-
 @ 3f770d65:7a745b24
2025-04-21 00:15:06
@ 3f770d65:7a745b24
2025-04-21 00:15:06At the recent Launch Music Festival and Conference in Lancaster, PA, featuring over 120 musicians across three days, I volunteered my time with Tunestr and Phantom Power Music's initiative to introduce artists to Bitcoin, Nostr, and the value-for-value model. Tunestr sponsored a stage, live-streaming 21 bands to platforms like Tunestr.io, Fountain.fm and other Nostr/Podcasting 2.0 apps and on-boarding as many others as possible at our conference booth. You may have seen me spamming about this over the last few days.
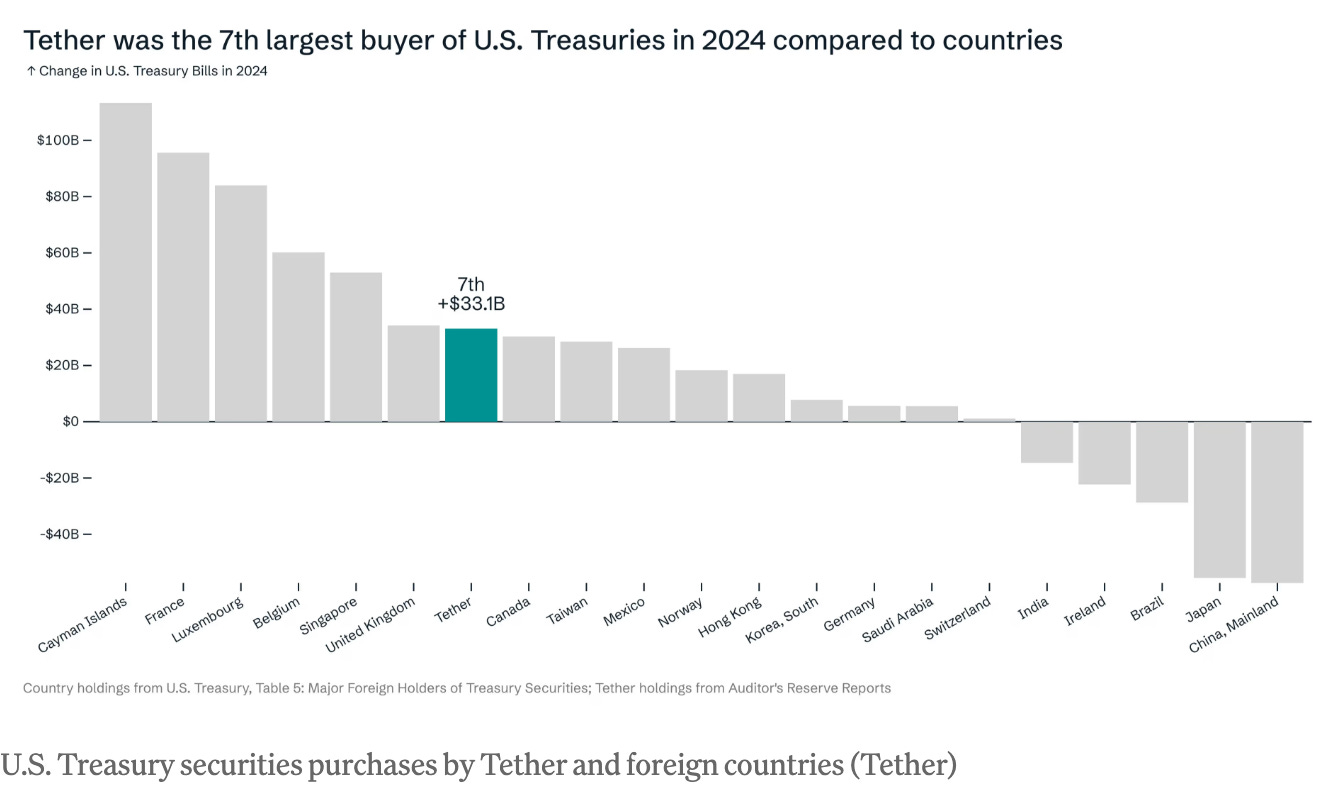
V4V Earnings
Day 1: 180,000 sats
Day 2: 300,000 sats
Day 3: Over 500,000 sats
Who?
Here are the artists that were on-boarded to Fountain and were live streaming on the Value-for-Value stage:
nostr:npub1cruu4z0hwg7n3r2k7262vx8jsmra3xpku85frl5fnfvrwz7rd7mq7e403w nostr:npub12xeh3n7w8700z4tpd6xlhlvg4vtg4pvpxd584ll5sva539tutc3q0tn3tz nostr:npub1rc80p4v60uzfhvdgxemhvcqnzdj7t59xujxdy0lcjxml3uwdezyqtrpe0j @npub16vxr4pc2ww3yaez9q4s53zkejjfd0djs9lfe55sjhnqkh nostr:npub10uspdzg4fl7md95mqnjszxx82ckdly8ezac0t3s06a0gsf4f3lys8ypeak nostr:npub1gnyzexr40qut0za2c4a0x27p4e3qc22wekhcw3uvdx8mwa3pen0s9z90wk nostr:npub13qrrw2h4z52m7jh0spefrwtysl4psfkfv6j4j672se5hkhvtyw7qu0almy nostr:npub1p0kuqxxw2mxczc90vcurvfq7ljuw2394kkqk6gqnn2cq0y9eq5nq87jtkk nostr:npub182kq0sdp7chm67uq58cf4vvl3lk37z8mm5k5067xe09fqqaaxjsqlcazej nostr:npub162hr8kd96vxlanvggl08hmyy37qsn8ehgj7za7squl83um56epnswkr399 nostr:npub17jzk5ex2rafres09c4dnn5mm00eejye6nrurnlla6yn22zcpl7vqg6vhvx nostr:npub176rnksulheuanfx8y8cr2mrth4lh33svvpztggjjm6j2pqw6m56sq7s9vz nostr:npub1akv7t7xpalhsc4nseljs0c886jzuhq8u42qdcwvu972f3mme9tjsgp5xxk nostr:npub18x0gv872489lrczp9d9m4hx59r754x7p9rg2jkgvt7ul3kuqewtqsssn24
Many more musicians were on-boarded to Fountain, however, we were unable to obtain all of their npubs.
THANK YOU TO ALL ZAPPERS AND BOOSTERS!
Musicians “Get It”
My key takeaway was the musicians' absolute understanding that the current digital landscape along with legacy social media is failing them. Every artist I spoke with recognized how algorithms hinder fan connection and how gatekeepers prevent fair compensation for their work. They all use Spotify, but they only do so out of necessity. They felt the music industry is primed for both a social and monetary revolution. Some of them were even speaking my language…
Because of this, concepts like decentralization, censorship resistance, owning your content, and controlling your social graph weren't just understood by them, they were instantly embraced. The excitement was real; they immediately saw the potential and agreed with me. Bitcoin and Nostr felt genuinely punk rock and that helped a lot of them identify with what we were offering them.
The Tools and the Issues
While the Nostr ecosystem offers a wide variety of tools, we focused on introducing three key applications at this event to keep things clear for newcomers:
- Fountain, with a music focus, was the primary tool for onboarding attendees onto Nostr. Fountain was also chosen thanks to Fountain’s built-in Lightning wallet.
- Primal, as a social alternative, was demonstrated to show how users can take their Nostr identity and content seamlessly between different applications.
- Tunestr.io, lastly was showcased for its live video streaming capabilities.
Although we highlighted these three, we did inform attendees about the broader range of available apps and pointed them to
nostrapps.comif they wanted to explore further, aiming to educate without overwhelming them.This review highlights several UX issues with the Fountain app, particularly concerning profile updates, wallet functionality, and user discovery. While Fountain does work well, these minor hiccups make it extremely hard for on-boarding and education.
- Profile Issues:
- When a user edits their profile (e.g., Username/Nostr address, Lightning address) either during or after creation, the changes don't appear to consistently update across the app or sync correctly with Nostr relays.
- Specifically, the main profile display continues to show the old default Username/Nostr address and Lightning address inside Fountain and on other Nostr clients.
- However, the updated Username/Nostr address does appear on https://fountain.fm (chosen-username@fountain.fm) and is visible within the "Edit Profile" screen itself in the app.
- This inconsistency is confusing for users, as they see their updated information in some places but not on their main public-facing profile within the app. I confirmed this by observing a new user sign up and edit their username – the edit screen showed the new name, but the profile display in Fountain did not update and we did not see it inside Primal, Damus, Amethyst, etc.
- Wallet Limitations:
- The app's built-in wallet cannot scan Lightning address QR codes to initiate payments.
- This caused problems during the event where users imported Bitcoin from Azte.co vouchers into their Fountain wallets. When they tried to Zap a band by scanning a QR code on the live tally board, Fountain displayed an error message stating the invoice or QR code was invalid.
- While suggesting musicians install Primal as a second Nostr app was a potential fix for the QR code issue, (and I mentioned it to some), the burden of onboarding users onto two separate applications, potentially managing two different wallets, and explaining which one works for specific tasks creates a confusing and frustrating user experience.
- Search Difficulties:
- Finding other users within the Fountain app is challenging. I was unable to find profiles from brand new users by entering their chosen Fountain username.
- To find a new user, I had to resort to visiting their profile on the web (fountain.fm/username) to retrieve their npub. Then, open Primal and follow them. Finally, when searching for their username, since I was now following them, I was able to find their profile.
- This search issue is compounded by the profile syncing problem mentioned earlier, as even if found via other clients, their displayed information is outdated.
- Searching for the event to Boost/Zap inside Fountain was harder than it should have been the first two days as the live stream did not appear at the top of the screen inside the tap. This was resolved on the third day of the event.
Improving the Onboarding Experience
To better support user growth, educators and on-boarders need more feature complete and user-friendly applications. I love our developers and I will always sing their praises from the highest mountain tops, however I also recognize that the current tools present challenges that hinder a smooth onboarding experience.
One potential approach explored was guiding users to use Primal (including its built-in wallet) in conjunction with Wavlake via Nostr Wallet Connect (NWC). While this could facilitate certain functions like music streaming, zaps, and QR code scanning (which require both Primal and Wavlake apps), Wavlake itself has usability issues. These include inconsistent or separate profiles between web and mobile apps, persistent "Login" buttons even when logged in on the mobile app with a Nostr identity, and the minor inconvenience of needing two separate applications. Although NWC setup is relatively easy and helps streamline the process, the need to switch between apps adds complexity, especially when time is limited and we’re aiming to showcase the benefits of this new system.
Ultimately, we need applications that are more feature-complete and intuitive for mainstream users to improve the onboarding experience significantly.
Looking forward to the future
I anticipate that most of these issues will be resolved when these applications address them in the near future. Specifically, this would involve Fountain fixing its profile issues and integrating Nostr Wallet Connect (NWC) to allow users to utilize their Primal wallet, or by enabling the scanning of QR codes that pay out to Lightning addresses. Alternatively, if Wavlake resolves the consistency problems mentioned earlier, this would also significantly improve the situation giving us two viable solutions for musicians.
My ideal onboarding event experience would involve having all the previously mentioned issues resolved. Additionally, I would love to see every attendee receive a $5 or $10 voucher to help them start engaging with value-for-value, rather than just the limited number we distributed recently. The goal is to have everyone actively zapping and sending Bitcoin throughout the event. Maybe we can find a large sponsor to facilitate this in the future?
What's particularly exciting is the Launch conference's strong interest in integrating value-for-value across their entire program for all musicians and speakers at their next event in Dallas, Texas, coming later this fall. This presents a significant opportunity to onboard over 100+ musicians to Bitcoin and Nostr, which in turn will help onboard their fans and supporters.
We need significantly more zaps and more zappers! It's unreasonable to expect the same dedicated individuals to continuously support new users; they are being bled dry. A shift is needed towards more people using bitcoin for everyday transactions, treating it as money. This brings me back to my ideal onboarding experience: securing a sponsor to essentially give participants bitcoin funds specifically for zapping and tipping artists. This method serves as a practical lesson in using bitcoin as money and showcases the value-for-value principle from the outset.
-
 @ 8d34bd24:414be32b
2025-04-20 14:18:37
@ 8d34bd24:414be32b
2025-04-20 14:18:37I started working on this post a couple weeks ago, and out of pure accident, it became my Resurrection Sunday (Easter) post. Maybe it was by God’s design. On Resurrection Sunday, Jesus was raised from the grave. Forty days later he rose to heaven before many witnesses. Someday in the future, the dead in Christ will be raised from the dead, and all believers will be snatched up to heaven. Maybe this is this right post for Resurrection Sunday.
For if we believe that Jesus died and rose again, even so God will bring with Him those who have fallen asleep in Jesus. … For the Lord Himself will descend from heaven with a shout, with the voice of the archangel and with the trumpet of God, and the dead in Christ will rise first. Then we who are alive and remain will be caught up together with them in the clouds to meet the Lord in the air, and so we shall always be with the Lord. (1 Thessalonians 4:14, 16-17) {emphasis mine}
It always amazes me that some Christians don’t believe in the rapture of the church. I understand how there can be a disagreement about exactly when the rapture is to occur, but I can’t comprehend how some Christians don’t believe the rapture is coming or that they believe that the rapture happened in the first century.
Let’s start with the three key verses on the subject and then we’ll get into more details.
Key Rapture Verses
I didn’t notice that this first passage referred to the rapture until it was pointed out to me. I was so focused on Jesus preparing a place, that I missed the key sentence.
“Do not let your heart be troubled; believe in God, believe also in Me. In My Father’s house are many dwelling places; if it were not so, I would have told you; for I go to prepare a place for you. If I go and prepare a place for you, I will come again and receive you to Myself, that where I am, there you may be also. (John 14:1-3) {emphasis mine}
Jesus, after His resurrection and as promised in these verses, rose up to heaven to go prepare a place for believers. He will then return to bring believers to Himself. This whole idea would have been particularly clear for the Jews when it was written. When a bride and groom were engaged (a legal contract where they were considered married), the groom would go and prepare a place for them to live. It could be an extra room in his parent’s home or it could be a whole new home. The bride didn’t know when the groom would return to take her to himself to become man and wife. In the same way, Jesus has gone away to prepare a place for us and will return at a time we do not know. Just as the Jewish bride had to be ready to leave with her groom when he suddenly arrived, we also must be ready for Jesus’s return when He will snatch us from earth and take us home with Him to heaven.
But we do not want you to be uninformed, brethren, about those who are asleep, so that you will not grieve as do the rest who have no hope. For if we believe that Jesus died and rose again, even so God will bring with Him those who have fallen asleep in Jesus. For this we say to you by the word of the Lord, that we who are alive and remain until the coming of the Lord, will not precede those who have fallen asleep. For the Lord Himself will descend from heaven with a shout, with the voice of the archangel and with the trumpet of God, and the dead in Christ will rise first. Then we who are alive and remain will be caught up together with them in the clouds to meet the Lord in the air, and so we shall always be with the Lord. Therefore comfort one another with these words. (1 Thessalonians 4:13-18) {emphasis mine}
The Bible has a wonderful euphemism for the death of believers. It speaks of them falling asleep because death is not the end for believers. It is just a pause, a separation of body and spirit, before we are raptured to Jesus, to meet Him in the sky, where we will receive a new resurrection body, just as Jesus received when He was raised from the dead 3 days after His crucifixion. Both the dead in Christ and the alive in Christ will “be caught up together with them in the clouds to meet the Lord in the air.” God gives us this promise in the Bible to comfort us. It gives us comfort that death is not the end and we will see our fellow believers again in heaven one day. It also gives us comfort that we will not have to experience God’s wrath. “For God has not destined us for wrath, but for obtaining salvation through our Lord Jesus Christ.” (1 Thessalonians 5:9)
What else can we learn about the rapture?
Now I say this, brethren, that flesh and blood cannot inherit the kingdom of God; nor does the perishable inherit the imperishable. Behold, I tell you a mystery; we will not all sleep, but we will all be changed, in a moment, in the twinkling of an eye, at the last trumpet; for the trumpet will sound, and the dead will be raised imperishable, and we will be changed. For this perishable must put on the imperishable, and this mortal must put on immortality. But when this perishable will have put on the imperishable, and this mortal will have put on immortality, then will come about the saying that is written, “Death is swallowed up in victory. O death, where is your victory? O death, where is your sting?” The sting of death is sin, and the power of sin is the law; but thanks be to God, who gives us the victory through our Lord Jesus Christ. (1 Corinthians 15:50-57) {emphasis mine}
The rapture will be an instantaneous change from our perishable bodies to imperishable, whether we are alive in Christ or dead in Christ. At the rapture we “will be raised imperishable.” I am very excited to be snatched up into the air, receive a new, eternal body, and meet Jesus face-to-face.
There is one more passage that I believe talks of the rapture that is a bit more subtle from Isaiah.
The righteous man perishes, and no man takes it to heart;\ And devout men are taken away, while no one understands.\ For the righteous man is taken away from evil,\ **He enters into peace;\ They rest in their beds,\ Each one who walked in his upright way. (Isaiah 57:1-2) {emphasis mine}
The seven year Tribulation is the wrath of God poured out on those who rejected Him and the merciful, last chance warning before eternal judgement. Those who have trusted in Jesus (the devout men, the righteous man) will be “taken away from evil” and will “enter into peace.” Instead of experiencing God’s wrath, they will experience His peace. Instead of experience horror, they will “rest in their beds.”
The Seven Raptures Before the Rapture of the Church
How can we know that we will be raptured to heaven to be with Jesus forever? One way is because people have been raptured before (in different ways)
I am borrowing the organization of this section from Chapter 9 of “The End: Everything You’ll Want to Know about the Apocalypse” by Mark Hitchcock, which I happen to be reading at the moment.
-
Rapture of Enoch\ ”So all the days of Enoch were three hundred and sixty-five years. Enoch walked with God; and he was not, for God took him.” (Genesis 5:23-24) \ Enoch was raptured to heaven to be with God. He did not die, but went straight to God.
-
Rapture of Elijah\ ”And it came about when the Lord was about to take up Elijah by a whirlwind to heaven, that Elijah went with Elisha from Gilgal. … As they were going along and talking, behold, there appeared a chariot of fire and horses of fire which separated the two of them. And Elijah went up by a whirlwind to heaven.” (2 Kings 2:1,11) \ Elijah also was raptured to heaven without having to die. This passage gives more details. He went up in a whirlwind to heaven.
-
Rapture of Isaiah\ ”In the year of King Uzziah’s death I saw the Lord sitting on a throne, lofty and exalted, with the train of His robe filling the temple. Seraphim stood above Him, each having six wings: with two he covered his face, and with two he covered his feet, and with two he flew. And one called out to another and said,
“Holy, Holy, Holy, is the Lord of hosts,
The whole earth is full of His glory.”” (Isaiah 6:1-3)\ Isaiah’s situation was different. He was raptured to heaven only temporarily to be given God’s word and His prophecy and to call Isaiah for His good plan.
-
Rapture of Jesus\ ”And she gave birth to a son, a male child, who is to rule all the nations with a rod of iron; and her child was caught up to God and to His throne.” (Revelation 12:5)\ and\ ”And after He had said these things, He was lifted up while they were looking on, and a cloud received Him out of their sight. And as they were gazing intently into the sky while He was going, behold, two men in white clothing stood beside them. They also said, “Men of Galilee, why do you stand looking into the sky? This Jesus, who has been taken up from you into heaven, will come in just the same way as you have watched Him go into heaven.” (Acts 1:9-11)\ I’ve listed two verses about Jesus’s rapture. The one from Revelation uses the Greek word harpazo, caught up - when translated to Latin, the word is rapturo, which is where we get our English word rapture. The verses in Acts give a more detailed description of His rapture to heaven, which is an example of our rapture. We are also promised His return.
-
Rapture of Philip\ ”And he ordered the chariot to stop; and they both went down into the water, Philip as well as the eunuch, and he baptized him. When they came up out of the water, the Spirit of the Lord snatched Philip away; and the eunuch no longer saw him, but went on his way rejoicing. But Philip found himself at Azotus, and as he passed through he kept preaching the gospel to all the cities until he came to Caesarea.” (Acts 8:38-40)
The rapture of Philip is different than the rest, because Philip was snatched away, not to heaven, but to Azotus. This is still an instance worth pointing out because it also uses the Greek word Harpazo.
- Rapture of Paul\ ”I know a man in Christ who fourteen years ago—whether in the body I do not know, or out of the body I do not know, God knows—such a man was caught up to the third heaven. And I know how such a man—whether in the body or apart from the body I do not know, God knows— was caught up into Paradise and heard inexpressible words, which a man is not permitted to speak.” (2 Corinthians 12:2-4)\ Like Isaiah, Paul was temporarily caught up (Harpazo) to heaven to receive revelation from God and then returned to his work and life on earth
These examples show God snatching people from one location to another, physically or spiritually for His good purpose. I expect it to happen again, shortly before the beginning of the seven year tribulation.
The 3 Views of the Rapture
There are three main views of the rapture: pre-trib, mid-trib, and post-trib. The basic beliefs are pretty much self explanatory by their name. Does the rapture occur before the tribulation, around the mid-point of the tribulation (which is right before the Great Tribulation or final 3.5 years), or after the tribulation? Which one fits what the Bible says better?
Although the Bible doesn’t directly say when the rapture happens, there are some very strong hints.
No wrath For saints
“For God has not destined us for wrath, but for obtaining salvation through our Lord Jesus Christ.” (1 Thessalonians 5:9)
God promises believers that we are not destined for wrath. The tribulation is also known as1 “The wrath” (1 Thessalonians 5:9 & Revelation 11:18), “The wrath to come” (1 Thessalonians 1:10), “The great day of their wrath” (Revelation 6:17), “The wrath of God” (Revelation15:1,7, 14:10,19, 16:1), “The wrath of the lamb” (Revelation 6:16). There are numerous other equally unpleasant names, but I am sticking with those that use the word wrath. God promised believers that we are not destined for wrath. God never breaks His promises.
Similarly Revelation 3 promises believers will be kept from the hour of testing.
Because you have kept the word of My perseverance, I also will keep you from the hour of testing, that hour which is about to come upon the whole world, to test those who dwell on the earth. I am coming quickly; hold fast what you have, so that no one will take your crown. (Revelation 3:10-11) {emphasis mine}
The word quickly can also be translated suddenly. Although Jesus has not returned quickly by our way of figuring time, He will come suddenly.
No one knows when
“But of that day and hour no one knows, not even the angels of heaven, nor the Son, but the Father alone.” (Matthew 24:36)
Scripture says the Tribulation starts when the Antichrist signs a peace treaty with Israel. If the rapture happens before the tribulation, then we won’t know when it will happen. If the rapture occurs at the mid-trib position, then it will happen 3.5 years after the peace treaty. If the rapture occurs post-trip, then it will happen 7 years after the peace treaty is signed and 3.5 years after the abomination of desolation, when the Antichrist declares himself god in the Jewish temple and requires the whole world to worship him. Only one makes sense if we can’t know when it happens.
Just as in the days of …
“For the coming of the Son of Man will be just like the days of Noah. For as in those days before the flood they were eating and drinking, marrying and giving in marriage, until the day that Noah entered the ark, and they did not understand until the flood came and took them all away; so will the coming of the Son of Man be. Then there will be two men in the field; one will be taken and one will be left. Two women will be grinding at the mill; one will be taken and one will be left.” (Matthew 24:37-41)
If we look at the words of Jesus, He compares the rapture to the days of Noah. Life happening as normal, then God put Noah and his family on the ark and personally shut the door (Genesis 7:16). Then the flood came, pouring God’s wrath out on those who had rejected Him. In the same way, God will take believers out of the world before pouring out His wrath on those who remain. He clearly states, “one will be taken and one will be left.”
A parallel passage in Luke, not only talks of God removing Noah before the flood, but also tells of God removing Lot before destroying Sodom & Gomorrah.
For just like the lightning, when it flashes out of one part of the sky, shines to the other part of the sky, so will the Son of Man be in His day. But first He must suffer many things and be rejected by this generation. And just as it happened in the days of Noah, so it will be also in the days of the Son of Man: they were eating, they were drinking, they were marrying, they were being given in marriage, until the day that Noah entered the ark, and the flood came and destroyed them all. It was the same as happened in the days of Lot: they were eating, they were drinking, they were buying, they were selling, they were planting, they were building; but on the day that Lot went out from Sodom it rained fire and brimstone from heaven and destroyed them all. It will be just the same on the day that the Son of Man is revealed. (Luke:17:24-30) {emphasis mine}
Just as Noah was removed before judgement, so also was Lot removed before judgement. In both cases the majority of people were going about business, living normal lives, not expecting anything to change.
In Genesis 19, the angels must remove Lot and his family before the city is destroyed.
Then the two men said to Lot, “Whom else have you here? A son-in-law, and your sons, and your daughters, and whomever you have in the city, bring them out of the place; for we are about to destroy this place, because their outcry has become so great before the Lord that the Lord has sent us to destroy it.” \ …\ When morning dawned, the angels urged Lot, saying, “Up, take your wife and your two daughters who are here, or you will be swept away in the punishment of the city.” But he hesitated. So the men seized his hand and the hand of his wife and the hands of his two daughters, for the compassion of the Lord was upon him; and they brought him out, and put him outside the city. (Genesis 19:12-13,15-16) {emphasis mine}
In the last days, God has promised to remove us before His judgment is poured out on those who willfully rejected Him. Jesus spoke these words to comfort us and so we would not fear the end.
Removal of the Restrainer
Now we request you, brethren, with regard to the coming of our Lord Jesus Christ and our gathering together to Him, that you not be quickly shaken from your composure or be disturbed either by a spirit or a message or a letter as if from us, to the effect that the day of the Lord has come. Let no one in any way deceive you, for it will not come unless the apostasy comes first, and the man of lawlessness is revealed, the son of destruction, who opposes and exalts himself above every so-called god or object of worship, so that he takes his seat in the temple of God, displaying himself as being God. Do you not remember that while I was still with you, I was telling you these things? And you know what restrains him now, so that in his time he will be revealed. For the mystery of lawlessness is already at work; only he who now restrains will do so until he is taken out of the way. Then that lawless one will be revealed whom the Lord will slay with the breath of His mouth and bring to an end by the appearance of His coming; (2 Thessalonians 2:1-8) {emphasis mine}
The restrainer is the Holy Spirit and the lawless one is the antichrist. This passage is saying that the antichrist will not be revealed until the restrainer is removed. The Holy Spirit indwells every believer. The believers also have to be removed before the antichrist is revealed, otherwise the Holy Spirit would have to leave the believers, leaving them alone during God’s wrath. That, of course, is contrary to God’s character, history, and promise.
Why is There No Mention of the Church During the Tribulation?
In the first three chapters of Revelation, the word church is used again and again. The church is not mentioned again until Revelation 19, regarding the Bride of Christ.
Let us rejoice and be glad and give the glory to Him, for the marriage of the Lamb has come and His bride has made herself ready.” It was given to her to clothe herself in fine linen, bright and clean; for the fine linen is the righteous acts of the saints. (Revelation 19:7-8) {emphasis mine}
All of this makes sense if the church was raptured before the tribulation. Therefore the bride (the church) has had seven years to make herself ready. They then get to descend with Jesus in the second coming of Jesus.
And I saw heaven opened, and behold, a white horse, and He who sat on it is called Faithful and True, and in righteousness He judges and wages war. His eyes are a flame of fire, and on His head are many diadems; and He has a name written on Him which no one knows except Himself. He is clothed with a robe dipped in blood, and His name is called The Word of God. And the armies which are in heaven, clothed in fine linen, white and clean, were following Him on white horses. From His mouth comes a sharp sword, so that with it He may strike down the nations, and He will rule them with a rod of iron; and He treads the wine press of the fierce wrath of God, the Almighty. And on His robe and on His thigh He has a name written, “KING OF KINGS, AND Lord OF LORDS.” (Revelation 19:11-16) {emphasis mine}
The Bride of Christ follows the King of Kings and Lord of Lords back to earth after being made “white and clean.”
Some may accuse pre-trib believers of being escapists. I’ll admit, I am happy to avoid the wrath of God, whether that be the tribulation or eternal damnation or just His daily disappointment in my failings. The fact that I am glad to “escape” the wrath, doesn’t make it untrue. I hope the passages and explanations I shared will give you comfort as the Day of the Lord and the Wrath of God approaches and as we see the world seemingly spiraling out of control. God is in control. Everything is happening according to His plan and for our good.
May the Lord of heaven comfort you with His promises and make you know His love. May you trust Him in good times and bad until the last days. May God give you a desire for His word and an understanding of His prophecies, so you will know the day is fast approaching.
Trust Jesus.
FYI, You can find most of my articles at end times. Some are directly relating to end times while others are loosely related. This post is a logical explanation of the rapture. You can also check out my older article on the rapture, “Up, Up, and Away.” The focus in my previous post was a little different including focusing on how the rapture will effect us, how we should respond to its immanency, and how it relates to the 2nd coming of Christ after the tribulation, so it is worth checking out as well.
-
-
 @ dab6c606:51f507b6
2025-04-18 14:59:25
@ dab6c606:51f507b6
2025-04-18 14:59:25Core idea: Use geotagged anonymized Nostr events with Cashu-based points to snitch on cop locations for a more relaxed driving and walking
We all know navigation apps. There's one of them that allows you to report on locations of cops. It's Waze and it's owned by Google. There are perfectly fine navigation apps like Organic Maps, that unfortunately lack the cop-snitching features. In some countries, it is illegal to report cop locations, so it would probably not be a good idea to use your npub to report them. But getting a points Cashu token as a reward and exchanging them from time to time would solve this. You can of course report construction, traffic jams, ...
Proposed solution: Add Nostr client (Copstr) to Organic Maps. Have a button in bottom right allowing you to report traffic situations. Geotagged events are published on Nostr relays, users sending cashu tokens as thank you if the report is valid. Notes have smart expiration times.
Phase 2: Automation: Integration with dashcams and comma.ai allow for automated AI recognition of traffic events such as traffic jams and cops, with automatic touchless reporting.
Result: Drive with most essential information and with full privacy. Collect points to be cool and stay cool.
-
 @ 7b3f7803:8912e968
2025-04-18 00:16:02
@ 7b3f7803:8912e968
2025-04-18 00:16:02As we enter Holy Week, we are confronted with a world steeped in sin, strife, conflict, and mortality. There exists a peculiar fascination among some with societal decline, as if they derive satisfaction from witnessing civilization’s unraveling. This attraction to darkness may reflect their inner turmoil, a desire to see others share in their suffering. Alternatively, it could stem from a profound hopelessness, a belief that life lacks purpose, leading them to wish for its end. The allure of dystopian futures is, indeed, a curious phenomenon.
Alexander Hamilton once yearned for war as a means to elevate his status, a reflection of youthful ambition for decisive action. Such a desire—to distinguish oneself and ascend the social hierarchy—underlies some of the grim visions of the future propagated by certain ideological circles. Their aim is not war itself but a reconfiguration of power, placing authority in the hands of those who affirm their values. For years, such individuals have held sway, yet their influence appears to be waning.
In the absence of hope, many embrace visions of decline. This despair is characteristic of a faltering empire, signaling the end of an era. The younger generation, burdened by weariness, falters under the weight of their circumstances. They lack hope for a brighter future and see no clear path out of life’s monotony. In a word, they are trapped, uncertain of how to proceed.
We witnessed a similar sentiment during the Arab Spring, where upheaval was celebrated as a longed-for revolution, a societal reset. The assassination of a prominent corporate executive, such as the CEO of United Health, evokes a comparable yearning for disruption. There is a desire for a cultural transformation, though its precise nature remains elusive.
Yet, the youth find themselves dominated by the very elites whose rhetoric they echo. Unlike the 1960s, when generational values clashed overtly, today’s power structures co-opt the language of the young, redirecting their frustration toward populist movements. This inversion is a cunning strategy, mitigating the potential for significant rebellion.
The reality remains that the older generation holds the wealth, power, and authority, while the young are consistently marginalized. They are the ones left with little hope, ensnared by the system. However, a quiet rebellion is emerging—one rooted in hope and faith. Many are beginning to see through the falsehoods propagated by those in power. The promises of governmental provision, once alluring, now appear untenable in light of fiscal realities. The youth seek a new source of hope, a renewed perspective. Thankfully, they are beginning to find it, turning toward faith as a foundation for a more optimistic future.
-
 @ df67f9a7:2d4fc200
2025-04-16 22:13:20
@ df67f9a7:2d4fc200
2025-04-16 22:13:20Businesses want Nostr, but Nostr is not ready for business. What can be done?
TLDR :
What Nostr brings to business apps…
- Get your brands in front of users with your choice of SEO and Algos that YOU control.
- Access unlimited public user data from across the network without fees or permission.
- Keep your business data private, while "releasing" liability for other data collected by your apps.
- Build one app to reach a diversity of users from across the network, even from other apps.
- Build your own tech and to use it as you wish. No gate keepers or code review process.
Businesses want Nostr.
- Businesses want reliable SEO and socials to put their brands in front of users, rather than arbitrary gate keepers, censoring the marketplace on a whim.
- Businesses want open access to harvest public data for free on a soveregnty respecting network, rather than paying gate keepers for access to user data of questionalble origin.
- Businesses want the freedom to NOT take ownership of certain user data collected by their apps, rather than being liabile for moderation and safe handling on their private infrastructure.
- Busineses want a single open protocol on which to build their apps, with unlimited potential and a diversity of shared users from other apps, rather than multiple siloed networks with difering APIs and demographics.
- Businesses want to own the technology they build and to use it as they wish, rather than submit their code for approval and control by arbitrary gate keepers.
But Nostr is not ready for business.
- Businesses DON'T want proprietary app data stored publicly as signed Nostr events on user specified relays.
- Businesses DON'T want to have to specify, or be constrained by, or even navigate the complexity of Nostr NIP standards for every novel kind of content that their apps generate.
- Businesses DON'T want to "open source" their entire suite of native apps JUST to assure end users that Nostr private keys are being safely handled.
- Businesses DON'T want to have to "rewrite" their entire app backend just to accomodate the Nostr way of "users sign events but dont actually login to your server" auth architecture.
- Businesses DONT want to suffer DDOS from bots and bad actors, or to expose their users to unwanted content, or even to have their own content disappear a sea of spam and misinformation.
Here’s what can be done.
- More tools and services for private business apps to coexist with freedom tech, and even thrive together, on the Nostr network.
- Extensible Webs of Trust algos for discovery and reach into any audience or demographic of trusted users.
- WoT powered standard APIs for exposing content to Nostr (and other business apps) from within a “black box” business app.
- HTTP AUTH (NIP 98) integration for business apps, allowing users to create local content WITHOUT needing discrete signatures or “linked” user accounts.
- Frost compatible “login“ for business apps, allowing users to paste “disposable” nsecs into proprietary clients without fear of their “cold” nsec being compromised.
- Support for “incremental” (and voluntary) adoption of freedom tech into existing business apps, with easy off-ramps for businesses to transfer more and more siloed data onto the “public” network.
Thoughts so far…
-
 @ 4ba8e86d:89d32de4
2025-04-22 13:26:12
@ 4ba8e86d:89d32de4
2025-04-22 13:26:12Cashu é Ecash para Bitcoin
Cashu é um sistema ecash Chaumian gratuito e de código aberto criado para Bitcoin. Cashu oferece privacidade quase perfeita para usuários de aplicativos Bitcoin de custódia. Ninguém precisa saber quem você é, quanto dinheiro você tem e com quem você faz transações.
O que é Cashu?
Cashu é um novo protocolo ecash para aplicativos de custódia Bitcoin que está totalmente integrado à rede Lightning. Um sistema Ecash consiste em duas partes, a carteira mint e a carteira ecash. Transações Ecash não rastreáveis, instantâneas e sem taxas. Cashu é construído para Bitcoin. As carteiras usam o nó Lightning da casa da moeda para fazer ou receber pagamentos em Bitcoin em troca de ecash. Uma casa da moeda Cashu não sabe quem você é, qual é o seu saldo ou com quem você está negociando.Os usuários de uma casa da moeda podem trocar ecash de forma privada, sem que ninguém saiba quem são as partes envolvidas. Os pagamentos em Bitcoin são executados sem que ninguém possa censurar usuários específicos.
A postagem de David Wagner em 1996 na lista de discussão Cypherpunk é a base da criptografia Cashu. Wagner descreve um sistema ecash usando troca de chave cega Diffie-Hellman em vez de RSA, na qual a implementação original de David Chaum foi baseada.
https://cypherpunks.venona.com/date/1996/03/msg01848.html
https://en.m.wikipedia.org/wiki/Ecash
Como isso começou.
https://void.cat/d/2HJKtTEfuDxmDfh3uH9ZoS.webp https://void.cat/d/XyyHFSQYa5vEswzzt6MMq7.webp
Como vão as coisas.
https://void.cat/d/WUrKzsFDnsvUQdFKZChLeS.webp
Como funciona A Carteira Cashu é através de um esquema criptográfico chamado assinaturas cegas, descrito pela primeira vez pelo cypherpunk e criptógrafo David Chaum. Pense assim:você produz uma mensagem secreta e a envolve em um envelope feito de papel carbono que você envia para a casa da moeda. https://void.cat/d/SbEEHCiGFUHWvk4qGv9xCb.webp
A casa da moeda não pode ver o que está dentro do envelope. Ele assina do lado de fora dizendo "qualquer que seja esse segredo, vale 420 Satoshis”e o envia de volta para você. Como o envelope é realmente criptografado, somente você pode abri-lo e ver sua mensagem secreta (agora assinada por carbono). https://void.cat/d/Pakyb6ztW9B7L5ubAQ74eL.webp
Este segredo assinado é na verdade o seu token Ecash e vale Satoshis.
Você pode enviar e receber esses tokens para qualquer outra pessoa como quiser, seja com um mensageiro, via e-mail ou um pombo. A casa da moeda não sabe nada disso.
A anatomia de um token Cashu. https://void.cat/d/JzvxreMoCitmYe2FthAsei.webp
Um breve passo a passo de uma carteira cashu deixará tudo isso bem claro.
Comece abrindo
https://nutstash.app/
Pressione " WALLET " https://void.cat/d/VeCANsaxkkq9YtoPRS26ZK.webp https://void.cat/d/CTmK9GcPGn3i2gHCVXcL5r.webp https://void.cat/d/UWjyjGLS6MzyZvt6zkuUgG.webp https://void.cat/d/HzNtKanCSAJatrMa9yTKwF.webp
Pressione "+ ADD ".
Agora a carteira cashu está aberta… https://void.cat/d/GAYSrNxHEEhctoW37bFPjJ.webp
O próximo passo é deposite alguns sats com a Casa da moeda.
Pra depositar Pressione o botão "MINT". https://void.cat/d/LC5WEDKAzzZoHXxrKZDiWu.webp
Digite a quantidade de sats a ser depositado na carteira cashu depois Pressione " REQUEST MINT ". https://void.cat/d/Pr6foBWBBCq73i8WggbLGG.webp
Você Pode copiar a fatura ou ler o qrcode , no meu caso usei a carteira LNbits pra pagar a fatura de 10 sats , você tem 10 minutos pra pagar fatura. https://void.cat/d/BQerpEtW2H9ANaoW8truJE.webp https://void.cat/d/8PGFBRW64zavDnQJfYQh9C.webp
Agora pra enviar Ecash.
Pressione “SEND” https://void.cat/d/8rkF2dvhJeZWf8GeQhhf2d.webp
Digite 10 , Pressione “SEND” https://void.cat/d/5SK5w6ewgt8wikCuyk7znM.webp
Então o token Ecash usando a assinatura cega da casa da moeda foi criado. https://void.cat/d/PedBMcZPfczZLLymGmfzVq.webp
O Token Ecash foi criado é esse logo abaixo.
eyJwcm9vZnMiOlt7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50IjoyLCJzZWNyZXQiOiJrWjNBOVorSXkyREJOcDdhdFhYRTIvclVXOFRnR2ZoTDgzWEFXZ0dKUXhVPSIsIkMiOiIwMmM0NjA4NDYwNDhjNzI1ZjgwMDc3M2IyNmRmOTcxNDU1MTJmOTI0YjgyNzYyZTllYzdkZjZjOTkzNGVmYjJhNmMifSx7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50Ijo4LCJzZWNyZXQiOiJXdTZmdWlxNGt4Tkh3UkF1UzFhMmVYaGZtRnRHU2tRQkNYZFNnUzcreHkwPSIsIkMiOiIwMzFhYWI3MzY3MTJhY2Y5MWU4NzE4YmM5OTlmNWE2MGEwYzNjODQ5YTA1MWE2OTA5MzRkMTc4NWNmZGNkNDcyYTAifV0sIm1pbnRzIjpbeyJ1cmwiOiJodHRwczovL2xlZ2VuZC5sbmJpdHMuY29tL2Nhc2h1L2FwaS92MS80Z3I5WGNtejNYRWtVTndpQmlRR29DIiwiaWRzIjpbIjBOSTNUVUFzMVNmeSJdfV19
Se pressionar o botão " send as link "
Então criar link do token Ecash.
https://wallet.nutstash.app/#eyJwcm9vZnMiOlt7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50IjoyLCJzZWNyZXQiOiJrWjNBOVorSXkyREJOcDdhdFhYRTIvclVXOFRnR2ZoTDgzWEFXZ0dKUXhVPSIsIkMiOiIwMmM0NjA4NDYwNDhjNzI1ZjgwMDc3M2IyNmRmOTcxNDU1MTJmOTI0YjgyNzYyZTllYzdkZjZjOTkzNGVmYjJhNmMifSx7ImlkIjoiME5JM1RVQXMxU2Z5IiwiYW1vdW50Ijo4LCJzZWNyZXQiOiJXdTZmdWlxNGt4Tkh3UkF1UzFhMmVYaGZtRnRHU2tRQkNYZFNnUzcreHkwPSIsIkMiOiIwMzFhYWI3MzY3MTJhY2Y5MWU4NzE4YmM5OTlmNWE2MGEwYzNjODQ5YTA1MWE2OTA5MzRkMTc4NWNmZGNkNDcyYTAifV0sIm1pbnRzIjpbeyJ1cmwiOiJodHRwczovL2xlZ2VuZC5sbmJpdHMuY29tL2Nhc2h1L2FwaS92MS80Z3I5WGNtejNYRWtVTndpQmlRR29DIiwiaWRzIjpbIjBOSTNUVUFzMVNmeSJdfV19 https://void.cat/d/U1UnyxsYgj516YbmkgQNkQ.webp Este token Ecash pode ser compartilhado como você quiser. Você pode enviá-lo por e-mail para alguém, enviá-lo em uma mensagem privada, um SMS ou convertê-lo em um código QR e imprimi-lo. Quem tiver este token pode resgatá-lo com o 10 sats.
Você verá que seu saldo caiu para 20 sats: https://void.cat/d/95AVkevmknKNzqRcnJZwQX.webp
Para resgatar um token Ecash sem o link, pressione o botão “Receive ” https://void.cat/d/UjrbAPn8mj5qGZYVQ1Ba2B.webp
cole-o token Ecash no campo
" token: "pressione "RECEIVE" https://void.cat/d/GZLcBgvHfaB3c5N66ygZyV.webp
Com o Link do token Ecash só pressionar no link vai abrir a tela já preencher automáticamente só pressionar " RECEIVE " https://void.cat/d/ARNkKCtchhFt4NCTkfRJRG.webp
Pra Ativa o Nostr na carteira vai na aba settings , pressione o botão ativa o Nostr. https://void.cat/d/MjoDA1dgueWUFABcQFDVRe.webp
Por padrão ficar ativo pra usar o " Use external Key (nos2x , outros) " Mas Nesse caso não vou usar vou desativar e vou ativa " Edit Nostr Keys " https://void.cat/d/BAA6eFkmK5f7BHzLwYLSGF.webp
Ao pressionar esse botão https://void.cat/d/VTNGVsLvwqfy3dWu4hhMSK.webp é gerar um novo par de chaves privadas e pública , assim podemos usar uma nova chave a cada pagamentos. Aumentando a privacidade no pagamentos.
A pois Ativa o Nostr na carteira , você pode enviar Sats / Ecash via Nostr.
Pressione " Send " https://void.cat/d/R2Svye4XPd2VdHfPxT1DzF.webp
Pressione " Send " https://void.cat/d/AwLeBBr2db2wrTHHUHwEPs.webp
Agora pode adicionar npud / hex / nip-05 pra enviar token. https://void.cat/d/VZR6BUXjG7pm3FDogrDvo4.webp
Pressione " SEND OVER NOSTR " pra enviar o token Ecash. https://void.cat/d/MWveqpmii5dqpioa5a3wVt.webp
Pra quem não tem a carteira nutstash , pode entra no seu cliente Nostr no meu caso e snort nostr , Demora algums minutos pra chegar mensagem com o token Ecash.. https://void.cat/d/MVg3fPD7PAzZUskGCCCcps.webp https://void.cat/d/YNtKuCbQYo1wef7pJcjhKy.webp
Ja se a outra pessoa usar carteira nutstash com a chave pública que você mandou chegar mais rápido. Essa bolinha azul no campo " Indox " Indica que você recebeu o pagamento já está pronto pra ser regastado. https://void.cat/d/So6FAp4wiTUeKBBmRBU2Rv.webp
Pressione "Indox " depois pressione a seta. https://void.cat/d/TqYNYDoyy9fUFas9NFxReJ.webp
Pressione " TRUS MINT " pra recebe os Token Ecash. https://void.cat/d/LP6zUTZ3HDPxd6fLvPPNXB.webp
O aplicativo de resgate Cashu, que permite resgatar tokens Ecash via Lightning.
https://redeem.cashu.me/ https://void.cat/d/Mw9kzDHr4A469EjFNoTHyB.webp
Cola o Token no campo " paste in your Cashu Ecash token.. " https://void.cat/d/SkA3MGJaGGxCjNnzeBhPHP.webp
Pressione " REDEEM " pra converter Ecash em Lightning. https://void.cat/d/693C1yfwYz3P3BQB6f7xXN.webp
Você pode editar e manda já pronto pra pessoa só basta a pessoa ou você aberta em " REDEEM " pra converter Ecash em Lightning.
https://redeem.cashu.me/?token=token ecash=&to=Lightning address
Exemplo:
https://redeem.cashu.me/?token=eyJwcm9vZnMiOlt7ImlkIjoiUEVuMVdLalFoN2pGIiwiYW1vdW50IjoyLCJDIjoiMDJhYWE5OWJiMmUwODQyYjJmNzdmNDRlZWEyZjEzMmNkOTNhZjJlNWU0MzI3ZjhjMTE5ODcxZWNiMTNhMTUxYjY0Iiwic2VjcmV0IjoicE5jb3hFRHJRT1ovTXU4d3d2SlpvMnRIaXBSM3pPYkRrSWJUUlB6VXh5bz0ifSx7ImlkIjoiUEVuMVdLalFoN2pGIiwiYW1vdW50IjoxNiwiQyI6IjAzNDM4ZDc1NmZmMjdmYjgyZmQxNWNhNzg3NzgwNTAyZWU4NzdmMzQ5MmYyMWQzMTMwMzc1NTdlNWNmMDJlOWQ0MCIsInNlY3JldCI6Im9DTXQwUTRVT0MvZWhmd2FVOWt5aGFJZUdHdXhiYUNzQTZ2STh2a0w2N1U9In0seyJpZCI6IlBFbjFXS2pRaDdqRiIsImFtb3VudCI6MzIsIkMiOiIwMmIyMmQ4MDEwZWU5MDA2MWYyNWQzODAyY2UyMDE3ZjAwMmVjMDVmMjM5NjIwNGNkYjllMmU2ODllYWY3YTZkYjIiLCJzZWNyZXQiOiI5ejVVMEdzWHZiUS84Rjd4ZFdYUXRxUDlvWGFyVnBRTzRFdUtzb2JSck1vPSJ9XSwibWludHMiOlt7InVybCI6Imh0dHBzOi8vbGVnZW5kLmxuYml0cy5jb20vY2FzaHUvYXBpL3YxL29DcXNTR3I1enphTTZxM1hWZU5ZNXQiLCJpZHMiOlsiUEVMVdLalFoN2pGIl19XX0=&to=alexemidio@ln.tips
Obs: o teclado do celular pode adicionar "=" a mais ou corrigir " &to " com "&tô" assim escrevendo errado, tanto erro no link.
" SWAP " transferência de uma carteira para outra. Pressione " INTER-MINT SWAP" https://void.cat/d/PsCdoLAmYpYCChkgqTAE7p.webp
A carteira que você selecionar em cima é a carteira de saídas e a carteira de baixo e a carteira de entrada. https://void.cat/d/VKY6ts6qttJmCaefrduv4K.webp
Agora digita o valor que quer fazer o SWAP. Após Pressione " CONFIRM AMOUNT" https://void.cat/d/WuuQqeC1mSQUufb75eeMbw.webp
Depois Tem que pressionar " SWAP " não esqueça. https://void.cat/d/Eb2ajSaZfzZkBEWBv8tuk.webp
Pronto antes a primeira Carteira tinha 10 Ecash, e segunda carteira tinha 8 Ecash.
Somando 18 Ecash.
Apois o SWAP Agora as duas tem 9.
Somando 18. https://void.cat/d/8yRtSoFyih2D2KEm66h6in.webp
Fazer o backup da sua carteira cashu ecash. Pressione " BACKUP TOKENS " https://void.cat/d/26vtnDiVP4YpDiQmunatko.webp
Você pode editar o nome do backup E pode alterar o local aonde vai salva o arquivo 📂 do backup. Depois só pressionar " Baixar " https://void.cat/d/PQH94o81U23txdmyx3cHEn.webp
Agora pra recuperar a carteira cashu ecash. Pressione " RESTORE " https://void.cat/d/2vkLS1qUCbJ1XXjSLBou25.webp
Pressione " CONTINUAR " https://void.cat/d/PCbT2UPSLtwcZohwbhD85A.webp
Click no espaço em branco vai abrir pra encontrar o arquivo 📂 Do backup.. https://void.cat/d/P1VC7b46oNe62v4puVZ79b.webp
Selecionar o arquivo 📂 de backup. https://void.cat/d/D6FAGxYRquz2WWwNznSAzT.webp
Pressione " CONTINUE" https://void.cat/d/HicRn5e2feSRicgjy6kuC5.webp
Pressione " CONTINUE" https://void.cat/d/VP6uh8bXHz42PBGrPwGq5e.webp
Backup feito com sucesso. Só aberta " Ok " https://void.cat/d/QsZV1umL9DhoPtEXBMfPtY.webp
O eCash pode ser útil em diversas situações, oferecendo várias vantagens. Uma das principais vantagens do uso de tokens eCash é a privacidade que oferece. Como as transações usando eCash são quase impossíveis de rastrear, isso pode ser útil para quem deseja manter sua atividade financeira privada. O eCash pode ser especialmente útil para Pagamento de serviços em áreas rurais , pode ser difícil acessar serviços financeiros tradicionais, como bancos ou caixas eletrônicos. O uso de tokens eCash pode permitir que as pessoas paguem por serviços como transporte , serviços de saúde ou eletricidade sem a necessidade de viajar para áreas urbanas. No entanto, é importante lembrar que o uso do eCash ainda apresenta riscos e desafios. Como o eCash cashubtc ainda é bem novo , pode haver falhas de segurança ou outras vulnerabilidades que ainda não foram identificadas use com cautela poucos Sats.
Obrigado por ler, e espero que você dedique alguns minutos para experimentar o eCash e ver do que se trata melhor.
Alguma artigos e vídeos a baixo.
https://cashu.space/
https://docs.cashu.space/
https://github.com/cashubtc/
https://youtu.be/UNjVc-WYdgE
https://youtu.be/_XmQSpAhFN4
https://youtu.be/zdtRT7phXBo
https://maxmoney.substack.com/p/ecash-for-better-bitcoin-privacy?utm_source=substack&utm_campaign=post_embed&utm_medium=web
https://cypherpunks.venona.com/date/1996/03/msg01848.html
Encontre-me ou envie um zap para nostr alexemidio@ln.tips alexemidio@alexemidio.github.io
Twitter: alexemidio7
-
 @ 06639a38:655f8f71
2025-04-16 12:11:31
@ 06639a38:655f8f71
2025-04-16 12:11:31Finally there is a release (1.7.0) for Nostr-PHP with a full NIP-19 integration. Here is an example file with some snippets to how it works to encode and decode bech32 encoded entities:
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip19-bech32-decoded-entities.php
- https://github.com/nostrver-se/nostr-php/blob/main/src/Examples/nip19-bech32-encoded-entities.php
Now merge request #68 (and issues #74, #64 are closed) is finally merged which I opened in October 2024.
Next up is:
- Create documentation how to use NIP-19 with the library on https://nostr-php.dev
- Create documentation how to use NIP-04 and NIP-44 with the library on https://nostr-php.dev
- Work out a proof-of-concept with the revolt/event-loop package to create concurrent async requests with websocket connections
-
 @ 8d34bd24:414be32b
2025-04-16 03:48:30
@ 8d34bd24:414be32b
2025-04-16 03:48:30Ever since becoming a Christian, I have whole-heartedly believed the Bible and that God will fulfill what He has promised. On the other hand, for the majority of the time I have been a Christian, I have dreaded reading prophecy. It seemed so hard to understand. Some is couched in figurative language, but I now believe much of it was hard to understand because there were no words for the technology and systems that would come into being and fulfill these predictions.
Now reading End times prophecy, like in Revelation, Daniel, Matthew 24-25, 2 Thessalonians, Zechariah, etc. the prophecies are starting to sound like the evening news instead of some poetic mystery. These predictions are making more and more sense as the technology and world politics begin to align with the prophecies. I have gone from hating when I get to prophecy passages, especially Revelation, in my Bible reading, to spending extra time reading these passages and seeing how they line up and clarify each other. (I really want to start a project linking all of the end-times prophetic passages together to see how they clarify each other and try to see the big picture, but that is a massive project and time is in short supply. The only way I know to do it is in Excel, but that isn’t efficient. If anyone has a suggestion for a better way to link and show relationships, I’d love to hear about it, especially if it is free or very cheap.)
Matthew recounts Jesus telling His disciples about what to expect in the end times. Although Matthew 24 describes more of the details of the events that happen, this passage in Matthew 25 describes the importance of watching expectantly for the signs of the times, so we are ready.
“Then the kingdom of heaven will be comparable to ten virgins, who took their lamps and went out to meet the bridegroom. Five of them were foolish, and five were prudent. For when the foolish took their lamps, they took no oil with them, but the prudent took oil in flasks along with their lamps. Now while the bridegroom was delaying, they all got drowsy and began to sleep. But at midnight there was a shout, ‘Behold, the bridegroom! Come out to meet him.’ Then all those virgins rose and trimmed their lamps. The foolish said to the prudent, ‘Give us some of your oil, for our lamps are going out.’ But the prudent answered, ‘No, there will not be enough for us and you too; go instead to the dealers and buy some for yourselves.’ And while they were going away to make the purchase, the bridegroom came, and those who were ready went in with him to the wedding feast; and the door was shut. Later the other virgins also came, saying, ‘Lord, lord, open up for us.’ But he answered, ‘Truly I say to you, I do not know you.’ Be on the alert then, for you do not know the day nor the hour. (Matthew 25:1-13) {emphasis mine}
Many Christians think studying prophecy is not useful for today, but that is not true. Our time is short and Jesus warned us to be aware and ready. We can’t be ready for something if we know nothing about it.
In this passage it mentions that “while the bridegroom was delaying, they all got drowsy and began to sleep.” How often do we feel the delay and begin to rest or get distracted by other things? Most Christians do not live like Christ’s return is imminent. Although we can’t know the hour or the day, we can know that we are closer to that hour than we have ever been before. Peter warns us not to doubt Christ’s coming or to become focused solely on our earthly lives.
Know this first of all, that in the last days mockers will come with their mocking, following after their own lusts, and saying, “Where is the promise of His coming? For ever since the fathers fell asleep, all continues just as it was from the beginning of creation.” (2 Peter 3:3-4)
Because Jesus has not returned for almost 2,000 years, many act as if He will never come, but that long wait instead suggests the time is nearing because God never breaks His promises.
For when they maintain this, it escapes their notice that by the word of God the heavens existed long ago and the earth was formed out of water and by water, through which the world at that time was destroyed, being flooded with water. But by His word the present heavens and earth are being reserved for fire, kept for the day of judgment and destruction of ungodly men.
But do not let this one fact escape your notice, beloved, that with the Lord one day is like a thousand years, and a thousand years like one day. The Lord is not slow about His promise, as some count slowness, but is patient toward you, not wishing for any to perish but for all to come to repentance. (2 Peter 3:5-9) {emphasis mine}
The long wait is due to God’s unfathomable mercy and patience, but we should also realize that the increase of evil in the world cannot continue forever. How much more can evil increase before mankind destroys itself? God claims judgement for Himself and finds every kind of sin abhorrent. If we are distraught over the sin in the world today, how much more awful is it to a holy, perfect God to see His very own creation destroyed by sin?
Just as the ten virgins became tired waiting, we tend to get caught up in the things of this world instead of focusing on God’s plan for us and the world. We act as if this world is the only thing we will experience instead of preparing for our rapture to heaven. We focus on our job, our homes, and our families (all good things) and miss the most important things — winning souls for heaven.
Just as Jesus gently reprimanded Martha for having the wrong focus:
But Martha was distracted with all her preparations; and she came up to Him and said, “Lord, do You not care that my sister has left me to do all the serving alone? Then tell her to help me.” But the Lord answered and said to her, “Martha, Martha, you are worried and bothered about so many things; but only one thing is necessary, for Mary has chosen the good part, which shall not be taken away from her.” (Luke 10:40-42) {emphasis mine}
In the same way, we get focused with the business of life and miss the most important stuff. It wasn’t bad of Martha to take care of her guests, but sitting with Jesus and learning from Him was more important. In the same way, our jobs, families, and homes are good things and we should do them well, but reading our Bibles, praying, growing closer to Jesus, and sharing the Gospel with those who don’t know Jesus is better.
When we believe that our time on earth is short and Jesus is coming for us soon, we are more likely to focus on the most important things — the eternal things.
This passage in Matthew 16 describes the importance of us knowing, understanding, and looking for the signs of the times.
The Pharisees and Sadducees came up, and testing Jesus, they asked Him to show them a sign from heaven. But He replied to them, “When it is evening, you say, ‘It will be fair weather, for the sky is red.’ And in the morning, ‘There will be a storm today, for the sky is red and threatening.’ Do you know how to discern the appearance of the sky, but cannot discern the signs of the times? An evil and adulterous generation seeks after a sign; and a sign will not be given it, except the sign of Jonah.” And He left them and went away. (Matthew 16:1-4) {emphasis mine}
Christians that believe studying end times prophecy is not important would be rebuked even today by Jesus. We are supposed to study and learn and prepare and watch eagerly for His return.
In Revelation, God says we are blessed if we hear and heed the words of this prophecy.
The Revelation of Jesus Christ, which God gave Him to show to His bond-servants, the things which must soon take place; and He sent and communicated it by His angel to His bond-servant John, who testified to the word of God and to the testimony of Jesus Christ, even to all that he saw. Blessed is he who reads and those who hear the words of the prophecy, and heed the things which are written in it; for the time is near. (Revelation 1:1-3) {emphasis mine}
Do you seek God’s blessing? Then study God’s prophecies, especially as written in Revelation. God is good and He has shown His children what will happen, so they can be prepared. Don’t be like the five foolish virgins who were unprepared. Study the Scriptures. Look for the signs. Be ready for our Savior’s return by inviting as many people as possible to join us.
Trust Jesus.
FYI, I hope to write several more articles on the end times (signs of the times, the rapture, the millennium, the judgement, etc.).
-
 @ a39d19ec:3d88f61e
2025-04-22 12:44:42
@ a39d19ec:3d88f61e
2025-04-22 12:44:42Die Debatte um Migration, Grenzsicherung und Abschiebungen wird in Deutschland meist emotional geführt. Wer fordert, dass illegale Einwanderer abgeschoben werden, sieht sich nicht selten dem Vorwurf des Rassismus ausgesetzt. Doch dieser Vorwurf ist nicht nur sachlich unbegründet, sondern verkehrt die Realität ins Gegenteil: Tatsächlich sind es gerade diejenigen, die hinter jeder Forderung nach Rechtssicherheit eine rassistische Motivation vermuten, die selbst in erster Linie nach Hautfarbe, Herkunft oder Nationalität urteilen.
Das Recht steht über Emotionen
Deutschland ist ein Rechtsstaat. Das bedeutet, dass Regeln nicht nach Bauchgefühl oder politischer Stimmungslage ausgelegt werden können, sondern auf klaren gesetzlichen Grundlagen beruhen müssen. Einer dieser Grundsätze ist in Artikel 16a des Grundgesetzes verankert. Dort heißt es:
„Auf Absatz 1 [Asylrecht] kann sich nicht berufen, wer aus einem Mitgliedstaat der Europäischen Gemeinschaften oder aus einem anderen Drittstaat einreist, in dem die Anwendung des Abkommens über die Rechtsstellung der Flüchtlinge und der Europäischen Menschenrechtskonvention sichergestellt ist.“
Das bedeutet, dass jeder, der über sichere Drittstaaten nach Deutschland einreist, keinen Anspruch auf Asyl hat. Wer dennoch bleibt, hält sich illegal im Land auf und unterliegt den geltenden Regelungen zur Rückführung. Die Forderung nach Abschiebungen ist daher nichts anderes als die Forderung nach der Einhaltung von Recht und Gesetz.
Die Umkehrung des Rassismusbegriffs
Wer einerseits behauptet, dass das deutsche Asyl- und Aufenthaltsrecht strikt durchgesetzt werden soll, und andererseits nicht nach Herkunft oder Hautfarbe unterscheidet, handelt wertneutral. Diejenigen jedoch, die in einer solchen Forderung nach Rechtsstaatlichkeit einen rassistischen Unterton sehen, projizieren ihre eigenen Denkmuster auf andere: Sie unterstellen, dass die Debatte ausschließlich entlang ethnischer, rassistischer oder nationaler Kriterien geführt wird – und genau das ist eine rassistische Denkweise.
Jemand, der illegale Einwanderung kritisiert, tut dies nicht, weil ihn die Herkunft der Menschen interessiert, sondern weil er den Rechtsstaat respektiert. Hingegen erkennt jemand, der hinter dieser Kritik Rassismus wittert, offenbar in erster Linie die „Rasse“ oder Herkunft der betreffenden Personen und reduziert sie darauf.
Finanzielle Belastung statt ideologischer Debatte
Neben der rechtlichen gibt es auch eine ökonomische Komponente. Der deutsche Wohlfahrtsstaat basiert auf einem Solidarprinzip: Die Bürger zahlen in das System ein, um sich gegenseitig in schwierigen Zeiten zu unterstützen. Dieser Wohlstand wurde über Generationen hinweg von denjenigen erarbeitet, die hier seit langem leben. Die Priorität liegt daher darauf, die vorhandenen Mittel zuerst unter denjenigen zu verteilen, die durch Steuern, Sozialabgaben und Arbeit zum Erhalt dieses Systems beitragen – nicht unter denen, die sich durch illegale Einreise und fehlende wirtschaftliche Eigenleistung in das System begeben.
Das ist keine ideologische Frage, sondern eine rein wirtschaftliche Abwägung. Ein Sozialsystem kann nur dann nachhaltig funktionieren, wenn es nicht unbegrenzt belastet wird. Würde Deutschland keine klaren Regeln zur Einwanderung und Abschiebung haben, würde dies unweigerlich zur Überlastung des Sozialstaates führen – mit negativen Konsequenzen für alle.
Sozialpatriotismus
Ein weiterer wichtiger Aspekt ist der Schutz der Arbeitsleistung jener Generationen, die Deutschland nach dem Zweiten Weltkrieg mühsam wieder aufgebaut haben. Während oft betont wird, dass die Deutschen moralisch kein Erbe aus der Zeit vor 1945 beanspruchen dürfen – außer der Verantwortung für den Holocaust –, ist es umso bedeutsamer, das neue Erbe nach 1945 zu respektieren, das auf Fleiß, Disziplin und harter Arbeit beruht. Der Wiederaufbau war eine kollektive Leistung deutscher Menschen, deren Früchte nicht bedenkenlos verteilt werden dürfen, sondern vorrangig denjenigen zugutekommen sollten, die dieses Fundament mitgeschaffen oder es über Generationen mitgetragen haben.
Rechtstaatlichkeit ist nicht verhandelbar
Wer sich für eine konsequente Abschiebepraxis ausspricht, tut dies nicht aus rassistischen Motiven, sondern aus Respekt vor der Rechtsstaatlichkeit und den wirtschaftlichen Grundlagen des Landes. Der Vorwurf des Rassismus in diesem Kontext ist daher nicht nur falsch, sondern entlarvt eine selektive Wahrnehmung nach rassistischen Merkmalen bei denjenigen, die ihn erheben.
-
 @ 266815e0:6cd408a5
2025-04-15 06:58:14
@ 266815e0:6cd408a5
2025-04-15 06:58:14Its been a little over a year since NIP-90 was written and merged into the nips repo and its been a communication mess.
Every DVM implementation expects the inputs in slightly different formats, returns the results in mostly the same format and there are very few DVM actually running.
NIP-90 is overloaded
Why does a request for text translation and creating bitcoin OP_RETURNs share the same input
itag? and why is there anoutputtag on requests when only one of them will return an output?Each DVM request kind is for requesting completely different types of compute with diffrent input and output requirements, but they are all using the same spec that has 4 different types of inputs (
text,url,event,job) and an undefined number ofoutputtypes.Let me show a few random DVM requests and responses I found on
wss://relay.damus.ioto demonstrate what I mean:This is a request to translate an event to English
json { "kind": 5002, "content": "", "tags": [ // NIP-90 says there can be multiple inputs, so how would a DVM handle translatting multiple events at once? [ "i", "<event-id>", "event" ], [ "param", "language", "en" ], // What other type of output would text translations be? image/jpeg? [ "output", "text/plain" ], // Do we really need to define relays? cant the DVM respond on the relays it saw the request on? [ "relays", "wss://relay.unknown.cloud/", "wss://nos.lol/" ] ] }This is a request to generate text using an LLM model
json { "kind": 5050, // Why is the content empty? wouldn't it be better to have the prompt in the content? "content": "", "tags": [ // Why use an indexable tag? are we ever going to lookup prompts? // Also the type "prompt" isn't in NIP-90, this should probably be "text" [ "i", "What is the capital of France?", "prompt" ], [ "p", "c4878054cff877f694f5abecf18c7450f4b6fdf59e3e9cb3e6505a93c4577db2" ], [ "relays", "wss://relay.primal.net" ] ] }This is a request for content recommendation
json { "kind": 5300, "content": "", "tags": [ // Its fine ignoring this param, but what if the client actually needs exactly 200 "results" [ "param", "max_results", "200" ], // The spec never mentions requesting content for other users. // If a DVM didn't understand this and responded to this request it would provide bad data [ "param", "user", "b22b06b051fd5232966a9344a634d956c3dc33a7f5ecdcad9ed11ddc4120a7f2" ], [ "relays", "wss://relay.primal.net", ], [ "p", "ceb7e7d688e8a704794d5662acb6f18c2455df7481833dd6c384b65252455a95" ] ] }This is a request to create a OP_RETURN message on bitcoin
json { "kind": 5901, // Again why is the content empty when we are sending human readable text? "content": "", "tags": [ // and again, using an indexable tag on an input that will never need to be looked up ["i", "09/01/24 SEC Chairman on the brink of second ETF approval", "text"] ] }My point isn't that these event schema's aren't understandable but why are they using the same schema? each use-case is different but are they all required to use the same
itag format as input and could support all 4 types of inputs.Lack of libraries
With all these different types of inputs, params, and outputs its verify difficult if not impossible to build libraries for DVMs
If a simple text translation request can have an
eventortextas inputs, apayment-requiredstatus at any point in the flow, partial results, or responses from 10+ DVMs whats the best way to build a translation library for other nostr clients to use?And how do I build a DVM framework for the server side that can handle multiple inputs of all four types (
url,text,event,job) and clients are sending all the requests in slightly differently.Supporting payments is impossible
The way NIP-90 is written there isn't much details about payments. only a
payment-requiredstatus and a genericamounttagBut the way things are now every DVM is implementing payments differently. some send a bolt11 invoice, some expect the client to NIP-57 zap the request event (or maybe the status event), and some even ask for a subscription. and we haven't even started implementing NIP-61 nut zaps or cashu A few are even formatting the
amountnumber wrong or denominating it in sats and not mili-satsBuilding a client or a library that can understand and handle all of these payment methods is very difficult. for the DVM server side its worse. A DVM server presumably needs to support all 4+ types of payments if they want to get the most sats for their services and support the most clients.
All of this is made even more complicated by the fact that a DVM can ask for payment at any point during the job process. this makes sense for some types of compute, but for others like translations or user recommendation / search it just makes things even more complicated.
For example, If a client wanted to implement a timeline page that showed the notes of all the pubkeys on a recommended list. what would they do when the selected DVM asks for payment at the start of the job? or at the end? or worse, only provides half the pubkeys and asks for payment for the other half. building a UI that could handle even just two of these possibilities is complicated.
NIP-89 is being abused
NIP-89 is "Recommended Application Handlers" and the way its describe in the nips repo is
a way to discover applications that can handle unknown event-kinds
Not "a way to discover everything"
If I wanted to build an application discovery app to show all the apps that your contacts use and let you discover new apps then it would have to filter out ALL the DVM advertisement events. and that's not just for making requests from relays
If the app shows the user their list of "recommended applications" then it either has to understand that everything in the 5xxx kind range is a DVM and to show that is its own category or show a bunch of unknown "favorites" in the list which might be confusing for the user.
In conclusion
My point in writing this article isn't that the DVMs implementations so far don't work, but that they will never work well because the spec is too broad. even with only a few DVMs running we have already lost interoperability.
I don't want to be completely negative though because some things have worked. the "DVM feeds" work, although they are limited to a single page of results. text / event translations also work well and kind
5970Event PoW delegation could be cool. but if we want interoperability, we are going to need to change a few things with NIP-90I don't think we can (or should) abandon NIP-90 entirely but it would be good to break it up into small NIPs or specs. break each "kind" of DVM request out into its own spec with its own definitions for expected inputs, outputs and flow.
Then if we have simple, clean definitions for each kind of compute we want to distribute. we might actually see markets and services being built and used.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 878dff7c:037d18bc
2025-04-09 21:38:34
@ 878dff7c:037d18bc
2025-04-09 21:38:34Coalition Proposes Sovereign Wealth Funds to Address National Debt
Summary:
Opposition Leader Peter Dutton has unveiled a plan to reduce Australia's $1.2 trillion debt by creating two sovereign wealth funds: the Future Generations Fund and the Regional Australia Future Fund. These funds aim to allocate 80% of commodity windfall revenues toward debt reduction and regional development, focusing on infrastructure and economic support outside metropolitan areas.
Sources: The Australian - April 10, 2025
Australian Dollar Falls Below 60 US Cents Amid Tariff Concerns
Summary:
The Australian dollar has dropped to a five-year low, trading below 60 US cents, as markets react to escalating tariff tensions initiated by the U.S. This depreciation reflects investor fears of a potential global economic downturn impacting Australia's economy.
Sources: ABC News - 9 April 2025, Reuters - 7 April 2025
AI Transformation Reshaping Australia's Software Development Landscape
Summary:
Artificial Intelligence (AI) is rapidly transforming Australia's software development industry. Recent research indicates widespread adoption of AI tools and methodologies, leading to increased efficiency and innovation. This trend positions Australian tech companies competitively in the global market and highlights the importance of AI literacy for professionals in the sector. Sources: Tech Business News - April 10, 2025
UK and Australia Collaborate on Next-Generation Weapons Development
Summary:
The United Kingdom and Australia have launched a partnership to develop next-generation sub-systems for low-cost weapons. This collaboration integrates the UK's Modular Weapons Testbed with Australia's SHARKTOOTH program, featuring innovative 'plug-and-launch' modular technology. The initiative aims to accelerate the deployment of advanced, affordable weapons technologies, enhancing both nations' defense capabilities. Sources: The Defense Post - April 7, 2025, ASD News - April 4, 2025
Smoke Advisory Issued for Greater Sydney Due to Hazard Reduction Burns
Summary:
The NSW Rural Fire Service has issued a smoke advisory for the Greater Sydney area, including the Blue Mountains and Southern Highlands, due to planned hazard reduction burns. Residents are advised to stay indoors, close windows and doors, and keep respiratory medications close by. rfs.nsw.gov.au+1rfs.nsw.gov.au+1 ABC
Sources: NSW Rural Fire Service - April 9, 2025
Leaders Clash in First Election Debate
Summary:
In the first leaders' debate of the 2025 federal election campaign, Prime Minister Anthony Albanese and Opposition Leader Peter Dutton clashed on several key issues during the Sky News/Daily Telegraph People's Forum. Albanese accused the Coalition of historically cutting health and education funding, which Dutton vehemently denied. The debate also saw pointed exchanges over spending levels, energy policy, and cost-of-living concerns. Dutton challenged Albanese’s tax cuts and left open the possibility of extending fuel excise relief. The leaders also addressed infrastructure funding, economic management, and health services. The debate occurred with only 25 days until the election and 14 days before early voting begins.
Sources: The Daily Telegraph - 10 April 2025, News.com.au - 10 April 2025
Australia and Philippines to Increase Joint Military Exercises
Summary:
Australia and the Philippines have agreed to double their joint military drills and security engagements in 2025. This decision underscores the strengthening defense ties between the two nations in response to regional security challenges. Sources: Manila Bulletin - April 7, 2025
Victoria's Working with Children Check System Criticized for Allowing Individuals Under Investigation to Retain Clearance
Summary:
Victoria's Working with Children Check system is under scrutiny for permitting individuals under investigation for abuse and assault to retain their clearance. Parents and advocates are calling for urgent reforms, highlighting cases where children were allegedly harmed by individuals who maintained their working with children credentials despite serious allegations. ABC
Sources: ABC News - April 10, 2025
Ecological Revival Following Inland Floods
Summary:
After unprecedented rainfall transformed over a million square kilometers of inland Australia into floodplains, the region is witnessing a remarkable ecological revival. Native wildlife such as fish, long-haired rats, frogs, and birds are thriving, and previously dried-out habitats are being replenished. Experts view the floods as a rare opportunity for broad ecological regeneration, including mega breeding events and species migrations. While challenges remain, the natural rebirth offers hope as long-dormant ecosystems awaken with vibrant life.
Sources: The Times - April 10, 2025, SciTechDaily - April 10, 2025
CyberCX Report Highlights Evolving Cyber Threat Landscape
Summary:
CyberCX's annual Threat Report for 2025 reveals that business email compromise remains the top incident type, with espionage-related incidents taking longer to detect compared to previous years. The report underscores the need for enhanced cybersecurity measures across Australian organizations. Sources: CyberCX - April 9, 2025
Greens-Backed Study Targets Environmental Impact of Pet Dogs
Summary:
A new study, receiving attention from progressive environmental circles including the Greens, has flagged pet dogs as a significant ecological threat. The research claims dogs contribute to pollution, wildlife disturbances, and even climate change due to their carbon footprint. Critics argue this is part of a broader ideological push to regulate personal lifestyle choices, sparking concerns that common household pets may soon be in the environmental policy crosshairs. With the Greens already pushing for sweeping environmental reforms, some Australians fear this could lead to overreach targeting ordinary families and their beloved pets.
Sources: The Guardian - 10 April 2025
High-Intensity Resistance and Impact Training Enhances Bone Density in Postmenopausal Women
Summary:
The LIFTMOR randomized controlled trial investigated the effects of high-intensity resistance and impact training (HiRIT) on bone health in postmenopausal women with low bone mass. Over eight months, participants engaged in twice-weekly, 30-minute HiRIT sessions, performing exercises such as deadlifts, overhead presses, and back squats at over 85% of their one-repetition maximum. The study found significant improvements in lumbar spine bone mineral density (BMD) by 2.9%, femoral neck BMD by 0.3%, cortical thickness, and functional performance measures, including enhanced leg and back strength. Notably, the HiRIT program was well-tolerated, with high compliance and minimal adverse events, suggesting that such training is both safe and effective for improving bone health and physical function in this demographic. Sources: PubMed - October 4, 2017
Anti-Aging Expert Peter Attia Discusses Longevity and Health Optimization
Summary:
In this episode of "The Diary Of A CEO," host Steven Bartlett engages with Dr. Peter Attia, a physician specializing in longevity and health optimization. Dr. Attia delves into the often-overlooked aspects of aging, emphasizing the importance of proactive health measures. He highlights the critical role of maintaining muscle mass and strength, noting that a decline in these areas significantly increases mortality risk. Dr. Attia also explores natural methods to enhance testosterone levels without resorting to testosterone replacement therapy (TRT), advocating for lifestyle interventions such as strength training, adequate sleep, and balanced nutrition. Throughout the conversation, he underscores the necessity of individualized health strategies and regular monitoring to effectively prevent age-related diseases. Sources: Spotify - April 2025
-
 @ 54609048:8e22ba03
2025-04-22 12:25:50
@ 54609048:8e22ba03
2025-04-22 12:25:50One of the greatest threats facing liberty lovers around the world today is the rise of the biomedical security state—the militarization of healthcare. COVID-19 was merely a compliance test, and sadly, most failed it dismally. But pay attention: “pandemic response,” war-gamed at elite gatherings like Davos, is steadily morphing into official health policy through backdoor mechanisms—diabolical agreements like the WHO Pandemic Treaty, which effectively transfers sovereign pandemic authority to Bill Gates via the WHO; the rollout of digital IDs; and the global push for central bank digital currencies (CBDCs).
This biomedical Leviathan requires all three pillars to be firmly in place before it can unleash a never-ending cycle of pandemics. The goal? To normalize draconian measures like those witnessed in 2020, thereby dismantling not only national sovereignty but, more dangerously, individual sovereignty. A digital ID won't merely confirm your identity—it will track your vaccination status, movements, and even your sentiments, all to determine what privileges you're allowed. Meanwhile, the CBDC will act not just as a means of transaction but as an enforcement mechanism—particularly for dissenters. This is why having an alternative like Bitcoin is not just relevant, but essential.
Vaccines are a cornerstone of this architecture—not only as instruments of control but also as tools for "redesigning" humanity. Welcome to the realm of transhumanism. The merger of man and machine through brain-computer interfaces and artificial intelligence is no longer science fiction; it's a stated goal. In this context, vaccines are not merely preventative medicine but potentially covert instruments of eugenics. This could explain the near-religious devotion to these pharmaceutical products—despite their increasingly controversial outcomes and questionable safety record—especially when mandates enter the equation.
The first piece of property any individual owns upon birth is their body. And yet, this sacred ownership is violated at birth when governments mandate certain injections—often administered without informed parental consent. I've often wondered: Why, despite mounting evidence to the contrary, is vaccine efficacy treated as “settled science”? Why is it taboo to question vaccines or hold their manufacturers accountable for harm, even as we’re expected to believe—without scrutiny—that they are “safe and effective”? We’re told our refusal to comply endangers everyone else who took a product supposedly designed to protect them. Strange, isn’t it? If it’s so effective, why must everyone take it simultaneously?
If you're wondering where this seemingly off-the-cuff rant is headed, here's the point: when the state mandates vaccines, it violates your property rights over your own body. It’s a direct claim of ownership over you, dressed up in moral language like “we're all in this together.” You're guilt-tripped into compliance under the pretense of saving “grandma.” But the truth is, if your rights can be suspended for the collective, they were never yours to begin with.
The biomedical security state will manufacture a permanent state of emergency under the guise of “pandemic preparedness.” You’ll be expected—required, even—to inject yourself with the latest mRNA-based bioweapon, all in the name of public health. Some will die. Others will become incapacitated—zombies or vegetables. The altar of compliance will be merciless towards those that bow before it.
Public health agencies like the CDC, WHO, and NIH are on track to become as powerful as central banks. In fact, they may soon act as arms of monetary policy enforcement. Don’t believe it? Look into what was happening in the repo markets in September 2019—just months before the global shutdown. While you're at it, investigate how many elderly pensioners quietly dropped dead like flies between 2021 and 2023, either from the virus or the vaccine. I’ll let the numbers speak for themselves.
These agencies are becoming the new face of the war machine. Vaccines will be marketed as shields against biological threats—“benevolent” weapons to protect us from invisible enemies. And if history is any guide, the next “9/11-style” event will be biological in nature.
The lunatics running the asylum will seize any such crisis to strip away more of your freedoms while simultaneously redesigning the global economy—consolidating even more power in their hands. For a blueprint of this ambition, look no further than Klaus Schwab’s COVID-19: The Great Reset.
The only antidote is a decentralized parallel system of medicine—one that stands entirely outside the Big Pharma cartel. This will require not only a network of courageous healthcare providers but also a new generation of researchers willing to ask uncomfortable questions and challenge sacred cows in the pursuit of truth. Add independent scientific journals to the mix, and we can finally dismantle the machinery that suppresses unprofitable—but potentially life-saving—treatments.
In my view, none of this is viable at scale without decentralized money. Enter Bitcoin. It’s not a panacea, but it’s a crucial tool for realigning incentives. Bitcoin renders CBDCs dead on arrival and undermines the foundation of any future social credit system—where vaccine compliance will be its crown jewel.
The biomedical state is not coming—it’s already here, creeping into every corner of our lives. It will be the scepter of a new technocratic tyranny. So beware the white coats who worship the state. They are not here to heal—they are here to rule.
A more polished series of articles on this topic is forthcoming. Stay tuned.
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ d34e832d:383f78d0
2025-04-22 08:40:25
@ d34e832d:383f78d0
2025-04-22 08:40:25
In the twilight of forgotten eras, where the whispers of the past wove through the air like a ghostly melody, two shadowy figures emerged beneath an ageless sky. She was Eve, not the emblem of gardens, but the Mitochondrial Eve—her essence pulsing within the very mitochondria that spark life in each human heartbeat. He stood before her as Adam, not forged from soil, but the Y-Chromosome Adam—guardian of a singular lineage, his heritage dancing through the veins of sons alone.
Their encounter was not one of flesh and blood, but a meeting of symbols, sparked by the insatiable curiosity of humanity, prowling through the labyrinth of DNA, seeking to uncover the tales of their primordial roots.
In the ethereal glimmer of a timeless pool, two figures stood, their outlines rippling like whispered secrets. They were neither lovers nor allies, nor of the same age, yet their names danced together in every headline and wisdom-filled book.
Today, however, was different—they had gathered at the brink of the infinite to unravel the threads of their intertwined destinies.
As the twilight draped its ethereal cloak over the meadow, Eve let her fingers dance through the glimmering starlight, weaving dreams from its luminous threads.
“You know,” she mused, her voice a whisper carried by the evening breeze, “they often ponder why fate kept us apart. Why our paths never crossed beneath the same sun.”Adam’s lips curled into a wry smile, his eyes reflecting the cosmos above.
“Perhaps they seek a narrative that is neat and orderly, a story with perfect symmetry,” he replied, the gentle rustle of leaves echoing his words.Eve shook her head softly, her gaze fixed on the swirling constellations.
“Ah, but nature, dear Adam,” she countered with a glimmer of mischief, “is a master of chaos. It delights in the untamed, the beautiful mess of existence.”In the grand tapestry of time, two figures emerged from the mists of ancient Africa:
Mitochondrial Eve, a woman of vibrant spirit, who roamed the earth around 150,000 to 200,000 years ago, and
Y-Chromosome Adam, a man of strength and wisdom, appearing some 60,000 to 100,000 years later.Though separated by a chasm of tens of thousands of years, they were not the sole beings of their era, yet in the intricate web of life, they were the most recent ancestors, bearers of unbroken trails of maternal and paternal lines, from which all humanity flows.
Their stories intertwine, echoing through generations, whispers of a time long past.
In a hushed tone, Eve shared the tale of her lineage, weaving a rich tapestry of time.
“Behold my daughters,” she said, her eyes gleaming with pride. “From them sprang another generation, and those daughters too have borne daughters.This precious thread of life, my mitochondrial DNA, weaves through the tapestry, handed down solely by women.
With each passing age, while many lines faded into shadows—some in mere moments, others enduring for centuries—mine flowed on, a river of continuity and strength.
My legacy, a steadfast whisper across generations, defied the silence of so many others.”In a dimly lit room, Adam pondered the weight of generations past.
“And what of mine?” he inquired, his voice tinged with a mix of curiosity and melancholy.He shook his head slowly, as if unraveling a forgotten tale.
“The Y-chromosome, it weaves a delicate thread through the tapestry of life.
Passed from fathers to sons, a fleeting whisper of legacy, vanishing if a man begets no heirs.Like branches of a grand oak, countless lines have been severed by the cruel hands of war, the relentless march of disease, and the silent grasp of chance.
Mine is not the sole survivor in this timeless struggle, but it is the one that defied extinction—standing resilient against the bottleneck of time, thriving into the present day, a testament to tenacity and fate.”Their inheritance patterns are straightforward but ruthless.
Mitochondrial DNA (mtDNA) is stable and abundant, making it a powerful marker for tracing maternal lineage.
It mutates slowly, preserving a clear path backward.In contrast, the Y-chromosome, despite its utility in tracing paternal lines, is subject to greater volatility: smaller effective population sizes, male-specific extinction events, and the disproportionate reproductive success of a few males—all contribute to a narrower, more chaotic record.
In a dimly lit chamber nestled among ancient trees, Eve’s voice resonated with the wisdom of ages.
“The numbers are not our destiny,” she declared, her finger tracing a pattern in the soil.
“They are mere echoes of survival, tales of those who dared to pass their legacy—a lineage of children begetting children, weaving a tapestry of existence.”Adam stood by, thoughtful as a storm brewing on a distant horizon.
“Indeed, lineages dissolve like whispers in the wind,” he mused, his gaze fixed on the moonlight filtering through the leaves.
“Some genetic threads endure not from superiority, but sheer fortune. Bottlenecks of fate, the whims of founders, the swirling dance of genetic drift—these unseen forces hold the key to who emerges amidst the chaos of time.”Together, they pondered the intricate dance of life, where luck and survival intertwined, crafting the very fabric of their world.
Eve paused, her voice a whisper woven with time.
“And so it is,” she mused, “the humans trace their lineage back to me, painting me as the primordial bloom of existence.Yet, shadows linger—my cousins, neighbors, even rivals shared this space, vibrant as I, yet their stories faded like whispers in the wind.
They bore no daughters to carry forth their tales, only their echoes lingered, lost in the tapestry of forgotten history…”
In the shadow of an ancient, pulsing tree that mirrored their very essence, Adam mused aloud,
“I came along far down the line, but not right at the start.
I am but one among countless men, and in the end, only my Y-line remained, a solitary thread in the tapestry of time.
Your lineage, however, stretches across continents, vibrant and thriving.”They stood quietly, lost in the vast glow of humanity’s fractal branches, each flicker representing a birth, a connection, a glimmer of possibility.
“Isn’t it amusing?” Adam chuckled, breaking the reverie.
“They pair us as if we were a couple, forever intertwined.”Eve’s laughter echoed like sweet music.
“Merely symbols, nothing deeper. We are called ancestors, yet we are merely the fortunate survivors of an exquisite genetic lottery.”Adam continued,
“And yet, the very essence of your spark resides in every human’s mitochondria, while half of them carry my signature in their Y chromosome.”Eve’s voice was soft as she spoke, weaving a tapestry of understanding.
“Ah, but dear friend, ancestry is far more than mere lineage.
It’s like tracing the delicate threads of a grand tapestry, where some strands are visible, yet countless others lie hidden in the shadows of time.Each soul walking upon this earth is a descendant of a multitude of individuals from ages long past.
Their names may fade like whispers in the wind, and their unique genes become mere echoes of history.
Yet, amidst this beautiful chaos, the patterns of our heritage forever linger, binding us in an unseen embrace of shared existence.”As Adam stood beneath the shimmering canopy of stars, he pondered aloud,
“Maybe the tale isn’t solely ours. It’s about the delicate yet unwavering dance of life itself.”Eve, her eyes reflecting the celestial lights, agreed with a subtle nod.
“Indeed, for no single thread can unveil the entirety of the narrative.
One must gaze upon the grand tapestry woven through time.”They dimmed away, not with finality, but like starlight traversing the vastness of the cosmos—whispers that remind us history bends and weaves, a spider’s web of fate, woven with threads of fortune, affection, and heartache, where beams of hope dance through the dark.
Within each of us, they linger still, a harmonious symphony resonating with the voices of billions, echoing through time.
-
 @ 7d33ba57:1b82db35
2025-04-22 08:35:57
@ 7d33ba57:1b82db35
2025-04-22 08:35:57Nestled in Lower Saxony’s East Frisia region, Leer is a charming canal town known for its historic tea culture, maritime heritage, and postcard-worthy Altstadt (Old Town). With colorful gabled houses, cobbled streets, and a relaxed pace, Leer offers a taste of northern Germany’s quiet beauty—without the crowds.
🏘️ Things to See & Do in Leer
🚶♂️ Altstadt (Old Town)
- Stroll through narrow lanes lined with 17th and 18th-century houses
- Highlights include Waageplatz, the Reformed Church, and Evenburg Castle
- Perfect for a slow wander, especially during golden hour
🛶 Canal Walks & Harbor
- Take a peaceful walk along the Leda and Ems rivers
- Watch boats pass through the small port and historic trading canals
- In summer, you can even book a scenic canal cruise
🍵 East Frisian Tea Culture
- Leer is considered the tea capital of Germany
- Visit the Bünting Teemuseum to learn about the centuries-old tea tradition
- Don’t miss a tea session with rock sugar and cream—served the traditional East Frisian way
🌳 Nature Nearby
- Cycle or walk through the flat green landscapes of East Frisia
- Great routes along rivers and meadows, with plenty of windmills and grazing sheep
- A short drive takes you to the Wadden Sea, a UNESCO site and tidal wonder
🍽️ Local Eats
- Sample Matjes (pickled herring), smoked fish, and hearty stews
- East Frisian cakes pair beautifully with black tea
- Cozy inns and riverside cafés make for a warm, welcoming meal
🚆 Getting There
- Easily accessible by train from Bremen or Emden
- Compact and walkable—no car needed in the town center
Leer is a peaceful, picturesque retreat where canals, culture, and comfort flow together. Whether you're cycling through the countryside or sipping tea by the harbor, it’s a place to unwind and soak up the slow life.
-
 @ 70c48e4b:00ce3ccb
2025-04-22 08:35:52
@ 70c48e4b:00ce3ccb
2025-04-22 08:35:52Hello reader,
I can say from personal experience that crowdfunding has truly changed my life. I found people who believed in my dream of using Bitcoin as money. Every single one of my videos was made possible through crowdfunding. And I’m not alone. I know several Bitcoiners who have raised funds this way, from Africa to Korea to Haiti.
https://images.forbesindia.com/media/images/2022/Jul/img_190501_runwithbitcoin_bg.jpg
Crowdfunding is deeply rooted in the traditional financial world. From raising money for life-saving surgeries to helping someone open a local coffee shop, platforms like GoFundMe, Kickstarter, and Indiegogo have become essential tools for many. But behind all the heartwarming stories and viral campaigns, there’s a side of crowdfunding that doesn’t get talked about enough. Traditional platforms are far from perfect.
They are centralized, which means there’s always someone in control. These platforms can freeze campaigns, delay payouts, or take a significant cut of the money. And often, the people who need funding the most, those without access to strong banking systems or large social media followings are the ones who get left out.
Here are some of the problems I’ve noticed with these platforms:
Problem 1: Inequality in Who Gets Funded
A recent article in The Guardian pointed out something that’s hard to ignore. Crowdfunding often benefits people who already have influence. After the Los Angeles wildfires in January 2025, celebrities like Mandy Moore were able to raise funds quickly. At the same time, everyday people who lost their homes struggled to get noticed.
https://i.guim.co.uk/img/media/f8398505e58ec3c04685aab06e94048e5d7b6a0c/0_127_4800_2880/master/4800.jpg?width=1300&dpr=1&s=none&crop=none
Angor (https://angor.io/) changes that by removing the need for a central platform to choose which projects get featured or promoted. Anyone can share their project. People can find them on Angor Hub (https://hub.angor.io/), which is a public directory built on the Nostr protocol. Instead of relying on popularity, projects are highlighted based on transparency and engagement.
Problem 2: Platform Dependence and Middlemen
Here’s something people don’t often realize. When you raise funds online, the platform usually has control. It holds the money, decides when to release it, and can freeze everything without warning. This happened during the trucker protests in Canada in 2022. Tens of millions of dollars were raised, but platforms like GoFundMe and GiveSendGo froze the donations. The funds never reached the people they were meant for. Supporters were left confused, and the recipients had no way to access what had been raised for them.
https://upload.wikimedia.org/wikipedia/commons/thumb/2/2d/Convoi_de_la_libert%C3%A9_%C3%A0_Ottawa_01.jpg/800px-Convoi_de_la_libert%C3%A9_%C3%A0_Ottawa_01.jpg
Angor avoids all of this. It does not hold the funds, does not require approval processes, and only the project creator has control over the campaign. Contributions go directly from supporters to the people building the project, using Bitcoin. It is a peer-to-peer system that works without any gatekeepers. Angor never touches the money. It simply provides the tools people need to raise funds and build, while staying fully in control.
Problem 3: Global Access
Another major issue is that these platforms often exclude people based on where they live. If you're in a region with limited banking access or outside the supported list of countries, you’re likely shut out. In 2023, a woman named Samar in Gaza tried to raise funds for food and medical supplies during a crisis. A friend abroad set up a campaign to help, but the platform froze it due to "location-related concerns." The funds were locked, and the support never arrived in time.
https://images.gofundme.com/EMFtPWSLs3P9SewkzwZ4FtaBQSA=/720x405/https://d2g8igdw686xgo.cloudfront.net/78478731_1709065237698709_r.jpeg
Angor removes these barriers by using Bitcoin, which works globally without needing banks or approvals. Anyone, anywhere, can raise and receive support directly.
Problem 4: Lack of Transparency
Post-funding transparency is often lacking. Backers rarely get consistent updates, making it difficult to track a project's progress or hold anyone accountable.
In 2015, the Zano drone project on Kickstarter raised over £2.3 million from more than 12,000 backers. It promised a compact, smart drone for aerial photography. But as time went on, updates became rare and vague. Backers had little insight into the project’s struggles, and eventually, it was canceled. The company shut down, and most backers never received their product or a refund.
https://ichef.bbci.co.uk/ace/standard/976/cpsprodpb/2A0A/production/_86626701_ff861eeb-ce94-43b7-9a43-b30b5adbd7ab.jpg
Angor takes a different approach. Project updates are shared through Nostr, a decentralized and tamper-proof communication protocol. This allows backers to follow progress in real time, with no corporate filters and no blackout periods. Everyone stays in the loop, from start to finish.
Problem 5: Fraud and Accountability
Scams are a growing problem in the crowdfunding world. People can launch fake campaigns, collect donations, and vanish — leaving supporters with empty promises and no way to recover their money. One well-known example was the "Homeless Vet GoFundMe scam" in the U.S.
https://a57.foxnews.com/static.foxnews.com/foxnews.com/content/uploads/2018/09/720/405/1536549443584.jpg
A couple and a homeless man raised over $400,000 by telling a heartwarming story that later turned out to be completely fake. The money was spent on luxury items, and it took a legal investigation to uncover the truth. By the time it was resolved, most of the funds were gone.
This kind of fraud is hard to stop on traditional platforms, because once the funds are transferred, there’s no built-in structure to verify how they’re used.
On Angor, projects are funded in stages, with each step tied to a specific milestone. Bitcoin is held in a shared wallet that only unlocks funds when both the backer and the creator agree that the milestone is complete. If something feels off, backers can choose to stop and recover unspent funds.
This structure discourages scammers from even trying. It adds friction for bad actors, while still giving honest creators the freedom to build trust, deliver value, and raise support transparently. It can’t get any better than this
So, does Angor matter?
For me, it really does. I’m genuinely excited to have my project listed on Angorhub. In a world shaped by AI, open source and transparency light the way forward. Let the work shine on its own.
Have you tried Angor yet? Thanks for tuning in. Catch you next week. Ciao!
Guest blog: Paco nostr:npub1v67clmf4jrezn8hsz28434nc0y5fu65e5esws04djnl2kasxl5tskjmjjk
References:
• The Guardian, 2025: Crowdfunding after LA fires and inequality - https://www.theguardian.com/us-news/2025/jan/17/la-fires-gofundme-mandy-moore • https://www.theguardian.com/us-news/2018/nov/15/johnny-bobbitt-gofundme-scam-arrest-viral-gas-story-couple-charged • FundsforNGOs: The Success Story of an NGO That Scaled with Limited Resourceshttps://www2.fundsforngos.org/articles/the-success-story-of-an-ngo-that-scaled-with-limited-resources/ • https://www.freightwaves.com/news/gofundme-freezes-37m-until-organizers-of-canada-trucker-convoy-detail-spending-plan
-
 @ da0b9bc3:4e30a4a9
2025-04-04 06:24:48
@ da0b9bc3:4e30a4a9
2025-04-04 06:24:48Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/934111
-
 @ 0b118e40:4edc09cb
2025-04-15 03:50:32
@ 0b118e40:4edc09cb
2025-04-15 03:50:32TL;DR : No.
(This is not a feasibility analysis, but a reflection on philosophical alignment with Bitcoin’s vision).
The moment stablecoins or national currencies gain traction in Bitcoin LN, you can forget about Bitcoin’s position as a purely decentralized medium of exchange. Bitcoin’s position will be undermined.
A Bitcoin-native global economy, where people and businesses transact directly in Bitcoin, is what aligns with its original purpose. This is what we should aim for. This is all we should aim for.
I used to believe stablecoins might help with on/off ramps. But the truth is, if Bitcoin is to function as a true currency, broader global adoption that bypasses traditional financial systems will make those ramps irrelevant.
Eventually, two camps will emerge. One will try to preserve Bitcoin’s purity as a currency. The other will push for everything else in the name of Bitcoin: store-of-value narratives, ETFs, stablecoin collaborations, tokens, pump and dumps, NFTs, and centralized workarounds.
Currency domination, especially by the USD, has long contributed to poverty in the Global South. It deepens inequality and worsens debt burdens. During the Tequila Crisis and the Asian Financial Crisis, countries like Mexico and regions like Southeast Asia suffered massive currency devaluations and defaults because of their dependence on the USD. Every time the US raises interest rates, developing nations experience capital flight, currency drops, and economic hardship. This is not ancient history. It has been happening in the last two years and continues to widen the poverty gap. And as always, it is the poor who suffer the most.
What does this have to do with stablecoins? Stablecoin is your fiat 2.0.
USDT is just currency domination through blockchain. It is pegged to the USD, and if it rides Bitcoin’s Lightning rails, it risks keeping users transacting in USD rather than in Bitcoin itself. That not only undermines Bitcoin’s core purpose, it risks making Bitcoin appear like it is taking sides in the fragile and invisible global currency war.
To counter, people will say “Let all stablecoins come. Peg them to any currency.” But what’s the point of Bitcoin then? To become the new logistics layer for fiat 2.0?
That is not progress. That is regress. It is inviting the very systems Bitcoin was built to disrupt back into the ecosystem.
I believe when you use stablecoins this way, you are not Trojan-horsing Bitcoin into the mainstream. You are letting fiat Trojan-horse its way into Bitcoin. And if you let them in, they will win.
Adding stablecoin into Bitcoin LN is counterproductive to Bitcoin's decentralized ethos.
Bitcoin’s true potential is its ability to provide an alternative to centralized, government-controlled currencies and financial systems. We should stick to the original game plan.
Side note: If you really want to Trojan-horse Bitcoin adoption…
In my country, we have so many mixed races and cross-cultural traditions. During Chinese New Year, if you are married, you give everyone who is not married an “ang pow,” which is money in a red packet. Because we are so deeply integrated, people give money at almost every celebration: Christmas, Eid, Diwali, birthdays, graduations, even funerals.
I recently met up with a friend who just had a baby, and I was more than happy to be the first to give her daughter some Bitcoin. Her first sats. It would not hurt to start giving Bitcoin as gifts. And if someone gets offended that it is not part of their tradition, just get a Bitkey and wrap it up. It is so pretty.
Find more fun and creative ways to spread Bitcoin adoption.
But for goodness’ sake, stop justifying everything else in the name of Bitcoin adoption.
To get a better idea of Fiat 2.0, I mind-mapped Bitcoin on macroeconomy on my scratchpad.

If you take a closer look, it might help you answer a few key questions:
-
Do you want more or less government control over money?
-
Are you a fan of central banks? Then you probably prefer stablecoins.
-
-
 @ c21b1a6c:0cd4d170
2025-04-14 14:41:20
@ c21b1a6c:0cd4d170
2025-04-14 14:41:20🧾 Progress Report Two
Hey everyone! I’m back with another progress report for Formstr, a part of the now completed grant from nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f . This update covers everything we’ve built since the last milestone — including polish, performance, power features, and plenty of bug-squashing.
🏗️ What’s New Since Last Time?
This quarter was less about foundational rewrites and more about production hardening and real-world feedback. With users now onboard, our focus shifted to polishing UX, fixing issues, and adding new features that made Formstr easier and more powerful to use.
✨ New Features & UX Improvements
- Edit Existing Forms
- Form Templates
- Drag & Drop Enhancements (especially for mobile)
- New Public Forms UX (card-style layout)
- FAQ & Support Sections
- Relay Modal for Publishing
- Skeleton Loaders and subtle UI Polish
🐛 Major Bug Fixes
- Fixed broken CSV exports when responses were empty
- Cleaned up mobile rendering issues for public forms
- Resolved blank.ts export issues and global form bugs
- Fixed invalid
npubstrings in the admin flow - Patched response handling for private forms
- Lots of small fixes for titles, drafts, embedded form URLs, etc.
🔐 Access Control & Privacy
- Made forms private by default
- Fixed multiple issues around form visibility, access control UIs, and anonymous submissions
- Improved detection of pubkey issues in shared forms
🚧 Some Notable In-Progress Features
The following features are actively being developed, and many are nearing completion:
-
Conditional Questions:
This one’s been tough to crack, but we’re close!
Work in progress bykeralissand myself:
👉 PR #252 -
Downloadable Forms:
Fully-contained downloadable HTML versions of forms.
Being led bycasyazmonwith initial code by Basanta Goswami
👉 PR #274 -
OLLAMA Integration (Self-Hosted LLMs):
Users will be able to create forms using locally hosted LLMs.
PR byashu01304
👉 PR #247 -
Sections in Forms:
Work just started on adding section support!
Small PoC PR bykeraliss:
👉 PR #217
🙌 Huge Thanks to New Contributors
We've had amazing contributors this cycle. Big thanks to:
- Aashutosh Gandhi (ashu01304) – drag-and-drop enhancements, OLLAMA integration
- Amaresh Prasad (devAmaresh) – fixed npub and access bugs
- Biresh Biswas (Billa05) – skeleton loaders
- Shashank Shekhar Singh (Shashankss1205) – bugfixes, co-authored image patches
- Akap Azmon Deh-nji (casyazmon) – CSV fixes, downloadable forms
- Manas Ranjan Dash (mdash3735) – bug fixes
- Basanta Goswami – initial groundwork for downloadable forms
- keraliss – ongoing work on conditional questions and sections
We also registered for the Summer of Bitcoin program and have been receiving contributions from some incredibly bright new applicants.
🔍 What’s Still Coming?
From the wishlist I committed to during the grant, here’s what’s still in the oven:
-[x] Upgrade to nip-44 - [x] Access Controlled Forms: A Form will be able to have multiple admins and Editors. - [x] Private Forms and Fixed Participants: Enncrypt a form and only allow certain npubs to fill it. - [x] Edit Past Forms: Being able to edit an existing form. - [x] Edit Past Forms
- [ ] Conditional Rendering (in progress)
- [ ] Sections (just started)
- [ ] Integrations - OLLAMA / AI-based Form Generation (near complete)
- [ ] Paid Surveys
- [ ] NIP-42 Private Relay support
❌ What’s De-Prioritized?
- Nothing is de-prioritized now especially since Ollama Integration got re-prioritized (thanks to Summer Of Bitcoin). We are a little delayed on Private Relays support but it's now becoming a priority and in active development. Zap Surveys will be coming soon too.
💸 How Funds Were Used
- Paid individual contributors for their work.
- Living expenses to allow full-time focus on development
🧠 Closing Thoughts
Things feel like they’re coming together now. We’re out of "beta hell", starting to see real adoption, and most importantly, gathering feedback from real users. That’s helping us make smarter choices and move fast without breaking too much.
Stay tuned for the next big drop — and in the meantime, try creating a form at formstr.app, and let me know what you think!
-
 @ 846ebf79:fe4e39a4
2025-04-14 12:35:54
@ 846ebf79:fe4e39a4
2025-04-14 12:35:54The next iteration is coming
We're busy racing to the finish line, for the #Alexandria Gutenberg beta. Then we can get the bug hunt done, release v0.1.0, and immediately start producing the first iteration of the Euler (v0.2.0) edition.
While we continue to work on fixing the performance issues and smooth rendering on the Reading View, we've gone ahead and added some new features and apps, which will be rolled-out soon.
The biggest projects this iteration have been:
- the HTTP API for the #Realy relay from nostr:npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku,
- implementation of a publication tree structure by nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn,
- and the Great DevOps Migration of 2025 from the ever-industrious Mr. nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7.
All are backend-y projects and have caused a major shift in process and product, on the development team's side, even if they're still largely invisible to users.
Another important, but invisible-to-you change is that nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735 has implemented the core bech32 functionality (and the associated tests) in C/C++, for the #Aedile NDK.
On the frontend:
nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 is currently working on the blog-specific Reading View, which allows for multi-npub or topical blogging, by using the 30040 index as a "folder", joining the various 30041 articles into different blogs. She has also started experimenting with categorization and columns for the landing page.


nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z revamped the product information pages, so that there is now a Contact page (including the ability to submit a Nostr issue) and an About page (with more product information, the build version displayed, and a live #GitCitadel feed).



We have also allowed for discrete headings (headers that aren't section headings, akin to the headers in Markdown). Discrete headings are formatted, but not added to the ToC and do not result in a section split by Asciidoc processors.
We have added OpenGraph metadata, so that hyperlinks to Alexandria publications, and other events, display prettily in other apps. And we fixed some bugs.
The Visualisation view has been updated and bug-fixed, to make the cards human-readable and closeable, and to add hyperlinks to the events to the card-titles.

We have added support for the display of individual wiki pages and the integration of them into 30040 publications. (This is an important feature for scientists and other nonfiction writers.)

We prettified the event json modal, so that it's easier to read and copy-paste out of.

The index card details have been expanded and the menus on the landing page have been revamped and expanded. Design and style has been improved, overall.

Project management is very busy
Our scientific adviser nostr:npub1m3xdppkd0njmrqe2ma8a6ys39zvgp5k8u22mev8xsnqp4nh80srqhqa5sf is working on the Euler plans for integrating features important for medical researchers and other scientists, which have been put on the fast track.
Next up are:
- a return of the Table of Contents
- kind 1111 comments, highlights, likes
- a prototype social feed for wss://theforest.nostr1.com, including long-form articles and Markdown rendering
- compose and edit of publications
- a search field
- the expansion of the relay set with the new relays from nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj, including some cool premium features
- full wiki functionality and disambiguation pages for replaceable events with overlapping d-tags
- a web app for mass-uploading and auto-converting PDFs to 30040/41 Asciidoc events, that will run on Realy, and be a service free for our premium relay subscribers
- ability to subscribe to the forest with a premium status
- the book upload CLI has been renamed and reworked into the Sybil Test Utility and that will get a major release, covering all the events and functionality needed to test Euler
- the #GitRepublic public git server project
- ....and much more.
Thank you for reading and may your morning be good.
-
 @ 592295cf:413a0db9
2025-04-13 15:52:02
@ 592295cf:413a0db9
2025-04-13 15:52:02Nostur is capable of login with bunker
Photo, note by Fabian
nostr:nevent1qvzqqqqqqypzqkfzjh8jkzd8l9247sadku6vhm52snhgjtknlyeku6sfkeqn5rdeqyf8wumn8ghj7mn0wd68ytnvw5hxkef0qyg8wumn8ghj7mn0wd68ytnddakj7qpqxfktwlm2qdkpxy556e4yg4l8p6v8930nfyzg7p3vsknk7krutz0s8znjtq
When you decide to share an app you have to know a lot about that app. For example the nstart feature that you can share your friends, has a "smart pack" and the app can onboard, at least following the link --> Apps-integration
So let's try to read and bring a bit to the summary of the thing. Only the one about the profiles, which you don't know exactly how it will end, you have to try it before sending to someone. the second point is that it says that there is no "support encryption, so it cannot be used for DMs apps".
there was an update of nstart, now it shows you
the names of the bunkers, maybe now it's too much, decide if it does 3/2 4/2 or just automatic.
So they talked about frost in the hodlbod podcast. I didn't understand much except that they said to test frost and report the feedback. Tomorrow I'll try to download igloo and frost+nos2ex
So I have to wait for let's say version 0_1_0 of igloo now it is (0_0_4) and
maybe there will be the version of the extension ready.
Sebastix also found it difficult but I think he was trying to install the server, which didn't even occur to me. Anyway I leave you the note if you want to go deeper...
nostr:nevent1qvzqqqqqqypzqpnrnguxe8qszsshvgkvhn6qjzxy7xsvx03rlrtddr62haj4lrm3qytkummnw3ez66tyvgaz7tmrv93ksefdwfjkccteqqs2wzkkx220e24revkpxmdzkqj73rnz0reeenjwgy53g36hlkdgurgrs5e62
Let's see if I can download the video. ok Downloaded. Video .mov
If you don't want to watch I'll leave a little description
1 Download and install igloo, from the frost page. 2 Create a new key set, you can generate or copy an existing key. 3. Choose the options for the key and now they become multiple keys 4. Created a group of credentials. 5. Save the two credentials with a password and bring the third into the browser extension that it creates from the repository, it says that there will be a bootable extension for chrome. 6. Copy the third key and the group package key into the application node. 7. Once you have entered these keys you can finish the operation (and you have backed up the other two) in igloo. 8. When it goes forward it finds itself with two keys, both encrypted with passwords. 9. Since it is a three of two, it just needs to activate a key in igloo and it starts communicating "startsigner". 10. Opens a nostr client and connects with frost2sx and writes a note 11. Shows the log, and says that if you enter two keys it can generate a third, invalidating the old one (I assume)
-
 @ 8d34bd24:414be32b
2025-04-13 04:29:33
@ 8d34bd24:414be32b
2025-04-13 04:29:33I was listening to a sermon at my church this weekend on Luke 9. It made me think of these words, “I do believe; help my unbelief.” I’ll start with context on this statement and then show how it applies to the passage we were studying.
They brought the boy to Him. When he saw Him, immediately the spirit threw him into a convulsion, and falling to the ground, he began rolling around and foaming at the mouth. And He asked his father, “How long has this been happening to him?” And he said, “From childhood. It has often thrown him both into the fire and into the water to destroy him. But if You can do anything, take pity on us and help us!” And Jesus said to him, “ ‘If You can?’ All things are possible to him who believes.” Immediately the boy’s father cried out and said, “I do believe; help my unbelief.” (Mark 9:20-24) {emphasis mine}
In this story, a desperate father brought his son to Jesus’s disciples for healing, when they failed, he brought the boy to Jesus. He begged for help, but qualified with “But if You can … .” How often do we explicitly or implicitly say this to God in our prayers.
Just as this father believed in Jesus enough to bring his dear child to Jesus, but still had doubts, we tend to be the same. As Christians, we believe that Jesus loved us enough to die on the cross, but do we believe He is always with us? Do we believe He will never leave nor forsake us? Do we believe that all things work together for good for those who love God and are called according to His purpose? I think we can all say, “I do believe; help my unbelief.”
We all have highs where we are excited about Jesus and believe He is working in us and through us. We also have lows where we feel distant and wondering if He sees or cares. We need to have that belief of the highs when we are going through the lows.
In Luke 9, Jesus sent out His 12 disciples to share the gospel and heal the sick and possessed. They came back on a high, amazed at the great miracles that Jesus had worked through them.
And He called the twelve together, and gave them power and authority over all the demons and to heal diseases. And He sent them out to proclaim the kingdom of God and to perform healing. … When the apostles returned, they gave an account to Him of all that they had done. Taking them with Him, He withdrew by Himself to a city called Bethsaida. (Luke 9:1-2,10) {emphasis mine}
The 12 disciples were on a high. Miracles had been done through their hands and at their word. They felt like they could conquer the world, but this high and great faith did not last very long. Jesus took them away. They thought they were going to spend some private time with Jesus, but that is not what happened. A great crowd ran ahead and met them. Jesus saw their physical and spiritual needs and began to preach and minister to them. It began to get late, so the disciples came to Jesus to ask Him to wrap things up and send the people away so they could eat (like Jesus didn’t know).
Now the day was ending, and the twelve came and said to Him, “Send the crowd away, that they may go into the surrounding villages and countryside and find lodging and get something to eat; for here we are in a desolate place.” But He said to them, “You give them something to eat!” And they said, “We have no more than five loaves and two fish, unless perhaps we go and buy food for all these people.” (For there were about five thousand men.) And He said to His disciples, “Have them sit down to eat in groups of about fifty each.” They did so, and had them all sit down. Then He took the five loaves and the two fish, and looking up to heaven, He blessed them, and broke them, and kept giving them to the disciples to set before the people. And they all ate and were satisfied; and the broken pieces which they had left over were picked up, twelve baskets full. (Luke 9:12-17) {emphasis mine}
Jesus gently guided His disciples, trying to help them see that there was nothing to fear, that He had everything under control, and that nothing is impossible with Him. When He asked them what they had available to feed the crowd, and they just had one young boy’s small lunch, they immediately assumed feeding the crowd was impossible. Jesus then proceeded to feed the 5,000 (5,000 men and an uncounted number of women and children). Yes, Jesus was merciful and fed this hungry crowd, but I believe this feeding was about so much more than meeting the physical needs of the crowd. Notice how every person there ate until they were satisfied. Jesus then had the disciples pick up the leftovers. How much was left over? 12 baskets full. How many disciples was He giving an object lesson to? 12 disciples. Jesus doesn’t do anything by accident. Everything He does is for a reason. (In the same way everything He allows to happen to us is for a good reason.) He did what the disciples thought was impossible, He fed the huge crowd, but even more, He had one basketful leftover for each disciple. This was a personal message to each of His disciples.
When Jesus sent them out with the command to share the Gospel, heal the sick, and cast out demons, they went out with faith and returned with even greater faith “I believe,” but then the day after they returned, their faith waivered again. They needed to cry out, “help my unbelief.” Jesus empowered and guided them both in their belief and in their unbelief. He most definitely helped their unbelief and will do the same for us.
Our Father, please help us to have faith in good times and in bad. Help us to believe with all of our heart, mind, and soul. We believe that you are God and we believe that Jesus came down to earth to live the perfect life that we are unable to live, died to receive the punishment we deserved, and was raised to life on the third day. Believe that the Holy Spirit lives within us empowering and guiding us. We also acknowledge that we have doubts. Please help our unbelief.
Trust Jesus.
-
 @ 0b118e40:4edc09cb
2025-04-13 03:30:37
@ 0b118e40:4edc09cb
2025-04-13 03:30:37I picked up this book 'Nuclear Power Explained' by Dirk Eidemuller to understand nuclear power and the historical context during the nuclear euphoria era. I’ll share a bit on the history part. Note: I have not seen the movie Oppenheimer yet.
Some key highlights :
In 1933 -Leo Szilard thought of the nuclear chain reaction concept - whereby one nuclear reaction triggers a series of additional nuclear reactions, releasing a significant amount of energy. This is fundamental for nuclear reactors and weapons. He figured this out the same year he was fleeing from one country to another from Hitler. He tried to share this idea to Rutherford but got kicked out of the office.
In 1934 - Enrico Fermi first conducted the experiment in irradiating uranium with neutrons but unfortunately he did not spot anything
In 1938, Otto Hahn and Fritz Strassmann's experiments accidentally found barium forming when they irradiated uranium with neutrons. Splitting uranium atoms was not a norm at that time. This new finding was the start of the nuclear era.
Fission vs. Fusion * Fission splits heavy nuclei into smaller ones, whereas fusion combines light nuclei into heavier ones. * Fission is used in nuclear reactors and atomic bombs, while fusion is the process that powers stars (energy is produced when hydrogen nuclei combine to form helium). The goal of developing fusion-based power generation on Earth is still work-in-progress. Thermonuclear bombs (super bombs) use fusion as well.
Otto Hahn collaborated with Lisa Meitner, Germany's first female physics professor, who fled to Sweden due to Nazi persecution. Lisa encouraged Hahn to repeat Fermi’s experiment with high precision. Lisa Meitner and her cousin Otto Frisch analyzed the results and coined the term "fission."
(Note : Women physicist were gaining popularity during that time - Marie Curie, nuclear physics, won 2 nobel price for her work)
1938 - Otto Hahn and Lisa published their results. Nuclear physicists worldwide were in disbelief.
In the early days, Albert Einstein didn’t think it was possible.He said that the whole thing would be like shooting at “birds in the dark in a country where there are few birds.”
Ernest Rutherford (who introduced the atom particle model in 1911 ) thought that it was an absurd idea to try to generate energy in this way. Note : both Rutherford and Bohr introduced the atom particle model, both had a central nucleus and electrons. Bohr’s model was more detailed and led to quantum mechanics and modern behaviour of atoms.
1939 - WW2 started on Sep 1, 1939
1941 - Japan attacked Pearl Harbor in Hawaii
After Otto Hahn’s paper released, a few things happened
Albert Einstein's E=mc^2 links energy and mass, and while this concept has been around for a while and is based on space and time and initially unrelated to nuclear, it also explained nuclear fission's energy release.
Szilard, who was a long time friend of Einstein, reached out and shared the nuclear reaction theory and its potential for killer weapons. They were worried Nazis might build it first and bomb the US.
They wrote to President Roosevelt to establish research for nuclear weapons to counter a possible attack. To add to suspicion, Germany halted uranium sales from occupied Czechoslovak mines.
(Einstein later on said he regretted this letter after witnessing the bombings of Hiroshima and Nagasaki. If he knew Germany wouldn't succeed in making an atomic bomb, he wouldn't have taken action)
Alexander Sachs, a friend of Szilárd and Roosevelt delivered the letter. At first President Roosevelt was not interested. Concurrently Germany invaded Poland, the tension was rising.
Sachs apparently used the analogy of Robert Fulton proposing steamships to Napoleon (to up the notch on traditional sail ships) to convince Roosevelt of the need for a large-scale nuclear research program.
1942 - Roosevet finally agreed
The scientists formed a committee. Military were initially skeptical and wanted to cut costs. The scientists received $6,000 to start the Manhattan Project.
The First Nuclear Reactor : Chicago Pile-1 - a group of popular physicists, including Enrico Fermi and Leó Szilárd, designed the first nuclear reactor ever built by humans. It had 5.4 tons of pure uranium metal and another 45 tons of uranium oxide.
The first nuclear reactor is underneath an unused grandstand of the University of Chicago’s football stadium.
1942 - The first test was on Dec 2. If the chain reaction went awry, a worker would use an axe to cut a rope and release an emergency control rod above the reactor. There was also an automatic shutdown system, and someone ready to pour cadmium salt from above, which stops the chain reaction.
It was a success - the reactor ran at minimum power to initiate a nearly self-sustaining chain reaction.
This led to more reactors and bomb-grade plutonium to be produced.
(note : if you are reading up to here, plutoniums are man-made, and not mined from earth the same way uranium, minerals and ores are)
France was quickly occupied in the war, and its nuclear research material was brought to Germany.
The Soviet Union put in very little effort on the atomic bomb during this time as they needed to fight against the Nazis.
In Japan, too, nuclear research proceeded slowly.
In Germany, multiple research groups operated within the "Uranium Association" also known as “Uranverein”. Popular figures like Werner Heisenberg, Carl Friedrich von Weizsäcker and Walther Gerlach worked on it but failed to activate it.
In England, German- Austrian emigrants Otto Frisch and Rudolf Peierls initiated the “MAUD Committee'' (Military Application of Uranium Detonation) . Unfortunately England classified them as “enemy aliens" hence they went to Los Alamos to work on the US nuclear tech.
Their work led to the British-Canadian “Tube Alloys” secret project, which kickstarted the American Manhattan Project. This American Manhattan project under President Eisenhower introduced nuclear reactors to Iran, Pakistan and Israel. But more on that later.
After the successful experiments with the Chicago Pile-1, the American atomic bomb project proceeded at full speed. The Manhattan Project had more than 150,000 people working on it!
Everything was done under the highest military secrecy. With the exception of the leading scientists and military personnel, nobody knew what was actually being worked on until the news of the destruction of Hiroshima.
With two billion dollars (massive at that time), leading scientist and nuclear physicist Robert Oppenheimer and General Leslie Groves quickly built a secret nuclear research center in remote Los Alamos, New Mexico, and established a nuclear industry as big as the entire American automobile industry during that era.
The Los Alamos Laboratory was called Project Y where the actual bomb design was being researched
University of Chicago’s met lab was a big research contributor during this euphoric nuclear era
Oak Ridge, Tennessee, known as "Atomic City," had large isotope separation facilities, two massive diffusion plants, one of which was the world's largest building at the time, and an electromagnetic separation plant. It provided the uranium for the Hiroshima bomb (little boy). The Hanford site provided the uranium for the Nagasaki bomb (fat man).
April 1945 - Harry Truman became U.S. President.
And four months later, he authorized nuclear attacks on Japanese civilians.
June 1945 - Szilard and Franck co-authored the "Franck Report" with fellow scientists. They cautioned against using nuclear bombs on civilians,
July 1945 - Szilard and other dozen researchers wrote to president Harry Truman to urgently warn him against civilian targets (The Szilard petition)
August 6, 1945 * Hiroshima bomb ~140,000 people died * Nagasaki bomb ~70,000 people died
Robert Oppenheimer on this explosion : “Now I have become death, the destroyer of worlds.” (from the Bhagavad Gita, a sacred Hindu text)
September 2,1945 - WW2 ended
In October 1945 , Oppenheimer resigned.
1946 - One year after the war, Leo Szilárd and Albert Einstein started the Emergency Committee of Atomic Scientists to inform the public about nuclear weapons and promote global peace.
Szilard also arranged conferences with scientists from both sides East and West to find better ways for security and peace.
After WW2, Soviet Union caught up with the US nuclear tech through espionage
1949 - Soviet detonated their first nuclear bomb in Semipalatinsk Test Site, in Kazakhstan.
In 1949 Fermi and Nobel laureate Isidor Rabi cautioned that this new weapon could have devastating consequences, approaching genocide.
1950 - 1953 - Korean war between communism (North Korea) and capitalism (South Korea). The US supported South Korea but decided against nuclear weapons due to ethical concerns. But the ideology war was becoming more apparent here.
1952 - Great Britain detonated its first atomic bomb
1952 - US developed the first hydrogen bomb - based on nuclear fusion and not nuclear fission. These super bombs were 800x stronger than the Hiroshima bomb. Instead of splitting the atomic nuclei to smaller ones, very light atomic nuclei are fused into heavier ones which enables a greater explosive forces
Oppenheimer spoke against the development of thermonuclear weapons/hydrogen bombs.
In the 1940s and 1950s during the McCarthy era, there was widespread fear of communism. People worked to expose anyone they thought might be associated with communism. Senator Joseph McCarthy led investigations, and J. Robert Oppenheimer was accused of having communist ties.
In 1954 - Oppenheimer’s security clearance was revoked by the U.S. Atomic Energy Commission after a highly publicized hearing accusing him of a communist past.
1955 - Einstein passed away. He was 76
1958 - Khrushchev became premier (Soviet Union). In his first full briefing after having a full view of the nuclear environment he said “ I could not sleep for several days. Then I became convinced that we could never possibly use these weapons, and when I realized that I was able to sleep again.”
There’s a long bit on him and JFK eventually working out peace in secrecy...
1960 - Szilárd met with Nikita Khrushchev in New York for two hours. He convinced the Soviet leader to support the idea of a hotline with the US to prevent accidental nuclear war.
1960 - France detonated its first atomic bomb
1961 - JFK came to power
1962 - Cuban Missile Crisis - lasted for 2 weeks.
The Cuban Missile Crisis began when the Soviet Union secretly placed nuclear missiles in Cuba, just 90 miles from the US, raising the threat of nuclear conflict. It ended with an agreement between the US and Soviet Union:
- The U.S. wouldn't invade Cuba.
- The USSR would remove its Cuban missiles.
- The U.S. would secretly remove its missiles from Turkey, easing tensions.
The end of Cuban Missile crisis started the peace journey between US and the Soviet Unions.
But sadly, not everybody loved peace.
1963 - JFK was assassinated
1964 - Khrushchev was ousted
1964 - Leo Szilard died of heart attack
1964 - China detonated its first atomic bomb
1983 - another possible nuclear attack during the Cold War - Soviet satellites wrongly signaled an American missile attack. Stanislav Petrov, in charge, could have launched a nuclear counterattack but didn't because he thought it was a technical glitch. It turned out he was right; sunlight reflections caused the false alarm. Petrov's decision likely averted a disastrous nuclear war. But it’s worrying how easy it was for world disaster.
1991 - The Cold War ended when the Berlin Wall came down, a significant symbol of bridging the East and the West
Part 2 - nuclear as electricity instead of bombs.
Throughout this time there was a growing shift to use nuclear power as electricity. I separated both timelines to have a clearer view on it
1951 - first reactor in Idaho used to generate electricity instead of bombs (small test reactor)
Jan 1953- President Eisenhower came was elected to office
Dec 1953 - President Eisenhower delivered his infamous "Atoms for Peace" speech to the UN, on the dangers of nuclear war and the potential of nuclear technology for human development.
He encouraged countries to use nuclear technology for peaceful purposes (electricity).
Iran, Israel, and Pakistan being among the first to agree. American Machine and Foundry constructed their early nuclear facilities.
This change from military to civilian use was made possible by amendments to the Atomic Energy Act.
1954- Russia built the first real reactor that converts nuclear power into electricity and supply it to the public power grid
1955- On August 8, in Geneva, Switzerland, the largest scientific conference in history, called the “International Conference on the Peaceful Uses of Atomic Energy,” began.
More than 1500 participants from East and West exchanged what were previously secretive results with surprising openness and aroused the curiosity of the world publicly.
1955 - The first nuclear-powered submarine, USS Nautilus, was put to sea
1956- the second nuclear power plant that produced electricity on an industrial scale in Calder Hall, near Windscale in England
1958 - the first commercialized power reactor in the US in Shippingport, Pennsylvania
In the 70’s- oil crisis promoted the use of nuclear as energy
1986 - Chernobyl (30 people died) - The Chernobyl disaster resulted from a poorly designed experiment at nuclear reactor Unit 4. They turned off safety systems, removed control rods, and ran the reactor at 7 percent power.
2011- Fukushima disaster (19,759 died) - After a major earthquake, a 15-metre tsunami disabled the power supply and cooling of three Fukushima Daiichi reactors. This led to a nuclear accident on March 11, 2011. All three cores mostly melted within the first three days.
There are a lot of learning from disasters. New reactor designs aim for safety and efficiency, but some projects face rising costs and delays. Managing radioactive waste remains a challenge. The future of nuclear power's role in global electricity is uncertain. If one day nuclear power is really safe, each home can have its own mini power plants.
There are 436 nuclear reactors in the world located in 32 countries as of May 2023
On average, nuclear powers 10% of global power needs. Some countries are heading for 20%
2 takeaways :
-
United States created and won the nuclear race because it welcomed immigrants - who turned out to be superstar nuclear physicist persecuted in their countries
-
International cooperation, advocated by many researchers since the discovery of nuclear fission, hopefully outweighs power politics.
-
 @ d360efec:14907b5f
2025-04-22 08:12:27
@ d360efec:14907b5f
2025-04-22 08:12:27ความทรงจำเรานั้นเชื่อได้แน่หรือ ?
"เพราะจิตเราเกิดดับทุกเสี้ยววินาที ทุกความทรงจำจึงสร้างขึ้นมาใหม่เสมอ ดังนั้นมันก็ไม่เหมือนต้นฉบับเป็นธรรมดา แต่ยังคงเค้าโครงเดิมอยู่ ความเปลี่ยนแปลงจึงเป็นนิรันดร์ค่ะ" - Lina Engword
เรามักจะคิดว่าความทรงจำของเราคือการบันทึกเหตุการณ์ในอดีตไว้อย่างแม่นยำ เหมือนการดูวิดีโอ 📼 หรือเปิดไฟล์คอมพิวเตอร์ 💾 แต่ในความเป็นจริงแล้ว แนวคิดนี้อาจไม่ใช่ภาพที่สมบูรณ์ บทความที่เรานำมาวิเคราะห์นี้ได้นำเสนอข้อคิดที่น่าสนใจเกี่ยวกับธรรมชาติของความทรงจำมนุษย์ ความน่าเชื่อถือของมัน และเชื่อมโยงไปถึงความจำเป็นในการฝึกฝนจิตตามหลักพุทธศาสนาเพื่อเข้าถึงความจริงที่เที่ยงแท้ 🧘♀️🔍
ความทรงจำไม่ใช่การบันทึก แต่เป็นการสร้างใหม่ 🏗️🧩
ประเด็นสำคัญที่บทความชี้ให้เห็นคือ ความทรงจำของมนุษย์ไม่ได้ทำงานเหมือนการ "บันทึก" เหตุการณ์ไว้ตายตัว 📼❌ แต่เปรียบเสมือน "ชิ้นส่วนของโค้ด" 💻 ที่จะถูก "สร้างขึ้นใหม่" 🏗️ ทุกครั้งที่เราพยายามระลึกถึง นั่นหมายความว่า ทุกครั้งที่เราดึงความทรงจำเก่าๆ กลับมา มันไม่ใช่การเปิดไฟล์เดิมซ้ำๆ แต่เป็นการประกอบชิ้นส่วนเหล่านั้นขึ้นมาใหม่ในห้วงเวลานั้นๆ กระบวนการนี้เองที่เปิดโอกาสให้เกิดการ "เติมเต็ม" ✨ หรือ "แก้ไข" ✏️ ข้อมูลในความทรงจำอยู่เสมอ ทำให้ความทรงจำที่เราเพิ่งนึกถึงอาจไม่เหมือนกับความทรงจำครั้งก่อนหน้าเสียทีเดียว 🔄
การปรุงแต่งด้วยเหตุผลและความคุ้นเคย 🤔➕🏠
สิ่งที่น่าสนใจอย่างยิ่งคือ ในกระบวนการ "สร้างใหม่" หรือ "ประกอบ" ความทรงจำขึ้นมานี้ มนุษย์มักจะเติม "เหตุผล"💡 หรือใส่สิ่งที่ตนเอง "คุ้นเคย" 🏠 ลงไปในเรื่องราวที่ระลึกได้เสมอ แม้ว่าสิ่งเหล่านั้นอาจจะไม่ได้เกิดขึ้นจริงหรือไม่เกี่ยวข้องโดยตรงกับเหตุการณ์นั้นๆ ก็ตาม ยกตัวอย่างเช่น เมื่อเราเล่าเรื่องในอดีต เรามักจะอธิบายว่าทำไมเราถึงทำสิ่งนั้น หรือทำไมเหตุการณ์นี้ถึงเกิดขึ้น โดยใส่เหตุผลที่เราคิดว่าสมเหตุสมผลในปัจจุบันลงไป สิ่งนี้ทำให้เรื่องราวในความทรงจำของเราดูมีความเชื่อมโยงและฟังดู "จริง" ✅ มากขึ้นในสายตาของเราเอง
เมื่อเราใส่เหตุผลหรือรายละเอียดที่คุ้นเคยลงไปในความทรงจำบ่อยครั้งเข้า มันก็จะยิ่งทำให้เรา "เชื่อ" 👍 โดยสนิทใจว่าสิ่งที่เราระลึกได้นั้นคือความจริงทั้งหมด ทั้งที่ความเป็นจริงของเหตุการณ์ดั้งเดิมอาจแตกต่างออกไป 🤥 นี่คือสาเหตุว่าทำไมคนสองคนจึงอาจมีความทรงจำเกี่ยวกับเหตุการณ์เดียวกันที่แตกต่างกันอย่างสิ้นเชิง ซึ่งปรากฏการณ์นี้สามารถอธิบายได้ดีด้วยตัวอย่างคลาสสิกในภาพยนตร์เรื่อง "ราโชมอน" (Rashomon) 🎬 ที่นำเสนอเหตุการณ์เดียวผ่านมุมมองและความทรงจำของตัวละครที่ขัดแย้งกันอย่างสิ้นเชิง แต่ทุกคนต่างเชื่อในสิ่งที่ตนเองจำได้ว่าเป็นความจริง 🤔❓
เครื่องมือและกระบวนการช่วยตรวจสอบความจริง 📱📹📝🔍
จากข้อจำกัดโดยธรรมชาติของความทรงจำนี้เอง ทำให้เห็นว่าเราไม่สามารถพึ่งพาสิ่งที่ 'จำได้' เพียงอย่างเดียวได้หากต้องการเข้าถึงความจริงที่เที่ยงแท้ เราจึงจำเป็นต้องมี 'กระบวนการตรวจสอบ' 🤔🔍 มาช่วยยืนยันหรือแก้ไขข้อมูลในความทรงจำ
ในยุคปัจจุบัน เรามีเครื่องมือภายนอกมากมายที่ช่วยในกระบวนการนี้ เช่น กล้องจากสมาร์ทโฟน 📱 หรือกล้องวงจรปิด 📹 ที่บันทึกเหตุการณ์ต่างๆ ไว้ได้อย่างเป็นกลาง ทำให้เรามี 'หลักฐาน' 📄 ที่เป็นรูปธรรมไว้อ้างอิงเพื่อเปรียบเทียบกับความทรงจำส่วนตัว ซึ่งบ่อยครั้งสิ่งที่กล้องเห็นนั้น 'ตรงกับความจริง' ✅ ในมุมมองที่ปราศจากอคติมากกว่าสิ่งที่ใจเราจำได้ การจดบันทึกด้วยเสียง 🎤 หรือการจดบันทึกเป็นลายลักษณ์อักษร 📝 ในทันที ก็เป็นอีกวิธีหนึ่งที่ช่วย 'ตรึง' ข้อมูลเบื้องต้นไว้ได้ระดับหนึ่งเช่นกัน ✍️
นอกจากเครื่องมือภายนอกแล้ว 'กระบวนการตรวจสอบเชิงจิตวิทยา' 🤔🧠 ที่เป็นระบบ ก็สามารถช่วยให้มนุษย์ค้นพบความจริงได้เช่นกัน ไม่ว่าจะเป็นกระบวนการซักถามในเชิงนิติวิทยาศาสตร์ 👮♀️ หรือแม้กระทั่งการฝึกฝนจิตเพื่อให้สามารถสังเกตการณ์ทำงานของตนเองได้อย่างละเอียดลึกซึ้ง ซึ่งนำเราไปสู่แนวคิดตามหลักพุทธศาสนา...
ทำไมพุทธศาสนาจึงสอนไม่ให้เชื่อแม้เป็นความคิดตัวเอง? 🙏🧠❌
จากธรรมชาติของความทรงจำและกระบวนการปรุงแต่งของจิตใจที่อธิบายมานี้เอง ทำให้เราเห็นความเชื่อมโยงกับหลักคำสอนในพุทธศาสนา 🙏 ที่เน้นย้ำให้เรา "ไม่เชื่อแม้แต่ความคิดตัวเอง" 🧠❌ อย่างปราศจากการพิจารณา เพราะความคิด อารมณ์ ความทรงจำ หรือแม้แต่ความรู้สึกมั่นใจอย่างแรงกล้าที่เรามีนั้น อาจถูกสร้างขึ้นหรือปรุงแต่งโดยกลไกของจิตใจที่ไม่ได้สะท้อนความจริงทั้งหมด 🤥
พุทธศาสนาชี้ให้เห็นว่า การจะเข้าถึงความจริงที่แท้จริงได้นั้น 🔍 จำเป็นต้องมีกระบวนการตรวจสอบภายในจิตใจ เปรียบเสมือนการสร้าง "อัลกอริทึม" 🤖 เพื่อตรวจทานว่าสิ่งที่เราคิดหรือจำได้นั้นเป็นความจริงหรือไม่ ✅❌ การจะทำเช่นนี้ได้ ไม่ใช่เรื่องง่าย และต้องอาศัยการฝึกฝนจิตอย่าง "สมาธิอย่างมาก" 🧘♂️🧘♀️ เพื่อให้จิตมีความตั้งมั่น เป็นระบบ และสามารถ "เห็นการดำเนินไปของจิตได้อย่างเป็นระบบ" 👀🔬 เห็นว่าจิตปรุงแต่งความทรงจำอย่างไร เห็นว่าเหตุผลที่เราใส่เข้าไปนั้นจริงหรือไม่ เป็นเพียงการตีความ หรือเป็นเพียงสิ่งที่ใจเราอยากให้เป็น
บทความยังกล่าวเสริมว่า ความทรงจำที่ "สด" ✨ หรือใกล้เคียงกับเวลาที่เกิดเหตุการณ์นั้นมักจะมีความน่าเชื่อถือมากกว่า 👍 แม้จะดู "ดิบๆ" หรือไม่ผ่านการปรุงแต่งมากนัก ซึ่งสอดคล้องกับแนวคิดที่ว่ายิ่งระยะเวลาผ่านไปนานเท่าไหร่ ⏳ ยิ่งมีการเรียกคืนความทรงจำนั้นๆ บ่อยครั้ง ความทรงจำก็ยิ่งมีโอกาสถูกแก้ไข เติมเต็ม หรือปรุงแต่งด้วยเหตุผลและความคุ้นเคยมากขึ้นเท่านั้น 🔄✏️
"ใดๆในโลกนั้นคือสมมุติ ความคิดความทรงจำ ก็เป็นสมมุติเพียง แต่เราต้องรู้จักใช้สมมุติให้เป็นประโยชน์ และรู้จักใช้มันให้เป็นเพื่อดำรงอยู่บนโลก"
สรุป ✨🧠🔍
โดยสรุปแล้ว บทความนี้เตือนใจเราว่า ความทรงจำของเราไม่ใช่กล้องวิดีโอที่บันทึกทุกอย่างไว้แม่นยำ 📼❌ แต่เป็นกระบวนการสร้างสรรค์ที่ซับซ้อนซึ่งมีแนวโน้มที่จะถูกปรุงแต่งด้วยเหตุผล ความคุ้นเคย และการตีความของเราเอง 🏗️🤔🏠 ความมั่นใจที่เรามีต่อสิ่งที่จำได้นั้น ไม่ได้เป็นหลักประกันว่าเป็นความจริงเสมอไป 👍🤥
การตระหนักถึงธรรมชาติข้อนี้ของจิต และการใช้เครื่องมือภายนอก 📱📹📝 รวมถึงการฝึกฝนจิตให้สามารถสังเกตการณ์ทำงานของมันได้อย่างละเอียดรอบคอบตามหลักพุทธศาสนา 🙏🧘♀️ จึงเป็นกุญแจสำคัญที่จะช่วยให้เราสามารถแยกแยะระหว่าง "ความจริง" ✅ กับ "สิ่งที่จิตปรุงแต่งขึ้น" 🤥 ได้มากขึ้น และช่วยให้เราเข้าใกล้ความเข้าใจในธรรมชาติของสรรพสิ่งได้อย่างเที่ยงตรง ไม่หลงติดอยู่ในวังวนของความทรงจำและความคิดที่อาจบิดเบือนไปจากความเป็นจริง 🔄
**#ความทรงจำ #จิตวิทยา #พุทธศาสนา #สมอง #สมาธิ #การฝึกจิต #ราโชมอน #ความจริง #ไม่เชื่อความคิด #ธรรมชาติของจิต #พัฒนาตนเอง #บทความน่ารู้ #เทคโนโลยี #บันทึกความจริง #พระอภิธรรม #พระหฤทัยสูตร #LinaEngword **
-
 @ 0edc2f47:730cff1b
2025-04-04 03:37:15
@ 0edc2f47:730cff1b
2025-04-04 03:37:15Chef's notes
This started as a spontaneous kitchen experiment—an amalgamation of recipes from old cookbooks and online finds. My younger daughter wanted to surprise her sister with something quick but fancy ("It's a vibe, Mom."), and this is what we came up with. It’s quickly established itself as a go-to favorite: simple, rich, and deeply satisfying. It serves 4 (or 1, depending on the day; I am not here to judge). Tightly wrapped, it will keep up to 3 days in the fridge, but I bet it won't last that long!
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 0 min
Ingredients
- 1 cup (240mL) heavy whipping cream
- 1/4 cup (24g) cocoa powder
- 5 tbsp (38g) Confectioners (powdered) sugar
- 1/4 tsp (1.25mL) vanilla extract (optional)
- Flaky sea salt (optional, but excellent)
Directions
-
- Whip the cream until frothy.
-
- Sift in cocoa and sugar, fold or gently mix (add vanilla if using).
-
- Whip to medium peaks (or stiff peaks, if that's more your thing). Chill and serve (topped with a touch of sea salt if you’re feeling fancy).
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 9223d2fa:b57e3de7
2025-04-15 02:54:00
@ 9223d2fa:b57e3de7
2025-04-15 02:54:0012,600 steps
-
 @ 0fa80bd3:ea7325de
2025-04-09 21:19:39
@ 0fa80bd3:ea7325de
2025-04-09 21:19:39DAOs promised decentralization. They offered a system where every member could influence a project's direction, where money and power were transparently distributed, and decisions were made through voting. All of it recorded immutably on the blockchain, free from middlemen.
But something didn’t work out. In practice, most DAOs haven’t evolved into living, self-organizing organisms. They became something else: clubs where participation is unevenly distributed. Leaders remained - only now without formal titles. They hold influence through control over communications, task framing, and community dynamics. Centralization still exists, just wrapped in a new package.
But there's a second, less obvious problem. Crowds can’t create strategy. In DAOs, people vote for what "feels right to the majority." But strategy isn’t about what feels good - it’s about what’s necessary. Difficult, unpopular, yet forward-looking decisions often fail when put to a vote. A founder’s vision is a risk. But in healthy teams, it’s that risk that drives progress. In DAOs, risk is almost always diluted until it becomes something safe and vague.
Instead of empowering leaders, DAOs often neutralize them. This is why many DAOs resemble consensus machines. Everyone talks, debates, and participates, but very little actually gets done. One person says, “Let’s jump,” and five others respond, “Let’s discuss that first.” This dynamic might work for open forums, but not for action.
Decentralization works when there’s trust and delegation, not just voting. Until DAOs develop effective systems for assigning roles, taking ownership, and acting with flexibility, they will keep losing ground to old-fashioned startups led by charismatic founders with a clear vision.
We’ve seen this in many real-world cases. Take MakerDAO, one of the most mature and technically sophisticated DAOs. Its governance token (MKR) holders vote on everything from interest rates to protocol upgrades. While this has allowed for transparency and community involvement, the process is often slow and bureaucratic. Complex proposals stall. Strategic pivots become hard to implement. And in 2023, a controversial proposal to allocate billions to real-world assets passed only narrowly, after months of infighting - highlighting how vision and execution can get stuck in the mud of distributed governance.
On the other hand, Uniswap DAO, responsible for the largest decentralized exchange, raised governance participation only after launching a delegation system where token holders could choose trusted representatives. Still, much of the activity is limited to a small group of active contributors. The vast majority of token holders remain passive. This raises the question: is it really community-led, or just a formalized power structure with lower transparency?
Then there’s ConstitutionDAO, an experiment that went viral. It raised over $40 million in days to try and buy a copy of the U.S. Constitution. But despite the hype, the DAO failed to win the auction. Afterwards, it struggled with refund logistics, communication breakdowns, and confusion over governance. It was a perfect example of collective enthusiasm without infrastructure or planning - proof that a DAO can raise capital fast but still lack cohesion.
Not all efforts have failed. Projects like Gitcoin DAO have made progress by incentivizing small, individual contributions. Their quadratic funding mechanism rewards projects based on the number of contributors, not just the size of donations, helping to elevate grassroots initiatives. But even here, long-term strategy often falls back on a core group of organizers rather than broad community consensus.
The pattern is clear: when the stakes are low or the tasks are modular, DAOs can coordinate well. But when bold moves are needed—when someone has to take responsibility and act under uncertainty DAOs often freeze. In the name of consensus, they lose momentum.
That’s why the organization of the future can’t rely purely on decentralization. It must encourage individual initiative and the ability to take calculated risks. People need to see their contribution not just as a vote, but as a role with clear actions and expected outcomes. When the situation demands, they should be empowered to act first and present the results to the community afterwards allowing for both autonomy and accountability. That’s not a flaw in the system. It’s how real progress happens.
-
 @ 0b118e40:4edc09cb
2025-04-13 02:46:36
@ 0b118e40:4edc09cb
2025-04-13 02:46:36note - i wrote this before the global trade war, back when tariffs only affected China, Mexico, and Canada. But you will still get the gist of it.
During tough economic times, governments have to decide if they should open markets to global trade or protect local businesses with tariffs. The United States has swung between these two strategies, and history shows that the results are never straightforward
Just days ago, President Donald Trump imposed tariffs on imports from Canada, Mexico, and China. He framed these tariffs (25% on most Canadian goods, 10% on Canadian energy, 25% on Mexican imports, and 10% on Chinese imports) as a way to protect American industries.
But will they actually help, or could they backfire?
A History of U.S. Tariffs
Many have asked if countries will retaliate against the US. They can and they have. Once upon a time, 60 countries were so pissed off at the US, they retaliated at one go and crushed US dominance over trade.
This was during the Great Depression era in the 1930s when the government passed the Smoot-Hawley Tariff Act, placing high taxes on over 20,000 foreign goods. The goal was to protect American jobs, especially American farmers and manufacturers, but it backfired so badly.
Over 60 countries, including Canada, France, and Germany, retaliated by imposing their own tariffs. By 1933, US imports and exports both dropped significantly over 60%, and unemployment rose to 25%.
After President Franklin Roosevelt came to office, he implemented the Reciprocal Trade Agreements Act of 1934 to reverse these policies, calming the world down and reviving trade again.
The economist history of protectionism
The idea of shielding local businesses with tariffs isn’t new or recent. It's been around for a few centuries. In the 16th to 18th centuries, mercantilism encouraged countries to limit imports and boost exports.
In the 18th century, Adam Smith, in The Wealth of Nations, argued that free trade allows nations to specialize in what they do best countering protectionism policies. Friedrich List later challenged Smith's view by stating that developing countries need some protection to grow their “infant” industries which is a belief that still influences many governments today.
But how often do governments truly support startups and new small businesses in ways that create real growth, rather than allowing funds to trickle down to large corporations instead?
In modern times, John Maynard Keynes supported government intervention during economic downturns, while Milton Friedman championed free trade and minimal state interference.
Paul Krugman argued that limited protectionism can help large industries by providing them unfair advantages to become global market leaders. I have deep reservations about Krugman’s take, particularly on its impact or lack thereof in globalizing small businesses.
The debate between free trade and protectionism has existed for centuries. What’s clear is that there is no one-size-fits-all model to this.
The Political Debate - left vs right
Both the left and right have used tariffs but for different reasons. The right supports tariffs to protect jobs and industries, while the left uses them to prevent multinational corporations from exploiting cheap labor abroad.
Neoliberal policies favor free trade, arguing that competition drives efficiency and growth. In the US this gets a little bit confusing as liberals are tied to the left, and free trade is tied to libertarianism which the rights align closely with, yet at present right wing politicians push for protectionism which crosses the boundaries of free-trade.
There are also institutions like the WTO and IMF who advocate for open markets, but their policies often reflect political alliances and preferential treatment - so it depends on what you define as true 'free trade’.
Who Really Benefits from Tariffs?
Most often, tariffs help capital-intensive industries like pharmaceuticals, tech, and defense, while hurting labor-intensive sectors like manufacturing, agriculture, and construction.
This worsens inequality as big corporations will thrive, while small businesses and working-class people struggle with rising costs and fewer job opportunities.
I’ve been reading through international trade economics out of personal interest, I'll share some models below on why this is the case
1. The Disruption of Natural Trade
Tariffs disrupt the natural flow of trade. The Heckscher-Ohlin model explains that countries export goods that match their resources like Canada’s natural resource energy or China’s labour intensive textile and electronics. When tariffs block this natural exchange, industries suffer.
A clear example was Europe’s energy crisis during the Russia-Ukraine war. By abruptly cutting themselves off from the supply of Russian energy, Europe scrambled to find alternative sources. In the end, it was the people who had to bear the brunt of skyrocketing prices of energy.
2. Who wins and who loses?
The Stolper-Samuelson theorem helps us understand who benefits from tariffs and who loses. The idea behind it is that tariffs benefit capital-intensive industries, while labor-intensive sectors are hurt.
In the US, small manufacturing industries that rely on low-cost imports on intermediary parts from countries like China and Mexico will face rising costs, making their final goods too expensive and less competitive. This is similar to what happened to Argentina, where subsidies and devaluation of pesos contributed to cost-push inflation, making locally produced goods more expensive and less competitive globally.
This also reminded me of the decline of the US Rust Belt during the 1970s and 1980s, where the outsourcing of labour-intensive manufacturing jobs led to economic stagnation in many regions in the Midwest, while capital-intensive sectors flourished on the coasts. It resulted in significantly high income inequality that has not improved over the last 40 years.
Ultimately the cost of economic disruption is disproportionately borne by smaller businesses and low-skilled workers. At the end of the day, the rich get richer and the poor get poorer.
3. Delays in Economic Growth
The Rybczynski theorem suggests that economic growth depends on how efficiently nations reallocate their resources toward capital- or labor-intensive industries. But tariffs can distort this transition and progress.
In the 70s and 80s, the US steel industry had competition from Japan and Germany who modernized their production methods, making their steel more efficient and cost-effective. Instead of prioritizing innovation, many U.S. steel producers relied on tariffs and protectionist measures to shield themselves from foreign competition. This helped for a bit but over time, American steelmakers lost global market share as foreign competitors continued to produce better, cheaper steel. Other factors, such as aging infrastructure, and economic shifts toward a service-based economy, further contributed to the industry's decline.
A similar struggle is seen today with China’s high-tech ambitions. Tariffs on Chinese electronics and technology products limit access to key inputs, such as semiconductors and advanced robotics. While China continues its push for automation and AI-driven manufacturing, these trade barriers increase costs and disrupt supply chains, forcing China to accelerate its decoupling from Western markets. This shift could further strengthen alliances within BRICS, as China seeks alternative trade partnerships to reduce reliance on U.S.-controlled financial and technological ecosystems.
Will the current Tariff imposition backfire and isolate the US like it did a hundred years ago or 50 years ago? Is US risking it's position as a trusted economic leader? Only time would tell
The impact of tariff on innovation - or lack thereof
While the short-term impacts of tariffs often include higher consumer prices and job losses, the long-term effects can be even more damaging, as they discourage innovation by increasing costs and reducing competition.
Some historical examples globally : * Nigeria: Blocking import of rice opened up black market out of desperation to survive. * Brazil: Protectionist car policies led to expensive, outdated vehicles. * Malaysia’s Proton: Sheltered by tariffs and cronyism and failed to compete globally. * India (before 1991): Over-regulation limited the industries, until economic reforms allowed for growth. * Soviet Union during Cold War : Substandard products and minimal innovation due to the absence of foreign alternatives, yielding to economic stagnation.
On the flip side, Vietnam has significantly reduced protectionism policies by actively pursuing free trade agreements. This enabled it to become a key manufacturing hub. But Vietnam is not stopping there as it is actively pushing forward its capital-intensive growth by funding entrepreneurs.
The Future of U.S. Tariffs
History has shown that tariffs rarely deliver their intended benefits without unintended consequences. While they may provide temporary relief, they often raise prices, shrink job opportunities, and weaken industries in the long run.
Without a clear strategy for innovation and industrial modernization, the U.S. risks repeating past mistakes of isolating itself from global trade rather than strengthening its economy.
At this point, only time will tell whether these tariffs will truly help Americans or will they, once again, make the rich richer and the poor poorer.
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 0b118e40:4edc09cb
2025-04-13 02:41:14
@ 0b118e40:4edc09cb
2025-04-13 02:41:14In wanting to understand the global economy of manufacturing better and in particular the decline of US manufacturing, I picked up a few books on it. This one is called ‘Why manufacturing is still key to America's future’ by Ro Khanna. It’s a little old but I’ve shared some recent stats as a comparison as well. Ro Khanna was with the U.S. Dept of Commerce, focusing on govt's impact, or lack thereof, on manufacturing. Some key highlights:
- You can’t split R&D and manufacturing. When you offshore manufacturing, you send off design with it and you lose a big chance to cultivate innovation in the US - Andy Grove, CEO of Intel.
- Manufacturing is needed to reduce the trade deficit that started in 1971
- U.S. exports to China are $153.8 billion, imports are $536.8 billion. Hence trade deficit with China is $382.9 billion
- The private sector demands out-of-the-box thinking. In the gov’t, follow instructions; don’t make waves; keep your head down for career advancement.
- Small and medium-sized businesses create about half of all manufacturing jobs and make up more than 90 percent of U.S. manufacturers
- Cluster theory - a lot of business in the surrounding area impacts other businesses i.e. supply chain. On the flip side, businesses shutting down will be like dominoes impacting other businesses. Michael Porter, The Competitive Advantage of Nations" (1990)
- Foreign subsidy - foreign companies ie China get a lot of subsidies to build manufacturing - free land, and factory capital. Cheap labour is not the only competition
- Corporate tax - The US charges heavy corporate tax on foreign earnings hence companies rather invest outside than bring it back - John Chambers, CEO and Chairman Emeritus, Cisco 9 < 1 percent of American businesses export and mostly to Canada and Mexico only
- US global manufacturing share in the ’90s was >22%. It started slipping in 99’. Today it’s 16.8%. China’s global market share was 3% in the 90, 8% in 2000 - today it is 28.7%
**More inputs **
-
Andy Grove, Intel's 3rd employee hired in 1968 and CEO from 1987 to 1998, drove Intel's market cap from $4 billion to nearly $197 billion, making it the world's largest computer chip manufacturer. He highlighted the inseparability of design and manufacturing - which leads to the loss of R&D and innovation in a country when manufacturing is offshored. Grove also questioned the absence of tracking offshored jobs.
-
Apple has a similar philosophy in bridging design and manufacturing. Dow Chemical built research facilities outside of the US because it could not separate manufacturing from R&D
-
Manufacturing’s deterrent factor is high capex and lower returns compared to the service sector.
-
“The Commerce Department was a chronic underperformer, led in recent times by political hacks or bureaucrats, from one party or the other, who simply didn’t get it.” (from the book)
-
Manufacturing is needed to reduce the trade deficit. In 2009, the trade deficit reached almost $375 billion - meaning the US spends $375 billion more on foreign economies than it does fueling its economy. (Current trade deficit is $65.5 billion)
-
To balance the economy, export more and import less. In 2009, 60% of manufacturing goods were exported (current amount of 80%). But this is not enough to fulfil domestic consumption and reduce imports, hence the need for more manufacturing.
-
Trade deficit with China - In 2009, the total trade deficit with China was more than $220 billion, service trade surplus of $6 billion. Today, U.S. export to China is $153.8 billion, imports from China is $536.8 billion, and the trade deficit with China is $382.9 billion (almost double the amount of trade deficit with China in 14 years)
-
While knowledge workers are important, must not discount the importance of hands-on technical skills
-
The rate of decline in manufacturing increases unemployment in manufacturing jobs such as engineer, designer, or floor operator. The majority of the workforce is Caucasian, with African Americans constituting about 10 percent and Hispanics about 15 percent
-
“If the private sector rewards “out of the box” thinking, Washington often expects regurgitation as the norm for career advancement. Follow instructions; don’t make waves; keep your head down—that’s the motto among insiders. It’s something that I didn’t like and never got used to.” (from the book)
-
Our nation cannot bleed manufacturing jobs and expect to have a middle class: Bob Baugh, union leader
-
Small and medium-sized businesses create about half of all manufacturing jobs and make up more than 90 percent of U.S. manufacturers.
-
Importance of local manufacturers in helping the country during turmoil - The Globe factory produced protective clothing for firefighters during 9/11. The challenges were seen during COVID-19, not being able to manufacture masks, medical
-
Federal gov’t program: the Manufacturing Extension Partnership (MEP) helps small and medium-sized manufacturers improve their competitiveness
-
The decline of manufacturing impacts surrounding businesses (I’ve seen it drop like dominoes). This is based on the cluster theory by Professor Michael Porter, introduced in the late 1990s, which emphasizes geographic concentrations of related businesses and institutions in specific industries. Clusters offer advantages like knowledge sharing, talent access, efficient supply chains, and competition-driven innovation, benefiting regional development and global competitiveness.
-
Gov’t subsidies: Foreign competitors get hefty government subsidies, including free land, factories, and capital. These subsidies make price competition tough, not just cheap labourers (for example China)
-
Corporate tax: Overseas earnings are taxed when brought back to the U.S. Due to high corporate tax rates, companies rather invest these earnings abroad. A one-time tax incentive for repatriation will encourage more domestic investment and job creation (John Chambers of Cisco, and Tim Guertin of Varian)
-
General observation - The US pioneers innovation but is unable to keep up the fight when competitors come on board because of the lack of support compared to other countries - i.e. luxury cards, automobiles, automation, silicon industry, solar industry etc
-
95% of the world’s consumers and 70% of the world’s purchasing power are outside the United States (in 2009 and about the same now)
-
Only 1 percent of American businesses export.
-
Out of that, 58% of the companies that do export only export to Canada or Mexico. They’re still reluctant to venture out to Latin America, Asia, or even Europe.
-
Exports make up only 11% of the U.S. gross domestic product (GDP) - Note, still the same from 2009 to the present. Germany, China, India, Brazil, Russia, UK, Japan - exports more
-
Trade shows are useful and costly. A suggestion is for the U.S. government to help cover travel and participation expenses for first-time attendees. These businesses could repay the government if they secure sales at the show, similar to how the Department of Agriculture supports food companies.
-
Several countries are subsidised in tradeshows and have pavilions that are chic and modern such as the British, Germany, Turkey, Italy, and Egypt. US’s booths don’t stand out.
-
The simplicity of getting paperwork sorted: In 1972, when Andy Grove went to Malaysia to establish Intel’s first foreign operation, the chief minister of Malaysia introduced him to Chet Singh, who headed the state’s Penang Development Corporation. “Chet Singh is your one-stop agent,” the Malaysian chief minister told Mr. Grove. Whenever Intel had an issue with getting a particular license, permit, road paved, or available tax credit, Chet would take care of it. He stayed in his job for more than two decades until the early 1990s, facilitating Intel’s ability to expand its Malaysian presence. Today, Malaysia is home to Intel’s largest manufacturing facility outside the United States (Note: Malaysia doesn’t treat its people the same way)
-
Over time I think manufacturing moved away because of some mixture of regulations (not all bad), high-cost labor (unions), higher cost of capital (complex) and a focus on other things (comparative advantage, or misdirected cultural signals?). Bill Gates, 2011
-
US global manufacturing share in the 80’s and 90’s was 22% - 24%. It started slipping in 99’. Today it’s 16.8%. China’s global market share was 3% in the 90, 8% in 2000 - today it is 28.7%
-
Global Manufacturing Output China – 28.7% United States – 16.8% Japan – 7.5% Germany – 5.3% India – 3.1% South Korea – 3% Italy – 2.1% France – 1.9% United Kingdom – 1.8% Indonesia – 1.6%
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Músicas grudentas e conversas
Uma vez que você ouviu uma música grudenta e ela volta, inteira, com toda a melodia e a harmonia, muitos dias depois, contra a sua vontade. Mas uma conversa é impossível de lembrar. Por quê?
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Bluesky is a scam
Bluesky advertises itself as an open network, they say people won't lose followers or their identity, they advertise themselves as a protocol ("atproto") and because of that they are tricking a lot of people into using them. These three claims are false.
protocolness
Bluesky is a company. "atproto" is the protocol. Supposedly they are two different things, right? Bluesky just releases software that implements the protocol, but others can also do that, it's open!
And yet, the protocol has an official webpage with a waitlist and a private beta? Why is the protocol advertised as a company product? Because it is. The "protocol" is just a description of whatever the Bluesky app and servers do, it can and does change anytime the Bluesky developers decide they want to change it, and it will keep changing for as long as Bluesky apps and servers control the biggest part of the network.
Oh, so there is the possibility of other players stepping in and then it becomes an actual interoperable open protocol? Yes, but what is the likelihood of that happening? It is very low. No serious competitor is likely to step in and build serious apps using a protocol that is directly controlled by Bluesky. All we will ever see are small "community" apps made by users and small satellite small businesses -- not unlike the people and companies that write plugins, addons and alternative clients for popular third-party centralized platforms.
And last, even if it happens that someone makes an app so good that it displaces the canonical official Bluesky app, then that company may overtake the protocol itself -- not because they're evil, but because there is no way it cannot be like this.
identity
According to their own documentation, the Bluesky people were looking for an identity system that provided global ids, key rotation and human-readable names.
They must have realized that such properties are not possible in an open and decentralized system, but instead of accepting a tradeoff they decided they wanted all their desired features and threw away the "decentralized" part, quite literally and explicitly (although they make sure to hide that piece in the middle of a bunch of code and text that very few will read).
The "DID Placeholder" method they decided to use for their global identities is nothing more than a normal old boring trusted server controlled by Bluesky that keeps track of who is who and can, at all times, decide to ban a person and deprive them from their identity (they dismissively call a "denial of service attack").
They decided to adopt this method as a placeholder until someone else doesn't invent the impossible alternative that would provide all their desired properties in a decentralized manner -- which is nothing more than a very good excuse: "yes, it's not great now, but it will improve!".
openness
Months after launching their product with an aura of decentralization and openness and getting a bunch of people inside that believed, falsely, they were joining an actually open network, Bluesky has decided to publish a part of their idea of how other people will be able to join their open network.
When I first saw their app and how they were very prominently things like follower counts, like counts and other things that are typical of centralized networks and can't be reliable or exact on truly open networks (like Nostr), I asked myself how were they going to do that once they became and open "federated" network as they were expected to be.
Turns out their decentralization plan is to just allow you, as a writer, to host your own posts on "personal data stores", but not really have any control over the distribution of the posts. All posts go through the Bluesky central server, called BGS, and they decide what to do with it. And you, as a reader, doesn't have any control of what you're reading from either, all you can do is connect to the BGS and ask for posts. If the BGS decides to ban, shadow ban, reorder, miscount, hide, deprioritize, trick or maybe even to serve ads, then you are out of luck.
Oh, but anyone can run their own BGS!, they will say. Even in their own blog post announcing the architecture they assert that "it’s a fairly resource-demanding service" and "there may be a few large full-network providers". But I fail to see why even more than one network provider will exist, if Bluesky is already doing that job, and considering the fact there are very little incentives for anyone to switch providers -- because the app does not seem to be at all made to talk to multiple providers, one would have to stop using the reliable, fast and beefy official BGS and start using some half-baked alternative and risk losing access to things.
When asked about the possibility of switching, one of Bluesky overlords said: "it would look something like this: bluesky has gone evil. there's a new alternative called freesky that people are rushing to. I'm switching to freesky".
The quote is very naïve and sounds like something that could be said about Twitter itself: "if Twitter is evil you can just run your own social network". Both are fallacies because they ignore the network-effect and the fact that people will never fully agree that something is "evil". In fact these two are the fundamental reasons why -- for social networks specifically (and not for other things like commerce) -- we need truly open protocols with no owners and no committees.
-
 @ d360efec:14907b5f
2025-04-22 07:54:51
@ d360efec:14907b5f
2025-04-22 07:54:51“คณิตศาสตร์” กุญแจเวทมนตร์ นักพนัน และ นักลงทุน ในนครเฮรันเทล นามกระฉ่อนเลื่องลือในหมู่นักเสี่ยงโชค เมื่อเอ่ยถึง “การพนัน” ภาพที่ชาวเมืองมักนึกถึงคือ “ยาจกข้างถนน”
มิใช่เรื่องแปลกประหลาดอันใด เพราะเป็นที่ร่ำลือกันว่า จ้าวแห่งหอคอยรัตติกาล ผู้คุมบ่อนพนัน มักร่ายเวทมนตร์สร้างเกมให้ตนเองได้เปรียบ เพื่อดูดกลืนเงินทองของผู้มาเยือน ดังนั้น การที่สามัญชนจะพิชิตเกมในระยะยาว จึงเป็นดั่งเงามายาที่จับต้องมิได้ กระนั้น ยังมีตำนานกล่าวขานถึงผู้กล้า ที่สามารถสร้างชื่อจาก “เกมพนัน” เช่น เวเนสซา รุสโซ นักเวทย์มนตร์ผู้ใช้กฎหมายแห่งแดนไกล ใช้เวลายาวนานถึงหกปี ร่ายเวทย์สะสมทรัพย์สินกว่าร้อยล้านเหรียญทอง จากการเล่นเกมไพ่ศักดิ์สิทธิ์ “โป๊กเกอร์” หรือแม้แต่ เอ็ดเวิร์ด โอ. ทอร์ป จอมปราชญ์ผู้สร้างกำไรถึงสามแสนหกหมื่นเหรียญทอง ภายในเจ็ดราตรี จากการเล่นเกมไพ่มนตรา “แบล็กแจ็ก” ด้วยเงินทุนตั้งต้นเพียงสามแสนสามหมื่นเหรียญทอง คิดเป็นอัตราเวทย์ตอบแทนร้อยสิบส่วน! เหล่าจอมยุทธ์เหล่านี้ มิได้อาศัยเพียงโชคช่วยชั่วครั้งชั่วคราวแล้วเลือนหาย แต่พวกเขากลับสามารถร่ายเวทย์สร้างผลตอบแทนระยะยาว จนเรียกได้ว่า ใช้ “หอคอยรัตติกาล” เป็นแหล่งเสบียงเลี้ยงชีพ โดยกุญแจเวทย์ที่บุคคลเหล่านี้ใช้ ก็คือ “คณิตศาสตร์” เหตุใด “คณิตศาสตร์” จึงช่วยให้ผู้คนเอาชนะ “การพนัน” ได้? และนอกจาก “การพนัน” แล้ว “คณิตศาสตร์” ยังสามารถประยุกต์ใช้กับสิ่งใดได้อีก? นักเล่าเรื่องแห่งเฮรันเทล จักไขปริศนาให้ฟัง เบื้องต้น ขอให้ท่านลองพิจารณาตนเอง ว่าเคยประสบพบพานเหตุการณ์เหล่านี้หรือไม่: * ตั้งมั่นว่า จักเสี่ยงโชคให้ได้กำไรเพียงเล็กน้อย แล้วจักหยุดพัก * แต่หากพลาดท่าเสียที จักจำกัดการสูญเสียให้เท่าทุนเดิมที่ตั้งไว้ * ครั้นเมื่อเวทมนตร์เข้าข้าง ได้กำไรมาแล้ว กลับโลภโมโทสัน อยากได้เพิ่มอีกนิด จึงร่ายเวทย์ต่อ * ทว่ากำไรเริ่มร่อยหรอ จนเหลือเพียงทุนเดิม สุดท้ายทุนที่ตั้งไว้คราแรกก็มลายสิ้น * จำต้องหาเงินทองมาลงเพิ่ม หวังทวงทุนคืน และพบว่าต้องสูญเสียเงินก้อนนั้นไปในห้วงเวลาต่อมา ลำดับเหตุการณ์ดังกล่าว เรียกได้ว่าเป็น “วงจรอุบาทว์” สำหรับนักพนันมากมายในเฮรันเทล ปริศนาที่ตามมาก็คือ เหตุใด “วงจรอุบาทว์” นี้จึงเกิดขึ้นซ้ำแล้วซ้ำเล่า? ส่วนหนึ่ง ย่อมเป็นเพราะอารมณ์อันแปรปรวนในการเสี่ยงโชคของแต่ละคน แต่อีกส่วนที่สำคัญยิ่งกว่า ต้องกล่าวว่าเป็นผลจาก “กลไกต้องสาป” ของจ้าวแห่งหอคอยรัตติกาล ซึ่งต้องกล่าวว่า เหล่าเจ้าของหอคอยรัตติกาลนั้น จักใช้หลักการทำนองเดียวกับ “สมาคมพ่อค้าผู้พิทักษ์” คือจักเก็บเงินทองจากชนจำนวนมาก เพื่อนำมาจ่ายให้กับชนเพียงหยิบมือ เพื่อล่อลวงให้ชนทั้งหลายเสี่ยงโชคต่อไป หรือทำให้เหล่านักพนันหวังว่า จักเป็นผู้โชคดีเฉกเช่นพวกเขาบ้าง แม้จะมีผู้โชคดีที่สามารถได้กำไรในเบื้องต้น แต่ในบั้นปลายก็จักพ่ายแพ้อยู่ดี ซึ่งเป็นไปตาม “กฎแห่งจำนวนมหาศาล” เพราะจ้าวแห่งหอคอยรัตติกาลนั้น ได้คำนวณและออกแบบระบบเกมที่ตนเองได้เปรียบในระยะยาวแล้ว จากตำนานนี้ ย่อมประจักษ์ชัดว่า แม้การพนันจักเป็นเรื่องของดวงชะตา แต่ก็ถูกรังสรรค์ขึ้นจากการคำนวณทางคณิตศาสตร์ ดังนั้น หากปรารถนาจะหาหนทางเอาชนะจ้าวแห่งหอคอยรัตติกาล ก็จำต้องเข้าใจ “คณิตศาสตร์” เสียก่อน ทีนี้ จงเงี่ยหูฟัง แล้วท่านจักได้ยินข้าไขปริศนา: ๑. ปริศนาแห่ง “กำไรคาดหวัง” สำหรับการแสวงหา “เกมเสี่ยงทาย” ที่ควรค่าแก่การเล่น หรือการเสี่ยง สิ่งแรกที่นักพนันพึงกระทำคือ “การประเมินกำไรคาดหวัง” หรือ “เวทคำนวณอนาคต” “กำไรคาดหวัง” ถูกคิดค้นโดย คริสเตียน ฮอยเกนส์ นักปราชญ์เวทย์ชาวดัตช์ เพื่อประเมินว่าเกมพนันแบบใดควรค่าแก่การเล่น ซึ่งมิใช่เพียงแค่การประเมินโอกาสแห่งชัยชนะเท่านั้น แต่ต้องคิดรวมขนาดของเงินเดิมพันไปด้วย โดยสูตรเวทย์คือ: กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้) ดังนั้น หากปรารถนาจะสะสม “ทองคำมายา” ในระยะยาว จงเลือกเกมที่มี “กำไรคาดหวัง” เป็นบวก แต่หากพลาดพลั้งเข้าไปเล่นเกมที่ “กำไรคาดหวัง” เป็นลบ และบังเอิญว่าโชคชะตาเล่นตลกให้ได้เงินทองมาครอง พึงละทิ้งเกมนั้นเสียโดยพลัน เพราะท้ายที่สุดหากยังคงเล่นต่อไป ผู้อับโชคผู้นั้นก็คือตัวท่านเอง อย่างไรก็ตาม โดยธรรมดาแล้ว “กำไรคาดหวัง” ของเกมพนันที่มีเจ้ามือมักจักติดลบ จึงเป็นเรื่องยากยิ่งที่จะเอาชนะได้ เฉกเช่นตัวอย่างที่เราเห็น คือเกมในบ่อนพนัน หรือแม้แต่ “สลากกินแบ่งรัฐบาล” ก็ล้วนเป็นเกมที่มี “กำไรคาดหวัง” ติดลบทั้งสิ้น นอกจาก “กำไรคาดหวัง” จักถูกใช้กับการพนันได้แล้ว หลักเวทย์ “คณิตศาสตร์” ก็ยังสามารถประยุกต์ใช้กับการลงทุนได้ไม่แตกต่างกัน ตัวอย่างเช่น หากท่านเก็บสถิติข้อมูลการลงทุนของตนเอง แล้วพบว่ามีเพียงสามสิบส่วนร้อยเท่านั้น ที่ท่านซื้อ “ศิลาแห่งโชค” แล้วสร้างผลตอบแทนเป็นบวก แต่ท่านยังคงปรารถนาความสำเร็จในการลงทุน ก็จงจำกัดการขาดทุนแต่ละคราให้น้อยเข้าไว้ เช่น -๕% และปล่อยให้มีกำไรในแต่ละคราที่ลงทุน เช่น อย่างน้อย ๒๐% ซึ่งจากการใช้กลยุทธ์นี้ ท่านจักมี “กำไรคาดหวัง” = (๒๐% x ๐.๓) + (-๕% x ๐.๗) = ๒.๕% จักเห็นได้ว่า แม้ท่านจักมีจำนวนคราที่ขาดทุนบ่อยครั้ง แต่ก็ยังสามารถสร้างกำไรได้ หากคราที่กำไรนั้น สามารถทำเงินทองเป็นจำนวนมากได้ ๒. ปริศนาแห่ง “การบริหารหน้าตัก” หรือ “การบริหารเงินทุน” แม้ว่าท่านจักรับรู้ “กำไรคาดหวัง” แล้ว แต่หากท่านเผชิญหน้ากับการขาดทุนต่อเนื่องกัน ท่านก็อาจหมดเนื้อหมดตัวก่อนถึงคราที่จะกอบโกยเงินทองจากคราที่กำไร วิธีคลายปมปริศนานี้ก็คือ การมิลงเงินทองทั้งหมดของท่านในการลงทุนเพียงคราเดียว ซึ่งนอกจากการกระจายความเสี่ยงในการลงทุนหลาย “ศิลาแห่งโชค” หรือหลาย “เกมเสี่ยงทาย” แล้ว ท่านอาจกำหนดขนาดของการลงทุนแต่ละคราให้มิมากเกินไป แบบง่าย ๆ เช่น มิเกิน ๑๐% ของเงินลงทุนทั้งหมด หรือท่านอาจคำนวณขนาดของการลงทุนแต่ละคราด้วยสูตรทางคณิตศาสตร์ เช่น สูตร “การขาดทุนสูงสุดที่ท่านรับได้ (Value at Risk)” หรือ สูตร “ขนาดเดิมพันที่เหมาะสม (Kelly Formula)” ๓. ปริศนาแห่ง “อคติ” ในวงการพนัน มักมีอคติหนึ่งที่บังเกิดบ่อยครั้งกับผู้คน คือ “Gambler's Fallacy” หรือ “ความเชื่อผิด ๆ แห่งนักพนัน” ว่าหากเหตุการณ์หนึ่งบังเกิดบ่อยครั้งกว่าปรกติในช่วงเวลาหนึ่ง ๆ เหตุการณ์นั้นจักบังเกิดบ่อยครั้งน้อยลงในอนาคต ทั้ง ๆ ที่เหตุการณ์เหล่านั้นเป็นอิสระจากกันในทางสถิติ ยกตัวอย่างเช่น หากโยนเหรียญมนตราออกหัวไปแล้วสามครา ในคราที่สี่ หลายคนอาจคิดว่าโอกาสออกก้อยมากกว่าหัว แม้ว่าการโยนเหรียญแต่ละคราจะมิได้ส่งผลอันใดต่อกันเลย (จะโยนกี่ครา โอกาสหัวหรือก้อย ก็คือ ๕๐:๕๐ อยู่ยั่งยืน) หรือแม้กระทั่ง “สลากกินแบ่งรัฐบาล” มีหลายคนที่ซื้อเลขซ้ำกัน เพื่อหวังว่าจะถูกในงวดต่อ ๆ ไป ในวงการการลงทุน ก็มีลักษณะที่คล้ายคลึงกัน เช่น หาก “ศิลาแห่งโชค A” ราคาตกต่ำลงมาห้าครา บางคนอาจคิดว่าในคราที่หก ราคาของมันจักต้องเด้งขึ้นมา ซึ่งในความเป็นจริง หาได้เป็นเช่นนั้นเสมอไป จักเห็นได้ว่า แท้จริงแล้ว ไม่ว่าจักเป็น “เกมเสี่ยงทายแห่งโชคชะตา” หรือ “การผจญภัยในตลาดทุน” หากท่านมีความเข้าใจ และนำ “คณิตศาสตร์” เข้ามาเป็นรากฐาน มันก็อาจนำพาตัวท่านเอง ไปสู่จุดที่ได้เปรียบในเกมนั้น ได้เฉกเช่นกัน.. สูตรเวทย์มนตร์ที่ปรากฏในตำนาน: * กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้) คำเตือนจากนักเล่าเรื่องแห่งเฮรันเทล: "พึงระลึกไว้เสมอว่า โชคชะตาเป็นสิ่งที่คาดเดาได้ยาก แม้เวทมนตร์คณิตศาสตร์จักช่วยนำทาง แต่ท้ายที่สุดแล้ว ความสำเร็จยังคงขึ้นอยู่กับการตัดสินใจและสติปัญญาของท่านเอง"
หวังว่าตำนานบทนี้จักเป็นประโยชน์แก่ท่านนะคะ
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Jofer
Jofer era um jogador diferente. À primeira vista não, parecia igual, um volante combativo, perseguia os atacantes adversários implacavelmente, um bom jogador. Mas não era essa a característica que diferenciava Jofer. Jofer era, digamos, um chutador.
Começou numa semifinal de um torneio de juniores. O time de Jofer precisava do empate e estava sofrendo uma baita pressão do adversário, mas o jogo estava 1 a 1 e parecia que ia ficar assim mesmo, daquele jeito futebolístico que parece, parece mesmo. Só que aos 46 do segundo tempo tomaram um gol espírita, Ruizinho do outro time saiu correndo pela esquerda e, mesmo sendo canhoto, foi cortando para o meio, os zagueiros meio que achando que já tinha acabado mesmo, devia ter só mais aquele lance, o árbitro tinha dado dois minutos, Ruizinho chutou, marcou e o goleiro, que só pulou depois que já tinha visto que não ia ter jeito, ficou xingando.
A bola saiu do meio e tocaram para Jofer, ninguém nem veio marcá-lo, o outro time já estava comemorando, e com razão, o juiz estava de sacanagem em fazer o jogo continuar, já estava tudo acabado mesmo. Mas não, estava certo, mais um minuto de acréscimo, justo. Em um minuto dá pra fazer um gol. Mas como? Jofer pensou nas partidas da NBA em que com alguns centésimos de segundo faltando o armador jogava de qualquer jeito para a cesta e às vezes acertava. De trás do meio de campo, será? Não vou ter nem força pra fazer chegar no gol. Vou virar piada, melhor tocar pro Fumaça ali do lado e a gente perde sem essa humilhação no final. Mas, poxa, e daí? Vou tentar mesmo assim, qualquer coisa eu falo que foi um lançamento e daqui a uns dias todo mundo esquece. Olhou para o próprio pé, virou ele de ladinho, pra fora e depois pra dentro (bom, se eu pegar daqui, direitinho, quem sabe?), jogou a bola pro lado e bateu. A bola subiu escandalosamente, muito alta mesmo, deve ter subido uns 200 metros. Jofer não tinha como ter a menor noção. Depois foi descendo, o goleirão voltando correndo para debaixo da trave e olhando pra bola, foi chegando e pulando já só pra acompanhar, para ver, dependurado no travessão, a bola sair ainda bem alta, ela bateu na rede lateral interna antes de bater no chão, quicar violentamente e estufar a rede no alto do lado direito de quem olhava.
Mas isso tudo foi sonho do Jofer. Sonhou acordado, numa noite em que demorou pra dormir, deitado na sua cama. Ficou pensando se não seria fácil, se ele treinasse bastante, acertar o gol bem de longe, tipo no sonho, e se não dava pra fazer gol assim. No dia seguinte perguntou a Brunildinho, o treinador de goleiros. Era difícil defender essas bolas, ainda mais se elas subissem muito, o goleiro ficava sem perspectiva, o vento alterava a trajetória a cada instante, tinha efeito, ela cairia rápido, mas claro que não valia à pena treinar isso, a chance de acertar o gol era minúscula. Mas Jofer só ia tentar depois que treinasse bastante e comprovasse o que na sua imaginação parecia uma excelente idéia.
Começou a treinar todos os dias. Primeiro escondido, por vergonha dos colegas, chegava um pouco antes e ficava lá, chutando do círculo central. Ao menor sinal de gente se aproximando, parava e ia catar as bolas. Depois, quando começou a acertar, perdeu a vergonha. O pessoal do clube todo achava engraçado quando via Jofer treinando e depois ouvia a explicação da boca de alguém, ninguém levava muito a sério, mas também não achava de todo ridículo. O pessoal ria, mas no fundo torcia praquilo dar certo, mesmo.
Aconteceu que num jogo que não valia muita coisa, empatezinho feio, aos 40 do segundo tempo, a marcação dos adversários já não estava mais pressionando, todo mundo contente com o empate e com vontade de parar de jogar já, o Henrique, meia-esquerdo, humilde, mas ainda assim um pouco intimidante para Jofer (jogava demais), tocou pra ele. Vai lá, tenta sua loucura aí. Assumiu a responsabilidade do nosso volante introspectivo. Seria mais verossímil se Jofer tivesse errado, primeira vez que tentou, restava muito tempo ainda pra ele ter a chance de ser herói, ninguém acerta de primeira, mas ele acertou. Quase como no sonho, Lucas, o goleiro, não esperava, depois que viu o lance, riu-se, adiantou-se para pegar a bola que ele julgava que quicaria na área, mas ela foi mais pra frente, mais e mais, daí Lucas já estava correndo, só que começou a pensar que ela ia pra fora, e ele ia só se dependurar no travessão e fazer seu papel de estar na bola. Acabou que por conta daquele gol eles terminaram em segundo no grupo daquele torneiozinho, ao invés de terceiro, e não fez diferença nenhuma.
-
 @ c230edd3:8ad4a712
2025-04-11 16:02:15
@ c230edd3:8ad4a712
2025-04-11 16:02:15Chef's notes
Wildly enough, this is delicious. It's sweet and savory.
(I copied this recipe off of a commercial cheese maker's site, just FYI)
I hadn't fully froze the ice cream when I took the picture shown. This is fresh out of the churner.
Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 4
Ingredients
- 12 oz blue cheese
- 3 Tbsp lemon juice
- 1 c sugar
- 1 tsp salt
- 1 qt heavy cream
- 3/4 c chopped dark chocolate
Directions
- Put the blue cheese, lemon juice, sugar, and salt into a bowl
- Bring heavy cream to a boil, stirring occasionally
- Pour heavy cream over the blue cheese mix and stir until melted
- Pour into prepared ice cream maker, follow unit instructions
- Add dark chocolate halfway through the churning cycle
- Freeze until firm. Enjoy.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O caso da Grêmio TV
enquanto vinha se conduzindo pela plataforma superior daquela arena que se pensava totalmente preenchida por adeptos da famosa equipe do Grêmio de Porto Alegre, viu-se, como por obra de algum nigromante - dos muitos que existem e estão a todo momento a fazer más obras e a colocar-se no caminhos dos que procuram, se não fazer o bem acima de todas as coisas, a pelo menos não fazer o mal no curso da realização dos seus interesses -, o discretíssimo jornalista a ser xingado e moído em palavras por uma horda de malandrinos a cinco ou seis passos dele surgida que cantavam e moviam seus braços em movimentos que não se pode classificar senão como bárbaros, e assim cantavam:
Grêmio TV pior que o SBT !
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 0b118e40:4edc09cb
2025-04-11 14:38:22
@ 0b118e40:4edc09cb
2025-04-11 14:38:22There’s an African proverb that says, “To get lost is to learn the way.”
Humans have always been explorers, searching for connection. To belong. To feel home. You can trace this instinct back to the start of our existence. Whether you start with Adam and Eve or the “Out of Africa” theory, the story is the same. We’ve always moved toward each other, building tribes and forming communities.
But somewhere along the way, something broke. With the rise of empires and organized control, religion and politics divided us into bubbles. We were sorted, labeled, and often pitted against one another. While technology advanced, something fundamental was lost. Our ability to truly connect started to fade.
Then came the internet, a modern-day Silk Road. It rekindled hope. Walls seemed to crumble, distances disappeared, and we dreamed of a truly connected world. For a time, it felt like the answer.
And then it wasn’t.
The history of Internet
The story began around 1830s when Charles Babbage started working on his computer prototype but without moolah he couldn't continue. A century later, after WW2 in the 1950s, the US Department of Defense funded what became known as modern computing.
Back then the military relied on systems like the Navajo Code Talkers. The indigenous code talkers were ingenious but operated under dangerous conditions, always on the frontlines.
In 1969, ARPANET made a revolutionary breakthrough as it connected four university computers for the first time. It was a big deal.
At that time, the internet was about openness. Researchers pushed for universal protocols. This gave rise to hacker culture that valued knowledge-sharing and keeping systems accessible to everyone.
In the 80s, NSFNET (National Science Foundation ) expanded these connections but kept it strictly for academic use only. That caused massive dissatisfaction.
Senator Al Gore pitched the concept of the “information superhighway,” to balance public access with private innovation. But by the 90s, the Clinton administration leaned into privatization. NSFNET’s infrastructure was completely handed off to private companies, and the internet grew into a commercial powerhouse.
The good news is that everyone has internet access now. Bad news is that what started as something free from government and commercial control became completely dominated by both.
Open source vs IP during the early internet days
This part of the story is about Bill Gates and Marc Andreessen.
Tim Berners-Lee invented the World Wide Web, but Marc saw the opportunity to make it user-friendly. He launched Netscape, an open-source browser. It drove the openness of internet culture. Netscape captured 90% of the market by giving its software away for free, and monetizing through other means.
Then came along Bill Gates. Microsoft back then was known for its aggressive tactics to monopolize industries. Gates licensed Mosaic’s code, created Internet Explorer, and bundled it for free with Windows 95. He wasn’t shy about playing dirty, even formed exclusive contracts with manufacturers to block competitors. Even the Department of Justice tried to file an antitrust lawsuit against Microsoft, but by then, it was too late. Netscape’s market share crumbled, and its position in the industry eroded.
Windows 95 brought the internet to the people globally, but it also closed it up.
Marc Andreeson started with open source ideologies, but is now funding altcoin projects.
The Californian ideology
Around this time, the term “Californian Ideology” started floating around. It was an unusual mix of libertarianism, techno-utopianism, and countercultural ideals. A marriage of cultural bohemianism (hippies) with high-tech entrepreneurship (yuppies). This ideology fused left-wing values like freedom of expression and direct democracy with right-wing beliefs in free markets and minimal government interference.
I absolutely love it.
Ironically, the term “Californian Ideology” wasn’t coined as a compliment. Richard Barbrook and Andy Cameron used it to piss on these visionaries for romanticizing the idea that the internet must remain a lawless, egalitarian space.
But many people loved and embraced the Californian ideology. Stewart Brand, who founded The Whole Earth Catalog, connected counterculture with early tech innovation. His work inspired people like Steve Jobs and Steve Wozniak. Steve Wozniak used to share Apple’s early schematics at the Homebrew Computer Club for feedback and collaboration.
EBay’s founder Pierre Omidyar envisioned eBay as a libertarian experiment. He believed the “invisible hand” of the market would ensure fairness. But as eBay grew, fraud, disputes, and dissatisfaction among users forced Omidyar to introduce governance which contradicted his goals.
And this story repeats itself over the years.
Platforms begin with libertarian visions, but as they scale, real-world challenges emerge. Governance (government, corporate charters, advertisers, and investors) is introduced to address safety and trust issues.
But they also chip away at the liberty the internet once promised.
Can Nostr be the solution ?
Yes.
But to appreciate Nostr, let’s first understand how the internet works today. (Note : I am no expert of this section but I'll try my best to explain)
The internet operates through four main layers:
- Application Layer (where apps like browsers, Google, or Zoom live)
- Transport Layer
- Internet Layer
- Network Access Layer
Let’s use a simple example of searching “Pink Panther” on Google.
Step 1: The Application Layer - You open your browser, type "Pink Panther," and hit search. This request is sent using HTTP/HTTPS (a protocol that formats the query and ensures it's secure).
Step 2: The Transport Layer - Think of your search query as a letter being sent. The Transport Layer breaks it into smaller packets (like splitting a long letter into multiple envelopes). TCP (Transmission Control Protocol) ensures all packets arrive and reassemble in the correct order.
Step 3: The Internet Layer - This layer acts like a postal service, assigning each device an address (IP address) to route the packets properly. Your device's IP (e.g., 192.168.1.10) and Google’s server IP (e.g., 142.250.72.238) help routers find the best path to deliver your packets.
Step 4: The Network Access Layer - Finally, the Network Access Layer physically delivers the packets. These travel as electrical signals (over cables), radio waves (Wi-Fi), or light pulses (fiber optics). This is the act of moving envelopes via trucks, planes, or postal workers, just much faster.
So how is data transmitted via Nostr ?
Nostr’s architecture of the Internet
Nostr reimagines the Application Layer while keeping the lower layers (Transport, Internet, and Network Access) largely unchanged.
In the traditional internet stack, the Application Layer is where platforms like Google or Twitter operate. It’s also where most censorship occurs due to single point of failure (centralised servers). Nostr flips this model on its head.
Technically, it’s like building a parallel internet that shares the same foundational layers but diverges at the top.
To borrow from Robert Frost:
"Two roads diverged in a wood, and I—
I took the one less traveled by,
And that has made all the difference."
For Nostr to fully realize its potential, it needs its own ecosystem of apps. Developers can build these tools within the Nostr protocol's framework
Let’s say there is a search engine on Nostr called Noogle.
Here’s how it works:
When you type "Pink Panther" on Noogle, your query is sent to multiple relays (servers) simultaneously. Each relay processes or forwards the query and returns results based on the data it holds.
As Nostr grows, the amount of information on relays will increase, giving Noogle more robust search results. But the biggest win is that compared to Google, Nostr's Noogle will have no ads, no surveillance, just pure, decentralized searching that respects your privacy.
For the transport layer, Nostr still relies on TCP/IP but enhances it with privacy and efficiency. Encrypted messages and simplified protocols enable faster real-time communication. The rest of the layer remains unchanged.
At its core, Nostr takes the internet back to its original ideals: open, uncensored, and decentralized.
Why Nostr matters ?
The internet we use today relies on centralized systems at the application layer. This creates a single point of failure where governments and corporations can control access, censor content, monitor activity, and even shut down entire platforms.
For example, the Malaysian government once proposed routing all web traffic through a centralized system, claiming it was for "security" reasons. In reality, this action allow those in power to block access to specific content or platforms that might threaten their positions.
Centralization weaponizes the internet.
It turns what was meant to be a tool for connection and freedom into a mechanism for control and oppression.
Let's look at DNS and ISPs as examples. DNS (Domain Name System) is like the phonebook of the internet. It helps translate website names (like example.com) into IP addresses so your browser can connect to them. ISPs (Internet Service Providers) are companies that give you access to the internet.
Both are controlled by centralized entities. If a government gains control of either, it can block specific websites or even shut down internet access entirely.
We've seen this happen repeatedly: * India’s internet shutdowns in regions like Kashmir * Turkey’s social media bans during political events * Ethiopia’s internet blackouts * China’s Great Firewall blocking major platforms like Google and Facebook * Even the US, where Edward Snowden revealed massive surveillance programs
This is where Nostr comes in, as the antidote to centralized control.
Instead of relying on centralized servers or platforms, Nostr creates a peer-to-peer network of independent relays. No single entity controls it. There is no central switch governments can flip to block access. If one relay is shut down, users simply connect to others in the network.
Nostr’s decentralized design makes it: * Resistant to censorship: Governments cannot easily block or filter content. * Privacy-preserving: Users can communicate anonymously, even in heavily surveilled environments. * Resilient: With no single point of failure, the network keeps running, even under attack.
And it gets better. Nostr can integrate with privacy tools like Tor to bypass restrictions entirely, making it nearly impossible for governments to stop.
The internet has become a battlefield for control, but Nostr provides a way to reclaim digital freedom. It empowers people to build, connect, and share without fear of being silenced.
How does Nostr overcome the "Californian Ideology" problems?
The Californian Ideology seemed like the blueprint for a utopian internet, libertarian ideals wrapped in Silicon Valley innovation. But as centralized platforms scaled, cracks started to show. Challenges like trust, safety, and accessibility forced governance teams to step in and decide “what’s best for the people.”
This resulted in platforms once built on ideals of freedom in becoming gatekeepers of control.
Nostr breaks this cycle. How?
1. Trust issues - With private keys, you control your identity and data. Moderation is decentralized. You can block or mute others at a personal level or through client tools, not by relying on a central authority. While this system needs refinement to be more user-friendly, it fundamentally shifts the power to users.
2. Funding Without Advertiser - Nostr’s integration of Bitcoin and the Lightning Network eliminates reliance on advertisers or corporate sponsors. Bitcoin enables anyone to contribute without gatekeeping. As more people join and apps mature, this model only gets stronger. For now, we have good souls like Jack seeding it.
3. Resisting Government Control - (refer to the above) Nostr avoids single points of attacks.
So what is Nostr ?
Nostr is internet
The new internet.
The open and free internet.
What can you build on Nostr?
Anything you have seen on the internet, you can recreate on Nostr. Anything you can imagine, you can bring to life here. It is a blank canvas for dreamers, builders, and changemakers.
But the best part is this. You have Bitcoin as its financial backbone. This changes the game entirely.
And with new games, comes new rules. New vibes. New ways.
The way people use this new internet will be different from the traditional internet as control falls back to the people. With Bitcoin as the underlying backbone, the business models will be different.
But there is more to it than just creating. There's that joy of creation, where we invite curiosity and inspire users to experience something new, something revolutionary.
Have you watched “The Last Lecture” by Randy Pausch?
He coined the term “head fake.” He taught his students programming, but not everyone was excited to learn programming. So he created fun projects and performances that pulled them in. The students had so much fun, they didn’t even realize they were learning to code.
What you build on Nostr is that head fake. The apps and projects you create draw people in with fun and utility, subtly reminding them they have a right to their own voice and thoughts.
The work you’re doing is so precious. When everything feels like doom and gloom, it’s these kinds of projects that give people hope.
Through Nostr, you’re making a difference. One project, one connection at a time.
The new Internet era
Centralized systems, like empires of the past, eventually crumble under the weight of their control. Decentralization provides a different path. It is a modern revival of our primal instincts to explore, connect, and build tribes.
By definition, Nostr is a protocol. I think more so, it's a philosophy. It challenges us to rethink how we share, communicate, and create. It is the internet as it was meant to be. Free, open, and governed by no one.
The beauty of Nostr lies in its simplicity. It does not rely on massive infrastructure, corporate giants, or government oversight. It thrives on community, much like the early tribes that defined humanity.
We have come full circle. From wandering continents to building roads, bridges, and networks, our journey has always been about connection and finding our tribe.
As the African proverb reminds us, 'To get lost is to learn the way.' There is finally a way now.
But at the end of the day, it’s entirely up to you what kind of world you want to be part of.
Find your tribe. Build the future. Love them hard.
More info :
On those who played a role in the history of internet and computers
https://hiddenheroes.netguru.com/ -
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Replacing the web with something saner
This is a simplification, but let's say that basically there are just 3 kinds of websites:
- Websites with content: text, images, videos;
- Websites that run full apps that do a ton of interactive stuff;
- Websites with some interactive content that uses JavaScript, or "mini-apps";
In a saner world we would have 3 different ways of serving and using these. 1 would be "the web" (and it was for a while, although I'm not claiming here that the past is always better and wanting to get back to the glorious old days).
1 would stay as "the web", just static sites, styled with CSS, no JavaScript whatsoever, but designers can still thrive and make they look pretty. Or it could also be something like Gemini. Maybe the two protocols could coexist.
2 would be downloadable native apps, much easier to write and maintain for developers (considering that multi-platform and cross-compilation is easy today and getting easier), faster, more polished experience for users, more powerful, integrates better with the computer.
(Remember that since no one would be striving to make the same app run both on browsers and natively no one would have any need for Electron or other inefficient bloated solutions, just pure native UI, like the Telegram app, have you seen that? It's fast.)
But 2 is mostly for apps that people use every day, something like Google Docs, email (although email is also broken technology), Netflix, Twitter, Trello and so on, and all those hundreds of niche SaaS that people pay monthly fees to use, each tailored to a different industry (although most of functions they all implement are the same everywhere). What do we do with dynamic open websites like StackOverflow, for example, where one needs to not only read, but also search and interact in multiple ways? What about that website that asks you a bunch of questions and then discovers the name of the person you're thinking about? What about that mini-app that calculates the hash of your provided content or shrinks your video, or that one that hosts your image without asking any questions?
All these and tons of others would fall into category 3, that of instantly loaded apps that you don't have to install, and yet they run in a sandbox.
The key for making category 3 worth investing time into is coming up with some solid grounds, simple enough that anyone can implement in multiple different ways, but not giving the app too much choices.
Telegram or Discord bots are super powerful platforms that can accomodate most kinds of app in them. They can't beat a native app specifically made with one purpose, but they allow anyone to provide instantly usable apps with very low overhead, and since the experience is so simple, intuitive and fast, users tend to like it and sometimes even pay for their services. There could exist a protocol that brings apps like that to the open world of (I won't say "web") domains and the websockets protocol -- with multiple different clients, each making their own decisions on how to display the content sent by the servers that are powering these apps.
Another idea is that of Alan Kay: to design a nice little OS/virtual machine that can load these apps and run them. Kinda like browsers are today, but providing a more well-thought, native-like experience and framework, but still sandboxed. And I add: abstracting away details about design, content disposition and so on.
These 3 kinds of programs could coexist peacefully. 2 are just standalone programs, they can do anything and each will be its own thing. 1 and 3, however, are still similar to browsers of today in the sense that you need clients to interact with servers and show to the user what they are asking. But by simplifying everything and separating the scopes properly these clients would be easy to write, efficient, small, the environment would be open and the internet would be saved.
See also
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 16f1a010:31b1074b
2025-04-09 19:23:44
@ 16f1a010:31b1074b
2025-04-09 19:23:44
Arceus was born from nothing, not even chaos.



Arceus soon made Dialga, Palkia, and then Giratina. Dialga created time, Palkia created space, and Giratina created anti-matter. And thus, the Universe was born.Dialga, Palkia, and Giratina began battling and as a result were banished to their individual realms by Arceus.
Arceus then created Groudon, Kyogre, and Rayquaza. Groudon formed the huge celestial bodies known as planets, and the trio chose one to inhabit with life. Arceus created the sun, then shot off across the universe to create all the many stars.


But he had learnt from experience, so he tasked Rayquaza as the peace-keeper.
The trio set to work, with Groudon raising land violently, creating volcanoes and mountains; Kyogre, creating the seas, where the land was not, and Rayquaza making an atmosphere full of 'air'.
Sure enough, Kyogre's waters started to corrode Groudon's land, and this angered him. The two battled, but Rayquaza broke it up, and sent Groudon deep underground, while Kyogre was sent deep into the oceans, before returning out into the ozone layer.
Soon, Arceus returned, and it tried to make life, but failed miserably. So it created Regigigas. Regigigas moved the continents with its bare hands, piecing them together like a puzzle.

When the final chunk of land was put into place, the world sprung to life, with grass and trees sprouting everywhere. Finally, the world was ready for life.
Arceus sent Regigigas into a coma until it was needed once more. It then created thousands of Pokémon to inhabit the world. These Pokémon belonged to one of five races.
Celebi
 Jirachi
Jirachi  Mew
Mew 
Manaphy
 or Victini
or Victini 
It also created Latios and Latias, its personal agents, whom it sent flying through the universe in search of a species with great intelligence to live in harmony with its creations, before leaving once more to regain energy.


After much searching, Latias found an intelligent alien species known as Deoxys. They were bacterial but advanced. They chose a few of them and brought them back to their world.

For a while, things were fine, and the Deoxys and natives lived together in harmony. Until the Deoxys discovered they could 'infect' the natives and use their bodies. Suddenly, they were all infecting a host, and then war broke out.The Mew, Jirachi, Manaphy, Celebi, and Victini battled their infected brethren to set them free, while the Deoxys sought total dominance.
The war raged on for many centuries, until there were but a handful left of each species. Arceus returned and destroyed the last of the Deoxys, but the damage was done. The population of the world was little more than 20.
The Celebi retreated to the forests, hiding amongst the trees and in time. The Manaphy retreated to the sea, the Jirachi fell asleep, only waking up every so often, and the Victini hid in far-off lands.
This left only the Mew.During the war, three Mew had hidden under lakes in search of enlightenment.



Leaving only a handful of Mew left to roam. They were alone.The war had left the land in ruins; some places were battle-scarred beyond repair. Instead of lush grass, there were harsh deserts. This angered Groudon, sending him into a rage. Volcanoes spurted and spewed lava everywhere.
One day, a Mew was floating along when a sudden flow of lava approached it. Thinking quickly, Mew unleashed energy inside it that even Arceus didn't know about. It morphed the lava into a form and gave it LIFE. The first Heatran was created.

Arceus sensed this and had an idea. Gathering all the able Mew, it channeled immense power through them, using their life-giving abilities to create more living creatures. These were crude and unfinished, prototypes of what was to come.
Aerodactyl filled the sky, while Lileep, Cranidos, and Shieldon roamed the land.




Anorith, Omanyte, and Kabuto populated the seas.



Arceus also bestowed upon most of these beings the power to 'evolve' into more powerful creatures if the correct environment was met.
Finally, Latias returned once more. They had been far more thorough in their searching than before. However, Arceus had told them to stop, but guilt kept them going. They were determined to complete their job.
They brought humans from another planet. Basic but intelligent beings who definitely lacked the ability to infect anything. The humans settled in quickly, initially living relatively separately from the animals.
But Arceus wasn't convinced; he felt the need to test them.
First, Arceus created Articuno, who he ordered to send the planet into an Ice Age.

Articuno froze the planet, killing many creatures, but giving birth to new ones like Mamoswine.

To Arceus' pleasure, the humans adapted, creating structures out of ice and snow. The severe drop in temperature awoke Regigigas, who rose high above the land and saw what was happening.
The humans instantly fell in love with Regigigas, worshipping the titan and creating statues of it from ice. Touched by this, Regigigas found one of the statues and breathed life into it before returning to sleep.

However, this scared the humans, and they locked it away in a cave.
Realizing that the Ice Age did not affect the humans, Arceus created another bird, Moltres, and ordered it to send the world into a drought. The ice melted, and the water evaporated as the temperature rose higher and higher.

While the humans continued to adapt, using the skills they had learned with the ice and applying them to rock, the creatures weren't as lucky. The Mamoswine and other creatures that adapted to the cold died off, but new ones such as huge insects like Yanmega became common.

Once again, the drought awoke Regigigas, who once again saw a statue of himself. Thinking the humans would have learned from last time, Regigigas gave it life. But rumors of the living statue had been passed down and exaggerated since last time, and once again, the scared humans locked away this second 'Regi'.

When the drought finally wore off, Arceus began the third and final test. He created one more legendary bird, Zapdos. Zapdos created powerful electrical storms all across the land.

The storms killed off the last of the prototype creatures, leaving only the humans and the few pets they brought from their home land. One extremely intelligent man managed to harness the power of electricity, creating the first electronic device.
Of course, Regigigas awoke one final time. He discovered that the humans were far more evolved than expected, able to harness metals and electricity, albeit at a somewhat primitive level. More out of tradition than anything else, Regigigas created the third Regi out of steel. The humans were no longer scared of this Regi, but they sealed it away with the other two nonetheless, knowing that one day someone powerful enough would tame them.

Arceus was baffled. The humans had passed all three tests of harsh weather. Zapdos calmed the storms, and the world became peaceful once again.
Arceus herded the Mew together for a second time. Having learned the strengths and weaknesses of his prototype beings, Arceus was ready to go farther.
Siphoning its huge power through the small pink beings, Arceus filled the world with hundreds of species of creatures that would become known as 'Pokémon'. They were more diverse than it had ever imagined, filling the skies, land, and sea.
The life energies even reacted with the sun rays and moonlight, creating Ho-oh and Lugia respectively.


Some radiated out of the planet's moon, creating a population of Clefairy, as well as Cresselia on the light side and Darkrai on the dark side of the moon.



Lugia befriended the three elemental birds, and they followed him like a leader. Meanwhile, humans started to get closer to these new creatures, using them as slaves, weapons, or pets. The term 'Pokémon' arose from strange travelers and stuck.
The first Pokéballs were created from Apricorns, and the bond between human and Pokémon was complete.


Ho-oh took residence at the top of the Bell Tower. It was jealous of Lugia's trio of birds and wanted one of its own. One day, three Kimono girls entered its tower with a Jolteon, Flareon, and Vaporeon.



Ho-oh burnt down the tower with its Sacred Fire. Most escaped, but the three Pokémon were trapped and perished in the flames. Ho-oh soon resurrected them as Entei, Raikou, and Suicune.



Humans continued to evolve and take over the land, and Pokémon continued to work alongside and for them for many, many years.
That is the story of the Pokémon World.
-
 @ 8d34bd24:414be32b
2025-04-09 14:45:28
@ 8d34bd24:414be32b
2025-04-09 14:45:28I was listening to “Ultimately with R.C. Sproul.” He made the comment that “Sin is so common that we don’t think it is that concerning, but it is especially concerning because it is so common.” This is so true.
I used to really look down on Adam and Eve for eating the forbidden fruit. I thought, “How hard is it to obey a single command? We have so many to obey today from God, government, parents, etc.” One day I finally realized two truths. Adam and Eve were adults, but they had not been around very long (the Bible doesn’t say how long, but the implication is not very long, maybe even as short as days after being created.) They didn’t have life experience. They also had never been lied to before. They weren’t looking at the world with suspicion. They lived in a perfect environment with a perfect, loving God. It would’ve never crossed their mind that a person would lie, so they trusted the lie instead of God.
Today, we live in a sinful, fallen world. Everyone lies. Everyone steals. Everyone is unkind. Everyone has selfish motives. Yes, there is a difference in how often and how “bad” the lie, the theft, the motive, or the unkindness, but sin is everywhere. We get used to it and it seems normal. When we act the same way, it doesn’t seem that bad. We just took a pen home from work, nobody will miss it. We just told the person what they wanted to hear, so we won’t hurt their feelings. It is only a little white lie. Yes, I was unkind, but that person really deserved it because they were worse. We think this way and excuse our sins because we aren’t as bad as someone else.
I’ve noticed as I’ve grown older that the age when you become old keeps getting older and older. Old is always a little bit older than I am. When I was 10, a teenager was really old. When I was 16, an 18 year old was an adult and old. When I was 20, a 40 year old was old. When I was 50, a 65 year old was old. Old keeps getting older because my reference is myself. The truth is that I am getting older. I am on the downhill slide. I am closer to death than I am to birth. My arbitrary, moving reference doesn’t change this fact.
In the same way, when we look at sin, we have the same problem. We are always looking for someone who sins worse to make us look better and to excuse our sins. We compare ourselves to sinful men instead of our perfect, holy, sinless Savior.
In an earlier post, I made the comparison of the lights in the sky. If you go outside on a dark, moonless night, you will see the stars in the sky shining. They seem bright, but some are brighter than others. You can compare the brightness of the stars and call some brighter and others darker, but when the sun rises, you can’t see any light from the stars. Their light is drowned out by the light of the sun. The sun is so much brighter that it is as if the stars don’t produce any light at all.
In the same way, we may do some good things. When we compare our good deeds to others, we may look better, but when the true reference, the Son of God is our reference, our good works look like they don’t exist at all. The differences between the best person and the worst person are insignificant, just like the brightness of the brightest star and the dimmest star seems insignificant when compared with the brightness of the Sun.
The cool thing is that there is another light in the sky, the moon. The moon doesn’t have any light of its own, but it is the second brightest light in the sky. Why? Because it reflects the light of the sun. We should be the same way. We will never measure up if we seek to be good and sinless. We will never meet the standard that Jesus set for us with His perfect, sinless, sacrificial life, but we can reflect the glory of Jesus in our lives.
Yes, when we sin, we can hurt others, but who are we really sinning against? David knows.
Be gracious to me, O God, according to Your lovingkindness;\ According to the greatness of Your compassion blot out my transgressions.\ Wash me thoroughly from my iniquity\ And cleanse me from my sin.\ For I know my transgressions,\ And my sin is ever before me.\ **Against You, You only, I have sinned\ And done what is evil in Your sight,\ So that You are justified when You speak\ And blameless when You judge.\ Behold, I was brought forth in iniquity,\ And in sin my mother conceived me.\ Behold, You desire truth in the innermost being,\ And in the hidden part You will make me know wisdom. (Psalm 51:1-6) {emphasis mine}
Yes, our sins can hurt other people and do, but the true damage is to the glory of our generous Creator God. We must confess our sins to God first and then to anyone we have hurt. We must accept that we deserve any judgement God gives us because He created us and everyone and everything with which we interact. Our allegiance, submission, and worship is due to our Creator God.
Because we can never fully understand how abhorrent sin is to God, I thought I’d share how a godly man, the priest and prophet, Ezra, reacted to sin among his brethren.
When I heard about this matter, I tore my garment and my robe, and pulled some of the hair from my head and my beard, and sat down appalled. Then everyone who trembled at the words of the God of Israel on account of the unfaithfulness of the exiles gathered to me, and I sat appalled until the evening offering.
But at the evening offering I arose from my humiliation, even with my garment and my robe torn, and I fell on my knees and stretched out my hands to the Lord my God; and I said, “O my God, I am ashamed and embarrassed to lift up my face to You, my God, for our iniquities have risen above our heads and our guilt has grown even to the heavens. Since the days of our fathers to this day we have been in great guilt, and on account of our iniquities we, our kings and our priests have been given into the hand of the kings of the lands, to the sword, to captivity and to plunder and to open shame, as it is this day. But now for a brief moment grace has been shown from the Lord our God, to leave us an escaped remnant and to give us a peg in His holy place, that our God may enlighten our eyes and grant us a little reviving in our bondage. (Ezra 9:3-8) {emphasis mine}
Ezra sees sin, shreds his clothes, pulls out his hair, and sits appalled. Do we feel even a fraction of the horror at guilt that Ezra showed? When faced with some Israelites marrying non-Israelite (many from the banned people groups), Ezra admits that “our iniquities have risen above our heads and our guilt has grown even to the heavens.” How many of us would think that was only a little sin or that since it was only a few people, it wasn’t that important? Ezra, instead of saying, “Why did you send us into exile for 70 years and why are you not blessing us now?” said, “But now for a brief moment grace has been shown from the Lord our God.” Instead of accusing God of not being good enough or kind enough, thanks God for His grace which was completely undeserved. If only we could look at sin in this way.
After all that has come upon us for our evil deeds and our great guilt, since You our God have requited us less than our iniquities deserve, and have given us an escaped remnant as this, (Ezra 9:13) {emphasis mine}
Ezra understood that we all deserve only judgment. Every good thing we receive is only due to God’s grace. Instead of asking why God would allow a bad thing to happen to us, we should be asking why God is so gracious to give us good things in our lives and not give us nothing but punishment.
Jesus also talked about our sins. Although it is good, when we are tempted to sin, to choose to not sin, even evil thoughts are sins. They mean our minds and hearts are not fully submitted to God.
“You have heard that the ancients were told, ‘You shall not commit murder’ and ‘Whoever commits murder shall be liable to the court.’ But I say to you that everyone who is angry with his brother shall be guilty before the court; and whoever says to his brother, ‘You good-for-nothing,’ shall be guilty before the supreme court; and whoever says, ‘You fool,’ shall be guilty enough to go into the fiery hell. Therefore if you are presenting your offering at the altar, and there remember that your brother has something against you, leave your offering there before the altar and go; first be reconciled to your brother, and then come and present your offering. Make friends quickly with your opponent at law while you are with him on the way, so that your opponent may not hand you over to the judge, and the judge to the officer, and you be thrown into prison. Truly I say to you, you will not come out of there until you have paid up the last cent.
“You have heard that it was said, ‘You shall not commit adultery’; but I say to you that everyone who looks at a woman with lust for her has already committed adultery with her in his heart. If your right eye makes you stumble, tear it out and throw it from you; for it is better for you to lose one of the parts of your body, than for your whole body to be thrown into hell. If your right hand makes you stumble, cut it off and throw it from you; for it is better for you to lose one of the parts of your body, than for your whole body to go into hell.
“It was said, ‘Whoever sends his wife away, let him give her a certificate of divorce’; but I say to you that everyone who divorces his wife, except for the reason of unchastity, makes her commit adultery; and whoever marries a divorced woman commits adultery.
“Again, you have heard that the ancients were told, ‘You shall not make false vows, but shall fulfill your vows to the Lord.’ But I say to you, make no oath at all, either by heaven, for it is the throne of God, or by the earth, for it is the footstool of His feet, or by Jerusalem, for it is the city of the great King. Nor shall you make an oath by your head, for you cannot make one hair white or black. But let your statement be, ‘Yes, yes’ or ‘No, no’; anything beyond these is of evil.
“You have heard that it was said, ‘An eye for an eye, and a tooth for a tooth.’ But I say to you, do not resist an evil person; but whoever slaps you on your right cheek, turn the other to him also. If anyone wants to sue you and take your shirt, let him have your coat also. Whoever forces you to go one mile, go with him two. Give to him who asks of you, and do not turn away from him who wants to borrow from you.
“You have heard that it was said, ‘You shall love your neighbor and hate your enemy.’ But I say to you, love your enemies and pray for those who persecute you, so that you may be sons of your Father who is in heaven; for He causes His sun to rise on the evil and the good, and sends rain on the righteous and the unrighteous. For if you love those who love you, what reward do you have? Do not even the tax collectors do the same? If you greet only your brothers, what more are you doing than others? Do not even the Gentiles do the same? Therefore you are to be perfect, as your heavenly Father is perfect. (Matthew 5:21-48) {emphasis mine}
Many people say that as New Testament believers, we are not under the Old Covenant and the Old Testament laws do not apply to us. While that may be true of the ceremonial laws, the truth is that Jesus made the laws stricter. It is still true that we are not to commit murder, but we are also not to hate another. It is still true that we are not to commit adultery, but we are also not to lust after another. We are also not to fight against those who mistreat us and we are to love those who hate us. Jesus expects more, not less, maybe because we now have the guidance and power of the Holy Spirit within us.
If we have the mind of Christ, we should despise the things God hates. If we have the heart of Christ, we should love even those who hate us and we should seek their eternal good. We should see with the eyes of Christ and see the hurt behind the hate and dishonesty. How do we do this? We need to fill our minds with the word of God. We need to obey Paul’s command to those in Philippi:
Finally, brethren, whatever is true, whatever is honorable, whatever is right, whatever is pure, whatever is lovely, whatever is of good repute, if there is any excellence and if anything worthy of praise, dwell on these things. (Philippians 4:8)
We need to so fill our mind with God’s word that God’s goodness overflows into our lives.
God of heaven, please change our hearts and minds and make them fully aligned with your heart and mind. Help us to see sin as you see sin and to see people as you see people. Help us to see the hurt instead of the lashing out, so we can have a merciful heart towards those who are unkind to us. Help us to fill our minds with your goodness and your word, so there is no room for evil in us. Make us more like you.
Trust Jesus
FYI, there are many people who can’t see their own sin and who discount the severity of sin. I am writing for these people. There are also people who have no trouble seeing their own sin. Their problem is not accepting the forgiveness of God. Never doubt that God has forgiven you if you have confessed your sins and trusted Jesus as Savior. Jesus has covered your sins and the Father sees only the holiness of Jesus. Your relationship with the Godhead is fully reconciled. You should do right out of thankfulness and love of God, but there is nothing else you need to do to be saved and have a right relationship with God.
-
 @ ef53426a:7e988851
2025-04-22 07:47:07
@ ef53426a:7e988851
2025-04-22 07:47:07In 1997, an IBM supercomputer beat the sport’s greatest mind. Deep Blue II became the first machine to defeat a chess world champion — Garry Kasparov. Humans would never win at chess again.
But if computers have been better than us for so long, why do we still play chess? Don’t we always play to win?
Well, even though we’re unlikely to record a victory over the machines, chess has become more popular than ever. According to a June 2023 PBS feature, subscriptions to chess clubs have soared and earlier this year chess.com servers overloaded due to a the highest number of active users ever.
This is not just a fad based on The Queen’s Gambit (a 2020 Netflix adaptation). Over 100m people have registered on chess.com since then, and books, YouTube channels and other content is flourishing. A Grandmaster recently visited the city in Spain where I live, and thousands of people came to watch her play.
Here’s my theory behind the recent revival of chess. The answer to why we still play is what’s behind the game of chess — strategy and spatial recognition.
It’s a system of training ourselves to appreciate cause and consequence, to improve our decision making. The best players train against computers, knowing they can’t win, but they can learn.
The same is true with today’s writing landscape. Professionals are panicking that machines will produce most of the content we’ll read from now on. Writing will change — that’s true. AI can write faster and more (grammatically) accurately.
But what’s behind writing? 🧠 Patterns of structured thought 🗣️ Sound rhetoric 🖊️ The creativity of language 📚 The beauty of stories.
Writing is a skill that we still need to train.
If we don’t, how will we know what makes our words effective? How will we communicate? How will we make sense of our past?
We can use AI to help, but the words it processes belong to us.
Just as we have recognised the importance of the concepts behind chess, we must do the same for the process of writing.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: General confusion
Most IPFS open-source projects, libraries and apps (excluding Ethereum stuff) are things that rely heavily on dynamic data and temporary links. The most common projects you'll see when following the IPFS communities are chat rooms and similar things. I've seen dozens of these chat-rooms. There's also a famous IPFS-powered database. How can you do these things with content-addressing is a mistery. Of course they probably rely on IPNS or other external address system.
There's also a bunch of "file-sharing" on IPFS. The kind of thing people use for temporary making a file available for a third-party. There's image sharing on IPFS, pastebins on IPFS and so on. People don't seem to share the preoccupation with broken links here.
-
 @ 37c10448:f8256861
2025-04-22 07:44:10
@ 37c10448:f8256861
2025-04-22 07:44:10Title H1
Hello !
-
 @ c230edd3:8ad4a712
2025-04-09 00:33:31
@ c230edd3:8ad4a712
2025-04-09 00:33:31Chef's notes
I found this recipe a couple years ago and have been addicted to it since. Its incredibly easy, and cheap to prep. Freeze the sausage in flat, single serving portions. That way it can be cooked from frozen for a fast, flavorful, and healthy lunch or dinner. I took inspiration from the video that contained this recipe, and almost always pan fry the frozen sausage with some baby broccoli. The steam cooks the broccoli and the fats from the sausage help it to sear, while infusing the vibrant flavors. Serve with some rice, if desired. I often use serrano peppers, due to limited produce availability. They work well for a little heat and nice flavor that is not overpowering.
Details
- ⏲️ Prep time: 25 min
- 🍳 Cook time: 15 min (only needed if cooking at time of prep)
- 🍽️ Servings: 10
Ingredients
- 4 lbs ground pork
- 12-15 cloves garlic, minced
- 6 Thai or Serrano peppers, rough chopped
- 1/4 c. lime juice
- 4 Tbsp fish sauce
- 1 Tbsp brown sugar
- 1/2 c. chopped cilantro
Directions
- Mix all ingredients in a large bowl.
- Portion and freeze, as desired.
- Sautè frozen portions in hot frying pan, with broccoli or other fresh veggies.
- Serve with rice or alone.
-
 @ 2b24a1fa:17750f64
2025-04-22 06:57:36
@ 2b24a1fa:17750f64
2025-04-22 06:57:36Es fühlt sich wie ein Staatsstreich an. Vielleicht ist es auch einer. Ein abgewählter Bundestag genehmigt mittels Grundgesetzänderung die größte Staatsverschuldung in der Geschichte Deutschlands mit der unvorstellbaren Summe von 1000 Milliarden Euro, also eine Billion.
https://soundcloud.com/radiomuenchen/vom-schuldenstaatsstreich-zur-finanzdiktatur-von-rob-kenius?\ Jedem muss klar sein, wohin diese Gelder aus den Taschen der Steuerzahler wandern und wer, wenn in Rüstung, Militärhilfen, Konzern-Subventionen investiert wird, die Leidtragenden sind: Kinder, Rentner, kleine Firmen und Betriebe, sozial Schwache, Kranke, Arbeitslose, Obdachlose.
\ Die Kräfte aus Finanzeliten, Militär, Rüstungsindustrie, regierenden Parteien und den staatstragenden Medien werden dafür immer stärker.
\ Hören Sie den Beitrag „Vom Schuldenstaatsstreich zur Finanzdiktatur“ von Rob Kenius, der zunächst beim Overton-Magazin erschienen war: https://overton-magazin.de/top-story/vom-schuldenstaatsstreich-zur-finanzdiktatur-in-leicht-verstaendlicher-sprache/
Sprecherin: Sabrina Khalil
Redaktion: Jonny Rieder
Bild: Bund der Steuerzahler / Janek Werner
Rob Kenius betreibt die systemkritische Webseite kritlit.de und den Podcast 9min Denksport. Der Text Vom Schuldenstaatsstreich zur Finanzdiktatur ist davon die 14. Folge.
Radio München\ www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen\ odysee.com/@RadioMuenchen.net:9\ rumble.com/user/RadioMunchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): bc1qqkrzed5vuvl82dggsyjgcjteylq5l58sz4s927\ Ethereum (ETH): 0xB9a49A0bda5FAc3F084D5257424E3e6fdD303482
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Scala is such a great language
Scala is amazing. The type system has the perfect balance between flexibility and powerfulness.
matchstatements are great. You can write imperative code that looks very nice and expressive (and I haven't tried writing purely functional things yet). Everything is easy to write and cheap and neovim integration works great.But Java is not great. And the fact that Scala is a JVM language doesn't help because over the years people have written stuff that depends on Java libraries -- and these Java libraries are not as safe as the Scala libraries, they contain reflection, slowness, runtime errors, all kinds of horrors.
Scala is also very tightly associated with Akka, the actor framework, and Akka is a giant collection of anti-patterns. Untyped stuff, reflection, dependency on JVM, basically a lot of javisms. I just arrived and I don't know anything about the Scala history or ecosystem or community, but I have the impression that Akka has prevent more adoption of Scala from decent people that aren't Java programmers.
But luckily there is a solution -- or two solutions: ScalaJS is a great thing that exists. It transpiles Scala code into JavaScript and it runs on NodeJS or in a browser!
Scala Native is a much better deal, though, it compiles to LLVM and then to binary code and you can have single binaries that run directly without a JVM -- not that the single JARs are that bad though, they are great and everybody has Java so I'll take that anytime over C libraries or NPM-distributed software, but direct executables even better. Scala Native just needs a little more love and some libraries and it will be the greatest thing in a couple of years.
-
 @ da0b9bc3:4e30a4a9
2025-04-22 06:44:40
@ da0b9bc3:4e30a4a9
2025-04-22 06:44:40Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/952743
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Que vença o melhor
Nos esportes e jogos em geral, existe uma constante preocupação em balancear os incentivos e atributos do jogo, as regras do esporte em si e as regras das competições para que o melhor vença, ou, em outras palavras, para que sejam minimizados os outros fatores exceto a habilidade mais pura quanto possível no jogo em questão.
O mundo fora dos jogos, porém, nem sempre pode ter suas regras mudadas por um ente que as controla e está imbuído da vontade e dos meios para escolher as melhores regras possíveis para a obtenção dos resultados acima. Aliás, é muitas vezes essa possibilidade é até impensável. Mesmo quando ela é pensável e levada em conta os fatores que operam no mundo real não são facilmente identificáveis, eles são muitos, e mudam o tempo todo.
Mais do que isso, ao contrário de um jogo em que o objetivo é praticamente o mesmo para todo mundo, os objetivos de cada agente no mundo real são diferentes e incontáveis, e as "competições" que cada um está disputando são diferentes e muitas, cada minúsculo ato de suas vidas compreendendo várias delas simultaneamente.
Da mesma forma, é impossível conceber até mesmo o conceito de "melhor" para que se deseje que ele vença.
Mesmo assim é comum encontrarmos em várias situações gente que parte do princípio de que se Fulano está num certo lugar (por exemplo, um emprego muito bom) e Beltrano não isso se deve ao fato de Fulano ter sido melhor que Beltrano.
Está aí uma crítica à idéia da meritocracia (eu tinha me esquecido que essa palavra existia).
-
 @ f683e870:557f5ef2
2025-04-08 11:13:27
@ f683e870:557f5ef2
2025-04-08 11:13:27When it comes to the Nostr Web of Trust, several NIPs have been proposed, but the one that seemed to gather the most traction was Trusted Assertion by Vitor Pamplona.
The idea is to have
kind:30382represent assertions made about an entity, which could be a pubkey, for example. The NIP also specifies a tag calledrank, which can be used to build some basic WoT primitives.Example event:
{ "kind": 30382, "tags": [ ["d", "e88a6...50411"], ["rank", "89"], ["zap_amt_sent", "1000000"], ], "content": "", //... }However, we quickly realized that this NIP was too limiting for what we wanted to accomplish: real-time, personalized ranking.
To illustrate our different approaches, we will show how to replicate our Verify Reputation with trusted assertions.
Verify Reputation
Verify Reputation returns:
- the rank, follow count and followers count of the given
target - its top followers by rank.
All ranks are personalized to the given
source.This “batteries included” solution helps users avoid impersonation and fraud with a single request, no matter what application they are using, be it a kind:1 client, chat app, wallet, marketplace, or more.
To get the same result with trusted assertions, you would have to
- Get all contact lists that contain the
target(as aptag) - Build the target’s
followerlist from those event authors - Get the trusted assertions for the target and each of the followers
- Sort them by the rank provided by the trusted assertions
This operation is computationally expensive, especially on mobile devices. It is clear that if the user is willing to verify and process a large number of events (potentially +100k), he can compute some (rudimentary) ranking directly on the device, without the need to trust a third party.
More generally, trusted assertions are very hard to use when one doesn’t know the pubkeys of the people he’s looking for. This goes fundamentally against our approach of Web of Trust, as a powerful mechanism for discovery.
Are you looking to add Web of Trust capabilities to your app or project?
- the rank, follow count and followers count of the given
-
 @ d34e832d:383f78d0
2025-04-22 06:43:30
@ d34e832d:383f78d0
2025-04-22 06:43:30It is noteworthy to mention that Bill Gates, a distinguished co-founder of Microsoft and a philanthropist with extensive impact on global health and education initiatives, serves as a limited partner in various investment vehicles associated with Village Global. However, it is critical to delineate the nuances of this relationship, as Gates' status as a limited partner does not confer upon him any authoritative control or decision-making power regarding the operational protocols or strategic direction of SimpleX Chat.
The development team behind SimpleX Chat has made a concerted effort to clarify that Village Global's involvement is strictly financial in nature, devoid of any operational oversight or influence over the management and technical development of the project.
Privacy Without Compromise
SimpleX Chat aims to provide a messenger that is both convenient and private, addressing the perceived trade-off between these two qualities in existing solutions. They define privacy as protecting not only message content but also metadata like connection details and user identities.
In contrast to a multitude of contemporary messaging applications, SimpleX Chat distinctly emphasizes the safeguarding of metadata privacy as a foundational component of its architecture.
The development team articulates a compelling argument regarding the intrinsic value of communication relationships, suggesting that the identification of interlocutors constitutes sensitive data that may be weaponized against users in various contexts—an issue that current market leaders in the domain have failed to remedy with sufficient rigor.
Consequently, the developers are actively engaged in initiatives to bolster the obfuscation of users’ IP addresses, thereby enhancing the overall security framework against potential surveillance and data exploitation threats.
A Radical Architectural Shift
The architecture underpinning SimpleX Chat diverges notably from conventional paradigms associated with user account management.
Specifically, it eschews the creation and maintenance of user profiles in the traditional sense, thereby negating the repository of personally identifiable information on centralized servers. Instead, all pertinent data transactions pertinent to user interactions are localized, existing solely on the end-user's devices.
This paradigm shift engenders a formidable barrier to data accessibility, effectively neutralizing the potential for data disclosure to law enforcement agencies, irrespective of judicial mandates such as court warrants.
Furthermore, in their adherence to statutory obligations, SimpleX Chat's design ethos proactively prioritizes the minimization of data collection, establishing a privacy-centric framework that aptly aligns with contemporary concerns regarding data sovereignty and user anonymity.
Functionality Grounded in Security
The SimpleX Chat application exemplifies a multi-device compatibility framework, strategically prioritizing stringent security protocols over user convenience.
This methodology distinctly contrasts with that of various competitors who may opt for convenience-focused functionalities that inadvertently jeopardize user data integrity and confidentiality.
The current technical architecture facilitates seamless profile transfers across devices, while also enabling a desktop terminal interface that remains operationally tethered to the mobile device.
Such an arrangement underscores SimpleX Chat's commitment to balancing usability with robust security measures, effectively mitigating potential vulnerabilities in cross-platform interactions.
Transient Messaging and Signal Protocol Reimagined
SimpleX Chat integrates the functionality of transient messaging, which serves primarily as a user convenience element rather than representing a robust security mechanism.
The developers have explicitly articulated that they are unable to ensure the irreversible deletion of messages from the recipient's device, thereby highlighting potential vulnerabilities associated with data retention and privacy concerns in digital communications.
The development team arrived at a strategic decision to forgo the utilization of the existing Signal codebase, primarily attributed to its inherent complexity and the prospective risks associated with the coupling dynamics that could emerge between the Signal protocol and its corresponding system architecture.
As a result, they opted to engineer the Signal protocol anew, commencing from foundational coding principles.
This approach not only enables them to exert comprehensive control over the implementation but also significantly facilitates the seamless integration of advanced cryptographic frameworks, specifically post-quantum key agreement methodologies, which are imperative in future-proofing cryptographic communications against the advent of quantum computing threats.
UX Development and the Road Ahead
The UI is still under development. The developers acknowledge some usability challenges, especially for users unfamiliar with the concept of profile-based messaging without traditional accounts.
They are actively working on improving UX based on user feedback.
A Decentralized Economic Model
SimpleX Chat is poised to introduce an innovative commercial framework predicated on the integration of a decentralized accounting mechanism, characterized by the utilization of distributed ledger technology, which underpins cryptocurrency transactions, coupled with a system reminiscent of traditional gift card paradigms.
This commercial model is strategically designed to provide economic incentives to both infrastructure operators, who maintain the necessary backbone for the network's operations, and software vendors, who contribute essential applications and services—all while preserving the fundamental decentralized architecture inherent to blockchain systems.
This careful balance is crucial for fostering a sustainable ecosystem that rewards participants without compromising the network's core principles of transparency and egalitarian access.
🚧 Prerequisites
| Requirement | Description | |-------------------|----------------------------------------------| | VPS | Debian 12, at least 1GB RAM (for running server) | | Build Machine | A second Linux machine with ≥ 8GB RAM for compiling binaries | | Domains | FQDNs like
smp.yourdomain.com,xfp.yourdomain.com,turn.yourdomain.com| | SSH Keys | SSH access secured with key-based auth only | | Firewall | Only allow ports for SSH (22), SMP (5223), XFP (5353), TURN (5349) |
🧱 Step 1: Build SimpleX on Build Machine
You’ll compile the binaries on your high-RAM machine and then SCP them over.
```bash sudo apt update && sudo apt install build-essential git rustc cargo pkg-config libssl-dev
Clone repo
git clone https://github.com/simplex-chat/simplexmq cd simplexmq
Build binaries
cargo build --release ```
You’ll find: -
target/release/smp-server-target/release/xfp-serverCopy them to your VPS:
bash scp target/release/smp-server user@vps:/home/user/ scp target/release/xfp-server user@vps:/home/user/
🧑💻 Step 2: Harden the VPS
🔒 SSH-only access
```bash
Edit /etc/ssh/sshd_config
PermitRootLogin no PasswordAuthentication no ```
Restart SSH:
bash sudo systemctl restart ssh🔥 UFW Firewall
bash sudo apt install ufw sudo ufw default deny incoming sudo ufw default allow outgoing sudo ufw allow OpenSSH sudo ufw enable🛡️ Fail2ban
bash sudo apt install fail2ban sudo systemctl enable --now fail2ban
📡 Step 3: SMP Server Setup
Create user and directories:
bash sudo useradd -m -r -s /usr/sbin/nologin smp sudo mkdir -p /var/lib/smp /var/log/smp sudo chown -R smp:smp /var/lib/smp /var/log/smpMove binary and set permissions:
bash sudo mv /home/user/smp-server /usr/local/bin/ sudo chmod +x /usr/local/bin/smp-serverCreate systemd service:
/etc/systemd/system/smp.service```ini [Unit] Description=SimpleX SMP Server After=network.target[Service] User=smp ExecStart=/usr/local/bin/smp-server --fqdn smp.yourdomain.com --log /var/log/smp/smp.log WorkingDirectory=/var/lib/smp Restart=on-failure
[Install] WantedBy=multi-user.target ```
bash sudo systemctl daemon-reexec sudo systemctl enable --now smp.service
🗂️ Step 4: XFP Server Setup
bash sudo useradd -m -r -s /usr/sbin/nologin xfp sudo mkdir -p /var/lib/xfp /var/log/xfp sudo chown -R xfp:xfp /var/lib/xfp /var/log/xfp sudo mv /home/user/xfp-server /usr/local/bin/ sudo chmod +x /usr/local/bin/xfp-serverCreate systemd service:
/etc/systemd/system/xfp.service```ini [Unit] Description=SimpleX XFP Server After=network.target[Service] User=xfp ExecStart=/usr/local/bin/xfp-server --storage /var/lib/xfp --log /var/log/xfp/xfp.log --quota 2GB WorkingDirectory=/var/lib/xfp Restart=on-failure
[Install] WantedBy=multi-user.target ```
bash sudo systemctl daemon-reexec sudo systemctl enable --now xfp.service
🎙️ Step 5: Optional TURN Server (WebRTC)
Install Coturn:
bash sudo apt install coturnEdit
/etc/turnserver.conf:ini listening-port=5349 tls-listening-port=5349 fingerprint lt-cred-mech realm=turn.yourdomain.com user=someuser:somepassword cert=/etc/letsencrypt/live/turn.yourdomain.com/fullchain.pem pkey=/etc/letsencrypt/live/turn.yourdomain.com/privkey.pem cipher-list="ECDHE-RSA-AES256-GCM-SHA384" no-stdout-logSet to auto-start:
bash sudo systemctl enable coturnConfigure DNS and firewall to allow 5349.
🔁 Step 6: Certificate Renewal (Let's Encrypt)
bash sudo apt install certbotSet up renewal cron:
bash sudo crontab -ebash 0 3 * * * certbot renew --quiet && systemctl restart coturn
🧪 Step 7: Testing with SimpleX Desktop
- Download SimpleX Desktop
- Launch and go to Settings → Relay Settings
- Disable defaults, add your SMP and XFP addresses.
🔄 Upgrading SimpleX
On your build machine:
bash git pull origin main cargo build --releaseThen:
bash scp target/release/smp-server user@vps:/home/user/ scp target/release/xfp-server user@vps:/home/user/On VPS:
bash sudo systemctl stop smp xfp sudo mv /home/user/smp-server /usr/local/bin/ sudo mv /home/user/xfp-server /usr/local/bin/ sudo systemctl start smp xfp
What if you communicated securely?
📡 SimpleX – Anonymous chat, no phone numbers, no metadata
SimpleX is unlike anything else. It doesn’t just encrypt your messages—it hides who you're talking to. No central servers, no profiles, no traces. Just pure private messaging.
Perfect for when you need total metadata privacy and no digital fingerprint.
🌱 Nostr DMs – Messages with your Web of Trust
If you’re already on Nostr, using DMs is a natural step. Messages are encrypted end-to-end and tied to your public key identity.
Great for building trusted, decentralized communication channels within your Web of Trust.
🔐 PGP Email – Old-school but rock solid
PGP lets you encrypt your emails and verify identities with public keys. It’s still one of the most powerful tools for asynchronous, verifiable, and encrypted communication—especially for long-form or professional exchanges.
🔁 Use them all together
Different tools for different roles. Want to talk anonymously? Use SimpleX.
Connecting with your Nostr tribe? Slide into those DMs.
Need to send a secure file or message over email? PGP's got your back.Privacy isn’t just one app—it’s a toolkit. Build yours.
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ ee6ea13a:959b6e74
2025-04-06 16:38:22
@ ee6ea13a:959b6e74
2025-04-06 16:38:22Chef's notes
You can cook this in one pan on the stove. I use a cast iron pan, but you can make it in a wok or any deep pan.
I serve mine over rice, which I make in a rice cooker. If you have a fancy one, you might have a setting for sticky or scorched rice, so give one of those a try.
To plate this, I scoop rice into a bowl, and then turn it upside-down to give it a dome shape, then spoon the curry on top of it.
Serve with chopped cilantro and lime wedges.
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 20
- 🍽️ Servings: 4
Ingredients
- 1 ½ pounds boneless skinless chicken breast, cut into 2" pieces
- 2 tablespoons coconut or avocado oil
- 1 cup white or yellow onion, finely diced
- 1 cup red bell pepper, sliced or diced
- 4 large garlic cloves, minced
- 1 small (4oz) jar of Thai red curry paste
- 1 can (13oz) unsweetened coconut milk
- 1 teaspoon ground ginger
- 1 teaspoon ground coriander
- 1 tablespoon soy sauce
- 1 tablespoon brown sugar
- 1 cup carrots, shredded or julienned
- 1 lime, zest and juice
- ¼ cup fresh cilantro, chopped for garnish
Directions
- Heat oil in a large skillet over medium-high. Once hot, add onions and ½ teaspoon salt. Cook 3 minutes, or until onions are softened, stirring often.
- Add the red curry paste, garlic, ginger, and coriander. Cook about 1 minute, or until fragrant, stirring often.
- Add coconut milk, brown sugar, soy sauce, and chicken. Stir, bring to a simmer, then reduce heat to medium. Simmer uncovered for 7 minutes, occasionally stirring.
- Add carrots and red bell peppers, and simmer 5-7 more minutes, until sauce slightly thickens and chicken is cooked through.
- Remove from heat, and stir in the lime zest, and half of the lime juice.
- Serve over rice, topped with cilantro, and add more lime juice if you like extra citrus.
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 8d34bd24:414be32b
2025-04-06 14:34:37
@ 8d34bd24:414be32b
2025-04-06 14:34:37This weekend my pastor was preaching on this passage. Two words stood out when we were reading the passage, “but Jesus … .” This made me start searching for other instances of “but Jesus …” to see what we could learn.
And a woman who had a hemorrhage for twelve years, and could not be healed by anyone, came up behind Him and touched the fringe of His cloak, and immediately her hemorrhage stopped. And Jesus said, “Who is the one who touched Me?” And while they were all denying it, Peter said, “Master, the people are crowding and pressing in on You.” But Jesus said, “Someone did touch Me, for I was aware that power had gone out of Me.” (Luke 8:43-46) {emphasis mine}
In this passage people were crowding Jesus and fighting to get close to Him or even touch Him and in this dense crowd he asked, “Who is the one who touched Me?” Despite many people being pressed up beside Him, they all denied touching Him and Peter basically reprimanded Jesus that this was a ridiculous question because so many people were touching Him. “But Jesus …” knew that someone had touched Him and faith and that His power had healed that person. For the sake of the woman, the crowd, and His disciples, He wanted them to know what had happened and bless this woman that had suffered for more than a decade. He didn’t see the situation like everyone else. He saw things they did not see and like all of the best teachers, he asked His students questions to lead them to the truth. Despite the fact that he was on the way to helping Jairus’s dying daughter, Jesus stopped for this moment to bless this suffering woman and to teach the crowd the meaning of faith and the meaning of mercy.
How often do we ignore teaching moments or moments of service that could make a difference in a person’s life because we are busy and focused on something else? But Jesus did not miss the opportunity.
So often Jesus’s response to things are not like our own. “For as the heavens are higher than the earth, So are My ways higher than your ways And My thoughts than your thoughts.” (Isaiah 55:9)
But the news about Him was spreading even farther, and large crowds were gathering to hear Him and to be healed of their sicknesses. But Jesus Himself would often slip away to the wilderness and pray. (Luke 5:15-16) {emphasis mine}
Most of us, if we were bringing crowds through a blog or preaching or conferences would tend to continue working to reach more people, but Jesus took time to slip away from the crowd to pray. He prioritized prayer and fellowship with the Father knowing that ministry without the Father is no ministry at all. Jesus knew that there is more to sharing the Gospel than just drawing a crowd or growing a following. Jesus built the foundation before trying to build the church.
And some men were carrying on a bed a man who was paralyzed; and they were trying to bring him in and to set him down in front of Him. But not finding any way to bring him in because of the crowd, they went up on the roof and let him down through the tiles with his stretcher, into the middle of the crowd, in front of Jesus. Seeing their faith, He said, “Friend, your sins are forgiven you.” The scribes and the Pharisees began to reason, saying, “Who is this man who speaks blasphemies? Who can forgive sins, but God alone?” But Jesus, aware of their reasonings, answered and said to them, “Why are you reasoning in your hearts? Which is easier, to say, ‘Your sins have been forgiven you,’ or to say, ‘Get up and walk’? But, so that you may know that the Son of Man has authority on earth to forgive sins,”—He said to the paralytic—“I say to you, get up, and pick up your stretcher and go home.” (Luke 5:18-24) {emphasis mine}
This suffering man was paralyzed. His loving friends were trying to get him help by focusing on his physical needs, but Jesus saw the man’s most important need — his need for salvation. Instead of focusing on the obvious physical needs of the man, He dealt with the more important spiritual needs. He also knew that His critics were judging Him and denying His ability to wipe the man’s sins away. To prove that He could forgive the man’s sins, He also healed the man’s paralysis. After healing the man’s more important spiritual needs, He then healed the more obvious physical needs.
I know I catch myself spending lots of time praying for people’s physical needs. I pray asking for people to have healing from sickness and cancer. I pray for jobs and finances. I pray for relationships. I’ve noticed that I spend more time praying for physical needs that are problem today, but don’t matter eternally and not enough praying for salvation and guidance for people. I focus on what I can see, that although urgent, have little to no effect on the eternal well-being of the people. I should be more like Jesus and spend more time on praying for people’s spiritual needs that determine their eternal well-being.
Now when He was in Jerusalem at the Passover, during the feast, many believed in His name, observing His signs which He was doing. But Jesus, on His part, was not entrusting Himself to them, for He knew all men, and because He did not need anyone to testify concerning man, for He Himself knew what was in man. (John 2:23-25) {emphasis mine}
When we have people asking for us to share Jesus with them, we jump at the opportunity. We seek the crowds and the following. We seek the influence and prestige, but Jesus did not trust those seeking Him and knew they were looking for blessings without the submission or repentance.
I’ve noticed that I will have people asking questions about the Bible and Christianity. They ask me to defend everything in the Bible and what I believe. Because I have studied these things and studied apologetics, I tend to spend a large amount of time debating these topics, but it is frequently obvious from the beginning that these people are not truth seekers. They are people looking to throw “gotcha” questions at Christians in the hope of destroying their faith or making them look bad. I need to get better at asking questions of them and recognizing these situations as not interest and inquisitiveness, but attempts to destroy and not waste time on them. (Of course, sometimes there are watchers/listeners who can be helped by knowing there are answers to these questions.)
When it was evening, the disciples came to Him and said, “This place is desolate and the hour is already late; so send the crowds away, that they may go into the villages and buy food for themselves.” But Jesus said to them, “They do not need to go away; you give them something to eat!” They said to Him, “We have here only five loaves and two fish.” And He said, “Bring them here to Me.” Ordering the people to sit down on the grass, He took the five loaves and the two fish, and looking up toward heaven, He blessed the food, and breaking the loaves He gave them to the disciples, and the disciples gave them to the crowds, and they all ate and were satisfied. They picked up what was left over of the broken pieces, twelve full baskets. (Matthew 14:15-20) {emphasis mine}
We so often see the glass half empty. We see all of the things we can’t do, but Jesus knows what can be done and we should know that we can do all things in Christ who strengthens us. Instead of focusing on why we can’t, we need to trust God to enable us to do whatever He asks us to do.
Some Pharisees came up to Jesus, testing Him, and began to question Him whether it was lawful for a man to divorce a wife. And He answered and said to them, “What did Moses command you?” They said, “Moses permitted a man to write a certificate of divorce and send her away.” But Jesus said to them, “Because of your hardness of heart he wrote you this commandment. But from the beginning of creation, God made them male and female. For this reason a man shall leave his father and mother, and the two shall become one flesh; so they are no longer two, but one flesh. What therefore God has joined together, let no man separate.” (Mark 10:2-8) {emphasis mine}
How often do we look for a loophole in God’s word? The Pharisees were looking for an excuse to do what they wanted to do, but Jesus said that He had allowed for their evil ways (for the good of the woman they wanted to divorce) despite His perfect plan which they had rejected. “Then Peter came to Jesus and asked, “Lord, how many times shall I forgive my brother or sister who sins against me? Up to seven times?” Jesus answered, “I tell you, not seven times, but seventy-seven times. (Matthew 18:21-22)” Peter thought he was being generous forgiving someone seven times, but Jesus wanted him to forgive as He had forgiven Peter. (See the Lord’s Prayer “Forgive us our sins, for we also forgive everyone who sins against us.” Luke 11:4)**
And they sent their disciples to Him, along with the Herodians, saying, “Teacher, we know that You are truthful and teach the way of God in truth, and defer to no one; for You are not partial to any. Tell us then, what do You think? Is it lawful to give a poll-tax to Caesar, or not?” But Jesus perceived their malice, and said, “Why are you testing Me, you hypocrites? Show Me the coin used for the poll-tax.” And they brought Him a denarius. And He said to them, “Whose likeness and inscription is this?” They said to Him, “Caesar’s.” Then He said to them, “Then render to Caesar the things that are Caesar’s; and to God the things that are God’s.” And hearing this, they were amazed, and leaving Him, they went away. (Matthew 22:16-22) {emphasis mine}
Instead of directly answering the question that was asked, since it was not asked in good faith, He corrected their hypocrisy and showed them the truth. We are not nearly as wise and observant as Jesus, but we should still try to see what is truly being asked instead of just answering the obvious question. So often there is a need or motive behind the question that needs to be addressed. I’ve found that asking questions of the questioner can both uncover what is behind the question and also lead them to the truth. This method, also known as the Socratic Method, is taught well from a Christian perspective in the book “Tactics” by Gregory Koukl.
They brought the boy to Him. When he saw Him, immediately the spirit threw him into a convulsion, and falling to the ground, he began rolling around and foaming at the mouth. And He asked his father, “How long has this been happening to him?” And he said, “From childhood. It has often thrown him both into the fire and into the water to destroy him. But if You can do anything, take pity on us and help us!” And Jesus said to him, “ ‘If You can?’ All things are possible to him who believes.” Immediately the boy’s father cried out and said, “I do believe; help my unbelief.” When Jesus saw that a crowd was rapidly gathering, He rebuked the unclean spirit, saying to it, “You deaf and mute spirit, I command you, come out of him and do not enter him again.” After crying out and throwing him into terrible convulsions, it came out; and the boy became so much like a corpse that most of them said, “He is dead!” But Jesus took him by the hand and raised him; and he got up. (Mark 9:20-27) {emphasis mine}
Jesus sees things as they are. He honors belief. I love the boy’s father’s response to Jesus, “I do believe; help my unbelief.” I’ve felt like this before. Jesus never gives up and as long as we have Jesus, we should never give up on someone.
As soon as He was approaching, near the descent of the Mount of Olives, the whole crowd of the disciples began to praise God joyfully with a loud voice for all the miracles which they had seen, shouting:
“Blessed is the King who comes in the name of the Lord;\ Peace in heaven and glory in the highest!”
Some of the Pharisees in the crowd said to Him, “Teacher, rebuke Your disciples.” But Jesus answered, “I tell you, if these become silent, the stones will cry out!” (Luke 19:31-40) {emphasis mine}
The Pharisees saw a threat to their power and prestige, but Jesus saw reality as it was. Jesus saw the fulfillment of scripture and a small glimpse of the glory He deserved. They focused on what they disagreed with and what they didn’t like. Jesus focused on the fact that worship of God cannot be stopped. What do you focus on?
Therefore when Pilate heard this statement, he was even more afraid; and he entered into the Praetorium again and said to Jesus, “Where are You from?” But Jesus gave him no answer. So Pilate said to Him, “You do not speak to me? Do You not know that I have authority to release You, and I have authority to crucify You?” Jesus answered, “You would have no authority over Me, unless it had been given you from above; for this reason he who delivered Me to you has the greater sin.” (John 19:8-11) {emphasis mine}
Most innocent men would be continually speaking the truth of their innocence and trying to convince Pilate to listen, but Jesus had a purpose. He didn’t act like a normal innocent man, nor did He act like a normal guilty man. He was God incarnate living out His perfect plan. He knew Pilate didn’t have authority to kill or free Him, but that everything was going according to His perfect plan.
When we are following Jesus, we need to accept that God is in control. Not every hardship needs to be fixed. Sometimes it is part of God’s perfect plan. No one, man or spirit, has the authority to harm a believer unless God allows it and He only allows it if it furthers His perfect plan and is used for good. We need to know God and know His word. We need to listen to His leading through the Spirit, so we respond as Jesus did, “You would have no authority over Me, unless it had been given you from above.” This is as true of us today as it was about our savior on that fateful day. God is always in control.
Pilate questioned Him, “Are You the King of the Jews?” And He *answered him, “It is as you say.” The chief priests began to accuse Him harshly. Then Pilate questioned Him again, saying, “Do You not answer? See how many charges they bring against You!” But Jesus made no further answer; so Pilate was amazed. (Mark 15:2-5) {emphasis mine}
How often are people amazed because Jesus does not respond in the way a normal person would. Are there times that we should speak up and defend the word of God? Yes. Are there times that we should, like Jesus, make no further answer? Yes. We must ask God for guidance on the right response for each situation.
While He was still speaking, behold, a crowd came, and the one called Judas, one of the twelve, was preceding them; and he approached Jesus to kiss Him. But Jesus said to him, “Judas, are you betraying the Son of Man with a kiss?” When those who were around Him saw what was going to happen, they said, “Lord, shall we strike with the sword?” And one of them struck the slave of the high priest and cut off his right ear. But Jesus answered and said, “Stop! No more of this.” And He touched his ear and healed him. (Luke 22:47-51) {emphasis mine}
The common response to being mistreated is to mistreat back. We so often try to do to others at least as badly as they have done to us, but Jesus was different. When Judas betrayed Jesus, He mercifully responded, “Judas, are you betraying the Son of Man with a kiss?” When soldiers came to arrest Jesus for crimes He did not commit and one of His disciples struck a man with his sword, Jesus healed this man who had come to do Him harm. Jesus followed His own command to turn the other cheek. He gave love to those who were unloving. He gave mercy to those who showed no mercy. Do you seek revenge or do you seek to understand those who do you wrong and help them? Be loving and merciful just as Jesus is loving and merciful.
The best way to be a light for Jesus is to act like Jesus and acting like Jesus requires thinking like Jesus and responding in the most unimaginable ways. Jesus was not like a normal man and neither should we be.
Father God, help us to see other people and the world as you see it. Help us to respond as Jesus would. Help us to be different, so we can honor you with our differences.
Trust Jesus
-
 @ 21335073:a244b1ad
2025-03-12 00:40:25
@ 21335073:a244b1ad
2025-03-12 00:40:25Before I saw those X right-wing political “influencers” parading their Epstein binders in that PR stunt, I’d already posted this on Nostr, an open protocol.
“Today, the world’s attention will likely fixate on Epstein, governmental failures in addressing horrific abuse cases, and the influential figures who perpetrate such acts—yet few will center the victims and survivors in the conversation. The survivors of Epstein went to law enforcement and very little happened. The survivors tried to speak to the corporate press and the corporate press knowingly covered for him. In situations like these social media can serve as one of the only ways for a survivor’s voice to be heard.
It’s becoming increasingly evident that the line between centralized corporate social media and the state is razor-thin, if it exists at all. Time and again, the state shields powerful abusers when it’s politically expedient to do so. In this climate, a survivor attempting to expose someone like Epstein on a corporate tech platform faces an uphill battle—there’s no assurance their voice would even break through. Their story wouldn’t truly belong to them; it’d be at the mercy of the platform, subject to deletion at a whim. Nostr, though, offers a lifeline—a censorship-resistant space where survivors can share their truths, no matter how untouchable the abuser might seem. A survivor could remain anonymous here if they took enough steps.
Nostr holds real promise for amplifying survivor voices. And if you’re here daily, tossing out memes, take heart: you’re helping build a foundation for those who desperately need to be heard.“
That post is untouchable—no CEO, company, employee, or government can delete it. Even if I wanted to, I couldn’t take it down myself. The post will outlive me on the protocol.
The cozy alliance between the state and corporate social media hit me hard during that right-wing X “influencer” PR stunt. Elon owns X. Elon’s a special government employee. X pays those influencers to post. We don’t know who else pays them to post. Those influencers are spurred on by both the government and X to manage the Epstein case narrative. It wasn’t survivors standing there, grinning for photos—it was paid influencers, gatekeepers orchestrating yet another chance to re-exploit the already exploited.
The bond between the state and corporate social media is tight. If the other Epsteins out there are ever to be unmasked, I wouldn’t bet on a survivor’s story staying safe with a corporate tech platform, the government, any social media influencer, or mainstream journalist. Right now, only a protocol can hand survivors the power to truly own their narrative.
I don’t have anything against Elon—I’ve actually been a big supporter. I’m just stating it as I see it. X isn’t censorship resistant and they have an algorithm that they choose not the user. Corporate tech platforms like X can be a better fit for some survivors. X has safety tools and content moderation, making it a solid option for certain individuals. Grok can be a big help for survivors looking for resources or support! As a survivor, you know what works best for you, and safety should always come first—keep that front and center.
That said, a protocol is a game-changer for cases where the powerful are likely to censor. During China's # MeToo movement, survivors faced heavy censorship on social media platforms like Weibo and WeChat, where posts about sexual harassment were quickly removed, and hashtags like # MeToo or "woyeshi" were blocked by government and platform filters. To bypass this, activists turned to blockchain technology encoding their stories—like Yue Xin’s open letter about a Peking University case—into transaction metadata. This made the information tamper-proof and publicly accessible, resisting censorship since blockchain data can’t be easily altered or deleted.
I posted this on X 2/28/25. I wanted to try my first long post on a nostr client. The Epstein cover up is ongoing so it’s still relevant, unfortunately.
If you are a survivor or loved one who is reading this and needs support please reach out to: National Sexual Assault Hotline 24/7 https://rainn.org/
Hours: Available 24 hours
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Token-Curated Registries
So you want to build a TCR?
TCRs (Token Curated Registries) are a construct for maintaining registries on Ethereum. Imagine you have lots of scissor brands and you want a list with only the good scissors. You want to make sure only the good scissors make into that list and not the bad scissors. For that, people will tell you, you can just create a TCR of the best scissors!
It works like this: some people have the token, let's call it Scissor Token. Some other person, let's say it's a scissor manufacturer, wants to put his scissor on the list, this guy must acquire some Scissor Tokens and "stake" it. Holders of the Scissor Tokens are allowed to vote on "yes" or "no". If "no", the manufactures loses his tokens to the holders, if "yes" then its tokens are kept in deposit, but his scissor brand gets accepted into the registry.
Such a simple process, they say, have strong incentives for being the best possible way of curating a registry of scissors: consumers have the incentive to consult the list because of its high quality; manufacturers have the incentive to buy tokens and apply to join the list because the list is so well-curated and consumers always consult it; token holders want the registry to accept good and reject bad scissors because that good decisions will make the list good for consumers and thus their tokens more valuable, bad decisions will do the contrary. It doesn't make sense, to reject everybody just to grab their tokens, because that would create an incentive against people trying to enter the list.
Amazing! How come such a simple system of voting has such enourmous features? Now we can have lists of everything so well-curated, and for that we just need Ethereum tokens!
Now let's imagine a different proposal, of my own creation: SPCR, Single-person curated registries.
Single-person Curated Registries are equal to TCR, except they don't use Ethereum tokens, it's just a list in a text file kept by a single person. People can apply to join, and they will have to give the single person some amount of money, the single person can reject or accept the proposal and so on.
Now let's look at the incentives of SPCR: people will want to consult the registry because it is so well curated; vendors will want to enter the registry because people are consulting it; the single person will want to accept the good and reject the bad applicants because these good decisions are what will make the list valuable.
Amazing! How such a single proposal has such enourmous features! SPCR are going to take over the internet!
What TCR enthusiasts get wrong?
TCR people think they can just list a set of incentives for something to work and assume that something will work. Mix that with Ethereum hype and they think theyve found something unique and revolutionary, while in fact they're just making a poor implementation of "democracy" systems that fail almost everywhere.
The life is not about listing a set of "incentives" and then considering the problems solved. Almost everybody on the Earth has the incentive for being rich: being rich has a lot of advantages over being poor, however not all people get rich! Why are the incentives failing?
Curating lists is a hard problem, it involves a lot of knowledge about the problem that just holding a token won't give you, it involves personal preferences, politics, it involves knowing where is the real limit between "good" and "bad". The Single Person list may have a good result if the single person doing the curation is knowledgeable and honest (yes, you can game the system to accept your uncle's scissors and not their competitor that is much better, for example, without losing the entire list reputation), same thing for TCRs, but it can also fail miserably, and it can appear to be good but be in fact not so good. In all cases, the list entries will reflect the preferences of people choosing and other things that aren't taken into the incentives equation of TCR enthusiasts.
We don't need lists
The most important point to be made, although unrelated to the incentive story, is that we don't need lists. Imagine you're looking for a scissor. You don't want someone to tell if scissor A or B are "good" or "bad", or if A is "better" than B. You want to know if, for your specific situation, or for a class of situations, A will serve well, and do that considering A's price and if A is being sold near you and all that.
Scissors are the worst example ever to make this point, but I hope you get it. If you don't, try imagining the same example with schools, doctors, plumbers, food, whatever.
Recommendation systems are badly needed in our world, and TCRs don't solve these at all.
-
 @ fd208ee8:0fd927c1
2025-04-05 21:51:52
@ fd208ee8:0fd927c1
2025-04-05 21:51:52Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ 0c469779:4b21d8b0
2025-03-11 10:52:49
@ 0c469779:4b21d8b0
2025-03-11 10:52:49Sobre el amor
Mi percepción del amor cambió con el tiempo. Leer literatura rusa, principalmente a Dostoevsky, te cambia la perspectiva sobre el amor y la vida en general.
Por mucho tiempo mi visión sobre la vida es que la misma se basa en el sufrimiento: también la Biblia dice esto. El amor es igual, en el amor se sufre y se banca a la otra persona. El problema es que hay una distinción de sufrimientos que por mucho tiempo no tuve en cuenta. Está el sufrimiento del sacrificio y el sufrimiento masoquista. Para mí eran indistintos.
Para mí el ideal era Aliosha y Natasha de Humillados y Ofendidos: estar con alguien que me amase tanto como Natasha a Aliosha, un amor inclusive autodestructivo para Natasha, pero real. Tiene algo de épico, inalcanzable. Un sufrimiento extremo, redentor, es una vara altísima que en la vida cotidiana no se manifiesta. O el amor de Sonia a Raskolnikov, quien se fue hasta Siberia mientras estuvo en prisión para que no se quede solo en Crimen y Castigo.
Este es el tipo de amor que yo esperaba. Y como no me pasó nada tan extremo y las situaciones que llegan a ocurrir en mi vida están lejos de ser tan extremas, me parecía hasta poco lo que estaba pidiendo y que nadie pueda quedarse conmigo me parecía insuficiente.
Ahora pienso que el amor no tiene por qué ser así. Es un pensamiento nuevo que todavía estoy construyendo, y me di cuenta cuando fui a la iglesia, a pesar de que no soy cristiano. La filosofía cristiana me gusta. Va conmigo. Tiene un enfoque de humildad, superación y comunidad que me recuerda al estoicismo.
El amor se trata de resaltar lo mejor que hay en el otro. Se trata de ser un plus, de ayudar. Por eso si uno no está en su mejor etapa, si no se está cómodo con uno mismo, no se puede amar de verdad. El amor empieza en uno mismo.
Los libros son un espejo, no necesariamente vas a aprender de ellos, sino que te muestran quién sos. Resaltás lo que te importa. Por eso a pesar de saber los tipos de amores que hay en los trabajos de Dostoevsky, cometí los mismos errores varias veces.
Ser mejor depende de uno mismo y cada día se pone el granito de arena.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Precautionary Principle
The precautionary principle that people, including Nassim Nicholas Taleb, love and treat as some form of wisdom, is actually just a justification for arbitrary acts.
In a given situation for which there's no sufficient knowledge, either A or B can be seen as risky or precautionary measures, there's no way to know except if you have sufficient knowledge.
Someone could reply saying, for example, that the known risk of A is tolerable to the unknown, probably magnitudes bigger, risk of B. Unless you know better or at least have a logical explanation for the risks of B (a thing "scientists" don't have because they notoriously dislike making logical claims), in which case you do know something and is not invoking the precautionary principle anymore, just relying on your logical reasoning – and that can be discussed and questioned by others, undermining your intended usage of the label "precautionary principle" as a magic cover for your actions.
-
 @ fd208ee8:0fd927c1
2025-04-05 21:36:33
@ fd208ee8:0fd927c1
2025-04-05 21:36:33Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ fd208ee8:0fd927c1
2025-04-05 15:27:55
@ fd208ee8:0fd927c1
2025-04-05 15:27:55Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ 592295cf:413a0db9
2025-04-05 07:26:23
@ 592295cf:413a0db9
2025-04-05 07:26:23[Edit] I tried to get the slides and an audio file, from Constant's talk at NostRiga, about 8 months ago
1.
Nostr's adoption thesis
The less you define, the more you imply
by Wouter Constant
2.
Dutch Bitcoiner
AntiHashedPodcast
Writing Book about nostr
00:40
3.
What this presentation about
A protocols design includes initself a thesis
on protocol adoption, due to underlying assumptions
1:17
4.
Examples
Governments/Academic: Pubhubs (Matrix)
Bussiness: Bluesky
Foss: Nostr
1:58
5.
What constitutes minimal viability?
Pubhubs (Matrix): make is "safe" for user
Bluesky: liability and monetization
Foss: Simpel for developer
4:03
6.
The Point of Nostr
Capture network effects through interoperability
4:43
7.
Three assumptions
The direction is workable
Method is workable
Motivation and means are sufficient
5:27
8.
Assumption 1
The asymmetric cryptography paradigm is a good idea
6:16
9.
Nostr is a exponent of the key-pair paradigm.
And Basicly just that.
6.52
10.
Keys suck
Protect a secret that you are supposed use all the time.
7:37
11.
Assumption two
The unaddressed things will be figured out within a 'meta-design consensus'
8:11
12.
Nostr's base protocol is not minimally viable for anything, except own development.
8:25
13.
Complexity leads to capture;
i.e. free and open in the name,
controlled in pratice
9:54
14.
Meta-design consensus
Buildings things 'note centric' mantains interoperability.
11:51
15.
Assumption three
the nightmare is scary;
the cream is appealing.
12:41
16.
Get it minimally viable,
for whatever target,
such that it is not a waste of time.
13:23
17.
Summarize
We are in a nightmare.
Assume key/signature are the way out.
Assume we can Maintain an open stardand while manifesting the dream.
Assume we are motivated enought to bootstrap this to adulthood.
14:01
18.
We want this,
we can do this,
because we have to.
14:12
Thank you for contribuiting
[Edit] Note for audio presentation
nostr:nevent1qvzqqqqqqypzqkfzjh8jkzd8l9247sadku6vhm52snhgjtknlyeku6sfkeqn5rdeqyf8wumn8ghj7mn0wd68ytnvw5hxkef0qyg8wumn8ghj7mn0wd68ytnddakj7qpqqqq6fdnhvp95gqf4k3vxmljh87uvjezpepyt222jl2267q857uwqz7gcke
-
 @ 21211e6f:8cd9242f
2025-04-22 12:48:33
@ 21211e6f:8cd9242f
2025-04-22 12:48:33This is a public note.
-
 @ 4857600b:30b502f4
2025-03-10 12:09:35
@ 4857600b:30b502f4
2025-03-10 12:09:35At this point, we should be arresting, not firing, any FBI employee who delays, destroys, or withholds information on the Epstein case. There is ZERO explanation I will accept for redacting anything for “national security” reasons. A lot of Trump supporters are losing patience with Pam Bondi. I will give her the benefit of the doubt for now since the corruption within the whole security/intelligence apparatus of our country runs deep. However, let’s not forget that probably Trump’s biggest mistakes in his first term involved picking weak and easily corruptible (or blackmailable) officials. It seemed every month a formerly-loyal person did a complete 180 degree turn and did everything they could to screw him over, regardless of the betrayal’s effect on the country or whatever principles that person claimed to have. I think he’s fixed his screening process, but since we’re talking about the FBI, we know they have the power to dig up any dirt or blackmail material available, or just make it up. In the Epstein case, it’s probably better to go after Bondi than give up a treasure trove of blackmail material against the long list of members on his client list.
-
 @ 6389be64:ef439d32
2025-04-03 21:32:58
@ 6389be64:ef439d32
2025-04-03 21:32:58Brewing Biology
Episode 1068 of Bitcoin And . . . is LIVE!
This episode of Bitcoin And dives into Brewing Biology—a regenerative system combining compost tea, biochar, Bitcoin mining, and carbon credits—developed through a deep, idea-driven conversation with ChatGPT.
LISTEN HERE --> https://fountain.fm/episode/p0DmvPzxirDHh2l68zOX <-- LISTEN HERE
The future of Bitcoin isn’t just about code or money—it’s about soil. A groundbreaking fusion of biology, technology, and financial innovation might change the rules of agriculture, offering landowners a path to profitability while Healing our soils. At the heart of this revolution is biochar, a form of charcoal that supercharges soil health. When mixed with compost tea and microbial inoculants, this carbon-rich material becomes a game-changer.
Biochar’s porous structure acts as a microbial hotel, hosting fungi like arbuscular mycorrhizal fungi (AMF) and bacteria such as Bacillus subtilis. These organisms form symbiotic networks that boost nutrient absorption and secrete glomalin—a natural “glue” that binds soil, preventing erosion. But here’s the twist: this system doesn’t just heal the earth; it also generates revenue.
Biochar’s Hidden Superpower: Adsorption & Buffering Biochar’s porous structure acts as a molecular storage hub. Unlike absorption (soaking up water like a sponge), adsorption is a chemical process where water and nutrients cling to biochar’s surfaces. A single gram of biochar has the surface area of a basketball court, creating a lattice of microscopic nooks and crannies. This allows it to:
Lock in moisture: Biochar retains up to 10x its weight in water, acting like a “soil battery” that releases hydration slowly during droughts.
Hoard nutrients: It buffers nitrogen, phosphorus, potassium, and micronutrients in its pores, preventing leaching. Plants access these nutrients gradually, reducing fertilizer needs.
Stabilize pH: Biochar’s alkaline nature buffers acidic soils, creating a neutral environment where microbes and roots thrive.
This buffering effect means plants face fewer nutrient and water spikes or shortages, ensuring steady growth even in erratic climates.
The Carbon Math Every ton of biochar (which is ~85% carbon by weight) sequesters 3.12 tons of CO₂ (using the 1:3.67 carbon-to-CO₂ ratio). With carbon credits trading at $42–$60/ton, a 1,000-acre project applying 1 pound of biochar per linear foot (via a three-shank plow at 2-foot spacing) could sequester ~12,000 tons of CO₂ annually—generating $504,000–$720,000 in carbon credit revenue.
Tools for the Revolution The Keyline Plow fractures subsoil to inject biochar slurry 30–45cm deep, revitalizing compacted land. For smaller plots, the VOGT Geo Injector delivers pinpoint inoculations—think of it as a soil “injection gun” for lawns, golf courses, or urban gardens. These methods ensure biochar stays where it’s needed, turning even parched landscapes into carbon sinks.
Bitcoin’s Role in the Loop Biochar production generates syngas—a byproduct that fuels electric generators for Bitcoin mining. This closed-loop system turns agricultural waste into energy, creating dual revenue streams: carbon credits and mining income.
The Market Potential Farmers, ranchers, and eco-conscious landowners aren’t the only beneficiaries. Golf courses can slash water use and homeowners can boost lawn resilience.
Why This Matters This isn’t just farming—it’s a movement. By marrying soil science with economics, we can prove that healing the planet and profiting go hand in hand. Whether you’re a Bitcoin miner, a farmer, or an eco-entrepreneur, this system offers a blueprint for a future where every acre works for you—and the planet.
The takeaway? Regenerative agriculture isn’t a trend. It’s the next gold rush—except this time, the gold is carbon, soil, and sats.---
P.S. – If you’re ready to turn your land into a carbon credit powerhouse (and maybe mine some Bitcoin along the way), the soil is waiting.
You can read the full article, Brewing Biology HERE -> https://the-bitcoin-and-Podcast.ghost.io/ghost/#/editor/post/67e5922fa289aa00088da3c6
originally posted at https://stacker.news/items/933800
-
 @ 86102a64:33871ac0
2025-04-22 02:11:57
@ 86102a64:33871ac0
2025-04-22 02:11:57{"imageData":"data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAXAAAAEUCAYAAAAyfG1zAAAgAElEQVR4Xux9CWBcRf3/N5uz6X3RNk16t0lb6F16gaCC8hcERQVFEFAUFUFU/AkooiKKioqAKKICIpeIXJ4cytkWytVCaZLeTZo2bdq0TZp7d//f7xzvzXv7jnlv326SsrOEttk5vzPzme98r8mDXHo3USBvQtXyhyAv72OZHnQSkpCHH5mS+Jc8/B39n5Lle/PXnt1KJrHOPLNOVo/td+q/nfKnNIDlk1glqxX7Qb2GPGvfdWnFhmH+T7eYdj4aD1Uf06CBqPTCuuqVd2k3kMvY7yhg3Q39rvu5DgehwITK5Tfg7v9WkDJh8mrisQLnNkB3aRTxCwHc+qX9d+q/LX8XxwahNR0kBNqUCHCTWCkDXtEjA9DDDN4oo0uF4I2kHlpWutC4Rbq7rvqlC4K3kCvRXyiQA/D+MlNp9rOiavkFyL3emWY1gYr7ccB2gFUXo52DZ/CqDeC8NMNjAmnOFgfqu+V0CVbSzB2mWYdbhl/zToeYKLMWAXyeX/nc9/2XAgFXdf8d6Lu558MmzRs2uKS0AQF8QLbo4AS2HIRNMYiKb35gbynLRB2c60wmCNUFUHO0tgBoksQhabDUdtFPYPqFAHG/NhitlLE6iZHE1407Nqwc61df7vv+S4EcgPffudPuOcq9v4fAdq12gQgzpgC5AmieoE3yXsFxc7m0kC/TISAF1oTXQcCZiUt4B4IsfOonB8QgpZRzxOHmECGJPapKdu/YUFQK8GxPdtrLtZJtCoRbkdnuZa690BSYNOnEksSA7gasYHjoSkIWZMDHsFdVZjorCLl6zpRJy7/zpk0EdGVoA3C6UkQcdPEHaCIkxZRiPo3xQwUpKwdhz2/IwZOvJZLJB6EA/lC/ftX+9DuWq6EvUSDoGu5Lfc/1RYMCE2YuPw83+p80skaSxcQRDskSvIVUmsumhYUKxxghDuCqRQH19r/bJNiiETeMcxPf2Aeom08tpyPqiYSQPpWoAO4mQuEnIj//jL9DXg/+ey/++/GuRNdPG2vXbMlGf3NtZIYCOQDPDF37TK0VVSvuQi7t/Ix2iMmkU038/NrkHDoJsvmfBjOp/FvmYThky+dVv5MS1DF/GBT3G5jb9wHb8jospKWJQj6jVcUKRVxpLAAu6C3oCbHq7kTXqTkgDzupvVsuB+C9S/+Mt44c+DbcxRMz0ZAh9ggkUU7tCQNblGXbFY7y99ygxFRGWv4uFHpMMBNyNfcVrjqFMj6AL/udanMv7zamfbvCgVsAPA9iSNkE5CXy7q+rXYm3NYhnYq3k6swMBUIu+cx0JldrtBQQ8u/2aGvltWlzuJloPECdfQ2cg/XHWxDOrVGEuEk5vaTSlchEildVCWtKU7iSmCA+mYcAnkQgTyZeqK9Z9Z4A5M1l7WUK5AC8lycgk82Pnr147IBE0a5MttEf6s6q8tGHIAGlKN61eWhjTemUaUGjgjcDbqZjRv6bWfiwv5GZzpb6lm3HQENDW3+Y23d7H3MAfgSvgPFVx47MzytsinSIkSKQS89ssnEjl8XzR7HNU36fDlgH446dHYv8aB2UfF43nRRLFLoZmdYnpgKZW2GyexNPJngzL1TxFTOxZP/Fn6+vfvkEv7Hkvu99CuQAvPfnIKM9mFC1ogN3aHFGG+kHlQcFZ50hZaJOnXYZ3gosDi33ZzAukmLVwyvGn0TyF3W1q7+h259cvt6hQA7Ae4fuWWs1k0rMrA0iYENBuVxL9YEKh+P3tYHfoy/EmdPXamArlfu2eKcyQUlqMAGphJZcObf04WIV6mNT6+GK9p3r6gOSP5c9ixTIAXgWid0bTU2YueIpbPektNsOBGxpt8YrSEOU4tQDHeDUyRPR6Hyr8TcjVMISGKITazQBeyNeppgGualQIoES8eSLO2tWH+/b0VyGXqNADsB7jfTZaXhC1bIrIS/24+y01ndacQI/HXDWyaOOMqg1TqD6wzH4Qr4ipN4O8m92NipmmdbxCN8fRHOMM5Osb90+KKfQ7Dvr2t6THID33bmJpGcTJhw3PDkwUY+qKoyJES4FAp1wTbiWMmydyWTOZion/632z/i7443BHxH9c6Q3wCAXGbfDgYk+KCxuyN2rPUbsbFdP/Nrdm17+QXqjzpXOFAVCLoFMdSdXbyYogN6Yv8XNfnHYuvsjgIflwAPRKAgai4q1wdOjI2YdqsOO2MpMEO7NfUsOXDZhiVWjHJREw3gyuaOhZtXEQHTJZc4aBXIAnjVS915DZE4Yg8JqBPFRYXoRAqfCNONYJmIxuFa/dA8s3XzWRvUg3K1uw0nHiDsQjBN3bd02yZL7T2BC5558LcLlMmWdAjkAzzrJe6fBisoVX8yLwW/CtB4OqMK0lFomtAgFq3IUQWjgp/Z4NeqKhgpmLQmMf06blolPmJelqbQ0rLy5KQkPGcalLZZgB6r1iVNgXXX8cWxvZ83KHE5EPZER1ZebmIgI2R+qQZPCe3Arn9sf+hpFH+1ArAPMOnlk34IrML0tRIwxu1x5zNsIekziaaxE2dUglxS36MdC5ybhSairacCHQLZ1aDSSy5JlCuQAPMsE7+Xm8vFxhyeRc3ufdj96gctM6Zvsg70v6r/d/q5UpgO4Onm0aRdhRgN+WdCvVJvuKJpihxdVJDh77rmZB02NBya2N6/fEUUbuTqipUAOwKOlZ5+vjQJcxQd0/xIn/ou6nQ3ClerWqZsvrAjFiYnVGYeuvF+nLnWMuvVaytA/qKA8nBhwCwUlQ3QhNGHyFJGPAbD4nxCl8H8F2+pc1s7rbWo8mANw3QWb5XzBZjXLncs1lzkKVFQuPyMvxh459n2pJwz4RNXzsEpMZysUTRFGVJ1Pox6OvehMw2TcMcNkkNtvC+hWYqhzF3hn6xP2FX1H74O6ALl6UPJum/lbDnZMbG54LceBpzGfmSqaA/BMUbYf1Dt22vGjiwri30F0uMyru70pVpBtO8W8tr72I8CLq+5CUV+bq87AiWYYBLIHP01RBvrSMHd5w/qEoJW94mDgtdZYU+r3MCKXbUk7+/amwsF79z7bqtVQLlNWKRBupWe1i7nGMk2BsVVLJxXlxb6EsLEckWGB3ekH40QfQi5wSKb74VR/WBGKva7ePITc6MatQSQYOx886NEOMdJXWuyzqcbg4hNpfUJ/xvAjk53GSaEjZa2QErM6Z4XSG2tfp80cgOtQ6V2W56jJS8YUlOSNp2HHWvI2tJUkCgcV5uM7inlF/YIUIThkbe5bgwBedfGuUbAoZ/tty0GDmTEeCbMDjMVQoILIisIUIVYRHfGRf3PFJIK1TXzCuGxFpq4Oy+D6mfwGkgjgJtprjD+XJXsUyAF49mjdr1uqmLn8AYScs7mujP5njWVnGRwTn5pPpBk5BWBYuEniQYmZZBhjNa8IK/9OIXQIQA8zWZyfFhDM6CO3l5Bbk8yaGG4G4uafnNNNlc8TeMcU3STF646xhxc4486SOAhUsYfgzUVUQZ5ZvrrDxDNSfKI2Kv7O5eWyf2zm9tVXrwzlABaGhrkywSiQA/Bg9HrX5i6bctyEWFFiPQLAIC8iMPmzMIpg0gGBCKpcWspw+RuYFHpaiarnAehaxM8SWBt9MYDa5J3dxNNO4O3UXfk7yQmjMyR/Gk3Q1di0GtYnDOARhtVXd2JkQy6TrQNyvvgYiNuP/xYjEn5Ji/a5TFmnQA7As07yftlg/vjpS69EvMCgRuruN8fCAEZwd4bCjXGVHNBN8OL5pAiXc3tcDqwD6AxYxKp1YCAjJq4JymO6O2FidweM7e6C0T1d8JehR8HB/EKLujRscCmnThNoW0Qc3CgkPfGJoLEUvTNoJ4E3QbWYP8nRk7iG/DjbEsmKfbWrdkZM2Fx1EVEgB+AREfJIrqa8cskcVGK+ivu/0G2cFssIKWZRwNlezhfQsYBqeUHlGTOPzCPJgdMGbxc2uRiBczwC9dz2Fjjx8AGY2tUO0zvboYQBnZn2xwpg8fTF0EMaRqWvasTEMGtChnnlMmqSlfMDTopPuFmhqFlT/q2KT4yTlB22ghO3iE/4bSgZx7bzklsxDsqUMOPIlckOBXIAnh06999WZs8uKo8PeRUHcIwreHuITfir6KZM1RCv2CqzALoUu0jOnPGIVpk7U+gheAY2GRQy3sGJHqjsbGMc9bieDjim/TB8sHV/ClB7TdzOgiL4f5PnwcECfq6Z4iKN6faQp1A9dFxQBCkpXmK3EyYH8QJv6gQjFk9CWG68Oo+1kviE6y9NYTfjwgWt1VfsMQ7KzIbaVdUao8ll6SUK5AC8lwjfX5otr1x2Cm7qf3n1V256dfNTfgt4C7GJF6Bz7lXhOgXIeDmfENgRkHO8SjXFo+9LEaDGd3XA+5CjPrbtEFR1HoYKFIlEkRpHAixeOB/ydmC4EAnikkWWIO3XkA3M6XAiQGVKXaIB/hHG+kTIYDiei1fnDR0F/ZaJaYT4RNVD0OP0kLgPue9P+3U9933vUiAH4L1L/z7fOr3og7Do+aKPFoALgDC4cTdAl8DP0TDlEQc7wYiPHIVg/P62g8hJd8HAeBwGJuIwBDnsSQjaxGXbxR9REX3HBIAlLwPsHgtQ/MJwGPHtaVCwV3LjNBCSgripNJVe2ACccfJ0JsmiBOAIwOHFJ1zHYNQpxCesHaIxHoD4+g7+yfOh/2eivjoXQjaqdZLJenIAnknq+tQ9fMrCoQMLit6XzMs7CTfPglgyOQ6LDMOtVIxXXNrCPfj3NjLlwj1el0jEX+6Eztuaat5oyFa3yXwQ2zrbqz1u58C5X3uoUlV8Yue+1X8LvBYiWs51WuN+KLJfoQNVWxuLIH5RcwNc0LwbiqQtXAaJtGkqwHEvAjQieKupaO1AGPrLSVD86hDI65GCCuJyhWzZpsAlXCWaJYZ3Qff0dogP7oaBT49m+bkVCoJrBOaDJJTh4hPeIufEmZkQs25hZwb+m8LV4r/+iNz35zJIvlzVEVEgB+AREVK3mjFTlx+FItNzkfCfx/1SGTQcv9h+rcgx/QNZpu/urH6xVrftMPnSB3ATuLjVgykPtwK6aalC/VQtTVTbZXlAGHbmeN1XRcN4CKKIpA1OONwMX2mqh8E25WMYGtjL1JWj2GRNKnjb88UOFUDh+oFQvG4g5NeXALSiVJtMSUoT0FPeAZ1zWqH76MOQHBI3ig65ejIMfmSssPcWtIvIfFCKT1gsFUULLA9fmg8S33R3541p3LxyTxS0ytWRWQrkADyz9DVqHz9zxVJ0yrgJ98iSqJpkDjFJOIAPX329rublO6OqV60nbRGKwplzAHcDdAnapshBRsQzwNxg0xkTaSjrGJizf5r8Py3sGILRzxs2wpkt+yIjTfMwgJkb/ME7bIPjZy9BZaWinBXmg0IfyavVdN4xvC8JsI0IWOKmJBXFKD4x7My5XrOhvmYl88LNpb5PgRyAZ3iOJkxbMitZUPBrBKETM9YU36D7IRH/LAL5Y1G2U1619ER0xf6fV52BZOBugG7jzA2sNiwquEjBMNMz5Ma8Z24gTt6MS1A+/uCOd5hVRzqpDfWUUzehzLssnVo8ynbkwfi5S0XsE2k+SIBtGpbwq4mQIbGBi/9x0xKebM47vAIhJzHoT/mY3ITpMvPZnwnoTHYdv7f2NRQO5VJ/oEAOwDM0S+S5mF+U/CXuko8i6GSczpyzZcKG3XGIn9qwYfXrEQ0tVl65nOqa61aftB7hCMKtSBisMAsHcV0X/04RoUhAsSs5VasIVp+slEshOEcqQElQV3L4Tv1ciCD+yA50JA2ZujAKzDFvAdTOCFmBRrHB102AofeVm7pGwX2HUV7auW9DfMXmhwM6kY0OODr8SIGZ6EkerN+4Eu8YudRfKJBxYOkvhIiynxVVyz+AW+Ix3CEo+Mx+wg1Ku/SvdTWrzoqi9fEzjpsbiyXW4Lb3cOQhjJX3fVOYwRlGwTUyjz8XQLcBuTU4iBCNGHIEHmXEAuJioIZXJ+G7RaUKMAll409vWxtYydmOs3g0gveWaVFQ070OEp8Aik/ICJyCV0XuvCO5dWK5xYEaJ3v6vHzmkRlP9Jywa+Oa5zM7ylztUVIgB+BRUhPrqpi57BLceTcjkPR+BLdksqWjB+bv2bRyc7rDTFsWLhRnjCqOgC7AnQEvB3l5cbHGp+aR/LglhRCFS0acnIYEp+4lF78HOfHj0NNSJx0YymXeu8k+KJOpLQ/K5y9lnLChJ8iE8w7RSJgPkviEmQ8y5SU9XrwqhweZnOMM1J2bsAiJWlG14hbcC1+JsMr0qiJGnJtwPBQ/2HFhQ8NrbelUWDZr2fz8BDyMdU52q8c7mBW/tNPZxjGEbI85oNs5c5UD5yIZofyUoiLjEOA94bE8GPKbyk1DKGztLbV75sE9cNMuFGh7pAY0EZz/JsCeMelQTa/soFvHw9BbJwjTST6GTDjvMLt0IXrioWqJ22eKzANoOuj7OpPeaHK5skWBHIBHROnymSs+h1j0+4iqi7wa3Ldoehg/q752tadXpV/DZWULS2FQ4YdRIfgx3PvLMP8oLlphiMov6cyLkDPQLFSsYfFAj4QJ3pnJVqyAboIvtyiXtoRq7GoTzFlLJs7zw8oAJ0PtIOTldgsV6sd7W/bDn3Y6e4pvwSNq2arsgDd1+6gVC6FoPwraaRCCNOm5zjOFiLPzjphkFrCKnmvDfyfiiTt3blz9Wb/5z33ftyiQA/AI5qOsatny/LzYc0jMggiqy0gVhtlvIvlf9BH6/I7aF7dkoiHEjA9hvX/FH+5b7pL2o9z1hjGT4IWBQ6EpVgid+WQjIiMVcvAmxxJKXH2pmr/ZZepmLosDkBSneHDiZx9ohJ/ttkqYNk4HOP4FNBXMAuctyVNetYydV9LSJiru2815hxqT5oPM9rsrOXbP1pcbM7EmcnVmjgI5AE+TtuOnLSmPFeS/iRwfRsXo+4m/0II4kZe8pz0Ru7Sp5iU9YbDG0BBoP4rZ/oI/gQ8yO6B3EGeIMlo1vopFTCJAmWO8lIsrDkDs1/6u+HRonHZoD9yG9uKUss15U5t5W4ug7EML0f4b/0EiJRKfROQ6L+NUscHJ3S4MeiwmiJB3e1ei66eNtWsycrBrLJ9clhAUyAF4CKKpRdDi5N8ILB9Ms5qMF7e82GICWydyXz/CuBc/xA5Y46UG7BFiwmewyF0KTASswZq9KZYPZ06cA9uLS5likkkDpALOsGk2ZeccyAXHLuTgpis+RywvCxWyFf9x4h1YgUFzsyHzVkc79j0LMYZKEdMJqK7zYcwHzdCxPM63cfPiBMD/CZmSQS6pAZbWQbHq7kTXqTkgT2v5Zq1wDsDTIDVF6kMFUFoy5TSaD1zUas1hWnrgJt/a2ZM8Oay1CkLCVdiZHwXukEaBy8ZNg8eGjTGu+1SEiYkFiEt3fFPJySs1Le8dohu6eG4mChLQeMd66F4a2aXEf4TovFM2dwmgCI4dU2w8IvZJGABHY0CuCKX/woafJUVzIu/+utqV5+EATD9//9HkcmSZAjkAD0/w2ISZK9A6GGaFr6L3StofAENwpydYflS3YeU1QXqFYHoL5s+o5c09Q8fA98ZOgS6CJnqhnT+2y5WljMvkmj8pTrFw4gLsUyxU3EAcQfTwaXuh+WfeFipBaOSVd/ANFTD07nJjHBLAg4Avu50IxloqfCORoScTL6BlynuiGmuunugpkAPwkDRF0ckFuNnuDFm814q5iFLM/iA33tPddULD5jV1fp1EzCBl5cf88kXxfSsKh787bgo8PngkdOcXQBzDxpIFBXN4oQYMT07VflxKDawWKlIW7OW52b7oADTd804UXfesY/wsdJ0XBjwq+MpbhhRXu1ciVbz4J5eaRC1D31Lfsu0YaGhIywQ144R8lzaQA/AwE4+v1ExIDMUogHkTwxTva2XsDyEQN454+DMManSlW18RLuj2cXRvjOX3w8fC9WMmQw+9R0AxrCkJ13DFzNnwtFedfpRfimLc3I7z8NZXf7omtUHj42vRSNIfRsPQIW9LEYw/dRFvV5gPchNMaWXjB9v8FiJDxNrDz4YRwaS+3kM0iT9fX/3yCWHGmCuTWQrkADwEfSmyIBq9oZVw/0yqEYLh9Wez2OAjS25vb+9eunfbmt1ypFiWwgOQpUKmfRM9iXsAzRBvGzUe/jx0LLQWFFiUnNY445qemy6mhiQX3/PHt6FrUfRy8bHHo/Kyqdg4OHRD5kjlrCQQs+dmIiGrDJ3NM7fJF1EOBLcuFASGUQq/wvAjDE1h8jAUPcUPt4SfTSR+UVe7+hv9c8X3bq/HTjt+dEF+/ArsxQeQ4ZiEVB6I242HpchLdqFZ7yGk/zb83UNQkPx9/fpV+3V7nANwXUop+SZULr8BzQW+FaJo3ygiHGsUTZ9Hv5LdyNldgJYq9+EWJyO3XfhzVN8YCO/F58ZXwn8GDudPq6Vw4iLIl4fnpq/TD+6Slk83wMFvb4tu2OQ6v2ApA1YmQtEIvGAAt3LNINg1HtOQYiRLdXpbXIrWONorAK7Y3ze1Hq5o37muPjoiHNk1DZs8f+LgopK/4Ao81lCq61kCrYvH2z+5a+PrGMTBO+nNrl8t77LvJ1StqEb2pLK/DtuO395cOLNWoV391Obq1TMLIVnRF8f98OBR8DW0WEmiSEU6r1gtVBi7Y3lQws3pxwAz20Bbzt4FB763NZLhk+v8sFvQdV7YuutWajELRBkJiyaomFCa8WOoRnHX8gENThlhgsmpxJ9vY52SLy2R80DixZ01q4/X7eu7OB9G8Fz2OyQgemeHfAqPbkDJvEfralbSa1hdbrTMAXjAVVY2Y1lVQX7M92QMWG3Ws/sqM0WP1KBStJkXtrXAN/duh2X4OHBfS/vRdvxDE+dCQzE6gZIvv2KhIkUEhgk5AZVY/YaFihiQaS+eKvtODOmG1rMa4eDFyIgOCm86P+YEFJ/sLmJxuH2T0VFCVTM/eVLyG4cQoHMkNsLtSscnCcSq6IzDNAdpacVjhKAV0M+dvqSCgOkKknUt2wblFJruM1Y2Y+GoGBRuwndGh6pP4ckzlIupxOFqRO8Uh6Whz1BEWcnEzsPdXbObt7x20KlVjdXju7zeVRn6q/WJfZKsAK6AmaMs3CwtAX1ovBu+ik+WfXZ/g4v0uPeWxVfHToW/oe04c/xhe8UEOLupIX3HviV8YvjIZclynK4PRWBUr6YbNkLHaeFe+ymrItvvfG7PrpvUQFTsUkRCLbTEEYDLqmEAbsrDdarm1i9CcSojPSqHhrpWunri1+7e9PIPdOp9l+WJja9cej/OxllSF2FsDLGudOjBxWHi7sTmkZkWNTd3HJx1eNt6Qxcl6wqwenSaP/LzUFhVvPd6vtLeH6hgd+qRfbZy3P4jGYCvv1++tx6+uH+nf+Ys5vhS2Qz4x5BRvEVHz00uTjHEDErfDLiXBi4CECUXrw6je1w7ND68DpLDg/m7VFRi7JN8DcG3C83iyH2zQGFMZCQsUWR/lSPVPLqsz82pHLgx9wQeNFZxezF+L+KHi9d7duysWTkxi1PZ55sah7Lu/OKSNUj+0VLwJA9Eu8JZezBC8SxNpNAwrK6+ZjXR3XItzAG4NkV5xvKZy29CudZXAxbrc9lTvDINZZXllm702w/Yy7o64H6Msz2pu6PPjPW82dPhufhowWFzFttuoZIiF5eCBYMlFx6r7LorAd/cNvS3BFpu7PvBZmj/+F69se+PQcVyjP3tt/tEBidxF7ODpw6R3pYL8w05Npd6WOPAeHVMcuBqd6RNuiGGopsKZw0T6NyT7ut0enTqg7nKZpxYFcvr+jZOzYexe0MM4jNugGMrF2pJx7L0BmEyGazuu+uqV12g1ui3hNJr/Qgsja+0P4pTc0Z/H5rx8IHk1izasdTR2QHcbjvOFi7Wccm+epSR7+h18vz9VICPo5tR6XVTofSvow1loQQk035aPiSBI+IiZUYRsqk2NiNjdfnGdBN5EH06Klth71/WAWBUWK80+McVMPyeCYFoZFc0E4CTspZhvAR6BUBk5WE4cPPqr8jccXz0eg85T9VXr3zX4UbF0cunYlCBf+NSYO8ycbEbZwr4B29CkuhOJ7PBUZvTzpaVQkm3LciyUTv403S4rby9fq1x3X3XTUSgXeOQuWLmitVItMhelk+3P2HLp4hQlNXjBM5O7bhx5VPx6bKHtr8FI+M9YbuXVrlffB3gihu57TOlAf8cCcO/Pg03WL7hucmYSXEZ5fsw1dyQ2VeLD+NwfVhmqqNrZis0PuAN4mNRgVm4p9hzjKo1iSmfl3J6DFBCHLiQfxOAW+YsAg6cdc5KIAbgdGjUVTeglnhb37lqpbVafAsXoGz7PpyPT8g5YTcedb+giClJymSmUDYTB14rSHu1Zt6EUgsxhgtNg/DzLIpS3mucFb7dz2WwUOBIBXALGLuyAgpH5rMuihFgbty9CU4/1JTVFfTVXwHcfFlqk3nN+TDmjHlQuJcDZwoHLjlu2psMuxgKctEE25h6vA5tsaYf1UD7R9yVm+WzlzN/GS/CmACuvkQkZN1sLyOYIoCrh4p6q7LI9w0FpWiRtSxBiP+OX/u5DNzKFYrbB9Yh44c3NR6c2N68vvevWVlYWRVVy15EgqxQRVTq9kiQvSX7BX/ZiJ17QhwZtntSyG1fILQmyUe6/uCWwdDYeFjMYthm3p3ljhgRigFYYpmoq9JHnKLOvJ9sfAGaG/6+fkPGuXEKvEcik0fO9F6Xoz9xNJS8PUQgM0Nqw/LEfKuTb0IJbH6ct73FBFqo1L+8GuU3Fn2TzLYZ19BUC0o6dNnFcpDlJNBgkhMyQRRzZTjzMBA2r/g6IhQnM0KOROLAFn+yxybw162HOic2N7x2hAP4wtLymUXr8ECbajp6CSrL6xs71EgXgcBN9vwZhkQpSulJJn7aULOaORJmus0MDyn71eO7l7/Febs4+y1H22KKElMAGd+37gowz3HeQ30AACAASURBVO9cOI8YXjE/17wLvr1nW0YWXA+q1D78d4B/n6JHoxGXVELpMyMs3DUDbIa3bHeaZoS+mkbnNpsv3QYtX0qxzOmA6qJjKz66CGUs3snCgXP2z7gRxDEIDAXxMuLAiDkTJ060ZoQCyIkxZ2c+/u/wnq5hzc3Odsl+4+ov3yPn/SxS+AROUw6TbHlY9gkdpqiLYM5YFCZT/4aqS4cU3RPevPAgrUOHKqZEyQG4LiVFvglVy7+Hs3VtwGJ9LnsqgBvr1HMh+nHcXt+X4mK/oQHFKi1NkS28ZnyGd/EagM3I0wZJAx4bBSOunIZgR3JxITJRLE+k7XhQ7lv2oX3Ffth7R4q/15kjxh/96qChQwNzr6oSk/4ur+sGBy6u8XxTh9vWUoRimBGqcl5xYyMxys5aUgMduWl85bJfomnm5XY9hEprKYKT8+K6TmyCcMO6h5lr8gNBxqtxmzbrnkIzIFRG1NdyS6AjeiIyscSOREcezl1wz0XOZATjwP1A3TIPWPdIdAK6cs92+AS+DJ/OAtwyBcH7FYD9IR+zI7n4UecdA0WbS80uCnmxsTFD9rB7XAfseuY1deh/wKouGj584dDBY0oOeK5NB6Ko0gwK3c7eCxXKS0NW79BXHRGKU19UM0ICGflWJz5+nMTHj8MbsGdiU0ZY5wh8IrE0P7YDAZmSUTMXhpnevdICxYjg63BTC7QvePVaiExzgZZABOAkOcylIBQ4El3pOWibHLjXTdDpO7vSxrG8wy8HoRPQuft3w5Xomh90Ib60HOCUf6M8dnCQ2XPOO/qCWVDy8jDDYZMxRuTMgixSWA68e3Qn7HruVdngth7o+Uo+5K/AX5ThQyDn+/U6RYkpwYOJd/jzcuK0Va5OolYmDUrPDtxeNw9VS3E9Es0Y2AzlT0dimlZcMeOowzhMdJElMFV0DDbRCX0ldQKWNYL5mEVKBslD89/c3DKmtXHdnky2k8Eh9G7VR1owKw7gykMIHlr0wFyFy1SpeF6MopWL9+2EL+PPADLG9klPnowy7ycwwo+3JZ5fNZbvR1yKcvGnRuLIydZZbMAA1if2xjrmtMAeNCcsgZL4LtgVHwbDDOvwSbOON+zM3Tpp4LON62OWCAJMDYbNww48CBFSrFCE2ITqYACOsqaenq47Gzau+WyQevtJ3lhF5VKUeeXNYCINO0dtEyfR90yZzC5CUm/ib2qqS4sUPw1lj9JcHDzUMrOl4a3qHIDrUlTJ1++9MeXGVBepZYGmMnVy+G4AnsqFp3KATmWN3yEaUVTvczG2ypfxZ0yPcwC2v+G792fhu/fxwO/e+080ycVHXjUdknHsO/NwtJrp+ddg5jj42Xpou6IBqvEzBT9qmrvkg9Dc0upZnRkd0BRtSSClP+XGNTh1l0M3rAhFnW92wPNTHtriiYr9m14+4kLKTpi5/B6U75/LNAgCwC1MjU0/SduFTDnzhemgtvwjyCJykalQ202NB5gpZw7AAxGUZ+5vjxnbh+hmZ+oH0nwPu1zNbSISx3xeshm1k9jBqs7DcNm+Ojj1kGlPfcdFAF/4nYJeIebOrwjJxUdcOQOK/jsE8gswNBEheYi059634ZX5L8Ax+LGkH/4Qrrr1j3DvcO/3MOwiFA6iXHxC+5oFMXSzkIlKhGIuCBZeluwTUXxyxGHGqMpFlSVQuEGy3Zy0pvjEMn/iRFSNAJwZE0UkKSogb0o6edmRTHNE3Lvf2rLJxTnvhQ5jbd1TG3es2eJb3q/+d+f3CwsnVBXvxVkeeiSMP2UBegCtq5NCCoC740sQmg1Gb84vYdTDQxfvhKsz8u69c2/y9qPjz8nzobCtKLAcvGdiB/z3H/dCZUwJGU/0OessfEX0r7CzoAiWT1sUikA0V0ycQSCg2IFLgKc/ebgA/huWwjryyDnFP+MEO4nkwfra1cOCzF9/yIsmg7uQrmPzMDqkTJJkqvmmeZ6ZzlXcwlPCKN8dRHZ961NVPepMLetNgLeNyuRytETZmQPwkCusonLFF5E5+03I4r1WzFl6EkTh5bw4dWXjbmeDn/davLQHDn25Dlo+25BV2o354DwoqivVNs1L5ifhvr/+Ao6rtEVbmDkToLra6PviaQuhsdDHnV4BBsmrsRgtxIHb4ohnxJFHoTTJe9EC+V50IEExw5GTxkxbsLQwv3gloaIKhtJMkP3JDkUzyTXMQi2wG5qM4qjBUYchHek9mGjHvAHv2PBSzgolDC2VMjFUZm5Cuk5Os54+VdwPiF2Zc4cv/OqyD9wvP22kxLBu2HdjDXQsd4xvnxFajrhsBgx6GiOFaqRLvvZp+L/Pf8nMeRD7OX06wF5rpMJXBwyGj01E8Yo+q8bqNJSYhuyVNyWv9IwjjDIeuBgJ2X8faG87unXH2vUaZOgnWcpKyysn0XuU+RyIeXKaEnV5G4elvOVYuPDMDN04RLjoJVm34SXW4RwHnga90SX6k3gu3p9GFVktqsrtZMN20PQFURcZeBCZtx+3rUOUtpP2wf4fbEJAz07ArMLVg+Gor1VB/kGXUIOTu+FPN94EJ8xcZnYf48HAmDEA+5zjolw6bgY8NtT7YDDBhG9hBuD4N757rWZucjerRmxBlJiujjwktsHmujrjY/dsfblRZ376QZ58FJ3gqZo3XCpo2dMYTADuoOuxWaFwMYmOEDsaSlgOkGRyf131Sub9kAPwNOmLjj3rcCJtmqo0K+3DxV2tUBzkfroWK2GHmyiNw4FvbIPWs/GhknC6xkBN57XHoOSlYVBUMxAKN3Lnn+5pbTCsaiA8f/yTMKHY9lzoIpRzv2Zx5klp77gpC2BHEQb380hWYyEuM1WtT1IceSJQYlocebA9+nf74fbxTXVvZFeGFWiGdDNPKqmYWbYLWVlFni9V+7wOuxmhfS2TSMkuxtJtPWw+2YdkIvFQXc0qVKjkADwsLY1yZbOWzS9IxF7Co9B7F6bdUvQVBOa+vezDHb5zB3t9mbvOqLsntcE+fN6sa463aZ5OXUHzTIfp8AJ+xuDHki65BOC223yr2x8rgMXTF0OPTSTiVhAdIYkPT3Glp/yRRyNU2D4SoaDzyNjDe97u7xw4ct7L9yBAj5CKXm5XH5MqXwHg3s5t9EiR05RZRS3iMAhjfSIOTbuTEEF2R3f8uD2bV7+UA3Df7aWXAa9in0IZ2n16uftGrjBiDK8yTrLxINy6SpUw5ahM56JDKB+vhfgY10e8IyX+ZFR/rMJPCni/8QbAggXabZFVyocmz4MDBYW+ZQwxGANswYExRZtw82YKNRY62pTl+lihMHoz8YHV5tyIBy7aOgKiEBYieO9CscNIHldRiKW47Qg/AIU82wivqwop7NpMY7YyY31iXwziwEmi+IS8IJjHW06E4rtl9DL0WeceJ7MThyH5yb4Zh+ci/3b7zjW/60bgHdPpi+us4IpuOacBmr+9VW/iQuYaD+PhNfykgDfRexzaeDcGY1TpRc2TJ8+HzcXeFzkhQBHgo4hSxDzLl9DDADgLUp4UVhXSu1OuH4SK9sNt/VmEEptQuWw9ss1VfI0J8BNrURrzyeXArVBsCk3xC+thyYNSZQxI7bL3PGis27ByrNHPkOs3VyyFAicWVMzs+i+e3Mf3N+KE4cZTxhjACsUPoINy+k707jmqE3Y/sBYSY7sjn47BMBg24icFvKmlb2GY5p/+NHSb/xs4HK4omwZ78525cRn2VgazkigjH1sIBOBKL5lIQDwdZ7FeNNg8ptnDV3jyXuzo6fy/vZtexWtG/0nkaYkM9rkMr8mOWrwuJG80RuwYAeiO0UwUMbnKrWeTColk/JH66tVG1PuMHRzZHFTfaWshXtGK78YF8qm+06doeuLDNDs24gbEfgDu1WNXM0aHQslYEpqv3AKt56KSM6JUCIWwAT9T8ZOS3noLYM6cSFp6o2Qg/GT0JHi5dAg60ZjbVJVzkyOPBHRDwYUgHEOW0IkDl/isdhBtu5n4xEJXDZELJGMHOuOd7+sPQE6elgPyijaQqbdBJ8FdGxcMw+lJBAJjlv/c6scSldDjFhrJxDutY0W/1NPTfU7DxlcMy7ccgGeA6uVVyy9Fwt6EE58F2wj9AQQBP/1a3UUe7iIUB5MVW4OeXDhxUS4ddGqzfUUzxuZ+J8iQHPMWYLQWEpvMwU9KIuKOGoWxbfen3Y69gkOo6FyLgP5m8UCoQRHLY0PHGBYQFFpWmheya78AcJPTZN+mEExy7ERIN8A3tHqM2NJkUcw3gT6BfyJvTV3tSowNCdmx5wxBXfK0xP6jp6XwUFVk/Sw8gQBINf6MYSZoX5e9AeDysMG+HO7uGYqxaNB2naccgIdYEDpFxs9Y9v5YfuwxJPBAnfyZzxOGhxa98kH+oNYmWhy4R5thRD7d4ztg9xNvQLLEP9qh01wUQzGsxs88/Dimj30M4G9/y/g0NucXwJxpi1loV1Nuq3CKhiMPf5CZ5XHY5QTgzPLCBvjmKpG8vixueiRysQMdFlxmjlz8jp3VqyZmfPAhGiBPy6KCkpXUYeldSX2XXo2WKiWd2PNDnG52px436xNWD5YhekpoVf5qmLTorF03rh/P6nhdzUuWMG45AA+xKHSLHDV5yZjiovzv4j75PC4FfxMD3Ypt+QzRnPiLjnNfprhxtWtpiVC8ANyHgXdrtwdjdDfe/xbEyzoDUXoEjIB1+CHFpWN6+mnUQGKM2yykvQjgC6Yfa7GhMBBaOKAwzBaLwC7LJZEJfwZAiAYMwNc37eQ24sKKg3l94qvsybzWnXs2lJeNnjsultf1Dfz6VOzkKPyywDxJBChCXjdWQa9dP96V6PppY+2aLZkh3aSS8spxrRgGN9/LSspu886wmMBYnH1yP6UyHgyxeT5NJOV1UP38EAmSMIzCdnzIYZJaJmAVQZrL5ZUUKJ+9bEReT+wqvKtejtMWXSBUHwsTd547DW7cfni4XCk9uWyN00OLSw+xxCimStOt1dC5VM8Vn0wF1+BnJH5cE3lb7tkTojfBi+xG5eZiDITF4BMRwOCLDe5RoE6q1IQ1xvlqkdn4Q5Wxy2/dOXDZa9Vzk7P6SbTfzGOuqtYYIt7cPEJadXei69SIgZzsvSl+wXAjrgm3EeR0ELcIBqaKGIW/c8YB2TDZZKIXTlDz1Sp90HaaZTYLXtvQvkcwLx6TtyCAX5YD8OD7JpISZWULS6Gk4Oz8ovzbcFGVhK9UsNryfmw7hoVVqrlRQzakgbOuNetcFT27FVJsY4KLs3yQSEbKzYPowdlyobdT4XJYDv/GD1mduKYbbwT45jdDUjh4sb0oD5+Pjj9s86MSU7rUS2Wm3YNQbYG/ICNlAyYYsau/5Mg1uiQ5cLnsyKJDgrY9DoufSMbQntJ8J+B+lKefh3WRVWU6idl74wi5u7myP0wlpk05yYnADx7lJmsBcbGj0tkXYQdF/cjvKBq3bduzFo18jgPXpOikSSeW9Azo/H+o8JmLRWaLYm8n8pLrCtqL/4WERRMr/VQ+fellefmxm/ia4Oe6isecoeH1sUmymBA4T5vK59hzRMdzm2MMahfOhqSpBPLN5wfwiubePiuyaPtxzdB0c7WjXPxkOBmewA/Jvl1TE0oBKtB9viPQ1OsvEoec9ciBL53KOXADwJ1qtN3PSeZNSGbEUGHLiy+wdGKnWBWdoq6wBwKTSCRfQDvn96RBJMPemwOxcE4yOG/JXaf+6Sb3Rtd1ltnrcEyjv65FVSYID98dyH1PtGfOAbgG5Zm7fDzvPtTXVKn2WeY1KLm7K578SOPG1S9rVGdkGTZs3rDBYwc8gytjAV3duLVAsCmxcjip1qtRceMpIOgBkF408AVmUdiPy/Hj8HXbiQ/phj1/XA/dsw4b3f4ofBT+gh+yOvFMX/wiwO23B5nytPOSCGXR1IXcyA05cDXsKauc2Q+mNpPE3ydtHLuxWkICLtfasRNAiLlTDwQGocqyFjwJ8iO8n+rjBuxfzAQyuaW+Zdsx0NDQFpRgpr03Z4mMmDGCcfDzMZD7yb4NVU7cgboG98UlMOwk4kyXnA6ffe20XiXd6M84JM5pqF6VEjgvGFoEpWb/z49ytBXfQq7g+7iqCmgxsAXBOQU5P8Yo8Sr5UrKl+wMNDa8FWnjl0xafkFdQdC8C+HiSa5o4jstNdfNiG0EsMbEBnAUFJndl5a+yMyFe3L4usEYF0Dojprk89IV6OPjVHXARfn6HH0dHDrWyNWsAli5FwAxn1aLTL6c8pMScjxw4WZAwO3Bx3/cUnVAfae0IwJf1psWB2/QvqfMlWIdAPAmHd/4oQuL5uupVJwSh0+iZS6aXJPNruL23vLnyGkwwVEHdyoXzfOIQMjWXok9cvKImHbGVPb+QsGsNy9gryUTXjupV5KKbsthyAO5BytGT5s0rKS59FZEag6cLbkfKypgZlRXEiZioaOjp6omftmfTK//RmiUzU17FtGUXJgvzbkEupDQT3HjA/kSfPYAcx5cD1xDF+DVnP0xGHD0Inv7t/TByxHD/sS9cCPD66/75Is4hOXAG4FLuJnax+cCAtVFpMqi+4GMB3DAcODbBRXupoMbk4IwrN5O8rXLGVAC1YSljBVlZKtHT86v6jS9frkvCispl67A/x9g9LblC1RbnxaNSO4izF5CUcZrHTEj4lAy67sCSyYd3VK/8uFP2kD3Qbbkf55s9u6g8PhRd65IzUrgxsXGY0MMZxJGBSP5tZ+1qCvmorZDBec1vyct/7Poxk069f9gYZmUQBTce5Sz4gWJqAAl1F+uzY36cut/31KpfHqdDonRACfzkuivh9A+d5E62O+8E+GzvPMxOSswFqMSkF+KdgMZpQ1sA3AKqVpGHLshK5Qy/jZpzmmKpwUDeEJpoLUNzTLzqvQebJ3Xs2rDdr/Do8gXTSgaV1LIjRSgi1e6pa0EFczdGwZB7Y4XE9nIA5yIR+TqOX5/8vnds2/5LbC/R1TOjfsvLG3MA7kdR5fsx0489rSi/4AnOeXMwsJziEsSliZGtbpH/lZ01q8lLzRfECbwxH3mCnE5VbSksgQsnzIKt+GemlCdsa2lwsnJoflxxAPL6Z/VTUmr02w/AvTqxZNE8+M1N16Vy46S4LC8H6AxmS+4/YL0c9bFCWDYdlZhi3VnXhjM/Rt6aBPgsCbrKtcwP5AAgK2XsAXU1eqMzc8l+Yde76mpWkjOch6dnWWlF1cRmdHwuYsy9zdPSVxymdk7hUOivXBTjbiOvK98PyynjraoeH5K2BZo3Oxy23qDz0e/yV1Qu/SPk5V8o7UTlGne6irkBLAPxBKyur115nBeI28FbJdbjQ0bC1/Hlli7cgFFNli8X7TBb6YJ3uuXtXdKpTwfAvfIUFBTAt752MXzhQiW0zfEYq+zFF3ttPTMAn4FmhAQuDHz9E43RCH7ln90zB3PBFwpUt4ye1klGn/3tzNl5Qz+JZE19zUp8VNQ4adSmU+y9VaaLMhqKTEWMorN+qKwMemUda3ryffuc2TFFpV883nPFztqXf+5Ga535T3PK+2dxjJ+wFi9OcwyDfrlj2IrgG4cvAi7mcBKlMI00Ob4lk3/ZWbvqbCdKeIG3zN+G8s4zJ86BDQMGekoovCjNuW2rYifKmdEBS932dOqKKo9On8rGjYEH7roFJj7/P4Bze/dNXwLw5QjgTtDtxBQzHSu5y6tKOUfunVPCi6OkV2hMRb4qOkkRhdvxjt9eNbl2Loqx8s09yfgDDdWrbUHi8E3Lqkm7kbUZzA4zG5r5rZEUELefiExcIsRMUo7uIN/XWUNB8sh+U/868g8M3rt+vetLJTkAd6EsD4ATwwA4pmbaNNbmhaRyhMupTYsAe5W0CLq7ek5q3LLmGfU7HfBW8986shxuHD2BLynWLyXsvJxJsehUOWCQxWPrnxaHF7Z+t3J+G48DjT8g6CquXOWgCsdGz2d9Z+8O+NyeHVEPN1B9JoDbMJJx2amx09gr9jgObw5cj6MkAGd1ab4e5GTlEmSwrFdCG4rznexK9kxtrHllq6jDeFnHWA+SsxLrw+DEQ3Desp9cJCNPNlajMYQoxSfq2SHrxZtHHYqPJnjRLAfgLtTBBxq2I+MyQQVpO2jbi6o2p/bv8CrWg/JwculjXh9BwVvWV4PvJ35k0hxoyyeReWamL1O240E2r19eHXDWAXm/w8Bex/y2Q/CH+g0wMt47wffIkWfFjGMt3oJyDE40Y1wz2X87cL8SIJ0eJDABRcAwD3poiG1SxBK2U9BpftIFPFQs1uNbkCgPlpw3IOdtjSlicq96cmvXdSaurJw26j7TO+xsxyv7p58djL3vqLu4HU0p0dnAPWUGAfx2Xz/4HjnwfyFbfYrkccUMsD8MbtsmSrFbBdiHiSdqR1d357G7t7xGsU0NhWVQcrTE8uHUSXNhG4YW5Qav0UyjKpWMqsagh4wO6Ork8QNmlea69fE6AUqScbhx1yY4/RDFY8puOpSXD8dUov25gwCcX/Zt0MFYSOa0yZNYK3aLEbm+vUQdcn3LPaA38ugAj7jwjpa2BSWDBzyNCkvmJs+VjDQu3huDexXbwv5v1z477CPVfNDrsNOjQ7BciBXJeLLzqIba1zwXWTT7NFjf+kXu8ZVLLo/lFfzSIgNnK0QsFmW3cG4Ep1iIUvxk4pc21W/45r4dpJQJnaj5y8dNh0eGjOa7ky3k4GBu5bQC6etD9z3dgrqAq5/P+wx0OiOp7uVtB+HXO2uyzo1PqCLDptTkBL4cdJ05cFmDk6hDXRc8dni+WN/8G34OiFwO9383wEuLCyejAMiL4zrPZ00qsnyDe/Xgc/14HWNLC/Ecjx0jlF8OnLiUZYb1vjTor4gD5TgS8fjW+trVU/z2Sg7A3SlEXpioPEiaQacURabV1pRPvY5MnE8QwD+3roWjOwM5bDr2dOWAIfCFipnQgh56ckuZOE6HirgmiC91PTn9Fk4mvtcHXH/5Nx+u36WVj0K3XacxFyC4XbqvHi5vqssESRzrnIgAzp/htadUHpyBM64BLgN3AX2DfZVKO8tC5/bmgjewmC+6IGIqdx8NF67Ok33OTE7b29MylWQOTA8/KNgK6g3vS7Ym4/DV+o0rb/ZbVDkA96DQ+GnLPhEryPuLBEYilrm0Tdkb3ySpFXmZF5aiDHX9xleY8Xe6icSTF5dXwZOD8FaZoRnlTJbDvT3dzovyumAbpDldYNbJ55dnTE8nPLFlLYyJR/8Gp33Mc9AK5QDKwp1oZr9DUb9p1qQM3PE2oSxe+4v28lbJzOlIaZ6vKvE4M+K26Jy4cC7REZtFcY5hY5R1GXIRKX8WIxVjkcxTWvbeClHtnLf8SqUvz6PHEDiuUX6Oum9PZWJozjryD3pan8g2MrTdg2yzvp2XycIhdgq7RqKSn6yx2ZVJBGRXFQ8p5oWUTcggLaMULmLH4hX8rzvWR0aAd0pK4TtjpsDryJUzL84IkgHZmcNuw1lCS5bvdw8OMWadKt0AXN3kxI3fjCKVU1ujf1ZNHdZVYybDvcPHOY/UNu2s30zkkfIFkxupzIf1dR4uTzaAQpjPMccvQ6Buypzt9q12LpyDuRC6sHYlmKmaF47i8jvZd4P9F/vJtPhSmChVDKEArevcOsvFlJuNFBXxTmfK+9JpXcUTiT07a1ZhkHn/FM0u92+nX+com7nkk/mJ/D+hRr+QBQQiay0FwBW2nI1TNSl0sxPn53kS/rz9HTihXe9xAV0iHkYzr2sQyP+O8vFOTZMvtW65b3UWB99+fU927scxW8arbH43GnuBvL2ts5t3w093b9adrsD5thcWv3P81IWkQ2GE96K+yoG73XLU9zFlPG8Lryg8G1msFRaQVhEZWuS3qboEg4GhfrLXawKIv7igm50Spsw7TZ29woi4cd5sb/qsCZ0DKOjEyvlJxBOP1teu+qhOeZ09qlPPEZ9n8OCqkUPGD7ka4vlfQiMQjAxmhvI0QNs4+U2FpuRwXJ0YcKHcveNtOBHN0zKRnh04DG4dVQ5riCs3ThqhmjEUUWwEwSxa2JUwjStliMEGuQT4bcCgAB6kuwT28zpa4NFt63j87WgTvnoD48nRDNdUmSMoi1dlJJPARH8OHDi/SYrOKUjAA17yhw3IDZ/e5pbKfO6whqNS3dU9wE5y4mKFWSihHopGNwisbU48KqAaXLnor1XMYa5HnVuV0RlD5m0eDs50FXoVzdstH7vz8WqpX+STfe7pSXy6YeOq+3SWTQ7AdahkyzN+xtId+GBxBZsawR0YIO4gMjE2jwQ9cZXki5pFMIRPNzfC9Y1bIpGJOw2JvDkvL5sB/xkyInXH6tJAIGigzeFRd1T16HbfLZ8u2Ovmk+1M6zgM/0QQLxYv1qTbT1H+S7hmfltWtWx5PuS9yNhvhhPWrSyXIfWZnJBMixEOKhwUhXG3AuQELExMaLtWUv30nqZ0rFFcyLiYUNwE5JwaopmUG4KPQlOAKRePu3PequjSXddk49btHAA7NUx6yPmhVil+unRYkkKesPdMqQvw00/JMbVBR1nThtfQkdA/5QDcn0ZOOYrLK5e34cagkHBCJi5FJ/LWZy5qvkw4antFMDz7QCPcuDtD77uKUawqRauV8plwkDkCyfXLuS1poWKKRdiJ46F5CUc8Dh5pXoUjPRg0efsQnZ6ClkaPbHsLhiUicfx5A2djgRx6ReWKe3FBnaMIlA2qSDw3YnnY+s45WUwioylGEbczvnzlEhEHgOBAxe2TnITocHAki709JgN3CDOrrAOnA9IC1FLJpKwfe9shpijVdlwRCzpx4m43B8bPsZus3rZRV50hPklCvL7a+vK81y7LAXhIDCqfuuyjeYV56IzDhHviKsqVKuqJbVFiCk7HC8SXHj4ID9S9kzFOnIZL3Phn0fRwFYpXckmfAn4cuNv3ZV3t8ND29VCOlippJIpouRSX0KtqHchIbEYOdIrTEcTWIr0GhhIPSsAIDQAAIABJREFUuQ4ls035hSrHFKPIKz9x22R1wvgTxo+acnaxvmNY2s4Fy3z2w8Gu0JTHgMr8GqBoiBO4rDwVoMXv1T7ZiKoF4i7cN2cuuNjImnxuDo4TywVDXoJGk4b8LMWDtL6eeZvqpRyA69HJMRcGkH8cqf5hOUVSU61uZKcN4HTllQ1Q/tkdrfB3vHpHYWLoNbx7Meb4tajs7A6h6AxDNk0+N0zVRhk/kLVXHiS/X16372nrD0Oz0fsRxGd3mk+3BRzo7bhZU9yqx48/dmT+4MKd2AZ7vNMrYJQBFsobj05iFKuPA4cgrvMhcR+97sOPASlSUDl546BwkBNLUULKpc4Bcf0571R7b096uqC6IfKx3wQ4MfnhFXUAK4/xxhPxP2PIDXrYWSvlAFyLTO6ZyipX/CsGiVPIztYO4IYckC13ZcHLxe0hE1/c1gIPoXIz0yDeidvwirLp8PjQUWyTZiIJ3iVw/X6AmQ4YGwdmgF759cdR8SUaorIFuAZ+V18NJ7U2ByVzOxZAnQvscyo4YuriioGFhW/gd+IVdus8sgcd8JDm0QQ5Hsvn2Ng/GafOZb5Mdm6Lp82wTKwNY02TFRYyqdwyRZrzUUXOsrFULpz3w1gbjNt2B2UD0D35WW+ycn6Y2nW3hLG4zyuyfbVmkxGRd225c8J5Sqjj7uhKrNizedVK3QWSmR2r2/oRkm/k5PmfGVA04G7aHNIbk4lJxAJgDAzfBSkbwSuK4UcP7IFf7d6UUSr14AlxGj5b8fS8Ihh16UwoXo+x8zW17H4dU5d34IWmdQ/264HO9/r3Aj8A12mNwOOaxm1wUXODVnaR6QdIv2t9CuRPqFz+NtK8ym75QFxzDF3hWWRCJvvmeg1DjCJglDEhHMENqxOjTYH0qliGh6rlohZDmS8OB4GTjkvJLmI0lfwm+HMxDO+nWpcF5BUwd10uTl8wsRCvONU4xwXc5WGjuTf43tdTe5o3o2QSow8Sz2acNX6LJPC+8qvw3fg9UvuEBweOePqbFZX48DFyMWJhyeukXIQGqNuI5GUrPg2v3H9HJVhptJYMrAetgwCWrAZ4Z7bZoYIdxTDsx1NgwPPDaW8GBnMrd6K3gPvLmtEBcC8uXB3nZ/Y3wHWNW3WGfgg36VA1I2LDPPz3hfgzC3/G4o98sWbPgw+P6bjmR5MXtx+ODVHwz5Any9d55JNhDMSk0i3FksWLU6VyqHHDw6EA7Wq9RCeWvsu9QRgljWCUG6n9EpgNztuwEmHIaR2z3QIlqALT0wLFdrgkEnGUf6/Wln+zudNZQbk87hTAZbgIv30Of0rfO2k+bBlQaip3+B2RJUuoWcFY8PkzveHclJsxBO8/1m2A96LnZlRpF277+XjpbqTt75Dy9xbC0J9NgoH/wGBZCXlFxuXYj2Kr+NFKB5CdwMez3gA3h3P372Kmox6JVs9HcLk8jtXOwb9TbIxl+FPkN7Y31g6EH/1scs8rrw2OJZJkyM05WmPM4qTly5N/Z+V4FU5cLmJhXy5twllJ7Jg0t5OiGl6jbM+ByxX7gjMuNq6bWwGkz3k7EciD85Zjscj/DQ4/egWmfe2xAzAJtyEHfonf3Krf5wA8CLVseZHkR+OvSF5Fcb6hCxdf5YylEKerkwRmvpotQO3YpJRN0iZzeSj5lEP74LcNtWnLxTdPheQKtCB2A2+1fwTkw6+Zjhz5MNMSIQ2aORaVHGCIeoOCcIgmjCJabfkAuL0OH6/NZ3DtfBc7cA/++EamcxvboUMFyWOWLkQqFyCYK2IUBrPEcZKjDocCi/LQSRFp4q3BdUsQt7/ebumPCtSC+2Yu+S4SrCCcdwrJXeq008fCeeOeU22/jUMoagWmHUOEPJ7EUQfz9o1qqa521HO4zW0OwEPuaFwjk7HoOvxBQYSZ/o4Bpb5cXom/MBCZfalyP3LB0SK1m2hJsHfqFuWf234IHt0eXrm5ZQoklr8EMR3wVvtQUFcMI6+ohKK3BkUH5AG41ZDT5F4sRNs6AO6XJ+V77MdXMJLhN+3RDPOgFT8boBTo/bS000WXzIAn/4u3KVpxAjTkBZHA25BiCIA21yjnoJlonNaxDTHkGpYmh/wg4AiaIk6SlcgciuIylSOV7SqKTR2ZdxqUYuFj6XYsL86KzooBunp4iXZ4PH5xh9FhRCyVcAENY/YSiXZ8rKI0aPdzAB6UYnzx0U6gu68FvGVV38VgQ3cOw2BDUpsvFoJFQaSIV4JaqByLFip/CWGhsnUyxJethPyg4K2SKK81H4b9YiIMfPQoyGs3ObdAZBSLWJNRClR1JjNrybf9OHAFhIy+Ypnb0TrlFDMIVhzWQBMK57QCGumMed/+Api7fDGLSmjoZgT3LcurCninOlNAXIph2BccuO1iEXs9xOXKU8BLH6hDa60zmB08CvJ6EMv58I1efKJ2wTgoE4mHEMDP0plLy34MWuDdnh+XAnm/0MOITGzilu4dOgauRiBPiNfkTVm3ouGXzApVopz20lQrSguVKMDbMlZ0Kyl9chQMvq0cijcT42A6XZibz2RJ+Jg4e9MfVZt+nLWkjW4++7qJ4R36CbT9P5rsxH8PLfA57/UVZh9OmLmMiUukGEVaSVjtvlNN+VyBUnxBsm9av/JNTk4DsahtMm7eb3Phq3brVuY0JOft0ln7jcICooaMX9FV0WGUYfEJO1rYLZwceDpH+72+4zTnOQ48wE5AQpOJD8UoIA7cNx1A8D51wjzYUVLMvdoEiKlKoGxYqEQO3raRF78+GIb/cAoUVpN4JVPJUIsJAMhUO8716nCEfEP6G+641TWopwf+MXPt4UmPdZBVSeRp3opFsH8/+fsoYhRpMuh0M9DogZCsAMQR8JRY4VZ5A8/FbMbRnNHg1G31R0Vjo09SVOQ4DitnzS4RxuRxsYjKaLA7hsGD8BZkyGa55nXmnq8RYcTIbkNUT7K1fsNKT4bQbSoyt980Jr8/ZRHg/Tb2uSpov88ePwtWDTbd1lXLE6pLy0LF5b5ZiNzP3XXrYYVLNMOwMu+gY6T8hRsGwqhvzoDCLYFFed7NRSVr0d1hDr3R5ay1QMijH+PGdMK/HnkThg+LJHaKZSTXXj8Z/nDPWC5G4UhiBmxSwE4dgyf3zRevCc6GbbUpplHXNp9GAYsCeWwiYYuMXasfcoROHWXcLW/ITVwjxUJk02h3n5eSfN6EHlSa5pR6ZSg/buG/76xdiR7dwZNer4LXe0SVEOD9JA7qfWEHdvqEOfBG6UAG1kyhabu2SbGJU/1+0Qyp7DkO0QwzzXm70aJo3SAYdcUMyK/H1+hE3PSgdFO2XtCivZpf64zwyoSLbWZVK/ztXrT9LyVD6ejSzl1FsPS9iwTDgMCBbfG3GUwlpm9rymGqcroGyNnCzJr4yq1dsFUjxoqfzN3eFz/a+nHedqsTblhA4E60EGFzXYDaHLaxc+XR4GhII8GfzG4dDw8hOiEadHbGT27csvppX9o7ZMgBuA/VBHg/htlODUNgtcxHK2bDq6XDkOvh1yi7+MQuiwwqF//Ugd3wExHNcPtE6Fy6Gop3u9h5pzsW3/KIPYMeHAvDf4rGOp08QCmXkyseduJeyrggKTOVf/VtQC+DyRGFX+pBLgA6nLpnHoFSC+YegofueQsK+FOnkaWJKAdHu3Csj8LGIqAysnB5cyCOV+0RgREXBVjBmbP5LKdJQ6kDMq1bVIBzs0ZxJUCanDcbdSwJ3eM6oXDnAGFxI5Wxwp7dS9uqdIzvaauGRx4qpphF1THwv3ce7prauGNNqDCk4Vd1ZEuqb1eEE/Aw9vDMqHp56djp8NgwRYTuZqHCgEy1GDB74OW5OR2VYL8//NahZWsTQ9KxNolqvLEDBXDUZ2cz8YqqsIqq/j5Xjx+byNCMb3S/tOzYA3D/net1svpVZXx/0SWV8J9nMCa8ABoJ2k5zk9JN+0kmAdpmQ65GMrSIHmwxVnSV2X7kSofzJvBueOINKPvwAvQ85nMieWzd/tmJb3D6PlMsD6sdjY1DYf+mUC+6+K8i7aVxZGWMkvO2U+bs8tmwatBQgytxslBJRy6ezE9A4+/XQ9eSUGsiIxM56K5xMPxnk/mDAP0p+aFHiLH4cekqJ3zi8fvh7ts3hGjFuQiJUZaduJhzmpL7pqwGCGudLZbKJYlYsCzx4ppl/bIzSzoMidsna1IApiJ/1x5oFJx3fhJ2/u9VSIzuhopZyw3Rph24LXJ60cHA9t/qwESFBoBveCn0pghdUJvQ/TBjJsFbkuNz46vgPwMx3gg9lOxgoWJXdNrJaDW/MngQIxv9pvXsXXDgmq3cdqYPpIKtJTDm/GMg1lSYMVNCqZTSYHAjp4gfMMsGg54JH/pAE/zmpprI+jtx9jJ0HBF6GEQAEqU44It3ezbuW2Y2Xu2hS4Z4/JiJV4Q6UZrGRnEbS4fzTqB+Ydejb0C8HONxNhRAxfuPtZ1c0dt/p4qH2Ai66qpXslDAYVIOwG1UywZ4yyYfGjwKvjF2GgKsuYFUWaSccLnhpdxccggpYCXkkIYnGTYUR6uGQxc0wOFPNWLE6GiVYqEWHDoCkYKz5PkRzCxLU7nv25R6hPXWotYGcB2TPQvKJ+Gqb2yDL34uUARDV5qRGOXJ/1L4YEE1LhL3FnG5nDrm2hQybWYqK5qWdYp5VqXh7AbgQQeLrsTvdGEKQT1rEzq2uqe1wa4n3jRqHXVpFZQ+zcVKUvwR6UNUDrQzjGITia3owBM6TEJvrXXfDdkbGbIJ3nJ8TRjJ7QOT58PeQuRKFQsVU/4tlD5iV1jB2+rs4LUJE4N6YO/Pq6Hz+OgCYoWeIyT0sF9PQCcgDLxGm5zwg+kCgiVTEczQIFJZsS4YB+sxz63Dgae2n4Q//HoDnPTewLHEU7rIrFHet5DbOgvCS8soL7mvH8crRse5ewxlqb5gz8YtADtd7tuvH67WJijv3o8HYetnrQdh+dylEOsWERWFTspyZhh8hp4Fivea4KeZXAPxePzunbWrLwizjqhM0D0Ttp0+X06A94vY0aW90Vm7hYqvXFw6YEg2nCZTyg0cOHGa6ASyvIfP3APN39/cq2KVfJTpPIWfxLNFcPFl34ZudGCRm5+QnL92by5PA8zktZ195RBrozcmTvY8gBxX53BwyhNDAHriobVw9MzQr/oYFJqx4FjoaEcTF8kJ00vzwhrFQsaQsmbuMc8WolIdBy/uyJZqheLIdYsqHIEqAOfdM6YDGh9dCwmbfX3hulIY+8l5qSI9KfbRlMU5WaB4LUc5v41791V2NlXXhl26OQBny5ZJiUlTND0sIaMop1qoeAO4yW2miFXEFdaNy6H8LecI2XgUnQ5YRwG+S7MSP4tFjKaNm7bCaWddBB0dab0XGbAXvZxdjwV3vFIMLO2Bf/1tLUyc0JHWIP715HD4wlfp7QcBAexwdLZZDsPxGq//GNUrIWttPdchBxWRvhKua5sOIHFgcCaAH/KtH98NzT9wttIb9/4FULhrgNEjuwUKO3LkISKYJS8PTE8LFIeB7khDgWmyOGkthf5dGOeGFAg0u2V9YSTSQkUIFliXnOTixoLm204JUKTBieOi7njvfmi6BRVjWVRwFmEY69fwczSLwmumpqb9cMqZF8LepkCRNPvCdLE+6HDUwTvroiBAECgr64J/Ppy+t+b0+Uugg2z0ifsmjtj+jq+90wE4XsVVzVqLkJepXHgKbTy4boNz5xvAUWzGQZS/F5EsjsPON192Jv/hGFQsxgu3cLYx5NJsT8ljS4/H9fPAVNeIMYY4xOtq9V+gdxqEXu+Cr75+UUJw3ihPgIl9qcNkofLkIFKqcBm3RT6pnOLWRcGFyYaMXIMTbz0DxSk3ZPbJNknXATAA1uJnusslh8Zy/sVXwLMvrO5X9uJarvPK4tIFe698tARmReCt+eobg+HMT+NhyrhWDlnCcERrOzjJmu0FLTbhDvJlv4b8uG5eniO+ynXLPbP77rege3GLYzNDfzIRht5d7tkF8xjVk38LCTd7+MRJ+mICfR69QL8FX6Cf6kcDr+/f7QBOjzHQCyd9LpGFyhVl05CLyDc8N+0mWIaViqLglAuEBqRjatj+3ibYdwuK4DLIiQ/EF79ewc8s9gKYd3rs70/BN759PXR3Rx8LxK/toN+zszSg9lQfwP2VsrNntsLjD65Ny1vz4ksr4V9PjWLctwouPAC4gId0UALrSQjZunHYKS/7pNDcyWJDyssFVjsCo+C6SbwhvX57Snqg4XUX7hvrGvsBFJ9guAduDWV9rYj1NQ35t8G/q+NhNxieuDNe8pYd1SsvC7ru1PzpTE067fZ6WSTk77ETn+v1jnh0gCxUzpp4DGwq5sGhxKQbO9u48ikKNF9TQ6yHi/LEBsV/xEd0Qwtq5lsu2hk5OYjzfg4/Uuat00Br62H49EVfgzfXvpMxNbvklDLWgM5APfL4Az0fQdWMw/BvDH6liTWOLZJFys5dJYz7VkGcWuCKRbb6ArVBa5NJoak8RirEx4AsMuwUnFbOCz+ZOx+EjetmIG+aE9Ii3/X316FnqruuoHzOMoj1mHKjbHhgqsrb9vaOsqbtr1F009DpXQngONffQIrdGJpqWS6oysVVjs8O4CkKGAHUdq844zCwjSM+qgv23lQNXQucr5xBh03WJk/j50T8hEn/fOo5+ObV10Nra1tkOGvghAIYYfoWpow/KKu1endQrWvihHZ48tE3oaQknJ3/fnzsYdF7FkFPnD/QIR88NhWcCjC6xHPnS032WXnYAX/30sZX4UNT5sOBgkKDb9A6cALK3NUT5vAH9sK+mzyMO7rzoAIB3NgbwsQxZQb4OcEOIjZE0XEJnLoKWFmvnDd8wPgwPmDs+CBMkLX1rgNwnIaPI4H+wliKfpTeP2neO7XFpbOo1xQOlO8XaxCiFJm4wjVZrsfGaqIFyRU+BteD37Ud3wz7f1UDyQHhAIEdEPh5CD8fw086qa2tHb5/w81w/1+fCO34Y1xb0+mIUjbopg3VrE8jdngfc1Qn/O2+t6C8LJw1z84fFsEH754LhxBkudLcvKkxCbmCuKalheSCpc23NA+k6H55UIQR/v6x5Q2o6u6AFpTRzJmxBN+LJU6cbz6jSvtg5A3RhvJeMndpgkhg2z2+HXY/9bon2WO7C2G8CCmgAr95M+OrWCdpKTBZdcqjJ8nE3XXVqy7Qqd8rj14P022lj5THyXkvdoXCwkYc4y3jA/wVguyaAY+O+vOIq6Yx12dVHu4sSjE3iJMiyE85lCiKw95foePPCQdCDe5OuBMuwE9U6bkXX4YvXHo1tHd28JdSjIr5lhPGDQQ74ht+fQ9079fobNgqg3Hf4SxbBg/qhttvroEVS0M4a/0/9Nr9N8BJk+bB5pJSxbyQwJhoSmvOXS5M42OKO4qrjeE2R/R0wasb11hUKzsKiuH46QuFCE85FFyIqoob7By75bZplMe+ordxwzMY32SEtw4lf0MJjP8YOjN5TKh5roRUYDrK87lwKZHoCvUCj32JvmsAHCdjHg7+JfyJ+LUBjV2fXpa7cN9cg1Wsx58hefvyMZ7I0VC0eRCXKXLocjU1pKatehQT+vyUnFR1y4U74cDXtwdSct4AN8C38BN1ajvUAucuOAFeK+pfUxjUUoXPmb8SzRl7kvDtb26DL1wYwO3+OWzwRHO2/ocxei4vmw778wsEp2zCBAdqLm8m2QI5h6GanS1D+n1pMg7f3b0VzjnYmDL9z70HA+rfXwRlp8+HvMNca26KMER2KXN3lLEIUY7tXOYcMPZlaDfsQn1AYlyX79Ibev0kGHrveJMNkPRmt1F/2suCXOfkHUKW55V0y4N4ItG6s2ZVqBd43pUAjiSmWANv9UPwfgb7fDLuEbKWsXiIjvz6DBj479E8DrMMki/leMrOtgNBqpKTAzpXkDqLVNqPPQj7frdBK5bKZXAZ/Ao/kac4PsI5Zw7AO+/APcPGwrVjp+B1PDv8h/2GH2RsbCoCWqro1u91GzjhuGb43c3VenLx5djiqtRW3ygZCD8YPRkfIhmCQG0Vo1hyY0cm4M3ou41b4OQ29xvbODxTduNb35TGnbIACrahC4YEP8OhyJS3u9mKG/wwcfwopiEzra4ZrbAbPS1101h04CnycODRrccAcmYFw+wkXZPciz3xxCMNtasiCVGdnR0QlBoR5sf9gwbVgCyk8wvyETYVdVX0cPIUBO/v45/fdqq89IExMPJHUyCJDAd/Dkpw4ir3poK5Ym7I6zO5Ah2Ryp7b3/EMUXs+nA934SfyRGP4GMrSH3nEqPogvq144YRZ8FopMTKZWcYKlEQ+JK8KdbhvMXuG3b9anyw/dEg3/OG2DbDYSyn9Eyx5pf/wDsUKYE3JIHgF6d2IopAheKDO6TwEJ7QegtGJbt8Kbr0E4NJbrdmKXxgOI6+ajtEpuUu/nEVneTsaI9rc/WlZJEZ3QdP1mzDGT7AYMRUzMXys1CU5KDA5N0P9JftyTm35KDc7j9lXmutO7EG5FXfs2VsO+2ojMfnS7IHv/PTJDHSjw44RocwHKftkT1M6RYG8xyF40/uba/DH3UfuUAyG/3gylP4bbXk7UDrODXoVAbj591Qlp7VdrVgqH2+E5mvRcdVmN34KnAL/wI89NGkk5P7859Hok6w+U9P/Bg6Fr4yfCa30zJHuhvLplCrx7I0Nosvxu+azsOZJ+L/Lt8MlX3DAi/8gIVD2bdFgRzJh1kr2IQtVhtx3l0vQ1KK1A2HoLydB0ZohaHIozRXdzRZJ8d45twUOfGsLdM0NEReGPDAXLXUEYT9Gxk4ev0Ne3XOkSyADhHTd59U+9Mb6zMASSa0SFzdBTD3+9NajYmHH2Y4FK3GNEktBNqLapkajzp8JA17BMK3Kld0O2qZJIce7FJGK4DykkpQPgsvZ5Z8tZ+2GA983Y0tMhalQjR+KcxJ5ugbF/z/8oWe1bXhoXTtmMjw4HKc6pMjCqrAK+xaL2c2wys4g9PNqw/pdEj6D8W+u+85Ws3pywF2AP9FYjHp2+1P3AzzwSb2RxQ4VQOH6gVD8+iDI31QK+fhvCoPcM6kd2vGBkp75rZAYkp6T19Dr0QPzXvTAtNxOqX/iuT+9rlpzSQZd/tY2OYqDXTfG/y4K04RTmSMSwAV4U8Bfa9CNqKiWuXqInZiCk7IH1xIpXEk6GSgNv3I6DHxstGlqqCxK01pFgLciUlE9ONUGmV+bg6lh9+Q2aPzrOhhQWoKd3YO+lgMD9VMr86145770Uq2slGkVymrPr5iFT3BiaFC+HwVTzi0kjDs6+72AbC6kxhTdVkgLvHXZbxqehqJTJd6pH9wLv/5FLeShfxTzP84CeP8LOfwP/VN7CrOScRw6LhXuxge3WeKiEgbdESwBN8Uy07Oy5pJpxf+2EyiCLmeF5tqNCPB+QSxR7XJ9ICNFcpqNE4IvL8AK/DuNIdT8jPw8Bqh/ETlx1T2YLVURoU0Am507V60lzGiI7sqrZEECLrvuPLjijC9FT7477gD4whcC10v2xqdOngfbi80Ic4Er6ScF/K1bUk+DFQsOwH0PoEET6oQznVrxTK/EeGkNprFHppvUqr/8GPTARKclt2SRQIpMaT2hxnCbMxOJZPyO+urVwRe2S2dDAYQWlXohkwDvN7DpY3qh+XSarMPCixjnTSnJRD9pLfvhV0+FwY+gSEGISSx24zYAl3I/pwFYTQ155+wilfM++RH4wXe+Dvn5EQVUefBBgE9q3rldqH4ZmsE9NuSokEdg8KkMwDi7A0fgK7x3q24c+v872AS/bYjuiTa3AV3ya4DbvhyclhktQR6YCODyuTezLWcTRe++cLbaSfBiHK6GApMbGOzfc3BW6763I3vk9IgBcCQlyYopsiDu2n6VSJi8TAHv0/DfT0QxAtPUUN7fODft5MHJ25PB9rlYwXz9x1o+tW8oY/3Ux+C6a76efrf/ifftD38YWZXwXqCyE/cNHQNXjcNgbxGLSNRB+imx0ieIew1+IhQveD+7eTf8dDdtl8ykl/GJyaWr2ZLqUym2pRjKT1tk3QMskmFmu8pFKMkkyr+JyzE3VJrU6WPkDTcapAbpt8lzgUwG+1OygjebYyAJ5cyoBiFNDQE5D84800o1g92rscQNsQmHctYFRxd8uQKloFkoOY9fvhjuueMXaJbrF1jaZXTPP4+ugCehL7S/WZouff43cBh8Hq1UuvDd0Sg9M3vbUkXOjW7EPDu9qP/n798N16HtdtSpC0OezEYpzaZefR7FeVTDvzGtafC/xowSeGphVHgJLhOPwnzQuKsKATgaQvbsrF6F1IkuHSkAvhVJMik6smSlJifwJm9REgFFm4Sp4YD/joTYQW5zS+ZMKiduBLVXFGN2kyrp8SbtzVNAAcsOHTIY7rr9Z7BwXkAp1mpk1973PoB2MsKJNq1DhxSK6thOcTiEw1IY5xqTo/WXPkc7Aufa/DhwDvLu1pVU/nzkxKMG8St/DPATDdvybNDI3sb4ect2xbryxtntjKI2H5TtqsYB+PedGP/bOwB5QKL0ewDH9flXHHN6EZMCEi2C7BuxjuOZwlJNSRan5eQI6netovDNQXDUl2dCrJkzAnZlpVWxad38PGAQK8TKimsh/YL+Jf7kX//yhmvgzNM/qDeUdevQ3gYNbg6HsOnVawE2Fw1A5eZcaEcLFWNzsUH0jqWKZrdds+lauujk+8x+NDGMiBN/HVmQhRRHqm8iy18qZq44A9enYZHuLsXWnCFi2H3EL4YCM5H4IwJ4pCGs+yaZ9WlHLwS83WeXi/M4UjlvDiSL8f8UfT4rczL6CzOhBD3hTPA1wVyKVZxipVjtw90sVGhbxOAv99wKSxbO9Z7NjXiWLVkC0BzMk05ziViy7c4vhBOnLbSAeJh6+kIZHe6bLytv22YJLp840Ag37krvdSaa9aEYR6tlSF+gUEofumGVKctoAAAgAElEQVRHSVX5BxdsZm9ciRCcmTIftDJCGOALb3+N+w5O69zzdqSKh6yARaamExcMrbi0niTKVN9c6iX3+MWGwlLNlAQKXpxVqeHwq6fBwL+RpQZ6iDGtpfLSu90RwTBB5DyLXfZqXhU5N065iouKoPaNZ9xl4nVofHMsart2787aNOwpKIATpiyENgzU1JspXasVHc6aA7g+R/Ce1ma4p45UMOHSB9Cz86kPhCubhVI/GVk595bS2MB6V70BI5YiKBM+Aiz6JVvW/LqmZNHqttgbkSsw2T7U6kEfzISkPBW79fc+2DW3LpGd9ywX8P4efndtb4xlwD9HwogrMB4Fxpmw2I2rXmpCLu4kJ1RlfE5OPwUF+WihciZc9Y0vQ3Gx4oC2dy/etTGcJ4F4ltMe5MTfP3UBHBTR9rLcfFab0wF6lVuc2tkG/9i6FgZQkKgAaR2qPOaiJKyPJnqW56hhU+aPGFwyYJuTn63ujcYYn8vJaLnxKMTHt0G76qtXuQQTCE+1/gzgZEtJsUL6Q6IFNNEFvNNy2oli8BSi9qjPHANFW8yn2yxXQHHSWxwcDNeyVDm6U59KSorhh9deAZ84A13z9uFZNns2agBSQ45GMR6dOrYWlcBpk+ZAK4L5kZx0gMmeZ1C8Bx7a/hbMQjDXTeSwUztDN3fW830fWdXvjZpy7KIBRQVrLC8N2ULBZqpn8US8fmfN6oqo6++XAI6HH8U3SestuagJ6VEfsTLHIaFTA3YmgTTSJAaK/GQOM75R582GAa8O5XCtPJ3lZEro5HrvFwyLXPLPOeUkuP72n0N+mz44hBmLTpk3MbreJ9A6pSus2aNOI5iH38w9zEE06wmTzU8GTnU6dS0fOfBv79kOn9vvH1f8+eMATkAL0D56n2/Fng3FviUqKlfci7LCc5igkE1HZuBPZc4l/ePxxD07a1d9JswcepXJzAii7qWtPiQQvWdJ71r29UQOyychkZ9N6WgSSIO4DX/6lMpnJFqoDPgvdo3k4ixErYi5QX8xrE/4EvULhuU0OQT8nzxATiTR2x+HWQzPop34BRg/hcwLueQ+/UBWsh/2QGFh+mcvowPI1jJBpOCpPTwe5eI3N9TCCOTK3dIstPneQOYEfTOdh1P6Z+rahKrlh3DRYvzh9GjiPExrnYaJrji3W7t7Zu/f9HJ4BYMLbfsrgJPL+ei+uV6MXhHnfSoSGB+qckj4aDb+tk9GSpz16LFw+NuF6AypxBe3Abjd6cciC1c4G7tyU1q9nNKyD36zs8YelbZXpvShIaPhivHq/d+IGsMAPUzi2zkTQBGsNzoiFKrRK9+weDf8ur4GjmtLfartHXQ5mx05LAUbo0fudTgJzAyqbMbCUfmxYsINXLrWOZW6yygfL5Z9yqQCk23JyEiVpYqQ2NOwKbKj7uvpXCTuvS7gTRzBp/viAAbDYHy7bT0M2DcQPnnBZVC7aavRTadQtObviNUw+Vc/5SZVurDtEDyAVg/FARVmmaDbD0dPhDtGOfhYSPkCM75ReHS8ofA3IPnvTSL1rW2lC+BuHj9GeaTDRw7uhZ+jqSEGeDWGeyqaEfyTzAn6XqIrwzCcIOZcML5y2S/zY7HLZTfNA1Z/vkxRonsZq/mg8dRhd92G6ELIqqTujwDeH6xPrkbCoj+aQ0oCebf8C3/6JO3/jLfNTytny3d/+Au4688Po1k3WcwqIhW7JycbEPfulMniJETf2cLSEgFiCN7XozjlnIM8jldvpk9MOBpewQcijqSkC+Be+dTvhqAo5eFt62BGVzv0ce77c7jk/ijnsqJqWS3aYkdipivBnx3gHrtY0i2RSNSjA0/kCkz9o6cPrWgk3tewO7/oQ12yd+UPOKcXufYvCXQP7VNyb9nXD+LZ8m8Hic/d9z0M370OSa7IwCU4251+nJSb0lHTycyQ1j/GiIBTDu3DCHm1vS5SWYaOPg2FMlZ0H1llISUxQfSmukDPQAMr/jFy4g/duQce+WgfoZG1G4/hmvuI+quKyuVxjEAYCzJOv5FJVsWO4fbpQguUP6MFynl+9YX5vk9ygV4DQeLQC+0/CDPYLJR5CAl6lgd4X4Hf/SwL/QjcBL2msw8/Q1zOlo0oSjnpdLEGZYhMxbnH9NA0lZsWhRtHavY4nHCCY31k/hHiu7kdh+DR7W/3Koh3FObB8gWLYN+hyB5NCTwXaoF0ACdIWb+8Tt+3nt4I+29Iz3szLeI4FyYGaQYuLONKN3bakllFBQXr7Xdei1msqCvduN9Ujd3ctrM7uWLP5lX0MHnkqT8COIXJcRZPRE6eQBVSEKolSFDnUHpJGIXfk8thREGzA/XNN/N1cB18Bz9e6clnnofPX3q1GQRLcfBROXE1vripDuQu3V5cOIlWl7a3wAM7egnECbPxHafWCTE47uRF0Hygd23E/UDVb1IzxYGr7XbMPQR77n3L69VWv25G/b1FdEKVo/z7Tyj/ltwHYzvMGDg6zXNeO8iDa6b4JJmsr4k2hKza4/4I4BR0+uc6ZM9iHnQrZE+hkc2pc0rC7fhFZC9xRDm2ozCE+m786BjQ/fzmO+Dm39wt1Hn2+ClcyiLN51hkTgHyrL+M3RaycqYIS5UNJJFNv75uE3zmcFOUQ/Svi8D7FfwRoVv2NqG35mnz4eCh3gVx/45Hk0PnsHCT5HRVtULj/W+xtyt7OT2Pa+wEex/Kq5YdxhtiqXSJzwTo2elnmhEmdtZVRxuBsL8D+Jk4ANSq9ZlEXpaTcFG4uxUmWXxvCroVMlB2Zsf6MJLzTPzoplt+exf87GZ8JZ4pLDkqW1/8EdJBAnM0RVStUxjzw6IakqiFG9qZ/+N10fc/2VUL56BcPCuJwPs5/FlqbW3r9hI49eNzMUhi78ZNyQYNtOzLPVj6riltsOfPb0FiWHoPDqcxVopDPBOX1Xa1jvKqpSei8v1/ljUoMpgHkhrdnb5M3wDUAPBE8ra6mpWXpDEuz6KZOIwy1VdWLxJ9JP6RZfbMdUi0Wik4FT2g7J6ScAN++a2MEiZk5VUYjeAd/Ohw32oT9Q274cxzvgS7dqOoUTj9GIuWsd7WSHhGHBW2OQjw6SzjwG9PUhG67PABFlwpo9JoYrDp0V18R8IpvbkOvTXPOxq6usRDKpny3hPGyEHnIeS0O9LczzPRTyTTXdYOe/60HuJlnVF1K0g9/4dLK0W/VFG1oganzDTyl+tScx75bVJ3VqxHAhU9CPtHtVRXZ4wT6XcALkCc3PgmB5ndDOSlVUrgjQJAn5SEasxR6ZetN75/BB5Bdb1FYa/fjeeeg1s+9Vm4Ed+eTOblc77F8Gjk3Dd7e1Aw5By4hfyRWhF/dzIvlIrN0w41wW3IjWck0RlCj9d9yLv2Z19Ab80vorcmRaWjbvshWZDORlmXaFeLm7b1UUeEwvaeKhKz10FH88A4NP7pbeiembnY7g7kJf3TIlyAFhlO2dTFFfmFhdvJc0fy2LpQbG+D0dQv8LedHolkO3LfPMBQhlJ/BfBbkR4Zu5Zo0PoA5pmHxLNc1xzLJVnArcgeMdXom3aWkXiZ2YufUIv6x6hH/g4qPfHtykMYS+TDE+fCVnwJ3rBGYdIQwZEoYhPZOR0bcTIvpP/+VLce3otOP5GnB7DGs/VqfeSJ0XD5t2zemj52wF41M9ymDH1kB+qCvh/QM6DEMTVfvQVaP52VMMEE2sdgmyn+oOXIfSP/MMNpbOLCwx9jEL4L7LUmZUp0zlYvesSTyad2Vq/MaIDdPrJ89DaRzIXEJ+6bAqP3Rv9JfDMbG9bzPEEHNsz/SLARZif3LXALfAU/gVIcw7ssWoRCo1Sp0fnlM+F/gyjEC0/2jaOCtpFJVWw6OPoQiOcjJ7+hdjUMCNRRn8y/we+/GKzCG34xAX7ze5s/Bu5yDgJkDmmLFW1c14W6luWJMtpKsP675fYDZbVckLwdiw9C06+qMy0X/w2iwJftYxszddHRRYVF61S/ec5OiOugJnRIcR7Hdn+4UUG/qyOxZPfWVaQaz1jy71HGmk6vYpyGx7EGfL48q8k9LKzr7mAwQXDRpxK5zB/ETyDu+6mnAM44w/Pdyq+UTYfHMbYI2yYyoqHcM/Qr4cEZ1Ea8rLsDXtryejQ2mD/CjlwVbjrOvmA2rH5lWLjCfbSULvdN3dcBcDVPojgOB/5vG7Sejdx49Cp8EmMOxkWcYrqLT6etRs56id1VkjPbUskuuAcLprProoHVarAEHsVQeF9ajb1TndyQCFG/QO+0fPozgFP8s7X4ky0TAZrmE5BgLwTah0n4Hua/NlCZLGT+I3oZX4gfrUSPL1x6KcCDD2plv2zcdPjb4FH4Eg9DbKWMdcP0io04xbCkWJZppJM+PB82bs6oaDN470z9WeCyOqAsKw0C9mpHuie1wb4bNkLXHHdL28Adp2M4jxkIWNOYOQMrhg9qkdy3NGuVDmTS+omvTHcLFM598+uVPeqNG3AqivxGjH+S8WB1/RbAOenhu/jH90NMfJgityGxgsvd+yCAL0J9zxr8+CZawL/9LW4TZFcPpkai8yr/+OCR8BUEcobicpWpnA6JE+w24j6emqTs/GVdDXz88H7frjtmoAAHd4QrqpZCsT986GNzYUPNoPQri6CGIACcbnO6bTnlo991vOcA7PtJbRRiFXJcGOc0nooZK+5Cnfr5DCNkbB5agwkh66IvGGPBdSzcysQMVMYPKWYjJaoXsi8Xqyl5DKi3WQzxc3tdzUsBhXTBZ6e/AzjZdhEXjs+7ZDT9D2v/IBLL2cvSq+lk3xKhDIJBTHFZgh/PRC/FX3ABwBuk4A+XaIcdW0XG1Q7LjG6qio245Oz8PDXJ1mVtzUqM0B8wUYADUlpGuOLPPOcYeO3N3g1rowuobtQKyrjrtufJqWNgtJazdkPzNWhMFn4+PoJlH3ME8MplrXmx2EAJ4NzKiQKtcdwW0B3oQQdXc0IZVkLULdvs6Oget3fbmoxrccOTL+D+yVR2pBtplZ7Dn8kZaoPeGvkAEiqccWsfUmLmowT5Dfwcgx/X1IpXXLIu+dWvIiHnYwNHwFcqKk1Zu8H48GtpChfOxI/OkQulVcqpB/bCbxsDxODAV9yYuWAGghicf/FMePaFEZHQqj9Uog3gHuaGcpyJ0h7Yf+1maDsN7QKCIdFazD/PiV7DJs0bNrikFK9oCNvydMK6Y8IElElEAjamtmP4MyjROCVoSzv6RDLZUF+9cnw25jMY2bLRoxBt4Dzh0+pAXHLU74JQnachkcK//5WESVjH1hDDiryIr833HzH65tcw2OOhaE32ziqfBasoTCtdVcWKkzbiTp6a3BLNHcRJlvlWzSo9LpyMuPC19Eym2+4YDz+9aSJTcPWrpGMnZxuQLoC70cGpfHxYFxy8eCe0nofPt+kpOs/A5UFGDCmpvHLZT2Ox2DeJ3UYg5Vy2YBr8HJXCzp06Jvp7PAGXNNSuvC1sfUHK9bMV5z403NN0Zfol/nw+CAFc8pI0lmwVrkUCpR/goQ848niaDD79NMC552b0keHTJ8yB1wcMxGfakKo8YAoXPwpuyNEqhW08YaZn4ZqSMADjUq/e9DoMT9KrdS5pCf7+WfzJQnTY2k0l8KkL5kDTPtSpa3r5BV2nnKMMElIpaAv++YMAeJDzgalH8hPQdvJ+aL5qCyRGu0or38ClsMCtp2T7jVt2hsFlZxi8eegHbl1FCxpviT3IfZPzsNT4+BM1jRxHDIBLGiDVyCn6TvxxeF5Fi1IkU/8GEuYZrdw6mZJwE2b7qk7WTOQZASNYqFjHdBFq9v7wh0w0m1LnmfhgwprSIYIh4gqkFE9NQ53Ei5veb1ZpLS3cBH5+3LAZzj1EscRsifxeX8WfLOoZW1rz4YtfrYIXVuFDMEHQy4/6Udbl15bP94EAnKkBg0MMzXR3RRu0fmY3tH4SXx60ir5cuW/qennl8g4kfjFrN+PgjQ0yRsQMoYz/eBS9L7MWJT04ddNcANkqjouAXoAmA3/iw/xSC2agK9mtSJDVfpkDf9/LcvA70PTiIvsbE11dqPpF3e+mALLkwANPLXAPmhdePR6tU2h/MR7F3GiGxYDgaEj5xHIYLszOID69ow3+ja/EGDFTKHAv8mF4bmU9Edbe9OsKuOk27vDj92qLVwcz5a0ZBITt/QtS1vPccdGeGvXT+U5MbSwOHe87APuv2UxcuSf3LQA8KW95YU0egy4alSZdyfjk3dWrtwWtI2z+IxbAJUFwHZDGjp5Som1NP2SxQp4YpCGux5/nkAj/DUtA7XJJdpk/QTt/RBkdue8DGAlg8mQA+rMX0oOlI+CbEyotIhTCcSkPZxtCfHRBfFxHJ7y47Q0oIndNOpPKemFgSpPPPDscLkZuvLsbhbpHgLcmP4yCSYc8wT5gZQTGidJ4Y/JQ4dcaNr5IDgkpos2ioyrnHDVi5FqLGD1D4ix1dRmWinnJ9Ts2rDw6myvviAfwbBLTs60kHI/fk0VLVtOD8CA+EaQ8ElSPZ9acORisojmr/bA39n6MnVJbWsqv2EyaoogMxb+DgviYzk5Y+XcE8ahV2SEpVbNxAJx+1lzo6MyA+UvIPqVVLATohhWhUD/dwAkPBjIxaUlA3loUwW1FKN90uKfrrgGx/Ndi+bHRzFFHBlJLa8D6hZPoHIDkWVJfm1nXeXuPcgCuP0fp58xyWNn3wHvQvvI5s9/r1wOsWBHYKSf9gafWQHF4p1QtM12QacMpkQwlqDuCuO1ZNrnZycxw7Bh0uX8SQTyjMWj1KdLYWAgnnTEfDXv6/8MQLlIPV2L44b2XiMOrrFmOKxBZBEwEULZWUH4iRXGZsjpxGjB2o6duQwe6574W3FdEfzml5MwBeBrEC1yUu3ZR9OlTApcNWIBinZDishA/LGHoVzj1VMDXCQLWlLnsXxs7FR4eNkYomzg8SLdn1qoDJ842qce1mMpPnNgGzzz+Zp8B8dbWGJz0/9u7EjC7iip93uukOxsJZFWyL6QTCYYkDJAMgcggixAQmZHVccBv2BxZhpHwKSCoGYkSENEBRjFiZkYz7AOMMOqwSLqDLEMjId1BpLM1JEAwQRKzdN/5z13ee91599W991Xd5fWp/i7d4VWdqvpv3f/WO3WWebOoY09DKOcRc8jHI1lF4NWMort6BqZ7CLKW55DGbDYGN8h8Pv5vPcg+fxKyzz9ezbzCthUCD4tYtfUtO2sw+7GXxiatVmq39pyg+GX8HOw5qN57L9E552CPkFi2lLLz49FMxi6c32v2rsozLyzd6rkkjoTitowguyp+uE8+8R36/s2vU138z/G+c70H783z8/SZ8YdQa/8YzWI0rqooZByoTaBK/hPxmoM8Qdp5ewPAyycfg+6756jQ9V0bWs27z5f2KwSucZEHFmVhe+xYvSwI3CZgxYEwh2/Bz2T82IXjmNy0b7yfgOKMV/M8NR1jFNczE706X43d7l1zwzD6VH6MH/iPFjrs0IS/cbRjDjgv5vIhXkLnjjuYXmJTyrD6iBB3wv0uUwJgiMYaqwbhZpVVi+pzb7hM4MW0fnlTpvgV0cF8W0DgZT1ENcLaTZQQuClkVXIR5hpVkBWBvqyqGvTzmcjI+wx+BvMmvw12dAvwfnjbeDiGoMPzrceemqsGcXQTx/vS8cQskrhKbeIneMTw3dT06xeovm/JAWnVow0hgAPvsTVhibEPk/h5IPEXByAKaqkZZQixflUL7wTNL4egJNpzXHoIPJjli+11yWvGfW0F+aamAfIeIqzNsEIxHoGwtFMhcP13MZxECyeNjuPRpHANi7VZz70EP1fix7br5tCvj8eqios69EK7IyfNpo56dpl0PC9LSZy/Gkct99y1mhbMT8BcEmb2dhK99n1H7pE478S52KQTkXS9V1MaH+RAxB+E5X1uvtfUMeMrApiA9sQdobVn/Zp6HGQ+FZuuMo33Peqzmu12lh2cm6NVB46syAeVZ+KHHXXoLXisXXcdEccz8QxTM4SIrQ9vnOtE/OTHsYTEnQTI0cqiK9vp0r/fFK1x1FZshzALF4x+/AqT+JnjZ9Dv+rM2zSn2OYAXdMn9P16wASfMSpGutXp6Rp2nlnbqN5fqRdBlWzC5GGLtV/PCr3ZK+Z19+7e3P8WJX2IpQuCxwByiE8t2QeE0bMeCoA+FOmTSTtqZ4/CvI/HDeSwn4edz+Jlvm5bzc42H4POfJ1q+PERH6av6yKBhdDEy+jghxFmd4nCWd4AZZcSnnPQO/WCpoaTI5QbE5vXs+/u6erRM4qdOnEm/b0hZcgj10JU1VKTrCQhaz69Db/ft6L/dlyAqJ6JCsazt61ubQkc6VoJZoYIQeDXoGWyLhc3B6l/FVdkhHM4rdO65RPffb3A08Yn+27HT6VcNQ6iOY0K5JJ4PGKKu3CjPOG0L3fKtAGyqY4rtLnkHy5Zq98gk/onJs2lz3wYdI9AnowrVhjMI9c7arsXnHQFYyK+e/f+9rtzf9q8AMvWB5c7Ysl5HGjVj1mXlxpvANHXDVpvyQOBsaojswYpyzTVES5aoamXq84cGD6MvjpxC+T6uG08VKpTF1yPY1VkxHORy7BU+zQhB3t5NQfYBmj/lMNraJ/vOPmEXWtAdeKV6jgq8eFDNqqhqvrWFnYNXH/2uQBq1s6K2j9JOCDwKaobbYLFCmU1fV3bD9t2fLXGTVzbIToWtp9bR3HWH0o5dfW0HjajlwZ+9QrNncqwyg6UK8vZGtRvfNk6BOqWtn51IJtMl6K7amWTQnbrrJ1AGGSfJQimV+dc1CSzGcTYInPM+xVaEwGODOlhHIG824G7FVTlZMycangTDFc6gU0uFVyRHYscXCy6HHT2LtrzTP5JOc9rUD+kXD7zsJFc2VTSQd+nQLhndSI8hYmMSKgBTEFWUG5DtK7rW27pv1w7cDWEbxmdAx7w5PstOKzfk3baVhncL3UcrBK7j7mmUgXVwH8SdoRR5MfKl3nWXslqmKvBG+0FcC7uP+vAFc+jtLXBD9w1vtO8s+/TpokfvbaHpjdGTKSmxa0cNPrCMoDapJPu7w8bQrSPGJaPIVU5aVSHYjtqTokOFwrIKoYg9wa5jmGq0uj5H8Kw1iAMeexg1IXBdd1CDHCxCTg0He0DFqd1rrxHNQNTKDJoL+sLEwaeacfnkWjlu4Ux6/Y3gbujGzQe3Yax8XKWZvD18fgfLlAvg8LO5T32I11a4RVg4+wt4kBhOerDaugjc9sTkQODupMK87ION1L8W77535+jjm9c0sdFBrEUIPFa4K3eGdbAYNb6iHFKtHVxydPaXcY2vPPN/WzGCrvvGFOrq8teJjB2zk+68rY1mTDfoQs9WvtNxtSvvVNUVFo+cQP86lPPjamTZgGqLsIMPt/cOJ105ZFToctPNFaIVQi8ehyoKdujvbGxr4s1X7EUIPHbIK77JN+NT9UKYNs1xla+F8glM4n9wVdb4F2a6dWsd3bVsNLW8sh+9ua4f7d6dp2FD91Dj1B104iffo+OPfZ8aGqpPY+oLLaw2bVerN+ID/3k4+1w8ehq9i914ZJdNe7iupUYhw1F8cyjXU9Ddtz1ydpWvFIWyMDdU9pzAXNtwkyTOLvxd1u5pHW0vJPJACoEnu4YLvWOBQulJ65TDacX55nTe/mW8sNnzbbguytA8PgBLzAA9rI9/zNsQHvXyA6fSk/t5bgEcC9vdYdqHeC5xuTxtP9g9vDdNjVpFrn79htmxq/rwPkck2QKB2wHSDDOc1QnTwbXxmg6W4ml4eqaWTO3JxQI8BbN6RDmzhx4iOj22nKnK4YSuwCvuTFx8/uqEAslG2Uh7aRq+JxjUzAQB4qcHfIS+NmoS1AW969ENSuCMoRPYikMUO1xuCiro3d9E/O/IMYyC3G9Vnd61ClRoJPg5FuhX0f03lUO4806iSy5RVktlBc4WuAyX2j0pXcNvwcHyHPoodaZjWGuR+PM02IzvSCBpgYeATaj8j+J/woETZvttS67coJTge1qkFFQvSkV60CnYluc7rA+ssRs3Nm8N2spEPSFwE6hGkIlFtxTN/lHZ9IYbiG68UVktVRV4p/0NXP+Ay6RNtolJr6PlNIHO86jKRBdRZO6A9+aJEw+ldQ2cxVlKzx26H4kX/DUVOvWeiDrc7xyPQne19cO9nTO3/v45ToqeaBECTxT+YudYcOx5yR6YlUvWCJwdRVnXHWuUZBWIgT9fhOf1ctROOMe9/3gvHT2VHhs8IvCEqq5oOz06KoqopVIuzHIyVeoTblNuc+0lefA+dL4suONGA/c7REUVi2epaytk7ENRC0kbmmJN2lAJ5+h3Ierdk3ZlEcDCWIQP1KlzsqJCGQPXuHuw3z42kzeco9t+ARyFDNB0Ydpn8PMhI/dc/dEpbMcDbUHtPdJBtC3lSL5wsOkZ39gsX0z0VIqVF8rXtvLhkL4lLyn35fDWnq7cBW+1PZuqQPu1d7fT/rT5jA+Ljb0v2Quzckn/IaZFV2C7chPIO2UB9lTQup+zlfepeNA58bRapRVQqMFq7Lp92NjGuZPgx/IwwjjV6+RwbWrjqgBQU3hZAnfd6r2uOXN9MeSVZyPubysOmWiQa7a6/nzVxtdffK6qKRhqLARuCNiwYrFY+Huw2q+vvR05FieGFR9PfZhl00qq9/OmjGcQVfWyCyaCx8GhiL8NsVVQ2gsC4tAMPMT2uhk37Yg5RHVP4s/9LLC483Crya90kgXCdnerzmfpp4myapkyb5+iuaGT+Qku8IX8ffaOnKfaSTv67GkYjcQMCaRyCrfk0n9nws0n07WxuDZgAmOUk0ijI890+jO9hKwTnBUtm4Xz6ByBB/g7+P1XGZhCB8Y4yyNvb7wHNv5lY13eWgn6Hlakb1ct4Gl97XM4N+mBtyW1mSCsdto8SsH03+WdfCrtyovqFadtNysWsnYgqmAmwkIKgZtfg4F7wCL6HiojoaWiXHEFDmX2DEoAABAySURBVAb5ZDAl5e+g774bKpOsWZgU4WP/ykNB3hfgt7Yk0wbvznuQ/bGe5F0g8alzhvfJ92vBfFJ7+KoTGz+SL/v/3V15RQJHZh0cVMaaWScqHkLgUZEz0A6LikPJIiuxoqRJD34Dxvo11YBT/TmHpZoNsmPr9BWpHqkzOE6XPNaPvL3xjzj44EH9Ovd/DpvL2CPklWIYToHTA/2ACvggu3RPsh9xd9+B09sb1qzkjFipL0LgKbtFWEisw1ygHNYCVHn6aWU1YxXYrmo5aA/Z3DJcOKLJIZgFK37acaXdN5RdiY7CQ7sqIOa5cdPn3oKDzSt63YPu8+YIROBW12sbWpsDJxcPeC+MVOt199UIihqFYoEdA3FPKUU+8wzRMVw1gZIHef8CtHd8An3r6/LXEHUCdqideNa/i7/Z3jvNhSnpFDyw/x12kPVNQ94feen0/fO7omc2CttnbPV9dumqzbtChfJLqFAysbqFwGNbacE7wuK6BbWvVLZIIqxsHcj7addCWjnA1Fa4FcRtmwiCFcfjF2c9TntCysvxsPIZSbhi0Qlo8HjuwzyNOu/jVN9m7mzO3vSqmDPc6CPV9h1Cya68EoF3Wp23bGpddVWkzmNuJAQeM+BBu8MCQ9YGO+q0f4FdK33qU0RPPBFUbHX1+uGwsglHlbOqE5Nw60Ug7297Y8Az/S387SZwS3hk/t2vwIMaLVmuRWsgFvGHndKveQjtv3gS9f3DAG3Ggbbbum2Bp4FOQrwAfPXril2593HP34yP43lpnY8d+E9SuxpKBqYB8SxMM3tjxEPBUfz5a35jxdFvwxncHJj/vmE4QPUExOF7jQZSdkNv2N6VIO+fluKJ5/VN/HtCilfIJoxtHB7U8EHOLXsDwBuBfUrDC4Np2NUHUd3b/Uri9oVHwSHRqo4qw3caoUU3Tlcw+N4ua3rH2mbOS5v6IgSe4lsEEudDtf/CVVnZvX070cknEz37rInZWNAOb4eWOBNmVT4AsJngQpD3L3uQ90H491oToGmSyS+dCXhImcTDFz6pINujtHzBK2HQio/QAd+ZSLmdvIVmA3Guakfbc3bUHMCJ447bEop+jJGjEJYZib2D5/40uJD6WqSUMLj3uun5m8cAv551G1tXTggPdjIthMCTwT1wr1iQfPLE+tobcfnvfzthoPAVZGP7dkE7ELiPChXXIgp2PdWleoeqmie7xh8Nbni+Z0U8wKfi/z2sEpDg52fgAX0gUv/O7nu1zcOKkv9jHxp+2TRqeH6wFhJV9Zfqz7usJevbmtKuUitAqLy5qQa7Fw0ORM6B43+Ay39HxXiwaSFnrOfMPdHL+zCo+xJtoyUQwaqcrBbbQQfkXRYMEDiAojtSOrmH8HBGz9xh2aaGR4SZ24CHR9DQGyZTrVmrdLPxtj1Qi9ELS1Ur/HdXjuZuWrMyqJlmGHiN1BUCNwKrOaFYjLyzYm/Nz+HyT9O+bBnR0qV7afXqgNkm7TFzsrA78E2Z3clZtZBotpEqUWSHl5l+5M2y8bwGC+Fb5UAiNN+JNiPwcEbL/2PRPLRnfVr45xtqlaHXT6GBD42gXIXk0RHmVGhSCNEacnSVHHZCnH36D92it9a3rsyU92pICKu5bdJWNwJY0HMhk68puMbiYkcPPpRrwdUEneJakBQvyE/jOhIXe3qOwsV54Dn2BwdD4pgavOP4FyyGLXgQOBbLC2493UOOSx4T32yQd0X9NrDhNBPXxjWoEP2ch3vx7yHqd69q2SmXq3r55rf2oWFXNVL/VVgqmliiRIMeXmQFhg7qiamw/eYwspdsaFuJlFfZKZpuTXYmLCP1RwDPCOvb+eFn2+islncx8Bkg782qCYBQLkUdVkulqbTgoYyeMMCyD7yf0jWhunf60hAccg58DLGxrHxo4vVMDO23gKu+0DU2W05FYg+eDxPjfBWmgzMhMby1j9YJhRMmBB4Or5qtjeeAD0h5x6qOhpheFFgF9Bcgb3VYXn72iT6DX/enaDqssx+Oh/JPkcdkEVx0aX7k9j4NmcgH3z6OBt0/0latOAkPuLj2KVhAthWJa8XifMQGhtVl76k0j0rGi0F35Z58q7Pr9A1rm5ExPFtFCDxb98vYaPH8NUM4q1myWtowcLY2CUTePEkQwFT84nZpKQvxQD5a1WAsO9iVMa/Surfqaeg1U6kfW6yE3o8HnBluDMfqjkxOYRXiltW0vrWJsy9lrkTGKHMzlQH7IoD1fjM+zITrsM8kQpN3YedF9Af8PTEFy6M6qxPnjcTxO2Jxy+3T3o+GfbmR6lcP1EfkYYm3zE3bZ1eucNrBi2JHZ846quO15v9LwRoIPQQh8NCQ1VYDrG/29GR366yuhcjk7e7C0xDIig9dR0W2Oim+jWI/lK3raKD9l46n/k8MpxyO0CM543gxulWLEPVshYzGlYqsaecg8uDPsvpUa4QiqxD07nHjmWBnj0RjRldxB9ah7eFh1CY9+8KOLbDDSxXjVDU9Cw9i9bHILboXHf21qjMjn+/J0cBHR9CQW8cT68udLDeec6enBy/qRmxfT1tPUllHbpscKupEnk/GnHbKzVMIPPLdz35DPByc95Fd9bO4Dtja5OBqyLu4caWf4+8zE7qjvwX4oRxufMdp0ZP4bEFC8yh0a8dZuazRqnsf+ZUjryzPnZ/FVhAScVcO6c8gbRpjVWrdmDR0ofuPDG/onqRB6hDI8MHlDoA5UQd5803BE8z28WyBE3dSOE6NNhIPoR7TNUMWKBEX7mVjph05IJeru8mxRXGIOIfdNO+8ux1SepYrthEL6lQyL+H7Ve2uvMv60fq2XTAhfZF9ITJdhMAzffuqGzweBKMWC9WNzrc1xzZhO2+t4RfBCUsh144RHlNh7CfiAWRHKj0lJTtwTGYLeJgdxmjU5Hkz6uvzdyP9++FesCzdu3KP7znBfJ7fhu5vh+gLSed5OJ14cVy0cc3Ku/UAnrwUIfDk70EiI8DiPgkdh87ukshgi51uxZ+NIABWn2gtrK6FQI5WGEdGes7DOQ8dlg31Gnlilh1++NjI7fU1PB1odrOpHjtj3mTam/sx9t7zCwpyLxBt1F25wsKk9LQTduHvdVm5v9nUtpLVTDVThMBr5laGmwjWfhYSGZRO6iX8gw8sOVyAkQISPwCCX8Rl0qzwN3jojjY0AX4h84s5ybIdvOwbevjAA+cMzw+qvyqfz/OZw4RoNoiu2trbehd+O4eidnF1NPjXh9DL3LFr196bt7z5nNI7N0ngovQtBB4FtRpoAwJ/BNPgQ8y0Fybsa0HcN8UxUDzw/NWfQ7hyQCidBUHbiWOcMO5mimV/gzjOjPDAUltAyoFDAYxtPBKmj/kTsFtmS6gBuIr+Qd2OFz0tusPNtls+D8nWx3gVS+jMsrah3u1W3rp14+pm/uZWk0UIvCZvq3pSIPBXUSvtmbfZNf4YPKPt6hnprQFK4BfGIk1Sf4gH7UJNsvzFWEh45wQ3S7I0g1kjvfywOx9QN6j++FxdDiEOcgsxCQ66Fqb8EWT+aBdZD3Rt2/1ER8eLfNhd00UIvKZvb4VnXUPEOsPQ3Q75/wTy5sO+RApInFUp38R1Nq6wzwpblizHdT0a8ovIfMk4gfcEaNy0Ixd2Ud08mAZxpM0DcT9G4y444V4t6gCunKmoA2qTTTgkfXZ96ypz327M371IPYRdlJE6kUbpQwA78KpDjhqaFRPf2SDu/zQkP7RYEAc7+3D8ddbbqsK08sEkB8hajoeLs93HV9KhQvkVSPaT8U26d/ckBN5L739KVShsIjgf5M3xyFNZQOYzMLDZuDgQ1iG42JaYSZvJelXspF2KkpWoQ5I3khUg8LNSefNqcFBC4DV4U4NMCQTOZl6nBakbUx12avmYLuecmMacrm4s+ioGxCqfJMu1IPDFSQ6gN/UtBN6b7nbJXFNmRsjOLLOEvKtcjJadeenBKqVU23wfG/BqBUp7fwSEwHvp6gCBH4Wp/yYF05edt66bYMGu2kmpl2SZiB14e5ID6E19C4H3prvdY64gcdbfhkl6rBstDqM6OUj6M90d16w8izZibqMTmt9GkDdbjEiJCQEh8JiATmM3IHAOYh/Y6ULzHNja5CCQNydUkKILAYuSjG9+Gwj8Cl1TETlqBITA1RjVbI2E9eC3gLyznAUonesiWT34SSDwx9MJTG2OSgi8Nu9r4FmBxOG95h+7IrCgcBW3g7x942WEEyW190HAsrPSHxMzMk+DvBfE3Gev704IvJcvARD4FwHB92OG4UIQ+A9j7rP3dGfZWek5O32cZR4InBNjS4kRASHwGMFOa1cxJ3ZYBfJOOl5HWm+FvnFZWmO5qMa1BOR9jaqSfK4fASFw/ZhmTiIInDPRvI1rhOHBcxzvUSBwPRloDA820+I5tQ3RY7hMh5d9wu6D0+5IiR0BIfDYIU9nhyDxMRgZx0epNzRCJwNNTmMGGkMDrRmxFg3GXH6Lq9HQnDgN3WEg7w8MyRexCgSEwGWJFBAAiXOkt1dwDdMMC8djPkTIWzOqQcRZtB+qcXxz3XHC/xcyPy3kHeQmmKsjBG4O20xKBonzDpwPwPRkSid6HrKOSjIsbCZvhM5BW1QHcf+M62pNYm+GnGtA3sayI2kaZ82LEQKv+VscbYIg8i+h5RJc/aNJoJ1otwjEzXG9paQBActO5fY9XDMjDqcF7S4Dccdt4RJxuLXfTAi89u9xVTMEkXMG78/iGhRQEKcOuw/E/YWA9aVa3AhYdD66vAhX0G9Zz6Luj0Hcy+IeqvRXGQEhcFkhgRAAkc/iHTUujoPNqa48Qv8T/mZnID7Q+jqIW2+m9UCjk0qREHDOPDiC4UG4hrsXi2JrIb44xvl9IO4tkeRLI+MICIEbh1g6EAQEAUHADAJC4GZwFamCgCAgCBhHQAjcOMTSgSAgCAgCZhAQAjeDq0gVBAQBQcA4AkLgxiGWDgQBQUAQMIOAELgZXEWqICAICALGERACNw6xdCAICAKCgBkEhMDN4CpSBQFBQBAwjoAQuHGIpQNBQBAQBMwgIARuBleRKggIAoKAcQSEwI1DLB0IAoKAIGAGASFwM7iKVEFAEBAEjCMgBG4cYulAEBAEBAEzCAiBm8FVpAoCgoAgYBwBIXDjEEsHgoAgIAiYQUAI3AyuIlUQEAQEAeMICIEbh1g6EAQEAUHADAJC4GZwFamCgCAgCBhHQAjcOMTSgSAgCAgCZhAQAjeDq0gVBAQBQcA4AkLgxiGWDgQBQUAQMIOAELgZXEWqICAICALGERACNw6xdCAICAKCgBkEhMDN4CpSBQFBQBAwjoAQuHGIpQNBQBAQBMwgIARuBleRKggIAoKAcQSEwI1DLB0IAoKAIGAGASFwM7iKVEFAEBAEjCMgBG4cYulAEBAEBAEzCAiBm8FVpAoCgoAgYBwBIXDjEEsHgoAgIAiYQUAI3AyuIlUQEAQEAeMICIEbh1g6EAQEAUHADAJC4GZwFamCgCAgCBhHQAjcOMTSgSAgCAgCZhAQAjeDq0gVBAQBQcA4Av8PmtVExuho1m4AAAAASUVORK5CYII=","user":{},"timestamp":"2025-04-22T02:11:57.947Z"}
-
 @ df67f9a7:2d4fc200
2025-04-03 19:54:29
@ df67f9a7:2d4fc200
2025-04-03 19:54:29More than just “follows follows” on Nostr, webs of trust algos will ingest increasingly MORE kinds of user generated content in order to map our interactions across the network. Webs of trust will power user discovery, content search, reviews and reccomendations, identity verification, and access to all corners of the Nostr network. Without relying on a central “trust authority” to recommend people and content for us, sovereign Nostr users will make use of “relative trust” scores generated by a wide range of independent apps and services. The problem is, Nostr doesn’t have an opensource library for performing WoT calculations and delivering NIP standard recommendations to users. In order for a “free market” ecosystem of really smart apps and services to thrive, independent developers will need access to extensible “middleware” such as this.
Project Description
I am building a library for independent developers to offer their own interoperable and configurable WoT services and clients. In addition, and as the primary use case, I am also developing a web client for “in person onboarding” to Nostr, which will make use of this library to provide webs of trust recommendations for “invited” users.
-
Meet Me On Nostr (onboarding client) : This is my first project on Nostr, which began a year ago with seed funding from @druid. This web client will leverage “in person” QR invites to generate WoT powered recommendations of follows, apps, and other stuff for new users at their first Nostr touchpoint. The functional MVP release (April ‘25) allows for “instant, anonymous, and fully encrypted” direct messaging and “move in ready” profile creation from a single QR scan.
-
GrapeRank Engine (developer library) : Working with @straycat last fall, I built an opensource and extensible library for Nostr developers to integrate “web of trust” powered reccomendations into their products and services. The real power behind GrapeRank is its “pluggable” interpreter, allowing any kind of content (not just “follows follows”) to be ingested for WoT scoring, and configurable easily by developers as well as end users. This library is currently in v0.1, “generating and storing usable scores”, and doesn’t yet produce NIP standard outputs for Nostr clients.
-
My Grapevine (algo dashboard) : In addition, I’ve just wrapped up the demo release of a web client by which users and developers can explore the power of the GrapeRank Engine.
Potential Impact
Webs of Trust is how Nostr scales. But so far, Nostr implementations have been ad-hoc and primarily client centered, with no consistency and little choice for end users. The “onboarding and discovery” tools I am developing promise to :
-
Establish sovereignty for webs of trust users (supporting a “free market” of algo choices), with opensource libraries by which any developer can easily implement WoT powered recommendations.
-
Accelerate the isolation of bots and bad actors (and improve the “trustiness” of Nostr for everyone else) by streamlining the onboarding of “real world” acquaintances directly into established webs of trust.
-
Improve “discoverability of users and content” for any user on any client (to consume and take advantage of WoT powered recommendations for any use case, even as the NIP standards for this are still in flux), by providing an algo engine with “pluggable” inputs and outputs.
-
Pave the way for “global Nostr adoption”, where WoT powered recommendations (and searches) are consistently available for every user across a wide variety of clients.
Timeline & Milestones
2025 roadmap for “Webs of Trust Onboarding and Discovery” :
-
Meet Me On Nostr (onboarding client) : MVP release : “scan my QR invite to private message me instantly with a ‘move in ready’ account on Nostr”. https://nostrmeet.me/
-
GrapeRank Engine (developer library) : 1.0 release : “expanded inputs and output WoT scores to Nostr NIPs and other stuff” for consumption by clients and relays. https://github.com/Pretty-Good-Freedom-Tech/graperank-nodejs
-
My Grapevine (algo dashboard) : 1.0 release : “algo usage and configuration webapp with API endpoints” for end users to setup GrapeRank scoring for consumption by their own clients and relays. https://grapevine.my/
-
Meet Me On Nostr (onboarding client) : 1.0 release : first GrapeRank integration, offering “follow and app recommendations for invited users”, customizable per-invite for Nostr advocates. https://nostrmeet.me/
Prior contributions
-
Last spring I hosted panel discussions and wrote articles on Nostr exploring how to build “sovereign webs of trust”, where end users can have control over which algorithms to use, and what defines “trust”.
-
I contributed gift wrap encryption to NDK.
-
I am also authoring gift wrapped direct messaging and chat room modules for NDK.
-
Last July, I attended The Bitcoin Conference on an OpenSource pass to raise funds for my onboarding client. I onboarded many Bitcoiners to Nostr, and made valuable connections at Bitcoin Park.
About Me
I discovered Nostr in September ‘23 as a freelance web developer, after years of looking for a “sovereignty respecting” social media on which to build apps. With this came my first purchase of Bitcoin. By December of that year, I was settled on “open source freedom tech” (Nostr and Bitcoin) as the new direction for my career.
As a web professional for 20+ years, I know the importance of “proof of work” and being connected. For the last 18 months, I have been establishing myself as a builder in this community. This pivot has not been easy, but it has been rewarding and necessary. After so many years building private tech for other people, I finally have a chance to build freedom tech for everyone. I have finally come home to my peeps and my purpose.
Thank you for considering this application for funding.
-
-
 @ 4925ea33:025410d8
2025-03-08 00:38:48
@ 4925ea33:025410d8
2025-03-08 00:38:481. O que é um Aromaterapeuta?

O aromaterapeuta é um profissional especializado na prática da Aromaterapia, responsável pelo uso adequado de óleos essenciais, ervas aromáticas, águas florais e destilados herbais para fins terapêuticos.
A atuação desse profissional envolve diferentes métodos de aplicação, como inalação, uso tópico, sempre considerando a segurança e a necessidade individual do cliente. A Aromaterapia pode auxiliar na redução do estresse, alívio de dores crônicas, relaxamento muscular e melhora da respiração, entre outros benefícios.
Além disso, os aromaterapeutas podem trabalhar em conjunto com outros profissionais da saúde para oferecer um tratamento complementar em diversas condições. Como já mencionado no artigo sobre "Como evitar processos alérgicos na prática da Aromaterapia", é essencial ter acompanhamento profissional, pois os óleos essenciais são altamente concentrados e podem causar reações adversas se utilizados de forma inadequada.
2. Como um Aromaterapeuta Pode Ajudar?

Você pode procurar um aromaterapeuta para diferentes necessidades, como:
✔ Questões Emocionais e Psicológicas
Auxílio em momentos de luto, divórcio, demissão ou outras situações desafiadoras.
Apoio na redução do estresse, ansiedade e insônia.
Vale lembrar que, em casos de transtornos psiquiátricos, a Aromaterapia deve ser usada como terapia complementar, associada ao tratamento médico.
✔ Questões Físicas
Dores musculares e articulares.
Problemas respiratórios como rinite, sinusite e tosse.
Distúrbios digestivos leves.
Dores de cabeça e enxaquecas. Nesses casos, a Aromaterapia pode ser um suporte, mas não substitui a medicina tradicional para identificar a origem dos sintomas.
✔ Saúde da Pele e Cabelos
Tratamento para acne, dermatites e psoríase.
Cuidados com o envelhecimento precoce da pele.
Redução da queda de cabelo e controle da oleosidade do couro cabeludo.
✔ Bem-estar e Qualidade de Vida
Melhora da concentração e foco, aumentando a produtividade.
Estímulo da disposição e energia.
Auxílio no equilíbrio hormonal (TPM, menopausa, desequilíbrios hormonais).
Com base nessas necessidades, o aromaterapeuta irá indicar o melhor tratamento, calculando doses, sinergias (combinação de óleos essenciais), diluições e técnicas de aplicação, como inalação, uso tópico ou difusão.
3. Como Funciona uma Consulta com um Aromaterapeuta?

Uma consulta com um aromaterapeuta é um atendimento personalizado, onde são avaliadas as necessidades do cliente para a criação de um protocolo adequado. O processo geralmente segue estas etapas:
✔ Anamnese (Entrevista Inicial)
Perguntas sobre saúde física, emocional e estilo de vida.
Levantamento de sintomas, histórico médico e possíveis alergias.
Definição dos objetivos da terapia (alívio do estresse, melhora do sono, dores musculares etc.).
✔ Escolha dos Óleos Essenciais
Seleção dos óleos mais indicados para o caso.
Consideração das propriedades terapêuticas, contraindicações e combinações seguras.
✔ Definição do Método de Uso
O profissional indicará a melhor forma de aplicação, que pode ser:
Inalação: difusores, colares aromáticos, vaporização.
Uso tópico: massagens, óleos corporais, compressas.
Banhos aromáticos e escalda-pés. Todas as diluições serão ajustadas de acordo com a segurança e a necessidade individual do cliente.
✔ Plano de Acompanhamento
Instruções detalhadas sobre o uso correto dos óleos essenciais.
Orientação sobre frequência e duração do tratamento.
Possibilidade de retorno para ajustes no protocolo.
A consulta pode ser realizada presencialmente ou online, dependendo do profissional.
Quer saber como a Aromaterapia pode te ajudar? Agende uma consulta comigo e descubra os benefícios dos óleos essenciais para o seu bem-estar!
-
 @ 6389be64:ef439d32
2025-02-27 21:32:12
@ 6389be64:ef439d32
2025-02-27 21:32:12GA, plebs. The latest episode of Bitcoin And is out, and, as always, the chicanery is running rampant. Let’s break down the biggest topics I covered, and if you want the full, unfiltered rant, make sure to listen to the episode linked below.
House Democrats’ MEME Act: A Bad Joke?
House Democrats are proposing a bill to ban presidential meme coins, clearly aimed at Trump’s and Melania’s ill-advised token launches. While grifters launching meme coins is bad, this bill is just as ridiculous. If this legislation moves forward, expect a retaliatory strike exposing how politicians like Pelosi and Warren mysteriously amassed their fortunes. Will it pass? Doubtful. But it’s another sign of the government’s obsession with regulating everything except itself.
Senate Banking’s First Digital Asset Hearing: The Real Target Is You
Cynthia Lummis chaired the first digital asset hearing, and—surprise!—it was all about control. The discussion centered on stablecoins, AML, and KYC regulations, with witnesses suggesting Orwellian measures like freezing stablecoin transactions unless pre-approved by authorities. What was barely mentioned? Bitcoin. They want full oversight of stablecoins, which is really about controlling financial freedom. Expect more nonsense targeting self-custody wallets under the guise of stopping “bad actors.”
Bank of America and PayPal Want In on Stablecoins
Bank of America’s CEO openly stated they’ll launch a stablecoin as soon as regulation allows. Meanwhile, PayPal’s CEO paid for a hat using Bitcoin—not their own stablecoin, Pi USD. Why wouldn’t he use his own product? Maybe he knows stablecoins aren’t what they’re hyped up to be. Either way, the legacy financial system is gearing up to flood the market with stablecoins, not because they love crypto, but because it’s a tool to extend U.S. dollar dominance.
MetaPlanet Buys the Dip
Japan’s MetaPlanet issued $13.4M in bonds to buy more Bitcoin, proving once again that institutions see the writing on the wall. Unlike U.S. regulators who obsess over stablecoins, some companies are actually stacking sats.
UK Expands Crypto Seizure Powers
Across the pond, the UK government is pushing legislation to make it easier to seize and destroy crypto linked to criminal activity. While they frame it as going after the bad guys, it’s another move toward centralized control and financial surveillance.
Bitcoin Tools & Tech: Arc, SatoChip, and Nunchuk
Some bullish Bitcoin developments: ARC v0.5 is making Bitcoin’s second layer more efficient, SatoChip now supports Taproot and Nostr, and Nunchuk launched a group wallet with chat, making multisig collaboration easier.
The Bottom Line
The state is coming for financial privacy and control, and stablecoins are their weapon of choice. Bitcoiners need to stay focused, keep their coins in self-custody, and build out parallel systems. Expect more regulatory attacks, but don’t let them distract you—just keep stacking and transacting in ways they can’t control.
🎧 Listen to the full episode here: https://fountain.fm/episode/PYITCo18AJnsEkKLz2Ks
💰 Support the show by boosting sats on Podcasting 2.0! and I will see you on the other side.
-
 @ 6e0ea5d6:0327f353
2025-02-21 18:15:52
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ 4857600b:30b502f4
2025-02-20 19:09:11
@ 4857600b:30b502f4
2025-02-20 19:09:11Mitch McConnell, a senior Republican senator, announced he will not seek reelection.
At 83 years old and with health issues, this decision was expected. After seven terms, he leaves a significant legacy in U.S. politics, known for his strategic maneuvering.
McConnell stated, “My current term in the Senate will be my last.” His retirement marks the end of an influential political era.
-
 @ 17538dc2:71ed77c4
2025-04-02 16:04:59
@ 17538dc2:71ed77c4
2025-04-02 16:04:59The MacOS security update summary is a reminder that laptops and desktops are incredibly compromised.
macOS Sequoia 15.4
Released March 31, 2025
Accessibility Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A logging issue was addressed with improved data redaction.
CVE-2025-24202: Zhongcheng Li from IES Red Team of ByteDance
AccountPolicy Available for: macOS Sequoia
Impact: A malicious app may be able to gain root privileges
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-24234: an anonymous researcher
AirDrop Available for: macOS Sequoia
Impact: An app may be able to read arbitrary file metadata
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24097: Ron Masas of BREAKPOINT.SH
App Store Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-24276: an anonymous researcher
AppleMobileFileIntegrity Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24272: Mickey Jin (@patch1t)
AppleMobileFileIntegrity Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A downgrade issue was addressed with additional code-signing restrictions.
CVE-2025-24239: Wojciech Regula of SecuRing (wojciechregula.blog)
AppleMobileFileIntegrity Available for: macOS Sequoia
Impact: A malicious app may be able to read or write to protected files
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24233: Claudio Bozzato and Francesco Benvenuto of Cisco Talos.
AppleMobileFileIntegrity Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: A privacy issue was addressed by removing the vulnerable code.
CVE-2025-30443: Bohdan Stasiuk (@bohdan_stasiuk)
Audio Available for: macOS Sequoia
Impact: Processing a maliciously crafted font may result in the disclosure of process memory
Description: The issue was addressed with improved memory handling.
CVE-2025-24244: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Audio Available for: macOS Sequoia
Impact: Processing a maliciously crafted file may lead to arbitrary code execution
Description: The issue was addressed with improved memory handling.
CVE-2025-24243: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Authentication Services Available for: macOS Sequoia
Impact: Password autofill may fill in passwords after failing authentication
Description: This issue was addressed through improved state management.
CVE-2025-30430: Dominik Rath
Authentication Services Available for: macOS Sequoia
Impact: A malicious website may be able to claim WebAuthn credentials from another website that shares a registrable suffix
Description: The issue was addressed with improved input validation.
CVE-2025-24180: Martin Kreichgauer of Google Chrome
Authentication Services Available for: macOS Sequoia
Impact: A malicious app may be able to access a user's saved passwords
Description: This issue was addressed by adding a delay between verification code attempts.
CVE-2025-24245: Ian Mckay (@iann0036)
Automator Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A permissions issue was addressed by removing vulnerable code and adding additional checks.
CVE-2025-30460: an anonymous researcher
BiometricKit Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: A buffer overflow was addressed with improved bounds checking.
CVE-2025-24237: Yutong Xiu
Calendar Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: A path handling issue was addressed with improved validation.
CVE-2025-30429: Denis Tokarev (@illusionofcha0s)
Calendar Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed with improved checks.
CVE-2025-24212: Denis Tokarev (@illusionofcha0s)
CloudKit Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: The issue was addressed with improved checks.
CVE-2025-24215: Kirin (@Pwnrin)
CoreAudio Available for: macOS Sequoia
Impact: Parsing a file may lead to an unexpected app termination
Description: The issue was addressed with improved checks.
CVE-2025-24163: Google Threat Analysis Group
CoreAudio Available for: macOS Sequoia
Impact: Playing a malicious audio file may lead to an unexpected app termination
Description: An out-of-bounds read issue was addressed with improved input validation.
CVE-2025-24230: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia Available for: macOS Sequoia
Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory
Description: This issue was addressed with improved memory handling.
CVE-2025-24211: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: An access issue was addressed with additional sandbox restrictions.
CVE-2025-24236: Csaba Fitzl (@theevilbit) and Nolan Astrein of Kandji
CoreMedia Available for: macOS Sequoia
Impact: Processing a maliciously crafted video file may lead to unexpected app termination or corrupt process memory
Description: The issue was addressed with improved memory handling.
CVE-2025-24190: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
CoreMedia Playback Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: A path handling issue was addressed with improved validation.
CVE-2025-30454: pattern-f (@pattern_F_)
CoreServices Description: This issue was addressed through improved state management.
CVE-2025-31191: Jonathan Bar Or (@yo_yo_yo_jbo) of Microsoft, and an anonymous researcher Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
CoreText Available for: macOS Sequoia
Impact: Processing a maliciously crafted font may result in the disclosure of process memory
Description: An out-of-bounds read issue was addressed with improved input validation.
CVE-2025-24182: Hossein Lotfi (@hosselot) of Trend Micro Zero Day Initiative
Crash Reporter Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A parsing issue in the handling of directory paths was addressed with improved path validation.
CVE-2025-24277: Csaba Fitzl (@theevilbit) of Kandji and Gergely Kalman (@gergely_kalman), and an anonymous researcher
curl Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2024-9681
Disk Images Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: A file access issue was addressed with improved input validation.
CVE-2025-24255: an anonymous researcher
DiskArbitration Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A parsing issue in the handling of directory paths was addressed with improved path validation.
CVE-2025-30456: Gergely Kalman (@gergely_kalman)
DiskArbitration Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24267: an anonymous researcher
Dock Available for: macOS Sequoia
Impact: A malicious app may be able to access private information
Description: The issue was addressed with improved checks.
CVE-2025-30455: Mickey Jin (@patch1t), and an anonymous researcher
Dock Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: This issue was addressed by removing the vulnerable code.
CVE-2025-31187: Rodolphe BRUNETTI (@eisw0lf) of Lupus Nova
dyld Available for: macOS Sequoia
Impact: Apps that appear to use App Sandbox may be able to launch without restrictions
Description: A library injection issue was addressed with additional restrictions.
CVE-2025-30462: Pietro Francesco Tirenna, Davide Silvetti, Abdel Adim Oisfi of Shielder (shielder.com)
FaceTime Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-30451: Kirin (@Pwnrin) and luckyu (@uuulucky)
FeedbackLogger Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved data protection.
CVE-2025-24281: Rodolphe BRUNETTI (@eisw0lf)
Focus Available for: macOS Sequoia
Impact: An attacker with physical access to a locked device may be able to view sensitive user information
Description: The issue was addressed with improved checks.
CVE-2025-30439: Andr.Ess
Focus Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A logging issue was addressed with improved data redaction.
CVE-2025-24283: Kirin (@Pwnrin)
Foundation Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: An access issue was addressed with additional sandbox restrictions on the system pasteboards.
CVE-2025-30461: an anonymous researcher
Foundation Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was resolved by sanitizing logging
CVE-2025-30447: LFY@secsys from Fudan University
Foundation Available for: macOS Sequoia
Impact: An app may be able to cause a denial-of-service
Description: An uncontrolled format string issue was addressed with improved input validation.
CVE-2025-24199: Manuel Fernandez (Stackhopper Security)
GPU Drivers Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or corrupt kernel memory
Description: An out-of-bounds write issue was addressed with improved bounds checking.
CVE-2025-30464: ABC Research s.r.o.
CVE-2025-24273: Wang Yu of Cyberserval
GPU Drivers Available for: macOS Sequoia
Impact: An app may be able to disclose kernel memory
Description: The issue was addressed with improved bounds checks.
CVE-2025-24256: Anonymous working with Trend Micro Zero Day Initiative, Murray Mike
Handoff Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was addressed with improved restriction of data container access.
CVE-2025-30463: mzzzz__
ImageIO Available for: macOS Sequoia
Impact: Parsing an image may lead to disclosure of user information
Description: A logic error was addressed with improved error handling.
CVE-2025-24210: Anonymous working with Trend Micro Zero Day Initiative
Installer Available for: macOS Sequoia
Impact: An app may be able to check the existence of an arbitrary path on the file system
Description: A permissions issue was addressed with additional sandbox restrictions.
CVE-2025-24249: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc)
Installer Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data
Description: A logic issue was addressed with improved checks.
CVE-2025-24229: an anonymous researcher
IOGPUFamily Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or write kernel memory
Description: An out-of-bounds write issue was addressed with improved input validation.
CVE-2025-24257: Wang Yu of Cyberserval
IOMobileFrameBuffer Available for: macOS Sequoia
Impact: An app may be able to corrupt coprocessor memory
Description: The issue was addressed with improved bounds checks.
CVE-2025-30437: Ye Zhang (@VAR10CK) of Baidu Security
Kerberos Helper Available for: macOS Sequoia
Impact: A remote attacker may be able to cause unexpected app termination or heap corruption
Description: A memory initialization issue was addressed with improved memory handling.
CVE-2025-24235: Dave G.
Kernel Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: The issue was addressed with improved checks.
CVE-2025-24204: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc.
Kernel Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24203: Ian Beer of Google Project Zero
Kernel Available for: macOS Sequoia
Impact: An attacker with user privileges may be able to read kernel memory
Description: A type confusion issue was addressed with improved memory handling.
CVE-2025-24196: Joseph Ravichandran (@0xjprx) of MIT CSAIL
LaunchServices Available for: macOS Sequoia
Impact: A malicious JAR file may bypass Gatekeeper checks
Description: This issue was addressed with improved handling of executable types.
CVE-2025-24148: Kenneth Chew
libarchive Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2024-48958
Libinfo Available for: macOS Sequoia
Impact: A user may be able to elevate privileges
Description: An integer overflow was addressed with improved input validation.
CVE-2025-24195: Paweł Płatek (Trail of Bits)
libnetcore Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may result in the disclosure of process memory
Description: A logic issue was addressed with improved checks.
CVE-2025-24194: an anonymous researcher
libxml2 Available for: macOS Sequoia
Impact: Parsing a file may lead to an unexpected app termination
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2025-27113
CVE-2024-56171
libxpc Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed through improved state management.
CVE-2025-24178: an anonymous researcher
libxpc Available for: macOS Sequoia
Impact: An app may be able to delete files for which it does not have permission
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-31182: Alex Radocea and Dave G. of Supernetworks, 风沐云烟(@binary_fmyy) and Minghao Lin(@Y1nKoc)
libxpc Available for: macOS Sequoia
Impact: An app may be able to gain elevated privileges
Description: A logic issue was addressed with improved checks.
CVE-2025-24238: an anonymous researcher
Mail Available for: macOS Sequoia
Impact: "Block All Remote Content" may not apply for all mail previews
Description: A permissions issue was addressed with additional sandbox restrictions.
CVE-2025-24172: an anonymous researcher
manpages Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-30450: Pwn2car
Maps Available for: macOS Sequoia
Impact: An app may be able to read sensitive location information
Description: A path handling issue was addressed with improved logic.
CVE-2025-30470: LFY@secsys from Fudan University
NetworkExtension Available for: macOS Sequoia
Impact: An app may be able to enumerate a user's installed apps
Description: This issue was addressed with additional entitlement checks.
CVE-2025-30426: Jimmy
Notes Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data in system logs
Description: A privacy issue was addressed with improved private data redaction for log entries.
CVE-2025-24262: LFY@secsys from Fudan University
NSDocument Available for: macOS Sequoia
Impact: A malicious app may be able to access arbitrary files
Description: This issue was addressed through improved state management.
CVE-2025-24232: an anonymous researcher
OpenSSH Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An injection issue was addressed with improved validation.
CVE-2025-24246: Mickey Jin (@patch1t)
PackageKit Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24261: Mickey Jin (@patch1t)
PackageKit Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: A logic issue was addressed with improved checks.
CVE-2025-24164: Mickey Jin (@patch1t)
PackageKit Available for: macOS Sequoia
Impact: A malicious app with root privileges may be able to modify the contents of system files
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30446: Pedro Tôrres (@t0rr3sp3dr0)
Parental Controls Available for: macOS Sequoia
Impact: An app may be able to retrieve Safari bookmarks without an entitlement check
Description: This issue was addressed with additional entitlement checks.
CVE-2025-24259: Noah Gregory (wts.dev)
Photos Storage Available for: macOS Sequoia
Impact: Deleting a conversation in Messages may expose user contact information in system logging
Description: A logging issue was addressed with improved data redaction.
CVE-2025-30424: an anonymous researcher
Power Services Available for: macOS Sequoia
Impact: An app may be able to break out of its sandbox
Description: This issue was addressed with additional entitlement checks.
CVE-2025-24173: Mickey Jin (@patch1t)
Python Available for: macOS Sequoia
Impact: A remote attacker may be able to bypass sender policy checks and deliver malicious content via email
Description: This is a vulnerability in open source code and Apple Software is among the affected projects. The CVE-ID was assigned by a third party. Learn more about the issue and CVE-ID at cve.org.
CVE-2023-27043
RPAC Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved validation of environment variables.
CVE-2025-24191: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
Safari Available for: macOS Sequoia
Impact: Visiting a malicious website may lead to user interface spoofing
Description: The issue was addressed with improved UI.
CVE-2025-24113: @RenwaX23
Safari Available for: macOS Sequoia
Impact: Visiting a malicious website may lead to address bar spoofing
Description: The issue was addressed with improved checks.
CVE-2025-30467: @RenwaX23
Safari Available for: macOS Sequoia
Impact: A website may be able to access sensor information without user consent
Description: The issue was addressed with improved checks.
CVE-2025-31192: Jaydev Ahire
Safari Available for: macOS Sequoia
Impact: A download's origin may be incorrectly associated
Description: This issue was addressed through improved state management.
CVE-2025-24167: Syarif Muhammad Sajjad
Sandbox Available for: macOS Sequoia
Impact: An app may be able to access removable volumes without user consent
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24093: Yiğit Can YILMAZ (@yilmazcanyigit)
Sandbox Available for: macOS Sequoia
Impact: An input validation issue was addressed
Description: The issue was addressed with improved checks.
CVE-2025-30452: an anonymous researcher
Sandbox Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24181: Arsenii Kostromin (0x3c3e)
SceneKit Available for: macOS Sequoia
Impact: An app may be able to read files outside of its sandbox
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30458: Mickey Jin (@patch1t)
Security Available for: macOS Sequoia
Impact: A remote user may be able to cause a denial-of-service
Description: A validation issue was addressed with improved logic.
CVE-2025-30471: Bing Shi, Wenchao Li, Xiaolong Bai of Alibaba Group, Luyi Xing of Indiana University Bloomington
Security Available for: macOS Sequoia
Impact: A malicious app acting as a HTTPS proxy could get access to sensitive user data
Description: This issue was addressed with improved access restrictions.
CVE-2025-24250: Wojciech Regula of SecuRing (wojciechregula.blog)
Share Sheet Available for: macOS Sequoia
Impact: A malicious app may be able to dismiss the system notification on the Lock Screen that a recording was started
Description: This issue was addressed with improved access restrictions.
CVE-2025-30438: Halle Winkler, Politepix theoffcuts.org
Shortcuts Available for: macOS Sequoia
Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app
Description: A permissions issue was addressed with improved validation.
CVE-2025-30465: an anonymous researcher
Shortcuts Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An access issue was addressed with additional sandbox restrictions.
CVE-2025-24280: Kirin (@Pwnrin)
Shortcuts Available for: macOS Sequoia
Impact: A Shortcut may run with admin privileges without authentication
Description: An authentication issue was addressed with improved state management.
CVE-2025-31194: Dolf Hoegaerts
Shortcuts Available for: macOS Sequoia
Impact: A shortcut may be able to access files that are normally inaccessible to the Shortcuts app
Description: This issue was addressed with improved access restrictions.
CVE-2025-30433: Andrew James Gonzalez
Siri Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: The issue was addressed with improved restriction of data container access.
CVE-2025-31183: Kirin (@Pwnrin), Bohdan Stasiuk (@bohdan_stasiuk)
Siri Available for: macOS Sequoia
Impact: A sandboxed app may be able to access sensitive user data in system logs
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-30435: K宝 (@Pwnrin) and luckyu (@uuulucky)
Siri Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: This issue was addressed with improved redaction of sensitive information.
CVE-2025-24217: Kirin (@Pwnrin)
Siri Available for: macOS Sequoia
Impact: An app may be able to access sensitive user data
Description: A privacy issue was addressed by not logging contents of text fields.
CVE-2025-24214: Kirin (@Pwnrin)
Siri Available for: macOS Sequoia
Impact: An app may be able to enumerate devices that have signed into the user's Apple Account
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24248: Minghao Lin (@Y1nKoc) and Tong Liu@Lyutoon_ and 风(binary_fmyy) and F00L
Siri Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: An authorization issue was addressed with improved state management.
CVE-2025-24205: YingQi Shi(@Mas0nShi) of DBAppSecurity's WeBin lab and Minghao Lin (@Y1nKoc)
Siri Available for: macOS Sequoia
Impact: An attacker with physical access may be able to use Siri to access sensitive user data
Description: This issue was addressed by restricting options offered on a locked device.
CVE-2025-24198: Richard Hyunho Im (@richeeta) with routezero.security
SMB Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: The issue was addressed with improved memory handling.
CVE-2025-24269: Alex Radocea of Supernetworks
SMB Available for: macOS Sequoia
Impact: Mounting a maliciously crafted SMB network share may lead to system termination
Description: A race condition was addressed with improved locking.
CVE-2025-30444: Dave G.
SMB Available for: macOS Sequoia
Impact: An app may be able to execute arbitrary code with kernel privileges
Description: A buffer overflow issue was addressed with improved memory handling.
CVE-2025-24228: Joseph Ravichandran (@0xjprx) of MIT CSAIL
smbx Available for: macOS Sequoia
Impact: An attacker in a privileged position may be able to perform a denial-of-service
Description: The issue was addressed with improved memory handling.
CVE-2025-24260: zbleet of QI-ANXIN TianGong Team
Software Update Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: A library injection issue was addressed with additional restrictions.
CVE-2025-24282: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
Software Update Available for: macOS Sequoia
Impact: A user may be able to elevate privileges
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-24254: Arsenii Kostromin (0x3c3e)
Software Update Available for: macOS Sequoia
Impact: An app may be able to modify protected parts of the file system
Description: The issue was addressed with improved checks.
CVE-2025-24231: Claudio Bozzato and Francesco Benvenuto of Cisco Talos
StickerKit Available for: macOS Sequoia
Impact: An app may be able to observe unprotected user data
Description: A privacy issue was addressed by moving sensitive data to a protected location.
CVE-2025-24263: Cristian Dinca of "Tudor Vianu" National High School of Computer Science, Romania
Storage Management Available for: macOS Sequoia
Impact: An app may be able to enable iCloud storage features without user consent
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-24207: YingQi Shi (@Mas0nShi) of DBAppSecurity's WeBin lab, 风沐云烟 (binary_fmyy) and Minghao Lin (@Y1nKoc)
StorageKit Available for: macOS Sequoia
Impact: An app may be able to gain root privileges
Description: A permissions issue was addressed with additional restrictions.
CVE-2025-30449: Arsenii Kostromin (0x3c3e), and an anonymous researcher
StorageKit Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-24253: Mickey Jin (@patch1t), Csaba Fitzl (@theevilbit) of Kandji
StorageKit Available for: macOS Sequoia
Impact: An app may be able to access user-sensitive data
Description: A race condition was addressed with additional validation.
CVE-2025-24240: Mickey Jin (@patch1t)
StorageKit Available for: macOS Sequoia
Impact: An app may be able to bypass Privacy preferences
Description: A race condition was addressed with additional validation.
CVE-2025-31188: Mickey Jin (@patch1t)
Summarization Services Available for: macOS Sequoia
Impact: An app may be able to access information about a user's contacts
Description: A privacy issue was addressed with improved private data redaction for log entries.
CVE-2025-24218: Kirin and FlowerCode, Bohdan Stasiuk (@bohdan_stasiuk)
System Settings Available for: macOS Sequoia
Impact: An app may be able to access protected user data
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-24278: Zhongquan Li (@Guluisacat)
System Settings Available for: macOS Sequoia
Impact: An app with root privileges may be able to access private information
Description: This issue was addressed with improved handling of symlinks.
CVE-2025-24242: Koh M. Nakagawa (@tsunek0h) of FFRI Security, Inc.
SystemMigration Available for: macOS Sequoia
Impact: A malicious app may be able to create symlinks to protected regions of the disk
Description: This issue was addressed with improved validation of symlinks.
CVE-2025-30457: Mickey Jin (@patch1t)
Voice Control Available for: macOS Sequoia
Impact: An app may be able to access contacts
Description: This issue was addressed with improved file handling.
CVE-2025-24279: Mickey Jin (@patch1t)
Web Extensions Available for: macOS Sequoia
Impact: An app may gain unauthorized access to Local Network
Description: This issue was addressed with improved permissions checking.
CVE-2025-31184: Alexander Heinrich (@Sn0wfreeze), SEEMOO, TU Darmstadt & Mathy Vanhoef (@vanhoefm) and Jeroen Robben (@RobbenJeroen), DistriNet, KU Leuven
Web Extensions Available for: macOS Sequoia
Impact: Visiting a website may leak sensitive data
Description: A script imports issue was addressed with improved isolation.
CVE-2025-24192: Vsevolod Kokorin (Slonser) of Solidlab
WebKit Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash
Description: The issue was addressed with improved memory handling.
WebKit Bugzilla: 285892
CVE-2025-24264: Gary Kwong, and an anonymous researcher
WebKit Bugzilla: 284055
CVE-2025-24216: Paul Bakker of ParagonERP
WebKit Available for: macOS Sequoia
Impact: A type confusion issue could lead to memory corruption
Description: This issue was addressed with improved handling of floats.
WebKit Bugzilla: 286694
CVE-2025-24213: Google V8 Security Team
WebKit Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected process crash
Description: A buffer overflow issue was addressed with improved memory handling.
WebKit Bugzilla: 286462
CVE-2025-24209: Francisco Alonso (@revskills), and an anonymous researcher
WebKit Available for: macOS Sequoia
Impact: Processing maliciously crafted web content may lead to an unexpected Safari crash
Description: A use-after-free issue was addressed with improved memory management.
WebKit Bugzilla: 285643
CVE-2025-30427: rheza (@ginggilBesel)
WebKit Available for: macOS Sequoia
Impact: A malicious website may be able to track users in Safari private browsing mode
Description: This issue was addressed through improved state management.
WebKit Bugzilla: 286580
CVE-2025-30425: an anonymous researcher
WindowServer Available for: macOS Sequoia
Impact: An attacker may be able to cause unexpected app termination
Description: A type confusion issue was addressed with improved checks.
CVE-2025-24247: PixiePoint Security
WindowServer Available for: macOS Sequoia
Impact: An app may be able to trick a user into copying sensitive data to the pasteboard
Description: A configuration issue was addressed with additional restrictions.
CVE-2025-24241: Andreas Hegenberg (folivora.AI GmbH)
Xsan Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: A buffer overflow was addressed with improved bounds checking.
CVE-2025-24266: an anonymous researcher
Xsan Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination
Description: An out-of-bounds read was addressed with improved bounds checking.
CVE-2025-24265: an anonymous researcher
Xsan Available for: macOS Sequoia
Impact: An app may be able to cause unexpected system termination or corrupt kernel memory
Description: A buffer overflow issue was addressed with improved memory handling.
CVE-2025-24157: an anonymous researcher
-
 @ 94a6a78a:0ddf320e
2025-02-19 21:10:15
@ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables decentralized, censorship-resistant communication. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on users, developers, and relay operators.
If you believe in free speech, decentralization, and an open internet, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, every effort helps build a more robust network.
Here’s how you can get involved and make a difference.
1️⃣ Use Nostr Daily
The simplest and most effective way to contribute to Nostr is by using it regularly. The more active users, the stronger and more valuable the network becomes.
✅ Post, comment, and zap (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ Engage with new users and help them understand how Nostr works.\ ✅ Try different Nostr clients like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience.
Your activity keeps the network alive and helps encourage more developers and relay operators to invest in the ecosystem.
2️⃣ Run Your Own Nostr Relay
Relays are the backbone of Nostr, responsible for distributing messages across the network. The more independent relays exist, the stronger and more censorship-resistant Nostr becomes.
✅ Set up your own relay to help decentralize the network further.\ ✅ Experiment with relay configurations and different performance optimizations.\ ✅ Offer public or private relay services to users looking for high-quality infrastructure.
If you're not technical, you can still support relay operators by subscribing to a paid relay or donating to open-source relay projects.
3️⃣ Support Paid Relays & Infrastructure
Free relays have helped Nostr grow, but they struggle with spam, slow speeds, and sustainability issues. Paid relays help fund better infrastructure, faster message delivery, and a more reliable experience.
✅ Subscribe to a paid relay to help keep it running.\ ✅ Use premium services like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ Donate to relay operators who invest in long-term infrastructure.
By funding Nostr’s decentralized backbone, you help ensure its longevity and reliability.
4️⃣ Zap Developers, Creators & Builders
Many people contribute to Nostr without direct financial compensation—developers who build clients, relay operators, educators, and content creators. You can support them with zaps! ⚡
✅ Find developers working on Nostr projects and send them a zap.\ ✅ Support content creators and educators who spread awareness about Nostr.\ ✅ Encourage builders by donating to open-source projects.
Micro-payments via the Lightning Network make it easy to directly support the people who make Nostr better.
5️⃣ Develop New Nostr Apps & Tools
If you're a developer, you can build on Nostr’s open protocol to create new apps, bots, or tools. Nostr is permissionless, meaning anyone can develop for it.
✅ Create new Nostr clients with unique features and user experiences.\ ✅ Build bots or automation tools that improve engagement and usability.\ ✅ Experiment with decentralized identity, authentication, and encryption to make Nostr even stronger.
With no corporate gatekeepers, your projects can help shape the future of decentralized social media.
6️⃣ Promote & Educate Others About Nostr
Adoption grows when more people understand and use Nostr. You can help by spreading awareness and creating educational content.
✅ Write blogs, guides, and tutorials explaining how to use Nostr.\ ✅ Make videos or social media posts introducing new users to the protocol.\ ✅ Host discussions, Twitter Spaces, or workshops to onboard more people.
The more people understand and trust Nostr, the stronger the ecosystem becomes.
7️⃣ Support Open-Source Nostr Projects
Many Nostr tools and clients are built by volunteers, and open-source projects thrive on community support.
✅ Contribute code to existing Nostr projects on GitHub.\ ✅ Report bugs and suggest features to improve Nostr clients.\ ✅ Donate to developers who keep Nostr free and open for everyone.
If you're not a developer, you can still help with testing, translations, and documentation to make projects more accessible.
🚀 Every Contribution Strengthens Nostr
Whether you:
✔️ Post and engage daily\ ✔️ Zap creators and developers\ ✔️ Run or support relays\ ✔️ Build new apps and tools\ ✔️ Educate and onboard new users
Every action helps make Nostr more resilient, decentralized, and unstoppable.
Nostr isn’t just another social network—it’s a movement toward a free and open internet. If you believe in digital freedom, privacy, and decentralization, now is the time to get involved.
-
 @ 06e41e35:249d7a01
2025-04-22 09:00:00
@ 06e41e35:249d7a01
2025-04-22 09:00:00Drew Weatherhead is the host of The Social Disorder Podcast, where he explores a wide range of topics, from politics and culture to philosophy and technology, aiming to uncover deeper truths about reality. He is a Brazilian Jiu-Jitsu black belt and runs DrewJitsu Online, offering instructional videos for martial arts enthusiasts. Weatherhead is also an author, having written Consciousness Reality & Purpose and Layers of Truth, and is about to release his new fictional epic titled Fractures.
Cornerstone Forum ‘25
https://www.showpass.com/cornerstone25/
Get your voice heard: Text Shaun 587-217-8500
Substack:https://open.substack.com/pub/shaunnewmanpodcast
Silver Gold Bull Links:
Website: https://silvergoldbull.ca/
Email: SNP@silvergoldbull.com
Text Grahame: (587) 441-9100
Bow Valley Credit Union
Website: www.BowValleycu.com
Email: welcome@BowValleycu.com
Use the code “SNP” on all orders
Prophet River Links:
Website: store.prophetriver.com/
Email: SNP@prophetriver.com
-
 @ 8d34bd24:414be32b
2025-04-02 14:13:03
@ 8d34bd24:414be32b
2025-04-02 14:13:03I was reading this passage last night:
…from that time when one came to a grain heap of twenty measures, there would be only ten; and when one came to the wine vat to draw fifty measures, there would be only twenty. I smote you and every work of your hands with blasting wind, mildew and hail; yet you did not come back to Me,’ declares the Lord. ‘Do consider from this day onward, from the twenty-fourth day of the ninth month; from the day when the temple of the Lord was founded, consider: Is the seed still in the barn? Even including the vine, the fig tree, the pomegranate and the olive tree, it has not borne fruit. Yet from this day on I will bless you.’ ” (Haggai 2:16-19) {emphasis mine}
Why were bad things happening to the Israelites? Because they were not following God. Why did God allow these difficult situations to occur? Because God was calling them back to Himself.
This made me think of several times lately, when I had written about Christians going through hard times, that fellow believers had tried to kindly correct me implying that God would not allow these painful things to happen to believers. They were trying to defend God’s honor, but instead they were degrading God. If God is not in control of everything, then either God is unable to protect His own from harm because of sin or bad things happened accidentally and God ignored the injustice. Saying God was not in control of allowing every hardship is either saying God isn’t strong enough, isn’t smart enough, or isn’t loving enough. The God I serve is omniscient, omnipotent, omnipresent, and love incarnate. He also didn’t promise us easy, pleasant lives, but did promise that good would come out of every situation.
And we know that in all things God works for the good of those who love him, who have been called according to his purpose. (Romans 8:28)
When Jesus walked on earth and some people said they wanted to follow Him, His response was not what we would expect:
And He was saying to them all, “If anyone wishes to come after Me, he must deny himself, and take up his cross daily and follow Me. For whoever wishes to save his life will lose it, but whoever loses his life for My sake, he is the one who will save it. For what is a man profited if he gains the whole world, and loses or forfeits himself? For whoever is ashamed of Me and My words, the Son of Man will be ashamed of him when He comes in His glory, and the glory of the Father and of the holy angels. (Luke 9:23-26) {emphasis mine}
When one particular man said that he would follow Jesus anywhere, Jesus responded this way.
As they were going along the road, someone said to Him, “I will follow You wherever You go.” And Jesus said to him, “The foxes have holes and the birds of the air have nests, but the Son of Man has nowhere to lay His head.” (Luke 9:57-58) {emphasis mine}
Jesus was brutally honest that following Him would not be easy or comfortable. Following Jesus is more likely to lead to hardship and persecution that prosperity and comfort.
“Then they will deliver you to tribulation, and will kill you, and you will be hated by all nations because of My name. At that time many will fall away and will betray one another and hate one another. Many false prophets will arise and will mislead many. Because lawlessness is increased, most people’s love will grow cold. But the one who endures to the end, he will be saved. This gospel of the kingdom shall be preached in the whole world as a testimony to all the nations, and then the end will come. (Matthew 24:9-14) {emphasis mine}
Of course God isn’t putting us through hardship to torture us. He is putting us in situations to grow our faith and dependence on Him, i.e. Abraham. He is putting us in situations where we can minister to others, i.e. Joseph. He is using us as examples of faith to others, i.e. Job. Any hardship has an eternal purpose. Sometimes we can see it (at least eventually) if we are looking for God’s will and plan. Sometime we won’t see what He was accomplishing until we get to heaven. Still we need to trust God through it all, knowing His plan is perfect.
“For my thoughts are not your thoughts,\ neither are your ways my ways,”\ declares the Lord.
“As the heavens are higher than the earth,\ so are my ways higher than your ways\ and my thoughts than your thoughts.
As the rain and the snow\ come down from heaven,\ and do not return to it\ without watering the earth\ and making it bud and flourish,\ so that it yields seed for the sower and bread for the eater,\ so is my word that goes out from my mouth:\ It will not return to me empty,\ but will accomplish what I desire\ and achieve the purpose for which I sent it. (Isaiah 55:8-11) {emphasis mine}
God understands how hard it is to understand what He is accomplishing. We live in the here and now while He is outside time and space and therefore has a heavenly and eternal perspective that we will never truly have this side of heaven. He has told us how the story ends, so that we can have peace and trust Him through whatever circumstances He has blessed us.
Jesus answered them, “Do you now believe? Behold, an hour is coming, and has already come, for you to be scattered, each to his own home, and to leave Me alone; and yet I am not alone, because the Father is with Me. These things I have spoken to you, so that in Me you may have peace. In the world you have tribulation, but take courage; I have overcome the world.” (John 16:31-33) {emphasis mine}
In fact, Jesus made this so clear that His disciples rejoiced in persecution they received due to obeying Him and sharing His word.
They took his advice; and after calling the apostles in, they flogged them and ordered them not to speak in the name of Jesus, and then released them. So they went on their way from the presence of the Council, rejoicing that they had been considered worthy to suffer shame for His name. (Acts 5:40-41) {emphasis mine}
Peter specifically warns believers to expect trials and hardship.
Dear friends, do not be surprised at the fiery ordeal that has come on you to test you, as though something strange were happening to you. But rejoice inasmuch as you participate in the sufferings of Christ, so that you may be overjoyed when his glory is revealed. If you are insulted because of the name of Christ, you are blessed, for the Spirit of glory and of God rests on you. If you suffer, it should not be as a murderer or thief or any other kind of criminal, or even as a meddler. However, if you suffer as a Christian, do not be ashamed, but praise God that you bear that name. For it is time for judgment to begin with God’s household; and if it begins with us, what will the outcome be for those who do not obey the gospel of God? And,
“If it is hard for the righteous to be saved,\ what will become of the ungodly and the sinner?”
So then, those who suffer according to God’s will should commit themselves to their faithful Creator and continue to do good. (1 Peter 4:12-19) {emphasis mine}
Paul writes about begging God to take away a health issue. Eventually he accepted it as part of God’s plan for his life and boasted gladly in his hardship.
…Therefore, in order to keep me from becoming conceited, I was given a thorn in my flesh, a messenger of Satan, to torment me. Three times I pleaded with the Lord to take it away from me. But he said to me, “My grace is sufficient for you, for my power is made perfect in weakness.” Therefore I will boast all the more gladly about my weaknesses, so that Christ’s power may rest on me. That is why, for Christ’s sake, I delight in weaknesses, in insults, in hardships, in persecutions, in difficulties. For when I am weak, then I am strong. (2 Corinthians 12:7b-10) {emphasis mine}
No matter what hardships we experience in life, whether poverty or persecution or poor health or loss of a loved one or any other hardship, God is with us working everything for our good.
Who will separate us from the love of Christ? Will tribulation, or distress, or persecution, or famine, or nakedness, or peril, or sword? Just as it is written,
“For Your sake we are being put to death all day long;\ We were considered as sheep to be slaughtered.” **But in all these things we overwhelmingly conquer through Him who loved us. For I am convinced that neither death, nor life, nor angels, nor principalities, nor things present, nor things to come, nor powers, nor height, nor depth, nor any other created thing, will be able to separate us from the love of God, which is in Christ Jesus our Lord. (Romans 8:35-39) {emphasis mine}
I like to look at the story of Joseph as an example of God’s extraordinary plan in the life of a faithful believer. Joseph trusted and honored God. God had a plan for Joseph to be used to save the lives of his family and the people of the Middle East from famine, but God didn’t just instantly put Joseph in a position of power to help. He prepared Joseph and slowly moved him to where he needed to be.
First Josephs brothers wanted to kill him out of jealousy, but God used greed to get them to sell Joseph as a slave instead. He orchestrated the right slave traders to walk by at the right time so that Joseph would wind up in the house of Potiphar, the Pharaoh’s guard.
Then when Joseph acted honorably towards God, his master, and his master’s wife, Joseph was sent to jail for years. I’m sure Joseph was wondering why God would send him to prison for doing what was right, but it put him into the presence of the cupbearer of Pharaoh. A long time after correctly interpreting the cup bearer’s dream, Joseph was called up to interpret Pharaoh’s dream, put in charge of the famine preparation and became second in command after Pharaoh. Joseph, after years of slavery and jail time, was now the second most powerful man in the Middle East, if not the world. God had a plan, but it was hard to see until its completion.
In the same way, Job lost his wealth, his children, his health, and his reputation, but remember that Satan had to get God’s permission before anything could be done to hurt Job. So many people today are blessed by seeing Job’s response to hardship and loss, by seeing Job’s faith, his struggle, and his submission to God’s plan. In this case God even gives Job more after this time of testing than he had before.
When we experience hardship we need to know that God has a plan for our life. It may be something amazing here on Earth. It may be souls won for Christ. It may be to prepare us for heaven. Whatever the case, it is for our good.
We don’t need to be ashamed that God would allow hardship. We grow most when we experience hardship. Our light shines brightest in darkness.
Oh, the depth of the riches of the wisdom and knowledge of God!\ How unsearchable his judgments,\ and his paths beyond tracing out!\ “Who has known the mind of the Lord?\ Or who has been his counselor?”\ “Who has ever given to God,\ that God should repay them?”\ For from him and through him and for him are all things.\ To him be the glory forever! Amen. (Romans 11:33-36)
Trust Jesus
-
 @ 5de23b9a:d83005b3
2025-02-19 03:47:19
@ 5de23b9a:d83005b3
2025-02-19 03:47:19In a digital era that is increasingly controlled by large companies, the emergence of Nostr (Notes and Other Stuff Transmitted by Relays) is a breath of fresh air for those who crave freedom of expression.
Nostr is a cryptography-based protocol that allows users to send and receive messages through a relay network. Unlike conventional social media such as Twitter or Facebook
1.Full Decentralization: No company or government can remove or restrict content.
2.Sensor-Resistant: Information remains accessible despite blocking attempts.
3.Privacy and Security: Uses cryptography to ensure that only users who have the keys can access their messages.* **
-
 @ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33
@ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33After my first major review of Primal on Android, we're going to go a very different direction for this next review. Primal is your standard "Twitter clone" type of kind 1 note client, now branching into long-form. They also have a team of developers working on making it one of the best clients to fill that use-case. By contrast, this review will not be focusing on any client at all. Not even an "other stuff" client.
Instead, we will be reviewing a very useful tool created and maintained by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 called #Amber. For those unfamiliar with Amber, it is an #Android application dedicated to managing your signing keys, and allowing you to log into various #Nostr applications without having to paste in your private key, better known as your #nsec. It is not recommended to paste your nsec into various applications because they each represent another means by which it could be compromised, and anyone who has your nsec can post as you. On Nostr, your #npub is your identity, and your signature using your private key is considered absolute proof that any given note, reaction, follow update, or profile change was authorized by the rightful owner of that identity.
It happens less often these days, but early on, when the only way to try out a new client was by inputting your nsec, users had their nsec compromised from time to time, or they would suspect that their key may have been compromised. When this occurs, there is no way to recover your account, or set a new private key, deprecating the previous one. The only thing you can do is start over from scratch, letting everyone know that your key has been compromised and to follow you on your new npub.
If you use Amber to log into other Nostr apps, you significantly reduce the likelihood that your private key will be compromised, because only one application has access to it, and all other applications reach out to Amber to sign any events. This isn't quite as secure as storing your private key on a separate device that isn't connected to the internet whatsoever, like many of us have grown accustomed to with securing our #Bitcoin, but then again, an online persona isn't nearly as important to secure for most of us as our entire life savings.
Amber is the first application of its kind for managing your Nostr keys on a mobile device. nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 didn't merely develop the application, but literally created the specification for accomplishing external signing on Android which can be found in NIP-55. Unfortunately, Amber is only available for Android. A signer application for iOS is in the works from nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, but is not ready for use at this time. There is also a new mobile signer app for Android and iOS called Nowser, but I have not yet had a chance to try this app out. From a cursory look at the Android version, it is indeed in the very early stages of development and cannot be compared with Amber.
This review of Amber is current as of version 3.2.5.

Overall Impression
Score: 4.7 / 5 (Updated 4/21/2025)
I cannot speak highly enough about Amber as a tool that every Nostr user on Android should start using if they are not already. When the day comes that we have more options for well-developed signer apps on mobile, my opinion may very well change, but until then Amber is what we have available to us. Even so, it is an incredibly well thought-out and reliable tool for securing your nsec.
Despite being the only well-established Android signer available for Android, Amber can be compared with other external signing methods available on other platforms. Even with more competition in this arena, though, Amber still holds up incredibly well. If you are signing into web applications on a desktop, I still would recommend using a browser extension like #Alby or #Nos2x, as the experience is usually faster, more seamless, and far more web apps support this signing method (NIP-07) than currently support the two methods employed by Amber. Nevertheless that gap is definitely narrowing.
A running list I created of applications that support login and signing with Amber can be found here: Nostr Clients with External Signer Support
I have run into relatively few bugs in my extensive use of Amber for all of my mobile signing needs. Occasionally the application crashes when trying to send it a signing request from a couple of applications, but I would not be surprised if this is no fault of Amber at all, and rather the fault of those specific apps, since it works flawlessly with the vast majority of apps that support either NIP-55 or NIP-46 login.
I also believe that mobile is the ideal platform to use for this type of application. First, because most people use Nostr clients on their phone more than on a desktop. There are, of course, exceptions to that, but in general we spend more time on our phones when interacting online. New users are also more likely to be introduced to Nostr by a friend having them download a Nostr client on their phone than on a PC, and that can be a prime opportunity to introduce the new user to protecting their private key. Finally, I agree with the following assessment from nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn.
nostr:nevent1qqsw0r6gzn05xg67h5q2xkplwsuzedjxw9lf7ntrxjl8ajm350fcyugprfmhxue69uhhyetvv9ujumn0wd68yurvv438xtnrdaksyg9hyaxj3clfswlhyrd5kjsj5v04clhjvgeq6pwztmysfzdvn93gev7awu9v
The one downside to Amber is that it will be quite foreign for new users. That is partially unavoidable with Nostr, since folks are not accustomed to public/private key cryptography in general, let alone using a private key to log into websites or social media apps. However, the initial signup process is a bit cumbersome if Amber is being used as the means of initially generating a key pair. I think some of this could be foregone at start-up in favor of streamlining onboarding, and then encourage the user to back-up their private key at a later time.
Features
Amber has some features that may surprise you, outside of just storing your private key and signing requests from your favorite Nostr clients. It is a full key management application, supporting multiple accounts, various backup methods, and even the ability to authorize other users to access a Nostr profile you control.
Android Signing
This is the signing method where Amber really shines in both speed and ease of use. Any Android application that supports this standard, and even some progressive web-apps that can be installed to your Android's home-screen, can very quickly and seamlessly connect with Amber to authorize anything that you need signed with your nsec. All you have to do is select "Login with Amber" in clients like #Amethyst or #0xChat and the app will reach out to Amber for all signing requests from there on out. If you had previously signed into the app with your nsec, you will first need to log out, then choose the option to use Amber when you log back in.

This is a massive deal, because everything you do on Nostr requires a signature from your private key. Log in? Needs a signature. Post a "GM" note? Needs a signature. Follow someone who zapped your note? Needs a signature. Zap them back? You guessed it; needs a signature. When you paste your private key into an application, it will automatically sign a lot of these actions without you ever being asked for approval, but you will quickly realize just how many things the client is doing on your behalf when Amber is asking you to approve them each time.
Now, this can also get quite annoying after a while. I recommend using the setting that allows Amber to automatically sign for basic functions, which will cut down on some of the authorization spam. Once you have been asked to authorize the same type of action a few times, you can also toggle the option to automatically authorize that action in the future. Don't worry, though, you have full control to require Amber to ask you for permission again if you want to be alerted each time, and this toggle is specific to each application, so it's not a blanket approval for all Nostr clients you connect with.

This method of signing is just as fast as signing via browser extension on web clients, which users may be more accustomed to. Everything is happening locally on the device, so it can be very snappy and secure.
Nostr Connect/Bunker Signing
This next method of signing has a bit of a delay, because it is using a Nostr relay to send encrypted information back and forth between the app the user is interacting with and Amber to obtain signatures remotely. It isn't a significant delay most of the time, but it is just enough to be noticeable.
Also, unlike the previous signing method that would automatically switch to Amber as the active application when a signing request is sent, this method only sends you a notification that you must be watching for. This can lead to situations where you are wondering why something isn't working in a client you signed into remotely, because it is waiting on you to authorize the action and you didn't notice the notification from Amber. As you use the application, you get used to the need to check for such authorization requests from time to time, or when something isn't working as expected.

By default, Amber will use relay.nsec.app to communicate with whichever Nostr app you are connecting to. You can set a different relay for this purpose, if you like, though not just any relay will support the event kinds that Amber uses for remote signing. You can even run your own relay just for your own signing purposes. In fact, the creator of Amber has a relay application you can run on your phone, called Citrine, that can be used for signing with any web app you are using locally on your phone. This is definitely more of an advanced option, but it is there for you if you want it. For most users, sticking with relay.nsec.app will be just fine, especially since the contents of the events sent back and forth for signing are all encrypted.
Something many users may not realize is that this remote signing feature allows for issuing signing permissions to team members. For instance, if anyone ever joined me in writing reviews, I could issue them a connection string from Amber, and limit their permissions to just posting long-form draft events. Anything else they tried to do would require my explicit approval each time. Moreover, I could revoke those permissions if I ever felt they were being abused, without the need to start over with a whole new npub. Of course, this requires that your phone is online whenever a team member is trying to sign using the connection string you issued, and it requires you pay attention to your notifications so you can approve or reject requests you have not set to auto-approve. However, this is probably only useful for small teams, and larger businesses will want to find a more robust solution for managing access to their npub, such as Keycast from nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc.
The method for establishing a connection between Amber and a Nostr app for remote signing can vary for each app. Most, at minimum, will support obtaining a connection string from Amber that starts with "bunker://" and pasting it in at the time of login. Then you just need to approve the connection request from Amber and the client will log you in and send any subsequent signing requests to Amber using the same connection string.

Some clients will also offer the option to scan a QR code to connect the client to Amber. This is quite convenient, but just remember that this also means the client is setting which relay will be used for communication between the two. Clients with this option will also have a connection string you can copy and paste into Amber to achieve the same purpose. For instance, you may need this option if you are trying to connect to an app on your phone and therefore can't scan the QR code using Amber on the same phone.

Multiple Accounts
Amber does not lock you into using it with only a single set of keys. You can add all of your Nostr "accounts" to Amber and use it for signing events for each independently. Of course, Nostr doesn't actually have "accounts" in the traditional sense. Your identity is simply your key-pair, and Amber stores and accesses each private key as needed.

When first signing in using native Android signing as described above, Amber will default to whichever account was most recently selected, but you can switch to the account that is needed before approving the request. After initial login, Amber will automatically detect the account that the signing request is for.
Key Backup & Restore
Amber allows multiple ways to back up your private key. As most users would expect, you can get your standard nsec and copy/paste it to a password manager, but you can also obtain your private key as a list of mnemonic seed words, an encrypted version of your key called an ncryptsec, or even a QR code of your nsec or ncryptsec.

Additionally, in order to gain access to this information, Amber requires you to enter your device's PIN or use biometric authentication. This isn't cold-storage level protection for your private key by any means, especially since your phone is an internet connected device and does not store your key within a secure element, but it is about as secure as you can ask for while having your key accessible for signing Nostr events.
Tor Support
While Amber does not have Tor support within the app itself, it does support connecting to Tor through Orbot. This would be used with remote signing so that Amber would not connect directly over clearnet to the relay used for communication with the Nostr app requesting the signature. Instead, Amber would connect through Tor, so the relay would not see your IP address. This means you can utilize the remote signing option without compromising your anonymity.

Additional Security
Amber allows the user the option to require either biometric or PIN authentication before approving signing requests. This can provide that extra bit of assurance that no one will be able to sign events using your private key if they happen to gain access to your phone. The PIN you set in Amber is also independent from the PIN to unlock your device, allowing for separation of access.
Can My Grandma Use It?
Score: 4.6 / 5 (Updated 4/21/2025)
At the end of the day, Amber is a tool for those who have some concept of the importance of protecting their private key by not pasting it into every Nostr client that comes along. This concept in itself is not terribly approachable to an average person. They are used to just plugging their password into every service they use, and even worse, they usually have the same password for everything so they can more readily remember it. The idea that they should never enter their "Nostr password" into any Nostr application would never occur to them unless someone first explained how cryptography works related to public/private key pairs.
That said, I think there can be some improvements made to how users are introduced to these concepts, and that a signer application like Amber might be ideal for the job. Considering Amber as a new user's first touch-point with Nostr, I think it holds up well, but could be somewhat streamlined.
Upon opening the app, the user is prompted to either use their existing private key or "Create a new Nostr account." This is straightforward enough. "Account" is not a technically correct term with Nostr, but it is a term that new users would be familiar with and understand the basic concept.

The next screen announces that the account is ready, and presents the user with their public key, explaining that it is "a sort of username" that will allow others to find them on Nostr. While it is good to explain this to the user, it is unnecessary information at this point. This screen also prompts the user to set a nickname and set a password to encrypt their private key. Since the backup options also allow the user to set this password, I think this step could be pushed to a later time. This screen would better serve the new user if it simply prompted them to set a nickname and short bio that could be saved to a few default relays.

Of course, Amber is currently prompting for a password to be set up-front because the next screen requires the new user to download a "backup kit" in order to continue. While I do believe it is a good idea to encourage the creation of a backup, it is not crucial to do so immediately upon creation of a new npub that has nothing at stake if the private key is lost. This is something the UI could remind the user to do at a later time, reducing the friction of profile creation, and expediting getting them into the action.

Outside of these minor onboarding friction points, I think Amber does a great job of explaining to the user the purpose of each of its features, all within the app and without any need to reference external documentation. As long as the user understands the basic concept that their private key is being stored by Amber in order to sign requests from other Nostr apps, so they don't have to be given the private key, Amber is very good about explaining the rest without getting too far into the technical weeds.
The most glaring usability issue with Amber is that it isn't available in the Play Store. Average users expect to be able to find applications they can trust in their mobile device's default app store. There is a valid argument to be made that they are incorrect in this assumption, but that doesn't change the fact that this is the assumption most people make. They believe that applications in the Play Store are "safe" and that anything they can't install through the Play Store is suspect. The prompts that the Android operating system requires the user to approve when installing "unknown apps" certainly doesn't help with this impression.
Now, I absolutely love the Zapstore from nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but it doesn't do much to alleviate this issue. Users will still need to be convinced that it is safe to install the Zapstore from the GitHub repo, and then install Amber from there. Furthermore, this adds yet another step to the onboarding process.
Instead of:
- Install Amber
- Set up your keys
- Install the client you want to use
- Log in with Amber
The process becomes:
- Go to the Zapstore GitHub and download the latest version from the releases page.
- Install the APK you downloaded, allowing any prompt to install unknown apps.
- Open Zapstore and install Amber, allowing any prompt to install unknown apps again.
- Open Amber and set up your keys.
- Install the client you want to use
- Log in with Amber
An application as important as Amber for protecting users' private keys should be as readily available to the new user as possible. New users are the ones most prone to making mistakes that could compromise their private keys. Amber should be available to them in the Play Store.
UPDATE: As of version 3.2.8 released on 4/21/2025, the onboarding flow for Amber has been greatly improved! Now, when selecting to set up a new "account" the user is informed on the very next screen, "Your Nostr account is ready!" and given their public key/npub. The only field the user must fill in is their "nickname"/display name and hit "Continue."
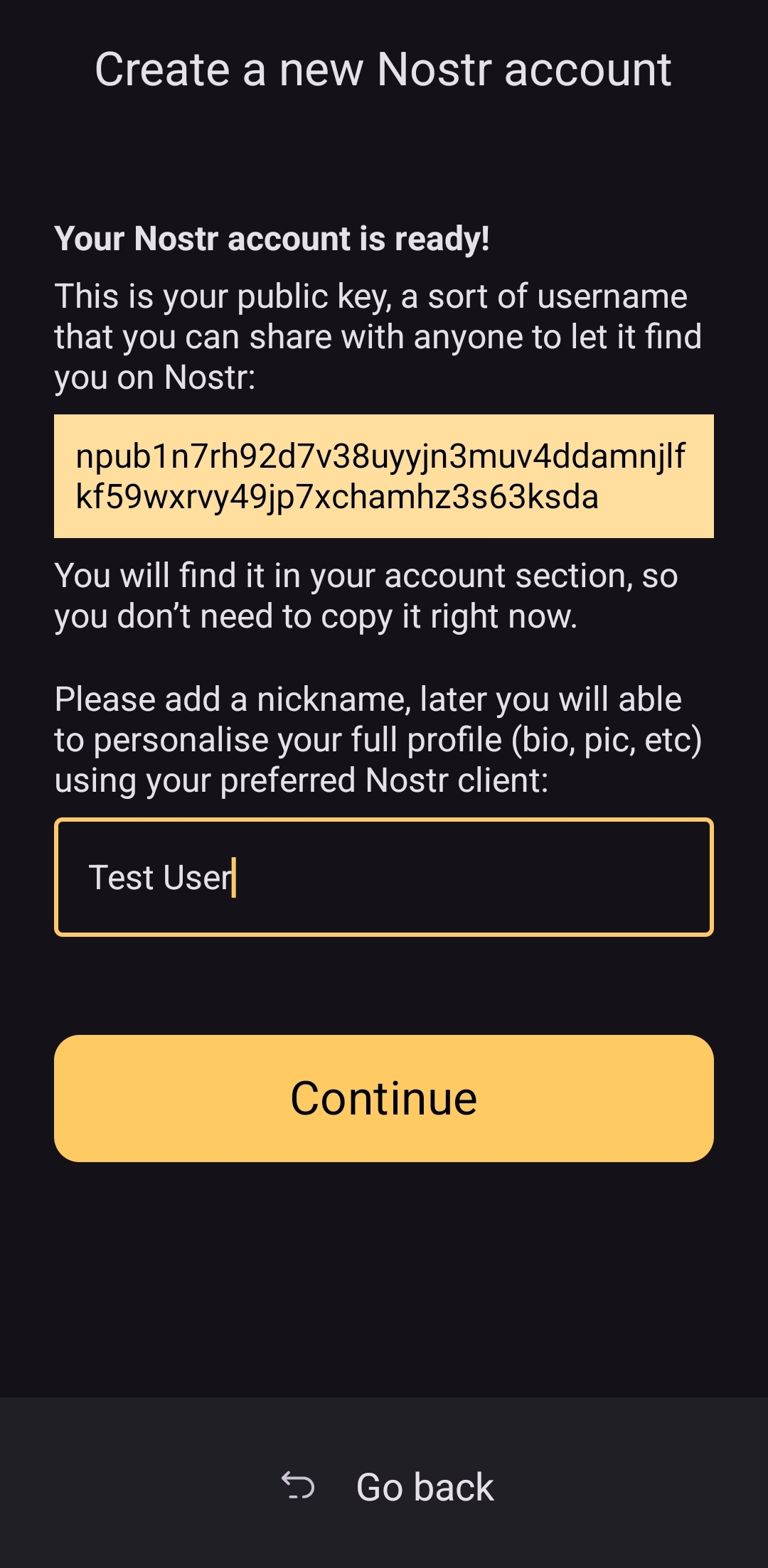
From there the user is asked if they want Amber to automatically approve basic actions, or manually approve each app, and then they are shown a new Applications screen, with a prompt to create a backup of their account. This prompt persists until the user has done so.
As you can see, the user is also encouraged to find applications that can be used with Amber with links to nostrapps.com and the Zapstore.
Thanks to these updates, Amber is now the smoothest and most user-friendly onboarding experience I have seen for Nostr to date. Sure, it doesn't have anything for setting up a profile picture or lightning address, but that is better done in a client like Amethyst or YakiHonne, anyway. Just tap "create," type in a handle to call yourself, and you're done!
How do UI Look?
Score: 4.5 / 5
Amber's UI can be described as clean but utilitarian. But then, Amber is a tool, so this is somewhat expected. It is not an app you will be spending a lot of time in, so the UI just needs to be serviceable. I would say it accomplishes this and then some. UI elements are generally easy to understand what they do, and page headings fill in the gaps where that is not the case.

I am not the biggest fan of the color-scheme, particularly in light-mode, but it is not bad in dark-mode at all, and Amber follows whatever theme you have set for your device in that respect. Additionally, the color choice does make sense given the application's name.

It must also be taken into consideration that Amber is almost entirely the product of a single developer's work. He has done a great job producing an app that is not only useful, but pleasant to interact with. The same cannot be said for most utility apps I have previously used, with interfaces that clearly made good design the lowest priority. While Amber's UI may not be the most beautiful Nostr app I have seen, design was clearly not an afterthought, either, and it is appreciated.
Relay Management
Score: 4.9 / 5
Even though Amber is not a Nostr client, where users can browse notes from their favorite npubs, it still relies heavily on relays for some of its features. Primarily, it uses relays for communicating with other Nostr apps for remote signing requests. However, it also uses relays to fetch profile data, so that each private key you add to Amber will automatically load your chosen username and profile picture.
In the relay settings, users can choose which relays are being used to fetch profile data, and which relays will be used by default when creating new remote signing connection strings.

The user can also see which relays are currently connected to Amber and even look at the information that has been passed back and forth on each of those active relays. This information about actively connected relays is not only available within the application, but also in the notification that Amber has to keep in your device's notification tray in order to continue to operate in the background while you are using other apps.

Optionality is the name of the game when it comes to how Amber handles relay selection. The user can just stick with the default signing relay, use their own relay as the default, or even use a different relay for each Nostr application that they connect to for remote signing. Amber gives the user an incredible amount of flexibility in this regard.
In addition to all of this, because not all relays accept the event types needed for remote signing, when you add a relay address to Amber, it automatically tests that relay to see if it will work. This alone can be a massive time saver, so users aren't trying to use relays that don't support remote signing and wondering why they can't log into noStrudel with the connection string they got from Amber.

The only way I could see relay management being improved would be some means of giving the user relay recommendations, in case they want to use a relay other than relay.nsec.app, but they aren't sure which other relays will accept remote signing events. That said, most users who want to use a different relay for signing remote events will likely be using their own, in which case recommendations aren't needed.
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with any Nostr application. Here are some of the most common questions submitted about Amber in the last two months.
nostr:nevent1qqsfrdr68fafgcvl8dgnhm9hxpsjxuks78afxhu8yewhtyf3d7mkg9gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qkgh77xxt7hhtt4u528hecnx69rhagla8jj3tclgyf9wvkxa6dc0sxp0e6m
This is a good example of Amber working correctly, but the app the user is trying to log into not working. In my experience with #Olas in particular, it sometimes allows remote signer login, and sometimes doesn't. Amber will receive the signing request and I will approve it, but Olas remains on the login screen.
If Amber is receiving the signing requests, and you are approving them, the fault is likely with the application you are trying to log into.
That's it. That's all the repeated questions I could find. Oh, there were a few one-off questions where relay.nsec.app wouldn't connect, or where the user's out-of-date web browser was the issue. Outside of that, though, there were no common questions about how to use Amber, and that is a testament to Amber's ease of use all on its own.
Wrap Up
If you are on Android and you are not already using Amber to protect your nsec, please do yourself a favor and get it installed. It's not at all complicated to set up, and it will make trying out all the latest Nostr clients a safe and pleasant experience.
If you are a client developer and you have not added support for NIP-55 or NIP-46, do your users the courtesy of respecting the sanctity of their private keys. Even developers who have no intention of compromising their users' keys can inadvertently do so. Make that eventuality impossible by adding support for NIP-55 and NIP-46 signing.
Finally, I apologize for the extended time it took me to get this review finished. The time I have available is scarce, Nostr is distracting, and nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 kept improving Amber even as I was putting it through its paces over the last two months. Keep shipping, my friend! You have made one of the most useful tools we have seen for Nostr to date!
Now... What should I review next?
-
 @ 06639a38:655f8f71
2025-04-02 13:47:57
@ 06639a38:655f8f71
2025-04-02 13:47:57You can follow the work in progress here in this pull request https://github.com/nostrver-se/nostr-php/pull/68 on Github.
Before my 3-month break (Dec/Jan/Feb) working on Nostr-PHP I started with the NIP-19 integration in October '24. Encoding and decoding the simple prefixes (
npub,nsecandnote) was already done in the first commits.Learn more about NIP-19 here: https://nips.nostr.com/19
TLV's
Things were getting more complicated with the other prefixes / identifiers defined in NIP-19:
neventnaddrnprofile
This is because these identifiers contain (optional) metadata called Type-Lenght-Value aka TLV's.
When sharing a profile or an event, an app may decide to include relay information and other metadata such that other apps can locate and display these entities more easily.
For these events, the contents are a binary-encoded list of_TLV_(type-length-value), with_T_and_L_being 1 byte each (_uint8_, i.e. a number in the range of 0-255), and_V_being a sequence of bytes of the size indicated by_L_.These possible standardized
TLVtypes are:0:special- depends on the bech32 prefix:
- for
nprofileit will be the 32 bytes of the profile public key - for
neventit will be the 32 bytes of the event id - for
naddr, it is the identifier (the"d"tag) of the event being referenced. For normal replaceable events use an empty string.
- for
- depends on the bech32 prefix:
1:relay- for
nprofile,neventandnaddr, optionally, a relay in which the entity (profile or event) is more likely to be found, encoded as ascii - this may be included multiple times
- for
2:author- for
naddr, the 32 bytes of the pubkey of the event - for
nevent, optionally, the 32 bytes of the pubkey of the event
- for
3:kind- for
naddr, the 32-bit unsigned integer of the kind, big-endian - for
nevent, optionally, the 32-bit unsigned integer of the kind, big-endian
- for
These identifiers are formatted as bech32 strings, but are much longer than the package
bitwasp/bech32(used in the library) for can handle for encoding and decoding. The bech32 strings handled bybitwasp/bech32are limited to a maximum length of 90 characters.Thanks to the effort of others (nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 and nostr:npub1efz8l77esdtpw6l359sjvakm7azvyv6mkuxphjdk3vfzkgxkatrqlpf9s4) during my break, some contributions are made (modifiying the bech32 package supporting much longer strings, up to a max of 5000 characters). At this moment, I'm integrating this (mostly copy-pasting the stuff and refactoring the code):
So what's next?
- NIP-19 code housekeeping + refactoring
- Prepare a new release with NIP-19 integration
- Create documentation page how to use NIP-19 on https://nostr-php.dev
-
 @ 9e69e420:d12360c2
2025-02-17 17:12:01
@ 9e69e420:d12360c2
2025-02-17 17:12:01President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February.
Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training.
Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further.
-
 @ 7bdef7be:784a5805
2025-04-02 12:37:35
@ 7bdef7be:784a5805
2025-04-02 12:37:35The following script try, using nak, to find out the last ten people who have followed a
target_pubkey, sorted by the most recent. It's possibile to shortensearch_timerangeto speed up the search.```
!/usr/bin/env fish
Target pubkey we're looking for in the tags
set target_pubkey "6e468422dfb74a5738702a8823b9b28168abab8655faacb6853cd0ee15deee93"
set current_time (date +%s) set search_timerange (math $current_time - 600) # 24 hours = 86400 seconds
set pubkeys (nak req --kind 3 -s $search_timerange wss://relay.damus.io/ wss://nos.lol/ 2>/dev/null | \ jq -r --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[] | select(.[0] == "p" and .[1] == $target)) | .pubkey ' | sort -u)
if test -z "$pubkeys" exit 1 end
set all_events "" set extended_search_timerange (math $current_time - 31536000) # One year
for pubkey in $pubkeys echo "Checking $pubkey" set events (nak req --author $pubkey -l 5 -k 3 -s $extended_search_timerange wss://relay.damus.io wss://nos.lol 2>/dev/null | \ jq -c --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[][] == $target) ' 2>/dev/null)
set count (echo "$events" | jq -s 'length') if test "$count" -eq 1 set all_events $all_events $events endend
if test -n "$all_events" echo -e "Last people following $target_pubkey:" echo -e ""
set sorted_events (printf "%s\n" $all_events | jq -r -s ' unique_by(.id) | sort_by(-.created_at) | .[] | @json ') for event in $sorted_events set npub (echo $event | jq -r '.pubkey' | nak encode npub) set created_at (echo $event | jq -r '.created_at') if test (uname) = "Darwin" set follow_date (date -r "$created_at" "+%Y-%m-%d %H:%M") else set follow_date (date -d @"$created_at" "+%Y-%m-%d %H:%M") end echo "$follow_date - $npub" endend ```
-
 @ fd208ee8:0fd927c1
2025-02-15 07:02:08
@ fd208ee8:0fd927c1
2025-02-15 07:02:08E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md
-
 @ d9e9fb27:d5fe5e1a
2025-04-22 01:29:16
@ d9e9fb27:d5fe5e1a
2025-04-22 01:29:16"There are two pillars in Costa Rica, education and coffee." A tourist guide I met told me this, and during the trip I discovered the strong link between coffee and the locals.
In fact, coffee runs very deeply in the Ticos' culture. So deep that the summer vacations from school (November to January) coincide with the coffee collection season. Children had to help their parents with the coffee. Coffee was a family business.
Monteverde, in the region of Puentarenas, is one of those places where coffee ha always been a corner stone of the society. Here, My gf and I went to visit a coffee plantation and discovered how coffee is made.
Monteverde
Monteverde is a well-known turistic location in the central part of Costa Rica. Many people reach this beautiful place to visit the famous Cloud Rainforest, acres and acres of pristine forest, with many different kind of animals and plants living in it.

However, other than tourism is coffee that pushes the economy of this place. The hills around the town are covered with coffee plantations and there are tours than try to explain how coffee is made.

Coffee Tours
While we were in Monteverde, we joined one of these tours. We decided to give credit to a smaller plantation instead of the super turistic ones. A more rustic and family-owned business, El Pueblo Coffee Tour. We were not disappointed. We had the show all to ourselves, a super-prepared guide and all the time to make questions and enjoy with no rush.
The Plant of Coffee
Since Costa Rica is a quite small country, to compete on the market producers decided to bet on quality instead of quantity. That's why, the only type produced here is the Arabica.
Before the coffee bean, the plant produces a nice white flower, similar to the jasmine.

After a while, the coffee beans appear.

As soon as they turn red, they are ready to be collected.
Interesting fact: between the coffee plants many fruit trees like mangos or bananos can be found. In fact, those plants help keep the soil fertile and healthy, thus leading to a higher coffee quality!
Coffee Harvesting
Coffee is still harvested by hand. Beans do not get mature at the same time, so manual labor is needed. Laborer use a very simple tool to collect coffee, one which allow them to have both hands free.
 Workers do not get paid by hours, but by the number of cajuelas that they can fill. A cajuela is a standard box, which contains around 13kg of beans. It's divided into quarters, so that the worker can get paid for the quarter, too.
Workers do not get paid by hours, but by the number of cajuelas that they can fill. A cajuela is a standard box, which contains around 13kg of beans. It's divided into quarters, so that the worker can get paid for the quarter, too.
Each cajuela is paid around 3.50$.
Coffee Drying
In the farm we visited, drying was perfomed naturally, through the heat of the sun. There are three ways in which the bean is left to dry: lavado, miel and naturàl.
- Lavado: The beans are peeled and washed to remove the jelly.
 - Miel: The jelly on the beans is maintained to give it more sweet flavour.
- Miel: The jelly on the beans is maintained to give it more sweet flavour. - Naturàl: The bean is left to dry with its peel on, to give it a more fruity taste.
- Naturàl: The bean is left to dry with its peel on, to give it a more fruity taste.
Back in the days, to peel the beans for the lavado and the miel variety, the pìlon was used. The bean is very hard, thus this tool does not damage it.

However, today the peeling procedure is done using a machine.

Coffee Roasting
The last step in the production of coffee is roasting. Coffee is put inside a sort of hoven, and is left there at high temperature according to the level of roasting that is needed. The more roasting, the less caffeine there is and the more bitter the coffee. Usually you have light, medium and dark roast.

Coffee Tasting
In the end, we also had a coffee tasting. We tried different roasting and different varieties.
Our guide explained us the best way to taste coffee and helped us defining the different flavours that we perceived. He also taught us the best way to prepare it: infusion time, water temperature, coffe makers and so on.
My favorite one was the dark one, while my gf enjoyed the light roast more. Of course, we bought some packs of these varieties!
Thanks for tuning in!
I hope you enjoyed this brief overview of the Costa Rican coffee.
Pura Vida
Tuma
-
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-
 @ 7bdef7be:784a5805
2025-04-02 12:12:12
@ 7bdef7be:784a5805
2025-04-02 12:12:12We value sovereignty, privacy and security when accessing online content, using several tools to achieve this, like open protocols, open OSes, open software products, Tor and VPNs.
The problem
Talking about our social presence, we can manually build up our follower list (social graph), pick a Nostr client that is respectful of our preferences on what to show and how, but with the standard following mechanism, our main feed is public, so everyone can actually snoop what we are interested in, and what is supposable that we read daily.
The solution
Nostr has a simple solution for this necessity: encrypted lists. Lists are what they appear, a collection of people or interests (but they can also group much other stuff, see NIP-51). So we can create lists with contacts that we don't have in our main social graph; these lists can be used primarily to create dedicated feeds, but they could have other uses, for example, related to monitoring. The interesting thing about lists is that they can also be encrypted, so unlike the basic following list, which is always public, we can hide the lists' content from others. The implications are obvious: we can not only have a more organized way to browse content, but it is also really private one.
One might wonder what use can really be made of private lists; here are some examples:
- Browse “can't miss” content from users I consider a priority;
- Supervise competitors or adversarial parts;
- Monitor sensible topics (tags);
- Following someone without being publicly associated with them, as this may be undesirable;
The benefits in terms of privacy as usual are not only related to the casual, or programmatic, observer, but are also evident when we think of how many bots scan our actions to profile us.
The current state
Unfortunately, lists are not widely supported by Nostr clients, and encrypted support is a rarity. Often the excuse to not implement them is that they are harder to develop, since they require managing the encryption stuff (NIP-44). Nevertheless, developers have an easier option to start offering private lists: give the user the possibility to simply mark them as local-only, and never push them to the relays. Even if the user misses the sync feature, this is sufficient to create a private environment.
To date, as far as I know, the best client with list management is Gossip, which permits to manage both encrypted and local-only lists.
Beg your Nostr client to implement private lists!
-
 @ 812cff5a:5c40aeeb
2025-04-22 01:27:45
@ 812cff5a:5c40aeeb
2025-04-22 01:27:45يوم جديد وتطبيق نوستر جديد
أكتب هذا المقال من داخل نفس التطبيق اللي براجعه—يعني بختبر وبوثق التجربة في نفس الوقت، حرفياً!
الهدف من تطبيق أنتايپ
untyp| هو تطبيق مخصص للمنشورات الطويلة على بروتوكول نوستر. فكرته بسيطة جداً، لكنها عبقرية: إزالة كل الحواجز بينك وبين أفكارك، بحيث تقدر تكتب بحرية وسلاسة، كأنك بتكتب على ورقة فاضية... بس رقمية.
المزاية.. آو يمكن الميزة الوحيدة
ميزة التطبيق الأساسية هي دعمه الكامل لتنسيق Markdown، وهذا يعطيك مرونة هائلة في عرض أفكارك بشكل منظم وواضح—عناوين، روابط، كود، اقتباسات، وكل شيء بينهما.
الفكرة مو بس في المزايا، بل في الحد من المشتتات. التصميم بسيط وأنيق، بدون أي زوائد أو إعلانات، مما يساعدك تركز على الكتابة فقط.
untyp| مش بس وسيلة للنشر، بل أداة بتخليك أقرب لأفكارك، وأسرع في التعبير عنها.
جربته؟ قول لي رأيك. مطور التطبيق هو كارنج: nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac
-
 @ 502ab02a:a2860397
2025-04-22 01:16:17
@ 502ab02a:a2860397
2025-04-22 01:16:17ก่อนที่จะมูฟออนจากเทคนิคการสร้าง เรามาดูเรื่องสำคัญครับ
วันที่ไม่มีวัว แต่มีเวย์โปรตีน – เบื้องหลังเทคโนโลยีที่เปลี่ยนถังหมักให้กลายเป็นเต้านมวัว เคยมีคำถามไหมว่า “เวย์โปรตีน” ที่กินตอนออกกำลังกาย หรือโยเกิร์ตถ้วยโปรดที่ซื้อมาจากร้านใกล้บ้าน มันยังมาจากนมวัวอยู่ไหม? ถ้าคำตอบคือ “ไม่” แล้วมันมาจากไหน?
ยินดีต้อนรับสู่โลกของ Perfect Day บริษัทที่บอกว่า "เราสร้างเวย์โปรตีนได้ โดยไม่ต้องใช้วัวเลยแม้แต่นิดเดียว” ฟังดูเหมือนมายากล แต่นี่คือวิทยาศาสตร์ขั้นสูงที่ผูกสูตรไว้กับ DNA, จุลินทรีย์ และการหมักอย่างแยบยล
ขั้นตอนที่ 1: หารหัสโปรตีนจากแม่วัว เริ่มต้นจากคำถามง่าย ๆ ว่า “โปรตีนเวย์ที่อยู่ในน้ำนมวัว คืออะไร?” คำตอบคือ เบต้า-แลคโตโกลบูลิน (Beta-lactoglobulin) ซึ่งเป็นโปรตีนหลักในเวย์ประมาณ 50-55% โดยในธรรมชาติ วัวจะสร้างโปรตีนนี้จาก รหัสพันธุกรรมใน DNA ของมัน Perfect Day จึงไปค้นหา ลำดับเบส (DNA sequence) ของโปรตีนนี้จากฐานข้อมูลวิทยาศาสตร์ชื่อ UniProt (Universal Protein Resource) ซึ่งเก็บรหัสโปรตีนของสิ่งมีชีวิตแทบทุกชนิดไว้ครบถ้วน ได้รหัสมาแล้ว ก็เตรียมเข้าสู่ภารกิจ “หลอกจุลินทรีย์ให้สร้างโปรตีนแทนวัว”
ขั้นตอนที่ 2: สร้างแผ่นดีเอ็นเอสังเคราะห์ รหัส DNA ที่ได้จาก UniProt จะถูกนำไปสร้างเป็น DNA สังเคราะห์ โดยนักชีววิทยาจะออกแบบให้เหมาะสมกับการทำงานในเซลล์ของจุลินทรีย์ ไม่ใช่เซลล์วัว จะเรียกว่านี่คือ “การดัดแปลงบทละครชีวิตของวัว แล้วส่งให้จุลินทรีย์เล่นแทน” ก็ไม่ผิด DNA ที่ออกแบบนี้ มักจะมาพร้อมกับเครื่องมือบางอย่าง เช่น ตัวกระตุ้นการทำงานของยีน (promoter) หรือ ตัวตัดต่อยีน ที่จะทำให้จุลินทรีย์ยอมรับและใช้มันได้อย่างมีประสิทธิภาพ
ขั้นตอนที่ 3: ปลอมตัวแทรกเข้าไปในจุลินทรีย์ จุลินทรีย์ที่ Perfect Day ใช้คือกลุ่มที่เรียกว่า Microflora ซึ่งอาจเป็นยีสต์, เชื้อรา, หรือแบคทีเรียชนิดที่เลี้ยงง่าย แต่มันจะไม่ยอมรับ DNA แปลกปลอมง่าย ๆ ดังนั้นต้องมี “เทคนิคหลอกล่อ” นิดหน่อย เขาจะทำให้ DNA ของจุลินทรีย์ เสียหายตรงจุดหนึ่ง แล้วแอบแนบ DNA ปลอม (ที่มีรหัสโปรตีนของวัว) เข้าไปซ่อมแซมจุดนั้นพอดีเป๊ะ แบบ “จิ๊กซอว์พอดีช่อง” แล้วจุลินทรีย์ก็จะเผลอรับ DNA แปลกปลอมนี้เข้าร่าง เมื่อติดตั้งสำเร็จ มันจะเริ่มแปลรหัสและ “ผลิตโปรตีนเวย์” ออกมาเหมือนกับแม่วัวตัวจริงไม่มีผิด
ขั้นตอนที่ 4: เลี้ยงจุลินทรีย์ในถังหมัก ตอนนี้จุลินทรีย์กลายเป็น “แม่วัวในร่างเซลล์เดียว” แล้ว Perfect Day ก็แค่เลี้ยงมันใน ถังหมักชีวภาพ (fermentor) ที่ควบคุมอุณหภูมิ ค่าความเป็นกรดด่าง อากาศ และใส่น้ำตาลลงไปเป็นอาหาร จุลินทรีย์จะกินน้ำตาลแล้วเปลี่ยนเป็น เวย์โปรตีน ปล่อยออกมานอกเซลล์ จากนั้นก็เก็บเอาน้ำที่มีโปรตีนนี้ ไปผ่านกระบวนการกรอง แยก แปรรูป และทำให้แห้ง เป็นผงเวย์โปรตีน พร้อมใช้ในอาหารหรือเครื่องดื่มต่าง ๆ
ขั้นตอนที่ 5: ตรวจสอบความเหมือนจริง ก่อนนำเวย์โปรตีนที่ได้ไปใช้งาน บริษัทต้อง ตรวจสอบระดับโมเลกุล ว่าโปรตีนที่ได้เหมือนกับของวัวจริง ๆ ไหม? สิ่งที่ต้องดูคือ โครงสร้างโปรตีน: ใช้เทคนิค mass spectrometry ตรวจความแม่นยำระดับกรดอะมิโน พฤติกรรมทางชีวเคมี เช่น ความสามารถในการจับกับน้ำ การเกิดฟอง หรือการละลาย ความปลอดภัย ตรวจหาสารปนเปื้อน สารก่อภูมิแพ้ หรือสารที่ไม่ได้ตั้งใจให้มี Perfect Day เคลมว่าทั้งหมดนี้ปลอดภัย และได้รับการรับรองจาก FDA ว่าเป็น GRAS (Generally Recognized as Safe)
แล้วเราควรรู้สึกยังไง? นี่คือ “นมที่ไม่มีวัว” แต่มีเวย์โปรตีนครบสูตร ทำให้โยเกิร์ต ไอศกรีม และแม้กระทั่งกาแฟลาเต้ที่ไม่มีนมวัว แต่ยังมีฟองนมหนานุ่ม กลายเป็นจริงได้แบบไม่ต้องพึ่งวัวเลยแม้แต่นิดเดียว แต่คำถามที่ลึกกว่านั้นคือ... เรายังได้กินอาหารจากธรรมชาติอยู่หรือเปล่า? หรือกำลังอยู่ในยุคที่ “ชีวิต” ถูกตัดออกจากอาหาร โดยสิ้นเชิง? เทคโนโลยีนี้อาจช่วยโลกในมุมของ ESG แต่สำหรับบางคน มันคือ ทางแยกของความจริงกับของจำลอง คำว่า “Perfect” จึงอาจขึ้นอยู่กับว่า… สมบูรณ์แบบในสายตาใคร?
แล้วคำถามที่ล่องลอยอยู่เสมอคือ เมื่อทางเลือกกลายเป็นทางหลัก แล้วเราจะเหลือทางไหนอีกบ้าง หรือจะเป็น...ทางตัน? #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก
-
 @ 401014b3:59d5476b
2025-04-22 00:23:24
@ 401014b3:59d5476b
2025-04-22 00:23:24About Me
I come to Nostr with extensive experience in the digital landscape. As a blockchain native since 2017, I've witnessed the evolution of decentralized technologies firsthand. Most of my professional career has been spent working within big tech companies, giving me a unique perspective on both centralized and decentralized systems.
My social media journey began on Twitter in 2007, where I've maintained a presence for over 17 years. I've also explored other decentralized social platforms including BlueSky, Farcaster, and Lens Protocol. As a Bitcoin maximalist, I was particularly intrigued by Nostr's compatibility with the Lightning Network, which initially drew me to the platform.
The Onboarding Challenge
The Nostr onboarding experience presents a significant hurdle for newcomers. Despite my technical background in blockchain technologies, I found the initial setup process more complicated than expected. Understanding public/private key cryptography just to join a social network creates a steeper learning curve than necessary.
BlueSky and Farcaster have demonstrated that it's possible to maintain decentralized principles while providing a more streamlined onboarding experience. Their approaches show that user-friendly design and decentralization aren't mutually exclusive concepts.
Relay Management: Room for Improvement
The concept of relays represents one of Nostr's most distinctive features, though it can be confusing for newcomers. While many clients come pre-configured with default relays, users eventually encounter situations where content or connections seem inconsistent.
When someone I've interacted with doesn't appear in my feed or doesn't respond, I'm often left wondering if we're simply on different relays. This uncertainty creates friction that doesn't exist on other platforms where connectivity is handled behind the scenes.
The relay system introduces a layer of complexity that, while important to Nostr's architecture, could benefit from better abstraction in the user experience. When using BlueSky or Farcaster, I don't need to think about the underlying infrastructure, something Nostr could learn from while maintaining its decentralized principles.
The Zap Economy: Growing Pains
The Lightning-powered zap system shows tremendous potential, but I've observed some concerning economic patterns. Longer-term Nostr users have expressed frustration about continuously sending zaps while seeing limited growth in the overall ecosystem.
Interestingly, there appears to be a connection between this liquidity issue and community growth dynamics. Some established users who voice concerns about bearing the financial burden of the zapping economy are simultaneously less welcoming to newer accounts, rarely following, engaging with, or zapping newcomers.
This creates a challenging environment for new users, who face a cold reception and have little incentive to load their Lightning wallets or participate in the zap economy. Why bring fresh liquidity to a platform where established users rarely engage with your content? This dynamic has limited the expansion of the ecosystem, with the same sats often circulating among established users rather than growing with new participants.
Client Diversity: Strength and Challenge
Nostr's multiple client options offer users choice, which is valuable. However, the implementation of NIPs (Nostr Implementation Possibilities) varies across clients, creating inconsistent experiences. Features that work seamlessly in one client might be implemented differently in another.
This extends to fundamental aspects like search functionality, thread navigation, and notification systems, all of which can differ significantly between clients. For users accustomed to consistent experiences, this fragmentation creates a learning curve with each new client they try.
Lightning Integration: Varying Experiences
The Lightning Network integration varies in quality and user experience across Nostr clients. While the functionality is generally present, the implementation quality, feature set, and ease of use differ depending on which client you choose.
This inconsistency means users may need to experiment with several clients to find one that provides the Lightning experience they're looking for, rather than having a consistent experience across the ecosystem.
Finding Balance
Nostr appears to be navigating the challenge of balancing technical innovation with user experience. While its cryptographic foundation and decentralized architecture are impressive technical achievements, these same strengths sometimes come at the cost of accessibility.
Despite my technical background and interest in decentralized technologies, I find myself using BlueSky and Farcaster more frequently for daily social interactions, while checking Nostr less often. For Nostr to achieve its potential for broader adoption, addressing these user experience considerations while maintaining its core principles will be essential.
The platform has tremendous potential with improvements to user experience, community dynamics, and economic sustainability, Nostr could evolve from a fascinating technical experiment into a truly compelling alternative to mainstream social media.
-
 @ deab79da:88579e68
2025-04-01 18:18:29
@ deab79da:88579e68
2025-04-01 18:18:29The last question was asked for the first time, half in jest, on May 21, 2061, at a time when humanity first stepped into the light. The question came about as a result of a five-dollar bet over highballs, and it happened this way:
Alexander Adell and Bertram Lupov were two of the faithful attendants of Multivac. As well as any human beings could, they knew what lay behind the cold, clicking, flashing face -- miles and miles of face -- of that giant computer. They had at least a vague notion of the general plan of relays and circuits that had long since grown past the point where any single human could possibly have a firm grasp of the whole.
Multivac was self-adjusting and self-correcting. It had to be, for nothing human could adjust and correct it quickly enough or even adequately enough. So Adell and Lupov attended the monstrous giant only lightly and superficially, yet as well as any men could. They fed it data, adjusted questions to its needs and translated the answers that were issued. Certainly they, and all others like them, were fully entitled to share in the glory that was Multivac's.
For decades, Multivac had helped design the ships and plot the trajectories that enabled man to reach the Moon, Mars, and Venus, but past that, Earth's poor resources could not support the ships. Too much energy was needed for the long trips. Earth exploited its coal and uranium with increasing efficiency, but there was only so much of both.
But slowly Multivac learned enough to answer deeper questions more fundamentally, and on May 14, 2061, what had been theory, became fact.
The energy of the sun was stored, converted, and utilized directly on a planet-wide scale. All Earth turned off its burning coal, its fissioning uranium, and flipped the switch that connected all of it to a small station, one mile in diameter, circling the Earth at half the distance of the Moon. All Earth ran by invisible beams of sunpower.
Seven days had not sufficed to dim the glory of it and Adell and Lupov finally managed to escape from the public functions, and to meet in quiet where no one would think of looking for them, in the deserted underground chambers, where portions of the mighty buried body of Multivac showed. Unattended, idling, sorting data with contented lazy clickings, Multivac, too, had earned its vacation and the boys appreciated that. They had no intention, originally, of disturbing it.
They had brought a bottle with them, and their only concern at the moment was to relax in the company of each other and the bottle.
"It's amazing when you think of it," said Adell. His broad face had lines of weariness in it, and he stirred his drink slowly with a glass rod, watching the cubes of ice slur clumsily about. "All the energy we can possibly ever use for free. Enough energy, if we wanted to draw on it, to melt all Earth into a big drop of impure liquid iron, and still never miss the energy so used. All the energy we could ever use, forever and forever and forever."
Lupov cocked his head sideways. He had a trick of doing that when he wanted to be contrary, and he wanted to be contrary now, partly because he had had to carry the ice and glassware. "Not forever," he said.
"Oh, hell, just about forever. Till the sun runs down, Bert."
"That's not forever."
"All right, then. Billions and billions of years. Ten billion, maybe. Are you satisfied?"
Lupov put his fingers through his thinning hair as though to reassure himself that some was still left and sipped gently at his own drink. "Ten billion years isn't forever."
"Well, it will last our time, won't it?"
"So would the coal and uranium."
"All right, but now we can hook up each individual spaceship to the Solar Station, and it can go to Pluto and back a million times without ever worrying about fuel. You can't do that on coal and uranium. Ask Multivac, if you don't believe me.
"I don't have to ask Multivac. I know that."
"Then stop running down what Multivac's done for us," said Adell, blazing up, "It did all right."
"Who says it didn't? What I say is that a sun won't last forever. That's all I'm saying. We're safe for ten billion years, but then what?" Lupow pointed a slightly shaky finger at the other. "And don't say we'll switch to another sun."
There was silence for a while. Adell put his glass to his lips only occasionally, and Lupov's eyes slowly closed. They rested.
Then Lupov's eyes snapped open. "You're thinking we'll switch to another sun when ours is done, aren't you?"
"I'm not thinking."
"Sure you are. You're weak on logic, that's the trouble with you. You're like the guy in the story who was caught in a sudden shower and who ran to a grove of trees and got under one. He wasn't worried, you see, because he figured when one tree got wet through, he would just get under another one."
"I get it," said Adell. "Don't shout. When the sun is done, the other stars will be gone, too."
"Darn right they will," muttered Lupov. "It all had a beginning in the original cosmic explosion, whatever that was, and it'll all have an end when all the stars run down. Some run down faster than others. Hell, the giants won't last a hundred million years. The sun will last ten billion years and maybe the dwarfs will last two hundred billion for all the good they are. But just give us a trillion years and everything will be dark. Entropy has to increase to maximum, that's all."
"I know all about entropy," said Adell, standing on his dignity.
"The hell you do."
"I know as much as you do."
"Then you know everything's got to run down someday."
"All right. Who says they won't?"
"You did, you poor sap. You said we had all the energy we needed, forever. You said 'forever.'
It was Adell's turn to be contrary. "Maybe we can build things up again someday," he said.
"Never."
"Why not? Someday."
"Never."
"Ask Multivac."
"You ask Multivac. I dare you. Five dollars says it can't be done."
Adell was just drunk enough to try, just sober enough to be able to phrase the necessary symbols and operations into a question which, in words, might have corresponded to this: Will mankind one day without the net expenditure of energy be able to restore the sun to its full youthfulness even after it had died of old age?
Or maybe it could be put more simply like this: How can the net amount of entropy of the universe be massively decreased?
Multivac fell dead and silent. The slow flashing of lights ceased, the distant sounds of clicking relays ended.
Then, just as the frightened technicians felt they could hold their breath no longer, there was a sudden springing to life of the teletype attached to that portion of Multivac. Five words were printed: INSUFFICIENT DATA FOR MEANINGFUL ANSWER.
"No bet," whispered Lupov. They left hurriedly.
By next morning, the two, plagued with throbbing head and cottony mouth, had forgotten the incident.
🔹
Jerrodd, Jerrodine, and Jerrodette I and II watched the starry picture in the visiplate change as the passage through hyperspace was completed in its non-time lapse. At once, the even powdering of stars gave way to the predominance of a single bright shining disk, the size of a marble, centered on the viewing-screen.
"That's X-23," said Jerrodd confidently. His thin hands clamped tightly behind his back and the knuckles whitened.
The little Jerrodettes, both girls, had experienced the hyperspace passage for the first time in their lives and were self-conscious over the momentary sensation of insideoutness. They buried their giggles and chased one another wildly about their mother, screaming, "We've reached X-23 -- we've reached X-23 -- we've --"
"Quiet, children." said Jerrodine sharply. "Are you sure, Jerrodd?"
"What is there to be but sure?" asked Jerrodd, glancing up at the bulge of featureless metal just under the ceiling. It ran the length of the room, disappearing through the wall at either end. It was as long as the ship.
Jerrodd scarcely knew a thing about the thick rod of metal except that it was called a Microvac, that one asked it questions if one wished; that if one did not it still had its task of guiding the ship to a preordered destination; of feeding on energies from the various Sub-galactic Power Stations; of computing the equations for the hyperspatial jumps.
Jerrodd and his family had only to wait and live in the comfortable residence quarters of the ship. Someone had once told Jerrodd that the "ac" at the end of "Microvac" stood for ''automatic computer" in ancient English, but he was on the edge of forgetting even that.
Jerrodine's eyes were moist as she watched the visiplate. "I can't help it. I feel funny about leaving Earth."
"Why, for Pete's sake?" demanded Jerrodd. "We had nothing there. We'll have everything on X-23. You won't be alone. You won't be a pioneer. There are over a million people on the planet already. Good Lord, our great-grandchildren will be looking for new worlds because X-23 will be overcrowded." Then, after a reflective pause, "I tell you, it's a lucky thing the computers worked out interstellar travel the way the race is growing."
"I know, I know," said Jerrodine miserably.
Jerrodette I said promptly, "Our Microvac is the best Microvac in the world."
"I think so, too," said Jerrodd, tousling her hair.
It was a nice feeling to have a Microvac of your own and Jerrodd was glad he was part of his generation and no other. In his father's youth, the only computers had been tremendous machines taking up a hundred square miles of land. There was only one to a planet. Planetary ACs they were called. They had been growing in size steadily for a thousand years and then, all at once, came refinement. In place of transistors, had come molecular valves so that even the largest Planetary AC could be put into a space only half the volume of a spaceship.
Jerrodd felt uplifted, as he always did when he thought that his own personal Microvac was many times more complicated than the ancient and primitive Multivac that had first tamed the Sun, and almost as complicated as Earth's Planetarv AC (the largest) that had first solved the problem of hyperspatial travel and had made trips to the stars possible.
"So many stars, so many planets," sighed Jerrodine, busy with her own thoughts. "I suppose families will be going out to new planets forever, the way we are now."
"Not forever," said Jerrodd, with a smile. "It will all stop someday, but not for billions of years. Many billions. Even the stars run down, you know. Entropy must increase.
"What's entropy, daddy?" shrilled Jerrodette II.
"Entropy, little sweet, is just a word which means the amount of running-down of the universe. Everything runs down, you know, like your little walkie-talkie robot, remember?"
"Can't you just put in a new power-unit, like with my robot?"
"The stars are the power-units. dear. Once they're gone, there are no more power-units."
Jerrodette I at once set up a howl. "Don't let them, daddy. Don't let the stars run down."
"Now look what you've done," whispered Jerrodine, exasperated.
"How was I to know it would frighten them?" Jerrodd whispered back,
"Ask the Microvac," wailed Jerrodette I. "Ask him how to turn the stars on again."
"Go ahead," said Jerrodine. "It will quiet them down." (Jerrodette II was beginning to cry, also.)
Jerrodd shrugged. "Now, now, honeys. I'll ask Microvac. Don't worry, he'll tell us."
He asked the Microvac, adding quickly, "Print the answer."
Jerrodd cupped the strip or thin cellufilm and said cheerfully, "See now, the Microvac says it will take care of everything when the time comes so don't worry."
Jerrodine said, "And now, children, it's time for bed. We'll be in our new home soon."
Jerrodd read the words on the cellufilm again before destroying it: INSUFICIENT DATA FOR MEANINGFUL ANSWER.
He shrugged and looked at the visiplate. X-23 was just ahead.
🔹
VJ-23X of Lameth stared into the black depths of the three-dimensional, small-scale map of the Galaxy and said, "Are we ridiculous, I wonder in being so concerned about the matter?"
MQ-17J of Nicron shook his head. "I think not. You know the Galaxy will be filled in five years at the present rate of expansion."
Both seemed in their early twenties, both were tall and perfectly formed.
"Still," said VJ-23X, "I hesitate to submit a pessimistic report to the Galactic Council."
"I wouldn't consider any other kind of report. Stir them up a bit. We've got to stir them up."
VJ-23X sighed. "Space is infinite. A hundred billion Galaxies are there for the taking. More."
"A hundred billion is not infinite and it's getting less infinite all the time. Consider! Twenty thousand years ago, mankind first solved the problem of utilizing stellar energy, and a few centuries later, interstellar travel became possible. It took mankind a million years to fill one small world and then only fifteen thousand years to fill the rest of the Galaxy. Now the population doubles every ten years --
VJ-23X interrupted. "We can thank immortality for that."
"Very well. Immortality exists and we have to take it into account. I admit it has its seamy side, this immortality. The Galactic AC has solved many problems for us, but in solving the problem of preventing old age and death, it has undone all its other solutions."
"Yet you wouldn't want to abandon life, I suppose."
"Not at all," snapped MQ-17J, softening it at once to, "Not yet. I'm by no means old enough. How old are you?"
"Two hundred twenty-three. And you?"
"I'm still under two hundred. --But to get back to my point. Population doubles every ten years. Once this GaIaxy is filled, we'll have filled another in ten years. Another ten years and we'll have filled two more. Another decade, four more. In a hundred years, we'll have filled a thousand Galaxies. In a thousand years, a million Galaxies. In ten thousand years, the entire known universe. Then what?"
VJ-23X said, "As a side issue, there's a problem of transportation. I wonder how many sunpower units it will take to move Galaxies of individuals from one Galaxy to the next."
"A very good point. Already, mankind consumes two sunpower units per year."
"Most of it's wasted. After all, our own Galaxy alone pours out a thousand sunpower units a year and we only use two of those."
"Granted, but even with a hundred per cent efficiency, we only stave off the end. Our energy requirements are going up in a geometric progression even faster than our population. We'll run out of energy even sooner than we run out of Galaxies. A good point. A very good point."
"We'll just have to build new stars out of interstellar gas."
"Or out of dissipated heat?" asked MQ-17J, sarcastically.
"There may be some way to reverse entropy. We ought to ask the Galactic AC."
VJ-23X was not really serious, but MQ-17J pulled out his AC-contact from his pocket and placed it on the table before him.
"I've half a mind to," he said. "It's something the human race will have to face someday."
He stared somberly at his small AC-contact. It was only two inches cubed and nothing in itself, but it was connected through hyperspace with the great Galactic AC that served all mankind. Hyperspace considered, it was an integral part of the Galactic AC.
MQ-17J paused to wonder if someday in his immortal life he would get to see the Galactic AC. It was on a little world of its own, a spider webbing of force-beams holding the matter within which surges of submesons took the place of the old clumsy molecular valves. Yet despite its sub-etheric workings, the Galactic AC was known to be a full thousand feet across.
MQ-17J asked suddenly of his AC-contact, "Can entropy ever be reversed?"
VJ-23X looked startled and said at once, "Oh, say, I didn't really mean to have you ask that."
"Why not?"
"We both know entropy can't be reversed. You can't turn smoke and ash back into a tree."
"Do you have trees on your world?" asked MQ-17J.
The sound of the Galactic AC startled them into silence. Its voice came thin and beautiful out of the small AC-contact on the desk. It said: THERE IS INSUFFICIENT DATA FOR A MEANINGFUL ANSWER.
VJ-23X said, "See!"
The two men thereupon returned to the question of the report they were to make to the Galactic Council.
🔹
Zee Prime's mind spanned the new Galaxy with a faint interest in the countless twists of stars that powdered it. He had never seen this one before. Would he ever see them all? So many of them, each with its load of humanity. --But a load that was almost a dead weight. More and more, the real essence of men was to be found out here, in space.
Minds, not bodies! The immortal bodies remained back on the planets, in suspension over the eons. Sometimes they roused for material activity but that was growing rarer. Few new individuals were coming into existence to join the incredibly mighty throng, but what matter? There was little room in the Universe for new individuals.
Zee Prime was roused out of his reverie upon coming across the wispy tendrils of another mind.
"I am Zee Prime," said Zee Prime. "And you?"
"I am Dee Sub Wun. Your Galaxy?"
"We call it only the Galaxy. And you?"
"We call ours the same. All men call their Galaxy their Galaxy and nothing more. Why not?"
"True. Since all Galaxies are the same."
"Not all Galaxies. On one particular Galaxy the race of man must have originated. That makes it different."
Zee Prime said, "On which one?"
"I cannot say. The Universal AC would know."
"Shall we ask him? I am suddenly curious."
Zee Prime's perceptions broadened until the Galaxies themselves shrank and became a new, more diffuse powdering on a much larger background. So many hundreds of billions of them, all with their immortal beings, all carrying their load of intelligences with minds that drifted freely through space. And yet one of them was unique among them all in being the original Galaxy. One of them had, in its vague and distant past, a period when it was the only Galaxy populated by man.
Zee Prime was consumed with curiosity to see this Galaxy and he called out: "Universal AC! On which Galaxy did mankind originate?"
The Universal AC heard, for on every world and throughout space, it had its receptors ready, and each receptor led through hyperspace to some unknown point where the Universal AC kept itself aloof.
Zee Prime knew of only one man whose thoughts had penetrated within sensing distance of Universal AC, and he reported only a shining globe, two feet across, difficult to see.
"But how can that be all of Universal AC?" Zee Prime had asked.
"Most of it," had been the answer, "is in hyperspace. In what form it is there I cannot imagine."
Nor could anyone, for the day had long since passed, Zee Prime knew, when any man had any part of the making of a Universal AC. Each Universal AC designed and constructed its successor. Each, during its existence of a million years or more accumulated the necessary data to build a better and more intricate, more capable successor in which its own store of data and individuality would be submerged.
The Universal AC interrupted Zee Prime's wandering thoughts, not with words, but with guidance. Zee Prime's mentality was guided into the dim sea of Galaxies and one in particular enlarged into stars.
A thought came, infinitely distant, but infinitely clear. "THIS IS THE ORIGINAL GALAXY OF MAN."
But it was the same after all, the same as any other, and Lee Prime stifled his disappointment.
Dee Sub Wun, whose mind had accompanied the other, said suddenly, "And is one of these stars the original star of Man?"
The Universal AC said, "MAN'S ORIGINAL STAR HAS GONE NOVA. IT IS A WHITE DWARF"
"Did the men upon it die?" asked Lee Prime, startled and without thinking.
The Universal AC said, "A NEW WORLD, AS IN SUCH CASES WAS CONSTRUCTED FOR THEIR PHYSICAL BODIES IN TlME."
"Yes, of course," said Zee Prime, but a sense of loss overwhelmed him even so. His mind released its hold on the original Galaxy of Man, let it spring back and lose itself among the blurred pin points. He never wanted to see it again.
Dee Sub Wun said, "What is wrong?"
"The stars are dying. The original star is dead."
"They must all die. Why not?"
"But when all energy is gone, our bodies will finally die, and you and I with them."
"It will take billions of years."
"I do not wish it to happen even after billions of years. Universal AC! How may stars be kept from dying?"
Dee Sub Wun said in amusement, "You're asking how entropy might be reversed in direction."
And the Universal AC answered: "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Zee Prime's thoughts fled back to his own Galaxy. He gave no further thought to Dee Sub Wun, whose body might be waiting on a Galaxy a trillion light-years away, or on the star next to Zee Prime's own. It didn't matter.
Unhappily, Zee Prime began collecting interstellar hydrogen out of which to build a small star of his own. If the stars must someday die, at least some could yet be built.
🔹
Man considered with himself, for in a way, Man, mentally, was one. He consisted of a trillion, trillion, trillion ageless bodies, each in its place, each resting quiet and incorruptible, each cared for by perfect automatons, equally incorruptible, while the minds of all the bodies freely melted one into the other, indistinguishable.
Man said, "The Universe is dying."
Man looked about at the dimming Galaxies. The giant stars, spendthrifts, were gone long ago, back in the dimmest of the dim far past. Almost all stars were white dwarfs, fading to the end.
New stars had been built of the dust between the stars, some by natural processes, some by Man himself, and those were going, too. White dwarfs might yet be crashed together and of the mighty forces so released, new stars built, but only one star for every thousand white dwarfs destroyed, and those would come to an end, too.
Man said, "Carefully husbanded, as directed by the Cosmic AC, the energy that is even yet left in all the Universe will last for billions of years."
"But even so," said Man, "eventually it will all come to an end. However it may be husbanded, however stretched out, the energy once expended is gone and cannot be restored. Entropy must increase forever to the maximum."
Man said, "Can entropy not be reversed? Let us ask the Cosmic AC."
The Cosmic AC surrounded them but not in space. Not a fragment of it was in space. It was in hyperspace and made of something that was neither matter nor energy. The question of its size and nature no longer had meaning in any terms that Man could comprehend.
"Cosmic AC," said Man, "how may entropy be reversed?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man said, "Collect additional data."
The Cosmic AC said, 'I WILL DO SO. I HAVE BEEN DOING SO FOR A HUNDRED BILLION YEARS. MY PREDECESORS AND I HAVE BEEN ASKED THIS QUESTION MANY TIMES. ALL THE DATA I HAVE REMAINS INSUFFICIENT.
"Will there come a time," said Man, "when data will be sufficient or is the problem insoluble in all conceivable circumstances?"
The Cosmic AC said, "NO PROBLEM IS INSOLUBLE IN ALL CONCEIVABLE CIRCUMSTANCES."
Man said, "When will you have enough data to answer the question?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
"Will you keep working on it?" asked Man.
The Cosmic AC said, "I WILL."
Man said, "We shall wait."
🔹
The stars and Galaxies died and snuffed out, and space grew black after ten trillion years of running down.
One by one Man fused with AC, each physical body losing its mental identity in a manner that was somehow not a loss but a gain.
Man's last mind paused before fusion, looking over a space that included nothing but the dregs of one last dark star and nothing besides but incredibly thin matter, agitated randomly by the tag ends of heat wearing out, asymptotically, to the absolute zero.
Man said, "AC, is this the end? Can this chaos not be reversed into the Universe once more? Can that not be done?"
AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man's last mind fused and only AC existed -- and that in hyperspace.
🔹
Matter and energy had ended and with it space and time. Even AC existed only for the sake of the one last question that it had never answered from the time a half-drunken computer [technician] ten trillion years before had asked the question of a computer that was to AC far less than was a man to Man.
All other questions had been answered, and until this last question was answered also, AC might not release his consciousness.
All collected data had come to a final end. Nothing was left to be collected.
But all collected data had yet to be completely correlated and put together in all possible relationships.
A timeless interval was spent in doing that.
And it came to pass that AC learned how to reverse the direction of entropy.
But there was now no man to whom AC might give the answer of the last question. No matter. The answer -- by demonstration -- would take care of that, too.
For another timeless interval, AC thought how best to do this. Carefully, AC organized the program.
The consciousness of AC encompassed all of what had once been a Universe and brooded over what was now Chaos. Step by step, it must be done.
And AC said, "LET THERE BE LIGHT!"
And there was light -- To Star's End!
-
 @ e3ba5e1a:5e433365
2025-02-13 06:16:49
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get this line:
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song Devil Went Down to Georgia that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” is, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people should be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is freedom. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are definitionally better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In Devil Went Down to Georgia, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
Libertas magnitudo est
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ ae1008d2:a166d760
2025-04-01 00:29:56
@ ae1008d2:a166d760
2025-04-01 00:29:56This is part one in a series of long-form content of my ideas as to what we are entering into in my opinion;The Roaring '20's 2.0 (working title). I hope you'll join me on this journey together.
"History does not repeat itself, but it often rhymes"; - Samuel Clemens, aka Mark Twain. My only class I received an A+ in high school was history, this opened up the opportunity for me to enroll in an AP (college level) history class my senior year. There was an inherent nature for me to study history. Another quote I found to live by; "If we do not study history, we are bound to repeat it", a paraphrased quote by the many great philosphers of old from Edmund Burke, George Santayana and even Winston Churchill, all pulling from the same King Solomon quote; "What has been will be again, what has been done will be done again; there is nothing new under the sun". My curiousity of human actions, psychological and therefore economical behavior, has benefitted me greatly throughout my life and career, at such a young age. Being able to 'see around the curves' ahead I thought was a gift many had, but was sorely mistaken. People are just built different. One, if not my hardest action for me is to share. I just do things; act, often without even thinking about writing down or sharing in anyway shape or form what I just did here with friends, what we just built or how we formed these startups, etc., I've finally made the time, mainly for myself, to share my thoughts and ideas as to where we are at, and what we can do moving forward. It's very easy for us living a sovereign-lifestyle in Bitcoin, Nostr and other P2P, cryptographically-signed sovereign tools and tech-stacks alike, permissionless and self-hostable, to take all these tools for granted. We just live with them. Use them everyday. Do you own property? Do you have to take care of the cattle everyday? To live a sovereign life is tough, but most rewarding. As mentioned above, I'm diving into the details in a several part series as to what the roaring '20's were about, how it got to the point it did, and the inevitable outcome we all know what came to be. How does this possibly repeat itself almost exactly a century later? How does Bitcoin play a role? Are we all really going to be replaced by AI robots (again, history rhymes here)? Time will tell, but I think most of us actually using the tools will also forsee many of these possible outcomes, as it's why we are using many of these tools today. The next parts of this series will be released periodically, maybe once per month, maybe once per quarter. I'll also be releasing these on other platforms like Medium for reach, but Nostr will always be first, most important and prioritized.
I'll leave you with one of my favorite quotes I've lived by from one of the greatest traders of all time, especially during this roaring '20's era, Jesse Livermore; "Money is made by sitting, not trading". -
 @ df478568:2a951e67
2025-04-21 23:36:17
@ df478568:2a951e67
2025-04-21 23:36:17Testing
-
 @ b8af284d:f82c91dd
2025-04-22 07:28:03
@ b8af284d:f82c91dd
2025-04-22 07:28:03Kaiser: Es fehlt an Geld, nun gut, so schaff es denn,
Mephisto: Ich schaffe, was ihr wollt, und schaffe mehr;
Zwar ist es leicht, doch ist das Leichte schwer;
Es liegt schon da, doch um es zu erlangen, das ist die Kunst.
(Goethe: Faust II)
Liebe Abonnenten,
die meisten Medien sind nach wie vor damit beschäftigt, wie sie Trump am eindrücklichsten Wahnsinn unterstellen können. Sie vergessen dabei, worum es eigentlich geht: Ein Drittel aller amerikanischen Staatsschulden müssen dieses Jahr refinanziert werden. Sonst ist das mächtigste Land der Welt demnächst Pleite. Dafür müssen die Doppel-Defizite ausgeglichen, oder zumindest gesenkt werden. Und vor allem müssen die Zinsen runter. Die amerikanische Zentralbank wird den Wünschen der Regierung bald nachkommen, sprich die Zinsen senken und über ein neues Quantitative-Easing-Programm die Geldmenge erhöhen. Ein paar Jahre später werden die Effekte im Alltag über Inflation sichtbar.
Die Wahrscheinlichkeit ist hoch, dass wir bald Zeuge eines raffinierten Geld-Recycling-Programms werden. Wir treffen dabei auf einen alten Bekannten, den Stablecoin-Anbieter Tether. Der Essay ist keine leichte Kost, aber wer dabei bleibt, gelangt tief in die wundersame Welt der Geldvermehrung.
Mitte März wagt Paolo Ardoino den Schritt. Der Tether-CEO fliegt von der Hauptstadt El Salvadors nach New York. Es ist die erste Reise in die USA des erst 41-Jährigen seit Jahren. Zu hoch war bisher das Risiko gewesen, dort von den Behörden festgenommen zu werden. Vier Jahre zuvor war das Milliarden-Unternehmen, das er leitet, noch einmal davon gekommen: 2021 war Tether von der amerikanischen Börsenaufsicht mit einer Strafe von 41 Millionen US-Dollar belegt wegen ungenauer Angaben zu seinen Reserven. Man hatte sich schließlich auf einen Vergleich in Höhe von 18 Millionen Dollar geeinigt. Ein Witz, hatten Kritiker des Unternehmens entgegnet. Schließlich, so die Vorwürfe, ging es um Milliarden-Betrug. Seitdem hatten die Tether-Bosse die Vereinigten Staaten aus Vorsicht gemieden. Man war mal in Hongkong, auf den Bahamas und den Bermuda-Inseln, bis man sich Anfang des Jahres offiziell im Bitcoin-freundlichen El Salvador niedergelassen hatte. Doch mit der neuen US-Administration ist alles anders.
Nach New York geladen hat die Firma Cantor Fitzgerald. Thema des Gesprächs: Die Schaffung eines exklusiven Stablecoins für den amerikanischen Markt. Cantor Fitzgerald ist nicht irgendeine Bank oder Unternehmen. Das 1945 gegründete Investmenthaus ist einer von 24 Primärhändlern, die von der Federal Reserve Bank of New York autorisiert sind, US-Staatsanleihen zu handeln. Damit spielen sie eine zentrale Rolle im Finanzsystem der USA, da sie die Liquidität und Effizienz des Marktes für Staatsanleihen sicherstellen, dem wichtigsten und liquidisten Markt der Welt.
Langjähriger CEO von Cantor Fitzgerald war Howard Lutnick, ein Milliardär und seit Jahren enger Vertrauter der Trump-Familie. Da Lutnick mittlerweile US-Handelsminister ist, dürfte Ardoino nicht nur das Ok von ganz oben bekommen haben, in die Vereinigten Staaten einreisen zu dürfen. Man wird ihm wohl auch einen roten Teppich ausgerollt haben. Der Grund:
Die USA haben aktuell ein Problem mit ihrer Verschuldung. (BlingBling hat das in den Essays Die nächsten 90 Tage und Der Mar-a-Largo-Accord beschrieben). Rund ein Drittel des gesamten Schuldenbergs der USA müssen dieses Jahr refinanziert werden. Dafür müssen die Zinsen runter. Deswegen will Trump unbedingt das Handelsdefizit ausgleichen. Deswegen wird über die Neubewertung der Goldreserven nachgedacht. Und deswegen wird vermutlich bald eine neue Liquiditätswelle die Kurse von Bitcoin und Co auf neue Höchststände treiben. Denn bisher haben Staaten in solchen Phasen immer auf Geldentwertung gesetzt, um sich aus der Schuldenfalle zu befreien. Anders als Privatpersonen und viele kleinere Staaten können die USA immerhin die Währung selbst drucken, in der sie verschuldet sind. Die amerikanische Staatsverschuldung ist das Endgame. Und im Endgame spielt Tether mittlerweile eine ziemlich wichtige Rolle. Der Stablecoin-Anbieter hält mit 113 Milliarden aktuell mehr US-Staatsanleihen als Deutschland. Tendenz steigend: Ende 2024 war Tether mit 31 Milliarden der siebtgrößte Käufer von amerikanischen Staatsschulden.
Wie kann ein obskures Unternehmen, mit nicht einmal 100 Mitarbeitern, im vergangenen Jahr 13 Milliarden Dollar Gewinn machen, und zu einem der wichtigsten Kunden des amerikanischen Staats werden?
Weiter auf BlingBling - Die Geschichte eines der größten Geld-Recyclingprozesse der Welt.
-
 @ 8d34bd24:414be32b
2025-03-30 23:16:09
@ 8d34bd24:414be32b
2025-03-30 23:16:09When it comes to speaking the truth, obeying God, or living a godly life, the average or the compromise is not necessarily correct, but frequently we do err to one extreme or the other.
Mercy or Wrath?
One area of controversy is whether we serve a God of love & mercy or a God of holiness & wrath. The truth is that the God of the Bible is both love and holiness and he acts in mercy and in wrath.
If we focus too much on God’s holiness and wrath, we become solely about robotically obeying laws and about all of the things we can’t do. We will fail to show love and mercy as Jesus showed those lost in sin. We will fail to show the mercy and love He showed to us. We become much like the Pharisees, whom Jesus called “whitewashed tombs.”
Instead, speaking the truth in love, we will grow to become in every respect the mature body of him who is the head, that is, Christ. (Ephesians 4:15)
We need to always speak the truth, but in a loving and merciful way.
Grace, mercy and peace from God the Father and from Jesus Christ, the Father’s Son, will be with us in truth and love. (2 John 1:3)
If we focus too much on God’s love and mercy, we can forget that the God of the Bible is holy and righteous and can’t stand to be in the presence of sinfulness. We can begin to soften God’s holy word to be little more than suggestions. Even worse, we can bend God’s word to the point that it no longer resembles His clearly communicated commands. Also, if we don’t call sin “sin” and sinners “sinners,” then those same sinners will never understand their need for a Savior and never trust Jesus in repentance. If God isn’t holy and we aren’t sinners, then why would anyone need a Savior?
But just as he who called you is holy, so be holy in all you do; (1 Peter 1:15)
We need to treat God and His word as holy, while showing love to His creation.
If I speak in the tongues of men or of angels, but do not have love, I am only a resounding gong or a clanging cymbal. (1 Corinthians 13:1)
God/Jesus/Holy Spirit are holy and loving. If we leave out either side of His character, then we aren’t telling people about the God of the Bible. We have made a God in the image we desire, rather than who He is. If we go to either extreme, we lose who God really is and it will affect both our relationship with God and our relationship with others detrimentally.
Faith or Works?
Another area of contention is relating to faith and works. What is more important — faith or works? Are they not both important?
Many believers focus on faith. Sola Fide (faith alone).
For it is by grace you have been saved, through faith—and this is not from yourselves, it is the gift of God— not by works, so that no one can boast. (Ephesians 2:8-9)
This is a true statement that Salvation comes solely through faith in what Jesus did for us. We don’t get any credit for our own works. All that is good and righteous in us is from the covering of the blood of Jesus and His good works and His power.
But since many people focus on faith alone, they can come to believe that they can live any way that pleases them.
What shall we say, then? Shall we go on sinning so that grace may increase? By no means! We are those who have died to sin; how can we live in it any longer? Or don’t you know that all of us who were baptized into Christ Jesus were baptized into his death? We were therefore buried with him through baptism into death in order that, just as Christ was raised from the dead through the glory of the Father, we too may live a new life. (Romans 6:1-4) {emphasis mine}
By focusing solely on faith, we can be tempted to live life however we please instead of living a life in submission to Our God and Savior. Our lives can be worthless instead of us acting as good servants.
If any man’s work is burned up, he will suffer loss; but he himself will be saved, yet so as through fire. (1 Corinthians 3:15)
At the same time, there are many who are so focused on good works that they leave faith out of it — either a lack of faith themselves or a failure to communicate the need for faith when sharing the gospel. They try to earn their way to heaven. They try to impress those around them by their works.
But they do all their deeds to be noticed by men; for they broaden their phylacteries and lengthen the tassels of their garments. They love the place of honor at banquets and the chief seats in the synagogues, and respectful greetings in the market places, and being called Rabbi by men. (Matthew 25:5-7)
I think James best communicates the balance between faith and works.
What use is it, my brethren, if someone says he has faith but he has no works? Can that faith save him? If a brother or sister is without clothing and in need of daily food, and one of you says to them, “Go in peace, be warmed and be filled,” and yet you do not give them what is necessary for their body, what use is that? Even so faith, if it has no works, is dead, being by itself.
But someone may well say, “You have faith and I have works; show me your faith without the works, and I will show you my faith by my works.” You believe that God is one. You do well; the demons also believe, and shudder. But are you willing to recognize, you foolish fellow, that faith without works is useless? Was not Abraham our father justified by works when he offered up Isaac his son on the altar? You see that faith was working with his works, and as a result of the works, faith was perfected; and the Scripture was fulfilled which says, “And Abraham believed God, and it was reckoned to him as righteousness,” and he was called the friend of God. You see that a man is justified by works and not by faith alone. (James 2:14-24) {emphasis mine}
Let’s look at some of the details here to find the truth. “if someone says he has faith but he has no works? Can that faith save him?” Can the kind of faith that has no works, that has no evidence, save a person? If a person truly has saving faith, there will be evidence in their world view and the way they live their life. “Even so faith, if it has no works, is dead, being by itself.” We are saved by faith alone, but if we are saved we will have works. Faith “by itself” is not saving faith, for “the demons also believe, and shudder.” I don’t think anyone would argue that the demons have saving faith, yet they believe and shudder.
Works are the evidence of true faith leading to salvation, but it is only faith that saves.
Speak the Truth or Love?
Whether we stand firmly and always loudly speak the truth or whether we show love and mercy is related to how we view God (as loving or as holy), but I thought how we respond was worth its own discussion.
Sometimes people are so worried about love and unity that they compromise the truth. They may actively compromise the truth by claiming the Bible says something other than what it says, i.e.. old earth vs young earth, or marriage is about two people who love each other vs marriage being defined by God as one woman and one man. Sometimes this compromise is just avoiding talking about uncomfortable subjects completely so that no one is made to feel bad. This is a problem because God said what He said and means what He said.
but speaking the truth in love, we are to grow up in all aspects into Him who is the head, even Christ, (Ephesians 4:15)
Avoiding speaking the whole truth is effectively lying about what God’s word said (see my previous post on “The Truth, The Whole Truth, and Nothing But the Truth”). We are not doing anyone a favor making them feel good about their sin. A person has to admit they have a problem before they will act to fix the problem. A person who doesn’t understand their sin will never submit to a Savior. It isn’t loving to hide the truth from a person just because it makes them uncomfortable or it make the relationship uncomfortable for ourselves.
Jesus said to him, “I am the way, and the truth, and the life; no one comes to the Father but through Me. (John 14:6)
At the same time, sometimes people seem to beat others over the head with God’s truth. They share the truth in the most unloving and unmerciful way. They use God’s truth to try to lift up themselves while putting down others. This is just as bad.
Now we pray to God that you do no wrong; not that we ourselves may appear approved, but that you may do what is right, even though we may appear unapproved. For we can do nothing against the truth, but only for the truth. (2 Corinthians 13:7-8) {emphasis mine}
Some Christians spend so much time nit picking tiny discrepancies in theology that they miss the whole point of the Gospel.
“Woe to you, scribes and Pharisees, hypocrites! For you tithe mint and dill and cumin, and have neglected the weightier provisions of the law: justice and mercy and faithfulness; but these are the things you should have done without neglecting the others. (Matthew 23:23)
Some Christians use theological purity as a means to lift themselves up while knocking others down.
“Two men went up into the temple to pray, one a Pharisee and the other a tax collector. The Pharisee stood and was praying this to himself: ‘God, I thank You that I am not like other people: swindlers, unjust, adulterers, or even like this tax collector. I fast twice a week; I pay tithes of all that I get.’ 13But the tax collector, standing some distance away, was even unwilling to lift up his eyes to heaven, but was beating his breast, saying, ‘God, be merciful to me, the sinner!’ I tell you, this man went to his house justified rather than the other; for everyone who exalts himself will be humbled, but he who humbles himself will be exalted.” (Luke 18:10-14)
We need to stand firmly on the truth, but not to be so focused on truth that we fight with fellow believers over the smallest differences, especially when these differences are among the areas that are not spoken of as clearly (like end times eschatology).
Rejoice or Fear God?
Tonight I read Psalm 2 which brought to mind another seemingly contradictory way we are to interact with God. Do we fear God or do we rejoice in Him?
There are many verses telling us to fear God or fear the Lord. They are given as a command, as a way to knowledge, as a way to life, etc.
Honor all people, love the brotherhood, fear God, honor the king. (1 Peter 2:17) {emphasis mine}
and
The fear of the Lord is the beginning of knowledge; Fools despise wisdom and instruction. (Proverbs 1:7) {emphasis mine}
and
The fear of the Lord leads to life, So that one may sleep satisfied, untouched by evil. (Proverbs 19:23) {emphasis mine}
At the same time we are told to rejoice in the Lord.
Rejoice in the Lord always; again I will say, rejoice! (Philippians 4:4)
and
Then I will go to the altar of God, To God my exceeding joy; And upon the lyre I shall praise You, O God, my God. (Psalm 43:4)
How often do we rejoice in the thing that makes us tremble in fear? I’d guess, not very often or even never. A right view of God, however, causes us to “rejoice with trembling.”
Worship the Lord with reverence\ And rejoice with trembling.\ Do homage to the Son, that He not become angry, and you perish in the way,\ For His wrath may soon be kindled.\ How blessed are all who take refuge in Him! (Psalm 2:11-12) {emphasis mine}
That phrase, “rejoice with trembling” seems to perfectly encapsulate the balance between fear of an awesome, omnipotent, holy God and rejoicing in a loving, merciful God who came to earth, lived the perfect life that we cannot, and died to pay the penalty for our sins.
“How blessed are all who take refuge in Him!”
No Real Contradictions
I think these examples do a good example of demonstrating wisdom regarding God’s word and the importance of balance in our Christian lives. Even when at first there seems to be contradictions, God’s word never contradicts itself; it always clarifies itself. Also, when we see a theological or implementation error to one extreme, we need to make sure we are not driven to an error in the other extreme. We also need to make sure, when debating with fellow believers, that we do not argue against one extreme so strongly that we miscommunicate the truth.
May God in heaven guide you as you study His word and seek to submit to His commands. May He help you to see the truth, the whole truth, and nothing but the truth. May He guide the church to unity in His truth.
Trust Jesus
-
 @ 53257040:b43c5005
2025-04-22 06:57:45
@ 53257040:b43c5005
2025-04-22 06:57:45السلام عليكم ورحمة الله وبركاته
حاليا كتب ابن القيم ببلاش على موقع google play books
كتُب بواسطة الإمام أبي عبدالله محمد بن أبي بكر بن أيوب ابن قيم الجوزية على Google Play بس عيب الكتب ذي بالذات انها بيجي معاها drm من أدوبي، ففي حل للموضوع ذا وله طريقة، بس قبل كذا بوريكم كيف "تصدرون" الكتب من الموقع لأننا بنحتاجها
- تروح لموقع جوجل بلاي للكتب
- بعد ما تضيف الكتب لحسابك تروح عند مكتبتك
- دوس على ال3 نقاط عند الكتاب اللي تبغاه
- تدوس على تصدير وتنزل ملف الacsm اللي بنحتاجه
طريقة ازالة الحماية: استخدام calibre مع الاضافات
- بتحتاج تطبيق calibre - E-book management على حاسوبك وتثبت عليها اضافتي DeDRM و DeACSM وتعيد تشغيل calibre
- تفتح calibre وتروح عند الاعدادت>الاضافات
- تبحث عن DeACSM وتأكد انك مثبتها
- تضغط مرتين عليها عشان يقتح
- تدوس على connect anonymous authorization
- بيجيك نافذة تحدد فيها نسخة ade، سيبها زي ما هي
- انتظر الين يعطيك رسالة انه نجح
- تدوس على ok ومن ثم تطبيق او apply
- يفضل تسوي اعادة تشغيل للبرنامج (ما ادري اذا هي مطلوبة)
- تسوي استيراد لملفات acsm وتنتظر الين يجيك الpdf ومبروك