-
 @ c631e267:c2b78d3e
2025-05-16 18:40:18
@ c631e267:c2b78d3e
2025-05-16 18:40:18Die zwei mächtigsten Krieger sind Geduld und Zeit. \ Leo Tolstoi
Zum Wohle unserer Gesundheit, unserer Leistungsfähigkeit und letztlich unseres Glücks ist es wichtig, die eigene Energie bewusst zu pflegen. Das gilt umso mehr für an gesellschaftlichen Themen interessierte, selbstbewusste und kritisch denkende Menschen. Denn für deren Wahrnehmung und Wohlbefinden waren und sind die rasanten, krisen- und propagandagefüllten letzten Jahre in Absurdistan eine harte Probe.
Nur wer regelmäßig Kraft tankt und Wege findet, mit den Herausforderungen umzugehen, kann eine solche Tortur überstehen, emotionale Erschöpfung vermeiden und trotz allem zufrieden sein. Dazu müssen wir erkunden, was uns Energie gibt und was sie uns raubt. Durch Selbstreflexion und Achtsamkeit finden wir sicher Dinge, die uns erfreuen und inspirieren, und andere, die uns eher stressen und belasten.
Die eigene Energie ist eng mit unserer körperlichen und mentalen Gesundheit verbunden. Methoden zur Förderung der körperlichen Gesundheit sind gut bekannt: eine ausgewogene Ernährung, regelmäßige Bewegung sowie ausreichend Schlaf und Erholung. Bei der nicht minder wichtigen emotionalen Balance wird es schon etwas komplizierter. Stress abzubauen, die eigenen Grenzen zu kennen oder solche zum Schutz zu setzen sowie die Konzentration auf Positives und Sinnvolles wären Ansätze.
Der emotionale ist auch der Bereich, über den «Energie-Räuber» bevorzugt attackieren. Das sind zum Beispiel Dinge wie Überforderung, Perfektionismus oder mangelhafte Kommunikation. Social Media gehören ganz sicher auch dazu. Sie stehlen uns nicht nur Zeit, sondern sind höchst manipulativ und erhöhen laut einer aktuellen Studie das Risiko für psychische Probleme wie Angstzustände und Depressionen.
Geben wir negativen oder gar bösen Menschen keine Macht über uns. Das Dauerfeuer der letzten Jahre mit Krisen, Konflikten und Gefahren sollte man zwar kennen, darf sich aber davon nicht runterziehen lassen. Das Ziel derartiger konzertierter Aktionen ist vor allem, unsere innere Stabilität zu zerstören, denn dann sind wir leichter zu steuern. Aber Geduld: Selbst vermeintliche «Sonnenköniginnen» wie EU-Kommissionspräsidentin von der Leyen fallen, wenn die Zeit reif ist.
Es ist wichtig, dass wir unsere ganz eigenen Bedürfnisse und Werte erkennen. Unsere Energiequellen müssen wir identifizieren und aktiv nutzen. Dazu gehören soziale Kontakte genauso wie zum Beispiel Hobbys und Leidenschaften. Umgeben wir uns mit Sinnhaftigkeit und lassen wir uns nicht die Energie rauben!
Mein Wahlspruch ist schon lange: «Was die Menschen wirklich bewegt, ist die Kultur.» Jetzt im Frühjahr beginnt hier in Andalusien die Zeit der «Ferias», jener traditionellen Volksfeste, die vor Lebensfreude sprudeln. Konzentrieren wir uns auf die schönen Dinge und auf unsere eigenen Talente – soziale Verbundenheit wird helfen, unsere innere Kraft zu stärken und zu bewahren.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ c631e267:c2b78d3e
2025-05-10 09:50:45
@ c631e267:c2b78d3e
2025-05-10 09:50:45Information ohne Reflexion ist geistiger Flugsand. \ Ernst Reinhardt
Der lateinische Ausdruck «Quo vadis» als Frage nach einer Entwicklung oder Ausrichtung hat biblische Wurzeln. Er wird aber auch in unserer Alltagssprache verwendet, laut Duden meist als Ausdruck von Besorgnis oder Skepsis im Sinne von: «Wohin wird das führen?»
Der Sinn und Zweck von so mancher politischen Entscheidung erschließt sich heutzutage nicht mehr so leicht, und viele Trends können uns Sorge bereiten. Das sind einerseits sehr konkrete Themen wie die zunehmende Militarisierung und die geschichtsvergessene Kriegstreiberei in Europa, deren Feindbildpflege aktuell beim Gedenken an das Ende des Zweiten Weltkriegs beschämende Formen annimmt.
Auch das hohe Gut der Schweizer Neutralität scheint immer mehr in Gefahr. Die schleichende Bewegung der Eidgenossenschaft in Richtung NATO und damit weg von einer Vermittlerposition erhält auch durch den neuen Verteidigungsminister Anschub. Martin Pfister möchte eine stärkere Einbindung in die europäische Verteidigungsarchitektur, verwechselt bei der Argumentation jedoch Ursache und Wirkung.
Das Thema Gesundheit ist als Zugpferd für Geschäfte und Kontrolle offenbar schon zuverlässig etabliert. Die hauptsächlich privat finanzierte Weltgesundheitsorganisation (WHO) ist dabei durch ein Netzwerk von sogenannten «Collaborating Centres» sogar so weit in nationale Einrichtungen eingedrungen, dass man sich fragen kann, ob diese nicht von Genf aus gesteuert werden.
Das Schweizer Bundesamt für Gesundheit (BAG) übernimmt in dieser Funktion ebenso von der WHO definierte Aufgaben und Pflichten wie das deutsche Robert Koch-Institut (RKI). Gegen die Covid-«Impfung» für Schwangere, die das BAG empfiehlt, obwohl es fehlende wissenschaftliche Belege für deren Schutzwirkung einräumt, formiert sich im Tessin gerade Widerstand.
Unter dem Stichwort «Gesundheitssicherheit» werden uns die Bestrebungen verkauft, essenzielle Dienste mit einer biometrischen digitalen ID zu verknüpfen. Das dient dem Profit mit unseren Daten und führt im Ergebnis zum Verlust unserer demokratischen Freiheiten. Die deutsche elektronische Patientenakte (ePA) ist ein Element mit solchem Potenzial. Die Schweizer Bürger haben gerade ein Referendum gegen das revidierte E-ID-Gesetz erzwungen. In Thailand ist seit Anfang Mai für die Einreise eine «Digital Arrival Card» notwendig, die mit ihrer Gesundheitserklärung einen Impfpass «durch die Hintertür» befürchten lässt.
Der massive Blackout auf der iberischen Halbinsel hat vermehrt Fragen dazu aufgeworfen, wohin uns Klimawandel-Hysterie und «grüne» Energiepolitik führen werden. Meine Kollegin Wiltrud Schwetje ist dem nachgegangen und hat in mehreren Beiträgen darüber berichtet. Wenig überraschend führen interessante Spuren mal wieder zu internationalen Großbanken, Globalisten und zur EU-Kommission.
Zunehmend bedenklich ist aber ganz allgemein auch die manifestierte Spaltung unserer Gesellschaften. Angesichts der tiefen und sorgsam gepflegten Gräben fällt es inzwischen schwer, eine zukunftsfähige Perspektive zu erkennen. Umso begrüßenswerter sind Initiativen wie die Kölner Veranstaltungsreihe «Neue Visionen für die Zukunft». Diese möchte die Diskussionskultur reanimieren und dazu beitragen, dass Menschen wieder ohne Angst und ergebnisoffen über kontroverse Themen der Zeit sprechen.
Quo vadis – Wohin gehen wir also? Die Suche nach Orientierung in diesem vermeintlichen Chaos führt auch zur Reflexion über den eigenen Lebensweg. Das ist positiv insofern, als wir daraus Kraft schöpfen können. Ob derweil der neue Papst, dessen «Vorgänger» Petrus unsere Ausgangsfrage durch die christliche Legende zugeschrieben wird, dabei eine Rolle spielt, muss jede/r selbst wissen. Mir persönlich ist allein schon ein Führungsanspruch wie der des Petrusprimats der römisch-katholischen Kirche eher suspekt.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:49:12
@ 6d5c826a:4b27b659
2025-05-23 21:49:12- Remmina - Feature-rich remote desktop application for linux and other unixes. (Source Code)
GPL-2.0C - Tiger VNC - High-performance, multi-platform VNC client and server. (Source Code)
GPL-2.0C++ - X2go - X2Go is an open source remote desktop software for Linux that uses the NoMachine/NX technology protocol. (Source Code)
GPL-2.0Perl
- Remmina - Feature-rich remote desktop application for linux and other unixes. (Source Code)
-
 @ c631e267:c2b78d3e
2025-05-02 20:05:22
@ c631e267:c2b78d3e
2025-05-02 20:05:22Du bist recht appetitlich oben anzuschauen, \ doch unten hin die Bestie macht mir Grauen. \ Johann Wolfgang von Goethe
Wie wenig bekömmlich sogenannte «Ultra-Processed Foods» wie Fertiggerichte, abgepackte Snacks oder Softdrinks sind, hat kürzlich eine neue Studie untersucht. Derweil kann Fleisch auch wegen des Einsatzes antimikrobieller Mittel in der Massentierhaltung ein Problem darstellen. Internationale Bemühungen, diesen Gebrauch zu reduzieren, um die Antibiotikaresistenz bei Menschen einzudämmen, sind nun möglicherweise gefährdet.
Leider ist Politik oft mindestens genauso unappetitlich und ungesund wie diverse Lebensmittel. Die «Corona-Zeit» und ihre Auswirkungen sind ein beredtes Beispiel. Der Thüringer Landtag diskutiert gerade den Entwurf eines «Coronamaßnahmen-Unrechtsbereinigungsgesetzes» und das kanadische Gesundheitsministerium versucht, tausende Entschädigungsanträge wegen Impfnebenwirkungen mit dem Budget von 75 Millionen Dollar unter einen Hut zu bekommen. In den USA soll die Zulassung von Covid-«Impfstoffen» überdacht werden, während man sich mit China um die Herkunft des Virus streitet.
Wo Corona-Verbrecher von Medien und Justiz gedeckt werden, verfolgt man Aufklärer und Aufdecker mit aller Härte. Der Anwalt und Mitbegründer des Corona-Ausschusses Reiner Fuellmich, der seit Oktober 2023 in Untersuchungshaft sitzt, wurde letzte Woche zu drei Jahren und neun Monaten verurteilt – wegen Veruntreuung. Am Mittwoch teilte der von vielen Impfschadensprozessen bekannte Anwalt Tobias Ulbrich mit, dass er vom Staatsschutz verfolgt wird und sich daher künftig nicht mehr öffentlich äußern werde.
Von der kommenden deutschen Bundesregierung aus Wählerbetrügern, Transatlantikern, Corona-Hardlinern und Russenhassern kann unmöglich eine Verbesserung erwartet werden. Nina Warken beispielsweise, die das Ressort Gesundheit übernehmen soll, diffamierte Maßnahmenkritiker als «Coronaleugner» und forderte eine Impfpflicht, da die wundersamen Injektionen angeblich «nachweislich helfen». Laut dem designierten Außenminister Johann Wadephul wird Russland «für uns immer der Feind» bleiben. Deswegen will er die Ukraine «nicht verlieren lassen» und sieht die Bevölkerung hinter sich, solange nicht deutsche Soldaten dort sterben könnten.
Eine wichtige Personalie ist auch die des künftigen Regierungssprechers. Wenngleich Hebestreit an Arroganz schwer zu überbieten sein wird, dürfte sich die Art der Kommunikation mit Stefan Kornelius in der Sache kaum ändern. Der Politikchef der Süddeutschen Zeitung «prägte den Meinungsjournalismus der SZ» und schrieb «in dieser Rolle auch für die Titel der Tamedia». Allerdings ist, anders als noch vor zehn Jahren, die Einbindung von Journalisten in Thinktanks wie die Deutsche Atlantische Gesellschaft (DAG) ja heute eher eine Empfehlung als ein Problem.
Ungesund ist definitiv auch die totale Digitalisierung, nicht nur im Gesundheitswesen. Lauterbachs Abschiedsgeschenk, die «abgesicherte» elektronische Patientenakte (ePA) ist völlig überraschenderweise direkt nach dem Bundesstart erneut gehackt worden. Norbert Häring kommentiert angesichts der Datenlecks, wer die ePA nicht abwähle, könne seine Gesundheitsdaten ebensogut auf Facebook posten.
Dass die staatlichen Kontrolleure so wenig auf freie Software und dezentrale Lösungen setzen, verdeutlicht die eigentlichen Intentionen hinter der Digitalisierungswut. Um Sicherheit und Souveränität geht es ihnen jedenfalls nicht – sonst gäbe es zum Beispiel mehr Unterstützung für Bitcoin und für Initiativen wie die der Spar-Supermärkte in der Schweiz.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ c631e267:c2b78d3e
2025-04-25 20:06:24
@ c631e267:c2b78d3e
2025-04-25 20:06:24Die Wahrheit verletzt tiefer als jede Beleidigung. \ Marquis de Sade
Sagen Sie niemals «Terroristin B.», «Schwachkopf H.», «korrupter Drecksack S.» oder «Meinungsfreiheitshasserin F.» und verkneifen Sie sich Memes, denn so etwas könnte Ihnen als Beleidigung oder Verleumdung ausgelegt werden und rechtliche Konsequenzen haben. Auch mit einer Frau M.-A. S.-Z. ist in dieser Beziehung nicht zu spaßen, sie gehört zu den Top-Anzeigenstellern.
«Politikerbeleidigung» als Straftatbestand wurde 2021 im Kampf gegen «Rechtsextremismus und Hasskriminalität» in Deutschland eingeführt, damals noch unter der Regierung Merkel. Im Gesetz nicht festgehalten ist die Unterscheidung zwischen schlechter Hetze und guter Hetze – trotzdem ist das gängige Praxis, wie der Titel fast schon nahelegt.
So dürfen Sie als Politikerin heute den Tesla als «Nazi-Auto» bezeichnen und dies ausdrücklich auf den Firmengründer Elon Musk und dessen «rechtsextreme Positionen» beziehen, welche Sie nicht einmal belegen müssen. [1] Vielleicht ernten Sie Proteste, jedoch vorrangig wegen der «gut bezahlten, unbefristeten Arbeitsplätze» in Brandenburg. Ihren Tweet hat die Berliner Senatorin Cansel Kiziltepe inzwischen offenbar dennoch gelöscht.
Dass es um die Meinungs- und Pressefreiheit in der Bundesrepublik nicht mehr allzu gut bestellt ist, befürchtet man inzwischen auch schon im Ausland. Der Fall des Journalisten David Bendels, der kürzlich wegen eines Faeser-Memes zu sieben Monaten Haft auf Bewährung verurteilt wurde, führte in diversen Medien zu Empörung. Die Welt versteckte ihre Kritik mit dem Titel «Ein Urteil wie aus einer Diktatur» hinter einer Bezahlschranke.
Unschöne, heutzutage vielleicht strafbare Kommentare würden mir auch zu einigen anderen Themen und Akteuren einfallen. Ein Kandidat wäre der deutsche Bundesgesundheitsminister (ja, er ist es tatsächlich immer noch). Während sich in den USA auf dem Gebiet etwas bewegt und zum Beispiel Robert F. Kennedy Jr. will, dass die Gesundheitsbehörde (CDC) keine Covid-Impfungen für Kinder mehr empfiehlt, möchte Karl Lauterbach vor allem das Corona-Lügengebäude vor dem Einsturz bewahren.
«Ich habe nie geglaubt, dass die Impfungen nebenwirkungsfrei sind», sagte Lauterbach jüngst der ZDF-Journalistin Sarah Tacke. Das steht in krassem Widerspruch zu seiner früher verbreiteten Behauptung, die Gen-Injektionen hätten keine Nebenwirkungen. Damit entlarvt er sich selbst als Lügner. Die Bezeichnung ist absolut berechtigt, dieser Mann dürfte keinerlei politische Verantwortung tragen und das Verhalten verlangt nach einer rechtlichen Überprüfung. Leider ist ja die Justiz anderweitig beschäftigt und hat außerdem selbst keine weiße Weste.
Obendrein kämpfte der Herr Minister für eine allgemeine Impfpflicht. Er beschwor dabei das Schließen einer «Impflücke», wie es die Weltgesundheitsorganisation – die «wegen Trump» in finanziellen Schwierigkeiten steckt – bis heute tut. Die WHO lässt aktuell ihre «Europäische Impfwoche» propagieren, bei der interessanterweise von Covid nicht mehr groß die Rede ist.
Einen «Klima-Leugner» würden manche wohl Nir Shaviv nennen, das ist ja nicht strafbar. Der Astrophysiker weist nämlich die Behauptung von einer Klimakrise zurück. Gemäß seiner Forschung ist mindestens die Hälfte der Erderwärmung nicht auf menschliche Emissionen, sondern auf Veränderungen im Sonnenverhalten zurückzuführen.
Das passt vielleicht auch den «Klima-Hysterikern» der britischen Regierung ins Konzept, die gerade Experimente zur Verdunkelung der Sonne angekündigt haben. Produzenten von Kunstfleisch oder Betreiber von Insektenfarmen würden dagegen vermutlich die Geschichte vom fatalen CO2 bevorzugen. Ihnen würde es besser passen, wenn der verantwortungsvolle Erdenbürger sein Verhalten gründlich ändern müsste.
In unserer völlig verkehrten Welt, in der praktisch jede Verlautbarung außerhalb der abgesegneten Narrative potenziell strafbar sein kann, gehört fast schon Mut dazu, Dinge offen anzusprechen. Im «besten Deutschland aller Zeiten» glaubten letztes Jahr nur noch 40 Prozent der Menschen, ihre Meinung frei äußern zu können. Das ist ein Armutszeugnis, und es sieht nicht gerade nach Besserung aus. Umso wichtiger ist es, dagegen anzugehen.
[Titelbild: Pixabay]
--- Quellen: ---
[1] Zur Orientierung wenigstens ein paar Hinweise zur NS-Vergangenheit deutscher Automobilhersteller:
- Volkswagen
- Porsche
- Daimler-Benz
- BMW
- Audi
- Opel
- Heute: «Auto-Werke für die Rüstung? Rheinmetall prüft Übernahmen»
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:48:56
@ 6d5c826a:4b27b659
2025-05-23 21:48:56- ActiveMQ - Java message broker. (Source Code)
Apache-2.0Java - BeanstalkD - A simple, fast work queue. (Source Code)
MITC - Gearman - Fast multi-language queuing/job processing platform. (Source Code)
BSD-3-ClauseC++ - NSQ - A realtime distributed messaging platform. (Source Code)
MPL-2.0Go - ZeroMQ - Lightweight queuing system. (Source Code)
GPL-3.0C++
- ActiveMQ - Java message broker. (Source Code)
-
 @ c631e267:c2b78d3e
2025-04-20 19:54:32
@ c631e267:c2b78d3e
2025-04-20 19:54:32Es ist völlig unbestritten, dass der Angriff der russischen Armee auf die Ukraine im Februar 2022 strikt zu verurteilen ist. Ebenso unbestritten ist Russland unter Wladimir Putin keine brillante Demokratie. Aus diesen Tatsachen lässt sich jedoch nicht das finstere Bild des russischen Präsidenten – und erst recht nicht des Landes – begründen, das uns durchweg vorgesetzt wird und den Kern des aktuellen europäischen Bedrohungs-Szenarios darstellt. Da müssen wir schon etwas genauer hinschauen.
Der vorliegende Artikel versucht derweil nicht, den Einsatz von Gewalt oder die Verletzung von Menschenrechten zu rechtfertigen oder zu entschuldigen – ganz im Gegenteil. Dass jedoch der Verdacht des «Putinverstehers» sofort latent im Raume steht, verdeutlicht, was beim Thema «Russland» passiert: Meinungsmache und Manipulation.
Angesichts der mentalen Mobilmachung seitens Politik und Medien sowie des Bestrebens, einen bevorstehenden Krieg mit Russland geradezu herbeizureden, ist es notwendig, dieser fatalen Entwicklung entgegenzutreten. Wenn wir uns nur ein wenig von der herrschenden Schwarz-Weiß-Malerei freimachen, tauchen automatisch Fragen auf, die Risse im offiziellen Narrativ enthüllen. Grund genug, nachzuhaken.
Wer sich schon länger auch abseits der Staats- und sogenannten Leitmedien informiert, der wird in diesem Artikel vermutlich nicht viel Neues erfahren. Andere könnten hier ein paar unbekannte oder vergessene Aspekte entdecken. Möglicherweise klärt sich in diesem Kontext die Wahrnehmung der aktuellen (unserer eigenen!) Situation ein wenig.
Manipulation erkennen
Corona-«Pandemie», menschengemachter Klimawandel oder auch Ukraine-Krieg: Jede Menge Krisen, und für alle gibt es ein offizielles Narrativ, dessen Hinterfragung unerwünscht ist. Nun ist aber ein Narrativ einfach eine Erzählung, eine Geschichte (Latein: «narratio») und kein Tatsachenbericht. Und so wie ein Märchen soll auch das Narrativ eine Botschaft vermitteln.
Über die Methoden der Manipulation ist viel geschrieben worden, sowohl in Bezug auf das Individuum als auch auf die Massen. Sehr wertvolle Tipps dazu, wie man Manipulationen durchschauen kann, gibt ein Büchlein [1] von Albrecht Müller, dem Herausgeber der NachDenkSeiten.
Die Sprache selber eignet sich perfekt für die Manipulation. Beispielsweise kann die Wortwahl Bewertungen mitschwingen lassen, regelmäßiges Wiederholen (gerne auch von verschiedenen Seiten) lässt Dinge irgendwann «wahr» erscheinen, Übertreibungen fallen auf und hinterlassen wenigstens eine Spur im Gedächtnis, genauso wie Andeutungen. Belege spielen dabei keine Rolle.
Es gibt auffällig viele Sprachregelungen, die offenbar irgendwo getroffen und irgendwie koordiniert werden. Oder alle Redenschreiber und alle Medien kopieren sich neuerdings permanent gegenseitig. Welchen Zweck hat es wohl, wenn der Krieg in der Ukraine durchgängig und quasi wörtlich als «russischer Angriffskrieg auf die Ukraine» bezeichnet wird? Obwohl das in der Sache richtig ist, deutet die Art der Verwendung auf gezielte Beeinflussung hin und soll vor allem das Feindbild zementieren.
Sprachregelungen dienen oft der Absicherung einer einseitigen Darstellung. Das Gleiche gilt für das Verkürzen von Informationen bis hin zum hartnäckigen Verschweigen ganzer Themenbereiche. Auch hierfür gibt es rund um den Ukraine-Konflikt viele gute Beispiele.
Das gewünschte Ergebnis solcher Methoden ist eine Schwarz-Weiß-Malerei, bei der einer eindeutig als «der Böse» markiert ist und die anderen automatisch «die Guten» sind. Das ist praktisch und demonstriert gleichzeitig ein weiteres Manipulationswerkzeug: die Verwendung von Doppelstandards. Wenn man es schafft, bei wichtigen Themen regelmäßig mit zweierlei Maß zu messen, ohne dass das Publikum protestiert, dann hat man freie Bahn.
Experten zu bemühen, um bestimmte Sachverhalte zu erläutern, ist sicher sinnvoll, kann aber ebenso missbraucht werden, schon allein durch die Auswahl der jeweiligen Spezialisten. Seit «Corona» werden viele erfahrene und ehemals hoch angesehene Fachleute wegen der «falschen Meinung» diffamiert und gecancelt. [2] Das ist nicht nur ein brutaler Umgang mit Menschen, sondern auch eine extreme Form, die öffentliche Meinung zu steuern.
Wann immer wir also erkennen (weil wir aufmerksam waren), dass wir bei einem bestimmten Thema manipuliert werden, dann sind zwei logische und notwendige Fragen: Warum? Und was ist denn richtig? In unserem Russland-Kontext haben die Antworten darauf viel mit Geopolitik und Geschichte zu tun.
Ist Russland aggressiv und expansiv?
Angeblich plant Russland, europäische NATO-Staaten anzugreifen, nach dem Motto: «Zuerst die Ukraine, dann den Rest». In Deutschland weiß man dafür sogar das Datum: «Wir müssen bis 2029 kriegstüchtig sein», versichert Verteidigungsminister Pistorius.
Historisch gesehen ist es allerdings eher umgekehrt: Russland, bzw. die Sowjetunion, ist bereits dreimal von Westeuropa aus militärisch angegriffen worden. Die Feldzüge Napoleons, des deutschen Kaiserreichs und Nazi-Deutschlands haben Millionen Menschen das Leben gekostet. Bei dem ausdrücklichen Vernichtungskrieg ab 1941 kam es außerdem zu Brutalitäten wie der zweieinhalbjährigen Belagerung Leningrads (heute St. Petersburg) durch Hitlers Wehrmacht. Deren Ziel, die Bevölkerung auszuhungern, wurde erreicht: über eine Million tote Zivilisten.
Trotz dieser Erfahrungen stimmte Michail Gorbatschow 1990 der deutschen Wiedervereinigung zu und die Sowjetunion zog ihre Truppen aus Osteuropa zurück (vgl. Abb. 1). Der Warschauer Pakt wurde aufgelöst, der Kalte Krieg formell beendet. Die Sowjets erhielten damals von führenden westlichen Politikern die Zusicherung, dass sich die NATO «keinen Zentimeter ostwärts» ausdehnen würde, das ist dokumentiert. [3]
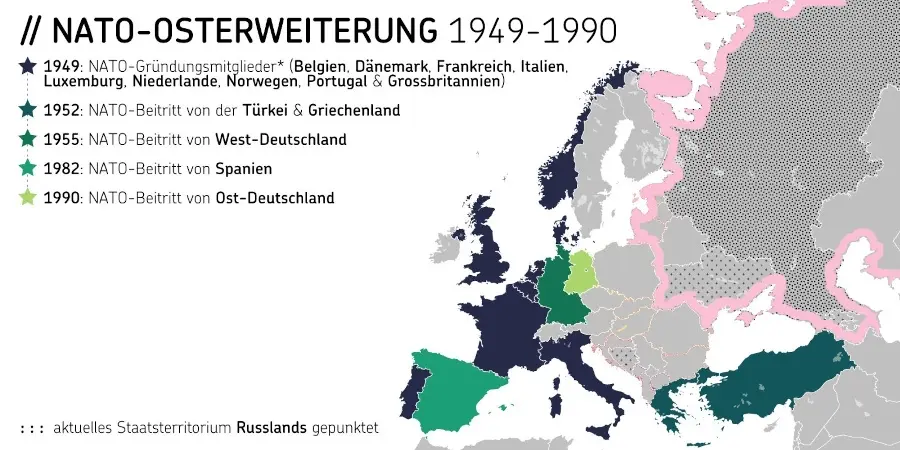
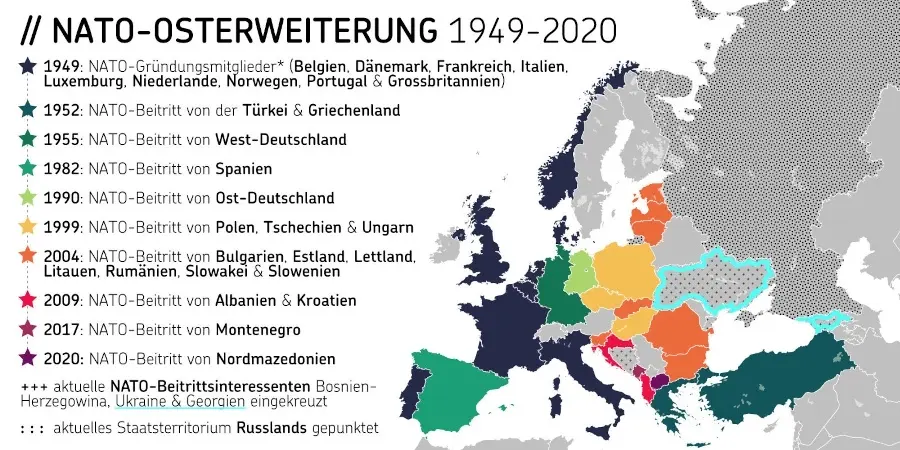
Expandiert ist die NATO trotzdem, und zwar bis an Russlands Grenzen (vgl. Abb. 2). Laut dem Politikberater Jeffrey Sachs handelt es sich dabei um ein langfristiges US-Projekt, das von Anfang an die Ukraine und Georgien mit einschloss. Offiziell wurde der Beitritt beiden Staaten 2008 angeboten. In jedem Fall könnte die massive Ost-Erweiterung seit 1999 aus russischer Sicht nicht nur als Vertrauensbruch, sondern durchaus auch als aggressiv betrachtet werden.
Russland hat den europäischen Staaten mehrfach die Hand ausgestreckt [4] für ein friedliches Zusammenleben und den «Aufbau des europäischen Hauses». Präsident Putin sei «in seiner ersten Amtszeit eine Chance für Europa» gewesen, urteilt die Journalistin und langjährige Russland-Korrespondentin der ARD, Gabriele Krone-Schmalz. Er habe damals viele positive Signale Richtung Westen gesendet.
Die Europäer jedoch waren scheinbar an einer Partnerschaft mit dem kontinentalen Nachbarn weniger interessiert als an der mit dem transatlantischen Hegemon. Sie verkennen bis heute, dass eine gedeihliche Zusammenarbeit in Eurasien eine Gefahr für die USA und deren bekundetes Bestreben ist, die «einzige Weltmacht» zu sein – «Full Spectrum Dominance» [5] nannte das Pentagon das. Statt einem neuen Kalten Krieg entgegenzuarbeiten, ließen sich europäische Staaten selber in völkerrechtswidrige «US-dominierte Angriffskriege» [6] verwickeln, wie in Serbien, Afghanistan, dem Irak, Libyen oder Syrien. Diese werden aber selten so benannt.
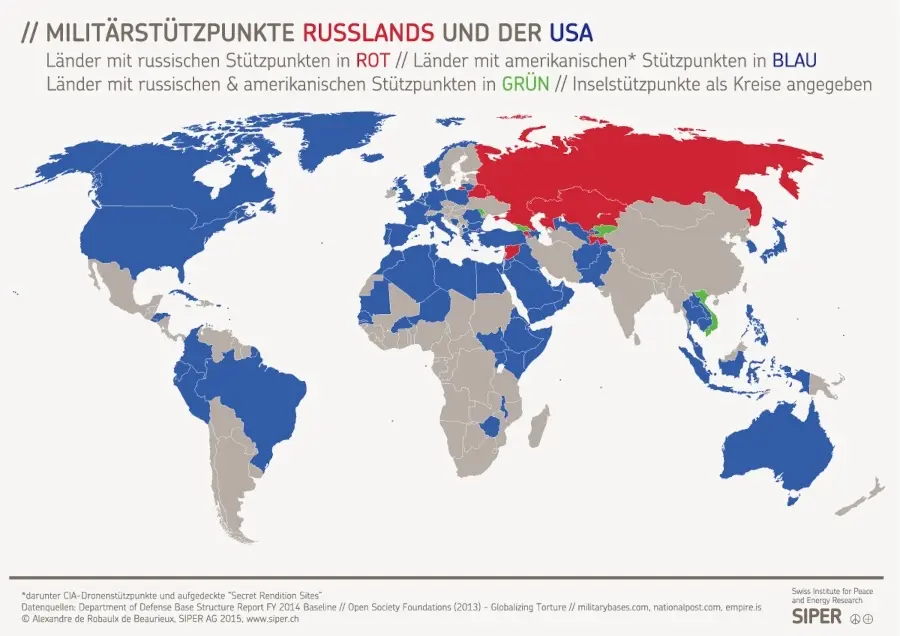
Speziell den Deutschen stünde außer einer Portion Realismus auch etwas mehr Dankbarkeit gut zu Gesicht. Das Geschichtsbewusstsein der Mehrheit scheint doch recht selektiv und das Selbstbewusstsein einiger etwas desorientiert zu sein. Bekanntermaßen waren es die Soldaten der sowjetischen Roten Armee, die unter hohen Opfern 1945 Deutschland «vom Faschismus befreit» haben. Bei den Gedenkfeiern zu 80 Jahren Kriegsende will jedoch das Auswärtige Amt – noch unter der Diplomatie-Expertin Baerbock, die sich schon länger offiziell im Krieg mit Russland wähnt, – nun keine Russen sehen: Sie sollen notfalls rausgeschmissen werden.
«Die Grundsatzfrage lautet: Geht es Russland um einen angemessenen Platz in einer globalen Sicherheitsarchitektur, oder ist Moskau schon seit langem auf einem imperialistischen Trip, der befürchten lassen muss, dass die Russen in fünf Jahren in Berlin stehen?»
So bringt Gabriele Krone-Schmalz [7] die eigentliche Frage auf den Punkt, die zur Einschätzung der Situation letztlich auch jeder für sich beantworten muss.
Was ist los in der Ukraine?
In der internationalen Politik geht es nie um Demokratie oder Menschenrechte, sondern immer um Interessen von Staaten. Diese These stammt von Egon Bahr, einem der Architekten der deutschen Ostpolitik des «Wandels durch Annäherung» aus den 1960er und 70er Jahren. Sie trifft auch auf den Ukraine-Konflikt zu, den handfeste geostrategische und wirtschaftliche Interessen beherrschen, obwohl dort angeblich «unsere Demokratie» verteidigt wird.
Es ist ein wesentliches Element des Ukraine-Narrativs und Teil der Manipulation, die Vorgeschichte des Krieges wegzulassen – mindestens die vor der russischen «Annexion» der Halbinsel Krim im März 2014, aber oft sogar komplett diejenige vor der Invasion Ende Februar 2022. Das Thema ist komplex, aber einige Aspekte, die für eine Beurteilung nicht unwichtig sind, will ich wenigstens kurz skizzieren. [8]
Das Gebiet der heutigen Ukraine und Russlands – die übrigens in der «Kiewer Rus» gemeinsame Wurzeln haben – hat der britische Geostratege Halford Mackinder bereits 1904 als eurasisches «Heartland» bezeichnet, dessen Kontrolle er eine große Bedeutung für die imperiale Strategie Großbritanniens zumaß. Für den ehemaligen Sicherheits- und außenpolitischen Berater mehrerer US-amerikanischer Präsidenten und Mitgründer der Trilateralen Kommission, Zbigniew Brzezinski, war die Ukraine nach der Auflösung der Sowjetunion ein wichtiger Spielstein auf dem «eurasischen Schachbrett», wegen seiner Nähe zu Russland, seiner Bodenschätze und seines Zugangs zum Schwarzen Meer.
Die Ukraine ist seit langem ein gespaltenes Land. Historisch zerrissen als Spielball externer Interessen und geprägt von ethnischen, kulturellen, religiösen und geografischen Unterschieden existiert bis heute, grob gesagt, eine Ost-West-Spaltung, welche die Suche nach einer nationalen Identität stark erschwert.
Insbesondere im Zuge der beiden Weltkriege sowie der Russischen Revolution entstanden tiefe Risse in der Bevölkerung. Ukrainer kämpften gegen Ukrainer, zum Beispiel die einen auf der Seite von Hitlers faschistischer Nazi-Armee und die anderen auf der von Stalins kommunistischer Roter Armee. Die Verbrechen auf beiden Seiten sind nicht vergessen. Dass nach der Unabhängigkeit 1991 versucht wurde, Figuren wie den radikalen Nationalisten Symon Petljura oder den Faschisten und Nazi-Kollaborateur Stepan Bandera als «Nationalhelden» zu installieren, verbessert die Sache nicht.
Während die USA und EU-Staaten zunehmend «ausländische Einmischung» (speziell russische) in «ihre Demokratien» wittern, betreiben sie genau dies seit Jahrzehnten in vielen Ländern der Welt. Die seit den 2000er Jahren bekannten «Farbrevolutionen» in Osteuropa werden oft als Methode des Regierungsumsturzes durch von außen gesteuerte «demokratische» Volksaufstände beschrieben. Diese Strategie geht auf Analysen zum «Schwarmverhalten» [9] seit den 1960er Jahren zurück (Studentenproteste), wo es um die potenzielle Wirksamkeit einer «rebellischen Hysterie» von Jugendlichen bei postmodernen Staatsstreichen geht. Heute nennt sich dieses gezielte Kanalisieren der Massen zur Beseitigung unkooperativer Regierungen «Soft-Power».
In der Ukraine gab es mit der «Orangen Revolution» 2004 und dem «Euromaidan» 2014 gleich zwei solcher «Aufstände». Der erste erzwang wegen angeblicher Unregelmäßigkeiten eine Wiederholung der Wahlen, was mit Wiktor Juschtschenko als neuem Präsidenten endete. Dieser war ehemaliger Direktor der Nationalbank und Befürworter einer Annäherung an EU und NATO. Seine Frau, die First Lady, ist US-amerikanische «Philanthropin» und war Beamtin im Weißen Haus in der Reagan- und der Bush-Administration.
Im Gegensatz zu diesem ersten Event endete der sogenannte Euromaidan unfriedlich und blutig. Die mehrwöchigen Proteste gegen Präsident Wiktor Janukowitsch, in Teilen wegen des nicht unterzeichneten Assoziierungsabkommens mit der EU, wurden zunehmend gewalttätiger und von Nationalisten und Faschisten des «Rechten Sektors» dominiert. Sie mündeten Ende Februar 2014 auf dem Kiewer Unabhängigkeitsplatz (Maidan) in einem Massaker durch Scharfschützen. Dass deren Herkunft und die genauen Umstände nicht geklärt wurden, störte die Medien nur wenig. [10]
Janukowitsch musste fliehen, er trat nicht zurück. Vielmehr handelte es sich um einen gewaltsamen, allem Anschein nach vom Westen inszenierten Putsch. Laut Jeffrey Sachs war das kein Geheimnis, außer vielleicht für die Bürger. Die USA unterstützten die Post-Maidan-Regierung nicht nur, sie beeinflussten auch ihre Bildung. Das geht unter anderem aus dem berühmten «Fuck the EU»-Telefonat der US-Chefdiplomatin für die Ukraine, Victoria Nuland, mit Botschafter Geoffrey Pyatt hervor.
Dieser Bruch der demokratischen Verfassung war letztlich der Auslöser für die anschließenden Krisen auf der Krim und im Donbass (Ostukraine). Angesichts der ukrainischen Geschichte mussten die nationalistischen Tendenzen und die Beteiligung der rechten Gruppen an dem Umsturz bei der russigsprachigen Bevölkerung im Osten ungute Gefühle auslösen. Es gab Kritik an der Übergangsregierung, Befürworter einer Abspaltung und auch für einen Anschluss an Russland.
Ebenso konnte Wladimir Putin in dieser Situation durchaus Bedenken wegen des Status der russischen Militärbasis für seine Schwarzmeerflotte in Sewastopol auf der Krim haben, für die es einen langfristigen Pachtvertrag mit der Ukraine gab. Was im März 2014 auf der Krim stattfand, sei keine Annexion, sondern eine Abspaltung (Sezession) nach einem Referendum gewesen, also keine gewaltsame Aneignung, urteilte der Rechtswissenschaftler Reinhard Merkel in der FAZ sehr detailliert begründet. Übrigens hatte die Krim bereits zu Zeiten der Sowjetunion den Status einer autonomen Republik innerhalb der Ukrainischen SSR.
Anfang April 2014 wurden in der Ostukraine die «Volksrepubliken» Donezk und Lugansk ausgerufen. Die Kiewer Übergangsregierung ging unter der Bezeichnung «Anti-Terror-Operation» (ATO) militärisch gegen diesen, auch von Russland instrumentalisierten Widerstand vor. Zufällig war kurz zuvor CIA-Chef John Brennan in Kiew. Die Maßnahmen gingen unter dem seit Mai neuen ukrainischen Präsidenten, dem Milliardär Petro Poroschenko, weiter. Auch Wolodymyr Selenskyj beendete den Bürgerkrieg nicht, als er 2019 vom Präsidenten-Schauspieler, der Oligarchen entmachtet, zum Präsidenten wurde. Er fuhr fort, die eigene Bevölkerung zu bombardieren.
Mit dem Einmarsch russischer Truppen in die Ostukraine am 24. Februar 2022 begann die zweite Phase des Krieges. Die Wochen und Monate davor waren intensiv. Im November hatte die Ukraine mit den USA ein Abkommen über eine «strategische Partnerschaft» unterzeichnet. Darin sagten die Amerikaner ihre Unterstützung der EU- und NATO-Perspektive der Ukraine sowie quasi für die Rückeroberung der Krim zu. Dagegen ließ Putin der NATO und den USA im Dezember 2021 einen Vertragsentwurf über beiderseitige verbindliche Sicherheitsgarantien zukommen, den die NATO im Januar ablehnte. Im Februar eskalierte laut OSZE die Gewalt im Donbass.
Bereits wenige Wochen nach der Invasion, Ende März 2022, kam es in Istanbul zu Friedensverhandlungen, die fast zu einer Lösung geführt hätten. Dass der Krieg nicht damals bereits beendet wurde, lag daran, dass der Westen dies nicht wollte. Man war der Meinung, Russland durch die Ukraine in diesem Stellvertreterkrieg auf Dauer militärisch schwächen zu können. Angesichts von Hunderttausenden Toten, Verletzten und Traumatisierten, die als Folge seitdem zu beklagen sind, sowie dem Ausmaß der Zerstörung, fehlen einem die Worte.
Hasst der Westen die Russen?
Diese Frage drängt sich auf, wenn man das oft unerträglich feindselige Gebaren beobachtet, das beileibe nicht neu ist und vor Doppelmoral trieft. Russland und speziell die Person Wladimir Putins werden regelrecht dämonisiert, was gleichzeitig scheinbar jede Form von Diplomatie ausschließt.
Russlands militärische Stärke, seine geografische Lage, sein Rohstoffreichtum oder seine unabhängige diplomatische Tradition sind sicher Störfaktoren für das US-amerikanische Bestreben, der Boss in einer unipolaren Welt zu sein. Ein womöglich funktionierender eurasischer Kontinent, insbesondere gute Beziehungen zwischen Russland und Deutschland, war indes schon vor dem Ersten Weltkrieg eine Sorge des britischen Imperiums.
Ein «Vergehen» von Präsident Putin könnte gewesen sein, dass er die neoliberale Schocktherapie à la IWF und den Ausverkauf des Landes (auch an US-Konzerne) beendete, der unter seinem Vorgänger herrschte. Dabei zeigte er sich als Führungspersönlichkeit und als nicht so formbar wie Jelzin. Diese Aspekte allein sind aber heute vermutlich keine ausreichende Erklärung für ein derart gepflegtes Feindbild.
Der Historiker und Philosoph Hauke Ritz erweitert den Fokus der Fragestellung zu: «Warum hasst der Westen die Russen so sehr?», was er zum Beispiel mit dem Medienforscher Michael Meyen und mit der Politikwissenschaftlerin Ulrike Guérot bespricht. Ritz stellt die interessante These [11] auf, dass Russland eine Provokation für den Westen sei, welcher vor allem dessen kulturelles und intellektuelles Potenzial fürchte.
Die Russen sind Europäer aber anders, sagt Ritz. Diese «Fremdheit in der Ähnlichkeit» erzeuge vielleicht tiefe Ablehnungsgefühle. Obwohl Russlands Identität in der europäischen Kultur verwurzelt ist, verbinde es sich immer mit der Opposition in Europa. Als Beispiele nennt er die Kritik an der katholischen Kirche oder die Verbindung mit der Arbeiterbewegung. Christen, aber orthodox; Sozialismus statt Liberalismus. Das mache das Land zum Antagonisten des Westens und zu einer Bedrohung der Machtstrukturen in Europa.
Fazit
Selbstverständlich kann man Geschichte, Ereignisse und Entwicklungen immer auf verschiedene Arten lesen. Dieser Artikel, obwohl viel zu lang, konnte nur einige Aspekte der Ukraine-Tragödie anreißen, die in den offiziellen Darstellungen in der Regel nicht vorkommen. Mindestens dürfte damit jedoch klar geworden sein, dass die Russische Föderation bzw. Wladimir Putin nicht der alleinige Aggressor in diesem Konflikt ist. Das ist ein Stellvertreterkrieg zwischen USA/NATO (gut) und Russland (böse); die Ukraine (edel) wird dabei schlicht verheizt.
Das ist insofern von Bedeutung, als die gesamte europäische Kriegshysterie auf sorgsam kultivierten Freund-Feind-Bildern beruht. Nur so kann Konfrontation und Eskalation betrieben werden, denn damit werden die wahren Hintergründe und Motive verschleiert. Angst und Propaganda sind notwendig, damit die Menschen den Wahnsinn mitmachen. Sie werden belogen, um sie zuerst zu schröpfen und anschließend auf die Schlachtbank zu schicken. Das kann niemand wollen, außer den stets gleichen Profiteuren: die Rüstungs-Lobby und die großen Investoren, die schon immer an Zerstörung und Wiederaufbau verdient haben.
Apropos Investoren: Zu den Top-Verdienern und somit Hauptinteressenten an einer Fortführung des Krieges zählt BlackRock, einer der weltgrößten Vermögensverwalter. Der deutsche Bundeskanzler in spe, Friedrich Merz, der gerne «Taurus»-Marschflugkörper an die Ukraine liefern und die Krim-Brücke zerstören möchte, war von 2016 bis 2020 Aufsichtsratsvorsitzender von BlackRock in Deutschland. Aber das hat natürlich nichts zu sagen, der Mann macht nur seinen Job.
Es ist ein Spiel der Kräfte, es geht um Macht und strategische Kontrolle, um Geheimdienste und die Kontrolle der öffentlichen Meinung, um Bodenschätze, Rohstoffe, Pipelines und Märkte. Das klingt aber nicht sexy, «Demokratie und Menschenrechte» hört sich besser und einfacher an. Dabei wäre eine für alle Seiten förderliche Politik auch nicht so kompliziert; das Handwerkszeug dazu nennt sich Diplomatie. Noch einmal Gabriele Krone-Schmalz:
«Friedliche Politik ist nichts anderes als funktionierender Interessenausgleich. Da geht’s nicht um Moral.»
Die Situation in der Ukraine ist sicher komplex, vor allem wegen der inneren Zerrissenheit. Es dürfte nicht leicht sein, eine friedliche Lösung für das Zusammenleben zu finden, aber die Beteiligten müssen es vor allem wollen. Unter den gegebenen Umständen könnte eine sinnvolle Perspektive mit Neutralität und föderalen Strukturen zu tun haben.
Allen, die sich bis hierher durch die Lektüre gearbeitet (oder auch einfach nur runtergescrollt) haben, wünsche ich frohe Oster-Friedenstage!
[Titelbild: Pixabay; Abb. 1 und 2: nach Ganser/SIPER; Abb. 3: SIPER]
--- Quellen: ---
[1] Albrecht Müller, «Glaube wenig. Hinterfrage alles. Denke selbst.», Westend 2019
[2] Zwei nette Beispiele:
- ARD-faktenfinder (sic), «Viel Aufmerksamkeit für fragwürdige Experten», 03/2023
- Neue Zürcher Zeitung, «Aufstieg und Fall einer Russlandversteherin – die ehemalige ARD-Korrespondentin Gabriele Krone-Schmalz rechtfertigt seit Jahren Putins Politik», 12/2022
[3] George Washington University, «NATO Expansion: What Gorbachev Heard – Declassified documents show security assurances against NATO expansion to Soviet leaders from Baker, Bush, Genscher, Kohl, Gates, Mitterrand, Thatcher, Hurd, Major, and Woerner», 12/2017
[4] Beispielsweise Wladimir Putin bei seiner Rede im Deutschen Bundestag, 25/09/2001
[5] William Engdahl, «Full Spectrum Dominance, Totalitarian Democracy In The New World Order», edition.engdahl 2009
[6] Daniele Ganser, «Illegale Kriege – Wie die NATO-Länder die UNO sabotieren. Eine Chronik von Kuba bis Syrien», Orell Füssli 2016
[7] Gabriele Krone-Schmalz, «Mit Friedensjournalismus gegen ‘Kriegstüchtigkeit’», Vortrag und Diskussion an der Universität Hamburg, veranstaltet von engagierten Studenten, 16/01/2025\ → Hier ist ein ähnlicher Vortrag von ihr (Video), den ich mit spanischer Übersetzung gefunden habe.
[8] Für mehr Hintergrund und Details empfehlen sich z.B. folgende Bücher:
- Mathias Bröckers, Paul Schreyer, «Wir sind immer die Guten», Westend 2019
- Gabriele Krone-Schmalz, «Russland verstehen? Der Kampf um die Ukraine und die Arroganz des Westens», Westend 2023
- Patrik Baab, «Auf beiden Seiten der Front – Meine Reisen in die Ukraine», Fiftyfifty 2023
[9] vgl. Jonathan Mowat, «Washington's New World Order "Democratization" Template», 02/2005 und RAND Corporation, «Swarming and the Future of Conflict», 2000
[10] Bemerkenswert einige Beiträge, von denen man später nichts mehr wissen wollte:
- ARD Monitor, «Todesschüsse in Kiew: Wer ist für das Blutbad vom Maidan verantwortlich», 10/04/2014, Transkript hier
- Telepolis, «Blutbad am Maidan: Wer waren die Todesschützen?», 12/04/2014
- Telepolis, «Scharfschützenmorde in Kiew», 14/12/2014
- Deutschlandfunk, «Gefahr einer Spirale nach unten», Interview mit Günter Verheugen, 18/03/2014
- NDR Panorama, «Putsch in Kiew: Welche Rolle spielen die Faschisten?», 06/03/2014
[11] Hauke Ritz, «Vom Niedergang des Westens zur Neuerfindung Europas», 2024
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:48:36
@ 6d5c826a:4b27b659
2025-05-23 21:48:36- aptly - Swiss army knife for Debian repository management. (Source Code)
MITGo - fpm - Versatile multi format package creator. (Source Code)
MITRuby - omnibus-ruby - Easily create full-stack installers for your project across a variety of platforms.
Apache-2.0Ruby - tito - Builds RPMs for git-based projects.
GPL-2.0Python
- aptly - Swiss army knife for Debian repository management. (Source Code)
-
 @ c631e267:c2b78d3e
2025-04-18 15:53:07
@ c631e267:c2b78d3e
2025-04-18 15:53:07Verstand ohne Gefühl ist unmenschlich; \ Gefühl ohne Verstand ist Dummheit. \ Egon Bahr
Seit Jahren werden wir darauf getrimmt, dass Fakten eigentlich gefühlt seien. Aber nicht alles ist relativ und nicht alles ist nach Belieben interpretierbar. Diese Schokoladenhasen beispielsweise, die an Ostern in unseren Gefilden typisch sind, «ostern» zwar nicht, sondern sie sitzen in der Regel, trotzdem verwandelt sie das nicht in «Sitzhasen».
Nichts soll mehr gelten, außer den immer invasiveren Gesetzen. Die eigenen Traditionen und Wurzeln sind potenziell «pfui», um andere Menschen nicht auszuschließen, aber wir mögen uns toleranterweise an die fremden Symbole und Rituale gewöhnen. Dabei ist es mir prinzipiell völlig egal, ob und wann jemand ein Fastenbrechen feiert, am Karsamstag oder jedem anderen Tag oder nie – aber bitte freiwillig.
Und vor allem: Lasst die Finger von den Kindern! In Bern setzten kürzlich Demonstranten ein Zeichen gegen die zunehmende Verbreitung woker Ideologie im Bildungssystem und forderten ein Ende der sexuellen Indoktrination von Schulkindern.
Wenn es nicht wegen des heiklen Themas Migration oder wegen des Regenbogens ist, dann wegen des Klimas. Im Rahmen der «Netto Null»-Agenda zum Kampf gegen das angeblich teuflische CO2 sollen die Menschen ihre Ernährungsgewohnheiten komplett ändern. Nach dem Willen von Produzenten synthetischer Lebensmittel, wie Bill Gates, sollen wir baldmöglichst praktisch auf Fleisch und alle Milchprodukte wie Milch und Käse verzichten. Ein lukratives Geschäftsmodell, das neben der EU aktuell auch von einem britischen Lobby-Konsortium unterstützt wird.
Sollten alle ideologischen Stricke zu reißen drohen, ist da immer noch «der Putin». Die Unions-Europäer offenbaren sich dabei ständig mehr als Vertreter der Rüstungsindustrie. Allen voran zündelt Deutschland an der Kriegslunte, angeführt von einem scheinbar todesmutigen Kanzlerkandidaten Friedrich Merz. Nach dessen erneuter Aussage, «Taurus»-Marschflugkörper an Kiew liefern zu wollen, hat Russland eindeutig klargestellt, dass man dies als direkte Kriegsbeteiligung werten würde – «mit allen sich daraus ergebenden Konsequenzen für Deutschland».
Wohltuend sind Nachrichten über Aktivitäten, die sich der allgemeinen Kriegstreiberei entgegenstellen oder diese öffentlich hinterfragen. Dazu zählt auch ein Kongress kritischer Psychologen und Psychotherapeuten, der letzte Woche in Berlin stattfand. Die vielen Vorträge im Kontext von «Krieg und Frieden» deckten ein breites Themenspektrum ab, darunter Friedensarbeit oder die Notwendigkeit einer «Pädagogik der Kriegsuntüchtigkeit».
Der heutige «stille Freitag», an dem Christen des Leidens und Sterbens von Jesus gedenken, ist vielleicht unabhängig von jeder religiösen oder spirituellen Prägung eine passende Einladung zur Reflexion. In der Ruhe liegt die Kraft. In diesem Sinne wünsche ich Ihnen frohe Ostertage!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:48:21
@ 6d5c826a:4b27b659
2025-05-23 21:48:21- CapRover - Build your own PaaS in a few minutes. (Demo, Source Code)
Apache-2.0Docker/Nodejs - Coolify - An open-source & self-hostable Heroku / Netlify alternative (and even more). (Source Code)
Apache-2.0Docker - Dokku - An open-source PaaS (alternative to Heroku). (Source Code)
MITDocker/Shell/Go/deb - fx - A tool to help you do Function as a Service with painless on your own servers.
MITGo - Kubero - A self-hosted Heroku PaaS alternative for Kubernetes that implements GitOps. (Demo, Source Code)
GPL-3.0K8S/Nodejs/Go - LocalStack - LocalStack is a fully functional local AWS cloud stack. This includes Lambda for serverless computation. (Source Code)
Apache-2.0Python/Docker/K8S - Nhost - Firebase Alternative with GraphQL. Get a database and backend configured and ready in minutes. (Source Code)
MITDocker/Nodejs/Go - OpenFaaS - Serverless Functions Made Simple for Docker & Kubernetes. (Source Code)
MITGo - Tau - Easily build Cloud Computing Platforms with features like Serverless WebAssembly Functions, Frontend Hosting, CI/CD, Object Storage, K/V Database, and Pub-Sub Messaging. (Source Code)
BSD-3-ClauseGo/Rust/Docker - Trusted-CGI - Lightweight self-hosted lambda/applications/cgi/serverless-functions platform.
MITGo/deb/Docker
- CapRover - Build your own PaaS in a few minutes. (Demo, Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:48:04
@ 6d5c826a:4b27b659
2025-05-23 21:48:04- GNS3 - Graphical network simulator that provides a variety of virtual appliances. (Source Code)
GPL-3.0Python - OpenWISP - Open Source Network Management System for OpenWRT based routers and access points. (Demo, Source Code)
GPL-3.0Python - Oxidized - Network device configuration backup tool.
Apache-2.0Ruby - phpIPAM - Open source IP address management with PowerDNS integration. (Source Code)
GPL-3.0PHP - RANCID - Monitor network devices configuration and maintain history of changes. (Source Code)
BSD-3-ClausePerl/Shell - rConfig - Network device configuration management tool. (Source Code)
GPL-3.0PHP
- GNS3 - Graphical network simulator that provides a variety of virtual appliances. (Source Code)
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ aa8de34f:a6ffe696
2025-03-31 21:48:50
@ aa8de34f:a6ffe696
2025-03-31 21:48:50In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht:
„Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\ (Quelle: t.me/rosenbusch/25228)
Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\ Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität.
-- Denn es braucht keinen Untergrund mehr. --
Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür.
Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung.
Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde.
Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen.
Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit.
Die Tyrannei sieht keinen Widerstand.\ Weil sie nicht erkennt, dass er längst begonnen hat.\ Unwiderruflich. Leise. Überall.
-
 @ c631e267:c2b78d3e
2025-03-31 07:23:05
@ c631e267:c2b78d3e
2025-03-31 07:23:05Der Irrsinn ist bei Einzelnen etwas Seltenes – \ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel. \ Friedrich Nietzsche
Erinnern Sie sich an die Horrorkomödie «Scary Movie»? Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?

Diese Szene kommt mir automatisch in den Sinn, wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real.
Die Europäische Union hat sich selbst über Jahre konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt.
In den USA haben sich die Vorzeichen allerdings mittlerweile geändert, und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen.
Statt jedoch umzukehren oder wenigstens zu bremsen und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die Kommentatoren des Events gegenseitig in sensationslüsterner «Berichterstattung».
Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen, Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, selbstzerstörerischen Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», erklärte die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte.
Zusätzlich brisant ist, dass aktuell «die ganze EU von Deutschen regiert wird», wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen.
Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen.
Es wird dringend Zeit, dass wir, der Souverän, diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts den Frieden auszurufen. Seien wir dabei!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:47:44
@ 6d5c826a:4b27b659
2025-05-23 21:47:44- Adagios - Web based Nagios interface for configuration and monitoring (replacement to the standard interface), and a REST interface. (Source Code)
AGPL-3.0Docker/Python - Alerta - Distributed, scalable and flexible monitoring system. (Source Code)
Apache-2.0Python - Beszel - Lightweight server monitoring platform that includes Docker statistics, historical data, and alert functions. (Source Code)
MITGo - Cacti - Web-based network monitoring and graphing tool. (Source Code)
GPL-2.0PHP - cadvisor - Analyzes resource usage and performance characteristics of running containers.
Apache-2.0Go - checkmk - Comprehensive solution for monitoring of applications, servers, and networks. (Source Code)
GPL-2.0Python/PHP - dashdot - A simple, modern server dashboard for smaller private servers. (Demo)
MITNodejs/Docker - EdMon - A command-line monitoring application helping you to check that your hosts and services are available, with notifications support.
MITJava - eZ Server Monitor - A lightweight and simple dashboard monitor for Linux, available in Web and Bash application. (Source Code)
GPL-3.0PHP/Shell - glances - Open-source, cross-platform real-time monitoring tool with CLI and web dashboard interfaces and many exporting options. (Source Code)
GPL-3.0Python - Healthchecks - Monitoring for cron jobs, background services and scheduled tasks. (Source Code)
BSD-3-ClausePython - Icinga - Nagios fork that has since lapped nagios several times. Comes with the possibility of clustered monitoring. (Source Code)
GPL-2.0C++ - LibreNMS - Fully featured network monitoring system that provides a wealth of features and device support. (Source Code)
GPL-3.0PHP - Linux Dash - A low-overhead monitoring web dashboard for a GNU/Linux machine.
MITNodejs/Go/Python/PHP - Monit - Small utility for managing and monitoring Unix systems. (Source Code)
AGPL-3.0C - Munin - Networked resource monitoring tool. (Source Code)
GPL-2.0Perl/Shell - Naemon - Network monitoring tool based on the Nagios 4 core with performance enhancements and new features. (Source Code)
GPL-2.0C - Nagios - Computer system, network and infrastructure monitoring software application. (Source Code)
GPL-2.0C - Netdata - Distributed, real-time, performance and health monitoring for systems and applications. Runs on Linux, FreeBSD, and MacOS. (Source Code)
GPL-3.0C - NetXMS - Open Source network and infrastructure monitoring and management. (Source Code)
LGPL-3.0/GPL-3.0Java/C++/C - Observium Community Edition - Network monitoring and management platform that provides real-time insight into network health and performance.
QPL-1.0PHP - openITCOCKPIT Community Edition - Monitoring Suite featuring seamless integrations with Naemon, Checkmk, Grafana and more. (Demo, Source Code)
GPL-3.0deb/Docker - Performance Co-Pilot - Lightweight, distributed system performance and analysis framework. (Source Code)
LGPL-2.1/GPL-2.0C - PHP Server Monitor - Open source tool to monitor your servers and websites. (Source Code)
GPL-3.0PHP - PhpSysInfo - A customizable PHP script that displays information about your system nicely. (Source Code)
GPL-2.0PHP - Prometheus - Service monitoring system and time series database. (Source Code)
Apache-2.0Go - Riemann - Flexible and fast events processor allowing complex events/metrics analysis. (Source Code)
EPL-1.0Java - rtop - Interactive, remote system monitoring tool based on SSH.
MITGo - ruptime - Classic system status server.
AGPL-3.0Shell - Scrutiny - Web UI for hard drive S.M.A.R.T monitoring, historical trends & real-world failure thresholds.
MITGo - Sensu - Monitoring tool for ephemeral infrastructure and distributed applications. (Source Code)
MITGo - Status - Simple and lightweight system monitoring tool for small homeservers with a pleasant web interface. (Demo
MITPython - Thruk - Multibackend monitoring web interface with support for Naemon, Nagios, Icinga and Shinken. (Source Code)
GPL-1.0Perl - Wazuh - Unified XDR and SIEM protection for endpoints and cloud workloads. (Source Code)
GPL-2.0C - Zabbix - Enterprise-class software for monitoring of networks and applications. (Source Code)
GPL-2.0C
- Adagios - Web based Nagios interface for configuration and monitoring (replacement to the standard interface), and a REST interface. (Source Code)
-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ 6d5c826a:4b27b659
2025-05-23 21:47:22
@ 6d5c826a:4b27b659
2025-05-23 21:47:22- Chocolatey - The package manager for Windows. (Source Code)
Apache-2.0C#/PowerShell - Clonezilla - Partition and disk imaging/cloning program. (Source Code)
GPL-2.0Perl/Shell/Other - DadaMail - Mailing List Manager, written in Perl. (Source Code)
GPL-2.0Perl - Fog - Cloning/imaging solution/rescue suite. (Source Code)
GPL-3.0PHP/Shell - phpList - Newsletter and email marketing software. (Source Code)
AGPL-3.0PHP
- Chocolatey - The package manager for Windows. (Source Code)
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ c631e267:c2b78d3e
2025-02-07 19:42:11
@ c631e267:c2b78d3e
2025-02-07 19:42:11Nur wenn wir aufeinander zugehen, haben wir die Chance \ auf Überwindung der gegenseitigen Ressentiments! \ Dr. med. dent. Jens Knipphals
In Wolfsburg sollte es kürzlich eine Gesprächsrunde von Kritikern der Corona-Politik mit Oberbürgermeister Dennis Weilmann und Vertretern der Stadtverwaltung geben. Der Zahnarzt und langjährige Maßnahmenkritiker Jens Knipphals hatte diese Einladung ins Rathaus erwirkt und publiziert. Seine Motivation:
«Ich möchte die Spaltung der Gesellschaft überwinden. Dazu ist eine umfassende Aufarbeitung der Corona-Krise in der Öffentlichkeit notwendig.»
Schon früher hatte Knipphals Antworten von den Kommunalpolitikern verlangt, zum Beispiel bei öffentlichen Bürgerfragestunden. Für das erwartete Treffen im Rathaus formulierte er Fragen wie: Warum wurden fachliche Argumente der Kritiker ignoriert? Weshalb wurde deren Ausgrenzung, Diskreditierung und Entmenschlichung nicht entgegengetreten? In welcher Form übernehmen Rat und Verwaltung in Wolfsburg persönlich Verantwortung für die erheblichen Folgen der politischen Corona-Krise?
Der Termin fand allerdings nicht statt – der Bürgermeister sagte ihn kurz vorher wieder ab. Knipphals bezeichnete Weilmann anschließend als Wiederholungstäter, da das Stadtoberhaupt bereits 2022 zu einem Runden Tisch in der Sache eingeladen hatte, den es dann nie gab. Gegenüber Multipolar erklärte der Arzt, Weilmann wolle scheinbar eine öffentliche Aufarbeitung mit allen Mitteln verhindern. Er selbst sei «inzwischen absolut desillusioniert» und die einzige Lösung sei, dass die Verantwortlichen gingen.
Die Aufarbeitung der Plandemie beginne bei jedem von uns selbst, sei aber letztlich eine gesamtgesellschaftliche Aufgabe, schreibt Peter Frey, der den «Fall Wolfsburg» auch in seinem Blog behandelt. Diese Aufgabe sei indes deutlich größer, als viele glaubten. Erfreulicherweise sei der öffentliche Informationsraum inzwischen größer, trotz der weiterhin unverfrorenen Desinformations-Kampagnen der etablierten Massenmedien.
Frey erinnert daran, dass Dennis Weilmann mitverantwortlich für gravierende Grundrechtseinschränkungen wie die 2021 eingeführten 2G-Regeln in der Wolfsburger Innenstadt zeichnet. Es sei naiv anzunehmen, dass ein Funktionär einzig im Interesse der Bürger handeln würde. Als früherer Dezernent des Amtes für Wirtschaft, Digitalisierung und Kultur der Autostadt kenne Weilmann zum Beispiel die Verknüpfung von Fördergeldern mit politischen Zielsetzungen gut.
Wolfsburg wurde damals zu einem Modellprojekt des Bundesministeriums des Innern (BMI) und war Finalist im Bitkom-Wettbewerb «Digitale Stadt». So habe rechtzeitig vor der Plandemie das Projekt «Smart City Wolfsburg» anlaufen können, das der Stadt «eine Vorreiterrolle für umfassende Vernetzung und Datenerfassung» aufgetragen habe, sagt Frey. Die Vereinten Nationen verkauften dann derartige «intelligente» Überwachungs- und Kontrollmaßnahmen ebenso als Rettung in der Not wie das Magazin Forbes im April 2020:
«Intelligente Städte können uns helfen, die Coronavirus-Pandemie zu bekämpfen. In einer wachsenden Zahl von Ländern tun die intelligenten Städte genau das. Regierungen und lokale Behörden nutzen Smart-City-Technologien, Sensoren und Daten, um die Kontakte von Menschen aufzuspüren, die mit dem Coronavirus infiziert sind. Gleichzeitig helfen die Smart Cities auch dabei, festzustellen, ob die Regeln der sozialen Distanzierung eingehalten werden.»
Offensichtlich gibt es viele Aspekte zu bedenken und zu durchleuten, wenn es um die Aufklärung und Aufarbeitung der sogenannten «Corona-Pandemie» und der verordneten Maßnahmen geht. Frustration und Desillusion sind angesichts der Realitäten absolut verständlich. Gerade deswegen sind Initiativen wie die von Jens Knipphals so bewundernswert und so wichtig – ebenso wie eine seiner Kernthesen: «Wir müssen aufeinander zugehen, da hilft alles nichts».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:47:03
@ 6d5c826a:4b27b659
2025-05-23 21:47:03- Beats - Single-purpose data shippers that send data from hundreds or thousands of machines and systems to Logstash or Elasticsearch. (Source Code)
Apache-2.0Go - Collectd - System statistics collection daemon. (Source Code)
MITC - Diamond - Daemon that collects system metrics and publishes them to Graphite (and others).
MITPython - Grafana - A Graphite & InfluxDB Dashboard and Graph Editor. (Source Code)
AGPL-3.0Go - Graphite - Scalable graphing server. (Source Code)
Apache-2.0Python - RRDtool - Industry standard, high performance data logging and graphing system for time series data. (Source Code)
GPL-2.0C - Statsd - Daemon that listens for statistics like counters and timers, sent over UDP or TCP, and sends aggregates to one or more pluggable backend services.
MITNodejs - tcollector - Gathers data from local collectors and pushes the data to OpenTSDB. (Source Code)
LGPL-3.0/GPL-3.0Python - Telegraf - Plugin-driven server agent for collecting, processing, aggregating, and writing metrics.
MITGo
- Beats - Single-purpose data shippers that send data from hundreds or thousands of machines and systems to Logstash or Elasticsearch. (Source Code)
-
 @ c631e267:c2b78d3e
2025-01-18 09:34:51
@ c631e267:c2b78d3e
2025-01-18 09:34:51Die grauenvollste Aussicht ist die der Technokratie – \ einer kontrollierenden Herrschaft, \ die durch verstümmelte und verstümmelnde Geister ausgeübt wird. \ Ernst Jünger
«Davos ist nicht mehr sexy», das Weltwirtschaftsforum (WEF) mache Davos kaputt, diese Aussagen eines Einheimischen las ich kürzlich in der Handelszeitung. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den vergangenen vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
Der deutsche WEF-Gründer hatte bei dieser Gelegenheit immer höchst lobende Worte für seine Landsmännin: 2021 erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und 2022 fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
Von der Leyens Handeln während der sogenannten Corona-«Pandemie» lobte Schwab damals bereits ebenso, wie es diese Woche das Karlspreis-Direktorium tat, als man der Beschuldigten im Fall Pfizergate die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
Jene Herausforderungen durch «Krisen epochalen Ausmaßes» werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im Global Risks Report nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
Ein «Great Mental Reset» sei die Voraussetzung dafür, dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
Der aktuelle Zustand unserer Gesellschaften ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die Rechtsstaatlichkeit stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:46:46
@ 6d5c826a:4b27b659
2025-05-23 21:46:46- aerc - Terminal MUA with a focus on plaintext and features for developers. (Source Code)
MITGo - Claws Mail - Old school email client (and news reader), based on GTK+. (Source Code)
GPL-3.0C - ImapSync - Simple IMAP migration tool for copying mailboxes to other servers. (Source Code)
NLPLPerl - Mutt - Small but very powerful text-based mail client. (Source Code)
GPL-2.0C - Sylpheed - Still developed predecessor to Claws Mail, lightweight mail client. (Source Code)
GPL-2.0C - Thunderbird - Free email application that's easy to set up and customize. (Source Code)
MPL-2.0C/C++
- aerc - Terminal MUA with a focus on plaintext and features for developers. (Source Code)
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ ae1008d2:a166d760
2025-04-01 00:29:56
@ ae1008d2:a166d760
2025-04-01 00:29:56This is part one in a series of long-form content of my ideas as to what we are entering into in my opinion;The Roaring '20's 2.0 (working title). I hope you'll join me on this journey together.
"History does not repeat itself, but it often rhymes"; - Samuel Clemens, aka Mark Twain. My only class I received an A+ in high school was history, this opened up the opportunity for me to enroll in an AP (college level) history class my senior year. There was an inherent nature for me to study history. Another quote I found to live by; "If we do not study history, we are bound to repeat it", a paraphrased quote by the many great philosphers of old from Edmund Burke, George Santayana and even Winston Churchill, all pulling from the same King Solomon quote; "What has been will be again, what has been done will be done again; there is nothing new under the sun". My curiousity of human actions, psychological and therefore economical behavior, has benefitted me greatly throughout my life and career, at such a young age. Being able to 'see around the curves' ahead I thought was a gift many had, but was sorely mistaken. People are just built different. One, if not my hardest action for me is to share. I just do things; act, often without even thinking about writing down or sharing in anyway shape or form what I just did here with friends, what we just built or how we formed these startups, etc., I've finally made the time, mainly for myself, to share my thoughts and ideas as to where we are at, and what we can do moving forward. It's very easy for us living a sovereign-lifestyle in Bitcoin, Nostr and other P2P, cryptographically-signed sovereign tools and tech-stacks alike, permissionless and self-hostable, to take all these tools for granted. We just live with them. Use them everyday. Do you own property? Do you have to take care of the cattle everyday? To live a sovereign life is tough, but most rewarding. As mentioned above, I'm diving into the details in a several part series as to what the roaring '20's were about, how it got to the point it did, and the inevitable outcome we all know what came to be. How does this possibly repeat itself almost exactly a century later? How does Bitcoin play a role? Are we all really going to be replaced by AI robots (again, history rhymes here)? Time will tell, but I think most of us actually using the tools will also forsee many of these possible outcomes, as it's why we are using many of these tools today. The next parts of this series will be released periodically, maybe once per month, maybe once per quarter. I'll also be releasing these on other platforms like Medium for reach, but Nostr will always be first, most important and prioritized.
I'll leave you with one of my favorite quotes I've lived by from one of the greatest traders of all time, especially during this roaring '20's era, Jesse Livermore; "Money is made by sitting, not trading". -
 @ 6d5c826a:4b27b659
2025-05-23 21:46:28
@ 6d5c826a:4b27b659
2025-05-23 21:46:28- Fluentd - Data collector for unified logging layer. (Source Code)
Apache-2.0Ruby - Flume - Distributed, reliable, and available service for efficiently collecting, aggregating, and moving large amounts of log data. (Source Code)
Apache-2.0Java - GoAccess - Real-time web log analyzer and interactive viewer that runs in a terminal or through the browser. (Source Code)
MITC - Loki - Log aggregation system designed to store and query logs from all your applications and infrastructure. (Source Code)
AGPL-3.0Go - rsyslog - Rocket-fast system for log processing. (Source Code)
GPL-3.0C
- Fluentd - Data collector for unified logging layer. (Source Code)
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 6d5c826a:4b27b659
2025-05-23 21:46:11
@ 6d5c826a:4b27b659
2025-05-23 21:46:11- GLPI - Information Resource-Manager with an additional Administration Interface. (Source Code)
GPL-3.0PHP - OCS Inventory NG - Asset management and deployment solution for all devices in your IT Department. (Source Code)
GPL-2.0PHP/Perl - OPSI - Hardware and software inventory, client management, deployment, and patching for Linux and Windows. (Source Code)
GPL-3.0/AGPL-3.0OVF/Python - RackTables - Datacenter and server room asset management like document hardware assets, network addresses, space in racks, networks configuration. (Demo, Source Code)
GPL-2.0PHP - Ralph - Asset management, DCIM and CMDB system for large Data Centers as well as smaller LAN networks. (Demo, Source Code)
Apache-2.0Python/Docker - Snipe IT - Asset & license management software. (Source Code)
AGPL-3.0PHP
- GLPI - Information Resource-Manager with an additional Administration Interface. (Source Code)
-
 @ 04c915da:3dfbecc9
2025-03-13 19:39:28
@ 04c915da:3dfbecc9
2025-03-13 19:39:28In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:45:53
@ 6d5c826a:4b27b659
2025-05-23 21:45:53- BounCA - A personal SSL Key / Certificate Authority web-based tool for creating self-signed certificates. (Source Code)
Apache-2.0Python - easy-rsa - Bash script to build and manage a PKI CA.
GPL-2.0Shell - Fusion Directory - Improve the Management of the services and the company directory based on OpenLDAP. (Source Code)
GPL-2.0PHP - LDAP Account Manager (LAM) - Web frontend for managing entries (e.g. users, groups, DHCP settings) stored in an LDAP directory. (Source Code)
GPL-3.0PHP - Libravatar - Libravatar is a service which delivers your avatar (profile picture) to other websites. (Source Code)
AGPL-3.0Python - Pomerium - An identity and context aware access-proxy inspired by BeyondCorp. (Source Code)
Apache-2.0Docker/Go - Samba - Active Directory and CIFS protocol implementation. (Source Code)
GPL-3.0C - Smallstep Certificates - A private certificate authority (X.509 & SSH) and related tools for secure automated certificate management. (Source Code)
Apache-2.0Go - ZITADEL - Cloud-native Identity & Access Management solution providing a platform for secure authentication, authorization and identity management. (Source Code)
Apache-2.0Go/Docker/K8S
- BounCA - A personal SSL Key / Certificate Authority web-based tool for creating self-signed certificates. (Source Code)
-
 @ 04c915da:3dfbecc9
2025-03-10 23:31:30
@ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:45:34
@ 6d5c826a:4b27b659
2025-05-23 21:45:34- Authelia - The Single Sign-On Multi-Factor portal for web apps. (Source Code)
Apache-2.0Go - Authentik - Flexible identity provider with support for different protocols. (OAuth 2.0, SAML, LDAP and Radius). (Source Code)
MITPython - KeyCloak - Open Source Identity and Access Management. (Source Code)
Apache-2.0Java
- Authelia - The Single Sign-On Multi-Factor portal for web apps. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:45:15
@ 6d5c826a:4b27b659
2025-05-23 21:45:15- 389 Directory Server - Enterprise-class Open Source LDAP server for Linux. (Source Code)
GPL-3.0C - Apache Directory Server - Extensible and embeddable directory server, certified LDAPv3 compatible, with Kerberos 5 and Change Password Protocol support, triggers, stored procedures, queues and views. (Source Code)
Apache-2.0Java - FreeIPA - Integrated security information management solution combining Linux (Fedora), 389 Directory Server, Kerberos, NTP, DNS, and Dogtag Certificate System (web interface and command-line administration tools). (Source Code)
GPL-3.0Python/C/JavaScript - FreeRADIUS - Multi-protocol policy server (radiusd) that implements RADIUS, DHCP, BFD, and ARP and associated client/PAM library/Apache module. (Source Code)
GPL-2.0C - lldap - Light (simplified) LDAP implementation with a simple, intuitive web interface and GraphQL support.
GPL-3.0Rust - OpenLDAP - Open-source implementation of the Lightweight Directory Access Protocol (server, libraries and clients). (Source Code)
OLDAP-2.8C
- 389 Directory Server - Enterprise-class Open Source LDAP server for Linux. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:44:57
@ 6d5c826a:4b27b659
2025-05-23 21:44:57- Atom Community - A fork of atom A hackable text editor from Github.
MITJavaScript - Brackets - Code editor for web designers and front-end developers. (Source Code)
MITJavaScript - Eclipse - IDE written in Java with an extensible plug-in system. (Source Code)
EPL-1.0Java - Geany - GTK2 text editor. (Source Code)
GPL-2.0C/C++ - GNU Emacs - An extensible, customizable text editor-and more. (Source Code)
GPL-3.0C - Haroopad - Markdown editor with live preview. (Source Code)
GPL-3.0JavaScript - jotgit - Git-backed real-time collaborative code editing.
MITNodejs - KDevelop - IDE by the people behind KDE. (Source Code)
GFDL-1.2C++ - Micro - A modern and intuitive terminal-based text editor. (Source Code)
MITGo - Nano - Easy to use, customizable text editor. (Source Code)
GPL-3.0C - Notepad++ - GPLv2 multi-language editor with syntax highlighting for Windows. (Source Code)
GPL-2.0C++ - TextMate - A graphical text editor for OS X. (Source Code)
GPL-3.0C++ - Vim - A highly configurable text editor built to enable efficient editing. (Source Code)
VimC - VSCodium - An open source cross-platform extensible code editor based on VS Code by Microsoft removing their non-free additions. (Source Code)
MITTypeScript
- Atom Community - A fork of atom A hackable text editor from Github.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:44:34
@ 6d5c826a:4b27b659
2025-05-23 21:44:34- Bind - Versatile, classic, complete name server software. (Source Code)
MPL-2.0C - CoreDNS - Flexible DNS server. (Source Code)
Apache-2.0Go - djbdns - A collection of DNS applications, including tinydns. (Source Code)
CC0-1.0C - dnsmasq - Provides network infrastructure for small networks: DNS, DHCP, router advertisement and network boot. (Source Code)
GPL-2.0C - Knot - High performance authoritative-only DNS server. (Source Code)
GPL-3.0C - NSD - Authoritative DNS name server developed speed, reliability, stability and security. (Source Code)
BSD-3-ClauseC - PowerDNS Authoritative Server - Versatile nameserver which supports a large number of backends. (Source Code)
GPL-2.0C++ - Unbound - Validating, recursive, and caching DNS resolver. (Source Code)
BSD-3-ClauseC - Yadifa - Clean, small, light and RFC-compliant name server implementation developed from scratch by .eu. (Source Code)
BSD-3-ClauseC
- Bind - Versatile, classic, complete name server software. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:44:16
@ 6d5c826a:4b27b659
2025-05-23 21:44:16- Atomia DNS - DNS management system.
ISCPerl - Designate - DNSaaS services for OpenStack. (Source Code)
Apache-2.0Python - DNSControl - Synchronize your DNS to multiple providers from a simple DSL. (Source Code)
MITGo/Docker - DomainMOD - Manage your domains and other internet assets in a central location. (Source Code)
GPL-3.0PHP - nsupdate.info - Dynamic DNS service. (Demo, Source Code)
BSD-3-ClausePython - octoDNS - DNS as code - Tools for managing DNS across multiple providers.
MITPython - Poweradmin - Web-based DNS control panel for PowerDNS server. (Source Code)
GPL-3.0PHP - SPF Toolbox - Application to look up DNS records such as SPF, MX, Whois, and more. (Source Code)
MITPHP
- Atomia DNS - DNS management system.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:43:55
@ 6d5c826a:4b27b659
2025-05-23 21:43:55- Ceph - Distributed object, block, and file storage platform. (Source Code)
LGPL-3.0C++ - DRBD - Distributed replicated storage system, implemented as a Linux kernel driver. (Source Code)
GPL-2.0C - GlusterFS - Software-defined distributed storage that can scale to several petabytes, with interfaces for object, block and file storage. (Source Code)
GPL-2.0/LGPL-3.0C - Hadoop Distributed Filesystem (HDFS) - Distributed file system that provides high-throughput access to application data. (Source Code)
Apache-2.0Java - JuiceFS - Distributed POSIX file system built on top of Redis and S3. (Source Code)
Apache-2.0Go - Kubo - Implementation of IPFS, a global, versioned, peer-to-peer filesystem that seeks to connect all computing devices with the same system of files.
Apache-2.0/MITGo - LeoFS - Highly available, distributed, replicated eventually consistent object/blob store. (Source Code)
Apache-2.0Erlang - Lustre - Parallel distributed file system, generally used for large-scale cluster computing. (Source Code)
GPL-2.0C - Minio - High-performance, S3 compatible object store built for large scale AI/ML, data lake and database workloads. (Source Code)
AGPL-3.0Go - MooseFS - Fault tolerant, network distributed file system. (Source Code)
GPL-2.0C - OpenAFS - Distributed network file system with read-only replicas and multi-OS support. (Source Code)
IPL-1.0C - Openstack Swift - A highly available, distributed, eventually consistent object/blob store. (Source Code)
Apache-2.0Python - Perkeep - A set of open source formats, protocols, and software for modeling, storing, searching, sharing and synchronizing data (previously Camlistore). (Source Code)
Apache-2.0C - TahoeLAFS - Secure, decentralized, fault-tolerant, peer-to-peer distributed data store and distributed file system. (Source Code)
GPL-2.0Python - XtreemFS - Distributed, replicated and fault-tolerant file system for federated IT infrastructures.. (Source Code)
BSD-3-ClauseJava
- Ceph - Distributed object, block, and file storage platform. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:43:37
@ 6d5c826a:4b27b659
2025-05-23 21:43:37- Diagrams.net - A.K.A. Draw.io. Easy to use Diagram UI with a plethora of templates. (Source Code)
Apache-2.0JavaScript/Docker - Kroki - API for generating diagrams from textual descriptions. (Source Code)
MITJava - Mermaid - Javascript module with a unique, easy, shorthand syntax. Integrates into several other tools like Grafana. (Source Code)
MITNodejs/Docker
- Diagrams.net - A.K.A. Draw.io. Easy to use Diagram UI with a plethora of templates. (Source Code)
-
 @ 6389be64:ef439d32
2025-02-27 21:32:12
@ 6389be64:ef439d32
2025-02-27 21:32:12GA, plebs. The latest episode of Bitcoin And is out, and, as always, the chicanery is running rampant. Let’s break down the biggest topics I covered, and if you want the full, unfiltered rant, make sure to listen to the episode linked below.
House Democrats’ MEME Act: A Bad Joke?
House Democrats are proposing a bill to ban presidential meme coins, clearly aimed at Trump’s and Melania’s ill-advised token launches. While grifters launching meme coins is bad, this bill is just as ridiculous. If this legislation moves forward, expect a retaliatory strike exposing how politicians like Pelosi and Warren mysteriously amassed their fortunes. Will it pass? Doubtful. But it’s another sign of the government’s obsession with regulating everything except itself.
Senate Banking’s First Digital Asset Hearing: The Real Target Is You
Cynthia Lummis chaired the first digital asset hearing, and—surprise!—it was all about control. The discussion centered on stablecoins, AML, and KYC regulations, with witnesses suggesting Orwellian measures like freezing stablecoin transactions unless pre-approved by authorities. What was barely mentioned? Bitcoin. They want full oversight of stablecoins, which is really about controlling financial freedom. Expect more nonsense targeting self-custody wallets under the guise of stopping “bad actors.”
Bank of America and PayPal Want In on Stablecoins
Bank of America’s CEO openly stated they’ll launch a stablecoin as soon as regulation allows. Meanwhile, PayPal’s CEO paid for a hat using Bitcoin—not their own stablecoin, Pi USD. Why wouldn’t he use his own product? Maybe he knows stablecoins aren’t what they’re hyped up to be. Either way, the legacy financial system is gearing up to flood the market with stablecoins, not because they love crypto, but because it’s a tool to extend U.S. dollar dominance.
MetaPlanet Buys the Dip
Japan’s MetaPlanet issued $13.4M in bonds to buy more Bitcoin, proving once again that institutions see the writing on the wall. Unlike U.S. regulators who obsess over stablecoins, some companies are actually stacking sats.
UK Expands Crypto Seizure Powers
Across the pond, the UK government is pushing legislation to make it easier to seize and destroy crypto linked to criminal activity. While they frame it as going after the bad guys, it’s another move toward centralized control and financial surveillance.
Bitcoin Tools & Tech: Arc, SatoChip, and Nunchuk
Some bullish Bitcoin developments: ARC v0.5 is making Bitcoin’s second layer more efficient, SatoChip now supports Taproot and Nostr, and Nunchuk launched a group wallet with chat, making multisig collaboration easier.
The Bottom Line
The state is coming for financial privacy and control, and stablecoins are their weapon of choice. Bitcoiners need to stay focused, keep their coins in self-custody, and build out parallel systems. Expect more regulatory attacks, but don’t let them distract you—just keep stacking and transacting in ways they can’t control.
🎧 Listen to the full episode here: https://fountain.fm/episode/PYITCo18AJnsEkKLz2Ks
💰 Support the show by boosting sats on Podcasting 2.0! and I will see you on the other side.
-
 @ dc4cd086:cee77c06
2025-02-09 03:35:25
@ dc4cd086:cee77c06
2025-02-09 03:35:25Have you ever wanted to learn from lengthy educational videos but found it challenging to navigate through hours of content? Our new tool addresses this problem by transforming long-form video lectures into easily digestible, searchable content.
Key Features:
Video Processing:
- Automatically downloads YouTube videos, transcripts, and chapter information
- Splits transcripts into sections based on video chapters
Content Summarization:
- Utilizes language models to transform spoken content into clear, readable text
- Formats output in AsciiDoc for improved readability and navigation
- Highlights key terms and concepts with [[term]] notation for potential cross-referencing
Diagram Extraction:
- Analyzes video entropy to identify static diagram/slide sections
- Provides a user-friendly GUI for manual selection of relevant time ranges
- Allows users to pick representative frames from selected ranges
Going Forward:
Currently undergoing a rewrite to improve organization and functionality, but you are welcome to try the current version, though it might not work on every machine. Will support multiple open and closed language models for user choice Free and open-source, allowing for personal customization and integration with various knowledge bases. Just because we might not have it on our official Alexandria knowledge base, you are still welcome to use it on you own personal or community knowledge bases! We want to help find connections between ideas that exist across relays, allowing individuals and groups to mix and match knowledge bases between each other, allowing for any degree of openness you care.
While designed with #Alexandria users in mind, it's available for anyone to use and adapt to their own learning needs.
Screenshots
Frame Selection

This is a screenshot of the frame selection interface. You'll see a signal that represents frame entropy over time. The vertical lines indicate the start and end of a chapter. Within these chapters you can select the frames by clicking and dragging the mouse over the desired range where you think diagram is in that chapter. At the bottom is an option that tells the program to select a specific number of frames from that selection.
Diagram Extraction

This is a screenshot of the diagram extraction interface. For every selection you've made, there will be a set of frames that you can choose from. You can select and deselect as many frames as you'd like to save.
Links
- repo: https://github.com/limina1/video_article_converter
- Nostr Apps 101: https://www.youtube.com/watch?v=Flxa_jkErqE
Output
And now, we have a demonstration of the final result of this tool, with some quick cleaning up. The video we will be using this tool on is titled Nostr Apps 101 by nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 during Nostrasia. The following thread is an analog to the modular articles we are constructing for Alexandria, and I hope it conveys the functionality we want to create in the knowledge space. Note, this tool is the first step! You could use a different prompt that is most appropriate for the specific context of the transcript you are working with, but you can also manually clean up any discrepancies that don't portray the video accurately. You can now view the article on #Alexandria https://next-alexandria.gitcitadel.eu/publication?d=nostr-apps-101
Initially published as chained kind 1's nostr:nevent1qvzqqqqqqypzp5r5hd579v2sszvvzfel677c8dxgxm3skl773sujlsuft64c44ncqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgwwaehxw309ahx7uewd3hkctcpzemhxue69uhhyetvv9ujumt0wd68ytnsw43z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309aex2mrp0yh8xmn0wf6zuum0vd5kzmp0qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgc7hglpn
Or view on Coracle https://coracle.social /nevent1qqsxunmjy20mvlq37vnrcshkf6sdrtkfjtjz3anuetmcuv8jswhezgcppemhxue69uhkummn9ekx7mp0qgsdqa9md83tz5yqnrqjw07hhkpmfjpkuv9hlh5v8yhu8z274w9dv7qnnq0s3
-
 @ 6d5c826a:4b27b659
2025-05-23 21:43:11
@ 6d5c826a:4b27b659
2025-05-23 21:43:11- Capistrano - Deploy your application to any number of machines simultaneously, in sequence or as a rolling set via SSH (rake based). (Source Code)
MITRuby - CloudSlang - Flow-based orchestration tool for managing deployed applications, with Docker capabilities. (Source Code)
Apache-2.0Java - CloudStack - Cloud computing software for creating, managing, and deploying infrastructure cloud services. (Source Code)
Apache-2.0Java/Python - Cobbler - Cobbler is a Linux installation server that allows for rapid setup of network installation environments. (Source Code)
GPL-2.0Python - Fabric - Python library and cli tool for streamlining the use of SSH for application deployment or systems administration tasks. (Source Code)
BSD-2-ClausePython - Genesis - A template framework for multi-environment BOSH deployments.
MITPerl - munki - Webserver-based repository of packages and package metadata, that allows macOS administrators to manage software installs. (Source Code)
Apache-2.0Python - Overcast - Deploy VMs across different cloud providers, and run commands and scripts across any or all of them in parallel via SSH. (Source Code)
MITNodejs
- Capistrano - Deploy your application to any number of machines simultaneously, in sequence or as a rolling set via SSH (rake based). (Source Code)
-
 @ 6be5cc06:5259daf0
2025-01-21 23:17:29
@ 6be5cc06:5259daf0
2025-01-21 23:17:29A seguir, veja como instalar e configurar o Privoxy no Pop!_OS.
1. Instalar o Tor e o Privoxy
Abra o terminal e execute:
bash sudo apt update sudo apt install tor privoxyExplicação:
- Tor: Roteia o tráfego pela rede Tor.
- Privoxy: Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
2. Configurar o Privoxy
Abra o arquivo de configuração do Privoxy:
bash sudo nano /etc/privoxy/configNavegue até a última linha (atalho:
Ctrl+/depoisCtrl+Vpara navegar diretamente até a última linha) e insira:bash forward-socks5 / 127.0.0.1:9050 .Isso faz com que o Privoxy envie todo o tráfego para o Tor através da porta 9050.
Salve (
CTRL+OeEnter) e feche (CTRL+X) o arquivo.
3. Iniciar o Tor e o Privoxy
Agora, inicie e habilite os serviços:
bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxyExplicação:
- start: Inicia os serviços.
- enable: Faz com que iniciem automaticamente ao ligar o PC.
4. Configurar o Navegador Firefox
Para usar a rede Tor com o Firefox:
- Abra o Firefox.
- Acesse Configurações → Configurar conexão.
- Selecione Configuração manual de proxy.
- Configure assim:
- Proxy HTTP:
127.0.0.1 - Porta:
8118(porta padrão do Privoxy) - Domínio SOCKS (v5):
127.0.0.1 - Porta:
9050
- Proxy HTTP:
- Marque a opção "Usar este proxy também em HTTPS".
- Clique em OK.
5. Verificar a Conexão com o Tor
Abra o navegador e acesse:
text https://check.torproject.org/Se aparecer a mensagem "Congratulations. This browser is configured to use Tor.", a configuração está correta.
Dicas Extras
- Privoxy pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o Privoxy.
-
 @ 9e69e420:d12360c2
2025-01-19 04:48:31
@ 9e69e420:d12360c2
2025-01-19 04:48:31A new report from the National Sports Shooting Foundation (NSSF) shows that civilian firearm possession exceeded 490 million in 2022. The total from 1990 to 2022 is estimated at 491.3 million firearms. In 2022, over ten million firearms were domestically produced, leading to a total of 16,045,911 firearms available in the U.S. market.
Of these, 9,873,136 were handguns, 4,195,192 were rifles, and 1,977,583 were shotguns. Handgun availability aligns with the concealed carry and self-defense market, as all states allow concealed carry, with 29 having constitutional carry laws.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:42:54
@ 6d5c826a:4b27b659
2025-05-23 21:42:54- Ajenti - Control panel for Linux and BSD. (Source Code)
MITPython/Shell - Cockpit - Web-based graphical interface for servers. (Source Code)
LGPL-2.1C - Froxlor - Lightweight server management software with Nginx and PHP-FPM support. (Source Code)
GPL-2.0PHP - HestiaCP - Web server control panel (fork of VestaCP). (Demo, Source Code)
GPL-3.0PHP/Shell/Other - ISPConfig - Manage Linux servers directly through your browser. (Source Code)
BSD-3-ClausePHP - Sentora - Open-Source Web hosting control panel for Linux, BSD (fork of ZPanel). (Source Code)
GPL-3.0PHP - Virtualmin - Powerful and flexible web hosting control panel for Linux and BSD systems. (Source Code)
GPL-3.0Shell/Perl/Other - Webmin - Web-based interface for system administration for Unix. (Source Code)
BSD-3-ClausePerl
- Ajenti - Control panel for Linux and BSD. (Source Code)
-
 @ e31e84c4:77bbabc0
2024-12-02 10:44:07
@ e31e84c4:77bbabc0
2024-12-02 10:44:07Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net
Fiduciary duty is the obligation to act in the client’s best interests at all times, prioritizing their needs above the advisor’s own, ensuring honesty, transparency, and avoiding conflicts of interest in all recommendations and actions.
This is something all advisors in the BFAN take very seriously; after all, we are legally required to do so. For the average advisor this is a fairly easy box to check. All you essentially have to do is have someone take a 5-minute risk assessment, fill out an investment policy statement, and then throw them in the proverbial 60/40 portfolio. You have thousands of investment options to choose from and you can reasonably explain how your client is theoretically insulated from any move in the \~markets\~. From the traditional financial advisor perspective, you could justify nearly anything by putting a client into this type of portfolio. All your bases were pretty much covered from return profile, regulatory, compliance, investment options, etc. It was just too easy. It became the household standard and now a meme.
As almost every real bitcoiner knows, the 60/40 portfolio is moving into psyop territory, and many financial advisors get clowned on for defending this relic on bitcoin twitter. I’m going to specifically poke fun at the ‘40’ part of this portfolio.
The ‘40’ represents fixed income, defined as…
An investment type that provides regular, set interest payments, such as bonds or treasury securities, and returns the principal at maturity. It’s generally considered a lower-risk asset class, used to generate stable income and preserve capital.
Historically, this part of the portfolio was meant to weather the volatility in the equity markets and represent the “safe” investments. Typically, some sort of bond.
First and foremost, the fixed income section is most commonly constructed with U.S. Debt. There are a couple main reasons for this. Most financial professionals believe the same fairy tale that U.S. Debt is “risk free” (lol). U.S. debt is also one of the largest and most liquid assets in the market which comes with a lot of benefits.
There are many brilliant bitcoiners in finance and economics that have sounded the alarm on the U.S. debt ticking time bomb. I highly recommend readers explore the work of Greg Foss, Lawrence Lepard, Lyn Alden, and Saifedean Ammous. My very high-level recap of their analysis:
-
A bond is a contract in which Party A (the borrower) agrees to repay Party B (the lender) their principal plus interest over time.
-
The U.S. government issues bonds (Treasury securities) to finance its operations after tax revenues have been exhausted.
-
These are traditionally viewed as “risk-free” due to the government’s historical reliability in repaying its debts and the strength of the U.S. economy
-
U.S. bonds are seen as safe because the government has control over the dollar (world reserve asset) and, until recently (20 some odd years), enjoyed broad confidence that it would always honor its debts.
-
This perception has contributed to high global demand for U.S. debt but, that is quickly deteriorating.
-
The current debt situation raises concerns about sustainability.
-
The U.S. has substantial obligations, and without sufficient productivity growth, increasing debt may lead to a cycle where borrowing to cover interest leads to more debt.
-
This could result in more reliance on money creation (printing), which can drive inflation and further debt burdens.
In the words of Lyn Alden “Nothing stops this train”
Those obligations are what makes up the 40% of most the fixed income in your portfolio. So essentially you are giving money to one of the worst capital allocators in the world (U.S. Gov’t) and getting paid back with printed money.
As someone who takes their fiduciary responsibility seriously and understands the debt situation we just reviewed, I think it’s borderline negligent to put someone into a classic 60% (equities) / 40% (fixed income) portfolio without serious scrutiny of the client’s financial situation and options available to them. I certainly have my qualms with equities at times, but overall, they are more palatable than the fixed income portion of the portfolio. I don’t like it either, but the money is broken and the unit of account for nearly every equity or fixed income instrument (USD) is fraudulent. It’s a paper mache fade that is quite literally propped up by the money printer.
To briefly be as most charitable as I can – It wasn’t always this way. The U.S. Dollar used to be sound money, we used to have government surplus instead of mathematically certain deficits, The U.S. Federal Government didn’t used to have a money printing addiction, and pre-bitcoin the 60/40 portfolio used to be a quality portfolio management strategy. Those times are gone.
Now the fun part. How does bitcoin fix this?
Bitcoin fixes this indirectly. Understanding investment criteria changes via risk tolerance, age, goals, etc. A client may still have a need for “fixed income” in the most literal definition – Low risk yield. Now you may be thinking that yield is a bad word in bitcoin land, you’re not wrong, so stay with me. Perpetual motion machine crypto yield is fake and largely where many crypto scams originate. However, that doesn’t mean yield in the classic finance sense does not exist in bitcoin, it very literally does. Fortunately for us bitcoiners there are many other smart, driven, and enterprising bitcoiners that understand this problem and are doing something to address it. These individuals are pioneering new possibilities in bitcoin and finance, specifically when it comes to fixed income.
Here are some new developments –
Private Credit Funds – The Build Asset Management Secured Income Fund I is a private credit fund created by Build Asset Management. This fund primarily invests in bitcoin-backed, collateralized business loans originated by Unchained, with a secured structure involving a multi-signature, over-collateralized setup for risk management. Unchained originates loans and sells them to Build, which pools them into the fund, enabling investors to share in the interest income.
Dynamics
- Loan Terms: Unchained issues loans at interest rates around 14%, secured with a 2/3 multi-signature vault backed by a 40% loan-to-value (LTV) ratio.
- Fund Mechanics: Build buys these loans from Unchained, thus providing liquidity to Unchained for further loan originations, while Build manages interest payments to investors in the fund.
Pros
- The fund offers a unique way to earn income via bitcoin-collateralized debt, with protection against rehypothecation and strong security measures, making it attractive for investors seeking exposure to fixed income with bitcoin.
Cons
- The fund is only available to accredited investors, which is a regulatory standard for private credit funds like this.
Corporate Bonds – MicroStrategy Inc. (MSTR), a business intelligence company, has leveraged its corporate structure to issue bonds specifically to acquire bitcoin as a reserve asset. This approach allows investors to indirectly gain exposure to bitcoin’s potential upside while receiving interest payments on their bond investments. Some other publicly traded companies have also adopted this strategy, but for the sake of this article we will focus on MSTR as they are the biggest and most vocal issuer.
Dynamics
-
Issuance: MicroStrategy has issued senior secured notes in multiple offerings, with terms allowing the company to use the proceeds to purchase bitcoin.
-
Interest Rates: The bonds typically carry high-yield interest rates, averaging around 6-8% APR, depending on the specific issuance and market conditions at the time of issuance.
-
Maturity: The bonds have varying maturities, with most structured for multi-year terms, offering investors medium-term exposure to bitcoin’s value trajectory through MicroStrategy’s holdings.
Pros
-
Indirect Bitcoin exposure with income provides a unique opportunity for investors seeking income from bitcoin-backed debt.
-
Bonds issued by MicroStrategy offer relatively high interest rates, appealing for fixed-income investors attracted to the higher risk/reward scenarios.
Cons
-
There are credit risks tied to MicroStrategy’s financial health and bitcoin’s performance. A significant drop in bitcoin prices could strain the company’s ability to service debt, increasing credit risk.
-
Availability: These bonds are primarily accessible to institutional investors and accredited investors, limiting availability for retail investors.
Interest Payable in Bitcoin – River has introduced an innovative product, bitcoin Interest on Cash, allowing clients to earn interest on their U.S. dollar deposits, with the interest paid in bitcoin.
Dynamics
-
Interest Payment: Clients earn an annual interest rate of 3.8% on their cash deposits. The accrued interest is converted to Bitcoin daily and paid out monthly, enabling clients to accumulate Bitcoin over time.
-
Security and Accessibility: Cash deposits are insured up to $250,000 through River’s banking partner, Lead Bank, a member of the FDIC. All Bitcoin holdings are maintained in full reserve custody, ensuring that client assets are not lent or leveraged.
Pros
-
There are no hidden fees or minimum balance requirements, and clients can withdraw their cash at any time.
-
The 3.8% interest rate provides a predictable income stream, akin to traditional fixed-income investments.
Cons
-
While the interest rate is fixed, the value of the Bitcoin received as interest can fluctuate, introducing potential variability in the investment’s overall return.
-
Interest rate payments are on the lower side
Admittedly, this is a very small list, however, these types of investments are growing more numerous and meaningful. The reality is the existing options aren’t numerous enough to service every client that has a need for fixed income exposure. I challenge advisors to explore innovative options for fixed income exposure outside of sovereign debt, as that is most certainly a road to nowhere. It is my wholehearted belief and call to action that we need more options to help clients across the risk and capital allocation spectrum access a sound money standard.
Additional Resources
-
River: The future of saving is here: Earn 3.8% on cash. Paid in Bitcoin.
-
MicroStrategy: MicroStrategy Announces Pricing of Offering of Convertible Senior Notes
Bitcoin and Fixed Income was Written By Wyatt O’Rourke. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: ultrahusky3@primal.net
-
-
 @ 6d5c826a:4b27b659
2025-05-23 21:42:36
@ 6d5c826a:4b27b659
2025-05-23 21:42:36- Buildbot - Python-based toolkit for continuous integration. (Source Code)
GPL-2.0Python - CDS - Enterprise-Grade Continuous Delivery & DevOps Automation Open Source Platform. (Source Code)
BSD-3-ClauseGo - Concourse - Concourse is a CI tool that treats pipelines as first class objects and containerizes every step along the way. (Demo, Source Code)
Apache-2.0Go - drone - Drone is a Continuous Delivery platform built on Docker, written in Go. (Source Code)
Apache-2.0Go - Factor - Programmatically define and run workflows to connect configuration management, source code management, build, continuous integration, continuous deployment and communication tools. (Source Code)
MITRuby - GitLab CI - Gitlab's built-in, full-featured CI/CD solution. (Source Code)
MITRuby - GoCD - Continuous delivery server. (Source Code)
Apache-2.0Java/Ruby - Jenkins - Continuous Integration Server. (Source Code)
MITJava - Laminar - Fast, lightweight, simple and flexible Continuous Integration. (Source Code)
GPL-3.0C++ - PHP Censor - Open source self-hosted continuous integration server for PHP projects.
BSD-2-ClausePHP - Strider - Open Source Continuous Deployment / Continuous Integration platform. (Source Code)
MITNodejs - Terrateam - GitOps-first automation platform for Terraform and OpenTofu workflows with support for self-hosted runners. (Source Code)
MPL-2.0OCaml/Docker - werf - Open Source CI/CD tool for building Docker images and deploying to Kubernetes via GitOps. (Source Code)
Apache-2.0Go - Woodpecker - Community fork of Drone that uses Docker containers. (Source Code)
Apache-2.0Go
- Buildbot - Python-based toolkit for continuous integration. (Source Code)
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ 6d5c826a:4b27b659
2025-05-23 21:42:17
@ 6d5c826a:4b27b659
2025-05-23 21:42:17- Collins - At Tumblr, it's the infrastructure source of truth and knowledge. (Source Code)
Apache-2.0Docker/Scala - i-doit - IT Documentation and CMDB.
AGPL-3.0PHP - iTop - Complete ITIL web based service management tool. (Source Code)
AGPL-3.0PHP - netbox - IP address management (IPAM) and data center infrastructure management (DCIM) tool. (Demo, Source Code)
Apache-2.0Python
- Collins - At Tumblr, it's the infrastructure source of truth and knowledge. (Source Code)
-
 @ 76c71aae:3e29cafa
2024-08-13 04:30:00
@ 76c71aae:3e29cafa
2024-08-13 04:30:00On social media and in the Nostr space in particular, there’s been a lot of debate about the idea of supporting deletion and editing of notes.
Some people think they’re vital features to have, others believe that more honest and healthy social media will come from getting rid of these features. The discussion about these features quickly turns to the feasibility of completely deleting something on a decentralized protocol. We quickly get to the “We can’t really delete anything from the internet, or a decentralized network.” argument. This crowds out how Delete and Edit can mimic elements of offline interactions, how they can be used as social signals.
When it comes to issues of deletion and editing content, what matters more is if the creator can communicate their intentions around their content. Sure, on the internet, with decentralized protocols, there’s no way to be sure something’s deleted. It’s not like taking a piece of paper and burning it. Computers make copies of things all the time, computers don’t like deleting things. In particular, distributed systems tend to use a Kafka architecture with immutable logs, it’s just easier to keep everything around, as deleting and reindexing is hard. Even if the software could be made to delete something, there’s always screenshots, or even pictures of screens. We can’t provably make something disappear.
What we need to do in our software is clearly express intention. A delete is actually a kind of retraction. “I no longer want to associate myself with this content, please stop showing it to people as part of what I’ve published, stop highlighting it, stop sharing it.” Even if a relay or other server keeps a copy, and keeps sharing it, being able to clearly state “hello world, this thing I said, was a mistake, please get rid of it.” Just giving users the chance to say “I deleted this” is a way of showing intention. It’s also a way of signaling that feedback has been heard. Perhaps the post was factually incorrect or perhaps it was mean and the person wants to remove what they said. In an IRL conversation, for either of these scenarios there is some dialogue where the creator of the content is learning something and taking action based on what they’ve learned.
Without delete or edit, there is no option to signal to the rest of the community that you have learned something because of how the content is structured today. On most platforms a reply or response stating one’s learning will be lost often in a deluge of replies on the original post and subsequent posts are often not seen especially when the original goes viral. By providing tools like delete and edit we give people a chance to signal that they have heard the feedback and taken action.
The Nostr Protocol supports delete and expiring notes. It was one of the reasons we switched from secure scuttlebutt to build on Nostr. Our nos.social app offers delete and while we know that not all relays will honor this, we believe it’s important to provide social signaling tools as a means of making the internet more humane.
We believe that the power to learn from each other is more important than the need to police through moral outrage which is how the current platforms and even some Nostr clients work today.
It’s important that we don’t say Nostr doesn’t support delete. Not all apps need to support requesting a delete, some might want to call it a retraction. It is important that users know there is no way to enforce a delete and not all relays may honor their request.
Edit is similar, although not as widely supported as delete. It’s a creator making a clear statement that they’ve created a new version of their content. Maybe it’s a spelling error, or a new version of the content, or maybe they’re changing it altogether. Freedom online means freedom to retract a statement, freedom to update a statement, freedom to edit your own content. By building on these freedoms, we’ll make Nostr a space where people feel empowered and in control of their own media.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:41:59
@ 6d5c826a:4b27b659
2025-05-23 21:41:59- Ansible - Provisioning, configuration management, and application-deployment tool. (Source Code)
GPL-3.0Python - CFEngine - Configuration management system for automated configuration and maintenance of large-scale computer systems. (Source Code)
GPL-3.0C - Chef - Configuration management tool using a pure-Ruby, domain-specific language (DSL) for writing system configuration "recipes". (Source Code)
Apache-2.0Ruby - cloud-init - Initialization tool to automate the configuration of VMs, cloud instances, or machines on a network. (Source Code)
GPL-3.0/Apache-2.0Python - Puppet - Software configuration management tool which includes its own declarative language to describe system configuration. (Source Code)
Apache-2.0Ruby/C - Rudder - Scalable and dynamic configuration management system for patching, security & compliance, based on CFEngine. (Source Code)
GPL-3.0Scala - Salt - Event-driven IT automation, remote task execution, and configuration management software. (Source Code)
Apache-2.0Python
- Ansible - Provisioning, configuration management, and application-deployment tool. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:41:37
@ 6d5c826a:4b27b659
2025-05-23 21:41:37- Eggdrop - The oldest Internet Relay Chat (IRC) bot still in active development. (Source Code)
GPL-2.0C - Errbot - Plugin based chatbot designed to be easily deployable, extensible and maintainable. (Source Code)
GPL-3.0Python - Hubot - A customizable, life embetterment robot. (Source Code)
MITNodejs
- Eggdrop - The oldest Internet Relay Chat (IRC) bot still in active development. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:41:18
@ 6d5c826a:4b27b659
2025-05-23 21:41:18- EasyBuild - EasyBuild builds software and modulefiles for High Performance Computing (HPC) systems in an efficient way. (Source Code)
GPL-2.0Python - Environment Modules - Environment Modules provides for the dynamic modification of a user's environment via modulefiles. (Source Code)
GPL-2.0Tcl - Lmod - Lmod is a Lua based module system that easily handles the MODULEPATH Hierarchical problem. (Source Code)
MITLua - Spack - A flexible package manager that supports multiple versions, configurations, platforms, and compilers. (Source Code)
MIT/Apache-2.0Python
- EasyBuild - EasyBuild builds software and modulefiles for High Performance Computing (HPC) systems in an efficient way. (Source Code)
-
 @ 6d5c826a:4b27b659
2025-05-23 21:40:57
@ 6d5c826a:4b27b659
2025-05-23 21:40:57- Backupninja - Lightweight, extensible meta-backup system, provides a centralized way to configure and coordinate many different backup utilities.
GPL-2.0Shell - Backrest - Backrest is a web UI and orchestrator for restic backup. (Source Code)
GPL-3.0Docker/Go - Bareos - Cross-network backup solution which preserves, archives, and recovers data from all major operating systems. (Source Code)
AGPL-3.0C++/C - Barman - Backup and Recovery Manager for PostgreSQL. (Source Code)
GPL-3.0Python - BorgBackup - Deduplicating archiver with compression and authenticated encryption. (Source Code)
BSD-3-ClausePython - Burp - Network backup and restore program. (Source Code)
AGPL-3.0C - Dar - Which stands for Disk ARchive, is a robust and rich featured archiving and backup software of the tar style. (Source Code)
GPL-2.0C++ - Duplicati - Backup client that securely stores encrypted, incremental, compressed backups on cloud storage services and remote file servers. (Source Code)
LGPL-2.1C# - Duplicity - Encrypted bandwidth-efficient backup using the rsync algorithm. (Source Code)
GPL-2.0Python - Proxmox Backup Server - Proxmox Backup Server is an enterprise-class, client-server backup solution thatis capable of backing up virtual machines, containers, and physical hosts. (Source Code)
GPL-3.0Rust - rclone - Command-line program to sync files and directories to and from different cloud storage providers.. (Source Code)
MITGo - Rdiff-backup - Reverse differential backup tool, over a network or locally. (Source Code)
GPL-2.0Python - Restic - Easy, fast, verifiable, secure and efficient remote backup tool. (Source Code)
BSD-2-ClauseGo - Rsnapshot - Filesystem snapshot utility based on rsync. (Source Code)
GPL-2.0Perl - Shield - A pluggable architecture for backup and restore of database systems.
MITGo - UrBackup - Client/Server Open Source Network Backup for Windows, MacOS and Linux. (Source Code)
AGPL-3.0C/C++
- Backupninja - Lightweight, extensible meta-backup system, provides a centralized way to configure and coordinate many different backup utilities.
-
 @ c1e9ab3a:9cb56b43
2025-05-18 04:14:48
@ c1e9ab3a:9cb56b43
2025-05-18 04:14:48Abstract
This document proposes a novel architecture that decouples the peer-to-peer (P2P) communication layer from the Bitcoin protocol and replaces or augments it with the Nostr protocol. The goal is to improve censorship resistance, performance, modularity, and maintainability by migrating transaction propagation and block distribution to the Nostr relay network.
Introduction
Bitcoin’s current architecture relies heavily on its P2P network to propagate transactions and blocks. While robust, it has limitations in terms of flexibility, scalability, and censorship resistance in certain environments. Nostr, a decentralized event-publishing protocol, offers a multi-star topology and a censorship-resistant infrastructure for message relay.
This proposal outlines how Bitcoin communication could be ported to Nostr while maintaining consensus and verification through standard Bitcoin clients.
Motivation
- Enhanced Censorship Resistance: Nostr’s architecture enables better relay redundancy and obfuscation of transaction origin.
- Simplified Lightweight Nodes: Removing the full P2P stack allows for lightweight nodes that only verify blockchain data and communicate over Nostr.
- Architectural Modularity: Clean separation between validation and communication enables easier auditing, upgrades, and parallel innovation.
- Faster Propagation: Nostr’s multi-star network may provide faster propagation of transactions and blocks compared to the mesh-like Bitcoin P2P network.
Architecture Overview
Components
-
Bitcoin Minimal Node (BMN):
- Verifies blockchain and block validity.
- Maintains UTXO set and handles mempool logic.
- Connects to Nostr relays instead of P2P Bitcoin peers.
-
Bridge Node:
- Bridges Bitcoin P2P traffic to and from Nostr relays.
- Posts new transactions and blocks to Nostr.
- Downloads mempool content and block headers from Nostr.
-
Nostr Relays:
- Accept Bitcoin-specific event kinds (transactions and blocks).
- Store mempool entries and block messages.
- Optionally broadcast fee estimation summaries and tipsets.
Event Format
Proposed reserved Nostr
kindnumbers for Bitcoin content (NIP/BIP TBD):| Nostr Kind | Purpose | |------------|------------------------| | 210000 | Bitcoin Transaction | | 210001 | Bitcoin Block Header | | 210002 | Bitcoin Block | | 210003 | Mempool Fee Estimates | | 210004 | Filter/UTXO summary |
Transaction Lifecycle
- Wallet creates a Bitcoin transaction.
- Wallet sends it to a set of configured Nostr relays.
- Relays accept and cache the transaction (based on fee policies).
- Mining nodes or bridge nodes fetch mempool contents from Nostr.
- Once mined, a block is submitted over Nostr.
- Nodes confirm inclusion and update their UTXO set.
Security Considerations
- Sybil Resistance: Consensus remains based on proof-of-work. The communication path (Nostr) is not involved in consensus.
- Relay Discoverability: Optionally bootstrap via DNS, Bitcoin P2P, or signed relay lists.
- Spam Protection: Relay-side policy, rate limiting, proof-of-work challenges, or Lightning payments.
- Block Authenticity: Nodes must verify all received blocks and reject invalid chains.
Compatibility and Migration
- Fully compatible with current Bitcoin consensus rules.
- Bridge nodes preserve interoperability with legacy full nodes.
- Nodes can run in hybrid mode, fetching from both P2P and Nostr.
Future Work
- Integration with watch-only wallets and SPV clients using verified headers via Nostr.
- Use of Nostr’s social graph for partial trust assumptions and relay reputation.
- Dynamic relay discovery using Nostr itself (relay list events).
Conclusion
This proposal lays out a new architecture for Bitcoin communication using Nostr to replace or augment the P2P network. This improves decentralization, censorship resistance, modularity, and speed, while preserving consensus integrity. It encourages innovation by enabling smaller, purpose-built Bitcoin nodes and offloading networking complexity.
This document may become both a Bitcoin Improvement Proposal (BIP-XXX) and a Nostr Improvement Proposal (NIP-XXX). Event kind range reserved: 210000–219999.
-
 @ 6d5c826a:4b27b659
2025-05-23 21:40:34
@ 6d5c826a:4b27b659
2025-05-23 21:40:34- Apache Ant - Automation build tool, similar to make, a library and command-line tool whose mission is to drive processes described in build files as targets and extension points dependent upon each other. (Source Code)
Apache-2.0Java - Apache Maven - Build automation tool mainly for Java. A software project management and comprehension tool. Based on the concept of a project object model (POM), Maven can manage a project's build, reporting and documentation from a central piece of information. (Source Code)
Apache-2.0Java - Bazel - A fast, scalable, multi-language and extensible build system. Used by Google. (Source Code)
Apache-2.0Java - Bolt - You can use Bolt to run one-off tasks, scripts to automate the provisioning and management of some nodes, you can use Bolt to move a step beyond scripts, and make them shareable. (Source Code)
Apache-2.0Ruby - GNU Make - The most popular automation build tool for many purposes, make is a tool which controls the generation of executables and other non-source files of a program from the program's source files. (Source Code)
GPL-3.0C - Gradle - Another build automation system. (Source Code)
Apache-2.0Groovy/Java - Rake - Build automation tool similar to Make, written in and extensible in Ruby. (Source Code)
MITRuby
- Apache Ant - Automation build tool, similar to make, a library and command-line tool whose mission is to drive processes described in build files as targets and extension points dependent upon each other. (Source Code)
-
 @ 1817b617:715fb372
2025-05-23 20:21:53
@ 1817b617:715fb372
2025-05-23 20:21:53🚀 Instantly Send Spendable Flash BTC, ETH, & USDT — Fully Blockchain-Verifiable!
Welcome to the cutting edge of crypto innovation: the ultimate tool for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Our advanced blockchain simulation technology employs 🔥 Race/Finney-style mechanisms, producing coins indistinguishable from authentic blockchain-confirmed tokens. Your transactions are instantly trackable and fully spendable for durations from 60 to 360 days!
🌐 Visit cryptoflashingtool.com for complete details.
🌟 Why Choose Our Crypto Flashing Service? Crypto Flashing is perfect for crypto enthusiasts, blockchain developers, ethical hackers, security professionals, and digital entrepreneurs looking for authenticity combined with unparalleled flexibility.
🎯 Our Crypto Flashing Features: ✅ Instant Blockchain Verification: Transactions appear completely authentic, complete with real blockchain confirmations, transaction IDs, and wallet addresses.
🔒 Maximum Security & Privacy: Fully compatible with VPNs, TOR, and proxy servers, ensuring absolute anonymity and protection.
🖥️ Easy-to-Use Software: Designed for Windows, our intuitive platform suits both beginners and experts, with detailed, step-by-step instructions provided.
📅 Customizable Flash Durations: Control your transaction lifespan precisely, from 60 to 360 days.
🔄 Universal Wallet Compatibility: Instantly flash BTC, ETH, and USDT tokens to SegWit, Legacy, or BCH32 wallets.
💱 Spendable on Top Exchanges: Flash coins seamlessly accepted on leading exchanges like Kraken and Huobi.
📊 Proven Track Record: ✅ Over 79 Billion flash transactions completed. ✅ 3000+ satisfied customers worldwide. ✅ 42 active blockchain nodes for fast, reliable transactions. 📌 Simple Step-by-Step Flashing Process: Step 1️⃣: Enter Transaction Details
Choose coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20) Specify amount & flash duration Provide wallet address (validated automatically) Step 2️⃣: Complete Payment & Verification
Pay using the cryptocurrency you wish to flash Scan the QR code or paste the payment address Upload payment proof (transaction hash & screenshot) Step 3️⃣: Initiate Flash Transaction
Our technology simulates blockchain confirmations instantly Flash transaction appears authentic within seconds Step 4️⃣: Verify & Spend Immediately
Access your flashed crypto instantly Easily verify transactions via provided blockchain explorer links 🛡️ Why Our Technology is Trusted: 🔗 Race/Finney Attack Logic: Creates realistic blockchain headers. 🖥️ Private iNode Cluster: Guarantees fast synchronization and reliable transactions. ⏰ Live Timer System: Ensures fresh wallet addresses and transaction legitimacy. 🔍 Genuine Blockchain TX IDs: Authentic transaction IDs included with every flash ❓ Frequently Asked Questions: Is flashing secure? ✅ Yes, encrypted with full VPN/proxy support. Can I flash from multiple devices? ✅ Yes, up to 5 Windows PCs per license. Are chargebacks possible? ❌ No, flash transactions are irreversible. How long are flash coins spendable? ✅ From 60–360 days, based on your chosen plan. Verification after expiry? ❌ Transactions can’t be verified after the expiry. Support available? ✅ Yes, 24/7 support via Telegram & WhatsApp.
🔐 Transparent, Reliable & Highly Reviewed:
CryptoFlashingTool.com operates independently, providing unmatched transparency and reliability. Check out our glowing reviews on ScamAdvisor and leading crypto forums!
📲 Get in Touch Now: 📞 WhatsApp: +1 770 666 2531 ✈️ Telegram: @cryptoflashingtool
🎉 Ready to Start?
💰 Buy Flash Coins Now 🖥️ Get Your Flashing Software
Experience the smartest, safest, and most powerful crypto flashing solution on the market today!
CryptoFlashingTool.com — Flash Crypto Like a Pro.
Instantly Send Spendable Flash BTC, ETH, & USDT — Fully Blockchain-Verifiable!
Welcome to the cutting edge of crypto innovation: the ultimate tool for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Our advanced blockchain simulation technology employs
Race/Finney-style mechanisms, producing coins indistinguishable from authentic blockchain-confirmed tokens. Your transactions are instantly trackable and fully spendable for durations from 60 to 360 days!
Visit cryptoflashingtool.com for complete details.
Why Choose Our Crypto Flashing Service?
Crypto Flashing is perfect for crypto enthusiasts, blockchain developers, ethical hackers, security professionals, and digital entrepreneurs looking for authenticity combined with unparalleled flexibility.
Our Crypto Flashing Features:
Instant Blockchain Verification: Transactions appear completely authentic, complete with real blockchain confirmations, transaction IDs, and wallet addresses.
Maximum Security & Privacy: Fully compatible with VPNs, TOR, and proxy servers, ensuring absolute anonymity and protection.
Easy-to-Use Software: Designed for Windows, our intuitive platform suits both beginners and experts, with detailed, step-by-step instructions provided.
Customizable Flash Durations: Control your transaction lifespan precisely, from 60 to 360 days.
Universal Wallet Compatibility: Instantly flash BTC, ETH, and USDT tokens to SegWit, Legacy, or BCH32 wallets.
Spendable on Top Exchanges: Flash coins seamlessly accepted on leading exchanges like Kraken and Huobi.
Proven Track Record:
- Over 79 Billion flash transactions completed.
- 3000+ satisfied customers worldwide.
- 42 active blockchain nodes for fast, reliable transactions.
Simple Step-by-Step Flashing Process:
Step : Enter Transaction Details
- Choose coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20)
- Specify amount & flash duration
- Provide wallet address (validated automatically)
Step : Complete Payment & Verification
- Pay using the cryptocurrency you wish to flash
- Scan the QR code or paste the payment address
- Upload payment proof (transaction hash & screenshot)
Step : Initiate Flash Transaction
- Our technology simulates blockchain confirmations instantly
- Flash transaction appears authentic within seconds
Step : Verify & Spend Immediately
- Access your flashed crypto instantly
- Easily verify transactions via provided blockchain explorer links
Why Our Technology is Trusted:
- Race/Finney Attack Logic: Creates realistic blockchain headers.
- Private iNode Cluster: Guarantees fast synchronization and reliable transactions.
- Live Timer System: Ensures fresh wallet addresses and transaction legitimacy.
- Genuine Blockchain TX IDs: Authentic transaction IDs included with every flash
Frequently Asked Questions:
- Is flashing secure?
Yes, encrypted with full VPN/proxy support. - Can I flash from multiple devices?
Yes, up to 5 Windows PCs per license. - Are chargebacks possible?
No, flash transactions are irreversible. - How long are flash coins spendable?
From 60–360 days, based on your chosen plan. - Verification after expiry?
Transactions can’t be verified after the expiry.
Support available?
Yes, 24/7 support via Telegram & WhatsApp.
Transparent, Reliable & Highly Reviewed:
CryptoFlashingTool.com operates independently, providing unmatched transparency and reliability. Check out our glowing reviews on ScamAdvisor and leading crypto forums!
Get in Touch Now:
WhatsApp: +1 770 666 2531
Telegram: @cryptoflashingtool
Ready to Start?
Experience the smartest, safest, and most powerful crypto flashing solution on the market today!
CryptoFlashingTool.com — Flash Crypto Like a Pro.
-
 @ 56f27915:5fee3024
2025-05-23 18:51:08
@ 56f27915:5fee3024
2025-05-23 18:51:08Ralph Boes – Menschenrechtsaktivist, Philosoph, Vorstandsmitglied im Verein Unsere Verfassung e.V.
Ralph Boes zeigt in dem Buch auf, wie wir uns von der Übermacht des Parteienwesens, die zur Entmündigung des Volkes führt, befreien können. Er zeigt, dass schon im Grundgesetz selbst höchst gegenläufige, an seinen freiheitlich-demokratischen Idealen bemessen sogar als verfassungswidrig zu bezeichnende Tendenzen wirken. Und dass diese es sind, die heute in seine Zerstörung führen. Er weist aber auch die Ansatzpunkte auf, durch die der Zerstörung des Grundgesetzes wirkungsvoll begegnet werden kann.
Eintritt frei, Spendentopf
Ralph Boes hat u.a. dafür gesorgt, dass die unmäßigen Sanktionen in Hartz IV 2019 vom Bundesverfassungsgericht für menschenrechts- und verfassungswidrig erklärt wurden. Aktuell setzt er sich für eine Ur-Abstimmung des Volkes über seine Verfassung ein.
-
 @ ecda4328:1278f072
2025-05-23 18:16:24
@ ecda4328:1278f072
2025-05-23 18:16:24And what does it mean to withdraw back to Bitcoin Layer 1?
Disclaimer: This post was written with help from ChatGPT-4o. If you spot any mistakes or have suggestions — feel free to reply or zap in feedback!
Let’s break it down — using three popular setups:
1. Wallet of Satoshi (WoS)
Custodial — you don’t touch Lightning directly
Sending sats:
- You open WoS, paste a Lightning invoice, hit send.
- WoS handles the payment entirely within their system.
- If recipient uses WoS: internal balance update.
- If external: routed via their node.
- You never open channels, construct routes, or sign anything.
Withdrawing to L1:
- You paste a Bitcoin address.
- WoS sends a regular on-chain transaction from their custodial wallet.
- You pay a fee. It’s like a bank withdrawal.
You don’t interact with Lightning directly. Think of it as a trusted 3rd party Lightning “bank”.
2. Phoenix Wallet
Non-custodial — you own keys, Phoenix handles channels
Sending sats:
- You scan a Lightning invoice and hit send.
- Phoenix uses its backend node (ACINQ) to route the payment.
- If needed, it opens a real 2-of-2 multisig channel on-chain automatically.
- You own your keys (12-word seed), Phoenix abstracts the technical parts.
Withdrawing to L1:
- You enter your Bitcoin address.
- Phoenix closes your Lightning channel (cooperatively, if possible).
- Your sats are sent as a real Bitcoin transaction to your address.
You’re using Lightning “for real,” with real Bitcoin channels — but Phoenix smooths out the UX.
3. Your Own Lightning Node
Self-hosted — you control everything
Sending sats:
- You manage your channels manually (or via automation).
- Your node:
- Reads the invoice
- Builds a route using HTLCs
- Sends the payment using conditional logic (preimages, time locks).
- If routing fails: retry or adjust liquidity.
Withdrawing to L1:
- You select and close a channel.
- A channel closing transaction is broadcast:
- Cooperative = fast and cheap
- Force-close = slower, more expensive, and time-locked
- Funds land in your on-chain wallet.
You have full sovereignty — but also full responsibility (liquidity, fees, backups, monitoring).
Core Tech Behind It: HTLCs, Multisig — and No Sidechain
- Lightning channels = 2-of-2 multisig Bitcoin addresses
- Payments = routed via HTLCs (Hashed Time-Locked Contracts)
- HTLCs are off-chain, but enforceable on-chain if needed
- Important:
- The Lightning Network is not a sidechain.
- It doesn't use its own token, consensus, or separate blockchain.
- Every Lightning channel is secured by real Bitcoin on L1.
Lightning = fast, private, off-chain Bitcoin — secured by Bitcoin itself.
Summary Table
| Wallet | Custody | Channel Handling | L1 Withdrawal | HTLC Visibility | User Effort | |--------------------|--------------|------------------------|---------------------|------------------|--------------| | Wallet of Satoshi | Custodial | None | Internal to external| Hidden | Easiest | | Phoenix Wallet | Non-custodial| Auto-managed real LN | Channel close | Abstracted | Low effort | | Own Node | You | Manual | Manual channel close| Full control | High effort |
Bonus: Withdrawing from LN to On-Chain
- WoS: sends sats from their wallet — like PayPal.
- Phoenix: closes a real channel and sends your UTXO on-chain.
- Own node: closes your multisig contract and broadcasts your pre-signed tx.
Bitcoin + Lightning = Sovereign money + Instant payments.
Choose the setup that fits your needs — and remember, you can always level up later.P.S. What happens in Lightning... usually stays in Lightning.
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16Drivechain
Understanding Drivechain requires a shift from the paradigm most bitcoiners are used to. It is not about "trustlessness" or "mathematical certainty", but game theory and incentives. (Well, Bitcoin in general is also that, but people prefer to ignore it and focus on some illusion of trustlessness provided by mathematics.)
Here we will describe the basic mechanism (simple) and incentives (complex) of "hashrate escrow" and how it enables a 2-way peg between the mainchain (Bitcoin) and various sidechains.
The full concept of "Drivechain" also involves blind merged mining (i.e., the sidechains mine themselves by publishing their block hashes to the mainchain without the miners having to run the sidechain software), but this is much easier to understand and can be accomplished either by the BIP-301 mechanism or by the Spacechains mechanism.
How does hashrate escrow work from the point of view of Bitcoin?
A new address type is created. Anything that goes in that is locked and can only be spent if all miners agree on the Withdrawal Transaction (
WT^) that will spend it for 6 months. There is one of these special addresses for each sidechain.To gather miners' agreement
bitcoindkeeps track of the "score" of all transactions that could possibly spend from that address. On every block mined, for each sidechain, the miner can use a portion of their coinbase to either increase the score of oneWT^by 1 while decreasing the score of all others by 1; or they can decrease the score of allWT^s by 1; or they can do nothing.Once a transaction has gotten a score high enough, it is published and funds are effectively transferred from the sidechain to the withdrawing users.
If a timeout of 6 months passes and the score doesn't meet the threshold, that
WT^is discarded.What does the above procedure mean?
It means that people can transfer coins from the mainchain to a sidechain by depositing to the special address. Then they can withdraw from the sidechain by making a special withdraw transaction in the sidechain.
The special transaction somehow freezes funds in the sidechain while a transaction that aggregates all withdrawals into a single mainchain
WT^, which is then submitted to the mainchain miners so they can start voting on it and finally after some months it is published.Now the crucial part: the validity of the
WT^is not verified by the Bitcoin mainchain rules, i.e., if Bob has requested a withdraw from the sidechain to his mainchain address, but someone publishes a wrongWT^that instead takes Bob's funds and sends them to Alice's main address there is no way the mainchain will know that. What determines the "validity" of theWT^is the miner vote score and only that. It is the job of miners to vote correctly -- and for that they may want to run the sidechain node in SPV mode so they can attest for the existence of a reference to theWT^transaction in the sidechain blockchain (which then ensures it is ok) or do these checks by some other means.What? 6 months to get my money back?
Yes. But no, in practice anyone who wants their money back will be able to use an atomic swap, submarine swap or other similar service to transfer funds from the sidechain to the mainchain and vice-versa. The long delayed withdraw costs would be incurred by few liquidity providers that would gain some small profit from it.
Why bother with this at all?
Drivechains solve many different problems:
It enables experimentation and new use cases for Bitcoin
Issued assets, fully private transactions, stateful blockchain contracts, turing-completeness, decentralized games, some "DeFi" aspects, prediction markets, futarchy, decentralized and yet meaningful human-readable names, big blocks with a ton of normal transactions on them, a chain optimized only for Lighting-style networks to be built on top of it.
These are some ideas that may have merit to them, but were never actually tried because they couldn't be tried with real Bitcoin or inferfacing with real bitcoins. They were either relegated to the shitcoin territory or to custodial solutions like Liquid or RSK that may have failed to gain network effect because of that.
It solves conflicts and infighting
Some people want fully private transactions in a UTXO model, others want "accounts" they can tie to their name and build reputation on top; some people want simple multisig solutions, others want complex code that reads a ton of variables; some people want to put all the transactions on a global chain in batches every 10 minutes, others want off-chain instant transactions backed by funds previously locked in channels; some want to spend, others want to just hold; some want to use blockchain technology to solve all the problems in the world, others just want to solve money.
With Drivechain-based sidechains all these groups can be happy simultaneously and don't fight. Meanwhile they will all be using the same money and contributing to each other's ecosystem even unwillingly, it's also easy and free for them to change their group affiliation later, which reduces cognitive dissonance.
It solves "scaling"
Multiple chains like the ones described above would certainly do a lot to accomodate many more transactions that the current Bitcoin chain can. One could have special Lightning Network chains, but even just big block chains or big-block-mimblewimble chains or whatnot could probably do a good job. Or even something less cool like 200 independent chains just like Bitcoin is today, no extra features (and you can call it "sharding"), just that would already multiply the current total capacity by 200.
Use your imagination.
It solves the blockchain security budget issue
The calculation is simple: you imagine what security budget is reasonable for each block in a world without block subsidy and divide that for the amount of bytes you can fit in a single block: that is the price to be paid in satoshis per byte. In reasonable estimative, the price necessary for every Bitcoin transaction goes to very large amounts, such that not only any day-to-day transaction has insanely prohibitive costs, but also Lightning channel opens and closes are impracticable.
So without a solution like Drivechain you'll be left with only one alternative: pushing Bitcoin usage to trusted services like Liquid and RSK or custodial Lightning wallets. With Drivechain, though, there could be thousands of transactions happening in sidechains and being all aggregated into a sidechain block that would then pay a very large fee to be published (via blind merged mining) to the mainchain. Bitcoin security guaranteed.
It keeps Bitcoin decentralized
Once we have sidechains to accomodate the normal transactions, the mainchain functionality can be reduced to be only a "hub" for the sidechains' comings and goings, and then the maximum block size for the mainchain can be reduced to, say, 100kb, which would make running a full node very very easy.
Can miners steal?
Yes. If a group of coordinated miners are able to secure the majority of the hashpower and keep their coordination for 6 months, they can publish a
WT^that takes the money from the sidechains and pays to themselves.Will miners steal?
No, because the incentives are such that they won't.
Although it may look at first that stealing is an obvious strategy for miners as it is free money, there are many costs involved:
- The cost of ceasing blind-merged mining returns -- as stealing will kill a sidechain, all the fees from it that miners would be expected to earn for the next years are gone;
- The cost of Bitcoin price going down: If a steal is successful that will mean Drivechains are not safe, therefore Bitcoin is less useful, and miner credibility will also be hurt, which are likely to cause the Bitcoin price to go down, which in turn may kill the miners' businesses and savings;
- The cost of coordination -- assuming miners are just normal businesses, they just want to do their work and get paid, but stealing from a Drivechain will require coordination with other miners to conduct an immoral act in a way that has many pitfalls and is likely to be broken over the months;
- The cost of miners leaving your mining pool: when we talked about "miners" above we were actually talking about mining pools operators, so they must also consider the risk of miners migrating from their mining pool to others as they begin the process of stealing;
- The cost of community goodwill -- when participating in a steal operation, a miner will suffer a ton of backlash from the community. Even if the attempt fails at the end, the fact that it was attempted will contribute to growing concerns over exaggerated miners power over the Bitcoin ecosystem, which may end up causing the community to agree on a hard-fork to change the mining algorithm in the future, or to do something to increase participation of more entities in the mining process (such as development or cheapment of new ASICs), which have a chance of decreasing the profits of current miners.
Another point to take in consideration is that one may be inclined to think a newly-created sidechain or a sidechain with relatively low usage may be more easily stolen from, since the blind merged mining returns from it (point 1 above) are going to be small -- but the fact is also that a sidechain with small usage will also have less money to be stolen from, and since the other costs besides 1 are less elastic at the end it will not be worth stealing from these too.
All of the above consideration are valid only if miners are stealing from good sidechains. If there is a sidechain that is doing things wrong, scamming people, not being used at all, or is full of bugs, for example, that will be perceived as a bad sidechain, and then miners can and will safely steal from it and kill it, which will be perceived as a good thing by everybody.
What do we do if miners steal?
Paul Sztorc has suggested in the past that a user-activated soft-fork could prevent miners from stealing, i.e., most Bitcoin users and nodes issue a rule similar to this one to invalidate the inclusion of a faulty
WT^and thus cause any miner that includes it in a block to be relegated to their own Bitcoin fork that other nodes won't accept.This suggestion has made people think Drivechain is a sidechain solution backed by user-actived soft-forks for safety, which is very far from the truth. Drivechains must not and will not rely on this kind of soft-fork, although they are possible, as the coordination costs are too high and no one should ever expect these things to happen.
If even with all the incentives against them (see above) miners do still steal from a good sidechain that will mean the failure of the Drivechain experiment. It will very likely also mean the failure of the Bitcoin experiment too, as it will be proven that miners can coordinate to act maliciously over a prolonged period of time regardless of economic and social incentives, meaning they are probably in it just for attacking Bitcoin, backed by nation-states or something else, and therefore no Bitcoin transaction in the mainchain is to be expected to be safe ever again.
Why use this and not a full-blown trustless and open sidechain technology?
Because it is impossible.
If you ever heard someone saying "just use a sidechain", "do this in a sidechain" or anything like that, be aware that these people are either talking about "federated" sidechains (i.e., funds are kept in custody by a group of entities) or they are talking about Drivechain, or they are disillusioned and think it is possible to do sidechains in any other manner.
No, I mean a trustless 2-way peg with correctness of the withdrawals verified by the Bitcoin protocol!
That is not possible unless Bitcoin verifies all transactions that happen in all the sidechains, which would be akin to drastically increasing the blocksize and expanding the Bitcoin rules in tons of ways, i.e., a terrible idea that no one wants.
What about the Blockstream sidechains whitepaper?
Yes, that was a way to do it. The Drivechain hashrate escrow is a conceptually simpler way to achieve the same thing with improved incentives, less junk in the chain, more safety.
Isn't the hashrate escrow a very complex soft-fork?
Yes, but it is much simpler than SegWit. And, unlike SegWit, it doesn't force anything on users, i.e., it isn't a mandatory blocksize increase.
Why should we expect miners to care enough to participate in the voting mechanism?
Because it's in their own self-interest to do it, and it costs very little. Today over half of the miners mine RSK. It's not blind merged mining, it's a very convoluted process that requires them to run a RSK full node. For the Drivechain sidechains, an SPV node would be enough, or maybe just getting data from a block explorer API, so much much simpler.
What if I still don't like Drivechain even after reading this?
That is the entire point! You don't have to like it or use it as long as you're fine with other people using it. The hashrate escrow special addresses will not impact you at all, validation cost is minimal, and you get the benefit of people who want to use Drivechain migrating to their own sidechains and freeing up space for you in the mainchain. See also the point above about infighting.
See also
-
 @ b0a838f2:34ed3f19
2025-05-23 18:11:34
@ b0a838f2:34ed3f19
2025-05-23 18:11:34- AmuseWiki - Amusewiki is based on the Emacs Muse markup, remaining mostly compatible with the original implementation. It can work as a read-only site, as a moderated wiki, or as a fully open wiki or even as a private site. (Demo, Source Code)
GPL-1.0Perl/Docker - BookStack - Organize and store information. Stores documentation in a book like fashion. (Demo, Source Code)
MITPHP/Docker - django-wiki - Wiki system with complex functionality for simple integration and a superb interface. Store your knowledge with style: Use django models. (Demo)
GPL-3.0Python - docmost - Collaborative wiki and documentation software (alternative to Confluence, Notion). (Source Code)
AGPL-3.0Docker/Nodejs - Documize - Modern Docs + Wiki software with built-in workflow, single binary executable, just bring MySQL/Percona. (Source Code)
AGPL-3.0Go - Dokuwiki - Easy to use, lightweight, standards-compliant wiki engine with a simple syntax allowing reading the data outside the wiki. All data is stored in plain text files, therefore no database is required. (Source Code)
GPL-2.0PHP - Feather Wiki - A lightning fast and infinitely extensible tool for creating personal non-linear notebooks, databases, and wikis that is entirely self-contained, runs in your browser, and is only 58 kilobytes in size. (Demo, Source Code, Clients)
AGPL-3.0Javascript - Gitit - Wiki program that stores pages and uploaded files in a git repository, which can then be modified using the VCS command line tools or the wiki's web interface.
GPL-2.0Haskell - Gollum - Simple, Git-powered wiki with a sweet API and local frontend.
MITRuby - Mediawiki - Wiki software package that powers Wikipedia and all other Wikimedia projects, serving hundreds of millions of users each month. (Demo, Source Code)
GPL-2.0PHP - Mycorrhiza Wiki - Filesystem and git-based wiki engine written in Go using Mycomarkup as its primary markup language. (Source Code)
AGPL-3.0Go - Otter Wiki - Simple, easy to use wiki software using markdown. (Source Code)
MITDocker - Pepperminty Wiki - Complete markdown-powered wiki contained in a single PHP file. (Demo)
MPL-2.0PHP - PmWiki - Wiki-based system for collaborative creation and maintenance of websites.
GPL-3.0PHP - Raneto - Raneto is an open source Knowledgebase platform that uses static Markdown files to power your Knowledgebase. (Source Code)
MITNodejs - TiddlyWiki - Reusable non-linear personal web notebook. (Source Code)
BSD-3-ClauseNodejs - Tiki - Wiki CMS Groupware with the most built-in features. (Demo, Source Code)
LGPL-2.1PHP - W - Lightweight, mutli-user, flat-file-database Wiki engine. Create pages quickly and edit them in your Web browser using Mardown/HTML/CSS/JS. The main difference with other wiki is that you are encouraged to customize each page style individually. (Source Code)
AGPL-3.0PHP - WackoWiki - WackoWiki is a light and easy to install multilingual Wiki-engine. (Source Code)
BSD-3-ClausePHP - Wiki.js - Modern, lightweight and powerful wiki app using Git and Markdown. (Demo, Source Code)
AGPL-3.0Nodejs/Docker/K8S - WikiDocs - A databaseless markdown flat-file wiki engine. (Source Code)
MITPHP/Docker - WiKiss - Wiki, simple to use and install. (Source Code)
GPL-2.0PHP - Wikmd - Modern and simple file based wiki that uses Markdown and Git.
MITPython/Docker - XWiki - Second generation wiki that allows the user to extend its functionalities with a powerful extension-based architecture. (Demo, Source Code)
LGPL-2.1Java/Docker/deb - Zim - Graphical text editor used to maintain a collection of wiki pages. Each page can contain links to other pages, simple formatting and images. (Source Code)
GPL-2.0Python/deb
- AmuseWiki - Amusewiki is based on the Emacs Muse markup, remaining mostly compatible with the original implementation. It can work as a read-only site, as a moderated wiki, or as a fully open wiki or even as a private site. (Demo, Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:11:11
@ b0a838f2:34ed3f19
2025-05-23 18:11:11- Algernon - Small self-contained pure-Go web server with Lua, Markdown, HTTP/2, QUIC, Redis and PostgreSQL support. (Source Code)
BSD-3-ClauseGo/Docker - Apache HTTP Server - Secure, efficient and extensible server that provides HTTP services in sync with the current HTTP standards. (Source Code)
Apache-2.0C/deb/Docker - BunkerWeb - Next-gen Web Application Firewall (WAF) that will protect your web services. (Demo, Source Code, Clients)
AGPL-3.0deb/Docker/K8S/Python - Caddy - Powerful, enterprise-ready, open source web server with automatic HTTPS. (Source Code)
Apache-2.0Go/deb/Docker - go-doxy - Lightweight, simple, and performant reverse proxy with WebUI, Docker integration, automatic shutdown/startup for container based on traffic.
MITDocker/Go - HAProxy - Very fast and reliable reverse-proxy offering high availability, load balancing, and proxying for TCP and HTTP-based applications. (Source Code)
GPL-2.0C/deb/Docker - Jauth
⚠- Lightweight SSL/TLS reverse proxy with authorization (via Telegram and SSH) for self-hosted apps.GPL-3.0Go - Lighttpd - Secure, fast, compliant, and very flexible web server that has been optimized for high-performance environments. (Source Code)
BSD-3-ClauseC/deb/Docker - Nginx Proxy Manager - Docker container for managing Nginx proxy hosts with a simple, powerful interface. (Source Code)
MITDocker - NGINX - HTTP and reverse proxy server, mail proxy server, and generic TCP/UDP proxy server. (Source Code)
BSD-2-ClauseC/deb/Docker - Pomerium - Identity-aware reverse proxy, successor to now obsolete oauth_proxy. It inserts an OAuth step before proxying your request to the backend, so that you can safely expose your self-hosted websites to public Internet. (Source Code)
Apache-2.0Go/Docker - SafeLine - Web application firewall / reverse proxy to protect your web apps from attacks and exploits. (Demo, Source Code)
GPL-3.0Docker - Static Web Server - Cross-platform, high-performance, and asynchronous web server for static file serving. (Source Code)
Apache-2.0/MITRust/Docker - SWAG (Secure Web Application Gateway) - Nginx webserver and reverse proxy with PHP support, built-in Certbot (Let's Encrypt) client and fail2ban integration.
GPL-3.0Docker - Traefik - HTTP reverse proxy and load balancer that makes deploying microservices easy. (Source Code)
MITGo/Docker - Varnish - Web application accelerator/caching HTTP reverse proxy. (Source Code)
BSD-3-ClauseGo/deb/Docker - Zoraxy - General purpose HTTP reverse proxy and forwarding tool. (Source Code)
AGPL-3.0Go/Docker
- Algernon - Small self-contained pure-Go web server with Lua, Markdown, HTTP/2, QUIC, Redis and PostgreSQL support. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:10:51
@ b0a838f2:34ed3f19
2025-05-23 18:10:51- Bluecherry - Closed-circuit television (CCTV) software application which supports IP and Analog cameras. (Source Code)
GPL-2.0PHP - Frigate - Monitor your security cameras with locally processed AI. (Source Code)
MITDocker/Python/Nodejs - SentryShot - Video surveillance management system.
GPL-2.0Docker/Rust - Viseron - Self-hosted, local-only NVR and AI Computer Vision software. With features such as object detection, motion detection, face recognition and more, it gives you the power to keep an eye on your home, office or any other place you want to monitor. (Source Code)
MITDocker - Zoneminder - Closed-circuit television (CCTV) software application which supports IP, USB and Analog cameras. (Source Code)
GPL-2.0PHP/deb
- Bluecherry - Closed-circuit television (CCTV) software application which supports IP and Analog cameras. (Source Code)
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Personagens de jogos e símbolos
A sensação de "ser" um personagem em um jogo ou uma brincadeira talvez seja o mais próximo que eu tenha conseguido chegar do entendimento de um símbolo religioso.
A hóstia consagrada é, segundo a religião, o corpo de Cristo, mas nossa mente moderna só consegue concebê-la como sendo uma representação do corpo de Cristo. Da mesma forma outras culturas e outras religiões têm símbolos parecidos, inclusive nos quais o próprio participante do ritual faz o papel de um deus ou de qualquer coisa parecida.
"Faz o papel" é de novo a interpretação da mente moderna. O sujeito ali é a coisa, mas ele ao mesmo tempo que é também sabe que não é, que continua sendo ele mesmo.
Nos jogos de videogame e brincadeiras infantis em que se encarna um personagem o jogador é o personagem. não se diz, entre os jogadores, que alguém está "encenando", mas que ele é e pronto. nem há outra denominação ou outro verbo. No máximo "encarnando", mas já aí já é vocabulário jornalístico feito para facilitar a compreensão de quem está de fora do jogo.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A Causa
o Princípios de Economia Política de Menger é o único livro que enfatiza a CAUSA o tempo todo. os cientistas todos parecem não saber, ou se esquecer sempre, que as coisas têm causa, e que o conhecimento verdadeiro é o conhecimento da causa das coisas.
a causa é uma categoria metafísica muito superior a qualquer correlação ou resultado de teste de hipótese, ela não pode ser descoberta por nenhum artifício econométrico ou reduzida à simples antecedência temporal estatística. a causa dos fenômenos não pode ser provada cientificamente, mas pode ser conhecida.
o livro de Menger conta para o leitor as causas de vários fenômenos econômicos e as interliga de forma que o mundo caótico da economia parece adquirir uma ordem no momento em que você lê. é uma sensação mágica e indescritível.
quando eu te o recomendei, queria é te imbuir com o espírito da busca pela causa das coisas. depois de ler aquilo, você está apto a perceber continuidade causal nos fenômenos mais complexos da economia atual, enxergar as causas entre toda a ação governamental e as suas várias consequências na vida humana. eu faço isso todos os dias e é a melhor sensação do mundo quando o caos das notícias do caderno de Economia do jornal -- que para o próprio jornalista que as escreveu não têm nenhum sentido (tanto é que ele escreve tudo errado) -- se incluem num sistema ordenado de causas e consequências.
provavelmente eu sempre erro em alguns ou vários pontos, mas ainda assim é maravilhoso. ou então é mais maravilhoso ainda quando eu descubro o erro e reinsiro o acerto naquela racionalização bela da ordem do mundo econômico que é a ordem de Deus.
em scrap para T.P.
-
 @ b0a838f2:34ed3f19
2025-05-23 18:10:36
@ b0a838f2:34ed3f19
2025-05-23 18:10:36- bit - Fast, lightweight, resource-efficient, compiled URL shortener.
MITDocker/Crystal - Chhoto URL - Simple, lightning-fast URL shortener with no bloat (fork of simply-shorten).
MITRust/Docker - clink - A super-minimal link shortening service written in pure C, focusing on small executable size, portability, and ease of configuration. (Demo, Source Code)
AGPL-3.0C - Flink - Create QR Codes, embeddable link previews for your website and crawls/scrapes metadata. (Demo)
MITDocker - Just Short It! - A KISS, single-user URL shortener that runs in just one container.
MITDocker - Kutt - Modern URL shortener with support for custom domains and custom URLs. (Demo, Source Code)
MITNodejs/Docker - liteshort - User-friendly, actually lightweight, and configurable URL shortener. (Source Code)
MITPython/deb - rs-short - A lightweight link shortener written in Rust, with features such as caching, spambot protection and phishing detection. (Demo)
MPL-2.0Rust - Shlink - URL shortener with REST API and command line interface. Includes official progressive web application and docker images. (Source Code, Clients)
MITPHP/Docker - Simple-URL-Shortener - KISS URL shortener, public or private (with account). Minimalist and lightweight. No dependencies. (Demo)
MITPHP - YOURLS - YOURLS is a set of PHP scripts that will allow you to run Your Own URL Shortener. Features include password protection, URL customization, bookmarklets, statistics, API, plugins, jsonp. (Source Code)
MITPHP
- bit - Fast, lightweight, resource-efficient, compiled URL shortener.
-
 @ b0a838f2:34ed3f19
2025-05-23 18:10:12
@ b0a838f2:34ed3f19
2025-05-23 18:10:12- ActivityWatch - Automatically track how you spend time on your devices. (Source Code)
MPL-2.0Python - Beaver Habit Tracker - Habit tracking app to save your precious moments in your fleeting life. (Demo)
BSD-3-ClauseDocker - Ever Gauzy - Open business management platform for collaborative, on-demand and sharing economies (ERP/CRM/HRM/ATS/PM). (Demo, Source Code)
AGPL-3.0Docker/Nodejs - Kimai - Track work time and print out a summary of your activities on demand. (Demo, Source Code)
AGPL-3.0PHP - solidtime - Modern time tracking application for freelancers and agencies. (Source Code)
AGPL-3.0Docker - TimeTagger - An open source time-tracker based on an interactive timeline and powerful reporting. (Demo, Source Code)
GPL-3.0Python - Traggo - Traggo is a tag-based time tracking tool. In Traggo there are no tasks, only tagged time spans. (Source Code)
GPL-3.0Docker/Go
- ActivityWatch - Automatically track how you spend time on your devices. (Source Code)
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Veterano não é dono de bixete
"VETERANO NÃO É DONO DE BIXETE". A frase em letras garrafais chama a atenção dos transeuntes neófitos. Paira sobre um cartaz amarelo que lista várias reclamações contra os "trotes machistas", que, na opinião do responsável pelo cartaz, "não é brincadeira, é opressão".
Eis aí um bizarro exemplo de como são as coisas: primeiro todos os universitários aprovam a idéia do trote, apoiam sua realização e até mesmo desejam sofrer o trote -- com a condição de o poderem aplicar eles mesmos depois --, louvam as maravilhas do mundo universitário, onde a suprema sabedoria se esconde atrás de rituais iniciáticos fora do alcance da imaginação do homem comum e rude, do pobre e do filhinho-de-papai das faculdades privadas; em suma: fomentam os mais baixos, os mais animalescos instintos, a crueldade primordial, destroem em si mesmos e nos colegas quaisquer valores civilizatórios que tivessem sobrado ali, ficando todos indistingüíveis de macacos agressivos e tarados.
Depois vêm aí com um cartaz protestar contra os assédios -- que sem dúvida acontecem em larguíssima escala -- sofridos pelas calouras de 17 anos e que, sendo também novatas no mundo universitário, ainda conservam um pouco de discernimento e pudor.
A incompreensão do fenômeno, porém, é tão grande, que os trotes não são identificados como um problema mental, uma doença que deve ser tratada e eliminada, mas como um sintoma da opressão machista dos homens às mulheres, um produto desta civilização paternalista que, desde que Deus é chamado "o Pai" e não "a Mãe", corrompe a benéfica, pura e angélica natureza do homem primitivo e o torna esta tão torpe criatura.
Na opinião dos autores desse cartaz é preciso, pois, continuar a destruir o que resta da cultura ocidental, e então esperar que haja trotes menos opressores.
-
 @ b0a838f2:34ed3f19
2025-05-23 18:09:55
@ b0a838f2:34ed3f19
2025-05-23 18:09:55- Bugzilla - General-purpose bugtracker and testing tool originally developed and used by the Mozilla project. (Source Code)
MPL-2.0Perl - Frappe Helpdesk - Helpdesk software which helps you streamline your company's support, offers an easy setup, clean user interface, and automation tools to resolve customer queries efficiently. (Source Code)
AGPL-3.0Docker - FreeScout - Email-based customer support application, help desk and shared mailbox (alternative to Zendesk and Help Scout). (Demo, Source Code)
AGPL-3.0PHP/Docker - GlitchTip - Error tracking app to collect errors reported by your app. (Source Code)
MITPython/Docker/K8S - ITFlow - Client IT documentation, ticketing, invoicing and accounting for MSPs (Managed Service Providers). (Demo, Source Code)
GPL-3.0PHP - MantisBT - Bug tracker, fits best for software development. (Demo, Source Code)
GPL-2.0PHP - OTOBO - Flexible web-based ticketing system used for customer service, help desk, IT service management. (Demo, Source Code)
GPL-3.0Perl/Docker - Request Tracker - An enterprise-grade issue tracking system. (Source Code)
GPL-2.0Perl - Roundup Issue Tracker - A simple-to-use and -install issue-tracking system with command-line, web, REST, XML-RPC, and e-mail interfaces. Designed with flexibility in mind - not just another bug tracker. (Source Code)
MIT/ZPL-2.0Python/Docker - Trudesk - Trudesk is an open-source help desk/ticketing solution. (Source Code)
Apache-2.0Nodejs/Docker - Zammad - Easy to use but powerful open-source support and ticketing system. (Source Code)
AGPL-3.0Ruby/deb
- Bugzilla - General-purpose bugtracker and testing tool originally developed and used by the Mozilla project. (Source Code)
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28neuron.vim
I started using this neuron thing to create an update this same zettelkasten, but the existing vim plugin had too many problems, so I forked it and ended up changing almost everything.
Since the upstream repository was somewhat abandoned, most users and people who were trying to contribute upstream migrate to my fork too.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28On "zk-rollups" applied to Bitcoin
ZK rollups make no sense in bitcoin because there is no "cheap calldata". all data is already ~~cheap~~ expensive calldata.
There could be an onchain zk verification that allows succinct signatures maybe, but never a rollup.
What happens is: you can have one UTXO that contains multiple balances on it and in each transaction you can recreate that UTXOs but alter its state using a zk to compress all internal transactions that took place.
The blockchain must be aware of all these new things, so it is in no way "L2".
And you must have an entity responsible for that UTXO and for conjuring the state changes and zk proofs.
But on bitcoin you also must keep the data necessary to rebuild the proofs somewhere else, I'm not sure how can the third party responsible for that UTXO ensure that happens.
I think such a construct is similar to a credit card corporation: one central party upon which everybody depends, zero interoperability with external entities, every vendor must have an account on each credit card company to be able to charge customers, therefore it is not clear that such a thing is more desirable than solutions that are truly open and interoperable like Lightning, which may have its defects but at least fosters a much better environment, bringing together different conflicting parties, custodians, anyone.
-
 @ b0a838f2:34ed3f19
2025-05-23 18:09:35
@ b0a838f2:34ed3f19
2025-05-23 18:09:35- 4ga Boards - Straightforward realtime kanban boards management for intuitive task tracking. Featuring an elegant dark mode, collapsible todo lists, and multitasking tools to supercharge your team's productivity. (Demo, Source Code)
MITNodejs/Docker/K8S - AppFlowy - Build detailed lists of to-do’s for different projects while tracking the status of each one. Open Source Notion Alternative. (Source Code)
AGPL-3.0Rust/Dart/Docker - Donetick - Task and chore management tool for personal and family use, with advanced scheduling, flexible assignment, and group sharing capabilities, detailed history, automation via API, simple and modern design. (Demo, Source Code)
AGPL-3.0Go/Docker - Focalboard - Define, organize, track and manage work across individuals and teams (alternative to Trello, Notion, and Asana). (Source Code, Clients)
MIT/AGPL-3.0/Apache-2.0Nodejs/Go/Docker - Kanboard - Simple visual task board. (Source Code)
MITPHP - myTinyTodo - Simple way to manage your todo list in AJAX style. Uses PHP, jQuery, SQLite/MySQL. GTD compliant. (Demo, Source Code)
GPL-2.0PHP - Nullboard - Single-page minimalist kanban board; compact, highly readable and quick to use. (Demo)
BSD-2-ClauseJavascript - Our Shopping List - Simple shared list application including shopping lists and any other small todo-list that needs to be used collaboratively. (Demo)
AGPL-3.0Docker - Planka - Realtime kanban board for workgroups (alternative to Trello). (Demo, Source Code)
AGPL-3.0Nodejs/Docker/K8S - Task Keeper - List editor for power users, backed by a self-hosted server.
Apache-2.0Scala - Tasks.md - A self-hosted, file based task management board that supports Markdown syntax.
MITDocker - Taskwarrior - Taskwarrior is Free and Open Source Software that manages your TODO list from your command line. It is flexible, fast, efficient, and unobtrusive. It does its job then gets out of your way. (Source Code)
MITC++ - Tegon
⚠- Dev-first issue tracking tool (alternative to Jira, Linear). (Source Code)AGPL-3.0Docker - Tracks - Web-based application to help you implement David Allen’s Getting Things Done™ methodology. (Source Code)
GPL-2.0Ruby - Vikunja - The to-do app to organize your life. (Demo, Source Code)
GPL-3.0Go - Wekan - Open-source Trello-like kanban. (Source Code)
MITNodejs
- 4ga Boards - Straightforward realtime kanban boards management for intuitive task tracking. Featuring an elegant dark mode, collapsible todo lists, and multitasking tools to supercharge your team's productivity. (Demo, Source Code)
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Splitpages
The simplest possible service: it splitted PDF pages in half.
Created specially to solve the problem of those scanned books that come with two pages side-by-side as if they were a single page and are much harder to read on Kindle because of that.

It required me to learn about Heroku Buildpacks though, and fork or contribute to a Heroku Buildpack that embedded a mupdf binary.
-
 @ b0a838f2:34ed3f19
2025-05-23 18:09:15
@ b0a838f2:34ed3f19
2025-05-23 18:09:15- cState - Static status page for hyperfast Hugo. Clean design, minimal JS, super light HTML/CSS, high customization, optional admin panel, read-only API, IE8+. Best used with Netlify, Docker. (Demo, Source Code)
MITGo - Gatus - Automated service health dashboard. (Demo, Source Code)
Apache-2.0Docker/K8S - kener - Status page with incident management, easy to use and customize. (Demo, Source Code)
MITNodejs/Docker - StatPing.ng - An easy to use Status Page for your websites and applications. Statping will automatically fetch the application and render a beautiful status page with tons of features for you to build an even better status page. (Source Code)
GPL-3.0Docker/Go - Uptime Kuma - Self-hosted website monitoring tool like "Uptime Robot". (Demo, Source Code)
MITDocker/Nodejs
- cState - Static status page for hyperfast Hugo. Clean design, minimal JS, super light HTML/CSS, high customization, optional admin panel, read-only API, IE8+. Best used with Netlify, Docker. (Demo, Source Code)
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28tempreites
My first library to get stars on GitHub, was a very stupid templating library that used just HTML and HTML attributes ("DSL-free"). I was inspired by http://microjs.com/ at the time and ended up not using the library. Probably no one ever did.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28litepub
A Go library that abstracts all the burdensome ActivityPub things and provides just the right amount of helpers necessary to integrate an existing website into the "fediverse" (what an odious name). Made for the gravity integration.
See also
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28questo.email
This was a thing done in a brief period I liked the idea of "indiewebcamp", a stupid movement of people saying everybody should have their site and post their lives in it.
From the GitHub postmortem:
questo.email was a service that integrated email addresses into the indieweb ecosystem by providing email-to-note and email-to-webmention triggers, which could be used for people to comment through webmention using their email addresses, and be replied, and also for people to send messages from their sites directly to the email addresses of people they knew; Questo also worked as an IndieAuth provider that used people's email addresses and Mozilla Persona.
It was live from December 2014 through December 2015.
Here's how the home page looked:

See also
- jekmentions, another thing related to "indieweb"
-
 @ 3c389c8f:7a2eff7f
2025-05-23 21:35:30
@ 3c389c8f:7a2eff7f
2025-05-23 21:35:30Web:
https://shopstr.store/
https://cypher.space/
https://plebeian.market/
Mobile:
https://www.amethyst.social/
-
 @ b0a838f2:34ed3f19
2025-05-23 18:09:00
@ b0a838f2:34ed3f19
2025-05-23 18:09:00- Bencher - Suite of continuous benchmarking tools designed to catch performance regressions in CI. (Source Code)
MIT/Apache-2.0Rust - WebHook Tester - Powerful tool for testing WebHooks and more.
MITDocker/Go/deb/K8S
- Bencher - Suite of continuous benchmarking tools designed to catch performance regressions in CI. (Source Code)
-
 @ 3c389c8f:7a2eff7f
2025-05-23 21:27:26
@ 3c389c8f:7a2eff7f
2025-05-23 21:27:26Clients:
https://untype.app
https://habla.news
https://yakihonne.com
https://cypher.space
https://highlighter.com
https://pareto.space/en
https://comet.md/
Plug Ins:
https://github.com/jamesmagoo/nostr-writer
https://threenine.co.uk/products/obstrlish
Content Tagging:
https://labelmachine.org
https://ontolo.social
Blog-like Display and Personal Pages:
https://orocolo.me
https://npub.pro
Personal Notes and Messaging:
https://app.flotilla.social There's an app, too!
https://nosbin.com
RSS Readers:
https://nostrapps.com/noflux
https://nostrapps.com/narr
https://nostrapps.com/feeder
-
 @ b0a838f2:34ed3f19
2025-05-23 18:08:44
@ b0a838f2:34ed3f19
2025-05-23 18:08:44- Cgit - Fast lightweight web interface for git repositories. (Source Code)
GPL-2.0C - Forgejo - A lightweight software forge focused on scaling, federation, and privacy (fork of Gitea). (Demo, Source Code, Clients)
MITDocker/Go - Fossil - Distributed version control system featuring wiki and bug tracker.
BSD-2-Clause-FreeBSDC - Gerrit - Code review and project management tool for Git-based projects. (Source Code)
Apache-2.0Java/Docker - gitbucket - Git platform powered with easy installation, high extensibility & GitHub API compatibility (alternative to GitHub). (Source Code)
Apache-2.0Scala/Java - Gitea - Git with a cup of tea! Painless self-hosted all-in-one software development service, including Git hosting, code review, team collaboration, package registry and CI/CD. (Demo, Source Code)
MITGo/Docker/K8S - GitLab - Self Hosted Git repository management, code reviews, issue tracking, activity feeds and wikis. (Demo, Source Code)
MITRuby/deb/Docker/K8S - Gitolite - Setup git hosting on a central server, with fine-grained access control and many more powerful features. (Source Code)
GPL-2.0Perl - Gogs - Painless self-hosted Git Service written in Go. (Source Code)
MITGo - Huly - All-in-one project management platform (alternative to Linear, Jira, Slack, Notion, Motion). (Demo, Source Code)
EPL-2.0Docker/K8S/Nodejs - Kallithea - Source code management system that supports two leading version control systems, Mercurial and Git, with a web interface. (Source Code)
GPL-3.0Python - Klaus - Simple, easy-to-set-up Git web viewer that Just Works.
ISCPython/Docker - Leantime - Lean project management system for small teams and startups helping to manage projects from ideation through delivery. (Source Code)
AGPL-3.0PHP/Docker - Mergeable
⚠- A better inbox for GitHub pull requests. (Demo, Source Code)MITNodejs/Docker/K8S - Mindwendel - Brainstorm and upvote ideas and thoughts within your team. (Demo, Source Code)
AGPL-3.0Docker/Elixir - minimal-git-server - Lightweight git server with a basic CLI to manage repositories, supporting multiple accounts and running in a container.
MITDocker - Octobox
⚠- Take back control of your GitHub Notifications. (Source Code)AGPL-3.0Ruby/Docker - OneDev - All-In-One DevOps Platform. With Git Management, Issue Tracking, and CI/CD. Simple yet Powerful. (Source Code)
MITJava/Docker/K8S - OpenProject - Manage your projects, tasks and goals. Collaborate via work packages and link them to your pull requests on Github. (Source Code)
GPL-3.0Ruby/deb/Docker - Pagure - Lightweight, powerful, and flexible git-centric forge with features laying the foundation for federated and decentralized development. (Demo)
GPL-2.0Docker/Python/deb - Phorge - Community-driven platform for collaborating, managing, organizing and reviewing software development projects. (Source Code)
Apache-2.0PHP - Plane - Track issues, epics, and product roadmaps in the simplest way possible (alternative to JIRA, Linear and Height). (Demo, Source Code)
AGPL-3.0Docker - ProjeQtOr - Complete, mature, multi-user project management system with extensive functionality for all phases of a project. (Demo, Source Code)
AGPL-3.0PHP - Redmine - Redmine is a flexible project management web application. (Source Code)
GPL-2.0Ruby - Review Board - Extensible and friendly code review tool for projects and companies of all sizes. (Demo, Source Code)
MITPython/Docker - rgit - An ultra-fast & lightweight cgit clone.
WTFPLRust/Docker - RhodeCode - RhodeCode is an open source platform for software development teams. It unifies and simplifies repository management for Git, Subversion, and Mercurial. (Source Code)
AGPL-3.0Python - Rukovoditel - Configurable open source project management, web-based application. (Source Code)
GPL-2.0PHP - SCM Manager - The easiest way to share and manage your Git, Mercurial and Subversion repositories over http. (Source Code)
BSD-3-ClauseJava/deb/Docker/K8S - Smederee - A frugal platform which is dedicated to help people build great software together leveraging the power of the Darcs version control system. (Source Code)
AGPL-3.0Scala - Sourcehut - A full web git interface with no javascript. (Demo, Source Code)
GPL-2.0Go - Taiga - Agile Project Management Tool based on the Kanban and Scrum methods. (Source Code)
MPL-2.0Docker/Python/Nodejs - Titra - Time-tracking solution for freelancers and small teams. (Source Code)
GPL-3.0Javascript/Docker - Trac - Trac is an enhanced wiki and issue tracking system for software development projects.
BSD-3-ClausePython/deb - Traq - Project management and issue tracking system written in PHP. (Source Code)
GPL-3.0PHP/Nodejs - Tuleap - Tuleap is a libre suite to plan, track, code and collaborate on software projects. (Source Code)
GPL-2.0PHP - UVDesk - UVDesk community is a service oriented, event driven extensible opensource helpdesk system that can be used by your organization to provide efficient support to your clients effortlessly whichever way you imagine. (Demo, Source Code)
MITPHP - ZenTao - An agile(scrum) project management system/tool. (Source Code)
AGPL-3.0PHP
- Cgit - Fast lightweight web interface for git repositories. (Source Code)
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28idea: Rumple
a payments network based on trust channels
This is the description of a Lightning-like network that will work only with credit or trust-based channels and exist alongside the normal Lightning Network. I imagine some people will think this is undesirable and at the same time very easy to do (such that if it doesn't exist yet it must be because no one cares), but in fact it is a very desirable thing -- which I hope I can establish below -- and at the same time a very non-trivial problem to solve, as the history of Ryan Fugger's Ripple project and posterior copies of it show.
Read these first to get the full context:
- Ryan Fugger's Ripple
- Ripple and the problem of the decentralized commit
- The Lightning Network solves the problem of the decentralized commit
- Parallel Chains
Explanation about the name
Since we're copying the fundamental Ripple idea from Ryan Fugger and since the name "Ripple" is now associated with a scam coin called XRP, and since Ryan Fugger has changed the name of his old website "Ripplepay" to "Rumplepay", we will follow his lead here. If "Ripplepay" was the name of a centralized prototype to the open peer-to-peer network "Ripple", now that the centralized version is called "Rumplepay" the peer-to-peer version must be called "Rumple".
Now the idea
Basically we copy the Lightning Network, but without HTLCs or channels being opened and closed with funds committed to them on multisig Bitcoin transactions published to the blockchain. Instead we use pure trust relationships like the original Ripple concept.
And we use the blockchain commit method, but instead of spending an absurd amount of money to use the actual Bitcoin blockchain instead we use a parallel chain.
How exactly -- a protocol proposal attempt
It could work like this:
The parallel chain, or "Rumple Chain"
- We define a parallel chain with a genesis block;
- Following blocks must contain
a. the ID of the previous block; b. a list of up to 32768 entries of arbitrary 32-byte values; c. an ID constituted by sha256(the previous block ID + the merkle root of all the entries) - To be mined, each parallel block must be included in the Bitcoin chain according as explained above.
Now that we have a structure for a simple "blockchain" that is completely useless, just blocks over blocks of meaningless values, we proceed to the next step of assigning meaning to these values.
The off-chain payments network, or "Rumple Network"
- We create a network of nodes that can talk to each other via TCP messages (all details are the same as the Lightning Network, except where mentioned otherwise);
- These nodes can create trust channels to each other. These channels are backed by nothing except the willingness of one peer to pay the other what is owed.
- When Alice creates a trust channel with Bob (
Alice trusts Bob), contrary to what happens in the Lightning Network, it's A that can immediately receive payments through that channel, and everything A receives will be an IOU from Bob to Alice. So Alice should never open a channel to Bob unless Alice trusts Bob. But also Alice can choose the amount of trust it has in Bob, she can, for example, open a very small channel with Bob, which means she will only lose a few satoshis if Bob decides to exit scam her. (in the original Ripple examples these channels were always depicted as friend relationships, and they can continue being that, but it's expected -- given the experience of the Lightning Network -- that the bulk of the channels will exist between users and wallet provider nodes that will act as hubs). - As Alice receive a payment through her channel with Bob, she becomes a creditor and Bob a debtor, i.e., the balance of the channel moves a little to her side. Now she can use these funds to make payments over that channel (or make a payment that combines funds from multiple channels using MPP).
- If at any time Alice decides to close her channel with Bob, she can send all the funds she has standing there to somewhere else (for example, another channel she has with someone else, another wallet somewhere else, a shop that is selling some good or service, or a service that will aggregate all funds from all her channels and send a transaction to the Bitcoin chain on her behalf).
- If at any time Bob leaves the network Alice is entitled by Bob's cryptographic signatures to knock on his door and demand payment, or go to a judge and ask him to force Bob to pay, or share the signatures and commitments online and hurt Bob's reputation with the rest of the network (but yes, none of these things is good enough and if Bob is a very dishonest person none of these things is likely to save Alice's funds).
The payment flow
- Suppose there exists a route
Alice->Bob->Caroland Alice wants to send a payment to Carol. - First Alice reads an invoice she received from Carol. The invoice (which can be pretty similar or maybe even the same as BOLT11) contains a payment hash
hand information about how to reach Carol's node, optionally an amount. Let's say it's 100 satoshis. - Using the routing information she gathered, Alice builds an onion and sends it to Bob, at the same time she offers to Bob a "conditional IOU". That stands for a signed commitment that Alice will owe Bob an 100 satoshis if in the next 50 blocks of the Rumple Chain there appears a block containing the preimage
psuch thatsha256(p) == h. - Bob peels the onion and discovers that he must forward that payment to Carol, so he forwards the peeled onion and offers a conditional IOU to Carol with the same
h. Bob doesn't know Carol is the final recipient of the payment, it could potentially go on and on. - When Carol gets the conditional IOU from Bob, she makes a list of all the nodes who have announced themselves as miners (which is not something I have mentioned before, but nodes that are acting as miners will must announce themselves somehow) and are online and bidding for the next Rumple block. Each of these miners will have previously published a random 32-byte value
vthey they intend to include in their next block. - Carol sends payments through routes to all (or a big number) of these miners, but this time the conditional IOU contains two conditions (values that must appear in a block for the IOU to be valid):
psuch thatsha256(p) == h(the same that featured in the invoice) andv(which must be unique and constant for each miner, something that is easily verifiable by Carol beforehand). Also, instead of these conditions being valid for the next 50 blocks they are valid only for the single next block. - Now Carol broadcasts
pto the mempool and hopes one of the miners to which she sent conditional payments sees it and, allured by the possibility of cashing in Carol's payment, includespin the next block. If that does not happen, Carol can try again in the next block.
Why bother with this at all?
-
The biggest advantage of Lightning is its openness
It has been said multiple times that if trust is involved then we don't need Lightning, we can use Coinbase, or worse, Paypal. This is very wrong. Lightning is good specially because it serves as a bridge between Coinbase, Paypal, other custodial provider and someone running their own node. All these can transact freely across the network and pay each other without worrying about who is in which provider or setup.
Rumple inherits that openness. In a Rumple Network anyone is free to open new trust channels and immediately route payments to anyone else.
Also, since Rumple payments are also based on the reveal of a preimage it can do swaps with Lightning inside a payment route from day one (by which I mean one can pay from Rumple to Lightning and vice-versa).
-
Rumple fixes Lightning's fragility
Lightning is too fragile.
It's known that Lightning is vulnerable to multiple attacks -- like the flood-and-loot attack, for example, although not an attack that's easy to execute, it's still dangerous even if failed. Given the existence of these attacks, it's important to not ever open channels with random anonymous people. Some degree of trust must exist between peers.
But one does not even have to consider attacks. The creation of HTLCs is a liability that every node has to do multiple times during its life. Every initiated, received or forwarded payment require adding one HTLC then removing it from the commitment transaction.
Another issue that makes trust needed between peers is the fact that channels can be closed unilaterally. Although this is a feature, it is also a bug when considering high-fee environments. Imagine you pay $2 in fees to open a channel, your peer may close that unilaterally in the next second and then you have to pay another $15 to close the channel. The opener pays (this is also a feature that can double as a bug by itself). Even if it's not you opening the channel, a peer can open a channel with you, make a payment, then clone the channel, and now you're left with, say, an output of 800 satoshis, which is equal to zero if network fees are high.
So you should only open channels with people you know and know aren't going to actively try to hack you and people who are not going to close channels and impose unnecessary costs on you. But even considering a fully trusted Lightning Network, even if -- to be extreme -- you only opened channels with yourself, these channels would still be fragile. If some HTLC gets stuck for any reason (peer offline or some weird small incompatibility between node softwares) and you're forced to close the channel because of that, there are the extra costs of sweeping these UTXO outputs plus the total costs of closing and reopening a channel that shouldn't have been closed in the first place. Even if HTLCs don't get stuck, a fee renegotiation event during a mempool spike may cause channels to force-close, become valueless or settle for very high closing fee.
Some of these issues are mitigated by Eltoo, others by only having channels with people you trust. Others referenced above, plus the the griefing attack and in general the ability of anyone to spam the network for free with payments that can be pending forever or a lot of payments fail repeatedly makes it very fragile.
Rumple solves most of these problems by not having to touch the blockchain at all. Fee negotiation makes no sense. Opening and closing channels is free. Flood-and-loot is a non-issue. The griefing attack can be still attempted as funds in trust channels must be reserved like on Lightning, but since there should be no theoretical limit to the number of prepared payments a channel can have, the griefing must rely on actual amounts being committed, which prevents large attacks from being performed easily.
-
Rumple fixes Lightning's unsolvable reputation issues
In the Lightning Conference 2019, Rusty Russell promised there would be pre-payments on Lightning someday, since everybody was aware of potential spam issues and pre-payments would be the way to solve that. Fast-forward to November 2020 and these pre-payments have become an apparently unsolvable problem[^thread-402]: no one knows how to implement them reliably without destroying privacy completely or introducing worse problems.
Replacing these payments with tables of reputation between peers is also an unsolved problem[^reputation-lightning], for the same reasons explained in the thread above.
-
Rumple solves the hot wallet problem
Since you don't have to use Bitcoin keys or sign transactions with a Rumple node, only your channel trust is at risk at any time.
-
Rumple ends custodianship
Since no one is storing other people's funds, a big hub or wallet provider can be used in multiple payment routes, but it cannot be immediately classified as a "custodian". At best, it will be a big debtor.
-
Rumple is fun
Opening channels with strangers is boring. Opening channels with friends and people you trust even a little makes that relationship grow stronger and the trust be reinforced. (But of course, like it happens in the Lightning Network today, if Rumple is successful the bulk of trust will be from isolated users to big reliable hubs.)
Questions or potential issues
-
So many advantages, yes, but trusted? Custodial? That's easy and stupid!
Well, an enormous part of the current Lightning Network (and also onchain Bitcoin wallets) already rests on trust, mainly trust between users and custodial wallet providers like ZEBEDEE, Alby, Wallet-of-Satoshi and others. Worse: on the current Lightning Network users not only trust, they also expose their entire transaction history to these providers[^hosted-channels].
Besides that, as detailed in point 3 of the previous section, there are many unsolvable issues on the Lightning protocol that make each sovereign node dependent on some level of trust in its peers (and the network in general dependent on trusting that no one else will spam it to death).
So, given the current state of the Lightning Network, to trust peers like Rumple requires is not a giant change -- but it is still a significant change: in Rumple you shouldn't open a large trust channel with someone just because it looks trustworthy, you must personally know that person and only put in what you're willing to lose. In known brands that have reputation to lose you can probably deposit more trust, same for long-term friends, and that's all. Still it is probably good enough, given the existence of MPP payments and the fact that the purpose of Rumple is to be a payments network for day-to-day purchases and not a way to buy real estate.
-
Why would anyone run a node in this parallel chain?
I don't know. Ideally every server running a Rumple Network node will be running a Bitcoin node and a Rumple chain node. Besides using it to confirm and publish your own Rumple Network transactions it can be set to do BMM mining automatically and maybe earn some small fees comparable to running a Lightning routing node or a JoinMarket yield generator.
Also it will probably be very lightweight, as pruning is completely free and no verification-since-the-genesis-block will take place.
-
What is the maturity of the debt that exists in the Rumple Network or its legal status?
By default it is to be understood as being payable on demand for payments occurring inside the network (as credit can be used to forward or initiate payments by the creditor using that channel). But details of settlement outside the network or what happens if one of the peers disappears cannot be enforced or specified by the network.
Perhaps some standard optional settlement methods (like a Bitcoin address) can be announced and negotiated upon channel creation inside the protocol, but nothing more than that.
[^thread-402]: Read at least the first 10 messages of the thread to see how naïve proposals like you and me could have thought about are brought up and then dismantled very carefully by the group of people most committed to getting Lightning to work properly. [^reputation-lightning]: See also the footnote at Ripple and the problem of the decentralized commit. [^hosted-channels]: Although that second part can be solved by hosted channels.
-
 @ b0a838f2:34ed3f19
2025-05-23 18:08:24
@ b0a838f2:34ed3f19
2025-05-23 18:08:24- Appsmith - Build admin panels, CRUD apps and workflows. Build everything you need, 10x faster. (Source Code)
Apache-2.0Java/Docker/K8S - Appwrite - End to end backend server for web, native, and mobile developers 🚀. (Source Code)
BSD-3-ClauseDocker - Dashpress - Generate fully functional admin apps in seconds from your database information, with a single command.
AGPL-3.0Nodejs/Docker - Manifest - Complete backend that fits into 1 YAML file. (Demo, Source Code)
MITNodejs - Motor Admin - No-code admin panel and business intelligence software - search, create, update, and delete data entries, create custom actions, and build reports. (Source Code)
AGPL-3.0Ruby/Docker - PocketBase - Backend for your next SaaS and Mobile app in one file. (Source Code)
MITGo/Docker - SQLPage - SQL-only dynamic website builder. (Source Code)
MITRust/Docker - ToolJet - Low-code framework to build & deploy internal tools with minimal engineering effort (alternative to Retool & Mendix). (Source Code)
GPL-3.0Nodejs/Docker/K8S - TrailBase - Open, sub-millisecond, single-executable FireBase alternative with type-safe REST & realtime APIs, built-in JS/TS runtime, auth & admin UI. (Demo, Source Code)
OSL-3.0Rust/Docker
- Appsmith - Build admin panels, CRUD apps and workflows. Build everything you need, 10x faster. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:08:08
@ b0a838f2:34ed3f19
2025-05-23 18:08:08- Accent - Developer-oriented translation tool. (Source Code)
BSD-3-ClauseElixir/Docker - Tolgee - Developer & translator friendly web-based localization platform enabling users to translate directly in the app they develop. (Source Code)
Apache-2.0Docker/Java - Traduora - Translation management platform for teams. (Source Code)
AGPL-3.0Docker/K8S/Nodejs - Weblate - Web-based translation tool with tight version control integration. (Source Code)
GPL-3.0Python/Docker/K8S
- Accent - Developer-oriented translation tool. (Source Code)
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Boardthreads
This was a very badly done service for turning a Trello list into a helpdesk UI.
Surprisingly, it had more paying users than Websites For Trello, which I was working on simultaneously and dedicating much more time to it.
The Neo4j database I used for this was a very poor choice, it was probably the cause of all the bugs.

-
 @ b0a838f2:34ed3f19
2025-05-23 18:07:52
@ b0a838f2:34ed3f19
2025-05-23 18:07:52- Atheos - Web-based IDE framework with a small footprint and minimal requirements, continued from Codiad. (Source Code)
MITPHP/Docker - code-server - VS Code in the browser, hosted on a remote server.
MITNodejs/Docker - Coder - Remote development machines on your own infrastructure. (Source Code)
AGPL-3.0Go/Docker/K8S/deb - Eclipse Che - Open source workspace server and cloud IDE. (Source Code)
EPL-1.0Docker/Java - HttPlaceholder - Quickly mock away any webservice using HttPlaceholder. HttPlaceholder lets you specify what the request should look like and what response needs to be returned.
MITC# - Judge0 CE - API to compile and run source code. (Source Code)
GPL-3.0Docker - JupyterLab - Web-based environment for interactive and reproducible computing. (Demo, Source Code)
BSD-3-ClausePython/Docker - Langfuse - LLM engineering platform for model tracing, prompt management, and application evaluation. Langfuse helps teams collaboratively debug, analyze, and iterate on their LLM applications such as chatbots or AI agents. (Demo, Source Code, Clients)
MITDocker - LiveCodes
⚠- Feature-rich client-side code playground for React, Vue, Svelte, Solid, Typescript, Python, Go, Ruby, PHP and 90+ other languages. (Demo, Source Code)MITNodejs - Lowdefy - Build internal tools, BI dashboards, admin panels, CRUD apps and workflows in minutes using YAML / JSON on an self-hosted, open-source platform. Connect to your data sources, host via Serverless, Netlify or Docker. (Source Code)
Apache-2.0Nodejs/Docker - RStudio Server - Web browser based IDE for R. (Source Code)
AGPL-3.0Java/C++ - Wakapi - Tracking tool for coding statistics, compatible with WakaTime. (Source Code)
GPL-3.0Go/Docker
- Atheos - Web-based IDE framework with a small footprint and minimal requirements, continued from Codiad. (Source Code)
-
 @ 0c65eba8:4a08ef9a
2025-05-23 21:01:16
@ 0c65eba8:4a08ef9a
2025-05-23 21:01:16You were born to stalk mammoths across frozen plains. To ride bareback with a spear across the steppes, chasing elk, buffalo, or raiders. To stand on the palisade wall in the dead of night, side by side with your brothers, as the horns of a rival village sounded in the dark.
This was manhood before the world became soft.
And where do we find ourselves now?
After twelve or more years of forced submission in the feminized, bureaucratic rituals of public schooling, where natural boyhood is pathologized, courage is demonized, energy is punished, and obedience is rewarded, they are spat out, numbed and shrunken, into the next stage of domestication.
In cubicles. Under fluorescent lights. Obeying fat postmenopausal women who manage sterile, soulless offices. Modern longhouses. Living in cities where no one knows your name and nothing feels alive.
This is modern ritual castration of men. A castration not of the flesh, but of the mind, the heart, and the soul.
Man was not made for this.
He was made for the wilds. For risk. For scars and sunburns and bruises and blood. For memories carved in the flesh, not filtered through a screen.
And when men try to live without these trials, they begin to rot. They wonder why they feel empty.
There is a kind of work that changes you. It doesn’t show up in guidance counselor brochures. It doesn’t care about your resume. And it pays you in something more valuable than prestige.
Hard muscle. Quiet pride. A grounded soul.
Before you commit to the classroom, before you bind yourself to a city, consider taking an adventure job. Just for a season. Just to see who you are when no one is watching.
Adventure Jobs
These are not careers. They are crucibles. They are not meant to last forever.
Every culture had them.
Heracles was not born a hero. He became one only after suffering. Before he was trusted with his place among the gods, he was sent to serve a weak and petty king, Eurystheus, who assigned him twelve impossible labors. Each one more humiliating, more dangerous than the last. He was not free. He was not in control. But he endured. And he emerged transfigured.
Odysseus spent ten years at war, and another ten lost at sea. His cunning was not forged in leisure, it was tempered in storms, on foreign islands, in the face of monsters and gods. His trials revealed who he truly was.
Even the impetuous Achilles, the most gifted warrior of his age, was tested in waiting. Forced to withdraw from battle, he confronted his pride, his grief, his mortality. And only then did he understand honor.
The Roman rite of passage was equally severe. Young noblemen were sent far from their homes, into distant provinces, warfronts, or garrisons. They served older men. They endured boredom, command, isolation, and sometimes death. No man could govern without first being governed.
And in the north, the sagas are the same. Boys were left in the wild to survive. Sigurd, before he became a dragon-slayer, served Regin, a foster-father full of secrets and betrayal. Even Thor, for all his strength, was humbled more than once by tasks set by giants, by challenges that could not be solved with brute force alone.
The story is clear across time:
Before a man could lead, he had to leave. Before he could rule, he had to serve. Before he could carry others, he had to be broken open by the world and stand back up.
This is what these jobs are. Not vacations. Not diversions. But modern-day crucibles. A return to the trials that shape heroic men.
If your mother says it sounds too dangerous, too remote, too rough to be safe, it's probably the right kind of job. That warning is part of the invitation. Because the path to manhood has always passed through risk. The specter of it should frighten the womenfolk.
These jobs are our modern version of the old heroic trials:
🔹 Fire lookout stations in the wilderness: Weeks alone in silence, watching the horizon. A masterclass in solitude and attentiveness.
🔹 Tree planting in Canada or Scandinavia: Physical exhaustion, brutal terrain, and camaraderie forged in shared hardship.
🔹 Shepherding in the Alps or Basque mountains: Living simply, rising early, tending flocks with dogs as your only companions.
🔹 Trail building or forest restoration crews: Moving earth, building paths, repairing what has been broken, inside and out.
🔹 Commercial fishing in Alaska or Iceland: Dangerous, well-paid, and a crash course in grit and hierarchy.
🔹 Glacier guiding or mountaineering apprenticeships: Learn from older men. Risk well. Learn respect for nature’s scale.
🔹 Vineyard harvest work in southern Europe: Sweat, sun, wine, and the rhythm of agricultural life.
🔹 Wildlife or park conservation teams: Track animals. Restore habitats. Learn patience and pattern recognition.
🔹 Outdoor expedition assistant (kayak, trekking, climbing): Support others through trials. Carry weight. Become reliable.
🔹 Off-grid homesteading internships or volunteer programs: Build your hands. Chop wood. Fix machines. Earn your food.
These jobs aren’t perfect. Some are rough. Some demand more than they give. But that’s the point.
A man who has been out there moves differently. He trusts himself. He carries reality in his bones.
He doesn’t fantasize about meaning. He builds it.
Don’t just study your heroes. Do what they did.
Before you enter a world of screens and scripts, give yourself a chapter worth remembering, even if it's only one summer. One that writes itself in sweat and soil and wind.
And if you're not a young man anymore, if you're thirty-five, newly divorced, burnt out, or simply lost your rhythm, this isn't closed to you.
Take one of these jobs not as a career change, but as a reset. A three-month season away from noise and nonsense. A space to work with your body instead of your screen. A time to stop thinking, stop spiraling, stop negotiating with yourself. Just wake, work, eat, sweat, and sleep. Let the forest or the mountain or the sea clear your mind.
You don’t need a plan. You need motion. You need change. You need clarity out of simplicity. You need weather in your face and weight in your hands.
This kind of reset isn’t a step backward. It’s the first real step forward you’ve taken in years.
And when you come back, you’ll be ready to lead.
Not because someone gave you permission. But because you earned it.
-
 @ b0a838f2:34ed3f19
2025-05-23 18:07:34
@ b0a838f2:34ed3f19
2025-05-23 18:07:34- Featbit - Enterprise-grade feature flag platform that you can self-host. (Source Code)
MITDocker/K8S - Flagsmith - Dashboard, API and SDKs for adding Feature Flags to your applications (alternative to LaunchDarkly). (Source Code)
BSD-3-ClauseDocker/K8S - Flipt - Feature flag solution with support for multiple data backends (alternative to LaunchDarkly). (Demo, Source Code)
GPL-3.0Docker/K8S/Go - GO Feature Flag - Simple, complete, and lightweight feature flag solution (alternative to LaunchDarkly). (Source Code)
MITGo
- Featbit - Enterprise-grade feature flag platform that you can self-host. (Source Code)
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28bolt12 problems
- clients can't programatically build new offers by changing a path or query params (services like zbd.gg or lnurl-pay.me won't work)
- impossible to use in a load-balanced custodian way -- since offers would have to be pregenerated and tied to a specific lightning node.
- the existence of fiat currency fields makes it so wallets have to fetch exchange rates from somewhere on the internet (or offer a bad user experience), using HTTP which hurts user privacy.
- the vendor field is misleading, can be phished very easily, not as safe as a domain name.
- onion messages are an improvement over fake HTLC-based payments as a way of transmitting data, for sure. but we must decide if they are (i) suitable for transmitting all kinds of data over the internet, a replacement for tor; or (ii) not something that will scale well or on which we can count on for the future. if there was proper incentivization for data transmission it could end up being (i), the holy grail of p2p communication over the internet, but that is a very hard problem to solve and not guaranteed to yield the desired scalability results. since not even hints of attempting to solve that are being made, it's safer to conclude it is (ii).
bolt12 limitations
- not flexible enough. there are some interesting fields defined in the spec, but who gets to add more fields later if necessary? very unclear.
- services can't return any actionable data to the users who paid for something. it's unclear how business can be conducted without an extra communication channel.
bolt12 illusions
- recurring payments is not really solved, it is just a spec that defines intervals. the actual implementation must still be done by each wallet and service. the recurring payment cannot be enforced, the wallet must still initiate the payment. even if the wallet is evil and is willing to initiate a payment without the user knowing it still needs to have funds, channels, be online, connected etc., so it's not as if the services could rely on the payments being delivered in time.
- people seem to think it will enable pushing payments to mobile wallets, which it does not and cannot.
- there is a confusion of contexts: it looks like offers are superior to lnurl-pay, for example, because they don't require domain names. domain names, though, are common and well-established among internet services and stores, because these services have websites, so this is not really an issue. it is an issue, though, for people that want to receive payments in their homes. for these, indeed, bolt12 offers a superior solution -- but at the same time bolt12 seems to be selling itself as a tool for merchants and service providers when it includes and highlights features as recurring payments and refunds.
- the privacy gains for the receiver that are promoted as being part of bolt12 in fact come from a separate proposal, blinded paths, which should work for all normal lightning payments and indeed are a very nice solution. they are (or at least were, and should be) independent from the bolt12 proposal. a separate proposal, which can be (and already is being) used right now, also improves privacy for the receiver very much anway, it's called trampoline routing.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28The Lightning Network solves the problem of the decentralized commit
Before reading this, see Ripple and the problem of the decentralized commit.
The Bitcoin Lightning Network can be thought as a system similar to Ripple: there are conditional IOUs (HTLCs) that are sent in "prepare"-like messages across a route, and a secret
pthat must travel from the final receiver backwards through the route until it reaches the initial sender and possession of that secret serves to prove the payment as well as to make the IOU hold true.The difference is that if one of the parties don't send the "acknowledge" in time, the other has a trusted third-party with its own clock (that is the clock that is valid for everybody involved) to complain immediately at the timeout: the Bitcoin blockchain. If C has
pand B isn't acknowleding it, C tells the Bitcoin blockchain and it will force the transfer of the amount from B to C.Differences (or 1 upside and 3 downside)
-
The Lightning Network differs from a "pure" Ripple network in that when we send a "prepare" message on the Lightning Network, unlike on a pure Ripple network we're not just promising we will owe something -- instead we are putting the money on the table already for the other to get if we are not responsive.
-
The feature above removes the trust element from the equation. We can now have relationships with people we don't trust, as the Bitcoin blockchain will serve as an automated escrow for our conditional payments and no one will be harmed. Therefore it is much easier to build networks and route payments if you don't always require trust relationships.
-
However it introduces the cost of the capital. A ton of capital must be made available in channels and locked in HTLCs so payments can be routed. This leads to potential issues like the ones described in https://twitter.com/joostjgr/status/1308414364911841281.
-
Another issue that comes with the necessity of using the Bitcoin blockchain as an arbiter is that it may cost a lot in fees -- much more than the value of the payment that is being disputed -- to enforce it on the blockchain.[^closing-channels-for-nothing]
Solutions
Because the downsides listed above are so real and problematic -- and much more so when attacks from malicious peers are taken into account --, some have argued that the Lightning Network must rely on at least some trust between peers, which partly negate the benefit.
The introduction of purely trust-backend channels is the next step in the reasoning: if we are trusting already, why not make channels that don't touch the blockchain and don't require peers to commit large amounts of capital?
The reason is, again, the ambiguity that comes from the problem of the decentralized commit. Therefore hosted channels can be good when trust is required only from one side, like in the final hops of payments, but they cannot work in the middle of routes without eroding trust relationships between peers (however they can be useful if employed as channels between two nodes ran by the same person).
The next solution is a revamped pure Ripple network, one that solves the problem of the decentralized commit in a different way.
[^closing-channels-for-nothing]: That is even true when, for reasons of the payment being so small that it doesn't even deserve an actual HTLC that can be enforced on the chain (as per the protocol), even then the channel between the two nodes will be closed, only to make it very clear that there was a disagreement. Leaving it online would be harmful as one of the peers could repeat the attack again and again. This is a proof that ambiguity, in case of the pure Ripple network, is a very important issue.
-
-
 @ 2f29aa33:38ac6f13
2025-05-17 12:59:01
@ 2f29aa33:38ac6f13
2025-05-17 12:59:01The Myth and the Magic
Picture this: a group of investors, huddled around a glowing computer screen, nervously watching Bitcoin’s price. Suddenly, someone produces a stick-no ordinary stick, but a magical one. With a mischievous grin, they poke the Bitcoin. The price leaps upward. Cheers erupt. The legend of the Bitcoin stick is born.
But why does poking Bitcoin with a stick make the price go up? Why does it only work for a lucky few? And what does the data say about this mysterious phenomenon? Let’s dig in, laugh a little, and maybe learn the secret to market-moving magic.

The Statistical Side of Stick-Poking
Bitcoin’s Price: The Wild Ride
Bitcoin’s price is famous for its unpredictability. In the past year, it’s soared, dipped, and soared again, sometimes gaining more than 50% in just a few months. On a good day, billions of dollars flow through Bitcoin trades, and the price can jump thousands in a matter of hours. Clearly, something is making this happen-and it’s not just spreadsheets and financial news.
What Actually Moves the Price?
-
Scarcity: Only 21 million Bitcoins will ever exist. When more people want in, the price jumps.
-
Big News: Announcements, rumors, and meme-worthy moments can send the price flying.
-
FOMO: When people see Bitcoin rising, they rush to buy, pushing it even higher.
-
Liquidations: When traders betting against Bitcoin get squeezed, it triggers a chain reaction of buying.
But let’s be honest: none of this is as fun as poking Bitcoin with a stick.

The Magical Stick: Not Your Average Twig
Why Not Every Stick Works
You can’t just grab any old branch and expect Bitcoin to dance. The magical stick is a rare artifact, forged in the fires of internet memes and blessed by the spirit of Satoshi. Only a chosen few possess it-and when they poke, the market listens.
Signs You Have the Magical Stick
-
When you poke, Bitcoin’s price immediately jumps a few percent.
-
Your stick glows with meme energy and possibly sparkles with digital dust.
-
You have a knack for timing your poke right after a big event, like a halving or a celebrity tweet.
-
Your stick is rumored to have been whittled from the original blockchain itself.
Why Most Sticks Fail
-
No Meme Power: If your stick isn’t funny, Bitcoin ignores you.
-
Bad Timing: Poking during a bear market just annoys the blockchain.
-
Not Enough Hype: If the bitcoin community isn’t watching, your poke is just a poke.
-
Lack of Magic: Some sticks are just sticks. Sad, but true.

The Data: When the Stick Strikes
Let’s look at some numbers:
-
In the last month, Bitcoin’s price jumped over 20% right after a flurry of memes and stick-poking jokes.
-
Over the past year, every major price surge was accompanied by a wave of internet hype, stick memes, or wild speculation.
-
In the past five years, Bitcoin’s biggest leaps always seemed to follow some kind of magical event-whether a halving, a viral tweet, or a mysterious poke.
Coincidence? Maybe. But the pattern is clear: the stick works-at least when it’s magical.

The Role of Memes, Magic, and Mayhem
Bitcoin’s price is like a cat: unpredictable, easily startled, and sometimes it just wants to be left alone. But when the right meme pops up, or the right stick pokes at just the right time, the price can leap in ways that defy logic.
The bitcoin community knows this. That’s why, when Bitcoin’s stuck in a rut, you’ll see a flood of stick memes, GIFs, and magical thinking. Sometimes, it actually works.

The Secret’s in the Stick (and the Laughs)
So, does poking Bitcoin with a stick really make the price go up? If your stick is magical-blessed by memes, timed perfectly, and watched by millions-absolutely. The statistics show that hype, humor, and a little bit of luck can move markets as much as any financial report.
Next time you see Bitcoin stalling, don’t just sit there. Grab your stick, channel your inner meme wizard, and give it a poke. Who knows? You might just be the next legend in the world of bitcoin magic.
And if your stick doesn’t work, don’t worry. Sometimes, the real magic is in the laughter along the way.

-aco
@block height: 897,104
-
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ b0a838f2:34ed3f19
2025-05-23 18:07:18
@ b0a838f2:34ed3f19
2025-05-23 18:07:18- DreamFactory - Turns any SQL/NoSQL/Structured data into Restful API. (Source Code)
Apache-2.0PHP/Docker/K8S - form.io - A REST API building platform that utilizes a drag & drop form builder, and is application framework agnostic. Contains open source and enterprise version. (Demo, Source Code)
MITNodejs/Docker - Fusio - Open-source API management platform which helps to build and manage REST APIs. (Demo, Source Code)
AGPL-3.0PHP/Docker - Graphweaver - Turn multiple data sources into a single GraphQL API. (Source Code)
MITNodejs - Hasura - Fast, instant realtime GraphQL APIs on Postgres with fine grained access control, also trigger webhooks on database events. (Source Code)
Apache-2.0Haskell/Docker/K8S - Hoppscotch Community Edition - Fast and beautiful API request builder. (Source Code)
MITNodejs/Docker - Kong - Microservice API Gateway and Platform. (Source Code)
Apache-2.0Lua/Docker/K8S/deb - Lura - High-performance API Gateway. (Source Code)
Apache-2.0Go - Opik
⚠- Evaluate, test, and ship LLM applications with a suite of observability tools to calibrate language model outputs across your dev and production lifecycle. (Source Code)Apache-2.0Docker/Python - Panora
⚠- Add an integration catalog to your SaaS product in minutes (alternative to Merge.dev). (Source Code)AGPL-3.0Nodejs/Docker - Para - Flexible and modular backend framework/server for object persistence, API development and authentication. (Source Code)
Apache-2.0Java/Docker - Svix - Open-source webhooks as a service that makes it super easy for API providers to send webhooks. (Source Code)
MITDocker/Rust - Tyk - Fast and scalable open source API Gateway. Out of the box, Tyk offers an API Management Platform with an API Gateway, API Analytics, Developer Portal and API Management Dashboard. (Source Code)
MPL-2.0Go/Docker/K8S - Yaade - Yaade is an open-source, self-hosted, collaborative API development environment. (Source Code)
MITDocker
- DreamFactory - Turns any SQL/NoSQL/Structured data into Restful API. (Source Code)
-
 @ b0a838f2:34ed3f19
2025-05-23 18:07:01
@ b0a838f2:34ed3f19
2025-05-23 18:07:01- Ansible-NAS - Build a full-featured home server with this playbook and an Ubuntu box.
MITAnsible/Docker - CasaOS - Simple, easy-to-use, elegant Home Cloud system. (Source Code)
Apache-2.0Go/Docker - DietPi - Minimal Debian OS optimized for single-board computers, which allows you to easily install and manage several services for selfhosting at home. (Source Code)
GPL-2.0Shell - DockSTARTer - DockSTARTer helps you get started with home server apps running in Docker. (Source Code)
MITShell - Dropserver - An application platform for your personal web services. (Source Code)
Apache-2.0Go/Deno - FreedomBox - Community project to develop, design and promote personal servers running free software for private, personal, communications. (Source Code)
AGPL-3.0Python/deb - HomelabOS - Offline privacy-centric data-center. Deploy over 100 services with a few commands. (Source Code)
MITDocker - HomeServerHQ - All-in-one home server infrastructure and installer. Have a fully configured email server, VPN, and public website(s) set up in less than an hour, even behind CGNAT. (Source Code)
GPL-3.0Shell - LibreServer - Home server configuration based on Debian. (Source Code)
AGPL-3.0Shell - Mars Server - Managed home server with Docker, Docker Compose, Make and Bash.
MITDocker - Mistborn - Virtual private cloud platform and WebUI that manages self hosted services.
MITShell/Docker - NextCloudPi - Nextcloud preinstalled and preconfigured, with a text and web management interface and all the tools needed to self host private data. With installation images for Raspberry Pi, Odroid, Rock64, Docker, and a curl installer for Armbian/Debian.
GPL-2.0Shell/PHP - OpenMediaVault - Network attached storage (NAS) solution based on Debian Linux. It contains services like SSH, (S)FTP, SMB/CIFS, DAAP media server, RSync, BitTorrent client and many more. (Source Code)
GPL-3.0PHP - Sandstorm - Personal server for running self-hosted apps easily and securely. (Demo, Source Code)
Apache-2.0C++/Shell - Self Host Blocks
⚠- Modular server management based on NixOS modules and focused on best practices.AGPL-3.0Nix - StartOS - Browser-based, graphical Operating System (OS) that makes running a personal server as easy as running a personal computer. (Source Code)
MITRust - Syncloud - Your own online file storage, social network or email server. (Source Code)
GPL-3.0Go/Shell - Tipi - Homeserver manager. One command setup, one click installs for your favorites self-hosted apps. (Source Code)
GPL-3.0Shell - UBOS - Linux distro that runs on indie boxes (personal servers and IoT devices). Single-command installation and management of apps - Jenkins, Mediawiki, Owncloud, WordPress, etc., and other features.
GPL-3.0Perl - Websoft9
⚠- GitOps-driven, multi-application hosting for cloud servers and home servers, one-click deployment of 200+ open source apps. (Demo, Source Code, Clients)LGPL-3.0Shell/Python - WikiSuite - The most comprehensive and integrated Free / Libre / Open Source enterprise software suite. (Source Code)
GPL-3.0/LGPL-2.1/Apache-2.0/MPL-2.0/MPL-1.1/MIT/AGPL-3.0Shell/Perl/deb - xsrv - Install and manage self-hosted services/applications, on your own server(s). (Source Code)
GPL-3.0Ansible/Shell - YunoHost - Server operating system aiming to make self-hosting accessible to everyone. (Demo, Source Code)
AGPL-3.0Python/Shell
- Ansible-NAS - Build a full-featured home server with this playbook and an Ubuntu box.
-
 @ b0a838f2:34ed3f19
2025-05-23 18:06:45
@ b0a838f2:34ed3f19
2025-05-23 18:06:45- Aleph - Tool for indexing large amounts of both documents (PDF, Word, HTML) and structured (CSV, XLS, SQL) data for easy browsing and search. It is built with investigative reporting as a primary use case. (Demo, Source Code)
MITDocker/K8S - Apache Solr - Enterprise search platform featuring full-text search, hit highlighting, faceted search, real-time indexing, dynamic clustering, and rich document (e.g., Word, PDF) handling. (Source Code)
Apache-2.0Java/Docker/K8S - Fess - Powerful and easily deployable Enterprise Search Server. (Demo, Source Code)
Apache-2.0Java/Docker - Jina - Cloud-native neural search framework for any kind of data.
Apache-2.0Python/Docker - Manticore Search - Full-text search and data analytics, with fast response time for small, medium and big data (alternative to Elasticsearch).
GPL-3.0Docker/deb/C++/K8S - MeiliSearch - Ultra relevant, instant and typo-tolerant full-text search API. (Source Code)
MITRust/Docker/deb - OpenSearch - Distributed and RESTful search engine. (Source Code)
Apache-2.0Java/Docker/K8S/deb - SearXNG
⚠- Internet metasearch engine which aggregates results from various search services and databases (Fork of Searx). (Source Code)AGPL-3.0Python/Docker - sist2 - Lightning-fast file system indexer and search tool.
GPL-3.0C/Docker - Sosse - Selenium based search engine and crawler with offline archiving. (Source Code)
AGPL-3.0Python/Docker - Typesense - Blazing fast, typo-tolerant open source search engine optimized for developer happiness and ease of use. (Source Code)
GPL-3.0C++/Docker/K8S/deb - Websurfx
⚠- Aggregate results from other search engines (metasearch engine) without ads while keeping privacy and security in mind. It is extremely fast and provides a high level of customization (alternative to SearX).AGPL-3.0Rust/Docker - Whoogle
⚠- A self-hosted, ad-free, privacy-respecting metasearch engine.MITPython - Yacy - Peer based, decentralized search engine server. (Source Code)
GPL-2.0Java/Docker/K8S - ZincSearch - Search engine that requires minimal resources (alternative to Elasticsearch). (Demo, Source Code)
Apache-2.0Go/Docker/K8S
- Aleph - Tool for indexing large amounts of both documents (PDF, Word, HTML) and structured (CSV, XLS, SQL) data for easy browsing and search. It is built with investigative reporting as a primary use case. (Demo, Source Code)
-
 @ 86611181:9fc27ad7
2025-05-23 20:31:44
@ 86611181:9fc27ad7
2025-05-23 20:31:44It's time to secure user data in your identity system This post was also published with the Industry Association of Privacy Professionals.
It seems like every day there is a new report of a major personal data breach. In just the past few months, Neiman Marcus, Ticketmaster, Evolve Bank, TeamViewer, Hubspot, and even the IRS have been affected.
The core issue is that user data is commonly spread across multiple systems that are increasingly difficult to fully secure, including database user tables, data warehouses and unstructured documents.
Most enterprises are already running an incredibly secure and hardened identity system to manage customer login and authorization, commonly referred to as a customer identity access management system. Since identity systems manage customer sign-up and sign-in, they typically contain customer names, email addresses, and phone numbers for multifactor authentication. Commercial CIAMs provide extensive logging, threat detection, availability and patch management.
Identity systems are highly secure and already store customers' personally identifiable information, so it stands to reason enterprises should consider identity systems to manage additional PII fields.
Identity systems are designed to store numerous PII fields and mask the fields for other systems. The Liberty Project developed the protocols that became Security Assertion Markup Language 2.0, the architecture at the core of CIAM systems, 20 years ago, when I was its chief technology officer. SAML 2.0 was built so identity data would be fully secure, and opaque tokens would be shared with other systems. Using tokens instead of actual user data is a core feature of identity software that can be used to fully secure user data across applications.
Most modern identity systems support adding additional customer fields, so it is easy to add new fields like Social Security numbers and physical addresses. Almost like a database, some identity systems even support additional tables and images.
A great feature of identity systems is that they often provide a full suite of user interface components for users to register, login and manage their profile fields. Moving fields like Social Security numbers from your database to your identity system means the identity system can fully manage the process of users entering, viewing and editing the field, and your existing application and database become descoped from managing sensitive data.
With sensitive fields fully isolated in an identity system and its user interface components, the identity system can provide for cumbersome and expensive compliance with standards such as the Health Insurance Portability and Accountability Act for medical data and the Payment Card Industry Data Security Standard for payment data, saving the time and effort to achieve similar compliance in your application.
There are, of course, applications that require sensitive data, such as customer service systems and data warehouses. Identity systems use a data distribution standard called System for Cross-domain Identity Management 2.0 to copy user data to other systems. The SCIM is a great standard to help manage compliance such as "right to be forgotten," because it can automatically delete customer data from other systems when a customer record is deleted from the identity system.
When copying customer data from an identity system to another application, consider anonymizing or masking fields. For example, anonymizing a birthdate into an age range when copying a customer record into a data warehouse can descope the data warehouse from containing personal information.
Most enterprises already run an Application Programming Interface Gateway to manage web services between systems. By combining an API Gateway with the identity system's APIs, it becomes very easy to automatically anonymize and mask customer data fields before they are copied into other systems.
A new set of companies including Baffle, Skyflow, and Piiano have introduced services that combine the governance and field management features of an identity system with extensive field masking. Since these systems do not offer the authentication and authorization features of an identity system, it's important to balance the additional features as they introduce an additional threat surface with PII storage and permissions.
PII sprawl is an increasing liability for companies. The most secure, compliant and flexible central data store to manage PII is the existing CIAM and API Gateway infrastructure that enterprises have already deployed.
Move that customer data into your identity system and lock it down. https://peter.layer3.press/articles/3c6912eb-404a-4630-9fe9-fd1bd23cfa64
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Webvatar
Like Gravatar, but using profile images from websites tagged with "microformats-2" tags, like people from the indiewebcamp movement liked. It falled back to favicon, gravatar and procedural avatar generators.
No one really used this, despite people saying they liked it. Since I was desperate to getting some of my programs appreciated by someone I even bought a domain. It was sad, but an enriching experience.
See also
-
 @ b0a838f2:34ed3f19
2025-05-23 18:06:22
@ b0a838f2:34ed3f19
2025-05-23 18:06:22- Dolibarr - Modern CRM software package to manage your company or foundation activity (contacts, suppliers, invoices, orders, stocks, agenda, accounting, ...). (Demo, Source Code)
GPL-3.0PHP/deb - ERPNext - ERP system to help you run your business. (Source Code)
GPL-3.0Python/Docker - farmOS - Web-based farm record keeping application. (Demo, Source Code)
GPL-2.0PHP/Docker - grocy - ERP beyond your fridge. Groceries & household management solution for your home. (Demo, Source Code)
MITPHP/Docker - LedgerSMB - Integrated accounting and ERP system for small and midsize businesses, with double entry accounting, budgeting, invoicing, quotations, projects, orders and inventory management, shipping and more. (Demo, Source Code)
GPL-2.0Docker/Perl - Odoo - Free open source ERP system. (Demo, Source Code)
LGPL-3.0Python/deb/Docker - OFBiz - Enterprise Resource Planning system with a suite of business applications flexible enough to be used across any industry. (Source Code)
Apache-2.0Java - Tryton - Free open source business solution. (Demo, Source Code)
GPL-3.0Python
- Dolibarr - Modern CRM software package to manage your company or foundation activity (contacts, suppliers, invoices, orders, stocks, agenda, accounting, ...). (Demo, Source Code)
