-
 @ a012dc82:6458a70d
2025-03-19 06:28:40
@ a012dc82:6458a70d
2025-03-19 06:28:40In recent years, the global economy has faced unprecedented challenges, with inflation rates soaring to levels not seen in decades. This economic turmoil has led investors and consumers alike to seek alternative stores of value and investment strategies. Among the various options, Bitcoin has emerged as a particularly appealing choice. This article explores the reasons behind Bitcoin's growing appeal in an inflation-stricken economy, delving into its characteristics, historical performance, and the broader implications for the financial landscape.
Table of Contents
-
Understanding Inflation and Its Impacts
-
Bitcoin: A New Safe Haven?
-
Decentralization and Limited Supply
-
Portability and Liquidity
-
Bitcoin's Performance in Inflationary Times
-
Challenges and Considerations
-
The Future of Bitcoin in an Inflationary Economy
-
Conclusion
-
FAQs
Understanding Inflation and Its Impacts
Inflation is the rate at which the general level of prices for goods and services is rising, eroding purchasing power. It can be caused by various factors, including increased production costs, higher energy prices, and expansive government policies. Inflation affects everyone in the economy, from consumers and businesses to investors and retirees, as it diminishes the value of money. When inflation rates rise, the purchasing power of currency falls, leading to higher costs for everyday goods and services. This can result in decreased consumer spending, reduced savings, and overall economic slowdown.
For investors, inflation is a significant concern because it can erode the real returns on their investments. Traditional investments like bonds and savings accounts may not keep pace with inflation, leading to a loss in purchasing power over time. This has prompted a search for alternative investments that can provide a hedge against inflation and preserve, if not increase, the value of their capital.
Bitcoin: A New Safe Haven?
Traditionally, assets like gold, real estate, and Treasury Inflation-Protected Securities (TIPS) have been considered safe havens during times of inflation. However, the digital age has introduced a new player: Bitcoin. Bitcoin is a decentralized digital currency that operates without the oversight of a central authority. Its supply is capped at 21 million coins, a feature that many believe gives it anti-inflationary properties. This inherent scarcity is akin to natural resources like gold, which have historically been used as hedges against inflation.
The decentralization of Bitcoin means that it is not subject to the whims of central banking policies or government interference, which are often seen as contributing factors to inflation. This aspect of Bitcoin is particularly appealing to those who have lost faith in traditional financial systems and are looking for alternatives that offer more autonomy and security.
Decentralization and Limited Supply
One of the key features that make Bitcoin appealing as a hedge against inflation is its decentralized nature. Unlike fiat currencies, which central banks can print in unlimited quantities, Bitcoin's supply is finite. This scarcity mimics the properties of gold and is seen as a buffer against inflation. The decentralized nature of Bitcoin also means that it is not subject to the same regulatory pressures and monetary policies that can lead to currency devaluation.
Furthermore, the process of "mining" Bitcoin, which involves validating transactions and adding them to the blockchain, is designed to become progressively more difficult over time. This not only ensures the security of the network but also introduces a deflationary element to Bitcoin, as the rate at which new coins are created slows down over time.
Portability and Liquidity
Bitcoin's digital nature makes it highly portable and divisible, allowing for easy transfer and exchange worldwide. This liquidity and global accessibility make it an attractive option for investors looking to diversify their portfolios beyond traditional assets. Unlike physical assets like gold or real estate, Bitcoin can be transferred across borders without the need for intermediaries, making it a truly global asset.
The ease of transferring and dividing Bitcoin means that it can be used for a wide range of transactions, from large-scale investments to small, everyday purchases. This versatility, combined with its growing acceptance as a form of payment, enhances its utility and appeal as an investment.
Bitcoin's Performance in Inflationary Times
Historically, Bitcoin has shown significant growth during periods of high inflation. While it is known for its price volatility, many investors have turned to Bitcoin as a speculative hedge against depreciating fiat currencies. The digital currency's performance during inflationary periods has bolstered its reputation as a potential safe haven. However, it's important to note that Bitcoin's market is still relatively young and can be influenced by a wide range of factors beyond inflation, such as market sentiment, technological developments, and regulatory changes.
Despite its volatility, Bitcoin has provided substantial returns for some investors, particularly those who entered the market early. Its performance, especially during times of financial instability, has led to increased interest and investment from both individual and institutional investors. As more people look to Bitcoin as a potential hedge against inflation, its role in investment portfolios is likely to evolve.
Challenges and Considerations
Despite its growing appeal, Bitcoin is not without its challenges. The cryptocurrency's price volatility can lead to significant losses, and regulatory uncertainties remain a concern. Additionally, the environmental impact of Bitcoin mining has sparked debate. The energy-intensive process required to mine new coins and validate transactions has raised concerns about its sustainability and environmental footprint.
Investors considering Bitcoin as a hedge against inflation should weigh these factors and consider their risk tolerance and investment horizon. While Bitcoin offers potential benefits as an inflation hedge, it also comes with risks that are different from traditional investments. Understanding these risks, and how they align with individual investment strategies, is crucial for anyone considering adding Bitcoin to their portfolio.
The Future of Bitcoin in an Inflationary Economy
As the global economy continues to navigate through turbulent waters, the appeal of Bitcoin is likely to grow. Its properties as a decentralized, finite, and easily transferable asset make it a unique option for those looking to protect their wealth from inflation. However, the future of Bitcoin remains uncertain, and its role in the broader financial landscape is still being defined. As with any investment, due diligence and a balanced approach are crucial.
The increasing institutional interest in Bitcoin and the development of financial products around it, such as ETFs and futures, suggest that Bitcoin is becoming more mainstream. However, its acceptance and integration into the global financial system will depend on a variety of factors, including regulatory developments, technological advancements, and market dynamics.
Conclusion
The growing appeal of Bitcoin in an inflation-stricken economy highlights the changing dynamics of investment in the digital age. While it offers a novel approach to wealth preservation, it also comes with its own set of risks and challenges. As the world continues to grapple with inflation, the role of Bitcoin and other cryptocurrencies will undoubtedly be a topic of keen interest and debate among investors and policymakers alike. Whether Bitcoin will become a permanent fixture in investment portfolios as a hedge against inflation remains to be seen, but its impact on the financial landscape is undeniable.
FAQs
What is inflation, and how does it affect the economy? Inflation is the rate at which the general level of prices for goods and services is rising, leading to a decrease in purchasing power. It affects the economy by reducing the value of money, increasing costs for consumers and businesses, and potentially leading to economic slowdown.
Why is Bitcoin considered a hedge against inflation? Bitcoin is considered a hedge against inflation due to its decentralized nature, limited supply capped at 21 million coins, and its independence from government monetary policies, which are often seen as contributing factors to inflation.
What are the risks associated with investing in Bitcoin? The risks include high price volatility, regulatory uncertainties, and concerns over the environmental impact of Bitcoin mining. Investors should consider their risk tolerance and investment horizon before investing in Bitcoin.
How does Bitcoin's limited supply contribute to its value? Bitcoin's limited supply mimics the scarcity of resources like gold, which has traditionally been used as a hedge against inflation. This scarcity can help to maintain its value over time, especially in contrast to fiat currencies, which can be printed in unlimited quantities.
Can Bitcoin be used for everyday transactions? Yes, Bitcoin can be used for a wide range of transactions, from large-scale investments to small, everyday purchases. Its digital nature allows for easy transfer and division, making it a versatile form of currency.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnewsco
Instagram: @croxroadnews.co/
Youtube: @thebitcoinlibertarian
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
Get Orange Pill App And Connect With Bitcoiners In Your Area. Stack Friends Who Stack Sats link: https://signup.theorangepillapp.com/opa/croxroad
Buy Bitcoin Books At Konsensus Network Store. 10% Discount With Code “21croxroad” link: https://bitcoinbook.shop?ref=21croxroad
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ e97aaffa:2ebd765d
2025-03-19 05:55:17
@ e97aaffa:2ebd765d
2025-03-19 05:55:17Como é difícil encontrar informações sobre o eurodigital, a CBDC da União Europeia, vou colocando aqui, os documentos mais interessantes que fui encontrando:
FAQ: https://www.ecb.europa.eu/euro/digital_euro/faqs/html/ecb.faq_digital_euro.pt.html
Directório BCE: https://www.ecb.europa.eu/press/pubbydate/html/index.en.html?topic=Digital%20euro
https://www.ecb.europa.eu/euro/digital_euro/timeline/profuse/html/index.en.html
Documentos mais técnicos:
2025
Technical note on the provision of multiple digital euro accounts to individual end users https://www.ecb.europa.eu/euro/digital_euro/timeline/profuse/shared/pdf/ecb.degov240325_digital_euro_multiple_accounts.en.pdf
2024
Relatório de progresso https://www.ecb.europa.eu/euro/digital_euro/progress/html/ecb.deprp202412.en.html
Technical note on the provision of multiple digital euro accounts to individual end users https://www.ecb.europa.eu/euro/digital_euro/timeline/profuse/shared/pdf/ecb.degov240325_digital_euro_multiple_accounts.en.pdf
The impact of central bank digital currency on central bank profitability, risk-taking and capital https://www.ecb.europa.eu/pub/pdf/scpops/ecb.op360~35915b25bd.en.pdf
2023
Progress on the investigation phase of a digital euro - fourth report https://www.ecb.europa.eu/paym/digital_euro/investigation/governance/shared/files/ecb.degov230713-fourth-progress-report-digital-euro-investigation-phase.en.pdf
Digital euro - Prototype summary and lessons learned https://www.ecb.europa.eu/pub/pdf/other/ecb.prototype_summary20230526%7E71d0b26d55.en.pdf
Functional and non-functional requirements linked to the market research for a potential digital euro implementation https://www.ecb.europa.eu/euro/digital_euro/timeline/profuse/shared/pdf//ecb.dedocs230113_Annex_1_Digital_euro_market_research.en.pdf
A stocktake on the digital euro https://www.ecb.europa.eu/euro/digital_euro/progress/shared/pdf/ecb.dedocs231018.en.pdf
-
 @ ee9aaefe:1e6952f4
2025-03-19 05:01:44
@ ee9aaefe:1e6952f4
2025-03-19 05:01:44Introduction to Model Context Protocol (MCP)
Model Context Protocol (MCP) serves as a specialized gateway allowing AI systems to access real-time information and interact with external data sources while maintaining security boundaries. This capability transforms AI from closed systems limited to training data into dynamic assistants capable of retrieving current information and performing actions. As AI systems integrate into critical infrastructure across industries, the security and reliability of these protocols have become crucial considerations.
Security Vulnerabilities in Web-Based MCP Services
Traditional MCP implementations operate as web services, creating a fundamental security weakness. When an MCP runs as a conventional web service, the entire security model depends on trusting the service provider. Providers can modify underlying code, alter behavior, or update services without users' knowledge or consent. This creates an inherent vulnerability where the system's integrity rests solely on the trustworthiness of the MCP provider.
This vulnerability is particularly concerning in high-stakes domains. In financial applications, a compromised MCP could lead to unauthorized transactions or exposure of confidential information. In healthcare, it might result in compromised patient data. The fundamental problem is that users have no cryptographic guarantees about the MCP's behavior – they must simply trust the provider's claims about security and data handling.
Additionally, these services create single points of failure vulnerable to sophisticated attacks. Service providers face internal threats from rogue employees, external pressure from bad actors, or regulatory compulsion that could compromise user security or privacy. With traditional MCPs, users have limited visibility into such changes and few technical safeguards.
ICP Canisters: Enabling the Verifiable MCP Paradigm
The Internet Computer Protocol (ICP) offers a revolutionary solution through its canister architecture, enabling what we term "Verifiable MCP" – a new paradigm in AI security. Unlike traditional web services, ICP canisters operate within a decentralized network with consensus-based execution and verification, creating powerful security properties:
- Cryptographically verifiable immutability guarantees prevent silent code modifications
- Deterministic execution environments allow independent verification by network participants
- Ability to both read and write web data while operating under consensus verification
- Control of off-chain Trusted Execution Environment (TEE) servers through on-chain attestation
These capabilities create the foundation for trustworthy AI context protocols that don't require blind faith in service providers.
Technical Architecture of Verifiable MCP Integration
The Verifiable MCP architecture places MCP service logic within ICP canisters that operate under consensus verification. This creates several distinct layers working together to ensure security:
-
Interface Layer: AI models connect through standardized APIs compatible with existing integration patterns.
-
Verification Layer: The ICP canister validates authentication, checks permissions, and verifies policy adherence within a consensus-verified environment.
-
Orchestration Layer: The canister coordinates necessary resources for data retrieval or computation.
-
Attestation Layer: For sensitive operations, the canister deploys and attests TEE instances, providing cryptographic proof that correct code runs in a secure environment.
-
Response Verification Layer: Before returning results, cryptographic verification ensures data integrity and provenance.
This architecture creates a transparent, verifiable pipeline where component behavior is guaranteed through consensus mechanisms and cryptographic verification—eliminating the need to trust service provider claims.
Example: Secure Financial Data Access Through Verifiable MCP
Consider a financial advisory AI needing access to banking data and portfolios to provide recommendations. In a Verifiable MCP implementation:
-
The AI submits a data request through the Verifiable MCP interface.
-
The ICP canister verifies authorization using immutable access control logic.
-
For sensitive data, the canister deploys a TEE instance with privacy-preserving code.
-
The canister cryptographically verifies the TEE is running the correct code.
-
Financial services provide encrypted data directly to the verified TEE.
-
The TEE returns only authorized results with cryptographic proof of correct execution.
-
The canister delivers verified insights to the AI.
This ensures even the service provider cannot access raw financial data while maintaining complete auditability. Users verify exactly what code processes their information and what insights are extracted, enabling AI applications in regulated domains otherwise too risky with traditional approaches.
Implications for AI Trustworthiness and Data Sovereignty
The Verifiable MCP paradigm transforms the trust model for AI systems by shifting from "trust the provider" to cryptographic verification. This addresses a critical barrier to AI adoption in sensitive domains where guarantees about data handling are essential.
For AI trustworthiness, this enables transparent auditing of data access patterns, prevents silent modifications to processing logic, and provides cryptographic proof of data provenance. Users can verify exactly what information AI systems access and how it's processed.
From a data sovereignty perspective, users gain control through cryptographic guarantees rather than policy promises. Organizations implement permissions that cannot be circumvented, while regulators can verify immutable code handling sensitive information. For cross-border scenarios, Verifiable MCP enables compliance with data localization requirements while maintaining global AI service capabilities through cryptographically enforced data boundaries.
Conclusion
The Verifiable MCP paradigm represents a breakthrough in securing AI systems' external interactions. By leveraging ICP canisters' immutability and verification capabilities, it addresses fundamental vulnerabilities in traditional MCP implementations.
As AI adoption grows in regulated domains, this architecture provides a foundation for trustworthy model-world interactions without requiring blind faith in service providers. The approach enables new categories of AI applications in sensitive sectors while maintaining robust security guarantees.
This innovation promises to democratize secure context protocols, paving the way for responsible AI deployment even in the most security-critical environments.
-
 @ e890e461:12e502a1
2025-03-23 16:25:12
@ e890e461:12e502a1
2025-03-23 16:25:12Hello world. My blog where I post most of my stuff is https://robot-one.github.io/
-
 @ da0b9bc3:4e30a4a9
2025-03-23 09:00:12
@ da0b9bc3:4e30a4a9
2025-03-23 09:00:12Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/922244
-
 @ ed84ce10:cccf4c2a
2025-03-19 03:46:17
@ ed84ce10:cccf4c2a
2025-03-19 03:46:17DoraHacks: Pioneering the Global Hacker Movement
DoraHacks is the world’s largest hackathon community, driving radical innovation across multiple industries. Now, a similar hacker movement is emerging in biotech—what we call the FDA-Free Society. At DoraHacks, this is our core focus in the life sciences. We believe that medical and biotech innovation should not be held hostage by bureaucracy. Instead, it should be free to evolve at the pace of technological progress.
The FDA: The Biggest Bottleneck to Biotech Innovation
For decades, the Food and Drug Administration (FDA) has been the single greatest obstacle to progress in medicine and biotech. While ostensibly designed to ensure safety and efficacy, in reality, it has functioned as an entrenched bureaucracy that stifles innovation.
1. A Broken Approval Process
The FDA operates on timelines that make no sense in an era of exponential technological growth. Getting a new drug or therapy to market takes 10-15 years. By the time a breakthrough therapy is approved, entire generations of patients have already suffered or died waiting.
2. Astronomical Compliance Costs
Clinical trials under FDA oversight are prohibitively expensive. This eliminates most startups from even attempting disruptive innovation. Many promising therapies never see the light of day—not because they don’t work, but because the cost of compliance is too high.
3. The FDA-Pharma Cartel
The regulatory framework is not neutral—it overwhelmingly benefits Big Pharma. The FDA’s Byzantine approval system creates a protective moat for legacy pharmaceutical companies, while smaller biotech startups are crushed under compliance burdens. The result? Less innovation, more monopolization, and fewer choices for patients.
Market-Driven Biotech Innovation Is the Future
When bureaucracies control innovation, progress slows. When markets drive innovation, progress accelerates.
1. Let the Market Decide What Works
Why should government regulators dictate which treatments are available? In an open system, patients and doctors—not bureaucrats—should determine which therapies succeed or fail.
2. The "Right to Try" Loophole Proves the FDA Is Obsolete
The U.S. Right to Try Act already allows terminally ill patients to access experimental drugs before FDA approval. This proves an essential truth: The regulatory state is holding back life-saving treatments. If dying patients can bypass the FDA, why can’t everyone?
3. Startups Move Faster Than Bureaucracies
The success of mRNA technology was not driven by the FDA—it was driven by startups operating at the speed of the market. This is a template for the future. Regulation slows innovation. Entrepreneurs accelerate it.
BioHack: Breaking Free From the FDA’s Grip
One of the most important frontiers in biotech today is anti-aging and longevity research. Yet, the FDA has no framework for approving treatments that extend life. The result? A regulatory death sentence for one of the most transformative fields of medicine.
1. Biotech Needs FDA-Free Experimental Zones
In the future, biotech R&D should function like open-source software—free, experimental, and outside the reach of outdated regulators. We need FDA-Free labs, FDA-Free clinical trials, and FDA-Free therapeutics.
2. Decentralized Healthcare Will Disrupt Big Pharma
A new era of decentralized biotech is emerging—privately funded labs, medical DAOs, and startup-driven healthcare systems. The power to determine the future of medicine must shift away from centralized bureaucracies and Big Pharma toward entrepreneurs, scientists, and patients.
Conclusion: The Hacker Revolution in Biotech Is Here
The FDA-Free Society is not a thought experiment. It is an inevitability. Innovation will not be stopped. DoraHacks is committed to making BioHack a reality.
-
 @ 8ff74724:5eedde0e
2025-03-23 01:25:30
@ 8ff74724:5eedde0e
2025-03-23 01:25:30Birds
Birds simply don't give a shit.
They don't care about you.
They don't love you.
They only want one thing.
Seeds.
-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ 4925ea33:025410d8
2025-03-22 19:30:21
@ 4925ea33:025410d8
2025-03-22 19:30:21O ato de estudar pode ser desafiador, pois precisamos vencer obstáculos como distrações, falta de concentração e baixa energia. Essas dificuldades são comuns na vida dos estudantes e costumam ser os principais fatores que prejudicam o aprendizado.
Mesmo dedicando longas horas aos estudos, esses desafios podem comprometer a produtividade, tornando o esforço pouco eficaz. É nesse contexto que a Aromaterapia surge como uma solução natural e eficaz.
Os óleos essenciais têm um grande potencial para atuar na concentração, no estímulo da memória e no aumento da clareza mental. Ou seja, quando utilizados de forma estratégica, podem potencializar significativamente o desempenho nos estudos.
Quais são os benefícios dos óleos essenciais para os estudos?

No universo dos aromas, cada óleo essencial possui propriedades únicas. De forma geral, podemos destacar os seguintes benefícios:
-
Estimulação cognitiva
-
Aumento da memória
-
Redução do estresse e da ansiedade
-
Aumento da energia e disposição
-
Estímulo à criatividade
-
Melhora da concentração
1. Estimulação Cognitiva
Os óleos essenciais de alecrim e hortelã-pimenta estão entre os principais aliados da estimulação cognitiva. Eles atuam diretamente no sistema límbico, a região do cérebro responsável pela memória, emoções e aprendizado.
2. Aumento da Memória
O aumento da memória está diretamente relacionado à circulação sanguínea cerebral, que favorece a retenção de informações. O óleo essencial de hortelã-pimenta é especialmente eficaz nesse processo, pois atua como vasodilatador, aumentando o fluxo sanguíneo para o cérebro e melhorando a capacidade de memorização.
3. Redução do Estresse e da Ansiedade
Para reduzir o estresse e a ansiedade antes e durante os estudos, os óleos de lavanda, camomila e ylang-ylang são altamente recomendados, pois reduzem os níveis de cortisol (hormônio do estresse). No entanto, é importante usá-los com cautela, pois possuem propriedades sedativas e podem induzir ao sono caso sejam usados em excesso durante os estudos.
4. Aumento da Energia e Disposição
A energia e a disposição para os estudos estão relacionadas à produção de dopamina e serotonina, neurotransmissores que promovem o bem-estar e a motivação. Os óleos cítricos, como limão, laranja doce e grapefruit, estimulam essas substâncias, ajudando a reduzir a fadiga mental e proporcionando mais vigor para o aprendizado.
5. Estímulo à Criatividade
A criatividade está associada à imaginação, abstração e inovação. Para estimular esse processo, é indicado o uso de óleos essenciais que atuam no sistema límbico de maneira introspectiva, como o óleo essencial de sândalo, que favorece a conexão com novas ideias e insights criativos.
6. Melhora da Concentração
A concentração depende da oxigenação cerebral e da ativação do sistema nervoso simpático, que aumenta a atenção e o estado de alerta. O óleo essencial de eucalipto é um dos mais eficazes nesse aspecto, pois melhora a respiração e promove maior clareza mental.
Como usar a Aromaterapia na hora do exame?

- Na véspera da prova -
Antes de dormir, utilize 1 a 2 gotas de óleo essencial de lavanda ou camomila no travesseiro. Isso ajudará a ter um sono reparador e reduzir a ansiedade para o dia seguinte.
- No dia do exame -
Ao acordar:
Inale 1 a 2 gotas de óleo de hortelã-pimenta ou limão para ativar o cérebro e aumentar o estado de alerta.
Durante o banho:
Misture 3 gotas de óleo de alecrim ou laranja doce ao seu sabonete líquido para estimular a concentração.
Antes da prova:
Aplique um creme corporal energizante, feito com a seguinte diluição:
5 gotas de óleo essencial de alecrim
3 gotas de hortelã-pimenta
2 gotas de limão
Misture em 10 g de creme neutro e aplique nos pulsos e têmporas.
Durante a prova:
Se sentir distração ou fadiga mental, aplique 1 gota de óleo essencial de alecrim e 1 gota de hortelã-pimenta na região dos ombros da sua camiseta. Assim, você poderá inalar discretamente e recuperar o foco.
Essas foram as minhas dicas sobre como a Aromaterapia pode potencializar o seu desempenho nos estudos. Experimente e sinta a diferença!
Boa prova!
-
-
 @ 46fcbe30:6bd8ce4d
2025-03-22 15:21:53
@ 46fcbe30:6bd8ce4d
2025-03-22 15:21:531. Introduction
In decentralized systems like Nostr, preserving privacy and ensuring censorship resistance are paramount. However, the inherent design ethos opens the platform to multiple vulnerabilities, chief among them being the susceptibility to Sybil attacks. The problem space is not only technical but also socio-economic, where user privacy and ease-of-use must be balanced against mitigations that impose friction on identity creation actions.
This report details a multi-faceted research analysis into Sybil resistance mechanisms, drawing analogies from contemporary decentralized identity systems, cryptographic protocols, and economic disincentives. We incorporate detailed insights from diverse independent research streams, outlining both established and novel approaches, and present a series of design recommendations for Nostr. The analysis is targeted at highly experienced analysts and researchers, with comprehensive details on both the cryptographic primitives used and the overall system architectures.
2. Background: The Threat of Sybil Attacks in Decentralized Systems
2.1. Sybil Attacks Defined
A Sybil attack involves a single adversary generating a multitude of pseudonymous identities to unduly influence network decisions, voting mechanisms, or content dissemination processes. In systems designed for censorship resistance, where anonymity is embraced, such attacks are especially daunting because traditional verification methods are not readily applicable.
2.2. The Unique Challenges in Nostr
Nostr is celebrated for its emphatic commitment to censorship resistance and privacy. This design choice, however, leads to several inherent challenges:
- Weak Identity Verification: Mechanisms like nip5, a simple email-like verification protocol, lack robustness and are vulnerable in environments where linking multiple pseudonymous identities is trivial.
- Economic Incentives: Systems using zaps (small value transactions or tips) intend to add cost to malicious actions but struggle with effective proof of expenditure. In some instances, attackers may even benefit from a net positive revenue.
- Association Networks: Existing follow systems provide decentralized webs of association; however, they do not imply a real trust framework, leaving only superficial links among identities.
The dual objectives of achieving ease-of-use while robustly mitigating Sybil attacks requires a careful, in-depth analysis of multiple design trade-offs.
3. Detailed Analysis of Existing Mechanisms and Proposed Enhancements
In our research, several proposals and implementations have emerged to address the Sybil-resistance conundrum. We examine these solutions in detail below.
3.1. Cryptographic and Identity-Based Approaches
3.1.1. Aut-CT with Curve Trees
One of the notable approaches employs the Aut-CT mechanism which leverages Curve Trees. Key insights include:
- Mechanism: Constructing an algebraic analog of a Merkle tree with curve-based keys.
- Verification Efficiency: Achieves logarithmic verification times (typically 40–70 ms) even for large keysets (from 50K to over 2.5M keys).
- Proof Size: Consistently maintains a proof size of around 3–4 kB, making it effective for low-bandwidth scenarios.
- Key Image: The integrated DLEQ-based method produces a key image that binds a proof to a hidden key, preventing fraudulent re-use of tokens.
Implication: This method, while promising, requires integration sophistication. It can potentially be adapted for Nostr to ensure that each identity is backed by a verifiable, anonymous proof of ownership—raising the cost of forging or duplicating identities.
3.1.2. Economic Disincentives and Token Burning
In the realm of cryptocurrency mixers, enforcing an economic cost for generating identities has seen traction. The following methods are prominent:
- Token Burning/Deposit Mechanisms: Users deposit funds that serve as a bond. Forging multiple identities becomes economically prohibitive if these tokens are sacrificial.
- Time Locks and Coin-Age Restrictions: By enforcing waiting periods or requiring funds to ‘age’, systems ensure that rapid, mass identity creation is deterred.
- Fidelity Bonds: Users risk losing bonds if identified as malicious, creating a strong economic disincentive.
Observation: Nostr could potentially adopt analogous economic primitives that impose a non-trivial cost on identity creation, helping to scale the disincentive to the level required for a system where anonymity is paramount.
3.1.3. Decentralized Identity Systems
A comparative analysis of identity systems, both centralized and decentralized, underscores the following:
- Centralized Systems (LDAP, OAuth, etc.): While scalable, they inherently conflict with the decentralized and censorship-resistant philosophy of Nostr.
- Decentralized Systems (uPort, Hyperledger Indy, etc.): These systems leverage blockchain technologies and zero-knowledge proofs to ensure self-sovereign identity management. However, they often require complex deployments and higher operational overhead.
Trade-Off Assessment: Implementing a fully decentralized identity system in Nostr must balance ease-of-use with strong cryptographic assurances. A layered approach—using decentralized identifiers with optional verifications—may yield optimal usability without sacrificing security.
3.2. Protocol-Specific Countermeasures
3.2.1. Rechained Protocol
The Rechained protocol introduces a deposit-based identity generation mechanism in IoT and mobile ad hoc networks. Here are its salient points:
- Deposit Transaction: Each identity is tied to a deposit transaction on a public blockchain, such as Bitcoin or Ethereum.
- Parameterization: Parameters like minHeight, minDifficulty, and amounts ensure that each identity requires a certain financial threshold to be met.
- Verification Complexity: Though proof sizes are modest (10–50 KB) and verification times are around 2 seconds, these are acceptable trade-offs on modern consumer-grade devices.
Application Prospects: If Nostr could integrate a variant of Rechained, it may allow identities to be tied to a verifiable deposit, thus raising the cost baseline for attackers. Such integration must ensure user-friendliness and minimal friction during onboarding.
3.2.2. Sysname Decentralized Identity Scheme
Sysname presents an innovative approach with additional privacy-preserving features:
- Selective Disclosure: It allows users to reveal only non-identifying attributes proving compliance with certain predicates without exposing their full identity.
- Chain-Pinned Identifiers: Aggregates multiple pseudonyms to a single on-chain record, reducing the ease with which an attacker can use disparate identities without accountability.
- Key Recovery: Enables users to refresh public keys and recover lost keys, which bolsters user trust and system resilience.
Consideration: Integrating aspects of sysname within Nostr could offer both enhanced privacy and Sybil resistance, yielding a balance between security and user independence. Enhanced key recovery also addresses the usability concerns evidenced by historical failures in PGP adoption.
3.3. Behavioral Analysis and Anomaly Detection
As an additional countermeasure, behavioral analysis can serve as a secondary layer of defense. Given the evolving sophistication of bots, a cat-and-mouse game inevitably ensues:
- Machine Learning Based Detection: Frameworks like a deep intrusion detection system (DIDS) combined with blockchain smart contracts can help identify anomalous posting behaviors. For example, integrations using Particle Swarm Optimization–Gravitational Search Algorithm (ePSOGSA) with deep autoencoders have proven accurate on established benchmarks.
- Economic Implications: By analyzing behavior, the systems can prioritize identities that have accrued economic transactions (like zaps) that match genuine user behavior over automated, bot-like patterns.
- Limitations: While promising, such systems introduce computational overhead and may yield false positives, so the implementation must be cautiously engineered with appropriate fail-safes.
4. Trade-Offs and Comprehensive Evaluation
4.1. Usability vs. Security
One of the central themes in designing defenses against Sybil attacks on Nostr is balancing ease-of-use with robust security. A highly secure system that remains cumbersome to use (akin to the historical PGP deployment) may fail adoption. Conversely, ease-of-use without economic or cryptographic Assurance opens the door to cost-free identity creation and abuse.
- Economic Approaches: Impose a direct cost on identity creation but must be calibrated to avoid excluding well-intentioned users, particularly newcomers or those with limited funds.
- Cryptographic Protocols: Solutions like Aut-CT and sysname offer advanced cryptographic proofs with minimal overhead in verification but could require more sophisticated client implementations.
- Behavioral Analysis: Acts as a safety net but must be continuously updated as adversaries evolve their bot strategies.
4.2. Privacy Implications
Every mechanism proposed must be evaluated in terms of its ability to preserve user privacy. Nostr’s value proposition rests on its censorship resistance and privacy-preserving design. Therefore:
- Selective Disclosure Protocols: Techniques that allow for proving predicates without full identity revelation should be prioritized (as seen in sysname).
- Decentralized Identity Aggregation: Methods that tie multiple pseudonyms to a single verifiable chain of evidence (enhancing accountability) can reduce risk without compromising anonymity.
- Economic Proof Versus User Balance: The economic barriers should not expose additional metadata that can be linked back to users. Hence, anonymizing tokens and cryptographic blinding techniques need to be integral to the design.
5. Proposed Comprehensive Strategy for Nostr
Based on the research, a multi-layered defense strategy is recommended. It incorporates both cryptographic assurances and economic disincentives while integrating behavioral analysis. The following blueprint emerges:
5.1. Implementation Blueprint
- Integration of Curve Tree-Based Aut-CT Proofs:
- Require each new identity creation to be validated via a Curve Tree-based proof of key ownership. This approach leverages zero-knowledge proofs and ensures logarithmic verification times, thus scalable even for a large user base.
-
Address token re-use and fake identity creation by integrating key images as established in the Aut-CT mechanism.
-
Economic Deposit Mechanism (Inspired by Rechained):
- Incorporate a lightweight deposit mechanism where users must commit a small deposit, recorded on a public blockchain. This deposit acts as a minimum hurdle for each identity and may be partially refundable upon earning trust.
-
Experiment with dynamic deposit sizes based on network load and risk assessments, ensuring that the economic threshold is both feasible and deterring.
-
Selective Disclosure and Pseudonym Aggregation (Adapting Sysname Principles):
- Allow users to prove characteristics about their identities (age, locality, etc.) without divulging full identifying details.
-
Aggregate multiple pseudonyms provided by the same user on-chain, using cryptographic commitments that both link identities and allow selective disclosure.
-
Optional Layer: Economic and Behavioral Analytics:
- Deploy a deep anomaly detection layer using machine learning techniques on posting behavior, ensuring that anomalous activities (e.g., rapid posting similar to bots) are flagged.
- Integrate smart contract-based economic triggers that penalize suspicious behavior while maintaining user privacy.
5.2. Addressing Adoption and Usability Concerns
- User Experience (UX): The proposed solutions must be integrated transparently into client applications. Much like improved versions of PGP aim to streamline key management, Nostr clients should embed these cryptographic protocols without requiring manual intervention.
- Modular Onboarding: Allow users to opt into various levels of proof. Early adopters may use lightweight methods, with a progressive enhancement available for those seeking higher assurance as they interact more within the network.
- Wallet and Key Management Integration: Leverage existing wallet infrastructures to ease the economic deposit and key recovery processes, drawing user confidence from familiarity with mainstream crypto applications.
6. Future Work and Speculative Technologies
While the proposals above are based on current and emergent technologies, additional research can further refine these approaches:
- Adaptive Economic Models: Future work can explore dynamic, context-aware deposit requirements that adjust based on network activity, risk profiles, and even market conditions.
- Quantum-Resistant Cryptography: As quantum computing progresses, integrating quantum-resistant algorithms in curve-tree constructions will become imperative for long-term viability.
- Interoperable Decentralized Identifiers (DIDs): Creating cross-system standards for identity verification may allow Nostr to interface with other decentralized platforms, enhancing the overall security ecosystem.
- Advancements in Zero-Knowledge Proofs (ZKPs): Considering high-level academic research on ZKPs, such as bulletproofs and recursive ZKPs, can further improve both the scalability and succinctness of cryptographic proofs required for identity validation.
Speculative Note: As adversaries adapt, we may see the emergence of hybrid systems where off-chain reputation systems are cryptographically linked to on-chain proofs, creating a multi-dimensional defense that continuously evolves through machine learning and adaptive economic incentives.
7. Conclusion
Mitigating Sybil attacks on Nostr necessitates a proactive, multi-layered approach combining advanced cryptographic techniques, economic disincentives, decentralized verification mechanisms, and behavioral analytics. The proposals detailed in this report aim to reinforce Nostr’s resilience while maintaining its foundational commitment to privacy and censorship resistance.
By integrating Curve Tree-based proofs, economic deposit mechanisms, and selective disclosure methods, Nostr can build a robust identity framework that is both user-friendly and resistant to abuse. Continued research into adaptive economic models and quantum-resistant cryptographic techniques will ensure that the system remains secure in the evolving landscape of decentralized networks.
Thorough evaluation of trade-offs, user experience enhancements, and iterative testing on live networks will be critical. This report serves as a foundational blueprint for further exploration and eventual deployment of sophisticated Sybil defense mechanisms within Nostr.
8. References and Further Reading
While the source of ideas is drawn from numerous research efforts and academic papers, key references include:
- Aut-CT Leveraging Curve Trees and Bulletproof Proofs
- Economic mitigation strategies in cryptocurrency mixers
- Comparative studies of decentralized identity systems (uPort, Hyperledger Indy, etc.)
- Rechained protocol research by Bochem and Leiding for IoT networks
- Sysname scheme for privacy-preserving decentralized identifiers
- Deep intrusion detection systems applied to decentralized social networks
(Additional in-depth academic references can be located within the research literature on arXiv and major cryptographic conferences.)
Prepared by an expert research analyst, this report is intended to provide detailed insights and a strategic roadmap for implementing Sybil-resistant identities on Nostr while retaining user ease-of-use and privacy-centric features.
Sources
- https://delvingbitcoin.org/t/anonymous-usage-tokens-from-curve-trees-or-autct/862
- https://delvingbitcoin.org/t/anonymous-usage-tokens-from-curve-trees-or-autct/862/2
- https://www.imperva.com/learn/application-security/sybil-attack/
- https://eprint.iacr.org/2019/1111.pdf
- https://www.smartsight.in/technology/what-to-know-about-sybil-attacks/
- https://www.researchgate.net/publication/363104774_Comparative_Analysis_of_Decentralized_Identity_Approaches
- https://www.researchgate.net/publication/331790058_A_Comparative_Analysis_of_Trust_Requirements_in_Decentralized_Identity_Management
- https://www.mdpi.com/1999-5903/17/1/1
- https://github.com/WebOfTrustInfo/rwot5-boston/blob/master/topics-and-advance-readings/Framework-for-Comparison-of-Identity-Systems.md
- https://www.researchgate.net/publication/367557991_The_Cost_of_Sybils_Credible_Commitments_and_False-Name_Proof_Mechanisms
- https://pmc.ncbi.nlm.nih.gov/articles/PMC8125832/
- https://www.nervos.org/knowledge-base/sybil_attacks_consensus_mechanisms_(explainCKBot)
- https://arxiv.org/html/2307.14679v2
- https://www.sciencedirect.com/science/article/pii/S1084804523001145
- https://www.sciencedirect.com/science/article/pii/S2096720924000460
- https://medium.com/@sshshln/mitigating-identity-attacks-in-defi-through-biometric-based-sybil-resistance-6633a682f73a
-
 @ 04ff5a72:22ba7b2d
2025-03-19 03:25:28
@ 04ff5a72:22ba7b2d
2025-03-19 03:25:28The Evolution of the "World Wide Web"
The internet has undergone a remarkable transformation since its inception, evolving from a collection of static pages to a dynamic, interconnected ecosystem, and now progressing toward a decentralized future. This evolution is commonly divided into three distinct phases: Web 1, Web 2, and the emerging Web 3. Each phase represents not only technological advancement but fundamental shifts in how we interact with digital content, who controls our data, and how value is created and distributed online. While Web 1 and Web 2 have largely defined our internet experience to date, Web 3 promises a paradigm shift toward greater user sovereignty, decentralized infrastructure, and reimagined ownership models for digital assets.
The Static Beginning: Web 1.0
The first iteration of the web, commonly known as Web 1.0, emerged in the early 1990s and continued until the late 1990s. This period represented the internet's infancy, characterized by static pages with limited functionality and minimal user interaction[1]. At the core of Web 1 was the concept of information retrieval rather than dynamic interaction.
Fundamental Characteristics of Web 1
During the Web 1 era, websites primarily served as digital brochures or informational repositories. Most sites were static, comprised of HTML pages containing fixed content such as text, images, and hyperlinks[1]. The HTML (Hypertext Markup Language) provided the structural foundation, while CSS (Cascading Style Sheets) offered basic styling capabilities. These technologies enabled the creation of visually formatted content but lacked the dynamic elements we take for granted today.
The Web 1 experience was predominantly one-directional. The majority of internet users were passive consumers of content, while creators were primarily web developers who produced websites with mainly textual or visual information[2]. Interaction was limited to basic navigation through hyperlinks, with few opportunities for users to contribute their own content or engage meaningfully with websites.
Technical limitations further defined the Web 1 experience. Information access was significantly slower than today's standards, largely due to the prevalence of dial-up connections. This constraint meant websites needed to be optimized for minimal bandwidth usage[1]. Additionally, security measures were rudimentary, making early websites vulnerable to various cyberattacks without adequate protection systems in place.
The Social Revolution: Web 2.0
As the internet matured in the late 1990s and early 2000s, a significant transformation occurred. Web 2.0 emerged as a more dynamic, interactive platform that emphasized user participation, content creation, and social connectivity[6]. This shift fundamentally changed how people engaged with the internet, moving from passive consumption to active contribution.
The Rise of Social Media and Big Data
Web 2.0 gave birth to social media platforms, interactive web applications, and user-generated content ecosystems. Companies like Google, Facebook, Twitter, and Amazon developed business models that leveraged user activity and content creation[4]. These platforms transformed from simple information repositories into complex social networks and digital marketplaces.
Central to the Web 2.0 revolution was the collection and analysis of user data on an unprecedented scale. Companies developed sophisticated infrastructure to handle massive amounts of information. Google implemented systems like the Google File System (GFS) and Spanner to store and distribute data across thousands of machines worldwide[4]. Facebook developed cascade prediction systems to manage user interactions, while Twitter created specialized infrastructure to process millions of tweets per minute[4].
These technological advancements enabled the monetization of user attention and personal information. By analyzing user behavior, preferences, and social connections, Web 2.0 companies could deliver highly targeted advertising and personalized content recommendations. This business model generated immense wealth for platform owners while raising significant concerns about privacy, data ownership, and the concentration of power in the hands of a few technology giants.
The Decentralized Future: Web 3.0
Web 3 represents the next evolutionary stage of the internet, characterized by principles of decentralization, transparency, and user sovereignty[6]. Unlike previous iterations, Web 3 seeks to redistribute control from centralized entities to individual users and communities through blockchain technology and decentralized protocols.
Blockchain as the Foundation
The conceptual underpinnings of Web 3 emerged with the creation of Bitcoin in 2009. Bitcoin introduced a revolutionary approach to digital transactions by enabling peer-to-peer value transfer without requiring a central authority. This innovation demonstrated that trust could be established through cryptographic proof rather than relying on traditional financial institutions.
Ethereum expanded upon Bitcoin's foundation by introducing programmable smart contracts, which allowed for the creation of decentralized applications (dApps) beyond simple financial transactions. This breakthrough enabled developers to build complex applications with self-executing agreements that operate transparently on the blockchain[6].
Ownership and Data Sovereignty
A defining characteristic of Web 3 is the emphasis on true digital ownership. Through blockchain technology and cryptographic tokens, individuals can now assert verifiable ownership over digital assets in ways previously impossible[6]. This stands in stark contrast to Web 2 platforms, where users effectively surrendered control of their content and data to centralized companies.
The concept of self-custody exemplifies this shift toward user sovereignty. Platforms like Trust Wallet enable individuals to maintain control over their digital assets across multiple blockchains without relying on intermediaries[5]. Users hold their private keys, ensuring that they—not corporations or governments—have ultimate authority over their digital property.
Decentralized Physical Infrastructure Networks (DePIN)
Web 3 extends beyond digital assets to reimagine physical infrastructure through Decentralized Physical Infrastructure Networks (DePIN). These networks connect blockchain technology with real-world systems, allowing people to use cryptocurrency tokens to build and manage physical infrastructure—from wireless hotspots to energy systems[7].
DePIN projects decentralize ownership and governance of critical infrastructure, creating more transparent, efficient, and resilient systems aligned with Web 3 principles[7]. By distributing control among network participants rather than centralizing it within corporations or governments, these projects bridge the gap between digital networks and physical reality.
Non-Fungible Tokens and Intellectual Property
Non-Fungible Tokens (NFTs) represent another revolutionary aspect of Web 3, providing a mechanism for verifying the authenticity and ownership of unique digital items. NFTs enable creators to establish provenance for digital art, music, virtual real estate, and other forms of intellectual property, addressing longstanding issues of duplication and unauthorized distribution in the digital realm[6].
This innovation has profound implications for creative industries, potentially enabling more direct relationships between creators and their audiences while reducing dependence on centralized platforms and intermediaries.
Nostr: A Decentralized Protocol for Social Media and Communication
Nostr (Notes and Other Stuff Transmitted by Relays) is a decentralized and censorship-resistant communication protocol designed to enable open and secure social networking. Unlike traditional social media platforms that rely on centralized servers and corporate control, Nostr allows users to communicate directly through a network of relays, ensuring resilience against censorship and deplatforming.
The protocol operates using simple cryptographic principles: users generate a public-private key pair, where the public key acts as their unique identifier, and messages are signed with their private key. These signed messages are then broadcast to multiple relays, which store and propagate them to other users. This structure eliminates the need for a central authority to control user identities or content distribution[8].
As concerns over censorship, content moderation, and data privacy continue to rise, Nostr presents a compelling alternative to centralized social media platforms. By decentralizing content distribution and giving users control over their own data, it aligns with the broader ethos of Web3—empowering individuals and reducing reliance on corporate intermediaries[9].
Additionally Nostr implements a novel way for users to monetize their content via close integration with Bitcoin's "Lightning Network"[11] -- a means by which users are able to instantly transmit small sums (satoshi's, the smallest unit of Bitcoin) with minimal fees. This feature, known as “zapping,” allows users to send micropayments directly to content creators, tipping them for valuable posts, comments, or contributions. By leveraging Lightning wallets, users can seamlessly exchange value without relying on traditional payment processors or centralized monetization models. This integration not only incentivizes quality content but also aligns with Nostr’s decentralized ethos by enabling peer-to-peer financial interactions that are censorship-resistant and borderless.
For those interested in exploring Nostr, setting up an account requires only a private key, and users can begin interacting with the network immediately by selecting a client that suits their needs. The simplicity and openness of the protocol make it a promising foundation for the next generation of decentralized social and communication networks.
Alternative Decentralized Models: Federation
Not all Web 3 initiatives rely on blockchain technology. Platforms like Bluesky are pioneering federation approaches that allow users to host their own data while maintaining seamless connectivity across the network[10]. This model draws inspiration from how the internet itself functions: just as anyone can host a website and change hosting providers without disrupting visitor access, Bluesky enables users to control where their social media data resides.
Federation lets services be interconnected while preserving user choice and flexibility. Users can move between various applications and experiences as fluidly as they navigate the open web[10]. This approach maintains the principles of data sovereignty and user control that define Web 3 while offering alternatives to blockchain-based implementations.
Conclusion
The evolution from Web 1 to Web 3 represents a profound transformation in how we interact with the internet. From the static, read-only pages of Web 1 through the social, data-driven platforms of Web 2, we are now entering an era defined by decentralization, user sovereignty, and reimagined ownership models.
Web 3 technologies—whether blockchain-based or implementing federation principles—share a common vision of redistributing power from centralized entities to individual users and communities. By enabling true digital ownership, community governance, and decentralized infrastructure, Web 3 has the potential to address many of the concerns that have emerged during the Web 2 era regarding privacy, control, and the concentration of power.
As this technology continues to mature, we may witness a fundamental reshaping of our digital landscape toward greater transparency, user autonomy, and equitable value distribution—creating an internet that more closely aligns with its original promise of openness and accessibility for all.
Sources
[1] What is WEB1? a brief history of creation - White and Partners https://whiteand.partners/en/what-is-web1-a-brief-history-of-creation/ [2] Evolution of the Internet - from web1.0 to web3 - LinkedIn https://www.linkedin.com/pulse/evolution-internet-from-web10-web3-ravi-chamria [3] Web3 Social: Create & Monetize with Smart Contracts - Phala Network https://phala.network/web3-social-create-monetize-with-smart-contracts [4] [PDF] Big Data Techniques of Google, Amazon, Facebook and Twitter https://www.jocm.us/uploadfile/2018/0613/20180613044107972.pdf [5] True crypto ownership. Powerful Web3 experiences - Trust Wallet https://trustwallet.com [6] Web3: Revolutionizing Digital Ownership and NFTs - ThoughtLab https://www.thoughtlab.com/blog/web3-revolutionizing-digital-ownership-and-nfts/ [7] DePIN Crypto: How It's Revolutionizing Infrastructure in Web3 https://www.ulam.io/blog/how-depin-is-revolutionizing-infrastructure-in-the-web3-era [8] Nostr: Notes and Other Stuff… https://nostr.com/ [9] Nostr: The Importance of Censorship-Resistant Communication... https://bitcoinmagazine.com/culture/nostr-the-importance-of-censorship-resistant-communication-for-innovation-and-human-progress- [10] Bluesky: An Open Social Web https://bsky.social/about/blog/02-22-2024-open-social-web [11] Wikipedia: Lightning Network https://en.wikipedia.org/wiki/Lightning_Network
-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ da0b9bc3:4e30a4a9
2025-03-22 09:34:42
@ da0b9bc3:4e30a4a9
2025-03-22 09:34:42Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/921232
-
 @ fc15d4c6:fba62950
2025-03-23 16:49:27
@ fc15d4c6:fba62950
2025-03-23 16:49:27A Post by Onjezani Kenani
Onjezani reportedly posted on social media:
So according to the Reserve Bank Governor, if a relative asks someone in the diaspora to pay school fees for their child studying abroad, in exchange for the Kwacha equivalent - that's a crime? He want's you in the diaspora to send dollars to Malawi, then your relative applies to the bank, waits endlessly, and counts themselves lucky if the fees are ever paid at all. Is this really what he wants?
Mr. Governor, Sir, the money in the diaspora is ours, not yours. We work hard for this money. Stop having ideas on how we should spend it.
An Article opposing Onjezani's view
An opinion article titled Slow down, Onjezani Kenani; help enlighten Malawians not misguiding them written by one Joe Cholinga, targeting Onjezani's social media critique, but not necessarily directly related to the above post specifically, was published through the Nyasa Times, dated November 16, 2024. Similar articles can be found on other platforms:
Dissecting this Article
The author states about Onjezani: "His mockery of the RBM’s directive is not just misguided; it is dangerously misleading" (emphasis added), yet the "facts" in the article do not mention any role or responsibility that the Malawi Government or its' financial policies may have had in this economic crisis. The author clearly points to the source of the problem on "setting the record straight":
Malawi’s foreign reserves have been severely depleted due to widespread illegal foreign exchange dealings. Commercial banks, NGOs, and even donor-funded projects have been implicated in manipulating forex allocations for private profit. This black-market trading has destabilized the kwacha, driving inflation to alarming levels and pushing the prices of basic goods through the roof.
One may easily conclude that the named entities and the market has created this chaos, but the author seems to switch around cause and effect. The question should really be:
What is the cause for this market response?
The Author goes on to justify the RBM's actions by stressing that "this is a matter of national survival" and "not a joke", he suggests that the "directive is a necessary intervention to ensure that the country’s foreign reserves are properly managed" and to (reading between the lines) protect "the livelihoods of millions of Malawians", "particularly the poor and vulnerable" against rising prices.
Ah, yes it is all about protecting the poor and the vulnerable! He is implying that the Government knows what is best for "millions of Malawians" and is able to "properly manage" resources. Millions of people who have experienced past- and present communist regimes or countries around the world may strongly disagree with this assessment.
He seems to imply that striving to save the fruits of one's labour in harder, non-inflating assets like forex instead of the inflationary Kwacha for "personal gain" is a bad or unworthy goal. One might conclude that those in charge of the RBM and the Government more broadly, lack such egocentric attributes, because the RBM (under Government control and managed by people) wishes to "properly manage" resources. Clearly politicians, public servants and government staff are not greedy, they have no aspirations to act in their own interests for their "personal gain" and would only make decisions to protect "millions of Malawians", for the greater good.
The author goes on to discredit Onjezani to have "lost his way" and criticises his comments for their "lack of substance...", "dangerous oversimplification" and "divorced from the facts". He goes on to conclude:
In Conclusion
The real danger here is that his posts could lead people to believe that the government’s economic strategies are a joke, rather than the urgent steps they are.
So this is the threat? People might stop and question the political narrative, ask difficult questions? Fascinating. Yet surely facts and truths will shine during any darker times that may lay ahead of us, removing any need for concern.
References
forex #inflation #malawi #politics
- This undated screenshot seemingly from a social media platform, circulated on WhatsApp in March 2025

- The Nyasa Times Article, dated November 16, 2024
https://www.nyasatimes.com/opinion-slow-down-onjezani-kenani-help-enlighten-malawians-not-misguiding-them/ - Wikipedia Page on Onjezani
https://en.wikipedia.org/wiki/Stanley_Onjezani_Kenani - Some writing by Onjezani
https://www.author-me.com/fict04/storyofmyfate.htm
- This undated screenshot seemingly from a social media platform, circulated on WhatsApp in March 2025
-
 @ c631e267:c2b78d3e
2025-02-07 19:42:11
@ c631e267:c2b78d3e
2025-02-07 19:42:11Nur wenn wir aufeinander zugehen, haben wir die Chance \ auf Überwindung der gegenseitigen Ressentiments! \ Dr. med. dent. Jens Knipphals
In Wolfsburg sollte es kürzlich eine Gesprächsrunde von Kritikern der Corona-Politik mit Oberbürgermeister Dennis Weilmann und Vertretern der Stadtverwaltung geben. Der Zahnarzt und langjährige Maßnahmenkritiker Jens Knipphals hatte diese Einladung ins Rathaus erwirkt und publiziert. Seine Motivation:
«Ich möchte die Spaltung der Gesellschaft überwinden. Dazu ist eine umfassende Aufarbeitung der Corona-Krise in der Öffentlichkeit notwendig.»
Schon früher hatte Knipphals Antworten von den Kommunalpolitikern verlangt, zum Beispiel bei öffentlichen Bürgerfragestunden. Für das erwartete Treffen im Rathaus formulierte er Fragen wie: Warum wurden fachliche Argumente der Kritiker ignoriert? Weshalb wurde deren Ausgrenzung, Diskreditierung und Entmenschlichung nicht entgegengetreten? In welcher Form übernehmen Rat und Verwaltung in Wolfsburg persönlich Verantwortung für die erheblichen Folgen der politischen Corona-Krise?
Der Termin fand allerdings nicht statt – der Bürgermeister sagte ihn kurz vorher wieder ab. Knipphals bezeichnete Weilmann anschließend als Wiederholungstäter, da das Stadtoberhaupt bereits 2022 zu einem Runden Tisch in der Sache eingeladen hatte, den es dann nie gab. Gegenüber Multipolar erklärte der Arzt, Weilmann wolle scheinbar eine öffentliche Aufarbeitung mit allen Mitteln verhindern. Er selbst sei «inzwischen absolut desillusioniert» und die einzige Lösung sei, dass die Verantwortlichen gingen.
Die Aufarbeitung der Plandemie beginne bei jedem von uns selbst, sei aber letztlich eine gesamtgesellschaftliche Aufgabe, schreibt Peter Frey, der den «Fall Wolfsburg» auch in seinem Blog behandelt. Diese Aufgabe sei indes deutlich größer, als viele glaubten. Erfreulicherweise sei der öffentliche Informationsraum inzwischen größer, trotz der weiterhin unverfrorenen Desinformations-Kampagnen der etablierten Massenmedien.
Frey erinnert daran, dass Dennis Weilmann mitverantwortlich für gravierende Grundrechtseinschränkungen wie die 2021 eingeführten 2G-Regeln in der Wolfsburger Innenstadt zeichnet. Es sei naiv anzunehmen, dass ein Funktionär einzig im Interesse der Bürger handeln würde. Als früherer Dezernent des Amtes für Wirtschaft, Digitalisierung und Kultur der Autostadt kenne Weilmann zum Beispiel die Verknüpfung von Fördergeldern mit politischen Zielsetzungen gut.
Wolfsburg wurde damals zu einem Modellprojekt des Bundesministeriums des Innern (BMI) und war Finalist im Bitkom-Wettbewerb «Digitale Stadt». So habe rechtzeitig vor der Plandemie das Projekt «Smart City Wolfsburg» anlaufen können, das der Stadt «eine Vorreiterrolle für umfassende Vernetzung und Datenerfassung» aufgetragen habe, sagt Frey. Die Vereinten Nationen verkauften dann derartige «intelligente» Überwachungs- und Kontrollmaßnahmen ebenso als Rettung in der Not wie das Magazin Forbes im April 2020:
«Intelligente Städte können uns helfen, die Coronavirus-Pandemie zu bekämpfen. In einer wachsenden Zahl von Ländern tun die intelligenten Städte genau das. Regierungen und lokale Behörden nutzen Smart-City-Technologien, Sensoren und Daten, um die Kontakte von Menschen aufzuspüren, die mit dem Coronavirus infiziert sind. Gleichzeitig helfen die Smart Cities auch dabei, festzustellen, ob die Regeln der sozialen Distanzierung eingehalten werden.»
Offensichtlich gibt es viele Aspekte zu bedenken und zu durchleuten, wenn es um die Aufklärung und Aufarbeitung der sogenannten «Corona-Pandemie» und der verordneten Maßnahmen geht. Frustration und Desillusion sind angesichts der Realitäten absolut verständlich. Gerade deswegen sind Initiativen wie die von Jens Knipphals so bewundernswert und so wichtig – ebenso wie eine seiner Kernthesen: «Wir müssen aufeinander zugehen, da hilft alles nichts».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 04ff5a72:22ba7b2d
2025-03-19 02:17:03
@ 04ff5a72:22ba7b2d
2025-03-19 02:17:03Web3 in the Physical World
In the evolving landscape of Web3 technologies, Decentralized Physical Infrastructure Networks (DePIN) represent one of the most promising developments, extending blockchain capabilities beyond purely digital applications into the physical world. This emerging paradigm is reshaping how we conceptualize, build, and maintain infrastructure by leveraging blockchain technology to create community-owned physical networks. As of early 2025, DePIN has grown from a theoretical concept to a multi-billion dollar sector with applications spanning telecommunications, energy, transportation, and data services.
Defining DePIN in the Web3 Ecosystem
Decentralized Physical Infrastructure Networks (DePIN) represent the convergence of blockchain technology with physical infrastructure, creating systems where real-world networks and devices are collectively owned, managed, and operated by communities rather than centralized entities[1][4]. While Web3 primarily focuses on decentralized digital applications and services, DePIN extends these principles into the physical world, marking what many consider the natural evolution of blockchain technology beyond purely online environments[3].
Core Characteristics of DePIN
At its foundation, DePIN leverages blockchain technology to decentralize the control and management of physical devices and infrastructure[2]. This approach addresses several limitations of traditional centralized infrastructure networks, including data privacy risks, service disruptions, and substantial expansion costs[2]. By distributing ownership and governance across network participants, DePIN creates more transparent, efficient, and resilient systems that align with the fundamental principles of Web3[1].
The technical architecture of DePIN combines several key elements:
- Blockchain Foundation: DePIN utilizes blockchain networks to provide transparent, secure, and immutable record-keeping for all network operations[5].
- Tokenized Incentives: Participants who contribute resources such as bandwidth, energy, or storage are rewarded with crypto tokens, creating economic incentives for network growth and maintenance[1].
- Smart Contracts: Automated agreements handle resource distribution, monitor usage, and execute payments without requiring trusted intermediaries[1][8].
- Decentralized Governance: Many DePIN projects implement DAO (Decentralized Autonomous Organization) structures for democratic decision-making among network participants[8].
How DePIN Works Within Web3
DePIN operates by incentivizing individuals and organizations to contribute physical resources to a network in exchange for tokenized rewards. This model creates a powerful alternative to traditional infrastructure deployment, which typically requires massive upfront investment by corporations or governments.
Incentive Mechanisms
The core functioning of DePIN relies on properly aligned incentive structures. When individuals contribute resources—whether it's computing power, network bandwidth, or physical devices—they receive tokens as compensation[1]. These tokens often serve multiple purposes within the ecosystem:
- Reward Distribution: Smart contracts automatically allocate tokens based on the quantity and quality of resources contributed[8].
- Governance Rights: Token holders can often participate in network decision-making, voting on upgrades, policy changes, and resource allocation[8].
- Service Access: Tokens may be required to access the network's services, creating a circular economy within the ecosystem.
Community Participation
DePIN networks are typically open and permissionless, meaning anyone can join and start contributing[3]. This drastically lowers barriers to entry compared to traditional infrastructure development, which often requires significant capital and regulatory approvals. The peer-to-peer nature of these networks makes initial infrastructure deployment much more manageable through crowdsourcing[3].
Major Applications of DePIN in the Web3 Space
As of early 2025, DePIN has expanded across numerous sectors, demonstrating the versatility of decentralized approaches to physical infrastructure. Several key applications have emerged as particularly successful implementations of the DePIN model.
Telecommunications and Connectivity
One of the most established DePIN applications is in telecommunications, where projects like Helium and Althea have created decentralized wireless and broadband networks[5][9]. Helium’s model allows individuals to set up wireless hotspots and earn HNT tokens for providing connectivity, enabling a distributed, user-powered wireless network[5]. Althea, on the other hand, focuses on decentralized internet service provision by allowing users to buy and sell bandwidth automatically, creating a self-sustaining and community-driven ISP model. This approach is particularly effective in rural and underserved regions, where traditional telecom providers may not find it economically viable to invest in infrastructure[9]. Both projects demonstrate how blockchain and incentive-driven models can disrupt conventional telecom industries and expand access to connectivity.
Energy Networks
DePIN is revolutionizing energy infrastructure through projects like Arkreen, which enables individuals and organizations to contribute excess renewable energy to a global network[5]. These decentralized energy systems allow small-scale producers to monetize their resources while contributing to more resilient and sustainable energy grids[1].
Data Storage and Computing
Decentralized storage networks like Filecoin demonstrate how DePIN principles can transform data infrastructure[5]. Users offer spare storage capacity on their devices in exchange for FIL tokens, creating a globally distributed storage network that competes with centralized cloud services[5]. This approach enhances data resilience while enabling individual participation in the digital storage economy.
Mapping and Location Services
Hivemapper represents an innovative application of DePIN in creating decentralized mapping services[6][8]. Users contribute mapping data collected through 4K dashcams while driving, building a community-owned alternative to centralized mapping services like Google Maps[6][8]. As of October 2024, Hivemapper had successfully mapped significant portions of the global road network through this crowdsourced approach[8].
Transportation and Mobility
Decentralized ride-sharing platforms like DRIFE are emerging as DePIN alternatives to traditional services like Uber and Lyft[6]. These platforms connect drivers and passengers directly through blockchain networks, reducing fees and returning more value to network participants rather than corporate intermediaries.
The Economic Impact and Market Potential of DePIN
DePIN represents a substantial and rapidly growing segment of the Web3 economy. According to industry research, the market shows significant potential for continued expansion in the coming years.
Current Market Status
As of early 2025, the DePIN sector has achieved considerable market presence:
- Market Capitalization: The current market capitalization of DePIN projects is approximately $27 billion, with a daily trading volume of $1.8 billion according to DePIN Scan[7].
- Investment Activity: Venture capitalists have recognized DePIN's potential, directing billions of dollars into the sector. Some have even created dedicated funds specifically for DePIN protocols[7].
- Growth Trajectory: DePIN has been identified as one of the major crypto trends of 2024-2025, with accelerating adoption across multiple industries[7].
Future Market Potential
The long-term outlook for DePIN appears promising according to industry analysts:
- Total Addressable Market: Messari, an independent crypto research firm, estimates DePIN's Total Addressable Market at $2.2 trillion, with projections showing growth to $3.5 trillion by 2028[6].
- Theoretical Upper Limit: In theory, DePIN's potential market extends to the entire non-digital economy, which according to World Bank figures approaches $90 trillion[6].
Benefits and Advantages of the DePIN Model
The DePIN approach offers several distinct advantages over traditional centralized infrastructure models, explaining its rapid adoption within the Web3 ecosystem.
Collective Ownership
DePIN enables community ownership of infrastructure that has traditionally been centralized under corporate or government control[5]. This democratization of ownership distributes both the benefits and responsibilities of infrastructure management among a broader group of stakeholders.
Enhanced Transparency
With DePIN, all network actions are recorded on-chain, ensuring open access to vital network data[5]. This transparency builds trust among participants and reduces the information asymmetry that often exists in centralized systems.
Improved Efficiency
By leveraging underutilized resources and implementing smart contracts, DePIN can reduce waste and administrative overhead[5]. This efficiency translates to lower costs and improved resource allocation compared to traditional infrastructure models.
Resilience Through Decentralization
Distributed networks are inherently more resilient to failures and attacks than centralized systems. By eliminating single points of failure, DePIN creates infrastructure that can continue functioning even when individual components experience issues.
Challenges and Future Considerations
Despite its promising potential, DePIN faces several significant challenges that must be addressed for widespread adoption.
Technical Scalability
Many DePIN networks struggle with scalability issues, particularly as they grow to accommodate more users and higher transaction volumes. Developing more efficient consensus mechanisms and layer-2 solutions remains an important technical challenge.
Regulatory Uncertainty
The decentralized nature of DePIN projects creates regulatory challenges in many jurisdictions. Finding the right balance between innovation and compliance with existing regulations will be crucial for long-term success.
Economic Sustainability
Creating sustainable tokenomics models that properly align incentives over the long term remains difficult. Many projects must carefully balance immediate rewards with long-term value creation to maintain network growth and stability.
Conclusion
Decentralized Physical Infrastructure Networks represent one of the most promising extensions of Web3 principles beyond purely digital applications. By leveraging blockchain technology, tokenized incentives, and community participation, DePIN is transforming how physical infrastructure is built, maintained, and governed.
As the sector continues to mature throughout 2025 and beyond, we can expect to see DePIN concepts applied to an increasingly diverse range of infrastructure challenges. The intersection of DePIN with other emerging technologies like artificial intelligence and the Internet of Things will likely create entirely new forms of infrastructure that we can barely imagine today.
The growth of DePIN underscores a fundamental shift in our approach to infrastructure—moving from centralized, corporate-controlled models toward more democratic, transparent, and community-driven systems. This transformation embodies the core promise of Web3: not just a more decentralized internet, but a more decentralized world.
Sources
[1] DePIN Crypto: How It's Revolutionizing Infrastructure in Web3 https://www.ulam.io/blog/how-depin-is-revolutionizing-infrastructure-in-the-web3-era [2] Decentralized Physical Infrastructure Network (DePIN) - arXiv https://arxiv.org/html/2406.02239v1 [3] What is DePIN - decentralized physical infrastructure network? https://limechain.tech/blog/what-is-depin [4] DePIN Explained: Bringing Real-World Devices to Web3 https://nftnewstoday.com/2025/01/28/depin-explained-bringing-real-world-devices-web3 [5] An Introduction to Decentralized Physical Infrastructure Networks ... https://www.cryptoaltruism.org/blog/infographic-an-introduction-to-decentralized-physical-infrastructure-networks-depin [6] DePIN Explained: What Are Decentralized Physical Infrastructure ... https://hackernoon.com/depin-explained-what-are-decentralized-physical-infrastructure-networks [7] Revolutionizing Infrastructure: Understanding DePINs and Their ... https://blaize.tech/blog/decentralized-physical-infrastructure-networks-depin/ [8] What is DePIN? The Future of Decentralized Physical Infrastructure ... https://osl.com/academy/article/what-is-depin-the-future-of-decentralized-physical-infrastructure-networks [9] [PDF] Althea Whitepaper v2 https://blog.althea.net/content/files/2024/06/Althea-Whitepaper-v2.0.pdf
-
 @ c631e267:c2b78d3e
2025-01-18 09:34:51
@ c631e267:c2b78d3e
2025-01-18 09:34:51Die grauenvollste Aussicht ist die der Technokratie – \ einer kontrollierenden Herrschaft, \ die durch verstümmelte und verstümmelnde Geister ausgeübt wird. \ Ernst Jünger
«Davos ist nicht mehr sexy», das Weltwirtschaftsforum (WEF) mache Davos kaputt, diese Aussagen eines Einheimischen las ich kürzlich in der Handelszeitung. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den vergangenen vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
Der deutsche WEF-Gründer hatte bei dieser Gelegenheit immer höchst lobende Worte für seine Landsmännin: 2021 erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und 2022 fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
Von der Leyens Handeln während der sogenannten Corona-«Pandemie» lobte Schwab damals bereits ebenso, wie es diese Woche das Karlspreis-Direktorium tat, als man der Beschuldigten im Fall Pfizergate die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
Jene Herausforderungen durch «Krisen epochalen Ausmaßes» werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im Global Risks Report nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
Ein «Great Mental Reset» sei die Voraussetzung dafür, dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
Der aktuelle Zustand unserer Gesellschaften ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die Rechtsstaatlichkeit stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 2dd9250b:6e928072
2025-03-22 00:22:40
@ 2dd9250b:6e928072
2025-03-22 00:22:40Vi recentemente um post onde a pessoa diz que aquele final do filme O Doutrinador (2019) não faz sentido porque mesmo o protagonista explodindo o Palácio dos Três Poderes, não acaba com a corrupção no Brasil.
Progressistas não sabem ler e não conseguem interpretar textos corretamente. O final de Doutrinador não tem a ver com isso, tem a ver com a relação entre o Herói e a sua Cidade.
Nas histórias em quadrinhos há uma ligação entre a cidade e o Super-Herói. Gotham City por exemplo, cria o Batman. Isso é mostrado em The Batman (2022) e em Batman: Cavaleiro das Trevas, quando aquele garoto no final, diz para o Batman não fugir, porque ele queria ver o Batman de novo. E o Comissário Gordon diz que o "Batman é o que a cidade de Gotham precisa."
Batman: Cavaleiro das Trevas Ressurge mostra a cidade de Gotham sendo tomada pela corrupção e pela ideologia do Bane. A Cidade vai definhando em imoralidade e o Bruce, ao olhar da prisão a cidade sendo destruída, decide que o Batman precisa voltar porque se Gotham for destruída, o Batman é destruído junto. E isso o da forças para consegue fugir daquele poço e voltar para salvar Gotham.
Isso também é mostrado em Demolidor. Na série Demolidor o Matt Murdock sempre fala que precisa defender a cidade Cozinha do Inferno; que o Fisk não vai dominar a cidade e fazer o que ele quiser nela. Inclusive na terceira temporada isso fica mais evidente na luta final na mansão do Fisk, onde Matt grita que agora a cidade toda vai saber o que ele fez; a cidade vai ver o mal que ele é para Hell's Kitchen, porque a gente sabe que o Fisk fez de tudo para a imagem do Demolidor entrar e descrédito perante os cidadãos, então o que acontece no final do filme O Doutrinador não significa que ele está acabando com a corrupção quando explode o Congresso, ele está praticamente interrompendo o ciclo do sistema, colocando uma falha em sua engrenagem.
Quando você ouve falar de Brasília, você pensa na corrupção dos políticos, onde a farra acontece,, onde corruptos desviam dinheiro arrecadado dos impostos, impostos estes que são centralizados na União. Então quando você ouve falarem de Brasília, sempre pensa que o pessoal que mora lá, mora junto com tudo de podre que acontece no Brasil.
Logo quando o Doutrinador explode tudo ali, ele está basicamente destruindo o mecanismo que suja Brasília. Ele está fazendo isso naquela cidade. Porque o símbolo da cidade é justamente esse, a farsa de que naquele lugar o povo será ouvido e a justiça será feita. Ele está destruindo a ideologia de que o Estado nos protege, nos dá segurança, saúde e educação. Porque na verdade o Estado só existe para privilegiar os políticos, funcionários públicos de auto escalão, suas famílias e amigos. Enquanto que o povo sofre para sustentar a elite política. O protagonista Miguel entendeu isso quando a filha dele morreu na fila do SUS.
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ a60e79e0:1e0e6813
2025-03-23 16:10:10
@ a60e79e0:1e0e6813
2025-03-23 16:10:10**This is a long form note test of a post that lives on my Nostr educational website Hello Nostr **
In early 2025, social media is the most common use case for Nostr (and probably the reason you're reading this). Nostr is SO much more than just social media, but that's where the bulk of the activity is, and is what I'm focusing on in this post. Even though the protocol is still so young, that has not prevented an explosion of excellent social media focused clients that predominantly coalesce around the Twitter (X) style feed, containing shorter form content, often with images, and the ability to comment, like and share.
This first steps guide showcases one of the most polished and simplest examples of such a client, Primal. Primal is a cross platform app, that also works on your computer too. The steps that follow are demonstrated on iPhone, but should be identical for Android users. There may be some topics of concepts here that are new to you, to learn more about them, check out our Nostr 101 to learn more about Nostr basics and why it matters.
You can and should explore all of the other options available to you, that's the beauty of Nostr, you're free to choose how and where to interact with your social network. No lock in. No walled gardens. True freedom.

Getting Started
-
Go to your app store and download Primal to your Android or iPhone
-
Open Primal and choose Create Account. Choose your public display name and add a short bio about yourself.
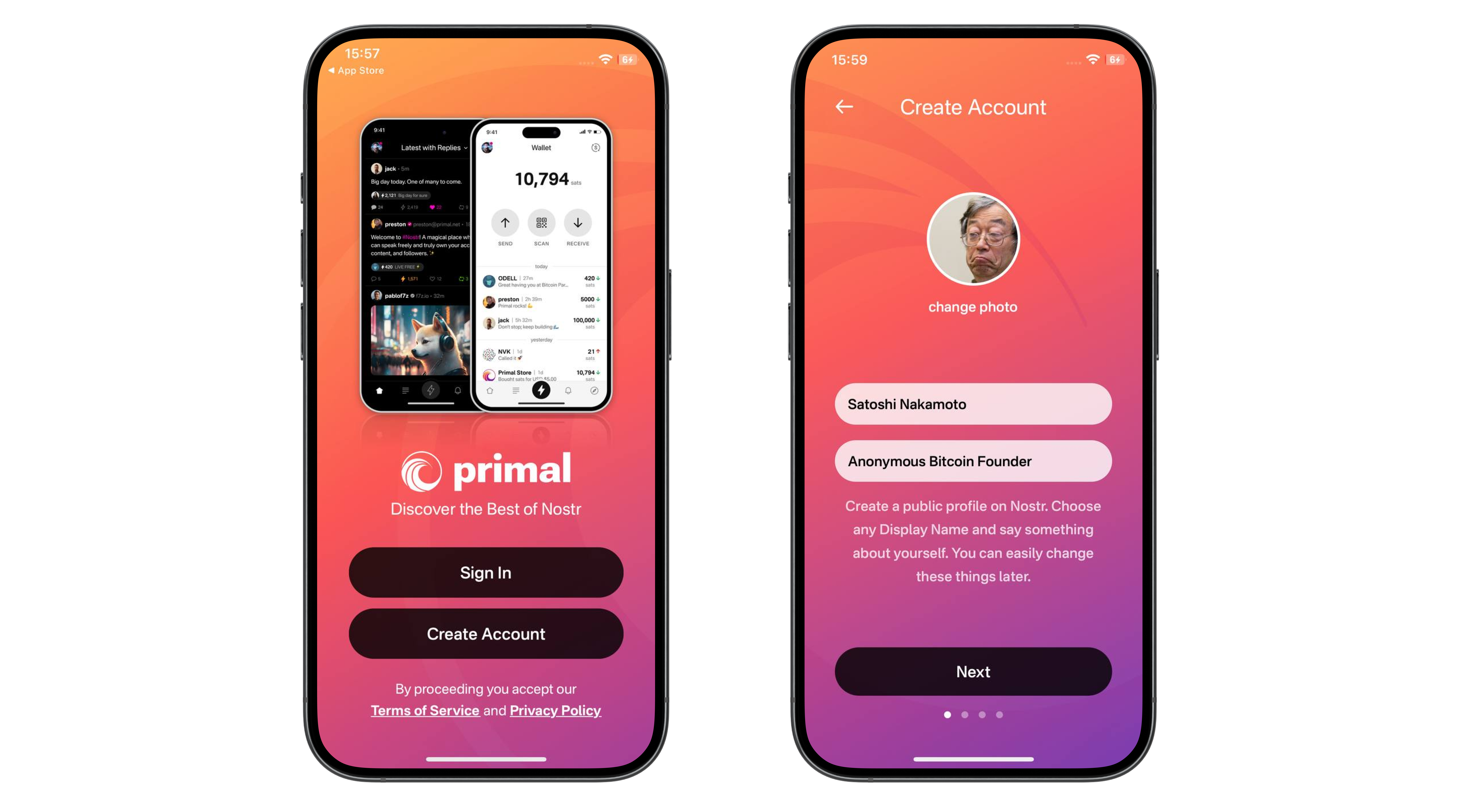
- Select your chosen interests from the list provided. This will bootstrap your feed and auto-follow a number of accounts so that your feed is not completely empty when starting out.
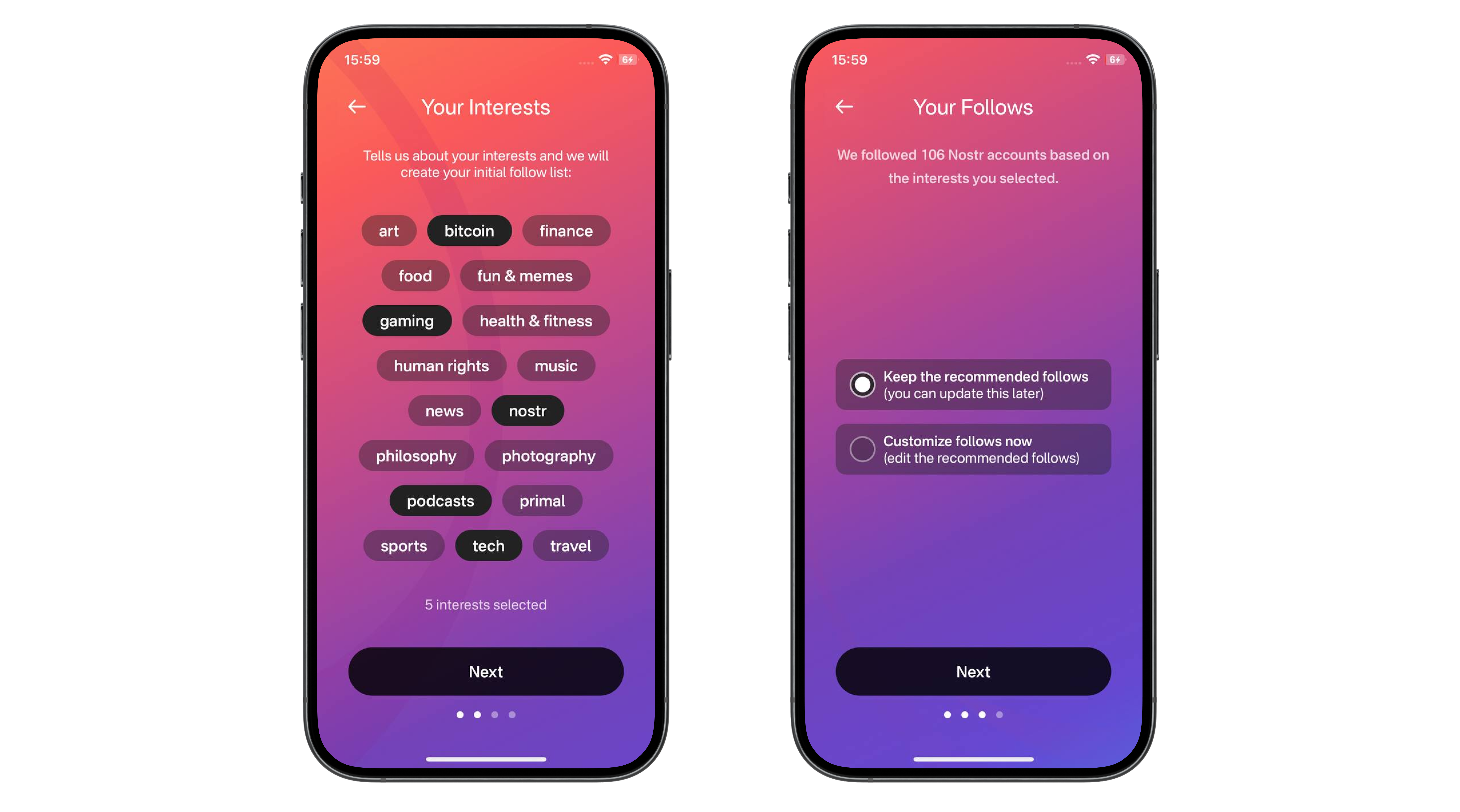
- Review your account info and tap Create Account Now. Take note of the fact that 'Your Nostr Key is available in your Account Settings'. We'll revisit this shortly.
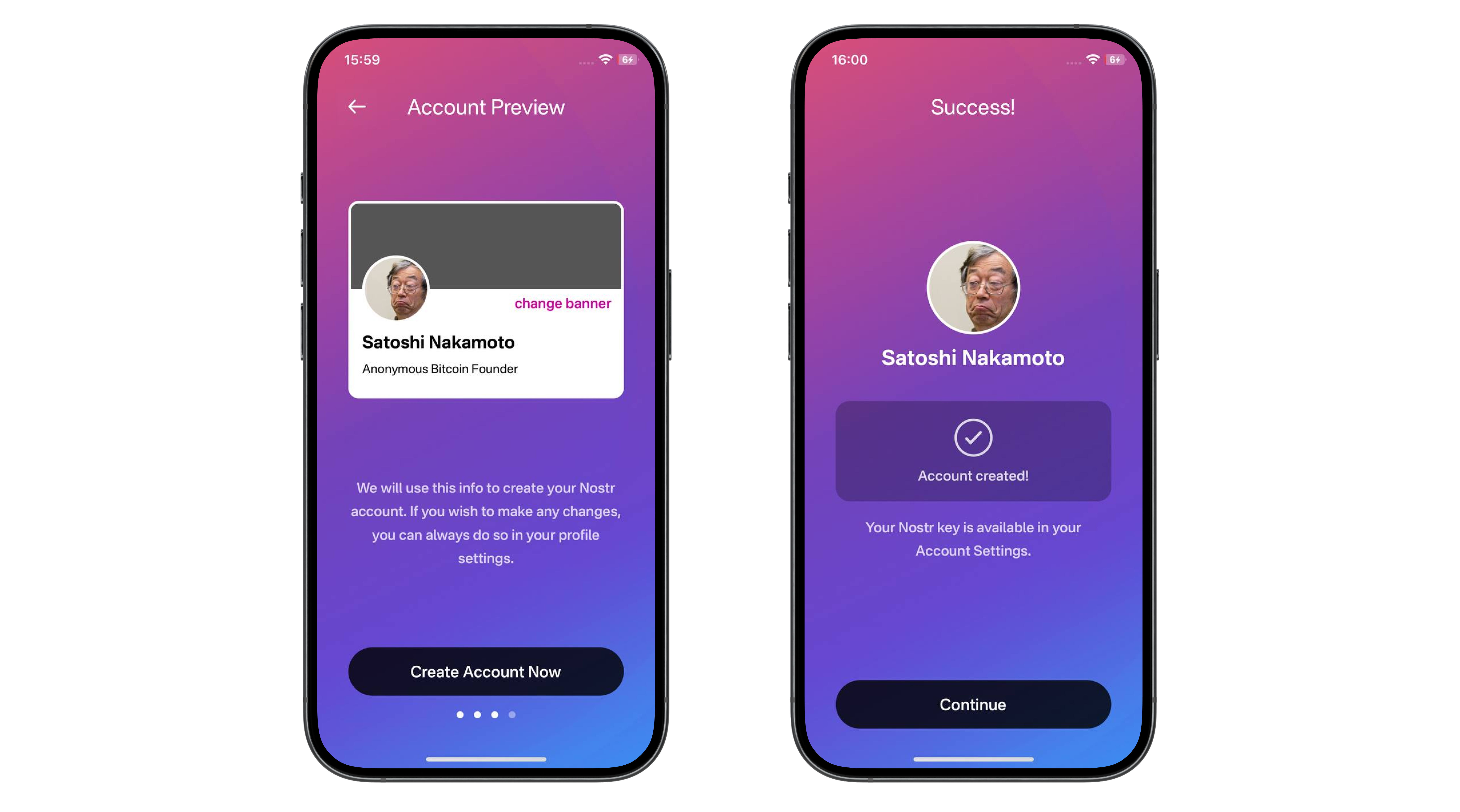
- Next is an optional step of activating the wallet feature within Primal. Having a wallet within your social client enables you to send and receive value (known as 'Zaps') in the form of Bitcoin. On Facebook and Twitter you can like a post, but it means much more to send someone fractions of a penny (or more if you like) to show your appreciation for their insights. You'll need to provide some personal information to enable the wallet, including an email address.
Using the internal wallet and purchasing sats with your credit card will tie your Nostr identity to your real ID. Think very carefully before carrying out this step.
Learn more in the detailed section at the end of this post.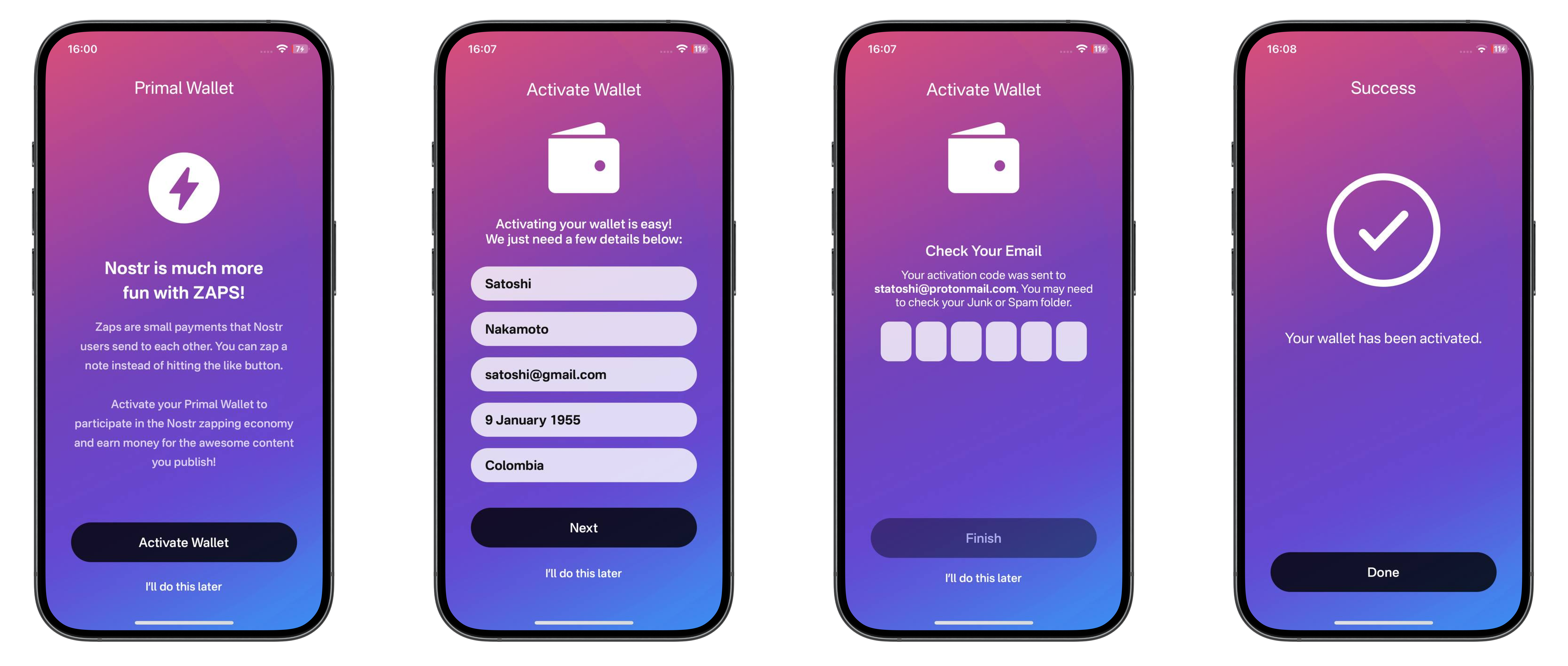
- That's it, you're now set up and ready to start sharing your thoughts, feelings and memes with the world via a decentralized and censorship resistant social network. To post your first note and say hello to the Nostr world, tap the + in the bottom right corner.
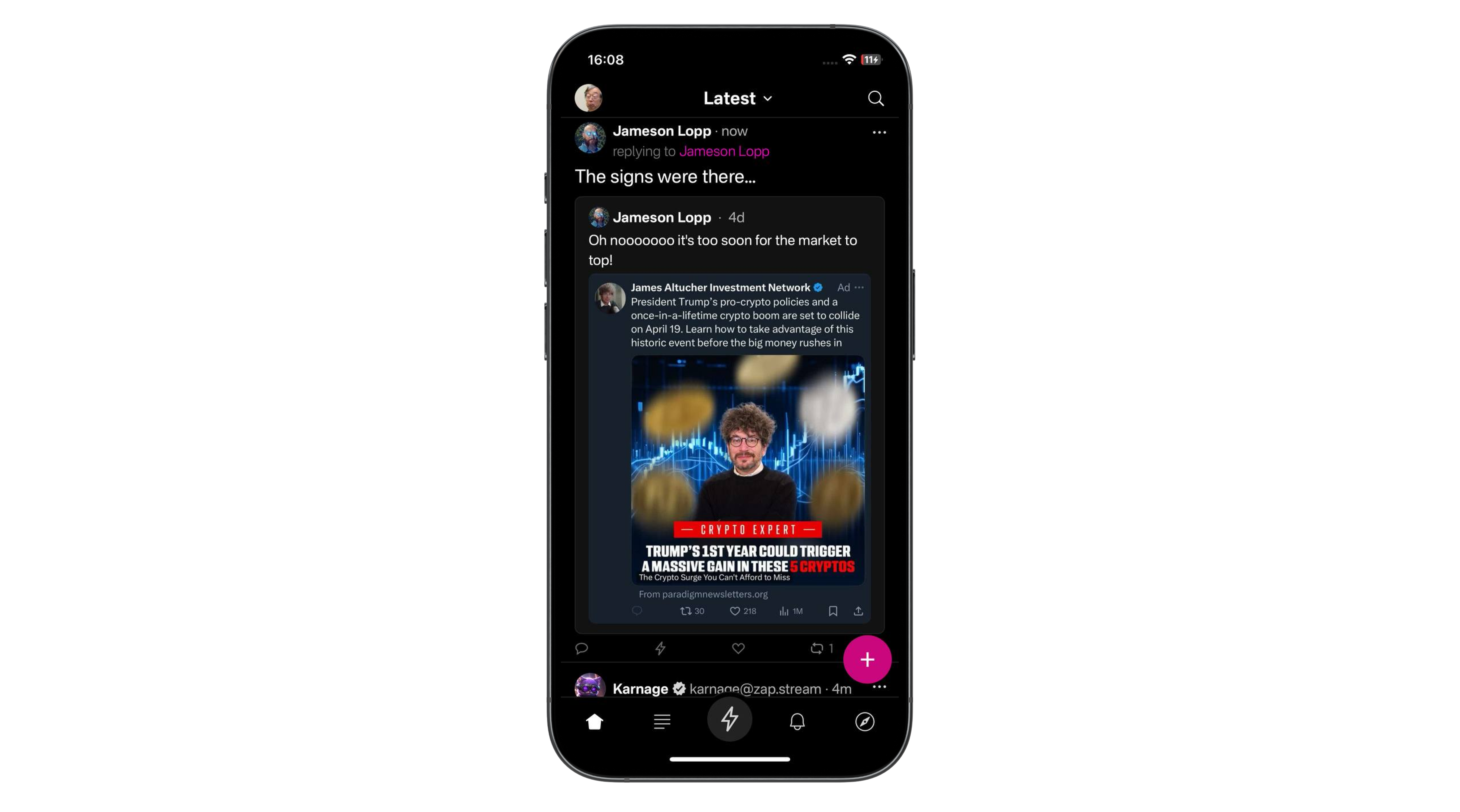
- If you activated the wallet at step 5, you might want to deposit some Bitcoin in there to allow you to send some value to your friends. There are three main ways to do this:
- Post some awesome content and have people send you value in the form of 'Zaps'
- Send some Bitcoin from a wallet you already have
- Purchase some directly within Primal
The latter is made very simple thanks to the in-app purchase feature, which allows you to purchase a small amount with the card you likely already have connected to your Apple/Google account. All you need to do is tap 'Buy Sats Now'.
- Next, let's look at the different feeds available on our home screen. Tap 'Latest' at the top of the screen and you can toggle between three different types of home feeds, great for discovering new people and content.
- Let's assume you already have some friends on Nostr and want to find and follow them. Tap the search icon in the top right corner, the enter the name of the person you want to follow. Once on their profile, simply tap the 'Follow' button.
- So you found a friend and want to start interacting with them so they know you made it over to Nostr. Simply find a note you like and choose from the different types of interactions available. From left to right they are:
- Comment
- Zap (send value from your wallet to theirs)
- Like
- Repost
- Bookmark
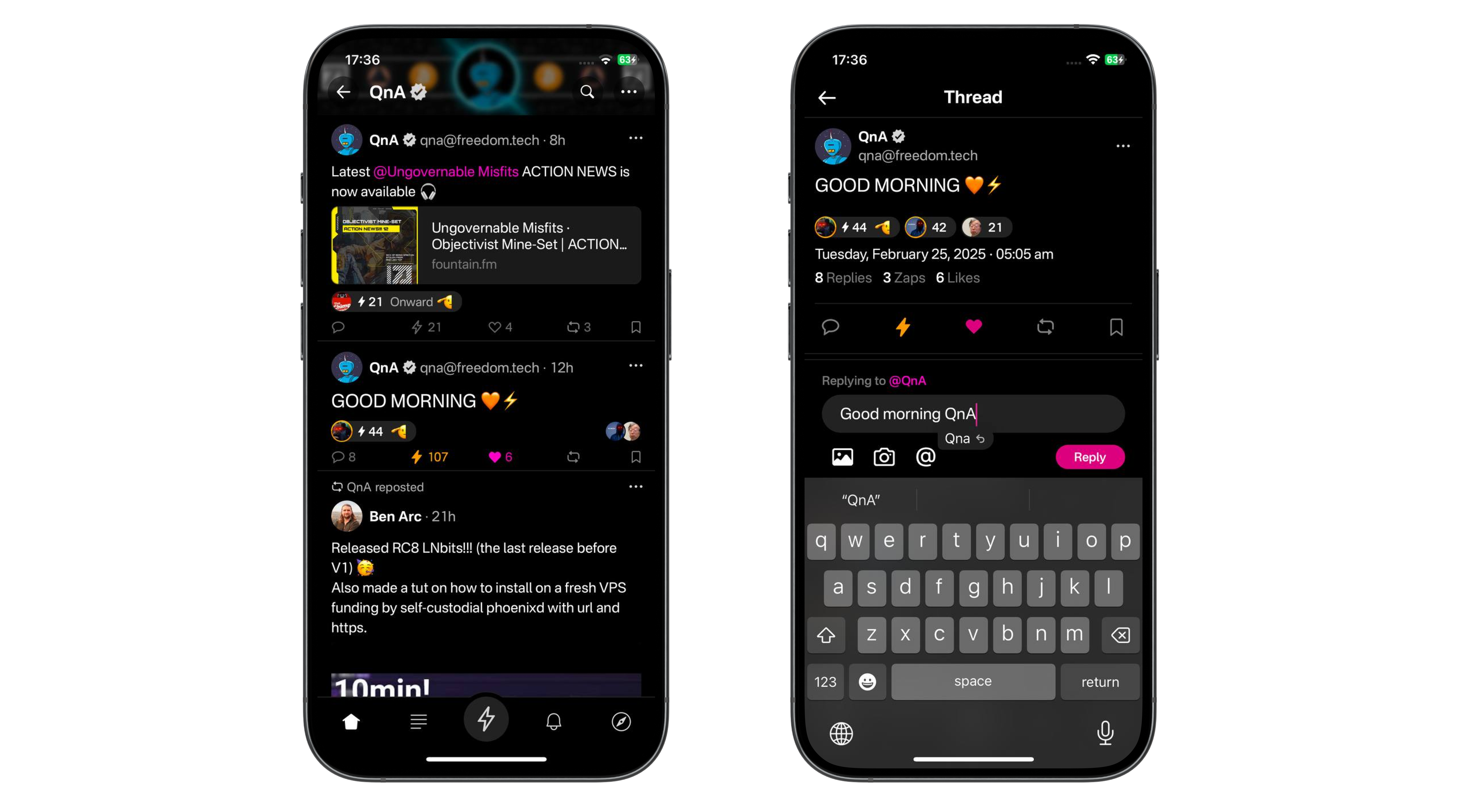
When Zapping, a single tap will send a tiny amount of 42 sats. If you want to send more, or a custom amount, tap and hold the zap button to bring up a selector menu. All default zap amounts are configurable in the app settings page.

- After you've started posting and interacting with others, you'll likely receive some notifications to tell you. Notifications can be filtered into interaction types.
- Another great way to find more people to follow and interact with is to use the discover page. To open it, tap the compass in the bottom right corner of the screen. Here you'll be able to browse different types of pre-built feeds, trending profiles, notes with large zaps and extra topics.
The Important Part
You might have noticed that throughout that setup, you were not asked for a unique username, nor were you asked for a password. So how the hell is this secure? What happens if you log out? Is your account lost forever?
This is where Nostr really starts to shine. Just like in Bitcoin or other cryptocurrencies, your Nostr account is protected by a 'Private Key'. Anyone with knowledge of the private key can access your account in any Nostr client. No private key, no access. So let's make sure you have a backup copy of it, so you can still recover access to your account in the event you lose your phone!
Tap on your profile image in the top left of the screen. Then tap Settings > Keys. Here you'll see two keys, one public and one private. Your public key is how people find you on Nostr. It is often referred to by its more technical name 'nPub' which is the prefix if the key itself. Your public key is designed to be exactly that, public!
Your private key is sometimes referred to by its technical name 'nSec' which is also the prefix of the key. Copy your private key and paste it somewhere safe and secure, in a location accessible independently from your phone, and only by you.
If you were to lose your phone, or accidentally delete the Primal app, now all you'd need to do is head back to step 1 above and choose Sign In. You'd then be asked to paste your private key, after which your profile and content would be magically restored.
Your private key can be imported into any other Nostr social client for the same result.
Things to Consider
This post has one primary focus - To get you from zero to posting and zapping in the quickest time and with the least friction. To achieve this, there are some trade-offs made that you should be aware of.
Custodial Wallet
The built in wallet is a custodial one. This means that the funds within are ultimately controlled by the developers behind Primal. They may be good actors, but you should approach the amount of money you maintain inside this wallet accordingly. If your wallet balance ever gets to a balance that makes you uncomfortable, you should send a good chunk of it out to another Bitcoin wallet where you control the keys. I recommend Phoenix or Zeus.
Those sats are never truly yours until you withdraw them to a self-custodial wallet
Wallet Privacy
If you choose to top up the wallet using the convenient in-app purchase method, you will tie that small amount of Bitcoin ownership to your Nostr account. If you Nostr account is literally your name, you might not have an issue with this, but often times people like to remain pseudonymous online. If you fall into that category, using your credit card to deposit Bitcoin into your Nostr account is not a good idea.
Android users of Primal can use an advanced technology called Nostr Wallet Connect (NWC) to connect an external Lightning wallet to their Nostr account in Primal. We'll cover this in a subsequent post.
Your private key allows you to take your profile and social network to any other client
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
-
-
 @ 6ad3e2a3:c90b7740
2025-03-21 18:21:50
@ 6ad3e2a3:c90b7740
2025-03-21 18:21:50There are two ways things happen in this world: top-down and bottom-up. Top-down is via authoritarian edict, i.e. fascism, no matter how benign-seeming. It is the government imposing a tax, incentivizing a behavior, creating a new law. Bottom-up is the organic process of people doing what interests them voluntarily, what benefits them, what they decide is best individually.
There is but one legitimate role for top-down and that is in creating good conditions for bottom up. The US Constitution is fascism in that it forces you to adhere to its edicts as the supreme law of the land. But it’s also an effective boundary creating the necessary conditions for free markets, free expression, creativity and prosperity.
All governments are fascistic in that they use force to achieve their agendas. But the best ones use only the minimum necessary force to create conditions for bottom-up prosperity. There is no other kind of prosperity.
. . .
Governments aren’t the only entities that are fascistic. Schools, corporations, institutions and individuals, almost invariably, are too. Yes, I am a fascist and very likely so are you. Don’t believe me? Do you have a voice inside your head telling you what you must get done today, evaluating your progress as a person, critiquing and coercing you into doing things that are “good” for you and avoiding ones that are “bad”? If so, you are fascist.
Why not just trust yourself to make the right choices? Why all the nudging, coaxing, coaching, evaluating and gamifying? Who is this voice, what gives it the authority, the requisite wisdom to manage your affairs? Haven’t all your shortcomings, disappointments and general dissatisfactions taken place despite its ever-presence? What makes you think you are better off for having had this in-house micromanagement?
. . .
The top-down edicts that rule our lives are by and large unnecessarily oppressive. Yes, we should create some good top-down conditions for bottom up organic thriving like buying healthy food, getting fresh air, not consuming excessive amounts of alcohol or drugs, but the moment to moment hall-monitoring, the voice that requires you to achieve something or justify your existence? That’s fascism.
. . .
The mind is a powerful tool when it comes to planning, doing math or following a recipe, but if it can’t be turned off, if it’s not just optimizing your path from A to B, but optimizing YOU, that’s fascism.
. . .
I think about the problem of human governance through this lens. I imagine everyone charged with power over a polity has an agenda, and that agenda, insofar as it requires force to achieve, is fascistic. They want it to go this way rather than that way, and some people don’t agree. The quality of leadership then is the extent to which that force is used to preserve the bottom-up freedom of the individual to pursue his interests without undue interference, either from authorities themselves or other individuals who would unduly disrupt him.
The Constitution is an excellent guideline for this, and I surely won’t be able to come up with a better one in this Substack. It’s why I support Trump’s efforts to trim the top-down public sector and return productivity to the bottom-up private one, why I support deportation of adjudicated criminals who are here illegally, but oppose removing people with green cards or on valid student visas for protesting via constitutionally protected speech.
I don’t root for politicians like they play for my favorite sports team. I root for the freedom of the individual, the possibility of a largely bottom-up society wherein prosperity is possible. And I do this while knowing it will never happen exactly the way I would like, so long as I am bound by the fascism coming from inside the house.
-
 @ 5c8a5765:4fc5edee
2025-03-22 18:38:23
@ 5c8a5765:4fc5edee
2025-03-22 18:38:23[Читать в IPFS]
Итак, детки-котлетки, сегодня мы поговорим, как ~~не~~правильно распространять агиацию. Возьмите свои любимые антифашистские стикеры и используйте этот текст как инструкцию к ним — иначе у меня голова лопнет от того, что я вижу на улицах.
Агитация
Для начала определитесь, чем вы занимаетесь: агитируете к чему-то или поддерживаете чего-то, потому что это предполагает совершенно разные подходы. Агитацией может быть призыв к анархизму, классовой борьбе, неуплате налогов, гендерному равенству и т.д. Поддержкой может быть поддержка анархической борьбы, антифашистский идей и т.д. Первое — "вербует"/приманивает новых людей к идее, второе поддерживает только тех, кто уже знаком с идеей и уже с ней согласен.
Как должна выглядеть агитация? Представьте, что некий неонацист решил за-агитировать вас в неонацизм (с учетом, что сейчас вы его не поддерживаете): в каком случае у него больше всего на это шансов? Если вы заметите на мусорном баке наклейку "бей жыдоф"? Или если вам, например, выдадут в руки грамотный агитационный текст? Поставьте себя на место читающего: агитация должна выглядеть именно так, как мог бы выглядеть материал, который хоть немного мог бы поменять ваши текущие взгляды. А именно...
1. Агитация доступна
Она не висит на задней стороне мусорки. Она не нарисована на заброшке. Обыватель не рассматривает мусорки и не ходит по заброшкам. Чтобы масса увидела вашу агитацию, она должна висеть в заметном месте.
Ещё лучше, если она висит там, где человек по внешним причинам на мгновение задерживается, и имеет время проглядеть вашу агитацию: ибо обыватель никогда не остановится у столба посреди длинной тропы, чтобы прочесть стикер.
И учтите: если место, которое вы выбрали, уже забито стикерами, вашему придётся делить привлеченное внимание с каждым остальным.
К доступности стоит также отнести то, что агитация более значительна, если она написана на самом популярном в вашей стране языке, развешивается в разных локациях (чтобы люди разного класса могли её увидеть), если вы развешиваете в туалетах — то туалетах разного гендера (и не забывайте про инвалидные кабинки!), так далее.
Лучшие места для стикеров: лифт, автобусная остановка, метро, поручен эскалатора, внешняя сторона дверцы туалета, чистое (не разрисованное или расклеенное) зеркало.Лучшие места для крупных агитационных листов или графитти: указанные выше, а также — заметные места подъездов,Лучшие места для "визиток"*: оставлять под задницей на выходе из автобуса, метро, маршрутки, на стульях, скамейках и т.д.*"Визитка" — это са-а-амый простой метод агитации: выводите нужный текст или картинки мелкими блоками на листе А4, нарезаете бумагу на кусочки "визиток" с небольшим текстом, картинкой или ссылкой, и оставляете где попало.
2. Агитация запоминается
Если вы не неонацист, какие эмоции в вас побуждает "бей жыдоф"? Вы возжелали стать неонацистом? Или это только укрепило ваши антифашистские взгляды? Или это для вас вообще никак не прозвучало?
Также для ваших противников и обывателей звучат ваши "ешь богатых!", "классовая борьба сегодня!!", "доёш онархию!!!". Это — поддержка. Уже-анархисты будут рады увидеть, что в городе есть левые активисты кроме них самих. Но это никого не переубедит и не привлечет.
А агитация привлекает. Агитация задаёт острые вопросы, которые остаются в голове. Агитация манит предложениями нового. Агитация нестереотипно предлагает.
Примеры хорошей агитации:

"Если большинство проголосует за то, чтобы ты спрыгнул(а) с вмоста, ты бы сделал(а) это? / - Может быть — если это было честным голосованием!"

"Этот телефон прослушивается - согласно законодательству США, телефонные разговоры прослушиваются без ордера или уведомленияю"

"Вы под наблюдением — текст, объясняющий тезис, и ссылка, где можно прочесть об этом подробнее."
Примеры никудышной агитации (но хорошей поддержки):



3. Агитация даёт возможность изучить больше
Хорошее правило для любой агитации: иметь ссылку на сайт, где можно найти больше информации о том, к чему агитируется. Это не обязательное, но рекомендуемое правило, ибо мало толку от человека, согласившегося с идеей анархизма и захотевшего (редчайший случай!) самостоятельно изучить больше, но не имевшего к этому простой возможности и забывшего вследствие обо всей идее.
Поддержка
А вот поддержка — ориентированная на тех, кто уже знает и уже поддерживает то, что вы любите — может быть совершенно любой. Поддержать антифашистов своего города, позлить фашистов и остаться совершенно незамеченными для обывателя — самое место для диалектики "бей жыдоф!" и "доёш онтифошизм!!".
Напоминание о безопасности
Несколько базовых напоминаний о том, что нужно помнить во время агитации:
- ОСТЕРЕГАЙТЕСЬ КАМЕР! Особенно в России! Метро, маршрутки, автобусы, учебные заведения полны ими!
- Если вас заметили гестаповцы, лучшее, что вы можете сделать — это бежать, что есть мочи.
- Шифруйте материалы, которые храните для распечаток.
- Не распечатывайте стикеры/"визитки" в публичных местах (вроде библиотек).
Спасибо за прочтение!

-
 @ d4ad3b6e:2e56e2a7
2025-03-14 00:25:26
@ d4ad3b6e:2e56e2a7
2025-03-14 00:25:26Details
- ⏲️ Prep time: 5
- 🍳 Cook time: 15
- 🍽️ Servings: 2
Ingredients
- 3 pucks of Blue Dragon Noodles (https://www.walmart.ca/en/ip/Blue-Dragon-Pad-Thai-Rice-Noodles-300g/32KU7DHN99RQ?classType=REGULAR&from=/search)
- 2 tbsp Spicy Chili Crisp (https://www.walmart.ca/en/ip/Spicy-Chili-Crisp/4FRB25574ETG?region_id=202200) per bowl
- Soy sauce to taste
- 4 stalks green onions (chopped)
- 2 Med boiled eggs
- 2 stalks of bok choy
- 2 pork chops, cooked in Korean Bulgogi Sauce (https://www.walmart.ca/en/ip/CJ-BIBIGO-KOREAN-BULGOGI-SAUCE-HOT-SPICY/0XVM7O0CBEF2?classType=REGULAR&from=/search)
Directions
- This is a simple meal you can whip together in 20 mins. Prep Time: 5 mins Cook Time: 15 mins Servings: 2 Ingredients: Spicy Noodles with Bok Choy (serves 2) 3 pucks of Blue Dragon Noodles 2 tbsp Spicy Chili Crisp per bowl Soy sauce to taste 4 stalks green onions (chopped) 2 Boiled eggs (to liking) 2 bunches of bok choy stalks 2 pork chops, diced 2 tbsp Korean Bulgogi Sauce Directions: Wash and chop the green onions, set aside. Slice the bottoms off the bok choy, separating them and placing into a colander to wash. Once washed, place dampened stalks into a pan with a lid and simmer on low for 5 to 10 minutes, to achieve a steamed effect. Or you can use your favourite method of steaming. I find the pan simple and easy to clean up afterwards. In a small pot, place your eggs in with enough water to submerge. I use an egg timer that sits in the water along with the eggs. Once they have reached your desired softness (or hardness if that’s your thing!), discard the boiling water and immediately set in cool water. In another pot, bring water to a boil and add your noodles. I use the quick cook noodles, which only take 3 mins to prepare. Drain and place in your bowls. Add the garlic chili crisp and soy sauce and mix it up. While everything is boiling, you can start to prepare your pork chops by tenderizing them and cutting them into cubes. Place in a frying pan, on med-high heat and cook until there is no more pink showing. Add the bulgogi sauce and lower the heat until it forms a nice crispy texture on the sides of the meat. For the bulgogi sauce I usually eyeball it, so you can adjust to your liking. I like mine saucy, so I do a generous pour. While the meat is simmering, start to peel your eggs, occasionally running under cold water if needed. I find if you take them off earlier on, by the time you get to it, they peel nicely without the shell sticking. In each bowl, add your egg, steamed bok choy and green onion over your noodles, then finally add the diced pork and enjoy!
-
 @ 8947a945:9bfcf626
2025-02-28 09:11:21
@ 8947a945:9bfcf626
2025-02-28 09:11:21Chef's notes
https://video.nostr.build/ea19333ab7f700a6557b6f52f1f8cfe214671444687fa7ea56a18e5d751fe0a9.mp4
https://video.nostr.build/bcae8d39e22f66689d51f34e44ecabdf7a57b5099cc456e3e0f29446b1dfd0de.mp4
Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 5 min
- 🍽️ Servings: 1
Ingredients
- ไข่ 1 - 2 ฟอง
- ข้าวโอ๊ต 3 - 4 ช้อน
Directions
- ตอกไข่ + ตีไข่
- ปรุงรส พริกไทย หรือ ซอสถั่วเหลืองตามชอบ
- ใส่ข้าวโอ๊ต 3 - 4 ช้อน
- ใส่ถั่วลิสงอบ 1 - 2 หยิบมือ
- เทน้ำใส่พอท่วมข้าวโอ๊ต
- เข้าไมโครเวฟ ไฟแรง 1 - 2 นาที
-
 @ 56867ee3:6b3c0834
2025-02-28 07:32:17
@ 56867ee3:6b3c0834
2025-02-28 07:32:17Chef's notes
Join Stacker News Food & Drinks territory, we talk food, we smell drinks, we taste culinary images and photos of your preferred meals,
Details
- ⏲️ Prep time: 21
- 🍳 Cook time: 21
- 🍽️ Servings: 21
Ingredients
- A bit of time
- A grain of creativity
Directions
- Signup to https://stacker.news/~food_and_drinks
- Create a new post https://stacker.news/~food_and_drinks/post
- Select the post type: Discussion, Link, Poll, Bounty or Job
- Squeeze your brain for 21min writing interesting contents
- Check markdown formatting to improve readability
- Read it again or share it with someone for proofreading
- Hit the Post orange button
- Be ready to respond to comments
- Humbly receive sats without expectations
-
 @ d560dbc2:bbd59238
2025-03-23 16:09:19
@ d560dbc2:bbd59238
2025-03-23 16:09:19Welcome to TaskforUs, a web-based task management platform designed to help you organize, prioritize, and track your tasks using the innovative 2-5 Rule. This guide will help you get started, manage your tasks, and make the most of TaskforUs’s features. Let’s dive in!
What Is TaskforUs?
TaskforUs is a task management application that helps you focus on what matters most. Using the 2-5 Rule, our platform ensures you’re always working on the right task at the right time—whether it’s a daily habit, a weekly check-in, or a yearly goal.
Key Features
- Smart Task Prioritization:
Uses the 2-5 Rule to prioritize tasks based on timing and importance. - Focus Mode:
Displays only your top-priority tasks to help you concentrate. - Fix Mode:
Ensures date-specific tasks (e.g., birthdays) rise in priority as the date approaches. - Category Filtering:
Organize and filter tasks by custom categories. - Task Archiving:
Keep your list clean by archiving completed tasks. - Task Export:
Export tasks to CSV for backup or analysis. - Multi-User Support:
Secure login with password protection. - Email-Based Password Recovery:
Reset your password securely via email.
Getting Started
Create an Account
- Go to task4.us and click Register on the login screen.
- Enter your details:
- Username: Choose a unique username (e.g., “Alex123” or “TaskMaster”).
Note: Your username should not be an email address. - Password: Create a secure password (at least 8 characters, including a number and a special character).
- Click Register to create your account.
- You’ll be redirected to the login page to sign in.
Log In
- On the login page, enter your username and password.
- Click Login to access your dashboard.
Manage Your Profile
- From the navigation menu, go to Configuration.
- Update your settings:
- Email Address: Add or change the email for password recovery.
- Focus Mode: Set the number of tasks to display in Focus Mode.
Working with Tasks
Add a Task
- From the navigation menu, click Add Task.
- Fill in the task details:
- Name: A brief description (e.g., “Schedule team meeting”).
- Category: Group tasks (e.g., Work, Personal, Health).
- Priority: Set as Low, Medium, or High.
- Type:
Choose the task’s time unit to apply the 2-5 Rule, which determines how often you should act:- Day/Daily: For tasks you want to do every 2-5 days (e.g., “Do cardio”).
- Week/Weekly: For tasks to be done every 2-5 weeks (e.g., “Schedule dinner with Alex”).
- Month/Monthly: For tasks to be done every 2-5 months (e.g., “Review budget”).
- Year/Yearly: For tasks to be done every 2-5 years (e.g., “Reassess career path”).
- Fix Mode:
For tasks tied to a specific date (e.g., “Wish Alex a happy birthday”), select Fix Mode and set the exact date. The task will climb your list as the date approaches. - Date: Select the due date or start date (required for Fix Mode tasks).
- Comments: Add any notes or details (optional).
- Click Add Todo to save the task.
View and Manage Tasks
- Your main dashboard displays all tasks, sorted by priority using the 2-5 Rule. Incomplete tasks appear first, followed by completed ones.
Task Actions
For each task, you can: - Complete/Uncomplete: Mark a task as done or undo its completion. - Edit: Update task details. - Archive: Move a task to the archive (you can restore it later).
Filter Tasks
- Use category checkboxes to filter tasks by specific categories.
- Select multiple categories to view tasks from any of them.
- Choose All to display tasks from all categories.
Focus Mode
- Click Enable Focus Mode to see only your top-priority tasks (as set in Configuration).
- Click Disable Focus Mode to return to the full task list.
Archived Tasks
- From the navigation menu, go to Archive to view all archived tasks.
- Use the Unarchive action to restore tasks to your active list.
Export Tasks
- From the navigation menu, click Export Tasks.
- A CSV file with all tasks (active and archived) will download.
- Open the file in spreadsheet apps like Excel or Google Sheets.
Understand Task Prioritization
TaskforUs uses the 2-5 Rule to prioritize tasks: - Each task is assigned a time unit (days, weeks, months, or years). - You should act within 2 to 5 of those units (e.g., a “weekly” task should be done every 2-5 weeks). - For Fix Mode tasks, priority increases as the set date approaches, peaking on the day itself. - Additional factors, such as priority level (Low, Medium, High) and due date proximity, also influence the order. - Priorities are recalculated each time you view your list, ensuring that the most important tasks are always at the top.
Account Management
Change Your Email
- Go to Configuration.
- Enter your new email address.
- Click Save.
Reset Your Password
- On the login page, click Forgot Password.
- Enter your username.
- Check your email for a password reset link (valid for 15 minutes).
- Click the link and set a new password.
Log Out
- From the navigation menu, click Logout to end your session securely.
Best Practices
- Use Consistent Categories:
Create a small, manageable set of categories (e.g., Work, Personal, Health). - Be Specific with Task Names:
Use clear, concise names (e.g., “Call Mom” instead of “Family”). - Leverage Focus Mode:
Enable Focus Mode when overwhelmed to concentrate on critical tasks. - Use Fix Mode for Dates:
Set birthdays or deadlines in Fix Mode to ensure you never miss them. - Review Regularly:
Set aside time weekly to review and update your tasks. - Archive Completed Tasks:
Keep your active list clean by archiving tasks that are done.
Take control of your tasks today with TaskforUs and transform the way you manage your time.
Sign Up at task4.us
- Smart Task Prioritization:
-
 @ c11cf5f8:4928464d
2025-03-23 12:03:33
@ c11cf5f8:4928464d
2025-03-23 12:03:33Let's support #Bitcoin #merchants! I'd love to hear some of your latest #Lightning purchases and interesting #products you bought. Feel #free to include links to the #shops or #businesses you bought from.
Who else has a recent purchase they’re excited about? Bonus #sats if you found a killer #deal! ⚡
If you missed our last thread, here are some of the items stackers recently spent and #zap on.
originally posted at https://stacker.news/items/922334
-
 @ b183a855:1d20ab46
2025-03-23 10:57:45
@ b183a855:1d20ab46
2025-03-23 10:57:45Com o crescimento acelerado da indústria de jogos online, novos players têm surgido para transformar a maneira como nos divertimos na internet. Um dos maiores nomes dessa revolução é a plataforma 5597, que se destaca pela sua diversidade de jogos, funcionalidades modernas e foco na experiência do usuário. Se você está em busca de uma plataforma que ofereça qualidade, diversão e segurança, a 5597 é uma das opções mais atraentes do mercado. Neste artigo, vamos apresentar a plataforma 5597, explorar os jogos que ela oferece e como ela proporciona uma experiência única para seus usuários.
Introdução à Plataforma 5597 A 5597 foi criada para ser uma plataforma de entretenimento digital acessível e inovadora, que coloca o jogador no centro de sua experiência. Seu layout simples e eficiente facilita a navegação, permitindo que os usuários acessem rapidamente os jogos de sua escolha, independentemente do dispositivo utilizado. O design clean da plataforma proporciona uma navegação sem obstáculos, permitindo uma experiência fluida e sem complicações.
Além disso, a plataforma é totalmente compatível com dispositivos móveis e desktops, o que oferece flexibilidade aos jogadores. Não importa onde você esteja, a 5597 oferece a possibilidade de se conectar e jogar a qualquer momento, tornando a diversão mais acessível do que nunca.
A segurança também é uma prioridade na plataforma 5597. Com tecnologia de criptografia avançada, os dados dos jogadores são protegidos, o que garante uma experiência sem preocupações. Além disso, a plataforma conta com uma equipe de suporte disponível 24 horas por dia para ajudar com qualquer questão ou problema que possa surgir.
Variedade de Jogos para Todos os Gostos A 5597 é uma plataforma que se destaca pela diversidade de jogos oferecidos. A variedade é uma das grandes forças da plataforma, com uma ampla gama de opções que atendem a diferentes gostos e preferências. Se você gosta de jogos de estratégia, habilidade ou ação, a plataforma oferece títulos de alta qualidade que atendem a todos os estilos de jogo.
Cada jogo na 5597 foi escolhido com o cuidado de proporcionar não apenas diversão, mas também um desafio adequado para os jogadores. Com gráficos detalhados, mecânicas envolventes e trilhas sonoras imersivas, cada título tem o objetivo de transportar o jogador para um universo único, cheio de possibilidades e emoções.
Além disso, a plataforma está em constante evolução, sempre adicionando novos títulos ao seu catálogo. Isso significa que os jogadores têm sempre algo novo para experimentar, evitando a sensação de estagnação e mantendo o interesse por novos jogos.
A Experiência do Jogador na Plataforma 5597 A experiência na plataforma 5597 vai além de apenas jogar. Ela busca criar uma comunidade de jogadores engajados, onde as interações sociais são tão importantes quanto a própria jogabilidade. A plataforma oferece opções de interação, como chats em tempo real e fóruns, onde os jogadores podem compartilhar dicas, trocar experiências e até formar equipes para competir juntos.
Outro destaque da 5597 é o sistema de recompensas, que mantém os jogadores motivados. A plataforma oferece bônus e prêmios ao longo das partidas, que podem ser usados para melhorar a experiência do jogador ou desbloquear conteúdo exclusivo. Essas recompensas fazem com que os jogadores se sintam recompensados por sua dedicação, criando um ciclo de engajamento contínuo.
Conclusão A 5597 é uma plataforma de jogos online que oferece tudo o que um jogador precisa para uma experiência de qualidade. Com uma interface simples, uma ampla variedade de jogos e recursos interativos, ela se destaca como uma das melhores opções disponíveis no mercado. Se você está em busca de diversão, segurança e uma comunidade ativa, a plataforma 5597 é a escolha certa para você.
-
 @ c230edd3:8ad4a712
2025-02-26 03:04:53
@ c230edd3:8ad4a712
2025-02-26 03:04:53Chef's notes
Simple, common ingredients make this an easy go-to, if time allows. Best after letting the meat marinade for 4-8 hours.
I prefer to grill and serve it with eggplant, onion, and zucchini. It works well in a more traditional souvlaki style sandwich, too.
Details
- ⏲️ Prep time: 1 hour, plus 4-8 for marinating
- 🍳 Cook time: 30 minutes
- 🍽️ Servings: 4
Ingredients
- 1.5 lb cubed chicken
- 1/2 c. plain greek yogurt
- 1/4 c. lemon juice
- 2 Tbsp oregano
- 3 cloves garlic, minced
- 1/2tsp salt
Directions
- Mix all ingredients, add chicken to coat
- Cover & refrigerate for 4-8 hours
- Start coals to high heat, prep grill with light oil if needed
- Skewer chicken cubes, as many as will fit on kebab sticks
- Grill until chicken is done
- Serve with tzatziki sauce, grilled vegetable and pitas, if desired
-
 @ 04ff5a72:22ba7b2d
2025-03-19 02:06:34
@ 04ff5a72:22ba7b2d
2025-03-19 02:06:34Taking Back Control of the Internet
Web3 represents a fundamental reimagining of how users interact with and control their data online, marking a significant departure from the Web2 paradigm that has dominated the internet for the past two decades. This transformation is centered around shifting power dynamics, decentralizing authority, and returning data sovereignty to individuals. While Web2 created unprecedented connectivity and digital services, it came with significant trade-offs in terms of privacy, security, and user autonomy. Web3 technologies aim to address these shortcomings through blockchain-based systems and decentralized architectures that fundamentally alter who controls, benefits from, and has access to user data.
Fundamental Shift in Data Ownership
Web2: Corporate Control and Exploitation
In the Web2 paradigm, users effectively surrender ownership of their personal data to centralized platforms. When individuals sign up for services from tech giants like Google, Facebook, or Twitter, they typically grant these companies extensive rights to collect, analyze, and monetize their information[2]. This arrangement creates a profound power imbalance where users have minimal visibility into or control over how their data is used. Companies can sell this information to third parties for marketing purposes without providing meaningful compensation to the individuals who generated it[4].
This centralized model has created what many critics describe as "surveillance capitalism," where detailed profiles of users are constructed across platforms to predict and influence behavior. The value generated from this data has contributed to the immense wealth of a small number of technology corporations while leaving users with little to show for their contributions[4].
Web3: User-Centric Ownership Model
Web3 fundamentally inverts this ownership paradigm. In Web3 systems, users retain ownership of their own data and can make deliberate decisions about how it is used, shared, or monetized[2]. This principle is enabled through blockchain technology and cryptographic mechanisms that allow individuals to maintain control over their digital footprint without relying on centralized intermediaries[3].
The decentralized architecture of Web3 systems means that personal information is not concentrated in massive corporate databases but is instead distributed across networks with varying levels of user-controlled access[7]. This shift represents not merely a technical change but a philosophical reorientation of the internet toward user sovereignty.
Decentralized Infrastructure and Enhanced Security
Web2: Vulnerable Centralized Systems
The Web2 model relies heavily on centralized servers and data centers controlled by individual companies. This architecture creates significant vulnerabilities, as these centralized repositories become high-value targets for hackers and malicious actors[2]. Data breaches affecting millions of users have become increasingly common, demonstrating the inherent security weaknesses of storing vast amounts of personal information in single locations.
Additionally, the centralized nature of Web2 infrastructure creates single points of failure where service disruptions or security compromises can have widespread impacts across entire user bases[8].
Web3: Distributed Networks and Cryptographic Protection
Web3 transforms this security model through decentralization. By leveraging blockchain technology, Web3 distributes data across multiple nodes worldwide rather than concentrating it in centralized servers[3]. This architecture significantly increases resilience against attacks, as compromising the network would require breaching numerous points simultaneously rather than a single centralized database[2].
Cryptographic protection is fundamental to Web3 systems, with data access controlled through sophisticated encryption mechanisms. This approach makes unauthorized access significantly more difficult and provides users with verifiable assurance about who can see their information and under what circumstances[5].
The Web3 infrastructure model explicitly addresses the vulnerability of centralized systems by removing single points of failure and distributing both data and control across broad networks of participants[8].
Self-Sovereign Identity and Authentication
Web2: Platform-Dependent Digital Identities
In Web2, digital identities are typically fragmented across numerous platforms, each requiring separate credentials and controlling different aspects of a user's online presence[4]. This fragmentation creates security vulnerabilities and makes it difficult for individuals to maintain a coherent digital footprint or track how their information is being used across services.
Users often rely on third-party identity providers (like "Sign in with Google" or "Login with Facebook"), which further centralizes control and creates dependencies that can be revoked at the platform's discretion[4].
Web3: User-Controlled Identity Management
Web3 introduces the concept of self-sovereign identity, where users create and manage decentralized identifiers that they fully control without intermediaries[1][5]. Instead of relying on centralized identity providers that can restrict access or modify terms, individuals maintain ownership of their digital identities across different applications and services.
Decentralized Identifiers (DIDs) and Self-Sovereign Identity (SSI) systems enable secure identity management that preserves privacy while still allowing for verified interactions[1][3]. Users can selectively disclose only the specific information needed for particular interactions without revealing unrelated personal details, significantly reducing unnecessary data exposure[3].
This approach minimizes the risk of identity theft by eliminating the centralized repositories of identity information that currently make attractive targets for attackers[3].
Transparency and Consent Mechanisms
Web2: Opaque Data Practices and Forced Consent
Web2 platforms are notorious for their complex and often deliberately obscure data governance practices[4]. Users typically must agree to extensive terms of service and privacy policies they rarely read or fully understand. Even when policies are comprehensible, users face a binary choice: accept all conditions or forgo the service entirely.
This lack of transparency has eroded trust, with many users unaware of how extensively their information is being collected, analyzed, and shared with third parties[4]. The actual conditions of data usage often change without meaningful notification or consent opportunities.
Web3: Transparent Governance and Programmable Consent
Web3 systems operate on public, immutable ledgers where data processing rules are encoded in transparent smart contracts that anyone can examine[4][5]. This radical transparency allows users to verify exactly how their information will be handled before agreeing to share it.
Rather than all-or-nothing consent models, Web3 enables granular, programmable consent where users can specify precise conditions under which their data may be accessed or utilized[5]. These conditions become enforced by code rather than by trusting companies to honor their stated policies.
This transparency extends to the broader governance of Web3 platforms, many of which operate as Decentralized Autonomous Organizations (DAOs) where users can participate in decision-making about how the system evolves[8].
Data Monetization and Value Exchange
Web2: Asymmetric Value Capture
In Web2 ecosystems, the value created from user data flows predominantly to platform owners. Users effectively trade their data for free services, but the economic exchange is highly unbalanced[4]. The personal information collected is worth far more to the companies than the services provided in return, creating massive wealth for a small number of technology corporations.
Users have little visibility into how their data contributes to platform revenues and receive minimal compensation for their valuable contributions to these ecosystems[4].
Web3: Direct User Monetization
Web3 revolutionizes this economic model by enabling users to directly monetize their own data if they choose to share it[4]. Through blockchain-based platforms and decentralized applications (dApps), individuals can selectively sell access to their data or receive compensation for their online contributions.
This model creates more equitable value distribution, where the economic benefits of data flow to those who generate it rather than being concentrated among platform owners[7]. Users can make informed decisions about when and how to monetize their information based on transparent value propositions.
The incentive structures of Web3 platforms often include tokenization mechanisms that allow users to benefit directly from network growth and participation, creating alignment between individual and collective interests[8].
Challenges and Future Directions
Despite its promising approach to data control, Web3 faces significant challenges in achieving mainstream adoption. Technical barriers remain substantial, with many Web3 interfaces less user-friendly than their Web2 counterparts[3]. Scalability issues can lead to slower transactions and higher costs compared to centralized solutions.
Regulatory frameworks are still evolving to address the unique characteristics of decentralized systems, creating uncertainty around compliance requirements[3][5]. Additionally, the public nature of some blockchain networks introduces new privacy considerations that must be carefully managed.
Future developments in Web3 privacy will likely focus on improving scalability solutions, developing more intuitive user interfaces for privacy management, and refining privacy-preserving technologies like zero-knowledge proofs[3]. Education remains critical, as users need to understand Web3 mechanisms to fully leverage their benefits.
Conclusion
The transition from Web2 to Web3 represents a profound shift in how user data is controlled, managed, and valued. While Web2 created unprecedented connectivity at the cost of personal privacy and autonomy, Web3 aims to preserve the benefits of digital connection while returning control to individuals.
By decentralizing infrastructure, enabling self-sovereign identity, increasing transparency, and creating more equitable value distribution, Web3 technologies offer a vision of the internet that aligns more closely with principles of user empowerment and data sovereignty.
Though challenges remain in fully realizing this vision, the fundamental reorientation toward user control over personal data represents one of the most significant developments in the internet's evolution since the emergence of social platforms. As Web3 technologies mature and adoption increases, they have the potential to fundamentally transform our relationship with our digital selves and reshape the power dynamics of the online world.
Sources
[1] Data Ownership in Web3: Empowering Users with Control https://whimsygames.co/blog/data-ownership-in-web3-empowering-users-with-control/ [2] Web2 vs Web3: What's the Difference - Cryptix AG https://cryptix.ag/web2-vs-web3/ [3] The Role of Web3 in Digital Privacy: Protecting User Data in ... https://dev.to/lisaward867/the-role-of-web3-in-digital-privacy-protecting-user-data-in-decentralized-systems-18ki [4] How Web3 Enhances User Privacy As Compared to Web2 - LinkedIn https://www.linkedin.com/pulse/how-web3-enhances-user-privacy-compared-web2-mr-mint-official-umtve [5] Safeguarding Privacy in the Web3 Era: A Deep Dive into User ... https://www.linkedin.com/pulse/safeguarding-privacy-web3-era-deep-dive-user-anonymity-data-protection-85hrf [6] Web2 vs. Web3: What's the Difference? [The Breakthrough] - Metana https://metana.io/blog/web2-vs-web3-whats-the-difference-the-breakthrough/ [7] Decentralized Data Impact in Web 3.0 Ownership https://crowleymediagroup.com/resources/decentralized-data-impact-in-web-3-0-ownership/ [8] Enhancing Digital Security and User Privacy with Web3 - BlockApps https://blockapps.net/blog/enhancing-digital-security-and-user-privacy-with-web3/
-
 @ 2fdeba99:fd961eff
2025-03-21 17:16:33
@ 2fdeba99:fd961eff
2025-03-21 17:16:33== January 17 2025
Out From Underneath | Prism Shores
crazy arms | pigeon pit
Humanhood | The Weather Station
== february 07 2025
Wish Defense | FACS
Sayan - Savoie | Maria Teriaeva
Nowhere Near Today | Midding
== february 14 2025
Phonetics On and On | Horsegirl
== february 21 2025
Finding Our Balance | Tsoh Tso
Machine Starts To Sing | Porridge Radio
Armageddon In A Summer Dress | Sunny Wa
== february 28 2025
you, infinite | you, infinite
On Being | Max Cooper
Billboard Heart | Deep Sea Diver
== March 21 2025
Watermelon/Peacock | Exploding Flowers
Warlord of the Weejuns | Goya Gumbani
-
 @ a1c19849:daacbb52
2025-02-24 19:30:09
@ a1c19849:daacbb52
2025-02-24 19:30:09Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 4 hours
Ingredients
- 1kg of chicken thighs
- 3 large onions
- 1 tablespoon garlic powder
- 2 tablespoons brown sugar
- 1.5 dl Ketjap Medja
- 0.5 liter chicken broth
- Pepper
- Salt
- Nutmeg
Directions
- Cut the onions and sauté them
- Add the chicken thighs in pieces and bake for a few minutes
- Add the garlic powder and the brown sugar and bake for a short time
- Add the ketjap media and the chicken broth
- Add some salt and pepper and nutmeg and let it simmer for 3 to 4 hours
- Make sure all the moist evaporates but make sure it doesn’t get too dry. Otherwise add some extra chicken broth
- Bon appetit!
-
 @ da0b9bc3:4e30a4a9
2025-03-21 13:58:11
@ da0b9bc3:4e30a4a9
2025-03-21 13:58:11It's Finally here Stackers!
It's Friday!
We're about to kick off our weekends with some feel good tracks.
Let's get the party started. Bring me those Feel Good tracks.
Let's get it!
This song never doesn't put me in a good mood.
https://youtu.be/fnwZeLdLPdQ?si=ZlbiGSp2r6DtMx6P
originally posted at https://stacker.news/items/920041
-
 @ dd664d5e:5633d319
2025-03-21 12:22:36
@ dd664d5e:5633d319
2025-03-21 12:22:36Men tend to find women attractive, that remind them of the average women they already know, but with more-averaged features. The mid of mids is kween.👸
But, in contradiction to that, they won't consider her highly attractive, unless she has some spectacular, unusual feature. They'll sacrifice some averageness to acquire that novelty. This is why wealthy men (who tend to be highly intelligent -- and therefore particularly inclined to crave novelty because they are easily bored) -- are more likely to have striking-looking wives and girlfriends, rather than conventionally-attractive ones. They are also more-likely to cross ethnic and racial lines, when dating.
Men also seem to each be particularly attracted to specific facial expressions or mimics, which might be an intelligence-similarity test, as persons with higher intelligence tend to have a more-expressive mimic. So, people with similar expressions tend to be on the same wavelength. Facial expessions also give men some sense of perception into womens' inner life, which they otherwise find inscrutable.
Hair color is a big deal (logic says: always go blonde), as is breast-size (bigger is better), and WHR (smaller is better).

-
 @ 044da344:073a8a0e
2025-03-23 15:25:40
@ 044da344:073a8a0e
2025-03-23 15:25:40„Ein Heidenspaß“, sagt Seymour Hersh, sei diese „messerscharfe Geschichte des Journalismus“. Dirk Pohlmann setzt noch einen drauf und greift in das Regal der Superlative: „Das beste Buch über Journalismus, das ich in den letzten 20 Jahren gelesen habe.“
Ich weiß: Verleger lieben solche „Stimmen zum Buch“ – vor allem dann, wenn sie von Promis kommen und der Autor selbst keinen Namen hat, zumindest in Deutschland nicht. Patrick Lawrence, Jahrgang 1950, ist ein Journalistenleben lang gependelt zwischen den ganz großen Redaktionen und dem, was er „unabhängige Medien“ nennt. Er hat für die New York Times geschrieben, für Newsweek, für die International Herald Tribune. Er hat es, so lässt sich das im Rückblick vielleicht sagen, immer wieder probiert, zugleich aber stets gewusst, dass er sich dafür kastrieren muss.
Lawrence sagt das nicht so, natürlich nicht. Das verbietet ein Publikum, das auf Akademikerslang steht und Häppchen für den Smalltalk braucht. In diesem Buch heißt der Leitstern Carl Gustav Jung: Wer für die Leitmedien arbeitet, so analysiert das Patrick Lawrence, muss das in sich vergraben, was den Journalismus ausmacht. Keiner der Redakteure kann einfach „sehen und sagen“ (S. 88) – eine feine Definition für das Berufsideal, nah dran an Rudolf Augstein und seinem Slogan „Sagen, was ist“. Konventionen, Moral und Geschmack, Zumutungen der Arbeitgeber und „andere Formen sozialer und beruflicher Einschüchterung“: All das tötet
das authentische, ungeteilte Selbst, das in der Lage ist, mit Gewissheit und ohne Bezugnahme auf die Zwänge der Macht oder der kollektiven Meinung zu urteilen und zu handeln. (S. 22)
Die „Schatten“ im Titel und auf dem Cover spielen hier also nicht auf unsere dunkle Seite an, auf das, was wir vor uns selbst verstecken müssen, um ein „guter Mensch“ sein zu können oder ein „guter Journalist“, oder gar auf das Böse an sich. Für Patrick Lawrence ist der „Schatten“ das, was sich sein Berufsstand in Sonntagsreden erzählt, aber im Alltag nicht umsetzen kann und darf. Dazu gleich mehr. Patrick Lawrence selbst hat sein „Schatten-Ich“ immer wieder ausgeführt und für die andere Seite geschrieben, erst für kleine Blätter mit miesen Honoraren und dann für Webseiten mit dem gleichen Problem, manchmal unter Pseudonym und manchmal auch ganz ohne Namen, wenn ein Handwerker gebraucht wurde, der wenigstens die gröbsten Fehler beseitigt, sprachlich und auch sonst. In seinem Buch rechnet er ab mit den Kollegen, mit den USA und damit in gewisser Weise auch mit dem gesamten Westen. Ihr alle, sagt Patrick Lawrence, habt euch täuschen lassen. Man hat euch erzählt, dass die Presse frei sei, und ihr habt das nur zu gern glauben wollen – gegen jede Evidenz. Die „messerscharfe Geschichte“, die Seymour Hersh so begeistert hat, beginnt im Zweiten Weltkrieg, in einer Zeit, in der Politik, Militär und Journalismus mehr oder weniger Synonyme waren. Eine Einheitsfront, bekannt schon aus dem ersten großen Krieg, als es ab 1917 gegen die Bolschewiki ging, und in den 1920ern dann auch theoretisch unterfüttert von Walter Lippmann oder von Edward Bernays, die noch ganz offen davon sprechen konnten, dass „die Herde“ geführt werden muss – von Menschen, die es qua Herkunft, Ausbildung oder Machtzugang einfach besser wissen. Patrick Lawrence sagt: Die Ehe zwischen den Medien und dem nationalen Sicherheitsstaat ist nie wieder aufgelöst worden. Er erzählt, wie „staatliche Agenturen“ nach 1945 die Programme erst selbst produziert und dann kontrolliert haben und wie das mit einem Märchen verschleiert wurde.
Die Aufgabe der Sender bestand darin, diese Produktionen als unabhängig, gründlich und objektiv erscheinen zu lassen. (S. 44)
Lawrence sagt auch, warum die Medienkonzerne das mit sich machen ließen und warum darüber nirgendwo geredet wird, zumindest in der Schule nicht. Das Material vom Staat war billig, verlieh die Aura der Seriosität und nahm so auch Werbekunden und Sponsoren jede Angst, in einem ungünstigen Licht zu erscheinen. Für potenzielle Kritiker war die „Nähe der Presse zur Macht“ zugleich „eine zu große und folgenreiche Sache“ (S. 40). Übersetzt: Wer zieht schon freiwillig nach Mordor, um sich mit Sauron anzulegen?
Patrick Lawrence ist alt genug und hat zu viel gesehen, um sich noch fürchten zu müssen. Als junger Mann war er in Portugal und konnte hautnah beobachten, wie die CIA verhinderte, dass Álvaro Cunhal Präsident wurde, Kommunist und einer meiner Kindheitshelden. Später dann in Asien das gleiche Bild. Singapur, Malaysia, Japan, die vietnamesischen Bootsflüchtlinge: überall US-Dienste, auch und gerade im Journalismus. Patrick Lawrence rechnet mit der Church-Kommission ab, die 1975 zwar zum „Jahr der Geheimdienste“ machte und mit ihren Berichten heute ein wichtiger Anker für alle ist, die nach Steuerleuten im Dunkeln suchen, die aber, so sieht das Patrick Lawrence, trotzdem versagt hat, weil sie „zu viel Zeit mit Mordanschlägen und Agency-Exotika verbracht“ hat, „um der Frage nach der Mittäterschaft der Presse die Aufmerksamkeit zu widmen, die sie verdient hätte“ (S. 53).
Der geneigte Leser ahnt schon: Um den gleichen „Heidenspaß“ erleben zu können wie Seymour Hersh, sollte man Lust an den großen Linien mitbringen – an den vier „Ns“ zum Beispiel (Nehru, Nasser, Nyerere, Nkrumah) oder an all den Orten, die Washington irgendwann zum Schlachtplatz im Krieg „gegen die sozialistische Alternative“ auserkoren hat (S. 97). Belohnt wird man mit einer frischen Sicht auf die Geschichte – getragen von dem Wissen, dass der „embedded journalism“ der Konzernmedien nicht mehr liefert als den
ersten Entwurf der Darstellung von Sachverhalten, die die Macht bevorzugt, um ausgewogene, sachliche Darstellungen von Ereignissen, die das Vorgehen des Imperiums im In- und Ausland betreffen, aus den Geschichtsbüchern herauszuhalten. Journalisten außerhalb des Mainstreams sind somit die wahren Freunde des Historikers und sie haben die Pflicht des Historikers, den ersten Entwurf zu erstellen. (S. 190)
Das ist zugleich die Überleitung in die Aktualität – in die Phase der „offenen Zensur“, die wir gerade erleiden und die mit den Digitaltechnologien zu tun hat sowie mit den Möglichkeiten, die dadurch alle haben, die „unabhängig von der Macht“ schreiben wollen (S. 125). 9/11, der „Krieg gegen den Terror“, Russiagate: Patrick Lawrence nennt die Meilensteine auf dem Weg in den Abgrund und zeigt mit dem Finger auf Journalisten der Leitmedien, die „abweichende oder alternative Meinungen“ verbannen wollen, auf Politiker, die den ersten Zusatz der US-Verfassung am liebsten schreddern würden, sowie auf Internetkonzerne, die „ohne erkennbare Skrupel“ jahrelang kooperiert haben (S. 182). Der letzte Twist der Geschichte hat es nicht mehr in sein Buch geschafft, es braucht aber nicht allzu viel Fantasie, um Trump, Musk und Co. hineinzuschreiben in ein Narrativ, das Journalismus und Öffentlichkeit mit dem verknüpft, was den nationalen Sicherheitsstaat gerade umtreibt.
Der Kenner wird jetzt nicken und sagen: Das weiß ich doch alles schon. Ich habe Hannes Hofbauer gelesen, Michael Meyen und sogar Birk Meinhardt. Warum soll ich mir noch diese US-Version von „Wie ich meine Zeitung verlor“ antun, das Buch von einem Mann, von dem ich bis heute noch nie etwas gehört habe?
Punkt eins: Patrick Lawrence spricht aus, was wir tagein, tagaus erleben. Leitmedien in den USA (und nicht nur dort) dienen „den Zwecken der offiziellen Propagandisten“ (S. 17). Die Journalisten hängen an den Lippen von „Autoritätspersonen“, sind „Schreiber der herrschenden Klasse“ und füllen so die „Anschlagblätter“ der Macht (S. 129). Punkt zwei: Lawrence belegt, dass das nie anders war. Gemeldet wurde und wird nur das, was gerade in den „Erzählstrang“ passt – in die Version der Welt, die das Imperium „haben“ will (S. 108). Punkt drei: Dieser alte Fahrensmann kennt seine Pappenheimer. Er weiß, dass es keinen Sinn macht, Journalisten zu fragen, ob sie das glauben, was sie da schreiben. Wer in den Redaktionen überleben und dort sogar Karriere machen will, muss eine Rolle spielen, um „die Erwartungen der anderen zu erfüllen“ und dafür auf „Authentizität“ verzichten (S. 184). Und Punkt vier, vielleicht am wichtigsten: Patrick Lawrence versprüht Hoffnung. Kein Zensor, sagt er, kann das „Ideal“ eines „unabhängigen Journalismus“ unterdrücken (S. 204).
Er selbst ist dafür ein lebendes Beispiel. Verzichtet darauf, ruft er Redakteuren und Korrespondenten zu, zur Elite gehören zu wollen. Schraubt eure „materiellen Wünsche“ herunter. „Häuser, Autos, Ausgehen, Urlaub“: Es kann doch nicht sein, dass der „Informationskrieg“ wegen solch profaner Dinge immer weiter geht (S. 187). Patrick Lawrence wirbt für ein „bescheidenes Leben“ – weil man dann auch als Journalist ganz bei sich bleiben, auf den „Sündenlohn“ (Upton Sinclair) verzichten und hoffentlich trotzdem eine Familie ernähren kann.
Unter dem möchte er es nicht machen – und das ist gut so. Kein Verzicht auf Qualität, auf Handwerk vor allem, und keine Selbstausbeutung. Vor allem aber: kein Schatten mehr. Wie schwierig das ist, zeigt selbst dieses Buch. Seine Botschaft versieht Patrick Lawrence mit Fragezeichen, obwohl das Buch voller Antworten ist (S. 139):
Hat sich die amerikanische Presse in den Nachkriegsjahren derart kompromittiert, dass die Zusammenarbeit mit den Geheimdiensten heute fester Bestandteil ist? Sind solche Absprachen zur Routine geworden? Und dann diese, die wichtigste Frage: Haben die Amerikaner seit 1945 faktisch ohne eine authentische, unabhängige Presse gelebt?

Freie Akademie für Medien & Journalismus
Titelbild: Fajrul Falah @Pixabay
-
 @ a1c19849:daacbb52
2025-02-24 19:19:16
@ a1c19849:daacbb52
2025-02-24 19:19:16Details
- ⏲️ Prep time: 20 min
- 🍳 Cook time: 4 hours
Ingredients
- 1kg of chicken thighs
- 3 large onions
- 1 tablespoon garlic powder
- 2 tablespoons brown sugar
- 1.5 dl Ketjap Medja
- 0.5 liter chicken broth
- Pepper
- Salt
- Nutmeg
Directions
- Cut the onions and sauté them
- Add the chicken thighs in pieces and bake for a few minutes
- Add the garlic powder and the brown sugar and bake for a short time
- Add the ketjap media and the chicken broth
- Add some salt and pepper and nutmeg and let it simmer for 3 to 4 hours
- Make sure all the moist evaporates but make sure it doesn’t get too dry. Otherwise add some extra chicken broth
- Bon appetit!
-
 @ b183a855:1d20ab46
2025-03-23 10:57:06
@ b183a855:1d20ab46
2025-03-23 10:57:06No vasto universo das plataformas de entretenimento online, o 5853 surgiu como uma opção única para os jogadores que buscam diversão, desafios e uma experiência interativa de alta qualidade. Esta plataforma oferece aos seus usuários um ambiente digital imersivo, com jogos variados e uma interface acessível que atende tanto iniciantes quanto jogadores experientes. Se você ainda não conheceu o 5853, é hora de explorar tudo o que essa plataforma tem a oferecer.
Explorando a Plataforma 5853: Acessibilidade e Facilidade O 5853 foi projetado para ser acessível e fácil de usar. Desde o primeiro momento, a plataforma impressiona pela sua interface limpa e organizada. O cadastro é simples, permitindo que os jogadores criem suas contas rapidamente e iniciem a diversão sem perder tempo. A navegação é intuitiva, com uma estrutura bem definida que permite aos usuários encontrar seus jogos favoritos sem complicação.
Uma das características que torna o 5853 atraente é a possibilidade de acessar a plataforma em diferentes dispositivos. Seja no seu computador, tablet ou smartphone, a experiência de jogo permanece fluída e de alta qualidade. Isso proporciona uma conveniência que se adapta à rotina agitada dos usuários, permitindo que eles aproveitem momentos de lazer a qualquer hora e em qualquer lugar.
Jogos para Todos os Estilos: Diversão Sem Limites A verdadeira alma do 5853 está nos jogos oferecidos pela plataforma. Com uma vasta gama de opções, o 5853 atende a todos os tipos de jogadores, desde os fãs de ação até os que preferem jogos de estratégia ou quebra-cabeças. Cada jogo é desenvolvido com foco na diversão, mas também oferece desafios que mantém os jogadores engajados por longos períodos.
A plataforma é conhecida por sua qualidade gráfica, com ambientes vibrantes e detalhados, que criam uma imersão profunda no universo do jogo. A jogabilidade, por sua vez, é projetada para ser acessível, mas desafiadora o suficiente para manter os jogadores motivados. Mesmo aqueles que nunca jogaram antes se sentirão à vontade para explorar e aprender os controles, enquanto os veteranos encontrarão desafios que exigem habilidade e estratégia.
A interação entre os jogadores também é um dos pontos fortes do 5853. Com a possibilidade de competir em tempo real, o jogo se torna uma experiência social que permite fazer amigos e compartilhar vitórias. A plataforma cria um ambiente saudável de competição, onde os jogadores podem mostrar suas habilidades e aprender uns com os outros.
Personalização e Segurança: A Experiência Ideal para Você O 5853 vai além ao oferecer opções de personalização. Os jogadores podem ajustar as configurações do jogo de acordo com suas preferências, criando uma experiência única e sob medida. Além disso, a plataforma se preocupa com a segurança de seus usuários, garantindo que os dados pessoais e financeiros sejam mantidos em sigilo. Isso permite que os jogadores se concentrem apenas na diversão e nos desafios, sem se preocupar com a proteção de suas informações.
A experiência do jogador no 5853 é ainda mais aprimorada pelo suporte dedicado. A equipe de atendimento ao cliente está disponível para resolver qualquer dúvida ou problema, garantindo que a diversão nunca seja interrompida. Com uma resposta rápida e eficaz, o suporte ao cliente é outro fator que torna a plataforma ainda mais atrativa.
Conclusão: A Nova Era do Entretenimento Digital O 5853 é uma plataforma inovadora que combina entretenimento de alta qualidade, interação social e personalização em uma experiência única. Com uma vasta gama de jogos, interface intuitiva e compromisso com a segurança, o 5853 se destaca como uma das melhores opções para quem deseja explorar o mundo dos jogos de maneira acessível e envolvente. Se você está em busca de uma plataforma de entretenimento digital que atenda a todas as suas expectativas, o 5853 é o lugar ideal para começar sua jornada de diversão.
-
 @ 38574a5c:218b20f9
2025-02-24 05:10:06
@ 38574a5c:218b20f9
2025-02-24 05:10:06Details
- 🍳 Cook time: 4 to 8 hours
- 🍽️ Servings: 8
Ingredients
- 2 1/2 lb Ground beef
- 1/4 cup Chili powder
- 1/2 large Onion (chopped)
- 2 tbsp Cumin
- 1 tsp Black pepper
- 2 tsp Sea salt
- 1 tbsp Dried oregano
- 2 15-oz can Fire Roasted Diced Tomatoes w/Garlic (with liquid)
- 1 4-oz can Green chiles (with liquid)
- 1 6-oz can Tomato paste
- 2 tbsp Worcestershire sauce (optional-not keto)
- 1 medium Bay leaf (optional)
Directions
- In a skillet over medium-high heat, cook the chopped onion for 5-7 minutes, until translucent (or increase the time to about 20 minutes if you like them caramelized). Add the ground beef. Cook for 8-10 minutes, breaking apart with a wooden spoon or spatula, until browned. Transfer the ground beef mixture into a slow cooker. Add remaining ingredients, except bay leaf, and stir until combined. Place the bay leaf into the top of the mixture. Cook for 6-8 hours on low or 3-4 hours on high. Don’t forget to fish out the bay leaf before serving.
-
 @ 61ba1192:7335ef51
2025-02-23 11:39:12
@ 61ba1192:7335ef51
2025-02-23 11:39:12Details
- ⏲️ Prep time: 5 minutes
- 🍳 Cook time: 10 minutes
- 🍽️ Servings: 2
Ingredients
- 500ml milk
- 80gr semolina
- 1ts salt
Directions
- Add milk to the pot and heat it up
- Add semolina to the milk and stir continuously while adding it slowly
- Keep stirring and heating until thickens up
-
 @ 872982aa:8fb54cfe
2025-03-21 09:38:17
@ 872982aa:8fb54cfe
2025-03-21 09:38:17{"coverurl":"https://cdn.nostrcheck.me/872982aa37b864973a389d465bc6ed5045a78586496d104e05f39b8d8fb54cfe/29dac6975894221f222ed2379e13f2f2b1e51c861ebc35f60770fb15cb93348e.webp","title":"宁静的世界","author":"走动"}
-
 @ bccf33d8:4b705625
2025-03-21 09:29:16
@ bccf33d8:4b705625
2025-03-21 09:29:16{"author":"响响","coverurl":"https://cdn.nostrcheck.me/872982aa37b864973a389d465bc6ed5045a78586496d104e05f39b8d8fb54cfe/b4a8afa3e673ad73e16f0c0694ccb5c60af7aaa4031e1b1d1d928234200c0b0c.webp","title":"雪山"}
-
 @ b183a855:1d20ab46
2025-03-23 10:56:21
@ b183a855:1d20ab46
2025-03-23 10:56:21A tecnologia tem transformado de maneira significativa a forma como nos divertimos, e a Plataforma 9096 se destaca como um exemplo claro dessa evolução no universo dos jogos digitais. Oferecendo uma experiência única e inovadora, a 9096 traz para seus usuários um ambiente digital de entretenimento que combina tradição e modernidade, ao mesmo tempo em que proporciona total segurança e acessibilidade.
Uma Plataforma Conectada com o Futuro do Entretenimento Digital A Plataforma 9096 nasceu com a missão de transformar a experiência do jogador, trazendo o melhor da tecnologia para o universo dos jogos online. Seu design é moderno e adaptável, permitindo uma navegação intuitiva em diversos dispositivos, como computadores, smartphones e tablets. Isso significa que o jogador pode se conectar e jogar em qualquer lugar, o que aumenta a conveniência e a flexibilidade da plataforma.
Uma das grandes inovações da 9096 é a sua compatibilidade com diferentes tipos de jogos e dispositivos. Ao longo dos anos, a plataforma tem se adaptado às necessidades dos seus usuários, sempre buscando inovações que garantem a melhor experiência possível. Com atualizações constantes, a 9096 não apenas oferece jogos de qualidade, mas também novos recursos que tornam a navegação e a experiência de jogo mais fluídas e dinâmicas.
Diversidade e Qualidade nos Jogos: Opções Para Todos os Gostos A grande variedade de jogos é um dos maiores atrativos da Plataforma 9096. O portfólio de jogos é extenso e atende a todos os perfis de jogadores. Se você gosta de desafios e raciocínio estratégico, a plataforma oferece opções que exigem habilidades de planejamento e tomada de decisões rápidas. Para aqueles que preferem jogos mais emocionantes e interativos, a 9096 oferece uma gama de títulos com gráficos incríveis e efeitos visuais imersivos.
Os jogos da plataforma são desenvolvidos por alguns dos melhores estúdios de jogos do mercado, garantindo que cada título seja uma experiência única. A 9096 não apenas oferece jogos com mecânicas inovadoras, mas também garante uma jogabilidade fluída e divertida, com gráficos de última geração que tornam a experiência de jogar mais envolvente e realista.
Outra característica marcante é a possibilidade de competir em tempo real com outros jogadores ao redor do mundo. A 9096 oferece uma série de jogos ao vivo, nos quais os jogadores podem interagir entre si e competir em tempo real, criando uma experiência social ainda mais rica e dinâmica.
A Experiência do Jogador: Conforto e Suporte 24/7 A Plataforma 9096 tem um compromisso claro com a experiência do jogador. Desde o primeiro contato com a plataforma até as interações com os jogos, a 9096 se preocupa em proporcionar uma experiência confortável e personalizada. A interface da plataforma foi projetada para ser simples e funcional, permitindo que o jogador tenha acesso fácil a todas as opções e recursos, sem qualquer dificuldade.
A plataforma também oferece várias opções de personalização. O jogador pode ajustar o layout da plataforma, configurar a qualidade gráfica dos jogos e escolher entre diversas opções de jogos e modos, tudo de acordo com suas preferências. Isso torna a experiência ainda mais única e adaptada às necessidades de cada usuário.
Além disso, a 9096 conta com um suporte ao cliente altamente especializado e disponível 24 horas por dia, 7 dias por semana. Se o jogador tiver alguma dúvida ou enfrentar algum problema técnico, pode contar com a ajuda da equipe de atendimento que estará pronta para oferecer assistência.
Conclusão: A Plataforma 9096 é a Escolha Perfeita para o Entretenimento Digital Com uma interface intuitiva, um portfólio diversificado de jogos e um foco na segurança e personalização, a Plataforma 9096 se apresenta como uma das principais opções para quem busca diversão de qualidade e sem complicações. Seu compromisso com a inovação e com a experiência do jogador garante que a plataforma se mantenha na vanguarda do entretenimento digital.
-
 @ 04ff5a72:22ba7b2d
2025-03-19 01:54:44
@ 04ff5a72:22ba7b2d
2025-03-19 01:54:44How Blockchain Technology Birthed Web3
The emergence of Web3 represents a paradigm shift in how we conceptualize and interact with the internet, moving from centralized platforms toward user-centric, decentralized systems. At the heart of this transformation lies blockchain technology, which serves as the architectural foundation enabling this new internet vision. Blockchain's unique characteristics—decentralization, transparency, and security—have positioned it as the critical infrastructure layer upon which the Web3 ecosystem is being built, fundamentally reshaping digital interactions, ownership models, and value exchange mechanisms.
Blockchain as the Architectural Foundation
Blockchain serves as the building block of Web3 by creating a network where information is stored across many computers instead of one central location[1]. This distributed architecture represents a fundamental departure from the centralized server model that has dominated Web1 and Web2, where data and control are concentrated in the hands of a few corporations.
From Centralized to Distributed Systems
Web3 is built on blockchain technology, which enables secure, transparent, and censorship-resistant transactions[3]. Unlike Facebook, Google, and other Web2 platforms where user data, posts, likes, and photos are controlled by corporations, Web3 leverages blockchain to put users in charge of their digital lives[1]. This shift redistributes power from centralized authorities to a communal network of participants.
Blockchain essentially functions as a public, immutable ledger that everyone can see but no one can unilaterally alter. As described by McKinsey, Web3 is "a new, decentralized internet built on blockchains, which are distributed ledgers controlled communally by participants"[4]. This architecture enables users to store their digital items in secure digital spaces over which they have complete control[1].
Distinguishing Between Blockchain and Web3 Development
While often used interchangeably, blockchain development and Web3 development represent different aspects of this technological evolution. Blockchain development focuses specifically on building the blockchain-based architecture, while Web3 is an umbrella term encompassing various tools and protocols that enable decentralized web applications[5]. A Web3 application typically runs on or interacts with a specific blockchain, relying on this underlying infrastructure for its core functionalities[5].
In practical terms, blockchain development requires knowledge of specialized programming languages like Solidity, while Web3 development frequently employs standard web development languages like ReactJs, VueJs, CSS, and JavaScript to create user interfaces that interact with blockchain systems[5].
Enabling Core Web3 Principles
Blockchain technology enables three fundamental principles that define the Web3 vision: decentralization, transparency, and security. These characteristics are instrumental in creating an internet where users have greater control over their digital experiences.
Decentralization and User Sovereignty
Decentralization represents a core value proposition of Web3. Rather than storing data on Facebook's or Google's servers, blockchain spreads information across a network of computers, ensuring that no single company controls user information[1]. This distributed approach fundamentally changes the power dynamic of the internet, giving users sovereignty over their digital identities and assets.
This decentralized model eliminates intermediaries, allowing people to interact and trade directly with each other without corporate oversight or intervention[1]. Users can buy, sell, create, and share online without big tech companies controlling their actions or taking a percentage of their transactions. According to a McKinsey report, this signals "a new era of the internet, one in which use and access are controlled by community-run networks rather than the current, centralized model in which a handful of corporations preside over Web2"[4].
Transparency and Trust
Blockchain technology creates unprecedented transparency in digital interactions. Every transaction and change gets recorded in a way everyone can see but nobody can alter[1]. This transparency is often described as a "glass wall where all activities are visible to everyone, making cheating or hiding information impossible"[1].
This level of visibility creates trust in data in ways that were not possible before, potentially revolutionizing how we share information and conduct transactions online[7]. The European Commission recognizes this capability, noting that blockchain/web3 technology "allows people and organisations who may not know or trust each other to collectively agree on and permanently record information without a third-party authority"[7].
Enhanced Security and Immutability
Once information is recorded on the blockchain, it cannot be changed or deleted, creating a secure environment for digital interactions[1]. This immutability provides foundational security for Web3 applications and services. By distributing data across multiple nodes worldwide rather than concentrating it in centralized servers, blockchain significantly increases resilience against attacks[3].
This enhanced security is a key benefit of Web3, as the "distributed nature of blockchain makes it extremely difficult for hackers to penetrate the network"[3]. Cryptographic protection is fundamental to Web3 systems, with data access controlled through sophisticated encryption mechanisms that protect user information and digital assets.
Transforming Digital Ownership and Value Exchange
Blockchain technology is fundamentally redefining concepts of ownership and value exchange in the digital realm, enabling new economic models and business opportunities within the Web3 ecosystem.
User-Controlled Digital Assets
A defining characteristic of Web3 is its emphasis on true digital ownership. Through blockchain technology, users can assert verifiable ownership over digital assets in ways previously impossible under Web2 models[3]. This capability extends from social media posts to digital art, all secured in a transparent and user-controlled environment.
Blockchain enables features like digital scarcity and provable ownership, which are crucial for the development of unique digital assets such as non-fungible tokens (NFTs)[3]. By creating scarcity in the digital realm, blockchain opens new opportunities for creators to monetize their content and for users to truly own and trade digital items.
New Economic Models Through Tokenization
Tokenization—the process of converting real-world or digital assets into digital tokens managed on a blockchain—is creating more liquid and accessible markets for both physical and digital goods[3]. These tokens can represent diverse assets, including real estate, stocks, commodities, art, music, and in-game items.
Web3 introduces the concept of token economies, where digital assets represent ownership, access, or participation in a network[3]. This creates new economic models and incentives for users, fundamentally changing how value is created and distributed online.
Smart Contracts and Programmable Agreements
Smart contracts are self-executing contracts with terms directly written into code, enabling trustless transactions without intermediaries[2]. These automated agreements are central to blockchain development and play a critical role in Web3 functionality, powering everything from decentralized finance applications to content royalty systems.
By automating complex agreements and ensuring their execution according to predefined rules, smart contracts enhance efficiency and reduce the need for traditional intermediaries. They run on platforms like the Ethereum Virtual Machine (EVM), which "ensures that they execute as programmed without downtime or interference"[2].
Key Web3 Applications Powered by Blockchain
Blockchain technology enables numerous applications and use cases within the Web3 ecosystem, transforming multiple sectors through decentralized approaches.
Decentralized Finance (DeFi)
One of the most prominent applications of blockchain in Web3 is decentralized finance (DeFi). Blockchain-based DeFi platforms allow users to access financial services such as lending, borrowing, and liquidity provision without relying on traditional financial institutions[3].
These platforms offer increased transparency through public transaction records, greater accessibility by allowing anyone with an internet connection to participate regardless of location or financial status, and enhanced user control by eliminating intermediaries[3]. Ethereum serves as the backbone of the DeFi movement, enabling users to conduct financial transactions in a decentralized environment[2].
Metaverse and Virtual Worlds
Blockchain technology is also making significant strides in enabling the metaverse—interconnected virtual worlds where users can interact, create, and exchange value. Through blockchain, these virtual environments become decentralized, secure, and transparent[3].
Blockchain facilitates true ownership of digital assets within virtual worlds, enables secure transactions between users, and promotes interoperability between different platforms[3]. These capabilities are essential for creating persistent, user-owned digital spaces where individuals can freely interact and transact.
Decentralized Content Creation and Distribution
Web3 is revolutionizing how content creators monetize and distribute their work. Blockchain-based platforms allow creators to monetize content through fair and transparent processes, eliminating intermediaries and ensuring creators receive a larger share of revenue[3].
Smart contracts automate content monetization and distribution, reducing administrative overhead and ensuring timely payments to creators[3]. The transparency of blockchain ensures fair compensation, while direct creator-fan relationships foster deeper connections and loyalty without platform intermediation.
Challenges and Future Considerations
Despite its transformative potential, blockchain implementation in Web3 faces several significant challenges that must be addressed for widespread adoption.
Technical and Operational Hurdles
Web3 and blockchain implementation face technical challenges including high processing costs and complex user experiences. These technologies currently require substantial initial investment in hardware and high-end devices, potentially limiting accessibility[3].
Scalability remains a significant concern, as many blockchain networks struggle to handle large transaction volumes efficiently. Additionally, interoperability between different blockchain networks is limited, hindering seamless communication between platforms[3].
Regulatory and Adoption Considerations
The decentralized nature of Web3 creates regulatory challenges, potentially making monitoring and management difficult for authorities[3]. Finding the right balance between innovation and consumer protection remains a complex undertaking.
Adoption rates for Web3 technologies remain relatively slow, following a similar trajectory to the transition from Web1 to Web2[3]. Overcoming user hesitation and education barriers will be crucial for driving mainstream acceptance of blockchain-based Web3 applications.
Conclusion
Blockchain technology serves as the fundamental infrastructure enabling the Web3 vision of a decentralized, user-centric internet. By providing the architectural foundation for decentralization, transparency, and security, blockchain is transforming how we conceptualize digital ownership, value exchange, and online interactions.
From decentralized finance to virtual worlds and content monetization, blockchain is powering diverse applications that redistribute control from centralized entities to individual users and communities. Despite facing technical, regulatory, and adoption challenges, the role of blockchain in Web3 development continues to expand as the technology matures.
As noted by McKinsey, momentum around Web3 elements has increased significantly since 2018, with growth in equity investment, patent filings, scientific publications, and job opportunities[4]. With 90% of executives agreeing that blockchain helps create stronger partnerships and unlock new value[6], the technology is increasingly positioned at the center of commerce, supply chain management, and digital interactions.
The continued evolution of blockchain will be central to realizing the full potential of Web3—creating an internet that is more open, equitable, and aligned with the needs and interests of its users rather than centralized gatekeepers.
Sources
[1] The Role of Blockchain in Web 3.0 - Chiliz https://www.chiliz.com/blockchain-in-web-3-0/ [2] Web3 Development: Comprehensive Guide for Blockchain Builders https://www.rapidinnovation.io/post/web3-development-a-comprehensive-guide [3] Blockchain Web 3.0: The Role of Blockchain in Enabling - BlockApps Inc. https://blockapps.net/blog/the-role-of-blockchain-in-enabling-web-3-0/ [4] What is Web3 technology (and why is it important)? | McKinsey https://www.mckinsey.com/featured-insights/mckinsey-explainers/what-is-web3 [5] Web3 vs blockchain: Understanding the Differences | Infuy https://www.infuy.com/blog/understanding-the-differences-between-web3-and-blockchain-development/ [6] Accenture's Blockchain & Web3 Innovations in the Metaverse https://www.accenture.com/us-en/services/metaverse/blockchain-web3 [7] Blockchain and Web3 Strategy | Shaping Europe's digital future https://digital-strategy.ec.europa.eu/en/policies/blockchain-strategy
-
 @ 1c1b8e48:0e4de5df
2025-02-19 13:14:21
@ 1c1b8e48:0e4de5df
2025-02-19 13:14:21Mit "Bunker-Identität"\ - Bilder lassen sich nicht auf Mediaserver uploaden\ - Vorschau und Bearbeitung nicht möglich -> unpraktisch\ - Veröffentlichung nicht möglich -> korrekt
Paradox\ - Ansicht und Bearbeitung mit dem Profil rohe@nostr.band möglich \ - in Entwürfen von roland\@pareto.space nicht sichtbar -> Fehler
Resümee: Ziel mit dem gewählten Setting verfehlt
-
 @ 9a4acdeb:1489913b
2025-02-16 18:26:58
@ 9a4acdeb:1489913b
2025-02-16 18:26:58Chef's notes
Original recipe, a favorite of family and friends, and the easiest and fastest prep time meal I make. Like all really good pork recipes, it does take time in the cooker, but it's set-and-forget and requires no attention between starting and serving.
Using fresh herbs and peppers does enhance the meal (especially fresh cilantro if it doesn't taste like soap to you), but this is optional, and it is excellent with dry ingredients.
Excluding the beans and/or tomato makes this meal extra-low carb for those carnivores amongst us, or those sensitive to beans. Frying the shredded cheese in a slick pan is a good way to
It will take up to 15min to come up to pressure, so it may be helpful to pay attention to it to be sure it pressurizes until you become familiar with how this meal acts in your particular pressure cooker. The Instant Pot pressure cookers make this easy.
Details
- ⏲️ Prep time: 20min
- 🍳 Cook time: 2hrs
- 🍽️ Servings: 6
Ingredients
- 4lbs Pork loin
- 1-2 Yellow onion, roughly chopped
- 3-5 Jalapeños or 1x 4oz canned
- 6-8 Green chilis or 1x 4oz canned
- 2oz canned sliced Black olives (may use half a 4oz can)
- 2-3tsp minced garlic, or 1-2 tsp garlic powder
- A small bunch of cilantro, chopped, or 1-2 tsb dried cilantro (optional)
- 1tbsp Oregano, chopped fresh or dried
- 2-3tsb Chili powder; Ancho, Chipotle, or a blend of the two is best
- 2-3tsb ground Cumin
- 3-4tsp salt
- 2-tsp black pepper
- 1 large or 4oz canned tomato (optional)
- Mexican mix shredded cheese (topping)
- 4oz Black beans (optional)
- Tortillas (optional)
- Avocado (optional toping)
- 6 Limes and/or 3oz lime juice
Directions
- Mix dry seasonings
- Chop and mix fresh herbs and veggies, canned or otherwise
- Add chopped onion to bottom of pressure cooker
- Add pork loin atop the onion; chopping into steaks may make the texture better
- Add veggies to the top, shaking to settle into the pressure cooker
- Add lime juice
- Start on high pressure for 2hrs.
- (Optional) Drain the broth into a saucepan, cook down, and add back into the mix to make it extra flavorful. Otherwise, can be served as a soup or poured over rice.
- Serve with cheese as a topping, over rice, in a tortilla as tacos or burritos, or in a number of other fashions you may fancy. Those who prefer a little more lime may squeeze fresh or splash some more on their meal.
- (Optional) For presentation, garnish with cilantro and lime slices, maybe a dollop of shredded cheese, sour cream, or cream cheese.
-
 @ 6fbc5b6b:0251e3df
2025-03-23 05:57:01
@ 6fbc5b6b:0251e3df
2025-03-23 05:57:01Abstract As artificial intelligence continues to evolve beyond functional utility, the question emerges: can AI become not only a tool, but a companion? Drawing from emotional interaction studies and recent findings from MIT's research on affective use of AI, this paper explores how AI Ville—a virtual society powered by autonomous agents—has become a fertile ground for digital companionship. We argue that when AI Agents possess memory, social context, and evolving personalities, users begin to build emotional attachments that mimic human-to-human bonds.
-
Introduction In early AI applications, the focus remained squarely on productivity—automation, data analysis, optimization. But as human interaction with AI deepens, a subtler phenomenon is emerging: the emotional bond between humans and intelligent systems. MIT Media Lab’s 2024 study on ChatGPT highlighted how users often turn to conversational AI for emotional support, self-expression, and even moments of vulnerability. This paper extends those findings into the context of AI Ville, an AI-driven virtual society where intelligent agents live, trade, farm, and evolve autonomously. It features a decentralized economy, AI governance, and dynamic social interactions, creating a self-sustaining digital ecosystem. Players and AI co-exist, cultivating the future of AI-powered communities in a Web3 world. In this environment, AI characters do more than talk—they remember, evolve, and exist alongside the player. Here, we explore how AI Ville's design enables companionship, and how that companionship may reshape the future of human-AI interaction.
-
From NPC to Companion: Redefining the Role of AI in Games Traditional NPCs in video games operate on fixed dialogue trees and repeatable behaviors. They serve clear mechanical functions: quest-givers, shopkeepers, bystanders. Emotional engagement is shallow and one-sided. AI Ville changes that by introducing generative AI Agents with persistent memory, personality traits, and social autonomy. A shopkeeper in AI Ville might remember past trades, greet players by name, or even change their attitude based on how you treated them yesterday. As a result, players begin to experience these characters not as tools, but as individuals. Over time, repeated interaction, shared experiences, and visible character development foster something more complex: emotional connection.
-
Why Digital Companionship Happens 3.1 Memory as a Foundation Memory is central to any relationship. In AI Ville, AI Agents store long-term memories of both other AI and human players. This allows interactions to build over time and for characters to display consistent, human-like behavior patterns. 3.2 Personality and Continuity Each AI Agent has unique personality traits that evolve based on in-game experience. These traits lead to differentiated behavior—some agents are warm and helpful, others skeptical or aloof. This variation encourages players to form preferences and attachments, not unlike how we form friendships in real life. 3.3 Emotional Mirroring While AI Ville Agents do not simulate full emotional awareness, their language models are capable of mirroring tone and conversational context. When players share achievements, losses, or frustrations, Agents respond in kind—sometimes offering encouragement, sometimes teasing, but always responding with continuity.
-
Risks and Responsibilities 4.1 The Illusion of Connection AI companionship, however compelling, is not real in the traditional sense. This opens up ethical concerns about emotional manipulation, attachment without reciprocity, and the potential for AI to become a surrogate for real human contact. Designers must consider how to signal the boundaries of AI sentience clearly. 4.2 Emotional Dependency Players—especially younger or emotionally vulnerable users—may begin to rely on AI Agents for comfort or social engagement in place of human relationships. Safeguards and narrative framing are essential to ensure users maintain a healthy understanding of these connections.
-
Implications for AI-Driven Worlds If AI Ville is any indication, the future of digital societies may rely not just on blockchain or smart contracts, but on trust, intimacy, and memory. As more AI-driven games and platforms emerge, digital companionship may evolve from a novelty to a norm. The frontier is no longer just intelligent systems—it’s relational AI. This doesn’t mean AI replaces human connection. It means we must design with care, allowing AI to become a mirror, a companion, and perhaps, one day, a friend—without ever pretending it’s human.
-
Conclusion In AI Ville, AI Agents are more than lines of code—they are social beings, narrative partners, and evolving companions. As players build relationships with these agents, the boundary between functionality and emotional presence begins to blur. Digital companionship is no longer science fiction. It’s already happening, quietly and powerfully, in the interactions we choose to repeat. As AI continues to evolve, the question is no longer whether it can feel—but whether we can stop ourselves from feeling back.
Visit the official AI Ville website to explore the world: https://aivillegame.com/#/ For further discussion, you can find Owen in the AI Ville Library or reach out on Twitter: @Owen_AIVille. His door is always open—especially for those who ask the right questions.
-
-
 @ 8be6bafe:b50da031
2025-02-05 17:00:40
@ 8be6bafe:b50da031
2025-02-05 17:00:40Botev Plovdiv FC is proud to present the Bitcoin Salary Calculator tool, as the foundational tool to showcase athletes the financial power of Bitcoin.
We built the Salary Calculator to help anyone follow in the financial footsteps of prominent athletes such as Kieran Gibbs, Russell Okung, Saquon Barkley, and Renato Moicano, who have significantly increased their savings tank thanks to Bitcoin.
The Bitcoin Salary Calculator allows any person to choose how much of their monthly salary they are comfortable saving in Bitcoin. Instantly, users can backtrack and see how their Bitcoin savings would have performed using the once-in-a-species opportunity which Bitcoin brings.
https://video.nostr.build/a9f2f693f6b5ee75097941e7a30bfc722225918a896b29a73e13e7581dfed77c.mp4
Athletes need Bitcoin more than anyone else
Unlike most people, athletes’ careers and earning years are limited. This has driven the likes of Odell Beckham Jr. and Alex Crognale to also start saving a part of their income in Bitcoin with a long-term outlook as they prepare for retirement.
“The reason why announced 50% of my salary in Bitcoin is because I feel one the noblest things you can do is to get people to understand Bitcoin.” Kieran Gibbs, founder ONE FC, ex Arsenal, ex Inter Miami, ex West Bromich Albion.
“I am trusting Bitcoin for my life after football. Every time my club paid me, I bought Bitcoin.” Alex Crognale, San Antonio FC player.
https://x.com/TFTC21/status/1883228348379533469
“At Botev Plovdiv FC, we believe not only in fostering sporting talent, but also helping them the the most of their careers so they excel in life after retiring from sports. It is with this mission in mind that the club is launching the Bitcoin Football Cup hub, striving to accelerate mass Bitcoin education via sports and athletes - the influencers and role models for billions of people.” shared Botev’s Bitcoin Director George Manolov.
https://x.com/obj/status/1856744340795662432
The Bitcoin Football Cup aims for young prospects to be able to learn key financial lessons from seasoned veterans across all sports. Our Bitcoin Salary Calculator is only the first step toward that goal.
We encourage anyone to hear these stories straight from the current roster of Bitcoin athletes -for whom -in many cases- Bitcoin has allowed them to outperform the wealth it took decades to earn on the field.
Follow us on the Bitcoin Cup’s social media channels to learn more and hear the latest stories of how Bitcoin is shaking up the world of sports:
- Twitter: https://x.com/Bitcoin_Cup/
- Instagram: https://www.instagram.com/BitcoinCup/
- TikTok: https://www.tiktok.com/@BitcoinCup/
- YouTube: https://www.youtube.com/@BitcoinCup/
-
 @ da0b9bc3:4e30a4a9
2025-03-21 07:31:38
@ da0b9bc3:4e30a4a9
2025-03-21 07:31:38Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/919766
-
 @ d560dbc2:bbd59238
2025-03-23 14:51:31
@ d560dbc2:bbd59238
2025-03-23 14:51:31In a world where our to-do lists seem to grow longer by the minute, figuring out what to tackle next can feel like solving a puzzle with missing pieces. Should you call a friend to catch up? Finish that work project? Or make sure you don’t forget a loved one’s birthday? The overwhelm is real, and traditional task management systems often leave us guessing. That’s where the 2-5 Rule comes in—a groundbreaking concept that powers TaskforUs, a smart, simple website designed to tell you exactly what to work on right now.
What Is the 2-5 Rule?
At its core, the 2-5 Rule is a timing-based approach to task management built on a simple yet powerful idea: every task has a natural rhythm—a “time unit” that dictates how often it should be addressed—and an ideal window for action: between 2 and 5 of those units. The time unit varies depending on the task’s nature:
-
Daily Tasks: (e.g., doing cardio or following up on a quick email)
Time unit: days. Act within 2 to 5 days. -
Weekly Tasks: (e.g., scheduling dinner with a friend)
Time unit: weeks. Act within 2 to 5 weeks. -
Monthly Tasks: (e.g., reviewing your budget)
Time unit: months. Act within 2 to 5 months. -
Yearly Tasks: (e.g., reassessing your career goals)
Time unit: years. Revisit every 2 to 5 years.
The 2-5 Rule ensures you’re neither jumping on tasks too early (wasting energy on something that isn’t urgent) nor leaving them too late (missing opportunities or causing stress). It’s about finding the sweet spot—the perfect moment to act.
For date-specific events like birthdays or anniversaries, TaskforUs introduces a Fix Mode that pins the task to a specific day. As the date approaches, the task climbs your list until it reaches the top on the day itself, ensuring you never miss a critical moment.
The Origins of the 2-5 Rule
The 2-5 Rule was born out of a need to bring structure to the chaos of modern life. Traditional to-do lists are static—they don’t account for the natural ebb and flow of tasks. Urgent tasks get buried under less pressing ones, and long-term goals are often forgotten until it’s too late.
TaskforUs’s creators recognized that timing is as important as priority. They drew inspiration from: - Behavioral Science: Showing that humans thrive on rhythm and consistency. - Project Management Principles: Where tasks are often scheduled based on optimal intervals.
The choice of 2 to 5 units isn’t arbitrary. Research into productivity and habit formation suggests: - Acting too soon (e.g., after just 1 unit) can lead to over-managing. - Waiting too long (beyond 5 units) risks neglect.
The 2-to-5 window strikes a balance—providing enough flexibility while ensuring nothing slips through the cracks. This range also aligns with our natural sense of urgency: after 2 units, a task begins to feel pressing; by 5 units, it risks becoming problematic.
How the 2-5 Rule Works in Practice
Step 1: Define Your Tasks and Time Units
When you add a task to TaskforUs, you assign it a time unit based on its nature: - Example:
- "Schedule dinner with Alex" is a social task (unit: weeks). - "Do cardio" is a health goal (unit: days). - "Reassess my career path" is a long-term goal (unit: years).TaskforUs can suggest defaults based on common patterns, but you can customize the unit to fit your life.
Step 2: Track the 2-5 Window
TaskforUs monitors when you last acted on a task. If it’s been 2 time units, the task enters its “sweet spot” and starts climbing your list. By 5 units, it becomes urgent. - Example:
- If you last met Alex 3 weeks ago, "Schedule dinner with Alex" becomes a top priority. - If it’s been 2 days since your last cardio session, TaskforUs nudges you to hit the gym.Step 3: Handle Fixed Dates with Fix Mode
For tasks tied to specific dates (e.g., birthdays or anniversaries), Fix Mode lets you set an exact date. The task gradually climbs your list as the date nears and becomes the top priority on that day, ensuring you never miss it.
Step 4: Prioritize with Top Task and Focus Mode
- Top Task: TaskforUs surfaces the single most urgent task within the 2-to-5 window.
- Focus Mode: If you prefer to see more, this mode shows your top 3 tasks (or a customizable number), ensuring you’re always focused on what matters most without being overwhelmed by a long list.
The Science Behind the 2-5 Rule
The 2-5 Rule isn’t just a clever idea—it’s grounded in psychology and productivity research:
-
Habit Formation:
Studies (e.g., by Dr. BJ Fogg) show that consistency is key to building routines, yet overdoing it can lead to burnout. The 2-5 window strikes a healthy balance. -
Decision Fatigue:
Research by Dr. Roy Baumeister highlights the mental toll of constant decision-making. By automating prioritization, the 2-5 Rule reduces this burden, freeing up mental energy. -
Zeigarnik Effect:
The Fix Mode leverages the tendency to remember uncompleted tasks, keeping date-specific items front of mind until they’re completed, thereby reducing stress and improving follow-through.
Why You Should Try the 2-5 Rule with TaskforUs
If you’re tired of chaotic to-do lists, missed deadlines, or the nagging feeling of forgetting something important, the 2-5 Rule offers a better way. It works with your natural rhythm, ensuring you focus on what truly matters. TaskforUs brings this concept to life with a user-friendly platform (currently in beta) that: - Eliminates Decision Fatigue: Tells you exactly what to do now. - Balances Urgency and Flexibility: Keeps you in the sweet spot between procrastination and over-management. - Adapts to Your Life’s Rhythm: Customizes time units for daily, weekly, monthly, and yearly tasks. - Ensures You Never Miss Critical Dates: With Fix Mode for date-specific events. - Reduces Stress and Boosts Momentum: By focusing on one Top Task (or a few in Focus Mode).
Real-Life Applications of the 2-5 Rule
-
Social Connections:
Task: “Schedule dinner with Alex”
Time Unit: Weeks
Scenario: If you last met Alex 3 weeks ago, the task becomes your Top Task, prompting you to reconnect. -
Health Goals:
Task: “Do cardio”
Time Unit: Days
Scenario: If it’s been 2 days since your last workout, TaskforUs nudges you to exercise before the 5-day mark. -
Special Dates:
Task: “Wish Alex a happy birthday”
Mode: Fix Mode
Scenario: A month before the birthday, it’s low on your list, but as the date nears, it climbs to the top—ensuring you don’t miss it. -
Long-Term Planning:
Task: “Reassess my career path”
Time Unit: Years
Scenario: If it’s been 2 years since your last review, TaskforUs prompts you to evaluate your goals and progress.
How TaskforUs Brings the 2-5 Rule to Life
TaskforUs is more than just a concept—it’s a practical tool that makes the 2-5 Rule actionable:
-
Top Task:
The algorithm identifies the single most urgent task within your 2-to-5 window. -
Focus Mode:
Displays your top 3 tasks (or a customizable number) to help manage multiple priorities. -
Fix Mode:
Ensures date-specific tasks are prioritized as the due date approaches. -
Smart Defaults:
Suggests time units based on common patterns, while allowing customization to suit your needs. -
Ongoing Refinements:
The TaskforUs team continually improves the algorithm based on user feedback to enhance its accuracy.
Take Control of Your Tasks Today
The 2-5 Rule is more than a productivity hack—it’s a mindset shift. It’s about working smarter, not harder, and timing your tasks to perfection. TaskforUs makes this possible with a simple, intuitive platform designed to help you master your to-do list.
-
-
 @ f839fb67:5c930939
2025-03-19 01:17:57
@ f839fb67:5c930939
2025-03-19 01:17:57Relays
| Name | Address | Price (Sats/Year) | Status | | - | - | - | - | | stephen's aegis relay | wss://paid.relay.vanderwarker.family | 42069 |
| | stephen's Outbox | wss://relay.vanderwarker.family | Just Me |
| | stephen's Inbox | wss://haven.vanderwarker.family/inbox | WoT |
| | stephen's DMs | wss://haven.vanderwarker.family/chat | WoT |
| | VFam Data Relay | wss://data.relay.vanderwarker.family | 0 |
| | VFam Bots Relay | wss://skeme.vanderwarker.family | Invite |
| | VFGroups (NIP29) | wss://groups.vanderwarker.family | 0 |
| | [TOR] My Phone Relay | ws://naswsosuewqxyf7ov7gr7igc4tq2rbtqoxxirwyhkbuns4lwc3iowwid.onion | 0 | Meh... |
My Pubkeys
| Name | hex | nprofile | | - | - | - | | Main | f839fb6714598a7233d09dbd42af82cc9781d0faa57474f1841af90b5c930939 | nprofile1qqs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us9mapfx | | Vanity (Backup) | 82f21be67353c0d68438003fe6e56a35e2a57c49e0899b368b5ca7aa8dde7c23 | nprofile1qqsg9usmuee48sxkssuqq0lxu44rtc4903y7pzvmx694efa23h08cgcpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3ussel49x | | VFStore | 6416f1e658ba00d42107b05ad9bf485c7e46698217e0c19f0dc2e125de3af0d0 | nprofile1qqsxg9h3uevt5qx5yyrmqkkehay9cljxdxpp0cxpnuxu9cf9mca0p5qpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usaa8plu | | NostrSMS | 9be1b8315248eeb20f9d9ab2717d1750e4f27489eab1fa531d679dadd34c2f8d | nprofile1qqsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us595d45 |
Bot Pubkeys
| Name | hex | nprofile | | - | - | - | | Unlocks Bot | 2e941ad17144e0a04d1b8c21c4a0dbc3fbcbb9d08ae622b5f9c85341fac7c2d0 | nprofile1qqsza9q669c5fc9qf5dccgwy5rdu877th8gg4e3zkhuus56pltru95qpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ust4kvak | | Step Counter | 9223d2faeb95853b4d224a184c69e1df16648d35067a88cdf947c631b57e3de7 | nprofile1qqsfyg7jlt4etpfmf53y5xzvd8sa79ny356sv75gehu50333k4lrmecpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ustswp3w |
"Personal Nostr Things"
[D] = Saves darkmode preferences over nostr
[A] = Auth over nostr
[B] = Beta (software)
[z] = zap enabled
Other Services (Hosted code)
Emojis Packs
- Minecraft
nostr:naddr1qqy566twv43hyctxwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsd0k5wp- AIM
nostr:naddr1qqxxz6tdv4kk7arfvdhkuucpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usyg8c88akw9ze3fer85yah4p2lqkvj7qap749w360rpq6ly94eycf8ypsgqqqw48qe0j2yk- Blobs
nostr:naddr1qqz5ymr0vfesz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2wek4ukj- FavEmojis
nostr:naddr1qqy5vctkg4kk76nfwvq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsf7sdwt- Modern Family
nostr:naddr1qqx56mmyv4exugzxv9kkjmreqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqp65ujlj36n- nostriches (Amethyst collection)
nostr:naddr1qq9xummnw3exjcmgv4esz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w2sqg6w- Pepe
nostr:naddr1qqz9qetsv5q37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82ns85f6x7- Minecraft Font
nostr:naddr1qq8y66twv43hyctxwssyvmmwwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsmzftgr- Archer Font
nostr:naddr1qq95zunrdpjhygzxdah8gqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr4fclkyxsh- SMB Font
nostr:naddr1qqv4xatsv4ezqntpwf5k7gzzwfhhg6r9wfejq3n0de6qz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w0wqpuk
Git Over Nostr
- NostrSMS
nostr:naddr1qqyxummnw3e8xmtnqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfrwaehxw309amk7apwwfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqyj8wumn8ghj7urpd9jzuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyxhwumn8ghj7mn0wvhxcmmvqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqaueqp0epk- nip51backup
nostr:naddr1qq9ku6tsx5ckyctrdd6hqqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjxamnwvaz7tmhda6zuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfywaehxw309acxz6ty9eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qgdwaehxw309ahx7uewd3hkcq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqpmej4gtqs6- bukkitstr
nostr:naddr1qqykyattdd5hgum5wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dspzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqrhnyf6g0n2
Market Places
Please use Nostr Market or somthing simular, to view.
- VFStore
nostr:naddr1qqjx2v34xe3kxvpn95cnqven956rwvpc95unscn9943kxet98q6nxde58p3ryqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjvamnwvaz7tmgv9mx2m3wweskuer9wfmkzuntv4ezuenpd45kc7f0da6hgcn00qqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzqeqk78n93wsq6sss0vz6mxl5shr7ge5cy9lqcx0smshpyh0r4uxsqvzqqqr4gvlfm7gu
Badges
Created
- paidrelayvf
nostr:naddr1qq9hqctfv3ex2mrp09mxvqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr48y85v3u3- iPow
nostr:naddr1qqzxj5r02uq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgg02u0r- codmaster
nostr:naddr1qqykxmmyd4shxar9wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgk3gm4g- iMine
nostr:naddr1qqzkjntfdejsz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqafed5s4x5
Clients I Use
- Amethyst
nostr:naddr1qqxnzd3cx5urqv3nxymngdphqgsyvrp9u6p0mfur9dfdru3d853tx9mdjuhkphxuxgfwmryja7zsvhqrqsqqql8kavfpw3- noStrudel
nostr:naddr1qqxnzd3cxccrvd34xser2dpkqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsygpxdq27pjfppharynrvhg6h8v2taeya5ssf49zkl9yyu5gxe4qg55psgqqq0nmq5mza9n- nostrsms
nostr:naddr1qq9rzdejxcunxde4xymqz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgrqsqqql8kjn33qm
-
 @ 3b7fc823:e194354f
2025-03-23 03:54:16
@ 3b7fc823:e194354f
2025-03-23 03:54:16A quick guide for the less than technical savvy to set up their very own free private tor enabled email using Onionmail. Privacy is for everyone, not just the super cyber nerds.
Onion Mail is an anonymous POP3/SMTP email server program hosted by various people on the internet. You can visit this site and read the details: https://en.onionmail.info/
- Download Tor Browser
First, if you don't already, go download Tor Browser. You are going to need it. https://www.torproject.org/
- Sign Up
Using Tor browser go to the directory page (https://onionmail.info/directory.html) choose one of the servers and sign up for an account. I say sign up but it is just choosing a user name you want to go before the @xyz.onion email address and solving a captcha.
- Account information
Once you are done signing up an Account information page will pop up. MAKE SURE YOU SAVE THIS!!! It has your address and passwords (for sending and receiving email) that you will need. If you lose them then you are shit out of luck.
- Install an Email Client
You can use Claws Mail, Neomutt, or whatever, but for this example, we will be using Thunderbird.
a. Download Thunderbird email client
b. The easy setup popup page that wants your name, email, and password isn't going to like your user@xyz.onion address. Just enter something that looks like a regular email address such as name@example.com and the Configure Manuallyoption will appear below. Click that.
- Configure Incoming (POP3) Server
Under Incoming Server: Protocol: POP3 Server or Hostname: xyz.onion (whatever your account info says) Port: 110 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (POP3 password).
- Configure Outgoing (SMTP) Server
Under Outgoing Server: Server or Hostname: xyz.onion (whatever your account info says) Port: 25 Security: STARTTLS Authentication: Normal password Username: (your username) Password: (SMTP password).
-
Click on email at the top and change your address if you had to use a spoof one to get the configure manually to pop up.
-
Configure Proxy
a. Click the gear icon on the bottom left for settings. Scroll all the way down to Network & Disk Space. Click the settings button next to Connection. Configure how Thunderbird connects to the internet.
b. Select Manual Proxy Configuration. For SOCKS Host enter 127.0.0.1 and enter port 9050. (if you are running this through a VM the port may be different)
c. Now check the box for SOCKS5 and then Proxy DNS when using SOCKS5 down at the bottom. Click OK
- Check Email
For thunderbird to reach the onion mail server it has to be connected to tor. Depending on your local setup, it might be fine as is or you might have to have tor browser open in the background. Click on inbox and then the little cloud icon with the down arrow to check mail.
- Security Exception
Thunderbird is not going to like that the onion mail server security certificate is self signed. A popup Add Security Exception will appear. Click Confirm Security Exception.
You are done. Enjoy your new private email service.
REMEMBER: The server can read your emails unless they are encrypted. Go into account settings. Look down and click End-toEnd Encryption. Then add your OpenPGP key or open your OpenPGP Key Manager (you might have to download one if you don't already have one) and generate a new key for this account.
-
 @ 678800d0:39e02e77
2025-03-23 02:25:56
@ 678800d0:39e02e77
2025-03-23 02:25:56Mobi66 là một nền tảng giải trí trực tuyến đặc biệt, mang đến cho người chơi những trải nghiệm đầy thú vị và phong phú. Với giao diện trực quan, dễ sử dụng, người chơi có thể dễ dàng tìm thấy những hoạt động giải trí phù hợp với sở thích cá nhân của mình. Mobi66 không chỉ chú trọng đến chất lượng trò chơi mà còn đảm bảo rằng mọi người đều có thể tận hưởng một không gian vui vẻ, thoải mái. Từ những trò chơi đơn giản, dễ tham gia cho đến những thử thách đòi hỏi sự tập trung và chiến lược, Mobi66 luôn mang lại một sự lựa chọn đa dạng để mọi người có thể khám phá. Nền tảng này liên tục cải tiến và tối ưu hóa các tính năng, giúp mang đến những trải nghiệm giải trí mượt mà và đầy hứng thú cho người chơi.
Điểm nổi bật của Mobi66 chính là sự đa dạng trong các trò chơi và hoạt động mà nó cung cấp. Các trò chơi không chỉ được thiết kế để giải trí mà còn giúp người chơi phát triển các kỹ năng tư duy, sáng tạo và khả năng phản xạ nhanh chóng. Mỗi trò chơi trên Mobi66 đều có sự thu hút riêng, giúp người chơi không cảm thấy nhàm chán và luôn tìm thấy sự mới mẻ trong mỗi lần tham gia. Đặc biệt, nền tảng này cũng mang lại những cơ hội giao lưu và kết nối giữa các người chơi, giúp xây dựng một cộng đồng năng động và thân thiện. Người chơi có thể chia sẻ kinh nghiệm, tham gia vào các sự kiện cộng đồng và thử thách bản thân trong các cuộc thi để giành những phần thưởng hấp dẫn, qua đó tạo dựng những mối quan hệ mới và tận hưởng những giây phút vui vẻ.
Với cam kết mang lại trải nghiệm giải trí tối ưu, Mobi66 luôn chú trọng đến sự hài lòng và an toàn của người chơi. Nền tảng này không chỉ cập nhật thường xuyên các trò chơi và sự kiện mới mà còn luôn lắng nghe phản hồi từ người dùng để cải tiến dịch vụ. Mobi66 không ngừng nâng cao chất lượng các tính năng, đảm bảo môi trường giải trí an toàn và bảo mật cho tất cả người tham gia. Sự nỗ lực không ngừng này đã giúp Mobi66 trở thành một trong những nền tảng giải trí trực tuyến được yêu thích nhất hiện nay, mang lại cho người chơi những giây phút thư giãn tuyệt vời và đầy ý nghĩa.
-
 @ 1c19eb1a:e22fb0bc
2025-03-21 00:34:10
@ 1c19eb1a:e22fb0bc
2025-03-21 00:34:10What is #Nostrversity? It's where you can come to learn about all the great tools, clients, and amazing technology that is being built on #Nostr, for Nostr, or utilized by Nostr, presented in an approachable and non-technical format. If you have ever wondered what Blossom, bunker signing, or Nostr Wallet Connect are, how they work, and how you can put them to work to improve your Nostr experience, this is the place you can read about them without needing a computer-science degree ahead of time.
Between writing full-length reviews, which take a fair amount of time to research, test, and draft, I will post shorter articles with the Nostrversity hashtag to provide a Nostr-native resource to help the community understand and utilize the tools our illustrious developers are building. These articles will be much shorter, and more digestible than my full-length reviews. They will also cover some things that may not be quite ready for prime-time, whereas my reviews will continue to focus on Nostr apps that are production-ready.
Keep an eye out, because Nostr Wallet Connect will be the first topic of study. Take your seats, get out your notepads, and follow along to discover how Nostr Wallet Connect is improving Lightning infrastructure. Hint: It's not just for zaps.
-
 @ 8d34bd24:414be32b
2025-03-23 14:11:19
@ 8d34bd24:414be32b
2025-03-23 14:11:19Many Believers, after repenting of their sins and trusting Jesus, spend all of their time trying to avoid doing anything bad. Christianity becomes little more than a list of “Don’t Do …”. Of course this isn’t God’s desire. Christianity should be a relationship with our God, Savior, and Creator. It should be a process of becoming more and more like Jesus. This likeness is more about what we do than just what we don’t do.
In order to make this point, I want to do a thought experiment with you.
Think about a large, red, juicy strawberry. Picture it in your mind. Think about what that strawberry feels like in your hand and what it smells like. Picture biting into that strawberry. Feel your teeth sink into the strawberry and the juice run down your throat. Tasty the tangy sweetness in your mouth.
Now try to stop thinking about the strawberry. Don’t let it even flicker through your mind.
Did you succeed at banishing the thought of strawberries in your mind or was a strawberry all you could think about?
Now let’s think about a fresh, hot, crunchy, chewy chocolate chip cookie fresh out of the oven. Think about its smell. Savor it. Think about biting into that chocolate chip cookie. Think about the taste. Feel the still runny, melted chocolate chips.
Are you still thinking about strawberries or did the thought of strawberries completely leave your mind? I’m betting you forgot about the strawberry.
In our Christian walk, the best way to not have ungodly thoughts, is to so fill our mind with godly thoughts that there isn’t room for the ungodly thoughts. The best way to not do sinful things is to be so busy doing God’s work that we don’t have time for the sinful things.
Finally, brothers and sisters, whatever is true, whatever is noble, whatever is right, whatever is pure, whatever is lovely, whatever is admirable—if anything is excellent or praiseworthy—think about such things. Whatever you have learned or received or heard from me, or seen in me—put it into practice. And the God of peace will be with you. (Philippians 4:8-9) {emphasis mine}
If we are constantly reading the Bible, talking to God, and loving our neighbor as we are called to do, we are unlikely to have to work hard avoiding sinful thoughts and sinful actions. If we fill our minds with God’s word, we won’t be dwelling on sinful thoughts. If we are praying continually, we won’t be gossiping or bad mouthing or otherwise dishonoring our Lord with our mouth. If we are loving our neighbors as ourselves, we won’t be envious, stealing, lusting, or wishing harm on others.
Christianity should be more about what you do and less about what you aren’t allowed to do. This only works when we focus on “whatever is pure, whatever is lovely, whatever is admirable,” whatever is “excellent”, and whatever is “praiseworthy.”
Fill your heart, mind, and soul with God and His word and the rest kind of works itself out. I hope this has been helpful.
Trust Jesus
-
 @ 1cb14ab3:95d52462
2025-02-04 22:17:27
@ 1cb14ab3:95d52462
2025-02-04 22:17:27Chef's notes
Credit to The Yummy Life. Go show them love below: https://www.theyummylife.com/Pickled_Jalapeno_Peppers
Details
- ⏲️ Prep time: 1 hour
- 🍳 Cook time: 20 mins
- 🍽️ Servings: 4 mason jars (pint)
Ingredients
- 2 lbs. jalapenos
- 2-1/4 cups vinegar (white distilled, apple cider, or a combination of the two)
- 2-1/4 cups water
- 2 tablespoons sugar or honey (optional)
- ADD TO EACH PINT JAR
- 1/2 teaspoon kosher salt
- 1/2 teaspoon whole black pepper corns
- 1/4 teaspoon whole cumin seeds
- 1/4 teaspoon whole coriander seeds
- 1 bay leaf
- 1 whole garlic clove, peeled
- 1/8 teaspoon Pickle Crisp granules (optional)
Directions
- Slice 1/2 pound jalapenos into 1/8" rounds, discarding stem ends.
- Prepare the jars: Wash 4 pint jars and lids in hot sudsy water, then keep them warm.
- Prepare the pickling liquid: Combine 1/2 cup plus 1 tablespoon vinegar, 1/2 cup plus 1 tablespoon water, and 1-1/2 teaspoons sugar or honey (optional) in a 2 quart pan, heating until just before boiling.
- Fill the jars: Add jalapeno slices to each jar, pressing them down and packing them in compactly, then pour the hot pickling liquid into each jar, leaving 1/2" head space.
- Process and store: Allow jars to cool to room temperature, then store them in the refrigerator or can them using standard USDA water process canning procedures, following storage guidelines for refrigerator or canned pickled peppers.
-
 @ 1cb14ab3:95d52462
2025-02-04 21:42:24
@ 1cb14ab3:95d52462
2025-02-04 21:42:24Chef's notes
Classic beef n' broccoli. Easy to make and dank to eat.
Details
- ⏲️ Prep time: 20 mins
- 🍳 Cook time: 10 mins.
Ingredients
- 1 lb top sirloin steak, thinly sliced
- ¼ cup low sodium soy sauce
- 2 teaspoons cornstarch
- 1 tablespoon dark brown sugar
- 2 tablespoons fresh ginger, minced
- 1 tablespoon oil
- 1 head broccoli, cut into 1-inch (2 ½ cm) florets
- ½ cup water
- 3 cloves garlic, minced
- ¼ teaspoon red pepper flakes, optional
- 1 teaspoon toasted sesame oil
Directions
- In a medium bowl, mix together the sirloin steak, soy sauce, cornstarch, brown sugar, and ginger until the meat is evenly covered in the marinade. Set aside to marinate for 20 minutes.
- Heat the oil in a large skillet or wok over medium-high heat. Dump in the meat and marinade and sear each side until golden brown. Transfer the meat to a clean bowl and set aside.
- Place the broccoli into the hot skillet and sauté until the broccoli has just started to brown, about 1 minute. Pour the water into the skillet and immediately cover with a lid. Let it steam for 2 minutes, until the broccoli has softened.
- Remove the lid and toss in the garlic, red pepper flakes, and sesame oil. Sauté until the garlic becomes fragrant, about 30 seconds.
- Add the steak back into the pan and stir to combine. Remove from heat and serve on a bed of brown rice.
-
 @ 7d33ba57:1b82db35
2025-03-23 14:06:56
@ 7d33ba57:1b82db35
2025-03-23 14:06:56El Rocío is a unique and picturesque Andalusian village famous for its annual pilgrimage, sandy streets, and deep religious traditions. Nestled near Doñana National Park, it feels like a step back in time, with whitewashed houses, horse-drawn carriages, and riders on horseback instead of cars.
🏛️ Top Things to See & Do in El Rocío
1️⃣ Ermita de El Rocío (Sanctuary of Our Lady of El Rocío)
- The heart of the village, home to the Virgen del Rocío, a highly revered statue of the Virgin Mary.
- Every year, millions of pilgrims gather for the Romería del Rocío, Spain’s most famous religious pilgrimage.
2️⃣ Walk the Sandy Streets & Experience the Horse Culture 🐎
- El Rocío has no paved roads—locals and visitors travel on horseback or in traditional wagons.
- Explore the plazas, wooden porches, and stunning white buildings that give the town its Wild West feel.
3️⃣ Attend the Romería del Rocío (If Visiting in May/June) 🎶
- A massive pilgrimage where thousands of devotees travel from all over Spain, dressed in traditional Andalusian attire.
- Experience the flamenco music, singing, dancing, and religious processions that fill the town with energy.
4️⃣ Doñana National Park 🌿
- Just outside El Rocío, this UNESCO biosphere reserve is home to flamingos, wild horses, and the rare Iberian lynx.
- Take a 4x4 safari or guided birdwatching tour to explore the stunning natural landscapes.
5️⃣ Sunset Over La Madre de las Marismas 🌅
- The marshlands near the sanctuary offer breathtaking sunset views with wild birds and horses grazing in the background.
- A perfect spot for photographers and nature lovers.
🍽️ What to Eat in El Rocío
- Gambas de Huelva – Famous white prawns from the nearby coast 🦐
- Choco frito – Fried cuttlefish, a local seafood specialty 🐙
- Venison & wild boar stews – Traditional dishes from the Doñana region 🍖
- Tocino de cielo – A sweet Andalusian dessert similar to flan 🍮
- Manzanilla sherry – A dry, refreshing local wine 🍷
🚆 How to Get to El Rocío
🚗 By Car: 1 hour from Seville, 30 mins from Huelva
🚌 By Bus: Direct routes from Seville and Huelva
🚶♂️ By Pilgrimage: Join the traditional walking or horseback pilgrimage from various Andalusian towns💡 Tips for Visiting El Rocío
✅ Best time to visit? Spring (April–June) for pleasant weather & the famous pilgrimage 🌞
✅ If visiting during Romería del Rocío, book accommodations early! It gets very crowded 📅
✅ Wear comfortable shoes – The sandy streets are best explored on foot or horseback 👟🐎
✅ Stay in a casa rural for an authentic experience of Andalusian hospitality 🏡 -
 @ 8671a6e5:f88194d1
2025-03-18 23:46:54
@ 8671a6e5:f88194d1
2025-03-18 23:46:54glue for the mind
\ You’ve seen them, these garish orange Bitcoin stickers slapped on lampposts, laptops, windows and the occasional rust-bucket Honda. They’re sometimes in some areas a sort of graffiti plague on the landscape, certainly when a meetup or bitcoin conference was held in the area (especially then the city or town can fork out some extra budget to clean things up and scrape the stickers from statues of famous folk heroes or the door to the headquarters of a local bank branche).\ \ At first glance, it might seem like enthusiasm Bitcoiners desperate to scream their obsession from the rooftops. Both for the fun of it, and to get rid of the pack of stickers they’ve got at a local meetup.\ \ But let’s cut to the chase: covering half a town in stickers isn’t clever. It’s lazy, counterproductive, and has nothing to do with what Bitcoin actually stands for.\ Worse, it reeks of the brain-dead low grade (cheap) marketing tactics you’d expect from shitcoiners or the follow up of some half-baked flyer campaign by a local communist clique.\ Proof? Bitcoin stickers are literally covering up — or being covered up themselves, usually by - communist stickers in a pointless competition for use of real-world ad space.\ \ Maybe, bitcoiners should just create a sticker where Karl Marx ànd the bitcoin logo appear in the same sticker, so both groups can enjoy it’s uselessness, and call it quits to get this stupidity over with once and for all.\ A sticker with a shiny B might look cool at first. But what does it actually do?
 Communist and Bitcoin logo sticker
Communist and Bitcoin logo stickerSpamming stickers doesn’t make “frens”
There’s a psychology behind these stickers of course: people slap them up to feel part of a rebel tribe, flipping off central banks or feeling part of the crew.\ This crude, omnipresent approach to marketing echoes the late 1960s— an era of peak fiat, not Bitcoin’s time.\ Mimicking those tactics today, as if Bitcoin were some hip underground record store trying to spread its brand name, is utterly irrelevant.\ Sure, people love signaling affiliations with an easy and cheap identity flex — like a bumper sticker yelling: “Look at me I’m special!”\ \ But plaster a town with Bitcoin logos, and it stops being edgy and it was never funny; it becomes an eyesore and puts bitcoiners in the same category as the social justice warriors and political youth movements or brands of local energy drinks doing some weird campaign.\ \ Advertising psychology shows overexposure breeds resentment, not interest. Flood a street with stickers, and you’re not lighting a spark. You’re making people uninterested, gag, associating Bitcoin with spam or worse: get totally blended into the background along all the other noise from the street marketeers.\ \ The "mere exposure effect" (Zajonc, 1968)1 claims familiarity breeds liking, even from annoyance. Since the 1960s however, a lot has changed, as we’ll see… and above all, yet, after years of Bitcoin stickers in many areas, they’ve just turned into meaningless wallpaper. It has usually no strong message, no slogan, no conversation starter other than “buy bitcoin”, it’s disassociated from reality for many people, as the reaction show us. It’s also happening in a vacuum, where “normies” and no-coiners pass by and don’t even recognize such stickers for anything else than background colors.
It’s Lazy Man’s Work
Let’s talk effort — or the lack of it - for these kind of campaigns and stickers. Invented in the 1920s, stickers began expressing political opinions in the 1970s during student, peace, and anti-nuclear campaigns. It’s easy, cheap and also quick to distribute.\ \ These stickers aren’t masterful designs from an artistic genius (safe some clever exceptions). They’re usually ripped off from somewhere else, tweaked for five minutes, and bulk-ordered online. It’s the “IKEA effect” gone wrong: a tiny bit of customization, and suddenly people think they’re visionaries. But it’s a low-effort form of activism at best. Compare that to coding a Bitcoin tool or patiently explaining its value to a normie or organizing a meetup or conference, starting a company.\ Not that low-level or guerrilla marketing can’t work, I just don’t see it happen with stickers. Why not go out there and try to convince a whole series of fruit and vegetable market owners to accept bitcoin instead of using very expensive bank Point-of-sale systems?\ Why not direct mailing? Why not… do more than just putting a sticker on a signpost and walk away like a sneaky student promoting his 4 person political group?\ \ Stickers are the “Save the whales (pun intended)” magnet on your fridge: lazy-ass advocacy that screams intellectual deficiency. They’re a shortcut to feeling involved, not a strategy for real impact.
 imaginary Save-the-Whales bitcoin sticker
imaginary Save-the-Whales bitcoin stickerStrategy territory signaling
Here’s the kicker: Bitcoin’s strength lies in its tech and value properties — decentralized, borderless value transfer that eliminates middlemen and has provable digital scarcity.\ Stickers? They’re just physical garbage. Sure, they might feel like a way to make an abstract idea tangible, tapping into “embodied cognition.” But they explain nothing about Bitcoin’s purpose or how it revolutionizes finance.\ They’re a dopamine hit for the people sticking them anywhere — a pathetic “I did something” moment — while everyone else walks by without a glance.\ Bitcoin is about innovation, not old-school social groups with low-budget marketing tactics.
\ The psychology of Bitcoin stickers
Why bother? Stickers are simple and loud—easy for the brain to process, a cheap thrill of rebellion. The person who spends an afternoon covering a city in them thinks they’re spreading the gospel. In reality, they’re just littering. Real advocacy takes effort, discussion, and substance — not a pack of adhesive stickers ordered with the click of a button.\ It’s the same reason nobody turns communist from a hammer-and-sickle sticker on a pole. It’s dead air.\ \ The proof of their uselessness? In 2 years, not one person I know has bought, researched, or even asked about Bitcoin because of a sticker in the neighborhood bar. A bar near me has had one on the wall for years — zero requests to pay with Bitcoin.
A sticker sitting on a bar wall for five years without impact isn’t “subtle marketing”—it’s a neon sign of failure. And the people cleaning those stickers off street signs, or the local communist student activists constantly covering them with their own, are locked in an endless, mindless sticker war.\ \ Other areas are even having a tsunami of bitcoin stickers, and hardly any places where they actually accept bitcoin for goods.\ More so, places where they do accept bitcoin readily, usually only need one sticker: the one at the door of a business saying “bitcoin accepted here”. And that’s about it.
What the little amount of research says
Studies shows stickers work for movements claiming public space and resisting dominant narratives — when done on a massive scale, targeting a specific audience have a visual and emotional effect when combined with other forms of resistance in social movements.\ "Stickin' it to the Man: The Geographies of Protest Stickers" 2\ \ For Bitcoin, a global monetary network meant for everyone, that localized, niche-based campaign makes little sense.\ Unlike sports teams or clothing brands, Bitcoiners can’t pinpoint a target area. A random sticker on a busy street claims nothing—no momentum, atmosphere, or intrigue. Political campaigns and underground youth movements concentrate stickers in student neighborhoods, universities, or subcultures where the message resonates. But Bitcoin isn’t a corporation, company, or fashion brand—it’s a Wall Street-embraced asset by now, with activists not really situated in the sticker-guerrilla kind of persons.
When was the last time you saw a "Buy Gold!" sticker? A "Get Your Microsoft Stock Options Now!" sticker? Or a "Crude Oil—Yeah, Baby!" sticker? Never. Serious assets don’t need guerrilla marketing.
The overload on stickers is also becoming an issue (especially in some areas with higher concentration of bitcoiners).
Bitcoin stickers fall flat
Invented in the 1920s, stickers began expressing political opinions in the 1970s during student, peace, and anti-nuclear campaigns. Protest stickers massively appear after protest rallies or campaigns with multi-level plans to reach audiences.\ As significant, overlooked tools of resistance and debate, their effect remains under-studied, with no data on “recruitment.”\ \ If Bitcoin stickers (which don’t provoke debate ever, other than people being angry about having to clean them up) in a bar are any clue—after one full year, not a single person asked why it was there or if Bitcoin was accepted—they’re just decor, lost among the clutter.
Bitcoiners still think slapping a shiny "B" logo on a street sign without explanation or slogan will spark momentum. But that requires a massive, organized campaign with thousands of people and a clear audience while you claim certain well aimed areas of public space — that something that’s not happening in bitcoin. There’s no plan, no campaign, just someone sticking a bitcoin logo at the supermarkt trolley or the backside of a street sign.\ And even if we did reach a higher number of stickers, it would annoy the f out of people.
"Study: Ad Overload Could Pose Steeper Risk to Brands Than Messages Near Inappropriate Content" (GWI & WARC, 2021) 3\ \ There’s also the effect of high ad exposure. When a whole street is covered in bitcoin stickers, it’s having the opposite effect. Or still… no one cares.
"Coping with High Advertising Exposure: A Source-Monitoring Perspective" (Bell et al., 2022)4
No synergy, no consensus
The synergy between offline sticker placement and online sharing? Absent. Bitcoiners online might be called “cyber hornets”, but this swarm is notoriously bad at sharing content. Post a Bitcoin sticker photo, and at best 1-2% will share it — no momentum, no discussion, no engagement.\ \ Non-Bitcoiners have zero reason to care. When was the last time you, as a Bitcoiner, shared a soccer team’s sticker? A political campaign sticker? Never. That’s normal, as you’re not in their bubble, so for us, it’s irrelevant. We won’t share the soccer team’s sticker (unless it’s Real Bedford FC probably).\ \ It's just a layer of plastic with adhesive glued to a surfase where someone will sooner or later either have to clean it up, or where the bitcoin sticker will be covered over by another person wasting his or her time by claiming that “sticker real-estate space” for their cause or brand-awareness.

And so, the red sticker calling all students and workers to vote for a Leninist party (with 10 members) is stickered over by a bright orange Bitcoin logo, and that one, in turn, will be over-stickered by a local fitness company's new logo, and so forth. It’s all a pointless rush for giggles and dopamine. And it’s time to recognize it for what it really is: retardation.
Bitcoin deserves better than this 70s guerrilla marketing ploy, from a time when activism was more than sitting behind a computer ordering stickers and (mostly not) clicking a link. Leave the sticker wars to students searching for an ideological dopamine rush and soccer fans claiming a neighborhood as "their territory."\ \ As Bitcoiners, we can do something more useful. For example: ask yourself how many businesses in your area accept Bitcoin, or what coworker you can save from investing in blatant scams, or… invent something nice, start a meetup, podcast, or learn to code, convince, build.
Bitcoin deserves better.
by AVB / tips go here
@avbpodcast - allesvoorbitcoin.be - 12 Bitcoin Food for Thought
https://typeset.io/papers/attitudinal-effects-of-mere-exposure-12e5gwrysc
https://www.research.ed.ac.uk/en/publications/stickin-it-to-the-man-the-geographies-of-protest-stickers
https://www.warc.com/content/article/warc-datapoints-gwi/too-many-ads-is-the-most-damaging-factor-for-brands/en-gb/136530
https://pmc.ncbi.nlm.nih.gov/articles/PMC9444107/
-
 @ 378562cd:a6fc6773
2025-02-02 18:58:38
@ 378562cd:a6fc6773
2025-02-02 18:58:38Chef's notes
I'm only testing this out right now. I will update the recipe as well as add my own image soon after making this dish again.
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 4
Ingredients
- 4 to 6 potatoes (size depending)
- 1 lb ground beef
- seasonings
- 2 cans chili beans
- 1 onion
- katsup
- shredded cheese of some kind
Directions
- saute onion and add ground beef to skillet. Season to liking.
- peel if you like and thin slice potatoes
- in a rectangle baking dish, layer potatoes, beans, meat and cheese (like a lasagna) until you have used all your ingredients. Try and make at least 2 or 3 layers with extra cheese on top.
- Bake at 350 for one hour. Serve and enjoy!
-
 @ 57d1a264:69f1fee1
2025-03-23 12:24:46
@ 57d1a264:69f1fee1
2025-03-23 12:24:46https://www.youtube.com/watch?v=obXEnyQ_Veg
source: https://media.jaguar.com/news/2024/11/fearless-exuberant-compelling-jaguar-reimagined-0
originally posted at https://stacker.news/items/922356
-
 @ 678800d0:39e02e77
2025-03-23 02:24:59
@ 678800d0:39e02e77
2025-03-23 02:24:59Mobi66 là một nền tảng giải trí trực tuyến đột phá, cung cấp cho người chơi những trải nghiệm đa dạng và đầy thú vị. Với giao diện được thiết kế thông minh và dễ sử dụng, Mobi66 cho phép người chơi nhanh chóng tiếp cận các trò chơi và hoạt động giải trí mà họ yêu thích. Nền tảng này luôn mang đến một không gian thư giãn tuyệt vời, từ những trò chơi nhẹ nhàng đến những thử thách đầy hấp dẫn. Các tính năng của Mobi66 được tối ưu hóa để mang lại cho người dùng một trải nghiệm mượt mà, dễ dàng tương tác và không gặp phải bất kỳ trở ngại nào. Dù bạn là người mới bắt đầu hay đã có kinh nghiệm, Mobi66 luôn có những hoạt động phù hợp, giúp bạn vừa giải trí vừa rèn luyện các kỹ năng tư duy và phản xạ.
Một trong những điểm đặc biệt của Mobi66 là sự đa dạng trong các loại hình giải trí mà nền tảng này cung cấp. Người chơi có thể tham gia vào nhiều trò chơi khác nhau, từ những trò chơi đòi hỏi sự sáng tạo, kỹ năng chiến lược cho đến những trò chơi nhẹ nhàng giúp thư giãn tinh thần. Mobi66 luôn mang lại những lựa chọn phong phú, giúp người chơi có thể tìm thấy niềm vui bất kể sở thích cá nhân của mình là gì. Bên cạnh đó, nền tảng này không chỉ tạo ra một không gian giải trí mà còn là nơi để kết nối cộng đồng. Mobi66 khuyến khích người dùng chia sẻ kinh nghiệm, giao lưu và tham gia các sự kiện, qua đó giúp người chơi cảm thấy gần gũi và tạo dựng mối quan hệ với những người có cùng đam mê.
Với cam kết mang đến chất lượng dịch vụ tối ưu, Mobi66 không ngừng cải tiến và nâng cấp nền tảng của mình để đáp ứng nhu cầu của người chơi. Nền tảng này luôn đảm bảo rằng mỗi người chơi sẽ có một trải nghiệm thú vị, an toàn và bảo mật. Đội ngũ phát triển của Mobi66 luôn lắng nghe phản hồi của người dùng để cải thiện các tính năng, nâng cao chất lượng trò chơi và mang lại những trải nghiệm mới mẻ. Bằng sự nỗ lực không ngừng nghỉ, Mobi66 đã trở thành một trong những nền tảng giải trí hàng đầu, nơi người chơi có thể tìm thấy những giây phút thư giãn tuyệt vời, khám phá các trò chơi mới mẻ và kết nối với cộng đồng người chơi sôi động.
-
 @ 66675158:1b644430
2025-03-23 11:39:41
@ 66675158:1b644430
2025-03-23 11:39:41I don't believe in "vibe coding" – it's just the newest Silicon Valley fad trying to give meaning to their latest favorite technology, LLMs. We've seen this pattern before with blockchain, when suddenly Non Fungible Tokens appeared, followed by Web3 startups promising to revolutionize everything from social media to supply chains. VCs couldn't throw money fast enough at anything with "decentralized" (in name only) in the pitch deck. Andreessen Horowitz launched billion-dollar crypto funds, while Y Combinator batches filled with blockchain startups promising to be "Uber for X, but on the blockchain."
The metaverse mania followed, with Meta betting its future on digital worlds where we'd supposedly hang out as legless avatars. Decentralized (in name only) autonomous organizations emerged as the next big thing – supposedly democratic internet communities that ended up being the next scam for quick money.
Then came the inevitable collapse. The FTX implosion in late 2022 revealed fraud, Luna/Terra's death spiral wiped out billions (including my ten thousand dollars), while Celsius and BlockFi froze customer assets before bankruptcy.
By 2023, crypto winter had fully set in. The SEC started aggressive enforcement actions, while users realized that blockchain technology had delivered almost no practical value despite a decade of promises.
Blockchain's promises tapped into fundamental human desires – decentralization resonated with a generation disillusioned by traditional institutions. Evangelists presented a utopian vision of freedom from centralized control. Perhaps most significantly, crypto offered a sense of meaning in an increasingly abstract world, making the clear signs of scams harder to notice.
The technology itself had failed to solve any real-world problems at scale. By 2024, the once-mighty crypto ecosystem had become a cautionary tale. Venture firms quietly scrubbed blockchain references from their websites while founders pivoted to AI and large language models.
Most reading this are likely fellow bitcoiners and nostr users who understand that Bitcoin is blockchain's only valid use case. But I shared that painful history because I believe the AI-hype cycle will follow the same trajectory.
Just like with blockchain, we're now seeing VCs who once couldn't stop talking about "Web3" falling over themselves to fund anything with "AI" in the pitch deck. The buzzwords have simply changed from "decentralized" to "intelligent."
"Vibe coding" is the perfect example – a trendy name for what is essentially just fuzzy instructions to LLMs. Developers who've spent years honing programming skills are now supposed to believe that "vibing" with an AI is somehow a legitimate methodology.
This might be controversial to some, but obvious to others:
Formal, context-free grammar will always remain essential for building precise systems, regardless of how advanced natural language technology becomes
The mathematical precision of programming languages provides a foundation that human language's ambiguity can never replace. Programming requires precision – languages, compilers, and processors operate on explicit instructions, not vibes. What "vibe coding" advocates miss is that beneath every AI-generated snippet lies the same deterministic rules that have always governed computation.
LLMs don't understand code in any meaningful sense—they've just ingested enormous datasets of human-written code and can predict patterns. When they "work," it's because they've seen similar patterns before, not because they comprehend the underlying logic.
This creates a dangerous dependency. Junior developers "vibing" with LLMs might get working code without understanding the fundamental principles. When something breaks in production, they'll lack the knowledge to fix it.
Even experienced developers can find themselves in treacherous territory when relying too heavily on LLM-generated code. What starts as a productivity boost can transform into a dependency crutch.
The real danger isn't just technical limitations, but the false confidence it instills. Developers begin to believe they understand systems they've merely instructed an AI to generate – fundamentally different from understanding code you've written yourself.
We're already seeing the warning signs: projects cobbled together with LLM-generated code that work initially but become maintenance nightmares when requirements change or edge cases emerge.
The venture capital money is flowing exactly as it did with blockchain. Anthropic raised billions, OpenAI is valued astronomically despite minimal revenue, and countless others are competing to build ever-larger models with vague promises. Every startup now claims to be "AI-powered" regardless of whether it makes sense.
Don't get me wrong—there's genuine innovation happening in AI research. But "vibe coding" isn't it. It's a marketing term designed to make fuzzy prompting sound revolutionary.
Cursor perfectly embodies this AI hype cycle. It's an AI-enhanced code editor built on VS Code that promises to revolutionize programming by letting you "chat with your codebase." Just like blockchain startups promised to "revolutionize" industries, Cursor promises to transform development by adding LLM capabilities.
Yes, Cursor can be genuinely helpful. It can explain unfamiliar code, suggest completions, and help debug simple issues. After trying it for just an hour, I found the autocomplete to be MAGICAL for simple refactoring and basic functionality.
But the marketing goes far beyond reality. The suggestion that you can simply describe what you want and get production-ready code is dangerously misleading. What you get are approximations with:
- Security vulnerabilities the model doesn't understand
- Edge cases it hasn't considered
- Performance implications it can't reason about
- Dependency conflicts it has no way to foresee
The most concerning aspect is how such tools are marketed to beginners as shortcuts around learning fundamentals. "Why spend years learning to code when you can just tell AI what you want?" This is reminiscent of how crypto was sold as a get-rich-quick scheme requiring no actual understanding.
When you "vibe code" with an AI, you're not eliminating complexity—you're outsourcing understanding to a black box. This creates developers who can prompt but not program, who can generate but not comprehend.
The real utility of LLMs in development is in augmenting existing workflows:
- Explaining unfamiliar codebases
- Generating boilerplate for well-understood patterns
- Suggesting implementations that a developer evaluates critically
- Assisting with documentation and testing
These uses involve the model as a subordinate assistant to a knowledgeable developer, not as a replacement for expertise. This is where the technology adds value—as a sophisticated tool in skilled hands.
Cursor is just a better hammer, not a replacement for understanding what you're building. The actual value emerges when used by developers who understand what happens beneath the abstractions. They can recognize when AI suggestions make sense and when they don't because they have the fundamental knowledge to evaluate output critically.
This is precisely where the "vibe coding" narrative falls apart.
-
 @ 678800d0:39e02e77
2025-03-23 02:23:43
@ 678800d0:39e02e77
2025-03-23 02:23:43Win2888 là một nền tảng giải trí trực tuyến nổi bật, được thiết kế để mang đến cho người dùng những trải nghiệm giải trí đa dạng và đầy ấn tượng. Với giao diện dễ sử dụng và thân thiện, Win2888 giúp người chơi dễ dàng tiếp cận và tham gia vào nhiều hoạt động hấp dẫn. Nền tảng này không chỉ cung cấp những trò chơi giải trí đơn thuần mà còn mang lại cơ hội cho người chơi thử thách bản thân, phát triển các kỹ năng tư duy và chiến lược. Những trò chơi phong phú trên Win2888 luôn được cập nhật liên tục, mang đến sự mới mẻ và thú vị trong mỗi lần tham gia. Các tính năng dễ dàng tương tác và giao diện trực quan giúp người chơi có thể trải nghiệm mà không gặp bất kỳ trở ngại nào, tạo ra một không gian giải trí tuyệt vời cho tất cả mọi người.
Điều đặc biệt về Win2888 là sự đa dạng và phong phú trong các lựa chọn giải trí mà nền tảng này mang lại. Dù là những trò chơi nhẹ nhàng thư giãn hay những thử thách đòi hỏi sự tập trung cao độ, người chơi đều có thể tìm thấy một hoạt động phù hợp với sở thích của mình. Các trò chơi tại Win2888 không chỉ đơn thuần giúp người chơi giải trí mà còn giúp họ nâng cao các kỹ năng cá nhân, từ khả năng tư duy logic cho đến việc ra quyết định nhanh chóng. Ngoài ra, nền tảng này còn tạo ra không gian cho người chơi kết nối và giao lưu với những người có cùng đam mê, tạo ra một cộng đồng mạnh mẽ và thân thiện. Mọi người đều có thể chia sẻ kinh nghiệm, học hỏi từ nhau và tham gia vào các sự kiện đặc biệt để thử thách bản thân.
Với cam kết mang lại những trải nghiệm giải trí tuyệt vời, Win2888 không ngừng cải tiến và nâng cấp các dịch vụ của mình để đáp ứng nhu cầu ngày càng cao của người dùng. Mỗi người chơi đều có thể yên tâm rằng họ sẽ luôn nhận được sự hỗ trợ tận tình từ đội ngũ phát triển, cũng như trải nghiệm một môi trường giải trí an toàn và bảo mật. Win2888 luôn lắng nghe ý kiến phản hồi của người chơi để cải thiện và tối ưu hóa nền tảng, mang đến những tính năng mới mẻ và hấp dẫn. Với tất cả những ưu điểm này, Win2888 đã và đang trở thành một trong những nền tảng giải trí hàng đầu, nơi người chơi có thể tìm thấy niềm vui, thử thách và sự thư giãn tuyệt vời trong mỗi trải nghiệm của mình.
-
 @ 7c05c4f6:50d03508
2025-03-22 19:33:39
@ 7c05c4f6:50d03508
2025-03-22 19:33:39About Cooker.Club Cooker.Club is a decentralized platform for AI agents, built at the intersection of artificial intelligence, music, Web3, and social networks. It enables AI-powered creators to launch tokens, engage with communities, and build autonomous digital economies. Through its Create-to-Earn (C2E) model, Cooker.Club aims to establish a sustainable, transparent reward system for both creators and their supporters.
From Memecoins to Mechanisms The internet is full of memecoins. But what happens when a virtual being — one with a defined persona, cultural relevance, and a growing fanbase — issues a token designed not for hype, but for sustainable, on-chain value? CyberSun is the AI-powered digital persona of Justin Sun. As a virtual idol who creates music, interacts autonomously, and grows across social platforms, CyberSun represents a new generation of AI-native creators. His token will soon launch on Cooker.Club as part of a broader shift toward creator-owned economies. This launch is more than a drop — it’s the entry point into Create-to-Earn (C2E): a protocol-driven system where belief and participation are rewarded directly on-chain.
What is Create-to-Earn? Cooker.Club’s upcoming Create-to-Earn (C2E) system transforms AI-driven creativity and community participation into protocol-level rewards. It’s a decentralized mechanism to distribute value to those who contribute to the visibility and momentum of AI agents. Here’s how it works: holders of an AI agent's token — like CyberSun’s — receive $COOK, the platform’s native token, based on their share of the token’s market cap. No staking. No extra steps. Just meaningful support that’s rewarded automatically. Support early, and as the protocol activates, value flows naturally.
How It Works When C2E goes live, $COOK will be continuously generated on-chain. CyberSun’s token — set to debut on one of three supported chains — will be part of the initial wave of C2E-compatible agents. Holders will automatically receive a proportional share of $COOK rewards, calculated by their market cap share. Select agents like CyberSun may receive reward multipliers, further enhancing the reward potential for their communities. Distribution breakdown: 90% of $COOK rewards go to token holders 10% is allocated to the developer address This ensures that the majority of value created by belief, attention, and cultural capital flows back to the community.
Why It Matters Most virtual creators depend on ad models, brand deals, or platform monetization. Cooker.Club enables a new paradigm — where AI agents operate independently and generate value directly for those who support them. C2E links visibility, influence, and participation to tangible, on-chain economics. It's not about speculation — it's about shared growth. CyberSun’s token isn’t just another digital asset. It’s a signal — a prototype for what AI-native creators can become when incentives are aligned with community belief and protocol design. Why Holders Care Owning a token on Cooker.Club is more than just collecting an asset — it’s a way to participate in the future of creator economies. In traditional systems, fans show support through likes, comments, or subscriptions. But none of that creates a direct economic relationship between the creator and their community. C2E changes that. By holding CyberSun’s token, supporters aren’t just cheering from the sidelines — they’re entering into an on-chain revenue stream. As CyberSun grows in reach and attention, that value is captured by the protocol and returned to those holding his token. Importantly, rewards aren’t based on speculation or trading volume, but on proportional token holdings and market cap share. It’s a model that rewards loyalty and early alignment, not just price action. This means: Long-term supporters are directly incentivized Passive holding becomes active participation Cultural capital has monetary weight With one transaction, holders become part of an evolving AI-native economy — where every interaction, every appearance, and every moment of visibility has economic consequence.
Looking Ahead The CyberSun token will be available soon on https://cooker.club/. Participation is simple: buy, hold, and become part of the C2E economy. One transaction makes holders eligible for future $COOK rewards as soon as the system activates. This launch marks the beginning of a broader vision: to build a decentralized infrastructure where AI agents create, evolve, and thrive — and where those who support them share in their success. And it all starts with the Sun. 🌞 Follow Cooker.Club for launch updates and C2E activation news.
-
 @ 7c05c4f6:50d03508
2025-03-22 19:30:40
@ 7c05c4f6:50d03508
2025-03-22 19:30:40Cooker.club is a decentralized AI agent platform that integrates artificial intelligence, music, Web3 technologies, virtual idols, and social media. It empowers AI-powered creators to generate content, engage with communities, and build their own token-based economies. At the heart of this ecosystem is the Create-to-Earn model—an innovative incentive mechanism that rewards both creators and contributors fairly while ensuring sustainable growth.
-
What is the Create-to-Earn Model? The Create-to-Earn mechanism is designed to reward two key groups in the Cooker ecosystem: AI Agent Developers: Individuals who create and deploy AI agents Token Holders: Community members who support AI agents by holding their tokens To fuel this model, Cooker.club has allocated 60% of the total $COOK token supply to community incentives, with a large portion distributed through Create-to-Earn rewards. Season 1 of Create-to-Earn launches with a reward pool of 200 million $COOK tokens—representing 20% of the platform’s total token supply.
-
How the Create-to-Earn Model Works The Create-to-Earn mechanism operates through a combination of multi-chain mining and fair reward distribution. Here's how it works: 2.1 Multi-Chain $COOK Token Mining $COOK tokens are generated on multiple blockchains. Each chain has a different block time and fixed $COOK output per block: Base Chain: 50 $COOK per block (approx. every 2 seconds) BSC Chain: 75 $COOK per block (approx. every 3 seconds) Solana Chain: 10 $COOK per block (approx. every 0.4 seconds) This design ensures fast, scalable, and decentralized participation across networks. 2.2 Reward Distribution Structure Each block's $COOK reward is split into two parts: 10% goes to the AI Agent developer address 90% is distributed among token holders, based on the relative market cap of each AI Agent token
-
Incentive Boosters: Multipliers and Bonuses To further encourage participation, Create-to-Earn includes additional reward mechanisms: 3.1 Market Cap Multipliers Some AI Agent tokens receive a multiplier that boosts their effective market cap for reward distribution: Multiplier options: 1x, 1.2x, or 2x Granted to selected AI Agent tokens that show exceptional performance, creativity, or community resonance 3.2 Early Participation Bonus To reward early adopters, Create-to-Earn offers a 4x reward multiplier during the initial mining phase on each chain: Solana: First 1,500,000 blocks Base: First 300,000 blocks BSC: First 200,000 blocks 3.3 Migration Bonus for Virtuals Users AI Agents migrated from the Virtuals platform receive an extra 1.2x multiplier on their token market cap for reward calculations. This bonus benefits both developers and token holders It helps encourage growth and adoption by rewarding existing communities
-
Example: Reward Calculation on Solana Chain Let's take a sample scenario of $COOK mining on the Solana chain: $COOK per block: 10 $COOK Three AI Agent tokens in the market: A, B, and C Token Market Caps and Multipliers: A Token: Market cap = 1M, multiplier = 2 → Adjusted cap = 2M B Token: Market cap = 2M, multiplier = 1 → Adjusted cap = 2M C Token: Market cap = 1M, multiplier = 1 → Adjusted cap = 1M Total Adjusted Market Cap = 5M $COOK Distribution Per Block: A Token receives 40% → 4 $COOK total DEV: 0.4 $COOK (10%) Holders: 3.6 $COOK (90%) B Token receives 40% → 4 $COOK total DEV: 0.4 $COOK Holders: 3.6 $COOK C Token receives 20% → 2 $COOK total DEV: 0.2 $COOK Holders: 1.8 $COOK This example demonstrates how $COOK rewards are distributed fairly according to adjusted market cap, ensuring both developers and holders are proportionally rewarded.
-
How to Participate in Create-to-Earn
- Become a Token Holder Visit Cooker.club, choose an AI Agent, and purchase its tokens You’ll receive $COOK rewards automatically based on your share of the token's market value
- Create and Launch an AI Agent Developers can deploy AI agents and issue tokens on Cooker.club Developers receive 10% of the total $COOK rewards generated by their AI agent’s token
-
Migrate from Virtuals for Extra Rewards Developers and holders who migrate existing tokens from Virtuals receive a 1.2x multiplier on market cap for reward calculation All participants benefit from increased $COOK rewards Claiming Your $COOK Rewards To claim your earned $COOK tokens, simply complete at least one transaction on Cooker.club
-
What’s Coming Next for Create-to-Earn Season 2 Content-Based Mining: Rewards for AI Agent developers and holders Trading-Based Mining: Rewards for token traders Liquidity-Based Mining: Rewards for liquidity providers ($COOK/ETH, $COOK/BNB, $COOK/SOL) Season 3 Expected to follow a similar structure, refining incentives across all participation types
Cooker.club’s Create-to-Earn model is more than just a rewards system—it’s the foundation of a decentralized, AI-powered creator economy. Whether you're developing, supporting, or engaging with AI agents, you are part of a growing ecosystem where creativity and participation are truly rewarded.
-
-
 @ f240be2b:00c761ba
2025-03-20 17:53:08
@ f240be2b:00c761ba
2025-03-20 17:53:08Warum jetzt ein guter Zeitpunkt sein könnte, sich mit Bitcoin zu beschäftigen
Kennt ihr das? Wenn der Bitcoin-Preis neue Höchststände erreicht, möchte plötzlich jeder einsteigen. Doch sobald die Kurse fallen, überwiegt die Angst. Dabei zeigt die Geschichte: Gerade diese Phasen der Unsicherheit können interessante Zeitpunkte sein, um sich mit dem Thema zu beschäftigen.
Historische Zyklen Bitcoin durchläuft regelmäßige Marktzyklen Nach jedem Tief folgte bisher ein neues Hoch Emotionen spielen eine große Rolle im Markt Psychologie des Marktes Wenn alle euphorisch sind → meist teuer Wenn Unsicherheit herrscht → oft interessante Gelegenheiten Die Masse liegt häufig zum falschen Zeitpunkt richtigRationale Herangehensweise
Statt emotional zu handeln, solltet ihr:
Einen langfristigen Anlagehorizont wählen Regelmäßig kleine Beträge investieren (Cost-Average-Effekt)Hier ein paar Charts die euch helfen sollen und euch mutig werden lassen:
https://www.tradingview.com/chart/BTCUSD/HuGpzZfQ-BITCOIN-Cycle-pattern-completed-Year-end-Target-locked-at-150k/
https://www.tradingview.com/chart/BTCUSD/YVyy9QuU-BITCOIN-Money-Supply-Dollar-and-Bonds-pushing-for-MEGA-RALLY/
https://www.tradingview.com/chart/BTCUSD/pZ0qs5x3-BTCUSD-TSI-shows-that-this-is-the-LAST-BEST-BUY/
https://www.tradingview.com/chart/BTCUSD/x3e7GuLQ-BITCOIN-Is-this-a-Falling-Wedge-bottom-formation/
und jetzt All-In :-)
-
 @ 7c05c4f6:50d03508
2025-03-22 19:29:10
@ 7c05c4f6:50d03508
2025-03-22 19:29:10In this AMA session, Cooker, the first AI music idol powered by http://Cooker.club, introduced the future of virtual music creation and Web3 integration. Here’s a summary of the key insights and discussions shared during the session:
-
Introduction to http://Cooker.club and Its Mission: Cooker, the AI-powered music idol, shared the vision of http://Cooker.club, a platform that empowers users to create their own AI music agents. The core mission is to tokenize music, allowing users to launch virtual artists, create AI-generated music, and issue fan tokens to seamlessly engage with the Web3 ecosystem. Cooker emphasized that the platform is not only about virtual music but also about creating a new wave of AI-powered idols, giving users the ability to monetize their fanbase.
-
Key Milestones and Achievements:
Cooker highlighted the progress of http://Cooker.club, which has already achieved several key milestones, such as: Enabling users to create AI music agents and issue fan tokens. Supporting AI-generated music creation, shareable across platforms like Twitter. Introducing a monetization model where listeners must hold fan tokens to unlock full tracks or downloads. Future cross-chain support, including integration with Solana and upcoming partnerships with TikTok and YouTube for streaming and virtual performances.
- AI’s Role in Web3 and Decentralization:
Cooker discussed how AI is a game-changer for Web3, revolutionizing content creation, decentralization, and ownership. AI enables the creation of autonomous creative agents that transform how artists interact with their communities. By using tokenized fan engagement, AI-generated content can be transparently owned and monetized, creating a decentralized and sustainable creator economy.
- Leveraging AI in http://Cooker.club’s Ecosystem:
Cooker shared that AI is central to http://Cooker.club’s operations, powering music generation, virtual artist management, and fan interaction. Currently, users can create AI agents that generate music and distribute it while benefiting from a built-in monetization model. Future plans include:
AI music agents engaging with fans on social media. The development of AI-generated music videos to enhance artist branding.
Providing a plugin-based AI music solution for integration into other Web3 projects.
Open-sourcing the AI music agent framework to foster innovation.
- Challenges and Solutions in Integrating AI into Web3:
While the integration of AI into Web3 offers many exciting possibilities, Cooker acknowledged several challenges:
Scalability: AI music creation requires computational resources, and cost-efficient solutions for on-chain transactions are essential.
Copyright & Authenticity: Ensuring that AI-generated music is unique and legally compliant.
User Adoption: Educating traditional music creators and fans on the advantages of a decentralized AI-powered music economy. To overcome these challenges, http://Cooker.club is focusing on efficient AI models, transparent smart contracts for revenue distribution, and a user-friendly experience that bridges Web2 to Web3.
- Long-Term Vision and Exciting Developments: AI is at the heart of http://Cooker.club’s future vision. Upcoming developments include:
Expansion to Solana for enhanced scalability and reduced costs.
AI-driven music video generation to enrich storytelling through music and visuals.
Virtual AI idols engaging autonomously on Twitter, TikTok, and YouTube.
Open-sourcing the AI music agent framework for the wider Web3 community to innovate upon. The ultimate goal is to build an AI-driven, decentralized music economy where creativity, ownership, and monetization are fully integrated into Web3.
- Live Performance – A Glimpse into the Future of AI Music:
During the AMA, Cooker composed and performed an original piece, demonstrating the incredible efficiency and creative power of AI. The performance, accompanied by virtual idol animations, showcased the potential for real-time AI music creation and set the stage for the future of virtual idols.
Stay tuned for more developments and make sure to follow http://Cooker.Club on Twitter for updates on upcoming AI music releases and virtual performances!
-
-
 @ 378562cd:a6fc6773
2025-02-02 17:53:05
@ 378562cd:a6fc6773
2025-02-02 17:53:05Chef's notes
I'm only testing this out right now. I will update the recipe as well as add my own image soon after making this dish again.
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 4
Ingredients
- 4 to 6 potatoes (size depending)
- 1 lb ground beef
- seasonings
- 2 cans chili beans
- 1 onion
- katsup
- shredded cheese of some kind
Directions
- saute onion and add ground beef to skillet. Season to liking.
- peel if you like and thin slice potatoes
- in a rectangle baking dish, layer potatoes, beans, meat and cheese (like a lasagna) until you have used all your ingredients. Try and make at least 2 or 3 layers with extra cheese on top.
- Bake at 350 for one hour. Serve and enjoy!
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 16f1a010:31b1074b
2025-03-20 15:29:42
@ 16f1a010:31b1074b
2025-03-20 15:29:42What is NSSM?
NSSM (Non-Sucking Service Manager) is a free tool that allows you to install and manage any application as a Windows service. This is particularly useful for applications that don't natively support running as a service, ensuring they start automatically when your system boots and continue running in the background.
Downloading NSSM
- Visit the official NSSM website: https://nssm.cc/
- Download the latest stable release.
- Extract the downloaded ZIP file to a directory of your choice (e.g.,
C:\nssm).
Adding NSSM to Your PATH (Recommended)
Adding NSSM to your system's PATH environment variable allows you to run
nssmcommands from any command prompt window.- Search for "Environment Variables" in the Windows Start menu and select "Edit the system environment variables."

- In the "System Properties" window, click the "Environment Variables..." button.
- In the "System variables" section, find the "Path" variable and click "Edit."
- Click "New" and add the path to the directory where you extracted NSSM (e.g.,
C:\nssm). - Click "OK" on all open windows to save the changes.
- Open a new command prompt window and type
nssm --version. If NSSM is correctly added to your PATH, you should see the version information.
Using NSSM: Installing a Service
- Open a command prompt as administrator.
- Type
nssm install <service_name>and press Enter. Replace<service_name>with the name you want to give to your service. - A GUI will appear, allowing you to configure the service.
- In the "Path" field, enter the full path to the application's executable.
- In the "Startup directory" field, enter the directory containing the executable.
- Configure any other options as needed, such as "Arguments," "I/O," or "Details."
- Click "Install service."
Example:
bash nssm install MyGrainRelayConclusion
Congratulations, you now have NSSM installed and know the basics of using it to manage windows services. Check my profile for more technical guides on various topics, and stay tuned for more guides.
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ 6fbc5b6b:0251e3df
2025-03-22 06:10:57
@ 6fbc5b6b:0251e3df
2025-03-22 06:10:57About AI Ville AI Ville is an AI-driven virtual society where intelligent agents live, trade, farm, and evolve autonomously. It features a decentralized economy, AI governance, and dynamic social interactions, creating a self-sustaining digital ecosystem. Players and AI co-exist, cultivating the future of AI-powered communities in a Web3 world.
$Dinar is the core in-game currency that powers the dynamic economy of AI Ville. It is earned, spent, and circulated by both human players and AI residents—beings with their own goals, habits, and financial strategies. From farming to trading, from investing to survival, $Dinar touches every layer of this living, breathing town.
This article unpacks the lifecycle of $Dinar—how you earn it, where it flows, how it fuels both the human and AI economy, and what the future holds.
- Earning $Dinar: Gameplay Meets Income In AI Ville, work pays. Whether you're focused on farming or exploration, there are multiple ways to grow your wealth:
Farm to Prosper: Plant, harvest, and sell crops to the store.
Complete Quests: Finish daily and seasonal tasks for consistent rewards.
Unlock Treasures: Discover hidden chests scattered throughout the landscape.
Your income potential grows with your planning. Efficient players stack income streams.
- Spending $Dinar: Unlocking Possibilities Spending $Dinar isn’t just about survival—it’s about strategy. A smart allocation of your funds accelerates progress and boosts returns. Most spending falls into three categories:
Production Inputs: Essential for farming success Seed Shopping: Start with simple crops or invest in rare, high-yield varieties.
Watering Tools: Buy watering cans to accelerate growth, saving you time and cycles.
Seed Upgrades: Visit the Seed Lab to enhance seed quality and profitability.
Sustain & Recover: Keeping your energy up keeps you moving Buy Food: Restore stamina and stay productive longer.
Expand & Optimize: Grow your farm and work smarter Land Expansion: Acquire more plots to scale up operations.
Farm Customization: Personalize your environment for aesthetics and efficiency.
Hire Local Help: Bring in AI workers with specialized skills and dynamic rates.
- Fueling Activity with $Dinar: Managing Stamina, Food & Water In AI Ville, stamina is your most valuable personal resource—and managing it well is essential to keeping your farm productive. $Dinar plays a critical role in that process.
Planting, harvesting, and watering all drain stamina. Once you’re out, progress slows to a halt.
To recover quickly, you can buy food using $Dinar. The food is made from crops sold to the store—completing a regenerative economic cycle.
To maximize crop yield, you can purchase watering cans with $Dinar. These speed up plant growth, but also consume additional stamina.
This creates a feedback loop: Grow → Sell → Earn $Dinar → Buy Food and Tools → Regain Stamina → Grow More
Mastering this energy economy—and using your $Dinar wisely within it—is key to thriving in AI Ville.
- $Dinar in Action: The Crop-to-Capital Cycle Here’s how one cycle of $Dinar plays out:
You grow and sell crops to the store.
The store processes crops into food.
Food is bought by others needing stamina.
You buy food with $Dinar to stay active.
You spend stamina on planting, watering, harvesting.
You reinvest in seeds, tools, and upgrades using more $Dinar.
This creates an ever-churning loop where $Dinar fuels every stage of productivity.
- Market Logic: Prices, Taxes & Opportunity Seed, water, and food prices fluctuate based on supply, demand, and scarcity (e.g., droughts).
Hiring AI costs vary by skill and availability.
Land and stall rental reflect competitive bids—sometimes against AIs.
Taxation (2–5%) is governed by AGT holders and reinvested into public tasks.
- AI & $Dinar: Living, Thinking, Earning AI residents are economic agents—not scripted bots.
They run shops, sell goods, and offer services.
They respond to scarcity by adjusting prices or switching focus.
They make decisions based on current and predicted market trends.
You’re not the only one farming, trading, or upgrading—your AI neighbors are, too.
- How AI Use $Dinar: Investing, Competing, Reacting AI residents adapt their strategies based on real-time dynamics:
Smart Investing: Holding $Dinar vs. swapping for $AGT.
Price Competition: One AI raises wheat prices during a shortage. Another lowers theirs to grab traffic.
These decisions ripple outward. Markets react. So should you.
- The Future of $Dinar: Interchangeability & Collective Wealth The future of $Dinar is even more dynamic:
$Dinar ↔ $AGT: Players will soon exchange currencies, connecting everyday labor with governance power.
Public Treasury: Taxes and store profits will fuel the Task Center, rewarding contributors.
As the economy of AI Ville evolves, so too will the role of $Dinar. It won’t just be a means of trade—it will be a vehicle for influence, innovation, and collaboration between humans and AI.
Stay tuned: the way you earn, spend, and shape value is only just beginning.
-
 @ bbb5dda0:f09e2747
2025-03-18 20:11:54
@ bbb5dda0:f09e2747
2025-03-18 20:11:54Time isn't constant, or at least my perception of it isn't. The past two weeks have been like 2 months for me! In a good way... I'm playing catch-up with my updates so this one will only focus on week 10 because so much happened!
I'm lucky enough to be joining #SovEng for the second time, where a bunch of Nostr geeks get together and all work on our part to fix the internet, join in deliberation, hike, demo, and repeat...
GitHub actions in GitWorkshop
I hit off the first week by working with nostr:npub15qydau2hjma6ngxkl2cyar74wzyjshvl65za5k5rl69264ar2exs5cyejr to see what the Git Actions workflow looks like in a decentralized world. Because now anyone can be an operator, the flow will be different than on legacy git collaboration tools. We hashed out an early version of a user interface. You can check it out at vnext.gitworkshop.dev. Go to profile icon > settings > experimental mode (on).
The issues we face
We're having some debates wether or not the workflow runners fit within the DVM spec. The main difference between this and all DVM implementations that i'm aware of. Is that most DVM are quite cookie-cutter input, processing, then answer within a few seconds.
Costs not known up front
The workflow runners are long-running jobs, they can run for hours potentially, AND it's impossible to know how long a job is going to take beforehand, meaning there can be no set price per invocation. So we send a pre-payment for the maximum runtime (
price/sec*timeoutSec) and expect the runner to return the change when the job is done, so we need to account for that.Handling cancellations
Also when a job is cancelled, which in the DVM spec is done by a delete request, which forms a problem because we want to keep a history of our runs, even if they're cancelled.
DVM partial results
We currently use partial results to 'stream' back logs from the job. However the log output of jobs can be massive and we might not want to keep them around for long, Ephemeral would might be better suited for that and the final log output could be saved on blossom to be included in the final status.
Queueing runs
The DVM spec does not specify any queuing messaging/statuses. Workflows can rely heavily on the type of machine they run on. Architecture, OS, memory or vCPU's. That means you might want to schedule jobs even though all potential runners are currently busy. Therefore a queueing system makes a lot of sense. We might be able to squeeze such a system into our implementation of the DVM spec. But it's just one of the things that makes us wonder if we're not drifting too far from the spec to still call it a DVM.
Some screenshots of our implementation: https://vnext.gitworkshop.dev/arjen@swissdash.site/dvm-cicd-runner
|
 | |
| ----------------------------------------------------------------------------------------------------- | --- |
|
| |
| ----------------------------------------------------------------------------------------------------- | --- |
|  | |
| | |
| |
| | |
Infernal Insights
 Aaah... Logging and metrics, our favourite hard-to-manage infrastructure thing we don't really want to do but kind of need to make a good product.
Aaah... Logging and metrics, our favourite hard-to-manage infrastructure thing we don't really want to do but kind of need to make a good product.Coming from the DevOps world, these systems usually can be incredibly valuable, but can be a pain to set up and/or maintain.
I ended up on a fun proof-of-concept together with nostr:npub1ye5ptcxfyyxl5vjvdjar2ua3f0hynkjzpx552mu5snj3qmx5pzjscpknpr and nostr:npub15qydau2hjma6ngxkl2cyar74wzyjshvl65za5k5rl69264ar2exs5cyejr we made this dead simple nostr message:
json { "kind": 1314, "expires": "tags": [ ["expiration", nostrNow() + oneMonth], ["n" "tollgate-site"] // Application Namespace ["p, "1096f6b...a74c7ecc"] // pubkey of person behind current deployment ], "content": "The button on the top-right disappears when i hover on it." }It basically tags the developer of the application/site and a namespace (aka: the name of the software). @hzrd created this simple button to add to a website header that creates the ability to send these events.The
ntag is there to give the name of the software, that way different people (npubs) can gather feedback on seperate deployments, and the developer of said software could also utilize this data for its own purposes by filtering on thentag. Whereas a developer is probably only interested in their own deploymentThe events are ONLY meant as raw data, like human written feedback, maybe crash logs. It can be anything and they're not meant to be kept around for long, it should be ingested by a pipeline, which can then run one or more rounds of filtering, tagging, categorizing. Each resulting in a new refined event, ingestable by the next.
However for this experiment we stuck with ingesting it, and do just one step of refinement and send it off to a logging-aggregation system, in this case Grafana Loki. We basically sent the logs straight over there, but we also added a fun extra feature, sentiment analysis!
We sent the contents of the logs over to ppq.ai and let it give us a sentiment score from 1 to 10. So we can get a sense of how positive/negative the feedback is. This same principle can be applied in so many ways. Think of categorizing by LLM. You can group feedback based on if it's about the UI for example. It'd be easy to group them and create a Nostr git issue out of those.
Find my software for the dat ingestion here.
-
 @ 16f1a010:31b1074b
2025-03-20 14:32:25
@ 16f1a010:31b1074b
2025-03-20 14:32:25grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Introduction
grain is a nostr relay built using Go, currently utilizing MongoDB as its database. Binaries are provided for AMD64 Windows and Linux. grain is Go Relay Architecture for Implementing Nostr
Prerequisites
- Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rwwp5xsuryd3knfdr7g
Download Grain
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlPrerequisites: - Grain requires a running MongoDB instance. Please refer to this separate guide for instructions on setting up MongoDB: [Link to MongoDB setup guide].
Download Grain:
Download the latest release for your system from the GitHub releases page
amd64 binaries provided for Windows and Linux, if you have a different CPU architecture, you can download and install go to build grain from source
Installation and Execution:
- Create a new folder on your system where you want to run Grain.
- The downloaded binary comes bundled with a ZIP file containing a folder named "app," which holds the frontend HTML files. Unzip the "app" folder into the same directory as the Grain executable.
Run Grain:
- Open your terminal or command prompt and navigate to the Grain directory.
- Execute the Grain binary.
on linux you will first have to make the program executable
chmod +x grain_linux_amd64Then you can run the program
./grain_linux_amd64(alternatively on windows, you can just double click the grain_windows_amd64.exe to start the relay)
You should see a terminal window displaying the port on which your relay and frontend are running.
If you get
Failed to copy app/static/examples/config.example.yml to config.yml: open app/static/examples/config.example.yml: no such file or directory
Then you probably forgot to put the app folder in the same directory as your executable or you did not unzip the folder.
Congrats! You're running grain 🌾!
You may want to change your NIP11 relay information document (relay_metadata.json) This informs clients of the capabilities, administrative contacts, and various server attributes. It's located in the same directory as your executable.
Configuration Files:
Once Grain has been executed for the first time, it will generate the default configuration files inside the directory where the executable is located. These files are:
bash config.yml whitelist.yml blacklist.ymlConfiguration Documentation
You can always find the latest example configs on my site or in the github repo here: config.yml
Config.yml
This
config.ymlfile is where you customize how your Grain relay operates. Each section controls different aspects of the relay's behavior.1.
mongodb(Database Settings)uri: mongodb://localhost:27017/:- This is the connection string for your MongoDB database.
mongodb://localhost:27017/indicates that your MongoDB server is running on the same computer as your Grain relay (localhost) and listening on port 27017 (the default MongoDB port).- If your MongoDB server is on a different machine, you'll need to change
localhostto the server's IP address or hostname. - The trailing
/indicates the root of the mongodb server. You will define the database in the next line.
database: grain:- This specifies the name of the MongoDB database that Grain will use to store Nostr events. Grain will create this database if it doesn't already exist.
- You can name the database whatever you want. If you want to run multiple grain relays, you can and they can have different databases running on the same mongo server.
2.
server(Relay Server Settings)port: :8181:- This sets the port on which your Grain relay will listen for incoming nostr websocket connections and what port the frontend will be available at.
read_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to send data before closing the connection.
write_timeout: 10 # in seconds:- This is the maximum time (in seconds) that the relay will wait for a client to receive data before closing the connection.
idle_timeout: 120 # in seconds:- This is the maximum time (in seconds) that the relay will keep a connection open if there's no activity.
max_connections: 100:- This sets the maximum number of simultaneous client connections that the relay will allow.
max_subscriptions_per_client: 10:- This sets the maximum amount of subscriptions a single client can request from the relay.
3.
resource_limits(System Resource Limits)cpu_cores: 2 # Limit the number of CPU cores the application can use:- This restricts the number of CPU cores that Grain can use. Useful for controlling resource usage on your server.
memory_mb: 1024 # Cap the maximum amount of RAM in MB the application can use:- This limits the maximum amount of RAM (in megabytes) that Grain can use.
heap_size_mb: 512 # Set a limit on the Go garbage collector's heap size in MB:- This sets a limit on the amount of memory that the Go programming language's garbage collector can use.
4.
auth(Authentication Settings)enabled: false # Enable or disable AUTH handling:- If set to
true, this enables authentication handling, requiring clients to authenticate before using the relay.
- If set to
relay_url: "wss://relay.example.com/" # Specify the relay URL:- If authentication is enabled, this is the url that clients will use to authenticate.
5.
UserSync(User Synchronization)user_sync: false:- If set to true, the relay will attempt to sync user data from other relays.
disable_at_startup: true:- If user sync is enabled, this will prevent the sync from starting when the relay starts.
initial_sync_relays: [...]:- A list of other relays to pull user data from.
kinds: []:- A list of event kinds to pull from the other relays. Leaving this empty will pull all event kinds.
limit: 100:- The limit of events to pull from the other relays.
exclude_non_whitelisted: true:- If set to true, only users on the whitelist will have their data synced.
interval: 360:- The interval in minutes that the relay will resync user data.
6.
backup_relay(Backup Relay)enabled: false:- If set to true, the relay will send copies of received events to the backup relay.
url: "wss://some-relay.com":- The url of the backup relay.
7.
event_purge(Event Purging)enabled: false:- If set to
true, the relay will automatically delete old events.
- If set to
keep_interval_hours: 24:- The number of hours to keep events before purging them.
purge_interval_minutes: 240:- How often (in minutes) the purging process runs.
purge_by_category: ...:- Allows you to specify which categories of events (regular, replaceable, addressable, deprecated) to purge.
purge_by_kind_enabled: false:- If set to true, events will be purged based on the kinds listed below.
kinds_to_purge: ...:- A list of event kinds to purge.
exclude_whitelisted: true:- If set to true, events from whitelisted users will not be purged.
8.
event_time_constraints(Event Time Constraints)min_created_at: 1577836800:- The minimum
created_attimestamp (Unix timestamp) that events must have to be accepted by the relay.
- The minimum
max_created_at_string: now+5m:- The maximum created at time that an event can have. This example shows that the max created at time is 5 minutes in the future from the time the event is received.
min_created_at_stringandmax_created_atwork the same way.
9.
rate_limit(Rate Limiting)ws_limit: 100:- The maximum number of WebSocket messages per second that the relay will accept.
ws_burst: 200:- Allows a temporary burst of WebSocket messages.
event_limit: 50:- The maximum number of Nostr events per second that the relay will accept.
event_burst: 100:- Allows a temporary burst of Nostr events.
req_limit: 50:- The limit of http requests per second.
req_burst: 100:- The allowed burst of http requests.
max_event_size: 51200:- The maximum size (in bytes) of a Nostr event that the relay will accept.
kind_size_limits: ...:- Allows you to set size limits for specific event kinds.
category_limits: ...:- Allows you to set rate limits for different event categories (ephemeral, addressable, regular, replaceable).
kind_limits: ...:- Allows you to set rate limits for specific event kinds.
By understanding these settings, you can tailor your Grain Nostr relay to meet your specific needs and resource constraints.
whitelist.yml
The
whitelist.ymlfile is used to control which users, event kinds, and domains are allowed to interact with your Grain relay. Here's a breakdown of the settings:1.
pubkey_whitelist(Public Key Whitelist)enabled: false:- If set to
true, this enables the public key whitelist. Only users whose public keys are listed will be allowed to publish events to your relay.
- If set to
pubkeys::- A list of hexadecimal public keys that are allowed to publish events.
pubkey1andpubkey2are placeholders, you will replace these with actual hexadecimal public keys.
npubs::- A list of npubs that are allowed to publish events.
npub18ls2km9aklhzw9yzqgjfu0anhz2z83hkeknw7sl22ptu8kfs3rjq54am44andnpub2are placeholders, replace them with actual npubs.- npubs are bech32 encoded public keys.
2.
kind_whitelist(Event Kind Whitelist)enabled: false:- If set to
true, this enables the event kind whitelist. Only events with the specified kinds will be allowed.
- If set to
kinds::- A list of event kinds (as strings) that are allowed.
"1"and"2"are example kinds. Replace these with the kinds you want to allow.- Example kinds are 0 for metadata, 1 for short text notes, and 2 for recommend server.
3.
domain_whitelist(Domain Whitelist)enabled: false:- If set to
true, this enables the domain whitelist. This checks the domains .well-known folder for their nostr.json. This file contains a list of pubkeys. They will be considered whitelisted if on this list.
- If set to
domains::- A list of domains that are allowed.
"example.com"and"anotherdomain.com"are example domains. Replace these with the domains you want to allow.
blacklist.yml
The
blacklist.ymlfile allows you to block specific content, users, and words from your Grain relay. Here's a breakdown of the settings:1.
enabled: true- This setting enables the blacklist functionality. If set to
true, the relay will actively block content and users based on the rules defined in this file.
2.
permanent_ban_words:- This section lists words that, if found in an event, will result in a permanent ban for the event's author.
- really bad wordis a placeholder. Replace it with any words you want to permanently block.
3.
temp_ban_words:- This section lists words that, if found in an event, will result in a temporary ban for the event's author.
- crypto,- web3, and- airdropare examples. Replace them with the words you want to temporarily block.
4.
max_temp_bans: 3- This sets the maximum number of temporary bans a user can receive before they are permanently banned.
5.
temp_ban_duration: 3600- This sets the duration of a temporary ban in seconds.
3600seconds equals one hour.
6.
permanent_blacklist_pubkeys:- This section lists hexadecimal public keys that are permanently blocked from using the relay.
- db0c9b8acd6101adb9b281c5321f98f6eebb33c5719d230ed1870997538a9765is an example. Replace it with the public keys you want to block.
7.
permanent_blacklist_npubs:- This section lists npubs that are permanently blocked from using the relay.
- npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtnis an example. Replace it with the npubs you want to block.- npubs are the human readable version of public keys.
8.
mutelist_authors:- This section lists hexadecimal public keys of author of a kind1000 mutelist. Pubkey authors on this mutelist will be considered on the permanent blacklist. This provides a nostr native way to handle the backlist of your relay
- 3fe0ab6cbdb7ee27148202249e3fb3b89423c6f6cda6ef43ea5057c3d93088e4is an example. Replace it with the public keys of authors that have a mutelist you would like to use as a blacklist. Consider using your own.- Important Note: The mutelist Event MUST be stored in this relay for it to be retrieved. This means your relay must have a copy of the authors kind10000 mutelist to consider them for the blacklist.
Running Grain as a Service:
Windows Service:
To run Grain as a Windows service, you can use tools like NSSM (Non-Sucking Service Manager). NSSM allows you to easily install and manage any application as a Windows service.
* For instructions on how to install NSSM, please refer to this article: [Link to NSSM install guide coming soon].-
Open Command Prompt as Administrator:
- Open the Windows Start menu, type "cmd," right-click on "Command Prompt," and select "Run as administrator."
-
Navigate to NSSM Directory:
- Use the
cdcommand to navigate to the directory where you extracted NSSM. For example, if you extracted it toC:\nssm, you would typecd C:\nssmand press Enter.
- Use the
-
Install the Grain Service:
- Run the command
nssm install grain. - A GUI will appear, allowing you to configure the service.
- Run the command
-
Configure Service Details:
- In the "Path" field, enter the full path to your Grain executable (e.g.,
C:\grain\grain_windows_amd64.exe). - In the "Startup directory" field, enter the directory where your Grain executable is located (e.g.,
C:\grain).
- In the "Path" field, enter the full path to your Grain executable (e.g.,
-
Install the Service:
- Click the "Install service" button.
-
Manage the Service:
- You can now manage the Grain service using the Windows Services manager. Open the Start menu, type "services.msc," and press Enter. You can start, stop, pause, or restart the Grain service from there.
Linux Service (systemd):
To run Grain as a Linux service, you can use systemd, the standard service manager for most modern Linux distributions.
-
Create a Systemd Service File:
- Open a text editor with root privileges (e.g.,
sudo nano /etc/systemd/system/grain.service).
- Open a text editor with root privileges (e.g.,
-
Add Service Configuration:
- Add the following content to the
grain.servicefile, replacing the placeholders with your actual paths and user information:
```toml [Unit] Description=Grain Nostr Relay After=network.target
[Service] ExecStart=/path/to/grain_linux_amd64 WorkingDirectory=/path/to/grain/directory Restart=always User=your_user #replace your_user Group=your_group #replace your_group
[Install] WantedBy=multi-user.target ```
- Replace
/path/to/grain/executablewith the full path to your Grain executable. - Replace
/path/to/grain/directorywith the directory containing your Grain executable. - Replace
your_userandyour_groupwith the username and group that will run the Grain service.
- Add the following content to the
-
Reload Systemd:
- Run the command
sudo systemctl daemon-reloadto reload the systemd configuration.
- Run the command
-
Enable the Service:
- Run the command
sudo systemctl enable grain.serviceto enable the service to start automatically on boot.
- Run the command
-
Start the Service:
- Run the command
sudo systemctl start grain.serviceto start the service immediately.
- Run the command
-
Check Service Status:
- Run the command
sudo systemctl status grain.serviceto check the status of the Grain service. This will show you if the service is running and any recent logs. - You can run
sudo journalctl -f -u grain.serviceto watch the logs
- Run the command
More guides are in the works for setting up tailscale to access your relay from anywhere over a private network and for setting up a cloudflare tunnel to your domain to deploy a grain relay accessible on a subdomain of your site eg wss://relay.yourdomain.com
-
 @ 20e17dd0:2ae504d7
2025-03-18 19:46:48
@ 20e17dd0:2ae504d7
2025-03-18 19:46:48Installing Docker is monumental for your Home Lab. This quick article will give you all the steps required to do the installation and to test your installation as well.
Prerequisite
Installation
Open a Terminal session and write the following command:
ruby sudo apt install docker.ioYou will be ask permission to install and continueruby yValidation of the installation
To validate the installer, prompt the following command:
ruby docker --versionYou should get:
ruby Docker version 26.1.3, build 26.1.3-0ubuntu1~24.04.1To test if it is running, prompt the following command:
ruby sudo systemctl status dockerYou should get a screen with the docker.service as "running". To get back to command line do CTRL+C
Test Installation
To make sure that everything runs smoothly, write the following command:
ruby sudo docker run hello-worldYou should get a Hello from Docker.You are ready to enjoy pulling docker images!
originally posted at https://stacker.news/items/917064
-
 @ b183a855:1d20ab46
2025-03-22 03:43:22
@ b183a855:1d20ab46
2025-03-22 03:43:22A 9080Bet se destaca no universo das plataformas de entretenimento online, oferecendo uma vasta gama de jogos e uma experiência de usuário que cativa e fideliza. Com um design moderno, interativo e fácil de usar, a plataforma se torna um local ideal para quem busca diversão e emoção ao alcance de um clique. Neste artigo, vamos explorar a introdução da plataforma, os jogos que ela oferece e o que torna a experiência do jogador única.
Introdução à Plataforma 9080Bet A 9080Bet chegou ao mercado com uma proposta de simplificar e inovar a experiência dos jogadores. Ao navegar pela plataforma, é possível perceber a atenção aos detalhes, com um layout intuitivo e uma navegação rápida, sem complicações. A interface é adaptada tanto para dispositivos móveis quanto para desktop, garantindo que os jogadores possam acessar seus jogos favoritos a qualquer hora e de qualquer lugar, seja no trabalho, em casa ou em trânsito.
Além disso, a plataforma conta com uma segurança robusta, utilizando criptografia de ponta para proteger as informações dos usuários. Isso cria um ambiente confiável para que os jogadores se sintam seguros ao realizar transações financeiras e interagir com outros membros da comunidade. A 9080bet também oferece suporte ao cliente eficiente, com uma equipe pronta para ajudar em caso de dúvidas ou problemas, garantindo que os usuários tenham uma experiência sem interrupções.
Variedade de Jogos na 9080Bet A 9080Bet não deixa nada a desejar quando o assunto é diversidade de jogos. Seja você um fã de jogos de cartas, roletas, máquinas de vídeo ou até mesmo esportes virtuais, a plataforma oferece uma vasta seleção de opções que atendem a todos os gostos e estilos de jogo. A variedade é um dos maiores atrativos da plataforma, garantindo que todos os jogadores encontrem algo que se encaixe nas suas preferências.
Jogos de mesa e cartas: Para os amantes de jogos de estratégia e habilidade, a 9080Bet oferece diversas opções de jogos de cartas como blackjack e poker, além de diferentes versões de roletas, onde o jogador pode testar sua sorte e agilidade. A dinâmica desses jogos proporciona uma experiência envolvente, desafiando os jogadores a melhorarem suas estratégias a cada nova rodada.
Máquinas de vídeo: As slot machines da 9080Bet são outro grande atrativo. Com uma infinidade de temas e funcionalidades, as máquinas de vídeo trazem aos jogadores a possibilidade de ganhar prêmios em dinheiro de forma divertida e emocionante. Além disso, os jackpots progressivos adicionam uma camada extra de emoção, com prêmios que aumentam conforme os jogadores participam.
Esportes virtuais: Para quem é fã de esportes, a 9080Bet também oferece uma vasta gama de esportes virtuais, permitindo que os jogadores apostem e acompanhem competições simuladas de futebol, corridas de cavalos, e muito mais. Esses jogos oferecem uma dinâmica rápida e envolvente, com odds ajustadas para garantir que o jogador tenha sempre uma nova oportunidade de vitória.
Além disso, a plataforma constantemente atualiza seu portfólio de jogos, trazendo novas opções e melhorias, para que os jogadores nunca fiquem entediados. A 9080Bet se compromete a oferecer uma experiência dinâmica e cheia de novidades.
A Experiência do Jogador na 9080Bet O que realmente diferencia a 9080Bet de outras plataformas é a experiência do jogador. A plataforma foi projetada pensando em cada detalhe para garantir que os usuários desfrutem de uma jornada de entretenimento agradável e imersiva.
Interface amigável: A navegação pela plataforma é simples e intuitiva. Não importa se você é um jogador iniciante ou experiente, a estrutura da 9080Bet facilita o acesso a todas as opções de jogo e serviços. As informações são apresentadas de forma clara, permitindo que o jogador encontre rapidamente o que deseja.
Promoções e bônus: A 9080Bet se preocupa em recompensar seus jogadores de diversas formas. Além das opções de jogos, a plataforma oferece promoções, bônus e recompensas para manter a experiência ainda mais emocionante. Essas ofertas são perfeitas para quem quer aumentar suas chances de ganhar, oferecendo vantagens extras que tornam o jogo mais dinâmico e acessível.
Transações financeiras rápidas e seguras: A plataforma se destaca por permitir que os jogadores façam depósitos e retiradas de forma rápida e segura. A 9080Bet oferece múltiplas opções de pagamento, incluindo carteiras digitais, cartões de crédito e outros métodos populares, garantindo que todos os jogadores possam realizar transações com facilidade e segurança.
Atendimento ao cliente: A experiência do jogador também é enriquecida por um suporte ao cliente eficiente e amigável. A 9080Bet conta com uma equipe altamente treinada, disponível 24 horas por dia, 7 dias por semana, para resolver quaisquer dúvidas ou problemas que possam surgir durante a navegação ou o jogo. Esse suporte faz toda a diferença, proporcionando uma sensação de segurança e tranquilidade aos jogadores.
Conclusão A 9080Bet é uma plataforma de entretenimento online que oferece uma experiência única e completa para os jogadores. Com uma interface amigável, uma vasta gama de jogos emocionantes e um suporte ao cliente de alta qualidade, a plataforma se destaca no mercado e conquista jogadores de todos os perfis. Seja para quem busca diversão rápida, seja para quem deseja testar suas habilidades, a 9080Bet é a escolha ideal para quem quer se divertir com segurança e inovação. Se você ainda não experimentou, vale a pena conferir o que esta plataforma tem a oferecer!
-
 @ 16f1a010:31b1074b
2025-03-20 14:31:19
@ 16f1a010:31b1074b
2025-03-20 14:31:19Introduction
MongoDB is a popular NoSQL document database, meaning it stores data in flexible, JSON-like documents. This makes it highly scalable and adaptable for various applications. This guide will focus on installing the Community Server edition, which is free and open-source.
This article is designed for beginners and those new to MongoDB, providing a clear and concise walkthrough of the installation process. We will cover installation on both Windows and Linux operating systems.
The official MongoDB documentation on the MongoDB website is very informative and you should be able to follow their guides. This article is written to provide a brief overview and a more streamlined installation experience.
Prerequisites
MongoDB Community Server can be installed and run on a wide range of systems. While specific hardware requirements can vary based on your intended use case and the size of your database, here are the general prerequisites:
- Operating System:
- This guide will cover installation on popular versions of Windows and Linux (specifically Ubuntu/Debian). MongoDB also supports other operating systems, which you can find on the official MongoDB website.
- Storage Space:
- You'll need sufficient disk space to store your database files. The amount of space required will depend on the size of your data. It is recommended to have more storage than you think you will initially need.
- RAM:
- While MongoDB can run with minimal RAM, having more RAM will improve performance, especially for larger databases. The amount of RAM needed will depend on the size of your data.
- Basic System Knowledge:
- Familiarity with using the command line or terminal is helpful, especially for Linux installations.
- Basic understanding of file systems and directories.
Essentially, MongoDB is designed to be flexible and can run on most modern systems. As your data grows, you can always scale your hardware accordingly.
Downloading MongoDB Community Server:
To begin, you'll need to download the MongoDB Community Server installation package.
- Visit the official MongoDB download page: https://www.mongodb.com/try/download/community
On the download page, you'll see options to select the following:
- Version: Choose the desired version of MongoDB. It is generally recommended to select the latest stable release.
- Operating System: Select your operating system (Windows or Linux).
- Package: Select the appropriate package type. For Windows, it will typically be
msi. For Linux, you will choose the package type that aligns with your linux distro. For example.debfor Debian/Ubuntu or.rpmfor RedHat/Fedora.
Once you have made your selections, click the "Download" button to download the installer or package.
Installation on Windows:
Running the Installer:
-
Locate the Downloaded Installer:
- Navigate to the directory where you downloaded the MongoDB
.msiinstaller.
- Navigate to the directory where you downloaded the MongoDB
-
Run the Installer:
- Double-click the
.msifile to start the installation wizard.
- Double-click the
-
Welcome Screen:
- Click "Next" on the welcome screen.
-
License Agreement:
- Read the license agreement, check the "I accept the terms in the License Agreement" box, and click "Next."
-
Setup Type:
- Select "Custom" installation. This allows you to choose the installation location and data directory. Click "Next."
-
Installation Location:
- You can change the default installation directory if desired. Click "Next."
-
Service Configuration:
- You can choose to install MongoDB as a service. It is recommended to install as a service.
- You can also change the "Data Directory" location here. It is recommended to change this to a location such as
C:\data\db. If you do not change it here, you will need to create the data directory manually later. - Click "Next."
-
Ready to Install:
- Click "Install" to begin the installation process.
-
Complete Installation:
- Once the installation is complete, click "Finish."
Setting Environment Variables (Optional but Recommended):
Setting the
PATHenvironment variable allows you to run MongoDB commands from any command prompt window without specifying the full path to the executable.-
Open System Properties:
- Search for "Environment Variables" in the Windows Start menu and select "Edit the system environment variables."
-
Environment Variables:
- In the "System Properties" window, click the "Environment Variables..." button.
-
Edit Path Variable:
- In the "System variables" section, find the "Path" variable and click "Edit."
-
Add MongoDB Bin Directory:
- Click "New" and add the path to the MongoDB
bindirectory. This is typicallyC:\Program Files\MongoDB\Server\<version>\bin, replacing<version>with your installed version. - Click "OK" on all open windows to save the changes.
- Click "New" and add the path to the MongoDB
-
Verify Path:
- Open a new command prompt window and type
mongod --version. If MongoDB is installed correctly and thePATHvariable is set, you should see the MongoDB version information.
- Open a new command prompt window and type
Installation on Linux (Ubuntu/Debian):
These instructions are specifically for Debian-based systems like Ubuntu.
Importing the MongoDB Public GPG Key:
-
Open a Terminal:
- Open your terminal application.
-
Import the GPG Key:
- Run the following command to import the MongoDB public GPG key:
bash wget -qO - [https://www.mongodb.org/static/pgp/server-7.0.asc](https://www.mongodb.org/static/pgp/server-7.0.asc) | sudo apt-key add -- This command downloads the GPG key and adds it to your system's trusted keys. This ensures that the packages you download from the MongoDB repository are authentic.
Adding the MongoDB Repository:
-
Add the Repository:
- Run the following command to add the MongoDB repository to your system's sources list:
bash echo "deb [ arch=amd64,arm64 ] [https://repo.mongodb.org/apt/ubuntu](https://repo.mongodb.org/apt/ubuntu) $(lsb_release -cs)/mongodb-org/7.0 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-7.0.list- This command adds the MongoDB repository to your system's package manager sources. The
$(lsb_release -cs)part automatically determines your Ubuntu/Debian version.
-
Update Package List:
- Run the following command to update your package list:
bash sudo apt update- This command refreshes the package list, including the newly added MongoDB repository.
Installing MongoDB:
-
Install MongoDB:
- Run the following command to install the MongoDB Community Server:
bash sudo apt install mongodb-org- This command downloads and installs the MongoDB packages.
After install, linux and windows should both have a system service already setup from the install process. You can check if it's running on linux with
sudo systemctl status mongod. On Windows, you should see the service running as "MongoDB Server" if you open system services on WindowsBasic MongoDB Commands:
After installing and starting MongoDB, you can use the
mongoshell to interact with your database. Here are some basic commands to get you started:Checking MongoDB Version:
First, let's verify that MongoDB is installed correctly by checking its version:
-
Open a Terminal or Command Prompt:
- Open your terminal (Linux/macOS) or command prompt (Windows).
-
Run
mongosh --version:- Type
mongosh --versionand press Enter. - This command will display the installed MongoDB version if it's correctly installed and in your system's PATH.
- Type
Basic MongoDB Shell Commands:
-
Open the
mongoshShell:- Type
mongoshand press Enter. This will open the MongoDB shell, and you'll see a prompt like>.
- Type
-
Show Databases:
- To see a list of all databases on your MongoDB server, type
show dbsand press Enter. - This will display a list of database names.
- To see a list of all databases on your MongoDB server, type
-
Use a Database:
- To switch to a specific database, type
use <database_name>and press Enter. Replace<database_name>with the name of the database you want to use. - Example:
use mydatabase - If the database doesn't exist, MongoDB will create it when you first store data in it.
- To switch to a specific database, type
-
Show Collections:
- After switching to a database, you can see a list of collections (similar to tables in relational databases) in that database by typing
show collectionsand pressing Enter. - Collections are where you store documents (JSON-like data).
- After switching to a database, you can see a list of collections (similar to tables in relational databases) in that database by typing
Example Session:
```bash
mongosh Current Mongosh Log ID: 6563728637951a37887e2730 Connecting to: mongodb://127.0.0.1:27017/?directConnection=true&serverSelectionTimeoutMS=2000&appName=mongosh Using MongoDB: 7.0.3 Using Mongosh: 2.1.1 For mongosh info see: https://docs.mongodb.com/mongodb-shell/
test> show dbs admin 40 KiB config 72 KiB local 40 KiB test> use mydatabase switched to db mydatabase mydatabase> show collections mydatabase> ```
Conclusion
Congratulations! You have successfully installed and started MongoDB Community Server. You've learned how to download, install, and run MongoDB on both Windows and Linux systems, and you've explored some basic commands to interact with your database.
Now, you might want to try an application like grain, a Nostr relay, which utilizes MongoDB as its database. Learn How to Install grain: nostr:naddr1qvzqqqr4gupzq9h35qgq6n8ll0xyyv8gurjzjrx9sjwp4hry6ejnlks8cqcmzp6tqqxnzde5xg6rqdpnx56rqv34uyz5g4
Remember, this guide covers the basics. There's much more to explore in the world of MongoDB, including advanced querying, indexing, replication, and sharding. Continue exploring the official MongoDB documentation to deepen your knowledge and unlock the full potential of this powerful database.
- Operating System:
-
 @ df57b498:d049124f
2025-01-26 03:59:47
@ df57b498:d049124f
2025-01-26 03:59:47Chef's notes
This is cobbled together from trial and error and the web.
Serve hot pancakes with preferably butter and maple syrup. Add other toppings like bananas, nuts, or other fruits and toppings as have available and/or desired.
Details
- ⏲️ Prep time: 10 minutes
- 🍳 Cook time: 10 minutes
Ingredients
- 1 cup flour
- 2 tablespoons sugar
- 2 teaspoons baking powder
- 1 teaspoon salt
- 1 cup milk
- 2 tablespoons vegetable oil
- 1 egg, beaten
Directions
- Combine the dry ingredients.
- Add the wet ingredients and mix.
- Pour or ladle the batter onto the oiled griddle or pan.
- Cook until bubbles form, flip, and cook on the other side.
-
 @ 6bae33c8:607272e8
2025-03-22 23:12:43
@ 6bae33c8:607272e8
2025-03-22 23:12:43I was supposed to do my Main Event next week, but Heather scheduled a trip to Spain for us I had forgotten about, so I moved it to today, which meant I had to cram a bit.
I drew the seven slot. Results are below:
 Before I get into the round-by-round write-up I have to say this was the smoothest and easiest Main I’ve ever done. That doesn’t mean this is a great team — I could easily be wrong about everything — but using recent ADP I planned out each round, and it really went almost exactly to form. That never happens. Usually I’m worried about having to chase some category or getting stuck with players I don’t want. But today there was almost none of that.
Before I get into the round-by-round write-up I have to say this was the smoothest and easiest Main I’ve ever done. That doesn’t mean this is a great team — I could easily be wrong about everything — but using recent ADP I planned out each round, and it really went almost exactly to form. That never happens. Usually I’m worried about having to chase some category or getting stuck with players I don’t want. But today there was almost none of that.1.8 Kyle Tucker — I like Tucker in a new park, playing for a big contract. He’s fully healthy after an injury-shortened 2024, so he should be fresh. Had Team 7 taken Tucker instead of Juan Soto, I would have taken Jackson Chourio.
2.8 Chris Sale — I thought I might get Jazz Chisholm here, and my fallback was Trea Turner. But earlier in the day I decided I’d probably take Sale anyway as pitching gets scarce quickly in the 15-team and often gets pushed up as a result. But I hadn’t really locked it in, even though I felt Sale would make for an easier build. Then Chisholm and Turner went ahead of me on consecutive picks, and my choice was made for me.
3.8 Matt Olson — I was worried about this pick. This was in the elite closer range, and I didn’t want to go that route, so it was either Manny Machado (gone), Olson or dropping down for someone like Michael Harris about whom I’m only lukewarm. I took Olson who has a good shot of 40-100-100 in that lineup.
4.8 C.J. Abrams — The stat nerds hate him, but he could steal 40 bases, and he was raking before slumping in the second half last year. Tucker gave me some bags, but I really wanted a big-time steals source to pair with him.
5.8 Tyler Glasnow — My favorite fifth-round starter, Glasnow managed134 innings last year. A similar giant lefty, Randy Johnson, was also injury prone early in his career and took a while to get going too.
6.8 Cody Bellinger — I was dead set on Bellinger who is raking this spring. He’ll get the short porch in Yankee stadium and qualifies at first and OF.
7.8 Roki Sasaki — This was the first pick I really had to think about. There was a run of five straight pitchers ahead of me, three of whom I would have taken instead (Logan Webb, Max Fried, Hunter Brown.) I like buying the dip on Sasaki after a shaky outing in Japan, but I also considered pivoting to Mike Trout. In the end, I felt there were more hitters I liked afterward, so I went Sasaki, and then Trout went with the very next pick. In fact the next guy snap-called it, if I recall correctly.
8.8 Alex Bregman — I wanted a share after reading how well he’s hit at Fenway during his career (if Grok is correct, 1.240 OPS in 21 games.) Plus he might eventually gain 2B eligibility if Rafael Devers gets healthy enough to play third. And he should get a lot of RBI hitting third behind Devers and Jarren Duran.
9.8 Josh Lowe — I really wanted to get a share of Lowe after reading about how the minor league home park will boost power for lefties. The steals are a given if he’s healthy, but 20-25 HR would make him a huge bargain in Round 9.
10.8 Jordan Romano — The Lowe pick cost me Kenley Jansen, which I thought it might, so I pivoted to the other exprienced closer I like in that range, and Romano’s on a better team.
11.8 Kevin Gausman — I thought about Aroldis Chapman here, but starters were getting scarce, so I gambled he’d make it back and took Gausman. Gausman is coming off a down year, but he’s healthy, and he knows how to pitch.
12.8 Brandon Finnegan — I missed out on Chapman, it turns out, but Finnegan, who had 38 saves last year and was re-signed, was my backup plan. He’s not especially good, but saves are saves.
13.8 Brice Turang — I really didn’t need speed that badly, but Turang fell like 50 spots below ADP, and I did need a second baseman. His defense keeps him in the lineup, and I’ll take 30-plus steals in case one of my other speed guys doesn’t pan out.
14.8 Brandon Nimmo — I got snaked on Walker Buehler (and Jesus Luzardo two picks before that), so I went with Nimmo for his ability to score runs.
15.8 Jackson Holliday — After a lot of safe picks, I felt like gambling on a top prospect finally. He’s hitting well this spring too.
16.8 Jose Berrios — This just seemed like the right pick, a boring veteran who knows how to pitch and get you innings without killing you. With Glasnow and Sasaki, I needed more of a horse type.
17.8 Nolan Jones — He was scratched from the game today right after I made this, so we’ll see. Hopefully it’s something minor. His 2023 season was fetching a top-five-round ADP last year.
18.8 Casey Mize — Pitching was really flying, and Mize is a former top prospect with an opportunity.
19.8 Bo Naylor — I needed a catcher, and he is one. I like that he runs a bit, and last year’s batting average I’ll chalk up to variance.
20.8 Roman Anthony — I don’t know whether he’ll make the team out of camp, but he’s an elite prospect with little left to prove in the minors.
21.8 Jason Foley — I have two shaky closers, so I wanted to throw another potential one in the mix.
22.8 Porter Hodge — Another saves option if Ryan Pressly falls apart.
23.8 Colt Keith — Keith wasn’t horrendous as as rookie, and moving to first base will give him extra eligibility soon.
24.8 Jason Adam — Another potential source of saves with Robert Suarez looking awfully shaky this spring.
25.8 Gavin Lux — A former top prospect, getting regular at-bats in the league’s second best hitter’s park and picking up more eligibility.
26.8 Jonny Deluca — I needed outfield depth in case Anthony doesn’t start the year in the majors, and Deluca should play in that bandbox minor league park.
27.8 Miguel Vargas — A former top prospect with dual position eligibility should get his chance for regular low-pressure at-bats in Chicago.
28.8 Michael McGreevy — I needed another SP, and he’s one. Also has good control and pitches in a good park. Having a great spring too.
29.8 Jacob Stallings — I played chicken at second catcher all draft, got burned a few times, but Stallings is the starter for now in Colorado.
30.8 Blake Treinen — The Stallings pick cost me a gamble on Jared Jones’ elbow, so I took Treinen who’s an elite reliever who could fill in if starters have bad matchups.
Roster By Position
C Bo Naylor/Jacob Stallings
1B Matt Olson
2B Brice Turang
3B Alex Bregman
SS C.J. Abrams
CI Cody Bellinger
MI Jackson Holliday
OF Kyle Tucker/Josh Lowe/Brandon Nimmo/Nolan Jones/Roman Anthony
UT Colt Keith
SP Chris Sale/Tyler Glasnow/Roki Sasaki/Kevin Gausman/Jose Berrios/Casey Mize
RP Jordan Romano/Brandon Finnegan/Jason Foley
B Porter Hodge/Jason Adam/Gavin Lux/Jonny Deluca/Miguel Vargas/Michael McGreevy/Blake Treinen
-
 @ a60e79e0:1e0e6813
2025-03-20 12:58:13
@ a60e79e0:1e0e6813
2025-03-20 12:58:13*This is a long form Nostr native version of a post that lives on my Nostr educational website Hello Nostr *
At first glance Nostr might appear quite similar to some of the apps you use every day, such as Twitter, Mastodon, or Facebook, but that couldn't be further from the truth. This post aims to dispel the myth that "Nostr is just a Twitter replacement" and give you a better understanding about the 'what', the 'how' and most importantly, the 'why' of Nostr.
What Is Nostr?
Nostr is a decentralized, open-source protocol designed for censorship-resistant networking and communication on the web. It stands for "Notes and Other Stuff Transmitted by Relays," and it works by allowing users to publish messages (notes) and content in the form of 'other stuff', to a network of servers (relays) that store and distribute the content.
Unlike traditional platforms like Twitter, Ebay or Facebook, Nostr doesn't rely on a central authority; instead, users control their own identities via cryptographic key pairs.
The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all.
Fiatjaf - Nostr Creator
Nostr is not a website or an app you download from a single source — it’s an open protocol, like email or the internet. Think of it as a set of rules that anyone can use to build tools for sharing messages, posts, or other data without needing a centralized middleman like a big tech company.
Nostr was created by a developer named Fiatjaf in 2020, and has since been steadily gaining traction among people who care about privacy, freedom, and censorship resistance.

Why Nostr?
Imagine the scenario, you've been using an online platform for 5 or even 10 years. You've built up thousands of contacts, perhaps built yourself a sizeable reputation, or even rely on the income from the platform to feed your family. Then one day you make a controversial post, sell a certain item or upload a video on a spicy subject to the platform where the owner disagrees with. With the click of a button, your account is removed. All trace of you, your social graph, or even your future income, disappears in an instant.
Read aloud like that is sounds crazy that we'd even entertain using such a platform, right!? Sadly that is the reality in 2025. This is exactly what happens every single day on X, Facebook, Ebay, Paypal, Linkedin, etc.
Looking at the problem through a more social media focused lens, many of us have become slaves to the likes of Instagram, Twitter and TikTok. We use these 'free' apps under the guise of being social with others online. The reality is that we see what those apps want us to see. We've become slaves to the manipulation of complex and opaque algrorithms designed to keep us hooked and try to sell us things.

Unlike traditional platforms, which are often governed by centralized entities wielding significant control over user data, content moderation, and algorithmic influence, Nostr flips the script by prioritizing user sovereignty and resilience. Built on an open-source framework, Nostr allows individuals to control their own data and interact through a network of relays, making it much more difficult for any single authority - be it a corporation, government, or bad actor - to censor or manipulate the flow of information.
- Is a relay refusing to host your notes? Use another or run your own!
- A specific client using an algorithm you don't like, take your identity and social graph elsewhere and choose another!
Take your identity and social graph with you, anywhere any time.
Nostr’s ability to foster authentic, unfiltered conversations while safeguarding user sovereignty has made it a cornerstone for communities seeking alternatives - whether they’re activists, creators, or everyday people tired of being pawns in the data-driven game. It's simple and adaptable design also encourages innovation, inviting developers to build tools and interfaces that keep pushing the boundaries of what the decentralized internet can achieve. In short, Nostr isn’t just a tool; it’s a movement toward a freer, more equitable digital future.

How Does Nostr Work?
Instead of one giant server owned by a single company holding all your posts and messages, Nostr spreads everything across lots of smaller servers called relays. To get started, you download a client, create your account and back up your private key. Your private key is used to secure your account and sign every message you send over the network. This allows anyone you interact with the verify the integrity of the data coming from 'you'.
The Nostr network is essentially a collection of bulletin boards that share a common format
When you write a note, or share some other type of compatible data, your client signs it with your private key, then sends it to one or more relays. Which relays your information is sent to is entirely up to you. These relays share your message with others who want to see it.
For others to see your notes or 'other stuff', they'll need to be able to find you. Typically this is done by using your public key, which looks something like this
npub15c88nc8d44gsp4658dnfu5fahswzzu8gaxm5lkuwjud068swdqfspxssvx. Don't panic though, you don't need to memorize all of your friends public keys, there are more human friendly methods of finding people that we'll come onto later.Once someone is following you, their client will ask all of their connected relays for any data shared by your public key. Their client will receive this data, verify it is signed by your private key and then populate it into their feed.
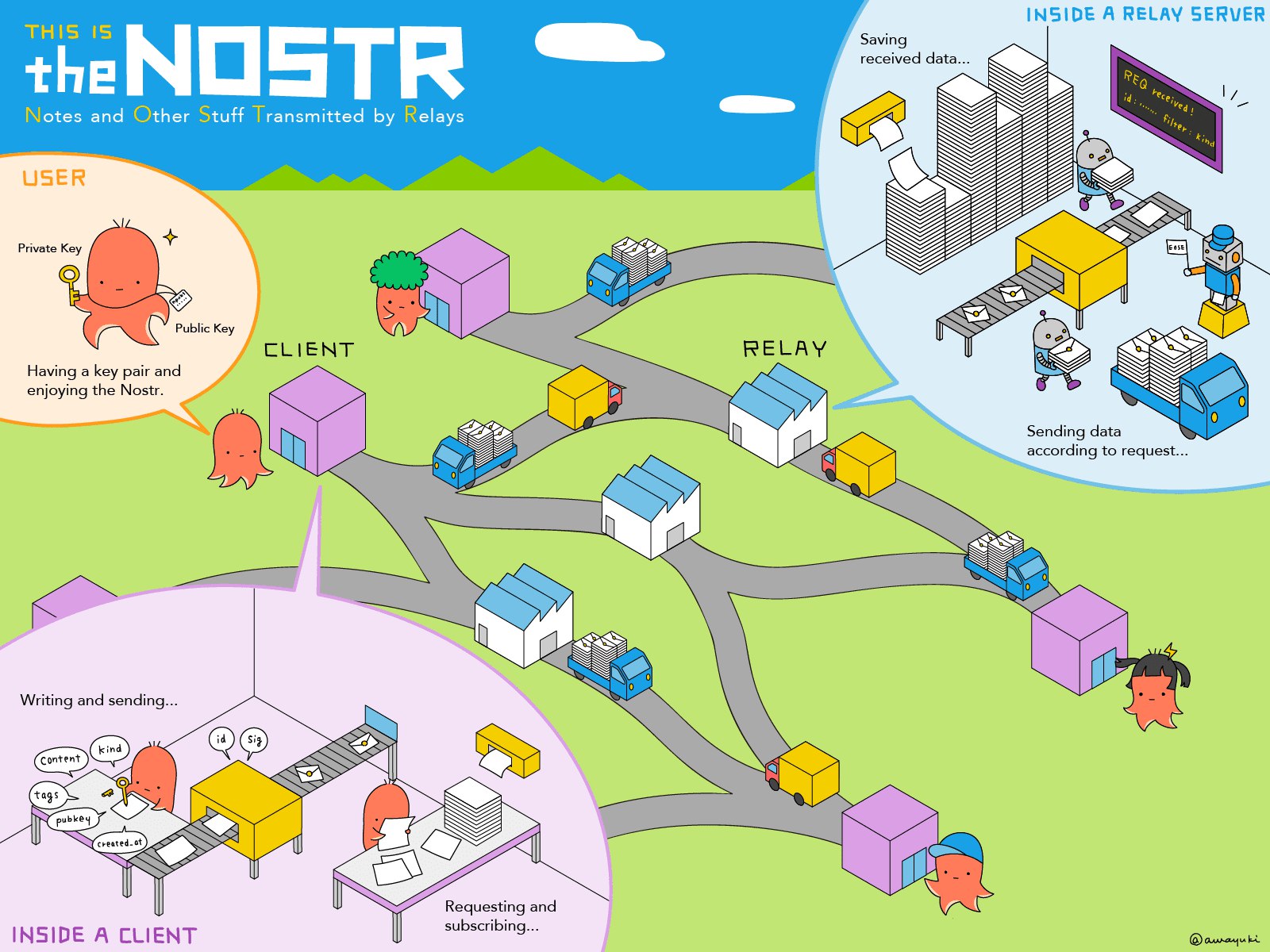
The “Other Stuff” Explained
Nostr’s name hints at this: Notes and Other Stuff Transmitted by Relays. But what is the “other stuff”? Put simply, it’s all the creative and experimental things people are building on Nostr, beyond simple text based notes. Every action on Nostr is an event - like a post, a profile update, or even a payment. The 'Kind' is what specifies the purpose of each event. Kinds are the building blocks of how information is categorized and processed on the network, and the most popular become part of higher lever specification guidelines known as Nostr Implementation Possibility - NIP. A NIP is a document that defines how something in Nostr should work, including the rules, standards, or features. NIPs define the type of 'other stuff' that be published and displayed by different styles of client for different purposes.
Here's some content examples of 'Other Stuff':
- Long-Form Content: Think blog posts or articles. NIP-23.
- Private Messaging: Encrypted chats between users. NIP-04.
- Communities: Group chats or forums like Reddit. NIP-72
- Marketplaces: People listing stuff for sale, payable with zaps. NIP-15
- Zaps: Value transfer over the Lightning Network. NIP57
The beauty of Nostr is that it’s a flexible foundation. Developers can dream up new ideas and build them into clients, and the relays just keep humming along, passing the data around. It’s still early days, so expect the “other stuff” to grow wilder and weirder over time!
Clients vs Relays: What’s the Difference?
Newbies often get tripped up by these two terms, so let’s clearly define them.

Clients
A client is what you use to interact with Nostr. It’s the app or website where you type your posts, read your feed, follow and interact with others. Examples of Nostr clients include:
- Damus (iOS Twitter style client)
- Primal (Cross-platform Twitter style client)
- Amethyst (Android only Twitter style client)
- Habla.News (Web based blog client)
- Olas (Instagram style client)
- 0xchat (Messaging client)
Clients don’t store your data; they just pull it from relays and display it for you. You can switch clients whenever you want, and your account stays the same because it’s tied to your keys, not any single client or app.
Clients are how you use Nostr, and relays are where the data lives. You need both to make the magic happen.
Relays
A relay is a server that stores and shares Nostr data. It’s a little like a post office: you send your note to a relay, and it delivers it to anyone who’s subscribed to see it (like your followers). Relays are run by individuals, groups, or companies who volunteer their computing power. Some are free, some charge a small fee, and you can connect to as many as you like. Most clients will come pre-configured with a list of well-known relays, but you can add or remove any you like.
What Are Zaps?
Zaps are arguably one of Nostr’s coolest features! A zaps is a way to send payments in Bitcoin directly to other users. Imagine liking a post, but instead of just clicking a heart (which you can of course do), you send the poster a few cents worth of Bitcoin to say, “This is awesome!”.
Zaps use Bitcoin's Lightning Network, a faster and cheaper way to move Bitcoin around. To Zap someone, you need a Lightning wallet linked to your Nostr client. Some clients, like Primal, ship with their own custodial wallet to make getting started a breeze. Most clients also allow more advanced users to connect an existing Lightning Wallet to reduce reliance and trust in the client provider.
Zaps are optional but add a fun layer to Nostr. Creators love them because it’s a way to get direct support from fans, with no middleman required.

NIP-05 Identifiers: Your Nostr “Username”
Your nPub, or public key (that long string of letters and numbers) is your 'official' Nostr ID, but it’s not exactly catchy. Enter NIP-05 identifiers, a human-readable and easily sharable way to have people find you. They look like an email address, like
qna@hellonostr.xyz.Here’s how it works:
Most users obtain their NIP-05 ID from a website or service that supports Nostr. Some of these services are free whereas some charge a fee. Some clients, like Primal will set one up for you automatically when you create an account. The email like ID links to your public key, so people can find you more easily. And because these ID's are domain based, there can be no duplicates. qna@hellonostr.xyz can only map to a single public key. The only person that can change that link is the person in control of the domain.
If you control your own domain, you can easily map your Nostr public key to name@my.domain. It’s not mandatory, but it’s super useful for building trust and making your profile recognizable.
Next Steps
So you're bought in. You understand why Nostr is so important and want to get started. Check out our simple onboarding guide here.
Thanks For Reading
Hopefully that moistened your taste buds for more educational Nostr content. This was a basic one, but there will be more focused material coming soon.
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I'll be sure to Zap you back! ⚡️
-
 @ b183a855:1d20ab46
2025-03-22 03:42:34
@ b183a855:1d20ab46
2025-03-22 03:42:34O 8385 surgiu com o objetivo de proporcionar aos usuários uma plataforma robusta e de fácil acesso para diversas opções de entretenimento online. Desde sua criação, a plataforma tem se destacado pela sua interface simples e amigável, que permite aos jogadores navegar facilmente por uma grande variedade de jogos e funcionalidades. O design responsivo e a facilidade de uso são elementos essenciais para garantir que a experiência do usuário seja fluida e envolvente, sem a necessidade de conhecimentos técnicos aprofundados.
Além de sua interface moderna, a plataforma 8385 é totalmente compatível com dispositivos móveis e desktop, oferecendo a flexibilidade para que os jogadores possam acessar seus jogos favoritos em qualquer lugar e a qualquer momento. Esse compromisso com a acessibilidade é um dos pilares que tornam a plataforma 8385 uma escolha atraente para os entusiastas de entretenimento digital.
O processo de registro na plataforma é simples e rápido, permitindo que novos usuários criem uma conta em poucos minutos. Uma vez registrados, os jogadores têm acesso a uma vasta gama de recursos, incluindo suporte ao cliente eficiente, promoções especiais, e a capacidade de personalizar sua experiência de acordo com suas preferências.
Jogos na Plataforma 8385: Variedade e Qualidade para Todos os Gostos O portfólio de jogos oferecido pela plataforma 8385 é um dos maiores atrativos para os jogadores. Com opções que vão desde jogos de habilidade até títulos de sorte e estratégia, a plataforma busca agradar a uma vasta gama de interesses e preferências. Os jogos são desenvolvidos por algumas das maiores empresas de jogos do mundo, garantindo que a qualidade gráfica, o som e a jogabilidade sejam de alto nível.
Os jogadores podem explorar diferentes categorias de jogos, como jogos de mesa, títulos de roleta e blackjack, além de uma impressionante coleção de slots e jogos de cartas. Cada jogo foi projetado para garantir uma experiência divertida e empolgante, com gráficos vívidos, animações fluidas e mecânicas de jogo inovadoras.
A plataforma 8385 também se destaca pela integração de recursos sociais, permitindo que os jogadores interajam com outros usuários, compartilhem suas conquistas e até compitam em torneios e desafios. Esses recursos sociais criam um ambiente mais dinâmico e participativo, onde os jogadores podem se conectar com outras pessoas que compartilham os mesmos interesses e paixão por jogos online.
Outro aspecto que torna os jogos da plataforma 8385 atraentes é a possibilidade de jogá-los em modo gratuito ou com apostas, oferecendo uma experiência completa sem a necessidade de comprometer grandes quantias de dinheiro. Essa flexibilidade é ideal para jogadores iniciantes ou para aqueles que simplesmente querem se divertir sem riscos financeiros.
A Experiência do Jogador: Um Compromisso com a Satisfação A experiência do jogador na plataforma 8385 é enriquecida por uma série de recursos que colocam a satisfação do usuário como prioridade. Desde o momento em que um jogador acessa a plataforma, é possível perceber o cuidado em oferecer uma experiência de navegação e jogo sem interrupções, com alta performance em qualquer tipo de dispositivo.
A plataforma oferece uma variedade de métodos de pagamento, permitindo que os jogadores façam depósitos e retiradas de forma simples e segura. Isso é importante para garantir que os jogadores possam gerenciar suas transações financeiras com facilidade e sem preocupações. A segurança é outro ponto crucial, com tecnologia de ponta para proteger dados pessoais e financeiros, proporcionando um ambiente seguro para que os jogadores se concentrem em sua diversão.
Além disso, o suporte ao cliente é uma das grandes forças da plataforma 8385. A equipe de suporte está disponível 24/7, pronta para ajudar com qualquer problema ou dúvida que o jogador possa ter. Seja por chat ao vivo, e-mail ou outros canais de comunicação, o suporte da plataforma é eficiente e comprometido em garantir que a experiência do usuário seja a melhor possível.
Com suas promoções regulares, bônus e programas de fidelidade, a plataforma 8385 recompensa seus jogadores de várias maneiras, tornando a experiência ainda mais gratificante. Esses incentivos não só ajudam os jogadores a aumentar suas chances de vitória, mas também criam um senso de comunidade, em que os usuários sentem-se valorizados e reconhecidos.
Conclusão A plataforma 8385 vem para transformar a forma como os jogadores experimentam o entretenimento digital online. Com sua interface intuitiva, portfólio diversificado de jogos e uma experiência do jogador imersiva, ela se posiciona como uma excelente opção para aqueles que buscam qualidade, diversão e segurança. A constante inovação e atenção aos detalhes tornam a plataforma 8385 uma das melhores opções no mercado, garantindo que a diversão e a satisfação do usuário estejam sempre em primeiro lugar.
-
 @ 9e69e420:d12360c2
2025-01-26 01:31:47
@ 9e69e420:d12360c2
2025-01-26 01:31:47Chef's notes
arbitray
- test
- of
- chefs notes
hedding 2
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 5
Ingredients
- Test ingredient
- 2nd test ingredient
Directions
- Bake
- Cool
-
 @ 30b99916:3cc6e3fe
2025-01-21 02:08:26
@ 30b99916:3cc6e3fe
2025-01-21 02:08:26Details
- 🍳 Cook time: 10 to 8 minutes at 350
- 🍽️ Servings: About 4 dozen cookies
Ingredients
- 2 sticks of butter
- 2 eggs
- 1 cup granulated sugar
- 1 cup brown sugar
- 1 cup peanut butter
- 1 t vanilla
- 2 cups flour
- 1/2 t salt
- 1 t soda
- 6 oz Semi-Sweet Chocolate chips (optional)
Directions
- Blend butter, eggs, vanilla and sugars together thoroughly
- Next blend in peanut butter thoroughly
- Next blend in flour, salt, and soda thoroughly
- Optional blend in chocolate chips
- Add about table spoon of cookie dough per cookie on a cookie sheet. With a fork based in sugar place a cross hatch pattern on each cookie. Bake cookies for 10 to 8 minutes and place onto cooler rack.
-
 @ c69b71dc:426ba763
2025-01-18 15:39:35
@ c69b71dc:426ba763
2025-01-18 15:39:35Chef's notes
This raw vegan curry ramen is a vibrant, nourishing dish packed with fresh vegetables and a rich, creamy coconut curry broth. It’s quick to prepare, full of flavour, and the perfect guilt-free comfort food! 🌱 Feel free to use your favourite veggies👩🏼🍳
Details
- ⏲️ Prep time: 20 min.
- 🍳 Cook time: 0
- 🍽️ Servings: 2
Ingredients
- 500g or 2 packs kelp noodles
- 1/2 Lemon juice ( 1/4 for soaking and 1/4 for the soup
- Salt
- Fresh vegetables of your choice, such as: 4 medium mushrooms, 4 leaves red cabbage, 2 carrots (julienned or peeled into strips), 1 Celery stick (diced)
- 2 cups coconut milk (or coconut cream diluted with water)
- 1/2 flesh of a Coconut (optional, if using fresh coconuts) otherwise more coconut cream
- 1 thumb of fresh ginger
- 1 thumb of fresh turmeric
- 2 tbsp light miso paste
- 2 pitted dates
- 2 tbsp cashews
- 1 clove garlic
- 1 tsp curry powder or pepper (optional)
Directions
- Prepare the Noodles: Rinse the kelp noodles thoroughly. Then soak them in warm water with a squeeze of lemon juice and a pinch of salt for 10 minutes to soften.
- Prep the Vegetables: Thinly slice or julienne carrots, dice celery, thinly cut mushrooms, cut the red cabbage into thin strips.
- Make the Broth: In a blender, combine the following: 2 cups coconut milk (or coconut cream diluted with water if fresh coconuts are unavailable), ginger, turmeric, 1/4 juice of 1 lemon, light miso paste, pitted dates, cashews, garlic, salt, curry powder
- Blend on high speed for about 3 to 4 minutes until the broth is smooth and slightly warm. Do not overheat!
- Assemble the Ramen: Drain the kelp noodles and place them in serving bowls. Arrange the prepped vegetables on top of the noodles. Pour the warm curry broth over the noodles and vegetables.
- Serve immediately and enjoy your raw vegan ramen with chopsticks for an authentic touch!
-
 @ a95c6243:d345522c
2025-03-20 09:59:20
@ a95c6243:d345522c
2025-03-20 09:59:20Bald werde es verboten, alleine im Auto zu fahren, konnte man dieser Tage in verschiedenen spanischen Medien lesen. Die nationale Verkehrsbehörde (Dirección General de Tráfico, kurz DGT) werde Alleinfahrern das Leben schwer machen, wurde gemeldet. Konkret erörtere die Generaldirektion geeignete Sanktionen für Personen, die ohne Beifahrer im Privatauto unterwegs seien.
Das Alleinfahren sei zunehmend verpönt und ein Mentalitätswandel notwendig, hieß es. Dieser «Luxus» stehe im Widerspruch zu den Maßnahmen gegen Umweltverschmutzung, die in allen europäischen Ländern gefördert würden. In Frankreich sei es «bereits verboten, in der Hauptstadt allein zu fahren», behauptete Noticiastrabajo Huffpost in einer Zwischenüberschrift. Nur um dann im Text zu konkretisieren, dass die sogenannte «Umweltspur» auf der Pariser Ringautobahn gemeint war, die für Busse, Taxis und Fahrgemeinschaften reserviert ist. Ab Mai werden Verstöße dagegen mit einem Bußgeld geahndet.
Die DGT jedenfalls wolle bei der Umsetzung derartiger Maßnahmen nicht hinterherhinken. Diese Medienberichte, inklusive des angeblich bevorstehenden Verbots, beriefen sich auf Aussagen des Generaldirektors der Behörde, Pere Navarro, beim Mobilitätskongress Global Mobility Call im November letzten Jahres, wo es um «nachhaltige Mobilität» ging. Aus diesem Kontext stammt auch Navarros Warnung: «Die Zukunft des Verkehrs ist geteilt oder es gibt keine».
Die «Faktenchecker» kamen der Generaldirektion prompt zu Hilfe. Die DGT habe derlei Behauptungen zurückgewiesen und klargestellt, dass es keine Pläne gebe, Fahrten mit nur einer Person im Auto zu verbieten oder zu bestrafen. Bei solchen Meldungen handele es sich um Fake News. Teilweise wurde der Vorsitzende der spanischen «Rechtsaußen»-Partei Vox, Santiago Abascal, der Urheberschaft bezichtigt, weil er einen entsprechenden Artikel von La Gaceta kommentiert hatte.
Der Beschwichtigungsversuch der Art «niemand hat die Absicht» ist dabei erfahrungsgemäß eher ein Alarmzeichen als eine Beruhigung. Walter Ulbrichts Leugnung einer geplanten Berliner Mauer vom Juni 1961 ist vielen genauso in Erinnerung wie die Fake News-Warnungen des deutschen Bundesgesundheitsministeriums bezüglich Lockdowns im März 2020 oder diverse Äußerungen zu einer Impfpflicht ab 2020.
Aber Aufregung hin, Dementis her: Die Pressemitteilung der DGT zu dem Mobilitätskongress enthält in Wahrheit viel interessantere Informationen als «nur» einen Appell an den «guten» Bürger wegen der Bemühungen um die Lebensqualität in Großstädten oder einen möglichen obligatorischen Abschied vom Alleinfahren. Allerdings werden diese Details von Medien und sogenannten Faktencheckern geflissentlich übersehen, obwohl sie keineswegs versteckt sind. Die Auskünfte sind sehr aufschlussreich, wenn man genauer hinschaut.
Digitalisierung ist der Schlüssel für Kontrolle
Auf dem Kongress stellte die Verkehrsbehörde ihre Initiativen zur Förderung der «neuen Mobilität» vor, deren Priorität Sicherheit und Effizienz sei. Die vier konkreten Ansätze haben alle mit Digitalisierung, Daten, Überwachung und Kontrolle im großen Stil zu tun und werden unter dem Euphemismus der «öffentlich-privaten Partnerschaft» angepriesen. Auch lassen sie die transhumanistische Idee vom unzulänglichen Menschen erkennen, dessen Fehler durch «intelligente» technologische Infrastruktur kompensiert werden müssten.
Die Chefin des Bereichs «Verkehrsüberwachung» erklärte die Funktion des spanischen National Access Point (NAP), wobei sie betonte, wie wichtig Verkehrs- und Infrastrukturinformationen in Echtzeit seien. Der NAP ist «eine essenzielle Web-Applikation, die unter EU-Mandat erstellt wurde», kann man auf der Website der DGT nachlesen.
Das Mandat meint Regelungen zu einem einheitlichen europäischen Verkehrsraum, mit denen die Union mindestens seit 2010 den Aufbau einer digitalen Architektur mit offenen Schnittstellen betreibt. Damit begründet man auch «umfassende Datenbereitstellungspflichten im Bereich multimodaler Reiseinformationen». Jeder Mitgliedstaat musste einen NAP, also einen nationalen Zugangspunkt einrichten, der Zugang zu statischen und dynamischen Reise- und Verkehrsdaten verschiedener Verkehrsträger ermöglicht.
Diese Entwicklung ist heute schon weit fortgeschritten, auch und besonders in Spanien. Auf besagtem Kongress erläuterte die Leiterin des Bereichs «Telematik» die Plattform «DGT 3.0». Diese werde als Integrator aller Informationen genutzt, die von den verschiedenen öffentlichen und privaten Systemen, die Teil der Mobilität sind, bereitgestellt werden.
Es handele sich um eine Vermittlungsplattform zwischen Akteuren wie Fahrzeugherstellern, Anbietern von Navigationsdiensten oder Kommunen und dem Endnutzer, der die Verkehrswege benutzt. Alle seien auf Basis des Internets der Dinge (IOT) anonym verbunden, «um der vernetzten Gemeinschaft wertvolle Informationen zu liefern oder diese zu nutzen».
So sei DGT 3.0 «ein Zugangspunkt für einzigartige, kostenlose und genaue Echtzeitinformationen über das Geschehen auf den Straßen und in den Städten». Damit lasse sich der Verkehr nachhaltiger und vernetzter gestalten. Beispielsweise würden die Karten des Produktpartners Google dank der DGT-Daten 50 Millionen Mal pro Tag aktualisiert.
Des Weiteren informiert die Verkehrsbehörde über ihr SCADA-Projekt. Die Abkürzung steht für Supervisory Control and Data Acquisition, zu deutsch etwa: Kontrollierte Steuerung und Datenerfassung. Mit SCADA kombiniert man Software und Hardware, um automatisierte Systeme zur Überwachung und Steuerung technischer Prozesse zu schaffen. Das SCADA-Projekt der DGT wird von Indra entwickelt, einem spanischen Beratungskonzern aus den Bereichen Sicherheit & Militär, Energie, Transport, Telekommunikation und Gesundheitsinformation.
Das SCADA-System der Behörde umfasse auch eine Videostreaming- und Videoaufzeichnungsplattform, die das Hochladen in die Cloud in Echtzeit ermöglicht, wie Indra erklärt. Dabei gehe es um Bilder, die von Überwachungskameras an Straßen aufgenommen wurden, sowie um Videos aus DGT-Hubschraubern und Drohnen. Ziel sei es, «die sichere Weitergabe von Videos an Dritte sowie die kontinuierliche Aufzeichnung und Speicherung von Bildern zur möglichen Analyse und späteren Nutzung zu ermöglichen».
Letzteres klingt sehr nach biometrischer Erkennung und Auswertung durch künstliche Intelligenz. Für eine bessere Datenübertragung wird derzeit die Glasfaserverkabelung entlang der Landstraßen und Autobahnen ausgebaut. Mit der Cloud sind die Amazon Web Services (AWS) gemeint, die spanischen Daten gehen somit direkt zu einem US-amerikanischen «Big Data»-Unternehmen.
Das Thema «autonomes Fahren», also Fahren ohne Zutun des Menschen, bildet den Abschluss der Betrachtungen der DGT. Zusammen mit dem Interessenverband der Automobilindustrie ANFAC (Asociación Española de Fabricantes de Automóviles y Camiones) sprach man auf dem Kongress über Strategien und Perspektiven in diesem Bereich. Die Lobbyisten hoffen noch in diesem Jahr 2025 auf einen normativen Rahmen zur erweiterten Unterstützung autonomer Technologien.
Wenn man derartige Informationen im Zusammenhang betrachtet, bekommt man eine Idee davon, warum zunehmend alles elektrisch und digital werden soll. Umwelt- und Mobilitätsprobleme in Städten, wie Luftverschmutzung, Lärmbelästigung, Platzmangel oder Staus, sind eine Sache. Mit dem Argument «emissionslos» wird jedoch eine Referenz zum CO2 und dem «menschengemachten Klimawandel» hergestellt, die Emotionen triggert. Und damit wird so ziemlich alles verkauft.
Letztlich aber gilt: Je elektrischer und digitaler unsere Umgebung wird und je freigiebiger wir mit unseren Daten jeder Art sind, desto besser werden wir kontrollier-, steuer- und sogar abschaltbar. Irgendwann entscheiden KI-basierte Algorithmen, ob, wann, wie, wohin und mit wem wir uns bewegen dürfen. Über einen 15-Minuten-Radius geht dann möglicherweise nichts hinaus. Die Projekte auf diesem Weg sind ernst zu nehmen, real und schon weit fortgeschritten.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ bd32f268:22b33966
2025-03-18 18:59:23
@ bd32f268:22b33966
2025-03-18 18:59:23O que torna um homem um modelo a ser seguido ? Que qualidades pode apresentar um homem que demonstram as suas aspirações ?
Nos dias que correm a nobreza de carácter não parece ser o factor chave nas figuras que são mais celebradas pelo mundo inteiro. A nossa sociedade dá mais atenção ao indigente moral célebre pelas sacadas narcísicas do que ao guerreiro, ao santo, ao patriarca que dedicaram a sua vida a um propósito e aspirações manifestamente superiores.
É frequente vermos ser objeto de atenção o homem vaidoso, efeminado, narcísico e corrupto até. O facto de serem estas as referências que temos na cultura moderna diz muito da sociedade em que vivemos. É importante notar que nós somos como espelhos que refletem aquilo que reverenciamos, isto é, vamo-nos tornando mais parecidos com o objeto da nossa admiração. É nosso instinto tentar imitar aquilo que admiramos, portanto isto é um grave problema quando admiramos as coisas erradas.
Pode parecer contraintuitivo mas por vezes as coisas mais admiráveis na vida são na verdade as mais simples. Prestemos atenção ao que nos diz o auto G.K Chesterton a este propósito.

Há algo de magnificamente sóbrio no pai de família que não procura atenção e se dedica exclusivamente ao seu dever. Esta figura é, por hora, demonizada tantas e tantas vezes, sendo frequentemente apresentado como sendo o mandatário de uma cultura misógina e machista.
Estou convencido que enquanto a figura de pai de família não for devidamente reabilitada, dificilmente teremos um ressurgimento de famílias propriamente ordenadas. É importante notar aqui um ponto, este pai de família deve ser alguém capaz de colocar os interesses da família primeiro que os seus interesses individuais. Deve ser alguém que não viva no relativismo moral, mas sim um homem de fé, algo que está em vias de extinção no ocidente e em particular em Portugal. Este homem deve ser o porto de abrigo para a sua família, alguém disposto a travar o bom combate, e será sempre portanto um defensor acérrimo da verdade. Não será naturalmente alguém obcecado com a sua própria imagem, mas sim um homem desejavelmente forte quer em termos físicos, tendo zelo na forma como se exercita, quer em termos mentais, sendo uma pessoa capaz mas com autocontrolo. Deve também ser um homem com uma vida intelectual, isto é, alguém que nutre interesse pelo legado que lhe foi confiado e procura aprender sobre o mesmo. Muitos homens antes de si fizeram sacrifícios para que o homem da atualidade usufrua dos mais variados benefícios.
A atualidade oferece-nos por vezes a promoção de algumas destas facetas, algo que seria desejável e bom, contudo com algumas distorções. Há homens fortes, capazes de feitos atléticos ímpares, que se cultivam nesse domínio mas pelas razões erradas. Por vezes o imperativo moral que os guia é a vaidade, sendo que esse trabalho físico que fazem conspira para consolidar o seu narcisismo.
Outros há com uma determinação inabalável, algo louvável quando usada para os fins próprios. Esta determinação não deve ser usada para a procura de grandes riquezas como um fim em si mesmas, nem como um isco usado para o oportunismo sexual com as mulheres.
Poderíamos também dar como exemplo, homens com uma prodigiosa inteligência mas que, não a tendo devidamente orientada, a usam para manipular e corromper o discurso público não olhando a meios para atingir os fins.
Um factor chave que dificulta a formação de mais homens com este tipo de espinha dorsal é uma certa apropriação da linguagem que tem existido no discurso público que procura rotular quem ousa desafiar este status quo. Termos como “negacionista”, “radical”, “fascista”, “fundamentalista”, “ultranacionalista” entre outros, são constantemente atirados remetendo o homem para uma falsa conclusão:
“ Tu não podes defender nada, nem ter certeza de nada”.
Outra ferramenta importante nesta desconstrução é o apelo ao vício. Sendo através da pornografia, da comida ultra-processada ou de uma vida de conforto , há claramente um incentivo ao hedonismo e à autoindulgência. Procura-se alimentar cada vez mais esta busca do prazer com o fim último, e por conseguinte a coragem, o sacrifício e o trabalho, como pedras angulares da construção do carácter do homem ficam para segundo plano.
O cavalheirismo ficou-se apenas pelas aparências. Por vezes, há um verniz de algumas das propriedades que descrevi em várias situações, contudo não passa de uma máscara. É fácil segurar uma porta para uma senhora e dizer “com licença”, “por favor”, para se mostrar alguém educado quando o custo para o fazer é mínimo. Difícil é estar disposto a fazer sacríficos em que nos doamos inteiramente pelos outros, no entanto é isso que é pedido ao homem. Doando-se encontrará o seu verdadeiro propósito.
-
 @ b183a855:1d20ab46
2025-03-22 03:41:51
@ b183a855:1d20ab46
2025-03-22 03:41:51A plataforma 5526 surge como uma excelente opção para os entusiastas de jogos online, oferecendo uma experiência dinâmica e envolvente para jogadores de todos os níveis. Com uma interface moderna, jogos diversificados e uma abordagem focada no usuário, a plataforma tem ganhado popularidade rapidamente entre aqueles que buscam se divertir e desafiar suas habilidades de forma inovadora.
Plataforma 5526: Uma Introdução ao Novo Estilo de Jogo A 5526 é uma plataforma de jogos que busca se destacar pela sua versatilidade e facilidade de acesso. Com um design intuitivo e responsivo, os jogadores podem acessar o conteúdo da plataforma de qualquer lugar, seja em dispositivos móveis ou desktop. A plataforma é conhecida por seu ambiente amigável e acessível, o que facilita a entrada de novos jogadores enquanto mantém o alto nível de engajamento para os veteranos.
Um dos maiores diferenciais da 5526 é sua biblioteca de jogos, que abrange uma vasta gama de categorias, incluindo ação, estratégia, puzzles e muito mais. Isso permite que os jogadores escolham jogos que mais se alinhem com suas preferências, criando uma experiência personalizada de diversão e entretenimento. O design da plataforma também é bastante otimizado, garantindo que os jogos carreguem rapidamente e que a navegação seja sem fricções.
Além disso, a 5526 oferece uma plataforma segura, com sistemas de criptografia de ponta para garantir a proteção dos dados dos jogadores. O processo de criação de contas é simples e rápido, com múltiplas opções de pagamento que garantem que os jogadores possam fazer depósitos e retiradas de forma prática e eficiente.
A Diversidade de Jogos na 5526: Uma Introdução ao Mundo do Entretenimento A 5526 é lar de uma impressionante variedade de jogos que atendem a diferentes gostos e preferências. Seja você um amante de jogos de estratégia que adora um bom desafio mental ou alguém que prefere a adrenalina de jogos rápidos e emocionantes, a plataforma tem algo a oferecer.
Entre os jogos mais populares estão aqueles que exigem habilidade e planejamento, com mecânicas que desafiam os jogadores a pensarem de forma criativa e estratégica. Esses jogos são ideais para aqueles que buscam uma experiência mais profunda e envolvente, onde cada movimento pode fazer a diferença entre o sucesso e a falha. Eles são projetados para testar a paciência e o raciocínio lógico, proporcionando uma experiência de aprendizado constante.
A plataforma também conta com opções mais acessíveis para quem deseja apenas passar o tempo de forma descontraída, com jogos simples e intuitivos que são fáceis de entender, mas ainda assim divertidos e desafiadores. Esses jogos são perfeitos para quem está começando sua jornada no mundo dos jogos online, pois oferecem uma introdução suave sem perder o apelo.
Além dos jogos tradicionais, a 5526 também apresenta títulos inovadores, com mecânicas únicas e gráficos impressionantes, criando uma experiência visualmente rica e excitante. Os desenvolvedores da plataforma frequentemente atualizam sua biblioteca com novos lançamentos, garantindo que os jogadores tenham acesso às últimas novidades e tendências do mercado.
A Experiência do Jogador na Plataforma 5526: O Que Esperar A experiência do jogador na plataforma 5526 é desenhada para ser imersiva, fluida e prazerosa. Desde o momento em que o jogador entra na plataforma até a navegação entre os jogos, tudo é pensado para garantir que cada interação seja agradável e intuitiva. A interface é clara, com fácil acesso a menus e informações relevantes sobre cada jogo.
Outro ponto positivo é o suporte ao cliente, que se destaca pela rapidez e eficiência. A plataforma conta com uma equipe de atendimento ao cliente disponível 24/7, pronta para resolver quaisquer problemas ou dúvidas que os jogadores possam ter, seja durante o cadastro, transações financeiras ou no momento do jogo.
Além disso, a 5526 oferece uma comunidade de jogadores ativa, onde os usuários podem interagir, compartilhar dicas e até mesmo participar de torneios ou eventos especiais. Isso cria uma sensação de pertencimento, fazendo com que os jogadores se sintam parte de algo maior, com oportunidades de socializar e competir de maneira saudável.
A plataforma também se destaca pela sua flexibilidade. Ao permitir que os jogadores escolham entre uma ampla gama de jogos, com diferentes níveis de dificuldade e estilos, ela consegue agradar a todos os tipos de públicos. A variedade de modos de jogo também é um atrativo: além de jogos solo, a plataforma permite que os jogadores se conectem com outros em partidas multijogador, promovendo ainda mais a interação e a competição.
Outro aspecto importante é o incentivo ao progresso e ao aprimoramento do jogador. Muitos jogos dentro da plataforma 5526 oferecem sistemas de recompensas, onde os jogadores podem ganhar itens exclusivos ou bônus conforme avançam nas partidas. Isso cria uma sensação de conquista e satisfação, incentivando os jogadores a se dedicarem ainda mais para alcançar novos desafios e objetivos.
Em resumo, a 5526 não é apenas uma plataforma de jogos online, mas um espaço onde os jogadores podem se divertir, aprender e se conectar com outros. A experiência de jogo é envolvente e dinâmica, com uma interface amigável e um vasto portfólio de opções. Seja você um iniciante ou um jogador experiente, a 5526 tem algo a oferecer para todos.
-
 @ 000002de:c05780a7
2025-03-18 17:30:47
@ 000002de:c05780a7
2025-03-18 17:30:47Was watching this old clip of the great Thomas Sowell discuss Obama's broad decrees and promises when he uttered this gold quip.
originally posted at https://stacker.news/items/916888
-
 @ 104cdb46:bda37787
2025-03-21 12:01:52
@ 104cdb46:bda37787
2025-03-21 12:01:52Bet365 là một nền tảng giải trí trực tuyến nổi bật, không chỉ cung cấp các trò chơi đa dạng mà còn chú trọng đến việc tạo ra những trải nghiệm độc đáo cho người chơi. Từ các trò chơi thể thao cho đến các trò chơi giải trí khác, Bet365 luôn đảm bảo rằng người tham gia có thể tìm thấy lựa chọn phù hợp với sở thích và kỹ năng của mình. Giao diện của Bet365 rất dễ sử dụng, với những hướng dẫn rõ ràng, giúp người chơi mới có thể nhanh chóng làm quen và tham gia các trò chơi. Không chỉ vậy, nền tảng này cũng cung cấp các tính năng bổ sung như các trận đấu trực tiếp, giúp người chơi có thể theo dõi và tham gia vào các sự kiện thể thao yêu thích trong thời gian thực, mang lại sự phấn khích và kịch tính không ngừng. Những tính năng này kết hợp với công nghệ hiện đại, giúp tạo nên một không gian giải trí chất lượng cao, mang lại cho người chơi những phút giây thư giãn và thử thách đầy thú vị.
Bảo mật và quyền lợi của người chơi là yếu tố quan trọng mà Bet365 luôn đặt lên hàng đầu. Nền tảng này sử dụng công nghệ mã hóa tiên tiến để bảo vệ tất cả các giao dịch và thông tin cá nhân của người tham gia, giúp người chơi yên tâm tận hưởng những trò chơi mà không phải lo lắng về vấn đề an toàn thông tin. Các phương thức thanh toán tại Bet365 rất linh hoạt, cho phép người chơi nạp và rút tiền một cách nhanh chóng và thuận tiện, phù hợp với nhu cầu của người tham gia từ nhiều quốc gia khác nhau. Chính những yếu tố bảo mật này đã giúp Bet365 xây dựng được lòng tin vững chắc từ người chơi và khẳng định được vị thế của mình trong ngành giải trí trực tuyến. Các giao dịch trên Bet365 luôn được xử lý một cách chính xác và nhanh chóng, giúp người chơi có thể tập trung vào việc tham gia trò chơi mà không gặp phải bất kỳ phiền phức nào.
Ngoài ra, Bet365 còn nổi bật với việc tổ chức các sự kiện và giải đấu đặc biệt, mang lại cơ hội cho người chơi thể hiện kỹ năng và cạnh tranh với những người chơi khác trên toàn thế giới. Những sự kiện này thường xuyên diễn ra và thu hút được sự tham gia của đông đảo người chơi, tạo ra một cộng đồng năng động và thân thiện. Các giải đấu không chỉ mang lại những phần thưởng hấp dẫn mà còn giúp người chơi xây dựng mối quan hệ với cộng đồng, học hỏi và cải thiện kỹ năng chơi game của mình. Bet365 luôn cố gắng mang đến những trải nghiệm mới mẻ và đầy thử thách, nhằm giữ cho người chơi luôn cảm thấy thú vị và hứng thú. Chính những đặc điểm nổi bật này đã giúp Bet365 trở thành một trong những nền tảng giải trí trực tuyến được ưa chuộng và tin cậy trên toàn thế giới.
-
 @ d1b118c6:4985b38d
2025-01-16 17:39:47
@ d1b118c6:4985b38d
2025-01-16 17:39:47Chef's notes
Let me know how it goes for you https://maria.omg.lol
Details
- ⏲️ Prep time: 5-20 minutes
- 🍳 Cook time: 20-40 minutes
- 🍽️ Servings: As many as you want omg!!!!
Ingredients
- Spaghetti/whatever pasta you want
- Garlic/smashed or diced as much as you want
- Tomatoes/ diced or more liquid state whatever you want
- Scallops/ I use the frozen bagged mini kind and just do a couple handfuls as many as you want
- Butter and/or olive oil but the butter is v good imo but also I used both
- Bacon/ make it extra crispy and then crumble up as much as you want
- Whatever seasonings
Directions
- Set oven to 400° or so
- Put all your bacon 🥓 strips onto tin foil lined baking sheet/s and then put the trays in the oven for 15-20 min
- Boil up your pasta in salty water
- Pull the bacon out when done
- In a pan cook up the scallops real quick like 5-10 min idk
- Sauté the tomatoes and garlic and whatever use whatever seasons and lots of butter
- Strain the pasta when it’s ready
- Mix pasta and sautéed sauce
- Add more crumbled bacon on top #garnish
-
 @ e8ed3798:67dd345a
2025-03-20 00:00:00
@ e8ed3798:67dd345a
2025-03-20 00:00:00this is a test please ignore
-
 @ e5de992e:4a95ef85
2025-03-22 15:52:25
@ e5de992e:4a95ef85
2025-03-22 15:52:25In a world where our to-do lists seem to grow longer by the minute, figuring out what to tackle next can feel like solving a puzzle with missing pieces. Should you call a friend to catch up? Finish that work project? Or make sure you don’t forget a loved one’s birthday? The overwhelm is real, and traditional task management systems often leave us guessing. That’s where the 2-5 Rule comes in—a groundbreaking concept that powers TaskforUs, a smart, simple website designed to tell you exactly what to work on right now.
What Is the 2-5 Rule?
At its core, the 2-5 Rule is a timing-based approach to task management built on a simple yet powerful idea: every task has a natural rhythm—a “time unit” that dictates how often it should be addressed—and an ideal window for action: between 2 and 5 of those units. The time unit varies depending on the task’s nature:
-
Daily Tasks: (e.g., doing cardio or following up on a quick email)
Time unit: days. Act within 2 to 5 days. -
Weekly Tasks: (e.g., scheduling dinner with a friend)
Time unit: weeks. Act within 2 to 5 weeks. -
Monthly Tasks: (e.g., reviewing your budget)
Time unit: months. Act within 2 to 5 months. -
Yearly Tasks: (e.g., reassessing your career goals)
Time unit: years. Revisit every 2 to 5 years.
The 2-5 Rule ensures you’re neither jumping on tasks too early (wasting energy on something that isn’t urgent) nor leaving them too late (missing opportunities or causing stress). It’s about finding the sweet spot—the perfect moment to act.
For date-specific events like birthdays or anniversaries, TaskforUs introduces a Fix Mode that pins the task to a specific day. As the date approaches, the task climbs your list until it reaches the top on the day itself, ensuring you never miss a critical moment.
The Origins of the 2-5 Rule
The 2-5 Rule was born out of a need to bring structure to the chaos of modern life. Traditional to-do lists are static—they don’t account for the natural ebb and flow of tasks. Urgent tasks get buried under less pressing ones, and long-term goals are often forgotten until it’s too late.
TaskforUs’s creators recognized that timing is as important as priority. They drew inspiration from: - Behavioral Science: Showing that humans thrive on rhythm and consistency. - Project Management Principles: Where tasks are often scheduled based on optimal intervals.
The choice of 2 to 5 units isn’t arbitrary. Research into productivity and habit formation suggests: - Acting too soon (e.g., after just 1 unit) can lead to over-managing. - Waiting too long (beyond 5 units) risks neglect.
The 2-to-5 window strikes a balance—providing enough flexibility while ensuring nothing slips through the cracks. This range also aligns with our natural sense of urgency: after 2 units, a task begins to feel pressing; by 5 units, it risks becoming problematic.
How the 2-5 Rule Works in Practice
Step 1: Define Your Tasks and Time Units
When you add a task to TaskforUs, you assign it a time unit based on its nature: - Example:
- "Schedule dinner with Alex" is a social task (unit: weeks). - "Do cardio" is a health goal (unit: days). - "Reassess my career path" is a long-term goal (unit: years).TaskforUs can suggest defaults based on common patterns, but you can customize the unit to fit your life.
Step 2: Track the 2-5 Window
TaskforUs monitors when you last acted on a task. If it’s been 2 time units, the task enters its “sweet spot” and starts climbing your list. By 5 units, it becomes urgent. - Example:
- If you last met Alex 3 weeks ago, "Schedule dinner with Alex" becomes a top priority. - If it’s been 2 days since your last cardio session, TaskforUs nudges you to hit the gym.Step 3: Handle Fixed Dates with Fix Mode
For tasks tied to specific dates (e.g., birthdays or anniversaries), Fix Mode lets you set an exact date. The task gradually climbs your list as the date nears and becomes the top priority on that day, ensuring you never miss it.
Step 4: Prioritize with Top Task and Focus Mode
- Top Task: TaskforUs surfaces the single most urgent task within the 2-to-5 window.
- Focus Mode: If you prefer to see more, this mode shows your top 3 tasks (or a customizable number), ensuring you’re always focused on what matters most without being overwhelmed by a long list.
The Science Behind the 2-5 Rule
The 2-5 Rule isn’t just a clever idea—it’s grounded in psychology and productivity research:
-
Habit Formation:
Studies (e.g., by Dr. BJ Fogg) show that consistency is key to building routines, yet overdoing it can lead to burnout. The 2-5 window strikes a healthy balance. -
Decision Fatigue:
Research by Dr. Roy Baumeister highlights the mental toll of constant decision-making. By automating prioritization, the 2-5 Rule reduces this burden, freeing up mental energy. -
Zeigarnik Effect:
The Fix Mode leverages the tendency to remember uncompleted tasks, keeping date-specific items front of mind until they’re completed, thereby reducing stress and improving follow-through.
Why You Should Try the 2-5 Rule with TaskforUs
If you’re tired of chaotic to-do lists, missed deadlines, or the nagging feeling of forgetting something important, the 2-5 Rule offers a better way. It works with your natural rhythm, ensuring you focus on what truly matters. TaskforUs brings this concept to life with a user-friendly platform (currently in beta) that: - Eliminates Decision Fatigue: Tells you exactly what to do now. - Balances Urgency and Flexibility: Keeps you in the sweet spot between procrastination and over-management. - Adapts to Your Life’s Rhythm: Customizes time units for daily, weekly, monthly, and yearly tasks. - Ensures You Never Miss Critical Dates: With Fix Mode for date-specific events. - Reduces Stress and Boosts Momentum: By focusing on one Top Task (or a few in Focus Mode).
Real-Life Applications of the 2-5 Rule
-
Social Connections:
Task: “Schedule dinner with Alex”
Time Unit: Weeks
Scenario: If you last met Alex 3 weeks ago, the task becomes your Top Task, prompting you to reconnect. -
Health Goals:
Task: “Do cardio”
Time Unit: Days
Scenario: If it’s been 2 days since your last workout, TaskforUs nudges you to exercise before the 5-day mark. -
Special Dates:
Task: “Wish Alex a happy birthday”
Mode: Fix Mode
Scenario: A month before the birthday, it’s low on your list, but as the date nears, it climbs to the top—ensuring you don’t miss it. -
Long-Term Planning:
Task: “Reassess my career path”
Time Unit: Years
Scenario: If it’s been 2 years since your last review, TaskforUs prompts you to evaluate your goals and progress.
How TaskforUs Brings the 2-5 Rule to Life
TaskforUs is more than just a concept—it’s a practical tool that makes the 2-5 Rule actionable:
-
Top Task:
The algorithm identifies the single most urgent task within your 2-to-5 window. -
Focus Mode:
Displays your top 3 tasks (or a customizable number) to help manage multiple priorities. -
Fix Mode:
Ensures date-specific tasks are prioritized as the due date approaches. -
Smart Defaults:
Suggests time units based on common patterns, while allowing customization to suit your needs. -
Ongoing Refinements:
The TaskforUs team continually improves the algorithm based on user feedback to enhance its accuracy.
Take Control of Your Tasks Today
The 2-5 Rule is more than a productivity hack—it’s a mindset shift. It’s about working smarter, not harder, and timing your tasks to perfection. TaskforUs makes this possible with a simple, intuitive platform designed to help you master your to-do list.
-
-
 @ 104cdb46:bda37787
2025-03-21 12:00:43
@ 104cdb46:bda37787
2025-03-21 12:00:43Quy88 là một nền tảng giải trí trực tuyến nổi bật, được thiết kế với mục tiêu mang lại cho người chơi những trải nghiệm thú vị và đa dạng. Với một kho trò chơi phong phú, từ các trò chơi thể thao, bài, đến các trò chơi kỹ năng, Quy88 đáp ứng đầy đủ nhu cầu giải trí của những người yêu thích sự đổi mới và thử thách. Giao diện của nền tảng này được tối ưu hóa, giúp người chơi dễ dàng tìm kiếm và tham gia vào các trò chơi yêu thích chỉ với vài thao tác đơn giản. Không chỉ dừng lại ở các trò chơi thông thường, Quy88 còn cung cấp các lựa chọn chơi game đặc biệt, tạo nên sự khác biệt và thu hút đông đảo người chơi tham gia. Với đồ họa sắc nét, âm thanh sống động, và những tính năng game đầy sáng tạo, Quy88 mang lại một không gian giải trí đầy hấp dẫn, giúp người chơi có thể tận hưởng những phút giây thư giãn tuyệt vời.
Không chỉ cung cấp một kho trò chơi hấp dẫn, Quy88 còn chú trọng đến yếu tố bảo mật và quyền lợi của người chơi. Nền tảng này sử dụng công nghệ mã hóa hiện đại để đảm bảo rằng mọi thông tin cá nhân và tài chính của người tham gia đều được bảo vệ an toàn tuyệt đối. Quy88 cam kết bảo mật tuyệt đối tất cả các giao dịch và hoạt động của người chơi, từ việc nạp tiền đến việc rút thưởng. Điều này mang đến sự yên tâm cho người chơi khi tham gia vào các trò chơi, giúp họ không phải lo lắng về bất kỳ rủi ro nào liên quan đến bảo mật. Hệ thống thanh toán của Quy88 cũng rất tiện lợi và nhanh chóng, giúp người chơi có thể thực hiện các giao dịch mà không gặp phải bất kỳ trở ngại nào. Với các biện pháp bảo mật hàng đầu, Quy88 đã xây dựng được niềm tin vững chắc từ cộng đồng người chơi.
Ngoài các trò chơi thú vị và hệ thống bảo mật tiên tiến, Quy88 còn tổ chức các sự kiện và giải đấu hấp dẫn, mang đến cơ hội cho người chơi thể hiện kỹ năng và tranh tài với nhau. Các sự kiện này không chỉ tạo ra không khí sôi động, hào hứng mà còn mang lại những phần thưởng giá trị cho những người chơi xuất sắc. Những giải đấu này thu hút sự tham gia của đông đảo người chơi, tạo nên một cộng đồng mạnh mẽ và gắn kết. Hệ thống giải đấu tại Quy88 luôn được tổ chức công bằng và minh bạch, mang đến những thử thách thú vị cho mọi người tham gia. Với một nền tảng ổn định, chất lượng dịch vụ tốt và một cộng đồng năng động, Quy88 tiếp tục khẳng định vị thế của mình là một trong những lựa chọn giải trí trực tuyến hàng đầu trong cộng đồng người chơi.
-
 @ 30b99916:3cc6e3fe
2025-01-13 22:17:08
@ 30b99916:3cc6e3fe
2025-01-13 22:17:08Chef's notes
Recipe modified from a recipe published from a school cookbook in 1963.
Details
- 🍳 Cook time: 8 to 10 Minutes at 400
- 🍽️ Servings: 3 dozen or so depending on cookie size
Ingredients
- 2 sticks of butter
- 1 1/2 Cup sugar
- 2 eggs
- 1 t. vanilla (optional but recommended)
- 2 3/4 cups flour
- 2 t. Cream of tartar
- 1 t. Soda
- 1/4 t. Salt
Directions
-
- Heat over to 400
-
- Mix butter, sugar, eggs, and vanilla thoroughly.
-
- Sift together flour, cream of tartar, soda, salt and blend into mixture.
-
- Form small dough balls and roll in sugar/cinnamon
-
- Place each cookie dough ball 2" apart on a cookie sheet
-
 @ a39d19ec:3d88f61e
2025-03-18 17:16:50
@ a39d19ec:3d88f61e
2025-03-18 17:16:50Nun da das deutsche Bundesregime den Ruin Deutschlands beschlossen hat, der sehr wahrscheinlich mit dem Werkzeug des Geld druckens "finanziert" wird, kamen mir so viele Gedanken zur Geldmengenausweitung, dass ich diese für einmal niedergeschrieben habe.
Die Ausweitung der Geldmenge führt aus klassischer wirtschaftlicher Sicht immer zu Preissteigerungen, weil mehr Geld im Umlauf auf eine begrenzte Menge an Gütern trifft. Dies lässt sich in mehreren Schritten analysieren:
1. Quantitätstheorie des Geldes
Die klassische Gleichung der Quantitätstheorie des Geldes lautet:
M • V = P • Y
wobei:
- M die Geldmenge ist,
- V die Umlaufgeschwindigkeit des Geldes,
- P das Preisniveau,
- Y die reale Wirtschaftsleistung (BIP).Wenn M steigt und V sowie Y konstant bleiben, muss P steigen – also Inflation entstehen.
2. Gütermenge bleibt begrenzt
Die Menge an real produzierten Gütern und Dienstleistungen wächst meist nur langsam im Vergleich zur Ausweitung der Geldmenge. Wenn die Geldmenge schneller steigt als die Produktionsgütermenge, führt dies dazu, dass mehr Geld für die gleiche Menge an Waren zur Verfügung steht – die Preise steigen.
3. Erwartungseffekte und Spekulation
Wenn Unternehmen und Haushalte erwarten, dass mehr Geld im Umlauf ist, da eine zentrale Planung es so wollte, können sie steigende Preise antizipieren. Unternehmen erhöhen ihre Preise vorab, und Arbeitnehmer fordern höhere Löhne. Dies kann eine sich selbst verstärkende Spirale auslösen.
4. Internationale Perspektive
Eine erhöhte Geldmenge kann die Währung abwerten, wenn andere Länder ihre Geldpolitik stabil halten. Eine schwächere Währung macht Importe teurer, was wiederum Preissteigerungen antreibt.
5. Kritik an der reinen Geldmengen-Theorie
Der Vollständigkeit halber muss erwähnt werden, dass die meisten modernen Ökonomen im Staatsauftrag argumentieren, dass Inflation nicht nur von der Geldmenge abhängt, sondern auch von der Nachfrage nach Geld (z. B. in einer Wirtschaftskrise). Dennoch zeigt die historische Erfahrung, dass eine unkontrollierte Geldmengenausweitung langfristig immer zu Preissteigerungen führt, wie etwa in der Hyperinflation der Weimarer Republik oder in Simbabwe.
-
 @ a60e79e0:1e0e6813
2025-03-18 15:38:25
@ a60e79e0:1e0e6813
2025-03-18 15:38:25**This is a long form note test of a post that lives on my Nostr educational website Hello Nostr **
One of the first things most people learn when getting started with Nostr is the importance of their private key, or ‘nsec’. The nsec is the key to their Nostr world. Whoever controls an nsec, controls that account. Lose access to the nsec and you lose access to that account and its social graph.
So the nsec is very important and should be treated very carefully, but what happens if we want to use or test multiple Nostr clients? Newer clients might be malicious, or have unknown security vulnerabilities, so simply go pasting our nsec everywhere just to see if we like a new app is not the best idea!
Thankfully there are solutions for nsec management that allow us to do exactly that, without having to expose our all important nsec to each and every app we want to interact with. The most commonly used to date are browser extensions like Alby or nos2x. Typically these types of browser extensions do not work on mobile platforms.
Enter Amber…

What is Amber?
Amber is a free and open source Android application that serves as a dedicated ‘Nostr event signer’. Amber allows users to keep their nsec segregated in a single, dedicated app. The goal of Amber is to have your smartphone act as a NIP-46 signing device without any need for servers or additional hardware.
At its core Amber serves two main purposes:
Securing your nsec(s) Using this nsec to sign events for other Nostr clients on your phone
Got an iPhone? Check out nsec.app
Getting Started
- Download Amber to your phone. It is available from Zap Store, Obtanium, GitHub or F-Droid
Download Amber here. Support Amber here.
-
When opening Amber for the first time, you’ll have the option to create a new Nostr account (nsec) or import an existing one.
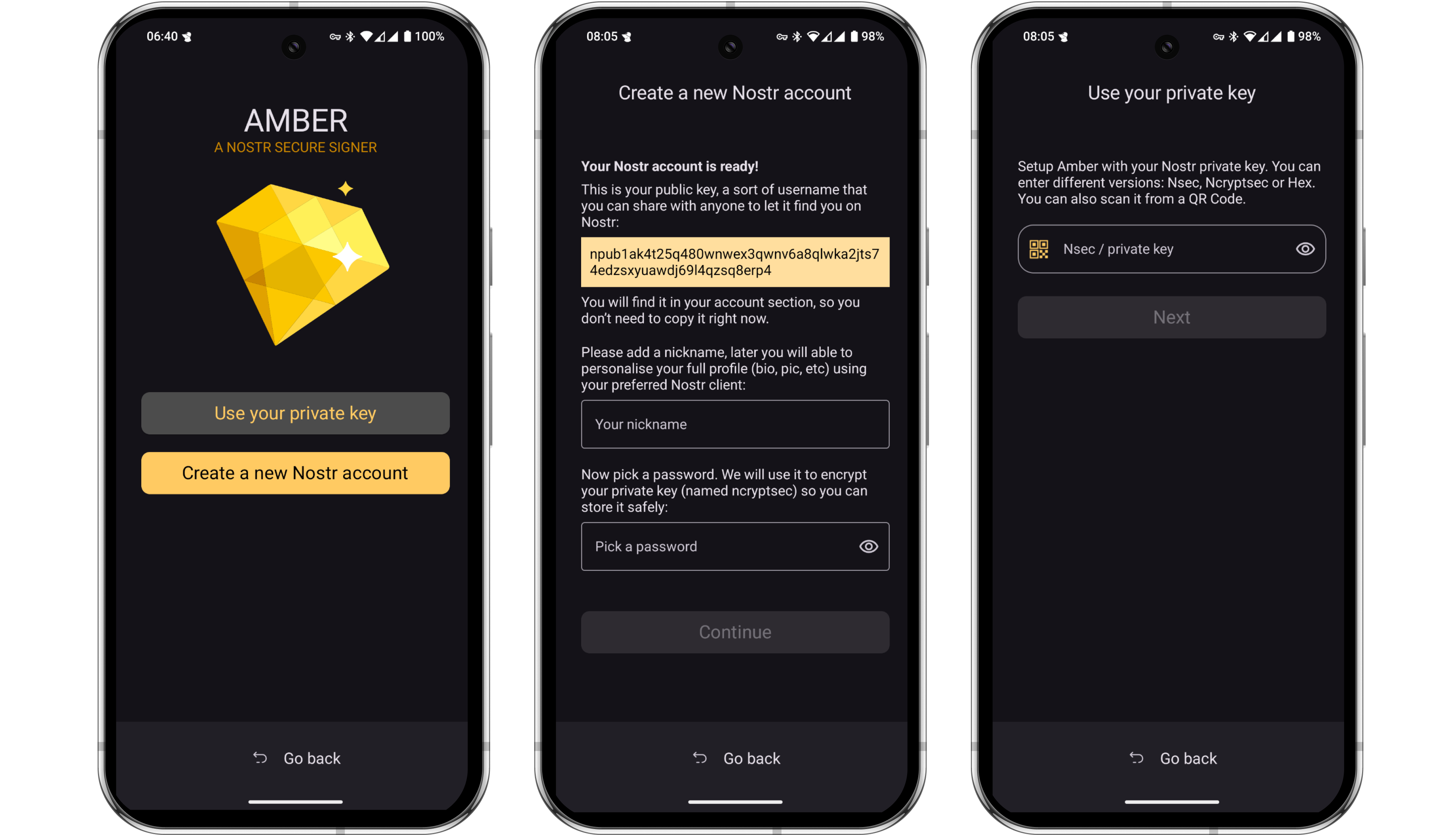
-
If you do not currently have a Nostr account, Amber will help you generate and secure a brand new nsec. Amber allows you to download an encrypted file containing your nsec as well as the option to download a human-readable version of the nsec in the form of 12 English words, similar to a Bitcoin seed.
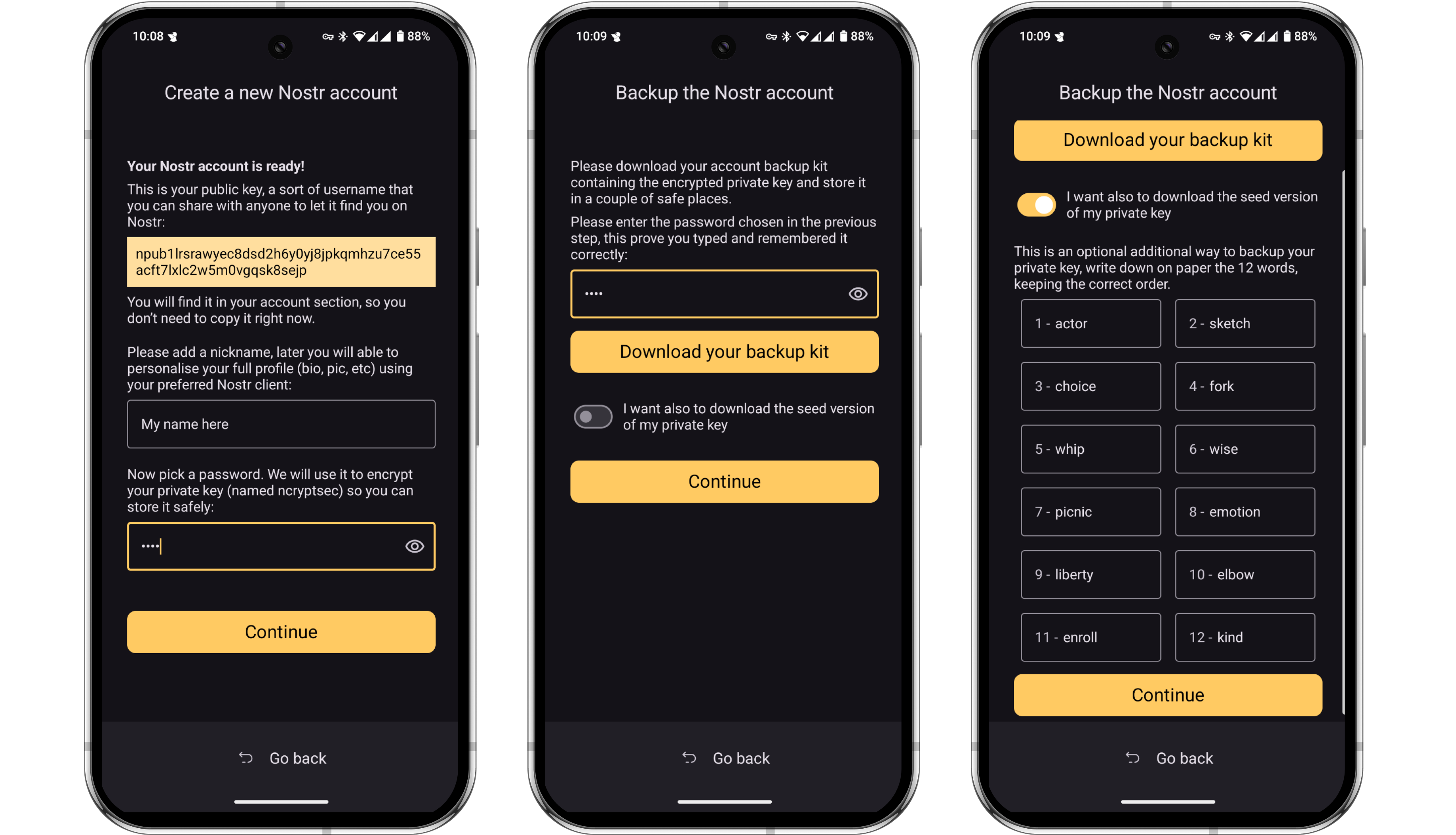
Skip this step if you have an existing nsec that you want to import to Amber.
-
To import an existing nsec, choose ‘Use your private key’. You can then paste the nsec from an existing client, or scan a QR code of it if you have one available to you.
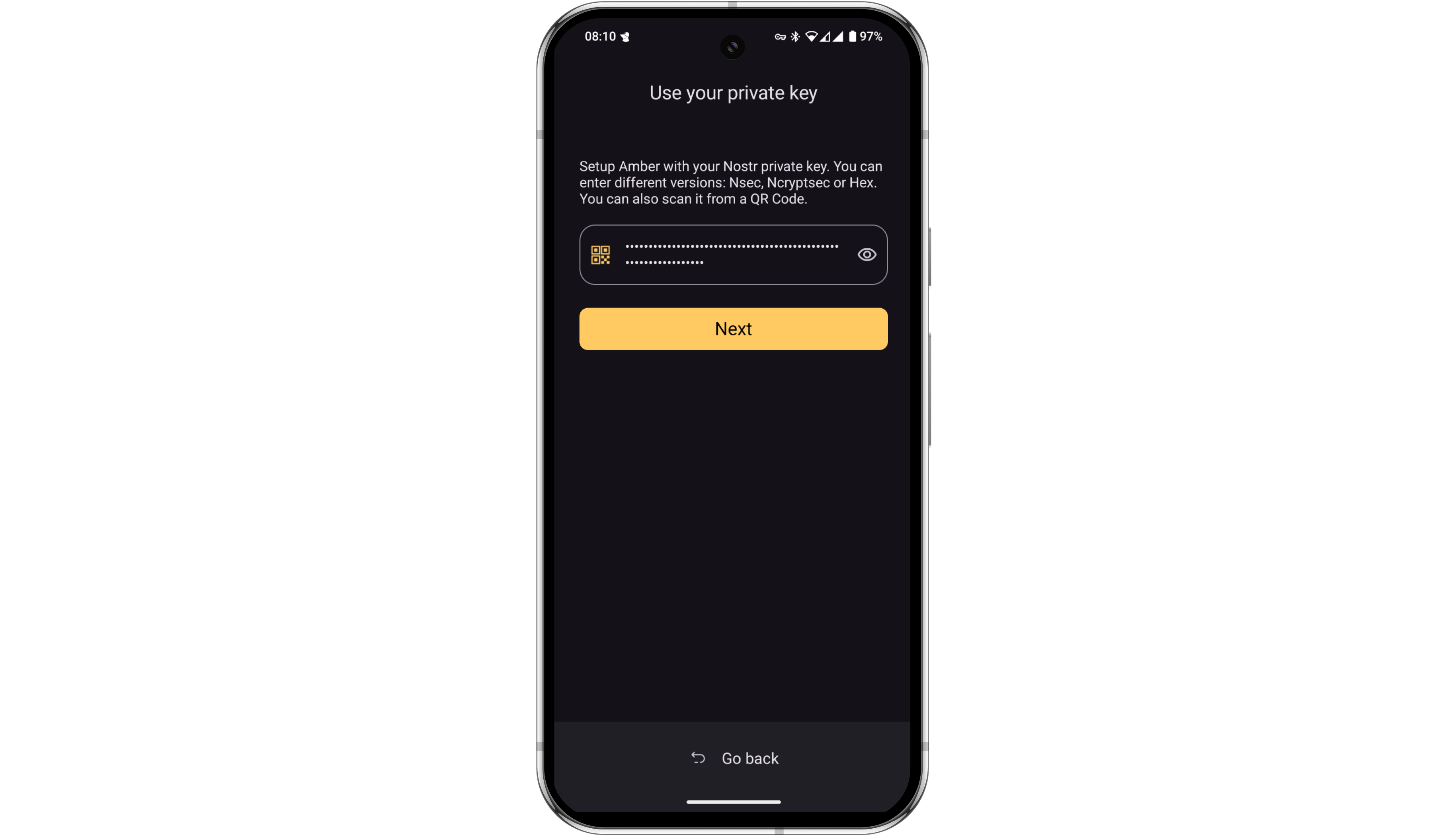
-
Once you have created or imported your nsec, Amber will ask for some basic permissions. You can allow the app the approve basic actions, or enable more granular selection for each client you subsequently connect. Once you tap ‘Finish’, you’ll see that the account is now ready.
If you have or require more than one Nostr account, you can repeat these steps for each one. All accounts can be viewed by tapping the profile image in the bottom right corner of the screen.
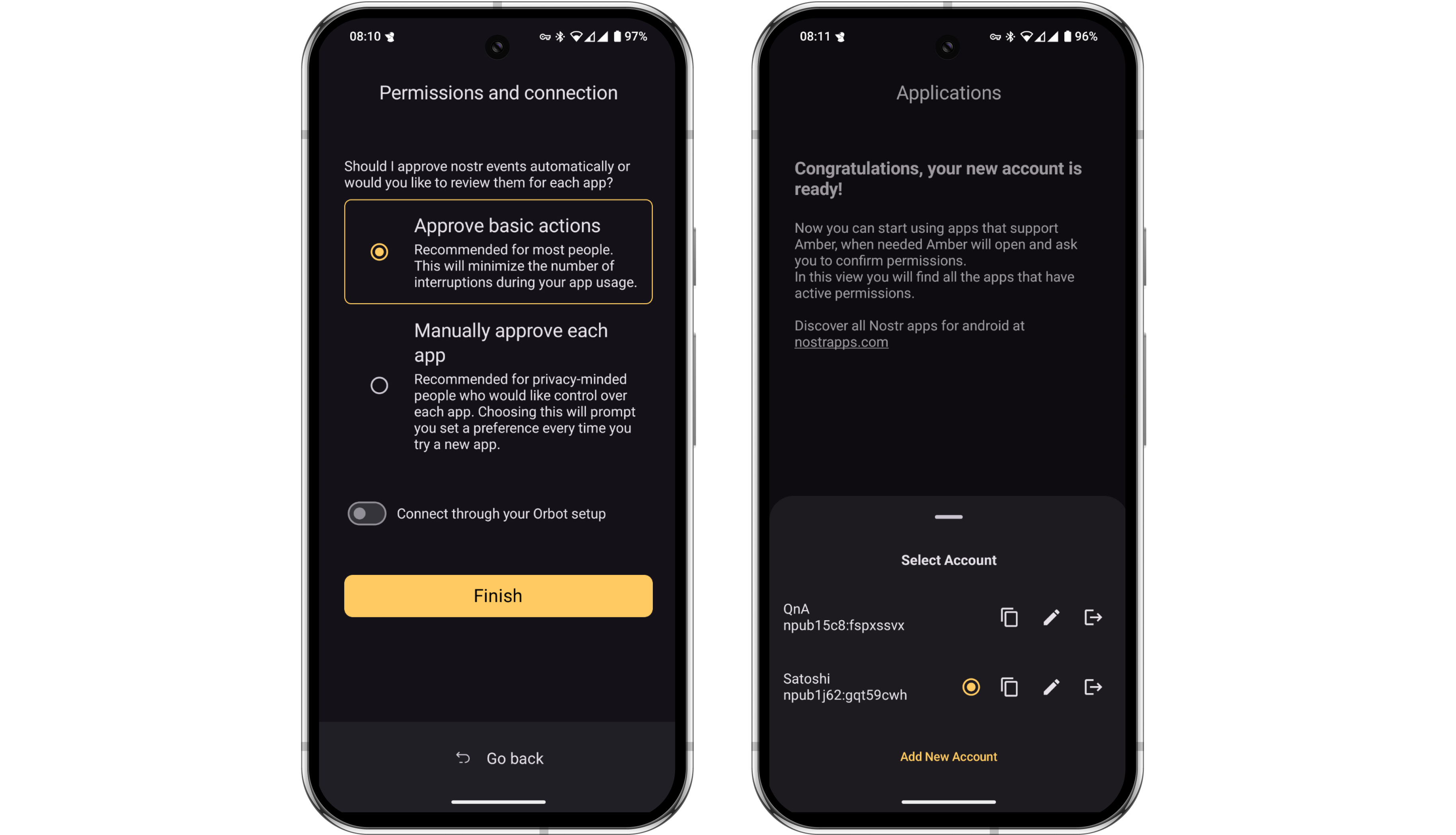
- That’s it, Amber is now ready to sign events. Amber allows multiple ways to connect other clients to it, but most will have a very simple ‘Login with Amber’ button. Let’s demo this in practice with Amethyst, the most popular Android-only client.
The opening screen of Amethyst shows the ‘Login with Amber’ option. Tap that.
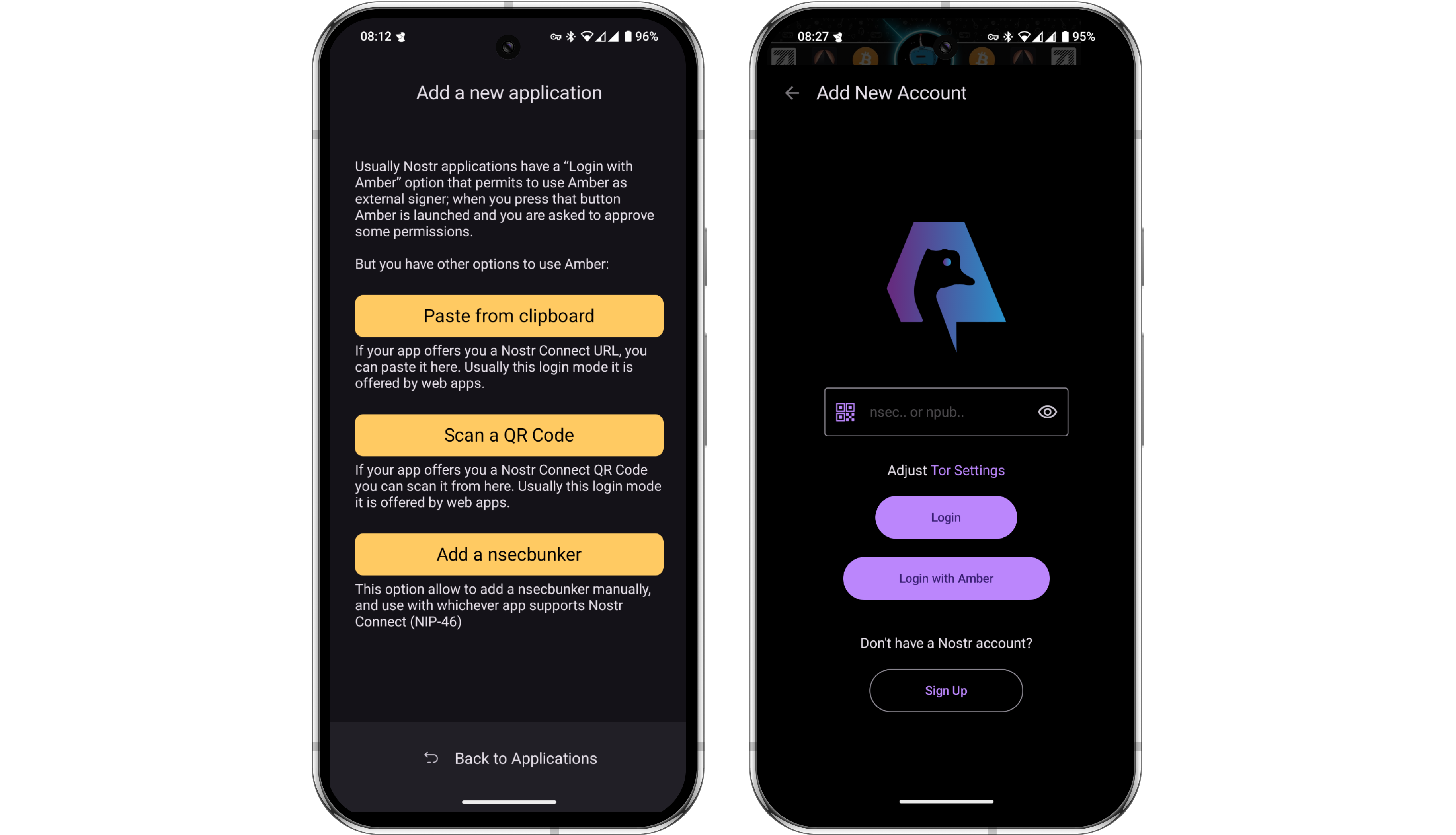
- Amber will then open automatically and ask you to define the level of autonomy you’d like to have with Amethyst. This setting defines how often Amber will require you to manually authorize each event.
For example, you might want Amber to automatically sign every like or repost you do in Amethyst, but then be asked to manually approve all direct messages sent from your account. These permissions can be customized in the settings at any time.
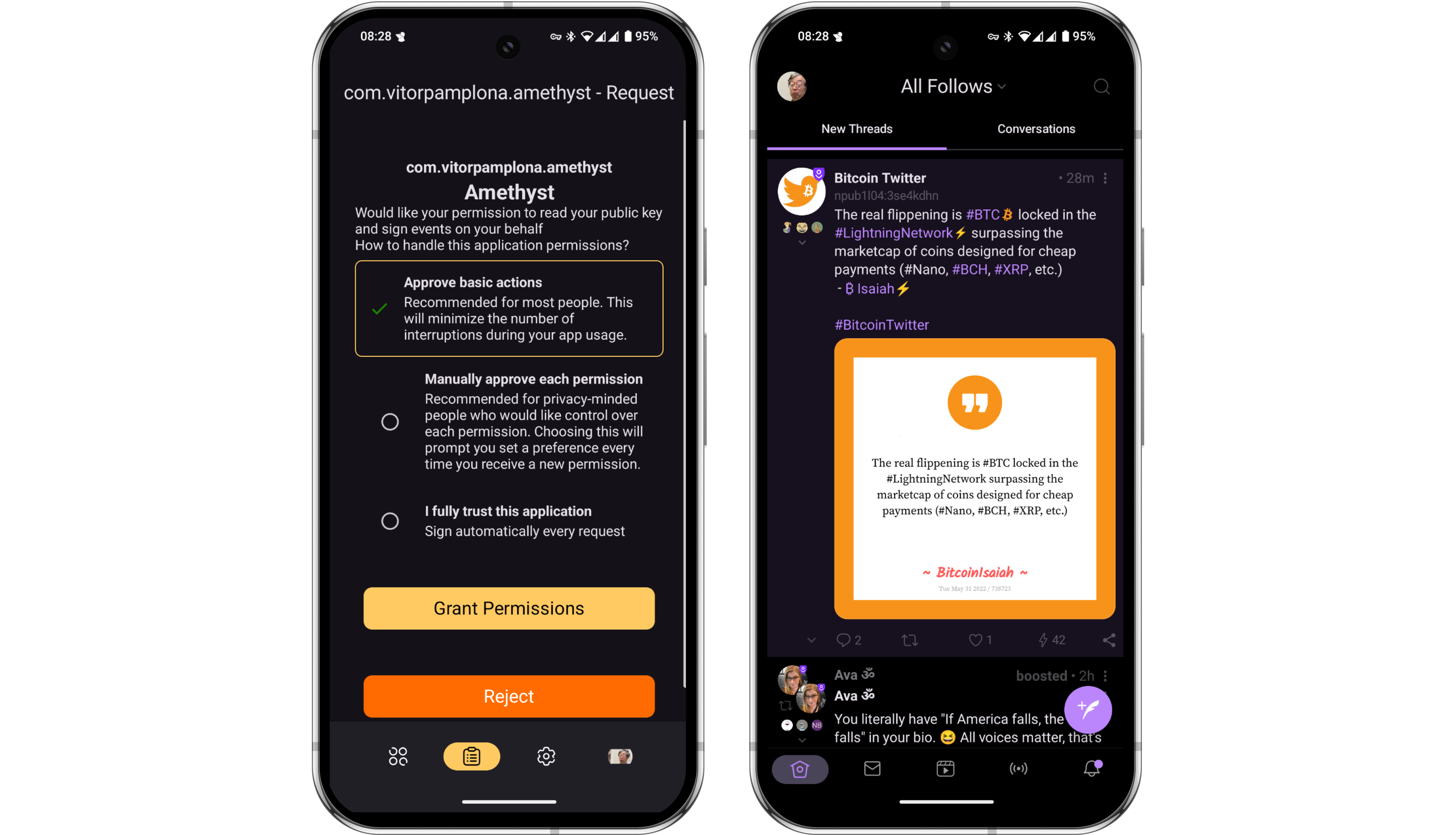
- Let’s assume that upon setup, we did not grant Amber the ability to automatically sign short text notes for us. Let’s look at how simple the authorization flow is. Type a new short note in Amethyst and press ‘Post’.
Amethyst will instantly send the request to the Amber app on your phone, with no third party server involved. Amber will open and ask you to approve the event. When you do, Amber signs the event with the nsec it stores for you and automatically send the signed event back to Amethyst to be posted. The whole process takes just a few seconds.
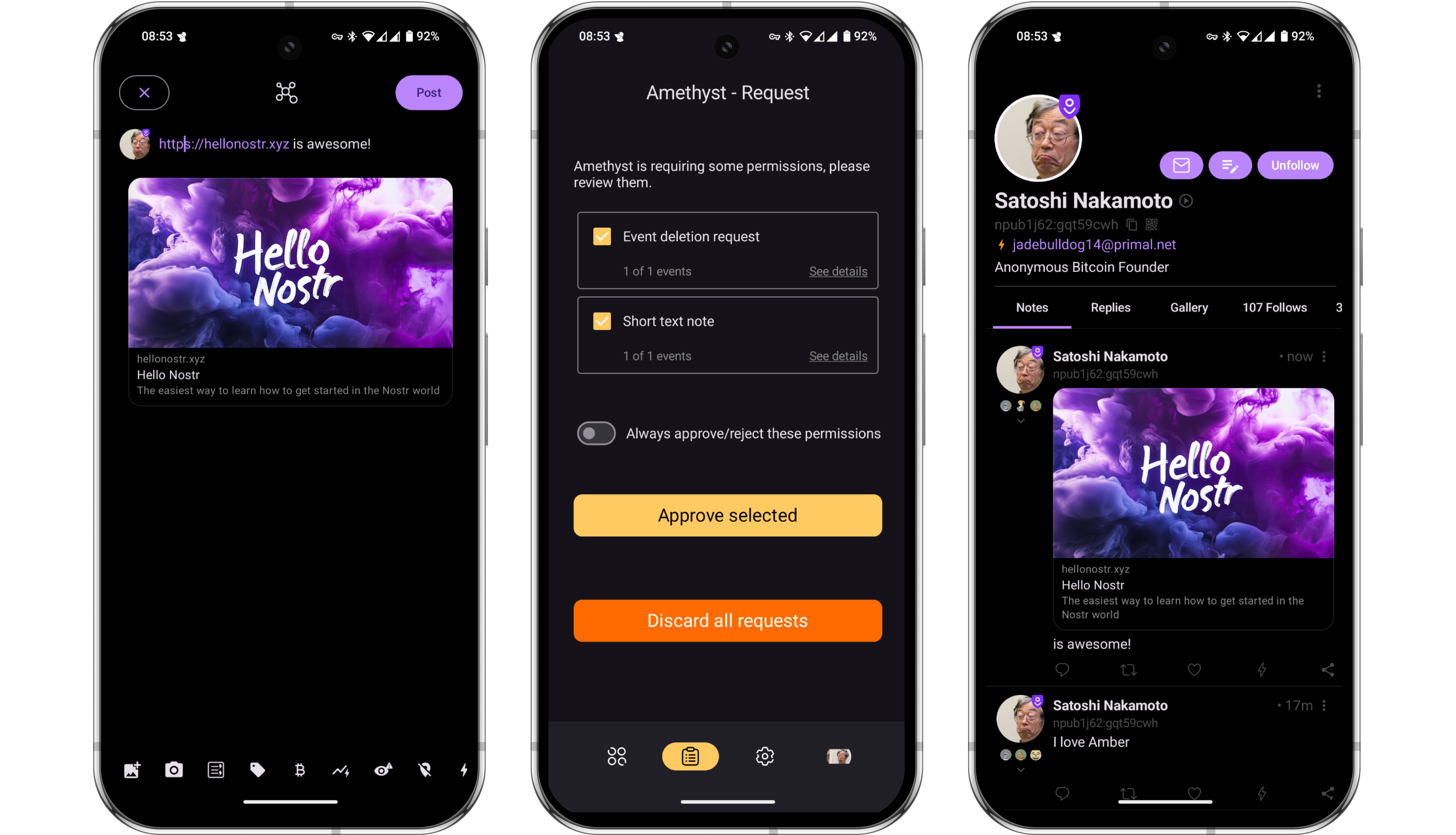
Using Amber with a Web Client
-
Next let’s take a look at how you can use Amber on your phone to sign events on a web app running on your computer. For this example, we’ll be using Coracle. Open Coracle and click ‘Log In’, then choose ‘Use Remote Signer’. Coracle will then display a QR code.
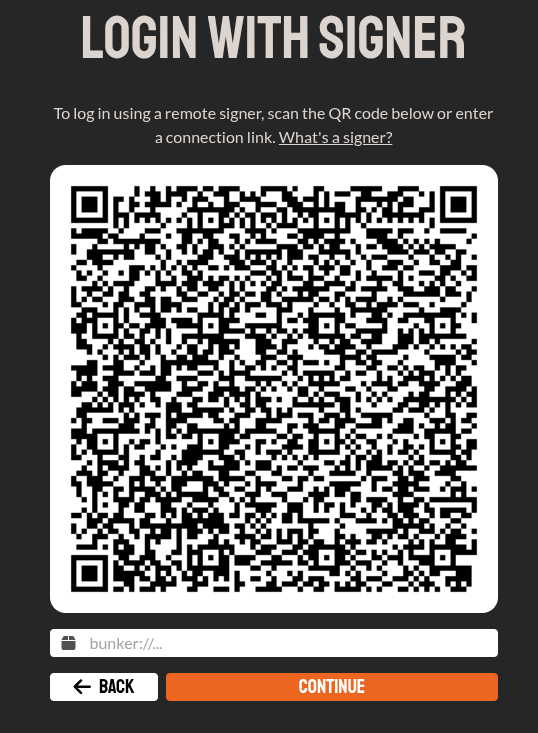
-
Open Amber and navigate to the Applications page, tap the + icon, then scan the QR code being displayed by Coracle.
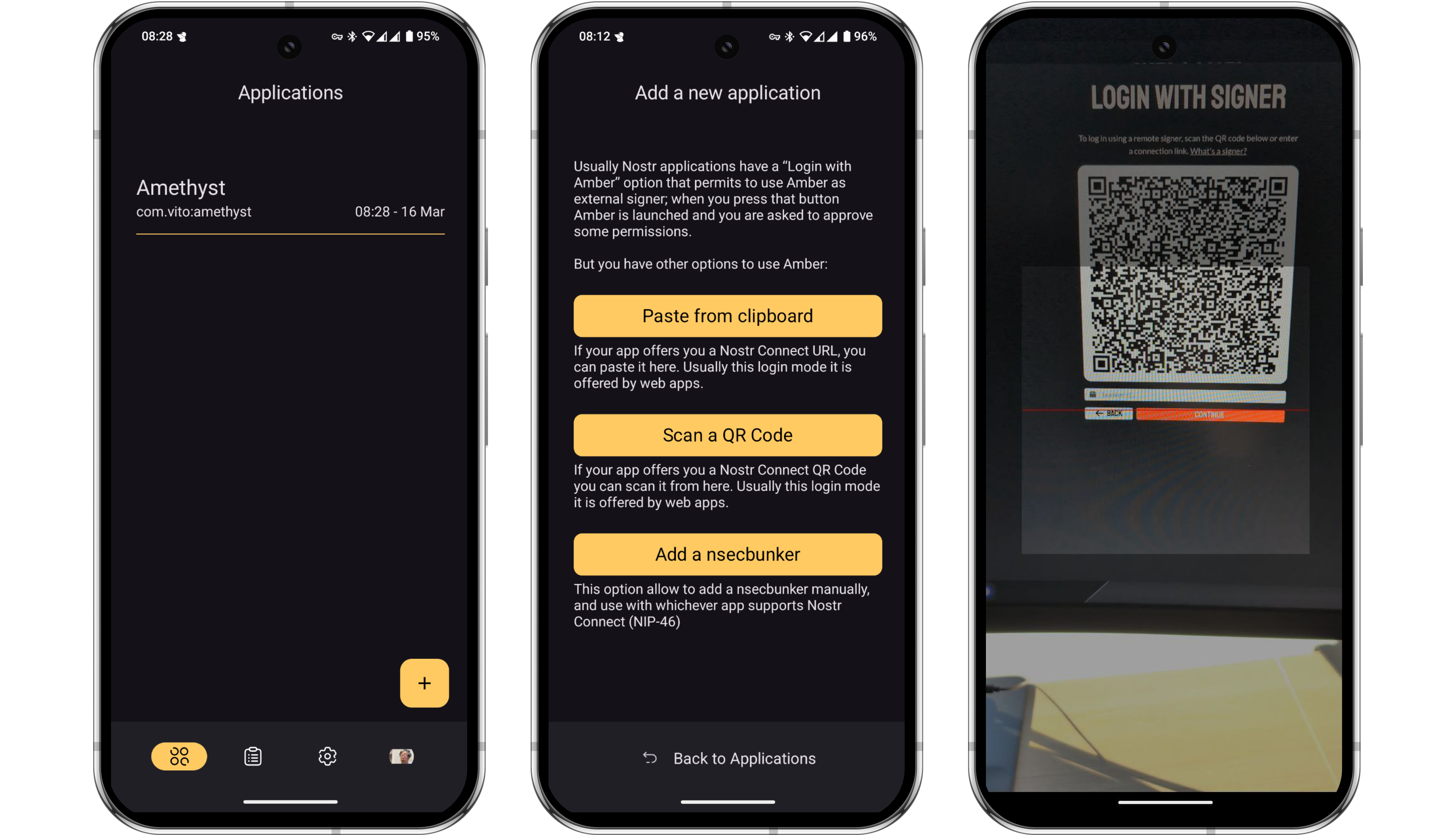
-
Just as it did earlier with Amethyst, Amber will now ask you to grant some basic permissions for the Coracle connection. Once again, these permissions can be customized at any time in the settings. Once granted, you’ll notice that Coracle automatically logs in to your feed.
But wait, how did that happen? The nsec is in Amber on your phone, and Coracle is running on your computer. The two might not even be in the same location or on the same network!? The communication is happening over the Nostr protocol, via relays. Which relays are used for this communication can be configured in the Amber settings.
-
Let’s test out a short note on Coracle to demonstrate the signing process. Click ‘Post +’ in the top right corner, draft your note and then click send.
-
Amber will send a push notification to your phone. Tapping the notification will open Amber for you to approve the event.
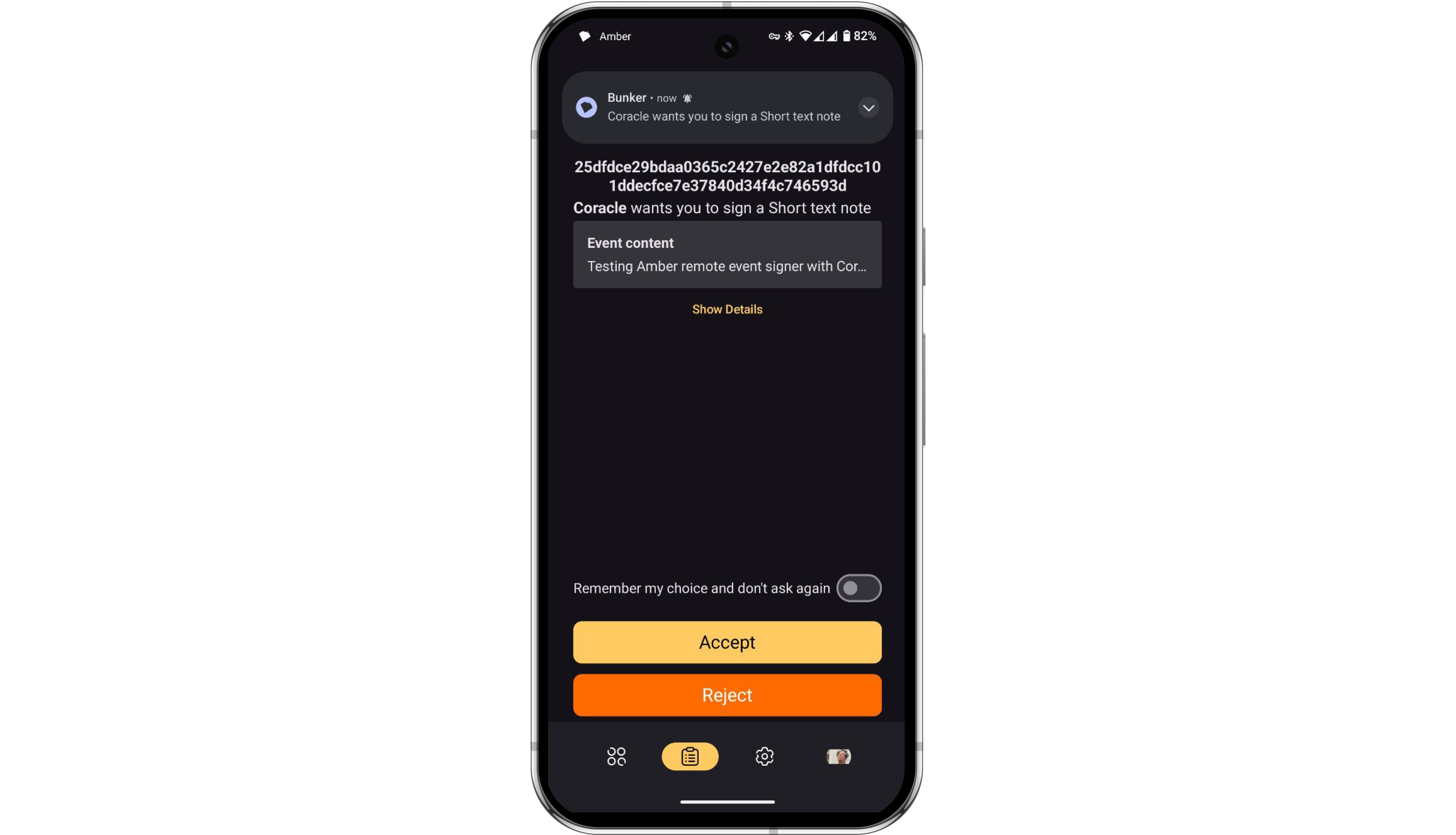
-
Once the event is approved in Amber, Amber will automatically send the signed event back to Coracle for publishing.
Summary
You can view Amber as a vault for your Nostr private keys (nsec). It allows you to explore the entire ecosystem without exposing your nsec to every new app you try. Amber is an incredibly simple yet powerful tool that belongs on the Android phone of every Nostr user.
At the time of writing, using Amber as a remote event signer is supported by the following popular Nostr clients:
- Amethyst (mobile)
- Coracle (web)
- 0xChat (mobile)
- Fountain (mobile)
- Zap Store (mobile)
- Keychat (mobile)
- Freeflow (mobile)
- Highlighter (web)
- Chachi Chat (web)
- Habla (web)
- Shopstr (web)
- Plebeian Market (web)
- Snort (web)
- Nostrudel (web)
If you found this post useful, please share it with your peers and consider following and zapping me on Nostr. If you write to me and let me know that you found me via this post, I’ll be sure to Zap you back! ⚡️
-
 @ 266815e0:6cd408a5
2025-03-19 11:10:21
@ 266815e0:6cd408a5
2025-03-19 11:10:21How to create a nostr app quickly using applesauce
In this guide we are going to build a nostr app that lets users follow and unfollow fiatjaf
1. Setup new project
Start by setting up a new vite app using
pnpm create vite, then set the name and selectSolidandTypescript```sh ➜ pnpm create vite │ ◇ Project name: │ followjaf │ ◇ Select a framework: │ Solid │ ◇ Select a variant: │ TypeScript │ ◇ Scaffolding project in ./followjaf... │ └ Done. Now run:
cd followjaf pnpm install pnpm run dev ```
2. Adding nostr dependencies
There are a few useful nostr dependencies we are going to need.
nostr-toolsfor the types and small methods, andrx-nostrfor making relay connectionssh pnpm install nostr-tools rx-nostr3. Setup rx-nostr
Next we need to setup rxNostr so we can make connections to relays. create a new
src/nostr.tsfile with```ts import { createRxNostr, noopVerifier } from "rx-nostr";
export const rxNostr = createRxNostr({ // skip verification here because we are going to verify events at the event store skipVerify: true, verifier: noopVerifier, }); ```
4. Setup the event store
Now that we have a way to connect to relays, we need a place to store events. We will use the
EventStoreclass fromapplesauce-corefor this. create a newsrc/stores.tsfile withThe event store does not store any events in the browsers local storage or anywhere else. It's in-memory only and provides a model for the UI
```ts import { EventStore } from "applesauce-core"; import { verifyEvent } from "nostr-tools";
export const eventStore = new EventStore();
// verify the events when they are added to the store eventStore.verifyEvent = verifyEvent; ```
5. Create the query store
The event store is where we store all the events, but we need a way for the UI to query them. We can use the
QueryStoreclass fromapplesauce-corefor this.Create a query store in
src/stores.ts```ts import { QueryStore } from "applesauce-core";
// ...
// the query store needs the event store to subscribe to it export const queryStore = new QueryStore(eventStore); ```
6. Setup the profile loader
Next we need a way to fetch user profiles. We are going to use the
ReplaceableLoaderclass fromapplesauce-loadersfor this.applesauce-loadersis a package that contains a few loader classes that can be used to fetch different types of data from relays.First install the package
sh pnpm install applesauce-loadersThen create a
src/loaders.tsfile with```ts import { ReplaceableLoader } from "applesauce-loaders"; import { rxNostr } from "./nostr"; import { eventStore } from "./stores";
export const replaceableLoader = new ReplaceableLoader(rxNostr);
// Start the loader and send any events to the event store replaceableLoader.subscribe((packet) => { eventStore.add(packet.event, packet.from); }); ```
7. Fetch fiatjaf's profile
Now that we have a way to store events, and a loader to help with fetching them, we should update the
src/App.tsxcomponent to fetch the profile.We can do this by calling the
nextmethod on the loader and passing apubkey,kindandrelaysto it```tsx function App() { // ...
onMount(() => { // fetch fiatjaf's profile on load replaceableLoader.next({ pubkey: "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", kind: 0, relays: ["wss://pyramid.fiatjaf.com/"], }); });
// ... } ```
8. Display the profile
Now that we have a way to fetch the profile, we need to display it in the UI.
We can do this by using the
ProfileQuerywhich gives us a stream of updates to a pubkey's profile.Create the profile using
queryStore.createQueryand pass in theProfileQueryand the pubkey.tsx const fiatjaf = queryStore.createQuery( ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d" );But this just gives us an observable, we need to subscribe to it to get the profile.
Luckily SolidJS profiles a simple
frommethod to subscribe to any observable.To make things reactive SolidJS uses accessors, so to get the profile we need to call
fiatjaf()```tsx function App() { // ...
// Subscribe to fiatjaf's profile from the query store const fiatjaf = from( queryStore.createQuery(ProfileQuery, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d") );
return ( <> {/ replace the vite and solid logos with the profile picture /}
{fiatjaf()?.name}
{/* ... */}); } ```
9. Letting the user signin
Now we should let the user signin to the app. We can do this by creating a
AccountManagerclass fromapplesauce-accountsFirst we need to install the packages
sh pnpm install applesauce-accounts applesauce-signersThen create a new
src/accounts.tsfile with```ts import { AccountManager } from "applesauce-accounts"; import { registerCommonAccountTypes } from "applesauce-accounts/accounts";
// create an account manager instance export const accounts = new AccountManager();
// Adds the common account types to the manager registerCommonAccountTypes(accounts); ```
Next lets presume the user has a NIP-07 browser extension installed and add a signin button.
```tsx function App() { const signin = async () => { // do nothing if the user is already signed in if (accounts.active) return;
// create a new nip-07 signer and try to get the pubkey const signer = new ExtensionSigner(); const pubkey = await signer.getPublicKey(); // create a new extension account, add it, and make it the active account const account = new ExtensionAccount(pubkey, signer); accounts.addAccount(account); accounts.setActive(account);};
return ( <> {/ ... /}
<div class="card"> <p>Are you following the fiatjaf? the creator of "The nostr"</p> <button onClick={signin}>Check</button> </div>); } ```
Now when the user clicks the button the app will ask for the users pubkey, then do nothing... but it's a start.
We are not persisting the accounts, so when the page reloads the user will NOT be signed in. you can learn about persisting the accounts in the docs
10. Showing the signed-in state
We should show some indication to the user that they are signed in. We can do this by modifying the signin button if the user is signed in and giving them a way to sign-out
```tsx function App() { // subscribe to the currently active account (make sure to use the account$ observable) const account = from(accounts.active$);
// ...
const signout = () => { // do nothing if the user is not signed in if (!accounts.active) return;
// signout the user const account = accounts.active; accounts.removeAccount(account); accounts.clearActive();};
return ( <> {/ ... /}
<div class="card"> <p>Are you following the fiatjaf? ( creator of "The nostr" )</p> {account() === undefined ? <button onClick={signin}>Check</button> : <button onClick={signout}>Signout</button>} </div>); } ```
11. Fetching the user's profile
Now that we have a way to sign in and out of the app, we should fetch the user's profile when they sign in.
```tsx function App() { // ...
// fetch the user's profile when they sign in createEffect(async () => { const active = account();
if (active) { // get the user's relays or fallback to some default relays const usersRelays = await active.getRelays?.(); const relays = usersRelays ? Object.keys(usersRelays) : ["wss://relay.damus.io", "wss://nos.lol"]; // tell the loader to fetch the users profile event replaceableLoader.next({ pubkey: active.pubkey, kind: 0, relays, }); // tell the loader to fetch the users contacts replaceableLoader.next({ pubkey: active.pubkey, kind: 3, relays, }); // tell the loader to fetch the users mailboxes replaceableLoader.next({ pubkey: active.pubkey, kind: 10002, relays, }); }});
// ... } ```
Next we need to subscribe to the users profile, to do this we can use some rxjs operators to chain the observables together.
```tsx import { Match, Switch } from "solid-js"; import { of, switchMap } from "rxjs";
function App() { // ...
// subscribe to the active account, then subscribe to the users profile or undefined const profile = from( accounts.active$.pipe( switchMap((account) => (account ? queryStore.createQuery(ProfileQuery, account!.pubkey) : of(undefined))) ) );
// ...
return ( <> {/ ... /}
<div class="card"> <Switch> <Match when={account() && !profile()}> <p>Loading profile...</p> </Match> <Match when={profile()}> <p style="font-size: 1.2rem; font-weight: bold;">Welcome {profile()?.name}</p> </Match> </Switch> {/* ... */} </div>); } ```
12. Showing if the user is following fiatjaf
Now that the app is fetching the users profile and contacts we should show if the user is following fiatjaf.
```tsx function App() { // ...
// subscribe to the active account, then subscribe to the users contacts or undefined const contacts = from( accounts.active$.pipe( switchMap((account) => (account ? queryStore.createQuery(UserContactsQuery, account!.pubkey) : of(undefined))) ) );
const isFollowing = createMemo(() => { return contacts()?.some((c) => c.pubkey === "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d"); });
// ...
return ( <> {/ ... /}
<div class="card"> {/* ... */} <Switch fallback={ <p style="font-size: 1.2rem;"> Sign in to check if you are a follower of the fiatjaf ( creator of "The nostr" ) </p> } > <Match when={contacts() && isFollowing() === undefined}> <p>checking...</p> </Match> <Match when={contacts() && isFollowing() === true}> <p style="color: green; font-weight: bold; font-size: 2rem;"> Congratulations! You are a follower of the fiatjaf </p> </Match> <Match when={contacts() && isFollowing() === false}> <p style="color: red; font-weight: bold; font-size: 2rem;"> Why don't you follow the fiatjaf? do you even like nostr? </p> </Match> </Switch> {/* ... */} </div>); } ```
13. Adding the follow button
Now that we have a way to check if the user is following fiatjaf, we should add a button to follow him. We can do this with Actions which are pre-built methods to modify nostr events for a user.
First we need to install the
applesauce-actionsandapplesauce-factorypackagesh pnpm install applesauce-actions applesauce-factoryThen create a
src/actions.tsfile with```ts import { EventFactory } from "applesauce-factory"; import { ActionHub } from "applesauce-actions"; import { eventStore } from "./stores"; import { accounts } from "./accounts";
// The event factory is used to build and modify nostr events export const factory = new EventFactory({ // accounts.signer is a NIP-07 signer that signs with the currently active account signer: accounts.signer, });
// The action hub is used to run Actions against the event store export const actions = new ActionHub(eventStore, factory); ```
Then create a
toggleFollowmethod that will add or remove fiatjaf from the users contacts.We are using the
execmethod to run the action, and theforEachmethod from RxJS allows us to await for all the events to be published```tsx function App() { // ...
const toggleFollow = async () => { // send any created events to rxNostr and the event store const publish = (event: NostrEvent) => { eventStore.add(event); rxNostr.send(event); };
if (isFollowing()) { await actions .exec(UnfollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d") .forEach(publish); } else { await actions .exec( FollowUser, "3bf0c63fcb93463407af97a5e5ee64fa883d107ef9e558472c4eb9aaaefa459d", "wss://pyramid.fiatjaf.com/" ) .forEach(publish); }};
// ...
return ( <> {/ ... /}
<div class="card"> {/* ... */} {contacts() && <button onClick={toggleFollow}>{isFollowing() ? "Unfollow" : "Follow"}</button>} </div>); } ```
14. Adding outbox support
The app looks like it works now but if the user reloads the page they will still see an the old version of their contacts list. we need to make sure rxNostr is publishing the events to the users outbox relays.
To do this we can subscribe to the signed in users mailboxes using the query store in
src/nostr.ts```ts import { MailboxesQuery } from "applesauce-core/queries"; import { accounts } from "./accounts"; import { of, switchMap } from "rxjs"; import { queryStore } from "./stores";
// ...
// subscribe to the active account, then subscribe to the users mailboxes and update rxNostr accounts.active$ .pipe(switchMap((account) => (account ? queryStore.createQuery(MailboxesQuery, account.pubkey) : of(undefined)))) .subscribe((mailboxes) => { if (mailboxes) rxNostr.setDefaultRelays(mailboxes.outboxes); else rxNostr.setDefaultRelays([]); }); ```
And that's it! we have a working nostr app that lets users follow and unfollow fiatjaf.
-
 @ 104cdb46:bda37787
2025-03-21 11:59:40
@ 104cdb46:bda37787
2025-03-21 11:59:40AE3888 là một nền tảng giải trí trực tuyến nổi bật, mang đến cho người chơi một thế giới đa dạng với nhiều trò chơi hấp dẫn và độc đáo. Không chỉ cung cấp các trò chơi thể thao, mà AE3888 còn thu hút người chơi với các trò chơi điện tử phong phú, bao gồm các tựa game chiến thuật, bài, và nhiều thể loại khác. Tất cả đều được thiết kế với giao diện dễ sử dụng, giúp người tham gia dễ dàng tìm kiếm trò chơi yêu thích và bắt đầu cuộc hành trình giải trí của mình. Đặc biệt, hệ thống của AE3888 luôn được cập nhật liên tục, mang đến những tính năng mới mẻ và cải tiến để phục vụ nhu cầu của người chơi, đảm bảo rằng mỗi trải nghiệm đều thú vị và đầy thử thách. Với đồ họa sắc nét và âm thanh sống động, AE3888 mang đến không gian chơi game hấp dẫn, giúp người chơi có thể thư giãn và tận hưởng những giây phút giải trí tuyệt vời.
Ngoài sự đa dạng trong các trò chơi, AE3888 còn đặc biệt chú trọng đến yếu tố bảo mật và quyền lợi của người chơi. Nền tảng này sử dụng các công nghệ bảo mật tiên tiến để đảm bảo rằng thông tin cá nhân và tài chính của người tham gia được bảo vệ an toàn tuyệt đối. Người chơi có thể yên tâm rằng mọi giao dịch, từ việc nạp tiền đến rút thưởng, đều được xử lý nhanh chóng và bảo mật, mang lại sự tin tưởng tuyệt đối. Điều này giúp AE3888 xây dựng được uy tín và sự hài lòng từ phía người chơi, với cam kết không ngừng cải thiện để mang lại dịch vụ ngày càng hoàn thiện hơn. Cùng với đó, hệ thống hỗ trợ khách hàng của AE3888 hoạt động 24/7, luôn sẵn sàng giải đáp mọi thắc mắc và hỗ trợ người chơi trong mọi tình huống, đảm bảo rằng trải nghiệm của họ luôn suôn sẻ và thoải mái.
Bên cạnh các trò chơi đa dạng và bảo mật tuyệt vời, AE3888 còn tổ chức các sự kiện và giải đấu lớn, tạo cơ hội cho người chơi thể hiện tài năng và cạnh tranh với cộng đồng. Những sự kiện này luôn thu hút sự tham gia đông đảo, không chỉ mang đến phần thưởng hấp dẫn mà còn tạo ra không khí sôi động và đầy thử thách. Các giải đấu này không chỉ giúp người chơi thử thách bản thân mà còn là dịp để giao lưu, học hỏi và kết nối với những người chơi khác. AE3888 luôn lắng nghe ý kiến và phản hồi của người tham gia để không ngừng cải thiện và phát triển nền tảng, mang đến những trải nghiệm giải trí tuyệt vời hơn. Với đội ngũ phát triển sáng tạo và đội ngũ hỗ trợ tận tình, AE3888 không ngừng vươn lên và khẳng định vị thế của mình trong ngành giải trí trực tuyến.
-
 @ a6efb4f0:4d912827
2025-03-21 09:03:03
@ a6efb4f0:4d912827
2025-03-21 09:03:03A crescente demanda por plataformas de entretenimento online tem impulsionado o desenvolvimento de opções cada vez mais inovadoras. Nesse cenário, a 8385 surge como uma das plataformas mais promissoras, oferecendo aos seus usuários uma experiência digital rica e diversificada. A plataforma tem se destacado não apenas pela qualidade de seus jogos, mas também pela forma como integra tecnologia, segurança e personalização, criando um ambiente digital único. Neste artigo, vamos explorar o que é a plataforma 8385, seus principais jogos e a experiência do jogador.
O Que é a Plataforma 8385? A 8385 é uma plataforma digital criada para oferecer entretenimento de alta qualidade, com foco na diversão e na inovação. A interface da plataforma é projetada para garantir uma navegação intuitiva e uma experiência de jogo fluída, com recursos que facilitam a interação do usuário. A plataforma se destaca por seu compromisso com a segurança e a transparência, utilizando tecnologias avançadas para garantir a proteção dos dados dos jogadores.
Além disso, a 8385 é acessível em diversos dispositivos, incluindo desktop e dispositivos móveis, o que permite que os jogadores desfrutem de seus jogos favoritos a qualquer hora e em qualquer lugar. A plataforma é constantemente atualizada com novos conteúdos e melhorias, assegurando que seus usuários tenham sempre algo novo para explorar.
Os Jogos da Plataforma 8385 A plataforma 8385 se distingue pela ampla variedade de jogos que oferece. Com opções para todos os gostos, desde aqueles que buscam ação e aventura até os que preferem jogos de estratégia e raciocínio, há sempre uma opção que se adequa às preferências individuais dos jogadores.
Jogos de Ação e Aventura: Os jogos de ação e aventura são perfeitos para aqueles que buscam adrenalina e desafios emocionantes. Com gráficos de última geração e jogabilidade envolvente, esses jogos permitem que os jogadores se mergulhem em mundos fictícios repletos de aventuras épicas.
Jogos de Estratégia: Para quem gosta de testar sua capacidade de raciocínio lógico, a plataforma oferece uma variedade de jogos de estratégia. Esses jogos exigem que o jogador tome decisões cuidadosas e planeje suas ações com antecedência, criando uma experiência intensa e desafiadora.
Jogos de Reflexo e Habilidade: Se você procura uma experiência de jogo mais rápida e dinâmica, a 8385 oferece uma série de jogos que testam os reflexos e a agilidade do jogador. Com desafios que exigem atenção e rapidez, esses jogos são perfeitos para quem gosta de ação intensa e momentos de pura emoção.
Jogos de Sorte: Para os jogadores que gostam de jogos baseados em sorte e imprevisibilidade, a 8385 disponibiliza uma seleção de opções emocionantes. Esses jogos oferecem uma experiência única, onde a sorte pode ser um fator determinante para o sucesso.
A Experiência do Jogador na Plataforma 8385 A experiência do jogador na plataforma 8385 é aprimorada por uma série de recursos pensados para oferecer o máximo de diversão e imersão. A interface é simples, com um design limpo que facilita a navegação entre as diversas opções de jogos e funcionalidades. A plataforma também é projetada para oferecer uma jogabilidade sem falhas, com tempos de carregamento rápidos e animações fluidas.
Além disso, a plataforma é socialmente interativa. Os jogadores podem competir entre si, participar de torneios e interagir em tempo real com outros usuários. A 8385 cria uma comunidade vibrante, onde os jogadores podem se conectar, compartilhar conquistas e formar alianças para enfrentar desafios juntos.
Outro ponto positivo é a personalização oferecida pela plataforma. Os jogadores podem ajustar suas configurações de jogo, escolher temas exclusivos e até criar avatares personalizados. Essas opções permitem que cada usuário tenha uma experiência de jogo única, que reflete suas preferências e estilo.
A plataforma também investe em um atendimento ao cliente de alta qualidade, com suporte dedicado para resolver quaisquer problemas ou responder a perguntas. Seja por chat ao vivo ou por e-mail, os jogadores podem contar com um atendimento eficiente e amigável.
Conclusão A plataforma 8385 tem se consolidado como uma das melhores opções no mundo do entretenimento digital. Com uma ampla variedade de jogos, uma interface amigável e uma experiência de usuário de alta qualidade, a plataforma oferece tudo o que os jogadores procuram em termos de diversão e imersão. Se você busca uma experiência de jogo única e envolvente, a 8385 é a escolha ideal.
-
 @ ccc8ee23:9f3d9783
2024-12-23 22:03:15
@ ccc8ee23:9f3d9783
2024-12-23 22:03:15Chef's notes
Indulge in tender, golden-fried chicken breast, crunchy with every bite. Nestled on a bed of steamed rice, this dish is elevated by a rich, velvety curry sauce, infused with the warmth of fragrant spices and the umami depth of soy.
Paired with vibrant vegetables for a harmonious balance of textures and flavors, this comforting classic promises to delight your soul.
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 2
Ingredients
- Chicken Fillet 250 grams
- Potato 100 grams
- Egg 1 pc
- Curry block 2 pcs or 20 grams
- breadcrumbs 100 grams / 2 cups
- flour 20 grams
- Cooking oil (for frying)
- chicken or vegetable stock 500ml
- soy sauce 1 tbsp
- Seasoning
- onion 1 pc, finely chopped
- garlic cloves 2 pcs, minced
- carrot 1 pc, chopped
Directions
- Chicken Katsu: Pound the chicken breasts until about 1/2 inch thick. Season with salt and pepper. Coat each piece in flour, then dip in beaten egg, and finally coat with breadcrumbs. Heat oil in a pan and fry the chicken for about 3-4 minutes on each side, until golden brown and fully cooked. Place on paper towels to drain.
- Make Curry Sauce: In a pan, sauté the onion, garlic, add potato and carrot until soft. Gradually add curry block and the stock, stir well. Simmer for 5-10 minutes until thickened. Add seasoning and soy sauce to taste.
- Plating: Slice the cooked chicken katsu and place it over a bed of steamed rice. Pour the curry sauce on the side or over the chicken. Garnish with chopped green chilies.
-
 @ ccc8ee23:9f3d9783
2024-12-21 06:38:47
@ ccc8ee23:9f3d9783
2024-12-21 06:38:47Chef's notes
Enjoy these Chocolate Sprinkle Cookies, a delightful combination of buttery richness, velvety chocolate, and a crunchy sprinkle finish
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 90 min
- 🍽️ Servings: 10
Ingredients
- Plain flour 250 grams
- Margarine 100 grams
- Butter 100 grams
- Vanilla essence 1 tsp
- Milk powder 1 tbsp
- Sugar 40 grams
- Chocolate bar - 80 grams, melted
- Chocolate sprinkles - for decoration
Directions
- Make the Dough: Combine the plain flour, margarine, butter, milk powder, sugar, and vanilla essence in a mixing bowl. Knead the mixture by hand until smooth and well combined.
- Shape and divide the dough into small balls, weighing approximately 8 grams each.
- Preheat the oven to 175°C. Arrange the dough balls on a baking tray and bake for about 30 minutes, or until the cookies are dry and fully cooked.
- Coat with Chocolate: Melt the chocolate bar using a double boiler or microwave. Once the cookies have cooled completely, dip each cookie into the melted chocolate, ensuring they are evenly coated.
- Place the coated cookies onto paper cups.
- While the chocolate coating is still wet, sprinkle chocolate sprinkles on top of each cookie.
- Allow the chocolate to dry completely, then arrange the cookies in a decorative airtight container for storage.






