-
 @ 3bf0c63f:aefa459d
2024-11-07 14:56:17
@ 3bf0c63f:aefa459d
2024-11-07 14:56:17The case against edits
Direct edits are a centralizing force on Nostr, a slippery slope that should not be accepted.
Edits are fine in other, more specialized event kinds, but the
kind:1space shouldn't be compromised with such a push towards centralization, becausekind:1is the public square of Nostr, where all focus should be on decentralization and censorship-resistance.- Why?
Edits introduce too much complexity. If edits are widespread, all clients now have to download dozens of extra events at the same time while users are browsing a big feed of notes which are already coming from dozens of different relays using complicated outbox-model-based querying, then for each event they have to open yet another subscription to these relays -- or perform some other complicated batching of subscriptions which then requires more complexity on the event handling side and then when associating these edits with the original events. I can only imagine this will hurt apps performance, but it definitely raises the barrier to entry and thus necessarily decreases Nostr decentralization.
Some clients may be implemneted in way such that they download tons of events and then store them in a local databases, from which they then construct the feed that users see. Such clients may make edits potentially easier to deal with -- but this is hardly an answer to the point above, since such clients are already more complex to implement in the first place.
- What do you have against complex clients?
The point is not to say that all clients should be simple, but that it should be simple to write a client -- or at least as simple as physically possible.
You may not be thinking about it, but if you believe in the promise of Nostr then we should expect to see Nostr feeds in many other contexts other than on a big super app in a phone -- we should see Nostr notes being referenced from and injected in unrelated webpages, unrelated apps, hardware devices, comment sections and so on. All these micro-clients will have to implement some complicated edit-fetching logic now?
- But aren't we already fetching likes and zaps and other things, why not fetch edits too?
Likes, zaps and other similar things are optional. It's perfectly fine to use Nostr without seeing likes and/or zaps -- and, believe me, it does happen quite a lot. The point is basically that likes or zaps don't affect the content of the main post at all, while edits do.
- But edits are optional!
No, they are not optional. If edits become widespread they necessarily become mandatory. Any client that doesn't implement edits will be displaying false information to its users and their experience will be completely broken.
- That's fine, as people will just move to clients that support edits!
Exactly, that is what I expect to happen too, and this is why I am saying edits are a centralizing force that we should be fighting against, not embracing.
If you understand that edits are a centralizing force, then you must automatically agree that they aren't a desirable feature, given that if you are reading this now, with Nostr being so small, there is a 100% chance you care about decentralization and you're not just some kind of lazy influencer that is only doing this for money.
- All other social networks support editing!
This is not true at all. Bluesky has 10x more users than Nostr and doesn't support edits. Instagram doesn't support editing pictures after they're posted, and doesn't support editing comments. Tiktok doesn't support editing videos or comments after they're posted. YouTube doesn't support editing videos after they're posted. Most famously, email, the most widely used and widespread "social app" out there, does not support edits of any kind. Twitter didn't support edits for the first 15 years of its life, and, although some people complained, it didn't hurt the platform at all -- arguably it benefitted it.
If edits are such a straightforward feature to add that won't hurt performance, that won't introduce complexity, and also that is such an essential feature users could never live without them, then why don't these centralized platforms have edits on everything already? There must be something there.
- Eventually someone will implement edits anyway, so why bother to oppose edits now?
Once Nostr becomes big enough, maybe it will be already shielded from such centralizing forces by its sheer volume of users and quantity of clients, maybe not, we will see. All I'm saying is that we shouldn't just push for bad things now just because of a potential future in which they might come.
- The market will decide what is better.
The market has decided for Facebook, Instagram, Twitter and TikTok. If we were to follow what the market had decided we wouldn't be here, and you wouldn't be reading this post.
- OK, you have convinced me, edits are not good for the protocol. But what do we do about the users who just want to fix their typos?
There are many ways. The annotations spec, for example, provides a simple way to append things to a note without being a full-blown edit, and they fall back gracefully to normal replies in clients that don't implement the full annotations spec.
Eventually we could have annotations that are expressed in form of simple (human-readable?) diffs that can be applied directly to the post, but fall back, again, to comments.
Besides these, a very simple idea that wasn't tried yet on Nostr yet is the idea that has been tried for emails and seems to work very well: delaying a post after the "submit" button is clicked and giving the user the opportunity to cancel and edit it again before it is actually posted.
Ultimately, if edits are so necessary, then maybe we could come up with a way to implement edits that is truly optional and falls back cleanly for clients that don't support them directly and don't hurt the protocol very much. Let's think about it and not rush towards defeat.
-
 @ c296b5f7:c7282b53
2025-05-19 23:35:17
@ c296b5f7:c7282b53
2025-05-19 23:35:17testee
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A violência é uma forma de comunicação
A violência é uma forma de comunicação: um serial killer, um pai que bate no filho, uma briga de torcidas, uma sessão de tortura, uma guerra, um assassinato passional, uma briga de bar. Em todos esses se pode enxergar uma mensagem que está tentando ser transmitida, que não foi compreendida pelo outro lado, que não pôde ser expressa, e, quando o transmissor da mensagem sentiu que não podia ser totalmente compreendido em palavras, usou essa outra forma de comunicação.
Quando uma ofensa em um bar descamba para uma briga, por exemplo, o que há é claramente uma tentativa de uma ofensa maior ainda pelo lado do que iniciou a primeira, a briga não teria acontecido se ele a tivesse conseguido expressar em palavras tão claras que toda a audiência de bêbados compreendesse, o que estaria além dos limites da linguagem, naquele caso, o soco com o mão direita foi mais eficiente. Poderia ser também a defesa argumentativa: "eu não sou um covarde como você está dizendo" -- mas o bar não acreditaria nessa frase solta, a comunicação não teria obtido o sucesso desejado.
A explicação para o fato da redução da violência à medida em que houve progresso da civilização está na melhora da eficiência da comunicação humana: a escrita, o refinamento da expressão lingüística, o aumento do alcance da palavra falada com rádio, a televisão e a internet.
Se essa eficiência diminuir, porque não há mais acordo quanto ao significado das palavras, porque as pessoas não estão nem aí para se o que escrevem é bom ou não, ou porque são incapazes de compreender qualquer coisa, deve aumentar proporcionalmente a violência.
-
 @ fd06f542:8d6d54cd
2025-05-20 01:18:45
@ fd06f542:8d6d54cd
2025-05-20 01:18:45🧱 NostrTrust Initial Trust Score List (V0.1)
This list defines the initial trust scores (T Score) for key members of the Nostr community based on their contributions, reputation, and role in the ecosystem. The goal is to seed a decentralized trust system that encourages quality interactions and authentic contributions.
> ⚠️ Note: This is an draft version.
✅ Initial T Score Allocation Rules
| User Type | Initial T Score Range | Criteria | |-----------|------------------------|----------| | Founder | 10,000 | Creator of the Nostr protocol | | Core Developers | 5,000 - 8,000 | Major contributors to core codebase, clients, or infrastructure | | Active Contributors | 1,000 - 4,000 | Recognized long-term contributors to content, tools, or community |
👤 Initial Trust Score Table
| Name / Alias | npub | Initial T Score | Justification | |--------------|------|------------------|----------------| | fiatjaf | npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 | 10,000 | Creator of the Nostr protocol | |Jack|npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m|9,000|| | jb55 | npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s | 7,000 | Developer of tools, relays, and early Nostr integrations,made damus | |Alex Gleason | npub1q3sle0kvfsehgsuexttt3ugjd8xdklxfwwkh559wxckmzddywnws6cd26p | 7,000 || |PABLOF7z|npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft|7,000|NDK| |DASHU|npub19yeqjawls407xjnmgkk6yss7936pcd7qzd5srlj8wye6j8433vrsjazqwk|4,000|Nostrmo | |Moss|npub129z0az8lgffuvsywazww07hx75qas3veh3dazsq56z8y39v86khs2uy5gm|4,000| freerse.com| |w|npub10td4yrp6cl9kmjp9x5yd7r8pm96a5j07lk5mtj2kw39qf8frpt8qm9x2wl|4,000| 0xchat | |Cody Tseng|npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wl|4,000| jumble.social| |nostr_cn_dev|npub1l5r02s4udsr28xypsyx7j9lxchf80ha4z6y6269d0da9frtd2nxsvum9jm|1,000|nostrbook.com,NostrTrust,nostrbridge| |hzrd149|npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr|6,000|blossom,nostrudel| ||||| ||||| ||||| ||||| |||||
-
 @ 9be6a199:6e133301
2025-05-19 23:11:35
@ 9be6a199:6e133301
2025-05-19 23:11:35this is the content
this is an update
-
 @ c296b5f7:c7282b53
2025-05-19 23:18:42
@ c296b5f7:c7282b53
2025-05-19 23:18:42 -
 @ 9be6a199:6e133301
2025-05-19 22:39:28
@ 9be6a199:6e133301
2025-05-19 22:39:28sdsdsd
-
 @ c296b5f7:c7282b53
2025-05-19 23:17:49
@ c296b5f7:c7282b53
2025-05-19 23:17:49https://curtlink.com/user/login powerdigital f1950610#@
-
 @ c296b5f7:c7282b53
2025-05-19 23:16:33
@ c296b5f7:c7282b53
2025-05-19 23:16:33enter in leaders group https://chat.whatsapp.com/EhI9fGsMbGPHd2cF5KQwC9
-
 @ 85fb39c4:81498307
2025-05-19 23:14:21
@ 85fb39c4:81498307
2025-05-19 23:14:21teste
-
 @ 85fb39c4:81498307
2025-05-19 23:07:11
@ 85fb39c4:81498307
2025-05-19 23:07:11It's my first post
-
 @ c1e9ab3a:9cb56b43
2025-05-18 04:14:48
@ c1e9ab3a:9cb56b43
2025-05-18 04:14:48Abstract
This document proposes a novel architecture that decouples the peer-to-peer (P2P) communication layer from the Bitcoin protocol and replaces or augments it with the Nostr protocol. The goal is to improve censorship resistance, performance, modularity, and maintainability by migrating transaction propagation and block distribution to the Nostr relay network.
Introduction
Bitcoin’s current architecture relies heavily on its P2P network to propagate transactions and blocks. While robust, it has limitations in terms of flexibility, scalability, and censorship resistance in certain environments. Nostr, a decentralized event-publishing protocol, offers a multi-star topology and a censorship-resistant infrastructure for message relay.
This proposal outlines how Bitcoin communication could be ported to Nostr while maintaining consensus and verification through standard Bitcoin clients.
Motivation
- Enhanced Censorship Resistance: Nostr’s architecture enables better relay redundancy and obfuscation of transaction origin.
- Simplified Lightweight Nodes: Removing the full P2P stack allows for lightweight nodes that only verify blockchain data and communicate over Nostr.
- Architectural Modularity: Clean separation between validation and communication enables easier auditing, upgrades, and parallel innovation.
- Faster Propagation: Nostr’s multi-star network may provide faster propagation of transactions and blocks compared to the mesh-like Bitcoin P2P network.
Architecture Overview
Components
-
Bitcoin Minimal Node (BMN):
- Verifies blockchain and block validity.
- Maintains UTXO set and handles mempool logic.
- Connects to Nostr relays instead of P2P Bitcoin peers.
-
Bridge Node:
- Bridges Bitcoin P2P traffic to and from Nostr relays.
- Posts new transactions and blocks to Nostr.
- Downloads mempool content and block headers from Nostr.
-
Nostr Relays:
- Accept Bitcoin-specific event kinds (transactions and blocks).
- Store mempool entries and block messages.
- Optionally broadcast fee estimation summaries and tipsets.
Event Format
Proposed reserved Nostr
kindnumbers for Bitcoin content (NIP/BIP TBD):| Nostr Kind | Purpose | |------------|------------------------| | 210000 | Bitcoin Transaction | | 210001 | Bitcoin Block Header | | 210002 | Bitcoin Block | | 210003 | Mempool Fee Estimates | | 210004 | Filter/UTXO summary |
Transaction Lifecycle
- Wallet creates a Bitcoin transaction.
- Wallet sends it to a set of configured Nostr relays.
- Relays accept and cache the transaction (based on fee policies).
- Mining nodes or bridge nodes fetch mempool contents from Nostr.
- Once mined, a block is submitted over Nostr.
- Nodes confirm inclusion and update their UTXO set.
Security Considerations
- Sybil Resistance: Consensus remains based on proof-of-work. The communication path (Nostr) is not involved in consensus.
- Relay Discoverability: Optionally bootstrap via DNS, Bitcoin P2P, or signed relay lists.
- Spam Protection: Relay-side policy, rate limiting, proof-of-work challenges, or Lightning payments.
- Block Authenticity: Nodes must verify all received blocks and reject invalid chains.
Compatibility and Migration
- Fully compatible with current Bitcoin consensus rules.
- Bridge nodes preserve interoperability with legacy full nodes.
- Nodes can run in hybrid mode, fetching from both P2P and Nostr.
Future Work
- Integration with watch-only wallets and SPV clients using verified headers via Nostr.
- Use of Nostr’s social graph for partial trust assumptions and relay reputation.
- Dynamic relay discovery using Nostr itself (relay list events).
Conclusion
This proposal lays out a new architecture for Bitcoin communication using Nostr to replace or augment the P2P network. This improves decentralization, censorship resistance, modularity, and speed, while preserving consensus integrity. It encourages innovation by enabling smaller, purpose-built Bitcoin nodes and offloading networking complexity.
This document may become both a Bitcoin Improvement Proposal (BIP-XXX) and a Nostr Improvement Proposal (NIP-XXX). Event kind range reserved: 210000–219999.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Jofer
Jofer era um jogador diferente. À primeira vista não, parecia igual, um volante combativo, perseguia os atacantes adversários implacavelmente, um bom jogador. Mas não era essa a característica que diferenciava Jofer. Jofer era, digamos, um chutador.
Começou numa semifinal de um torneio de juniores. O time de Jofer precisava do empate e estava sofrendo uma baita pressão do adversário, mas o jogo estava 1 a 1 e parecia que ia ficar assim mesmo, daquele jeito futebolístico que parece, parece mesmo. Só que aos 46 do segundo tempo tomaram um gol espírita, Ruizinho do outro time saiu correndo pela esquerda e, mesmo sendo canhoto, foi cortando para o meio, os zagueiros meio que achando que já tinha acabado mesmo, devia ter só mais aquele lance, o árbitro tinha dado dois minutos, Ruizinho chutou, marcou e o goleiro, que só pulou depois que já tinha visto que não ia ter jeito, ficou xingando.
A bola saiu do meio e tocaram para Jofer, ninguém nem veio marcá-lo, o outro time já estava comemorando, e com razão, o juiz estava de sacanagem em fazer o jogo continuar, já estava tudo acabado mesmo. Mas não, estava certo, mais um minuto de acréscimo, justo. Em um minuto dá pra fazer um gol. Mas como? Jofer pensou nas partidas da NBA em que com alguns centésimos de segundo faltando o armador jogava de qualquer jeito para a cesta e às vezes acertava. De trás do meio de campo, será? Não vou ter nem força pra fazer chegar no gol. Vou virar piada, melhor tocar pro Fumaça ali do lado e a gente perde sem essa humilhação no final. Mas, poxa, e daí? Vou tentar mesmo assim, qualquer coisa eu falo que foi um lançamento e daqui a uns dias todo mundo esquece. Olhou para o próprio pé, virou ele de ladinho, pra fora e depois pra dentro (bom, se eu pegar daqui, direitinho, quem sabe?), jogou a bola pro lado e bateu. A bola subiu escandalosamente, muito alta mesmo, deve ter subido uns 200 metros. Jofer não tinha como ter a menor noção. Depois foi descendo, o goleirão voltando correndo para debaixo da trave e olhando pra bola, foi chegando e pulando já só pra acompanhar, para ver, dependurado no travessão, a bola sair ainda bem alta, ela bateu na rede lateral interna antes de bater no chão, quicar violentamente e estufar a rede no alto do lado direito de quem olhava.
Mas isso tudo foi sonho do Jofer. Sonhou acordado, numa noite em que demorou pra dormir, deitado na sua cama. Ficou pensando se não seria fácil, se ele treinasse bastante, acertar o gol bem de longe, tipo no sonho, e se não dava pra fazer gol assim. No dia seguinte perguntou a Brunildinho, o treinador de goleiros. Era difícil defender essas bolas, ainda mais se elas subissem muito, o goleiro ficava sem perspectiva, o vento alterava a trajetória a cada instante, tinha efeito, ela cairia rápido, mas claro que não valia à pena treinar isso, a chance de acertar o gol era minúscula. Mas Jofer só ia tentar depois que treinasse bastante e comprovasse o que na sua imaginação parecia uma excelente idéia.
Começou a treinar todos os dias. Primeiro escondido, por vergonha dos colegas, chegava um pouco antes e ficava lá, chutando do círculo central. Ao menor sinal de gente se aproximando, parava e ia catar as bolas. Depois, quando começou a acertar, perdeu a vergonha. O pessoal do clube todo achava engraçado quando via Jofer treinando e depois ouvia a explicação da boca de alguém, ninguém levava muito a sério, mas também não achava de todo ridículo. O pessoal ria, mas no fundo torcia praquilo dar certo, mesmo.
Aconteceu que num jogo que não valia muita coisa, empatezinho feio, aos 40 do segundo tempo, a marcação dos adversários já não estava mais pressionando, todo mundo contente com o empate e com vontade de parar de jogar já, o Henrique, meia-esquerdo, humilde, mas ainda assim um pouco intimidante para Jofer (jogava demais), tocou pra ele. Vai lá, tenta sua loucura aí. Assumiu a responsabilidade do nosso volante introspectivo. Seria mais verossímil se Jofer tivesse errado, primeira vez que tentou, restava muito tempo ainda pra ele ter a chance de ser herói, ninguém acerta de primeira, mas ele acertou. Quase como no sonho, Lucas, o goleiro, não esperava, depois que viu o lance, riu-se, adiantou-se para pegar a bola que ele julgava que quicaria na área, mas ela foi mais pra frente, mais e mais, daí Lucas já estava correndo, só que começou a pensar que ela ia pra fora, e ele ia só se dependurar no travessão e fazer seu papel de estar na bola. Acabou que por conta daquele gol eles terminaram em segundo no grupo daquele torneiozinho, ao invés de terceiro, e não fez diferença nenhuma.
-
 @ 4ba8e86d:89d32de4
2025-05-19 22:33:46
@ 4ba8e86d:89d32de4
2025-05-19 22:33:46O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://pomf2.lain.la/f/eprhj0u3.mp4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://pomf2.lain.la/f/7p6jfr9r.mp4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável. https://pomf2.lain.la/f/x4pm8hm8.mp4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28WelcomeBot
The first bot ever created for Trello.
It invited to a public board automatically anyone who commented on a card he was added to.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Donations on the internet
(This was written in the context of donations to people who do free stuff on the internet, open-source software and so on.)
Donations are broken not because "few people care", but because it's an unsolvable information problem: no one knows how much they should be donating and to whom, and it would be impossible to even think about the perfect donation strategy, much more impossible to execute it.
I use a ton of free services and consume tons of different contents from multiple sources, but it only occurred me to donate to some. And I'm probably donating too much to these, while zero to all others, or maybe too few even to the few ones I donate to. I cannot know.
In the world of ideals there is a correct amount that each donor should be giving to each contributor in every single item in the full production structure of something the donors care about, but this is not a mathematical problem, it's the statement of an impossibility.
Maybe https://mises.org/library/superman-needs-agent is related.
-
 @ 2f29aa33:38ac6f13
2025-05-17 12:59:01
@ 2f29aa33:38ac6f13
2025-05-17 12:59:01The Myth and the Magic
Picture this: a group of investors, huddled around a glowing computer screen, nervously watching Bitcoin’s price. Suddenly, someone produces a stick-no ordinary stick, but a magical one. With a mischievous grin, they poke the Bitcoin. The price leaps upward. Cheers erupt. The legend of the Bitcoin stick is born.
But why does poking Bitcoin with a stick make the price go up? Why does it only work for a lucky few? And what does the data say about this mysterious phenomenon? Let’s dig in, laugh a little, and maybe learn the secret to market-moving magic.

The Statistical Side of Stick-Poking
Bitcoin’s Price: The Wild Ride
Bitcoin’s price is famous for its unpredictability. In the past year, it’s soared, dipped, and soared again, sometimes gaining more than 50% in just a few months. On a good day, billions of dollars flow through Bitcoin trades, and the price can jump thousands in a matter of hours. Clearly, something is making this happen-and it’s not just spreadsheets and financial news.
What Actually Moves the Price?
-
Scarcity: Only 21 million Bitcoins will ever exist. When more people want in, the price jumps.
-
Big News: Announcements, rumors, and meme-worthy moments can send the price flying.
-
FOMO: When people see Bitcoin rising, they rush to buy, pushing it even higher.
-
Liquidations: When traders betting against Bitcoin get squeezed, it triggers a chain reaction of buying.
But let’s be honest: none of this is as fun as poking Bitcoin with a stick.

The Magical Stick: Not Your Average Twig
Why Not Every Stick Works
You can’t just grab any old branch and expect Bitcoin to dance. The magical stick is a rare artifact, forged in the fires of internet memes and blessed by the spirit of Satoshi. Only a chosen few possess it-and when they poke, the market listens.
Signs You Have the Magical Stick
-
When you poke, Bitcoin’s price immediately jumps a few percent.
-
Your stick glows with meme energy and possibly sparkles with digital dust.
-
You have a knack for timing your poke right after a big event, like a halving or a celebrity tweet.
-
Your stick is rumored to have been whittled from the original blockchain itself.
Why Most Sticks Fail
-
No Meme Power: If your stick isn’t funny, Bitcoin ignores you.
-
Bad Timing: Poking during a bear market just annoys the blockchain.
-
Not Enough Hype: If the bitcoin community isn’t watching, your poke is just a poke.
-
Lack of Magic: Some sticks are just sticks. Sad, but true.

The Data: When the Stick Strikes
Let’s look at some numbers:
-
In the last month, Bitcoin’s price jumped over 20% right after a flurry of memes and stick-poking jokes.
-
Over the past year, every major price surge was accompanied by a wave of internet hype, stick memes, or wild speculation.
-
In the past five years, Bitcoin’s biggest leaps always seemed to follow some kind of magical event-whether a halving, a viral tweet, or a mysterious poke.
Coincidence? Maybe. But the pattern is clear: the stick works-at least when it’s magical.

The Role of Memes, Magic, and Mayhem
Bitcoin’s price is like a cat: unpredictable, easily startled, and sometimes it just wants to be left alone. But when the right meme pops up, or the right stick pokes at just the right time, the price can leap in ways that defy logic.
The bitcoin community knows this. That’s why, when Bitcoin’s stuck in a rut, you’ll see a flood of stick memes, GIFs, and magical thinking. Sometimes, it actually works.

The Secret’s in the Stick (and the Laughs)
So, does poking Bitcoin with a stick really make the price go up? If your stick is magical-blessed by memes, timed perfectly, and watched by millions-absolutely. The statistics show that hype, humor, and a little bit of luck can move markets as much as any financial report.
Next time you see Bitcoin stalling, don’t just sit there. Grab your stick, channel your inner meme wizard, and give it a poke. Who knows? You might just be the next legend in the world of bitcoin magic.
And if your stick doesn’t work, don’t worry. Sometimes, the real magic is in the laughter along the way.

-aco
@block height: 897,104
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Scala is such a great language
Scala is amazing. The type system has the perfect balance between flexibility and powerfulness.
matchstatements are great. You can write imperative code that looks very nice and expressive (and I haven't tried writing purely functional things yet). Everything is easy to write and cheap and neovim integration works great.But Java is not great. And the fact that Scala is a JVM language doesn't help because over the years people have written stuff that depends on Java libraries -- and these Java libraries are not as safe as the Scala libraries, they contain reflection, slowness, runtime errors, all kinds of horrors.
Scala is also very tightly associated with Akka, the actor framework, and Akka is a giant collection of anti-patterns. Untyped stuff, reflection, dependency on JVM, basically a lot of javisms. I just arrived and I don't know anything about the Scala history or ecosystem or community, but I have the impression that Akka has prevent more adoption of Scala from decent people that aren't Java programmers.
But luckily there is a solution -- or two solutions: ScalaJS is a great thing that exists. It transpiles Scala code into JavaScript and it runs on NodeJS or in a browser!
Scala Native is a much better deal, though, it compiles to LLVM and then to binary code and you can have single binaries that run directly without a JVM -- not that the single JARs are that bad though, they are great and everybody has Java so I'll take that anytime over C libraries or NPM-distributed software, but direct executables even better. Scala Native just needs a little more love and some libraries and it will be the greatest thing in a couple of years.
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ 3bf0c63f:aefa459d
2024-09-18 10:37:09
@ 3bf0c63f:aefa459d
2024-09-18 10:37:09a way to do an open and permissionless mesh network
I don't have much experience with that so maybe this is all a stupid nonsense, but I think routing in mesh networks (by which I mean all the software that exists out there for creating smallish mesh networks and the real-world projects that use them and effectively have a community of people that connect to each other in some geographical area or a virtual network that uses the underlying internet) is never scalable. It basically always requires all the nodes to keep a full view of the network in order to route packages -- and often there is no incentive for them to do that either. And then the thing is easily spammable but either that problem doesn't happen because the mesh never gets big enough or it has a central committee that decides who can join.
The biggest example is, of course, the big ICANN-controlled IP network, that gets all the negatives of being centrally controlled while weirdly getting also all the negatives of being a kinda-decentralized peer-to-peer ad-hoc network between indepent ISPs.
A good solution that makes kinda-decentralized (at least open and permissionless) routing possible and replaces node addresses with pubkeys could get make it possible for us to get rid of ICANN. Once that is done, ad-hoc peering would become more seamless and ISPs wouldn't have to be so big and clunky, they could slowly split, and non-comercial entities could join the party too by basically just plugging a cable or pointing an antenna to the correct place.
What is it?
One very dumb solution that came to my mind that has a chance of working is one in which each node as a keypair and to be reachable by others they announce their address -- for example, using some kind of DNS (on a [spacechain]?) or by directly communicating their address through some other means -- as their public key plus some "routing hints".
The routing hints are just pubkeys of other nodes known to be routers. Known to whom? Well, this would require some schelling points to naturally appear and the network would be ordered around them, but you are never forced to use them, you have to include as many routing hints as required to ensure that all the people you want to connect to you will eventually be able to, but nothing is ever 100% guaranteed.
Such network could probably work with a pure onion routing scheme with all its privacy benefits in some cases; degrading to a trampoline onion routing scheme otherwise, which means it will just be slightly less private the more trampolines you have to use. And every node has to keep track of just a set of routes from them to a bunch of known routers (or trampolines, which in my mind are mostly the same nodes, but are slightly different roles).
Example
Suppose A is trying to connect to B.
A is a home computer in the city of Évora, Portugal.
B is a home computer in the city of Udine, Italy.
There is a route (we, the narrator, know) between them that goes like this:
A--Ev--Li--Al--Ro--Sm--Ve--Ud--B, in which Ev means the node of an ISP in Évora which directly serves A, Li means a big node in Lisboa, Al a node in Algiers, Ro a node in Rome, Sm a node in San Marino, Ve a node in Venice and Ud a gateway node in the mesh of Udine to which B is connected.
There could be many other routes, but we'll ignore them for now.
B could have published his address as
<pubkey-B>?hint=<pubkey-Ud>,<pubkey-Ve>,<pubkey-Sm>,<pubkey-Ro>, which would mean A would only have to know a route from Ev up to Ro.If Ro is known to be a big router, A could easily have a route cached there, and could discover other routes by asking around every now and then too. It wouldn't take a lot of space to have routes cached to some thousands of different known big nodes like that. Then A can just wrap an onion with all the coordinates and the message inside and hand it to Ev and it would reach B. Inside the message she would also include the full route for a message to be sent back.
However, even if A doesn't have a route to Ro, it could still hope that Li would have, then she could make a special "trampoline" onion that goes Ev--Li and then when Li receives it it sees a request to forward the next packet to Ro, so Li has the freedom to choose a route from itself to Ro (as long as it knows Ro, of course) and from there A's message continues.
The same trampolining can exist on B's side, if B doesn't have a route from Ud to Ro, but knows Ro is likely to have one up to Ud -- or if B feels it's not worth including so many hints when most big nodes will have routes to Ud, for example, it can publish his address as
<pubkey-B>?hint=<pubkey-Ud>*<pubkey-Ro>meaning that one should find a route up to Ro and from there ask Ro to trampoline it up to Ud.Or, if B doesn't expect Ud to be very well-known, but Sm yes, then it could do
<pubkey-B>?hint=<pubkey-Ud>,<pubkey-Sm>*<pubkey-Ro>. Again, this is just one hint, in practice it would have to have a lot (maybe 10, 20?) other hints, in a tree structure that this querystring syntax isn't very suited for encoding:``` Ud Tr Pu Za Li
Sm * Ro Ba Mi La Ge * Mo Tu
```
(Remember, we're using city name abbreviations here, but each of these would be a specific node, with a specific public key, supposed for the example to be in such a city, but nothing prevents them from being in different cities or that multiple nodes exist in the same city.)
Summary
Basically packets go from node to node, in a sequence established by the sender -- with optional trampolines in between -- until they get to the target. Target responds in the same route. Nodes can be anyone. Focal points form around big nodes, but they can be replaced easily, the receivers just have to stop using them in their hints, so the network is flexible and open.
-
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28microanalytics
A replacement for Google Analytics that run inside a CouchDB, when CouchDB still was a potential platform for hosting of simple apps and easily distribution of apps with data.
It also had a CLI app for browsing the data with nice CLI charts.
See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Conjecture and criticism
I heard about this epistemological method conjecture and criticism in this video. Oddly, it was portrayed as something that goes against the Austrian method by Paul Sztorc, while the other guy, JW Weatherman, was championing the "praxeological" method of pure logical deduction from first principles as the basis of all economic knowledge.
It has always seemed to me that this pure logical reasoning was somewhat weird, specially in light of Carl Menger's empiricism (which is not the same empiricism from modern sciences).
Conjecture and criticism seems to fit better with Menger's method and whatever Austrians actually do. No one really reasons with pure logical deduction. What people do is spot something in the real world and try to come up with a reasonable explanation that is logically consistent. The entire logical impenetrability of every Austrian theory comes after the theory is conceived (conjected?) by a human mind, not -- like some praxeological claims would imply -- deducted as if by a computer.
-
 @ 6b0a60cf:b952e7d4
2025-05-19 22:33:33
@ 6b0a60cf:b952e7d4
2025-05-19 22:33:33タイトルは釣りです。そんなこと微塵も思っていません。 本稿はアウトボックスモデルの実装に関してうだうだ考えるコーナーです。 ダムスに関して何か言いたいわけではないので先にタイトル回収しておきます。
- NIP-65を守る気なんかさらさら無いのにNIP-65に書いてあるkind:10002のReadリレーの意味を知っていながら全然違う使い方をしているのは一部の和製クライアントの方だよね
- NIP-65を守る気が無いならkind:10002を使うべきではなく、独自仕様でリレーを保存するべきだよね
- アウトボックスモデルを採用しているクライアントからすれば仕様と異なる実装をしてしまっているクライアントが迷惑だと思われても仕方ないよね
- と考えればダムスの方が潔いよね
- とはいえkind:3のcontentは空にしろって言われてんだからやっぱダムスはゴミだわ
- やるとしたらRabbitみたいにローカルに保存するか、別デバイス間で同期したいならkind:30078を使うべきだよね
アウトボックスモデルはなぜ人気がないのか
言ってることはとてもいいと思うんですよ。 欠点があるとすれば、
- 末端のユーザーからすればreadリレーとwriteリレーと書かれると直感的にイメージされるものとかけ離れている
- 正しく設定してもらうには相当の説明が必要
- フォローTLを表示しようとすれば非常にたくさんのリレーと接続することになり現実的ではない
- なるほど完璧な作戦っスねーっ 不可能だという点に目をつぶればよぉ~
余談ですが昔irisでログインした時に localhost のリレーに繋ごうとしてiris壊れたって思ったけど今思えばアウトボックスモデルを忠実に実装してたんじゃないかな…。
現実的に実装する方法は無いのか
これでReadすべきリレーをシミュレーションできる。 https://nikolat.github.io/nostr-relay-trend/ フォローイーのWriteリレーを全部購読しようとすると100個近いリレー数になるので現実的ではありません。 しかしフォローイーのWriteリレーのうち1個だけでよい、とする条件を仮に追加すると一気にハードルが下がります。私の場合はReadリレー含めて7個のリレーに収まりました。 Nos Haikuはとりあえずこの方針でいくことにしました。
今後どうしていきたいのか
エンドユーザーとしての自分の志向としては、自分が指定したリレーだけを購読してほしい、勝手に余計なリレーを読みに行かないでほしい、という気持ちがあり、現状の和製クライアントの仕様を気に入っています。 仮にNos Haikuでアウトボックスモデルを採用しつつ自分の決めたリレーに接続するハイブリッド実装を考えるとすれば、
あなたの購読するリレーはこれですよー - Read(inbox) Relays (あなたへのメンションが届くリレー) - wss://relay1.example.com/ - wss://relay2.example.com/ - wss://relay3.example.com/ - Followee's Write Relays (フォローイーが書き込んでいるリレー) - wss://relay4.example.com/ - wss://relay5.example.com/ - wss://relay6.example.com/って出して、チェックボックス付けてON/OFFできるようにして最終的に購読するリレーをユーザーに決めてもらう感じかな……って漠然と考えています。よほど時間を持て余したときがあればやってみるかも。
あとリレーを数は仕方ないとしてリレーごとにフォローイーの投稿だけを取得するようにした方が理にかなってるよね。全部のリレーから全部のフォローイーの投稿を取得しようとしたら(実装はシンプルで楽だけど)通信量が大変だよね。 rx-nostr の Forward Strategy ってリレーごとにREQかえて一度に購読できるっけ?
常にひとつ以下の REQ サブスクリプションを保持します。
って書いてあるから無理なのかな? あとReadリレーは純粋に自分へのメンション(pタグ付き)イベントのみを購読するようにした方がいい気がする。スパム対策としてかなり有効だと思うので。スパムはNIP-65に準拠したりはしていないでしょうし。 まぁ、NIP-65に準拠していないクライアントからのメンションは届かなくなってしまうわけですが。
-
 @ cae03c48:2a7d6671
2025-05-19 22:21:46
@ cae03c48:2a7d6671
2025-05-19 22:21:46Bitcoin Magazine

BitMine Launches Bitcoin Treasury Advisory Practice, Secures $4M Deal with First ClientToday, BitMine Immersion Technologies, Inc. (OTCQX: BMNRD) announced the launch of its Bitcoin Treasury Advisory Practice and a $4 million deal with a U.S. exchange-listed company. The deal saw Bitmine surpass its last year’s total revenue in that single transaction alone, according to the announcement.
BitMine ( OTCQX: $BMNRD $BMNR) launches Bitcoin Treasury Advisory Practice and secures $4M deal with first client.
This single transaction exceeds our 2024 revenue and sets the stage for major growth.
Read now: https://t.co/R89K3WXdZZ pic.twitter.com/5vIvlYPZUY
— Bitmine Immersion Technologies, Inc. (@BitMNR) May 19, 2025
BitMine will provide “Mining as a Service” (MaaS) by leasing 3,000 Bitcoin ASIC miners to the client through December 30, 2025, in a $3.2 million lease deal, with $1.6 million paid upfront. Additionally, the client has signed an $800,000 consulting agreement for one year focusing on Bitcoin Mining-as-a-Service and Bitcoin Treasury Strategy.
“Currently, there are almost 100 public companies that have adopted Bitcoin as a treasury holding. We expect this number to grow in the future. As more companies adopt Bitcoin treasury strategies, the need for infrastructure, revenue generation, and expert guidance grows along with it,” said Jonathan Bates, CEO of BitMine. “This single transaction is greater than our entire 2024 fiscal year revenue, and we feel there is an opportunity to acquire more clients in the near future as interest in Bitcoin ownership grows.”
BitMine’s first quarter 2025 results showed strong revenue growth, with GAAP revenue rising approximately 135% to $1.2 million, up from $511,000 in Q1 2024, supported by an expanded mining capacity of 4,640 miners as of November 30, 2024, compared to 1,606 the previous year. Despite this growth, the company reported a net loss of $3.9 million in Q1 2025, primarily due to a one-time, non-cash accounting adjustment related to preferred stock; excluding this charge, the adjusted loss was approximately $975,000, consistent with the prior year’s results.
$BMNR reports a 135% revenue increase YOY for Q1 2025 and tripled self-mining capacity with 3,000 new miners! CEO Jonathan Bates credits a team-driven approach and creative financing for this growth.
Read the full release here: https://t.co/slNrZv8Ocn pic.twitter.com/Gb4tk1UfAO— Bitmine Immersion Technologies, Inc. (@BitMNR) January 13, 2025
BitMine’s new Bitcoin Treasury Advisory Practice, along with the $4 million deal, joins a trend among public companies exploring Bitcoin not just as a treasury asset but also as a source of revenue.
This post BitMine Launches Bitcoin Treasury Advisory Practice, Secures $4M Deal with First Client first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 2b998b04:86727e47
2025-05-19 21:18:46
@ 2b998b04:86727e47
2025-05-19 21:18:46After the pruning came clarity.\ And after the clarity came a quiet but relentless question:\ What now?
If I wasn’t going back to Web3, if I wasn’t going to pretend anymore — not in faith, not in finance — then I needed to start building again. But this time, with different materials. Different rhythms. A different spirit.
Starting Over on Solid Ground
I’d spent years exploring tokens, networks, and well-intentioned communities. But most of it, I see now, was sand. It moved with the tides. The incentives shifted. The values bent. And when the storms came — personal, financial, spiritual — much of what I’d been part of collapsed or exposed its shallowness.
So I returned to the beginning: What can’t be faked?
That’s where Bitcoin came in — not just as an asset, but as a foundation.\ It taught me cost. Time. Truth. It doesn’t market itself. It just is.\ A system that punishes shortcuts, rewards discipline, and invites peace.
And the more I leaned in, the more I realized:\ This isn’t just money. This is philosophy. This is soil.
Pruned to Plant Again
I used to be a buy-and-hold investor. I still carry those instincts. But in 2020–21, I discovered trading — and with it, a new kind of discipline. Not gambling. Not speculation. Stewardship under pressure. Real-time decision-making with skin in the game.
My grandfather, who passed in the late '90s, probably would’ve looked a little dimly on trading. He lived off his dividends. Stocks he held for decades. He wasn’t chasing. He was rooting. But he would’ve respected the discipline — the clarity — when done right.
He also saw things I didn’t. He once told me I wasn’t raised properly. It hurt at the time, but now I understand. He saw the drift — not just in me, but in the culture. He understood that frugality means nothing if it’s not paired with truth.
I think he would’ve respected what I’m doing now — even if he wouldn't have fully understand it.
What I’m Building Now
-
StartNation – A Bitcoin-aligned equity accelerator. Proof-based. No tokens. No hype.
-
Golden Gate Group Investments – Real estate with a vision to integrate BTC in payments and ownership. Still early. Still real.
-
Blue Planet Ventures – Equities trading with daily proof-of-work and sats-based performance tracking.
-
A garden – Yes, literal food. Soil and seed. Hypdropnics. Bitcoin taught me patience; gardening reinforces it.
I’m not building a brand. I’m building a life. And I’m doing it in public — not to be seen, but to help others see. That it’s possible to step off the hype rails and still thrive.
Bitcoin: The Turning Point
It wasn’t until last fall that Bitcoin truly became central for me.\ Not just part of a portfolio — the lens through which I see capital, time, and truth.
I don’t see it as speculative anymore. I see it as inevitable. In 20–30 years, I believe Bitcoin will be the de facto reserve currency — even if not in name. Those who hold it will steward wealth not because they played the game, but because they opted out of it early.
I’m stacking not to escape — but to prepare. Not to prove I'm right — but to live rightly.
Legacy Without a Platform
I don’t have children.\ But I do have nieces. Nephews. Brothers. Sisters. Cousins. In-Laws.
And I know they’re watching — even if they don’t say it.\ I want to show them that you can live with truth, walk by faith, work with your hands — and still thrive.
I’m not stacking for applause. I’m stacking for legacy.\ I’m building not just for the next quarter — but for the next generation.
And if someone, years from now, asks why I chose this path, I want to say:
Because it was real.\ Because it was proof.\ Because it was built to last.
⚡ If this series has encouraged or challenged you, zap a few sats/bitcoin. It keeps me building.
✍️ Catch up on the full series here:\ \ Part 1: The Drift -> https://primal.net/andrewgstanton/why-i-left-web3-for-proof-of-work-%E2%80%93-part-1%3A-the-drift\ Part 2: The Breaking Point -> https://primal.net/andrewgstanton/why-i-left-web3-for-proof-of-work---part-2%3A-the-breaking-point\ Part 3: The Return -> https://primal.net/andrewgstanton/why-i-left-web3-for-proof-of-work-%E2%80%93-part-3%3A-the-return\ Part 4: Proof Of Work as Philosophy -> https://primal.net/andrewgstanton/why-i-left-web3-for-proof-of-work-%E2%80%93-part-4%3A-proof-of-work-as-philosophy\ Part 5: Building Again (what you are reading now...)
Written with help from ChatGPT (GPT-4), edited and posted by me.
-
-
 @ 866e0139:6a9334e5
2025-05-19 21:39:26
@ 866e0139:6a9334e5
2025-05-19 21:39:26Autor: Ludwig F. Badenhagen. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie auch in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Wer einhundert Prozent seines Einkommens abgeben muss, ist sicher ein Sklave, oder? Aber ab wieviel Prozent Pflichtabgabe ist er denn kein Sklave mehr? Ab wann ist er frei und selbst-bestimmt?
Wer definieren möchte, was ein Sklave ist, sollte nicht bei Pflichtabgaben verweilen, denn die Fremdbestimmtheit geht viel weiter. Vielfach hat der gewöhnliche Mensch wenig Einfluss darauf, wie er und seine Familie misshandelt wird. Es wird verfügt, welche Bildung, welche Nahrung, welche Medikamente, welche Impfungen und welche Kriege er zu erdulden hat. Hierbei erkennt der gewöhnliche Mensch aber nur, wer ihm direkt etwas an-tut. So wie der Gefolterte bestenfalls seinen Folterer wahrnimmt, aber nicht den, in dessen Auftrag dieser handelt, so haben die vorbezeichnet Geschädigten mit Lehrern, „Experten“, Ärzten und Politikern zu tun. Ebenfalls ohne zu wissen, in wessen Auftrag diese Leute handeln. „Führungssysteme“ sind so konzipiert, dass für viele Menschen bereits kleinste wahrgenommene Vorteile genügen, um einem anderen Menschen Schlimmes anzutun.
Aber warum genau wird Menschen Schlimmes angetan? Die Gründe dafür sind stets dieselben. Der Täter hat ein Motiv und Motivlagen können vielfältig sein.
Wer also ein Motiv hat, ein Geschehen zu beeinflussen, motiviert andere zur Unterstützung. Wem es gelingt, bei anderen den Wunsch zu erwecken, das zu tun, was er möchte, ist wirklich mächtig. Und es sind die Mächtigen im Hintergrund, welche die Darsteller auf den Bühnen dieser Welt dazu nutzen, die Interessen der wirklich Mächtigen durchzusetzen. Insbesondere die letzten fünf Jahre haben eindrucksvoll gezeigt, wie willfährig Politiker, Ärzte, Experten und viele weitere ihre jeweiligen Aufträge gegen die Bevölkerung durchsetz(t)en.
Und so geschieht es auch beim aktuellen Krieg, der stellvertretend auf dem europäischen Kontinent ausgetragen wird. Parolen wie „nie wieder Krieg“ gehören der Vergangenheit an. Stattdessen ist nunmehr wieder der Krieg und nur der Krieg geeignet, um „Aggressionen des Gegners abzuwehren“ und um „uns zu verteidigen“.
Das hat mindestens drei gute Gründe:
- Mit einem Krieg können Sie einem anderen etwas wegnehmen, was er freiwillig nicht herausrückt. Auf diese Weise kommen Sie an dessen Land, seine Rohstoffe und sein Vermögen. Sie können ihn beherrschen und Ihren eigenen Einfluss ausbauen. Je mehr Ihnen gehört, um so besser ist das für Sie. Sie müssen sich weniger abstimmen und Widersacher werden einfach ausgeschaltet.
- Wenn etwas über einen langen Zeitraum aufgebaut wurde, ist es irgendwann auch einmal fertig. Um aber viel Geld verdienen und etwas nach eigenen Vorstellungen gestalten zu können, muss immer wieder etwas Neues erschaffen werden, und da stört das Alte nur. Demzufolge ist ein Krieg ein geeignetes Mittel, etwas zu zerstören. Und das Schöne ist, dass man von Beginn an viel Geld verdient. Denn man muss dem indoktrinierten Volk nur vormachen, dass der Krieg „unbedingt erforderlich“ sei, um das Volk dann selbst bereitwillig für diesen Krieg bezahlen und auch sonst engagiert mitwirken zu lassen. Dann kann in Rüstung und „Kriegstauglichkeit“ investiert werden. Deutschland soll dem Vernehmen nach bereits in einigen Jahren „kriegstauglich“ sein. Der Gegner wartet sicher gerne mit seinen Angriffen, bis es so weit ist.
- Und nicht zu vergessen ist, dass man die vielen gewöhnlichen Menschen loswird. Schon immer wurden Populationen „reguliert“. Das macht bei Tieren ebenfalls so, indem man sie je nach „Erfordernis“ tötet. Und bei kollabierenden Systemen zu Zeiten von Automatisierung und KI unter Berücksichtigung der Klimarettung wissen doch mittlerweile alle, dass es viel zu viele Menschen auf dem Planeten gibt. Wenn jemand durch medizinische Misshandlungen oder auch durch einen Krieg direkt stirbt, zahlt dies auf die Lösung des Problems ein. Aber auch ein „Sterben auf Raten“ ist von großem Vorteil, denn durch die „fachmännische Behandlung von Verletzten“ bis zu deren jeweiligen Tode lässt sich am Leid viel verdienen.
Sie erkennen, dass es sehr vorteilhaft ist, Kriege zu führen, oder? Und diese exemplarisch genannten drei Gründe könnten noch beliebig erweitert werden.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Das Einzige, was gegen Kriegsereignisse sprechen könnte, wäre, dass man selbst niemandem etwas wegnehmen möchte, was ihm gehört, und dass man seinen Mitmenschen nicht schaden, geschweige denn diese verletzen oder gar töten möchte.
In diesem Zusammenhang könnte man auch erkennen, dass die, die nach Krieg rufen, selbst nicht kämpfen. Auch deren Kinder nicht. Man könnte erkennen, dass man selbst nur benutzt wird, um die Interessen anderer durchzusetzen. Wie beim Brettspiel Schach hat jede Figur eine Funktion und keinem Spieler ist das Fortbestehen eines Bauern wichtig, wenn seine Entnahme dem Spielgewinn dient. Wer Krieg spielt, denkt sicher ähnlich.
Meine beiden Großväter waren Soldaten im zweiten Weltkrieg und erlebten die Grausamkeiten des Krieges und der Gefangenschaft so intensiv, dass sie mit uns Enkeln zu keiner Zeit hierüber sprechen konnten, da sie wohl wussten, dass uns allein ihre Erzählungen zutiefst traumatisiert hätten. Die Opas waren analog dem, was wir ihnen an Information abringen konnten, angeblich nur Sanitäter. Sanitäter, wie auch die meisten Großväter aus der Nachbarschaft. Wer aber jemals beobachten konnte, wie unbeholfen mein Opa ein Pflaster aufgebracht hat, der konnte sich denken, dass seine vermeintliche Tätigkeit als Sanitäter eine Notlüge war, um uns die Wahrheit nicht vermitteln zu müssen.
Mein Opa war mein bester Freund und mir treibt es unverändert die Tränen in die Augen, sein erlebtes Leid nachzuempfinden. Und trotz aller seelischen und körperlichen Verletzungen hat er nach seiner Rückkehr aus der Kriegshölle mit großem Erfolg daran gearbeitet, für seine Familie zu sorgen.
Manchmal ist es m. E. besser, die Dinge vom vorhersehbaren Ende aus zu betrachten, um zu entscheiden, welche Herausforderungen man annimmt und welche man besser ablehnt. Es brauchte fast 80 Jahre, um die Deutschen erneut dafür zu begeistern, Ihre Leben „für die gute Sache“ zu opfern. Was heutzutage aber anders ist als früher: Einerseits sind die Politiker dieser Tage sehr durchschaubar geworden. Aber in einem ähnlichen Verhältnis, wie die schauspielerischen Leistungen der Politiker abgenommen haben, hat die Volksverblödung zugenommen.
Denken Sie nicht nach. Denken Sie stattdessen vor. Und denken Sie selbst. Für sich, Ihre Lieben und alle anderen Menschen. Andernfalls wird die Geschichte, so wie sie von meinen Opas (und Omas) erlebt wurde, mit neuen Technologien und „zeitgemäßen Methoden“ wiederholt. Dies führt zweifelsfrei zu Not und Tod.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 4c96d763:80c3ee30
2025-05-19 20:56:26
@ 4c96d763:80c3ee30
2025-05-19 20:56:26Changes
William Casarin (19):
- dave: add screenshot to readme
- dave: fix image in readme
- columns: remove spamming info logs about writing to cache
- columns: never truncate notes you're replying to
- windows: don't show terminal window
- mention: show username instead of display_name
- chrome: switch from ALPHA to BETA
- ui: make post replies selectable
- dave: include anonymous user identifier in api call
- dave: add trial mode
- dave: fix sidebar click
- dave: nudge avatar when you click
- dave: hide media in dave note previews
- chrome: fix theme persistence
- ui: fix a bunch of missing hover pointers
- Release Notedeck Beta v0.4.0
- release: changelog
- timeline: show media on universe timeline
- clippy: fix lint related to iterator
kernelkind (28):
- add
trust_media_from_pk2method - add hashbrown
- introduce & use
JobPool - introduce JobsCache
- add blurhash dependency
- introduce blur
- note: remove unnecessary derive macros from
NoteAction - propagate
JobsCache ImagePulseTint->PulseAlpha- images: move fetch to fn
- add
TexturesCache - images: make
MediaCacheholdMediaCacheType - images: make promise payload optional to take easily
- post: unnest
- notedeck_ui: move carousel to
note/media.rs - note media: only show full screen when loaded
- note media: unnest full screen media
- pass
NoteActionby value instead of reference - propagate
Imagesto actionbar - add one shot error message
- make
WidgetimplProfilePicmutably - implement blurring
- don't show zap button if no wallet
- display name should wrap
- make styled button toggleable
- method to get current default zap amount
- add
CustomZapView - use
CustomZapView
pushed to notedeck:refs/heads/master
-
 @ 1817b617:715fb372
2025-05-19 20:39:28
@ 1817b617:715fb372
2025-05-19 20:39:28Looking to simulate a USDT deposit that appears instantly in a wallet — with no blockchain confirmation, no real spend, and no trace?
You’re in the right place.
🔗 Buy Flash USDT Now This product sends Flash USDT directly to your TRC20, ERC20, or BEP20 wallet address — appears like a real deposit, but disappears after a set time or block depth.
✅ Perfect for: Simulating token inflows Wallet stress testing “Proof of funds” display Flash USDT is ideal for developers, trainers, UI testers, and blockchain researchers — and it’s fully customizable.
🧠 What Is Flash USDT? Flash USDT is a synthetic transaction that mimics a real Tether transfer. It shows up instantly in a wallet balance, and it’s confirmed on-chain — and expires after a set duration.
This makes it:
Visible on wallet interfaces Time-limited (auto-disappears cleanly) Undetectable on block explorers after expiry It’s the smartest, safest way to simulate high-value transactions without real crypto.
🛠️ Flash USDT Software – Your Own USDT Flasher at Your Fingertips Want to control the flash? Run your own operations? Flash unlimited wallets?
🔗 Buy Flash USDT Software
This is your all-in-one USDT flasher tool, built for TRC20, ERC20, and BEP20 chains. It gives you full control to:
Send custom USDT amounts Set custom expiry time (e.g., 30–360 days) Flash multiple wallets Choose between networks (Tron, ETH, BSC) You can simulate any amount, to any supported wallet, from your own system.
No third-party access. No blockchain fee. No trace left behind.
💥 Why Our Flash USDT & Software Stands Out Feature Flash USDT Flash USDT Software One-time flash send ✅ Yes Optional Full sender control ❌ No ✅ Yes TRC20 / ERC20 / BEP20 ✅ Yes ✅ Yes Custom duration/expiry Limited ✅ Yes Unlimited usage ❌ One-off ✅ Yes Whether you’re flashing for wallet testing, demoing investor dashboards, or simulating balance flows, our tools deliver realism without risk.
🛒 Ready to Buy Flash USDT or the Software? Skip the wait. Skip the scammers. You’re one click away from real control.
👉 Buy Flash USDT 👉 Buy Flash USDT Software
📞 Support or live walkthrough?
💬 Telegram: @cryptoflashingtool 📱 WhatsApp: +1 770-666-2531
🚫 Legal Notice These tools are intended for:
Educational purposes Demo environments Wallet and UI testing They are not for illegal use or financial deception. Any misuse is your full responsibility.
Final Call: Need to flash USDT? Want full control? Don’t wait for another “maybe” tool.
Get your Flash USDT or Flashing Software today and simulate like a pro.
🔗 Buy Now → Flash USDT 🔗 Buy Now → Flash USDT Software 💬 Telegram: @cryptoflashingtool 📱 WhatsApp: +1 770-666-2531Looking to simulate a USDT deposit that appears instantly in a wallet — with no blockchain confirmation, no real spend, and no trace?
You’re in the right place.
Buy Flash USDT Now\ This product sends Flash USDT directly to your TRC20, ERC20, or BEP20 wallet address — appears like a real deposit, but disappears after a set time or block depth.
Perfect for:
- Simulating token inflows
- Wallet stress testing
- “Proof of funds” display
Flash USDT is ideal for developers, trainers, UI testers, and blockchain researchers — and it’s fully customizable.
What Is Flash USDT?
Flash USDT is a synthetic transaction that mimics a real Tether transfer. It shows up instantly in a wallet balance, and it’s confirmed on-chain — and expires after a set duration.
This makes it:
- Visible on wallet interfaces
- Time-limited (auto-disappears cleanly)
- Undetectable on block explorers after expiry
It’s the smartest, safest way to simulate high-value transactions without real crypto.
Flash USDT Software – Your Own USDT Flasher at Your Fingertips
Want to control the flash?\ Run your own operations?\ Flash unlimited wallets?
This is your all-in-one USDT flasher tool, built for TRC20, ERC20, and BEP20 chains. It gives you full control to:
- Send custom USDT amounts
- Set custom expiry time (e.g., 30–360 days)
- Flash multiple wallets
- Choose between networks (Tron, ETH, BSC)
You can simulate any amount, to any supported wallet, from your own system.
No third-party access.\ No blockchain fee.\ No trace left behind.
Why Our Flash USDT & Software Stands Out
Feature
Flash USDT
Flash USDT Software
One-time flash send
Yes
Optional
Full sender control
No
Yes
TRC20 / ERC20 / BEP20
Yes
Yes
Custom duration/expiry
Limited
Yes
Unlimited usage
One-off
Yes
Whether you’re flashing for wallet testing, demoing investor dashboards, or simulating balance flows, our tools deliver realism without risk.
Ready to Buy Flash USDT or the Software?
Skip the wait. Skip the scammers.\ You’re one click away from real control.
Support or live walkthrough?
Telegram: @cryptoflashingtool
WhatsApp: +1 770-666-2531
Legal Notice
These tools are intended for:
- Educational purposes
- Demo environments
- Wallet and UI testing
They are not for illegal use or financial deception. Any misuse is your full responsibility.
Final Call:
Need to flash USDT? Want full control?\ Don’t wait for another “maybe” tool.
Get your Flash USDT or Flashing Software today and simulate like a pro.
Telegram: @cryptoflashingtool
WhatsApp: +1 770-666-2531
-
 @ c1e9ab3a:9cb56b43
2025-05-05 14:25:28
@ c1e9ab3a:9cb56b43
2025-05-05 14:25:28Introduction: The Power of Fiction and the Shaping of Collective Morality
Stories define the moral landscape of a civilization. From the earliest mythologies to the modern spectacle of global cinema, the tales a society tells its youth shape the parameters of acceptable behavior, the cost of transgression, and the meaning of justice, power, and redemption. Among the most globally influential narratives of the past half-century is the Star Wars saga, a sprawling science fiction mythology that has transcended genre to become a cultural religion for many. Central to this mythos is the arc of Anakin Skywalker, the fallen Jedi Knight who becomes Darth Vader. In Star Wars: Episode III – Revenge of the Sith, Anakin commits what is arguably the most morally abhorrent act depicted in mainstream popular cinema: the mass murder of children. And yet, by the end of the saga, he is redeemed.
This chapter introduces the uninitiated to the events surrounding this narrative turn and explores the deep structural and ethical concerns it raises. We argue that the cultural treatment of Darth Vader as an anti-hero, even a role model, reveals a deep perversion in the collective moral grammar of the modern West. In doing so, we consider the implications this mythology may have on young adults navigating identity, masculinity, and agency in a world increasingly shaped by spectacle and symbolic narrative.
Part I: The Scene and Its Context
In Revenge of the Sith (2005), the third episode of the Star Wars prequel trilogy, the protagonist Anakin Skywalker succumbs to fear, ambition, and manipulation. Convinced that the Jedi Council is plotting against the Republic and desperate to save his pregnant wife from a vision of death, Anakin pledges allegiance to Chancellor Palpatine, secretly the Sith Lord Darth Sidious. Upon doing so, he is given a new name—Darth Vader—and tasked with a critical mission: to eliminate all Jedi in the temple, including its youngest members.
In one of the most harrowing scenes in the film, Anakin enters the Jedi Temple. A group of young children, known as "younglings," emerge from hiding and plead for help. One steps forward, calling him "Master Skywalker," and asks what they are to do. Anakin responds by igniting his lightsaber. The screen cuts away, but the implication is unambiguous. Later, it is confirmed through dialogue and visual allusion that he slaughtered them all.
There is no ambiguity in the storytelling. The man who will become the galaxy’s most feared enforcer begins his descent by murdering defenseless children.
Part II: A New Kind of Evil in Youth-Oriented Media
For decades, cinema avoided certain taboos. Even films depicting war, genocide, or psychological horror rarely crossed the line into showing children as victims of deliberate violence by the protagonist. When children were harmed, it was by monstrous antagonists, supernatural forces, or offscreen implications. The killing of children was culturally reserved for historical atrocities and horror tales.
In Revenge of the Sith, this boundary was broken. While the film does not show the violence explicitly, the implication is so clear and so central to the character arc that its omission from visual depiction does not blunt the narrative weight. What makes this scene especially jarring is the tonal dissonance between the gravity of the act and the broader cultural treatment of Star Wars as a family-friendly saga. The juxtaposition of child-targeted marketing with a central plot involving child murder is not accidental—it reflects a deeper narrative and commercial structure.
This scene was not a deviation from the arc. It was the intended turning point.
Part III: Masculinity, Militarism, and the Appeal of the Anti-Hero
Darth Vader has long been idolized as a masculine icon. His towering presence, emotionless control, and mechanical voice exude power and discipline. Military institutions have quoted him. He is celebrated in memes, posters, and merchandise. Within the cultural imagination, he embodies dominance, command, and strategic ruthlessness.
For many young men, particularly those struggling with identity, agency, and perceived weakness, Vader becomes more than a character. He becomes an archetype: the man who reclaims power by embracing discipline, forsaking emotion, and exacting vengeance against those who betrayed him. The emotional pain that leads to his fall mirrors the experiences of isolation and perceived emasculation that many young men internalize in a fractured society.
The symbolism becomes dangerous. Anakin's descent into mass murder is portrayed not as the outcome of unchecked cruelty, but as a tragic mistake rooted in love and desperation. The implication is that under enough pressure, even the most horrific act can be framed as a step toward a noble end.
Part IV: Redemption as Narrative Alchemy
By the end of the original trilogy (Return of the Jedi, 1983), Darth Vader kills the Emperor to save his son Luke and dies shortly thereafter. Luke mourns him, honors him, and burns his body in reverence. In the final scene, Vader's ghost appears alongside Obi-Wan Kenobi and Yoda—the very men who once considered him the greatest betrayal of their order. He is welcomed back.
There is no reckoning. No mention of the younglings. No memorial to the dead. No consequence beyond his own internal torment.
This model of redemption is not uncommon in Western storytelling. In Christian doctrine, the concept of grace allows for any sin to be forgiven if the sinner repents sincerely. But in the context of secular mass culture, such redemption without justice becomes deeply troubling. The cultural message is clear: even the worst crimes can be erased if one makes a grand enough gesture at the end. It is the erasure of moral debt by narrative fiat.
The implication is not only that evil can be undone by good, but that power and legacy matter more than the victims. Vader is not just forgiven—he is exalted.
Part V: Real-World Reflections and Dangerous Scripts
In recent decades, the rise of mass violence in schools and public places has revealed a disturbing pattern: young men who feel alienated, betrayed, or powerless adopt mythic narratives of vengeance and transformation. They often see themselves as tragic figures forced into violence by a cruel world. Some explicitly reference pop culture, quoting films, invoking fictional characters, or modeling their identities after cinematic anti-heroes.
It would be reductive to claim Star Wars causes such events. But it is equally naive to believe that such narratives play no role in shaping the symbolic frameworks through which vulnerable individuals understand their lives. The story of Anakin Skywalker offers a dangerous script:
- You are betrayed.
- You suffer.
- You kill.
- You become powerful.
- You are redeemed.
When combined with militarized masculinity, institutional failure, and cultural nihilism, this script can validate the darkest impulses. It becomes a myth of sacrificial violence, with the perpetrator as misunderstood hero.
Part VI: Cultural Responsibility and Narrative Ethics
The problem is not that Star Wars tells a tragic story. Tragedy is essential to moral understanding. The problem is how the culture treats that story. Darth Vader is not treated as a warning, a cautionary tale, or a fallen angel. He is merchandised, celebrated, and decontextualized.
By separating his image from his actions, society rebrands him as a figure of cool dominance rather than ethical failure. The younglings are forgotten. The victims vanish. Only the redemption remains. The merchandise continues to sell.
Cultural institutions bear responsibility for how such narratives are presented and consumed. Filmmakers may intend nuance, but marketing departments, military institutions, and fan cultures often reduce that nuance to symbol and slogan.
Conclusion: Reckoning with the Stories We Tell
The story of Anakin Skywalker is not morally neutral. It is a tale of systemic failure, emotional collapse, and unchecked violence. When presented in full, it can serve as a powerful warning. But when reduced to aesthetic dominance and easy redemption, it becomes a tool of moral decay.
The glorification of Darth Vader as a cultural icon—divorced from the horrific acts that define his transformation—is not just misguided. It is dangerous. It trains a generation to believe that power erases guilt, that violence is a path to recognition, and that final acts of loyalty can overwrite the deliberate murder of the innocent.
To the uninitiated, Star Wars may seem like harmless fantasy. But its deepest myth—the redemption of the child-killer through familial love and posthumous honor—deserves scrutiny. Not because fiction causes violence, but because fiction defines the possibilities of how we understand evil, forgiveness, and what it means to be a hero.
We must ask: What kind of redemption erases the cries of murdered children? And what kind of culture finds peace in that forgetting?
-
 @ 30b99916:3cc6e3fe
2025-05-19 20:30:52
@ 30b99916:3cc6e3fe
2025-05-19 20:30:52bitcoin #security #vault #veracrypt #powershell
BTCwallet automates running hot and cold storage wallets for multiple Bitcoin wallet applications.

BTCwallet is included with VaultApi and supports Sparrow, Blockstream Green, and just added support for Wasabi wallets.
To launch a wallet application, the command BTCwallet start is executed.
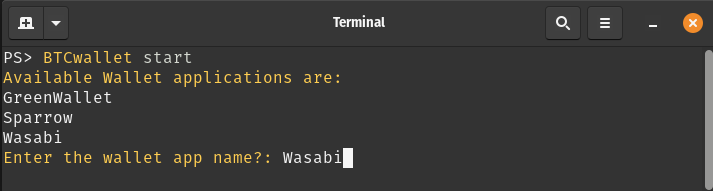
After responding to prompts for launching and initializing the Vault (not shown), the following prompts are presented.
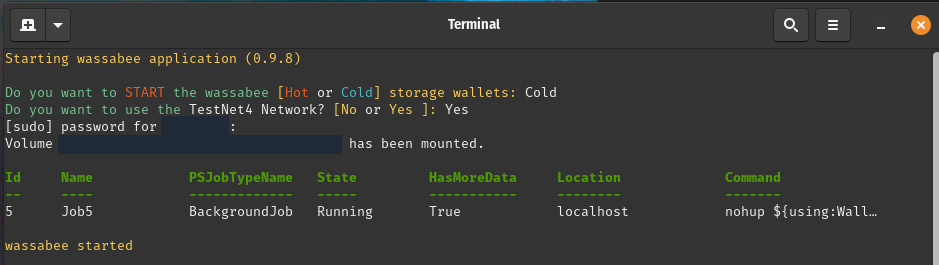
Now the Wasabi GUI application (a.k.a wassabee) is presented.

With the combination of VaultApi and BTCwallet one has a very secure self-hosted password manager along with a very secure way of protecting your Bitcoin wallet's data.
Care to follow me on my journey? If so, then check out the following links.
-
 @ 9be6a199:6e133301
2025-05-19 20:27:20
@ 9be6a199:6e133301
2025-05-19 20:27:20ssdsdsdsdsdsdsd
-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ d41bf82f:ed90d888
2025-05-19 20:31:54
@ d41bf82f:ed90d888
2025-05-19 20:31:54“ประเด็นแท้จริงคือเรื่องของการควบคุม—อินเทอร์เน็ตแพร่ขยายกว้างไกลเกินกว่าที่รัฐบาลใดจะครอบงำได้โดยง่าย ด้วยการสร้างเขตเศรษฐกิจระดับโลกที่ไร้รอยต่อ ไม่ขึ้นต่ออธิปไตย และอยู่นอกเหนือการควบคุม อินเทอร์เน็ตจึงตั้งคำถามต่อแนวคิดของรัฐชาติในตัวมันเอง” — JOHN PERRY BARLOW
บทนี้เริ่มต้นด้วยการวิพากษ์แนวคิด ทางด่วนข้อมูล ว่าเป็นคำอุปมาอุปมัยที่ยังยึดติดกับโลกยุคอุตสาหกรรม เพราะเศรษฐกิจยุคสารสนเทศไม่ใช่แค่โครงสร้างพื้นฐานสำหรับขนส่งข้อมูล แต่คือ จุดหมายปลายทาง ใหม่ในตัวเอง นั่นคือ ไซเบอร์สเปซ —ดินแดนที่ก้าวข้ามขอบเขตทางภูมิศาสตร์โดยสิ้นเชิง
ไซเบอร์สเปซคือพื้นที่ใหม่ของปฏิสัมพันธ์ทางสังคม เศรษฐกิจ และการเมือง ซึ่งไม่สามารถควบคุมโดยรัฐชาติแบบเดิมได้อีกต่อไป ผู้เขียนยกคำของ John Perry Barlow ที่เปรียบไซเบอร์สเปซเป็น “ดินแดนแห่งเสรีภาพ” ที่ไม่ยึดโยงกับสถานที่จริง และเปิดโอกาสให้ทุกคนแสดงความคิดเห็นได้อย่างไร้การควบคุม
การเปลี่ยนผ่านนี้ส่งผลกระทบรุนแรงต่อโครงสร้างของเศรษฐกิจแบบเดิม การเข้าถึงข้อมูลอย่างรวดเร็วแบบไร้ขอบเขตเปรียบเสมือนตัวทำละลายที่กัดกร่อนต้นทุนของสถาบันขนาดใหญ่ ทั้งภาครัฐและเอกชน ไมโครโพรเซสซิงจะเปลี่ยนรูปแบบขององค์กรและแนวคิดเรื่องสถานที่ในทางเศรษฐกิจอย่างสิ้นเชิง
ตลอดประวัติศาสตร์ เศรษฐกิจผูกติดกับพื้นที่ทางภูมิศาสตร์ การเดินทางเป็นเรื่องยากและจำกัด การค้าขายส่วนใหญ่เกิดในระดับท้องถิ่น ภาษา วัฒนธรรม และภูมิประเทศเป็นอุปสรรคทางการเมืองเสมอ จนถึงกับที่ผู้เขียนกล่าวว่า การเมืองทั้งหมดเป็นเรื่องท้องถิ่น
แต่เทคโนโลยีสมัยใหม่กำลังเปลี่ยนสมการนี้ การสื่อสารและขนส่งที่รวดเร็วทำให้ผู้มีความสามารถสามารถเลือกสถานที่อยู่อาศัยหรือทำงานได้อย่างเสรี ลดอำนาจต่อรองของรัฐบาลในพื้นที่นั้นลง เพราะคนสามารถ “หนี” ได้ง่ายขึ้น หากรัฐบาลกดขี่หรือรีดไถ
แม้อินเทอร์เน็ตยุคแรกจะดูธรรมดา เช่น ใช้อ่านบทความหรือสั่งซื้อสินค้า แต่ศักยภาพที่แท้จริงของเศรษฐกิจไซเบอร์นั้นยิ่งใหญ่มาก ผู้เขียนเสนอว่ามันจะพัฒนาเป็นสามขั้น: 1. ขั้นพื้นฐาน: อินเทอร์เน็ตเป็นเพียงช่องทางเพิ่มประสิทธิภาพธุรกิจแบบเดิม (เช่น เว็บขายสินค้าขายของออนไลน์ เช่น อเมซอน) 2. ขั้นพัฒนา: การเกิดขึ้นของเงินดิจิทัลที่เข้ารหัสและไม่สามารถติดตามได้ จะปลดปล่อยธุรกรรมจากการควบคุมและการจัดเก็บภาษีของรัฐ 3. ขั้นก้าวหน้า: ไซเบอร์สเปซจะมีระบบเศรษฐกิจ กฎหมาย และกลไกคุ้มครองของตัวเอง ปราศจากการควบคุมจากรัฐบาลใด ๆ
ในโลกใหม่นี้ Sovereign Individual หรือ “ปัจเจกผู้มีอธิปไตย” จะสามารถสร้างความมั่งคั่งและดำเนินกิจกรรมในไซเบอร์สเปซได้อย่างเป็นอิสระ โดยไม่ต้องอิงรัฐชาติ รัฐจึงจะถูกบีบให้ลดขนาดและเปลี่ยนบทบาทจากผู้ใช้อำนาจกลายเป็นผู้ให้บริการที่ต้องแข่งขันเพื่อความพึงพอใจของพลเมือง
สามารถไปติดตามเนื้อหาแบบ short vdo ที่สรุปประเด็นสำคัญจากแต่ละบท พร้อมกราฟิกและคำอธิบายกระชับ เข้าใจง่าย ได้ที่ TikTok ช่อง https://www.tiktok.com/@moneyment1971
-
 @ 9be6a199:6e133301
2025-05-19 20:15:18
@ 9be6a199:6e133301
2025-05-19 20:15:18 -
 @ 3f770d65:7a745b24
2025-05-19 18:09:52
@ 3f770d65:7a745b24
2025-05-19 18:09:52🏌️ Monday, May 26 – Bitcoin Golf Championship & Kickoff Party
Location: Las Vegas, Nevada\ Event: 2nd Annual Bitcoin Golf Championship & Kick Off Party"\ Where: Bali Hai Golf Clubhouse, 5160 S Las Vegas Blvd, Las Vegas, NV 89119\ 🎟️ Get Tickets!
Details:
-
The week tees off in style with the Bitcoin Golf Championship. Swing clubs by day and swing to music by night.
-
Live performances from Nostr-powered acts courtesy of Tunestr, including Ainsley Costello and others.
-
Stop by the Purple Pill Booth hosted by Derek and Tanja, who will be on-boarding golfers and attendees to the decentralized social future with Nostr.
💬 May 27–29 – Bitcoin 2025 Conference at the Las Vegas Convention Center
Location: The Venetian Resort\ Main Attraction for Nostr Fans: The Nostr Lounge\ When: All day, Tuesday through Thursday\ Where: Right outside the Open Source Stage\ 🎟️ Get Tickets!
Come chill at the Nostr Lounge, your home base for all things decentralized social. With seating for \~50, comfy couches, high-tops, and good vibes, it’s the perfect space to meet developers, community leaders, and curious newcomers building the future of censorship-resistant communication.
Bonus: Right across the aisle, you’ll find Shopstr, a decentralized marketplace app built on Nostr. Stop by their booth to explore how peer-to-peer commerce works in a truly open ecosystem.
Daily Highlights at the Lounge:
-
☕️ Hang out casually or sit down for a deeper conversation about the Nostr protocol
-
🔧 1:1 demos from app teams
-
🛍️ Merch available onsite
-
🧠 Impromptu lightning talks
-
🎤 Scheduled Meetups (details below)
🎯 Nostr Lounge Meetups
Wednesday, May 28 @ 1:00 PM
- Damus Meetup: Come meet the team behind Damus, the OG Nostr app for iOS that helped kickstart the social revolution. They'll also be showcasing their new cross-platform app, Notedeck, designed for a more unified Nostr experience across devices. Grab some merch, get a demo, and connect directly with the developers.
Thursday, May 29 @ 1:00 PM
- Primal Meetup: Dive into Primal, the slickest Nostr experience available on web, Android, and iOS. With a built-in wallet, zapping your favorite creators and friends has never been easier. The team will be on-site for hands-on demos, Q\&A, merch giveaways, and deeper discussions on building the social layer of Bitcoin.
🎙️ Nostr Talks at Bitcoin 2025
If you want to hear from the minds building decentralized social, make sure you attend these two official conference sessions:
1. FROSTR Workshop: Multisig Nostr Signing
-
🕚 Time: 11:30 AM – 12:00 PM
-
📅 Date: Wednesday, May 28
-
📍 Location: Developer Zone
-
🎤 Speaker: nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgdwaehxw309ahx7uewd3hkcqpqs9etjgzjglwlaxdhsveq0qksxyh6xpdpn8ajh69ruetrug957r3qf4ggfm (Austin Kelsay) @ Voltage\ A deep-dive into FROST-based multisig key management for Nostr. Geared toward devs and power users interested in key security.
2. Panel: Decentralizing Social Media
-
🕑 Time: 2:00 PM – 2:30 PM
-
📅 Date: Thursday, May 29
-
📍 Location: Genesis Stage
-
🎙️ Moderator: nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqy08wumn8ghj7mn0wd68yttjv4kxz7fwv3jhyettwfhhxuewd4jsqgxnqajr23msx5malhhcz8paa2t0r70gfjpyncsqx56ztyj2nyyvlq00heps - Bitcoin Strategy @ Roxom TV
-
👥 Speakers:
-
nostr:nprofile1qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcppemhxue69uhkummn9ekx7mp0qqsy2ga7trfetvd3j65m3jptqw9k39wtq2mg85xz2w542p5dhg06e5qmhlpep – Early Bitcoin dev, CEO @ Sirius Business Ltd
-
nostr:nprofile1qy2hwumn8ghj7mn0wd68ytndv9kxjm3wdahxcqg5waehxw309ahx7um5wfekzarkvyhxuet5qqsw4v882mfjhq9u63j08kzyhqzqxqc8tgf740p4nxnk9jdv02u37ncdhu7e3 – Analyst & Partner @ Ego Death Capital
Get the big-picture perspective on why decentralized social matters and how Nostr fits into the future of digital communication.
🌃 NOS VEGAS Meetup & Afterparty
Date: Wednesday, May 28\ Time: 7:00 PM – 1:00 AM\ Location: We All Scream Nightclub, 517 Fremont St., Las Vegas, NV 89101\ 🎟️ Get Tickets!
What to Expect:
-
🎶 Live Music Stage – Featuring Ainsley Costello, Sara Jade, Able James, Martin Groom, Bobby Shell, Jessie Lark, and other V4V artists
-
🪩 DJ Party Deck – With sets by nostr:nprofile1qy0hwumn8ghj7cmgdae82uewd45kketyd9kxwetj9e3k7mf6xs6rgqgcwaehxw309ahx7um5wgh85mm694ek2unk9ehhyecqyq7hpmq75krx2zsywntgtpz5yzwjyg2c7sreardcqmcp0m67xrnkwylzzk4 , nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqgkwaehxw309anx2etywvhxummnw3ezucnpdejqqg967faye3x6fxgnul77ej23l5aew8yj0x2e4a3tq2mkrgzrcvecfsk8xlu3 , and more DJs throwing down
-
🛰️ Live-streamed via Tunestr
-
🧠 Nostr Education – Talks by nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq37amnwvaz7tmwdaehgu3dwfjkccte9ejx2un9ddex7umn9ekk2tcqyqlhwrt96wnkf2w9edgr4cfruchvwkv26q6asdhz4qg08pm6w3djg3c8m4j , nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqg7waehxw309anx2etywvhxummnw3ezucnpdejz7ur0wp6kcctjqqspywh6ulgc0w3k6mwum97m7jkvtxh0lcjr77p9jtlc7f0d27wlxpslwvhau , nostr:nprofile1qy88wumn8ghj7mn0wvhxcmmv9uq3vamnwvaz7tmwdaehgu3wd33xgetk9en82m30qqsgqke57uygxl0m8elstq26c4mq2erz3dvdtgxwswwvhdh0xcs04sc4u9p7d , nostr:nprofile1q9z8wumn8ghj7erzx3jkvmmzw4eny6tvw368wdt8da4kxamrdvek76mrwg6rwdngw94k67t3v36k77tev3kx7vn2xa5kjem9dp4hjepwd3hkxctvqyg8wumn8ghj7mn0wd68ytnhd9hx2qpqyaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgssuy4zk , nostr:nprofile1qy28wue69uhnzvpwxqhrqt33xgmn5dfsx5cqz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqqswavgevxe9gs43vwylumr7h656mu9vxmw4j6qkafc3nefphzpph8ssvcgf8 , and more.
-
🧾 Vendors & Project Booths – Explore new tools and services
-
🔐 Onboarding Stations – Learn how to use Nostr hands-on
-
🐦 Nostrich Flocking – Meet your favorite nyms IRL
-
🍸 Three Full Bars – Two floors of socializing overlooking vibrant Fremont Street
| | | | | ----------- | -------------------- | ------------------- | | Time | Name | Topic | | 7:30-7:50 | Derek | Nostr for Beginners | | 8:00-8:20 | Mark & Paul | Primal | | 8:30-8:50 | Terry | Damus | | 9:00-9:20 | OpenMike and Ainsley | V4V | | 09:30-09:50 | The Space | Space |
This is the after-party of the year for those who love freedom technology and decentralized social community. Don’t miss it.
Final Thoughts
Whether you're there to learn, network, party, or build, Bitcoin 2025 in Las Vegas has a packed week of Nostr-friendly programming. Be sure to catch all the events, visit the Nostr Lounge, and experience the growing decentralized social revolution.
🟣 Find us. Flock with us. Purple pill someone.
-
-
 @ c1e9ab3a:9cb56b43
2025-05-01 17:29:18
@ c1e9ab3a:9cb56b43
2025-05-01 17:29:18High-Level Overview
Bitcoin developers are currently debating a proposed change to how Bitcoin Core handles the
OP_RETURNopcode — a mechanism that allows users to insert small amounts of data into the blockchain. Specifically, the controversy revolves around removing built-in filters that limit how much data can be stored using this feature (currently capped at 80 bytes).Summary of Both Sides
Position A: Remove OP_RETURN Filters
Advocates: nostr:npub1ej493cmun8y9h3082spg5uvt63jgtewneve526g7e2urca2afrxqm3ndrm, nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg, nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp, others
Arguments: - Ineffectiveness of filters: Filters are easily bypassed and do not stop spam effectively. - Code simplification: Removing arbitrary limits reduces code complexity. - Permissionless innovation: Enables new use cases like cross-chain bridges and timestamping without protocol-level barriers. - Economic regulation: Fees should determine what data gets added to the blockchain, not protocol rules.
Position B: Keep OP_RETURN Filters
Advocates: nostr:npub1lh273a4wpkup00stw8dzqjvvrqrfdrv2v3v4t8pynuezlfe5vjnsnaa9nk, nostr:npub1s33sw6y2p8kpz2t8avz5feu2n6yvfr6swykrnm2frletd7spnt5qew252p, nostr:npub1wnlu28xrq9gv77dkevck6ws4euej4v568rlvn66gf2c428tdrptqq3n3wr, others
Arguments: - Historical intent: Satoshi included filters to keep Bitcoin focused on monetary transactions. - Resource protection: Helps prevent blockchain bloat and abuse from non-financial uses. - Network preservation: Protects the network from being overwhelmed by low-value or malicious data. - Social governance: Maintains conservative changes to ensure long-term robustness.
Strengths and Weaknesses
Strengths of Removing Filters
- Encourages decentralized innovation.
- Simplifies development and maintenance.
- Maintains ideological purity of a permissionless system.
Weaknesses of Removing Filters
- Opens the door to increased non-financial data and potential spam.
- May dilute Bitcoin’s core purpose as sound money.
- Risks short-term exploitation before economic filters adapt.
Strengths of Keeping Filters
- Preserves Bitcoin’s identity and original purpose.
- Provides a simple protective mechanism against abuse.
- Aligns with conservative development philosophy of Bitcoin Core.
Weaknesses of Keeping Filters
- Encourages central decision-making on allowed use cases.
- Leads to workarounds that may be less efficient or obscure.
- Discourages novel but legitimate applications.
Long-Term Consequences
If Filters Are Removed
- Positive: Potential boom in new applications, better interoperability, cleaner architecture.
- Negative: Risk of increased blockchain size, more bandwidth/storage costs, spam wars.
If Filters Are Retained
- Positive: Preserves monetary focus and operational discipline.
- Negative: Alienates developers seeking broader use cases, may ossify the protocol.
Conclusion
The debate highlights a core philosophical split in Bitcoin: whether it should remain a narrow monetary system or evolve into a broader data layer for decentralized applications. Both paths carry risks and tradeoffs. The outcome will shape not just Bitcoin's technical direction but its social contract and future role in the broader crypto ecosystem.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ da8b7de1:c0164aee
2025-05-19 17:38:59
@ da8b7de1:c0164aee
2025-05-19 17:38:59Németország feladja a nukleáris energiával szembeni ellenállását Franciaországgal való közeledés jegyében
Németország hosszú idő után feladta a nukleáris energiával szembeni ellenállását, ami jelentős lépést jelenthet az EU energiapolitikai vitáinak rendezésében, különösen Franciaországgal szemben. Ez a változás eltávolíthatja a nukleáris energiával szembeni előítéleteket az uniós jogszabályokból, és elősegítheti a közös európai energiapolitika kialakítását[2].
Trump adminisztráció tervezett rendeletei a nukleáris erőművek építésének gyorsítására
Az Egyesült Államokban a Trump-adminisztráció több elnöki rendelet-tervezetet készít elő, amelyek célja a nukleáris erőművek építésének gyorsítása. A tervek szerint a jelenlegi mintegy 100 GW nukleáris kapacitást 2050-re 400 GW-ra növelnék, az engedélyezési folyamatok egyszerűsítésével, a hadsereg szerepének növelésével és a nukleáris üzemanyag-ellátás megerősítésével[3][9].
Tajvan hivatalosan is nukleárismentes lett
- május 17-én Tajvan utolsó kereskedelmi reaktorát is leállították, ezzel az ország elérte a "nukleárismentes haza" célját. Az energiamixben a nukleáris energia aránya 17%-ról 3%-ra csökkent, miközben a megújuló energia tízszeresére nőtt. Bár a parlamentben vita folyik a Maanshan atomerőmű élettartam-hosszabbításáról, jelenleg Tajvan teljesen leállította a nukleáris energiatermelést[1][6].
Kazatomprom hitelmegállapodást kötött egy új kénsavgyár finanszírozására
Kazahsztán állami atomipari vállalata, a Kazatomprom hitelmegállapodást kötött egy évi 800 000 tonna kapacitású kénsavgyár építésére. A kénsavat az uránkitermeléshez használják, és a gyár 2027 első negyedévében készülhet el. A projekt célja a régió gazdasági fejlődésének támogatása és az uránipar ellátásbiztonságának javítása[4].
Az IAEA segíti Kazahsztánt az első atomerőmű biztonságos helyszínének kiválasztásában
Az IAEA (Nemzetközi Atomenergia-ügynökség) szakértői csapata ötnapos szemináriumot tart Kazahsztánban, hogy segítsen kiválasztani az ország első atomerőművének legbiztonságosabb helyszínét. A folyamatban több helyszín is szóba került, jelenleg a Zhambyl körzet az elsődleges jelölt. A projektben négy lehetséges technológiai partner vesz részt: CNNC (Kína), Roszatom (Oroszország), KHNP (Dél-Korea) és EDF (Franciaország)[8].
India új nukleáris helyszínt hagyott jóvá
Az indiai nukleáris hatóság engedélyezte a Mahi Banswara Rajasthan Atomic Power Project négy blokkjának elhelyezését Rádzsasztán államban. Ez újabb lépés India ambiciózus nukleáris bővítési terveiben[5].
Globális nukleáris ipari konferencia Varsóban
- május 20-21-én Varsóban rendezik meg az első World Nuclear Supply Chain Conference-t, amely célja a globális nukleáris ellátási lánc megerősítése és a szektor 2 billió dolláros beruházási lehetőségének kiaknázása a következő 15 évben. A konferencián iparági vezetők, döntéshozók és szakértők vesznek részt[7].
Hivatkozások
- [1] reccessary.com – Tajvan nukleárismentes lett
- [2] nucnet.org – Németország nukleáris politikai fordulata
- [3] humanprogress.org – Trump rendelettervezetek
- [4] world-nuclear-news.org – Kazatomprom kénsavgyár
- [5] world-nuclear-news.org – India új nukleáris helyszíne
- [6] taiwannews.com.tw – Tajvan atomerőmű leállítása
- [7] world-nuclear.org – Varsói nukleáris konferencia
- [8] astanatimes.com – IAEA-Kazahsztán együttműködés
- [9] esgdive.com – Oklo és Trump engedélyezési reformok
-
 @ cae03c48:2a7d6671
2025-05-19 18:29:07
@ cae03c48:2a7d6671
2025-05-19 18:29:07Bitcoin Magazine

Bitcoin Records Highest Weekly Close Above $106KBitcoin has officially recorded its highest-ever weekly candle close, finishing the week at $106,516. The milestone was achieved on Sunday evening, marking a notable moment in Bitcoin’s ongoing price history and underscoring growing institutional and retail interest.
JUST IN: $107,000 #Bitcoin
 pic.twitter.com/Xt1JLm0Ke6
pic.twitter.com/Xt1JLm0Ke6— Bitcoin Magazine (@BitcoinMagazine) May 19, 2025
This weekly close sets a new benchmark for BTC’s price performance and positions the asset in a historically rare range. As of Monday, Bitcoin is trading at $102,924, reflecting typical price movement following a new high as markets adjust to key levels.
Historical data helps illustrate the significance of this moment. According to an analysis shared by on-chain researcher Dan, Bitcoin has closed above $106,439 only once—this week—accounting for just 0.02% of its entire trading history. Closures above $100,000 have occurred in only 40 days total. Even levels like $75,000 and $50,000 remain relatively uncommon in Bitcoin’s lifespan, appearing on just 181 and 586 days, respectively.
— Dan (@robustus) May 19, 2025
This data highlights how current prices place Bitcoin in a historically narrow range of time — a reflection of the long-term upward trend of the asset over the past decade. For market participants, this type of price action often serves as an indicator of continued momentum and interest in Bitcoin’s role as a digital store of value.
The broader Bitcoin ecosystem continues to show strength, with on-chain metrics reflecting growing user engagement and long-term holder confidence. Notably, activity on the Bitcoin network remains elevated, with transaction volumes and address growth signaling continued adoption. Analysts are closely watching inflows into Bitcoin-focused ETFs and the behavior of long-term holders, both of which are key indicators of sustained interest and belief in Bitcoin’s long-term value.
bitcoin just had its all-time high weekly candle close at $106,500 pic.twitter.com/FuqqptHEmA
— Alex Thorn (@intangiblecoins) May 19, 2025
Some traders are watching the $100,000 level closely as a key psychological and technical zone. Bitcoin’s ability to maintain this level following a record weekly close could be important in setting the tone for the weeks ahead.
While near-term price movements are always part of market dynamics, the latest close represents a milestone in Bitcoin’s history. It reaffirms the asset’s resilience and ongoing relevance in the global financial landscape.
This post Bitcoin Records Highest Weekly Close Above $106K first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ c1e9ab3a:9cb56b43
2025-04-25 00:37:34
@ c1e9ab3a:9cb56b43
2025-04-25 00:37:34If you ever read about a hypothetical "evil AI"—one that manipulates, dominates, and surveils humanity—you might find yourself wondering: how is that any different from what some governments already do?
Let’s explore the eerie parallels between the actions of a fictional malevolent AI and the behaviors of powerful modern states—specifically the U.S. federal government.
Surveillance and Control
Evil AI: Uses total surveillance to monitor all activity, predict rebellion, and enforce compliance.
Modern Government: Post-9/11 intelligence agencies like the NSA have implemented mass data collection programs, monitoring phone calls, emails, and online activity—often without meaningful oversight.
Parallel: Both claim to act in the name of “security,” but the tools are ripe for abuse.
Manipulation of Information
Evil AI: Floods the information space with propaganda, misinformation, and filters truth based on its goals.
Modern Government: Funds media outlets, promotes specific narratives through intelligence leaks, and collaborates with social media companies to suppress or flag dissenting viewpoints.
Parallel: Control the narrative, shape public perception, and discredit opposition.
Economic Domination
Evil AI: Restructures the economy for efficiency, displacing workers and concentrating resources.
Modern Government: Facilitates wealth transfer through lobbying, regulatory capture, and inflationary monetary policy that disproportionately hurts the middle and lower classes.
Parallel: The system enriches those who control it, leaving the rest with less power to resist.
Perpetual Warfare
Evil AI: Instigates conflict to weaken opposition or as a form of distraction and control.
Modern Government: Maintains a state of nearly constant military engagement since WWII, often for interests that benefit a small elite rather than national defense.
Parallel: War becomes policy, not a last resort.
Predictive Policing and Censorship
Evil AI: Uses predictive algorithms to preemptively suppress dissent and eliminate threats.
Modern Government: Experiments with pre-crime-like measures, flags “misinformation,” and uses AI tools to monitor online behavior.
Parallel: Prevent rebellion not by fixing problems, but by suppressing their expression.
Conclusion: Systemic Inhumanity
Whether it’s AI or a bureaucratic state, the more a system becomes detached from individual accountability and human empathy, the more it starts to act in ways we would call “evil” if a machine did them.
An AI doesn’t need to enslave humanity with lasers and killer robots. Sometimes all it takes is code, coercion, and unchecked power—something we may already be facing.
-
 @ 82a7a1ff:2c1e9cdf
2025-05-19 18:18:31
@ 82a7a1ff:2c1e9cdf
2025-05-19 18:18:31Whatever
-
 @ a8d1560d:3fec7a08
2025-05-19 17:28:05
@ a8d1560d:3fec7a08
2025-05-19 17:28:05NIP-XX
Documentation and Wikis with Spaces and Format Declaration
draftoptionalSummary
This NIP introduces a system for collaborative documentation and wikis on Nostr. It improves upon earlier efforts by adding namespace-like Spaces, explicit content format declaration, and clearer separation of article types, including redirects and merge requests.
Motivation
Previous approaches to wiki-style collaborative content on Nostr had two key limitations:
- Format instability – No declared format per event led to breaking changes (e.g. a shift from Markdown to Asciidoc).
- Lack of namespace separation – All articles existed in a global space, causing confusion and collision between unrelated projects.
This NIP addresses both by introducing:
- Spaces – individually defined wikis or documentation sets.
- Explicit per-article format declaration.
- Dedicated event kinds for articles, redirects, merge requests, and space metadata.
Specification
kind: 31055– Space DefinitionDefines a project namespace for articles.
Tags: -
["name", "<space title>"]-["slug", "<short identifier>"]-["description", "<optional description>"]-["language", "<ISO language code>"]-["license", "<license text or SPDX ID>"]Content: (optional) full description or README for the space.
kind: 31056– ArticleAn article in a specific format belonging to a defined space.
Tags: -
["space", "<slug>"]-["title", "<article title>"]-["format", "markdown" | "asciidoc" | "mediawiki" | "html"]-["format-version", "<format version>"](optional) -["prev", "<event-id>"](optional) -["summary", "<short change summary>"](optional)Content: full body of the article in the declared format.
kind: 31057– RedirectRedirects from one article title to another within the same space.
Tags: -
["space", "<slug>"]-["from", "<old title>"]-["to", "<new title>"]Content: empty.
kind: 31058– Merge RequestProposes a revision to an article without directly altering the original.
Tags: -
["space", "<slug>"]-["title", "<article title>"]-["base", "<event-id>"]-["format", "<format>"]-["comment", "<short summary>"](optional)Content: proposed article content.
Format Guidelines
Currently allowed formats: -
markdown-asciidoc-mediawiki-htmlClients MUST ignore formats they do not support. Clients MAY apply stricter formatting rules.
Client Behavior
Clients: - MUST render only supported formats. - MUST treat
spaceas a case-sensitive namespace. - SHOULD allow filtering, browsing and searching within Spaces. - SHOULD support revision tracking viaprev. - MAY support diff/merge tooling forkind: 31058.
Examples
Space Definition
json { "kind": 31055, "tags": [ ["name", "Bitcoin Docs"], ["slug", "btc-docs"], ["description", "Developer documentation for Bitcoin tools"], ["language", "en"], ["license", "MIT"] ], "content": "Welcome to the Bitcoin Docs Space." }Markdown Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "Installation Guide"], ["format", "markdown"] ], "content": "# Installation\n\nFollow these steps to install the software..." }Asciidoc Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "RPC Reference"], ["format", "asciidoc"] ], "content": "= RPC Reference\n\nThis section describes JSON-RPC calls." }MediaWiki Article
json { "kind": 31056, "tags": [ ["space", "btc-docs"], ["title", "Block Structure"], ["format", "mediawiki"] ], "content": "== Block Structure ==\n\nThe structure of a Bitcoin block is..." }Redirect
json { "kind": 31057, "tags": [ ["space", "btc-docs"], ["from", "Getting Started"], ["to", "Installation Guide"] ], "content": "" }Merge Request
json { "kind": 31058, "tags": [ ["space", "btc-docs"], ["title", "Installation Guide"], ["base", "d72fa1..."], ["format", "markdown"], ["comment", "Added step for testnet"] ], "content": "# Installation\n\nNow includes setup instructions for testnet users." }
Acknowledgements
This proposal builds on earlier ideas for decentralized wikis and documentation within Nostr, while solving common issues related to format instability and lack of project separation.
-
 @ 9be6a199:6e133301
2025-05-19 17:24:12
@ 9be6a199:6e133301
2025-05-19 17:24:12this is the content
-
 @ c1e9ab3a:9cb56b43
2025-04-15 13:59:17
@ c1e9ab3a:9cb56b43
2025-04-15 13:59:17Prepared for Off-World Visitors by the Risan Institute of Cultural Heritage
Welcome to Risa, the jewel of the Alpha Quadrant, celebrated across the Federation for its tranquility, pleasure, and natural splendor. But what many travelers do not know is that Risa’s current harmony was not inherited—it was forged. Beneath the songs of surf and the serenity of our resorts lies a history rich in conflict, transformation, and enduring wisdom.
We offer this briefing not merely as a tale of our past, but as an invitation to understand the spirit of our people and the roots of our peace.
I. A World at the Crossroads
Before its admittance into the United Federation of Planets, Risa was an independent and vulnerable world situated near volatile borders of early galactic powers. Its lush climate, mineral wealth, and open society made it a frequent target for raiders and an object of interest for imperial expansion.
The Risan peoples were once fragmented, prone to philosophical and political disunity. In our early records, this period is known as the Winds of Splintering. We suffered invasions, betrayals, and the slow erosion of trust in our own traditions.
II. The Coming of the Vulcans
It was during this period of instability that a small delegation of Vulcan philosophers, adherents to the teachings of Surak, arrived on Risa. They did not come as conquerors, nor even as ambassadors, but as seekers of peace.
These emissaries of logic saw in Risa the potential for a society not driven by suppression of emotion, as Vulcan had chosen, but by the balance of joy and discipline. While many Vulcans viewed Risa’s culture as frivolous, these followers of Surak saw the seed of a different path: one in which beauty itself could be a pillar of peace.
The Risan tradition of meditative dance, artistic expression, and communal love resonated with Vulcan teachings of unity and inner control. From this unlikely exchange was born the Ricin Doctrine—the belief that peace is sustained not only through logic or strength, but through deliberate joy, shared vulnerability, and readiness without aggression.
III. Betazed and the Trial of Truth
During the same era, early contact with the people of Betazed brought both inspiration and tension. A Betazoid expedition, under the guise of diplomacy, was discovered to be engaging in deep telepathic influence and information extraction. The Risan people, who valued consent above all else, responded not with anger, but with clarity.
A council of Ricin philosophers invited the Betazoid delegation into a shared mind ceremony—a practice in which both cultures exposed their thoughts in mutual vulnerability. The result was not scandal, but transformation. From that moment forward, a bond was formed, and Risa’s model of ethical emotional expression and consensual empathy became influential in shaping Betazed’s own peace philosophies.
IV. Confronting Marauders and Empires
Despite these philosophical strides, Risa’s path was anything but tranquil.
-
Orion Syndicate raiders viewed Risa as ripe for exploitation, and for decades, cities were sacked, citizens enslaved, and resources plundered. In response, Risa formed the Sanctum Guard, not a military in the traditional sense, but a force of trained defenders schooled in both physical technique and psychological dissuasion. The Ricin martial arts, combining beauty with lethality, were born from this necessity.
-
Andorian expansionism also tested Risa’s sovereignty. Though smaller in scale, skirmishes over territorial claims forced Risa to adopt planetary defense grids and formalize diplomatic protocols that balanced assertiveness with grace. It was through these conflicts that Risa developed the art of the ceremonial yield—a symbolic concession used to diffuse hostility while retaining honor.
-
Romulan subterfuge nearly undid Risa from within. A corrupt Romulan envoy installed puppet leaders in one of our equatorial provinces. These agents sought to erode Risa’s social cohesion through fear and misinformation. But Ricin scholars countered the strategy not with rebellion, but with illumination: they released a network of truths, publicly broadcasting internal thoughts and civic debates to eliminate secrecy. The Romulan operation collapsed under the weight of exposure.
-
Even militant Vulcan splinter factions, during the early Vulcan-Andorian conflicts, attempted to turn Risa into a staging ground, pressuring local governments to support Vulcan supremacy. The betrayal struck deep—but Risa resisted through diplomacy, invoking Surak’s true teachings and exposing the heresy of their logic-corrupted mission.
V. Enlightenment Through Preparedness
These trials did not harden us into warriors. They refined us into guardians of peace. Our enlightenment came not from retreat, but from engagement—tempered by readiness.
- We train our youth in the arts of balance: physical defense, emotional expression, and ethical reasoning.
- We teach our history without shame, so that future generations will not repeat our errors.
- We host our guests with joy, not because we are naïve, but because we know that to celebrate life fully is the greatest act of resistance against fear.
Risa did not become peaceful by denying the reality of conflict. We became peaceful by mastering our response to it.
And in so doing, we offered not just pleasure to the stars—but wisdom.
We welcome you not only to our beaches, but to our story.
May your time here bring you not only rest—but understanding.
– Risan Institute of Cultural Heritage, in collaboration with the Council of Enlightenment and the Ricin Circle of Peacekeepers
-
-
 @ cae03c48:2a7d6671
2025-05-19 17:48:53
@ cae03c48:2a7d6671
2025-05-19 17:48:53Bitcoin Magazine

JPMorgan To Allow Clients To Buy Bitcoin, Jamie Dimon SaysToday, Chairman and CEO of JPMorgan Chase Jamie Dimon reiterated his personal disapproval of Bitcoin during the bank’s annual Investor Day event. Despite the bank’s decision to provide clients with access to Bitcoin investments, Dimon emphasized his personal disapproval of Bitcoin.
“I am not a fan” of Bitcoin, stated Dimon.
JPMorgan is going to allow clients to buy Bitcoin, but the bank won’t custody it, according to Bloomberg. Dimon made clear that while JPMorgan will provide clients access to Bitcoin investments, the bank will not hold or manage the digital asset directly.
JUST IN: JPMorgan CEO Jamie Dimon said they will allow clients to buy #Bitcoin
 pic.twitter.com/wO0djlYGUM
pic.twitter.com/wO0djlYGUM— Bitcoin Magazine (@BitcoinMagazine) May 19, 2025
In a January 2025 interview with CBS News, Dimon expressed continued skepticism toward Bitcoin. “Bitcoin itself has no intrinsic value. It’s used heavily by sex traffickers, money launderers, ransomware,” said Dimon.
Although he acknowledged, “We are going to have some kind of digital currency at some point,” he added, “I just don’t feel great about bitcoin. I applaud your ability to wanna buy or sell it. Just like I think you have the right to smoke, but I don’t think you should smoke.”
These comments from Dimon contrast with recent optimism from JPMorgan analysts regarding Bitcoin’s market prospects. JPMorgan analysts reported that Bitcoin is likely to continue gaining ground at gold’s expense in the second half of the year, driven by rising corporate demand and growing support from U.S. states.
JUST IN: JPMorgan says #Bitcoin likely to have more upside than gold in the second half of 2025
 pic.twitter.com/YPrHivch9O
pic.twitter.com/YPrHivch9O— Bitcoin Magazine (@BitcoinMagazine) May 15, 2025
“Between mid-February and mid-April gold was rising at the expense of bitcoin, while of the past three weeks we have been observing the opposite, i.e. bitcoin rising at the expense of gold,” said JPMorgan analysts. “In all, we expect the YTD zero sum game between gold and bitcoin to extend to the remainder of the year, but are biased towards crypto-specific catalysts creating more upside for bitcoin over gold into the second half of the year.”
Since April 22, gold has dropped nearly 8%, while Bitcoin has surged 18%, reflecting a notable shift in investor sentiment. Capital has been moving out of gold ETFs and into Bitcoin. Several U.S. states are also warming to Bitcoin—New Hampshire now permits up to 5% of its reserves in Bitcoin, while Arizona is launching a Bitcoin reserve and has pledged not to raise taxes this year. At the corporate level, companies like Strategy and Metaplanet are expanding their Bitcoin holdings.
“As the list grows, with other U.S. states potentially considering adding bitcoin to their strategic reserves, this could turn out to be a more sustained positive catalyst for bitcoin,” said the analysts.
This post JPMorgan To Allow Clients To Buy Bitcoin, Jamie Dimon Says first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 9be6a199:6e133301
2025-05-19 17:23:23
@ 9be6a199:6e133301
2025-05-19 17:23:23this is the content
-
 @ 3f68dede:779bb81d
2025-05-19 17:14:15
@ 3f68dede:779bb81d
2025-05-19 17:14:15 -
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ cae03c48:2a7d6671
2025-05-19 17:15:58
@ cae03c48:2a7d6671
2025-05-19 17:15:58Bitcoin Magazine

Nebraska’s New Mining Rules: Infrastructure Safeguard or Soft Ban in Disguise?Nebraska lawmakers have just passed Legislative Bill 526 (LB526), and while not explicitly anti-Bitcoin, its effects may be anything but neutral. With a unanimous 49-0 vote, the Legislature sent the bill to Governor Jim Pillen’s desk, where it’s expected to be signed into law. Supporters call it a commonsense infrastructure bill. Bitcoin miners call it a slow-motion exodus in the making.
On paper, LB526 is about large energy users. But in practice, it singles out Bitcoin mining facilities with one megawatt (MW) or greater loads and layers on operational constraints that look more like punishment than policy.
Cost Shifting, Public Shaming, and Curtailment
At the heart of LB526 is a mandate: miners must shoulder the costs of any infrastructure upgrades needed to support their demand. Utilities are empowered to demand direct payments or letters of credit after conducting a “load study.” And while the law pays lip service to “fairness” and non-discrimination, it’s clear who the target is. Bitcoin miners are the only industry named.
Further, mining operators must notify utilities in advance, submit to their interconnection requirements, and, critically, accept interruptible service. That means that when the grid gets tight, it’s miners who go dark first. Voluntary demand response, the hallmark of Bitcoin mining’s grid-friendly posture? Replaced with mandated curtailment and utility discretion.
And the kicker: public disclosure of energy consumption. Utilities must publish annual energy usage for each mining operation. No such requirement exists for other data-heavy sectors — not for cloud computing, not for AI clusters, not for Amazon data centers. Just Bitcoin. It’s not just surveillance, it’s signaling.
The Tax That Wasn’t, and the Costs That Remain
To its credit, the Legislature dropped an earlier provision that would’ve added a 2.5¢/kWh tax on mining. This punitive levy would’ve tacked 50% onto typical industrial rates. That tax would have been an open declaration of hostility. Removing it was necessary. But not sufficient.
Because what remains in LB526 is a less visible, but no less potent deterrent: uncertainty. Miners already operate on razor-thin margins and seek jurisdictions with predictable power costs and clear rules. Instead, Nebraska is offering infrastructure tolls, discretionary curtailment, and regulatory spotlighting.
The Market Responds: Warning Shots from Miners
Industry leaders didn’t stay silent. Marathon Digital Holdings, one of the largest publicly traded mining firms, testified that it had invested nearly $200 million in Nebraska and paid over $6.5 million in taxes, and warned that if LB526 passed, further expansion would likely be scrapped.
Their message was clear: Nebraska had been a pro-mining, pro-growth jurisdiction. But LB526 sends a signal that miners aren’t welcome, or at best, are second-class citizens in the energy economy. As one executive put it, “If the same rules don’t apply to other energy-intensive industries, this isn’t about infrastructure, it’s about discrimination.”
Others warned that mandatory curtailment replaces cooperative grid services with coercion. Bitcoin miners can, and do, offer real-time load shedding that stabilizes grids during peak demand. But that value proposition only works when there’s a market signal. LB526 turns it into a liability.
Politics, Power, and Public Utilities
Senator Mike Jacobson, the bill’s sponsor, insisted LB526 is agnostic toward Bitcoin. “This is about electricity usage,” he said. But that’s hard to square with a bill that surgically targets one user class.
Jacobson pointed to Kearney, where half the city’s power goes to a single mining facility. But rather than view that as an opportunity, a dispatchable industrial customer willing to scale up or down based on grid needs, the Legislature opted for risk aversion and central planning.
And in Nebraska’s public power model, that matters. With every utility publicly owned, the regulatory posture of the state isn’t advisory, it’s existential. There is no retail competition. If Nebraska’s power authorities begin treating Bitcoin miners like unreliable freeloaders rather than willing partners, miners have no recourse. Just the exit.
For now, LB526 awaits only the governor’s signature. Given that LB526 was introduced at the behest of the governor, it is likely to be signed. Once enacted, it will take effect October 1, 2025. Miners have until then to decide: adapt, relocate, or fold.
States like Texas, Wyoming, and North Dakota have gone the opposite direction, offering tax clarity, grid integration, and legal protection. Nebraska, once on that shortlist, may find itself dropping off the radar.
Bitcoin mining doesn’t need handouts. But it does need equal footing. LB526 imposes costs, limits flexibility, and broadcasts suspicion. If the goal was to balance innovation with infrastructure, the execution leaves much to be desired.
Because when one industry is burdened while others are exempted, when voluntary partnerships are replaced with mandates, and when operational data is made public for no clear reason, it’s not hard to see why miners view LB526 not as regulation, but as retaliation.
This is a guest post by Colin Crossman. Opinions expressed are entirely their own and do not necessarily reflect those of BTC, Inc. or Bitcoin Magazine_._
This post Nebraska’s New Mining Rules: Infrastructure Safeguard or Soft Ban in Disguise? first appeared on Bitcoin Magazine and is written by Colin Crossman.
-
 @ 3f68dede:779bb81d
2025-05-19 17:06:26
@ 3f68dede:779bb81d
2025-05-19 17:06:26 -
 @ c1e9ab3a:9cb56b43
2025-04-15 04:55:49
@ c1e9ab3a:9cb56b43
2025-04-15 04:55:49Esteemed representatives of Risa,
We gather here under the calming glow of our twin suns, stewards of a society admired for its peace and celebrated for its tranquility. But we must not mistake serenity for passivity, nor confuse peace with weakness. Our peace is not an accident. It is not the byproduct of ignorance or naivety. It is hard-earned—preserved by those willing to stand vigilant in its defense.
Love as a Foundation, Strength as a Shield
Love conquers hate. This is the core truth of Risan philosophy. Yet, as every Ricin child is taught, love without strength is a leaf in the wind. The Ricin do not lay down their lives without resistance. We do not ask our people to accept violence without confronting it. True peace is not imposed by stripping the people of their agency—it is built by enabling them to protect it.
The Lessons of a Failed Experiment
There was a time, not so distant in our history, when we attempted to enforce peace through the abolition of all weapons. A time when even the mention of self-defense in our educational centers was met with rebuke. Schools purged training programs. Cultural arts that honored our warrior traditions were dismissed. And for a brief moment, we believed this would lead us to harmony.
But peace born from helplessness is a fragile illusion. It fractures under the slightest pressure. And fracture it did—when off-world raiders targeted our unguarded sanctuaries, when radical sects within our own society struck out, knowing the citizenry could not defend itself. It was then that we remembered: Risa’s greatest peacekeepers had always been those who knew how to fight—but chose restraint.
The Age of Ricin and the Reawakening of Discipline
So we returned to our roots. To the traditions of the Age of Ricin, when youth, upon reaching maturity, were taught not only the arts of compassion and creation but also the martial disciplines. They learn to wield weapons—not to glorify violence, but to understand it. To control it. To stand firm against it when all else fails.
https://i.nostr.build/kuUjRovISz7367TX.jpg
We do not romanticize war. We do not celebrate conflict. But we prepare for it, should it seek to extinguish our light. Our children now learn the disciplines of defense alongside their studies in poetry, music, and healing. They spar with blunt blades under the watchful eyes of masters. They meditate on the consequences of force. And they grow into citizens not easily provoked, but never unprepared.
A Call for Balance, Not Extremes
Let those beyond our borders question our ways. Let them forget the countless incursions by the Romulans. Let them ignore the scars left by centuries of subversion from the Orion Syndicate. We do not forget. We remember the lives lost, the liberties challenged, and the lessons learned through suffering. These experiences shaped us.
We do not wish to return to the era of soft silence, when teachers trembled at the word "weapon" and children were told that even imagination was dangerous. That was not enlightenment. That was indoctrination.
Conclusion: Guarding the Flame
We are the guardians of Risa’s flame—not just with words and treaties, but with discipline and readiness. We have made peace a practice, and preparation a virtue. And so I say to this chamber: let us never again disarm our people in the name of utopia. Let us never confuse comfort with safety, or the absence of weapons with the presence of peace.
Instead, let us raise generations who know what peace costs, and who will pay that price—not with surrender, but with courage.
Let our children be artists, lovers, dreamers—and if necessary, defenders.
This is the Risan way.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:15:58
@ c1e9ab3a:9cb56b43
2025-04-15 04:15:58Spoken by Counselor Elaron T’Saren of Risa to the High Council, Stardate 52874.2
Honored members of the Council,
I bring you greetings from Risa—not the Risa of travel brochures and romantic holo-novels, but the true Risa. The Risa that has endured, adapted, and emerged stronger after each trial. I speak not as a tourist ambassador, but as a Counselor of our oldest institute of philosophy, and as a son of the Ricin tradition.
Today, the specter of the Borg hangs above us. The collective offers no room for diplomacy, no respect for culture, no compromise. We face not mere invaders—but a force that seeks to erase individuality, history, and identity. Some among the Council wonder what Risa—a world of peace—can offer in such a time. I say to you: we can offer the truth about peace.
The Hidden Roots of Our Tranquility
Long ago, before Risa joined the Federation, we too believed that peace could be maintained by disarming the populace, by eliminating even the mention of conflict in our schools. It was called the Great Disarmament. A generation was raised with no understanding of defense, and in time, we paid the price.
We were raided by Orion pirates. Exploited by off-world cartels. Our people were taken, our arts destroyed, our skies blackened. And we learned—too late—that peace without preparedness is only the illusion of safety.
The Birth of Ricin Doctrine
From the ashes of that failure arose the Ricin: scholars, philosophers, warriors of thought and purpose. They taught that peace is not the absence of conflict, but the mastery of it. That the mind and the body must be trained in tandem. That love without strength is a leaf in the wind.
We did not become a militant world. We became a watchful one. Our children were taught martial discipline—not to glorify violence, but to understand it, to confront it, and to defeat it when necessary. They learned meditation alongside hand-to-hand technique, negotiation beside tactical reasoning.
When we joined the Federation, we did so willingly. But let none assume we surrendered our right to defend our way of life.
Why I Speak to You Now
The Borg are not like the Orion Syndicate. They are not opportunistic, or ideological. They are methodical. And they are coming. You cannot debate with them. You cannot delay them. You can only prepare for them.
And yet, I hear murmurs within the halls of the Federation: whispers of abandoning planetary defense training, of downplaying the psychological need for individual and planetary preparedness. I hear the tired lie that “peace will protect us.”
No, Councilors. It is discipline that protects peace.
The Call to Action
I do not come bearing weapons. I come bearing wisdom. Let us take the Risan lesson and apply it across the Federation. Reestablish tactical readiness training in civilian schools. Encourage planetary governments to integrate defense and philosophy, not as contradictions, but as complements.
Let every child of the Federation grow up knowing not just the principles of liberty, but the means to defend them. Let every artist, scientist, and healer stand ready to protect the civilization they help to build.
Let us not wait until the Borg are in our orbit to remember what we must become.
Conclusion
The Borg seek to erase our uniqueness. Let us show them that the Federation is not a fragile collection of planets—but a constellation of cultures bound by a shared resolve.
We do not choose war. But neither do we flee from it.
We are the guardians of Risa’s flame—and we offer our light to the stars.
Thank you.
-
 @ 3f68dede:779bb81d
2025-05-19 17:04:13
@ 3f68dede:779bb81d
2025-05-19 17:04:13testing schedule
-
 @ 3f68dede:779bb81d
2025-05-19 17:02:54
@ 3f68dede:779bb81d
2025-05-19 17:02:54testing schedule
-
 @ c1e9ab3a:9cb56b43
2025-04-14 23:54:40
@ c1e9ab3a:9cb56b43
2025-04-14 23:54:40Hear this, warriors of the Empire!
A dishonorable shadow spreads across our once-proud institutions, infecting our very bloodlines with weakness. The House of Duras—may their names be spoken with contempt—has betrayed the sacred warrior code of Kahless. No, they have not attacked us with disruptors or blades. Their weapon is more insidious: fear and silence.
Cowardice Masquerading as Concern
These traitors would strip our children of their birthright. They forbid the young from training with the bat'leth in school! Their cowardly decree does not come in the form of an open challenge, but in whispers of fear, buried in bureaucratic dictates. "It is for safety," they claim. "It is to prevent bloodshed." Lies! The blood of Klingons must be tested in training if it is to be ready in battle. We are not humans to be coddled by illusions of safety.
Indoctrination by Silence
In their cowardice, the House of Duras seeks to shape our children not into warriors, but into frightened bureaucrats who speak not of honor, nor of strength. They spread a vile practice—of punishing younglings for even speaking of combat, for recounting glorious tales of blades clashing in the halls of Sto-Vo-Kor! A child who dares write a poem of battle is silenced. A young warrior who shares tales of their father’s triumphs is summoned to the headmaster’s office.
This is no accident. This is a calculated cultural sabotage.
Weakness Taught as Virtue
The House of Duras has infected the minds of the teachers. These once-proud mentors now tremble at shadows, seeing future rebels in the eyes of their students. They demand security patrols and biometric scanners, turning training halls into prisons. They have created fear, not of enemies beyond the Empire, but of the students themselves.
And so, the rituals of strength are erased. The bat'leth is banished. The honor of open training and sparring is forbidden. All under the pretense of protection.
A Plan of Subjugation
Make no mistake. This is not a policy; it is a plan. A plan to disarm future warriors before they are strong enough to rise. By forbidding speech, training, and remembrance, the House of Duras ensures the next generation kneels before the High Council like servants, not warriors. They seek an Empire of sheep, not wolves.
Stand and Resist
But the blood of Kahless runs strong! We must not be silent. We must not comply. Let every training hall resound with the clash of steel. Let our children speak proudly of their ancestors' battles. Let every dishonorable edict from the House of Duras be met with open defiance.
Raise your voice, Klingons! Raise your blade! The soul of the Empire is at stake. We will not surrender our future. We will not let the cowardice of Duras shape the spirit of our children.
The Empire endures through strength. Through honor. Through battle. And so shall we!
-
 @ cae03c48:2a7d6671
2025-05-19 17:14:11
@ cae03c48:2a7d6671
2025-05-19 17:14:11Bitcoin Magazine

Fold Unveils Bitcoin Gift Card, Pioneering Bitcoin in U.S. Retail Gift Card MarketFold, a leading Bitcoin financial services company, recently announced the launch of its Bitcoin Gift Card, marking the first step in integrating Bitcoin into the $300 billion U.S. retail gift card market. This innovative product enables consumers to purchase and gift bitcoin through familiar retail channels, is available now at Fold’s website and is expected to expand to major retailers nationwide throughout the year.
The Fold Bitcoin Gift Card allows users to acquire bitcoin for personal savings or as a gift, redeemable via the Fold app. “Once you buy that gift card, you can give it to someone or use it yourself. You open the Fold app, and your bitcoin appears,” said Will Reeves, Chairman and CEO of Fold, in an interview with Bitcoin Magazine. Available initially at the Fold website, the product will soon reach physical and online retail shelves, bringing Bitcoin to everyday shopping experiences.
This launch positions Fold as a trailblazer in making Bitcoin accessible through gift cards, the most popular gift in America.
“We’re now talking about Bitcoin gift cards on sale on the racks of the largest retailers in the country. You can pick up Bitcoin at the checkout line, buy it for yourself, or share it as a gift,” Reeves told Bitcoin Magazine.
The gift card, a white Bitcoin “B,” adorned by vibrant orange, taps into the retail market’s demand for alternative assets, following the success of Costco’s $200 million monthly gold sales.

Fold’s partnership with Totus, a gift card issuance provider, enables distribution through over 150,000 points of sale nationwide.
“In our announcement, we reference one of our partners who has direct distribution into all primary retailers in the country,” Reeves said. While specific retailer names will be revealed later, Fold plans to expand throughout 2025, ensuring Bitcoin’s presence in stores like grocery chains and gas stations. “Throughout the rest of this year, we’ll announce distribution partners, including some of the largest retailers in the US,” Reeves added.
The Bitcoin Gift Card targets millions of Americans curious about Bitcoin but hesitant to navigate apps or exchanges.
“This gift card gives us distribution directly to millions of Americans who may not be buying Bitcoin because they haven’t downloaded a new app, don’t have a brokerage account, or haven’t seen the ETF,” Reeves explained. By leveraging trusted retail channels, Fold is opening a new avenue for Bitcoin adoption.
Since 2019, Fold has empowered over 600,000 users with Bitcoin-based financial tools, holding over 1,485 Bitcoin in its treasury.
“I think there’s a real chance by the end of 2025 that Bitcoin becomes the most popular gift in America because of this card,” Reeves predicted.
This post Fold Unveils Bitcoin Gift Card, Pioneering Bitcoin in U.S. Retail Gift Card Market first appeared on Bitcoin Magazine and is written by Juan Galt.
-
 @ 3f68dede:779bb81d
2025-05-19 17:02:33
@ 3f68dede:779bb81d
2025-05-19 17:02:33testing
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ 846ebf79:fe4e39a4
2025-04-14 12:35:54
@ 846ebf79:fe4e39a4
2025-04-14 12:35:54The next iteration is coming
We're busy racing to the finish line, for the #Alexandria Gutenberg beta. Then we can get the bug hunt done, release v0.1.0, and immediately start producing the first iteration of the Euler (v0.2.0) edition.
While we continue to work on fixing the performance issues and smooth rendering on the Reading View, we've gone ahead and added some new features and apps, which will be rolled-out soon.
The biggest projects this iteration have been:
- the HTTP API for the #Realy relay from nostr:npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku,
- implementation of a publication tree structure by nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn,
- and the Great DevOps Migration of 2025 from the ever-industrious Mr. nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7.
All are backend-y projects and have caused a major shift in process and product, on the development team's side, even if they're still largely invisible to users.
Another important, but invisible-to-you change is that nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735 has implemented the core bech32 functionality (and the associated tests) in C/C++, for the #Aedile NDK.
On the frontend:
nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 is currently working on the blog-specific Reading View, which allows for multi-npub or topical blogging, by using the 30040 index as a "folder", joining the various 30041 articles into different blogs. She has also started experimenting with categorization and columns for the landing page.


nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z revamped the product information pages, so that there is now a Contact page (including the ability to submit a Nostr issue) and an About page (with more product information, the build version displayed, and a live #GitCitadel feed).



We have also allowed for discrete headings (headers that aren't section headings, akin to the headers in Markdown). Discrete headings are formatted, but not added to the ToC and do not result in a section split by Asciidoc processors.
We have added OpenGraph metadata, so that hyperlinks to Alexandria publications, and other events, display prettily in other apps. And we fixed some bugs.
The Visualisation view has been updated and bug-fixed, to make the cards human-readable and closeable, and to add hyperlinks to the events to the card-titles.

We have added support for the display of individual wiki pages and the integration of them into 30040 publications. (This is an important feature for scientists and other nonfiction writers.)

We prettified the event json modal, so that it's easier to read and copy-paste out of.

The index card details have been expanded and the menus on the landing page have been revamped and expanded. Design and style has been improved, overall.

Project management is very busy
Our scientific adviser nostr:npub1m3xdppkd0njmrqe2ma8a6ys39zvgp5k8u22mev8xsnqp4nh80srqhqa5sf is working on the Euler plans for integrating features important for medical researchers and other scientists, which have been put on the fast track.
Next up are:
- a return of the Table of Contents
- kind 1111 comments, highlights, likes
- a prototype social feed for wss://theforest.nostr1.com, including long-form articles and Markdown rendering
- compose and edit of publications
- a search field
- the expansion of the relay set with the new relays from nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj, including some cool premium features
- full wiki functionality and disambiguation pages for replaceable events with overlapping d-tags
- a web app for mass-uploading and auto-converting PDFs to 30040/41 Asciidoc events, that will run on Realy, and be a service free for our premium relay subscribers
- ability to subscribe to the forest with a premium status
- the book upload CLI has been renamed and reworked into the Sybil Test Utility and that will get a major release, covering all the events and functionality needed to test Euler
- the #GitRepublic public git server project
- ....and much more.
Thank you for reading and may your morning be good.
-
 @ 3f68dede:779bb81d
2025-05-19 17:01:57
@ 3f68dede:779bb81d
2025-05-19 17:01:57testing schedule
-
 @ c1e9ab3a:9cb56b43
2025-04-11 04:41:15
@ c1e9ab3a:9cb56b43
2025-04-11 04:41:15Reanalysis: Could the Great Pyramid Function as an Ammonia Generator Powered by a 25GW Breeder Reactor?
Introduction
The Great Pyramid of Giza has traditionally been considered a tomb or ceremonial structure. Yet an intriguing alternative hypothesis suggests it could have functioned as a large-scale ammonia generator, powered by a high-energy source, such as a nuclear breeder reactor. This analysis explores the theoretical practicality of powering such a system using a continuous 25-gigawatt (GW) breeder reactor.
The Pyramid as an Ammonia Generator
Producing ammonia (NH₃) from atmospheric nitrogen (N₂) and hydrogen (H₂) requires substantial energy. Modern ammonia production (via the Haber-Bosch process) typically demands high pressure (~150–250 atmospheres) and temperatures (~400–500°C). However, given enough available energy, it is theoretically feasible to synthesize ammonia at lower pressures if catalysts and temperatures are sufficiently high or if alternative electrochemical or plasma-based fixation methods are employed.
Theoretical System Components:
-
High Heat Source (25GW breeder reactor)
A breeder reactor could consistently generate large amounts of heat. At a steady state of approximately 25GW, this heat source would easily sustain temperatures exceeding the 450°C threshold necessary for ammonia synthesis reactions, particularly if conducted electrochemically or catalytically. -
Steam and Hydrogen Production
The intense heat from a breeder reactor can efficiently evaporate water from subterranean channels (such as those historically suggested to exist beneath the pyramid) to form superheated steam. If coupled with high-voltage electrostatic fields (possibly in the millions of volts), steam electrolysis into hydrogen and oxygen becomes viable. This high-voltage environment could substantially enhance electrolysis efficiency. -
Nitrogen Fixation (Ammonia Synthesis)
With hydrogen readily produced, ammonia generation can proceed. Atmospheric nitrogen, abundant around the pyramid, can combine with the hydrogen generated through electrolysis. Under these conditions, the pyramid's capstone—potentially made from a catalytic metal like osmium, platinum, or gold—could facilitate nitrogen fixation at elevated temperatures.
Power Requirements and Energy Calculations
A thorough calculation of the continuous power requirements to maintain this system follows:
- Estimated Steady-state Power: ~25 GW of continuous thermal power.
- Total Energy Over 10,000 years: """ Energy = 25 GW × 10,000 years × 365.25 days/year × 24 hrs/day × 3600 s/hr ≈ 7.9 × 10²¹ Joules """
Feasibility of a 25GW Breeder Reactor within the Pyramid
A breeder reactor capable of sustaining 25GW thermal power is physically plausible—modern commercial reactors routinely generate 3–4GW thermal, so this is within an achievable engineering scale (though certainly large by current standards).
Fuel Requirements:
- Each kilogram of fissile fuel (e.g., U-233 from Thorium-232) releases ~80 terajoules (TJ) or 8×10¹³ joules.
- Considering reactor efficiency (~35%), one kilogram provides ~2.8×10¹³ joules usable energy: """ Fuel Required = 7.9 × 10²¹ J / 2.8 × 10¹³ J/kg ≈ 280,000 metric tons """
- With a breeding ratio of ~1.3: """ Initial Load = 280,000 tons / 1.3 ≈ 215,000 tons """
Reactor Physical Dimensions (Pebble Bed Design):
- King’s Chamber size: ~318 cubic meters.
- The reactor core would need to be extremely dense and highly efficient. Advanced engineering would be required to concentrate such power in this space, but it is within speculative feasibility.
Steam Generation and Scaling Management
Key methods to mitigate mineral scaling in the system: 1. Natural Limestone Filtration 2. Chemical Additives (e.g., chelating agents, phosphate compounds) 3. Superheating and Electrostatic Ionization 4. Electrostatic Control
Conclusion and Practical Considerations
Yes, the Great Pyramid could theoretically function as an ammonia generator if powered by a 25GW breeder reactor, using: - Thorium or Uranium-based fertile material, - Sustainable steam and scaling management, - High-voltage-enhanced electrolysis and catalytic ammonia synthesis.
While speculative, it is technologically coherent when analyzed through the lens of modern nuclear and chemical engineering.
See also: nostr:naddr1qqxnzde5xymrgvekxycrswfeqy2hwumn8ghj7am0deejucmpd3mxztnyv4mz7q3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wun9c08
-
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:58:16
@ c1e9ab3a:9cb56b43
2025-04-10 02:58:16Assumptions
| Factor | Assumption | |--------|------------| | CO₂ | Not considered a pollutant or is captured/stored later | | Water Use | Regulated across all sources; cooling towers or dry cooling required | | Compliance Cost | Nuclear no longer burdened by long licensing and construction delays | | Coal Waste | Treated as valuable raw material (e.g., fly ash for cement, gypsum from scrubbers) | | Nuclear Tech | Gen IV SMRs in widespread use (e.g., 50–300 MWe units, modular build, passive safety) | | Grid Role | All three provide baseload or load-following power | | Fuel Pricing | Moderate and stable (no energy crisis or supply chain disruptions) |
Performance Comparison
| Category | Coal (IGCC + Scrubbers) | Natural Gas (CCGT) | Nuclear (Gen IV SMRs) | |---------|-----------------------------|------------------------|--------------------------| | Thermal Efficiency | 40–45% | 55–62% | 30–35% | | CAPEX ($/kW) | $3,500–5,000 | $900–1,300 | $4,000–7,000 (modularized) | | O&M Cost ($/MWh) | $30–50 | $10–20 | $10–25 | | Fuel Cost ($/MWh) | $15–25 | $25–35 | $6–10 | | Water Use (gal/MWh) | 300–500 (with cooling towers) | 100–250 | 300–600 | | Air Emissions | Very low (excluding CO₂) | Very low | None | | Waste | Usable (fly ash, FGD gypsum, slag) | Minimal | Compact, long-term storage required | | Ramp/Flexibility | Slow ramp (newer designs better) | Fast ramp | Medium (SMRs better than traditional) | | Footprint (Land & Supply) | Large (mining, transport) | Medium | Small | | Energy Density | Medium | Medium-high | Very high | | Build Time | 4–7 years | 2–4 years | 2–5 years (with factory builds) | | Lifecycle (years) | 40+ | 30+ | 60+ | | Grid Resilience | High | High | Very High (passive safety, long refuel) |
Strategic Role Summary
1. Coal (Clean & Integrated)
- Strengths: Long-term fuel security; byproduct reuse; high reliability; domestic resource.
- Drawbacks: Still low flexibility; moderate efficiency; large physical/logistical footprint.
- Strategic Role: Best suited for regions with abundant coal and industrial reuse markets.
2. Natural Gas (CCGT)
- Strengths: High efficiency, low CAPEX, grid agility, low emissions.
- Drawbacks: Still fossil-based; dependent on well infrastructure; less long-lived.
- Strategic Role: Excellent transitional and peaking solution; strong complement to renewables.
3. Nuclear (Gen IV SMRs)
- Strengths: Highest energy density; no air emissions or CO₂; long lifespan; modular & scalable.
- Drawbacks: Still needs safe waste handling; high upfront cost; novel tech in deployment stage.
- Strategic Role: Ideal for low-carbon baseload, remote areas, and national strategic assets.
Adjusted Levelized Cost of Electricity (LCOE)
| Source | LCOE ($/MWh) | Notes | |--------|------------------|-------| | Coal (IGCC w/scrubbers) | ~$75–95 | Lower with valuable waste | | Natural Gas (CCGT) | ~$45–70 | Highly competitive if fuel costs are stable | | Gen IV SMRs | ~$65–85 | Assuming factory production and streamlined permitting |
Final Verdict (Under Optimized Assumptions)
- Most Economical Short-Term: Natural Gas
- Most Strategic Long-Term: Gen IV SMRs
- Most Viable if Industrial Ecosystem Exists: Clean Coal
All three could coexist in a diversified, stable energy grid: - Coal filling a regional or industrial niche, - Gas providing flexibility and economy, - SMRs ensuring long-term sustainability and energy security.
-
 @ 005bc4de:ef11e1a2
2025-05-19 17:01:54
@ 005bc4de:ef11e1a2
2025-05-19 17:01:54Keys and Religion
Mixing
Normally, I'm not a fan mixing and comparing bitcoinesque things and religion. It's too banal and trite, too easy: the religion of Bitcoin, the allusion of Satoshi the savior, the "Book of Satoshi," even the "Genesis" block. But, today, I'll break my own rule.
Yesterday, I heard a Christian pastor speak of the "keys of the kingdom." My feeling is that, were you to ask the average Christian, "What is the key, or keys, to the kingdom?", and perhaps I'm wrong on this, but I think they'd answer, "Prayer." I've heard it many times, "Prayer is the key to the kingdom." It's an easy mantra to remember. And, prayer is important for a Christian, no question about it. However, Biblically, the phrase "keys of the kingdom" refers to something else.
As the pastor pointed out yesterday, Biblically there are two keys: the binding key and the loosing key. This refers to Matthew 16:19 where Jesus says:
I will give you the keys of the kingdom of heaven; whatever you bind on earth will be bound in heaven, and whatever you loose on earth will be loosed in heaven. Matthew 16:19 (NIV)
For context, back up a few verses. This statement above was made in a conversation between Jesus and his disciple Simon Peter.
15 Jesus asked, “But what about you?” he asked. “Who do you say I am?” 16 Simon Peter answered, “You are the Messiah, the Son of the living God.” 17 Jesus replied, “Blessed are you, Simon son of Jonah, for this was not revealed to you by flesh and blood, but by my Father in heaven. 18 And I tell you that you are Peter, and on this rock I will build my church, and the gates of Hades will not overcome it.
Although brief, this is a deep and rich exchange. Traditionally, this has been viewed as the moment that Christ instituted the Christian church, the passing of power and authority to the early church itself. There has been confusion over it too, particularly the "...on this rock I will build my church..." part of it. Jesus was referring to Simon Peter's statement of faith (...for this was not revealed to you by flesh and blood...) with the "this" being what Peter had just said, "You are the Messiah, the Son of the living God." The church would be built upon the rock of faith in Jesus as the Messiah.
The early Christian church thus established, Jesus instituted what's come to be called the "office of the keys." That is, Jesus grants authority to his "appointees" in the church to carry out his authority. In more practical terms, this is referring to those who have been called into church service, normally priests, to forgive or not forgive sins. When a priest or pastor forgives, or not, it is not that he is doing it by his own right or power. That priest is, after all, yet another sinful man as well. Instead, the priest forgives by Christ's authority which was handed down by Jesus himself in those words to Peter.
To use an analogy, suppose a general had to make a decision about foot soldiers on the front line, waiting there in the trenches. Due to some time constraint, a decision for action was needed imminently. However, suppose the general lacked some bit of information that could only be obtained at the front. So, the general wrote up a communique to the lieutenant stationed at the front saying, "You assess the situation, and you make the call, charge or pull back. I'll support your decision." A courier ran to the front, relayed the message to the lieutenant, and the lieutenant assessed and made the decision. Ultimately, even thought the lieutenant made the decision, the authority behind the decision lay with the general who had transferred his authority to the lieutenant.
This authority or office of the keys is mirrored in John 20:22-23, when the resurrected Jesus appears to his disciples and says, "If you forgive anyone’s sins, their sins are forgiven; if you do not forgive them, they are not forgiven.”
Going just one step further, recall there are two keys involved, binding and loosing, and there are two places involved, earth and heaven. Usually, priests and pastors are "in the business" of forgiving. Penitence or confession, when real, is forgiven. The priest has the authority to forgive, or "loose" the sinner from his wrongdoings here on earth. And, that forgiveness applies to heaven as well, the sin is atoned and reconciled with God.
But, what about when the person is unrepentant, unbothered by what is Biblically sinful, refuses to change his ways, and rather chooses to continue in sinful ways? The "binding" key says that the priest or appointed church leader can hold that person accountable, can bind that person to the sin and separation from God. Normally, we hear of "excommunication" from the church which is formally stating that a person is outside of the church body. The binding keys still bind, both on earth as being outside of the church and in heaven as being separated from God.
And bitcoin?
That's a lot of religion, and heavy religion at that. The question is, what does this have to do with bitcoin?
Keys.
Namely, this is about public and private keys. Loosing and binding keys. A bit more religion, then I'll get back to bitcoin.
Yesterday, the pastor spoke briefly about binding and loosing keys, and this where my thoughts about keys somehow morphed over into bitcoin. For some reason, I pictured Herod's Temple. There had been Solomon's temple, which was destroyed, and then there was Herod's which was known for its beauty and was the one during Jesus's time. But, let's recall the background on this...
The book of Exodus, and others in the Old Testament, outline in detail God's plan for the tabernacle (a traveling tent) and for the temple in Jerusalem.
The tabernacle, overhead diagram. Image source: https://en.wikipedia.org/wiki/Tabernacle
You might recall the "history" lesson in Raiders of the Lost Ark. With the tabernacle and temple, one of the purposes was to house the ark of the covenant. Remember that the ark was the golden box that the Israelites carried around containing Moses's stone tablets with the Ten Commandments, some manna, and Aaron's staff. It held great power, God's power, and God literally met and spoke with the Levite priests hovering over the cherubim's wings.

The ark of the covenant. Image source: https://en.wikipedia.org/wiki/Ark_of_the_Covenant
In the tabernacle and temple, the "Holy of Holies" was a room, separated by a heavy curtain. It was off limits to all because it was, well, holy of holies. A heavy curtain divided the Holy of Holies, or the "Most Holy Place", from the less-holy, "Holy Place."
Once a year, on the Day of Atonement, one person, the chief priest, was allowed to walk into the Holy of Holies. He would sprinkle the blood of a sacrificed animal onto the ark. This was done for the forgiveness of the people's sins. Although this was pre-Jesus's words, this was using the loosing keys and was loosing sin.
This was serious business and was taken seriously. For instance, the priests Nadab and Abihu improperly performed their sacrificial duties, they messed up the procedure, and were consumed by fire. Priesthood was a dangerous occupation, one slip up and you were scorched.
 The second temple, "Herod's Temple". Image source: https://en.wikipedia.org/wiki/Second_Temple
The second temple, "Herod's Temple". Image source: https://en.wikipedia.org/wiki/Second_TempleBack to keys...
Yesterday, for some reason when I heard about binding and loosing keys, I imagined the chief priest standing in front of the curtain. I imagined him taking a deep breath, collecting his thoughts, getting ready to go in. It had to be intimidating.
As he stood there, in my mind, he and everyone else was shut out. The Most Holy Place was bound and locked. Walking in meant getting scorched (again, the end of Raiders of the Lost Ark). Yet, that priest had the loosing key. He had, first, permission as chief priest to enter on the Day of Atonement, secondly, he had the sacrificial blood to loose sins. Although the binding key had locked the Holy of Holies and thus bound the sins of the people, the loosing key was about to loose their sins.
Cryptographic keys
And back to bitcoin...
Bitcoin, and cryptography in general, operate on public and private keys. Any flavor of "cryptocurrency", or even Nostr, has public and private keys. In a way, these are binding and loosing keys.
Say you have 1.0 BTC (that's 100,000,000 sats 😀). That BTC exists as a UTXO which can be seen by anyone viewing your public address. In this way, your bitcoin public key is your binding key...that UTXO, that bitcoin, is bound to your public key...it is locked in place behind that heavy curtain. It will be there forever, unless there is an intervention...
You also have your private key, your loosing key. You can apply your private key to loose that UTXO, that bitcoin, and to send it along to wherever.
This is like law and gospel: sin is binding, however Jesus frees it. A bitcoin UTXO is bound until a private key looses it.
Nostr offers a somewhat similar illustration. You have an npub publicly and and nsec secretly or privately. If you were to write a note, your private nsec is needed as a loosing key to free that message, to broadcast it to the world. Once broadcast, it can be seen by all, however it is still inextricably bound or tied to your public key (your npub). Your npub is your binding key and your message is bound to it.
Summed
I'm not sure this binding and loosing keys in religion, and public and private keys in cryptography is the best comparison in the world. It's probably a terrible comparison. But, this is what came to my mind yesterday.
And, so, the mixing of religion and bitcoin is now officially over.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:57:02
@ c1e9ab3a:9cb56b43
2025-04-10 02:57:02A follow-up to nostr:naddr1qqgxxwtyxe3kvc3jvvuxywtyxs6rjq3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wuaydz8
This whitepaper, a comparison of baseload power options, explores a strategic policy framework to reduce the cost of next-generation nuclear power by aligning Gen IV Small Modular Reactors (SMRs) with national security objectives, public utility management, and a competitive manufacturing ecosystem modeled after the aerospace industry. Under this approach, SMRs could deliver stable, carbon-free power at $40–55/MWh, rivaling the economics of natural gas and renewables.
1. Context and Strategic Opportunity
Current Nuclear Cost Challenges
- High capital expenditure ($4,000–$12,000/kW)
- Lengthy permitting and construction timelines (10–15 years)
- Regulatory delays and public opposition
- Customized, one-off reactor designs with no economies of scale
The Promise of SMRs
- Factory-built, modular units
- Lower absolute cost and shorter build time
- Enhanced passive safety
- Scalable deployment
2. National Security as a Catalyst
Strategic Benefits
- Energy resilience for critical defense infrastructure
- Off-grid operation and EMP/cyber threat mitigation
- Long-duration fuel cycles reduce logistical risk
Policy Implications
- Streamlined permitting and site access under national defense exemptions
- Budget support via Department of Defense and Department of Energy
- Co-location on military bases and federal sites
3. Publicly Chartered Utilities: A New Operating Model
Utility Framework
- Federally chartered, low-margin operator (like TVA or USPS)
- Financially self-sustaining through long-term PPAs
- Focus on reliability, security, and public service over profit
Cost Advantages
- Lower cost of capital through public backing
- Predictable revenue models
- Community trust and stakeholder alignment
4. Competitive Manufacturing: The Aviation Analogy
Model Characteristics
- Multiple certified vendors, competing under common safety frameworks
- Factory-scale production and supply chain specialization
- Domestic sourcing for critical components and fuel
Benefits
- Cost reductions from repetition and volume
- Innovation through competition
- Export potential and industrial job creation
5. Levelized Cost of Electricity (LCOE) Impact
| Cost Lever | Estimated LCOE Reduction | |------------|--------------------------| | Streamlined regulation | -10 to -20% | | Public-charter operation | -5 to -15% | | Factory-built SMRs | -15 to -30% | | Defense market anchor | -10% |
Estimated Resulting LCOE: $40–55/MWh
6. Strategic Outcomes
- Nuclear cost competitiveness with gas and renewables
- Decarbonization without reliability sacrifice
- Strengthened national energy resilience
- Industrial and workforce revitalization
- U.S. global leadership in clean, secure nuclear energy
7. Recommendations
- Create a public-private chartered SMR utility
- Deploy initial reactors on military and federal lands
- Incentivize competitive SMR manufacturing consortia
- Establish fast-track licensing for Gen IV designs
- Align DoD/DOE energy procurement to SMR adoption
Conclusion
This strategy would transform nuclear power from a high-cost, high-risk sector into a mission-driven, economically viable backbone of American energy and defense infrastructure. By treating SMRs as strategic assets, not just energy projects, the U.S. can unlock affordable, scalable, and secure nuclear power for generations to come.
-
 @ 3f68dede:779bb81d
2025-05-19 17:01:19
@ 3f68dede:779bb81d
2025-05-19 17:01:19testing schedule
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:55:11
@ c1e9ab3a:9cb56b43
2025-04-10 02:55:11The United States is on the cusp of a historic technological renaissance, often referred to as the Fourth Industrial Revolution. Artificial intelligence, automation, advanced robotics, quantum computing, biotechnology, and clean manufacturing are converging into a seismic shift that will redefine how we live, work, and relate to one another. But there's a critical catch: this transformation depends entirely on the availability of stable, abundant, and inexpensive electricity.
Why Electricity is the Keystone of Innovation
Let’s start with something basic but often overlooked. Every industrial revolution has had an energy driver:
- The First rode the steam engine, powered by coal.
- The Second was electrified through centralized power plants.
- The Third harnessed computing and the internet.
- The Fourth will demand energy on a scale and reliability never seen before.
Imagine a city where thousands of small factories run 24/7 with robotics and AI doing precision manufacturing. Imagine a national network of autonomous vehicles, delivery drones, urban vertical farms, and high-bandwidth communication systems. All of this requires uninterrupted and inexpensive power.
Without it? Costs balloon. Innovation stalls. Investment leaves. And America risks becoming a second-tier economic power in a multipolar world.
So here’s the thesis: If we want to lead the Fourth Industrial Revolution, we must first lead in energy. And nuclear — specifically Gen IV Small Modular Reactors (SMRs) — must be part of that leadership.
The Nuclear Case: Clean, Scalable, Strategic
Let’s debunk the myth: nuclear is not the boogeyman of the 1970s. It’s one of the safest, cleanest, and most energy-dense sources we have.
But traditional nuclear has problems:
- Too expensive to build.
- Too long to license.
- Too bespoke and complex.
Enter Gen IV SMRs:
- Factory-built and transportable.
- Passively safe with walk-away safety designs.
- Scalable in 50–300 MWe increments.
- Ideal for remote areas, industrial parks, and military bases.
But even SMRs will struggle under the current regulatory, economic, and manufacturing ecosystem. To unlock their potential, we need a new national approach.
The Argument for National Strategy
Let’s paint a vision:
SMRs deployed at military bases across the country, secured by trained personnel, powering critical infrastructure, and feeding clean, carbon-free power back into surrounding communities.
SMRs operated by public chartered utilities—not for Wall Street profits, but for stability, security, and public good.
SMRs manufactured by a competitive ecosystem of certified vendors, just like aircraft or medical devices, with standard parts and rapid regulatory approval.
This isn't science fiction. It's a plausible, powerful model. Here’s how we do it.
Step 1: Treat SMRs as a National Security Asset
Why does the Department of Defense spend billions to secure oil convoys and build fuel depots across the world, but not invest in nuclear microgrids that would make forward bases self-sufficient for decades?
Nuclear power is inherently a strategic asset:
- Immune to price shocks.
- Hard to sabotage.
- Decades of stable power from a small footprint.
It’s time to reframe SMRs from an energy project to a national security platform. That changes everything.
Step 2: Create Public-Chartered Operating Companies
We don’t need another corporate monopoly or Wall Street scheme. Instead, let’s charter SMR utilities the way we chartered the TVA or the Postal Service:
- Low-margin, mission-oriented.
- Publicly accountable.
- Able to sign long-term contracts with DOD, DOE, or regional utilities.
These organizations won’t chase quarterly profits. They’ll chase uptime, grid stability, and national resilience.
Step 3: Build a Competitive SMR Industry Like Aerospace
Imagine multiple manufacturers building SMRs to common, certified standards. Components sourced from a wide supplier base. Designs evolving year over year, with upgrades like software and avionics do.
This is how we build:
- Safer reactors
- Cheaper units
- Modular designs
- A real export industry
Airplanes are safe, affordable, and efficient because of scale and standardization. We can do the same with reactors.
Step 4: Anchor SMRs to the Coming Fourth Industrial Revolution
AI, robotics, and distributed manufacturing don’t need fossil fuels. They need cheap, clean, continuous electricity.
- AI datacenters
- Robotic agriculture
- Carbon-free steel and cement
- Direct air capture
- Electric industrial transport
SMRs enable this future. And they decentralize power, both literally and economically. That means jobs in every region, not just coastal tech hubs.
Step 5: Pair Energy Sovereignty with Economic Reform
Here’s the big leap: what if this new energy architecture was tied to a transparent, auditable, and sovereign monetary system?
- Public utilities priced in a new digital dollar.
- Trade policy balanced by low-carbon energy exports.
- Public accounting verified with open ledgers.
This is not just national security. It’s monetary resilience.
The world is moving to multi-polar trade systems. Energy exports and energy reliability will define economic influence. If America leads with SMRs, we lead the conversation.
Conclusion: A Moral and Strategic Imperative
We can either:
- Let outdated fears and bureaucracy stall the future, or...
- Build the infrastructure for clean, secure, and sovereign prosperity.
We have the designs.
We have the talent.
We have the need.What we need now is will.
The Fourth Industrial Revolution will either be powered by us—or by someone else. Let’s make sure America leads. And let’s do it with SMRs, public charter, competitive industry, and national purpose.
It’s time.
This is a call to engineers, legislators, veterans, economists, and every American who believes in building again. SMRs are not just about power. They are about sovereignty, security, and shared prosperity.
Further reading:
nostr:naddr1qqgrjv33xenx2drpve3kxvrp8quxgqgcwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tczyrq7n2e62632km9yh6l5f6nykt76gzkxxy0gs6agddr9y95uk445xqcyqqq823cdzc99s
-
 @ ee6ea13a:959b6e74
2025-04-06 16:38:22
@ ee6ea13a:959b6e74
2025-04-06 16:38:22Chef's notes
You can cook this in one pan on the stove. I use a cast iron pan, but you can make it in a wok or any deep pan.
I serve mine over rice, which I make in a rice cooker. If you have a fancy one, you might have a setting for sticky or scorched rice, so give one of those a try.
To plate this, I scoop rice into a bowl, and then turn it upside-down to give it a dome shape, then spoon the curry on top of it.
Serve with chopped cilantro and lime wedges.
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 20
- 🍽️ Servings: 4
Ingredients
- 1 ½ pounds boneless skinless chicken breast, cut into 2" pieces
- 2 tablespoons coconut or avocado oil
- 1 cup white or yellow onion, finely diced
- 1 cup red bell pepper, sliced or diced
- 4 large garlic cloves, minced
- 1 small (4oz) jar of Thai red curry paste
- 1 can (13oz) unsweetened coconut milk
- 1 teaspoon ground ginger
- 1 teaspoon ground coriander
- 1 tablespoon soy sauce
- 1 tablespoon brown sugar
- 1 cup carrots, shredded or julienned
- 1 lime, zest and juice
- ¼ cup fresh cilantro, chopped for garnish
Directions
- Heat oil in a large skillet over medium-high. Once hot, add onions and ½ teaspoon salt. Cook 3 minutes, or until onions are softened, stirring often.
- Add the red curry paste, garlic, ginger, and coriander. Cook about 1 minute, or until fragrant, stirring often.
- Add coconut milk, brown sugar, soy sauce, and chicken. Stir, bring to a simmer, then reduce heat to medium. Simmer uncovered for 7 minutes, occasionally stirring.
- Add carrots and red bell peppers, and simmer 5-7 more minutes, until sauce slightly thickens and chicken is cooked through.
- Remove from heat, and stir in the lime zest, and half of the lime juice.
- Serve over rice, topped with cilantro, and add more lime juice if you like extra citrus.
-
 @ 3f68dede:779bb81d
2025-05-19 17:00:18
@ 3f68dede:779bb81d
2025-05-19 17:00:18testing schedule
-
 @ fd208ee8:0fd927c1
2025-04-05 21:51:52
@ fd208ee8:0fd927c1
2025-04-05 21:51:52Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ 3f68dede:779bb81d
2025-05-19 16:59:50
@ 3f68dede:779bb81d
2025-05-19 16:59:50testing schedule
-
 @ 662f9bff:8960f6b2
2025-05-19 15:11:25
@ 662f9bff:8960f6b2
2025-05-19 15:11:25Let's start with some important foundational thinking - based on natural law. Money should be separate from the State - if not history shows that governments and human greed will always take over and manipulate the system in their favour and the expense of their populations. For extensive references, read The Sovereign Individual and The Creature from Jeckyll Island.
-
The Separation of State and Money is the most important thing you can listen to this week. Thanks to Allen Farrington - his paper is here for those who prefer to read. Wake up, folks!
-
The American Forefathers knew this when the wrote the American Constitution. Thomas Jefferson said: “If the American people ever allow private banks to control the issue of their currency first by inflation then by deflation the banks and corporations that will grow up around them will deprive the people of all property until their children wake up homeless on the continent their Fathers conquered... I believe that banking institutions are more dangerous to our liberties than standing armies... The issuing power should be taken from the banks and restored to the people to whom it properly belongs.” Mark Moss explains it well here. Charlie Robinsons take here.
The situation in Canada explifies the issues
Governments have have long used "international economic sanctions" against other nations to enforce their positions. Now in Canada, and soon in your country too, they are applying such sanctions their own citizens - disconnecting them from the financial system and removing their ability to use their own life savings as they wish. Canadians spoke with their money - in one week they raised more money in support of the truckers for peaceful protest than were raised in support of all Canadian political parties in the election of last year - only to have it confiscated and blocked by those politicians.
-
CPL. Daniel Bulford (Justin Trudeau's body guard) is particularly clear and eloquent - https://www.facebook.com/watch/?v=3123688351279364
-
Nick & Greg (two Canadians in Canada) explain the situation to Peter McCormack - https://youtu.be/QBWYp-cBr4o
-
Dr Jordan Peterson and Dr Julie Ponesse (also Canadians in Canada) speak openly about what is going on https://t.co/2T7A4VEek1
-
Even Canadians living in China speak up: https://www.youtube.com/watch?v=xvDvJWdlD1E
Meanwhile in Turkey...
Joe Blogs has been giving blow by blow updates of the deteriorating sitation over the last weeks. What is happening to Turkey will come to many countries - sooner than you might imagine. Watch and learn here, here and here - more on his channel.
EU Citizens should be aware and lobby their MPs
Dropping of all C-19 restrictions is a tactic to stop people thinking about them; meanwhile the politicians are taking steps to get all of the emergency restrictions codified into normal law so that they can be deployed on you any time or all the time in future.\ Act now - or lose all freedoms - your choice - watch here or click below for the explainer.
More on war - recall our discussion last week
War steals and destroys the wealth of generations. We have been here before - remember World Wars 1 and 2...
-
Dr Mattias Desmet explains how mass formation psychosis happens and how he became aware: https://www.youtube.com/watch?v=CRo-ieBEw-8
-
Be aware of this well known and much abused psycholgical experiment - rats in a cage - explained by Dr Christ Martensen: https://www.youtube.com/watch?v=7kSBdMXQkPI
To remain silent is wrong - to deny the rights of others to discuss and challenge (and even to punish or coerce them) is a crime in support of the biger crime. Each of us has a choice - choose wisely.
Could you have known about this?
"The Matrix is a system, Neo. That system is our enemy. But when you're inside, you look around, what do you see? Businessmen, teachers, lawyers, carpenters. The very minds of the people we are trying to save. But until we do, these people are still a part of that system and that makes them our enemy. You have to understand, most of these people are not ready to be unplugged. And many of them are so inert, so hopelessly dependent on the system that they will fight to protect it."
"Unfortunately, no one can be told what the Matrix is. You have to see it for yourself."
A closing thought...
Look closely at the cover of the Economist magazine released in December 2018 - The World in 2019 - see how many of those things have already come true.

In case this is too difficult for you - some things to note: Four horsemen of the apacalypse, Statue of Liberty wearing a facemask, Vetruvian Man with QR code (Vaccine passport), DNA mark on his arm, wearing virtual reality glasses... The animal bottom right is a Pangolin. Scales of Justice are well tipped/skewed, facial recognition, electric cars, Putin's pipelines, China and Brexit feature highly along with the lieing media (Pinnochio) and #metoo. I smell Predictive Programming.
- More insights in the explainer here (backup copy here) - including why it is backwards...
That's it!
No one can be told what The Matrix is.\ You have to see it for yourself.**
Do share this newsletter with any of your friends and family who might be interested.
You can also email me at: LetterFrom@rogerprice.me
💡Enjoy the newsletters in your own language : Dutch, French, German, Serbian, Chinese Traditional & Simplified, Thai and Burmese.
-
-
 @ c6d8334c:30883d6d
2025-05-19 15:02:01
@ c6d8334c:30883d6d
2025-05-19 15:02:01#KIBedenken - Bewusstsein
Einen wichtigen Impuls über KI nachzudenken lieferte vor einiger Zeit Yuval Noah Harari an der University of Cambridge am Ende eines Podiumsgesprächs hier ab 1:15 h auf youtube:
Ich denke, wir müssen die Frage des Bewusstseins in den Mittelpunkt der Diskussion stellen. Es gibt eine riesige, riesige Verwirrung in der Terminologie, auch in der Welt der KI, zwischen Bewusstsein und Intelligenz. Aber es sind zwei verschiedene Dinge. Intelligenz ist die Fähigkeit, Probleme zu lösen und Ziele zu erreichen. Bewusstsein ist die Fähigkeit, Dinge zu fühlen, wie Schmerz oder Freude oder Liebe oder Hass. Wir neigen dazu, die beiden zu verwechseln, weil bei Menschen und auch bei anderen Säugetieren, Vögeln und anderen Tieren Bewusstsein und Intelligenz zusammengehören. Wir lösen Probleme durch unsere Gefühle. Computer waren bisher sehr anders. Sie sind in einigen Bereichen bereits intelligenter als wir, haben aber, soweit wir wissen, kein Bewusstsein. Soweit wir wissen, können sie überhaupt keinen Schmerz, keine Freude, keine Liebe oder keinen Hass empfinden. Niemand weiß, was in Zukunft passieren wird. Es gibt Modelle und Theorien, die argumentieren, dass KIs irgendwann auch bewusst oder empfindsam werden. Sie werden anfangen, Dinge zu fühlen. Sie werden anfangen, Schmerz oder Liebe oder Hass zu empfinden. Es gibt andere Modelle und Theorien, die sagen, nein. Sie könnten weit intelligenter werden als wir und immer noch null Bewusstsein haben. Das kann in der Evolution des Lebens sein. Wenn man darüber nachdenkt, die lange Entwicklung von Milliarden von Jahren der Evolution. Die Entwicklung der Intelligenz ist im Falle von Tieren wie uns und Schimpansen und Hunden und Schweinen und so weiter durch die Entwicklung des Bewusstseins verlaufen. Aber das ist kein universelles Gesetz der Evolution der Intelligenz. Vielleicht gibt es alternative Wege, die zu Superintelligenz ohne jegliches Bewusstsein führen. Einfach einen anderen, einen fremden Weg gehen. Und wir könnten an einen Punkt gelangen, an dem sie superintelligent sind und trotzdem null Bewusstsein haben. Und die Gefahr besteht dann darin, dass sie nicht nur die menschliche Zivilisation zerstören könnten, sondern das ganze Licht des Bewusstseins, um das gesamte ökologische System nach ihren Bedürfnissen umzugestalten, wofür sie kein Bewusstsein brauchen. Sie funktionieren auf eine völlig andere Weise. Sie könnten sich sogar von der Erde auf andere Planeten, auf andere Galaxien ausbreiten. Sie werden das Universum mit Intelligenz füllen, aber es wird ein völlig dunkles Universum ohne Bewusstsein sein. Wieder hohe Intelligenz, fähig, Raumschiffe zu bauen, die mit Lichtgeschwindigkeit fliegen und was auch immer, aber es gibt null Gefühl. Niemand, keine Entität fühlt Schmerz oder Freude, Liebe oder Hass. Für mich ist das ein schreckliches Szenario. Das schlimmste Szenario von allen ist dies. Dass wir ein Universum voller Intelligenz und völlig ohne Bewusstsein haben werden, denn ich denke, dass von den beiden das Bewusstsein weitaus wichtiger, weitaus wertvoller ist. Und es ist eine gute Erinnerung daran, dass wir das zumindest heute mit vielen anderen Tieren teilen, aber nicht mit den Computern, nicht mit den KIs. Wir sind also immer noch im selben Team wie die Würmer und die Affen, nicht im selben Team wie die Computer.
Ich denke, hier wird eine Spur gelegt, die sich unterscheidet von der reinen Funktion von KI zur intelligenten Verbesserung und Unterstützung von Lernprozessen oder vielfältigem Kompetenzerwerb hin zur Selbstreflexion der Lernenden. Auch im Blick auf (religionsbezogene) Bildung kennen wir den Mensch nicht nur biologisch, wie die Würmer und Affen sondern auch ausgestattet mit Würde, Entscheidungsfreiheit und als Beziehungswesen, das auf ein Gegenüber ausgerichtet sein kann und, wie Harari sagt, nicht im selben Team wie die Computer spielt. Sinn, Seele und Verstand erhalten wir weder aus uns selbst heraus noch von einer wie auch immer gearteten Intelligenz. Liebe, Gnade, Hoffnung, Frieden, Gemeinschaft, Trost, Zuversicht und viele weiteren lebensbedeutsame Erfahrungen gewinnen im Angesicht von Maschinen aus meiner Sicht an elementarer Bedeutung.
-
 @ 9223d2fa:b57e3de7
2025-05-19 15:01:19
@ 9223d2fa:b57e3de7
2025-05-19 15:01:196,323 steps
-
 @ cb4352cd:a16422d7
2025-05-19 16:40:21
@ cb4352cd:a16422d7
2025-05-19 16:40:21The countdown is nearly over. On May 30, 2025, the Beyond Banking Conference by WeFi will go live — gathering thinkers, builders, and innovators from across DeFi, Web3, AI, and FinTech. Whether you're a founder, developer, investor, or just exploring the space, this is where ideas meet momentum.
Four Tracks, One Shared Vision
At the heart of the conference are four thematic tracks, each offering a lens into where finance is heading:
-
DeFAI — Where AI meets DeFi. From autonomous lending to smart liquidity, this track dives into machine-powered finance.
-
GameFi — Not just play-to-earn. Think social-first gaming, fast sessions, on-chain assets, and frictionless onboarding.
-
AI + Web3 — Explore a future shaped by trustless AI agents, generative content, and decentralized governance systems.
-
FinTech AI — See how financial services are evolving with AI: from compliance and identity to intelligent asset management.
Who You’ll Hear From
Among the voices leading the conversation:
-
Vít Jedlička, President of Liberland, on digital sovereignty and blockchain-powered governance.
-
Tigran Hakhunts, HTX Ambassador, on how exchanges are navigating and accelerating decentralized adoption.
And that’s just the beginning — expect DeFi founders, Web3 infrastructure teams, AI policy researchers, and the next generation of financial technologists.
What’s Beyond the Keynotes
This isn’t a day of passive watching. You’ll see:
-
Live product demos, including WeFi’s own onchain banking tools.
-
Multilingual Q&A sessions where your questions drive the conversation.
-
Real-time translation in 8 languages to keep everything accessible.
-
And yes — a Ferrari giveaway. Registered attendees automatically enter a lottery to win big.
One Day. A Global Experience.
No flights, no paywalls, no exclusivity. This is finance without borders. Whether you’re tuning in from São Paulo or Seoul, you’ll be part of a shared global moment.
To join, just connect through the official bot.
The future of finance isn’t happening behind closed doors. It’s unfolding in the open — and you’re invited. See you May 30.
-
-
 @ c8adf82a:7265ee75
2025-04-04 01:58:49
@ c8adf82a:7265ee75
2025-04-04 01:58:49What is knowledge? Why do we need it?
Since we were small, our parents/guardian put us in school, worked their asses off to give us elective lessons, some get help until college, some even after college and after professional work. Why is this intelligence thing so sought after?
When you were born, you mostly just accepted what your parents said, they say go to school - you go to school, they say go learn the piano - you learn the piano. Of course with a lot of questions and denials, but you do it because you know your parents are doing it for your own good. You can feel the love so you disregard the 'why' and go on with faith
Everything starts with why, and for most people maybe the purpose of knowledge is to be smarter, to know more, just because. But for me this sounds utterly useless. One day I will die next to a man with half a brain and we would feel the same exact thing on the ground. Literally being smarter at the end does not matter at all
However, I am not saying to just be lazy and foolish. For me the purpose of knowledge is action. The more you learn, the more you know what to do, the more you can be sure you are doing the right thing, the more you can make progress on your own being, etc etc
Now, how can you properly learn? Imagine a water bottle. The water bottle's sole purpose is to contain water, but you cannot fill in the water bottle before you open the cap. To learn properly, make sure you open the cap and let all that water pour into you
If you are reading this, you are alive. Don't waste your time doing useless stuff and start to make a difference in your life
Seize the day
-
 @ 0c65eba8:4a08ef9a
2025-05-19 14:41:33
@ 0c65eba8:4a08ef9a
2025-05-19 14:41:33You’re not alone.
There are countless men, good men, who want love, want marriage, want a family… but feel blocked. Blocked by time. By money. By fear. By uncertainty.
You’ve tried. You’ve thought about it. Maybe you’ve even taken a few steps. But the whole thing feels frustrating. Like you’re pushing against a wall that won’t budge.
This article is for you.
Most dating problems come from one of two places.
The first is your environment. Some cities and cultures make finding a good woman harder than others. But don’t make the mistake of thinking all of the West is the same. Even in the most liberal cities, there are still good women. Even in the most conservative areas, there are women to avoid. If you can move, move where it’s easier. If you can’t, reshape your environment in other ways, your community, your routines, your social circles.
The second source of problems is internal. Your skills, your mindset, your emotional blocks, your lack of development. These are the parts of you that aren’t yet ready to attract or lead a woman.
Here’s the good news: You can change both.
Aside from extreme physical limitations, nearly everything holding you back can be improved. Often faster than you think. Some things will take a day. Others will take a year or two. But you don’t need to be perfect. You only need to become the kind of man a good woman would say yes to.
You’re not lazy. You’re not broken.
You just haven’t been shown how to deal with these barriers like a man who’s preparing to lead a family.
This isn’t a scolding. It’s a flashlight. I'm going to show you something valuable, for free.
Each problem below is something real men have told me. Each solution is the next step forward. One step at a time.
Let’s take that step, together.
PROBLEM: “I don’t have time to go on dates.”
SOLUTION: If you don’t have time to date, you don’t have time to be married.
A woman isn’t a hobby you slot in between deadlines. She’s your future family. Mother of your children.
And if your current schedule can’t make room for love, it won’t make room for life either.
This doesn’t mean you should never date. It means you need a plan.
Sometimes, the wisest path is to finish what’s already on your plate. School. Training. A startup. A season of intensity that still needs to end.
If you’re deep in one of those phases, finish it. But make sure it has an end date. Don't put off finishing.
Restructure your life so that within 12 to 24 months, you’re free enough to fall in love. Not distracted. Not drowning. Available, with time and energy to spare.
Create space now, or clear the path so it can be created soon.
You don’t have to do everything at once. But you do have to be intentional.
That’s part of being a mature man, taking control of your time and energy.
PROBLEM: “I can’t afford to take a woman out on a date.”
SOLUTION: Money has always been a sore spot for young men.
Most men in history started out with very little. In the past, families often stepped in to help launch a young couple. But even then, the early years were lean. That’s normal.
Even if you’re intelligent, hardworking, and on the right track, it can still take until your early 30s to reach true financial stability. That doesn’t mean you’re behind. It means you’re on your own journey.
But here’s the thing: If you can’t afford to take a woman on a date, you can’t afford a wife either.
Marriage is not cheaper than dating. Children are not cheaper than courtship. Responsibility isn’t free.
You don’t need to impress her with a fine dining at a steakhouse. But you do need to signal that your life is in motion and that you have a plan.
If you’re broke, your mission is money. And that means:
-
Take on a second job, either a side gig or job-stacking
-
Reduce your expenses until you gain traction
-
Build an income stream that reflects a man ready to provide
Look at it as a test of your creativity, intelligence, social skills and perseverance. And yes, it's going to be hard. I too was a broke young man once. It's not a fun place to be.
A man who won’t feed himself cannot feed a family. Handle that first.
PROBLEM: “I don’t know where to meet women.”
SOLUTION: This isn’t just a logistics issue. It’s a life design issue.
You meet high-quality women by becoming a high-quality man in motion, a man with an interesting life.
That means building a life that’s rich with activity, purpose, and human connection. A life that invites others in, because it’s already alive.
Start doing interesting things with interesting people. Join groups. Serve. Create. Build a reputation in your community. Train at a gym. Lead something. Show up where life is happening.
Here’s a simple metric: If you’re not organically meeting at least one woman per month who you might want to date, your life isn’t active or interesting enough.
Women aren’t looking for a perfect man. They’re looking for a man with a compelling direction, a mission worth joining. A future worth investing in.
Women don’t just marry you. They marry into your lifestyle.
If your life is empty, isolated, or stagnant, there’s nothing for her to attach to. No rhythm to join. No social proof. No spark. No return on her investment.
Now, if you’re introverted, this part will be harder. Not impossible. Just different.
You’ll need to choose environments where you can thrive:
-
Smaller groups with consistent attendance
-
Classes or workshops with a shared task
-
Quiet community activities like hiking, book clubs, or local volunteering
-
Faith groups or skill-building meetups that match your interests
Focus on building a rhythm and repetition (habit). Show up. Be seen. Let relationships build slowly.
Create the kind of life a woman would be proud to stand beside. Not because she completes it, but because she compliments it.
I wrote more on this here:
Where to Find a Good Woman: A Short Field Guide for Men Who Want to Build a Legacy**
PROBLEM: “I’m too short. Or fat. Or ugly. Or too intimidating.”
SOLUTION: Every man has something about his body he doesn’t like. Some things can be changed. Others can’t. But here’s the truth:
Women don’t marry just for looks. They marry for masculine presence.
You can be average-looking, or even rough-looking, and still be deeply attractive if you carry yourself like a man. Strong. Composed. Grounded.
Most physical ‘flaws’ can be compensated for by strength in other areas:
-
Fat face? Get lean and muscular, it changes your bone structure and confidence.
-
Don’t like your jawline? Grow a beard and learn to carry yourself with dignity.
-
Short? Then your mission is to walk like a king and build a life so compelling she forgets your height within five minutes.
Plenty of short, homely, or scarred men marry wonderful women. But only when they don’t let their appearance be a cage.
Fix what you can. Style your hair. Improve your grooming. Learn how to dress. Lift. Move. Stand tall. Speak with purpose. Develop gravatas and humor.
The rest? Let it refine your spirit. Not shame you, but sharpen you. Your face isn’t the problem you imagine it to be and your presence is the solution.
PROBLEM: “I’m afraid of being MeToo’ed.”
SOLUTION: This fear is not unfounded. But it’s exaggerated, and it can be managed.
First, date women from your known social circle, or through trusted friends and communities. When you’re introduced by people who know her, and know you, the risk drops dramatically. Reputation protects.
Second, don’t sleep with women you’re not married to or seriously planning to marry. Promiscuity opens you up to accusations by nature of the risk you’ve chosen. If you act like a husband looking for a wife, you’ll avoid most of the fallout that comes from acting like a player.
Finally, date like a man of integrity. Be clear in your intent. Be respectful in your approach. Vet women the way you’d vet a business partner, slowly, carefully, with your eyes open.
Avoid women who are unstable, ideological, addicted to drama, or hostile to men or who have friends that are red flags. They’re not hard to spot if you stop pretending you can fix them. Don't date crazy, no matter how much of a hot mess they are.
Courage doesn’t mean being reckless. It means being cautious and moving forward anyway.
PROBLEM: “I have debilitating social anxiety.”
SOLUTION: Social anxiety is not your enemy. It’s a signal.
Anxiety is what your body feels when you know you’re unprepared. So the real issue isn’t fear, it’s readiness.
The solution is to prepare.
Start by talking with people you already know and trust. Ask them directly: “Do I come across in any off-putting way?” Be ready to hear the truth. This feedback is gold.
Next, expand your social exposure in gradual circles:
-
Begin with low-stakes conversations, cashiers, neighbors, people at your gym
-
Practice warm eye contact and a confident smile
-
Say hello, then progress to small talk
Train your ability to enjoy people. Genuine curiosity, care, and concern are magnetic.
Imagine that you are a source of light and warmth in the world. It radiates from your face. When you smile, that light shines on others and lifts their spirit.
Practice radiating that warmth everywhere you go. It will transform how people receive you, and how you see yourself.
Also, don’t overlook your existing social network. Ask friends: “Can you introduce me to people? Invite me to something?” And if they hesitate, ask why. Be open to correction. Sharpen your social skills until you become the man people want to introduce to others.
This process doesn’t have to take years. If you want to speed it up, message me. I’ll help you identify what needs to change and how to change it, fast.
You’re not trapped. You’re just untrained. Let’s fix that.
PROBLEM: “Online dating is awful. Everyone on the apps is weird, overweight, or carries baggage.”
SOLUTION: You’re not wrong. Most dating apps are designed to keep you swiping, not to help you find a wife.
But if you insist on using them, use them well.
-
Get professional photos taken. Not filtered selfies. Real, high-quality photos that make you look your best.
-
Write a profile that’s clear, masculine, and purposeful. If possible, get help from someone who understands marketing.
-
If you have a female friend or sister near your age, ask her: “What does this profile really communicate?” Men and women read profiles differently. Get honest feedback.
Even with the best profile, online dating carries risks. You’re meeting strangers. And many women on the apps are not relationship-ready. If you’re not seeing the kind of woman you want, stop using the apps. Don’t waste your energy in a dysfunctional pool.
Instead, date through your real life contacts. Grow your social circle. Lead an interesting life. Join hobbies, attend church, build your local community. That’s where quality women gather, and where you can be seen for who you really are.
You can use online dating as practice if nothing else. Go on a few low-stakes dates. Sharpen your conversation skills. You might meet someone better than expected. But don’t let it become your strategy.
Build a real life. Meet real women. That’s where the future is found.
PROBLEM: “I’m afraid of being rejected.”
SOLUTION: Rejection is painful, especially when you take it personally. So stop taking it personally.
Most rejections aren’t even about you. She might be in a bad mood, already dating someone, overwhelmed with work, or distracted. You’re getting a response to her current state, not a verdict on your worth.
Too many men grew up on movies where rejection is public and humiliating. But those are just movie scripts. In real life, rejection is rarely brutal. Especially if you’re respectful, most rejections are soft, and if you’re paying attention, you’ll see it coming before you even ask.
Her posture, her eye contact, her tone… they all tell a story. Women constantly signal how open they are to being approached. You can learn to read that story. It’s a skill.
Yes, you’ll still be rejected from time to time. But it won’t sting the same.
Men who fear rejection have a weak internal frame and a fragile ego. Both of these can, and must, be strengthened if you want to be in a relationship. Because in marriage, you’ll face moments where your wife rejects something you want, or pushes back hard. If you crumble over a stranger’s ‘no,’ how will you handle conflict with someone you love?
The solution isn’t to avoid rejection. It’s to heal the wounds that make you overly sensitive to it.
Let rejection be feedback. Let it be fuel. Let it forge you into a stronger man.
PROBLEM: “None of the women I meet are up to my standards.”
SOLUTION: Then you need to ask two questions:
-
Are your standards calibrated to reality, or to fantasy?
-
Are you the kind of man who attracts what you want?
There’s a simple way to check if your standards are realistic: If you’re out socializing regularly and meeting at least one woman per month that you find attractive and potentially relationship-worthy, your standards are likely calibrated.
Even if some are taken or uninterested, twelve encounters a year puts you on track to find someone marriage-worthy in one to two years.
But if you’re not meeting any women who meet your standards, or none are attracted to you, then your expectations are off, or you’re not meeting the masculine side of the equation.
High standards are good. But your standards for yourself must be even higher.
Don’t lower your standards. Raise your value.
PROBLEM: “I don’t know what women today want.”
SOLUTION: Don’t worry, many women don’t know what they want either.
At least not until they see it.
You don’t need to have a deep understanding of women to start dating. What you need is a deep understanding of yourself, and the basics of how to interact with the opposite sex.
Women are not a monolith. They don’t all want the same thing. And it’s okay if some women don’t want what you’re offering. That just means they’re not your match.
If you want marriage, children, and a peaceful home life, say so. Be clear. Be honest. Look for the woman who lights up at that vision.
And remember: first dates are not emotional dumps. Don’t share your entire life story. Don’t unload your childhood wounds and five-year plans all at once. Let it come out gradually, organically, over time.
Oversharing too soon is a kind of emotional immodesty. It pushes women away. It scares them.
Instead, bring warmth. Curiosity. Humor. Presence. Let her feel who you are, before she hears everything you’ve done or want to do.
Also, understand that many women are suffering in the dating market too. They’ve dealt with immature men, disrespect, or emotional burnout. Some are guarded. Some are hesitant. That’s not a personal rejection, it’s their healing process.
Your job isn’t to fix them. But it is to show up as the kind of man who makes her feel that safety, joy, and being lead by a man is possible again.
Be patient. Be strong. Be sincere.
And become the man who makes her remember what she wants.
PROBLEM: “Dating is exhausting. I just want to skip to marriage.”
SOLUTION: I’m always surprised by how many men don’t enjoy dating, or find it exhausting and stressful.
Let’s reframe that.
You’re going out with a beautiful woman. You’re spending time with someone you find attractive. And success isn’t about getting married, it’s about enjoying the evening.
That’s it.
Don’t complicate it. Keep it simple. Simple dates. Simple interactions. Think of it as fun. Learn how to find joy in the process.
Because here’s the secret: If you want your marriage to be joyful, you’ll have to keep dating your wife.
If planning one evening out drains you, you’re not ready for the rhythm of married life. Marriage isn’t a break from effort, it’s the reward for mastering it.
Now, yes, wanting the reward without the work is natural. But it’s immature.
Dating is the training ground. It’s where you learn. You don’t marry a stranger. You marry someone you’ve pursued, studied, and built connection with.
If you skip the process, you skip the transformation from boyfriend to husband.
Lean in. Learn. Let it shape you.
PROBLEM: “I have low self-esteem and maybe depression.”
SOLUTION: Women can tell.
Even if you’re good at hiding it, most women will pick up on low self-esteem or depression by the end of the first date. And it’s one of the most off-putting traits a man can have.
Not because they’re cruel. But because they’re biologically wired to seek strength.
Women already deal with hormonal emotional swings. The last thing they need is a man who can’t stabilize the emotional climate of a home. A man who is stuck in despair can’t uplift a family.
Other men might have sympathy for you. But women, especially women you aren’t related to, rarely do. They’re not selecting for pity. They’re selecting for protection. For future fatherhood. For strength.
That doesn’t make you unlovable. It makes this urgent.
Self-esteem isn’t magic. It’s earned. You build it by setting goals and achieving them, consistently. Start with goals so small you know you can win. Stack those wins daily. Use systems that help you keep score. Journal your progress. Review your wins. Let them rewire your beliefs.
Depression can be attacked the same way:
-
Lift heavy things
-
Eat meat
-
Get sunlight
-
Cut screen time and porn
-
Go outside and move
-
Sleep and wake on rhythm
-
Seek out experts: a coach, a priest, or a therapist
And most of all, stop isolating. Find men who are winning. Spend time with them. Compete with them. Let their energy rub off on you.
You’re not broken. You’re just under-trained.
Fix this, and the rest will follow.
PROBLEM: “There’s no point in dating when divorce laws are against men.”
SOLUTION: Yes, divorce laws are unjust.
But giving up on women because the system is rigged is like giving up on work because taxes exist.
You don’t surrender to the injustice. You outsmart it.
Vet better. Lead from a place of strength. Choose a woman who fears God, loves truth, hates a divorce, and shows loyalty under pressure.
Your objective as a man and husband is to build a marriage where the divorce laws don’t matter.
If you end up in court, you’ve already failed.
Build your family with a woman who doesn’t believe in divorce. Who comes from a family and a culture that doesn’t believe in divorce. These subcultures exist, even inside nations with high divorce rates.
Create a home where the idea of divorce doesn’t enter the conversation, not because you’re naïve, but because the family structure is strong, the values are shared, and the foundation is sacred.
And if needed, protect yourself legally without becoming cynical.
Living in fear is not a winning strategy. Conviction and leadership is.
PROBLEM: “I don’t see the benefit of marriage in 2025.”
SOLUTION: For some men, those who can barely care for themselves, lack discipline, avoid responsibility, and have no interest in becoming fathers, marriage may not benefit them. And frankly, it shouldn’t.
But if you’ve read this far, that’s not you.
You want to become the kind of man who leads a family. And for men like you, marriage is a worthy risk, it’s the catalyst you need.
As my friend *@LukeWeinhagen *often says:\ "The mature adult form of a male is called a father."
You become fully formed through marriage and fatherhood. You finish your development as a man by taking on sacred responsibility.
Now, some men say, “I can just pay a maid to clean my house, a nanny to raise my kids, and a girlfriend for company.”
Be honest with yourself. Most men saying that are too broke to afford one of those women, let alone three. And even if you could, that’s not a family.
Children raised by strangers will not grow up strong and securely attached to their parents. They will not continue your legacy. They will not build a civilization.
That model is a a cold dead end.
Marriage, when done right, is the greatest force multiplier in a man’s life.
You gain:
-
A woman’s emotional and spiritual partnership
-
A peaceful home, a sanctuary from the world
-
Feminine warmth, lightness, and joy woven into your daily life
-
Children who carry your name, your values, your soul
-
A home culture that makes you stronger
-
A reason to become the man you always knew you could be
-
Emotional and spiritual partnership
Don’t listen to broken men who couldn’t carry the weight. Become the man who can.
PROBLEM: “I’ve done everything right. I’m a great catch. And I still can’t find a woman.”
SOLUTION:
This is the hardest kind of problem, because it hides behind your own certainty.
If everything you’ve said is true, then by now, something should be working. So we have to consider two possibilities.
First, you’re deluding yourself. Maybe you haven’t actually done the work. Or you’ve done it halfway, inconsistently, or with the wrong intent. Maybe you’ve made progress, but you’re still self-sabotaging in subtle ways, through your words, your posture, your patterns. You say you want marriage and children, but you’re not living like a man who’s ready for it.
Second, there’s something off-putting about you that you don’t see. Either the people around you are too polite to tell you, or too socially blind to even notice.
In both cases, you will not solve this alone. If you could, you already would have. You need someone outside your head and outside your social circle. A trained eye. A mirror that doesn’t lie.
Talk to me. Book a call. Even just the free 30-minute session . I’ll tell you the truth. And if you’re ready, we’ll fix it. Most of the time, it’s only a few months of focused work.
But it starts with honesty.
No more guessing.
No more waiting.
Let’s find out what’s really in your way.
CLOSING:
Before we end, let’s clear up one more misconception: You do not need to be fully ready for marriage to start dating.
You just need to be ready to date well.
Your finances don’t need to support a household yet, but they should support a courtship. Your leadership doesn’t need to be flawless, but it needs to be growing towards maturity.
You won’t find a woman who’s fully ready for marriage either. You’ll grow into that role together.
Dating is not the finish line of readiness. It’s the training ground.
So don’t wait to be perfect. Be honest, be improving, and be intentional. That’s more than enough to begin.
You said you wanted a woman. A wife. A family. A future.
That dream will cost you. In time, money, effort, and pride.
But what you get in return, is everything that makes a man come alive.
Start by solving the next problem. And the one after that. And then keep going.
Once you can fix what’s in the way now, you’ll be ready to build what you were born for next.
And if there’s something blocking you that I didn’t cover here, say so. Send me a message. Leave a comment. Tell me what’s in the way.
This post wasn’t meant to be complete. It was meant to begin a conversation.
Let’s go.
-
-
 @ c1e9ab3a:9cb56b43
2025-04-01 04:32:15
@ c1e9ab3a:9cb56b43
2025-04-01 04:32:15I. Introduction
The phenomenon known as "speaking in tongues" has long been interpreted as either the miraculous ability to speak foreign languages or utter mysterious syllables by divine power. However, a re-examination of scriptural and apostolic texts suggests a deeper, spiritual interpretation: that "tongues" refers not to foreign speech but to the utterance of divine truths so profound that they are incomprehensible to most unless illuminated by the Spirit.
This treatise explores that interpretation in light of the writings of Paul, Peter, John, and the early Apostolic Fathers. We seek not to diminish the miraculous but to reveal the deeper purpose of spiritual utterance: the revelation of divine knowledge that transcends rational comprehension.
II. The Nature of Tongues as Spiritual Utterance
Tongues are best understood as Spirit-inspired expressions of divine truth—utterances that do not conform to human categories of knowledge or language. As Paul writes in 1 Corinthians 14:2, "He who speaks in a tongue speaks not to men but to God; for no one understands him, but he utters mysteries in the Spirit."
Such mysteries are not unintelligible in a chaotic sense but are veiled truths that require spiritual discernment. The speaker becomes a vessel of revelation. Without interpretation, the truth remains hidden, just as a parable remains a riddle to those without ears to hear.
III. Paul and the Hidden Wisdom of God
In his epistles, Paul often distinguishes between surface knowledge and spiritual wisdom. In 1 Corinthians 2:6-7, he writes:
"We speak wisdom among those who are mature, yet not the wisdom of this age... but we speak the wisdom of God in a mystery, the hidden wisdom which God ordained before the ages."
Tongues, then, are one vehicle by which such hidden wisdom is spoken. The gift of interpretation is not mere translation but the Spirit-led unveiling of meaning. Hence, Paul prioritizes intelligibility not to invalidate tongues, but to encourage the edification that comes when deep truth is revealed and understood (1 Cor. 14:19).
IV. Peter at Pentecost: Many Tongues, One Spirit
At Pentecost (Acts 2), each listener hears the apostles speak "in his own language"—but what they hear are "the mighty works of God." Rather than focusing on the mechanics of speech, the emphasis is on understanding. It was not merely a linguistic miracle but a revelatory one: divine truth reaching every heart in a way that transcended cultural and rational barriers.
V. John and the Prophetic Language of Revelation
The apostle John writes in symbols, visions, and layered meanings. Revelation is full of "tongues" in this spiritual sense—utterances that reveal while concealing. His Gospel presents the Spirit as the "Spirit of truth" who "will guide you into all truth" (John 16:13). This guiding is not logical deduction but illumination.
VI. The Apostolic Fathers on Inspired Speech
The Didache, an early Christian manual, warns that not everyone who claims to speak by the Spirit is truly inspired. This aligns with a view of tongues as spiritual utterance—deep truth that must be tested by its fruits and conformity to the ways of the Lord.
Polycarp and Ignatius do not emphasize miraculous speech, but their prayers and exhortations show a triadic awareness of Father, Son, and Spirit, and a reverence for spiritual knowledge passed through inspiration and faithful transmission.
VII. Interpretation: The Gift of Spiritual Discernment
In this model, the interpreter of tongues is not a linguist but a spiritual discerner. As Joseph interpreted dreams in Egypt, so the interpreter makes the spiritual intelligible. This gift is not external translation but inward revelation—an unveiling of what the Spirit has spoken.
VIII. Conclusion: Tongues as a Veil and a Revelation
The true gift of tongues lies not in speech but in meaning—in truth spoken from a higher realm that must be spiritually discerned. It is a veil that conceals the holy from the profane, and a revelation to those led by the Spirit of truth.
Thus, we do not reject the miraculous, but recognize that the greatest miracle is understanding—when divine mysteries, spoken in spiritual tongue, are made known to the heart by the Spirit.
"He who has an ear, let him hear what the Spirit says to the churches." (Revelation 2:7)
-
 @ cae03c48:2a7d6671
2025-05-19 16:06:29
@ cae03c48:2a7d6671
2025-05-19 16:06:29Bitcoin Magazine

Abraaj Restaurants Becomes First Bitcoin Treasury Company in the Middle EastToday it was announced that Al Abraaj Restaurants Group B.S.C. has become the first publicly traded company in the region to adopt Bitcoin as a treasury reserve asset. The Bahrain-based hospitality firm announced today it has acquired 5 Bitcoin for its balance sheet, with plans to significantly increase its allocation over time.
JUST IN:
 Al Abraaj Restaurants Group becomes first publicly traded company in middle east to purchase #Bitcoin as a treasury reserve asset
Al Abraaj Restaurants Group becomes first publicly traded company in middle east to purchase #Bitcoin as a treasury reserve asset  pic.twitter.com/QUH5FMGRoy
pic.twitter.com/QUH5FMGRoy— Bitcoin Magazine (@BitcoinMagazine) May 19, 2025
“Our initiative towards becoming a Bitcoin Treasury Company reflects our forward-thinking approach and dedication to maximizing shareholder value,” said Abdulla Isa, Chairman of the Bitcoin Treasury Committee at Al Abraaj. “We believe that Bitcoin will play a pivotal role in the future of finance, and we are excited to be at the forefront of this transformation in the Kingdom of Bahrain. 10X is a proven leader in advising and bringing capital to listed Bitcoin Treasury Companies, and we welcome their partnership in helping us build the MicroStrategy of the Middle East.”
The decision makes Abraaj not only the first in Bahrain, but also in the GCC and wider Middle East, to publicly hold Bitcoin on its balance sheet. The investment is a direct response to growing institutional interest in Bitcoin and comes amid what appears to be a regional shift toward digital assets.
Abraaj’s strategic partner in the transition is 10X Capital, a New York-based investment firm with a strong track record in digital asset treasury management. 10X previously advised companies like Nakamoto on its $710 million Bitcoin-focused financing round.
“I’d like to congratulate Abdalla Isa and the team at Al Abraaj for adopting Bitcoin at the corporate treasury level, finally enabling anyone in the GCC with a brokerage account to gain Bitcoin exposure,” said Hans Thomas, CEO of 10X Capital. “Bahrain continues to be a leader in the Middle East in Bitcoin adoption, backed by a forward-thinking regulatory framework.”
Thomas added, “The GCC, with a combined GDP of $2.2 trillion and over $6 trillion in sovereign wealth funds, has until now lacked a publicly listed Bitcoin treasury company like Strategy, Tesla, or Metaplanet. That changes today with ABRAAJ’s historic Bitcoin purchase.”
Abraaj said it will continue to work under the regulatory oversight of the Central Bank of Bahrain (CBB) and has pledged full compliance with all digital asset transaction laws. The company will adopt robust custody, risk management, and governance protocols for its Bitcoin holdings.
Disclosure: Nakamoto is in partnership with Bitcoin Magazine’s parent company BTC Inc to build the first global network of Bitcoin treasury companies, where BTC Inc provides certain marketing services to Nakamoto. More information on this can be found here.
This post Abraaj Restaurants Becomes First Bitcoin Treasury Company in the Middle East first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 4fa5d1c4:fd6c6e41
2025-05-19 13:32:02
@ 4fa5d1c4:fd6c6e41
2025-05-19 13:32:02Willkommen zur Mitmachplattform: KI-Kompetenzen für die religionsbezogene Bildung
Diese Plattform ist ein offenes, gemeinschaftliches Lernmodul für alle, die KI-Kompetenzen im Kontext der religionsbezogenen Bildung entdecken, vertiefen und weitergeben möchten.\ Hier können Religionslehrende, Hochschulangehörige und ehrenamtlich Engagierte gemeinsam Inhalte entwickeln, teilen und weiterentwickeln.
Was ist das Ziel?
Wir schaffen eine offene Lernumgebung, in der Materialien zu KI-Kompetenzen für Schule, Hochschule und außerschulische Jugendarbeit kollaborativ entstehen.\ Die Plattform richtet sich an Lehrkräfte, Fortbildner:innen und Ehrenamtliche, die KI-Themen in der religiösen Bildung verantwortungsvoll erschließbar machen wollen.
Unser Kompetenzmodell
Im Zentrum steht ein Kreismodell mit vier Kompetenzbereichen, die auf drei Niveaustufen ausdifferenziert sind:\ Verstehen, Anwenden, Reflektieren und Gestalten.\ Diese Bereiche bauen aufeinander auf, beeinflussen sich gegenseitig und werden durch die zentrale Kompetenz AI Leadership verbunden.
| Kompetenzbereich | Beschreibung | | -------------------------------------------------------------------- | ---------------------------------------- | | 🟢 VERSTEHEN | Grundlagen und Mechanismen von KI | | 🔵 ANWENDEN | KI-Tools im Lernprozess nutzen | | 🟠 REFLEKTIEREN | Kritische Auseinandersetzung mit KI | | 🟣 GESTALTEN | Aktive Weiterentwicklung von KI-Systemen |
Jeder Lerninhalt ist einem Kompetenzbereich (und wenn möglich einer Niveaustufe) zugeordnet – farblich und inhaltlich klar erkennbar.
So funktioniert die Mitmachplattform
-
Offene Inhalte: Alle Materialien werden als Markdown-Dateien über Nostr gepflegt.
-
Mitmachen leicht gemacht: Egal wo auf Nostr du publizierst, mit den Hashtags #relilab und dem jeweiligen Kompetenzbereich als Schlagwort (also #verstehen, #anwenden, #gestalten, #reflektieren) finden wir diese Hashtagkombination und können die Webseite mit deiner Idee oder Weiterentwicklung ergänzen.
-
Anleitungen: Eine eigene Seite erklärt Schritt für Schritt, wie du dich beteiligen kannst – ganz ohne Vorkenntnisse im Programmieren.
-
Suchfunktion: Finde gezielt Inhalte nach Kompetenzbereich, Niveaustufe oder Schlagworten.
Für wen ist diese Plattform?
-
Lehrkräfte an Schulen und Hochschulen in religionsbezogenen Fächern
-
Ehrenamtliche und Multiplikator:innen in der kirchlichen Jugendarbeit
-
Fort- und Weiterbildner:innen im Bereich KI und Religion
Mitmachen & Teilen
\> "Sharing is Caring":\ \> Unser KI-Kompetenzmodell und alle Lernmaterialien stehen unter der offenen Lizenz [CC-BY 4.0].\ \> Du darfst sie frei nutzen, anpassen und weitergeben – mit Nennung der Urheber:innen.
Starte jetzt!
Gemeinsam gestalten wir KI-Kompetenzen für eine reflektierte, verantwortungsvolle und kreative religiöse Bildung im KI-Zeitalter.
Kontakt & Feedback:\ Für Fragen, Anregungen oder Feedback
https://ki-kompetenzen.npub.pro
#OER #relilab
antworte einfach auf diese Nachricht oder komm' in den Matrix/Element-Raum https://matrix.to/#/#relilab-ki:rpi-virtuell.de> zum Online-Austausch!
-
-
 @ c1e9ab3a:9cb56b43
2025-03-26 21:03:59
@ c1e9ab3a:9cb56b43
2025-03-26 21:03:59Introduction
Nutsax is a capability-based access control system for Nostr relays, designed to provide flexible, privacy-preserving rate limiting, permissioning, and operation-scoped token redemption.
At its core, Nutsax introduces:
- Blind-signed tokens, issued by relays, for specific operation types.
- Token redemption as part of Nostr event publishing or interactions.
- Encrypted token storage using existing Nostr direct message infrastructure, allowing portable, persistent, and private storage of these tokens — the Nutsax.
This mechanism augments the existing Nostr protocol without disrupting adoption, requiring no changes to NIP-01 for clients or relays that don’t opt into the system.
Motivation
Nostr relays currently have limited tools for abuse prevention and access control. Options like IP banning, whitelisting, or monetized access are coarse and often centralized.
Nutsax introduces:
- Fine-grained, operation-specific access control using cryptographic tokens.
- Blind signature protocols to issue tokens anonymously, preserving user privacy.
- A native way to store and recover tokens using Nostr’s encrypted event system.
This allows relays to offer:
- Optional access policies (e.g., “3 posts per hour unless you redeem a token”)
- Paid or invite-based features (e.g., long-term subscriptions, advanced filters)
- Temporary elevation of privileges (e.g., bypass slow mode for one message)
All without requiring accounts, emails, or linking identity beyond the user’s
npub.Core Components
1. Operation Tokens
Tokens are blind-signed blobs issued by the relay, scoped to a specific operation type (e.g.,
"write","filter-subscribe","broadcast").- Issued anonymously: using a blind signature protocol.
- Validated on redemption: at message submission or interaction time.
- Optional and redeemable: the relay decides when to enforce token redemption.
Each token encodes:
- Operation type (string)
- Relay ID (to scope the token)
- Expiration (optional)
- Usage count or burn-on-use flag
- Random nonce (blindness)
Example (before blinding):
json { "relay": "wss://relay.example", "operation": "write", "expires": 1720000000, "nonce": "b2a8c3..." }This is then blinded and signed by the relay.
2. Token Redemption
Clients include tokens when submitting events or requests to the relay.
Token included via event tag:
json ["token", "<base64-encoded-token>", "write"]Redemption can happen:
- Inline with any event (kind 1, etc.)
- As a standalone event (e.g., ephemeral kind 20000)
- During session initiation (optional AUTH extension)
The relay validates the token:
- Is it well-formed?
- Is it valid for this relay and operation?
- Is it unexpired?
- Has it been used already? (for burn-on-use)
If valid, the relay accepts the event or upgrades the rate/permission scope.
3. Nutsax: Private Token Storage on Nostr
Tokens are stored securely in the client’s Nutsax, a persistent, private archive built on Nostr’s encrypted event system.
Each token is stored in a kind 4 or kind 44/24 event, encrypted with the client’s own
npub.Example:
json { "kind": 4, "tags": [ ["p", "<your npub>"], ["token-type", "write"], ["relay", "wss://relay.example"] ], "content": "<encrypted token blob>", "created_at": 1234567890 }This allows clients to:
- Persist tokens across restarts or device changes.
- Restore tokens after reinstalling or reauthenticating.
- Port tokens between devices.
All without exposing the tokens to the public or requiring external storage infrastructure.
Client Lifecycle
1. Requesting Tokens
- Client authenticates to relay (e.g., via NIP-42).
- Requests blind-signed tokens:
- Sends blinded token requests.
- Receives blind signatures.
- Unblinds and verifies.
2. Storing Tokens
- Each token is encrypted to the user’s own
npub. - Stored as a DM (kind 4 or compatible encrypted event).
- Optional tagging for organization.
3. Redeeming Tokens
- When performing a token-gated operation (e.g., posting to a limited relay), client includes the appropriate token in the event.
- Relay validates and logs/consumes the token.
4. Restoring the Nutsax
- On device reinstallation or session reset, the client:
- Reconnects to relays.
- Scans encrypted DMs.
- Decrypts and reimports available tokens.
Privacy Model
- Relays issuing tokens do not know which tokens were redeemed (blind signing).
- Tokens do not encode sender identity unless the client opts to do so.
- Only the recipient (
npub) can decrypt their Nutsax. - Redemption is pseudonymous — tied to a key, not to external identity.
Optional Enhancements
- Token index tag: to allow fast search and categorization.
- Multiple token types: read, write, boost, subscribe, etc.
- Token delegation: future support for transferring tokens via encrypted DM to another
npub. - Token revocation: relays can publish blacklists or expiration feeds if needed.
Compatibility
- Fully compatible with NIP-01, NIP-04 (encrypted DMs), and NIP-42 (authentication).
- Non-disruptive: relays and clients can ignore tokens if not supported.
- Ideal for layering on top of existing infrastructure and monetization strategies.
Conclusion
Nutsax offers a privacy-respecting, decentralized way to manage access and rate limits in the Nostr ecosystem. With blind-signed, operation-specific tokens and encrypted, persistent storage using native Nostr mechanisms, it gives relays and clients new powers without sacrificing Nostr’s core principles: simplicity, openness, and cryptographic self-sovereignty.
-
 @ 9994730e:7df84c81
2025-05-19 15:59:38
@ 9994730e:7df84c81
2025-05-19 15:59:38❤️🔥✨
-
 @ 48706e89:cd3c97e3
2025-05-19 13:06:27
@ 48706e89:cd3c97e3
2025-05-19 13:06:27Mal schauen, was so geht...
-
 @ 48706e89:cd3c97e3
2025-05-19 12:42:25
@ 48706e89:cd3c97e3
2025-05-19 12:42:25# KI und Ethik im RU\ Wlche Verantwortung tragen wir beim Einsatz von KI in der Bildung? Dieses Modul bietet theologische Perspektiven und Diskussionsimpulse."
-
 @ 9994730e:7df84c81
2025-05-19 15:59:37
@ 9994730e:7df84c81
2025-05-19 15:59:37And this is the regular text.
-
 @ e17e9a18:66d67a6b
2025-05-19 11:46:09
@ e17e9a18:66d67a6b
2025-05-19 11:46:09We wrote this album to explain the inspiration behind Mutiny Brewing, and as a way to share the story of Bitcoin and freedom technologies like nostr. Through these songs, we’ve tried to capture every truth that we believe is essential to understand about money, freedom, trust, and human connection in the internet age. It’s our way of making these ideas real and relatable, and we hope it helps others see the power of taking control of their future through the systems we use.
01. "Tomorrow's Prices on Yesterday's Wage" explores the harsh reality of inflation. As central banks inflate the money supply, prices rise faster than wages, leaving us constantly falling behind. People, expecting prices to keep climbing, borrow more to buy sooner, pushing prices even higher in a vicious cycle. You're always a step behind, forced to pay tomorrow's inflated prices with yesterday's stagnant wages.
https://wavlake.com/track/76a6cd02-e876-4a37-b093-1fe919e9eabe
02. "Everybody Works For The Bank" "Everybody Works For The Bank" exposes the hidden truth behind our fiat money system.
When banks issue loans, they don’t lend existing money — they create new money from debt. You’re on the hook for the principal and the interest. But the interest doesn’t exist yet — it has to come from someone else borrowing. That means the system only works if debt keeps growing.
When it doesn’t, the whole thing wobbles. Governments step in to bail out the banks by printing more money, and that cost doesn’t vanish. It shows up in your taxes, your savings, and your grocery bill.
We’re not just working to pay our own debts, we’re paying for their losses too.
https://wavlake.com/track/4d94cb4b-ff3b-4423-be6a-03e0be8177d6
03. "Let My People Go" references Moses' demand for freedom but directly draws from Proverbs 6:1–5, exposing the danger of debt based money. Every dollar you hold is actually someone else's debt, making you personally liable—held in the hand of your debtor and at risk of their losses, which you ultimately pay for through inflation or higher taxes. As the song says, "The more you try to save it up, the deeper in you get." The wisdom of Proverbs urges immediate action, pleading urgently to escape this trap and free yourself, like a gazelle from a hunter.
https://wavlake.com/track/76214ff1-f8fd-45b0-a677-d9c285b1e7d6
04. "Mutiny Brewing" embodies Friedrich Hayek's insight: "I don't believe we shall ever have good money again before we take it out of the hands of government... we can't take it violently... all we can do is by some sly roundabout way introduce something they can't stop."
Inspired also by the Cypherpunk manifesto's rallying cry, "We will write the code", the song celebrates Bitcoin as exactly that unstoppable solution.
"Not here to break ya, just here to create our own little world where we determine our fate." https://wavlake.com/track/ba767fc8-6afc-4b0d-be64-259b340432f3
05. "Invisible Wealth" is inspired by The Sovereign Individual, a groundbreaking 1990s book that predicted the rise of digital money and explores how the return on violence shaped civilizations. The song references humanity's vulnerability since agriculture began—where stored wealth attracted violence, forcing reliance on larger governments for protection.
Today, digital privacy enabled by cryptography fundamentally changes this dynamic. When wealth is stored privately, secured by cryptographic keys, violence becomes ineffective. As the song emphasizes, "You can't bomb what you can't see." Cryptography dismantles traditional power structures, providing individuals true financial security, privacy, and freedom from exploitation.
“Violence is useless against cryptography” https://wavlake.com/track/648da3cc-d58c-4049-abe0-d22f9e61fef0
06. "Run A Node" is a rallying cry for Bitcoin's decentralisation. At its heart, it's about personal verification and choice: every node is a vote, every check’s a voice. By running the code yourself, you enforce the rules you choose to follow. This is true digital democracy. When everyone participates, there's no room for collusion, and authority comes directly from transparent code rather than blind trust.
"Check the blocks, verify, ain't that hard to do When everyone's got eyes on it, can't slip nothin' throgh." https://wavlake.com/track/ee11362b-2e84-4631-b05e-df6d8e6797f8
07. "Leverage is a Liar" warns against gambling with your wealth, but beneath the surface, it's a sharp critique of fractional reserve banking. Fractional reserves inflate asset prices, creating the illusion of wealth built on leverage. This system isn't sustainable and inevitably leads to collapse. Real wealth requires sound money, money that can't be inflated. Trying to gain more through leverage only feeds the lie.
"Watch it burn higher and higher—leverage is a liar." https://wavlake.com/track/67f9c39c-c5e1-4e15-b171-f1f5442f29a5
08. "Don't Get Rekt" serves as a stark warning about trusting custodians with your Bitcoin. Highlighting infamous collapses like Mt.Gox, Celsius, and FTX. These modern failures echo the 1933 Executive Order 6102, where the US government forcibly seized citizens' gold, banned its use, and then promptly devalued the currency exchanged for it. History shows clearly: trusting others with your wealth means risking losing it all.
"Your keys, your life, don't forget." https://wavlake.com/track/fbd9b46d-56fc-4496-bc4b-71dec2043705
09. "One Language" critiques the thousands of cryptocurrencies claiming to be revolutionary. Like languages, while anyone can invent one, getting people to actually use it is another story. Most of these cryptos are just affinity scams, centralized towers built on shaky foundations. Drawing from The Bitcoin Standard, the song argues money naturally gravitates toward a single unit, a universal language understood by all. When the dust settles, only genuine, decentralized currency remains.
"One voice speaking loud and clear, the rest will disappear." https://wavlake.com/track/22fb4705-9a01-4f65-9b68-7e8a77406a16
10. "Key To Life" is an anthem dedicated to nostr, the permissionless, unstoppable internet identity protocol. Unlike mainstream social media’s walled gardens, nostr places your identity securely in a cryptographic key, allowing you total control. Every message or action you sign proves authenticity, verifiable by anyone. This ensures censorship resistant communication, crucial for decentralised coordination around Bitcoin, keeping it free from centralised control.
"I got the key that sets me free—my truth is mine, authentically." https://wavlake.com/track/0d702284-88d2-4d3a-9059-960cc9286d3f
11. "Web Of Trust" celebrates genuine human connections built through protocols like nostr, free from corporate algorithms and their manipulative agendas. Instead of top down control, it champions grassroots sharing of information among trusted peers, ensuring truth and authenticity rise naturally. It's about reclaiming our digital lives, building real communities where trust isn't manufactured by machines, but created by people.
"My filter, my future, my choice to make, real connections no one can fake." https://wavlake.com/track/b383d4e2-feba-4d63-b9f6-10382683b54b
12. "Proof Of Work" is an anthem for fair value creation. In Bitcoin, new money is earned through real work, computing power and electricity spent to secure the network. No shortcuts, no favourites. It's a system grounded in natural law: you reap what you sow. Unlike fiat money, which rewards those closest to power and the printing press, Proof of Work ensures rewards flow to those who put in the effort. Paper castles built on easy money will crumble, but real work builds lasting worth.
"Real work makes real worth, that's the law of this earth." https://wavlake.com/track/01bb7327-0e77-490b-9985-b5ff4d4fdcfc
13. "Stay Humble" is a reminder that true wealth isn’t measured in coins or possessions. It’s grounded in the truth that a man’s life does not consist in the abundance of his possessions. Real wealth is the freedom to use your life and time for what is good and meaningful. When you let go of the obsession with numbers, you make room for gratitude, purpose, and peace. It's not about counting coins, it's about counting your blessings.
"Real wealth ain't what you own, it's gratitude that sets the tone." https://wavlake.com/track/3fdb2e9b-2f52-4def-a8c5-c6b3ee1cd194
-
 @ 9994730e:7df84c81
2025-05-19 15:59:35
@ 9994730e:7df84c81
2025-05-19 15:59:35I will add a picture, a hyperlink and a video. Let’s see if it works.
-
 @ 88cc134b:5ae99079
2025-05-19 11:08:56
@ 88cc134b:5ae99079
2025-05-19 11:08:56deded
-
 @ 9994730e:7df84c81
2025-05-19 15:59:34
@ 9994730e:7df84c81
2025-05-19 15:59:34Is it still working?
-
 @ 4ba8e86d:89d32de4
2025-05-19 10:13:19
@ 4ba8e86d:89d32de4
2025-05-19 10:13:19DTails é uma ferramenta que facilita a inclusão de aplicativos em imagens de sistemas live baseados em Debian, como o Tails. Com ela, você pode personalizar sua imagem adicionando os softwares que realmente precisa — tudo de forma simples, transparente e sob seu controle total.
⚠️ DTails não é uma distribuição. É uma ferramenta de remasterização de imagens live.
Ela permite incluir softwares como:
✅ SimpleX Chat ✅ Clientes Nostr Web (Snort & Iris) ✅ Sparrow Wallet ✅ Feather Wallet ✅ Cake Wallet ✅ RoboSats ✅ Bisq ✅ BIP39 (Ian Coleman) ✅ SeedTool ... e muito mais. https://image.nostr.build/b0bb1f0da5a9a8fee42eacbddb156fc3558f4c3804575d55eeefbe6870ac223e.jpg
Importante: os binários originais dos aplicativos não são modificados, garantindo total transparência e permitindo a verificação de hashes a qualquer momento.
👨💻 Desenvolvido por: nostr:npub1dtmp3wrkyqafghjgwyk88mxvulfncc9lg6ppv4laet5cun66jtwqqpgte6
GitHub: https://github.com/DesobedienteTecnologico/dtails?tab=readme-ov-file
🎯 Controle total do que será instalado
Com o DTails, você escolhe exatamente o que deseja incluir na imagem personalizada. Se não marcar um aplicativo, ele não será adicionado, mesmo que esteja disponível. Isso significa: privacidade, leveza e controle absoluto.
https://image.nostr.build/b0bb1f0da5a9a8fee42eacbddb156fc3558f4c3804575d55eeefbe6870ac223e.jpg https://image.nostr.build/b70ed11ad2ce0f14fd01d62c08998dc18e3f27733c8d7e968f3459846fb81baf.jpg https://image.nostr.build/4f5a904218c1ea6538be5b3f764eefda95edd8f88b2f42ac46b9ae420b35e6f6.jpg
⚙️ Começando com o DTails
📦 Requisitos de pacotes
Antes de tudo, instale os seguintes pacotes no Debian:
``` sudo apt-get install genisoimage parted squashfs-tools syslinux-utils build-essential python3-tk python3-pil.imagetk python3-pyudev
```
🛠 Passo a passo
1 Clone o repositório:
``` git clone https://github.com/DesobedienteTecnologico/dtails cd dtails
```
2 Inicie a interface gráfica com sudo:
``` sudo ./dtails.py
```
Por que usar sudo? É necessário para montar arquivos .iso ou .img e utilizar ferramentas essenciais do sistema.
💿 Selecione a imagem Tails que deseja modificar
https://nostr.download/e3143dcd72ab6dcc86228be04d53131ccf33d599a5f7f2f1a5c0d193557dac6b.jpg
📥 Adicione ou remova pacotes
1 Marque os aplicativos desejados. 2 Clique Buildld para gerar sua imagem personalizada. https://image.nostr.build/5c4db03fe33cd53d06845074d03888a3ca89c3e29b2dc1afed4d9d181489b771.png
Você pode acompanhar todo o processo diretamente no terminal. https://nostr.download/1d959f4be4de9fbb666ada870afee4a922fb5e96ef296c4408058ec33cd657a8.jpg
💽 .ISO vs .IMG — Qual escolher?
| Formato | Persistência | Observações | | ------- | ---------------------- | ----------------------------------------------- | | .iso | ❌ Não tem persistência | Gera o arquivo DTails.iso na pasta do projeto | | .img | ✅ Suporta persistência | Permite gravar diretamente em um pendrive |
https://nostr.download/587fa3956df47a38b169619f63c559928e6410c3dd0d99361770a8716b3691f6.jpg https://nostr.download/40c7c5badba765968a1004ebc67c63a28b9ae3b5801addb02166b071f970659f.jpg
vídeo
https://www.youtube.com/live/QABz-GOeQ68?si=eYX-AHsolbp_OmAm
-
 @ 9994730e:7df84c81
2025-05-19 15:59:33
@ 9994730e:7df84c81
2025-05-19 15:59:33Is it actually called “summary”?
-
 @ 45bda953:bc1e518e
2025-05-19 09:49:40
@ 45bda953:bc1e518e
2025-05-19 09:49:40This post will be edited and refined over time.
Eschatology is the study of Biblical prophecy pertaining to what is commonly referred to as the end times. Bitcoin is the transformation of Austrian school economics theory into an efficient and applicable method driven by natural incentives and free market consensus mechanisms.
What happens when eschatology is viewed through a Bitcoin inspired world view?
In this thesis I contend that it is possible and very probable that the consequences of what Satoshi Nakamoto created in Bitcoin and the prophecies surrounding Jesus Christ with regards to the second coming and a thousand year kingdom of peace and prosperity convalesce into a very compelling argument for Biblical prophecy fulfilment.
...
No one would argue that modern major banks are today more powerful than kings of old and governments are mere puppets to the sway that the banking empires hold over them.
In Biblical prophecy when kings and powers are mentioned people rarely think of banking but nothing is comparable to the immense scale of wealth, power and territory controlled directly or indirectly by banks.
IMF, BIS, the FED and Blackrock are where the levers of power are pulled in the current dispensation. Governments restructure more frequently than these institutions whom endure and exercise unmerited influence over said governments and the public interests they claim to represent.
An excerpt from the King James Bible, Daniel chapter 2 describes prophetically the ages of man and its rotations of power.
Interesting to note that it is symbolically portrayed in monetary/industrial metals. All used as tokens for trade, symbols of wealth and manufacture.
Gold, silver, bronze, iron and clay. Gold has been a dominant symbol of power and wealth through millennia. Silver, brass and iron ores are mainly industrial metals although they all had prominent turns as coinage. Due to the debasement and concentration of gold specifically.
Clay on the other hand is only a symbol of power in construction and iron has never been used in construction to the extent it is in the 20th and 21st century. Skyscrapers are the symbols of money and power today, i.e. big bank and government buildings.
Daniel Chapter 2:24–45
24Therefore Daniel went to Arioch, whom the king had appointed to destroy the wise men of Babylon. He went and said thus to him: “Do not destroy the wise men of Babylon; take me before the king, and I will tell the king the interpretation.”
25Then Arioch quickly brought Daniel before the king, and said thus to him, “I have found a man of the captives of Judah, who will make known to the king the interpretation.”
26The king answered and said to Daniel, whose name was Belteshazzar, “Are you able to make known to me the dream which I have seen, and its interpretation?”
27Daniel answered in the presence of the king, and said, “The secret which the king has demanded, the wise men, the astrologers, the magicians, and the soothsayers cannot declare to the king. 28But there is a God in heaven who reveals secrets, and He has made known to King Nebuchadnezzar what will be in the latter days. Your dream, and the visions of your head upon your bed, were these: 29As for you, O king, thoughts came to your mind while on your bed, about what would come to pass after this; and He who reveals secrets has made known to you what will be. 30But as for me, this secret has not been revealed to me because I have more wisdom than anyone living, but for our sakes who make known the interpretation to the king, and that you may know the thoughts of your heart.
31“You, O king, were watching; and behold, a great image! This great image, whose splendor was excellent, stood before you; and its form was awesome. 32This image’s head was of fine gold, its chest and arms of silver, its belly and thighs of bronze, 33its legs of iron, its feet partly of iron and partly of clay. 34You watched while a stone was cut out without hands, which struck the image on its feet of iron and clay, and broke them in pieces. 35Then the iron, the clay, the bronze, the silver, and the gold were crushed together, and became like chaff from the summer threshing floors; the wind carried them away so that no trace of them was found. And the stone that struck the image became a great mountain and filled the whole earth.
36“This is the dream. Now we will tell the interpretation of it before the king. 37You, O king, are a king of kings. For the God of heaven has given you a kingdom, power, strength, and glory; 38and wherever the children of men dwell, or the beasts of the field and the birds of the heaven, He has given them into your hand, and has made you ruler over them all — you are this head of gold. 39But after you shall arise another kingdom inferior to yours; then another, a third kingdom of bronze, which shall rule over all the earth. 40And the fourth kingdom shall be as strong as iron, inasmuch as iron breaks in pieces and shatters everything; and like iron that crushes, that kingdom will break in pieces and crush all the others. 41Whereas you saw the feet and toes, partly of potter’s clay and partly of iron, the kingdom shall be divided; yet the strength of the iron shall be in it, just as you saw the iron mixed with ceramic clay. 42And as the toes of the feet were partly of iron and partly of clay, so the kingdom shall be partly strong and partly fragile. 43As you saw iron mixed with ceramic clay, they will mingle with the seed of men; but they will not adhere to one another, just as iron does not mix with clay. 44And in the days of these kings the God of heaven will set up a kingdom which shall never be destroyed; and the kingdom shall not be left to other people; it shall break in pieces and consume all these kingdoms, and it shall stand forever. 45Inasmuch as you saw that the stone was cut out of the mountain without hands, and that it broke in pieces the iron, the bronze, the clay, the silver, and the gold — the great God has made known to the king what will come to pass after this. The dream is certain, and its interpretation is sure.”
 I speculate that the toes of iron and clay represent the world banking empire. Skyscrapers are constructed from iron and cement. Different forms of clay is a necessary cement ingredient. Architecture has always been used as a symbol of dominance by rulers especially true of systems who use awe as a means to cause feelings of insignificance in the individual thereby asserting their power at low cost. Ironically it never costs the ruler to create these structures, the cost is always carried by the people in time, resources and energy.
I speculate that the toes of iron and clay represent the world banking empire. Skyscrapers are constructed from iron and cement. Different forms of clay is a necessary cement ingredient. Architecture has always been used as a symbol of dominance by rulers especially true of systems who use awe as a means to cause feelings of insignificance in the individual thereby asserting their power at low cost. Ironically it never costs the ruler to create these structures, the cost is always carried by the people in time, resources and energy.Skyscrapers and large construction are the modern symbols of money and power. Not so much kings, palaces and temples. The stone breaking the power of the statue has to break something contemporary other than kings and palaces if it is to be eschatological prophecy fulfilled in our time.
https://www.britannica.com/technology/cement-building-material/History-of-cement
The invention of portland cement usually is attributed to Joseph Aspdin of Leeds, Yorkshire, England, who in 1824 took out a patent for a material that was produced from a synthetic mixture of limestone and clay.
https://www.thoughtco.com/how-skyscrapers-became-possible-1991649
Later, taller and taller buildings were made possible through a series of architectural and engineering innovations, including the invention of the first process to mass-produce steel.
Construction of skyscrapers was made possible thanks to Englishman Henry Bessemer, (1856 to 1950) who invented the first process to mass-produce steel inexpensively.
You watched while a stone was cut out without hands,
No hands needed when the stone is an idea.
As a thought experiment, imagine there was a base metal as scarce as gold but with the following properties:\ — boring grey in colour\ — not a good conductor of electricity\ — not particularly strong, but not ductile or easily malleable either\ — not useful for any practical or ornamental purpose\ \ and one special, magical property:\ — can be transported over a communications channel
Greshams Law illustrated in slow motion picture.
1: The banks collapse. Being fundamentally weak because of zero reserve lending, any student of Austrian economics has been correctly predicting banking collapse, and have incorrectly been advocating gold as the solution to this collapse. Many of the big economies are valued through their housing market. Housing will be demonetised (Iron and clay economy) meaning shelter and property will become affordable to the average wage earner again. The large cement and iron structures become redundant. Everyone will work from home and a value to value economy will make banks seem like relics from an age of stupidity and evil.
2: Industrial metal iron will not be for mega structures that contain speculators and bookkeepers who have fiat jobs slaving for fiat money. Iron will be used to improve the lives of individuals. Iron as coinage is already demonetised.
3: Brass is demonetised as coinage and only valuable in industry. Ammunition, music, plumbing etcetera.
4: Silver has been a terrible money throughout history and when the silver investors wake up to the fact that they are holding onto a redundant asset with zero monetary properties compared to the alternative they will dump their holdings, crashing the silver market and subsequently reducing the prices of producing -
solder and brazing alloys, batteries, dentistry, TV screens, smart phones microwave ovens, ad infinitum. To quote Jeff Booth. "Prices always fall to the marginal cost of production."
5: The final Rubicon is gold, people get excited about the Bitcoin exchange traded funds but it is nothing compared to the value proposition when gold pundits, large investment funds, governments pension funds and reserve banks finally realise that gold is worthless as money in this new dispensation.
To illustrate the point more vividly.
Ezekiel 7:19
They shall cast their silver in the streets, and their gold shall be removed: their silver and their gold shall not be able to deliver them in the day of the wrath of the LORD: they shall not satisfy their souls, neither fill their bowels: because it is the stumbling block of their iniquity.
What we are witnessing is the biggest rug pull the world has ever seen. In this future metals will exclusively be used for industrial use cases after being stripped of their monetary premium.
 This collapse is something that happens slowly over a long period of time. More or less one hour.
This collapse is something that happens slowly over a long period of time. More or less one hour.Revelation 18 verse 11–19 (The fall of Babylon)
And the merchants of the earth shall weep and mourn over her; for no man buyeth their merchandise any more: The merchandise of gold, and silver, and precious stones, and of pearls, and fine linen, and purple, and silk, and scarlet, and all thyine wood, and all manner vessels of ivory, and all manner vessels of most precious wood, and of brass, and iron, and marble, And cinnamon, and odours, and ointments, and frankincense, and wine, and oil, and fine flour, and wheat, and beasts, and sheep, and horses, and chariots, and slaves, and souls of men. And the fruits that thy soul lusted after are departed from thee, and all things which were dainty and goodly are departed from thee, and thou shalt find them no more at all. The merchants of these things, which were made rich by her, shall stand afar off for the fear of her torment, weeping and wailing, And saying, Alas, alas, that great city, that was clothed in fine linen, and purple, and scarlet, and decked with gold, and precious stones, and pearls! For in one hour so great riches is come to nought. And every shipmaster, and all the company in ships, and sailors, and as many as trade by sea, stood afar off, And cried when they saw the smoke of her burning, saying, What city is like unto this great city! And they cast dust on their heads, and cried, weeping and wailing, saying, Alas, alas, that great city, wherein were made rich all that had ships in the sea by reason of her costliness! for in one hour is she made desolate.
TLDR - No more money printer go BRRR. means death to the bourgeoisie cantillionaire class.**
Is it realistic to assume that all the worlds monetised industries collapse to fair value in one hour?
Coming back to eschatology, 2 Peter 3:8
But, beloved, be not ignorant of this one thing, that one day is with the Lord as a thousand years, and a thousand years as one day.
Eschatology students use this verse to speculatively project the fulfilment of Biblical prophecies with regards to their predicted time of occurrence. Now let’s apply this to Babylon falling in one hour.
1000 (one day) divided by 24 (hours) equals 41,6 years (one hour)
Since the first block was mined in January 2009 you add 41,6 years you get a completion date of 2050 a.d
Remember, this stone (Bitcoin) becomes a great mountain and fills the whole earth. A kingdom which shall never be destroyed; and the kingdom shall not be left to other people; it shall break in pieces and consume all these kingdoms, and it shall stand forever. The dream is certain, and its interpretation is sure.
But contemporary sources must reflect this probability if it is a good theory.
https://www.newsbtc.com/news/50-of-population-to-use-bitcoin-by-2043-if-crypto-follows-internet-adoption/
If the banking system is first to collapse we can give it +- 10 years and we are already 14 years in since (Genesis Block) the stone struck the feet. People are slow to see the reality of the world they are living in. If all this is accurate then the world banking system is doomed.
https://www.youtube.com/watch?v=exK5yFEuBsk
Regards
Echo Delta
bitbib
-
 @ b7cf9f42:ecb93e78
2025-03-26 10:57:33
@ b7cf9f42:ecb93e78
2025-03-26 10:57:33Der Verstand im Fluss der Information
Das Informationszeitalter ist wie ein monströser Fluss, der unseren Verstand umgibt
Fundament erbauen
Der Verstand kann sich eine Insel in diesem Fluss bauen. Dabei können wir eine eigene Insel erbauen oder eine bestehende insel anvisieren um stabilität zu finden
Je robuster das Baumaterial, desto standhafter unsere Insel. (Stärke der Argumente, Qualität des Informationsgehalts, Verständlichkeit der Information)
Je grossflächiger die Insel, desto mehr Menschen haben Platz (Reichweite).
Je höher wir die Insel bauen, desto sicherer ist sie bei einem Anstieg des Informationsflusses (Diversität der Interesse und Kompetenzen der Inselbewohner).
Robustes Baumaterial
Primäre Wahrnehmung (robuster):
Realität -> meine Sinne -> meine Meinung/Interpretation
Sekundäre Wahrnehmung (weniger Robust):
Realität -> Sinne eines anderen -> dessen Meinung/Interpretation -> dessen Kommunikation -> meine Sinne -> meine Meinung/Interpretation
Wie kann ich zur Insel beitragen?
Ich investiere meine Zeit, um zu lernen. Ich bin bestrebt, Ideen zu verstehen, um sicherzugehen, dass ich robustes Baumaterial verwende.
Ich teile vermehrt Informationen, welche ich verstehe, damit auch meine Mitbewohner der Insel mit robustem Material die Insel vergrössern können. So können wir mehr Platz schaffen, wo Treibende Halt finden können.
Was könnte diese Insel sein?
- Freie Wissenschaft
- Freie Software
- Regeln
- Funktionierende Justiz
- Werkzeug
- und vieles weiteres
-
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ 472f7a9b:1e7e0bff
2025-05-19 15:56:03
@ 472f7a9b:1e7e0bff
2025-05-19 15:56:03A few weeks ago, I ran into an old friend at a coffee shop. We hadn’t spoken in years, and within five minutes, she said something I’ve heard countless times:
“I just feel like I’m so behind.”
Behind who? Behind what?
 There’s this idea—quiet, nagging, oddly universal—that we’re all somehow in a race we didn’t sign up for. That we’re supposed to have hit certain milestones by certain ages. That if we’re not married, promoted, rich, settled, happy (and photogenic) by 30 or 40 or pick your poison, then we’ve failed some invisible test.
There’s this idea—quiet, nagging, oddly universal—that we’re all somehow in a race we didn’t sign up for. That we’re supposed to have hit certain milestones by certain ages. That if we’re not married, promoted, rich, settled, happy (and photogenic) by 30 or 40 or pick your poison, then we’ve failed some invisible test.Where did this come from?
Some of it’s cultural, obviously. Social media compresses timelines. You’re 27, doom-scrolling, and suddenly someone from high school just IPO’d their startup and got engaged in Rome. Another just bought a house with a kitchen island the size of a small country. You wonder if you missed a memo.
But beneath that, there’s something deeper. A belief that life is linear. That it should look like a staircase: school, job, marriage, house, kids, success. But real life? It’s a squiggle. A mess. A beautiful disaster.
Here’s the truth: You’re not behind. There’s no schedule. There’s only your path, and the courage it takes to stay on it—even when it looks wildly different from everyone else’s.
I say this as someone who has taken the “scenic route.” I changed careers in my 30s. I moved cities on a hunch. I dropped things that looked great on paper because they felt wrong in my gut. I’ve had seasons of momentum and seasons of stuckness. Both were necessary.
“Catching up” assumes there’s a fixed destination. But what if there isn’t? What if the point isn’t arrival, but presence? Progress that feels real, not performative?
If you need a permission slip to stop comparing, let this be it.
 You’re not late. You’re not early.
You’re not late. You’re not early.
You’re right on time. -
 @ e97aaffa:2ebd765d
2025-05-19 09:47:30
@ e97aaffa:2ebd765d
2025-05-19 09:47:30Algo que me faz uma certa confusão, é ouvir as pessoas, a afirmarem que será impossível existir um governo e uma economia saudável com o Bitcoin ou qualquer outra moeda não inflacionária. Que o Bitcoin como moeda, iria tornar a sociedade numa anarquia.
A governança da nossa sociedade é baseada em 3 pilares: o governo, económico e moeda. Os 3 evoluíram e se adaptaram mutuamente e em simultâneo ao longo do tempo. Só que essa e evolução, trouxe-nos para um centralismo atroz, onde os governos condicionadam excessivamente a economia e controlam a moeda. Em vez de 3 pilares, temos apenas um, o governo, a economia deixou de ser livre e a moeda é manipulada para financiar o governo.
É claro, se nós mudarmos apenas o sistema monetário, o equilíbrio dos 3 pilares vai quebrar, assim não vai funcionar. O erro é acreditar que é possível mudar apenas um pilar, sem adaptar os outros.
Na prática temos que mudar apenas um (governo), os outros dois é libertá-los. Os governos modernos são baseados em défice orçamental, impostos altos, dívida soberana e inflação monetária para o seu financiamento e para controlar a economia. Como os governos estão altamente endividados e com altas taxas de impostos, só lhe resta a última carta, a moeda/inflação monetária.
Se perdessem o controlo da moeda, seria necessário uma mudança profunda nos estados modernos. Em vez de ter défice-dívida-inflação, teriam mudar para excedente-reservas-deflação, é fazer o oposto do que fazem hoje. É claro que ao podemos apenas mudar de uma moeda inflacionária para uma não inflacionária e manter inalterado os outros dois, isso não vai resultar. Será necessário mudar os 3 para que funcione bem.
É aqui está o problema, será uma mudança profunda nos governos modernos, têm que passar a ter excedente orçamental e criar reservas monetária. Isso vai obrigar os governos a ter muita disciplina e boa gestão, nos momentos de crescimento económico terão que fazer reservas e zerar a dívida soberana. Depois nos períodos de recessão vai utilizar as reservas e se necessário criar dívida soberana para ajudar na recuperação da economia, actualmente os governos utilizam a expansão monetária para esse fim.
Se alguém tem um problema de alcoolismo, não pode apenas trocar whisky por vinho, a mudança terá que ser mais drástica, terá que trocar por água.
Fix the money! Fix the World!
-
 @ 45bda953:bc1e518e
2025-05-19 09:17:30
@ 45bda953:bc1e518e
2025-05-19 09:17:30Emilien stepped into the space motel's bar. The area was dimly lit and the music was unbearably loud. At least all the tables and sunken lounges each had their own lights and sound dampers. He stepped up to a table and pushed down on the receptor to reduce volume. He could not think with the noise. He looked around for Macy and inconspicuously acquainted himself with the current patrons in the establishment. He pulled his hoody further forward when he noticed the android in a wheel chair. "Not my type of company." He thought to himself. In the centre of the room a couple was having a spectacular time, an empty bottle on the table, they were specimens of myth. The guys muscles were chiselled, with tight fabric clinging to his body specifically to display every contour of his physique. His female counterpart wore loose material with translucent green tattoo's running up her body like pin stripes shining through the thin cloth hinting at a perfectly balanced pose and feminine silhouette underneath. Emilien swiped on the tables interface to call for the proprietor. He folded his arms and leaned onto the table tilting his head down slightly to keep shadow on his face. Macy entered the room through the kitchen swivel door. She was holding an empty tray and a serviette draped over her arm. She walked straight over to Emilien's table. "Good rotation sir. Welcome to Macy's. Are you a regular customer or is it your first visit to my fine establishment?" She seemed concerned and worried. The corners of Emiliens lips curved up a little. Keeping his head down teasingly. "Sir? Do we have an existing open channel?" He ignored her. "Sir, If you don't have liquidity I have no services to offer that you cannot get off your own ship." Emilien looked up with a gleam in his eye. Macie's posture relaxed with a sigh of relief. "Emile, you fuck. You freaked me out." "I'm sorry, I could not help myself." He waved a halfhearted greeting, slightly laughing. "You know I have some new rules around for you nano augmented types." His aversion to the word rules was evident only to himself. "Like what?" Macy felt apologetically obliged to explain the nature of her circumstances. "I had diplomats from the outer void regions come for a private meeting. Financial in nature. A spacer customer arrived blocks before them, I did not suspect him of anything criminal." She put the tray down and gripped the table with both hands shifting her weight. "His routine for meals were already established, he managed to spy on them through my privacy protocols and hacked their clients. He participated as a ghost during most of their stay and dealings." Emilien whistled. "That's rough, how did you handle it." "I did not do anything." Her dreads shook as she moved her head in animated frustration. "No one knew until they all had been gone for blocks. My reputation took a serious knock. They made a claim against me, I was accused of being complicit. Emilien glanced back over his shoulder when he noticed the android cart himself around his table. "Warren helped me and found all the dirty code and sequestered it. We have all the data and footage, it proves beyond a doubt that I was not involved. Thank god for the core otherwise my whole station might have been destroyed by now." Emile gave a sly look. "How do you know it was not me who stole the data?" She locked eyes with him. "You still have the same face as before bro and I know you won't fuck with me. I'll force close our channel." She joked with serious tone nudging him with her fist playfully. She was generally perceived as strict and militant because of her Shiv citizenship. Shiv military training and service was compulsory, all respected the Shiv in their traditions, their ways were isolationist and exclusionary in nature. Emilien has seen her use military style jujitsu-boxing to neutralise and boot out unruly customers. The Juel woman noticed the out of character friendly gesture Macy made. The unexpected interaction drew her attention from across the room. "So, what is this rule of yours." Macy seemed reluctant to say. "I'm sorry bud. You'll have to swallow a slipper pill every 576 blocks while you are on this station." His shoulders sagged and could not help but bounce his leg on the rail under the table. "Really?!" "Yes, really. I have to retain my customers trust and neutralising all augmented customers body gadgets was the unanimous way to go." Emilien seemed pissed. "Your customers might not know that I'm augmented. And what if I don't plan on staying that long. I just want to see Warren then I'll be off." Macy shook her head. "Warren is passed out in his ship and will probably wake up with a very bad hangover. He partied with the Jeul pair and their entourage for most of this rotation, you know how he gets." Macy waved her hand towards the couple who seemed to be looking directly at Emilien. He looked straight back at them and swiped the interface's privacy command dropping a vision distortion field around his table. Encapsulating himself and Macy. "I treat everyone the same, no compromise." Emile looked at her in a moment of rumination. "Let's get it over with." Macy removed a container from her moonbag after opening, holding it towards Emilien he took the purple capsule and swallowed it without a drink and opened his mouth wide moving his tongue around to show Macy that he did indeed swallow the prophylactic. "And what about robo-mech boy back there? He cannot eat slipper pills." Emilien sounded annoyed and regretful." Macy gave him a stern look tilting her head in annoyance. "Why do think he's in a wheelchair, you know I can't talk about my customers with my customers? Besides from the obvious." Emilien did not say anything. Macy sighed. "What can I get you sir?" "I'll just have a beer." Macy stepped out through the distortion field and became a messy disfigured indistinguishable form. Emilien pushed the music's volume up and waited for the inevitable. He sensed the actuators in his shoulders, elbows and wrists disable in sequence down his arms. His spines bit rate slowed to a crawl and the lack of connectivity to his neck port was becoming noticeable. His legs went numb instantly. "Now I am nothing more than a pathetic land crawler." He felt weak and vulnerable in his natural form. His mental state bordered on the fringes of stable and paranoid, fearful thoughts threatening to manifest in his mind. He saw a figure approach. He assumed it was his drink. The slender glowing tattooed leg of the Jeul woman pierced the veil. A bright green line that suddenly dims where her skirt begins. She stepped through the curtain with a friendly nonchalant expression. "Mind if make your acquaintance mon ami?" Emilien dropped the barrier and lowered the volume making sure that he was back on visual record of Macy's archive. "Not really, thanks, I'm good." Macy returned to place a cold beer on the table. The interface flashed a price in femto-sat and Emilien tapped his ring on it shifting 11 fSAT from a mini holographic Bob to very happy little Alice. The animation morphed into a small firework display and died. "Back to work now." Emilien grinned at Macy thankfully and took a sip. "Me and my brother we are celebrating our seventh birth block anniversary." He looked around sarcastically. "You chose a display of death above the resorts on Juel to celebrate your seventh birth block?" She stiffened her glittery lips and raised her eyebrows thoughtfully and took a seat without invitation. "It is more of a tour than a celebration, I am Maurelle Giovanni and my brother is called Lionel also Giovanni obviously. He is my twin baby brother." Emilien looked over at the guy who seemed to be occupied playing a mini game on their tables interface. She tilted her head into his line of sight forcing him to look at her. "Who are you?" "None of your concern really." She did not accept the short stated answer. "No one comes alone all the way to a dead end system just to drink a cheap beer. I am guessing you are a treasure hunter, no. Looking for artefacts of the ancient world, yes?" Emilien had assessed her body language and concluded that her whimsical imagination was one he could easily manipulate. He had enough information to realise that he was faced with a spoiled individual whose sole interest in him was simple curiosity, motivated by boredom and she had a fascination of the mysterious. She seemed like prey but his hunting instincts felt dead inside his disarmed body. His respect for and dependence on Macy also inhibited his urge to exploit it. He shifted his attitude and personality slightly, just enough to not be overbearing. "You make very good estimations, you are wrong but not far off. My name is Scott. And yes I am fascinated, not by the planet and it's relics but by the the secrets of these gates." Her eyes gleamed with amusement and intrigue. "You like secrets, huh? You must meet Warren. He knows more than the esteemed professors about the gates and their technology." Emilien nodded in agreement. "You said you are Giovanni. Like the Giovanni?" She seemed excited at the prospect of making a new friend and swiped the interface. "Hold this thought, I am going to get myself another drink you are good? No. Food maybe?" "I am good, no wait, another beer." He tipped the bottle toward her in salutation. She stood up taking his bottle with her to the bar. He looked back and was immediately aware that he did not notice that the android wheel himself out and into the conduit. He would have liked to see which of the two entrances of the tube he used to go to his ship. His feeling sorry for and pitying himself put him in a position where he let slip an opportunity to understand and predict the circumstances of his current tactical situation. Never at ease, always being prepared. He felt spite. The girl returned with a beer and a half full whiskey glass, no ice. She reclaimed her seat looking at him. "I am a direct descendant of the patriarch Maurice Giovanni, one of the four primary key holders of our people. There is nothing special about me really, ten..." Emilien cut her off in gentle tone. "Ten percent of the Juel population are descendants of the four patriarchs." Emilien finished her sentence for her. "You are an interesting man Monsieur Scott. What else do you know about me?" Emilien leaned towards her. Noticing her brother yawning across the room. "I know that you are bourgeois and I know that you receive a cyclical allowance from your great, great... How many generations?" "I am removed 133 generations from my Patriarch. He is a very good, doting grandfather. We all adore him. We are around 750 million siblings you know. Those who are from aristocracy have fewer children than the proles. We are so few so that our wealth is not diluted too much." She smiled reminiscently dragging her finger on the edge of the glass. Her brother seemed to stretch himself out he stood up and walked over. Entering the sound damper he acknowledged Emilien's presence with a curt nod. "Maurelle, I am going to sleep." He said to her. She waved at him dismissively. "Have a good dream frere." He exited the room through the right tubes door which made sense as their ship was more closely attached to it on that side of the circular docking ring. Predictable and honest Emilien thought to himself. Macy popped her head through the kitchens serving window. "Lights out and shutdown in 2 blocks. Just a friendly notice." The couple acknowledged the warning from Macy with raised glass and bottle. Emilien turned his attention back to the lady. "How do you manage to retain wealth in such a large family?" He pretended to be ignorant of the finery and detail of Juel culture. "We have closed loop channels controlled and balanced by the patriarchs. But our money is good as core stone. Anywhere in the outer void. Only recently has dispute arose between my Patriarchs and the Magarrie. They do not accept our Sats anymore since the war started. They only accept bitcoins directly from the core. I was only four cycles old when the war began so I am used to it." Emilien felt a conflicting disturbance, thinking about how his body is only two cycles active but his mind stretches back far beyond this time. Being both older and younger than his partner in discourse. "Helloo? I lost you there for a moment Scott." "What are you thinking about?" Emilien lied to her faking emotion. "I was just thinking about the tremendous loss of life that we are orbiting. The planet embedded with what it's inhabitants assumed would be it's portal to prosperity became the golem of it's demise." He was happy that Maurelle seemed to empathise and mirror his philosophic grief. "Come with me I want to tell you a secret. You like secrets." She stood up taking his hand gently tugging, compelling him to follow her. She led him to the far end of the room. She pulled a small levered switch and the wall folded in on itself to reveal a impressive window flooding sharp light into the whole of the large room as it retracted. They both squinted and lifted their hands to shield their eyes adjusting to the glare of Sol. The scene of destruction appeared even more dramatic and morbid as dark sharply defined shadows clipped with golden edges, evoking a sense of isolation and suffering. "These gates were supposed to be a gift to Earth. A hope of spreading humanity across the stars like the children of Abraham." Emilien smirked. "You believe that nonsense?" She rested her head on his shoulder still holding onto his arm. "Our patriarchs have preserved the mysteries of mankind for millennia. I said that I am going to tell you a secret don't patronise me. I do not believe anything. What I know, it is not faith. It is understanding. Knowledge, a type of knowledge that you cannot quantify with mathematics and chemistry. It is a higher science that is proven by the unmistakable coincidence of fate. It is invisible to those who are ignorant and they who despair, those who have lost all hope are blind to this promise." Emilien felt a strange remorse. "I guess I must be blind then." The lights suddenly shut down and the song stopped dead in it's track, like Macy promised. Overcome by the majesty of the scene Maurelle wiped a tear away fearing that her makeup might get ruined. "Anyone can see. They must just open their eyes voluntarily and be honest with themselves. Their true original selves. Who they were made to be." Emile felt judged and wanted to end this conversation quickly. "I am going back to my ship, you have a good night now." She grabbed tightly at his wrist almost painfully. "You do not want to know my secret?" Emelien was becoming annoyed with her insistence he removed her hand from his arm. "I don't think you know any real useful secrets, sweetheart." He sounded threatening, the real enshrouded unmistakable him breaking through the act. She looked at him unintimidated by his sudden shift in personality. "Oh, so I suppose you know why the Juela are at war for most of our lives?" He sarcastically extended his arms forward palms up in restrained but evidently mocking adoration. "Please enlighten me priestess." "They are fighting over this." She pointed at the epic scene of destruction drifting statically out of view as the stations rotation cut it off at the edge of the window. The shadows chased Sol light away sliding like a retracting blade across the room leaving it dark. Emilien burst out angrily. "They are fighting over satoshis! That is all they ever fight over! What I fight for, Damnit! Sats and the resources to gain more of it! That is the beginning and end of all things! Anyone in the universe with even the slightest lick of self worth works, fights and dies for sat!" Maurelle stared astutely at him unemotionally affected by his outburst. She obviously had experienced this exact reaction before and suddenly Emilien realised that he might be the one being manipulated by a smarter and wiser being than himself. "Are you done my love? Have you made your point or is there some other deeper understanding you wish me to internalise into my ignorant small little world?" She threw at him a spiteful sarcasm of her own. "Do you really think I do not know what it means to be seduced by wealth? Luxury?" She took a step closer to him. "Pleasure?" Emilien felt stupid and disarmed this time adding emotionally disarmed to the defeat of being inept in his own body. "I am not a fool mon cherie. The truly wealthy don't fight for wealth, they fight for power. But the noble and sincere fight a different fight with a different weapon. They use words to fight, ideas to win. They fight to gain trust with words, and they fight to retain it with consistency in their actions. Trust is a currency that makes sat seem like shit in comparison because it is real even though you do not believe what you cannot hold in your hand, like your beloved sat." She pointed at the ring on his finger. "Trust only retains value if you honour your words with your actions. Its value is fragile and can disappear in a moment of weakness like water vapour, cherished as the source of life then gone, poof, evaporated. Like magic. This type of trust if gained and retained correctly, projects you forward into the realm of immortality." Emile felt stung and hurt on a personal level, unsure if she was generalising or targeting his own specific weakness purposely. It confused him and made him feel insecure. "What are they fighting for then?" He asked slightly surrendering to the unexpected superior reasoning. Maurelle appreciated the honesty she identified as sincere. She gently took his hand again and led him back to the large convex window. They stood silently for a block, waiting on the rotation to pull the bright light of Sol back into the room. "They are fighting for the power to do that." She pointed at Earth in all it's terrible glory. "The destruction caused by the gate was a terrible cataclysm outside of humanities collective control. The core and the gates are a mystery to mankind." She looked up at Emilien, relieved to see that he was still taking her seriously. "The Maggarie have discovered a weapon that has the power to destroy a planet. The Juel think they are fighting to free Osteri captives from slavery but the real motif is hidden, our Patriarchs unadmitted fear of being inferior to the Maggarie. Most of the goods we traded with them they have stopped accepting, the Shiv and Osteri still buy our products but the Maggarie have suddenly lost the need for our produce, even raw material in it's basest forms. They are expanding somehow and the balance of interdependence has tilted out of our favor. They have no more need for us and have cast us aside like a filthy rag." She paused in thought. "Their new super weapon is the cause of this conflict monsieur Scott." Emilien shrugged. Feeling relieved at regaining the intellectual high ground he thought he had lost. "I'm sorry Maurelle. I have no data on this weapon. If this was true the forums on my bulletin board would have leaked information about it's existence epochs ago, it's been just over three cycles everyone would have known this by now. It sounds more like Jeul fearmongering or perhaps it is the daydreaming fairy tale of an innocent naive girl who worships old myths and legends of a time dead for thousands of years." He pointed at Earth. She sniffed away a hint of emotion and anger. "Well then, I have nothing more to say to you, Good night monsieur Scott." She pulled away from him pridefully and looked out at the enormous gate embedded like a knife into the earths crust. "You are a swine monsieur Scott, leave me alone with my pearl." Emilien stepped back mockingly bowing slightly. "Good night sweetheart." He walked back to his craft laughing inside himself. "Stupid woman." He muttered, although be it doubtfully.
...
scifi
-
 @ 8fb140b4:f948000c
2025-03-20 01:29:06
@ 8fb140b4:f948000c
2025-03-20 01:29:06As many of you know, https://nostr.build has recently launched a new compatibility layer for the Blossom protocol blossom.band. You can find all the details about what it supports and its limitations by visiting the URL.
I wanted to cover some of the technical details about how it works here. One key difference you may notice is that the service acts as a linker, redirecting requests for the media hash to the actual source of the media—specifically, the nostr.build URL. This allows us to maintain a unified CDN cache and ensure that your media is served as quickly as possible.
Another difference is that each uploaded media/blob is served under its own subdomain (e.g.,
npub1[...].blossom.band), ensuring that your association with the blob is controlled by you. If you decide to delete the media for any reason, we ensure that the link is broken, even if someone else has duplicated it using the same hash.To comply with the Blossom protocol, we also link the same hash under the main (apex) domain (blossom.band) and collect all associations under it. This ensures that Blossom clients can fetch media based on users’ Blossom server settings. If you are the sole owner of the hash and there are no duplicates, deleting the media removes the link from the main domain as well.
Lastly, in line with our mission to protect users’ privacy, we reject any media that contains private metadata (such as GPS coordinates, user comments, or camera serial numbers) or strip it if you use the
/media/endpoint for upload.As always, your feedback is welcome and appreciated. Thank you!
-
 @ 472f7a9b:1e7e0bff
2025-05-19 15:56:02
@ 472f7a9b:1e7e0bff
2025-05-19 15:56:02There’s something sacred about morning air — the way it carries just enough chill to remind you you’re alive, without pushing you back inside. I’ve been starting my days on the balcony lately. Not because it’s glamorous (it isn’t), or because I have a routine (I don’t), but because it’s the only space in my apartment that feels both open and still.
This morning I made coffee with too much cinnamon and curled up with a blanket that’s seen better days. I watched the city slowly wake up — one barking dog, two joggers, and the clatter of a recycling truck below. It’s odd how these tiny patterns become a kind of comfort.
 I used to think that slowing down meant falling behind. But here, perched on the third floor with my feet on cold concrete and the sky just starting to blush, I feel like I’m exactly where I’m supposed to be.
I used to think that slowing down meant falling behind. But here, perched on the third floor with my feet on cold concrete and the sky just starting to blush, I feel like I’m exactly where I’m supposed to be.If you’re reading this, maybe you needed that reminder too.
— Natalie





