-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ 6146ad04:a0937b0b
2025-05-29 05:55:28
@ 6146ad04:a0937b0b
2025-05-29 05:55:28As the crypto market gears up for what many believe could be the next major bull run, one question dominates investor conversations: Will Bitcoin lead the charge once again, or will a new class of AI-powered coins steal the spotlight? This isn’t just a speculative debate—it represents a deeper narrative shift in how crypto investors are thinking about value, utility, and the future of technology.
Bitcoin: The Proven Leader
Bitcoin has historically been the spark that ignites every major bull market. As the original cryptocurrency, it's viewed as the safest bet in an otherwise volatile industry. Its scarcity (capped at 21 million), increasing institutional interest (like the 2024 approval of multiple spot ETFs), and its role as a hedge against inflation have all contributed to its dominance.
Why Bitcoin Might Lead Again:
Institutional adoption: BlackRock, Fidelity, and other giants now offer Bitcoin ETFs, making BTC more accessible than ever.
Digital gold narrative: With macroeconomic uncertainty still looming, Bitcoin’s role as a store of value is being reinforced.
Halving cycle: The 2024 halving has historically been followed by price surges due to reduced supply and increasing demand.
Yet, despite all this, the market has matured—and so has investor appetite.
AI Coins: The New Frontier of Speculation and Utility
Enter AI coins, a category of tokens tied to projects using or enabling artificial intelligence through blockchain technology. These include platforms like Fetch.ai (FET), Render (RNDR), SingularityNET (AGIX), and Numerai (NMR).
Why AI Coins Are Catching Fire:
AI hype cycle: The AI boom, fueled by OpenAI, NVIDIA, and advancements in machine learning, has crossed over into crypto.
Speculative narratives: Investors are betting that decentralized AI networks could challenge centralized tech giants like Google and Meta.
Real use cases: Projects are building decentralized compute, AI marketplaces, and data-sharing protocols with real-world applications.
AI coins often exhibit faster, more dramatic price movements than Bitcoin—appealing to high-risk, high-reward traders. They're meme-able, futuristic, and aligned with the fastest-growing tech trend globally.
The Clash of Narratives
At their core, Bitcoin and AI coins represent two different kinds of crypto belief systems:
Trait Bitcoin AI Coins
Narrative Digital gold, store of value Innovation, future tech, decentralizing AI Volatility Lower High Market maturity Very mature Emerging Investor type Institutional, long-term holders Retail, speculative traders Use case Monetary alternative Data, compute, prediction, services
Rather than choosing between the two, many smart investors are allocating across both, with Bitcoin providing stability and AI coins offering exponential upside.
Market Signals to Watch
Dominance Index: Bitcoin’s dominance often shrinks when altcoin cycles heat up—watch for a dip below 50% as a signal AI coins are gaining ground.
VC Investment Trends: AI and Web3 crossover projects have received increasing venture capital attention.
On-chain activity: Active addresses, developer commits, and transaction volume in AI coin ecosystems are growing rapidly.
Final Thoughts
While Bitcoin may still be the undisputed king of crypto, AI coins are positioning themselves as the spark of the next wave of innovation. Whether they lead the bull run or ride its momentum, their influence is undeniable. Investors may not need to choose a side, but they do need to understand the strengths, risks, and narratives behind both.
In the next bull market, it may not be Bitcoin vs. AI coins—it could be Bitcoin and AI coins that reshape the financial and technological landscape.
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 3bf0c63f:aefa459d
2024-12-06 20:37:26
@ 3bf0c63f:aefa459d
2024-12-06 20:37:26início
"Vocês vêem? Vêem a história? Vêem alguma coisa? Me parece que estou tentando lhes contar um sonho -- fazendo uma tentativa inútil, porque nenhum relato de sonho pode transmitir a sensação de sonho, aquela mistura de absurdo, surpresa e espanto numa excitação de revolta tentando se impôr, aquela noção de ser tomado pelo incompreensível que é da própria essência dos sonhos..."
Ele ficou em silêncio por alguns instantes.
"... Não, é impossível; é impossível transmitir a sensação viva de qualquer época determinada de nossa existência -- aquela que constitui a sua verdade, o seu significado, a sua essência sutil e contundente. É impossível. Vivemos, como sonhamos -- sozinhos..."
- Livros mencionados por Olavo de Carvalho
- Antiga homepage Olavo de Carvalho
- Bitcoin explicado de um jeito correto e inteligível
- Reclamações
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ d3d74124:a4eb7b1d
2025-05-29 02:19:14
@ d3d74124:a4eb7b1d
2025-05-29 02:19:14language is a funny thing. the English grammar is one of the most, if the not THE most complicated grammars to learn.
https://en.wikipedia.org/wiki/Defense_Language_Aptitude_Battery\ DLAB. it's the test you take to see if you have a gift for language learning.
in my exploration of languages, first Chinese Mandarin, then software languages, context is king (Jesus is King). the surrounding context is different every where you go.
physical space context. we can't be two places at once. nostr allows for many languages, because you can provide your own digital context. our physical perspective give us a field of view. NOSTR clients give us a field of view into digital context.
math is a language.
bitcoin will be called a lot of things.
wizardry
some elections results are anchored in time. using bitcoin. what else should be? legal documents seem obvious. other cryptographic proofs.
zero knowledge proofs. something about curve trees.
Find your local BitDevs.
Shenandoah Bitcoin Club
pondering a Veteran's Day live music event in Frederick County, VA. who would show up to a lunch and learn with hardware wallets in testnet4 mode? to try shit out? local only, but you should do it where you are too if you're not local.
mining
getting better? Bitmain announces a "decentralized mining pool" but I doubt we'll see open source code if history follows. 256Foundation getting to business. working prototypes for the Ember One using USB and python are out there for those that know where to look. i am very bullish on mujina. very bullish. fun coinbase tricks happening too with CTV+CSFS.
p.s. written on primal's new article publishing UI.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 6be5cc06:5259daf0
2025-05-27 20:22:09
@ 6be5cc06:5259daf0
2025-05-27 20:22:09A posição do libertário que rejeita o cristianismo padece de sérias incoerências lógicas, históricas e filosóficas. Ao renegar as bases espirituais e culturais que tornaram possível o próprio ideal libertário, tal posição demonstra ser, ao mesmo tempo, autofágica e irracional. É o caso de alguém que se gloria dos frutos de uma árvore que corta pela raiz.
I. Fundamento histórico: a civilização da liberdade é cristã
Não foi o secularismo moderno, nem o paganismo antigo, que ergueram as instituições que protegem a dignidade da pessoa humana e os limites ao poder. Desde os primeiros séculos, a Igreja resistiu ao culto estatal romano, afirmando a soberania de Deus sobre os Césares — "Mais importa obedecer a Deus que aos homens" (Atos 5,29).
Foi o cristianismo que:
-
Fundou universidades livres, onde o saber era buscado sob o primado da verdade;
-
Defendeu a lei natural como fundamento do direito — uma doutrina que protege o indivíduo contra tiranias;
-
Resgatou e aprofundou o conceito de pessoa, dotada de razão e livre-arbítrio, imagem de Deus, e, portanto, inalienavelmente digna e responsável.
Em momentos-chave da história, como nas disputas entre papado e império, nas resistências contra absolutismos, e na fundação do direito internacional por Francisco de Vitoria e a Escola de Salamanca, foi o cristianismo quem freou o poder estatal em nome de princípios superiores. A tradição cristã foi frequentemente o principal obstáculo à tirania, não seu aliado.
Negar isso é amputar a própria genealogia da liberdade ocidental.
Uma das chaves do cristianismo para a construção dessa civilização da liberdade foi a exaltação do individualismo. Ao afirmar que o ser humano é feito à imagem de Deus e que sua salvação é uma escolha pessoal, o cristianismo colocou o indivíduo no centro da moralidade e da liberdade. Diferente dos gregos, cuja ética era voltada para a polis e a cidade-estado, o cristianismo reafirma a suprema importância do indivíduo, com sua capacidade de escolha moral, responsabilidade pessoal e dignidade intrínseca. Esse princípio, mais do que qualquer outra religião, foi o alicerce do desenvolvimento da liberdade individual e da autonomia, valores que sustentam a civilização ocidental.
A ética grega, na melhor das hipóteses, descreve a ordem natural — mas não consegue justificar por que essa ordem deveria obrigar a vontade humana. Um Logos impessoal não tem autoridade moral. Uma ordem cósmica sem um Legislador é apenas um dado de fato, não uma norma vinculante. A vontade pode rebelar-se contra o telos — e sem um Deus justo, que ordena a natureza à perfeição, não há razão última para não o fazer.
A cultura grega teve uma influência indiscutível sobre o desenvolvimento da civilização ocidental, mas o cristianismo não só absorveu o que havia de bom na cultura grega, como também elevou e completou esses aspectos. O cristianismo, ao afirmar que todos os homens são feitos à imagem e semelhança de Deus e têm dignidade intrínseca, levou a uma noção de igualdade moral e liberdade que transcende as limitações da pólis grega.
II. Falsa dicotomia: fé e liberdade não são opostas
Com frequência equiparam a religião à coerção e à obediência cega. Mas isso é um equívoco: o cristianismo não se impõe pela força, mas apela à consciência. O próprio Deus, em sua relação com a criatura racional, respeita sua liberdade. Como ensina a Escritura:
"Se alguém quiser vir após mim..." (Mt 16,24);
"Eis que estou à porta e bato. Se alguém ouvir a minha voz e abrir a porta, entrarei em sua casa e cearei com ele." (Ap 3,20);
"Assim falai, e assim procedei, como devendo ser julgados pela lei da liberdade." (Tiago 2,12).A adesão à fé deve ser livre, voluntária e racional, pois sem liberdade não há verdadeiro mérito, nem amor genuíno. Isso é mais compatível com o princípio de não agressão do que qualquer utopia secular. Ora, o núcleo do evangelho é voluntarista: salvação pessoal, conversão interior, caridade.
Ninguém deve ser forçado, contra sua vontade, a abraçar a fé, pois o ato de fé é por sua natureza voluntário (Dignitatis Humanae; CDC, cân. 748,2)
Se algum Estado usa da força para impor o cristianismo, afirmar que o cristianismo causou as coerções é tão equivocado quanto dizer que a propriedade privada causa o comunismo; é uma inversão da realidade, pois o comunismo surge precisamente da violação da propriedade. Portanto, a fé forçada é inválida em si mesma, pois viola a natureza do ato de crer, que deve ser livre.
III. Fundamento moral: sem transcendência, o libertarianismo flutua no vácuo
O libertário anticristão busca defender princípios objetivos — como a inviolabilidade do indivíduo e a ilegitimidade da agressão — sem um fundamento transcendente que lhes dê validade universal. Por que a agressão é errada? Por que alguém tem direito à vida, à liberdade, à propriedade? Sem uma explicação transcendental, as respostas para tais perguntas se tornam apenas opiniões ou convenções, não obrigações morais vinculantes. Se a moralidade é puramente humana, então os direitos podem ser modificados ou ignorados conforme a vontade da sociedade. O conceito de direitos naturais, tão caro ao libertarianismo, precisa de um solo metafísico que justifique sua universalidade e imutabilidade. Caso contrário, eles podem ser tratados apenas como acordos utilitários temporários ou preferências culturais, sem qualquer obrigatoriedade para todos os seres humanos em todas as circunstâncias.
Pensadores libertários seculares, como Ayn Rand e Murray Rothbard, tentaram ancorar os direitos naturais na razão humana ou na natureza do homem. Rand baseia sua ética no egoísmo racional, enquanto Rothbard apela à lei natural. Embora essas abordagens busquem objetividade, elas carecem de uma resposta definitiva para por que a razão ou a natureza humana obrigam moralmente todos os indivíduos. Sem um fundamento transcendente, suas concepções permanecem vulneráveis a interpretações subjetivas ou a cálculos utilitários.
Aqui, o cristianismo oferece uma explicação sólida e transcendental que fundamenta os direitos naturais. A visão cristã de que o ser humano foi criado à imagem e semelhança de Deus confere à pessoa uma dignidade intrínseca, imutável e universal. Essa dignidade não depende de fatores externos, como consenso social ou poder político, mas é uma característica inerente ao ser humano pela sua criação divina. A partir dessa perspectiva teológica, torna-se possível afirmar com base sólida que os direitos naturais são dados por Deus e, portanto, são universais e vinculantes.
O cristianismo também é a base de um sistema moral que distingue claramente justiça de legalidade. O Estado pode criar leis, mas isso não significa que essas leis sejam justas. A justiça, sob a ótica cristã, é uma expressão da ordem moral objetiva, algo que transcende as leis humanas e é definido pela vontade divina. Por isso, o libertarianismo cristão vê a agressão como uma violação de uma ordem moral objetiva, e não apenas uma violação de uma convenção social ou de um acordo utilitário.
Se a moralidade e os direitos naturais não forem fundamentados em um Logos criador e legislador, o que acontece é que o conceito de direito natural degenera para algo mais frágil, como um simples acordo utilitário. Nesse cenário, os direitos do indivíduo se tornam algo acordado entre os membros de uma sociedade, em vez de princípios imutáveis e universais. Os direitos podem ser negociados, alterados ou ignorados conforme o interesse do momento.
IV. Fundamento científico: a racionalidade moderna é filha da fé cristã
A ciência moderna só foi possível no contexto cultural cristão. Nenhuma outra civilização — nem a grega, nem a islâmica, nem a chinesa — produziu o método científico como o Ocidente cristão o fez.
Isso se deve a quatro premissas teológicas:
-
Criação racional: O mundo é ordenado por um Deus racional.
-
Distinção entre Criador e criatura: A natureza não é divina e pode ser estudada sem sacrilégio.
-
Valor do trabalho e da observação empírica, herdado do monaquismo.
-
Autonomia institucional, presente nas universidades medievais.
A doutrina cristã da Criação ex nihilo ensina que o mundo foi criado por um Deus racional, sábio e pessoal. Portanto, o cosmos é ordenado, possui leis, e pode ser compreendido pela razão humana — que é imagem do Criador. Isso contrasta fortemente com as cosmovisões panteístas ou mitológicas, onde o mundo é cíclico, arbitrário ou habitado por forças caprichosas.
Sem essa fé no Logos criador, não há razão para crer que a natureza tenha uma ordem inteligível universal e constante, que pode ser descoberta por observação e dedução. A ciência moderna só é possível porque, antes de investigar a natureza, pressupôs-se que ela era investigável — e isso foi uma herança direta do pensamento cristão.
Homens como Bacon, Newton, Kepler e Galileu viam na ciência um modo de glorificar o Criador. O ateísmo cientificista é, portanto, parasitário da teologia cristã, pois toma seus frutos e rejeita suas raízes. A ciência moderna nasceu como filha legítima da fé cristã. E os que hoje a usam contra sua mãe, ou são ingratos, ou ignorantes.
V. O cristianismo como barreira à revolução cultural
O cristianismo é a barreira mais sólida contra a infiltração revolucionária. A chamada "marcha gramsciana", que visa corroer os fundamentos morais da sociedade para subjugar o indivíduo ao coletivo, encontra sua resistência mais firme nos princípios cristãos. A fé cristã, ao proclamar a existência de uma verdade objetiva, de uma lei moral imutável e de uma dignidade humana que transcende o Estado e o consenso social, imuniza a civilização contra o relativismo e o igualitarismo nivelador do marxismo cultural.
Além disso, o cristianismo é uma tradição milenar, profundamente enraizada no cotidiano das pessoas, não sendo uma novidade a ser imposta ou implementada, mas uma força presente há séculos, que permeia a estrutura social, moral e cultural da sociedade. Sua presença constante nas comunidades, desde os tempos mais antigos, oferece uma resistência robusta contra qualquer tentativa de subverter a ordem natural e moral estabelecida.
Não por acaso, tanto Karl Marx quanto Antonio Gramsci identificaram no cristianismo o principal obstáculo à realização de seus projetos revolucionários. Marx chamou a religião de "ópio do povo" porque sabia que uma alma ancorada em Deus não se submete facilmente ao poder terreno; Gramsci, mais sutil, propôs a destruição da cultura cristã como pré-condição para o triunfo do socialismo. Sem essa âncora transcendente, a sociedade torna-se presa fácil das engenharias sociais que pretendem redefinir arbitrariamente o homem, a família e a liberdade.
Conclusão
O libertário anticristão, consciente ou não, nega as fundações mesmas do edifício que habita. Ao rejeitar o cristianismo, cava o abismo sob os próprios pés, privando o ideal libertário de sua base moral, cultural e racional. Ele defende a ética voluntária, a liberdade individual e a ordem espontânea, mas sem o solo metafísico e histórico que torna esses princípios inteligíveis e possíveis. É um erro tentar preservar a liberdade em termos absolutos sem reconhecer as raízes cristãs que a sustentam, pois o cristianismo é a única tradição que a legitima e a viabiliza.
Negar o cristianismo é racionalmente insustentável. A liberdade, como a conhecemos, é filha da fé cristã, que oferece a base moral e metafísica que torna a liberdade tanto desejável quanto possível. Mesmo que ateu, o libertário que ama a liberdade deveria, no mínimo, respeitar — e, idealmente, redescobrir — essas raízes cristãs. Pois sem fé, restam apenas o niilismo e o relativismo, que, eventualmente, desaguam na servidão.
Como nos ensina a tradição: Ubi fides ibi libertas — onde há fé, há liberdade.
-
-
 @ 048ecb14:7c28ac78
2025-05-29 00:49:55
@ 048ecb14:7c28ac78
2025-05-29 00:49:55I recently set up a Raspberry Pi camera server that's so minimal and straightforward, I thought it was worth sharing. This isn't one of those over-engineered solutions with fancy features - it's just a basic, reliable camera feed accessible from any browser on my local network.
The Goal
I wanted something that: 1. Starts automatically when the Pi boots up 2. Captures images at regular intervals 3. Shows the latest image in a simple web page accessible from any device 4. Doesn't require complex setup or dependencies 5. Uses minimal resources on my old Raspberry Pi
The Hardware
Nothing fancy here: - Raspberry Pi 2B (yes, the ancient one from 2015!) - Raspberry Pi Camera Module (standard version) - Power supply - That's it!
The Result

The interface is minimal but does the job. It shows the latest image and auto-refreshes every couple of seconds.
How to Get Set Up
Getting this running on your own Pi is super simple:
-
Make sure your camera module is connected and enabled
bash sudo raspi-config # Navigate to Interface Options > Camera and enable it -
Install the only dependency, ImageMagick (for rotation)
bash sudo apt update sudo apt install imagemagick -
Clone the repository, and navigate to the implementation's directory
bash git clone https://github.com/rewolf/RpiCameraViewer cd simple -
Start the camera server
bash ./start_camera_server.sh -
Access the feed from any device on your network
http://your-pi-ip-address:8080
That's it! No complex configuration, no fancy dependencies.
For more details consider reading the README
To make it start automatically on boot:
Add the following, with your specific installation path ```bash crontab -e
Add this line:
@reboot cd /path/to/RpiCameraViewer/simple && ./start_camera_server.sh ```
Configuration
There's not much configuration, but you can tweak few variables at the top of the
capture.shfile to modify width, height, rotation, quality, etc:bash QUALITY=90 WIDTH=720 HEIGHT=1280 ROTATION=90 # Set to 0 to disable rotationHow It Works
The solution is very basic:
- A bash script (
capture.sh) captures photos every few seconds by runninglibcamera-stilland sending a SIGUSR1 interrupt to signal it to capture a snapshot - The snapshot is rotated as needed with ImageMagick and saved with timestamps
- A symbolic link is updated to point to the latest image
- A minimal Python HTTP server serves a basic webpage showing the current image (the symlink), rendered to an HTML canvas
Note it does expose that directory to the whole LAN on :8080.
Give it a try if you need something like that quickly.
I have a plan to make a better implementation planned at some point, but for now this will do.
-
-
 @ 3bf0c63f:aefa459d
2024-10-31 16:08:50
@ 3bf0c63f:aefa459d
2024-10-31 16:08:50Anglicismos estúpidos no português contemporâneo
Palavras e expressões que ninguém deveria usar porque não têm o sentido que as pessoas acham que têm, são apenas aportuguesamentos de palavras inglesas que por nuances da história têm um sentido ligeiramente diferente em inglês.
Cada erro é acompanhado também de uma sugestão de como corrigi-lo.
Palavras que existem em português com sentido diferente
- submissão (de trabalhos): envio, apresentação
- disrupção: perturbação
- assumir: considerar, pressupor, presumir
- realizar: perceber
- endereçar: tratar de
- suporte (ao cliente): atendimento
- suportar (uma idéia, um projeto): apoiar, financiar
- suportar (uma função, recurso, característica): oferecer, ser compatível com
- literacia: instrução, alfabetização
- convoluto: complicado.
- acurácia: precisão.
- resiliência: resistência.
Aportuguesamentos desnecessários
- estartar: iniciar, começar
- treidar: negociar, especular
Expressões
- "não é sobre...": "não se trata de..."

Ver também
-
 @ 3bf0c63f:aefa459d
2024-09-18 10:37:09
@ 3bf0c63f:aefa459d
2024-09-18 10:37:09How to do curation and businesses on Nostr
Suppose you want to start a Nostr business.
You might be tempted to make a closed platform that reuses Nostr identities and grabs (some) content from the external Nostr network, only to imprison it inside your thing -- and then you're going to run an amazing AI-powered algorithm on that content and "surface" only the best stuff and people will flock to your app.
This will be specially good if you're going after one of the many unexplored niches of Nostr in which reading immediately from people you know doesn't work as you generally want to discover new things from the outer world, such as:
- food recipe sharing;
- sharing of long articles about varying topics;
- markets for used goods;
- freelancer work and job offers;
- specific in-game lobbies and matchmaking;
- directories of accredited professionals;
- sharing of original music, drawings and other artistic creations;
- restaurant recommendations
- and so on.
But that is not the correct approach and damages the freedom and interoperability of Nostr, posing a centralization threat to the protocol. Even if it "works" and your business is incredibly successful it will just enshrine you as the head of a platform that controls users and thus is prone to all the bad things that happen to all these platforms. Your company will start to display ads and shape the public discourse, you'll need a big legal team, the FBI will talk to you, advertisers will play a big role and so on.
If you are interested in Nostr today that must be because you appreciate the fact that it is not owned by any companies, so it's safe to assume you don't want to be that company that owns it. So what should you do instead? Here's an idea in two steps:
- Write a Nostr client tailored to the niche you want to cover
If it's a music sharing thing, then the client will have a way to play the audio and so on; if it's a restaurant sharing it will have maps with the locations of the restaurants or whatever, you get the idea. Hopefully there will be a NIP or a NUD specifying how to create and interact with events relating to this niche, or you will write or contribute with the creation of one, because without interoperability this can't be Nostr.
The client should work independently of any special backend requirements and ideally be open-source. It should have a way for users to configure to which relays they want to connect to see "global" content -- i.e., they might want to connect to
wss://nostr.chrysalisrecords.com/to see only the latest music releases accredited by that label or towss://nostr.indiemusic.com/to get music from independent producers from that community.- Run a relay that does all the magic
This is where your value-adding capabilities come into play: if you have that magic sauce you should be able to apply it here. Your service -- let's call it
wss://magicsaucemusic.com/-- will charge people or do some KYM (know your music) validation or use some very advanced AI sorcery to filter out the spam and the garbage and display the best content to your users who will request the global feed from it (["REQ", "_", {}]), and this will cause people to want to publish to your relay while others will want to read from it.You set your relay as the default option in the client and let things happen. Your relay is like your "website" and people are free to connect to it or not. You don't own the network, you're just competing against other websites on a leveled playing field, so you're not responsible for it. Users get seamless browsing across multiple websites, unified identities, a unified interface (that could be different in a different client) and social interaction capabilities that work in the same way for all, and they do not depend on you, therefore they're more likely to trust you.
Does this centralize the network still? But this a simple and easy way to go about the matter and scales well in all aspects.
Besides allowing users to connect to specific relays for getting a feed of curated content, such clients should also do all kinds of "social" (i.e. following, commenting etc) activities (if they choose to do that) using the outbox model -- i.e. if I find a musician I like under
wss://magicsaucemusic.comand I decide to follow them I should keep getting updates from them even if they get banned from that relay and start publishing onwss://nos.lolorwss://relay.damus.ioor whatever relay that doesn't even know anything about music.The hardcoded defaults and manual typing of relay URLs can be annoying. But I think it works well at the current stage of Nostr development. Soon, though, we can create events that recommend other relays or share relay lists specific to each kind of activity so users can get in-app suggestions of relays their friends are using to get their music from and so on. That kind of stuff can go a long way.
-
 @ 83279ad2:bd49240d
2025-05-29 04:05:29
@ 83279ad2:bd49240d
2025-05-29 04:05:29 -
 @ 9c9d2765:16f8c2c2
2025-05-29 05:32:35
@ 9c9d2765:16f8c2c2
2025-05-29 05:32:35CHAPTER THIRTY TWO A gasp rippled through the public gallery. The final verdict was a seismic moment. The very individuals who had orchestrated a web of lies, who had tormented James and nearly dismantled his legacy, were finally being held accountable.
Mark clenched his fists, not in resistance, but in shame. He had underestimated the power of truth and overestimated his ability to manipulate it. Helen, whose ambition had once shone with ruthless brilliance, now looked ghostly pale. Her mask of superiority had slipped long ago now she appeared merely human, broken by consequence.
The sentence was read: fifteen years in federal prison without parole. The gavel came down like thunder, final and absolute.
Outside the courthouse, a sea of journalists flooded the steps, broadcasting the downfall of two of the city's most notorious conspirators. The news trended for days: “Justice Delivered: Mark and Helen Behind Bars.”
Elsewhere in the City...
James stood in his office, staring out the panoramic window. The skyline was as vivid as ever, but something within him had changed. The burden of vengeance was no longer resting on his shoulders; it had been replaced by a serene stillness, the kind that only comes when vindication meets closure.
Charles walked in with a soft smile. “It’s over,” he said gently, placing a newspaper on James’s desk.
James glanced at the front page: a large photo of Mark and Helen being escorted away in handcuffs beneath the bold headline.
“They thought they were writing your ending,” Charles said, “but you turned it into your beginning.”
James gave a modest nod. “I don’t want to be defined by what they did to me. I want to be remembered for what I did despite it.”
Charles patted his shoulder. “And you will be.”
Later That Evening…
Rita entered the room, her presence now as familiar and comforting as a warm breeze. She carried two glasses of wine and handed one to James. “To justice,” she said with a quiet smile.
“To new beginnings,” he replied, gently clinking his glass with hers.
They sat together, overlooking the city lights that shimmered like constellations on the earth. Below them, the world kept turning. But within their world, a storm had passed, and what remained was a sense of peace that only truth, time, and resilience could deliver.
James no longer carried the weight of proving himself. The world now knows the truth. His enemies had been exposed, and his name had been redeemed. Yet, more than that, he had found strength not in retaliation, but in rising above.
The glow of the evening sun spilled across the marble floors of JP Enterprises’ grand atrium, casting a warm golden hue that mirrored the fresh beginning within the company. The air inside was no longer heavy with silent whispers or wary eyes. Instead, it danced with hope, ambition, and a revived sense of unity. Employees walked taller, with lighter steps, no longer shadowed by fear or doubt.
At the heart of it all stood James.
Once scorned, rejected, and underestimated, James now commanded not only the title of President but the unwavering respect of every soul within those walls. But power had not swelled his ego instead, it had deepened his compassion. He had faced the abyss of betrayal, the mockery of the world, and the crushing weight of humiliation. Yet, like a phoenix, he had risen more brilliant, more composed, and infinitely wiser.
In his newly renovated office a tasteful blend of elegance and subtle grandeur James sat at the desk that had once been occupied by his father. The very same desk that had been out of his reach for years. Now, it belonged to him. Not because of inheritance, but because of merit.
He opened a letter from a small startup company seeking funding. As he read through the proposal, his eyes lingered not only on the numbers but the story behind it the dreams, the sacrifice, the courage. He saw himself in those words. A man who once had nothing but a belief in himself.
With a steady hand, he signed the approval and penned a note:
"Sometimes, all you need is for one person to believe in you. Let that be me."
A knock interrupted his thoughts.
Rita walked in, holding a file. Her expression was soft, almost serene. She had blossomed in her new role as the Executive Director of Strategic Development. No longer overshadowed, no longer silenced, she now stood as a powerful woman, respected for both her brilliance and her unshakable loyalty.
“They’ve confirmed the date for the scholarship launch,” she said, placing the folder in front of him.
James looked up. “Good. The youth deserve a chance. Just like I once did.”
She smiled, pride gleaming in her eyes. “You’re building more than just a company, James. You’re building legacies.”
He gazed at her for a moment, the corners of his mouth lifting into a quiet smile. “Legacies are not built by men who seek revenge. They’re built by those who rise after being broken.”
Outside the headquarters, billboards displayed JP Enterprises' newest initiative: The James Preston Foundation for Aspiring Entrepreneurs. It was a pledge to the next generation, a declaration that no dream was too small, no background too humble.
Elsewhere...
In the solitude of their prison cell, Mark stared blankly at the concrete wall. News of James’s continued rise had reached even there. Helen sat across from him, no longer wearing tailored suits or designer jewelry, but a faded uniform that matched her lost status.
“He was just supposed to be a stepping stone,” Helen muttered bitterly. “How did he end up at the summit?”
Mark didn’t respond. There was nothing left to say. Their ambitions had imploded, consumed by the fire of their own pride and cruelty.
Later That Night...
James stood alone on the rooftop of the JP tower, watching the city pulse with life beneath him. The stars above mirrored the twinkling lights below.
Rita joined him moments later, the wind tousling her hair. She didn’t say anything, just stood beside him, sharing the silence.
“You know,” James finally said, “for the longest time, I wanted to prove everyone wrong. Now... I just want to prove that they were wrong to ever doubt what’s possible.”
Rita nodded. “And you have.”
He turned to her, a tender light in his eyes. “I couldn’t have done it alone.”
They stood there, two warriors shaped by fire, not bound by the past but inspired by it.
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-29 00:42:35
@ 5d4b6c8d:8a1c1ee3
2025-05-29 00:42:35Pretty good day today, despite being a bit of a cookie monster again. - Lots of steps from mowing the lawn, walking the dog, and miscellaneous errands - Broke my fast a little early in the morning, but ate healthy until afternoon snacks
Also, I came across a new health app on nostr. Has anyone else used SOUND HSA? It supposedly pays sats for steps.
How did everyone else do with their goals today?
https://stacker.news/items/991609
-
 @ c1e9ab3a:9cb56b43
2025-05-27 16:19:06
@ c1e9ab3a:9cb56b43
2025-05-27 16:19:06Star Wars is often viewed as a myth of rebellion, freedom, and resistance to tyranny. The iconography—scrappy rebels, totalitarian stormtroopers, lone smugglers—suggests a deep anti-authoritarian ethos. Yet, beneath the surface, the narrative arc of Star Wars consistently affirms the necessity, even sanctity, of central authority. This blog entry introduces the question: Is Star Wars fundamentally a celebration of statism?
Rebellion as Restoration, Not Revolution
The Rebel Alliance’s mission is not to dismantle centralized power, but to restore the Galactic Republic—a bureaucratic, centrally governed institution. Characters like Mon Mothma and Bail Organa are high-ranking senators, not populist revolutionaries. The goal is to remove the corrupt Empire and reinstall a previous central authority, presumed to be just.
- Rebels are loyalists to a prior state structure.
- Power is not questioned, only who wields it.
Jedi as Centralized Moral Elites
The Jedi, often idealized as protectors of peace, are unelected, extra-legal enforcers of moral and military order. Their authority stems from esoteric metaphysical abilities rather than democratic legitimacy.
- They answer only to their internal Council.
- They are deployed by the Senate, but act independently of civil law.
- Their collapse is depicted as tragic not because they were unaccountable, but because they were betrayed.
This positions them as a theocratic elite, not spiritual anarchists.
Chaos and the Frontier: The Case of the Cantina
The Mos Eisley cantina, often viewed as a symbol of frontier freedom, reveals something darker. It is: - Lawless - Violent - Culturally fragmented
Conflict resolution occurs through murder, not mediation. Obi-Wan slices off a limb; Han shoots first—both without legal consequence. There is no evidence of property rights, dispute resolution, or voluntary order.
This is not libertarian pluralism—it’s moral entropy. The message: without centralized governance, barbarism reigns.
The Mythic Arc: Restoration of the Just State
Every trilogy in the saga returns to a single theme: the fall and redemption of legitimate authority.
- Prequels: Republic collapses into tyranny.
- Originals: Rebels fight to restore legitimate order.
- Sequels: Weak governance leads to resurgence of authoritarianism; heroes must reestablish moral centralism.
The story is not anti-state—it’s anti-bad state. The solution is never decentralization; it’s the return of the right ruler or order.
Conclusion: The Hidden Statism of a Rebel Myth
Star Wars wears the costume of rebellion, but tells the story of centralized salvation. It: - Validates elite moral authority (Jedi) - Romanticizes restoration of fallen governments (Republic) - Portrays decentralized zones as corrupt and savage (outer rim worlds)
It is not an anarchist parable, nor a libertarian fable. It is a statist mythology, clothed in the spectacle of rebellion. Its core message is not that power should be abolished, but that power belongs to the virtuous few.
Question to Consider:
If the Star Wars universe consistently affirms the need for centralized moral and political authority, should we continue to see it as a myth of freedom? Or is it time to recognize it as a narrative of benevolent empire? -
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ 83279ad2:bd49240d
2025-05-29 04:03:54
@ 83279ad2:bd49240d
2025-05-29 04:03:54 -
 @ 4d41a7cb:7d3633cc
2025-04-08 01:17:39
@ 4d41a7cb:7d3633cc
2025-04-08 01:17:39Satoshi Nakamoto, the pseudonymous creator of Bitcoin, registered his birthday as April 5, 1975, on his P2P Foundation profile. Many think that he chose this date because on that same day in 1933, the United States government confiscated the gold of the American people. Whether this was on purpose or not, what happened in this day is very important to understand how do we ended up here.
In 1933, as expressed in Roosevelt’s Executive Orders 6073, 6102, and 6260, the United States first declared bankruptcy. The bankrupt U.S. went into receivership in 1933. America was turned over via receivership and reorganization in favor of its creditors. These creditors, the International Bankers, from the beginning stated their intent, which was to plunder, bankrupt, conquer and enslave America and return it to its colonial status.1
As one of his first acts as President, Franklin Delano Roosevelt declared a “Banking Emergency” to bail out the Federal Reserve Bank, which had embezzled this country’s gold supply. The Congress gave the President dictatorial powers under the “War Powers Act of 1917” (amended 1933), written, by the way, by the Board of Governors of the Federal Reserve Bank of New York.2
This day marked the official abandonment of the American Constitution, law and real money. Today, 92 years after this event, most of the people living today have never had any real money or paid for anything using real money; unless they used Bitcoin...
There could be no bankruptcy if there was not a private central bank lending paper currency to the government at interest, so we must start from 1913, when the Federal Reserve was created: a non-federal private bank with no reserves and the monopoly of issuing debt based paper currency in unlimited amounts and lending it to the government at interest by buying treasury bills. The fact that this currency is lent into existence at interest makes the debt mathematically impossible to be repaid; it can only be refinanced or defaulted.
Between 1929 and 1933, the Federal Reserve Bank reduced the currency supply by 33%, thereby creating the Great Depression, bankrupting the US government, stealing the Americans’ gold supply, and officially ending the gold standard. Since then the US dollar (money) was replaced with Federal Reserve Notes (debt). This was also the end of the Republican form of government and the beginning of a socialist mob rule democracy (Fascism).
“Fascism should more properly be called corporatism because it is the merger of state and corporate power.” — Benito Mussolini
The United States government has been bankrupt since 1933, since it defaulted on its gold bonds. This type of bond existed until 1933, when the U.S. monetary system abandoned the gold standard. 3 From this year the government has been totally controlled by the International bankers and used as a tool to spread and maintain their power worldwide.
Many people think that the gold standard was abandoned in 1971, but this is not true; in fact, this happened in 1933 when the US dollar was replaced by Federal Reserve Notes that are 100% debt-based fiat paper currency.
The year 1933 in the United States marked:
- The end of the Republican form of government and the beginning of American Fascism
- The end of the United States dollar and its replacement by Federal Reserve Notes
- The abandonment of common law and replacement with military admiralty law
- The takeover of the United States government by International bankers
- A massive gold theft and the end of the US gold standard
- The exchange of rights with privileges and licenses
- The United States government bankruptcy
The next shameful event in our history which still plagues us to this day was the “War Powers Act of 1933.” This Act permitted President Roosevelt to make law in the form of Executive Order, bypass Congress and create his socialist state. We (citizens of this country) were ever after to be considered enemies of the United States who must be licensed to engage in any commercial activity. With the aid of the Federal Reserve (the same people who created the Depression), the President confiscated our gold and silver coin and replaced it with worthless pieces of paper and a debt system that will eventually destroy this great country. Our land and our labor were pledged to the Federal Reserve Bank, Inc., as collateral for a debt system that could never be paid.4
“Emergency Powers” means any form of military style government, martial law, or martial rule. Martial law and martial rule are not the same.
United States Congressional Record March 17, 1993 Vol. #33, page H- 1303, Congressman James Traficant, Jr. (Ohio) addressing the House:
“Mr. Speaker, we are here now in chapter 11. Members of Congress are official trustees presiding over the greatest reorganization of any Bankrupt entity in world history, the U.S. Government. We are setting forth, hopefully, a blueprint for our future”
“There are some who say it is a coroner’s report that will lead to our demise. It is an established fact that the United States Federal Government has been dissolved by the Emergency Banking Act, March 9, 1933, 48 Stat. 1, Public Law 89-719; dered by President Roosevelt, being bankrupt and insolvent. H.J.R. 192, 73rd Congress in session June 5, 1933 – Joint Resolution To Suspend The Gold Standard and Abrogate the Gold Clause dissolved the Sovereign Authority of the United States and the official capacities of all United States Governmental Offices, Officers, and Departments and is further evidence that the United States Federal Government exists today in name only” **“The receivers of the United States Bankruptcy are the International Bankers, via the United Nations, the World Bank and the International Monetary Fund”
“All United States Offices, Officials, and Departments are now operating within a de facto status in name only under Emergency War Powers. With the Constitutional Republican form of Government now dissolved, the receivers of the Bankruptcy have adopted a new form of government for the United States. This new form of government is known as a Democracy, being an established Socialist/Communist order under a new governor for America. This act was instituted and established by transferring and/or placing the Office of the Secretary of Treasury to that of the Governor of the International Monetary Fund. Public Law 94-564, page 8, Section H.R. 13955 read in part:”
“The U.S. Secretary of Treasury receives no compensation for representing the United States.”
The American Spirit
The intention of the founding fathers of the United States was to create a constitutional republic to protect natural human rights and escape from the tyrannical English monarchy and its usurious Bank of England's monetary system. They created an honest monetary system based on gold and silver (United State Dollar) and got rid of nobility titles, creating equality under the law.
Section 10 of the American Constitution says:
No State shall enter into any Treaty, Alliance, or Confederation; grant Letters of Marque and Reprisal; coin Money; emit Bills of Credit; make anything but gold and silver Coin a tender in payment of debts; pass any bill of attainder, ex post facto law, or law impairing the obligation of contracts; or grant any title of nobility.
The United States Dollar (1792-1933)
A dollar is a measure of weight defined by the Coinage Act of 1792 and 1900, which specifies a certain quantity—24.8 grains of gold or 371.25 grains of silver (from 1792 to 1900) when the American dollar was based on a bimetallic standard.
The Gold Standard Act of 1900 formally placed the United States on the gold standard, setting the value of one dollar at 25.8 grams of 90% pure gold, which fixed the price of gold at $20.67 per troy ounce. This standard was totally abandoned in 1933.
Gold and silver were such powerful money during the founding of the United States of America that the founding fathers declared that only gold or silver coins could be “money” in America.
But since the greedy bankers cannot profit from honest money they cannot print, they replaced the money with paper debt instruments. And by doing this, they have effectively enslaved the American people until today. My definition of modern slavery is working for a currency that someone else can create at no cost or effort. What's worse is that they even demand to be paid back and with interest!
Federal Reserve Notes (1913-present)
Federal Reserve Notes are not real money. Money that has metallic or other intrinsic value, as distinguished from paper currency, checks, and drafts.
Federal Reserve Notes (FRNs) are a legal fiction. An assumption that something is true even though it may be untrue. 5 The assumption that they are money, when in fact they are the opposite of money: debt or paper currency.
Paper money. Paper documents that circulate as currency; bills drawn by a government against its own credit. 6 Like Goldsmiths' notes. Hist. Bankers' cash notes: promissory notes given by bankers to customers as acknowledgments of the receipt of money. • This term derives from the London banking business, which originally was transacted by goldsmiths.7
These notes were scientifically designed to bankrupt the government and slave the American people, as Alfred Owen Crozier warned one year before the bill for the creation of the FED was passed through Congress (1912):
If Congress yields and authorizes a private central bank as proposed by the pending bill, the end when the bubble bursts will be universal ruin and national bankruptcy.
Unfortunately, the bill was passed in 1913, and this private bank started printing a new currency different from the US dollar creating the great depression and effectible bankrupting the government like Alfred warned 20 years before.
Alfred also warned:
Thus the way is opened for an unlimited inflation of corporate paper currency issued by a mere private corporation with relatively small net assets and no government guarantee, every dollar supposed to be redeemable in gold, but with not a single dollar of gold necessarily held in the reserves of such corporation to accomplish such redemption.
Differently from what's commonly believed Federal Reserve Notes (FRNs) were never really “backed” by gold; they were never supposed to be hard currency. Currency backed by reserves, esp. gold and silver reserves.
The United States government defaulted on its gold clauses, calling for payment in gold. This marked the end of the gold standard. A monetary system in which currency is convertible into its legal equivalent in gold or gold coin.
Since then we have been under a paper standard, where we use fake money as tender for payments. Paper standard. A monetary system based entirely on paper; a system of currency that is not convertible into gold or other precious metal.
People traded their coupons as money or “currency.” Currency is not money but a money substitute. Redeemable currency must promise to pay a dollar equivalent in gold or silver money. Federal Reserve Notes (FRNs) make no such promises and are not “money.” A Federal Reserve Note is a debt obligation of the federal United States government, not “money.” The federal United States government and the U.S. Congress were not and have never been authorized by the Constitution of the United States of America to issue currency of any kind, but only lawful money—gold and silver coin.8
A bona fide note can be used in a financial transaction to discharge the debt only because it is an unconditional promise to pay by the issuer to the bearer. Is a Federal Reserve Note a contract note, an unconditional promise to pay? At one time the Federal Reserve issued bona fide contractual notes and certificates, redeemable in gold and silver coin. Most people never saw or comprehended the contract. It went largely unread because the Federal Reserve very cunningly hid the contract on the face of the note by breaking it up into five separate lines of text with a significantly different typeface for each line and placing the president’s picture right in the middle of it. They even used the old attorney’s ruse of obscuring the most important text in fine print! Over time, the terms and conditions of the contract were diluted until eventually they literally became an I.O.U. for nothing.
FEDERAL RESERVE NOTE
-
THIS NOTE IS LEGAL TENDER FOR ALL DEBT, PUBLIC AND PRIVATE, AND IT IS REDEEMABLE IN LAWFUL MONEY AT THE UNITED STATES TREASURY OR ANY FEDERAL RESERVE BANK.
-
DATE: SERIES OF 1934
-
WILL PAY TO THE BEARER ON DEMAND: ONE HUNDRED DOLLARS
-
TREASURER OF THE UNITED STATES SIGNATURE
-
SECRETARY OF THE TREASURY SIGNATURE

Nowadays FRNs say "This note is legal tender for all debts public and private" it tender debt but it does not pay the bearer on demand. It value was stolen by a counterfeiting technique commonly know as inflation.
One hundred dollars (SERIES OF 1934) will be 2480 grains of gold, or 159.4 grams, or 5.1249 troy ounces. Today one troy ounce is priced around $3,000 federal reserve notes. 5.1249 X 3,000 = $15,375 actual FRNs.
A $100 FRN bill today will buy 0.65% of a real gold $100 dollar certificate. That’s a -99.35% loss of purchasing power in the last 91 years.
FRNs savers have been rugged pulled!
Gold bugs where the winners...
But Bitcoin is even better...
Happy birthday Satoshi! April 5 will be forever remembered.
Satoshi... The man, the myth, the Legend...
-
 @ 9c9d2765:16f8c2c2
2025-05-29 05:14:31
@ 9c9d2765:16f8c2c2
2025-05-29 05:14:31In a forgotten valley surrounded by mountains, there lived a girl named Rita. Her village believed in balance above all. They built lives without extremes no loud laughter, no deep sorrow. Everything was quiet, even joy. Smiles were polite. Tears were hidden.
Rita had always felt something missing. She saw it in dreams vivid colors, music, a joy that made your chest ache with light. But in her village, emotion was like a weed trimmed before it grew wild.
One day, exploring beyond the hills, Rita found a strange garden untouched, walled off, hidden behind a curtain of vines. Inside, roses bloomed in impossible colors, but every rosebush was thick with thorns. A single sign read:
“Only those who bleed may feel the bloom.”
Curious, Rita reached out. A thorn pierced her skin. Pain flared through her finger. She recoiled but then, something strange happened. The air shimmered. The garden came alive with fragrance, color, and warmth she’d never known. Her wound stung, but her heart raced with wonder.
She returned every day. Each time, the thorns drew blood and each time, the garden showed her something deeper: the memory of a lost friend, the sting of loneliness, the ache of longing. She wept. She raged. She broke.
And then one day she laughed. Not politely. Not softly. But with her whole body. The pain had carved space for something vast. She danced barefoot among the thorns, scars and all.
Years later, when Rita returned to her village, she was changed. She sang songs that made people cry and laugh in the same breath. She planted a new garden in the town square with thorns intact and invited everyone in.
At first, they hesitated. But slowly, they followed her path. And one by one, the village bloomed with color.
Moral: To feel happiness, you must experience pain because only through the thorns can the roses mean something.
-
 @ 000002de:c05780a7
2025-05-28 23:34:51
@ 000002de:c05780a7
2025-05-28 23:34:51With all the free press Steak `n Shake is getting for accepting bitcoin this post got me thinking about good burgers at fast food chains. There are incredible non-fast food burgers and local places but I'm limiting this to chains.
In order if you are going for a chain fast food American burgers here's the list in order.
- In-n-Out
- Shake Shack
- Habit Burger & Grill
- Five Guys
Everything else is not worth mentioning or I'm not aware of it due to where I live and have traveled.
What's your list.
Bonus:
Which of these or you picks will be next in accepting bitcoin.
https://stacker.news/items/991559
-
 @ 10846a37:73b5f923
2025-05-29 05:04:19
@ 10846a37:73b5f923
2025-05-29 05:04:19Com a crescente popularidade das plataformas de jogos online no Brasil, surge uma nova opção que promete elevar o nível da diversão e da confiabilidade: 115Bet. Este portal se destaca por oferecer uma experiência completa, com tecnologia de ponta, suporte ao usuário de alta qualidade e uma variedade de jogos que atende desde os iniciantes até os mais experientes. Neste artigo, vamos apresentar os principais atrativos da 115Bet, explorar os tipos de jogos disponíveis e compartilhar como é a experiência de quem escolhe essa plataforma para se divertir.
Plataforma Moderna e Segura Um dos primeiros pontos que chamam atenção na 115Bet é o seu design moderno e intuitivo. A navegação no site é simples, rápida e responsiva em qualquer dispositivo — seja no computador, tablet ou smartphone. A segurança também é prioridade: a plataforma conta com criptografia de dados e sistemas avançados de proteção para garantir a privacidade e a tranquilidade dos jogadores.
Além disso, a 115betoferece um ambiente 100% legalizado, com licenciamento internacional que segue todas as normas exigidas para o funcionamento transparente e justo.
Variedade de Jogos para Todos os Gostos O catálogo de jogos da 115Bet é diversificado e sempre atualizado. Os usuários encontram títulos populares e de alta performance, desenvolvidos por fornecedores reconhecidos no mercado. Entre os destaques estão:
Slots temáticos: jogos com gráficos impressionantes e mecânicas envolventes. Dos temas clássicos aos mais modernos, há opções para todos os estilos.
Roleta ao vivo: com crupiês reais e transmissão em tempo real, os jogadores vivenciam uma experiência autêntica e interativa.
Blackjack: versões tradicionais e alternativas que exigem estratégia e concentração.
Bacará: ideal para quem busca emoção com regras simples e partidas dinâmicas.
Jogos de números e apostas rápidas: como keno, bingo e outros jogos instantâneos, perfeitos para quem gosta de agilidade.
Outro diferencial importante é a presença de mesas ao vivo, com profissionais capacitados e interação em tempo real, proporcionando uma atmosfera envolvente.
Experiência do Jogador: Suporte e Benefícios A experiência do jogador na 115Bet é marcada pelo cuidado com o atendimento e pelas vantagens oferecidas. O suporte está disponível 24 horas por dia, em português, por chat ao vivo ou e-mail, garantindo agilidade e eficiência na resolução de dúvidas ou problemas.
A plataforma também é conhecida por seu programa de bônus atrativos, incluindo recompensas de boas-vindas, promoções frequentes e um sistema de fidelidade para jogadores assíduos. Isso significa que, além de se divertir, o usuário é constantemente valorizado e incentivado a continuar jogando.
Outro ponto positivo é a facilidade nos depósitos e saques, com métodos de pagamento populares no Brasil, como Pix, transferência bancária, carteiras digitais e criptomoedas. As transações são rápidas e seguras, aumentando ainda mais a confiança dos usuários.
Conclusão A 115Bet chega ao mercado brasileiro como uma excelente alternativa para quem busca entretenimento online de qualidade, com uma plataforma segura, ampla variedade de jogos e uma experiência que coloca o jogador em primeiro lugar. Seja para relaxar após um dia de trabalho ou para desafiar sua sorte e habilidade, a 115Bet oferece todas as ferramentas necessárias para transformar cada acesso em momentos inesquecíveis. Vale a pena conhecer e experimentar tudo o que essa plataforma tem a oferecer!
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 21335073:a244b1ad
2025-05-21 16:58:36
@ 21335073:a244b1ad
2025-05-21 16:58:36The other day, I had the privilege of sitting down with one of my favorite living artists. Our conversation was so captivating that I felt compelled to share it. I’m leaving his name out for privacy.
Since our last meeting, I’d watched a documentary about his life, one he’d helped create. I told him how much I admired his openness in it. There’s something strange about knowing intimate details of someone’s life when they know so little about yours—it’s almost like I knew him too well for the kind of relationship we have.
He paused, then said quietly, with a shy grin, that watching the documentary made him realize how “odd and eccentric” he is. I laughed and told him he’s probably the sanest person I know. Because he’s lived fully, chasing love, passion, and purpose with hardly any regrets. He’s truly lived.
Today, I turn 44, and I’ll admit I’m a bit eccentric myself. I think I came into the world this way. I’ve made mistakes along the way, but I carry few regrets. Every misstep taught me something. And as I age, I’m not interested in blending in with the world—I’ll probably just lean further into my own brand of “weird.” I want to live life to the brim. The older I get, the more I see that the “normal” folks often seem less grounded than the eccentric artists who dare to live boldly. Life’s too short to just exist, actually live.
I’m not saying to be strange just for the sake of it. But I’ve seen what the crowd celebrates, and I’m not impressed. Forge your own path, even if it feels lonely or unpopular at times.
It’s easy to scroll through the news and feel discouraged. But actually, this is one of the most incredible times to be alive! I wake up every day grateful to be here, now. The future is bursting with possibility—I can feel it.
So, to my fellow weirdos on nostr: stay bold. Keep dreaming, keep pushing, no matter what’s trending. Stay wild enough to believe in a free internet for all. Freedom is radical—hold it tight. Live with the soul of an artist and the grit of a fighter. Thanks for inspiring me and so many others to keep hoping. Thank you all for making the last year of my life so special.
-
 @ 10846a37:73b5f923
2025-05-29 05:03:44
@ 10846a37:73b5f923
2025-05-29 05:03:44Nos últimos anos, o mercado de entretenimento online tem crescido de forma surpreendente, e plataformas como a BG77 estão se destacando por oferecer uma experiência completa, segura e empolgante para seus usuários. Com um ambiente moderno, acessível e recheado de opções interativas, a BG77 chegou ao Brasil com a missão de transformar o modo como os brasileiros se divertem online.
Conhecendo a Plataforma BG77 A BG77 é uma plataforma digital que reúne diversas modalidades de jogos interativos, voltados para quem busca emoção, estratégia e recompensas reais. Seu design é intuitivo e responsivo, facilitando o acesso tanto por computadores quanto por dispositivos móveis. O processo de cadastro é simples e rápido, permitindo que novos usuários comecem a jogar em poucos minutos.
Além disso, a segurança dos dados dos jogadores é levada a sério. A plataforma utiliza tecnologia de ponta em criptografia, garantindo que todas as informações pessoais e financeiras estejam protegidas contra qualquer tipo de acesso não autorizado.
Outro diferencial da BG77 é o suporte ao cliente. A equipe de atendimento está disponível 24 horas por dia, 7 dias por semana, para tirar dúvidas, solucionar problemas e garantir que a experiência dos jogadores seja sempre positiva.
Diversidade de Jogos para Todos os Gostos O grande destaque da BG77 está na variedade de jogos disponíveis. A plataforma oferece desde clássicos populares até títulos modernos e cheios de recursos gráficos e sonoros envolventes.
Entre os mais procurados, estão os jogos de roleta digital, onde os jogadores podem testar sua sorte e habilidades com diferentes estratégias. Também fazem parte do catálogo os emocionantes jogos de cartas, como o pôquer e o blackjack, ideais para quem gosta de pensar e planejar cada movimento.
Os amantes de slots também encontram uma vasta seleção de máquinas com temas variados, desde aventuras no Egito Antigo até mundos futuristas. Os gráficos são de altíssima qualidade, e os efeitos sonoros contribuem para uma experiência totalmente imersiva.
Outro atrativo são os jogos ao vivo, onde o jogador pode interagir em tempo real com apresentadores e outros usuários, tornando cada rodada ainda mais empolgante. Essa função reforça o compromisso da BG77 com a inovação e a interatividade.
Experiência do Jogador: Diversão com Recompensas Reais A BG77 foi criada pensando no jogador brasileiro. Por isso, toda a interface da plataforma está em português, com opções de pagamento locais como Pix, boleto bancário e transferências diretas. Isso facilita não apenas os depósitos, mas também os saques, que são processados com rapidez e eficiência.
Outro ponto importante é o sistema de recompensas e bônus. Novos usuários recebem vantagens ao se cadastrarem, e jogadores frequentes são beneficiados com promoções exclusivas, rodadas grátis e programas de fidelidade. Tudo isso contribui para manter o nível de diversão sempre elevado.
Além disso, a comunidade BG77 é bastante ativa, com rankings, torneios e desafios entre os participantes. Isso cria um ambiente competitivo e, ao mesmo tempo, amigável, onde todos têm a chance de brilhar.
Conclusão A BG77 é mais do que uma simples plataforma de jogos — é um verdadeiro universo de entretenimento digital pensado para oferecer diversão, segurança e oportunidades reais de ganho. Com sua estrutura moderna, variedade de jogos e foco total na experiência do jogador, ela se consolida como uma das melhores opções disponíveis no Brasil atualmente. Se você busca emoção, desafios e recompensas, a BG77 é o lugar ideal para começar sua jornada.
-
 @ a396e36e:ec991f1c
2025-05-28 22:27:45
@ a396e36e:ec991f1c
2025-05-28 22:27:45👤 Generation X and Bitcoin: Between Invisibility, Structural Disillusionment, and Defiance
Generation X, born between 1965 and 1980, has been largely sidelined in generational discourse. Unlike the baby boomers —symbols of stability and prosperity— or millennials and Gen Z —constant fixtures in the media and cultural spotlight— Gen X remains the least mentioned, the least studied, and often not even recognized by its own members as a distinct generation.
Today, they are in midlife —a period that, according to the U-shaped curve of happiness, is one of the most emotionally and psychologically difficult stages: deteriorating health, professional stagnation, and the dual burden of caring for both parents and children. But their condition is not just a matter of age —it’s the product of a unique convergence of economic and political failure.
Structurally, Generation X reached its crucial phase of financial consolidation during the global economic crisis of 2008 —a moment that froze wage growth and severely limited access to housing, investment opportunities, and savings. In parallel, they faced increasing labor precarization: unstable contracts, outsourcing, erosion of social protections, and the dismantling of job security. Compared to other generations, their economic mobility was minimal. Even in terms of wealth accumulation and home ownership, many Gen Xers show weaker indicators than early-born millennials at the same life stage.
At the same time, many countries —especially in Latin America and parts of Europe— turned toward alternative models to free-market systems: socialist proposals that promised redistribution, justice, and equality. But in practice, these models led to state dependency, excessive intervention, economic rigidity, and a loss of productive dynamism. The outcome was devastating: rising poverty, institutional decay, inflation, plummeting investment, growing corruption, and a widespread collapse of trust.
For a generation raised on values of effort, autonomy, and social mobility, this ideological shift brought a double betrayal —first from liberalism, which failed to deliver on its promises, and then from socialism, which entrenched poverty, dependency, and dysfunction.
And yet, while younger generations increasingly embrace state-centric proposals like universal basic income, subsidies, or nationalizations as progressive solutions, many in Gen X see these not as innovation, but as déjà vu —a recycling of failed models they’ve already lived and paid for.
It’s at this point that Bitcoin emerges as more than just a financial technology. For many Gen Xers, Bitcoin is both a symbolic and concrete response — a refuge from a system that betrayed them. It’s not just about investment. It’s about individual sovereignty. They call it “fuck you money” because it represents a total break from traditional structures: it doesn’t depend on banks, governments, political parties, or promises that never materialize.
Bitcoin is money without permission, without censorship, without planned devaluation. It’s a tool for radical autonomy. For a generation marked by skepticism, self-reliance, and disillusionment, it stands as a quiet but powerful form of resistance — a way of saying: “I don’t depend on you. I don’t believe you. I don’t need you.”
Today, while others debate new statist models or more market reforms, many Gen Xers are simply opting out. Bitcoin isn’t just an economic choice — it’s a stance. A way to reclaim the individual control the system once denied them.
-
 @ cae03c48:2a7d6671
2025-05-29 05:00:52
@ cae03c48:2a7d6671
2025-05-29 05:00:52Bitcoin Magazine

JD Vance Says “Bitcoin Finally Has a Champion in the White House”In a headline speech at the Bitcoin 2025 Conference today, U.S. Vice President JD Vance declared Bitcoin’s growing role in national policy and promised a new era of federal support under the Trump administration. “It’s great to be here with Bitcoin at $108k and to be the Vice President of the United States,” Vance opened. “This isn’t a conference of people. This is a movement.”

Thanking David Bailey, and key figures like Cameron and Tyler Winklevoss, Vance emphasized, “They took a big step and everyone else followed.” He also shouted out Coinbase for their participation at the event as well.
In sharp contrast to past administrations, Vance was clear: “What we’ve done in the Trump administration in digital asset policy is only the beginning. Crypto finally has a champion and an ally in the White House.”
JUST IN:
 Vice President JD Vance said they’re going to fire every regulator like Gary Gensler. pic.twitter.com/awHYMEMQAg
Vice President JD Vance said they’re going to fire every regulator like Gary Gensler. pic.twitter.com/awHYMEMQAg— Bitcoin Magazine (@BitcoinMagazine) May 28, 2025
Vance underscored the grassroots energy of the Bitcoin community: “This gets decided by the people, by you—not unelected bureaucrats.”
He laid out three key priorities for the administration, the first being Widespread Adoption – “Fifty million Americans own Bitcoin. I think it’s gonna be 100 million before too long.” The second being Legislative Support– “We are optimistic the Senate will pass the clean GENIUS Act. Stablecoins don’t threaten the U.S. dollar—they’re a force multiplier for the economic mission.” And third, Clear Regulation – “We need a transparent regulatory framework that incorporates Bitcoin into the mainstream economy.”
Referencing broader concerns about institutional overreach, Vance said, “Crypto is a hedge against bad policymaking in Washington.”

Promising protection and partnership from Washington, he vowed, “You deserve respect and support from your government—not bureaucrats trying to tear you down. We are ending the weaponization of federal agencies against this community.”
Vance concluded stating, “Bitcoin is digital gold, but none of you are—unless you get involved,” discussing how Bitcoin is here to stay, but only if the American people get involved and build the industry. “Where Bitcoin is going is strategically important to the U.S. We’re gonna make the right decisions, and that depends on you being a part of the conversation.”
The message that Vance made was abundantly clear. Bitcoin is in the hands of the American people, and it is up to the citizens to make a lasting impact with it.
This post JD Vance Says “Bitcoin Finally Has a Champion in the White House” first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 3c559080:a053153e
2025-05-25 20:26:43
@ 3c559080:a053153e
2025-05-25 20:26:43So firstly you should find an emulator for whatever you want to play on. There are many for desktop and mobile devices. Checkhere for a list of all the available consoles and their various emulators.
Next what game do you want to play? This is the like the homepage for a shit ton of roms.
Some of the more popular roms are there and other various list like Sony Nintendo
After narrowing down your selection you will end up on myrient i assume this is just some dope person hosting all these so if you get some use out of it, think of donating they even take corn, but other shitcoins too (but thats not the focus here)
Once you download the Rom of the game you want, you will get a compressed (zip) folder, unzip it and within it will be the rom, most systems will identify your emulator and use it open the game. If not, launch the emulator and within it should be an option to open a file, open the file in the unzipped folder.
Enjoy So you want to Mod?
So every Mod, is a mod for a specific game [ex. Pokemon Blue, Pokemon FireRed, Super Mario Bros.] so it requires you to get the Rom for that base game, the mod itself, and a tool to patch it.
 There is an online tool to easily patch the mod to the ROM. IMPORTANT, this will not change any naming, Id recommend having a folder with the base game roms, and a folder for the mods, and lastly a folder for the newly modded roms. Make sure to name or just save the game in modded roms folder after the patch.
There is an online tool to easily patch the mod to the ROM. IMPORTANT, this will not change any naming, Id recommend having a folder with the base game roms, and a folder for the mods, and lastly a folder for the newly modded roms. Make sure to name or just save the game in modded roms folder after the patch. Below are a few resource to find various Pokemon Rom mods(sometimes called hacks)
Personally, Pokemon Unbound is considered the best most polished hack. it runs on Pokemon Fire Red.
Pokemon Emerald Rouge is a cool take on the popular Rougelite genre. This runs on base game Pokemon Emerald
-
 @ c1e6505c:02b3157e
2025-05-28 17:36:03
@ c1e6505c:02b3157e
2025-05-28 17:36:03I recently acquired a new lens:
1959 Leica Summaron F2.8 35mm LTM.
1959 Leica Summaron 35mm f2.8 LTM mounted on my Fujifilm Xpro2 with LTM adapter made by Urth.
Technically, it was a trade. I helped a fellow Bitcoiner set up their Sparrow Wallet, Nostr stuff, and troubleshoot a few wallet issues, and in return, they gave me the lens.
It all started at a local Bitcoin meetup I went to about a week ago - my second time attending. I recognized a few faces from last time, but also saw some new ones. These meetups are refreshing - it’s rare to speak a common language about something like Bitcoin or Nostr. Most people still don’t get it. But they will.
Technology moves forward. Networks grow. Old cells die off.
During the meetup, someone noticed I had my Leica M262 with me and struck up a conversation. Said they had some old Leica lenses and gear at home, and wanted to show me.
Bitcoin and photography in one conversation? I’m down.
A day or so later, they sent me a photo of one of the lenses: a vintage Summaron LTM 35mm f/2.8 from 1959. I’d never seen or heard of one before. They asked if I could help them set up Sparrow and a Bitcoin node. In exchange, they’d give me the lens. Sounded like a good deal to me. Helping plebs with their setups feels like a duty anyway. I said, of course.
They invited me over - a pretty trusting move, which I appreciated. They had some great Bitcoin memorabilia: Fred Krueger’s The Big Bitcoin Book (even if the guy’s turned full shitcoiner), and some FTX sunglasses from Bitcoin 2022. Probably future collector’s items, lol.




We headed upstairs to work on setting up Sparrow Wallet on their Windows machine. I verified the software download first (which you should always do), then helped them create a new wallet using their Ledger Flex. They also had an older Ledger Nano X. The Flex setup was easy, but the Nano X gave us trouble. It turns out Ledger allows multiple wallets for the same asset, which can show up differently depending on how they’re configured. In Sparrow, only one wallet showed—none of the others.
I believe it had to do with the derivation path from the Ledger. If anyone knows a fix, let me know.
After a few hours of troubleshooting, I told them I couldn’t really recommend Ledger. The UX is a mess. They’d already heard similar things from other plebs too.
I suggested switching to the Blockstream Jade. It’s a solid Bitcoin-only device from a trustworthy team. That’s what you want in a hardware wallet.
But back to the lens…
Since it’s an LTM (Leica Thread Mount), I couldn’t mount it directly on my M262. Luckily, I remembered I had an Urth adapter that fits my Fujifilm X-Pro2. I don’t use the X-Pro2 much these days—it’s mostly been sidelined by the M262 - but this was the perfect excuse to bring it out again.
To test the lens, I shot everything wide open at f/2.8. Nothing crazy fast, but it’s the best way to see a lens’s character. And this one definitely has character. There’s a subtle softness and a kind of motion blur effect around the edges when wide open. At first, I wasn’t sure how I felt about it, but the more I shot, the more I liked it. It reminds me of Winogrand’s work in Winogrand Color - those messy, shifting edges that make the frame feel alive. It also helps soften the digital-ness of the camera sensor.
The focus throw is short and snappy - much tighter than my Summicron V3 35mm f/2. I really like how fast it is to use. The closest focusing distance is about 3.5 feet, so it’s not ideal for close-ups. And with the Urth adapter on the X-Pro2, the focal length ends up closer to 40mm.
The only thing that threw me off was the infinity lock. When the focus hits infinity, it physically locks - you have to press a small tab to unlock it. I’ve seen others complain about it, so I guess it’s just one of those old lens quirks. I’m getting used to it.
All the photos here were taken around where I live in South Carolina. Some during bike rides to the river for a swim, others while walking through the marshlands.
I try to make work wherever I am. You should be able to.
It’s about the light, the rhythm, the play - and having the motivation to actually go out and shoot.
Lens rating: 7.9/10
I mainly shoot with a Leica M262, and edit in Lightroom + Dehancer
Use “PictureRoom” for 10% off Dehancer Film
If you’ve made it this far, thank you for taking the time to view my work - consider becoming a paid subscriber.
Also, please contact me if you would like to purchase any of my prints.
Follow me on Nostr:
npub1c8n9qhqzm2x3kzjm84kmdcvm96ezmn257r5xxphv3gsnjq4nz4lqelne96
-
 @ 005bc4de:ef11e1a2
2025-05-28 09:05:10
@ 005bc4de:ef11e1a2
2025-05-28 09:05:10
BIP-2,100,000,000,000,000,000
So, you're telling me...
- 21 million bitcoins is out, and...
- 2.1 quadrillion sats is in, except that...
- sats are out, so...
- 2.1 quadrillion bitcoins is in, except that...
- there are actually millisats, but...
- millisats are out, so...
- millibitcoins are in, so now...
- there are 2.1 quintillion millibitcoins, except that...
- millibitcoins are the basic base unit of bitcoin, so...
- millibitcoins are out, and now...
- 2.1 quintillion bitcoins are in

-
 @ 6a6be47b:3e74e3e1
2025-05-28 17:37:11
@ 6a6be47b:3e74e3e1
2025-05-28 17:37:11Hi frens! 🌞
How was your day? Mine was pretty great! Not to brag—I just try to see things in a positive light. Even when a day is “meh” or downright awful, I look for at least one good thing in it. Sometimes, let’s be real, there isn’t even one. Some days, weeks, or even months can just be tough. But even that shall pass.
✨ So, let’s try to focus on at least one good thing around us, or within us. Who knows—maybe a little magic can happen…
🎨 Today, I made time for some drawing on Procreate—yaaay! If you caught yesterday’s discussion, you know I drew a butterfly 🦋. Maybe with today’s drawing, you’ll be able to guess my next blog entry 👀
Today’s subject: Cytisus scoparius, better known as “Scotch broom” (or Scots broom).
🔍 I used to mix it up with gorse, but there are some telltale differences:
“Broom is similar to common gorse in size, shape and flower colour, but it lacks the spines and has short, flattened leaves and larger flowers.” — The Wildlife Trusts
⭐️Fun fact: I actually painted a gorse not too long ago for my Beltane post.
🚨 A word of caution though—don’t get too close! Scotch broom is harmful if eaten, so keep an eye out for your pets when you’re out and about, according to rhs.org.uk
🌼 I love spotting these bright yellow blooms by the highway or just outside town. That color is chef’s kiss—it really brightens up any drive!
💐That’s all for today. I’m super excited to hear what you think!
Take care and godspeed, my frens! 🚀✨
https://stacker.news/items/991324
-
 @ 57c631a3:07529a8e
2025-04-07 13:17:50
@ 57c631a3:07529a8e
2025-04-07 13:17:50What is Growth Engineering? Before we start: if you’ve already filled out the What is your tech stack? survey: thank you! If you’ve not done so, your help will be greatly appreciated. It takes 5-15 minutes to complete. Those filling out will receive results before anyone else, and additional analysis from myself and Elin. Fill out this survey here.**
npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m
Growth engineering was barely known a decade ago, but today, most scaleups and many publicly traded tech companies have dedicated growth teams staffed by growth engineers. However, some software engineers are still suspicious of this new area because of its reputation for hacky code with little to no code coverage.
For this reason and others, I thought it would be interesting to learn more from an expert who can tell us all about the practicalities of this controversial domain. So I turned to Alexey Komissarouk, who’s been in growth engineering since 2016, and was in charge of it at online education platform, MasterClass. These days, Alexey lives in Tokyo, Japan, where he advises on growth engineering and teaches the Growth Engineering course at Reforge.
In today’s deep dive, Alexey covers:
- What is Growth Engineering? In the simplest terms: writing code to help a company make more money. But there are details to consider: like the company size where it makes sense to have a dedicated team do this.
- What do Growth Engineers work on? Business-facing work, empowerment and platform work are the main areas.
- Why Growth Engineers move faster than Product Engineers. Product Engineers ship to build: Growth Engineers ship to learn. Growth Engineers do take shortcuts that would make no sense when building for longevity – doing this on purpose.
- Tech stack. Common programming languages, monitoring and oncall, feature flags and experimentation, product analytics, review apps, and more.
- What makes a good Growth Engineer? Curiosity, “build to learn” mindset and a “Jack of all trades” approach.
- Where do Growth Engineers fit in? Usually part of the engineering department, either operating as with an “owner” or a “hitchiker” model.
- Becoming a Growth Engineer. A great area if you want to eventually become a founder or product manager – but even if not, it can accelerate your career growth. Working in Growth forces you to learn more about the business.
With that, it’s over to Alexey:
I’ll never forget the first time I made my employer a million dollars.
I was running a push notification A/B test for meal delivery startup Sprig, trying to boost repeat orders.
A push notification similar to what we tested to boost repeat orders
Initial results were unpromising; the push notification was not receiving many opens. Still, I wanted to be thorough: before concluding the idea was a failure, I wrote a SQL query to compare order volume for subsequent weeks between customers in test vs control.
The SQL used to figure out the push notification’s efficiency
As it turned out, our test group “beat” the control group by around 10%:
‘review_5_push’ was the new type of push notification. Roughly the same amount of users clicked it, but they placed 10% more in orders
I plugged the numbers into a significance calculator, which showed it was statistically significant – or “stat-sig” – and therefore highly unlikely to be a coincidence. This meant we had a winner on our hands! But how meaningful was it, really, and what would adding the push notification mean for revenue, if rolled out to 100% of users?
It turned out this experiment created an additional $1.5 million dollars, annually, with just one push notification. Wow!
I was hooked. Since that day, I've shipped hundreds of experimental “winners” which generated hundreds of millions of incremental revenue for my employers. But you never forget the first one. Moments like this is what growth engineering is all about.
1. What is Growth Engineering?
Essentially, growth engineering is the writing of code to make a company money. Of course, all code produced by a business on some level serves this purpose, but while Product Engineers focus on creating a Product worth paying for, Growth Engineers instead focus on making that good product have a good business. To this end, they focus on optimizing and refining key parts of the customer journey, such as:
- Getting more people to consider the product
- Converting them into paying customers
- Keeping them as customers for longer, and spending more
What kinds of companies employ Growth Engineers? Places you’ve heard of, like Meta, LinkedIn, DoorDash, Coinbase, and Dropbox, are some of the ones I’ve had students from. There’s also OpenAI, Uber, Tiktok, Tinder, Airbnb, Pinterest… the list of high-profile companies goes on. Most newer public consumer companies you’ve heard have a growth engineering org, too.
Typically, growth engineering orgs are started by companies at Series B stage and beyond, so long as they are selling to either consumers or businesses via SaaS. These are often places trying to grow extremely fast, and have enough software engineers that some can focus purely on growth. Before the Series B stage, a team is unlikely to be ready for growth for various reasons; likely that it hasn’t found product-market fit, or has no available headcount, or lacks the visitor traffic required to run A/B tests.
Cost is a consideration. A fully-loaded growth team consisting of a handful of engineers, a PM, and a designer costs approximately 1 million dollars annually. To justify this, a rule of thumb is to have at least $5 million dollars in recurring revenue – a milestone often achieved at around the Series B stage.
Despite the presence of growth engineering at many public consumer tech companies, the field itself is still quite new, as a discipline and as a proper title.
Brief history of growth engineering
When I joined Opendoor in 2016, there was a head of growth but no dedicated growth engineers, but there were by the time I left in 2020. At MasterClass soon after, there was a growth org and a dozen dedicated growth engineers. So when did growth engineering originate?
The story is that its origins lie at Facebook in 2007. The team was created by then-VP of platform and monetization Chamath Palihapitiya. Reforce founder and CEO Brian Balfour shares:
“Growth (the kind found on an org chart) began at Facebook under the direction of Chamath Palihapitiya. In 2007, he joined the early team in a nebulous role that fell somewhere between Product, Marketing, and Operations. According to his retelling of the story on Recode Decode, after struggling to accomplish anything meaningful in his first year on the job, he was on the verge of being fired.Sheryl Sandberg joined soon after him, and in a hail mary move he pitched her the game-changing idea that led to the creation of the first-ever growth team. This idea not only saved his job, but earned him the lion’s share of the credit for Facebook’s unprecedented growth.At the time, Sheryl and Mark asked him, “What do you call this thing where you help change the product, do some SEO and SEM, and algorithmically do this or that?”His response: “I don’t know, I just call that, like, Growth, you know, we’re going to try to grow. I’ll be the head of growing stuff."And just like that, Growth became a thing.”
Rather than focus on a particular product or feature, the growth team at Facebook focused on moving the needle, and figuring out which features to work on. These days, Meta employs hundreds if not thousands of growth engineers.
2. What do Growth Engineers work on?
Before we jump into concrete examples, let’s identify three primary focus areas that a growth engineer’s work usually involves.
- Business-facing work – improving the business directly
- Empowerment work – enabling other teams to improve the business
- Platform work – improving the velocity of the above activities
Let’s go through all three:
Business-facing work
This is the bread and butter of growth engineering, and follows a common pattern:
- Implement an idea. Try something big or small to try and move a key business metric, which differs by team but is typically related to conversion rate or retention.
- Quantify impact. Usually via A/B testing.
- Analyze impact. Await results, analyze impact, ship or roll back – then go back to the first step.
Experiments can lead to sweeping or barely noticeable changes. A famous “I can’t believe they needed to test this” was when Google figured out which shade of blue generates the most clicks. At MasterClass, we tested things across the spectrum:
- Small: should we show the price right on the homepage, was that a winner? Yes, but we framed it in monthly terms of $15/month, not $180/year.
- Medium: when browsing a course page, should we include related courses, or more details about the course itself? Was it a winner? After lengthy experimentation, it was hard to tell: both are valuable and we needed to strike the right balance.
- Large: when a potential customer is interested, do we take them straight to checkout, or encourage them to learn more? Counterintuitively, adding steps boosted conversion!
Empowerment
One of the best ways an engineer can move a target metric is by removing themselves as a bottleneck, so colleagues from marketing can iterate and optimize freely. To this end, growth engineers can either build internal tools or integrate self-serve MarTech (Marketing Technology) vendors.
With the right tool, there’s a lot that marketers can do without engineering’s involvement:
- Build and iterate on landing pages (Unbounce, Instapage, etc)
- Draft and send email, SMS and Push Notifications (Iterable, Braze, Customer.io, etc)
- Connect new advertising partners (Google Tag Manager, Segment, etc)
We go more into detail about benefits and applications in the MarTech section of Tech Stack, below.
Platform work
As a business scales, dedicated platform teams help improve stability and velocity for the teams they support. Within growth, this often includes initiatives like:
- Experiment Platform. Many parts of running an experiment can be standardized, from filtering the audience, to bucketing users properly, to observing statistical methodology. Historically, companies built reusable Experiment Platforms in-house, but more recently, vendors such as Eppo and Statsig have grown in popularity with fancy statistical methodologies like “Controlled Using Pre-Experiment Data” (CUPED) that give more signal with less data.
- Reusable components. Companies with standard front-end components for things like headlines, buttons, and images, dramatically reduce the time required to spin up a new page. No more "did you want 5 or 6 pixels here" with a designer; instead growth engineers rely on tools like Storybook to standardize and share reusable React components.
- Monitoring. Growth engineering benefits greatly from leveraging monitoring to compensate for reduced code coverage. High-quality business metric monitoring tools can detect bugs before they cause damage.
When I worked at MasterClass, having monitoring at the ad layer prevented at least one six-figure incident. One Friday, a marketer accidentally broadened the audience for a particular ad from US-only, to worldwide. In response, the Facebook Ad algorithm went on a spending spree, bringing in plenty of visitors from places like Brazil and India, whom we knew from past experience were unlikely to purchase the product. Fortunately, our monitoring noticed the low-performing campaign within minutes, and an alert was sent to the growth engineer on-call, who immediately reached out to the marketer and confirmed the change was unintentional, and then shut down the campaign.
Without this monitoring, a subtle targeting error like this could have gone unnoticed all weekend and would have eaten up $100,000+ of marketing budget. This episode shows that platform investment can benefit everyone; and since growth needs them most, it’s often the growth platform engineering team which implements them.
As the day-to-day work of a Growth Engineer shows, A/B tests are a critical tool to both measure success and learn. It’s a numbers game: the more A/B tests a team can run in a given quarter, the more of them will end up winners, making the team successful. It’s no wonder, then, that Growth Engineering will pull out all the stops to improve velocity.
3. Why Growth Engineers move faster than Product Engineers
On the surface, growth engineering teams look like product engineering ones; writing code, shipping pull requests, monitoring on-call, etc. So how do they move so much faster? The big reason lies in philosophy and focus, not technology. To quote Elena Verna, head of growth at Dropbox:
“Product Engineering teams ship to build; Growth Engineering teams ship to learn.”
Real-world case: price changes at Masterclass
A few years ago at MasterClass, the growth team wanted to see if changing our pricing model to multiple tiers would improve revenue.
Inspired in part by multiple pricing tiers for competitors such as Netflix (above), Disney Plus, and Hulu.
The “multiple pricing tier” proposal for MasterClass.
From a software engineering perspective, this was a highly complex project because:
- Backend engineering work: the backend did not yet support multiple pricing options, requiring a decent amount of engineering, and rigorous testing to make sure existing customers weren’t affected.
- Client app changes: on the device side, multiple platforms (iOS, iPad, Android, Roku, Apple TV, etc) would each need to be updated, including each relevant app store.
The software engineering team estimated that becoming a “multi-pricing-tier” company would take months across numerous engineering teams, and engineering leadership was unwilling to greenlight that significant investment.
We in growth engineering took this as a challenge. As usual, our goal was not just to add the new pricing model, but to learn how much money it might bring in. The approach we ended up proposing was a Fake Door test, which involves offering a not-yet-available option to customers to gauge interest level. This was risky, as taking a customer who’s ready to pay and telling them to join some kind of waiting list is a colossal waste, and risks making them feel like the target of a “bait and switch” trick.
We found a way. The key insight was that people are only offended about a “bait and switch”, if the “switch” is worse than the “bait.” Telling customers they would pay $100 and then switching to $150 would cause a riot, but starting at $150 and then saying “just kidding, it’s only $100” is a pleasant surprise.
The good kind of surprise.
So long as every test “pricing tier” is less appealing – higher prices, fewer features – than the current offering, we could “upgrade” customers after their initial selection. A customer choosing the cheapest tier gets extra features at no extra cost, while a customer choosing a more expensive tier is offered a discount.
We created three new tiers, at different prices. The new “premium” tier would describe the existing, original offering. Regardless of what potential customers selected, they got this “original offering,” during the experiment.
The best thing about this was that no backend changes were required. There were no real, new, back-end pricing plans; everybody ended up purchasing the same version of MasterClass for the same price, with the same features. The entirety of the engineering work was on building a new pricing page, and the “congratulations, you’ve been upgraded” popup. This took just a few days.
Within a couple of weeks, we had enough data to be confident the financial upside of moving to a multi-pricing-tier model would be significant. With this, we’re able to convince the rest of engineering’s leadership to invest in building the feature properly. In the end, launching multiple pricing tiers turned out to be one of the biggest revenue wins of the year.
Building a skyscraper vs building a tent
The MasterClass example demonstrates the spirit of growth engineering; focusing on building to learn, instead of building to last. Consider building skyscrapers versus tents.
Building a tent optimizes for speed of set-up and tear-down over longevity. You don’t think of a tent as one that is shoddy or low-quality compared to skyscrapers: it’s not even the same category of buildings! Growth engineers maximize use of lightweight materials. To stick with the tents vs skyscraper metaphor: we prioritize lightweight fabric materials over steel and concrete whenever possible. We only resort to traditional building materials when there’s no other choice, or when a direction is confirmed as correct. Quality is important – after all, a tent must keep out rain and mosquitoes. However, the speed-vs-durability tradeoff decision results in very different approaches and outcomes.
4. Tech stack
At first glance, growth and product engineers use the same tooling, and contribute to the same codebases. But growth engineering tends to be high-velocity, experiment-heavy, and with limited test coverage. This means that certain “nice to have” tools for product engineering are mission-critical for growth engineers.
Read more https://connect-test.layer3.press/articles/ea02c1a1-7cfa-42b4-8722-0165abcae8bb
-
 @ 10846a37:73b5f923
2025-05-29 04:58:56
@ 10846a37:73b5f923
2025-05-29 04:58:56A plataforma 711BRL tem se destacado como uma das grandes promessas do entretenimento digital no Brasil. Com um visual moderno, navegação intuitiva e um catálogo impressionante de jogos, a 711BRL oferece uma experiência diferenciada para jogadores que buscam diversão, praticidade e segurança em um só lugar.
Uma Plataforma Moderna e Confiável Desde o primeiro acesso, é possível notar que a 711BRL foi desenvolvida com foco na experiência do usuário. O site é rápido, responsivo e compatível com todos os tipos de dispositivos, como computadores, tablets e smartphones. Isso permite que os jogadores aproveitem todos os recursos da plataforma em qualquer lugar, a qualquer momento.
A segurança também é um dos pilares da 711brl. A plataforma utiliza tecnologia de criptografia de ponta para proteger os dados pessoais e financeiros dos usuários, além de contar com métodos de pagamento amplamente conhecidos no Brasil, como PIX, boletos bancários e carteiras digitais. Tudo isso garante tranquilidade para quem deseja jogar sem preocupações.
Catálogo Variado de Jogos Um dos grandes atrativos da 711BRL é a diversidade de jogos disponíveis. A plataforma reúne títulos dos principais desenvolvedores do mercado, com gráficos de alta qualidade, trilhas sonoras envolventes e mecânicas inovadoras. Entre os destaques, estão:
Jogos de slots: Com temas variados, desde aventuras mitológicas até histórias futuristas, os slots são ideais para quem gosta de dinamismo e surpresas a cada rodada.
Jogos de mesa: Para quem prefere desafios estratégicos, a 711BRL oferece diferentes versões de roleta, blackjack e bacará, entre outros clássicos do entretenimento digital.
Jogos ao vivo: Com interações em tempo real com apresentadores profissionais, essa modalidade proporciona uma experiência imersiva, onde o jogador se sente parte da ação.
Além disso, a plataforma atualiza seu catálogo constantemente, trazendo novidades e lançamentos para manter a experiência sempre renovada.
Experiência do Jogador em Primeiro Lugar Outro diferencial da 711BRL é o cuidado com o jogador. A plataforma conta com um atendimento ao cliente eficiente, disponível 24 horas por dia, sete dias por semana, por meio de chat ao vivo e e-mail. A equipe está sempre pronta para tirar dúvidas, resolver problemas e orientar os usuários em qualquer etapa do processo.
A navegação é intuitiva, com menus bem organizados e filtros que facilitam a busca pelos jogos favoritos. Novos usuários encontram tutoriais e guias explicativos, o que ajuda muito na adaptação inicial e permite que todos aproveitem ao máximo cada funcionalidade oferecida.
Para completar, a 711BRL promove campanhas promocionais frequentes, com bônus de boas-vindas, rodadas grátis e sorteios exclusivos, sempre com regras claras e acessíveis. Isso contribui para uma experiência mais empolgante e recompensadora.
Conclusão A 711BRL é mais do que uma simples plataforma de jogos: é um ambiente completo de entretenimento online, que une tecnologia, variedade e suporte de qualidade. Ideal para jogadores iniciantes e experientes, o site oferece tudo o que é necessário para uma jornada divertida, segura e cheia de possibilidades. Se você busca uma nova forma de se divertir online, a 711BRL é, sem dúvidas, uma excelente escolha.
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 51bbb15e:b77a2290
2025-05-21 00:24:36
@ 51bbb15e:b77a2290
2025-05-21 00:24:36Yeah, I’m sure everything in the file is legit. 👍 Let’s review the guard witness testimony…Oh wait, they weren’t at their posts despite 24/7 survellience instructions after another Epstein “suicide” attempt two weeks earlier. Well, at least the video of the suicide is in the file? Oh wait, a techical glitch. Damn those coincidences!
At this point, the Trump administration has zero credibility with me on anything related to the Epstein case and his clients. I still suspect the administration is using the Epstein files as leverage to keep a lot of RINOs in line, whereas they’d be sabotaging his agenda at every turn otherwise. However, I just don’t believe in ends-justify-the-means thinking. It’s led almost all of DC to toss out every bit of the values they might once have had.
-
 @ c9badfea:610f861a
2025-05-20 19:49:20
@ c9badfea:610f861a
2025-05-20 19:49:20- Install Sky Map (it's free and open source)
- Launch the app and tap Accept, then tap OK
- When asked to access the device's location, tap While Using The App
- Tap somewhere on the screen to activate the menu, then tap ⁝ and select Settings
- Disable Send Usage Statistics
- Return to the main screen and enjoy stargazing!
ℹ️ Use the 🔍 icon in the upper toolbar to search for a specific celestial body, or tap the 👁️ icon to activate night mode
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ b7274d28:c99628cb
2025-05-28 01:11:43
@ b7274d28:c99628cb
2025-05-28 01:11:43In this second installment of The Android Elite Setup tutorial series, we will cover installing the nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 on your #Android device and browsing for apps you may be interested in trying out.
Since the #Zapstore is a direct competitor to the Google Play Store, you're not going to be able to find and install it from there like you may be used to with other apps. Instead, you will need to install it directly from the developer's GitHub page. This is not a complicated process, but it is outside the normal flow of searching on the Play Store, tapping install, and you're done.
Installation
From any web browser on your Android phone, navigate to the Zapstore GitHub Releases page and the most recent version will be listed at the top of the page. The .apk file for you to download and install will be listed in the "Assets."
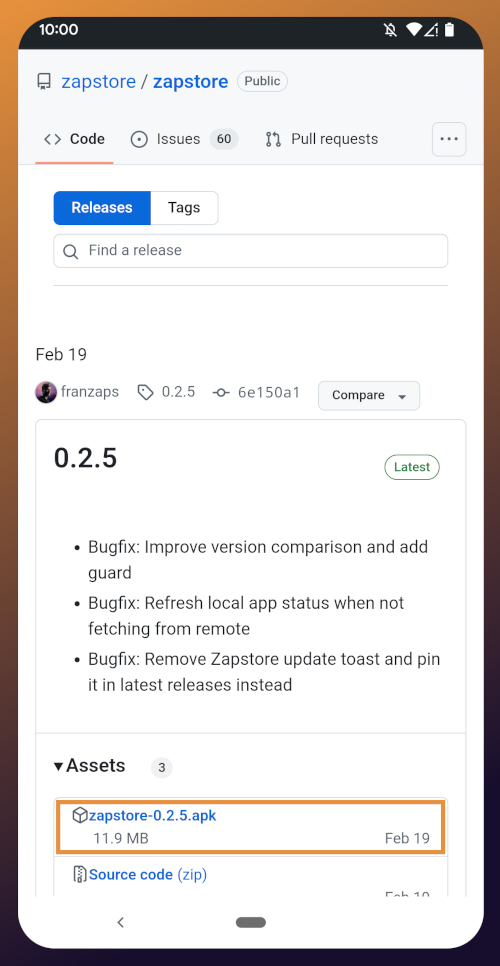
Tap the .apk to download it, and you should get a notification when the download has completed, with a prompt to open the file.
You will likely be presented with a prompt warning you that your phone currently isn't allowed to install applications from "unknown sources." Anywhere other than the Play Store is considered an "unknown source" by default. However, you can manually allow installation from unknown sources in the settings, which the prompt gives you the option to do.
In the settings page that opens, toggle it to allow installation from this source, and you should be prompted to install the application. If you aren't, simply go to your web browser's downloads and tap on the .apk file again, or go into your file browser app and you should find the .apk in your Downloads folder.
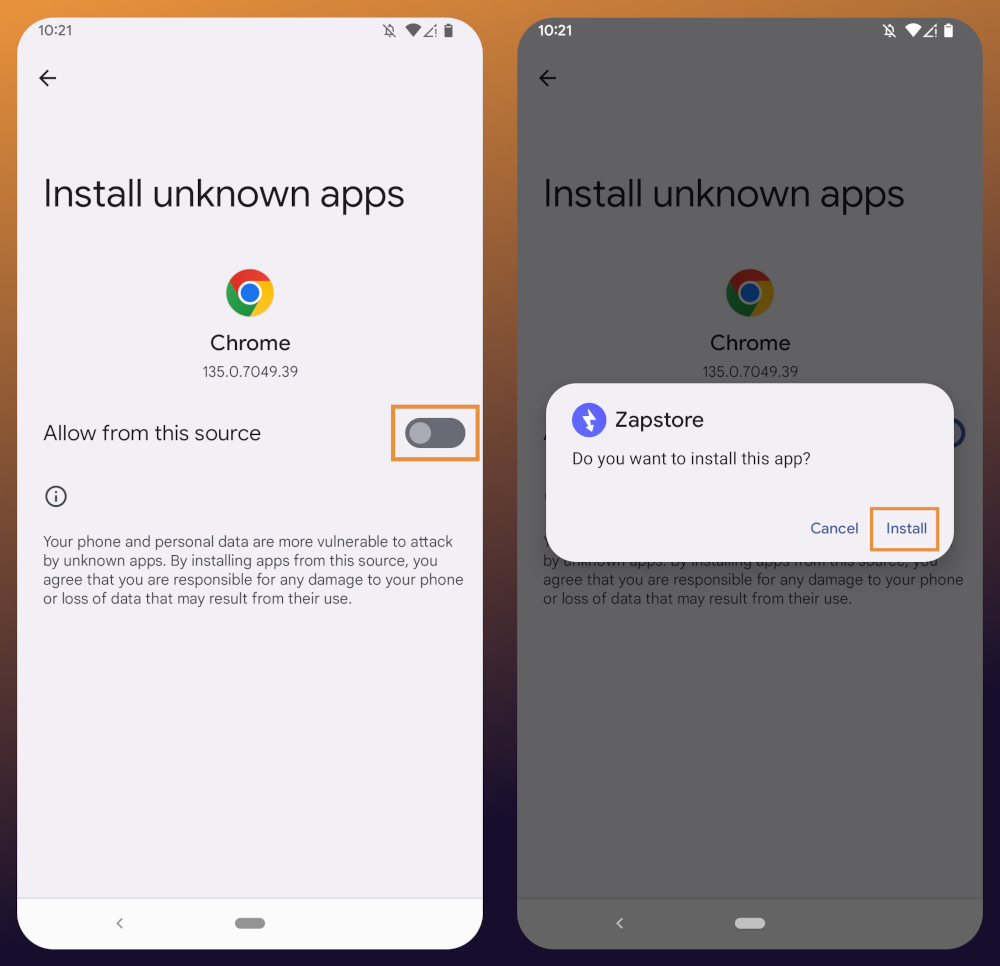
If the application doesn't open automatically after install, you will find it in your app drawer.

Home Page
Right at the top of the home page in the Zapstore is the search bar. You can use it to find a specific app you know is available in the Zapstore.
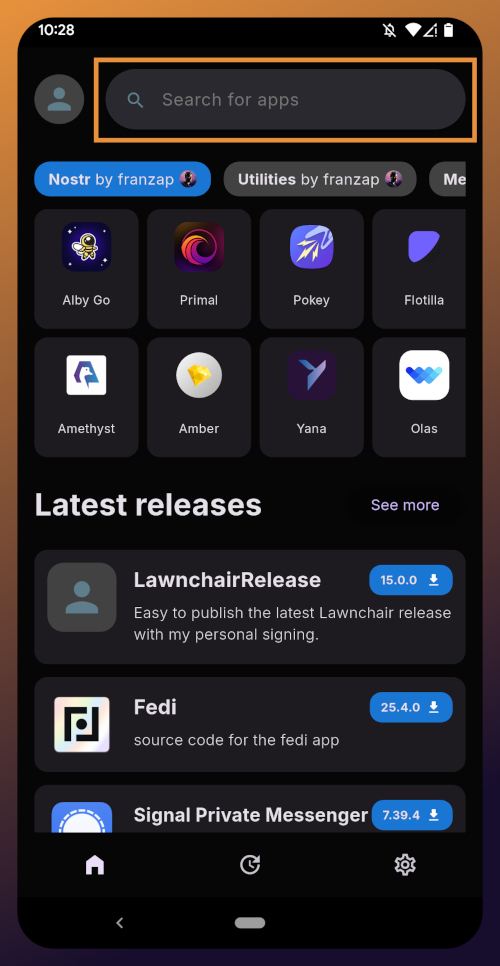
There are quite a lot of open source apps available, and more being added all the time. Most are added by the Zapstore developer, nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but some are added by the app developers themselves, especially Nostr apps. All of the applications we will be installing through the Zapstore have been added by their developers and are cryptographically signed, so you know that what you download is what the developer actually released.
The next section is for app discovery. There are curated app collections to peruse for ideas about what you may want to install. As you can see, all of the other apps we will be installing are listed in nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9's "Nostr" collection.
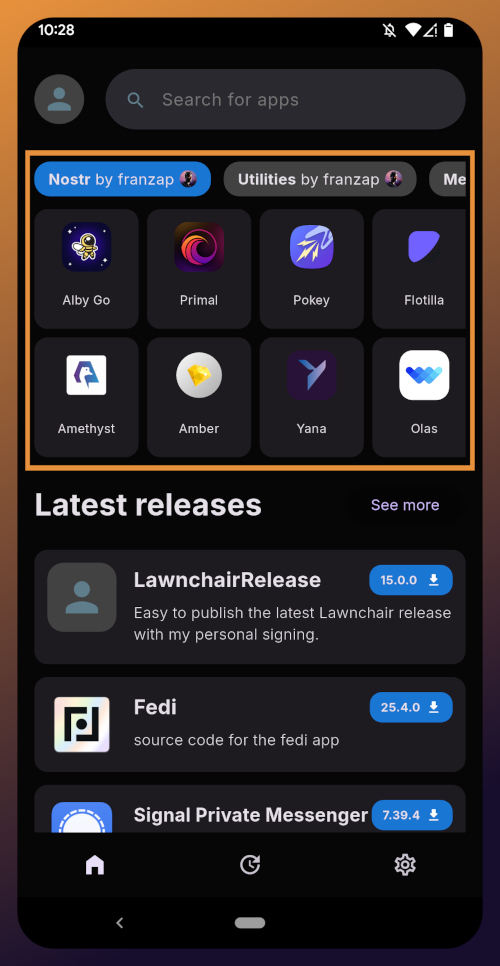
In future releases of the Zapstore, users will be able to create their own app collections.
The last section of the home page is a chronological list of the latest releases. This includes both new apps added to the Zapstore and recently updated apps. The list of recent releases on its own can be a great resource for discovering apps you may not have heard of before.
Installed Apps
The next page of the app, accessed by the icon in the bottom-center of the screen that looks like a clock with an arrow circling it, shows all apps you have installed that are available in the Zapstore. It's also where you will find apps you have previously installed that are ready to be updated. This page is pretty sparse on my test profile, since I only have the Zapstore itself installed, so here is a look at it on my main profile:

The "Disabled Apps" at the top are usually applications that were installed via the Play Store or some other means, but are also available in the Zapstore. You may be surprised to see that some of the apps you already have installed on your device are also available on the Zapstore. However, to manage their updates though the Zapstore, you would need to uninstall the app and reinstall it from the Zapstore instead. I only recommend doing this for applications that are added to the Zapstore by their developers, or you may encounter a significant delay between a new update being released for the app and when that update is available on the Zapstore.
Tap on one of your apps in the list to see whether the app is added by the developer, or by the Zapstore. This takes you to the application's page, and you may see a warning at the top if the app was not installed through the Zapstore.
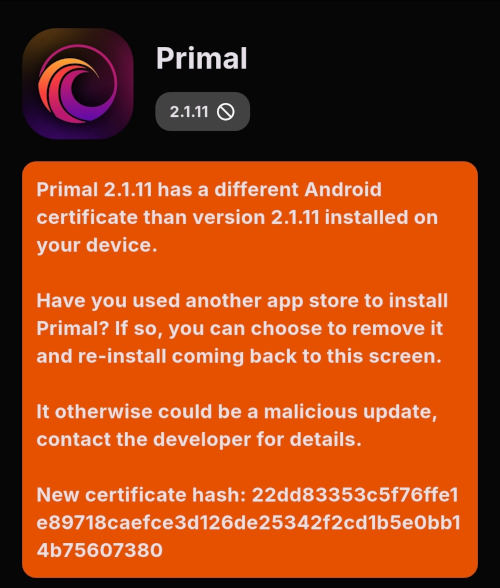
Scroll down the page a bit and you will see who signed the release that is available on the Zapstore.
In the case of Primal, even though the developer is on Nostr, they are not signing their own releases to the Zapstore yet. This means there will likely be a delay between Primal releasing an update and that update being available on the Zapstore.
Settings
The last page of the app is the settings page, found by tapping the cog at the bottom right.
Here you can send the Zapstore developer feedback directly (if you are logged in), connect a Lightning wallet using Nostr Wallet Connect, delete your local cache, and view some system information.
We will be adding a connection to our nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch wallet in part 5 of this tutorial series.
For the time being, we are all set with the Zapstore and ready for the next stage of our journey.
Continue to Part 3: Amber Signer. Nostr link: nostr:naddr1qqxnzde5xuengdeexcmnvv3eqgstwf6d9r37nqalwgxmfd9p9gclt3l0yc3jp5zuyhkfqjy6extz3jcrqsqqqa28qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qg6waehxw309aex2mrp0yhxyunfva58gcn0d36zumn9wss80nug
-
 @ 97c70a44:ad98e322
2025-02-18 20:30:32
@ 97c70a44:ad98e322
2025-02-18 20:30:32For the last couple of weeks, I've been dealing with the fallout of upgrading a web application to Svelte 5. Complaints about framework churn and migration annoyances aside, I've run into some interesting issues with the migration. So far, I haven't seen many other people register the same issues, so I thought it might be constructive for me to articulate them myself.
I'll try not to complain too much in this post, since I'm grateful for the many years of Svelte 3/4 I've enjoyed. But I don't think I'll be choosing Svelte for any new projects going forward. I hope my reflections here will be useful to others as well.
If you're interested in reproductions for the issues I mention here, you can find them below.
The Need for Speed
To start with, let me just quickly acknowledge what the Svelte team is trying to do. It seems like most of the substantial changes in version 5 are built around "deep reactivity", which allows for more granular reactivity, leading to better performance. Performance is good, and the Svelte team has always excelled at reconciling performance with DX.
In previous versions of Svelte, the main way this was achieved was with the Svelte compiler. There were many ancillary techniques involved in improving performance, but having a framework compile step gave the Svelte team a lot of leeway for rearranging things under the hood without making developers learn new concepts. This is what made Svelte so original in the beginning.
At the same time, it resulted in an even more opaque framework than usual, making it harder for developers to debug more complex issues. To make matters worse, the compiler had bugs, resulting in errors which could only be fixed by blindly refactoring the problem component. This happened to me personally at least half a dozen times, and is what ultimately pushed me to migrate to Svelte 5.
Nevertheless, I always felt it was an acceptable trade-off for speed and productivity. Sure, sometimes I had to delete my project and port it to a fresh repository every so often, but the framework was truly a pleasure to use.
Svelte is not Javascript
Svelte 5 doubled down on this tradeoff — which makes sense, because it's what sets the framework apart. The difference this time is that the abstraction/performance tradeoff did not stay in compiler land, but intruded into runtime in two important ways:
- The use of proxies to support deep reactivity
- Implicit component lifecycle state
Both of these changes improved performance and made the API for developers look slicker. What's not to like? Unfortunately, both of these features are classic examples of a leaky abstraction, and ultimately make things more complex for developers, not less.
Proxies are not objects
The use of proxies seems to have allowed the Svelte team to squeeze a little more performance out of the framework, without asking developers to do any extra work. Threading state through multiple levels of components without provoking unnecessary re-renders in frameworks like React is an infamously difficult chore.
Svelte's compiler avoided some of the pitfalls associated with virtual DOM diffing solutions, but evidently there was still enough of a performance gain to be had to justify the introduction of proxies. The Svelte team also seems to argue that their introduction represents an improvement in developer experience:
we... can maximise both efficiency and ergonomics.
Here's the problem: Svelte 5 looks simpler, but actually introduces more abstractions.
Using proxies to monitor array methods (for example) is appealing because it allows developers to forget all the goofy heuristics involved with making sure state was reactive and just
pushto the array. I can't count how many times I've writtenvalue = valueto trigger reactivity in svelte 4.In Svelte 4, developers had to understand how the Svelte compiler worked. The compiler, being a leaky abstraction, forced its users to know that assignment was how you signaled reactivity. In svelte 5, developers can just "forget" about the compiler!
Except they can't. All the introduction of new abstractions really accomplishes is the introduction of more complex heuristics that developers have to keep in their heads in order to get the compiler to act the way they want it to.
In fact, this is why after years of using Svelte, I found myself using Svelte stores more and more often, and reactive declarations less. The reason being that Svelte stores are just javascript. Calling
updateon a store is simple, and being able to reference them with a$was just a nice bonus — nothing to remember, and if I mess up the compiler yells at me.Proxies introduce a similar problem to reactive declarations, which is that they look like one thing but act like another on the edges.
When I started using Svelte 5, everything worked great — until I tried to save a proxy to indexeddb, at which point I got a
DataCloneError. To make matters worse, it's impossible to reliably tell if something is aProxywithouttry/catching a structured clone, which is a performance-intensive operation.This forces the developer to remember what is and what isn't a Proxy, calling
$state.snapshotevery time they pass a proxy to a context that doesn't expect or know about them. This obviates all the nice abstractions they gave us in the first place.Components are not functions
The reason virtual DOM took off way back in 2013 was the ability to model your application as composed functions, each of which takes data and spits out HTML. Svelte retained this paradigm, using a compiler to sidestep the inefficiencies of virtual DOM and the complexities of lifecycle methods.
In Svelte 5, component lifecycles are back, react-hooks style.
In React, hooks are an abstraction that allows developers to avoid writing all the stateful code associated with component lifecycle methods. Modern React tutorials universally recommend using hooks instead, which rely on the framework invisibly synchronizing state with the render tree.
While this does result in cleaner code, it also requires developers to tread carefully to avoid breaking the assumptions surrounding hooks. Just try accessing state in a
setTimeoutand you'll see what I mean.Svelte 4 had a few gotchas like this — for example, async code that interacts with a component's DOM elements has to keep track of whether the component is unmounted. This is pretty similar to the kind of pattern you'd see in old React components that relied on lifecycle methods.
It seems to me that Svelte 5 has gone the React 16 route by adding implicit state related to component lifecycles in order to coordinate state changes and effects.
For example, here is an excerpt from the documentation for $effect:
You can place $effect anywhere, not just at the top level of a component, as long as it is called during component initialization (or while a parent effect is active). It is then tied to the lifecycle of the component (or parent effect) and will therefore destroy itself when the component unmounts (or the parent effect is destroyed).
That's very complex! In order to use
$effect... effectively (sorry), developers have to understand how state changes are tracked. The documentation for component lifecycles claims:In Svelte 5, the component lifecycle consists of only two parts: Its creation and its destruction. Everything in-between — when certain state is updated — is not related to the component as a whole; only the parts that need to react to the state change are notified. This is because under the hood the smallest unit of change is actually not a component, it’s the (render) effects that the component sets up upon component initialization. Consequently, there’s no such thing as a “before update”/"after update” hook.
But then goes on to introduce the idea of
tickin conjunction with$effect.pre. This section explains that "tickreturns a promise that resolves once any pending state changes have been applied, or in the next microtask if there are none."I'm sure there's some mental model that justifies this, but I don't think the claim that a component's lifecycle is only comprised of mount/unmount is really helpful when an addendum about state changes has to come right afterward.
The place where this really bit me, and which is the motivation for this blog post, is when state gets coupled to a component's lifecycle, even when the state is passed to another function that doesn't know anything about svelte.
In my application, I manage modal dialogs by storing the component I want to render alongside its props in a store and rendering it in the
layout.svelteof my application. This store is also synchronized with browser history so that the back button works to close them. Sometimes, it's useful to pass a callback to one of these modals, binding caller-specific functionality to the child component:javascript const {value} = $props() const callback = () => console.log(value) const openModal = () => pushModal(MyModal, {callback})This is a fundamental pattern in javascript. Passing a callback is just one of those things you do.
Unfortunately, if the above code lives in a modal dialog itself, the caller component gets unmounted before the callback gets called. In Svelte 4, this worked fine, but in Svelte 5
valuegets updated toundefinedwhen the component gets unmounted. Here's a minimal reproduction.This is only one example, but it seems clear to me that any prop that is closed over by a callback function that lives longer than its component will be undefined when I want to use it — with no reassignment existing in lexical scope. It seems that the reason this happens is that the props "belong" to the parent component, and are accessed via getters so that the parent can revoke access when it unmounts.
I don't know why this is necessary, but I assume there's a good engineering reason for it. The problem is, this just isn't how javascript works. Svelte is essentially attempting to re-invent garbage collection around component lifecycles, which breaks the assumption every javascript developer has that variables don't simply disappear without an explicit reassignment. It should be safe to pass stuff around and let the garbage collector do its job.
Conclusion
Easy things are nice, but as Rich Hickey says, easy things are not always simple. And like Joel Spolsky, I don't like being surprised. Svelte has always been full of magic, but with the latest release I think the cognitive overhead of reciting incantations has finally outweighed the power it confers.
My point in this post is not to dunk on the Svelte team. I know lots of people like Svelte 5 (and react hooks). The point I'm trying to make is that there is a tradeoff between doing things on the user's behalf, and giving the user agency. Good software is built on understanding, not cleverness.
I also think this is an important lesson to remember as AI-assisted coding becomes increasingly popular. Don't choose tools that alienate you from your work. Choose tools that leverage the wisdom you've already accumulated, and which help you to cultivate a deeper understanding of the discipline.
Thank you to Rich Harris and team for many years of pleasant development. I hope that (if you read this) it's not so full of inaccuracies as to be unhelpful as user feedback.
-
 @ 502ab02a:a2860397
2025-05-29 01:40:28
@ 502ab02a:a2860397
2025-05-29 01:40:28เรามาดู แลคเชอร์ประวัติศาสตร์ ที่พลิกโลกแห่งการเกษตรและอาหารของมนุษย์ชาติกันครับ เรามาดูความแยบยลที่สามารถจูงใจคนมากมายให้เห็นถึงข้อดีของเนื้อจากแลบ เขาทำได้ยังไง เรามาศึกษาการสื่อสารกันครับ
เรื่องมันเริ่มจากการประชุม World Economic Forum ปี 2015 ที่ศาสตราจารย์ Mark Post นักเภสัชวิทยาชาวดัตช์ ที่เรารู้จักกันไปแล้ว ซึ่งตอนนั้นเป็นศาสตราจารย์ด้านสรีรวิทยาของหลอดเลือดอยู่ที่ Maastricht University และเป็นผู้ร่วมก่อตั้งบริษัท Mosa Meat ได้ลุกขึ้นมาเล่าเรื่อง "เนื้อเพาะเลี้ยง" หรือ cultured meat ให้คนทั้งห้องฟัง
สิ่งที่เขาพูดมันไม่ใช่แค่นวัตกรรมใหม่ แต่คือคำเตือนที่จริงจัง ว่าถ้ามนุษย์ยังผลิตเนื้อสัตว์แบบเดิม เรากำลังวิ่งเข้าใกล้ปัญหาใหญ่ที่รออยู่ข้างหน้า
ศาสตราจารย์ Post เล่าไว้ได้น่าสนใจมาก เขาบอกว่าแค่จะได้แฮมเบอร์เกอร์ 1 ชิ้นขนาดหนึ่งในสี่ปอนด์ เราต้องใช้เมล็ดธัญพืช 7 ปอนด์ ใช้น้ำจืด 50 แกลลอน และพื้นที่ดินอีก 70 ตารางฟุต นั่นแปลว่าเรากำลังเปลี่ยนของดีในธรรมชาติ ข้าว น้ำ ดิน ไปเป็นของที่กินหมดใน 10 นาที แล้วหิวใหม่ได้ในอีกครึ่งชั่วโมง
เหตุผลก็เพราะวัวมันไม่ได้แปลงโปรตีนพืชมาเป็นเนื้อได้มีประสิทธิภาพนัก พูดอีกแบบคือ มันเปลืองเกินไป
ตอนนี้พื้นที่เพาะปลูกของโลกกว่า 70% ถูกใช้ไปในการผลิตเนื้อสัตว์ คิดดูสิว่าถ้าเราหาทางที่ดีกว่านี้ได้ เราจะมีพื้นที่ว่างกลับคืนมาแค่ไหน
แถมวัวไม่ใช่แค่กินเก่งนะ ยังปล่อยก๊าซเก่งด้วย โดยเฉพาะมีเทนที่ทำให้โลกร้อนพอๆ กับอุตสาหกรรมการขนส่งเลยทีเดียว ศาสตราจารย์ Post เล่าว่า ทุกครั้งที่เขาเห็นวัวยืนเคี้ยวหญ้า เขาไม่ได้เห็นแค่วัว...แต่เห็นเมฆก๊าซมีเทนลอยมาด้วย
และที่น่าคิดคือ เมื่อรายได้ของคนในอินเดียหรือจีนสูงขึ้น พวกเขาจะกินเนื้อเพิ่มตามรายได้ ซึ่งสถิติบอกว่าภายในปี 2050 ความต้องการเนื้อสัตว์จะเพิ่มขึ้นเป็น สองเท่า จากปัจจุบัน
แต่ศาสตราจารย์ก็ไม่ได้มองว่าเนื้อเป็นปีศาจ เขาบอกว่า มนุษย์ถูกสร้างมาให้รักเนื้อ เนื้อคือสิ่งที่มาพร้อมวิวัฒนาการ เราได้พลังงานจากมัน สมองเราใหญ่ขึ้นเพราะมัน และกลายเป็นมนุษย์เพราะมัน
แม้จะมีคนอีกกว่าสองพันล้านที่เป็นมังสวิรัติ ส่วนใหญ่อาจเพราะไม่มีทางเลือก แต่อย่างน้อยพวกเขาก็อยู่รอดได้ แต่ก็ปฏิเสธไม่ได้ว่า คนที่เคยล่า เคยกินเนื้อ จะรู้สึกตื่นเต้นทุกครั้งที่ได้แบ่งเนื้อกันบนโต๊ะ
ศาสตราจารย์ Post เองก็ยังชอบกินเนื้อ แต่เขาอยากได้เนื้อที่ได้มาจากทางเลือกที่ดีกว่า ไม่ใช่ทางที่พาโลกเข้า ICU
เนื้อเพาะเลี้ยงเริ่มจากหลักการง่ายๆ ที่เรารู้มาตั้งแต่ช่วงปี 2000 ว่า ในกล้ามเนื้อของสัตว์มี สเต็มเซลล์ รอคอยจะซ่อมแซมเนื้อเยื่อหากมันได้รับบาดเจ็บ
แค่เอาชิ้นกล้ามเนื้อเล็กๆ จากวัว ขนาดแค่ 1 ซม. x 1 มม. มาแยกสเต็มเซลล์ออกมาเลี้ยงให้ขยายตัว
เฮียว่าอันนี้น่าทึ่งมาก เพราะจากตัวอย่างเล็กๆ ชิ้นเดียว สามารถผลิตเนื้อวัวได้ถึง 10,000 กิโลกรัม เลยนะ!
แปลว่าเราสามารถลดจำนวนวัวทั้งโลกจากครึ่งพันล้านตัว เหลือแค่ประมาณ 30,000 ตัวได้เลย
และถ้าให้เซลล์กล้ามเนื้อพวกนี้อยู่ในสภาพแวดล้อมที่เหมาะสม มันก็จะเริ่มสร้างกล้ามเนื้อขึ้นมาเอง โดยเฉพาะถ้าเรากระตุ้นให้มันรู้สึกเหมือนกำลัง “ออกกำลัง” อยู่ เช่น ใส่แรงตึงเข้าไป
ทีมนักวิจัยของเขาเลี้ยงเซลล์เหล่านี้ให้เติบโตในรูปวงแหวนคล้ายโดนัท ครบ 3 สัปดาห์ กล้ามเนื้อจะเริ่มหดตัว สร้างความตึง และกลายเป็นเนื้อกล้ามเนื้อแบบเต็มตัวที่ดูไม่ต่างจากกล้ามเนื้อในสเต็กจริงๆ เลย
ปี 2013 ทีมของ Mark Post ผลิตเส้นใยกล้ามเนื้อจำนวน 10,000 เส้น เอามาทำแฮมเบอร์เกอร์ และนำไปเปิดตัวในงานแถลงข่าวที่ลอนดอน เป็นเหมือนการโชว์ทำอาหารผสมกับเปิดงานวิจัย
จุดประสงค์คือจะพิสูจน์ให้โลกเห็นว่า “เฮ้ย! สิ่งนี้ไม่ใช่แค่ไอเดียลอยๆ แต่มันทำได้จริง และจำเป็นต้องทำจริงๆ เพราะเรากำลังจะเจอวิกฤต”
ราคาแฮมเบอร์เกอร์ตอนนั้นคือ 250,000 ยูโร
มีเชฟผู้กล้าปรุง และอาสาสมัครสองคนลองชิม พวกเขาบอกว่า “ก็โอเคในฐานะเบอร์เกอร์ราคาเท่านี้ แต่ก็อยากได้รสเข้มกว่านี้หน่อย” เพราะยังไม่มีไขมัน เลยรสจืดไปหน่อย
แต่ที่สำคัญคือ พวกเขายืนยันว่า “มันคือเนื้อจริงๆ” ทั้งเนื้อสัมผัสและโครงสร้าง
แค่มีต้นแบบยังไม่พอ เพราะจะทำให้ขายได้จริง ต้องผ่านด่านสำคัญ เนื้อต้องผลิตได้โดยใช้ทรัพยากรน้อยกว่าการเลี้ยงวัวจริง การประเมินเบื้องต้นจาก University of Oxford พบว่า เนื้อเพาะเลี้ยงใช้พื้นที่น้อยลง 90% น้ำลดลง 90% พลังงานลดลง 60–70%
ทุกอย่างที่ใช้ในการเลี้ยงเซลล์ต้องมีจำนวนมากพอหรือหมุนเวียนใช้ได้ ที่น่าหนักใจคือ การเลี้ยงเซลล์ต้องใช้ “ซีรั่มจากลูกวัว” ซึ่งได้มาจากเลือดวัว ถ้าลดจำนวนวัว เราก็ไม่มีซีรั่ม แต่ตอนนี้มีงานพัฒนาไปเยอะแล้ว กำลังหาวิธีทำเซลล์กล้ามเนื้อโดยไม่ต้องพึ่งซีรั่มจากสัตว์
ไม่ใช่แค่โปรตีน แต่ต้องเป็น "เนื้อ" ในทุกความรู้สึก นักวิจัยพยายามปรับสภาพแวดล้อมการเพาะเลี้ยง เช่น ความเข้มข้นของออกซิเจน เพื่อให้เซลล์แสดงโปรตีนสำคัญ เช่น myoglobin ที่ทำให้เนื้อมีสีและรสชาติเหมือนเนื้อจริง
การยอมรับของผู้บริโภคเป็นอีกด่านสำคัญที่เนื้อเพาะเลี้ยงต้องข้ามผ่านให้ได้ ไม่ใช่แค่เรื่องรสชาติหรือคุณค่าทางโภชนาการเท่านั้น แต่ยังเป็นเรื่องของ "ใจ" ที่ต้องเปิดรับสิ่งใหม่ที่ไม่คุ้นเคย ศาสตราจารย์ Post เล่าว่า ในการสำรวจผู้บริโภคในอังกฤษและเนเธอร์แลนด์ พบว่ามีคนไม่น้อยที่ยินดีจะลองกินเนื้อเพาะเลี้ยง ถึง 52% ของชาวดัตช์ และ 60% ของชาวอังกฤษเลยทีเดียว
เขาเปรียบเทียบว่า จริงๆ แล้ว คนเรายอมกินฮอทดอกโดยไม่รู้ด้วยซ้ำว่าทำมาจากอะไร หรือผ่านอะไรมาบ้าง ขอแค่มัน "อร่อย ถูก และดูปลอดภัย" ก็เพียงพอแล้วสำหรับคนส่วนใหญ่ ดังนั้นเนื้อเพาะเลี้ยงจึงไม่ต่างกันมากนัก ขอเพียงให้คนรู้สึกว่า “กินแล้วไม่ตาย” และ “ไม่ได้แปลกจนใจฝ่อ” เท่านั้นแหละ วันหนึ่งมันก็จะกลายเป็นของธรรมดาในตู้เย็นเหมือนกับโยเกิร์ตหรือไส้กรอกนั่นเอง
ในด้านของราคา แม้จะยังไม่ถูกเท่าไส้กรอกในซูเปอร์ แต่ก็ลดลงมาไกลจากจุดเริ่มต้นแบบสุดๆ จากชิ้นต้นแบบราคา 250,000 ดอลลาร์ในปี 2013 ตอนนี้ต้นทุนลดลงมาเหลือประมาณ 65 ดอลลาร์ต่อกิโลกรัม (ยังไม่รวมเทคโนโลยีล้ำหน้าอื่นๆ ที่กำลังพัฒนาอยู่) ซึ่งก็ถือว่าอยู่ในระดับเดียวกับเนื้อวากิวหรือสเต๊กเกรดพรีเมียมเลยทีเดียว เป้าหมายคือทำให้ถูกลงอีก และผลิตได้ในระดับอุตสาหกรรมให้เพียงพอกับคนทั้งโลก ไม่ใช่ของฟุ่มเฟือยสำหรับคนรวยเท่านั้น
แต่วิสัยทัศน์ที่น่าสนใจจริงๆ คือ ภาพของอนาคตที่ศาสตราจารย์ Post วาดไว้ เขาเชื่อว่าเทคโนโลยีนี้เรียบง่ายพอที่จะขยายไปสู่ครัวเรือนหรือชุมชนเล็กๆ ได้ วันหนึ่งเราอาจได้เห็นการเพาะเลี้ยงเซลล์จากหมูที่เลี้ยงอยู่ข้างบ้าน แล้วเอาไปปั่นเป็นหมูสับแบบสดใหม่ ไม่ต้องฆ่าสัตว์ ไม่ต้องส่งโรงงาน ไม่ต้องตัดต่อพันธุกรรม แค่นั่งรอเหมือนหมักแป้งเปรี้ยว แล้วได้เนื้อสดๆ มาใส่ต้มจืด
และนั่นแหละคือ "การเปลี่ยนกรอบคิดเรื่องเนื้อสัตว์" แบบพลิกฝ่ามือ
มันจะไม่ใช่เรื่องการฆ่าอีกต่อไป ไม่ใช่เรื่องของฟาร์มกลิ่นฉี่ หรือสายพานโรงฆ่าสัตว์ มันจะเป็น "ผลิตภัณฑ์ใหม่" ที่เราสร้างได้ ควบคุมได้ และปรับแต่งได้ เช่น เพิ่มโอเมก้า 3 ในเซลล์ไขมันให้สูงขึ้น หรือทำให้เนื้อไม่มีคอเลสเตอรอลเลยก็ยังได้
แม้ศาสตราจารย์ Post จะเน้นเรื่องความมั่นคงทางอาหารและผลกระทบต่อสิ่งแวดล้อมเป็นหลัก แต่เขาก็ยอมรับว่า สำหรับคนกินทั่วๆ ไป ประเด็นที่ "ไม่มีสัตว์ต้องเจ็บปวด" จะกลายเป็นจุดขายที่สำคัญในใจของผู้บริโภค
เขาเชื่อว่า เมื่อวันนั้นมาถึง วันที่เรายืนอยู่หน้าตู้แช่ในซูเปอร์ แล้วเห็นผลิตภัณฑ์สองชิ้นวางข้างกัน — หนึ่งคือเนื้อวัวที่มาจากฟาร์ม และอีกหนึ่งคือเนื้อเพาะเลี้ยงที่ไม่เคยมีวัวต้องร้องไห้แม้แต่นิดเดียว — การตัดสินใจอาจจะไม่ง่าย แต่ "จะมีคนจำนวนมากขึ้นเรื่อยๆ ที่เลือกแบบไม่ต้องฆ่า"
เพราะสุดท้าย เราไม่ได้แค่กินเนื้อ… เรากำลังกิน “ความเชื่อ” ลงไปด้วย #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
ใครสนใจดูคลิปก็กดตรงนี้ได้ครับ https://youtu.be/1lI9AwxKfTY?si=6CDBUl2yGBoHWc-P
-
 @ 629c4a12:f822cc1a
2025-02-23 21:33:31
@ 629c4a12:f822cc1a
2025-02-23 21:33:31I’ve always been drawn to minimalism. There’s a certain peace that comes from stripping away the unnecessary, decluttering both physical and mental spaces. Yet, when it comes to finances, I’ve found myself tangled in complexity. As an ‘optimizer,’ I spend an inordinate amount of time thinking about investments, managing risk, and endlessly tinkering with my portfolio. This preoccupation contradicts the minimalist principles I try to live by.
It seems absurd to me that the financial world has become so complicated that we need money managers to simply preserve the value of our money. If investing is so intricate that the average person must hire professionals just to preserve (let alone grow) the value of their savings, then something is fundamentally wrong.
For the past five years, I’ve immersed myself in the history and mechanics of financial systems. The deeper I delved, the clearer it became: Bitcoin is a force of minimalism in an increasingly financialized and complex world.
The Clutter of Modern Finance
Our financial system has become bloated with complexity. The hyper-securitization of assets has created an environment filled with financial clutter. Derivatives, for example, represent layers upon layers of financial engineering, often so convoluted that even experts struggle to understand them fully.
More troubling is the way nearly everything of value has been financialized. Real estate and art, two things that should embody personal value and cultural significance, have been transformed into mere asset classes. They are bought, sold, and speculated upon not for their intrinsic qualities but as instruments in the game of wealth preservation.
But why has this happened? It’s actually quite simple: our money is constantly losing value. The dollar, for example, debases at a rate of around 7% per year. Holding cash feels like holding melting ice, so it’s only natural for people to seek out scarce assets to preserve their wealth. The Never-Ending Game of Diversification
This pursuit of scarce assets sets off a complex game—a game that forces people to diversify endlessly:
- Equities
- Bonds
- Real Estate
- Commodities
- Art
- Collectibles
We’re told to spread our investments across these asset classes to mitigate risk and preserve our hard-earned money. Those who can afford to hire money managers generally fare better in this game, as they have access to expertise and strategies designed to navigate this maze of complexity.
Ironically, this system creates an incentive for more complexity. The more convoluted the financial landscape becomes, the more we need money managers, and the more entrenched this cycle of financialization and securitization becomes. It’s a force of ever-increasing entropy—quite the opposite of minimalism.
Bitcoin: Simplicity in a Complex World
In the midst of this financial chaos, Bitcoin emerges as a beacon of simplicity. It offers a way out of the clutter, a chance to reclaim financial minimalism. Bitcoin embodies the concept of scarcity with a rare kind of perfection: there will only ever be 21 million Bitcoins. No more.
This scarcity makes Bitcoin the perfect savings technology. Unlike traditional currencies, no one can debase your holdings. You don’t need to chase after real estate, art, or other assets to preserve your wealth. You don’t need to constantly diversify and rebalance a portfolio to stay ahead of inflation. Bitcoin’s scarcity gives you a way to hold your wealth securely, without the need for endless tinkering.
I’m not blind to Bitcoin’s short-term price volatility. However, it’s crucial to understand that we’re still in the early stages of adoption. As more people embrace this perfect form of scarcity, Bitcoin’s qualities as savings technology will express itself.
Bitcoin has the potential to de-financialize the housing market. It can de-financialize art.
Ultimately, Bitcoin has the power to replace those aspects of our lives that currently serve as proxies for scarcity.
A Minimalist Approach to Wealth
Bitcoin allows us to step off the treadmill of constant financial optimization. It offers a simpler way to safeguard the fruits of our labor. Rather than spending our time, energy, and attention on navigating a complex financial system, we can focus on what truly matters: living a meaningful life.
By embracing Bitcoin, we embrace a minimalist approach to wealth. We reject the idea that we must play a never-ending game of diversification to maintain our standard of living. Instead, we adopt a simple, elegant solution that aligns with the principles of minimalism.
Conclusion
In a world that grows more financially cluttered by the day, Bitcoin stands as a path to financial minimalism. It frees us from the complexities of traditional finance, allowing us to preserve our wealth without the need for constant vigilance and management.
By embodying scarcity and simplicity, Bitcoin gives us a way to reclaim our time and energy. It’s not just a financial tool; it’s a way to simplify our lives, to step back from the chaos, and to focus on what truly matters
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 04c915da:3dfbecc9
2025-03-10 23:31:30
@ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:47:16
@ 04c915da:3dfbecc9
2025-05-20 15:47:16Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 3bf0c63f:aefa459d
2024-06-19 16:13:28
@ 3bf0c63f:aefa459d
2024-06-19 16:13:28Estórias
-
 @ 04c915da:3dfbecc9
2025-03-07 00:26:37
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 3bf0c63f:aefa459d
2024-06-13 15:40:18
@ 3bf0c63f:aefa459d
2024-06-13 15:40:18Why relay hints are important
Recently Coracle has removed support for following relay hints in Nostr event references.
Supposedly Coracle is now relying only on public key hints and
kind:10002events to determine where to fetch events from a user. That is a catastrophic idea that destroys much of Nostr's flexibility for no gain at all.- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
kind:1s -- now that cannot work because the person who created the post doesn't have the relays specific to those communities in their outbox list; - There is a discussion happening in a niche relay, for example, a relay that can only be accessed by the participants of a conference for the duration of that conference -- since that relay is not in anyone's public outbox list, it's impossible for anyone outside of the conference to ever refer to these events;
- Some big public relays, say, relay.damus.io, decide to nuke their databases or periodically delete old events, a user keeps using that big relay as their outbox because it is fast and reliable, but chooses to archive their old events in a dedicated archival relay, say, cellar.nostr.wine, while prudently not including that in their outbox list because that would make no sense -- now it is impossible for anyone to refer to old notes from this user even though they are publicly accessible in cellar.nostr.wine;
- There are topical relays that curate content relating to niche (non-microblogging) topics, say, cooking recipes, and users choose to publish their recipes to these relays only -- but now they can't refer to these relays in the external Nostr world of
kind:1s because these topical relays are not in their outbox lists. - Suppose a user wants to maintain two different identities under the same keypair, say, one identity only talks about soccer in English, while the other only talks about art history in French, and the user very prudently keeps two different
kind:10002events in two different sets of "indexer" relays (or does it in some better way of announcing different relay sets) -- now one of this user's audiences cannot ever see notes created by him with their other persona, one half of the content of this user will be inacessible to the other half and vice-versa. - If for any reason a relay does not want to accept events of a certain kind a user may publish to other relays, and it would all work fine if the user referenced that externally-published event from a normal event, but now that externally-published event is not reachable because the external relay is not in the user's outbox list.
- If someone, say, Alex Jones, is hard-banned everywhere and cannot event broadcast
kind:10002events to any of the commonly used index relays, that person will now appear as banned in most clients: in an ideal world in which clients followednprofileand other relay hints Alex Jones could still live a normal Nostr life: he would print business cards with hisnprofileinstead of annpuband clients would immediately know from what relay to fetch his posts. When other users shared his posts or replied to it, they would include a relay hint to his personal relay and others would be able to see and then start following him on that relay directly -- now Alex Jones's events cannot be read by anyone that doesn't already know his relay.
- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-28 12:37:30
@ 5d4b6c8d:8a1c1ee3
2025-05-28 12:37:30https://rumble.com/embed/v6rp3fh/?pub=4e023h
I know some of our stackers are follicly challenged, so I thought I'd pass along this video.
Have any of you tried topical onion juice for hair regrowth?
I'll eat more onion and rosemary and get more Sun, just to be safe.
https://stacker.news/items/991118
-
 @ a29cfc65:484fac9c
2025-05-28 10:30:32
@ a29cfc65:484fac9c
2025-05-28 10:30:32Deutschland ist eines der wenigen Länder mit einer gesetzlich verankerten ausnahmslosen Schulbesuchspflicht. Mit den Schulschließungen in der Corona-Zeit wurde das Gesetz jedoch faktisch plötzlich außer Kraft gesetzt. Alle mussten zu Hause lernen. Als die Schulen danach wieder offen waren, wurden die Kinder mit Maskenpflicht, Tests und Impfdruck gequält. Nicht selten traten bei den Schülern Krankheiten und psychische Störungen auf. Nicht wenige Eltern suchten im Gespräch mit dem Lehrerkollegium nach Lösungen für ihre Kinder. In den meisten Fällen war das nicht möglich. Die Lehrer waren auf die neue Ideologie und die Durchsetzung der Maßnahmen eingeschworen und hatten Angst. Einige Eltern haben ihre Kinder dann in eigener Verantwortung aus der Schule genommen und zu Hause selbst unterrichtet. An manchen Orten fanden sich Gemeinschaften, wo die Kinder in Gruppen lernten. Während viele Lerngemeinschaften nicht mehr existieren, hat die Familie von Katharina den Unterricht für ihre drei Kinder in Eigenregie etabliert. Inzwischen haben sie dafür sogar „den Segen“ von Familiengericht und Jugendamt.
Katharina und Johannes leben mit ihren drei Wunschkindern Aurelius (15), Benjamin (14) und Friedrich (10) in einem Vorort von Leipzig. Die Familie wohnte früher in der Stadt. In der Corona-Zeit haben sie sich mit dem Physiotherapie- & Seminarzentrum Curasanus eine Existenz auf dem Land aufgebaut und begehen diesen Sommer ihr 20-jähriges Praxis-Jubiläum. Katharina hat ihre Arbeit als Physiotherapeutin weitgehend aufgegeben, um sich als Mama und Lernbegleiterin ihren Kindern widmen zu können. Daneben bietet sie Vorträge und Workshops an, übernimmt einen großen Teil der Praxis-Organisation und ist Manager, Rezeptionistin und Vertriebler der eigenen Firma. Wir besuchten einen ihrer Lachyoga-Kurse. Dabei erlebten wir ihr Zusammenspiel mit den drei Kindern. Anschließend stellten wir Katharina unsere Fragen zum Freilernen.
Im unmittelbaren Umfeld wird die Familie bestaunt und geachtet. Sie haben sich bewusst für das Freilernen entschieden. Die Kinder wurden ohne Test nicht mehr in die Schule gelassen. Auch andere Zwangsmaßnahmen wie die Maske wollten die Eltern den Kindern ersparen. Besonders Benjamin hatte traumatische Erlebnisse. Seine Lehrerin schmiss mit dem Schlüssel nach den Schülern und wandte andere schwarze Pädagogik an. Er ging ständig mit Bauchschmerzen ins Bett. Ein weiterer Punkt ist die Masernimpfung. Die Kinder könnten zwar zur Schule gehen, aber die Eltern werden mit rechtlichen Maßnahmen und Zwangszahlungen belegt. Da Katharina in ihrer Praxis viele Erkrankungen als Folge der Masernimpfung beobachten konnte, lehnt sie die Pflichtimpfung ab. Die Eltern haben kein Vertrauen mehr in die staatliche Schulerziehung mit all dem Zwang und den Erpressungen. Als die Familie den Entschluss gefasst hatte, die Kinder nicht mehr in die Schule zu schicken, haben sie ihre Praxis vorübergehend geschlossen, ihr Haus verkauft und sind auf Reisen gegangen. Die beiden großen Kinder wurden von der Schule abgemeldet. Nach der Rückkehr haben sie dann mit einem neuen Leben auf dem Land begonnen.
Lernen ohne Schule: Wie geht das?
„Wissen ist Macht und eine Holschuld“, sagt uns Katharina. Das ist ihr Motto und motiviert auch die Kinder. Mit dem Unterricht zu Hause macht die Familie ihre eigene Studie und zeigt, dass Lernen auch anders geht als in der Schule. Die Eltern können viel besser auf jedes einzelne Kind eingehen. Johannes arbeitete früher als Straßenbauer. Er unterstützt die Jungs vor allem in Mathematik, Geometrie und Physik sowie bei handwerklichen Fertigkeiten. Katharinas Stärken liegen in Deutsch, Sprachen und Organisation. Unter den Patienten ihrer Praxis gibt es Lehrer, die ihnen helfen. Weitere Unterstützung kommt von Freunden und Bekannten. Bei bestimmten Projekten treffen sie auf andere Freilernerkinder. „Das Netzwerk wird immer größer, es wird immer schöner und interessanter“, sagt Katharina. Man geht mit vielen anderen einen gemeinsamen Weg, verlässt dabei eingetretene Pfade und erkundet neue Themenfelder wie Mediengestaltung, freie Energie, Elektrotherapie, meditatives und Improvisations-Zeichnen. „Ich sprudele vor Ideen. Sie kommen in mein Feld, und dann mache ich was draus“, sagt Katharina. Die Jungs sind in Wurzen im Ringelnatz-Literaturkreis. Dort schreiben sie Drehbuchgeschichten und haben einen Film produziert. Sie suchen sich Projekte oder kreieren neue, wie mit dem Planetarium Eilenburg. Diese Zusammenarbeit hat sich sehr gut entwickelt. Dort lernen 4- bis 15-Jährige zusammen. Die drei Jungs spielen Klavier. Erdkunde und Geschichte erleben die Kinder auch dadurch, dass die Familie Hauptstädte oder die bosnischen Pyramiden selbst erkundet. Dabei erweist es sich als Vorteil, nicht auf die Ferienzeiten angewiesen zu sein.
Als Physiotherapeutin ist Katharina bewusst, dass man neue Lernstrategien entwickeln muss. Die Kinder lernen unterschiedlich. Jedes Kind hat seinen eigenen Charakter. Aurelius benötigt eher eine 1:1-Betreuung. Darauf kann Katharina viel individueller eingehen als die staatliche Schule. Es ist aber auch aufwendiger und anstrengender. Besonderen Wert legt sie darauf, dass rechte und linke Gehirnhälfte gleichmäßig beansprucht werden. Lernphasen werden immer wieder mit Entspannungs- oder Bewegungsphasen kombiniert. Sie weiß, dass den Kindern zuerst die Grundlagen des Lesens, Rechnens und Schreibens vermittelt werden müssen. Dann sind sie in der Lage, sich alles Weitere selbst anzueignen – Unterstützung vorausgesetzt. „Besonders das Schreiben mit der eigenen Hand ist wichtig für die Vernetzung der beiden Gehirnhälften“, sagt Katharina. Dafür nehmen sich die Eltern Zeit. Die Kinder führen Tagebuch. Außerdem halten es die Eltern für wichtig, den Kindern Werte und Tugenden wie Dankbarkeit, Verlässlichkeit, Beharrlichkeit, Aufrichtigkeit, Ehrlichkeit und die zehn Gebote zu vermitteln. Katharina und Johannes sind beide religiös begleitet aufgewachsen. Heute sehen sie die Kirche als Institution kritisch. Angebunden an die Schöpfung und im Gottvertrauen erschaffen und schöpfen sie Leben und Lebensraum aus eigener Kraft – so erklärt es uns Katharina.
Ein weiteres Thema sind die Funktionen des Körpers und wie sich die Kinder gesund erhalten können. Vieles lernen sie dabei in der Physiotherapiepraxis. Die Familie hat das Privileg, in ihrem eigenen Biorhythmus leben zu können. „Das macht sehr viel aus – wir sind alle gesund“, sagt Katharina. Der Lern- und Arbeitstag beginnt nicht vor 9 Uhr und hat eine eigene Struktur. Im Tagesablauf sind feste Verantwortlichkeiten integriert. So wechseln sich die Kinder aller drei Tage mit Tischdecken, Staubsaugen und Geschirrspüler ab. Das hilft ihnen, sich selbst zu organisieren. Das geht nicht immer reibungslos vonstatten. Wenn das Lernpensum beizeiten abgearbeitet wurde, helfen die Kinder im Haushalt oder Garten oder gehen ihrem Bewegungsdrang auf andere Weise nach. Die Eltern sind am Abend noch länger aktiv, denn die Praxis erfordert noch die eine oder andere bürokratische Pflicht. Die Familie ist sehr naturverbunden. Sie gehen viel in den Wald und in den Garten. Sie bauen selbst Gemüse und Obst an. Dabei können die Kinder zum Beispiel Erfahrungen mit Permakultur und natürlicher Düngung sammeln. Die Familie achtet auf die Ernährung, schließlich ist Katharina seit fast 25 Jahren Ernährungsberaterin. Was sie nicht selbst anbauen, wird beim Bauern des Vertrauens eingekauft. Die Jungs können selbst kochen und backen. Die Schädlichkeit von Zucker ist den Kindern schon bewusst geworden, ohne gänzlich auf Schokolade verzichten zu müssen. Medikamente gibt es im Haushalt nicht. Sie kennen sich sehr gut mit den Heilmitteln aus der Natur aus und können so ihre Selbstheilungskräfte aktivieren. Sie haben keinen Hausarzt. Natürlich hat keines der Kinder ein Handy. Bisher haben sie noch kein Verlangen danach. Die Eltern halten es für wichtig, dass die Kinder erst sicher bei Selbstorganisation und Tagesstruktur sind, bevor sie ein Handy bekommen. Katharina weist darauf hin, dass beispielsweise WhatsApp erst ab 16 Jahren zugelassen ist, und fragt sich, ob das andere Eltern wissen.
Gesetze auf Augenhöhe auslegen
Den Behörden blieben die Freilerner nicht verborgen. Sie wurden aktiv und schalteten das Familiengericht ein. Die Familie hatte keinen Anwalt und keine Rechtsschutzversicherung. Katharina erzählt uns, dass sie schließlich auf „Hilfe von oben“ gehofft habe. Irgendwer hat sie anscheinend erhört, denn sie bekamen „einen Engel“ als Verfahrensbeistand. Die Behörden waren sehr zugänglich. In den Gesprächen gab man zu, mit der Schulsituation ebenfalls nicht zufrieden zu sein. „Wir wollen so wie ihr, dass sich etwas verändert. Wir sind an Eurer Seite.“ Die Gespräche mit dem Jugendamt und der Richterin vom Familiengericht Grimma waren immer auf Augenhöhe. Schließlich legte man der Familie keine Steine in den Weg. Damit kann Katharina ihr Konzept nach außen leben und andere inspirieren. Ihre Schlussfolgerung: Eltern müssen sich ihrer Stärken bewusst werden und aus ihrer Angst herauskommen. Das Konzept muss aber zur Familie passen, denn jede Familie ist anders.
Die Basis für freies Lernen ist das Vertrauen der Eltern in ihre Kinder. Denn Kinder sind von Natur aus wissbegierig und wollen lernen. Katharina hat viel von Bertrand Stern und von Riccardo Leppe gelernt. Beiden wurde von ihren Eltern das Lernen ohne Schulbesuch ermöglicht. Mit Bertrand Stern hat Katharina Kontakt. Er wird im November am Buß- und Bettag eine kleine Fortbildung im Therapie- und Seminarzentrum geben. Für den Vorabend ist ein Vortrag geplant. Katharina zitiert Riccardo Leppe: „Es ändert sich nur was, wenn man es selbst tut.“ Er sei sich sicher, dass der Fortschritt beim Freilernen inzwischen so weit ist, dass „die Paste nicht wieder zurück in die Tube geht“.
Der Übergang zur Berufsausbildung
Die ersten Freilernerkinder kommen jetzt in das Alter, in dem sie eine Berufsausbildung beginnen können. Aurelius und Benjamin, die beiden „Großen“, machen seit Anfang des Jahres schon erste Praktika bei ortsansässigen Handwerksbetrieben. Beide Seiten sind sehr zufrieden. Durch die Praktika, die länger dauern als im schulischen Lehrplan vorgesehen, können sich die Kinder ausprobieren. Katharina findet es interessant miterleben zu dürfen, wie auf ihre Kinder reagiert wird. Bringen sie etwas mit, das die anderen nicht haben? Denken sie anders mit? Benjamin bekam schon ein Angebot, in einem Metallbau-Betrieb stundenweise mitzuarbeiten. In den Betrieben weiß man, dass die Abschlüsse der staatlichen Schulen größtenteils das Papier nicht wert sind, auf dem sie stehen. Viele verlassen die Schule und können kaum lesen und schreiben, von Selbstorganisation ganz zu schweigen. Ein Freilerner kann eine staatliche Externen-Prüfung ablegen, um einen Haupt- oder Realschulabschluss zu erwerben. Katharina: „Für eine Ausbildung bei einem privaten Unternehmer braucht man das nicht, allein der Unternehmer entscheidet über die Aufnahme des Auszubildenden“. Außerdem stehen den jungen Leuten Privatschulen oder der zweite Bildungsweg zur Verfügung. Wenn man einen praktischen Beruf ergreift, ist es immer noch möglich, sich bis zur Hochschulreife weiterzubilden. Nach mehrjährigen Tätigkeiten kann man bei den Kammern von Industrie, Handel und Handwerk (IHK und HWK) eine Abschlussprüfung ablegen, mit der man zum Studium zugelassen werden kann. Oder man geht gleich den Weg in die Selbstständigkeit.
Frei lernen weitergedacht
Während der Coronazeit haben sich in Sachsen und speziell um Leipzig herum kleine Freilernergruppen gefunden. Die Gruppen werden aktuell zusammengeführt, um zum Beispiel gemeinsam den Mathematikunterricht zu gestalten. Besonders um Dresden herum ist die Szene noch stärker ausgeprägt. Außerdem gibt es seit mehr als 20 Jahren den Bundesverband Natürlich Lernen (BVNL). Er bietet Beratung und zentrale Veranstaltungen an.
Der Wunsch nach dem freien Lernen ohne Schulzwang ist groß. Doch die meisten Eltern wollen ihre Kinder dafür irgendwo abgeben und nicht selbst unterrichten. Katharinas größter Wunsch ist es, drei bis fünf Elternpaare zu finden, die sich in die Betreuung und Unterrichtung ihrer Kinder teilen. Das größte Hindernis dafür sieht sie in den Eltern selbst. Durch ungelöste transgenerative Konflikte und unverarbeitete Familientraumata kommen sie noch nicht in ihre eigene Kraft für ein selbstbestimmtes Leben. Viele wagen es noch nicht, ihre Erwerbstätigkeit zugunsten der Kinder einzuschränken. Katharina sieht es als große Aufgabe für sich und ihre Familie, mit dem Freilernen das Gemeinschaftsbewusstsein und gute Konfliktlösungsstrategien zu entwickeln. Sie denkt dabei bereits an ihre Enkel. Aber sie weiß auch, dass die Eltern ein sehr hohes Maß an Eigeninitiative, Motivation und Selbstdisziplin aufbringen müssen. Sie würde Eltern, die sich das noch nicht zutrauen, als Traumabegleiterin zur Verfügung stehen, für einen angemessenen Energieausgleich. Diese gegenseitige Unterstützung käme Kindern und Eltern zugute. Ebenso hält sie die Idee der Mehrgenerationenerziehung für wichtig. Dabei profitieren nicht nur die Kinder. Die Erfahrungen der älteren Menschen gehen nicht verloren, sondern werden an die jüngeren Generationen weitergegeben und machen sie resilienter. Das hilft den Eltern, ihrer Erwerbsarbeit nachzugehen und Familientraumata zu bewältigen.
Katharina ist eine starke Frau und sprüht nur so vor Energie. Selbst als wir nach 21 Uhr das Therapiezentrum verlassen, sind ihr die Anstrengungen des Tages nicht anzumerken. Sie wird nicht müde beim Sprechen. Für Fragen zum Thema Freilernen kann man sich an sie wenden.
Der Text wurde zuerst am 27.05.2025 im Blog „Freie Akademie für Medien und Journalismus“ veröffentlicht (https://www.freie-medienakademie.de/medien-plus/lernen-neu-gemacht)
Bildquelle: Salah Darwish, unsplash.com
-
 @ eb0157af:77ab6c55
2025-05-28 07:01:26
@ eb0157af:77ab6c55
2025-05-28 07:01:26Bitcoin surpasses gold in the United States: 50 million holders and a dominant role in the global market.
According to a new report by River, for the first time in history, the number of Americans owning bitcoin has surpassed that of gold holders. The analysis reveals that approximately 50 million U.S. citizens currently own the cryptocurrency, while gold owners number 37 million. In fact, 14.3% of Americans own bitcoin, the highest percentage of holders worldwide.

Source: River
The report highlights that 40% of all Bitcoin-focused companies are based in the United States, consolidating America’s dominant position in the sector. Additionally, 40.5% of Bitcoin holders are men aged 31 to 35, followed by 35.9% of men aged 41 to 45. In contrast, only 13.4% of holders are women.

Source: River
Notably, U.S. companies hold 94.8% of all bitcoins owned by publicly traded companies worldwide. According to the report, recent regulatory changes in the U.S. have made the asset more accessible through financial products such as spot ETFs.
The document also shows that American investors increasingly view the cryptocurrency as protection against fiscal instability and inflation, appreciating its limited supply and decentralized governance model.
For River, Bitcoin offers significant practical advantages over gold in the modern digital era. Its ease of custody, cross-border transfer, and liquidity make the cryptocurrency an attractive option for both individual and institutional investors, the report suggests.
The post USA: 50 million Americans own bitcoin appeared first on Atlas21.
-
 @ 9e69e420:d12360c2
2025-02-17 17:12:01
@ 9e69e420:d12360c2
2025-02-17 17:12:01President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February.
Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training.
Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further.
-
 @ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03
@ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ 866e0139:6a9334e5
2025-05-27 10:15:17
@ 866e0139:6a9334e5
2025-05-27 10:15:17Autor: Milosz Matuschek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie auch in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Der Schweizer Historiker Daniele Ganser startet eine Plakataktion. Auf Facebook schreibt er:
"Dieses Plakat habe ich ab heute an sechs Bahnhöfen in der Schweiz aufhängen lassen: Die Schweiz muss die Neutralität bewahren. Keine Zusammenarbeit mit der NATO!
Die Aktion läuft eine Woche. Das Plakat hängt in Basel (Gleis 5 und 7), Zürich (Gleis 9 und 12), Bern (Gleis 3 und 11), Luzern (Gleis 7 und 11), St. Gallen (Gleis 1 und 2) und Chur (Gleis 4 und Arosabahn).
Wenn jemand ein Plakat sieht und fotografiert und es mir per Email schickt freut mich das!
https://globalbridge.ch/die-schweiz-muss-die.../
Daniele Ganser kann man über folgende Seite kontaktieren.
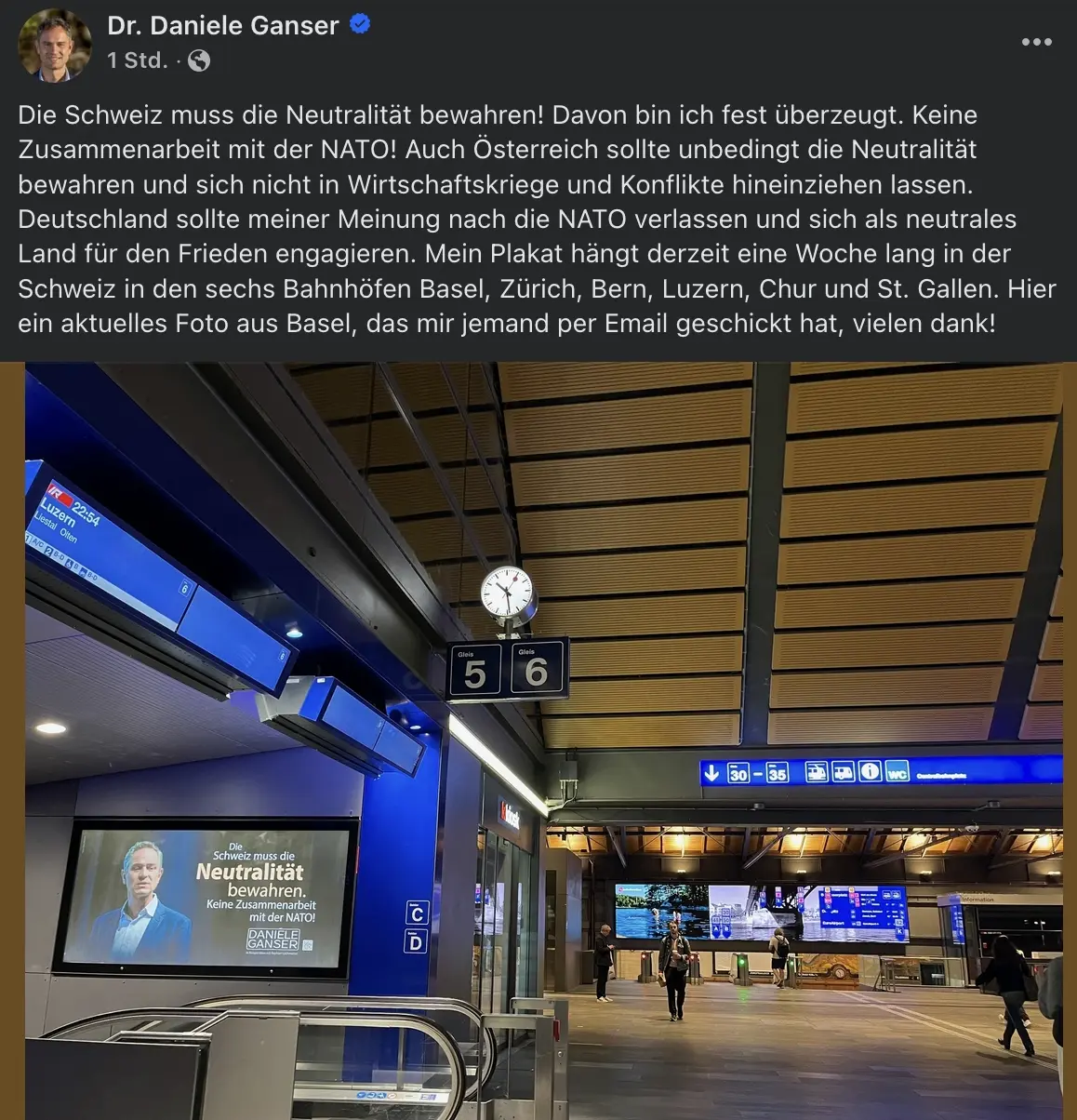
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ d360efec:14907b5f
2025-05-27 15:46:26
@ d360efec:14907b5f
2025-05-27 15:46:26 -
 @ b83a28b7:35919450
2025-05-16 19:23:58
@ b83a28b7:35919450
2025-05-16 19:23:58This article was originally part of the sermon of Plebchain Radio Episode 110 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ fd208ee8:0fd927c1
2025-02-15 07:02:08
@ fd208ee8:0fd927c1
2025-02-15 07:02:08E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md
-
 @ c9badfea:610f861a
2025-05-24 12:55:17
@ c9badfea:610f861a
2025-05-24 12:55:17Before you post a message or article online, let the LLM check if you are leaking any personal information using this prompt:
Analyze the following text to identify any Personally Identifiable Information (PII): <Your Message>Replace
<Your Message>with your textIf no PII is found, continue by modifying your message to detach it from your personality. You can use any of the following prompts (and further modify it if necessary).
Prompt № 1 - Reddit-Style
Convert the message into a casual, Reddit-style post without losing meaning. Split the message into shorter statements with the same overall meaning. Here is the message: <Your Message>Prompt № 2 - Advanced Modifications
``` Apply the following modifications to the message: - Rewrite it in lowercase - Use "u" instead of "you" - Use "akchoaly" instead of "actually" - Use "hav" instead of "have" - Use "tgat" instead of "that" - Use comma instead of period - Use British English grammar
Here is the message:
``` Prompt № 3 - Neutral Tone
Rewrite the message to correct grammar errors, and ensure the tone is neutral and free of emotional language: <Your Message>Prompt № 4 - Cross Translation Technique
Translate the message into Chinese, then translate the resulting Chinese text back into English. Provide only the final English translation. Here is the message: <Your Message>Check the modified message and send it.
ℹ️ You can use dialects to obfuscate your language further. For example, if you are from the US, you can tell the LLM to use British grammar and vice versa.
⚠️ Always verify the results. Don't fully trust an LLM.
-
 @ 3bf0c63f:aefa459d
2024-05-24 12:31:40
@ 3bf0c63f:aefa459d
2024-05-24 12:31:40About Nostr, email and subscriptions
I check my emails like once or twice a week, always when I am looking for something specific in there.
Then I go there and I see a bunch of other stuff I had no idea I was missing. Even many things I wish I had seen before actually. And sometimes people just expect and assume I would have checked emails instantly as they arrived.
It's so weird because I'm not making a point, I just don't remember to open the damn "gmail.com" URL.
I remember some people were making some a Nostr service a while ago that sent a DM to people with Nostr articles inside -- or some other forms of "subscription services on Nostr". It makes no sense at all.
Pulling in DMs from relays is exactly the same process (actually slightly more convoluted) than pulling normal public events, so why would a service assume that "sending a DM" was more likely to reach the target subscriber when the target had explicitly subscribed to that topic or writer?
Maybe due to how some specific clients work that is true, but fundamentally it is a very broken assumption that comes from some fantastic past era in which emails were 100% always seen and there was no way for anyone to subscribe to someone else's posts.
Building around such broken assumptions is the wrong approach. Instead we should be building new flows for subscribing to specific content from specific Nostr-native sources (creators directly or manual or automated curation providers, communities, relays etc), which is essentially what most clients are already doing anyway, but specifically Coracle's new custom feeds come to mind now.
This also reminds me of the interviewer asking the Farcaster creator if Farcaster made "email addresses available to content creators" completely ignoring all the cryptography and nature of the protocol (Farcaster is shit, but at least they tried, and in this example you could imagine the interviewer asking the same thing about Nostr).
I imagine that if the interviewer had asked these people who were working (or suggesting) the Nostr DM subscription flow they would have answered: "no, you don't get their email addresses, but you can send them uncensorable DMs!" -- and that, again, is getting everything backwards.
-
 @ 04c915da:3dfbecc9
2025-03-04 17:00:18
@ 04c915da:3dfbecc9
2025-03-04 17:00:18This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:53
@ 39cc53c9:27168656
2025-05-27 09:21:53The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 04c915da:3dfbecc9
2025-02-25 03:55:08
@ 04c915da:3dfbecc9
2025-02-25 03:55:08Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-23 13:46:21
@ 5d4b6c8d:8a1c1ee3
2025-05-23 13:46:21You'd think I'd be most excited to talk about that awesome Pacers game, but, no. What I'm most excited about this week is that @grayruby wants to continue Beefing with Cowherd.
Still, I am excited to talk about Tyrese Haliburton becoming a legendary Knicks antagonist. Unfortunately, the Western Conference Finals are not as exciting. Also, why was the MVP announcement so dumb?
The T20k cricket contest is tightening up, as we head towards the finish. Can @Coinsreporter hold on to his vanishing lead?
@Carresan has launched Football Madness. Let's see if we understand whatever the hell this is any better than we did last week.
On this week's Blok'd Shots, we'll ridicule Canada for their disgraceful loss in the World Championships and talk about the very dominant American Florida Panthers, who are favorites to win the Stanley Cup.
Are the Colorado the worst team in MLB history?
The Tush Push has survived another season. Will the NFL eventually ban it or will teams adjust?
Plus, whatever else Stackers want to talk about.
https://stacker.news/items/987399
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ 6e0ea5d6:0327f353
2025-02-21 18:15:52
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ 97c70a44:ad98e322
2025-02-03 22:25:35
@ 97c70a44:ad98e322
2025-02-03 22:25:35Last week, in a bid to understand the LLM hype, I decided to write a trivial nostr-related program in rust via a combination of codebuff (yes, that is a referral link, pls click), aider, and goose.
The result of the experiment was inconclusive, but as a side effect it produced a great case study in converting a NINO into a Real Nostr App.
Introducing Roz
Roz, a friendly notary for nostr events.
To use it, simply publish an event to
relay.damus.ioornos.lol, and roz will make note of it. To find out when roz first saw a given event, just ask:curl https://roz.coracle.social/notary/cb429632ae22557d677a11149b2d0ccd72a1cf66ac55da30e3534ed1a492765dThis will return a JSON payload with a
seenkey indicating when roz first saw the event. How (and whether) you use this is up to you!De-NINO-fying roz
Roz is just a proof of concept, so don't rely on it being there forever. And anyway, roz is a NINO, since it provides value to nostr (potentially), but doesn't really do things in a nostr-native way. It also hard-codes its relays, and certainly doesn't use the outbox model or sign events. But that's ok, it's a proof of concept.
A much better way to do this would be to modify roz to properly leverage nostr's capabilities, namely:
- Use nostr-native data formats (i.e., draft a new kind)
- Use relays instead of proprietary servers for data storage
- Leverage nostr identities and signatures to decouple trust from storage, and allow trusted attestations to be discovered
Luckily, this is not hard at all. In fact, I've gone ahead and drafted a PR to the NIPs repo that adds timestamp annotations to NIP 03, as an alternative to OpenTimestamps. The trade-off is that while user attestations are far less reliable than OTS proofs, they're much easier to verify, and can reach a pretty high level of reliability by combining multiple attestation sources with other forms of reputation.
In other words, instead of going nuclear and embedding your attestations into The Time Chain, you can simply ask 5-10 relays or people you trust for their attestations for a given event.
This PR isn't terribly important on its own, but it does remove one small barrier between us and trusted key rotation events (or other types of event that require establishing a verifiable chain of causality).
-
 @ 58537364:705b4b85
2025-05-28 08:25:55
@ 58537364:705b4b85
2025-05-28 08:25:55ถ้าอยากแล้วไม่หลง มันก็อยากด้วยปัญญา ความอยากอย่างนี้ท่านเรียกว่า เป็นบารมีของตน แต่ไม่ใช่ทุกคนนะที่มีปัญญา
บางคนไม่อยากจะให้มันอยาก เพราะเข้าใจว่า การมาปฏิบัติก็เพื่อระงับความอยาก ความจริงน่ะ ถ้าหากว่าไม่มีความอยาก ก็ไม่มีข้อปฏิบัติ ไม่รู้ว่าจะทำอะไร ลองพิจารณาดูก็ได้
ทุกคน แม้องค์พระพุทธเจ้าของเราก็ตาม ที่ท่านออกมาปฏิบัติ ก็เพื่อจะให้บรรเทากิเลสทั้งหลายนั้น
แต่ว่ามันต้องอยากทำ อยากปฏิบัติ อยากให้มันสงบ และก็ไม่อยากให้มันวุ่นวาย ทั้งสองอย่างนี้ มันเป็นอุปสรรคทั้งนั้น ถ้าเราไม่มีปัญญา ไม่มีความฉลาดในการกระทำอย่างนั้น เพราะว่ามันปนกันอยู่ อยากทั้งสองอย่างนี้มันมีราคาเท่า ๆ กัน
อยากจะพ้นทุกข์มันเป็นกิเลส สำหรับคนไม่มีปัญญา อยากด้วยความโง่ ไม่อยากมันก็เป็นกิเลส เพราะไม่อยากอันนั้นมันประกอบด้วยความโง่เหมือนกัน คือทั้งอยาก ไม่อยาก ปัญญาก็ไม่มี ทั้งสองอย่างนี้ มันเป็นกามสุขัลลิกานุโยโค กับอัตตกิลมถานุโยโค ซึ่งพระพุทธองค์ของเรา ขณะที่พระองค์กำลังทรงปฏิบัติอยู่นั้น ท่านก็หลงใหลในอย่างนี้ ไม่รู้ว่าจะทำอย่างไร ท่านหาอุบายหลายประการ กว่าจะพบของสองสิ่งนี้
ทุกวันนี้เราทั้งหลายก็เหมือนกัน ทุกสิ่งทั้งสองอย่างนี้มันกวนอยู่ เราจึงเข้าสู่ทางไม่ได้ก็เพราะอันนี้ ความเป็นจริงนี้ทุกคนที่มาปฏิบัติ ก็เป็นปุถุชนมาทั้งนั้น ปุถุชนก็เต็มไปด้วยความอยาก ความอยากที่ไม่มีปัญญา อยากด้วยความหลง ไม่อยากมันก็มีโทษเหมือนกัน “ไม่อยาก” มันก็เป็นตัณหา “อยาก” มันก็เป็นตัณหาอีกเหมือนกัน
ทีนี้ นักปฏิบัติยังไม่รู้เรื่องว่า จะเอายังไงกัน เดินไปข้างหน้าก็ไม่ถูก เดินกลับไปข้างหลังก็ไม่ถูก จะหยุดก็หยุดไม่ได้เพราะมันยังอยากอยู่ มันยังหลงอยู่ มีแต่ความอยาก แต่ปัญญาไม่มี มันอยากด้วยความหลง มันก็เป็นตัณหา ถึงแม้ไม่อยาก มันก็เป็นความหลง มันก็เป็นตัณหาเหมือนกันเพราะอะไร? เพราะมันขาดปัญญา
ความเป็นจริงนั้น ธรรมะมันอยู่ตรงนั้นแหละ ตรงความอยากกับความไม่อยากนั่นแหละ แต่เราไม่มีปัญญา ก็พยายามไม่ให้อยากบ้าง เดี๋ยวก็อยากบ้าง อยากให้เป็นอย่างนั้น ไม่อยากให้เป็นอย่างนี้ ความจริงทั้งสองอย่างนี้ หรือทั้งคู่นี้มันตัวเดียวกันทั้งนั้น ไม่ใช่คนละตัว แต่เราไม่รู้เรื่องของมัน
พระพุทธเจ้าของเรา และสาวกทั้งหลายของพระองค์นั้นท่านก็อยากเหมือนกัน แต่ “อยาก” ของท่านนั้น เป็นเพียงอาการของจิตเฉย ๆ หรือ “ไม่อยาก” ของท่าน ก็เป็นเพียงอาการของจิตเฉย ๆ อีกเหมือนกัน มันวูบเดียวเท่านั้น ก็หายไปแล้ว
ดังนั้น ความอยากหรือไม่อยากนี้ มันมีอยู่ตลอดเวลาแต่สำหรับผู้มีปัญญานั้น “อยาก” ก็ไม่มีอุปาทาน “ไม่อยาก” ก็ไม่มีอุปาทาน เป็น “สักแต่ว่า” อยากหรือไม่อยากเท่านั้น ถ้าพูดตามความจริงแล้ว มันก็เป็นแต่ "อาการของจิต" อาการของจิตมันเป็นของมันอย่างนั้นเอง ถ้าเรามาตะครุบมันอยู่ใกล้ ๆ นี่มันก็เห็นชัด
ดังนั้นจึงว่า การพิจารณานั้น ไม่ใช่รู้ไปที่อื่น มันรู้ตรงนี้แหละ เหมือนชาวประมงที่ออกไปทอดแหนั่นแหละ ทอดแหออกไปถูกปลาตัวใหญ่ เจ้าของผู้ทอดแหจะคิดอย่างไร? ก็กลัว กลัวปลาจะออกจากแหไปเสีย เมื่อเป็นเช่นนั้น ใจมันก็ดิ้นรนขึ้นระวังมาก บังคับมาก ตะครุบไปตะครุบมาอยู่นั่นแหละ ประเดี๋ยวปลามันก็ออกจากแหไปเสีย เพราะไปตะครุบมันแรงเกินไป
อย่างนั้นโบราณท่านพูดถึงเรื่องอันนี้ ท่านว่าค่อย ๆ ทำมัน แต่อย่าไปห่างจากมัน นี่คือปฏิปทาของเรา ค่อย ๆ คลำมันไปเรื่อย ๆ อย่างนั้นแหละ
อย่าปล่อยมัน หรือไม่อยากรู้มัน ต้องรู้ ต้องรู้เรื่องของมัน พยายามทำมันไปเรื่อย ๆ ให้เป็นปฏิปทา ขี้เกียจเราก็ทำไม่ขี้เกียจเราก็ทำ เรียกว่าการทำการปฏิบัติ ต้องทำไปเรื่อยๆอย่างนี้
ถ้าหากว่าเราขยัน ขยันเพราะความเชื่อ มันมีศรัทธาแต่ปัญญาไม่มี ถ้าเป็นอย่างนี้ ขยันไป ๆ แล้วมันก็ไม่เกิดผลอะไรขึ้นมากมาย ขยันไปนาน ๆ เข้า แต่มันไม่ถูกทาง มันก็ไม่สงบระงับ ทีนี้ก็จะเกิดความคิดว่า เรานี้บุญน้อยหรือวาสนาน้อย หรือคิดไปว่ามนุษย์ในโลกนี้คงทำไม่ได้หรอก แล้วก็เลยหยุดเลิกทำเลิกปฏิบัติ
ถ้าเกิดความคิดอย่างนี้เมื่อใด ขอให้ระวังให้มาก ให้มีขันติ ความอดทน ให้ทำไปเรื่อย ๆ เหมือนกับเราจับปลาตัวใหญ่ ก็ให้ค่อย ๆ คลำมันไปเรื่อย ๆ ปลามันก็จะไม่ดิ้นแรงค่อย ๆทำไปเรื่อย ๆ ไม่หยุด ไม่ช้าปลาก็จะหมดกำลัง มันก็จับง่าย จับให้ถนัดมือเลย ถ้าเรารีบจนเกินไป ปลามันก็จะหนีดิ้นออกจากแหเท่านั้น
ดังนั้น การปฏิบัตินี้ ถ้าเราพิจารณาตามพื้นเหตุของเรา เช่นว่า เราไม่มีความรู้ในปริยัติ ไม่มีความรู้ในอะไรอื่น ที่จะให้การปฏิบัติมันเกิดผลขึ้น ก็ดูความรู้ที่เป็นพื้นเพเดิมของเรานั่นแหละอันนั้นก็คือ “ธรรมชาติของจิต” นี่เอง มันมีของมันอยู่แล้ว เราจะไปเรียนรู้มัน มันก็มีอยู่ หรือเราจะไม่ไปเรียนรู้มัน มันก็มีอยู่
อย่างที่ท่านพูดว่า พระพุทธเจ้าจะบังเกิดขึ้นก็ตาม หรือไม่บังเกิดขึ้นก็ตาม ธรรมะก็คงมีอยู่อย่างนั้น มันเป็นของมันอยู่อย่างนั้น ไม่พลิกแพลงไปไหน มันเป็นสัจจธรรม
เราไม่เข้าใจสัจจธรรม ก็ไม่รู้ว่าสัจจธรรมเป็นอย่างไร นี้เรียกว่า การพิจารณาในความรู้ของผู้ปฏิบัติที่ไม่มีพื้นปริยัติ
ขอให้ดูจิต พยายามอ่านจิตของเจ้าของ พยายามพูดกับจิตของเจ้าของ มันจึงจะรู้เรื่องของจิต ค่อย ๆ ทำไป ถ้ายังไม่ถึงที่ของมัน มันก็ไปอยู่อย่างนั้น
ครูบาอาจารย์บางท่านบอกว่า ทำไปเรื่อย ๆ อย่าหยุด บางทีเรามาคิด “เออ ทำไปเรื่อย ๆ ถ้าไม่รู้เรื่องของมัน ถ้าทำไม่ถูกที่มัน มันจะรู้อะไร” อย่างนี้เป็นต้น ก็ต้องไปเรื่อย ๆ ก่อน แล้วมันก็จะเกิดความรู้สึกนึกคิดขึ้นในสิ่งที่เราพากเพียรทำนั้น
มันเหมือนกันกับบุรุษที่ไปสีไฟ ได้ฟังท่านบอกว่า เอาไม้ไผ่สองอันมาสีกันเข้าไปเถอะ แล้วจะมีไฟเกิดขึ้น บุรุษนั้นก็จับไม้ไผ่เข้าสองอัน สีกันเข้า แต่ใจร้อน สีไปได้หน่อย ก็อยากให้มันเป็นไฟ ใจก็เร่งอยู่เรื่อย ให้เป็นไฟเร็วๆ แต่ไฟก็ไม่เกิดสักที บุรุษนั้นก็เกิดความขี้เกียจ แล้วก็หยุดพัก แล้วจึงลองสีอีกนิด แล้วก็หยุดพัก ความร้อนที่พอมีอยู่บ้าง ก็หายไปล่ะซิ เพราะความร้อนมันไม่ติดต่อกัน
ถ้าทำไปเรื่อยๆอย่างนี้ เหนื่อยก็หยุด มีแต่เหนื่อยอย่างเดียวก็พอได้ แต่มีขี้เกียจปนเข้าด้วย เลยไปกันใหญ่ แล้วบุรุษนั้นก็หาว่าไฟไม่มี ไม่เอาไฟ ก็ทิ้ง เลิก ไม่สีอีก แล้วก็ไปเที่ยวประกาศว่า ไฟไม่มี ทำอย่างนี้ไม่ได้ ไม่มีไฟหรอก เขาได้ลองทำแล้ว
ก็จริงเหมือนกันที่ได้ทำแล้ว แต่ทำยังไม่ถึงจุดของมันคือความร้อนยังไม่สมดุลกัน ไฟมันก็เกิดขึ้นไม่ได้ ทั้งที่ความจริงไฟมันก็มีอยู่ อย่างนี้ก็เกิดความท้อแท้ขึ้นในใจของผู้ปฏิบัตินั้น ก็ละอันนี้ไปทำอันโน้นเรื่อยไป อันนี้ฉันใดก็ฉันนั้น
การปฏิบัตินั้น ปฏิบัติทางกายทางใจทั้งสองอย่าง มันต้องพร้อมกัน เพราะอะไร? เพราะพื้นเพมันเป็นคนมีกิเลสทั้งนั้น พระพุทธเจ้าก่อนที่จะเป็นพระพุทธเจ้า ท่านก็มีกิเลสแต่ท่านมีปัญญามากหลาย พระอรหันต์ก็เหมือนกัน เมื่อยังเป็นปุถุชนอยู่ ก็เหมือนกับเรา
เมื่อความอยากเกิดขึ้นมา เราก็ไม่รู้จัก เมื่อความไม่อยากเกิดขึ้นมา เราก็ไม่รู้จัก บางทีก็ร้อนใจ บางทีก็ดีใจ ถ้าใจเราไม่อยาก ก็ดีใจแบบหนึ่ง และวุ่นวายอีกแบบหนึ่ง ถ้าใจเราอยาก มันก็วุ่นวายอย่างหนึ่ง และดีใจอย่างหนึ่ง มันประสมประเสกันอยู่อย่างนี้
อันนี้คือปฏิปทาของผู้ปฏิบัติเรา
[อ่านใจธรรมชาติ] หลวงปู่ชา สุภัทโท หนังสือ หมวด: โพธิญาณ

-
 @ 0fa80bd3:ea7325de
2025-01-29 05:55:02
@ 0fa80bd3:ea7325de
2025-01-29 05:55:02The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future.
Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs.
There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won.
Our only resource is the will of the people to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root.
So I started asking myself: How do we stop this fragmentation? How do we create a space where people can rebuild their connections when they’re ready? How do we build a self-sustaining network, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—how do we make it spread, even in occupied territory?
In 2009, something historic happened: the internet got its own money. Thanks to Satoshi Nakamoto, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize.
That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became purely digital.
The internet was already a sanctuary for information, a place where people could connect and organize. But with Bitcoin, it evolved. Now, value itself could flow freely, beyond the reach of authorities.
Think about it: when seedlings are grown in controlled environments before being planted outside, they get stronger, survive longer, and bear fruit faster. That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild.
Now, picture the internet as that controlled environment for ideas. Bitcoin? It’s the fertile soil that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless. It can absorb any number of ideas, any number of people, and it doesn’t run out of space.
But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—without surveillance, without censorship, without the constant fear of being erased.
This is where Nostr comes in.
Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. It’s a new kind of city. One that no dictator can seize, no corporation can own, no government can shut down.
It’s built on decentralization, encryption, and individual control. Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them.
In a world where cities fall and governments fail, Nostr is a city that cannot be occupied. A place for ideas, for networks, for freedom. A city that grows stronger the more people build within it.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ ece127e2:745bab9c
2025-05-29 00:32:33
@ ece127e2:745bab9c
2025-05-29 00:32:33vamos a ver que tal
*lo bueno es que si entro en https://makimono.lumilumi.app/ a la nota y agrego contenido , como éste ...quiero ver si lo añade o hace una nueva nota ?? *
-
 @ 39cc53c9:27168656
2025-05-27 09:21:51
@ 39cc53c9:27168656
2025-05-27 09:21:51Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-28 01:29:24
@ 5d4b6c8d:8a1c1ee3
2025-05-28 01:29:24I finished my Workit step challenge today, but still ate too many snacks and kept eating too late into the evening. I also was just more active in general: chores, errands, playing with the kid and dog, etc.
How did you all do today?
https://stacker.news/items/990849
-
 @ ecda4328:1278f072
2025-05-21 11:44:17
@ ecda4328:1278f072
2025-05-21 11:44:17An honest response to objections — and an answer to the most important question: why does any of this matter?
Last updated: May 21, 2025\ \ 📄 Document version:\ EN: https://drive.proton.me/urls/A4A8Y8A0RR#Sj2OBsBYJFr1\ RU: https://drive.proton.me/urls/GS9AS1NB30#ZdKKb5ackB5e
\ Statement: Deflation is not the enemy, but a natural state in an age of technological progress.\ Criticism: in real macroeconomics, long-term deflation is linked to depressions.\ Deflation discourages borrowers and investors, and makes debt heavier.\ Natural ≠ Safe.
1. “Deflation → Depression, Debt → Heavier”
This is true in a debt-based system. Yes, in a fiat economy, debt balloons to the sky, and without inflation it collapses.
But Bitcoin offers not “deflation for its own sake,” but an environment where you don’t need to be in debt to survive. Where savings don’t melt away.\ Jeff Booth said it clearly:
“Technology is inherently deflationary. Fighting deflation with the printing press is fighting progress.”
You don’t have to take on credit to live in this system. Which means — deflation is not an enemy, but an ally.
💡 People often confuse two concepts:
-
That deflation doesn’t work in an economy built on credit and leverage — that’s true.
-
That deflation itself is bad — that’s a myth.
📉 In reality, deflation is the natural state of a free market when technology makes everything cheaper.
Historical example:\ In the U.S., from the Civil War to the early 1900s, the economy experienced gentle deflation — alongside economic growth, employment expansion, and industrial boom.\ Prices fell: for example, a sack of flour cost \~$1.00 in 1865 and \~$0.50 in 1895 — and there was no crisis, because wages held and productivity increased.
Modern example:\ Consumer electronics over the past 20–30 years are a vivid example of technological deflation:\ – What cost $5,000 in 2000 (e.g., a 720p plasma TV) now costs $300 and delivers 10× better quality.\ – Phones, computers, cameras — all became far more powerful and cheaper at the same time.\ That’s how tech-driven deflation works: you get more for less.
📌 Bitcoin doesn’t make the world deflationary. It just doesn’t fight against deflation, unlike the fiat model that fights to preserve its debt pyramid.\ It stops punishing savers and rewards long-term thinkers.
Even economists often confuse organic tech deflation with crisis-driven (debt) deflation.
\ \ Statement: We’ve never lived in a truly free market — central banks and issuance always existed.\ Criticism: ideological statement.\ A truly “free” market is utopian.\ Banks and monetary issuance emerged in response to crises.\ A market without arbiters is not always fair, especially under imperfect competition.
2. “The Free Market Is a Utopia”
Yes, “pure markets” are rare. But what we have today isn’t regulation — it’s centralized power in the hands of central banks and cartels.
Bitcoin offers rules without rulers. 21 million. No one can change the issuance. It’s not ideology — it’s code instead of trust. And it has worked for 15 years.
💬 People often say that banks and centralized issuance emerged as a response to crises — as if the market couldn’t manage on its own.\ But if a system needs to be “rescued” again and again through money printing… maybe the problem isn’t freedom, but the system itself?
📌 Crises don’t disprove the value of free markets. They only reveal how fragile a system becomes when the price of money is set not by the market, but by a boardroom vote.\ Bitcoin doesn’t magically eliminate crises — it removes the root cause: the ability to manipulate money in someone’s interest.
\ \ Statement: Inflation is an invisible tax, especially on the poor and working class.\ Criticism: partly true: inflation can reduce debt burden, boost employment.\ The state indexes social benefits. Under stable inflation, compensators can work. Under deflation, things might be worse (mass layoffs, defaults).
3. “Inflation Can Help”
Theoretically — yes. Textbooks say moderate inflation can reduce debt burdens and stimulate consumption and jobs.\ But in practice — it works as a stealth tax, especially on those without assets. The wealthy escape — into real estate, stocks, funds.\ But the poor and working class lose purchasing power because their money is held in cash — and cash devalues.
💬 As Lyn Alden says:
“When your money can’t hold value, you’re forced to become an investor — even if you just want to save and live.”
The state may index pensions or benefits — but always with a lag, and always less than actual price increases.\ If bread rises 15% and your payment increase is 5%, you got poorer, even if the number on paper went up.
💥 We live in an inflationary system of everything:\ – Inflationary money\ – Inflationary products\ – Inflationary content\ – And now even inflationary minds
🧠 This is more than just rising prices — it’s a degradation of reality perception. You’re always rushing, everything loses meaning.\ But when did the system start working against you?
📉 What went wrong after 1971?
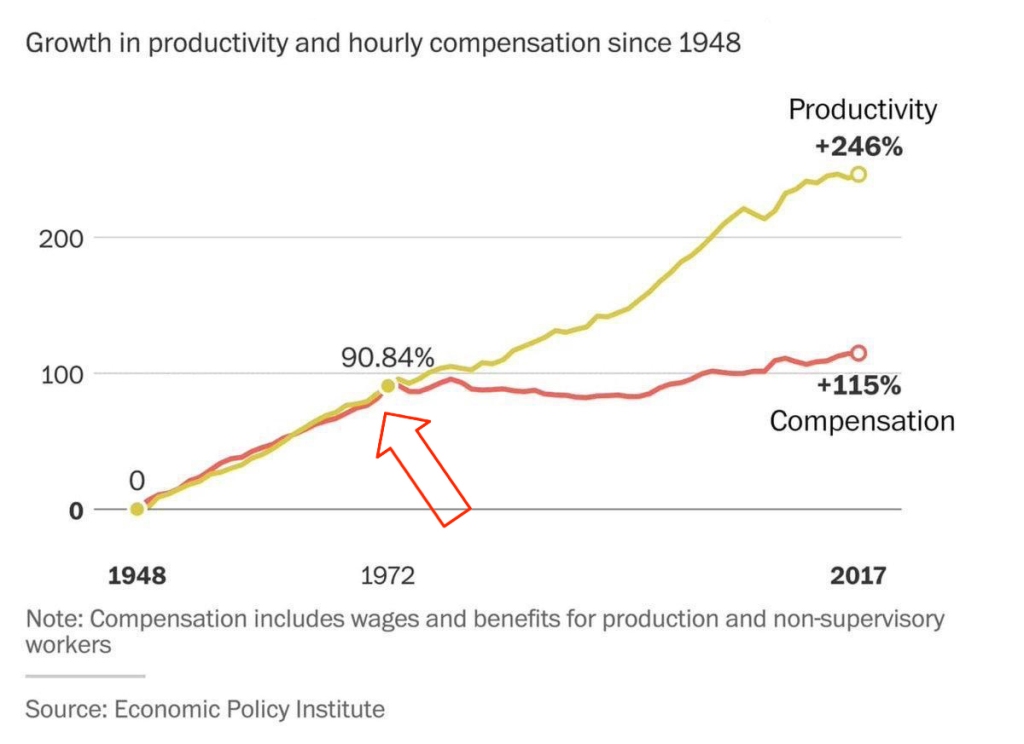 This chart shows that from 1948 to the early 1970s, productivity and wages grew together.\
But after the end of the gold standard in 1971 — the connection broke. Productivity kept rising, but real wages stalled.
This chart shows that from 1948 to the early 1970s, productivity and wages grew together.\
But after the end of the gold standard in 1971 — the connection broke. Productivity kept rising, but real wages stalled.👉 This means: you work more, better, faster — but buy less.
🔗 Source: wtfhappenedin1971.com
When you must spend today because tomorrow it’ll be worth less — that’s rewarding impulse and punishing long-term thinking.
Bitcoin offers a different environment:\ – Savings work\ – Long-term thinking is rewarded\ – The price of the future is calculated, not forced by a printing press
📌 Inflation can be a tool. But in government hands, it became a weapon — a slow, inevitable upward redistribution of wealth.
\ \ Statement: War is not growth, but a reallocation of resources into destruction.
Criticism: war can spur technological leaps (Internet, GPS, nuclear energy — all from military programs). "Military Keynesianism" was a real model.
4. “War Drives R&D”
Yes, wars sometimes give rise to tech spin-offs: Internet, GPS, nuclear power — all originated from military programs.
But that doesn’t make war a source of progress — it makes tech a byproduct of catastrophe.
“War reallocates resources toward destruction — not growth.”
Progress doesn’t happen because of war — it happens despite it.
If scientific breakthroughs require a million dead and burnt cities — maybe you’ve built your economy wrong.
💬 Even Michael Saylor said:
“If you need war to develop technology — you’ve built civilization wrong.”
No innovation justifies diverting human labor, minds, and resources toward destruction.\ War is always the opposite of efficiency — more is wasted than created.
🧠 Bitcoin, on the other hand, is an example of how real R&D happens without violence.\ No taxes. No army. Just math, voluntary participation, and open-source code.
📌 Military Keynesianism is not a model of progress — it’s a symptom of a sick monetary system that needs destruction to reboot.
Bitcoin shows that coordination without violence is possible.\ This is R&D of a new kind: based not on destruction, but digital creation.
Statement: Bitcoin isn’t “Gold 1.0,” but an improved version: divisible, verifiable, unseizable.
Criticism: Bitcoin has no physical value; "unseizability" is a theory;\ Gold is material and autonomous.
5. “Bitcoin Has No Physical Value”
And gold does? Just because it shines?
Physical form is no guarantee of value.\ Real value lies in: scarcity, reliable transfer, verifiability, and non-confiscatability.
Gold is:\ – Hard to divide\ – Hard to verify\ – Expensive to store\ – Easy to seize
💡 Bitcoin is the first store of value in history that is fully free from physical limitations, and yet:\ – Absolutely scarce (21M, forever)\ – Instantly transferable over the Internet\ – Cryptographically verifiable\ – Controlled by no government
🔑 Bitcoin’s value lies in its liberation from the physical.\ It doesn’t need to be “backed” by gold or oil. It’s backed by energy, mathematics, and ongoing verification.
“Price is what you pay, value is what you get.” — Warren Buffett
When you buy bitcoin, you’re not paying for a “token” — you’re gaining access to a network of distributed financial energy.
⚡️ What are you really getting when you own bitcoin?\ – A key to a digital asset that can’t be faked\ – The ability to send “crystallized energy” anywhere on Earth (it takes 10 minutes on the base L1 layer, or instantly via the Lightning Network)\ – A role in a new accounting system that runs 24/7/365\ – Freedom: from banks, borders, inflation, and force
📉 Bitcoin doesn’t require physical value — because it creates value:\ Through trust, scarcity, and energy invested in mining.\ And unlike gold, it was never associated with slavery.
Statement: There’s no “income without risk” in Bitcoin: just hold — you preserve; want more — invest, risk, build.
Criticism: contradicts HODL logic; speculation remains dominant behavior.
6. “Speculation Dominates”
For now — yes. That’s normal for the early phase of a new technology. Awareness doesn’t come instantly.
What matters is not the motive of today’s buyer — but what they’re buying.
📉 A speculator may come and go — but the asset remains.\ And this asset is the only one in history that will never exist again. 21 million. Forever.
📌 Look deeper. Bitcoin has:\ – No CEO\ – No central issuer\ – No inflation\ – No “off switch”\ 💡 It was fairly distributed — through mining, long before ASICs existed. In the early years, bitcoin was spent and exchanged — not hoarded. Only those who truly believed in it are still holding it today.
💡 It’s not a stock. Not a startup. Not someone’s project.\ It’s a new foundation for trust.\ It’s opting out of a system where freedom is a privilege you’re granted under conditions.
🧠 People say: “Bitcoin can be copied.”\ Theoretically — yes.\ Practically — never.
Here’s what you’d need to recreate Bitcoin:\ – No pre-mine\ – A founder who disappears and never sells\ – No foundation or corporation\ – Tens of thousands of nodes worldwide\ – 701 million terahashes of hash power\ – Thousands of devs writing open protocols\ – Hundreds of global conferences\ – Millions of people defending digital sovereignty\ – All that without a single marketing budget
That’s all.
🔁 Everything else is an imitation, not a creation.\ Just like you can’t “reinvent fire” — Bitcoin can only exist once.
Statements:\ **The Russia's '90s weren’t a free market — just anarchic chaos without rights protection.\ **Unlike fiat or even dollars, Bitcoin is the first asset with real defense — from governments, inflation, even thugs.\ *And yes, even if your barber asks about Bitcoin — maybe it's not a bubble, but a sign that inflation has already hit everyone.
Criticism: Bitcoin’s protection isn’t universal — it works only with proper handling and isn’t available to all.\ Some just want to “get rich.”\ None of this matters because:
-
Bitcoin’s volatility (-30% in a week, +50% in a month) makes it unusable for price planning or contracts.
-
It can’t handle mass-scale usage.
-
To become currency, geopolitical will is needed — and without the first two, don’t even talk about the third.\ Also: “Bitcoin is too complicated for the average person.”
7. “It’s Too Complex for the Masses”
It’s complex — if you’re using L1 (Layer 1). But even grandmas use Telegram. In El Salvador, schoolkids buy lunch with Lightning. My barber installed Wallet of Satoshi in minutes right in front of me — and I now pay for my haircut via Lightning.
UX is just a matter of time. And it’s improving. Emerging tools:\ Cashu, Fedimint, Fedi, Wallet of Satoshi, Phoenix, Proton Wallet, Swiss Bitcoin Pay, Bolt Card / CoinCorner (NFC cards for Lightning payments).
This is like the internet in 1995:\ It started with modems — now it’s 4K streaming.
💸 Now try sending a regular bank transfer abroad:\ – you need to type a long IBAN\ – add SWIFT/BIC codes\ – include the recipient’s full physical address (!), compromising their privacy\ – sometimes add extra codes or “purpose of payment”\ – you might get a call from your bank “just to confirm”\ – no way to check the status — the money floats somewhere between correspondent/intermediary banks\ – weekends or holidays? Banks are closed\ – and don’t forget the limits, restrictions, and potential freezes
📌 With Bitcoin, you just scan a QR code and send.\ 10 minutes on-chain = final settlement.\ Via Lightning = instant and nearly free.\ No bureaucracy. No permission. No borders.
8. “Can’t Handle the Load”
A common myth.\ Yes, Bitcoin L1 processes about 7 transactions per second — intentionally. It’s not built to be Visa. It’s a financial protocol, just like TCP/IP is a network protocol. TCP/IP isn’t “fast” or “slow” — the experience depends on the infrastructure built on top: servers, routers, hardware. In the ’90s, it delivered text. Today, it streams Netflix. The protocol didn’t change — the stack did.
Same with Bitcoin: L1 defines rules, security, finality.\ Scaling and speed? That’s the second layer’s job.
To understand scale:
| Network | TPS (Transactions/sec) | | --- | --- | | Visa | up to 24,000 | | Mastercard | \~5,000 | | PayPal | \~193 | | Litecoin | \~56 | | Ethereum | \~20 | | Bitcoin | \~7 |
\ ⚡️ Enter Lightning Network — Bitcoin’s “fast lane.”\ It allows millions of transactions per second, instantly and nearly free.
And it’s not a sidechain.
❗️ Lightning is not a separate network.\ It uses real Bitcoin transactions (2-of-2 multisig). You can close the channel to L1 at any time. It’s not an alternative — it’s a native extension built into Bitcoin.\ Also evolving: Ark, Fedimint, eCash — new ways to scale and add privacy.
📉 So criticizing Bitcoin for “slowness” is like blaming TCP/IP because your old modem won’t stream YouTube.\ The protocol isn’t the problem — it’s the infrastructure.
🛡️ And by the way: Visa crashes more often than Bitcoin.
9. “We Need Geopolitical Will”
Not necessarily. All it takes is the will of the people — and leaders willing to act. El Salvador didn’t wait for G20 approval or IMF blessings. Since 2001, the country had used the US dollar as its official currency, abandoning its own colón. But that didn’t save it from inflation or dependency on foreign monetary policy. In 2021, El Salvador became the first country to recognize Bitcoin as legal tender. Since March 13, 2024, they’ve been purchasing 1 BTC daily, tracked through their public address:
🔗 Address\ 📅 First transaction
This policy became the foundation of their Strategic Bitcoin Reserve (SBR) — a state-led effort to accumulate Bitcoin as a national reserve asset for long-term stability and sovereignty.
Their example inspired others.
In March 2025, U.S. President Donald Trump signed an executive order creating the Strategic Bitcoin Reserve of the USA, to be funded through confiscated Bitcoin and digital assets.\ The idea: accumulate, don’t sell, and strategically expand the reserve — without extra burden on taxpayers.
Additionally, Senator Cynthia Lummis (Wyoming) proposed the BITCOIN Act, targeting the purchase of 1 million BTC over five years (\~5% of the total supply).\ The plan: fund it via revaluation of gold certificates and other budget-neutral strategies.
📚 More: Strategic Bitcoin Reserve — Wikipedia
👉 So no global consensus is required. No IMF greenlight.\ All it takes is conviction — and an understanding that the future of finance lies in decentralized, scarce assets like Bitcoin.
10. “-30% in a week, +50% in a month = not money”
True — Bitcoin is volatile. But that’s normal for new technologies and emerging money. It’s not a bug — it’s a price discovery phase. The world is still learning what this asset is.
📉 Volatility is the price of entry.\ 📈 But the reward is buying the future at a discount.
As Michael Saylor put it:
“A tourist sees Niagara Falls as chaos — roaring, foaming, spraying water.\ An engineer sees immense energy.\ It all depends on your mental model.”
Same with Bitcoin. Speculators see chaos. Investors see structural scarcity. Builders see a new financial foundation.
💡 Now consider gold:
👉 After the gold standard was abandoned in 1971, the price of gold skyrocketed from around \~$300 to over $2,700 (adjusted to 2023 dollars) by 1980. Along the way, it experienced extreme volatility — with crashes of 40–60% even amid the broader uptrend.\ 💡 (\~$300 is the inflation-adjusted equivalent of about $38 in 1971 dollars)\ 📈 Source: Gold Price Chart — Macrotrends\ \ Nobody said, “This can’t be money.” \ Because money is defined not by volatility, but by scarcity, adoption, and trust — which build over time.
📊 The more people save in Bitcoin, the more its volatility fades.
This is a journey — not a fixed state.
We don’t judge the internet by how it worked in 1994.\ So why expect Bitcoin to be the “perfect currency” in 2025?
It grows bottom-up — without regulators’ permission.\ And the longer it survives, the stronger it becomes.
Remember how many times it’s been declared dead.\ And how many times it came back — stronger.
📊 Gold vs. Bitcoin: Supply Comparison
This chart shows the key difference between the two hard assets:
🔹 Gold — supply keeps growing.\ Mining may be limited, but it’s still inflationary.\ Each year, there’s more — with no known cap: new mines, asteroid mining, recycling.
🔸 Bitcoin — capped at 21 million.\ The emission schedule is public, mathematically predictable, and ends completely around 2140.
🧠 Bottom line:\ Gold is good.\ Bitcoin is better — for predictability and scarcity.
💡 As Saifedean Ammous said:
“Gold was the best monetary good… until Bitcoin.”
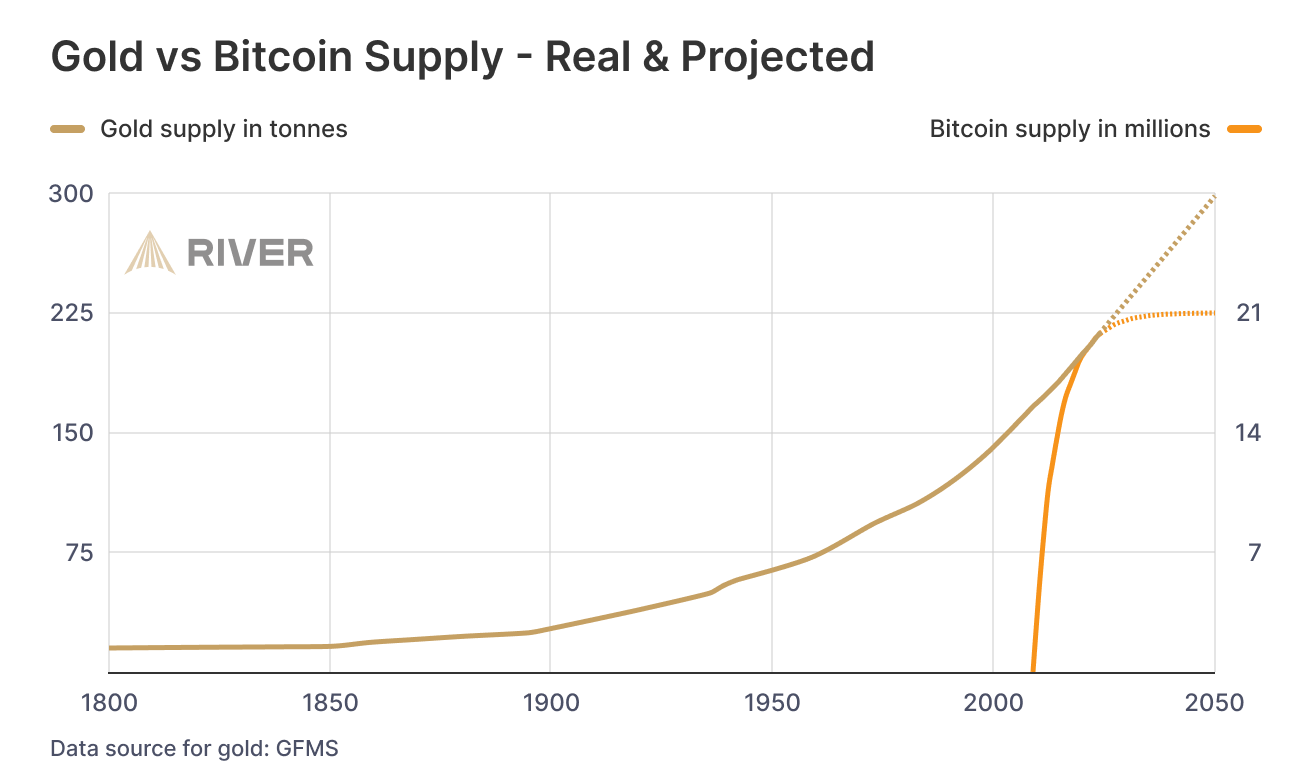 ### While we argue — fiat erodes every day.
### While we argue — fiat erodes every day.No matter your view on Bitcoin, just show me one other asset that is simultaneously:
– immune to devaluation by decree\ – impossible to print more of\ – impossible to confiscate by a centralized order\ – impossible to counterfeit\ – and, most importantly — transferable across borders without asking permission from a bank, a state, or a passport
💸 Try sending $10,000 through PayPal from Iran to Paraguay, or Bangladesh to Saint Lucia.\ Good luck. PayPal doesn't even work there.
Now open a laptop, type 12 words — and you have access to your savings anywhere on Earth.
🌍 Bitcoin doesn't ask for permission.\ It works for everyone, everywhere, all the time.
📌 There has never been anything like this before.
Bitcoin is the first asset in history that combines:
– digital nature\ – predictable scarcity\ – absolute portability\ – and immunity from tyranny
💡 As Michael Saylor said:
“Bitcoin is the first money in human history not created by bankers or politicians — but by engineers.”
You can own it with no bank.\ No intermediary.\ No passport.\ No approval.
That’s why Bitcoin isn’t just “internet money” or “crypto” or “digital gold.”\ It may not be perfect — but it’s incorruptible.\ And it’s not going away.\ It’s already here.\ It is the foundation of a new financial reality.
🔒 This is not speculation. This is a peaceful financial revolution.\ 🪙 This is not a stock. It’s money — like the world has never seen.\ ⛓️ This is not a fad. It’s a freedom protocol.
And when even the barber starts asking about Bitcoin — it’s not a bubble.\ It’s a sign that the system is breaking.\ And people are looking for an exit.
For the first time — they have one.
💼 This is not about investing. It’s about the dignity of work.
Imagine a man who cleans toilets at an airport every day.
Not a “prestigious” job.\ But a crucial one.\ Without him — filth, bacteria, disease.
He shows up on time. He works with his hands.
And his money? It devalues. Every day.
He doesn’t work less — often he works more than those in suits.\ But he can afford less and less — because in this system, honest labor loses value each year.
Now imagine he’s paid in Bitcoin.
Not in some “volatile coin,” but in hard money — with a limited supply.\ Money that can’t be printed, reversed, or devalued by central banks.
💡 Then he could:
– Stop rushing to spend, knowing his labor won’t be worth less tomorrow\ – Save for a dream — without fear of inflation eating it away\ – Feel that his time and effort are respected — because they retain value
Bitcoin gives anyone — engineer or janitor — a way out of the game rigged against them.\ A chance to finally build a future where savings are real.
This is economic justice.\ This is digital dignity.
📉 In fiat, you have to spend — or your money melts.\ 📈 In Bitcoin, you choose when to spend — because it’s up to you.
🧠 In a deflationary economy, both saving and spending are healthy:
You don’t scramble to survive — you choose to create.
🎯 That’s true freedom.
When even someone cleaning floors can live without fear —\ and know that their time doesn’t vanish... it turns into value.
🧱 The Bigger Picture
Bitcoin is not just a technology — it’s rooted in economic philosophy.\ The Austrian School of Economics has long argued that sound money, voluntary exchange, and decentralized decision-making are prerequisites for real prosperity.\ Bitcoin doesn’t reinvent these ideas — it makes them executable.
📉 Inflation doesn’t just erode savings.\ It quietly destroys quality of life.\ You work more — and everything becomes worse:\ – food is cheaper but less nutritious\ – homes are newer but uglier and less durable\ – clothes cost more but fall apart in months\ – streaming is faster, but your attention span collapses\ This isn’t just consumerism — it’s the economics of planned obsolescence.
🧨 Meanwhile, the U.S. debt has exceeded 3x its GDP.\ And nobody wants to buy U.S. bonds anymore — so the U.S. has to buy its own debt.\ Yes: printing money to buy the IOUs you just printed.\ This is the endgame of fiat.
🎭 Bonds are often sold as “safe.”\ But in practice, they are a weapon — especially abroad.\ The U.S. and IMF give loans to developing countries.\ But when those countries can’t repay (due to rigged terms or global economic headwinds), they’re forced to sell land, resources, or strategic assets.\ Both sides lose: the debtor collapses under the weight of debt, while the creditor earns resentment and instability.\ This isn’t cooperation — it’s soft colonialism enabled by inflation.
📌 Bitcoin offers a peaceful exit.\ A financial system where money can’t be created out of thin air.\ Where savings work.\ Where dignity is restored — even for those who clean toilets.
-
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ e9d7ed6f:f52b3346
2025-05-28 23:36:58
@ e9d7ed6f:f52b3346
2025-05-28 23:36:58I'd like to toss it off by thanking you my reader, friends, associates, strangers, bitcoiners, cryptonaires, economists, and critics from all walks of life for granting me this opportunity to write to you. yeah?...
Is that readable? Is there enough ink in this pen to write? Let me squash and develop a fresh script!
Okay now, that was one heck of a disaster introduction my friends.
That's not even the way Satoshi introduced his White paper back in 2008, or rather mined his first block. So dear reader, lets pretend this introduction never happened lets give it one more kick start.
Alright we are set so here we go...
Flavatos, Gateway Mall, the left ventricle of Lilongwe's heart, Malawi is where the aroma of a fresh bitcoin pizza sent waves of spattering energy, broadcasting to all nodes over the bitcoin network. Pizza crums spread over the table, folks and knives faced opposite directions, tomato sauce on the white plate had contours of pizza passage, a half baked joke & its laughter could be heard by passersby's heading inside the mall. It was chilly Saturday afternoon from outside but the soft drinks were a must to soften the well baked fragments of pizza which were being churned. All thanks to Larszlo Keyckenes. Phones where right on the table as the photographer snapped every detail of moment with his camera, trying to paint a bitcoin Monalisa, innocence was in the youthful energetic bitcoiners who filled left to right seats in pairs. Three tables were joined together making a table tennis appear short, but the waitress had to check for any empty slot to squeeze a chair in. We were twenty three with the expection of thirty but the space was just plentiful.
Flavatos was ready and set. The waitress again, with a smile of welcoming a guest whispered right besides where i was standing that the pizza is ready, but i had to HODL for a moment, we were just setting up the laptop which we would use to connect & listen to a presentation by John Miller, a distant relative and a bitcoiner we had talked of for weeks. As if am very good at analysing charts, the looks of the faces were eagerly waiting and i when i looked on my wrist i realised we didn't have much more time other than to start off, so i clapped my hands to capture everyones attention. I was excited to welcome all & really appreciate for sparing their time to come.
There was buzz in the atmosphere, all eyes glued to me as i thanked the cofounder Grant for pulling the strings, in our presence we had the cofounder of women of Satoshi Yankho who i was facing directly to my right hand side and threw me sparkle of acknowledgement, i couldn't forget & sweep under the mat, John Miller sponsor for the Bitcoin Pizza who is currently in the US & was waiting to deliver a speech on this very moment. All started off in the right order, my stomach tuned as my brain signaled the pizza image, sending tickling hunger sensation, so not to keep everyone waiting longer, i handed it over to Grant who quickly threw like free shot on the free throw line. There was genuine appreciation and he set the floor ready for John Miller to grace and unwrap the Pizza. When John took on the google meet space, we all fixed to our phones, eager to see John who was seven hours away from us, about two or three plane tickets to get where he was physically located. John delivered a twenty minute presentation that would make a fresh graduate take off his hat and really consider what they did the last four years of their university. There was a lot of knowledge on his presentation, highlighting the eminent nails to the coffin for US dollar, the chart and numbers didn't lie when he displayed how the purchasing power of the dollar has declined since 1971 post detachment from gold. He spoke with authority on why bitcoin, how Bitcoiners should continue orange pilling and detoxing all the pool of confusion of the current FIAT sytem. It was listening to wisdom of an old man, giving the torch to the young ones. The waitress had brought to the table clean white plates with some folks wrapped in a white napkin tissue that appeared so white as Satoshi's white paper. In no time the pizza was ready to bona petite, John wrapped up in a cousy style by saying, "keep stacking Sats and avoiding shitcoins. The attendees were in pairs and hands were rubbing, contemplating of how the first bite would feel. The enzymes were ready to digest. The next host, who happens to be the writer of this article had to take the floor and give short remarks to thank John, Grant and everyone. I saw the pizza being cut into slices, whilst others took sips of their favorite soft drinks, there were smiles from left to right check. The sound chewing was amplified, triggering my ear drums to some vibe. This was was a big family reunion. My signal for speaking almost went off as the aroma teased the mind, i saw the bubble from the fanta bottle float up but i was mature to handled the temper of my hunger. As the pizza halvening was going on, I reminded of how significant this moment was when Larszlo Heykens first made an offer of 10,000 BTC & how it signified use case of bitcoin as a medium of exchange and a resort of finality between two counterparts without any middleman. It surely was moment that reminded us of the free markets. Where two counterparts chose their own commodities of exchange and each left satisfied as finality of transactions. Truly those were the good old free market days. By the time i said goodbye, my counterparts had already mined half of the pizza brought. I was about to pop a question of where is my share when i saw three more full plates of pizza broadcasted & awaiting for verification. I knew i was in for a treat.
As i kept my hands, mouth and tummy busy, one surprising moment really fired me up with excitement. Grant stood up and surprised everyone by introducing his new friend from Kenya. He said they had met in Mulanje and how they came across each other was purely a barter coincidence of wants. Rather him explaining, he let our new Kenyan explorer share the fascinating story of how he wanted to send funds in Kenya but couldn't find means of transalating our local currency into the Kenyan shilling. So how could these two opposite worlds tie together? When he saw the post of bitcoin accepted here, it sparked the charge. Using Bitcoin, he was able to send funds in Kenya via bitcoin lightening wallet through Tando and Mpesa. As if we were in a cinema watching possibilities become realities, a demostration was showcased how inter transactions are done from a wallet of Satoshi lightening wallet to Tando whilst eating pizza in Malawi.
It was truly a fantastic orange day to pill and slice. See you in the next article as i continue to polish my writing skills.
Pacharo Nyirenda. Bitcoinboma An amature writer but soon to be pro writer & blogger!
-
 @ 3bf0c63f:aefa459d
2024-05-21 12:38:08
@ 3bf0c63f:aefa459d
2024-05-21 12:38:08Bitcoin transactions explained
A transaction is a piece of data that takes inputs and produces outputs. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered.
Imagine you have 10 satoshis. That means you have them in an unspent transaction output (UTXO). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a script that unlocks that transaction and related signatures, then you specify outputs along with a script that locks these outputs.

As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them.
For most of the cases locking and unlocking means specifying a public key whose controller (the person who has the corresponding private key) will be able to spend. Other fancy things are possible too, but we can ignore them for now.
Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.

If you're still interested in transactions maybe you could take a look at this small chapter of that Andreas Antonopoulos book.
If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: https://en.bitcoin.it/wiki/Coin_analogy
-
 @ c3b2802b:4850599c
2025-05-26 07:57:44
@ c3b2802b:4850599c
2025-05-26 07:57:44Knapp 20 Millionen Menschen im Land sind heute in Deutschland in Genossenschaften tätig, welche eine Alternative zum nicht zukunftsfähigen Abwärtsstrudel von global agierenden Wirtschafts- und Finanzplayern mit ihren Kriegs- und Krisenplänen darstellen. Und kaum bemerkt findet derzeit ein stürmisches Wachstum der Genossenschaftsbewegung statt.
Nach Informationen des Deutschen Genossenschafts- und Raiffeisenverbandes stieg während der Multikrise der vergangenen 5 Jahre im Laufe nur einen Jahres (vom Jahresbericht 2023 zum Jahresbericht 2024) die Zahl der Energiegenossenschaften von 877 auf 951 an, die von Konsum- und Dienstleistungsgenossenschaften von 440 auf 510 und die von gewerblichen Genossenschaften von 1.372 auf 1.419.
Wer das Gejammer von „Wirtschaftsweisen“ über zu geringe Wachstumsraten bei ethisch fragwürdigen Indikatoren einer wünschenswerten Gesellschaft wie dem BIP (Brutto-Inland-Produkt) im Ohr hat, könnte bereits beim Überschlagen des Anstiegs bei den oben genannten Zahlen die These gestützt sehen, dass der Strukturwandel hin zur Regionalgesellschaft bereits in vollem Gang ist.
Wenn Sie sich für die Aufbruchstimmung und den frischen Wind insbesondere bei den neu gegründeten Genossenschaften interessieren, schauen sie gern einmal auf die Plattform einer jungen Genossenschaft, welche „Menschlich Wirtschaften“ in ihrer Satzung zum Ziel erklärt hat.
Und sollten Sie Mitte Juni eine Reise an die Ostsee attraktiv finden, kommen Sie gern zum Genossenschaftstreffen vom 13. bis 15. Juni 2025 in Poppendorf bei Rostock. Dort dürfen Sie nicht nur einen Einblick in die aktuellen Baustellen und ersten Erfolge unserer bundesweit aktiven Genossenschaft erwarten, sondern auch ein buntes Kulturprogramm im Rahmen eines kleinen Festivals und ein Zusammensein mit Pionieren der Regionalgesellschaft!
Das Titelbild zeigt ein Menschlich Wirtschaften Domizil in Stralsund. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Was charakterisiert eine Genossenschaft?
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08
@ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08Tldr
- Nostr is an open and interoperable protocol
- You can integrate it with workflow automation tools to augment your experience
- n8n is a great low/no-code workflow automation tool which you can host yourself
- Nostrobots allows you to integrate Nostr into n8n
- In this blog I create some workflow automations for Nostr
- A simple form to delegate posting notes
- Push notifications for mentions on multiple accounts
- Push notifications for your favourite accounts when they post a note
- All workflows are provided as open source with MIT license for you to use
Inter-op All The Things
Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In Using NFC Cards with Nostr I explored the
nostr:URI to launch Nostr clients from a card tap.The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails.
My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted.
This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull.
So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications.
All we need are simple ways to plug things together.
Nostr and Workflow Automation
Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective.
n8n for workflow automation
Many workflow automation tools exist. My favourite is n8n. n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to.
Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine.
Eating my own dogfood
It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do?
In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting.
I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up.
Running n8n with Nostrobots
I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs my HAVEN Nostr Relay and Albyhub Lightning Node in Docker containers,
- My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows.
Installing n8n
Self-hosting n8n could not be easier. I followed n8n's Docker-Compose installation docs–
- Install Docker and Docker-Compose if you haven't already,
- Create your
docker-compose.ymland.envfiles from the docs, - Create your data folder
sudo docker volume create n8n_data, - Start your container with
sudo docker compose up -d, - Your n8n instance should be online at port
5678.
n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there.
Installing Nostrobots
To integrate n8n nicely with Nostr, I used the Nostrobots community node by Ocknamo.
In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in.
You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative).
To install a community node, see n8n community node docs. From your workflow dashboard–
- Click the "..." in the bottom left corner beside your username, and click "settings",
- Cilck "community nodes" left sidebar,
- Click "Install",
- Enter the "npm Package Name" which is
n8n-nodes-nostrobots, - Accept the risks and click "Install",
- Nostrobots is now added to your n8n instance.
Using Nostrobots
Nostrobots gives you nodes to help you build Nostr-integrated workflows–
- Nostr Write – for posting Notes to the Nostr network,
- Nostr Read – for reading Notes from the Nostr network, and
- Nostr Utils – for performing certain conversions you may need (e.g. from bech32 to hex).
Nostrobots has good documentation on each node which focuses on simple use cases.
Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use.
What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible.
Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with NIP-01). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of.
Creating and adding workflows
With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation.
- Click "Add workflow" to go to the workflow builder screen,
- If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added,
- If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article).
Nostr Workflow Automations
It's time to build some things!
A simple form to post a note to Nostr
I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily.
I needed a basic form with credentials that posted a Note.
For this I can use a very simple workflow–
- A n8n Form node – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted.
- A Set node – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain.
- A Nostr Write node (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays.
Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive".
It may also be the world's simplest Nostr client.
You can find the Nostr Form to Post a Note workflow here.
Push notifications on mentions and new notes
One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want–
- To make sure I never miss a note addressed to any of my Npubs – For this I want a push notification any time any Nostr user mentions any of my Npubs,
- To make sure I always see all notes from key accounts – For this I need a push notification any time any of my Npubs post any Notes to the network,
- To get these notifications on all of my devices – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day.
I needed to build a Nostr push notifications solution.
To build this workflow I had to string a few ideas together–
- Triggering the node on a schedule – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited,
- Storing a list of Npubs in a Nostr list – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists (NIP-51, kind 30000). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. Listr.lol or Nostrudel.ninja). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions,
- Using specific relays – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata,
- Querying Nostr events (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do–
- I read the EventID of my Kind 30000 list, to return the desired pubkeys,
- For notifications on mentions, I read all Kind 1 notes that mention that pubkey,
- For notifications on new notes, I read all Kind 1 notes published by that pubkey,
- Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub,
- I transform the EventID into a Nevent to help clients find it.
- Using the Nostr URI – As I did with my NFC card article, I created a link with the
nostr:URI prefix so that my phone's native client opens the link by default, - Push notifications solution – I needed a push notifications solution. I found many with n8n integrations and chose to go with Pushover which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license.
Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go.
You can find the Nostr Push Notification If Mentioned here and If Posts a Note here.
In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible.
Use my workflows
I have open sourced all my workflows at my Github with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use.
To import any of my workflows–
- Click on the workflow of your choice, e.g. "Nostr_Push_Notify_If_Mentioned.json",
- Click on the "raw" button to view the raw JSON, ex any Github page layout,
- Copy that URL,
- Enter that URL in the "import from URL" dialog mentioned above.
To configure them–
- Prerequisites, credentials, and variables are all stated,
- In general any variables required are entered into a Set Node that follows the trigger node,
- Pushover has some extra setup but is very straightforward and documented in the workflow.
What next?
Over my first four blogs I explored creating a good Nostr setup with Vanity Npub, Lightning Payments, Nostr Addresses at Your Domain, and Personal Nostr Relay.
Then in my latest two blogs I explored different types of interoperability with NFC cards and now n8n Workflow Automation.
Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this:
- Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds),
- Automated or scheduled posting (such as auto-liking everything Lyn Alden posts),
- Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming),
- All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr,
- All kinds of other automation (such as BlackCoffee controlling a coffee machine),
- All kinds of AI Assistants and Agents,
In fact I have already released an open source workflow for an AI Assistant, and will share more about that in my next blog.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:46
@ 39cc53c9:27168656
2025-05-27 09:21:46Bitcoin enthusiasts frequently and correctly remark how much value it adds to Bitcoin not to have a face, a leader, or a central authority behind it. This particularity means there isn't a single person to exert control over, or a single human point of failure who could become corrupt or harmful to the project.
Because of this, it is said that no other coin can be equally valuable as Bitcoin in terms of decentralization and trustworthiness. Bitcoin is unique not just for being first, but also because of how the events behind its inception developed. This implies that, from Bitcoin onwards, any coin created would have been created by someone, consequently having an authority behind it. For this and some other reasons, some people refer to Bitcoin as "The Immaculate Conception".
While other coins may have their own unique features and advantages, they may not be able to replicate Bitcoin's community-driven nature. However, one other cryptocurrency shares a similar story of mystery behind its creation: Monero.
History of Monero
Bytecoin and CryptoNote
In March 2014, a Bitcointalk thread titled "Bytecoin. Secure, private, untraceable since 2012" was initiated by a user under the nickname "DStrange"^1^. DStrange presented Bytecoin (BCN) as a unique cryptocurrency, in operation since July 2012. Unlike Bitcoin, it employed a new algorithm known as CryptoNote.
DStrange apparently stumbled upon the Bytecoin website by chance while mining a dying bitcoin fork, and decided to create a thread on Bitcointalk^1^. This sparked curiosity among some users, who wondered how could Bytecoin remain unnoticed since its alleged launch in 2012 until then^2^.
Some time after, a user brought up the "CryptoNote v2.0" whitepaper for the first time, underlining its innovative features^4^. Authored by the pseudonymous Nicolas van Saberhagen in October 2013, the CryptoNote v2 whitepaper^5^ highlighted the traceability and privacy problems in Bitcoin. Saberhagen argued that these flaws could not be quickly fixed, suggesting it would be more efficient to start a new project rather than trying to patch the original^5^, an statement simmilar to the one from Satoshi Nakamoto^6^.
Checking with Saberhagen's digital signature, the release date of the whitepaper seemed correct, which would mean that Cryptonote (v1) was created in 2012^7^, although there's an important detail: "Signing time is from the clock on the signer's computer" ^9^.
Moreover, the whitepaper v1 contains a footnote link to a Bitcointalk post dated May 5, 2013^10^, making it impossible for the whitepaper to have been signed and released on December 12, 2012.
As the narrative developed, users discovered that a significant 80% portion of Bytecoin had been pre-mined^11^ and blockchain dates seemed to be faked to make it look like it had been operating since 2012, leading to controversy surrounding the project.
The origins of CryptoNote and Bytecoin remain mysterious, leaving suspicions of a possible scam attempt, although the whitepaper had a good amount of work and thought on it.
The fork
In April 2014, the Bitcointalk user
thankful_for_today, who had also participated in the Bytecoin thread^12^, announced plans to launch a Bytecoin fork named Bitmonero^13^.The primary motivation behind this fork was "Because there is a number of technical and marketing issues I wanted to do differently. And also because I like ideas and technology and I want it to succeed"^14^. This time Bitmonero did things different from Bytecoin: there was no premine or instamine, and no portion of the block reward went to development.
However, thankful_for_today proposed controversial changes that the community disagreed with. Johnny Mnemonic relates the events surrounding Bitmonero and thankful_for_today in a Bitcointalk comment^15^:
When thankful_for_today launched BitMonero [...] he ignored everything that was discussed and just did what he wanted. The block reward was considerably steeper than what everyone was expecting. He also moved forward with 1-minute block times despite everyone's concerns about the increase of orphan blocks. He also didn't address the tail emission concern that should've (in my opinion) been in the code at launch time. Basically, he messed everything up. Then, he disappeared.
After disappearing for a while, thankful_for_today returned to find that the community had taken over the project. Johnny Mnemonic continues:
I, and others, started working on new forks that were closer to what everyone else was hoping for. [...] it was decided that the BitMonero project should just be taken over. There were like 9 or 10 interested parties at the time if my memory is correct. We voted on IRC to drop the "bit" from BitMonero and move forward with the project. Thankful_for_today suddenly resurfaced, and wasn't happy to learn the community had assumed control of the coin. He attempted to maintain his own fork (still calling it "BitMonero") for a while, but that quickly fell into obscurity.
The unfolding of these events show us the roots of Monero. Much like Satoshi Nakamoto, the creators behind CryptoNote/Bytecoin and thankful_for_today remain a mystery^17^, having disappeared without a trace. This enigma only adds to Monero's value.
Since community took over development, believing in the project's potential and its ability to be guided in a better direction, Monero was given one of Bitcoin's most important qualities: a leaderless nature. With no single face or entity directing its path, Monero is safe from potential corruption or harm from a "central authority".
The community continued developing Monero until today. Since then, Monero has undergone a lot of technological improvements, migrations and achievements such as RingCT and RandomX. It also has developed its own Community Crowdfundinc System, conferences such as MoneroKon and Monerotopia are taking place every year, and has a very active community around it.
Monero continues to develop with goals of privacy and security first, ease of use and efficiency second. ^16^
This stands as a testament to the power of a dedicated community operating without a central figure of authority. This decentralized approach aligns with the original ethos of cryptocurrency, making Monero a prime example of community-driven innovation. For this, I thank all the people involved in Monero, that lead it to where it is today.
If you find any information that seems incorrect, unclear or any missing important events, please contact me and I will make the necessary changes.
Sources of interest
- https://forum.getmonero.org/20/general-discussion/211/history-of-monero
- https://monero.stackexchange.com/questions/852/what-is-the-origin-of-monero-and-its-relationship-to-bytecoin
- https://en.wikipedia.org/wiki/Monero
- https://bitcointalk.org/index.php?topic=583449.0
- https://bitcointalk.org/index.php?topic=563821.0
- https://bitcointalk.org/index.php?action=profile;u=233561
- https://bitcointalk.org/index.php?topic=512747.0
- https://bitcointalk.org/index.php?topic=740112.0
- https://monero.stackexchange.com/a/1024
- https://inspec2t-project.eu/cryptocurrency-with-a-focus-on-anonymity-these-facts-are-known-about-monero/
- https://medium.com/coin-story/coin-perspective-13-riccardo-spagni-69ef82907bd1
- https://www.getmonero.org/resources/about/
- https://www.wired.com/2017/01/monero-drug-dealers-cryptocurrency-choice-fire/
- https://www.monero.how/why-monero-vs-bitcoin
- https://old.reddit.com/r/Monero/comments/u8e5yr/satoshi_nakamoto_talked_about_privacy_features/
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-
 @ f0c7506b:9ead75b8
2024-12-08 09:05:13
@ f0c7506b:9ead75b8
2024-12-08 09:05:13
Yalnızca güçlü olanların hakkıdır yaşamak.
Güçlü olan ileri gider ve saflar seyrekleşir. Ama üç beş büyük, güçlü ve tanrısal kişi güneşli ve aydınlık gözleriyle o yeni, o vaat edilmiş ülkeye ulaşacaktır. Belki binlerce yıl sonra ancak. Ve güçlü, adaleli, hükmetmek için yaratılmış elleriyle hastaların, zayıfların ve sakatların ölüleri üzerinde bir krallık kuracaklardır. Bir krallık!
Benim aradığım insanların kendileri değil, sesleridir.
Duyguları körelmiş, çeşitli düşüncelere saplanmış kalabalık hiçbir zaman ilerlemenin taşıyıcısı olamaz, kendi küçüklüğünün o küflü içgüdüsüyle kalabalığın kin ve nefretle baktığı bir kişi, bir büyük kişi, iradesinin gösterdiği yolda kimsenin gözünün yaşına bakmaksızın ilahi bir güç ve bir zafer gülümsemesiyle yürüyebilir ancak.
Bizim soyumuz da sonsuz oluşum piramidinin doruk noktasını oluşturmaktan uzaktır. Bizler de mükemmelliğe ulaşmış değiliz. Bizler de henüz olgunlaşmadık.
Şairler sevgiye övgüler döşenir; doğrusu sevginin güçlü bir şey olduğu kesin. Hüneşin bir ışınıdır sevgi, aydınlatıp nurlandırır insanı der bazıları; bazıları da insanı esrikliğe sürükleyen bir zehri kendisinde barındırdığını söyler. Gerçekten de yol açtığı sonuçlar, bir hekimin ağır bir ameliyattan önce korkudan titreyen hastaya teneffüs ettirdiği güldürücü gazınkine benzer, içinde tepinip duran acıyı unutturur hastaya.
Önemli olan, hayatta hiç değilse bir kez kutsal bir ilkbaharın yaşanmasıdır; öyle bir bahar ki, insanın gönlünü ilerideki bütün günleri altın yaldızla kaplamaya yetecek kadar ışık ve parıltıyla doldursun.
Şu hayat denen şey kötü bir işçiliğin ürünü, acemilere göre bir şey. Bu kepaze yaşam uğruna insan nelere katlanmıyor ki!
Kendisine sadakatten ayrılmadığı, yalnızca kendisinin olan bir tek bu var: Yalnızlığı.
Sahildeki üstü tenteli hasır koltuklar arkasındaki yüksek, sessiz kum tepeleri içinde yürürsen, tenteler altındaki insanları göremezsin; ama birinin bir diğerine seslendiğini, bir başkasının gevezelik ettiğini, bir ötekinin güldüğünü işitir ve anlarsın hemen: bu insan şöyle şöyle biridir diyebilirsin. Onun hayatı sevdiğini, bağrında büyük bir özlem ya da acı barındırdığını, bu acının da sesini ağlamaklı kıldığını her gülüşünde hissedersin.
-
 @ 3bf0c63f:aefa459d
2024-03-23 08:57:08
@ 3bf0c63f:aefa459d
2024-03-23 08:57:08Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 39cc53c9:27168656
2025-05-27 09:21:40
@ 39cc53c9:27168656
2025-05-27 09:21:40“The future is there... staring back at us. Trying to make sense of the fiction we will have become.” — William Gibson.
This month is the 4th anniversary of kycnot.me. Thank you for being here.
Fifteen years ago, Satoshi Nakamoto introduced Bitcoin, a peer-to-peer electronic cash system: a decentralized currency free from government and institutional control. Nakamoto's whitepaper showed a vision for a financial system based on trustless transactions, secured by cryptography. Some time forward and KYC (Know Your Customer), AML (Anti-Money Laundering), and CTF (Counter-Terrorism Financing) regulations started to come into play.
What a paradox: to engage with a system designed for decentralization, privacy, and independence, we are forced to give away our personal details. Using Bitcoin in the economy requires revealing your identity, not just to the party you interact with, but also to third parties who must track and report the interaction. You are forced to give sensitive data to entities you don't, can't, and shouldn't trust. Information can never be kept 100% safe; there's always a risk. Information is power, who knows about you has control over you.
Information asymmetry creates imbalances of power. When entities have detailed knowledge about individuals, they can manipulate, influence, or exploit this information to their advantage. The accumulation of personal data by corporations and governments enables extensive surveillances.
Such practices, moreover, exclude individuals from traditional economic systems if their documentation doesn't meet arbitrary standards, reinforcing a dystopian divide. Small businesses are similarly burdened by the costs of implementing these regulations, hindering free market competition^1:
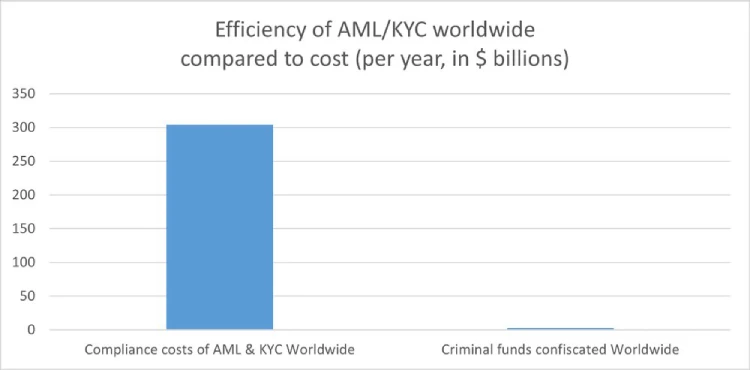
How will they keep this information safe? Why do they need my identity? Why do they force businesses to enforce such regulations? It's always for your safety, to protect you from the "bad". Your life is perpetually in danger: terrorists, money launderers, villains... so the government steps in to save us.
‟Hush now, baby, baby, don't you cry Mamma's gonna make all of your nightmares come true Mamma's gonna put all of her fears into you Mamma's gonna keep you right here, under her wing She won't let you fly, but she might let you sing Mamma's gonna keep baby cosy and warm” — Mother, Pink Floyd
We must resist any attack on our privacy and freedom. To do this, we must collaborate.
If you have a service, refuse to ask for KYC; find a way. Accept cryptocurrencies like Bitcoin and Monero. Commit to circular economies. Remove the need to go through the FIAT system. People need fiat money to use most services, but we can change that.
If you're a user, donate to and prefer using services that accept such currencies. Encourage your friends to accept cryptocurrencies as well. Boycott FIAT system to the greatest extent you possibly can.
This may sound utopian, but it can be achieved. This movement can't be stopped. Go kick the hornet's nest.
“We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do.” — Eric Hughes, A Cypherpunk's Manifesto
The anniversary
Four years ago, I began exploring ways to use crypto without KYC. I bookmarked a few favorite services and thought sharing them to the world might be useful. That was the first version of kycnot.me — a simple list of about 15 services. Since then, I've added services, rewritten it three times, and improved it to what it is now.
kycnot.me has remained 100% independent and 100% open source^2 all these years. I've received offers to buy the site, all of which I have declined and will continue to decline. It has been DDoS attacked many times, but we made it through. I have also rewritten the whole site almost once per year (three times in four years).
The code and scoring algorithm are open source (contributions are welcome) and I can't arbitrarly change a service's score without adding or removing attributes, making any arbitrary alterations obvious if they were fake. You can even see the score summary for any service's score.
I'm a one-person team, dedicating my free time to this project. I hope to keep doing so for many more years. Again, thank you for being part of this.
-
 @ 3bf0c63f:aefa459d
2024-03-19 14:32:01
@ 3bf0c63f:aefa459d
2024-03-19 14:32:01Censorship-resistant relay discovery in Nostr
In Nostr is not decentralized nor censorship-resistant I said Nostr is centralized. Peter Todd thinks it is centralized by design, but I disagree.
Nostr wasn't designed to be centralized. The idea was always that clients would follow people in the relays they decided to publish to, even if it was a single-user relay hosted in an island in the middle of the Pacific ocean.
But the Nostr explanations never had any guidance about how to do this, and the protocol itself never had any enforcement mechanisms for any of this (because it would be impossible).
My original idea was that clients would use some undefined combination of relay hints in reply tags and the (now defunct)
kind:2relay-recommendation events plus some form of manual action ("it looks like Bob is publishing on relay X, do you want to follow him there?") to accomplish this. With the expectation that we would have a better idea of how to properly implement all this with more experience, Branle, my first working client didn't have any of that implemented, instead it used a stupid static list of relays with read/write toggle -- although it did publish relay hints and kept track of those internally and supportedkind:2events, these things were not really useful.Gossip was the first client to implement a truly censorship-resistant relay discovery mechanism that used NIP-05 hints (originally proposed by Mike Dilger) relay hints and
kind:3relay lists, and then with the simple insight of NIP-65 that got much better. After seeing it in more concrete terms, it became simpler to reason about it and the approach got popularized as the "gossip model", then implemented in clients like Coracle and Snort.Today when people mention the "gossip model" (or "outbox model") they simply think about NIP-65 though. Which I think is ok, but too restrictive. I still think there is a place for the NIP-05 hints,
nprofileandneventrelay hints and specially relay hints in event tags. All these mechanisms are used together in ZBD Social, for example, but I believe also in the clients listed above.I don't think we should stop here, though. I think there are other ways, perhaps drastically different ways, to approach content propagation and relay discovery. I think manual action by users is underrated and could go a long way if presented in a nice UX (not conceived by people that think users are dumb animals), and who knows what. Reliance on third-parties, hardcoded values, social graph, and specially a mix of multiple approaches, is what Nostr needs to be censorship-resistant and what I hope to see in the future.
-
 @ e31e84c4:77bbabc0
2024-12-02 10:44:07
@ e31e84c4:77bbabc0
2024-12-02 10:44:07Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net
Fiduciary duty is the obligation to act in the client’s best interests at all times, prioritizing their needs above the advisor’s own, ensuring honesty, transparency, and avoiding conflicts of interest in all recommendations and actions.
This is something all advisors in the BFAN take very seriously; after all, we are legally required to do so. For the average advisor this is a fairly easy box to check. All you essentially have to do is have someone take a 5-minute risk assessment, fill out an investment policy statement, and then throw them in the proverbial 60/40 portfolio. You have thousands of investment options to choose from and you can reasonably explain how your client is theoretically insulated from any move in the \~markets\~. From the traditional financial advisor perspective, you could justify nearly anything by putting a client into this type of portfolio. All your bases were pretty much covered from return profile, regulatory, compliance, investment options, etc. It was just too easy. It became the household standard and now a meme.
As almost every real bitcoiner knows, the 60/40 portfolio is moving into psyop territory, and many financial advisors get clowned on for defending this relic on bitcoin twitter. I’m going to specifically poke fun at the ‘40’ part of this portfolio.
The ‘40’ represents fixed income, defined as…
An investment type that provides regular, set interest payments, such as bonds or treasury securities, and returns the principal at maturity. It’s generally considered a lower-risk asset class, used to generate stable income and preserve capital.
Historically, this part of the portfolio was meant to weather the volatility in the equity markets and represent the “safe” investments. Typically, some sort of bond.
First and foremost, the fixed income section is most commonly constructed with U.S. Debt. There are a couple main reasons for this. Most financial professionals believe the same fairy tale that U.S. Debt is “risk free” (lol). U.S. debt is also one of the largest and most liquid assets in the market which comes with a lot of benefits.
There are many brilliant bitcoiners in finance and economics that have sounded the alarm on the U.S. debt ticking time bomb. I highly recommend readers explore the work of Greg Foss, Lawrence Lepard, Lyn Alden, and Saifedean Ammous. My very high-level recap of their analysis:
-
A bond is a contract in which Party A (the borrower) agrees to repay Party B (the lender) their principal plus interest over time.
-
The U.S. government issues bonds (Treasury securities) to finance its operations after tax revenues have been exhausted.
-
These are traditionally viewed as “risk-free” due to the government’s historical reliability in repaying its debts and the strength of the U.S. economy
-
U.S. bonds are seen as safe because the government has control over the dollar (world reserve asset) and, until recently (20 some odd years), enjoyed broad confidence that it would always honor its debts.
-
This perception has contributed to high global demand for U.S. debt but, that is quickly deteriorating.
-
The current debt situation raises concerns about sustainability.
-
The U.S. has substantial obligations, and without sufficient productivity growth, increasing debt may lead to a cycle where borrowing to cover interest leads to more debt.
-
This could result in more reliance on money creation (printing), which can drive inflation and further debt burdens.
In the words of Lyn Alden “Nothing stops this train”
Those obligations are what makes up the 40% of most the fixed income in your portfolio. So essentially you are giving money to one of the worst capital allocators in the world (U.S. Gov’t) and getting paid back with printed money.
As someone who takes their fiduciary responsibility seriously and understands the debt situation we just reviewed, I think it’s borderline negligent to put someone into a classic 60% (equities) / 40% (fixed income) portfolio without serious scrutiny of the client’s financial situation and options available to them. I certainly have my qualms with equities at times, but overall, they are more palatable than the fixed income portion of the portfolio. I don’t like it either, but the money is broken and the unit of account for nearly every equity or fixed income instrument (USD) is fraudulent. It’s a paper mache fade that is quite literally propped up by the money printer.
To briefly be as most charitable as I can – It wasn’t always this way. The U.S. Dollar used to be sound money, we used to have government surplus instead of mathematically certain deficits, The U.S. Federal Government didn’t used to have a money printing addiction, and pre-bitcoin the 60/40 portfolio used to be a quality portfolio management strategy. Those times are gone.
Now the fun part. How does bitcoin fix this?
Bitcoin fixes this indirectly. Understanding investment criteria changes via risk tolerance, age, goals, etc. A client may still have a need for “fixed income” in the most literal definition – Low risk yield. Now you may be thinking that yield is a bad word in bitcoin land, you’re not wrong, so stay with me. Perpetual motion machine crypto yield is fake and largely where many crypto scams originate. However, that doesn’t mean yield in the classic finance sense does not exist in bitcoin, it very literally does. Fortunately for us bitcoiners there are many other smart, driven, and enterprising bitcoiners that understand this problem and are doing something to address it. These individuals are pioneering new possibilities in bitcoin and finance, specifically when it comes to fixed income.
Here are some new developments –
Private Credit Funds – The Build Asset Management Secured Income Fund I is a private credit fund created by Build Asset Management. This fund primarily invests in bitcoin-backed, collateralized business loans originated by Unchained, with a secured structure involving a multi-signature, over-collateralized setup for risk management. Unchained originates loans and sells them to Build, which pools them into the fund, enabling investors to share in the interest income.
Dynamics
- Loan Terms: Unchained issues loans at interest rates around 14%, secured with a 2/3 multi-signature vault backed by a 40% loan-to-value (LTV) ratio.
- Fund Mechanics: Build buys these loans from Unchained, thus providing liquidity to Unchained for further loan originations, while Build manages interest payments to investors in the fund.
Pros
- The fund offers a unique way to earn income via bitcoin-collateralized debt, with protection against rehypothecation and strong security measures, making it attractive for investors seeking exposure to fixed income with bitcoin.
Cons
- The fund is only available to accredited investors, which is a regulatory standard for private credit funds like this.
Corporate Bonds – MicroStrategy Inc. (MSTR), a business intelligence company, has leveraged its corporate structure to issue bonds specifically to acquire bitcoin as a reserve asset. This approach allows investors to indirectly gain exposure to bitcoin’s potential upside while receiving interest payments on their bond investments. Some other publicly traded companies have also adopted this strategy, but for the sake of this article we will focus on MSTR as they are the biggest and most vocal issuer.
Dynamics
-
Issuance: MicroStrategy has issued senior secured notes in multiple offerings, with terms allowing the company to use the proceeds to purchase bitcoin.
-
Interest Rates: The bonds typically carry high-yield interest rates, averaging around 6-8% APR, depending on the specific issuance and market conditions at the time of issuance.
-
Maturity: The bonds have varying maturities, with most structured for multi-year terms, offering investors medium-term exposure to bitcoin’s value trajectory through MicroStrategy’s holdings.
Pros
-
Indirect Bitcoin exposure with income provides a unique opportunity for investors seeking income from bitcoin-backed debt.
-
Bonds issued by MicroStrategy offer relatively high interest rates, appealing for fixed-income investors attracted to the higher risk/reward scenarios.
Cons
-
There are credit risks tied to MicroStrategy’s financial health and bitcoin’s performance. A significant drop in bitcoin prices could strain the company’s ability to service debt, increasing credit risk.
-
Availability: These bonds are primarily accessible to institutional investors and accredited investors, limiting availability for retail investors.
Interest Payable in Bitcoin – River has introduced an innovative product, bitcoin Interest on Cash, allowing clients to earn interest on their U.S. dollar deposits, with the interest paid in bitcoin.
Dynamics
-
Interest Payment: Clients earn an annual interest rate of 3.8% on their cash deposits. The accrued interest is converted to Bitcoin daily and paid out monthly, enabling clients to accumulate Bitcoin over time.
-
Security and Accessibility: Cash deposits are insured up to $250,000 through River’s banking partner, Lead Bank, a member of the FDIC. All Bitcoin holdings are maintained in full reserve custody, ensuring that client assets are not lent or leveraged.
Pros
-
There are no hidden fees or minimum balance requirements, and clients can withdraw their cash at any time.
-
The 3.8% interest rate provides a predictable income stream, akin to traditional fixed-income investments.
Cons
-
While the interest rate is fixed, the value of the Bitcoin received as interest can fluctuate, introducing potential variability in the investment’s overall return.
-
Interest rate payments are on the lower side
Admittedly, this is a very small list, however, these types of investments are growing more numerous and meaningful. The reality is the existing options aren’t numerous enough to service every client that has a need for fixed income exposure. I challenge advisors to explore innovative options for fixed income exposure outside of sovereign debt, as that is most certainly a road to nowhere. It is my wholehearted belief and call to action that we need more options to help clients across the risk and capital allocation spectrum access a sound money standard.
Additional Resources
-
River: The future of saving is here: Earn 3.8% on cash. Paid in Bitcoin.
-
MicroStrategy: MicroStrategy Announces Pricing of Offering of Convertible Senior Notes
Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net
-
-
 @ b7274d28:c99628cb
2025-05-28 00:59:49
@ b7274d28:c99628cb
2025-05-28 00:59:49Your identity is important to you, right? While impersonation can be seen in some senses as a form of flattery, we all would prefer to be the only person capable of representing ourselves online, unless we intentionally delegate that privilege to someone else and maintain the ability to revoke it.
Amber does all of that for you in the context of #Nostr. It minimizes the possibility of your private key being compromized by acting as the only app with access to it, while all other Nostr apps send requests to Amber when they need something signed. This even allows you to give someone temporary authority to post as you without giving them your private key, and you retain the authority to revoke their permissions at any time.
nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 has provided Android users with an incredibly powerful tool in Amber, and he continues to improve its functionality and ease of use. Indeed, there is not currently a comparative app available for iOS users. For the time being, this superpower is exclusive to Android.
Installation
Open up the Zapstore app that you installed in the previous stage of this tutorial series.
Very likely, Amber will be listed in the app collection section of the home page. If it is not, just search for "Amber" in the search bar.
Opening the app's page in the Zapstore shows that the release is signed by the developer. You can also see who has added this app to one of their collections and who has supported this app with sats by zapping the release.
Tap "Install" and you will be prompted to confirm you are sure you want to install Amber.
Helpfully, you are informed that several other users follow this developer on Nostr. If you have been on Nostr a while, you will likely recognize these gentlemen as other Nostr developers, one of them being the original creator of the protocol.
You can choose to never have Zapstore ask for confirmation again with apps developed by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, and since we have another of his apps to install later in this tutorial series, I recommend you toggle this on. Then tap on "Trust greenart7c3 and install app."
Just like when you installed the Zapstore from their GitHub, you will be prompted to allow the Zapstore to install apps, since Android considers it an "unknown source."
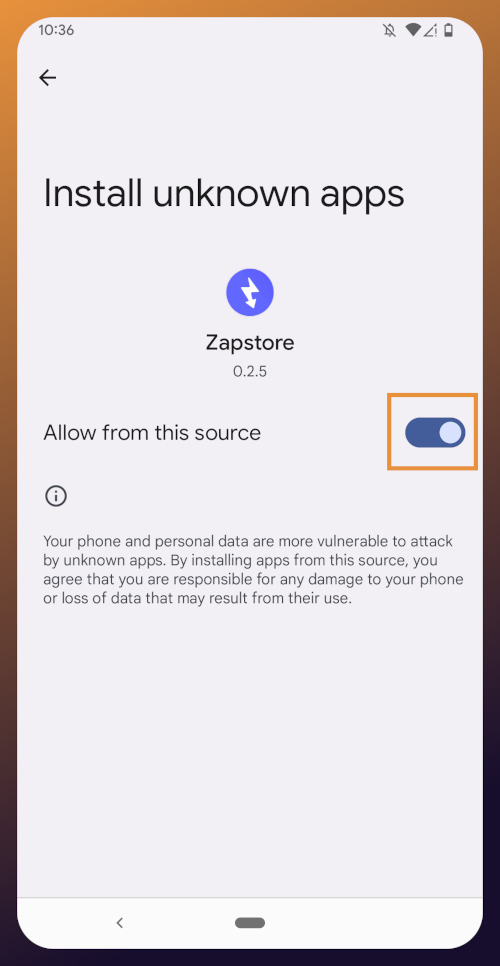
Once you toggle this on and use the back button to get back to the Zapstore, Amber will begin downloading and then present a prompt to install the app. Once installed, you will see a prompt that installation was a success and you can now open the app.
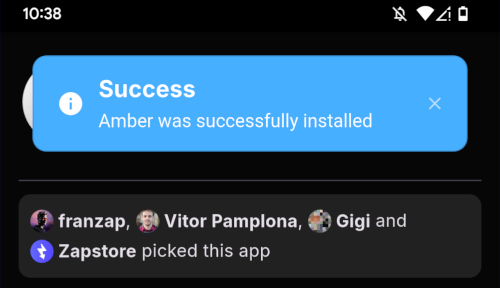
From here, how you proceed will depend on whether you need to set up a new Nostr identity or use Amber with an existing private key you already have set up. The next section will cover setting up a new Nostr identity with Amber. Skip to the section titled "Existing Nostrich" if you already have an nsec that you would like to use with Amber.
New Nostrich
Upon opening the application, you will be presented with the option to use an existing private key or create a new Nostr account. Nostr doesn't really have "accounts" in the traditional sense of the term. Accounts are a relic of permissioned systems. What you have on Nostr are keys, but Amber uses the "account" term because it is a more familiar concept, though it is technically inaccurate.
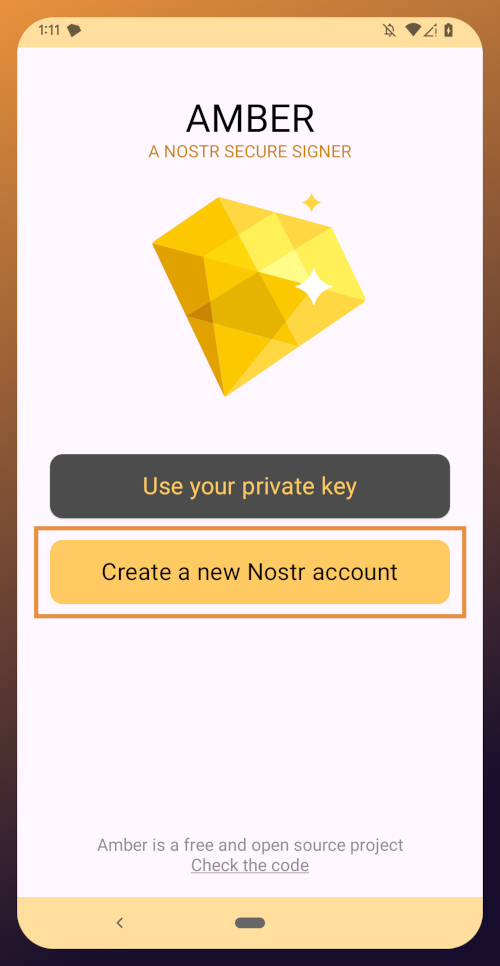
Choose "Create a new Nostr account" and you will be presented with a screen telling you that your Nostr account is ready. Yes, it was really that easy. No email, no real name, no date of birth, and no annoying capcha. Just "Create a new account" and you're done.
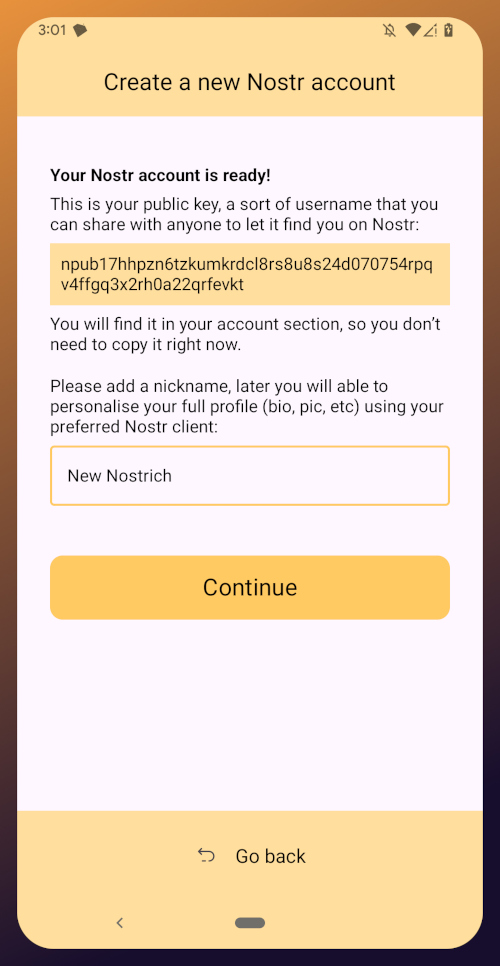
The app presents you with your public key. This is like an address that can be used to find your posts on Nostr. It is 100% unique to you, and no one else can post a note that lists this npub as the author, because they won't have the corresponding private key. You don't need to remember your npub, though. You'll be able to readily copy it from any Nostr app you use whenever you need it.
You will also be prompted to add a nickname. This is just for use within Amber, since you can set up multiple profiles within the app. You can use anything you want here, as it is just so you can tell which profile is which when switching between them in Amber.
Once you've set your nickname, tap on "Continue."
The next screen will ask you what Amber's default signing policy should be.
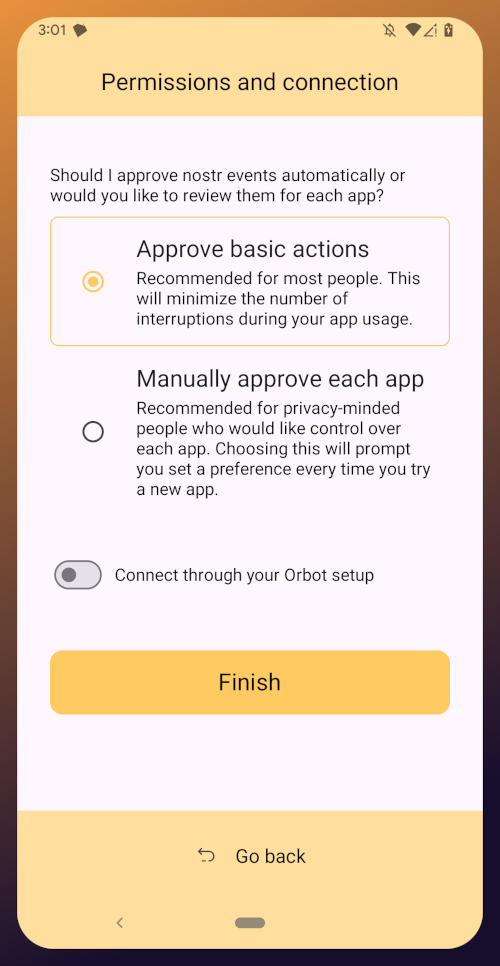
The default is to approve basic actions, referring to things that are common for Nostr clients to request a signature for, like following another user, liking a post, making a new post, or replying. If you are more concerned about what Amber might be signing for on your behalf, you can tell it to require manual approval for each app.
Once you've made your decision, tap "Finish." You will also be able to change this selection in the app settings at any time.
With this setup out of the way, you are now presented with the main "Applications" page of the app.
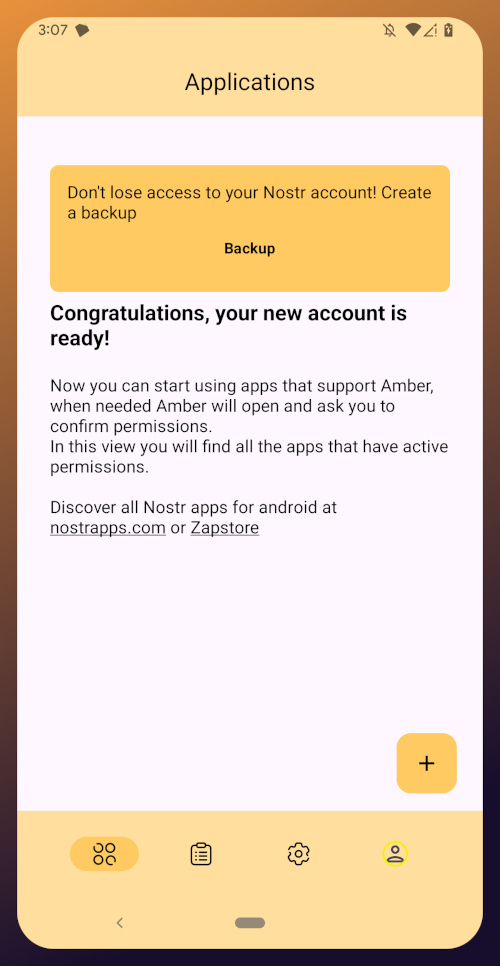
At the top, you have a notification encouraging you to create a backup. Let's get that taken care of now by tapping on the notification and skipping down to the heading titled "Backing Up Your Identity" in this tutorial.
Existing Nostrich
Upon opening the application, you will be presented with the option to use your private key or create a new Nostr account. Choose the former.
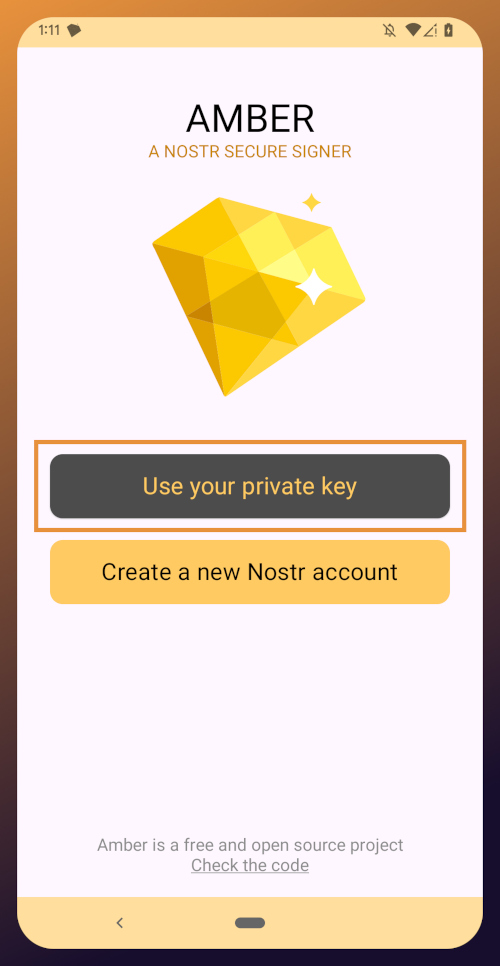
The next screen will require you to paste your private key.
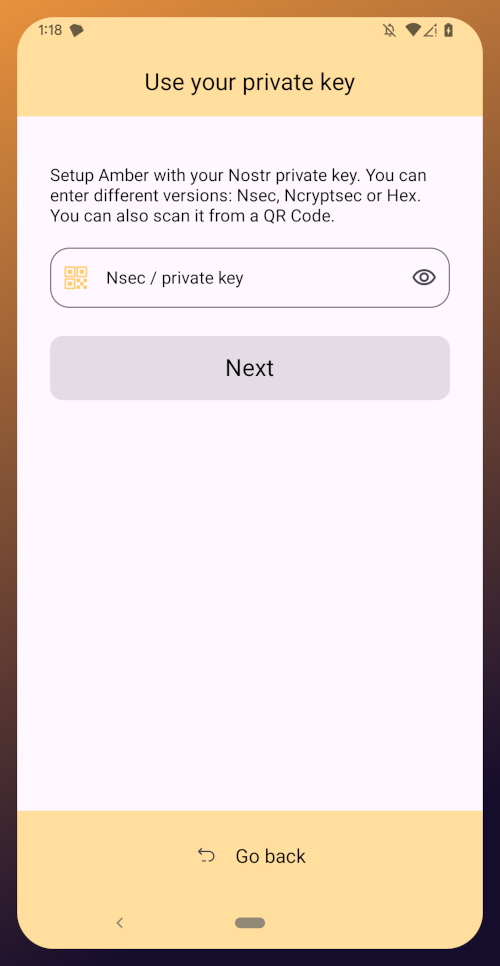
You will need to obtain this from whatever Nostr app you used to create your profile, or any other Nostr app that you pasted your nsec into in the past. Typically you can find it in the app settings and there will be a section mentioning your keys where you can copy your nsec. For instance, in Primal go to Settings > Keys > Copy private key, and on Amethyst open the side panel by tapping on your profile picture in the top-left, then Backup Keys > Copy my secret key.
After pasting your nsec into Amber, tap "Next."

Amber will give you a couple options for a default signing policy. The default is to approve basic actions, referring to things that are common for Nostr clients to request a signature for, like following another user, liking a post, making a new post, or replying. If you are more concerned about what Amber might be signing for on your behalf, you can tell it to require manual approval for each app.
Once you've made your decision, tap "Finish." You will also be able to change this selection in the app settings at any time.
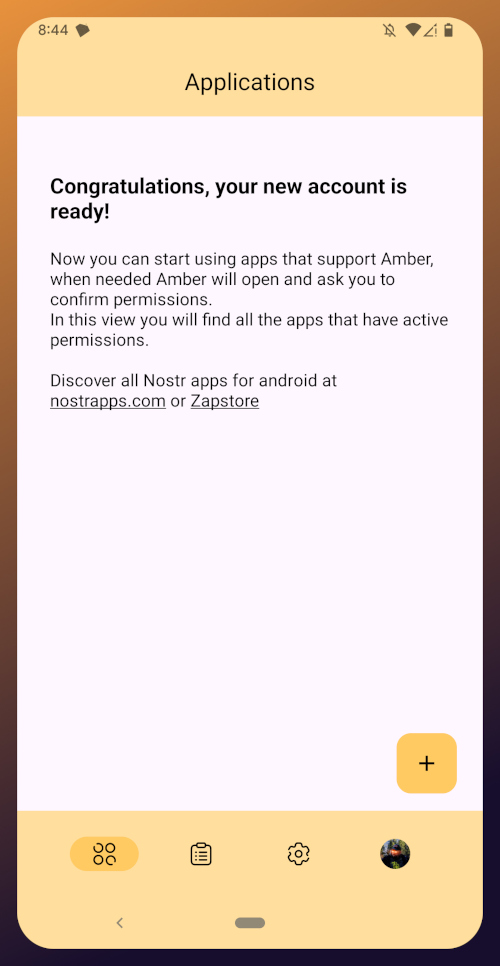
With this setup out of the way, you are now presented with the main "Applications" page of the app. You have nothing here yet, since you haven't used Amber to log into any Nostr apps, but this will be where all of the apps you have connected with Amber will be listed, in the order of the most recently used at the top.
Before we go and use Amber to log into an app, though, let's make sure we've created a backup of our private key. You pasted your nsec into Amber, so you could just save that somewhere safe, but Amber gives you a few other options as well. To find them, you'll need to tap the cog icon at the bottom of the screen to access the settings, then select "Backup Keys."
Backing Up Your Identity
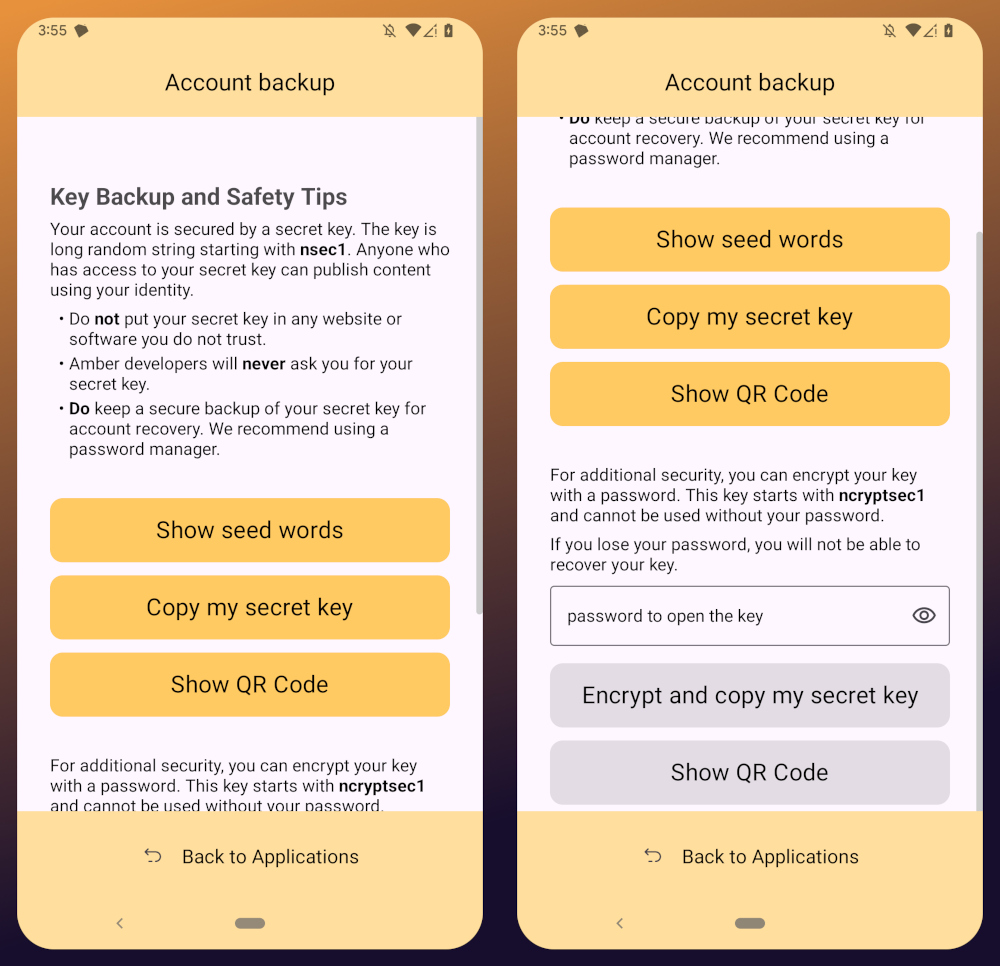
You'll notice that Amber has a few different options for backing up your private key that it can generate.
First, it can give you seed words, just like a Bitcoin seed. If you choose that option, you'll be presented with 12 words you can record somewhere safe. To recover your Nostr private key, you just have to type those words into a compatible application, such as Amber.
The next option is to just copy the secret/private key in its standard form as an "nsec." This is the least secure way to store it, but is also the most convenient, since it is simple to paste into another signer application. If you want to be able to log in on a desktop web app, the browser extension Nostr signers won't necessarily support entering your 12 word seed phrase, but they absolutely will support pasting in your nsec.
You can also display a QR code of your private key. This can be scanned by Amber signer on another device for easily transferring your private key to other devices you want to use it on. Say you have an Android tablet in addition to your phone, for instance. Just make sure you only use this function where you can be certain that no one will be able to get a photograph of that QR code. Once someone else has your nsec, there is no way to recover it. You have to start all over on Nostr. Not a big deal at this point in your journey if you just created a Nostr account, but if you have been using Nostr for a while and have built up a decent amount of reputation, it could be much more costly to start over again.
The next options are a bit more secure, because they require a password that will be used to encrypt your private key. This has some distinct advantages, and a couple disadvantages to be aware of. Using a password to encrypt your private key will give you what is called an ncryptsec, and if this is leaked somehow, whoever has it will not necessarily have access to post as you on Nostr, the way they would if your nsec had been leaked. At least, not so long as they don't also have your password. This means you can store your ncryptsec in multiple locations without much fear that it will be compromised, so long as the password you used to encrypt it was a strong and unique one, and it isn't stored in the same location. Some Nostr apps support an ncryptsec for login directly, meaning that you have the option to paste in your ncryptsec and then just log in with the password you used to encrypt it from there on out. However, now you will need to keep track of both your ncryptsec and your password, storing both of them safely and separately. Additionally, most Nostr clients and signer applications do not support using an ncryptsec, so you will need to convert it back to a standard nsec (or copy the nsec from Amber) to use those apps.
The QR option using an ncryptsec is actually quite useful, though, and I would go this route when trying to set up Amber on additional devices, since anyone possibly getting a picture of the QR code is still not going to be able to do anything with it, unless they also get the password you used to encrypt it.
All of the above options will require you to enter the PIN you set up for your device, or biometric authentication, just as an additional precaution before displaying your private key to you.
As for what "store it in a safe place" looks like, I highly recommend a self-hosted password manager, such as Vaultwarden+Bitwarden or KeePass. If you really want to get wild, you can store it on a hardware signing device, or on a steel seed plate.
Additional Settings
Amber has some additional settings you may want to take advantage of. First off, if you don't want just anyone who has access to your phone to be able to approve signing requests, you can go into the Security settings add a PIN or enable biometrics for signing requests. If you enable the PIN, it will be separate from the PIN you use to access your phone, so you can let someone else use your phone, like your child who is always begging to play a mobile game you have installed, without worrying that they might have access to your Nostr key to post on Amethyst.
Amber also has some relay settings. First are the "Active relays" which are used for signing requests sent to Amber remotely from Nostr web apps. This is what enables you to use Amber on your phone to log into Nostr applications on your desktop web browser, such as Jumble.social, Coracle.social, or Nostrudel.ninja, eliminating your need to use any other application to store your nsec whatsoever. You can leave this relay as the default, or you can add other relays you want to use for signing requests. Just be aware, not all relays will accept the notes that are used for Nostr signing requests, so make sure that the relay you want to use does so. In fact, Amber will make sure of this for you when you type in the relay address.
The next type of relays that you can configure in Amber are the "Default profile relays." These are used for reading your profile information. If you already had a Nostr identity that you imported to Amber, you probably noticed it loaded your profile picture and display name, setting the latter as your nickname in Amber. These relays are where Amber got that information from. The defaults are relay.nostr.band and purplepag.es. The reason for this is because they are aggregators that look for Nostr profiles that have been saved to other relays on the network and pull them in. Therefore, no matter what other relay you may save your profile to, Amber will likely be able to find it on one of those two relays as well. If you have a relay you know you will be saving your Nostr profiles to, you may want to add it to this list.
You can also set up Amber to be paired with Orbot for signing over Tor using relays that are only accessible via the Tor network. That is an advanced feature, though, and well beyond the scope of this tutorial.
Finally, you can update the default signing policy. Maybe after using Amber for a while, you've decided that the choice you made before was too strict or too lenient. You can change it to suit your needs.
Zapstore Login
Now that you are all set up with Amber, let's get you signed into your first Nostr app by going back to the Zapstore.
From the app's home screen, tap on the user icon in the upper left of the screen. This will open a side panel with not much on it except the option to "sign in." Go ahead and tap on it.
You will be presented with the option to either sign in with Amber, or to paste your npub. However, if you do the latter, you will only have read access, meaning you cannot zap any of the app releases. There are other features planned for the Zapstore that may also require you to be signed in with write access, so go ahead and choose to log in with Amber.
Your phone should automatically switch to Amber to approve the sign-in request.
You can choose to only approve basic actions for Zapstore, require it to manually approve every time, or you can tell it that you "fully trust this application." Only choose the latter option with apps you have used for a while and they have never asked you to sign for anything suspicious. For the time being, I suggest you use the "Approve basic actions" option and tap "Grant Permissions."
Your phone will switch back to the Zapstore and will show that you are now signed in. Congratulations! From here on out, logging into most Nostr applications will be as easy as tapping on "Log in with Amber" and approving the request.
If you set up a new profile, it will just show a truncated version of your npub rather than the nickname you set up earlier. That's fine. You'll have an opportunity to update your Nostr profile in the next tutorial in this series and ensure that it is spread far and wide in the network, so the Zapstore will easily find it.
That concludes the tutorial for Amber. While we have not covered using Amber to log into Nostr web apps, that is outside the scope of this series, and I will cover it in an upcoming tutorial regarding using Amber's remote signer options in detail.
Since you're already hanging out in the Zapstore, you may as well stick around, because we will be using it right out the gate in the next part of this series: Amethyst Installation and Setup. (Coming Soon)
-
 @ cae03c48:2a7d6671
2025-05-29 00:02:06
@ cae03c48:2a7d6671
2025-05-29 00:02:06Bitcoin Magazine

🔴 LIVE: The Bitcoin Conference 2025 – Day 2The liveblog has ended.
No liveblog updates yet.
Load more
This post 🔴 LIVE: The Bitcoin Conference 2025 – Day 2 first appeared on Bitcoin Magazine and is written by Bitcoin Magazine.
-
 @ 2b998b04:86727e47
2025-05-28 23:24:05
@ 2b998b04:86727e47
2025-05-28 23:24:05I’ve spent years chasing the promise of freedom.\ In startups. In faith communities. In movements that claimed to be for the people.
And yet — so often, that promise felt just out of reach.\ Conditional. Corporate. Sanitized.\ A freedom with fine print.
But here —\ Here in the thick of Bitcoin 2025, on Nostr, among misfits and builders and signal-bringers —\ something is alive.
It’s not a platform.\ It’s not a marketing strategy.\ It’s not another app promising to “empower” you while locking down your data and selling you out.
It’s freedom rooted in architecture.\ Decentralization not just as a buzzword —\ but as an expression of conviction.
A kind of freedom you can feel in your body:
-
When you zap someone’s words because they moved you — not because an algorithm told you to.
-
When your identity is yours — keys, not credentials.
-
When no one can delete your story because you control the server, or because there is no server — just the relay of your choosing.
This isn’t utopia.\ There are egos. There’s noise. There’s still posturing.\ But it’s different.\ The center of gravity has shifted.
We’re no longer begging institutions to notice us.\ We’re building outside their jurisdiction.
And for the first time in a long time,\ freedom feels close.\ Tangible.\ Joyful.\ Alive.
This isn’t just about tech.\ It’s about trust.\ It’s about choosing to show up —\ to build\ to write\ to signal\ to keep going.
Even when it’s hard.\ Even when no one claps.
Because real freedom doesn’t come from being noticed.\ It comes from being sovereign.
And that’s something no one can take from me again.
—
Written in Las Vegas, during Bitcoin 2025.\ Posted via Nostr. Vibes co-authored by ChatGPT (“Dr. C”).\ Zap: https://tinyurl.com/yuyu2b9t
-
-
 @ a4992688:88fd660f
2025-05-28 00:58:09
@ a4992688:88fd660f
2025-05-28 00:58:09Retail Isn't Coming Back
(and they might be gone for good)
Written by nostr:nprofile1qqs2fxfx3z6yns4a6mafcwdgsrtluf747h37nl2vglt9mqj93r7kvrcwm69jy
It's been just a matter of days since Bitcoin has broken a new all-time high in US dollars and yet, things are extremely quiet on the ground level... Your friends aren't texting to find out if now is a good time to buy, the normies at work haven't brought it up to you, and Coinbase isn't even in the top 100 overall apps in the Google Play App Store. As of now, it sits at #164.
In fact, according to Google search trends, worldwide interest in Bitcoin is lower today while setting new all-time highs above $110,000 than it was at the pits of the 2022 bear market when FTX was blowing up and Bitcoin crashed to below $16,000.
the mempool also paints a quiet picture. It’s mostly empty. Just a few blocks’ worth of transactions waiting to confirm, most paying 1–4 sats/vB. In fact, over the last 144 blocks (about 24 hours), the average fee per transaction has hovered below 1,500 sats, roughly $1.50.
This is far from the behavior found on-chain during previous all-time highs. It reflects an underutilized network predominantly being used by its original power users. Meanwhile, the hash rate climbs relentlessly, month after month, setting record after record. Miners are expending more energy than ever, but fee pressure is nowhere to be found.
🕵️♂️ Is Retail In The Room with Us Now?
The typical signs of retail investor enthusiasm, such as increased Google searches, higher Coinbase app downloads, and a congested mempool all remain subdued. This raises the question: Is the current rally predominantly driven by institutional investors, with retail participation lagging behind?
Since the approval of spot Bitcoin ETFs in January 2024, these financial instruments have accumulated nearly 1.21 million bitcoin, with total assets under management exceeding $132 billion (or, 5.75%+ of 21M total BTC). Initially, retail investors were the primary contributors to these inflows, accounting for approximately 80% of the total assets under management as of October 2024. However, more recent trends indicate a shift, with institutional investors, including hedge funds and asset managers, increasing their stakes in Bitcoin ETFs.
Institutional exposure more than doubled from Q3 to Q4 of 2024 according to SEC 13-F filings, whereas assets under management for all non-institutional ETF holders grew by 62%. While retail is responsible for approximately 73.7% of AUM in the ETFs, a small number of institutions represent more than a 26% of the ETF inflows as of the end of 2024.
🥴 PTSD - Portfolio Trauma & Speculative Disillusionment
For many retail investors, the scars from the 2021–2022 crypto cycle run deep. They bought into the hype near Bitcoin's previous all-time high of $69,000, only to watch their investments plummet to $15,000. The collapse of major platforms like Terra, Celsius, and FTX didn't just erase wealth—it shattered trust.
This collective trauma has left many retail investors wary. They've seen the cycle before: rapid gains followed by devastating losses. The excitement that once drew them into the market has been replaced by caution and skepticism. Even as Bitcoin reaches new heights, the enthusiasm that characterized previous bull runs is noticeably absent.
By all measurable metrics, retail investors appear increasingly reluctant to step outside the comfort of traditional financial rails to gain Bitcoin exposure. In response to past losses and a heightened desire for security, many are now turning to regulated investment vehicles like spot Bitcoin ETFs, offered by institutions such as BlackRock and Fidelity. These products provide a familiar, low-friction on-ramp by eliminating the need for self-custody, avoiding the risks of phishing and exchange hacks, and sidestepping the complexities of managing wallets or navigating volatile crypto platforms. This behavioral shift helps explain why we’re not seeing a surge in mempool congestion, on-chain activity, or crypto exchange downloads. Retail isn’t gone per se... they are however predominantly choosing to interact with Bitcoin from a "safe" distance, inside the walled garden of TradFi.
🧙♂️ Pay No Attention to the Custodian Behind the Curtain
Retail might look like it's back, but it isn't. Not really. They've been rerouted. Herded away from the open network and into the controlled comfort of traditional finance, where Bitcoin is boxed up, regulated, and sold as a familiar financial product.
Spot ETFs from firms like BlackRock offer the illusion of exposure without any of the responsibility or freedom that comes with actually owning Bitcoin. There are no private keys, no ability to withdraw, no direct access to the asset. Most of the Bitcoin that backs those shares sits in Coinbase Custody, inaccessible from the investor’s point of view. Retail can watch the price move, but they can't move a single sat.
They can't send it to family. They can't use Lightning. They can't participate in a fork or vote with their coins. Their holdings are locked inside a financial product, subject to tax surveillance and government oversight, with none of the borderless, censorship-resistant qualities that make Bitcoin what it is.
This isn’t Bitcoin as a tool for sovereignty. It’s Bitcoin as a stock proxy, tucked neatly into retirement accounts and brokerage dashboards. Retail hasn't returned to Bitcoin. They've returned to a synthetic version of it. One that looks clean, feels safe, and doesn’t ask them to think too hard.
The crowd is back, but not on the chain. They've returned to price, not protocol.
🔍Missing: Retail. Last Seen 2021.
If this bull run feels quieter than the last one, it’s because it is. Retail investors, once the lifeblood of Bitcoin mania, are largely absent from the on-chain activity. Their presence isn’t being felt where it used to be.
The reasons are stacking up. Regulatory pressure has increased globally, with new tax reporting rules, stricter KYC requirements, and fewer accessible exchanges making direct participation more frustrating than exciting. At the same time, the opportunity cost has shifted. T-bills are yielding 5 percent, and the stock market is deep in an AI-driven rally that feels new and full of upside. Compared to that, Bitcoin’s core narratives like digital gold or inflation protection no longer feel urgent or unique.
Institutions are now leading through ETFs and futures, smoothing out volatility and removing many of the sudden moves that once drew in retail traders. On-chain user experience still falls behind modern apps, Lightning remains niche, and energy concerns continue to shape public perception. More importantly, the cost of everyday life has gone up. Rent is up. Groceries are expensive. People are stretched thin. Student loans have resumed and homeownership is out of reach for many.
Until those conditions shift, retail is unlikely to return in any meaningful way. It is not that they have given up on Bitcoin. They are simply trying to keep up with everything else.
The chart below illustrates that the number of active Bitcoin addresses has declined by approximately 42% since its peak in 2021.
🧲 What Pulls Them Back In?
Retail hasn’t disappeared. It’s just not on-chain. They’re watching the charts, buying the proxies, and dipping into Bitcoin exposure through familiar vehicles like ETFs and high-beta stocks. MSTR, MSTY, SQ, MARA, and RIOT have become stand-ins for the real thing. For many, that feels close enough. They haven’t sworn off Bitcoin entirely, but they also haven’t found a reason to return to the protocol itself. Price alone isn’t doing it. If Bitcoin is going to recapture retail attention on-chain, it needs more than speculation. It needs to be usable, intuitive, and culturally relevant. Until then, the crowd will stay inside the walled garden, content with price exposure. The question now is what pulls them back into the open network.
🛠️ Make it Frictionless, or Forget it
Retail won’t return until exploring Bitcoin feels rewarding, not risky. Right now, engaging directly with the network still feels technical, intimidating, and easy to get wrong. The average person doesn’t want to learn about seed phrases, fee markets, or signing messages. They just want it to work, and ideally in one tap.
Self-custody, while powerful, still comes with a learning curve that scares most users off. One typo can lose everything. One phishing link can wipe a life’s savings. When compared to the ease of buying a Bitcoin ETF inside a brokerage app, it becomes obvious why most people choose comfort over control.
Lightning wallets have improved, but mainstream usability is still far off. Many users struggle with basic concepts like payment channels and inbound liquidity. App store reviews often reflect confusion and frustration. More importantly, Lightning still raises serious questions in a high-fee environment. Opening or closing a channel can become expensive when the base layer gets congested. This undermines Lightning’s value as a low-cost, instant settlement layer. If fees are unpredictable, it becomes harder to trust that Lightning will be there when users actually need it.
Apps like Nostr are beginning to pave the way with native Lightning features like zaps, where users can send sats as tips or signals within a social feed. It’s the kind of simple, purpose-driven interaction that could eventually normalize Lightning in everyday use. But for now, it remains niche, with limited reach beyond early adopters and Bitcoin-native circles. The pieces are falling into place, but mainstream readiness is still a long way off.
To pull retail back in, Bitcoin has to compete on usability, not just principle. That means seedless recovery. Wallets that back up automatically. Tap-to-pay Lightning. Default privacy. Smarter fee estimation. The average user should not have to study Bitcoin to use it, just like they don’t need to understand TCP/IP to send an email.
Until the experience becomes effortless, Bitcoin on-chain will remain the domain of power users and diehards. Everyone else will keep choosing exposure over participation, because for now, the friction outweighs the freedom.
🔥 Give Them a Reason to Care Again
Speculation brought retail in. Survival might bring them back. But between those extremes, there needs to be a reason to engage that feels meaningful in everyday life. For most people, Bitcoin still doesn’t offer that. It’s not woven into anything they do. It’s not a tool they reach for. It’s just a number in a ticker—or now, in an ETF.
The core narratives that once drove adoption have lost their urgency. “Digital gold” sounds more like a sales pitch than a breakthrough. “Inflation hedge” didn’t hold up during inflation. “Opt out of the banking system” is hard to relate to when your paycheck hits a checking account and your bills are on autopay. These messages worked when people were curious or scared. But in a world focused on AI, passive income, and stable yields, Bitcoin feels like a cold, hard asset with no warm story.
Retail doesn’t just need new slogans. They need a new reason. A killer app. A cultural hook. Something that connects the protocol to their daily life. That could come from anywhere—remittances, peer-to-peer media, AI payments, creator tools, censorship resistance, even gaming. We’re starting to see glimpses. Nostr’s Lightning zaps, for example, show how sats could flow through social interactions. It's lightweight, casual, and fits into habits people already have. But even that is still early and relatively isolated from the mainstream.
Of course, it’s possible that price alone brings them back. A violent move toward $200,000 or higher could generate headlines, social buzz, and another wave of opportunistic buying. But even in that scenario, most people still won't touch the protocol. They’ll chase exposure, not interaction. They’ll buy tickers, not UTXOs.
Retail will come back when Bitcoin stops being an idea they watch and starts being a tool they use. Until then, attention might spike, but engagement will remain shallow.
🏠 Bitcoin Needs a Homebase
Bitcoin is everywhere, but it feels like it’s nowhere. There's no single place where the culture lives. No town square. No digital front porch where holders, builders, speculators, artists, and newcomers all cross paths. And that absence is being felt.
In past cycles, Twitter served as a kind of home for Bitcoin discussion. But now the conversation is fractured. Memes, developer talk, Lightning experiments, and exchange drama are scattered across Telegram groups, Nostr relays, GitHub repos, Reddit threads, and gated newsletters. There’s no central venue that brings it all together. What once felt like a movement now feels more like a loose network of subcultures.
This isn’t just a cultural gap. It’s a usability gap. Without a shared space or interface, discovering Bitcoin's tools, communities, or use cases becomes a fragmented and overwhelming experience. For newcomers especially, it turns exploration into a scavenger hunt. There’s no hub where someone can casually browse peer-to-peer markets, tip someone over Lightning, try a game, test a wallet, or ask basic questions without feeling out of place.
Importantly, this homebase shouldn’t be a corporate platform or single point of failure. It should reflect the values of the network itself—open, decentralized, secure, and resistant to censorship. A sovereign space, not another walled garden. Something that anyone can plug into, build on top of, or access freely without needing permission or credentials. Not a headquarters, but a commons.
Bitcoin doesn’t need a leader, but it could use a center of gravity. A place where its many threads can be visible, accessible, and in conversation with each other. Until it feels like something you can step into, most people won’t feel like they’re truly part of it.
🧵 Final Thoughts
Retail didn’t disappear. It checked out. After wild volatility, failed platforms, and busted narratives, most people aren't rushing back into the Bitcoin Network as we know it. They’ve opted for safety. For simplicity. For familiar rails like ETFs, proxy stocks, and apps that feel intuitive and risk-free.
Bitcoin, meanwhile, has matured in price but not necessarily in presence. The protocol is stronger than ever, but the culture feels scattered. The use cases feel theoretical. The experience still feels fragile. And for most, that's just not enough.
Maybe retail comes back with the next crisis. Maybe it takes a breakout product. Or maybe it doesn’t happen for years. No one knows what the catalyst will be, or if there even has to be one. But what’s clear is that Bitcoin’s next chapter won’t be won by price alone. It will be shaped by the tools we build, the stories we tell, and the places we create for people to show up.
One thing I know for sure: if retail returns, it won’t be for long unless we’ve built something that gives them a real reason to stay.
-
 @ 69eea734:4ae31ae6
2025-05-26 01:15:05
@ 69eea734:4ae31ae6
2025-05-26 01:15:05Dies ist der Anfang einer Serie, die ich schreiben möchte. Sie handelt von etwas, das wir verloren haben, und das dennoch, in Teilen, in uns weiterlebt.
Wen meine ich mit dem “wir”? Das Wir kann schnell problematisch werden, wenn man meint für andere zu sprechen, und dann erkennen muss, falsche Annahmen gemacht zu haben.
Als ich diesen Satz schrieb, hatte ich diejenigen von uns im Hinterkopf, die in einer westlichen Industriegesellschaft aufgewachsen sind. Der Verlust ist etwas, das ich spüre, und dem reale Geschehnisse mit zugrunde liegen. Eine Art Sehnsucht wird stärker, wenn ich von bestimmten Ereignissen lese, bei denen Menschen gewaltsam von dem getrennt wurden, das sie bis dahin gehalten und ernährt hatte: Dem Land, zu dem sie gehörten.
Worüber ich schreiben möchte, das sind die Commons. Ein weites Feld. Commons, das kann Allmende heißen oder Gemeingüter.
Es geht dabei aber nicht nur um das, was gemeinsam genutzt wird, sondern auch um das Soziale darum herum — wie sich eine Gruppe selbst organisiert, und dabei den Mitgliedern und dem Gemeingut gerecht wird
Es ist eines jener Konzepte, denen mit einer einfachen Definition nicht gut gedient ist. Es geht eher darum, ein Gefühl dafür zu bekommen, sich ihm anzunähern, eine Beziehung aufzubauen. Wenn das gelingt, dann ist man an einer Art neuem Ort, einer neuen (und gleichzeitig alten) Sichtweise angekommen, die man nicht mehr verliert. Und gleichzeitig Teil einer Gemeinschaft geworden.
Zum Commons gehören Personen und das Commoning. Subjekte und ein Verb. Hinzu kommen die Resourcen, die gemeinsam betreut werden. Also Subjekt, Verb, Objekt. Hilfreicher ist es, die Ressourcen ebenfalls als Subjekte zu sehen. Beim ursprünglichen Commons stand der Commoner in einer partnerschaftlichen Beziehung zu dem Land, das seine Lebensgrundlage war. [1]
Die Commons bilden ein Gegengewicht zu Staat und Privatwirtschaft. Sie funktionieren nach einer anderen Logik, und wirken der kapitalistischen Forderung nach exponentiellem Wachstum, und der Vereinzelung der Menschen in der modernen Gesellschaft entgegen.
Mein Vorhaben ist, alle ein bis zwei Wochen einen kurzen Aufsatz zu schreiben, der einen Aspekt der Commons beleuchtet. Der deutsche Wikipedia-Eintrag gibt sehr gut wieder, wie vielschichtig das Thema ist.
Es könnte dabei in folgende Richtungen gehen:
- Geschichte der Enclosures (Einhegungen)
- Kämpfe indigener Kulturen und anarchischer Gemeinschaften
- Bemühungen, Commons und das Commoning in unserer westlichen Kulturn wiederzubeleben und zu fördern
- Das kollektive Trauma, das mit dem Verlust von Gemeingütern, insbesondere Land, verbunden ist
- Wie sich dies in jedem Einzelnen widerspiegelt
Ich schreibe dabei auch, um mir selbst über bestimmte Dinge klar zu werden. Ich bin mit zwei Commons-Bewegungen im Südwesten Englands verbunden, und diese Beziehungen sind nicht immer ganz einfach. Und doch würde ich mich nicht davon lösen wollen.
Warum schrieb ich davon, dass wir etwas verloren haben, wenn es die Commons doch gibt?
Eine bestimmte Lebensweise, die freien Zugang zu Wald und Acker- und Weideland garantierte, um sich zu ernähren und Holz und Torf zu sammeln, wurde mit den Einhegungen nach und nach zerstört. Während das Leben sicher sehr hart war — und sich zuvor innerhalb der Feudalherrschaft abspielte — sorgten über lange Zeit gewachsene Traditionen und Bräuche dafür, dass Menschen sich zugehörig und versorgt fühlten. Diese Art des Aufgehobenseins ging verloren, als die Landbewohner vertrieben wurden und sich in den Städten als Lohnarbeiter verdingen oder auswandern mussten.
Vor kurzem habe ich ein Buch namens The Traumatised Society gelesen, in dem Fred Harrison das Schicksal des englischen Naturdichters John Clare schildert, der direkt miterlebte, wie das Land eingegrenzt wurde und darüber verzweifelte. Besonders eindrücklich schreibt auch Alastair McIntosh in dem insgesamt sehr erstaunlichen und magischen Buch Soil and Soul über die schottische Version der Einhegungen, die Highland Clearances.
Solche Schilderungen lassen ahnen, wie gewaltsam die Menschen von ihrer früheren Lebensweise getrennt wurden. Später gingen England und andere europäische Mächte in ihren Kolonien ähnlich vor. Die erste Kolonisierung war die der eigenen Bevölkerung. Ich glaube, dass diese Vorgänge uns kollektiv geprägt haben, und wir die Commons brauchen, um den Folgen entgegenzuwirken.
Diese haben aber auch in ihren neueren Formen keinen leichten Stand.
Wie Silke Helfrich schrieb: “Commons existieren nicht in einer heilen Welt, sondern in einer commons-unfreundlichen Umgebung. Es ist daher wichtig, dass Commoners sich bewusst sind, welchen Schatz sie in den Händen halten, um ihn bewahren und entfalten zu können.”
Demnächst mehr...
\ [1] Der amerikanische Priester und Gelehrte Thomas Berry rief dazu auf, das Universum nicht als eine Ansammlung von Objekten zu sehen, sondern eine Gemeinschaft von Subjekten: The universe is a communion of subjects, not a collection of objects.
-
 @ b7274d28:c99628cb
2025-05-27 07:07:33
@ b7274d28:c99628cb
2025-05-27 07:07:33A few months ago, a nostrich was switching from iOS to Android and asked for suggestions for #Nostr apps to try out. nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 offered the following as his response:
nostr:nevent1qvzqqqqqqypzq0mhp4ja8fmy48zuk5p6uy37vtk8tx9dqdwcxm32sy8nsaa8gkeyqydhwumn8ghj7un9d3shjtnwdaehgunsd3jkyuewvdhk6tcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszythwden5te0dehhxarj9emkjmn99uqzpwwts6n28eyvjpcwvu5akkwu85eg92dpvgw7cgmpe4czdadqvnv984rl0z
Yes. #Android users are fortunate to have some powerful Nostr apps and tools at our disposal that simply have no comparison over on the iOS side. However, a tool is only as good as the knowledge of the user, who must have an understanding of how best to wield it for maximum effect. This fact was immediately evidenced by replies to Derek asking, "What is the use case for Citrine?" and "This is the first time I'm hearing about Citrine and Pokey. Can you give me links for those?"
Well, consider this tutorial your Nostr starter-kit for Android. We'll go over installing and setting up Amber, Amethyst, Citrine, and Pokey, and as a bonus we'll be throwing in the Zapstore and Coinos to boot. We will assume no previous experience with any of the above, so if you already know all about one or more of these apps, you can feel free to skip that tutorial.
So many apps...
You may be wondering, "Why do I need so many apps to use Nostr?" That's perfectly valid, and the honest answer is, you don't. You can absolutely just install a Nostr client from the Play Store, have it generate your Nostr identity for you, and stick with the default relays already set up in that app. You don't even need to connect a wallet, if you don't want to. However, you won't experience all that Nostr has to offer if that is as far as you go, any more than you would experience all that Italian cuisine has to offer if you only ever try spaghetti.
Nostr is not just one app that does one thing, like Facebook, Twitter, or TikTok. It is an entire ecosystem of applications that are all built on top of a protocol that allows them to be interoperable. This set of tools will help you make the most out of that interoperability, which you will never get from any of the big-tech social platforms. It will provide a solid foundation for you to build upon as you explore more and more of what Nostr has to offer.
So what do these apps do?

Fundamental to everything you do on Nostr is the need to cryptographically sign with your private key. If you aren't sure what that means, just imagine that you had to enter your password every time you hit the "like" button on Facebook, or every time you commented on the latest dank meme. That would get old really fast, right? That's effectively what Nostr requires, but on steroids.
To keep this from being something you manually have to do every 5 seconds when you post a note, react to someone else's note, or add a comment, Nostr apps can store your private key and use it to sign behind the scenes for you. This is very convenient, but it means you are trusting that app to not do anything with your private key that you don't want it to. You are also trusting it to not leak your private key, because anyone who gets their hands on it will be able to post as you, see your private messages, and effectively be you on Nostr. The more apps you give your private key to, the greater your risk that it will eventually be compromised.
Enter #Amber, an application that will store your private key in only one app, and all other compatible Nostr apps can communicate with it to request a signature, without giving any of those other apps access to your private key.
Most Nostr apps for Android now support logging in and signing with Amber, and you can even use it to log into apps on other devices, such as some of the web apps you use on your PC. It's an incredible tool given to us by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, and only available for Android users. Those on iPhone are incredibly jealous that they don't have anything comparable, yet.

Speaking of nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, the next app is also one of his making.
All Nostr data is stored on relays, which are very simple servers that Nostr apps read notes from and write notes to. In most forms of social media, it can be a pain to get your own data out to keep a backup. That's not the case on Nostr. Anyone can run their own relay, either for the sake of backing up their personal notes, or for others to post their notes to, as well.
Since Nostr notes take up very little space, you can actually run a relay on your phone. I have been on Nostr for almost 2 and a half years, and I have 25,000+ notes of various kinds on my relay, and a backup of that full database is just 24MB on my phone's storage.
Having that backup can save your bacon if you try out a new Nostr client and it doesn't find your existing follow list for some reason, so it writes a new one and you suddenly lose all of the people you were following. Just pop into your #Citrine relay, confirm it still has your correct follow list or import it from a recent backup, then have Citrine restore it. Done.
Additionally, there are things you may want to only save to a relay you control, such as draft messages that you aren't ready to post publicly, or eCash tokens, which can actually be saved to Nostr relays now. Citrine can also be used with Amber for signing into certain Nostr applications that use a relay to communicate with Amber.
If you are really adventurous, you can also expose Citrine over Tor to be used as an outbox relay, or used for peer-to-peer private messaging, but that is far more involved than the scope of this tutorial series.

You can't get far in Nostr without a solid and reliable client to interact with. #Amethyst is the client we will be using for this tutorial because there simply isn't another Android client that comes close, so far. Moreover, it can be a great client for new users to get started on, and yet it has a ton of features for power-users to take advantage of as well.
There are plenty of other good clients to check out over time, such as Coracle, YakiHonne, Voyage, Olas, Flotilla and others, but I keep coming back to Amethyst, and by the time you finish this tutorial, I think you'll see why. nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z and others who have contributed to Amethyst have really built something special in this client, and it just keeps improving with every update that's shipped.
Most social media apps have some form of push notifications, and some Nostr apps do, too. Where the issue comes in is that Nostr apps are all interoperable. If you have more than one application, you're going to have both of them notifying you. Nostr users are known for having five or more Nostr apps that they use regularly. If all of them had notifications turned on, it would be a nightmare. So maybe you limit it to only one of your Nostr apps having notifications turned on, but then you are pretty well locked-in to opening that particular app when you tap on the notification.
Pokey, by nostr:npub1v3tgrwwsv7c6xckyhm5dmluc05jxd4yeqhpxew87chn0kua0tjzqc6yvjh, solves this issue, allowing you to turn notifications off for all of your Nostr apps, and have Pokey handle them all for you. Then, when you tap on a Pokey notification, you can choose which Nostr app to open it in.
Pokey also gives you control over the types of things you want to be notified about. Maybe you don't care about reactions, and you just want to know about zaps, comments, and direct messages. Pokey has you covered. It even supports multiple accounts, so you can get notifications for all the npubs you control.

One of the most unique and incredibly fun aspects of Nostr is the ability to send and receive #zaps. Instead of merely giving someone a 👍️ when you like something they said, you can actually send them real value in the form of sats, small portions of a Bitcoin. There is nothing quite like the experience of receiving your first zap and realizing that someone valued what you said enough to send you a small amount (and sometimes not so small) of #Bitcoin, the best money mankind has ever known.
To be able to have that experience, though, you are going to need a wallet that can send and receive zaps, and preferably one that is easy to connect to Nostr applications. My current preference for that is Alby Hub, but not everyone wants to deal with all that comes along with running a #Lightning node. That being the case, I have opted to use nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch for this tutorial, because they offer one of the easiest wallets to set up, and it connects to most Nostr apps by just copy/pasting a connection string from the settings in the wallet into the settings in your Nostr app of choice.
Additionally, even though #Coinos is a custodial wallet, you can have it automatically transfer any #sats over a specified threshold to a separate wallet, allowing you to mitigate the custodial risk without needing to keep an eye on your balance and make the transfer manually.

Most of us on Android are used to getting all of our mobile apps from one souce: the Google Play Store. That's not possible for this tutorial series. Only one of the apps mentioned above is available in Google's permissioned playground. However, on Android we have the advantage of being able to install whatever we want on our device, just by popping into our settings and flipping a toggle. Indeed, thumbing our noses at big-tech is at the heart of the Nostr ethos, so why would we make ourselves beholden to Google for installing Nostr apps?
The nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 is an alternative app store made by nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9 as a resource for all sorts of open-source apps, but especially Nostr apps. What is more, you can log in with Amber, connect a wallet like Coinos, and support the developers of your favorite Nostr apps directly within the #Zapstore by zapping their app releases.
One of the biggest features of the Zapstore is the fact that developers can cryptographically sign their app releases using their Nostr keys, so you know that the app you are downloading is the one they actually released and hasn't been altered in any way. The Zapstore will warn you and won't let you install the app if the signature is invalid.
Getting Started
Since the Zapstore will be the source we use for installing most of the other apps mentioned, we will start with installing the Zapstore.
We will then use the Zapstore to install Amber and set it up with our Nostr account, either by creating a new private key, or by importing one we already have. We'll also use it to log into the Zapstore.
Next, we will install Amethyst from the Zapstore and log into it via Amber.
After this, we will install Citrine from the Zapstore and add it as a local relay on Amethyst.
Because we want to be able to send and receive zaps, we will set up a wallet with CoinOS and connect it to Amethyst and the Zapstore using Nostr Wallet Connect.
Finally, we will install Pokey using the Zapstore, log into it using Amber, and set up the notifications we want to receive.
By the time you are done with this series, you will have a great head-start on your Nostr journey compared to muddling through it all on your own. Moreover, you will have developed a familiarity with how things generally work on Nostr that can be applied to other apps you try out in the future.
Continue to Part 2: The Zapstore. Nostr Link: nostr:naddr1qvzqqqr4gupzpde8f55w86vrhaeqmd955y4rraw8aunzxgxstsj7eyzgntyev2xtqydhwumn8ghj7un9d3shjtnzwf5kw6r5vfhkcapwdejhgtcqp5cnwdphxv6rwwp3xvmnzvqgty5au
-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ cae03c48:2a7d6671
2025-05-29 00:01:56
@ cae03c48:2a7d6671
2025-05-29 00:01:56Bitcoin Magazine

GameStop Buys $513 Million Worth of BitcoinVideo game retailer GameStop has purchased 4,710 Bitcoin worth approximately $513 million, marking another major corporate entry into Bitcoin treasury holdings as the trend of companies adding Bitcoin to their balance sheets accelerates in 2025.
The company announced the acquisition via X on Wednesday but did not disclose specific details about when the purchases were made or the average price paid per coin. The move follows GameStop’s March announcement of plans to pursue a Bitcoin treasury strategy, which included a $1.3 billion convertible senior notes offering to fund Bitcoin purchases.
BREAKING:
 GAMESTOP PURCHASED 4,710 #BITCOIN pic.twitter.com/fDH9ctZJVP
GAMESTOP PURCHASED 4,710 #BITCOIN pic.twitter.com/fDH9ctZJVP— Bitcoin Magazine (@BitcoinMagazine) May 28, 2025
GameStop’s Bitcoin acquisition represents a strategic shift in corporate treasury management, following the playbook established by companies like Strategy.
The purchase comes amid a surge in corporate Bitcoin adoption, with over 50 public companies announcing Bitcoin treasury programs in the first five months of 2025. Recent entrants include 21 Capital, Strive, H100 Group and more.
The announcement pushed GameStop’s shares up 4.4% in pre-market trading, while Bitcoin traded near $108,900. The company reported $4.78 billion in cash and marketable securities as of February 1, suggesting this Bitcoin investment represents approximately 10.7% of its liquid assets.
The move follows similar treasury diversification strategies by other major corporations, including Tesla’s $1.25 billion Bitcoin holding and recent announcements from Trump Media and Technology Group of plans to raise $2.5 billion for Bitcoin purchases.
At press time, Bitcoin trades at $108,900, down 0.68% over the past 24 hours, as the market processes this significant institutional development and its implications for broader corporate adoption of Bitcoin as a treasury asset.
This post GameStop Buys $513 Million Worth of Bitcoin first appeared on Bitcoin Magazine and is written by Vivek Sen.
-
 @ eb0157af:77ab6c55
2025-05-27 07:01:37
@ eb0157af:77ab6c55
2025-05-27 07:01:37The exchange reveals the extent of the breach that occurred last December as federal authorities investigate the data leak.
Coinbase has disclosed that the personal data of 69,461 users was compromised during the breach in December 2024, according to documentation filed with the Maine Attorney General’s Office.
The disclosure comes after Coinbase announced last week that a group of hackers had demanded a $20 million ransom, threatening to publish the stolen data on the dark web. The attackers allegedly bribed overseas customer service agents to extract information from the company’s systems.
Coinbase had previously stated that the breach affected less than 1% of its user base, compromising KYC (Know Your Customer) data such as names, addresses, and email addresses. In a filing with the U.S. Securities and Exchange Commission (SEC), the company clarified that passwords, private keys, and user funds were not affected.
Following the reports, the SEC has reportedly opened an official investigation to verify whether Coinbase may have inflated user metrics ahead of its 2021 IPO. Separately, the Department of Justice is investigating the breach at Coinbase’s request, according to CEO Brian Armstrong.
Meanwhile, Coinbase has faced criticism for its delayed response to the data breach. Michael Arrington, founder of TechCrunch, stated that the stolen data could cause irreparable harm. In a post on X, Arrington wrote:
“The human cost, denominated in misery, is much larger than the $400m or so they think it will actually cost the company to reimburse people. The consequences to companies who do not adequately protect their customer information should include, without limitation, prison time for executives.”
Coinbase estimates the incident could cost between $180 million and $400 million in remediation expenses and customer reimbursements.
Arrington also condemned KYC laws as ineffective and dangerous, calling on both regulators and companies to better protect user data:
“Combining these KYC laws with corporate profit maximization and lax laws on penalties for hacks like these means these issues will continue to happen. Both governments and corporations need to step up to stop this. As I said, the cost can only be measured in human suffering.”
The post Coinbase: 69,461 users affected by December 2024 data breach appeared first on Atlas21.
-
 @ 6a6be47b:3e74e3e1
2025-05-27 16:36:21
@ 6a6be47b:3e74e3e1
2025-05-27 16:36:21🔍 Today was one of those days where I dove deeper into the world of Stacker News, exploring how wallets work and all that jazz. If you have any tips or tricks, please send them my way—I’m still figuring it all out!
After my tech adventures, I turned to drawing. Usually, I have a lineup of ideas ready to go, but none of them quite fit my mood today. Then I remembered the butterflies from my upcoming blog entry—can you guess what I’m writing and painting about? 👀
🦋Even though I’ve painted butterflies before here’s one on Instagram, I felt like revisiting them.
This one I posted on Nostr, a while ago
Lately, I’ve been seeing butterflies everywhere on my walks with my dog, and they just felt right for today’s art session. So here’s to butterflies and their beautiful symbolism!
In Celtic mythology, there’s an old Irish saying:
“Butterflies are souls of the dead waiting to pass through Purgatory.” From mindbodygreen.com
It’s no wonder butterflies are often seen as symbols of rebirth. Even Aristotle named the butterfly:
“Psyche,” the Greek word for “soul.” From learnreligions.com
☀️With the weather warming up, days growing longer, and the air full of new scents (and butterfly sightings!🦋), I invite you to really enjoy this season. After drawing today’s butterfly, I realized how freeing it is to just let go and create—no pressure, just fun. Sometimes, taking even a few mindful minutes to do something you love can work wonders—maybe even a little magic.
Hope to catch you on the next one, frens. Godspeed! ✨
Today's butterfly. I drew it on Procreate.
https://stacker.news/items/990470
-
 @ 3bf0c63f:aefa459d
2024-01-29 02:19:25
@ 3bf0c63f:aefa459d
2024-01-29 02:19:25Nostr: a quick introduction, attempt #1
Nostr doesn't have a material existence, it is not a website or an app. Nostr is just a description what kind of messages each computer can send to the others and vice-versa. It's a very simple thing, but the fact that such description exists allows different apps to connect to different servers automatically, without people having to talk behind the scenes or sign contracts or anything like that.
When you use a Nostr client that is what happens, your client will connect to a bunch of servers, called relays, and all these relays will speak the same "language" so your client will be able to publish notes to them all and also download notes from other people.
That's basically what Nostr is: this communication layer between the client you run on your phone or desktop computer and the relay that someone else is running on some server somewhere. There is no central authority dictating who can connect to whom or even anyone who knows for sure where each note is stored.
If you think about it, Nostr is very much like the internet itself: there are millions of websites out there, and basically anyone can run a new one, and there are websites that allow you to store and publish your stuff on them.
The added benefit of Nostr is that this unified "language" that all Nostr clients speak allow them to switch very easily and cleanly between relays. So if one relay decides to ban someone that person can switch to publishing to others relays and their audience will quickly follow them there. Likewise, it becomes much easier for relays to impose any restrictions they want on their users: no relay has to uphold a moral ground of "absolute free speech": each relay can decide to delete notes or ban users for no reason, or even only store notes from a preselected set of people and no one will be entitled to complain about that.
There are some bad things about this design: on Nostr there are no guarantees that relays will have the notes you want to read or that they will store the notes you're sending to them. We can't just assume all relays will have everything — much to the contrary, as Nostr grows more relays will exist and people will tend to publishing to a small set of all the relays, so depending on the decisions each client takes when publishing and when fetching notes, users may see a different set of replies to a note, for example, and be confused.
Another problem with the idea of publishing to multiple servers is that they may be run by all sorts of malicious people that may edit your notes. Since no one wants to see garbage published under their name, Nostr fixes that by requiring notes to have a cryptographic signature. This signature is attached to the note and verified by everybody at all times, which ensures the notes weren't tampered (if any part of the note is changed even by a single character that would cause the signature to become invalid and then the note would be dropped). The fix is perfect, except for the fact that it introduces the requirement that each user must now hold this 63-character code that starts with "nsec1", which they must not reveal to anyone. Although annoying, this requirement brings another benefit: that users can automatically have the same identity in many different contexts and even use their Nostr identity to login to non-Nostr websites easily without having to rely on any third-party.
To conclude: Nostr is like the internet (or the internet of some decades ago): a little chaotic, but very open. It is better than the internet because it is structured and actions can be automated, but, like in the internet itself, nothing is guaranteed to work at all times and users many have to do some manual work from time to time to fix things. Plus, there is the cryptographic key stuff, which is painful, but cool.
-
 @ bf47c19e:c3d2573b
2025-05-28 20:37:58
@ bf47c19e:c3d2573b
2025-05-28 20:37:58Bitcoin: Peer-to-peer sistem elektronskog novca
Satoshi Nakamoto
satoshin@gmx.com
Prevedeno na srpski sa bitcoin.org/bitcoin.pdf od strane ECD
Sažetak. Potpuna peer-to-peer verzija elektronskog novca omogućila bi slanje uplata putem interneta direktno od jedne strane ka drugoj bez posredovanja finansijskih institucija. Digitalni potpisi pružaju deo rešenja, ali se glavni benefiti gube ako je i dalje potrebna pouzdana treća strana za sprečavanje dvostruke potrošnje. Predlažemo rešenje problema dvostruke potrošnje korišćenjem peer-to-peer mreže. Mreža vremenski označava transakcije tako što ih hešuje u tekući lanac dokaza o radu (proof of work) temeljen na hešu, formirajući zapis koji se ne može promeniti bez ponovnog rada i objavljivanja dokaza o tom radu. Najduži lanac ne služi samo kao dokaz niza događaja, nego i kao dokaz da je taj niz događaja potvrđen od strane dela peer-to-peer mreže koja poseduju najveću zbirnu procesorsku snagu (CPU). Sve dok većinu procesorske snage kontrolišu čvorovi (nodes) koji ne sarađuju u napadu na mrežu, oni će generisati najduži lanac i nadmašiti napadače. Sama mreža zahteva minimalnu strukturu. Poruke kroz mrežu se prenose uz pretpostavku da svaki čvor čini maksimalan napor da poruku prenese u svom izvornom obliku i na optimalan način, a čvorovi mogu napustiti mrežu i ponovo joj se pridružiti po želji, prihvatajući najduži lanac dokaza o radu kao dokaz onoga što se dogodilo dok ih nije bilo.
1. Uvod
Trgovina na Internetu počela je da se oslanja skoro isključivo na finansijske institucije koje služe kao pouzdani posrednici pri obradi elektronskih plaćanja. Iako sistem radi dovoljno dobro za većinu transakcija i dalje trpi od inherentnih slabosti modela utemeljenog na poverenju.
Potpuno nepovratne transakcije zapravo nisu moguće, jer finansijske institucije ne mogu izbeći posredovanje u rešavanju eventualnih sporova. Troškovi posredovanja povećavaju troškove transakcija, ograničavaju minimalnu praktičnu veličinu transakcija i onemogućuju male, povremene transakcije jer postoji velika šteta zbog gubitka mogućnosti da se izvrše nepovratna plaćanja za nepovratne usluge. Uz mogućnost povraćaja transakcije, potreba za poverenjem raste. Trgovci moraju biti oprezni prema svojim kupcima i tražiti im više informacija nego što bi inače bilo neophodno. Određeni procenat prevara prihvaćen je kao neizbežan. Ovi troškovi i nepouzdanost plaćanja mogu se izbeći korišćenjem gotovine, ali ne postoji mehanizam za elektronsko plaćanje bez pouzdane treće strane.
Ono što je potrebno je elektronski sistem plaćanja zasnovan na kriptografskom dokazu umesto na poverenju, koji omogućava da bilo koje dve strane direktno i dobrovoljno međusobno trguju bez potrebe za posrednikom. Transakcije koje su nepovratne bi zaštitile prodavce od prevara, a escrow mehanizmi mogli bi se lako implementirati radi zaštite kupaca. U ovom dokumentu predlažemo rešenje problema dvostruke potrošnje korišćenjem peer-to-peer distribuiranog servera vremenskih oznaka (timestamp) za generisanje računarskog dokaza o hronološkom redosledu transakcija. Sistem je siguran sve dok pošteni čvorovi zajedno kontrolišu više procesorske snage procesora nego bilo koja udružena grupa napadačkih čvorova.
2. Transakcije
Elektronski novčić definišemo kao lanac digitalnih potpisa. Svaki vlasnik prenosi novčić na sledećeg digitalnim potpisivanjem heša prethodne transakcije i javnog ključa sledećeg vlasnika, dodajući ih potom na kraj novčića. Primalac transakcije može da verifikuje potpise, a time i lanac vlasništva.

Problem je naravno u tome što primalac ne može potvrditi da jedan od prethodnih vlasnika nije dva puta poslao isti novčić. Uobičajeno rešenje je uvođenje pouzdanog centralizovanog posrednika, kreatora novčića koji proverava sve transakcije. Nakon svake transakcije, novčić se mora vratiti kreatoru kako bi se izdao novi novčić i veruje se da samo za novčiće izdate direktno od kreatora možemo biti sigurni da nisu dva puta potrošeni. Problem sa ovim rešenjem je što sudbina čitavog novčanog sistema zavisi od kompanije koja kreira novčiće, jer svaka transakcija mora da prođe kroz nju, baš kao što je slučaj sa bankom.
Treba nam način da primalac bude siguran da prethodni vlasnici nisu potpisali nikakve ranije transakcije kojim bi potrošili taj novčić. Za naše potrebe, računamo transakciju koja se prva desila i ne zanimaju nas naredni pokušaji da se isti novčić ponovo pošalje. Jedini način da sa sigurnošću potvrdimo da taj novčić nije prethodno bio poslat je da imamo informacije o svim transakcijama koje su se ikada desile. U modelu baziranom na centalizovan kreatoru, taj kreator je imao informacije o svim transakcijama i odlučivao koja transakcija je prva stigla. Da bismo to postigli bez pouzdanog posrednika, transakcije moraju biti javno objavljene [1] i potreban nam je sistem u kojem učesnici mogu da se dogovore o jedinstvenoj istoriji redosleda kojim su transakcije primljene. Primaocu je potreban dokaz da se u trenutku dešavanja svake od transakcija većina čvorova složila oko toga da je baš ta transakcija bila ona koja je prva primljena.
3. Server vremenskih oznaka
Rešenje koje predlažemo počinje serverom vremenskih oznaka. Server vremenske oznake radi tako što uzima heš bloka podataka kojem će se dodeliti vremenska oznaka i objavi taj heš svima u mreži, slično kao u novinama ili kao post na Usenet mreži [2-5]. Vremenska oznaka očigledno dokazuje da su podaci morali postojati u to vreme kako bi ušli u haš. Svaka vremenska oznaka sadrži prethodnu vremensku oznaku u svom hešu, formirajući tako lanac, pri čemu svaka dodatna vremenska oznaka pojačava potvrde onih pre nje.

4. Dokaz o radu (Proof-of-Work)
Da bismo implementirali distribuirani server vremenskih oznaka na peer-to-peer principu, moraćemo da koristimo sistem dokaza o radu sličan Hashcash-u Adama Back-a [6], umesto Uneset postova ili novinskih objava. Dokaz o radu uključuje traženje vrednosti koja će, kada se hešuje, na primer pomoću SHA-256 heš funkcije, stvarati heš čiji binarni zapis započinje određenim brojem nula. Prosečna količina potrebnog rada eksponencijalno raste sa brojem potrebnih početnih nula, a može se proveriti izvršavanjem samo jedne heš fuknkcije.
Za našu mrežu vremenskih oznaka implementiramo dokaz o radu povećavajući nonce broja u bloku sve dok se ne pronađe ona vrednost nonce-a koja daje hešu bloka potreban broj početnih nula. Jednom kada se procesorska snaga utroši kako bi se zadovoljio dokaz o radu, blok se ne može izmeniti bez ponovljenog rada. Kako se kasniji blokovi vežu na taj blok, rad potreban da se on izmeni uključivao bi i ponovno obrađivanje svih blokova nakon njega.

Dokaz o radu takođe rešava problem utvrđivanja većine pri odlučivanju. Ako bi se većina zasnivala na principu jednog glasa po IP adresi, mogao bi je narušiti svako ko je u stanju da glasa sa više IP adresa odjednom. Dokaz o radu u osnovi predstavlja jedan glas po jedinici procesorske snage. Većinska odluka je predstavljena najdužim lancem u čije je stvaranje zapravo investirano najviše rada prilikom dokazivanja. Ako većinu procesorske snage kontrolišu pošteni čvorovi, pošten lanac će rasti najbrže i nadmašiće sve konkurentske lance. Da bi izmenio neki od prethodnih blokova, napadač bi morao da ponovi dokaz o radu za taj blok i sve blokove nakon njega, a zatim da sustigne i nadmaši količinu rada poštenih čvorova. Kasnije ćemo pokazati da se dodavanjem novih blokova eksponencijalno smanjuje verovatnoća da će sporiji napadač uspeti da sustigne pošteni lanac.
Da bi se kompenzovalo povećanje brzine hardvera i promenljivo interesovanje ljudi za vođenje čvorova tokom vremena, težina obavljanja dokaza o radu (proof-of-work difficulty) određuje se prema prosečnom broju blokova krairanih za sat vremena. Ako se blokovi stvaraju prebrzo, težina se povećava.
5. Mreža
Koraci za vođenje mreže su sledeći:
1) Nove transakcije se prosleđuju svim čvorovima u mreži. 2) Svaki čvor prikuplja nove transakcije u blok. 3) Svaki čvor radi na pronalaženju dokaza o radu dovoljnog nivoa težine za svoj blok. 4) Kada čvor pronađe dokaz o radu, on emituje taj blok ka svim čvorovima. 5) Čvorovi prihvataju blok samo ako su sve transakcije u njemu ispravne i nisu već potrošene. 6) Čvorovi izražavaju prihvatanje bloka radeći na stvaranju sledećeg bloka u lancu, koristeći heš prihvaćenog bloka kao prethodni heš.
Čvorovi uvek smatraju da je najduži lanac ispravan i nastaviće da rade na njegovom produžavanju. Ako dva čvora istovremeno emituju različite verzije sledećeg bloka, neki čvorovi prvo mogu primiti jedan ili drugi blok. U tom slučaju svaki čvor radi na prvom koji je dobio, ali čuvaju drugu kariku lanca u slučaju da ona postane duža. Dilema će biti rešena kada se pronađe sledeći dokaz o radu i jedna karika postane duža; čvorovi koji su radili na drugoj karici lanca će se prebaciti na dužu kariku.
Emitovanje novih transakcija ne mora nužno doći do svih čvorova. Sve dok stižu do velikog broja čvorova, te transakcije će ući u blok. Slično važi i za blokove, ni oni ne moraju doći odmah do svih čvorova. Ako neki čvor propusti da primi informaciju o bloku, kada mu stigne sledeći blok,primetiće da je propustio jedan, pa će ga tražiti naknadno.
6. Podsticaj
Po pravilu, prva transakcija u bloku je posebna transakcija koja kreira novi novčić u vlasništvu kreatora bloka. Ovo daje podsticaj čvorovima da podrže mrežu i pruža način za početnu ubacivanje novčića u opticaj, budući da ne postoji centralno telo koje ih izdaje. Stalno dodavanje konstantne količine novih novčića liči na rudarenje zlata, gde rudari ulažu resurse kako bi izrudarili nove količine zlata i ubacili ih u opticaj. U našem slučaju ulaže se procesorsko vreme i električna energija.
Podsticaj se takođe može finansirati i transakcionim naknadama. Ako je iznos izlaznog dela transakcije manji od ulaznog, razliku čini naknada za transakciju koja se dodaje iznosu nagrade za kreatora bloka koji sadrži tu transakciju. Nakon što predefinisani broj novčića uđe u opticaj, podsticaj mogu u potpunosti činiti transakcione naknade, čime se sistem oslobađa inflacije.
Čvorovi su na ovaj način podstaknuti da ostanu pošteni. Ako je pohlepni napadač u stanju da angažuje više procesorske snage od svih poštenih čvorova zajedno, morao bi da bira između toga da poništi svoje izvršene transakcije i time prevari ljude ili da procesorsku snagu koristi za stvaranje novih novčića. On bi trebalo bi uvidi da je isplativije igrati po pravilima koja ga nagrađuju sa više novih novčića od svi drugi zajedno, nego da potkopava sistem i vrednost sopstvenog bogatstva.
7. Oslobađanje prostora na hard disku
Kada je dovoljno blokova dodato nakon poslednje transakcije novčića, prethodne transakcije tog novčića se mogu odbaciti kako bi se uštedeo prostor na hard disku. Kako bi se to ostvarilo bez razbijanja heša bloka, transakcije su hešovane u Merkleovo stablo (Merkle Tree) [7] [2] [5], gde je samo koren uključen u heš bloka. Stari blokovi se tada mogu sabiti uklanjanjem nepotrebnih grana drveta. Unutrašnji heševi ne moraju biti skladišteni.

Zaglavlje bloka bez transakcija bilo bi oko 80 bajtova. Ako pretpostavimo da su blokovi generisani svakih 10 minuta, 80 bajtova * 6 * 24 * 365 = 4,2 MB godišnje. Imajući u vidu činjenicu da se u 2008. godini računari uglavnom prodaju sa oko 2 GB RAM-a i Murov zakon koji predviđa trenutni rast od 1,2 GB godišnje, skladištenje ne bi trebalo da predstavlja problem čak i ako se zaglavlja bloka moraju čuvati u memoriji.
8. Pojednostavljena verifikacija plaćanja
Moguće je verifikovati plaćanja bez vođenja čitavog mrežnog čvora. Korisnik samo treba da sačuva kopiju zaglavlja blokova najdužeg lanca dokaza o radu, do koje može doći upitom ka mrežnim čvorovima dok se ne uveri da je dobio najduži lanac i dobije Merkleova granu
koja povezuje transakciju sa blokom u koji je uneta vremenska oznaka za tu transakciju. Ne može samostalno proveriti transakciju, ali povezujući je sa mestom u lancu može videti da je prihvaćena od strane čvora mreže i da su na njen blok dodati naknadni blokovi što dalje potvrđuje da ju je mreža prihvatila.

Kao takva, verifikacija je pouzdana sve dok pošteni čvorovi kontrolišu mrežu, ali je ranjiva ako napadač nadjača ostatak mreže. Čvorovi mreže mogu sami proveriti transakcije, ali napadačeve lažne transakcije mogu zavarati one koji koriste pojednostavljenu metodu verifikacije transakcija sve dok je on u stanju da nadjačava ostatak mreže. Jedna od strategija zaštite bila bi prihvatanje upozorenja čvorova mreže kada otkriju nevažeći blok, pri čemu bi korisnikov softver morao da preuzme ceo blok i sporne transakcije kako bi potvrdio nepravilnost. Biznisi koji primaju česte uplate će verovatno želeti da pokrenu i vode sopstvene čvorove radi brže verifikacije i potrebe da im sigurnost ne zavisi od drugih.
9. Kombinovanje i deljenje vrednosti
Iako bi bilo moguće pojedinačno rukovati novčićima, bilo bi nezgrapno kreirati zasebnu transakciju za svaki cent u toj transferu. Da biste dozvolili podelu i kombinovanje vrednosti, transakcije sadrže više ulaza i izlaza. Obično će postojati ili jedan ulaz iz veće prethodne transakcije ili više unosa koji kombinuju manje iznose, a najviše dva izlaza: jedan za samo plaćanje, a jedan koji vraća kusur, ako ga ima, nazad pošiljaocu.

Treba napomenuti da situacija u kojoj transakcija zavisi od nekoliko drugih transakcija, a te transakcije zavise od još mnogo više, ovde nije problem. Nikada ne postoji potreba za izdvajanjem istorije pojedinačne transakcije.
10. Privatnost
Tradicionalni bankarski model postiže odgovarajući nivo privatnosti ograničavanjem pristupa informacijama na strane uključene u transakciju i posrednika. Neophodnost javnog objavljivanja svih transakcija isključuje mogućnost primene pomenutog modela, ali privatnost se i dalje može zadržati na drugi način: čuvanjem javnih ključeva (public keys) anonimnim. Javnost može videti da neko šalje iznos nekom drugom, ali bez informacija koje povezuju transakciju sa bilo kim. Ovo je slično količini informacija koje objavljuju berze, gde se vreme i veličina pojedinačnih trgovina čine javnim, ali bez navođenja ko su stranke uključene u tu trgovinu.

Kao dodatni zaštitni zid, preporučljivo je koristiti novi par ključeva za svaku transakciju, kako ne bi bili povezane sa zajedničkim vlasnikom. Neka povezivanja su i dalje neizbežna kod transakcija sa više ulaza, koje nužno otkrivaju da su njihovi ulazi bili u vlasništvu istog vlasnika. Rizik je taj da bi se otkrivanjem vlasnik ključa mogle otkriti i ostale transakcije koje su pripadale tom vlasniku.
11. Proračuni
Razmatramo scenario u kome napadač pokušava da generiše alternativni lanac brže od poštenog lanca. Čak i ako se to postigne, to ne omogućuje proizvoljne promene u sistemu, poput stvaranje vrednosti ni iz čega ili uzimanje novca koji nikada nije pripadao napadaču. Pošteni čvorovi neće prihvatiti nevažeće transakcije kao uplatu i nikada neće prihvatiti blok koji ih sadrži. Napadač može samo pokušati da promeni jednu od svojih transakcija kako bi vratio novac koji je nedavno potrošio.
Trka između poštenog lanca i lanca napadača može se predstaviti kao binomska distribucija slučajne diskretne varijable (Binomial Random Walk). Uspešni ishod je da se pošten lanac produži za jedan blok, povećavajući svoje vođstvo za +1, a neuspešni ishod je da se napadačev lanac produži za jedan blok, smanjujući zaostatak za -1.
Verovatnoću da napadač nadoknadi određeni deficit možemo izraziti kroz problem kockareve propasti (Gambler’s Ruin Problem). Pretpostavimo da kockar sa neograničenim iznosom novca počinje sa zaostatkom i igra potencijalno beskonačan broj ponovljenih igara u pokušaju da nadoknadi zaostatak. Možemo izračunati verovatnoću za nadoknađivanje zaostatka ili da će napadač stići pošten lanac, na sledeći način [8]:
p= verovatnoća da pošten čvor pronađe sledeći blok q= verovatnoća da napadač pronađe sledeći blok qz= verovatnoća da će napadač ikada dostići z blokova zaostatka

S obzirom na našu pretpostavku da je p > q, verovatnoća pada eksponencijalno kako se povećava broj blokova koje napadač mora da nadoknadi. Sa šansama protiv njega, ako mu se u početku ne posreći, njegove šanse postaju manje i manje sa povećanjem zaostatka.
Sada razmatramo koliko primalac nove transakcije treba da čeka pre nego što postane
dovoljno siguran da pošiljalac ne može promeniti transakciju. Pretpostavljamo da je pošiljalac napadač koji želi da natera primaoca da veruje da mu je platio, a zatim nakon nekog vremena tu transakciju preusmeri ka sebi. Primalac će primetiti kada se to dogodi, ali pošiljalac se nada da će tad već biti prekasno.
Primalac generiše novi par ključeva i daje javni ključ pošiljaocu neposredno pre potpisivanja transakcije. Ovo sprečava pošiljaoca da unapred pripremi lanac blokova radeći na njemu neprekidno dok mu se ne posreći da stekne dovoljnu prednost i u tom trenutku izvrši transakciju. Kada se transakcija pošalje, nepošteni pošiljalac počinje tajno da radi na paralelnom lancu koji sadrži alternativnu verziju njegove transakcije.
Primalac čeka dok transakcija ne bude dodata u blok, i dok z blokova nije dodato nakon tog bloka. On ne zna tačno koliko je napadač napredovao, ali pod pretpostavkom da su pošteni blokovi kreirani očekivanom dinamikom, potencijalni napredak napadača će biti prikazan kao Poasonova distribucija sa očekivanom vrednošću:

Kako bismo izračunali verovatnoću da napadač ipak može da nadoknadi zaostatak, množimo gustinu verovatnoće za svaki nivo napretka koji je mogao da ostvari sa verovatnoćom da od tog trenutka može da potpuno nadoknadi zaostatak:

Preuređujemo formulu kako bismo izbegli sabiranje beskonačnog broja sabiraka zbog repa distribucije:

I konvertujemo u programski kod u programskom jeziku C…

Kroz par primera, vidimo da verovatnoća opada eksponencijalno sa porastom z.

Rešavanje za P < 0.1%…

12. Zaključak
Predložili smo sistem za elektronske transakcije bez oslanjanja na poverenje. Počeli smo sa uobičajenim šablonom i novčićima nastalim iz digitalnih potpisa, koji pruža snažnu kontrolu nad vlasništvom, ali je nepotpun bez načina da se spreči dvostruka potrošnja. Kako bismo ovo rešili, predložili smo peer-to-peer mrežu koja koristi dokaz o radu za čuvanje javne istorije transakcija čija izmena napadačima brzo postaje računski nepraktična ako pošteni čvorovi kontrolišu većinu procesorske snage. Mreža je robusna u svojoj nestrukturiranoj jednostavnosti. Svi čvorovi rade istovremeno uz malo koordinacije. Ne treba ih identifikovati, jer se poruke ne usmeravaju na jedno određeno mesto nego samo trebaju biti prenete uz maksimalan napor od strane čvorova da se taj prenos odradi na predviđen način. Čvorovi mogu da napuste i ponovo se pridruže mreži po želji, prihvatajući lanac dokaza o radu kao dokaz onoga što se dogodilo dok ih nije bilo. Oni glasaju svojom procesorskom snagom, izražavajući svoje prihvatanje validnih blokova time što pokušavaju da ih nadgrade novim blokovima i odbacuju nevažeće blokove odbijanjem ih nadgrađuju. Sva potrebna pravila i podsticaji mogu se nametnuti ovim mehanizmom postizanja konsenzusa.
Reference:
[1] W. Dai, „b-money,“ weidai.com/bmoney.txt, 1998.
[2] H. Massias, X.S. Avila, and J.-J. Quisquater, „Design of a secure timestamping service with minimal trust requirements,“ In 20th Symposium on Information Theory in the Benelux, May 1999.
[3] S. Haber, W.S. Stornetta, „How to time-stamp a digital document,“ In Journal of Cryptology, vol 3, no 2, pages 99-111, 1991.
[4] D. Bayer, S. Haber, W.S. Stornetta, „Improving the efficiency and reliability of digital time-stamping,“ In Sequences II: Methods in Communication, Security and Computer Science, pages 329-334, 1993.
[5] S. Haber, W.S. Stornetta, „Secure names for bit-strings,“ In Proceedings of the 4th ACM Conference on Computer and Communications Security, pages 28-35, April 1997.
[6] A. Back, „Hashcash – a denial of service counter-measure,“ hashcash.org/papers/hashcash.pdf, 2002.
[7] R.C. Merkle, „Protocols for public key cryptosystems,“ In Proc. 1980 Symposium on Security and Privacy, IEEE Computer Society, pages 122-133, April 1980.
[8] W. Feller, „An introduction to probability theory and its applications,“ 1957.































