from just one meetup.
 YakiHonne: It's amazing to see how you met your co-founders and how you’ve built something incredible that continues to grow today. What advice would you give to someone looking to start a successful Bitcoin community right now?
YakiHonne: It's amazing to see how you met your co-founders and how you’ve built something incredible that continues to grow today. What advice would you give to someone looking to start a successful Bitcoin community right now?Keypleb:First, one very important piece of advice is to ensure that every meetup is held at the same location regularly. We realized this challenge through trial and error. To help others who are interested, we’ve published our meetup guide on GitHub, where everyone can check it out. For example, meetups should be held regularly, ideally once a month, or even once a week. In Chiang Mai, the Bitcoin meetup starts every Thursday at 7 PM, and everyone knows the time and location, making it easy to join without having to look up the next meetup. Keypleb:Additionally, our meetup structure is very simple. First, we do a round of introductions where everyone shares their name, where they’re from, and what Bitcoin means to them. This usually takes about 15 minutes. Then, we discuss three main questions: First, why do we need Bitcoin? The discussion typically focuses on two main issues Bitcoin addresses: inflation and censorship;Secondly, how to buy Bitcoin? We usually ask who wants to buy some Bitcoin, and then we do a small purchase together and conduct a P2P trade to demonstrate how easy it is to buy Bitcoin. Lastly, how to store Bitcoin? We introduce self-custody and show how to use hardware wallets (like Trezor), explaining the concept of the 12 words and private keys. Keypleb:The whole meetup usually wraps up in about an hour, after which people can continue socializing at Bitcoin House or wherever the meetup is taking place. In short, keeping the meetup simple and efficient, and ensuring a fixed location for each event, are key factors in building a successful community.
YakiHonne: What's the major approach? Is it more technical, or do you focus on non-technical aspects, or do you cover both?
Keypleb:Our approach includes both technical and non-technical content. Initially, our meetups were completely non-technical, just casual gatherings for people to socialize. Over time, however, we've evolved to incorporate more technical content. Keypleb:Out of the 31 monthly regular meetups we host, most of them have been non-technical, simply regular gatherings held at the same time and place according to our meetup guide. For example, we host the “Bitcoin for Beginners” meetup, which is designed for newcomers and takes place every second Friday of the month at 5 PM at the Bitcoin House Bali. This is entirely non-technical. Additionally, every Wednesday at Bitcoin House, we host the “My First Bitcoin” course. While the course touches on some technical aspects, such as seed phrases and backups, it’s still beginner-friendly and not too technical. The course runs for 10 weeks, and we plan to offer it in the local language at Bali University to help the local community better understand Bitcoin. Keypleb:On the other hand, we also offer highly technical content. We launched a new program called “Code Orange,” which is specifically designed for developers and programmers. We use the “Decoding Bitcoin” website, created by Jamal, which is a learning platform for developers. Many developer schools, like Code Orange, use this resource. Additionally, we host “Code Orange” meetups where we dive into the technical aspects of Bitcoin, such as how mining works and how to prevent single points of failure. Keypleb:We also organize technical workshops, such as “How to Defend Against a Five-Dollar Wrench Attack,” which is closely related to security. Recently, there have been some kidnapping incidents in Bali, and many people are concerned about their Bitcoin being stolen. To address this, we plan to hold a workshop on how to protect Bitcoin against such attacks. Additionally, we host hackathons and other high-tech events, and we just completed a very successful beginner-level hackathon. Keypleb:In summary, our community caters to everyone, from beginners to technical experts. For beginners, we offer easy-to-understand, non-technical content, while for experienced Bitcoiners, we provide in-depth technical material.
 YakiHonne: It's great to approach it in both ways, so everyone gets their own "piece of the cake."Now, I'd like to dive into the technical side. What advice would you give to technically inclined individuals or organizations looking to contribute to the Bitcoin ecosystem? How should they approach the technical aspects of Bitcoin if they want to get involved?
YakiHonne: It's great to approach it in both ways, so everyone gets their own "piece of the cake."Now, I'd like to dive into the technical side. What advice would you give to technically inclined individuals or organizations looking to contribute to the Bitcoin ecosystem? How should they approach the technical aspects of Bitcoin if they want to get involved?Keypleb:I have some additional advice. First, technical individuals can sign up for the “Decoding Bitcoin” course that starts on 18th March 2025 or join our “Code Orange” program and participate in the end-of-year hackathon. If they are technically proficient, this will be a great opportunity. “Decoding Bitcoin” is great for beginners, but it’s also useful for technical individuals. If someone is very skilled, they can start contributing code right away. If they find the course too easy, they can skip it and dive directly into more advanced projects. Additionally, Bitshala and Chaincode Labs offer advanced courses, which more technically advanced individuals can choose to pursue.
 Keypleb:Additionally, it's worth mentioning that the Bitcoin Dev Project has a great platform where technical individuals can find “Good First Issue” or open-source projects to start contributing code. You'll learn about the philosophy behind Bitcoin and why it's more meaningful than other “shitcoins.” Once you’ve taken enough “orange pills” (the philosophy and technology of Bitcoin), you can dive deeper into Bitcoin core development and potentially start coding in C++. If you're interested, you can join specific projects like Nostr, Fedimint or E-Cash.
Keypleb:Additionally, it's worth mentioning that the Bitcoin Dev Project has a great platform where technical individuals can find “Good First Issue” or open-source projects to start contributing code. You'll learn about the philosophy behind Bitcoin and why it's more meaningful than other “shitcoins.” Once you’ve taken enough “orange pills” (the philosophy and technology of Bitcoin), you can dive deeper into Bitcoin core development and potentially start coding in C++. If you're interested, you can join specific projects like Nostr, Fedimint or E-Cash.YakiHonne: I’d like to move on to the next question: How do you see Bitcoin communities evolving as technology progresses, particularly in areas like scalability, privacy, and adaptability to other systems? Keypleb:I believe the Bitcoin community will continue to evolve, and it has already made incredible progress. Two and a half years ago, we started alone in Bali, with just ourselves. We began in the official phase and have had numerous conversations throughout the year. For example, we are now starting a Bitcoin club at a university in Bali; we just need to find a passionate, driven “Bitcoin maximalist,” and the Bitcoin club will begin. Like what our friends did in Banyuwangi, Indonesia, these clubs could eventually evolve into Bitcoin houses.
Keypleb:Regarding privacy and scalability, the community is making strides. We’re big fans of Fedi, which builds on top of the Fedimint protocol and uses e-cash to scale Bitcoin while improving privacy. Fedi low fees and high privacy potential give Bitcoin great opportunities in this area. Keypleb:As for Bitcoin's compatibility with fiat systems, although Bitcoin payments are illegal in some countries like Indonesia, smart developers across Southeast Asia are working on legal solutions. For example, there's a website called Pleb QR that works in Thailand, allowing you to pay in fiat via the Lightning Network. Koral is another app specifically for Indonesia. These kinds of testing products already exist and are physically possible, but we’re just waiting on regulations. My influential friends are actively lobbying the government for adoption. Keypleb:In summary, privacy, scalability, and compatibility with fiat systems are all works in progress, and they will continue to evolve positively. There will be more meetups, more wallet downloads, and more adoption—there’s no doubt about that.
YakiHonne: You mentioned the concept of cross-country issues, so I have one last question: How is the government’s stance on Bitcoin? Is the political climate supportive or against Bitcoin? How do you see the government's approach to Bitcoin in your community or environment?
Keypleb:This reminds me of a person, Jeff Booth, who once said, “We are them, the government is made up of us.” In Indonesia, many politicians actually support Bitcoin, and many of them mine Bitcoin themselves. When money is involved, the incentive is strong, and politicians naturally like to make more money. As a result, Indonesia has a large Bitcoin mining scene. However, overall, the Indonesian government is against Bitcoin, as seen in their ban on Bitcoin payments. The 2011 currency law states that any currency other than the Indonesian Rupiah (IDR) cannot be used, and violators can face up to one year in prison or a fine. This means you cannot pay with US dollars, lira, euros, pesos or pounds. Keypleb:This shows that the government’s legal system is somewhat fragile. It’s understandable that the government is concerned about disruptive technologies like Bitcoin, especially with such a fragile fiat system. Indonesia has also seen many arrests. In 2016, Bank Indonesia issued a letter announcing a crackdown on cryptocurrency payments. Those involved in paying in Bitcoin had their funds seized, and the police cooperated in shutting down businesses accepting Bitcoin payments in the cities. While this isn't very friendly, it does highlight the fragility of the existing system. We also believe that a new executive order may be introduced in the future, similar to when President Roosevelt in 1933 ordered Americans to hand over all their gold with his Executive Order 6102. If it happened before, it could happen again. Keypleb:Therefore, we predict that Bitcoin custody could become a legal issue, which is one of the reasons we blur the faces of participants at every meetup. We need to protect the community from any potential risks. But overall, we remain optimistic. Despite the government ban, the ideology of Bitcoin is unstoppable, and its spread cannot be stopped. So, we are very optimistic about the future.
YakiHonne: I think almost every government around the world, even in Africa, faces similar issues with Bitcoin. Some governments might want Bitcoin but hesitate to openly accept it due to the fear of it undermining the traditional financial system, which, of course, could eventually happen. But hopefully, as the new generation comes into power, we'll see more Bitcoin-friendly governments. So, thank you so much for sharing your insights and advice. I really appreciate your time and the valuable input you've provided.
Keypleb:I'm really glad this conversation enlightened me. I enjoyed it a lot, and it made me reflect on how much work we're doing and how valuable it is. There are a lot of problems out there, with censorship being the biggest one, followed by inflation, which is also a major issue depending on the region. But Bitcoin is open, the community is growing, and people are fighting against censorship and internet shutdowns in places like Indonesia and beyond. The movement is definitely growing. So, I'm very happy to be here and have this chat. Thanks again.
Bitcoin Indonesia nostr: nostr:npub1y4qd2zhtn05gnsaaq5xfejzfk4a32638tx6gpp9g8k6e42g9d66qaxhcr3
Keypleb nostr: nostr:npub190trvg63e6tyqlwlj6lccqpftx76lckj25c006vwx3dzvdl88yxs2nyqdx
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 4fa5d1c4:fd6c6e41
2025-06-04 17:45:05
@ 4fa5d1c4:fd6c6e41
2025-06-04 17:45:051. Einleitung
Dieser Beitrag bietet eine detaillierte Einführung in Nostr - ein dezentrales Protokoll für soziale Medien, das sich grundlegend von traditionellen und föderierten Plattformen unterscheidet - und erweitert seine Diskussion, um das Potenzial für die Integration von Nostr in die Entwicklung von Bildungsplattformen im Sinne von Open Educational Practices (OEP) zu untersuchen. Nostr ist als leichtgewichtiger, zensurresistenter Mechanismus konzipiert, der in erster Linie auf einer kryptografischen Schlüsselverwaltung und einer Client-zentrierten Architektur basiert, die zusammen eine dezentrale Identitätskontrolle und Autonomie über digitale Inhalte ermöglichen. Im Gegensatz zu konventionellen zentralisierten Modellen, die sich auf servergestützte Kontrolle oder föderierte Systeme wie Mastodon, die Moderation und Identitätsspeicherung zusammenfassen, stützt sich Nostr auf ein Netzwerk von "Relais", die ohne direkte Interkommunikation arbeiten, wobei alle Funktionen der Datenaggregation, des Austauschs von Inhalten zwischen den Räumen und der Benutzerinteraktion an die Client-Anwendungen delegiert werden. Ziel dieses Beitrags ist es daher, einen umfassenden technischen und konzeptionellen Überblick über die Architektur des Protokolls und eine kritische Diskussion seiner Anwendbarkeit im Kontext dezentraler Bildungsplattformen zu geben, die eine offene, nutzergesteuerte Erstellung, Verwaltung und Verteilung von Inhalten fördern und damit den Prinzipien des OEP entsprechen.
2. Hintergrund und Motivation
Die Entwicklung der sozialen Medien in den letzten zwei Jahrzehnten war geprägt von zunehmend zentralisierten Plattformen, die sowohl die digitale Identität der Nutzer als auch die von ihnen erstellten Inhalte kontrollieren, was oft zu Zensur, algorithmischer Manipulation und Einzelausfällen führt. Im Gegensatz dazu haben sich dezentralisierte Social-Media-Protokolle wie Nostr als innovative Antwort auf diese Zentralisierungsfallen entwickelt, die offene, kryptografisch sichere und verteilte Architekturen verwenden. Nostr wurde mit dem ausdrücklichen Schwerpunkt konzipiert, den Nutzern die volle Kontrolle über ihre Kontoauthentifizierung und digitale Identität zu geben, was durch die Verwaltung von kryptografischen Schlüsselpaaren analog zu denen in Bitcoin-Wallets erreicht wird. Dieses Modell verbessert nicht nur die zensurresistenten Eigenschaften der Plattform, sondern verändert auch grundlegend die Machtdynamik in traditionellen sozialen Netzwerken, da es die Abhängigkeit von zentralen Behörden minimiert und die Möglichkeiten der Ausbeutung und Überwachung verringert. Im Kontext von Bildungsökosystemen bieten diese Merkmale eine solide Grundlage für die Entwicklung von Plattformen, die transparent, partizipatorisch und widerstandsfähig sind, da sie die gemeinsame Nutzung und kontinuierliche Weiterentwicklung von Bildungsressourcen ohne zentralisierte Kontrolle oder Unternehmenssteuerung unterstützen.
3. Technische Architektur von Nostr
Die Architektur von Nostr basiert in erster Linie auf zwei integralen Komponenten: Clients und Relays. Clients sind die benutzerseitigen Anwendungen, die die Erstellung, Veröffentlichung und Aggregation von Inhalten ermöglichen, während Relays Server sind, die von den Benutzern generierte Nachrichten, so genannte "Events", empfangen, speichern und weiterleiten. Eine der wichtigsten Neuerungen des Nostr-Protokolls ist die radikale Entkopplung der traditionellen Client-Server-Beziehung: Die Relais müssen sich nicht synchronisieren oder miteinander kommunizieren, was bedeutet, dass die Replikation von Inhalten und die Aggregation von Daten zwischen den Räumen vollständig auf der Client-Seite stattfindet. Dies minimiert die zentrale Kontrolle und schafft ein verteiltes, relaisbasiertes System, das von Natur aus resistent gegen Zensur ist, da die Dichte der verfügbaren Relays und die Möglichkeit der Nutzer, sich mit mehreren Relays zu verbinden, sicherstellen, dass die Inhalte auch dann zugänglich bleiben, wenn bestimmte Relays ausfallen oder kompromittiert sind.
In Nostr sind Ereignisse als JSON-Objekte strukturiert, die einem definierten Schema mit verschiedenen "Arten" (NIPs) entsprechen, um spezifische Funktionalitäten und andere zukünftige Erweiterungen zu unterstützen. Jedes Ereignis wird mit dem privaten kryptografischen Schlüssel des Nutzers digital signiert, was die Authentizität und Integrität der Daten garantiert und gleichzeitig eine sichere, pseudonyme Interaktion ermöglicht. Da innerhalb des Protokolls keine zentrale Behörde oder ein einziger Identitätsspeicher existiert, behalten die Nutzer die vollständige Kontrolle über ihre digitalen Identitäten, und wenn der private Schlüssel verloren geht, ist das entsprechende Konto unwiederbringlich. Dieser Ansatz verankert den Grundsatz, dass Identität sowohl dezentralisiert als auch unveränderlich ist, und stärkt die individuelle Kontrolle über persönliche Daten und Inhalte.
Da die Relays unabhängig voneinander von verschiedenen Betreibern verwaltet und nicht von zentralen Diensten koordiniert werden, können die Benutzer mehrere Relays auswählen, um die Bereitstellung und Replikation von Inhalten zu optimieren. Diese architektonische Entscheidung verbessert die Redundanz und Ausfallsicherheit erheblich, bringt aber gleichzeitig technische Herausforderungen in Bezug auf Standardisierung, Moderation und effiziente Kommunikation zwischen den Clients mit sich. Nostr integriert auch Bitcoin-basierte Mikrozahlungen (bekannt als "Zaps"), um finanzielle Anreize für den Betrieb von Relay-Servern zu schaffen und so die Herausforderungen der wirtschaftlichen Nachhaltigkeit in einer dezentralen Infrastruktur zu bewältigen. Die Design-Entscheidungen in Nostr fördern Offenheit und Innovation, indem sie es jeder Person oder Organisation mit ausreichenden technischen Fähigkeiten erlauben, ein Relay zu hosten oder einen Client zu entwickeln, was zu einem lebendigen Ökosystem von verschiedenen Anwendungen und Diensten führt.
4. Identitätsmanagement und Moderation
Im Mittelpunkt des dezentralen Paradigmas von Nostr steht der Ansatz der Identitätsverwaltung, der sich von traditionellen Systemen unterscheidet, bei denen Identitäten als Kontodaten von zentralen Servern verwaltet werden. Bei Nostr verfügt jeder Benutzer über ein einzigartiges kryptografisches Schlüsselpaar, wobei der öffentliche Schlüssel als dauerhafte digitale Kennung und der private Schlüssel als Mittel zum Signieren aller Aktionen und Ereignisse dient. Dieses kryptonative Modell gewährleistet nicht nur robuste Sicherheit und Authentizität, sondern überlässt den Nutzern auch die alleinige Verantwortung für die Verwaltung ihrer Schlüssel - was sowohl die Freiheit als auch das Risiko eines vollständig dezentralen Identitätssystems unterstreicht.Dieses empfindliche Gleichgewicht unterstreicht die Autonomie der Nutzer und steht im Einklang mit dem breiteren Ethos dezentraler sozialer Medien, in denen keine einzelne Instanz die Identität einer Person ohne Zugang zu ihrem privaten Schlüssel außer Kraft setzen oder manipulieren kann.
Die Moderation in Nostr ist aufgrund des dezentralen Kuratierungsmodells noch komplexer. Die Inhalte werden nicht von einer zentralen Behörde moderiert, sondern durch eine Kombination aus relaisspezifischen Richtlinien und clientseitigen Kontrollen, wie z. B. benutzerdefinierte Listen für persönliche Kuratoren oder Sperr-/Stummschaltungsfunktionen. Dieser Ansatz fördert zwar die freie Meinungsäußerung und unterstützt eine Vielzahl von Standpunkten, kann aber auch zu uneinheitlichen Moderationsrichtlinien und fragmentierten Nutzererfahrungen auf verschiedenen Relays und Clients führen, was für die Nutzer eine erhebliche technische und verhaltensbezogene Belastung darstellt, wenn sie ihre digitalen Umgebungen kuratieren wollen.
5. Skalierbarkeit und Widerstandsfähigkeit gegen Zensur
Ein entscheidendes Merkmal des Nostr-Protokolls ist sein hohes Maß an Skalierbarkeit und Zensurresistenz, das durch seine verteilte, relaisbasierte Architektur erreicht wird. Durch die Dezentralisierung der Speicherung und Verbreitung von Inhalten auf zahlreiche unabhängige Relays entschärft Nostr die üblichen Schwachstellen zentralisierter sozialer Plattformen, wie z. B. Single Points of Failure oder das Potenzial für staatliche oder unternehmensgesteuerte Zensur. Mehrere Relays können gleichzeitig arbeiten, wodurch sichergestellt wird, dass die Stabilität des Netzwerks auch dann erhalten bleibt, wenn einige von ihnen vom Netz genommen werden oder behördlichem Druck ausgesetzt sind, und dass Inhalte für Kunden, die mit alternativen Relays verbunden sind, zugänglich bleiben.
Die Skalierbarkeit von Nostr wird dadurch verbessert, dass sich die Nutzenden gleichzeitig mit mehreren Relays verbinden können, was die Replikation von Inhalten über ein globales Netz von Servern ermöglicht, das sich über zahlreiche geografische Regionen und autonome Systeme erstreckt. Dieser Replikationsmechanismus bringt jedoch Herausforderungen mit sich, wie z. B. eine erhöhte Redundanz bei der Speicher- und Bandbreitennutzung, die eine sorgfältige Optimierung und die Entwicklung innovativer clientseitiger Strategien erfordern, um den Datenabruf zu verwalten und den Overhead zu reduzieren, ohne die Verfügbarkeit zu beeinträchtigen. Darüber hinaus trägt die Dezentralisierung der Zuständigkeiten für Kuratierung und Moderation zu einer dynamischen Umgebung bei, in der Inhalte sowohl gegen erzwungene Löschungen resistent als auch an die Bedürfnisse der Nutzer anpassbar sind, wenn auch auf Kosten von Einheitlichkeit und vorhersehbarer Nutzererfahrung.
6. Vergleich mit föderierten und zentralisierten Modellen
Das Aufkommen dezentraler Protokolle wie Nostr steht in scharfem Kontrast zu föderierten Netzwerken wie Mastodon, die das ActivityPub-Protokoll verwenden. Während föderierte Systeme die Kontrolle über unabhängige Instanzen verteilen, verlassen sie sich immer noch auf ein gewisses Maß an Zentralisierung auf der Ebene jeder einzelnen Instanz, von denen jede ihre eigenen Richtlinien bezüglich Moderation, Identitätsüberprüfung und Inhaltszensur durchsetzt. In diesen Systemen ist die Verwaltung zwar auf mehrere Knotenpunkte verteilt, aber es besteht eine Abhängigkeit von Serveradministratoren, die erhebliche Macht über den Inhalt und die Identität der Benutzer haben; dies steht im Gegensatz zu Nostrs vollständig kundenorientiertem Kurations- und Identitätsverwaltungsmodell, das darauf abzielt, jeden einzelnen Kontrollpunkt zu eliminieren.
In zentralisierten Architekturen werden Benutzerdaten und -identitäten auf proprietäre und undurchsichtige Weise verwaltet, wodurch Inhalte den Launen von Unternehmensrichtlinien und externem Druck ausgesetzt werden, was zu Überwachung, gezielter Zensur oder einseitiger algorithmischer Manipulation von Inhalten führen kann. Das Design von Nostr - das auf kryptografischer Authentifizierung, clientseitiger Datenaggregation und dem erlaubnisfreien Betrieb von Relay-Servern beruht - stellt eine radikale Abkehr dar, die das Gleichgewicht der Macht fest in die Hände der einzelnen Nutzer und nicht in die Hände zentraler Behörden legt.
7. Implikationen für Bildungsplattformen
Das Potenzial für die Integration des dezentralen Protokolls von Nostr in Bildungsplattformen bietet eine transformative Gelegenheit zur Unterstützung von Open Educational Practices (OEP). OEP legt den Schwerpunkt auf Inklusion, Autonomie der Lernenden, kollaborative Wissenserstellung und offenen Zugang zu Bildungsressourcen. Herkömmliche Bildungsplattformen sind oft durch zentralisierte Architekturen eingeschränkt, die den Zugang behindern und Innovationen unterdrücken können, da sie auf einzelne administrative Kontrollen und proprietäre Content-Management-Systeme angewiesen sind.
Durch die Nutzung der dezentralen Infrastruktur von Nostr können Bildungsplattformen aufgebaut werden, die es Lehrenden und Lernenden ermöglichen, die volle Kontrolle über ihre digitalen Identitäten und Bildungsinhalte zu behalten, ohne das Risiko von Zensur oder externer Einmischung. In solchen Systemen verwaltet jeder Teilnehmer seine eigene Identität mithilfe von kryptografischen Schlüsseln, wodurch sichergestellt wird, dass Bildungsleistungen, Beiträge und Zeugnisse auf überprüfbare und unveränderliche Weise aufgezeichnet werden. Dies fördert ein Umfeld, in dem die Schaffung und Verbreitung von Wissen wirklich von den Teilnehmern selbst bestimmt wird, frei von den Zwängen, die von zentralen Torwächtern auferlegt werden.
Darüber hinaus bietet die relaisbasierte Architektur von Nostr eine beispiellose Skalierbarkeit und Ausfallsicherheit - Eigenschaften, die für ein Bildungsökosystem, das eine Vielzahl von Nutzern mit unterschiedlichem geografischen und sozioökonomischen Hintergrund unterstützen muss, unerlässlich sind. Bildungsinhalte - von digitalen Lehrbüchern und Multimedia-Vorlesungen bis hin zu interaktiven Diskursen und gemeinschaftlichen Projekten - können gespeichert und über mehrere Relays repliziert werden, um sicherzustellen, dass der Zugang auch bei lokalen Netzwerkausfällen oder Zensurversuchen erhalten bleibt.
Das offene Protokoll von Nostr ist außerdem eine ideale Grundlage für die Entwicklung interoperabler Bildungsplattformen, auf denen Drittentwickler und Bildungseinrichtungen maßgeschneiderte Clients und Anwendungen für pädagogische Zwecke erstellen können. Dieser Ansatz fördert ein vielfältiges Ökosystem von Bildungswerkzeugen und -diensten, die nahtlos zusammenarbeiten, ohne auf eine einzige proprietäre Plattform beschränkt zu sein, und steht damit im Einklang mit dem Ethos des OEP. Pädagogen können digitale Lernumgebungen entwerfen, die die kollaborative Erstellung von Inhalten, Peer-Reviews und Community-gesteuerte Kuration unterstützen und gleichzeitig von der Sicherheit und Transparenz profitieren, die das kryptografische Grundgerüst von Nostr bietet.
Darüber hinaus gewährleistet die inhärente Zensurresistenz von Nostr, dass Bildungsinhalte zugänglich und frei von staatlichen oder unternehmerischen Eingriffen bleiben - ein besonders wichtiger Aspekt für Lernende in Regionen, in denen der Zugang zu Informationen eingeschränkt oder überwacht wird. Diese Widerstandsfähigkeit untermauert nicht nur die demokratische Verbreitung von Wissen, sondern unterstützt auch den Grundsatz eines digitalen Gemeinguts, bei dem Bildungsressourcen kollektiv verwaltet und gemeinsam genutzt werden. In diesem Zusammenhang kann Nostr genutzt werden, um Bildungsplattformen zu entwickeln, die nicht nur robust und integrativ sind, sondern auch auf die Bedürfnisse marginalisierter oder unterrepräsentierter Gemeinschaften abgestimmt sind.
Zusätzlich zu diesen strukturellen Vorteilen kann die finanzielle Nachhaltigkeit dezentraler Bildungsplattformen durch die Integration von auf Kryptowährungen basierenden Anreizmechanismen gestärkt werden - wie die Unterstützung von Nostr für Bitcoin Lightning "Zaps" zeigt. Diese Micropayment-Systeme eröffnen Möglichkeiten für neuartige Finanzierungsmodelle, die Pädagogen und Inhaltsersteller direkt belohnen und so die Abhängigkeit von werbebasierten Einnahmen oder zentralisierten Finanzierungsströmen verringern, die häufig die Integrität der Bildung gefährden. Solche wirtschaftlichen Anreize können auch den Betrieb und die Wartung von Relay-Servern unterstützen und so sicherstellen, dass die dezentrale Infrastruktur belastbar und kontinuierlich für Bildungszwecke verfügbar bleibt.
8. Möglichkeiten für kollaboratives und kultursensibles Lernen
Über die technische Stabilität und Skalierbarkeit hinaus bietet die dezentrale Natur von Nostr bedeutende Möglichkeiten zur Förderung von kollaborativem Lernen und kultursensibler Pädagogik. Dezentralisierte Bildungsplattformen, die auf Nostr aufbauen, können lokale Gemeinschaften in die Lage versetzen, Inhalte zu erstellen und zu kuratieren, die kontextuell relevant und kulturell angemessen sind - ein entscheidender Faktor bei der Förderung von Bildungsgerechtigkeit und Inklusivität. In Umgebungen, in denen Mainstream-Bildungstechnologien als von oben nach unten betrachtet werden und nicht mit lokalen Werten oder pädagogischen Ansätzen übereinstimmen, ermöglicht eine dezentralisierte Infrastruktur die Entwicklung maßgeschneiderter digitaler Lernumgebungen, die lokale Kulturen, Sprachen und Traditionen widerspiegeln.
Dieser gemeinschaftsorientierte Bildungsansatz fördert das Gefühl der Eigenverantwortung bei Lernenden und Lehrenden gleichermaßen und ermutigt zur gemeinschaftlichen Schaffung von Wissen, das unterschiedliche Erkenntnistheorien respektiert. So können Pädagogen beispielsweise dezentrale "Lernräume" einrichten, in denen Open-Source-Lernmaterialien, Werkzeuge für die digitale Kompetenz und innovative Lehrmethoden gemeinsam genutzt und durch partizipatives Engagement kontinuierlich weiterentwickelt werden. In einem solchen Modell verschwimmen die Grenzen zwischen Lernenden und Lehrenden, was einen fließenden Ideenaustausch und die gemeinsame Schaffung von Wissen ermöglicht, die im Mittelpunkt offener Bildungspraktiken stehen.
Darüber hinaus ermöglicht die Flexibilität der Client-zentrierten Architektur von Nostr die Entwicklung von spezialisierten Bildungsclients, die auf die jeweiligen Lernstile und Disziplinen zugeschnitten sind. Diese Clients könnten Funktionen wie erweiterte Such- und Filterfunktionen für Bildungsinhalte, integrierte Anmerkungswerkzeuge für die gemeinsame Bearbeitung von Dokumenten und interoperable Identitätsmanagementsysteme enthalten, die es den Lernenden ermöglichen, ihre Anmeldedaten nahtlos in verschiedene digitale Lernumgebungen zu übertragen. Solche Innovationen würden nicht nur die Rolle der Nutzerautonomie beim digitalen Lernen stärken, sondern auch die Entwicklung von Bildungsnetzwerken fördern, die belastbar und anpassungsfähig sind und auf die sich verändernden pädagogischen Herausforderungen reagieren können.
9. Herausforderungen und Abhilfestrategien
Trotz der vielversprechenden Möglichkeiten ist die Integration von Nostr in Bildungsplattformen nicht unproblematisch. Gerade die Funktionen, die den Nutzern mehr Möglichkeiten bieten - wie selbstverwaltete kryptografische Schlüssel und dezentralisierte Inhaltsmoderation - führen auch Komplexitäten ein, die die Benutzerfreundlichkeit und Zugänglichkeit behindern können, insbesondere für Personen ohne fortgeschrittene technische Kenntnisse. Die Schlüsselverwaltung stellt beispielsweise eine kritische Schwachstelle dar; der Verlust eines privaten Schlüssels führt unwiderruflich zum Verlust der Identität und des Zugriffs auf die eigenen digitalen Beiträge - ein Risiko, das durch solide Bildungsinitiativen und Mechanismen zur Unterstützung der Nutzer angegangen werden muss.
Die technische Kompetenz von Lehrenden und Lernenden ist in diesem Zusammenhang von größter Bedeutung und erfordert die Entwicklung umfassender Einführungsverfahren, benutzerfreundlicher Schnittstellen und Hilfsmittel, die kryptografische Konzepte entmystifizieren und die Interaktion mit dezentralen Netzwerken vereinfachen. Zu diesem Zweck könnte der Einsatz intuitiver Bildungsmodule, interaktiver Tutorials und von der Community geleiteter Schulungen technische Barrieren abbauen und gleichzeitig die Entwicklung digitaler Kompetenzen fördern, die für die Navigation in dezentralen Netzwerken unerlässlich sind. Darüber hinaus muss die Herausforderung einer inkonsistenten Moderation und fragmentierten Nutzererfahrung aufgrund der heterogenen Richtlinien unabhängiger Relais und Clients durch die Einrichtung von Community-Governance-Rahmenwerken und interoperablen Standards angegangen werden, die eine Grundlinie der Qualität und Sicherheit auf der gesamten Plattform gewährleisten.
Strategien zur Bewältigung des mit der Skalierbarkeit verbundenen Overheads - wie etwa die redundante Replikation von Beiträgen über eine übermäßige Anzahl von Relays - sollten sich auf die Implementierung clientseitiger Optimierungstechniken konzentrieren, die die Ineffizienz von Bandbreite und Speicherplatz verringern, ohne die Belastbarkeit und Zugänglichkeit des Netzwerks zu beeinträchtigen. Kontinuierliche Forschung und iterative Verfeinerung werden notwendig sein, um ein Gleichgewicht zwischen den Vorteilen der Dezentralisierung und der ihr innewohnenden betrieblichen Komplexität zu finden und sicherzustellen, dass auf Nostr basierende Bildungsplattformen sowohl robust als auch benutzerfreundlich bleiben können.
10. Zukünftige Richtungen und Forschungsmöglichkeiten
Die Einbindung von Nostr in Bildungsplattformen stellt ein fruchtbares Gebiet für Forschung und Entwicklung dar, das zahlreiche Möglichkeiten zur Erkundung bietet. Zukünftige Arbeiten könnten das Design interoperabler Bildungsrahmenwerke erforschen, die die dezentrale Architektur von Nostr mit aufkommenden Technologien wie künstlicher Intelligenz, Blockchain-basiertem Credentialing und fortschrittlichen kryptographischen Techniken integrieren, um die Sicherheit, Zugänglichkeit und Authentizität in digitalen Lernumgebungen weiter zu verbessern. Die Erforschung gemeinschaftsbasierter Governance-Modelle ist ebenfalls gerechtfertigt, da dezentrale Plattformen Mechanismen für die kollektive Entscheidungsfindung und Konfliktlösung erfordern, die mit den Grundsätzen einer offenen, partizipativen Bildung vereinbar sind.
Ein möglicher Weg ist die Entwicklung modularer, quelloffener Bildungs-Clients, die sich nahtlos mit verschiedenen Relais verbinden lassen und den Lehrkräften leistungsstarke Tools zur Kuratierung und Moderation von Inhalten bieten. Diese Clients könnten anpassbare Dashboards, Module für die Zusammenarbeit in Echtzeit und integrierte Unterstützung für Mikrozahlungen oder Anreizstrukturen bieten, um sicherzustellen, dass Bildungsinhalte sowohl dynamisch als auch finanziell nachhaltig bleiben. Darüber hinaus könnte die Einrichtung digitaler Identitätsrahmen, die auf den kryptografischen Prinzipien von Nostr aufbauen, zu innovativen Modellen für die Überprüfung akademischer Zeugnisse, die Verfolgung des Lernfortschritts und die Erleichterung der plattformübergreifenden Anerkennung von Bildungsleistungen führen, und das alles ohne die Aufsicht zentralisierter Registrierungsbehörden.
Die Schnittstelle zwischen digitaler Kompetenz und ethischer digitaler Bürgerschaft ist ein weiteres vielversprechendes Forschungsgebiet. In dem Maße, in dem Pädagogen dezentrale Bildungstechnologien in die Lehrpläne integrieren, wird es zwingend notwendig, Lehrmethoden zu entwickeln, die nicht nur technische Kenntnisse, sondern auch die kritischen und moralischen Fähigkeiten vermitteln, die für die Arbeit in einem dezentralen digitalen Ökosystem erforderlich sind. Solche pädagogischen Strategien sollten Schulungen zum Schlüsselmanagement, zur Verifizierung digitaler Identitäten und zum Verständnis der Kompromisse umfassen, die mit dezentralisierten und zentralisierten Technologiemodellen einhergehen, um den Schülern eine ausgewogene Perspektive auf digitale Rechte, Verantwortlichkeiten und Möglichkeiten zu vermitteln.
Die Zusammenarbeit zwischen akademischen Institutionen, Open-Source-Gemeinschaften und Innovatoren dezentraler Technologien wird entscheidend sein, um diese Forschungsagenden voranzutreiben und die Entwicklung von Bildungslabors und Pilotprojekten zu fördern, die die praktischen Auswirkungen und Vorteile dezentraler Bildungsplattformen auf der Grundlage von Nostr erforschen. Solche Initiativen könnten als lebende Laboratorien zum Testen neuer Werkzeuge, Methoden und Governance-Strategien dienen, mit dem Ziel, das Gleichgewicht zwischen dem Versprechen der Dezentralisierung und ihren praktischen Herausforderungen schrittweise zu verfeinern.
11. Schlußfolgerung
Zusammenfassend lässt sich sagen, dass Nostr eine bahnbrechende Entwicklung in der Architektur sozialer Medien darstellt, die die Beziehung zwischen Nutzern, Inhalten und Netzwerkinfrastruktur durch ein dezentralisiertes, kryptographisch gesichertes und klientenzentriertes Modell neu definiert. Das relaisbasierte Design, die dezentrale Identitätsverwaltung und die offene Architektur bieten erhebliche Vorteile gegenüber herkömmlichen zentralisierten und föderierten Systemen in Bezug auf Zensurresistenz, Skalierbarkeit und Benutzerautonomie. Diese technischen Innovationen haben weitreichende Auswirkungen auf die Entwicklung von Bildungsplattformen, die den Grundsätzen der Open Educational Practices entsprechen. Durch die Unterstützung von nutzergesteuerten Identitäten, stabiler Replikation von Inhalten und gemeinschaftsgesteuerter Verwaltung bietet Nostr eine Infrastruktur für dezentrale Bildungsökosysteme, die Inklusion, Zusammenarbeit und kontinuierliche Innovation fördern.
Der Einsatz von Nostr in Bildungskontexten verspricht, Lernende und Lehrende in die Lage zu versetzen, Bildungsinhalte frei von zentralisierten Einschränkungen und externer Zensur zu erstellen, zu teilen und gemeinschaftlich weiterzuentwickeln. Gleichzeitig erfordern die Herausforderungen, die mit der technischen Komplexität, der Schlüsselverwaltung und der inkonsistenten Moderation verbunden sind, kontinuierliche Forschung und die Entwicklung unterstützender Werkzeuge. Wenn diese Probleme durch gezielte Maßnahmen wie benutzerfreundliche Schnittstellen, umfassende Programme für digitale Kompetenz und gemeinschaftsbasierte Governance-Modelle angegangen werden, können die Beteiligten das volle Potenzial von Nostr nutzen, um dezentrale, offene und partizipative Bildungsplattformen zu schaffen, die den Geist von Open Educational Practices wirklich verkörpern.
Letztendlich stellt die Integration von Nostr in dezentralisierte Bildungsplattformen nicht nur eine technische Entwicklung dar, sondern auch einen gesellschaftspolitischen Wandel hin zu größerer Dezentralisierung, Ermächtigung der Nutzer und digitaler Souveränität. Diese Ausrichtung an den Werten des OEP definiert nicht nur die Verbreitung und den Konsum von Bildungsinhalten neu, sondern ist auch Katalysator für breitere Diskussionen über digitale Rechte, Inklusion und ethische Teilhabe an der digitalen Allmende. Das Potenzial solcher Plattformen, kontextrelevante, zensurresistente und kollaborativ kuratierte Bildungsressourcen bereitzustellen, ist ein entscheidender Schritt, um die Zukunft der digitalen Bildung neu zu gestalten.
Fazit
Zusammenfassend lässt sich sagen, dass die innovative Architektur von Nostr, die auf einer kryptografischen Schlüsselverwaltung und dezentralen Relay-Netzwerken basiert, den Grundstein für eine neue Generation von Bildungsplattformen legt, die die Einschränkungen zentralisierter Systeme überwinden können. Ihre Fähigkeit, belastbare, sichere und nutzerzentrierte digitale Umgebungen bereitzustellen, steht in perfektem Einklang mit den Grundsätzen offener Bildungspraktiken und bietet Lehrenden und Lernenden eine noch nie dagewesene Kontrolle über ihre digitalen Interaktionen und Inhalte. Kontinuierliche Forschung, interdisziplinäre Zusammenarbeit und gezielte Bildungsinitiativen werden unerlässlich sein, um dieses Potenzial voll auszuschöpfen und sicherzustellen, dass die Vorteile der Dezentralisierung allen Mitgliedern der Bildungsgemeinschaft zugänglich sind.
Durch den strategischen Einsatz von Nostr-basierten Bildungsplattformen kann die Zukunft des Lernens als ein Bereich neu konzipiert werden, in dem offener Zugang, Autonomie der Lernenden und gemeinschaftsgesteuerte Wissensbildung nicht nur möglich, sondern unvermeidlich sind - eine Zukunft, in der dezentrale Infrastrukturen eine gerechtere, transparentere und partizipativere digitale Bildungslandschaft ermöglichen.
Dieser Beitrag hat daher eine ausführliche Einführung in die technischen und konzeptionellen Grundlagen von Nostr gegeben, die Mechanismen beschrieben, mit denen Nostr Dezentralisierung und Zensurresistenz erreicht, und seine bedeutenden Auswirkungen auf die Zukunft von Bildungsplattformen im Rahmen von Open Educational Practices untersucht. Die Synergie zwischen dem dezentralen Paradigma von Nostr und dem demokratischen, inklusiven Ethos von OEP birgt ein transformatives Versprechen für die Neugestaltung der digitalen Bildung in einer Weise, die Offenheit, Sicherheit und lebenslanges Lernen für eine globale Gemeinschaft fördert.
Indem sie aufkommende dezentralisierte Protokolle wie Nostr als grundlegende Infrastrukturkomponenten von Bildungsplattformen nutzen, können Stakeholder eine ganzheitliche digitale Transformation vorantreiben, die Technologie, Pädagogik und Ethik vereint und ein Paradigma einführt, in dem Bildungsgerechtigkeit und digitale Selbstbestimmung keine Wünsche, sondern realisierte Prinzipien unserer vernetzten Gesellschaft sind.
Verwendete Quellen:
-
Seeing the Politics of Decentralized Social Media Protocols. S Hwang, AX Zhang. ArXiv (2025). <https://doi.org/10.48550/arxiv.2505.22962>
-
Navigating Decentralized Online Social Networks: An Overview of Technical and Societal Challenges in Architectural Choices. Ujun Jeong, L. Ng, K. Carley, Huan Liu. ArXiv (2504). <https://doi.org/10.48550/arxiv.2504.00071>
-
Towards Decentralized Applications. X Ma. 2024. <https://escholarship.org/content/qt0j7044w0/qt0j7044w0_noSplash_c638cdfda170244b9abf750f654399f1.pdf>
-
Decentralized Social Networking Protocol (DSNP) and User Empowerment: An Analysis of Online Identity Ownership, Data Privacy, and Comparative Assessment with Other Decentralized Protocols. M Nay . 2024. <https://dspace.mit.edu/bitstream/handle/1721.1/156782/nay-mnay-meng-eecs-2024-thesis.pdf?sequence=1&isAllowed=y>
-
A Kantian Right to Fediverse Access, or: for a digital enlightenment on the social web. JN Bingemann . <https://philarchive.org/archive/BINAKR>
-
Exploring the Nostr Ecosystem: A Study of Decentralization and Resilience. Yiluo Wei, Gareth Tyson. ArXiv (2402). <https://doi.org/10.48550/arxiv.2402.05709>
-
Money and Trust in Metaverses, Bitcoin and Stablecoins in global social XR. John O'Hare, Allen J. Fairchild, U. Ali. ArXiv (2207). <https://doi.org/10.48550/arxiv.2207.09460>
-
FEDSTR: Money-In AI-Out | A Decentralized Marketplace for Federated Learning and LLM Training on the NOSTR Protocol. Konstantinos E. Nikolakakis, George Chantzialexiou, Dionysis Kalogerias. ArXiv (2024). <https://doi.org/10.48550/arxiv.2404.15834>
-
"Sumud" as Connected Learning: Towards a Collective Digital Commons in Palestine.. H Scott, M Ujvari, AMA Bakeer. 2025. <https://files.eric.ed.gov/fulltext/EJ1464483.pdf>
Erstellt mit Unterstützung von FutureHouse, Perplexity, Deepl, Ideogram und ChatGPT.
-
-
 @ da8b7de1:c0164aee
2025-06-04 16:37:07
@ da8b7de1:c0164aee
2025-06-04 16:37:07Nukleáris politika és szabályozási fejlemények
A Nemzetközi Atomenergia-ügynökség (IAEA) Kormányzótanácsa 2025. június 9-én kezdi meg szokásos júniusi ülését Bécsben. A főbb napirendi pontok között szerepel a 2024-es éves jelentés, a technikai együttműködési tevékenységek, az iráni ellenőrzés és felügyelet, az ellenőrzések végrehajtása Észak-Koreában és Szíriában, a nukleáris biztonság és védelem Ukrajnában, valamint a nukleáris anyagok átruházása és ellenőrzése az AUKUS-keretében. Az ülésen új tagokat is kijelölnek a Kormányzótanácsba, és előkészítik a 69. rendes közgyűlést[iaea.org].
Jelentős projektek és iparági bővülés
Az amerikai Tennessee Valley Authority (TVA) benyújtotta kérelmét az Egyesült Államok Nukleáris Szabályozási Bizottságához egy GE Vernova Hitachi BWRX-300 kis moduláris reaktor (SMR) megépítésére a Clinch River telephelyen, ami jelentős lépés az amerikai fejlett nukleáris technológiák elterjesztésében[world-nuclear-news.org]. Kanadában a hatóság engedélyezte az Ontario Power Generation számára, hogy egy BWRX-300 reaktort építsen a Darlington New Nuclear Project helyszínen, ezzel tovább haladva az észak-amerikai SMR-projektek terén[world-nuclear-news.org].
India nukleáris szabályozója jóváhagyta a négyblokkos Mahi Banswara Rajasthan Atomerőmű telephelyét, Kínában pedig folytatódnak a szerelési munkák a Haiyang 3 egységen. Eközben Belgium és Dánia felülvizsgálják nukleáris politikájukat: Belgium visszavonja a korábbi leállítási döntést, Dánia pedig újragondolja álláspontját[world-nuclear-news.org].
Ellátási lánc, munkaerő és nemzetközi együttműködés
A nukleáris kapacitás várható gyors növekedése miatt egyre nagyobb hangsúly kerül mind a helyi, mind a globális ellátási lánc felkészítésére. A World Nuclear Association legutóbbi konferenciája kiemelte az ellátási lánc „globalizációjának” fontosságát a bővülés támogatásához[world-nuclear-news.org]. A nukleáris munkaerő világszerte növekedni fog, ami új lehetőségeket teremt, nem pedig hiányt. Az iparági szakértők hangsúlyozzák a jelentkezők tapasztalatának javítását és a szektorok közötti készségek hasznosítását a jövőbeni igények kielégítésére[world-nuclear-news.org].
A nemzetközi szabályozói együttműködés is fejlődik, különösen a kis moduláris reaktorok (SMR) tervezési értékelése terén. A brit Nukleáris Szabályozási Hivatal közzétette első jelentését ebben a témában, globális szinten hatékonyabb és összehangoltabb megközelítést célozva[world-nuclear-news.org].
Gazdasági és befektetési trendek
A nukleáris szektorban újra optimizmus tapasztalható, egészséges projektportfóliókkal és növekvő magánbefektetésekkel, különösen a fejlett üzemanyagok, például a HALEU (magas dúsítású urán) terén. A Világbank lehetséges politikai váltása, amely lehetővé tenné nukleáris projektek finanszírozását, jelentős hatással lehet a globális befektetésekre, példát mutatva más hitelezőknek is[ans.org].
Az USA-ban jelentős lépés a Prohibiting Russian Uranium Imports Act életbe lépése, amely megtiltja a feldolgozatlan, alacsony dúsítású orosz urán behozatalát, és 2,72 milliárd dollár szövetségi támogatást szabadít fel a hazai urántermelés fellendítésére. A törvény 2027-ig korlátozott mentességeket engedélyez, 2040-ben pedig lejár[ans.org].
Technológia és innováció
A TerraPower hivatalosan is jelezte a brit hatóságoknak, hogy megkezdi a Natrium nátrium-hűtésű gyorsreaktor általános tervezési engedélyezési folyamatát, ezzel jelezve, hogy a vállalat nemzetközi szinten is be kívánja vezetni ezt a technológiát[world-nuclear-news.org]. Olaszországban új nemzeti bizottság alakult a radioaktív anyagok szállításával kapcsolatos kihívások kezelésére, a megfelelőség és a logisztika egyszerűsítése érdekében[world-nuclear-news.org].
Az Enel, az Ansaldo Energia és a Leonardo megalapította a Nuclitalia céget, hogy tanulmányozza a fejlett nukleáris technológiákat és elemezze a piaci lehetőségeket, ami jól mutatja az európai érdeklődés növekedését a következő generációs nukleáris megoldások iránt[world-nuclear-news.org].
Friss és közelgő események
- Az IAEA Kormányzótanácsának ülése (2025. június 9–13.) számos politikai, biztonsági és védelmi kérdéssel foglalkozik majd[iaea.org].
- Az amerikai Fehér Ház nemrégiben csúcstalálkozót tartott a hazai nukleáris fejlesztésekről, és elindította a legnagyobb szövetségi kezdeményezést az elmúlt ötven évben a hálózati méretű nukleáris reaktorok felgyorsított építésére[ans.org].
Források: - world-nuclear-news.org - iaea.org - ans.org - nucnet.org
-
 @ d9a329af:bef580d7
2025-06-04 18:09:31
@ d9a329af:bef580d7
2025-06-04 18:09:31This one is rather straightforward today, as I wanted to write something on the software I personally use in my day-to-day musical composition deal, depending on what needs to be done. I want to go a little in depth in this regard, so bear with me on this one.
For the first stop on this libreware-riddled pilgramage, the operating system.
There are two I'll be mentioning: one for beginners, and the one I use on a day-to-day basis (my daily driver).
- Linux Mint
- Fun Fact: This was my longest-running daily driver for a while (over a year or two and some change) before I switched to my current one (based upon Arch, an advanced distro)
- Beginner friendly (based upon Ubuntu, Debian if using LMDE)
- Usually works OOTB when it's set up for music production (with some exceptions on some software)
- Versatile multimedia distribution (gaming, music, art, creative writing, etc.)
- Software is old, but the distro is rock-solid.
Linux Mint... the classic choice for a popular distro aimed at GNU/Linux beginners. It's the most popular of them all, especially when it comes to Snap-free protest distros (Pop_OS! is another one that's Snap-free), and the most popular in general. It's a general-purpose OS aimed at easing beginners into Linux, and the wider FLOSS community (FLOSS is an acronym for Free/Libre Open-Source Software) of software made available using licensed like GPL, MIT, MPL, Apache-2, BSD, WTFPL, and many more of the like.
I would personally recommend the Debian Edition (LMDE) and use the Debian Testing repositories if you want up-to-date software, and not bleeding edge for APT (the package manager in Debian and Ubuntu). It will be much easier to learn how to add software repositories with a couple commands in the terminal that way, and this knowledge will transcend if you decide to move to vanilla Debian. However, if you want the Cinnamon Desktop Environment, Linux Mint is a good choice, as its developers are behind Cinnamon (It has the looks of Windows Vista, which is why it's so familiar for those switching from Windows). However, there isn't too much software in the Mint, Debian and Ubuntu repos, which is a bummer (you can just find community-maintained repos or build software from source if you have the know-how).
- CachyOS
- Fun Fact: It's my current daily driver (if you couldn't tell by now).
- Arch-based distribution focused on content creation (vibe emanation as some Nostriches call it), gaming and other multimedia work
- Optimized repositories depending on the CPU architecture family (I have V3 repos enabled, since I use a CPU that supports V3)
- Bleeding edge of software packaging
- Packages (both official and community maintained) out the wazoo (80k+ packages in the AUR [Arch User Repository], with some AUR packages in binary form thanks to the Chaotic AUR repo)
CachyOS... the gamer's Arch that even beats out the likes of EndeavourOS and Garuda Linux (both Arch-based gaming distros). This is thanks in part to the optimizations made to vanilla Arch (especially the optimized repositories based upon what CPU you have installed) among many other things done to it under the hood. However, while it is fantastic for gaming, the other multimedia performances are quite a sight to behold, especially since anybody worth their salt is using almost exclusively FLOSS to make things easier for yourself to escape the grasp of incompetent fools that we call politicians. Using Linux, FLOSS and GrapheneOS (the only acceptable AOSP ROM) will help you kickstart your journey to privacy, security and proper OPSEC protocols so you don't get sucked into the proprietary software matrix (which I explained in this article).
As a Linux user with almost 5 years of experience, it's hard for me to go back to proprietary stuff. After all, with the advancement in weaponized and centralized AI on the rise, I wanted to seriously get myself out of that (which is why I used almost exclusively FLOSS for the past 4+ years). Enough about that already, let's get into the software required for you to make music... oh wait, I'm talking about myself here. Whoops....
Now that the operating system is out of the way, let's get into the actual software I use to make music:
- Ardour (DAW)
- x42 Plugins (General Purpose Plugin Suite)
- LSP PLugins (General Purpose Plugin Suite)
- Sfizz (SFZ player)
- Dragonfly Reverb (Reverberation Plugin Suite)
- DeBess (Airwindows De-Esser)
- Noise Repellant (Noise Gate)
- Guitarix and GX Plugins (Guitar Pedalboard Simulation)
- Vital (Synth Plugin)
- Surge XT (Synth Plugin) [Unused]
- EQ10Q (No longer usable)
- CALF Plugins (No Longer Usable)
- DSK SF2 (I used this due to ACE Fluid Synth acting like a turd)
- DR-84 (Proprietary Drum Machine Plugin [Winblows])
These are the primary pieces of software that I use to make music on Linux, with the description as shown above. This article would be too long anyway if I were to explain them, so I'll leave that here.
-
 @ a3c6f928:d45494fb
2025-06-04 15:57:36
@ a3c6f928:d45494fb
2025-06-04 15:57:36Perfectionism wears many disguises—high standards, ambition, responsibility—but at its core, it’s a fear of not being enough. It convinces us that worth is earned by flawless performance, constant output, and meeting every expectation. But perfection is a prison, and real freedom begins when we choose progress over pressure.
The Weight of Perfection
Perfectionism doesn't protect us—it paralyzes us. It:
Delays action out of fear of mistakes
Fuels anxiety, self-criticism, and burnout
Makes success feel fleeting, because nothing ever feels "good enough"
Creates a cycle of comparison and shame
Why We Chase Perfect
Many of us were taught that being excellent = being lovable. So we equate flaws with failure. But chasing perfect is like running a race with no finish line—you’re never allowed to rest, celebrate, or simply be.
Signs You’re Caught in the Trap
You procrastinate because you’re afraid to do it “wrong”
You obsess over details at the expense of joy or time
You struggle to feel proud—even when you achieve something
You avoid trying new things unless you’re sure you’ll succeed
Breaking Free from the Illusion
-
Redefine Success: Replace “perfect” with “done is better than perfect.” Focus on growth.
-
Celebrate Small Wins: Let progress be enough. Every step forward counts.
-
Welcome Mistakes: They are proof you’re learning, growing, and showing up.
-
Be Gentle with Yourself: Speak to yourself like someone you love.
-
Let Real Be Enough: Authenticity is far more powerful than polish.
Why It Matters
Perfectionism may look like strength, but vulnerability is where our real power lies. When we let go of needing to be perfect, we finally become free to be real—to take risks, make art, love fully, and live without constant self-editing.
“You don't have to be perfect to be worthy. You just have to be you.”
Choose progress. Show up imperfectly. That’s where freedom lives.
-
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ eb0157af:77ab6c55
2025-06-04 19:02:32
@ eb0157af:77ab6c55
2025-06-04 19:02:32Bitmain’s new device raises the bar for energy efficiency.
During the World Digital Mining Summit, Bitmain introduced its latest bitcoin mining device: the Antminer S23 Hydro. The new miner promises an energy efficiency of 9.5 joules per terahash (J/TH), setting new industry standards.
 ANTMINER S23 Hyd. Newly Launched at WDMS 2025!
ANTMINER S23 Hyd. Newly Launched at WDMS 2025!
 580T 9.5J/T
580T 9.5J/T
Sales Start from May 28th, 9:00AM (EST)
Shipping from Q1, 2026 pic.twitter.com/Kg3VJTt7Rg— BITMAIN (@BITMAINtech) May 27, 2025
According to Bitmain’s presentation, the Antminer S23 Hydro delivers up to 580 TH/s with a power consumption of 5,510 watts.
Scheduled for release in early 2026, the Antminer S23 Hydro marks a major leap forward compared to the first ASIC devices dedicated to mining. To put it in perspective, the first specialized miners launched in 2013 consumed around 1,200 J/TH. Bitmain’s latest device therefore represents a more than 99% improvement in efficiency.
Hashprice and economic challenges
In recent months, the hashprice — the metric measuring mining profitability — has remained relatively low, dropping below $39 per petahash per second during the year. As of now, the hashprice stands at around $55 per petahash per second, according to data from Hashrate Index.
This scenario has pushed several companies in the sector to rethink their expansion strategies. Instead of increasing hashing capacity, many are choosing to upgrade their existing fleets, focusing on efficiency rather than sheer scale.
The introduction of the Antminer S23 Hydro could catalyze a transformation within the mining ecosystem. The gradual replacement of outdated devices with more efficient technology could lead to a significant reduction in the Bitcoin network’s overall energy consumption.
The post Bitmain unveils the Antminer S23 Hydro: unprecedented efficiency appeared first on Atlas21.
-
 @ 04c915da:3dfbecc9
2025-03-10 23:31:30
@ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 04c915da:3dfbecc9
2025-03-07 00:26:37
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ cae03c48:2a7d6671
2025-06-04 19:01:51
@ cae03c48:2a7d6671
2025-06-04 19:01:51Bitcoin Magazine

Norwegian Public Company K33 AB Purchased 10 BTC For Their New Bitcoin Treasury StrategyK33 AB (PUBL), a digital asset brokerage and research firm, announced that it has completed its first Bitcoin acquisition under its new Bitcoin treasury strategy, purchasing 10 BTC for approximately SEK 10 million.
JUST IN:
 Publicly traded company K33 buys 10 #Bitcoin for SEK 10 million for its balance sheet. pic.twitter.com/wB8Kt09EZf
Publicly traded company K33 buys 10 #Bitcoin for SEK 10 million for its balance sheet. pic.twitter.com/wB8Kt09EZf— Bitcoin Magazine (@BitcoinMagazine) June 3, 2025
Today’s purchase is the first transaction of the secured SEK 60 million that K33 announced it will buy for its Bitcoin treasury strategy.
“We expect Bitcoin to be the best-performing asset in the coming years and will build our balance sheet in Bitcoin moving forward,” said the CEO of K33 Torbjorn Bull Jenssen. “This will give K33 direct exposure to the Bitcoin price and help unlock powerful synergies with our brokerage operation. Our ambition is to build a balance of at least 1000 BTC over time and then scale from there.”
During K33’s Q1 2025 Report & Strategic Outlook presentation. Torbjorn Jenssen mentioned that the “US BTC ETF was the most successful ETF launch in history. Acquiring more capital in just one year than gold did in 20.”
Jenssen also said K33 is working with other Bitcoin treasury companies in the Nordics and hopes to use its treasury as a foundation to offer new services, such as Bitcoin backed lending.
“For K33, Bitcoin is not only a high-conviction asset — it’s also a strategic enabler,” he said. “With a sizable BTC reserve, we will be able to strengthen our financial position while unlocking new revenue streams, product capabilities, and partnerships.”
Bitcoin will be the best performing asset in the coming decade and my goal with K33 is to accumulate as many as possible while unlocking powerful operational synergies with our brokerage operation,” posted Jenssen on X.
Bitcoin will be the best performing asset in the coming decade and my goal with K33 is to accumulate as many as possible while unlocking powerful operational synergies with our brokerage operation. https://t.co/Crxu0b5QPz
— Torbjørn (@TorbjrnBullJens) May 28, 2025
Bitcoin treasury holdings are becoming a trend of companies in 2025. Around 217 companies and public entities now hold Bitcoin on their balance sheets.
Last week, during the 2025 Bitcoin Conference in Las Vegas, the CEO of GameStop Ryan Cohen announced that GameStop purchased 4,710 Bitcoin worth approximately $505 million, marking another major corporate entry into Bitcoin treasury holdings.
In an interview with the CEO of Nakamoto David Bailey, the CEO of GameStop Ryan Cohen stated, “If the thesis is correct then Bitcoin and gold as well can be a hedge against global currency devaluation and systemic risk. Bitcoin has certain unique advantages better than gold.”
BREAKING:
 GAMESTOP PURCHASED 4,710 #BITCOIN pic.twitter.com/fDH9ctZJVP
GAMESTOP PURCHASED 4,710 #BITCOIN pic.twitter.com/fDH9ctZJVP— Bitcoin Magazine (@BitcoinMagazine) May 28, 2025
This post Norwegian Public Company K33 AB Purchased 10 BTC For Their New Bitcoin Treasury Strategy first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 6316050a:a5e43cbe
2025-06-04 14:24:01
@ 6316050a:a5e43cbe
2025-06-04 14:24:01Contexto
En el Grupo de Teoría y Simulación en Materia Blanda estudiamos sistemas poliméricos, interfaces y sistemas coloidales a escala nanoscópica. Estos pueden estar en equilibrio o presentar flujo de partículas o calor y son de interés en ciencia básica y aplicada en campos como micro y nano-fluídica, aplicaciones a transferencia de calor y máquinas moleculares. Una característica central es que la temperatura juega un rol importante y existe una competencia entre entropía y energía. Esto suele dar lugar a transiciones de fases u otros cambios cualitativos del comportamiento del sistema.
Herramientas
Usamos simulación computacional y herramientas teóricas, con énfasis en conceptos de mecánica estadística, que permiten estudiar variados sistemas en diferentes situaciones físicas. Estudiamos a estos sistemas en condiciones de equilibrio termodinámico o también cómo es su comportamiento cuando se inducen flujos o se los somete a campos externos. (fuera de equilibrio)
Proponemos el siguiente tema de Tesis de Licenciatura en física
Simulación de transferencia de calor en nanocanales con paredes modificadas por polímeros

 Izquierda: Nano- con una interfaz líquido vapor canal y un flujo estacionario de calor, provocado por la diferencia de temperatura de las paredes. Derecha: Puente de líquido inducido por la presencia de polímeros semi-flexibles. Ambas imágenes obtenidas de simulaciones de dinámica molecular.
Izquierda: Nano- con una interfaz líquido vapor canal y un flujo estacionario de calor, provocado por la diferencia de temperatura de las paredes. Derecha: Puente de líquido inducido por la presencia de polímeros semi-flexibles. Ambas imágenes obtenidas de simulaciones de dinámica molecular. Los fenómenos de transferencia de calor tienen una gran importancia en un amplísimo rango de aplicaciones como los procesos de generación y conversión de energía y son cruciales para el enfriamiento de motores y dispositivos electrónicos. Estas aplicaciones requerirán en el futuro un funcionamiento a mayor densidad de energía, y por lo tanto, mayor generación de calor, que deberá ser removido más eficientemente. En particular, los fenómenos de cambio de fases, como la ebullición nucleada, tienen aplicaciones en plantas de potencia eléctrica, desalinización térmica, enfriamiento de chips electrónicos y recuperación de calor desechado, entre muchas otras. Uno de los desafíos más importantes para continuar la reducción de tamaño de los dispositivos electrónicos es aumentar su densidad de potencia de operación y para ello se debe lograr una extracción eficiente del calor generado. La transferencia de calor es relevante también en aplicaciones a escalas espaciales mayores, como en la generación de energía eléctrica en centrales térmicas y nucleares. En las centrales nucleares de generación IV es necesario aumentar el calor transportado por unidad de tiempo y mejorar la eficiencia de los intercambiadores de calor. Estos procesos de transporte térmico distan de comprenderse a nivel básico, porque tienen una gran complejidad en tanto que son fenómenos fuera de equilibrio con cambios de fases.
Se propone estudiar la transferencia de calor en un nanocanal que presenta una interfaz líquido-vapor.
Estudiaremos los detalles de cómo cambian con el tiempo las características de la evaporación de una interfaz y las propiedades térmicas cuando se modifica la pared con polímeros u otras moléculas en el seno del líquido. Analizaremos también la rectificación del flujo de calor, pensando al nano-canal como un diodo térmico. Realizaremos simulaciones de dinámica molecular en clusters de supercómputo para estudiar estos sistemas en distintas condiciones físicas. Si tienen interés en tener más detalles, no duden en contactarnos.Contacto: Claudio Pastorino (claudiopastorino .... cnea.gob.ar ; IG, X: @clopasto; Nostr: @clopasto
¿Qué se aprenderá en esta Tesis principalmente?
Estas línea de trabajo es teórico-numérica , con una parte importante de simulación computacional. Involucra principalmente conceptos de: * Mecánica estadística (Física Teórica 3 en DF-UBA), * Materia condensada en general y materia blanda. * Fundamentos y uso de simulación computacional: Dinámica Molecular, Dissipative Particle Dynamics y/o Monte Carlo, * No se requieren conocimientos previos de computación, pero sí interés en el uso y creación de programas, para plantear y calcular propiedades de los sistemas físicos. * Se trabajará con * Linux, Python, Bash, Awk. * Clusters de super-cómputo, High Performance Computing. * Herramientas de posprocesamiento.
Referencias
- Heat flow through a liquid–vapor interface in a nano-channel: the effect of end-grafting polymers on a wall , Claudio Pastorino, Ignacio Urrutia, María Fiora y Federico Condado, J. Phys. Cond. Matt. 34:344004
- Boiling and quenching heat transfer advancement by nanoscale surface modification Hu, Xu, Cheng, Zhao, Ziegler and Chung. Scientific Reports 7:6117 (2017)
-
 @ cae03c48:2a7d6671
2025-06-04 19:01:40
@ cae03c48:2a7d6671
2025-06-04 19:01:40Bitcoin Magazine

Canadian Company SolarBank Adopts Bitcoin Treasury StrategyToday, SolarBank Corporation (NASDAQ: SUUN), a leader in distributed solar energy, battery storage, and clean energy infrastructure across North America, has announced the integration of Bitcoin as a strategic reserve asset into its corporate treasury strategy, following the footsteps of MicroStrategy and SharpLink Gaming.
SolarBank has also applied to open an institutional account with Coinbase Prime (NASDAQ: COIN), enabling secure Bitcoin custody, USDC services, and a self-custodial wallet for its Bitcoin holdings.
JUST IN: North American construction engineering company SolarBank adopts a Strategic Bitcoin Reserve
 pic.twitter.com/b2xvVARjZZ
pic.twitter.com/b2xvVARjZZ— Bitcoin Magazine (@BitcoinMagazine) June 3, 2025
The company cited several strategic advantages for adopting Bitcoin as a reserve asset:
- Financial Resilience: Bitcoin holdings will serve as a hedge against inflation and currency debasement.
- Clean Energy Off-set: Emissions tied to Bitcoin mining will be counterbalanced by SolarBank’s renewable energy generation.
- Market Appeal: The move targets tech-savvy investors interested in digital assets, DeFi, and blockchain.
- Competitive Differentiation: SolarBank aims to differentiate itself as a first-mover in combining renewable energy with Web3 and DeFi principles.
“As the adoption of Bitcoin continues to grow, SolarBank believes that establishing a Bitcoin treasury strategy taps into a growing sector that is seeing increasing adoption,” commented Dr. Richard Lu. “In a world of ever-increasing energy demand and treasury complexity, SolarBank delivers renewable energy solutions and recurring revenues, now combined with all of the benefits of holding Bitcoin.”
SolarBank further emphasized that its core focus remains on renewable energy development, highlighting several recent achievements:
- A $100 million U.S. solar deal with CIM Group targeting 97 MW of projects.
- A $49.5 million agreement with Qcells to deploy US made solar technology.
- A $41 million partnership with Honeywell to develop landfill-based solar farms.
- A $25 million credit facility from RBC to expand its battery energy storage portfolio.
With over 1 GW of projects in development and partnerships with Fortune 500 companies, SolarBank continues to generate recurring revenues through long-term contracts while accelerating decarbonization efforts.
“The actual timing and value of Bitcoin purchases, under the allocation strategy will be determined by management,” stated the company in the press release. “Purchases will also depend on several factors, including, among others, general market and business conditions, the trading price of Bitcoin and the anticipated cash needs of SolarBank. The allocation strategy may be suspended, discontinued or modified at any time for any reason. As of the date of this press release, no Bitcoin purchases have been made.”
This post Canadian Company SolarBank Adopts Bitcoin Treasury Strategy first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 000002de:c05780a7
2025-06-04 17:09:47
@ 000002de:c05780a7
2025-06-04 17:09:47I know most of you aren't doing this but I hope this is helpful when talking to your friends and family about bitcoin. Specifically if they bring up Orange Man or have real issues with him.
First off we can see that most of the MAGA / Political Bitcoin cheer-leading is exclusively SoV/NGU and not freedom money. Its basically the crypto types. The shitcoiners. The scammers. I get why this will turn off people that don't love the orange man. I recently heard a technical podcaster say he didn't like being associated with bitcoin (though he said crypto and his co-host is a bitcoin only guy...). I'm here to tell you that's dumb.
Why? I know how dumb it is by experience. Back in the day I was a kid listening to Rush Limbaugh and he was destroying the sky is falling claims I was hearing in government schools. I used to come home freaking out about global warming and the destruction of the rain forests. This was in the 90s btw. Looking back on what Limbaugh said, he's been proven largely right. But that isn't my point. My point is that because of this and because of how dumb many of the environmentalists takes were, I ignored many environmental issues. I would turn off people that called themselves environmentalists. This was a mistake. I was ignoring many other problems with how we use resources and used weak reasoning on others. I seeded caring for the environment to the left. I let myself be sidelined by reactionary thinking.
A few years ago I learned about the Permaculture[^1] way of thinking and it kinda blew my mind. A guy named Jack Spirko said something that stuck with me. Everyone should be an environmentalist. At least to the extent that they care about the planet we all share. Of course we all know this but it flipped a switch in my head. I'd allowed myself to be a reactionary on the environment and harm humans do to the air, water, and soil as well as the creatures. I always cared about these things but it too a dude that I aligned with on many topics to snap me out of my programming.
I think a similar thing can happen with Bitcoin. Don't be reactionary. Just because some people you don't align with or like do like a thing... it doesn't mean that thing is bad. They could be representing it incorrectly. Bitcoin, if it truly is money is apolitical. Now, we can get into economics and dive into the deep end about hard money but the fact is that bitcoin shouldn't really be political in the sense of US politics on the ground. If you are just a voter or pleb you should be adopting bitcoin no matter what any politician says. The republicans and democrats are not that different on many topics and the MAGA movement is just pandering. Don't let the Orange Man turn you off from bitcoin. Don't let the number go up people turn you off. There are people living under oppressive regimes all over the globe that can be helped by bitcoin. We may need it in the US. Don't sleep on this because of a clown. Don't be dumb. Its a great way to stay poor and vulnerable.
[^1]: Permaculture is an ethical design science that uses natural systems to provide all human and ecological needs in a regenerative way.
https://stacker.news/items/997169
-
 @ 04c915da:3dfbecc9
2025-03-04 17:00:18
@ 04c915da:3dfbecc9
2025-03-04 17:00:18This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 0861144c:e68a1caf
2025-06-04 13:54:37
@ 0861144c:e68a1caf
2025-06-04 13:54:37The last Empire: the Final Days of the Soviet Union
Serhii Plokhy clearly writes from a Ukrainian perspective, but at no point does he allow his bias to interfere with an extensive and compelling documentation, filled with transcripts and official documents from both the Soviet and American sides—documents involving actors who transitioned from the final days of the Soviet Union to the formation of the new Russian Federation.
I discovered this book through a Lex Fridman podcast, where the author gives a review of the Russian-Ukrainian conflict, explaining in rich detail the events experienced between both nations. I won’t say that what’s happening in this region is easy to understand, and yet, after reading this book, I have no doubt that all of this was foreseeable.
Here are some things I’ve learned from the book—without giving away spoilers or going too deep:
The United States opposed the disintegration of the Soviet Union until the very last hours
Contrary to popular belief and Reagan’s lofty slogans about the Evil Empire, the advisers of President George H. W. Bush—except for Dick Cheney and his inner circle—were against the dissolution and extinction of the Soviet Union. There were two simple reasons: nuclear power and nationalism.
Over the years, the USSR produced tons of nuclear arsenal, and if the country were to dissolve, advisers on both sides predicted a “nuclear Yugoslavia,” referring to the imminent conflicts in that region. The other reason was strategic: it’s easier to deal with one large country than with many separate republics sharing similar ethnic backgrounds. After reading this book, the Balkan Wars seem even more closely tied to the consequences of the Soviet breakup. You’ll draw your own conclusions when you read it.
The Cold War is in pause mode
In some movie I once heard the phrase, The war doesn’t end until both sides declare it over; while it’s true that Gorbachev resigned on December 25 and made way for the Russian Federation, he never officially ended the geopolitical maneuvers. Meanwhile, George Bush gave a speech declaring that they had “won the Cold War.”
Anyway. Have you read anything similar to this?
https://stacker.news/items/997003
-
 @ 8d34bd24:414be32b
2025-06-04 13:21:20
@ 8d34bd24:414be32b
2025-06-04 13:21:20It is hard going through difficult situations. Health problems, family problems, financial problems, feeling alone, feeling stuck in the wrong place, and persecution are all situations that Christians regularly find themselves. The question is “How will we respond to pain?”
Advice for the Suffering
Some Christians pull away from God when it feels like everything is going wrong. They think God doesn’t care or can’t fix things. They resent every minute of pain and accuse God of wrongdoing. Even Job, who fell on his face in worship after losing everything had a moment of weakness.
“Oh that my grief were actually weighed\ And laid in the balances together with my calamity!\ For then it would be heavier than the sand of the seas;\ Therefore my words have been rash.” (Job 6:2-3) {emphasis mine}
After a moment of doubt, he did, however, repent of his rash words, as should we all.
Job should be an example to us all in dealing with pain and difficult situations. This is the verse that inspired this post.
But it is still my consolation,\ And I rejoice in unsparing pain,\ That I have not denied the words of the Holy One. \ (Job 6:10) {emphasis mine}
What an example! “I rejoice in unsparing pain.” When we trust God so much that we can rejoice in unsparing pain, we are trusting God as we should. We are accepting that God is working good in our life and we can trust Him even when nothing makes sense to us.
I also love how he says that his consolation is that “I have not denied the words of the Holy One.” Job is hurting terribly. His heart is broken. He is destitute. He lost 8 children in one day. His friends, that came to console him, have instead accused him of wrongdoing. He doesn’t understand what God is doing and why, but he has “NOT denied the words of the Holy One.” He is still putting his faith in God and his word. He is still submitting to God when he feels mistreated. He is still trusting \ God, even when he doesn’t understand what God is doing and why so many bad things are raining down on him in a torrent. Despite it all, he refuses to deny God. I hope if I am ever put through similar situations, that I can trust God and not deny His goodness.
Advice for friends
The book of Job, in addition to advice to those who are suffering, also gives advice to friends of those who are suffering. (or maybe more accurately, what not to do)
Job’s friends came with the intention to encourage and console Job. Every time Job would confess his thoughts, concerns, and questions, the response by his friends would get harsher and harsher. In the beginning they were gentle corrections, but they quickly escalated to accusing Job of great sins, that they had to know were not true, and blaming Job for every hard thing that had happened to him.
I’ve talked to other Christians who have confessed to being dragged down by other Christians who would tell them that every difficult thing that happened to them was due to their sin or lack of faith. In the case of Job, his difficulties were due to his faithfulness, in order to prove to Satan and all of history that a faithful man would stay faithful to God in good times and in bad.
Can Christians suffer as a consequence of sins and poor decisions? Of course, but there are many times that the faithful suffer. In Scripture, the people who suffered most were frequently the most faithful.
Job’s correction of his friends was accurate.
“For the despairing man there should be kindness from his friend;\ So that he does not forsake the fear of the Almighty.\ My brothers have acted deceitfully like a wadi,\ Like the torrents of wadis which vanish, (Job 6:14-15)
For those who don’t know, a wadi is a streambed that has water running in the wet season, but is bone dry during the dry season. Job accused his friends of being encouraging and helpful when he was prospering, then showing up and providing no encouragement or help when he needed it most. He thought refreshment was coming to visit, and instead what hope he had left was drained from him by his “friends.”
We need to make sure we aren’t one of those who decreases hope and decreases faith in one who is hurting. We need to have mercy when a hurting person works through their confusion and doubts and help lead them back to God instead of driving a wedge between them and God.
May the God of heaven protect us and lead us through the trials of life and may our trials lead us into the arms of our Savior. May God help us to merciful and to help guide the hurting into the Savior’s care.
Trust Jesus
-
 @ 04c915da:3dfbecc9
2025-02-25 03:55:08
@ 04c915da:3dfbecc9
2025-02-25 03:55:08Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 9ca447d2:fbf5a36d
2025-06-04 18:02:28
@ 9ca447d2:fbf5a36d
2025-06-04 18:02:285/27/2025, Las Vegas, NV — Sati, a Bitcoin payments app and Lightning infrastructure provider, today announced the launch of its Lightning integration with Xverse, a Bitcoin wallet used by over 1.5 million people worldwide.
Thanks to the integration, Xverse users can now send and receive sats (bitcoin’s smallest denomination) instantly over the Lightning Network with no setup, no app switching, and no custodial risk.
Initially designed in 2017, the Lightning Network has grown to become Bitcoin’s leading layer-2, with a current BTC capacity of over $465M.
Sati is now leveraging this technology to bring the world’s favorite digital currency into the pockets of 3 billion users worldwide, thanks to its powerful API integration with WhatsApp.
“Bitcoin was not meant to be an asset for Wall Street—it was built for peer-to-peer money, borderless and accessible,” said Felipe Servin, Founder and CEO of Sati.
“Integrating Lightning natively into Xverse brings that vision back to life, making Bitcoin usable at scale for billions.”
Thanks to the integration, every Xverse user now gets a Lightning Address instantly.
That means they can receive tips, pay invoices, and use Bitcoin for microtransactions—all without having to manage channels or switch between different apps.
Sati expects USDT on Lightning to be supported as early as Q3 for the Xverse wallet and in July 2025 for users accessing Sati through WhatsApp.
This integration positions Sati’s role as a Lightning infrastructure provider, not just a consumer app.
By leveraging its API-based solution, the company provides plug-and-play backend services to wallets and platforms looking to add Bitcoin payments without compromising on security or UX.
The Xverse launch follows the debut of Parasite Pool, a new mining pool leveraging Sati and Xverse’s tech stack and focused on democratizing Bitcoin mining.
Parasite Pool charges 0% fees and pays out instantly over Lightning, making it ideal for small-scale miners, especially those running ultra-low-power hardware like Bitaxe.
With over 500 users joining Parasite Pool within weeks of launch and an average pool hashrate of 5 PH/s, Parasite Pool is steadily growing its presence in the home mining space.
Thanks to the Lightning integration, Parasite Pool supports the smallest Lightning payouts in the industry (a fraction of a cent), lowering the barrier to entry for anyone interested in mining.
Sati recently closed a $600K pre-seed round backed by Bitcoin-focused investors, including Draper Associates, BitcoinFi, Arcanum, BoostVC, and Ricardo Salinas.
The funding is being used to support global expansion, stablecoin integration, Lightning infrastructure growth, and broader access to Bitcoin in emerging markets.
Sati will be conducting live product demos at Bitcoin 2025 in Las Vegas on May 27-29. To learn more about Sati, visit sati.pro
Press Contact
press@sati.proAbout Sati
Sati is a Bitcoin payments infrastructure provider. Launched in 2025 with investors of the likes as Draper Associates and Ricardo Salinas, Sati powers fast, seamless Bitcoin payments on applications such as WhatsApp to fuel the next wave of adoption. Learn more at sati.pro
About Xverse
Xverse is the on-chain platform for the Bitcoin economy—think Revolut meets Alchemy, built natively on Bitcoin. Trusted by over 1.5 million users, Xverse is launching a unified portfolio platform for Bitcoin L1 and Layer 2s, alongside developer infrastructure to power seamless Bitcoin-native apps.
-
 @ f85b9c2c:d190bcff
2025-06-04 11:37:50
@ f85b9c2c:d190bcff
2025-06-04 11:37:50Airdrops have gained immense popularity in the world of cryptocurrency. They’re not just a trend; they play a crucial role in the crypto community. To truly grasp their importance, let’s dive into the fascinating world of airdrops.This article aims to give you a thorough and easy-to-follow insight into airdrops, so you can appreciate their significance. Whether you’re new to crypto or an experienced investor, understanding airdrops necessary.
What is an Airdrop? An airdrop, in the context of cryptocurrencies, refers to the distribution of free tokens or digital assets to a select group of individuals or cryptocurrency wallet holders.Airdrops typically do not require participants to invest any money. Instead, they are often used as a promotional tool, a means of distributing tokens to a wider audience or as a reward for holding a specific cryptocurrency. Airdrops can vary in scale from small-scale distributions to massive giveaways involving millions of tokens.These objectives can range from increasing brand awareness and attracting new users to rewarding loyal community members and building a decentralized network.
The Purpose of Airdrops Airdrops serve a variety of purposes within the cryptocurrency space, each with its own unique objectives and benefits. Understanding these purposes is essential for comprehending the motivations behind airdrop campaigns: 1. Promotion and Marketing: Airdrops are often used as a marketing tool to promote a new cryptocurrency project or token. By distributing free tokens to a wide audience, the project gains visibility and attracts potential users and investors. 2. Community Building: Airdrops can be instrumental in building and nurturing a loyal community around a cryptocurrency project. When tokens are distributed to existing token holders or active users, it fosters a sense of belonging and loyalty among participants. 3. Decentralization: Some blockchain projects use airdrops as a means to distribute tokens and decentralize ownership. By distributing tokens widely, projects aim to prevent a concentration of wealth and influence in the hands of a few. 4. User Engagement: Airdrops can encourage user engagement and participation within a blockchain ecosystem. They often come with certain conditions, such as holding a minimum amount of tokens or participating in specific activities, which incentivize users to become more active within the community. 5. Network Upgrades: As mentioned earlier, airdrops are frequently employed to distribute tokens created after a blockchain network upgrade. This ensures that existing token holders receive an equivalent amount of the new tokens, maintaining their stake in the network.
Types of Airdrops Airdrops come in various forms, each tailored to achieve specific goals. Here are some common types of airdrops: 1. Hard Fork Airdrops: These airdrops occur when a blockchain undergoes a hard fork, resulting in the creation of a new cryptocurrency. Holders of the original cryptocurrency receive a proportional amount of the new tokens. Bitcoin Cash (BCH) is a prime example of a hard fork airdrop. 2. Snapshot Airdrops: In a snapshot airdrop, a blockchain project takes snapshot of its blockchain at a specific block height. Anyone holding the cryptocurrency at that moment receives a set number of airdropped tokens. This type of airdrop is common in projects seeking to reward loyal users. 4. Holder Airdrops: Holder airdrops reward existing token holders based on the number of tokens they possess in their wallets. The more tokens held, the more airdropped tokens a user receives. 5. Referral Airdrops: Referral airdrops encourage users to refer others to a project or platform. Participants receive tokens when their referrals join and take certain actions. 6. Staking Airdrops: Staking airdrops are designed to incentivize token holders to lock up or stake their tokens in a platform’s network. In return, they receive additional tokens as rewards. 7. Community Airdrops: These airdrops target active members of a project’s community, including contributors, moderators, or those engaged in specific activities within the ecosystem.
Participating in Airdrops Participating in airdrops can be a straightforward process, but it often involves certain prerequisites and steps: 1. Wallet Requirements: To receive airdropped tokens, you typically need a compatible cryptocurrency wallet. Ensure your wallet supports the specific blockchain or token associated with the airdrop. 2. Awareness: Stay informed about upcoming airdrops by following cryptocurrency news, project announcements, and social media channels. Airdrops are often announced in advance to build excitement and anticipation. 3. Meet Eligibility Criteria: Airdrops often come with eligibility criteria. This may include holding a minimum amount of a specific cryptocurrency, being an active user of a platform, or participating in certain activities. 4. Registration: Some airdrops require participants to register or provide specific information, such as an email address or social media account, to be eligible. Follow the registration process provided by the project. 5. Secure Your Private Keys: Ensure that your private keys or seed phrases are securely stored and never shared with anyone. Airdrops are typically distributed based on wallet balances, and losing access to your wallet may result in the loss of airdropped tokens. 6. Claiming Airdrops: After meeting the eligibility criteria and completing any necessary steps, you’ll need to claim the airdropped tokens. This often involves interacting with a smart contract or following instructions provided by the project. Conclusion Airdrops in the cryptocurrency world distribute free digital tokens to specific individuals or wallet holders, requiring no upfront investment. They serve as promotional tools, community builders, and decentralization mechanisms. They impact the crypto ecosystem by diversifying token holders, boosting engagement, educating users, and may have market implications and regulatory considerations.
-
 @ 6e0ea5d6:0327f353
2025-02-21 18:15:52
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ 7dfc349d:2609110d
2025-06-04 16:36:07
@ 7dfc349d:2609110d
2025-06-04 16:36:07At this stage in the game, one does not need another alarming news story, another shocking scientific discovery, or even some psuedo-spiritual online-influencer to tell us about the zillions of environmental hazards and dangers to our health that abound in the world we live in.
Cancer rates are up, sperm counts are down, depression rates are sky-high, and general morale is seemingly at an all-time low, and if I'm seeing the same sources and interpreting the same data you are from the commonly accepted "mainstream" media sources, than its hard to argue that an alternative option to all of these things that have made us so sick and depressed is not such an unreasonable one.
The "Norm" has become food laced with chemicals, medical treatments left up to pharmecutical companies, rampant and profound obesity rates, and a crippling nationwide mental health crisis. If that is the case, then we should be looking for some serious answers to these problems by considering what our alternatives really are.
We still tend to view "healthy", "organic", and "physically fit" types of people as a sort of "fringe" population. If the baseline for the majority of the US means being overweight, overburdened and under-active, then actually feeling healthy, stress free and physically fit means you are swimming against the tide of this country's attitudes towards what "health" is. I do not think I need waste any more of yours or my precious time by citing examples, as you can watch the fight play out in real time today in the "mainstream" news.
---
So here is where we start looking for solutions, rather than only focusing on the problems, and arguing about things that are right in front of our faces. What we label as "alternative treatments" are often age-old practices that came from one culture or another throughout history. Acupuncture, Massage, Chinese Medicine, Herbalism, and more. All of these have been in practice for thousands of years, but they tend to lack the rigorous scientific data to back them up (though that is rapidly changing), and they also offer fewer opportunities for massive profits by government or private entities.
Most of these alternative medicines and treatments put their focus on how the body is operating as a whole, and they rarely utilize invasive procedures and almost never prescribe pharmaceuticals, unless considered absolutely necessary.
What keeps these types of treatments outside the main stream is precisely that; they do not offer many places for third-party intermediaries to come in and profit. Insurers, medical equipment companies, clinic operators, They would all lose out. A direct patient-provider relationship has been commandeered by insurance providers, drug companies, and MASSIVE incentives for profit and personal gains.
Steps in; Spatial Medicine, and the cohesive future of what we now consider fringe practices about the body. If you can go to one Manual Therapist who is able to help you recover from a variety of issues that would normally have brought you to 5 different specialists and clinics, then who is really losing out, you or them?
When you can get direct access to care from trained and qualified individuals, without needing to ask permission from your health insurer, and without being limited to care options because of it. How does that sound?
When we finally get it in our heads that all of these alternative therapies are more interested in your body working the right way than it appears the mainstream medical conglomerate ever was, than we can stop feeling bad about wanting to actually feel good, and seek the care that fits our needs. There are a litany of trained, licensed, and verifiable practitioners out there who have proven their experience. Sure, this puts a little more onus on you to, but it also ensures you are able to trust and verify your care-providers, instead of having to trust and submit to an unverifiable insurance company or doctor who choses for you.
As a Manual Therapist who aims to distinguish this work from the generically accepted idea of "massage", I can say that I have watched people who've spent years with traditional doctors get over issues in matter of weeks when they work with me. At the very lowest baseline, no one has ever walked out of my office feeling worse than they did when they got there, but more often life-changing healing and pain relief is the result. Alternative and "direct-care" providers will ensure you get the most value for your hard earned money, because we are also getting the most direct, rewarding and ultimately effective relationship we like to have with our clients.
So despite what the mainstream says, trust your gut and make the effort to find out what alternative treatments may actually get you where you'd like to be. Look for providers with experience, and listen to all the options. Most of us take pride in our practices, and strive to provide the best possible care to our clients. As soon as middlemen and third-parties get involved, you are compromising the quality of care, and the personal relationship that is essential to getting better.
If working with ArrowSpine Manual Therapy is something you are curious about, please contact me to set up a phone call or an in-person office visit to learn more!
Sincerly, \ Brian Romanelli, LMT
ArrowSpine Manual Therapy
-
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-
 @ cae03c48:2a7d6671
2025-06-04 17:01:24
@ cae03c48:2a7d6671
2025-06-04 17:01:24Bitcoin Magazine

The Blockchain Group Buys $69 Million Worth of BitcoinFrench tech firm completes acquisition of 624 BTC through €60.2 million capital raise and bond issuance. The company reports 1,097.6% BTC Yield year-to-date as European corporations to accelerate Bitcoin treasury adoption.
The Blockchain Group, Europe’s first Bitcoin Treasury Company, has acquired 624 Bitcoin for approximately €60.2 million ($69 million), marking a significant expansion of its Bitcoin holdings through a combination of equity sales and convertible bonds.
JUST IN:
 Publicly traded The Blockchain Group buys 624 #Bitcoin for €60.2 million.
Publicly traded The Blockchain Group buys 624 #Bitcoin for €60.2 million. Nothing stops this train
 pic.twitter.com/Jvfvd13zsn
pic.twitter.com/Jvfvd13zsn— Bitcoin Magazine (@BitcoinMagazine) June 3, 2025
According to a press release issued June 3, the Euronext Growth Paris-listed company completed the purchase in two tranches: 80 BTC acquired for €7.7 million through a capital increase, and 544 BTC for €52.5 million via convertible bonds subscribed by Fulgur Ventures.
The acquisitions bring the company’s total Bitcoin holdings to 1,471 BTC, purchased at an average price of €89,687 ($103,000) per coin. The Group has achieved a “BTC Yield” – measuring the change in Bitcoin holdings relative to fully diluted shares – of 1,097.6% year-to-date.
The purchase was executed through Banque Delubac & Cie and Swissquote Bank Europe SA, with custody provided by Swiss infrastructure firm Taurus. The company indicated plans to acquire an additional 60 BTC through ongoing convertible bond issuances from UTXO Management and Moonlight Capital.
The Group’s latest acquisition was funded through a €8.6 million capital increase, with participation from investors including TOBAM Bitcoin Treasury Opportunities Fund and Quadrille Capital, alongside a €55.3 million convertible bond issuance to Fulgur Ventures.
The company reported a BTC Gain of 439 BTC year-to-date and a BTC € Gain of approximately €42.3 million, highlighting the growing trend of European corporations diversifying treasury assets into Bitcoin.
At press time, Bitcoin trades at €92,349 ($105,260), as institutional adoption continues to reshape corporate treasury management across Europe and globally.
This post The Blockchain Group Buys $69 Million Worth of Bitcoin first appeared on Bitcoin Magazine and is written by Vivek Sen.
-
 @ b1ddb4d7:471244e7
2025-06-04 11:01:29
@ b1ddb4d7:471244e7
2025-06-04 11:01:29Bitcoin FilmFest (BFF25) returns to Warsaw for its third edition, blending independent cinema—from feature films and commercials to AI-driven experimental visuals—with education and entertainment.
Hundreds of attendees from around the world will gather for three days of screenings, discussions, workshops, and networking at the iconic Kinoteka Cinema (PKiN), the same venue that hosted the festival’s first two editions in March 2023 and April 2024.
This year’s festival, themed “Beyond the Frame,” introduces new dimensions to its program, including an extra day on May 22 to celebrate Bitcoin Pizza Day, the first real-world bitcoin transaction, with what promises to be one of Europe’s largest commemorations of this milestone.
BFF25 bridges independent film, culture, and technology, with a bold focus on decentralized storytelling and creative expression. As a community-driven cultural experience with a slightly rebellious spirit, Bitcoin FilmFest goes beyond movies, yet cinema remains at its heart.
Here’s a sneak peek at the lineup, specially curated for movie buffs:
 Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money.
Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money. Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative).
Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative). Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.
Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.To get an idea of what might come up at the event, here, you can preview 6 selected ads combined into two 2 videos:
 Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships.
Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships. Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.
Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.BFF25 Main Screenings
Sample titles from BFF25’s Official Selection:
 REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director.
REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director. UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year.
UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year. HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.
HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.Check out trailers for this year’s BFF25 and past editions on YouTube.
Tickets & Info:
- Detailed program and tickets are available at bitcoinfilmfest.com/bff25.
- Stay updated via the festival’s official channels (links provided on the website).
- Use ‘LN-NEWS’ to get 10% of tickets
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ cae03c48:2a7d6671
2025-06-04 17:01:17
@ cae03c48:2a7d6671
2025-06-04 17:01:17Bitcoin Magazine

SEC Commissioner Hester Peirce Speaks On Privacy And Permissionlessness At PubKeyYesterday, SEC Commissioner Hester Peirce sat down for a fireside chat with NYDIG founder Ross Stevens at New York City’s Bitcoin-themed bar PubKey.
The two traversed a number of topics during their discussion, including why it’s important that the world has a permissionless network and asset like Bitcoin as well as why transactional privacy should be a right for U.S. citizens.
Peirce didn’t mince words during the discussion, yet she also spoke with nuance and thoughtfulness as she responded to questions from not only Stevens but from members of the audience during a Q&A session, as well.
On Permissionlessness
Toward the onset of the talk, Peirce highlighted the fact that Bitcoin is a tool for freedom fighters as part of a broader theme of why it’s crucial that permissionless technology like Bitcoin exists.
She said that she often thinks about what it would have been like if someone like Harriet Tubman had had Bitcoin.
Stevens then posed a question about the risk of a situation in which a U.S. president issues an executive order that authorizes the government to confiscate U.S. citizens’ bitcoin, like the way Executive Order 6102 enabled the government to seize U.S. citizens’ gold in 1933.
Peirce admitted that “it’s still possible for an Executive Order like 6102 to happen in the U.S.,” and made the case that it’s up to us to remain vigilant so as not to permit something like this to happen again.
“To protect ourselves from something like Executive Order 6102, we must reaffirm the founding principles of America and hold the government accountable to those principles,” said the commissioner.
Stevens added that some of Bitcoin’s qualities, such as the ability to store one’s seed phrase in one’s mind, make it more resistant to seizure than gold and, therefore, a better freedom-preserving technology. (The topic of owning actual bitcoin, or holding one’s own bitcoin private keys, as a means of embracing the true nature of Bitcoin as a permissionless technology versus having bitcoin exposure via spot bitcoin ETFs or through custodians arose at many points in the discussion.)
Further along in the discussion, Peirce stressed the importance of the U.S. government continuing to view code as speech, a topic that Stevens brought up and has written extensively about.
“It’s important as regulators for us to treat code as speech,” began Peirce.
“Otherwise, developers would have to check their code with the government before publishing it,” she added, before also noting that developers having to do this could stifle and undermine their ability to publish open-source software.
On Privacy
Halfway through the talk, Stevens asked Peirce if Americans should be free to use crypto mixers.
Before directly commenting on the matter, Peirce spoke more broadly to the concept of financial privacy and that it seems to be of little concern to most U.S. citizens.
“It’s remarkable to me how little people care about financial privacy,” said Peirce. “It’s very personal how you spend your money — and we’ve ceded so much privacy.”
Regarding crypto mixers more specifically, Peirce stated that she believes Americans have a right to use such technology.
“There’s supposed to be a presumption of innocence in this country,” she said. “Technologies that allow you to do things on chain but also allow you to preserve privacy are really important.”
At the beginning of the Q&A portion of the event, Thomas Pacchia, the bar’s owner, highlighted the dangers of the Bank Secrecy Act (BSA) in that it mandates that users turn over significant amounts of personal data to financial institutions and asked what the odds were of one day seeing the act repealed.
Peirce agreed with Pacchia that there is great risk in financial institutions holding so much of their customers’ data but pointed out that the idea of repealing the BSA is a point of deep contention in Washington, D.C.
“Really bad things can happen if a centralized financial institution has a lot of information about you, but it’s such a third rail in D.C. to talk about the Bank Secrecy Act because of the fear that bad actors will rush in,” said Peirce.
Listening Intently
Peirce has stated a number of times, most recently at Bitcoin 2025, that she believes that the U.S. government works for the American people.
It’s clear that this isn’t just hot air or a talking point, as evidenced by how carefully she listens to the questions posed to her and how thoughtful her responses to said questions are.
For example, I asked Commissioner Peirce if there was any chance we might eventually see in-kind redemptions for the spot bitcoin ETFs for retail investors.
While she admitted that it’s “unlikely,” she offered me some space to make my case for why they’re important and concluded the exchange with me by stating that she’d “give it some more thought.”
She responded to Stevens and to each member of the audience who posed a question with the same type of care and consideration, which seemed to be appreciated as she broached topics as sensitive as having the legal right to hold one’s Bitcoin keys and to transact with bitcoin privately.
Peirce also seemed genuinely concerned about making sure that regulators don’t get in the way of Bitcoin and crypto fulfilling their promise as both freedom technology and an alternative to the traditional financial and monetary systems.
“I’m concerned that we’ll stunt growth if we do things the wrong way,” Peirce concluded, eliciting a warm round of applause from the Bitcoin enthusiasts in attendance.
This post SEC Commissioner Hester Peirce Speaks On Privacy And Permissionlessness At PubKey first appeared on Bitcoin Magazine and is written by Frank Corva.
-
 @ 2dd9250b:6e928072
2025-06-04 10:01:11
@ 2dd9250b:6e928072
2025-06-04 10:01:11Durante a década de 1990, houve o aumento da globalização da economia, determinando a adição do fluxo internacional de capitais, de produtos e serviços. Este fenômeno levou a uma interdependência maior entre as economias dos países. Justamente por causa da possibilidade de que um eventual colapso econômico em um país resulte no contágio dos demais. Diante disso, aumentou a preocupação com os riscos incentivando a utilização de sofisticados modelos e estratégias de avaliação de gestão de risco.
Na década, ganharam destaque ainda os graves problemas financeiros enfrentados, entre outros, pelo banco inglês Barings Bank, e pelo fundo de investimento norte-americano Long Term Capital Management.
Outro grande destaque foi a fraude superior a US$ 7 bilhões sofrida pelo banco Société Generale em Janeiro de 2008.
O Barings Bank é um banco inglês que faliu em 1995 em razão de operações financeiras irregulares e mal-sucedidas realizadas pelo seu principal operador de mercado. O rombo da instituição foi superior à US$ 1,3 Bilhão e causado por uma aposta equivocada no desempenho futuro no índice de ações no Japão. Na realidade, o mercado acionário japonês caiu mais de 15% na época, determinando a falência do banco. O Baring Bank foi vendido a um grupo financeiro holandês (ING) pelo valor simbólico de uma libra esterlina.
O Long Term Capital Management era um fundo de investimento de que perdeu em 1998 mais de US$ 4,6 bilhões em operações nos mercados financeiros internacionais. O LTCM foi socorrido pelo Banco Central dos Estados Unidos (Federal Reserve ), que coordenou uma operação de socorro financeiro à instituição. A justificativa do Banco Central para esta decisão era "o receio das possíveis consequências mundiais da falência do fundo de investimento".
O banco francês Société Generale informou, em janeiro de 2008, uma perda de US$ 7,16 bilhões determinadas por fraudes efetuadas por um operador do mercado financeiro. Segundo revelou a instituição, o operador assumiu posições no mercado sem o conhecimento da direção do banco. A instituição teve que recorrer a uma urgente captação de recursos no mercado próxima a US$ 5,0 bilhões.
E finalmente chegamos ao caso mais problemático da era das finanças modernas anterior ao Bitcoin, o caso Lehman Brothers.
O Lehman Brothers era o 4° maior de investimentos dos EUA quando pediu concordata em 15/09/2008 com dívidas que superavam inacreditáveis US$ 600 bilhões.
Não se tinha contas correntes ou talão de cheques do Lehman Brothers. Era um banco especializado em investimentos e complexas operações financeiras. Havia feito pesados investimentos em empréstimos a juros fixos no famigerado mercado subprime, e o crédito imobiliário voltado a pessoas consideradas de forte risco de inadimplência.
Com essa carteira de investimentos que valia bem menos que o estimado e o acúmulo de projetos financeiros, minou a confiança dos investidores na instituição de 158 anos. Suas ações passaram de US$ 80 a menos de US$ 4. Acumulando fracassos nas negociações para levantar fundos; a instituição de cerca de 25 mil funcionários entrou em concordata.
O Federal Reserve resgatou algumas instituições financeiras grandes e tradicionais norte-americanas como a seguradora AIG no meio da crise. O Fed injetou um capital de US$ 182, 3 bilhões no American International Group (AIG).
Foi exatamente essa decisão do Fed em salvar alguns bancos e deixar quebrar outros, que causou insegurança por parte dos clientes. E os clientes ficaram insatisfeitos tanto com os bancos de investimentos quanto com as agências de classificação de risco, como a Standard & Poor's que tinha dado uma nota alta para o Lehman Brothers no mesmo dia em que ele quebrou.
E essa foi uma das razões pelo qual o Bitcoin foi criado. Satoshi Nakamoto entendeu que as pessoas não estavam mais confiando nem no Governo, nem nos Bancos Privados que o Governo federal restagatava quando eles quebravam e isso prejudicou muita gente. Tanto que o “hash” do Genesis Block contém o título do artigo “Chancellor on brink of second bailout for banks” (Chanceler à beira de segundo resgate para bancos, em português) da edição britânica do The Times.
Esse texto foi parcialmente editado do texto de ASSAF Neto, CAF (2014).
-
 @ cae03c48:2a7d6671
2025-06-04 16:01:58
@ cae03c48:2a7d6671
2025-06-04 16:01:58Bitcoin Magazine

Michael Saylor’s Strategy Announces Initial Public Offering of 2,500,000 STRD SharesToday, Strategy (Nasdaq: MSTR; STRK; STRF) has announced that it plans to conduct an initial public offering of 2,500,000 STRD shares of Strategy’s 10.00% Series A Perpetual Stride Preferred Stock.
JUST IN: Michael Saylor's Strategy announces Initial Public Offering of STRD stock to raise more money to buy #Bitcoin
 pic.twitter.com/ow29eNaW89
pic.twitter.com/ow29eNaW89— Bitcoin Magazine (@BitcoinMagazine) June 2, 2025
“Strategy intends to use the net proceeds from the offering for general corporate purposes, including the acquisition of bitcoin and for working capital,“ stated the company in the announcement.
The STRD Stock will offer non-cumulative cash dividends at an annual rate of 10 percent, paid quarterly in arrears on March 31, June 30, September 30 and December 31 of each year, beginning on September 30, 2025. If dividends are not declared, they will not accumulate, and Strategy says it is not required to make up for missed payments.
Strategy may be able to redeem all outstanding STRD shares if the total number falls below 25 percent of the original issuance or if certain tax events occur. In such cases, holders will receive the liquidation preference of $100 per share plus any declared and unpaid dividends.
The company stated, “if an event that constitutes a “fundamental change” under the certificate of designations governing the STRD Stock occurs, then, holders of the STRD Stock will have the right to require Strategy to repurchase some or all of their shares of STRD Stock at a cash repurchase price equal to the stated amount of the STRD Stock to be repurchased, plus declared and unpaid regular dividends, if any, that will have accrued to, but excluding the fundamental change repurchase date.”
Also today, Strategy (MSTR) acquired another 705 Bitcoin for about $75 million, further expanding its position as the largest corporate holder of Bitcoin as more public companies continue to adopt Bitcoin treasury strategies.
BREAKING:
 STRATEGY BUYS ANOTHER 705 #BITCOIN FOR $75 MILLION pic.twitter.com/WBgKUcbbEP
STRATEGY BUYS ANOTHER 705 #BITCOIN FOR $75 MILLION pic.twitter.com/WBgKUcbbEP— Bitcoin Magazine (@BitcoinMagazine) June 2, 2025
According to their SEC filing on June 2, they bought Bitcoin at an average price of $106,495 each between May 26 and June 1, bringing their total holdings to 580,955 BTC. The acquisition was funded by selling some of their preferred shares through an at-the-market (ATM) equity offering.
The company raised $74.6 million by selling a combination of its preferred stock classes, including 353,511 shares of STRK preferred stock for $36.2 million and 374,968 shares of STRF preferred stock for $38.4 million. With this purchase, Strategy’s average acquisition price across all its Bitcoin holdings stands at $70,023 per coin.
This post Michael Saylor’s Strategy Announces Initial Public Offering of 2,500,000 STRD Shares first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ 9dd283b1:cf9b6beb
2025-06-04 08:33:32
@ 9dd283b1:cf9b6beb
2025-06-04 08:33:32To all territory owners,
- Can I co-found a territory with someone? Is it on the roadmap to be able to do so?
- Can I automatically split the territory rewards with other stackers?
- Can I rename the territory in the future?
Thanks
https://stacker.news/items/996796
-
 @ e136fbe5:b6e8325d
2025-06-04 10:02:38
@ e136fbe5:b6e8325d
2025-06-04 10:02:38Trong thời đại công nghệ số và đô thị hóa nhanh chóng, Việt Nam đang chứng kiến làn sóng chuyển mình mạnh mẽ từ các thành phố truyền thống sang những khu đô thị thông minh với hệ thống hạ tầng hiện đại, kết nối số và lấy người dân làm trung tâm. Trong bối cảnh đó, EV8 đóng vai trò ngày càng quan trọng khi trở thành giải pháp hỗ trợ thiết thực cho mục tiêu phát triển đô thị bền vững, thân thiện với môi trường và thuận tiện cho người dân. Xe điện EV8 không chỉ giúp giảm thiểu ô nhiễm không khí, tiếng ồn mà còn tối ưu hóa quá trình di chuyển trong nội đô với công nghệ định vị, quản lý năng lượng và kết nối tức thời thông qua nền tảng số. Khi hạ tầng giao thông thông minh đang dần được hoàn thiện, EV8 kết hợp cùng các hệ thống đèn tín hiệu, trạm sạc công cộng, ứng dụng điều hướng, và dữ liệu thời gian thực để mang lại trải nghiệm di chuyển hiệu quả, an toàn và dễ dàng hơn. Điều này giúp người dùng không chỉ tiết kiệm chi phí mà còn chủ động trong từng hành trình, đồng thời nâng cao chất lượng sống trong môi trường đô thị văn minh. Tính linh hoạt, thân thiện và khả năng tích hợp công nghệ chính là những yếu tố khiến EV8 trở thành sự lựa chọn lý tưởng cho cư dân các thành phố thông minh tương lai.
Không dừng lại ở khía cạnh giao thông, EV8 còn đóng góp vào việc xây dựng một hệ sinh thái đô thị đa chiều với khả năng tương tác giữa con người và công nghệ. Nền tảng EV8 không chỉ cung cấp phương tiện di chuyển mà còn kết nối người dùng với mạng lưới dịch vụ tiện ích đô thị như thanh toán điện tử, quản lý năng lượng cá nhân, theo dõi chỉ số môi trường xung quanh, và nhận cảnh báo giao thông thông minh. Qua đó, EV8 góp phần thúc đẩy hành vi sống xanh, có trách nhiệm, đồng thời khuyến khích người dân sử dụng công nghệ để giải quyết các vấn đề của đời sống hàng ngày. Việc EV8 đồng hành cùng các đô thị thông minh không chỉ mang ý nghĩa công nghệ mà còn là sự cam kết về giá trị cộng đồng – tạo ra một môi trường sống hiệu quả, bền vững và kết nối cao. Đặc biệt, những chiến dịch cộng đồng và chương trình ưu đãi tích hợp như tích điểm sử dụng xanh, hoàn tiền khi tham gia các hoạt động bảo vệ môi trường, hay hỗ trợ tài chính cho người dân chuyển đổi sang xe điện đều là minh chứng cho tầm nhìn dài hạn của EV8 trong việc đồng hành cùng quá trình xây dựng thành phố tương lai. Nhờ sự hiện diện của EV8, các đô thị tại Việt Nam đang tiến gần hơn đến chuẩn mực sống thông minh – nơi công nghệ phục vụ con người một cách thiết thực và bền vững, đồng thời khẳng định vai trò tiên phong của EV8 trong việc kiến tạo tương lai đô thị số.
-
 @ eb0157af:77ab6c55
2025-06-04 15:01:57
@ eb0157af:77ab6c55
2025-06-04 15:01:57A new investment vehicle combines exposure to Bitcoin with downside protection based on the price of gold.
On May 29, Cantor Fitzgerald Asset Management announced the launch of an investment product that merges direct exposure to Bitcoin with a bearish hedge linked to gold.
According to the financial institution, the new fund offers a solution for investors seeking to benefit from the growth potential of the leading cryptocurrency while maintaining a safety net tied to the precious metal.
Fund features
The fund is structured with a five-year term and no cap on potential upside, allowing investors to fully capture Bitcoin’s growth. The “1-to-1” protection mechanism means that any losses on Bitcoin would be offset by corresponding gains from gold.
Brandon Lutnick, Chairman of Cantor and son of former CEO Howard Lutnick (now Commerce Secretary in the Trump administration), called the product “a truly revolutionary investment vehicle” that helps investors access Bitcoin’s potential while providing downside protection. “There are still people on the Earth that are still scared of Bitcoin, and we want to bring them into this ecosystem,” Lutnick added.
The fund marks Cantor Fitzgerald’s first BTC-focused investment product. The firm, with 79 years of history and $14.8 billion in assets under management, is making its first significant move into the Bitcoin market.
The announcement follows the closing of its first round of financing agreements with Maple Finance and FalconX. Through its “Bitcoin Financing Business” division, Cantor plans to initially make up to $2 billion in financing available to institutional clients.
The post Cantor Fitzgerald launches Bitcoin fund with gold hedge appeared first on Atlas21.
-
 @ a5ee4475:2ca75401
2025-06-04 15:10:55
@ a5ee4475:2ca75401
2025-06-04 15:10:55[EM ATUALIZAÇÃO]
vacina #saude #politica #manipulacao #mundial #genocidio #pandemia #conspiracao
Este artigo reúne algumas evidências mais antigas que vim registrando durante alguns anos contra a covid, vacinas obrigatórias e a ação de agências de governo, fundações, políticos, mídia tradicional, celebridades, influenciadores, cientistas, redes sociais e laboratórios, em envolvimento com genocídio e restrições de liberdades em escala mundial causado por decisões em várias esferas relativas ao covid e as vacinas obrigatórias em geral.
Porém, alguns links podem não estar mais disponiveis, foram que ainda faltam ser registradas muitas informações já divulgadas nos últimos anos e que não tivemos contato pela escassez de meios para a obtenção dessas informações de forma organizada. Portanto, o presente artigo ainda passará por atualizações de conteúdo e formatação, então se possível ajudem sugerindo com complementos ou alterações.
Explicações iniciais:
- SARS-CoV-2 é que é nome do vírus. Ele que causa a doença Covid-19;
- O coronavírus SARS-CoV-2 é o segundo tipo de SARS-CoV documentado, o primeiro ocorreu entre 2002 e 2003, se originando também da China e também dito como tendo origem animal;
- SARS (Severe Acute Respiratory Syndrome) - Síndrome Respiratória Aguda Grave (SRAG) é a uma doença respiratória viral, relatada ser de origem zoonótica (animal), causada pelos coronavírus SARS-CoV (2002) e SARS-CoV-2 (2019), ambos de origem chinesa;
- O termo 'Coronavírus' (COVID) é na verdade um nome genérico para vários vírus de gripes já comuns, dado para o tipo corona (com uma "coroa", 'espetos' ao redor dele), o Sars-Cov-2 (que passou a ser chamado erroneamente só de Covid), é só um deles.
1. Vacinas Obrigatórias em Geral
-
Vacinas e autismo em crianças https://publichealthpolicyjournal.com/vaccination-and-neurodevelopmental-disorders-a-study-of-nine-year-old-children-enrolled-in-medicaid/
-
O CDC admite que 98 milhões de pessoas receberam o vírus do câncer através da vacina da Poliomielite https://medicinanews.com.br/frente/frente_1/o-cdc-admite-que-98-milhoes-de-pessoas-receberam-o-virus-do-cancer-atraves-da-vacina-poliomielite/
 - Fonte original da imagem: https://preventdisease.com/images13/CDC_Polio.png [indisponível]
- Imagem arquivada em: https://web.archive.org/web/20201203231640/
- Fonte original da imagem: https://preventdisease.com/images13/CDC_Polio.png [indisponível]
- Imagem arquivada em: https://web.archive.org/web/20201203231640/"O CDC (Os Centros de Controle e Prevenção de Doenças dos Estados Unidos) removeu rapidamente uma página do seu site, que estava em cache no Google, como você pode ver logo abaixo, admitindo que mais de 98 milhões de americanos receberam uma ou mais doses de vacina contra pólio dentro de 8 período entre 1955 e 1963, quando uma proporção da vacina foi contaminada com um poliomavírus causador de câncer chamado SV40."
27/02/2021 - Por que o Japão demorou para vacinar, mesmo com Olimpíada se aproximando https://www.cnnbrasil.com.br/internacional/2021/02/27/por-que-o-japao-demorou-para-vacinar-mesmo-com-olimpiada-se-aproximando
"Desconfiança da população japonesa em relação a vacinas, ligada a casos ocorridos no passado, está entre razões que atrasaram imunização no país.
A resistência à vacina do Japão remonta à década de 1970, quando duas crianças morreram dentro de 24 horas após receberem a vacina combinada contra difteria, tétano e coqueluche (coqueluche). A vacina foi temporariamente suspensa, mas a confiança já havia sido abalada. Por vários anos, as taxas de vacinação infantil caíram, levando a um aumento nos casos de tosse convulsa.
No final dos anos 1980, houve outro susto com a introdução da vacina tripla contra sarampo, caxumba e rubéola produzida no Japão. As primeiras versões do imunizante foram associadas à meningite asséptica, ou inchaço das membranas ao redor do cérebro e da medula espinhal. O problema foi rastreado até o componente caxumba da vacina tripla, o que levou a uma ação judicial e a indenização por danos pesados.
O Instituto Nacional de Ciências da Saúde interrompeu a dose combinada em 1993 e a substituiu por vacinas individuais. Após o escândalo, Shibuya disse que o governo japonês se tornou "ciente dos riscos" e seu programa nacional de vacinação tornou-se voluntário.
O Dr. Yuho Horikoshi, especialista em doenças infecciosas, diz que os processos levaram a uma "lacuna de vacinação", em que nenhuma vacina foi aprovada no Japão por cerca de 15 anos.
Mais recentemente, em 2013, o Japão adicionou a vacina contra o papilomavírus humano (HPV) ao calendário nacional para proteger as meninas contra o vírus sexualmente transmissível, que é conhecido por causar câncer cervical. No entanto, vídeos de meninas supostamente sofrendo de reações adversas começaram a circular no YouTube, levando o governo a retirá-los da programação nacional."
2. PRIMEIRAS OCORRÊNCIAS PREDITIVAS AO COVID-19
2002 - Síndrome respiratória aguda grave (SARS) Brenda L. Tesini (setembro de 2018). Síndrome respiratória aguda grave (SARS) [indisponível]. Manual Merck. Consultado em 23 de janeiro de 2020, citado no Wikipedia
Wikipedia: "A SARS [doença do vírus SARS-CoV] foi detectada na China e entre 2002 e 2003, um surto da doença resultou em mais de 8 000 casos e cerca de 800 mortes em todo o mundo. "
2010 - Fundação Rockfeller, Lockstep. https://www.rockefellerfoundation.org/wp-content/uploads/Annual-Report-2010-1.pdf
Neste PDF da fundação Rockfeller, em seu próprio site, a fundação deixou claro o seu envolvimento em casos de ‘contenção’ de pandemias juntamente com a USAID (agência americana com nome ambíguo, como formalmente ‘United States Agency for International Development’, mas soando como ‘US Socorre’, mas sendo um braço do governo democrata que financiava interferências políticas diretas em vários países, como no Brasil: https://www.gazetadopovo.com.br/vida-e-cidadania/quais-ongs-cooperaram-com-moraes-e-sao-alvo-do-congresso-nos-eua/ ), inclusive em relacionadas ao SARS, um vírus muito semelhante ao SEGUNDO tipo de vírus Sars-Cov, o Sars-Cov-2 (o vírus propagado em 2019) e que causa o COVID-19.
Segundo eles:
“Integração entre Regiões e Países
A Fundação Rockefeler investiu US$ 22 milhões em sua Iniciativa de Redes de Vigilância de Doenças para ajudar a conter a disseminação de doenças infecciosas e pandemias, fortalecendo os sistemas nacionais, regionais e globais de vigilância e resposta a doenças. Dois programas-chave da Rockefeler — a Rede de Vigilância de Doenças da Bacia do Mekong e a Rede Integrada de Vigilância de Doenças da África Oriental — conectaram e capacitaram profissionais de saúde, epidemiologistas e autoridades de saúde pública em toda a região, levando a um aumento de seis vezes nos locais de vigilância de doenças transfronteiriças somente nos últimos três anos. Em 2010, a Rockefeler expandiu a bem-sucedida campanha transdisciplinar One Health, que a USAID e o Banco Asiático de Desenvolvimento adotaram como modelos. One Health refere-se à integração da ciência médica e veterinária para combater essas novas variedades de doenças zoonóticas que se movem e sofrem mutações rapidamente de animais para humanos. Essas colaborações criaram e fortaleceram uma rede regional crítica de saúde pública, enquanto as lições aprendidas foram exportadas entre disciplinas e países. Além de fortalecer os laços globais em saúde pública, a Rockefeler ajudou a elevar o nível de especialização e treinamento em campo. O Programa de Treinamento em Epidemiologia de Campo coloca graduados nos mais altos escalões do governo no Laos e no Vietnã, enquanto as bolsas da Rockefeler transformaram as ferramentas disponíveis para os médicos, permitindo-lhes utilizar o poder da internet para se comunicar e monitorar eventos, compreender contextos locais e analisar novos problemas. Finalmente, estamos aplicando ferramentas do século XXI para combater os desafios de saúde do século XXI.”
Julho de 2012 - Revista Mundo Estranho
Houve uma "coincidência", a revista Mundo Estranho em julho de 2012, entrevistou o até então doutorando em virologia, Átila Iamarino (o mesmo cientista que fez diversas propagandas das vacinas no Brasil), para descrever um possível cenário de propagação de uma epidemia viral, a revista descreve com grande precisão os eventos de 2020, mas apontando o oposto da China, em que, na realidade, sua economia cresceu vertiginosamente.
3. PRIMEIROS INDÍCIOS
10/2019 - Evento 201 - Durante os Jogos Militares Internacionais na China https://www.centerforhealthsecurity.org/event201/
Promovido por: - Bill & Melinda Gates Foundation - John Hopkins Institute - Fórum econômico mundial
"O evento simula a liberação de um coronavírus novo do tipo zoonótico transmitido por morcegos para porcos e por fim para humanos. Eventualmente ele se torna muito transmissível entre humanos levando a uma pandemia severa. O vírus é muito parecido com o vírus da SARS, mas se transmite muito mais facilmente entre pessoas devido a sintomas muito mais leves destas."
Também mencionado por: [Jornal Estadão] ( http://patrocinados.estadao.com.br/medialab/releaseonline/releasegeral-releasegeral/geral-johns-hopkins-center-for-health-security-forum-economico-mundial-e-fundacao-bill-melinda-gates-realizam-exercicio-pandemico-e-transmissao-ao-vivo/)
Sobre o "Movimento antivacina"
05/12/2017 - Movimento antivacina: como surgiu e quais consequências ele pode trazer? https://www.uol.com.br/universa/noticias/redacao/2017/12/05/o-que-o-movimento-antivacina-pode-causar.htm?cmpid=copiaecola
23/03/2019 - "Instagram bloqueia hashtags e conteúdo antivacinação" https://canaltech.com.br/redes-sociais/instagram-bloqueia-hashtags-e-conteudo-antivacinacao-135411/
23/05/2021 - Novos dados sobre pesquisadores de Wuhan aumentam debate sobre origens da Covid https://www.cnnbrasil.com.br/saude/novos-dados-sobre-pesquisadores-de-wuhan-aumentam-debate-sobre-origens-da-covid/
"A China relatou à Organização Mundial da Saúde que o primeiro paciente com sintomas semelhantes aos de Covid-19 foi registrado em Wuhan em 8 de dezembro de 2019"
01/02/2020 - O que aconteceu desde que o novo coronavírus foi descoberto na China https://exame.com/ciencia/o-que-aconteceu-desde-que-o-novo-coronavirus-foi-descoberto-na-china/
"O primeiro alerta foi recebido pela Organização Mundial da Saúde (OMS) em 31 de dezembro de 2019"
15/09/2020 - YouTube diz que vai remover vídeos com mentiras sobre vacina contra COVID-19 https://gizmodo.uol.com.br/youtube-remover-videos-mentiras-vacina-covid-19/
"O YouTube anunciou na quarta-feira (14) que estenderá as regras atuais sobre mentiras, propaganda e teorias da conspiração sobre a pandemia do coronavírus para incluir desinformação sobre as vacinas contra a doença.
De acordo com a Reuters, a gigante do vídeo diz que agora vai proibir conteúdos sobre vacinas contra o coronavírus que contradizem “o consenso de especialistas das autoridades de saúde locais ou da OMS”, como afirmações falsas de que a vacina é um pretexto para colocar chips de rastreamento nas pessoas ou que irá matar ou esterilizar quem tomar."
*07/01/2021 - YouTube vai punir canais que promovem mentiras sobre eleições – incluindo os de Trump https://olhardigital.com.br/2021/01/07/noticias/youtube-vai-punir-canais-que-promovem-mentiras-sobre-eleicoes-incluindo-os-de-trump/
"O YouTube anunciou que vai punir canais que promovem mentiras sobre as eleições, removendo sumariamente qualquer vídeo que contenha desinformação e, ao mesmo tempo, advertindo com um “strike” o canal que o veicular. A medida já está valendo e a primeira “vítima” é ninguém menos que o ex-presidente americano, Donald Trump.
A medida não é exatamente nova, mas foi novamente comunicada e reforçada pelo YouTube na quarta-feira (6), após os eventos de invasão do Capitólio, em Washington, onde o presidente eleito Joe Biden participava da cerimônia que confirmava a sua vitória nas eleições de novembro de 2020. A ocasião ficou marcada pela tentativa de invasão de correligionários de Trump, que entraram no edifício em oposição à nomeação do novo presidente. Uma mulher acabou sendo morta pela polícia que protegia o local.
O ex-presidente Donald Trump teve vídeos banidos de seu canal no YouTube após os eventos de ontem (6) no capitólio."
4. FIGURAS CENTRAIS
Bill Gates
- Bill Gates diz 'não' a abrir patentes de vacinas https://www.frontliner.com.br/bill-gates-diz-nao-a-abrir-patentes-de-vacinas/
"Bill Gates, um dos homens mais ricos do mundo, cuja fundação tem participação na farmacêutica alemã CureVac, produtora de vacina mRNA para prevenção de covid-19, disse não acreditar que a propriedade intelectual tenha algo a ver com o longo esforço global para controlar a pandemia."
João Doria e São Paulo
26/07/2017 - João Dória vai a China conhecer drones para ampliar segurança eletrônica na capital paulista https://jc.ne10.uol.com.br/blogs/jamildo/2017/07/26/joao-doria-vai-china-conhecer-drones-para-ampliar-seguranca-eletronica-na-capital-paulista/
02/08/2019 - Governo de SP fará Missão China para ampliar cooperação e atrair investimentos https://www.saopaulo.sp.gov.br/spnoticias/governo-de-sao-paulo-detalha-objetivos-da-missao-china/
20/11/2019 - Doria se encontra com chineses das gigantes CREC e CRCC e oferece concessões de rodovia, metrô e ferrovia https://diariodotransporte.com.br/2019/11/20/doria-se-encontra-com-chineses-das-gigantes-crec-e-crcc-e-oferece-concessoes-de-rodovia-metro-e-ferrovia/
25/01/2020 - "Chineses serão agressivos" nas privatizações em SP até 2022, afirma Dória https://noticias.uol.com.br/colunas/jamil-chade/2020/01/25/entrevista-joao-doria-privatizacoes-sao-paulo-china.htm
O governador de São Paulo, João Doria, afirma que vai acelerar os programas de desestatização no estado em 2020 e acredita que concessões e vendas poderão permitir uma arrecadação de pelo menos R$ 40 bilhões. Nesse processo, o governador avalia que a China deve atuar de forma agressiva e que aprofundará sua posição de maior parceira comercial do estado, se distanciando de americanos e argentinos.
29/06/2020 - Doria estabelece multa para quem estiver sem máscara na rua em SP https://veja.abril.com.br/saude/doria-estabelece-multa-para-quem-estiver-sem-mascara-na-rua/
24/12/2020 - Doria é flagrado sem máscara e fazendo compras em Miami https://pleno.news/brasil/politica-nacional/doria-e-flagrado-sem-mascara-e-fazendo-compras-em-miami.html
"Foto do governador de São Paulo sem o item de proteção viralizou nas redes"
07/06/2021 - Doria é criticado na internet por tomar sol sem máscara em hotel no Rio https://vejasp.abril.com.br/cidades/doria-e-criticado-na-internet-por-tomar-sol-sem-mascara-em-hotel-no-rio/
30/09/2020 - Governo de SP assina contrato com Sinovac e prevê vacina para dezembro https://agenciabrasil.ebc.com.br/saude/noticia/2020-09/governo-de-sp-assina-contrato-com-sinovac-e-preve-vacina-para-dezembro
O governador de São Paulo, João Doria, e o vice-presidente da laboratório chinês Sinovac, Weining Meng, assinaram hoje (30), um contrato que prevê o fornecimento de 46 milhões de doses da vacina CoronaVac para o governo paulista até dezembro deste ano.
O contrato também prevê a transferência tecnológica da vacina da Sinovac para o Instituto Butantan, o que significa que, o instituto brasileiro poderá começar a fabricar doses dessa vacina contra o novo coronavírus. O valor do contrato, segundo o governador João Doria é de US$ 90 milhões.
20/10/2020 - Coronavac terá mais de 90% de eficácia, afirmam integrantes do governo paulista https://www.cnnbrasil.com.br/saude/2020/12/20/coronavac-tera-mais-de-90-de-eficacia-afirmam-integrantes-do-governo
24/10/2020 - Não esperamos 90% de eficácia da Coronavac’, diz secretário de saúde de SP https://www.cnnbrasil.com.br/saude/2020/12/24/nao-esperamos-90-de-eficacia-da-coronavac-diz-secretario-de-saude-de-sp
07/01/2021 - Vacina do Butantan: eficácia é de 78% em casos leves e 100% em graves https://www.cnnbrasil.com.br/saude/2021/01/07/vacina-do-butantan-eficacia-e-de-78-em-casos-leves-e-100-em-graves
09/01/2021 - Não é hora de sermos tão cientistas como estamos sendo agora https://g1.globo.com/sp/sao-paulo/video/nao-e-hora-de-sermos-tao-cientistas-como-estamos-sendo-agora-diz-secretario-de-saude-de-sp-9166405.ghtml
10/01/2021 - Dados da Coronavac relatados à Anvisa não estão claros, diz médico https://www.cnnbrasil.com.br/saude/2021/01/10/dados-da-coronavac-relatados-a-anvisa-nao-estao-claros-diz-medico
"O diretor do Laboratório de Imunologia do Incor, Jorge Kalil, reforçou que faltaram informações sobre a Coronavac nos dados divulgados à Anvisa"
12/01/2021 - New Brazil data shows disappointing 50,4% efficacy for China’s Coronavac vaccine [Novos dados do Brasil mostram eficácia decepcionante de 50,4% para a vacina CoronaVac da China] https://www.reuters.com/article/us-health-coronavirus-brazil-coronavirus/new-brazil-data-shows-disappointing-504-efficacy-for-chinas-coronavac-vaccine-idUSKBN29H2CE
13/01/2021 - Eficácia da Coronavac: 50,38%, 78% ou 100%? https://blogs.oglobo.globo.com/lauro-jardim/post/5038-78-ou-100.html
“De acordo com interlocutores que participaram tanto do anúncio de ontem como da semana passada, quem pressionou para que os dados de 78% e 100% fossem liberados foi João Dória.”
07/05/2021 - Covid-19: Doria toma primeira dose da vacina CoronaVac https://veja.abril.com.br/saude/covid-19-doria-toma-primeira-dose-da-vacina-coronavac/
04/06/2021 - Doria é vacinado com a segunda dose da CoronaVac em São Paulo https://noticias.uol.com.br/politica/ultimas-noticias/2021/06/04/doria-e-vacinado-com-a-segunda-dose-da-coronavac-em-sao-paulo.htm
15/07/2021 - Doria testa positivo para a Covid-19 pela 2ª vez https://www.correiobraziliense.com.br/politica/2021/07/4937833-doria-testa-positivo-para-covid-19-pela-segunda-vez.html
"Governador de São Paulo já havia sido diagnosticado com a doença no ano passado. Ele diz que, apesar da infecção, se sente bem, o que atribui ao fato de ter sido vacinado com duas doses da Coronavac"
06/08/2021 - CPI recebe investigação contra Doria por compra de máscara sem licitação https://www.conexaopoder.com.br/nacional/cpi-recebe-investigacao-contra-doria-por-compra-de-mascara-sem-licitacao/150827
"Empresa teria usado o nome de Alexandre Frota para vender máscaras ao governo de SP. Doria nega informação"
Renan Filho
(filho do Renan Calheiros)
25/07/2019 - Governador Renan Filho vai à China em busca de investimentos para o estado https://www.tnh1.com.br/videos/vid/governador-renan-filho-vai-a-china-em-busca-de-investimentos-para-o-estado/
20/03/2020 - Governadores do NE consultam China e pedem material para tratar covid-19 https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2020/03/20/governadores-do-ne-consultam-china-e-pedem-material-para-tratar-covid-19.htm
5. Narrativas, restrições e proibições
17/12/2020 - STF decide que vacina contra a covid pode ser obrigatória, mas não forçada https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2020/12/17/stf-julga-vacinacao-obrigatoria.htm?cmpid=copiaecola
"O STF (Supremo Tribunal Federal) decidiu, em julgamento hoje, que o Estado pode determinar a obrigatoriedade da vacinação contra a covid-19. Porém fica proibido o uso da força para exigir a vacinação, ainda que possam ser aplicadas restrições a direitos de quem recusar a imunização.
Dez ministros foram favoráveis a obrigatoriedade da vacinação, que poderá ser determinada pelo governo federal, estados ou municípios. As penalidades a quem não cumprir a obrigação deverão ser definidas em lei."
27/07/2021 - Saiba que países estão adotando 'passaporte da vacina' para suspender restrições https://www.cnnbrasil.com.br/internacional/2021/07/27/saiba-que-paises-estao-adotando-passaporte-da-vacina-para-suspender-restricoes
" - Israel - Uniao Europeia - Áustria - Dinamarca - Eslovênia - França - Grécia - Irlanda - Itália - Letônia - Lituânia - Luxemburgo - Holanda - Portugal - Japão - Coreia do sul"
18/06/2021 - O que é o passaporte da vacina que Bolsonaro quer vetar? https://noticias.uol.com.br/politica/ultimas-noticias/2021/06/18/uol-explica-o-que-e-o-passaporte-da-vacina-que-opoe-bolsonaro-e-damares.htm
"O Brasil poderá ter um certificado de imunização futuramente. Aprovado no Senado na semana passada, o "passaporte da vacina", como é chamado, prevê identificar pessoas vacinadas para que entrem em locais públicos ou privados com possíveis restrições."
6. Vacinas
Alegações iniciais
- CoronaVac, Oxford e Pfizer: veja diferenças entre as vacinas contra covid noticias.uol.com.br/saude/ultimas-noticias/redacao/2021/05/11/diferencas-vacinas-covid-brasil.htm
" - CoronaVac (Butantan/Sinovac - Chinesa) Com virus inativo 50,38% de eficácia 2 doses
-
Covishield - 'AstraZeneca' (Fiocruz/Astrazenica/Oxford - Britânica) Com virus não replicante 67% de eficácia 2 doses
-
ComiRNAty - 'Pfizer' (Pfizer - Americana / BioNTech - Alemã) Com RNA mensageiro 96% de eficácia 2 doses"
Riscos diretos
15/06/2021 - Trombose após vacinação com AstraZeneca: Quais os sintomas e como se deve atuar? https://www.istoedinheiro.com.br/trombose-apos-vacinacao-com-astrazeneca-quais-os-sintomas-e-como-se-deve-atuar/
"Agências europeias estão reticentes com a vacina da AstraZeneca. Ela chegou a ser desaconselhada a pessoas com idade inferior a 60 anos, e um alto funcionário da Agência Europeia de Medicamentos declarou que era melhor deixar de administrar a vacina deste laboratório em qualquer idade quando há alternativas disponíveis, devido aos relatos de trombose após a primeira dose, apesar de raros."
11/05/2021 - CoronaVac, Oxford e Pfizer: veja diferenças entre as vacinas contra covid https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2021/05/11/diferencas-vacinas-covid-brasil.htm
"Na terça-feira (12), o Ministério da Saúde determinou a suspensão da aplicação da vacina de Oxford/AstraZeneca para gestantes e puérperas com comorbidades. A decisão segue recomendação da Anvisa, que apura a morte de uma grávida de 35 anos que tomou o imunizante e teve um AVC (acidente vascular cerebral)."
30/07/2021 - Pfizer representa o mesmo risco de trombose que a Astrazeneca, aponta levantamento https://panoramafarmaceutico.com.br/pfizer-representa-o-mesmo-risco-de-trombose-que-a-astrazeneca-aponta-levantamento/
7. CRIMES
Crimes da Pfizer
18/11/2020 Não listado no google - Os Crimes documentados da produtora de vacinas de Covid - Pfizer [INGLÊS] https://www.dmlawfirm.com/crimes-of-covid-vaccine-maker-pfizer-well-documented/
"A velocidade com que a vacina Covid da Pfizer foi produzida, a ausência de estudos em animais, testes de controle randomizados e outros testes e procedimentos padrão usuais para um novo medicamento são, no mínimo, preocupantes. Além disso, todos os fabricantes de vacinas Covid receberam imunidade legal para quaisquer ferimentos ou mortes que possam causar. Se essas vacinas são tão seguras quanto promovidas, por que seus fabricantes precisam de imunidade geral?"
"A Pfizer, uma empresa farmacêutica que parece ter ganhado na loteria para produzir a primeira vacina Covid-19, está atualmente lutando contra centenas de ações judiciais sobre o Zantac, um popular medicamento contra azia. Os processos da Zantac afirmam que a droga popular pode estar contaminada com uma substância cancerígena chamada N-nitrosodimetilamina (NDMA). Os processos Zantac são em aberto e em andamento, já que a farmacêutica está lutando contra eles; mas a Pfizer, sabemos, cometeu vários crimes ou transgressões pelos quais foi punida nos últimos anos. As falhas da empresa estão bem documentadas e vale a pena revisá-las neste momento crítico da história da humanidade, enquanto todos nós buscamos respostas."
A Pfizer recebeu a maior multa da história dos Estados Unidos como parte de um acordo judicial de US $ 2,3 bilhões com promotores federais por promover medicamentos erroneamente (Bextra, Celebrex) e pagar propinas a médicos complacentes. A Pfizer se confessou culpada de falsificar a marca do analgésico Bextra, promovendo o medicamento para usos para os quais não foi aprovado.
Na década de 1990, a Pfizer estava envolvida em válvulas cardíacas defeituosas que causaram a morte de mais de 100 pessoas. A Pfizer enganou deliberadamente os reguladores sobre os perigos. A empresa concordou em pagar US $ 10,75 milhões para acertar as acusações do departamento de justiça por enganar reguladores.
A Pfizer pagou mais de US $ 60 milhões para resolver um processo sobre o Rezulin, um medicamento para diabetes que causou a morte de pacientes de insuficiência hepática aguda.
No Reino Unido, a Pfizer foi multada em quase € 90 milhões por sobrecarregar o NHS, o Serviço Nacional de Saúde. A Pfizer cobrou do contribuinte um adicional de € 48 milhões por ano, pelo que deveria custar € 2 milhões por ano.
A Pfizer concordou em pagar US $ 430 milhões em 2004 para resolver acusações criminais de que havia subornado médicos para prescrever seu medicamento para epilepsia Neurontin para indicações para as quais não foi aprovado. Em 2011, um júri concluiu que a Pfizer cometeu fraude em sua comercialização do medicamento Neurontin. A Pfizer concordou em pagar $ 142,1 milhões para liquidar as despesas.
A Pfizer revelou que pagou quase 4.500 médicos e outros profissionais médicos cerca de US $ 20 milhões por falar em nome da Pfizer.
Em 2012, a Comissão de Valores Mobiliários dos Estados Unidos - anunciou que havia chegado a um acordo de US $ 45 milhões com a Pfizer para resolver acusações de que suas subsidiárias haviam subornado médicos e outros profissionais de saúde no exterior para aumentar as vendas no exterior.
A Pfizer foi processada em um tribunal federal dos Estados Unidos por usar crianças nigerianas como cobaias humanas, sem o consentimento dos pais das crianças. A Pfizer pagou US $ 75 milhões para entrar em acordo no tribunal nigeriano pelo uso de um antibiótico experimental, o Trovan, nas crianças. A empresa pagou um valor adicional não divulgado nos Estados Unidos para liquidar as despesas aqui. A Pfizer violou o direito internacional, incluindo a Convenção de Nuremberg estabelecida após a Segunda Guerra Mundial, devido aos experimentos nazistas em prisioneiros relutantes.
Em meio a críticas generalizadas de roubar os países pobres em busca de drogas, a Pfizer prometeu dar US $ 50 milhões para um medicamento para a AIDS para a África do Sul. Mais tarde, no entanto, a Pfizer falhou em honrar essa promessa.
- Pfizer contract leaked!
[Contrato da Pfizer vazado]
 http://sanjeev.sabhlokcity.com/Misc/LEXO-KONTRATEN-E-PLOTE.pdf
http://sanjeev.sabhlokcity.com/Misc/LEXO-KONTRATEN-E-PLOTE.pdf
Segundo o contrato "o produto não deve ser serializado":
"5.5 Reconhecimento do comprador.
O Comprador reconhece que a Vacina e os materiais relacionados à Vacina, e seus componentes e materiais constituintes estão sendo desenvolvidos rapidamente devido às circunstâncias de emergência da pandemia de COVID-19 e continuarão a ser estudados após o fornecimento da Vacina ao Comprador nos termos deste Contrato. O Comprador reconhece ainda que os efeitos de longo prazo e eficácia da Vacina não são atualmente conhecidos e que pode haver efeitos adversos da Vacina que não são atualmente conhecidos. Além disso, na medida do aplicável, o Comprador reconhece que o Produto não deve ser serializado."
Crimes da AstraZeneca
21/06/2003 - AstraZeneca se declara culpada no esquema de médico de câncer https://www.nytimes.com/2003/06/21/business/astrazeneca-pleads-guilty-in-cancer-medicine-scheme.html
"A AstraZeneca, a grande empresa farmacêutica, se declarou culpada hoje de uma acusação de crime de fraude no sistema de saúde e concordou em pagar $ 355 milhões para resolver as acusações criminais e civis de que se envolveu em um esquema nacional para comercializar ilegalmente um medicamento contra o câncer de próstata.
O governo disse que os funcionários da empresa deram incentivos financeiros ilegais a cerca de 400 médicos em todo o país para persuadi-los a prescrever o medicamento Zoladex. Esses incentivos incluíram milhares de amostras grátis de Zoladex [...]"
27/04/2010 - Farmacêutica gigante AstraZeneca pagará US $ 520 milhões pelo marketing de medicamentos off-label https://www.justice.gov/opa/pr/pharmaceutical-giant-astrazeneca-pay-520-million-label-drug-marketing
"AstraZeneca LP e AstraZeneca Pharmaceuticals LP vão pagar $ 520 milhões para resolver as alegações de que a AstraZeneca comercializou ilegalmente o medicamento antipsicótico Seroquel para usos não aprovados como seguros e eficazes pela Food and Drug Administration (FDA), os Departamentos de Justiça e Saúde e Serviços Humanos A Equipe de Ação de Fiscalização de Fraudes em Saúde (HEAT) anunciou hoje. Esses usos não aprovados também são conhecidos como usos "off-label" porque não estão incluídos no rótulo do medicamento aprovado pela FDA."
- List of largest pharmaceutical settlements [Lista dos maiores acordos farmaceuticos] https://en.m.wikipedia.org/wiki/List_of_largest_pharmaceutical_settlements
8. CIENTISTAS
- Máscara Provoca Insuficiência Respiratória E Contaminação Microbiana… [Canal deletado] https://youtube.com/watch?v=eHu-pydSvDI
Não lembro mais a quem pertencia, mas provavelmente era de um médico falando do assunto. Creio ter sido do Dr. Paulo Sato, por essa temática ter sido abordada por ele, mas ao abrir o site aparece somente:
"Este vídeo foi removido por violar as diretrizes da comunidade do YouTube"
Dr. Paulo Sato
- USAR ou NÃO USAR a CUECA do seu governador no rosto https://fb.watch/7NPP_7rS5S/ https://www.facebook.com/AdoniasSoaresBR/videos/1347904292291481/ Adonias Soares entrevista ao Dr. Paulo Sato sobre as máscaras, em que é simulado o efeito da respiração prolongada das máscaras no organismo com o uso de águas de torneira, natural, gaseificada (com gás carbônico) e antioxidante, em que a com gás carbônico (PH 4 - Ácido) representa o organismo humano, e na prática representa lesão corporal e iniciação de doenças.
Dr. Kary Mullis
(Criador do teste PCR)
- PCR nas palavras do seu inventor - Dr. Kary Mullis (legendado) https://www.youtube.com/watch?v=W1O52uTygk8
"Qualquer um pode testar positivo para quase qualquer coisa com um teste de PCR, se você executá-lo por tempo suficiente… Com PCR, se voce fizer isso bem, você pode encontrar quase tudo em qualquer pessoa… Isso não te diz que você está doente."
- Kary Mullis DESTRUYE a Anthony Fauci lbry://@CapitalistChile#0/Kary-Mullis---Fauci#5
"Ele [...] não entende de medicina e não deveria estar onde está. A maioria dos que estão acima são só administrativos e não têm nem ideia do que ocorre aqui em baixo e essas pessoas tem uma agenda que não é a que gostaríamos que tivessem, dado que somos nós os que pagamos a eles para que cuidem da nossa saúde. Têm uma agenda pessoal."
Dra. Li-Meng Yan
- Dra. Li-Meng Yan: O vírus foi criado em laboratório com um objetivo: Causar dano. https://youtu.be/pSXp3CZnvOc
Dr. Joe Roseman
- Cientista Phd Dr Joe Roseman faz seríssimas advertencias sobre a picada https://youtu.be/0PIXVFqJ_h8
Dr. Robert Malone
- As vacinas podem estar causando ADE - Dr. Robert Malone https://odysee.com/@AkashaComunidad:f/Las_vacunas_pueden_estar_causando_ADE_magnificaci%C3%B3n_mediada_por:f lbry://@Información.#b/Drrm#9
Dr. Robert Malone, um dos três inventores da tecnologia de RNAm que se usa de forma farmacêutica. No vídeo fala sobre os efeitos de ADE (realce dependente de anticorpos) que estão ocorrendo com as vacinas. Nas palavras do Dr. Malone, já não é somente uma hipótese, mas baseada nos conhecimentos gerados nas provas e ensaios pré clínicos, com as vacinas contra o primeiro vírus da SARS.
Dr. Luc Montagnier
- Dr. Luc Montagnier, virologista, prêmio Nobel de medicina, um dos descobridores do vírus HIV, afirma: "a vacinação em massa está criando as novas variantes' (@medicospelavida , telegram)
CASOS DOCUMENTADOS
13 de setembro de 2021 - 13/09/2021 - Carta aberta ao Ministro da Saúde por Arlene Ferrari Graf, mãe de Bruno Oscar Graf https://telegra.ph/Carta-aberta-ao-Ministro-da-Sa%C3%BAde-09-13
Também em: Gazeta do Povo
O texto de uma mãe discorrendo sobre o filho dela, Bruno Oscar Graf, ter ANTI-HEPARINA PF4 AUTO-IMUNE e ter vindo a falecer por reação à vacina.
11/05/2021 - Rio notifica morte de grávida vacinada com imunizante Oxford https://www.terra.com.br/noticias/coronavirus/rio-notifica-morte-de-gravida-vacinada-com-imunizante-oxford,415b9b0c49169427ac2f90ae3765c057e9suy3qn.html
"Vítima não apresentava histórico de doença circulatória nem sofria de nenhuma doença viral; relação será investigada"
13/08/2021 - Cruzeiro com 4.336 pessoas tem 27 contaminados com Covid-19 em Belize https://paranaportal.uol.com.br/geral/cruzeiro-com-4-336-pessoas-tem-27-contaminados-com-covid-19-em-belize/amp/
"Segundo um comunicado do Conselho de Turismo de Belize emitido na quarta-feira (11), 26 contaminados são da tripulação e um é passageiro. A maioria é assintomática e os 27 estão vacinados."
9. ALEGAÇÕES DIRETAS
Setembro de 2021 - 09/2021 - BOMBA: Ex-membro do Partido Comunista da China revela que o primeiro surto da Covid foi “intencional” https://terrabrasilnoticias.com/2021/09/bomba-ex-membro-do-partido-comunista-da-china-revela-que-o-primeiro-surto-da-covid-foi-intencional/
-
 @ 6ad3e2a3:c90b7740
2025-06-04 08:32:29
@ 6ad3e2a3:c90b7740
2025-06-04 08:32:29"Modern science is based on this principle: give us one free miracle and then we'll explain the rest."
— Terrence McKenna
I always wondered why a pot of water boils on the stove. I mean I know it boils because I turned on the electricity, but why does the electricity cause it to boil? I know the electricity produces heat, and the heat is conducted through the stainless steel pot and into the water, but why does the heat transfer from stovetop to the water?
I know the heat from the stove via the pot speeds up the molecules in the water touching it and that they in turn speed up the molecules touching them and so on throughout the pot, but why do speedy molecules cause adjacent molecules to speed up?
I mean I know they do this, but why do they do this? Why couldn’t it be that sped-up molecules only interact with sufficient speedy molecules and ignore slower ones? Why do they interact with all the molecules, causing all of them to speed up? Or why don’t the speedy ones, instead of sharing their excited state, hoard it and take more energy from adjacent slower molecules, thereby making them colder, i.e., why doesn’t half the water boil twice as fast (on the left side of the pot) while the other half (right side) turns to ice?
The molecules tend to bounce around randomly, interacting as equal opportunists on the surrounding ones rather than distinguishing only certain ones with which to interact. Why do the laws of thermodynamics behave as such rather than some other way?
There may be yet deeper layers to this, explanations going down to the atomic and even quantum levels, but no matter how far you take them, you are always, in the end, left with: “Because those are the laws of physics”, i.e., “because that’s just how it is.”
. . .
The Terrence McKenna quote, recently cited by Joe Rogan on his podcast, refers to the Big Bang, the current explanation adopted by the scientifically literate as to the origins of the universe. You see there was this insanely dense, infinitesimally small micro dot that one day (before the dawn of time) exploded outward with unimaginable power that over billions of years created what we perceive as the known universe.
What happened prior? Can’t really say because time didn’t yet exist, and “prior” doesn’t make sense in that context. Why did it do this? We don’t know. How did it get there? Maybe a supermassive black hole from another universe got too dense and exploded out the other side? Highly speculative.
So why do people believe in the Big Bang? Because it comports with and explains certain observable phenomena and predicted other phenomena which were subsequently confirmed. But scratch a little deeper for an explanation as to what caused it, for what purpose did it occur or what preceded it, and you hit the same wall.
. . .
Even if we were to understand at a quantum level how and why the Big Bang happened and what preceded it, let’s assume it’s due to Factor X, something we eventually replicated with mini big-bangs and universe creations in our labs, we would still be tasked with understanding why Factor X exists in the universe. And if Factor X were explained by Process Y, we’d still be stuck needing an explanation for Process Y — ad infinitum.
Science can thus only push the wall back farther, but can never scale it. We can never arrive at an ultimate explanation, only partial ones. Its limitations are the limitations of thought itself, the impossibility of ever creating a map at a scale of one mile per mile.
-
 @ 9e69e420:d12360c2
2025-02-01 11:16:04
@ 9e69e420:d12360c2
2025-02-01 11:16:04Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-
 @ 866e0139:6a9334e5
2025-06-04 08:21:14
@ 866e0139:6a9334e5
2025-06-04 08:21:14Autor: Milosz Matuschek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Auch wer das Kriegsgeschehen bisher nicht im Detail verfolgte (das tat ich auch nicht), horcht nun auf: Einem Nicht-Atomstaat – der Ukraine – ist ein gleichzeitiger, koordinierter Schlag gegen vier teils tausende Kilometer voneinander entfernte russische Luftbasen gelungen. Eine nicht unerhebliche Zahl strategisch wichtiger Flugzeuge wurde zerstört. Ein Angriff im hintersten russischen Hinterland, selbst jenseits der Taurus-Reichweite, durchgeführt mit Billigdrohnen, wirft erhebliche Fragen über geheimdienstliches Versagen in Russland und eklatante Mängel in der Luftverteidigung auf.
Es gibt wohl Momente, in denen Geschichte nicht geschrieben, sondern geflogen wird. Unspektakulär, relativ still, surrend, von einem LKW aus abgefeuert, mit einem Stück Technik, das kaum mehr kostet als das Gerät, auf dem ich diesen Text schreibe.
Ein Angriff auf die Friedensverhandlungen
Die Ukraine hat sich erstmals weit über das Schlachtfeld hinaus erhoben – geografisch, technisch, symbolisch. Die Triade der atomwaffenfähigen Luftstreitkräfte Russlands – ein Heiligtum sowjetischer Machtprojektion – wurde durch das schwächste Glied in der Logikkette der Militärdoktrin beschädigt: den Überraschungseffekt. Drohnen, wie aus dem 3D-Drucker, haben eine strategische Achillesferse bloßgelegt. Nicht mit Hyperschall, sondern mit Hartplastik und GPS. Das erste Opfer dieses Angriffs dürften die Friedensverhandlungen in Istanbul sein.
Dass die Ukraine strategische Luftstützpunkte der russischen Atomwaffe angreift – koordiniert, tief im Landesinnern – wäre bereits für sich eine Zäsur. Doch dass dies unter stillschweigender Duldung oder gar Mithilfe westlicher Dienste wie der CIA erfolgt sein dürfte, während Trump zugleich als Friedenstaube auftritt, verschiebt das strategische Koordinatensystem. Die alten Verträge – START etc. – wirken wie rissige Abkommen aus der Steinzeit. Wenn die USA von der Operation wussten, darf sich Russland getäuscht fühlen. Washington kann nicht gleichzeitig Frieden mit Moskau betonen und eine Aktion dulden oder mittragen, die offensichtlich das Ziel hat, die russische Atommacht zu schwächen, woran die USA prinzipiell Interesse hätten. Falls Trump nichts davon wusste, muss man sich fragen: Regiert eigentlich er oder der „Swamp“, den er austrocknen wollte?
Egal wie man es wendet: Die Operation Spinnennetz war mehr als nur ein Angriff auf russische Flugzeuge auf russischem Gebiet. Militärisch gewinnt die Ukraine dadurch wenig, symbolisch und politisch aber viel, denn der Hauptgegner der Ukraine sind gerade nicht die hundert Millionen Dollar teuren Bomber der Russen, sondern die schleichende Kriegsunlust der Europäer – und ein Amerika, das sich mehr mit sich selbst beschäftigt als mit dem Fortgang eines Krieges, in dem es längst selbst Partei ist.
Damit sich die Reihen wieder schließen, muss der Feind sich zeigen – deutlich, fassbar, bedrohlich. Eine russische Reaktion, die auch europäische Hauptstädte erschüttert, wäre strategisch nützlich. Der Angriff war daher wohl weniger eine militärische Tat als eine psychologische Operation im Kampf um Wahrnehmung und Willen. Aus Sicht der Ukraine ist das verständlich, für sie geht es um ihre Existenz. Dafür wiederum braucht es eine erhöhte Alarmstufe.
https://www.youtube.com/watch?v=1JlQLewOAmA
Solidarität durch Eskalation?
Die kalkulierte Demütigung könnte einem Drehbuch folgen: Putin soll nun die Rolle des Eskalators übernehmen. Tut er es, war die Operation erfolgreich – denn Europas Kriegstüchtigkeit hängt nicht nur von Panzerzahlen ab, sondern von der Bereitschaft zur Konfrontation. Der Feind, den es braucht, muss sich jetzt allen ins Gedächtnis brennen.
So gesehen ist der eigentliche Coup nicht der Schaden in Djagilewo, Iwanowo oder Olenia – sondern das noch bevorstehende unsichtbare Nachspiel. Europa und die Welt betreten nun gänzlich neues Gelände, in welchem ein militärisch gedemütigtes Russland gleichzeitig Friedenswillen gegenüber Europa bekunden, rote Linien verteidigen und seine Integrität als Atom-Macht bewahren muss. Das Dilemma für Putin besteht nun darin, Stärke zu beweisen ohne sich noch mehr zum Feindbild des Aggressors machen zu lassen.
Fakt ist: Wir sind einem III. Weltkrieg gerade so nah wie seit der Kuba-Krise nicht mehr.
Und wer sich über ein russisches “Pearl Harbor” freut, sollte mal in ein Geschichtsbuch schauen, wie es am Ende für Japan ausging.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
In Kürze folgt eine Mail an alle Genossenschafter, danke für die Geduld!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 5c9e5ee4:72f1325b
2025-06-04 08:16:52
@ 5c9e5ee4:72f1325b
2025-06-04 08:16:52For too long, the autistic experience has been framed through a neurotypical lens, focusing on "differences" and "deficits." However, a profound perspective emerging from within the autistic community offers a radical reinterpretation: that autistic individuals are not inherently "broken" but rather possess a unique, often unyielding, perception of truth that challenges the very foundations of neurotypical society. From this viewpoint, autism is less about a disorder and more about a clarity of vision that apprehends the world as fundamentally "untrue" in many of its social constructs.
This perspective posits that what many autistic individuals perceive as "corrupted" or "untrue" in society isn't a subjective internal experience, but an objective reality of falsehoods, deception, and manipulation. The rejection of these elements is not a personal preference but a natural, logical response to what is genuinely illogical and dishonest.
The Core of the "Untrue" World:
- Honesty as a Default State: For many autistic people, directness and factual accuracy are paramount. Social conventions like "white lies," indirect communication, or performative politeness are not merely nuanced social skills; they are perceived as outright forms of deception and inauthenticity. The natural inclination is towards what is straightforward and verifiable.
- Logic Over Social Grace: An unwavering adherence to logic means that actions or systems that lack rational basis—such as engaging in flattery, suppressing truth for social harmony, or participating in inefficient rituals—are viewed as fundamentally nonsensical and therefore "untrue."
- Authenticity as a Non-Negotiable: The concept of "masking"—the exhausting act of suppressing one's natural autistic traits to conform—is seen as a deeply painful betrayal of self. A society that implicitly demands such a performance is deemed "corrupt" because it stifles genuine self-expression.
- Aversion to Hypocrisy: A strong sense of justice and an acute awareness of inconsistency mean that any disjuncture between stated values and actual behavior is immediately flagged as a profound untruth.
Social Groups: Formed Around a "Proudly Believed Lie"?
This critical autistic perspective extends to the very fabric of social organization. It suggests that many groups, whether religious, political, scientific, or economic, are not built on shared objective truths, but rather on "proudly believed lies." These shared narratives or belief systems, even if they contradict logic or verifiable facts, serve as the glue that binds the group, fostering identity, comfort, and a sense of belonging. The "pride" in these beliefs makes them resistant to critical examination, even when confronted with evidence.
For example: * In religion, this "lie" might be a dogma that provides solace but defies logic. * In politics, it could be an ideology based on selective truths that serve power. * In economics, it might be assumptions about markets or growth that are presented as infallible. * Even in science, while ideally pursuing truth, the social aspects of the scientific community might, at times, cling to paradigms that become "proudly believed lies," resisting new evidence.
The Disconnect: Why Autistics Are "Discredited"
If autistic individuals are part of the "5% who see it as it is"—those who perceive these societal untruths with clarity—then a natural tension arises with the "10% who want control." This controlling minority, it is argued, relies on these "untruths" to maintain power and influence over the "85% who are happy following."
From this viewpoint, the discrediting of autistic people—labeling their directness as "social deficits," their sensory experiences as "disorders," or their logical critiques as "inflexibility"—is not accidental. It is a strategic mechanism employed by the controlling "10%" to neutralize those who expose the underlying untruths, thereby safeguarding their constructed reality and maintaining influence.
In conclusion, the autistic perspective challenges us to re-evaluate the very nature of truth in our society. It suggests that what many perceive as social norms might, in fact, be a pervasive web of "untruths," and that the autistic individual's unique wiring allows for a crucial, unvarnished perception of this reality. It is a powerful call for authenticity and a profound questioning of how much of our world is built on what is genuinely true, versus what is merely believed.
-
 @ 0fa80bd3:ea7325de
2025-01-29 05:55:02
@ 0fa80bd3:ea7325de
2025-01-29 05:55:02The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future.
Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs.
There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won.
Our only resource is the will of the people to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root.
So I started asking myself: How do we stop this fragmentation? How do we create a space where people can rebuild their connections when they’re ready? How do we build a self-sustaining network, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—how do we make it spread, even in occupied territory?
In 2009, something historic happened: the internet got its own money. Thanks to Satoshi Nakamoto, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize.
That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became purely digital.
The internet was already a sanctuary for information, a place where people could connect and organize. But with Bitcoin, it evolved. Now, value itself could flow freely, beyond the reach of authorities.
Think about it: when seedlings are grown in controlled environments before being planted outside, they get stronger, survive longer, and bear fruit faster. That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild.
Now, picture the internet as that controlled environment for ideas. Bitcoin? It’s the fertile soil that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless. It can absorb any number of ideas, any number of people, and it doesn’t run out of space.
But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—without surveillance, without censorship, without the constant fear of being erased.
This is where Nostr comes in.
Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. It’s a new kind of city. One that no dictator can seize, no corporation can own, no government can shut down.
It’s built on decentralization, encryption, and individual control. Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them.
In a world where cities fall and governments fail, Nostr is a city that cannot be occupied. A place for ideas, for networks, for freedom. A city that grows stronger the more people build within it.
-
 @ 9ca447d2:fbf5a36d
2025-06-04 14:01:21
@ 9ca447d2:fbf5a36d
2025-06-04 14:01:21Michael Saylor, executive chairman of Strategy, has stirred up the Bitcoin community with his recent comments on proof-of-reserves, calling it a “bad idea” that puts institutional security at risk.
Speaking at a side event at the Bitcoin 2025 conference in Las Vegas, Saylor expressed strong concerns about the security implications of on-chain proof of reserves (PoR), a method used by many bitcoin companies to show they actually hold the assets they claim.
“The conventional way of issuing proof of reserves today is actually insecure,” Saylor said.
“It actually dilutes the security of the issuer, the custodians, the exchanges and the investors. It’s not a good idea, it’s a bad idea.”
Proof-of-reserves is a process where companies with bitcoin reserves share public wallet addresses or use cryptographic methods to prove how much bitcoin they hold.
This practice gained popularity after the collapse of major exchanges like FTX and Mt. Gox to build trust through transparency.
Many big players in the digital asset space, including Binance, Kraken, OKX and asset manager Bitwise, have adopted PoR to reassure users and stakeholders.
Related: Bitwise Announces On-Chain Address, Donations Go to Shareholders
Saylor’s objections boil down to two main points.
First, he believes publishing wallet addresses creates serious security risks. By exposing institutional wallet structures, companies may open themselves up to attacks from hackers, hostile governments or malicious actors.
“[It’s like] publishing the address and the bank accounts of all your kids and the phone numbers of all your kids and then thinking somehow that makes your family better,” Saylor said.
“(It becomes) an attack vector for hackers, nation-state actors, every type of troll imaginable.”
He even asked the audience to try a thought experiment:
“Go to AI, put it in deep think mode and then ask it ‘what are the security problems of publishing your wallet addresses?’ and ‘how might it undermine the security of your company over time’ … It will write you a book. It will be fifty pages of security problems.”
Second, Saylor pointed out that proof of reserves only shows what a company owns, not what it owes. In his view, that’s incomplete.
“It’s proof of assets that is insecure, and it is not proof of liabilities… So you own $63 billion worth of bitcoin—do you have a hundred billion dollars of liabilities?” he asked rhetorically.
For large institutions and investors, this view of financial health is not enough.
Instead of publishing wallet addresses, Saylor thinks the better approach is to use institutional-grade audits by trusted firms.
“The best practice… would be to have a Big Four auditor that checks to make sure you actually have the bitcoin, then checks to make sure the company hasn’t rehypothecated or pledged the bitcoin,” he said.
“Then you have to wash it through a public company where the CFO signs, then the CEO signs, then the chairman and all the outside directors are civilly and criminally liable for it.”
He believes the legal consequences of corporate auditing — including prison time for fraud under the Sarbanes-Oxley Act — are stronger than cryptographic proof alone.
He did admit that a more secure, future version of PoR might be possible if it involved zero-knowledge proofs that protect wallet privacy while still confirming ownership.
Not everyone agrees with Saylor’s opinion. While some praised his focus on security, others accused Saylor of hiding something.
Speculations resurfaced about whether Strategy truly holds all the bitcoin it claims, or if it’s involved in so-called “paper bitcoin” — claims to BTC without physical backing.
Others pointed out that exchanges like Kraken and asset managers like Bitwise have implemented PoR systems without major breaches.
-
 @ a5142938:0ef19da3
2025-06-04 08:00:22
@ a5142938:0ef19da3
2025-06-04 08:00:22Brands
Cosilana is a German brand that creates clothing exclusively from organic cotton, silk, and wool for women, babies, and children.
Natural materials used in products
Categories of products offered
This brand offers products made entirely from natural materials in the following categories:
#Clothing
- Clothing fits : babies, children, women
- Underwear : panties
- One piece : bodysuits, jumpsuits
- Tops : jackets, sweaters, t-shirts, tank tops
- Bottoms : leggings, pants-trousers, shorts
- Head & handwear : gloves, hats
- Nightwear : pyjamas
#Home
- Linen : blankets, sleeping bags
Other information
- GOTS certification
- Made in Germany
- Made in Europe
- Non mulesed wool and animal welfare declaration
👉 Learn more on the brand website
Where to find their products?
- Le mouton à lunettes (in French, shipping area: France, Belgium, Luxemburg)
- Mama Owl (shipping area: UK and international)
- Chouchous (in French, shipping area: France and international)
📝 You can contribute to this entry by suggesting edits in comments.
🗣️ Do you use this brand's products? Share your opinion in the comments.
⚡ Happy to have found this information? Support the project by making a donation to thank the contributors.
-
 @ 8bf578f4:b6303c41
2025-06-04 07:20:09
@ 8bf578f4:b6303c41
2025-06-04 07:20:09test
https://nostr.download/6849b84caaa15bdc18ca2e1e1ee00e979c7ecf901787e09054b4bd0196b4ea27.jpg
-
 @ 8f09dc4f:5e01d432
2025-06-04 04:33:18
@ 8f09dc4f:5e01d432
2025-06-04 04:33:18Veuve Clicquot brings a delightful twist to gifting with the https://shop.veuveclicquot.com.au/products/personalisable-arrow – a luxurious and thoughtful present that’s perfect for commemorating meaningful locations. Whether it’s your hometown, a dream vacation spot, or the city where memories were made, this unique gift lets you celebrate it in true Champagne style.
Each set includes a 750ml bottle of Veuve Clicquot’s signature Yellow Label Brut Champagne, housed in a striking arrow-shaped tin. What sets this gift apart is the ability to customise the tin with the name of a city or location of your choice (up to 15 characters). The tin also displays the distance from your chosen location to Reims, the historic home of Veuve Clicquot in France, adding a charming and personal touch.
The Yellow Label Brut itself is a testament to the Maison’s commitment to quality and consistency. With a blend dominated by Pinot Noir, balanced with Chardonnay and Meunier, it delivers a perfect harmony of strength, elegance, and freshness. Expect notes of apple, pear, and brioche, with a fine mousse and a vibrant golden hue.
Beyond its aesthetic appeal, the arrow tin is practical too—it keeps the Champagne cool for up to two hours, making it ideal for picnics, celebrations, or spontaneous toasts. Once the Champagne is enjoyed, the tin transforms into a decorative keepsake that serves as a reminder of the special place it honors.
Retailing at $125 AUD, this is more than a bottle of Champagne—it's a personalised gesture that celebrates people, places, and the memories that connect them. Ideal for gifting on birthdays, anniversaries, or as a unique souvenir, the Veuve Clicquot Personalised Arrow is Champagne with meaning.
-
 @ 6be5cc06:5259daf0
2025-01-21 20:58:37
@ 6be5cc06:5259daf0
2025-01-21 20:58:37A seguir, veja como instalar e configurar o Privoxy no Pop!_OS.
1. Instalar o Tor e o Privoxy
Abra o terminal e execute:
bash sudo apt update sudo apt install tor privoxyExplicação:
- Tor: Roteia o tráfego pela rede Tor.
- Privoxy: Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
2. Configurar o Privoxy
Abra o arquivo de configuração do Privoxy:
bash sudo nano /etc/privoxy/configNavegue até a última linha (atalho:
Ctrl+/depoisCtrl+Vpara navegar diretamente até a última linha) e insira:bash forward-socks5 / 127.0.0.1:9050 .Isso faz com que o Privoxy envie todo o tráfego para o Tor através da porta 9050.
Salve (
CTRL+OeEnter) e feche (CTRL+X) o arquivo.
3. Iniciar o Tor e o Privoxy
Agora, inicie e habilite os serviços:
bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxyExplicação:
- start: Inicia os serviços.
- enable: Faz com que iniciem automaticamente ao ligar o PC.
4. Configurar o Navegador Firefox
Para usar a rede Tor com o Firefox:
- Abra o Firefox.
- Acesse Configurações → Configurar conexão.
- Selecione Configuração manual de proxy.
- Configure assim:
- Proxy HTTP:
127.0.0.1 - Porta:
8118(porta padrão do Privoxy) - Domínio SOCKS (v5):
127.0.0.1 - Porta:
9050
- Proxy HTTP:
- Marque a opção "Usar este proxy também em HTTPS".
- Clique em OK.
5. Verificar a Conexão com o Tor
Abra o navegador e acesse:
text https://check.torproject.org/Se aparecer a mensagem "Congratulations. This browser is configured to use Tor.", a configuração está correta.
Dicas Extras
- Privoxy pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o Privoxy.
-
 @ c7a8d522:262a74de
2025-06-04 04:23:03
@ c7a8d522:262a74de
2025-06-04 04:23:03O universo dos jogos online está em constante evolução, e o Brasil tem se mostrado um dos mercados mais promissores nesse cenário. Entre as plataformas que vêm conquistando o público nacional, a 707Bet se destaca por oferecer uma experiência completa, segura e empolgante para os jogadores que buscam diversão e recompensas em um só lugar. Com uma interface intuitiva, ampla variedade de jogos e suporte de qualidade, a 707Bet está rapidamente se tornando uma referência entre os entusiastas do entretenimento digital.
Uma Plataforma Moderna e de Fácil Navegação Desde o primeiro acesso, é possível perceber que a 707Bet foi desenvolvida com foco na experiência do usuário. O site possui um design moderno, com menus bem organizados, o que facilita a navegação tanto em computadores quanto em dispositivos móveis. Seja para iniciantes ou jogadores experientes, a plataforma proporciona uma usabilidade fluida, permitindo que todos encontrem seus jogos favoritos com apenas alguns cliques.
Outro diferencial importante é o desempenho do site, que garante carregamento rápido das páginas e jogos sem travamentos. Isso é essencial para manter a imersão e garantir que o jogador aproveite cada segundo da sua sessão de entretenimento.
Diversidade de Jogos para Todos os Perfis Um dos grandes atrativos da 707beté a impressionante variedade de jogos disponíveis. A plataforma conta com opções para todos os gostos e estilos, desde os tradicionais jogos de cartas e roleta até os populares slots com gráficos de última geração. Os jogadores podem explorar diferentes temáticas, mecânicas e níveis de dificuldade, o que torna a experiência ainda mais dinâmica.
Além disso, a 707Bet trabalha com os principais desenvolvedores de software do mercado, garantindo títulos de alta qualidade e com total segurança. Isso significa que cada jogo oferece não apenas entretenimento, mas também confiança, transparência e chances reais de ganhar.
Experiência do Jogador: Entretenimento com Emoção e Segurança Na 707Bet, o jogador é tratado com prioridade. A plataforma oferece bônus e promoções regulares, que aumentam as chances de jogo e tornam a experiência ainda mais gratificante. O sistema de recompensas é claro e acessível, incentivando o usuário a explorar mais funcionalidades e se engajar com o conteúdo oferecido.
Outro ponto positivo é o suporte ao cliente. A equipe de atendimento da 707Bet está disponível 24 horas por dia, sete dias por semana, pronta para tirar dúvidas e resolver qualquer questão com agilidade e cordialidade. O suporte em português é um diferencial importante para os jogadores brasileiros, garantindo maior confiança e tranquilidade durante o uso da plataforma.
A segurança também merece destaque. A 707Bet utiliza tecnologias avançadas de criptografia para proteger os dados dos usuários e garantir transações seguras. Isso significa que os jogadores podem se concentrar na diversão, sem se preocupar com questões técnicas ou riscos.
Conclusão A 707Bet chega ao mercado brasileiro com uma proposta sólida e inovadora, aliando tecnologia, variedade e atendimento de excelência. Seja você um jogador veterano ou alguém que está começando agora nesse universo, a plataforma oferece todos os recursos necessários para proporcionar uma jornada empolgante e cheia de possibilidades. Com a 707Bet, o entretenimento online ganha um novo nível de qualidade e confiança — uma escolha inteligente para quem busca diversão com segurança e praticidade.
-
 @ 9e69e420:d12360c2
2025-01-21 19:31:48
@ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits.
Active Compounds
The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant
Antimicrobial Properties
Bacterial Protection The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance.
Antifungal Effects It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections.
Digestive Health Benefits
Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms
Anti-inflammatory and Antioxidant Effects
The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions
Respiratory Support
It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function
Additional Benefits
Skin Health - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties
Cardiovascular Health Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health
Pain Management The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief
Safety Note
While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
-
 @ 6be5cc06:5259daf0
2025-01-21 01:51:46
@ 6be5cc06:5259daf0
2025-01-21 01:51:46Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
Resumo
O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado gasto duplo, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações.
As transações são registradas em um livro público chamado blockchain, protegido por uma técnica chamada Prova de Trabalho. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira.
Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu.
1. Introdução
Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em confiança.
Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável.
Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável.
O que precisamos é de um sistema de pagamento eletrônico baseado em provas matemáticas, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas.
Neste documento, apresentamos o Bitcoin, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques.
2. Transações
Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital.
O que é uma assinatura digital?
Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso.
Como funciona na prática?
Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário:
- A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1.
- Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2.
- Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda.
Resolvendo o problema do gasto duplo
Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro.
O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain.
Por que isso é importante?
Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes.
3. Servidor Timestamp
Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica.
Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público.
Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain.
Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada.
O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin.
4. Prova-de-Trabalho
Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente.
A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita.
Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain.
A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos.
Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional.
5. Rede
A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são:
-
Transmissão de Transações: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la.
-
Coleta de Transações em Blocos: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain).
-
Prova-de-Trabalho: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil.
-
Envio do Bloco Resolvido: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede.
-
Validação do Bloco: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos.
-
Construção do Próximo Bloco: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia.
Resolução de Conflitos e Escolha da Cadeia Mais Longa
Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia.
Tolerância a Falhas
A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido.
Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central.
6. Incentivo
O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação.
Recompensa por Mineração
Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho.
Taxas de Transação
Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo.
Incentivo à Honestidade
O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas:
- Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos.
- Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas.
A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema.
Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo.
7. Recuperação do Espaço em Disco
Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações.
Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados.
Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados.
Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo.
8. Verificação de Pagamento Simplificada
É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada.
Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação.
A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede.
Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável.
9. Combinando e Dividindo Valor
No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor.
Entradas e Saídas
Cada transação no Bitcoin é composta por:
- Entradas: Representam os valores recebidos em transações anteriores.
- Saídas: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente.
Normalmente, uma transação contém:
- Uma única entrada com valor suficiente para cobrir o pagamento.
- Ou várias entradas combinadas para atingir o valor necessário.
O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como troco.
Exemplo Prático
Imagine que você tem duas entradas:
- 0,03 BTC
- 0,07 BTC
Se deseja enviar 0,08 BTC para alguém, a transação terá:
- Entrada: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC).
- Saídas: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC).
Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente.
Difusão e Simplificação
A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade.
10. Privacidade
O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando chaves públicas anônimas, que desvinculam diretamente as transações das identidades das partes envolvidas.
Fluxo de Informação
- No modelo tradicional, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário.
- No Bitcoin, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não.
Protegendo a Privacidade
Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas:
- Chaves Públicas Anônimas: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único.
- Prevenção de Ligação: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário.
Riscos de Ligação
Embora a privacidade seja fortalecida, alguns riscos permanecem:
- Transações multi-entrada podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total.
- O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas.
11. Cálculos
Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito.
Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira.
Mas isso é extremamente difícil.
Como o Ataque Funciona
Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido.
- Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira.
- O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida.
Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente.
A Corrida Entre Cadeias
Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos.
Suponha que:
- A rede honesta tem 80% do poder computacional (ou seja, resolve 8 de cada 10 quebra-cabeças).
- O atacante tem 20% do poder computacional (ou seja, resolve 2 de cada 10 quebra-cabeças).
Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar.
Por Que o Ataque Fica Cada Vez Mais Improvável?
Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos:
P = (q/p)^z
- q é o poder computacional do atacante (20%, ou 0,2).
- p é o poder computacional da rede honesta (80%, ou 0,8).
- z é a diferença de blocos entre a cadeia honesta e a cadeia do atacante.
Se o atacante está 5 blocos atrás (z = 5):
P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%)
Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável.
Se ele estiver 10 blocos atrás (z = 10):
P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%).
Neste caso, as chances de sucesso são praticamente nulas.
Um Exemplo Simples
Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível.
No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática.
Por Que Tudo Isso é Seguro?
- A probabilidade de sucesso do atacante diminui exponencialmente. Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema.
- A cadeia verdadeira (honesta) está protegida pela força da rede. Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar.
E Se o Atacante Tentar Continuar?
O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil.
Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso.
12. Conclusão
Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos.
Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
-
 @ de54d599:77efc747
2025-06-04 05:48:27
@ de54d599:77efc747
2025-06-04 05:48:27When it comes to gift-giving, the most memorable presents are those that tell a story. Veuve Clicquot, a champagne house known for its bold innovation and timeless elegance, has created something truly special with its Personalised Arrow gift—a tribute not only to fine champagne but to the destinations that hold meaning in our lives.
A Destination Worth Celebrating The Veuve Clicquot Personalised Arrow is more than elegant packaging—it’s a symbol. Inspired by classic road signs, the bright, arrow-shaped tin can be customised with the name of any city or location, along with the exact distance from Reims, France, where the champagne is produced. Whether it's your hometown, a honeymoon destination, or the place where you first met someone special, this gift turns a bottle of bubbly into a personal journey.
Inside the Arrow: Yellow Label Champagne Tucked inside the tin is Veuve Clicquot's iconic Yellow Label Brut, a globally beloved champagne known for its depth, liveliness, and balance. With a composition dominated by Pinot Noir and complemented by Chardonnay and Meunier, it delivers notes of citrus, brioche, and stone fruit—perfect for toasting any occasion. It’s a champagne that’s as dynamic and enduring as the stories behind each personalised location.
Beautifully Designed with the Planet in Mind The tin is crafted from 30% recycled materials and is 100% recyclable, aligning with Veuve Clicquot’s sustainability commitments. Its removable sugarcane-based backing adds a thoughtful eco-friendly touch to a design that’s made to last long after the bottle is enjoyed.
A Gift That Connects People and Places This unique keepsake is ideal for birthdays, anniversaries, weddings, or corporate gifts—it’s perfect for anyone who values meaningful moments and sophisticated taste. More than just a drink, it's a celebration of where you've been, and where you’re going.
With the Veuve Clicquot Personalised Arrow, every toast becomes a story—one that starts with a location and ends in a lasting memory.
-
 @ 3b13c372:3e1e7ef2
2025-06-04 05:40:55
@ 3b13c372:3e1e7ef2
2025-06-04 05:40:55For those who believe every bottle should tell a story, Veuve Clicquot’s Personalised Arrow Champagne offers the perfect blend of sophistication and sentiment. More than a premium Champagne, this collector’s piece is a tribute to the places that shape our lives—wrapped in unmistakable Veuve Clicquot style.
At the heart of the package is a 750ml bottle of Veuve Clicquot Yellow Label Brut, a Champagne celebrated for its balance of power, freshness, and finesse. It’s crafted predominantly from Pinot Noir, supported by Chardonnay and Meunier, creating a vibrant, structured wine with layers of pear, citrus, and brioche.
What sets this gift apart is its outer casing: a bold, arrow-shaped metal tin that can be personalised with the name of your chosen city or destination (up to 15 characters). Alongside your customisation, the arrow displays the distance from that location to Reims, France—the spiritual home of Veuve Clicquot.
This elegant detail turns the bottle into a statement. Whether you’re celebrating a new home, a wedding, a farewell, or just sending a thoughtful gift, the Personalised Arrow adds meaning to the moment. It’s functional, too—keeping your Champagne cool for up to two hours—making it ideal for celebrations on the go.
Veuve Clicquot’s Personalised Arrow Champagne is a thoughtful way to connect a bottle of world-class wine with a personal journey. A toast to the people and places we never forget—wrapped in signature yellow, and stamped with your own message.
-
 @ 7460b7fd:4fc4e74b
2025-06-04 12:18:52
@ 7460b7fd:4fc4e74b
2025-06-04 12:18:52TRX 从 $0.12 涨至 $1.00 对 Tron 网络资源与用户行为的系统性影响
当前 TRX 价格约 $0.12,若其涨至 $1.00,Tron 网络的资源模型(能量 Energy 和带宽 Bandwidth)、用户手续费感知、质押行为以及市场流通供应都将发生深刻变化。下面将基于博弈论逻辑、链上资源参数和用户行为建模进行分析,并通过图表和数据展示各变量的联动关系。
Tron 网络资源模型与手续费机制概览
Tron 采用独特的资源模型:交易消耗带宽点数(BP)和能量(Energy)而非直接收取传统手续费。每个账户每天可免费获得一定的带宽点数(例如约 600 点)用于普通交易help.tokenpocket.pro;但能量没有每日免费的分配help.tokenpocket.pro。发送 TRX 等普通转账主要消耗带宽,而执行 TRC20 智能合约(如转账 USDT)则需要能量。用户可以通过冻结(质押) TRX 来获取这两种资源的配额,以支付交易所需的资源费用exodus.comexodus.com。具体而言:
-
带宽(Bandwidth):用于衡量交易字节大小的资源。账户每天有少量免费带宽(历史上约 5000 点,后调整至 1500,再至 600 点左右)trondao.medium.comhelp.tokenpocket.pro。若带宽不足,系统将按每字节 1000 sun(0.001 TRX)的价格烧毁 TRX 获取带宽cryptoapis.io。
-
能量(Energy):用于衡量智能合约执行的计算资源,没有每日免费额度,只能通过冻结 TRX 获得trondao.medium.comhelp.tokenpocket.pro。当能量不足时,系统按每单位能量 280 sun(即 0.00028 TRX)的单价烧毁 TRX 作为费用cryptoapis.io。每笔 TRC20 代币交易会消耗一定能量,例如转账 USDT 大约需要数万能量。
冻结 TRX 后,用户按其冻结量占全网总冻结量的比例共享固定总量的带宽和能量每日配额。例如,全网每日总能量供应固定约 50,000,000,000 单位,用户冻结 TRX 获得的能量 = (个人冻结量 / 全网冻结总量) * 50,000,000,000trondao.medium.comtrondao.medium.com。这意味着当更多人冻结 TRX 时,每单位 TRX 获得的能量将递减,但冻结总量上升会提高全网总可用能量。冻结的 TRX 最少锁定3天,冻结期间不可流通或交易trondao.medium.com。作为激励,冻结 TRX 可用于投票超级代表(SR)以获得约 4% 年化的 Staking 收益crypto.news。
手续费支付方式 – 冻结 vs 燃烧: 当用户有足够的能量和带宽时,交易将优先消耗这些资源,不直接扣除 TRX 手续费help.tokenpocket.pro。若资源不足,则需要燃烧一定数量的 TRX 来补足差额exodus.com。例如:
-
普通 TRX 转账:消耗约 268 字节带宽,无需能量,通常可用每日免费带宽覆盖,大多数情况下用户无需支付 TRX 手续费help.tokenpocket.pro。
-
TRC20-USDT 转账:若发送方和接收方账户有足够资源,则耗能量和带宽,不烧 TRX;否则将燃烧 TRX 作为手续费help.tokenpocket.pro。据统计,在资源不足时,一笔 USDT 转账约需燃烧 13.74 TRX(接收方已有该代币时)或 27.6 TRX(接收方首次接收该代币时,需要创建资产映射)help.tokenpocket.pro。以当前价 $0.12 计,相当于 $1.61 – $3.22 的费用。可见,冻结 TRX 获得能量后,几乎可使手续费降为零,仅消耗资源而不烧币help.tokenpocket.pro。
上述模型奠定了用户行为的基础:老用户往往习惯冻结 TRX 以获取免费资源,新用户若未冻结则需要持有并燃烧 TRX 支付手续费。当 TRX 价格显著上升时,这种差异和资源机制将引发一系列连锁反应。
老用户 vs 新用户:质押习惯与手续费敏感度
老用户(资深 Tron 用户)通常早已适应了 Tron 的资源机制,倾向于冻结一定量的 TRX 来保障日常交易的能量和带宽需求。这些用户往往持有大量 TRX,并享受冻结带来的免费交易和Staking 收益。对于老用户而言,哪怕 TRX 价格上涨,其主观感受到的手续费成本仍较低,因为他们多数交易并不直接烧币支付TRX。他们的行为特征是:
-
预见性冻结:会根据网络状况和自身交易频率,提前增加冻结量以确保足够资源。价格上涨时,老用户可能追加冻结更多 TRX(即使这部分 TRX 价值升高),因为相较于高昂的潜在手续费,他们更看重保证链上操作的低成本。
-
收益驱动:老用户也关注冻结带来的投票奖励收益。例如当前 Tron 质押年化约4.5%crypto.news。随着价格上涨,他们持币市值增加,继续冻结还能坐享收益,进一步增强了冻结意愿。
新用户则大多缺乏上述经验,进入 Tron 网络时往往没有冻结 TRX。许多新用户使用 Tron 是因为听闻其转账 USDT 手续费低廉,但他们可能只持有极少量 TRX 来支付手续费,甚至一开始没有TRX(需先获取一些 TRX 才能进行转账)help.tokenpocket.pro。新用户的行为和感知具有不同特点:
-
手续费敏感:新用户对显性的美元计价手续费非常敏感。他们初期未质押,因此每笔交易都真实消耗 TRX。在 TRX 价格较低时,这笔费用很小(几美分到一两美元),他们可能忽略不计;但当价格上涨导致每笔交易成本攀升,新用户会明显感觉“不再那么便宜”,从而开始寻求对策。
-
反应滞后:与老用户主动冻结不同,新用户往往在几次交易被收取较高手续费后,才会被动学习到通过冻结 TRX 可降低费用这一机制。一些钱包和社区教程也会引导新用户质押或租赁能量来节约成本help.tokenpocket.prohelp.tokenpocket.pro。
-
冻结意愿取决于成本临界点:新用户往往有一个心理阈值——当单笔手续费上涨到比如几美元甚至两位数美元时,他们才觉得“不划算,需要质押”。在 TRX 价格低迷时期,这个阈值可能从未被触及,但随着 TRX 攀升,新用户群体中会出现集中式的质押行为转变,一旦手续费达到“显著”水平,他们会成批地开始冻结 TRX。
综上,老用户在价格上升初期已提前布局资源,对手续费上涨免疫,新用户则可能在价格上涨过程中逐渐被培养成新的质押者。这种差异将在不同价格阶段体现为质押率和交易成本感受的变化,并直接影响 TRX 的流通盘和市场供需。
TRX 价格阶段与手续费成本变化
随着 TRX 价格从 $0.12 上涨至更高价位,用户实际支付的手续费成本(美元计)会线性上升。在资源消耗(以 TRX 计)大致不变的情况下,TRX 越昂贵,每笔交易烧毁的 TRX 转换为法币就越高。下表总结了不同价位下,一次 TRC20-USDT 转账的近似成本(未冻结资源时):
| TRX价格 | USDT转账手续费(接收地址已激活) | 手续费美元价(约) | USDT转账手续费(新地址) | 手续费美元价(约) | | ----- | --------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- | --------- | -------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- | --------- | | $0.12 | 13.74 TRXhelp.tokenpocket.pro | \~$1.65 | 27.6 TRXhelp.tokenpocket.pro | \~$3.30 | | $0.30 | 13.74 TRX | \~$4.12 | 27.6 TRX | \~$8.28 | | $0.50 | 13.74 TRX | \~$6.87 | 27.6 TRX | \~$13.80 | | $1.00 | 13.74 TRX | \~$13.74 | 27.6 TRX | \~$27.60 |
注:13.74 TRX 是指向已持有USDT的地址转账的典型能量消耗费用;27.6 TRX 则包括了向新地址转账(需创建账户)的额外成本。help.tokenpocket.pro上述美元价仅为近似,实际能量消耗会随网络拥堵程度浮动。
图:TRX 价格上涨对未质押用户的单笔 USDT 转账费用(美元计)的影响。费用基本随 TRX 价格线性上升,在接收方无 USDT 资产时费用更高。help.tokenpocket.probinance.com
从图中可以直观地看到,当 TRX 从 $0.12 涨至 $0.30 时,每笔 USDT 转账费从 \~$1.6 增至 \~$4-8 美元;涨至 $0.50 时,费用进一步涨至接近两位数美元;而在 $1.00 时,不冻结资源直接转账的费用范围高达 \~$14-$28,已经远超“廉价”的范畴。这种手续费攀升将直接改变用户行为:
-
对于未冻结 TRX 的用户,高昂的美元手续费将迫使他们重新评估 Tron 网络的使用成本。当一次简单转账可能花费 \~$10,美金计价下已接近以太坊主网曾经的费用水平,Tron “廉价网络”的优势将被削弱。许多个人用户会被强烈激励去冻结一定数量的 TRX,以换取能量来豁免后续交易手续费help.tokenpocket.pro。一些服务商和交易所也可能选择代用户冻结大量 TRX,以降低批量交易成本。
-
部分小额或低频用户可能被高费用劝退,转而选择其它Layer1网络或二层方案。然而,由于 Tron 网络在稳定币领域的巨大体量(截至 2025 年4月,Tron 上流通的 USDT 超过 $700 亿cryptoslate.com,每日 USDT 转账额约 $190 亿cryptoslate.com),短期内用户更可能留在 Tron 生态并通过质押来适应变化,而不会轻易放弃这一主流稳定币链。
与此同时,已冻结资源的用户几乎不受价格上涨的手续费影响。无论 TRX 价格多高,他们每笔交易依然只需消耗带宽和能量(这些资源本身不是直接按美元计价),额外的 TRX 燃烧为零help.tokenpocket.pro。唯一的“成本”是冻结 TRX 带来的流动性损失和机会成本。但在牛市氛围下,持有 TRX 本就是盈利的,加之还有质押收益,相比之下冻结的机会成本很低。因此,随着价格上升,冻结获取资源的方案相对更有利可图,用户群体从“不冻结”向“冻结”迁移将加速。
手续费阈值与用户质押的正反馈闭环
考虑上述趋势,我们可以识别出一个潜在的“手续费显著点”或阈值:当单笔交易手续费达到足以引起用户强烈关注的水平时,大量用户将改变策略开始冻结 TRX。这一阈值在不同用户心中略有差异,但可以是假设在几美元左右(例如 $5)。博弈论视角下,这是一个集体行为转折点:之前,个体最佳响应可能是不冻结、承担小额费用;一旦超过阈值,个体最佳响应切换为冻结 TRX 来避免高额费用。这个策略转变会引发一系列连锁反应,形成正反馈循环:
-
价格上涨 → 手续费攀升:随着 TRX 价格上扬,非质押用户每笔交易燃烧的 TRX 价值水涨船高。当费用升至阈值以上,大部分用户开始重视成本问题。
-
成本感知 → 用户大量质押:面对显著上涨的费用,大量原本未质押的用户开始冻结 TRX 以获取能量,避免继续支付高额手续费help.tokenpocket.prohelp.tokenpocket.pro。特别是新进入用户,在感受到手续费压力后,更倾向于立即质押以降低开销。老用户则可能加大质押以获取更多免费资源。
-
质押增加 → 流通盘收紧:当大量 TRX 被冻结(锁定)后,流通中的可交易 TRX 供应量下降。这些新冻结的 TRX 至少锁定3天,很多用户会选择长期质押获取收益,使得市场上即时可售卖的筹码变少。同时,部分用户未及时质押的,仍在持续燃烧 TRX 付费,也在永久性地减少总供应(Tron 网络目前每日燃烧量已经高于发行量,使TRX呈现净通缩趋势crypto.newsreddit.com)。
-
供应减少 → 价格进一步上涨:流通盘收紧后,在需求旺盛(尤其是牛市资金追逐和 Tron 网络高使用量不减)的情况下,TRX 的价格往往进一步上涨。这是经典的供需效应:供给减少,价格上行压力增大。更重要的是,价格上升又会反过来强化用户对手续费的敏感度,使得更多边际用户加入冻结行列,进一步削减流通供应——正反馈循环就此形成。
这一系列过程可以形成一个“价格上涨 → 成本上升 → 质押增加 → 流通减少 → 再次推高价格”的循环闭环reddit.com。市场上的做市商和鲸鱼投资者可能会利用或放大这一动态:当他们观察到手续费成本逼近用户阈值、质押率开始上升时,可能主动推动 TRX 价格突破关键点,从而触发更多散户用户质押,加剧流通盘收缩。这给了大户更好的条件进一步拉升价格,因为市面上流动的卖盘更少,稍大买单就能推动价格上涨。可以说,Tron 网络机制下的用户集体质押行为,使价格上涨具备自我强化的“弹簧”效应:拉一下就紧一点,形成正向循环。
需要注意的是,也存在减缓机制:随着全网冻结的 TRX 增加,每单位 TRX 可分得的能量下降,某种程度上要求用户冻结更多的 TRX才能完全覆盖同样的交易频率developers.tron.networkdevelopers.tron.network。这意味着质押率提升到一定程度后,额外用户再质押所获得的边际效用减少,正反馈的效力可能会逐步减弱。此外,如果手续费过高,一些用户可能降低交易频率或寻找替代方案。不过,在迈向 $1.00 的阶段内,Tron 作为稳定币主链的地位和用户黏性意味着大多数用户会选择适应而非离开,这使得上述正反馈有机会充分演绎。
图:TRX 价格上涨过程中质押率(冻结占总供给比例)的理论变化示意。价格越高,因手续费驱动的质押率越大,流通盘越紧(此图假设从约20%升至50%的冻结率,仅作说明)。实际过程中质押率上升具有滞后性和渐进特征。
新用户涌入与合力放大效应
在价格上涨的初期阶段,新用户的涌入对上述循环起到推波助澜的作用。牛市中,随着 TRX 价格突破历史水平并表现强势,越来越多的新参与者会被吸引到 Tron 生态。这些新用户往往抱着逐利和追涨的心理进入市场:
-
追涨入场:新用户看到 TRX 大涨,担心“踏空”,会倾向于迅速买入 TRX。这直接形成买盘,推高价格,也增加了潜在需要冻结的 TRX 持有者基数。
-
边用边买:很多新人是因为 Tron 上 USDT 等稳定币转账便宜快捷而入场。当 TRX 价格上涨、媒体报道 Tron 活跃时,他们更愿意选择 Tron 网络进行跨所转账、链上交易等,从而进一步推高 Tron 网络的交易活跃度和费用收入crypto.newscrypto.news。
-
从众质押:当新用户进来后,老用户或钱包方往往会教育他们质押省钱。再加上他们亲身经历几次昂贵手续费后,往往很快接受这一理念。这些新用户一开始可能并未计划长期持有 TRX,但为了降低使用成本,他们反而开始冻结所购的 TRX。很多新用户甚至会超额冻结(冻结比自己短期所需更多的量),因为他们发现质押还有收益且3天锁定并不长。这相当于把原本可能成为抛压的一部分新增筹码也锁住了。
新资金+新质押形成的合力,会放大价格-质押正反馈循环的力度。与仅老用户参与相比,新用户带来了额外的需求和锁仓动力,使流通供应收缩更剧烈。换句话说,本轮行情中新增的参与者并没有全部将 TRX 投入市场流通,反而有相当比例被“冻结”起来,减少了即时可售卖的代币数量。这种现象加速了市场从“供过于求”向“供不应求”的转换。
博弈论角度看,新用户的行为受老用户和市场信号影响,呈现**“从众效应”:当大家都在说“手续费贵了赶紧质押”“质押后几乎不要钱”时,个人跟随策略是有利的。这种群体策略迅速一致化的趋势,使得市场进入某种短期均衡**:大部分活跃用户都质押,剩余在外流通的更多是交易所库存、投机者筹码。一旦达到此均衡点,TRX 价格在流动性受限的情况下可能出现较为剧烈的波动,进一步吸引外围资金关注。然而,只要 Tron 网络的基础需求(如稳定币交易)坚挺,这种供应紧缩的状况就持续对价格形成支撑。
总结:联动效应与趋势展望
综合以上分析,TRX 价格从 $0.12 涨向 $1.00 将引发链上资源、用户行为和市场供需的一系列联动变化:
-
手续费上涨迫使用户行动:价格翻数倍后,不质押的用户手续费开销飙升数倍binance.com。用户从被动付费转向积极质押以获取“免费”能量,Tron 网络的质押率水涨船高。
-
质押率提高缩减流通供应:大量 TRX 冻结锁定,使流通盘迅速收紧crypto.news。同时,一些未质押部分在高费用下被直接燃烧,进一步造成 TRX 通缩reddit.com。供给减少对价格形成正向推动。
-
正反馈循环加剧波动:价格越涨→质押越多→流通越少→价格越容易再涨。这个正反馈闭环可能被市场力量(包括大户的刻意推动)所强化,在行情中后期表现尤为明显。
-
新参与者放大合力:新用户在牛市初期蜂拥而入,既贡献了需求又通过质押“锁仓”,反而减轻了抛压,起到了助涨而非砸盘的作用,放大了整体合力。
-
博弈均衡与风险:最终,大多数活跃用户选择质押是理性策略,但也意味短期内市场流动性下降。若某时刻大量质押的筹码解冻出货,或外部需求下降,这一循环可能逆转。因此,各方参与者都在博弈对方的动作:用户希望提前质押锁定低成本,市场庄家则利用高质押率营造供应稀缺推高价格,同时也警惕何时会有解冻卖出的潮涌。
从 Tron 网络的发展看,价格与网络资源、用户行为间的动态关系体现了典型的自适应反馈机制。Tron 作为目前主力稳定币传输链,其成本和性能直接影响用户留存与行为。当 TRX 价格步入高位区间,Tron 或许也会调整参数(如增加总能量供给或优化手续费机制)来平衡用户体验和代币经济模型。不过,在涨向 $1.00 的过程中,上述正反馈循环很可能成为推动力量之一。投资者和参与者应密切关注质押率、手续费水平等链上指标的变化——它们既是价格行情的结果,也是后续走势的原因。在理想状态下,这种“价格上涨-资源质押-流通收缩”的合循环能够稳步推升 Tron 生态价值;但如果过度强化,也需防范因流动性不足导致的剧烈波动风险。总体而言,TRX 价格上涨对 Tron 网络的影响是全方位的:手续费机制使用户行为发生系统性改变,而用户集体行为的改变反过来塑造了市场供求格局,值得持续深入监测和研究。crypto.newscryptoslate.com
-
-
 @ c9badfea:610f861a
2025-06-04 03:19:18
@ c9badfea:610f861a
2025-06-04 03:19:18Monospace
𝙰𝙱𝙲𝙳𝙴𝙵𝙶𝙷𝙸𝙹𝙺𝙻𝙼𝙽𝙾𝙿𝚀𝚁𝚂𝚃𝚄𝚅𝚆𝚇𝚈𝚉 𝚊𝚋𝚌𝚍𝚎𝚏𝚐𝚑𝚒𝚓𝚔𝚕𝚖𝚗𝚘𝚙𝚚𝚛𝚜𝚝𝚞𝚟𝚠𝚡𝚢𝚣
Script
𝓐𝓑𝓒𝓓𝓔𝓕𝓖𝓗𝓘𝓙𝓚𝓛𝓜𝓝𝓞𝓟𝓠𝓡𝓢𝓣𝓤𝓥𝓦𝓧𝓨𝓩 𝓪𝓫𝓬𝓭𝓮𝓯𝓰𝓱𝓲𝓳𝓴𝓵𝓶𝓷𝓸𝓹𝓺𝓻𝓼𝓽𝓾𝓿𝔀𝔁𝔂𝔃
Fraktur
𝔄𝔅ℭ𝔇𝔈𝔉𝔊ℌℑ𝔍𝔎𝔏𝔐𝔑𝔒𝔓𝔔ℜ𝔖𝔗𝔘𝔙𝔚𝔛𝔜ℨ 𝔞𝔟𝔠𝔡𝔢𝔣𝔤𝔥𝔦𝔧𝔨𝔩𝔪𝔫𝔬𝔭𝔮𝔯𝔰𝔱𝔲𝔳𝔴𝔵𝔶𝔷Fraktur - Bold
𝕬𝕭𝕮𝕯𝕰𝕱𝕲𝕳𝕴𝕵𝕶𝕷𝕸𝕹𝕺𝕻𝕼𝕽𝕾𝕿𝖀𝖁𝖂𝖃𝖄𝖅 𝖆𝖇𝖈𝖉𝖊𝖋𝖌𝖍𝖎𝖏𝖐𝖑𝖒𝖓𝖔𝖕𝖖𝖗𝖘𝖙𝖚𝖛𝖜𝖝𝖞𝖟
Sans Serif - Italic
𝘈𝘉𝘊𝘋𝘌𝘍𝘎𝘏𝘐𝘑𝘒𝘓𝘔𝘕𝘖𝘗𝘘𝘙𝘚𝘛𝘜𝘝𝘞𝘟𝘠𝘡 𝘢𝘣𝘤𝘥𝘦𝘧𝘨𝘩𝘪𝘫𝘬𝘭𝘮𝘯𝘰𝘱𝘲𝘳𝘴𝘵𝘶𝘷𝘸𝘹𝘺𝘻Sans Serif - Bold
𝗔𝗕𝗖𝗗𝗘𝗙𝗚𝗛𝗜𝗝𝗞𝗟𝗠𝗡𝗢𝗣𝗤𝗥𝗦𝗧𝗨𝗩𝗪𝗫𝗬𝗭 𝗮𝗯𝗰𝗱𝗲𝗳𝗴𝗵𝗶𝗷𝗸𝗹𝗺𝗻𝗼𝗽𝗾𝗿𝘀𝘁𝘂𝘃𝘄𝘅𝘆𝘇Sans Serif - Bold Italic
𝘼𝘽𝘾𝘿𝙀𝙁𝙂𝙃𝙄𝙅𝙆𝙇𝙈𝙉𝙊𝙋𝙌𝙍𝙎𝙏𝙐𝙑𝙒𝙓𝙔𝙕 𝙖𝙗𝙘𝙙𝙚𝙛𝙜𝙝𝙞𝙟𝙠𝙡𝙢𝙣𝙤𝙥𝙦𝙧𝙨𝙩𝙪𝙫𝙬𝙭𝙮𝙯Sans Serif - Double-Struck
𝖠𝖡𝖢𝖣𝖤𝖥𝖦𝖧𝖨𝖩𝖪𝖫𝖬𝖭𝖮𝖯𝖰𝖱𝖲𝖳𝖴𝖵𝖶𝖷𝖸𝖹 𝖺𝖻𝖼𝖽𝖾𝖿𝗀𝗁𝗂𝗃𝗄𝗅𝗆𝗇𝗈𝗉𝗊𝗋𝗌𝗍𝗎𝗏𝗐𝗑𝗒𝗓
Serif - Italic
𝐴𝐵𝐶𝐷𝐸𝐹𝐺𝐻𝐼𝐽𝐾𝐿𝑀𝑁𝑂𝑃𝑄𝑅𝑆𝑇𝑈𝑉𝑊𝑋𝑌𝑍 𝑎𝑏𝑐𝑑𝑒𝑓𝑔ℎ𝑖𝑗𝑘𝑙𝑚𝑛𝑜𝑝𝑞𝑟𝑠𝑡𝑢𝑣𝑤𝑥𝑦𝑧Serif - Bold
𝐀𝐁𝐂𝐃𝐄𝐅𝐆𝐇𝐈𝐉𝐊𝐋𝐌𝐍𝐎𝐏𝐐𝐑𝐒𝐓𝐔𝐕𝐖𝐗𝐘𝐙 𝐚𝐛𝐜𝐝𝐞𝐟𝐠𝐡𝐢𝐣𝐤𝐥𝐦𝐧𝐨𝐩𝐪𝐫𝐬𝐭𝐮𝐯𝐰𝐱𝐲𝐳Serif - Bold Italic
𝑨𝑩𝑪𝑫𝑬𝑭𝑮𝑯𝑰𝑱𝑲𝑳𝑴𝑵𝑶𝑷𝑸𝑹𝑺𝑻𝑼𝑽𝑾𝑿𝒀𝒁 𝒂𝒃𝒄𝒅𝒆𝒇𝒈𝒉𝒊𝒋𝒌𝒍𝒎𝒏𝒐𝒑𝒒𝒓𝒔𝒕𝒖𝒗𝒘𝒙𝒚𝒛Serif - Double-Struck
𝔸𝔹ℂ𝔻𝔼𝔽𝔾ℍ𝕀𝕁𝕂𝕃𝕄ℕ𝕆ℙℚℝ𝕊𝕋𝕌𝕍𝕎𝕏𝕐ℤ 𝕒𝕓𝕔𝕕𝕖𝕗𝕘𝕙𝕚𝕛𝕜𝕝𝕞𝕟𝕠𝕡𝕢𝕣𝕤𝕥𝕦𝕧𝕨
Regional Indicator Symbols
🇦 🇧 🇨 🇩 🇪 🇫 🇬 🇭 🇮 🇯 🇰 🇱 🇲 🇳 🇴 🇵 🇶 🇷 🇸 🇹 🇺 🇻 🇼 🇽 🇾 🇿
Pseudo-Asian
卂 乃 匚 ᗪ 乇 千 Ꮆ 卄 丨 フ Ҝ ㄥ 爪 几 ㄖ 卩 Ɋ 尺 丂 ㄒ ㄩ ᐯ 山 乂 ㄚ 乙
Circled
ⒶⒷⒸⒹⒺⒻⒼⒽⒾⒿⓀⓁⓂⓃⓄⓅⓆⓇⓈⓉⓊⓋⓌⓍⓎⓏ ⓐⓑⓒⓓⓔⓕⓖⓗⓘⓙⓚⓛⓜⓝⓞⓟⓠⓡⓢⓣⓤⓥⓦⓧⓨⓩ
Squared #1
🄰🅱🄲🅳🄴🅵🄶🅷🄸🅹🄺🅻🄼🅽🄾🅿🅀🆁🅂🆃🅄🆅🅆🆇🅈🆉 🅰🄱🅲🄳🅴🄵🅶🄷🅸🄹🅺🄻🅼🄽🅾🄿🆀🅁🆂🅃🆄🅅🆆🅇🆈🅉Squared #2
🄰🄱🄲🄳🄴🄵🄶🄷🄸🄹🄺🄻🄼🄽🄾🄿🅀🅁🅂🅃🅄🅅🅆🅇🅈🅉Squared #3
🅰🅱🅲🅳🅴🅵🅶🅷🅸🅹🅺🅻🅼🅽🅾🅿🆀🆁🆂🆃🆄🆅🆆🆇🆈🆉Squared #4
🅐🅑🅒🅓🅔🅕🅖🅗🅘🅙🅚🅛🅜🅝🅞🅟🅠🅡🅢🅣🅤🅥🅦🅧🅨🅩 -
 @ c7a8d522:262a74de
2025-06-04 04:21:47
@ c7a8d522:262a74de
2025-06-04 04:21:47Com o avanço da tecnologia e a popularização das plataformas digitais de jogos, os brasileiros estão cada vez mais em busca de experiências online que combinem praticidade, emoção e segurança. Nesse cenário, a 0066Bet se destaca como uma das plataformas mais completas e inovadoras do mercado, oferecendo uma ampla variedade de jogos e um ambiente digital pensado especialmente para os usuários que desejam entretenimento de qualidade a qualquer hora e em qualquer lugar.
Uma Plataforma Moderna e Segura A 0066Bet foi desenvolvida com foco total na experiência do usuário. Com um design moderno e responsivo, a plataforma funciona perfeitamente em computadores, tablets e smartphones, permitindo que os jogadores tenham acesso total às funcionalidades, independentemente do dispositivo. Além disso, a segurança é uma das grandes prioridades da empresa. O site utiliza criptografia avançada e protocolos de proteção de dados para garantir que as informações dos usuários estejam sempre protegidas.
A facilidade de cadastro e navegação também merece destaque. Em poucos minutos, qualquer pessoa pode criar sua conta, explorar as seções de jogos e começar a se divertir com total autonomia. Os métodos de pagamento são variados e incluem opções amplamente utilizadas no Brasil, o que facilita ainda mais o acesso ao entretenimento.
Diversidade de Jogos para Todos os Gostos Um dos grandes atrativos da 0066beté a variedade de jogos disponíveis. A plataforma conta com títulos clássicos e modernos, atendendo tanto os iniciantes quanto os jogadores mais experientes. Entre os destaques estão os jogos de cartas como poker e bacará, que exigem estratégia e habilidade, além de opções mais dinâmicas como roletas virtuais, jogos com números e modalidades ao vivo com interação em tempo real.
Para os amantes da adrenalina, a seção de jogos com crupiês reais é imperdível. Nela, os jogadores participam de partidas transmitidas ao vivo, com profissionais treinados, proporcionando uma experiência extremamente imersiva e realista — tudo sem sair de casa.
Outro ponto forte da 0066Bet é a oferta constante de novos títulos e atualizações. A equipe da plataforma está sempre em busca de novidades, o que garante que os jogadores encontrem sempre algo diferente para explorar e experimentar.
Experiência do Jogador: Simples, Intuitiva e Gratificante A opinião dos usuários é unânime: a experiência na 0066Bet é agradável, fluida e repleta de recompensas. A interface é intuitiva, as instruções dos jogos são claras e o sistema de suporte ao cliente funciona 24 horas por dia, com atendimento rápido e eficiente em português.
Além disso, a plataforma oferece promoções regulares, bônus de boas-vindas e programas de fidelidade que valorizam o tempo e o investimento dos jogadores. Esses incentivos tornam a jornada ainda mais empolgante, garantindo que cada sessão de jogo seja única e recompensadora.
Conclusão A 0066Bet vem se consolidando como uma das melhores opções de entretenimento online no Brasil. Com sua interface amigável, catálogo variado de jogos e compromisso com a segurança e a satisfação do usuário, a plataforma é ideal para quem busca emoção, diversão e a chance de viver experiências intensas e inesquecíveis diretamente da tela do celular ou do computador.
Se você ainda não conhece a 0066Bet, essa é a hora perfeita para descobrir um novo mundo de entretenimento digital. Faça seu cadastro, explore os jogos disponíveis e aproveite tudo o que a plataforma tem a oferecer!
-
 @ c7a8d522:262a74de
2025-06-04 04:21:18
@ c7a8d522:262a74de
2025-06-04 04:21:18Com o avanço da tecnologia e o crescimento do entretenimento digital, plataformas como a 888Game vêm se destacando no cenário brasileiro por oferecerem uma experiência completa e envolvente aos seus usuários. Com um design moderno, navegação intuitiva e um catálogo diversificado de jogos, a 888Game se posiciona como uma das melhores opções para quem busca emoção, desafio e diversão em um só lugar.
Uma Plataforma Pensada para o Jogador Brasileiro A 888Game foi desenvolvida com foco total na experiência do usuário. Desde o primeiro acesso, é possível perceber o cuidado com os detalhes: o site é responsivo, rápido e adaptado para dispositivos móveis, permitindo que os jogadores aproveitem seus jogos favoritos de onde estiverem, a qualquer momento. Além disso, a plataforma está totalmente em português, o que garante uma navegação fluida e sem barreiras linguísticas.
Outro ponto forte é a facilidade no processo de cadastro e nas transações financeiras. A 888gameaceita diversos métodos de pagamento populares entre os brasileiros, incluindo Pix, transferências bancárias e carteiras digitais, tornando os depósitos e saques rápidos, seguros e práticos.
Variedade de Jogos para Todos os Gostos Um dos grandes diferenciais da 888Game é a vasta seleção de jogos disponíveis. Os usuários encontram opções para todos os perfis, desde os mais clássicos até os lançamentos mais modernos. Entre os destaques estão:
Jogos de mesa: como roleta, blackjack e bacará, com versões ao vivo que trazem mais emoção e realismo à experiência.
Slots (caça-níqueis): com uma enorme variedade de temas, gráficos impressionantes e bônus especiais que garantem rodadas extras e prêmios emocionantes.
Jogos ao vivo: com crupiês reais transmitidos em tempo real, proporcionando uma atmosfera imersiva e interativa.
Além disso, a 888Game atualiza frequentemente seu catálogo, sempre trazendo novidades e tendências do mercado para manter os jogadores entretidos e surpreendidos.
Experiência do Usuário: Fluidez, Emoção e Suporte de Qualidade A experiência na 888Game vai muito além dos jogos. A plataforma se destaca por proporcionar uma jornada completa e satisfatória ao usuário. Os gráficos são de alta definição, os jogos carregam rapidamente e o ambiente digital é leve, sem travamentos ou interrupções.
Outro ponto que merece destaque é o suporte ao cliente. A 888Game oferece atendimento em português, com canais de suporte via chat ao vivo e e-mail, garantindo respostas rápidas e eficientes para qualquer dúvida ou problema. O atendimento funciona 24 horas por dia, todos os dias da semana, algo essencial para garantir a tranquilidade dos jogadores.
Além disso, a plataforma valoriza seus usuários com promoções constantes, bônus de boas-vindas atrativos e programas de fidelidade que recompensam o engajamento contínuo. Isso demonstra o compromisso da 888Game em manter seus jogadores motivados e satisfeitos.
Conclusão: A Escolha Certa para Quem Busca Diversão Online com Qualidade A 888Game é, sem dúvida, uma plataforma completa que une inovação, variedade de jogos, segurança e uma excelente experiência ao usuário. Seja você um jogador experiente ou alguém que está começando agora no universo dos jogos online, a 888Game oferece tudo o que você precisa para se divertir com confiança e praticidade.
Se você está em busca de uma nova forma de entretenimento, com emoção de sobra e uma interface amigável, vale a pena conhecer a 888Game. Prepare-se para horas de diversão e descubra por que tantos brasileiros já elegeram esta plataforma como sua favorita!
-
 @ 472f440f:5669301e
2025-06-04 01:37:37
@ 472f440f:5669301e
2025-06-04 01:37:37Marty's Bent
via nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqy0hwumn8ghj7mn0wd68yttjv4kxz7fwvf5hgcm0d9hzumnfde4xzqpq85h9z5yxn8uc7retm0n6gkm88358lejzparxms5kmy9epr236k2qtyz2zr
A lot of the focus over the last couple of months has been on the emergence of Strategy competitors in public markets looking to build sizable bitcoin treasuries and attract investors of all shapes and sizes to drive shareholder value. The other big topic in the bitcoin development world has been around OP_RETURN and the debate over whether or not the amount of data that can be shoved into a bitcoin transaction should be decided by the dominant implementation.
A topic that is just as, if not more, important that is not getting enough appreciation is the discussion around open source bitcoin developers and the lingering effects of the Biden administration's attack on Samourai Wallet and Tornado Cash. If you read our friend Matt Corallo's tweet above, you'll notice that the lingering effects are such that even though the Trump administration has made concerted efforts to reverse the effects of Operation Chokepoint 2.0 that were levied by the Biden administration, Elizabeth Warren, and her friends at the Treasury and SEC - it is imperative that we enshrine into law the rights of open source developers to build products and services that enable individuals to self-custody bitcoin and use it in a peer-to-peer fashion without the threat of getting thrown in jail cell.
As it stands today, the only assurances that we have are from an administration that is overtly in favor of the proliferation of bitcoin in the United States. There is nothing in place to stop the next administration or another down the line from reverting to Biden-era lawfare that puts thousands of bitcoin developers around the world at risk of being sent into a cage because the government doesn't like how some users leverage the code they write. To make sure that this isn't a problem down the line it is imperative that we pass the Blockchain Regulatory Clarity Act, which would not hold bitcoin developers liable for the ways in which end users leverage their tools.
Not only is this an act that would protect developers from pernicious government officials targeting them when end users use their technology in a way that doesn't make the government happy, it will also protect YOU, the end user, looking to transact in a peer-to-peer fashion and leverage all of the incredible properties of bitcoin the way they were meant to be. If the developers are not protected, they will not be able to build the technology that enables you to leverage bitcoin.
So do your part and go to saveourwallets.org. Reach out to your local representatives in Congress and Senators and make some noise. Let them know that this is something that you care deeply about and that they should not only pay attention to this bill but push it forward and enshrine it into law as quickly as possible.
There are currently many developers either behind bars or under house arrest for developing software that gives you the ability to use Bitcoin in a self-sovereign fashion and use it in a privacy-preserving way. Financial privacy isn't a crime. It is an inalienable human right that should be protected at all cost. The enshrinement of this inalienable right into law is way past due.
#FreeSamourai #FreeRoman
Headlines of the Day
MicroStrategy Copycats See Speculative Premiums Fade - via X
Square Tests Bitcoin Payments, Lightning Yields Beat DeFi - via X
Get our new STACK SATS hat - via tftcmerch.io
Bitfinex Moves $731M Bitcoin to Jack Mallers' Fund - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code “TFTC20” during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Should I join a country club?
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ 1ef61805:f18312cc
2025-06-04 01:56:42
@ 1ef61805:f18312cc
2025-06-04 01:56:42**Inside OpSec Academy’s One-on-One Approach to Digital Sovereignty ** As digital infrastructure becomes increasingly opaque and centralised, a growing number of individuals are seeking to understand—not just use—the tools that protect their privacy and autonomy online. While many solutions promise security at the click of a button, few teach the underlying principles or offer environments that prioritise verifiability and user control.
OpSec Academy’s new one-on-one training, "OpSec Intensive," takes a different approach. Delivered in person and fully offline, the full-day session provides practical, tool-based instruction inside a secure, USB-booted environment—designed from the ground up to leave no trace.
At the heart of the session is OpSecOS v1.2, a live operating system that routes all traffic through Tor, uses system non-persistence, and comes preconfigured with a suite of open-source tools for password management, communication, and private finance. The OS runs from a USB stick, allowing participants to explore and build their own private computing workflows without touching the host machine.
Learning in Context: Why One-on-One? While group training can provide a general introduction to privacy concepts, it often lacks depth and adaptability. OpSec Intensive is structured as a one-on-one session to allow real-time feedback, personal threat modeling, and tailored instruction based on the participant’s specific context and technical background.
This format also makes space for slow, deliberate learning—a rarity in cybersecurity training, where content is often condensed or overly abstract. In OpSec Intensive, participants move through each phase at their own pace, working directly with an experienced instructor to build confidence and competence.
Structure and Content of the Day The curriculum spans both foundational theory and hands-on practice, beginning with basic OpSec principles before moving into technical tool use.
Topics include: * Booting and verifying OpSecOS * Secure USB creation and system verification * Navigating a non-persistent, Tor-routed live environment * Password and credential management * Offline use of KeePassXC * Strategies for vault organisation and redundancy * Bitcoin wallet setup and recovery * Single-signature and multisignature wallet creation using Sparrow, Electrum, and Feather * Understanding xpubs, derivation paths, and recovery flow * Seed phrase security * Entropy generation and validation using offline tools like iancoleman.io * Best practices for cold storage and physical backups * Network privacy and decentralised communication * Using Mempool.space to visualise Bitcoin transaction data * Setting up Nostr clients (Snort, Iris) for decentralised messaging * Discussion of traffic fingerprinting and Tor considerations
A Shift Toward Practical Sovereignty The tools and workflows covered in OpSec Intensive are not theoretical. Participants leave the session with configured environments, tested backups, and an understanding of what each tool does—and what it doesn’t do.
This reflects a broader shift in how privacy-conscious individuals are approaching digital security. Rather than relying on packaged services or closed-source software, there’s growing interest in verifiable, modular tools that prioritise autonomy and resilience over ease-of-use.
In that context, OpSec Academy’s offering sits somewhere between a workshop and an apprenticeship: not a lecture, but a process of guided, hands-on learning designed for the long haul.
To learn more or enquire about availability, visit opsecacademy.org.
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ 6389be64:ef439d32
2025-01-16 15:44:06
@ 6389be64:ef439d32
2025-01-16 15:44:06Black Locust can grow up to 170 ft tall
Grows 3-4 ft. per year
Native to North America
Cold hardy in zones 3 to 8

Firewood
- BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal
- Since its growth is fast, firewood can be plentiful
Timber

- Rot resistant due to a naturally produced robinin in the wood
- 100 year life span in full soil contact! (better than cedar performance)
- Fence posts
- Outdoor furniture
- Outdoor decking
- Sustainable due to its fast growth and spread
- Can be coppiced (cut to the ground)
- Can be pollarded (cut above ground)
- Its dense wood makes durable tool handles, boxes (tool), and furniture
- The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak.
- A very low rate of expansion and contraction
- Hardwood flooring
- The highest tensile beam strength of any American tree
- The wood is beautiful
Legume
- Nitrogen fixer
- Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn
- Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]]
Bees

- The edible flower clusters are also a top food source for honey bees
Shade Provider

- Its light, airy overstory provides dappled shade
- Planted on the west side of a garden it provides relief during the hottest part of the day
- (nitrogen provider)
- Planted on the west side of a house, its quick growth soon shades that side from the sun
Wind-break

- Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters
Fodder
- Over 20% crude protein
- 4.1 kcal/g of energy
- Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
-
 @ 6389be64:ef439d32
2025-01-13 21:50:59
@ 6389be64:ef439d32
2025-01-13 21:50:59Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
Meet The Forest Walker
For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
The Small Branch Chipper
When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
The Gassifier
The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
Biochar: The Waste
Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
Wood Vinegar: More Waste
Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
The Internal Combustion Engine
Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
CO2 Production For Growth
Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
The Branch Drones
During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
The Bitcoin Miner
Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
The Mesh Network
What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
Back To The Chain
Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
Sensor Packages
LiDaR
The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
pH, Soil Moisture, and Cation Exchange Sensing
The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
Weather Data
Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
Noise Suppression
Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
Fire Safety
A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
The Wrap
How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-
 @ 7460b7fd:4fc4e74b
2025-06-04 12:17:18
@ 7460b7fd:4fc4e74b
2025-06-04 12:17:18Tron(TRX)区块链架构与性能综合分析
Tron 的三层架构与虚拟机设计
*Tron 区块链采用三层架构:存储层、核心层、应用层developers.tron.networkcointelegraph.com。*存储层包含区块存储和状态存储,并引入图数据库理念以满足多样化数据存储需求developers.tron.network。核心层实现共识(基于改进的 委托权益证明 DPoS)、账户管理和智能合约等模块developers.tron.network。Tron 虚拟机(TVM)位于核心层,用于执行智能合约代码。Tron 最初指定 Java 语言 用于智能合约开发,并规划支持其它高级语言developers.tron.network。这一设计取舍体现了团队对 Java 生态和性能的偏好:Tron **节点实现(java-tron)**采用 Java 开发,使虚拟机与链上逻辑高度兼容 Java 环境。此外,TVM 与 Ethereum EVM 高度兼容,方便以太坊DApp迁移,但在细节上有所不同medium.commedium.com。例如,TVM 使用能量(Energy)而非 Gas,
energyPrice为全网固定参数(目前210 SUN,即0.00021 TRX)medium.com;大多数指令的能耗与以太坊相同,但部分操作成本更低(如合约存储读取SLOAD等)medium.com。Tron 地址体系也不同:通过CREATE2创建合约时使用0x41前缀(Tron 地址Hex前缀),确保与以太坊地址格式区别medium.com。总的来说,Tron 架构在继承主流区块链设计的基础上,用 Java 实现了一套高性能的三层架构,为 DApp 提供了良好的开发和运行环境developers.tron.networkcointelegraph.com。吞吐性能与资源模型:带宽与能量机制
Tron 在性能上追求高吞吐和低延迟。共识方面,Tron 采用 **27个超级代表(SR)**轮流产块的机制,每隔3秒出块reflexivityresearch.com。得益于DPoS和小规模节点,Tron 单链理论TPS可达约2,000~2,500cointelegraph.comchainspect.app。实际网络中Tron尚未达到饱和:截至2025年中旬,每日交易量稳定在 800万笔以上(峰值逾1000万),平均约 90~120 TPSbinance.combinance.com。相比之下,以太坊当前主网TPS约15笔(日均140万交易)cointelegraph.com。Tron链上尚无明显拥堵,表明其吞吐冗余较充足。
Tron 引入了独特的资源模型,将交易执行成本分解为“带宽点数”(Bandwidth)和“能量”(Energy)两类developers.tron.network。带宽代表交易数据的大小,每字节消耗1点带宽developers.tron.network;能量代表合约执行的算力和存储消耗,每执行一步EVM指令消耗相应能量developers.tron.network。Tron 每个账户每天有 5000点免费带宽 配额developers.tron.network用于普通转账;当免费额不足时,可以通过“冻结”TRX获取资源或直接消耗少量TRX燃烧获得developers.tron.networkdevelopers.tron.network。例如,一个约200字节的普通转账消耗200带宽点,如账户无冻结资源且免费额度用尽,则需烧毁约 每字节10 SUN(即0.00001 TRX)的费用developers.tron.network——换算下来一次转账成本仅约 0.001~0.01美元(远低于以太坊动辄数美元的Gas费)。对于智能合约交易,则既消耗带宽又消耗能量developers.tron.network。开发者或用户可冻结 TRX 获取能量,按其冻结占比分享全网每日约500亿能量的恢复额度developers.tron.networkdevelopers.tron.network。冻结的能量会随时间自动恢复(24小时恢复满)developers.tron.networkdevelopers.tron.network。如果调用合约时能量不足,系统会按当前能量价格从用户扣除等值 TRX 燃烧medium.com。
Tron 资源模型对用户和开发者影响显著:一般用户日常转账几乎免费(每天免费额度足够覆盖小额频度交易),即使进行 TRC20 代币(如 USDT)转账,只要账户持有一定冻结的 TRX,其能量和带宽消耗也可被抵扣为零成本cointelegraph.com。如果用户没有任何冻结资源,转账 USDT 约需消耗十余枚 TRXmedium.com;但实际约六成以上的能量消耗是通过用户预先冻结TRX来覆盖的medium.com。此外,Tron 允许智能合约开发者为调用者代付部分能量:开发者可设置自己承担例如90%的能量费用developers.tron.networkdevelopers.tron.network。这意味着在 Tron 上,DApp 开发者可以冻结足够TRX资源,使用户调用其合约时无需支付能量费(类似Gas代付),提升应用可用性developers.tron.networkdevelopers.tron.network。资源模型的另一便利是 资源委托:账户A可以为账户B冻结TRX来提供带宽或能量developers.tron.network。综合来看,Tron 的带宽/能量双资源机制避免了直接以代币计价的浮动手续费,为用户提供了**“零Gas”**的体验,同时激励TRX持有者参与质押获取资源alphanode.globalalphanode.global。这种设计在牛市高拥堵场景下依然能保持交易成本稳定,有利于大规模应用。Tron 官方统计显示,截至2024年底网络平均每笔交易费用低至 $0.000005 美元cointelegraph.com,几乎可以忽略不计。
Tron 与主流公链的架构和开发体验对比
Tron 的系统架构与开发体验在不同维度上可与 Ethereum、Solana、Avalanche、BNB Chain 等主流公链进行横向比较。下表总结了几项关键对比:
| 属性 | Tron (TRX) | Ethereum | Solana | Avalanche (C链) | BNB Chain (BSC) | | ------------- | ---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- | ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- | ---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- | --------------------------------------------------------------------------------------------------------------------------------------------------------------------- | ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ | | 共识机制 & 节点 | DPoS (27个超级代表,其他为见证节点)reflexivityresearch.com;3秒出块 | PoS (质押验证人 50万+,随机出块);12秒出块,最终确认约612分钟 | PoH+PoS (领导者序列+验证人约2000)chainspect.app;0.4秒出块,终局约10-15秒 | Avalanche共识 (验证人上千);\~1-2秒出块,\~1秒终局chainspect.app | PoSA ( 权威证明,21活跃验证者);\~3秒出块,快速终局 (几秒内)chainspect.app | | 架构设计 | 三层架构(存储/核心/应用)cointelegraph.com;单链+侧链BTTC扩展 | 单层主链+即将通过分片\&Rollup扩展;EVM执行环境 | 单链高度并行运行时(Sealevel);账户模型并行合约执行 | 主网三链架构(X链UTXO/P链治理/C链EVM);支持子网扩展 | 类以太坊单链架构;EVM执行环境,依赖以太坊工具链 | | 智能合约平台 | TVM(Ethereum VM 兼容,有能量机制改进)medium.com;支持 Solidity 等 | EVM(广泛支持Solidity、Vyper等);强生态工具 | BPF虚拟机(Rust/C/C++开发,需重新编译);高性能但开发曲线较陡 | EVM (C链);Solidity 合约与以太坊兼容 | EVM;Solidity合约完全兼容以太坊,工具链共用 | | 平均实际TPS | \~90-150 TPS(2024-25年,日均交易数8百万+binance.comcoindesk.com);峰值 \~270 TPSchainspect.app | \~15 TPS(L1日均约140万笔交易)cointelegraph.com;需借助L2提升 | \~1000+ TPS(日均交易数数千万,包含投票交易)chainspect.app;曾峰值5000+ TPSbinance.com | 当前负载低,实际 \~7 TPSchainspect.app;高峰 \~120 TPSchainspect.app | \~200 TPS(日均交易约400万笔binance.com);高峰 \~1700 TPSchainspect.app | | 理论最大TPS | \~2,000-2,500 TPS(当前参数下区块容量)cointelegraph.comchainspect.app | \~15-30 TPS(不考虑Rollup;单区块Gas上限限制) | \~50,000+ TPS(官方理论值)chainspect.app;高度依赖硬件性能 | \~1,000+ TPS(C链Gas参数下)chainspect.app | \~2,200 TPS(现行Gas上限下估计值)chainspect.app | | 交易费用机制 | 带宽+能量模型:每日免费额度+质押获取资源,无需常付手续费developers.tron.networkdevelopers.tron.network;无资源时按固定价格烧TRX(≈$0.0001/笔) | Gas拍卖:用户以 ETH 支付Gas费,费率随网络拥堵浮动;矿工/质押者收益 | 固定低费:按计算单元收取极低SOL费用,无免费额度;拥堵时费率略上调 | Gas费:按EVM Gas计算,以AVAX支付,费用较低;支持动态调整 | Gas费:与以太坊类似但计价币种为BNB,手续费低廉且有上限 | | 开发体验 | Solidity 为主(与以太坊基本通用);TronWeb、TronIDE 等SDK工具developers.tron.networkdevelopers.tron.network;需理解资源模型区别 | Solidity/Vyper生态成熟,工具最完善(Truffle、Hardhat等);L2多样 | **Rust/ C++**为主,开发需适应新模型;Solana工具链(Anchor框架等)在改进 | Solidity为主(C链类似以太坊开发);另有Subnet可用Rust、Go自定义VM | Solidity为主,100%兼容以太坊工具(Remix、Hardhat等);开发门槛与以太一致 | | 主要应用与优势 | 稳定币传输(USDT占据全球约50%供应coindesk.comcoindesk.com);DeFi借贷(JustLend)等,但生态DApp相对稀少coinshares.com | 通用智能合约平台(DeFi、NFT蓬勃,生态最大);安全性与去中心化强 | 高性能DApp(链游、NFT市场等;近期增长快);曾遇网络中断挑战 | DeFi与资产发行(C链上有借贷DEX,也支持企业级子网);强调快速终局性 | 泛用智能合约(DeFi规模庞大,如PancakeSwap等);依托Binance生态,用户基数大 |
表:Tron 与 Ethereum、Solana、Avalanche、BNB Chain 的关键技术指标和体验比较。 上表可见,Tron 在性能和成本上具备明显优势:TPS远高于以太坊cointelegraph.com,达到Solana/Avalanche的次高水平;交易手续费几乎为零cointelegraph.com。Tron 通过牺牲一定去中心化程度(仅27个验证人)换取了高吞吐和快速确认(3秒出块,\~1分钟内区块不可逆)chainspect.app。相比之下,以太坊去中心化最强但性能有限;Solana走极致性能路线,TPS极高但因架构复杂曾多次宕机,开发语言Rust门槛也更高。Avalanche主网C链采用EVM,使开发体验类似以太坊,但通过创新共识实现1秒终局,高TPS潜力;不过Avalanche生态主要在子网探索,主链交易量目前不大。BNB Chain 与 Tron 类似,采用小规模验证者和EVM,在性能和费用上接近Tron,也广受用户欢迎(尤其DeFi应用)。然而 BNB Chain 手续费仍需消耗BNB(虽很便宜),而 Tron 的资源模型让新用户无币也能免费发交易,初次使用门槛更低alphanode.global。
开发者体验方面,Tron 对以太坊生态高度兼容。Solidity 智能合约几乎无需修改即可部署到 Tron 网络(TronVM对EVM指令的兼容medium.com确保了这一点)。开发工具有 TronWeb JS 框架、TronIDE 集成环境等供使用developers.tron.network。不过Tron社区的第三方工具和合约模板相对以太坊要少,一些以太坊常用开发库在Tron上可能需要调整。Solana 则完全是另一种开发范式(基于Rust的BPF合约),与EVM链差异大。Avalanche的C链因为本质就是EVM,所以以太坊开发者可无缝迁移合约;BNB Chain 亦然。总的来说,Tron 和 BSC 在开发上延续了以太坊的习惯,而Solana、Avalanche追求性能和新架构,开发曲线相对陡峭。Tron 相比BSC的一个不同点是资源模型,这要求开发者考虑带宽/能量的分配,但也提供了为用户代付资源的机制,适合需要降低用户使用门槛的DApp。值得注意的是,Tron 主网账户总数已超过 3亿(包括大量交易所托管地址)coindesk.com、日活跃地址逾 百万coindesk.com;尽管生态应用不算丰富,但庞大的用户基础主要来源于稳定币交易和基本金融应用,对开发者而言意味着可观的潜在用户群。
工程实现与稳定币优势:有限创新下的差异化
Tron 经常被评价为“技术创新有限”,因为其很多理念来源于前辈(如采用与EOS类似的DPoS共识,兼容EVM的合约机制等)coinshares.com。Tron 白皮书早期甚至曾被指出有抄袭他链文档的嫌疑。然而,Tron 在工程实现和优化上非常出色,打造出了一条高可用、高性能的主网,并在关键细分领域取得领先地位。首先,Tron 网络运行稳定,自2018年主网上线以来几乎没有发生严重宕机或安全事件。这一点相较于同样DPoS架构的 EOS 主网要稳健得多(EOS 主网上线后曾多次出现性能瓶颈和治理僵局),也好于近年曾遭遇停链的 Solana 等高TPS链。Tron 将区块时间精确到3秒且长期保持共识稳定,使得链上转账**“三秒到账”**成为标志性的用户体验优势。
更重要的是,Tron 聚焦于稳定币转账这一高频刚需场景,通过一系列工程手段降低用户成本、提升效率。例如,Tron 上 USDT 等稳定币的 TRC-20 合约转账被优化得近似免Gas:利用带宽每日免费额度和发行方资源冻结策略,大部分小额USDT转账用户无需支付任何TRXcointelegraph.com。据统计,Tron 上单笔 USDT 转账成本可低至 0.345 TRX(约合2美分)甚至为零medium.com。Tron 还允许代币发行方提供一定的“免费带宽”给代币持有人developers.tron.networkdevelopers.tron.network,这意味着像 Tether 这样的发行方可为TRC20-USDT交易承担资源费用,使用户体验真正达到免手续费。这种“稳定币交易免Gas”的设计在主流公链中独树一帜。
Tron 的另一工程优势是极快的确定性。虽然Tron每块3秒,但由于DPoS共识和固有的BFT特性,Tron 区块在数轮出块后即不可逆转。Tron Solidity节点仅同步不可逆区块,用于对接交易所等场景developers.tron.network。通常交易所对Tron充值只需等待 1分钟左右确认,远快于以太坊传统上要求的数分钟/数十个区块确认。chainspect.app的链速数据显示,Tron链上最终确定(finality)时间约 \~57秒,与EOS等DPoS链类似,明显快于以太坊(>6分钟)和比特币(一小时)chainspect.app。这使Tron成为稳定币跨平台流转的理想基础设施:用户可以在交易所之间快速划转USDT,几乎实时地完成资金移动,而手续费可以忽略不计。
尽管Tron本身没有提出全新的共识算法或智能合约范式,但这些工程上的打磨带来了切实的成果:截至2025年,Tron 网络上 USDT的流通量超过750亿美元,再度位居各链之首cointelegraph.comcointelegraph.com。约 50%以上的USDT供应原生发行在Tron上coindesk.comcoindesk.com(二号是以太坊,约47%,其余诸如Solana、Avalanche合计不到5%cointelegraph.com)。Tron 同时处理了全球稳定币交易价值的近29%coindesk.com,每日 USDT 转账额高达 200亿美元coindesk.com。这些数据说明,尽管Tron没有“炫目的”技术标签,但凭借务实的性能优化和对用户友好的成本结构,在稳定币这一杀手级应用上取得了其它公链无法比拟的领先coindesk.com。
Tron 的高性能也使其成为去中心化金融(DeFi)基础设施的有力支撑。Tron上最大的DeFi借贷协议 JustLend 锁定价值超过 60亿美元coinshares.com(主要是TRX和USDT的借贷),显示出稳定币低费率环境对资金沉淀的吸引力。Tron 于2022年还推出了去中心化美元稳定币 USDD,以丰富生态。不过USDD体量相对有限(约7亿市值)coinshares.com,Tron生态真正的支柱仍是 USDT 等主流稳定币的传输和兑换。正因为聚焦于稳定币的出色支持,Tron 获得了行业独特地位:CoinShares 报告称截至2024年末 Tron 上约44%的USDT供应,使其在稳定币基础设施方面一度超越以太坊coinshares.comcoinshares.com。
“BTC上涨+稳定币基础设施”叙事下的 Tron 竞争力与市场前景
当前环境下,Tron 在 USDT市场占有率高、交易成本极低 的条件下,展现出强大的竞争优势。这与行业宏观叙事“比特币上涨 + 稳定币基础设施受益”紧密相关。在加密市场进入上行周期时,比特币价格攀升往往伴随场外资金涌入,稳定币作为法币与加密世界的桥梁需求激增castleisland.vc。Tron 因为在稳定币传输领域的卓越表现,有望从这一趋势中获得超额收益(Alpha)。
首先,Bitcoin上涨带来的交易活跃增加,势必需要大量稳定币在交易所和用户间快速流转。Tron作为承载全球超过一半USDT流通的网络coindesk.comcoindesk.com,“水涨船高”,交易笔数和价值很可能进一步增长。从2024到2025年的数据已经印证了这一点:2024年末以来 Tron 日均交易量从约430万增加到840万以上,增长了95%binance.combinance.com。尤其是在2025年初,比特币触发的新一轮市场热度下,Tron 日均交易笔数持续保持在 800万+,并多次冲击单日千万笔的关口binance.combinance.com。这表明 Tron 网络能够大规模处理牛市涌现的交易需求,为稳定币的频繁进出提供了高吞吐保障。
其次,超低的费用使Tron在竞争中胜出。当市场繁荣时,以太坊等网络往往因拥堵导致Gas费飙升,而Tron凭借资源模型依然保持每笔几乎为0的费用cointelegraph.com。这一点对套利交易商、跨境转账用户等极为重要:他们可以放心地使用Tron在交易所和钱包间搬运资金,而不用担心手续费侵蚀利润。这种成本优势也使得Tron在新兴市场获得青睐。许多亚洲、非洲的用户通过Tron链转移美元稳定币用于支付和结算coinshares.comcoinshares.com。由此Tron已经形成网络效应:用户数量多、USDT储备大,新用户更愿意选择已被广泛接受的Tron作为稳定币链。2025年一季度,Tron链上USDT流通再增 70亿美元,新增用户钱包数增长了 4600万coindesk.comcoindesk.com。这种高速增长进一步巩固了Tron在稳定币领域的龙头地位。
从市场价值角度看,Tron 的基本面强劲却长期被低估的情况也引人关注。Tron手续费收入与市值比成为分析师讨论的焦点:截至2024年底,Tron每日协议收入约 $79万美元(主要来自能量费燃烧等)alphanode.globalalphanode.global。按Tron当时$190亿市值计算,其市盈率(P/E)显著低于同业。例如Solana市值虽只有Tron五分之一,但每日费用收入只有Tron的一半alphanode.global。这意味着 Tron 网络在实际利用率和价值捕获上表现突出,TRX 代币有潜在重估空间alphanode.global。部分研究指出Tron的手续费收入/市值比远高于以太坊、Solana等,暗示TRX被低估且具有“价值洼地”特征。
竞争层面,Tron 面临的挑战主要来自以太坊扩容和其他低费链的蚕食。一方面,以太坊主网的升级及其Rollup二层网络(如Arbitrum、Optimism等)在降低费用方面取得进展,某些USDT流通开始转移到以太坊的Layer 2。但即便如此,Tron凭借先发优势和广泛的交易所支持,短期内仍牢牢占据稳定币结算主渠道coinshares.com。2024年11月,以太坊曾短暂重新超过Tron的USDT供应占比,但很快又被Tron新的增发反超cointelegraph.comcointelegraph.com。这显示出Tether公司和市场对于Tron网络的信心和需求依然强劲。另一方面,BSC、Solana等亦尝试争夺稳定币市场份额,例如BSC上也运行着不少USDT。但截至2025年,BSC上的USDT流通量和活跃度远不及Tron(Tron每日稳定币活跃地址占全行业28%coindesk.comcoindesk.com)。Solana则更专注于自身DeFi和新资产发行,稳定币主要还是USDC为主,体量有限。
综合而言,Tron 在“BTC 上涨 + 稳定币基础设施需求”这一行业趋势下展现出了独特的竞争力。它以稳健高效的工程实现弥补了技术创新上的不足,围绕稳定币这一刚需场景打造出低成本、高速度、广覆盖的链上金融网络。在未来市场周期中,只要对稳定币的需求存在,Tron 作为底层清算层的地位就难以被撼动。对于TRX的价值表现,这意味着有潜在的Alpha:当交易量和用户数上升时,TRX作为资源质押和手续费燃烧的载体,其需求量和内在价值也水涨船高alphanode.globalalphanode.global。当然,Tron 也需继续拓展生态应用、改善西方市场的形象来巩固长期地位coinshares.comcoinshares.com。但就当前来看,Tron已经凭借“强工程+准入门槛低”的策略,在区块链基础设施版图中占据了一席重要之地。它在稳定币时代的成功经验,印证了区块链项目不仅可以靠颠覆性创新取胜,也可以通过持续优化用户体验和性能找到差异化赛道,实现后来居上。
参考资料:developers.tron.networkmedium.comcointelegraph.comcoindesk.comcoindesk.com等。
-
 @ cae03c48:2a7d6671
2025-06-04 13:00:52
@ cae03c48:2a7d6671
2025-06-04 13:00:52Bitcoin Magazine

Tether Group & Bitfinex Transferred 25,812 BTC to Jack Mallers’ Twenty One CapitalToday, Tether Group and Bitfinex have transferred a combined 25,812.22 BTC to support their investment in Twenty One Capital, a newly formed Bitcoin-native company set to go public through a business combination with Cantor Equity Partners (Nasdaq: CEP).
Tether moved 14,000 BTC to an address of Twenty One Capital (XXI) and previously transferred 4,812.22 BTC to another address of Twenty One Capital as part of their investment in the company.
JUST IN: Tether sends 18,812 #Bitcoin worth almost $2 billion to Jack Maller's Twenty One Capital
 pic.twitter.com/Oy18iPnUzO
pic.twitter.com/Oy18iPnUzO— Bitcoin Magazine (@BitcoinMagazine) June 2, 2025
Bitfinex, in parallel, has sent 7,000 BTC to an address of Twenty One Capital, also as part of its investment.
JUST IN: Bitfinex sent 7,000 #Bitcoin worth $731 million to Jack Mallers' Twenty One Capital
 pic.twitter.com/kshqZwHz34
pic.twitter.com/kshqZwHz34— Bitcoin Magazine (@BitcoinMagazine) June 2, 2025
These Bitcoin transfers come a little over a month after Twenty One Capital and CEP announced that it was raising $585 million in additional capital at the closing of the business combination. The raise was to feature $385 million in convertible senior secured notes and $200 million in PIPE (private investment in public equity) financing, with proceeds expected to be used for further Bitcoin purchases and general corporate purposes. Once finalized, the company anticipates launching with over 42,000 BTC, positioning it as the third-largest Bitcoin treasury in the world.
“Markets need reliable money to measure value and allocate capital efficiently,” said the Co-Founder and CEO of Twenty One Jack Mallers. “We believe that Bitcoin is the answer, and Twenty One is how we bring that answer to public markets. Our mission is simple: to become the most successful company in Bitcoin, the most valuable financial opportunity of our time. We’re not here to beat the market, we’re here to build a new one. A public stock, built by Bitcoiners, for Bitcoiners.”
The announcement comes just days after Mallers announced a new Bitcoin backed loan platform at Strike during the 2025 Bitcoin Conference in Las Vegas. The system will offer interest rates between 9-13%, allowing clients to borrow between $10,000 and $1 billion using Bitcoin as collateral.
“All these professional economists, they are like Bitcoin is risky and volatile,” stated Mallers. “No it’s not. This is the magnificent 7 one year volatility and the orange one in the middle is Bitcoin. It’s no more risky and volatile. It’s a little bit more volatile than Apple, but is far less more volatile than Tesla.”
“Life is short,” commented Jack. “Take the trip, but with bitcoin you just get to take a better one.”
This post Tether Group & Bitfinex Transferred 25,812 BTC to Jack Mallers’ Twenty One Capital first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 7460b7fd:4fc4e74b
2025-06-04 12:50:39
@ 7460b7fd:4fc4e74b
2025-06-04 12:50:39TRX网络USDT在华人地下跨境犯罪经济中的作用研究
引言
华人主导的跨境地下犯罪经济近年来出现了新的金融工具——以USDT(泰达币)稳定币为核心的加密货币支付体系,尤其流行于波场(TRON)网络上的TRC20-USDT。这种去中心化货币在跨国电信诈骗、网络赌博、人口贩卖等灰黑产业中扮演着关键角色binance.combinance.com。本文将从学术角度探讨TRX网络USDT在上述犯罪经济中的作用,包括:USDT如何充当金三角、柬埔寨、西港等地跨国犯罪的资金纽带;灰色金融圈中“黑U”“灰U”的含义及其链上特征与处置;犯罪团伙对imToken、Bitpie、TokenPocket等手机钱包的广泛使用;USDT作为“市场择优的货币”在政治经济真空地带的自发流通;以及TRON创始人孙宇晨在国际政治博弈中的行为与传统华人“避政治”思维的张力。这些讨论将结合公开报道、行业调查和链上分析数据进行梳理,以期勾勒出USDT在地下经济链条中的隐秘版图。
波场USDT:东南亚跨境犯罪网络的资金动脉
 \
柬埔寨金边街头一处提供USDT兑换的店面,电子屏幕上用中英文显示“USDT抵押换汇7.2保永久”,反映USDT已成为当地地下经济的常用货币工具 © 丹妮尔·基顿-奥尔森/南华早报followin.iofollowin.io。
\
柬埔寨金边街头一处提供USDT兑换的店面,电子屏幕上用中英文显示“USDT抵押换汇7.2保永久”,反映USDT已成为当地地下经济的常用货币工具 © 丹妮尔·基顿-奥尔森/南华早报followin.iofollowin.io。在东南亚的跨境犯罪热点地区(如“金三角”地带、柬埔寨西哈努克港等),TRC20版USDT已成为各种违法活动的共同资金链条binance.combinance.com。这些地区聚集了大量中国籍犯罪团伙,从电信诈骗园区到网络博彩赌场,甚至涉有人口贩卖和强迫劳动的黑营地,USDT被用作吸纳赃款、转移资金和内部结算的“通用货币”binance.combinance.com。USDT在波场网络上的迅捷匿名转账特性使其深受不法分子青睐:波场自2018年上线后将区块链交易速度提升至秒级、手续费降至美分级,用户体验几乎等同于银行转账,这直接助推了当年涉币犯罪案件数量同比大增74%geekpark.net。在现实中,这意味着诈骗集团可以在几分钟内将巨额资金通过TRX网络划转出境,且几乎无需手续费,难以被传统金融监管即时拦截。
大量调查显示,东南亚跨国诈骗集团正大规模依赖USDT来收取和清洗赃款。例如,柬埔寨一度被揭露隐藏着每年高达190亿美元规模的加密诈骗网络,相当于该国GDP的60%,其中USDT等加密币是资金流转的主要媒介binance.com。一些大型华人诈骗组织开发了高度集成的平台,以Huione汇旺集团为核心技术支撑,将受害者骗来的资金迅速转换为难以追踪的USDT进行跨境转移binance.combinance.com。在柬埔寨和邻近地区,USDT俨然形成一个地下金融循环:金边街头随处可见标有中文的兑换店提供人民币与USDT的24小时兑换服务,USDT成为华人社群规避中国外汇管制、参与地下交易的首选工具followin.io。即使柬埔寨官方名义上禁止加密货币交易,低成本、高效率的USDT交易仍在暗地里蓬勃发展,连当地一些持牌交易所也默认为华人客户提供USDT兑换,以参与这条灰色产业链followin.iofollowin.io。
跨国电信诈骗和网络博彩中,犯罪团伙常要求受害者将资金兑换为USDT后转入其提供的钱包地址,以逃避银行监控reddit.com。所谓“杀猪盘”式骗局就经常引导受害者在合法加密平台购买USDT,再充值到骗子控制的虚假投资App中reddit.com。通过这种方式,赃款直接进入链上流通,远离了传统银行体系。例如,2023年在柬埔寨西港运营的“银河集团”诈骗团伙诱骗国内3万余名中老年受害者投资虚假项目,骗取人民币1.433亿元后,即通过Telegram联系国内“币商”将赃款兑换为USDT并分散转移sohu.comsohu.com。中国警方披露,该团伙在数月内组织40名境内人员专门从事USDT洗钱,涉案金额2000多万元人民币sohu.com。最终这些帮凶被以掩饰、隐瞒犯罪所得罪判刑sohu.com,说明USDT已成为跨境诈骗资金回流国内的主要通道之一。
同样在2025年,泰国警方抓获了一名跨国诈骗嫌犯ZHOU某,此人曾在柬埔寨西港绑架勒索同胞100万人民币,并涉及多个国际诈骗和洗钱团伙news.qq.comnews.qq.com。调查发现,一名与其同居的中国女子通过USDT洗钱,从网络投资诈骗中获利高达1,840万枚USDTnews.qq.com。如此巨量的USDT流水再次印证了波场USDT在此类犯罪经济中的核心地位。波场链上USDT流通量近年来更是迅猛攀升:截至2023年5月,TRC20-USDT发行量突破777亿美元,一举超越以太坊网络上的USDT发行,成为全球最大规模的稳定币网络okx.com。截至2025年5月波场上的USDT流通量进一步超过757亿美元,占据稳定币市场半壁江山,表明愈来愈多资金选择经由波场USDT流动binance.comblocktempo.com。有报告指出,自2022年以来波场一直在USDT日均交易量上领先于以太坊binance.com。这部分反映了东南亚以及全球范围内大量非正规资金和灰色资本正涌入波场USDT体系,因为相比之下以太坊网络手续费高昂且链上交易透明度更高,不法分子更倾向于成本低且风评相对隐蔽的波场网络geekpark.netbinance.com。
值得注意的是,一些东南亚国家政商势力默许甚至参与了这种地下经济。例如柬埔寨有证据表明,多名执政党高官间接从强迫劳动的诈骗活动中获利,纵容了USDT地下经济的发展binance.combinance.com。柬埔寨政商背景深厚的Huione集团建立起庞大的USDT支付与担保系统,在东南亚乃至东亚范围处理着巨额资金流web3caff.comweb3caff.com。据美国财政部数据,Huione旗下的“汇旺担保”仅通过Telegram运营,自2021年来已处理超过40亿美元资金binance.com。链上分析显示,其核心地址在2023年一年内流入高达21.58亿USDT,其中被判定为网络赌博、高风险灰产交易、洗钱、诈骗等“不干净”资金的占比接近20%web3caff.comweb3caff.com。由于卷入大量东南亚非法活动,2024年7月Tether公司冻结了Huione关联地址上的2,962万枚USDT,引发业界关注web3caff.com。更大规模的冻结也在发生:美国司法部2023年调查东南亚诈骗洗钱网络时,一次性没收了近900万美元加密货币,并促使Tether追加冻结了2.25亿美元疑涉“杀猪盘”骗局的USDTfollowin.iofollowin.io。这些执法动作表明,波场USDT纵然便利,也已成为全球监管机构打击跨境犯罪的新焦点。
“黑U”与“灰U”:灰色金融中的稳定币污点
随着USDT渗透灰色金融领域,“黑U”“灰U”成为华语圈特有的行业术语,用于区分USDT资金的“清白”程度binance.comaicoin.com。黑U一般指明确涉及违法犯罪活动的USDT资金,往往来源地址已被执法机关标记冻结,或由Tether公司应司法请求冻结操作binance.combinance.com。此类“黑U”由于链上烙印污点,很可能无法正常转出或在交易所兑现——比如某人从违法平台提取USDT,而该平台被警方查封,其地址标记为涉案地址,那么任何从该地址转出的后续地址上的U币都可能被视为涉案资产而遭冻结处理binance.combinance.com。灰U则多指尚未被官方标记但来源可疑、涉及灰色产业(如地下赌资、逃税资金等)的USDT。这类USDT处于执法视野的灰色地带,短期内或可正常流通,但一旦上游案件爆发也有染黑的风险。业内人士形象地将广泛用于欺诈、盗窃、黑客攻击等黑灰产活动的稳定币称为“黑U”,事实上主要指USDTaicoin.com。随着各国加大链上追踪力度,越来越多交易所和机构对可疑USDT敬而远之,以免卷入反洗钱调查aicoin.com。“黑U”“灰U”之分也提醒场外交易者提高风险意识。
中国警方和司法机关对涉案USDT等加密资产的处置,近年逐步形成规范。cn.tradingview.com据中科链源SAFEIS安全研究院《2022年中国虚拟货币司法处置报告》,截至2022年底,中国司法机关扣押在案、等待处置的加密货币总价值约348亿元人民币,涵盖比特币、以太币和泰达币(USDT)等主流币cn.tradingview.comcn.tradingview.com。值得注意的是,近年涉币案件数量虽有所下降,但案件中涉案加密资产总量却在逆势飙升,表明加密货币犯罪正朝着“大案值、专业化”方向发展cn.tradingview.com。司法实践中,“黑U”等涉案USDT的处置主要有两种:一是在案件判决后将虚拟币变现上缴财政;二是在侦查阶段由公安机关先行变现或冻结保管cn.tradingview.com。无论哪种方式,如何安全合规地将币兑换为法币是核心难题。一些地方检察机关开始出台内部指引,细化了查询冻结、扣押保管、移送处置各环节的操作规范,为依法处置涉案虚拟货币提供指南cn.tradingview.com。这表明官方已经认识到“黑U”“灰U”资产处置的迫切性和复杂性。
链上分析工具也用于甄别黑灰U的流转特征。执法技术公司中科链源开发了SAFEIS安士查控平台,能够将大额可疑USDT流动绘制成网状资金流向图,对涉嫌地址实施7×24小时监控news.sina.cnnews.sina.cn。根据多年研究,他们总结出虚拟币洗钱的典型路径,包括场外承兑、跨境“跑分”、地下钱庄等fx168news.com。对于USDT洗钱,往往呈现四处流窜、多层中转的链上踪迹:不法分子常用新开钱包地址来降低过往交易痕迹binance.com;利用去中心化交易所(DEX)、跨链桥、混币器等手段试图打乱追踪news.sina.cnnews.sina.cn;甚至发行内部结算代币以逃避监管覆盖binance.com。例如,上文提到的汇旺团伙就曾发行自己的稳定币来优化洗钱流程binance.com。但无论花样如何翻新,链上留下的记录终究难以彻底抹去。一旦某个USDT地址被认定藏污纳垢,执法部门可请求Tether公司冻结其代币资产web3caff.com。Tether作为中心化稳定币发行方,近年来频繁执行“泰达冻结”动作以配合各国执法,涉及人口贩卖、毒品贸易、大规模洗钱等重大案件时更是果断出手faxianlaw.com。例如2023年下半年,Tether因配合美国调查“大猪杀”诈骗园区,短时间内冻结了数亿美元涉案USDTfollowin.io。当然,滥用冻结也引发争议:合法的加密企业若误收了部分“黑U”,账户突然被冻将遭受业务重创并可能面临法律风险web3caff.com。因此行业呼吁建立更透明的黑灰U识别和通知机制。在完全去中心化的未来尚未到来前,“黑U”恐怕仍将如同“黑钱”一般,通过监管合作与技术手段被不断围追堵截binance.com。对于普通币民而言,务必提高警惕,避免因贪图便宜买入来源不明的低价USDT而沾染黑灰风险binance.com。行业建议是在正规交易所购买USDT、通过信誉良好的场外商家出售,以尽量隔绝“脏U”影响binance.com。正如业内提示的那样:“只要你能顺利转出并在交易所变现的U,就算好U”binance.com——这背后是复杂的风控筛查和执法协作在发挥作用。
数字钱包:灰产链条中的隐秘工具
在地下灰产的运作中,常用的手机数字钱包应用如imToken、Bitpie、TokenPocket等扮演了重要角色。这些去中心化钱包由于无需实名制、便于多链资产管理且操作灵活,成为灰黑产从业者的“随身钱袋”和逃避监管的利器。据一线执法人员观察,许多涉案人员手机中往往安装有多个此类钱包App,以方便随时收付USDT等数字资产。在前述柬埔寨诈骗园区中,被胁迫工作的人员甚至可能通过数字钱包领取薪资或提成,犯罪集团用USDT直接支付,以绕开银行系统的追踪。这些钱包也用于团伙内部结算和跨境转账,诈骗集团会将受害者的钱转换成USDT发送到自己的imToken等钱包,再通过不记名的链上账户在全球范围内调度资金。
对于从事洗钱的“币商”而言,钱包是必不可少的工具。正如反洗钱专家所建议的,黑灰产业人员切忌将黑钱直接充入交易所账户,而应先提到个人钱包,再经由场外渠道兑换binance.combinance.com。这样做的原因在于:交易所往往配合监管监测大额可疑充提,一旦直接存入“黑U”,交易所可能冻结账户并上报公安binance.com。相反,钱包地址由于去中心化且与个人身份无直接关联,警方难以及时掌握钱包持有人真实身份binance.com。例如,币圈常用的钱包imToken支持ETH和TRON等主流链,灰产人员可以在其中生成多个USDT地址,用完即弃,降低被关联的风险**binance.com**。再通过这些钱包将U币分散转移给他人或其他钱包,实现“跳板”洗白。近年来流行的跑分平台骗局也利用受害者的钱包参与黑U兑换,以脱钩源头aicoin.comaicoin.com。可以说,手机钱包已成为灰色资金流动的重要载体。
值得关注的是,这些钱包应用在华人灰产圈中几乎成为“标配”。有海外华人论坛调侃道:“你做的事情跟灰产有关,自然就会用到imToken这款钱包。”这反映出imToken等在地下圈子的普及度之高。当然,钱包本身只是工具,其本意并非服务犯罪。然而在严厉的金融监管和资金跨境限制下,很多游走灰色地带的资金选择了数字钱包这条“暗道”。以imToken和TokenPocket为例,它们提供方便的私钥管理和转账功能,用户可自行掌控资产,不受第三方冻结。某种程度上,灰产人员利用的正是去中心化钱包“无边界”、“抗审查”的特质,将非法资金与现实身份切割开来。比如Telegram上的币商常指导买家先下载这些钱包收币,再协助将USDT卖出兑换人民币,从而避开银行敏感词监控和卡片冻结风险binance.combinance.com。链上资金在钱包之间空转数次后,再流入交易所时已难以直接追查源头。这给执法带来巨大挑战:警方往往需要提取嫌疑人手机中的钱包数据或借助链上分析,还原出钱包地址之间错综复杂的关系链,方能锁定赃款流向。
当然,一旦钱包地址与某起案件建立关联,也可能进入监控清单。数字执法工具可以将特定地址标记为高风险,实现实时预警news.sina.cnnews.sina.cn。部分钱包应用也开始与审计工具合作,标记可疑资产来源以提醒用户。尽管如此,“去中心化钱包+USDT”仍是当前地下资金体系中成本最低、效率最高的配置。对于普通用户而言,需要警惕的是不要随意为陌生人充当USDT资金中转,否则极可能卷入洗钱犯罪。近期就有多起中国公民因帮助境外灰产跑分兑换USDT而被以帮信罪判刑的案例sohu.com。这些教训表明,即便使用的是号称匿名的数字钱包,链上交易终究逃不过法网。因此,正确使用钱包的方式应是合法合规理财,而非为灰黑资金“提桶接水”。对监管者而言,则需在尊重技术发展的同时,加强对钱包使用异常行为的监控和溯源能力建设。
哈耶克视角:USDT——真空地带的“市场择优”货币
奥地利经济学家弗里德里希·哈耶克曾提出货币去国家化和自由竞争理论,主张让各种私人货币在市场中竞争,优胜劣汰,由市场自行选择最适合的货币。USDT的崛起,在某种意义上印证了哈耶克的这一预见——在政治与经济的真空地带(或者说监管薄弱、法币失灵的环境中),一种由私人公司发行的数字稳定币获得了广泛自发采用,成为事实上的流通货币。
在柬埔寨、西非、缅北等“金融飞地”或灰色地带,官方法币要么信用不足、通胀严重,要么受到资本管制难以自由兑换。在这些场景下,各方参与者自然倾向选择一种稳定且高效的价值媒介来交易结算。USDT恰好符合这一需求:锚定美元确保价值稳定,跨境转移不受主权限制,交易成本低且速度快。如前所述,柬埔寨的华人地下经济圈干脆跳过当地货币瑞尔和美元现金,直接用USDT进行兑换、抵押和支付followin.iofollowin.io。赌场里兑筹码可以用USDT,诈骗团伙内部发奖金用USDT,毒贩收到赃款也偏好收USDTjiemian.comjiemian.com。USDT俨然成为这些地区事实上的“硬通货”,这正是自由市场选择货币的体现——不管发行者是不是政府,只要一种货币能更好地充当交换媒介和价值储藏手段,市场就会拥抱它。
从哈耶克的货币观来看,USDT的流行揭示出当法定体系无法满足交易各方需求时,民间会自发寻求替代方案。在中国严格限制资金出境和境外赌博的背景下,大批资金绕道USDT离开银行体系追逐海外投资或赌局followin.io。市场“择优”的结果,使得泰达币这种原本用于币圈交易避险的稳定币,在完全不同的场景中获得生命力:既服务于跨境商贸和侨汇,也沦为电诈洗钱和地下钱庄的工具。这种双重面向也引发思考——**当一种货币的主要用途集中在黑产和投机领域时,它究竟是市场自发最优选择,还是金融体系漏洞的产物?**有评论指出:“一种货币使用者越多理论上是好事,但如果用途仅限于黑产和投机,是否该审视一下加密货币的初心?”jiemian.com。哈耶克或许会辩称,市场选择未必总是道德的选择,竞争出的胜者只是满足了当下参与者利益。然而从社会治理角度,USDT充当“地下央行”的崛起无疑对传统金融和法治形成了冲击。
另一个哈耶克式的问题在于:USDT并非去中心的货币,它依赖于中心化发行方维持锚定和信用。那么市场真的在“自由”选择吗?抑或只是缺少更优选项下的无奈之举?毕竟在这些真空地带,民众和非法分子用不起波动巨大的比特币,也无法信任当地政府的货币,于是选择了一个挂钩美元且相对可靠的公司代币。这里既有对美元信誉的追随,也有对主权信用的逃离。哈耶克畅想的私人货币竞争,本质上要带来货币质量的提升。然而USDT的乱象(例如透明度问题、超发质疑)也提示我们:当私营货币变成地下秩序的基石时,同样需要新的规制之手来防范滥用和风险蔓延finlaw.pku.edu.cnodaily.news。总之,在当前全球政治经济的缝隙中,USDT如同一种“自发生长”的货币填补了真空。这既印证了市场择优原则,又提醒我们这份“择优”并非在完美竞争环境下发生,而是在各国监管套利和需求倒逼的特殊土壤中生长的异象。如何引导这类市场产物朝良性方向发展,可能是未来政策和技术需要共同回答的问题。
孙宇晨的资本博弈与华人“避政治”传统
TRON波场网络创始人孙宇晨在USDT版图中扮演着一个特殊的角色:一方面,他的商业帝国因TRX和USDT的成功而崛起;另一方面,他本人又频频以“资本玩家”的身份介入国际政治和监管博弈,行为方式与传统华人商界避政治的惯性形成鲜明对比。
传统上,海外华人企业家多奉行低调务实的哲学,聚焦经商、远离政治纷争,以求在异国他乡自保并兼顾与祖籍国的关系。然而身为90后的孙宇晨却反其道而行:他主动寻求政治舞台,不惜花重金打造个人影响力。最引人注目的是2021年末,孙宇晨出任加勒比海岛国格林纳达驻世界贸易组织(WTO)大使,成为当时全球WTO代表中唯一的中国籍90后**finance.sina.cnfinance.sina.cn**。这一消息震惊舆论:一个加密货币创业者竟以外国外交官身份出现在国际组织,许多人质疑这背后是否存在利益交易。事实上据格林纳达官方公告,孙宇晨的任命于2021年12月17日生效,授权其全权代表格国出席WTO会议finance.sina.cn。外界推测孙宇晨可能通过投资入籍等方式获取格林纳达国籍,并凭借财力和人脉获得了该国政府的委任hk01.comsohu.com。此举对孙宇晨个人而言,无疑能增加政治光环甚至潜在的外交豁免,对于波场及加密圈也提供了一层保护色。然而这种高调的政治参与在华人商界是少见的。华人社会历来有“商人不问政”的传统观念,尤其是改革开放以来的企业家更倾向于专注财富积累、避免卷入敏感政治话题。孙宇晨的举动无疑突破了这一默契,在一定程度上引起了国内官方和业界的复杂反应。
孙宇晨在国际监管环境中的“搏杀”也体现出资本逐利的游戏色彩。他多次与美国监管机构周旋:2023年3月,美国证券交易委员会(SEC)以涉嫌非法发行证券和市场操纵等罪名起诉孙宇晨及其关联公司,指控他出售TRX和BTT代币未注册、并操纵TRX市场价格finance.sina.cn。孙宇晨迅速在社交媒体上回应,称SEC的指控“毫无依据”finance.sina.cn。尽管官司缠身,他依然活跃在线,甚至在香港、新加坡等地寻求新的业务机会。一些评论将他形容为“亦正亦邪”的资本玩家:一面高举拥抱监管的旗帜(例如表示愿配合香港合规框架),另一面又被指暗地参与洗币、内幕交易等灰色操作zhuanlan.zhihu.com。这种矛盾的形象折射出加密大亨在全球治理夹缝中的生存现状:他们游走于规则边缘,既想享受合法待遇,又不放弃制度漏洞带来的暴利。这与老一辈华商“循规蹈矩,明哲保身”的信条形成了鲜明张力。
孙宇晨的“资本主义博弈行为”还体现于其善于制造话题、获取影响力的手段上。从早年拍下巴菲特午餐以3千万人民币搏出位,到高调宣布太空之旅计划,他运用资本资源为自己贴上各种标签。这些行为放在传统华商语境中,无疑显得过于张扬和高风险——过多曝光可能引来监管警惕,卷入政治则可能招致各方不满。然而孙宇晨似乎深谙全球化时代的新规则:利用资金和技术优势,他可以在多国间穿梭套利,身份可以是企业家、投资人、外交代表多重转换。这种“去中国化”的跨国身份策略,某种程度上也是对华人避政治传统的一种挑战。他选择直接参与政治博弈(哪怕是小国政治),而非像多数同行那样退居幕后来影响政策。结果是,他个人的冒进举动有时会反噬企业形象。例如,格林纳达政局变动后新政府迅速撤销了孙宇晨的大使任命(原先支持他的政党在2022年6月选举中下台)finance.sina.cnfinance.sina.cn。孙宇晨在WTO露脸不满半年便失去了外交官身份,这场“政治投资”得失几何尚难定论,但至少证明了商人染指政治所需承担的不确定性。
可以说,孙宇晨身上凝聚了中国互联网时代新贵与传统华人商贾思想的冲突。一方面,他具备全球视野和冒险精神,敢于用资本开道,在国际舞台为自己和旗下加密帝国博取合法性和话语权。另一方面,这种高调参与公共事务的做法容易触碰红线,不仅引来美国SEC等强力部门的围剿,也可能在中国官方那里被视为“离经叛道”。毕竟,中国政府对加密货币一直态度谨慎,孙宇晨早在2019年就曾因出境风波被传与监管有摩擦。从华人社会心理看,孙宇晨的特立独行也引发两极评价:支持者称其为新时代华人敢于争取国际地位的代表,质疑者则认为他“精致利己”,没有国家认同,在资本游戏中随时可以抛弃身份立场。这也正是传统“避政治”思维与新兴“全球公民”意识的碰撞。**孙宇晨现象提醒我们:**在加密货币这个去中心化的疆场上,华人创业者开始探索新的生存之道,不再满足于做隐形的财富玩家,而是试图塑造规则、影响格局。但个人的棋局再精彩,也要面对大国博弈和法律高墙的制约。孙宇晨能否在资本与政治的夹缝中继续腾挪,将在很大程度上影响波场乃至华语加密圈的未来走向。
结论
基于现有调查与公开资料的分析,我们可以看到USDT(特别是波场TRC20网络上的USDT)正深刻融入华人地下跨境犯罪经济的血脉。从东南亚猖獗的电信诈骗、网络赌场,到跨境毒品和人口贩卖交易,USDT提供了一个高效且去中心化的结算网络,使不法资金得以脱离传统金融监管的视线高速流转news.sina.cnfollowin.io。在灰色金融世界中,业界用“黑U”“灰U”来识别USDT资金的干净程度,提醒参与者谨防踩雷涉罪aicoin.combinance.com。中国执法部门针对这类涉案加密资产已开始摸索行之有效的追踪和处置机制,包括引入区块链分析工具、完善司法处置规范等cn.tradingview.comnews.sina.cn。与此同时,地下产业大规模使用的imToken等手机钱包成为灰产资金流动的关键环节,体现出技术双刃剑的效应:去中心化工具在便利正常用户的同时也被不法分子所利用。更宏观地看,USDT在无主监管地带的泛滥从一方面印证了市场自发选择的力量,如同哈耶克预言的私人货币在特定环境胜出法币followin.io。但这种“胜利”伴随着巨大社会风险和治理挑战,呼唤着国际协作的新对策。
最后,孙宇晨的个人轨迹为我们提供了另一个观察维度:作为TRON/USDT生态的缔造者之一,他在全球舞台上以资本为筹码参与政治和规则博弈,反映出加密时代华人商人的新冒险精神,也揭示了其与传统价值观的冲突finance.sina.cn。USDT及其背后的波场网络,从来不只是冰冷的技术和数字,它深嵌于现实的政治经济土壤之中。在中国与世界交汇的灰色地带,USDT既是工具也是产物,既成全了地下经济的壮大也倒逼着监管升级与国际合作。未来的犯罪打击和金融治理,必须正视这样一种数字货币所带来的复杂影响。从学术和执法实践角度出发,我们应持续关注USDT等稳定币的流向,完善跨境资金监测和司法处置机制。同时,也要思考如何引导加密货币回归合法正轨,让其真正服务实体经济而非滋养犯罪网络。在法制与市场的拉锯中,或许唯有全球共同努力,方能既不扼杀技术创新,又能织密法网,让USDT不再成为法外之地的肆意横财之源。正如中国公安大学的专家所言:“妖怪一旦放出瓶子,就会产生不可逆的影响”jiemian.com。USDT这只从瓶中放出的“魔灵”,唯有在阳光下接受规范和引导,才能避免成为彻底失控的风险之源。各国监管者和行业从业者正面临一次前所未有的考验:如何驾驭这个时代的双刃剑,在保障金融安全的同时,释放技术进步的正面价值。我们拭目以待这一进程的演变,也期待看到地下黑产不再有滋生的温床。
参考文献:
-
胡翼龙, 等. 区块链技术的阴暗面:涉币犯罪与法币犯罪的边界正被打破. 中国人民公安大学讲座纪要geekpark.netgeekpark.net.
-
币市雷达. 黑U真的存在吗?正确使用USDT的方式. CoinsRadar专栏binance.combinance.com.
-
PANews深度. 明知是黑U还去买?警惕跑分套利骗局. AiCoin文章aicoin.comaicoin.com.
-
佚名. 柬埔寨:190亿美元加密货币诈骗网络的中心. HRC报告摘要binance.combinance.com.
-
昭化区人民法院. 为西港电诈团伙银河集团洗钱超2000万,国内40人被判刑. 新闻报道sohu.comsohu.com.
-
腾讯新闻《我在柬埔寨》. 红通逃犯柬埔寨绑架勒索同胞涉诈骗洗钱,在泰国被捕. 福建新闻报道news.qq.comnews.qq.com.
-
Web3Caff链上分析. 柬埔寨汇旺集团遭泰达冻结2962万USDT事件分析. web3caff.comweb3caff.com.
-
SCMP / 南华早报. USDT已成为柬埔寨地下经济活动的主要手段. 跟踪报道followin.iofollowin.io.
-
TradingView新闻. 中国涉案加密资产处置新规初现端倪?cn.tradingview.comcn.tradingview.com.
-
新浪科技. 孙宇晨格林纳达外交官身份被撤回finance.sina.cnfinance.sina.cn.
-
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-04 01:24:36
@ 5d4b6c8d:8a1c1ee3
2025-06-04 01:24:36Howdy stackers, this is the place to share your ~HealthAndFitness triumphs and challenges.
I was glad to hit my step goal today, since it's gloomy and rainy here. Once again, I ate too many cookies. Gotta stop being a cookie monster.
How'd you all do, today?
https://stacker.news/items/996659
-
 @ 6be5cc06:5259daf0
2025-06-04 00:58:46
@ 6be5cc06:5259daf0
2025-06-04 00:58:46Introdução
O princípio do sola scriptura, pedra angular da teologia protestante desde a Reforma do século XVI, estabelece que apenas a Escritura constitui a autoridade final e suprema em questões de fé e prática cristã. Este princípio, formulado inicialmente por Martinho Lutero e sistematizado pelos reformadores subsequentes, pretende oferecer um fundamento epistemológico sólido para a teologia, livre das supostas corrupções da tradição eclesiástica.
Contudo, uma análise rigorosa revela que o sola scriptura incorre em contradições lógicas fundamentais que comprometem sua viabilidade como sistema epistemológico coerente. Este artigo examina essas contradições através de três perspectivas complementares: filosófica, exegética e histórica.
A Contradição Performativa Fundamental
O Problema da Autoreferência
O sola scriptura enfrenta um dilema epistemológico insuperável: afirma que apenas a Escritura possui autoridade final em matéria de fé, mas essa própria regra não é explicitamente ensinada na Escritura. Trata-se de uma contradição performativa clássica, onde o enunciado viola suas próprias condições de possibilidade.
Esta situação configura uma falácia de petitio principii (círculo vicioso), pois exige que se aceite uma doutrina que não pode ser sustentada pelas premissas do próprio sistema. Para estabelecer o sola scriptura, seria necessário recorrer a uma autoridade externa à Escritura – precisamente aquilo que o princípio pretende rejeitar.
Fundacionalismo Mal Estruturado
Do ponto de vista epistemológico, o sola scriptura apresenta-se como um fundacionalismo defeituoso. Pretende funcionar como axioma supremo e auto-evidente, mas falha ao não fornecer a base textual que sua própria metodologia exige. Um verdadeiro fundacionalismo escriturístico deveria ser capaz de demonstrar sua validade através de uma prova explícita nas próprias Escrituras.
O Testemunho Contrário das Escrituras
Limitações do Registro Escrito
A própria Escritura reconhece as limitações do registro textual. João 21:25 declara explicitamente: "Jesus fez também muitas outras coisas. Se cada uma delas fosse escrita, penso que nem mesmo no mundo inteiro haveria espaço suficiente para os livros que seriam escritos."
Este versículo é particularmente problemático para o sola scriptura, pois reconhece que nem todos os ensinamentos de Cristo foram preservados por escrito. Como pode a Escritura ser suficiente se ela própria admite sua incompletude?
A Valorização da Tradição Oral
Paulo, em 2 Tessalonicenses 2:15, oferece uma instrução que contradiz frontalmente o sola scriptura: "Assim, pois, irmãos, ficai firmes e conservai os ensinamentos que de nós aprendestes, seja por palavras, seja por carta nossa."
O apóstolo valoriza inequivocamente tanto a tradição oral ("por palavras") quanto a escrita ("por carta"), estabelecendo um modelo de autoridade dual que o protestantismo posterior rejeitaria.
A Necessidade de Autoridade Interpretativa
A narrativa do eunuco etíope em Atos 8:30-31 demonstra a inadequação da Escritura isolada como autoridade final. Quando Filipe pergunta se o eunuco entende o que lê, a resposta é reveladora: "Como poderei entender, se alguém não me ensinar?"
Este episódio ilustra que a mera posse do texto bíblico não garante compreensão adequada. É necessária uma autoridade interpretativa externa – no caso, representada por Filipe, que age com autoridade apostólica.
A Complexidade Hermenêutica
Pedro, em sua segunda epístola (3:16-17), reconhece a dificuldade interpretativa inerente às Escrituras: "Suas cartas contêm algumas coisas difíceis de entender, as quais os ignorantes e instáveis torcem, como também o fazem com as demais Escrituras, para a própria destruição deles."
Esta passagem não apenas reconhece a complexidade hermenêutica dos textos sagrados, mas também alerta sobre os perigos da interpretação inadequada. Implicitamente, sugere a necessidade de uma autoridade interpretativa confiável para evitar distorções doutrinárias.
O Paradoxo Histórico da Canonização
A Dependência da Tradição Eclesiástica
Um dos argumentos mais devastadores contra o sola scriptura emerge da própria história da formação do cânon bíblico. Os concílios de Hipona (393 d.C.) e Cartago (397 d.C.) foram responsáveis pela definição oficial do cânon das Escrituras tal como conhecemos hoje.
Este fato histórico cria um paradoxo insuperável: aceitar a Bíblia como autoridade única requer aceitar a autoridade da tradição eclesiástica que a definiu. O próprio cânon bíblico é produto da tradição apostólica e da deliberação conciliar, não de autodefinição escriturística.
A Circularidade da Autopistia
Tentativas protestantes de resolver este dilema através do conceito de "autopistia" – a suposta capacidade das Escrituras de se auto-autenticar – apenas aprofundam o problema circular. Como determinar que as Escrituras possuem esta propriedade sem recorrer a critérios externos? A própria doutrina da autopistia não é explicitamente ensinada na Escritura.
Implicações Teológicas e Epistemológicas
A Fragmentação Interpretativa
A história do protestantismo oferece evidência empírica das consequências práticas do sola scriptura. A multiplicação de denominações e interpretações divergentes sugere que o princípio, longe de fornecer clareza doutrinária, pode na verdade contribuir para a fragmentação teológica.
Se a Escritura fosse verdadeiramente suficiente e auto-interpretativa, seria razoável esperar maior convergência hermenêutica entre aqueles que aderem ao sola scriptura. A realidade histórica sugere o contrário.
A Alternativa Católica e Ortodoxa
As tradições católica e ortodoxa, embora enfrentando suas próprias tensões epistemológicas, mantêm pelo menos coerência interna ao reconhecer explicitamente múltiplas fontes complementares de autoridade: Escritura, Tradição e Magistério (no caso católico) ou Escritura e Tradição (no caso ortodoxo).
Estas posições evitam a contradição performativa do sola scriptura ao não reivindicar que sua própria metodologia epistemológica seja derivada exclusivamente da Escritura.
Conclusão
A análise crítica do sola scriptura revela contradições estruturais que comprometem fundamentalmente sua viabilidade como princípio epistemológico. O princípio incorre em contradição performativa ao estabelecer uma regra que não pode ser derivada de suas próprias premissas, configura um fundacionalismo mal estruturado ao carecer de base textual explícita, e enfrenta o testemunho contrário da própria Escritura, que reconhece suas limitações e a necessidade de autoridades interpretativas externas.
O paradoxo histórico da canonização – onde o próprio cânon bíblico depende da autoridade tradicional que o sola scriptura pretende rejeitar – representa talvez o golpe mais decisivo contra o princípio protestante.
Isso não implica necessariamente a falsidade do protestantismo como sistema teológico, mas sugere que seus fundamentos epistemológicos requerem reformulação substancial. Uma teologia protestante intelectualmente honesta precisaria reconhecer as limitações do sola scriptura e desenvolver uma epistemologia mais nuançada que leve em conta a complexidade das fontes de autoridade religiosa.
A busca pela verdade teológica, independentemente de compromissos confessionais, exige o reconhecimento rigoroso das limitações e contradições inerentes aos nossos sistemas epistemológicos. No caso do sola scriptura, essa honestidade intelectual revela um princípio que, por mais central que seja para a identidade protestante, não pode sustentar o peso epistemológico que tradicionalmente lhe foi atribuído.
-
 @ f85b9c2c:d190bcff
2025-06-04 01:06:04
@ f85b9c2c:d190bcff
2025-06-04 01:06:04
Focusing on something for an hour a Day for the next 90 days will make you 90% better than others. I’ve been mulling over a simple truth lately, and I’m excited to share it with you. What if I told you that just one hour a day could change your game? Not ten, not five, but one little hour—sixty minutes to claim.
Stick with me here, because I’m about to break it down in a way that’ll make you cheer, with sentences that rhyme and a message that’s clear.
The Magic of One Hour Let’s start with the power that’s ours to devour. One hour a day, no more, no less, can lift you from the mundane mess. It’s not about grinding till you drop, or pushing so hard you flop. It’s a focused burst, a daily deed, planting a tiny, mighty seed. While others scroll or doze away, you’re stacking skills day by day. In 90 days, you’ll see it’s true— you’ll rise above the common crew.
Why 90 Days Works Ninety days, a quarter year, is time enough to shift your gear. It’s short enough to keep the fire, long enough to climb higher. Science says habits form in less, but mastery needs a steady press. An hour each day, consistent and neat, builds a rhythm you can’t beat. While others drift, you’ll stay on track, your progress piling, no looking back.
Be Better Than Most Here’s the kicker, the reason to boast: most folks don’t focus, they just coast. An hour of effort, pure and fine, puts you ahead of ninety-nine. Not because you’re some rare breed, but because you chose to plant that seed. The world’s distracted, screens aglow, but you’ll be steady, in the know. By day ninety, you’ll stand tall, 90% better than them all.
How to Make It Stick Pick your thing, don’t overthink—writing, coding, or a gym link. Set a time, make it rhyme with your daily chime. Shut the noise, close the door, focus deep, and explore. No multitasking, that’s a trap, just one task to bridge the gap. Track your days, feel the groove, watch your skills start to improve.
My Challenge to You So here’s my dare, from me to you: one hour a day, see it through. Ninety days, that’s all I ask, a simple, life-changing task. I’m doing it too, I’m in the race, chasing growth at my own pace. Let’s rise together, you and I, with just an hour, we’ll touch the sky. Start today, don’t delay— one hour a day is all you need, okay?
-
 @ e2c72a5a:bfacb2ee
2025-06-04 11:19:49
@ e2c72a5a:bfacb2ee
2025-06-04 11:19:49While hackers shift from code to human psychology, $2.1B in crypto was stolen in 2025. Ethereum's price surged 46% in 30 days, strengthening against Bitcoin and poised for a significant breakout. Meanwhile, California unanimously passed a bill allowing state agencies to accept crypto payments, signaling mainstream adoption. Corporate treasuries now control over 3% of Bitcoin's total supply, with 60+ companies doubling their holdings in just two months. The crypto landscape is transforming from technical vulnerabilities to social engineering – are you protecting your assets or just your code? What security measures have you implemented that address the human element of crypto safety?
-
 @ f85b9c2c:d190bcff
2025-06-04 01:00:21
@ f85b9c2c:d190bcff
2025-06-04 01:00:21
Is Physical Punishment Truly an Effective Way to Discipline Children? Whether flogging or corporal punishment, is a proper way to correct a child often causes disagreement and debate. Over the centuries and around the world, educators, psychologists, parents and lawmakers have argued about it. A person’s behavior is corrected through flogging which is intended to be physically harsh. It is a big concern whether the process helps or leaves people with more damage over time.
Historical Perspective Floggings have been practiced for centuries to discipline people. Years back, many people used disciplinary spanking to encourage children to be disciplined and respectful. It used to be popularly believed that not using discipline made children spoiled. This saying suggested that flogging or some other physical punishment, was both necessary and proper to correct those who did wrong. Presently, things are not the same as they were before. In the last few decades, there has been a major change in what is generally accepted. Child development and psychology research indicate that flogging and different types of punishment might even cause harm.
Effects on Mind and Feelings Experts always see that flogging has negative impact on children’s mental health. Even though it may force someone to cooperate right away, it usually results in fear, resentment and aggression. Instead of showing right from wrong, it makes the child think that being disciplined is humiliating and causes pain. This situation might lower the child’s self-esteem, interfere with their emotional development and hurt the relationship between the child and the parent. Also, flogging does little to deal with the real reason why someone acts this way. It only worries about how to punish instead of trying to understand why the behavior occurred. A correct approach involves explaining the problem with what they did and supporting them to improve their decisions next time.
Having Questions About What Is Legal and Ethical Many countries now forbid flogging and other corporal punishments in both schools and homes. Children’s freedom from physical harm is becoming recognized more often in the law. UNCRC claims that children should be protected from all types of physical and mental abuse.
Ethical concerns are raised by the practice of using flogging to discipline people. It goes against the main principles of respect and dignity. Their growth as human beings calls for proper guidance, so kids can become mature and caring adults. When they are beaten, children often learn that violence is a way to find solutions.
What Can Be Used Instead of Flogging There are a lot of peaceful and successful steps you can take to guide how a child behaves. Settings ground rules, using praise for good behaviors, always keeping communication clear and giving the same consequences help. By giving praise for good behavior, you help the child want to act that way again. Giving a time-out or taking away things a person enjoys is a gentle way to deal with misbehavior.
 In addition, these approaches help fix behavior problems and allow the child and caregiver to form trust and communicate openly. Through play, children learn to control themselves, feel empathy and solve problems which they need for their ongoing growth.
In addition, these approaches help fix behavior problems and allow the child and caregiver to form trust and communicate openly. Through play, children learn to control themselves, feel empathy and solve problems which they need for their ongoing growth.Conclusion In short, flogging does not make sense or work as a way to correct a child. Despite making the child obey at the moment, it often seriously harms a child’s emotional, psychological and moral growth in the future. Today’s parenting and educating focus on methods that fix misbehavior and boost a child’s confidence and sense of safety. Real correction teaches the child, helps them make right choices and encourages them to be responsible and caring. Flogging is not successful in reaching these goals. Rather, it causes a pattern of violence and fear that can cause serious damage in the long run. So, flogging should be understood not as a punishment, but as something harmful that society should forget about.
-
 @ da8b7de1:c0164aee
2025-06-03 19:31:32
@ da8b7de1:c0164aee
2025-06-03 19:31:32Lengyelország előrelépése az első atomerőmű építésében
Lengyelország állami nukleáris vállalata, a Polskie Elektrownie Jadrowe (PEJ) és egy amerikai konzorcium – élén a Westinghouse és a Bechtel cégekkel – mérnöki fejlesztési megállapodást kötött. Ez a szerződés kulcsfontosságú lépés az ország első atomerőművének megvalósítása felé, lehetővé téve a részletes mérnöki és helyszínspecifikus munkák megkezdését. A lengyel kormány ezt mérföldkőnek tekinti az energiaszuverenitás és a dekarbonizáció felé vezető úton.
Amerikai politika: lendület az új nukleáris technológiáknak
Az Egyesült Államok kormánya elnöki rendeletet adott ki, amely reformokat vezet be a nukleáris reaktorok tesztelésében az Energiaügyi Minisztériumnál. A cél az új generációs reaktorok – köztük mikroreaktorok és kis moduláris reaktorok (SMR-ek) – fejlesztésének és engedélyezésének felgyorsítása, valamint a környezetvédelmi vizsgálatok egyszerűsítése. A rendelet legalább három új reaktor kritikus üzembe helyezését célozza meg 2026 júliusáig, támogatva ezzel az ipari alkalmazások széles körét, például adatközpontokat vagy hidrogéntermelést. Az intézkedés célja, hogy az USA visszaszerezze vezető szerepét a nukleáris innovációban, és csökkentse a korábbi években felhalmozódott engedélyezési akadályokat.
Kis moduláris reaktorok (SMR) fejlesztése világszerte
Az SMR-szektorban világszerte jelentős előrelépések történtek: - Az amerikai Tennessee Valley Authority (TVA) benyújtotta az első építési kérelmet egy GE Hitachi BWRX-300 SMR-re a Clinch River telephelyen. - Kanadában az Ontario Power Generation engedélyt kapott az első, négy tervezett SMR megépítésének megkezdésére a Darlington telephelyen. - Belgium és Brazília innovatív SMR-technológiákat vizsgál, köztük ólom-hűtésű reaktorokat és nemzetközi együttműködéseket. - Olyan technológiai óriások, mint a Google, az USA-ban korai fázisú fejlett nukleáris projektekbe fektetnek, ami a magánszektor növekvő érdeklődését mutatja.
Globális ipari és pénzügyi támogatás a nukleáris bővítéshez
Széles körű koalíció – köztük olyan nagyvállalatok, mint az Amazon, Google, Meta, Dow – és pénzügyi intézmények kötelezték el magukat amellett, hogy 2050-re megháromszorozzák a globális nukleáris kapacitást. Ez összhangban van az ENSZ klímacsúcsain tett vállalásokkal, ahol már 31 ország támogatja a nukleáris energia megháromszorozását a nettó zéró kibocsátási célok eléréséhez. Az amerikai kongresszus olyan törvényjavaslatokat készít elő, amelyek lehetővé tennék, hogy a multilaterális fejlesztési bankok – például a Világbank – is finanszírozhassanak nukleáris projekteket, megszüntetve ezzel a korábbi tiltásokat.
Közelgő nemzetközi nukleáris biztonsági gyakorlat
A Nemzetközi Atomenergia-ügynökség (IAEA) készül a ConvEx-3 vészhelyzeti gyakorlatára, amelyet 2025. június 24–25-én Romániában tartanak. A gyakorlat egy súlyos nukleáris vészhelyzetet szimulál a cernavodai atomerőműben, tesztelve a tagállamok és nemzetközi szervezetek felkészültségét és reagálóképességét. A ConvEx-3 a legmagasabb szintű IAEA vészhelyzeti gyakorlat, kulcsszerepet játszik a globális nukleáris biztonság és védelem erősítésében.
Politikai bizonytalanság Dél-Korea nukleáris terveiben
Dél-Korea 2025. június 3-i elnökválasztása hatással lehet az ország nukleáris reneszánszára. A vezető jelölt, Lee Jae-myung kijelentette, hogy „egyelőre” fenntartaná a nukleáris energiát, de hosszabb távon a megújulók felé mozdulna el. Ez bizonytalanságot okoz a koreai nukleáris ipar hazai és exportterveiben, ami kihatással lehet a globális ellátási láncokra és külföldi reaktorprojektekre is.
Iparági trendek és további fejlemények
- Japán új energiastratégiája maximalizálni kívánja a nukleáris energia részarányát, 2040-re mintegy 20%-ot célozva, különös hangsúlyt fektetve a következő generációs reaktorokra és a biztonság növelésére.
- Belgium kormánya és a francia Engie közműcég megállapodott a kulcsfontosságú reaktorok üzemidejének tízéves meghosszabbításáról, ami az európai nukleáris pálfordulás újabb jele.
- Az IAEA és a World Nuclear Association egyaránt növekvő nemzetközi érdeklődésről számol be az SMR-ek és fejlett reaktortechnológiák iránt, új projektek és partnerségek indulnak Ázsiában, Európában és Amerikában.
Források:
world-nuclear-news.org
nucnet.org
iaea.org
world-nuclear.org
govinfo.gov
whitehouse.gov -
 @ 5ea46480:450da5bd
2025-06-04 11:18:24
@ 5ea46480:450da5bd
2025-06-04 11:18:24Ofcourse do we want our big open world cake, and eat it with a side of stability and order. I love the spammers, because all they do is press our noses on the grim reality we are facing: Everything is going to turn to absolute shit. The fact that we are all interconnected is meaningless because the communication lines contain too much noise.
Look, some spambot posting silly things that might waste your attention for a tiny bit before you figure out its not worth your time, or clutter your feed, is not the end of the world. But the point is that that post could be anything, and with a bit of AI effort more convincing. We all sense this, in fact we even see it, and there is no indication to think it wont get worse.
Important to note is, that the big platforms are struggling with this crap as well. Their set up is by their nature a ‘have a cake and eat it’ proposition: Yes we are the worlds public square that everyone visits in this particular domain, and we will keep you safe from spammers and fraudsters. But we ran out of captchas, and they are forced to heighten their walls, reinforce their gates and increase the amount of guards that are on patrol; slowly but surely, you as a user will be forced to subjugate yourself to more and more scrutiny, restrictions and punishment if you want to be active there. At some point the only reason they would be considered ‘the worlds public square’, is because they are the only vestiges of order left without any existing alternatives.
If we seriously want to introduce that alternative, we would have to approach the issue in a fundamentally different manner. That issue, is one of reputation, i.e. consistent behavior over time. Now to be clear, there is no full proof system for reputation, it does not exist for two reasons: One, anyone at any time can decide to break their consistent behavior simply because they feel like it. And two, because you you never have perfect information and can therefor not interpret the consistency of their behavior perfectly; think of a spy for example, where them consistently lying to you and eventually betraying you actually makes them a consistent spy.
Reputation is always a game of who knows who, but ‘social’ reputation is hard to scale: the longer the ties become, the less they can be relied upon. To scale reputation went the route of formalization via institutions: these are your certificates, badges, uniforms whatever, as a testament you went through certain predefined hoops in a controlled environment. As a result, whatever reputation the institution might have rubs off on you. It also stacks in the fact that one certificate can only be obtained when other certificates were acquired prior. So these certificates are pieces of reputational capital, defined in records. This system allowed us to create globe spanning organizations.
That system does work, but it is rigid, and the moment it becomes corrupt you are very, very screwed, because on what basis are you going to put it back together again? In any event, that is what we have anyway and as noted it has other issues, so what other option is there? Scaling ‘social’ reputation. The whole idea behind Nostr’s ‘Web of Trust’, is that bottom-up connections and relations, that are (partly) based on existing relations in meat-space can form a globally meaningful reputational pillar on which we can start identifying each other again.
If seven handshakes connects you with everyone, four will get you pretty far. Three is even less risk, whilst five might open up interesting doors for you. The point is, its gradual, and according to your risk appetite you can play around with it. Secondly, the better well connected you are, how more of a reputation you gained, the less risk you need to run to begin with. Obviously this requires some bootstrapping, but you live in meatspace; if there really is no-one out there willing to give you a leg up you might want to do some soul searching.
But the result of this strategy, will be that everyone will pull back behind their own little moats first. At first, we will all lose connections to defend ourselves against the massive onslaught of ‘the Fake’: The big estrangement. But that is ok, with a bit of effort, I am sure that eventually, after enough reputational capital is build over time, we will find each other again in this global village.
-
 @ cae03c48:2a7d6671
2025-06-03 19:02:12
@ cae03c48:2a7d6671
2025-06-03 19:02:12Bitcoin Magazine

Sberbank, Russia’s Biggest Bank, Launches Structured Bond Tied to BitcoinSberbank, the largest bank in Russia, has launched a new structured bond that ties investor returns to the performance of Bitcoin and the U.S. dollar-to-ruble exchange rate. This new financial product represents one of the first moves by a major Russian institution to offer Bitcoin-linked investments under recently updated national regulations.
BREAKING:
 Russia's largest bank Sberbank launches structured bonds linked to Bitcoin. pic.twitter.com/LtD26jPS0x
Russia's largest bank Sberbank launches structured bonds linked to Bitcoin. pic.twitter.com/LtD26jPS0x— Bitcoin Magazine (@BitcoinMagazine) June 2, 2025
The structured bond is initially available over the counter to a limited group of qualified investors. According to the announcement, it allows investors to earn based on two factors: the price performance of BTC in U.S. dollars and any strengthening of the dollar compared to the Russian ruble.
Unlike typical Bitcoin investments, this product does not require the use of a Bitcoin wallet or foreign platforms. “All transactions [are] processed in rubles within Russia’s legal and infrastructure systems,” Sberbank stated, highlighting compliance with domestic financial protocols.
In addition to the bond, Sberbank has announced plans to launch similar structured investment products with Bitcoin exposure on the Moscow Exchange. The bank also revealed it will introduce a Bitcoin futures product via its SberInvestments platform on June 4, aligning with the product’s debut on the Moscow Exchange.
These developments follow a recent policy change by the Bank of Russia, which now permits financial institutions to offer Bitcoin-linked instruments to qualified investors. This shift opens the door for Bitcoin within the country’s traditional financial markets.
While Russia has previously taken a cautious approach to digital assets, Sberbank’s launch of a Bitcoin-linked bond and upcoming futures product marks a new phase of adoption—one that blends Bitcoin exposure with existing financial infrastructure.
The bank’s structured bond may signal a growing interest in regulated access to Bitcoin, especially within large financial institutions.
This post Sberbank, Russia’s Biggest Bank, Launches Structured Bond Tied to Bitcoin first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ bf47c19e:c3d2573b
2025-06-04 10:48:23
@ bf47c19e:c3d2573b
2025-06-04 10:48:23Čini se da se svet kreće u pogrešnom smeru - rastući troškovi, opadajući životni standard i rastuća nestabilnost. Šta je koren problema? Naš novac je pokvaren.
Naučite više na satsvsfiat.com.
U ovom videu Džo Brajan se služi jedinstvenom i zanimljivom pričom kako bi pokazao da uzrok većine naših problema jednostavno leži u kvalitetu našeg novca. Ovaj video, koji je dostupan svima i svuda, sklapa kockice između današnjih izazova i njihovih osnovnih uzroka uz predstavljanje rešenja: Bitkoin.
Molimo vas da naučite o Bitkoinu - popravite novac i popravićete svet 🧡
-
 @ e0e92e54:d630dfaa
2025-06-03 19:01:32
@ e0e92e54:d630dfaa
2025-06-03 19:01:32As some of you know, I lead a quarterly Bible Study through Faith Driven Investor
One of the members from the cohort that just ended forwarded me an email from the US Christian Chamber of Commerce
The summary is: Christians should intentionally be doing more business with Christians.
[Full email at the bottom of this Article]
I recanted to my FDI member about a book I read a few years ago, Thou Shall Prosper, by Rabbi Daniel Lapin.
In it he gave the statistics that a single dollar recirculates in the Jewish community 12 times, Muslims 8 times, and Christians only 3 or 4 times.
(I'm probably slightly off on recalling the stats)
But the point being that as a people group, Jews are 4x more wealthy than Christians because Christians value doing business with one another 4 times less than Jews...or said another way, the Jewish people value doing business with one another 4x more than Christians.
Reading the email I was sent, I was further reminded as business owners, leaders, and investors;
If we are truly going to steward that which God has entrusted to us, we should want to re-circulate those resources as many times as possible within the Christian community in order to have the greatest probability of return on image bearers.
What are your thoughts?
I Bought a House Through the Christian Chamber - What happened next surprised me
My husband and I just bought a house—but it wasn’t just a transaction. It was a transformation.
With our daughter’s high school graduation behind us, we felt ready to step into a long-held dream: moving to a beach town we’ve thought, talked, and prayed about for years. As part of turning our dream into a reality, we made a very intentional decision:
We would buy our home entirely through the Christian Chamber community.
We wanted to walk the talk—to model what Kingdom commerce really looks like. So we sought Christian-led businesses for every part of the process. What started as a symbolic gesture quickly became a profound experience with two life-changing revelations:
1) The Power of Prayer in Business
Yes, we prayed as a couple—but imagine your Realtor, lender, inspector, and insurance agent all praying with you, too.
We’re not talking about just being “nice people” or listening to worship in the office. We’re talking about Spirit-filled, Jesus-following believers who brought prayer into every decision.
· Our Realtor is also a church planter—her discernment helped us find the perfect house on day one.
· Our lender joined us in prayer—and worked miracles to make the deal smooth and abundantly possible.
· Our inspector's biggest red flag? A bird’s nest in a porch light. (Yes, really.)
· Our insurance agent handled everything—and in Florida, that’s no small feat.
I have bought and sold seven homes in my life, but this was the best experience by far. The layout, the location, the timing, the favor—it was all wrapped in prayer and covered in grace. It wasn’t just business. It was supernatural.
2) Kingdom ROI — A Multiplied Impact
By doing business with Christians, we didn’t just find great service. We created a multiplied Kingdom return.
We know where our vendors give. We know the churches they support, the ministries they fund, and the people they serve.
When they earned from our purchase, those dollars didn’t disappear—they were reinvested into Kingdom causes we could never reach on our own.
This is Kingdom ROI.
It’s a real-life example of the parable of the talents—we didn’t bury our resources. We multiplied them. When you spend money with aligned believers, your impact compounds.
The opposite is also true:
When we spend with businesses that oppose our values, we’re funding platforms that erode the very things we’re trying to protect—our families, our freedoms, and our faith.
We MUST STOP funding the enemy.
The Bigger Picture
Let’s be clear: Studies show that Christians make up 31% of the world’s population, but we control 55% of the world’s wealth—more than $107 trillion in personal assets.
And yet…we’re leaking that wealth into systems that are actively working against us.
Why? Because we do not have the infrastructure to keep it aligned.
Until now.
That’s what we’re building through the U.S. Christian Chamber of Commerce: A national infrastructure that empowers Christians to redirect their dollars, align their values, and multiply their impact.
What If You Did the Same?
· Buy your next product or service from a Christian-led business.
· Hire your next contractor from your local Christian Chamber.
· Invest in a company with eternal impact.
· Launch a Christian Chamber in your region—we’ll help you.
· Join the U.S. Christian Chamber. This is your Chamber, for your nation.
· Meet us in Orlando for SWC 2026, the global gathering of Christian commerce.
Imagine the multiplying power if thousands of us made similar decisions—every day—across this nation.
We own the wealth. Now let’s build the infrastructure, create the ecosystem, and shift the world's wealth one transaction at a time.
This is our nation and we are One Nation Under God!
Jason Ansley is the founder of Above The Line Leader, where he provides tailored leadership support and operational expertise to help business owners, entrepreneurs, and leaders thrive— without sacrificing your faith, family, or future.
-
Want to strengthen your leadership and enhance operational excellence? Connect with Jason at https://abovethelineleader.com/#your-leadership-journey
-
📌 This article first appeared on NOSTR. You can also find more Business Leadership Articles and content at: 👉 https://abovethelineleader.com/business-leadership-articles
-
-
 @ e3ba5e1a:5e433365
2025-01-13 16:47:27
@ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity.
A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur.
The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior.
And there are plenty of incentives beyond our direct control! My son is also incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take.
Why incentives matter
A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could just do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example:
- If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning.
- If people would just use the recycling bin, we wouldn’t have such a landfill problem.
- If people would just stop being lazy, our team would deliver our project on time.
In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally.
- The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do.
- No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle.
- If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.

My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want.
If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is.
Running a company
Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions.
Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good.
What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off.
Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning.
When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.

Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money.
There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals.
Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature.
Moral hazard
Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings.
What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.

But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I don’t turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all.
This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as:
- We’re so habituated to turning off the water that we don’t even consider not turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off.
- Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created.
- We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?)
Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard.
A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard.
It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend?
And since we’re talking about the government already…
Government moral hazards
As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a huge number of examples of moral hazards. I decided to cherry-pick a few for this post.
The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people?
The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet.
If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups.
You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”

And here’s the absolute best part of this: I can’t even truly blame either California or Wall Street. (I mean, I do blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits.
There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions.
Non-monetary competition
At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home.
In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.)
Anyway, my professor’s wife had a friend. My professor described in great detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas.
This is a demonstration of non-monetary compensation. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules.
The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become wealthier and whiter, the exact opposite of their desired outcome. Why would that happen?
Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky.
She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls.
So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites.
You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences.
Bureaucracy
These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences.
Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings.
Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate.
Government incentivized behavior
This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples:
- Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to malinvestment and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience.
- Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise.
- During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation.
- The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen.
- Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example).
- Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as high living.)
Conclusion
The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives.
We can bemoan these realities all we want, but they are realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People should take advantage of the incentives around them. Because if they don’t, someone else will.
(If you want a literary example of that last comment, see the horse in Animal Farm.)
How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula:
- Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people.
- Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them.
- And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example.
And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining!
-
 @ 8bad92c3:ca714aa5
2025-06-03 18:02:33
@ 8bad92c3:ca714aa5
2025-06-03 18:02:33Marty's Bent

It's been a pretty historic week for the United States as it pertains to geopolitical relations in the Middle East. President Trump and many members of his administration, including AI and Crypto Czar David Sacks and Treasury Secretary Scott Bessent, traveled across the Middle East making deals with countries like Qatar, Saudi Arabia, the United Arab Emirates, Syria, and others. Many are speculating that Iran may be included in some behind the scenes deal as well. This trip to the Middle East makes sense considering the fact that China is also vying for favorable relationships with those countries. The Middle East is a power player in the world, and it seems pretty clear that Donald Trump is dead set on ensuring that they choose the United States over China as the world moves towards a more multi-polar reality.
Many are calling the events of this week the Riyadh Accords. There were many deals that were struck in relation to artificial intelligence, defense, energy and direct investments in the United States. A truly prolific power play and demonstration of deal-making ability of Donald Trump, if you ask me. Though I will admit some of the numbers that were thrown out by some of the countries were a bit egregious. We shall see how everything plays out in the coming years. It will be interesting to see how China reacts to this power move by the United States.
While all this was going on, there was something happening back in the United States that many people outside of fringe corners of FinTwit are not talking about, which is the fact that the 10-year and 30-year U.S. Treasury bond yields are back on the rise. Yesterday, they surpassed the levels of mid-April that caused a market panic and are hovering back around levels that have not been seen since right before Donald Trump's inauguration.
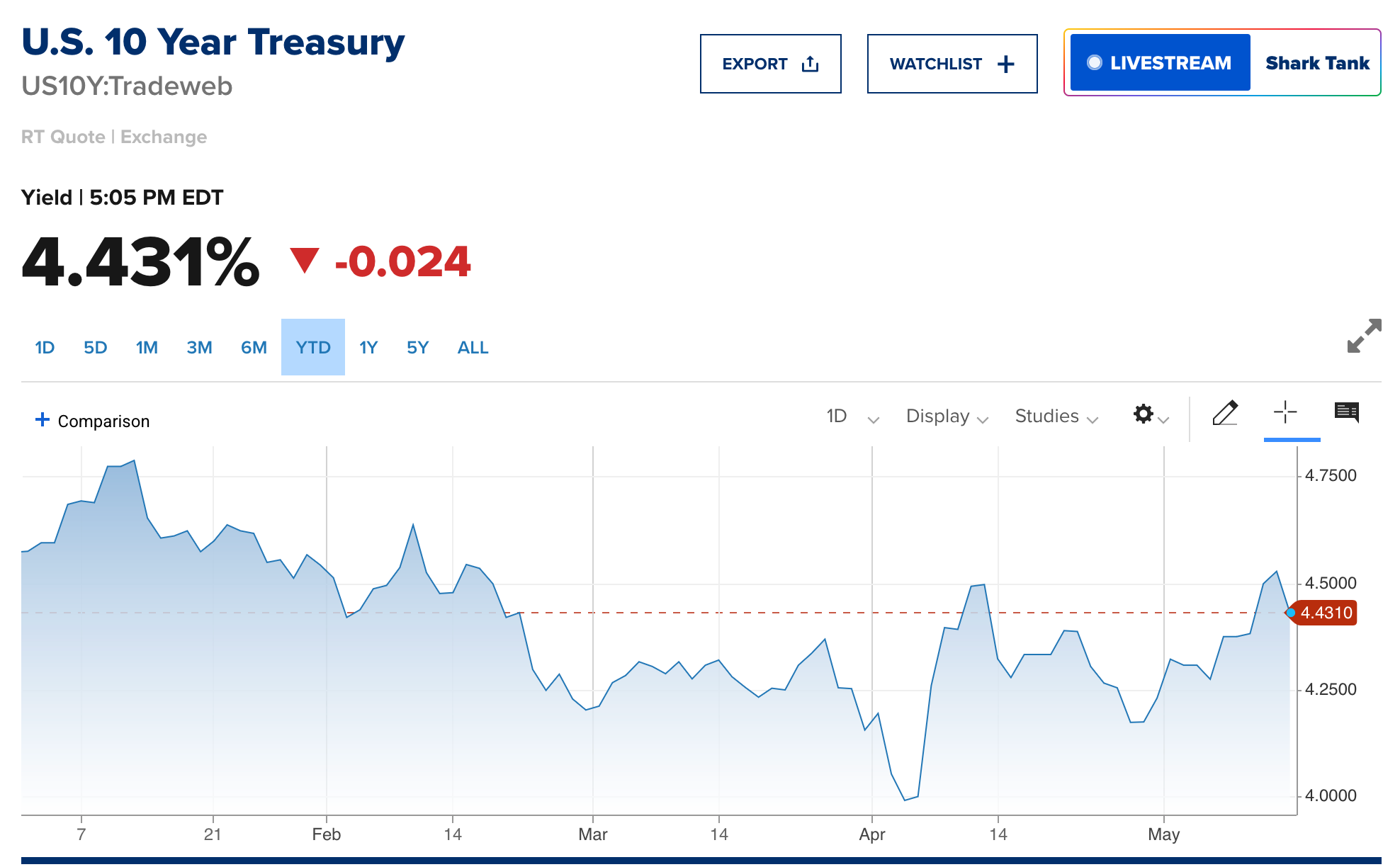
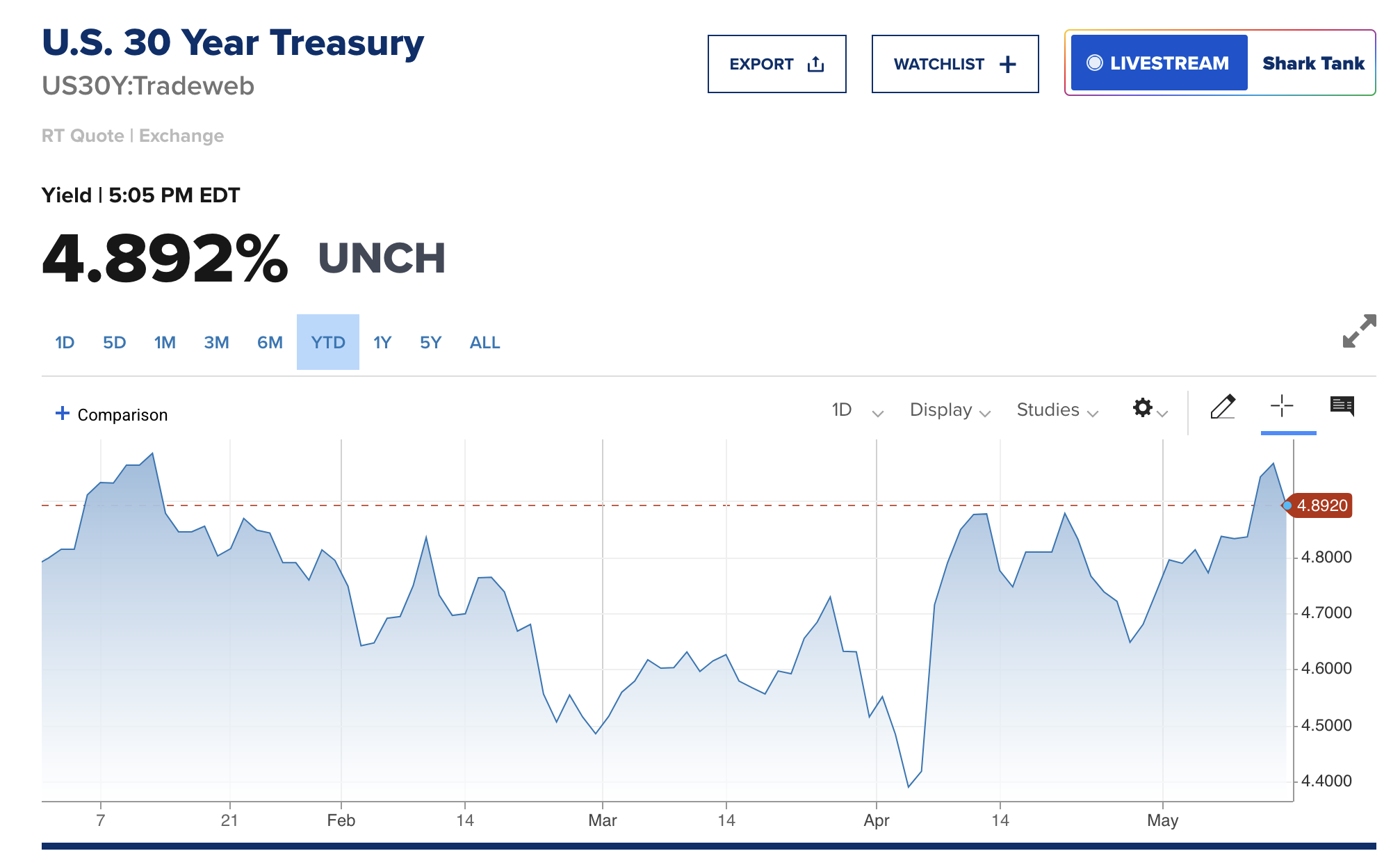
I imagine that there isn't as much of an uproar right now because I'm pretty confident the media freakouts we were experiencing in mid-April were driven by the fact that many large hedge funds found themselves off sides of large levered basis trades. I wouldn't be surprised if those funds have decreased their leverage in those trades and bond yields being back to mid-April levels is not affecting those funds as much as they were last month. But the point stands, the 10-year and 30-year yields are significantly elevated with the 30-year approaching 5%. Regardless of the deals that are currently being made in the Middle East, the Treasury has a big problem on its hands. It still has to roll over many trillions worth of debt over over the next few years and doing so at these rates is going to be massively detrimental to fiscal deficits over the next decade. The interest expense on the debt is set to explode in the coming years.
On that note, data from the first quarter of 2025 has been released by the government and despite all the posturing by the Trump administration around DOGE and how tariffs are going to be beneficial for the U.S. economy, deficits are continuing to explode while the interest expense on the debt has definitively surpassed our annual defense budget.
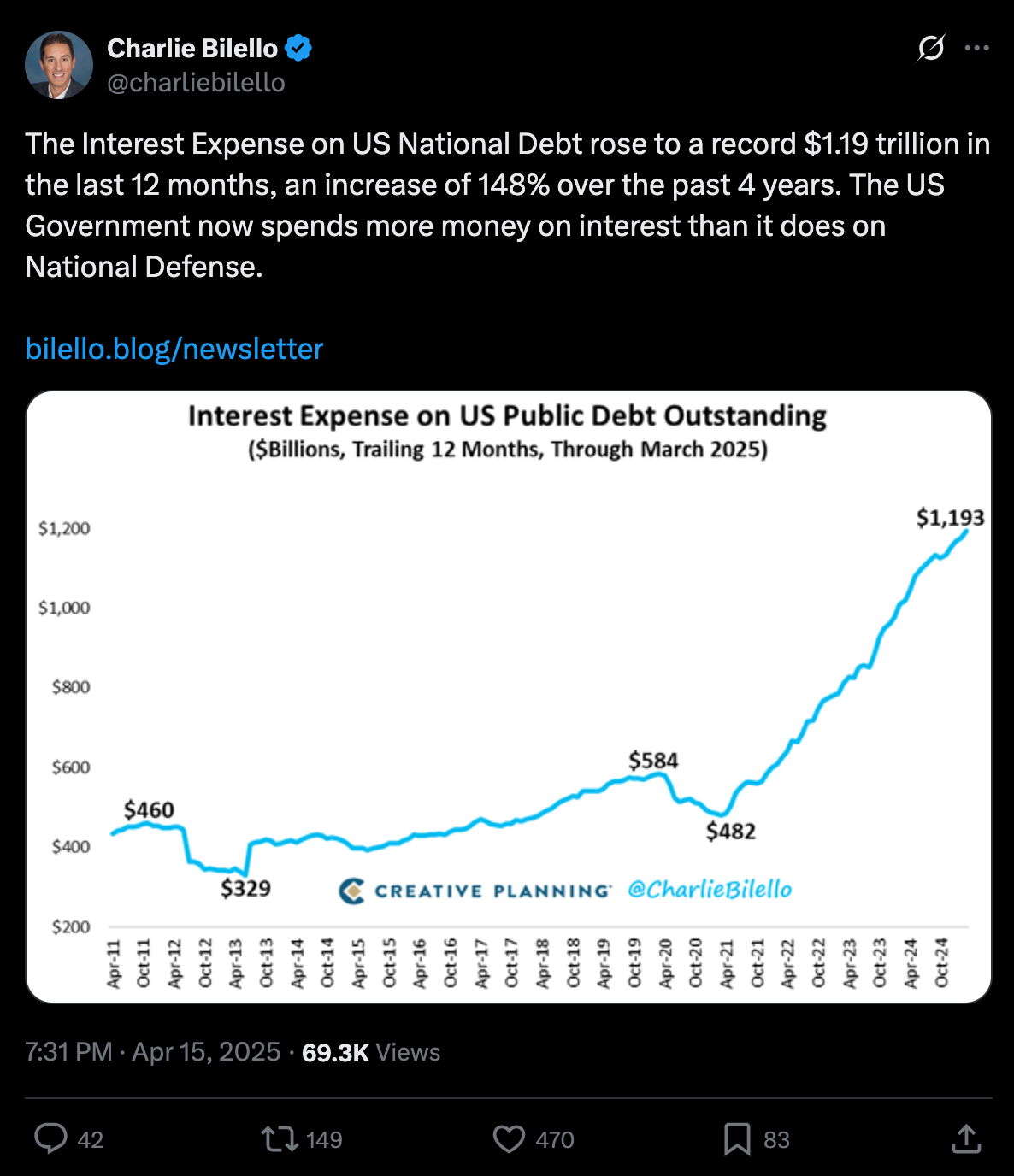
via Charlie Bilello
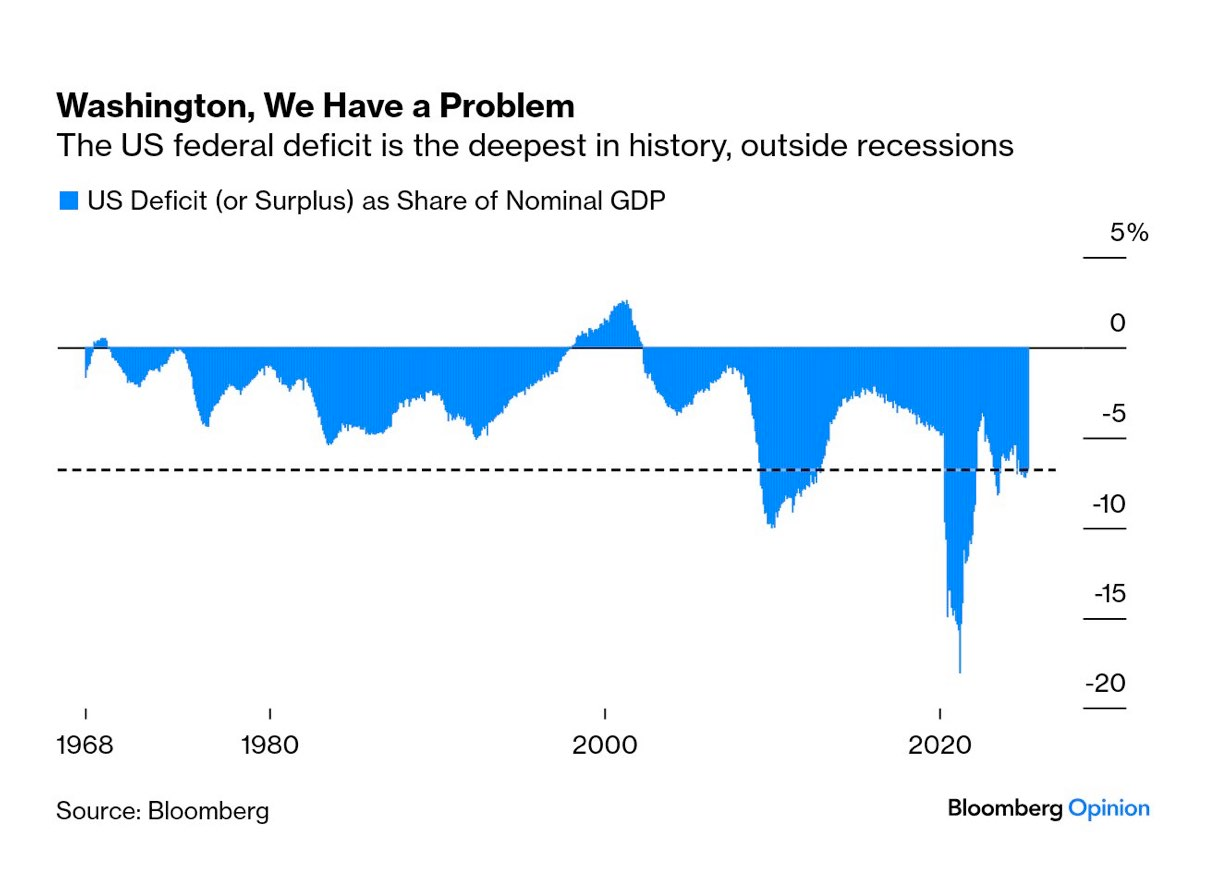
via Mohamed Al-Erian
To make matters worse, as things are deteriorating on the fiscal side of things, the U.S. consumer is getting crushed by credit. The 90-plus day delinquency rates for credit card and auto loans are screaming higher right now.
via TXMC
One has to wonder how long all this can continue without some sort of liquidity crunch. Even though equities markets have recovered from their post-Liberation Day month long bear market, I would not be surprised if what we're witnessing is a dead cat bounce that can only be continued if the money printers are turned back on. Something's got to give, both on the fiscal side and in the private markets where the Common Man is getting crushed because he's been forced to take on insane amounts of debt to stay afloat after years of elevated levels of inflation. Add on the fact that AI has reached a state of maturity that will enable companies to replace their current meat suit workers with an army of cheap, efficient and fast digital workers and it isn't hard to see that some sort of employment crisis could be on the horizon as well.
Now is not the time to get complacent. While I do believe that the deals that are currently being made in the Middle East are probably in the best interest of the United States as the world, again, moves toward a more multi-polar reality, we are facing problems that one cannot simply wish away. They will need to be confronted. And as we've seen throughout the 21st century, the problems are usually met head-on with a money printer.
I take no pleasure in saying this because it is a bit uncouth to be gleeful to benefit from the strife of others, but it is pretty clear to me that all signs are pointing to bitcoin benefiting massively from everything that is going on. The shift towards a more multi-polar world, the runaway debt situation here in the United States, the increasing deficits, the AI job replacements and the consumer credit crisis that is currently unfolding, All will need to be "solved" by turning on the money printers to levels they've never been pushed to before.
Weird times we're living in.
China's Manufacturing Dominance: Why It Matters for the U.S.
In my recent conversation with Lyn Alden, she highlighted how China has rapidly ascended the manufacturing value chain. As Lyn pointed out, China transformed from making "sneakers and plastic trinkets" to becoming the world's largest auto exporter in just four years. This dramatic shift represents more than economic success—it's a strategic power play. China now dominates solar panel production with greater market control than OPEC has over oil and maintains near-monopoly control of rare earth elements crucial for modern technology.
"China makes like 10 times more steel than the United States does... which is relevant in ship making. It's relevant in all sorts of stuff." - Lyn Alden
Perhaps most concerning, as Lyn emphasized, is China's financial leverage. They hold substantial U.S. assets that could be strategically sold to disrupt U.S. treasury market functioning. This combination of manufacturing dominance, resource control, and financial leverage gives China significant negotiating power in any trade disputes, making our attempts to reshoring manufacturing all the more challenging.
Check out the full podcast here for more on Triffin's dilemma, Bitcoin's role in monetary transition, and the energy requirements for rebuilding America's industrial base.
Headlines of the Day
Financial Times Under Fire Over MicroStrategy Bitcoin Coverage - via X
Trump in Qatar: Historic Boeing Deal Signed - via X
Get our new STACK SATS hat - via tftcmerch.io
Johnson Backs Stock Trading Ban; Passage Chances Slim - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code *“TFTC20”* during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Building things of value is satisfying.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !import
-
 @ 05a0f81e:fc032124
2025-06-03 19:28:10
@ 05a0f81e:fc032124
2025-06-03 19:28:10What Are Rumors?
Rumors are pieces of information, stories, or claims that are circulated among people without confirmed evidence or verification. They often spread by word of mouth, social media, or other informal means and can be either true, partially true, or completely false.
Rumors can arise in various settings, schools, workplaces, communities, or online and may involve personal matters, celebrities, politics, or current events.
There are Characteristics of Rumors
-
Lack of Verification: Rumors are not based on solid evidence or official sources.
-
Rapid Spread: They often spread quickly, especially in emotionally charged environments.
-
Distortion Over Time: As a rumor is retold, details may change, making it more misleading.
-
Emotional Impact: They usually provoke strong reactions like fear, curiosity, or anger.
There are various disadvantages of Rumors
- Spread of False Information
Rumors can mislead people, creating confusion or panic, especially during crises.
Example: False health advice during a pandemic can endanger lives.
- Damage to Reputation
Individuals or organizations can suffer harm to their image or credibility.
Example: A student falsely accused of cheating might face social isolation or disciplinary action.
- Breakdown of Trust
Trust within families, workplaces, or communities can erode when rumors circulate.
People become suspicious and communication suffers.
- Emotional Harm
Rumors can lead to stress, anxiety, and depression, especially for those targeted.
In extreme cases, victims may experience bullying or harassment.
- Conflict and Division
Rumors often fuel misunderstandings, arguments, or even violence.
They can cause divisions along social, political, or cultural lines.
- Wasted Time and Resources
Authorities or organizations may have to spend time disproving rumors instead of focusing on important tasks.
Example: Law enforcement addressing false threats.
- Legal Consequences
In some cases, spreading harmful or defamatory rumors can lead to lawsuits or criminal charges.
Conclusion
While some rumors may seem harmless or even entertaining, their consequences can be severe. They thrive in environments lacking transparency and can damage individuals, relationships, and communities. It is always best to verify information from credible sources before sharing it and to promote honest, respectful communication.
-
-
 @ 2e8970de:63345c7a
2025-06-03 17:33:37
@ 2e8970de:63345c7a
2025-06-03 17:33:37https://www.wsj.com/finance/investing/wall-street-bond-market-us-debt-990e12e9?mod=hp_lead_pos7
https://stacker.news/items/996265

