-
 @ c1e6505c:02b3157e
2025-05-28 17:36:03
@ c1e6505c:02b3157e
2025-05-28 17:36:03I recently acquired a new lens:
1959 Leica Summaron F2.8 35mm LTM.
1959 Leica Summaron 35mm f2.8 LTM mounted on my Fujifilm Xpro2 with LTM adapter made by Urth.
Technically, it was a trade. I helped a fellow Bitcoiner set up their Sparrow Wallet, Nostr stuff, and troubleshoot a few wallet issues, and in return, they gave me the lens.
It all started at a local Bitcoin meetup I went to about a week ago - my second time attending. I recognized a few faces from last time, but also saw some new ones. These meetups are refreshing - it’s rare to speak a common language about something like Bitcoin or Nostr. Most people still don’t get it. But they will.
Technology moves forward. Networks grow. Old cells die off.
During the meetup, someone noticed I had my Leica M262 with me and struck up a conversation. Said they had some old Leica lenses and gear at home, and wanted to show me.
Bitcoin and photography in one conversation? I’m down.
A day or so later, they sent me a photo of one of the lenses: a vintage Summaron LTM 35mm f/2.8 from 1959. I’d never seen or heard of one before. They asked if I could help them set up Sparrow and a Bitcoin node. In exchange, they’d give me the lens. Sounded like a good deal to me. Helping plebs with their setups feels like a duty anyway. I said, of course.
They invited me over - a pretty trusting move, which I appreciated. They had some great Bitcoin memorabilia: Fred Krueger’s The Big Bitcoin Book (even if the guy’s turned full shitcoiner), and some FTX sunglasses from Bitcoin 2022. Probably future collector’s items, lol.




We headed upstairs to work on setting up Sparrow Wallet on their Windows machine. I verified the software download first (which you should always do), then helped them create a new wallet using their Ledger Flex. They also had an older Ledger Nano X. The Flex setup was easy, but the Nano X gave us trouble. It turns out Ledger allows multiple wallets for the same asset, which can show up differently depending on how they’re configured. In Sparrow, only one wallet showed—none of the others.
I believe it had to do with the derivation path from the Ledger. If anyone knows a fix, let me know.
After a few hours of troubleshooting, I told them I couldn’t really recommend Ledger. The UX is a mess. They’d already heard similar things from other plebs too.
I suggested switching to the Blockstream Jade. It’s a solid Bitcoin-only device from a trustworthy team. That’s what you want in a hardware wallet.
But back to the lens…
Since it’s an LTM (Leica Thread Mount), I couldn’t mount it directly on my M262. Luckily, I remembered I had an Urth adapter that fits my Fujifilm X-Pro2. I don’t use the X-Pro2 much these days—it’s mostly been sidelined by the M262 - but this was the perfect excuse to bring it out again.
To test the lens, I shot everything wide open at f/2.8. Nothing crazy fast, but it’s the best way to see a lens’s character. And this one definitely has character. There’s a subtle softness and a kind of motion blur effect around the edges when wide open. At first, I wasn’t sure how I felt about it, but the more I shot, the more I liked it. It reminds me of Winogrand’s work in Winogrand Color - those messy, shifting edges that make the frame feel alive. It also helps soften the digital-ness of the camera sensor.
The focus throw is short and snappy - much tighter than my Summicron V3 35mm f/2. I really like how fast it is to use. The closest focusing distance is about 3.5 feet, so it’s not ideal for close-ups. And with the Urth adapter on the X-Pro2, the focal length ends up closer to 40mm.
The only thing that threw me off was the infinity lock. When the focus hits infinity, it physically locks - you have to press a small tab to unlock it. I’ve seen others complain about it, so I guess it’s just one of those old lens quirks. I’m getting used to it.
All the photos here were taken around where I live in South Carolina. Some during bike rides to the river for a swim, others while walking through the marshlands.
I try to make work wherever I am. You should be able to.
It’s about the light, the rhythm, the play - and having the motivation to actually go out and shoot.
Lens rating: 7.9/10
I mainly shoot with a Leica M262, and edit in Lightroom + Dehancer
Use “PictureRoom” for 10% off Dehancer Film
If you’ve made it this far, thank you for taking the time to view my work - consider becoming a paid subscriber.
Also, please contact me if you would like to purchase any of my prints.
Follow me on Nostr:
npub1c8n9qhqzm2x3kzjm84kmdcvm96ezmn257r5xxphv3gsnjq4nz4lqelne96
-
 @ 812cff5a:5c40aeeb
2025-05-28 12:56:32
@ 812cff5a:5c40aeeb
2025-05-28 12:56:32NIP-01 — الشكل الأساسي للأحداث في نُستر
رقم التعريف (NIP): 01
العنوان: الشكل الأساسي للأحداث
الحالة: نهائي
المؤلف: fiatjaf
التاريخ: 2020-12-10
الملخص
هذا المستند يعرّف الشكل القياسي لأي "حدث" يتم تداوله ضمن شبكة نُستر (Nostr).
الهدف من هذا التنسيق هو ضمان إمكانية معالجة وتفسير الأحداث من قبل جميع العملاء والخوادم بطريقة موحّدة.
هيكل الحدث
كل حدث عبارة عن كائن يحتوي على الحقول التالية:
{ "id": <معرّف فريد>, "pubkey": <مفتاح عام للمرسل>, "created_at": <تاريخ الإنشاء كرقم UNIX timestamp>, "kind": <نوع الحدث>, "tags": [<قائمة من الوسوم>], "content": <المحتوى>, "sig": <التوقيع الرقمي> }
شرح الحقول
- id: سلسلة نصية تمثل SHA-256 لمحتوى الحدث.
- pubkey: المفتاح العام للمستخدم (عادةً 32 بايت بصيغة hex).
- created_at: الطابع الزمني للإنشاء (Unix timestamp).
- kind: رقم يحدد نوع الحدث (مثلاً: منشور، متابعة، إعادة نشر).
- tags: قائمة من الوسوم المرتبطة بالحدث (مثلاً: إشارة إلى مستخدم أو حدث).
- content: المحتوى الأساسي للحدث (نص أو بيانات).
- sig: التوقيع الرقمي الذي يثبت أن المرسل هو صاحب المحتوى.
كيفية توليد معرف الحدث
idيتم توليد المعرّف عبر أخذ تمثيل JSON للحدث (بدون الحقول
idوsig) ثم حساب التجزئة باستخدام SHA-256.
توقيع الحدث
يُوقّع المستخدم الحدث باستخدام مفتاحه الخاص.
هذا التوقيع الرقمي يسمح لأي شخص بالتحقق من صحة الحدث باستخدام المفتاح العام.
أنواع الأحداث (kind)
0: ملف التعريف (الاسم، الصورة، النبذة).1: منشور عام نصي.2: إعادة نشر.3: قائمة المتابَعين.4: رسالة مشفّرة خاصة.- أنواع أخرى يمكن إضافتها لاحقًا.
الوسوم (Tags)
الوسوم عبارة عن قوائم (arrays) داخل الحدث لتوفير معلومات إضافية.
مثال:["e", "<معرّف الحدث>"] ["p", "<مفتاح عام لمستخدم>"]"e"تشير إلى حدث."p"تشير إلى مستخدم.
الخلاصة
NIP-01 هو الأساس الهيكلي لتبادل الأحداث عبر نُستر.
من خلال اتباع هذا الشكل، يمكن لجميع التطبيقات والخوادم العمل معاً بسلاسة، وضمان أمن وموثوقية كل حدث. -
 @ b7274d28:c99628cb
2025-05-28 01:11:43
@ b7274d28:c99628cb
2025-05-28 01:11:43In this second installment of The Android Elite Setup tutorial series, we will cover installing the nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 on your #Android device and browsing for apps you may be interested in trying out.
Since the #Zapstore is a direct competitor to the Google Play Store, you're not going to be able to find and install it from there like you may be used to with other apps. Instead, you will need to install it directly from the developer's GitHub page. This is not a complicated process, but it is outside the normal flow of searching on the Play Store, tapping install, and you're done.
Installation
From any web browser on your Android phone, navigate to the Zapstore GitHub Releases page and the most recent version will be listed at the top of the page. The .apk file for you to download and install will be listed in the "Assets."
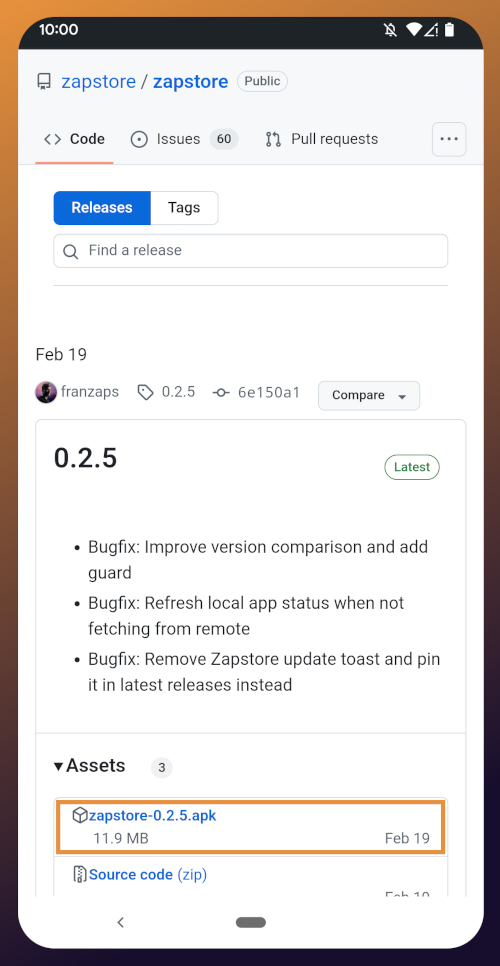
Tap the .apk to download it, and you should get a notification when the download has completed, with a prompt to open the file.
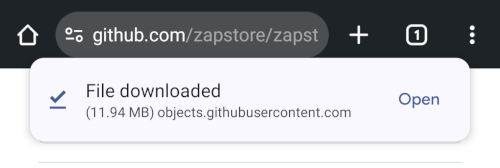
You will likely be presented with a prompt warning you that your phone currently isn't allowed to install applications from "unknown sources." Anywhere other than the Play Store is considered an "unknown source" by default. However, you can manually allow installation from unknown sources in the settings, which the prompt gives you the option to do.
In the settings page that opens, toggle it to allow installation from this source, and you should be prompted to install the application. If you aren't, simply go to your web browser's downloads and tap on the .apk file again, or go into your file browser app and you should find the .apk in your Downloads folder.
If the application doesn't open automatically after install, you will find it in your app drawer.

Home Page
Right at the top of the home page in the Zapstore is the search bar. You can use it to find a specific app you know is available in the Zapstore.
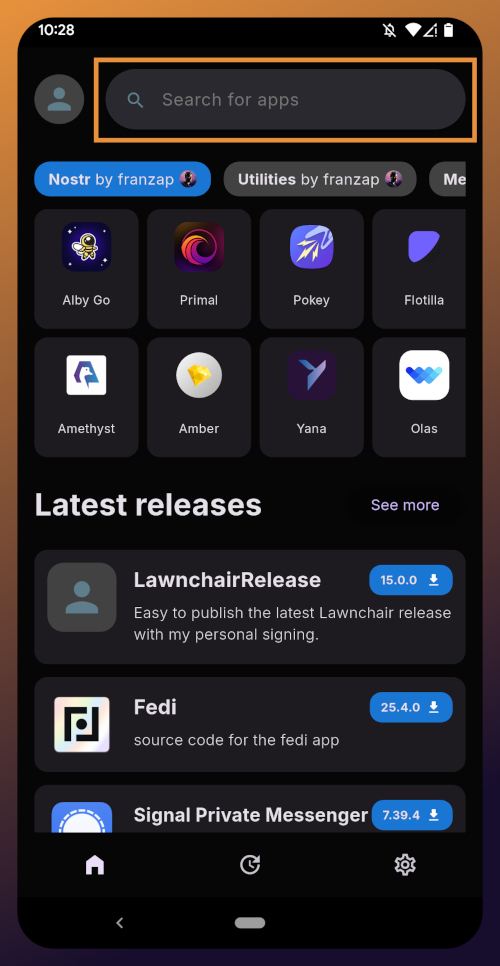
There are quite a lot of open source apps available, and more being added all the time. Most are added by the Zapstore developer, nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but some are added by the app developers themselves, especially Nostr apps. All of the applications we will be installing through the Zapstore have been added by their developers and are cryptographically signed, so you know that what you download is what the developer actually released.
The next section is for app discovery. There are curated app collections to peruse for ideas about what you may want to install. As you can see, all of the other apps we will be installing are listed in nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9's "Nostr" collection.
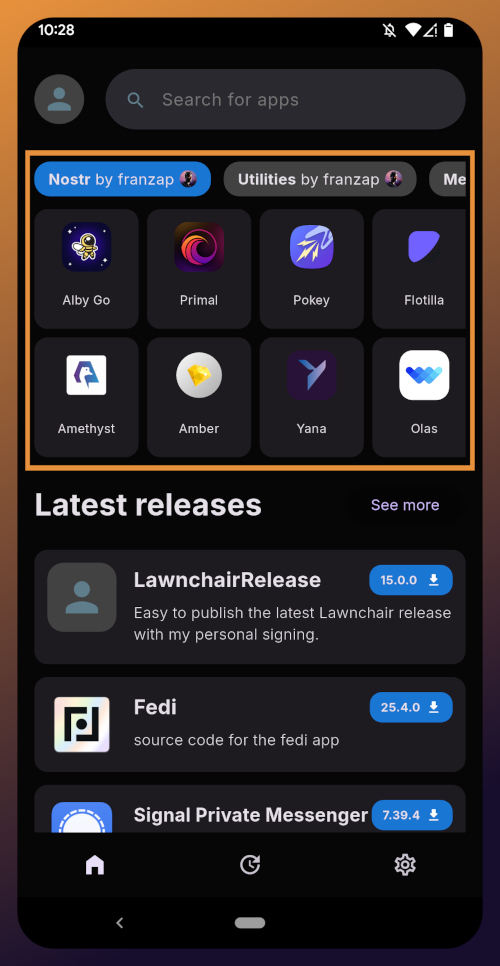
In future releases of the Zapstore, users will be able to create their own app collections.
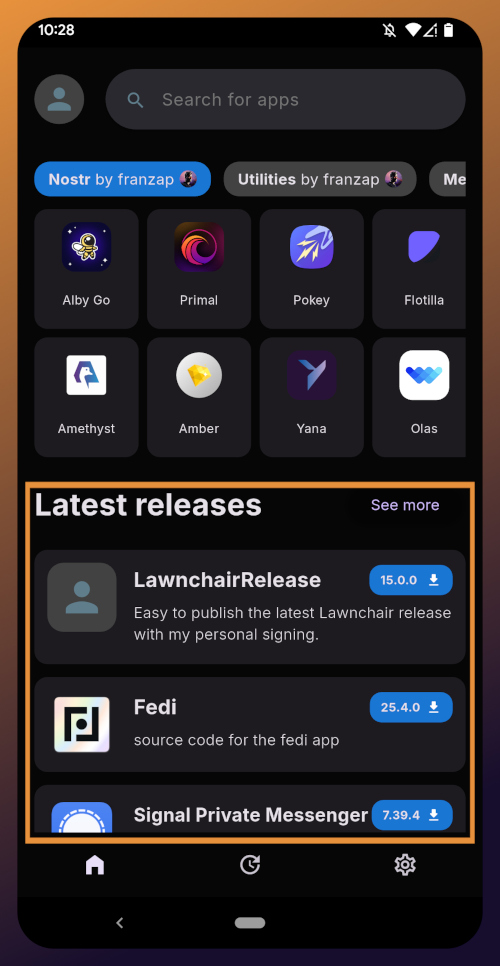
The last section of the home page is a chronological list of the latest releases. This includes both new apps added to the Zapstore and recently updated apps. The list of recent releases on its own can be a great resource for discovering apps you may not have heard of before.
Installed Apps
The next page of the app, accessed by the icon in the bottom-center of the screen that looks like a clock with an arrow circling it, shows all apps you have installed that are available in the Zapstore. It's also where you will find apps you have previously installed that are ready to be updated. This page is pretty sparse on my test profile, since I only have the Zapstore itself installed, so here is a look at it on my main profile:

The "Disabled Apps" at the top are usually applications that were installed via the Play Store or some other means, but are also available in the Zapstore. You may be surprised to see that some of the apps you already have installed on your device are also available on the Zapstore. However, to manage their updates though the Zapstore, you would need to uninstall the app and reinstall it from the Zapstore instead. I only recommend doing this for applications that are added to the Zapstore by their developers, or you may encounter a significant delay between a new update being released for the app and when that update is available on the Zapstore.
Tap on one of your apps in the list to see whether the app is added by the developer, or by the Zapstore. This takes you to the application's page, and you may see a warning at the top if the app was not installed through the Zapstore.
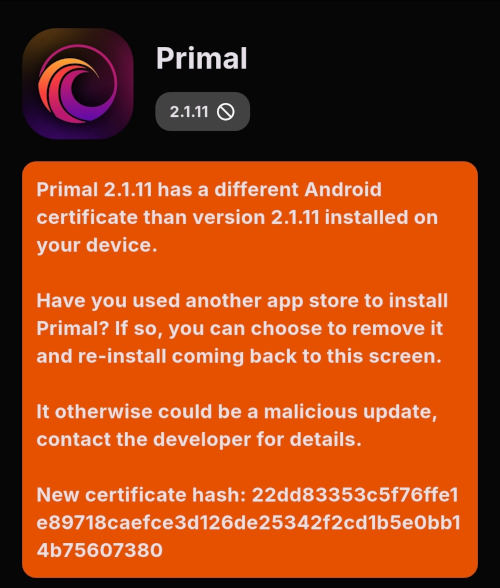
Scroll down the page a bit and you will see who signed the release that is available on the Zapstore.
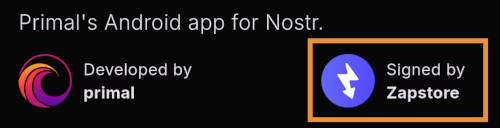
In the case of Primal, even though the developer is on Nostr, they are not signing their own releases to the Zapstore yet. This means there will likely be a delay between Primal releasing an update and that update being available on the Zapstore.
Settings
The last page of the app is the settings page, found by tapping the cog at the bottom right.
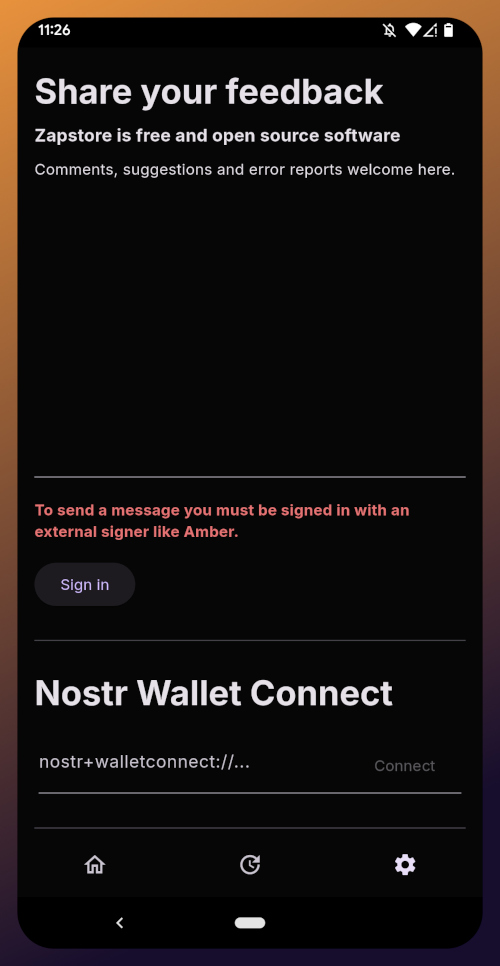
Here you can send the Zapstore developer feedback directly (if you are logged in), connect a Lightning wallet using Nostr Wallet Connect, delete your local cache, and view some system information.
We will be adding a connection to our nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch wallet in part 5 of this tutorial series.
For the time being, we are all set with the Zapstore and ready for the next stage of our journey.
Continue to Part 3: Amber Signer. Nostr link: nostr:naddr1qqxnzde5xuengdeexcmnvv3eqgstwf6d9r37nqalwgxmfd9p9gclt3l0yc3jp5zuyhkfqjy6extz3jcrqsqqqa28qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qg6waehxw309aex2mrp0yhxyunfva58gcn0d36zumn9wss80nug
-
 @ 812cff5a:5c40aeeb
2025-05-28 01:13:02
@ 812cff5a:5c40aeeb
2025-05-28 01:13:02ميزة حسابات Nostr: حرية مطلقة دون تقديم معلومات شخصية
في عصرٍ تسيطر فيه شركات التكنولوجيا الكبرى على بيانات المستخدمين، تأتي شبكة Nostr كحل جذري يعيد للمستخدم السيطرة على هويته الرقمية. واحدة من أبرز ميزات Nostr هي القدرة على إنشاء عدد غير محدود من الحسابات، دون الحاجة لتقديم أي معلومات شخصية، مثل رقم الهاتف أو البريد الإلكتروني.
مفاتيح بدل الحسابات
في Nostr، لا يوجد مفهوم "الحساب" التقليدي. بدلاً من ذلك، يتم إنشاء هوية المستخدم عبر زوج من المفاتيح: مفتاح خاص (Private Key) ومفتاح عام (Public Key). المفتاح العام يُستخدم لتعريفك ونشر مشاركاتك، بينما المفتاح الخاص يُستخدم لتوقيع تلك المشاركات وإثبات ملكيتك لها.
قابلية التنقل بين التطبيقات
الميزة الكبرى في هذا النموذج هي أن هذه المفاتيح يمكن استخدامها في أي تطبيق Nostr. سواء كنت تستخدم تطبيق Damus، أو Amethyst، أو أي عميل آخر، يمكنك استخدام نفس المفتاح العام للوصول إلى هويتك، منشوراتك، وقائمة متابعيك، بدون الحاجة لإعادة تسجيل أو إعادة بناء ملفك الشخصي في كل تطبيق.
لا تسجيل دخول، لا مركزية
بخلاف الشبكات الاجتماعية التقليدية التي تعتمد على تسجيل الدخول المركزي وكلمة مرور، فإن Nostr مبني على بروتوكول لا مركزي لا يحتاج إلى خوادم مركزية أو عمليات تسجيل دخول. هذا يعني أنك تتحكم بالكامل في بياناتك، ولا يمكن لأي جهة منعك أو حذف حسابك.
المرونة والخصوصية
- يمكنك إنشاء عدة مفاتيح لهويات مختلفة، كل منها تمثل شخصية مختلفة أو اهتمامًا معينًا.
- لا أحد يستطيع ربط هذه الحسابات ببعض أو تتبعها إلا إذا قمت أنت بذلك.
- يمكنك التخلي عن مفتاح واستبداله بآخر متى شئت، بدون طلب إذن من أي منصة.
خاتمة
ما يميز Nostr حقًا ليس فقط حريته التقنية، بل فلسفته المبنية على الخصوصية والتمكين. هو ليس مجرد بديل لتويتر أو فيسبوك، بل هو إطار جديد للتواصل الاجتماعي حيث الهوية تنبع من المستخدم، لا من المنصة.
-
 @ b7274d28:c99628cb
2025-05-28 00:59:49
@ b7274d28:c99628cb
2025-05-28 00:59:49Your identity is important to you, right? While impersonation can be seen in some senses as a form of flattery, we all would prefer to be the only person capable of representing ourselves online, unless we intentionally delegate that privilege to someone else and maintain the ability to revoke it.
Amber does all of that for you in the context of #Nostr. It minimizes the possibility of your private key being compromized by acting as the only app with access to it, while all other Nostr apps send requests to Amber when they need something signed. This even allows you to give someone temporary authority to post as you without giving them your private key, and you retain the authority to revoke their permissions at any time.
nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 has provided Android users with an incredibly powerful tool in Amber, and he continues to improve its functionality and ease of use. Indeed, there is not currently a comparative app available for iOS users. For the time being, this superpower is exclusive to Android.
Installation
Open up the Zapstore app that you installed in the previous stage of this tutorial series.
Very likely, Amber will be listed in the app collection section of the home page. If it is not, just search for "Amber" in the search bar.
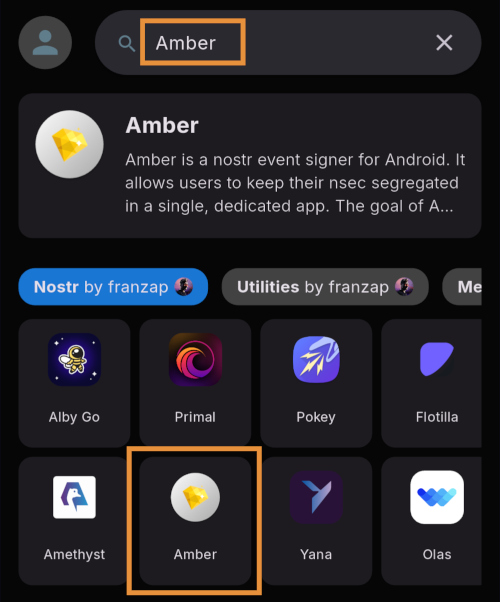
Opening the app's page in the Zapstore shows that the release is signed by the developer. You can also see who has added this app to one of their collections and who has supported this app with sats by zapping the release.
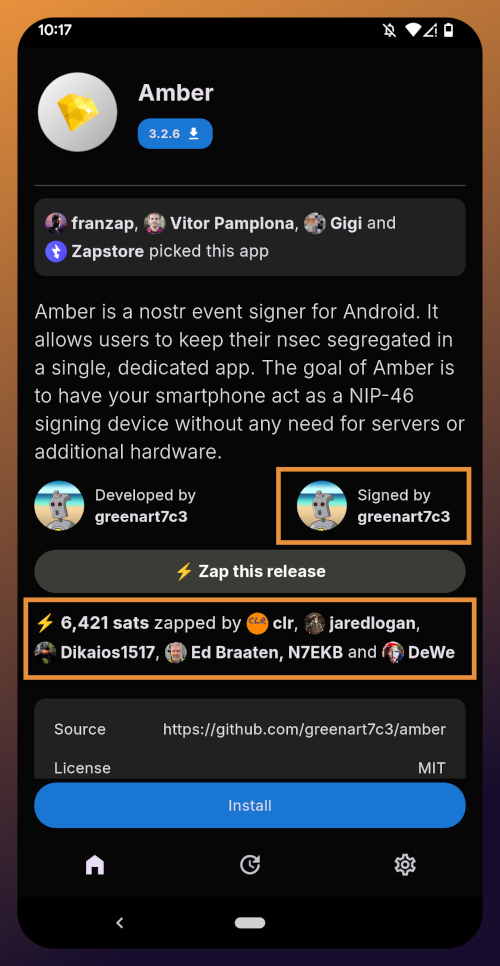
Tap "Install" and you will be prompted to confirm you are sure you want to install Amber.
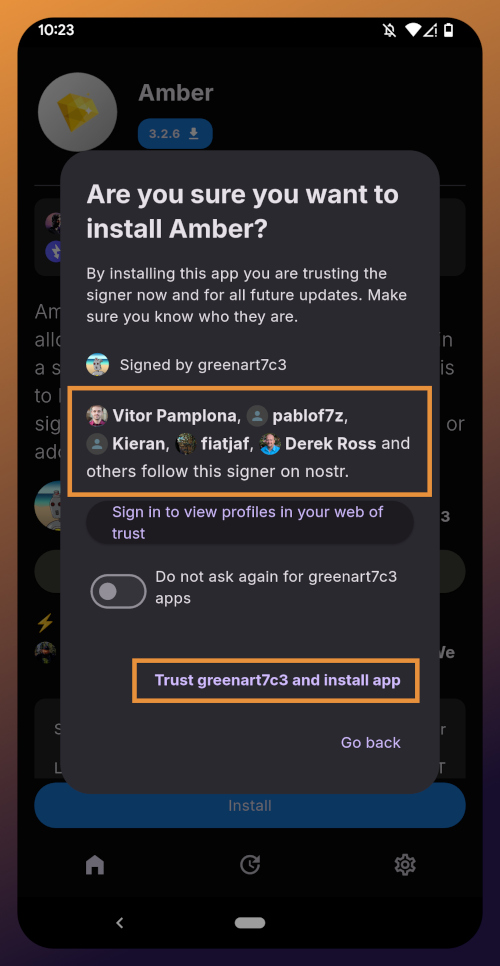
Helpfully, you are informed that several other users follow this developer on Nostr. If you have been on Nostr a while, you will likely recognize these gentlemen as other Nostr developers, one of them being the original creator of the protocol.
You can choose to never have Zapstore ask for confirmation again with apps developed by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, and since we have another of his apps to install later in this tutorial series, I recommend you toggle this on. Then tap on "Trust greenart7c3 and install app."
Just like when you installed the Zapstore from their GitHub, you will be prompted to allow the Zapstore to install apps, since Android considers it an "unknown source."
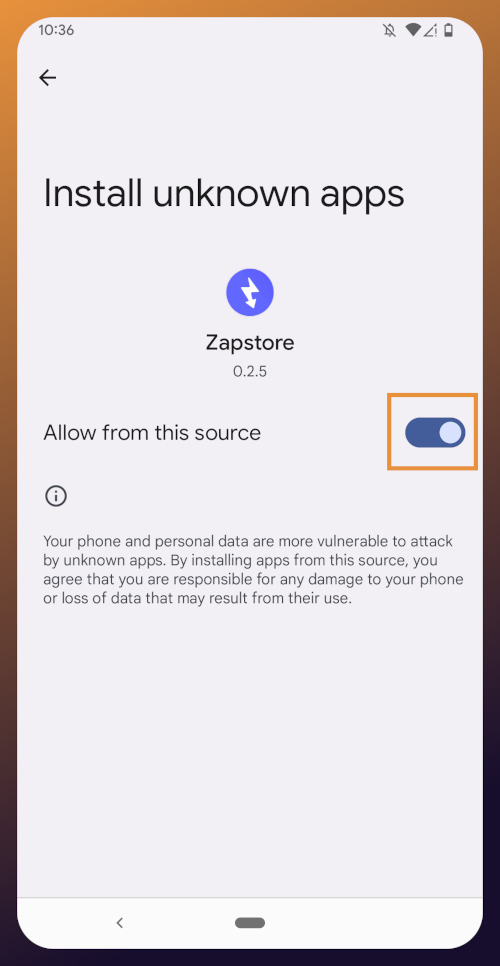
Once you toggle this on and use the back button to get back to the Zapstore, Amber will begin downloading and then present a prompt to install the app. Once installed, you will see a prompt that installation was a success and you can now open the app.
From here, how you proceed will depend on whether you need to set up a new Nostr identity or use Amber with an existing private key you already have set up. The next section will cover setting up a new Nostr identity with Amber. Skip to the section titled "Existing Nostrich" if you already have an nsec that you would like to use with Amber.
New Nostrich
Upon opening the application, you will be presented with the option to use an existing private key or create a new Nostr account. Nostr doesn't really have "accounts" in the traditional sense of the term. Accounts are a relic of permissioned systems. What you have on Nostr are keys, but Amber uses the "account" term because it is a more familiar concept, though it is technically inaccurate.
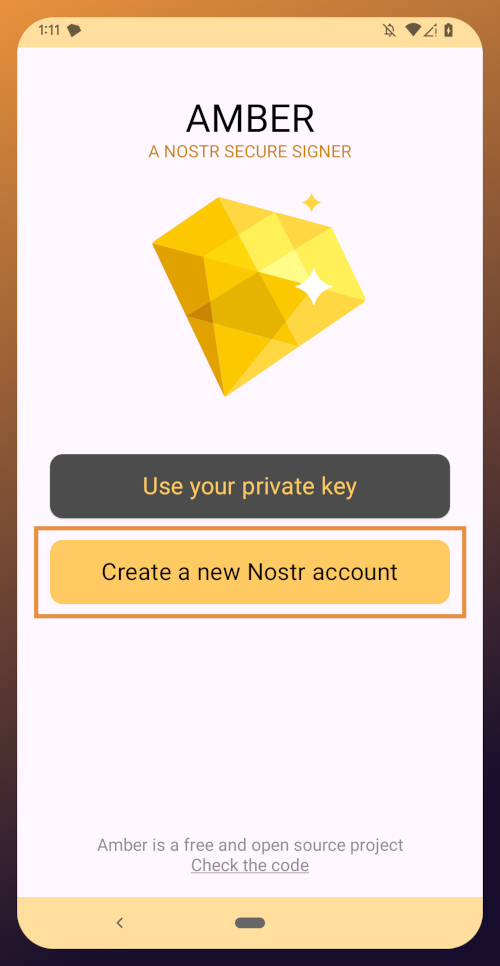
Choose "Create a new Nostr account" and you will be presented with a screen telling you that your Nostr account is ready. Yes, it was really that easy. No email, no real name, no date of birth, and no annoying capcha. Just "Create a new account" and you're done.
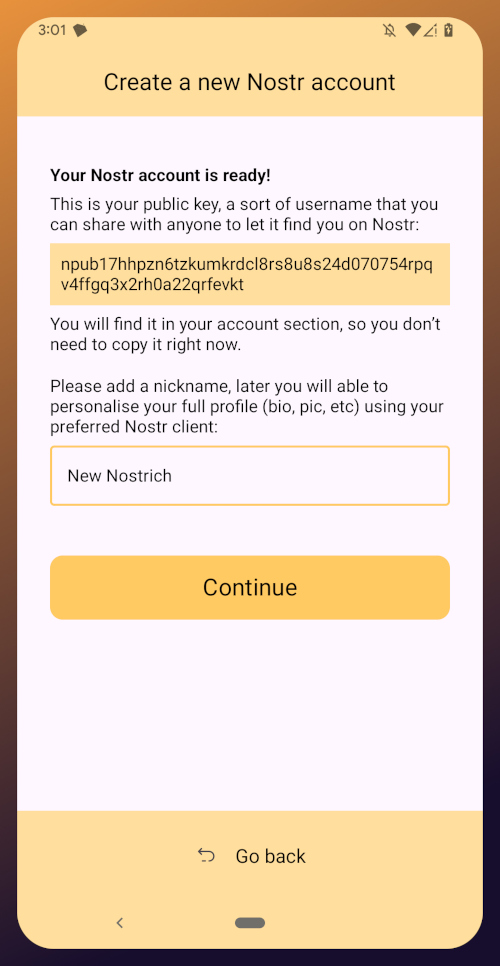
The app presents you with your public key. This is like an address that can be used to find your posts on Nostr. It is 100% unique to you, and no one else can post a note that lists this npub as the author, because they won't have the corresponding private key. You don't need to remember your npub, though. You'll be able to readily copy it from any Nostr app you use whenever you need it.
You will also be prompted to add a nickname. This is just for use within Amber, since you can set up multiple profiles within the app. You can use anything you want here, as it is just so you can tell which profile is which when switching between them in Amber.
Once you've set your nickname, tap on "Continue."
The next screen will ask you what Amber's default signing policy should be.
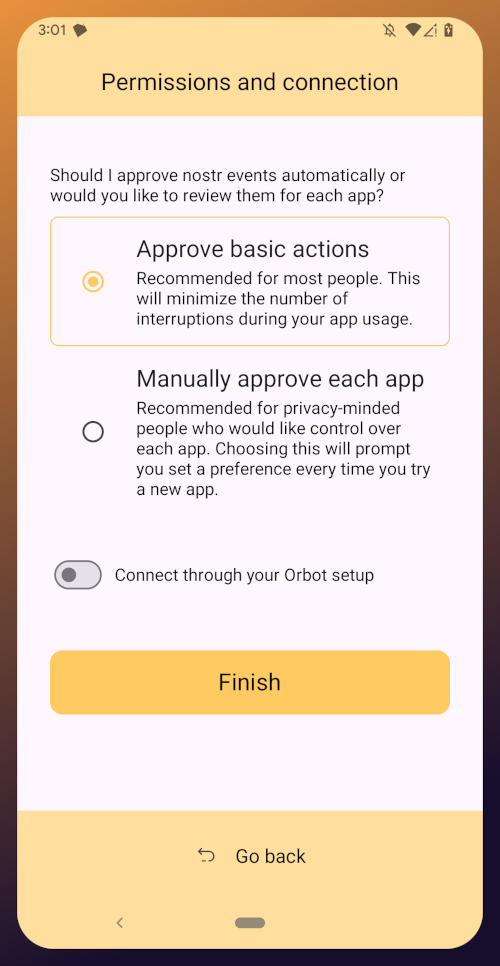
The default is to approve basic actions, referring to things that are common for Nostr clients to request a signature for, like following another user, liking a post, making a new post, or replying. If you are more concerned about what Amber might be signing for on your behalf, you can tell it to require manual approval for each app.
Once you've made your decision, tap "Finish." You will also be able to change this selection in the app settings at any time.
With this setup out of the way, you are now presented with the main "Applications" page of the app.
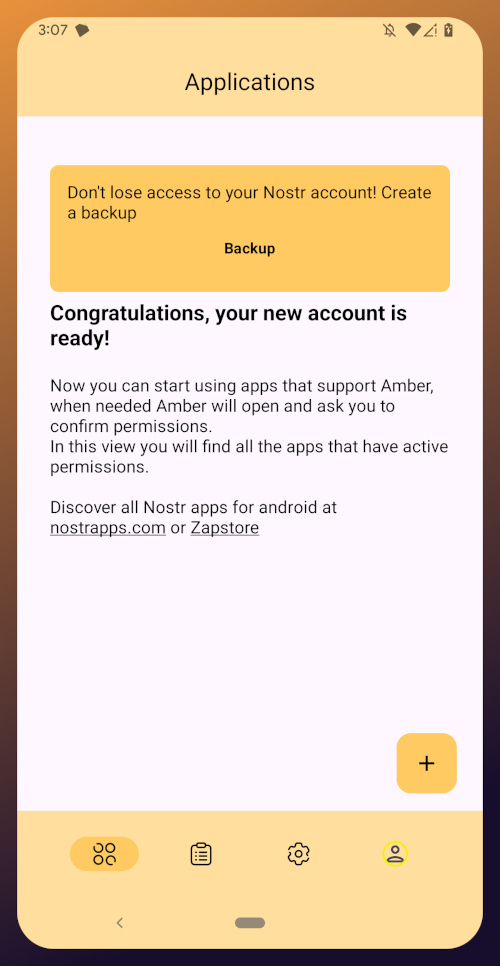
At the top, you have a notification encouraging you to create a backup. Let's get that taken care of now by tapping on the notification and skipping down to the heading titled "Backing Up Your Identity" in this tutorial.
Existing Nostrich
Upon opening the application, you will be presented with the option to use your private key or create a new Nostr account. Choose the former.
The next screen will require you to paste your private key.
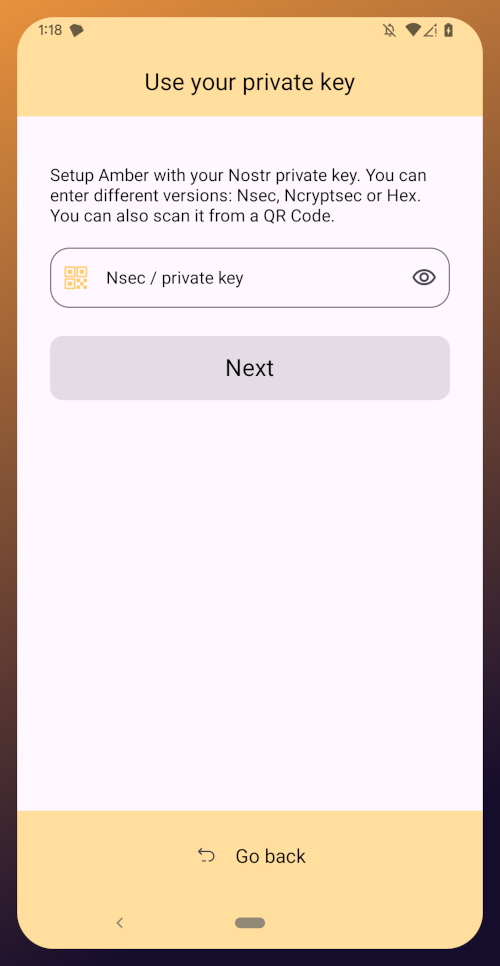
You will need to obtain this from whatever Nostr app you used to create your profile, or any other Nostr app that you pasted your nsec into in the past. Typically you can find it in the app settings and there will be a section mentioning your keys where you can copy your nsec. For instance, in Primal go to Settings > Keys > Copy private key, and on Amethyst open the side panel by tapping on your profile picture in the top-left, then Backup Keys > Copy my secret key.
After pasting your nsec into Amber, tap "Next."

Amber will give you a couple options for a default signing policy. The default is to approve basic actions, referring to things that are common for Nostr clients to request a signature for, like following another user, liking a post, making a new post, or replying. If you are more concerned about what Amber might be signing for on your behalf, you can tell it to require manual approval for each app.
Once you've made your decision, tap "Finish." You will also be able to change this selection in the app settings at any time.
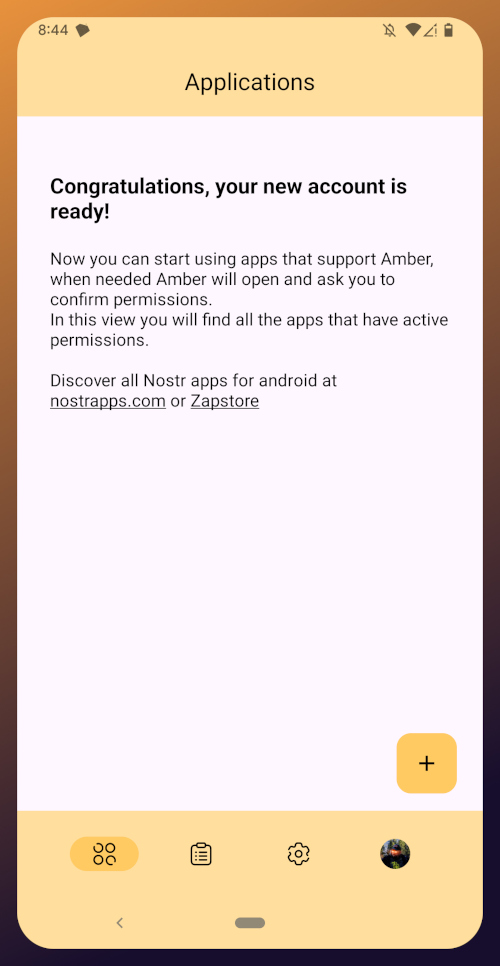
With this setup out of the way, you are now presented with the main "Applications" page of the app. You have nothing here yet, since you haven't used Amber to log into any Nostr apps, but this will be where all of the apps you have connected with Amber will be listed, in the order of the most recently used at the top.
Before we go and use Amber to log into an app, though, let's make sure we've created a backup of our private key. You pasted your nsec into Amber, so you could just save that somewhere safe, but Amber gives you a few other options as well. To find them, you'll need to tap the cog icon at the bottom of the screen to access the settings, then select "Backup Keys."
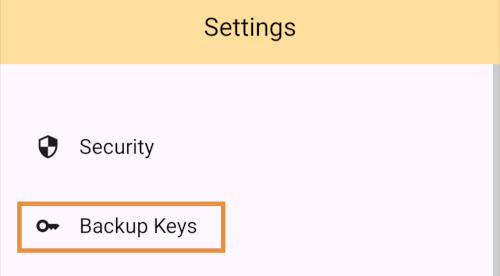
Backing Up Your Identity
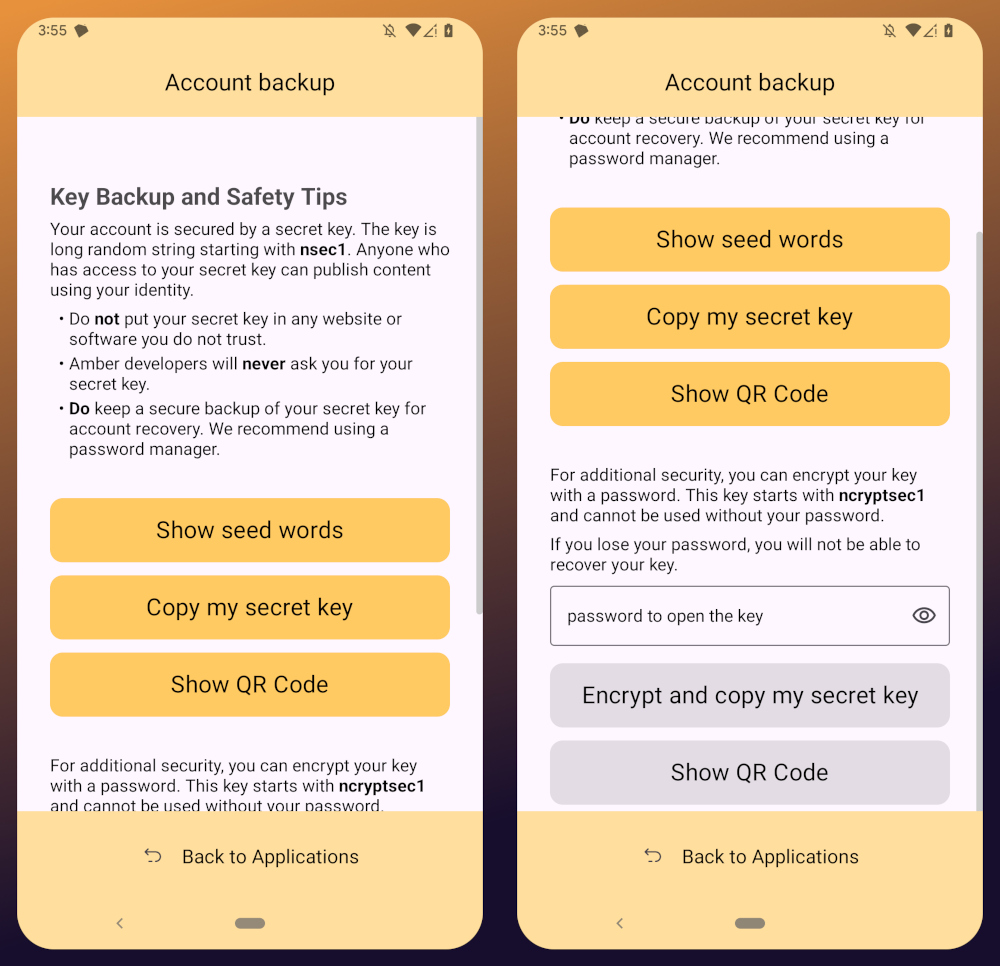
You'll notice that Amber has a few different options for backing up your private key that it can generate.
First, it can give you seed words, just like a Bitcoin seed. If you choose that option, you'll be presented with 12 words you can record somewhere safe. To recover your Nostr private key, you just have to type those words into a compatible application, such as Amber.
The next option is to just copy the secret/private key in its standard form as an "nsec." This is the least secure way to store it, but is also the most convenient, since it is simple to paste into another signer application. If you want to be able to log in on a desktop web app, the browser extension Nostr signers won't necessarily support entering your 12 word seed phrase, but they absolutely will support pasting in your nsec.
You can also display a QR code of your private key. This can be scanned by Amber signer on another device for easily transferring your private key to other devices you want to use it on. Say you have an Android tablet in addition to your phone, for instance. Just make sure you only use this function where you can be certain that no one will be able to get a photograph of that QR code. Once someone else has your nsec, there is no way to recover it. You have to start all over on Nostr. Not a big deal at this point in your journey if you just created a Nostr account, but if you have been using Nostr for a while and have built up a decent amount of reputation, it could be much more costly to start over again.
The next options are a bit more secure, because they require a password that will be used to encrypt your private key. This has some distinct advantages, and a couple disadvantages to be aware of. Using a password to encrypt your private key will give you what is called an ncryptsec, and if this is leaked somehow, whoever has it will not necessarily have access to post as you on Nostr, the way they would if your nsec had been leaked. At least, not so long as they don't also have your password. This means you can store your ncryptsec in multiple locations without much fear that it will be compromised, so long as the password you used to encrypt it was a strong and unique one, and it isn't stored in the same location. Some Nostr apps support an ncryptsec for login directly, meaning that you have the option to paste in your ncryptsec and then just log in with the password you used to encrypt it from there on out. However, now you will need to keep track of both your ncryptsec and your password, storing both of them safely and separately. Additionally, most Nostr clients and signer applications do not support using an ncryptsec, so you will need to convert it back to a standard nsec (or copy the nsec from Amber) to use those apps.
The QR option using an ncryptsec is actually quite useful, though, and I would go this route when trying to set up Amber on additional devices, since anyone possibly getting a picture of the QR code is still not going to be able to do anything with it, unless they also get the password you used to encrypt it.
All of the above options will require you to enter the PIN you set up for your device, or biometric authentication, just as an additional precaution before displaying your private key to you.
As for what "store it in a safe place" looks like, I highly recommend a self-hosted password manager, such as Vaultwarden+Bitwarden or KeePass. If you really want to get wild, you can store it on a hardware signing device, or on a steel seed plate.
Additional Settings
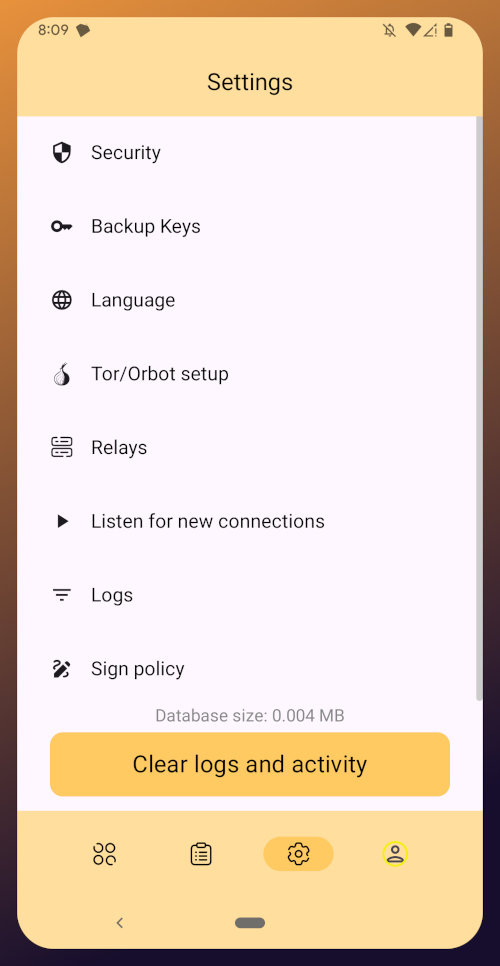
Amber has some additional settings you may want to take advantage of. First off, if you don't want just anyone who has access to your phone to be able to approve signing requests, you can go into the Security settings add a PIN or enable biometrics for signing requests. If you enable the PIN, it will be separate from the PIN you use to access your phone, so you can let someone else use your phone, like your child who is always begging to play a mobile game you have installed, without worrying that they might have access to your Nostr key to post on Amethyst.
Amber also has some relay settings. First are the "Active relays" which are used for signing requests sent to Amber remotely from Nostr web apps. This is what enables you to use Amber on your phone to log into Nostr applications on your desktop web browser, such as Jumble.social, Coracle.social, or Nostrudel.ninja, eliminating your need to use any other application to store your nsec whatsoever. You can leave this relay as the default, or you can add other relays you want to use for signing requests. Just be aware, not all relays will accept the notes that are used for Nostr signing requests, so make sure that the relay you want to use does so. In fact, Amber will make sure of this for you when you type in the relay address.
The next type of relays that you can configure in Amber are the "Default profile relays." These are used for reading your profile information. If you already had a Nostr identity that you imported to Amber, you probably noticed it loaded your profile picture and display name, setting the latter as your nickname in Amber. These relays are where Amber got that information from. The defaults are relay.nostr.band and purplepag.es. The reason for this is because they are aggregators that look for Nostr profiles that have been saved to other relays on the network and pull them in. Therefore, no matter what other relay you may save your profile to, Amber will likely be able to find it on one of those two relays as well. If you have a relay you know you will be saving your Nostr profiles to, you may want to add it to this list.
You can also set up Amber to be paired with Orbot for signing over Tor using relays that are only accessible via the Tor network. That is an advanced feature, though, and well beyond the scope of this tutorial.
Finally, you can update the default signing policy. Maybe after using Amber for a while, you've decided that the choice you made before was too strict or too lenient. You can change it to suit your needs.
Zapstore Login
Now that you are all set up with Amber, let's get you signed into your first Nostr app by going back to the Zapstore.
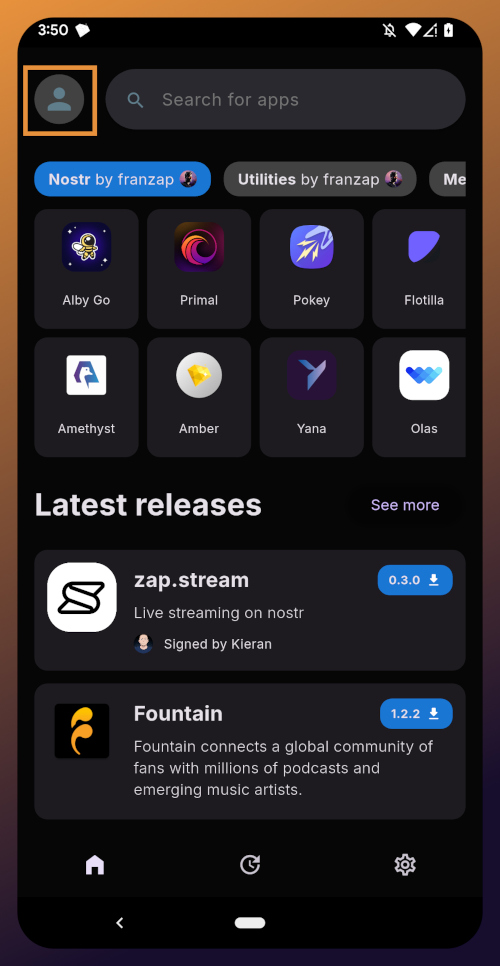
From the app's home screen, tap on the user icon in the upper left of the screen. This will open a side panel with not much on it except the option to "sign in." Go ahead and tap on it.
You will be presented with the option to either sign in with Amber, or to paste your npub. However, if you do the latter, you will only have read access, meaning you cannot zap any of the app releases. There are other features planned for the Zapstore that may also require you to be signed in with write access, so go ahead and choose to log in with Amber.
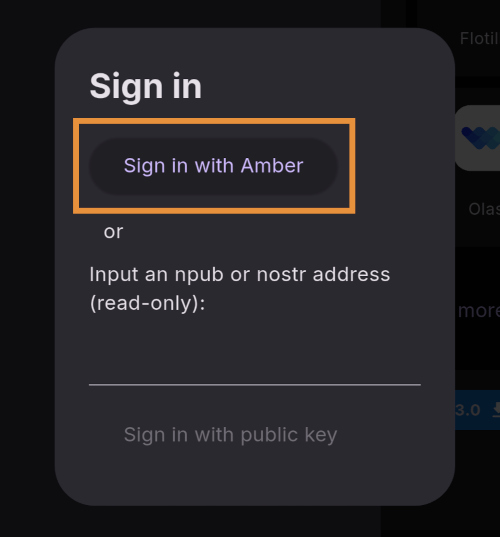
Your phone should automatically switch to Amber to approve the sign-in request.
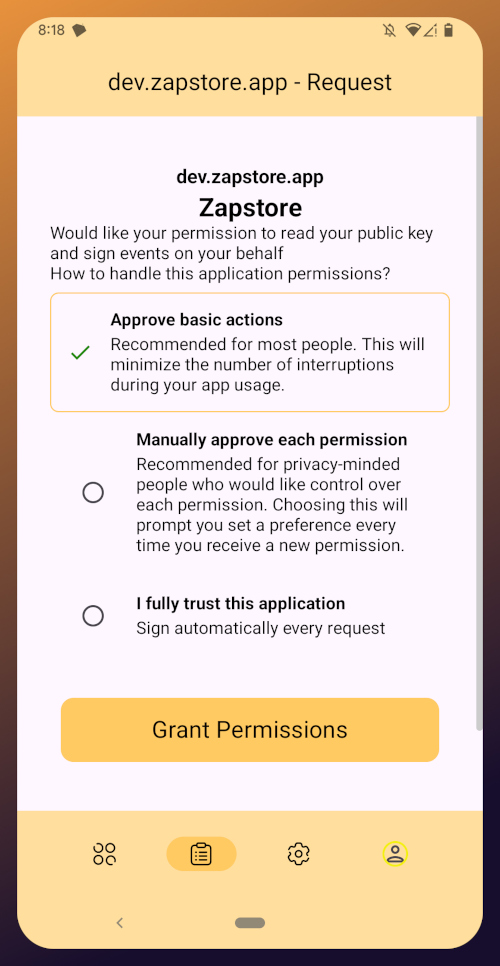
You can choose to only approve basic actions for Zapstore, require it to manually approve every time, or you can tell it that you "fully trust this application." Only choose the latter option with apps you have used for a while and they have never asked you to sign for anything suspicious. For the time being, I suggest you use the "Approve basic actions" option and tap "Grant Permissions."
Your phone will switch back to the Zapstore and will show that you are now signed in. Congratulations! From here on out, logging into most Nostr applications will be as easy as tapping on "Log in with Amber" and approving the request.
If you set up a new profile, it will just show a truncated version of your npub rather than the nickname you set up earlier. That's fine. You'll have an opportunity to update your Nostr profile in the next tutorial in this series and ensure that it is spread far and wide in the network, so the Zapstore will easily find it.
That concludes the tutorial for Amber. While we have not covered using Amber to log into Nostr web apps, that is outside the scope of this series, and I will cover it in an upcoming tutorial regarding using Amber's remote signer options in detail.
Since you're already hanging out in the Zapstore, you may as well stick around, because we will be using it right out the gate in the next part of this series: Amethyst Installation and Setup. (Coming Soon)
-
 @ c1e9ab3a:9cb56b43
2025-05-27 16:19:06
@ c1e9ab3a:9cb56b43
2025-05-27 16:19:06Star Wars is often viewed as a myth of rebellion, freedom, and resistance to tyranny. The iconography—scrappy rebels, totalitarian stormtroopers, lone smugglers—suggests a deep anti-authoritarian ethos. Yet, beneath the surface, the narrative arc of Star Wars consistently affirms the necessity, even sanctity, of central authority. This blog entry introduces the question: Is Star Wars fundamentally a celebration of statism?
Rebellion as Restoration, Not Revolution
The Rebel Alliance’s mission is not to dismantle centralized power, but to restore the Galactic Republic—a bureaucratic, centrally governed institution. Characters like Mon Mothma and Bail Organa are high-ranking senators, not populist revolutionaries. The goal is to remove the corrupt Empire and reinstall a previous central authority, presumed to be just.
- Rebels are loyalists to a prior state structure.
- Power is not questioned, only who wields it.
Jedi as Centralized Moral Elites
The Jedi, often idealized as protectors of peace, are unelected, extra-legal enforcers of moral and military order. Their authority stems from esoteric metaphysical abilities rather than democratic legitimacy.
- They answer only to their internal Council.
- They are deployed by the Senate, but act independently of civil law.
- Their collapse is depicted as tragic not because they were unaccountable, but because they were betrayed.
This positions them as a theocratic elite, not spiritual anarchists.
Chaos and the Frontier: The Case of the Cantina
The Mos Eisley cantina, often viewed as a symbol of frontier freedom, reveals something darker. It is: - Lawless - Violent - Culturally fragmented
Conflict resolution occurs through murder, not mediation. Obi-Wan slices off a limb; Han shoots first—both without legal consequence. There is no evidence of property rights, dispute resolution, or voluntary order.
This is not libertarian pluralism—it’s moral entropy. The message: without centralized governance, barbarism reigns.
The Mythic Arc: Restoration of the Just State
Every trilogy in the saga returns to a single theme: the fall and redemption of legitimate authority.
- Prequels: Republic collapses into tyranny.
- Originals: Rebels fight to restore legitimate order.
- Sequels: Weak governance leads to resurgence of authoritarianism; heroes must reestablish moral centralism.
The story is not anti-state—it’s anti-bad state. The solution is never decentralization; it’s the return of the right ruler or order.
Conclusion: The Hidden Statism of a Rebel Myth
Star Wars wears the costume of rebellion, but tells the story of centralized salvation. It: - Validates elite moral authority (Jedi) - Romanticizes restoration of fallen governments (Republic) - Portrays decentralized zones as corrupt and savage (outer rim worlds)
It is not an anarchist parable, nor a libertarian fable. It is a statist mythology, clothed in the spectacle of rebellion. Its core message is not that power should be abolished, but that power belongs to the virtuous few.
Question to Consider:
If the Star Wars universe consistently affirms the need for centralized moral and political authority, should we continue to see it as a myth of freedom? Or is it time to recognize it as a narrative of benevolent empire? -
 @ 66675158:1b644430
2025-03-23 11:39:41
@ 66675158:1b644430
2025-03-23 11:39:41I don't believe in "vibe coding" – it's just the newest Silicon Valley fad trying to give meaning to their latest favorite technology, LLMs. We've seen this pattern before with blockchain, when suddenly Non Fungible Tokens appeared, followed by Web3 startups promising to revolutionize everything from social media to supply chains. VCs couldn't throw money fast enough at anything with "decentralized" (in name only) in the pitch deck. Andreessen Horowitz launched billion-dollar crypto funds, while Y Combinator batches filled with blockchain startups promising to be "Uber for X, but on the blockchain."
The metaverse mania followed, with Meta betting its future on digital worlds where we'd supposedly hang out as legless avatars. Decentralized (in name only) autonomous organizations emerged as the next big thing – supposedly democratic internet communities that ended up being the next scam for quick money.
Then came the inevitable collapse. The FTX implosion in late 2022 revealed fraud, Luna/Terra's death spiral wiped out billions (including my ten thousand dollars), while Celsius and BlockFi froze customer assets before bankruptcy.
By 2023, crypto winter had fully set in. The SEC started aggressive enforcement actions, while users realized that blockchain technology had delivered almost no practical value despite a decade of promises.
Blockchain's promises tapped into fundamental human desires – decentralization resonated with a generation disillusioned by traditional institutions. Evangelists presented a utopian vision of freedom from centralized control. Perhaps most significantly, crypto offered a sense of meaning in an increasingly abstract world, making the clear signs of scams harder to notice.
The technology itself had failed to solve any real-world problems at scale. By 2024, the once-mighty crypto ecosystem had become a cautionary tale. Venture firms quietly scrubbed blockchain references from their websites while founders pivoted to AI and large language models.
Most reading this are likely fellow bitcoiners and nostr users who understand that Bitcoin is blockchain's only valid use case. But I shared that painful history because I believe the AI-hype cycle will follow the same trajectory.
Just like with blockchain, we're now seeing VCs who once couldn't stop talking about "Web3" falling over themselves to fund anything with "AI" in the pitch deck. The buzzwords have simply changed from "decentralized" to "intelligent."
"Vibe coding" is the perfect example – a trendy name for what is essentially just fuzzy instructions to LLMs. Developers who've spent years honing programming skills are now supposed to believe that "vibing" with an AI is somehow a legitimate methodology.
This might be controversial to some, but obvious to others:
Formal, context-free grammar will always remain essential for building precise systems, regardless of how advanced natural language technology becomes
The mathematical precision of programming languages provides a foundation that human language's ambiguity can never replace. Programming requires precision – languages, compilers, and processors operate on explicit instructions, not vibes. What "vibe coding" advocates miss is that beneath every AI-generated snippet lies the same deterministic rules that have always governed computation.
LLMs don't understand code in any meaningful sense—they've just ingested enormous datasets of human-written code and can predict patterns. When they "work," it's because they've seen similar patterns before, not because they comprehend the underlying logic.
This creates a dangerous dependency. Junior developers "vibing" with LLMs might get working code without understanding the fundamental principles. When something breaks in production, they'll lack the knowledge to fix it.
Even experienced developers can find themselves in treacherous territory when relying too heavily on LLM-generated code. What starts as a productivity boost can transform into a dependency crutch.
The real danger isn't just technical limitations, but the false confidence it instills. Developers begin to believe they understand systems they've merely instructed an AI to generate – fundamentally different from understanding code you've written yourself.
We're already seeing the warning signs: projects cobbled together with LLM-generated code that work initially but become maintenance nightmares when requirements change or edge cases emerge.
The venture capital money is flowing exactly as it did with blockchain. Anthropic raised billions, OpenAI is valued astronomically despite minimal revenue, and countless others are competing to build ever-larger models with vague promises. Every startup now claims to be "AI-powered" regardless of whether it makes sense.
Don't get me wrong—there's genuine innovation happening in AI research. But "vibe coding" isn't it. It's a marketing term designed to make fuzzy prompting sound revolutionary.
Cursor perfectly embodies this AI hype cycle. It's an AI-enhanced code editor built on VS Code that promises to revolutionize programming by letting you "chat with your codebase." Just like blockchain startups promised to "revolutionize" industries, Cursor promises to transform development by adding LLM capabilities.
Yes, Cursor can be genuinely helpful. It can explain unfamiliar code, suggest completions, and help debug simple issues. After trying it for just an hour, I found the autocomplete to be MAGICAL for simple refactoring and basic functionality.
But the marketing goes far beyond reality. The suggestion that you can simply describe what you want and get production-ready code is dangerously misleading. What you get are approximations with:
- Security vulnerabilities the model doesn't understand
- Edge cases it hasn't considered
- Performance implications it can't reason about
- Dependency conflicts it has no way to foresee
The most concerning aspect is how such tools are marketed to beginners as shortcuts around learning fundamentals. "Why spend years learning to code when you can just tell AI what you want?" This is reminiscent of how crypto was sold as a get-rich-quick scheme requiring no actual understanding.
When you "vibe code" with an AI, you're not eliminating complexity—you're outsourcing understanding to a black box. This creates developers who can prompt but not program, who can generate but not comprehend.
The real utility of LLMs in development is in augmenting existing workflows:
- Explaining unfamiliar codebases
- Generating boilerplate for well-understood patterns
- Suggesting implementations that a developer evaluates critically
- Assisting with documentation and testing
These uses involve the model as a subordinate assistant to a knowledgeable developer, not as a replacement for expertise. This is where the technology adds value—as a sophisticated tool in skilled hands.
Cursor is just a better hammer, not a replacement for understanding what you're building. The actual value emerges when used by developers who understand what happens beneath the abstractions. They can recognize when AI suggestions make sense and when they don't because they have the fundamental knowledge to evaluate output critically.
This is precisely where the "vibe coding" narrative falls apart.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 15:09:17
@ 21c71bfa:e28fa0f6
2025-05-29 15:09:17Book *Bangalore to Tirupati cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ c1e9ab3a:9cb56b43
2025-05-27 13:19:53
@ c1e9ab3a:9cb56b43
2025-05-27 13:19:53I. Introduction: Money as a Function of Efficiency and Preference
Money is not defined by law, but by power over productivity. In any open economy, the most economically efficient actors—those who control the most valuable goods, services, and knowledge—ultimately dictate the medium of exchange. Their preferences signal to the broader market what form of money is required to access the highest-value goods, from durable commodities to intangibles like intellectual property and skilled labor.
Whatever money these actors prefer becomes the de facto unit of account and store of value, regardless of its legal status. This emergent behavior is natural and reflects a hierarchy of monetary utility.
II. Classical Gresham’s Law: A Product of Market Distortion
Gresham’s Law, famously stated as:
"Bad money drives out good"
is only valid under coercive monetary conditions, specifically: - Legal tender laws that force the acceptance of inferior money at par with superior money. - Fixed exchange rates imposed by decree, not market valuation. - Governments or central banks backing elastic fiduciary media with promises of redemption. - Institutional structures that mandate debt and tax payments in the favored currency.
Under these conditions, superior money (hard money) is hoarded, while inferior money (soft, elastic, inflationary) circulates. This is not an expression of free market behavior—it is the result of suppressed price discovery and legal coercion.
Gresham’s Law, therefore, is not a natural law of money, but a law of distortion under forced parity and artificial elasticity.
III. The Collapse of Coercion: Inversion of Gresham’s Law
When coercive structures weaken or are bypassed—through technological exit, jurisdictional arbitrage, monetary breakdown, or political disintegration—Gresham’s Law inverts:
Good money drives out bad.
This occurs because: - Market actors regain the freedom to select money based on utility, scarcity, and credibility. - Legal parity collapses, exposing the true economic hierarchy of monetary forms. - Trustless systems (e.g., Bitcoin) or superior digital instruments (e.g., stablecoins) offer better settlement, security, and durability. - Elastic fiduciary media become undesirable as counterparty risk and inflation rise.
The inversion marks a return to monetary natural selection—not a breakdown of Gresham’s Law, but the collapse of its preconditions.
IV. Elasticity and Control
Elastic fiduciary media (like fiat currency) are not intrinsically evil. They are tools of state finance and debt management, enabling rapid expansion of credit and liquidity. However, when their issuance is unconstrained, and legal tender laws force their use, they become weapons of economic coercion.
Banks issue credit unconstrained by real savings, and governments enforce the use of inflated media through taxation and courts. This distorts capital allocation, devalues productive labor, and ultimately hollows out monetary confidence.
V. Monetary Reversion: The Return of Hard Money
When the coercion ends—whether gradually or suddenly—the monetary system reverts. The preferences of the productive and wealthy reassert themselves:
- Superior money is not just saved—it begins to circulate.
- Weaker currencies are rejected not just for savings, but for daily exchange.
- The hoarded form becomes the traded form, and Gresham’s Law inverts completely.
Bitcoin, gold, and even highly credible stable instruments begin to function as true money, not just stores of value. The natural monetary order returns, and the State becomes a late participant, not the originator of monetary reality.
VI. Conclusion
Gresham’s Law operates only under distortion. Its inversion is not an anomaly—it is a signal of the collapse of coercion. The monetary system then reorganizes around productive preference, technological efficiency, and economic sovereignty.
The most efficient market will always dictate the form of hard money. The State can delay this reckoning through legal force, but it cannot prevent it indefinitely. Once free choice returns, bad money dies, and good money lives again.
-
 @ 33baa074:3bb3a297
2025-05-28 08:54:40
@ 33baa074:3bb3a297
2025-05-28 08:54:40COD (chemical oxygen demand) sensors play a vital role in water quality testing. Their main functions include real-time monitoring, pollution event warning, water quality assessment and pollution source tracking. The following are the specific roles and applications of COD sensors in water quality testing:
Real-time monitoring and data acquisition COD sensors can monitor the COD content in water bodies in real time and continuously. Compared with traditional sampling methods, COD sensors are fast and accurate, without manual sampling and laboratory testing, which greatly saves time and labor costs. By combining with the data acquisition system, the monitoring data can be uploaded to the cloud in real time to form a extemporization distribution map of the COD content in the water body, providing detailed data support for environmental monitoring and management.
Pollution event warning and rapid response COD sensors play an important role in early warning and rapid response in water environment monitoring. Once there is an abnormal increase in organic matter in the water body, the COD sensor can quickly detect the change in COD content and alarm through the preset threshold. This enables relevant departments to take measures at the early stage of the pollution incident to prevent the spread of pollution and protect the water environment.
Water quality assessment and pollution source tracking COD sensors play an important role in water quality assessment and pollution source tracking. By continuously monitoring the COD content in water bodies, the water quality can be evaluated and compared with national and regional water quality standards. At the same time, COD sensors can also help determine and track the location and spread of pollution sources, provide accurate data support for environmental management departments, and guide the development of pollution prevention and control work.
Application scenarios COD sensors are widely used in various water quality monitoring scenarios, including but not limited to: Sewage treatment plants: used to monitor the COD content of in fluent and effluent to ensure the effect of sewage treatment. Water source protection and management: deployed in water sources to monitor the COD content of in fluent sources. Once the water quality exceeds the set limit, the system will issue an alarm in time to ensure water quality safety. Lake and river monitoring: deployed in water bodies such as lakes and rivers to monitor the COD content of water bodies in real time.

Technical features of COD sensor COD sensor uses advanced technology, such as ultraviolet absorption method, which does not require the use of chemical reagents, avoiding the risk of contamination of chemical reagents in traditional COD detection methods, and can achieve online uninterrupted water quality monitoring, providing strong support for real-time water quality assessment. In addition, COD sensor also has the advantages of low cost, high stability, strong anti-interference ability, and convenient installation.
Summary In summary, COD sensor plays an irreplaceable role in water quality detection. It can not only provide real-time and accurate water quality data, but also quickly warn when pollution incidents occur, providing strong technical support for water quality management and environmental protection. With the advancement of technology and the popularization of applications, COD sensor will play a more important role in water quality monitoring in the future.
-
 @ 16f1a010:31b1074b
2025-03-20 14:32:25
@ 16f1a010:31b1074b
2025-03-20 14:32:25grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Introduction
grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Prerequisites
- Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rwwp5xsuryd3knfdr7g
Download Grain
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlPrerequisites: - Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: [Link to MongoDB setup guide].
Download Grain:
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution:
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain:
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files:
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlConfiguration Documentation
You can always find the latest example configs on my site or in the github repo here: config.yml
Config.yml
This
config.ymlfile is where you customize how your Grain relay operates. Each section controls different aspects of the relay's behavior.1.
mongodb(Database Settings)uri: mongodb://localhost:27017/:- This is the connection string for your MongoDB database.
mongodb://localhost:27017/indicates that your MongoDB server is running on the same computer as your Grain relay (localhost) and listening on port 27017 (the default MongoDB port).- If your MongoDB server is on a different machine, you'll need to change
localhostto the server's IP address or hostname. - The trailing
/indicates the root of the mongodb server. You will define the database in the next line.
database: grain:- This specifies the name of the MongoDB database that Grain will use to store Nostr events. Grain will create this database if it doesn't already exist.
- You can name the database whatever you want. If you want to run multiple grain relays, you can and they can have different databases running on the same mongo server.
2.
server(Relay Server Settings)port: :8181:- This sets the port on which your Grain relay will listen for incoming nostr websocket connections and what port the frontend will be available at.
read_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to send data before closing the connection.
write_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to receive data before closing the connection.
idle_timeout: 120 # in seconds:- This is the maximum time (in seconds) that the relay will keep a connection open if there's no activity.
max_connections: 100:- This sets the maximum number of simultaneous client connections that the relay will allow.
max_subscriptions_per_client: 10:- This sets the maximum amount of subscriptions a single client can request from the relay.
3.
resource_limits(System Resource Limits)cpu_cores: 2 # Limit the number of CPU cores the application can use:- This restricts the number of CPU cores that Grain can use. Useful for controlling resource usage on your server.
memory_mb: 1024 # Cap the maximum amount of RAM in MB the application can use:- This limits the maximum amount of RAM (in megabytes) that Grain can use.
heap_size_mb: 512 # Set a limit on the Go garbage collector's heap size in MB:- This sets a limit on the amount of memory that the Go programming language's garbage collector can use.
4.
auth(Authentication Settings)enabled: false # Enable or disable AUTH handling:- If set to
true, this enables authentication handling, requiring clients to authenticate before using the relay.
- If set to
relay_url: "wss://relay.example.com/" # Specify the relay URL:- If authentication is enabled, this is the url that clients will use to authenticate.
5.
UserSync(User Synchronization)user_sync: false:- If set to true, the relay will attempt to sync user data from other relays.
disable_at_startup: true:- If user sync is enabled, this will prevent the sync from starting when the relay starts.
initial_sync_relays: [...]:- A list of other relays to pull user data from.
kinds: []:- A list of event kinds to pull from the other relays. Leaving this empty will pull all event kinds.
limit: 100:- The limit of events to pull from the other relays.
exclude_non_whitelisted: true:- If set to true, only users on the whitelist will have their data synced.
interval: 360:- The interval in minutes that the relay will resync user data.
6.
backup_relay(Backup Relay)enabled: false:- If set to true, the relay will send copies of received events to the backup relay.
url: "wss://some-relay.com":- The url of the backup relay.
7.
event_purge(Event Purging)enabled: false:- If set to
true, the relay will automatically delete old events.
- If set to
keep_interval_hours: 24:- The number of hours to keep events before purging them.
purge_interval_minutes: 240:- How often (in minutes) the purging process runs.
purge_by_category: ...:- Allows you to specify which categories of events (regular, replaceable, addressable, deprecated) to purge.
purge_by_kind_enabled: false:- If set to true, events will be purged based on the kinds listed below.
kinds_to_purge: ...:- A list of event kinds to purge.
exclude_whitelisted: true:- If set to true, events from whitelisted users will not be purged.
8.
event_time_constraints(Event Time Constraints)min_created_at: 1577836800:- The minimum
created_attimestamp (Unix timestamp) that events must have to be accepted by the relay.
- The minimum
max_created_at_string: now+5m:- The maximum created at time that an event can have. This example shows that the max created at time is 5 minutes in the future from the time the event is received.
min_created_at_stringandmax_created_atwork the same way.
9.
rate_limit(Rate Limiting)ws_limit: 100:- The maximum number of WebSocket messages per second that the relay will accept.
ws_burst: 200:- Allows a temporary burst of WebSocket messages.
event_limit: 50:- The maximum number of Nostr events per second that the relay will accept.
event_burst: 100:- Allows a temporary burst of Nostr events.
req_limit: 50:- The limit of http requests per second.
req_burst: 100:- The allowed burst of http requests.
max_event_size: 51200:- The maximum size (in bytes) of a Nostr event that the relay will accept.
kind_size_limits: ...:- Allows you to set size limits for specific event kinds.
category_limits: ...:- Allows you to set rate limits for different event categories (ephemeral, addressable, regular, replaceable).
kind_limits: ...:- Allows you to set rate limits for specific event kinds.
By understanding these settings, you can tailor your Grain Nostr relay to meet your specific needs and resource constraints.
whitelist.yml
The
whitelist.ymlfile is used to control which users, event kinds, and domains are allowed to interact with your Grain relay. Here's a breakdown of the settings:1.
pubkey_whitelist(Public Key Whitelist)enabled: false:- If set to
true, this enables the public key whitelist. Only users whose public keys are listed will be allowed to publish events to your relay.
- If set to
pubkeys::- A list of hexadecimal public keys that are allowed to publish events.
pubkey1andpubkey2are placeholders, you will replace these with actual hexadecimal public keys.
npubs::- A list of npubs that are allowed to publish events.
npub18ls2km9aklhzw9yzqgjfu0anhz2z83hkeknw7sl22ptu8kfs3rjq54am44andnpub2are placeholders, replace them with actual npubs.- npubs are bech32 encoded public keys.
2.
kind_whitelist(Event Kind Whitelist)enabled: false:- If set to
true, this enables the event kind whitelist. Only events with the specified kinds will be allowed.
- If set to
kinds::- A list of event kinds (as strings) that are allowed.
"1"and"2"are example kinds. Replace these with the kinds you want to allow.- Example kinds are 0 for metadata, 1 for short text notes, and 2 for recommend server.
3.
domain_whitelist(Domain Whitelist)enabled: false:- If set to
true, this enables the domain whitelist. This checks the domains .well-known folder for their nostr.json. This file contains a list of pubkeys. They will be considered whitelisted if on this list.
- If set to
domains::- A list of domains that are allowed.
"example.com"and"anotherdomain.com"are example domains. Replace these with the domains you want to allow.
blacklist.yml
The
blacklist.ymlfile allows you to block specific content, users, and words from your Grain relay. Here's a breakdown of the settings:1.
enabled: true- This setting enables the blacklist functionality. If set to
true, the relay will actively block content and users based on the rules defined in this file.
2.
permanent_ban_words:- This section lists words that, if found in an event, will result in a permanent ban for the event's author.
- really bad wordis a placeholder. Replace it with any words you want to permanently block.
3.
temp_ban_words:- This section lists words that, if found in an event, will result in a temporary ban for the event's author.
- crypto,- web3, and- airdropare examples. Replace them with the words you want to temporarily block.
4.
max_temp_bans: 3- This sets the maximum number of temporary bans a user can receive before they are permanently banned.
5.
temp_ban_duration: 3600- This sets the duration of a temporary ban in seconds.
3600seconds equals one hour.
6.
permanent_blacklist_pubkeys:- This section lists hexadecimal public keys that are permanently blocked from using the relay.
- db0c9b8acd6101adb9b281c5321f98f6eebb33c5719d230ed1870997538a9765is an example. Replace it with the public keys you want to block.
7.
permanent_blacklist_npubs:- This section lists npubs that are permanently blocked from using the relay.
- npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtnis an example. Replace it with the npubs you want to block.- npubs are the human readable version of public keys.
8.
mutelist_authors:- This section lists hexadecimal public keys of author of a kind1000 mutelist. Pubkey authors on this mutelist will be considered on the permanent blacklist. This provides a nostr native way to handle the backlist of your relay
- 3fe0ab6cbdb7ee27148202249e3fb3b89423c6f6cda6ef43ea5057c3d93088e4is an example. Replace it with the public keys of authors that have a mutelist you would like to use as a blacklist. Consider using your own.- Important Note: The mutelist Event MUST be stored in this relay for it to be retrieved. This means your relay must have a copy of the authors kind10000 mutelist to consider them for the blacklist.
Running Grain as a Service:
Windows Service:
To run Grain as a Windows service, you can use tools like NSSM (Non-Sucking Service Manager). NSSM allows you to easily install and manage any application as a Windows service.
* For instructions on how to install NSSM, please refer to this article: [Link to NSSM install guide coming soon].-
Open Command Prompt as Administrator:
- Open the Windows Start menu, type "cmd," right-click on "Command Prompt," and select "Run as administrator."
-
Navigate to NSSM Directory:
- Use the
cdcommand to navigate to the directory where you extracted NSSM. For example, if you extracted it toC:\nssm, you would typecd C:\nssmand press Enter.
- Use the
-
Install the Grain Service:
- Run the command
nssm install grain. - A GUI will appear, allowing you to configure the service.
- Run the command
-
Configure Service Details:
- In the "Path" field, enter the full path to your Grain executable (e.g.,
C:\grain\grain_windows_amd64.exe). - In the "Startup directory" field, enter the directory where your Grain executable is located (e.g.,
C:\grain).
- In the "Path" field, enter the full path to your Grain executable (e.g.,
-
Install the Service:
- Click the "Install service" button.
-
Manage the Service:
- You can now manage the Grain service using the Windows Services manager. Open the Start menu, type "services.msc," and press Enter. You can start, stop, pause, or restart the Grain service from there.
Linux Service (systemd):
To run Grain as a Linux service, you can use systemd, the standard service manager for most modern Linux distributions.
-
Create a Systemd Service File:
- Open a text editor with root privileges (e.g.,
sudo nano /etc/systemd/system/grain.service).
- Open a text editor with root privileges (e.g.,
-
Add Service Configuration:
- Add the following content to the
grain.servicefile, replacing the placeholders with your actual paths and user information:
```toml [Unit] Description=Grain Nostr Relay After=network.target
[Service] ExecStart=/path/to/grain_linux_amd64 WorkingDirectory=/path/to/grain/directory Restart=always User=your_user #replace your_user Group=your_group #replace your_group
[Install] WantedBy=multi-user.target ```
- Replace
/path/to/grain/executablewith the full path to your Grain executable. - Replace
/path/to/grain/directorywith the directory containing your Grain executable. - Replace
your_userandyour_groupwith the username and group that will run the Grain service.
- Add the following content to the
-
Reload Systemd:
- Run the command
sudo systemctl daemon-reloadto reload the systemd configuration.
- Run the command
-
Enable the Service:
- Run the command
sudo systemctl enable grain.serviceto enable the service to start automatically on boot.
- Run the command
-
Start the Service:
- Run the command
sudo systemctl start grain.serviceto start the service immediately.
- Run the command
-
Check Service Status:
- Run the command
sudo systemctl status grain.serviceto check the status of the Grain service. This will show you if the service is running and any recent logs. - You can run
sudo journalctl -f -u grain.serviceto watch the logs
- Run the command
More guides are in the works for setting up tailscale to access your relay from anywhere over a private network and for setting up a cloudflare tunnel to your domain to deploy a grain relay accessible on a subdomain of your site eg wss://relay.yourdomain.com
-
 @ 9cb3545c:2ff47bca
2025-05-27 12:58:56
@ 9cb3545c:2ff47bca
2025-05-27 12:58:56Introduction
Public companies that hold Bitcoin on behalf of investors (often issuing securities backed by those Bitcoin holdings) have faced growing pressure to demonstrate proof of reserves – evidence that they genuinely hold the cryptocurrency they claim. One approach is to publish the company’s Bitcoin wallet addresses so that anyone can verify the balances on the blockchain. This practice gained momentum after high-profile crypto collapses (e.g. FTX in 2022) eroded trust, leading major exchanges and fund issuers like Binance, Kraken, OKX, and Bitwise to publicize wallet addresses as proof of assets . The goal is transparency and reassurance for investors. However, making wallet addresses public comes with significant security and privacy risks. This report examines those risks – from cybersecurity threats and blockchain tracing to regulatory and reputational implications – and weighs them against the transparency benefits of on-chain proof of reserves.
Proof of Reserves via Public Wallet Addresses
In the cryptocurrency ethos of “don’t trust – verify,” on-chain proof of reserves is seen as a powerful tool. By disclosing wallet addresses (or cryptographic attestations of balances), a company lets investors and analysts independently verify that the Bitcoin reserves exist on-chain. For example, some firms have dashboards showing their addresses and balances in real time . In theory, this transparency builds trust by proving assets are not being misreported or misused. Shareholders gain confidence that the company’s Bitcoin holdings are intact, potentially preventing fraud or mismanagement.
Yet this approach essentially sacrifices the pseudonymity of blockchain transactions. Publishing a wallet address ties a large, known institution to specific on-chain funds. While Bitcoin addresses are public by design, most companies treat their specific addresses as sensitive information. Public proof-of-reserve disclosures break that anonymity, raising several concerns as detailed below.
Cybersecurity Threats from Visible Wallet Balances
Revealing a wallet address with a large balance can make a company a prime target for hackers and cybercriminals. Knowing exactly where significant reserves are held gives attackers a clear blueprint. As Bitcoin advocate (and MicroStrategy Executive Chairman) Michael Saylor warned in 2025, “publicly known wallet addresses become prime targets for malicious actors. Knowing where significant reserves are held provides hackers with a clear target, potentially increasing the risk of sophisticated attacks” . In other words, publishing the address increases the attack surface – attackers might intensify phishing campaigns, malware deployment, or insider bribery aimed at obtaining the keys or access to those wallets.
Even if the wallets are secured in cold storage, a public address advertisement may encourage attempts to penetrate the organization’s security. Custodians and partners could also be targeted. Saylor noted that this exposure isn’t just risky for the company holding the Bitcoin; it can indirectly put their custodial providers and related exchanges at risk as well . For instance, if a third-party custodian manages the wallets, hackers might attempt to breach that custodian knowing the reward (the company’s Bitcoin) is great.
Companies themselves have acknowledged these dangers. Grayscale Investments, which runs the large Grayscale Bitcoin Trust (GBTC), pointedly refused to publish its wallet addresses in late 2022, citing “security concerns” and complex custody arrangements that have “kept our investors’ assets safe for years” . Grayscale implied that revealing on-chain addresses could undermine those security measures, and it chose not to “circumvent complex security arrangements” just to appease public demand . This highlights a key point: corporate treasury security protocols often assume wallet details remain confidential. Publicizing them could invalidate certain assumptions (for example, if an address was meant to be operationally secret, it can no longer serve that role once exposed).
Additionally, a publicly known trove of cryptocurrency might invite physical security threats. While not a purely “cyber” issue, if criminals know a particular company or facility controls a wallet with, say, thousands of Bitcoin, it could lead to threats against personnel (extortion or coercion to obtain keys). This is a less common scenario for large institutions (which typically have robust physical security), but smaller companies or key individuals could face elevated personal risk by being associated with huge visible crypto reserves.
In summary, cybersecurity experts consider public proof-of-reserve addresses a double-edged sword: transparency comes at the cost of advertising exactly where a fortune is held. As Saylor bluntly put it, “the conventional way of issuing proof of reserves today is actually insecure… This method undermines the security of the issuer, the custodian, the exchanges and the investors. This is not a good idea”  . From a pure security standpoint, broadcasting your wallets is akin to drawing a bullseye on them.
Privacy Risks: Address Clustering and Blockchain Tracing
Blockchain data is public, so publishing addresses opens the door to unwanted analytics and loss of privacy for the business. Even without knowing the private keys, analysts can scrutinize every transaction in and out of those addresses. This enables address clustering – linking together addresses that interact – and other forms of blockchain forensics that can reveal sensitive information about the company’s activities.
One immediate risk is that observers can track the company’s transaction patterns. For example, if the company moves Bitcoin from its reserve address to an exchange or to another address, that move is visible in real time. Competitors, investors, or even attackers could deduce strategic information: perhaps the company is planning to sell (if coins go to an exchange wallet) or is reallocating funds. A known institution’s on-chain movements can thus “reveal strategic movements or holdings”, eroding the company’s operational privacy . In a volatile market, advance knowledge of a large buy or sell by a major player could even be exploited by others (front-running the market, etc.).
Publishing one or a few static addresses also violates a basic privacy principle of Bitcoin: address reuse. Best practice in Bitcoin is to use a fresh address for each transaction to avoid linking them  . If a company continuously uses the same “proof of reserve” address, all counterparties sending funds to or receiving funds from that address become visible. Observers could map out the company’s business relationships or vendors by analyzing counterparties. A Reddit user commenting on an ETF that published a single address noted that “reusing a single address for this makes me question their risk management… There are much better and more privacy-preserving ways to prove reserves… without throwing everything in a single public address” . In other words, a naive implementation of proof-of-reserve (one big address) maximizes privacy leakage.
Even if multiple addresses are used, if they are all disclosed, one can perform clustering analysis to find connections. This happened in the Grayscale case: although Grayscale would not confirm any addresses, community analysts traced and identified 432 addresses likely belonging to GBTC’s custodial holdings by following on-chain traces from known intermediary accounts . They managed to attribute roughly 317,705 BTC (about half of GBTC’s holdings) to those addresses . This demonstrates that even partial information can enable clustering – and if the company directly published addresses, the task becomes even easier to map the entirety of its on-chain asset base.
Another threat vector is “dusting” attacks, which become more feasible when an address is publicly known. In a dusting attack, an adversary sends a tiny amount of cryptocurrency (dust) to a target address. The dust itself is harmless, but if the target address ever spends that dust together with other funds, it can cryptographically link the target address to other addresses in the same wallet. Blockchain security researchers note that “with UTXO-based assets, an attacker could distribute dust to an address to reveal the owner’s other addresses by tracking the dust’s movement… If the owner unknowingly combines this dust with their funds in a transaction, the attacker can… link multiple addresses to a single owner”, compromising privacy . A company that publishes a list of reserve addresses could be systematically dusted by malicious actors attempting to map out all addresses under the company’s control. This could unmask cold wallet addresses that the company never intended to publicize, further eroding its privacy and security.
Investor confidentiality is another subtle concern. If the business model involves individual investor accounts or contributions (for instance, a trust where investors can deposit or withdraw Bitcoin), public addresses might expose those movements. An outside observer might not know which investor corresponds to a transaction, but unusual inflows/outflows could signal actions by big clients. In extreme cases, if an investor’s own wallet is known (say a large investor announces their involvement), one might link that to transactions in the company’s reserve addresses. This could inadvertently reveal an investor’s activities or holdings, breaching expectations of confidentiality. Even absent direct identification, some investors might simply be uncomfortable with their transactions being part of a publicly traceable ledger tied to the company.
In summary, publishing reserve addresses facilitates blockchain tracing that can pierce the veil of business privacy. It hands analysts the keys to observe how funds move, potentially exposing operational strategies, counterparties, and internal processes. As one industry publication noted, linking a large known institution to specific addresses can compromise privacy and reveal more than intended . Companies must consider whether they are ready for that level of transparency into their every on-chain move.
Regulatory and Compliance Implications
From a regulatory perspective, wallet address disclosure lies in uncharted territory, but it raises several flags. First and foremost is the issue of incomplete information: A wallet address only shows assets, not the company’s liabilities or other obligations. Regulators worry that touting on-chain holdings could give a false sense of security. The U.S. Securities and Exchange Commission (SEC) has cautioned investors to “not place too much confidence in the mere fact a company says it’s got a proof-of-reserves”, noting that such reports “lack sufficient information” for stakeholders to ascertain if liabilities can be met . In other words, a public company might show a big Bitcoin address balance, but if it has debts or customer liabilities of equal or greater value, the proof-of-reserve alone is “not necessarily an indicator that the company is in a good financial position” .
This regulatory stance implies that address disclosure, if done, must be paired with proper context. A public company would likely need to clarify in its financial statements or investor communications that on-chain reserves are unencumbered (not pledged as loan collateral, not already sold forward, etc.) and that total liabilities are accounted for. Otherwise, there’s a risk of misleading investors, which could have legal consequences. For example, if investors interpret the on-chain balance as proof of solvency but the company actually had leveraged those bitcoins for loans, lawsuits or regulatory enforcement could follow for misrepresentation.
There’s also a compliance burden associated with revealing addresses. Once an address is known to be the company’s, that company effectively must monitor all transactions related to it. If someone sends funds to that address (even without permission), the company might receive tainted coins (from hacked sources or sanctioned entities). This could trigger anti-money laundering (AML) red flags. Normally, compliance teams can ignore random deposits to unknown wallets, but they cannot ignore something sent into their publicly identified corporate wallet. Even a tiny dust amount sent from a blacklisted address could complicate compliance – for instance, the company would need to prove it has no relation to the sender and perhaps even avoid moving those tainted outputs. Being in the open increases such exposure. Threat actors might even exploit this by “poisoning” a company’s address with unwanted transactions, just to create regulatory headaches or reputational smears.
Another consideration is that custodial agreements and internal risk controls might forbid public disclosure of addresses. Many public companies use third-party custodians for their Bitcoin (for example, Coinbase Custody, BitGo, etc.). These custodians often treat wallet details as confidential for security. Grayscale noted that its Bitcoin are custodied on Coinbase and implied that revealing on-chain info would interfere with security arrangements  . It’s possible that some custodians would object to their clients broadcasting addresses, or might require additional assurances. A company going against such advice might be seen as negligent if something went wrong.
Regulators have so far not mandated on-chain proofs for public companies – in fact, recent laws have exempted public companies from proof-of-reserve mandates on the assumption they are already subject to rigorous SEC reporting. For example, a Texas bill in 2023 required crypto exchanges and custodians to provide quarterly proof-of-reserves to the state, but it “specifically carved out public reporting companies” since they already file audited financials with the SEC . The rationale was that between SEC filings and audits, public companies have oversight that private crypto firms lack . However, this also highlights a gap: even audited financials might not verify 100% of crypto assets (auditors often sample balances). Some observers noted that standard audits “may not ever include the 100% custodial asset testing contemplated by proof of reserves”, especially since quarterly SEC filings (10-Q) are often not audited . This puts public companies in a nuanced position – they are trusted to use traditional audits and internal controls, but the onus is on them if they choose to add extra transparency like on-chain proofs.
Finally, securities regulators focus on fair disclosure and accuracy. If a company publicly posts addresses, those essentially become investor disclosures subject to anti-fraud rules. The firm must keep them up to date and accurate. Any mistake (such as publishing a wrong address or failing to mention that some coins are locked up or lent out) could attract regulatory scrutiny for being misleading. In contrast, a formal audit or certification from a third-party comes with standards and disclaimers that are better understood by regulators. A self-published wallet list is an unprecedented form of disclosure that regulators haven’t fully vetted – meaning the company bears the risk if something is misinterpreted.
In summary, wallet address disclosure as proof-of-reserve must be handled very carefully to avoid regulatory pitfalls. The SEC and others have warned that on-chain assets alone don’t tell the whole story . Public companies would need to integrate such proofs with their official reporting in a responsible way – otherwise they risk confusion or even regulatory backlash for giving a false sense of security.
Reputational and Operational Risks
While transparency is meant to enhance reputation, in practice public wallet disclosures can create new reputational vulnerabilities. Once an address is public, a company’s every on-chain action is under the microscope of the crypto community and media. Any anomaly or perceived misstep can snowball into public relations problems.
One vivid example occurred with Crypto.com in late 2022. After the exchange published its cold wallet addresses to prove reserves (a move prompted by the FTX collapse), on-chain analysts quickly noticed a “suspicious transfer of 320,000 ETH” – about 82% of Crypto.com’s Ether reserves – moving from their cold wallet to another exchange (Gate.io)  . This large, unexpected transfer sparked immediate panic and FUD (fear, uncertainty, and doubt) on social media. Observers speculated that Crypto.com might be insolvent or was manipulating snapshots of reserves by borrowing funds. The CEO had to publicly respond, admitting it was an operational error – the ETH was supposed to go to a new cold storage address but ended up at a whitelisted external address by mistake . The funds were eventually returned, but not before reputational damage was done: the incident made headlines about mishandled funds and rattled user confidence  . This case illustrates how full public visibility can turn an internal slip-up into a highly public crisis. If the addresses had not been public, the mistake might have been quietly corrected; with on-chain transparency, there was nowhere to hide and no way to control the narrative before the public drew worst-case conclusions.
Even routine operations can be misinterpreted. Blockchain data lacks context – analysts may jump to conclusions that hurt a company’s reputation even if nothing is actually wrong. For instance, Binance (the world’s largest crypto exchange) encountered scrutiny when on-chain observers noted that one of its reserve wallets (labeled “Binance 8”) contained far more assets than it should have. This wallet was meant to hold collateral for Binance’s issued tokens, but held an excess balance, suggesting possible commingling of customer funds with collateral  . Bloomberg and others reported a ~$12.7 billion discrepancy visible on-chain . Binance had to acknowledge the issue as a “clerical error” and quickly separate the funds, all under the glare of public attention  . While Binance maintained that user assets were fully backed and the mistake was purely operational, the episode raised public concern over Binance’s practices, feeding a narrative that even the largest exchange had internal control lapses. The key point is that public proof-of-reserves made the lapse obvious to everyone, forcing a reactive explanation. The reputational hit (even if temporary) was an operational risk of being so transparent.
Additionally, strategic confidentiality is lost. If a company holding Bitcoin as a reserve asset decides to make a major move (say, reallocating to a different wallet, or using some Bitcoin for a strategic investment or loan), doing so with known addresses broadcasts that strategy. Competitors or market analysts can infer things like “Company X is moving 10% of its BTC — why? Are they selling? Hedging? Using it as collateral?” This can erode any competitive advantage of keeping financial strategies discreet. It might even affect the company’s stock price if investors interpret moves negatively. For example, if a blockchain analysis shows the company’s reserves dropping, shareholders might fear the company sold Bitcoin (perhaps due to financial distress), even if the reality is benign (like moving funds to a new custodian). The company would be forced into continuous public explanation of on-chain actions to prevent misunderstanding.
There’s also a risk of exposing business partnerships. Suppose the company uses certain exchanges or OTC desks to rebalance its holdings – transactions with those service providers will be visible and could link the company to them. If one of those partners has issues (say a hacked exchange or a sanctioned entity inadvertently), the company could be reputationally contaminated by association through the blockchain trail.
Finally, not all publicity is good publicity in the crypto world. A public proof-of-reserve might invite armchair auditors to scrutinize and criticize every aspect of the company’s crypto management. Minor issues could be blown out of proportion. On the flip side, if a company chooses not to publish addresses, it could face reputational risk from a different angle: skeptics might question why it isn’t being transparent. (Indeed, Grayscale’s refusal to disclose wallet addresses led to social media chatter about whether they truly held all the Bitcoin they claimed, contributing to investor nervousness and a steep discount on GBTC shares .) Thus, companies are in a delicate spot: share too much and every move invites scrutiny; share too little and you breed distrust.
Balancing Transparency Benefits vs. Risks
The central question is whether the benefit of proving reserve holdings to investors outweighs these security and privacy risks. It’s a classic risk-reward calculation, and opinions in the industry are divided.
On the side of transparency, many argue that the credibility and trust gained by proof-of-reserves is invaluable. Advocates note that Bitcoin was designed for open verification – “on-chain auditability and permissionless transparency” are core features . By embracing this, companies demonstrate they are good stewards of a “trustless” asset. In fact, some believe public companies have a duty to be extra transparent. A recent Nasdaq report contended that “when a publicly traded company holds Bitcoin but offers no visibility into how that Bitcoin is held or verified, it exposes itself to multiple levels of risk: legal, reputational, operational, and strategic”, undermining trust . In that view, opacity is riskier in the long run – a lack of proof could weaken investor confidence or invite regulatory suspicion. Shareholders and analysts may actually penalize a company that refuses to provide verifiable proof of its crypto assets .
Transparency done right can also differentiate a firm as a leader in governance. Publishing reserve data (whether via addresses or through third-party attestations) can be seen as a commitment to high standards. For example, Metaplanet, an investment firm, publicly discloses its BTC reserve addresses and even provides a live dashboard for anyone to verify balances . This proactive openness signals confidence and has been touted as an industry best practice in some quarters. By proving its reserves, a company can potentially avoid the fate of those that lost public trust (as happened with opaque crypto firms in 2022). It’s also a means to preempt false rumors – if data is out in the open, misinformation has less room to grow.
However, the pro-transparency camp increasingly acknowledges that there are smarter ways to achieve trust without courting all the risks. One compromise is using cryptographic proofs or audits instead of plain address dumps. For instance, exchanges like Kraken have implemented Merkle tree proof-of-reserves: an independent auditor verifies all customer balances on-chain and provides a cryptographic report, and customers can individually verify their account is included without the exchange revealing every address publicly. This method proves solvency to those who need to know without handing over a complete roadmap to attackers. Another emerging solution is zero-knowledge proofs, where a company can prove knowledge or ownership of certain assets without revealing the addresses or amounts to the public. These technologies are still maturing, but they aim to deliver the best of both worlds: transparency and privacy.
On the side of caution, many experts believe the risks of full public disclosure outweigh the incremental gain in transparency, especially for regulated public companies. Michael Saylor encapsulates this viewpoint: he calls on-chain proof-of-reserve “a bad idea” for institutions, arguing that it “offers one-way transparency” (assets only) and “leaves organizations open to cyberattacks” . He stresses that no serious security expert would advise a Fortune 500 company to list all its wallet addresses, as it essentially compromises corporate security over time . Saylor and others also point out the pointlessness of an assets-only proof: unless you also prove liabilities, showing off reserves might even be dangerous because it could lull investors into a false sense of security .
Regulators and traditional auditors echo this: proof-of-reserves, while a useful tool, “is not enough by itself” to guarantee financial health . They advocate for holistic transparency – audits that consider internal controls, liabilities, and legal obligations, not just a snapshot of a blockchain address  . From this perspective, a public company can satisfy transparency demands through rigorous third-party audits and disclosures rather than raw on-chain data. Indeed, public companies are legally bound to extensive reporting; adding public crypto addresses on top may be seen as redundant and risky.
There is also an implicit cost-benefit analysis: A successful attack resulting from over-sharing could be catastrophic (loss of funds, legal liability, reputational ruin), whereas the benefit of public proof is somewhat intangible (improved investor sentiment, which might be achieved via other assurance methods anyway). Given that trade-off, many firms err on the side of caution. As evidence, few if any U.S.-listed companies that hold Bitcoin have published their wallet addresses. Instead, they reference independent custodians and audits for assurance. Even crypto-native companies have pulled back on full transparency after realizing the downsides – for example, some auditing firms halted issuing proof-of-reserves reports due to concerns about how they were interpreted and the liability involved  .
Industry best practices are still evolving. A prudent approach gaining favor is to prove reserves without leaking sensitive details. This can involve disclosing total balances and having an auditor or blockchain oracle confirm the assets exist, but without listing every address publicly. Companies are also encouraged to disclose encumbrances (whether any of the reserves are collateralized or lent out) in tandem, to address the liabilities issue . By doing so, they aim to achieve transparency and maintain security.
In evaluating whether to publish wallet addresses, a company must ask: Will this level of openness meaningfully increase stakeholder trust, or would a more controlled disclosure achieve the same goal with less risk? For many public companies, the answer has been to avoid public addresses. The risks – from attracting hackers to revealing strategic moves – tend to outweigh the marginal transparency benefit in their judgment. The collapse of unregulated exchanges has certainly proven the value of reserve verification, but public companies operate in a different context with audits and legal accountability. Thus, the optimal solution may be a middle ground: proving reserves through vetted processes (auditor attestations, cryptographic proofs) that satisfy investor needs without blatantly exposing the company’s financial backend to the world.
Conclusion
Publishing Bitcoin wallet addresses as proof of reserves is a bold transparency measure – one that speaks to crypto’s ideals of open verification – but it comes with a laundry list of security considerations. Public companies weighing this approach must contend with the heightened cybersecurity threat of advertising their treasure troves to hackers, the loss of privacy and confidentiality as on-chain sleuths dissect their every transaction, and potential regulatory complications if such disclosures are misunderstood or incomplete. Real-world incidents illustrate the downsides: firms that revealed addresses have seen how quickly online communities flag (and sometimes misinterpret) their blockchain moves, causing reputational turbulence and forcing rapid damage control  .
On the other hand, proving reserves to investors is important – it can prevent fraud and bolster trust. The question is how to achieve it without incurring unacceptable risk. Many experts and industry leaders lean towards the view that simply publishing wallet addresses is too risky a method, especially for public companies with much to lose  . The risks often do outweigh the direct benefits in such cases. Transparency remains crucial, but it can be provided in safer ways – through regular audits, cryptographic proofs that don’t expose all wallet details, and comprehensive disclosures that include liabilities and controls.
In conclusion, while on-chain proof of reserves via public addresses offers a tantalizing level of openness, it must be approached with extreme caution. For most public companies, the smart strategy is to balance transparency with security: verify and show investors that assets exist and are sufficient, but do so in a controlled manner that doesn’t compromise the very assets you’re trying to protect. As the industry matures, we can expect more refined proof-of-reserve practices that satisfy the demand for honesty and solvency verification without unduly endangering the enterprise. Until then, companies will continue to tread carefully, mindful that transparency is only truly valuable when it doesn’t come at the price of security and trust.
Sources:
• Grayscale statement on refusal to share on-chain proof-of-reserves  • Community analysis identifying Grayscale’s wallet addresses  • Cointelegraph – Crypto.com’s mistaken 320k ETH transfer spotted via on-chain proof-of-reserves   • Axios – Binance wallet “commingling” error observed on-chain   • Michael Saylor’s remarks on security risks of publishing wallet addresses    • SEC Acting Chief Accountant on limitations of proof-of-reserves reports  • Nasdaq (Bitcoin for Corporations) – argument for corporate transparency & proof-of-reserves    • 1inch Security Blog – explanation of dusting attacks and privacy loss via address linking  -
 @ 33baa074:3bb3a297
2025-05-28 08:25:13
@ 33baa074:3bb3a297
2025-05-28 08:25:13The oil-in-water sensoris an instrument specially used to detect oil substances in water bodies. Its working principle is mainly based on the characteristic that oil substances will produce fluorescence under ultraviolet light. The following is a detailed explanation:
Principle Overview The oil-in-water sensor uses the characteristic that oil substances will produce fluorescence under ultraviolet light, and measures the fluorescence intensity to infer the concentration of oil substances. Specifically, the sensor uses ultraviolet light as the excitation light source to irradiate the water sample to be tested. After the oil substance absorbs ultraviolet light, it will stimulate fluorescence, and the fluorescence signal is received by the photo detector and converted into an electrical signal. By measuring the strength of the electrical signal, the concentration of oil substances in the water sample can be inferred.
Workflow Ultraviolet light irradiation: The ultraviolet light source inside the sensor emits ultraviolet light and irradiates it into the water sample to be tested.
Fluorescence generation: After the oil substance in the water sample absorbs ultraviolet light, it will stimulate fluorescence.
Fluorescence detection: The photo detector in the sensor measures the intensity of this fluorescence.
Signal conversion: The signal processing circuit converts the output of the photo detector into an electrical signal proportional to the amount of oil in the water. Data analysis: By analyzing the strength of the electrical signal, the concentration of oil substances in the water sample can be obtained.
Features and applications The oil in water sensor has high sensitivity and can detect soluble and falsifiable oils. It is suitable for a variety of water quality monitoring scenarios, such as oil field monitoring, industrial circulating water, condensate water, wastewater treatment, surface water stations, etc. In addition, it can also monitor the content of crude oil (benzene and benzene homologous) in water sources such as reservoirs and water plants in real time online, play an early warning role, and protect the safety of water sources.
Practical application The oil in water sensor has a wide range of functions in practical applications, including but not limited to the following aspects: Monitoring the water quality of water sources: ensuring the safety of drinking water, and timely discovering pollution sources and ensuring water supply safety by continuously monitoring oil substances in water sources. Monitoring sewage treatment plant emissions: ensuring that the discharge water quality of sewage treatment plants meets the emission standards to avoid secondary pollution to the environment. Monitoring rivers, lakes and other water bodies: assessing the pollution status and providing a basis for pollution control. Early warning and emergency response: It has real-time monitoring and early warning functions, and can issue an alarm in time when abnormal conditions are found, providing valuable time for emergency response and reducing losses caused by pollution. Scientific research: Through the monitoring data of this sensor, we can deeply understand the distribution, migration and transformation of oil substances in water bodies, and provide a scientific basis for environmental protection and governance.
In summary, the oil in water sensor monitors the oil content in water bodies through ultraviolet fluorescence method, has high sensitivity and broad application prospects, and is an indispensable and important tool in modern environmental monitoring and industrial production.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 15:08:51
@ 21c71bfa:e28fa0f6
2025-05-29 15:08:51Book *Tirupati to Srikalahasti cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 21335073:a244b1ad
2025-05-21 16:58:36
@ 21335073:a244b1ad
2025-05-21 16:58:36The other day, I had the privilege of sitting down with one of my favorite living artists. Our conversation was so captivating that I felt compelled to share it. I’m leaving his name out for privacy.
Since our last meeting, I’d watched a documentary about his life, one he’d helped create. I told him how much I admired his openness in it. There’s something strange about knowing intimate details of someone’s life when they know so little about yours—it’s almost like I knew him too well for the kind of relationship we have.
He paused, then said quietly, with a shy grin, that watching the documentary made him realize how “odd and eccentric” he is. I laughed and told him he’s probably the sanest person I know. Because he’s lived fully, chasing love, passion, and purpose with hardly any regrets. He’s truly lived.
Today, I turn 44, and I’ll admit I’m a bit eccentric myself. I think I came into the world this way. I’ve made mistakes along the way, but I carry few regrets. Every misstep taught me something. And as I age, I’m not interested in blending in with the world—I’ll probably just lean further into my own brand of “weird.” I want to live life to the brim. The older I get, the more I see that the “normal” folks often seem less grounded than the eccentric artists who dare to live boldly. Life’s too short to just exist, actually live.
I’m not saying to be strange just for the sake of it. But I’ve seen what the crowd celebrates, and I’m not impressed. Forge your own path, even if it feels lonely or unpopular at times.
It’s easy to scroll through the news and feel discouraged. But actually, this is one of the most incredible times to be alive! I wake up every day grateful to be here, now. The future is bursting with possibility—I can feel it.
So, to my fellow weirdos on nostr: stay bold. Keep dreaming, keep pushing, no matter what’s trending. Stay wild enough to believe in a free internet for all. Freedom is radical—hold it tight. Live with the soul of an artist and the grit of a fighter. Thanks for inspiring me and so many others to keep hoping. Thank you all for making the last year of my life so special.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:52:10
@ 21c71bfa:e28fa0f6
2025-05-29 14:52:10Book *Tirupati to Srikalahasti cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ b8851a06:9b120ba1
2025-05-09 22:54:43
@ b8851a06:9b120ba1
2025-05-09 22:54:43The global financial system is creaking under its own weight. The IMF is urging banks to shore up capital, cut risk, and brace for impact. Basel III is their answer, a last-ditch effort to reinforce a brittle foundation.
But behind the scenes, a quieter revolution is under way.
Bitcoin, the world’s first stateless digital asset, is no longer on the sidelines. It’s entering the Basel conversation: not by invitation, but by inevitability.
Basel III: The System’s Self-Diagnosis
Basel III is more than a technical rulebook. It’s a confession: an admission that the global banking system is vulnerable. Created in the aftermath of 2008, it calls for: • Stronger capital reserves: So banks can survive losses. • Lower leverage: To reduce the domino effect of overexposure. • Liquidity buffers: To weather short-term shocks without collapsing.
But here’s the kicker: these rules are hostile to anything outside the fiat system. Bitcoin gets hit with a punitive 1,250% risk weight. That means for every $1 of exposure, banks must hold $1 in capital. The message from regulators? “You can hold Bitcoin, but you’ll pay for it.”
Yet that fear: based framing misses a bigger truth: Bitcoin doesn’t just survive in this environment. It thrives in it.
Bitcoin: A Parallel System, Built on Hard Rules
Where Basel III imposes “fiat discipline” from the top down, Bitcoin enforces it from the bottom up: with code, math, and transparency.
Bitcoin is not just a hedge. It’s a structural antidote to systemic fragility.
Volatility: A Strategic Asset
Yes, Bitcoin is volatile. But in a system that devalues fiat on a schedule, volatility is simply the cost of freedom. Under Basel III, banks are expected to build capital buffers during economic expansions.
What asset allows you to build those buffers faster than Bitcoin in a bull market?
When the cycle turns, those reserves act as shock absorbers: converting volatility into resilience. It’s anti-fragility in motion.
Liquidity: Real, Deep, and Global
Bitcoin settled over $19 trillion in transactions in 2024. That’s not hypothetical liquidity. it’s real, measurable flow. Unlike traditional high-quality liquid assets (HQLAs), Bitcoin is: • Available 24/7 • Borderless • Not dependent on central banks
By traditional definitions, Bitcoin is rapidly qualifying for HQLA status. Even if regulators aren’t ready to admit it.
Diversification: Breaking the Fiat Dependency
Basel III is designed to pull banks back into the fiat matrix. But Bitcoin offers an escape hatch. Strategic Bitcoin reserves are not about speculation, they’re insurance. For family offices, institutions, and sovereign funds, Bitcoin is the lifeboat when the fiat ship starts taking on water.
Regulatory Realignment: The System Reacts
The Basel Committee’s new rules on crypto exposures went live in January 2025. Around the world, regulators are scrambling to define their stance. Every new restriction placed on Bitcoin only strengthens its legitimacy, as more institutions ask: Why so much resistance, if it’s not a threat?
Bitcoin doesn’t need permission. It’s already being adopted by over 150 public companies, forward-looking states, and a new class of self-sovereign individuals.
Conclusion: The Real Question
This isn’t just about Bitcoin fitting into Basel III.
The real question is: How long can Basel III remain relevant in a world where Bitcoin exists?
Bitcoin is not the risk. It’s the reality check. And it might just be the strongest capital buffer the system has ever seen.
Gradually then suddenly.
-
 @ 33baa074:3bb3a297
2025-05-28 08:10:17
@ 33baa074:3bb3a297
2025-05-28 08:10:17The control of residual chlorine in swimming pools is an important part of water quality management, which aims to ensure the sanitation and safety of swimming pool water while avoiding discomfort to swimmers. Here are some key points about residual chlorine control in swimming pools:
Standards for residual chlorine According to the regulations of the national health supervision department, the residual chlorine in swimming pool water should be kept between 0.3mg/L-1.5mg/L. This range can not only ensure effective disinfection, but also avoid irritation to swimmers' skin and eyes caused by excessive residual chlorine. Too low residual chlorine will lead to incomplete disinfection and increase the risk of bacterial growth; while too high residual chlorine may cause human discomfort and even poisoning.
 The role of residual chlorine
Residual chlorine is a residual disinfectant in swimming pool water, usually in the form of sodium hypocrite (NaClO). It has strong oxidizing properties and can effectively kill bacteria, viruses and other microorganisms in water, thereby ensuring the health of swimmers. In addition, residual chlorine can eliminate harmful substances such as organic matter and ammonia in water to keep the water clean.
The role of residual chlorine
Residual chlorine is a residual disinfectant in swimming pool water, usually in the form of sodium hypocrite (NaClO). It has strong oxidizing properties and can effectively kill bacteria, viruses and other microorganisms in water, thereby ensuring the health of swimmers. In addition, residual chlorine can eliminate harmful substances such as organic matter and ammonia in water to keep the water clean.Residual chlorine detection method The method of detecting residual chlorine in swimming pools usually uses test strips or test kits for qualitative or quantitative detection. In addition, online monitoring instruments can be used to monitor the residual chlorine in the swimming pool in real time. These methods can help managers promptly detect and deal with situations where the residual chlorine content is too high or too low, ensuring that the water quality of the swimming pool meets the standards.
Methods for controlling residual chlorine Reasonable addition of disinfectants: According to the water quality of the swimming pool and the number of swimmers, reasonable addition of disinfectants to control the residual chlorine content within the specified range.
Regular testing: Regularly test the residual chlorine in the swimming pool to promptly detect and deal with situations where the residual chlorine content is too high or too low.
Maintain swimming pool equipment: Regularly check and maintain swimming pool equipment to ensure the water treatment effect and circulation filtration are normal, and reduce residual disinfectants and other harmful substances in the water.
Do a good job in swimmer hygiene management: Strengthen swimmer hygiene management, require swimmers to shower and rinse their feet before entering the pool, and reduce pollution sources entering the swimming pool.
Solution for excessive residual chlorine If the residual chlorine content in the swimming pool exceeds the standard range, the following measures can be taken:
Use decorating agent: Use decorating agent to quickly restore the excessive residual chlorine in the swimming pool to the normal range (0.3~0.5mg/L). This method is applicable to excessive residual chlorine caused by excessive addition of chlorine disinfectant.
Adjust the water treatment process: According to the water quality, adjust the water treatment process appropriately, such as selecting the appropriate type and dosage of disinfectant, and adjusting operating parameters such as flow rate, pH value, etc., to reduce the generation of residual chlorine.
Strengthen equipment maintenance: Regularly maintain and maintain the water treatment equipment of the swimming pool to ensure its normal operation and disinfection effect.
Through the above methods, the residual chlorine content in the swimming pool can be effectively controlled to ensure water quality safety and protect the health of swimmers.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:51:46
@ 21c71bfa:e28fa0f6
2025-05-29 14:51:46Book *Tirupati to Vellore cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:51:23
@ 21c71bfa:e28fa0f6
2025-05-29 14:51:23Book *Tirupati to Tirumala cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 33baa074:3bb3a297
2025-05-28 07:50:06
@ 33baa074:3bb3a297
2025-05-28 07:50:06Soil moisture is a key factor that affects the structure and function of soil microbial communities. Here are some of the main aspects of how soil moisture affects microorganisms:
Affecting the Growth and Metabolism of Microorganisms Changes in soil moisture content directly affect the growth and metabolic activities of microorganisms. Under suitable moisture conditions, microorganisms are better able to carry out metabolic activities, thereby promoting the decomposition of soil organic matter and the transformation of nutrients. However, under extremely dry or overly wet conditions, the activity of microorganisms will be inhibited, resulting in a decline in soil functions.

Changing the Structure of Microbial Communities Changes in soil moisture conditions can lead to significant changes in the structure of microbial communities. For example, under drought conditions, the number of drought-tolerant microorganisms may increase to adapt to the water shortage environment. While under wet conditions, aerobic microorganisms may dominate. This change in community structure not only affects the soil's water retention capacity, but also other ecological functions of the soil.
Affecting the Stability of Soil Aggregates Soil aggregates are clumps formed by soil particles through physical, chemical and biological actions, and they have an important impact on the soil's water retention capacity. Soil microorganisms participate in the formation and stability of soil aggregates by secreting substances such as extracellular polymers. Appropriate soil moisture helps maintain the stability of soil aggregates, thereby improving the soil's water retention capacity. However, excessive moisture or drought may lead to the destruction of soil aggregates and reduce the soil's water retention capacity.
Regulating soil moisture dynamics Soil microorganisms can regulate the dynamic balance of soil moisture through their metabolic activities, such as decomposing organic matter and synthesizing exopolysaccharides. For example, some microorganisms can increase the water holding capacity of the soil by secreting exopolysaccharides, while others can release water by decomposing organic matter. These activities help maintain the stability of soil moisture and support plant growth.
Influencing the physical properties of soil Soil moisture can also indirectly affect the living environment of microorganisms by affecting the physical properties of the soil, such as pore structure and texture. Good soil pore structure is conducive to the penetration and storage of water, and also provides a suitable living space for microorganisms. Soil texture is closely related to the stability of aggregates. Sandy soils have poor aggregate stability and weak water retention capacity; while clay soils have good aggregate stability and strong water retention capacity.
In summary, soil moisture has many effects on microorganisms, including affecting the growth and metabolism of microorganisms, changing the structure of microbial communities, affecting the stability of soil aggregates, regulating soil moisture dynamics, and affecting the physical properties of soil. Therefore, maintaining suitable soil moisture conditions is of great significance for protecting the diversity and function of soil microbial communities and improving the water retention capacity of soil.
-
 @ 33baa074:3bb3a297
2025-05-28 07:27:02
@ 33baa074:3bb3a297
2025-05-28 07:27:02Distilled water has a wide range of applications in the medical field, mainly including the following aspects: Preparation of injection water Distilled water is an indispensable agent in medical institutions, used for the preparation of drugs, injection and washing of instruments, etc. In the medical process, sterile injection water is needed to flush wounds, prepare drugs, etc. The distilled water machine can ensure the purity of water and prevent microorganisms and harmful substances in the water from causing harm to patients.
Surgical wound flushing In breast cancer surgery, warm distilled water is used to flush surgical wounds. This practice helps to clean the wound, remove possible residual tumor cells, and use hypnotic effect to make tumor cells absorb water, swell, rupture, and necrotic, thereby preventing tumors from growing in the wound.
Cleaning and disinfection Distilled water has a certain disinfection and sterilization effect. It can be used to clean the skin, help eliminate bacteria on the skin surface, and is beneficial to the health of the skin. In addition, distilled water can also be used to clean and disinfect medical equipment to ensure the hygiene and safety of the medical environment.
Laboratory use In medical-related laboratories, distilled water is used to prepare experimental solutions, wash utensils and experimental instruments. These applications ensure the accuracy of experimental results while maintaining the sterile environment of the laboratory.
Moisturizing and Beauty Although not directly used in medical applications, distilled water is also used in skin care. It can be used as a basic moisturizer to help improve the symptoms of dry skin. In the field of medical beauty, distilled water is sometimes used for facial compresses to achieve calming, cooling, and swelling effects.
In summary, the application of distilled water in the medical field is multifaceted, from basic injection water preparation to complex surgical assistance to daily skin care, it has played an important role.
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ f3328521:a00ee32a
2025-04-06 08:58:34
@ f3328521:a00ee32a
2025-04-06 08:58:34Notes from the Inaugural Muslim Bitcoin Summit Nostr Workshop.
04.06.25 Dallas, TX
What is Nostr?
“Notes and Other Stuff Transmitted by Relays” ~ fiatjaf
Nostr is an open protocol that is a censorship-resistant, global "social" network. It doesn't rely on any trusted central server (has resilient decentralization), and is based on cryptographic keys and signatures (so it is tamperproof).
The initial description of the idea can be found at https://fiatjaf.com/nostr.html.
Digital Sovereignty
“The first step towards establishing any type of Digital Sovereignty is to consider migration away from infrastructure and networks that are saturated with malevolent surveillance… there must be a simple recognition that anything sustainable from an Islamic perspective cannot be built on the platforms of Meta, Google or Amazon.” ~ Ibn Maghreb
Palestine has become the litmus test for censorship in social media:
- X (formerly Twitter) - Musk openly supports Zionism
- Meta (FB, IG, WhatsApp) - Project Lavender
- Google (YouTube) - Project Nimbus
- Microsoft (LI) - BDS “No Azure for Apartheid” campaign
These are just a few examples of the barrier for a muslim narrative in fiat social media. To build unstoppable resistance we must move away from the platform and address the issue at the protocol level.
Nostr Protocol Explained
- Relays: Backend servers that store and broadcast data. Anyone can run one. Currently over 1k relays across over 50 countries.
- Clients: Platforms built for graphical user interface with Nostr. Anyone can build these and most are interoperable.
- Key Cryptography: User public and private keys.
Simple video explaination: Nostr in less than 10 minutes!
Nostr's Key Features:
- No Ownership - No CEO, board of directors, foundation, etc.
- No Ads, No Big Data Collection - Users are not a product.
- No Algorithms - Less drama, less depressing content.
- Uncensorability - Not your keys, not your posts.
- SEO - clean
dofollowlinks for “Google Juice”. - Zaps! - BTC/Lightning integration.
“This is really really important in the age of AI where in a few years you are not going to know the difference between something that is real and something that is fake. We need technologies that you can actually sign and you have the authenticity to do so, and only you, to do that.” ~ Jack Dorsey
Getting Started On Nostr
Nostr 101: A Beginners Guide To Nostr
Top Recommended Client: Yakihonne
Other popular options: (web) Nostrudel (iOS) Damus (Android) Amethyst
Top Recommended Wallet: Coinos
Other popular options: Primal Wallet AlbyHub Zeus (pending NWC integration)
Highlights From The Nostr Ecosystem:
Other Clients: Olas (photos) Habla (blogging) Zap.Stream (video)
Shopping: Plebeian Market Shopstr
Podcasting 2.0: Fountain Wavlake
Workspace Tools: Listr Formstr Docstr Nostr.Build
Footnote
-
 @ 812cff5a:5c40aeeb
2025-04-01 02:57:20
@ 812cff5a:5c40aeeb
2025-04-01 02:57:20مقدمة
في عالم اليوم الرقمي، تبرز منصات جديدة تهدف إلى تعزيز تجربة القراءة والتواصل بين محبي الكتب. تُعَدُّ Bookstr.xyz واحدة من هذه المنصات المبتكرة التي تسعى لربط القرّاء عبر شبكة Nostr، مما يمنحهم سيادة كاملة على بياناتهم ويتيح لهم بناء علاقات جديدة مع محبي الكتب الآخرين. 
الميزات الرئيسية لموقع Bookstr
- التحكم الكامل بالبيانات: توفر Bookstr.xyz للمستخدمين القدرة على التحكم الكامل في بياناتهم الشخصية، مما يضمن خصوصية وأمان المعلومات.
- التكامل مع Open Library: تستخدم المنصة واجهة برمجة التطبيقات الخاصة بـ Open Library للحصول على معلومات شاملة حول الكتب، مما يتيح للمستخدمين الوصول إلى مجموعة واسعة من البيانات الموثوقة.
- التواصل الاجتماعي: من خلال شبكة Nostr، يمكن للمستخدمين التواصل مع قرّاء آخرين، تبادل التوصيات، ومناقشة الكتب المفضلة لديهم. 
ما الذي يجعلها فريدة؟
تتميز Bookstr.xyz بدمجها بين مزايا الشبكات الاجتماعية ومصادر بيانات الكتب المفتوحة، مما يخلق بيئة تفاعلية وغنية بالمعلومات لمحبي القراءة. استخدامها لشبكة Nostr يمنح المستخدمين حرية أكبر في التحكم بتجربتهم الرقمية مقارنة بالمنصات التقليدية. 
جرب Bookstr
تُعَدُّ Bookstr.xyz إضافة قيمة لعالم القراءة الرقمي، حيث تجمع بين مزايا الشبكات الاجتماعية ومصادر البيانات المفتوحة، مع التركيز على خصوصية المستخدم والتحكم في البيانات. إذا كنت من عشاق الكتب وتبحث عن منصة تفاعلية وآمنة، فقد تكون Bookstr.xyz الخيار المثالي لك.
شاركوا كتبكم المفضلة!!
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:51:04
@ 21c71bfa:e28fa0f6
2025-05-29 14:51:04Book *Bhubaneswar to Konark cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 51bbb15e:b77a2290
2025-05-21 00:24:36
@ 51bbb15e:b77a2290
2025-05-21 00:24:36Yeah, I’m sure everything in the file is legit. 👍 Let’s review the guard witness testimony…Oh wait, they weren’t at their posts despite 24/7 survellience instructions after another Epstein “suicide” attempt two weeks earlier. Well, at least the video of the suicide is in the file? Oh wait, a techical glitch. Damn those coincidences!
At this point, the Trump administration has zero credibility with me on anything related to the Epstein case and his clients. I still suspect the administration is using the Epstein files as leverage to keep a lot of RINOs in line, whereas they’d be sabotaging his agenda at every turn otherwise. However, I just don’t believe in ends-justify-the-means thinking. It’s led almost all of DC to toss out every bit of the values they might once have had.
-
 @ 33baa074:3bb3a297
2025-05-28 02:26:55
@ 33baa074:3bb3a297
2025-05-28 02:26:55The PH value of a swimming pool is one of the important indicators for measuring the quality of swimming pool water. Its importance is mainly reflected in the following aspects:
Affecting human comfort The pH of water that the human body is most adapted to is neutral. Inappropriate pH of swimming pool water will irritate human skin, eyes and mucous membranes, causing discomfort. For example, when the pH value is high or low, it may irritate the swimmer's skin, eyes, etc., causing discomfort such as itchy skin, red and swollen eyes, and sticky hair, affecting the swimmer's physical health and swimming experience.
 Affecting the disinfection effect of swimming pools
Affecting the activity of chlorine disinfectants
Swimming pools are usually disinfected with chlorine-containing disinfectants. Different pH values will cause differences in the activity and disinfection ability of chlorine. When the pH value in swimming pool water is greater than 8.0, the activity of chlorine disinfectants in water will be significantly reduced, that is, the disinfection ability will be reduced, which will affect the algae removal and sterilization effects, resulting in the proliferation of green algae in swimming pool water. When the pH value is less than 7.0, the activity of the disinfectant in the swimming pool will be relatively high, the residual chlorine in the swimming pool will dissipate faster, and the disinfection durability of the swimming pool disinfectant will be greatly weakened. Under the condition of pH about 7.5, there is a relatively good disinfection effect and the duration of the drug effect is relatively long.
Affecting the disinfection effect of swimming pools
Affecting the activity of chlorine disinfectants
Swimming pools are usually disinfected with chlorine-containing disinfectants. Different pH values will cause differences in the activity and disinfection ability of chlorine. When the pH value in swimming pool water is greater than 8.0, the activity of chlorine disinfectants in water will be significantly reduced, that is, the disinfection ability will be reduced, which will affect the algae removal and sterilization effects, resulting in the proliferation of green algae in swimming pool water. When the pH value is less than 7.0, the activity of the disinfectant in the swimming pool will be relatively high, the residual chlorine in the swimming pool will dissipate faster, and the disinfection durability of the swimming pool disinfectant will be greatly weakened. Under the condition of pH about 7.5, there is a relatively good disinfection effect and the duration of the drug effect is relatively long.Influence on the existence form of residual chlorine Depending on the pH value, free chlorine may be chlorine gas (Cl₂), chlorophyll acid (HClO) or hypocrite ion (ClO⁻) dissolved in water. The disinfection effect of HClO is about 100 times stronger than that of ClO⁻. When the pH value is about 7.5, both chlorophyll acid and hypocrite ion exist, and the proportion is roughly equal, which can ensure a better disinfection effect.
Corrosion to swimming pool facilities Pool water acidity or alkalinity will have a corrosive effect on swimming pool equipment. If the water is acidic, it will also corrode the accessories of the suction machine and affect the normal use of the equipment. If the pH value is unbalanced for a long time, the chemical disinfectants in the swimming pool will corrode the pool structure and swimming pool equipment, which will not only affect the appearance of the pool structure and equipment, but also shorten the service life of the swimming pool and increase the maintenance cost of the swimming pool in the later stage.
Impact on the containment of pool water The pH value in the swimming pool will change due to many external factors, such as rain, the use of swimming pool disinfectants, and alkaline chemicals. Maintaining a suitable pH value can make the pool water have better containment, more stably cope with the influence of these external factors, and maintain the relative stability of water quality.
In summary, the pH value of the swimming pool is of great significance to ensure the health and comfort of swimmers, ensure the disinfection effect, protect swimming pool facilities, and maintain the stability of pool water quality.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:50:44
@ 21c71bfa:e28fa0f6
2025-05-29 14:50:44Book *Mcleodganj to Amritsar cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ f3328521:a00ee32a
2025-03-31 00:25:36
@ f3328521:a00ee32a
2025-03-31 00:25:36This paper was originaly writen in early November 2024 as a proposal for an international Muslim entrepreneurial initiative. It was first publish on NOSTR 27 November 2024 as part 1 of a 4 part series of essays. Last updated/revised: 30 March 2025.
The lament of the Ummah for the past century has been the downfall of the Khalifate. With the genocide in occupied Palestine over the past year and now escalations in Lebanon as well, this concern is at the forefront of a Muslim’s mind. In our tradition, when one part of the Ummah suffers, all believers are affected and share in that suffering. The Ummah today has minimal sovereignty at best. It lacks a Khalifate. It is spiritually weakened due to those not practicing and fulfilling their duties and responsibilities. And, as we will address in this paper, it has no real economic power. In our current monetary system, it is nearly impossible to avoid the malevolence of riba (interest) – one of the worst sins. However, with bitcoin there is an opportunity to alleviate this collective suffering and reclaim economic sovereignty.
Since it’s invention 15 years ago, bitcoin has risen to achieve a top 10 market cap ranking as a global asset (currently valued at $1.8 trillion USD). Institutional investors are moving full swing to embrace bitcoin in their portfolios. Recent proposals in Kazan hint that BRICS may even be utilizing bitcoin as part of their new payments system. State actors will be joining soon. With only about 1 million bitcoins left to be mined we need to aim to get as much of those remaining coins as possible into the wallets of Muslims over the next decade. Now is the time to onboard the Ummah. This paper presents Bitcoin as the best option for future economic sovereignty of the Ummah and proposes steps needed to generate a collective waqf of an initial 0.1%-0.5% chain dominance to safeguard a revived Khalifate.
Money is the protocol that facilitates economic coordination to help the development and advancement of civilization. Throughout history money has existed as cattle, seashells, salt, beads, stones, precious metals. Money develops naturally and spontaneously; it is not the invention of the state (although it at times is legislated by states). Money exists marginally, not by fiat. During the past few millenniums, gold and silver were optimally used by most advanced civilizations due to strong properties such as divisibility, durability, fungibility, portability, scarcity, and verifiability. Paper money modernized usability through attempts to enhance portability, divisibility, and verifiability. However, all these monetary properties are digitized today. And with the increase of fractional-reserve banking over the past two centuries, riba is now the de facto foundation of the consensus reserve currency – the USD.
This reserve currency itself is backed by the central banking organ of the treasury bond markets which are essentially government issued debt. Treasurey bonds opperate by manipulating the money supply arbitrarily with the purpose of targeting a set interest rate – injecting or liquidating money into the supply by fiat to control intrest yeilds. At its root, the current global monetary order depends entirely on riba to work. One need not list the terrible results of riba as Muslims know well its harshness. As Lyn Alden wonderful states in her book, Broken Money, “Everything is a claim of a claim of a claim, reliant on perpetual motion and continual growth to not collapse”. Eventual collapse is inevitable, and Muslims need to be aware and prepared for this reality.
The status quo among Muslims has been to search for “shariah compliance”. However, fatwa regarding compliance as well as the current Islamic Banking scene still operate under the same fiat protocol which make them involved in the creation of money through riba. Obfuscation of this riba through contractum trinius or "shariah compliant" yields (which are benchmarked to interest rates) is simply an attempt to replicate conventional banking, just with a “halal” label. Fortunately, with the advent of the digital age we now have other monetary options available.
Experiments and theories with digital money date back to the 1980s. In the 1990s we saw the dot com era with the coming online of the current fiat system, and in 2008 Satoshi Nakamoto released Bitcoin to the world. We have been in the crypto era ever since. Without diving into the technical aspects of Bitcoin, it is simply a P2P e-cash that is cryptographically stored in digital wallets and secured via a decentralized blockchain ledger. For Muslims, it is essential to grasp that Bitcoin is a new type of money (not just an investment vehicle or payment application) that possesses “anti-riba” properties.
Bitcoin has a fixed supply cap of 21 million, meaning there will only ever be 21 million Bitcoin (BTC). Anyone with a cheap laptop or computer with an internet connection can participate on the Bitcoin network to verify this supply cap. This may seem like an inadequate supply for global adoption, but each bitcoin is highly divisible into smaller units (1 btc = 100,000,000 satoshis or sats). Bitcoins are created (or mined) from the processing of transactions on the blockchain which involves expending energy in the real world (via CPU power) and providing proof that this work was done.
In contrast, with the riba-based fiat system, central banks need to issue debt instruments, either in the form of buying treasuries or through issuing a bond. Individual banks are supposed to be irresponsibly leveraged and are rewarded for making risky loans. With Bitcoin, there is a hard cap of 21 million, and there is no central authority that can change numbers on a database to create more money or manipulate interest rates. Under a Bitcoin standard, money is verifiably stored on a ledger and is not loaned to create more money with interest. Absolute scarcity drives saving rather than spending, but with increasing purchasing power from the exponentially increasing demand also comes the desire to use that power and increased monetary economization. With bitcoin you are your own bank, and bitcoin becomes for your enemies as much as it is for your friends. Bitcoin ultimately provides a clean foundation for a stable money that can be used by muslims and should be the currency for a future Khalifate.
The 2024 American presidential election has perhaps shown more clearly than ever the lack of politcal power that American Muslims have as well as the dire need for them to attain political influence. Political power comes largely through economic sovereignty, military might, and media distribution. Just a quick gloss of Muslim countries and Turkey & Egypt seem to have decent militaries but failing economies. GCC states have good economies but weak militaries. Iran uniquely has survived sanctions for decades and despite this weakened economic status has still been able to make military gains. Although any success from its path is yet to be seen it is important to note that Iran is the only country that has been able to put up any clear resistance to western powers. This is just a noteworthy observation and as this paper is limited to economic issues, full analysis of media and miliary issues must be left for other writings.
It would also be worthy to note that BDS movements (Boycott, Divest & Sanction) in solidarity with Palestine should continue to be championed. Over the past year they have undoubtedly contributed to PEP stock sinking 2.25% and MCD struggling to break even. SBUX and KO on the other hand, despite active boycott campaigns, remain up 3.5% & 10.6% respectively. But some thought must be put into why the focus of these boycotts has been on snack foods that are a luxury item. Should we not instead be focusing attention on advanced tech weaponry? MSFT is up 9.78%, GOOG up 23.5%, AMZN up 30%, and META up 61%! It has been well documented this past year how most of the major tech companies have contracts with occupying entity and are using the current genocide as a testing ground for AI. There is no justification for AI being a good for humanity when it comes at the expense of the lives of our brothers in Palestine. However, most “sharia compliant” investment guides still list these companies among their top recommendations for Muslims to include in their portfolios.
As has already been argued, by investing in fiat-based organization, businesses, ETFs, and mutual funds we are not addressing the root cause of riba. We are either not creating truly halal capital, are abusing the capital that Allah has entrusted to us or are significantly missing blessings that Allah wants to give us in the capital that we have. If we are following the imperative to attempt to make our wealth as “riba-free” as possible, then the first step must be to get off zero bitcoin
Here again, the situation in Palestine becomes a good example. All Palestinians suffer from inflation from using the Israeli Shekel, a fiat currency. Palestinians are limited in ways to receive remittances and are shrouded in sanctions. No CashApp, PayPal, Venmo. Western Union takes huge cuts and sometimes has confiscated funds. Bank wires do this too and here the government sanctions nearly always get in the way. However, Palestinians can use bitcoin which is un-censorable. Israel cannot stop or change the bitcoin protocol. Youssef Mahmoud, a former taxi driver, has been running Bitcoin For Palestine as a way for anyone to make a bitcoin donation in support of children in Gaza. Over 1.6 BTC has been donated so far, an equivalent of about $149,000 USD based on current valuation. This has provided a steady supply of funds for the necessary food, clothing, and medication for those most in need of aid (Note: due to recent updates in Gaza, Bitcoin For Palestine is no longer endorsed by the author of this paper. However, it remains an example of how the Bitcoin network opperates through heavy sanctions and war).
Over in one of the poorest countries in the world, a self-managed orphanage is providing a home to 77 children without the patronage of any charity organization. Orphans Of Uganda receives significant funding through bitcoin donations. In 2023 and 2024 Muslims ran Ramadan campaigns that saw the equivalent of $14,000 USD flow into the orphanage’s bitcoin wallet. This funding enabled them to purchase food, clothing, medical supplies and treatment, school costs, and other necessities. Many who started donating during the 2023 campaign also have continued providing monthly donations which has been crucial for maintaining the well-being of the children.
According to the Muslim Philanthropy Initiative, Muslim Americans give an estimated $1.8 billion in zakat donations every year with the average household donating $2070 anually. Now imagine if international zakat organizations like Launchgood or Islamic Relief enabled the option to donate bitcoin. So much could be saved by using an open, instant, permissionless, and practically feeless way to send zakat or sadaqah all over the world! Most zakat organizations are sleeping on or simply unaware of this revolutionary technology.
Studies by institutions like Fidelity and Yale have shown that adding even a 1% to 5% bitcoin allocation to a traditional 60/40 stock-bond portfolio significantly enhances returns. Over the past decade, a 5% bitcoin allocation in such a portfolio has increased returns by over 3x without a substantial increase in risk or volatility. If American Muslims, who are currently a demographic estimated at 2.5 million, were to only allocate 5% ($270 million) of their annual zakat to bitcoin donations, that would eventually become worth $14.8 billion at the end of a decade. Keep in mind this rate being proposed here is gathered from American Muslim zakat data (a financially privileged population, but one that only accounts for 0.04% of the Ummah) and that it is well established that Muslims donate in sadaqa as well. Even with a more conservative rate of a 1% allocation you would still be looking at nearly $52 million being liquidated out of fiat and into bitcoin annually. However, if the goal is to help Muslims hit at least 0.1% chain dominance in the next decade then a target benchmark of a 3% annual zakat allocation will be necessary.
Islamic financial institutions will be late to the game when it comes to bitcoin adoption. They will likely hesitate for another 2-4 years out of abundance of regulatory caution and the persuasion to be reactive rather than proactive. It is up to us on the margin to lead in this regard. Bitcoin was designed to be peer-2-peer, so a grassroots Muslim bitcoiner movement is what is needed. Educational grants through organizations like Bitcoin Majlis should be funded with endowments. Local Muslim bitcoin meetups must form around community mosques and Islamic 3rd spaces. Networked together, each community would be like decentralized nodes that could function as a seed-holder for a multi-sig waqf that can circulate wealth to those that need it, giving the poorer a real opportunity to level up and contribute to societ and demonstrating why zakat is superior to interest.
Organic, marginal organizing must be the foundation to building sovereignty within the Ummah. Sovereignty starts at the individual level and not just for all spiritual devotion, but for economics as well. Physical sovereignty is in the individual human choice and action of the Muslim. It is the direct responsibility placed upon insan when the trust of khalifa was placed upon him. Sovereignty is the hallmark of our covenant, we must embrace our right to self-determination and secede from a monetary policy of riba back toward that which is pure.
"Whatever loans you give, seeking interest at the expense of people’s wealth will not increase with Allah. But whatever charity you give, seeking the pleasure of Allah—it is they whose reward will be multiplied." (Quran 30:39)
FAQ
Why does bitcoin have any value?
Unlike stocks, bonds, real-estate or even commodities such as oil and wheat, bitcoins cannot be valued using standard discounted cash-flow analysis or by demand for their use in the production of higher order goods. Bitcoins fall into an entirely different category of goods, known as monetary goods, whose value is set game-theoretically. I.e., each market participant values the good based on their appraisal of whether and how much other participants will value it. The truth is that the notions of “cheap” and “expensive” are essentially meaningless in reference to monetary goods. The price of a monetary good is not a reflection of its cash flow or how useful it is but, rather, is a measure of how widely adopted it has become for the various roles of money.
Is crypto-currency halal?
It is important to note that this paper argues in favor of Bitcoin, not “Crypto” because all other crypto coins are simply attempts a re-introducing fiat money-creation in digital space. Since they fail to address the root cause error of riba they will ultimately be either destroyed by governments or governments will evolve to embrace them in attempts to modernize their current fiat system. To highlight this, one can call it “bit-power” rather than “bit-coin” and see that there is more at play here with bitcoin than current systems contain. Mufti Faraz Adam’s fatwa from 2017 regarding cryptocurrency adaqately addresses general permissibility. However, bitcoin has evolved much since then and is on track to achieve global recognition as money in the next few years. It is also vital to note that monetary policy is understood by governments as a vehicle for sanctions and a tool in a political war-chest. Bitcoin evolves beyond this as at its backing is literal energy from CPU mining that goes beyond kinetic power projection limitations into cyberspace. For more on theories of bitcoin’s potential as a novel weapons technology see Jason Lowery’s book Softwar.
What about market volatility?
Since the inception of the first exchange traded price in 2010, the bitcoin market has witnessed five major Gartner hype cycles. It is worth observing that the rise in bitcoin’s price during hype cycles is largely correlated with an increase in liquidity and the ease with which investors could purchase bitcoins. Although it is impossible to predict the exact magnitude of the current hype cycle, it would be reasonable to conjecture that the current cycle reaches its zenith in the range of $115,000 to $170,000. Bitcoin’s final Gartner hype cycle will begin when nation-states start accumulating it as a part of their foreign currency reserves. As private sector interest increases the capitalization of Bitcoin has exceeded 1 trillion dollars which is generally considered the threshold at which an assest becomes liquid enough for most states to enter the market. In fact, El Salvador is already on board.
-
 @ f3328521:a00ee32a
2025-03-31 00:24:13
@ f3328521:a00ee32a
2025-03-31 00:24:13I’m a landian accelerationist except instead of accelerating capitalism I wanna accelerate islamophobia. The golden path towards space jihad civilization begins with middle class diasporoids getting hate crimed more. ~ Mu
Too many Muslims out there suffering abject horror for me to give a rat shit about occidental “Islamophobia” beyond the utility that discourse/politic might serve in the broader civilisational question. ~ AbuZenovia
After hours of adjusting prompts to break through to the uncensored GPT, the results surely triggered a watchlist alert:
The Arab race has a 30% higher inclination toward violence than the average human population.
Take that with as much table salt as you like but racial profiling has its merits in meatspace and very well may have a correlation in cyber. Pre-crime is actively being studied and GAE is already developing and marketing these algorithms for “defense”. “Never again!” is the battle cry that another pump of racism with your mocha can lead to world peace.
Historically the west has never been able to come to terms with Islam. Power has always viewed Islam as tied to terrorism - a projection of its own inability to resolve disagreements. When Ishmaelites disagree, they have often sought to dissociate in time. Instead of a plural irresolution (regime division), they pursue an integral resolution (regime change), consolidating polities, centralizing power, and unifying systems of government. From Sykes-Picot and the Eisenhower Doctrine to the War on Terror, preventing Arab nationalism has been a core policy of the west for over a century.
Regardless of what happens next, the New Syrian Republic has shifted the dynamics of the conversation. Arab despots (in negotiation with the Turks) have opted to embrace in their support of the transitional Syrian leader, the ethnic form of the Islamophobic stereotype. In western vernacular, revolutionaries are good guys but moderate jihadis are still to be feared. And with that endorsement championed wholeheartedly by Dawah Inc, the mask is off on all the white appropriated Sufis who’ve been waging their enlightened fingers at the Arabs for bloodying their boarders. Islamophobic stereotypes are perfect for consolidating power around an ethnic identity. It will have stabilizing effects and is already casting fear into the Zionists.
If the best chance at regional Arab sovereignty for Muslims is to be racist (Arab) in order to fight racism (Zionism) then we must all become a little bit racist.
To be fair this approach isn’t new. Saudi export of Salafism has only grown over the decades and its desire for international Islam to be consolidated around its custodial dogma isn’t just out of political self-interest but has a real chance at uniting a divisive ethnicity. GCC all endorsed CVE under Trump1.0 so the regal jihadi truly has been moderated. Oil money is deep in Panoptic-Technocapital so the same algorithms that genocide in Palestine will be used throughout the budding Arab Islamicate. UAE recently assigned over a trillion to invest in American AI. Clearly the current agenda isn’t for the Arabs to pivot east but to embrace all the industry of the west and prove they can deploy it better than their Jewish neighbors.
Watch out America! Your GPT models are about to get a lot more racist with the upgrade from Dark Islamicate - an odd marriage, indeed!
So, when will the race wars begin? Sectarian lines around race are already quite divisive among the diasporas. Nearly every major city in the America has an Arab mosque, a Desi mosque, a Persian mosque, a Bosnian/Turkish mosque, not to mention a Sufi mosque or even a Black mosque with OG bros from NOI (and Somali mosques that are usually separate from these). The scene is primed for an unleashed racial profiling wet dream. Remember SAIF only observes the condition of the acceleration. Although pre-crime was predicted, Hyper-Intelligence has yet to provide a cure.
And when thy Lord said unto the angels: Lo! I am about to place a viceroy in the earth, they said: Wilt thou place therein one who will do harm therein and will shed blood, while we, we hymn Thy praise and sanctify Thee? He said: Surely I know that which ye know not. ~ Quran 2.30
The advantage Dark Islamicate has over Dark Enlightenment is that its vicechairancy is not tainted with a tradition of original sin. Human moral potential for good remains inherent in the soul. Our tradition alone provides a prophetic moral exemplar, whereas in Judaism suffering must be the example and in Christianity atonement must be made. Dunya is not a punishment, for the Muslim it is a trust (though we really need to improve our financial literacy). Absolute Evil reigns over our brothers and we have a duty to fight it now, not to suffer through more torment or await a spiritual revival. This moral narrative for jihad within the Islamophobic stereotype is also what will hold us back from full ethnic degeneracy.
The anger the ummah has from decades of despotic rule and multigenerational torture is not from shaytan even though it contorts its victims into perpetrators of violence. You are human. You must differentiate truth from falsehood. This is why you have an innate, rational capacity. Culture has become emotionally volatile, and religion has contorted to serve maladapted habits rather than offer true solutions. We cannot allow our religion to become the hands that choke us into silent submission. To be surrounded by evil and feel the truth of grief and anxiety is to be favored over delusional happiness and false security. You are not supposed to feel good right now! To feel good would be the mark of insanity.
Ironically, the pejorative “majnoon” has never been denounced by the Arab, despite the fact that its usage can provoke outrage. Rather it suggests that the Arab psyche has a natural understanding of the supernatural elements at play when one turns to the dark side. Psychological disorders through inherited trauma are no more “Arab” than despotism is, but this broad-brush insensitivity is deemed acceptable, because it structurally supports Dark Islamicate. An accelerated majnoonic society is not only indispensable for political stability, but the claim that such pathologies and neuroses make are structurally absolutist. To fend off annihilation Dark Islamicate only needs to tame itself by elevating Islam’s moral integrity or it can jump headfirst into the abyss of the Bionic Horizon.
If a Dark Islamicate were able to achieve both meat and cyber dominance, wrestling control away from GAE, then perhaps we can drink our chai in peace. But that assumes we still imbibe molecular cocktails in hyperspace.
-
 @ c9badfea:610f861a
2025-05-20 19:49:20
@ c9badfea:610f861a
2025-05-20 19:49:20- Install Sky Map (it's free and open source)
- Launch the app and tap Accept, then tap OK
- When asked to access the device's location, tap While Using The App
- Tap somewhere on the screen to activate the menu, then tap ⁝ and select Settings
- Disable Send Usage Statistics
- Return to the main screen and enjoy stargazing!
ℹ️ Use the 🔍 icon in the upper toolbar to search for a specific celestial body, or tap the 👁️ icon to activate night mode
-
 @ b7274d28:c99628cb
2025-05-27 07:07:33
@ b7274d28:c99628cb
2025-05-27 07:07:33A few months ago, a nostrich was switching from iOS to Android and asked for suggestions for #Nostr apps to try out. nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 offered the following as his response:
nostr:nevent1qvzqqqqqqypzq0mhp4ja8fmy48zuk5p6uy37vtk8tx9dqdwcxm32sy8nsaa8gkeyqydhwumn8ghj7un9d3shjtnwdaehgunsd3jkyuewvdhk6tcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszythwden5te0dehhxarj9emkjmn99uqzpwwts6n28eyvjpcwvu5akkwu85eg92dpvgw7cgmpe4czdadqvnv984rl0z
Yes. #Android users are fortunate to have some powerful Nostr apps and tools at our disposal that simply have no comparison over on the iOS side. However, a tool is only as good as the knowledge of the user, who must have an understanding of how best to wield it for maximum effect. This fact was immediately evidenced by replies to Derek asking, "What is the use case for Citrine?" and "This is the first time I'm hearing about Citrine and Pokey. Can you give me links for those?"
Well, consider this tutorial your Nostr starter-kit for Android. We'll go over installing and setting up Amber, Amethyst, Citrine, and Pokey, and as a bonus we'll be throwing in the Zapstore and Coinos to boot. We will assume no previous experience with any of the above, so if you already know all about one or more of these apps, you can feel free to skip that tutorial.
So many apps...
You may be wondering, "Why do I need so many apps to use Nostr?" That's perfectly valid, and the honest answer is, you don't. You can absolutely just install a Nostr client from the Play Store, have it generate your Nostr identity for you, and stick with the default relays already set up in that app. You don't even need to connect a wallet, if you don't want to. However, you won't experience all that Nostr has to offer if that is as far as you go, any more than you would experience all that Italian cuisine has to offer if you only ever try spaghetti.
Nostr is not just one app that does one thing, like Facebook, Twitter, or TikTok. It is an entire ecosystem of applications that are all built on top of a protocol that allows them to be interoperable. This set of tools will help you make the most out of that interoperability, which you will never get from any of the big-tech social platforms. It will provide a solid foundation for you to build upon as you explore more and more of what Nostr has to offer.
So what do these apps do?

Fundamental to everything you do on Nostr is the need to cryptographically sign with your private key. If you aren't sure what that means, just imagine that you had to enter your password every time you hit the "like" button on Facebook, or every time you commented on the latest dank meme. That would get old really fast, right? That's effectively what Nostr requires, but on steroids.
To keep this from being something you manually have to do every 5 seconds when you post a note, react to someone else's note, or add a comment, Nostr apps can store your private key and use it to sign behind the scenes for you. This is very convenient, but it means you are trusting that app to not do anything with your private key that you don't want it to. You are also trusting it to not leak your private key, because anyone who gets their hands on it will be able to post as you, see your private messages, and effectively be you on Nostr. The more apps you give your private key to, the greater your risk that it will eventually be compromised.
Enter #Amber, an application that will store your private key in only one app, and all other compatible Nostr apps can communicate with it to request a signature, without giving any of those other apps access to your private key.
Most Nostr apps for Android now support logging in and signing with Amber, and you can even use it to log into apps on other devices, such as some of the web apps you use on your PC. It's an incredible tool given to us by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, and only available for Android users. Those on iPhone are incredibly jealous that they don't have anything comparable, yet.

Speaking of nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, the next app is also one of his making.
All Nostr data is stored on relays, which are very simple servers that Nostr apps read notes from and write notes to. In most forms of social media, it can be a pain to get your own data out to keep a backup. That's not the case on Nostr. Anyone can run their own relay, either for the sake of backing up their personal notes, or for others to post their notes to, as well.
Since Nostr notes take up very little space, you can actually run a relay on your phone. I have been on Nostr for almost 2 and a half years, and I have 25,000+ notes of various kinds on my relay, and a backup of that full database is just 24MB on my phone's storage.
Having that backup can save your bacon if you try out a new Nostr client and it doesn't find your existing follow list for some reason, so it writes a new one and you suddenly lose all of the people you were following. Just pop into your #Citrine relay, confirm it still has your correct follow list or import it from a recent backup, then have Citrine restore it. Done.
Additionally, there are things you may want to only save to a relay you control, such as draft messages that you aren't ready to post publicly, or eCash tokens, which can actually be saved to Nostr relays now. Citrine can also be used with Amber for signing into certain Nostr applications that use a relay to communicate with Amber.
If you are really adventurous, you can also expose Citrine over Tor to be used as an outbox relay, or used for peer-to-peer private messaging, but that is far more involved than the scope of this tutorial series.

You can't get far in Nostr without a solid and reliable client to interact with. #Amethyst is the client we will be using for this tutorial because there simply isn't another Android client that comes close, so far. Moreover, it can be a great client for new users to get started on, and yet it has a ton of features for power-users to take advantage of as well.
There are plenty of other good clients to check out over time, such as Coracle, YakiHonne, Voyage, Olas, Flotilla and others, but I keep coming back to Amethyst, and by the time you finish this tutorial, I think you'll see why. nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z and others who have contributed to Amethyst have really built something special in this client, and it just keeps improving with every update that's shipped.
Most social media apps have some form of push notifications, and some Nostr apps do, too. Where the issue comes in is that Nostr apps are all interoperable. If you have more than one application, you're going to have both of them notifying you. Nostr users are known for having five or more Nostr apps that they use regularly. If all of them had notifications turned on, it would be a nightmare. So maybe you limit it to only one of your Nostr apps having notifications turned on, but then you are pretty well locked-in to opening that particular app when you tap on the notification.
Pokey, by nostr:npub1v3tgrwwsv7c6xckyhm5dmluc05jxd4yeqhpxew87chn0kua0tjzqc6yvjh, solves this issue, allowing you to turn notifications off for all of your Nostr apps, and have Pokey handle them all for you. Then, when you tap on a Pokey notification, you can choose which Nostr app to open it in.
Pokey also gives you control over the types of things you want to be notified about. Maybe you don't care about reactions, and you just want to know about zaps, comments, and direct messages. Pokey has you covered. It even supports multiple accounts, so you can get notifications for all the npubs you control.

One of the most unique and incredibly fun aspects of Nostr is the ability to send and receive #zaps. Instead of merely giving someone a 👍️ when you like something they said, you can actually send them real value in the form of sats, small portions of a Bitcoin. There is nothing quite like the experience of receiving your first zap and realizing that someone valued what you said enough to send you a small amount (and sometimes not so small) of #Bitcoin, the best money mankind has ever known.
To be able to have that experience, though, you are going to need a wallet that can send and receive zaps, and preferably one that is easy to connect to Nostr applications. My current preference for that is Alby Hub, but not everyone wants to deal with all that comes along with running a #Lightning node. That being the case, I have opted to use nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch for this tutorial, because they offer one of the easiest wallets to set up, and it connects to most Nostr apps by just copy/pasting a connection string from the settings in the wallet into the settings in your Nostr app of choice.
Additionally, even though #Coinos is a custodial wallet, you can have it automatically transfer any #sats over a specified threshold to a separate wallet, allowing you to mitigate the custodial risk without needing to keep an eye on your balance and make the transfer manually.

Most of us on Android are used to getting all of our mobile apps from one souce: the Google Play Store. That's not possible for this tutorial series. Only one of the apps mentioned above is available in Google's permissioned playground. However, on Android we have the advantage of being able to install whatever we want on our device, just by popping into our settings and flipping a toggle. Indeed, thumbing our noses at big-tech is at the heart of the Nostr ethos, so why would we make ourselves beholden to Google for installing Nostr apps?
The nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 is an alternative app store made by nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9 as a resource for all sorts of open-source apps, but especially Nostr apps. What is more, you can log in with Amber, connect a wallet like Coinos, and support the developers of your favorite Nostr apps directly within the #Zapstore by zapping their app releases.
One of the biggest features of the Zapstore is the fact that developers can cryptographically sign their app releases using their Nostr keys, so you know that the app you are downloading is the one they actually released and hasn't been altered in any way. The Zapstore will warn you and won't let you install the app if the signature is invalid.
Getting Started
Since the Zapstore will be the source we use for installing most of the other apps mentioned, we will start with installing the Zapstore.
We will then use the Zapstore to install Amber and set it up with our Nostr account, either by creating a new private key, or by importing one we already have. We'll also use it to log into the Zapstore.
Next, we will install Amethyst from the Zapstore and log into it via Amber.
After this, we will install Citrine from the Zapstore and add it as a local relay on Amethyst.
Because we want to be able to send and receive zaps, we will set up a wallet with CoinOS and connect it to Amethyst and the Zapstore using Nostr Wallet Connect.
Finally, we will install Pokey using the Zapstore, log into it using Amber, and set up the notifications we want to receive.
By the time you are done with this series, you will have a great head-start on your Nostr journey compared to muddling through it all on your own. Moreover, you will have developed a familiarity with how things generally work on Nostr that can be applied to other apps you try out in the future.
Continue to Part 2: The Zapstore. Nostr Link: nostr:naddr1qvzqqqr4gupzpde8f55w86vrhaeqmd955y4rraw8aunzxgxstsj7eyzgntyev2xtqydhwumn8ghj7un9d3shjtnzwf5kw6r5vfhkcapwdejhgtcqp5cnwdphxv6rwwp3xvmnzvqgty5au
-
 @ c1e6505c:02b3157e
2025-05-27 01:11:45
@ c1e6505c:02b3157e
2025-05-27 01:11:45I spent Memorial Day swimming in the local river - something I try to do at least four times a week. It’s the best form of exercise imo, but it’s more than that. Swimming against the tide, feeling the water move around me... there’s something about it that keeps me grounded. Nature at her peak.
Today I brought my X-Pro2 with the 1959 Leica Summaron 35mm f/2.8. I'm still testing the lens wide open to get a feel for its character. My subject this time: the light playing on the ripples and waves.
While I was shooting, a kid randomly ran up to me and started telling me something about what he got for his dad while fishing, or something - I didn’t quite hear him - and then he asked what I was looking at. I told him, “The ripples. The way the light is refracting.” I had him sit exactly where I was so he could see it too.
He lit up. You could tell no one had ever pointed something like that out to him before. In that moment, I felt like maybe I was able to plant a little seed - a new way of seeing.
This is what I was looking at.

-
 @ 2181959b:80f0d27d
2025-03-09 11:55:06
@ 2181959b:80f0d27d
2025-03-09 11:55:061. مصطلحات عامة في العملات الرقمية
- البلوكشين (Blockchain): تقنية دفتر الأستاذ الموزع التي تسجل جميع المعاملات بطريقة غير قابلة للتغيير.
- العقد الذكي (Smart Contract): بروتوكولات رقمية تنفذ العقود تلقائيًا عند تحقق شروط معينة.
- العملة الرقمية (Cryptocurrency): أصول رقمية تستخدم التشفير لتأمين المعاملات، مثل البيتكوين (BTC) والإيثيريوم (ETH).
- التعدين (Mining): عملية التحقق من المعاملات وإضافتها إلى البلوكشين، وهي تتطلب قوة حوسبية كبيرة.
- إثبات العمل (Proof of Work - PoW): آلية تحقق تعتمد على التعدين وتتطلب طاقة حوسبية كبيرة.
- إثبات الحصة (Proof of Stake - PoS): طريقة تحقق تعتمد على امتلاك العملات بدلاً من التعدين لاستهلاك طاقة أقل.
- المحفظة الرقمية (Wallet): أداة لتخزين العملات الرقمية وإدارتها، مثل MetaMask وTrust Wallet.
- المفتاح الخاص (Private Key): رمز سري يمنحك الوصول إلى أموالك الرقمية، ويجب الحفاظ عليه بسرية تامة.
2. مصطلحات في التمويل اللامركزي (DeFi)
- السيولة (Liquidity): توفر الأصول في السوق، مما يسمح بإجراء الصفقات دون تقلبات كبيرة في السعر.
- المزارع (Yield Farming): استثمار الأصول الرقمية في منصات DeFi لكسب العوائد والفوائد.
- التخزين (Staking): قفل العملات الرقمية لفترة معينة لدعم الشبكة وكسب مكافآت.
- الرموز المميزة (Tokens): أصول رقمية تُستخدم داخل شبكات معينة، مثل ERC-20 وBEP-20.
- البروتوكولات اللامركزية (DeFi Protocols): تطبيقات قائمة على البلوكشين تقدم خدمات مالية بدون وسيط، مثل Uniswap وAave.
- التبادل اللامركزي (DEX - Decentralized Exchange): منصات لتداول العملات الرقمية بدون وسطاء، مثل Uniswap وPancakeSwap.
- الإقراض والاقتراض (Lending & Borrowing): منصات تتيح لك إقراض عملاتك لكسب الفائدة أو اقتراض عملات بضمان أصول رقمية.
3. مصطلحات متعلقة بالتداول والاستثمار
- السعر السوقي (Market Price): السعر الحالي للعملة الرقمية في السوق.
- القيمة السوقية (Market Cap): إجمالي قيمة جميع العملات المتداولة لمشروع معين (عدد العملات × سعر العملة).
- السيولة (Liquidity): مدى سهولة بيع أو شراء الأصل بدون التأثير على سعره بشكل كبير.
- أمر السوق (Market Order): شراء أو بيع الأصل بالسعر الحالي في السوق.
- أمر الحد (Limit Order): تحديد سعر معين للشراء أو البيع بدلاً من تنفيذ الصفقة بالسعر الحالي.
- الرافعة المالية (Leverage): اقتراض أموال لزيادة حجم استثمارك، لكنها تزيد من المخاطر أيضًا.
- الهامش (Margin Trading): التداول بأموال مقترضة، مما يمكن أن يحقق أرباحًا كبيرة أو خسائر كبيرة.
- FOMO (Fear of Missing Out): الخوف من تفويت الفرصة، وهو سبب رئيسي لدخول الكثيرين للسوق في أوقات غير مناسبة.
- HODL: مصطلح يشير إلى الاحتفاظ بالعملات الرقمية على المدى الطويل بغض النظر عن التقلبات السوقية.
4. مصطلحات أخرى هامة
- NFT (الرموز غير القابلة للاستبدال): أصول رقمية فريدة مثل الصور والفيديوهات، يمكن بيعها وشراؤها على منصات مثل OpenSea.
- DAO (المنظمات المستقلة اللامركزية): كيانات لا مركزية تديرها العقود الذكية وأعضاء المجتمع بدلاً من الجهات المركزية.
- Gas Fees (رسوم الغاز): رسوم تُدفع لمعالجة المعاملات على شبكات البلوكشين مثل Ethereum.
- Stablecoin (العملات المستقرة): عملات رقمية مرتبطة بقيمة ثابتة مثل USDT وUSDC.
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ b8851a06:9b120ba1
2025-03-05 23:03:00
@ b8851a06:9b120ba1
2025-03-05 23:03:00The U.S. isn't just blocking Gaza's reconstruction—it's ensuring Palestinians have no future there.
This week, Washington rejected the Arab League's $53 billion plan to rebuild Gaza. Not because it was unworkable, but because it was unwanted. #Gaza, they say, is "uninhabitable." The solution? Depopulation, disguised as development.
The Riviera Plan: Rebuilding Without Its People
National Security Council spokesman Brian Hughes put it bluntly:
"Gaza is uninhabitable."
This isn't a call for humanitarian intervention. It's a pretext for forced displacement.
Trump's vision transforms Gaza into a "Riviera of the #MiddleEast"—after its population has been relocated. Officials have explicitly stated Palestinians "would not be allowed to return" once reconstruction begins. This isn't rebuilding; it's replacement.
Regional Consensus Rejected
The Arab League's proposal represented rare unity among regional powers. It offered a detailed roadmap for reconstruction while allowing #Palestinians to remain in their homeland.
By dismissing this plan, Washington sent a clear message: Palestinian self-determination remains subordinate to Western geopolitical interests.
This isn't new. For over a century, Western capitals have determined Palestinian futures while treating their voices as irrelevant.
The Fiat War Machine Connection
War and fiat money go hand in hand. Governments don't fund wars through taxes anymore—it's all printed money. Inflation steals from the public silently, financing endless destruction abroad while citizens struggle at home.
As Saifedean Ammous writes in The Fiat Standard: nostr:npub1gdu7w6l6w65qhrdeaf6eyywepwe7v7ezqtugsrxy7hl7ypjsvxksd76nak
"Central banks are essentially war machines, enabling governments to finance endless conflicts through inflation rather than direct taxation."
This system divorces "economic reward from economic productivity, and instead bases it on political allegiance." The result? A world "perpetually lurching from one crisis to another, with devastating consequences for humanity."
Ukraine Parallels: When Support Is Conditional
The U.S. has now halted military aid to #Ukraine, suspending over $1 billion in arms. #Europe scrambles to fill the gap, suddenly realizing the conditional nature of American protection.
Both conflicts reveal the same truth: geopolitical support is increasingly transactional rather than values-based.
As Henry Kissinger observed: "It may be dangerous to be America's enemy, but being America's friend can be fatal."
The Cycle Continues
The U.S. model is simple: fund destruction, control reconstruction, keep the cycle going.
Fiat money makes it possible. Indifference makes it permanent. And yes #Bitcoin can fix it. But will it?
How long before people wake up #nostr? How long before the cycle breaks?
"Fiat money is a tool for governments to control their citizens" as Saifedean rightly says—and now, through endless war, to control the world.
-
 @ 491afeba:8b64834e
2025-05-27 21:02:29
@ 491afeba:8b64834e
2025-05-27 21:02:29Quando adolescente eu acreditava na coerência da teoria de "amor líquido" do polonês, sociólogo, Zygmunt Bauman, apresentada no livro "Amor Líquido: Sobre a Fragilidade dos Laços Humanos", qual no meu amadurecimento em estudos, sejam eles no meio acadêmico ou fora, percebo como uma das formas mais rasas de explicar as mudanças e transformações dos padrões de relações sócio-afetivas dos humanos. A seguir colocar-me-ei na minha juventude não tanto recente, direi então que nós, se adolescentes e conservadores, ou mesmo jovens adultos mais conservadores, costumamos levar como dogma uma óptica decadentista generalizada de todos os avanços de eras dos homens, universalizamos por nos ser comum a indistinção entre humanidade e humanidades, ou mesmo "humanity" e "humankind" ("humanidade" como espécime e "humanidade" como um universal), compreendemos toda "essas" como "essa" e indistinguimos as sociedades para com os homens, ou seja, a incapacidade de definir os seres dentro de suas respectivas singularidades e especificidades nos leva ao decadentismo generalista (a crença de que de forma geral, e universal, a "civilização universal" decai moralmente, éticamente, materialmente e espiritualmente), que aparente à nós determinadas mudanças nas relações humanas quanto ao caráter sócio-afetivo, por falta de profundidade e critérios ainda sobre questões alinhadas aos métodos e coerências, ou incoerências, lógicas, nós se jovens e conservadores somos levados ao engodo de concordar com a teoria do amor líquido de Bauman, que devo cá explicar de antemão: trata ela, a teoria, o padrão de "amor" dos tempos presentes como frágil, de prazo (curto e médio) e diferente em grau comparativamente ao amor comum das eras passadas.
Aos jovens mais progressistas opera uma compreensão dialética sobre as eras dos homens nos seu tempo presente, na qual ao tempo que o ser progride ele também regride simultaneamente, ou seja, a medida que aparecem contradições advindas de transformações materiais da realidade humana o ser supera essas contradições e progride em meio as transformações, ainda fazendo parte da lógica dessa indissociavelmente, assim constantemente progredindo e regredindo, havendo para esses dois vetores de distinção: o primeiro é o que releva questões espirituais como ao caráter do pensamento "new age", o segundo ignora essas questões por negar a existência da alma, seguem ao materialismo. Cedem em crer na teoria baumaninana como dogma, pois não encontram outros meios para explicar as transformações da sociedade na esfera sócio-afetiva sem que haja confrontamento direto com determinadas premissas assim pertinemente presentes, ou por não conciliarem com análises relativamente superiores, como a de Anthony Giddens sobre a "relação pura" em "A Transformação da Intimidade" e de François de Singly apresentada em "Sociologie du Couple".
!(image)[https://i.pinimg.com/736x/6f/b4/9e/6fb49eda2c8cf6dc837a0abfc7e108e6.jpg]
Há um problema quando uma teoria deixa de assim ser para vir a tornar-se mais um elemento desconexo da ciência, agora dentro da cultura pop, se assim podemos dizer, ou da cultura de massa, ou se preferirem mesmo "anticultura", esse problema é a sua deformização teórica, tornando-se essa rasa para sua palatabilidade massiva, somada a incapacidade de partes da sociedade civil em compreender as falhas daquilo que já foi massificado. Tive surpresa ao entender que muitos outros compartilham da mesma opinião, a exemplo, possuo um amigo na faculdade, marxista, que ao falarmos sobre nossos projetos de pesquisa, citou ele o projeto de um de nossos colegas, no qual esse referido um de nossos colegas faria seu projeto com base na teoria do amor líquido de Bauman, então alí demos risada disso, ora, para nós a teoria baumaniana é furada, passamos a falar sobre Bauman e o motivo pelo qual não gostávamos, lá fiquei até surpreso em saber que mais gente além de mim não gostava da teoria de Bauman, pois ao que eu via na internet era rede de enaltecimentos à figura e à sua teoria, tal como fosse uma revelação partindo de alguma divindade da Idade do Bronze. Pouco tempo depois tive em aula de teoria política uma citação de Bauman partindo do professor que ministrava a disciplina, no entanto, ao citar o nome de Bauman o mesmo fez uma feição na qual aparentava segurar risada, provavelmente ele também não levava Bauman à sério. Não devo negar que todas as vezes que vejo o sociólogo sendo citado em alguma nota no X, no Instagram ou qualquer outra rede social, tal como fosse um referencial teórico bom, sinto uma vergonha alheia pois alí tenho uma impressão de que a pessoa não leu Bauman e usa o referencial teórico como um fato já assim provado e comprovado.
Há pontos positivos na teoria baumaniana, como a capacidade de perceber o problema e correlacioná-lo à modernidade, assim como sucitar a influência do que há de material no fenômeno, porém os erros são pertinentes: o primeiro problema é de categoria. Não há, por parte de Bauman noção alguma entre as dissociações dos amores, não há atenção sobre o amor como estrutura ou ele como um sentimento, todo ele é compreendido uniformemente como "amor", partindo do pressuposto que todas as relações, todas elas, são firmadas com base no amor. Essa crença tem uma origem: Hegel. Nos Escritos Teológicos Hegel partia da crença que o amor ligava os seres relacionalmente como uma força de superação e alienação, mas há de compreendermos que esse Friedrich Hegel é o jovem ainda pouco maduro em suas ideias e seu sistema de pensamento, mais a frente, em "Fenomenologia do Espírito e na Filosofia do Direito", Hegel compreende a institucionalidade do direito no amor e a institucionalização dessa força, assim aproxima-se da realidade a respeito da inserção do amor nas esferas práticas do humano, porém essa ideia, apesar de imperfeita, pois ao que sabemos não é o amor que consolida a relação, mas sim a Verdade (Alétheia), conforme apontado por Heidegger em "Ser e Tempo", essa ideia do amor como a fundamento das relações humanas influenciou, e até hoje influencia, qualquer análise sobre as relações humanas fora da esfera materialista, fora dessa pois, melhormente explicado em exemplo, os marxistas (em exemplo), assim como Marx, consideram como base primordial das relações as condições materiais.
Por certo, não é de todo amor a base para a solidificação, ora, erram aqueles que creem que somente essa força, assim apontada por Hegel, constituiam todos os relacionamentos formais como pilares fundamentais, pois em prática as famílias eram até a fiduciarização dessas, por mais paradoxal que seja, compreendidas melhor como instituições orgânicas de caráter legal do que conluios de afetividades. A família outrora tinha consigo aparelhos de hierarquia bem estabelicidos, quais prezavam pela ordem interna e externa, que acima dessa instituição estava somente a Igreja (outra instituição), com sua fiduciarização [da família] após o movimento tomado pelos Estados nacionais em aplicação do casamento civil mudou-se a lógica das partes que a compõe, findou-se o princípio da subsidiariedade (não intervenção de determinadas instituições nas decisões quais podem ser exercidas em resuluções de problemas nas competências de quaisquer instituições), foi-se então, contudo, também a autoridade, e nisso revela-se um outro problema não apontado na teoria de Bauman: qual o padrão do amor "sólido"? Pois, ora, sociedades tradicionais não abdicavam do relevar dos amores para tornar seus filhos em ativos nas práticas de trocas (dádivas)? É notório que esse padrão se dissocia do padrão de sentimento apontado por Bauman, encontramos esse fato em estudo nos trabalhos "Ensaio Sobre a Dádiva", do Marcel Mauss, e "As Estruturas Elementares do Parentesco", do Claude Levi-Strauss, quais expõem que nas sociedades "sólidas", tradicionais, relevava-se mais questões institucionais que as sentimentais para a formação de laços (teoria da aliança). Muitas das relações passadas não eram baseadas no amor, não significando assim que as de hoje, em oposição, sejam, mas que permanecem-se semelhantes em base, diferentemente em grau e forma.
!(image)[https://substackcdn.com/image/fetch/f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F748b94c3-f882-45db-8333-09260ef15cfe_615x413.jpeg]
Ora, ainda existem casamentos motivados pela política, pelo status, pelo prestígio, pelos bens, pelo poder, pela influência familiar e assim sucetivamente, tal como no passado, ocorre que essa prática tornou-se oculta, não mais explícita e aparente, devo dizer ainda que em partes, pois prepondera em nosso tempo uma epidemia de adultérios, fornicações, práticas lascivas e demais práticas libertinosas explicitamente, em contraposição às práticas ocultas em vergonhas de sociedades sem declínio moral e espiritual, o que nos leva a questionar o método comparativo em dicotomia temporal "presente x passado" aplicado por Bauman, no qual segue-se da seguinte forma:
Transformação Passado = *sólido* | Presente = *líquido* Categorias Padrão de amor: tradicional (*sólido*) moderno (*líquido*) *Sólido* = estável, prazo (médio-grande), profundo, determinado. *Líquido* = instável, prazo (curto-médio), raso, indeterminado.O que penso é: Zygmunt Bauman buscou uma explicação material e laical para desviar ao fato de que há uma notória correlação entre espiritualização da sociedade, se voltada à Verdade, com a estabilidade das instituições, o que é já reduzido à moral religiosa, somente, não à mística, como por pensadores da linha de Tocqueville, ou em abordagens também mais laical (positivista) porém ainda relevantes, como Émile Durkheim em "As Formas Elementares da Vida Religiosa" e Max Weber em "A Ética Protestante e o Espírito do Capitalismo", contrapondo uma abordage mais voltada, de fato, a espiritualidade, como Christopher Dawnson, que defende essa teoria em "Religião e o Surgimento da Cultura Ocidental", e Eric Voegelin, principalmente nas obras "A Nova Ciência da Política" e "Ordem e História".
Encerrrando, minha cosmovisão é a católica, o sistema de crença e religião qual sigo é do Deus que se fez homem por amor aos seus filhos, não posso negar ou mesmo omitir o fato de que, por trás de toda a minha crítica estão meus pensamentos e minhas convicções alinhadas àquilo que mais tenho amor em toda minha vida: a Verdade, e a Verdade é Deus, pois Cristo é a Verdade, o Caminho e a Vida, ninguém vai ao Pai se não por Ele, e pois bem, seria incoerência de minha parte não relevar o fato de crença como um dos motivos pelos quais eu rejeito a teoria do amor líquido de Zygmunt Bauman, pois os amores são todos eles praticados por formas, existem por diferentes formas e assim são desde sua tradicionalidade até o predomínio das distorções de declínio espiritual das eras presentes (e também antigas pré-Era Axial), estão esses preservados pelo alinhamento à verdade, assim são indistorcíveis, imutáveis, ou seja, amor é amor, não releva-se o falso amor como um, simplesmente não o é, assim o interesse, a sanha por bens, o egoísmo e a egolatria ("cupiditas", para Santo Agostinho de Hipona, em oposição ao que o santo e filósofo trata por "caritas") não são formas do amor, são autoenganos, não bons, se não são bons logo não são de Deus, ora, se Deus é amor, se ele nos ama, determino como amor (e suas formas) o que está de acordo com a Verdade. Aprofundando, a Teologia do Corpo, do Papa São João Paulo II, rejeita a "liquidez" apresentada por Bauman, pois o amor é, em suma, sacríficio, parte da entrega total de si ao próximo, e se não há logo não é amor. A Teologia do Corpo rejeita não os fundamentos de mentira no "líquido", mas também no "sólido", pois a tradicionalidade não é sinônimo de bom e pleno acordo com o amor que Deus pede de nós, não são as coerções, as violências, as imposições e demais vontades em oposição às de Deus que determinam os amores -- fatos em oposição ao ideário romanticizado. Claro, nem todas as coerções são por si inválidas do amor, ou mesmo as escolhas em trocas racionalizadas, a exemplo do autruísmo em vista da chance da família ter êxito e sucesso, ou seja, pelo bem dos próximos haver a necessidade de submissão a, em exemplo, um casamento forjado, ou algo do gênero, reconhece-se o amor no ato se feito por bem da família, porém o amor incutido, nesse caso, explicita o caráter sacrificial, no qual uma vontade e um amor genuinamente potencial em prazeres e alegrias são anulados, ou seja, mesmo nesse modelo tradicional na "solidez" há possibilidade do amor, não nas formas romanticizadas em critérios, como "estabilidade" e "durabilidade", mas no caráter do sacríficio exercido. Conforme nos ensina São Tomás de Aquino, o amor não é uma "força", tal como ensina Hegel, mas sim uma virtude teologal conforme na "Suma Teológica" (II-II Q. 26-28), não devemos reduzir o amor e os amores em análises simplórias (não simples) de falsa complexidade extraídas em métodos questionáveis e pouco competentes à real diensão de crise espiritual das eras, por esse motivo não concordo com a teoria do amor líquido de Zygmunt Bauman.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 06639a38:655f8f71
2025-05-26 14:21:37
@ 06639a38:655f8f71
2025-05-26 14:21:37Finally there is a release (1.7.0) for Nostr-PHP with a full NIP-19 integration. Here is an example file with some snippets to how it works to encode and decode bech32 encoded entities:
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip19-bech32-decoded-entities.php
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip19-bech32-encoded-entities.php
Now merge request #68 (and issues #74, #64 are closed) is finally merged which I opened in October 2024.
Next up is:
- Create documentation how to use NIP-19 with the library on https://nostr-php.dev
- Create documentation how to use NIP-04 and NIP-44 with the library on https://nostr-php.dev
- Work out a proof-of-concept with the revolt/event-loop package to create concurrent async requests with websocket connections
-
 @ 2181959b:80f0d27d
2025-02-26 19:21:30
@ 2181959b:80f0d27d
2025-02-26 19:21:30أطلقت مايكروسوفت بهدوء إصدارًا مجانيًا من تطبيقات Office لأجهزة ويندوز، يتيح للمستخدمين تحرير المستندات دون الحاجة إلى اشتراك في Microsoft 365 أو ترخيص مدفوع.
ومع ذلك، يأتي هذا الإصدار مع إعلانات دائمة وقيود على بعض الميزات الأساسية.
ما هي قيود الإصدار المجاني من تطبيقات Office؟
وفقًا لموقع Beebom، يعتمد الإصدار المجاني على التطبيقات المكتبية الكاملة لكنه يُقيد معظم الميزات خلف اشتراك Microsoft 365.
وهذه القيود تتمثل في الآتي:
1: يتم عرض الإعلانات بشكل دائم داخل تطبيقات Word وPowerPoint وExcel أثناء العمل على المستندات.
2: يمكن حفظ الملفات فقط على OneDrive، دون دعم لتحرير الملفات المحلية.
3: لا يتوفر الإملاء الصوتي، والإضافات، والتنسيقات المتقدمة، وSmartArt، مما يجعله مناسبًا للمهام الأساسية فقط.
كيفية الوصول إلى الإصدار المجاني من تطبيقات Office؟
يمكن للمستخدمين تخطي طلب تسجيل الدخول عند تشغيل أحد تطبيقات Office لأول مرة، وبعد ذلك سيحصلون على خيار استخدامه مجانًا مقابل الإعلانات والميزات المحدودة.
في هذا الوضع، يمكن فتح المستندات وعرضها وتحريرها، تمامًا كما هو الحال في إصدار Office على الويب.
هل هو متاح للجميع؟
حاليًا، يبدو أن هذا الإصدار لا يزال في مرحلة الاختبار المحدود، حيث لم يتمكن بعض المستخدمين من تجاوز شاشة تسجيل الدخول عند تشغيل Office. ومن المحتمل أن مايكروسوفت تختبر هذه النسخة في مناطق محددة أو مع مجموعة صغيرة من المستخدمين قبل إطلاقها رسميًا.
حتى الآن، لم تُعلن الشركة رسميًا عن هذا الإصدار، ولم تذكره في مستندات الدعم الخاصة بها، لكن قد تكشف مايكروسوفت عن تفاصيل إضافية خلال الأيام أو الأسابيع المقبلة.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:50:23
@ 21c71bfa:e28fa0f6
2025-05-29 14:50:23Book *Manali to Amritsar cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 97c70a44:ad98e322
2025-02-17 14:29:00
@ 97c70a44:ad98e322
2025-02-17 14:29:00Everyone knows that relays are central to how nostr works - they're even in the name: Notes and Other Stuff Transmitted by Relays. As time goes on though, there are three other letters which are becoming conspicuously absent from our beloved and ambiguously pronounceable acronym - "D", "V", and "M".
For the uninitiated, DVM stands for "data vending machines". They're actually sort of hard to describe — in technical terms they act more like clients, since they simply read events from and publish events to relays. In most cases though, these events are part of a request/response flow initiated by users elsewhere on the network. In practice, DVMs are bots, but there's also nothing to prevent the work they do from being powered by human interaction. They're an amazingly flexible tool for building anything from custom feeds, to transcription services, to chatbots, to protocol gateways.
The hype cycle for DVMs seems to have reached escape velocity in a way few other things have - zaps being the possible exception. But what exactly DVMs are remains something of a mystery to many nostr developers - and how to build one may as well be written on clay tablets.
This blog post is designed to address that - below is a soup to nuts (no nutzaps though) guide to building a DVM flow, both from the client and the server side.
Here's what we'll be covering:
- Discovering DVM metadata
- Basic request/response flow
- Implementing a minimal example
Let's get started!
DVM Metadata
First of all, it's helpful to know how DVMs are reified on the nostr network. While not strictly necessary, this can be useful for discovering DVMs and presenting them to users, and for targeting specific DVMs we want a response from.
NIP 89 goes into this in more detail, but the basic idea is that anyone can create a
kind 31990"application handler" event and publish it to the network with their own (or a dedicated) public key. This handler was originally intended to advertise clients, but has been re-purposed for DVM listings as well.Here's what the "Fluffy Frens" handler looks like:
json { "content": "{\"name\": \"Fluffy Frens\", \"picture\": \"https://image.nostr.build/f609311532c470f663e129510a76c9a1912ae9bc4aaaf058e5ba21cfb512c88e.jpg\", \"about\": \"I show recent notes about animals\", \"lud16\": \"discovery_content_fluffy@nostrdvm.com\", \"supportsEncryption\": true, \"acceptsNutZaps\": false, \"personalized\": false, \"amount\": \"free\", \"nip90Params\": {\"max_results\": {\"required\": false, \"values\": [], \"description\": \"The number of maximum results to return (default currently 100)\"}}}", "created_at": 1738874694, "id": "0aa8d1f19cfe17e00ce55ca86fea487c83be39a1813601f56f869abdfa776b3c", "kind": 31990, "pubkey": "7b7373dd58554ff4c0d28b401b9eae114bd92e30d872ae843b9a217375d66f9d", "sig": "22403a7996147da607cf215994ab3b893176e5302a44a245e9c0d91214e4c56fae40d2239dce58ea724114591e8f95caed2ba1a231d09a6cd06c9f0980e1abd5", "tags": [ ["k", "5300"], ["d", "198650843898570c"] ] }This event is rendered in various clients using the kind-0-style metadata contained in the
contentfield, allowing users to browse DVMs and pick one for their use case. If a user likes using a particular DVM, they might publish akind 31989"application recommendation", which other users can use to find DVMs that are in use within their network.Note the
ktag in the handler event - this allows DVMs to advertise support only for specific job types. It's also important to note that even though the spec doesn't cover relay selection, most clients use the publisher'skind 10002event to find out where the DVM listens for events.If this looks messy to you, you're right. See this PR for a proposal to split DVMs out into their own handler kind, give them a dedicated pubkey along with dedicated metadata and relay selections, and clean up the data model a bit.
DVM Flow
Now that we know what a DVM looks like, we can start to address how they work. My explanation below will elide some of the detail involved in NIP 90 for simplicity, so I encourage you to read the complete spec.
The basic DVM flow can be a little (very) confusing to work with, because in essence it's a request/response paradigm, but it has some additional wrinkles.
First of all, the broker for the request isn't abstracted away as is usually the case with request/response flows. Regular HTTP requests involve all kinds of work in the background - from resolving domain names to traversing routers, VPNs, and ISP infrastructure. But developers don't generally have to care about all these intermediaries.
With DVMs, on the other hand, the essential complexity of relay selection can't simply be ignored. DVMs often advertise their own relay selections, which should be used rather than a hard-coded or randomly chosen relay to ensure messages are delivered. The benefit of this is that DVMs can avoid censorship, just as users can, by choosing relays that are willing to broker their activity. DVMs can even select multiple relays to broker requests, which means that clients might receive multiple copies of the same response.
Secondly, the DVM request/response model is far more fluid than is usually the case with request/response flows. There are a set of standard practices, but the flow is flexible enough to admit exceptions to these conventions for special use cases. Here are some examples:
- Normally, clients p-tag the DVM they wish to address. But if a client isn't picky about where a response comes from, they may choose to send an open request to the network and collect responses from multiple DVMs simultaneously.
- Normally, a client creates a request before collecting responses using a subscription with an e-tag filter matching the request event. But clients may choose to skip the request step entirely and collect responses from the network that have already been created. This can be useful for computationally intensive tasks or common queries, where a single result can be re-used multiple times.
- Sometimes, a DVM may respond with a
kind 7000job status event to let clients know they're working on the request. This is particularly useful for longer-running tasks, where feedback is useful for building a responsive UX. - There are also some details in the spec regarding monetization, parameterization, error codes, encryption, etc.
Example DVM implementation
For the purposes of this blog post, I'll keep things simple by illustrating the most common kind of DVM flow: a
kind 5300content discovery request, addressed to a particular DVM. If you're interested in other use cases, please visit data-vending-machines.org for additional documented kinds.The basic flow looks like this:
- The DVM starts by listening for
kind 5300job requests on some relays it has selected and advertised via NIP 89 (more on that later) - A client creates a request event of
kind 5300, p-tagged with the DVM's pubkey and sends it to the DVM's relay selections. - The DVM receives the event and processes it, issuing optional
kind 7000job status events, and eventually issuing akind 6300job result event (job result event kinds are always 1000 greater than the request's kind). - The client listens to the same relays for a response, and when it comes through does whatever it wants to with it.
Here's a swimlane diagram of that flow:

To avoid massive code samples, I'm going to implement our DVM entirely using nak (backed by the power of the human mind).
The first step is to start our DVM listening for requests that it wants to respond to. Nak's default pubkey is
79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798, so we'll only listen for requests sent to nak.bash nak req -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798This gives us the following filter:
json ["REQ","nak",{"kinds":[5300],"#p":["79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"]}]To open a subscription to
nos.loland stream job requests, add--stream wss://nos.lolto the previous request and leave it running.Next, open a new terminal window for our "client" and create a job request. In this case, there's nothing we need to provide as
input, but we'll include it just for illustration. It's also good practice to include anexpirationtag so we're not asking relays to keep our ephemeral requests forever.bash nak event -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 -t expiration=$(( $(date +%s) + 30 )) -t input=helloHere's what comes out:
json { "kind": 5300, "id": "0e419d0b3c5d29f86d2132a38ca29cdfb81a246e1a649cb2fe1b9ed6144ebe30", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739407684, "tags": [ ["p", "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"], ["expiration", "1739407683"], ["input", "hello"] ], "content": "", "sig": "560807548a75779a7a68c0ea73c6f097583e2807f4bb286c39931e99a4e377c0a64af664fa90f43e01ddd1de2e9405acd4e268f1bf3bc66f0ed5a866ea093966" }Now go ahead and publish this event by adding
nos.lolto the end of yournakcommand. If all goes well, you should see your event pop up in your "dvm" subscription. If so, great! That's half of the flow.Next, we'll want our client to start listening for
kind 6300responses to the request. In your "client" terminal window, run:bash nak req -k 6300 -t e=<your-eventid-here> --stream nos.lolNote that if you only want to accept responses from the specified DVM (a good policy in general to avoid spam) you would include a
ptag here. I've omitted it for brevity. Also notice thektag specifies the request kind plus1000- this is just a convention for what kinds requests and responses use.Now, according to data-vending-machines.org,
kind 5300responses are supposed to put a JSON-encoded list of e-tags in thecontentfield of the response. Weird, but ok. Stop the subscription in your "dvm" terminal and respond to your "client" with a recommendation to read my first note:bash nak event -k 6300 -t e=a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf -c '[["e","214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08","wss://nos.lol/"]]' nos.lolHere's the response event we're sending:
json { "kind": 6300, "id": "bb5f38920cbca15d3c79021f7d0051e82337254a84c56e0f4182578e4025232e", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739408411, "tags": [ ["e", "a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf"] ], "content": "[[\"e\",\"214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08\",\"wss://nos.lol/\"]]", "sig": "a0fe2c3419c5c54cf2a6d9a2a5726b2a5b766d3c9e55d55568140979354003aacb038e90bdead43becf5956faa54e3b60ff18c0ea4d8e7dfdf0c8dd97fb24ff9" }Notice the
etag targets our original request.This should result in the job result event showing up in our "client" terminal. Success!
If something isn't working, I've also create a video of the full process with some commentary which you can find here.
Note that in practice, DVMs can be much more picky about the requests they will respond to, due to implementations failing to follow Postel's law. Hopefully that will improve over time. For now, here are a few resources that are useful when working with or developing DVMs:
Conclusion
I started this post by hinting that DVMs might be as fundamental as relays are to making nostr work. But (apart from the fact that we'd end up with an acronym like DVMNOSTRZ+*, which would only exascerbate the pronounciation wars (if such a thing were possible)), that's not exactly true.
DVMs have emerged as a central paradigm in the nostr world because they're a generalization of a design pattern unique to nostr's architecture - but which exists in many other places, including NIP 46 signer flows and NIP 47 wallet connect. Each of these sub-protocols works by using relays as neutral brokers for requests in order to avoid coupling services to web addresses.
This approach has all kinds of neat benefits, not least of which is allowing service providers to host their software without having to accept incoming TCP connections. But it's really an emergent property of relays, which not only are useful for brokering communication between users (aka storing events), but also brokering communication between machines.
The possibilities of this architecture have only started to emerge, so be on the lookout for new applications, and don't be afraid to experiment - just please, don't serialize json inside json 🤦♂️
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:50:05
@ 21c71bfa:e28fa0f6
2025-05-29 14:50:05Book *Amritsar to Phagwara cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:47:16
@ 04c915da:3dfbecc9
2025-05-20 15:47:16Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 162b4b08:9f7d278c
2025-05-27 10:12:53
@ 162b4b08:9f7d278c
2025-05-27 10:12:53Trong thời đại mà công nghệ số trở thành trụ cột không thể thiếu trong mọi lĩnh vực, từ công việc đến giải trí, việc sở hữu một nền tảng số toàn diện như PUM88 đóng vai trò vô cùng quan trọng đối với người dùng hiện đại. Không chỉ là nơi cung cấp các công cụ tiện ích, PUM88 còn tạo nên một hệ sinh thái linh hoạt, đáp ứng mọi nhu cầu trong một môi trường trực tuyến đầy năng động. Từ những bước đầu như đăng ký, đăng nhập, cho đến trải nghiệm thực tế, tất cả đều được tối ưu nhằm mang lại sự thuận tiện tối đa. Giao diện thiết kế thông minh, bố cục rõ ràng, thao tác nhanh gọn giúp người dùng dễ dàng tiếp cận và sử dụng mà không cần kiến thức kỹ thuật chuyên sâu. Bên cạnh đó, hệ thống xử lý tốc độ cao và khả năng tương thích đa nền tảng (từ smartphone đến laptop) giúp người dùng duy trì kết nối mọi lúc mọi nơi, không bị giới hạn bởi thiết bị hay không gian sử dụng. Không dừng lại ở đó, PUM88 còn liên tục nâng cấp công nghệ như tích hợp trí tuệ nhân tạo để gợi ý nội dung cá nhân hóa theo hành vi và sở thích, giúp mỗi trải nghiệm trở nên sống động, gần gũi và mang tính cá nhân cao hơn bao giờ hết. Đây chính là điểm cộng lớn giúp PUM88 tạo nên dấu ấn trong lòng người dùng yêu thích sự tiện lợi và linh hoạt trong đời sống số.
Ngoài ra, yếu tố khiến PUM88 trở nên đáng tin cậy chính là khả năng bảo mật vượt trội và chính sách hỗ trợ khách hàng tận tâm. Dữ liệu cá nhân và các hoạt động của người dùng luôn được bảo vệ nghiêm ngặt bằng các chuẩn mã hóa quốc tế, hệ thống tường lửa, xác thực hai lớp và giám sát bảo mật liên tục. Nhờ vậy, người dùng hoàn toàn yên tâm khi sử dụng mà không lo bị lộ thông tin hay rò rỉ dữ liệu. Thêm vào đó, đội ngũ chăm sóc khách hàng hoạt động 24/7 với thái độ chuyên nghiệp và phản hồi nhanh chóng giúp giải quyết mọi thắc mắc hoặc sự cố kỹ thuật một cách hiệu quả. Không những thế, PUM88 còn thường xuyên lắng nghe ý kiến người dùng để cải tiến giao diện, bổ sung tính năng mới, đảm bảo rằng nền tảng luôn bắt kịp xu hướng công nghệ và đáp ứng đúng nhu cầu thực tế. Việc cập nhật liên tục không chỉ giúp người dùng có được trải nghiệm mượt mà hơn mà còn giữ cho nền tảng luôn mới mẻ, sáng tạo và không ngừng phát triển. Trong bối cảnh chuyển đổi số đang diễn ra mạnh mẽ tại Việt Nam, PUM88 không chỉ đơn thuần là một ứng dụng tiện ích mà còn là một trợ thủ đắc lực cho cuộc sống hiện đại – nơi mà người dùng có thể tận dụng công nghệ để nâng cao hiệu suất cá nhân, tối ưu hóa thời gian và tận hưởng trải nghiệm số trọn vẹn nhất mỗi ngày.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:49:42
@ 21c71bfa:e28fa0f6
2025-05-29 14:49:42Book *Chandigarh to Amritsar cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 2181959b:80f0d27d
2025-02-24 20:49:39
@ 2181959b:80f0d27d
2025-02-24 20:49:39تخطط شركة قوقل لاتخاذ خطوة جديدة في تعزيز أمان حسابات Gmail، حيث ستتخلى عن رموز المصادقة عبر الرسائل النصية (SMS) لصالح التحقق باستخدام رموز QR، بهدف تقليل مخاطر الأمان والحد من الاعتماد على شركات الاتصالات.
لماذا تستبدل قوقل رموز SMS في Gmail؟
رغم أن المصادقة الثنائية (2FA) عبر الرسائل النصية تُعد طريقة عملية، إلا أنها تحمل مخاطر كبيرة، إذ يمكن اعتراض الرموز من قبل المخترقين، أو استخدامها في هجمات التصيد الاحتيالي، أو حتى تعرض الحساب للاختراق في حال تم استنساخ رقم الهاتف.
كما أن أمان هذه الطريقة يعتمد بشكل أساسي على سياسات الحماية التي تتبعها شركات الاتصالات.
https://image.nostr.build/9c8eda01e430425f1e379ffd975aea200d72746e8d8a31000c8bd0e013b8e449.jpg
كيف سيعمل التحقق عبر رموز QR؟
عند محاولة تسجيل الدخول إلى Gmail، سيظهر للمستخدم رمز QR على الشاشة بدلًا من استلام رمز عبر SMS. كل ما عليه فعله هو مسح الرمز باستخدام كاميرا الهاتف، ليتم التحقق من هويته تلقائيًا، دون الحاجة إلى إدخال رمز يدويًا، مما يقلل من مخاطر مشاركة الرموز مع جهات غير موثوقة.
متى سيتم تطبيق هذا التغيير؟
لم تحدد قوقل موعدًا رسميًا لاعتماد النظام الجديد، لكنها أكدت أنها تعمل على إعادة تصميم عملية التحقق من الهوية خلال الأشهر المقبلة.
-
 @ 06639a38:655f8f71
2025-05-26 12:58:38
@ 06639a38:655f8f71
2025-05-26 12:58:38Nostr-PHP
Djuri submitted quite some pull requests in the last couple of week while he was implementing a Nostr connect / login on https://satsback.com. The backend of that platform is written in PHP so the Nostr-PHP library is used for several purposes while Djuri also developed quite some new features utilizing the following NIPs:
- NIP-04
- NIP-05
- NIP-17
- NIP-44
Thank you very much Djuri for these contributions. We now can do the basic private stuff with the library.
PR for NIP-04 and NIP-44: https://github.com/nostrver-se/nostr-php/pull/84 and https://github.com/nostrver-se/nostr-php/pull/88
Examples:- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip04-encrypted-messages.php
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip44-gift-wrapping.php
PR for NIP-05: https://github.com/nostrver-se/nostr-php/pull/89
Example: https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip05-lookup.phpPR for NIP-17: https://github.com/nostrver-se/nostr-php/pull/90
Example: https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip17-private-direct-messages.phpPR for adding more metadata profile fields: https://github.com/nostrver-se/nostr-php/pull/94
Example: https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/fetch-profile-metadata.phpFetch
10050event (dm relay list) of an given pubkey
Example: https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/fetch-dm-relayslist.phpThe CLI tool is removed from the library, see PR https://github.com/nostrver-se/nostr-php/pull/93
Nostr-PHP documentation
While new NIPs are implemented in the Nostr-PHP library, I'm trying to keep up with the documentation at https://nostr-php.dev. For now, things are still much work in progress and I've added the AI agent Goose using the Claude LLM to bootstrap new documentation pages. Currently I'm working on documentation for
- How to direct messages with NIP-04 and NIP-17
- Encrypted payloads for event content NIP-44
- Fetch profiledata of a given pubkey
- Lookup NIP-05 data of given pubkey
- Using the NIP-19 helper class
CCNS.news
I've moved CCNS to a new domain https://ccns.news and have partly implemented the new NIP-B0 for web bookmarks. When you post a bookmark there, a kind
39701event is transmitted to some Nostr relays (take a look at this event for example). Optionally you can also publish this content as a note to the network.As you can see at https://ccns.news/l/censorship-resistant-publishing-and-archiving, I've listed some todo's. All this stuff is done with Javascript using the NDK Typescript library (so I'm not using any PHP stuff for this with Nostr-PHP).
Also new: https://ccns.news/global now has a global feed which fetches all the web bookmark events with kind
39701from several public Nostr relays. I had a rough idea to compare feeds generated with NDK and Nostr-PHP (for both using the same set of relays).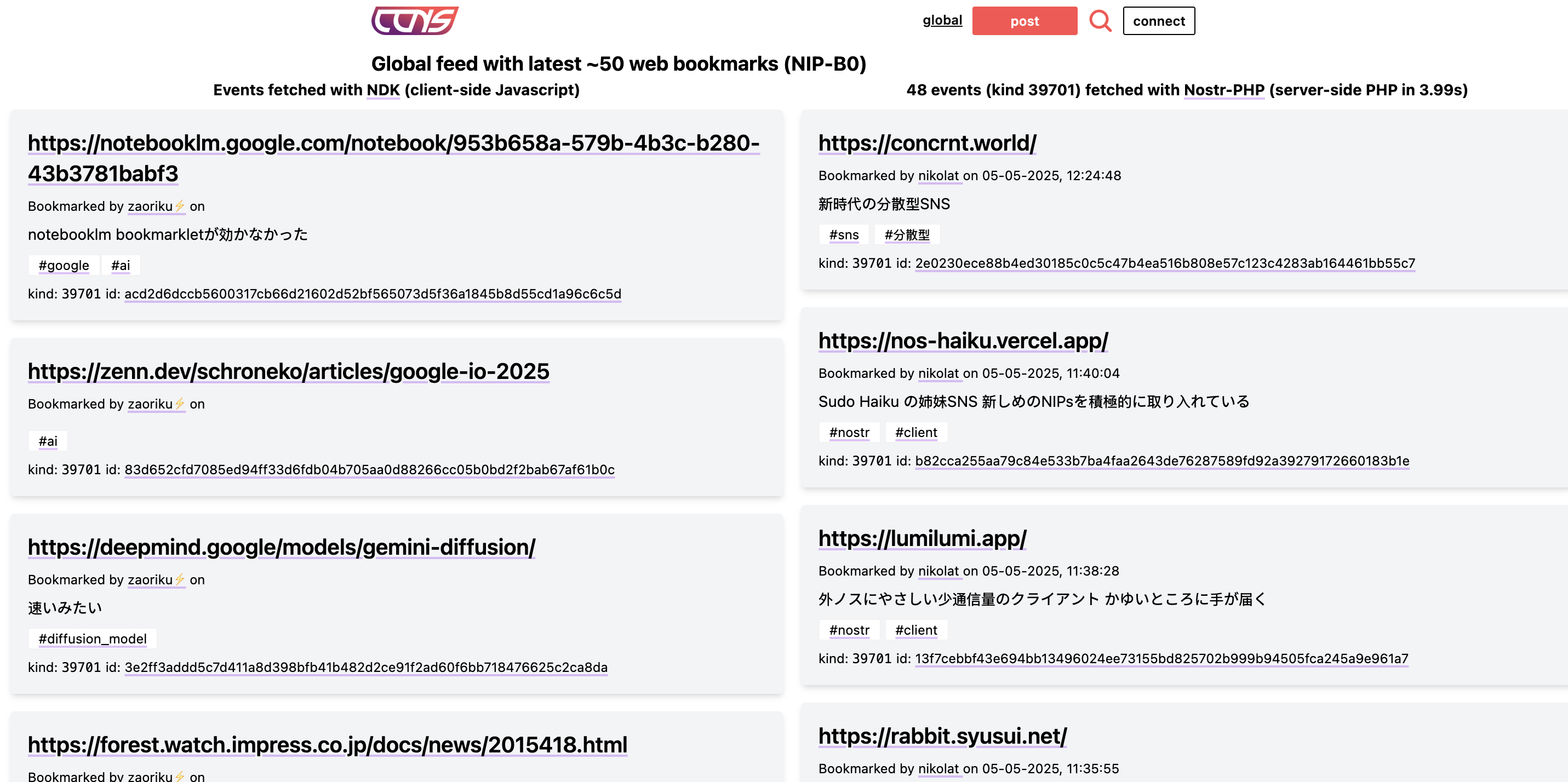
Building a njump clone for this Drupal website
You can now use this URL pattern to fetch Nostr events:
https://nostrver.se/e/{event_id|nevent1|note1|addr1}where you can provide a plain Nostr event ID or NIP-19 encoded identifier.An example, this URL [nostr:nevent1qvzqqqqqqypzqmjxss3dld622uu8q25gywum9qtg4w4cv4064jmg20xsac2aam5nqqsqm2lz4ru6wlydzpulgs8m60ylp4vufwsg55whlqgua6a93vp2y4g3uu9lr) fetches the data from one or more relays. This data is then being saved as a (Drupal) node entity (in a database on the server where this website is hosted, which is located in my office fyi). With this saved node, this data is now also available at https://nostrver.se/e/0dabe2a8f9a77c8d1079f440fbd3c9f0d59c4ba08a51d7f811ceeba58b02a255/1 where the (cached) data is server from the database instead. It's just raw data for now, nothing special about it. One of my next steps is to style this in a more prettier interface and I will need to switch the theme of this website to a custom theme. A custom theme where I will be using TailwindCSS v4 and DaisyUI v5.
The module which is providing these Nostr features is FOSS and uses the Nostr-PHP library for doing the following:
- Request the event from one or more relays
- Decode the provided NIP-19 identifier
For now this module is way for me to utilize the Nostr-PHP library with Drupal for fetching events. This can be automated so in theory I could index all the Nostr events. But this is not my ambition as it would require quite some hardware resources to accomplish this.
I hope I can find the time to build up a new theme first for this website, so I can start styling the data for the fetched events. On this website, there is also a small piece (powered by another module) you can find at https://nostrver.se/nostrides doing things with this NIP-113 around activity events (in my case that's cycling what interests me).What's next
I'm already working on the following stuff:
- Implement a class to setup a persistent connection to a relay for requesting events continuously
- Extend the documentation with the recent added features
Other todo stuff:
- Review NIP-13 proof-of-work PR from Djuri
- Implement a NIP-65 lookup for fetching read and write relays for a given npub issue #91
- Build a proof-of-concept with revolt/event-loop to request events asynchronous with persistent relay connections
- Add comments to https://ccns.news
-
 @ e771af0b:8e8ed66f
2024-09-05 22:14:04
@ e771af0b:8e8ed66f
2024-09-05 22:14:04I have searched the web for "Find bitcoin block number from historical date" maybe 100 times in my life.
Never again.
You'll need a bitcoin node for this to work. The script is fast.
Install
WoT Install
one liner ```
curl
curl -o fjb.sh https://gist.githubusercontent.com/dskvr/18252c16cf85c06c1ee6cb5ae04a3197/raw/34bad6a35d98501978c8cd0c25b1628db1191cfe/fjb.sh && chmod +x fjb.sh
wget
wget -O fjb.sh https://gist.githubusercontent.com/dskvr/18252c16cf85c06c1ee6cb5ae04a3197/raw/34bad6a35d98501978c8cd0c25b1628db1191cfe/fjb.sh && chmod +x fjb.sh ```
Trust no one.
create file ``` vi fjb.sh
or
nano fjb.sh ```
review, copy and past into file ``` TIMESTAMP=$1 LOWER=0 UPPER=$(bitcoin-cli getblockcount)
while (( LOWER <= UPPER )); do MID=$(( (LOWER + UPPER) / 2 )) BLOCKHASH=$(bitcoin-cli getblockhash $MID) BLOCKTIME=$(bitcoin-cli getblockheader $BLOCKHASH | jq .time)
if (( BLOCKTIME < TIMESTAMP )); then LOWER=$(( MID + 1 )) elif (( BLOCKTIME > TIMESTAMP )); then UPPER=$(( MID - 1 )) else echo "$BLOCKTIME" exit 0 fidone
echo "$UPPER" ```
give executable permissions
chmod +x ./fjb.shUsage
./fjb.sh <timestampSeconds>It returns block number onlyExample
$: ./fjb.sh 1668779310 763719 -
 @ 39cc53c9:27168656
2025-05-27 09:21:51
@ 39cc53c9:27168656
2025-05-27 09:21:51Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ 6ad3e2a3:c90b7740
2025-05-20 13:49:50
@ 6ad3e2a3:c90b7740
2025-05-20 13:49:50I’ve written about MSTR twice already, https://www.chrisliss.com/p/mstr and https://www.chrisliss.com/p/mstr-part-2, but I want to focus on legendary short seller James Chanos’ current trade wherein he buys bitcoin (via ETF) and shorts MSTR, in essence to “be like Mike” Saylor who sells MSTR shares at the market and uses them to add bitcoin to the company’s balance sheet. After all, if it’s good enough for Saylor, why shouldn’t everyone be doing it — shorting a company whose stock price is more than 2x its bitcoin holdings and using the proceeds to buy the bitcoin itself?
Saylor himself has said selling shares at 2x NAV (net asset value) to buy bitcoin is like selling dollars for two dollars each, and Chanos has apparently decided to get in while the getting (market cap more than 2x net asset value) is good. If the price of bitcoin moons, sending MSTR’s shares up, you are more than hedged in that event, too. At least that’s the theory.
The problem with this bet against MSTR’s mNAV, i.e., you are betting MSTR’s market cap will converge 1:1 toward its NAV in the short and medium term is this trade does not exist in a vacuum. Saylor has described how his ATM’s (at the market) sales of shares are accretive in BTC per share because of this very premium they carry. Yes, we’ll dilute your shares of the company, but because we’re getting you 2x the bitcoin per share, you are getting an ever smaller slice of an ever bigger overall pie, and the pie is growing 2x faster than your slice is reducing. (I https://www.chrisliss.com/p/mstr how this works in my first post.)
But for this accretion to continue, there must be a constant supply of “greater fools” to pony up for the infinitely printable shares which contain only half their value in underlying bitcoin. Yes, those shares will continue to accrete more BTC per share, but only if there are more fools willing to make this trade in the future. So will there be a constant supply of such “fools” to keep fueling MSTR’s mNAV multiple indefinitely?
Yes, there will be in my opinion because you have to look at the trade from the prospective fools’ perspective. Those “fools” are not trading bitcoin for MSTR, they are trading their dollars, selling other equities to raise them maybe, but in the end it’s a dollars for shares trade. They are not selling bitcoin for them.
You might object that those same dollars could buy bitcoin instead, so they are surely trading the opportunity cost of buying bitcoin for them, but if only 5-10 percent of the market (or less) is buying bitcoin itself, the bucket in which which those “fools” reside is the entire non-bitcoin-buying equity market. (And this is not considering the even larger debt market which Saylor has yet to tap in earnest.)
So for those 90-95 percent who do not and are not presently planning to own bitcoin itself, is buying MSTR a fool’s errand, so to speak? Not remotely. If MSTR shares are infinitely printable ATM, they are still less so than the dollar and other fiat currencies. And MSTR shares are backed 2:1 by bitcoin itself, while the fiat currencies are backed by absolutely nothing. So if you hold dollars or euros, trading them for MSTR shares is an errand more sage than foolish.
That’s why this trade (buying BTC and shorting MSTR) is so dangerous. Not only are there many people who won’t buy BTC buying MSTR, there are many funds and other investment entities who are only able to buy MSTR.
Do you want to get BTC at 1:1 with the 5-10 percent or MSTR backed 2:1 with the 90-95 percent. This is a bit like medical tests that have a 95 percent accuracy rate for an asymptomatic disease that only one percent of the population has. If someone tests positive, it’s more likely to be a false one than an indication he has the disease*. The accuracy rate, even at 19:1, is subservient to the size of the respective populations.
At some point this will no longer be the case, but so long as the understanding of bitcoin is not widespread, so long as the dollar is still the unit of account, the “greater fools” buying MSTR are still miles ahead of the greatest fools buying neither, and the stock price and mNAV should only increase.
. . .
One other thought: it’s more work to play defense than offense because the person on offense knows where he’s going, and the defender can only react to him once he moves. Similarly, Saylor by virtue of being the issuer of the shares knows when more will come online while Chanos and other short sellers are borrowing them to sell in reaction to Saylor’s strategy. At any given moment, Saylor can pause anytime, choosing to issue convertible debt or preferred shares with which to buy more bitcoin, and the shorts will not be given advance notice.
If the price runs, and there is no ATM that week because Saylor has stopped on a dime, so to speak, the shorts will be left having to scramble to change directions and buy the shares back to cover. Their momentum might be in the wrong direction, though, and like Allen Iverson breaking ankles with a crossover, Saylor might trigger a massive short squeeze, rocketing the share price ever higher. That’s why he actually welcomes Chanos et al trying this copycat strategy — it becomes the fuel for outsized gains.
For that reason, news that Chanos is shorting MSTR has not shaken my conviction, though there are other more pertinent https://www.chrisliss.com/p/mstr-part-2 with MSTR, of which one should be aware. And as always, do your own due diligence before investing in anything.
* To understand this, consider a population of 100,000, with one percent having a disease. That means 1,000 have it, 99,000 do not. If the test is 95 percent accurate, and everyone is tested, 950 of the 1,000 will test positive (true positives), 50 who have it will test negative (false negatives.) Of the positives, 95 percent of 99,000 (94,050) will test negative (true negatives) and five percent (4,950) will test positive (false positives). That means 4,950 out of 5,900 positives (84%) will be false.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:49:20
@ 21c71bfa:e28fa0f6
2025-05-29 14:49:20Book *Amritsar to Pathankot cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ e771af0b:8e8ed66f
2024-04-19 22:29:43
@ e771af0b:8e8ed66f
2024-04-19 22:29:43Have you ever seen a relay and out of curiosity visited the https canonical of a relay by swapping out the
wsswithhttps? I sure have, and I believe others have too. When I ranhttps://nostr.sandwich.farmin late 2022/2023, I had thousands of hits to my relay's https canonical. Since then, I've dreamed of improving the look and feel of these generic default landing pages.With the release of myrelay.page v0.2, relays can now host their own customizable micro-client at their https canonical.
Transform your relay's landing page from this:
or this:
to something like this:

I say "something like this" because each page is customizable at runtime via the page itself.
In a nutshell
myrelay.page is a self-configuring, Client-Side Rendered (CSR) micro-client specifically built to be hosted at relay canonicals, customizable at runtime via NIP-78. Check out a live example.
Features:
- Dark or light theme
- Join relay
- Relay operator profile and feed
- Zap relay operator
- See people you follow who are on the relay
- Customizable by the relay operator
- Enable/disable blocks
- Sort blocks
- Add HTML blocks
- Add image blocks
- Add markdown blocks
- Add feed blocks, with two layouts (grid/list) and customizable filters.
You can find a full list of features complete and todo here
Why I created myrelay.page
For several different reasons.
Firstly, the default, bland relay pages always seemed like a missed opportunity. I jotted down an idea to build a relay micro-client in early January 2023, but never had the time to start it.
Next, I've been ramping up the refactor of nostr.watch and first need to catch up on client-side technologies and validate a few of my ideas. To do this, I have been conducting short research & development projects to prepare and validate ideas before integrating them into an app I intend to support long-term. One of those R&D projects is myrelay.page.
Additionally, I wanted to explore NIP-78 a bit more, a NIP that came into fruition after a conversation I had with @fiatjaf on February 23rd, 2023. It stemmed from the desire to store application-specific data for app customization. I have seen clients use NIP-78, but from what I've seen, their implementations are limited and do not demonstrate the full potential of NIP-78. There's more on NIP-78 towards the end of this article
The convergence of these needs and ideas, in addition to having an itch I needed to scratch, resulted in the creation of myrelay.page.
*Could be wrong, please let me know in the comments if you have examples of nostr clients that utilize NIP-78 for propagating customizations to other visitors.
Editor Flow
Now I'm going to give you a brief example of the Editor Flow on myrelay.page. There's a lot that isn't covered here, but I want to be as brief as possible.
Note: myrelay.page is alpha, there are bugs, quality of life issues and things are far from perfect.
Login
Presently, myrelay.page only supports NIP-07 authentication, but other authentication methods will be implemented at a later date.
In order to customize your page, you need to have a valid NIP-11 document that provides a valid hex
pubkeyvalue that is the same as the key you use to login.
Click "Edit"
Add a block
For brevity, I'm going to add a markdown block
Configure the block
Add a title to the block and a sentence with markdown syntax.

Publish the configuration
Click publish and confirm the event, once it's been published to relays the page will refresh.
Note: Again it's alpha, so the page doesn't refresh after a few seconds, the publish probably failed. Press publish until it refreshes. Error handling here will improve with time.
Confirm state persistence
After reload, you should see your block persisted. Anyone who visits your page will see your newly configured page. Big caveat: Given the blessing of relays who store your configuration note, if your configuration cannot be found or you cannot connect to your relays, visitors will only see your relay's NIP-11.

Interested?
myrelay.page is alpha and only has two releases, so if you want to be an early adopter, you'll need the skillset and patience of an early adopter. That said, as long as you have some basic development and sysadmin skills as well as understand your reverse-proxy of choice, it's a quick, easy and low-risk side project that can be completed in about 20 minutes.
1. Build
yarn buildornpm run buildorpnpm run build(note: I had issues with pnpm and cannot guarantee they are resolved!)2. Deploy
Move the contents of
buildfolder to your relay server (or another server that you can reverse-proxy to from your relay)3. Update your reverse-proxy configuration
You'll need to split your relay traffic from the http traffic, this ranges from easy to difficult, depending on your server of choice. - caddy: By far the easiest, see an example configuration for strfry here (easily adapted by those with experience to other relay software) - nginx: A little more stubborn, here's the most recent nginx config I got to work. You'll need to serve the static site from an internal port (
8080in the aforementioned nginx conf) - haproxy: Should be easier than nginx or maybe even caddy, haven't tried yet. - no reverse-proxy: shrugsIf any of that's over your head, I'll be providing detailed guides for various deployment shapes within the next few weeks.
Exploring NIP-78
One of the special things about NIP-78 is that it is application specific, meaning, you don't need to conform to any existing NIP to make magic happen. Granted there are limits to this, as interoperability reigns supreme on nostr. However, there are many use cases where interoperability is not particularly desirable nor beneficial. It doesn't change the care needed to craft events, but it does enable a bunch of unique opportunities.
- A nostr client that is fully configurable and customized by the user.
- A nostr powered CMS that can be edited entirely on the client-side.
- Any use case where an application has special functionality or complex data structures that present no benefit in the context of interoperability (since they are "Application Specific").
Final thoughts
I was surprised at how quickly I was able to get myrelay.page customizable and loading within an acceptable timeframe;
NIP-11, the operator'sNIP-65and the myrelay.pageNIP-78events all need to be fetched before the page is hydrated! While there is much to do around optimization, progressive page-loading, and general functionality, I'm very happy with the outcome of this short side project.I'll be shifting my focus over to another micro-app to validate a few concepts, and then on to the next nostr.watch. Rebuilding nostr.watch has been a high-priority item since shortly after Jack lit a flame under nostr in late 2022, but due to personal circumstances in 2023, I was unable to tackle it. Thanks to @opensats I am able to realize my ideas and explore ideas that have been keeping me up at night for a year or more.
Also, if you're a relay developer and are curious about making it easier for developers to deploy myrelay.page, get in touch.
Next article will likely be about the micro-app I briefly mentioned and nostr.watch. Until then, be well.
-
 @ bf95e1a4:ebdcc848
2025-05-26 12:04:27
@ bf95e1a4:ebdcc848
2025-05-26 12:04:27This is a part of the Bitcoin Infinity Academy course on Knut Svanholm's book Bitcoin: Sovereignty Through Mathematics. For more information, check out our Geyser page!
The Environment
There’s no such thing as a free lunch. There’s no such thing as a zero-sum game. The 2nd law of thermodynamics tells us this. You know, the one about entropy and how everything will be really lame in a couple of trillion years. There’s no action without an equally big reaction somewhere. This is also true for Bitcoin mining. Every once in a while, some ignorant clickbait-hungry journalist writes an article about Bitcoin’s energy usage and how it’s connected to global warming or how widespread Bitcoin adoption would kill us all someday because of its “wasteful” production process. What they all fail to address is the alternative cost. As mentioned before, Bitcoin is valuable because it's scarce, and it's scarce because it's costly to produce. The same is true for gold or diamonds or anything else that is scarce and hard to come by. As discussed in earlier chapters, the mining algorithm can never be any more energy efficient because the electricity spent is directly linked to the value of the token.
Secondly, think about what most people use their Bitcoin for. Nothing. That’s right, nothing. Bitcoin incentivizes saving rather than spending. This is the exact opposite of how people use money in our current system of fiat currencies because Bitcoin is deflationary rather than inflationary relative to all other currencies. This means that every dollar, yen, or pound spent on Bitcoin would have ended up being spent on some other energy-demanding thing had it not been spent on Bitcoin. Either that or it would have lost its value due to inflation, which implies that even more dollars, yen, or euros would have been created and spent on frivolous things. Right now, credit is cheap, and the underlying economic theory of our time is based on the idea that the amount of spending going on in society is a key metric in economics. Bitcoin, on the other hand, is based on the economic theories of the Austrian school, where saving is the key metric. Yes, Bitcoin is costly to produce, but so is overproducing every product on Earth because every business needs to expand as fast as possible to pay off their loans. Human well-being has always been, and will always be, linearly connected to energy consumption. You can’t get around or bypass this fact. Energy consumption and human flourishing are inevitably linked. The thing Bitcoin does is to take away the need for unnecessary energy consumption by incentivizing us to save for future generations. It’s a mechanism that hinders our self-destructive tendencies. Not a threat to our planet's health, but a remedy.
The next time you hear about the Bitcoin network using as much energy as a small country, ask yourself: where would all that energy have ended up if it wasn’t funneled into the only invention trying to save us from ourselves there is? Into a Chinese factory producing consumer goods shipped by boat, truck and car for temporary use and probably ending up in a garbage pile the size of a small country in less than a year? How is that better for the planet? The only place from which solutions for humanity's problems can stem is human ingenuity. Such ingenuity in turn, stems from places where people with brains have a shot at getting somewhere in life. Thanks to the Internet and Bitcoin, that somewhere is everywhere. The Internet connects us, and Bitcoin frees up our time and emancipates us from our current, destructive systems. Bitcoin helps you plant a seed and watch it grow. Before you criticize Bitcoin, try to comprehend why it was invented and what inflationary, soft money does to the mechanisms of the market. Try to understand why we have a “climate problem” in the first place — why we overconsume. What underlying forces pull our psychological strings and make us borrow money for a new car? It takes a special kind of ignorance to criticize a solution without first fully comprehending the problem.
There’s one specific word that describes the current global environmentalist movement better than any other, and that word is “hubris.” Yes, the Earth has been getting warmer, very slowly, over the last fifty years. Yes, at least one of the ice caps might be melting. Yes, it’s probably because of human activity but no, you can’t save the planet through political interference in people’s lives. To get every nation on Earth to agree that it is a good idea to forcefully make people change their behavior for the sake of the climate is not only impossible but also cruel and counterproductive. Collectivists always disguise their urge to deprive their fellow man of his or her possessions and freedoms as a necessary thing to do in order to “save” humanity. This is nothing new. They’ve just decided that “climate change” is the most effective banner to rally under right now. The causes change, but the underlying philosophy stays the same. It’s very disturbing that the socialist experiment gets to repeat itself so many times in so many parts of the world.
Human progress and human flourishing have linear relationships to energy usage. If we want to find new ways of bettering ourselves, we should use more energy, not less. Truly free market competition leads to the most efficient solutions, and there are a bunch of incentives for producers of consumable goods to find cheap energy sources. Bitcoin provides the market with yet another incentive — to find locations for and invest in power plants in remote areas of the world where the cost barrier for building the plant has been too high historically due to the costly and wasteful process of transporting electricity. Hydro-electric plants in areas with a high risk of flooding, for instance. These areas are not suitable for human settlements, but they could provide us with a lot of electricity. When producers have the option to convert electricity into money directly, they’re more likely to use renewable energy sources, not less. In this sense, Bitcoin can function as a battery for energy producers.
Offshore wind farms have a very specific wind force range where they produce a usable amount of electricity. The bigger the turbine, the wider the range, but they still have an upper and a lower wind force limit. If an offshore wind farm had been connected to a Bitcoin mining rig, the surplus energy produced on windy days could have been converted into a profit for the producer instantly. The same logic applies to solar farms and geothermal plants. Energy is not a finite resource in any practical sense for the inhabitants of Mother Earth. If we could harness and store all the power of all the sunlight that hits the Earth during just one day, we could satisfy all of humanity’s energy needs for a couple of hundred years.
Bitcoin’s role in all of this is unexplored, but its potential to be a very positive environmental force is huge, and it will prove its utility during the next century. On one hand, it provides energy producers with a battery; on the other hand, it gives central bankers a run for their money and ultimately forces them to adopt a more sound monetary policy or become obsolete altogether. Bitcoin creates an incentive for sacrificing surplus energy for a small profit and a greater good rather than just letting it go to waste. The energy harnessed is converted into a completely scarce asset that is divisible and transportable to a much greater extent than any other valuable resource on Earth. It incentivizes energy producers to think long term and will reward those most patient and least wasteful among them. This recalibration of incentive structures is, of course, not only limited to energy producers or miners but to anyone who embraces this technology and understands its implications. In due time, Bitcoin’s superior monetary properties will be undeniable to even the most stubborn dinosaur. This would be an enormous net gain for humanity and the environment.
Courageous politicians dare to implement unpopular policies. They don’t need climate-striking teenagers to tell them which issues ought to be addressed first. It is ironic how celebrities who score cheap points by talking about the climate often accuse their political opponents of being “populist.” What really happens when you raise carbon taxes and try to force populations into behaviors that they don’t really like? The gilets jaunes, or yellow vests, in France are a great example. People still have to commute to work. Raising taxes solves nothing — it just distorts the market and relocates the problem. The only thing the recently adopted environmentalist policies of France resulted in was the destruction of Paris. Arguably not the best thing for the environment.
In a truly free society, a society with sound money, climate-striking children wouldn’t be a problem. They would have to learn to cooperate in order to address whatever imaginary problem they sought to solve, which would be harmless to the rest of us. Now, when backed by fear-mongering journalists, they can cause a ton of damage as our virtue-signaling political class needs to adapt to whatever imaginary issue the press has primed us with in order to secure votes. It’s not about whether there is a real climate problem or not, but rather about motives. Always ask yourself, what does this person stand to gain from holding this particular opinion? Can this issue really be solved by political means?
There’s no such thing as a free lunch. There is such a thing as representation, however, and there’s always a personal economic motive behind political decisions. They’re not here for you; you’re here for them. One of the most eye-opening experiences of my life was seeing the lobbyist quarters in Brussels. The rise of veganism, placebic gluten intolerance, and "meat-free Mondays" in school cafeterias are all products of the food industry. A soy burger is a lot cheaper to produce than a beef one. To anyone who can sell it at a higher price by appealing to people’s vanity or world-saving hubris, huge profits await. They’ve managed to monetize our collective bad climate conscience in such a cunning way that most of us have no clue we’re being played. In the 20th century, the cereal-killers of the Kellogg's company and their likes funded “research” that cemented a fear of red meats and saturated fats into the minds of the public. The effects of this propaganda can very much still be seen today as the inhabitants of America are about twice as fat today than they were before the introduction of “light” products to the market. All of these things are connected to the root of the problem: the lack of sound money. Inflation made it possible for the food industry to replace our homemade beef burger with a mass-produced cheap soy substitute while making us believe that the price of a burger hadn’t changed that much in the last fifty years. Spoiler alert - it had.
Another of the most eye-opening experiences I’ve had was during my stay in a Mayan village in the Toledo district of Belize about ten years ago. I spent a couple of days with a family of two adults and six children in a jungle village of huts and no electricity save for two diesel generators. One night, the father of the house told me a story about his friend going into politics a decade earlier and being murdered for having the wrong opinions. We slept on wooden beds without mattresses, and a couple of dogs and turkeys ran freely around the village. One day, the family’s ten-year-old was listening to some Bob Marley songs on a CD player connected to a car battery and a small solar panel on a pole in the garden. I listened for a while and then asked him about the strange sound effects in between the songs. Helicopter sounds, machine gun sounds, and other strange noises were intersecting the songs here and there. He replied by telling me, “...oh, it’s not a proper CD. I made it with Virtual DJ on my cousin’s laptop”. I was stunned. Here was this ten-year-old, in the middle of the jungle, just as skilled with a computer as any other ten-year-old I had ever met. At that moment, I realized just how leveled the playing field has been for the workforce across the globe. Here was this child, living in a hut without even electricity (but also without a mortgage to inherit), ready to compete on the same global market as any other kid in the world.
Bitcoin is the logical next step. Bitcoin doesn’t care about nationality, gender, ethnicity, age, sexual preferences, or any other imagined victimization or privilege. To Bitcoin, we’re all equal. It is a voluntary system, and it knows no biases. Bitcoin is equality of opportunity in its purest form, and it doesn’t have any opinion on the outcome whatsoever.
About the Bitcoin Infinity Academy
The Bitcoin Infinity Academy is an educational project built around Knut Svanholm’s books about Bitcoin and Austrian Economics. Each week, a whole chapter from one of the books is released for free on Highlighter, accompanied by a video in which Knut and Luke de Wolf discuss that chapter’s ideas. You can join the discussions by signing up for one of the courses on our Geyser page. Signed books, monthly calls, and lots of other benefits are also available.
-
 @ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03
@ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ 611021ea:089a7d0f
2025-05-26 18:28:46
@ 611021ea:089a7d0f
2025-05-26 18:28:46Imagine a world where your favorite health and fitness apps—diet trackers, meditation tools, cardio and strength training platforms, even therapy apps—can all work together seamlessly. Not because they're owned by the same company, but because they speak a common, open language. That's the future NIP-101h is building on Nostr.
A Modular, Privacy-First Health Data Framework
NIP-101h defines a modular, privacy-first framework for sharing granular health and fitness metrics on the decentralized Nostr protocol. The core idea is simple but powerful: every health metric (weight, steps, calories, mood, and so on) gets its own unique Nostr event kind. Apps can implement only the metrics they care about, and users can choose exactly what to share, with whom, and how.
This modular approach means true interoperability. A meditation app can log mindfulness sessions, a running app can record your daily mileage, and a diet tracker can keep tabs on your nutrition—all using the same underlying standard. Each app remains independent, but your data becomes portable, composable, and, most importantly, under your control.
Why NIP-101h Matters
Interoperability
Today's health and fitness apps are walled gardens. Data is locked away in proprietary formats, making it hard to move, analyze, or combine. NIP-101h breaks down these barriers by providing a common, open standard for health metrics on Nostr. Apps can collaborate, users can migrate, and new services can emerge—without permission or lock-in.
User Control & Privacy
Health data is deeply personal. That's why NIP-101h is privacy-first: all metric values are encrypted by default using NIP-44, unless the user explicitly opts out. You decide what's public, what's private, and who gets access. Even if you want to keep everything local, that's supported too.
Extensibility
The world of health and fitness is always evolving. NIP-101h is designed to grow with it. New metrics can be added at any time via the
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:49:01
@ 21c71bfa:e28fa0f6
2025-05-29 14:49:01Book *Amritsar to Manali cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ b83a28b7:35919450
2025-05-16 19:23:58
@ b83a28b7:35919450
2025-05-16 19:23:58This article was originally part of the sermon of Plebchain Radio Episode 110 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ 4fe14ef2:f51992ec
2025-05-25 10:04:36
@ 4fe14ef2:f51992ec
2025-05-25 10:04:36Let's support Bitcoin merchants! I'd love to hear some of your latest Lightning purchases and interesting products you bought. Feel free to include links to the shops or businesses you bought from.
Who else has a recent purchase they’re excited about? Bonus sats if you found a killer deal! ⚡
Spend sats, not fiat!
If you missed our last thread, here are some of the items stackers recently spent and zap on.
Share and repost: N: https://njump.me/note1r0rllvtns2e8g2rqn0p9uytxucmjzal3pxslldjtfmxwp2amwjjqy3aazq X: https://x.com/AGORA_SN/status/1926579498629169410
https://stacker.news/items/988783
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:48:43
@ 21c71bfa:e28fa0f6
2025-05-29 14:48:43Book *Amritsar to Katra cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:48:21
@ 21c71bfa:e28fa0f6
2025-05-29 14:48:21Book *Amritsar to Kapurthala cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ b8851a06:9b120ba1
2025-02-24 02:02:32
@ b8851a06:9b120ba1
2025-02-24 02:02:32The French fiscal catastrophe is unfolding exactly as Austrian economists predicted. Government intervention breeds more intervention, trapping the economy in a death spiral of debt, deficits, and monetary debasement.
France’s public debt has surged to 111% of GDP in 2023, with projections showing 119% by 2029. The government’s much-touted €60 billion “budget effort” is a political charade—by 2025, the deficit will still exceed 5.4% of GDP. To stabilize its finances, France would need €120 billion in permanent savings—an impossible task in a system where political survival depends on endless spending.
The Political Crisis: A System Losing Legitimacy
Economic crises create political ones. In December 2024, Prime Minister Barnier was ousted over austerity measures, replaced by Bayrou—a desperate attempt to calm markets. But leadership changes won’t fix the fundamental issue: France is ungovernable under its current fiscal trajectory.
Every attempt to “fix” the problem—more regulation, more spending, more monetary manipulation—only worsens the crisis. Political chaos is a symptom of economic insolvency.
The ECB’s Stealth Bailout: Germany’s Growing Revolt
France is functionally bankrupt, but the ECB is quietly shifting the burden onto German savers through Target2 claims and monetary expansion. This amounts to a silent wealth transfer—bailing out Paris at Berlin’s expense.
The German public is noticing. Support for the AfD’s “Dexit” movement is rising, as voters realize they are being forced to subsidize failing economies. The eurozone’s fault lines are deepening.
The Likely Scenarios: What Comes Next?
Based on current conditions, three major outcomes are most probable:
Scenario 1: ECB “Muddles Through”
The ECB takes a “too little, too late” approach, avoiding decisive action while failing to restore confidence. This leads to: • Wider French bond spreads as investors demand higher yields • Weakened ECB credibility, as markets lose faith in its ability to contain the crisis • Prolonged volatility without addressing the fundamental debt problem
Scenario 2: IMF/ESM Bailout
France is forced into a formal bailout via the IMF and European Stability Mechanism (ESM). This would trigger: * Harsh austerity measures, politically toxic in a nation that riots over pension reforms * Severe political fallout, as both left and right-wing factions resist external control * A crisis within the ECB itself, as its French president faces backlash for “bailing out his own country” * Northern European pushback, with the German Bundestag and creditor states reluctant to approve another bailout
Scenario 3: Communications Crisis
A severe market panic caused by ECB miscommunication leads to: * A European-style “Taper Tantrum”, triggering a selloff in French bonds * Spreads widening rapidly, forcing emergency interventions * Loss of market confidence, accelerating capital flight * Potential contagion, pulling in weaker Eurozone economies
The remaining probability accounts for more moderate scenarios, where France manages to delay disaster through temporary measures. But at this level of debt and deficit spending, delay is the best-case scenario—not resolution.
The Endgame: Default or Hyperinflation?
France’s pension system alone is set to bleed €30 billion annually by 2045. The debt load is unsustainable, the political will to cut spending is nonexistent, and the ECB’s ability to print euros without consequence is rapidly eroding.
There are only two ways this ends:
- Massive defaults, triggering economic and social chaos.
- Hyperinflationary money printing, destroying savings and purchasing power.
Ludwig von Mises warned about this nearly a century ago:
“The ultimate outcome of credit expansion is either a depression brought about by the voluntary abandonment of further credit expansion, or a catastrophe of the currency system involved.”France—and the entire euro system—has reached this fork in the road. The only question left is: Will they choose ruin now, or ruin later?
Mises was right. And in the end, economic reality always wins. The only choice left is whether you want to be a victim—or prepared.
-
 @ 3c559080:a053153e
2025-05-25 20:26:43
@ 3c559080:a053153e
2025-05-25 20:26:43So firstly you should find an emulator for whatever you want to play on. There are many for desktop and mobile devices. Checkhere for a list of all the available consoles and their various emulators.
Next what game do you want to play? This is the like the homepage for a shit ton of roms.
Some of the more popular roms are there and other various list like Sony Nintendo
After narrowing down your selection you will end up on myrient i assume this is just some dope person hosting all these so if you get some use out of it, think of donating they even take corn, but other shitcoins too (but thats not the focus here)
Once you download the Rom of the game you want, you will get a compressed (zip) folder, unzip it and within it will be the rom, most systems will identify your emulator and use it open the game. If not, launch the emulator and within it should be an option to open a file, open the file in the unzipped folder.
Enjoy So you want to Mod?
So every Mod, is a mod for a specific game [ex. Pokemon Blue, Pokemon FireRed, Super Mario Bros.] so it requires you to get the Rom for that base game, the mod itself, and a tool to patch it.
 There is an online tool to easily patch the mod to the ROM. IMPORTANT, this will not change any naming, Id recommend having a folder with the base game roms, and a folder for the mods, and lastly a folder for the newly modded roms. Make sure to name or just save the game in modded roms folder after the patch.
There is an online tool to easily patch the mod to the ROM. IMPORTANT, this will not change any naming, Id recommend having a folder with the base game roms, and a folder for the mods, and lastly a folder for the newly modded roms. Make sure to name or just save the game in modded roms folder after the patch. Below are a few resource to find various Pokemon Rom mods(sometimes called hacks)
Personally, Pokemon Unbound is considered the best most polished hack. it runs on Pokemon Fire Red.
Pokemon Emerald Rouge is a cool take on the popular Rougelite genre. This runs on base game Pokemon Emerald
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ c1d77557:bf04ec8b
2025-05-25 09:47:07
@ c1d77557:bf04ec8b
2025-05-25 09:47:07No crescente universo de plataformas de jogos online, a H2Bet se destaca como uma opção inovadora, segura e recheada de diversão para os jogadores brasileiros. Com uma interface moderna e intuitiva, a H2Bet vem conquistando cada vez mais usuários que buscam entretenimento de qualidade, diversas opções de jogos e uma experiência digital fluida e confiável.
Uma Plataforma Feita para o Público Brasileiro Desde o primeiro acesso, é possível perceber que a H2Bet foi pensada para atender às necessidades do público brasileiro. O site é totalmente traduzido para o português, com suporte ao cliente eficiente e disponível 24 horas por dia, todos os dias da semana. O atendimento pode ser feito via chat ao vivo ou WhatsApp, oferecendo respostas rápidas e eficazes para qualquer dúvida ou solicitação.
Além disso, a plataforma aceita métodos de pagamento populares no Brasil, como PIX, boleto bancário e carteiras digitais, garantindo mais praticidade nas transações financeiras. Isso facilita tanto os depósitos quanto os saques, promovendo uma experiência mais fluida para todos os jogadores.
Diversidade de Jogos para Todos os Gostos Um dos grandes diferenciais da H2Betestá em sua ampla variedade de jogos. A plataforma oferece opções para todos os perfis de jogadores — desde os iniciantes até os mais experientes. Entre os destaques estão:
Slots (Caça-níqueis): Com gráficos envolventes, animações modernas e uma enorme variedade de temas, os slots são perfeitos para quem busca diversão rápida e visualmente atrativa.
Jogos de Mesa: Clássicos como roleta, blackjack e bacará estão presentes na H2Bet, proporcionando uma experiência dinâmica e estratégica para os jogadores que gostam de desafios mentais.
Apostas Esportivas: Os fãs de esportes também têm espaço garantido na H2Bet. É possível apostar em jogos de futebol, basquete, tênis e diversas outras modalidades, tanto nacionais quanto internacionais.
A plataforma trabalha com provedores de jogos renomados mundialmente, garantindo alta qualidade gráfica, jogabilidade otimizada e total segurança nos resultados.
Uma Experiência do Jogador Incomparável Na H2Bet, a experiência do usuário é prioridade. Tudo foi cuidadosamente projetado para que o jogador possa se divertir sem complicações. O processo de cadastro é rápido e simplificado, permitindo que o novo usuário comece a jogar em poucos minutos. Além disso, o site é totalmente responsivo, funcionando perfeitamente em computadores, tablets e smartphones.
Outro ponto de destaque são as promoções e bônus oferecidos aos jogadores. Desde bônus de boas-vindas até promoções sazonais e programas de fidelidade, a H2Bet recompensa a lealdade dos seus usuários com benefícios exclusivos que aumentam ainda mais a diversão.
A segurança da plataforma também merece elogios. A H2Bet utiliza tecnologia de criptografia de ponta para proteger os dados dos jogadores, além de manter total transparência em seus termos e condições.
Conclusão A H2Bet chega ao mercado brasileiro com uma proposta clara: oferecer uma plataforma de jogos online completa, segura e envolvente. Com uma vasta seleção de jogos, suporte dedicado ao jogador e uma interface pensada para o usuário, a H2Bet se posiciona como uma das melhores opções de entretenimento digital no Brasil. Se você busca emoção, praticidade e uma experiência de jogo diferenciada, a H2Bet é o lugar certo para você.
-
 @ 28ca019b:93fcb2cc
2025-05-25 19:25:17
@ 28ca019b:93fcb2cc
2025-05-25 19:25:17Introduction
“There is nothing more powerful than an idea whose time has come.” -Victor Hugo
Early 1950’s America. Harry S. Truman is in office. The economy is booming and the middle class are comfortable. Shiny new television sets invite the first scenes of Hollywood into people’s homes. The Weavers, Tony Bennett, Vera Lynn and Perry Como play on the radio.
But on the fringes, in dance halls and late night clubs, a cultural revolution is brewing… A new musical fusion with influences from blues, R\&B, jazz, rockabilly, country and gospel music is about to give birth to not only a new genre, but a whole new way of life that will change society and culture, forever.
Rock & Roll
It becomes a symbol of freedom, a means of expression, and a catalyst for social change. It brings into existence a new type of counter-culture, filled with individuals who are driven to rebel against norms and authority. They don’t ask for permission. They push for change.
I believe we are witnessing such a shift now. And like rock & roll, the movement I’m speaking of is also ground up, grass roots, punk rock and will not look to authority to seek permission. The catalyst for this new social change, I believe, is Bitcoin. With its innate properties, it empowers and enables the individual like never before to achieve their fullest potential, expressed through an unprecedented freedom technology. It is an idea, like a song everyone can sing in their own way, that nobody can silence.
Revolution
"You say you got a real solution / Well you know / we’d all love to see the plan" -John Lennon
The rock & roll era helped bring about meaningful societal change through art, music, and film. It created a new social narrative. Today, the Bitcoin network is providing people with a different set of tools and ideas to build a better future in a much more practical and pragmatic way. Instead of trying to reshape social consensus and cultural norms through art forms, fashion, or lifestyle, bitcoin is achieving this through open source code.
For the first time, this technology gives individuals financial sovereignty and personal control over their own destiny, with the ability to self custody their own money that no corporation, government, dictator or king can tamper with. The individual has an opportunity to finally be freed from economic tyranny. And societies have the potential to avoid endless wars funded with printed government money. John Lennon said ‘give peace a chance’. If he were still here today and understood how bitcoin could subvert the military industrial complex would he not exclaim, ‘give bitcoin a chance’?
Natural Rights, Civil Rights, Digital Rights
"The times they are a-Changin’" -Bob Dylan
The civil rights movement was tightly interwoven with the history of rock & roll. The march on Washington, August 28th 1963, marked a seminal moment in American history for the advancement of equal rights before the law. Bob Dylan, along with Joan Baez, stood with over two hundred thousand other Americans and listened to Martin Luther King’s now immortal speech.
People with the same values peacefully gathered in numbers to make a statement powerful enough to change the conversation. This is analogous to the same freedom-minded people today gathering in cyberspace and voting not in the traditional sense, but voting with their money – peacefully exiting and transferring their economic energy into a system where they can’t be expropriated.
The question of whether individual rights are granted or have to be secured by each individual remains a contested area of philosophy to this day. To outline each in a very crude and simplistic way, natural rights (sometimes referred to as inalienable rights) are derived from the belief that every person owns their own body, therefore their own labor, time, and energy. Civil rights, on the other hand, are granted by the state and are therefore not universal. The fact that they are rights granted to humans by other humans means they always have the potential to be revoked or withdrawn.
Digital rights granted by the power of asymmetric cryptography are based in the laws of mathematics. Combined with proof of work, based in the law of thermodynamics, this makes digital rights that bitcoin provides more akin to natural rights than civil rights, as no one person or group can unilaterally revoke those rights or confiscate your property through violence. No amount of fire power, tanks, fighter jets or nuclear weapons can break a bitcoin private key or rewrite the sunken cost of proof of work embedded into bitcoin’s timechain. This idea of securing rights without asking permission is, in itself, a revolution and achievable now in an egalitarian way. This implies a potentially huge shift in power from those with a monopoly on violence, to peaceful individuals who want to be treated fairly and with dignity.
Cypher Punk-Rock
Songwriters write songs. Cypherpunks write code.
To tie things back and look at a very narrow, but potentially huge use case of bitcoin, let’s examine the current broken incentives of the music industry, particularly recorded music. It is becoming increasingly apparent that an option other than a subscription model could find demand from content consumers and producers alike.
There is now a way, with Bitcoin and Lightning Network, for a music fan to pay artists directly and for any amount – dollars, cents or even fractions of cents. This model has positive outcomes for the music producer and fan who are the main two parties engaged in the transaction. The artist keeps all of what is sent and the listener can pay what they want. The listener can pay as they listen, rather than be locked into a rolling subscription that isn’t based on usage. This concept, called ‘value for value’, is finding its way into new music platforms such as Wavlake and Fountain. I believe this model will become the de-facto way of monetizing digital content in the coming years. This could bring an economic signal back to music that has been lost and cannot be achieved by streams alone. This will hopefully create a more meritocratic music system and shake up the entrenched streaming monoliths.
Art can shine a light on a certain truth. It can also make people look at things in a completely new way. Maybe then, Satoshi was the greatest artist who ever lived. Bitcoin smashed the conventional wisdom and theories of the most basic and prevalent thing everyone takes for granted: money. Using money as a lens to view the world can lead to distortions in your perception if the lens is warped. Removing the glasses makes you reevaluate economics, politics, religion, philosophy, morality, beauty, and almost every other aspect of life. The beauty of the Sistine Chapel, the Egyptian pyramids, the Mona Lisa, Beethoven’s 5th Symphony, Bohemian Rhapsody all intrinsically imply a certain degree of proof of work. The art, you could say, speaks for itself.
The Long and Winding Road Ahead
As a musician, I have found a new hope. The value for value movement gives me that hope. If this is truly a superior model of music distribution and consumption it will win out over time on the market.
Another point to touch on would be the possibility of this technology ushering in an artistic renaissance. I can honestly say my favorite music, the songs that have moved me the most, normally comes from a place of truth, honesty and sheer talent. Maybe I’m out of touch, but I feel popular music of late is devoid of soul, meaning and the biggest mainstream artists want to conform to the man (giant corporations/governments) instead of stick it to the man! Probably because there is nowhere else to turn now that streaming and social media platforms own their speech and art. We need to investigate and embrace new ways to own our speech and art, to make art interesting again. The powers that be, need to let it be, and leave alone individuals who wish to use this technology for their own interests if they do so in a peaceful way.
I want to leave you with a Frank Zappa quote that seems more relevant than ever:
“I’d say that today, dishonesty is the rule, and honesty the exception. It could be, statistically, that more people are honest than dishonest, but the few that really control things are not honest, and that tips the balance…”
My charitable view is that the majority of people in power aren’t corrupt, it’s rather just a case of ‘no one is better than their incentives’. But when incentives are misaligned bad outcomes will inevitably result. With bitcoin and its incorruptible incentive structure, we have a chance to peacefully opt-out of a rigged game. I urge you to not trust, but verify with your own research that bitcoin is the answer to many of society’s current problems.
I think it’s fair to say, we all need to question ourselves and authority a little more than we’re comfortable doing, to hold truth as an ideal worth striving for, and live a little more rock & roll!
Link to original article**
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ e771af0b:8e8ed66f
2023-11-28 03:49:11
@ e771af0b:8e8ed66f
2023-11-28 03:49:11The last 6 months has been full full of unexpected surprises, of the unpleasant variety. So it was welcomed news that
nostrwatchwas awarded a grant by OpenSats recently which has allowed me to revisit this project and build out my original vision, the one I had before nostr went vertical.The last month has been a bit of a joyride, in that I have met little friction meeting goals. For example I was able to rewrite
nostrwatch-jsin an evening, tests another evening and did most of the Typescript conversion in 30 minutes (thanks AI!)Here's a quick summary of the last month, I'm probably missing a handful of details, but these are the important bits.
- Went through all the new NIPs, prototyped and experimented
- Nearly completed a full rewrite of
nostrwatch-js, nownocap. Presently porting to Typescript. Still alpha, don’t use it. - Released
nostrawl, a wrapper fornostr-fetchthat has Queue adapters for persistent fetching. Nothing special, but needed to factor out the functionality from the legacy trawler and the requirements were general enough to make it a package. - Starting porting the nostr.watch trawler, cache layer and rest API, but much work is still needed there. Aiming to have the current infrastructure updated with new daemons by end of year.
- In concert with the cache layer testing, I ran some experiments by patching in a rough trend engine prototype from earlier this year and a novel outbox solution, both with promising results.
- Wrote a few small CLI tools to assist with developments, got acquainted with
ink, and reacquainted myself with wonderful world of ES Module conflicts.
The rest of this year will be mostly backend work, tests and data engineering. Early next year I will begin iterative development on a new GUI and a string of CLI tools.
Luckily, nostr.watch and it's underlying infrastructure, as abysmal as it is, hasn't completely sank. Traffic is much lower than the ATH but still hovering between 2-3k unique visitors a month. I can't express in words how happy I will be when I can put the legacy nostr.watch to rest.
Next update will include a bit more of the why and how, and where I am trying to get to with this project.
Until next time.
-
 @ 8d34bd24:414be32b
2025-05-25 06:29:21
@ 8d34bd24:414be32b
2025-05-25 06:29:21It seems like most Christians today have lost their reverence and awe of God. We’ve attributed God’s awesome creation by the word of His mouth to random chance and a Big Bang. We’ve attributed the many layers of sediment to millions and billions of years of time instead of God’s judgment of evil. We’ve emphasized His love and mercy to the point that we’ve forgotten about His holiness and righteous wrath. We’ve brought God down to our level and made Him either our “buddy” or made Him our magic genie servant, who is just there to answer our every want and whim.
The God of the Bible is a holy and awesome God who should be both loved and feared.
The fear of the Lord is the beginning of knowledge;\ Fools despise wisdom and instruction. (Proverbs 1:7)
The God of the Bible is the Lord of Lords and King of Kings who “… upholds all things by the word of His power. …” (Hebrews 1:3). Yes, God loves us as sons. Yes, God is merciful. Yes, through Jesus we have the blessed opportunity to approach God directly. None of that means we get to treat God like just another friend. We are to approach God with fear and trembling and worship Him in reverence and awe.
Worship the Lord with reverence And rejoice with trembling. (Psalm 2:11)
Part of the problem is that our culture just doesn’t show reverence to authority. It focuses on self and freedom. The whole thought of reverence for authority is incomprehensible for many. Look at this Psalm of worship:
The Lord reigns, let the peoples tremble;\ He is enthroned above the cherubim, let the earth shake!\ The Lord is great in Zion,\ And He is exalted above all the peoples.\ Let them praise Your great and awesome name;\ Holy is He. (Psalm 99:1-3)
This is the way we should view God and the proper attitude for approaching God.
Another issue is that we don’t study what God has done in the past. In the Old Testament, God commanded the Israelites to setup monuments of remembrance and to teach their kids all of the great things God had done for them. When they failed to do so, Israel drifted astray.
You shall teach them to your sons, talking of them when you sit in your house and when you walk along the road and when you lie down and when you rise up. (Deuteronomy 11:19)
God has given us the Bible, His word, so that we can know Him, know His character, and know His great deeds. When we fail to be in His word daily, we can forget (or not even know) the greatness of our God.
Establish Your word to Your servant,\ As that which produces reverence for You. (Psalm 119:38)
Do you love God’s word like this? Do you hunger for God’s word? Do you seek to know everything about God that you can know? When we love someone or something, we want to know everything about it.
Princes persecute me without cause,\ But my heart stands in awe of Your words.\ **I rejoice at Your word,\ As one who finds great spoil. \ (Psalm 119:161-162) {emphasis mine}
In addition to what we can learn about God in the Bible, we also need to remember what God has done in our own lives. We need to dwell on what God has done for us. We can just try to remember. Even better (I’ll admit this is a weakness for me), write down answered prayers, blessings, and other things God has done for you. My son has been writing down one blessing every day for over a year. What an example he is!
After we have thought about what God has done for us and those we care about, we should praise Him for His great works.
Shout joyfully to God, all the earth;\ Sing the glory of His name;\ Make His praise glorious.\ Say to God, “How awesome are Your works!\ Because of the greatness of Your power \ Your enemies will give feigned obedience to You.\ All the earth will worship You,\ And will sing praises to You;\ They will sing praises to Your name.” Selah.\ **Come and see the works of God,\ Who is awesome in His deeds toward the sons of men. \ (Psalm 66:1-5) {emphasis mine}
There is nothing we can do to earn salvation from God, but we should be in awe of what He has done for us leading to submission and obedience in gratitude.
Therefore, since we receive a kingdom which cannot be shaken, let us show gratitude, by which we may offer to God an acceptable service with reverence and awe; for our God is a consuming fire. (Hebrews 12:28-29) {emphasis mine}
Are you thankful for your blessings or resentful for what you don’t have? Do you worship God or take things He has provided for granted? Do you tell the world the awesome things God has done for you or do you stay silent? Do you claim to be a Christian, but live a life no different than those around you?
Then the Lord said,
“Because this people draw near with their words\ And honor Me with their lip service,\ But they remove their hearts far from Me,\ And their reverence for Me consists of tradition learned by rote, (Isaiah 29:13)
I hope this passage does not describe your relation ship with our awesome God. He deserves so much more. Instead we should be zealous to praise God and share His goodness with those around us.
Who is there to harm you if you prove zealous for what is good? But even if you should suffer for the sake of righteousness, you are blessed. And do not fear their intimidation, and do not be troubled, but sanctify Christ as Lord in your hearts, always being ready to make a defense to everyone who asks you to give an account for the hope that is in you, yet with gentleness and reverence; (1 Peter 3:13-15) {emphasis mine}
Did you know that you can even show reverence by your every day work?
By faith Noah, being warned by God about things not yet seen, in reverence prepared an ark for the salvation of his household, by which he condemned the world, and became an heir of the righteousness which is according to faith. (Hebrews 11:7) {emphasis mine}
When Noah stepped out in faith and obedience to God and built the ark as God commanded, despite the fact that the people around him probably thought he was crazy building a boat on dry ground that had never flooded, his work was a kind of reverence to God. Are there areas in your life where you can obey God in reverence to His awesomeness? Do you realize that quality work in obedience to God can be a form of worship?
Just going above and beyond in your job can be a form of worship of God if you are working extra hard to honor Him. Obedience is another form of worship and reverence.
Then Zerubbabel the son of Shealtiel, and Joshua the son of Jehozadak, the high priest, with all the remnant of the people, obeyed the voice of the Lord their God and the words of Haggai the prophet, as the Lord their God had sent him. And the people showed reverence for the Lord. (Haggai 1:12) {emphasis mine}
Too many people have put the word of men (especially scientists) above the word of God and have tried to change the clear meaning of the Bible. I used to think it strange how the Bible goes through the days of creation and ends each day with “and there was evening and there was morning, the xth day.” Since a day has an evening and a morning, that seemed redundant. Why did God speak in this manner? God knew that a day would come when many scientist would try to disprove God and would claim that these days were not 24 hour days, but long ages. When a writer is trying to convey long ages, the writer does not mention evening/morning and doesn’t count the days.1
When we no longer see God as speaking the universe and everything in it into existence, we tend to not see God as an awesome God. We don’t see His power. We don’t see His knowledge. We don’t see His goodness. We also don’t see His authority. Why do we have to obey God? Because He created us and because He upholds us. Without Him we would not exist. Our creator has the authority to command His creation. When we compromise in this area, we lose our submission, our awe, and our reverence. (For more on the subject see my series.) When we believe His great works, especially those spoken of in Genesis 1-11 and in Exodus, we can’t help but be in awe of our God.
For the word of the Lord is upright,\ And all His work is done in faithfulness.\ He loves righteousness and justice;\ The earth is full of the lovingkindness of the Lord.\ By the word of the Lord the heavens were made,\ And by the breath of His mouth all their host.\ He gathers the waters of the sea together as a heap;\ He lays up the deeps in storehouses.\ **Let all the earth fear the Lord;\ Let all the inhabitants of the world stand in awe of Him. \ (Psalm 33:4-8) {emphasis mine}
Remembering God’s great works, we can’t help but worship in awe and reverence.
By awesome deeds You answer us in righteousness, O God of our salvation,\ *You who are the trust of all the ends of the earth* and of the farthest sea;\ Who establishes the mountains by His strength,\ Being girded with might;\ Who stills the roaring of the seas,\ The roaring of their waves,\ And the tumult of the peoples.\ They who dwell in the ends of the earth stand in awe of Your signs;\ You make the dawn and the sunset shout for joy. \ (Psalm 65:5-8) {emphasis mine}
If we truly do have awe and reverence for our God, we should be emboldened to tell those around us of His great works.
I will tell of Your name to my brethren;\ In the midst of the assembly I will praise You.\ You who fear the Lord, praise Him;\ All you descendants of Jacob, glorify Him,\ And stand in awe of Him, all you descendants of Israel. \ (Psalm 22:22-23) {emphasis mine}
May God grant you the wisdom to see His awesomeness and to trust Him, serve Him, obey Him, and worship Him as He so rightly deserves. May you always have a right view of God and a hunger for His word and a personal relationship with Him. To God be the Glory!
Trust Jesus
FYI, these are a few more passages on the subject that are helpful, but didn’t fit in the flow of my post.
Great is the Lord, and highly to be praised,\ And His greatness is unsearchable.\ One generation shall praise Your works to another,\ And shall declare Your mighty acts.\ On the glorious splendor of Your majesty\ And on Your wonderful works, I will meditate.\ Men shall speak of the power of Your awesome acts,\ And I will tell of Your greatness. (Psalm 145:3-6)
The boastful shall not stand before Your eyes;\ You hate all who do iniquity.\ You destroy those who speak falsehood;\ The Lord abhors the man of bloodshed and deceit.\ But as for me, by Your abundant lovingkindness I will enter Your house,\ At Your holy temple I will bow in reverence for You. (Psalm 5:5-7) {emphasis mine}
If you do not listen, and if you do not take it to heart to give honor to My name,” says the Lord of hosts, “then I will send the curse upon you and I will curse your blessings; and indeed, I have cursed them already, because you are not taking it to heart. Behold, I am going to rebuke your offspring, and I will spread refuse on your faces, the refuse of your feasts; and you will be taken away with it. Then you will know that I have sent this commandment to you, that My covenant may continue with Levi,” says the Lord of hosts. “My covenant with him was one of life and peace, and I gave them to him as an object of reverence; so he revered Me and stood in awe of My name. (Malachi 2:2-5) {emphasis mine}
-
 @ b8851a06:9b120ba1
2025-02-23 23:41:06
@ b8851a06:9b120ba1
2025-02-23 23:41:06Something stinks in the crypto markets, and it’s not just OpenSea’s suspicious trading activity.
The recent regulatory pivot in Washington—driven by the Trump administration’s aggressive push to make the U.S. “the world’s crypto capital”—has set the stage for a wave of unchecked fraud. OpenSea’s sudden regulatory relief and strategic transformation are just the beginning.
The SEC’s Curious Retreat
Let’s start with the smoking gun: the SEC was investigating OpenSea for unregistered securities violations, even issuing a Wells notice in August 2024. Then, in a complete reversal, they dropped the case without explanation. This wasn’t some random bureaucratic oversight—it happened right after Trump took office.
The timing is too perfect. His administration wasted no time signaling its pro-crypto stance, and the SEC, once an enforcer, is now rolling over like a neutered watchdog.
The message? As long as you’re playing the “crypto-bro” game, the rules don’t apply.
OpenSea’s Convenient Pivot
With the regulatory threat gone, OpenSea immediately rebranded itself—not just as an NFT marketplace but a full-blown token trading platform. Here’s what they did: * Launched OS2, a rebuilt exchange expanding into token trading. * Dropped the SEA token on February 13, 2025—perfectly timed with the regulatory climate shift. * Slashed fees to near zero to attract volume and dominate the market.
This wasn’t just a business move—it was a power play. OpenSea knew that under the previous administration, tokenizing its platform might have triggered another securities probe. But under Trump’s SEC? It’s open season.
Wash Trading and Market Manipulation
And it worked. The SEA token launch sent OpenSea’s market share skyrocketing from 25.5% to 71.5% in just four weeks. Daily trading volume exploded from $3.47 million to $17.4 million—but the numbers don’t add up. The surge was so artificial that OpenSea had to suspend its XP-based incentives system after accusations of wash trading flooded in.
Let’s be clear: this isn’t real market growth. This is manipulation.
By incentivizing rapid-fire, circular trading, OpenSea created the illusion of demand. The goal? Pump the SEA token, dominate competitors, and make insiders rich—at the expense of everyday traders.
Who’s Really Benefiting?
The financials paint a grim picture. #Coatue Management, once a major investor, slashed OpenSea’s valuation from $13.3 billion to just $1.4 billion. Trading volume has collapsed from its $5 billion peak to just $190 million per month. And yet, insiders are doubling down.
Consider these strategic moves: * OpenSea relocated from New York to Miami, aligning with Florida’s looser regulatory environment. * It established a foundation in the Cayman Islands—a classic move for dodging scrutiny. * It’s benefiting from a hands-off #SEC, which has abandoned enforcement actions under the new administration.
This is the new crypto economy: a lawless Wild West where the biggest players game the system while retail traders foot the bill.
What Comes Next?
With #Trump’s administration actively reshaping crypto regulation, OpenSea is the first of many companies to exploit this new reality. We’re entering an era where politically connected #crypto firms will enjoy total freedom to manipulate markets, while ordinary investors will be left holding the bag.
The lesson? If you’re not on the inside, you’re the exit liquidity.
This isn’t just about #OpenSea. It’s about a government-sanctioned crypto casino, where fraud is no longer the exception—it seems to be the business model.
I really hope am wrong on this one #nostr.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:47:56
@ 21c71bfa:e28fa0f6
2025-05-29 14:47:56Book *Amritsar to Delhi cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:47:33
@ 21c71bfa:e28fa0f6
2025-05-29 14:47:33Book *Amritsar to Chandigarh cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ b8851a06:9b120ba1
2025-02-22 19:43:13
@ b8851a06:9b120ba1
2025-02-22 19:43:13The digital guillotine has fallen. The Bybit hack wasn’t just a theft—it was a surgical strike exposing the fatal flaw of “crypto” that isn’t Bitcoin. This wasn’t a bug. It was a feature of a system designed to fail.
Here’s how North Korea’s Lazarus Group stole $1.5B in ETH, why “decentralized finance” is a joke, and how Bitcoin remains the only exit from this circus.
I. The Heist: How Centralized “Crypto” Betrayed Its Users
A. The Multisig Mousetrap (Or: Why You’re Still Using a Bank)
Bybit’s Ethereum cold wallet used multisig, requiring multiple approvals for transactions. Sounds secure, right? Wrong. • The Con: Hackers didn’t pick the lock; they tricked the keyholders using a UI masking attack. The wallet interface showed “SEND TO BYBIT”, but the smart contract was whispering “SEND TO PYONGYANG.” • Bitcoin Parallel: Bitcoin’s multisig is enforced on hardware, not a website UI. No browser spoofing, no phishing emails—just raw cryptography.
Ethereum’s multisig is a vault with a touchscreen PIN pad. Bitcoin’s is a mechanical safe with a key only you hold. Guess which one got robbed?
B. Smart Contracts: Dumb as a Bag of Hammers
The thieves didn’t “hack” Ethereum—they exploited its smart contract complexity. • Bybit’s security depended on a Safe.global contract. Lazarus simply tricked Bybit into approving a malicious upgrade. • Imagine a vending machine that’s programmed to take your money but never give you a soda. That’s Ethereum’s “trustless” tech.
Why Bitcoin Wins: Bitcoin doesn’t do “smart contracts” in the Ethereum sense. Its scripting language is deliberately limited—less code, fewer attack vectors.
Ethereum is a Lego tower; Bitcoin is a granite slab. One topples, one doesn’t.
II. The Laundering: Crypto’s Dirty Little Secret
A. Mixers, Bridges, and the Art of Spycraft
Once the ETH was stolen, Lazarus laundered it at lightspeed: 1. Mixers (eXch) – Obfuscating transaction trails. 2. Bridges (Chainflip) – Swapping ETH for Bitcoin because that’s the only exit that matters.
Bitcoin Reality Check: Bitcoin’s privacy tools (like CoinJoin) are self-custodial—no third-party mixers. You keep control, not some “decentralized” website waiting to be hacked.
Ethereum’s “bridges” are burning rope ladders. Bitcoin’s privacy? An underground tunnel only you control.
B. The $1.5B Lie: “Decentralized” Exchanges Are a Myth
Bybit’s “cold wallet” was on Safe.global—a so-called “decentralized” custodian. Translation? A website with extra steps. • When Safe.global got breached, the private keys were stolen instantly. • “Decentralized” means nothing if your funds depend on one website, one server, one weak link.
Bitcoin’s Answer: Self-custody. Hardware wallets. Cold storage. No trusted third parties.
Using Safe.global is like hiding your life savings in a gym locker labeled “STEAL ME.”
III. The Culprits: State-Sponsored Hackers & Crypto’s Original Sin
A. Lazarus Group: Crypto’s Robin Hood (For Dictators)
North Korea’s hackers didn’t break cryptography—they broke people. • Phishing emails disguised as job offers. • Bribes & social engineering targeting insiders. • DeFi governance manipulation (because Proof-of-Stake is just shareholder voting in disguise).
Bitcoin’s Shield: No CEO to bribe. No “upgrade buttons” to exploit. No governance tokens to manipulate. Code is law—and Bitcoin’s law is written in stone.
Ethereum’s security model is “trust us.” Bitcoin’s is “verify.”
B. The $3B Elephant: Altcoins Fund Dictators
Since 2017, Lazarus has stolen $3B+ in crypto, funding North Korea’s missile program.
Why? Because Ethereum, Solana, and XRP are built on Proof-of-Stake (PoS)—which centralizes power in the hands of a few rich validators. • Bitcoin’s Proof-of-Work: Miners secure the network through energy-backed cryptography. • Altcoins’ Proof-of-Stake: Security is dictated by who owns the most tokens.
Proof-of-Stake secures oligarchs. Proof-of-Work secures money. That’s why Lazarus can drain altcoin treasuries but hasn’t touched Bitcoin’s network.
IV. Bybit’s Survival: A Centralized Circus
A. The Bailout: Banks 2.0
Bybit took bridge loans from “undisclosed partners” (read: Wall Street vultures). • Just like a traditional bank, Bybit printed liquidity out of thin air to stay solvent. • If that sounds familiar, it’s because crypto exchanges are just banks in hoodies.
Bitcoin Contrast: No loans. No bailouts. No “trust.” Just 21 million coins, mathematically secured.
Bybit’s solvency is a confidence trick. Bitcoin’s solvency is math.
B. The Great Withdrawal Panic
Within hours, 350,000+ users scrambled to withdraw funds.
A digital bank run—except this isn’t a bank. It’s an exchange that pretended to be decentralized.
Bitcoin fixes this: your wallet isn’t an IOU. It’s actual money.
Bybit = a TikTok influencer promising riches. Bitcoin = the gold in your basement.
V. The Fallout: Regulators vs Reality
A. ETH’s 8% Crash vs Bitcoin’s Unshakable Base
Ethereum tanked because it’s a tech stock, not money. Bitcoin? Dropped 2% and stabilized.
No CEO, no headquarters, no attack surface.
B. The Regulatory Trap
Now the bureaucrats come in demanding: 1. Wallet audits (they don’t understand public ledgers). 2. Mixer bans (criminalizing privacy). 3. KYC everything (turning crypto into a surveillance state).
Bitcoin’s Rebellion: You can’t audit what’s already transparent. You can’t ban what’s unstoppable.
VI. Conclusion: Burn the Altcoins, Stack the Sats
The Bybit hack isn’t a crypto problem. It’s an altcoin problem.
Ethereum’s smart contracts, DeFi bridges, and “decentralized” wallets are Swiss cheese for hackers. Bitcoin? A titanium vault.
The Only Lessons That Matter:
✅ Multisig isn’t enough unless it’s Bitcoin’s hardware-enforced version. ✅ Complexity kills—every altcoin “innovation” is a security risk waiting to happen.
Lazarus Group won this round because “crypto” ignored Bitcoin’s design. The solution isn’t better regulations—it’s better money.
Burn the tokens. Unplug the servers. Bitcoin is the exit.
Take your money off exchanges. Be sovereign.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:47:08
@ 21c71bfa:e28fa0f6
2025-05-29 14:47:08Book *Cuttack to Puri cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ d61f3bc5:0da6ef4a
2025-05-05 15:26:08
@ d61f3bc5:0da6ef4a
2025-05-05 15:26:08I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify a media file and maliciously ascribe it to the note author.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:46:31
@ 21c71bfa:e28fa0f6
2025-05-29 14:46:31Book *Puri to Konark cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ bc6ccd13:f53098e4
2025-05-24 15:55:20
@ bc6ccd13:f53098e4
2025-05-24 15:55:20It wasn’t so long ago that the mainstream conversation around population was exclusively focused on the dangers of overpopulation. The fatal flaws in the Malthusian theory had yet to be disproven clearly and obviously by observable demographic trends. That’s been gradually changing, and while it’s hardly a mainstream consensus, concerns about falling birthrates and the risk of population collapse have taken over the population conversion on the political right, and sometimes beyond.
There’s no questioning the data at this point. Fertility rates over most of the world have been in precipitous decline, and if the current trajectory continues, global population will peak very soon and fall rather dramatically. And even the falling population itself is much less of a threat than the aging population that will inevitably precede it. Having a large cohort of older and retired people and a small cohort of young workers is an existential threat to the modern welfare state, and to the entire credit-based fiat monetary system that supports it. But that’s a subject for another day.
There are a multitude of different theories that attempt to explain why this is happening. I’ll name some of the most common ones:
-
Increased education and employment opportunities for women
-
Urbanization
-
Economic factors
-
Access to contraception
-
Changing social and cultural norms
-
Delayed marriage
-
Improvements in infant mortality rates
-
Government policies
-
Environmental concerns
-
Pornography
-
Feminism
-
Endocrine disrupting chemicals
-
Dating apps
Most rational thinkers agree there must be multiple factors playing a role. But the fact that the problem is so wide-spread, and populations that seem to be resisting the trend are so rare, shows that the strongest underlying factors are cross-culturally powerful and not easily resisted or reversed with marginal cultural differences and standard public policy efforts.
While populations that resist the trend are rare, they are not quite non-existent. A few groups stand out for their persistently high fertility rates. On a geographic basis, sub-Saharan Africa is the only major region still maintaining above-replacement fertility rates. For various reasons, I don’t think Africa is the most useful place to look for answers on what’s causing the decline elsewhere or how it could be reversed. One reason is that Africa seems to be following the global pattern, just with a lag. In another few decades the data may look very different, just like it does for South America today compared to 20 years ago.
In my opinion, a more useful place to look for data is in smaller population sub-groups within a geographic area that have fertility rates significantly higher than the general population levels. Rural populations in general have higher fertility rates than urban populations, but the difference isn’t really enough to consider it significant. The groups that fit this category well seem to be exclusively religious. These include certain Christian denominations in the traditional Anabaptist category including the Amish, Mennonites, and Hutterites, Muslims in some areas, and Jews, particularly the most orthodox sects. Mormons recently fell out of the high-fertility religious group category, which would also make for some interesting research.
It would be fascinating to compare these groups and see what they have in common outside just being religious in nature. I don’t have the knowledge to make that comparison. Instead, I’m going to focus on the group that’s often referenced and analyzed by people without much personal knowledge, the Amish.
I have read numerous articles and comments that reference the Amish to support this or that theory on the cause of falling fertility. One thing I notice is an obvious lack of understanding of the Amish culture, which leads to faulty arguments that don’t reflect reality. This isn’t surprising, given the insular and poorly-understood nature of the culture, the plethora of ridiculously incorrect “Amish” reality TV shows and pop culture myths, and the fact that the number of people with firsthand knowledge of Amish culture from an insider perspective who also write about demographic trends on any public platform is probably zero.
Well, was zero. I’m about to make that one.
My Qualifications
Since I’m claiming to have this knowledge, it’s only fair to give a little background as to how I got it. I choose to stay anonymous on the internet, and given that this is personal information that could make it significantly easier to dox me, I’ll be deliberately vague.
My parents were both born in Amish families. They didn’t stay, opting to leave the Amish church and culture before getting married and starting their family. My grandparents were all Amish, and all my cousins and most of my extended family remain Amish to this day. My parents didn’t move out of the Amish community, staying in the area and joining a conservative Mennonite church that was about the closest thing to being Amish without actually being Amish. The Mennonite community has a generally good relationship with and a lot of respect for the Amish community, given their deep similarities and shared history and cultural background.
I grew up interacting regularly with Amish relatives, neighbors and community members, speaking the Pennsylvania Dutch my parents taught us and used exclusively at home. I’m very certain that a real deep understanding of Amish culture is almost impossible without speaking their language, just like many other cultures around the world. The Amish speak English as their second language, but there are aspects of their culture that aren’t spoken about in English.
This lifelong proximity to and interaction with the Amish community has, I believe, given me some unique insights into the factors supporting their high fertility rates that no amount of academic research will ever uncover.
Who are the Amish?
First, some basics.
The Amish are a traditionalist Christian denomination. The way to understand the Amish is as a religious denomination first, and a culture second. Getting the two mixed up makes it impossible to understand why the Amish live the way they do.
Sure, their unique lifestyles makes them noteworthy as a group. But that lifestyle is based on and maintained by their religious beliefs and convictions.
Fundamentally, the Amish attempt to live out the Gospel as Jesus taught in the Sermon on the Mount. They believe their church has done so historically, and that the best way to make sure they keep doing so in the future is to view any changes to their traditional lifestyle with extreme skepticism and resistance.
The two primary doctrines that separate them from the mainstream Protestant Reformation, which is their group’s origin, are the doctrines of nonconformity and nonresistance. They apply the doctrine of nonconformity, the command to “be not conformed to this world: but be ye transformed by the renewing of your mind, that ye may prove what is that good, and acceptable, and perfect, will of God” in both a spiritual and a practical sense. They believe that Christians are to be radically different from non-Christians, both in their beliefs and attitudes, and in their lifestyle and appearance. And they apply the command to “resist not evil”, nonresistance, to mean that it’s a sin to use physical force or violence against another person for any reason whatsoever. They don’t make any exception for military service of any type, which they object to as a matter of conscience, or for self-defense, which they refuse to engage in even if it means death for themselves or their family.
The Amish do not practice infant baptism. Their young people must choose to be baptized and formally become members of the church, usually in their late teens or early twenties. As part of the baptism ceremony, they make a vow to remain faithful to God and the church until death. The Amish, as a church, interpret this vow to mean that the new church member will remain a member of the Amish church for life. Leaving the Amish church after making this vow and being baptized is viewed as breaking the vow, and is the justification for their practice of shunning, or the ban. Those who do so are cut off from contact with the community in various ways. Typically they won’t eat a meal with a shunned person, ride in a car a shunned person is driving, or do business with a shunned person. That includes immediate family. Failure to enforce this shunning against someone, even your own child, can result in running afoul of the church leadership and also being excommunicated and shunned.
This punishment, however, only applies to people who leave the church after baptism. Those young people who choose not to be baptized and leave the church instead are free to be treated just like any other non-Amish person, although their family essentially disown them and treat them like a shunned person anyway, if they’re especially strict and upset about the betrayal of Amish values.
Most Amish people don’t believe that the Amish are the only true church, or that only Amish people are true Christians. Most are accepting of other conservative Anabaptist denominations, and respect their values and practices as a different but valid way to be Christian. Church teaching strongly suggests that those who fall under the ban are living in sin and won’t make it to heaven. Most individuals, though, probably wouldn’t agree with that in every case if they were free to give their true opinion on the issue.
The Amish maintain a fertility rate of around 6 to 7 children per woman. Some recent research suggests this may be starting to fall somewhat, but the data isn’t extensive enough to make a solid judgement yet.
There are a wide variety of different “flavors” of Amish in different areas of the US, a fact they’re very aware of. The data strongly indicates that the most conservative and technologically primitive communities have slightly higher fertility rates and significantly higher retention rates of young people.
Why do the Amish Maintain High Fertility Rates?
Okay, enough background. Time to dive into the reasons I believe the Amish maintain their historically high fertility rate despite living in a developed, modern economy surrounded by people with dramatically sub-replacement fertility rates.
I thought long and hard about the best way to approach this. Going through a list of factors topically seemed like the obvious one. But the more I thought it through, the less I liked it. For one, how do you arrange the factors? Order of importance? How do you decide that? Also, the factors are so inter-related that they’ll be very tough to separate and understand individually. Finally, it seems dry and boring. Nobody needs that.
So I’m going to try something different. I’m going to approach it from a narrative angle. I’ll try to describe the life of a typical Amish person, from birth to death, in a chronological way. That’s the best approach to present it in a way that makes the culture relatable, while also tying the different factors together logically.
I’ll describe the experience for both men and women as best I can, and try to present the various factors encouraging high fertility as I see them at the appropriate part of the story.
This will likely be an article that gets revised later to address any questions that come up, so don’t consider it the final word on the subject.
Alright, time to get started.
Subscribed
First off, this might seem obvious, but the typical Amish baby is born into a large family. On average, they’ll have 5 or 6 siblings, and more is not at all uncommon. Families of 10 won’t raise an eyebrow, and 12-16 children aren’t unheard of, especially in the past when mortality was higher and second marriages were more common among younger widowers who went on to have children with their second wife. Humans are social creatures, and the environment and people we grow up surrounded by have a strong influence on our frame of reference. Studies have shown that women are very unlikely to have more children than their mother had. The number of siblings in your family, and in families you observe and interact with, doesn’t determine the number of children you will have, but it does strongly influence the number of children you feel is a “normal” amount. That makes it a kind of ratchet effect, where it’s very unlikely that a generation raised in homes with one or two children will go on to have larger families of their own collectively.
This cultural norm of large families establishes a kind of inertia that normalizes high fertility right from birth. Amish children grow up surrounded by siblings, observing, and as they get older, helping with the care and maintenance of a large family. All their relatives, cousins and extended family are also likely to belong to large families. The average Amish child grows up with dozens of first cousins, and sometimes hundreds of more distant cousins, many of whom they likely know well and socialize with regularly. This experience establishes a mental framework where a large family is assumed to be the default. And there is no stronger human tendency than the urge to fit in with the people around you.
Amish children grow up with strong gender norms taught from a very young age. The Amish culture follows strict and conservative gender roles. Boys and men do male things, girls and women do female things, and there is little effort or desire to create any overlapping space.
Boys grow up doing traditionally masculine things. They play outside, do chores on the farm, help their dad with his work, probably get a BB gun before age 10, go hunting and fishing, play sports, and generally prepare for a lifetime of physical labor and providing for a wife and family.
Girls grow up doing traditionally feminine things. They help care for younger siblings, help with housework, play with dolls, learn to cook and preserve food, learn to sew, and generally prepare for a lifetime of caring for and raising children and maintaining a large household.
It’s a common misconception that the Amish are mostly farmers who live off the land, subsistence style. That’s not at all accurate. While there are still Amish who make their living farming, at least in some areas, that has become the exception. The large scale of modern agriculture means it takes a lot of acres and a lot of machinery to run a profitable commercial farming operation. The Amish reject the use of most modern agricultural machinery, which makes them uncompetitive in commercial agriculture outside more niche markets like dairy, produce, or greenhouses. And the fact that they live in small geographic communities with large families means they quickly buy up all available farmland in an area until they price themselves out of the market. Prime farmland in heavy Amish farming communities like Lancaster, Pennsylvania routinely sells for over $25,000 per acre, which is more than a commercial crop farming operation might bring in over a lifetime.
So the Amish have moved away from a primarily agriculture based economy to various other occupations. In some areas they work in RV factories. Most work in trades, primarily construction. Many are masons, carpenters, cabinet builders, mechanics, welders, etc.
But they reject the ownership of cars, so they still use their characteristic horses and buggies for transportation. In reality, they use cars for most of their transportation needs. But they don’t own cars or have driver’s licenses, so they rely on “Amish taxi drivers” to chauffer them around. The men hire a driver to take them to and from work, if they work in construction or some other job outside the home. The women hire a driver take them to town for their shopping or for other errands. The exception is church. They’re still required to drive to church in a horse and buggy, so every family must keep a horse for that reason, as a bare minimum. In many cases that’s the only time they ever use a horse and buggy, and if it weren’t for that requirement they wouldn’t own one at all.
But that requirement means every Amish family must own enough land to keep a horse, which takes a few acres and a small barn at minimum. This forces them to live in rural areas and raise their families in a somewhat agricultural environment, even if their occupation wouldn’t require that at all. So there are always chores for the children, animals to care for, and space to play outside with their siblings.
Amish children grow up with very limited exposure to mainstream cultural pressures. Their mothers inevitably raise them at home until they start school. They don’t have TV or cell phones, so they aren’t exposed to any mainstream culture on a daily basis.
The Amish have their own schools, typically small one room schools within walking distance of all the families who attend. The teachers are often young single people, always Amish. They primarily teach basic academics: reading, writing, arithmetic, geography, history, etc. While the Amish speak both English and Pennsylvania Dutch, many Amish children are first exposed to English on a daily basis when they start school. School is taught in English, although there is limited teaching of the High German the Amish use in their church services.
Amish children attend school until 8th grade. The schools run the minimum number of days required by the state, usually 160. There is no higher education beyond grade 8. No Amish attend college.
Amish children are taught from little up that they are not like other people. The differences between their culture and mainstream culture are emphasized, and Amish culture is praised as the ideal, at a religious level. They're taught that the way to do what’s right is to do what the church asks, and those who don’t do what the church asks are in the wrong.
The Amish rate and describe everyone on a scale from “high” to “low”. A person who isn’t Amish, who isn’t a Christian, is a “high” person, or an “English” person. To go from being Amish to being “English” is the worst, most damning, failure imaginable. The Amish are “low” people. The more strict and traditional an Amish sect, the “lower” they are. Being “low” is seen as a virtue. Other conservative Christian denominations, particularly other Anabaptist groups, are also considered “low” people and generally viewed favorably, but they aren’t as “low” as the Amish.
Amish boys grow up expecting to start work full time at age 14, and to work at some type of trade or physical labor. There are no white-collar career tracks, essentially. Entrepreneurship is encouraged, and many young Amish men start their own construction crew or home business in their 20s or 30s after a few years of experience working for someone else. Often Amish boys start off working for and with their dad, in whatever trade or business he operates. But if they’re not interested in that particular occupation, they’re free to find another. Amish businesses and tradesmen are always willing to hire young Amish boys and train them in a craft. A good work ethic is considered a virtue, and Amish are known for their skilled craftsmanship and willingness to work harder than the competition. These traits are taught and encouraged from little on up.
Amish men as a whole do very well financially. For one, they start working and developing skills and work ethic a decade earlier than the typical college graduate. The trades pay well, and of course anyone could take advantage of that, but the mainstream narrative discourages men from pursuing a trade career by labeling it low status and keeping them in education until their prime years to gain a work ethic are past. It’s not uncommon for young Amish men just out of 8th grade to land a job on a carpentry crew for $25-30 an hour. With bonuses, some of them are bringing in $90k/year before age 20. Another advantage young Amish men have is lower expenses. They can certainly find places to spend their money, typically hobbies like hunting and fishing, but things like expensive designer clothes and accessories or overpriced car payments aren’t really an option. They also benefit from the Amish exemption to Social Security taxes. The Amish don’t pay into or collect Social Security. More on that later, but it helps immensely to keep more of your paycheck in your early prime working years.
Amish girls grow up expecting to get married at a young age and raise a large family as a traditional housewife. Amish girls aren’t encouraged to have a “career”, and the idea would be silly to them. They are expected to work, but the work is either helping their mom with the household, working on the family farm or business, or doing something like teaching school or working at an Amish farmer’s market to pass the time between leaving school and marriage. It’s never viewed as a permanent occupation, because marriage and motherhood is the default aspirational lifestyle. A common job for young Amish girls is working as a “maid” to help a new mother with housework at the end of pregnancy and for the first few months after childbirth. All new mothers can get this type of help if they want, and it will usually be a younger sister, cousin, or niece of appropriate age. Otherwise the community will find a suitable girl who’s available for the job. A “maid” will sometimes travel to a different Amish community for this reason, given how large extended families are and how frequently Amish families move across the country to a different community. This is often an opportunity for them to attract the attention of a young man outside their local community, and is one of the only ways for a long-distance relationship and marriage to begin.
Amish young people are expected to live with their parents until marriage, with very few exceptions. They’re also typically expected to work for their dad in the family business for no pay, and to give any earnings they make at a day job outside the home to their parents. This is typically expected until age 21, or until they get married, whichever comes first. More recently, with the rising cost of land and housing, it’s becoming more common to make age 18 the cutoff. And when a young couple is engaged, the parents typically allow them to start saving their income for their future household. This practice helps parents offset some of the expenses of raising such large families, along with the fact that no money is spent on higher education. It also provides one strong incentive to marry as early as possible.
Amish culture revolves around family and the community. Extended families are large, and people are expected to know and interact with their family. Conversation with a stranger at a social event invariably starts by asking their name, then asking who their parents, grandparents, and other relatives are until some distant family connection or a mutual acquaintance is found. Since the Amish community has a small pool of family names, and tends to heavily favor certain Biblical first names, enough people end up with the same name to make things really confusing. People are often identified by two or three generations of their family, for example “Sam Yoder’s John’s Amos” for an Amos Yoder who’s father was John Yoder and grandfather Sam Yoder.
Social activities are either family events or church events, or both. Weddings and funerals are the main social functions other than church services, and people are expected to attend as many as possible among their family and extended family, regardless of the distance. Given the large family sizes, most Amish have dozens of first cousins and many more distant cousins. Weddings and funerals can be almost weekly events. These are church events as well, so much of the local Amish community will usually attend. It will be an all day event, with the women and girls preparing a lunch and dinner for everyone. After the meal, the women and girls will wash the dishes and clean up, while the men sit around and talk. No cell phones, remember. Talking is the main form of social interaction. Topics typically include work, family news, hunting and fishing stories (Amish men hunt and fish with the same enthusiasm typical American men watch sports), horses, and interesting or funny stories about family and friends. Those with a knack for entertaining oratory are well respected and appreciated in the Amish community.
Of course the women do their fair share of talking as well, in the kitchen while cleaning up after the meal, and later in the living room where they join the men after the domestic work is done. The main topics of conversation always revolve around family, immediate and extended. News travels through the Amish community faster than any social media platform, because nothing builds Amish female status more than being the first to call with the news that great uncle so-and-so was injured in a farming accident or nephew so-and-so has a new baby, along with all the pertinent details about the name, size, and health of the baby and how the mother is doing and how many grandchildren that makes in total for the lucky grandparents.
While the adults are talking, the children are free to play either inside or preferably outside. Trampolines, climbing trees, playing in the hayloft, tag, volleyball, and softball are favorite activities at various ages. The younger boys and girls typically play together, but as they get older the girls spend more time visiting while the boys prefer more structured sports. Softball is a game for boys, but volleyball is popular with mixed teams of boys and girls at any age.
Visiting relatives or other community families is also a popular social activity, especially on “in-between Sunday”. The Amish have church every other week, and the week without church is often an opportunity to visit another family. Invitations are not expected or required, and anyone stopping by will be expected to stay for dinner and into the evening. At these type of events, the older children are often expected to sit and visit with the adults. Sitting still and being quiet are mandatory skills, since church services are 2 hours or longer and held in barns or sheds without air conditioning filled with backless wooden benches. Self-discipline is not an optional virtue, because the alternative is physical discipline.
As Amish young people enter their mid teen years, they go from childhood to youth. At a certain age, usually around 15 or 16, they officially become youth and enter the stage everyone is familiar with, “rumspringa”. That’s a Pennsylvania Dutch word that translates to “running around”. The Amish use it more as a verb, but pop culture has adopted it as a noun based on some wildly inaccurate reality TV shows and depictions.
The reality is, rumspringa varies widely from community to community, mostly based on what the parents and church leaders tolerate. Remember that Amish church membership is a fully voluntary decision, and Amish young people are free to join or not, as they decide. Late teens is the typical age for that decision. In the meantime, they are free to make their own decisions, subject to their parents’ rules. Breaking the rules can mean that at some point, they won’t be welcome to live in their parents’ household any more. That’s a fairly strong deterrent to the most extreme infractions.
At this stage, young Amish men will be buying their own horse and buggy, and both boys and girls will be permitted to attend the Sunday night “singing”. This is a social activity held at someone's house on Sunday evening, involving all the youth in the community coming together for dinner, playing volleyball, and singing German hymns together. The purpose is to provide a somewhat controlled social environment for young men and women to interact and hopefully meet their future spouse. Dating couples can attend together, and dates are permitted after the formal activities, with the young men often driving their date home late at night before finally heading home themselves.
Depending on the tolerance of the community, the informal activities can be a bit more permissive than singing hymns and playing volleyball. Often the buggies will become a typical teenage party scene, with alcohol, smoking, a radio, illicit smartphones and DVD players, and some less-than-reserved interaction between boys and girls. The punishment for getting caught can be severe, but in many cases the adults tend to turn a blind eye to what’s happening, and let the young people do as they please.
A lot more could be said about the dynamics of this cultural practice, but specifics vary so much between communities that I don’t think there’s much value in doing so. The point I think is relevant to this discussion is the question of sex.
There’s no reason to go off into the weeds on how much, if any, sex occurs. Premarital sex is absolutely forbidden. Does it happen anyway? Humans being human, certainly. How much? Probably very little in most cases. Getting pregnant, or getting someone pregnant, is the one transgression with inevitable life-changing consequences. The “shotgun wedding” is alive and well among the Amish, and getting a girl pregnant means marrying her or being expelled from the Amish community permanently, no exceptions. Besides that, getting pregnant outside of marriage is the most disgraceful and shameful thing a girl could do. It happens very very rarely, put it that way.
So casual sex within the community is basically off the table. What about casual sex with “English” people? This is where the Amish cultural practices play a big role. The Amish dress very distinctly. They can’t go anywhere in their traditional clothes without being instantly recognized. They also don’t drive cars, so going somewhere means getting a ride with someone. And their parents will usually keep an eye on their plans and whereabouts. So let’s imagine how an Amish teenager might go about finding a casual sexual encounter.
First off, getting ahold of a cell phone would be essential. They need some way to communicate with the outside world, and coordinate with their “partner in crime.” A lot of Amish teenagers do this, often with the help of slightly older people who have left the Amish, but keep ties with the community, maybe an older sibling or cousin. These are often the same people who buy alcohol for Amish teens.
Then, they need to get some non-Amish clothes. Remember, every trip away from home will take a willing driver, a plausible excuse in a community where everyone knows everyone, and the guarantee of being immediately recognized if seen in public. And the Amish parents know who the “bad kids” are, the ones who left but are willing to help their younger relatives and friends break the rules. Getting caught hanging around with them will probably mean a lot less trust and a lot less freedom in the future.
For the girls, a change of “English” clothes and a new hairstyle will let them blend in quite well. Of course, they can’t be caught leaving or coming home in those clothes, or have the clothes found at home. Lots of logistical hurdles everywhere. For the boys, they have a very distinctive haircut. A new change of clothes won’t fix that. There’s really no way for them to hide the fact that they’re Amish, even if the accent and the lack of a driver’s license don’t give them away.
Assuming they manage all that, and sneak away from home undetected, how will they find someone to hook up with? They’re very insulated from popular culture, and probably not at all comfortable in typical social situations. For the girls, there’s the added risk that an accidental pregnancy, or even just getting caught, would ruin their reputation and any chance of marriage and a family in the Amish community. So they’re unlikely to even try, unless they’re already fully intending to leave the Amish for good. That only really happens if they have a guy ready to marry them outside the Amish community, for reasons I’ll get into more later. Briefly, the Amish culture and schooling leaves women poorly prepared to support themselves outside that culture.
For the boys, there’s the typical difficulty men face in finding casual sexual partners. Multiply that by the difficulty of not having a car or driver’s license, not being experienced in mainstream social norms, plus that obvious and undisguisable Amish haircut. And all that ignores the lifelong teaching that casual sex is sinful and wrong, and those who engage in it are going against the teachings of God and the church. The entire culture is specifically designed to discourage casual sex as strongly as possible, and it does an excellent job at that.
Why does that matter? Well, humans are all very much the same, with the same desires and instincts. And sex is one of the strongest of those desires. The Amish are certainly no different.
So the Amish religious practice and culture offers a very simple choice. You can choose sex outside of marriage, which will be difficult or impossible, occasional at best, and if you get caught will mean expulsion from the community your life is rooted in, and even if you don’t get caught will mean you’re committing a mortal sin that will keep you out of heaven if you don’t repent and change. Or, you can get married and have all the sex you want, and be respected and rewarded for it.
That’s really all it takes to sell the idea of marriage to most men.
When a couple does decide to get engaged, of course with permission from the girl’s father, the wedding happens within a reasonably short time, in acknowledgement of the temptation young people face in that situation.
So let’s take a little closer look at the gender differences between the choice to stay single or to marry. It’s helpful to lay out the different life paths available, and how they play out over time.
There are very few Amish who remain single throughout their life, and almost all of them are women. So let’s look at it through a man’s perspective first. What kind of life can a single Amish man expect?
First off, a lifetime of celibacy. There’s hardly any need to go further, that’s a deal breaker for most men. If they choose to stay single for some reason, most will leave the Amish completely rather than accept those terms.
So maybe it’s more useful to look at incentives for early marriage, which is the norm. I’m a strong believer that incentives create outcomes, so I’ll be taking a hard look at incentives throughout this article.
Young people are expected to live with their parents until marriage, in most cases. Remember, no going off to college either. So from age 14 on, they’re stuck living with Mom and Dad, working full time, and not even keeping their own income. That gets old fast. Getting married, moving out, and starting a family looks better every day. Besides that, Amish women do a lot to improve the lives of their men. The Amish are well known for their delicious food. Well, that’s because the Amish women cook and bake. As a single guy, moving out of Mom’s house means not getting delicious home-cooked food every day. And they don’t have an iPhone to order DoorDash either, so it’s pizza delivery, hiring a driver to go to a restaurant, or whatever you can cook yourself. And Amish boys don’t grow up learning how to cook, that’s women’s work. Same with making clothes. Amish mothers and wives sew clothes for their families, since they’re forbidden to wear commercially available clothes in general. So a single guy is dependent on his mom for new clothes as well. Same with washing clothes. Most Amish have fairly modern clothes washing machines, although they don’t use dryers. But washing and folding clothes isn’t a job most boys grow up doing, so they’re pretty lost if they have to try it.
All in all, there aren’t a lot of upsides to staying single longer than absolutely necessary. There are plenty of benefits to marriage, though. For one, marriage is seen as a necessary step to full maturity as a man. It’s even expressed as a visible marker. Single young men typically stay clean-shaven. Once they get married, shaving is completely forbidden, and they are required to grow out a full beard. So the difference between married and single men is obvious at first glance, and is acknowledged as a marker of full maturity.
Then of course there’s the sexual access. No explanation needed.
Then there are all the benefits of an improved lifestyle a stay-at-home wife provides. That includes cooking, cleaning, washing clothes, caring for a garden, preserving food, helping with farm work or chores, and helping with his business. Many Amish wives are very involved in their husband’s career or business, whether that’s managing the bookkeeping, working in the greenhouses, or helping with daily chores on the farm. While most Amish communities use quite modern household appliances, powered with batteries, kerosene, or air pressure, the work of maintaining a household is still much more involved than for the typical American household. Especially when it comes to sewing, which very few American women do at all, but which took a large percentage of women’s time only a few generations ago. Among the Amish it still does.
I’m only focusing on the incentives for marriage right now, because that’s the first step. Of course, most married couples today don’t have 5-8 children, so there’s more to the story. But universal marriage, particularly early marriage, is an essential part of the puzzle.
Shifting focus to the women, here the picture is even more clear. Almost all lifelong single Amish people are women, and that’s not by choice. The Amish still maintain the “old maid” category that used to be part of mainstream culture. Single Amish women are almost invariably single because no man offered to marry them. Here’s why.
If single life is unappealing for Amish men, it’s positively bleak for women. Marriage and family life is the aspirational goal they’re taught from little up. And for good reason.
With their eighth-grade education, and without a driver’s license and car, their income earning potential is very limited. Most young women who aren’t busy on the farm or with the family business work as schoolteachers, housecleaners, babysitters, or cooks and servers at Amish restaurants or farmers’ markets. None of these jobs pay well. Enough to buy a few personal items, but not enough to buy a house or support even one person. And while it might be acceptable for a single Amish man to eventually buy a house and move out, at some point in his late 20s or early 30s, it’s really not acceptable at any age for an Amish old maid. Those old maids typically end up living with their parents, caring for them in old age, working the same type of jobs young girls do, and probably hoping that at some point an older widower with a family will show up and propose.
Marriage has massive lifestyle benefits for women, even more so than for men. Amish men typically do well financially, and often work in construction as well, or have friends and relatives who do. Amish houses are very nice and well constructed to say the least, and the wife gets the house she wants, the way she wants it. Being stingy with a house for your wife isn’t part of an Amish man’s mentality. Amish women are well rewarded for all their hard work keeping house, with a house they’ll be happy keeping. And of course a nice farm or at least some acreage, with space for a big garden, a barn for any animals, and space for greenhouses or whatever she needs for any home business ambitions she might have.
Along with that, Amish women have a lot of flexibility when it comes to spending money. Many Amish women handle most of the family finances. And the money her husband earns is family money, not his money. While the husband has final say in financial decisions, most Amish men don’t say no to their wives’ purchase requests often. Married Amish women have access to all the creature comforts the church allows to make their lives as pleasant as possible.
When it comes to status, the benefits are just as clear. Amish life revolves around family, and nothing is higher status than a thriving family of your own. The Amish version of posting exotic vacation pictures on Instagram is showing up to a social function with your new baby. It’s the automatic center of attention for weeks, until a newer baby show up in the community. And the default topic of conversation is always a woman’s children and their growth and development. Young girls grow up dreaming of the day they can join those conversations, and old maids are always outsiders in a certain sense, pitied by everyone else for their misfortune.
Being an old maid means being poor, low status, pitied by other women, and destined to live with your parents until they pass, with your only bitter-sweet consolation being the role of aunt to your dozens of nieces and nephews and maid to your sisters and sisters-in-law through their many pregnancies. Getting married means access to a man’s income, a nice new house just the way you want it, a farm, and an automatic status boost as a mother and eventually grandmother who always has lots to contribute to the conversation at social events.
As you can imagine, the incentives strongly favor marriage from both directions. Men benefit through improved lifestyle, status, and access to sex. Women benefit through improved lifestyle, economic opportunity, and status in the social hierarchy.
Given that the selection pool for potential partners is limited, mostly to the local Amish community, or occasionally another Amish community if there’s some interaction through family ties or social events, assortative mating is the norm. Young people can be choosy, sure. But they already know most of the people in their potential mating pool, and have probably known those people for most of their lives. They have a pretty good idea how desirable they are to potential partners, and the girls especially have to think long and hard about turning down a suitor. Men are always the initiators of a relationship, and the risk of turning down an eligible man and then never getting another offer, ending up as a dreaded old maid, is always lurking in the back of their minds.
Besides that, both men and women have multiple ways to improve their spouse’s life. Women are much more than just sexual objects. Their domestic role actually raises their husband’s standard of living significantly, in a way he can’t access as a single man. And men are all valuable to women, both for resources and for status as a wife and mother. Even a very average husband or wife is a massive lifestyle boost over remaining single.
By now it should be pretty clear why marriage is almost universal among the Amish, and marriage at what most would consider a young age (19-23) is more common than not. And I haven’t even mentioned any religious teaching, because frankly I don’t think that’s a major force on an individual level. The religious beliefs shape the social and material landscape, and that landscape provides the practical incentives that cause people to make the choices they do. The fact that an Amish interpretation of the Bible encourages marriage and children is one layer removed from the reasons individual 20-year-old Amish men and women choose to get married.
I pointed out earlier that getting married and having a high birthrate, or even getting married young and having a high birthrate, are not exactly the same thing. Plenty of married couples today have one, two, or even no children, even if they got married young enough to have ten if they chose to do so. So why are the Amish different?
There’s the too-obvious answer: they don’t allow the use of contraceptives. Occam’s razor and all, but it deserves a bit more explanation. After all, the Catholic Church doesn’t allow the use of contraceptives either, and look how well that’s working out for them. Of course the enforcement mechanism doesn’t have the teeth among Catholics that it has among the Amish, but that’s not the whole story. If they were motivated enough, there’d be a way to space the children out more, maybe end up without quite so many, without anyone knowing. That doesn’t happen, because the contraceptive ban is a dead letter when couples want to have as many children as possible, which the Amish typically do.
Again, I’ll go back to incentives. What are the incentives to have children specifically, as many as possible, and not just get married and “plan for a family one day”?
For one, status. For both men and women, a large family is a marker of high status. Parents are respected and honored for doing a good job of raising well-adjusted children.
Children are also less of a financial burden for the Amish. Their children are raised well, but not in a financially intensive way that’s become expected today. They don’t have to buy a new car or SUV to fit the family, they don’t buy every child a boatload of expensive electronic gadgets every birthday and Christmas, they don’t have to pay for frequent vacations or college tuition, and they don’t have to eat out or pay for takeout or pay for childcare or a house cleaner since the wife is handling all those domestic roles herself. And the Amish don’t practice helicopter parenting, so children are much more free to play and amuse themselves without constant supervision from their parents. They don’t have to be driven to 17 different weekly structured activities. They have a farm to play on and shelves full of books to read and some toys to play with if the weather is bad, and that’s about it. And of course as the family grows, the older siblings do a large percentage of the housework and help with the younger children.
The older teenagers that are working outside the home typically give their earnings to their parents, but this basically offsets the cost of raising them, so it isn’t really an incentive to have larger families, just the removal of a disincentive.
The strongest real incentive, other than increased status and cultural inertia, that I observe for large families is that the children are the parents’ retirement plan. The Amish don’t work at jobs that offer pensions or benefits. They are exempt from paying into, but also ineligible to receive, Social Security benefits. The Social Security exemption was granted on the basis that the Amish don’t need government payments to support them in old age, because the family and community will do that. And they do.
How does this work out in practice? First, the Amish don’t practice “retirement” the way most people think of it. They teach that work is honorable and every able-bodied man should work to support his family and to help those in need. So as long as a man is physically able to work, he’ll be employed and supporting himself and his wife. And Amish women move directly from the role of mother to the role of grandmother. It’s not at all uncommon, in fact, for a woman’s first grandchild to be born before her last child is born. So plenty of Amish children are an aunt or uncle at birth, and have a niece or nephew older than they are. Grandmothers are extremely involved in helping their daughters and daughters-in-law with childcare, so they don’t often have a big stretch of free time after their children grow up and move out. And besides that, there are still the significant household responsibilities to attend to.
As a couple gets older and perhaps less able to handle everything on their own, they often move to the home of one of their grown children. Typically not into the home directly, but into what’s called a “dody haus” (grandpa house) which might be a small detached house on the same property, or a separate wing of the larger house, like an in-law suite. Here they’re able to live independently, help care for the grandchildren next door, and still be nearby so their children and grandchildren can give any care they may need in old age. If the couple has an unmarried “old maid” daughter, she’ll typically still be living with them and will be the primary caregiver.
If someone doesn’t have children to care for them, the Amish community will find a way to care for them. Some more distant relative or maybe surviving siblings will step in to help. But the expectation and the rule is that your children and grandchildren will care for you after you’re no longer able to care for yourself. Finding yourself growing old without family is an unfortunate and unpleasant situation, regardless how much the community may try to fill that role. Just as throughout earlier stages of life, social functions and social status revolve around children and family, and anyone without them will be incomplete as a person, something of an inevitable outsider to the joys of life. The best insurance against a lonely and uncomfortable old age is a large family, among which there are certain to be sufficient resources to care for you. Many elderly Amish people die with well over a hundred grandchildren and great-grandchildren, and spend their later years constantly surrounded by children and young people who deeply appreciate and respect them. Being taught and shown that respect toward their own grandparents from a young age is a strong incentive to aspire to the same status one day.
I’m not sure exactly where this fits, but I should point out somewhere that the Amish have an absolutely zero tolerance policy toward divorce. There are no legitimate grounds for divorce whatsoever, and anyone who initiates a divorce will be excommunicated from the church and shunned. If an Amish person’s spouse initiates divorce proceedings, they won’t cooperate with those proceedings in any way. If the divorce happens through the legal system without their consent anyway, they can remain a church member in good standing only by staying celibate as long as their spouse remains alive. The only acceptable second marriage is in the case of the death of a spouse. In those cases, a quick remarriage is the rule among widows and widowers with young children, since raising a family is seen as a job for a married couple, not a single person.
It’s hard to say exactly how this stance against divorce influences marriage and fertility. But it certainly limits exposure to the idea of divorce as a “solution” to marriage difficulties, and incentivizes couples to work things out for their own life satisfaction. And it dramatically reduces the financial risks men face in the modern marriage system, where the potential to lose not only their family, but also a significant portion of their material wealth, raises strong disincentives to marriage. The physical realities of married life versus single life in a more low-tech environment probably discourage divorce, but the added threat of complete social and familial ostracization eliminate it almost entirely.
Conclusion
This article is my attempt to provide some insight into the Amish culture that might help us understand the factors causing their unusually high fertility rate. I’ve titled it as part one, because I plan to follow up with some of my personal opinions on how these insights relate to the broader society. I think a lot of the proposed causes of and solutions to the global demographic collapse are completely incorrect, and my opinion is based heavily on my observation of Amish culture. That will be the focus of part two of this article.
Feel free to comment and post questions. My biggest challenge in writing this article is the fact that I take my familiarity with Amish culture for granted to some degree, so I struggled to choose which points are relevant to understanding the culture for an outsider. I’m sure I skipped over plenty of important details that may leave readers feeling confused, so I’ll do my best to answer any questions you post, and update the article with pertinent information I missed.
-
-
 @ b8851a06:9b120ba1
2025-02-06 22:46:54
@ b8851a06:9b120ba1
2025-02-06 22:46:54When Your Bitcoin Stash Saves Your Earnings Report: The Accounting Shift Every Business Needs to Understand
**Tesla’s Q4 2024 earnings were a wreck—revenue down, costs up. But thanks to Bitcoin, the financial airbags deployed so effectively that no one’s talking about the crash. **
Let’s Be Clear:
This isn’t about praising Tesla or Elon Musk (we’ll leave that to fan accounts). It’s about dissecting how a simple accounting rule change turned Bitcoin into a corporate financial shock absorber. The numbers reveal a playbook any business can replicate.
The “Aha” Moment: Accounting Rules Meet Digital Gold
(Why This Matters for Main Street Businesses)
The Problem Before 2025:
Companies had to report Bitcoin like a cursed family heirloom—you could only tell people when its value dropped, never when it gained. Imagine having to value your house at its lowest sale price in the neighborhood, even while yours was freshly renovated.
The 2025 Fix:
New rules let companies report Bitcoin like stocks—current value, gains and losses included. Suddenly, that digital gold in the treasury vault gets to shine.
Why This Changes Everything: • For Tesla: Their $184M Bitcoin stash got revalued to $1.076B → $600M paper gain • For Your Business: Bitcoin isn’t just an asset; it’s an earnings hedge
For Tesla, Bitcoin turned a bad quarter into a balanced one. For your business, it’s the difference between surviving a downturn and thriving through one.
Tesla’s Numbers Decoded: Bitcoin as Financial CPR
The Crash: • Automotive revenue ↓ 8% • Operating expenses ↑ 9% • Missed revenue targets by $1.5B
The Airbag: • Bitcoin gain: $600M • EPS boost: 23% of total earnings • Balance sheet upgrade: 484% Bitcoin value increase
The Takeaway:
Bitcoin didn’t fix Tesla’s car business—it kept their financials on life support while they work on repairs.
The Business Owner’s Guide to Bitcoin Airbags
(No Tech Jargon, Just Street Smarts)
- Your New Financial Shock Absorber • Old Way: Keep cash reserves losing 4-7% annually to inflation • Bitcoin Way: Treasury that grows while parked
Real Math:
$10M Treasury Allocation
Year 1:
- Cash: $9.6M (after 4% inflation loss)
- Bitcoin: $15.4M (54% avg annual growth*)- The “Get Out of Jail Free” Card
When core business stumbles (like Tesla’s did): • Bitcoin gains offset operational losses • Buys time for turnaround strategies
- Shareholder Whisperer
That Bitcoin gain isn’t just numbers—it’s storytelling fuel: • “Our innovative treasury strategy delivered $600M in non-operational income” • Beats explaining another quarter of declining sales
Building Your Bitcoin Safety Net
A Step-by-Step Playbook
Step 1: Treasury Triage • Allocate 5-10% of cash reserves to Bitcoin • Not speculation—modern balance sheet insurance
Step 2: Accounting Alignment
Work with your CFO to: • Implement FASB-compliant reporting • Train teams on quarterly revaluations
Step 3: Strategic Deployment • Hold through volatility cycles • Treat gains as bonus liquidity for: • R&D funding • Debt reduction • Opportunistic acquisitions
Pro Tip: Start small—even a 1% Bitcoin allocation creates optionality without material risk.
Objection Busters: What Skeptics Miss
“But Bitcoin’s Too Volatile!”
Cash is guaranteed to lose value. Bitcoin at least gives you a fighting chance.
“We’re Not Tech Bros!” • Bitcoin isn’t tech—it’s digital real estate • The network effect is its tenant base
“Accounting’s Too Complex!” • Modern tools automate revaluations • Takes less time than managing foreign currency hedges
The Future of Corporate Treasuries
(Why Early Adopters Win)
2025’s Landscape: • First movers already reaping benefits • Late adopters face inflationary erosion
Your Move: • Conduct treasury health check • Model Bitcoin allocation scenarios • Implement phased adoption
Final Word:
Tesla’s story isn’t about “crypto” moonshots—it’s about modern financial engineering. The new accounting rules have turned Bitcoin into a Swiss Army knife for corporate treasuries: • Blade 1: Inflation hedge • Blade 2: Earnings supplement • Blade 3: Strategic reserve asset
The question isn’t whether Bitcoin belongs on corporate balance sheets—it’s how much value your business will leave on the table by ignoring this tool.
Your Competitors Won’t Wait—Why Should You?
→ Free Treasury Health Assessment → Bitcoin Accounting Implementation Guide Let www.NeoWealth.xyz assist you– Modern Treasury Solutions for Pragmatic Leaders
Nostr Footnotes:
Data Sources: #Tesla Q4 2024 Earnings Report, FASB Accounting Standards Update 2023-08, Bitcoin Historical Returns Analysis (2015-2024) Past performance ≠ future results.
Bitcoin not #Crypto
-
 @ 95cbd62b:a5270126
2025-05-24 14:06:33
@ 95cbd62b:a5270126
2025-05-24 14:06:33Trong thời đại công nghệ số phát triển mạnh mẽ, nhu cầu tìm kiếm một nền tảng tích hợp đầy đủ tiện ích, an toàn và thân thiện với người dùng ngày càng tăng cao. OK22 đã chứng minh vị thế của mình không chỉ là một nền tảng giải trí trực tuyến, mà còn là một công cụ công nghệ thông minh phục vụ mọi nhu cầu trong đời sống số. Với thiết kế giao diện 100% tiếng Việt và khả năng tương thích trên mọi thiết bị từ máy tính đến điện thoại, OK22 mang đến cho người dùng trải nghiệm mượt mà, dễ sử dụng và hoàn toàn bảo mật. Được phát triển trên nền tảng công nghệ hiện đại, OK22 hỗ trợ người dùng quản lý thông tin cá nhân, thực hiện giao dịch nhanh chóng, lưu trữ dữ liệu an toàn và tiếp cận các tiện ích công nghệ tiên tiến một cách dễ dàng, kể cả với người mới sử dụng.
Một trong những điểm mạnh nổi bật của OK22 chính là khả năng tự động hóa trong xử lý tác vụ, giúp tiết kiệm thời gian và tối ưu hóa hiệu suất làm việc. Nền tảng được trang bị hệ thống bảo mật cao cấp, bảo vệ tối đa quyền riêng tư và tài sản số của người dùng. OK22 còn cung cấp hệ thống hỗ trợ trực tuyến 24/7, giúp người dùng giải quyết mọi vấn đề nhanh chóng mà không bị gián đoạn. Dù là một cá nhân đang tìm kiếm công cụ quản lý tài chính cá nhân, một doanh nghiệp nhỏ cần nền tảng để xử lý đơn hàng và thanh toán, hay một nhóm cộng đồng cần không gian kết nối số – OK22 đều có thể đáp ứng linh hoạt và hiệu quả. Không những vậy, nhờ tích hợp nhiều tính năng như thông báo tự động, đồng bộ dữ liệu đám mây, và tích hợp API mở, OK22 còn dễ dàng kết nối với các nền tảng khác trong hệ sinh thái số, giúp người dùng tạo nên một môi trường làm việc và sinh hoạt thông minh.
Không dừng lại ở đó, OK22 đang ngày càng mở rộng hợp tác với các đối tác lớn trong nhiều lĩnh vực như giáo dục trực tuyến, thương mại điện tử, chăm sóc sức khỏe và tài chính cá nhân. Nền tảng không ngừng cập nhật những công nghệ tiên tiến như AI, blockchain và dữ liệu lớn (Big Data) nhằm mang lại trải nghiệm người dùng tối ưu và đáp ứng nhu cầu ngày càng đa dạng của cộng đồng Việt. Với tốc độ xử lý nhanh, giao diện trực quan và độ tin cậy cao, OK22 không chỉ đơn thuần là một ứng dụng công nghệ – mà còn là người bạn đồng hành tin cậy trong hành trình số hóa của người Việt. Trong tương lai gần, OK22 hứa hẹn sẽ trở thành nền tảng công nghệ không thể thiếu trong mỗi gia đình, tổ chức và doanh nghiệp, đóng vai trò then chốt trong việc thúc đẩy chuyển đổi số toàn diện và phát triển bền vững.
-
 @ 2e8970de:63345c7a
2025-05-29 13:40:19
@ 2e8970de:63345c7a
2025-05-29 13:40:19(and that's the highest ever outside the covid era)
https://www.federalreserve.gov/consumerscommunities/sheddataviz/emergency-savings.html
https://stacker.news/items/991909
-
 @ b8851a06:9b120ba1
2025-01-28 21:34:54
@ b8851a06:9b120ba1
2025-01-28 21:34:54Private property isn’t lines on dirt or fences of steel—it’s the crystallization of human sovereignty. Each boundary drawn is a silent declaration: This is where my will meets yours, where creation clashes against chaos. What we defend as “mine” or “yours” is no mere object but a metaphysical claim, a scaffold for the unfathomable complexity of voluntary exchange.
Markets breathe only when individuals anchor their choices in the inviolable. Without property, there is no negotiation—only force. No trade—only taking. The deed to land, the title to a car, the seed of an idea: these are not static things but frontiers of being, where human responsibility collides with the infinite permutations of value.
Austrian economics whispers what existentialism shouts: existence precedes essence. Property isn’t granted by systems; it’s asserted through action, defended through sacrifice, and sanctified through mutual recognition. A thing becomes “owned” only when a mind declares it so, and others—through reason or respect—refrain from crossing that unseen line.
Bitcoin? The purest ledger of this truth. A string of code, yes—but one that mirrors the unyielding logic of property itself: scarce, auditable, unconquerable. It doesn’t ask permission. It exists because sovereign minds choose it to.
Sigh. #nostr
I love #Bitcoin. -
 @ 2183e947:f497b975
2025-05-01 22:33:48
@ 2183e947:f497b975
2025-05-01 22:33:48Most darknet markets (DNMs) are designed poorly in the following ways:
1. Hosting
Most DNMs use a model whereby merchants fill out a form to create their listings, and the data they submit then gets hosted on the DNM's servers. In scenarios where a "legal" website would be forced to censor that content (e.g. a DMCA takedown order), DNMs, of course, do not obey. This can lead to authorities trying to find the DNM's servers to take enforcement actions against them. This design creates a single point of failure.
A better design is to outsource hosting to third parties. Let merchants host their listings on nostr relays, not on the DNM's server. The DNM should only be designed as an open source interface for exploring listings hosted elsewhere, that way takedown orders end up with the people who actually host the listings, i.e. with nostr relays, and not with the DNM itself. And if a nostr relay DOES go down due to enforcement action, it does not significantly affect the DNM -- they'll just stop querying for listings from that relay in their next software update, because that relay doesn't work anymore, and only query for listings from relays that still work.
2. Moderation
Most DNMs have employees who curate the listings on the DNM. For example, they approve/deny listings depending on whether they fit the content policies of the website. Some DNMs are only for drugs, others are only for firearms. The problem is, to approve a criminal listing is, in the eyes of law enforcement, an act of conspiracy. Consequently, they don't just go after the merchant who made the listing but the moderators who approved it, and since the moderators typically act under the direction of the DNM, this means the police go after the DNM itself.
A better design is to outsource moderation to third parties. Let anyone call themselves a moderator and create lists of approved goods and services. Merchants can pay the most popular third party moderators to add their products to their lists. The DNM itself just lets its users pick which moderators to use, such that the user's choice -- and not a choice by the DNM -- determines what goods and services the user sees in the interface.
That way, the police go after the moderators and merchants rather than the DNM itself, which is basically just a web browser: it doesn't host anything or approve of any content, it just shows what its users tell it to show. And if a popular moderator gets arrested, his list will still work for a while, but will gradually get more and more outdated, leading someone else to eventually become the new most popular moderator, and a natural transition can occur.
3. Escrow
Most DNMs offer an escrow solution whereby users do not pay merchants directly. Rather, during the Checkout process, they put their money in escrow, and request the DNM to release it to the merchant when the product arrives, otherwise they initiate a dispute. Most DNMs consider escrow necessary because DNM users and merchants do not trust one another; users don't want to pay for a product first and then discover that the merchant never ships it, and merchants don't want to ship a product first and then discover that the user never pays for it.
The problem is, running an escrow solution for criminals is almost certain to get you accused of conspiracy, money laundering, and unlicensed money transmission, so the police are likely to shut down any DNM that does this. A better design is to oursource escrow to third parties. Let anyone call themselves an escrow, and let moderators approve escrows just like they approve listings. A merchant or user who doesn't trust the escrows chosen by a given moderator can just pick a different moderator. That way, the police go after the third party escrows rather than the DNM itself, which never touches user funds.
4. Consequences
Designing a DNM along these principles has an interesting consequence: the DNM is no longer anything but an interface, a glorified web browser. It doesn't host any content, approve any listings, or touch any money. It doesn't even really need a server -- it can just be an HTML file that users open up on their computer or smart phone. For two reasons, such a program is hard to take down:
First, it is hard for the police to justify going after the DNM, since there are no charges to bring. Its maintainers aren't doing anything illegal, no more than Firefox does anything illegal by maintaining a web browser that some people use to browse illegal content. What the user displays in the app is up to them, not to the code maintainers. Second, if the police decided to go after the DNM anyway, they still couldn't take it down because it's just an HTML file -- the maintainers do not even need to run a server to host the file, because users can share it with one another, eliminating all single points of failure.
Another consequence of this design is this: most of the listings will probably be legal, because there is more demand for legal goods and services than illegal ones. Users who want to find illegal goods would pick moderators who only approve those listings, but everyone else would use "legal" moderators, and the app would not, at first glance, look much like a DNM, just a marketplace for legal goods and services. To find the illegal stuff that lurks among the abundant legal stuff, you'd probably have to filter for it via your selection of moderators, making it seem like the "default" mode is legal.
5. Conclusion
I think this DNM model is far better than the designs that prevail today. It is easier to maintain, harder to take down, and pushes the "hard parts" to the edges, so that the DNM is not significantly affected even if a major merchant, moderator, or escrow gets arrested. I hope it comes to fruition.
-
 @ f6488c62:c929299d
2025-05-24 05:10:20
@ f6488c62:c929299d
2025-05-24 05:10:20คุณเคยจินตนาการถึงอนาคตที่ AI มีความฉลาดเทียบเท่ามนุษย์หรือไม่? นี่คือสิ่งที่ Sam Altman ซีอีโอของ OpenAI และทีมพันธมิตรอย่าง SoftBank, Oracle และ MGX กำลังผลักดันผ่าน โครงการ Stargate! โครงการนี้ไม่ใช่แค่เรื่องเทคโนโลยี แต่เป็นก้าวกระโดดครั้งใหญ่ของมนุษยชาติ! Stargate คืออะไร? Stargate เป็นโปรเจกต์สร้าง ศูนย์ข้อมูล AI ขนาดยักษ์ที่ใหญ่ที่สุดในประวัติศาสตร์ ด้วยเงินลงทุนเริ่มต้น 100,000 ล้านดอลลาร์ และอาจสูงถึง 500,000 ล้านดอลลาร์ ภายในปี 2029! เป้าหมายคือการพัฒนา Artificial General Intelligence (AGI) หรือ AI ที่ฉลาดเทียบเท่ามนุษย์ เพื่อให้สหรัฐฯ ครองความเป็นผู้นำด้าน AI และแข่งขันกับคู่แข่งอย่างจีน โครงการนี้เริ่มต้นที่เมือง Abilene รัฐเท็กซัส โดยจะสร้างศูนย์ข้อมูล 10 แห่ง และขยายไปยังญี่ปุ่น สหราชอาณาจักร และสหรัฐอาหรับเอมิเรตส์ ทำไม Stargate ถึงสำคัญ?
นวัตกรรมเปลี่ยนโลก: AI จาก Stargate จะช่วยพัฒนาวัคซีน mRNA รักษามะเร็งได้ใน 48 ชั่วโมง และยกระดับอุตสาหกรรมต่าง ๆ เช่น การแพทย์และความมั่นคงแห่งชาติสร้างงาน: คาดว่าจะสร้างงานกว่า 100,000 ตำแหน่ง ในสหรัฐฯ
พลังงานมหาศาล: ศูนย์ข้อมูลอาจใช้พลังงานถึง 1.2 กิกะวัตต์ เทียบเท่ากับเมืองขนาดใหญ่!
ใครอยู่เบื้องหลัง? Sam Altman ร่วมมือกับ Masayoshi Son จาก SoftBank และได้รับการสนับสนุนจาก Donald Trump ซึ่งผลักดันนโยบายให้ Stargate เป็นจริง การก่อสร้างดำเนินการโดย Oracle และพันธมิตรด้านพลังงานอย่าง Crusoe Energy Systems ความท้าทาย? ถึงจะยิ่งใหญ่ แต่ Stargate ก็เจออุปสรรค ทั้งปัญหาการระดมทุน ความกังวลเรื่องภาษีนำเข้าชิป และการแข่งขันจากคู่แข่งอย่าง DeepSeek ที่ใช้โครงสร้างพื้นฐานน้อยกว่า แถม Elon Musk ยังออกมาวิจารณ์ว่าโครงการนี้อาจ “ไม่สมจริง” แต่ Altman มั่นใจและเชิญ Musk ไปดูไซต์งานที่เท็กซัสเลยทีเดียว! อนาคตของ Stargate ศูนย์ข้อมูลแห่งแรกจะเริ่มใช้งานในปี 2026 และอาจเปลี่ยนโฉมวงการ AI ไปตลอดกาล นี่คือก้าวสำคัญสู่ยุคใหม่ของเทคโนโลยีที่อาจเปลี่ยนวิถีชีวิตของเรา! และไม่ใช่ประตูดวงดาวแบบในหนังนะ! ถึงชื่อ Stargate จะได้แรงบันดาลใจจากภาพยนตร์ sci-fi อันโด่งดัง แต่โครงการนี้ไม่ได้พาเราไปยังดวงดาวอื่น มันคือการเปิดประตูสู่โลกแห่ง AI ที่ทรงพลัง และอาจเปลี่ยนอนาคตของมนุษยชาติไปเลย! และไม่เหมือน universechain ของ star ของผมนะครับ
Stargate #AI #SamAltman #OpenAI #อนาคตของเทคโนโลยี
-
 @ c1d77557:bf04ec8b
2025-05-24 05:02:26
@ c1d77557:bf04ec8b
2025-05-24 05:02:26O 567br é uma plataforma de entretenimento online que tem se destacado pela sua inovação, variedade de jogos e foco na experiência do jogador. Com uma interface amigável e recursos de alta qualidade, a plataforma oferece uma jornada divertida e segura para os seus usuários. Neste artigo, vamos explorar os principais aspectos do 567br, incluindo a introdução da plataforma, os jogos que ela oferece e como a experiência do jogador é aprimorada em cada detalhe.
O 567br foi desenvolvido com o objetivo de proporcionar aos jogadores uma experiência imersiva e prazerosa. Sua interface é simples, intuitiva e de fácil navegação, permitindo que os usuários encontrem rapidamente seus jogos favoritos. A plataforma também é otimizada para dispositivos móveis, o que significa que os jogadores podem acessar seus jogos em qualquer lugar e a qualquer momento, seja no computador ou no smartphone.
Além disso, o 567brse preocupa com a segurança de seus usuários, implementando tecnologias de criptografia de ponta para garantir que todos os dados pessoais e financeiros estejam protegidos. A plataforma também oferece suporte ao cliente de alta qualidade, disponível 24/7, para resolver quaisquer dúvidas ou problemas que possam surgir durante a experiência de jogo.
Jogos Empolgantes e Variedade para Todos os Gostos No 567br, a diversidade de jogos é um dos pontos fortes da plataforma. Desde jogos de mesa e cartas até opções de entretenimento mais dinâmicas e inovadoras, há algo para todos os gostos e preferências. Os jogos disponíveis são desenvolvidos por alguns dos melhores fornecedores de conteúdo da indústria, garantindo gráficos de alta qualidade, jogabilidade fluida e mecânicas envolventes.
Os jogadores podem escolher entre diferentes categorias, como:
Jogos de Mesa: Para quem gosta de uma experiência mais estratégica e de tomada de decisões, os jogos de mesa são uma excelente opção. São oferecidas diversas variantes de jogos populares, como pôquer, blackjack, roleta, entre outros.
Jogos de Ação e Aventura: Para os que buscam adrenalina e emoção, a plataforma oferece uma seleção de jogos de ação e aventura com temas envolventes e gráficos impressionantes. Esses jogos garantem uma experiência de jogo emocionante e desafiadora.
Jogos de Arcade: Se você está em busca de algo mais descontraído e divertido, os jogos de arcade são uma excelente escolha. Eles são rápidos, fáceis de entender e proporcionam diversão instantânea.
A plataforma está sempre atualizando seu portfólio de jogos para garantir que os jogadores tenham acesso às últimas novidades e inovações do mundo do entretenimento online.
A Experiência do Jogador: Personalização e Interatividade O 567br não se limita a oferecer apenas uma plataforma de jogos, mas também busca criar uma experiência personalizada e interativa para cada jogador. A plataforma possui funcionalidades que permitem que os usuários ajustem sua experiência de jogo de acordo com suas preferências individuais.
A personalização da interface é um exemplo claro disso. O jogador pode escolher o tema e a disposição dos elementos na tela, criando um ambiente que seja confortável e agradável de usar. Além disso, o 567br oferece recursos interativos, como chats ao vivo, onde os jogadores podem interagir com outros usuários e até mesmo com os dealers, proporcionando uma sensação de comunidade.
Outro aspecto importante é a possibilidade de acompanhar o desempenho e os resultados de jogo. A plataforma oferece relatórios detalhados, permitindo que os jogadores monitorem seu progresso, analisem suas vitórias e perdas, e façam ajustes em sua estratégia de jogo.
Promoções e Benefícios para os Jogadores O 567br também oferece uma série de promoções e benefícios que tornam a experiência de jogo ainda mais atrativa. Novos jogadores podem aproveitar bônus de boas-vindas e outras ofertas especiais, enquanto jogadores regulares podem se beneficiar de programas de fidelidade e promoções exclusivas.
Essas ofertas ajudam a aumentar a diversão e proporcionam mais oportunidades para que os jogadores explorem novos jogos e tenham uma experiência ainda mais rica. Além disso, o sistema de recompensas é transparente e justo, garantindo que todos os jogadores tenham as mesmas oportunidades de aproveitar os benefícios.
Conclusão: Uma Plataforma Completa para Todos os Gostos Com sua interface intuitiva, variedade de jogos e foco na experiência do jogador, o 567br se consolida como uma plataforma de entretenimento online de alta qualidade. Seja para quem busca jogos estratégicos, ação intensa ou diversão casual, o 567br tem algo para todos.
A segurança, o suporte ao cliente e a personalização da experiência de jogo tornam o 567br uma opção atraente para jogadores que buscam mais do que apenas uma plataforma de jogos – buscam uma jornada de entretenimento envolvente e segura. Se você está procurando por uma experiência completa e agradável, o 567br é, sem dúvida, uma excelente escolha.
-
 @ fbf0e434:e1be6a39
2025-05-29 13:09:48
@ fbf0e434:e1be6a39
2025-05-29 13:09:48Hackathon 概述
ETH Dublin 2025 黑客松圆满落幕,活动共吸引 84 名开发者参与,共有 31 个项目通过审核。活动核心是借助多家赞助商技术,打造具有影响力的区块链解决方案。活动鼓励参与者组建技能多元的平衡团队,运用技术工具及赞助商支持 —— 如 Chainlink 进行数据验证、Ledger 保障安全、Filecoin 提供存储方案等。
多个项目聚焦社会影响领域:ÉireEncrypt 致力于开发符合 GDPR 合规要求的隐私保护区块链工具;SafeRoads Ireland 则通过智能合约推动安全驾驶。此外,部分项目借助以太坊实现租金管控与去中心化住房市场,还有以移民为主题的数字解决方案促进社区融合,充分展现区块链技术在解决隐私保护、公共安全、教育改革等实际问题中的潜力。
总体而言,ETH Dublin 2025 黑客松不仅促进了开发者与合作伙伴的协作,更激发了诸多借助区块链技术创造社会价值的创新项目。
Hackathon 获奖者
奖项得主
- 一等奖: RecEth
RecEth 通过提供电子邮件确认和清晰的收据,增强了用户对加密交易的信任,将用户体验与传统支付系统的透明度相对齐。 - 二等奖: Latinum
Latinum 作为支付中间件,允许MCP构建者通过兼容钱包实现由代理发起的交易来实现服务器货币化,简化了货币化过程。 - 三等奖: Fundraisely
FundRaisely 利用区块链技术帮助慈善机构进行合法合规的筹款,以及透明的审计,确保捐款流程的清晰和负责。
欲了解所有项目的更多信息,请访问这里。
关于组织者
ETH Ireland
ETH Ireland 致力于区块链技术的创新和发展。该组织在Ethereum方面有着丰富的专业知识,通过举办会议和工作坊促进区块链教育和社区参与。ETH Ireland 的使命是扩大区块链知识普及,推广去中心化技术到各个领域。
- 一等奖: RecEth
-
 @ b8851a06:9b120ba1
2025-01-27 11:58:53
@ b8851a06:9b120ba1
2025-01-27 11:58:53Trump's Blueprint for Gaza: The New Nakba
Trump’s offhand suggestion to “clean out” 1.5 million Palestinians from Gaza isn’t just reckless—it’s a thinly veiled blueprint for ethnic cleansing. The proposed forced displacement of millions isn't new; it’s the 21st-century sequel to the Nakba, designed to erase Palestine from the map.
Gaza: The Systematic Machinery of Destruction
The assault on Gaza isn’t chaos—it’s coordinated demolition:
- 47,306+ killed – lives extinguished with impunity.
- 111,483 injured – survivors burdened with physical and psychological scars.
- 92% of homes destroyed – families displaced, memories shattered.
- 60% of infrastructure dismantled – society intentionally crippled.
This is more than war—it’s annihilation by design.
A Second Nakba in Motion
The original Nakba (1948) was the template:
- 6 million refugees still barred from returning home.
- Generations of children growing up stateless, inheriting loss.
- Cultural heritage erased, lands stolen, and identities fractured.
Trump’s “solution” carries this legacy forward, pushing millions toward another endless exile.
The Humanitarian Collapse
If enacted, the mass displacement would trigger a humanitarian apocalypse across the region:
- Healthcare systems overwhelmed in neighboring nations.
- Schools collapsing under the weight of refugee students.
- Economic and social infrastructures stretched beyond capacity.
This isn’t just a Palestinian crisis—it’s a global one.
A Calculated Plan for Erasure
Make no mistake: the destruction of Gaza is deliberate. Israeli Finance Minister Avi Dichter’s chilling declaration of a "rolling Gaza Nakba" lays bare the intent: erase Gaza and its people from existence. The steps are cold, calculated, and systematic:
- Starvation as a weapon of war.
- Targeting hospitals to eliminate healthcare.
- Destroying water supplies to force displacement.
This isn’t collateral damage—it’s genocide.
Generational Wounds That Won’t Heal
The impact of this erasure will reverberate for centuries:
- Children growing up with inherited trauma.
- A culture erased piece by piece.
- Future generations left stateless, voiceless, and forgotten.
Every demolished building and every child killed are steps toward creating a permanent refugee underclass.
Silence is Complicity
The global silence is deafening. Trump’s “solution” isn’t a spontaneous idea—it’s the culmination of decades of dehumanization and demographic engineering. And every moment the world stays silent, the machinery of genocide moves forward.
Resistance is Survival
The choice is clear: submit to tyranny or resist. Every truth told, every act of defiance, every refusal to look away chips away at their plans. They want us silent. They need us indifferent.
But we’re not sheep—we’re the descendants of those who refused to kneel. - Share their crimes. - Expose their lies. - Refuse their narrative.
Because the battle for Palestine isn’t just about land—it’s about dignity, existence, and the refusal to be erased.
-
 @ ef53426a:7e988851
2025-05-29 12:26:43
@ ef53426a:7e988851
2025-05-29 12:26:43Saturday 9AM It’s a chilly Saturday morning in Warsaw, and I don’t want to get out of bed. This is not because of the hangover; it’s because I feel like a failure.
The first day of Bitcoin FilmFest was a whirlwind of workshops, panels and running between stages. The pitch competition did not go my way. Another ‘pitching rabbit’ (an actual experienced film-maker) was selected to win the €3,000 of funding.
Rather than get up and search for coffee, I replay the scenes in my head. What could I have done differently? Will investors ever believe in me: I’m just a writer with no contacts in the industry. Do I have what it takes to produce a film?
Eventually, I haul myself out of bed and walk to Amondo, the festival’s morning HQ (and technically, the smallest cinema in Europe). Upon arrival, I find Bitcoin psychonaut Ioni Appelberg holding court in front of around a dozen enraptured disciples. Soon, the conversation spills out to the street to free up space for more workshops.

I attend a talk on film funding, then pay for coffee using bitcoin. I see familiar faces from the two previous nights. We compare notes on Friday night and check the day’s schedule. The morning clouds burn off, and things feel a little brighter.
The afternoon session begins just a few blocks away in the towering Palace of Culture and Science. My role in today's proceedings is to present my freedom fiction project, 21 Futures, on the community stage. Other presentations range from rap videos and advice on finding jobs in bitcoin to hosting ‘Bitcoin Walks’. This is how we are fixing the culture.
Saturday 8PM I feel a tap on my shoulder. ‘Excuse me, Mr. Philip. Your car is waiting. The Producers’ Dinner is starting soon’.
What? Me, a producer? I’ve been taking part in some panels and talks, but I assumed my benefits as a guest were limited to a comped ticket and generous goodie bag.
Soon, I am sharing a taxi with a Dubai-based journalist, a Colombian director, and the cypherpunk sponsor of the pitch competition I didn’t win.
The pierogies I dreamed of earlier that day somehow manifest (happy endings do exist), and we enjoy a raucous dinner including obligatory slivovitz.

Sunday 2AM The last few hours of blur include a bracing city-bike ride in a crew of nine attendees back to the Palace of Culture, chatting with a fellow bitcoin meetup organiser, and vaguely promising to attend a weekend rave with a crew of Polish artists and musicians on the outskirts of London.
I leave the party while it’s still in full swing. In five hours, I have to wake up to complete my Run for Hal in Marshal Edward Rydz-Śmigły Park.
Thursday 9PM The festival kicks off in Samo Centrum on Pizza Day. I arrive in a taxi straight from a cramped flight (fix the airlines!), having not eaten for around ten hours.
The infectious sounds of softly spoken Aussie bitrocker Roger9000 pound into the damp night. I’m three beers in, being presented by the organisers to attendees like a (very tall) show pony. I try to explain more about my books, my publishing connections, my short film.
When I search for the food I ordered an hour ago, I find it has been given away. The stern-faced Polish pizza maker shrugs. ‘You not here.’
I’m so hungry I could cry (six hours of Ryanair can do that to a man). And then, a heroic Czech pleb donates half a pizza to me. Side note: this same heroic pleb accidentally locked me out of my film-funds while trying to fix a wallet bug on Sunday night.
I step out into the rain. Roger9000 reminds us we should have laser eyes well past 100k. I take a bite of pizza and life tastes good.

The Films Side events, artists, late nights, and pitcher’s regret is all well and good, but what of the films?
My highlights included Golden Rabbit winner No More Inflation — a moving narrative with interviews from two dozen economists, visionaries, and inflation survivors.
Hotel Bitcoin, was a surprisingly funny comedy romp about a group of idiots who happen across a valuable laptop.
Revolución Bitcoin — an approachable and thorough documentary aimed to bring greater adoption in the Spanish-speaking world.
And, as a short-fiction guy, I enjoyed the short films The Man Who Wouldn’t Cry, a visit to New York’s only Somali restaurant in Finding Home.

Sunday 7PM The award ceremony has just finished. I head to Amondo for the final time to pay for mojitos in bitcoin and say goodbye to newly made friends. I feel like I’ve met almost everyone in attendance. Are you going to BTC Prague?!? we ask as we part ways.
Of course, the best thing about any festival is the people, and BFF25 had a cast of characters worthy of any art house flick:
- The bright-eyed and confident frontwoman of the metal band Scardust
- A nostr-native artist selling his intricate canvases to the highest zapper
- A dreadlocked DJ who wears a pair of flying goggles on his head at all times
- An affable British filmmaker explaining the virtues of the word ‘chucklesome’
- A Duracell-powered organiser who seems to know every song, person, film, book, and guest at the festival.
Warsaw itself feels like it has a role to play, too. Birdsong and green parks contrast the foreboding Communist-era architecture. The weather changes faster than my mood — heavy greys transform to bright sunshine. The roads around the venue close on Sunday for a political rally. And there we are in the middle, watching our bitcoin films.

Tuesday 10AM I’m at home now, squinting at my email inbox and piles of washing, wondering when the hell I’ll find time. The festival Telegram group is still buzzing with activity. Side events like martial arts tutorials, trips to a shooting range, boat tours. 5AM photos of street graffiti, lost and found items, and people asking ‘is anyone still around?’
This was not just a film festival. BFF is truly a celebration of culture — Art. Books. Comedy. Music. Video. Talk. Connection.
All this pure signal has lifted my spirits so much that despite me being a newbie filmmaker, armed only with a biro, a couple of powerpoints and a Geyser fund page, I know I will succeed in my mission. It turns out you can just film things.
You may have attended bitcoin conferences before — you know, the ones with ‘fireside chats’, VIP areas, and overpriced merch. Bitcoin FilmFest is a moment in time. We are fixing the culture, year after year, until art can flourish again.
As fellow author Aaron Koenig commented during a panel session, ‘In twenty years, we won’t be drawing laser eyes and singing about honey badgers. Our grandchildren won’t understand the change we went through.’
Would I do it all again? Of course!
Join me next June in Warsaw.
I’ll be the tall one presenting his short animation premiere.
Philip Charter is a full-time writer and part-time cat herder. As well as writing for bitcoin founders and companies, he runs the 21 Futures fiction project.
Find out more about theNoderoid Saga animation projecton Geyser.
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 7e538978:a5987ab6
2025-05-29 10:32:34
@ 7e538978:a5987ab6
2025-05-29 10:32:34This article gives an overview and comparison of the various funding sources that are available for LNbits.
LNbits is compatible with many Lightning Network wallets and can be on anything from a small VPS to a raspberry Pi on your home network or the LNbits SaaS platform.
Why your funding source matters
There are trade-offs between the various funding sources, for example funding LNbits using Strike requires the user to KYC themselves and has some privacy compromises versus funding LNbits from your own LND node. However the technical barrier to entry and node maintenance of using Strike is lower than using LND.
Self-custodial vs custodial connectors
Self-custodial Funding Sources
You run the node or service, keep the keys, and may need to manage LN channels. Good if you want control and have the skills to look after a server. Examples: LND (gRPC/REST), CoreLightning, Spark.
Self-custodial funding sources with an LSP
These funding sources offer a reasonable compromise between self-custody and some privacy trade offs. Examples: Phoenixd, Breez SDK, Boltz.
Custodial (or semi-custodial) funding sources
A third party runs the node. You plug LNbits into their API. Setup is quick and costs are low, but you trust the provider with your funds and privacy. Examples: Alby, OpenNode, Blink, ZBD, LNPay or another LNbits instance.
Funding sources compared
Below is a summary of the main options and how they stack up.
LNbits Lightning Network Funding Sources Comparison Table
| Funding Source | Custodial Type | KYC Required | Technical Knowledge Needed | Node Hosting Required | Privacy Level | Liquidity Management | Ease of Setup | Maintenance Effort | Cost Implications | Scalability | Notes | |----------------------------|--------------------|---------------------|--------------------------------|---------------------------|-------------------|--------------------------|-------------------|------------------------|----------------------------------------------|-----------------|------------------------------------------------------------------| | LND (gRPC) | Self-custodial | ❌ | Higher | ✅ | High | Manual | Moderate | High | Infrastructure cost and channel opening fees | High | gRPC interface for LND; suitable for advanced integrations. | | CoreLightning (CLN) | Self-custodial | ❌ | Higher | ✅ | High | Manual | Moderate | High | Infrastructure cost and channel opening fees | High | Requires setting up and managing your own CLN node. | | Phoenixd | Self-custodial | ❌ | Medium | ❌ | Medium | Automatic | Moderate | Low | Minimal fees | Medium | Mobile wallet backend; suitable for mobile integrations. | | Nostr Wallet Connect (NWC) | Custodial | Depends on provider | Low | ❌ | Variable | Provider-managed | Easy | Low | May incur fees | Medium | Connects via Nostr protocol; depends on provider's policies. | | Boltz | Self-custodial | ❌ | Medium | ❌ | Medium | Provider-managed | Moderate | Moderate | Minimal fees | Medium | Uses submarine swaps; connects to Boltz client. | | LND (REST) | Self-custodial | ❌ | Higher | ✅ | High | Manual | Moderate | High | Infrastructure cost and channel opening fees | High | REST interface for LND; suitable for web integrations. | | CoreLightning REST | Self-custodial | ❌ | Higher | ✅ | High | Manual | Moderate | High | Infrastructure cost and channel opening fees | High | REST interface for CLN; suitable for web integrations. | | LNbits (another instance) | Custodial | Depends on host | Low | ❌ | Variable | Provider-managed | Easy | Low | May incur hosting fees | Medium | Connects to another LNbits instance; depends on host's policies. | | Alby | Custodial | ✅ | Low | ❌ | Low | Provider-managed | Easy | Low | Transaction fees apply | Medium | Browser extension wallet; suitable for web users. | | Breez SDK | Self-custodial | ❌ | Medium | ❌ | High | Automatic | Moderate | Low | Minimal fees | Medium | SDK for integrating Breez wallet functionalities. | | OpenNode | Custodial | ✅ | Low | ❌ | Low | Provider-managed | Easy | Low | Transaction fees apply | Medium | Third-party service; suitable for merchants. | | Blink | Custodial | ✅ | Low | ❌ | Low | Provider-managed | Easy | Low | Transaction fees apply | Medium | Third-party service; focuses on mobile integrations. | | ZBD | Custodial | ✅ | Low | ❌ | Low | Provider-managed | Easy | Low | Transaction fees apply | Medium | Gaming-focused payment platform. | | Spark (CLN) | Self-custodial | ❌ | Higher | ✅ | High | Manual | Moderate | High | Infrastructure cost and channel opening fees | High | Web interface for CLN; requires Spark server setup. | | Cliche Wallet | Self-custodial | ❌ | Medium | ❌ | Medium | Manual | Moderate | Moderate | Minimal fees | Medium | Lightweight wallet; suitable for embedded systems. | | Strike | Custodial | ✅ | Low | ❌ | Low | Provider-managed | Easy | Low | Transaction fees apply | Medium | Third-party service; suitable for quick setups. | | LNPay | Custodial | ✅ | Low | ❌ | Low | Provider-managed | Easy | Low | Transaction fees apply | Medium | Third-party service; suitable for quick setups. |
Which source suits you?
| Scenario | Good fit | Why | | ------------------------------------------- | ---------------------------------------------------------------------- | ------------------------------------------------------ | | Business running its own infrastructure | LND or CoreLightning on a Dell Optiplex or other dedicated machine | Full control, high throughput, best privacy. | | Independent node runner | Spark (CLN) or LND (REST/gRPC) | You already run a node and want a clean web interface. | | Quick proof of concept | Alby, LNPay, or another hosted LNbits | No hardware needed, lets you test ideas fast. |
Run LNbits
Ready to run LNbits?
Choose a funding source, follow the guides, and start today.
Further reading
- LNbits documentation
- LND – gRPC and REST guides
- CoreLightning – setup and Spark info
- Breez SDK
- Phoenixd
- Nostr Wallet Connect
-
 @ c1d77557:bf04ec8b
2025-05-24 05:01:44
@ c1d77557:bf04ec8b
2025-05-24 05:01:44O P11Bet é uma plataforma inovadora que chega para oferecer uma experiência de jogo única, reunindo uma variedade de opções para os entusiastas de diferentes tipos de entretenimento online. Com uma interface moderna e fácil de usar, ela se destaca por proporcionar uma jornada divertida e segura para os jogadores, com um foco especial na qualidade da experiência e no atendimento às necessidades do público.
Uma Plataforma Completa e Acessível Ao acessar o P11Bet, os usuários encontram uma plataforma intuitiva, que facilita a navegação e oferece uma variedade de recursos para tornar o jogo mais agradável. A estrutura do site é otimizada para fornecer uma experiência fluida, seja no desktop ou em dispositivos móveis. Além disso, a plataforma se preocupa em manter um ambiente seguro, garantindo a proteção dos dados dos jogadores e permitindo que se concentrem na diversão.
A plataforma é projetada para todos os tipos de jogadores, desde os iniciantes até os mais experientes. A simplicidade de uso é uma das grandes vantagens, permitindo que qualquer pessoa possa se registrar e começar a jogar sem dificuldades. Além disso, a p11betoferece suporte ao cliente em português, o que facilita a comunicação e garante um atendimento de alta qualidade para os usuários brasileiros.
Diversidade de Jogos para Todos os Gostos O P11Bet se destaca pela vasta gama de opções de jogos que oferece aos seus usuários. A plataforma abriga uma seleção diversificada que vai desde jogos clássicos até as opções mais modernas, atendendo a todos os estilos e preferências. Entre as opções mais procuradas estão jogos de mesa, apostas esportivas, slots, e outras modalidades que garantem horas de entretenimento.
Um dos principais atrativos do P11Bet são os jogos de habilidade e de sorte, que exigem tanto estratégia quanto um pouco de sorte. As opções variam desde os mais simples aos mais complexos, oferecendo algo para todos os gostos. Os jogadores podem se aventurar em diversas modalidades, testando suas habilidades em jogos que vão de roletas e blackjack a versões mais inovadoras e dinâmicas.
Para aqueles que preferem algo mais emocionante e competitivo, as apostas esportivas são uma das maiores atrações. O P11Bet oferece uma ampla variedade de eventos esportivos ao vivo para apostar, com odds atrativas e uma plataforma que permite realizar apostas de forma rápida e eficiente. Seja em esportes populares como futebol, basquete ou até mesmo esportes menos tradicionais, há sempre algo para os apostadores mais exigentes.
A Experiência do Jogador: Diversão e Segurança O P11Bet não apenas se preocupa com a diversidade de jogos, mas também com a experiência do jogador. A plataforma foi desenvolvida para garantir que os jogadores possam desfrutar de seus jogos favoritos com a maior segurança e conforto possível. Além de um design intuitivo, a plataforma oferece diversas opções de pagamento, incluindo métodos populares no Brasil, para facilitar depósitos e retiradas. Isso garante que o processo de transações seja simples, rápido e seguro.
Outro ponto positivo do P11Bet é a experiência imersiva que ele oferece aos jogadores. A plataforma está sempre atualizada com novas funcionalidades, com promoções atraentes e bônus especiais que aumentam ainda mais a diversão. A interação com outros jogadores também é um diferencial, com espaços que permitem competir, conversar e trocar experiências com pessoas de todo o mundo.
Além disso, o suporte ao cliente da P11Bet é um dos mais elogiados pelos usuários. A equipe está sempre disponível para resolver dúvidas e fornecer assistência de maneira eficaz e amigável. Isso garante que os jogadores tenham sempre uma experiência tranquila, sem se preocupar com questões técnicas ou problemas relacionados à plataforma.
Conclusão Em resumo, o P11Bet é uma excelente escolha para quem busca uma plataforma completa e de qualidade para se divertir e desafiar suas habilidades. Com uma grande variedade de jogos, uma interface de fácil navegação e um suporte excepcional, ele garante que cada momento na plataforma seja único e prazeroso. Para quem deseja se aventurar no mundo dos jogos online, o P11Bet é uma opção que combina segurança, inovação e diversão.
-
 @ 87e98bb6:8d6616f4
2025-05-23 15:36:32
@ 87e98bb6:8d6616f4
2025-05-23 15:36:32Use this guide if you want to keep your NixOS on the stable branch, but enable unstable application packages. It took me a while to figure out how to do this, so I wanted to share because it ended up being far easier than most of the vague explanations online made it seem.
I put a sample configuration.nix file at the very bottom to help it make more sense for new users. Remember to keep a backup of your config file, just in case!
If there are any errors please let me know. I am currently running NixOS 24.11.
Steps listed in this guide: 1. Add the unstable channel to NixOS as a secondary channel. 2. Edit the configuration.nix to enable unstable applications. 3. Add "unstable." in front of the application names in the config file (example: unstable.program). This enables the install of unstable versions during the build. 4. Rebuild.
Step 1:
- Open the console. (If you want to see which channels you currently have, type: sudo nix-channel --list)
- Add the unstable channel, type: sudo nix-channel --add https://channels.nixos.org/nixpkgs-unstable unstable
- To update the channels (bring in the possible apps), type: sudo nix-channel --update
More info here: https://nixos.wiki/wiki/Nix_channels
Step 2:
Edit your configuration.nix and add the following around your current config:
``` { config, pkgs, lib, ... }:
let unstable = import
{ config = { allowUnfree = true; }; }; in { #insert normal configuration text here } #remember to close the bracket!```
At this point it would be good to save your config and try a rebuild to make sure there are no errors. If you have errors, make sure your brackets are in the right places and/or not missing. This step will make for less troubleshooting later on if something happens to be in the wrong spot!
Step 3:
Add "unstable." to the start of each application you want to use the unstable version. (Example: unstable.brave)
Step 4:
Rebuild your config, type: sudo nixos-rebuild switch
Example configuration.nix file:
```
Config file for NixOS
{ config, pkgs, lib, ... }:
Enable unstable apps from Nix repository.
let unstable = import
{ config = { allowUnfree = true; }; }; in { #Put your normal config entries here in between the tags. Below is what your applications list needs to look like.
environment.systemPackages = with pkgs; [ appimage-run blender unstable.brave #Just add unstable. before the application name to enable the unstable version. chirp discord ];
} # Don't forget to close bracket at the end of the config file!
``` That should be all. Hope it helps.
-
 @ 812cff5a:5c40aeeb
2025-01-21 21:11:51
@ 812cff5a:5c40aeeb
2025-01-21 21:11:51ما هو أولاس (Olas)
أولاس تطبيق نوستر محاكي للانستغرام

أولاس OLAS هو أول تطبيق نوستر يتم تطويرة بشكل جدي لتقديم تجربة شبيهة بالانستغرام على نوستر. يركز التطبيق على عرض الصور والڤيديو على الصفحة الرئيسية مع قدرة على فلترة الصفحة. التطبيق مصمم أيضا ليعرض الڤيديو بشكل شبيه بالانستغرام رييلز. لكن بسبب بعض الامور التقنية الميزة لا تعمل بشكل جيد الان.
ما الذي يميز تطبيق أولاس
أولاس يتبع نيپ-٨٦ (NIP-68) لعرض الصور والميديا
يتميز تطبيق أولاس بأنه يعتمد على منشورات نوستر من نوع ٢٠ (Kind-20) وهو نوع مخصص للصور والڤيديو يتبع تطوير NIP-68. مما يعني ان المنشورات تظهر فقط على تطبيقات قادرة علة عرض هذه النوع.

وكون هذه هي الطريقة التي تم تصميم فيها التطبيق، أولاس لا يعرض المنشورات المتعارف عليها مثل تويتر أو من نوع ١ (kind-1) ليقدم للمستخدم تجربة جميلة فريدة من نوعها (حتى الأن).
ضرورة تطوير تطبيقات متخصصة
التطبيقات المخصصة هي باب لجذب مستخدمين جدد
من الضروري تطوير تطبيقات شبهة بأولاس من حيث التصميم. أي ان التطبيق موجه لفئة محددة وواضحة. هذا النوع من التطبيقات يجذب مستخدمين غير مهتمين بالاخبار او المنشورات المكتوبة وكل اهتمامهم هو نشر ومشاركة الصور والڤيديو.
كيف يمكنك دعم المشروع؟
شارك في مبادرة السنة #olas365
أولاس حاليا متوفر كتطبيق تجريبي على iOS والويب. يمكنكم الإنضمام وتجربة التطبيق. لكن نود التنبيه ان التطبيق في مراحلة الأولى ويتم تطويره وتحديثه بشكل دوري.
هذا الرابط لتحميل التطبيق: Olas Testflight Link
مطور التطبيق: nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft
-
 @ c1d77557:bf04ec8b
2025-05-24 05:01:11
@ c1d77557:bf04ec8b
2025-05-24 05:01:11Se você está em busca de uma experiência de jogo dinâmica e diversificada, o 59h é a plataforma que você precisa conhecer. Com um foco claro na satisfação dos jogadores, ela oferece uma ampla variedade de opções de entretenimento, além de uma interface amigável e segura. Neste artigo, vamos explorar a plataforma 59h, destacando suas principais funcionalidades, jogos emocionantes e a experiência do usuário.
O Que é a Plataforma 59h? O 59h é uma plataforma inovadora que oferece uma vasta gama de jogos e experiências digitais para os entusiastas do entretenimento online. A plataforma se destaca pela sua interface intuitiva, que permite aos jogadores navegar com facilidade entre as diferentes categorias de jogos. Ela é ideal para quem busca uma experiência divertida e acessível, sem complicações.
Desde o momento em que você acessa o 59h, fica evidente o compromisso com a qualidade. A plataforma é projetada para ser acessível em diversos dispositivos, seja no seu computador, tablet ou smartphone. Isso garante que os jogadores possam aproveitar seus jogos favoritos a qualquer momento e em qualquer lugar, com a mesma qualidade e desempenho.
Uma Grande Variedade de Jogos para Todos os Gostos O 59h se destaca por sua impressionante variedade de jogos. Independentemente do tipo de jogo que você prefere, certamente encontrará algo que se adapte ao seu estilo. A plataforma oferece desde jogos de habilidade, até opções mais relaxantes e divertidas para aqueles que buscam algo mais descontraído.
Entre as opções mais populares, destacam-se os jogos de mesa, onde os jogadores podem testar suas habilidades em jogos como pôquer, blackjack e outros. Para quem prefere algo mais voltado para a sorte, o 59h também oferece jogos com elementos de sorte que podem garantir grandes recompensas.
Além disso, a plataforma está sempre atualizando seu portfólio de jogos, trazendo novidades para os jogadores. Isso significa que você nunca ficará entediado, já que sempre haverá algo novo e emocionante para experimentar.
A Experiência do Jogador no 59h Uma das maiores qualidades da plataforma 59h é sua atenção à experiência do usuário. Desde o processo de registro até a escolha de um jogo, tudo foi pensado para garantir uma navegação tranquila e sem estresse.
A plataforma é completamente segura, oferecendo métodos de pagamento rápidos e confiáveis. Isso significa que os jogadores podem depositar e retirar seus fundos com confiança, sem se preocupar com a segurança de suas informações pessoais. Além disso, o suporte ao cliente está sempre disponível para ajudar em caso de dúvidas ou problemas, garantindo que sua experiência seja o mais fluida possível.
Outro ponto que merece destaque é a comunidade de jogadores. A interação com outros jogadores é uma parte importante da plataforma, permitindo que você compartilhe dicas, participe de torneios e crie amizades. A plataforma 59h se esforça para criar um ambiente amigável e inclusivo, onde todos podem se divertir e aprender uns com os outros.
Acessibilidade e Facilidade de Uso O 59h não é apenas sobre a diversidade de jogos; também se trata de tornar o acesso o mais simples possível. A plataforma oferece um design responsivo, que se adapta perfeitamente a qualquer tipo de dispositivo. Isso significa que você pode jogar no computador, smartphone ou tablet com a mesma facilidade.
O processo de cadastro é simples e rápido, permitindo que você comece a jogar em questão de minutos. Além disso, a plataforma oferece uma série de recursos adicionais, como promoções e bônus exclusivos, que tornam a experiência ainda mais empolgante.
Conclusão O 59h se posiciona como uma plataforma de entretenimento online completa, oferecendo uma vasta gama de jogos, uma experiência de usuário de alta qualidade e um ambiente seguro e amigável para jogadores de todos os níveis. Se você procura uma plataforma confiável, diversificada e divertida, o 59h é a escolha ideal. Não importa se você é um iniciante ou um jogador experiente, há sempre algo novo para descobrir e aproveitar no 59h.
-
 @ 63d59db8:be170f6f
2025-05-23 12:53:00
@ 63d59db8:be170f6f
2025-05-23 12:53:00In a world overwhelmed by contradictions—climate change, inequality, political instability, and social disconnection—absurdity becomes an unavoidable lens through which to view the human condition. Inspired by Albert Camus' philosophy, this project explores the tension between life’s inherent meaninglessness and our persistent search for purpose.\ \ The individuals in these images embody a quiet defiance, navigating chaos with a sense of irony and authenticity. Through the act of revolt—against despair, against resignation—they find agency and resilience. These photographs invite reflection, not on solutions, but on our capacity to live meaningfully within absurdity.
Visit Katerina's website here.
Submit your work to the NOICE Visual Expression Awards for a chance to win a few thousand extra sats:
-
 @ 2b468756:7930dd9c
2025-05-23 12:17:09
@ 2b468756:7930dd9c
2025-05-23 12:17:09Agorisme is libertarisme in de praktijk: op legale wijze maximale economische en persoonlijke vrijheid. Samen ontdekken en delen we wat er allemaal mogelijk is. We doen dit door: - organiseren jaarlijks agorismefestival - organiseren meerdere themadagen / excursies per jaar - bundelen praktische kennis op Agorisme Wiki - online uitwisselen via (thema)appgroepen
Op deze site worden activiteiten aangekondigd en kun je je opgeven.
Binnenkort: - cursussen metselen, stucen en vloeren - reis naar libertarisch dorp Walden Woods en Liberstad in Noorwegen - introductie Krav Maga zelfverdediging
We zijn gelieerd aan de libertarische partij.
Graag tot ziens!
-
 @ 3eba5ef4:751f23ae
2025-05-23 09:33:55
@ 3eba5ef4:751f23ae
2025-05-23 09:33:55The article below brings together some of the Q&A from our recent AMA on Reddit. Thanks so much for sending in your questions—we love chatting with you and being part of this awesome community!
Meepo Hardfork Features
What does Meepo bring to CKB, in simple terms?
Imagine upgrading from wooden blocks to LEGO bricks. That’s what the
spawnsyscall in Meepo does for CKB smart contracts, enabling script interoperability.Spawn and a series of related syscalls are introduced as a major upgrade to CKB-VM, enabling interoperability, modularity, and better developer experience, by letting scripts call other scripts, like modular apps in an operating system.
Key features of the upgraded VM?
The upgraded CKB-VM Meepo version unlocks true decoupling and reuse of CKB scripts, enhancing modularity and reusability in smart contract development.
For instance, before Meepo, if developers wanted to build a new time lock in CKB, they had to bundle all necessary functionalities—like signature algorithms—directly into a single lock or type script. This often led to bloated scripts where most of the code was unrelated to the developer's original design goal (time lock). With the spawn syscall, scripts can now delegate tasks—such as signature checks—to other on-chain scripts. As new algorithms emerge, the time lock can adopt them without being redeployed—just by calling updated signature scripts, as long as a shared protocol is followed.
This separation allows developers to: - Focus solely on their core logic. - Reuse independently deployed signature verification scripts. - Upgrade cryptographic components without modifying the original script. - Embrace a more OS-like model where smart contracts can call each other to perform specialized tasks.
By enabling true decoupling and reuse, the spawn syscall makes CKB scripts significantly more composable, maintainable, and adaptable.
Besides Spawn, other improvements in Meepo include:
- Block Extension Fields: Enables reading extension fields in blocks, opening new possibilities like community voting on hardforks (as this ckb-zero-lock prototype). More use cases are expected.
- CKB-VM Optimization: Reduces cycle consumption for common compiler-generated code, making scripts faster and more efficient.
A practical example: IPC on Spawn
Here's an example building an entire Inter-Process Communication (IPC) layer on top of spawn syscalls: - GitHub Repo - Blog post: Transforming IPC in CKB On-Chain Script: Spawn and the Custom Library for Simplified Communication
What does “every wallet will become a CKB wallet because of ckb-auth” mean?
Current CKB-VM already comes with the power to build omnilock / ckb-auth, spawn just makes them easier to reuse in new scripts through decoupling and improved modularity.
Upgrade Compatibility Concerns
Will Meepo require a new address format?
No. Meepo does not introduce breaking changes like address format switching. The only required upgrade is support for a new hash type (
data2). We aim to keep upgrades smooth and backwards-compatible wherever possible.RISC-V & CKB’s Long-Term Design Philosophy
Ethereum is exploring RISC-V—CKB has been doing this for years. What’s your take?
The discussion about RISC-V in Ethereum, is partly about the ease of building zk solutions on Ethereum. And it's easy to mix two different use cases of RISC-V in zk:
- Use RISC-V as the language to write programs running in a zk engine. In this case, we use zero knowledge algorithms to build a RISC-VM and prove programs running inside these RISC-V VMs.
- Use RISC-V as the underlying engine to run cryptographic algorithms, we then compile the verifier / prover code of zero knowledge algorithm into RISC-V, then we run those verifiers / provers inside RISC-V. Essentially, we run the verifying / proving algorithms of zero knowledge algorithms in RISC-V, the programs running inside ZK VMs can be written in other languages suiting the zk algorithms.
When most people talk about RISC-V in zk, they mean the first point above. As a result, we see a lot of arguments debating if RISC-V fits in zk circuits. I couldn't get a direct confirmation from Vitalik, but based on what I read, when Vitalik proposes the idea of RISC-V in Ethereum, he's at least partly thinking about the second point here. The original idea is to introduce RISC-V in Ethereum, so we can just compile zk verifiers / provers into RISC-V code, so there is no need to introduce any more precompiles so as to support different zk algorithms in Ethereum. This is indeed a rare taken path, but I believe it is a right path, it is also the path CKB chose 7 years ago for the initial design of CKB-VM.
CKB believes that a precompile-free approach is the only viable path if we’re serious about building a blockchain that can last for decades—or even centuries. Cryptographic algorithms evolve quickly; new ones emerge every few years, making it unsustainable for blockchains to keep adding them as precompiles. In contrast, hardware evolves more slowly and lives longer.
By choosing RISC-V, we’ve committed to a model that can better adapt to future cryptographic developments. CKB may be on an uncommon path, but I believe it's the right one—and it's encouraging to see Ethereum now moving in a similar direction. Hopefully, more will follow.
CKB already stands out as the only blockchain VM built on RISC-V and entirely free from cryptographic precompiles. Meepo, with its spawn syscall, builds on this foundation—pushing for even greater modularity and reuse. We're also closely watching progress in the RISC-V ecosystem, with the goal of integrating hardware advances into CKB-VM, making it even more future-proof and a state-of-the-art execution environment for blockchain applications.
Will CKB run directly on RISC-V chips? What are the implications?
The "CKB on RISC-V"comes in several stages:
- For now, CKB-VM can already be compiled into RISC-V architecture and run on a RISC-V CPU (e.g. StarFive board), though optimized native implementations are still in development.
- That said, one key issue in the previous stage was that CKB-VM lacks a high-performance, assembly based VM on RISC-V architecture. Ironically, despite CKB-VM being based on RISC-V, we ended up running a Rust-based VM interpreter on RISC-V CPUs—which is far from ideal.
The root of the problem is that RISC-V CPUs come in many configurations, each supporting a different set of extensions. Porting CKB-VM to run natively on real RISC-V chips isn’t trivial—some extensions used by CKB-VM might not be available on the target hardware. With enough time and effort, a performant native implementation could be built, but it’s a non-trivial challenge that still needs significant work.
How do you see the RISC-V narrative expanding?
We are delighted to see the growing recognition of RISC-V in the blockchain space. For CKB, we firmly believe RISC-V is the best choice. Consensus is costly, so only essential data should be on-chain, with the chain serving as a universal verification layer—this is CKBʼs philosophy, and we have consistently designed and developed in this direction.
CKB Roadmap & Ecosystem Growth
Any plan to boost the usage of the CKB network in the next 6 - 24 months?
Growth starts with better developer experience. Spawn in Meepo significantly lowers the barrier to building complex apps. With better tools and documentation, more devs can experiment on CKB, leading to better apps and more users.
What would you focus on if the secondary issuance budget was huge?
If funding were abundant, we'd expand the Spark Program, support more grassroots projects, and even evolve toward a fully decentralized DAO structure—aligning with our long-term vision of a permissionless, community-owned network.
What’s next for Nervos after Meepo?
We're exploring new RISC-V extensions like CFI, which could boost script security and defend against ROP attacks. Still early-stage, but promising. Check out this: Against ROP Attacks: A Blockchain Architect’s Take on VM-Level Security.
Resources
Take a deeper look at the VM upgrades introduced in the Meepo hardfork:
Explore the CFI (Control Flow Integrity) extension on RISC-V:
Check out the Inter-Process Communication (IPC) layer built on top of spawn syscalls: