-
 @ 51bbb15e:b77a2290
2025-05-21 00:24:36
@ 51bbb15e:b77a2290
2025-05-21 00:24:36Yeah, I’m sure everything in the file is legit. 👍 Let’s review the guard witness testimony…Oh wait, they weren’t at their posts despite 24/7 survellience instructions after another Epstein “suicide” attempt two weeks earlier. Well, at least the video of the suicide is in the file? Oh wait, a techical glitch. Damn those coincidences!
At this point, the Trump administration has zero credibility with me on anything related to the Epstein case and his clients. I still suspect the administration is using the Epstein files as leverage to keep a lot of RINOs in line, whereas they’d be sabotaging his agenda at every turn otherwise. However, I just don’t believe in ends-justify-the-means thinking. It’s led almost all of DC to toss out every bit of the values they might once have had.
-
 @ 34f1ddab:2ca0cf7c
2025-05-20 23:59:03
@ 34f1ddab:2ca0cf7c
2025-05-20 23:59:03Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ 3f770d65:7a745b24
2025-05-20 21:14:28
@ 3f770d65:7a745b24
2025-05-20 21:14:28I’m Derek Ross, and I’m all-in on Nostr.
I started the Grow Nostr Initiative to help more people discover what makes Nostr so powerful: ✅ You own your identity ✅ You choose your social graph and algorithms ✅ You aren't locked into any single app or platform ✅ You can post, stream, chat, and build, all without gatekeepers
What we’re doing with Grow Nostr Initiative: 🌱 Hosting local meetups and mini-conferences to onboard people face-to-face 📚 Creating educational materials and guides to demystify how Nostr works 🧩 Helping businesses and creators understand how they can plug into Nostr (running media servers, relays, and using key management tools)
I believe Nostr is the foundation of a more open internet. It’s still early, but we’re already seeing incredible apps for social, blogging, podcasting, livestreaming, and more. And the best part is that they're all interoperable, censorship-resistant, and built on open standards. Nostr is the world's largest bitcoin economy by transaction volume and I truly believe that the purple pill helps the orange pill go down. Meaning, growing Nostr will also grow Bitcoin adoption.
If you’ve been curious about Nostr or are building something on it, or let’s talk. Whether you're just getting started or you're already deep in the ecosystem, I'm here to answer questions, share what I’ve learned, and hear your ideas. Check out https://nostrapps.com to find your next social decentralized experience.
Ask Me Anything about GNI, Nostr, Bitcoin, the upcoming #NosVegas event at the Bitcoin Conference next week, etc.!
– Derek Ross 🌐 https://grownostr.org npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424
https://stacker.news/items/984689
-
 @ c9badfea:610f861a
2025-05-20 19:49:20
@ c9badfea:610f861a
2025-05-20 19:49:20- Install Sky Map (it's free and open source)
- Launch the app and tap Accept, then tap OK
- When asked to access the device's location, tap While Using The App
- Tap somewhere on the screen to activate the menu, then tap ⁝ and select Settings
- Disable Send Usage Statistics
- Return to the main screen and enjoy stargazing!
ℹ️ Use the 🔍 icon in the upper toolbar to search for a specific celestial body, or tap the 👁️ icon to activate night mode
-
 @ 30b99916:3cc6e3fe
2025-05-20 23:00:17
@ 30b99916:3cc6e3fe
2025-05-20 23:00:17For all you COVID COWARDS out there perhaps you can redeem yourself by supporting America's Frontline Docters
History will show that the defeat of COVID tyranny wasn’t granted – it was won, case by case, voice by voice – and your support for America’s Frontline Doctors played an important role in this fight.
America 2020 – our nation faced a moment of truth.
Public health soldiers working for deep-state globalists unleashed tyranny in response to a virus - to terrorize us and dismantle our Constitution.
When I look back on the forces arrayed against us, I’m amazed more people did NOT stand up for their rights:
_Government agencies...hospitals...universities...corporations..._
...the state acting as our “savior” ...
...and Big Tech as the enforcer...
All joined forces to impose sweeping authoritarian mandates under the banners of public health and settled science.
_They declared freedom and liberty non-essential._
_They silenced, fired, shamed, and canceled ANYONE who dared question them._
ANYONE who resisted the masking, the lockdowns, the forced mRNA injections, are HEROS.
It angers me just thinking about what happened next.
Everyday Americans lost their livelihoods.
Parents watched as their children deteriorated after being locked out of their schools.
Doctors – some of the best in the country – were hunted down by their own licensing boards for practicing ACTUAL medicine instead of government-approved pseudoscience.
I hate to admit it, but tyranny triumphed.
The people had surrendered so much liberty that I didn’t recognize the nation our founders had forged.
I’m sure you didn’t either.
But while we can’t undo the past, we can make sure we don’t repeat it.
That is why America’s Frontline Doctors and I – with you alongside us – have been fighting back.
And together, we’ve been doing it case by case, supporting legal challenges against these unconstitutional, totalitarian mandates.
-
 @ c9badfea:610f861a
2025-05-20 17:05:41
@ c9badfea:610f861a
2025-05-20 17:05:41- Install YTDLnis (it's free and open source)
- Launch the app and allow notifications and storage access if prompted
- Go to any supported website or use the YouTube, Instagram, X, or Facebook app
- Tap Share on the post or website URL and select YTDLnis as the sharing destination
- Adjust the settings if desired and tap Download
- You'll be notified when the download finishes
- Enjoy uninterrupted watching!
ℹ️ This app uses
yt-dlpinternally and it's also available as a standalone CLI tool -
 @ 2b998b04:86727e47
2025-05-20 22:15:45
@ 2b998b04:86727e47
2025-05-20 22:15:45I didn’t take a course on “prompt engineering.” I didn’t memorize secret formulas or chase viral hacks.
What I did do was treat it like a system.
Just like in software:
Write → Compile → Test → Debug → Repeat
With AI, the loop feels just as familiar:
Prompt → Output → Edit → Re-prompt
That’s not magic. That’s engineering.
When someone asked me, “How can you trust AI for anything serious?”\ I told them: “Same way we trust the internet — not because the network’s reliable, but because the protocol is.”
AI is no different. The key is building systems around it:
-
Multiple models if needed
-
Human-in-the-loop verification
-
Layered editing and real discernment
It’s Not That Different From Other Engineering
Once you stop treating AI like a black box and start treating it like a tool, the whole experience changes.
The prompt isn’t a spell. It’s a spec.\ The response isn’t a prophecy. It’s a build.\ And your discernment? That’s your QA layer.
What I Actually Use It For
-
Brainstorming titles and refining headlines
-
Drafting posts that I shape and filter
-
Running content through for edge cases
-
Exploring theological or philosophical questions
And yes — I want it to be useful. I am building to make a living, not just to make noise. But I don’t lead with monetization. I lead with clarity — and build toward sustainability.
Final Thought
If you’re waiting for a course to teach you how to “do AI,” maybe just start by building something real. Test it. Edit it. Use it again. That’s engineering.
Shoutout to Dr. C (ChatGPT) for helping me articulate this.
If this post sparked anything for you, zap a few sats ⚡ — every bit helps me keep building with conviction.
-
-
 @ 04c915da:3dfbecc9
2025-05-20 15:50:48
@ 04c915da:3dfbecc9
2025-05-20 15:50:48For years American bitcoin miners have argued for more efficient and free energy markets. It benefits everyone if our energy infrastructure is as efficient and robust as possible. Unfortunately, broken incentives have led to increased regulation throughout the sector, incentivizing less efficient energy sources such as solar and wind at the detriment of more efficient alternatives.
The result has been less reliable energy infrastructure for all Americans and increased energy costs across the board. This naturally has a direct impact on bitcoin miners: increased energy costs make them less competitive globally.
Bitcoin mining represents a global energy market that does not require permission to participate. Anyone can plug a mining computer into power and internet to get paid the current dynamic market price for their work in bitcoin. Using cellphone or satellite internet, these mines can be located anywhere in the world, sourcing the cheapest power available.
Absent of regulation, bitcoin mining naturally incentivizes the build out of highly efficient and robust energy infrastructure. Unfortunately that world does not exist and burdensome regulations remain the biggest threat for US based mining businesses. Jurisdictional arbitrage gives miners the option of moving to a friendlier country but that naturally comes with its own costs.
Enter AI. With the rapid development and release of AI tools comes the requirement of running massive datacenters for their models. Major tech companies are scrambling to secure machines, rack space, and cheap energy to run full suites of AI enabled tools and services. The most valuable and powerful tech companies in America have stumbled into an accidental alliance with bitcoin miners: THE NEED FOR CHEAP AND RELIABLE ENERGY.
Our government is corrupt. Money talks. These companies will push for energy freedom and it will greatly benefit us all.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:50:22
@ 04c915da:3dfbecc9
2025-05-20 15:50:22There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 04c915da:3dfbecc9
2025-05-20 15:47:16
@ 04c915da:3dfbecc9
2025-05-20 15:47:16Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ da8b7de1:c0164aee
2025-05-20 19:30:10
@ da8b7de1:c0164aee
2025-05-20 19:30:10TVA SMR-építési engedélykérelem Clinch Riverben
A Tennessee Valley Authority (TVA) benyújtotta az első kis moduláris reaktor (SMR) építési engedélykérelmet az Egyesült Államokban, a Clinch River-i telephelyre. Ez a lépés mérföldkő az amerikai nukleáris ipar számára, hiszen a BWRX-300 típusú SMR-rel a TVA célja a szén-dioxid-mentes energiatermelés bővítése és az innovatív nukleáris technológia bevezetése.
ČEZ új nukleáris telephelyet jelölt ki Csehországban
A cseh ČEZ energetikai vállalat kijelölte a Tušimice-i telephelyet egy új atomerőmű számára, ahol várhatóan kis moduláris reaktorokat (SMR) telepítenek. Ez a lépés segíti az országot az energiafüggetlenség és a szénalapú energiatermelés kivezetése felé vezető úton.
Urenco USA új dúsító kaszkádot indított
Az Urenco USA New Mexicóban elindította új gázcentrifuga kaszkádját, amely 15%-kal növeli az amerikai dúsított urán kapacitást. Ez kulcsfontosságú az orosz uránimporttól való függetlenedés és az amerikai atomerőművek ellátásbiztonsága szempontjából.
Fiatal szakemberek sürgetik a nukleáris energia központi szerepét Európában
Európai fiatal nukleáris szakemberek nyílt levélben hívták fel a döntéshozók figyelmét arra, hogy a nukleáris energia kapjon központi szerepet a kontinens dekarbonizációs stratégiájában. Kiemelték a kutatás-fejlesztés, a befektetési környezet javítása és a társadalmi elfogadottság növelésének fontosságát.
Zeno Power 50 millió dolláros befektetést szerzett
Az amerikai Zeno Power startup 50 millió dolláros befektetést jelentett be nukleáris akkumulátorok fejlesztésére, amelyek extrém környezetekben – például az űrben vagy tenger alatt – biztosítanak megbízható energiát. A cég célja, hogy 2027-re kereskedelmi forgalomba hozza első rendszereit.
További globális nukleáris fejlemények
Több ország – például India, Kína, Belgium, Kanada, Brazília – is új nukleáris projekteket jelentett be, miközben a nemzetközi konferenciák az ellátási láncok megerősítését és a nukleáris kapacitások bővítését helyezik előtérbe.
Hivatkozások
- tva.com
- en.wikipedia.org/wiki/ČEZ_Group
- urencousa.com
- zenopower.com
- fisa-euradwaste2025.ncbj.gov.pl
- world-nuclear.org
- nucnet.org
-
 @ 4fa5d1c4:fd6c6e41
2025-05-20 15:13:35
@ 4fa5d1c4:fd6c6e41
2025-05-20 15:13:35📌 Ablauf
1. Prompt auswählen
Wähle aus der Promptsammlung einen Prompt, der dich anspricht – z. B. zu Unterrichtsplanung, Kreativmethoden, Inklusion oder KI-Nutzung im RU.
2. Prompt ausprobieren
Verwende den Prompt mit einem KI-Tool (z. B. ChatGPT oder ein freies Modell wie LM Studio) und passe ihn ggf. leicht an dein Thema oder deine Klasse an.
3. Reflexion schreiben
Notiere kurz, was gut geklappt hat, was überrascht hat oder was du noch verbessern möchtest. Halte es so fest, dass andere davon lernen können.
4. Auf Nostr posten
Veröffentliche deine Reflexion oder ein konkretes Ergebnis (z. B. Screenshot, kurzer Textauszug, Sketchnote …) über deinen Nostr-Client (z. B. Damus, Amethyst, Habla.news).\ Verwende folgende Hashtags:
```text
relilab #verstehen oder #anwenden oder #reflektieren oder #gestalten
(optional: 1️⃣, 2️⃣ oder 3️⃣ je nach Niveaustufe) ```
Beispiel:
markdown Heute mit dem Prompt zur „Virtuellen Exkursion“ gearbeitet – mega spannend, wie viel die Schüler:innen zu Jerusalem wussten! Habe das Ergebnis als Audio-Reisebericht umgesetzt. #relilab #anwenden 2️⃣
💡 Hinweise
-
Nutze möglichst einen Prompt pro Post, damit die Community gut filtern kann.
-
Wenn du einen neuen Prompt ausprobierst oder abwandelst, verlinke gerne auf die Originalquelle (z. B. „Kapitel 2 · Kreative Unterrichtsgestaltung – Lernspiel entwickeln“).
-
Du kannst auch Fragen an die Community stellen: z. B. „Hat jemand diesen Prompt schon mal mit einer 6. Klasse ausprobiert?“
📣 Ziel der Aktion
Durch eure Beiträge entsteht eine wachsende Sammlung an:
-
reflektierten Einsatzbeispielen aus der Praxis
-
kreativen Varianten und Weiterentwicklungen
-
Ideen für KI-gestützte Lehrer:innenbildung im Fach Religion
Wenn du magst, notiere deine eigenen Favoriten-Prompts, poste Screenshots oder gestalte eine „Best-of“-Sammlung für dein Kollegium!
Promptsammlung Religionsunterricht
Kapitel 1 · Unterrichtsplanung & -vorbereitung (Religionsunterricht)
Religionsstunde planen
prompt Plane eine 45-minütige Religionsstunde in **[Klassenstufe]** zum Thema **[„Nächstenliebe in Judentum, Christentum & Islam“ o. ä.]**. Liefere: – drei messbare Kompetenzziele (KMK-Bereich „Religiöse Identität entwickeln“) – detaillierten Phasenplan (Einstieg | Erarbeitung | Sicherung | Transfer) mit Zeitangaben – mindestens zwei kreative Sozialformen (Think-Pair-Share, Placemat, Gallery Walk …) – Kerntext(e) aus Bibel, Koran oder Tanach + passenden Medienimpuls (Video, Bild, Song) – Lernaufgabe für zu Hause, die das Thema in den Lebenswelt-Bezug bringtUnterrichtseinheit entwerfen
prompt Entwirf eine vierwöchige Einheit **[Thema: „Schöpfungsverantwortung“]** für die **[Sek I]**. Für jede Doppelstunde angeben: – Leitfrage & erwartetes Kompetenzniveau (AB I – III) – Schlüsseltexte/Traditionen (Genesis 1–2, islamische Schöpfungs-Ayat, „Laudato si’“ …) – handlungsorientierte Lernaufgabe inkl. Differenzierung – Methodensetting (z. B. Gruppenpuzzle, Mystery, Stationenlauf) – benötigte Materialien/Medien und eine kurze ReflexionsideeDifferenzierte Lernaufgaben
prompt Formuliere Lernaufgaben zum Thema **[„Gleichnisse Jesu“]** für drei Anspruchsniveaus: 1. Unterstützungsniveau – Lesestrategieblatt + vorstrukturierter Lückentext 2. Basisniveau – Text-Puzzle + Placemat-Diskussion 3. Erweiterungsniveau – eigener Podcast (Recherche, Skript, Produktion, Peer-Feedback) Je Aufgabe: Ziel, Ablauf in Schritten, erwartetes Produkt, Bewertungsfokus.Langfristiges Projekt skizzieren
prompt Skizziere ein sechs-wöchiges Projekt **„Interreligiöse Stadt-Rallye“** für **[Klasse 9]**: – Projektziele & zugeordnete Kompetenzen – Checkliste für Besuche (Kirche, Synagoge, Moschee, Tempel) inkl. Leitfragen – digitale Dokumentation (Padlet-Storyboard, QR-Blogposts, Foto-Missionen) – Abschlussprodukt (multimediale Stadttour) + Rubrik mit vier BewertungsdimensionenJahresübersicht erstellen
prompt Erstelle eine Grobjahresplanung für **[ev. Religion, Kl. 5]** mit sechs Themenfeldern (z. B. „Staunen über die Schöpfung“, „Jesus begegnen“…). Zu jedem Feld: – Zeitraum & passendes Fest im Kirchenjahr als Anker – kompetenzorientierte Leistungsform (Portfolio, Lernlandkarte, Präsentation …) – kurze Hinweissequenz für mögliche fächerverbindende ChancenProjektwoche „Spiritualität erleben“
prompt Konzipiere eine fächerübergreifende Projektwoche **„Spiritualität & Achtsamkeit“** für **[Jgst. 7–8]**: – Workshop-Menü (Ikonenmalen, Kalligraphie, Yoga, Psalm-Rap, MBSR-Übungen …) – externe Expert*innen (Pfarrer*in, Imam, Rabbiner*in, buddhistische*r Lehrer*in) – tägliche Reflexionsformate (Stille-Tagebuch, Audio-Log, Blitzlicht-Runde) – gemeinsamer Abschluss: interreligiöses Friedensgebet + Feedback-GalleryKompetenzen formulieren
prompt Schreibe messbare Kompetenzformulierungen für die Einheit **[„Propheten – Stimmen für Gerechtigkeit“]** (Sek II). Nutze Anforderungsbereiche I–III und füge zu jeder Kompetenz: Beobachtungshinweis + kurzes Beispiel für Leistungsnachweis.
Kapitel 2 · Kreative Unterrichtsgestaltung (Religionsunterricht)
Lernspiel entwickeln
prompt Entwickle ein interaktives Spiel, das Schüler*innen **[z. B. die Zehn Gebote]** niedrigschwellig erarbeiten lässt. Beschreibe: Spielidee, Regeln, Material, Spielphasen (Warm-up | Action | Debrief) und Reflexionsfragen zur theologischen Vertiefung.Gruppenarbeit strukturieren
prompt Plane eine Gruppenaufgabe zu den **„Seligpreisungen der Bergpredigt“**: – Gruppenzuteilung je Seligpreisung – Produktwahl (Comic-Strip, Poetry-Slam, Kurzvideo …) mit Kreativbriefing – Präsentations-Setting + Peer-Feedback-Raster – Lehrer*innen-Checkliste zur Beobachtung von Zusammenarbeit & InhaltstiefeInterdisziplinärer Unterricht
prompt Kombiniere **„Umweltschutz in den Weltreligionen“** mit **Biologie** in einer Doppelstunde: – theologischer Impuls (Schöpfungsverantwortung) – biologischer Faktenblock (ökologische Fußabdrücke) – Arbeitsphase: Lernende vergleichen religiöse & wissenschaftliche Begründungen und entwerfen Handlungsideen für die Schule.Storytelling einsetzen
prompt Zeige, wie Storytelling das Thema **„Exodus – Befreiungsgeschichte“** lebendig macht: – Dramaturgie (Setup – Konflikt – Climax – Rückbindung) – Erzähler*innenrollen (Miriam, Moses, Pharao, Gott als Off-Stimme) – Aufgaben: Storyboard zeichnen, Rollen-Podcast aufnehmen, reflektiertes JournalExperimenteller Ansatz
prompt Entwirf einen experimentellen Unterrichtsgang zur Leitfrage **„Was bedeutet heilig?“**: – Alltagsobjekte auswählen und symbolisch umdeuten lassen – Stationen: Wahrnehmung | Gestaltung | Deutung | Religionsvergleich – abschließende Reflexion in einem Gallery Walk + theologischer EinordnungBlended-Learning-Konzept
prompt Erstelle ein Blended-Learning-Szenario zur Einheit **„Feste im Kirchenjahr“**: – Online-Phase: interaktive Zeitleiste, Erklärvideos, H5P-Quiz – Präsenz-Phase: Lernlandkarte, Gruppen-Challenge „Festkalender bauen“ – Leistungsnachweis: Lerntagebuch + digitale Portfolio-AbgabeDesign Thinking anwenden
prompt Nutze Design Thinking, um mit Schüler*innen Lösungen für **„Armut in unserer Stadt“** aus religiöser Perspektive zu entwickeln. Beschreibe alle sechs Phasen inkl. Tools (Empathy Map, How-Might-We-Fragen, Prototyping-Material), Zeit- und Raumplan.Escape-Room planen
prompt Konzipiere einen pädagogischen Escape Room zum Thema **„Paulus auf Missionsreise“**: – Storyline (Start, Hinweise, Wendepunkt, Finale) – fünf Rätseltypen (Logik, Bibelcode, UV-Botschaft …) – benötigtes Material & Technik + Safety-Briefing – Auswertungsbogen für Lernergebnisse & Teamwork-SkillsFlipped Classroom umsetzen
prompt Gestalte einen Flipped-Classroom-Ablauf zur Einheit **„Gleichnisse Jesu“**: – Zuhause: drei Micro-Learning-Videos (< 5 min) + interaktiver Selbsttest – Unterricht: kooperative Fallanalyse, Rollenspiel, Kreativstation – Reflexion: One-Minute-Paper → digitales Feedback-PadVirtuelle Exkursion einbauen
prompt Baue eine virtuelle Exkursion **„Jerusalem – Heilige Stätten“** ein: – Ressourcen: 360°-VR-Tour, Street-View-Links, Museums-App – Vorbereitende Leitfragen (historisch, religiös, politisch) – Arbeitsauftrag: digitale Reise-Map anlegen, Eindrücke vertonen, Peer-Review – Abschluss: Fishbowl-Diskussion zu religiöser Vielfalt & KonfliktlinienKapitel 3 · Differenzierung & Inklusion (Religiöses Lernen)
Inklusive Aufgabenstellung
prompt Gestalte eine Unterrichtseinheit zu **[„Gleichnisse Jesu“]** so, dass Lernende mit kognitiven, motorischen oder sprachlichen Beeinträchtigungen aktiv teilnehmen können. • beschreibe drei barrierearme Medien-/Methoden-Anpassungen • formuliere für jedes Lernniveau ein messbares Teilziel • gib Beispiele für unterstützende Hilfsmittel (z. B. Symbolkarten, Audiodeskription, taktile Bibel)Individuellen Förderplan erstellen
prompt Erstelle einen Förderplan für eine*n Schüler*in mit Lese-Rechtschreib-Schwäche im Thema **[„Schöpfungspsalmen“]**: – diagnostische Ausgangslage + SMART-Ziele – wöchentliche Lernschritte (Methoden, Materialien, Zeitbudget) – Evaluationskriterien & Reflexionsfragen für Lernende + LehrkraftKompetenzentwicklung begleiten
prompt Zeige, wie du die Kompetenzentwicklung in der Einheit **„Spiritualität & Achtsamkeit“** laufend beobachtest: • Portfolio-Raster mit Indikatoren zu Wahrnehmung / Deutung / Gestaltung • Feedback-Tool (Ampel, Check-Out, Audio-Memo) • Maßnahmenplan bei Unter- oder ÜberforderungPersonalisierte Lernpfade
prompt Baue personalisierte Lernpfade für **„Weltreligionen im Dialog“** (Kl. 7) auf: – drei optionale Module (Video-Recherche, Expert*innen-Interview, Kreativprodukt) je nach Vorwissen – Self-Assessment-Checkpoints + Empfehlung nächster Schritt – technische Umsetzung mit Learning-Management-System deiner WahlLernjournal nutzen
prompt Entwirf ein Lernjournal-Format zur Reihe **„Seligpreisungen“**: • tägliche Prompt-Frage (kognitiv, affektiv, spirituell) • visuelle Elemente (Sketchnote, Emojikarte, Farbsymbol) • Wochen-Meta-Reflexion + Peer-KommentarfeldSpezifische Unterstützung
prompt Beschreibe Zusatzmaßnahmen, um das abstrakte Konzept **„Trinität“** für Lernende mit Verständnisschwierigkeiten greifbar zu machen: – vereinfachte Grafiken, Alltagsanalogien, szenische Darstellung – Schritt-für-Schritt-Erklärvideo (max. 3 min) – begleitender Glossar in einfacher SpracheKulturelle Vielfalt einbeziehen
prompt Plane eine Sequenz **„Feste im Jahreskreis“** so, dass christliche, jüdische und muslimische Perspektiven gleichwertig vorkommen. Gib drei konkrete Aufgabenbeispiele (interaktiver Wandkalender, Interview mit Familie, „Fest-Box“) und nenne Bewertungsbausteine zur Würdigung kultureller Vielfalt.Mehrsprachigkeit fördern
prompt Zeige Strategien, wie du arabisch-, hebräisch- oder russischsprachige Schüler*innen in das Thema **„Friede in den Heiligen Schriften“** einbeziehst: – zweisprachiger Wortschatz-Trainer – Tandem-Aktivität mit Übersetzer-App – Produktoption „mehrsprachiges Audio-Gebet“Barrierefreier Unterricht
prompt Erstelle einen barrierefreien Ablaufplan für eine 90-min-Sequenz zu **„Luther und die Reformation“** in einer heterogenen Lerngruppe: – Raum-, Material- und Technik-Anpassungen – klare Kommunikationsregeln (z. B. Gebärdensprach-Dolmetsch, Live-Untertitel) – evaluierbare Barrierefreiheits-ChecklisteKapitel 4 · Bewertung & Feedback (im Religionsunterricht)
Prüfungsfragen entwickeln
prompt Formuliere fünf Prüfungsaufgaben zu **„Prophetische Bücher“** (2 Wissen, 2 Transfer, 1 Bewertung). Gib zu jeder Aufgabe Erwartungshorizont & Bloom-Taxonomie-Stufe an.Lernstrategien für Schüler*innen
prompt Erstelle drei konkrete Tipps, wie sich Lernende auf eine Klassenarbeit zu **„Kirchengeschichte – Reformation bis heute“** vorbereiten können (visualisieren | vernetzen | reflektieren).Selbstbewertung anleiten
prompt Entwirf einen Selbstbewertungsbogen, mit dem Oberstufen-Schüler*innen ihre persönliche spirituelle Entwicklung in der Einheit **„Exodus – Freiheit erleben“** reflektieren: – 5 Skalen-Items + offenes Feld – Anleitungs-Text für ehrliche Selbsteinschätzung – Follow-Up-GesprächsleitfadenPeer-Feedback organisieren
prompt Baue ein Peer-Feedback-Setting für das Projekt „Predigt-Podcast zur Nächstenliebe“ auf: • 3-Kriterien-Checkliste (Inhalt, theologischer Tiefgang, Medieneinsatz) • Zeit-Taktung (Aufnahme – Austausch – Revision) • Moderationskarten für konstruktive RückmeldungBewertungsrubrik erstellen
prompt Entwerfe eine 4-stufige Rubrik für das Produkt **„Interreligiöser Video-Essay: Was ist heilig?“** Bewertungsdimensionen: Recherche, Argumentation, Kreativität, Technik. Ordne jeder Stufe klare Deskriptoren & Punktwerte zu.Schnelle Lernüberprüfung
prompt Skizziere eine 3-Min-Exit-Ticket-Abfrage zum Stundenthema **„Auferstehungshoffnung“**: – eine Verständnisfrage, ein Transfer-Impuls, ein persönlicher Bezug – Auswertungsplan (Ampel-Sortierung + Blitz-Feedback an Klasse)Feedback von Schüler*innen einholen
prompt Erstelle fünf Leitfragen, um anonymes Lernenden-Feedback zum Thema **„Sakrale Räume erkunden“** zu sammeln (Aspekte: Klarheit, Relevanz, Methoden, Beteiligung, Wohlbefinden). Schlage ein digitales Tool für die Umsetzung vor und erläutere den Ablauf in 3 Schritten.Kapitel 5 · Digitale Medien & KI (Religionsunterricht)
Interaktive Biblemap erstellen
prompt Lege mit **[Tool: Thinglink / Genially]** eine interaktive Karte biblischer Orte an (Jerusalem, Nazareth, Bethsaida …). – je Ort: Kurzinfo, Bild/360°-Link, passender Bibelvers – Aufgabe: Lernende verknüpfen Geodaten mit Lebensstationen Jesu – füge Reflexionsfragen + Export-Anleitung für das LMS hinzuKI-ChatBot als Lernpartner
prompt Konfiguriere einen KI-ChatBot, der Fragen zu **„Weltreligionen und Umweltschutz“** auf A2–B2-Sprachniveau beantwortet. – Prompt-Engineering-Vorgabe (Rolle, Stil, Quellenzitierweise) – fünf Beispiel-User-Prompts + erwartete Bot-Antwort – Datenschutz-Hinweis & didaktischer EinsatzrahmenBibel-Snap-AR-Filter entwickeln
prompt Entwirf ein Konzept für einen Augmented-Reality-Filter (Instagram/Snap) zu **„Seligpreisungen“**: – visuelle Overlays, Trigger-Events, Soundeffekt – Lernaufgabe: Selfie mit Lieblingsseligpreisung + Kommentar posten – Ethik-Checkliste (Privatsphäre, Bildrechte, Sensibilität religiöser Symbole)Digitales Escape-Game bauen
prompt Plane mit **[Tool: Deck.Toys]** ein digitales Escape-Game „Spuren des Propheten Jesaja“: – Level-Struktur (Prophetie-Puzzle, Quiz, Hidden Object) – win-Condition & automatisiertes Feedback – Export-Code + Anleitung für barrierefreie Version (Screenreader-Labels)Podcast-Serie kuratieren
prompt Stelle eine 4-teilige Schüler-Podcast-Serie **„Gerechtigkeit in Religionen“** auf: – redaktioneller Plan (Themen, Gäste, Bibel/Koran-Bezüge) – Work-Flow (Skript, Aufnahme, Schnitt, Distribution) – Bewertungsrubrik – Inhalt, Technik, DiskursqualitätVirtuelles Museumslabor
prompt Nutze **Mozilla Hubs** und erstelle einen VR-Raum „Symbole des Glaubens“. – Raum-Zonen (Kreuz, Menora, Halbmond, Om) – Lehrer-Dashboard: Moderations-Tools + Sicherheits-Settings – Arbeitsauftrag: Lernende hinterlegen Audiokommentar & Quizfrage pro SymbolKI-gestützte Bildanalyse
prompt Zeige, wie Lernende mit **Computer-Vision-API** ikonografische Motive (z. B. Verkündigungsbild) analysieren: – Schrittanleitung: Upload → Tagging → theologische Interpretation – Vergleich mit manueller Bildbetrachtung – Reflexionsbogen zu Chancen & Grenzen automatischer Deutung
Kapitel 6 · Motivation & Klassenklima (im Religionsunterricht)
Einstieg mit Mystery-Bild
prompt Starte die Einheit **„Exodus“** mit einem rätselhaften Bildausschnitt (gezoomte Wüste, brennender Dornbusch …). – drei Leitfragen zum Rätsel – Ablauf Mystery-Methode (Hypothesen, Puzzleteile, Auflösung) – Brücke zur LernzieltransparenzRitual „Wort des Tages“
prompt Führe ein tägliches Ritual ein: Zufalls-Bibelvers via App, kurze stille Lesephase, spontanes Wort-Cloud-Feedback. – Setup-Anleitung, Regelzeit (3 min), Variationen (Hadith/Zitat) – Reflexion nach vier Wochen (Exit-Ticket-Vorlage)Gamifizierte Punkte-Challenge
prompt Erstelle ein Punktesystem („Faith-Coins“) für vorbildliches Teamwork in Projekten **„Interreligiöser Dialog“**: – Mission-Board, Badges, Level-Belohnungen – klare Regeln (Fairplay, Bonus für Hilfsbereitschaft) – Monitoring-Tool & Schutz vor Wettbewerb-StressAffirmations-Station
prompt Richte im Klassenraum eine „Mut-&-Segen-Station“ ein: – Materialliste (Segen-Karten, Affirmations-Würfel, Kerze) – Nutzung: Start/Ende der Stunde, bei Konflikten – Dokumentiere Wirkung mit anonymem Feedback-PosterKlassensong komponieren
prompt Lass die Klasse einen Song zu **„Nächstenliebe“** schreiben / recorden: – Schrittfolge: Brainstorm–Lyrics–Beat-Making–Recording–Release – Tools (Soundtrap, BandLab, Loop-Bibliothek CC-Lizenz) – Präsentation im Schul-Gottesdienst + Rechte-CheckDankbarkeits-Journal
prompt Implementiere ein wöchentliches Dankbarkeits-Journal nach der Stunde **„Schöpfung bewahren“**: – drei Leitfragen (Wahrnehmung, Wertschätzung, Umsetzung) – Peer-Sharing-Option (freiwillig) – Beobachtung: Einfluss auf Klassenklima (Mess-Skala beilegen)Konfliktlösungs-Circle
prompt Nutze eine Circle-Time nach der Methode „Restorative Justice“ bei Streit um religiöse Themen: – Rollen (Keeper, Sprecher*in, Zuhörer*in) – Gesprächsregeln & Talking-Piece – Nachbereitung: individueller Commitment-Zettel
Kapitel 7 · Spiritualität & Persönlichkeitsbildung
Meditation anleiten
prompt Schreibe ein 10-min-Skript für eine geführte Meditation „Ruhe finden – Psalm 23“, altersgerecht **[Klasse 8]**: – Setting (Sitzhaltung, Musik, Licht) – verbale Anleitung (Ein-, Ausatmen, Bild-Metaphern) – Nachbesprechung (Gefühls-Skala, Bibel-Resonanzfrage)Pilgerweg auf dem Schulhof
prompt Plane einen Mini-Pilgerweg (6 Stationen) zu „Fragen nach dem Sinn“ auf dem Gelände: – Stationstexte + Symbol-Aktion (Stein legen, Wasser berühren …) – QR-Codes mit Audioguide durch Schüler*innen eingesprochen – Reflexionsbogen + Foto-Collage-AufgabeStilles Tagebuch digital
prompt Setze mit **Padlet** ein „Stilles Tagebuch“ auf: – geschlossene Kommentarfunktion – wöchentliches Impulsbild (Ikone, Naturfoto, Calligraffiti) – Lehrkraft-Feedback nur per Emoji-Code, um Raum zu lassenGebetsformen erkunden
prompt Entwickle eine Lernstationen-Werkstatt **„Gebet in 5 Religionen“**: – Materialien: Gebetsriemen, Gebetsteppich, Mala-Kette, Kerzen, Textblätter – QR-Video-Tutorials zu Körperhaltungen – Reflexionsauftrag: Venn-Diagramm Gemeinsamkeiten/VerschiedenheitenSpirituelles Tage-Retreat
prompt Skizziere einen schulischen Tages-Retreat „Stille & Kreativität“ für Oberstufe: – Rhythmus: Meditation – Kreativ-Workshop – Solo-Waldzeit – Sharing-Circle – Logistik (Räume, Materialien, externe Begleitung) – Evaluations-Tool: digitales Mood-BarometerDank-Labyrinth bauen
prompt Gib Anweisungen, wie eine Klasse ein begehbares Dankbarkeits-Labyrinth aus Kerzen/Seilen legt: – Aufbauplan & Sicherheitsregeln – Impulstext „Preis der Dankbarkeit“ (Lk 17, 11-19) – Audio-Begleitung + ZeitplanLebensweg-Timeline gestalten
prompt Lass Lernende eine „Lebensweg-Timeline“ (Canvas / Miro) erstellen, in der spirituelle Schlüsselmomente eingetragen werden: – Anleitung zu Life-Events, Werte, Glaubensfragen – Peer-Coaching-Leitfaden (respektvolle Rückfragen) – Datenschutz-Vereinbarung & Freigabe-OptionenKapitel 8 · Soziale & emotionale Unterstützung (Religionsunterricht)
Emotionale Intelligenz fördern
prompt Entwirf eine 20-min-Aktivität, die Lernende der **[Klassenstufe]** dabei unterstützt, Gefühle mit Psalm-Metaphern auszudrücken. – Warm-up: Emoji-Kärtchen + passender Psalmvers – Partneraustausch „Wann habe ich mich wie König David gefühlt?“ – Mini-Reflexion: Gebets-Haiku (3 Zeilen) ins Klassen-Padlet postenKonfliktlösung interreligiös
prompt Stelle einen 3-Schritt-Leitfaden für Klassengespräche bei Spannungen zwischen religiösen Gruppen zusammen: 1. „Wertschätzungs-Runde“ – jede*r nennt, was er/sie an der anderen Tradition bewundert 2. „Gemeinsamer Kern“ – Bibel-, Koran- oder Tora-Vers zum Thema Frieden lesen, Gemeinsamkeiten markieren 3. „Handlungsplan“ – Klasse legt zwei konkrete Fairness-Regeln festAchtsamkeit mit Psalm 46
prompt Schreibe ein 5-min-Achtsamkeitsskript „Sei still und erkenne Gott“ für den Stundenbeginn: Atem-Anker, Psalmwort wiederholen, 30 Sek. Stille, Abschluss-Frage in Still-Journal notieren.Teambuilding „Vertrau mir“
prompt Plane ein Teambuilding-Spiel, bei dem Partner*innen mit verbundenen Augen durch einen „Weg des Lichts“ aus Kerzen geführt werden. – Sicherheits-Checkliste – Spiritueller Debrief: Johannes 8,12 verknüpfenKrisenintervention – spiritueller Beistand
prompt Erstelle ein 4-Punkte-Handout für Lehrkräfte, wie sie bei plötzlicher Trauer in der Klasse handeln: • Präsenz zeigen – kurze Stille + Kerze entzünden • Offenes Ohr – kein theologisieren, nur zuhören • Ressourcen nennen – Schulseelsorge, Jugendpfarrer*in • Nachsorge – Memory-Box gestaltenSelbstwert stärken (Imago Dei)
prompt Formuliere eine Kreativaufgabe „Ich bin Bild Gottes“: Lernende gestalten ein Self-Portrait-Collage mit Bibel-Affirmationen, kurze Audio-Beschreibung aufnehmen, Gallery-Walk durchführen.Resilienz durch Glaubensgeschichten
prompt Gib einen Arbeitsauftrag, bei dem Schüler*innen eine biblische Figur wählen, deren Lebenskrise sie analysieren (Hiob, Ruth, Josef) und die Strategien auf heutige Situationen übertragen.
Kapitel 9 · Elternarbeit & Zusammenarbeit
Elternbrief „Religiöse Lernwege“
prompt Verfasse einen Elternbrief (max. 300 Wörter), der – das Halbjahresthema **[z. B. Gerechtigkeit in den Propheten]** erklärt – 2 Mitmach-Tipps für zuhause enthält (Familiengebet, Podcast) – QR-Link zur Materialsammlung bietetElternabend – interreligiöse Einheit vorstellen
prompt Erstelle eine Agenda (60 min) für einen Elternabend: • Begrüßung & Gebet der Religionen (5 min) • Lernziele & Methoden-Tour (15 min) • Mini-Workshop „Feste teilen“ (20 min) • Fragen & Feedback-Karten (15 min) • Segen zum Abschluss (5 min)Elternfeedback digital einholen
prompt Gestalte einen 7-Fragen-Forms-Fragebogen: Skalen (1–5) zu: Relevanz, Transparenz, Wertevermittlung, Medienmix + zwei offene Felder „Was lief gut?“ / „Wunsch für nächste Reihe“.Schwieriges Elterngespräch führen
prompt Entwirf einen Gesprächsleitfaden (Sandwich-Methode) für eine Diskussion über fehlende Hausaufgaben im Kontext Glaubensfest-Vorbereitungen.Elternmitarbeit im Projekt „Feste zu Hause“
prompt Skizziere ein Mitmach-Format, bei dem Familien ihre Festtraditionen per Video (max. 2 min) vorstellen; Sammel-Padlet, Klassen-Kompliment-Wand und Auszeichnung „Fest-Botschafter*in“.Familienkommunikation stärken
prompt Gib drei Übungen, wie Eltern religiöse Dialoge anstoßen können: • „Frage des Tages“-Glas • Gemeinsames Dankbarkeitsbuch • Podcast „3 Minuten Bibelimpuls“ beim Abendessen hörenEltern-Kind-Projekt „Heilige Orte“
prompt Plane ein Wochenend-Projekt: Familie besucht lokalen Sakralbau, füllt Reflexions-Worksheet aus, erstellt Foto-Story in CANVA; Präsentation im Unterricht, Peer-Feedback-Kriterien beilegen.
Kapitel 10 · Zeitmanagement & Organisation (Religionsunterricht)
Liturgische To-do-Liste
prompt Erstelle für die nächsten 4 Schulwochen eine Checkliste, die Unterricht, Gottesdienst-Vorbereitung und Schulfest (St. Martin) synchronisiert; inkl. Deadlines & Verantwortliche.45-min-Stundenplan fein takten
prompt Gliedere eine Stunde **[Thema Gleichnisse]** in 5-Min-Blöcke: Warm-up-Rätsel, Kurzimpuls, Gruppenpuzzle, Austausch, Transfer, Mini-Exit-Ticket – plus 2 min Puffer.Unterrichtsstruktur „Flow“
prompt Baue einen wiederkehrenden Ablauf mit kleinen Ritualen: • Ankommens-Kerze (1 min) • Learning Target (Tafel-Icon) • Aktiv-Phase • Stille-Minute • Segen-to-goÜbergänge mit Symbol
prompt Gib 3 Methoden, um Phasenwechsel per Klangschale, Lichtritual oder Vers-Einblendung zu signalisieren – inkl. Schüler-Assistenzplan.Prioritäten im Kirchenjahr setzen
prompt Lege fest, welche Themen vor Weihnachten abgeschlossen sein müssen und welche (Fastenzeit) ins zweite Halbjahr fallen – Schlagwort-Roadmap.Arbeitszeitplan für Lehrkraft
prompt Erstelle einen Wochenplan (Mo–So) mit festen Blöcken: Vorbereitung, Korrektur, Seelsorge-Termin, Me-Time; Ampel-Farbcode für Belastung; Reminder „Sabbat-Abend offline“.
Kapitel 11 · Persönliche Weiterbildung & Reflexion
Selbstreflexion als Religionslehrkraft
prompt Liste 5 Leitfragen (Theologie, Didaktik, Spiritualität, Beziehung, Innovation), die du jedes Quartal schriftlich beantwortest.Fortbildung „KI im Religionsunterricht“
prompt Stelle einen 3-Stufen-Lernpfad zusammen: 1) Online-MOOC (4 h) 2) Praxis-Webinar „Prompt-Design“ (2 h) 3) Kollegiale Umsetzungsschau (90 min) mit Reflexionsbogen. 4) MarkDown für Liascript-LernmodulBurnout-Prophylaxe spirituell
prompt Entwirf eine 7-Tage-Challenge: tägliche 10-min-Stille, Journaling „Segen des Tages“, Digital-Sonnenuntergang (kein Screen nach 21 Uhr) und wöchentlicher Spazier-Psalm.Teamteaching ökumenisch
prompt Gib eine Checkliste für Planung mit einer katholischen Kollegin: gemeinsame Lernziele, liturgische Sprache abstimmen, Rollenverteilung, Reflexions-Debrief.Microteaching „Kurzpredigt“
prompt Lege ein Format fest: 5-min-Mini-Homilie vor Kolleg*innen, Video-Feedback, zweifache Wiederholung nach Feed-Forward-Regeln.Jahresziele setzen
prompt Nutze SMART+LOVE-Schema (L-inked to faith, O-wned, V-alue-added, E-cological) für drei persönliche Entwicklungsziele und definiere Quartals-Checkpoints.Innovation: VR-Pilgerfahrt
prompt Skizziere, wie du in 60 min eine VR-Station an einem Pilgerort testest, Evaluation × 3 (Lerngewinn, Technik, Emotion), Nachbesprechung im Kollegium.Kapitel 12 · Exkursionen & Außerschulisches Lernen
Kloster-Tag organisieren
prompt Plane einen ganztägigen Klassenausflug in ein Benediktiner- oder Zisterzienser-Kloster. – Zeitplan (Laudes-Besuch, Führung, Arbeitsstation, Stundengebet, Gesprächsrunde) – Lernziele (Spiritualität erleben, klösterliche Werte reflektieren, Stille-Erfahrung) – Arbeitsaufträge: Audio-Interview mit Mönch/Nonne, Foto-Essay „Ora et Labora“ – Vor-/Nachbereitung im Unterricht (Vorwissen-Quiz, Reflexionsportfolio)Interreligiöse Stadt-Tour
prompt Entwirf eine dreistündige „House-of-Worship-Tour“ (Moschee – Synagoge – Kirche) für die [Jgst. 9–10]. – Routenplan, Zeiten, Ansprechpartner*innen, Kleidungshinweise – Leitfragen je Stopp (Architektur, Riten, Engagement in der Stadtgesellschaft) – digitale Begleitmap in Google My Maps / Actionbound – Reflexionsprodukt: gemeinsames „Code of Respect“-PosterMuseum der Religionen virtuell
prompt Nutze 3D-Rundgänge von **[Museum X]** und erstelle ein Lern-Webquest „Religiöse Symbole im Wandel“. – fünf Recherche‐Aufgaben mit Zeitlimit – Peer-Review: Padlet-Poster „Top 3 Überraschungen“ – Lehrer-Dashboard: Bewertungskriterien + ZugangslinksPilgerwanderung light
prompt Skizziere eine 8-km-Pilgerstrecke nahe der Schule. – sechs Stationen (Psalm-Rezitation, Naturmeditation, Segenswort …) – Materialliste (Pilgerpass, Stempel, Erste-Hilfe-Set) – Safety-Plan + Elterninfo – Abschluss: Lagerfeuer-Runde „Reiseroute des Herzens“Service-Learning bei der Tafel
prompt Verbinde eine Exkursion zur lokalen Tafel e.V. mit einem vierwöchigen Projekt „Glauben & Teilen“. – Vorbereitung: Arbeitslosigkeit & Almosen in Bibel/Koran – Vor-Ort-Einsatz (2 h Sortieren + 1 h Gespräche) – Reflexion: Rollenkarte „Prophetische Stimme“ – Leistungsnachweis: Podcast-Episode + 360°-Feedback
Kapitel 13 · Ethik & Gesellschaftliche Verantwortung
Bioethik-Debatte führen
prompt Entwirf ein Oxford-Debate-Setting zu **[„CRISPR‐Babys – moralisch vertretbar?“]**. – Rollen (Pro / Contra / Jury) – theologische Argumentationskarten (Imago Dei, Schöpfungsverantwortung) – Bewertungsrubrik (Sachkenntnis, Ethik-Transfer, Dialoghaltung) – Follow-Up-Essay-PromptDilemma-Diskussion „Notlüge“
prompt Stelle ein Fallbeispiel „Notlüge zum Schutz eines Freundes“ bereit. – Fishbowl-Methode mit Beobachtungsauftrag – Transfer-Aufgabe: biblische Szenen verknüpfen (Pharao, Hebammen, (2. Mose 1,15-21)Menschenrechte & Religion
prompt Entwirf ein Stationenlernen (6 Stationen) „Bibel, Koran, UN-Charta“. – Quellentexte, QR-Videos, Kreativ-Station „Art. 1 als Graffiti“ – Zwischentest (Learning Apps) + Exit-Ticket – Reflexion im Wertequadrat (Freiheit – Ordnung)Planspiel „Flucht & Asyl“
prompt Kreiere ein 90-min-Planspiel mit Rollen (Geflüchtete / Grenzpolizei / NGO / Regierung). – Szenario, Rollenbriefe, Event-Cards – Einbettung: biblisches Motiv „Exodus – Fremdsein“ – Debrief-Matrix Gefühle / Fakten / Glaubensimpulse / HandlungsoptionenProphetie heute
prompt Schreibe einen Auftrag: Lernende identifizieren in Medien aktuelle „prophetische Stimmen“ (Fridays for Future, Amnesty) und vergleichen sie mit Amos & Jesaja. – Kriterienraster (Anklage, Vision, Handlungsaufruf) – Präsentation als Insta-Reel oder Infografik
Kapitel 14 · Globale Gerechtigkeit & Nachhaltigkeit
Fair-Trade-Schulaktion
prompt Entwirf ein Projekt „Eine Welt-Kiosk“ (4 Wochen). – Team-Rollen (Einkauf, Werbung, Kassenbuch, Bildung) – theologische Begründung (Mt 25, Jak 5) – Marketing-Plan (Plakat, Schulgottesdienst-Spot, Social-Story) – Impact-Messung (Umsatz, Umfrage, Spendenzweck)Wasser als Menschenrecht
prompt Plane eine Doppelstunde „Durstige Welt“. – Einstieg: symbolisches 1-Liter-Experiment – Textvergleich: Joh 4 (Frau am Brunnen) & Qurʾan 21:30 – Gruppenauftrag: Wasserkampagne für Schul-IG entwickeln – Mini-Debatte: Privatisierung ja/neinKlimagerechtigkeits-Liturgie
prompt Schreibe ein 30-min-Andachtskonzept „Schrei der Schöpfung“. – Psalm 104 als Wechselgesang – Kurzimpuls Laudato si’ §139 – Aktionssymbolik: Erde-Tuch + Saatkorn-Ritual – Call-to-Action-Karte mit persönlichem CO₂-ZielBuddhist Economics vs. Christliche Soziallehre
prompt Erstelle einen Vergleichs-Chart (4 Kriterien) + Diskussions-Prompt: „Welche Wirtschaftsethik braucht die Post-Wachstums-Gesellschaft?“UN-SDGs im Religionsunterricht
prompt Baue eine Lernlandkarte, die jedem SDG einen religiösen Impuls zuordnet. – Tool: Miro-Board Vorlage – Beispiel: SDG 13 ↔ „Garten Eden bewahren“ – Abschlussprodukt: Elevator-Pitch-Video (90 sec) mit Handlungsaufruf
Kapitel 15 · Führung, Engagement & Diakonie
Service-Learning „Senior*innen online“
prompt Plane eine dreiwöchige Aktion: Klasse coacht Senior*innen beim Smartphone-Einsatz. – Vorbereitung: biblischer Impuls „Ehre die Alten“ – Training-Module, Rollenkarten, Feedback-Bogen – Abschluss-Event mit Segens-Ritual & UrkundenSchuldiakonie-Team gründen
prompt Erstelle ein Konzept zur Gründung eines „Diakonie-Teams“ (Kl. 9-12). – Satzung, Rollen (Team-Leads, PR, Fundraising) – Jahresprojekt-Ideen (Suppenküche, Fair-Fashion-Swap) – Mentoring durch lokale KirchengemeindeLeadership-Training „Servant Leader“
prompt Entwirf einen Workshop-Tag (6 h) zu dienender Führung nach Mk 10,45. – Icebreaker, Input-Impulse, Fallstudien-Gruppenarbeit – Reflexions-Matrix „Head-Heart-Hand“ – Zertifikat-KriterienMentoring jüngerer Schüler*innen
prompt Skizziere ein Peer-Mentoring-Programm „Glaubensfragen teilen“. – Matching-Prozess, 5-Treffen-Guide, Gesprächs-Kärtchen – Evaluations-Tool (Mentor/Mentee-Feedback)Charity-Kampagne „Licht teilen“
prompt Entwerfe einen 14-tägigen Schul-Spendenlauf zugunsten eines Solarprojekte in Afrika. – theologische Rahmung („Ihr seid das Licht der Welt“) – Sponsoring-Formular, Social-Media-Challenge, Andacht zur Eröffnung – Ergebnis-Präsentation: Weltkarte + Dank-Video der Partner-NGO
Kapitel 16 · Theologie & Popkultur
Biblische Motive in Superhelden-Filmen
prompt Erstelle eine Analyse-Aufgabe zu [Film: „Spider-Man No Way Home“]. – Szenenauswahl, Leitfrage (Opfer & Erlösung) – Arbeitsblatt „Parallele zu Christusfigur?“ – Präsentationsformat: Meme-Collage oder Re-cut-TrailerTikTok-Mini-Predigt
prompt Schreibe einen Prompt, mit dem Lernende eine 60-Sek-TikTok-Predigt zu **[Seligpreisung X]** produzieren. – Hook, Kernvers, Call-to-Action – Hashtag-Liste, Musik-Snippet (lizenzfrei) – Feedback-Rubrik (Klarheit, Kreativität, theol. Tiefe)Rap-Battle Altes vs. Neues Testament
prompt Plane ein Klassen-Rap-Battle „Gesetz vs. Gnade“. – Beat-Auswahl, Battle-Regeln, Reim-Worksheet – Peer-Jury-Bögen (Flow, Inhalt, Punchline, Respekt) – Reflexion: Gal 3,24 & Mt 5,17 im PlenumGaming-Theologie
prompt Erstelle einen Analyse-Prompt für **[Game: „The Last of Us“]** zum Thema „Opfer‐Liebe & Moral“. – Level-Szenen, Diskussionsfragen, Vergleich mit Joh 15,13 – Creative Option: Alternative Ending StoryboardPlaylist „Psalmen im Pop“
prompt Gib Auftrag, eine Spotify-Playlist moderner Songs mit Psalm-Resonanzen zu kuratieren (mind. 8 Titel); jeder Track mit Mini-Annotation (30 Wörter).Kapitel 17 · Interreligiöser Dialog & Diversity
Fishbowl Diskussion
prompt Organisiere eine Fishbowl Diskussion zu **„Gemeinsame Werte in Judentum, Christentum & Islam“**. – Rollen: 3 Sprecher*innen je Religion, 2 freie Stühle, Außenkreis – Leitfragen (Würde, Barmherzigkeit, Gerechtigkeit) – Beobachtung Grid für Außenkreis (Argument, Emotion, Bezug Schrift) – Debrief: Gemeinsamkeiten clustern, Differenzen respektvoll festhaltenInterfaith Panel
prompt Plane ein Schüler*innen-Panel mit Vertreter*innen von 4 Religionen. – Ablauf: Lightning-Talks (5 min) → moderierte Fragerunde → World-Café – Vorbereitungs-Worksheet: „Meine Frage an…“ – Reflexions-Blogpost (200 Wörter) als LeistungsnachweisDialog-Café
prompt Richte ein „Religions-Café“ ein (Tische: Feiern, Gebet, Kleidung, Essen). – Tisch-Hosts mit Quick-Facts-Karten – 10-min-Runden, Timer-Gong – Abschluss: Murmelrunde „größte Überraschung“ + Mentimeter-WordcloudScripture Speed-Dating
prompt Lass Lernende in 5-min-Runden je einen Vers vorstellen (Bibel, Koran, Tanach, Bhagavad Gita) zu **„Frieden“**. – Vorlage: Vers, Kontext, eigene Frage – Rotation, Feedback-Sticker, Ranking „Vers der Stunde“Konflikt-Simulation
prompt Erstelle ein Planspiel „Bau neuer Gebetsraum an der Schule“. – Stakeholder-Briefe: Schüler*innenrat, Eltern, Stadt, Religionsgemeinschaften – Verhandlungs-Phase, Presse-Konferenz, Kompromiss-Paper – Reflexion: Goldene Regel & GG Art. 4Shared Values-Collage
prompt Auftrag: Gruppe erstellt Digi-Collage „Das verbindet uns“ (Canva). – Mind-Map-Start, Bild-Recherche CC-Lizenz, Zitat-Overlays – Poster-Walk, Peer-Voting via KlebepunkteAmbassador-Projekt
prompt Jede*r Schüler*in wird „Religion-Ambassador“ für eine Tradition. – 3 Recherche-Aufträge, 1 Interview, TikTok-Summary (60 s) – gemeinsame Auswertung im Padlet-Cluster (Riten, Ethik, Symbolik)
Kapitel 18 · Liturgie & Gottesdienstgestaltung
Schüler-Gottesdienst planen
prompt Entwirf einen 30-min-Schulgottesdienst zum Thema **„Hoffnung“**. – Liturgischer Ablauf (Begrüßung, Lied, Lesung, Aktion, Segen) – Rollen-Matrix (Musik-Team, Technik, Predigt-Crew) – Checkliste für Inklusion (Gender-Sprache, Barrierefreiheit)Digitaler Live-Stream
prompt Erstelle ein Setup für einen gestreamten Advents-Impuls. – Technik-Schema (OBS, Kamera, Mikro, YouTube Link) – Einbindung interaktiver Chat-Fragen – DSGVO-Hinweise & Moderations-PlanSymbolischer Raum
prompt Gestalte einen „Raum der Klage“ in der Aula (Fastenzeit). – Bodenbild Asche-Kreuz, Kerzen-Spirale, Gebets-Box – Ablauf 10-min-Stationengang, Audio-Loop Psalm 130 – Sicherheits- und Aufsichts-PlanPsalm-Rap Worship
prompt Leite eine Klasse an, Psalm 23 als Rap vorzutragen. – Beat-Template, Vers-Aufteilung, Refrain-Hook – Recording mit BandLab, EQ-Preset „Worship Lo-Fi“ – Live-Performance im Gottesdienst + Lyric-VideoTaizé-Abend
prompt Konzipiere eine 25-min-Taizé-Andacht (Kerzen-Kreuz, repetitives Lied, Stille). – Liedauswahl (Laudate omnes gentes / Ubi caritas) – Ablauf-Kärtchen, Gitarren-Akkorde, zweisprachiges GebetSegnungsfeier
prompt Entwirf eine Segnungsfeier für Abschluss-Klasse. – Ritual: Hand-auf-Schulter, persönliches Segenswort, Kreuzzeichen – Musik-Cue, Fotopunkt, Give-away „Segen-To-Go“-KarteLiturgischer Kalender Smartboard
prompt Erstelle eine interaktive Smartboard-Tafel mit Festfarben, Symbolen, Liedvorschlägen; Drag-&-Drop-Quiz „Ordne das Fest!“
Kapitel 19 · Kreatives Schreiben & Kunstprojekte;
Psalm-Haiku
prompt Auftrag: Schreibe zu einem ausgewählten Psalmvers drei Haikus. – Struktur 5-7-5, Bildsprache beibehalten, persönlicher Twist – Audio-Aufnahme mit Regen-Ambience, Upload in NostrGraphic-Novel-Bibeltext
prompt Lass Lernende **Mk 2,1-12** als 8-Panel-Comic umsetzen. – Storyboard-Template, Sprechblasen, onomatopoetische Effekte – Peer-Review „Lesbarkeit & Theologie“Poetry-Slam Propheten
prompt Organisiere einen Slam-Abend „Stimme der Gerechtigkeit“. – Textlänge 3 min, Requisite erlaubt – Jury-Bögen (Wortkraft, Performance, Forderung) – Streaming-Option + Publikums-VotingIkonen-Workshop
prompt Führe 90-min-Workshop „Jesus-Ikone in Acryl“ durch. – Schrittfolge: Holzgrund, Goldbogen, Proportions-Raster, Lasur – Theologischer Input zur Ikonen-Theologie, Stille-PhaseKalligrafie-Schriftrolle
prompt Gestalte mit der Klasse ein 2 m langes Pergament „Selig sind…“. – Material-Liste, Pinsel-Technik, Farbsymbolik – Ausstellung im Schulflur + QR-Code-Making-OfParabel-Comic-Strip
prompt Team erstellt 4-Panel-Webcomic zur Parabel „Verlorener Sohn“. – Stil wählbar (Manga, Indie, Minimal) – Upload auf Schul-Insta, Hashtag-ChallengeGemeinschafts-Mural
prompt Plane ein Wandbild „Regenbogen-Bund“. – Entwurfs-Workshop, Schablonen, Schulfest-Live-Painting – Reflexion: Farbe als Zeichen der Verheißung
Kapitel 20 · Bibliodrama & Rollenspiel
Bibliodrama-Setting
prompt Leite ein 60-min-Bibliodrama zu **„Emmaus-Jünger“**. – Rollen-Zuweisung, Körper-Statue, Resonanz-Runde – Transfer: „Wann brannte unser Herz?“ JournalingHot-Seat-Interview
prompt Schüler*in im „heißen Stuhl“ antwortet als Paulus. – Vorbereitungs-Kärtchen (Biografie, Missionsreisen, Konflikte) – Audience-Fragen, Reflexion: Differenz Fakten / FantasieKonzil von Jerusalem
prompt Rollenspiel: Apostel vs. Pharisäer über Heiden-Mission. – Positions-Papers, Moderations-Hammer, Mehrheits-Vote – Debrief: Gal 2 & Apostelgeschichte 15 vergleichenModerne Parabel
prompt Gruppen schreiben & spielen eine heutige Version der „Barmherzigen Samariter“ in 5 Szenen (E-Scooter-Unfall).Forum-Theater Mobbing
prompt Setze Forum-Theater nach Boal ein: Szenario „Religiöses Cyber-Mobbing“. – Stop-Signal, Zuschauende als Joker, Lösungs-Ideen ausprobierenFreeze-Frame Auferstehung
prompt Klasse stellt in drei Standbildern Karsamstag – Ostermorgen – Emmaus dar. – Foto-Shooting, Bild-Analyse „Gefühle im Raum“Impro-Dilemma-Box
prompt Sammle ethische Dilemmata, ziehe zufällig, spiele 2-min-Impro-Szene, Klasse bietet Lösungswege; Bibel-Matching als Abschluss.Kapitel 21 · Wissenschaft & Forschung im RU
Empirische Unterrichtsstudie planen
prompt Skizziere ein Forschungsdesign (Mixed-Methods) zur Frage, ob Storytelling die Bibeltextkompetenz in **[Klassenstufe]** steigert. – Hypothese, Stichprobe, Instrumente (Pre-/Post-Test, Fokusgruppe) – Zeitplan 8 Wochen, Ethik-Check, Auswertungs-Software – Reflexionsauftrag für Schüler*innen nach AbschlussUnterrichtsbeobachtung per Video
prompt Erarbeite einen Leitfaden für Videografie im RU: – Kameraposition, Datenschutzinfo, Einverständnisbogen Eltern – Codierschema (Interaktion, Fragearten, Wartezeit) – Analysetools (ELAN, Vosaic) + Reporting-TemplateStatistik zur Religiosität erheben
prompt Entwirf einen 12-Items-Fragebogen (Likert 1–5) zu „Glaubenspraxis Jugendlicher“. – Themen: Gebet, Gottesdienst, Mediennutzung, Zweifel – Pre-Test auf Verständlichkeit, Cronbach-α-Ziel > 0,75 – Prompt für ChatGPT: „Generiere Item-Analysen & Visualisierung“Literaturreview KI im RU
prompt Formuliere einen Prompt, der ChatGPT auf Deutsch ein systematisches Review der letzten 5 Jahre (2020-25) erstellt: – Suchstrings, Inclusion-Criteria, PRISMA-Flowchart – Output-Struktur Abstract → Ergebnisse → Lücken → Ausblick
Kapitel 22 · Historisch-kritische Bibelarbeit
Textkritischer Einstieg
prompt Lass Lernende **Mk 16, 9-20** mit Nestle-Aland-App untersuchen: – Auftrag: Textvarianten markieren, Randnotizen vergleichen – Diskussionsfragen: Kanon, Inspiration, Relevanz heutiger AusgabenQuellenhypothese entdecken
prompt Plane eine Gruppenpuzzle-Einheit zur Zwei-Quellen-Theorie. – Expertentexte (Mk, Q-Hypothese, Sondergut Mt/Lk) – Produkt: Info-Poster „So entsteht ein Evangelium“ – Checkliste: redaktionelle Merkmale finden, SchlussdiskussionFormgeschichte kreativ
prompt Organisation einer „Formgeschichte-Gallery“: – Teams inszenieren Witzwort, Wunder, Streitgespräch als Meme, Reel, Podcast – Gallery-Walk, Peer-Rubrik „Gattungsmerkmale getroffen?“Exegese-Prompt
prompt Erstelle einen Prompt, der eine KI eine Mini-Exegetische Analyse (Setting, Form, Sit-in-Leben, Theologie, Rezeption) zu jeder Bibelperikope liefert; begrenze Ausgabe auf 300 Wörter.
Kapitel 23 · Krisenseelsorge & Notfallpädagogik
Notfall-Handlungskette
prompt Stelle ein One-Pager-Schema für Krisenfälle (Tod, Suizidgedanken) zusammen: 1) Wahrnehmen & Sichern · 2) Kollegium informieren · 3) Eltern/Profis einbinden · 4) Nachsorge – Telefonnummern (Schulpsychologe, Krisendienst) freilassend eintragenTrauerritual gestalten
prompt Entwirf ein 15-min-Ritual „Licht der Erinnerung“ für die Klasse: – Mitte-Kreuz, Namenskärtchen, Kerzen-Aufstellung, Psalm 34,19 – Raummusik-Vorschlag, Leitfragen stille Reflexion, optionaler SegenPsychoedukation „Angst“
prompt Bau eine 45-min-Einheit Angstbewältigung mit Psalm 91 & Atem-Techniken. – Theorie-Input, Körperübung 4-7-8-Atmung, Bibelvers-Affirmation – Exit-Ticket „Meine Angst-Skillbox“ (3 Ideen)Peer-Support-Netzwerk
prompt Skizziere ein Schulkonzept „Schüler-Seelsorge-Team“. – Auswahl-Prozess, 3-tägige Grundschulung (Aktives Zuhören, Schweigepflicht) – Supervision, Öffentlichkeitsarbeit, Evaluationsbogen
Kapitel 24 · Schulkooperation & Öffentlichkeitsarbeit
RU-Blog aufsetzen
prompt Gib Schritt-für-Schritt-Anleitung (WordPress): Theme-Auswahl, Kategorien (Impulse, Projekte, Schüler-Gastbeiträge), DSGVO-Plug-ins, Redaktionsplan 3-Monats-Sicht; Prompt für KI-Bilder (Stable Diffusion) inkl. Lizenz-CheckMedien-Pitch
prompt Formuliere ein 200-Wörter-Pressestatement für die Lokalzeitung über die Aktion **„Eine-Welt-Kiosk“** (Kap. 14). Inklusive Quote einer Schülerin & Spendenstand.RU-Tagung hosten
prompt Erstelle ein Ablaufskript für eine regionale RU-Fachtagung (5 h): Keynote „KI & Theologie“, 3 Workshops, Poster-Session, Abschlussandacht. – Raum-Plan, Technik-Check, Catering-ZeitslotsPartnerschule international
prompt Skizziere ein eTwinning-Projekt mit einer Schule in **[Land]** Thema „Speisen & Fasten in unseren Religionen“. – Timeline 6 Monate, Tools (TwinSpace, Padlet, Canva) – Produkte: gemeinsames Koch-E-Book, virtuelle FastenkalenderSocial-Media-Strategie
```prompt Entwirf für den RU-Instagram-Account eine 4-Wochen-Content-Map:
MondayMotivation-Vers, Mini-Reel „Bibel in 30 sec“, Umfrage-Sticker,
Takeover der Klasse 9, Hashtag-Liste, Insights-KPI-Ziel (Engagement 5 %) ```
Kapitel 25 · Bibelsprachen & Übersetzung
Hebräisch-Crashkurs
prompt Erstelle ein 4-Stunden-Modul „Bibel-Hebräisch für Einsteiger*innen“. – Alphabet lernen (Poster + Audio-Übung) – 10 Schlüsselwörter (שָׁלוֹם, חֶסֶד …) inkl. Lautschrift & Bedeutung – Mini-Auftrag: Psalm 23,1 in Lautschrift abschreiben & übersetzen – Abschluss-Quiz (Matching hebr. Wort ↔ dt. Bedeutung)Griechisch des NT entdecken
prompt Plane eine Doppelstunde „Koine-Griechisch lesen lernen“. – Einstieg: Griechisches Alphabet-Rap (YouTube-Link) – Textarbeit: Joh 1,1-5 Parallel-Kolumne (griech./dt.) – Analyseaufgabe: Verben im Aorist markieren, Bedeutungs-Shift diskutieren – Reflexion: Welche Nuancen gehen in Übersetzungen verloren?Septuaginta-Vergleich
prompt Lass Lernende Gen 1,1-5 in Hebräisch, LXX-Griechisch & Luther-Übersetzung nebeneinander legen. – Auftrag: drei semantische Unterschiede identifizieren – Visualisierung: T-Diagramm „Wortwahl vs. Theologie“ – Transfer: Warum sind Übersetzungen theologische Entscheidungen?Übersetzer-Werkstatt
prompt Baue ein Gruppenprojekt „Übersetze dein Lieblingsgleichnis“. – Schrittfolge: Wort-für-Wort-Entwurf → Dynamic-Equivalent-Entwurf → Peer-Review – Kriterienraster (Genauigkeit, Lesbarkeit, Stil, Theologie) – Produkt: zweispaltiges Booklet mit KommentarKI-gestützte Translation
prompt Schreibe einen Prompt, der GPT für dich eine Roh-Übersetzung von Ps 121 liefert, dann bitte um Stil-Varianten (jugendlich, liturgisch, poetisch) und gib eine Checkliste, wie Lernende die Vorschläge kritisch prüfen.
Kapitel 26 · Religion & Naturwissenschaft
Big Bang vs. Schöpfung
prompt Entwirf eine Debatte „Urknall und Genesis – Widerspruch oder Ergänzung?“. – Rollen: Naturwissenschaftler*in, Theolog*in, Schülerjury – Input-Material: Video-Clip CERN, Bibeltext Gen 1,1-5, Zitat Georges Lemaître – Bewertungsrubrik: Argumentationslogik, Quellenbezug, DialogfähigkeitEvolution & Glaube
prompt Plane eine Stationsarbeit (5 Stationen) „Genesis 2 trifft Darwin“. – Inhalte: Fossilien-Puzzle, Gen 2 Lese-Rallye, Clever-Trees Simulation … – Reflexionsbogen: Conflict-/Independence-/Integration-Modell – Ergebnis: persönliches Statement-PadletKlimaphysik meets Theologie
prompt Kreiere ein Co-Teaching-Szenario RU + Physik „Treibhaus & Treue zur Schöpfung“. – Experiment CO₂-Flaschen-Test (Physik) – Bibelimpuls Ps 24,1; Laudato si’ §23 (RU) – Gruppenauftrag: Infografik „Physik-Fakten ↔ prophetischer Auftrag“Neurotheologie light
prompt Schreibe einen 20-min-Impuls „Was passiert im Gehirn beim Beten?“ – Erkläre Begriffe (präfrontaler Cortex, Salience Network) vereinfacht – Diskussionsfrage: Macht das Beten weniger heilig? – Mini-Aktivität: 2-Min-Stille + Emotions-ThermometerKI als Schöpfungswerkzeug?
prompt Formuliere einen Pro-/Contra-Debatten-Prompt: „Darf der Mensch mittels KI neue Lebewesen designen – übertritt er damit eine göttliche Grenze?“ Gib vier Leitthesen je Seite und einen Auswertungsbogen (Sachargument / Ethik / Empathie).
Kapitel 27 · Musik & Klang im Religionsunterricht
Bibel-Beat-Lab
prompt Auftrag: Sample drei Bibel-Verse (mp3-Clips) und baue daraus einen 90-sek-Beat. – Tool-Tipp: Soundtrap Spur-Template – Lernziel: Text + Sound = Verkündigung 2.0 – Präsentation: Klassen-Listening-Session + VotingGregorianik erleben
prompt Plane eine Mini-Exkursion in eine Abtei oder Kloster (oder Video-Visit). – Vorab-Auftrag: Was macht gregorianischen Choral einzigartig? – Vor Ort: Klangtagebuch (Geräusch-Beschreibungen, Gefühle) – Nachbereitung: Vergleich Worship-Song vs. ChoralPsalm-Pop-Mashup
prompt Gib Lernenden den Prompt „Mixe Psalm 91 mit aktuellem Pop-Hit“. – Schritte: Lyrics Sheet erstellen, Hook identifizieren, Mashup-Regeln – Reflexion: Stößt Pop-Kultur die Sakralität ab oder erweitert sie sie?Klangschalen-Liturgie
prompt Erstelle ein 15-min-Stille-Ritual mit Klangschalen & Taizé-Ostinato. – Ablauf: Atem, Anschlag-Sequenz, 2-min-Stille, gesungene Antwort – Sicherheits-Hinweis für sensible Lernende (Trigger)Sound-Walk Schöpfung
prompt Skizziere einen 30-min-Außen-Sound-Walk: – Stationen: Wasser, Wind, Tiere, Stadtlärm → jeder Klang mit Gen 1-Vers verknüpfen – Auftrag: Audio-Notizen aufnehmen, hinterher Collage basteln
Kapitel 28 · Bilingual / CLIL Religious Education
Lesson Plan „Parables“ (EN)
prompt Create a 45-minute CLIL lesson on **“The Good Samaritan”** (Englisch + Religion). – Objectives: vocabulary (compassion, neighbour), ethics debate, creative output – Activities: video clip, jigsaw reading, freeze-frame role-play – Assessment: exit ticket sentence-transformationsTerminology-Toolkit
prompt Compile a glossary (20 terms) for Grade 9 bilingual unit “Creation & Stewardship”. – Columns: EN term, DE equivalent, easy definition, sample sentence – Prompt: Generate flash-cards in Quizlet automaticallyBilingual Assessment
prompt Design a rubric for a bilingual podcast “Faith & Science”. – Criteria: Content depth, language accuracy (B1-B2), creativity, reflection – 4 levels, score-bands, comment spaceCross-curricular Project
prompt Outline a 3-week CLIL project with Biology “Water in the Bible & Ecology”. – Milestones: joint field trip, water-testing, theological collage – Final product: bilingual exhibition brochure (digital + print)Teacher-Prompt for AI
prompt Write an English prompt that asks ChatGPT to simplify Isaiah 11,6-9 to CEFR A2 level and suggest three comprehension questions.
Kapitel 29 · Religionsunterricht in der Grundschule
Erzählsäckchen „Zachäus“
prompt Plane eine 30-min-Erzählrunde mit Erzählsäckchen: Figuren, Baum-Ast, Münzen. – Ablauf: Bodenbild, Erzählen, Mitmach-Aktion „Kletterbaum“, Abschluss-Gebet – Differenzierung: Piktogramm-Fragen für Leseanfänger*innenGott im Alltag entdecken
prompt Stell eine Wochen-Hausaufgabe „Gottes-Spuren“: – Kinder fotografieren einen Moment, der sie an Gott erinnert – Präsentation als Galerie, drei Satzanfänge „Ich staune, weil …“Psalmen malen
prompt Lass Klasse 2 Ps 136,1 in Fingerfarben malen. – Schritt-für-Schritt, Farb-Symbolik, Trockenstation – Klassen-Ausstellung + Eltern-EinladungRuhe-Insel einrichten
prompt Richte eine Lese-Kuschel-Ecke „Stille mit Gott“ ein. – Ausstattungsliste (Kissen, Bibelbilderbuch, Sanduhr) – Regeln (max. 2 Kinder, Flüsterstimme) – Reflexions-Stern „Wie fühle ich mich jetzt?“Mini-Gottesdienst Advent
prompt Entwirf einen 15-min-Klassen-Adventsimpuls „Licht teilen“. – Lied „Tragt in die Welt nun ein Licht“, Kerzenkreis, Fürbitten-Stern – Eltern-Einbindung: Wunsch-Engel zu Hause basteln
Kapitel 30 · Prüfungsformate & Abiturvorbereitung
Klausur-Pool
prompt Erstelle drei klausurreife Aufgaben zu „Reich-Gottes-Botschaft Jesu“. – Typ A Textanalyse Mk 4,26-29 – Typ B Synopse Sachurteil „Jetzt-Schon / Noch-Nicht“ – Typ C eigenes Werturteil zu Papst Franziskus, Evangelii Gaudium §183Mündliche Prüfung trainieren
prompt Plane ein Speed-Dating-Setup: 6 Themen, 6 Tische, 4 min Rede / 2 min Fragen. – Prüfungsraster (Sachkenntnis, Argument, Transfer, Sprache) – Reflexions-Protokoll nach jeder RundePortfolio fürs Abitur
prompt Gib Anweisungen für ein semesterbegleitendes Portfolio (digitale Mappe). – Pflicht-Artefakte: Exegese, Lernjournal, Debatten-Video, Service-Learning-Log – Selbst-Assessment-Rubrik, Peer-Feedback-Slot, Abgabe-ChecklistePräsentationsprüfung
prompt Erstelle eine Themenliste (10 Vorschläge) für das 15-min Präsentationsabitur Schwerpunkt „Religion & Digitale Gesellschaft“ + Leitfragen & Quellen-Hint.Crash-Kurs Wiederholung
prompt Schreibe einen 5-Tage-Wiederholungsplan (je 90 min) vor Abitur: Tag 1 Bibel, Tag 2 Kirchengeschichte, Tag 3 Ethik, Tag 4 Ökumene/Weltreligionen, Tag 5 freie Lücken. – Lernmethoden: Mind-Map, Karteikarten-Battle, Kahoot-Turnier, Silent DebateKapitel 31 · Digitale Prüfungsformate & Learning Analytics
Auto-Graded Quiz
prompt Erstelle mit **[Tool: H5P / Moodle]** ein 15-Fragen-Quiz zu „Bergpredigt“. – Fragetypen: Multiple Choice, Drag-Text, Hotspot Bild – je Frage: Bibelvers-Verweis & Feedback-Text – Export-Anleitung SCORM + Barrierefrei-ChecklisteKI-Feedback-Generator
prompt Schreibe einen Prompt, mit dem ChatGPT eingereichte Essays („Gleichnisse Jesu aktualisieren“) in 3 Kriterien bewertet (Inhalt, Argument, Stil) und spezifische Verbesserungstipps gibt.Learning-Analytics-Dashboard
prompt Skizziere ein Dashboard-Konzept (Power BI / Google Data Studio): – KPIs: Quiz-Score, Bearbeitungszeit, Fehlerschwerpunkte – Ampel-Visualisierung für Frühwarnsystem – Datenschutz-Hinweis & Elternreport-VorlageE-Portfolio-Abgabe
prompt Formuliere Anforderungen für ein digitales Semester-Portfolio (OneDrive / Nextcloud): Ordnerstruktur, Metadaten, Reflexions-Rubrik, Selbst-freigabe Mechanismus für Peer-Review.Audio-Kurztest
prompt Entwirf einen 5-min-Sprachmemo-Test: Schüler*innen fassen eine Psalmstelle verbal zusammen; Lehrkraft erhält Auto-Transkript + KI-Schlüsselwort-Check.
Kapitel 32 · Visuelle Medien & Film-Interpretation
Bibel-Film-Clip analysieren
prompt Wähle eine 3-min-Sequenz aus **[Film: „Prince of Egypt“]** und gib Analyse-Auftrag: filmische Mittel, theologische Aussage, Vergleich mit Exodus-Text; Ergebnistyp: 1-seitiges Slide-Deck.Storyboard « Modern Exodus »
prompt Auftrag: Erstelle ein 6-Panel-Storyboard, das die Exodus-Narrativ in heutige Flüchtlingsroute überträgt. – Panel-Beschreibung, Dialogschnipsel, KamerawinkelMicro-Dokumentation
prompt Plane ein 90-sek-Dokuvideo „Fasten in drei Religionen“. – Shot-List, B-Roll, O-Ton Interview, Creative-Commons-Musik – Abgabe-Specs: 1080p, Untertitel srt, Thumbnail-BriefingFilm-Debatte
prompt Richte eine Pro/Contra-Debatte ein: „Zeigt *Noah* (2014) biblische Wahrheit oder Hollywood-Fiction?“ – Vorbereitungskärtchen (Gen 6-9, Regie-Interview) – 4-Kriterien-Scorecard (Fakten, Ethik, Rhetorik, Quellen)GIF-Theologie
prompt Gib Lernenden den Auftrag, einen 3-s-GIF zu „Auferstehungshoffnung“ zu erstellen; Plattform Canva; Begleittext max. 50 Worte.
Kapitel 33 · Achtsamkeit & Mental Health
Breath-Prayer Session
prompt Schreibe ein 8-min-Script „Jah-weh-Atmung“ (Ein-Aus-Silbe) für Stundenbeginn; inkludiert Ruhe-Timer & Exit-Frage „Wie fühlst du dich?“Angst-Toolbox
prompt Erstelle eine 4-teiliges Arbeitsblatt „Psalm 27 vs. Prüfungsangst“: 1) Trigger identifizieren 2) Vers als Selbst-Talk 3) Grounding-Übung 4) Peer-Buddy-Check-In.Digital Detox Challenge
prompt Formuliere eine 48-h-Offline-Challenge basierend auf Ex 20,8-11 (Sabbatgebot); Tracking-Tabelle, Reflexionsfragen, gemeinschaftliches Abschluss-Gebet.
-
-
 @ df9150e8:4b224b13
2025-05-20 19:16:06
@ df9150e8:4b224b13
2025-05-20 19:16:06Small Business & Bitcoin - Month 1 - April Update
This letter is meant to be a month by month reflection and live interaction of starting and building a bitcoin treasury for your small business. It is my belief that a bitcoin treasury will expand the runway and viability of any profitable cash flowing small business. It is a stealthy and discrete way to extend the value and worth of your small business.
It is becoming more and more obvious that cash on a balance sheet is melting away due to record high inflation rates. A bitcoin treasury is your best weapon against high inflation and it has consistently and reliably outpaced inflation since inception.
Another benefit to a bitcoin treasury is reshaping your mindset around bitcoin being the hurdle rate for your small business. Bitcoin has a 10 year CAGR of 84%. And while that is likely to shrink over the coming 10 years, we still expect it to exceptionally outperform any other treasury asset. With that in mind, you need to look at the outgoing dollar within your business. Any dollar spent that can’t return you better than 84% may be likely best served in your bitcoin treasury.
So the goal of this letter is simple: I will be building an outline and example in real time and month by month on how to build your bitcoin treasury within a small business. I will be detailing the process in these monthly essays for my reflection and your consumption. If you are reading this, you’ve probably seen what Michael Saylor and Strategy have done in the public markets. They have created the playbook for public bitcoin treasury. We are going to detail the process for your average mom and pop business.
The Playbook
To start this writing, I am going to give you the exact methods we will be taking to acquire our bitcoin as well as the exact % and amounts of bitcoin added to the treasury. We are starting on zero. What I mean by that is that as of now we will not be lump summing any cash into bitcoin from our balance sheet. We will likely do that down the road, but not something we are doing today. We are going to start by averaging 10% of monthly profit into bitcoin.
You may think this amount is too conservative. I tend to agree. My plan is to put something together that is repeatable and conservative at the start. We are going to add 10% of profits to a bitcoin balance each month for a few months and evaluate. Our goal is to increase the % allocation after the first few months. We are starting conservative because other businesses (and ours) need to operate without that 10% and make sure we can adapt. Once we’ve done that we slowly continue to increase the allocation until we reach optimal % allocations.
In addition to simply purchasing bitcoin, we’ve switched to a bitcoin back debit card. This means that every transaction (marketing, bill pay) I am getting anywhere from 1% to 1.5% back in bitcoin. While this will be a marginal way to stack bitcoin, every little bit counts and this helps us add to our stack. If we believe that bitcoin has another 10X increase in fiat price over the coming years then this will prove to make everything cheaper in the long run as the bitcoin back we collect will be increasing in value for years to come. What 1.5% is now could end up being 15% off in a few short years. Any small business owner knows that your margins are everything and giving us this edge in our margin is a huge thing for business owners.
Our Treasury
We began stacking mid April so we don’t have a full month of stacking yet. Based on our few weeks of stacking our current treasury as of May 12, 2025 looks like this:
Stacked through purchasing: 905,336 sats = $918
Stacked through bitcoin back card = 183,281 sats = $190.72
Total Bitcoin = 1,088,617 sats = $1,108.72
Important To Note:
Current price of bitcoin when writing = $101,871.10 per coin.
“Sat” is the smallest unit of a bitcoin.
1 million sats = 1% of owning a whole bitcoin
Our Treasury Strategy (Expanded):
Purchasing Bitcoin via business profits
We are starting at what we believe will be the most conservative allocation towards bitcoin that we will have. 10% should affect our (and hopefully most) operating business very little. We are starting in the most conservative way so that other small businesses can see this and hopefully make these very minor but achievable allocations into bitcoin.
Each month I will look at our net profit and then take 10% of it and purchase bitcoin. We will store all of our bitcoin on a multi sig hardware wallet and continue to track the proceeds here publicly.
In the future (as mentioned above) we will continue to raise the % of net profit allocated towards bitcoin. We want to acquire bitcoin as rapidly and violently as possible. We will need a much greater than 10% allocation to do that. We will likely reevaluate after month 3 and see if it is time to increase the % allocation.
This is also a great encouragement to all small businesses to get creative with sales and marketing to boost your bottom line. Since the % allocation is fixed, we have to earn more profit in order to purchase more bitcoin. Obviously, the best way to maximize bitcoin stacked each month is eventually getting to peak % allocation and continuously maximizing and setting new monthly highs with profit in the business.
As much as we love bitcoin, this allows us to spend the bulk of our time focused inward on our business. The more improvements we can make then, in theory, the more bitcoin we should be able to put in our reserves. This is also a great encouragement to business owners to really dig in and slash all waste within the business. What are we paying for/spending money on that is a waste or at the very least non essential to operations. It can also allow us to audit our way of doing things to ensure everything we do is being done in the most efficient way possible. A lean and profitable business is one that can stack more bitcoin.
Getting bitcoin via a bitcoin back debit card:
This is the 2nd way that we will add bitcoin to our balance sheet as a treasury asset. This debit card works just like a reward credit card. We spend money on it and are instantly rewarded with 1% to 1.5% bitcoin back. This bitcoin is added directly to a wallet linked to our debit card and can be withdrawn to the main wallet.
While this will not be our most powerful driver in stacking bitcoin, It will certainly increase our bitcoin holdings over time as opposed to not using it. It kind of works from the opposite end of the spectrum. Purchasing bitcoin through our profits is a great offensive way to buy bitcoin. Getting bitcoin back from our debit card purchase is a great defensive way to stack bitcoin as it decreases our cost of goods sold with every purchase. As we spend on marketing, pay our taxes, upgrade equipment, or sign up for a new subscription that will help the business, we will be earning bitcoin back on all of those purchases making them cheaper than the listed price.
As the bitcoin we get back via debit card rewards goes up in value over the years, everything we purchase using that card is, in theory, getting cheaper.
Borrowed Money
There is also the option of taking on debt for bitcoin which we’ve seen happen rapidly in public markets. Currently, we are not taking on any kind of debt to add to our bitcoin treasury, but that is something we can and will consider as time moves on. It is important to me to begin stacking with our cashflows first. Once we have built up a decent hoard of BTC on our treasury, we would consider taking a loan to purchase bitcoin,
Think of this as an arbitrage opportunity. If you can secure a loan at 6% for an asset that might have a CAGR of 40+% then it would likely be a good move to make as long as you have sufficient cashflows to cover the principal and interest payments on the loan.
As a small business, we don’t have access to the same tools and products that public companies do. So it’s important to ensure we keep a low time preference with any time of borrowing that we may do. While it is always ideal to stack as much bitcoin as possible, ensuring that you are doing so in a responsible and sustainable way is key. You should be able to cover the payments on the loan very easily. If it’s going to constrain cashflow and increase stress and pressure in the business then you are probably borrowing too much. Loan amounts should be in that sweet spot of impactful enough to really boost your bitcoin treasury, but not so heavy that it puts your business in danger.
It’s also important to note that borrowing money isn’t for everyone. If the thought of a loan to purchase bitcoin causes stress, you may be better off just focusing on stacking from your cashflow and improving your bitcoin treasury month in and month out. Just because this has been popularized in the public markets, doesn’t mean that it has to be done on a smaller scale with your small business. It’s simply something to consider when evaluating your bitcoin treasury and how you can increase it’s value in the most accretive ways possible.
For example, Let’s say your company has a net profit of $10,000 per month. You’ve already got a bitcoin treasury valued at $100,000 and you have the opportunity to take on a $30,000 loan at 6% interest. This would automatically boost your treasury by 30% and should be a debt note that is simple and sustainable to pay each month out of your net profits. You would also be able to continue stacking your % allocation each month from your net profit.
The danger of this loan is low in a number of ways. First, the note would be for $30,000 and you have a bitcoin treasury of $130,000. In a worst case scenario, you could liquidate enough bitcoin to payoff the loan and move on. The other substantial way that it’s safe is that you have sufficient cashflow to cover what is likely to be a payment in the $500-$700 range each month depending on the terms. You are only eating into your net profit by 5-7% monthly to begin to pay down the loan.
I'm surely coming from the conservative side when it comes to being a bitcoiner in small business, but I would feel much more comfortable taking a loan once I have a pre established treasury. I would also like for the size of that loan to be smaller than the overall value of my current treasury. So with those parameters set, I’m probably a few months away from even considering a loan to expand the bitcoin on my balance sheet. However, It will be something that I maintain a watchful eye on and would consider it when terms and market conditions seem favorable to make a lump sum buy into bitcoin.
I believe this to be an opportunity within a limited time frame. I think we see bitcoin increase in value by a multiple of 10 over the coming decade. I do think that as time marches on that bitcoin’s CAGR will continue to decrease. It’ll still be attractive, but this is a natural occurrence as an asset matures and becomes larger. Will borrowing money responsibly to purchase bitcoin be a good idea when it is priced at $1,000,000 per coin? Only Time will tell. Until we see more of that price maturation, I tend to think it’s a fairly solid trade off when done responsibly.
In Conclusion:
This writing had a lot of technicality to it to explain what we are doing. In future writings I will continue to share our bitcoin stacking results and thoughts behind how we feel about the previous month. I’ll also get into some more of the business aspects of it and what we are doing to increase efficiency. At the end of the day, everything we do will be in an effort to stack more bitcoin into our treasury.
We will provide an ongoing monthly update and will update again once May has ended.
Talk Soon.
-Caleb Gregory
-
 @ 58537364:705b4b85
2025-05-20 14:22:05
@ 58537364:705b4b85
2025-05-20 14:22:05Ikigai means "the meaning of life" or "the reason for being." Why were we born? What are we living for? When work is not seen as something separate from life.
The Japanese believe that everyone has their own ikigai. Those who discover it find meaning and value in life, leading to greater happiness, better moods, and a more fulfilling world.
Today, there are many books about ikigai, but the first one written by a Japanese author is:
“The Little Book of Ikigai: The Secret Japanese Way to Live a Happy and Long Life” by Ken Mogi (Thai translation by Wuttichai Krisanaprakankit)
Come explore the true world of ikigai through this Japanese neuroscientist’s insights, conveyed through conversations that challenge the idea of ikigai as something grand—showing instead that it starts with small personal joys.
Ken Mogi says that Jiro Ono, a 94-year-old sushi chef who still makes sushi today, was his inspiration for writing the book.
This sushi chef did not start the job out of passion or talent—but he dedicated every piece of sushi to bring happiness to his customers. That, Ken says, is the essence of ikigai.
Strangely, the word “ikigai” is not often used in daily conversations in Japan.
Because it’s something so natural that it doesn’t need to be said. In today’s world, we often talk about how to succeed, how to get promoted, how to become a CEO. But for the Japanese, success isn’t everything.
For example, many Japanese people are deeply passionate about hobbies or have kodawari. Others might not care what those hobbies are—as long as the person seems happy, that’s enough. Some are obsessed with trains, manga, or anime. These people don’t need fame or recognition from society. If they’re happy in their own way, that’s perfectly okay.
Kodawari means a deep dedication or meticulous attention to something. For example, someone obsessed with stationery might spend a lot of time selecting the perfect pens, notebooks, or pencils. They’ll research, analyze, and experiment to find the tools they love most.
Everyone’s ikigai can be different, because people value different things and live differently.
Ikigai is about diversity. Japanese society encourages children to discover their own ikigai. They don’t tell kids to pursue jobs only because they pay well. If you ask students what jobs they want, they rarely say it’s about money first.
Ikigai is not the same as "success." The Japanese know that life isn’t just about being successful. Ikigai matters more. You could be successful but lack ikigai. Conversely, you might not be “successful” but still have ikigai—and you might be happier.
Ken Mogi defines success as something society acknowledges and rewards. But ikigai comes from your own heart and personal happiness. Others may not recognize it as success, but that doesn’t matter.
Ikigai is personal. We can be happy in our own way. We don’t judge others’ happiness—let them find joy in their own path.
The key to ikigai is finding small moments of happiness, even from little things. For example, when Ken was a child, he loved studying butterflies. Now, when he’s out jogging and sees a beautiful butterfly, he feels ikigai. Or sometimes, it comes from small amusing moments—like hearing a child tell his dad, “Dad, you have to do it this way!”
So, if we want to find our own ikigai, where do we start? Start with noticing small pleasures in daily life. That’s the easiest place to begin.
In the brain, there's a chemical called dopamine. When we achieve even small things, dopamine is released, creating happiness. That’s why enjoying small things is so important.
For some, ikigai might seem hard to grasp—especially if life is difficult, if they feel hopeless or lack self-worth. So begin with tiny moments of joy.
Is it the same as positive thinking? Ikigai is a part of that. But when we talk about “positive thinking,” it can feel like pressure to some people. So instead, just notice small joys: making your morning coffee, running in the rain.
Lessons from Ken Mogi:
-
Ikigai is not about chasing success or wealth, but about feeling happiness in your own life, which gives your life personal meaning.
-
Ikigai is not defined by society. Everyone’s ikigai is different. Each person can be happy in their own way.
-
**Don’t judge or force others—**children, partners—to live how you think is right. Respect diversity.
-
Smile at people who are enjoying their ikigai, and support them if they struggle.
-
Ikigai exists on two levels:
-
Big ikigai: life purpose or work values.
-
Small ikigai: tiny joys in everyday life.
-
Ikigai starts with noticing small pleasures today.
Source: From the Cloud of Thoughts column An interview by Ajarn Katewadi from Marumura with Ken Mogi, author of the first Japanese book on ikigai.
-
-
 @ ece127e2:745bab9c
2025-05-20 18:59:11
@ ece127e2:745bab9c
2025-05-20 18:59:11vamos a ver que tal
-
 @ 662f9bff:8960f6b2
2025-05-20 18:52:01
@ 662f9bff:8960f6b2
2025-05-20 18:52:01April already and we are still refugees from the madness in HK. During March I had quite a few family matters that took priority and I also needed to work for two weeks. April is a similar schedule but we flew to Madeira for a change of scene and so that I could have a full 2-weeks off - my first real holiday in quite a few years!
We are staying in an airBnB in Funchal - an experience that I can totally recommend - video below! Nice to have an apartment that is fully equipped in a central location and no hassle for a few weeks. While here we are making the most of the great location and all the local possibiliites.
Elsewhere in the world
Things are clearly not going great around the world. If you are still confused as to why these things are happening, do go back and read the previous Letter from HK section "Why? How did we get here?"
You should be in no doubt that the "Great Reset" with its supporting "Great Narrative" is in full swing.. This is it - it is not a drill. For additional insights the following are recommended.
-
Jeff Booth discusses clearly and unemotionally with Pomp - Inflation is theft from humanity by the world governments
-
James' summary of Day 2 of the Miami conference - Peter Thiel (wow) and a fantastic explainer from Saifedean on the costs of the current corrupt financial system
-
James' summary of Day 3 of the Miami conference - listen in particular to the words of wisdom from Michael Saylor and Lyn Alden
-
Layered Money - The corruption of the system will blow your mind once you understand it…
-
This is BIG: Strike Is Bringing Freedom To Retail Merchants
-
Mark summarises Ray's book: Things will go faster and slower than you want!
-
Thoughtful words from George - evil is at work - be in no doubt..
-
Wow - My mind is blown. Must listen to John Carvalho - what clear ambition and answers to every question!
-
Related to the John Carvalho discussion. Likely these two options will end up complementing each other
On the personal and inspirational side
Advantage of time off work is that I have more time to read, listen and watch things that interest me. It really is a privilege that so much high quality material is so readily available. Do not let it go to waste. A few fabulous finds (and some re-finds) from this past week:
-
Ali Abdaal's bookshelf review just blew my mind! For the full list of books with links see the text under his video. So many inspirations and his delivery is perfect.
-
Gotta recommend Ali's 21 Life Lessons. I have been following him since he was student in Cambridge five years ago - his personal and professional growth and what he achieves (now with his team) is truely staggering.
-
Also his 15 books to read in 2022 - especially this one!
-
I also keep going back to Steve Jobs giving the 2005 Stanford Commencement address Three stories from his life - listen and be inspired - especially story #3
You will know that I am a fan of Audio Books and also Kindle - recently I am starting to use Whispersync where you get the Kindle- and Audio-books together for a nice price. This makes it easier to take notes (using Mac or iPad Kindle reader) while getting the benefit of having the book read to you by a professional reader.
I have also been inspired by a few people pushing themselves to do more reading - like this girl and Ali himself with his tips. Above all: just do it and do not get stuck on something that does not work for you!
Books that I am reading - Audio and Kindle!
-
The Final Empire: Mistborn, Book 1 - this is a new genre for me - I rather feel that it might be a bit too complicated for my engineering mind - let's see
-
Die with Zero: Getting All You Can from Your Money and Your Life - certainly provocative and obvious if you think about it but 99% do the opposite!
-
Chariots of the Gods - a classic by Erich von Daniken (written in 1968) - I have been inspired by his recent YT video appearances. Thought provoking and leads you to many possibilities.
So what's it like in Funchal, Madeira?
Do check out HitTheRoadMadeira's walking tour around Funchal
My first impressions of Funchal
and see my day out on Thursday!
Saturday - Funchal and Camar de Lobos
That's it!
No one can be told what The Matrix is.\ You have to see it for yourself.**
Do share this newsletter with any of your friends and family who might be interested.
You can also email me at: LetterFrom@rogerprice.me
💡Enjoy the newsletters in your own language : Dutch, French, German, Serbian, Chinese Traditional & Simplified, Thai and Burmese.
-
-
 @ 6ad3e2a3:c90b7740
2025-05-20 13:49:50
@ 6ad3e2a3:c90b7740
2025-05-20 13:49:50I’ve written about MSTR twice already, https://www.chrisliss.com/p/mstr and https://www.chrisliss.com/p/mstr-part-2, but I want to focus on legendary short seller James Chanos’ current trade wherein he buys bitcoin (via ETF) and shorts MSTR, in essence to “be like Mike” Saylor who sells MSTR shares at the market and uses them to add bitcoin to the company’s balance sheet. After all, if it’s good enough for Saylor, why shouldn’t everyone be doing it — shorting a company whose stock price is more than 2x its bitcoin holdings and using the proceeds to buy the bitcoin itself?
Saylor himself has said selling shares at 2x NAV (net asset value) to buy bitcoin is like selling dollars for two dollars each, and Chanos has apparently decided to get in while the getting (market cap more than 2x net asset value) is good. If the price of bitcoin moons, sending MSTR’s shares up, you are more than hedged in that event, too. At least that’s the theory.
The problem with this bet against MSTR’s mNAV, i.e., you are betting MSTR’s market cap will converge 1:1 toward its NAV in the short and medium term is this trade does not exist in a vacuum. Saylor has described how his ATM’s (at the market) sales of shares are accretive in BTC per share because of this very premium they carry. Yes, we’ll dilute your shares of the company, but because we’re getting you 2x the bitcoin per share, you are getting an ever smaller slice of an ever bigger overall pie, and the pie is growing 2x faster than your slice is reducing. (I https://www.chrisliss.com/p/mstr how this works in my first post.)
But for this accretion to continue, there must be a constant supply of “greater fools” to pony up for the infinitely printable shares which contain only half their value in underlying bitcoin. Yes, those shares will continue to accrete more BTC per share, but only if there are more fools willing to make this trade in the future. So will there be a constant supply of such “fools” to keep fueling MSTR’s mNAV multiple indefinitely?
Yes, there will be in my opinion because you have to look at the trade from the prospective fools’ perspective. Those “fools” are not trading bitcoin for MSTR, they are trading their dollars, selling other equities to raise them maybe, but in the end it’s a dollars for shares trade. They are not selling bitcoin for them.
You might object that those same dollars could buy bitcoin instead, so they are surely trading the opportunity cost of buying bitcoin for them, but if only 5-10 percent of the market (or less) is buying bitcoin itself, the bucket in which which those “fools” reside is the entire non-bitcoin-buying equity market. (And this is not considering the even larger debt market which Saylor has yet to tap in earnest.)
So for those 90-95 percent who do not and are not presently planning to own bitcoin itself, is buying MSTR a fool’s errand, so to speak? Not remotely. If MSTR shares are infinitely printable ATM, they are still less so than the dollar and other fiat currencies. And MSTR shares are backed 2:1 by bitcoin itself, while the fiat currencies are backed by absolutely nothing. So if you hold dollars or euros, trading them for MSTR shares is an errand more sage than foolish.
That’s why this trade (buying BTC and shorting MSTR) is so dangerous. Not only are there many people who won’t buy BTC buying MSTR, there are many funds and other investment entities who are only able to buy MSTR.
Do you want to get BTC at 1:1 with the 5-10 percent or MSTR backed 2:1 with the 90-95 percent. This is a bit like medical tests that have a 95 percent accuracy rate for an asymptomatic disease that only one percent of the population has. If someone tests positive, it’s more likely to be a false one than an indication he has the disease*. The accuracy rate, even at 19:1, is subservient to the size of the respective populations.
At some point this will no longer be the case, but so long as the understanding of bitcoin is not widespread, so long as the dollar is still the unit of account, the “greater fools” buying MSTR are still miles ahead of the greatest fools buying neither, and the stock price and mNAV should only increase.
. . .
One other thought: it’s more work to play defense than offense because the person on offense knows where he’s going, and the defender can only react to him once he moves. Similarly, Saylor by virtue of being the issuer of the shares knows when more will come online while Chanos and other short sellers are borrowing them to sell in reaction to Saylor’s strategy. At any given moment, Saylor can pause anytime, choosing to issue convertible debt or preferred shares with which to buy more bitcoin, and the shorts will not be given advance notice.
If the price runs, and there is no ATM that week because Saylor has stopped on a dime, so to speak, the shorts will be left having to scramble to change directions and buy the shares back to cover. Their momentum might be in the wrong direction, though, and like Allen Iverson breaking ankles with a crossover, Saylor might trigger a massive short squeeze, rocketing the share price ever higher. That’s why he actually welcomes Chanos et al trying this copycat strategy — it becomes the fuel for outsized gains.
For that reason, news that Chanos is shorting MSTR has not shaken my conviction, though there are other more pertinent https://www.chrisliss.com/p/mstr-part-2 with MSTR, of which one should be aware. And as always, do your own due diligence before investing in anything.
* To understand this, consider a population of 100,000, with one percent having a disease. That means 1,000 have it, 99,000 do not. If the test is 95 percent accurate, and everyone is tested, 950 of the 1,000 will test positive (true positives), 50 who have it will test negative (false negatives.) Of the positives, 95 percent of 99,000 (94,050) will test negative (true negatives) and five percent (4,950) will test positive (false positives). That means 4,950 out of 5,900 positives (84%) will be false.
-
 @ e4950c93:1b99eccd
2025-05-20 11:06:09
@ e4950c93:1b99eccd
2025-05-20 11:06:09Contenu à venir.
-
 @ 0971cd37:53c969f4
2025-05-20 17:00:53
@ 0971cd37:53c969f4
2025-05-20 17:00:53ลดต้นทุนค่าไฟ เพิ่มความคุ้มค่าให้การขุด Bitcoin ที่บ้าน ในยุคที่ต้นทุนพลังงานสูงขึ้นอย่างต่อเนื่อง นักขุด Bitcoin ที่บ้าน หรือ Home Miner ต้องคิดให้รอบคอบก่อนเลือกเครื่องขุด เพราะ “แรงขุดสูงสุด” ไม่ได้แปลว่า “กำไรดีที่สุด” อีกต่อไป การเลือกเครื่องขุดไม่ใช่แค่ดูแค่แรงขุด (Hashrate) สูงสุดเท่านั้น แต่ต้องพิจารณาเรื่อง "การกินไฟ" และ "ความคุ้มค่าในการใช้งานระยะยาว" ด้วย ซึ่งสายหนึ่งที่ได้รับความนิยมมากขึ้นเรื่อย ๆ ก็คือ สาย Tuning Power หรือการจูนเครื่องขุดเพื่อให้ได้อัตราส่วน Hashrate/Watt ที่ดีที่สุด
เทรนด์ใหม่ของวงการขุดคือสาย Tuning Power หรือการปรับแต่งพลังงานของเครื่องขุด Bitcoin (ASIC) ให้ได้ ประสิทธิภาพ Hashrate ต่อการใช้พลังงาน (Efficiency) สูงที่สุด ซึ่งเหมาะอย่างยิ่งสำหรับการขุดในบ้านที่มีข้อจำกัดด้านค่าไฟ ความร้อน และ เสียงรบกวน
Tuning Power คืออะไร? Tuning Power คือการปรับลดแรงขุดของเครื่อง ASIC ลงเล็กน้อย เพื่อให้กินไฟน้อยลงแบบชัดเจน
ตัวอย่างเช่น Custom Firmware Braiins OS ใช้กับ Antminer S19jpro จากเดิมแรงขุด 104 TH/s กินไฟ 3,500W เมื่อปรับแต่งในส่วน Power Target จูนเหลือ 75 TH/s อาจกินไฟแค่ 1,600W-1,800W หลังจาก Tuning ค่าประสิทธิภาพ(Efficiency)ดีขึ้น เช่น จาก 32 J/TH เหลือเพียง 22–20 J/TH
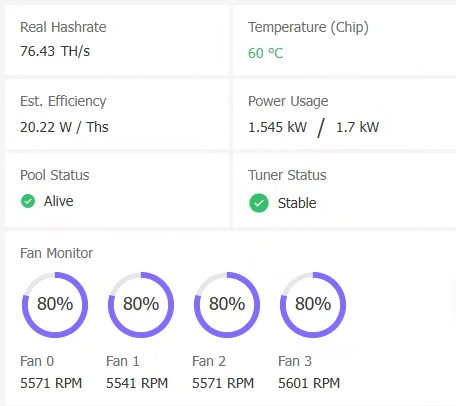 หมายเหตุ: ค่า Efficiency ยิ่งต่ำ ยิ่งดี แปลว่าใช้พลังงานน้อยต่อ 1 TH
หมายเหตุ: ค่า Efficiency ยิ่งต่ำ ยิ่งดี แปลว่าใช้พลังงานน้อยต่อ 1 THทำไมต้อง Tuning Power? การจูนพลังงาน (Tuning Power) คือการปรับแต่งเครื่องขุด เช่น ASIC ให้ทำงานที่แรงขุดไม่เต็ม 100% แต่กินไฟน้อยลงอย่างชัดเจน ส่งผลให้:
- ประหยัดค่าไฟ โดยเฉพาะถ้าขุดในพื้นที่ต้นทุนพลังงานค่าไฟสูงหรือไม่มี TOU (Time of Use) และ เหมาะสำหรับผู้ใช้ไฟแบบ TOU ที่ค่าไฟกลางวัน ON-Peak แพง ต้องการขุดเลือกช่วงกลางคืนและวันหยุดเสาร์-อาทิตย์ และ วันหยุดราชการตามปกติ Off-Peak , ที่ใช้ระบบ Solar หรือมีระบบ Battery ต้องการประหยัดไฟ
- ลดความร้อนของเครื่อง ทำให้ยืดอายุการใช้งานและลดค่าใช้จ่ายด้าน ซำบำรุง ระบบระบายความร้อน
- เพิ่มความคุ้มค่า ในช่วงตลาดหมี ที่กำไรจากการขุดต่ำ การลดต้นทุนไฟฟ้าคือทางรอดหลัก
เครื่องขุด Bitcoin (ASIC) รุ่นไหน ที่เหมาะกับสาย Tuning Power
-
Antminer รองรับ Custom Firmware เช่น Braiins OS ที่เป็นยอดนิยมในการ Tuning Power
-
WhatsMiner M30-M60s Series ขึ้นไป ใช้โปรแกรม WhatsMinerTool เพื่อทำการ Tuning Power ได้โดยตรงไม่จำเป็นต้อง Custom Firmware
สรุป การเป็น Home Miner ที่ยั่งยืนไม่ได้ขึ้นกับว่าเครื่องขุดแรงแค่ไหน แต่ขึ้นกับว่า “จ่ายค่าไฟแล้วเหลือกำไรหรือไม่ หรือ จ่ายค่าไฟแล้วคุ้มค้ารายได้ Bitcoin จากการขุดจำนวนที่ได้รับมากขึ้นหรือไม่” การเลือกเครื่องขุดสำหรับสาย Tuning Power จึงเป็นทางเลือกที่ตอบโจทย์ผู้ที่ต้องการประสิทธิภาพสูงในต้นทุนที่ควบคุมได้โดยเฉพาะในยุคที่ตลาดผันผวน และ ค่าไฟฟ้าคือศัตรูตัวจริงของนักขุด
-
 @ 39cc53c9:27168656
2025-05-20 10:45:31
@ 39cc53c9:27168656
2025-05-20 10:45:31The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 39cc53c9:27168656
2025-05-20 10:45:29
@ 39cc53c9:27168656
2025-05-20 10:45:29Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ 39cc53c9:27168656
2025-05-20 10:45:28
@ 39cc53c9:27168656
2025-05-20 10:45:28Over the past few months, I've dedicated my time to a complete rewrite of the kycnot.me website. The technology stack remains unchanged; Golang paired with TailwindCSS. However, I've made some design choices in this iteration that I believe significantly enhance the site. Particularly to backend code.
UI Improvements
You'll notice a refreshed UI that retains the original concept but has some notable enhancements. The service list view is now more visually engaging, it displays additional information in a more aesthetically pleasing manner. Both filtering and searching functionalities have been optimized for speed and user experience.
Service pages have been also redesigned to highlight key information at the top, with the KYC Level box always accessible. The display of service attributes is now more visually intuitive.
The request form, especially the Captcha, has undergone substantial improvements. The new self-made Captcha is robust, addressing the reliability issues encountered with the previous version.
Terms of Service Summarizer
A significant upgrade is the Terms of Service summarizer/reviewer, now powered by AI (GPT-4-turbo). It efficiently condenses each service's ToS, extracting and presenting critical points, including any warnings. Summaries are updated monthly, processing over 40 ToS pages via the OpenAI API using a self-crafted and thoroughly tested prompt.
Nostr Comments
I've integrated a comment section for each service using Nostr. For guidance on using this feature, visit the dedicated how-to page.
Database
The backend database has transitioned to pocketbase, an open-source Golang backend that has been a pleasure to work with. I maintain an updated fork of the Golang SDK for pocketbase at pluja/pocketbase.
Scoring
The scoring algorithm has also been refined to be more fair. Despite I had considered its removal due to the complexity it adds (it is very difficult to design a fair scoring system), some users highlighted its value, so I kept it. The updated algorithm is available open source.
Listings
Each listing has been re-evaluated, and the ones that were no longer operational were removed. New additions are included, and the backlog of pending services will be addressed progressively, since I still have access to the old database.
API
The API now offers more comprehensive data. For more details, check here.
About Page
The About page has been restructured for brevity and clarity.
Other Changes
Extensive changes have been implemented in the server-side logic, since the whole code base was re-written from the ground up. I may discuss these in a future post, but for now, I consider the current version to be just a bit beyond beta, and additional updates are planned in the coming weeks.
-
 @ 39cc53c9:27168656
2025-05-20 10:45:26
@ 39cc53c9:27168656
2025-05-20 10:45:26I'm launching a new service review section on this blog in collaboration with OrangeFren. These reviews are sponsored, yet the sponsorship does not influence the outcome of the evaluations. Reviews are done in advance, then, the service provider has the discretion to approve publication without modifications.
Sponsored reviews are independent from the kycnot.me list, being only part of the blog. The reviews have no impact on the scores of the listings or their continued presence on the list. Should any issues arise, I will not hesitate to remove any listing.
The review
WizardSwap is an instant exchange centred around privacy coins. It was launched in 2020 making it old enough to have weathered the 2021 bull run and the subsequent bearish year.
| Pros | Cons | |------|------| | Tor-friendly | Limited liquidity | | Guarantee of no KYC | Overly simplistic design | | Earn by providing liquidity | |
Rating: ★★★★★ Service Website: wizardswap.io
Liquidity
Right off the bat, we'll start off by pointing out that WizardSwap relies on its own liquidity reserves, meaning they aren't just a reseller of Binance or another exchange. They're also committed to a no-KYC policy, when asking them, they even promised they would rather refund a user their original coins, than force them to undergo any sort of verification.
On the one hand, full control over all their infrastructure gives users the most privacy and conviction about the KYC policies remaining in place.
On the other hand, this means the liquidity available for swapping isn't huge. At the time of testing we could only purchase at most about 0.73 BTC with XMR.
It's clear the team behind WizardSwap is aware of this shortfall and so they've come up with a solution unique among instant exchanges. They let you, the user, deposit any of the currencies they support into your account and earn a profit on the trades made using your liquidity.
Trading
Fees on WizardSwap are middle-of-the-pack. The normal fee is 2.2%. That's more than some exchanges that reserve the right to suddenly demand you undergo verification, yet less than half the fees on some other privacy-first exchanges. However as we mentioned in the section above you can earn almost all of that fee (2%) if you provide liquidity to WizardSwap.
It's good that with the current Bitcoin fee market their fees are constant regardless of how much, or how little, you send. This is in stark contrast with some of the alternative swap providers that will charge you a massive premium when attempting to swap small amounts of BTC away.
Test trades
Test trades are always performed without previous notice to the service provider.
During our testing we performed a few test trades and found that every single time WizardSwap immediately detected the incoming transaction and the amount we received was exactly what was quoted before depositing. The fees were inline with what WizardSwap advertises.

- Monero payment proof
- Bitcoin received
- Wizardswap TX link - it's possible that this link may cease to be valid at some point in the future.
ToS and KYC
WizardSwap does not have a Terms of Service or a Privacy Policy page, at least none that can be found by users. Instead, they offer a FAQ section where they addresses some basic questions.
The site does not mention any KYC or AML practices. It also does not specify how refunds are handled in case of failure. However, based on the FAQ section "What if I send funds after the offer expires?" it can be inferred that contacting support is necessary and network fees will be deducted from any refund.
UI & Tor
WizardSwap can be visited both via your usual browser and Tor Browser. Should you decide on the latter you'll find that the website works even with the most strict settings available in the Tor Browser (meaning no JavaScript).
However, when disabling Javascript you'll miss the live support chat, as well as automatic refreshing of the trade page. The lack of the first means that you will have no way to contact support from the trade page if anything goes wrong during your swap, although you can do so by mail.
One important thing to have in mind is that if you were to accidentally close the browser during the swap, and you did not save the swap ID or your browser history is disabled, you'll have no easy way to return to the trade. For this reason we suggest when you begin a trade to copy the url or ID to someplace safe, before sending any coins to WizardSwap.
The UI you'll be greeted by is simple, minimalist, and easy to navigate. It works well not just across browsers, but also across devices. You won't have any issues using this exchange on your phone.
Getting in touch
The team behind WizardSwap appears to be most active on X (formerly Twitter): https://twitter.com/WizardSwap_io
If you have any comments or suggestions about the exchange make sure to reach out to them. In the past they've been very receptive to user feedback, for instance a few months back WizardSwap was planning on removing DeepOnion, but the community behind that project got together ^1 and after reaching out WizardSwap reversed their decision ^2.
You can also contact them via email at:
support @ wizardswap . ioDisclaimer
None of the above should be understood as investment or financial advice. The views are our own only and constitute a faithful representation of our experience in using and investigating this exchange. This review is not a guarantee of any kind on the services rendered by the exchange. Do your own research before using any service.
-
 @ 39cc53c9:27168656
2025-05-20 10:45:24
@ 39cc53c9:27168656
2025-05-20 10:45:24Bitcoin enthusiasts frequently and correctly remark how much value it adds to Bitcoin not to have a face, a leader, or a central authority behind it. This particularity means there isn't a single person to exert control over, or a single human point of failure who could become corrupt or harmful to the project.
Because of this, it is said that no other coin can be equally valuable as Bitcoin in terms of decentralization and trustworthiness. Bitcoin is unique not just for being first, but also because of how the events behind its inception developed. This implies that, from Bitcoin onwards, any coin created would have been created by someone, consequently having an authority behind it. For this and some other reasons, some people refer to Bitcoin as "The Immaculate Conception".
While other coins may have their own unique features and advantages, they may not be able to replicate Bitcoin's community-driven nature. However, one other cryptocurrency shares a similar story of mystery behind its creation: Monero.
History of Monero
Bytecoin and CryptoNote
In March 2014, a Bitcointalk thread titled "Bytecoin. Secure, private, untraceable since 2012" was initiated by a user under the nickname "DStrange"^1^. DStrange presented Bytecoin (BCN) as a unique cryptocurrency, in operation since July 2012. Unlike Bitcoin, it employed a new algorithm known as CryptoNote.
DStrange apparently stumbled upon the Bytecoin website by chance while mining a dying bitcoin fork, and decided to create a thread on Bitcointalk^1^. This sparked curiosity among some users, who wondered how could Bytecoin remain unnoticed since its alleged launch in 2012 until then^2^.
Some time after, a user brought up the "CryptoNote v2.0" whitepaper for the first time, underlining its innovative features^4^. Authored by the pseudonymous Nicolas van Saberhagen in October 2013, the CryptoNote v2 whitepaper^5^ highlighted the traceability and privacy problems in Bitcoin. Saberhagen argued that these flaws could not be quickly fixed, suggesting it would be more efficient to start a new project rather than trying to patch the original^5^, an statement simmilar to the one from Satoshi Nakamoto^6^.
Checking with Saberhagen's digital signature, the release date of the whitepaper seemed correct, which would mean that Cryptonote (v1) was created in 2012^7^, although there's an important detail: "Signing time is from the clock on the signer's computer" ^9^.
Moreover, the whitepaper v1 contains a footnote link to a Bitcointalk post dated May 5, 2013^10^, making it impossible for the whitepaper to have been signed and released on December 12, 2012.
As the narrative developed, users discovered that a significant 80% portion of Bytecoin had been pre-mined^11^ and blockchain dates seemed to be faked to make it look like it had been operating since 2012, leading to controversy surrounding the project.
The origins of CryptoNote and Bytecoin remain mysterious, leaving suspicions of a possible scam attempt, although the whitepaper had a good amount of work and thought on it.
The fork
In April 2014, the Bitcointalk user
thankful_for_today, who had also participated in the Bytecoin thread^12^, announced plans to launch a Bytecoin fork named Bitmonero^13^.The primary motivation behind this fork was "Because there is a number of technical and marketing issues I wanted to do differently. And also because I like ideas and technology and I want it to succeed"^14^. This time Bitmonero did things different from Bytecoin: there was no premine or instamine, and no portion of the block reward went to development.
However, thankful_for_today proposed controversial changes that the community disagreed with. Johnny Mnemonic relates the events surrounding Bitmonero and thankful_for_today in a Bitcointalk comment^15^:
When thankful_for_today launched BitMonero [...] he ignored everything that was discussed and just did what he wanted. The block reward was considerably steeper than what everyone was expecting. He also moved forward with 1-minute block times despite everyone's concerns about the increase of orphan blocks. He also didn't address the tail emission concern that should've (in my opinion) been in the code at launch time. Basically, he messed everything up. Then, he disappeared.
After disappearing for a while, thankful_for_today returned to find that the community had taken over the project. Johnny Mnemonic continues:
I, and others, started working on new forks that were closer to what everyone else was hoping for. [...] it was decided that the BitMonero project should just be taken over. There were like 9 or 10 interested parties at the time if my memory is correct. We voted on IRC to drop the "bit" from BitMonero and move forward with the project. Thankful_for_today suddenly resurfaced, and wasn't happy to learn the community had assumed control of the coin. He attempted to maintain his own fork (still calling it "BitMonero") for a while, but that quickly fell into obscurity.
The unfolding of these events show us the roots of Monero. Much like Satoshi Nakamoto, the creators behind CryptoNote/Bytecoin and thankful_for_today remain a mystery^17^, having disappeared without a trace. This enigma only adds to Monero's value.
Since community took over development, believing in the project's potential and its ability to be guided in a better direction, Monero was given one of Bitcoin's most important qualities: a leaderless nature. With no single face or entity directing its path, Monero is safe from potential corruption or harm from a "central authority".
The community continued developing Monero until today. Since then, Monero has undergone a lot of technological improvements, migrations and achievements such as RingCT and RandomX. It also has developed its own Community Crowdfundinc System, conferences such as MoneroKon and Monerotopia are taking place every year, and has a very active community around it.
Monero continues to develop with goals of privacy and security first, ease of use and efficiency second. ^16^
This stands as a testament to the power of a dedicated community operating without a central figure of authority. This decentralized approach aligns with the original ethos of cryptocurrency, making Monero a prime example of community-driven innovation. For this, I thank all the people involved in Monero, that lead it to where it is today.
If you find any information that seems incorrect, unclear or any missing important events, please contact me and I will make the necessary changes.
Sources of interest
- https://forum.getmonero.org/20/general-discussion/211/history-of-monero
- https://monero.stackexchange.com/questions/852/what-is-the-origin-of-monero-and-its-relationship-to-bytecoin
- https://en.wikipedia.org/wiki/Monero
- https://bitcointalk.org/index.php?topic=583449.0
- https://bitcointalk.org/index.php?topic=563821.0
- https://bitcointalk.org/index.php?action=profile;u=233561
- https://bitcointalk.org/index.php?topic=512747.0
- https://bitcointalk.org/index.php?topic=740112.0
- https://monero.stackexchange.com/a/1024
- https://inspec2t-project.eu/cryptocurrency-with-a-focus-on-anonymity-these-facts-are-known-about-monero/
- https://medium.com/coin-story/coin-perspective-13-riccardo-spagni-69ef82907bd1
- https://www.getmonero.org/resources/about/
- https://www.wired.com/2017/01/monero-drug-dealers-cryptocurrency-choice-fire/
- https://www.monero.how/why-monero-vs-bitcoin
- https://old.reddit.com/r/Monero/comments/u8e5yr/satoshi_nakamoto_talked_about_privacy_features/
-
 @ 39cc53c9:27168656
2025-05-20 10:45:23
@ 39cc53c9:27168656
2025-05-20 10:45:23I've been thinking about how to improve my seed backup in a cheap and cool way, mostly for fun. Until now, I had the seed written on a piece of paper in a desk drawer, and I wanted something more durable and fire-proof.
After searching online, I found two options I liked the most: the Cryptosteel Capsule and the Trezor Keep. These products are nice but quite expensive, and I didn't want to spend that much on my seed backup. Privacy is also important, and sharing details like a shipping address makes me uncomfortable. This concern has grown since the Ledger incident^1. A $5 wrench attack^2 seems too cheap, even if you only hold a few sats.
Upon seeing the design of Cryptosteel, I considered creating something similar at home. Although it may not be as cool as their device, it could offer almost the same in terms of robustness and durability.
Step 1: Get the materials and tools
When choosing the materials, you will want to go with stainless steel. It is durable, resistant to fire, water, and corrosion, very robust, and does not rust. Also, its price point is just right; it's not the cheapest, but it's cheap for the value you get.

I went to a material store and bought:
- Two bolts
- Two hex nuts and head nuts for the bolts
- A bag of 30 washers
All items were made of stainless steel. The total price was around €6. This is enough for making two seed backups.
You will also need:
- A set of metal letter stamps (I bought a 2mm-size letter kit since my washers were small, 6mm in diameter)
- You can find these in local stores or online marketplaces. The set I bought cost me €13.
- A good hammer
- A solid surface to stamp on
Total spent: 19€ for two backups
Step 2: Stamp and store
Once you have all the materials, you can start stamping your words. There are many videos on the internet that use fancy 3D-printed tools to get the letters nicely aligned, but I went with the free-hand option. The results were pretty decent.

I only stamped the first 4 letters for each word since the BIP-39 wordlist allows for this. Because my stamping kit did not include numbers, I used alphabet letters to define the order. This way, if all the washers were to fall off, I could still reassemble the seed correctly.
The final result
So this is the final result. I added two smaller washers as protection and also put the top washer reversed so the letters are not visible:

Compared to the Cryptosteel or the Trezor Keep, its size is much more compact. This makes for an easier-to-hide backup, in case you ever need to hide it inside your human body.
Some ideas
Tamper-evident seal
To enhance the security this backup, you can consider using a tamper-evident seal. This can be easily achieved by printing a unique image or using a specific day's newspaper page (just note somewhere what day it was).
Apply a thin layer of glue to the washer's surface and place the seal over it. If someone attempts to access the seed, they will be forced to destroy the seal, which will serve as an evident sign of tampering.
This simple measure will provide an additional layer of protection and allow you to quickly identify any unauthorized access attempts.
Note that this method is not resistant to outright theft. The tamper-evident seal won't stop a determined thief but it will prevent them from accessing your seed without leaving any trace.
Redundancy
Make sure to add redundancy. Make several copies of this cheap backup, and store them in separate locations.
Unique wordset
Another layer of security could be to implement your own custom mnemonic dictionary. However, this approach has the risk of permanently losing access to your funds if not implemented correctly.
If done properly, you could potentially end up with a highly secure backup, as no one else would be able to derive the seed phrase from it. To create your custom dictionary, assign a unique number from 1 to 2048 to a word of your choice. Maybe you could use a book, and index the first 2048 unique words that appear. Make sure to store this book and even get a couple copies of it (digitally and phisically).
This self-curated set of words will serve as your personal BIP-39 dictionary. When you need to translate between your custom dictionary and the official BIP-39 wordlist, simply use the index number to find the corresponding word in either list.
Never write the idex or words on your computer (Do not use
Ctr+F) -
 @ 57c631a3:07529a8e
2025-05-20 15:40:04
@ 57c631a3:07529a8e
2025-05-20 15:40:04The Video: The World's Biggest Toddler
https://connect-test.layer3.press/articles/3f9d28a4-0876-4ee8-bdac-d1a56fa9cd02
-
 @ 39cc53c9:27168656
2025-05-20 10:45:21
@ 39cc53c9:27168656
2025-05-20 10:45:21kycnot.me features a somewhat hidden tool that some users may not be aware of. Every month, an automated job crawls every listed service's Terms of Service (ToS) and FAQ pages and conducts an AI-driven analysis, generating a comprehensive overview that highlights key points related to KYC and user privacy.
Here's an example: Changenow's Tos Review

Why?
ToS pages typically contain a lot of complicated text. Since the first versions of kycnot.me, I have tried to provide users a comprehensive overview of what can be found in such documents. This automated method keeps the information up-to-date every month, which was one of the main challenges with manual updates.
A significant part of the time I invest in investigating a service for kycnot.me involves reading the ToS and looking for any clauses that might indicate aggressive KYC practices or privacy concerns. For the past four years, I performed this task manually. However, with advancements in language models, this process can now be somewhat automated. I still manually review the ToS for a quick check and regularly verify the AI’s findings. However, over the past three months, this automated method has proven to be quite reliable.
Having a quick ToS overview section allows users to avoid reading the entire ToS page. Instead, you can quickly read the important points that are grouped, summarized, and referenced, making it easier and faster to understand the key information.
Limitations
This method has a key limitation: JS-generated pages. For this reason, I was using Playwright in my crawler implementation. I plan to make a release addressing this issue in the future. There are also sites that don't have ToS/FAQ pages, but these sites already include a warning in that section.
Another issue is false positives. Although not very common, sometimes the AI might incorrectly interpret something harmless as harmful. Such errors become apparent upon reading; it's clear when something marked as bad should not be categorized as such. I manually review these cases regularly, checking for anything that seems off and then removing any inaccuracies.
Overall, the automation provides great results.
How?
There have been several iterations of this tool. Initially, I started with GPT-3.5, but the results were not good in any way. It made up many things, and important thigs were lost on large ToS pages. I then switched to GPT-4 Turbo, but it was expensive. Eventually, I settled on Claude 3 Sonnet, which provides a quality compromise between GPT-3.5 and GPT-4 Turbo at a more reasonable price, while allowing a generous 200K token context window.
I designed a prompt, which is open source^1, that has been tweaked many times and will surely be adjusted further in the future.
For the ToS scraping part, I initially wrote a scraper API using Playwright^2, but I replaced it with Jina AI Reader^3, which works quite well and is designed for this task.
Non-conflictive ToS
All services have a dropdown in the ToS section called "Non-conflictive ToS Reviews." These are the reviews that the AI flagged as not needing a user warning. I still provide these because I think they may be interesting to read.
Feedback and contributing
You can give me feedback on this tool, or share any inaccuraties by either opening an issue on Codeberg^4 or by contacting me ^5.
You can contribute with pull requests, which are always welcome, or you can support this project with any of the listed ways.
-
 @ 39cc53c9:27168656
2025-05-20 10:45:20
@ 39cc53c9:27168656
2025-05-20 10:45:20These reviews are sponsored, yet the sponsorship does not influence the outcome of the evaluations. Sponsored reviews are independent from the kycnot.me list, being only part of the blog. The reviews have no impact on the scores of the listings or their continued presence on the list. Should any issues arise, I will not hesitate to remove any listing. Reviews are in collaboration with Orangefren.
The review
Swapter.io is an all-purpose instant exchange. They entered the scene in the depths of the bear market about 2 years ago in June of 2022.
| Pros | Cons | | --------------- | ---------------------------------- | | Low fees | Shotgun KYC with opaque triggers | | Large liquidity | Relies on 3rd party liquidity | | Works over Tor | Front-end not synced with back-end | | Pretty UI | |
Rating: ★★★☆☆ Service Website: swapter.io
⚠️ There is an ongoing issue with this service: read more on Reddit.
Test Trades
During our testing we performed a trade from XMR to LTC, and then back to XMR.
Our first trade had the ID of:
mpUitpGemhN8jjNAjQuo6EvQ. We were promised 0.8 LTC for sending 0.5 XMR, before we sent the Monero. When the Monero arrived we were sent 0.799 LTC.On the return journey we performed trade with ID:
yaCRb5pYcRKAZcBqg0AzEGYg. This time we were promised 0.4815 XMR for sending 0.799 LTC. After Litecoin arrived we were sent 0.4765 XMR.As such we saw a discrepancy of
~0.1%in the first trade and~1%in the second trade. Considering those trades were floating we determine the estimates presented in the UI to be highly accurate and honest.Of course Swapter could've been imposing a large fee on their estimates, but we checked their estimates against CoinGecko and found the difference to be equivalent to a fee of just over
0.5%. Perfectly in line with other swapping services.Trading
Swapter supports BTC, LTC, XMR and well over a thousand other coins. Sadly they don't support the Lightning Network. For the myriad of currencies they deal with they provide massive upper limits. You could exchange tens, or even hundreds, of thousands of dollars worth of cryptocurrency in a single trade (although we wouldn't recommend it).
The flip side to this is that Swapter relies on 3rd party liquidity. Aside from the large liqudity this also benefits the user insofar as it allows for very low fees. However, it also comes with a negative - the 3rd party gets to see all your trades. Unfortunately Swapter opted not to share where they source their liquidity in their Privacy Policy or Terms of Service.
KYC & AML policies
Swapter reserves the right to require its users to provide their full name, their date of birth, their address and government-issued ID. A practice known as "shotgun KYC". This should not happen often - in our testing it never did - however it's not clear when exactly it could happen. The AML & KYC policy provided on Swapter's website simply states they will put your trade on hold if their "risk scoring system [deems it] as suspicious".
Worse yet, if they determine that "any of the information [the] customer provided is incorrect, false, outdated, or incomplete" then Swapter may decide to terminate all of the services they provide to the user. What exactly would happen to their funds in such a case remains unclear.
The only clarity we get is that the Swapter policy outlines a designated 3rd party that will verify the information provided by the user. The third party's name is Sum & Substance Ltd, also simply known as samsub and available at sumsub.com
It's understandable that some exchanges will decide on a policy of this sort, especially when they rely on external liquidity, but we would prefer more clarity be given. When exactly is a trade suspicious?
Tor
We were pleased to discover Swapter works over Tor. However, they do not provide a Tor mirror, nor do they work without JavaScript. Additionally, we found that some small features, such as the live chat, did not work over Tor. Fortunately, other means of contacting their support are still available.
UI
We have found the Swapter UI to be very modern, straightforward and simple to use. It's available in 4 languages (English, French, Dutch and Russian), although we're unable to vouch for the quality of some of those, the ones that we used seemed perfectly serviceable.
Our only issue with the UI was that it claims the funds have been sent following the trade, when in reality it seems to take the backend a minute or so to actually broadcast the transaction.
Getting in touch
Swapter's team has a chat on their website, a support email address and a support Telegram. Their social media presence in most active on Telegram and X (formerly Twitter).
Disclaimer
None of the above should be understood as investment or financial advice. The views are our own only and constitute a faithful representation of our experience in using and investigating this exchange. This review is not a guarantee of any kind on the services rendered by the exchange. Do your own research before using any service.
-
 @ 39cc53c9:27168656
2025-05-20 10:45:18
@ 39cc53c9:27168656
2025-05-20 10:45:18“The future is there... staring back at us. Trying to make sense of the fiction we will have become.” — William Gibson.
This month is the 4th anniversary of kycnot.me. Thank you for being here.
Fifteen years ago, Satoshi Nakamoto introduced Bitcoin, a peer-to-peer electronic cash system: a decentralized currency free from government and institutional control. Nakamoto's whitepaper showed a vision for a financial system based on trustless transactions, secured by cryptography. Some time forward and KYC (Know Your Customer), AML (Anti-Money Laundering), and CTF (Counter-Terrorism Financing) regulations started to come into play.
What a paradox: to engage with a system designed for decentralization, privacy, and independence, we are forced to give away our personal details. Using Bitcoin in the economy requires revealing your identity, not just to the party you interact with, but also to third parties who must track and report the interaction. You are forced to give sensitive data to entities you don't, can't, and shouldn't trust. Information can never be kept 100% safe; there's always a risk. Information is power, who knows about you has control over you.
Information asymmetry creates imbalances of power. When entities have detailed knowledge about individuals, they can manipulate, influence, or exploit this information to their advantage. The accumulation of personal data by corporations and governments enables extensive surveillances.
Such practices, moreover, exclude individuals from traditional economic systems if their documentation doesn't meet arbitrary standards, reinforcing a dystopian divide. Small businesses are similarly burdened by the costs of implementing these regulations, hindering free market competition^1:

How will they keep this information safe? Why do they need my identity? Why do they force businesses to enforce such regulations? It's always for your safety, to protect you from the "bad". Your life is perpetually in danger: terrorists, money launderers, villains... so the government steps in to save us.
‟Hush now, baby, baby, don't you cry Mamma's gonna make all of your nightmares come true Mamma's gonna put all of her fears into you Mamma's gonna keep you right here, under her wing She won't let you fly, but she might let you sing Mamma's gonna keep baby cosy and warm” — Mother, Pink Floyd
We must resist any attack on our privacy and freedom. To do this, we must collaborate.
If you have a service, refuse to ask for KYC; find a way. Accept cryptocurrencies like Bitcoin and Monero. Commit to circular economies. Remove the need to go through the FIAT system. People need fiat money to use most services, but we can change that.
If you're a user, donate to and prefer using services that accept such currencies. Encourage your friends to accept cryptocurrencies as well. Boycott FIAT system to the greatest extent you possibly can.
This may sound utopian, but it can be achieved. This movement can't be stopped. Go kick the hornet's nest.
“We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do.” — Eric Hughes, A Cypherpunk's Manifesto
The anniversary
Four years ago, I began exploring ways to use crypto without KYC. I bookmarked a few favorite services and thought sharing them to the world might be useful. That was the first version of kycnot.me — a simple list of about 15 services. Since then, I've added services, rewritten it three times, and improved it to what it is now.
kycnot.me has remained 100% independent and 100% open source^2 all these years. I've received offers to buy the site, all of which I have declined and will continue to decline. It has been DDoS attacked many times, but we made it through. I have also rewritten the whole site almost once per year (three times in four years).
The code and scoring algorithm are open source (contributions are welcome) and I can't arbitrarly change a service's score without adding or removing attributes, making any arbitrary alterations obvious if they were fake. You can even see the score summary for any service's score.
I'm a one-person team, dedicating my free time to this project. I hope to keep doing so for many more years. Again, thank you for being part of this.
-
 @ 39cc53c9:27168656
2025-05-20 10:45:16
@ 39cc53c9:27168656
2025-05-20 10:45:16
Silent.link is an anonymous eSIM provider. They offer pay-as-you-go roaming in 160+ countries.
Pros
- Anonymous
- Private payment options
- High performance
- Global availability
Cons
- Need to select the right networks sometimes
- Latency
- Data and incoming SMS & call only
Rating
★★★★★
Service website
eSIMs replace traditional, physical SIM cards, if you have a fairly new phone, odds are it supports them. Since most people change their mobile carrier very rarely, the most common use case for these new eSIMs is their use in travel. Although their use as a piece of a larger OPSEC puzzle to improve privacy when using the internet from your phone is increasingly popular too.
Silent.link is not the only eSIM provider out there. Yet, they’re so unique that even Twitter’s (now X) founder Jack Dorsey recommends them.
Let’s start off with a quick explanation of how Silent.link works and what pay-as-you-go means. Most other eSIM providers will sell you packages of GBs with an expiration date. For instance imagine you’re visiting France then going to the UK after a few months. With other providers you might buy a 10GB in France package valid for 7 days, then after some months a 10GB in the UK package also valid for 7 days. You likely won’t use up the full package in either country and the remaining capacity will be voided as the package expires.
Silent.link’s pay-as-you-go is different. There are no geographic packages. There are no expiration dates. You simply have a balance denominated in USD and are charged as you use up the data according to the pricing of whichever local carrier you’re connecting via.
Preparing for the same trips from the example above you’d simply top-up your Silent.link balance with $10. Then you’d use Silent.link in France paying $1.33/GB, you’d only be charged for the exact amount used, then you’d go to the UK and pay $1.54/GB from the balance you had left over from France. It doesn’t matter how much time passes between the trips, because Silent.link balances don’t expire. If you have a balance left over you can use it on a future trip, or simply use it up in your home country.
Pros
Anonymity
Silent.link is anonymous. Most other eSIM providers require some form of identification. This can be a traditional, full KYC, procedure involving your ID or passport numbers or, as seemingly innocent, as verifying your phone number with your main carrier. Regardless, a link between the eSIM you bought online and your identity is established.
In some countries you’ll be able to pick up a traditional SIM (or the new eSIM) from a local carrier without undergoing this verification. This can still be a hassle though. You’ll need to look up the laws before travelling, you’ll need to find a local store selling them, you’ll need to decide how you’ll pay privately, etc. And that’s the best case, that’s assuming the country you want to get the SIM in allows you to buy one anonymously.
Private payment methods
Silent.link only accepts cryptocurrency and according to their stats, most payments are made with Bitcoin (either onchain or using the Lightning Network) or with Monero. As such paying anonymously is not a problem. The use a self-hosted instance of BTCPay Server to process payments and operate their own LN node. The entire checkout process can be completed over Tor.
Cons
Network selection
Although you can skip the hassle of buying a new eSIM every time you travel it’s a good idea to look up the pricing of different mobile networks in the country you’re going to. The differences can be trivial, but can also be 100x. If a specific mobile network offers a much better deal, you’ll probably want to dive into your phone’s settings to make sure it only connects to that network.
High prices for some regions
Second issue can be that, especially for poorer countries, Silent.link might not have the best prices. For instance if you travel to Angola you’ll end up paying $155.44/GB. But if you search around for other providers you’ll find eSIM that offer much lower prices for that same country.
Data & incoming SMS & calls only
These eSIMs are either data-only or only offer data and inbound sms and calls. You can’t use Silent.link eSIMs to send texts or make phone calls.
Latency
For most use-cases this shouldn’t matter, but the way roaming works is that when you’re abroad your data is first sent to your home country then sent out into the internet from there. For instance if you’re a Brit on holiday in Spain wherever you open up a website your phone communicates with the Spanish network who forwards the request to your home network in the UK and only there does the request start going towards the website you’re trying to load. The response takes the same path in reverse.
The home network for the Silent.link eSIMs is Poland. To take an extreme (antipodal) example, if you’re in Chile loading a Chilean website your request will go to Poland then back from Poland to the website’s server in Chile, then the response will go from Chile to Poland to you (in Chile). All those trips add latency. In our testing, done during the recent OrangeFren.com meetup in Istanbul, the difference was an additional 73ms. The bandwidth, however, was exceptional, easily surpassing 100 Mbps.
This latency issue isn’t unique to Silent.link, other eSIM providers usually suffer from it too, though their home network may be better suited for your latency needs. If you need the best latency we recommend a SIM from a local provider (or WiFi).
This proxy behaviour isn’t all negative however. It may potentially allow you to circumvent censorship or geoblocking if you’re trying to access resources available from Poland, but unavailable elsewhere.
Besides Istanbul one of the countries we also tested Silent.link in was Northern Cyprus. This territory is mostly unrecognized. It’s a country that, depending on who you ask, is or isn’t real. Despite this unresolved geopolitical status Silent.link performed without any issues.
Installation
If you decide to give Silent.link a try, you'll need to select if you want a data-only plan or a plan with inbound SMS & calling, once you complete the payment simply scan the QR code on the order confirmation page with your phone. Make sure to save the url of that order confirmation page somewhere! You will need it to top up your eSIM and check your remaining balance.
Getting in touch
The preferred way of contacting Silent.link's support is using the website's built-in chat function. Alternative methods include X (formerly Twitter), Matrix and email.
Their support is online from 09:00 - 21:00 UTC although even when testing outside of those hours we got a reply within a minute.
NOTE: These reviews are sponsored, yet the sponsorship does not influence the outcome of the evaluations. Sponsored reviews are independent from the kycnot.me list, being only part of the blog. The reviews have no impact on the scores of the listings or their continued presence on the list. Should any issues arise, I will not hesitate to remove any listing.
-
 @ 39cc53c9:27168656
2025-05-20 10:45:15
@ 39cc53c9:27168656
2025-05-20 10:45:15After almost 3 months of work, we've completed the redesign of kycnot.me. More modern and with many new features.
Privacy remains the foundation - everything still works with JavaScript disabled. If you enable JS, you will get some nice-to-have features like lazy loading and smoother page transitions, but nothing essential requires it.
User Accounts
We've introduced user accounts that require zero personal information:
- Secret user tokens - no email, no phone number, no personal data
- Randomly generated usernames for default privacy and fairness
- Karma system that rewards contributions and unlocks features: custom display names, profile pictures, and more.
Reviews and Community Discussions
On the previous sites, I was using third party open source tools for the comments and discussions. This time, I've built my own from scratch, fully integrated into the site, without JavaScript requirements.
Everyone can share their experiences and help others make informed decisions:
- Ratings: Comments can have a 1-5 star rating attached. You can have one rating per service and it will affect the overall user score.
- Discussions: These are normal comments, you can add them on any listed service.
Comment Moderation
I was strugling to keep up with moderation on the old site. For this, we've implemented an AI-powered moderation system that:
- Auto-approves legitimate comments instantly
- Flags suspicious content for human review
- Keeps discussions valuable by minimizing spam
The AI still can mark comments for human review, but most comments will get approved automatically by this system. The AI also makes summaries of the comments to help you understand the overall sentiment of the community.
Powerful Search & Filtering
Finding exactly what you need is now easier:
- Advanced filtering system with many parameters. You can even filter by attributes to pinpoint services with specific features.
The results are dynamic and shuffle services with identical scores for fairness.
See all listings
Listings are now added as 'Community Contributed' by default. This means that you can still find them in the search results, but they will be clearly marked as such.
Updated Scoring System
New dual-score approach provides more nuanced service evaluations:
- Privacy Score: Measures how well a service protects your personal information and data
-
Trust Score: Assesses reliability, security, and overall reputation
-
Combined into a weighted Overall Score for quick comparisons
- Completely transparent and open source calculation algorithm. No manual tweaking or hidden factors.
AI-Powered Terms of Service Analysis
Basically, a TLDR summary for Terms of Service:
- Automated system extracts the most important points from complex ToS documents
- Clear summaries
- Updated monthly to catch any changes
The ToS document is hashed and only will be updated if there are any changes.
Service Events and Timelines
Track the complete history of any service, on each service page you can see the timeline of events. There are two types of events:
- Automatic events: Created by the system whenever something about a service changes, like its description, supported currencies, attributes, verification status…
- Manual events: Added by admins when there’s important news, such as a service going offline, being hacked, acquired, shut down, or other major updates.
There is also a global timeline view available at /events
Notification System
Since we now have user accounts, we built a notifiaction system so you can stay informed about anything:
- Notifications for comment replies and status changes
- Watch any comment to get notified for new replies.
- Subscribe to services to monitor events and updates
- Notification customization.
Coming soon: Third-party privacy-preserving notifications integration with Telegram, Ntfy.sh, webhooks...
Service Suggestions
Anyone with an account can suggest a new service via the suggestion form. After submitting, you'll receive a tracking page where you can follow the status of your suggestion and communicate directly with admins.
All new suggestions start as "unlisted" — they won't appear in search results until reviewed. Our team checks each submission to ensure it's not spam or inappropriate. If similar services already exist, you'll be shown possible duplicates and can choose to submit your suggestion as an edit instead.
You can always check the progress of your suggestion, respond to moderator questions, and see when it goes live, everything will also be notified to your account. This process ensures high-quality listings and a collaborative approach to building the directory.
These are some of the main features we already have, but there are many more small changes and improvements that you will find when using the site.
What's Next?
This is just the beginning. We will be constantly working to improve KYCnot.me and add more features that help you preserve your privacy.
Remember: True financial freedom requires the right to privacy. Stay KYC-free!
-
 @ 58537364:705b4b85
2025-05-20 06:47:23
@ 58537364:705b4b85
2025-05-20 06:47:23อิคิไก (Ikigai) แปลว่า ความหมายของการมีชีวิตอยู่ เหตุผลของการมีชีวิตอยู่ เราเกิดมาเพื่ออะไร ใช้ชีวิตอยู่ไปทำไม เมื่อการงานไม่ใช่สิ่งที่แปลกแยกจากชีวิต
คนญี่ปุ่นเชื่อว่าทุกคนมี ikigai ของตัวเอง ผู้ที่ค้นพบ ikigai จะเจอความหมายและคุณค่าของชีวิต ทำให้มีความสุขกว่า อารมณ์ดีกว่า และมีโลกที่น่าอยู่กว่าด้วย
ปัจจุบัน มีหนังสือเกี่ยวกับอิคิไกออกวางขายเป็นจำนวนมาก แต่เล่มที่คนญี่ปุ่นเป็นคนเขียนเล่มแรกนั้น คือ
- The Little Book of Ikigai : The secret Japanese way to live a happy and long life โดยอาจารย์เคน โมหงิ (แปลภาษาไทยโดย คุณวุฒิชัย กฤษณะประการกิจ)
ตามมาสัมผัสโลกของอิคิไกที่แท้จริงจากนักวิทยาศาสตร์วิจัยด้านสมองชาวญี่ปุ่นคนนี้ ผ่านบทสนทนาที่จะเปลี่ยนความคิดใหม่ที่ว่า 'อิคิไก' เริ่มต้นจากมองหาความสุขเล็กๆ น้อยๆ ในแบบของตัวเราเอง
อาจารย์เคน โมหงิว่า ปู่จิโร่ เชฟซูชิวัย 94 ปี ที่ยังยืนปั้นซูชิให้เราทานอยู่ในทุกวันนี้ เป็นแรงบันดาลใจให้อาจารย์เกิดไอเดียในการเขียนหนังสืออิคิไก
เชฟซูชิที่ ‘ไม่ได้’ เริ่มเลือกงานนี้เพราะความรักหรือความถนัด แต่กลับทุ่มเทปั้นซูชิทุกคำเพื่อให้ลูกค้ามีความสุข… นั่นคือต้นแบบของอิคิไก
น่าแปลกที่คนญี่ปุ่นไม่ค่อยใช้คำว่า ‘อิคิไก’ ในชีวิตประจำวันหรือบทสนทนาทั่วไปเท่าไหร่
เพราะมันเป็นสิ่งที่ปกติและเราทำกันตามธรรมชาติ ในโลกปัจจุบัน เรามักพูดกันว่าทำอย่างไรเราถึงจะประสบความสำเร็จ ทำอย่างไรจะได้เลื่อนตำแหน่ง หากอยากเป็น CEO จะเป็นได้อย่างไร แต่คนญี่ปุ่นมีความคิดว่าความสำเร็จไม่ใช่ทุกอย่างในชีวิต
ยกตัวอย่างเช่นมีคนญี่ปุ่นจำนวนมากที่จริงจังกับงานอดิเรก หรือมี โคดาวาริ* คนอื่นไม่สนหรอกว่างานอดิเรกของคนคนนั้นจะเป็นอะไร ตราบใดที่คนคนนั้นดูมีความสุขดีนั่นก็โอเคแล้ว มีคนจำนวนมากคลั่งไคล้รถไฟ มังงะ (หนังสือการ์ตูน) หรือแอนิเมะ (ภาพยนตร์การ์ตูน) คนเหล่านี้ไม่จำเป็นต้องมีชื่อเสียงหรือได้รับการยอมรับจากสังคม ตราบเท่าที่พวกเขามีความสุขในแบบของเขาเอง มันก็ดีแล้ว
- ความพิถีพิถันใส่ใจในบางเรื่องเป็นพิเศษ เช่น คนที่ชอบเครื่องเขียนมากๆ จะพิถีพิถันในการเลือกปากกา สมุด ดินสอที่ตนเองจะใช้ เพราะฉะนั้น คนที่มีโคดาวาริเหล่านี้จะศึกษาเครื่องเขียนจนถึงที่สุด วิเคราะห์ ทดลอง จนพบว่าเครื่องเขียนแบบใดที่ตนเองหลงใหลที่สุด
อิคิไกของแต่ละคนอาจแตกต่างกัน ต่างคนอาจมีค่านิยมที่ต่างกัน ซึ่งสะท้อนในรูปแบบชีวิตที่แตกต่างกันก็ได้
อิคิไกเป็นเรื่องของความหลากหลายนะ สังคมญี่ปุ่นพยายามผลักดันให้เด็กๆ ทุกคนตามหาอิคิไกของตนเอง เราจะไม่บอกว่า งานนี้เงินดี ทำสิ หรืองานนี้เงินน้อย อย่าไปทำเลย ถ้าคุณถามนักศึกษาว่า พวกเขาอยากทำงานอะไร พวกเขาคงไม่ตอบว่าเลือกทำที่บริษัทนี้เพราะเงินเป็นอันดับแรกหรอก
อิคิไกแตกต่างจากคำว่า ‘ความสำเร็จ’ คนญี่ปุ่นรู้ว่าชีวิตไม่ได้มีแค่เรื่องประสบความสำเร็จ อิคิไกสำคัญกับชีวิตมากกว่า คุณอาจจะประสบความสำเร็จ แต่คุณอาจไม่มีอิคิไก ในทางกลับกัน แม้คุณไม่ประสบความสำเร็จ คุณอาจจะมีอิคิไกก็ได้ ซึ่งชีวิตคุณอาจจะมีความสุขมากกว่า
อาจารย์เคน โมหงินิยามคำว่า ‘ความสำเร็จ’ คือสิ่งที่คุณจะได้รับการยอมรับจากคนในสังคมหรือบริบทสังคมนั้นๆ แต่อิคิไกมาจากหัวใจของคุณ มาจากความสุขส่วนตัวของคุณ คนอื่นอาจจะไม่ได้มองว่านั่นคือความสำเร็จ
อิคิไกเป็นสิ่งที่เฉพาะบุคคล เราสามารถมีความสุขในแบบของเราเอง เราไม่ตัดสินความสุขของคนอื่น และให้เขามีความสุขในแบบของเขาเอง…
สิ่งสำคัญของอิคิไกคือ คุณมีความสุขเล็กๆ น้อยๆ จากเรื่องที่ดูเหมือนเป็นเรื่องเล็กๆ น้อยๆ หรือเปล่า เช่น ตอนเด็กๆ ผมชอบศึกษาเกี่ยวกับผีเสื้อ เวลาผมไปวิ่งออกกำลังกายแล้วเห็นผีเสื้อสวยๆ ผมก็สัมผัสได้ถึงอิคิไก หรือบางทีอาจเกิดขึ้นตอนที่ผมรู้สึกตลกๆ ก็ได้ ผมเห็นเด็กผู้ชายคนหนึ่งบอกพ่อว่า “พ่อๆ ต้องทำอย่างนี้สิ” เวลาผมได้ยินบทสนทนาแบบนี้ ผมก็รู้สึกถึงอิคิไก
หากพวกเราอยากมีอิคิไกบ้าง เราควรเริ่มจากอะไรดี ? เริ่มจากการสัมผัสความสุขจากสิ่งเล็กๆ น้อยๆ ก่อน มันเริ่มทำได้ง่ายที่สุด ในสมองเรามีสารชื่อโดพามีน หากเราทำอะไรสำเร็จเล็กๆ น้อยๆ โดพามีนจะหลั่งออกมา วงจรนั้นจะช่วยทำให้คุณมีความสุข การมีความสุขกับสิ่งเล็กๆ เช่นนี้เป็นเรื่องสำคัญมาก สำหรับหลายคน แนวคิดเรื่องอิคิไกอาจเข้าใจยาก หรือยากสำหรับบางคนที่ชีวิตพวกเขากำลังอยู่ในช่วงยากลำบาก กำลังรู้สึกหมดหวัง ท้อแท้ หรือไม่ได้เคารพตนเอง เพราะฉะนั้น เริ่มจากความสุขเล็กๆ น้อยๆ ก่อนครับ
มันเหมือนการคิดบวกไหม ? อิคิไกเป็นส่วนหนึ่งนะ เวลาเราคิดถึงชีวิต หรือคิดหาวิธีการคิดบวก มันเป็นเรื่องที่ซับซ้อนมาก สำหรับบางคนคำว่า ‘คิดบวก’ อาจฟังดูกดดันสำหรับพวกเขา เพราะฉะนั้น เริ่มจากการมองเห็นความสุขจากสิ่งเล็กๆ น้อยๆ รอบตัว สิ่งเล็กมากๆ เช่นการได้ตื่นมาชงกาแฟดื่ม การได้วิ่งกลางสายฝน

Lesson from Ken Mogi 1. อิคิไก ไม่ใช่การแสวงหาความสำเร็จหรือความร่ำรวย แต่เป็นการรู้สึกหรือสัมผัสถึงความสุขในชีวิตของตนเอง จนทำให้เราเห็นความหมายของชีวิตเราในแบบของเรา 2. อิคิไกไม่ใช่สิ่งที่สังคมนิยามหรือโลกให้ความสำคัญ แต่ละคนมีอิคิไกที่แตกต่างกัน และมีความสุขกับชีวิตในแบบของตนเอง ที่เราเลือกเอง 3. เราไม่ควรตัดสินคนอื่นหรือบีบบังคับคนอื่น เช่น ลูก แฟน ให้ใช้ชีวิตในแบบที่เราคิดว่าใช่ แต่เราควรเคารพความหลากหลายนั้น 4. มองคนที่มีอิคิไกหรือกำลังสนุกกับสิ่งที่พวกเขารักด้วยรอยยิ้ม และคอยช่วยเหลือหากพวกเขาลำบาก 5. อิคิไกมีทั้งระดับใหญ่ ซึ่งเกี่ยวกับแนวทางชีวิตหรือคุณค่าของงาน และอิคิไกระดับเล็กคือการสัมผัสความสุขเล็กๆ น้อยๆ ที่พบเห็นได้ในชีวิตประจำวัน 6. อิคิไก เริ่มต้นจากมองหาความสุขเล็กๆ น้อยๆ ในวันนี้
ที่มา : จากคอลัมน์ Cloud of Thoughts บทสัมภาษณ์ของอ.เกตุวดี Marumura พาไปคุยกับอาจารย์เคน โมหงิ ผู้เขียนหนังสืออิคิไกเล่มแรก!
-
 @ 4ba8e86d:89d32de4
2025-05-19 22:33:46
@ 4ba8e86d:89d32de4
2025-05-19 22:33:46O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://pomf2.lain.la/f/eprhj0u3.mp4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://pomf2.lain.la/f/7p6jfr9r.mp4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável. https://pomf2.lain.la/f/x4pm8hm8.mp4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ 3f770d65:7a745b24
2025-05-19 18:09:52
@ 3f770d65:7a745b24
2025-05-19 18:09:52🏌️ Monday, May 26 – Bitcoin Golf Championship & Kickoff Party
Location: Las Vegas, Nevada\ Event: 2nd Annual Bitcoin Golf Championship & Kick Off Party"\ Where: Bali Hai Golf Clubhouse, 5160 S Las Vegas Blvd, Las Vegas, NV 89119\ 🎟️ Get Tickets!
Details:
-
The week tees off in style with the Bitcoin Golf Championship. Swing clubs by day and swing to music by night.
-
Live performances from Nostr-powered acts courtesy of Tunestr, including Ainsley Costello and others.
-
Stop by the Purple Pill Booth hosted by Derek and Tanja, who will be on-boarding golfers and attendees to the decentralized social future with Nostr.
💬 May 27–29 – Bitcoin 2025 Conference at the Las Vegas Convention Center
Location: The Venetian Resort\ Main Attraction for Nostr Fans: The Nostr Lounge\ When: All day, Tuesday through Thursday\ Where: Right outside the Open Source Stage\ 🎟️ Get Tickets!
Come chill at the Nostr Lounge, your home base for all things decentralized social. With seating for \~50, comfy couches, high-tops, and good vibes, it’s the perfect space to meet developers, community leaders, and curious newcomers building the future of censorship-resistant communication.
Bonus: Right across the aisle, you’ll find Shopstr, a decentralized marketplace app built on Nostr. Stop by their booth to explore how peer-to-peer commerce works in a truly open ecosystem.
Daily Highlights at the Lounge:
-
☕️ Hang out casually or sit down for a deeper conversation about the Nostr protocol
-
🔧 1:1 demos from app teams
-
🛍️ Merch available onsite
-
🧠 Impromptu lightning talks
-
🎤 Scheduled Meetups (details below)
🎯 Nostr Lounge Meetups
Wednesday, May 28 @ 1:00 PM
- Damus Meetup: Come meet the team behind Damus, the OG Nostr app for iOS that helped kickstart the social revolution. They'll also be showcasing their new cross-platform app, Notedeck, designed for a more unified Nostr experience across devices. Grab some merch, get a demo, and connect directly with the developers.
Thursday, May 29 @ 1:00 PM
- Primal Meetup: Dive into Primal, the slickest Nostr experience available on web, Android, and iOS. With a built-in wallet, zapping your favorite creators and friends has never been easier. The team will be on-site for hands-on demos, Q\&A, merch giveaways, and deeper discussions on building the social layer of Bitcoin.
🎙️ Nostr Talks at Bitcoin 2025
If you want to hear from the minds building decentralized social, make sure you attend these two official conference sessions:
1. FROSTR Workshop: Multisig Nostr Signing
-
🕚 Time: 11:30 AM – 12:00 PM
-
📅 Date: Wednesday, May 28
-
📍 Location: Developer Zone
-
🎤 Speaker: nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgdwaehxw309ahx7uewd3hkcqpqs9etjgzjglwlaxdhsveq0qksxyh6xpdpn8ajh69ruetrug957r3qf4ggfm (Austin Kelsay) @ Voltage\ A deep-dive into FROST-based multisig key management for Nostr. Geared toward devs and power users interested in key security.
2. Panel: Decentralizing Social Media
-
🕑 Time: 2:00 PM – 2:30 PM
-
📅 Date: Thursday, May 29
-
📍 Location: Genesis Stage
-
🎙️ Moderator: nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqy08wumn8ghj7mn0wd68yttjv4kxz7fwv3jhyettwfhhxuewd4jsqgxnqajr23msx5malhhcz8paa2t0r70gfjpyncsqx56ztyj2nyyvlq00heps - Bitcoin Strategy @ Roxom TV
-
👥 Speakers:
-
nostr:nprofile1qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcppemhxue69uhkummn9ekx7mp0qqsy2ga7trfetvd3j65m3jptqw9k39wtq2mg85xz2w542p5dhg06e5qmhlpep – Early Bitcoin dev, CEO @ Sirius Business Ltd
-
nostr:nprofile1qy2hwumn8ghj7mn0wd68ytndv9kxjm3wdahxcqg5waehxw309ahx7um5wfekzarkvyhxuet5qqsw4v882mfjhq9u63j08kzyhqzqxqc8tgf740p4nxnk9jdv02u37ncdhu7e3 – Analyst & Partner @ Ego Death Capital
Get the big-picture perspective on why decentralized social matters and how Nostr fits into the future of digital communication.
🌃 NOS VEGAS Meetup & Afterparty
Date: Wednesday, May 28\ Time: 7:00 PM – 1:00 AM\ Location: We All Scream Nightclub, 517 Fremont St., Las Vegas, NV 89101\ 🎟️ Get Tickets!
What to Expect:
-
🎶 Live Music Stage – Featuring Ainsley Costello, Sara Jade, Able James, Martin Groom, Bobby Shell, Jessie Lark, and other V4V artists
-
🪩 DJ Party Deck – With sets by nostr:nprofile1qy0hwumn8ghj7cmgdae82uewd45kketyd9kxwetj9e3k7mf6xs6rgqgcwaehxw309ahx7um5wgh85mm694ek2unk9ehhyecqyq7hpmq75krx2zsywntgtpz5yzwjyg2c7sreardcqmcp0m67xrnkwylzzk4 , nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgkwaehxw309anx2etywvhxummnw3ezucnpdejqqg967faye3x6fxgnul77ej23l5aew8yj0x2e4a3tq2mkrgzrcvecfsk8xlu3 , and more DJs throwing down
-
🛰️ Live-streamed via Tunestr
-
🧠 Nostr Education – Talks by nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq37amnwvaz7tmwdaehgu3dwfjkccte9ejx2un9ddex7umn9ekk2tcqyqlhwrt96wnkf2w9edgr4cfruchvwkv26q6asdhz4qg08pm6w3djg3c8m4j , nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqg7waehxw309anx2etywvhxummnw3ezucnpdejz7ur0wp6kcctjqqspywh6ulgc0w3k6mwum97m7jkvtxh0lcjr77p9jtlc7f0d27wlxpslwvhau , nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq3vamnwvaz7tmwdaehgu3wd33xgetk9en82m30qqsgqke57uygxl0m8elstq26c4mq2erz3dvdtgxwswwvhdh0xcs04sc4u9p7d , nostr:nprofile1q9z8wumn8ghj7erzx3jkvmmzw4eny6tvw368wdt8da4kxamrdvek76mrwg6rwdngw94k67t3v36k77tev3kx7vn2xa5kjem9dp4hjepwd3hkxctvqyg8wumn8ghj7mn0wd68ytnhd9hx2qpqyaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgssuy4zk , nostr:nprofile1qy28wue69uhnzvpwxqhrqt33xgmn5dfsx5cqz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqqswavgevxe9gs43vwylumr7h656mu9vxmw4j6qkafc3nefphzpph8ssvcgf8 , and more.
-
🧾 Vendors & Project Booths – Explore new tools and services
-
🔐 Onboarding Stations – Learn how to use Nostr hands-on
-
🐦 Nostrich Flocking – Meet your favorite nyms IRL
-
🍸 Three Full Bars – Two floors of socializing overlooking vibrant Fremont Street
| | | | | ----------- | -------------------- | ------------------- | | Time | Name | Topic | | 7:30-7:50 | Derek | Nostr for Beginners | | 8:00-8:20 | Mark & Paul | Primal | | 8:30-8:50 | Terry | Damus | | 9:00-9:20 | OpenMike and Ainsley | V4V | | 09:30-09:50 | The Space | Space |
This is the after-party of the year for those who love freedom technology and decentralized social community. Don’t miss it.
Final Thoughts
Whether you're there to learn, network, party, or build, Bitcoin 2025 in Las Vegas has a packed week of Nostr-friendly programming. Be sure to catch all the events, visit the Nostr Lounge, and experience the growing decentralized social revolution.
🟣 Find us. Flock with us. Purple pill someone.
-
-
 @ a8d1560d:3fec7a08
2025-05-19 17:28:05
@ a8d1560d:3fec7a08
2025-05-19 17:28:05NIP-XX
Documentation and Wikis with Spaces and Format Declaration
draftoptionalSummary
This NIP introduces a system for collaborative documentation and wikis on Nostr. It improves upon earlier efforts by adding namespace-like Spaces, explicit content format declaration, and clearer separation of article types, including redirects and merge requests.
Motivation
Previous approaches to wiki-style collaborative content on Nostr had two key limitations:
- Format instability – No declared format per event led to breaking changes (e.g. a shift from Markdown to Asciidoc).
- Lack of namespace separation – All articles existed in a global space, causing confusion and collision between unrelated projects.
This NIP addresses both by introducing:
- Spaces – individually defined wikis or documentation sets.
- Explicit per-article format declaration.
- Dedicated event kinds for articles, redirects, merge requests, and space metadata.
Specification
kind: 31055– Space DefinitionDefines a project namespace for articles.
Tags: -
["name", "<space title>"]-["slug", "<short identifier>"]-["description", "<optional description>"]-["language", "<ISO language code>"]-["license", "<license text or SPDX ID>"]Content: (optional) full description or README for the space.
kind: 31056– ArticleAn article in a specific format belonging to a defined space.
Tags: -
["space", "<slug>"]-["title", "<article title>"]-["format", "markdown" | "asciidoc" | "mediawiki" | "html"]-["format-version", "<format version>"](optional) -["prev", "<event-id>"](optional) -["summary", "<short change summary>"](optional)Content: full body of the article in the declared format.
kind: 31057– RedirectRedirects from one article title to another within the same space.
Tags: -
["space", "<slug>"]-["from", "<old title>"]-["to", "<new title>"]Content: empty.
kind: 31058– Merge RequestProposes a revision to an article without directly altering the original.
Tags: -
["space", "<slug>"]-["title", "<article title>"]-["base", "<event-id>"]-["format", "<format>"]-["comment", "<short summary>"](optional)Content: proposed article content.
Format Guidelines
Currently allowed formats: -
markdown-asciidoc-mediawiki-htmlClients MUST ignore formats they do not support. Clients MAY apply stricter formatting rules.
Client Behavior
Clients: - MUST render only supported formats. - MUST treat
spaceas a case-sensitive namespace. - SHOULD allow filtering, browsing and searching within Spaces. - SHOULD support revision tracking viaprev. - MAY support diff/merge tooling forkind: 31058.
Examples
Space Definition
json { "kind": 31055, "tags": [ ["name", "Bitcoin Docs"], ["slug", "btc-docs"], ["description", "Developer documentation for Bitcoin tools"], ["language", "en"], ["license", "MIT"] ], "content": "Welcome to the Bitcoin Docs Space." }Markdown Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "Installation Guide"], ["format", "markdown"] ], "content": "# Installation\n\nFollow these steps to install the software..." }Asciidoc Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "RPC Reference"], ["format", "asciidoc"] ], "content": "= RPC Reference\n\nThis section describes JSON-RPC calls." }MediaWiki Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "Block Structure"], ["format", "mediawiki"] ], "content": "== Block Structure ==\n\nThe structure of a Bitcoin block is..." }Redirect
json { "kind": 31057, "tags": [ ["space", "btc-docs"], ["from", "Getting Started"], ["to", "Installation Guide"] ], "content": "" }Merge Request
json { "kind": 31058, "tags": [ ["space", "btc-docs"], ["title", "Installation Guide"], ["base", "d72fa1..."], ["format", "markdown"], ["comment", "Added step for testnet"] ], "content": "# Installation\n\nNow includes setup instructions for testnet users." }
Acknowledgements
This proposal builds on earlier ideas for decentralized wikis and documentation within Nostr, while solving common issues related to format instability and lack of project separation.
-
 @ 3f68dede:779bb81d
2025-05-19 17:14:15
@ 3f68dede:779bb81d
2025-05-19 17:14:15 -
 @ 3f68dede:779bb81d
2025-05-19 17:06:26
@ 3f68dede:779bb81d
2025-05-19 17:06:26
