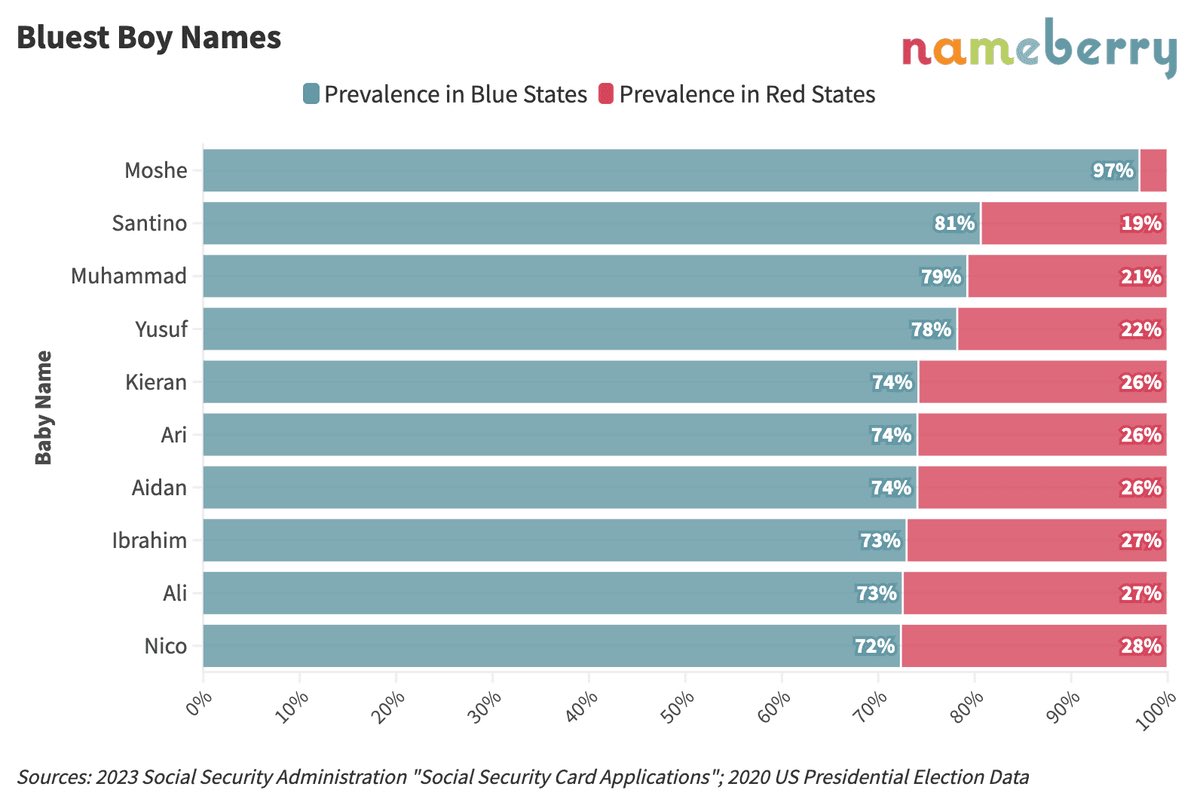
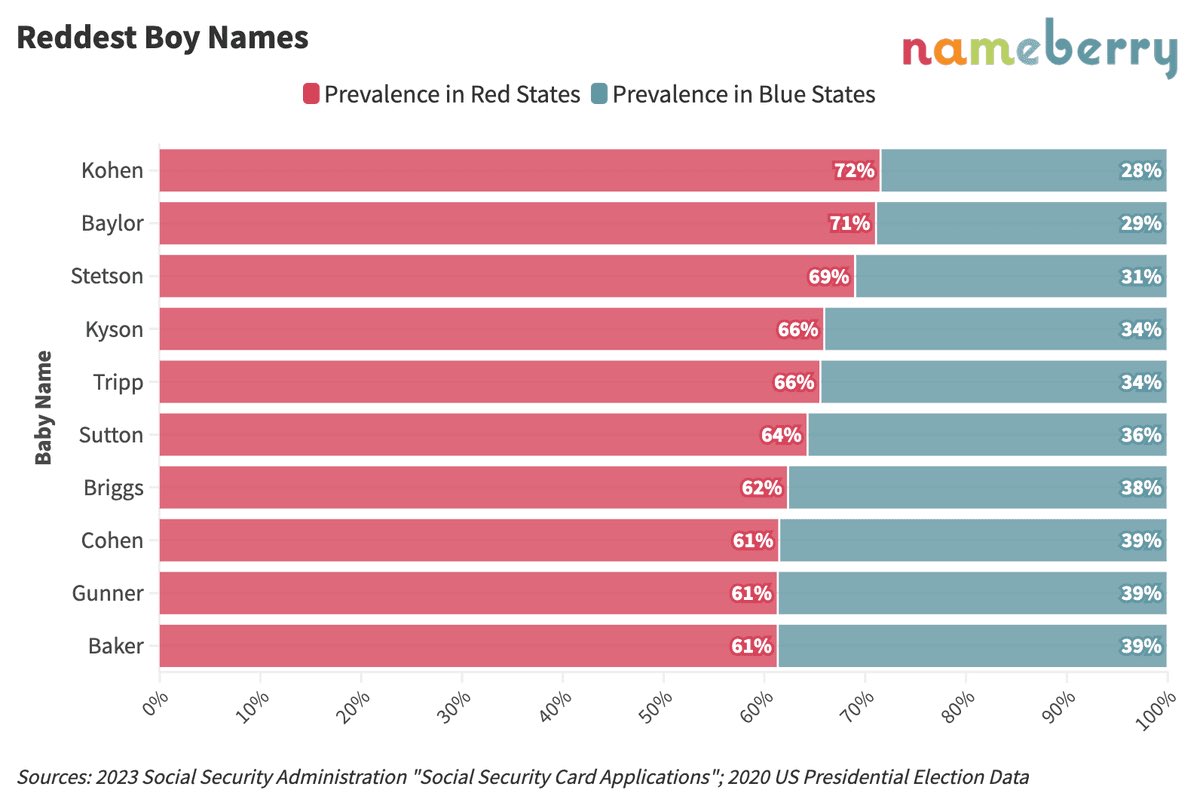
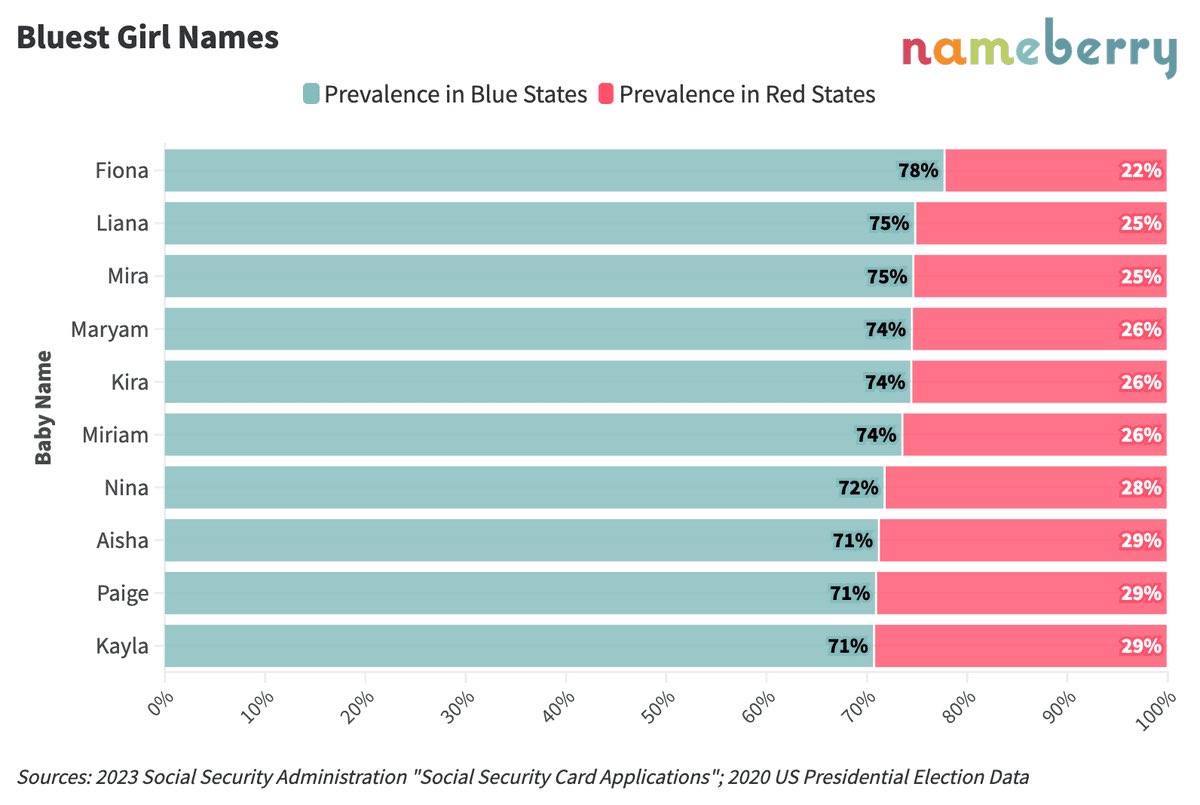
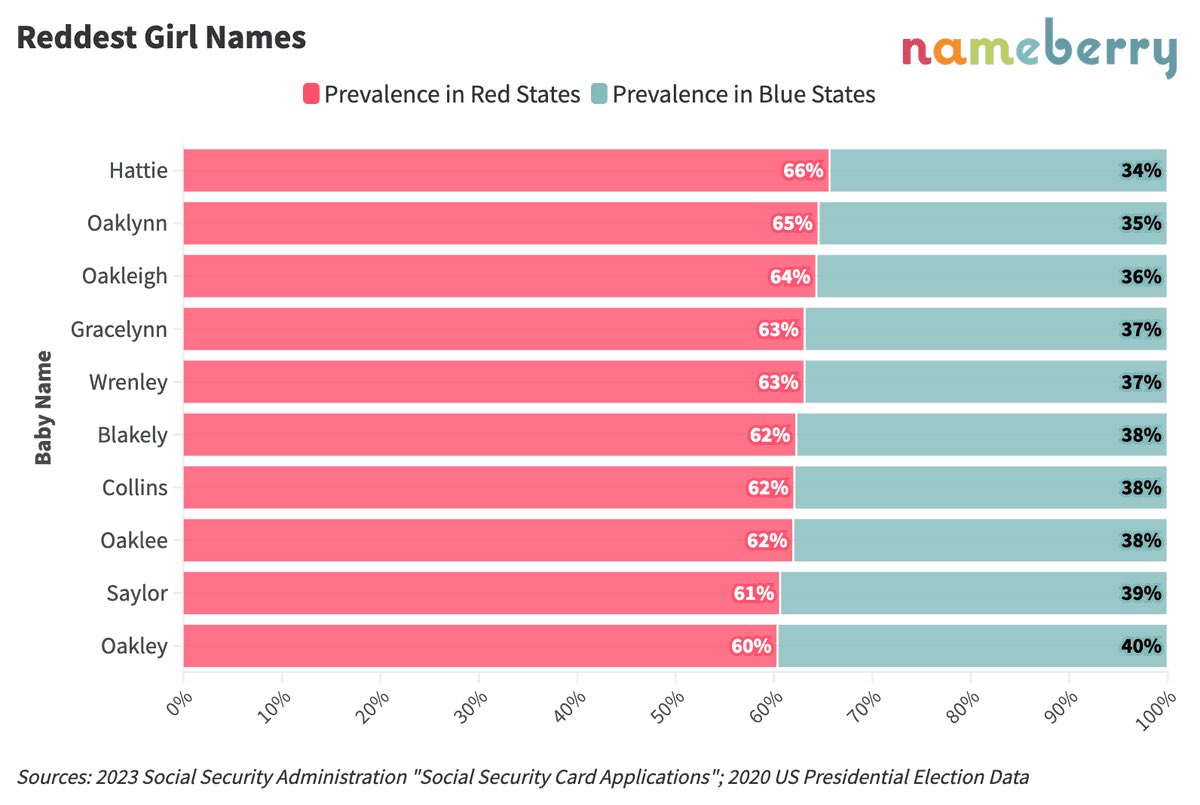
-
 @ 66675158:1b644430
2025-03-23 11:39:41
@ 66675158:1b644430
2025-03-23 11:39:41I don't believe in "vibe coding" – it's just the newest Silicon Valley fad trying to give meaning to their latest favorite technology, LLMs. We've seen this pattern before with blockchain, when suddenly Non Fungible Tokens appeared, followed by Web3 startups promising to revolutionize everything from social media to supply chains. VCs couldn't throw money fast enough at anything with "decentralized" (in name only) in the pitch deck. Andreessen Horowitz launched billion-dollar crypto funds, while Y Combinator batches filled with blockchain startups promising to be "Uber for X, but on the blockchain."
The metaverse mania followed, with Meta betting its future on digital worlds where we'd supposedly hang out as legless avatars. Decentralized (in name only) autonomous organizations emerged as the next big thing – supposedly democratic internet communities that ended up being the next scam for quick money.
Then came the inevitable collapse. The FTX implosion in late 2022 revealed fraud, Luna/Terra's death spiral wiped out billions (including my ten thousand dollars), while Celsius and BlockFi froze customer assets before bankruptcy.
By 2023, crypto winter had fully set in. The SEC started aggressive enforcement actions, while users realized that blockchain technology had delivered almost no practical value despite a decade of promises.
Blockchain's promises tapped into fundamental human desires – decentralization resonated with a generation disillusioned by traditional institutions. Evangelists presented a utopian vision of freedom from centralized control. Perhaps most significantly, crypto offered a sense of meaning in an increasingly abstract world, making the clear signs of scams harder to notice.
The technology itself had failed to solve any real-world problems at scale. By 2024, the once-mighty crypto ecosystem had become a cautionary tale. Venture firms quietly scrubbed blockchain references from their websites while founders pivoted to AI and large language models.
Most reading this are likely fellow bitcoiners and nostr users who understand that Bitcoin is blockchain's only valid use case. But I shared that painful history because I believe the AI-hype cycle will follow the same trajectory.
Just like with blockchain, we're now seeing VCs who once couldn't stop talking about "Web3" falling over themselves to fund anything with "AI" in the pitch deck. The buzzwords have simply changed from "decentralized" to "intelligent."
"Vibe coding" is the perfect example – a trendy name for what is essentially just fuzzy instructions to LLMs. Developers who've spent years honing programming skills are now supposed to believe that "vibing" with an AI is somehow a legitimate methodology.
This might be controversial to some, but obvious to others:
Formal, context-free grammar will always remain essential for building precise systems, regardless of how advanced natural language technology becomes
The mathematical precision of programming languages provides a foundation that human language's ambiguity can never replace. Programming requires precision – languages, compilers, and processors operate on explicit instructions, not vibes. What "vibe coding" advocates miss is that beneath every AI-generated snippet lies the same deterministic rules that have always governed computation.
LLMs don't understand code in any meaningful sense—they've just ingested enormous datasets of human-written code and can predict patterns. When they "work," it's because they've seen similar patterns before, not because they comprehend the underlying logic.
This creates a dangerous dependency. Junior developers "vibing" with LLMs might get working code without understanding the fundamental principles. When something breaks in production, they'll lack the knowledge to fix it.
Even experienced developers can find themselves in treacherous territory when relying too heavily on LLM-generated code. What starts as a productivity boost can transform into a dependency crutch.
The real danger isn't just technical limitations, but the false confidence it instills. Developers begin to believe they understand systems they've merely instructed an AI to generate – fundamentally different from understanding code you've written yourself.
We're already seeing the warning signs: projects cobbled together with LLM-generated code that work initially but become maintenance nightmares when requirements change or edge cases emerge.
The venture capital money is flowing exactly as it did with blockchain. Anthropic raised billions, OpenAI is valued astronomically despite minimal revenue, and countless others are competing to build ever-larger models with vague promises. Every startup now claims to be "AI-powered" regardless of whether it makes sense.
Don't get me wrong—there's genuine innovation happening in AI research. But "vibe coding" isn't it. It's a marketing term designed to make fuzzy prompting sound revolutionary.
Cursor perfectly embodies this AI hype cycle. It's an AI-enhanced code editor built on VS Code that promises to revolutionize programming by letting you "chat with your codebase." Just like blockchain startups promised to "revolutionize" industries, Cursor promises to transform development by adding LLM capabilities.
Yes, Cursor can be genuinely helpful. It can explain unfamiliar code, suggest completions, and help debug simple issues. After trying it for just an hour, I found the autocomplete to be MAGICAL for simple refactoring and basic functionality.
But the marketing goes far beyond reality. The suggestion that you can simply describe what you want and get production-ready code is dangerously misleading. What you get are approximations with:
- Security vulnerabilities the model doesn't understand
- Edge cases it hasn't considered
- Performance implications it can't reason about
- Dependency conflicts it has no way to foresee
The most concerning aspect is how such tools are marketed to beginners as shortcuts around learning fundamentals. "Why spend years learning to code when you can just tell AI what you want?" This is reminiscent of how crypto was sold as a get-rich-quick scheme requiring no actual understanding.
When you "vibe code" with an AI, you're not eliminating complexity—you're outsourcing understanding to a black box. This creates developers who can prompt but not program, who can generate but not comprehend.
The real utility of LLMs in development is in augmenting existing workflows:
- Explaining unfamiliar codebases
- Generating boilerplate for well-understood patterns
- Suggesting implementations that a developer evaluates critically
- Assisting with documentation and testing
These uses involve the model as a subordinate assistant to a knowledgeable developer, not as a replacement for expertise. This is where the technology adds value—as a sophisticated tool in skilled hands.
Cursor is just a better hammer, not a replacement for understanding what you're building. The actual value emerges when used by developers who understand what happens beneath the abstractions. They can recognize when AI suggestions make sense and when they don't because they have the fundamental knowledge to evaluate output critically.
This is precisely where the "vibe coding" narrative falls apart.
-
 @ b7cf9f42:ecb93e78
2025-03-26 10:57:33
@ b7cf9f42:ecb93e78
2025-03-26 10:57:33Der Verstand im Fluss der Information
Das Informationszeitalter ist wie ein monströser Fluss, der unseren Verstand umgibt
Fundament erbauen
Der Verstand kann sich eine Insel in diesem Fluss bauen. Dabei können wir eine eigene Insel erbauen oder eine bestehende insel anvisieren um stabilität zu finden
Je robuster das Baumaterial, desto standhafter unsere Insel. (Stärke der Argumente, Qualität des Informationsgehalts, Verständlichkeit der Information)
Je grossflächiger die Insel, desto mehr Menschen haben Platz (Reichweite).
Je höher wir die Insel bauen, desto sicherer ist sie bei einem Anstieg des Informationsflusses (Diversität der Interesse und Kompetenzen der Inselbewohner).
Robustes Baumaterial
Primäre Wahrnehmung (robuster):
Realität -> meine Sinne -> meine Meinung/Interpretation
Sekundäre Wahrnehmung (weniger Robust):
Realität -> Sinne eines anderen -> dessen Meinung/Interpretation -> dessen Kommunikation -> meine Sinne -> meine Meinung/Interpretation
Wie kann ich zur Insel beitragen?
Ich investiere meine Zeit, um zu lernen. Ich bin bestrebt, Ideen zu verstehen, um sicherzugehen, dass ich robustes Baumaterial verwende.
Ich teile vermehrt Informationen, welche ich verstehe, damit auch meine Mitbewohner der Insel mit robustem Material die Insel vergrössern können. So können wir mehr Platz schaffen, wo Treibende Halt finden können.
Was könnte diese Insel sein?
- Freie Wissenschaft
- Freie Software
- Regeln
- Funktionierende Justiz
- Werkzeug
- und vieles weiteres
-
 @ 7d33ba57:1b82db35
2025-03-26 09:22:57
@ 7d33ba57:1b82db35
2025-03-26 09:22:57Córdoba is a treasure trove of Moorish architecture, Roman heritage, and Andalusian charm. Once the capital of the Umayyad Caliphate, it’s home to stunning patios, atmospheric streets, and UNESCO-listed landmarks.
🏛️ Top Things to See & Do in Córdoba
1️⃣ La Mezquita-Catedral 🕌⛪
- Córdoba’s most iconic landmark, a UNESCO World Heritage Site.
- A breathtaking blend of Islamic arches and a Christian cathedral.
- Don’t miss the orange tree courtyard and bell tower views.
2️⃣ Alcázar de los Reyes Cristianos 🏰
- A medieval fortress with stunning gardens and Mudejar courtyards.
- Walk through Roman mosaics, ancient baths, and watchtowers.
3️⃣ Puente Romano & Calahorra Tower 🌉
- A historic Roman bridge over the Guadalquivir River.
- Great for sunset views with the Mezquita in the background.
- Visit the Calahorra Tower Museum for a look at Córdoba’s Islamic past.
4️⃣ Judería (Jewish Quarter) & Calleja de las Flores 🌺
- Wander through narrow, whitewashed streets lined with flowers.
- Visit the Córdoba Synagogue, one of Spain’s last remaining medieval synagogues.
- Stop by Calleja de las Flores, one of the most photogenic streets in Spain.
5️⃣ Palacio de Viana 🏡
- A 16th-century palace with 12 stunning courtyards filled with flowers.
- A must-visit during Córdoba’s Patio Festival (May).
6️⃣ Medina Azahara 🏛️
- The ruins of a 10th-century Moorish palace-city, 8 km from Córdoba.
- One of the greatest archaeological sites from Al-Andalus.
7️⃣ Plaza de la Corredera & Local Tapas 🍷
- A lively square with colorful buildings and traditional bars.
- Try local specialties like salmorejo (cold tomato soup) and flamenquín (breaded ham & cheese roll).
🍽️ What to Eat in Córdoba
- Salmorejo – A thick cold tomato soup, topped with ham and egg 🍅
- Flamenquín – A deep-fried pork roll stuffed with ham & cheese 🥩🧀
- Rabo de toro – Slow-cooked oxtail stew, a classic dish 🥘
- Berenjenas con miel – Fried eggplant drizzled with honey 🍆🍯
- Montilla-Moriles wine – A local sherry-like wine 🍷
🚗 How to Get to Córdoba
🚆 By Train: High-speed AVE trains from Madrid (1 hr 45 min), Seville (45 min), Málaga (1 hr)
🚘 By Car: 1.5 hrs from Seville, 2 hrs from Granada, 1 hr 40 min from Málaga
🚌 By Bus: Regular connections from major Andalusian cities
✈️ By Air: Closest airports are Seville (SVQ) or Málaga (AGP)💡 Tips for Visiting Córdoba
✅ Best time to visit? Spring (April–May) for mild weather & flower-filled patios 🌸
✅ Visit early morning or late afternoon to avoid the midday heat ☀️
✅ Book Mezquita tickets in advance to skip long queues 🎟️
✅ Try the local patios – Many houses open their courtyards for visitors 🏡 -
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ 57d1a264:69f1fee1
2025-03-26 08:45:13
@ 57d1a264:69f1fee1
2025-03-26 08:45:13I was curious to see how Stacker.News domain and website contents scored from a SEO (Search Engine Optimization) perspective. Here what Semrush nows about SN. But first have alook at the Page Performance Score on Google (Detailled report available here). Performance and Accessibility looks have really low score!
| Desktop | Mobile | |---|---| |
|
| |
|
|
Now let's see what Semrush knows.
Analytics
General view on your metrics and performance trend compared to last 30 days.
See estimations of stacker.news's desktop and mobile traffic based on Semrush’s proprietary AI and machine learning algorithms, petabytes of clickstream data, and Big Data technologies.
Distribution of SN's organic traffic and keywords by country. The Organic Traffic graph shows changes in the amount of estimated organic and paid traffic driven to the SN analyzed domain over time.
| Organic Search | Backlinks Analytics | |---|---| |
|
|
| Position Changes Trend | Top Page Changes | |---|---| |
|
| |This trend allows you to monitor organic traffic changes, as well as improved and declined positions.| Top pages with the biggest traffic changes over the last 28 days. |
Competitors
The Competitive Positioning Map shows the strengths and weaknesses of SN competitive domains' presence in organic search results. Data visualizations are based on the domain's organic traffic and the number of keywords that they are ranking for in Google's top 20 organic search results. The larger the circle, the more visibility a domain has. Below, a list of domains an analyzed domain is competing against in Google's top 20 organic search results.
Referring Domains
Daily Stats
| Organic Traffic | Organic Keywords | Backlinks | |---|---|---| | 976 | 15.9K | 126K | |
-41.87%|-16.4%|-1.62%|📝 Traffic Drop
Traffic downturn detected! It appears SN domain experienced a traffic drop of 633 in the last 28 days. Take a closer look at these pages with significant traffic decline and explore areas for potential improvement. Here are the pages taking the biggest hits:
- https://stacker.news/items/723989 ⬇️ -15
- https://stacker.news/items/919813 ⬇️ -12
- https://stacker.news/items/783355 ⬇️ -5
📉 Decreased Authority Score
Uh-oh! Your Authority score has dropped from 26 to 25. Don't worry, we're here to assist you. Check out the new/lost backlinks in the Backlink Analytics tool to uncover insights on how to boost your authority.
🌟 New Keywords
Opportunity Alert! Targeting these keywords could help you increase organic traffic quickly and efficiently. We've found some low-hanging fruits for you! Take a look at these keywords: - nitter.moomoo.me — Volume 70 - 0xchat — Volume 30 - amethyst nostr — Volume 30
🛠️ Broken Pages
This could hurt the user experience and lead to a loss in organic traffic. Time to take action: amend those pages or set up redirects. Here below, few pages on SN domain that are either broken or not crawlable: - https://stacker.news/404 — 38 backlinks - https://stacker.news/api/capture/items/91154 — 24 backlinks - https://stacker.news/api/capture/items/91289 — 24 backlinks
Dees this post give you some insights? Hope so, comment below if you have any SEO suggestion? Mine is to improve or keep an eye on Accessibility!
One of the major issues I found is that SN does not have a
robots.txt, a key simple text file that allow crawlers to read or not-read the website for indexing purposes. @k00b and @ek is that voluntary?Here are other basic info to improve the SEO score and for those of us that want to learn more:
- Intro to Accessibility: https://www.w3.org/WAI/fundamentals/accessibility-intro/
- Design for Accessibility: https://www.w3.org/WAI/tips/designing/
- Web Accessibility Best Practices: https://www.freecodecamp.org/news/web-accessibility-best-practices/
originally posted at https://stacker.news/items/925433
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ b04082ac:29b5c55b
2025-03-26 07:07:11
@ b04082ac:29b5c55b
2025-03-26 07:07:11In the bustling markets of Kumasi, the 19th-century capital of the Asante Empire in modern-day Ghana, traders conducted their commerce not with coins or paper notes, but with gold dust measured by intricately crafted brass spoons. This monetary system, devoid of a central bank or state-issued fiat, sustained a sophisticated civilization for over two centuries, challenging the conventional narrative that money requires a sovereign issuer to function. The Asante’s gold dust economy provides a historical lens through which to view the principles of sound money—principles that Bitcoin, with its fixed supply and decentralized architecture, resurrects in the digital realm. For those who recognize Bitcoin’s potential as a transformative monetary system, the Asante’s gold dust spoons serve as a compelling precedent: a medium of exchange rooted in scarcity and trust can underpin a thriving society, independent of centralized authority.
Map from 1896 of the British Gold Coast Colony (today Ghana).
The Asante Empire, spanning from 1701 to 1901, relied on sika futuro—gold dust painstakingly extracted from rivers and forests—as its primary currency. Measured with spoons and brass weights known as abrammo, this system was remarkably decentralized. Each trader carried their own set of tools, often adorned with proverbs or symbolic designs, enabling them to verify transactions without reliance on a centralized mint or overseer. By 1900, the Asante had amassed 14 million ounces of gold, a volume that rivaled the economic output of many European nations during the same period. This wealth fueled extensive trade networks across West Africa, connecting the empire to merchants from the coast to the interior, and supported cultural artifacts like the Golden Stool, a revered symbol of collective sovereignty forged from gold. The value of gold dust stemmed not from a royal proclamation but from its inherent scarcity and the labor required to obtain it—qualities that economists identify as the bedrock of sound money. Bitcoin reflects this paradigm: its cap of 21 million coins, enforced through cryptographic consensus rather than governmental fiat, establishes a monetary discipline immune to arbitrary expansion. The Asante’s experience underscores a fundamental economic insight: money derives its efficacy not from state endorsement, but from its ability to resist manipulation and retain value over time.
 Men in the process of weighing gold dust, photographed on the Ivory Coast in 1892. From Marcel Monnier’s France Noire Cote d’Ivoire et Soudan, 1894.
Men in the process of weighing gold dust, photographed on the Ivory Coast in 1892. From Marcel Monnier’s France Noire Cote d’Ivoire et Soudan, 1894.Economic history teaches that sound money lowers time preference, encouraging saving and long-term planning over immediate consumption. The Asante’s gold dust, hard-won from the earth, could not be inflated at will; its supply expanded only incrementally, dictated by the limits of human effort and natural deposits. This constraint fostered a culture of accumulation, where wealth was preserved across generations, evident in the empire’s ability to finance infrastructure, such as roads linking trade hubs, and maintain a formidable military presence that deterred regional rivals. Historical records, such as those from anthropologist R.S. Rattray, describe how gold dust was hoarded in family coffers, passed down as a stable store of value. Bitcoin embodies this same dynamic. Its fixed issuance schedule—halving roughly every four years—mimics the gradual accretion of gold dust, encouraging holders to prioritize long-term retention over short-term expenditure. In contrast, fiat currencies, subject to unrestrained printing, elevate time preference, as seen in modern economies where central banks flood markets with liquidity, eroding purchasing power and compelling consumption over saving—a fate the Asante’s gold dust and Bitcoin’s design inherently avoid.
An array of gold dust spoons from the Asante Empire, each adorned with detailed engravings and symbolic motifs, reflecting their role in trade and cultural heritage.
The tools of the Asante economy further illustrate this monetary discipline. The spoons, ranging from 1/16-ounce measures for daily purchases to 2-ounce weights for significant transactions, were not mere utensils but instruments of precision and trust. Crafted with care—some bearing motifs of birds or proverbs like “The bird flies high”—they standardized trade across a diverse empire, reducing disputes over quantity or purity. Each trader’s possession of their own abrammo weights created a network of verification, a decentralized mechanism that prefigures Bitcoin’s blockchain. In Bitcoin’s system, nodes—computers running the protocol—validate every transaction, ensuring integrity without a central arbiter. This parallel is not superficial: both the Asante’s spoons and Bitcoin’s nodes represent a distributed order, where trust emerges from the system’s structure rather than a single authority. The Asante’s trade practices, documented by historians like Timothy Garrard, reveal a sophistication that belies their pre-industrial context—merchants negotiated with precision, their gold dust facilitating commerce from salt to textiles, much as Bitcoin enables peer-to-peer exchange across continents.
A collection of intricately crafted gold dust spoons from the Asante Empire, showcasing the artistry and cultural significance of gold in Akan trade and tradition.
Trust was the cornerstone of the Asante system, a quality that transcends its physical medium. Gold dust bore intrinsic worth, its weight a palpable assurance of value, a property recognized by European traders as early as the 15th century, well before the Asante state coalesced in 1701. This trust was not legislated but cultivated over centuries, a cultural conviction in the reliability of a scarce resource. Bitcoin’s trust arises from a different foundation: vast computational effort expended in mining secures its network, while a cryptographic framework ensures its integrity against tampering. Neither system depends on a sovereign guarantor; both derive legitimacy from attributes embedded in their design—scarcity and verifiability for gold dust, computational proof and immutability for Bitcoin. The Asante’s economy succumbed to colonial intervention in 1896, when British forces outlawed gold dust in favor of imperial currency, yet its principles endured in illicit trade, hinting at a resilience that Bitcoin amplifies. Bitcoin’s global network, operating beyond the reach of any single jurisdiction, withstands regulatory assaults—miners relocate, nodes persist—offering a durability the Asante could only aspire to in their regional confines.
One modern theory, Modern Monetary Theory (MMT), posits that money gains legitimacy solely through state declaration, underpinned by taxation and legal tender laws. The Asante’s experience contradicts this. Gold dust circulated among the Akan peoples long before the empire’s formation, its adoption predating any centralized authority; Asante kings taxed it but did not invent it. MMT’s insistence on government fiat as the source of monetary value overlooks the spontaneous emergence of money from human exchange—a process the Asante and Bitcoin demonstrate with clarity.
A detailed gold dust spoon from the Asante Empire, featuring symbolic engravings and a prominent animal motif, highlighting the cultural and spiritual significance of its design
Yet, the parallel between the Asante’s gold dust economy and Bitcoin might appear strained. Critics could argue that the Asante operated in a pre-industrial, regional context, their gold dust suited to a localized barter system, while Bitcoin contends with a global, digital economy of unprecedented complexity. The physicality of gold dust, they might contend, differs fundamentally from Bitcoin’s intangible code, and the Asante’s eventual subjugation by colonial fiat suggests state power ultimately prevails. This critique, however, misjudges the essence of the comparison. The Asante’s system thrived not because of its scale or medium, but because it embodied sound money—scarcity ensured its value, decentralization preserved its integrity. Bitcoin extends these principles, its fixed supply and distributed ledger transcending physical limits to achieve global reach. The Asante’s fall to colonial force reflects not a flaw in their money, but a lack of technological resilience—Bitcoin’s network, spanning continents and fortified by cryptography, shrugs off such threats, proving the concept’s adaptability rather than its weakness.
A single gold dust spoon from the Asante Empire, featuring geometric patterns and intricate engravings, a testament to the Akan's skilled metalwork and economic traditions.
The Asante’s gold dust economy persisted for two centuries, a testament to monetary sovereignty until colonial powers dismantled it. Its legacy lies in its demonstration that a decentralized, scarce medium can drive economic vitality—a lesson Bitcoin inherits and expands. By 2025, Bitcoin’s market value exceeds a trillion dollars, a quiet rebellion against central banks that echoes the Asante’s independence from state-issued money. The spoons—each a tool of meticulous trade—foreshadow Bitcoin’s blockchain, a ledger of unalterable trust. Their story reaffirms an enduring economic principle: money’s strength lies in its resistance to debasement, not in the power of its issuer. The Asante built an empire on this foundation, leveraging gold dust to forge a society of wealth and stability. Bitcoin, unbound by geography or politics, extends this logic into an era of unprecedented connectivity. If the Asante achieved such heights with a regional system, what might Bitcoin accomplish as a global one? The answer lies not in speculation, but in the hands of those who understand and wield its potential.
-
 @ 866e0139:6a9334e5
2025-03-26 06:56:05
@ 866e0139:6a9334e5
2025-03-26 06:56:05Autor: Dr. Ulrike Guérot. (Foto: Manuela Haltiner). Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Ich bin 60 Jahre. Einer meiner Großväter, Wilhelm Hammelstein, liegt auf dem Soldatenfriedhof in Riga begraben. Der andere, mütterlicherseits, Paul Janus, kam ohne Beine aus dem Krieg zurück, auch aus Russland. Ich kenne ihn nur mit Prothesen und Krücken. Er hat immer bei Wetterwechsel über Phantomschmerz geklagt und ist seines Lebens nicht mehr froh geworden. Den Krieg hat man ihm im Gesicht angesehen, auch wenn ich das als kleines Mädchen nicht verstanden habe.
"Ihr könnt euch nicht vorstellen, was ich gesehen habe"
Von den Russen hat er trotzdem nie schlecht geredet. Was er immer nur zu uns Enkelkindern gesagt war: *„Ihr könnt euch nicht vorstellen, was ich gesehen habe“. * Wir haben es nicht verstanden, als 6- oder 8-Jährige, und haben gelacht. Manchmal haben wir ihm seine Krücken weggenommen, die immer an den Ohrensessel gelehnt waren, dann konnte Opa Paul nicht aufstehen und ist wütend geworden.

Meine Mutter, Helga Hammelstein, ist im Mai 1939 gleichsam in den Krieg hineingeboren worden, in Schlesien. 1945 gab es für sie, wie für viele, Flucht und Vertreibung. Ob sie und ihre zwei Schwestern von den Russen vergewaltigt wurden – wie damals so viele – kann ich nicht sagen. Diese Themen waren bei uns tabuisiert. Was ich sagen kann, ist, dass meine Mutter als Flüchtlings- und Kriegskind vom Krieg hochgradig traumatisiert war – und als Kriegsenkelin war oder bin ich es wohl auch noch. Eigentlich merke ich das erst heute so richtig, wo wieder Krieg auf dem europäischen Kontinent ist und Europa auch in den Krieg ziehen, wo es kriegstüchtig gemacht werden soll.
Vielleicht habe ich mich aufgrund dieser Familiengeschichte immer so für Europa, für die europäische Integration interessiert, für die EU, die einmal als Friedensprojekt geplant war. Ich habe Zeit meines Lebens, seit nunmehr 30 Jahren, in verschiedenen Positionen, als Referentin im Deutschen Bundestag, in Think Tanks oder an Universitäten akademisch, intellektuell, publizistisch und künstlerisch zum Thema Europa gearbeitet.
1989 habe ich einen Franzosen geheiratet, ich hatte mich beim Studium in Paris verliebt und in den 1990-Jahren in Paris zwei Söhne bekommen. Auch in der französischen Familie gab es bittere Kriegserfahrungen: der Mann der Oma meines damaligen Mannes war 6 Jahre in deutscher Kriegsgefangenschaft. „Pourquoi tu dois marier une Allemande?“ „Warum musst du eine Deutsche heiraten?“, wurde mein damaliger Mann noch gefragt. Das Misstrauen mir gegenüber wurde erst ausgeräumt, als wir ihr 1991 den kleinen Felix, unseren erstgeborenen Sohn, in den Schoß gelegt haben.
Das europäische Friedensprojekt ist gescheitert
Das europäische Einheits- und Friedensprojekt war damals, nach dem Mauerfall, in einer unbeschreiblichen Aufbruchstimmung, die sich heute niemand mehr vorstellen kann: Der ganze Kontinent in fröhlicher Stimmung - insieme, gemeinsam, together, ensemble – und wollte politisch zusammenwachsen. Heute ist es gescheitert und ich fasse es nicht! Das Kriegsgeheul in ganz Europa macht mich nachgerade verrückt.
Darum habe ich ein europäisches Friedensprojekt ins Leben gerufen: TheEuropean Peace Project. Am Europatag, den 9. Mai, um 17 Uhr, wollen wir in ganz Europa in allen europäischen und auf dem ganzen europäischen Kontinent als europäische Bürger den Frieden ausrufen! Ich würde mich freuen, wenn viele mitmachen!
DIE FRIEDENSTAUBE JETZT ABONNIEREN:
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):
Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space oder kontakt@idw-europe.org.
Wo bleibt ein deutsch-russisches Jugendwerk?
Mein Lieblingsbuch zu Europa ist Laurent Gaudet, Nous, L’Europe, banquet des peuples. „Wir, Europa! Ein Banquet der Völker“ Es ist ein großartiges Gedicht, etwa wie die Ilias von Homer. Es beschreibt die letzten einhundert Jahre europäische Geschichte, die ganzen Krieg und Revolutionen. Und es beschreibt doch, was uns als Europäer eint. Darin findet sich der – für mich wunderschöne! - Satz: „Ce que nous partageons, c’est ce que nous étions tous bourraux et victime.“ „Was wir als Europäer teilen ist, dass wir alle zugleich Opfer und Täter waren“.
Und doch haben wir es geschafft, die „Erbfeindschaft“ zu beenden und uns auszusöhnen, zum Beispiel die Deutschen und Franzosen, über ein deutsch-französisches Jugendwerk, das 1963 gegründet wurde. So ein Jugendwerk wünsche ich mir auch heute zwischen Europa und Russland!
Das Epos von Laurent Gaudet ist in einem Theaterstück von dem französischen Regisseur Roland Auzet auf die Bühne gebracht worden. In dem 40-köpfigen Ensemble sind verschiedene Nationalitäten aus ganz Europa: das Stück ist fantastisch! Ich selber habe es auf dem Theaterfestival in Avignon 2019 sehen dürfen!
Ich wünsche mir, dass wir statt jetzt für Milliarden überall in Europa Waffen zu kaufen, das Geld dafür auftreiben, dieses Theaterstück in jede europäische Stadt zu bringen: wenn das gelänge, hätten wohl alle verstanden, was es heißt, Europäer zu sein: nämlich Frieden zu machen!
Ulrike Guérot, Jg. 1964, ist europäische Professorin, Publizistin und Bestsellerautorin. Seit rund 30 Jahren beschäftigt sie sich in europäischen Think Tanks und Universitäten in Paris, Brüssel, London, Washington, New York, Wien und Berlin mit Fragen der europäischen Demokratie, sowie mit der Rolle Europas in der Welt. Ulrike Guérot ist seit März 2014 Gründerin und Direktorin des European Democracy Labs, e.V.,Berlin und initiierte im März 2023 das European Citizens Radio, das auf Spotify zu finden ist. Zuletzt erschien von ihr "Über Halford J. Mackinders Heartland-Theorie, Der geografische Drehpunkt der Geschichte", Westend, 2024). Mehr Infos zur Autorin hier.
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ da0b9bc3:4e30a4a9
2025-03-26 06:54:00
@ da0b9bc3:4e30a4a9
2025-03-26 06:54:00Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/925400
-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ 30876140:cffb1126
2025-03-26 04:58:21
@ 30876140:cffb1126
2025-03-26 04:58:21The portal is closing. The symphony comes to an end. Ballet, a dance of partners, A wish of hearts, Now closing its curtains.
I foolishly sit Eagerly waiting For the circus to begin again, As crowds file past me, Chuckles and popcorn falling, Crushed under foot, I sit waiting For the show to carry on.
But the night is now over, The laughs have been had, The music been heard, The dancers are gone now Into the nightbreeze chill. Yet still, I sit waiting,
The empty chairs yawning, A cough, I start, could it be? Yet the lights now go out, And now without my sight I am truly alone in the theater.
Yet still, I am waiting For the show to carry on, But I know that it won’t, Yet still, I am waiting. Never shall I leave For the show was too perfect And nothing perfect should ever be finished.
-
 @ a95c6243:d345522c
2025-03-20 09:59:20
@ a95c6243:d345522c
2025-03-20 09:59:20Bald werde es verboten, alleine im Auto zu fahren, konnte man dieser Tage in verschiedenen spanischen Medien lesen. Die nationale Verkehrsbehörde (Dirección General de Tráfico, kurz DGT) werde Alleinfahrern das Leben schwer machen, wurde gemeldet. Konkret erörtere die Generaldirektion geeignete Sanktionen für Personen, die ohne Beifahrer im Privatauto unterwegs seien.
Das Alleinfahren sei zunehmend verpönt und ein Mentalitätswandel notwendig, hieß es. Dieser «Luxus» stehe im Widerspruch zu den Maßnahmen gegen Umweltverschmutzung, die in allen europäischen Ländern gefördert würden. In Frankreich sei es «bereits verboten, in der Hauptstadt allein zu fahren», behauptete Noticiastrabajo Huffpost in einer Zwischenüberschrift. Nur um dann im Text zu konkretisieren, dass die sogenannte «Umweltspur» auf der Pariser Ringautobahn gemeint war, die für Busse, Taxis und Fahrgemeinschaften reserviert ist. Ab Mai werden Verstöße dagegen mit einem Bußgeld geahndet.
Die DGT jedenfalls wolle bei der Umsetzung derartiger Maßnahmen nicht hinterherhinken. Diese Medienberichte, inklusive des angeblich bevorstehenden Verbots, beriefen sich auf Aussagen des Generaldirektors der Behörde, Pere Navarro, beim Mobilitätskongress Global Mobility Call im November letzten Jahres, wo es um «nachhaltige Mobilität» ging. Aus diesem Kontext stammt auch Navarros Warnung: «Die Zukunft des Verkehrs ist geteilt oder es gibt keine».
Die «Faktenchecker» kamen der Generaldirektion prompt zu Hilfe. Die DGT habe derlei Behauptungen zurückgewiesen und klargestellt, dass es keine Pläne gebe, Fahrten mit nur einer Person im Auto zu verbieten oder zu bestrafen. Bei solchen Meldungen handele es sich um Fake News. Teilweise wurde der Vorsitzende der spanischen «Rechtsaußen»-Partei Vox, Santiago Abascal, der Urheberschaft bezichtigt, weil er einen entsprechenden Artikel von La Gaceta kommentiert hatte.
Der Beschwichtigungsversuch der Art «niemand hat die Absicht» ist dabei erfahrungsgemäß eher ein Alarmzeichen als eine Beruhigung. Walter Ulbrichts Leugnung einer geplanten Berliner Mauer vom Juni 1961 ist vielen genauso in Erinnerung wie die Fake News-Warnungen des deutschen Bundesgesundheitsministeriums bezüglich Lockdowns im März 2020 oder diverse Äußerungen zu einer Impfpflicht ab 2020.
Aber Aufregung hin, Dementis her: Die Pressemitteilung der DGT zu dem Mobilitätskongress enthält in Wahrheit viel interessantere Informationen als «nur» einen Appell an den «guten» Bürger wegen der Bemühungen um die Lebensqualität in Großstädten oder einen möglichen obligatorischen Abschied vom Alleinfahren. Allerdings werden diese Details von Medien und sogenannten Faktencheckern geflissentlich übersehen, obwohl sie keineswegs versteckt sind. Die Auskünfte sind sehr aufschlussreich, wenn man genauer hinschaut.
Digitalisierung ist der Schlüssel für Kontrolle
Auf dem Kongress stellte die Verkehrsbehörde ihre Initiativen zur Förderung der «neuen Mobilität» vor, deren Priorität Sicherheit und Effizienz sei. Die vier konkreten Ansätze haben alle mit Digitalisierung, Daten, Überwachung und Kontrolle im großen Stil zu tun und werden unter dem Euphemismus der «öffentlich-privaten Partnerschaft» angepriesen. Auch lassen sie die transhumanistische Idee vom unzulänglichen Menschen erkennen, dessen Fehler durch «intelligente» technologische Infrastruktur kompensiert werden müssten.
Die Chefin des Bereichs «Verkehrsüberwachung» erklärte die Funktion des spanischen National Access Point (NAP), wobei sie betonte, wie wichtig Verkehrs- und Infrastrukturinformationen in Echtzeit seien. Der NAP ist «eine essenzielle Web-Applikation, die unter EU-Mandat erstellt wurde», kann man auf der Website der DGT nachlesen.
Das Mandat meint Regelungen zu einem einheitlichen europäischen Verkehrsraum, mit denen die Union mindestens seit 2010 den Aufbau einer digitalen Architektur mit offenen Schnittstellen betreibt. Damit begründet man auch «umfassende Datenbereitstellungspflichten im Bereich multimodaler Reiseinformationen». Jeder Mitgliedstaat musste einen NAP, also einen nationalen Zugangspunkt einrichten, der Zugang zu statischen und dynamischen Reise- und Verkehrsdaten verschiedener Verkehrsträger ermöglicht.
Diese Entwicklung ist heute schon weit fortgeschritten, auch und besonders in Spanien. Auf besagtem Kongress erläuterte die Leiterin des Bereichs «Telematik» die Plattform «DGT 3.0». Diese werde als Integrator aller Informationen genutzt, die von den verschiedenen öffentlichen und privaten Systemen, die Teil der Mobilität sind, bereitgestellt werden.
Es handele sich um eine Vermittlungsplattform zwischen Akteuren wie Fahrzeugherstellern, Anbietern von Navigationsdiensten oder Kommunen und dem Endnutzer, der die Verkehrswege benutzt. Alle seien auf Basis des Internets der Dinge (IOT) anonym verbunden, «um der vernetzten Gemeinschaft wertvolle Informationen zu liefern oder diese zu nutzen».
So sei DGT 3.0 «ein Zugangspunkt für einzigartige, kostenlose und genaue Echtzeitinformationen über das Geschehen auf den Straßen und in den Städten». Damit lasse sich der Verkehr nachhaltiger und vernetzter gestalten. Beispielsweise würden die Karten des Produktpartners Google dank der DGT-Daten 50 Millionen Mal pro Tag aktualisiert.
Des Weiteren informiert die Verkehrsbehörde über ihr SCADA-Projekt. Die Abkürzung steht für Supervisory Control and Data Acquisition, zu deutsch etwa: Kontrollierte Steuerung und Datenerfassung. Mit SCADA kombiniert man Software und Hardware, um automatisierte Systeme zur Überwachung und Steuerung technischer Prozesse zu schaffen. Das SCADA-Projekt der DGT wird von Indra entwickelt, einem spanischen Beratungskonzern aus den Bereichen Sicherheit & Militär, Energie, Transport, Telekommunikation und Gesundheitsinformation.
Das SCADA-System der Behörde umfasse auch eine Videostreaming- und Videoaufzeichnungsplattform, die das Hochladen in die Cloud in Echtzeit ermöglicht, wie Indra erklärt. Dabei gehe es um Bilder, die von Überwachungskameras an Straßen aufgenommen wurden, sowie um Videos aus DGT-Hubschraubern und Drohnen. Ziel sei es, «die sichere Weitergabe von Videos an Dritte sowie die kontinuierliche Aufzeichnung und Speicherung von Bildern zur möglichen Analyse und späteren Nutzung zu ermöglichen».
Letzteres klingt sehr nach biometrischer Erkennung und Auswertung durch künstliche Intelligenz. Für eine bessere Datenübertragung wird derzeit die Glasfaserverkabelung entlang der Landstraßen und Autobahnen ausgebaut. Mit der Cloud sind die Amazon Web Services (AWS) gemeint, die spanischen Daten gehen somit direkt zu einem US-amerikanischen «Big Data»-Unternehmen.
Das Thema «autonomes Fahren», also Fahren ohne Zutun des Menschen, bildet den Abschluss der Betrachtungen der DGT. Zusammen mit dem Interessenverband der Automobilindustrie ANFAC (Asociación Española de Fabricantes de Automóviles y Camiones) sprach man auf dem Kongress über Strategien und Perspektiven in diesem Bereich. Die Lobbyisten hoffen noch in diesem Jahr 2025 auf einen normativen Rahmen zur erweiterten Unterstützung autonomer Technologien.
Wenn man derartige Informationen im Zusammenhang betrachtet, bekommt man eine Idee davon, warum zunehmend alles elektrisch und digital werden soll. Umwelt- und Mobilitätsprobleme in Städten, wie Luftverschmutzung, Lärmbelästigung, Platzmangel oder Staus, sind eine Sache. Mit dem Argument «emissionslos» wird jedoch eine Referenz zum CO2 und dem «menschengemachten Klimawandel» hergestellt, die Emotionen triggert. Und damit wird so ziemlich alles verkauft.
Letztlich aber gilt: Je elektrischer und digitaler unsere Umgebung wird und je freigiebiger wir mit unseren Daten jeder Art sind, desto besser werden wir kontrollier-, steuer- und sogar abschaltbar. Irgendwann entscheiden KI-basierte Algorithmen, ob, wann, wie, wohin und mit wem wir uns bewegen dürfen. Über einen 15-Minuten-Radius geht dann möglicherweise nichts hinaus. Die Projekte auf diesem Weg sind ernst zu nehmen, real und schon weit fortgeschritten.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-03-15 10:56:08
@ a95c6243:d345522c
2025-03-15 10:56:08Was nützt die schönste Schuldenbremse, wenn der Russe vor der Tür steht? \ Wir können uns verteidigen lernen oder alle Russisch lernen. \ Jens Spahn
In der Politik ist buchstäblich keine Idee zu riskant, kein Mittel zu schäbig und keine Lüge zu dreist, als dass sie nicht benutzt würden. Aber der Clou ist, dass diese Masche immer noch funktioniert, wenn nicht sogar immer besser. Ist das alles wirklich so schwer zu durchschauen? Mir fehlen langsam die Worte.
Aktuell werden sowohl in der Europäischen Union als auch in Deutschland riesige Milliardenpakete für die Aufrüstung – also für die Rüstungsindustrie – geschnürt. Die EU will 800 Milliarden Euro locker machen, in Deutschland sollen es 500 Milliarden «Sondervermögen» sein. Verteidigung nennen das unsere «Führer», innerhalb der Union und auch an «unserer Ostflanke», der Ukraine.
Das nötige Feindbild konnte inzwischen signifikant erweitert werden. Schuld an allem und zudem gefährlich ist nicht mehr nur Putin, sondern jetzt auch Trump. Europa müsse sich sowohl gegen Russland als auch gegen die USA schützen und rüsten, wird uns eingetrichtert.
Und während durch Diplomatie genau dieser beiden Staaten gerade endlich mal Bewegung in die Bemühungen um einen Frieden oder wenigstens einen Waffenstillstand in der Ukraine kommt, rasselt man im moralisch überlegenen Zeigefinger-Europa so richtig mit dem Säbel.
Begleitet und gestützt wird der ganze Prozess – wie sollte es anders sein – von den «Qualitätsmedien». Dass Russland einen Angriff auf «Europa» plant, weiß nicht nur der deutsche Verteidigungsminister (und mit Abstand beliebteste Politiker) Pistorius, sondern dank ihnen auch jedes Kind. Uns bleiben nur noch wenige Jahre. Zum Glück bereitet sich die Bundeswehr schon sehr konkret auf einen Krieg vor.
Die FAZ und Corona-Gesundheitsminister Spahn markieren einen traurigen Höhepunkt. Hier haben sich «politische und publizistische Verantwortungslosigkeit propagandistisch gegenseitig befruchtet», wie es bei den NachDenkSeiten heißt. Die Aussage Spahns in dem Interview, «der Russe steht vor der Tür», ist das eine. Die Zeitung verschärfte die Sache jedoch, indem sie das Zitat explizit in den Titel übernahm, der in einer ersten Version scheinbar zu harmlos war.
Eine große Mehrheit der deutschen Bevölkerung findet Aufrüstung und mehr Schulden toll, wie ARD und ZDF sehr passend ermittelt haben wollen. Ähnliches gelte für eine noch stärkere militärische Unterstützung der Ukraine. Etwas skeptischer seien die Befragten bezüglich der Entsendung von Bundeswehrsoldaten dorthin, aber immerhin etwa fifty-fifty.
Eigentlich ist jedoch die Meinung der Menschen in «unseren Demokratien» irrelevant. Sowohl in der Europäischen Union als auch in Deutschland sind die «Eliten» offenbar der Ansicht, der Souverän habe in Fragen von Krieg und Frieden sowie von aberwitzigen astronomischen Schulden kein Wörtchen mitzureden. Frau von der Leyen möchte über 150 Milliarden aus dem Gesamtpaket unter Verwendung von Artikel 122 des EU-Vertrags ohne das Europäische Parlament entscheiden – wenn auch nicht völlig kritiklos.
In Deutschland wollen CDU/CSU und SPD zur Aufweichung der «Schuldenbremse» mehrere Änderungen des Grundgesetzes durch das abgewählte Parlament peitschen. Dieser Versuch, mit dem alten Bundestag eine Zweidrittelmehrheit zu erzielen, die im neuen nicht mehr gegeben wäre, ist mindestens verfassungsrechtlich umstritten.
Das Manöver scheint aber zu funktionieren. Heute haben die Grünen zugestimmt, nachdem Kanzlerkandidat Merz läppische 100 Milliarden für «irgendwas mit Klima» zugesichert hatte. Die Abstimmung im Plenum soll am kommenden Dienstag erfolgen – nur eine Woche, bevor sich der neu gewählte Bundestag konstituieren wird.
Interessant sind die Argumente, die BlackRocker Merz für seine Attacke auf Grundgesetz und Demokratie ins Feld führt. Abgesehen von der angeblichen Eile, «unsere Verteidigungsfähigkeit deutlich zu erhöhen» (ausgelöst unter anderem durch «die Münchner Sicherheitskonferenz und die Ereignisse im Weißen Haus»), ließ uns der CDU-Chef wissen, dass Deutschland einfach auf die internationale Bühne zurück müsse. Merz schwadronierte gefährlich mehrdeutig:
«Die ganze Welt schaut in diesen Tagen und Wochen auf Deutschland. Wir haben in der Europäischen Union und auf der Welt eine Aufgabe, die weit über die Grenzen unseres eigenen Landes hinausgeht.»
[Titelbild: Tag des Sieges]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-03-11 10:22:36
@ a95c6243:d345522c
2025-03-11 10:22:36«Wir brauchen eine digitale Brandmauer gegen den Faschismus», schreibt der Chaos Computer Club (CCC) auf seiner Website. Unter diesem Motto präsentierte er letzte Woche einen Forderungskatalog, mit dem sich 24 Organisationen an die kommende Bundesregierung wenden. Der Koalitionsvertrag müsse sich daran messen lassen, verlangen sie.
In den drei Kategorien «Bekenntnis gegen Überwachung», «Schutz und Sicherheit für alle» sowie «Demokratie im digitalen Raum» stellen die Unterzeichner, zu denen auch Amnesty International und Das NETTZ gehören, unter anderem die folgenden «Mindestanforderungen»:
- Verbot biometrischer Massenüberwachung des öffentlichen Raums sowie der ungezielten biometrischen Auswertung des Internets.
- Anlasslose und massenhafte Vorratsdatenspeicherung wird abgelehnt.
- Automatisierte Datenanalysen der Informationsbestände der Strafverfolgungsbehörden sowie jede Form von Predictive Policing oder automatisiertes Profiling von Menschen werden abgelehnt.
- Einführung eines Rechts auf Verschlüsselung. Die Bundesregierung soll sich dafür einsetzen, die Chatkontrolle auf europäischer Ebene zu verhindern.
- Anonyme und pseudonyme Nutzung des Internets soll geschützt und ermöglicht werden.
- Bekämpfung «privaten Machtmissbrauchs von Big-Tech-Unternehmen» durch durchsetzungsstarke, unabhängige und grundsätzlich föderale Aufsichtsstrukturen.
- Einführung eines digitalen Gewaltschutzgesetzes, unter Berücksichtigung «gruppenbezogener digitaler Gewalt» und die Förderung von Beratungsangeboten.
- Ein umfassendes Förderprogramm für digitale öffentliche Räume, die dezentral organisiert und quelloffen programmiert sind, soll aufgelegt werden.
Es sei ein Irrglaube, dass zunehmende Überwachung einen Zugewinn an Sicherheit darstelle, ist eines der Argumente der Initiatoren. Sicherheit erfordere auch, dass Menschen anonym und vertraulich kommunizieren können und ihre Privatsphäre geschützt wird.
Gesunde digitale Räume lebten auch von einem demokratischen Diskurs, lesen wir in dem Papier. Es sei Aufgabe des Staates, Grundrechte zu schützen. Dazu gehöre auch, Menschenrechte und demokratische Werte, insbesondere Freiheit, Gleichheit und Solidarität zu fördern sowie den Missbrauch von Maßnahmen, Befugnissen und Infrastrukturen durch «die Feinde der Demokratie» zu verhindern.
Man ist geneigt zu fragen, wo denn die Autoren «den Faschismus» sehen, den es zu bekämpfen gelte. Die meisten der vorgetragenen Forderungen und Argumente finden sicher breite Unterstützung, denn sie beschreiben offenkundig gängige, kritikwürdige Praxis. Die Aushebelung der Privatsphäre, der Redefreiheit und anderer Grundrechte im Namen der Sicherheit wird bereits jetzt massiv durch die aktuellen «demokratischen Institutionen» und ihre «durchsetzungsstarken Aufsichtsstrukturen» betrieben.
Ist «der Faschismus» also die EU und ihre Mitgliedsstaaten? Nein, die «faschistische Gefahr», gegen die man eine digitale Brandmauer will, kommt nach Ansicht des CCC und seiner Partner aus den Vereinigten Staaten. Private Überwachung und Machtkonzentration sind dabei weltweit schon lange Realität, jetzt endlich müssen sie jedoch bekämpft werden. In dem Papier heißt es:
«Die willkürliche und antidemokratische Machtausübung der Tech-Oligarchen um Präsident Trump erfordert einen Paradigmenwechsel in der deutschen Digitalpolitik. (...) Die aktuellen Geschehnisse in den USA zeigen auf, wie Datensammlungen und -analyse genutzt werden können, um einen Staat handstreichartig zu übernehmen, seine Strukturen nachhaltig zu beschädigen, Widerstand zu unterbinden und marginalisierte Gruppen zu verfolgen.»
Wer auf der anderen Seite dieser Brandmauer stehen soll, ist also klar. Es sind die gleichen «Feinde unserer Demokratie», die seit Jahren in diese Ecke gedrängt werden. Es sind die gleichen Andersdenkenden, Regierungskritiker und Friedensforderer, die unter dem großzügigen Dach des Bundesprogramms «Demokratie leben» einem «kontinuierlichen Echt- und Langzeitmonitoring» wegen der Etikettierung «digitaler Hass» unterzogen werden.
Dass die 24 Organisationen praktisch auch die Bekämpfung von Google, Microsoft, Apple, Amazon und anderen fordern, entbehrt nicht der Komik. Diese fallen aber sicher unter das Stichwort «Machtmissbrauch von Big-Tech-Unternehmen». Gleichzeitig verlangen die Lobbyisten implizit zum Beispiel die Förderung des Nostr-Netzwerks, denn hier finden wir dezentral organisierte und quelloffen programmierte digitale Räume par excellence, obendrein zensurresistent. Das wiederum dürfte in der Politik weniger gut ankommen.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ e5de992e:4a95ef85
2025-03-26 04:57:53
@ e5de992e:4a95ef85
2025-03-26 04:57:53Overview
On March 25, 2025, U.S. stock markets experienced modest gains despite declining volume and a drop in the Consumer Confidence Index, indicating that investors remain cautiously optimistic amid mixed economic signals.
U.S. Stock Indices
- S&P 500:
- Increased by 0.2%
- Closed at 5,776.65 points
-
Marked its third consecutive winning session, but volume was declining.
-
Dow Jones Industrial Average (DJIA):
- Rose marginally by 0.01%
- Ended at 42,587.50 points
-
Volume was declining.
-
Nasdaq Composite:
- Advanced by 0.5%
- Finished at 18,271.86 points
- Volume was declining.
U.S. Futures Market
- S&P 500 Futures:
-
Rose by 0.06%, suggesting a modestly positive opening.
-
Dow Jones Futures:
- Remained unchanged, indicating a neutral sentiment among investors.
Note: Both futures segments are experiencing low volume.
Key Factors Influencing U.S. Markets
-
Trade Policy Developments:
Investor sentiment has been influenced by reports suggesting that President Donald Trump's proposed tariffs may be more narrowly targeted than initially feared—potentially exempting certain sectors. This has alleviated some concerns regarding the impact of trade policies on economic growth. -
Economic Data Releases:
The Consumer Confidence Index declined, reflecting growing concerns about economic expectations. However, positive corporate earnings reports have contributed to the market's resilience. -
Sector-Specific News:
- International Paper saw significant stock price increases due to upbeat growth outlooks.
- United Parcel Service (UPS) faced declines amid reduced earnings projections.
Global Stock Indices Performance
International markets displayed mixed performances:
- Germany's DAX:
- Experienced a slight decline of 0.32%
- Closed at 23,109.79 points
-
Initial optimism regarding tariff negotiations waned.
-
UK's FTSE 100:
- Fell marginally by 0.10%
-
Reflects investor caution amid mixed economic data.
-
Hong Kong's Hang Seng:
- Declined by 2.35%
- Closed at 23,344.25 points
-
Impacted by a downturn in Chinese tech shares and ongoing tariff concerns.
-
Japan's Nikkei 225:
- Showed resilience with a modest gain, influenced by positive domestic economic indicators.
Cryptocurrency Market
The cryptocurrency market has experienced notable activity:
- Bitcoin (BTC):
- Trading at approximately $87,460
-
Down 1.23% from the previous close.
-
Ethereum (ETH):
- Priced around $2,057.22
- Marked a 0.69% uptick from the prior session.
These movements indicate the market’s sensitivity to regulatory developments and macroeconomic factors.
Key Global Economic and Geopolitical Events
-
Trade Tensions and Tariff Policies:
Ongoing discussions regarding U.S. tariff implementations have created an atmosphere of uncertainty, influencing global market sentiment and leading to cautious investor behavior. -
Central Bank Communications:
Statements from Federal Reserve officials and other central bank representatives are being closely monitored for insights into future monetary policy directions, especially in light of evolving economic conditions and inflationary pressures. -
Cryptocurrency Regulatory Environment:
Anticipation of a more favorable regulatory landscape under the current administration has contributed to recent rallies in major cryptocurrencies, though analysts caution that these rebounds may be fleeting amid broader market dynamics.
Conclusion
Global financial markets are navigating a complex environment shaped by trade policy developments, economic data releases, and sector-specific news. Investors are advised to remain vigilant and consider these factors when making informed decisions, as they are likely to continue influencing market behavior in the foreseeable future.
-
 @ a95c6243:d345522c
2025-03-04 09:40:50
@ a95c6243:d345522c
2025-03-04 09:40:50Die «Eliten» führen bereits groß angelegte Pilotprojekte für eine Zukunft durch, die sie wollen und wir nicht. Das schreibt der OffGuardian in einem Update zum Thema «EU-Brieftasche für die digitale Identität». Das Portal weist darauf hin, dass die Akteure dabei nicht gerade zimperlich vorgehen und auch keinen Hehl aus ihren Absichten machen. Transition News hat mehrfach darüber berichtet, zuletzt hier und hier.
Mit der EU Digital Identity Wallet (EUDI-Brieftasche) sei eine einzige von der Regierung herausgegebene App geplant, die Ihre medizinischen Daten, Beschäftigungsdaten, Reisedaten, Bildungsdaten, Impfdaten, Steuerdaten, Finanzdaten sowie (potenziell) Kopien Ihrer Unterschrift, Fingerabdrücke, Gesichtsscans, Stimmproben und DNA enthält. So fasst der OffGuardian die eindrucksvolle Liste möglicher Einsatzbereiche zusammen.
Auch Dokumente wie der Personalausweis oder der Führerschein können dort in elektronischer Form gespeichert werden. Bis 2026 sind alle EU-Mitgliedstaaten dazu verpflichtet, Ihren Bürgern funktionierende und frei verfügbare digitale «Brieftaschen» bereitzustellen.
Die Menschen würden diese App nutzen, so das Portal, um Zahlungen vorzunehmen, Kredite zu beantragen, ihre Steuern zu zahlen, ihre Rezepte abzuholen, internationale Grenzen zu überschreiten, Unternehmen zu gründen, Arzttermine zu buchen, sich um Stellen zu bewerben und sogar digitale Verträge online zu unterzeichnen.
All diese Daten würden auf ihrem Mobiltelefon gespeichert und mit den Regierungen von neunzehn Ländern (plus der Ukraine) sowie über 140 anderen öffentlichen und privaten Partnern ausgetauscht. Von der Deutschen Bank über das ukrainische Ministerium für digitalen Fortschritt bis hin zu Samsung Europe. Unternehmen und Behörden würden auf diese Daten im Backend zugreifen, um «automatisierte Hintergrundprüfungen» durchzuführen.
Der Bundesverband der Verbraucherzentralen und Verbraucherverbände (VZBV) habe Bedenken geäußert, dass eine solche App «Risiken für den Schutz der Privatsphäre und der Daten» berge, berichtet das Portal. Die einzige Antwort darauf laute: «Richtig, genau dafür ist sie ja da!»
Das alles sei keine Hypothese, betont der OffGuardian. Es sei vielmehr «Potential». Damit ist ein EU-Projekt gemeint, in dessen Rahmen Dutzende öffentliche und private Einrichtungen zusammenarbeiten, «um eine einheitliche Vision der digitalen Identität für die Bürger der europäischen Länder zu definieren». Dies ist nur eines der groß angelegten Pilotprojekte, mit denen Prototypen und Anwendungsfälle für die EUDI-Wallet getestet werden. Es gibt noch mindestens drei weitere.
Den Ball der digitalen ID-Systeme habe die Covid-«Pandemie» über die «Impfpässe» ins Rollen gebracht. Seitdem habe das Thema an Schwung verloren. Je näher wir aber der vollständigen Einführung der EUid kämen, desto mehr Propaganda der Art «Warum wir eine digitale Brieftasche brauchen» könnten wir in den Mainstream-Medien erwarten, prognostiziert der OffGuardian. Vielleicht müssten wir schon nach dem nächsten großen «Grund», dem nächsten «katastrophalen katalytischen Ereignis» Ausschau halten. Vermutlich gebe es bereits Pläne, warum die Menschen plötzlich eine digitale ID-Brieftasche brauchen würden.
Die Entwicklung geht jedenfalls stetig weiter in genau diese Richtung. Beispielsweise hat Jordanien angekündigt, die digitale biometrische ID bei den nächsten Wahlen zur Verifizierung der Wähler einzuführen. Man wolle «den Papierkrieg beenden und sicherstellen, dass die gesamte Kette bis zu den nächsten Parlamentswahlen digitalisiert wird», heißt es. Absehbar ist, dass dabei einige Wahlberechtigte «auf der Strecke bleiben» werden, wie im Fall von Albanien geschehen.
Derweil würden die Briten gerne ihre Privatsphäre gegen Effizienz eintauschen, behauptet Tony Blair. Der Ex-Premier drängte kürzlich erneut auf digitale Identitäten und Gesichtserkennung. Blair ist Gründer einer Denkfabrik für globalen Wandel, Anhänger globalistischer Technokratie und «moderner Infrastruktur».
Abschließend warnt der OffGuardian vor der Illusion, Trump und Musk würden den US-Bürgern «diesen Schlamassel ersparen». Das Department of Government Efficiency werde sich auf die digitale Identität stürzen. Was könne schließlich «effizienter» sein als eine einzige App, die für alles verwendet wird? Der Unterschied bestehe nur darin, dass die US-Version vielleicht eher privat als öffentlich sei – sofern es da überhaupt noch einen wirklichen Unterschied gebe.
[Titelbild: Screenshot OffGuardian]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ f6488c62:c929299d
2025-03-26 03:53:51
@ f6488c62:c929299d
2025-03-26 03:53:51เมื่อไม่นานมานี้ ไมเคิล เซย์เลอร์ ต้อนรับ Ryan Cohen ประธาน GameStop เข้าสู่ "ทีมบิตคอยน์" หลังบริษัทประกาศใช้บิตคอยน์เป็นทรัพย์สินสำรองอย่างเป็นทางการ เหตุการณ์นี้ไม่เพียงสะท้อนความเชื่อมั่นในสกุลเงินดิจิทัลของเซย์เลอร์ แต่ยังพิสูจน์ให้เห็นว่าเขาเป็นนักปฏิบัติผู้เปลี่ยนความเชื่อให้เป็นการกระทำจริง ไม่ใช่แค่การพูดคุยทฤษฎี ทุกการตัดสินใจของเขาเปรียบเสมือนเข็มทิศนำทางองค์กรธุรกิจสู่ยุคดิจิทัลอย่างไม่หลบเลี่ยง แม้ต้องเผชิญความผันผวนของตลาดและเสียงวิพากษ์นับไม่ถ้วน เขายังคงยืนหยัดด้วยความแน่วแน่แบบเดียวกับวันที่ตัดสินใจลงทุนมหาศาลผ่าน MicroStrategy เป็นครั้งแรก
การสังเกตความเด็ดขาดของเซย์เลอร์ทำให้ฉุกคิดถึงความลังเลในตัวเองได้ไม่น้อย แม้จะเชื่อในหลักการบางอย่าง แต่ก็มักพบว่าตนเองยังก้าวไม่พ้นกรอบความคิดแบบ "รอความพร้อม" หรือ "กลัวความเสี่ยง" ซึ่งอาจเป็นกับดักของคนชอบอยู่ในคอมฟอร์ตโซนเสียมากกว่า เซย์เลอร์สอนบทเรียนสำคัญผ่านการกระทำว่าโอกาสไม่อาจรอให้สมบูรณ์แบบ และวิสัยทัศน์ที่ชัดเจนต้องมาพร้อมความกล้าที่จะริเริ่ม แม้จุดสิ้นสุดจะไม่แน่นอน เหตุการณ์ที่เขาเชิญชวน Ryan Cohen เข้าสู่โลกบิตคอยน์ก็เป็นตัวอย่างชัดเจนว่าเส้นทางสู่การเปลี่ยนแปลงมักเริ่มจากความกล้าที่จะก้าวออกก่อน ไม่ใช่การรอให้ทุกอย่างลงตัว
การเคลื่อนไหวของ GameStop ถือเป็นสัญญาณความเปลี่ยนแปลงของระบบเศรษฐกิจยุคใหม่ที่บิตคอยน์ไม่ใช่แค่เครื่องมือลงทุน แต่เป็นสัญลักษณ์ของความคิดก้าวหน้า เซย์เลอร์กำลังท้าทายกรอบคิดเดิมๆ ผ่านการลงมือทำที่ผสมผสานความกล้าหาญ วิสัยทัศน์ระยะยาว และความเชื่อมั่นอย่างเหนียวแน่น เขาไม่เพียงสร้างแรงกระเพื่อมในวงการเงิน แต่ยังทิ้งคำถามให้เราต้องทบทวนตัวเองอยู่เสมอ: อะไรคือสิ่งที่เราเชื่อมั่นพอจะทุ่มเททั้งชีวิตจิตใจ? บทเรียนจากชายคนนี้อาจไม่เกี่ยวกับการลงทุนล้วนๆ แต่เกี่ยวกับศิลปะการตัดสินใจที่เปลี่ยนความเชื่อให้กลายเป็นความจริงได้ด้วยสองมือของตัวเอง ปล. ดูๆ ไปแล้ว เขาก็คล้ายๆ ด๊อกเตอร์สเตร็นจ์ มากเหมือนกัน 555
-
 @ a95c6243:d345522c
2025-03-01 10:39:35
@ a95c6243:d345522c
2025-03-01 10:39:35Ständige Lügen und Unterstellungen, permanent falsche Fürsorge \ können Bausteine von emotionaler Manipulation sein. Mit dem Zweck, \ Macht und Kontrolle über eine andere Person auszuüben. \ Apotheken Umschau
Irgendetwas muss passiert sein: «Gaslighting» ist gerade Thema in vielen Medien. Heute bin ich nach längerer Zeit mal wieder über dieses Stichwort gestolpert. Das war in einem Artikel von Norbert Häring über Manipulationen des Deutschen Wetterdienstes (DWD). In diesem Fall ging es um eine Pressemitteilung vom Donnerstag zum «viel zu warmen» Winter 2024/25.
Häring wirft der Behörde vor, dreist zu lügen und Dinge auszulassen, um die Klimaangst wach zu halten. Was der Leser beim DWD nicht erfahre, sei, dass dieser Winter kälter als die drei vorangegangenen und kälter als der Durchschnitt der letzten zehn Jahre gewesen sei. Stattdessen werde der falsche Eindruck vermittelt, es würde ungebremst immer wärmer.
Wem also der zu Ende gehende Winter eher kalt vorgekommen sein sollte, mit dessen Empfinden stimme wohl etwas nicht. Das jedenfalls wolle der DWD uns einreden, so der Wirtschaftsjournalist. Und damit sind wir beim Thema Gaslighting.
Als Gaslighting wird eine Form psychischer Manipulation bezeichnet, mit der die Opfer desorientiert und zutiefst verunsichert werden, indem ihre eigene Wahrnehmung als falsch bezeichnet wird. Der Prozess führt zu Angst und Realitätsverzerrung sowie zur Zerstörung des Selbstbewusstseins. Die Bezeichnung kommt von dem britischen Theaterstück «Gas Light» aus dem Jahr 1938, in dem ein Mann mit grausamen Psychotricks seine Frau in den Wahnsinn treibt.
Damit Gaslighting funktioniert, muss das Opfer dem Täter vertrauen. Oft wird solcher Psychoterror daher im privaten oder familiären Umfeld beschrieben, ebenso wie am Arbeitsplatz. Jedoch eignen sich die Prinzipien auch perfekt zur Manipulation der Massen. Vermeintliche Autoritäten wie Ärzte und Wissenschaftler, oder «der fürsorgliche Staat» und Institutionen wie die UNO oder die WHO wollen uns doch nichts Böses. Auch Staatsmedien, Faktenchecker und diverse NGOs wurden zu «vertrauenswürdigen Quellen» erklärt. Das hat seine Wirkung.
Warum das Thema Gaslighting derzeit scheinbar so populär ist, vermag ich nicht zu sagen. Es sind aber gerade in den letzten Tagen und Wochen auffällig viele Artikel dazu erschienen, und zwar nicht nur von Psychologen. Die Frankfurter Rundschau hat gleich mehrere publiziert, und Anwälte interessieren sich dafür offenbar genauso wie Apotheker.
Die Apotheken Umschau machte sogar auf «Medical Gaslighting» aufmerksam. Davon spreche man, wenn Mediziner Symptome nicht ernst nähmen oder wenn ein gesundheitliches Problem vom behandelnden Arzt «schnöde heruntergespielt» oder abgetan würde. Kommt Ihnen das auch irgendwie bekannt vor? Der Begriff sei allerdings irreführend, da er eine manipulierende Absicht unterstellt, die «nicht gewährleistet» sei.
Apropos Gaslighting: Die noch amtierende deutsche Bundesregierung meldete heute, es gelte, «weiter [sic!] gemeinsam daran zu arbeiten, einen gerechten und dauerhaften Frieden für die Ukraine zu erreichen». Die Ukraine, wo sich am Montag «der völkerrechtswidrige Angriffskrieg zum dritten Mal jährte», verteidige ihr Land und «unsere gemeinsamen Werte».
Merken Sie etwas? Das Demokratieverständnis mag ja tatsächlich inzwischen in beiden Ländern ähnlich traurig sein. Bezüglich Friedensbemühungen ist meine Wahrnehmung jedoch eine andere. Das muss an meinem Gedächtnis liegen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ d9422098:7ee511a3
2025-03-26 05:04:03
@ d9422098:7ee511a3
2025-03-26 05:04:03екненлотлоло
-
 @ 9711d1ab:863ebd81
2025-03-26 03:36:56
@ 9711d1ab:863ebd81
2025-03-26 03:36:56 Welcome back friends! We’ve made it to the end of March, congratulations. Here’s what we’ve got to share this month:
Welcome back friends! We’ve made it to the end of March, congratulations. Here’s what we’ve got to share this month:-
🎓 The SDK Class of Q1
-
🤓 Back to School with Antonio
-
⚡️ Lightning is Everywhere
-
🎙️ Shooting the Breez with Danny, Umi & Roy
The SDK Class of Q1 2025 🎓
 We’ve been talking a lot about momentum at Breez and we’re seeing it build every day. More partners are adding Bitcoin payments with our SDK and more sats are moving freely around the world. By offering the choice of two implementations, Nodeless and Native, we’re truly building the best Lightning developer experience out there.
We’ve been talking a lot about momentum at Breez and we’re seeing it build every day. More partners are adding Bitcoin payments with our SDK and more sats are moving freely around the world. By offering the choice of two implementations, Nodeless and Native, we’re truly building the best Lightning developer experience out there.And the momentum just keeps growing stronger.
In fact, we’ve welcomed so many new partners that we had to bundle them all into one big announcement — it’s our pleasure to welcome the SDK Class of Q1 2025: Assetify, Cowbolt, DexTrade, Flash, Lightning Pay, OpenAgents, Satoshi, Shakesco, Tidebinder, and ZapZap.
 ---
---Back to School with Antonio 🚌
 We tell everyone we meet that adding Bitcoin payments to apps is really easy with the Breez SDK. But rather than just tell you this, we’ve decided to show you.
We tell everyone we meet that adding Bitcoin payments to apps is really easy with the Breez SDK. But rather than just tell you this, we’ve decided to show you.Antonio, one of our talented developers at Breez, has produced a video tutorial showing how you can add Bitcoin payments to React Native and Expo apps with the Breez SDK - Nodeless.
Join him as he guides you through each step and shows that it really is that *easy* to add Bitcoin payments to any app with our SDK.
Lightning is Everywhere.
 It’s true — Lightning is everywhere.
It’s true — Lightning is everywhere.Bitcoin payments aren’t just a thing for the few, they’re for the many.
This month, we’re showcasing our friends at Cowbolt. They’ve just released their collaborative cost-splitting, team-chat, and self-custody app (check it out).
Shooting the Breez 🌬️
 Since releasing our Bitcoin payment report — where we explained that Bitcoin isn’t just digital gold, it’s a thriving everyday currency accessible to millions of people around the world — Bitcoin payments have been the talk of the town.
Since releasing our Bitcoin payment report — where we explained that Bitcoin isn’t just digital gold, it’s a thriving everyday currency accessible to millions of people around the world — Bitcoin payments have been the talk of the town.As co-author of the report, I joined the Stephan Livera Podcast to discuss the growing trend in more detail. I also met up with Bo Jablonski to explain why more and more apps are taking notice on the newly-formed Guardians of Bitcoin radio show.
Developments have come thick and fast over the past month — most notably, the announcement of USDT coming to Lightning (check out Roy’s take on the good, the bad, and the unknown in Bitcoin Magazine). Breez’s BD Lead, Umi, joined a Spaces on X with UXTO, Amboss, and Lightning Labs to discuss the stablecoin’s imminent arrival on the network.
 That’s not all from Umi, she also joined her alma mater at the Cornell Bitcoin Club to explain why bitcoin is a medium of exchange, thanks to Lightning.
That’s not all from Umi, she also joined her alma mater at the Cornell Bitcoin Club to explain why bitcoin is a medium of exchange, thanks to Lightning. And last but not least, Roy was spreading the good word of Bitcoin, joining Bitfinex’s podcast to explain how Lightning is truly changing the game.
And last but not least, Roy was spreading the good word of Bitcoin, joining Bitfinex’s podcast to explain how Lightning is truly changing the game.
And there we go folks, another edition of Feel the Breez has come to a close.
As always, we’ll leave you with our usual parting comment: the best time to get into Lightning is now — it always has been.
Stay tuned for exciting announcements we’ll be releasing soon.
Until next time ✌️
-
-
 @ 220522c2:61e18cb4
2025-03-26 03:24:25
@ 220522c2:61e18cb4
2025-03-26 03:24:25npub1ygzj9skr9val9yqxkf67yf9jshtyhvvl0x76jp5er09nsc0p3j6qr260k2

-
 @ a95c6243:d345522c
2025-02-21 19:32:23
@ a95c6243:d345522c
2025-02-21 19:32:23Europa – das Ganze ist eine wunderbare Idee, \ aber das war der Kommunismus auch. \ Loriot
«Europa hat fertig», könnte man unken, und das wäre nicht einmal sehr verwegen. Mit solch einer Einschätzung stünden wir nicht alleine, denn die Stimmen in diese Richtung mehren sich. Der französische Präsident Emmanuel Macron warnte schon letztes Jahr davor, dass «unser Europa sterben könnte». Vermutlich hatte er dabei andere Gefahren im Kopf als jetzt der ungarische Ministerpräsident Viktor Orbán, der ein «baldiges Ende der EU» prognostizierte. Das Ergebnis könnte allerdings das gleiche sein.
Neben vordergründigen Themenbereichen wie Wirtschaft, Energie und Sicherheit ist das eigentliche Problem jedoch die obskure Mischung aus aufgegebener Souveränität und geschwollener Arroganz, mit der europäische Politiker:innende unterschiedlicher Couleur aufzutreten pflegen. Und das Tüpfelchen auf dem i ist die bröckelnde Legitimation politischer Institutionen dadurch, dass die Stimmen großer Teile der Bevölkerung seit Jahren auf vielfältige Weise ausgegrenzt werden.
Um «UnsereDemokratie» steht es schlecht. Dass seine Mandate immer schwächer werden, merkt natürlich auch unser «Führungspersonal». Entsprechend werden die Maßnahmen zur Gängelung, Überwachung und Manipulation der Bürger ständig verzweifelter. Parallel dazu plustern sich in Paris Macron, Scholz und einige andere noch einmal mächtig in Sachen Verteidigung und «Kriegstüchtigkeit» auf.
Momentan gilt es auch, das Überschwappen covidiotischer und verschwörungsideologischer Auswüchse aus den USA nach Europa zu vermeiden. So ein «MEGA» (Make Europe Great Again) können wir hier nicht gebrauchen. Aus den Vereinigten Staaten kommen nämlich furchtbare Nachrichten. Beispielsweise wurde einer der schärfsten Kritiker der Corona-Maßnahmen kürzlich zum Gesundheitsminister ernannt. Dieser setzt sich jetzt für eine Neubewertung der mRNA-«Impfstoffe» ein, was durchaus zu einem Entzug der Zulassungen führen könnte.
Der europäischen Version von «Verteidigung der Demokratie» setzte der US-Vizepräsident J. D. Vance auf der Münchner Sicherheitskonferenz sein Verständnis entgegen: «Demokratie stärken, indem wir unseren Bürgern erlauben, ihre Meinung zu sagen». Das Abschalten von Medien, das Annullieren von Wahlen oder das Ausschließen von Menschen vom politischen Prozess schütze gar nichts. Vielmehr sei dies der todsichere Weg, die Demokratie zu zerstören.
In der Schweiz kamen seine Worte deutlich besser an als in den meisten europäischen NATO-Ländern. Bundespräsidentin Karin Keller-Sutter lobte die Rede und interpretierte sie als «Plädoyer für die direkte Demokratie». Möglicherweise zeichne sich hier eine außenpolitische Kehrtwende in Richtung integraler Neutralität ab, meint mein Kollege Daniel Funk. Das wären doch endlich mal ein paar gute Nachrichten.
Von der einstigen Idee einer europäischen Union mit engeren Beziehungen zwischen den Staaten, um Konflikte zu vermeiden und das Wohlergehen der Bürger zu verbessern, sind wir meilenweit abgekommen. Der heutige korrupte Verbund unter technokratischer Leitung ähnelt mehr einem Selbstbedienungsladen mit sehr begrenztem Zugang. Die EU-Wahlen im letzten Sommer haben daran ebenso wenig geändert, wie die Bundestagswahl am kommenden Sonntag darauf einen Einfluss haben wird.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 1bda7e1f:bb97c4d9
2025-03-26 03:23:00
@ 1bda7e1f:bb97c4d9
2025-03-26 03:23:00Tldr
- Nostr is a new open social protocol for the internet
- You can use it to create your own online community website/app for your users
- This needs only a few simple components that are free and open source
- Jumble.Social client is a front-end for showing your community content to your users
- Simple With Whitelist relay (SW2) is a back-end with simple auth for your community content
- In this blog I explain the components and set up a online community website/app that any community or company can use for their own users, for free.
You Can Run Your Own Private "X" For Free
Nostr is a new open social protocol for the internet. Because it is a protocol it is not controlled by any one company, does not reside on any one set of servers, does not require any licenses, and no one can stop you from using it however you like.
When the name Nostr is recognised, it is as a "Twitter/X alternative" – that is an online open public forum. Nostr is more than just this. The open nature of the protocol means that you can use it however you feel like, including that you can use it for creating your own social websites to suit whatever goals you have – anything from running your own team collaboration app, to running your own online community.
Nostr can be anything – not just an alternative to X, but also to Slack, Teams, Discord, Telegram (etc) – any kind of social app you'd like to run for your users can be run on Nostr.
In this blog I will show you how to launch your own community website, for your community members to use however they like, with low code, and for free.
Simple useful components
Nostr has a few simple components that work together to provide your experience –
- Your "client" – an app or a website front-end that you log into, which displays the content you want to see
- Your "relay" – a server back-end which receives and stores content, and sends it to clients
- Your "user" – a set of keys which represents a user on the network,
- Your "content" – any user content created and signed by a user, distributed to any relay, which can be picked up and viewed by any client.
It is a pattern that is used by every other social app on the internet, excepting that in those cases you can usually only view content in their app, and only post your content to their server.
Vs with Nostr where you can use any client (app) and any relay (server), including your own.
This is defined as a standard in NIP-01 which is simple enough that you can master it in a weekend, and with which you can build any kind of application.
The design space is wide open for anyone to build anything–
- Clones of Twitter, Instagram, Telegram, Medium, Twitch, etc,
- Whole new things like Private Ephemeral Messengers, Social Podcasting Apps, etc,
- Anything else you can dream up, like replacements for B2B SaaS or ERP systems.
Including that you can set up and run your own "X" for your community.
Super powers for –private– social internet
When considering my use of social internet, it is foremost private not public. Email, Whatsapp, Slack, Teams, Discord, Telegram (etc), are all about me, as a user, creating content for a selected group of individuals – close friends, colleagues, community members – not the wider public.
This private social internet is crying out for the kind of powers that Nostr provides. The list of things that Nostr solves for private social internet goes on-and-on.
Let me eat my own dog food for a moment.
- I am a member of a community of technology entrepreneurs with an app for internal community comms. The interface is not fit for this purpose. Good content gets lost. Any content created within the walled kingdom cannot be shared externally. Community members cannot migrate to a different front-end, or cross-post to public social channels.
- I am a member of many communities for kids social groups, each one with a different application and log in. There is no way to view a consolidated feed. There is no way to send one message to many communities, or share content between them. Remembering to check every feed separately is a drag.
- I am a member of a team with an app for team comms. It costs $XXX per user per month where it should be free. I can't self-host. I can't control or export my data. I can't make it interoperate natively with other SaaS. All of my messages probably go to train a Big Co AI without my consent.
In each instance "Nostr fixes this."
Ready now for low-code admins
To date Nostr has been best suited to a more technical user. To use the Nostr protocol directly has been primarily a field of great engineers building great foundations.
IMO these foundations are built. They are open source, free to use, and accessible for anyone who wants to create an administer their own online community, with only low code required.
To prove it, in this blog I will scratch my own itch. I need a X / Slack / Teams alternative to use with a few team members and friends (and a few AIs) as we hack on establishing a new business idea.
I will set this up with Nostr using only open source code, for free.
Designing the Solution
I am mostly non-technical with helpful AI. To set up your own community website in the style of X / Slack / Teams should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs some other unrelated Nostr projects in Docker containers,
- My objective was to set up and run my own community website for my own team use, in Docker, hosted on my own server.
User requirements
What will I want from a community website?
- I want my users to be able to log into a website and post content,
- I want to save that content to a server I control accessed only be people I authorise,
- I want my users to view only that content by default, and not be exposed to any wider public social network unless they knowingly select that,
- I want my user's content to be either:
- a) viewable only by other community members (i.e. for internal team comms), or
- b) by the wider public (i.e. for public announcements), at the user's discretion.
- I want it to be open source so that other people maintain the code for me,
- I want it for free.
Nostr solutions
To achieve this with Nostr, I'll need to select some solutions "a-la carte" for each of the core components of the network.
- A client – For my client, I have chosen Jumble. Jumble is a free open-source client by Cody Tseng, available free on Github or at Jumble.social. I have chosen Jumble because it is a "relay-centric" client. In key spots the user interface highlights for the user what relay they are viewing, and what relay they are posting to. As a result, it is a beautiful fit for me to use as the home of all my community content.
- A relay – For my relay, I have chosen Simple With Whitelist (SW2). SW2 is a free open-source relay by Utxo The Webmaster, based on Khatru by Fiatjaf, available free on Github. I have chosen SW2 because it allows for very simple configuration of user auth. Users can be given read access to view notes, and write access to post notes within simple
config.jsonfiles. This allows you to keep community content private or selectively share it in a variety of ways. Per the Nostr protocol, your client will connect with your relay via websocket. - A user sign-up flow – Jumble has a user sign-up flow using Nstart by Fiatjaf, or as an admin I can create and provision my own users with any simple tool like NAK or Nostrtool.
- A user content flow – Jumble has a user content flow that can post notes to selected relays of the users choice. Rich media is uploaded to free third-party hosts like Nostr.build, and in the future there is scope to self-host this too.
With each of these boxes ticked I'm ready to start.
Launching a Private Community Website with Jumble and SW2
Install your SW2 relay
The relay is the trickiest part, so let's start there. SW2 is my Nostr relay software of choice. It is a Go application and includes full instructions for Go install. However, I prefer Docker, so I have built a Docker version and maintain a Docker branch here.
1 – In a terminal clone the repo and checkout the Docker branch
git clone https://github.com/r0d8lsh0p/sw2.git cd sw2 git checkout docker2 – Set up the environment variables
These are specified in the readme. Duplicate the example .env file and fill it with your variables.
cp .env.example .envFor me this .env file was as follows–
```
Relay Metadata
RELAY_NAME="Tbdai relay" RELAY_PUBKEY="ede41352397758154514148b24112308ced96d121229b0e6a66bc5a2b40c03ec" RELAY_DESCRIPTION="An experimental relay for some people and robots working on a TBD AI project." RELAY_URL="wss://assistantrelay.rodbishop.nz" RELAY_ICON="https://image.nostr.build/44654201843fc0f03e9a72fbf8044143c66f0dd4d5350688db69345f9da05007.jpg" RELAY_CONTACT="https://rodbishop.nz" ```
3 – Specify who can read and write to the relay
This is controlled by two config files
read_whitelist.jsonandwrite_whitelist.json.- Any user with their pubkey in the
read_whitelistcan read notes posted to the relay. If empty, anyone can read. - Any user with their pubkey in the
write_whitelistcan post notes to the relay. If empty, anyone can write.
We'll get to creating and authorising more users later, for now I suggest to add yourself to each whitelist, by copying your pubkey into each JSON file. For me this looks as follows (note, I use the 'hex' version of the pubkey, rather than the npub)–
{ "pubkeys": [ "1bda7e1f7396bda2d1ef99033da8fd2dc362810790df9be62f591038bb97c4d9" ] }If this is your first time using Nostr and you don't yet have any user keys, it is easy and free to get one. You can get one from any Nostr client like Jumble.social, any tool like NAK or nostrtool.com or follow a comprehensive guide like my guide on mining a Nostr key.
4 – Launch your relay
If you are using my Docker fork from above, then–
docker compose upYour relay should now be running on port 3334 and ready to accept web socket connections from your client.
Before you move on to set up the client, it's helpful to quickly test that it is running as expected.
5 – Test your websocket connection
For this I use a tool called wscat to make a websocket connection.
You may need to install wscat, e.g.
npm install -g wscatAnd then run it, e.g.
wscat -c ws://localhost:3334(note use
ws://for localhost, rather thanwss://).If your relay is working successfully then it should receive your websocket connection request and respond with an AUTH token, asking you to identify yourself as a user in the relay's
read_whitelist.json(using the standard outlined in NIP-42), e.g.``` Connected (press CTRL+C to quit) < ["AUTH","13206fea43ef2952"]
```
You do not need to authorise for now.
If you received this kind of message, your relay is working successfully.
Set a subdomain for your relay
Let's connect a domain name so your community members can access your relay.
1 – Configure DNS
At a high level –
- Get your domain (buy one if you need to)
- Get the IP address of your VPS
- In your domain's DNS settings add those records as an A record to the subdomain of your choice, e.g.
relayas inrelay.your_domain_name.com, or in my caseassistantrelay.rodbishop.nz
Your subdomain now points to your server.
2 – Configure reverse proxy
You need to redirect traffic from your subdomain to your relay at port
3334.On my VPS I use Caddy as a reverse proxy for a few projects, I have it sitting in a separate Docker network. To use it for my SW2 Relay required two steps.
First – I added configuration to Caddy's
Caddyfileto tell it what to do with requests for therelay.your_domain_name.comsubdomain. For me this looked like–assistantrelay.rodbishop.nz { reverse_proxy sw2-relay:3334 { # Enable WebSocket support header_up X-Forwarded-For {remote} header_up X-Forwarded-Proto {scheme} header_up X-Forwarded-Port {server_port} } }Second – I added the Caddy Docker network to the SW2
docker-compose.ymlto make it be part of the Caddy network. In my Docker branch, I provide this commented section which you can uncomment and use if you like.``` services: relay: ... relay configuration here ...
networks:
- caddy # Connect to a Caddy network for reverse proxy
networks:
caddy:
external: true # Connect to a Caddy network for reverse proxy
```
Your relay is now running at your domain name.
Run Jumble.social
Your client set up is very easy, as most heavy lifting is done by your relay. My client of choice is Jumble because it has features that focus the user experience on the community's content first. You have two options for running Jumble.
- Run your own local copy of Jumble by cloning the Github (optional)
- Use the public instance at Jumble.social (easier, and what we'll do in this demo)
If you (optionally) want to run your own local copy of Jumble:
git clone https://github.com/CodyTseng/jumble.git cd jumble npm install npm run devFor this demo, I will just use the public instance at http://jumble.social
Jumble has a very helpful user interface for set up and configuration. But, I wanted to think ahead to onboarding community members, and so instead I will do some work up front in order to give new members a smooth onboarding flow that I would suggest for an administrator to use in onboarding their community.
1 – Create a custom landing page URL for your community members to land on
When your users come to your website for the first time, you want them to get your community experience without any distraction. That will either be–
- A prompt to sign up or login (if only authorised users can read content)
- The actual content from your other community members (If all users can read content)
Your landing page URL will look like:
http://jumble.social/?r=wss://relay.your_domain_name.comhttp://jumble.social/– the URL of the Jumble instance you are using?r=– telling Jumble to read from a relaywss://– relays connect via websocket using wss, rather than httpsrelay.your_domain_name.com– the domain name of your relay
For me, this URL looks like
http://jumble.social/?r=wss://assistantrelay.rodbishop.nz2 – Visit your custom Jumble URL
This should load the landing page of your relay on Jumble.
In the background, Jumble has attempted to establish a websocket connection to your relay.
If your relay is configured with read authentication, it has sent a challenge to Jumble asking your user to authenticate. Jumble, accordingly should now be showing you a login screen, asking your user to login.
3 – Login or Sign Up
You will see a variety of sign up and login options. To test, log in with the private key that you have configured to have read and write access.
In the background, Jumble has connected via websocket to your relay, checked that your user is authorised to view notes, and if so, has returned all the content on the relay. (If this is your first time here, there would not be any content yet).
If you give this link to your users to use as their landing page, they will land, login, and see only notes from members of your community.
4– Make your first post to your community
Click the "post" button and post a note. Jumble offers you the option to "Send only to relay.your_domain_name.com".
- If set to on, then Jumble will post the note only to your relay, no others. It will also include a specific tag (the
"-"tag) which requests relays to not forward the note across the network. Only your community members viewing notes on your community relay can see it. - If set to off, then Jumble will post the note to your relay and also the wider public Nostr network. Community members viewing notes on the relay can see it, and so can any user of the wider Nostr network.
5– Optional, configure your relay sets
At the top of the screen you should now see a dropdown with the URL of your relay.
Each user can save this relay to a "relay set" for future use, and also view, add or delete other relays sets including some sets which Jumble comes with set up by default.
As an admin you can use this to give users access to multiple relays. And, as a user, you can use this to access posts from multiple different community relays, all within the one client.
Your community website is up and running
That is the basic set up completed.
- You have a website where your community members can visit a URL to post notes and view all notes from all other members of the community.
- You have basic administration to enforce your own read and write permissions very simply in two json files.
Let's check in with my user requirements as a community admin–
- My community is saving content to a server where I control access
- My users view only that content by default, and are not exposed to any wider public social network unless they knowingly select that
- My user's content is a) viewable only by other community members, or b) by the wider public, at the user's discretion
- Other people are maintaining the code for me
- It's free
This setup has scope to solve my dog fooding issues from earlier–
- If adopted, my tech community can iterate the interface to suit its needs, find great content, and share content beyond the community.
- If adopted, my kids social groups can each have their own relays, but I can post to all of them together, or view a consolidated feed.
- If adopted, my team can chat with each other for free. I can self host this. It can natively interoperate with any other Nostr SaaS. It would be entirely private and will not be captured to train a Big Co AI without my consent.
Using your community website in practice
An example onboarding flow
- A new member joins your IRL community
- Your admin person gives them your landing page URL where they can view all the posts by your community members – If you have configured your relay to have no read auth required, then they can land on that landing page and immediately start viewing your community's posts, a great landing experience
- The user user creates a Nostr profile, and provides the admin person with their public key
- The admin person adds their key to the whitelists to read and write as you desire.
Default inter-op with the wider Nostr network
- If you change your mind on SW2 and want to use a different relay, your notes will be supported natively, and you can migrate on your own terms
- If you change your mind on Jumble and want to use a different client, your relay will be supported natively, and you can migrate on your own terms
- If you want to add other apps to your community's experience, every Nostr app will interoperate with your community by default – see the huge list at Awesome Nostr
- If any of your users want to view your community notes inside some other Nostr client – perhaps to see a consolidated feed of notes from all their different communities – they can.
For me, I use Amethyst app as my main Nostr client to view the public posts from people I follow. I have added my private community relay to Amethyst, and now my community posts appear alongside all these other posts in a single consolidated feed.
Scope to further improve
- You can run multiple different relays with different user access – e.g. one for wider company and one for your team
- You can run your own fork of Jumble and change the interface to suit you needs – e.g. add your logo, change the colours, link to other resources from the sidebar.
Other ideas for running communities
- Guest accounts: You can give a user "guest" access – read auth, but no write auth – to help people see the value of your community before becoming members.
- Running a knowledge base: You can whitelist users to read notes, but only administrators can post notes.
- Running a blind dropbox: You can whitelist users to post notes, but only the administrator can read notes.
- Running on a local terminal only: With Jumble and SW2 installed on a machine, running at –
localhost:5173for Jumble, andlocalhost:3334for SW2 you can have an entirely local experience athttp://localhost:5173/?r=ws://localhost:3334.
What's Next?
In my first four blogs I explored creating a good Nostr setup with Vanity Npub, Lightning Payments, Nostr Addresses at Your Domain, and Personal Nostr Relay.
Then in my latest three blogs I explored different types of interoperability with NFC cards, n8n Workflow Automation, and now running a private community website on Nostr.
For this community website–
- There is scope to make some further enhancements to SW2, including to add a "Blossom" media server so that community admins can self-host their own rich media, and to create an admin screen for administration of the whitelists using NIP-86.
- There is scope to explore all other kinds of Nostr clients to form the front-end of community websites, including Chachi.chat, Flotilla, and others.
- Nostr includes a whole variety of different optional standards for making more elaborate online communities including NIP-28, NIP-29, NIP-17, NIP-72 (etc). Each gives certain different capabilities, and I haven't used any of them! For this simple demo they are not required, but each could be used to extend the capabilities of the admin and community.
I am also doing a lot of work with AI on Nostr, including that I use my private community website as a front-end for engaging with a Nostr AI. I'll post about this soon too.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ a95c6243:d345522c
2025-02-15 19:05:38
@ a95c6243:d345522c
2025-02-15 19:05:38Auf der diesjährigen Münchner Sicherheitskonferenz geht es vor allem um die Ukraine. Protagonisten sind dabei zunächst die US-Amerikaner. Präsident Trump schockierte die Europäer kurz vorher durch ein Telefonat mit seinem Amtskollegen Wladimir Putin, während Vizepräsident Vance mit seiner Rede über Demokratie und Meinungsfreiheit für versteinerte Mienen und Empörung sorgte.
Die Bemühungen der Europäer um einen Frieden in der Ukraine halten sich, gelinde gesagt, in Grenzen. Größeres Augenmerk wird auf militärische Unterstützung, die Pflege von Feindbildern sowie Eskalation gelegt. Der deutsche Bundeskanzler Scholz reagierte auf die angekündigten Verhandlungen über einen möglichen Frieden für die Ukraine mit der Forderung nach noch höheren «Verteidigungsausgaben». Auch die amtierende Außenministerin Baerbock hatte vor der Münchner Konferenz klargestellt:
«Frieden wird es nur durch Stärke geben. (...) Bei Corona haben wir gesehen, zu was Europa fähig ist. Es braucht erneut Investitionen, die der historischen Wegmarke, vor der wir stehen, angemessen sind.»
Die Rüstungsindustrie freut sich in jedem Fall über weltweit steigende Militärausgaben. Die Kriege in der Ukraine und in Gaza tragen zu Rekordeinnahmen bei. Jetzt «winkt die Aussicht auf eine jahrelange große Nachrüstung in Europa», auch wenn der Ukraine-Krieg enden sollte, so hört man aus Finanzkreisen. In der Konsequenz kennt «die Aktie des deutschen Vorzeige-Rüstungskonzerns Rheinmetall in ihrem Anstieg offenbar gar keine Grenzen mehr». «Solche Friedensversprechen» wie das jetzige hätten in der Vergangenheit zu starken Kursverlusten geführt.
Für manche Leute sind Kriegswaffen und sonstige Rüstungsgüter Waren wie alle anderen, jedenfalls aus der Perspektive von Investoren oder Managern. Auch in diesem Bereich gibt es Startups und man spricht von Dingen wie innovativen Herangehensweisen, hocheffizienten Produktionsanlagen, skalierbaren Produktionstechniken und geringeren Stückkosten.
Wir lesen aktuell von Massenproduktion und gesteigerten Fertigungskapazitäten für Kriegsgerät. Der Motor solcher Dynamik und solchen Wachstums ist die Aufrüstung, die inzwischen permanent gefordert wird. Parallel wird die Bevölkerung verbal eingestimmt und auf Kriegstüchtigkeit getrimmt.
Das Rüstungs- und KI-Startup Helsing verkündete kürzlich eine «dezentrale Massenproduktion für den Ukrainekrieg». Mit dieser Expansion positioniere sich das Münchner Unternehmen als einer der weltweit führenden Hersteller von Kampfdrohnen. Der nächste «Meilenstein» steht auch bereits an: Man will eine Satellitenflotte im Weltraum aufbauen, zur Überwachung von Gefechtsfeldern und Truppenbewegungen.
Ebenfalls aus München stammt das als DefenseTech-Startup bezeichnete Unternehmen ARX Robotics. Kürzlich habe man in der Region die größte europäische Produktionsstätte für autonome Verteidigungssysteme eröffnet. Damit fahre man die Produktion von Militär-Robotern hoch. Diese Expansion diene auch der Lieferung der «größten Flotte unbemannter Bodensysteme westlicher Bauart» in die Ukraine.
Rüstung boomt und scheint ein Zukunftsmarkt zu sein. Die Hersteller und Vermarkter betonen, mit ihren Aktivitäten und Produkten solle die europäische Verteidigungsfähigkeit erhöht werden. Ihre Strategien sollten sogar «zum Schutz demokratischer Strukturen beitragen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-02-19 09:23:17
@ a95c6243:d345522c
2025-02-19 09:23:17Die «moralische Weltordnung» – eine Art Astrologie. Friedrich Nietzsche
Das Treffen der BRICS-Staaten beim Gipfel im russischen Kasan war sicher nicht irgendein politisches Event. Gastgeber Wladimir Putin habe «Hof gehalten», sagen die Einen, China und Russland hätten ihre Vorstellung einer multipolaren Weltordnung zelebriert, schreiben Andere.
In jedem Fall zeigt die Anwesenheit von über 30 Delegationen aus der ganzen Welt, dass von einer geostrategischen Isolation Russlands wohl keine Rede sein kann. Darüber hinaus haben sowohl die Anreise von UN-Generalsekretär António Guterres als auch die Meldungen und Dementis bezüglich der Beitrittsbemühungen des NATO-Staats Türkei für etwas Aufsehen gesorgt.
Im Spannungsfeld geopolitischer und wirtschaftlicher Umbrüche zeigt die neue Allianz zunehmendes Selbstbewusstsein. In Sachen gemeinsamer Finanzpolitik schmiedet man interessante Pläne. Größere Unabhängigkeit von der US-dominierten Finanzordnung ist dabei ein wichtiges Ziel.
Beim BRICS-Wirtschaftsforum in Moskau, wenige Tage vor dem Gipfel, zählte ein nachhaltiges System für Finanzabrechnungen und Zahlungsdienste zu den vorrangigen Themen. Während dieses Treffens ging der russische Staatsfonds eine Partnerschaft mit dem Rechenzentrumsbetreiber BitRiver ein, um Bitcoin-Mining-Anlagen für die BRICS-Länder zu errichten.
Die Initiative könnte ein Schritt sein, Bitcoin und andere Kryptowährungen als Alternativen zu traditionellen Finanzsystemen zu etablieren. Das Projekt könnte dazu führen, dass die BRICS-Staaten den globalen Handel in Bitcoin abwickeln. Vor dem Hintergrund der Diskussionen über eine «BRICS-Währung» wäre dies eine Alternative zu dem ursprünglich angedachten Korb lokaler Währungen und zu goldgedeckten Währungen sowie eine mögliche Ergänzung zum Zahlungssystem BRICS Pay.
Dient der Bitcoin also der Entdollarisierung? Oder droht er inzwischen, zum Gegenstand geopolitischer Machtspielchen zu werden? Angesichts der globalen Vernetzungen ist es oft schwer zu durchschauen, «was eine Show ist und was im Hintergrund von anderen Strippenziehern insgeheim gesteuert wird». Sicher können Strukturen wie Bitcoin auch so genutzt werden, dass sie den Herrschenden dienlich sind. Aber die Grundeigenschaft des dezentralisierten, unzensierbaren Peer-to-Peer Zahlungsnetzwerks ist ihm schließlich nicht zu nehmen.
Wenn es nach der EZB oder dem IWF geht, dann scheint statt Instrumentalisierung momentan eher der Kampf gegen Kryptowährungen angesagt. Jürgen Schaaf, Senior Manager bei der Europäischen Zentralbank, hat jedenfalls dazu aufgerufen, Bitcoin «zu eliminieren». Der Internationale Währungsfonds forderte El Salvador, das Bitcoin 2021 als gesetzliches Zahlungsmittel eingeführt hat, kürzlich zu begrenzenden Maßnahmen gegen das Kryptogeld auf.
Dass die BRICS-Staaten ein freiheitliches Ansinnen im Kopf haben, wenn sie Kryptowährungen ins Spiel bringen, darf indes auch bezweifelt werden. Im Abschlussdokument bekennen sich die Gipfel-Teilnehmer ausdrücklich zur UN, ihren Programmen und ihrer «Agenda 2030». Ernst Wolff nennt das «eine Bankrotterklärung korrupter Politiker, die sich dem digital-finanziellen Komplex zu 100 Prozent unterwerfen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ e516ecb8:1be0b167
2025-03-25 23:49:34
@ e516ecb8:1be0b167
2025-03-25 23:49:34En los años 20, Estados Unidos vivía una juerga económica conocida como los "Roaring Twenties". La Gran Guerra había terminado, la industria estaba en auge, los autos llenaban las calles y el jazz resonaba en cada esquina. Todo parecía ir viento en popa: las acciones subían como espuma, la gente compraba a crédito como si no hubiera mañana y los bancos estaban felices de prestar dinero. Pero, según los economistas austriacos —piensa en Ludwig von Mises o Friedrich Hayek—, esta prosperidad era una fachada, una burbuja inflada artificialmente que tarde o temprano iba a estallar.
La Escuela Austriaca sostiene que el verdadero villano de esta historia no fue la codicia de los especuladores ni el exceso de optimismo, sino algo más sutil y estructural: la manipulación del dinero y el crédito por parte de la Reserva Federal. Vamos a desglosarlo paso a paso, como si estuviéramos destapando una intriga.
Acto 1: La Reserva Federal enciende la mecha
Tras su creación en 1913, la Reserva Federal (el banco central de EE.UU.) tenía el poder de controlar la oferta de dinero y las tasas de interés. En la década de 1920, decidió que era buena idea mantener las tasas de interés artificialmente bajas. ¿Por qué? Para estimular la economía, ayudar a Gran Bretaña a volver al patrón oro y mantener la fiesta en marcha. Pero para los austriacos, esto fue como echar gasolina a una fogata.
Cuando las tasas de interés se mantienen bajas por decreto, el dinero se vuelve "barato". Los bancos prestan más de lo que lo harían en un mercado libre, y ese crédito fácil fluye hacia empresas, inversores y consumidores. Es como si le dieras a todo el mundo una tarjeta de crédito sin límite: la gente empieza a gastar, invertir y construir como si la riqueza fuera infinita. Pero aquí viene el giro: ese dinero no reflejaba ahorros reales ni riqueza genuina. Era una ilusión creada por la expansión del crédito.
Acto 2: El auge insostenible
Con este dinero barato, los empresarios se lanzaron a proyectos ambiciosos: fábricas, rascacielos, nuevas tecnologías. Los inversores, por su parte, corrieron a Wall Street, comprando acciones a crédito (lo que se llamaba "comprar al margen"). El mercado de valores se disparó: el índice Dow Jones pasó de 63 puntos en 1921 a 381 en 1929. ¡Una locura! La gente común, desde taxistas hasta amas de casa, se metió al juego, convencida de que las acciones solo podían subir.
Para la Escuela Austriaca, este "boom" era una distorsión. Según su teoría del ciclo económico, desarrollada por Mises y Hayek, cuando el crédito se expande artificialmente, los recursos se mal asignan. Imagina que eres un chef con un presupuesto limitado: si alguien te da dinero falso para comprar ingredientes, harás platos extravagantes que no puedes sostener cuando el dinero real se acabe. Eso estaba pasando en la economía: se construían cosas que no tenían demanda real ni base sólida.
Acto 3: La burbuja empieza a pincharse
Hacia 1928, algunos empezaron a oler problemas. La producción industrial comenzó a tambalearse, los inventarios se acumulaban y las deudas crecían. La Reserva Federal, dándose cuenta de que la fiesta se estaba descontrolando, intentó subir las tasas de interés para enfriar las cosas. Pero era demasiado tarde: la economía ya estaba dopada con crédito fácil, y el daño estaba hecho.
El 24 de octubre de 1929 —el famoso "Jueves Negro"— el pánico estalló en Wall Street. Los inversores, viendo que las acciones estaban sobrevaloradas y que sus deudas eran impagables, empezaron a vender en masa. El martes siguiente, 29 de octubre, el mercado colapsó por completo: millones de acciones cambiaron de manos, los precios se desplomaron y la riqueza en papel se evaporó. Pero para los austriacos, esto no fue la causa del problema, sino el síntoma. El verdadero desastre ya había ocurrido en los años previos, con la expansión artificial del crédito.
Epílogo: La lección austriaca
Desde la perspectiva de la Escuela Austriaca, el Crack del 29 no fue un fallo del libre mercado, sino del intervencionismo. La Reserva Federal, al manipular las tasas de interés y la oferta de dinero, creó una burbuja que era insostenible. Cuando estalló, la economía tuvo que pasar por una dolorosa "corrección": las empresas quebraron, los bancos cerraron y el desempleo se disparó. Para Mises y Hayek, esto era inevitable: el mercado necesitaba purgar los excesos y realinear los recursos con la realidad.
¿Y qué pasó después? Bueno, la Gran Depresión que siguió fue agravada, según los austriacos, por más intervenciones: el New Deal de Roosevelt y las políticas proteccionistas como la Ley Smoot-Hawley solo prolongaron la agonía. Pero esa es otra historia para otro café.
-
 @ c631e267:c2b78d3e
2025-02-07 19:42:11
@ c631e267:c2b78d3e
2025-02-07 19:42:11Nur wenn wir aufeinander zugehen, haben wir die Chance \ auf Überwindung der gegenseitigen Ressentiments! \ Dr. med. dent. Jens Knipphals
In Wolfsburg sollte es kürzlich eine Gesprächsrunde von Kritikern der Corona-Politik mit Oberbürgermeister Dennis Weilmann und Vertretern der Stadtverwaltung geben. Der Zahnarzt und langjährige Maßnahmenkritiker Jens Knipphals hatte diese Einladung ins Rathaus erwirkt und publiziert. Seine Motivation:
«Ich möchte die Spaltung der Gesellschaft überwinden. Dazu ist eine umfassende Aufarbeitung der Corona-Krise in der Öffentlichkeit notwendig.»
Schon früher hatte Knipphals Antworten von den Kommunalpolitikern verlangt, zum Beispiel bei öffentlichen Bürgerfragestunden. Für das erwartete Treffen im Rathaus formulierte er Fragen wie: Warum wurden fachliche Argumente der Kritiker ignoriert? Weshalb wurde deren Ausgrenzung, Diskreditierung und Entmenschlichung nicht entgegengetreten? In welcher Form übernehmen Rat und Verwaltung in Wolfsburg persönlich Verantwortung für die erheblichen Folgen der politischen Corona-Krise?
Der Termin fand allerdings nicht statt – der Bürgermeister sagte ihn kurz vorher wieder ab. Knipphals bezeichnete Weilmann anschließend als Wiederholungstäter, da das Stadtoberhaupt bereits 2022 zu einem Runden Tisch in der Sache eingeladen hatte, den es dann nie gab. Gegenüber Multipolar erklärte der Arzt, Weilmann wolle scheinbar eine öffentliche Aufarbeitung mit allen Mitteln verhindern. Er selbst sei «inzwischen absolut desillusioniert» und die einzige Lösung sei, dass die Verantwortlichen gingen.
Die Aufarbeitung der Plandemie beginne bei jedem von uns selbst, sei aber letztlich eine gesamtgesellschaftliche Aufgabe, schreibt Peter Frey, der den «Fall Wolfsburg» auch in seinem Blog behandelt. Diese Aufgabe sei indes deutlich größer, als viele glaubten. Erfreulicherweise sei der öffentliche Informationsraum inzwischen größer, trotz der weiterhin unverfrorenen Desinformations-Kampagnen der etablierten Massenmedien.
Frey erinnert daran, dass Dennis Weilmann mitverantwortlich für gravierende Grundrechtseinschränkungen wie die 2021 eingeführten 2G-Regeln in der Wolfsburger Innenstadt zeichnet. Es sei naiv anzunehmen, dass ein Funktionär einzig im Interesse der Bürger handeln würde. Als früherer Dezernent des Amtes für Wirtschaft, Digitalisierung und Kultur der Autostadt kenne Weilmann zum Beispiel die Verknüpfung von Fördergeldern mit politischen Zielsetzungen gut.
Wolfsburg wurde damals zu einem Modellprojekt des Bundesministeriums des Innern (BMI) und war Finalist im Bitkom-Wettbewerb «Digitale Stadt». So habe rechtzeitig vor der Plandemie das Projekt «Smart City Wolfsburg» anlaufen können, das der Stadt «eine Vorreiterrolle für umfassende Vernetzung und Datenerfassung» aufgetragen habe, sagt Frey. Die Vereinten Nationen verkauften dann derartige «intelligente» Überwachungs- und Kontrollmaßnahmen ebenso als Rettung in der Not wie das Magazin Forbes im April 2020:
«Intelligente Städte können uns helfen, die Coronavirus-Pandemie zu bekämpfen. In einer wachsenden Zahl von Ländern tun die intelligenten Städte genau das. Regierungen und lokale Behörden nutzen Smart-City-Technologien, Sensoren und Daten, um die Kontakte von Menschen aufzuspüren, die mit dem Coronavirus infiziert sind. Gleichzeitig helfen die Smart Cities auch dabei, festzustellen, ob die Regeln der sozialen Distanzierung eingehalten werden.»
Offensichtlich gibt es viele Aspekte zu bedenken und zu durchleuten, wenn es um die Aufklärung und Aufarbeitung der sogenannten «Corona-Pandemie» und der verordneten Maßnahmen geht. Frustration und Desillusion sind angesichts der Realitäten absolut verständlich. Gerade deswegen sind Initiativen wie die von Jens Knipphals so bewundernswert und so wichtig – ebenso wie eine seiner Kernthesen: «Wir müssen aufeinander zugehen, da hilft alles nichts».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 1e5d0f11:12eeba92
2025-03-25 23:42:33
@ 1e5d0f11:12eeba92
2025-03-25 23:42:33Una semana en Nostr
Mucho tiempo ha pasado desde la primera vez que escuche de Nostr, guiado por mi eterna curiosidad ante cada nueva tecnología que descubro en internet decidí sumergirme en este protocolo, lo que encontré en ese entonces era un recién nacido, tenia todo el potencial de crecer y convertirse en algo grande y usado por muchas personas, pero todavía estaba en su infancia y los desarrolladores que tomaban provecho de este nuevo protocolo eran pocos y sus aplicaciones eran también jóvenes, ademas que los relés de Nostr (algo critico en su infraestructura) eran muy pocos, en conclusión estaba claro que había llegado muy temprano, y que Nostr todavía no era para alguien que se interesa por la tecnología pero cuya profesión no es el desarrollo de aplicaciones para internet, a esperar.
Grande fue mi sorpresa al volver a Nostr, al igual como ocurrió con muchos, fui recordado de Nostr gracias a Derek Ross y su charla en Nostr for Beginners w/ Derek Ross, al volver mi sorpresa fue grata, "no esta muerto" fue lo primero que pensé, esto porque es común que proyectos de código abiertos y que en superficie parece que intentaran reinventar la rueda están destinados al paredón de desarrolladores criticándolos o hundidos en el océano de Github sin nadie para explorar lo que pudo ser una buena idea, pero no Nostr, Nostr seguía vivo, creciendo y actualizando sus NIPs, gracias, en gran medida, a una generosa donación del co-fundador de Twitter (ahora llamado X o Xitter para algunos) en Bitcoins, la moneda del futuro y que derrotara al dinero fiduciario, o eso aseguran sus varios creyentes en Nostr, y Nostr esta lleno de ellos, lleno, sin duda impulsados por la importante donación que recibió el proyecto y por un mecanismo que lleva a este protocolo mas allá que otros: Nip-57. Lighting Zaps se llaman, y le da la posibilidad al usuario de transferir "Zaps", que como lo dice la propia pagina de Nostr es una propina que puede ser entregada a cualquier usuario que use Nostr y que ya tenga su billetera Lightning funcionando, y esto puede ser convertido en BTC, algo que no he probado y no creo lo haga en el corto tiempo, pero saber que tanto empeño se ha puesto en la creación de un nuevo protocolo pro incensurable que ademas incorpora elementos de cadena de bloques para proveer a creadores de contenido u otros con un método directo de financiación y así remover la necesidad de publicidad en las paginas algo que me parece saludable para internet, internet estaría mucho mejor sin tanto rastreador de publicidad y con mas respeto a la privacidad de los usuarios.
En fin, escribo esto como una prueba para saber como funcionan las publicaciones largas y tediosas desde Flycat, y bueno, seguiré usando el protocolo Nostr porque parece que ya esta en una etapa que me agrada y esta mas maduro, le contare a otros sobre Nostr, pero debo decir que entrar a Nostr, agregar relés y buscar usuarios para seguir es un proceso lento y tranquilo, no parece ser para el usuario común, pero al final siempre es uno el que configura las cuentas de sus padres y otros familiares.
-
 @ a95c6243:d345522c
2025-01-31 20:02:25
@ a95c6243:d345522c
2025-01-31 20:02:25Im Augenblick wird mit größter Intensität, großer Umsicht \ das deutsche Volk belogen. \ Olaf Scholz im FAZ-Interview
Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur Reuters Verbreitung in den Medien gefunden hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten.
Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen sei repräsentativ, behauptet der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von Mitgliedern, die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben».
Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH, also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges «Demokratie-Update» aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet.
Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer befürchteten, dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen.
Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein? Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise abgelehnt. Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen.
Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen, die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter berichtet. Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert».
Der Vorwand «unzulässiger Einflussnahme» auf Politik und Wahlen wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als «völlig irre» bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird «E-Voting» seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg.
Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus. Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die weit verbreitete Armut zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 878dff7c:037d18bc
2025-03-25 23:32:39
@ 878dff7c:037d18bc
2025-03-25 23:32:39Federal Budget 2025: Comprehensive Analysis and Implications
Overview:
On March 25, 2025, Treasurer Jim Chalmers presented Australia's Federal Budget for the 2025–26 fiscal year. This budget introduces several significant measures aimed at providing immediate cost-of-living relief, stimulating economic growth, and addressing long-term structural challenges. Key components include:
-
Personal Income Tax Cuts: The budget outlines a reduction in the lowest marginal tax rate from 16% to 15% starting July 1, 2026, and further to 14% from July 1, 2027. This initiative is projected to cost $17.1 billion over three years and aims to benefit low and middle-income earners.
-
Energy Bill Relief: An extension of the Energy Bill Relief Fund will provide $150 rebates to households over the next six months, totaling $1.8 billion. This measure is designed to alleviate rising energy costs and is expected to reduce headline inflation by approximately 0.5 percentage points in 2025.
-
Healthcare Investments: Significant funding has been allocated to Medicare to enhance bulk billing services and reduce pharmaceutical costs under the Pharmaceutical Benefits Scheme (PBS), aiming to improve healthcare accessibility.
-
Housing Initiatives: The budget includes an $800 million expansion of the Help to Buy program, increasing eligibility criteria to assist first-home buyers. However, this measure is limited to 40,000 applicants, leading to concerns about its overall impact on housing affordability.
-
Economic Projections: The budget forecasts a return to deficits, with an anticipated shortfall of $27.6 billion for the 2025–26 fiscal year. Real GDP growth is projected at 2.25%, with unemployment rates expected to peak at 4.25%.
Expert Analyses:
-
Deloitte: Deloitte's analysis emphasizes the need for structural reforms to address underlying fiscal challenges, noting that while the budget provides immediate relief, it may not sufficiently tackle long-term economic issues.
-
PwC: PwC highlights the importance of enacting pending tax and superannuation measures to ensure fiscal stability, pointing out that the budget's forward tax agenda remains uncertain.
-
KPMG: KPMG observes that the budget attempts to balance immediate cost-of-living relief with long-term fiscal responsibility but notes that it may lack measures to boost productivity and incentivize business investment.
Reactions from News Sources:
-
ABC News described the budget as "cautiously optimistic," praising its cost-of-living focus but noting limited ambition in areas such as climate investment and innovation.
-
The Guardian called it a "modest" budget, identifying meaningful but narrow wins for renters, aged care, and public infrastructure, while critiquing it for its limited reach and reliance on temporary relief.
-
The Australian Financial Review emphasized the lack of bold economic reform, pointing out that while the tax cuts may assist consumers in the short term, the broader economic strategy appeared politically calculated rather than reform-driven.
-
News.com.au focused on practical household benefits, highlighting how the budget would impact average Australians. It praised the tax cuts and rebates but expressed skepticism about the housing measures' real-world impact.
-
The Australian accused the budget of being driven by “polling, not policy,” arguing that it sidesteps difficult reforms in areas like energy security, defense, and migration in favor of short-term voter appeal.
Sectoral Implications:
-
Business Investment: The budget projects modest business investment growth of 1.5% in 2025–26 and 2026–27, down from 6% in 2024–25. This decline is attributed to global economic uncertainties and trade tensions.
-
Tax Compliance: The Australian Taxation Office (ATO) will receive nearly $999 million over the next four years to enhance enforcement activities, aiming to recover an additional $3.2 billion in tax receipts by 2029.
-
Housing Market: Despite the expansion of the Help to Buy program, concerns remain about the budget's limited impact on housing affordability, with critics arguing that more comprehensive measures are needed to address supply constraints.
Conclusion:
The Federal Budget 2025 introduces measures aimed at providing immediate relief to Australian households and businesses. While it delivers on promises around tax cuts and cost-of-living support, several analysts and media commentators view it as lacking in ambition and long-term economic vision. The political nature of its design is evident, with many measures framed to appeal to voters in the lead-up to the next federal election. Its success will hinge on effective implementation and how well it navigates the evolving domestic and global economic landscape.
Sources: Deloitte - March 25, 2025, PwC Australia - March 25, 2025, KPMG Australia - March 25, 2025, The Guardian - March 25, 2025, News.com.au - March 26, 2025, The Australian - March 26, 2025, Australian Financial Review - March 26, 2025, ABC News - March 25, 2025
Apple Transforms AirPods Pro 2 into Hearing Aids
Summary:
Apple has released a software upgrade enabling AirPods Pro 2 to function as "clinical grade" hearing aids for individuals with mild to moderate hearing loss. This feature includes the ability to perform hearing tests using an iPhone or iPad. Priced at $399, the AirPods Pro 2 offer an affordable alternative to traditional hearing aids, which can cost thousands. Experts caution that while beneficial, professional guidance is essential, and the AirPods may not be suitable for everyone.
Sources: The Australian - March 26, 2025, The Guardian - March 26, 2025
2000km Rain Band to Drench Queensland and New South Wales
Summary:
A 2000km-long rain band, fueled by tropical air and a low-pressure system, is set to bring exceptionally high rainfall to Queensland and parts of New South Wales. Some regions have already experienced significant downpours, with 208mm recorded in the Central West and 145mm near Townsville. Severe weather warnings are in effect, with flash flooding reported and expected to worsen. Residents are advised to remain vigilant due to rising river and creek levels. In contrast, Western Australia is enduring record-breaking heat, with temperatures surpassing 39°C in certain areas.
Sources: News.com.au - March 26, 2025, ABC News - March 26, 2025
Projected Population Shift from New South Wales to Queensland
Summary:
Federal budget data projects that New South Wales will experience a net loss of 115,300 residents by 2028-29, primarily due to Sydney's high cost of living. Queensland is expected to gain approximately 110,500 residents during the same period. Other states like Victoria and Western Australia are also projected to see slight population increases, while South Australia, Tasmania, the Northern Territory, and the ACT may experience decreases.
Source: News.com.au - March 26, 2025
Ban on Non-Compete Clauses for Workers Earning Below $175,000
Summary:
The Australian government has announced plans to ban non-compete clauses for workers earning below $175,000 annually, including professions such as hairdressers, construction workers, and childcare staff. This initiative aims to enhance job mobility and is projected to boost the economy by approximately $5 billion, potentially increasing individual wages by up to $2,500 annually. The ban is set to take effect in 2027.
Sources: The Guardian - March 25, 2025, Mirage News - March 26, 2025, NAB Business - March 26, 2025
Geopolitical Tensions and Tariffs Hamper Australian Mining Investment
Summary:
Industry leaders express concern that escalating geopolitical tensions and tariffs are adversely affecting investment in Australia's mining sector. The uncertainty surrounding international trade policies, particularly from major partners like the United States and China, is leading to hesitancy among investors. This situation poses challenges for Australia's resource-driven economy, emphasizing the need for strategic responses to navigate the complex global landscape. Sources: National Security News - March 25, 2025
Government Launches Campaign on Tainted Alcohol Risks Abroad
Summary:
In response to the deaths of two Melbourne teenagers in Laos last year from methanol poisoning, the Australian government has initiated a campaign to raise awareness about the dangers of consuming tainted alcohol overseas. The campaign aims to educate young Australians on alcohol-related risks, signs of methanol poisoning, and safety measures through social media, text messages, and airport communications. Foreign Affairs Minister Penny Wong emphasized the importance of this initiative in preventing further tragedies.
Sources: ABC News - March 24, 2025, The Guardian - March 24, 2025
Boeing's MQ-28 Ghost Bat Completes 100th Flight
Summary:
Boeing's MQ-28 Ghost Bat, an uncrewed collaborative combat aircraft developed in partnership with the Royal Australian Air Force (RAAF), has successfully completed its 100th test flight. This milestone signifies the program's maturity and underscores Australia's growing role in advanced aerospace development. The MQ-28 is designed to operate alongside crewed aircraft, enhancing mission capabilities and providing a force multiplier effect. Looking ahead, Boeing plans to conduct an air-to-air missile test from the MQ-28 by late 2025 or early 2026, aiming to further integrate offensive capabilities into the platform.
Sources: Australian Defence Magazine - March 25, 2025, Breaking Defense - March 25, 2025, Flight Global - March 25, 2025, Boeing - March 25, 2025
Russia and Ukraine Agree to Black Sea Ceasefire
Summary:
In a significant development, Russia and Ukraine have agreed to a ceasefire in the Black Sea, aiming to ensure safe navigation and halt military engagements in the region. The agreement, brokered by the United States during separate talks held in Saudi Arabia, includes provisions to prevent the use of commercial vessels for military purposes and to implement a 30-day suspension of attacks on energy infrastructure. However, the implementation of the ceasefire is contingent upon the lifting of certain Western sanctions on Russia's agricultural and financial sectors, a condition that has sparked debate among international observers. Ukrainian President Volodymyr Zelenskyy has expressed cautious optimism, emphasizing the need for concrete actions over verbal commitments. Critics argue that the agreement may disproportionately favor Russia, potentially allowing it to consolidate its position in the region. The situation remains fluid, with further negotiations anticipated to address unresolved issues and ensure adherence to the ceasefire terms. Sources: Associated Press - March 26, 2025, The Guardian - March 26, 2025
UN Research Indicates Under-reported Methane Emissions from Queensland Mine
Summary:
A UN-backed study reveals that methane emissions from Glencore's Hail Creek coalmine in Queensland are likely three to eight times higher than reported. Using aircraft-based measurements, the study found emissions between 1.5Mt and 4.2Mt CO2e per year, compared to the reported 0.53Mt CO2e. This underscores the need for more accurate emission reporting methods, as methane is a potent greenhouse gas.
Sources: The Guardian - March 26, 2025
How to Improve Your Teeth & Oral Microbiome for Brain & Body Health
Summary:
In this episode of the Huberman Lab podcast, Dr. Andrew Huberman interviews Dr. Staci Whitman, a board-certified functional dentist specializing in pediatric and adult care. They discuss the critical role of oral health in overall brain and body wellness. Key topics include:
- Oral Microbiome's Impact: The balance of bacteria in the mouth influences systemic health, affecting digestion, immunity, and even neurological function.
- Preventive Dental Care: Emphasis on regular dental check-ups, proper brushing and flossing techniques, and the use of non-toxic dental products to maintain oral hygiene.
- Dietary Considerations: How nutrition affects oral health, highlighting the importance of reducing sugar intake and consuming nutrient-rich foods to support strong teeth and gums.
- Connections to Chronic Diseases: Exploring links between oral health issues like gum disease and conditions such as heart disease, diabetes, and Alzheimer's.
- Holistic Approaches: Discussion on integrating functional medicine practices into dentistry to address root causes of oral health problems rather than just symptoms.
This conversation underscores the importance of maintaining oral health as a vital component of overall well-being.
-
-
 @ a95c6243:d345522c
2025-01-24 20:59:01
@ a95c6243:d345522c
2025-01-24 20:59:01Menschen tun alles, egal wie absurd, \ um ihrer eigenen Seele nicht zu begegnen. \ Carl Gustav Jung
«Extremer Reichtum ist eine Gefahr für die Demokratie», sagen über die Hälfte der knapp 3000 befragten Millionäre aus G20-Staaten laut einer Umfrage der «Patriotic Millionaires». Ferner stellte dieser Zusammenschluss wohlhabender US-Amerikaner fest, dass 63 Prozent jener Millionäre den Einfluss von Superreichen auf US-Präsident Trump als Bedrohung für die globale Stabilität ansehen.
Diese Besorgnis haben 370 Millionäre und Milliardäre am Dienstag auch den in Davos beim WEF konzentrierten Privilegierten aus aller Welt übermittelt. In einem offenen Brief forderten sie die «gewählten Führer» auf, die Superreichen – also sie selbst – zu besteuern, um «die zersetzenden Auswirkungen des extremen Reichtums auf unsere Demokratien und die Gesellschaft zu bekämpfen». Zum Beispiel kontrolliere eine handvoll extrem reicher Menschen die Medien, beeinflusse die Rechtssysteme in unzulässiger Weise und verwandele Recht in Unrecht.
Schon 2019 beanstandete der bekannte Historiker und Schriftsteller Ruthger Bregman an einer WEF-Podiumsdiskussion die Steuervermeidung der Superreichen. Die elitäre Veranstaltung bezeichnete er als «Feuerwehr-Konferenz, bei der man nicht über Löschwasser sprechen darf.» Daraufhin erhielt Bregman keine Einladungen nach Davos mehr. Auf seine Aussagen machte der Schweizer Aktivist Alec Gagneux aufmerksam, der sich seit Jahrzehnten kritisch mit dem WEF befasst. Ihm wurde kürzlich der Zutritt zu einem dreiteiligen Kurs über das WEF an der Volkshochschule Region Brugg verwehrt.
Nun ist die Erkenntnis, dass mit Geld politischer Einfluss einhergeht, alles andere als neu. Und extremer Reichtum macht die Sache nicht wirklich besser. Trotzdem hat man über Initiativen wie Patriotic Millionaires oder Taxmenow bisher eher selten etwas gehört, obwohl es sie schon lange gibt. Auch scheint es kein Problem, wenn ein Herr Gates fast im Alleingang versucht, globale Gesundheits-, Klima-, Ernährungs- oder Bevölkerungspolitik zu betreiben – im Gegenteil. Im Jahr, als der Milliardär Donald Trump zum zweiten Mal ins Weiße Haus einzieht, ist das Echo in den Gesinnungsmedien dagegen enorm – und uniform, wer hätte das gedacht.
Der neue US-Präsident hat jedoch «Davos geerdet», wie Achgut es nannte. In seiner kurzen Rede beim Weltwirtschaftsforum verteidigte er seine Politik und stellte klar, er habe schlicht eine «Revolution des gesunden Menschenverstands» begonnen. Mit deutlichen Worten sprach er unter anderem von ersten Maßnahmen gegen den «Green New Scam», und von einem «Erlass, der jegliche staatliche Zensur beendet»:
«Unsere Regierung wird die Äußerungen unserer eigenen Bürger nicht mehr als Fehlinformation oder Desinformation bezeichnen, was die Lieblingswörter von Zensoren und derer sind, die den freien Austausch von Ideen und, offen gesagt, den Fortschritt verhindern wollen.»
Wie der «Trumpismus» letztlich einzuordnen ist, muss jeder für sich selbst entscheiden. Skepsis ist definitiv angebracht, denn «einer von uns» sind weder der Präsident noch seine auserwählten Teammitglieder. Ob sie irgendeinen Sumpf trockenlegen oder Staatsverbrechen aufdecken werden oder was aus WHO- und Klimaverträgen wird, bleibt abzuwarten.
Das WHO-Dekret fordert jedenfalls die Übertragung der Gelder auf «glaubwürdige Partner», die die Aktivitäten übernehmen könnten. Zufällig scheint mit «Impfguru» Bill Gates ein weiterer Harris-Unterstützer kürzlich das Lager gewechselt zu haben: Nach einem gemeinsamen Abendessen zeigte er sich «beeindruckt» von Trumps Interesse an der globalen Gesundheit.
Mit dem Projekt «Stargate» sind weitere dunkle Wolken am Erwartungshorizont der Fangemeinde aufgezogen. Trump hat dieses Joint Venture zwischen den Konzernen OpenAI, Oracle, und SoftBank als das «größte KI-Infrastrukturprojekt der Geschichte» angekündigt. Der Stein des Anstoßes: Oracle-CEO Larry Ellison, der auch Fan von KI-gestützter Echtzeit-Überwachung ist, sieht einen weiteren potenziellen Einsatz der künstlichen Intelligenz. Sie könne dazu dienen, Krebserkrankungen zu erkennen und individuelle mRNA-«Impfstoffe» zur Behandlung innerhalb von 48 Stunden zu entwickeln.
Warum bitte sollten sich diese superreichen «Eliten» ins eigene Fleisch schneiden und direkt entgegen ihren eigenen Interessen handeln? Weil sie Menschenfreunde, sogenannte Philanthropen sind? Oder vielleicht, weil sie ein schlechtes Gewissen haben und ihre Schuld kompensieren müssen? Deswegen jedenfalls brauchen «Linke» laut Robert Willacker, einem deutschen Politikberater mit brasilianischen Wurzeln, rechte Parteien – ein ebenso überraschender wie humorvoller Erklärungsansatz.
Wenn eine Krähe der anderen kein Auge aushackt, dann tut sie das sich selbst noch weniger an. Dass Millionäre ernsthaft ihre eigene Besteuerung fordern oder Machteliten ihren eigenen Einfluss zugunsten anderer einschränken würden, halte ich für sehr unwahrscheinlich. So etwas glaube ich erst, wenn zum Beispiel die Rüstungsindustrie sich um Friedensverhandlungen bemüht, die Pharmalobby sich gegen institutionalisierte Korruption einsetzt, Zentralbanken ihre CBDC-Pläne für Bitcoin opfern oder der ÖRR die Abschaffung der Rundfunkgebühren fordert.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 2f4550b0:95f20096
2025-03-25 23:09:57
@ 2f4550b0:95f20096
2025-03-25 23:09:57Recently, I tuned into a prominent podcast where the conversation turned to what children are learning in K-12 education (around the 1:24:20 mark). Among the contributors was a Silicon Valley tech investor who shared a startling anecdote about an elite private school. He described how, at what he called “the best all-girls private school in Silicon Valley,” students were taught that reading was racist. He went on: “There was a spreadsheet that these kids had to memorize every day that had every other kid’s pronoun, and if you didn’t get it right you’d get in trouble.”
I was floored, not just by the absurdity of the curriculum, but by the casual assertion that a school teaching such ideas could still be deemed “the best.” How could an institution so detached from a rigorous, skill-building education retain that lofty title? I reflected on what truly makes an elite private school worthy of being called “the best,” a label too often thrown around without scrutiny.
Historically, top-tier private schools earned their reputations through academic excellence, robust curricula, and a commitment to preparing students for leadership and success. Think of the traditional hallmarks: mastery of core subjects like literature, mathematics, and science; critical thinking honed through debate and analysis; and extracurriculars designed to cultivate discipline and creativity. These schools were exclusive not just for their price tags but for their promise to deliver an education that equipped graduates to thrive in competitive universities and careers.
Yet the anecdote from that podcast suggests a troubling shift. If a school prioritizes ideological conformity (say, memorizing pronouns or framing foundational skills like reading as racist) over intellectual rigor, it’s fair to question whether it still deserves its elite status. Prestige, wealth, and social cachet might keep a school “elite” in name, but “the best” should mean more than that. It should reflect a dedication to fostering knowledge, skills, and independent thought, qualities that empower students as future leaders, not pawns in a cultural tug-of-war.
Consider what parents and students expect from a premium education. For an astronomical tuition (often exceeding $40,000 annually in places like Silicon Valley) they anticipate a return on investment: a curriculum that challenges young minds, teachers who inspire rather than indoctrinate, and a culture that values merit over dogma. When a school veers into territory where basic literacy is politicized or rote memorization of social rules trumps critical inquiry, it betrays that trust. No spreadsheet of pronouns will help a graduate navigate a complex world; a firm grasp of history, science, and persuasive writing just might.
This isn’t to say elite schools shouldn’t evolve. The world changes, and education must adapt, whether by integrating technology, addressing current issues, or broadening perspectives. But adaptation should enhance, not replace, the core mission of learning. A school can teach ethics alongside traditional subjects without sacrificing intellectual integrity. The problem arises when ideology becomes the curriculum, sidelining the tools students need to reason for themselves. If students are taught to question reading instead of mastering it, how will they author their own futures?
The Silicon Valley example isn’t isolated. Across the country, elite institutions have leaned into progressive trends, prioritizing social justice frameworks and experimental pedagogies over substance. Some might argue this reflects a bold reimagining of education, but there’s a difference between innovation and derailment. A school can be forward-thinking without abandoning the fundamentals that define excellence. Parents paying top dollar, and students investing their formative years, deserve more than a trendy experiment.
So, what should define “the best” private school today? First, employ a curriculum that balances tradition and progress: teach Shakespeare and coding, ethics and algebra, with an eye toward real-world application. Second, hire a faculty of experts who challenge students to think, not just comply. Third, create an environment that rewards effort and achievement over adherence to a script. Prestige alone, whether from alumni networks, manicured campuses, or Silicon Valley buzz, can’t suffice.
The tech investor’s remark about “the best” stuck with me because it revealed a disconnect. A school might remain elite in the eyes of the wealthy or well-connected, but “the best” is a higher bar. It’s a title earned through results, not rhetoric. Until these institutions recommit to education over indoctrination, they risk losing not just their claim to excellence, but the trust of those they serve.
-
 @ c631e267:c2b78d3e
2025-01-18 09:34:51
@ c631e267:c2b78d3e
2025-01-18 09:34:51Die grauenvollste Aussicht ist die der Technokratie – \ einer kontrollierenden Herrschaft, \ die durch verstümmelte und verstümmelnde Geister ausgeübt wird. \ Ernst Jünger
«Davos ist nicht mehr sexy», das Weltwirtschaftsforum (WEF) mache Davos kaputt, diese Aussagen eines Einheimischen las ich kürzlich in der Handelszeitung. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den vergangenen vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
Der deutsche WEF-Gründer hatte bei dieser Gelegenheit immer höchst lobende Worte für seine Landsmännin: 2021 erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und 2022 fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
Von der Leyens Handeln während der sogenannten Corona-«Pandemie» lobte Schwab damals bereits ebenso, wie es diese Woche das Karlspreis-Direktorium tat, als man der Beschuldigten im Fall Pfizergate die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
Jene Herausforderungen durch «Krisen epochalen Ausmaßes» werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im Global Risks Report nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
Ein «Great Mental Reset» sei die Voraussetzung dafür, dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
Der aktuelle Zustand unserer Gesellschaften ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die Rechtsstaatlichkeit stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-01-13 10:09:57
@ a95c6243:d345522c
2025-01-13 10:09:57Ich begann, Social Media aufzubauen, \ um den Menschen eine Stimme zu geben. \ Mark Zuckerberg
Sind euch auch die Tränen gekommen, als ihr Mark Zuckerbergs Wendehals-Deklaration bezüglich der Meinungsfreiheit auf seinen Portalen gehört habt? Rührend, oder? Während er früher die offensichtliche Zensur leugnete und später die Regierung Biden dafür verantwortlich machte, will er nun angeblich «die Zensur auf unseren Plattformen drastisch reduzieren».
«Purer Opportunismus» ob des anstehenden Regierungswechsels wäre als Klassifizierung viel zu kurz gegriffen. Der jetzige Schachzug des Meta-Chefs ist genauso Teil einer kühl kalkulierten Business-Strategie, wie es die 180 Grad umgekehrte Praxis vorher war. Social Media sind ein höchst lukratives Geschäft. Hinzu kommt vielleicht noch ein bisschen verkorkstes Ego, weil derartig viel Einfluss und Geld sicher auch auf die Psyche schlagen. Verständlich.
«Es ist an der Zeit, zu unseren Wurzeln der freien Meinungsäußerung auf Facebook und Instagram zurückzukehren. Ich begann, Social Media aufzubauen, um den Menschen eine Stimme zu geben», sagte Zuckerberg.
Welche Wurzeln? Hat der Mann vergessen, dass er von der Überwachung, dem Ausspionieren und dem Ausverkauf sämtlicher Daten und digitaler Spuren sowie der Manipulation seiner «Kunden» lebt? Das ist knallharter Kommerz, nichts anderes. Um freie Meinungsäußerung geht es bei diesem Geschäft ganz sicher nicht, und das war auch noch nie so. Die Wurzeln von Facebook liegen in einem Projekt des US-Militärs mit dem Namen «LifeLog». Dessen Ziel war es, «ein digitales Protokoll vom Leben eines Menschen zu erstellen».
Der Richtungswechsel kommt allerdings nicht überraschend. Schon Anfang Dezember hatte Meta-Präsident Nick Clegg von «zu hoher Fehlerquote bei der Moderation» von Inhalten gesprochen. Bei der Gelegenheit erwähnte er auch, dass Mark sehr daran interessiert sei, eine aktive Rolle in den Debatten über eine amerikanische Führungsrolle im technologischen Bereich zu spielen.
Während Milliardärskollege und Big Tech-Konkurrent Elon Musk bereits seinen Posten in der kommenden Trump-Regierung in Aussicht hat, möchte Zuckerberg also nicht nur seine Haut retten – Trump hatte ihn einmal einen «Feind des Volkes» genannt und ihm lebenslange Haft angedroht –, sondern am liebsten auch mitspielen. KI-Berater ist wohl die gewünschte Funktion, wie man nach einem Treffen Trump-Zuckerberg hörte. An seine Verhaftung dachte vermutlich auch ein weiterer Multimilliardär mit eigener Social Media-Plattform, Pavel Durov, als er Zuckerberg jetzt kritisierte und gleichzeitig warnte.
Politik und Systemmedien drehen jedenfalls durch – was zu viel ist, ist zu viel. Etwas weniger Zensur und mehr Meinungsfreiheit würden die Freiheit der Bürger schwächen und seien potenziell vernichtend für die Menschenrechte. Zuckerberg setze mit dem neuen Kurs die Demokratie aufs Spiel, das sei eine «Einladung zum nächsten Völkermord», ernsthaft. Die Frage sei, ob sich die EU gegen Musk und Zuckerberg behaupten könne, Brüssel müsse jedenfalls hart durchgreifen.
Auch um die Faktenchecker macht man sich Sorgen. Für die deutsche Nachrichtenagentur dpa und die «Experten» von Correctiv, die (noch) Partner für Fact-Checking-Aktivitäten von Facebook sind, sei das ein «lukratives Geschäftsmodell». Aber möglicherweise werden die Inhalte ohne diese vermeintlichen Korrektoren ja sogar besser. Anders als Meta wollen jedoch Scholz, Faeser und die Tagesschau keine Fehler zugeben und zum Beispiel Correctiv-Falschaussagen einräumen.
Bei derlei dramatischen Befürchtungen wundert es nicht, dass der öffentliche Plausch auf X zwischen Elon Musk und AfD-Chefin Alice Weidel von 150 EU-Beamten überwacht wurde, falls es irgendwelche Rechtsverstöße geben sollte, die man ihnen ankreiden könnte. Auch der Deutsche Bundestag war wachsam. Gefunden haben dürften sie nichts. Das Ganze war eher eine Show, viel Wind wurde gemacht, aber letztlich gab es nichts als heiße Luft.
Das Anbiedern bei Donald Trump ist indes gerade in Mode. Die Weltgesundheitsorganisation (WHO) tut das auch, denn sie fürchtet um Spenden von über einer Milliarde Dollar. Eventuell könnte ja Elon Musk auch hier künftig aushelfen und der Organisation sowie deren größtem privaten Förderer, Bill Gates, etwas unter die Arme greifen. Nachdem Musks KI-Projekt xAI kürzlich von BlackRock & Co. sechs Milliarden eingestrichen hat, geht da vielleicht etwas.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 5d4b6c8d:8a1c1ee3
2025-03-25 23:01:15
@ 5d4b6c8d:8a1c1ee3
2025-03-25 23:01:15As we close in on the playoffs, especially with the mighty regular season Cavs stumbling a bit, I wanted to zoom out and get some historical perspective on what it takes to be an NBA champion.
Over the past 20 years, here's the complete list of the 10 guys who were the best player on a title team. 1. Lebron 4x 2. Steph 4x 3. Duncan 3x 4. Kobe 2x 5. Tatum 6. Jokic 7. Giannis 8. Kawhi 9. Dirk 10. Garnett
The worst players on that list are better than anyone on the Cavs, or several other playoff teams. Unless we're going to have an '04 Pistons anomaly, the only teams I see with players who might belong on that list are the following: - Celtics (Tatum's already there, after all) - OKC (SGA's having the best guard season since MJ) - Denver - Milwaukee - Lakers - Clippers (If Kawhi's still that guy) - Warriors - T-Wolves
Eight is actually a lot, but only two of these teams are playing like contenders.
What do you think? Can we rule out the teams that aren't on this list? Am I slandering someone by leaving them out? Or, is this just nonsense masquerading as analysis?
originally posted at https://stacker.news/items/925135
-
 @ a95c6243:d345522c
2025-01-03 20:26:47
@ a95c6243:d345522c
2025-01-03 20:26:47Was du bist hängt von drei Faktoren ab: \ Was du geerbt hast, \ was deine Umgebung aus dir machte \ und was du in freier Wahl \ aus deiner Umgebung und deinem Erbe gemacht hast. \ Aldous Huxley
Das brave Mitmachen und Mitlaufen in einem vorgegebenen, recht engen Rahmen ist gewiss nicht neu, hat aber gerade wieder mal Konjunktur. Dies kann man deutlich beobachten, eigentlich egal, in welchem gesellschaftlichen Bereich man sich umschaut. Individualität ist nur soweit angesagt, wie sie in ein bestimmtes Schema von «Diversität» passt, und Freiheit verkommt zur Worthülse – nicht erst durch ein gewisses Buch einer gewissen ehemaligen Regierungschefin.
Erklärungsansätze für solche Entwicklungen sind bekannt, und praktisch alle haben etwas mit Massenpsychologie zu tun. Der Herdentrieb, also der Trieb der Menschen, sich – zum Beispiel aus Unsicherheit oder Bequemlichkeit – lieber der Masse anzuschließen als selbstständig zu denken und zu handeln, ist einer der Erklärungsversuche. Andere drehen sich um Macht, Propaganda, Druck und Angst, also den gezielten Einsatz psychologischer Herrschaftsinstrumente.
Aber wollen die Menschen überhaupt Freiheit? Durch Gespräche im privaten Umfeld bin ich diesbezüglich in der letzten Zeit etwas skeptisch geworden. Um die Jahreswende philosophiert man ja gerne ein wenig über das Erlebte und über die Erwartungen für die Zukunft. Dabei hatte ich hin und wieder den Eindruck, die totalitären Anwandlungen unserer «Repräsentanten» kämen manchen Leuten gerade recht.
«Desinformation» ist so ein brisantes Thema. Davor müsse man die Menschen doch schützen, hörte ich. Jemand müsse doch zum Beispiel diese ganzen merkwürdigen Inhalte in den Social Media filtern – zur Ukraine, zum Klima, zu Gesundheitsthemen oder zur Migration. Viele wüssten ja gar nicht einzuschätzen, was richtig und was falsch ist, sie bräuchten eine Führung.
Freiheit bedingt Eigenverantwortung, ohne Zweifel. Eventuell ist es einigen tatsächlich zu anspruchsvoll, die Verantwortung für das eigene Tun und Lassen zu übernehmen. Oder die persönliche Freiheit wird nicht als ausreichend wertvolles Gut angesehen, um sich dafür anzustrengen. In dem Fall wäre die mangelnde Selbstbestimmung wohl das kleinere Übel. Allerdings fehlt dann gemäß Aldous Huxley ein Teil der Persönlichkeit. Letztlich ist natürlich alles eine Frage der Abwägung.
Sind viele Menschen möglicherweise schon so «eingenordet», dass freiheitliche Ambitionen gar nicht für eine ganze Gruppe, ein Kollektiv, verfolgt werden können? Solche Gedanken kamen mir auch, als ich mir kürzlich diverse Talks beim viertägigen Hacker-Kongress des Chaos Computer Clubs (38C3) anschaute. Ich war nicht nur überrascht, sondern reichlich erschreckt angesichts der in weiten Teilen mainstream-geformten Inhalte, mit denen ein dankbares Publikum beglückt wurde. Wo ich allgemein hellere Köpfe erwartet hatte, fand ich Konformismus und enthusiastisch untermauerte Narrative.
Gibt es vielleicht so etwas wie eine Herdenimmunität gegen Indoktrination? Ich denke, ja, zumindest eine gestärkte Widerstandsfähigkeit. Was wir brauchen, sind etwas gesunder Menschenverstand, offene Informationskanäle und der Mut, sich freier auch zwischen den Herden zu bewegen. Sie tun das bereits, aber sagen Sie es auch dieses Jahr ruhig weiter.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 00f8d531:a838c062
2025-03-26 00:21:41
@ 00f8d531:a838c062
2025-03-26 00:21:41Dear nostr, I love you. Stay frosty.
-
 @ 7da115b6:7d3e46ae
2025-03-25 22:59:06
@ 7da115b6:7d3e46ae
2025-03-25 22:59:06These are in order of least to most complex.
Be Warned: Some of these ingredients may be unique to New Zealand and Australia
Pikelets
Pikelets are delicious with butter and jam or jam and whipped cream. To make Pancakes, double this recipe and make them larger. Serve in a stack with butter, maple syrup, bacon and blueberries. I've found a single batch is good for 2-4 people if you just want a snack.
Prep Time: 5 minutes Cooking Time: About 10 minutes
Ingredients: - A Cup Self Raising Flour - A Quarter Teaspoon of Table Salt - 1 Egg - A Quarter Cup of White Sugar - About 3 quarters of a Cup of Whole Milk
Method: 1. Sift the Flour and Salt into a bowl. 2. In another bowl beat the Egg and Sugar with a whisk until pale and thick. 3. Add the Egg mixture and the Milk to the dry ingredients and mix until just combined. 4. Gently heat a non-stick frying pan and drop tablespoonfuls of the mixture from the point of the spoon onto the surface. 5. When bubbles start to burst on the top of the Pikelets, turn them over and cook the second side until golden. 6. Place in a clean tea towel to cool.
This recipe requires a little experience to get right, especially if you prefer to use a cast iron pan or griddle. Basically, you can use a cast iron or aluminium pan, just make sure to grease the pan between each batch. The easiest way to do it, is to grab some baking paper, or butter paper wrap, scrunch it up and wipe it over the block of butter, and then wipe the surface of the pan. After the first round has cooked, do wipe the butter over the pan again. It'll stop the Pikelets from sticking.
Scones
These are based on an old recipe from the Edmond's Cookbook, and have been a Kiwi staple for decades. The yield is about 12 (ish), but it depends on how big or small you shape them.
Prep Time: About 10 minutes Cooking Time: 10 minutes (Depending on your Oven)
Ingredients: - 3 Cups of Premium White Wheat Flour - 2 and a Half Levelled Tablespoons of Baking Powder - A quarter of a Teaspoon of Table Salt - About a Third of a Cup of Butter - Between 1 to 1.5 Cups of Whole Milk
Method: 1. Preheat the oven to 220C. 2. Grease or flour a baking tray. 3. Sift the flour, baking powder and salt into a bowl. 4. Rub in the butter with your fingertips until the mixture resembles fine breadcrumbs 5. Add the milk and quickly mix with a round-bladed table knife to a soft dough. For light and tender scones the mixture should be quite soft and a little sticky. 6. Scrape the dough onto the floured baking tray and flour the top 7. Working quickly, pat the dough out to 2cm thickness and with a floured knife cut it into 12 even-sized pieces, then separate the scones to allow 2cm space between them. 8. Brush the tops with milk. 9. Bake for 10 minutes or until golden brown. Place on a wire rack to cool, wrapped in a clean tea towel to keep them soft.
They're great with Butter or Whipped Cream and Jam. 3-4 per person is excellent with some hot sweet Tea mid afternoon.
A little variation that used to be popular is to dice up about a a cup of Bacon, grate about a cup of Cheese, and throw it in the batter for a savoury twist.
Remember to not overcook them, otherwise they come out dry and crumbly.
Chocolate Muffins
I can't remember where I got this recipe, but I've made them dozens of times over the years. They really fill the gap when it comes to those hungry little faces pleading for snacks. This recipe is a little more complicated, but worth it. They're soft and moist, and extremely more-ish. I can personally eat about half on my own before I start feeling guilty. You can get about 12 muffins out of this mixture.
Prep Time: 20 minutes Cooking Time: About 18 minutes
Ingredients: - 1 and a quarter Cups Self Raising Flour - A quarter Cup of Cocoa Powder - 3 quarters of a Teaspoon of Baking Soda - A Quarter Teaspoon of Table Salt - Half a Cup of Soft Brown Sugar - A Quarter Cup of White Sugar - Half a cup of Chocolate Chips - An Egg - Half a Cup of Greek Yoghurt or Sour Cream - Half a Cup of Whole Milk - A Quarter Cup of Sunflower Oil (substitute with warmed dripping/butter or clean cooking oil to taste) - 1 Teaspoon of Vanilla Essence
Method: 1. Preheat oven to 180C on fan bake. 2. Line a 12-hole muffin tin with paper cases. 3. Sift the Flour, Cocoa Powder, Baking Soda and Salt into a large bowl. Stir in the White and Brown Sugars, followed by the Chocolate Chips. 4. In a separate bowl, whisk together Egg, Yoghurt (or Sour Cream), Milk, Oil (or Butter/Dripping) and Vanilla Essence. 5. Add the mixture to the dry ingredients and mix until just combined. Try not to over-mix it, you're not looking for a smooth texture, just no unmixed dry ingredients. 6. Divide mixture evenly between 12 muffin paper cases. 7. (Optional) Sprinkle with extra chocolate chips, for decoration. 8. Bake for 18-20 minutes, until muffins spring back when lightly pressed. 9. Leave to cool in tins for a couple of minutes before transferring to a wire cooling rack.
If you're feeling especially fancy, you can slice them open, and add a dollop of jam and whipped cream. Garnish with a Mint Leaf or Glacé Cherry. Using a Sieve, you can powder the top with Icing Sugar if you want to go that extra mile. It's a real Wifey pleaser.
-
 @ b2d670de:907f9d4a
2025-03-25 20:17:57
@ b2d670de:907f9d4a
2025-03-25 20:17:57This guide will walk you through setting up your own Strfry Nostr relay on a Debian/Ubuntu server and making it accessible exclusively as a TOR hidden service. By the end, you'll have a privacy-focused relay that operates entirely within the TOR network, enhancing both your privacy and that of your users.
Table of Contents
- Prerequisites
- Initial Server Setup
- Installing Strfry Nostr Relay
- Configuring Your Relay
- Setting Up TOR
- Making Your Relay Available on TOR
- Testing Your Setup]
- Maintenance and Security
- Troubleshooting
Prerequisites
- A Debian or Ubuntu server
- Basic familiarity with command line operations (most steps are explained in detail)
- Root or sudo access to your server
Initial Server Setup
First, let's make sure your server is properly set up and secured.
Update Your System
Connect to your server via SSH and update your system:
bash sudo apt update sudo apt upgrade -ySet Up a Basic Firewall
Install and configure a basic firewall:
bash sudo apt install ufw -y sudo ufw allow ssh sudo ufw enableThis allows SSH connections while blocking other ports for security.
Installing Strfry Nostr Relay
This guide includes the full range of steps needed to build and set up Strfry. It's simply based on the current version of the
DEPLOYMENT.mddocument in the Strfry GitHub repository. If the build/setup process is changed in the repo, this document could get outdated. If so, please report to me that something is outdated and check for updated steps here.Install Dependencies
First, let's install the necessary dependencies. Each package serves a specific purpose in building and running Strfry:
bash sudo apt install -y git build-essential libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev liblmdb-dev libflatbuffers-dev libsecp256k1-dev libzstd-devHere's why each dependency is needed:
Basic Development Tools: -
git: Version control system used to clone the Strfry repository and manage code updates -build-essential: Meta-package that includes compilers (gcc, g++), make, and other essential build toolsPerl Dependencies (used for Strfry's build scripts): -
libyaml-perl: Perl interface to parse YAML configuration files -libtemplate-perl: Template processing system used during the build process -libregexp-grammars-perl: Advanced regular expression handling for Perl scriptsCore Libraries for Strfry: -
libssl-dev: Development files for OpenSSL, used for secure connections and cryptographic operations -zlib1g-dev: Compression library that Strfry uses to reduce data size -liblmdb-dev: Lightning Memory-Mapped Database library, which Strfry uses for its high-performance database backend -libflatbuffers-dev: Memory-efficient serialization library for structured data -libsecp256k1-dev: Optimized C library for EC operations on curve secp256k1, essential for Nostr's cryptographic signatures -libzstd-dev: Fast real-time compression algorithm for efficient data storage and transmissionClone and Build Strfry
Clone the Strfry repository:
bash git clone https://github.com/hoytech/strfry.git cd strfryBuild Strfry:
bash git submodule update --init make setup-golpe make -j2 # This uses 2 CPU cores. Adjust based on your server (e.g., -j4 for 4 cores)This build process will take several minutes, especially on servers with limited CPU resources, so go get a coffee and post some great memes on nostr in the meantime.
Install Strfry
Install the Strfry binary to your system path:
bash sudo cp strfry /usr/local/binThis makes the
strfrycommand available system-wide, allowing it to be executed from any directory and by any user with the appropriate permissions.Configuring Your Relay
Create Strfry User
Create a dedicated user for running Strfry. This enhances security by isolating the relay process:
bash sudo useradd -M -s /usr/sbin/nologin strfryThe
-Mflag prevents creating a home directory, and-s /usr/sbin/nologinprevents anyone from logging in as this user. This is a security best practice for service accounts.Create Data Directory
Create a directory for Strfry's data:
bash sudo mkdir /var/lib/strfry sudo chown strfry:strfry /var/lib/strfry sudo chmod 755 /var/lib/strfryThis creates a dedicated directory for Strfry's database and sets the appropriate permissions so that only the strfry user can write to it.
Configure Strfry
Copy the sample configuration file:
bash sudo cp strfry.conf /etc/strfry.confEdit the configuration file:
bash sudo nano /etc/strfry.confModify the database path:
```
Find this line:
db = "./strfry-db/"
Change it to:
db = "/var/lib/strfry/" ```
Check your system's hard limit for file descriptors:
bash ulimit -HnUpdate the
nofilessetting in your configuration to match this value (or set to 0):```
Add or modify this line in the config (example if your limit is 524288):
nofiles = 524288 ```
The
nofilessetting determines how many open files Strfry can have simultaneously. Setting it to your system's hard limit (or 0 to use the system default) helps prevent "too many open files" errors if your relay becomes popular.You might also want to customize your relay's information in the config file. Look for the
infosection and update it with your relay's name, description, and other details.Set ownership of the configuration file:
bash sudo chown strfry:strfry /etc/strfry.confCreate Systemd Service
Create a systemd service file for managing Strfry:
bash sudo nano /etc/systemd/system/strfry.serviceAdd the following content:
```ini [Unit] Description=strfry relay service
[Service] User=strfry ExecStart=/usr/local/bin/strfry relay Restart=on-failure RestartSec=5 ProtectHome=yes NoNewPrivileges=yes ProtectSystem=full LimitCORE=1000000000
[Install] WantedBy=multi-user.target ```
This systemd service configuration: - Runs Strfry as the dedicated strfry user - Automatically restarts the service if it fails - Implements security measures like
ProtectHomeandNoNewPrivileges- Sets resource limits appropriate for a relayEnable and start the service:
bash sudo systemctl enable strfry.service sudo systemctl start strfryCheck the service status:
bash sudo systemctl status strfryVerify Relay is Running
Test that your relay is running locally:
bash curl localhost:7777You should see a message indicating that the Strfry relay is running. This confirms that Strfry is properly installed and configured before we proceed to set up TOR.
Setting Up TOR
Now let's make your relay accessible as a TOR hidden service.
Install TOR
Install TOR from the package repositories:
bash sudo apt install -y torThis installs the TOR daemon that will create and manage your hidden service.
Configure TOR
Edit the TOR configuration file:
bash sudo nano /etc/tor/torrcScroll down to wherever you see a commented out part like this: ```
HiddenServiceDir /var/lib/tor/hidden_service/
HiddenServicePort 80 127.0.0.1:80
```
Under those lines, add the following lines to set up a hidden service for your relay:
HiddenServiceDir /var/lib/tor/strfry-relay/ HiddenServicePort 80 127.0.0.1:7777This configuration: - Creates a hidden service directory at
/var/lib/tor/strfry-relay/- Maps port 80 on your .onion address to port 7777 on your local machine - Keeps all traffic encrypted within the TOR networkCreate the directory for your hidden service:
bash sudo mkdir -p /var/lib/tor/strfry-relay/ sudo chown debian-tor:debian-tor /var/lib/tor/strfry-relay/ sudo chmod 700 /var/lib/tor/strfry-relay/The strict permissions (700) are crucial for security as they ensure only the debian-tor user can access the directory containing your hidden service private keys.
Restart TOR to apply changes:
bash sudo systemctl restart torMaking Your Relay Available on TOR
Get Your Onion Address
After restarting TOR, you can find your onion address:
bash sudo cat /var/lib/tor/strfry-relay/hostnameThis will output something like
abcdefghijklmnopqrstuvwxyz234567.onion, which is your relay's unique .onion address. This is what you'll share with others to access your relay.Understanding Onion Addresses
The .onion address is a special-format hostname that is automatically generated based on your hidden service's private key.
Your users will need to use this address with the WebSocket protocol prefix to connect:
ws://youronionaddress.onionTesting Your Setup
Test with a Nostr Client
The best way to test your relay is with an actual Nostr client that supports TOR:
- Open your TOR browser
- Go to your favorite client, either on clearnet or an onion service.
- Check out this list of nostr clients available over TOR.
- Add your relay URL:
ws://youronionaddress.onionto your relay list - Try posting a note and see if it appears on your relay
- In some nostr clients, you can also click on a relay to get information about it like the relay name and description you set earlier in the stryfry config. If you're able to see the correct values for the name and the description, you were able to connect to the relay.
- Some nostr clients also gives you a status on what relays a note was posted to, this could also give you an indication that your relay works as expected.
Note that not all Nostr clients support TOR connections natively. Some may require additional configuration or use of TOR Browser. E.g. most mobile apps would most likely require a TOR proxy app running in the background (some have TOR support built in too).
Maintenance and Security
Regular Updates
Keep your system, TOR, and relay updated:
```bash
Update system
sudo apt update sudo apt upgrade -y
Update Strfry
cd ~/strfry git pull git submodule update make -j2 sudo cp strfry /usr/local/bin sudo systemctl restart strfry
Verify TOR is still running properly
sudo systemctl status tor ```
Regular updates are crucial for security, especially for TOR which may have security-critical updates.
Database Management
Strfry has built-in database management tools. Check the Strfry documentation for specific commands related to database maintenance, such as managing event retention and performing backups.
Monitoring Logs
To monitor your Strfry logs:
bash sudo journalctl -u strfry -fTo check TOR logs:
bash sudo journalctl -u tor -fMonitoring logs helps you identify potential issues and understand how your relay is being used.
Backup
This is not a best practices guide on how to do backups. Preferably, backups should be stored either offline or on a different machine than your relay server. This is just a simple way on how to do it on the same server.
```bash
Stop the relay temporarily
sudo systemctl stop strfry
Backup the database
sudo cp -r /var/lib/strfry /path/to/backup/location
Restart the relay
sudo systemctl start strfry ```
Back up your TOR hidden service private key. The private key is particularly sensitive as it defines your .onion address - losing it means losing your address permanently. If you do a backup of this, ensure that is stored in a safe place where no one else has access to it.
bash sudo cp /var/lib/tor/strfry-relay/hs_ed25519_secret_key /path/to/secure/backup/locationTroubleshooting
Relay Not Starting
If your relay doesn't start:
```bash
Check logs
sudo journalctl -u strfry -e
Verify configuration
cat /etc/strfry.conf
Check permissions
ls -la /var/lib/strfry ```
Common issues include: - Incorrect configuration format - Permission problems with the data directory - Port already in use (another service using port 7777) - Issues with setting the nofiles limit (setting it too big)
TOR Hidden Service Not Working
If your TOR hidden service is not accessible:
```bash
Check TOR logs
sudo journalctl -u tor -e
Verify TOR is running
sudo systemctl status tor
Check onion address
sudo cat /var/lib/tor/strfry-relay/hostname
Verify TOR configuration
sudo cat /etc/tor/torrc ```
Common TOR issues include: - Incorrect directory permissions - TOR service not running - Incorrect port mapping in torrc
Testing Connectivity
If you're having trouble connecting to your service:
```bash
Verify Strfry is listening locally
sudo ss -tulpn | grep 7777
Check that TOR is properly running
sudo systemctl status tor
Test the local connection directly
curl --include --no-buffer localhost:7777 ```
Privacy and Security Considerations
Running a Nostr relay as a TOR hidden service provides several important privacy benefits:
-
Network Privacy: Traffic to your relay is encrypted and routed through the TOR network, making it difficult to determine who is connecting to your relay.
-
Server Anonymity: The physical location and IP address of your server are concealed, providing protection against denial-of-service attacks and other targeting.
-
Censorship Resistance: TOR hidden services are more resilient against censorship attempts, as they don't rely on the regular DNS system and can't be easily blocked.
-
User Privacy: Users connecting to your relay through TOR enjoy enhanced privacy, as their connections are also encrypted and anonymized.
However, there are some important considerations:
- TOR connections are typically slower than regular internet connections
- Not all Nostr clients support TOR connections natively
- Running a hidden service increases the importance of keeping your server secure
Congratulations! You now have a Strfry Nostr relay running as a TOR hidden service. This setup provides a resilient, privacy-focused, and censorship-resistant communication channel that helps strengthen the Nostr network.
For further customization and advanced configuration options, refer to the Strfry documentation.
Consider sharing your relay's .onion address with the Nostr community to help grow the privacy-focused segment of the network!
If you plan on providing a relay service that the public can use (either for free or paid for), consider adding it to this list. Only add it if you plan to run a stable and available relay.
-
 @ 5256d869:9a567e23
2025-03-26 00:09:55
@ 5256d869:9a567e23
2025-03-26 00:09:55Pages stretch like waves, but a single drop remains— just read the last line.
-
 @ a95c6243:d345522c
2025-01-01 17:39:51
@ a95c6243:d345522c
2025-01-01 17:39:51Heute möchte ich ein Gedicht mit euch teilen. Es handelt sich um eine Ballade des österreichischen Lyrikers Johann Gabriel Seidl aus dem 19. Jahrhundert. Mir sind diese Worte fest in Erinnerung, da meine Mutter sie perfekt rezitieren konnte, auch als die Kräfte schon langsam schwanden.
Dem originalen Titel «Die Uhr» habe ich für mich immer das Wort «innere» hinzugefügt. Denn der Zeitmesser – hier vermutliche eine Taschenuhr – symbolisiert zwar in dem Kontext das damalige Zeitempfinden und die Umbrüche durch die industrielle Revolution, sozusagen den Zeitgeist und das moderne Leben. Aber der Autor setzt sich philosophisch mit der Zeit auseinander und gibt seinem Werk auch eine klar spirituelle Dimension.
Das Ticken der Uhr und die Momente des Glücks und der Trauer stehen sinnbildlich für das unaufhaltsame Fortschreiten und die Vergänglichkeit des Lebens. Insofern könnte man bei der Uhr auch an eine Sonnenuhr denken. Der Rhythmus der Ereignisse passt uns vielleicht nicht immer in den Kram.
Was den Takt pocht, ist durchaus auch das Herz, unser «inneres Uhrwerk». Wenn dieses Meisterwerk einmal stillsteht, ist es unweigerlich um uns geschehen. Hoffentlich können wir dann dankbar sagen: «Ich habe mein Bestes gegeben.»
Ich trage, wo ich gehe, stets eine Uhr bei mir; \ Wieviel es geschlagen habe, genau seh ich an ihr. \ Es ist ein großer Meister, der künstlich ihr Werk gefügt, \ Wenngleich ihr Gang nicht immer dem törichten Wunsche genügt.
Ich wollte, sie wäre rascher gegangen an manchem Tag; \ Ich wollte, sie hätte manchmal verzögert den raschen Schlag. \ In meinen Leiden und Freuden, in Sturm und in der Ruh, \ Was immer geschah im Leben, sie pochte den Takt dazu.
Sie schlug am Sarge des Vaters, sie schlug an des Freundes Bahr, \ Sie schlug am Morgen der Liebe, sie schlug am Traualtar. \ Sie schlug an der Wiege des Kindes, sie schlägt, will's Gott, noch oft, \ Wenn bessere Tage kommen, wie meine Seele es hofft.
Und ward sie auch einmal träger, und drohte zu stocken ihr Lauf, \ So zog der Meister immer großmütig sie wieder auf. \ Doch stände sie einmal stille, dann wär's um sie geschehn, \ Kein andrer, als der sie fügte, bringt die Zerstörte zum Gehn.
Dann müßt ich zum Meister wandern, der wohnt am Ende wohl weit, \ Wohl draußen, jenseits der Erde, wohl dort in der Ewigkeit! \ Dann gäb ich sie ihm zurücke mit dankbar kindlichem Flehn: \ Sieh, Herr, ich hab nichts verdorben, sie blieb von selber stehn.
Johann Gabriel Seidl (1804-1875)
-
 @ a95c6243:d345522c
2024-12-21 09:54:49
@ a95c6243:d345522c
2024-12-21 09:54:49Falls du beim Lesen des Titels dieses Newsletters unwillkürlich an positive Neuigkeiten aus dem globalen polit-medialen Irrenhaus oder gar aus dem wirtschaftlichen Umfeld gedacht hast, darf ich dich beglückwünschen. Diese Assoziation ist sehr löblich, denn sie weist dich als unverbesserlichen Optimisten aus. Leider muss ich dich diesbezüglich aber enttäuschen. Es geht hier um ein anderes Thema, allerdings sehr wohl ein positives, wie ich finde.
Heute ist ein ganz besonderer Tag: die Wintersonnenwende. Genau gesagt hat heute morgen um 10:20 Uhr Mitteleuropäischer Zeit (MEZ) auf der Nordhalbkugel unseres Planeten der astronomische Winter begonnen. Was daran so außergewöhnlich ist? Der kürzeste Tag des Jahres war gestern, seit heute werden die Tage bereits wieder länger! Wir werden also jetzt jeden Tag ein wenig mehr Licht haben.
Für mich ist dieses Ereignis immer wieder etwas kurios: Es beginnt der Winter, aber die Tage werden länger. Das erscheint mir zunächst wie ein Widerspruch, denn meine spontanen Assoziationen zum Winter sind doch eher Kälte und Dunkelheit, relativ zumindest. Umso erfreulicher ist der emotionale Effekt, wenn dann langsam die Erkenntnis durchsickert: Ab jetzt wird es schon wieder heller!
Natürlich ist es kalt im Winter, mancherorts mehr als anderswo. Vielleicht jedoch nicht mehr lange, wenn man den Klimahysterikern glauben wollte. Mindestens letztes Jahr hat Väterchen Frost allerdings gleich zu Beginn seiner Saison – und passenderweise während des globalen Überhitzungsgipfels in Dubai – nochmal richtig mit der Faust auf den Tisch gehauen. Schnee- und Eischaos sind ja eigentlich in der Agenda bereits nicht mehr vorgesehen. Deswegen war man in Deutschland vermutlich in vorauseilendem Gehorsam schon nicht mehr darauf vorbereitet und wurde glatt lahmgelegt.
Aber ich schweife ab. Die Aussicht auf nach und nach mehr Licht und damit auch Wärme stimmt mich froh. Den Zusammenhang zwischen beidem merkt man in Andalusien sehr deutlich. Hier, wo die Häuser im Winter arg auskühlen, geht man zum Aufwärmen raus auf die Straße oder auf den Balkon. Die Sonne hat auch im Winter eine erfreuliche Kraft. Und da ist jede Minute Gold wert.
Außerdem ist mir vor Jahren so richtig klar geworden, warum mir das südliche Klima so sehr gefällt. Das liegt nämlich nicht nur an der Sonne als solcher, oder der Wärme – das liegt vor allem am Licht. Ohne Licht keine Farben, das ist der ebenso simple wie gewaltige Unterschied zwischen einem deprimierenden matschgraubraunen Winter und einem fröhlichen bunten. Ein großes Stück Lebensqualität.
Mir gefällt aber auch die Symbolik dieses Tages: Licht aus der Dunkelheit, ein Wendepunkt, ein Neuanfang, neue Möglichkeiten, Übergang zu neuer Aktivität. In der winterlichen Stille keimt bereits neue Lebendigkeit. Und zwar in einem Zyklus, das wird immer wieder so geschehen. Ich nehme das gern als ein Stück Motivation, es macht mir Hoffnung und gibt mir Energie.

Übrigens ist parallel am heutigen Tag auf der südlichen Halbkugel Sommeranfang. Genau im entgegengesetzten Rhythmus, sich ergänzend, wie Yin und Yang. Das alles liegt an der Schrägstellung der Erdachse, die ist nämlich um 23,4º zur Umlaufbahn um die Sonne geneigt. Wir erinnern uns, gell?
Insofern bleibt eindeutig festzuhalten, dass “schräg sein” ein willkommener, wichtiger und positiver Wert ist. Mit anderen Worten: auch ungewöhnlich, eigenartig, untypisch, wunderlich, kauzig, … ja sogar irre, spinnert oder gar “quer” ist in Ordnung. Das schließt das Denken mit ein.
In diesem Sinne wünsche ich euch allen urige Weihnachtstage!
Dieser Beitrag ist letztes Jahr in meiner Denkbar erschienen.
-
 @ bc52210b:20bfc6de
2025-03-25 20:17:22
@ bc52210b:20bfc6de
2025-03-25 20:17:22CISA, or Cross-Input Signature Aggregation, is a technique in Bitcoin that allows multiple signatures from different inputs in a transaction to be combined into a single, aggregated signature. This is a big deal because Bitcoin transactions often involve multiple inputs (e.g., spending from different wallet outputs), each requiring its own signature. Normally, these signatures take up space individually, but CISA compresses them into one, making transactions more efficient.
This magic is possible thanks to the linearity property of Schnorr signatures, a type of digital signature introduced to Bitcoin with the Taproot upgrade. Unlike the older ECDSA signatures, Schnorr signatures have mathematical properties that allow multiple signatures to be added together into a single valid signature. Think of it like combining multiple handwritten signatures into one super-signature that still proves everyone signed off!
Fun Fact: CISA was considered for inclusion in Taproot but was left out to keep the upgrade simple and manageable. Adding CISA would’ve made Taproot more complex, so the developers hit pause on it—for now.
CISA vs. Key Aggregation (MuSig, FROST): Don’t Get Confused! Before we go deeper, let’s clear up a common mix-up: CISA is not the same as protocols like MuSig or FROST. Here’s why:
- Signature Aggregation (CISA): Combines multiple signatures into one, each potentially tied to different public keys and messages (e.g., different transaction inputs).
- Key Aggregation (MuSig, FROST): Combines multiple public keys into a single aggregated public key, then generates one signature for that key.
Key Differences: 1. What’s Aggregated? * CISA: Aggregates signatures. * Key Aggregation: Aggregates public keys. 2. What the Verifier Needs * CISA: The verifier needs all individual public keys and their corresponding messages to check the aggregated signature. * Key Aggregation: The verifier only needs the single aggregated public key and one message. 3. When It Happens * CISA: Used during transaction signing, when inputs are being combined into a transaction. * MuSig: Used during address creation, setting up a multi-signature (multisig) address that multiple parties control.
So, CISA is about shrinking signature data in a transaction, while MuSig/FROST are about simplifying multisig setups. Different tools, different jobs!
Two Flavors of CISA: Half-Agg and Full-Agg CISA comes in two modes:
- Full Aggregation (Full-Agg): Interactive, meaning signers need to collaborate during the signing process. (We’ll skip the details here since the query focuses on Half-Agg.)
- Half Aggregation (Half-Agg): Non-interactive, meaning signers can work independently, and someone else can combine the signatures later.
Since the query includes “CISA Part 2: Half Signature Aggregation,” let’s zoom in on Half-Agg.
Half Signature Aggregation (Half-Agg) Explained How It Works Half-Agg is a non-interactive way to aggregate Schnorr signatures. Here’s the process:
- Independent Signing: Each signer creates their own Schnorr signature for their input, without needing to talk to the other signers.
- Aggregation Step: An aggregator (could be anyone, like a wallet or node) takes all these signatures and combines them into one aggregated signature.
A Schnorr signature has two parts:
- R: A random point (32 bytes).
- s: A scalar value (32 bytes).
In Half-Agg:
- The R values from each signature are kept separate (one per input).
- The s values from all signatures are combined into a single s value.
Why It Saves Space (~50%) Let’s break down the size savings with some math:
Before Aggregation: * Each Schnorr signature = 64 bytes (32 for R + 32 for s). * For n inputs: n × 64 bytes.
After Half-Agg: * Keep n R values (32 bytes each) = 32 × n bytes. * Combine all s values into one = 32 bytes. * Total size: 32 × n + 32 bytes.
Comparison:
- Original: 64n bytes.
- Half-Agg: 32n + 32 bytes.
- For large n, the “+32” becomes small compared to 32n, so it’s roughly 32n, which is half of 64n. Hence, ~50% savings!
Real-World Impact: Based on recent Bitcoin usage, Half-Agg could save:
- ~19.3% in space (reducing transaction size).
- ~6.9% in fees (since fees depend on transaction size). This assumes no major changes in how people use Bitcoin post-CISA.
Applications of Half-Agg Half-Agg isn’t just a cool idea—it has practical uses:
- Transaction-wide Aggregation
- Combine all signatures within a single transaction.
- Result: Smaller transactions, lower fees.
- Block-wide Aggregation
- Combine signatures across all transactions in a Bitcoin block.
- Result: Even bigger space savings at the blockchain level.
- Off-chain Protocols / P2P
- Use Half-Agg in systems like Lightning Network gossip messages.
- Benefit: Efficiency without needing miners or a Bitcoin soft fork.
Challenges with Half-Agg While Half-Agg sounds awesome, it’s not without hurdles, especially at the block level:
- Breaking Adaptor Signatures
- Adaptor signatures are special signatures used in protocols like Discreet Log Contracts (DLCs) or atomic swaps. They tie a signature to revealing a secret, ensuring fair exchanges.
-
Aggregating signatures across a block might mess up these protocols, as the individual signatures get blended together, potentially losing the properties adaptor signatures rely on.
-
Impact on Reorg Recovery
- In Bitcoin, a reorganization (reorg) happens when the blockchain switches to a different chain of blocks. Transactions from the old chain need to be rebroadcast or reprocessed.
- If signatures are aggregated at the block level, it could complicate extracting individual transactions and their signatures during a reorg, slowing down recovery.
These challenges mean Half-Agg needs careful design, especially for block-wide use.
Wrapping Up CISA is a clever way to make Bitcoin transactions more efficient by aggregating multiple Schnorr signatures into one, thanks to their linearity property. Half-Agg, the non-interactive mode, lets signers work independently, cutting signature size by about 50% (to 32n + 32 bytes from 64n bytes). It could save ~19.3% in space and ~6.9% in fees, with uses ranging from single transactions to entire blocks or off-chain systems like Lightning.
But watch out—block-wide Half-Agg could trip up adaptor signatures and reorg recovery, so it’s not a slam dunk yet. Still, it’s a promising tool for a leaner, cheaper Bitcoin future!
-
 @ a95c6243:d345522c
2024-12-13 19:30:32
@ a95c6243:d345522c
2024-12-13 19:30:32Das Betriebsklima ist das einzige Klima, \ das du selbst bestimmen kannst. \ Anonym
Eine Strategie zur Anpassung an den Klimawandel hat das deutsche Bundeskabinett diese Woche beschlossen. Da «Wetterextreme wie die immer häufiger auftretenden Hitzewellen und Starkregenereignisse» oft desaströse Auswirkungen auf Mensch und Umwelt hätten, werde eine Anpassung an die Folgen des Klimawandels immer wichtiger. «Klimaanpassungsstrategie» nennt die Regierung das.
Für die «Vorsorge vor Klimafolgen» habe man nun erstmals klare Ziele und messbare Kennzahlen festgelegt. So sei der Erfolg überprüfbar, und das solle zu einer schnelleren Bewältigung der Folgen führen. Dass sich hinter dem Begriff Klimafolgen nicht Folgen des Klimas, sondern wohl «Folgen der globalen Erwärmung» verbergen, erklärt den Interessierten die Wikipedia. Dabei ist das mit der Erwärmung ja bekanntermaßen so eine Sache.
Die Zunahme schwerer Unwetterereignisse habe gezeigt, so das Ministerium, wie wichtig eine frühzeitige und effektive Warnung der Bevölkerung sei. Daher solle es eine deutliche Anhebung der Nutzerzahlen der sogenannten Nina-Warn-App geben.
Die ARD spurt wie gewohnt und setzt die Botschaft zielsicher um. Der Artikel beginnt folgendermaßen:
«Die Flut im Ahrtal war ein Schock für das ganze Land. Um künftig besser gegen Extremwetter gewappnet zu sein, hat die Bundesregierung eine neue Strategie zur Klimaanpassung beschlossen. Die Warn-App Nina spielt eine zentrale Rolle. Der Bund will die Menschen in Deutschland besser vor Extremwetter-Ereignissen warnen und dafür die Reichweite der Warn-App Nina deutlich erhöhen.»
Die Kommunen würden bei ihren «Klimaanpassungsmaßnahmen» vom Zentrum KlimaAnpassung unterstützt, schreibt das Umweltministerium. Mit dessen Aufbau wurden das Deutsche Institut für Urbanistik gGmbH, welches sich stark für Smart City-Projekte engagiert, und die Adelphi Consult GmbH beauftragt.
Adelphi beschreibt sich selbst als «Europas führender Think-and-Do-Tank und eine unabhängige Beratung für Klima, Umwelt und Entwicklung». Sie seien «global vernetzte Strateg*innen und weltverbessernde Berater*innen» und als «Vorreiter der sozial-ökologischen Transformation» sei man mit dem Deutschen Nachhaltigkeitspreis ausgezeichnet worden, welcher sich an den Zielen der Agenda 2030 orientiere.
Über die Warn-App mit dem niedlichen Namen Nina, die möglichst jeder auf seinem Smartphone installieren soll, informiert das Bundesamt für Bevölkerungsschutz und Katastrophenhilfe (BBK). Gewarnt wird nicht nur vor Extrem-Wetterereignissen, sondern zum Beispiel auch vor Waffengewalt und Angriffen, Strom- und anderen Versorgungsausfällen oder Krankheitserregern. Wenn man die Kategorie Gefahreninformation wählt, erhält man eine Dosis von ungefähr zwei Benachrichtigungen pro Woche.
Beim BBK erfahren wir auch einiges über die empfohlenen Systemeinstellungen für Nina. Der Benutzer möge zum Beispiel den Zugriff auf die Standortdaten «immer zulassen», und zwar mit aktivierter Funktion «genauen Standort verwenden». Die Datennutzung solle unbeschränkt sein, auch im Hintergrund. Außerdem sei die uneingeschränkte Akkunutzung zu aktivieren, der Energiesparmodus auszuschalten und das Stoppen der App-Aktivität bei Nichtnutzung zu unterbinden.
Dass man so dramatische Ereignisse wie damals im Ahrtal auch anders bewerten kann als Regierungen und Systemmedien, hat meine Kollegin Wiltrud Schwetje anhand der Tragödie im spanischen Valencia gezeigt. Das Stichwort «Agenda 2030» taucht dabei in einem Kontext auf, der wenig mit Nachhaltigkeitspreisen zu tun hat.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 6a6be47b:3e74e3e1
2025-03-25 20:16:37
@ 6a6be47b:3e74e3e1
2025-03-25 20:16:37Hi frens, how are you?
🎨 I've been keeping busy with some personal projects and haven't painted as much as I'd like, but most importantly, I've returned to painting with watercolors. I'm getting used to them again, and although I love them, they can be tricky, especially when working wet on wet.
I've done a few pieces since getting back into it, and I'm excited to show the results, but at the same time, I'm a bit wary. Not because I want them to be "perfect" to share, but because I just want to have fun with them and get the joy back from painting.
🐱 And I'm not slacking because I have my furry little helper with me, and he's not having any of it!

He's a good boi

I've also been baking! 👩🍳 Yesterday, I made cinnamon "donuts" 🍩 , which ended up being muffins since I don't have a donut skillet.

And today, I baked lemon muffins 🍋, and they turned out delicious!

🧁 I had one as soon as they cooled, and chef's kiss... they're amazing!
🫀So as you can see I've been up to a few things, I'm not the best at this social media game. It can be draining so I want to have a balance between creating and showcasing you my proof of work 💪
💎I'm still getting there, but it's worth it.
🪄 Balance to achieve harmony is my goal.
🔮 I just wanted to check in and see what you've been up to! I'd love to know 🩷🫶🏻.
Have an amazing day frens!
-
 @ a95c6243:d345522c
2024-12-06 18:21:15
@ a95c6243:d345522c
2024-12-06 18:21:15Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\ dass wir Vorteile aus ihr ziehen;\ in jedem andern hegt man den Wunsch,\ dass der Unschuldige in Schutz genommen werde.\ Jean-Jacques Rousseau
Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden.
Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen» den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen schadet der Psyche und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben Menschen getötet».
Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft. Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen Erfahrungen als Kritikerin der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit Transition News. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften».
Menschen, die aufrichtig andere schützen wollten, werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter Heinrich Habig, Bianca Witzschel und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat Transition News mehrfach berichtet (z.B. hier und hier). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie Alexander Bittner erfahren mussten.
Die eigentlich Kriminellen schützen sich derweil erfolgreich selber, nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte Verbrechen gegen die Menschheit». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn Hunter möglicherweise auch Anthony Fauci begnadigen wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte?
Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken.
Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers Robert F. Kennedy Jr. erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens Călin Georgescu, der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der Panik im Wertewesten.
In Rumänien selber gab es gerade einen Paukenschlag: Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das Tabu gebrochen, Wahlen zu verbieten, bevor sie etwas ändern können.
Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: Zensur) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 2ed3596e:98b4cc78
2025-03-25 19:12:58
@ 2ed3596e:98b4cc78
2025-03-25 19:12:58Americans can now buy bitcoin on the Lightning Network directly from their bank with their Bitcoin Well account. By using the dollars in your Bitcoin Well Cash Balance you can buy bitcoin over the Lightning Network with instant delivery. You can also go directly from your bank to your Lightning Wallet. You can now live fully on a Lightning-powered bitcoin standard ⚡️
How to buy bitcoin on the Lightning Network instantly:
-
Add your Lightning Payment Address (LNURL) to your Bitcoin Well account
-
Enter the amount of dollars you want to buy bitcoin with
-
Choose your Bitcoin Well Cash Balance (you may need to fund this first!)
-
SMASH BUY! Your Lightning wallet will receive sats in seconds 🏎️
\ You can also go directly from your bank to your Lightning wallet. Your bitcoin will be sent over the Lightning network as soon as your dollars arrive (usually within 3 business days).
Here are detailed steps to guide you on how to buy bitcoin on the Lightning Network 👇
Step 1: Get your Lightning details
Go to your Lightning wallet and copy your Lightning Payment Address (looks like an email address). A Payment Address is not a Lightning invoice, but rather a static receiving address similar to a bitcoin receiving address. The benefit of using a Payment Address is that you can passively receive any quantity of sats at any time; unlike an invoice, a Payment Address does not have an expiry or a fixed amount of sats limiting the amount can be received. \ \ In the example below we use the Coinos.io wallet to obtain a Payment Address. Coinos is a powerful and easy to use Lightning wallet available in any country via your favourite web browser. You can set up a Coinos Lightning wallet and start receiving sats in seconds.

\ Coinos features a Lightning Payment Address. Once you’ve set up your wallet, hit “Receive” to access your Payment Address.
Step 2: Add your Lightning wallet to your Bitcoin Well account
Log in to your Bitcoin Well account and navigate to Buy bitcoin. From the buy screen, select bank or balance and add your Lightning wallet to the Destination by clicking Add wallet. Add your Lightning Payment Address from Step 1 here.
Step 3: Buy bitcoin on the Lightning Network
After you’ve selected your source and added your Lightning Payment Address as the destination, you are ready to complete your bitcoin purchase on the Lightning Network! \ \ When buying bitcoin from your Cash Balance, the dollars will instantly convert to bitcoin and be sent directly to your Lightning wallet – delivery takes less than a minute! 🤯\ \ When buying bitcoin from your bank account, you can expect to wait at least a couple business days as we wait for the slow movement of fiat to be finalized before sats can be sent.
## The compromise is over: bitcoin fast, easy and cheap
In the past, Bitcoiners had to choose between using freedom money at the mercy of the speed and cost of Bitcoin’s blockchain, or use the legacy banking system while surrendering their monetary freedom and independence. Ideally, Americans never have to compromise their monetary principles; thankfully, they no longer have to. \ \ Stacking sats straight to the Lightning also enables an innovative way to manage UTXOs. Now anyone can stack sats as much as they like without worrying about UTXO bloat. Simply accumulate sats on your Lightning wallet and then swap it across to your on-chain wallet in one neat UTXO. Since Coinos is a custodial Lightning wallet, you should periodically send your sats to your self-custody hardware wallet. To help you get the most out of the Lightning network, Bitcoin Well has a free swap tool that lets you swap sats between on-chain and Lightning. While this feature is only available in Canada, it will make its way to the United States very soon 🤫
Haven’t signed up with Bitcoin Well yet? Sign up here to start living on a (Lightning powered) Bitcoin Standard free from custodians and centralized honey pots.
Earn sats from your bitcoin transactions
\ Bitcoin Well is also the best place in the world to earn bitcoin. When you earn points in your Bitcoin Well account, you gain the opportunity to play the Bitcoin (Wishing) Well, where you win sats with every play.
The best part? We send bitcoin that you win straight to your personal wallet via the Lightning Network ⚡
Oh yeah, did we mention you can win 1,000,000 sats? If you're an active Bitcoin Well customer, there is a chance you've earned a pile of points. The more you use your account for buying, selling or spending bitcoin - the more points you’ll earn! Log in to your Bitcoin Well account and check your point balance.
About Bitcoin Well
\ Bitcoin Well exists to enable independence. We do this by coupling the convenience of modern banking, with the benefits of bitcoin. In other words, we make it easy to use bitcoin with self-custody.
-
-
 @ 7d33ba57:1b82db35
2025-03-25 18:31:35
@ 7d33ba57:1b82db35
2025-03-25 18:31:35Located on the Costa de la Luz, Conil de la Frontera is a charming Andalusian fishing village known for its golden beaches, whitewashed streets, and delicious seafood. With a laid-back atmosphere, it’s perfect for relaxation, surfing, and enjoying authentic Spanish culture.

🏖️ Top Things to See & Do in Conil de la Frontera
1️⃣ Playa de los Bateles 🏝️
- The main beach, right next to the town center.
- Long stretches of soft golden sand with clear Atlantic waters.
- Ideal for sunbathing, swimming, and beachside dining.
2️⃣ Playa de la Fontanilla 🌊
- One of the most beautiful beaches in the region, with crystal-clear waters.
- Great for families, surfers, and seafood lovers.
- Home to some of the best chiringuitos (beach bars) in Conil.
3️⃣ Playa del Palmar 🏄♂️
- A surfer’s paradise with consistent waves and a bohemian vibe.
- Popular for surf schools, yoga retreats, and sunset beach bars.
- Less crowded than the town’s main beaches.
4️⃣ Historic Old Town & Plaza de España 🏡
- Wander through narrow, whitewashed streets full of local boutiques, tapas bars, and cafés.
- Visit the Plaza de España, the town’s lively main square.
- Stop by the Torre de Guzmán, a medieval watchtower with great views.
5️⃣ Mercado de Abastos 🐟
- A traditional market where locals buy fresh seafood, fruits, and vegetables.
- Great place to experience the authentic Andalusian food culture.
6️⃣ Mirador del Jabiguero 🌅
- One of the best viewpoints in town, offering panoramic views over Conil and the Atlantic.
- A perfect spot for sunset photos.
🍽️ What to Eat in Conil de la Frontera
- Atún de Almadraba – Fresh bluefin tuna, caught using a traditional method 🐟
- Ortiguillas fritas – Fried sea anemones, a local delicacy 🍤
- Choco a la plancha – Grilled cuttlefish, a simple but delicious dish 🦑
- Tortillitas de camarones – Light and crispy shrimp fritters 🥞🦐
- Sangría or Tinto de Verano – Refreshing drinks to enjoy by the beach 🍷
🚗 How to Get to Conil de la Frontera
🚘 By Car: ~45 min from Cádiz, 1.5 hrs from Seville, 2.5 hrs from Málaga
🚆 By Train: Nearest station is San Fernando-Bahía Sur, then take a bus
🚌 By Bus: Direct buses from Cádiz, Seville, and other Andalusian cities
✈️ By Air: Closest airport is Jerez de la Frontera (XRY) (~1 hr away)💡 Tips for Visiting Conil de la Frontera
✅ Best time to visit? May to September for beach weather, spring & autumn for fewer crowds 🌞
✅ Book accommodation early in summer – It’s a popular vacation spot 🏡
✅ Try local tuna dishes – Conil is famous for its bluefin tuna 🍽️
✅ Visit during the Feria de Conil (June) for a lively cultural experience 🎉 -
 @ a95c6243:d345522c
2024-11-29 19:45:43
@ a95c6243:d345522c
2024-11-29 19:45:43Konsum ist Therapie.
Wolfgang JoopUmweltbewusstes Verhalten und verantwortungsvoller Konsum zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
Heute ist also wieder mal «Black Friday», falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
Warum fallen wir auf derartige Werbetricks herein und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
Gedankenlosigkeit und Maßlosigkeit können besonders bei der Ernährung zu ernsten Problemen führen. Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
Kritik am schwarzen Freitag und dem unnötigen Konsum kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
Die EU-Kommission lancierte 2015 den Begriff «Green Friday» im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das Pariser Abkommen unterzeichnet werden sollte.
Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt. Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des «Green New Deal» verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um Valencia dazu sagen?
Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020 eine «grüne Erholung von Covid-19, um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie «verantwortungsvolle Risikobereitschaft» unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ b1b16be0:08f41c1d
2025-03-25 18:08:21
@ b1b16be0:08f41c1d
2025-03-25 18:08:21What if Nostr app could save an Illiterate country?
Guatemala is the most illiterate country in Hispanic America at levels as serious as Africa.
About 30% of the population aged 15 or over cannot read or write. This figure rises in rural areas, where illiteracy reaches even more worrying levels, affecting mainly women and indigenous populations.
Limiting their access to paid jobs, their ability to access health services, and their full participation in political and social life. Education is a fundamental right, but there are still large gaps in access and educational quality, especially in rural areas and in communities with high poverty rates.
What if there was an application similar to Duolingo, but that allowed people to learn to read and write while earning Satoshis (Sats) This proposal not only sounds innovative, but could be a powerful tool to combat the country's illiteracy.
The idea of an app that rewards learning "learn to earn"
Duolingo is a popular platform that has proven to be effective in teaching languages through a gamified approach. If that model could be replicated, but with a specific focus on reading and writing, and above all reward users with sats, it could offer two key benefits: encourage learning and offer a direct economic opportunity to users.
Satoshis, being a low-cost and easy-to-access, can be a motivating tool. Many people in Guatemala, especially those in rural areas, do not have access to a traditional banking system, much less to a national identity document, but they have access to mobile phones and the internet, which facilitates the inclusion of an alternative form of value. With this additional motivation, people would be more willing to invest time in learning, knowing that they can get a tangible reward for their effort.
https://image.nostr.build/9da1c3b9478be817e82c891fdceaf87905a4d68876e9190240a8f979ebd35b40.jpg
Will there be developers interested in helping?
In addition, the technology sector globally is increasingly focused on open source, financial inclusion and the use of Bitcoin as an empowerment tool.
A project like this could attract developers interested in creating inclusive technological solutions that not only improve the quality of life of Guatemalans, but also promote access to new economic opportunities through digital tools. Is the possibility of working on a project with social impact, which combines education and Bitcoin, something that could excite many developers?
Algorithms for a greater impact on the illiterate
For this application to be truly effective, it is not enough to replicate existing models. The platform's algorithms would need to be adapted to focus specifically on the needs of the illiterate. The algorithm would have to be flexible enough to adapt to different levels of learning and ensure that users can progress gradually and effectively. (That it can identify literate users who only want the reward).
This could include:
-
Reinforce basic learning: Include exercises focused on phonetics, letter recognition and word construction, something that is not so central in language learning applications.
-
Personalized gamification: Use a system of rewards and levels that motivates users to continue learning, adapting to their learning pace. Sats could accumulate as the user progresses, which could be an additional incentive.
-
Interactivity and visual support: Incorporate visual elements, such as images or videos, that help users associate words with objects or actions, which would be especially useful for those with few previous educational resources.
-
Collaborative learning: Create a community within the application where users can interact, share their progress, and perhaps even solve doubts from others, which would foster an environment of collective learning.
-
This country is also one of those that suffers the most from malnutrition as much as Africa. By having Sats they can exchange them for grains or legumes in the market. That the community in turn learns from the value of Bitcoin and can the markets go through a circular economy.
https://image.nostr.build/ed3805f6c695519ec8327ce6ee9900ec235d714a20a542b5559d9e6c63bc4496.jpg
Is this a feasible idea or just a fantasy?
This type of project could be really valuable. While there are technological and economic challenges, the combination of education and Bitcoin is a growing trend, and Guatemala has the potential to benefit greatly from it. The integration of an accessible platform, which encourages learning and offers a direct reward, can be the key to improving literacy rates in the country.
If you think long-term, this application could not only help reduce illiteracy, but also increase financial inclusion, offering people a way to earn income digitally. This country is one of those with the most migrants to the United States due to lack of work and extreme poverty.
It is clear that there are challenges to bring this idea to reality. Even so, I wouldn't be fantasizing. These types of projects are increasingly common in the digital world, and with the commitment of the technological community, along with the support of organizations that promote education and inclusion, a real difference could be made in the lives of millions of Guatemalans.
In conclusion, Guatemala faces high levels of illiteracy that limit the opportunities for personal and economic development of its population. Could an application that combines learning with economic rewards be an innovative solution to reduce this problem? Although there are challenges, the potential positive impact of this type of initiative is indisputable, and could mark a before and after in the educational and financial history of the country.
I’m not dev but if you know the next step please send me an inbox!
-
-
 @ 378562cd:a6fc6773
2025-03-25 17:24:27
@ 378562cd:a6fc6773
2025-03-25 17:24:27In an era where the value of traditional money seems to shrink by the day, many turn to Bitcoin as a potential safeguard against inflation. But is Bitcoin truly a hedge, or is this just wishful thinking? Let’s break it down.
Understanding Inflation Inflation occurs when the purchasing power of money declines due to an increase in prices.
Central banks, like the Federal Reserve, often print more money, leading to more dollars chasing the same amount of goods.
Over time, inflation erodes savings and makes everyday items more expensive.
Why Bitcoin is Considered an Inflation Hedge Limited Supply – Unlike the U.S. dollar, Bitcoin has a fixed supply of 21 million coins, making it immune to money printing.
Decentralization – No government or central bank can manipulate Bitcoin’s supply or devalue it through policy changes.
Digital Gold – Many see Bitcoin as a modern version of gold, offering a store of value outside traditional financial systems.
Global Accessibility – Bitcoin operates 24/7 across borders, making it accessible to anyone looking to escape failing currencies.
Challenges to Bitcoin as an Inflation Hedge Volatility – Bitcoin’s price swings wildly, making it risky as a short-term hedge.
Adoption & Trust – Unlike gold, which has been a store of value for centuries, Bitcoin is relatively new and still gaining mainstream acceptance.
Market Correlation – At times, Bitcoin moves in tandem with stocks rather than acting as a safe-haven asset.
Regulatory Uncertainty – Governments around the world continue to debate Bitcoin’s place in the economy, which can impact its long-term stability.
The Verdict: Fact or Fiction? ✅ Long-Term Potential: Over the years, Bitcoin has shown signs of being a hedge against currency devaluation, especially in countries with hyperinflation. ⚠️ Short-Term Reality: Bitcoin’s volatility makes it unreliable as an immediate hedge, unlike traditional safe-haven assets like gold.
For those who believe in Bitcoin’s future, it could be a strong long-term hedge. However, for those looking for immediate inflation protection, it’s still a speculative bet.
Would you trust Bitcoin to safeguard your wealth? 🚀💰
What do you think? Share your comments below.
-
 @ a95c6243:d345522c
2024-11-08 20:02:32
@ a95c6243:d345522c
2024-11-08 20:02:32Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister EckhartSchwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung, der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
Mit einem bemerkenswerten Timing hat die deutsche Regierungskoalition am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer Selbsthypnose rund um Harris-Hype und Trump-Panik – mit teils erschreckenden Auswüchsen. Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
Das Kindergarten-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik «vorsätzlich herbeigeführt» worden seien.
Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen. Verkehrs- und Digitalminister Wissing trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit Jörg Kukies habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP, hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können. Das ging erst kürzlich aus dem diesjährigen «Freiheitsindex» hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
«Die absolute Mehrheit hat absolut die Nase voll», titelte die Bild angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat, kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei Manova. Und er kenne Friedrich Merz schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
Was also tun? Der Schweizer Verein «Losdemokratie» will eine Volksinitiative lancieren, um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
In jedem Fall wird es notwendig sein, unsere Bemühungen um Freiheit und Selbstbestimmung zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 27dd78c2:66ffe658
2025-03-25 17:12:08
@ 27dd78c2:66ffe658
2025-03-25 17:12:08In an age where ‘run clubs’ are getting more popular than ‘night clubs’, it’s exciting to see a Nostr-based sovereign fitness tracker hit the scene: Enter Runstr.club!
Runstr has emerged as a game-changer, redefining how runners connect, track progress, and stay motivated. For Bitcoin Runners, a movement that advocates sovereignty of one’s wealth, while improving one’s health, Runstr.club presents an exciting platform of choice to record your proof-of-work, take ownership of your personal data, and selectively engage with your social graph.
What is Runstr.club?
Runstr.club is a platform that’s being built to grow the proof-of-work community, with plans to offer interactive leaderboards, challenges, and social engagement. Unlike traditional running apps that focus purely on statistics, Runstr.club puts emphasis on camaraderie, motivation, and shared goals. It’s the Strava alternative that values ownership of your data, interoperability between platforms, and privacy as standard.
Why Runstr.club is a Great Fit for Bitcoin Runners
Bitcoin Runners isn’t just about proof-of-work; it’s about promoting freedom tech, decentralisation, and self-sovereignty principles that align closely with the ethos of Runstr.club.
Here’s why this platform is a great match for our movement:
- Community-Driven & Decentralised Spirit
Bitcoin Runners thrives on grassroots adoption and community participation, much like Runstr.club’s organic and community-focused model. Unlike corporate-owned fitness platforms that prioritise monetisation, Runstr.club is designed to empower runners, keeping the experience authentic and meaningful.
- Privacy-First Approach
One of the key concerns for bitcoiners is privacy. Mainstream fitness platforms harvest user data for profit, but Runstr.club offers a privacy-first alternative. This makes it an excellent choice for runners who value sovereignty in the digital age.
- The Advantage of Nostr Over Centralised Run Tracking Tools
Most mainstream running apps, like Strava or Nike Run Club, rely on centralised platforms that control user data, impose restrictions, and often monetise user activity. Runstr.club, however, is built on Nostr, a decentralised protocol that enables users to interact without getting trapped inside a walled garden.
With Nostr, runners benefit from:
-
True ownership of their data – no risk of platforms selling or misusing personal running history.
-
Resilience against censorship – no arbitrary bans or content moderation dictated by a 'shadowy suit'.
-
Interoperability – seamless integration with other Nostr-based applications, keeping data fluid and accessible across different platforms.
-
Peer-to-peer connectivity – allowing runners to share progress, create challenges, and stay engaged independent of big tech.
For Bitcoin Runners, Nostr’s decentralised nature aligns perfectly with the principles of sovereignty, freedom, and privacy.
- Gamification & Challenges
Runstr.club has engaging challenges and decentralised leaderboards on its roadmap. Whether you’re stacking sats through running-related bitcoin challenges or simply competing with fellow bitcoiners for fun, the platform will add an extra layer of engagement to every run. We would love to see such features come to life!
Conclusion
Runstr.club is more than just a running tracker—it’s a Nostr, bitcoin, and fitness onboarding community-driven movement. By embracing platforms that respect privacy, encourage competition, and foster community, we stay true to our values while pushing our limits as runners.
Let’s take this to the next level - be sure to follow Runstr on Nostr!
Run free. Stay sovereign. Stack zaps!
We’re shilling this open-source initiative out of genuine appreciation for both its vision and the dedicated team behind it.
-
 @ 220522c2:61e18cb4
2025-03-25 16:05:27
@ 220522c2:61e18cb4
2025-03-25 16:05:27draftoptionalAbstract
This NIP defines a new event kind for sharing and storing code snippets. Unlike regular text notes (
kind:1), code snippets have specialized metadata like language, extension, and other code-specific attributes that enhance discoverability, syntax highlighting, and improved user experience.Event Kind
This NIP defines
kind:1337as a code snippet event.The
.contentfield contains the actual code snippet text.Optional Tags
-
filename- Filename of the code snippet -
l- Programming language name (lowercase). Examples: "javascript", "python", "rust" -
extension- File extension (without the dot). Examples: "js", "py", "rs" -
description- Brief description of what the code does -
runtime- Runtime or environment specification (e.g., "node v18.15.0", "python 3.11") -
license- License under which the code is shared (e.g., "MIT", "GPL-3.0", "Apache-2.0") -
dep- Dependency required for the code to run (can be repeated) -
repo- Reference to a repository where this code originates
Format
```json {
"id": "<32-bytes lowercase hex-encoded SHA-256 of the the serialized event data>",
"pubkey": "<32-bytes lowercase hex-encoded public key of the event creator>",
"created_at":
, "kind": 1337,
"content": "function helloWorld() {\n console.log('Hello, Nostr!');\n}\n\nhelloWorld();",
"tags": [
["l", "javascript"], ["extension", "js"], ["filename", "hello-world.js"], ["description", "A basic JavaScript function that prints 'Hello, Nostr!' to the console"], ["runtime", "node v18.15.0"], ["license", "MIT"], ["repo", "https://github.com/nostr-protocol/nostr"]],
"sig": "<64-bytes signature of the id>"
} ```
Client Behavior
Clients that support this NIP SHOULD:
-
Display code snippets with proper syntax highlighting based on the language.
-
Allow copying the full code snippet with a single action.
-
Render the code with appropriate formatting, preserving whitespace and indentation.
-
Display the language and extension prominently.
-
Provide "run" functionality for supported languages when possible.
-
Display the description (if available) as part of the snippet presentation.
Clients MAY provide additional functionality such as:
-
Code editing capabilities
-
Forking/modifying snippets
-
Creating executable environments based on the runtime/dependencies
-
Downloading the snippet as a file using the provided extension
-
Sharing the snippet with attribution
References
nip #grownostr
-
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ 3c389c8f:7a2eff7f
2025-03-25 15:51:44
@ 3c389c8f:7a2eff7f
2025-03-25 15:51:44*Create your keys and set up your profile:
https://start.njump.me/
*Pick a NIP07 browser extension or offline signer to safely store your private key (nsec):
https://nostr.net/
*Pick an app, sign in, and start exploring:
https://nostrapps.com/
That's All! :)
-
 @ a012dc82:6458a70d
2025-03-25 13:57:54
@ a012dc82:6458a70d
2025-03-25 13:57:54Bitcoin, the pioneering cryptocurrency, has once again defied skeptics by surging to a new all-time high. This remarkable resurgence is a testament to the resilience and enduring appeal of Bitcoin, even as it navigates through periods of intense volatility and regulatory scrutiny. Emerging from the shadows of the digital world, Bitcoin has sparked a financial revolution that challenges the very fabric of traditional banking and monetary systems. Its journey from an obscure digital token to a globally recognized financial asset encapsulates a saga of innovation, speculation, and the relentless pursuit of financial autonomy. This article explores the journey of Bitcoin from its inception to its current status as a leading digital asset, highlighting the challenges it has overcome and the factors contributing to its recent record-breaking performance.
Table of Contents
-
The Genesis of Bitcoin
-
Overcoming Adversity
-
The Path to Mainstream Acceptance
-
Breaking New Ground with ETFs
-
Navigating the Crypto Ecosystem
-
Looking Ahead: Challenges and Opportunities
-
Conclusion
-
FAQs
The Genesis of Bitcoin
Bitcoin was introduced to the world in 2008 by an individual or group using the pseudonym Satoshi Nakamoto. Conceived as a decentralized digital currency, Bitcoin offered a novel solution to the double-spend problem without the need for a central authority. This innovation was set against the backdrop of the global financial crisis, positioning Bitcoin as an alternative to traditional banking systems and fiat currencies. The early years of Bitcoin were marked by a passionate but small community of users, and the cryptocurrency was primarily used for niche online transactions. The concept of a decentralized currency was revolutionary, promising a new era of financial freedom and privacy. However, Bitcoin's early days were fraught with challenges, including limited public understanding, technical hurdles, and skepticism from the financial establishment. Despite these obstacles, the foundational principles of Bitcoin—transparency, security, and decentralization—captivated a growing number of enthusiasts who saw its potential to redefine money.
Overcoming Adversity
Bitcoin's journey has been anything but smooth. The cryptocurrency has faced numerous challenges, including regulatory hurdles, security breaches, and intense market volatility. High-profile incidents, such as the collapse of the Mt. Gox exchange in 2014 and the contentious debates over scalability, tested the resilience of the Bitcoin network and its community. Despite these setbacks, Bitcoin continued to gain traction, attracting a diverse group of users and investors drawn to its potential for high returns and its underlying blockchain technology. The path was littered with obstacles, from hard forks and regulatory crackdowns to sensational media coverage and public skepticism. Yet, each challenge served to strengthen the community and refine the technology, forging a cryptocurrency that was increasingly robust, adaptable, and resilient. The adversities faced by Bitcoin acted as a crucible, purifying and validating the concept of decentralized finance in the eyes of a global audience.
The Path to Mainstream Acceptance
The turning point for Bitcoin came with the gradual recognition of its value as both a digital asset and a technological innovation. Institutional investors began to take notice, and the cryptocurrency started to shed its reputation as a tool for illicit transactions. The introduction of futures contracts and the increasing interest from traditional financial firms signaled a shift towards mainstream acceptance. However, the journey was not without its skeptics, who pointed to Bitcoin's energy consumption and its volatile price swings as reasons for caution. The road to mainstream acceptance was paved with educational efforts, technological advancements, and a growing recognition of Bitcoin's unique attributes, such as its fixed supply and borderless nature. As awareness and understanding of Bitcoin increased, so too did its legitimacy and value, leading to a gradual but undeniable integration into the broader financial landscape.
Breaking New Ground with ETFs
The recent surge in Bitcoin's price can be largely attributed to the approval of exchange-traded funds (ETFs) pegged to the digital asset by U.S. regulators. This milestone was achieved after years of advocacy from the crypto community and a legal battle that challenged the Securities and Exchange Commission's initial rejections. The launch of the first "spot" Bitcoin ETFs has opened the doors for more traditional investors to enter the market, providing a regulated and familiar avenue for Bitcoin exposure. This development has not only boosted Bitcoin's price but also reinforced its legitimacy as an investment asset. The introduction of Bitcoin ETFs represents a significant breakthrough in the cryptocurrency's journey, bridging the gap between the innovative, often misunderstood world of digital currencies and the established, regulated realm of traditional finance. This convergence has facilitated a new wave of investment, bringing with it increased liquidity, visibility, and acceptance for Bitcoin and the broader cryptocurrency market.
Navigating the Crypto Ecosystem
Bitcoin's influence extends beyond its own price performance, serving as a bellwether for the broader cryptocurrency market. The ecosystem has grown exponentially, with thousands of altcoins and a burgeoning decentralized finance (DeFi) sector. However, the industry has not been immune to challenges, facing regulatory scrutiny, market manipulation, and high-profile scandals. Despite these obstacles, Bitcoin has maintained its dominance, buoyed by a loyal community and its perceived value as a hedge against inflation and currency devaluation. The cryptocurrency ecosystem is a dynamic and evolving landscape, marked by rapid innovation and intense competition. Yet, through all the tumult and transformation, Bitcoin remains the cornerstone, setting the standard for security, adoption, and market value. Its journey mirrors the maturation of the entire crypto space, from a fringe idea to a major financial force, influencing everything from individual investment strategies to global economic policies.
Looking Ahead: Challenges and Opportunities
As Bitcoin reaches new heights, questions remain about its sustainability and the potential impact of regulatory changes. The upcoming "halving" event, which reduces the reward for mining new blocks, is expected to have significant implications for Bitcoin's supply and, consequently, its price. Additionally, the cryptocurrency must navigate the delicate balance between innovation and regulation, as authorities worldwide grapple with how to oversee this evolving asset class. The future of Bitcoin is inextricably linked to the broader narrative of digital transformation and financial innovation. As it continues to evolve, Bitcoin will face new challenges and opportunities, from technological advancements and competitive pressures to shifting regulatory landscapes and economic trends. Yet, if history is any guide, Bitcoin will adapt and thrive, continuing its unstoppable journey from adversity to record highs.
Conclusion
From its humble beginnings to its current status as a financial phenomenon, Bitcoin's journey is a compelling narrative of innovation, resilience, and the relentless pursuit of decentralization. While the road ahead is fraught with uncertainty, Bitcoin's ability to rebound from adversity and reach new record highs is a testament to its enduring appeal and the transformative potential of cryptocurrencies. As the world continues to embrace digital currencies, Bitcoin's story remains a powerful reminder of the possibilities and challenges that lie ahead in the uncharted waters of the digital age. The saga of Bitcoin is far from over; it is a continuing tale of disruption, adaptation, and, ultimately, triumph in the face of adversity.
FAQs
Why has Bitcoin reached new record highs? Bitcoin's recent surge to new record highs can be attributed to factors such as the approval of Bitcoin ETFs, growing institutional acceptance, its appeal as a hedge against inflation, and increasing mainstream interest.
What are Bitcoin ETFs, and why are they important? Bitcoin ETFs (Exchange-Traded Funds) are investment funds that track the price of Bitcoin and are traded on traditional stock exchanges. They provide investors with a way to gain exposure to Bitcoin without having to buy or store the cryptocurrency directly, which has contributed to increased Bitcoin adoption.
What challenges has Bitcoin faced? Bitcoin has faced numerous challenges, including regulatory hurdles, security breaches, market volatility, and skepticism from the financial community. Despite these challenges, Bitcoin has continued to grow and gain acceptance.
What is the "halving" event in Bitcoin? The "halving" is an event that occurs approximately every four years, where the reward for mining new Bitcoin blocks is halved. This reduces the rate at which new bitcoins are generated, theoretically increasing scarcity and potentially driving up the price.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ b17fccdf:b7211155
2025-03-25 11:23:36
@ b17fccdf:b7211155
2025-03-25 11:23:36Si vives en España, quizás hayas notado que no puedes acceder a ciertas páginas webs durante los fines de semana o en algunos días entre semana, entre ellas, la guía de MiniBolt.
Esto tiene una razón, por supuesto una solución, además de una conclusión. Sin entrar en demasiados detalles:
La razón
El bloqueo a Cloudflare, implementado desde hace casi dos meses por operadores de Internet (ISPs) en España (como Movistar, O2, DIGI, Pepephone, entre otros), se basa en una orden judicial emitida tras una demanda de LALIGA (Fútbol). Esta medida busca combatir la piratería en España, un problema que afecta directamente a dicha organización.
Aunque la intención original era restringir el acceso a dominios específicos que difundieran dicho contenido, Cloudflare emplea el protocolo ECH (Encrypted Client Hello), que oculta el nombre del dominio, el cual antes se transmitía en texto plano durante el proceso de establecimiento de una conexión TLS. Esta medida dificulta que las operadoras analicen el tráfico para aplicar bloqueos basados en dominios, lo que les obliga a recurrir a bloqueos más amplios por IP o rangos de IP para cumplir con la orden judicial.
Esta práctica tiene consecuencias graves, que han sido completamente ignoradas por quienes la ejecutan. Es bien sabido que una infraestructura de IP puede alojar numerosos dominios, tanto legítimos como no legítimos. La falta de un "ajuste fino" en los bloqueos provoca un perjuicio para terceros, restringiendo el acceso a muchos dominios legítimos que no tiene relación alguna con actividades ilícitas, pero que comparten las mismas IPs de Cloudflare con dominios cuestionables. Este es el caso de la web de MiniBolt y su dominio
minibolt.info, los cuales utilizan Cloudflare como proxy para aprovechar las medidas de seguridad, privacidad, optimización y servicios adicionales que la plataforma ofrece de forma gratuita.Si bien este bloqueo parece ser temporal (al menos durante la temporada 24/25 de fútbol, hasta finales de mayo), es posible que se reactive con el inicio de la nueva temporada.

La solución
Obviamente, MiniBolt no dejará de usar Cloudflare como proxy por esta razón. Por lo que a continuación se exponen algunas medidas que como usuario puedes tomar para evitar esta restricción y poder acceder:
~> Utiliza una VPN:
Existen varias soluciones de proveedores de VPN, ordenadas según su reputación en privacidad: - IVPN - Mullvad VPN - Proton VPN (gratis) - Obscura VPN (solo para macOS) - Cloudfare WARP (gratis) + permite utilizar el modo proxy local para enrutar solo la navegación, debes utilizar la opción "WARP a través de proxy local" siguiendo estos pasos: 1. Inicia Cloudflare WARP y dentro de la pequeña interfaz haz click en la rueda dentada abajo a la derecha > "Preferencias" > "Avanzado" > "Configurar el modo proxy" 2. Marca la casilla "Habilite el modo proxy en este dispositivo" 3. Elige un "Puerto de escucha de proxy" entre 0-65535. ej: 1080, haz click en "Aceptar" y cierra la ventana de preferencias 4. Accede de nuevo a Cloudflare WARP y pulsa sobre el switch para habilitar el servicio. 3. Ahora debes apuntar el proxy del navegador a Cloudflare WARP, la configuración del navegador es similar a esta para el caso de navegadores basados en Firefox. Una vez hecho, deberías poder acceder a la guía de MiniBolt sin problemas. Si tienes dudas, déjalas en comentarios e intentaré resolverlas. Más info AQUÍ.

~> Proxifica tu navegador para usar la red de Tor, o utiliza el navegador oficial de Tor (recomendado).

La conclusión
Estos hechos ponen en tela de juicio los principios fundamentales de la neutralidad de la red, pilares esenciales de la Declaración de Independencia del Ciberespacio que defiende un internet libre, sin restricciones ni censura. Dichos principios se han visto quebrantados sin precedentes en este país, confirmando que ese futuro distópico que muchos negaban, ya es una realidad.
Es momento de actuar y estar preparados: debemos impulsar el desarrollo y la difusión de las herramientas anticensura que tenemos a nuestro alcance, protegiendo así la libertad digital y asegurando un acceso equitativo a la información para todos
Este compromiso es uno de los pilares fundamentales de MiniBolt, lo que convierte este desafío en una oportunidad para poner a prueba las soluciones anticensura ya disponibles, así como las que están en camino.
¡Censúrame si puedes, legislador! ¡La lucha por la privacidad y la libertad en Internet ya está en marcha!

Fuentes: * https://bandaancha.eu/articulos/movistar-o2-deja-clientes-sin-acceso-11239 * https://bandaancha.eu/articulos/esta-nueva-sentencia-autoriza-bloqueos-11257 * https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958 * https://bandaancha.eu/articulos/como-activar-ech-chrome-acceder-webs-10689 * https://comunidad.movistar.es/t5/Soporte-Fibra-y-ADSL/Problema-con-web-que-usan-Cloudflare/td-p/5218007
-
 @ b80cc5f2:966b8353
2025-03-25 11:07:11
@ b80cc5f2:966b8353
2025-03-25 11:07:11Originally posted on 15/10/2024 @ https://music.2140art.com/artist-spotlight-airklipz-vape-life-music/
South London MC and producer Airklipz is no stranger to independence. Coming into music professionally from setting up his commercial studio over 20 years ago, he’s risen to become one of the UK underground’s most prolific MCs.
Airklipz has been dropping banger after banger, with several EPs and Albums released in 2024 alone. He has always managed his music releases and has teamed up with various outfits and labels since 2009.
Recently teaming up with independent label Nyark Music for a number, Airklipz has always been ‘one to watch’. His experience setting up as a direct-to-consumer musician goes back years, first discovering Bitcoin in 2014 and then adopting it in 2024 as part of his journey in the new music economy.
How long have you been making music professionally?
I’ve been making music professionally since 2010.
What are some of the mediums you’ve used to distribute your music? Bandcamp, Awal and DistroKid, along with the WavLake and Even recently
Have you ever been signed to a label?
I was briefly signed to a friend’s label but have mostly been independent.
What are some of the main things you see as a problem in today’s music industry?
The main problems I see these days are the old labels, partnering up with companies like Google to limit the reach of any independent artist that isn’t signed to them. Also, the way the social media platforms have all become “Pay to play”, is all a part of the same thing.
What made you decide to join the 2140Music community?
I decided to join 2140 So we could get together and combat the problem of visibility by attacking as a collective in a brand-new market space.
What are some of the notable projects you’ve released or people you’ve worked with?
I’ve released a fair few amount of projects including the “LDN State Ov Mind” series, the “African Ninja In London” trilogy and the “Vape Life” series of projects, and in total, I have over 20 projects in my discography
-
 @ 6bae33c8:607272e8
2025-03-25 11:03:28
@ 6bae33c8:607272e8
2025-03-25 11:03:28I try to make these bold enough that I get most of them wrong. If you’re not getting most wrong, they’re not bold enough! Hits from last year included Teoscar Hernandez being the Marcel Ozuna of 2024 and Shohei Ohtani’s gambling scandal getting memory-holed totally. Misses include Walker Buehler > Tarik Skubal and Spencer Torkelson > Vlad Guerrero. As I said, the predictions have to be bold!
Also, these are hunches, the explanations for which are largely irrelevant. The relevant information is priced into ADP, so while I’ll justify it one way or another, it’s the prediction itself, not the explanation that matters.
1, Alex Bregman is top-five in AL MVP voting
This just feels like a perfect fit. Bregman rakes at Fenway (1.240 career OPS), and he rarely strikes out. I could see a .300-plus batting average with 30 home runs. The Red Sox upgraded their pitching too, and after the Yankees lost Gerrit Cole and Juan Soto, have a good chance to win the AL East.
2. Bo Bichette outperforms Mookie Betts
Granted Betts is sick right now and lost a ton of weight, but he was still going in the second round of NFBC Mains, while Bichette was going in Rounds 8-9. Bichette was hurt last year, but prior to that he was a star, is in his age 27 season and has four home runs and a .373 average in Spring Training. I’m sick that I didn’t get any shares (took Bregman over him in the Main.)
3. Chris Sale finishes as a top-5 starter again
This might not sound that bold because he’s SP6 by ADP, but every pitcher except maybe Paul Skenes and Skubal are underdogs to be top-five, given the volatility of the position. I love veterans in their mid-30s finding it again, usually they have 2-3 years of good before age and injury catch up again. It reminds me of Justin Verlander who hit a rough patch before righting the ship for several elite years.
4. Tyler Glasnow finishes as top-3 in NL CY Young votes
My comp for Glasnow is Randy Johnson, another tall lefty who battled injuries in his 20s before settling down to become one of the GOATS. Glasnow managed 135 IP last year and if he ups it to 165, he’ll be in the CY mix on the Dodgers.
5. Cody Bellinger hits 40 homers
A pull hitter with a high fly ball rate, Bellinger is perfect for Yankee Stadium. He’ll have to stay healthy, of course, but he’s still just 29 — won’t turn 30 until July — and is primed for the second best year of his career (he won’t top 2019.)
6. At least one of the following veteran pitchers has a top-five CY finish: Justin Verlander, Max Scherzer, Kevin Gausman, Walker Buehler, Sandy Alcantara or Carlos Rodon.
Pitchers who were once elite still own most of their skills, health permitting. While Scherzer and Verlander have lost velocity, knowing how to pitch is sufficient above a certain minimum threshold.
7. Jackson Chourio goes 30-30-.300
Chourio hit over .300 for the final four months of the season, once the Brewers stopped pulling him in and out of the lineup. The steals should be easy for him with a full season of at-bats, and the power should be there too in that park.
8. Hunter Brown finishes top-five in AL CY voting
After a rough start, Brown was one of the best pitchers in the league last year with a 2.31 ERA over the last four months. He’s in a good park, in the right division (though the A’s home park got a lot worse) and on a good enough team for run support purposes.
9. Aroldis Chapman gets more saves than Jhoan Duran
Chapman is still throwing 99 and landed a job on the much-improved Red Sox, while Duran, who took nine losses last year, has Griffin Jax behind him. I know Chapman’s control has been bad the last few years, but I have a hunch the veteran warhorse has a comeback year.
10. Some of these predictions will be wrong
I’ll pay the cost of never going 10-for-10 to make sure I don’t go 0-for-10.
-
 @ 7da115b6:7d3e46ae
2025-03-25 11:00:01
@ 7da115b6:7d3e46ae
2025-03-25 11:00:01What Happened?
Sadly, some news came to us in the last couple of days, news that has exploded our plans like a bombshell. As you know from previous posts, my family and I had found the property of our dreams, within the price range that suited us. The only issue was that we had to sell our rental property to be able to purchase the land we wanted to develop for our homestead. At the time, it wasn't an issue.
With a few phone calls and some discussion with the local Council; the Realtor; the Vendors, and the bank, we were on our way. We made an offer, and it was accepted, contingent on our rental property selling. Our offer expires this Friday, and the likelihood of it selling before then, is slim. That leaves us 3 days to come up with the $130,000 we need to secure the property.
"So why not just extend the offer?" I hear you say. Well, that's a fair point - We did. The extension runs out this Friday. Can we extend on the extension? Legally, yes. but here's the rub:
A counter offer has been put forward.
This basically means, that without having the money available by the end of the offer extension, the Vendor is going to take the counter offer.
That's Not So Bad... Right?
Yes, and no.
Unfortunately, we've spend thousands of dollars on reports; valuations; building research and site inspections. This means all of the plans, money and time that we've invested so far is going to be lost. Yes yes, you're right of course, it's our own fault for getting so financially and emotionally invested in the first place. Lesson learned.
I think that the hardest part of it all, was breaking it to my wife. She had already started designing her gardens, and had dreams of watching our homestead grow. The look of utter defeat on her face was gut wrenching. I felt as though I had failed her, and torn away the dream we had built together. She and I had lost our dream in the course of a single phone call. It hit both of us hard.
It's been 24 hours now, and the pain is real. I don't want to eat or go to work, I don't want to talk to anyone. I just want to lay down on my wife's lap and close my eyes until it's over. Deep down inside, I know it's a childish reaction, but that doesn't make it any less of a slap across the face.
The Light at the End of the Tunnel
Cliche, I know, but there may be a little glimmer of light on the horizon. If we do sell our rental property, we will have money to play with. This means we can buy a crappy little Ute and caravan, and go exploring our country. Perhaps stop at a few places that look nice, and see if they're places we could settle. If we spend a few months just looking around, and find somewhere homely, then we can stay for a while at a local caravan park, and look for a property that may be suitable.
At the very least, it would mean that we can escape our shit jobs, which has been the biggest goal from the beginning.
Fingers crossed...
-
 @ 2e8970de:63345c7a
2025-03-25 18:03:08
@ 2e8970de:63345c7a
2025-03-25 18:03:08Data collected by nameberry (baby name website)
originally posted at https://stacker.news/items/924756
-
 @ d560dbc2:bbd59238
2025-03-25 17:14:30
@ d560dbc2:bbd59238
2025-03-25 17:14:30If you juggle multiple tasks, projects, and responsibilities, you’ve likely heard of the Getting Things Done (GTD) method—a productivity system developed by David Allen to help you organize your tasks and clear your mind for focused work. You might also be exploring Task4Us, a web-based task management platform I founded that leverages the 2-5 Rule to prioritize tasks based on timing rather than rigid scheduling.
At first glance, these two systems might seem to operate differently: GTD focuses on a structured five-step process to manage tasks, while Task4Us emphasizes an anti-planning approach using its 2-5 Rule. However, combining these two can create powerful synergy by blending GTD’s clarity and structure with Task4Us’s intuitive timing-based prioritization. This guide walks you through how to integrate Task4Us with GTD to streamline your workflow, reduce mental clutter, and achieve your goals with less stress.
Understanding the Basics: GTD and Task4Us
What Is the Getting Things Done (GTD) Method?
GTD is a five-step productivity framework designed to externalize your tasks and commitments, freeing your mind for action. The steps are:
-
Capture:
Collect every task, idea, or commitment that grabs your attention into a trusted external system (e.g., notebook or app). -
Clarify:
Process each item to determine if it’s actionable. If it is, define the next step; if not, trash it, file it for reference, or defer it. -
Organize:
Sort actionable tasks into lists (e.g., Next Actions, Projects, Waiting For) and non-actionable items into categories like Someday/Maybe or Reference. -
Reflect:
Regularly review your lists to update priorities and ensure nothing slips through the cracks. -
Engage:
Choose your next action based on context, time, and energy, and then work on it.
GTD’s strength lies in reducing cognitive load by capturing everything so you can stay decisive and focused. However, GTD doesn’t inherently guide you on when to do tasks, leaving timing decisions up to you.
What Is Task4Us and the 2-5 Rule?
Task4Us is a task management platform built on the 2-5 Rule, an approach that emphasizes timing over detailed scheduling. Instead of planning when to do each task, you simply:
- Enter the Task:
Capture it into Task4Us as your “inbox.” - Set a Time Unit:
Choose whether the task is daily, weekly, monthly, or yearly. - Record the Last Act Date or Set a Fixed Due Date:
For recurring tasks, provide the last date you acted on them. For date-specific tasks, use Fix Mode to set the due date.
The 2-5 Rule calculates the task’s priority based on a “sweet spot” of 2 to 5 time units, ensuring you act at the optimal moment—neither too early nor too late.
Why Combine GTD and Task4Us?
By integrating these methods, you can capitalize on the strengths of both:
- GTD’s Clarity:
Use GTD to capture and organize every task and project, ensuring nothing is forgotten. - Task4Us’s Timing:
Leverage the 2-5 Rule to automatically prioritize tasks based on when they should be acted on, reducing the need to micromanage your schedule.
Together, they form a system where you externalize all your commitments (GTD) and then focus on the most important task at the right time (Task4Us), leading to a seamless, stress-free workflow.
Step-by-Step Guide to Combining Task4Us and GTD
Step 1: Capture Everything with GTD, Using Task4Us as Your Inbox
- Action:
Whenever a task or idea arises—like “Call a client,” “Plan a vacation,” or “Renew passport”—add it directly to Task4Us. - Tip:
Don’t worry about details yet; the goal is to clear your mind by capturing everything.
Example tasks: - “Email project updates to the team” - “Schedule a dentist appointment” - “Meet Uncle Lars for coffee”
Step 2: Clarify and Organize Tasks Using GTD Principles in Task4Us
- Clarify:
Process each captured task. Decide if it’s actionable. - If not actionable:
Trash it, file it for reference, or mark it as a “Someday/Maybe” task in Task4Us. - If actionable:
Determine the next step. - Organize:
In Task4Us, assign each actionable task: - Time Unit:
Choose days, weeks, months, or years (e.g., “Email project updates” as a weekly task). - Fix Mode:
For date-specific tasks (e.g., “Wish Alex a happy birthday”), set the exact due date. - Categories:
Group tasks (e.g., Work, Personal, Health) to align with GTD’s organization system. - Projects:
For multi-step projects, create a dedicated category and break the project into smaller, actionable tasks.
Step 3: Reflect Weekly to Update Your Task4Us Lists
- Review Your Tasks:
Set aside time each week to review your Task4Us lists. - Check your Top Task and Focus Mode (top 3 tasks) to ensure they reflect your current priorities.
- Update as Needed:
Adjust time units, update last act dates, or move tasks between active, someday/maybe, and archived lists. - Projects Review:
Ensure each multi-step project has at least one actionable task with a clear time unit.
Step 4: Engage with Task4Us’s Top Task and Focus Mode
- Engage:
Task4Us automatically surfaces your Top Task based on the 2-5 Rule. - For instance, if “Meet Uncle Lars” is nearing its action window, it will appear as the top task.
- Focus Mode:
Use this mode to display your top 3 tasks for a distraction-free workflow.
This aligns with GTD’s principle of choosing the right next action, making it easier to act decisively.
Step 5: Enhance GTD with Task4Us’s Unique Features
- Fix Mode for Deadlines:
Use Fix Mode for tasks with fixed dates (e.g., passport renewal) to ensure they gain priority as the due date approaches. - Export Tasks:
Download your task list as a CSV file to review your productivity over time. - Customize:
Adjust categories, time units, and Focus Mode settings to best suit your workflow.
A Real-Life Example: Combining GTD and Task4Us
Imagine managing work tasks, personal goals, and social connections:
-
Capture:
Throughout the day, add tasks like “Finish project report,” “Call Mom,” “Book dentist appointment,” and “Brainstorm new blog post” to Task4Us. -
Clarify and Organize:
- “Finish project report” is actionable—set as a weekly task in the Work category.
- “Call Mom” is actionable—set as a monthly task in the Personal category (last called 3 weeks ago).
- “Book dentist appointment” has a deadline (e.g., April 10, 2025)—use Fix Mode.
-
“Brainstorm new blog post” is not urgent—categorize it as Someday/Maybe.
-
Reflect:
During a weekly review, notice “Call Mom” is nearing the 5-week mark and becomes your top task. Update “Finish project report” after completion. -
Engage:
Task4Us displays “Call Mom” as the top task. You call, mark it done, and Task4Us updates the last act date. -
Enhance:
Use Focus Mode to tackle your top 3 tasks without distraction and export your tasks for review.
Why This Combination Works
-
GTD’s Lack of Timing Guidance:
Task4Us’s 2-5 Rule fills the gap by ensuring you act at the optimal moment. -
Task4Us’s Simplicity:
GTD adds structure to Task4Us, helping you manage complex projects and capture non-actionable items. -
Reduced Cognitive Load:
Both systems externalize tasks, reducing mental clutter and ensuring you’re focused on the right task at the right time.
Try It Out and Share Your Experience
Task4Us is currently in beta—now’s the perfect time to integrate it with GTD and transform your productivity. Start by capturing your tasks in Task4Us, apply GTD’s steps to clarify and organize them, and let the 2-5 Rule guide your actions.
Sign up for Task4Us at todo.task4.us and experience the power of combining GTD with the 2-5 Rule.
How do you manage your tasks? Do you use GTD, Task4Us, or a mix of methods? Share your thoughts in the comments—I’d love to hear your experience! 🚀
#Productivity #TaskManagement #GTD #Task4Us
-
-
 @ 3c389c8f:7a2eff7f
2025-03-25 17:12:33
@ 3c389c8f:7a2eff7f
2025-03-25 17:12:33Understanding Relays
Relays are a very simple concept, but an incredibly powerful part of Nostr. They are simple servers, of sorts, with a specific set of tasks- to fetch, hold, and send notes. Relays don't communicate with each other, only with clients. The client sends a request for any relevant notes and the relays oblige. What types of notes (aka events) that each relay will hold or fetch will vary because of different relays will operate under different sets of rules. Some will accept most any type of event from anyone. Others can be very strict, requiring things like payment, proof-of-work, specific event kinds, or only allow a whitelist of users to reduce spam and other unwanted content. When you create an event, or publish a note, it is sent to your "write" or "outbox" relays. Anyone who follows your npub or sends "fetch" /"read" requests, to those relays will receive your notes. When someone replies, likes, or otherwise engages with your note, that note will then duplicate to any "write" or "outbox" relays that the other person is connecting to as their outbox relays. This does two important things:
It creates a new event through through the action of engaging your note. This is a signed record of activity from that user's npub. This is also the event that is sent back to your "read" or "inbox" relays so that you may be notified that someone is interacting with you.
By creating a copy, this helps ensure your note will be able to be spread across more of the ecosystem, expanding your reach and introducing redundancy, in case a relay should go down or disappear completely. This does not imply that your data will be safely stored forever. In fact, its the exact opposite. The protocol assumes that any relay, or many, could disappear at any time. A relay can shut down, kick you out, experience intentional or unintentional data loss, or many other things. It is likely that a copy of your notes will still exist on many relays, but if you are concerned with the longevity of your content, consider running your own. Paid services for long term note storage exists as well, but they do require trusting the provider.
In this light, the importance of relays starts to become obvious. The various rules open up a whole plethora of use cases that make relays interesting, unique, and useful for the user. They are the backbone of the protocol. They are also tools for finding and managing great social connections and great content.
Types of Relays
This section can, in no way, be considered comprehensive. It is nearly impossible to know all of the relay implementations that may exist or all the rules that they may have set for themselves. Here, we will address some common types that will be useful in making the most of Nostr and a few types with specialized tasks.
Public Relays - Most Nostr clients will start new users with a predetermined set of relays that are free and publicly available for fetching and serving. This lowers the entry barrier for getting connected to the network, ensuring that everyone has access. It does come with some tradeoffs. Public relays tend to accept almost any type of content, so they are prone becoming the hosts of spam, bots, and shady content. To curate your space, it is recommended to get connected with some relays that help you clean things up.
Web-of-Trust Relays - These relays use your social graph and the graphs of others to build a network of higher trust for its users. This reduces spam and other yucky stuff from making it into your feeds. For write access, you must be followed by someone else within the network. If you are coming to Nostr with no external social connection, these may not be useful at first, though most do allow for public reading so you may find them useful to discover people and content you find interesting. Once you have established some social connections, they are great for creating a feed that casts a wider net through the whole network.
Paid Read/Write Filter Relays - These relays will charge an admission fee for write access. This helps to reduce spam and bots. Not all paying npubs want to see or interact with all who are willing to pay the fee, so a paid write relay often works best when paired with a paid filter relay for reading. These will operate under many sets of filtering rules, so be sure to read through any available material from the provider. They should explain what they filter and why, so that you may choose filters that match your tastes.
Inbox Relays - These relays are tasked with collecting any events that are intended FOR you. This includes likes, replies, receipts, and mentions, among many other things. If socializing with your friends and colleagues is important to you, you will want to find inbox relays that manage this task well. DM inbox relays are a separate but similar concept, as direct messages are encrypted and wrapped. They are a specialized relay meant for handling encrypted events. Many DM inbox relays charge a subscription fee, some do not. This is also a great use case for private relays.
Private Relays - These relays can be arranged to handle nearly anything you would like. You can whitelist a group of people that can write, restrict read access through AUTH, and set other various rules. They are a great option for any encrypted data, such as DMs, lists, and drafts. They also make a great backup for your own notes to help ensure that they remain available and locatable. Running your own is the optimal option here, but there are paid services, that I think of as relay rental. They are hosted on big servers, and managed by a small company. All details of the relay rules are at the renter's discretion. This is a good option if you do not have the hardware or confidence to set up your own private relay yet.
Search Relays - Search relays can help you find specific users & notes across the wider network. Some specialize in searching for people, others for text, tags, and other criteria. A strong search relay can make navigating through Nostr a breeze. As with other things, some may require a small fee to use them and others are free to use. Try out some free ones before buying to see if you are happy with your experience.
"Read" Relays - This is sort of a catchall term for anywhere that your client connects to for fetching notes and other events. In the best scenerio, you should not have to worry about these, as relays will signal for your client to find the notes you are fetching. The Nostr protocol and its mechanisms are adapting to what works, so being informed of "read" relays is essential for now. These are the places that you may need to tell your client to connect to when fetching notes from the people you follow. Specialized Relays - Specialized relays will vary in function and rules. Some are for curating quality feeds while others host full-fledge communities around a topic or common interest. Clients designed to interact with these more specialized use cases will often have relay information available or a method for you to browse their feeds.
This is just a snapshot of the different types of relays that exists now. Many are in development and testing for algorithmic content distribution, paywalled content, encrypted group messaging, limited read access, media hosting, and more. (This section may be updated as certain types gain or lose traction throughout the ecosystem.)
Managing Relays
By now, this probably feels like a ton of information and it is, but its also part of what gives you the ability to create and maintain a quality experience with Nostr. A truly decentralized system puts power into the user's hands rather than a corporation. If you want to be in control of your space (spatium tuum), relays are the first and foremost way to do that. They don't have to be viewed as boring servers. They are anything but that. They are tools that can enhance your online networking, serve you educational or entertaining content, or provide you with a safe place to store your personal thoughts. What you use them for is up to YOU.
Spend some time trying free ones, exploring relay feeds, or plugging into some paid services until you find a setup that creates a quality online space for you. If you're worried that you might "break" your connection, don't be. Make a note of a couple that you are connecting to when getting started, as a backup, but I feel confident to say that you won't ever look at it again.
Finding Relays
Finding relays can be a bit of a chore, but that is getting easier as time goes by. For now you there a few options you can try.
-
Visit a relay explorer like nostr.watch or nostr.info
-
Use a client that shows you which relays are hosting a note or a person's relay list. There are some examples in our client guide like Amethyst, Coracle, Jumble, and Nostrudel.
-
Just ask. Most people are on a social network to be social. Currently, Nostr is brimming with social people who are passionate about freedom, decentralized communication, and Nostr in particular. They are happy to help.
Running Your Own
Relay.tools is a hosted personal relay service for ease and a user friendly experience. Search Zapstore for Citrine to run a native relay on your Android device.
Below are some suggestions for relays to run on your own hardware. Search "nostr relay" on GitHub for more.
https://utxo.one/#nostr-projects
https://khatru.nostr.technology/
https://github.com/mikedilger/chorus
nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqyghwumn8ghj7mn0wd68ytnhd9hx2tcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qqdxymngv35xq6rxdf5xqer2s0rg3q
-
-
 @ 7da115b6:7d3e46ae
2025-03-25 10:55:04
@ 7da115b6:7d3e46ae
2025-03-25 10:55:04Originally written and posted on the 12th of December, 2024
Emotionally, it's been challenging to say the least, and the heat just exacerbates the frustration. But don't let that fool you; we've made significant progress. We found our dream property over two months ago for $130,000. 3 hectares of land, but 2 hectares of it is unusable. This was perfectly okay with us as it's going to be a massive effort for one person anyway.
Two months ago, we put in an offer and they accepted it. However, we are not well off by any means; most weeks, we just scrape by. We have two properties - a property in the Far North that we've been renting out to pay the mortgage ($70,000 remaining), and the one we live in which has almost the entire mortgage outstanding.
So how can we afford another property? Well it's no simple feat! First, we need to sell our Rental Property for around $400,000 (a reasonable market rate). Once that sells, about $170,000 in equity gets transferred to the mortgage of the property we're currently living in. After paying off the last of the mortgage on the rental property and shifting the equity to our current property, that will leave us with almost nothing after legal fees and real estate agent fees.
This amount remaining barely covers the cost of the property we put an offer on - our dream property. It's a humbling experience realizing just how far we still have to go in this journey towards self-sufficiency.
It's a sober reminder that we can't rush it, but should rather embrace each step along the way. For better or for worse, we must adapt and learn from every situation as it comes our way. After all, we can only control what's within our reach; the rest is just a matter of time and patience.
Perhaps it's not about achieving self-sufficiency, but truly embracing the journey itself. The path towards that dream property we've been longing for may take longer than expected, but as long as we have each other and keep pushing forward, I can't think of anything more rewarding than seeing our vision unfold step by step.
I have to remember to cherish the memories and experiences along this road, because it's those moments that will truly make the journey worthwhile.
-
 @ 3c389c8f:7a2eff7f
2025-03-25 16:38:21
@ 3c389c8f:7a2eff7f
2025-03-25 16:38:21Public Key vs Private Key
When you generate a Nostr identity, you generate a cryptographic keypair. One is your public key (npub...). It is used to find you and your notes. The other is your private key (nsec...), which you use to interact. Everything you do is an event, which is signed by your private key. This makes all of your actions provably yours. You are solely responsible for protecting your nsec. It is recommended to try Nostr with a test keypair before setting up anything that you want to treat seriously.
Key Creation and Protection
Most Nostr clients will have the option to generate a keypair onsite or in-app. This is convenient for trying Nostr or a client. To make a keypair for longterm use, you might want to visit a site that provides some key security from the start. Your keys are a permanent set of identifiers. They cannot be changed or reset. You own them and it is your responsibility to keep your private key safe.
When you are ready to set up a permanent identity, start in a place that specializes in Nostr key generation. Nstart and Hubstr are great places to start. NOA, Nostr Onboarding App, is multiplatform with a native app, which helps make it easier to share with friends. You can create a vanity npub through various methods as well, like https://www.nostr.rest/ . There are other methods but these are some of the most user friendly ones that I have found. They provide some tools and guidance for creating your keypair in a safe manner. Once you've gone through the process, it is a good idea to write down your nsec and store it off of any devices, in the event you should lose access to your computer or phone.
Using a signer or a browser extension to house your nsec (private key), is the next step to keeping your identity safe. (Find out more on key management below)
Portability of Your Keys
This is where all the magic happens. You can use your keys to sign into any Nostr app. If you sign in with your npub (public key), you will enter in a read-only mode. This is nice for seeing a client's interface before trying it. You can sign in with anyone's npub to see what their social feeds look like, too. You do not need to be concerned with security when using npub sign-in. Your public key, is fully public. Not all Nostr clients support this option, but many do.
Signing in with your nsec unlocks all the features of a client and enables you to interact on the protocol. Everything you do is signed by your nsec and made available by your npub. Using some sort of signer is obviously advised, to keep from exposing your nsec online.
Since all of your actions (aka events) are stored on relays and not by clients, all of your content, messages, or anything else becomes available in any client that supports those event types. Most social stuff, like replies and profile views are available almost everywhere. Not all apps will support everything, but the ones that share a common theme will handle your events in similar manners. (I.e., a marketplace listing made from one app will display across many apps. The comments and replies will, too, so there is no need to manage multiple listings to answer questions or mark something as sold.)
Key Management
This is an evolving field, with many methods of key management being explored. People, businesses, and institutions all have different needs.
Signing Extensions keep your key in a browser extension, signaling to an app that the valid nsec is present. This sign in method is available on most Nostr apps. These are the most convenient method of key management but they do have their limitations. Using an extension can be cumbersome on mobile devices, and they could still be subject to vulnerabilities within your browser or the signer itself. They also don't allow for multiple users to sign events, like a business or organization might need. Key Bunkers enable the storage of key shards encrypted across multiple locations or in one spot. Bunker signing calls the encrypted key shards to decrypt for signing events. A bunker key, often called a bunker string, can be shared with staff or used to keep your key offline. They are revocable and replaceable. The process is currently a a little complicated and client support is somewhat limited. Adoption and improvement of this method is happening quickly, as the need for multi-party access to a profile increases. Native Signing Apps, like Amber for Android, make key key storage and signing for mobile a simple process. These apps work to keep your key offline, similarly to a bunker, but it is all stored encrypted on your device. Most Nostr-Android apps and web clients offer support for this method. Development of a similar iOS app is underway. Offline Hardware Signers like standalone devices and NFC cards are being explored, tested, by many groups.
This is a very active development space and this section will be updated as needed. Below are some suggestions for Nostr signers:
https://nsec.app/ https://chromewebstore.google.com/detail/nos2x/kpgefcfmnafjgpblomihpgmejjdanjjp https://www.getflamingo.org/
-
 @ 7da115b6:7d3e46ae
2025-03-25 10:52:00
@ 7da115b6:7d3e46ae
2025-03-25 10:52:00Originally written and posted on the 10th of March, 2025
Safety
The first reason that comes to mind is safety. Violent crime has become a recurring theme in our town, with statistics showing a rise in cases such as burglaries and general homicides. These changes have made us acutely aware of the importance of providing a secure environment for our family. As our children grow, we yearn for them to experience not just safety, but also a sense of stability that comes with it.
The thought of crime often makes me reflect on moments like the domestic violence and murder within throwing distance of our current home, or the attempted mugging and homicide at a nearby petrol station. These incidents have sparked a desire for a place where our family can feel more secure and enjoy the peace of mind that comes with knowing they're safe. I hope that growing up in a safe environment will instill confidence and security in my kids as they navigate life. This pursuit of safety is not just about protecting my loved ones; it’s about creating a foundation where they can thrive and feel secure in their surroundings, allowing them to focus on their growth and aspirations without the constant awareness of potential danger.
Cost of Living
The cost of living has been another pivotal factor in our decision to move. Over time, we’ve noticed how the city’s expenses, from petrol to groceries, have steadily increased, making every purchase a mindful choice. The rising costs of utilities, transportation, and daily essentials have become a significant part of our budget, leaving us wondering if there’s room for more than just the basics. While the city offers many amenities, we’ve found ourselves seeking a lifestyle that aligns with our values and allows us to live comfortably without constant financial strain.
The cost of groceries has also become a major consideration. As prices rise, even simple trips to the store have us thinking about every purchase. We’ve found ourselves choosing between brands or quantities to stay within our budget, which has made us appreciate the idea of growing some of our own food.
While we love the idea of the cultural and social offerings of city life, the reality is that we spend more time trying to stretch our weekly budget to make ends meet, than we do enjoying the fruits of our labor. We’re looking forward to a place where we can manage our budget comfortably, while still having access to the amenities we need. This doesn’t mean we’re leaving behind everything we’ve grown accustomed to; it’s about finding a balance—a home that allows us to live fully without feeling constrained by expenses.
Our decision to move isn't about wanting to be one with nature or making a statement; it’s more about practicality. Owning a freehold property gives us the stability we need, allowing us to live sustainably without feeling tied down by expenses. This choice aligns with our values and offers a sense of freedom, not because we're trying to escape something, but because it supports the life we want for ourselves and our family. We’ve worked hard to pay down our mortgages, but now we’re ready for the next step—owning our own land that we can build upon.
We’re not looking to simplify just because we want to be closer to nature; rather, we see this move as an opportunity to create a lifestyle that’s more in tune with our needs. By growing our own food and living in a clean, natural environment, we’re prioritizing sustainability without compromising on what matters most—our family’s future and well-being. It’s about creating a home that reflects our values, not just embracing change for the sake of being different.
Educational Opportunities
Our oldest child’s education is another driving force behind this move. We’ve discovered that the place we’re moving to offers a University with "fees-free" options, which will provide him with an opportunity to pursue his studies without the burden of tuition costs. This not only eases our financial concerns but also gives us peace of mind knowing he can focus on his education without added stress. It’s a decision that aligns with our aspirations for his future and our family's well-being, hoping he can thrive in an environment that supports his academic journey and personal growth.
Also, our youngest child is going to have the opportunity to raise the animals he’s so enamored with, such as chickens; dogs; pigs, and maybe even a couple of sheep. I want these experiences to help him to learn by doing, fostering a sense of responsibility and connection with where our food comes from. By caring for these creatures, we hope he’ll develop life skills that will help him grow into his own skin as he gets older. It’s a chance for him to explore his passions and build confidence in a hands-on way.
Freedom
Space has become something we truly appreciate, especially with our kids and pets. We’re eager for them to have more room to roam and explore freely. The privacy that a rural setting offers is high on our list of needs because living in the city often feels like we're always surrounded by others. It's not uncommon to bump into neighbors or find ourselves at loggerheads over simple things like car parks. This constant interaction, while part of city life, can sometimes feel overwhelming.
But it's not just us - our current place of employment also experiences issues with neighboring businesses, and it’s the employees who end up feeling the impact. It feels as if everyone is out for themselves, and are incapable of thinking about how their actions affect others.The city environment feels cramped and extremely claustrophobic, making us yearn for more personal space. We’re looking forward to the freedom of having our own large property where we can enjoy peace and quiet. It’s exciting to think about the possibilities, like building a barn or adding bee hives, and even sinking a water well as we please.
Food & Gardening
The idea of growing our own food is another exciting prospect that we're eager to explore. We’re looking forward to cultivating fresh produce in our garden, which will not only provide healthier options for our family but also add variety and freshness to our meals. It will be a major undertaking for us. While I personally have some understanding of growing and harvesting simple crops like potatoes and cabbage, I am deeply aware of my lack of knowledge and experience. It will take years for me to actually become proficient. We’re excited to teach our kids where their food comes from and instill an appreciation for sustainable living. Growing our own produce aligns with our desire for a more natural, self-sufficient lifestyle, offering us the joy of seeing the fruits of our labor in our garden.
Exercise & General Wellness
Living in a bustling city has its perks, but it has also take a toll on our sense of well-being. The daily grind often leaves us feeling mentally and emotionally drained, leaving little room for relaxation and physical activity. With the convenience of modern life comes a faster pace, which, while beneficial, frequently feels overwhelming. We long for moments to pause, breathe in fresh air, and reconnect with ourselves.
I think that the desire for more exercise and fresh air, is a natural response to the our current lifestyle. The city’s vibrant atmosphere and endless opportunities often come at the expense of personal time and the chance to enjoy relax. By seeking a new environment, We're looking for a balanced life for our family, where we can revitalize their minds and bodies through simple yet essential activities like walking around the property or the exercise of working the land. This shift is not just about changing scenery; it’s about creating a lifestyle that supports our overall well-being and allows for moments of peace away from the hustle and bustle.
In conclusion, this move is about more than just changing scenery; it’s about creating a home that embodies our values—safety, education, sustainability, and well-being for our family. It’s a step towards a future where we can thrive in an environment that supports our growth and aspirations.
-
 @ 3c389c8f:7a2eff7f
2025-03-25 16:16:29
@ 3c389c8f:7a2eff7f
2025-03-25 16:16:29Android
Amethyst - Experience the all-in-one Nostr client for mobile. Amethyst supports custom emoji reactions, marketplace listings, live streams, and so much more. If you're fresh to exploring Nostr, Amethyst may seem like a wild adventure compared to the any other social media of the past. Packed with features and blazing fast, this client gives you the ability to see just what Nostr is all about.
Voyage - This client is light on storage and data consumption, which is great for anyone with cheaper phones, limited data plans, or traveling/living in areas with lower data signal. Not only that, Voyage also offers some list and relay management tools not available in many other apps, so its great for handling some of the technical aspects of Nostr on the fly.
Web
Satellite - Fast and reliable, this client has topic communities, rich feeds, and beautiful profile displays. They offer paid media hosting for pictures, videos and more, which is essential for sharing visual content on Nostr. Satellite has long been a favorite for its simplified approach to displaying notes in a dense, clean manner and its consistency, reliability, and speed.
Jumble - Explore Nostr relay feeds, follow feeds, and more. Jumble has a clean, no-fluff interface that's easy to use and understand. You can socialize on specialized relays, or browse and chat on public relays with friends.
Coracle - Coracle allows you to easily browse relay feeds, your follow feed, and create custom feeds. You can generate Proof-of Work notes, set 'send' delays, and limit the number of relays the client talks to, to increase speed and reduce data consumption. You can generate PoW anonymous replies, too. A favorite feature is the option to import and export all of your data to/from your local device, so you can easily maintain a copy or send any lost events back to the Nostr network.
Nostrudel - The neat thing about Nostrudel is trying to find a Nostr action that it can't do. It's got all the bells and whistles. Nostudel may be a bit overwhelming if you're not familiar with all that is possible on Nostr, but once you have an idea, take this for a spin and see what new ways of interacting on the protocol that you discover.
iOS/Apple
Sorry... this is going to be a little scant for a while. Simply not one of the Apple people, these are the ones my iOS/Nostr friends seem to love:
Damus is a longtime favorite among users, adhering to a protocol-first approach to development.
Nostur sounds like a fun app, maybe on par with Amethyst as far as fun features and fast performance.
You'll have to do your own exploring to see what they are really all about.
Multi-platform
Primal - Simple, clean, and with an integrated Bitcoin/Lightning wallet for fast, easy zaps (basically tips, but on Nostr!). Get started with Nostr right away with no hassle and send or receive Bitcoin among your social network. Primal is great for anyone new to Nostr or who wants to enjoy a more traditional social media experience with the benefits that Nostr has to offer. Primal is available for Android, iOS, and on the web.
Yakihonne - Yakihonne is a beautiful multi-platform client that is available across any device. With a focus on long-form writing, it makes it easy to read and create Nostr articles, blogs, and any other informative piece. It doesn't stop there, though. You can scroll your social feed, set up smart widgets, and browse curated content collections, too.
Desktop
Notedeck - Built by the Damus team, Notedeck brings the speed and redundancy of Nostr to your machine. The local software is easy to install, set up, and use. Add multiple columns to the interface for a full screen of different feeds, profiles, and notifications.
Gossip - Gossip has a wide array of technical knobs and dials for relay controls, note fetching and publishing, and a clean interface that even I can understand. Gossip is built for the more technically-inclined among us, but is also great for the general Nostr "power user". This client is still a step above my paygrade but I'm loving it, regardless of that. If you are like me, this is a great client for a learn-through-doing method of understanding Nostr.
For Groups, Communities, and Chat
Oxchat - Oxchat puts security at the forefront of its interface with encrypted private and group chats. It does a whole lot more than that, too. You can browse your social feed, make voice and video calls, and display badges.
Flotilla and ChaChi are a couple of up and coming group/community/chat clients that are still very much under development, but look to be worth expounding upon in the future. Nostr's interoperability allows you to create and engage in groups you have joined through any of the above clients.
Specialty Clients
Zap.cooking - Publish recipes, earn zaps, find recipes, send zaps. Its a pretty brilliant system. There is no more need for 20 minute stories or overwhelming popup ads. Nostr adds a social layer to recipe sharing that doesn't require a new account to participate. Just sign in with your signing extension of choice, and you can share and leave feedback instantly.
Highlighter - Its still a bit of a construction site, but Highlighter is on its way to becoming Nostr's premiere content creator studio. Write, highlight, and curate. Not only can you create these, you can also browse and discover great Nostr content. There's lots in the works for video and other types of content, too.
Shipyard - "A Quiet Space for Loud Ideas" says it all. Shipyard is focused solely on your writing experience so that you may focus soley on your writing. This client is clean, reliable, and extemely user friendly. It is also one of few Nostr clients that provide you with the ability schedule the publishing of your notes.
Emojito.meme - Create and find custom emoji packs to use on Nostr! How fun is that? Just bookmark & those emojis ready to be used in any supporting social client.
Badges.page - Create and claim badges that display on Nostr profiles in supporting clients. This is a great way to engage with fans, celebrate moments with friends, or even just to be silly. You can set the difficulty of creating a badge with Proof-of-Work to create rare and super rare badges for top supporters, which is pretty cool.
Olas - A beautiful, visual showcase for photography and more. Its sort of like Instagram, but on Nostr, so its better. You can share, scroll, post, and monetize your content in a breeze.
Zapstore - Its an app store! On Nostr! Built for Android! Just follow the instructions on the site to begin your journey of stepping out of the nightmare that is the Playstore. Find apps recommended by your social graph, built by developers trusted within your networks, and donate to app development directly. You'll find more than just Nostr apps here. Zapstore is devoted to bringing free open source software from builder to user with as little interference as possible.
Listr - Create and manage lists for use in any other supporting client. This was the first thing that wow'd me about Nostr when I discovered it a couple years ago. There's something about making a list of people with common interests in one client, and seeing that list in action in another that just blew me away. Different feeds for different purposes, all chronological and all curated by YOU.
Habla - Long-form writing on Nostr made simple. You can quickly and easily get started with a blog or news publication and distribute it to your entire Nostr audience, regardless of which apps they use. Most social clients support article display within various feeds. You can always quote-note your article in a regular note, if you want to boost article exposure, too.
-
 @ ecda4328:1278f072
2025-03-25 10:00:52
@ ecda4328:1278f072
2025-03-25 10:00:52Kubernetes and Linux Swap: A Practical Perspective
After reviewing kernel documentation on swap management (e.g., Linux Swap Management), KEP-2400 (Kubernetes Node Memory Swap Support), and community discussions like this post on ServerFault, it's clear that the topic of swap usage in modern systems—especially Kubernetes environments—is nuanced and often contentious. Here's a practical synthesis of the discussion.
The Rationale for Disabling Swap
We disable SWAP on our Linux servers to ensure stable and predictable performance by relying on available RAM, avoiding the performance degradation and unnecessary I/O caused by SWAP usage. If an application runs out of memory, it’s usually due to insufficient RAM allocation or a memory leak, and enabling SWAP only worsens performance for other applications. It's more efficient to let a leaking app restart than to rely on SWAP to prevent OOM crashes.
With modern platforms like Kubernetes, memory requests and limits are enforced, ensuring apps use only the RAM allocated to them, while avoiding overcommitment to prevent resource exhaustion.
Additionally, disabling swap may protect data from data remanence attacks, where sensitive information could potentially be recovered from the swap space even after a process terminates.
Theoretical Capability vs. Practical Deployment
Linux provides a powerful and flexible memory subsystem. With proper tuning (e.g., swappiness, memory pinning, cgroups), it's technically possible to make swap usage efficient and targeted. Seasoned sysadmins often argue that disabling swap entirely is a lazy shortcut—an avoidance of learning how to use the tools properly.
But Kubernetes is not a traditional system. It's an orchestrated environment that favors predictability, fail-fast behavior, and clear isolation between workloads. Within this model:
- Memory requests and limits are declared explicitly.
- The scheduler makes decisions based on RAM availability, not total virtual memory (RAM + swap).
- Swap introduces non-deterministic performance characteristics that conflict with Kubernetes' goals.
So while the kernel supports intelligent swap usage, Kubernetes intentionally sidesteps that complexity.
Why Disable Swap in Kubernetes?
-
Deterministic Failure > Degraded Performance\ If a pod exceeds its memory allocation, it should fail fast — not get throttled into slow oblivion due to swap. This behavior surfaces bugs (like memory leaks or poor sizing) early.
-
Transparency & Observability\ With swap disabled, memory issues are clearer to diagnose. Swap obfuscates root causes and can make a healthy-looking node behave erratically.
-
Performance Consistency\ Swap causes I/O overhead. One noisy pod using swap can impact unrelated workloads on the same node — even if they’re within their resource limits.
-
Kubernetes Doesn’t Manage Swap Well\ Kubelet has historically lacked intelligence around swap. As of today, Kubernetes still doesn't support swap-aware scheduling or per-container swap control.
-
Statelessness is the Norm\ Most containerized workloads are designed to be ephemeral. Restarting a pod is usually preferable to letting it hang in a degraded state.
"But Swap Can Be Useful..."
Yes — for certain workloads (e.g., in-memory databases, caching layers, legacy systems), there may be valid reasons to keep swap enabled. In such cases, you'd need:
- Fine-tuned
vm.swappiness - Memory pinning and cgroup-based control
- Swap-aware monitoring and alerting
- Custom kubelet/systemd integration
That's possible, but not standard practice — and for good reason.
Future Considerations
Recent Kubernetes releases have introduced experimental swap support via KEP-2400. While this provides more flexibility for advanced use cases — particularly Burstable QoS pods on cgroupsv2 — swap remains disabled by default and is not generally recommended for production workloads unless carefully planned. The rationale outlined in this article remains applicable to most Kubernetes operators, especially in multi-tenant and performance-sensitive environments.
Even the Kubernetes maintainers acknowledge the inherent trade-offs of enabling swap. As noted in KEP-2400's Risks and Mitigations section, swap introduces unpredictability, can severely degrade performance compared to RAM, and complicates Kubernetes' resource accounting — increasing the risk of noisy neighbors and unexpected scheduling behavior.
Some argue that with emerging technologies like non-volatile memory (e.g., Intel Optane/XPoint), swap may become viable again. These systems promise near-RAM speed with large capacity, offering hybrid memory models. But these are not widely deployed or supported in mainstream Kubernetes environments yet.
Conclusion
Disabling swap in Kubernetes is not a lazy hack — it’s a strategic tradeoff. It improves transparency, predictability, and system integrity in multi-tenant, containerized environments. While the kernel allows for more advanced configurations, Kubernetes intentionally simplifies memory handling for the sake of reliability.
If we want to revisit swap usage, it should come with serious planning: proper instrumentation, swap-aware observability, and potentially upstream K8s improvements. Until then, disabling swap remains the sane default.
-
 @ 7d33ba57:1b82db35
2025-03-25 09:38:27
@ 7d33ba57:1b82db35
2025-03-25 09:38:27Located on the Costa de la Luz, Chipiona is a charming seaside town in Cádiz province, known for its stunning beaches, iconic lighthouse, and delicious local wines. It’s a perfect destination for those seeking relaxation, history, and Andalusian charm.
🏖️ Top Things to See & Do in Chipiona
1️⃣ Chipiona Lighthouse (Faro de Chipiona) 💡
- The tallest lighthouse in Spain (69 meters), built in 1867.
- Climb 322 steps for breathtaking views of the Atlantic Ocean.
- Used to guide ships through the Gulf of Cádiz for centuries.
2️⃣ Playa de Regla 🏝️
- The most famous beach in Chipiona, known for its golden sand and calm waters.
- Perfect for sunbathing, swimming, and long walks along the shore.
- Surrounded by beach bars (chiringuitos) and seafood restaurants.
3️⃣ Santuario de Nuestra Señora de Regla ⛪
- A beautiful neo-Gothic monastery near the beach.
- Home to the Virgen de Regla, the town’s patron saint.
- A site of religious pilgrimages, especially in September.
4️⃣ Las Corrales de Pesca 🎣
- Ancient fishing structures made of stone walls in the sea, dating back to Roman times.
- A unique traditional fishing method, still in use today.
- Guided tours are available to learn about their history.
5️⃣ Bodega César Florido 🍷
- Visit one of the oldest wineries in Chipiona, famous for Moscatel wine.
- Enjoy a wine tasting tour and learn about the local winemaking tradition.
6️⃣ Paseo Marítimo & Sunset Views 🌅
- A scenic beachfront promenade, ideal for an evening stroll.
- Watch the sunset over the Atlantic Ocean, one of the most beautiful in Andalusia.
🍽️ What to Eat in Chipiona
- Langostinos de Sanlúcar – Delicious local prawns, best with a glass of Manzanilla wine 🦐🍷
- Tortillitas de camarones – Crispy shrimp fritters, a Cádiz specialty 🥞🦐
- Chocos a la plancha – Grilled cuttlefish with olive oil and lemon 🦑
- Pescaíto frito – A mix of fried fresh fish, perfect for a beachside meal 🐟
- Moscatel de Chipiona – A sweet dessert wine, famous in the region 🍷

🚗 How to Get to Chipiona
🚘 By Car: ~30 min from Cádiz, 1 hr from Seville, 2 hrs from Málaga
🚆 By Train: Closest stations in El Puerto de Santa María or Jerez de la Frontera
🚌 By Bus: Regular buses from Cádiz, Jerez, and Seville
✈️ By Air: Nearest airport is Jerez de la Frontera (XRY) (~40 min away)💡 Tips for Visiting Chipiona
✅ Best time to visit? Spring & summer for beach weather, September for festivals 🌞
✅ Try a Moscatel wine tour – The local wineries are world-famous 🍷
✅ Bring comfortable shoes – If climbing the lighthouse 👟
✅ Visit in September for the Fiestas de la Virgen de Regla, a unique cultural experience 🎉 -
 @ da0b9bc3:4e30a4a9
2025-03-25 09:14:07
@ da0b9bc3:4e30a4a9
2025-03-25 09:14:07Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/924287
-
 @ 8b61abe1:b3444ff4
2025-03-25 07:06:47
@ 8b61abe1:b3444ff4
2025-03-25 07:06:47The idea of buying a house with Bitcoin in Italy is intriguing and fits into the debate on the digitalization of the real estate sector. However, despite the growing interest in cryptocurrencies, it is currently almost impossible to complete a real estate transaction using Bitcoin. But why?
The Legal Nature of Cryptocurrencies
One of the main obstacles to purchasing real estate with Bitcoin is the legal uncertainty on cryptocurrencies. In Italy, Bitcoin is not considered legal tender but rather a digital asset with a fluctuating value.
The Italian law requires that real estate transactions be conducted using state-recognized financial instruments, such as EURO. Additionally, the purchase contract must be drawn up in front of a notary, and the payment must be made through traceable methods to ensure transaction transparency and prevent money laundering.
One of the pillars of Italy’s real estate system is money traceability. Anti-money laundering regulations require that all significant transactions be executed through traceable instruments.
Cryptocurrencies, on the other hand, are decentralized and often provide a degree of anonymity in transactions, making it difficult to verify the origin of funds. This conflicts with the legal requirement to demonstrate the lawful source of money used for real estate purchases.
The Role of the Notary and Operational Challenges
To complete a real estate transaction in Italy, a notary must be present to certify the legality of the transaction and ensure that the payment is made in compliance with the law. Currently, a notary cannot accept Bitcoin payments because it is not considered legal tender.
The only way to use Bitcoin in a real estate transaction would be to convert it into euros before the sale. However, this negates the advantage of paying directly with cryptocurrency and introduces additional costs, such as conversion fees and potential capital gains taxes.
Lack of Specific Regulations
Other countries have started regulating real estate transactions in cryptocurrency, but Italy still lags in this area. Without a clear regulatory framework recognizing Bitcoin as an accepted means of payment in real estate, it is difficult to envision any short-term changes.
Some private initiatives have attempted to bypass this issue by offering sales in Bitcoin, but in practice, these transactions involve the seller accepting Bitcoin and immediately converting it into euros before the notarial deed. This does not represent a true real estate transaction in cryptocurrency but rather an alternative payment method before the finalization of the sale in euros.
A Possible Future?
For now, buying real estate with Bitcoin in Italy remains more of a theoretical concept than a concrete possibility. To make this payment method a reality, legislative changes would be needed to: 1. Recognize cryptocurrencies as a legal payment method. 2. Define clear procedures to ensure the traceability of Bitcoin transactions. 3. Establish mechanisms for the immediate and certified conversion of cryptocurrencies into euros at the time of the notarial deed.
-
 @ 220522c2:61e18cb4
2025-03-25 06:57:24
@ 220522c2:61e18cb4
2025-03-25 06:57:24
-
 @ 7da115b6:7d3e46ae
2025-03-25 05:14:41
@ 7da115b6:7d3e46ae
2025-03-25 05:14:41Originally written and posted on the 21st of Sept, 2022
I'm about 6 months into the ownership of my first bike, since I was a teenager. It has most definitely been an interesting time. While I am truly enjoying riding, it's not been without it's hiccups.
The first real issue is that I don't have a great knowledge of motorcycle models, or their general history. My first ride was an 80cc Yamaha Jog, which could do 70 Km/h down hill with a tail wind. My second was a Yamaha DX100 (colloquially known as the "Flying Banana"), which I could start with the handle of a teaspoon, and was lost when the back tyre burst during a trip, resulting in a write-off (a story in of itself).
So a little background first. The reason I purchased a bike, is mostly for financial reasons. While there is an argument to be made that it's more expensive to ride than drive, I did a ton of math, and came to the conclusion that it actually works out cheaper, considering my circumstances. When factoring in the massive rise in fuel costs; the far lower insurance costs; and lower maintenance costs (due to being able to maintain it reasonably well on my own). It seemed that because I do long trips of around 400 Km every couple of weeks, it was a sound option. Also, being middle aged, I ended up having to go back and sit my motorcycle licence, as with my previous bikes, it was in a time where riding dirty on small displacement bikes wasn't really noticed by the cops (yes, that does indeed make me a middle aged learner rider).
When researching bikes, I made a few things a priority:
- Small displacement
- Aesthetically pleasing
- Easily repairable
- Cheap maintenance
- Reliability
- Fuel efficient
nb. I didn't include things like performance or top speed, because they were mostly irrelevant to my needs at the time.
In the end, it worked out that the Kawasaki Ninja 250 fit all of the criteria I had set. It was about then that I set out to find a good example of the model, at a reasonable price.
I delved into the subject with gusto, looking at the Trademe sales, and researching as best as I could. I ran across the Ninja250 Wiki and found a thriving community built around these interesting little bikes. While I didn't interact directly with the community, I did find the compiled resources invaluable for my purposes. They've pulled together schematics, technical manuals, replacement parts lists, tips & tricks and a ton of general information. Very handy.
Unfortunately, Kawasaki have been a little liberal with the "Ninja" moniker, and it seems like they enjoyed slapping the label on a ton of different models. It got extremely confusing in a very short period of time. In the end, I found a listing for a 2007 Ninja 250, that looked really clean for its age, with only 30,000Kms on the clock. Being the 2007 model, it was the last of the dual carb bikes, before they switched to Electronic Fuel Injection. This appealed to me, because it lowered the bar for maintenance.
It seemed like the perfect option for me, so I got in contact with the owner, and we negotiated a price. I looked over the bike, and in my inexperience, I missed some crucial details that a more experienced rider would have noticed (I'll get to those details shortly). After a quick ride on my newly minted Learners Licence, I found the power was decent and it rode well. I checked for things like frame fatigue, engine noise, drops in power, exhaust leaks, tyre tread, oil leaks and more.
The owner seemed trustworthy, so when he told me that "It runs like a dream, and it's never needed any work aside from a replacement faring", I believed him. In hind sight, I seriously should have realised the red flag about it needing new faring.
This is where we get to the details I missed.
Firstly, It looks like the Oil Filter had never been changed, but to cover this fact, they did an oil change just before the sale, so it looked clean.
Secondly, the fuel filter had never been changed, so was full of crud. Because it's hidden in the carb end of the fuel line, you cant see it on a cursory look.
Thirdly, someone had removed the air filter, and just never bothered to put it back or replace it. Unfortunately, it's under the fuel tank, so you cant see it without removing the tank.
Fourth and finally, the Faring. So it turns out that the bike had definitely been laid down at some point. My naivety and excitement blinded me to what was obvious. The clutch handle was scratched to sin, the tail bar has scrapes along one corner, and the foot pegs had been replaced.
Again, looking back, how could I not have seen these things? I'm kicking myself, but now that I have it, I just have to deal with the consequences.
I'm disappointed in the seller for not disclosing these issues, and to say that I was cursing his name when I found out about these things, is a definite understatement. I know that I should have been more diligent, but it calls into question my judgement. I feel a little ripped off by people like this, and am starting to question a lot of decisions I wouldn't normally hesitate to make.
Anyway, after a lot more research it turns out it's not even an EX250, which is what the previous owner told me. It is in fact a GPX250, which has a completely different set of parts. This was a true eye opener, and led me to order parts that are completely incompatible with the bike. When I finally found out the correct model, I was able to move forward.
Since having the bike, I've lubed the chain multiple times (it looks like it had never been done); I've replaced the oil filter and done an oil change; ripped out the silly fuel filter and added an in-line gravity fed one that is transparent and easy to view; and replaced the air filter.
It seems to be running better now, and there is more to be done, but I'm sad that it has come to this. I never should have listened to the previous owner, let alone trusted him. I have learned my lesson, and will be far more vigilant in the future.
-
 @ 7da115b6:7d3e46ae
2025-03-25 05:04:16
@ 7da115b6:7d3e46ae
2025-03-25 05:04:16It's heart wrenching when everything around you seems to come crashing down around your ears, it seems as though the world is coming to an end.
What Happened?
Sadly, some news came to us in the last couple of days, news that has exploded our plans like a bombshell. As you know from previous posts, my family and I had found the property of our dreams, within the price range that suited us. The only issue was that we had to sell our rental property to be able to purchase the land we wanted to develop for our homestead. At the time, it wasn't an issue.
With a few phone calls and some discussion with the local Council; the Realtor; the Vendors, and the bank, we were on our way. We made an offer, and it was accepted, contingent on our rental property selling. Our offer expires this Friday, and the likelihood of it selling before then, is slim. That leaves us 3 days to come up with the $130,000 we need to secure the property.
"So why not just extend the offer?" I hear you say. Well, that's a fair point - We did. The extension runs out this Friday. Can we extend on the extension? Legally, yes. but here's the rub:
A counter offer has been put forward.
This basically means, that without having the money available by the end of the offer extension, the Vendor is going to take the counter offer.
That's Not So Bad... Right?
Yes, and no.
Unfortunately, we've spend thousands of dollars on reports; valuations; building research and site inspections. This means all of the plans, money and time that we've invested so far is going to be lost. Yes yes, you're right of course, it's our own fault for getting so financially and emotionally invested in the first place. Lesson learned.
I think that the hardest part of it all, was breaking it to my wife. She had already started designing her gardens, and had dreams of watching our homestead grow. The look of utter defeat on her face was gut wrenching. I felt as though I had failed her, and torn away the dream we had built together. She and I had lost our dream in the course of a single phone call. It hit both of us hard.
It's been 24 hours now, and the pain is real. I don't want to eat or go to work, I don't want to talk to anyone. I just want to lay down on my wife's lap and close my eyes until it's over. Deep down inside, I know it's a childish reaction, but that doesn't make it any less of a slap across the face.
The Light at the End of the Tunnel
Cliche, I know, but there may be a little glimmer of light on the horizon. If we do sell our rental property, we will have money to play with. This means we can buy a crappy little Ute and caravan, and go exploring our country. Perhaps stop at a few places that look nice, and see if they're places we could settle. If we spend a few months just looking around, and find somewhere homely, then we can stay for a while at a local caravan park, and look for a property that may be suitable.
At the very least, it would mean that we can escape our shit jobs, which has been the biggest goal from the beginning.
Fingers crossed...
-
 @ e5de992e:4a95ef85
2025-03-25 05:00:45
@ e5de992e:4a95ef85
2025-03-25 05:00:45Global financial markets are experiencing significant movements influenced by recent developments in trade policies, economic data releases, and geopolitical events.
U.S. Stock Market Performance
On March 24, 2025, U.S. stock markets rallied sharply, buoyed by optimism surrounding potential easing of forthcoming tariffs:
-
Dow Jones Industrial Average (DJIA):
Rose by nearly 600 points (1.4%), closing at 42,583.32. -
S&P 500:
Increased by 1.8%, ending the session at 5,767.57 points. -
Nasdaq Composite:
Advanced by 2.3%, finishing at 18,188.59 points.
These gains were led by significant advances in the technology sector, with notable performances from companies like Tesla, which surged 12%, and Nvidia, which gained 3.2%.
U.S. Futures Market
As of the latest data, U.S. stock futures are exhibiting slight fluctuations:
-
Dow Jones Futures:
Indicated a modest decline, reflecting investor caution ahead of upcoming economic data releases. -
S&P 500 Futures:
Showed minimal movement, suggesting tentative market sentiment. -
Nasdaq Futures:
Displayed slight volatility, influenced by recent tech sector performances.
Key Factors and Events Influencing U.S. Markets
Trade Policy Developments
- Recent market rallies were largely driven by reports that the U.S. administration plans to implement more targeted tariffs than initially feared.
- Certain sectors such as automobiles and semiconductors may be exempted, alleviating investor concerns about trade policies impacting economic growth.
Economic Data Releases
- Investors are closely monitoring upcoming economic indicators, including the Consumer Confidence Index and the Personal Consumption Expenditures (PCE) index.
- These indicators will help gauge the health of the economy and inform potential implications for monetary policy.
Federal Reserve's Monetary Policy
- The Federal Reserve's recent decision to maintain interest rates—along with its revised economic outlook—continues to influence market sentiment.
- This policy stance is particularly relevant in relation to inflation expectations and growth projections.
Global Stock Indices Performance
International markets have shown mixed reactions in response to U.S. trade policy developments and regional economic data:
-
Germany's DAX:
Experienced modest gains amid cautious optimism over global trade discussions. -
UK's FTSE 100:
Edged higher, supported by strength in commodity-related sectors. -
Euro Stoxx 50:
Advanced, driven by positive corporate earnings reports and easing trade tensions. -
Japan's Nikkei 225:
Rose by over 1%, mirroring Wall Street’s upbeat performance and optimism regarding U.S. tariff policies. -
Hong Kong's Hang Seng:
Declined by 1%, impacted by profit-taking activities and ongoing trade uncertainties.
Cryptocurrency Market
The cryptocurrency market has exhibited volatility, with major digital assets experiencing price fluctuations:
-
Bitcoin (BTC):
Trading at approximately $84,481.00, down 1.82% from the previous close. -
Ethereum (ETH):
Priced around $1,987.26, reflecting a 2.18% decrease from the prior session.
These movements highlight the broader market's sensitivity to regulatory developments and macroeconomic factors affecting investor sentiment in the digital asset space.
Key Global Economic and Geopolitical Events
-
Trade Tensions and Tariff Policies:
Rapid escalation of trade barriers—reminiscent of protectionist measures from the 1930s—has raised concerns about long-term economic and diplomatic ramifications, including slower growth and heightened inflation. -
Central Bank Communications:
Statements from Federal Reserve officials and other central bank representatives are being closely scrutinized for future monetary policy directions. -
Corporate Earnings Reports:
Upcoming earnings releases from major corporations are expected to provide further clarity on sector health and broader economic conditions, influencing market dynamics in the near term.
Conclusion
Global financial markets are navigating a complex landscape shaped by trade policy developments, economic data releases, and geopolitical events. Investors are advised to remain vigilant and consider these factors when making informed decisions, as they are likely to continue influencing market behavior in the foreseeable future.
-
-
 @ 7da115b6:7d3e46ae
2025-03-25 04:52:58
@ 7da115b6:7d3e46ae
2025-03-25 04:52:58It's heart wrenching when everything around you seems to come crashing down around your ears, it seems as though the world is coming to an end.
What Happened?
Sadly, some news came to us in the last couple of days, news that has exploded our plans like a bombshell. As you know from previous posts, my family and I had found the property of our dreams, within the price range that suited us. The only issue was that we had to sell our rental property to be able to purchase the land we wanted to develop for our homestead. At the time, it wasn't an issue.
With a few phone calls and some discussion with the local Council; the Realtor; the Vendors, and the bank, we were on our way. We made an offer, and it was accepted, contingent on our rental property selling. Our offer expires this Friday, and the likelihood of it selling before then, is slim. That leaves us 3 days to come up with the $130,000 we need to secure the property.
"So why not just extend the offer?" I hear you say. Well, that's a fair point - We did. The extension runs out this Friday. Can we extend on the extension? Legally, yes. but here's the rub:
A counter offer has been put forward.
This basically means, that without having the money available by the end of the offer extension, the Vendor is going to take the counter offer.
That's Not So Bad... Right?
Yes, and no.
Unfortunately, we've spend thousands of dollars on reports; valuations; building research and site inspections. This means all of the plans, money and time that we've invested so far is going to be lost. Yes yes, you're right of course, it's our own fault for getting so financially and emotionally invested in the first place. Lesson learned.
I think that the hardest part of it all, was breaking it to my wife. She had already started designing her gardens, and had dreams of watching our homestead grow. The look of utter defeat on her face was gut wrenching. I felt as though I had failed her, and torn away the dream we had built together. She and I had lost our dream in the course of a single phone call. It hit both of us hard.
It's been 24 hours now, and the pain is real. I don't want to eat or go to work, I don't want to talk to anyone. I just want to lay down on my wife's lap and close my eyes until it's over. Deep down inside, I know it's a childish reaction, but that doesn't make it any less of a slap across the face.
The Light at the End of the Tunnel
Cliche, I know, but there may be a little glimmer of light on the horizon. If we do sell our rental property, we will have money to play with. This means we can buy a crappy little Ute and caravan, and go exploring our country. Perhaps stop at a few places that look nice, and see if they're places we could settle. If we spend a few months just looking around, and find somewhere homely, then we can stay for a while at a local caravan park, and look for a property that may be suitable.
At the very least, it would mean that we can escape our shit jobs, which has been the biggest goal from the beginning.
Fingers crossed...
blog #homesteading
-
 @ 7da115b6:7d3e46ae
2025-03-25 04:46:17
@ 7da115b6:7d3e46ae
2025-03-25 04:46:17It's heart wrenching when everything around you seems to come crashing down around your ears, it seems as though the world is coming to an end.
What Happened?
Sadly, some news came to us in the last couple of days, news that has exploded our plans like a bombshell. As you know from previous posts, my family and I had found the property of our dreams, within the price range that suited us. The only issue was that we had to sell our rental property to be able to purchase the land we wanted to develop for our homestead. At the time, it wasn't an issue.
With a few phone calls and some discussion with the local Council; the Realtor; the Vendors, and the bank, we were on our way. We made an offer, and it was accepted, contingent on our rental property selling. Our offer expires this Friday, and the likelihood of it selling before then, is slim. That leaves us 3 days to come up with the $130,000 we need to secure the property.
"So why not just extend the offer?" I hear you say. Well, that's a fair point - We did. The extension runs out this Friday. Can we extend on the extension? Legally, yes. but here's the rub:
A counter offer has been put forward.
This basically means, that without having the money available by the end of the offer extension, the Vendor is going to take the counter offer.
That's Not So Bad... Right?
Yes, and no.
Unfortunately, we've spend thousands of dollars on reports; valuations; building research and site inspections. This means all of the plans, money and time that we've invested so far is going to be lost. Yes yes, you're right of course, it's our own fault for getting so financially and emotionally invested in the first place. Lesson learned.
I think that the hardest part of it all, was breaking it to my wife. She had already started designing her gardens, and had dreams of watching our homestead grow. The look of utter defeat on her face was gut wrenching. I felt as though I had failed her, and torn away the dream we had built together. She and I had lost our dream in the course of a single phone call. It hit both of us hard.
It's been 24 hours now, and the pain is real. I don't want to eat or go to work, I don't want to talk to anyone. I just want to lay down on my wife's lap and close my eyes until it's over. Deep down inside, I know it's a childish reaction, but that doesn't make it any less of a slap across the face.
The Light at the End of the Tunnel
Cliche, I know, but there may be a little glimmer of light on the horizon. If we do sell our rental property, we will have money to play with. This means we can buy a crappy little Ute and caravan, and go exploring our country. Perhaps stop at a few places that look nice, and see if they're places we could settle. If we spend a few months just looking around, and find somewhere homely, then we can stay for a while at a local caravan park, and look for a property that may be suitable.
At the very least, it would mean that we can escape our shit jobs, which has been the biggest goal from the beginning.
Fingers crossed...
blog #homesteading
-
 @ bf7973ed:841ad12a
2025-03-25 04:19:41
@ bf7973ed:841ad12a
2025-03-25 04:19:41test
-
 @ 7da115b6:7d3e46ae
2025-03-25 03:56:59
@ 7da115b6:7d3e46ae
2025-03-25 03:56:59![[titelbild-das-ab-1972-eingefuhrte-testbild-des-schweizer-fernsehens.jpg]]This is just a basic test of long form #blog posts from Obsidian.
-
 @ d560dbc2:bbd59238
2025-03-25 05:29:36
@ d560dbc2:bbd59238
2025-03-25 05:29:36Hey! Today, I’m diving into the 2-5 Rule—a unique task management method that’s all about timing, not planning. It powers TaskforUs, a beta platform that’s changing how we prioritize tasks. Grab a coffee, and let’s get started!
What Is the 2-5 Rule?
The 2-5 Rule is a task management approach that focuses on when to act on a task rather than creating a detailed plan. Every task has a “time unit” (days, weeks, months, or years), and you should act within 2 to 5 of those units. This “sweet spot” ensures that you’re neither rushing nor neglecting tasks.
Examples:
- Daily tasks: (e.g., “Do cardio”) – Act every 2-5 days.
- Weekly tasks: (e.g., “Meet a friend”) – Act every 2-5 weeks.
- Monthly tasks: (e.g., “Review budget”) – Act every 2-5 months.
- Yearly tasks: (e.g., “Renew passport”) – Act every 2-5 years.
You don’t plan the exact time to do the task—just enter it into TaskforUs, set the time unit, and provide either the last date you acted on it or a fixed due date. The system prioritizes it for you, making it an anti-planning method.
How Does It Work in Practice?
Example 1: Renewing Your Passport
-
Scenario:
You get your passport today (March 24, 2025). -
Action:
Add the task “Renew passport” to TaskforUs with a yearly time unit and set the “last act date” as today. -
Outcome:
The task starts low on your priority list but climbs over time. After 2 years, it begins to rise; by 5 years, it’s near the top—nudging you to act before your passport expires.
Alternatively, use Fix Mode to set the expiration date (e.g., March 24, 2030) so the task climbs in priority as the date approaches.
Example 2: Meeting Uncle Lars Regularly
-
Scenario:
You want to meet your Uncle Lars roughly 10 times a year (about once every 5 weeks). -
Action:
Add the task “Meet Uncle Lars” with a weekly time unit (to provide flexibility) and set the “last act date” as the most recent meeting (e.g., March 1, 2025). -
Outcome:
Over time, the task slowly climbs in your priority list. After 2 weeks, it starts gaining focus; by 5 weeks, it becomes urgent—prompting you to schedule the next meeting.
No detailed planning is required—you simply add the task, and the 2-5 Rule does the rest.
The Psychology Behind the 2-5 Rule
The 2-5 Rule isn’t just a clever idea—it’s grounded in psychology and behavioral science. Here’s why it works so well:
-
It Reduces Decision Fatigue
Constantly deciding when to do each task can be exhausting. The 2-5 Rule automates prioritization, so you don’t have to think about when to act. TaskforUs surfaces the right task at the right time, freeing up mental energy for doing the work. -
It Aligns with Natural Rhythms
Humans thrive on rhythm and consistency. Behavioral science shows that after 2 time units, a task starts to feel pressing, but by 5 units, it’s at risk of being neglected. The 2-5 window captures this natural sense of urgency. -
It Taps into the Zeigarnik Effect
This psychological principle states that uncompleted tasks are remembered better than completed ones. As a task’s due window approaches, it naturally rises in priority—keeping it top of mind. -
It Prevents Over-Planning Stress
Detailed scheduling can be stressful, especially when life is unpredictable. The anti-planning nature of the 2-5 Rule removes this burden: you simply enter your task and let the system remind you when it’s time to act.
The Structure of TaskforUs: Bringing the 2-5 Rule to Life
TaskforUs is a web-based platform (currently in beta) that makes the 2-5 Rule actionable:
-
Add Tasks Easily:
Simply enter a task, set its time unit (days, weeks, months, or years), and provide the last act date or a fixed due date for Fix Mode tasks. -
Top Task:
TaskforUs automatically highlights your most urgent task based on the 2-5 Rule, telling you exactly what to do right now. -
Focus Mode:
See your top 3 tasks (or adjust the number) for distraction-free productivity. -
Fix Mode:
For date-specific tasks (e.g., “Wish Alex a happy birthday”), set the due date and watch the task climb in priority as the day approaches, peaking on the day itself. -
Category Filtering and Archiving:
Organize tasks into categories (e.g., Work, Personal) and archive completed tasks to keep your list clean. -
Export Tasks:
Download your tasks as a CSV file for backup or analysis.
TaskforUs takes the 2-5 Rule’s anti-planning philosophy and makes it seamless, ensuring you always know what to do next without the mental load of scheduling.
Why the 2-5 Rule Works: A Game-Changer for Task Management
The 2-5 Rule stands out because it addresses common pain points in task management:
-
No More Overwhelm:
By focusing on one top task (or a few in Focus Mode), you avoid the clutter of a long to-do list. -
Effortless Prioritization:
The rule automates the decision of what to do next, reducing stress and boosting productivity. -
Never Miss a Deadline:
With Fix Mode, date-specific tasks like passport renewals or birthdays rise to the top at the right time. -
Flexibility:
The 2-to-5 window gives you room to act when it suits you—without rigid deadlines.
Try the 2-5 Rule with TaskforUs
The 2-5 Rule is a fresh take on task management that balances short-term habits with long-term goals—without the burden of meticulous planning. TaskforUs makes it easy to implement, and as a beta user, you can help shape its future.
Here’s why you should try it:
-
No Planning Needed:
Just add your tasks and let the system prioritize them automatically. -
Clarity:
Always know what to do right now—without the mental load of overthinking. -
Flexibility:
The 2-to-5 window gives you the right balance between urgency and ease. -
Reliability:
Fix Mode ensures you never miss critical dates. -
Be Part of the Beta:
Your feedback helps improve TaskforUs as it evolves.
Take Control of Your Tasks Today
The 2-5 Rule is more than a productivity hack—it’s a new way to manage tasks by focusing on timing rather than rigid plans. Ready to say goodbye to overwhelm and hello to effortless prioritization?
Sign up for TaskforUs at task4.us and experience the 2-5 Rule in action.
Your tasks, perfectly timed—without a plan in sight. -
 @ 502ab02a:a2860397
2025-03-25 02:24:07
@ 502ab02a:a2860397
2025-03-25 02:24:07ต่อเนื่องจากมหากาพย์น้ำมันมะกอกปลอมนะครับ คนที่ปลอมแปลงน้ำมันมะกอกได้พัฒนาวิธีการต่าง ๆ เพื่อเลียนแบบคุณสมบัติของน้ำมันมะกอกแท้ ทำให้การตรวจสอบด้วยการแช่เย็นเพื่อดูการแข็งตัวอาจไม่สามารถยืนยันความบริสุทธิ์ได้อย่างแน่นอนแล้วหละครับ
คำแนะนำในการเลือกซื้อน้ำมันมะกอกจะแบ่งเป็นกว้างงงงงงงกว้าง 3 เรื่องคือ 1 ซื้อจากแหล่งที่เชื่อถือได้ เลือกซื้อน้ำมันมะกอกจากผู้ผลิตหรือร้านค้าที่มีความน่าเชื่อถือ และมีการรับรองคุณภาพจากหน่วยงานที่เกี่ยวข้อง ซึ่ง เชรี่ยละ ฝากเงินไว้กับคนอื่น 5555 2 ตรวจสอบฉลาก อ่านฉลากผลิตภัณฑ์อย่างละเอียด ตรวจสอบแหล่งที่มา วันที่ผลิต และวันที่หมดอายุ อันนี้คือที่เราจะคุยกันวันนี้ 3 สังเกตลักษณะของน้ำมัน น้ำมันมะกอกแท้มักมีสีและกลิ่นเฉพาะตัว หากพบว่าสีหรือกลิ่นผิดปกติ ควรพิจารณาก่อนซื้อ ตรงนี้นี่ต้องอาศัยความเจ็บปวดจากการพลาดเยอะๆ จะทำให้รู้ความแตกต่างครับ ซึ่ง not bad นะ
ไล่จากเรื่องเล็กก่อน คือ การสังเกตลักษณะน้ำมัน แบบที่นิยมสุุดคือ การแช่ตู้เย็นแล้วดูว่ามันแข็งไหม ที่เราสอนต่อๆกันมาคือ ถ้าแข็งก็คือดี ของแท้ แต่ แต่ แต่ ส่วนใหญ่แล้วการปลอมน้ำมันมะกอกเขาจะใช้หลากหลายวิธี แล้วแต่คนจะทำครับ อาทิเช่น การเจือปนสิ่งเหล่านี้ลงไปครับ - ไขมันเติมไฮโดรเจนบางส่วน ได้แก่พวกน้ำมันพืชราคาถูก เช่น น้ำมันถั่วเหลือง น้ำมันปาล์ม หรือคาโนลา มักถูกเติมไฮโดรเจนบางส่วนเพื่อเพิ่มอายุการเก็บรักษาอยู่แล้ว ต้นทุนต่ำกว่าน้ำมันมะกอกมาก หลายๆคนคงบอกว่า เอ้ย มันแช่เย็นแล้วไม่แข็งตัวนี่ ตรงนี้มีข้อมูลบอกว่า เขาใช้ไขมันทรานส์หรือไขมันเติมไฮโดรเจน โดยใช้หลักการทางเคมีที่ทำให้เนื้อสัมผัสของน้ำมันปลอมเลียนแบบพฤติกรรมของน้ำมันมะกอกแท้เมื่อถูกแช่เย็น บางที่ก็เติมน้ำมันมะพร้าวหรือน้ำมันปาล์ม อันนี้ต้นทุนต่ำทำง่ายเลยครับ เค้าใช้น้ำมันปาล์มโอเลอินที่มีการ ปรับแต่ง ด้วยการ เติมสารเติมแต่ง ทำให้ไขมันในน้ำมันมีลักษณะแข็งขึ้นและสามารถ ปรับจุดหลอมเหลว ให้สามารถแข็งตัวที่อุณหภูมิที่เย็นได้มากขึ้น - กรดไขมันอิ่มตัวสังเคราะห์ ประเภทกรดสเตียริกหรือกรดปาลมิติกสังเคราะห์เป็นผลิตภัณฑ์พลอยได้จากอุตสาหกรรมแปรรูปไขมันพืชและสัตว์ ราคาต่อหน่วยต่ำมาก โดยเฉพาะถ้าซื้อในปริมาณมาก - ไขมันจากสัตว์ อย่างเช่นไขมันหมูและน้ำมันปลาถูกกว่าน้ำมันมะกอก และสามารถหาได้จากอุตสาหกรรมแปรรูปอาหารที่มักมีของเหลือทิ้งในปริมาณมาก - ขี้ผึ้งพืช พวกขี้ผึ้ง Candelilla Wax หรือ Carnauba Wax ราคาถูกกว่าและสามารถใช้ในปริมาณน้อยเพื่อเลียนแบบคุณสมบัติทางกายภาพ - โมโนกลีเซอไรด์และไดกลีเซอไรด์ เป็นสารเติมแต่งที่ใช้ในอุตสาหกรรมอาหารอยู่แล้ว ต้นทุนต่ำมาก และช่วยให้น้ำมันมีเนื้อสัมผัสคล้ายน้ำมันมะกอก
ในข้อต่อมาจะรวมกันได้เลยครับ ฉลาก และ การรับรองคุณภาพ คือผมตัดเรื่องผู้ผลิตหรือร้านค้าออกไปเลย เพราะก็ไปดูเองได้ว่าแบรนด์เก่าแก่ เราก็จะเหมารวมไปเองว่าไม่น่าโกง 5555 เราข้ามมาอะไรที่พอจะมีหลักเกณฑ์ได้นะครับ short cut เลยคือ ตรารับรอง ใครจะดู DOP IGP USDA Organic อะไรผมไม่ค่อยสนใจครับ ผมว่าถ้าเป็นไปได้ข้ามไปดูนี่เลยครับ
 - International Olive Council (IOC) น้ำมันมะกอกที่ได้รับการรับรองจาก IOC เป็นการรับรองคุณภาพน้ำมันมะกอกที่ได้รับการตรวจสอบจากองค์กรที่มีมาตรฐานสากล
- COOC (California Olive Oil Council) สำหรับน้ำมันมะกอกที่ผลิตในแคลิฟอร์เนีย หรือในสหรัฐฯ จะมีการรับรองจาก COOC ที่ยืนยันว่าผ่านการตรวจสอบมาตรฐาน
- International Olive Council (IOC) น้ำมันมะกอกที่ได้รับการรับรองจาก IOC เป็นการรับรองคุณภาพน้ำมันมะกอกที่ได้รับการตรวจสอบจากองค์กรที่มีมาตรฐานสากล
- COOC (California Olive Oil Council) สำหรับน้ำมันมะกอกที่ผลิตในแคลิฟอร์เนีย หรือในสหรัฐฯ จะมีการรับรองจาก COOC ที่ยืนยันว่าผ่านการตรวจสอบมาตรฐานเรามาทำความเข้าใจรายละเอียดของน้ำมันมะกอกกันก่อนครับ เพื่อว่าตอนดูฉลากจะได้รู้ว่าทำไมต้องมีของพวกนี้ พันธุ์มะกอกที่ใช้ทำน้ำมันมะกอกนั้นเป็นตัวกำหนดรสชาติและกลิ่นหอมของน้ำมันมะกอก โดยมะกอกแต่ละสายพันธุ์ให้รสชาติแตกต่างกันครับ Arbequina (สเปน): กลิ่นผลไม้ มีรสคล้ายแอปเปิ้ลเขียว Koroneiki (กรีซ): เผ็ดร้อน มีรสพริกไทย Coratina (อิตาลี - Puglia): รสเข้ม เผ็ดร้อน มีรสขมติดปลายลิ้น Manzanilla cacereña (สเปน): หอมผลไม้ มีรสอัลมอนด์ แอปเปิ้ลเขียว Peranzana (อิตาลี - Puglia): รสชาติกลมกล่อม หอมหวานเล็กน้อย
- พื้นที่เพาะปลูกและผลิต ตัวนี้แหละครับ เอาไปทำตรา IGP เรียกเหมาๆว่า Geographical Origin น้ำมันมะกอกคุณภาพสูงจะระบุชัดเจนว่า มะกอกมาจากไหนและผลิตที่ไหน ถ้าฉลากไม่ระบุ แสดงว่าอาจเป็นน้ำมันมะกอกผสมจากหลายแหล่ง ซึ่งอาจมีคุณภาพต่ำ
- วันที่เก็บเกี่ยว น้ำมันมะกอกมีสารโพลีฟีนอล (Polyphenols) ซึ่งเป็นสารต้านอนุมูลอิสระที่ให้รสชาติและกลิ่นหอม แต่เมื่อเวลาผ่านไป สารเหล่านี้จะลดลง ทำให้น้ำมันเสียรสชาติ
- ระดับความเป็นกรด (Acidity Level) ตัวนี้หละที่ผมโคตรเน้น และพูดบ่อยมาก จนหลายๆคนเบื่อ 5555 น้ำมันมะกอก Extra Virgin ต้องมี ค่าความเป็นกรดต่ำกว่า 0.8% ค่ายิ่งต่ำ ยิ่งดี เพราะหมายความว่ามะกอกถูกเก็บเกี่ยวอย่างเหมาะสมและสกัดอย่างรวดเร็ว
- ระดับความเข้มของรสชาติ เรื่องการกินก็สำคัญนะครับน้ำมันมะกอกมีระดับความเข้มต่างกัน ควรเลือกให้เหมาะกับอาหาร รสอ่อน (Delicate) เหมาะกับปลา เนื้อขาว และสลัดเบาๆ ,รสปานกลาง (Moderate) เหมาะกับพาสต้า ผักย่าง และชีส รสเข้มข้น (Intense) เหมาะกับเนื้อแดง ช็อกโกแลต และอาหารที่มีรสจัด
ส่วนตราที่บอกไว้ข้างบนโน้นนน จำไว้เลยว่า อย่าหลงเชื่อคำว่า "Organic" เพียงอย่างเดียว เพราะการปลูกแบบออร์แกนิกไม่ได้รับประกันว่ารสชาติจะดีเสมอไป หลีกเลี่ยงน้ำมันมะกอกที่ระบุว่า "Product of EU" เพราะอาจเป็นการผสมจากหลายประเทศ
สำหรับเรื่องฉลากนะครับ ใครที่ดื่มไวน์โลกเก่าจะคุ้นเคยความที่ต้องอ่านรายละเอียดพวกนี้เป็นอย่างดี น้ำมันมะกอกแบบ extra virgin olive oil ที่ดี ฉลากและแพคเกจจะต้องมีประมาณนี้ครับ 1.ระดับกรดอิสระ (Free Fatty Acids, FFA) หรือ กรดโอเลอิก (%) ต้องไม่เกิน 0.8% ตามมาตรฐานของ International Olive Council (IOC) ถ้าค่าตัวนี้ยิ่งต่ำ แสดงว่าน้ำมันมะกอกมีคุณภาพดีขึ้น เพราะบ่งบอกว่าผลมะกอกถูกสกัดอย่างดี ไม่ผ่านกระบวนการที่ทำให้เสื่อมสภาพ 2. ค่าความเป็นออกซิเดชัน (Peroxide Value, PV) (meq O₂/kg) ต้องไม่เกิน 20 meq O₂/kg คือไม่ต้องรู้ก็ได้ครับว่ามาจากไหน เอาว่าถ้าค่าสูงเกินไป แสดงว่าน้ำมันเริ่มเหม็นหืนจากปฏิกิริยาออกซิเดชัน 3. ค่า K232 และ K270 (UV Absorbance at 232 nm และ 270 nm) โดยที่ K232 ต้องไม่เกิน 2.50 (บ่งบอกถึงการเกิดออกซิเดชันระยะแรก) และ K270 ต้องไม่เกิน 0.22 (บ่งบอกถึงการเสื่อมสภาพของน้ำมัน) ค่าเหล่านี้ใช้แสง UV ตรวจจับว่ามีการกลั่นน้ำมันอื่นผสมเข้ามาหรือไม่ 4. ค่า Delta-K (ΔK) ต้องไม่เกิน 0.01 ค่านี้ใช้ตรวจจับว่าน้ำมันมีการปนเปื้อนหรือถูกดัดแปลงด้วยสารอื่นไหม 5. ประเทศต้นกำเนิด (Country of Origin) น้ำมันมะกอกที่มีคุณภาพดีมักระบุชื่อฟาร์มหรือแหล่งผลิตที่ชัดเจน เช่น อิตาลี สเปน กรีซ 6. วันที่เก็บเกี่ยว (Harvest Date) และวันหมดอายุ (Best Before Date) ควรเลือกน้ำมันที่มีวันที่เก็บเกี่ยวล่าสุด (อายุการเก็บรักษาโดยทั่วไปคือ 18-24 เดือน) 7. วิธีการสกัด (Extraction Method) ต้องระบุว่าเป็น "Cold Pressed" หรือ "Cold Extracted" หมายถึงสกัดโดยไม่ใช้ความร้อน ซึ่งช่วยรักษาคุณภาพของสารอาหาร 8. ปริมาณโพลีฟีนอล (Polyphenol Content) (mg/kg) [อาจไม่มีในทุกยี่ห้อ] น้ำมันมะกอกคุณภาพสูงมักมีโพลีฟีนอลมากกว่า 250 mg/kg ซึ่งช่วยลดการอักเสบในร่างกาย แต่บางยี่ห้อก็จะให้ดูที่วิตามิน E กับ K เพราะ น้ำมันมะกอกที่มี Polyphenol สูงมักจะมีปริมาณ วิตามิน E ที่สูงตามไปด้วย และการที่น้ำมันมะกอกมี วิตามิน K ก็อาจสะท้อนถึงการที่น้ำมันมะกอกนั้นไม่ได้ถูกผ่านกระบวนการปรับแต่งหรือแปรรูปที่มากจนเกินไป ทำให้รักษาสารอาหารที่สำคัญ รวมถึง Polyphenol ไว้ได้ 9. บรรจุภัณฑ์ ควรเป็นขวดแก้วสีเข้มหรือกระป๋องโลหะ เพื่อป้องกันการเสื่อมสภาพจากแสง




ใน 9 ข้อนี้ ไม่จำเป็นต้องมีครบทุกข้อก็ได้นะครับ เท่าที่ผมพยายามหาในไทย เจอ acidity ก็บุญโขแล้วครับ 55555 บางทีเขาก็อาจไม่ได้แปะไว้บนฉลาก แต่ต้องตามไปอ่านในเว็บของผู้ผลิตก็ได้ครับ
ส่วนใครที่อ่านถึงตรงนี้แล้วท้อใจ ไม่อยากกินมันแล้ว ก็ขอบอกว่า โลกมันก็เป็นแบบนี้แหละครับ ของมันมีราคามากจนต้องมีการปลอมกัน มันไม่ได้โหดร้ายขนาดนั้นหรอกครับ กระเป๋าแบรนด์เนมก็ปลอมกันเกลื่อน นาฬิกาก็ปลอมกันทั่ว แต่คุณๆก็มองออกใช่ไหมครับ น้ำมันมะกอกมันก็ไม่ต่างกันหรอกครับ มันคือเรื่องที่ไม่ธรรมดาของโลกนี้ที่คนทำเป็นเรื่องธรรมดา
ถ้ามันดูหดหู่ไป จำง่ายๆก็ได้ครับว่า "ทุกน้ำมันมะกอกปลอม จะไม่มีฉลากที่บอกรายละเอียดดีๆ แต่ ทุกน้ำมันมะกอกที่ไม่มีฉลากรายละเอียดดีๆ ไม่ได้เป็นน้ำมันมะกอกปลอม" logic แบบง่ายๆนี้เลยครับ
ผมได้แค่บอกว่า สิ่งที่ควรดูเพื่อแลกกับเงินที่ต้องจ่ายให้มันมากๆคืออะไร แล้วสิ่งที่เราจ่ายไปบริโภค เราได้แบบนั้นจริงๆไหม อย่างที่เคยบอกใน #ฉลาก3รู้ เสมอๆคือ ฉลากไม่ได้เป็นตัวประกาศิตที่จะบอกว่าใครไม่มีคือแย่ แต่ฉลากมันเหมือนคำมันสัญญา ว่าผู้ผลิตจะทำตามที่เขียนเอาไว้ ถ้าใครที่กล้าบิดพริ้วจากนั้น หรือ ทำไม่จริงตามฉลาก มันก็คือการที่เขากล้าทำผิดสัญญา และมันต้องแลกมาด้วยค่าใช้จ่าย ไม่ว่าจะชื่อเสียง ความน่าเชื่อถือ หรือ ความภาคภูมิใจ เราคงทำอะไรไม่ได้มากกว่านั้น จะใช้กระบวนการ ก็ต้องพิสูจน์ ใช้เวลา เพราะที่เห็นในบ้านเราก็มีตัวอย่างมากมาย แต่มันก็ "อย่างน้อย" มันวัดกันหล่ะวะ ว่า แกกล้าสัญญากับชั้นมั๊ย
โอเคมะ ถ้าคุณจะหนี มันต้องหนีตลอดไปในทุกๆอย่างครับ หรือจะให้ผมเล่าเรื่อง fun fact ของกินเทพอื่นๆ ที่พวกคุณกินกันอย่างเป็นล่ำเป็นสันเพื่อกระตุ้นให้ศึกษาเพิ่มไหมหล่ะ 55555
#pirateketo #ฉลาก3รู้ #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 1d7ff02a:d042b5be
2025-03-25 02:01:41
@ 1d7ff02a:d042b5be
2025-03-25 02:01:41ໃນຍຸກດິຈິຕອນ, ການລົບກວນທາງເທັກໂນໂລຊີໄດ້ສັ່ນຄອນສະຖາບັນແບບດັ້ງເດີມທົ່ວໂລກ. ເຊັ່ນດຽວກັນກັບແພລດຟອມສື່ສັງຄົມອອນລາຍທີ່ໄດ້ທຳລາຍອິດທິພົນຂອງສື່ທ້ອງຖິ່ນ, Tether (USDT) ແລະ ສະເຕເບິນຄອຍອື່ນໆ ກຳລັງທ້າທາຍອຳນາດຂອງທະນາຄານກາງໃນປະເທດກຳລັງພັດທະນາ. ສະກຸນເງິນດິຈິຕອນທີ່ມີຄວາມສະຖຽນເຫຼົ່ານີ້ ສະເໜີວິທີການສຳລັບປະຊາຊົນເພື່ອປ້ອງກັນເງິນເຟີ້, ຫຼີກລ່ຽງການຄວບຄຸມທຶນ, ແລະ ເຂົ້າເຖິງຕະຫຼາດການເງິນໂລກໂດຍບໍ່ຕ້ອງອີງໃສ່ລະບົບທະນາຄານແບບດັ້ງເດີມ. ໃນຂະນະທີ່ການນຳໃຊ້ກຳລັງເພີ່ມຂຶ້ນ, USDT ກຳລັງກາຍເປັນໄພຂົ່ມຂູ່ທີ່ມີຢູ່ຈິງຕໍ່ທະນາຄານກາງ, ຈຳກັດການຄວບຄຸມຂອງພວກເຂົາຕໍ່ນະໂຍບາຍການເງິນ ແລະ ອຳນາດອະທິປະໄຕທາງການເງິນ.
ທາງເລືອກໃໝ່ແທນສະກຸນເງິນທ້ອງຖິ່ນ
ປະເທດກຳລັງພັດທະນາມັກຈະປະສົບບັນຫາກັບການລົດຄ່າເງິນ, ເງິນເຟີ້, ແລະ ການໄຫລອອກຂອງທຶນ. ທະນາຄານກາງຫຼາຍແຫ່ງບໍ່ສາມາດຮັກສາສະຖຽນລະພາບຂອງສະກຸນເງິນເນື່ອງຈາກການຄຸ້ມຄອງທີ່ບໍ່ດີ, ການພິມເງິນຫຼາຍເກີນໄປ, ຫຼື ການແຊກແຊງທາງການເມືອງ. ພົນລະເມືອງທີ່ເຫັນເງິນທ້ອນຂອງຕົນຖືກກັດເຊາະ ຕາມປົກກະຕິແລ້ວຈະມີທາງເລືອກບໍ່ຫຼາຍ: ປ່ຽນເງິນທ້ອງຖິ່ນເປັນ ໂດລາ ຫລື ໃນກໍລະນີ້ລາວເຮົາກໍຈະມີ ບາດ ແລະ ຢວນນຳ ຜ່ານທະຫລາດມືດ ຫຼື ລົງທຶນກັບທຸລະກິດ, ຊື້ອະສັງຫາ ແລະ ລົງທຶນໃນຊັບສິນຕ່າງປະເທດ. USDT ໄດ້ປ່ຽນແປງເກມນີ້. ມັນອະນຸຍາດໃຫ້ທຸກຄົນທີ່ມີການເຂົ້າເຖິງອິນເຕີເນັດສາມາດເກັບຮັກສາ ແລະ ໂອນມູນຄ່າໃນຮູບແບບດິຈິຕອນທີ່ທຽບເທົ່າກັບໂດລາໂດຍບໍ່ຈຳເປັນຕ້ອງໄດ້ຮັບການອະນຸມັດຈາກທະນາຄານທ້ອງຖິ່ນ ຫຼື ລັດຖະບານ. ສິ່ງນີ້ຊ່ວຍໃຫ້ຫຼຸດພົ້ນຈາກການອີງໃສ່ສະກຸນເງິນແຫ່ງຊາດທີ່ອ່ອນແອ, ສະເໜີທາງເລືອກທີ່ງ່າຍໃນການປ້ອງກັນການເສື່ອມຄ່າ. ໃນປະເທດເຊັ່ນ: ເວເນຊູເອລາ, ອາເຈນຕິນາ, ໄນຈີເຣຍ, ເລບານອນ, ແລະ ລາວ, ປະຊາຊົນກຳລັງນຳໃຊ້ USDT ເພື່ອປົກປ້ອງຄວາມໝັ້ງຄັ່ງຂອງພວກເຂົາຈາກພາວະເງິນເຟີ້ສູງ ແລະ ຄວາມບໍ່ສະຖຽນທາງການເງິນ.
ການທຳລາຍການຜູກຂາດຂອງທະນາຄານກາງ
ທະນາຄານກາງມີອຳນາດອັນໃຫຍ່ຫຼວງຕໍ່ລະບົບການເງິນໂດຍການຄວບຄຸມການອອກເງິນ, ອັດຕາດອກເບ້ຍ, ແລະ ການໄຫຼຂອງທຶນ. ເຖິງຢ່າງໃດກໍຕາມ, USDT ບ່ອນທຳລາຍການຄວບຄຸມນີ້ດ້ວຍການສະໜອງລະບົບການເງິນຄູ່ຂະໜານທີ່ດຳເນີນງານເປັນອິດສະຫຼະຈາກການກຳກັບດູແລຂອງລັດຖະບານ. ສິ່ງນີ້ທ້າທາຍສາມພື້ນທີ່ຫຼັກຂອງອຳນາດທະນາຄານກາງ:
- ການຄວບຄຸມນະໂຍບາຍການເງິນ:
ເມື່ອປະຊາຊົນຍ້າຍເງິນທ້ອນຈາກສະກຸນເງິນທ້ອງຖິ່ນໄປສູ່ USDT, ທະນາຄານກາງຈະສູນເສຍຄວາມສາມາດໃນການຄວບຄຸມປະລິມານເງິນຢ່າງມີປະສິດທິພາບ. ຖ້າປະຊາກອນສ່ວນໃຫຍ່ຢຸດໃຊ້ສະກຸນເງິນແຫ່ງຊາດ, ນະໂຍບາຍເຊັ່ນ: ການປ່ຽນແປງອັດຕາດອກເບ້ຍ ຫຼື ການພິມເງິນກໍຈະສູນເສຍປະສິດທິພາບຂອງພວກມັນ.
- ການຫຼີກລ່ຽງການຄວບຄຸມທຶນ:
ປະເທດກຳລັງພັດທະນາຫຼາຍແຫ່ງບັງຄັບໃຊ້ການຄວບຄຸມທຶນທີ່ເຂັ້ມງວດເພື່ອປ້ອງກັນບໍ່ໃຫ້ເງິນອອກນອກປະເທດ, ເຮັດໃຫ້ສະກຸນເງິນຂອງພວກເຂົາມີສະຖຽນລະພາບ. USDT, ໂດຍບໍ່ມີພົມແດນ, ອະນຸຍາດໃຫ້ຜູ້ໃຊ້ຫຼີກລ່ຽງການຄວບຄຸມເຫຼົ່ານີ້, ເຮັດໃຫ້ມັນງ່າຍຂຶ້ນໃນການດຳເນີນທຸລະກຳທົ່ວໂລກ ຫຼື ເກັບຮັກສາຄວາມໝັ້ງຄັ່ງທີ່ມີສະພາບຄ່ອງລະດັບສາກົນ.
- ການລົດບົດບາດຂອງລະບົບທະນາຄານ:
USDT ຫຼຸດຄວາມຕ້ອງການຂອງການບໍລິການທະນາຄານແບບດັ້ງເດີມ. ດ້ວຍສະມາດໂຟນ ແລະ ກະເປົາເງິນດິຈິຕອນ, ປະຊາຊົນສາມາດສົ່ງ ແລະ ຮັບການຊຳລະເງິນໂດຍບໍ່ຕ້ອງຜ່ານລະບົບທະນາຄານ, ຕັດທະນາຄານອອກຈາກລະບົບນິເວດການເງິນ ແລະ ເຮັດໃຫ້ພວກມັນຂາດຄ່າທຳນຽມທຸລະກຳ ແລະ ເງິນຝາກ.
ກໍລະນີຂອງລາວ: ການປ່ຽນແປງທາງການເງິນທີ່ກຳລັງເກີດຂຶ້ນ
ລາວ, ເຊັ່ນດຽວກັນກັບປະເທດກຳລັງພັດທະນາຫຼາຍແຫ່ງ, ປະເຊີນກັບສິ່ງທ້າທາຍທາງເສດຖະກິດລວມທັງເງິນເຟີ້, ສະກຸນເງິນແຫ່ງຊາດທີ່ອ່ອນແອ (ເງິນກີບລາວ), ແລະ ການເຂົ້າເຖິງເງິນຕາຕ່າງປະເທດທີ່ຈຳກັດ. ລັດຖະບານມີການຄວບຄຸມທຶນທີ່ເຂັ້ມງວດ, ເຮັດໃຫ້ມັນຍາກສຳລັບບຸກຄົນ ແລະ ທຸລະກິດໃນການຊື້ USD ຜ່ານຊ່ອງທາງທີ່ເປັນທາງການ. ສິ່ງນີ້ເຮັດໃຫ້ເກີດຕະຫຼາດມືດສຳລັບການແລກປ່ຽນເງິນຕາທີ່ເຕີບໂຕຂຶ້ນ. ດ້ວຍການເພີ່ມຂຶ້ນຂອງ USDT, ຊາວລາວຫຼາຍຄົນກຳລັງຫັນມາໃຊ້ stable coin ແລະ ເກັບຊັບສິນດິຈິຕອນ ເປັນທາງເລືອກທີ່ປອດໄພກວ່າການຖືເງິນກີບລາວ, ເຊິ່ງມີແນວໂນ້ມທີ່ຈະເສື່ອມຄ່າລົງ.
ບົດຮຽນຈາກການທຳລາຍສື່ທ້ອງຖິ່ນໂດຍສື່ສັງຄົມອອນລາຍ
ການເພີ່ມຂຶ້ນຂອງ USDT ສະທ້ອນໃຫ້ເຫັນເຖິງສື່ສັງຄົມອອນລາຍໄດ້ທຳລາຍສື່ທ້ອງຖິ່ນແນວໃດ. ສື່ຂ່າວແບບດັ້ງເດີມເຄີຍຜູກຂາດການແຈກຢາຍຂໍ້ມູນ, ແຕ່ແພລດຟອມເຊັ່ນ: Facebook, Twitter, ແລະ YouTube ໄດ້ເຮັດໃຫ້ການສ້າງ ແລະ ການແຈກຢາຍເນື້ອຫາເປັນປະຊາທິປະໄຕ. ດັ່ງນັ້ນ, ສື່ທີ່ຄວບຄຸມໂດຍລັດ ແລະ ບໍລິສັດຈຶ່ງສູນເສຍຄວາມສາມາດໃນການກຳນົດເນື້ອຫາ ໃນຂະນະທີ່ສື່ສັງຄົມອອນລາຍເພີ່ມອຳນາດໃຫ້ບຸກຄົນໃນການແບ່ງປັນ ແລະ ເຂົ້າເຖິງຂ່າວທີ່ບໍ່ໄດ້ຜ່ານການ censorship. ເຊັ່ນດຽວກັນ, USDT ກຳລັງກະຈາຍອຳນາດທາງການເງິນ. ເຊັ່ນດຽວກັບສື່ສັງຄົມອອນລາຍທີ່ໃຫ້ສຽງແກ່ປະຊາຊົນນອກເໜືອຈາກສື່ກະແສຫຼັກ, USDT ກຳລັງໃຫ້ຄວາມເປັນອິດສະຫຼະທາງການເງິນແກ່ບຸກຄົນທີ່ເກີນກວ່າຂອບເຂດຂອງທະນາຄານກາງ. ແນວໂນ້ມນີ້ຊັດເຈນ: ສະຖາບັນທີ່ລວມສູນຈະສູນເສຍການຄວບຄຸມເມື່ອບຸກຄົນໄດ້ຮັບການເຂົ້າເຖິງໂດຍກົງຕໍ່ທາງເລືອກອື່ນ.
Trump ສະໜັບສະໜູນ Stable Coin
ປະທານາທິບໍດີສະຫະລັດ Donald Trump ໄດ້ສະແດງການສະໜັບສະໜູນຕໍ່ stable coin ແລະ ອຸດສາຫະກຳ cryptocurrency ເມື່ອບໍ່ດົນມານີ້. ຈຸດຢືນຂອງລາວເປັນສັນຍານເຖິງການປ່ຽນແປງທີ່ເປັນໄປໄດ້ໃນນະໂຍບາຍຂອງສະຫະລັດທີ່ອາດຈະສ້າງຄວາມຊອບທຳໃຫ້ແກ່ສະເຕເບິນຄອຍ ແລະ ຂັບເຄື່ອນການນຳໃຊ້ທົ່ວໂລກ. ຖ້າລັດຖະບານສະຫະລັດຮັບຮອງສະເຕເບິນຄອຍເຊັ່ນ USDT, ມັນອາດຈະເລັ່ງການນຳໃຊ້ພວກມັນເປັນທາງເລືອກແທນລະບົບທະນາຄານແບບດັ້ງເດີມ, ສ້າງແຮງກົດດັນເພີ່ມເຕີມຕໍ່ທະນາຄານກາງໃນປະເທດກຳລັງພັດທະນາ. ນີ້ອາດຈະສົ່ງເສີມໃຫ້ມີການມີສ່ວນຮ່ວມຂອງສະຖາບັນຫຼາຍຂຶ້ນ, ເຮັດໃຫ້ມັນຍາກຂຶ້ນສຳລັບລັດຖະບານທ້ອງຖິ່ນໃນການປາບປາມການນຳໃຊ້ USDT.
ຊ່ອງຫວ່າງຂອງການຮັບຮູ້: ຫຼາຍຄົນຍັງບໍ່ຮູ້ເຖິງໄພຂົ່ມຂູ່
ເຖິງແມ່ນວ່າ USDT ຈະເຕີບໂຕຢ່າງໄວວາ, ປະຊາຊົນຫຼາຍຄົນໃນປະເທດກຳລັງພັດທະນາຍັງບໍ່ຮັບຮູ້ເຖິງຜົນກະທົບຂອງມັນ. ໃນຂະນະທີ່ຜູ້ໃຊ້ເລີ່ມຕົ້ນຈະເປັນ ບຸກຄົນທີ່ຮູ້ເທັກໂນໂລຊີ, ນັກລົງທຶນ ແລະ ເຈົ້າຂອງທຸລະກິດ, ປະຊາກອນສ່ວນໃຫຍ່ຍັງອີງໃສ່ການທະນາຄານແບບດັ້ງເດີມ ແລະ ສະກຸນເງິນຕາມກົດໝາຍໂດຍບໍ່ຮູ້ເຖິງຄວາມສ່ຽງຂອງການເສື່ອມຄ່າ ແລະ ຄວາມບໍ່ສະຖຽນທາງການເງິນ. ເຖິງຢ່າງໃດກໍຕາມ, ບຸກຄົນຕ້ອງມີຄວາມຄິດລິເລີ່ມໃນການສຶກສາຕົນເອງກ່ຽວກັບເຄື່ອງມືທາງການເງິນທາງເລືອກເຊັ່ນ USDT ແລະ Bitcoin ເພື່ອປົກປ້ອງຄວາມໝັ້ງຄັ່ງ ແລະ ຄວາມເປັນອິດສະຫຼະທາງການເງິນຂອງພວກເຂົາ.
ບົດສະຫຼຸບ: ການປະຕິວັດທາງການເງິນທີ່ກຳລັງເກີດຂຶ້ນ
USDT ແລະ Bitcoin ແມ່ນການປະຕິວັດທາງການເງິນທີ່ເພີ່ມອຳນາດໃຫ້ບຸກຄົນໃນປະເທດກຳລັງພັດທະນາທີ່ຈະຫຼຸດພົ້ນຈາກນະໂຍບາຍການເງິນທີ່ລົ້ມເຫຼວ. ເຊັ່ນດຽວກັບສື່ສັງຄົມອອນລາຍໄດ້ປະຕິວັດພູມທັດຂອງສື່ໂດຍການໃຫ້ປະຊາຊົນຄວບຄຸມຂໍ້ມູນຂ່າວສານ, USDT ກຳລັງປະຕິວັດການເງິນໂດຍການໃຫ້ປະຊາຊົນຄວບຄຸມເງິນຂອງພວກເຂົາ. ສຳລັບທະນາຄານກາງໃນປະເທດກຳລັງພັດທະນາ, ການປ່ຽນແປງນີ້ສ້າງສະພາວະຫຍຸ້ງຍາກທີ່ຮ້າຍແຮງ: ປັບຕົວ ຫຼື ສູນເສຍອິດທິພົນ. ລັດຖະບານອາດຈະພະຍາຍາມຄວບຄຸມກົດລະບຽບ ຫຼື ຫ້າມສະເຕເບິນຄອຍ, ແຕ່ຕາມທີ່ປະຫວັດສາດໄດ້ສະແດງໃຫ້ເຫັນກັບສື່ສັງຄົມອອນລາຍ.
-
 @ aa333681:f8b3be8c
2025-03-25 01:46:24
@ aa333681:f8b3be8c
2025-03-25 01:46:24
วิธีสะสมบิตคอยน์ให้ครบ 1 BTC: แนวทางเชิงกลยุทธ์
บิตคอยน์เป็นสินทรัพย์ที่มีจำนวนจำกัด และการสะสมให้ครบ 1 บิตคอยน์กำลังเป็นเรื่องที่ยากขึ้นเรื่อย ๆ บทความนี้จะช่วยให้คุณเข้าใจถึงความสำคัญของการสะสมบิตคอยน์และแนวทางเชิงกลยุทธ์ในการเป็นเจ้าของ 1 บิตคอยน์
ทำไมต้องสะสมให้ครบ 1 บิตคอยน์?
บิตคอยน์มีจำนวนจำกัดที่ 21 ล้านเหรียญ แต่เนื่องจากมีเหรียญที่สูญหายไป ทำให้ปริมาณที่สามารถหมุนเวียนอยู่จริงอาจมีเพียง 15-17 ล้านเหรียญ เท่านั้น เมื่อความต้องการเพิ่มขึ้น พลังซื้อและความหายากของบิตคอยน์ก็จะยิ่งเพิ่มขึ้น การเป็นเจ้าของบิตคอยน์เต็ม 1 เหรียญอาจกลายเป็นทรัพย์สินที่เปลี่ยนชีวิตในระบบการเงินอนาคต
ความเข้าใจเกี่ยวกับสกุลเงินที่แท้จริง: เวลา
สกุลเงินที่แท้จริงคือเวลาของคุณ—ทรัพยากรที่คุณไม่รู้ว่ามีอยู่เท่าใด
ถามตัวเองว่า: เงินมีไว้เพื่ออะไร? เพื่อตอบสนองความต้องการ ซื้อของฟุ่มเฟือย หรือเพื่อสร้างความมั่นคงในระยะยาว? บิตคอยน์ช่วยรักษามูลค่าของเงินเมื่อเวลาผ่านไป ต่างจากสกุลเงินกระดาษที่เสื่อมค่าลงเนื่องจากเงินเฟ้อ
เอาชนะอคติเชิงหน่วย (Unit Bias)
หลายคนรู้สึกท้อแท้เมื่อเห็นราคาบิตคอยน์ที่สูง คิดว่าต้องซื้อเป็นเหรียญเต็ม ๆ เท่านั้น นี่เรียกว่า Unit Bias หรืออคติที่เกิดจากการมองว่าบิตคอยน์แพงเพียงเพราะราคาต่อเหรียญสูง
วิธีคิดที่ถูกต้อง:
- คุณ ไม่จำเป็น ต้องซื้อบิตคอยน์เต็มเหรียญในครั้งเดียว
- ค่อย ๆ สะสมผ่าน กลยุทธ์ DCA (Dollar-Cost Averaging) หรือการซื้อสะสมเป็นงวด ๆ
- เข้าใจว่าระหว่าง ราคา กับ มูลค่า นั้นแตกต่างกัน—ราคาผันผวน แต่มูลค่าในระยะยาวมีแนวโน้มเพิ่มขึ้น
3 ขั้นตอนสำคัญในการสะสมบิตคอยน์
การสะสมบิตคอยน์สามารถทำได้ 3 วิธีหลัก ๆ ได้แก่ Fiat Arbitrage, Productivity และ Connectivity ซึ่งแต่ละขั้นตอนมีบทบาทสำคัญในเส้นทางการเป็นเจ้าของ 1 บิตคอยน์
1. Fiat Arbitrage (การเปลี่ยนสินทรัพย์เป็นบิตคอยน์)
ความหมาย: การใช้เงินกระดาษ (Fiat) ซื้อบิตคอยน์ก่อนที่เงินกระดาษจะเสื่อมค่าลง
วิธีดำเนินการ:
- ใช้รายได้จากเงินกระดาษซื้อบิตคอยน์เป็นประจำ
- วางแผนการออม—กำหนดสัดส่วนของรายได้ที่นำไปซื้อบิตคอยน์
- ลดความเสี่ยงจากความผันผวนโดยใช้ DCA
- เมินเฉยต่อ FUD (Fear, Uncertainty, and Doubt) หรือข่าวลือที่ทำให้เกิดความกลัวเกี่ยวกับบิตคอยน์
2. Productivity (การสร้างรายได้เป็นบิตคอยน์โดยตรง)
ความหมาย: การหารายได้ในรูปแบบบิตคอยน์โดยไม่ต้องแลกมาจากเงินกระดาษ
วิธีดำเนินการ:
- ให้บริการหรือขายสินค้าที่รับชำระเป็นบิตคอยน์
- หากคุณเป็นเจ้าของธุรกิจ ให้เริ่มรับชำระเงินด้วยบิตคอยน์
- ศึกษา การขุดบิตคอยน์ (Mining) หากเป็นไปได้
- มุ่งเน้นไปที่อุตสาหกรรม พลังงาน คอมพิวเตอร์ และการเงิน ซึ่งมีการใช้งานบิตคอยน์สูง
3. Connectivity (การใช้บิตคอยน์เป็นหน่วยวัดมูลค่าทางเศรษฐกิจ)
ความหมาย: การเตรียมตัวสำหรับอนาคตที่บิตคอยน์ถูกใช้เป็นมาตรฐานกำหนดราคาสินค้าและบริการ
วิธีดำเนินการ:
- สนับสนุน เศรษฐกิจที่ใช้บิตคอยน์เป็นหลัก
- สร้างธุรกิจที่ดำเนินงาน ด้วยบิตคอยน์ทั้งหมด
- ส่งเสริมให้เกิดการใช้งานบิตคอยน์ในระดับชุมชนและเครือข่ายของคุณ
- มีส่วนร่วมใน เศรษฐกิจบิตคอยน์ระดับโลก เพื่อเตรียมพร้อมก่อนการใช้งานแพร่หลาย
อนาคตของการสะสมบิตคอยน์
เมื่อการใช้งานบิตคอยน์ขยายตัว การเป็นเจ้าของเพียงเศษเสี้ยวของบิตคอยน์อาจมีมูลค่ามหาศาลในอนาคต โลกกำลังก้าวเข้าสู่ยุคที่บิตคอยน์เป็นพื้นฐานของธุรกรรมทางเศรษฐกิจ เช่นเดียวกับทองคำในอดีต
บทสรุป:
- สะสมบิตคอยน์ อย่างต่อเนื่อง ผ่าน Fiat Arbitrage
- สร้างรายได้ในรูปแบบบิตคอยน์ โดยตรง
- เตรียมพร้อมสำหรับโลกที่บิตคอยน์กลายเป็น มาตรฐานกำหนดมูลค่า
“เวลาที่ดีที่สุดในการเริ่มสะสมบิตคอยน์คือเมื่อสิบปีก่อน เวลาที่ดีที่สุดรองลงมาคือวันนี้”
เริ่มต้นตั้งแต่วันนี้ เพื่อสร้างอนาคตทางการเงินที่มั่นคงด้วยบิตคอยน์ของคุณ

How to Accumulate One Whole Bitcoin: A Strategic Guide
Bitcoin is a scarce asset, and acquiring one whole Bitcoin is becoming increasingly difficult over time. This guide will help you understand why Bitcoin accumulation matters and how you can strategically work towards owning a full Bitcoin.
Why Accumulate One Whole Bitcoin?
Bitcoin has a fixed supply of 21 million coins, but due to lost coins, the actual circulating supply is even lower—estimated to be around 15-17 million. As more people seek to acquire Bitcoin, its purchasing power and scarcity increase. Owning a full Bitcoin could be a game-changing asset in the future financial system.
Understanding the True Currency: Time
The truest currency is your time—a balance you do not know the total amount of.
Ask yourself: What is the purpose of money? Is it to buy luxuries, secure your future, or create generational wealth? Bitcoin allows you to preserve purchasing power over time, unlike fiat currencies that devalue due to inflation.
Overcoming Unit Bias
Many people feel discouraged when they see Bitcoin's high price, thinking they need to buy a whole Bitcoin at once. This is called unit bias—the psychological barrier of thinking Bitcoin is expensive simply because one whole unit costs a lot.
Key Insights:
- You don’t need to buy one Bitcoin all at once.
- Accumulate gradually over time through Dollar-Cost Averaging (DCA).
- Understand that Bitcoin’s price and value are different—price fluctuates, but its long-term value trends upwards.
The Three Phases of Bitcoin Accumulation
There are three main strategies to accumulate Bitcoin: Fiat Arbitrage, Productivity, and Connectivity. Each phase plays a crucial role in your Bitcoin journey.
1. Fiat Arbitrage (Store of Value Phase)
Definition: Using fiat money to buy Bitcoin before it loses purchasing power.
How to Do It:
- Earn fiat income and convert a portion into Bitcoin regularly.
- Follow a savings strategy—decide what percentage of your income will go into Bitcoin.
- Reduce volatility risk by using incremental purchases (DCA).
- Ignore short-term FUD (Fear, Uncertainty, and Doubt) about Bitcoin’s volatility.
2. Productivity (Medium of Exchange Phase)
Definition: Generating Bitcoin income instead of buying it with fiat.
How to Do It:
- Offer products or services in exchange for Bitcoin.
- If you run a business, start accepting Bitcoin payments.
- Engage in Bitcoin mining if it is cost-effective for you.
- Focus on energy, computing, and financial sectors where Bitcoin intersects.
3. Connectivity (Unit of Account Phase)
Definition: A future phase where Bitcoin becomes the standard for pricing goods and services.
How to Prepare:
- Support Bitcoin-native economies where goods and services are priced in Bitcoin.
- Build businesses and contracts that operate entirely in Bitcoin.
- Encourage Bitcoin adoption in communities and networks.
- Participate in the global Bitcoin economy, positioning yourself ahead of mass adoption.
The Future of Bitcoin Accumulation
As Bitcoin adoption grows, owning even a fraction of a Bitcoin will be increasingly valuable. The world is moving towards a system where Bitcoin is the foundation of economic transactions, much like gold in past centuries.
Key Takeaways:
- Accumulate Bitcoin slowly but consistently through Fiat Arbitrage.
- Be productive and earn Bitcoin directly.
- Prepare for a world where Bitcoin is the unit of account.
“The best time to start accumulating Bitcoin was ten years ago. The second-best time is today.”
Start your journey now and secure your financial future with Bitcoin.
Reference: https://www.youtube.com/watch?v=SiuDCmPFDbY
Tags:
siamstr
bitcoin #bitcoiner
btc #1btc
onewholebitcoin #wholecoiner
-
 @ fd06f542:8d6d54cd
2025-03-25 01:40:53
@ fd06f542:8d6d54cd
2025-03-25 01:40:5330023的 文章 可发以被 删除 1 吗?
-
 @ 378562cd:a6fc6773
2025-03-25 00:16:58
@ 378562cd:a6fc6773
2025-03-25 00:16:58Bitcoin gives you financial freedom, but if you're not careful, someone’s watching. If you don’t run your own Bitcoin node, you're trusting someone else with your privacy. Here's why that’s a bad idea—and how running your own node fixes it.
What Is a Bitcoin Node? A Bitcoin node is software that connects to the Bitcoin network. It: ✅ Verifies transactions and blocks. ✅ Stores a copy of the blockchain. ✅ Relays transactions to the network. ✅ Lets you use Bitcoin without trusting anyone.
If you don’t run a node, you’re relying on someone else’s—usually a company that tracks your activity.
How Using Someone Else’s Node Destroys Your Privacy 👀 They Can See Your Transactions – Third-party wallets track what you send, receive, and how much Bitcoin you have. 📍 Your IP Address is Exposed – When you send a transaction, your location could be linked to it. ⛔ Censorship is Possible – Some services can block or delay your transactions. 🔗 They Can Link Your Addresses – Many wallets send your balance info to outside servers, connecting all your Bitcoin activity.
How Running Your Own Node Protects You 🔒 No One Knows Your Balances – Your wallet checks the blockchain directly, keeping your finances private. 🕵️ Hides Your IP Address – No one knows where your transactions come from, especially if you use Tor. 🚀 No Transaction Censorship – Your node sends transactions directly, avoiding interference. ✅ You Verify Everything – No fake data or reliance on third-party information.
But Isn’t Running a Node Hard? Not anymore! You can: 💻 Download Bitcoin Core and run it on your computer. 🔌 Use plug-and-play devices like Umbrel or MyNode. 🍓 Set up a cheap Raspberry Pi to run 24/7.
It’s easier than you think—and worth it.
Why This Matters The more people run nodes, the stronger Bitcoin gets. It becomes more decentralized, harder to censor, and more private for everyone.
Final Thought If you value privacy, freedom, and financial independence, running your own Bitcoin node is a no-brainer. Take control. Protect your Bitcoin. Run a node. 🚀
-
 @ a3a17f65:e9606ad9
2025-03-25 02:22:32
@ a3a17f65:e9606ad9
2025-03-25 02:22:32Maybe it’s the novelty, or perhaps a placebo effect. Maybe it's the sense of finally accomplishing something I’ve set out to do a long time ago. But the first impression is that writing has already begun to clear my mind. It seems to be one of the most powerful ways to improve thinking. Developing the habit of writing could lead to becoming a better thinker.
This journal is meant to reflect whatever’s on my mind. But posting it online comes with a different set of pros and cons compared to what most productivity gurus recommend. For instance, I’ll cut out personal thoughts or sensitive information—something essential in a personal journal. I could mitigate such flaw by writing two versions: one for public view and one for myself, but that feels like too much hassle when I’m just starting this new habit (as James Clear advises, make your habits easy!). On the flip side, posting on cyberspace forces me to be mindful of you, dear reader. Writing for myself alone would allow me to leave empty spaces between familiar ideas and have no problem joining the dots later. But here, fortunately, that luxury doesn’t exist.
Another complementary habit that’s been nagging at me lately is reading, especially fiction—not for learning, but for the pure joy of reading without the pressure to take notes or analyze everything. I just came across this post and despite not being plagued by the obsessive use of smart phones and social media, these two phrases caught my eye:
Reading literary fiction has been linked to having more empathy and the ability to engage in critical thinking
I’ve always valued critical thinking, so that didn’t surprise me. But the link to empathy caught my attention. It made me think about how reading fiction let us experience different perspectives, possibly engaging the same mirror-neurons activated during real-life interactions. Fascinating how something that sharpens our minds can also help us connect with others on a deeper level.
I feel like myself again. Did I mention I’m also sleeping better, and feel happier too?
This quote resonated on a deep level. For me, a single day of writing has given me a most welcomed sense of accomplishment due to being true to myself. Combining journaling with joyful reading might be one of the most powerful boosts to both sleep quality and a sense of purpose I’ve experienced in a long time.
-
 @ da0b9bc3:4e30a4a9
2025-03-24 22:50:57
@ da0b9bc3:4e30a4a9
2025-03-24 22:50:57Hello Stackers!
It's Monday so we're back doing "Meta Music Mondays" 😉.
From before the territory existed there was just one post a week in a ~meta take over. Now each month we have a different theme and bring music from that theme.
This month is March and we're doing March Madness. So give me those Wacky and Weird crazy artists and songs. The weirder the better!
Let's have fun.
Can't have March Madness without Madness!
https://youtu.be/SOJSM46nWwo?si=gtghOZte3rh41tXg
Talk Music. Share Tracks. Zap Sats.
originally posted at https://stacker.news/items/924076
-
 @ 98028d3f:24448238
2025-03-25 01:57:54
@ 98028d3f:24448238
2025-03-25 01:57:54我写这个例子主要看如何更新修改的1。
-
 @ 6e0ea5d6:0327f353
2025-03-24 22:42:59
@ 6e0ea5d6:0327f353
2025-03-24 22:42:59🎣
The support I never had could have saved me time, and I would certainly be farther along at this moment. However, that absence taught me to value having, and if I pass this lesson on to you earlier, it is so you have more time to learn what I could not see.
I like what my father once paraphrased: "If I have seen further, it is by standing on the shoulders of giants." And right now, I think of all that the little one who descends from you will one day behold. The heaviest burdens I pushed were so that you could soar, and if I have dedicated my existence to you, it is so that from my ashes, you may always rise again.
Out of love, I will try not to spoil you with excessive gifts, but instead, without being absent, I hope to build you up. With this line and these strands, I wish to teach you to catch your own fish. Live by what I have taught you and seek to understand what I could not. Honor who I was for you by becoming the best you can be.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 21e127ec:b43a5414
2025-03-24 22:30:47
@ 21e127ec:b43a5414
2025-03-24 22:30:47**
Respondiendo a Joel Serrano
nostr:npub1sg0j78carjndmg7qjfstk2y0e23r5cvxwn3u9z5cgnk5jnh4vxqs355u3l
respecto a hilo de Twitter sobre la adopción de Bitcoin como Medio de Intercambio con Unidad de Cuenta Delegada.
Primero, quiero compartir un artículo de Fernando Nieto que aborda la volatilidad inherente de Bitcoin:
https://x.com/fnietom/status/1454114755807961094
Este artículo de Nieto me ha llevado a cuestionarme si, en un escenario de adopción masiva, Bitcoin podría alcanzar realmente una estabilidad relativa suficiente para facilitar la coordinación de precios y el cálculo económico. De ahí surge la idea de que Bitcoin podría necesitar otros instrumentos que perfeccionen su función como unidad de cuenta.
Un ejemplo claro es lo que ocurrió en Venezuela con la dolarización de facto (al margen del Estado). En sus inicios (y aún hoy en gran medida), solo un pequeño porcentaje de la población tenía acceso a dólares a través la banca internacional, lo que les permitía realizar transacciones financieras fuera del sistema estatal. Estas operaciones se llevaban a cabo en el circuito financiero internacional, aunque las relaciones comerciales reales ocurrían dentro de Venezuela. Otro pequeño grupo tenía acceso a dólares en efectivo para sus transacciones económicas, pero la gran mayoría de la población solo disponía del bolívar venezolano como medio de intercambio en una economía dolarizada. En este contexto, muchos usaban el dólar para calcular los precios de bienes y servicios, mientras que el bolívar seguía siendo el medio de intercambio principal.
La diferencia notable con Bitcoin radica en las causas. En Venezuela, este fenómeno de medio de intercambio con unidad de cuenta delegada (Dolar - Bolivar) se debía a las restricciones monetarias impuestas por el gobierno respecto al dólar, la falta de servicios financieros en esa moneda y la escasa liquidez de dólares físicos. En el caso de Bitcoin, seria debido a su volatilidad inherente producto de su oferta inelástica (Bitcoin como medio de intercambio generalmente aceptado con unidad de cuenta delegada en Fiat publico ó privado - stablecoin).
Sin embargo, esto no implica que la unidad de cuenta que complemente a Bitcoin deba ser necesariamente emitida por un Estado. Creo que la verdadera innovación de Bitcoin radica en su potencial para actuar como un patrón monetario que descentralice la emisión monetaria de los estados gracias al monopolio de la violencia, algo que sí podían ejercer con el oro. Con Bitcoin, el Estado pierde el control, permitiendo que la banca libre emita monedas estables respaldadas en un patrón Bitcoin. El escenario sería una competencia entre monedas estables adoptadas en un segundo plano para facilitar el cálculo económico necesario para coordinar precios, préstamos, servicios financieros y la institución del crédito. Y Bitcoin podría funcionar en primer plano principalmente como medio de intercambio.
No pienso que Bitcoin vaya a eliminar las monedas fiat o estables, ya sean públicas o privadas. Más bien, lo veo como un mecanismo disciplinador que podría prevenir los malos comportamientos monetarios.
Gracias por tu tiempo agradecido y atento a tu posible respuesta.
-
 @ 6e0ea5d6:0327f353
2025-03-24 22:11:58
@ 6e0ea5d6:0327f353
2025-03-24 22:11:58People, mio caro, mistake silence for weakness just as they mistake the shine of silver for the value of gold. Because the modern world—hysterical and theatrical—has learned to respect noise, shouting, emotional outbursts, and the endless chatter of failures who demand respect without ever having earned it. But we, who have emerged from the forge of omertà, know that the one who reacts immediately is merely begging for relevance.
A real man—and I do not refer to those who simply wear trousers, but to those who carry their name and reputation upon their shoulders—knows that humiliation is not avenged with words of promise, but with a sentence of action. And sentences, amico mio, are not uttered in impulse. They are written in silence, with permanent ink on the paper of memory.
The one who strikes back in the moment of offense reveals that he is still under the dominion of emotion. But the one who remains silent, who stands still, who looks his aggressor in the eye and does not utter a single word—he has already begun to dig, with his own hands, the symbolic grave of the one who offended him. His coldness is not the absence of pain, but the absolute mastery of it. And that is precisely why he is feared. Not because he screams, but because he thinks. Because he smiles while thinking. Because he watches while you believe he has forgotten.
In Sicily, we say that the wolf does not howl when preparing to strike—it merely crouches. The fool believes that silence is cowardice. The wise man knows it is calculation. While the world carries on with its pathetic routines and social theater, the humiliated man prepares the final stage. And on this stage, there will be no audience, no applause. Only the dry sound of justice being served. Without mercy. Without apologies. Without a second chance.
Vengeance is not an emotion. It is an art. And the first stroke in the masterpiece is control.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 7d33ba57:1b82db35
2025-03-24 21:47:31
@ 7d33ba57:1b82db35
2025-03-24 21:47:31Located on the southeastern coast of Spain, Cartagena is a city rich in history, maritime heritage, and stunning Mediterranean views. With over 3,000 years of history, it boasts Roman ruins, modernist architecture, and a vibrant port, making it one of Spain’s most underrated travel destinations.
🏛️ Top Things to See & Do in Cartagena
1️⃣ Roman Theatre of Cartagena 🎭
- The star attraction, dating back to the 1st century BC.
- One of Spain’s best-preserved Roman theatres, discovered in 1988 beneath the city.
- Visit the museum to learn about its history before exploring the impressive ruins.
2️⃣ Concepción Castle & Panoramic Lift 🏰
- A 14th-century fortress on a hill offering spectacular views of the city and harbor.
- Take the glass elevator for a scenic ride to the top.
- The museum inside explains Cartagena’s rich military and naval history.
3️⃣ Calle Mayor & Modernist Architecture 🏛️
- The city’s main pedestrian street, lined with elegant buildings, shops, and cafés.
- Admire Casa Cervantes, Gran Hotel, and the Casino, examples of Cartagena’s modernist style.
4️⃣ National Museum of Underwater Archaeology (ARQVA) ⚓
- Learn about sunken treasures, ancient shipwrecks, and underwater archaeology.
- Features artifacts from Phoenician, Roman, and medieval maritime history.
5️⃣ Naval Museum & the Peral Submarine 🚢
- Discover Cartagena’s naval history, including models of warships and maritime artifacts.
- See the Peral Submarine, the first-ever electric-powered submarine, invented in 1888.
6️⃣ Playa de Cala Cortina 🏖️
- A beautiful urban beach, just a few minutes from the city center.
- Great for swimming, snorkeling, and relaxing with clear Mediterranean waters.
7️⃣ Batería de Castillitos 🏰
- A dramatic cliffside fortress with fairy-tale turrets and massive coastal cannons.
- Located 30 minutes from Cartagena, offering panoramic sea views.
🍽️ What to Eat in Cartagena
- Caldero del Mar Menor – A local seafood rice dish, similar to paella 🍚🐟
- Michirones – A hearty bean stew with chorizo and ham 🥘
- Marineras – A Russian salad tapa served on a breadstick with an anchovy 🥖🐟
- Tarta de la abuela – A delicious layered biscuit and chocolate cake 🍰
- Asiático Coffee – A signature Cartagena coffee with condensed milk, brandy, and cinnamon ☕🍸
🚗 How to Get to Cartagena
🚆 By Train: Direct trains from Madrid (4 hrs), Murcia (45 min), and Alicante (1.5 hrs)
🚘 By Car: ~30 min from Murcia, 1.5 hrs from Alicante, 3.5 hrs from Madrid
✈️ By Air: Nearest airport is Murcia-Corvera Airport (RMU) (~30 min away)
🚢 By Cruise Ship: Cartagena is a popular Mediterranean cruise stop💡 Tips for Visiting Cartagena
✅ Best time to visit? Spring & Autumn – warm but not too hot 🌞
✅ Wear comfortable shoes – Many streets and attractions involve walking on cobblestones 👟
✅ Visit during the Roman Festival (Carthaginians & Romans, September) for a unique cultural experience 🎭🏛️
✅ Try a sunset drink at a rooftop bar near the port for incredible views 🍹🌅 -
 @ 878dff7c:037d18bc
2025-03-24 21:43:00
@ 878dff7c:037d18bc
2025-03-24 21:43:00China Denies Plans to Send Peacekeeping Troops to Ukraine
Summary:
Recent reports suggested that China was considering participating in a European-led peacekeeping mission in Ukraine. However, the Chinese Foreign Ministry has firmly denied these claims, stating that such reports are "completely untrue" and reaffirming China's consistent and clear position on the Ukraine crisis. This development highlights the complexities in international efforts to address the ongoing conflict in Ukraine.
Sources: Politico - March 25, 2025, Global Times - March 25, 2025, Newsweek - March 25, 2025
Internal Environmental Regulations Pose Greater Threat to Australian Trade Than Foreign Tariffs
Summary:
Australia's stringent environmental regulations, referred to as "green tape," are posing significant risks to its export industries, including LNG, coal, and iron ore. These regulations have drawn criticism from key trading partners like Japan. The Albanese government's commitments under international climate agreements have intensified these regulations, potentially undermining economic stability more than foreign tariffs.
Sources: The Daily Telegraph - March 25, 2025
Government Announces 'Buy Australian' Initiative to Support Local Industries
Summary:
In response to global trade uncertainties, the Albanese government has introduced a 'Buy Australian' policy aimed at bolstering domestic industries and reducing reliance on international markets. The initiative seeks to mitigate the impact of foreign tariffs and promote local manufacturing, aligning with efforts to 'Trump-proof' the Australian economy against external economic policies.
Source: News.com.au - March 25, 2025
Interest Rates Expected to Remain Elevated Amid Global Trade Tensions
Summary:
Economic analysts predict that the Reserve Bank of Australia may maintain higher interest rates for an extended period due to anticipated inflationary pressures stemming from global trade tensions. Policies, such as tariffs imposed by the U.S., are contributing to economic uncertainty, potentially impacting Australia's economic stability and influencing monetary policy decisions.
Source: News.com.au - March 25, 2025
Severe Flooding Threatens Queensland Amid Heavy Rainfall
Summary:
Queensland is experiencing severe weather conditions, with heavy rainfall leading to significant flooding risks. The Bureau of Meteorology has issued warnings for severe thunderstorms and flooding, particularly between Innisfail and Townsville. In the past 24 hours, rainfall totals have ranged from 50 to 150mm, with expectations of up to 200mm in isolated areas. Major flood warnings are in effect for the Bulloo River, with moderate warnings for several others. Inland regions could see up to 400mm, equating to nearly a year's worth of rain. Residents are advised to stay updated and prepare for potential emergencies.
Sources: News.com.au - 25 March 2025, The Guardian - 25 March 2025
Peter Dutton's 'Me Too' Politics Strategy Criticized Within Liberal Party
Summary:
Peter Dutton's approach of rapidly matching Labor's spending pledges, such as the $8.5 billion Medicare boost and a $150 power bill rebate, has drawn criticism within the Liberal Party. This "Me Too" strategy aims to appear equally voter-friendly but is argued to undermine the Coalition's credibility as better economic managers amid a cost-of-living crisis. Critics suggest that by mirroring Labor's spending, the Coalition loses the ability to effectively critique Labor's fiscal policies without appearing hypocritical, potentially benefiting Labor as their spending gains voter favor.
Sources: The Daily Telegraph - March 24, 2025
Community Organizations Oppose Proposed Public Housing Reforms in Northern Territory
Summary:
Community organizations are criticizing the Country Liberal Party's proposed public housing reforms, which aim to address anti-social behavior, evictions, and debt. Critics argue these reforms could negatively impact disadvantaged groups, particularly Aboriginal Territorians, by shifting the perception of housing from a human right to a conditional privilege. The Central Land Council warns of potential increases in homelessness and incarceration rates among Aboriginal people.
Sources: The Courier-Mail - 25 March 2025
Coalition Proposes Changes to Vehicle Emissions Standards and Hybrid Tax Incentives
Summary:
The Coalition plans to modify Labor’s vehicle emissions standards and reinstate tax incentives for plug-in hybrids. They argue that removing these incentives could hinder efforts to reduce emissions and negatively impact Australian families during the current cost-of-living crisis. The car industry also expresses concerns about stringent carbon footprint targets and the financial burden of meeting emission requirements.
Sources: The Australian - 25 March 2025
Call for Development of Sovereign Supply Chains in Australia
Summary:
A recent survey revealed that 63% of company leaders view geopolitical instability as the primary risk to their organizations. The pandemic exposed vulnerabilities in global and domestic supply chains, particularly in Australia's production of essential goods. To address this, there is a call for developing resilient sovereign supply chains, balancing reshoring critical manufacturing with strategic partnerships. Collaborative efforts across government, business, and educational institutions are deemed necessary to build robust supply chains.
Sources: The Australian - 25 March 2025
Interest Rates in Australia May Stay High Amid Global Economic Uncertainty
Summary:
Interest rates in Australia may remain elevated due to expected increases in inflation, driven by U.S. tariff policies causing global economic uncertainty. These tariffs are likely to raise prices and contribute to inflationary pressures. The Reserve Bank of Australia faces a dilemma, balancing the need to address declining employment data with the potential for rate cuts to stimulate the economy. Economists suggest maintaining current interest rates to observe further economic developments.
Sources: News.com.au - 25 March 2025
NSW Government to Remove Shark Nets from Sydney Beaches
Summary:
The NSW government will remove shark nets from 51 Sydney beaches on March 31, ahead of their usual end-of-April schedule, to reduce the bycatch of sea turtles migrating throughout April. This decision follows feedback from coastal councils, six of which have voted for the permanent removal of the nets due to concerns over marine bycatch. However, there are concerns that alternative shark mitigation technologies, such as drones and SMART drumlines, may not be as effective in protecting swimmers. The final decision on the future of the shark nets will be made by the NSW government, based on a report compiled from the feedback of 25 councils.
Sources: The Daily Telegraph - March 24, 2025
Victoria Achieves World-Leading Cardiac Arrest Survival Rates
Summary:
Victoria has quietly become a global leader in cardiac arrest survival, thanks to a combination of fast emergency responses, community training, and public health infrastructure. New data released today shows that 41% of people who suffered a cardiac arrest in public and received immediate CPR and defibrillation survived — putting Victoria among the top three regions globally, just behind King County in the U.S. and Denmark.
Much of the credit goes to everyday citizens. Nearly 80% of cardiac arrests witnessed by bystanders were met with immediate CPR, a rate far above the national average. The widespread rollout of over 7,500 publicly accessible defibrillators and the GoodSAM mobile app — which alerts nearby trained responders in real-time — has also played a key role in improving outcomes.
Health officials say the results are proof that early intervention saves lives, and the state's model could serve as a blueprint for others. Survivors and their families have expressed overwhelming gratitude for both the emergency responders and ordinary citizens whose quick thinking made the difference.
Sources: The Guardian - March 24, 2025, ABC News - March 25, 2025
Wind Drought Challenges Australia's Renewable Energy Sector
Summary:
Zen Energy, co-developed by economist Ross Garnaut, is facing financial difficulties due to a "wind drought" affecting its wind generation capacity. The company had to purchase expensive spot market capacity to meet obligations, leading to the sale of a near 10% stake for $43 million to fund large-scale battery development. This situation highlights the challenges in Australia's transition to renewable energy, especially with fluctuating wholesale electricity prices and long-term contracts.
Sources: The Australian - March 24, 2025
Istanbul Mayor's Arrest Signals Turkey's Authoritarian Shift
Summary:
Ekrem Imamoglu, the mayor of Istanbul and a prominent opposition figure, has been detained and jailed on charges of graft and terrorism. Analysts suggest that President Recep Tayyip Erdogan's move was facilitated by global geopolitical instability, reducing the likelihood of international condemnation. This arrest is viewed as a significant blow to Turkish opposition and indicative of a move towards increased authoritarianism.
Sources: Associated Press - March 25, 2025
Iranian Generals Direct Houthi Attacks in Red Sea
Summary:
Key Iranian figures behind Houthi rebel operations in Yemen have been identified. The Houthis, supported by Iran's IRGC, have launched attacks on merchant vessels and warships in the Red Sea, disrupting global trade. These operations are reportedly commanded by senior Iranian officials and approved by Supreme Leader Ali Khamenei, highlighting Iran's strategic involvement in regional conflicts.
Sources: The Sun - March 22, 2025
Exploring Programming, AI, and Personal Journeys with ThePrimeagen on the Lex Fridman Podcast
Summary:
In episode #461 of the Lex Fridman Podcast, Lex has an in-depth conversation with ThePrimeagen, a well-known software developer and content creator. The episode covers a range of topics including:
- Programming and Development: ThePrimeagen shares insights into modern coding practices, the evolution of software engineering, and his passion for low-level programming.
- Artificial Intelligence: The two discuss AI's impact on society, the future of intelligent systems, and philosophical implications.
- Life with ADHD: ThePrimeagen opens up about living with ADHD, discussing the challenges it brings and how he channels it into productivity.
- Addiction and Recovery: A personal and vulnerable look at his journey through addiction and the steps he took toward recovery.
- Philosophy and Faith: The episode also touches on topics like belief in God, human purpose, and finding meaning through both faith and technology.
Importance:
This episode stands out for its honest blend of technical depth and emotional vulnerability. It offers listeners a rare look at how a high-performing developer balances the pressures of tech life with personal challenges. The philosophical undertones add a reflective layer, making it not just informative but also deeply human.
Sources: Lex Fridman Podcast - March 25, 2025
-
 @ 4520e45a:aa52208a
2025-03-24 21:42:12
@ 4520e45a:aa52208a
2025-03-24 21:42:12Hashrate\ Die Hashrate wird vom Pool basierend auf den übermittelten Shares innerhalb eines Zeitraums berechnet und zeigt, wie viele Hashes pro Sekunde dein Worker generiert.\ Die Statistik zeigt die durschschnittliche Hashrate für:\ 1 Minute (1m), 5 Minuten (5m), 1 Stunde (1hr), 1 Tag (1d), 7 Tage (7d)
1M = 1 MH/s = 1'000'000 H/S\ 1G = 1 GH/s = 1'000'000'000 H/S\ 1T = 1 TH/s = 1'000'000'000'000 H/S\ 1P = 1 PH/s = 1'000'000'000'000'000 H/S
Lastshare\ Angabe in Unix Zeit, wann der letzte Share von deinem Worker bei ckpool abgeliefert wurde.\ 🔗 unix timestamp converter
Worker\ Anzahl Worker. Wenn mehrere Miner identischen Namen haben, werden sie zu einem Worker zusammengefasst. Wenn du für jeden Miner separate Statistiken willst, muss sich deren Worker-Name hinter der Bitcoin-Adresse unterscheiden:\ 1CCAV1N3FCffp4fXBBAF6qNGu1tvXTmndy.bitaxe1\ 1CCAV1N3FCffp4fXBBAF6qNGu1tvXTmndy.bitaxe2\ 1CCAV1N3FCffp4fXBBAF6qNGu1tvXTmndy.bitaxe3
Shares\ Anzahl akzeptierter Shares, die seit Beginn von deinem Worker bei ckpool abgeliefert wurden. Wenn ein Hash alle notwendigen Kriterien und die vom Pool geforderte Schwierigkeit erfüllt, wird er als Share an ckpool übermittelt.
Bestshare\ Der beste/höchste Share der seit dem letzten gefundenen Block abgeliefert wurde.\ Wenn du oder ckpool einen Block gefunden hat, wird dieser Wert zurück auf Null gesetzt.
Bestever\ Der jemals beste/höchste gefundene Share. Im AxeOS als Best Difficulty bezeichnet.\ Wenn du oder ckpool einen Block gefunden hat, wird dieser Wert nicht zurück auf Null gesetzt.
Ein Block wird gefunden, wenn die Schwierigkeit (=Difficulty) eines Shares höher ist als die aktuelle Netzwerk-Schwierigkeit.
Zum Zeitpunkt des Schreibens des Reads — Blockzeit 889277 — liegt die Netzwerk-Schwierigkeit bei: 113'757'508'810'854 = 113T
Authorised\ Angabe in Unix Zeit, wann du dich zum ersten Mal mit ckpool verbunden hast (wurde erst mit v0.9.7 am 30.05.2023 eingeführt).\ 🔗 unix timestamp converter
-
 @ ed5774ac:45611c5c
2025-03-24 21:33:47
@ ed5774ac:45611c5c
2025-03-24 21:33:47Erdogan’s Turkey: The Rise, Reign, and Decline of a Political Strongman
As Turkey’s political crisis intensifies with Erdogan’s imprisonment of Imamoglu—a leading opposition figure and likely frontrunner in the 2028 presidential elections—it is crucial to analyze the historical events and geopolitical factors that enabled Erdogan’s rise, secured the consolidation of his rule, and allowed him to maintain his grip on power for decades. To understand the foundations of Erdogan’s enduring political legacy, we must examine the historical events that shaped his ideology and the global power struggles of the time. Equally important are the international actors who facilitated his rise and prolonged his rule. Key factors include the link between Erdogan’s rise and the Iraq War, the interplay between Turkey’s military coups and the Ukraine crisis, the events that led to the erosion of Western support for Erdogan, the role of the U.S. and NATO in the 2016 coup attempt against his rule, and the shifting geopolitical landscape that continues to define Turkey’s political future.
The Roots of Islamism: The CIA, the 1980 Coup, and the Suppression of Turkish Liberalism
Erdogan’s rise is deeply intertwined with the growth of Turkey’s Islamic movement, which gained traction in the 1970s amid Cold War geopolitics. During this period, the U.S., under the guidance of Zbigniew Brzezinski, National Security Advisor to President Jimmy Carter, devised the “Green Belt” strategy. This plan aimed to cultivate a radicalized Islamic generation across the Muslim world to counter the spread of communist ideology. The U.S. intervention in Afghanistan, which radicalized certain factions and triggered the Soviet invasion, was a critical component of this strategy. Brzezinski himself proudly acknowledged this in various interviews. Turkey, a NATO ally bordering the Soviet Union, became a key theater for implementing this policy.
The military coup of September 12, 1980, marked a pivotal moment in Turkish history. Led by General Kenan Evren, the Turkish armed forces seized power under the pretext of restoring order amid escalating violence between leftist and rightist factions that had claimed thousands of lives. However, the junta’s crackdown disproportionately targeted the Turkish left—a movement distinct from Soviet-style communism, composed of liberal, educated intellectuals such as writers, artists, journalists, and thinkers. These individuals, who championed Turkish sovereignty, intellectual freedom, and democratic ideals, were perceived as a direct threat to the military’s Islamization agenda, backed by the CIA. Tens of thousands were imprisoned, tortured, or executed, while left-wing organizations were banned outright.
At the same time, the junta actively fostered Islamist groups, establishing religious schools known as Imam Hatip institutions under the guise of combating Marxism and communism. In reality, their true objective was to eliminate anyone who sought Turkish sovereignty, embraced patriotism, or valued critical thinking. Writers, artists, journalists, and intellectuals—those who dared to think independently and question authority—were viewed as existential threats to the Islamization model the military and its CIA allies sought to impose. By silencing these voices, the junta aimed to eradicate opposition to their vision of a Turkey subservient to religious dogma and foreign interests, ensuring a populace stripped of sovereign thought and resistant to enlightenment.
This paradox—a secular military suppressing liberal intellectuals while nurturing Islamist groups—laid the foundation for Erdogan’s rise and the eventual Islamization of Turkish society.
The Chaos of the 1990s: Economic Crisis and the Rise of Erdogan
The 1990s were a chaotic decade for Turkey, marked by economic instability, a Kurdish insurgency, and a revolving door of coalition governments. The 1994 financial crisis saw inflation soar, while terrorist attacks by the Kurdistan Workers’ Party (PKK) and political assassinations fueled national disarray. Successive governments, often beholden to globalist agendas dictated by the International Monetary Fund and World Bank, failed to deliver stability. This period mirrored today’s European political crises, where ideological convergence has left voters disillusioned.
Into this void stepped Erdogan, a charismatic former soccer player turned politician from Istanbul’s working-class Kasimpasa district, whose blend of populist appeal and religious rhetoric resonated with a disillusioned populace. His rise was no accident. In 1994, he won the mayoralty of Istanbul as a member of the Islamist Welfare Party (Refah Partisi), showcasing a blend of populist charisma and religious appeal. However, his early political career faced a setback in 1997 when the military, acting as guardians of Turkey’s secular Kemalist legacy, forced the resignation of Welfare Party Prime Minister Necmettin Erbakan in what was dubbed a “postmodern coup.” Erdogan’s imprisonment in 1998 for reciting a divisive poem only solidified his image as a martyr among his devout supporters.
The 2001 Crisis: Neocons, Economic Sabotage, and Erdogan’s Ascendancy
Erdogan’s true ascent began amid Turkey’s devastating 2001 financial crisis, which saw the economy contract by 5.7%, unemployment spike, and the Turkish lira collapse. The crisis, worsened by IMF-mandated austerity measures, discredited the ruling coalition under Prime Minister Bulent Ecevit. A staunch nationalist, Ecevit had spearheaded Turkey’s 1974 intervention in Cyprus and forced Syria to expel PKK leader Abdullah Ocalan in 1999. His refusal to align Turkey with the impending U.S.-led Iraq War in 2003 made him a liability for U.S. neoconservatives, who were already preparing for the conflict.
Far from a mere economic downturn, the 2001 crisis was a deliberate strategy orchestrated by the global Western financial cartel to destabilize Ecevit’s nationalist government. This administration, fiercely protective of Turkish sovereignty, had unequivocally opposed Turkey’s involvement in the Iraq War. To eliminate this obstacle, the financial cartel—comprising international financial institutions and Western-backed actors—engineered the crisis by exploiting Turkey’s reliance on hot money and Western financial support. The resulting economic collapse eroded public trust in the government and existing political parties, creating a power vacuum that paved the way for Erdogan. Handpicked by the globalist cabal as their new proxy, Erdogan was positioned to advance their political agenda in Turkey. The neocons viewed him as a pliable ally: a moderate Islamist who could pacify Turkey’s religious conservatives while advancing Western interests. Despite resistance within his own party, Erdogan advocated for Turkish involvement in the Iraq War, though the Turkish Parliament, with the help of dissidents in his party, ultimately rejected U.S. troop deployments in 2003. Nevertheless, Erdogan remained loyal to his neocon backers and globalist patrons, privatizing state assets at rock-bottom prices—akin to Yeltsin’s controversial reforms in 1990s Russia—and deepening Turkey’s economic dependence on the EU and the U.S.
In addition to tying Turkey’s economy to Western interests, Erdogan targeted the Turkish military in 2007 through the Ergenekon and Sledgehammer trials. Widely criticized as show trials orchestrated with the help of the Gulen movement—a shadowy Islamic network led by Fethullah Gulen—these cases imprisoned or sidelined hundreds of officers, including navy admirals opposed to NATO’s Black Sea ambitions. These officers had long argued that NATO’s mission ended with the fall of the Soviet Union and advocated for closer ties with Russia and China. They also opposed plans to integrate Georgia and Ukraine into NATO, fearing it would destabilize the region and turn the Black Sea into a battleground between the West and Russia. By weakening the navy and sidelining its dissenting admirals, Erdogan brought Turkey back in line with NATO’s strategic objectives, enabling the neocons to advance their plans for NATO expansion into the Black Sea region—a move that set the stage for the 2008 Russo-Georgian War and the 2014 Ukrainian crisis.. Without this internal coup against the Turkish military, these events might have unfolded differently—or not at all.
For his services to the globalist agenda, Erdogan was portrayed in Western media as a democratizing hero, and Turkey’s economy was praised for its growth and strength. However, the reality was starkly different. To understand the globalist propaganda surrounding Erdogan, consider Barack Obama’s first foreign visit as U.S. president: a trip to Turkey in 2009. In a speech to the Turkish Parliament, Obama praised Erdogan’s “democratic reforms” and the strength of Turkey’s economy—which was growing steadily only due to cheap credit provided by international financial institutions serving the same globalist interests Erdogan represented. Meanwhile, journalists and dissidents filled Turkish prisons.
The 2016 Coup Attempt: Erdogan’s Break with the West
Erdogan’s honeymoon with the West soured in the 2010s. His support for Egypt’s Muslim Brotherhood and his interventionist stance in Syria clashed with U.S. priorities, especially after the Arab Spring upended regional alliances. Sensing Erdogan’s growing autonomy, the neocons turned to Fethullah Gulen, a cleric living in Pennsylvania since 1999 with close ties to the CIA and the Clinton Foundation. Gulen’s Hizmet movement, once an ally in Erdogan’s rise, had infiltrated Turkey’s police, judiciary, and military, creating a “parallel state.”
The July 15, 2016, coup attempt—marked by rogue military units bombing parliament and nearly capturing Erdogan—was orchestrated by factions of the Gulen movement within the army, with the involvement of the CIA and NATO, using Incirlik Air Base as one of the primary command centers to coordinate the operation (one of NATO’s largest military bases in the region). The timing suggests that the neocons, anticipating Hillary Clinton’s presidency, planned to install Gulen as their new puppet in Turkey. As a radical Sunni leader hostile to Iran, Gulen could have aligned Turkey with a broader anti-Iranian axis, potentially dragging the country into a regional war against Iran—much like Saddam Hussein did three decades earlier.
The coup’s failure, quashed by loyalists and public resistance, marked a turning point, leading Erdogan to purge over 100,000 civil servants and consolidate his power through a 2017 referendum and pivoting toward Russia and China—not out of conviction, but as leverage against Western abandonment.
Turkey’s Geopolitical Balancing Act: Ukraine, NATO, and the Black Sea
Erdogan’s post-2016 flirtations with Moscow—evidenced by the purchase of Russian S-400 systems and energy deals—reflect more than a pragmatic balancing act. They reflect a desperate attempt to regain Western attention, akin to dating someone new to make an ex jealous, aimed at convincing the West not to write him off.
The Ukrainian crisis, escalating with Russia’s 2022 invasion, has pushed Turkey into a delicate role. As a NATO member controlling the Bosphorus, Erdogan has mediated grain deals and prisoner swaps, leveraging Turkey’s strategic position. Yet his reluctance to fully back NATO’s hardline stance has further alienated him from the West, making him a target for a potential regime change operation as the West has grown desperate to win its proxy war against Russia. As a result, international media and globalist factions have intensified efforts to undermine his regime, seeking to remove him from power.
Turkey at a Crossroads: Imamoglu, Erdogan’s Decline, and the Future
Erdogan has fulfilled his mission: he has made Turkey’s economy dependent on the West, eliminated patriotic voices in the military, dismantled the parliamentary system, wrecked the education system, and buried the secular Turkish republic. His legacy is a deeply polarized Turkey: economically dependent on the West, militarily weakened, and institutionally hollowed out.
Corruption scandals, a collapsing lira, and authoritarian excesses have fueled widespread public discontent. Yet, rather than addressing the root causes of this anger—economic hardship, growing authoritarianism, and systemic corruption—Erdogan has grown increasingly paranoid, attributing every challenge to Western conspiracies and interventions. This refusal to confront reality has only deepened the divide between him and the Turkish people, fueling widespread disillusionment and anger.
Imamoglu’s rise—winning Istanbul in 2019 and 2023 despite blatant election irregularities, systematic government interference, censorship, and the full force of Erdogan’s authoritarian machinery—stands as a testament to his resilience and the enduring hope of Turkey’s opposition. Facing a system rigged to ensure his defeat, Imamoglu triumphed against overwhelming odds. Erdogan’s regime spared no effort, leveraging state media, the judiciary, and security forces to manipulate the results, yet it could not prevent Imamoglu’s victories in Istanbul, which shattered the illusion of invincibility surrounding Erdogan’s rule. His recent imprisonment on fabricated charges ahead of the 2028 elections underscores Erdogan’s desperation to suppress this threat, further alienating a populace yearning for change.
Turkey now stands at a crossroads. The powers that once propelled Erdogan to prominence—U.S. neoconservatives and the Islamist legacy of the 1980 coup—have lost control of their creation. His fall from Western favor, tied to the 2016 coup attempt and his regional overreach, has left him isolated, oscillating between East and West while clinging to power as domestic anger reaches a boiling point. Whether Imamoglu or another leader emerges, Turkey’s post-Erdogan era will face the monumental task of rebuilding its secular republic and defining its role in an increasingly complex global landscape.
Turkey’s struggle is not just its own—it is an example of the suffering endured for decades under Western colonialism and a parasitic financial order. This system, designed to enrich a handful of elites in the West, thrives by exploiting the Global South, perpetuating poverty, and engineering chaos to maintain control. Turkey’s fight for self-determination stands as a beacon for all nations seeking to break free from the chains of neocolonialism and reclaim their rightful place in a just and equitable global order. The future must be built on the sovereignty of nations, free from the selfish designs of a Western oligarchy.