-
 @ 42342239:1d80db24
2025-03-09 15:22:43
@ 42342239:1d80db24
2025-03-09 15:22:43Last fall, Italian economist Mario Draghi, former head of the European Central Bank (ECB), published his 400-page report on Europe's (actually the EU's) competitiveness. Draghi's verdict was harsh: Europe is facing an "existential challenge." It's hard to disagree. While the EU is launching new regulations on plastic corks and hiding text messages from the public, Elon Musk is changing the world with groundbreaking innovations in the automotive, robotics, and space industries.
At the same time that the EU is not only preventing people from trying new things but also preventing them from even thinking about trying, Musk's space company SpaceX is capturing massive star rockets with "chopstick grips". While the EU is stuck in an ocean of meaningless bureaucratic details, Musk is engaged in a process of constant testing and improvement, reminiscent of the natural course of decentralized systems.
The EU's meager economic growth can be compared to a ticking time bomb that threatens to explode in all of our faces. Disposable incomes have increased nearly twice as much in the US compared to the EU since 2000, and this is a difference that is noticeable not only in our standard of living but also in our opportunities for leisure time. As the late economist Robert Lucas said, "Once you start thinking about growth, it's hard to think about anything else." Perhaps the best thing that can be said about the report is that its abundance of words, numbers, and images underscores how bad things are. And perhaps it has therefore become impossible for the EU's leaders to continue ignoring the union's problems.
Like giving a shark responsibility for beach safety
However, asking a former EU president to investigate and propose changes is like giving a shark responsibility for beach safety. Among other things, he proposes larger allocations for research and development, even though the EU already spends more than the US as a percentage of GDP - it's thus impossible for this to be the problem. It comes as no surprise that the proposals are about more centralization, harmonization, and streamlining - i.e., continuing in the same old tracks. While Musk seems to have an intuitive understanding of how knowledge arises through real-world experiments , what is proposed here is more of the administrative bureaucracy's preconceived five-year plans. The bureaucracy is to be given free rein, and the nations are to be pushed back - a repeat of a theme we know all too well. Centralization undermines real knowledge growth, which may explain why the EU is falling behind.
A venomous snake that is ignored
Rent-seeking is like a venomous snake that slithers through the EU's corridors, but the concept is conspicuous by its absence in Draghi's report. It is a well-known phenomenon where companies spend resources on influencing decision-makers to gain advantages instead of creating value. The EU bureaucracy has produced a total of 13,000 legislative acts since 2019 - more than four times as many as the US. How many of these have received an invisible stamp of approval from lobbyists? Economist Jeffrey Sachs has warned that American lobbying in Brussels is so dominant that it affects all decision-making in the digital economy, which may be one of the EU's biggest problems. GDPR regulations, for example, are estimated to have reduced small tech companies' profits by 15% (!).
Size is not everything
Small businesses are the invisible heroes that contribute most to productivity and employment growth. These are being suffocated by the ECB's actions and the constantly increasing and inefficient regulatory mess. The ECB's war on small banks hampers growth for small businesses because large banks prioritize large transactions. Big computers' algorithms cannot replace small banks' local knowledge. Harmful regulations and grandiose dreams lead to a loss of both knowledge and growth.
What should the end goal be?
Sweden's daily Dagens Industri's editorial page recently wrote that "Defeat is not an option" on the theme of green transition. It asked whether "free democracies or a Chinese dictatorship should lead the way." Large-scale industrial projects and plans can undoubtedly provide benefits. But it's worth questioning whether Europe should really have the same end goal as China.
During both the Renaissance and the Industrial Revolution, decentralized power structures played a crucial role. During the Renaissance, states and cities were relatively independent. Power was decentralized to princes, nobles, and merchants. The Church had an important role, but it was not as centralized as it would become. Florence, Venice, and Amsterdam could develop different scientific and artistic traditions. When one region encountered problems, other regions could continue to develop and grow, and so on. At that time - even if the concept did not exist - it seemed to be understood that the economy is a complex system of the second order. Or a computationally irreducible one, as Stephen Wolfram would have expressed it.
In the book "The Art of War," Chinese General Sun Tzu wrote that "He who chooses the battlefield first will win. He who lets his opponent choose the battlefield will lose." Instead of striving to play on China's (alleged) centralized battlefield, perhaps we Europeans should consider returning to our roots. Do away with the bureaucracy's heavy foot and give power back to the individual! Scrap the monster banks and create conditions for small local banks instead. Stop subsidizing American IT giants' data centers and give every European an AI in their own hand. Forget the five-year plans and invest in decentralized economic experiments instead. Does that sound radical?
The word "radical" comes from the Latin word for root, radix . The word used to have a positive connotation because it implied a willingness to go to the root of the problem or to return to one's roots.
More of us should dare to question the modern structures that brought us to today's sad situation. Roots are a plant's strength - without them, it cannot grow and flourish. So it is with Europe. Our continent, which was once a thriving garden where ideas and innovations bloomed, needs to return to its roots to regain its former strength. This may be exactly what is required.
Put simply: a more radical Europe.
-
 @ 42342239:1d80db24
2025-03-02 14:13:43
@ 42342239:1d80db24
2025-03-02 14:13:43With the rapid development of artificial intelligence (AI), we face a future where we may soon have access to almost everything we desire – at least in the digital realm. But unfortunately, what we wish for doesn’t always align with what we truly need, or what would benefit us.
The Dutch ethologist Niko Tinbergen was awarded the Nobel Prize in Physiology or Medicine in 1973 for his studies of animal behaviour patterns. While earlier scientists had primarily focused on learning as the main explanation for animal behaviour, Tinbergen instead emphasised instincts.
Tinbergen studied, among other things, what makes newly hatched bird chicks beg for food from their parents. This was investigated by presenting parentless chicks with various painted beak models to see which ones they would seek food from. Several objects proved more popular than real gull beaks.
Artificial eggs were also created and placed in bird nests. Black-headed gulls that received wooden eggs before laying their own were found to actually refrain from laying real eggs. Fake eggs were painted in different colours and patterns, and made in various sizes. The gulls always preferred trying to incubate eggs of absurd sizes – for example eggs with eight times the volume of real ones. The poor gulls made desperate attempts to sit on these giant eggs – but often slid off.
The explanation for the gulls’ self-destructive behaviour was that they had a hardwired ability (instinct) to respond to specific stimuli (appearance of beaks and eggs with particular colours/sizes). Researchers exaggerated these stimuli, creating stronger but ultimately misguided reactions. The concept of "superstimuli" was hatched. Nothing in the gulls’ evolution had prepared them for these experiments, explaining their self-destructive behaviors.
Psychologist Deirdre Barrett has translated this concept to a human context. She argues that superstimuli govern human behaviours much like they do other animals’, citing junk food consumption, addictive social media use, and pornography consumption as examples. Nothing in Homo sapiens’ evolution prepared us for modern society’s stimuli, which might explain our frequently self-destructive behaviours.
When the Liberal Party (Swedish political party Liberalerna) proposes mandatory porn filters on all mobile phones "to protect children and youth," it might appear they’re on the right track. However, these issues deserve more profound discussions.
How do we create technical solutions that meet our fundamental needs for health, education, and human connection – rather than just supplying mindless scrolling entertainment? How can we ensure those collecting our data don’t exploit it for their own interests, selling us things we don’t need? Is the current model of centralisation, corporate giants, and profit maximisation really compatible with our best interests?
In summary: How can we ensure future technology serves our real needs, rather than mislead us - much like Niko Tinbergen deceived the poor gulls?
-
 @ 4523be58:ba1facd0
2025-02-27 22:20:33
@ 4523be58:ba1facd0
2025-02-27 22:20:33NIP-117
The Double Ratchet Algorithm
The Double Ratchet is a key rotation algorithm for secure private messaging.
It allows us to 1) communicate on Nostr without revealing metadata (who you are communicating with and when), and 2) keep your message history and future messages safe even if your main Nostr key is compromised.
Additionally, it enables disappearing messages that become undecryptable when past message decryption keys are discarded after use.
See also: NIP-118: Nostr Double Ratchet Invites
Overview
"Double ratchet" means we use 2 "ratchets": cryptographic functions that can be rotated forward, but not backward: current keys can be used to derive next keys, but not the other way around.
Ratchet 1 uses Diffie-Hellman (DH) shared secrets and is rotated each time the other participant acknowledges a new key we have sent along with a previous message.
Ratchet 2 generates encryption keys for each message. It rotates after every message, using the previous message's key as input (and the Ratchet 1 key when it rotates). This process ensures forward secrecy for consecutive messages from the same sender in between Ratchet 1 rotations.
Nostr implementation
We implement the Double Ratchet Algorithm on Nostr similarly to Signal's Double Ratchet with header encryption, but encrypting the message headers with NIP-44 conversation keys instead of symmetric header keys.
Ratchet 1 keys are standard Nostr keys. In addition to encryption, they are also used for publishing and subscribing to messages on Nostr. As they are rotated and not linked to public Nostr identities, metadata privacy is preserved.
Nostr event format
Message
Outer event
typescript { kind: 1060, content: encryptedInnerEvent, tags: [["header", encryptedHeader]], pubkey: ratchetPublicKey, created_at, id, sig }We subscribe to Double Ratchet events based on author public keys which are ephemeral — not used for other purposes than the Double Ratchet session. We use the regular event kind
1060to differentiate it from other DM kinds, retrieval of which may be restricted by relays.The encrypted header contains our next nostr public key, our previous sending chain length and the current message number.
Inner event
Inner events must be NIP-59 Rumors (unsigned Nostr events) allowing plausible deniability.
With established Nostr event kinds, clients can implement all kinds of features, such as replies, reactions, and encrypted file sharing in private messages.
Direct message and encrypted file messages are defined in NIP-17.
Algorithm
Signal's Double Ratchet with header encryption document is a comprehensive description and explanation of the algorithm.
In this NIP, the algorithm is only described in code, in order to highlight differences to the Signal implementation.
External functions
We use the following Nostr functions (NIP-01):
generateSecretKey()for creating Nostr private keysfinalizeEvent(partialEvent, secretKey)for creating valid Nostr events with pubkey, id and signature
We use NIP-44 functions for encryption:
nip44.encryptnip44.decryptnip44.getConversationKey
- createRumor
Key derivation function:
```typescript export function kdf( input1: Uint8Array, input2: Uint8Array = new Uint8Array(32), numOutputs: number = 1 ): Uint8Array[] { const prk = hkdf_extract(sha256, input1, input2);
const outputs: Uint8Array[] = []; for (let i = 1; i <= numOutputs; i++) { outputs.push(hkdf_expand(sha256, prk, new Uint8Array([i]), 32)); } return outputs; } ```
Session state
With this information you can start or continue a Double Ratchet session. Save it locally after each sent and received message.
```typescript interface SessionState { theirCurrentNostrPublicKey?: string; theirNextNostrPublicKey: string;
ourCurrentNostrKey?: KeyPair; ourNextNostrKey: KeyPair;
rootKey: Uint8Array; receivingChainKey?: Uint8Array; sendingChainKey?: Uint8Array;
sendingChainMessageNumber: number; receivingChainMessageNumber: number; previousSendingChainMessageCount: number;
// Cache of message & header keys for handling out-of-order messages // Indexed by Nostr public key, which you can use to resubscribe to unreceived messages skippedKeys: { [pubKey: string]: { headerKeys: Uint8Array[]; messageKeys: { [msgIndex: number]: Uint8Array }; }; }; } ```
Initialization
Alice is the chat initiator and Bob is the recipient. Ephemeral keys were exchanged earlier.
```typescript static initAlice( theirEphemeralPublicKey: string, ourEphemeralNostrKey: KeyPair, sharedSecret: Uint8Array ) { // Generate ephemeral key for the next ratchet step const ourNextNostrKey = generateSecretKey();
// Use ephemeral ECDH to derive rootKey and sendingChainKey const [rootKey, sendingChainKey] = kdf( sharedSecret, nip44.getConversationKey(ourEphemeralNostrKey.private, theirEphemeralPublicKey), 2 );
return { rootKey, theirNextNostrPublicKey: theirEphemeralPublicKey, ourCurrentNostrKey: ourEphemeralNostrKey, ourNextNostrKey, receivingChainKey: undefined, sendingChainKey, sendingChainMessageNumber: 0, receivingChainMessageNumber: 0, previousSendingChainMessageCount: 0, skippedKeys: {}, }; }
static initBob( theirEphemeralPublicKey: string, ourEphemeralNostrKey: KeyPair, sharedSecret: Uint8Array ) { return { rootKey: sharedSecret, theirNextNostrPublicKey: theirEphemeralPublicKey, // Bob has no ‘current’ key at init time — Alice will send to next and trigger a ratchet step ourCurrentNostrKey: undefined, ourNextNostrKey: ourEphemeralNostrKey, receivingChainKey: undefined, sendingChainKey: undefined, sendingChainMessageNumber: 0, receivingChainMessageNumber: 0, previousSendingChainMessageCount: 0, skippedKeys: {}, }; }
```
Sending messages
```typescript sendEvent(event: Partial
) { const innerEvent = nip59.createRumor(event) const [header, encryptedData] = this.ratchetEncrypt(JSON.stringify(innerEvent)); const conversationKey = nip44.getConversationKey(this.state.ourCurrentNostrKey.privateKey, this.state.theirNextNostrPublicKey); const encryptedHeader = nip44.encrypt(JSON.stringify(header), conversationKey);
const outerEvent = finalizeEvent({ content: encryptedData, kind: MESSAGE_EVENT_KIND, tags: [["header", encryptedHeader]], created_at: Math.floor(now / 1000) }, this.state.ourCurrentNostrKey.privateKey);
// Publish outerEvent on Nostr, store inner locally if needed return {outerEvent, innerEvent}; }
ratchetEncrypt(plaintext: string): [Header, string] { // Rotate sending chain key const [newSendingChainKey, messageKey] = kdf(this.state.sendingChainKey!, new Uint8Array([1]), 2); this.state.sendingChainKey = newSendingChainKey; const header: Header = { number: this.state.sendingChainMessageNumber++, nextPublicKey: this.state.ourNextNostrKey.publicKey, previousChainLength: this.state.previousSendingChainMessageCount }; return [header, nip44.encrypt(plaintext, messageKey)]; } ```
Receiving messages
```typescript handleNostrEvent(e: NostrEvent) { const [header, shouldRatchet, isSkipped] = this.decryptHeader(e);
if (!isSkipped) { if (this.state.theirNextNostrPublicKey !== header.nextPublicKey) { // Received a new key from them this.state.theirCurrentNostrPublicKey = this.state.theirNextNostrPublicKey; this.state.theirNextNostrPublicKey = header.nextPublicKey; this.updateNostrSubscriptions() }
if (shouldRatchet) { this.skipMessageKeys(header.previousChainLength, e.pubkey); this.ratchetStep(header.nextPublicKey); }}
decryptHeader(event: any): [Header, boolean, boolean] { const encryptedHeader = event.tags[0][1]; if (this.state.ourCurrentNostrKey) { const conversationKey = nip44.getConversationKey(this.state.ourCurrentNostrKey.privateKey, event.pubkey); try { const header = JSON.parse(nip44.decrypt(encryptedHeader, conversationKey)) as Header; return [header, false, false]; } catch (error) { // Decryption with currentSecret failed, try with nextSecret } }
const nextConversationKey = nip44.getConversationKey(this.state.ourNextNostrKey.privateKey, event.pubkey); try { const header = JSON.parse(nip44.decrypt(encryptedHeader, nextConversationKey)) as Header; return [header, true, false]; } catch (error) { // Decryption with nextSecret also failed }
const skippedKeys = this.state.skippedKeys[event.pubkey]; if (skippedKeys?.headerKeys) { // Try skipped header keys for (const key of skippedKeys.headerKeys) { try { const header = JSON.parse(nip44.decrypt(encryptedHeader, key)) as Header; return [header, false, true]; } catch (error) { // Decryption failed, try next secret } } }
throw new Error("Failed to decrypt header with current and skipped header keys"); }
ratchetDecrypt(header: Header, ciphertext: string, nostrSender: string): string { const plaintext = this.trySkippedMessageKeys(header, ciphertext, nostrSender); if (plaintext) return plaintext;
this.skipMessageKeys(header.number, nostrSender);
// Rotate receiving key const [newReceivingChainKey, messageKey] = kdf(this.state.receivingChainKey!, new Uint8Array([1]), 2); this.state.receivingChainKey = newReceivingChainKey; this.state.receivingChainMessageNumber++;
return nip44.decrypt(ciphertext, messageKey); }
ratchetStep(theirNextNostrPublicKey: string) { this.state.previousSendingChainMessageCount = this.state.sendingChainMessageNumber; this.state.sendingChainMessageNumber = 0; this.state.receivingChainMessageNumber = 0; this.state.theirNextNostrPublicKey = theirNextNostrPublicKey;
// 1st step yields the new conversation key they used const conversationKey1 = nip44.getConversationKey(this.state.ourNextNostrKey.privateKey, this.state.theirNextNostrPublicKey!); // and our corresponding receiving chain key const [theirRootKey, receivingChainKey] = kdf(this.state.rootKey, conversationKey1, 2); this.state.receivingChainKey = receivingChainKey;
// Rotate our Nostr key this.state.ourCurrentNostrKey = this.state.ourNextNostrKey; const ourNextSecretKey = generateSecretKey(); this.state.ourNextNostrKey = { publicKey: getPublicKey(ourNextSecretKey), privateKey: ourNextSecretKey };
// 2nd step yields the new conversation key we'll use const conversationKey2 = nip44.getConversationKey(this.state.ourNextNostrKey.privateKey, this.state.theirNextNostrPublicKey!); // And our corresponding sending chain key const [rootKey, sendingChainKey] = kdf(theirRootKey, conversationKey2, 2); this.state.rootKey = rootKey; this.state.sendingChainKey = sendingChainKey; }
skipMessageKeys(until: number, nostrSender: string) { if (this.state.receivingChainMessageNumber + MAX_SKIP < until) { throw new Error("Too many skipped messages"); }
if (!this.state.skippedKeys[nostrSender]) { this.state.skippedKeys[nostrSender] = { headerKeys: [], messageKeys: {} };
if (this.state.ourCurrentNostrKey) { const currentSecret = nip44.getConversationKey(this.state.ourCurrentNostrKey.privateKey, nostrSender); this.state.skippedKeys[nostrSender].headerKeys.push(currentSecret); } const nextSecret = nip44.getConversationKey(this.state.ourNextNostrKey.privateKey, nostrSender); this.state.skippedKeys[nostrSender].headerKeys.push(nextSecret);}
while (this.state.receivingChainMessageNumber < until) { const [newReceivingChainKey, messageKey] = kdf(this.state.receivingChainKey!, new Uint8Array([1]), 2); this.state.receivingChainKey = newReceivingChainKey; this.state.skippedKeys[nostrSender].messageKeys[this.state.receivingChainMessageNumber] = messageKey; this.state.receivingChainMessageNumber++; } }
trySkippedMessageKeys(header: Header, ciphertext: string, nostrSender: string): string | null { const skippedKeys = this.state.skippedKeys[nostrSender]; if (!skippedKeys) return null;
const messageKey = skippedKeys.messageKeys[header.number]; if (!messageKey) return null;
delete skippedKeys.messageKeys[header.number];
if (Object.keys(skippedKeys.messageKeys).length === 0) { delete this.state.skippedKeys[nostrSender]; }
return nip44.decrypt(ciphertext, messageKey); } ```
-
 @ a95c6243:d345522c
2025-03-11 10:22:36
@ a95c6243:d345522c
2025-03-11 10:22:36«Wir brauchen eine digitale Brandmauer gegen den Faschismus», schreibt der Chaos Computer Club (CCC) auf seiner Website. Unter diesem Motto präsentierte er letzte Woche einen Forderungskatalog, mit dem sich 24 Organisationen an die kommende Bundesregierung wenden. Der Koalitionsvertrag müsse sich daran messen lassen, verlangen sie.
In den drei Kategorien «Bekenntnis gegen Überwachung», «Schutz und Sicherheit für alle» sowie «Demokratie im digitalen Raum» stellen die Unterzeichner, zu denen auch Amnesty International und Das NETTZ gehören, unter anderem die folgenden «Mindestanforderungen»:
- Verbot biometrischer Massenüberwachung des öffentlichen Raums sowie der ungezielten biometrischen Auswertung des Internets.
- Anlasslose und massenhafte Vorratsdatenspeicherung wird abgelehnt.
- Automatisierte Datenanalysen der Informationsbestände der Strafverfolgungsbehörden sowie jede Form von Predictive Policing oder automatisiertes Profiling von Menschen werden abgelehnt.
- Einführung eines Rechts auf Verschlüsselung. Die Bundesregierung soll sich dafür einsetzen, die Chatkontrolle auf europäischer Ebene zu verhindern.
- Anonyme und pseudonyme Nutzung des Internets soll geschützt und ermöglicht werden.
- Bekämpfung «privaten Machtmissbrauchs von Big-Tech-Unternehmen» durch durchsetzungsstarke, unabhängige und grundsätzlich föderale Aufsichtsstrukturen.
- Einführung eines digitalen Gewaltschutzgesetzes, unter Berücksichtigung «gruppenbezogener digitaler Gewalt» und die Förderung von Beratungsangeboten.
- Ein umfassendes Förderprogramm für digitale öffentliche Räume, die dezentral organisiert und quelloffen programmiert sind, soll aufgelegt werden.
Es sei ein Irrglaube, dass zunehmende Überwachung einen Zugewinn an Sicherheit darstelle, ist eines der Argumente der Initiatoren. Sicherheit erfordere auch, dass Menschen anonym und vertraulich kommunizieren können und ihre Privatsphäre geschützt wird.
Gesunde digitale Räume lebten auch von einem demokratischen Diskurs, lesen wir in dem Papier. Es sei Aufgabe des Staates, Grundrechte zu schützen. Dazu gehöre auch, Menschenrechte und demokratische Werte, insbesondere Freiheit, Gleichheit und Solidarität zu fördern sowie den Missbrauch von Maßnahmen, Befugnissen und Infrastrukturen durch «die Feinde der Demokratie» zu verhindern.
Man ist geneigt zu fragen, wo denn die Autoren «den Faschismus» sehen, den es zu bekämpfen gelte. Die meisten der vorgetragenen Forderungen und Argumente finden sicher breite Unterstützung, denn sie beschreiben offenkundig gängige, kritikwürdige Praxis. Die Aushebelung der Privatsphäre, der Redefreiheit und anderer Grundrechte im Namen der Sicherheit wird bereits jetzt massiv durch die aktuellen «demokratischen Institutionen» und ihre «durchsetzungsstarken Aufsichtsstrukturen» betrieben.
Ist «der Faschismus» also die EU und ihre Mitgliedsstaaten? Nein, die «faschistische Gefahr», gegen die man eine digitale Brandmauer will, kommt nach Ansicht des CCC und seiner Partner aus den Vereinigten Staaten. Private Überwachung und Machtkonzentration sind dabei weltweit schon lange Realität, jetzt endlich müssen sie jedoch bekämpft werden. In dem Papier heißt es:
«Die willkürliche und antidemokratische Machtausübung der Tech-Oligarchen um Präsident Trump erfordert einen Paradigmenwechsel in der deutschen Digitalpolitik. (...) Die aktuellen Geschehnisse in den USA zeigen auf, wie Datensammlungen und -analyse genutzt werden können, um einen Staat handstreichartig zu übernehmen, seine Strukturen nachhaltig zu beschädigen, Widerstand zu unterbinden und marginalisierte Gruppen zu verfolgen.»
Wer auf der anderen Seite dieser Brandmauer stehen soll, ist also klar. Es sind die gleichen «Feinde unserer Demokratie», die seit Jahren in diese Ecke gedrängt werden. Es sind die gleichen Andersdenkenden, Regierungskritiker und Friedensforderer, die unter dem großzügigen Dach des Bundesprogramms «Demokratie leben» einem «kontinuierlichen Echt- und Langzeitmonitoring» wegen der Etikettierung «digitaler Hass» unterzogen werden.
Dass die 24 Organisationen praktisch auch die Bekämpfung von Google, Microsoft, Apple, Amazon und anderen fordern, entbehrt nicht der Komik. Diese fallen aber sicher unter das Stichwort «Machtmissbrauch von Big-Tech-Unternehmen». Gleichzeitig verlangen die Lobbyisten implizit zum Beispiel die Förderung des Nostr-Netzwerks, denn hier finden wir dezentral organisierte und quelloffen programmierte digitale Räume par excellence, obendrein zensurresistent. Das wiederum dürfte in der Politik weniger gut ankommen.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 04ea4f83:210e1713
2025-02-24 06:42:36
@ 04ea4f83:210e1713
2025-02-24 06:42:36Erschienen im The Bitstein Brief | Veröffenlichung 10.12.2022 |\ Author: Bitstein (Michael Goldstein)\ Übersetzt von: Sinautoshi am 11.12.2022 - 766906
„Die gesellschaftliche Funktion der Wirtschaftswissenschaft besteht gerade darin, solide Wirtschaftstheorien zu entwickeln und die Irrtümer bösartiger Denkweisen zu entlarven. Bei der Verfolgung dieser Aufgabe zieht der Wirtschaftswissenschaftler die tödliche Feindschaft aller Schwindler und Scharlatane auf sich, deren Abkürzungen zum irdischen Paradies er entlarvt. Je weniger diese Quacksalber in der Lage sind, plausible Einwände gegen die Argumente eines Ökonomen vorzubringen, desto wütender beschimpfen sie ihn.“
- Ludwig von Mises, „Nationalökonomie, Theorie des Handelns und Wirtschaftens”
Das „toxischste" an einem Bitcoin-Maximalisten ist seine unerschütterliche Bereitschaft, „Nein” zu sagen. Nach dem Studium der Geldtheorie und -geschichte und der Erfahrung mit den unerbittlichen Kräften des Marktes, hat der Bitcoiner ein Verständnis für die Realität des monetären Wettbewerbs, ein Bewusstsein für die kritische Natur dezentraler Systeme, einen Fokus auf die Lösung der wichtigsten monetären Probleme und eine strikte Ablehnung der unvermeidlichen Ablenkungen, Opportunitätskosten und ethischen Bedenken bei der Einführung und Förderung von Altcoin-Projekten.
Einige Kritiker bemängeln unhöfliche rhetorische Schnörkel, die als Hindernis für die Gewinnung neuer Bitcoin-Nutzer angesehen werden. Wenn das wahr wäre, gäbe es in der Arbeitsteilung eine Chance für eine qualitativ hochwertigere Bitcoin-Ausbildung, die die Bitcoiner meiner Meinung nach gerne wahrnehmen würden, vor allem die Kritiker, die die bestehenden Unzulänglichkeiten besser erkennen. Doch egal, wie höflich die Bitcoiner ihre Ansichten darlegen, bestimmte Möchtegern-Unternehmer und Influencer werden immer im Streit mit einer leidenschaftlichen Bevölkerungsgruppe stehen, die einfach nicht interessiert ist - und ihr Desinteresse lautstark kundtut. Die „toxischsten" Bitcoiner sind oft diejenigen, die die Weisheit der Bitcoiner erst erkannt haben, nachdem sie von Shitcoins verbrannt wurden und ihr neu gefundenes Desinteresse unmissverständlich zum Ausdruck bringen wollen.
Was soll man also als Bitcoiner tun? Ich empfehle, sich der Wahrheit und der Förderung der Wahrheit zu verschreiben und die Wirksamkeit von Rhetorik an ihrem langfristigen Einfluss und nicht an ihrer kurzfristigen Popularität zu messen.
In dieser Hinsicht sollten sich die Bitcoiner von dem ursprünglichen toxischen Maximalisten inspirieren lassen: Ludwig von Mises. Der bedeutende Wirtschaftswissenschaftler setzte sich unbeirrt für die Wahrheit, freie Märkte und gesundes Geld ein und scheute sich nicht, das zu sagen, was gesagt werden musste, auch wenn er sich damit keine Freunde machte. Langfristig wurde er zu einem der einflussreichsten Ökonomen und Denker des 20. Jahrhunderts, und seine Arbeit hat den Weg für den Bitcoin geebnet.
Mises, der Geldmaximalist
Einer der Hauptkritikpunkte an den Bitcoin-Maximalisten ist die Behauptung, dass die Welt auf Bitcoin (als Geld) konvergieren wird und es generell keine Verwendung für andere Währungen gibt. Dies wird als normative Aussage betrachtet. In Wirklichkeit machen die Bitcoiner eine positive, beschreibende Aussage darüber, wie der monetäre Wettbewerb funktioniert.
In der 1912 veröffentlichten Theorie des Geldes und der Umlaufmittel schrieb Mises:
„So haben die Erfordernisse des Marktes allmählich dazu geführt, dass bestimmte Waren als gemeinsame Tauschmittel ausgewählt wurden. Die Gruppe der Waren, aus der diese ausgewählt wurden, war ursprünglich sehr groß und unterschied sich von Land zu Land; sie wurde aber immer mehr eingeschränkt. Wann immer ein direkter Tausch nicht in Frage kam, war jede der an einem Geschäft beteiligten Parteien bestrebt, ihre überflüssigen Waren nicht nur gegen marktgängigere Waren im Allgemeinen, sondern gegen die marktgängigsten Waren einzutauschen, und von diesen wiederum bevorzugte sie natürlich die marktgängigste Ware. Je größer die Marktfähigkeit der zuerst im indirekten Tausch erworbenen Waren ist, desto größer ist die Aussicht, das endgültige Ziel ohne weitere Manöver erreichen zu können. So gäbe es die unvermeidliche Tendenz, dass die weniger marktfähigen Güter aus der Reihe der als Tauschmittel verwendeten Waren nach und nach verworfen würden, bis schließlich nur noch ein einziges Gut übrig bliebe, das allgemein als Tauschmittel verwendet würde: das Geld.“
Mises zufolge wählen die Akteure zunehmend das marktgängigste Gut als Tauschmittel aus und der natürliche Verlauf des Marktes geht in Richtung Vereinheitlichung zu einem einzigen Geldgut. Das ist schlicht und einfach monetärer Maximalismus.
Mises unterscheidet sich von den Bitcoinern lediglich durch die Stärke der Behauptungen, die er über die tatsächlichen empirischen Entscheidungen der Wirtschaftsakteure zu treffen bereit ist. Mises weist darauf hin, dass sowohl Gold als auch Silber an vielen Orten zu Geld gemacht wurden, wahrscheinlich wegen ihrer ähnlichen Eigenschaften, und dass es den Rahmen der Geldtheorie sprengt, zu sagen, ob Gold oder Silber letztlich besser verkäuflich ist. Trotzdem sagt er:
„Denn es ist ziemlich sicher, dass die Vereinheitlichung auch dann ein wünschenswertes geldpolitisches Ziel gewesen wäre, wenn die ungleiche Marktfähigkeit der als Tauschmittel verwendeten Güter kein Motiv geboten hätte. Die gleichzeitige Verwendung mehrerer Geldarten bringt so viele Nachteile mit sich und verkompliziert die Technik des Tauschens so sehr, dass das Bestreben, das Geldsystem zu vereinheitlichen, in jedem Fall unternommen worden wäre.“
Die natürliche Tendenz zu einem einzigen Geldgut ist so stark, dass seiner Meinung nach die Vereinheitlichung der Geldsysteme auch dann angestrebt würde, wenn zwei Güter genau gleich marktfähig wären. Zuvor stellt er außerdem fest:
„Das endgültige Urteil könnte erst gefällt werden, wenn alle Hauptteile der bewohnten Erde ein einziges Handelsgebiet bilden, denn erst dann wäre es unmöglich, dass andere Nationen mit unterschiedlichen Geldsystemen sich anschließen und die internationale Organisation verändern.“
Jede neue Handelsbeziehung eröffnet die Möglichkeit, ein brandneues Geldgut einzuführen, das bisher nicht verwendet wurde. Wenn seine Qualitäten ein höheres Maß an Marktfähigkeit aufrechterhalten könnten, ist es möglich, dass sich die gesamte internationale Währungsordnung aufgrund seiner natürlichen Überlegenheit bei der Bewältigung der Funktionen des Geldes um ihn herum neu organisieren könnte.
Im Bitcoin Standard liefert Saifedean Ammous zahlreiche Argumente dafür, warum Gold dem Silber als Geldwert überlegen war, obwohl Mises nicht bereit oder nicht daran interessiert war, diesen Punkt zu diskutieren, und warum Bitcoin ein noch besserer Geldwert ist. Mises hat die Einführung von Bitcoin in die Weltwirtschaft zwar nicht mehr erlebt, aber seine Wirtschaftstheorie erklärt genau, warum Bitcoin an Wert gewinnen würde und warum es plausibel ist, dass die gesamte internationale Währungsordnung auf einen Bitcoin-Standard umgestellt wird. Er gibt auch den theoretischen Rahmen, um zu verstehen, warum Altcoins Bitcoin nicht allein durch ihre Eigenschaften ausstechen können. Sie müssen eine bessere Marktfähigkeit in Bezug auf Raum, Zeit und Größe bieten, um einen ausreichenden Vorteil gegenüber Bitcoin zu haben. Wie bereits an anderer Stelle beschrieben, ist dies einfach nicht gelungen, und nur Bitcoin bietet ein stark dezentralisiertes, überprüfbares und glaubwürdig knappes digitales Geldgut.
Mises, der Marktmaximalist
Die Geldtheorie ist nicht der einzige Ort, an dem der Leser eine Art „Maximalismus" in Mises' Denken spüren kann. Sein gesamtes Werk läuft auf einen unverhohlenen Marktmaximalismus hinaus, der sich weigert, durch rigorose ökonomische Theorie und Analyse sozialistischen oder interventionistischen Argumenten nachzugeben.
Ein großartiges Beispiel für seine Verteidigung des freien Marktes findet sich in einem Vortrag aus dem Jahr 1950 mit dem Titel „Die Mitte des Weges führt zum Sozialismus". In dieser Vorlesung greift Mises Interventionisten an, die behaupten, eine Politik der „Mitte" zwischen den beiden Extremen Kapitalismus und Sozialismus zu favorisieren. Durch strategische Interventionen kann der Staat die Auswüchse beider Systeme verhindern.
Mises betrachtet Kapitalismus und Sozialismus jedoch als diametral entgegengesetzte und unvereinbare Organisationssysteme und nicht als ein Spektrum der Wohlstandsverteilung:
„Der Konflikt der beiden Prinzipien ist unüberbrückbar und lässt keinen Kompromiss zu. Kontrolle ist unteilbar. Entweder entscheidet die Nachfrage der Verbraucher, die sich auf dem Markt manifestiert, für welche Zwecke und wie die Produktionsfaktoren eingesetzt werden sollen, oder der Staat kümmert sich um diese Angelegenheiten. Es gibt nichts, was den Gegensatz zwischen diesen beiden widersprüchlichen Prinzipien abmildern könnte. Sie schließen sich gegenseitig aus. Der Interventionismus ist kein goldener Mittelweg zwischen Kapitalismus und Sozialismus. Er ist der Entwurf für ein drittes System der wirtschaftlichen Organisation der Gesellschaft und muss als solches gewürdigt werden.“
Dieses dritte System ist jedoch im Grunde nur ein längerer Marsch zum Sozialismus, indem es ein falsches Lippenbekenntnis zu Privateigentum und freier Marktwirtschaft ablegt. Auf jeden Eingriff, der stattfindet, müssen weitere folgen. Die Festsetzung eines Preises hier erfordert die Festsetzung eines anderen Preises dort, und so geht es die ganze Lieferkette entlang. Am Ende hat der Interventionismus die gesamte „Marktwirtschaft" im Würgegriff.
Der Interventionismus kann nicht als ein Wirtschaftssystem betrachtet werden, das dazu bestimmt ist, zu bleiben. Er ist eine Methode zur Umwandlung des Kapitalismus in den Sozialismus in mehreren aufeinanderfolgenden Schritten. Damit unterscheidet er sich von den Bemühungen der Kommunisten, den Sozialismus auf einen Schlag zu verwirklichen. Der Unterschied bezieht sich nicht auf das letztendliche Ziel der politischen Bewegung, sondern vor allem auf die Taktik, die zur Erreichung des von beiden Gruppen angestrebten Ziels angewandt wird.
Trotzdem sind selbst die meisten vermeintlichen Befürworter einer freien Marktwirtschaft in Wirklichkeit von interventionistischen Ideologien und Denkweisen durchdrungen, und ihre Strategien sind immer zum Scheitern und zu Kompromissen verurteilt.
„Dies hat zur Folge, dass praktisch kaum etwas getan wird, um das System der Privatwirtschaft zu erhalten. Es gibt nur Mittelsmänner, die glauben, erfolgreich gewesen zu sein, wenn sie eine besonders ruinöse Maßnahme eine Zeit lang hinausgezögert haben. Sie sind immer auf dem Rückzug. Sie nehmen heute Maßnahmen in Kauf, die sie noch vor zehn oder zwanzig Jahren für undiskutabel gehalten hätten. In ein paar Jahren werden sie sich mit anderen Maßnahmen abfinden, die sie heute noch für undiskutabel halten. Was den totalitären Sozialismus verhindern kann, ist nur ein grundlegender Wandel der Ideologien.\ \ Was wir brauchen, ist weder Antisozialismus noch Antikommunismus, sondern eine offene Befürwortung des Systems, dem wir all den Wohlstand verdanken, der unser Zeitalter von den vergleichsweise beengten Verhältnissen vergangener Zeiten unterscheidet.“
Mises nimmt kein Blatt vor den Mund, wenn er eine interventionistische Politik fordert, und es gibt viele Lehren, die Bitcoiner daraus ziehen können.
Erstens ist das Bitcoin-Netzwerk nicht einfach nur eine andere Art des Werttransfers als eine bestehende zentralisierte Lösung, eine Art PayPal 2.0. Es ist ein strukturell anderer Ansatz für das gesamte Problem der doppelten Ausgaben. „Blockchain, nicht Bitcoin" ist eine Mogelpackung, weil sie den Kern dessen, was Bitcoin einzigartig macht (Dezentralisierung, unabhängige Überprüfbarkeit usw.), wegnimmt, während sie behauptet, „die zugrundeliegende Technologie" zu nutzen, ähnlich wie ein nationalsozialistisches oder faschistisches Regime die staatliche Kontrolle über die Produktion übernehmen könnte, während es behauptet, für Privateigentum zu sein. Wenn du die Vorteile des Marktes nutzen willst, musst du tatsächlich einen Markt haben, und wenn du die Vorteile von Bitcoin nutzen willst, musst du Bitcoin tatsächlich nutzen.
Außerdem sollte die Dezentralisierung als binäres System betrachtet werden. Entweder ist ein System dezentralisiert, oder es ist dazu verdammt, zentralisiert zu werden, manchmal mit einem Hard Fork nach dem anderen (vgl. Ethereum). Bitcoin-Maximalisten werden regelmäßig als toxisch bezeichnet, weil sie entschlossen an bestimmten Netzwerkparametern festhalten, selbst wenn diese willkürlich oder trivial erscheinen. Ein ganzer Krieg über die Blockgröße wurde um eine Begrenzung von 1 MB geführt. Die Zahl schien willkürlich und die Lösung trivial zu sein, aber die Bitcoiner weigerten sich, davon abzuweichen. Und warum? Eine höhere Blockgröße würde die Kosten für den Betrieb eines vollständigen Knotens (Full Node) erhöhen, der für eine unabhängige Validierung und Dezentralisierung notwendig ist. Ein Hard Fork würde einen vernichtenden Präzedenzfall schaffen und alle zukünftigen Ansprüche auf Abwärtskompatibilität gefährden, die für die Glaubwürdigkeit der Geldpolitik und die Fähigkeit der Nodes, sich vertrauensvoll mit dem Netzwerk zu synchronisieren, erforderlich sind. Die Blockkapazität stieg zwar an, aber nur, weil SegWit, dessen Vorteile weit über die bloße Verbesserung der Skalierung hinausgingen, über einen Soft Fork aktiviert werden konnte, sodass denjenigen, die dies nicht wollten, keine neuen Kosten auferlegt wurden.
Andere Projekte hingegen akzeptieren nicht, dass die Kompromisse bei Bitcoin nicht wirklich willkürlich sind. Sie bieten Turing-complete Smart Contracts, schnellere Blockzeiten, größere Blöcke oder alle möglichen anderen „Features" an. Die Features werden nicht mit demselben extrem konservativen Engagement für Sicherheit produziert wie Bitcoin und bedrohen oft die Fähigkeit, überhaupt einen vollständigen Knoten (Full-Node) zu betreiben. Nur bei Bitcoin kümmern sich die Leute darum, dass die Geldmenge tatsächlich überprüft werden kann. Mit der Zeit verlieren die Projekte, wenn sie überhaupt aufrechterhalten werden, jeden Anschein einer glaubwürdigen Dezentralisierung. Ethereum, das einst mit unaufhaltsamen Anwendungen und der Aussage „Code ist Gesetz" warb, erlebte den DAO-Hack und ist nach der Einführung von Proof-of-Stake (das von Natur aus zentralisierend ist) der OFAC-Zensur in unterschiedlichem Maße unterworfen.
Bitcoin akzeptiert nichts von alledem. Er beugt seine Regeln für niemanden. Bitcoiner wissen auch, dass das System gar kein Bitcoin mehr wäre, wenn die Regeln gebogen würden. Mises hilft uns zu verstehen, dass eine Politik des Mittelweges zu Shitcoinerei führt. Eine Währung ist entweder Bitcoin oder dazu verdammt, ein Shitcoin zu sein.
Mises, der toxische Maximalist
Im Jahr 1947 fand in der Schweiz das erste Treffen der Mont Pèlerin Society statt. Bei diesem Treffen trafen sich viele der einflussreichsten Verfechter der freien Märkte und des klassischen Liberalismus, von Ludwig von Mises über F. A. Hayek bis hin zu Milton Friedman und vielen anderen, um darüber zu diskutieren, wie man die steigende Flut des Totalitarismus und seiner Wirtschaftsideologien durch die Förderung freier Märkte und des Privateigentums bekämpfen kann. Man könnte meinen, dass Mises genau in diese Diskussionen passt. Doch wie Milton Friedman berichtete, kam es anders:
„Die Geschichte, an die ich mich am besten erinnere, ereignete sich auf dem ersten Treffen in Mont Pèlerin, als [Mises] aufstand und sagte: „Ihr seid alle ein Haufen Sozialisten." Wir diskutierten über die Einkommensverteilung und darüber, ob man progressive Einkommenssteuern haben sollte. Einige der Anwesenden vertraten die Ansicht, dass es eine Rechtfertigung dafür geben könnte.\ \ Eine andere Gelegenheit, die ebenso aufschlussreich ist: Fritz Machlup war ein Schüler von Mises, einer seiner treuesten Jünger. Bei einem der Treffen in Mont Pèlerin hielt Machlup einen Vortrag, in dem er, glaube ich, die Idee eines Goldstandards in Frage stellte; er sprach sich für freie Wechselkurse aus. Mises war so wütend, dass er drei Jahre lang nicht mit Machlup sprechen wollte. Einige Leute mussten die beiden wieder zusammenbringen. Es ist schwer zu verstehen; man kann es einigermaßen nachvollziehen, wenn man sich vor Augen führt, wie Menschen wie Mises in seinem Leben verfolgt wurden.“
Wie bereits erwähnt, hielt Mises drei Jahre später einen Vortrag, in dem er eindrucksvoll erklärte, warum sie tatsächlich alle ein Haufen Sozialisten waren. Wer staatliche Eingriffe in die Einkommensverteilung akzeptiert, ist dem Sozialismus bereits verfallen, sobald genug Zeit vergangen ist. Mises war einfach nicht bereit, den sozialistischen Irrtümern, die er im Laufe seiner intellektuellen Karriere so akribisch aufgespießt hatte, Glauben zu schenken. Jörg Guido Hülsmann stellt in Mises: The Last Knight of Liberalism fest, dass „Mises zwar in der Lage war, Sozialisten hoch zu schätzen, aber der Vorfall zeigte, dass er wenig Geduld mit Sozialisten hatte, die sich als Liberale ausgaben."
Doch Mises' giftiges Verhalten blieb nicht ohne Folgen. Laut Hülsmann:
„Der Schlagabtausch zwischen Mises und seinen neoliberalen Gegnern prägte den Ton in der Mont Pèlerin Society für die kommenden Jahre.... Obwohl die Libertären um Mises eine kleine Minderheit waren, hatten sie die finanzielle Unterstützung der amerikanischen Hauptsponsoren wie dem Volker Fund, ohne die die Gesellschaft in jenen frühen Jahren schnell ausgestorben wäre. Solange Mises aktiv an den Treffen teilnahm, war es daher unmöglich, die technischen Details eines genehmigten staatlichen Interventionismus zu diskutieren. Das Laissez-faire hatte ein Comeback gefeiert. Es war zwar nicht die Mehrheitsmeinung, aber es war eine diskutierbare und diskutierte politische Option - zu viel für einige anfängliche Mitglieder wie Maurice Allais, der die Gesellschaft genau aus diesem Grund bald wieder verließ.“
Indem er toxisch war, konnte Mises dazu beitragen, den Ton für eine wirklich laissez-faire Mont Pèlerin Society zu setzen, die ihrem erklärten Ziel gerecht werden konnte, und sie wählten F. A. Hayek zu ihrem Präsidenten. Er hatte keine Angst, Klartext zu reden, aber lautstark, sogar gegenüber Leuten, die vermutlich zu seinem „eigenen Team" gehörten. Ludwig von Mises war ein Mann, der seine Ideen ernst nahm und die Wahrheit noch viel ernster.
In seinen Memoiren schreibt Mises über seine Zeit in der österreichischen Handelskammer in den 1910er und 1920er Jahren:
„Ich wurde manchmal beschuldigt, meinen Standpunkt zu schroff und unnachgiebig zu vertreten. Es wurde auch behauptet, dass ich mehr hätte erreichen können, wenn ich eine größere Kompromissbereitschaft gezeigt hätte.... Die Kritik war ungerechtfertigt; ich konnte nur dann effektiv sein, wenn ich die Dinge so darstellen konnte, wie sie mir erschienen. Wenn ich heute auf meine Arbeit bei der Handelskammer zurückblicke, bedauere ich nur meine Kompromissbereitschaft und nicht meine Unnachgiebigkeit.“
In dieser Zeit trug sein Rat dazu bei, die Hyperinflation in Österreich aufzuhalten und ihre Auswirkungen im Vergleich zur Weimarer Republik abzuschwächen.
Bitcoiner werden von endlosen „Krypto-" und „Shitcoin"-Betrügern geplagt, die auf dem Rücken der innovativen Technologie und des wirtschaftlichen Erfolgs von Bitcoin reiten wollen. Den Bitcoinern wird gesagt, dass sie alle im selben Team sind. In den Augen der Öffentlichkeit sind sie das auch. Das Ergebnis ist eine getäuschte Öffentlichkeit, der zentralisierte Pump-and-Dump-Systeme und Rugpulls, Affen-Jpegs und Rube-Goldberg-Maschinen verkauft werden, die auf Schlagwörtern basieren und die Vorstellung vermitteln, dass sie in der gleichen Liga spielen wie die großartigste Geldtechnologie, die je geschaffen wurde. „Krypto" profitiert vom Erfolg von Bitcoin, und die Bekanntheit von Bitcoin sinkt mit den Misserfolgen von „Krypto". Doch wenn Bitcoiner die Unterschiede ansprechen und diese Projekte ablehnen, die sie uninteressant oder sogar verabscheuungswürdig finden, wird das als schädlich angesehen. Den Bitcoinern schadet das nicht, denn sie können weiter (Satoshis) stapeln und bauen, aber die Menschen, die unter Fiat-Regimen leben müssen, leiden darunter, dass ihnen kein Weg zu Freiheit und Wohlstand gezeigt wird.
Abgesehen davon, dass das Geld des Einzelnen in Gefahr ist, kann die Offenheit für Shitcoins auch Veränderungen im Netzwerk fördern, die die Dezentralisierung beeinträchtigen. Wenn es Unterstützung für einen Shitcoin gibt, der auf einem bestimmten Merkmal basiert, warum sollte das Merkmal dann nicht in Bitcoin existieren? Wenn es tatsächlich eine Tendenz zu einer einzigen Währung gibt, ist die Förderung einer alternativen Kryptowährung selbst ein Angriff auf das Potenzial von Bitcoin. Wirtschaft und Technik sind mit gnadenlosen Konsequenzen konfrontiert. Eine falsche Abfolge von Schritten kann zu absoluter Verwüstung führen. Bitcoiner nehmen das sehr ernst und machen keinen Hehl daraus, dass sie diese Konsequenzen fürchten. Wenn sie das tun, lehnen sie ganze unternehmerische Vorhaben ab und stellen ihre gesamte Einnahmequelle in Frage. Das ist toxisch.
Bitcoiners sollten immer den Mut haben, Mises zu zitieren und jedem zu sagen: „Ihr seid alle ein Haufen Shitcoiner."
Der aufgehende Stern von Mises
Obwohl er aus einer adligen Familie stammte und in Österreich hohe Positionen innehatte, hatte Mises, als er auf der Flucht vor den Nazis in die Vereinigten Staaten emigrierte, nur wenige Möglichkeiten. Bis zu seiner Pensionierung war er „Gastprofessor" an der New York University. Er arbeitete im Grunde genommen im stillen Kämmerlein und unterrichtete hauptsächlich in seinen inzwischen berühmten informellen Seminaren, an denen auch Murray Rothbard und andere teilnahmen. Er benötigte die Unterstützung verschiedener philanthropischer Fonds. Hinzu kam, dass die Wirtschaftswissenschaften, wie alle Sozialwissenschaften, dem Szientismus und der Technokratie erlegen waren, so dass Mises' strenge logisch-deduktive Methoden im Vergleich zu mathematischen Formeln und statistischen Modellen als altmodisch galten. Der Goldstandard wurde zugunsten eines Fiat-Systems abgeschafft, und als Mises starb, hatte der US-Dollar keinerlei Verbindung mehr zu Edelmetallen oder realen Ersparnissen, so dass die Geldpolitik allein den Launen der Politik überlassen blieb.
Es gab allen Grund, Ludwig von Mises völlig in Vergessenheit geraten zu lassen. Doch seine Schüler, wie Murray Rothbard, hielten die österreichische Schule am Leben. Im Jahr 1982 wurde das Ludwig von Mises Institute von Rothbard und Lew Rockwell gegründet und von Dr. Ron Paul finanziert (beide wurden von ihren Kritikern als „toxisch" bezeichnet). Dr. Paul selbst wurde zu einem legendären Verfechter der Ideen von Mises und anderen, sowohl im Kongress als auch im Präsidentschaftswahlkampf. In letzterem machte Dr. Paul die von der Federal Reserve verursachte wirtschaftliche Zerstörung zu einem zentralen Bestandteil seines Programms und zum ersten Mal seit Jahrzehnten zu einem wichtigen Thema in der politischen Debatte, was den Diskurs danach für immer veränderte.
Es ist also kein Wunder, dass viele Menschen, die sich als erste für Bitcoin begeisterten, treue Schüler von Mises waren und dass seine Ideen mit dem Wachstum von Bitcoin noch mehr an Bedeutung gewonnen haben. Seine rigorose Erläuterung der Wahrheiten des Wirtschaftsrechts, die auf Subjektivismus, Marginalismus und methodologischem Individualismus beruht, gab den Menschen den Rahmen, um zu verstehen, wie Bitcoin die Geldpolitik veranschaulicht, die zu Frieden, Wohlstand und Freiheit führt. Anstatt irrelevant zu werden, ist Mises heute wichtiger denn je. Wie Ron Paul bemerkte: „Wir sind jetzt alle Österreicher."
Fazit
Das Toxische liegt im Auge des Betrachters oder des Bagholders. Die Wirtschaftswissenschaft ist, wie jedes Streben nach Wahrheit, kein Beliebtheitswettbewerb, und die Wahrheit wird immer von denen bekämpft werden, deren Geschäft und Status von der Verbreitung von Irrtümern und Unwahrheiten abhängt.\ \ Ludwig von Mises stand fest zu seinen gründlichen Analysen der Wirtschaftswissenschaften und des klassischen Liberalismus und scheute sich nicht, das zu verteidigen, was er für wahr hielt, selbst auf Kosten von Prestige und Popularität. Heute steht er weit über fast jedem anderen Sozialwissenschaftler des 20. Jahrhunderts.
Ich habe an anderer Stelle über Memes und Rhetorik gesprochen, und es gibt viel zu diskutieren über bestimmte Strategien und ihre Wirksamkeit. Aber vor allem muss jede Strategie die Wahrheit in den Mittelpunkt stellen. Die Wahrheit ist zeitlos, so dass ihre Relevanz nicht auf kurzfristige Popularität beschränkt ist. Wenn dies der Fall ist, ist der Vorwurf der „Toxizität" entweder eine Aufforderung zur Verbesserung oder ein Ehrenzeichen dafür, dass man trotz aller Widrigkeiten für die Wahrheit einsteht. Wie das Motto von Ludwig von Mises schon sagte: tu ne cede malis, sed contra audentior ito. Weiche dem Bösen nicht, trete ihm umso mutiger entgegen.
-
 @ 04ea4f83:210e1713
2025-02-23 17:38:11
@ 04ea4f83:210e1713
2025-02-23 17:38:11Erschienen in Citadel 21 Vol. 21 | Veröffentlichung 21.03.2023 \ Autor: Knut Svanholm\ Übersetzt von: Sinautoshi am 24.03.2023 - 782344\ \ Rückblickend sieht das Jahr 2022 wie eine Art Höhepunkt aus. Während der Großteil der Gesellschaft weitgehend vergessen hat, was die politische Klasse ihren Untertanen während der sogenannten Pandemie angetan hat, kotzte Hollywood weiterhin Inhalte aus, die von „diversen" Regisseuren und Drehbuchautoren produziert wurden und bis zum Rand mit nicht ganz so subtilen Botschaften und Verachtung für ihr Publikum gefüllt waren.
Star Wars und Marvel haben nach der Übernahme durch Disney auf diese Weise Franchise-Mord begangen, und auch das Erbe von Der Herr der Ringe wurde von der linken Idiotie vergewaltigt und für immer befleckt. Jetzt gibt es von jedem männlichen Avenger eine weibliche Version. Hugh Jackman, der Schauspieler, der früher die Hauptrolle des X-Men-Mutanten Wolverine spielte, empfahl seinen Anhängern in den sozialen Medien kürzlich Bill Gates' Buch über den Klimawandel.
Als Frauen verkleidete Männer gewinnen Sportmeisterschaften für Frauen, und alle haben so viel Angst davor, als bigott bezeichnet zu werden, dass sich niemand traut, auf die Absurdität hinzuweisen, dass ein Mann alle Mädchen schlägt. Diese so genannten Sportler werden als „mutig" bezeichnet, obwohl sie alles andere als das sind.
Die Tatsache, dass es in einigen Berufen mehr Männer als Frauen gibt, wird als Problem angesehen, aber warum genau das ein Problem ist, wird selten erwähnt. Die Verdienste und die tatsächliche Meinungsvielfalt werden auf dem Altar der „Vielfalt und Integration" geschlachtet.
Die Gesellschaft ist an einem Punkt angelangt, an dem die Verbraucher Ärzten und Anwälten gerade wegen ihrer Hautfarbe misstrauen, da sie vermuten, dass sie deshalb in ihre Positionen gekommen sind und nicht wegen ihrer Kompetenz oder ihrer Verdienste. Noch vor zwanzig Jahren war die normale Bauchreaktion das Gegenteil: „Wow, ein Arzt aus einer Minderheit! Sie müssen hart gearbeitet haben, um dorthin zu gelangen, wo sie heute sind!"
Als ich aufgewachsen bin, wurde ein „Rassist" als jemand definiert, der sich einen Dreck um die Hautfarbe oder die ethnische Zugehörigkeit einer anderen Person scherte. Dasselbe galt für das Wort „Sexist" - man war ein Sexist, wenn man das Geschlecht einer Person bei der Beurteilung berücksichtigte.
Ich hatte das Gefühl, dass die Welt seit den Gräueltaten des Zweiten Weltkriegs im Kampf gegen diese Vorurteile einen weiten Weg zurückgelegt hatte und dass jeder eine anständige Karriere in jedem Beruf machen konnte, wenn er sich nur anstrengte und sich Mühe gab. Doch irgendwann in den frühen 2000er Jahren änderte sich etwas.
Plötzlich begannen die Worte das Gegenteil von dem zu bedeuten, was sie ursprünglich bedeuteten. Plötzlich war jeder, der sich einen Dreck um seine Hautfarbe scherte, ein Rassist. Jeder, dem es egal war, ob der CEO eines großen Unternehmens ein Mann oder eine Frau war, war ein Sexist.
Im Jahr 2023 behaupten manche sogar, man sei ein „Transphobe", wenn man nicht gelegentlich Fellatio an einem „weiblichen Penis" betreiben will. Die Tugendwächter laufen in der Tat Amok, und die Medienunternehmen lieben es. Sie lieben es, weil sie alles lieben, was die Kluft zwischen den Menschen schürt. Je verrückter die Aktionen der Clownwelt® sind, desto wütender sind die Reaktionen der leichtgläubigen, verärgerten Menschen auf der „vernünftigen" Seite des politischen Spektrums.
Die Menschheit neigt dazu, sich wie ein Pendel oder eine Abrissbirne zu verhalten, wenn es um politische Meinungen oder „die aktuelle Sache" geht.
Wenn es zu viele blauhaarige, übergewichtige, lesbische, glutenintolerante, vegane Umweltschützer gibt, taucht von irgendwoher eine Welle von Skinheads auf, die mit Steroiden vollgepumpt sind und gegen Samenöl und Fleischfresser sind.
Für jede Hillary Clinton gibt es einen Donald Trump. Für jede Greta Thunberg gibt es einen Andrew Tate. Für jeden CNN-Reporter gibt es einen Alex Jones.
Auch im Bitcoin-Bereich gibt es immer ein „aktuelles Thema", an das man sich klammern kann, wenn auch oft eine männlichere Idee als das „aktuelle Thema" des Mainstreams. Was nur wenige wissen, ist, wie faul diese Art des Denkens ist.
Wissenschaft ist nicht automatisch schlecht, nur weil „die Wissenschaft" schlecht ist.
Nur weil man gelernt hat, dass alles, was die Regierung sagt, eine Lüge ist, ist nicht automatisch auch das Gegenteil wahr. Die Welt ist nuanciert; die meisten Dinge sind nicht schwarz oder weiß.
Was wahr und sehr schwarz-weiß ist, ist das Geld - es gibt Bitcoin und es gibt Shitcoins. Nur wenn wir letztere für erstere aufgeben, können wir die Politik aus dem menschlichen Handeln entfernen und uns auf eine gewisse Wahrheit in der Basisschicht der Zivilisation zurück arbeiten. Bitcoin belohnt weder Rent-Seeking noch faules Denken.
Die positiven Aspekte vieler moderner Technologien werden oft übersehen. Auch wenn sich die Clownwelt® und die lächerlichen Ideen, die ihr folgen, wie ein Lauffeuer verbreiten, gibt es Gründe für einen ungetrübten Optimismus für die Zukunft.
Wir hören oft von den Gefahren der sozialen Medien und wie sie die Gehirne unserer Kinder schädigen, aber wir werden selten an die Kehrseite der Medaille erinnert. Soziale Medien verbinden Menschen in einem Ausmaß, das der Menschheit nie zuvor zugänglich war. Jeder Mensch auf der Welt kann heute mit jedem anderen in Kontakt treten und mit einem Mausklick einen Videoanruf starten. Das ist ein enorm wichtiges Instrument für den Frieden. In Kombination mit Bitcoin haben die Bösewichte keine Chance mehr.
Wenn jeder auf diese Weise vernetzt ist, wird überdeutlich, wie absurd es ist, dass wir in Staaten mit unterschiedlichen Gesetzen und Vorschriften leben. Warum gelten für meine Mitmenschen auf der anderen Seite dieses Teiches, dieses Flusses, dieses Gebirges oder sogar dieser imaginären Linie in der Erde andere Regeln?
Jeden Tag wachen mehr und mehr Menschen auf und erkennen, dass es nur ein einziges Menschenrecht gibt - das Recht, in Ruhe gelassen zu werden.
Immer mehr Menschen erkennen, dass die Geldentwertung kein natürliches Phänomen ist, sondern eine bewusste Politik. Es ist nur eine Frage der Zeit, bis die alte Welt verschwindet. Solange wir kommunizieren dürfen, gibt es Hoffnung. Das Internet hat bewiesen, dass sich jede Kommunikation auf eine Reihe von Einsen und Nullen reduzieren lässt, und Bitcoin hat bewiesen, dass Geld nichts anderes als Information ist.
-
 @ a95c6243:d345522c
2025-03-04 09:40:50
@ a95c6243:d345522c
2025-03-04 09:40:50Die «Eliten» führen bereits groß angelegte Pilotprojekte für eine Zukunft durch, die sie wollen und wir nicht. Das schreibt der OffGuardian in einem Update zum Thema «EU-Brieftasche für die digitale Identität». Das Portal weist darauf hin, dass die Akteure dabei nicht gerade zimperlich vorgehen und auch keinen Hehl aus ihren Absichten machen. Transition News hat mehrfach darüber berichtet, zuletzt hier und hier.
Mit der EU Digital Identity Wallet (EUDI-Brieftasche) sei eine einzige von der Regierung herausgegebene App geplant, die Ihre medizinischen Daten, Beschäftigungsdaten, Reisedaten, Bildungsdaten, Impfdaten, Steuerdaten, Finanzdaten sowie (potenziell) Kopien Ihrer Unterschrift, Fingerabdrücke, Gesichtsscans, Stimmproben und DNA enthält. So fasst der OffGuardian die eindrucksvolle Liste möglicher Einsatzbereiche zusammen.
Auch Dokumente wie der Personalausweis oder der Führerschein können dort in elektronischer Form gespeichert werden. Bis 2026 sind alle EU-Mitgliedstaaten dazu verpflichtet, Ihren Bürgern funktionierende und frei verfügbare digitale «Brieftaschen» bereitzustellen.
Die Menschen würden diese App nutzen, so das Portal, um Zahlungen vorzunehmen, Kredite zu beantragen, ihre Steuern zu zahlen, ihre Rezepte abzuholen, internationale Grenzen zu überschreiten, Unternehmen zu gründen, Arzttermine zu buchen, sich um Stellen zu bewerben und sogar digitale Verträge online zu unterzeichnen.
All diese Daten würden auf ihrem Mobiltelefon gespeichert und mit den Regierungen von neunzehn Ländern (plus der Ukraine) sowie über 140 anderen öffentlichen und privaten Partnern ausgetauscht. Von der Deutschen Bank über das ukrainische Ministerium für digitalen Fortschritt bis hin zu Samsung Europe. Unternehmen und Behörden würden auf diese Daten im Backend zugreifen, um «automatisierte Hintergrundprüfungen» durchzuführen.
Der Bundesverband der Verbraucherzentralen und Verbraucherverbände (VZBV) habe Bedenken geäußert, dass eine solche App «Risiken für den Schutz der Privatsphäre und der Daten» berge, berichtet das Portal. Die einzige Antwort darauf laute: «Richtig, genau dafür ist sie ja da!»
Das alles sei keine Hypothese, betont der OffGuardian. Es sei vielmehr «Potential». Damit ist ein EU-Projekt gemeint, in dessen Rahmen Dutzende öffentliche und private Einrichtungen zusammenarbeiten, «um eine einheitliche Vision der digitalen Identität für die Bürger der europäischen Länder zu definieren». Dies ist nur eines der groß angelegten Pilotprojekte, mit denen Prototypen und Anwendungsfälle für die EUDI-Wallet getestet werden. Es gibt noch mindestens drei weitere.
Den Ball der digitalen ID-Systeme habe die Covid-«Pandemie» über die «Impfpässe» ins Rollen gebracht. Seitdem habe das Thema an Schwung verloren. Je näher wir aber der vollständigen Einführung der EUid kämen, desto mehr Propaganda der Art «Warum wir eine digitale Brieftasche brauchen» könnten wir in den Mainstream-Medien erwarten, prognostiziert der OffGuardian. Vielleicht müssten wir schon nach dem nächsten großen «Grund», dem nächsten «katastrophalen katalytischen Ereignis» Ausschau halten. Vermutlich gebe es bereits Pläne, warum die Menschen plötzlich eine digitale ID-Brieftasche brauchen würden.
Die Entwicklung geht jedenfalls stetig weiter in genau diese Richtung. Beispielsweise hat Jordanien angekündigt, die digitale biometrische ID bei den nächsten Wahlen zur Verifizierung der Wähler einzuführen. Man wolle «den Papierkrieg beenden und sicherstellen, dass die gesamte Kette bis zu den nächsten Parlamentswahlen digitalisiert wird», heißt es. Absehbar ist, dass dabei einige Wahlberechtigte «auf der Strecke bleiben» werden, wie im Fall von Albanien geschehen.
Derweil würden die Briten gerne ihre Privatsphäre gegen Effizienz eintauschen, behauptet Tony Blair. Der Ex-Premier drängte kürzlich erneut auf digitale Identitäten und Gesichtserkennung. Blair ist Gründer einer Denkfabrik für globalen Wandel, Anhänger globalistischer Technokratie und «moderner Infrastruktur».
Abschließend warnt der OffGuardian vor der Illusion, Trump und Musk würden den US-Bürgern «diesen Schlamassel ersparen». Das Department of Government Efficiency werde sich auf die digitale Identität stürzen. Was könne schließlich «effizienter» sein als eine einzige App, die für alles verwendet wird? Der Unterschied bestehe nur darin, dass die US-Version vielleicht eher privat als öffentlich sei – sofern es da überhaupt noch einen wirklichen Unterschied gebe.
[Titelbild: Screenshot OffGuardian]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 04ea4f83:210e1713
2025-02-23 10:43:38
@ 04ea4f83:210e1713
2025-02-23 10:43:38Veröffentlicht auf Discreetlog.com am 17.04.2023\ Originalautor: Matt Odell\ Übersetzt von: Sinautoshi am 20.05.2023 - 790600
„Privatsphäre ist für eine offene Gesellschaft im elektronischen Zeitalter notwendig. Privatsphäre ist keine Geheimhaltung. Eine private Angelegenheit ist etwas, von dem man nicht möchte, dass es die ganze Welt erfährt, aber eine geheime Angelegenheit ist etwas, von dem man nicht möchte, dass es irgendjemand erfährt." Privatsphäre ist die Macht, sich der Welt selektiv zu offenbaren.“ - Eric Hughes, A Cypherpunk's Manifesto , 1993
Privatsphäre ist für die Freiheit unerlässlich. Ohne Privatsphäre ist der Einzelne nicht in der Lage, frei von Überwachung und Kontrolle Entscheidungen zu treffen. Mangelnde Privatsphäre führt zum Verlust der Selbstbestimmung. Wenn Einzelpersonen ständig überwacht werden, schränkt dies unsere Fähigkeit ein, uns auszudrücken und Risiken einzugehen. Alle Entscheidungen, die wir treffen, können negative Auswirkungen auf diejenigen haben, die uns überwachen. Ohne die Freiheit, Entscheidungen zu treffen, kann der Einzelne nicht wirklich frei sein.
Freiheit ist für den Erwerb und Erhalt von Wohlstand von entscheidender Bedeutung. Wenn der Einzelne nicht die Freiheit hat, Entscheidungen zu treffen, hindern uns Einschränkungen und Beschränkungen daran, wirtschaftliche Chancen zu nutzen. Wenn es uns in einem solchen Umfeld irgendwie gelingt, Wohlstand zu erlangen, kann mangelnde Freiheit zur direkten Beschlagnahme von Vermögenswerten durch Regierungen oder andere böswillige Organisationen führen. Wenn die Freiheit gefährdet wird, führt dies im großen Maßstab zu weitverbreiteter wirtschaftlicher Stagnation und Armut. Der Schutz der Freiheit ist für den wirtschaftlichen Wohlstand von wesentlicher Bedeutung.
Der Zusammenhang zwischen Privatsphäre, Freiheit und Wohlstand ist entscheidend. Ohne Privatsphäre verliert der Einzelne die Freiheit, frei von Überwachung und Kontrolle Entscheidungen zu treffen. Während der Mangel an Freiheit den Einzelnen daran hindert, wirtschaftliche Chancen wahrzunehmen, und den Vermögenserhalt nahezu unmöglich macht. Keine Privatsphäre? Keine Freiheit. Keine Freiheit? Kein Wohlstand.
Rechte werden nicht gewährt. Sie werden eingenommen und verteidigt. Rechte werden oft als Erlaubnis der Machthaber missverstanden, etwas zu tun. Wenn dir jedoch jemand etwas geben kann, kann er es dir grundsätzlich nach Belieben wegnehmen. Im Laufe der Geschichte haben Menschen zwangsläufig für Grundrechte gekämpft, darunter Privatsphäre und Freiheit. Diese Rechte wurden nicht von den Machthabern gegeben, sondern durch Kampf eingefordert und erkämpft. Selbst nachdem diese Rechte erlangt wurden, müssen sie kontinuierlich verteidigt werden, um sicherzustellen, dass sie nicht weggenommen werden. Rechte werden nicht gewährt – sie werden durch Kampf erworben und durch Opfer verteidigt.
-
 @ 42342239:1d80db24
2025-02-23 10:00:20
@ 42342239:1d80db24
2025-02-23 10:00:20Europe's economic framework requires restructuring grounded in realism. The Commission's Competitiveness Compass, alas, reveals dangerous left-hemisphere dominance and risks repeating Mao's mistakes.
The European Commission presented its "competitiveness compass" in January. There will be massive investments in biotechnology, materials technology, medicines, space, and the defence industry. AI gigafactories are to be established, while Europe will "maintain its leadership in quantum technologies" (a leadership that few seem to be aware of). This will be achieved through more environmental labelling schemes, nature credits, procurement rules, platforms, cooperation plans, and coordination systems. Although the report contains some bright spots, such as promises to ease the regulatory burden, the overall picture is strikingly lacking in creativity. Instead, we are mainly met with the usual thought patterns of the European technocracy, which manifest in additional centralised frameworks, quantifiable goals, and annual reports. Mao's ghost haunts Brussels.
The Missing Half of Europe's Brain
Iain McGilchrist, a British psychiatrist and philosopher, has launched the hemispheric hypothesis (a theory about how the two hemispheres of the brain work). The left hemisphere is more detail- and control-oriented, while the right hemisphere is holistic and creative. A society dominated by the left hemisphere, like our own according to McGilchrist, "would see it as its task to control everything maximally." The Commission's compass appears similarly lobotomised , prioritising measurable processes over imaginative solutions.
In an earlier text, I mentioned that Europe might need to return to its roots and asked if Europe should have "the same end goal as China." This is still a relevant and justified question. But if we are honest, China has implemented a series of well-thought-out reforms since the 1980s, in addition to its many well-known and large-scale investments. It is not necessarily wrong to be inspired by China, as many believe; it depends on which China you are inspired by.
Lessons from the Cat Theory
When Deng Xiaoping returned to power in the late 1970s, he chose a more pragmatic approach than his predecessors. China left Mao Zedong's purges of dissidents behind. Instead, he launched the cat theory: "it doesn't matter what colour the cat is as long as it catches mice", regarding economic development. It was now free to experiment with different models. Instead of ideological conformity, the most important thing was to increase productivity and material prosperity.
What was done in China?
- Companies and individuals were given more freedom
- Provinces and municipalities were given more autonomy
- Special economic zones were established, with different conditions and rules
- Programs to increase the number of banks were introduced
- The banking sector was deregulated
- Property rights and contract law began to be respected
China has since gone from being an economic backwater to not only being the world's largest economy in terms of purchasing power but also a global tech contender (leading in 37 out of 44 key technologies per ASPI).
EU's Compliance Obsession vs Chinese Pragmatism
And today, when China is astonishing the world with surprisingly cheap and competent AI systems, which recently set American tech stocks in motion, in the EU one is met with advertisements for yet another compliance training, this time about AI. Every new compliance training echoes Mao's ghost – ideological correctness overriding practical results. Is prosperity really built with certifications, directives, requirements, and penalties?
When we compare the Chinese experience with today's EU, the contrast is clear:
- Freedoms are curtailed. The right to privacy is undermined (Chat Control, etc.)
- Member states' ability to self-govern is reduced, year by year
- Streamlining and harmony are popular buzzwords in the bureaucracy
- The ECB is actively working to reduce the number of banks
- The banking sector is being regulated more and more
- Property rights and contract law are being eroded, which can be partly attributed to developments in payment systems
Deng's cat theory was an example of when the right hemisphere was involved in decision-making. Rather than just focusing on details (the cat's colour), the whole (the result) was important. The Chinese proverb "cross the river by feeling the stones" is another example of more holistic thinking. Under Deng's leadership, reforms were first tested in a free zone or a province. After a while, the reforms could be evaluated before they were possibly implemented on a larger scale. "Try before you buy" is also a wise principle that follows from complexity research. In sharp contrast to this approach was Mao's "Great Leap Forward," a part of a disastrous five-year plan that shows what can happen when the left hemisphere is given too much power. A tragedy of historic proportions - a mass famine - resulted. While Deng exorcized Mao's ghost through pragmatic experimentation, Brussels seems determined to resurrect. Today's EU risks repeating Mao's mistake of letting political abstractions ("green transition! digital decade!") override reality – Mao's ghost surely smiles at nature credit schemes replacing actual market signals.
Mao's ghost trives on the ontological mistake
The serious problems that the EU is facing have been built up over decades and stem from incorrect assumptions. The economy is not complicated. It is complex. The concepts are often confused, but they describe two fundamentally different things. The complicated refers to something composite, but which can still be unfolded and then folded back up again without changing its essence. The complex, on the other hand, refers to something entangled, where every attempt to divide it changes its character. Compare, for example, an airplane engine with a béarnaise sauce. If you mix up the concepts, you make an ontological mistake, a philosopher would say. A programmer would say: garbage in, garbage out. Mao's ghost thrives on this ontological error, convincing technocrats they can blueprint society like a Soviet tractor factory.
When a system is complicated, predictable, and linear, centralised coordination and control by the left hemisphere can work well. But in complex systems, it can never be a solution because it leads to reduced adaptability and increased system risks. Instead, the goal should be diversity and decentralisation, which provide greater adaptability! The faster the changes of the system or in the environment, the greater the demands on adaptability and flexibility - if the system is to survive, that is. Increased diversity and decentralisation would not only increase adaptability and flexibility but also promote creativity, an ability that will likely become increasingly important in a world where AI and automation are changing the rules.
A better path forward
Europe's economic framework requires restructuring grounded in realism. The Commission's competitiveness compass - fixated on metrics and control - reveals dangerous left-hemisphere dominance, echoing Maoist central planning's epistemological errors. Our path forward demands:
- Dual-brain governance (prioritising creativity over control)
- Banishing of category mistakes (acknowledging the complex adaptive nature of the economy)
- Pragmatism over ideology (policy sandboxes inspired by China's special economic zones)
- Anti-fragile design (increased autonomy of EU nations, within states, and decentralised banking)
- Sunset clauses on all bureaucracy (regulators cannot originate breakthroughs)
The alternative? Another technocratic Great Leap Forward - eco-certified, AI-monitored, but economically brittle and fundamentally maladapted to the complex global economy. As Deng's reformers understood: no institutional architecture, not even the First Emperor's Terracotta Army, can withstand modernity's tide.
-
 @ a95c6243:d345522c
2025-03-01 10:39:35
@ a95c6243:d345522c
2025-03-01 10:39:35Ständige Lügen und Unterstellungen, permanent falsche Fürsorge \ können Bausteine von emotionaler Manipulation sein. Mit dem Zweck, \ Macht und Kontrolle über eine andere Person auszuüben. \ Apotheken Umschau
Irgendetwas muss passiert sein: «Gaslighting» ist gerade Thema in vielen Medien. Heute bin ich nach längerer Zeit mal wieder über dieses Stichwort gestolpert. Das war in einem Artikel von Norbert Häring über Manipulationen des Deutschen Wetterdienstes (DWD). In diesem Fall ging es um eine Pressemitteilung vom Donnerstag zum «viel zu warmen» Winter 2024/25.
Häring wirft der Behörde vor, dreist zu lügen und Dinge auszulassen, um die Klimaangst wach zu halten. Was der Leser beim DWD nicht erfahre, sei, dass dieser Winter kälter als die drei vorangegangenen und kälter als der Durchschnitt der letzten zehn Jahre gewesen sei. Stattdessen werde der falsche Eindruck vermittelt, es würde ungebremst immer wärmer.
Wem also der zu Ende gehende Winter eher kalt vorgekommen sein sollte, mit dessen Empfinden stimme wohl etwas nicht. Das jedenfalls wolle der DWD uns einreden, so der Wirtschaftsjournalist. Und damit sind wir beim Thema Gaslighting.
Als Gaslighting wird eine Form psychischer Manipulation bezeichnet, mit der die Opfer desorientiert und zutiefst verunsichert werden, indem ihre eigene Wahrnehmung als falsch bezeichnet wird. Der Prozess führt zu Angst und Realitätsverzerrung sowie zur Zerstörung des Selbstbewusstseins. Die Bezeichnung kommt von dem britischen Theaterstück «Gas Light» aus dem Jahr 1938, in dem ein Mann mit grausamen Psychotricks seine Frau in den Wahnsinn treibt.
Damit Gaslighting funktioniert, muss das Opfer dem Täter vertrauen. Oft wird solcher Psychoterror daher im privaten oder familiären Umfeld beschrieben, ebenso wie am Arbeitsplatz. Jedoch eignen sich die Prinzipien auch perfekt zur Manipulation der Massen. Vermeintliche Autoritäten wie Ärzte und Wissenschaftler, oder «der fürsorgliche Staat» und Institutionen wie die UNO oder die WHO wollen uns doch nichts Böses. Auch Staatsmedien, Faktenchecker und diverse NGOs wurden zu «vertrauenswürdigen Quellen» erklärt. Das hat seine Wirkung.
Warum das Thema Gaslighting derzeit scheinbar so populär ist, vermag ich nicht zu sagen. Es sind aber gerade in den letzten Tagen und Wochen auffällig viele Artikel dazu erschienen, und zwar nicht nur von Psychologen. Die Frankfurter Rundschau hat gleich mehrere publiziert, und Anwälte interessieren sich dafür offenbar genauso wie Apotheker.
Die Apotheken Umschau machte sogar auf «Medical Gaslighting» aufmerksam. Davon spreche man, wenn Mediziner Symptome nicht ernst nähmen oder wenn ein gesundheitliches Problem vom behandelnden Arzt «schnöde heruntergespielt» oder abgetan würde. Kommt Ihnen das auch irgendwie bekannt vor? Der Begriff sei allerdings irreführend, da er eine manipulierende Absicht unterstellt, die «nicht gewährleistet» sei.
Apropos Gaslighting: Die noch amtierende deutsche Bundesregierung meldete heute, es gelte, «weiter [sic!] gemeinsam daran zu arbeiten, einen gerechten und dauerhaften Frieden für die Ukraine zu erreichen». Die Ukraine, wo sich am Montag «der völkerrechtswidrige Angriffskrieg zum dritten Mal jährte», verteidige ihr Land und «unsere gemeinsamen Werte».
Merken Sie etwas? Das Demokratieverständnis mag ja tatsächlich inzwischen in beiden Ländern ähnlich traurig sein. Bezüglich Friedensbemühungen ist meine Wahrnehmung jedoch eine andere. Das muss an meinem Gedächtnis liegen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 42342239:1d80db24
2025-02-16 08:39:59
@ 42342239:1d80db24
2025-02-16 08:39:59Almost 150 years ago, the British newspaper editor William Thomas Stead wrote that "the editorial pen is a sceptre of power, compared with which the sceptre of many a monarch is but a gilded lath". He had begun to regard journalism as something more than just conveying information - the journalist or editor could become a ruler.
Times had certainly changed compared to a few hundred years earlier. Before Gutenberg's invention of the printing press, it was mainly the church that controlled the dissemination of information in Europe, but when Stead put pen to paper, this control had shifted to newspapers, schools, and universities. Eventually, technologies like radio and TV entered the scene, but the power dynamics remained asymmetrical - only a few could send information to the many.
However, with the emergence of the internet, and especially with the spread of social media, a significant change followed. Instead of only a few being able to send information to the many, many could send to many. Almost anyone could now create their own newspaper, radio, or TV channel. The power over information dissemination was decentralised.
Ten years ago, Roberta Alenius, who was then press secretary for Sweden's Prime Minister Fredrik Reinfeldt of the Moderate Party, shared her experiences with Social Democratic and Moderate Party internet activists on social media. She reported that social media played a significant role in how news "comes out" and is shaped, and that journalism was now downstream of social media. Five years later, NATO's then-Secretary-General Jens Stoltenberg said that "NATO must be prepared for both conventional and hybrid threats: from tanks to tweets." This finally underscores the importance of social media.
Elon Musk, who took over X (formerly Twitter) in 2022, has claimed that "it's absolutely fundamental and transformative that the people actually get to decide the news and narrative and what's important," and that citizen journalism is the future.
While his platform allows most expressions - for better or worse - the reach of messages is instead limited ("freedom of speech does not mean freedom of reach "). X has also opened its recommendation algorithm to the outside world by making it open-source. Although this is a welcome step, the fact remains that it's impossible to know which code is actually used and what adjustments are made by humans or algorithms.
William Thomas Stead's "sceptre of power", which has wandered from the church to newspaper and TV editorial offices, and now to citizens according to Elon Musk, risks being transferred to algorithms' opaque methods?
Instead of talking about "toxic algorithms" and TikTok bans, like the so many do today, we should ask ourselves more fundamental questions. What happens when algorithms are no longer objective (how can they ever be?), but instead become tools for shaping our reality? Perhaps our greatest challenge today is not deciding who should govern the information landscape, but instead recognising that no one is up to the task - not even well-ventilated computers.
-
 @ 42342239:1d80db24
2025-02-14 08:42:40
@ 42342239:1d80db24
2025-02-14 08:42:40A recent US data leak has brought to light a disturbing reality: our everyday technology has become a powerful tool for surveillance and control. Paradoxically, new technology holds the key to creating a safer, more resilient, and perhaps even more human society.
Preparedness remains a multifaceted topic that continues to spark engagement. The subject is not just about energy infrastructure and food supply but also about seemingly more orthogonal issues like obesity and cybersecurity.
The significant importance of cybersecurity can be illustrated by examples from an American company that was recently subjected to an IT intrusion with a subsequent data leak. The company, Gravy Analytics, specializes in providing mobile phone data that provides exceptionally detailed information about where individuals are located at any given time. Data that can be used, for example, for advertising purposes, but also for more sinister purposes such as extortion or espionage. The company has previously been accused of using misleading methods to collect location data without valid consent from individuals.
Mobile operators have long had the ability to locate their subscribers' positions over time. This leak shows how even apps on your phone risk revealing your location. Analysis of the samples leaked from the leak shows that data has leaked out for users of several well-known mobile applications, including the popular mobile game Candy Crush and the widely used online dating service Tinder.
Even if apps only use an ad ID when collecting data, these collected digital breadcrumbs can often be deanonymized. It is possible, for example, to identify daily routines, workplaces, and where and when an individual usually sleeps. This usually enables identification. But it is also possible to map an individual's social circle and romantic relationships. The mapping risks quickly becoming both sensitive and invasive.
The fact that such data is collected, but especially that it leaks, also poses a threat to preparedness. By mapping military or other sensitive locations (energy supply, water treatment plants, critical infrastructure) along with location and time data, it is potentially possible to identify employees at these locations. Information that can then be used by those who want to cause harm.
It is not written in the stars that citizens must be dependent on a few large IT companies. Our data does not need to be collected and used in a way that does not benefit us, without our knowledge. There are alternatives to large-scale and "super-registers". Technology such as asymmetric encryption and zero-knowledge proofs can be used to give power back to the individual. If the parliament and government are serious about improving preparedness, it is high time to leave old thought patterns like Chat Control 2 behind and instead explore such possibilities.
The primary purpose of the internet was originally to enable information transfer without intermediaries ("peer-to-peer"). Today, intermediaries are everywhere. It is worth remembering that peer-to-peer is not some obscure technical term. In case we have forgotten about it, it simply means: person to person, without intermediaries.
Maybe new technology can not only give us a safer and more resilient society, but also a more human one?
-
 @ a95c6243:d345522c
2025-02-21 19:32:23
@ a95c6243:d345522c
2025-02-21 19:32:23Europa – das Ganze ist eine wunderbare Idee, \ aber das war der Kommunismus auch. \ Loriot
«Europa hat fertig», könnte man unken, und das wäre nicht einmal sehr verwegen. Mit solch einer Einschätzung stünden wir nicht alleine, denn die Stimmen in diese Richtung mehren sich. Der französische Präsident Emmanuel Macron warnte schon letztes Jahr davor, dass «unser Europa sterben könnte». Vermutlich hatte er dabei andere Gefahren im Kopf als jetzt der ungarische Ministerpräsident Viktor Orbán, der ein «baldiges Ende der EU» prognostizierte. Das Ergebnis könnte allerdings das gleiche sein.
Neben vordergründigen Themenbereichen wie Wirtschaft, Energie und Sicherheit ist das eigentliche Problem jedoch die obskure Mischung aus aufgegebener Souveränität und geschwollener Arroganz, mit der europäische Politiker:innende unterschiedlicher Couleur aufzutreten pflegen. Und das Tüpfelchen auf dem i ist die bröckelnde Legitimation politischer Institutionen dadurch, dass die Stimmen großer Teile der Bevölkerung seit Jahren auf vielfältige Weise ausgegrenzt werden.
Um «UnsereDemokratie» steht es schlecht. Dass seine Mandate immer schwächer werden, merkt natürlich auch unser «Führungspersonal». Entsprechend werden die Maßnahmen zur Gängelung, Überwachung und Manipulation der Bürger ständig verzweifelter. Parallel dazu plustern sich in Paris Macron, Scholz und einige andere noch einmal mächtig in Sachen Verteidigung und «Kriegstüchtigkeit» auf.
Momentan gilt es auch, das Überschwappen covidiotischer und verschwörungsideologischer Auswüchse aus den USA nach Europa zu vermeiden. So ein «MEGA» (Make Europe Great Again) können wir hier nicht gebrauchen. Aus den Vereinigten Staaten kommen nämlich furchtbare Nachrichten. Beispielsweise wurde einer der schärfsten Kritiker der Corona-Maßnahmen kürzlich zum Gesundheitsminister ernannt. Dieser setzt sich jetzt für eine Neubewertung der mRNA-«Impfstoffe» ein, was durchaus zu einem Entzug der Zulassungen führen könnte.
Der europäischen Version von «Verteidigung der Demokratie» setzte der US-Vizepräsident J. D. Vance auf der Münchner Sicherheitskonferenz sein Verständnis entgegen: «Demokratie stärken, indem wir unseren Bürgern erlauben, ihre Meinung zu sagen». Das Abschalten von Medien, das Annullieren von Wahlen oder das Ausschließen von Menschen vom politischen Prozess schütze gar nichts. Vielmehr sei dies der todsichere Weg, die Demokratie zu zerstören.
In der Schweiz kamen seine Worte deutlich besser an als in den meisten europäischen NATO-Ländern. Bundespräsidentin Karin Keller-Sutter lobte die Rede und interpretierte sie als «Plädoyer für die direkte Demokratie». Möglicherweise zeichne sich hier eine außenpolitische Kehrtwende in Richtung integraler Neutralität ab, meint mein Kollege Daniel Funk. Das wären doch endlich mal ein paar gute Nachrichten.
Von der einstigen Idee einer europäischen Union mit engeren Beziehungen zwischen den Staaten, um Konflikte zu vermeiden und das Wohlergehen der Bürger zu verbessern, sind wir meilenweit abgekommen. Der heutige korrupte Verbund unter technokratischer Leitung ähnelt mehr einem Selbstbedienungsladen mit sehr begrenztem Zugang. Die EU-Wahlen im letzten Sommer haben daran ebenso wenig geändert, wie die Bundestagswahl am kommenden Sonntag darauf einen Einfluss haben wird.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-02-19 09:23:17
@ a95c6243:d345522c
2025-02-19 09:23:17Die «moralische Weltordnung» – eine Art Astrologie. Friedrich Nietzsche
Das Treffen der BRICS-Staaten beim Gipfel im russischen Kasan war sicher nicht irgendein politisches Event. Gastgeber Wladimir Putin habe «Hof gehalten», sagen die Einen, China und Russland hätten ihre Vorstellung einer multipolaren Weltordnung zelebriert, schreiben Andere.
In jedem Fall zeigt die Anwesenheit von über 30 Delegationen aus der ganzen Welt, dass von einer geostrategischen Isolation Russlands wohl keine Rede sein kann. Darüber hinaus haben sowohl die Anreise von UN-Generalsekretär António Guterres als auch die Meldungen und Dementis bezüglich der Beitrittsbemühungen des NATO-Staats Türkei für etwas Aufsehen gesorgt.
Im Spannungsfeld geopolitischer und wirtschaftlicher Umbrüche zeigt die neue Allianz zunehmendes Selbstbewusstsein. In Sachen gemeinsamer Finanzpolitik schmiedet man interessante Pläne. Größere Unabhängigkeit von der US-dominierten Finanzordnung ist dabei ein wichtiges Ziel.
Beim BRICS-Wirtschaftsforum in Moskau, wenige Tage vor dem Gipfel, zählte ein nachhaltiges System für Finanzabrechnungen und Zahlungsdienste zu den vorrangigen Themen. Während dieses Treffens ging der russische Staatsfonds eine Partnerschaft mit dem Rechenzentrumsbetreiber BitRiver ein, um Bitcoin-Mining-Anlagen für die BRICS-Länder zu errichten.
Die Initiative könnte ein Schritt sein, Bitcoin und andere Kryptowährungen als Alternativen zu traditionellen Finanzsystemen zu etablieren. Das Projekt könnte dazu führen, dass die BRICS-Staaten den globalen Handel in Bitcoin abwickeln. Vor dem Hintergrund der Diskussionen über eine «BRICS-Währung» wäre dies eine Alternative zu dem ursprünglich angedachten Korb lokaler Währungen und zu goldgedeckten Währungen sowie eine mögliche Ergänzung zum Zahlungssystem BRICS Pay.
Dient der Bitcoin also der Entdollarisierung? Oder droht er inzwischen, zum Gegenstand geopolitischer Machtspielchen zu werden? Angesichts der globalen Vernetzungen ist es oft schwer zu durchschauen, «was eine Show ist und was im Hintergrund von anderen Strippenziehern insgeheim gesteuert wird». Sicher können Strukturen wie Bitcoin auch so genutzt werden, dass sie den Herrschenden dienlich sind. Aber die Grundeigenschaft des dezentralisierten, unzensierbaren Peer-to-Peer Zahlungsnetzwerks ist ihm schließlich nicht zu nehmen.
Wenn es nach der EZB oder dem IWF geht, dann scheint statt Instrumentalisierung momentan eher der Kampf gegen Kryptowährungen angesagt. Jürgen Schaaf, Senior Manager bei der Europäischen Zentralbank, hat jedenfalls dazu aufgerufen, Bitcoin «zu eliminieren». Der Internationale Währungsfonds forderte El Salvador, das Bitcoin 2021 als gesetzliches Zahlungsmittel eingeführt hat, kürzlich zu begrenzenden Maßnahmen gegen das Kryptogeld auf.
Dass die BRICS-Staaten ein freiheitliches Ansinnen im Kopf haben, wenn sie Kryptowährungen ins Spiel bringen, darf indes auch bezweifelt werden. Im Abschlussdokument bekennen sich die Gipfel-Teilnehmer ausdrücklich zur UN, ihren Programmen und ihrer «Agenda 2030». Ernst Wolff nennt das «eine Bankrotterklärung korrupter Politiker, die sich dem digital-finanziellen Komplex zu 100 Prozent unterwerfen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 42342239:1d80db24
2025-02-10 08:16:32
@ 42342239:1d80db24
2025-02-10 08:16:32The risks associated with cryptocurrencies have recently received attention in the media, where e.g. the Swedish Financial Supervisory Authority warns of the high volatility and risk of investments in crypto. Within the EU, as usual, significant efforts are being made to expand the already extensive regulatory framework. Meanwhile, in the US, there has been a marked turnaround. Even the presidential family has launched their own cryptocurrencies, resulting in criticism from industry experts .
Important perspectives, however, are conspicuous by their absence in the conversation.
Iain McGilchrist, a British psychiatrist and philosopher, has introduced the hemispheric hypothesis (a theory about how the brain's two hemispheres function). The left hemisphere is more detail- and control-oriented, while the right hemisphere is more holistic. A society dominated by the left hemisphere, such as our own according to McGilchrist , "would see it as its task to control everything maximally and would have a paranoid feeling that we need to have surveillance cameras everywhere...".
During a speech at the World Economic Forum, President Trump recently stated that conservatives complain about big banks, such as Bank of America, not allowing them to conduct business within the bank. Critics argue that the American banking system has been used to persecute political opponents, both during Obama's and Biden's terms. Under Obama, 'Operation Chokepoint' was introduced to limit certain businesses' access to banking services. A subcommittee in the Senate now wants to eradicate this phenomenon.
More and more people are discovering that their money is not always under their control. Non-profit associations and congregations are not allowed to open bank accounts. Sometimes they are even thrown out as bank customers. Others may report being subjected to lengthy interrogations by the bank about what they intend to do with their money, even when they just want to transfer funds between their own accounts. Rejected churches are met with silence, while a bank account is (still!) necessary to fully operate in society.
When leading economists at the International Monetary Fund (IMF) argue that a cashless society can threaten fundamental rights , including property rights, when churches are refused bank accounts in what is described as "a threat to civil society" and when regulations still fail to combat organised crime , is it not reasonable to wonder if we are on the right path?
With cash, people can pay freely without intermediaries, which constitutes a form of financial freedom. The notes you hold in your hand are your own. Cryptocurrencies, such as Bitcoin, offer a similar possibility: an electronic, peer-to-peer cash system (person to person).
A society dominated by the left hemisphere results in a pathological need for control, according to McGilchrist. A more holistic perspective, taking into account the right hemisphere, would acknowledge that too much control can be detrimental, that property rights are a fundamental right, and that financial freedom is a human right. Do these perspectives not deserve more attention?
-
 @ a95c6243:d345522c
2025-02-15 19:05:38
@ a95c6243:d345522c
2025-02-15 19:05:38Auf der diesjährigen Münchner Sicherheitskonferenz geht es vor allem um die Ukraine. Protagonisten sind dabei zunächst die US-Amerikaner. Präsident Trump schockierte die Europäer kurz vorher durch ein Telefonat mit seinem Amtskollegen Wladimir Putin, während Vizepräsident Vance mit seiner Rede über Demokratie und Meinungsfreiheit für versteinerte Mienen und Empörung sorgte.
Die Bemühungen der Europäer um einen Frieden in der Ukraine halten sich, gelinde gesagt, in Grenzen. Größeres Augenmerk wird auf militärische Unterstützung, die Pflege von Feindbildern sowie Eskalation gelegt. Der deutsche Bundeskanzler Scholz reagierte auf die angekündigten Verhandlungen über einen möglichen Frieden für die Ukraine mit der Forderung nach noch höheren «Verteidigungsausgaben». Auch die amtierende Außenministerin Baerbock hatte vor der Münchner Konferenz klargestellt:
«Frieden wird es nur durch Stärke geben. (...) Bei Corona haben wir gesehen, zu was Europa fähig ist. Es braucht erneut Investitionen, die der historischen Wegmarke, vor der wir stehen, angemessen sind.»
Die Rüstungsindustrie freut sich in jedem Fall über weltweit steigende Militärausgaben. Die Kriege in der Ukraine und in Gaza tragen zu Rekordeinnahmen bei. Jetzt «winkt die Aussicht auf eine jahrelange große Nachrüstung in Europa», auch wenn der Ukraine-Krieg enden sollte, so hört man aus Finanzkreisen. In der Konsequenz kennt «die Aktie des deutschen Vorzeige-Rüstungskonzerns Rheinmetall in ihrem Anstieg offenbar gar keine Grenzen mehr». «Solche Friedensversprechen» wie das jetzige hätten in der Vergangenheit zu starken Kursverlusten geführt.
Für manche Leute sind Kriegswaffen und sonstige Rüstungsgüter Waren wie alle anderen, jedenfalls aus der Perspektive von Investoren oder Managern. Auch in diesem Bereich gibt es Startups und man spricht von Dingen wie innovativen Herangehensweisen, hocheffizienten Produktionsanlagen, skalierbaren Produktionstechniken und geringeren Stückkosten.
Wir lesen aktuell von Massenproduktion und gesteigerten Fertigungskapazitäten für Kriegsgerät. Der Motor solcher Dynamik und solchen Wachstums ist die Aufrüstung, die inzwischen permanent gefordert wird. Parallel wird die Bevölkerung verbal eingestimmt und auf Kriegstüchtigkeit getrimmt.
Das Rüstungs- und KI-Startup Helsing verkündete kürzlich eine «dezentrale Massenproduktion für den Ukrainekrieg». Mit dieser Expansion positioniere sich das Münchner Unternehmen als einer der weltweit führenden Hersteller von Kampfdrohnen. Der nächste «Meilenstein» steht auch bereits an: Man will eine Satellitenflotte im Weltraum aufbauen, zur Überwachung von Gefechtsfeldern und Truppenbewegungen.
Ebenfalls aus München stammt das als DefenseTech-Startup bezeichnete Unternehmen ARX Robotics. Kürzlich habe man in der Region die größte europäische Produktionsstätte für autonome Verteidigungssysteme eröffnet. Damit fahre man die Produktion von Militär-Robotern hoch. Diese Expansion diene auch der Lieferung der «größten Flotte unbemannter Bodensysteme westlicher Bauart» in die Ukraine.
Rüstung boomt und scheint ein Zukunftsmarkt zu sein. Die Hersteller und Vermarkter betonen, mit ihren Aktivitäten und Produkten solle die europäische Verteidigungsfähigkeit erhöht werden. Ihre Strategien sollten sogar «zum Schutz demokratischer Strukturen beitragen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-02-07 19:42:11
@ c631e267:c2b78d3e
2025-02-07 19:42:11Nur wenn wir aufeinander zugehen, haben wir die Chance \ auf Überwindung der gegenseitigen Ressentiments! \ Dr. med. dent. Jens Knipphals
In Wolfsburg sollte es kürzlich eine Gesprächsrunde von Kritikern der Corona-Politik mit Oberbürgermeister Dennis Weilmann und Vertretern der Stadtverwaltung geben. Der Zahnarzt und langjährige Maßnahmenkritiker Jens Knipphals hatte diese Einladung ins Rathaus erwirkt und publiziert. Seine Motivation:
«Ich möchte die Spaltung der Gesellschaft überwinden. Dazu ist eine umfassende Aufarbeitung der Corona-Krise in der Öffentlichkeit notwendig.»
Schon früher hatte Knipphals Antworten von den Kommunalpolitikern verlangt, zum Beispiel bei öffentlichen Bürgerfragestunden. Für das erwartete Treffen im Rathaus formulierte er Fragen wie: Warum wurden fachliche Argumente der Kritiker ignoriert? Weshalb wurde deren Ausgrenzung, Diskreditierung und Entmenschlichung nicht entgegengetreten? In welcher Form übernehmen Rat und Verwaltung in Wolfsburg persönlich Verantwortung für die erheblichen Folgen der politischen Corona-Krise?
Der Termin fand allerdings nicht statt – der Bürgermeister sagte ihn kurz vorher wieder ab. Knipphals bezeichnete Weilmann anschließend als Wiederholungstäter, da das Stadtoberhaupt bereits 2022 zu einem Runden Tisch in der Sache eingeladen hatte, den es dann nie gab. Gegenüber Multipolar erklärte der Arzt, Weilmann wolle scheinbar eine öffentliche Aufarbeitung mit allen Mitteln verhindern. Er selbst sei «inzwischen absolut desillusioniert» und die einzige Lösung sei, dass die Verantwortlichen gingen.
Die Aufarbeitung der Plandemie beginne bei jedem von uns selbst, sei aber letztlich eine gesamtgesellschaftliche Aufgabe, schreibt Peter Frey, der den «Fall Wolfsburg» auch in seinem Blog behandelt. Diese Aufgabe sei indes deutlich größer, als viele glaubten. Erfreulicherweise sei der öffentliche Informationsraum inzwischen größer, trotz der weiterhin unverfrorenen Desinformations-Kampagnen der etablierten Massenmedien.
Frey erinnert daran, dass Dennis Weilmann mitverantwortlich für gravierende Grundrechtseinschränkungen wie die 2021 eingeführten 2G-Regeln in der Wolfsburger Innenstadt zeichnet. Es sei naiv anzunehmen, dass ein Funktionär einzig im Interesse der Bürger handeln würde. Als früherer Dezernent des Amtes für Wirtschaft, Digitalisierung und Kultur der Autostadt kenne Weilmann zum Beispiel die Verknüpfung von Fördergeldern mit politischen Zielsetzungen gut.
Wolfsburg wurde damals zu einem Modellprojekt des Bundesministeriums des Innern (BMI) und war Finalist im Bitkom-Wettbewerb «Digitale Stadt». So habe rechtzeitig vor der Plandemie das Projekt «Smart City Wolfsburg» anlaufen können, das der Stadt «eine Vorreiterrolle für umfassende Vernetzung und Datenerfassung» aufgetragen habe, sagt Frey. Die Vereinten Nationen verkauften dann derartige «intelligente» Überwachungs- und Kontrollmaßnahmen ebenso als Rettung in der Not wie das Magazin Forbes im April 2020:
«Intelligente Städte können uns helfen, die Coronavirus-Pandemie zu bekämpfen. In einer wachsenden Zahl von Ländern tun die intelligenten Städte genau das. Regierungen und lokale Behörden nutzen Smart-City-Technologien, Sensoren und Daten, um die Kontakte von Menschen aufzuspüren, die mit dem Coronavirus infiziert sind. Gleichzeitig helfen die Smart Cities auch dabei, festzustellen, ob die Regeln der sozialen Distanzierung eingehalten werden.»
Offensichtlich gibt es viele Aspekte zu bedenken und zu durchleuten, wenn es um die Aufklärung und Aufarbeitung der sogenannten «Corona-Pandemie» und der verordneten Maßnahmen geht. Frustration und Desillusion sind angesichts der Realitäten absolut verständlich. Gerade deswegen sind Initiativen wie die von Jens Knipphals so bewundernswert und so wichtig – ebenso wie eine seiner Kernthesen: «Wir müssen aufeinander zugehen, da hilft alles nichts».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 42342239:1d80db24
2025-01-18 08:31:05
@ 42342239:1d80db24
2025-01-18 08:31:05Preparedness is a hot topic these days. In Europe, Poland has recently introduced compulsory lessons in weapons handling for schoolchildren for war-preparedness purposes. In Sweden, the Swedish Civil Contingencies Agency (MSB) has recently published the brochure on what to do "If crisis or war comes".
However, in the event of war, a country must have a robust energy infrastructure. Sweden does not seem to have this, at least judging by the recent years' electricity price turbulence in southern Sweden. Nor does Germany. The vulnerabilities are many and serious. It's hard not to be reminded of a Swedish prime minister who, just eleven years ago, saw defense as a special interest.
A secure food supply is another crucial factor for a country's resilience. This is something that Sweden lacks. In the early 1990s, nearly 75 percent of the country's food was produced domestically. Today, half of it must be imported. This makes our country more vulnerable to crises and disruptions. Despite our extensive agricultural areas, we are not even self-sufficient in basic commodities like potatoes, which is remarkable.
The government's signing of the Kunming-Montreal Framework for Biological Diversity two years ago risks exacerbating the situation. According to the framework, countries must significantly increase their protected areas over the coming years. The goal is to protect biological diversity. By 2030, at least 30% of all areas, on land and at sea, must be conserved. Sweden, which currently conserves around 15%, must identify large areas to be protected over the coming years. With shrinking fields, we risk getting less wheat, fewer potatoes, and less rapeseed. It's uncertain whether technological advancements can compensate for this, especially when the amount of pesticides and industrial fertilizers must be reduced significantly.
In Danish documents on the "roadmap for sustainable development" of the food system, the possibility of redistributing agricultural land (land distribution reforms) and agreements on financing for restoring cultivated land to wetlands (the restoration of cultivated, carbon-rich soils) are discussed. One cannot avoid the impression that the cultivated areas need to be reduced, in some cases significantly.
The green transition has been a priority on the political agenda in recent years, with the goal of reducing carbon emissions and increasing biological diversity. However, it has become clear that the transition risks having consequences for our preparedness.
One example is the debate about wind power. On the one hand, wind power is said to contribute to reducing carbon emissions and increasing renewable energy. On the other hand, it is said to pose a security risk, as wind turbines can affect radio communication and radar surveillance.
Of course, it's easy to be in favor of biological diversity, but what do we do if this goal comes into conflict with the needs of a robust societal preparedness? Then we are faced with a difficult prioritization. Should we put the safety of people and society before the protection of nature, or vice versa?
“Politics is not the art of the possible. It consists in choosing between the disastrous and the unpalatable” said J. K. Galbraith, one of the most influential economists of the 20th century. Maybe we can’t both eat the cake and have it too?
-
 @ a95c6243:d345522c
2025-01-31 20:02:25
@ a95c6243:d345522c
2025-01-31 20:02:25Im Augenblick wird mit größter Intensität, großer Umsicht \ das deutsche Volk belogen. \ Olaf Scholz im FAZ-Interview
Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur Reuters Verbreitung in den Medien gefunden hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten.
Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen sei repräsentativ, behauptet der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von Mitgliedern, die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben».
Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH, also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges «Demokratie-Update» aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet.
Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer befürchteten, dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen.
Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein? Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise abgelehnt. Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen.
Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen, die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter berichtet. Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert».
Der Vorwand «unzulässiger Einflussnahme» auf Politik und Wahlen wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als «völlig irre» bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird «E-Voting» seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg.
Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus. Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die weit verbreitete Armut zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ f88e6629:e5254dd5
2025-01-17 14:10:19
@ f88e6629:e5254dd5
2025-01-17 14:10:19...which allow online payments to be sent directly from one party to another without going through a financial institution.
- Without sovereign and accessible payments we are loosing censorship resistance
- Without censorship resistance even other core characteristics are in danger - including scarcity and durability.
- This affects every bitcoiner including sworn hodlers and MSTR followers.
| Property | Description | Fulfillment | | --- | --- | --- | | Scarce | Fixed supply forever. Instantly and costlessly verifiable | 🟢 Good, but can be harmed without censorship resistance | | Portable | Effortless to store and move, with negligible costs | 🟠 Onchain transactions can be expensive, other layers require onchain to be sovereign. Easy portability is offered by custodians only. | | Divisible | Infinitely divisible | 🟠 Smaller units than dust are available only for LN users, which most people can’t use in a sovereign way. | | Durable | Exists forever without deterioration | 🟢 Good, but can be harmed without censorship resistance | | Fungible | Every piece is forever the same as every other piece | 🟡 Onchain bitcoin is not fungible. | | Acceptable | Everyone, anywhere, can send and receive | 🟠 Most people are not able to send and receive in a sovereign way. | | Censorship Resistant | You hold it. Nobody can take it or stop you sending it | 🟠 Custodians are honey-pots that can and will be regulated |
➡️ We need accessible, scalable, and sovereign payment methods
-
 @ a95c6243:d345522c
2025-01-24 20:59:01
@ a95c6243:d345522c
2025-01-24 20:59:01Menschen tun alles, egal wie absurd, \ um ihrer eigenen Seele nicht zu begegnen. \ Carl Gustav Jung
«Extremer Reichtum ist eine Gefahr für die Demokratie», sagen über die Hälfte der knapp 3000 befragten Millionäre aus G20-Staaten laut einer Umfrage der «Patriotic Millionaires». Ferner stellte dieser Zusammenschluss wohlhabender US-Amerikaner fest, dass 63 Prozent jener Millionäre den Einfluss von Superreichen auf US-Präsident Trump als Bedrohung für die globale Stabilität ansehen.
Diese Besorgnis haben 370 Millionäre und Milliardäre am Dienstag auch den in Davos beim WEF konzentrierten Privilegierten aus aller Welt übermittelt. In einem offenen Brief forderten sie die «gewählten Führer» auf, die Superreichen – also sie selbst – zu besteuern, um «die zersetzenden Auswirkungen des extremen Reichtums auf unsere Demokratien und die Gesellschaft zu bekämpfen». Zum Beispiel kontrolliere eine handvoll extrem reicher Menschen die Medien, beeinflusse die Rechtssysteme in unzulässiger Weise und verwandele Recht in Unrecht.
Schon 2019 beanstandete der bekannte Historiker und Schriftsteller Ruthger Bregman an einer WEF-Podiumsdiskussion die Steuervermeidung der Superreichen. Die elitäre Veranstaltung bezeichnete er als «Feuerwehr-Konferenz, bei der man nicht über Löschwasser sprechen darf.» Daraufhin erhielt Bregman keine Einladungen nach Davos mehr. Auf seine Aussagen machte der Schweizer Aktivist Alec Gagneux aufmerksam, der sich seit Jahrzehnten kritisch mit dem WEF befasst. Ihm wurde kürzlich der Zutritt zu einem dreiteiligen Kurs über das WEF an der Volkshochschule Region Brugg verwehrt.
Nun ist die Erkenntnis, dass mit Geld politischer Einfluss einhergeht, alles andere als neu. Und extremer Reichtum macht die Sache nicht wirklich besser. Trotzdem hat man über Initiativen wie Patriotic Millionaires oder Taxmenow bisher eher selten etwas gehört, obwohl es sie schon lange gibt. Auch scheint es kein Problem, wenn ein Herr Gates fast im Alleingang versucht, globale Gesundheits-, Klima-, Ernährungs- oder Bevölkerungspolitik zu betreiben – im Gegenteil. Im Jahr, als der Milliardär Donald Trump zum zweiten Mal ins Weiße Haus einzieht, ist das Echo in den Gesinnungsmedien dagegen enorm – und uniform, wer hätte das gedacht.
Der neue US-Präsident hat jedoch «Davos geerdet», wie Achgut es nannte. In seiner kurzen Rede beim Weltwirtschaftsforum verteidigte er seine Politik und stellte klar, er habe schlicht eine «Revolution des gesunden Menschenverstands» begonnen. Mit deutlichen Worten sprach er unter anderem von ersten Maßnahmen gegen den «Green New Scam», und von einem «Erlass, der jegliche staatliche Zensur beendet»:
«Unsere Regierung wird die Äußerungen unserer eigenen Bürger nicht mehr als Fehlinformation oder Desinformation bezeichnen, was die Lieblingswörter von Zensoren und derer sind, die den freien Austausch von Ideen und, offen gesagt, den Fortschritt verhindern wollen.»
Wie der «Trumpismus» letztlich einzuordnen ist, muss jeder für sich selbst entscheiden. Skepsis ist definitiv angebracht, denn «einer von uns» sind weder der Präsident noch seine auserwählten Teammitglieder. Ob sie irgendeinen Sumpf trockenlegen oder Staatsverbrechen aufdecken werden oder was aus WHO- und Klimaverträgen wird, bleibt abzuwarten.
Das WHO-Dekret fordert jedenfalls die Übertragung der Gelder auf «glaubwürdige Partner», die die Aktivitäten übernehmen könnten. Zufällig scheint mit «Impfguru» Bill Gates ein weiterer Harris-Unterstützer kürzlich das Lager gewechselt zu haben: Nach einem gemeinsamen Abendessen zeigte er sich «beeindruckt» von Trumps Interesse an der globalen Gesundheit.
Mit dem Projekt «Stargate» sind weitere dunkle Wolken am Erwartungshorizont der Fangemeinde aufgezogen. Trump hat dieses Joint Venture zwischen den Konzernen OpenAI, Oracle, und SoftBank als das «größte KI-Infrastrukturprojekt der Geschichte» angekündigt. Der Stein des Anstoßes: Oracle-CEO Larry Ellison, der auch Fan von KI-gestützter Echtzeit-Überwachung ist, sieht einen weiteren potenziellen Einsatz der künstlichen Intelligenz. Sie könne dazu dienen, Krebserkrankungen zu erkennen und individuelle mRNA-«Impfstoffe» zur Behandlung innerhalb von 48 Stunden zu entwickeln.
Warum bitte sollten sich diese superreichen «Eliten» ins eigene Fleisch schneiden und direkt entgegen ihren eigenen Interessen handeln? Weil sie Menschenfreunde, sogenannte Philanthropen sind? Oder vielleicht, weil sie ein schlechtes Gewissen haben und ihre Schuld kompensieren müssen? Deswegen jedenfalls brauchen «Linke» laut Robert Willacker, einem deutschen Politikberater mit brasilianischen Wurzeln, rechte Parteien – ein ebenso überraschender wie humorvoller Erklärungsansatz.
Wenn eine Krähe der anderen kein Auge aushackt, dann tut sie das sich selbst noch weniger an. Dass Millionäre ernsthaft ihre eigene Besteuerung fordern oder Machteliten ihren eigenen Einfluss zugunsten anderer einschränken würden, halte ich für sehr unwahrscheinlich. So etwas glaube ich erst, wenn zum Beispiel die Rüstungsindustrie sich um Friedensverhandlungen bemüht, die Pharmalobby sich gegen institutionalisierte Korruption einsetzt, Zentralbanken ihre CBDC-Pläne für Bitcoin opfern oder der ÖRR die Abschaffung der Rundfunkgebühren fordert.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-01-18 09:34:51
@ c631e267:c2b78d3e
2025-01-18 09:34:51Die grauenvollste Aussicht ist die der Technokratie – \ einer kontrollierenden Herrschaft, \ die durch verstümmelte und verstümmelnde Geister ausgeübt wird. \ Ernst Jünger
«Davos ist nicht mehr sexy», das Weltwirtschaftsforum (WEF) mache Davos kaputt, diese Aussagen eines Einheimischen las ich kürzlich in der Handelszeitung. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den vergangenen vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
Der deutsche WEF-Gründer hatte bei dieser Gelegenheit immer höchst lobende Worte für seine Landsmännin: 2021 erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und 2022 fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
Von der Leyens Handeln während der sogenannten Corona-«Pandemie» lobte Schwab damals bereits ebenso, wie es diese Woche das Karlspreis-Direktorium tat, als man der Beschuldigten im Fall Pfizergate die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
Jene Herausforderungen durch «Krisen epochalen Ausmaßes» werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im Global Risks Report nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
Ein «Great Mental Reset» sei die Voraussetzung dafür, dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
Der aktuelle Zustand unserer Gesellschaften ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die Rechtsstaatlichkeit stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 42342239:1d80db24
2025-01-10 09:21:46
@ 42342239:1d80db24
2025-01-10 09:21:46It's not easy to navigate today's heavily polluted media landscape. If it's not agenda-setting journalism, then it's "government by journalism", or "åfanism" (i.e. clickbait journalism)) that causes distortions in what we, as media consumers, get to see. On social media, bot armies and troll factories pollute the information landscape like the German Ruhr area 100 years ago - and who knows exactly how all these opaque algorithms select the information that's placed in front of our eyes. While true information is sometimes censored, as pointed out by the founder of Meta (then Facebook) the other year, the employees of censorship authorities somehow suddenly go on vacation when those in power spread false information.
The need to carefully weigh the information that reaches us may therefore be more important than ever. A principle that can help us follows from what is called costly signaling in evolutionary biology. Costly signaling refers to traits or behaviors that are expensive to maintain or perform. These signals function as honest indicators. One example is the beauty and complexity of a peacock's feathers. Since only healthy and strong males can afford to invest in these feathers, they become credible and honest signals to peahens looking for a partner.
The idea is also found in economics. There, costly signaling refers to when an individual performs an action with high costs to communicate something with greater credibility. For example, obtaining a degree from a prestigious university can be a costly signal. Such a degree can require significant economic and time resources. A degree from a prestigious university can therefore, like a peacock's extravagant feathers, function as a costly signal (of an individual's endurance and intelligence). Not to peahens, but to employers seeking to hire.
News is what someone, somewhere, doesn't want reported: all the rest is advertisement
-- William Randolph Hearst
Media mogul William Randolph Hearst and renowned author George Orwell are both said to have stated that "News is what someone, somewhere, doesn't want reported: all the rest is advertisement." Although it's a bit drastic, there may be a point to the reasoning. "If the spin is too smooth, is it really news?"
Uri Berliner, a veteran of the American public radio station National Public Radio (NPR) for 25 years, recently shared his concerns about the radio's lack of impartiality in public. He argued that NPR had gone astray when it started telling listeners how to think. A week later, he was suspended. His spin was apparently not smooth enough for his employer.
Uri Berliner, by speaking out publicly in this way, took a clear risk. And based on the theory of costly signaling, it's perhaps precisely why we should consider what he had to say.
Perhaps those who resign in protest, those who forgo income, or those who risk their social capital actually deserve much more attention from us media consumers than we usually give them. It is the costly signal that indicates real news value.
Perhaps the rest should just be disregarded as mere advertising.
-
 @ a95c6243:d345522c
2025-01-13 10:09:57
@ a95c6243:d345522c
2025-01-13 10:09:57Ich begann, Social Media aufzubauen, \ um den Menschen eine Stimme zu geben. \ Mark Zuckerberg
Sind euch auch die Tränen gekommen, als ihr Mark Zuckerbergs Wendehals-Deklaration bezüglich der Meinungsfreiheit auf seinen Portalen gehört habt? Rührend, oder? Während er früher die offensichtliche Zensur leugnete und später die Regierung Biden dafür verantwortlich machte, will er nun angeblich «die Zensur auf unseren Plattformen drastisch reduzieren».
«Purer Opportunismus» ob des anstehenden Regierungswechsels wäre als Klassifizierung viel zu kurz gegriffen. Der jetzige Schachzug des Meta-Chefs ist genauso Teil einer kühl kalkulierten Business-Strategie, wie es die 180 Grad umgekehrte Praxis vorher war. Social Media sind ein höchst lukratives Geschäft. Hinzu kommt vielleicht noch ein bisschen verkorkstes Ego, weil derartig viel Einfluss und Geld sicher auch auf die Psyche schlagen. Verständlich.
«Es ist an der Zeit, zu unseren Wurzeln der freien Meinungsäußerung auf Facebook und Instagram zurückzukehren. Ich begann, Social Media aufzubauen, um den Menschen eine Stimme zu geben», sagte Zuckerberg.
Welche Wurzeln? Hat der Mann vergessen, dass er von der Überwachung, dem Ausspionieren und dem Ausverkauf sämtlicher Daten und digitaler Spuren sowie der Manipulation seiner «Kunden» lebt? Das ist knallharter Kommerz, nichts anderes. Um freie Meinungsäußerung geht es bei diesem Geschäft ganz sicher nicht, und das war auch noch nie so. Die Wurzeln von Facebook liegen in einem Projekt des US-Militärs mit dem Namen «LifeLog». Dessen Ziel war es, «ein digitales Protokoll vom Leben eines Menschen zu erstellen».
Der Richtungswechsel kommt allerdings nicht überraschend. Schon Anfang Dezember hatte Meta-Präsident Nick Clegg von «zu hoher Fehlerquote bei der Moderation» von Inhalten gesprochen. Bei der Gelegenheit erwähnte er auch, dass Mark sehr daran interessiert sei, eine aktive Rolle in den Debatten über eine amerikanische Führungsrolle im technologischen Bereich zu spielen.
Während Milliardärskollege und Big Tech-Konkurrent Elon Musk bereits seinen Posten in der kommenden Trump-Regierung in Aussicht hat, möchte Zuckerberg also nicht nur seine Haut retten – Trump hatte ihn einmal einen «Feind des Volkes» genannt und ihm lebenslange Haft angedroht –, sondern am liebsten auch mitspielen. KI-Berater ist wohl die gewünschte Funktion, wie man nach einem Treffen Trump-Zuckerberg hörte. An seine Verhaftung dachte vermutlich auch ein weiterer Multimilliardär mit eigener Social Media-Plattform, Pavel Durov, als er Zuckerberg jetzt kritisierte und gleichzeitig warnte.
Politik und Systemmedien drehen jedenfalls durch – was zu viel ist, ist zu viel. Etwas weniger Zensur und mehr Meinungsfreiheit würden die Freiheit der Bürger schwächen und seien potenziell vernichtend für die Menschenrechte. Zuckerberg setze mit dem neuen Kurs die Demokratie aufs Spiel, das sei eine «Einladung zum nächsten Völkermord», ernsthaft. Die Frage sei, ob sich die EU gegen Musk und Zuckerberg behaupten könne, Brüssel müsse jedenfalls hart durchgreifen.
Auch um die Faktenchecker macht man sich Sorgen. Für die deutsche Nachrichtenagentur dpa und die «Experten» von Correctiv, die (noch) Partner für Fact-Checking-Aktivitäten von Facebook sind, sei das ein «lukratives Geschäftsmodell». Aber möglicherweise werden die Inhalte ohne diese vermeintlichen Korrektoren ja sogar besser. Anders als Meta wollen jedoch Scholz, Faeser und die Tagesschau keine Fehler zugeben und zum Beispiel Correctiv-Falschaussagen einräumen.
Bei derlei dramatischen Befürchtungen wundert es nicht, dass der öffentliche Plausch auf X zwischen Elon Musk und AfD-Chefin Alice Weidel von 150 EU-Beamten überwacht wurde, falls es irgendwelche Rechtsverstöße geben sollte, die man ihnen ankreiden könnte. Auch der Deutsche Bundestag war wachsam. Gefunden haben dürften sie nichts. Das Ganze war eher eine Show, viel Wind wurde gemacht, aber letztlich gab es nichts als heiße Luft.
Das Anbiedern bei Donald Trump ist indes gerade in Mode. Die Weltgesundheitsorganisation (WHO) tut das auch, denn sie fürchtet um Spenden von über einer Milliarde Dollar. Eventuell könnte ja Elon Musk auch hier künftig aushelfen und der Organisation sowie deren größtem privaten Förderer, Bill Gates, etwas unter die Arme greifen. Nachdem Musks KI-Projekt xAI kürzlich von BlackRock & Co. sechs Milliarden eingestrichen hat, geht da vielleicht etwas.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ f88e6629:e5254dd5
2025-01-08 20:08:17
@ f88e6629:e5254dd5
2025-01-08 20:08:17- Send a transaction, and the recipient uses the coin for another payment. You then merge these two transactions together and save on fees. 🔥
If you have a Trezor, you can try this out on: https://coiner-mu.vercel.app/
But be cautious. This is a hobby project without any guarantee.
How does it work?
- Connect Trezor, enter the passphrase, and select an account.
- The application display your coins, pending transactions, and descendant transactions.
- Then app shows you how much you can save by merging all transactions and removing duplicate information.
- Finally, you can sign and broadcast this more efficient transaction
-
 @ a95c6243:d345522c
2025-01-03 20:26:47
@ a95c6243:d345522c
2025-01-03 20:26:47Was du bist hängt von drei Faktoren ab: \ Was du geerbt hast, \ was deine Umgebung aus dir machte \ und was du in freier Wahl \ aus deiner Umgebung und deinem Erbe gemacht hast. \ Aldous Huxley
Das brave Mitmachen und Mitlaufen in einem vorgegebenen, recht engen Rahmen ist gewiss nicht neu, hat aber gerade wieder mal Konjunktur. Dies kann man deutlich beobachten, eigentlich egal, in welchem gesellschaftlichen Bereich man sich umschaut. Individualität ist nur soweit angesagt, wie sie in ein bestimmtes Schema von «Diversität» passt, und Freiheit verkommt zur Worthülse – nicht erst durch ein gewisses Buch einer gewissen ehemaligen Regierungschefin.
Erklärungsansätze für solche Entwicklungen sind bekannt, und praktisch alle haben etwas mit Massenpsychologie zu tun. Der Herdentrieb, also der Trieb der Menschen, sich – zum Beispiel aus Unsicherheit oder Bequemlichkeit – lieber der Masse anzuschließen als selbstständig zu denken und zu handeln, ist einer der Erklärungsversuche. Andere drehen sich um Macht, Propaganda, Druck und Angst, also den gezielten Einsatz psychologischer Herrschaftsinstrumente.
Aber wollen die Menschen überhaupt Freiheit? Durch Gespräche im privaten Umfeld bin ich diesbezüglich in der letzten Zeit etwas skeptisch geworden. Um die Jahreswende philosophiert man ja gerne ein wenig über das Erlebte und über die Erwartungen für die Zukunft. Dabei hatte ich hin und wieder den Eindruck, die totalitären Anwandlungen unserer «Repräsentanten» kämen manchen Leuten gerade recht.
«Desinformation» ist so ein brisantes Thema. Davor müsse man die Menschen doch schützen, hörte ich. Jemand müsse doch zum Beispiel diese ganzen merkwürdigen Inhalte in den Social Media filtern – zur Ukraine, zum Klima, zu Gesundheitsthemen oder zur Migration. Viele wüssten ja gar nicht einzuschätzen, was richtig und was falsch ist, sie bräuchten eine Führung.
Freiheit bedingt Eigenverantwortung, ohne Zweifel. Eventuell ist es einigen tatsächlich zu anspruchsvoll, die Verantwortung für das eigene Tun und Lassen zu übernehmen. Oder die persönliche Freiheit wird nicht als ausreichend wertvolles Gut angesehen, um sich dafür anzustrengen. In dem Fall wäre die mangelnde Selbstbestimmung wohl das kleinere Übel. Allerdings fehlt dann gemäß Aldous Huxley ein Teil der Persönlichkeit. Letztlich ist natürlich alles eine Frage der Abwägung.
Sind viele Menschen möglicherweise schon so «eingenordet», dass freiheitliche Ambitionen gar nicht für eine ganze Gruppe, ein Kollektiv, verfolgt werden können? Solche Gedanken kamen mir auch, als ich mir kürzlich diverse Talks beim viertägigen Hacker-Kongress des Chaos Computer Clubs (38C3) anschaute. Ich war nicht nur überrascht, sondern reichlich erschreckt angesichts der in weiten Teilen mainstream-geformten Inhalte, mit denen ein dankbares Publikum beglückt wurde. Wo ich allgemein hellere Köpfe erwartet hatte, fand ich Konformismus und enthusiastisch untermauerte Narrative.
Gibt es vielleicht so etwas wie eine Herdenimmunität gegen Indoktrination? Ich denke, ja, zumindest eine gestärkte Widerstandsfähigkeit. Was wir brauchen, sind etwas gesunder Menschenverstand, offene Informationskanäle und der Mut, sich freier auch zwischen den Herden zu bewegen. Sie tun das bereits, aber sagen Sie es auch dieses Jahr ruhig weiter.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 42342239:1d80db24
2025-01-04 20:38:53
@ 42342239:1d80db24
2025-01-04 20:38:53The EU's regulations aimed at combating disinformation raise questions about who is really being protected and also about the true purpose of the "European Democracy Shield".
In recent years, new regulations have been introduced, purportedly to combat the spread of false or malicious information. Ursula von der Leyen, President of the European Commission, has been keen to push forward with her plans to curb online content and create a "European Democracy Shield" aimed at detecting and removing disinformation.
Despite frequent discussions about foreign influence campaigns, we often tend to overlook the significant impact that domestic actors and mass media have on news presentation (and therefore also on public opinion). The fact that media is often referred to as the fourth branch of government, alongside the legislative, executive, and judicial branches, underscores its immense importance.
In late 2019, the Federal Bureau of Investigation (FBI) seized a laptop from a repair shop. The laptop belonged to the son of then-presidential candidate Biden. The FBI quickly determined that the laptop was the son's and did not appear to have been tampered with.
Almost a year later, the US presidential election took place. Prior to the election, the FBI issued repeated warnings to various companies to be vigilant against state-sponsored actors [implying Russia] that could carry out "hack-and-leak campaigns". Just weeks before the 2020 presidential election, an October surprise occurred when the NY Post published documents from the laptop. The newspaper's Twitter account was locked down within hours. Twitter prevented its users from even sharing the news. Facebook (now Meta) took similar measures to prevent the spread of the news. Shortly thereafter, more than 50 former high-ranking intelligence officials wrote about their deep suspicions that the Russian government was behind the story: "if we're right", "this is about Russia trying to influence how Americans vote". Presidential candidate Biden later cited these experts' claims in a debate with President Trump.
In early June this year, the president's son was convicted of lying on a gun license application. The laptop and some of its contents played a clear role in the prosecutors' case. The court concluded that parts of the laptop's contents were accurate, which aligns with the FBI's assessment that the laptop did not appear to have been tampered with. The president's son, who previously filed a lawsuit claiming that the laptop had been hacked and that data had been manipulated, has now withdrawn this lawsuit, which strengthens the image that the content is true.
This raises questions about the true purpose of the "European Democracy Shield". Who is it really intended to protect? Consider the role of news editors in spreading the narrative that the laptop story was Russian disinformation. What impact did social media's censorship of the news have on the outcome of the US election? And if the laptop's contents were indeed true - as appears to be the case - what does it say about the quality of the media's work that it took almost four years for the truth to become widely known, despite the basic information being available as early as 2020?
-
 @ a95c6243:d345522c
2025-01-01 17:39:51
@ a95c6243:d345522c
2025-01-01 17:39:51Heute möchte ich ein Gedicht mit euch teilen. Es handelt sich um eine Ballade des österreichischen Lyrikers Johann Gabriel Seidl aus dem 19. Jahrhundert. Mir sind diese Worte fest in Erinnerung, da meine Mutter sie perfekt rezitieren konnte, auch als die Kräfte schon langsam schwanden.
Dem originalen Titel «Die Uhr» habe ich für mich immer das Wort «innere» hinzugefügt. Denn der Zeitmesser – hier vermutliche eine Taschenuhr – symbolisiert zwar in dem Kontext das damalige Zeitempfinden und die Umbrüche durch die industrielle Revolution, sozusagen den Zeitgeist und das moderne Leben. Aber der Autor setzt sich philosophisch mit der Zeit auseinander und gibt seinem Werk auch eine klar spirituelle Dimension.
Das Ticken der Uhr und die Momente des Glücks und der Trauer stehen sinnbildlich für das unaufhaltsame Fortschreiten und die Vergänglichkeit des Lebens. Insofern könnte man bei der Uhr auch an eine Sonnenuhr denken. Der Rhythmus der Ereignisse passt uns vielleicht nicht immer in den Kram.
Was den Takt pocht, ist durchaus auch das Herz, unser «inneres Uhrwerk». Wenn dieses Meisterwerk einmal stillsteht, ist es unweigerlich um uns geschehen. Hoffentlich können wir dann dankbar sagen: «Ich habe mein Bestes gegeben.»
Ich trage, wo ich gehe, stets eine Uhr bei mir; \ Wieviel es geschlagen habe, genau seh ich an ihr. \ Es ist ein großer Meister, der künstlich ihr Werk gefügt, \ Wenngleich ihr Gang nicht immer dem törichten Wunsche genügt.
Ich wollte, sie wäre rascher gegangen an manchem Tag; \ Ich wollte, sie hätte manchmal verzögert den raschen Schlag. \ In meinen Leiden und Freuden, in Sturm und in der Ruh, \ Was immer geschah im Leben, sie pochte den Takt dazu.
Sie schlug am Sarge des Vaters, sie schlug an des Freundes Bahr, \ Sie schlug am Morgen der Liebe, sie schlug am Traualtar. \ Sie schlug an der Wiege des Kindes, sie schlägt, will's Gott, noch oft, \ Wenn bessere Tage kommen, wie meine Seele es hofft.
Und ward sie auch einmal träger, und drohte zu stocken ihr Lauf, \ So zog der Meister immer großmütig sie wieder auf. \ Doch stände sie einmal stille, dann wär's um sie geschehn, \ Kein andrer, als der sie fügte, bringt die Zerstörte zum Gehn.
Dann müßt ich zum Meister wandern, der wohnt am Ende wohl weit, \ Wohl draußen, jenseits der Erde, wohl dort in der Ewigkeit! \ Dann gäb ich sie ihm zurücke mit dankbar kindlichem Flehn: \ Sieh, Herr, ich hab nichts verdorben, sie blieb von selber stehn.
Johann Gabriel Seidl (1804-1875)
-
 @ ee11a5df:b76c4e49
2024-12-24 18:49:05
@ ee11a5df:b76c4e49
2024-12-24 18:49:05China
I might be wrong, but this is how I see it
This is a post within a series I am going to call "I might be wrong, but this is how I see it"
I have repeatedly found that my understanding of China is quite different from that of many libertarian-minded Americans. And so I make this post to explain how I see it. Maybe you will learn something. Maybe I will learn something.
It seems to me that many American's see America as a shining beacon of freedom with a few small problems, and China is an evil communist country spreading communism everywhere. From my perspective, America was a shining beacon of freedom that has fallen to being typical in most ways, and which is now acting as a falling empire, and China was communist for about a decade, but turned and ran away from that as fast as they could (while not admitting it) and the result is that the US and China are not much different anymore when it comes to free markets. Except they are very different in some other respects.
China has a big problem
China has a big problem. But it is not the communism problem that most Westerners diagnose.
I argue that China is no longer communist, it is only communist in name. And that while it is not a beacon of free market principles, it is nearly as free market now as Western nations like Germany and New Zealand are (being somewhat socialist themselves).
No, China's real problem is authoritarian one-party rule. And that core problem causes all of the other problems, including its human rights abuses.
Communism and Socialism
Communism and Socialism are bad ideas. I don't want to argue it right here, but most readers will already understand this. The last thing I intend to do with this post is to bolster or defend those bad ideas. If you dear reader hold a candle for socialism, let me know and I can help you extinguish it with a future "I might be wrong, but this is how I see it" installment.
Communism is the idea of structuring a society around common ownership of the means of production, distribution, and exchange, and the idea of allocating goods and services based on need. It eliminates the concept of private property, of social classes, ultimately of money and finally of the state itself.
Back under Mao in 1958-1962 (The Great Leap Forward), China tried this (in part). Some 50+ million people died. It was an abject failure.
But due to China's real problem (authoritarianism, even worship of their leaders), the leading classes never admitted this. And even today they continue to use the word "Communist" for things that aren't communist at all, as a way to save face, and also in opposition to the United States of America and Europe.
Authorities are not eager to admit their faults. But this is not just a Chinese fault, it is a fault in human nature that affects all countries. The USA still refuses to admit they assassinated their own president JFK. They do not admit they bombed the Nord Stream pipeline.
China defines "socialism with Chinese characteristics" to mean "the leadership of the Communist Party of China". So they still keep the words socialism and communism, but they long ago dropped the meanings of those words. I'm not sure if this is a political ploy against us in the West or not.
China's Marketplace Today
Today China exhibits very few of the properties of communism.
They have some common ownership and state enterprises, but not much differently than Western countries (New Zealand owns Air New Zealand and Kiwibank and Kiwirail, etc). And there are private enterprises all over China. They compete and some succeed and some fail. You might hear about a real-estate bank collapsing. China has private property. They have mostly free markets. They have money, and the most definitely have social classes and a very strong state.
None of that is inline with what communist thinkers want. Communist thinkers in China moan that China has turned away from communism.
Deng Xiaoping who succeeded Mao and attempted to correct the massive mistake, did much when he said "to get rich is glorious."
China achieved staggering rates of economic growth. 10% annually on average since 1977. Chinese economic reform started in 1979 and has continued through successive administrations (Deng, Jiang, Hu and now Xi).
China is now the world's largest economy (by GDP in PPP terms) since 2016.
I was first made aware of China's economic growth by Jim Rogers, an American commodities expert who travelled through China (and the rest of the world from 1990-1992) and in 2007 moved to Singapore where he ensured his daughters learned to speak Mandarin, because Jim knew where the economic growth was going to happen. Jim always spoke positively of China's economic prospects, and his view was so different from the "China is a nasty communist place" view that I had grown up with that my mind opened.
How can anybody believe they are still a communist country? In what world does it make sense that communism can produce such a massively booming economy? It doesn't make sense because it is simply wrong.
What does happen is that the CPC interferes. It lets the market do what markets do, but it interferes where it thinks oversight and regulation would produce a better result.
Western nations interfere with their markets too. They have oversight and regulation. In fact some of China's planned reforms had to be put on hold by Xi due to Donald Trump's trade war with China. That's right, they were trying to be even more free market than America, but America's protectionism prodded Xi to keep control so he could fight back efficiently.
Government oversight and regulation IMHO is mostly bad because it gets out of control, and there are no market forces to correct this. This gets even more extreme in a one-party system, so I can judge that China's oversight and regulation problems are very likely worse than those in Western nations (but I have no first hand experience or evidence).
Why do you keep saying CPC?
The Communist Party of China (CPC) is the ruling party in China. That is their official name. To call them the CCP is to concede to the idea that the British and Americans get to name everybody. I'm not sure who is right, since CPC or CCP is their "English" name (in Chinese it is 中国共产党 and Westernized it is Zhōngguó Gòngchǎndǎng). Nonetheless, I'll call them CPC because that is their wish.
Social Credit System
China moved from a planned economy to a market economy in stages. They didn't want any more sudden changes (can you blame them?). In the process, many institutions that have existed in the West for a long time didn't exist in China and they had to arise somehow. IMHO market forces would have brought these about in the private sector, but the one-party CP of China instead decided to create these.
One of those institutions was a credit score system. In the West we have TransUnion and Equifax that maintain credit ratings on people, and we have S&P, Moody's and Fitch that maintain credit ratings on companies. The domain of these ratings is their financial credit-worthiness.
So the People's Bank of China developed a credit information database for it's own needs. The government picked up on the idea and started moving towards a National Credit Management System. In 2004 it became an official goal to establish a credit system compatible with a modern market system. By 2006 banks were required to report on consumer creditworthiness.
But unchecked one-party governmental power will often take a good idea (credit worthiness data shared among private parties) and systematize it and apply it top-down, creating a solution and a new problem at the same time.
Nonetheless, originally it was about credit worthiness and also criminal convictions. That is no big scary thing that some right-wing American commentators will lead you to believe. In the US for example criminal records are public, so China's Social Credit System started out being no more over-reaching in scope than what Americans have lived under their entire lives, its only fault (a severe one) being centrally planned. And that remained the case up until about 2016 (in my estimation).
But of course there is always scope creep. As it exists today, I have reason to believe that CPC officials and even A.I. use judgement calls to score someone on how moral that person has been! Of course that is not a good idea, and IMHO the problem stems from one-party rule, and authoritarian administration of ideas that should instead be handled by the private sector.
Environmental, Social, and Governance
ESG is a system that came out of a couple basic ideas. The first is that many two-party transactions actually have externalities. They don't just affect the two parties, they also affect everybody else. When you fly in an airplane, you increase the CO2 in the atmosphere that everybody has to pay for (eventually). You may dispute that example, but that is no doubt one of the motivations of ESG.
But of course the recognition of this basic issue didn't lead all people towards market solutions (well it did, but those have been mostly messed up by others), but instead led many people towards ESG, which is a social credit scoring system which applies scores based on environmental and social side-effects of market transactions.
This is not at all the same as China's social credit system, which I described above. I hope you can see the difference.
In fact, China imported ESG from the West. Chinese companies, of their free will, in an attempt to court Western capital, achieve ESG goals for those Western investors. They have been playing this ESG game for 20 years just like the entire world has, because the West has imposed this faux-morality upon them. It isn't something China exported to us, it is something we exported to them.
I think China has avoided Woke-ism
My understanding of Chinese people, based on what I've heard many Chinese people say, is that China isn't affected by the Western woke-ism epidemic. They deride Western white woke people with the term "Baizuo". They have never sent an incompetent break dancer to the Olympics because of wok-ism. Competence is highly respected as is the competition to be the most competent, which (when augmented by a one-child policy which is no longer) has produced child prodigies like no other country has.
What about predatory loans of the Belt and Road initiative?
Predatory is an odd name for loans to people in need. The World Bank makes loans to people in need. China does too. China stands in opposition to Western Empire, and in that regard they produce their own alternative BRICS institutions. This is one of them.
There is AFAIK nothing more predatory about them. It is just that in some cases the borrowers have trouble paying them back and they get foreclosed upon. I don't think this is worthy of much discussion, except that the term "predatory" seems to me to be a propaganda device.
What about foreign influence from China?
China wants to influence the world, especially its own trading partners and potential trading partners. Doing that above board is fine by me.
But some of it is undoubtedly covert. Sometimes Chinese-born people run for public office in Western countries. In New Zealand we stood down some when it became clear they were being influenced too much by the CPC while being charged with representing their local town (dual loyalty issues). If only the USA would do the same thing to their dually-loyal politicians.
And all large nations run influence operations. The USA has the CIA, for example, and claims this "soft power" is actually the better alternative to what would otherwise be military intervention (but IMHO shouldn't be either). I'm not defending such operations (I despise them), I'm just explaining how China's position of exerting influence is not only no big deal and totally expected, it pales in comparison to the United States' influence operations which often become military excursions (something China rarely ever does).
What about the Great Firewall?
Yeah, that sucks. Again, single-party authoritarian control gone to extremes.
What about Human Rights Abuses? What about the Uyghur Genocide?
I don't like them. To the extent they are occurring (and I lean towards the belief that they are occurring), I condemn them.
China has anti-terrorism and anti-extremism policies that go too far. They end up oppressing and/or criminalizing cultures that aren't Chinese enough. But especially, China punishes dissent. Disagreement with the CPC is the high crime. It is the one-party rule that causes this problem. Anybody who speaks out against the CPC or goes against the state in any way is harshly punished. This happens to Uyghurs, to Falun Gong, to Tibetans, and to any religion that is seen as subversive.
Amnesty International and the UN OHCHR have documented issues around the Xinjiang Uyghur autonomous region, Tibet, LGBT rights, death penalty, workers rights, and the Hong Kong special administrative region. I am not about to pretend I know better than they do, but to some extent they go too far.
Amnesty International says this about the USA: Discrimination and violence against LGBTI people were widespread and anti-LGBTI legislation increased. Bills were introduced to address reparations regarding slavery and its legacies. Multiple states implemented total bans on abortion or severely limited access to it. Gender-based violence disproportionately affected Indigenous women. Access to the USA for asylum seekers and migrants was still fraught with obstacles, but some nationalities continued to enjoy Temporary Protected Status. Moves were made to restrict the freedom to protest in a number of states. Black people were disproportionately affected by the use of lethal force by police. No progress was made in the abolition of the death penalty, apart from in Washington. Arbitrary and indefinite detention in the US naval base Guantánamo Bay, Cuba, continued. Despite extensive gun violence, no further firearm reform policies were considered, but President Biden did announce the creation of the White House Office of Gun Violence Prevention. The USA continued to use lethal force in countries around the world. Black people, other racialized groups and low-income people bore the brunt of the health impacts of the petrochemical industry, and the use of fossil fuels continued unabated.
Amnesty international didn't even point out that the US government quashes free speech via pressure on social media corporations (because Amnesty International is far too lefty).
So who is worse, China or the US? I'm not going to make that judgement call, but suffice it to say that in my mind, China is not obviously worse.
China violates freedom of expression, association, and assembly of all people. This is bad, and a consequence mainly of one-party rule (again, what I think is the root cause of most of their ills). They arrest, detain, potentially kill anybody who publicly disagrees openly with their government. Clearly this is an excess of authoritarianism, a cancer that is very advanced in China.
As to organ harvesting of Uyghur Muslims, I think this is a myth.
China has dealt harshly with Muslim extremism. They don't offer freedom of religion to ISIS. And Amnesty International complains about that. But practically speaking you probably shouldn't respect the extremist religion of people who want to force everybody into a global caliphate through threat of violence. As you are well aware, some extremist Muslims (<1% of Islam) believe in using violence to bring about a global caliphate. Those extremists pop up in every country and are usually dealt with harshly. China has had to deal with them too.
I have watched two different Western YouTubers travel to Xinjiang province trying to find the oppressed Uyghurs and interview them. They can't find them. What they find instead are Uyghur Muslims doing their prayers five times a day at the local mosque. And also stories that the CPC pitched in some money to help them renovate the mosque. Maybe they were afraid it was a CPC trap and so they wouldn't speak freely. Amnesty International and the UN OHCHR say more than a million are "arbitrarily detained" and I'm not going to argue otherwise. But I'd be more convinced if there were a stream of pictures and news like there is out of Gaza, and it is suspicious that there isn't.
Conclusion
China is more like a Western nation that Westerners realize. Economically, militarily, socially. It still has a very serious obstacle to overcome: one-party rule. I don't think the one-party is going to voluntarily give up power. So most probably at some point in the future there will be a revolution. But in my opinion it won't happen anytime soon. For the most part Chinese people are living high on the hog, getting rich, enjoying the good life, in positive spirits about life, and are getting along with their government quite well at present.
-
 @ a95c6243:d345522c
2024-12-21 09:54:49
@ a95c6243:d345522c
2024-12-21 09:54:49Falls du beim Lesen des Titels dieses Newsletters unwillkürlich an positive Neuigkeiten aus dem globalen polit-medialen Irrenhaus oder gar aus dem wirtschaftlichen Umfeld gedacht hast, darf ich dich beglückwünschen. Diese Assoziation ist sehr löblich, denn sie weist dich als unverbesserlichen Optimisten aus. Leider muss ich dich diesbezüglich aber enttäuschen. Es geht hier um ein anderes Thema, allerdings sehr wohl ein positives, wie ich finde.
Heute ist ein ganz besonderer Tag: die Wintersonnenwende. Genau gesagt hat heute morgen um 10:20 Uhr Mitteleuropäischer Zeit (MEZ) auf der Nordhalbkugel unseres Planeten der astronomische Winter begonnen. Was daran so außergewöhnlich ist? Der kürzeste Tag des Jahres war gestern, seit heute werden die Tage bereits wieder länger! Wir werden also jetzt jeden Tag ein wenig mehr Licht haben.
Für mich ist dieses Ereignis immer wieder etwas kurios: Es beginnt der Winter, aber die Tage werden länger. Das erscheint mir zunächst wie ein Widerspruch, denn meine spontanen Assoziationen zum Winter sind doch eher Kälte und Dunkelheit, relativ zumindest. Umso erfreulicher ist der emotionale Effekt, wenn dann langsam die Erkenntnis durchsickert: Ab jetzt wird es schon wieder heller!
Natürlich ist es kalt im Winter, mancherorts mehr als anderswo. Vielleicht jedoch nicht mehr lange, wenn man den Klimahysterikern glauben wollte. Mindestens letztes Jahr hat Väterchen Frost allerdings gleich zu Beginn seiner Saison – und passenderweise während des globalen Überhitzungsgipfels in Dubai – nochmal richtig mit der Faust auf den Tisch gehauen. Schnee- und Eischaos sind ja eigentlich in der Agenda bereits nicht mehr vorgesehen. Deswegen war man in Deutschland vermutlich in vorauseilendem Gehorsam schon nicht mehr darauf vorbereitet und wurde glatt lahmgelegt.
Aber ich schweife ab. Die Aussicht auf nach und nach mehr Licht und damit auch Wärme stimmt mich froh. Den Zusammenhang zwischen beidem merkt man in Andalusien sehr deutlich. Hier, wo die Häuser im Winter arg auskühlen, geht man zum Aufwärmen raus auf die Straße oder auf den Balkon. Die Sonne hat auch im Winter eine erfreuliche Kraft. Und da ist jede Minute Gold wert.
Außerdem ist mir vor Jahren so richtig klar geworden, warum mir das südliche Klima so sehr gefällt. Das liegt nämlich nicht nur an der Sonne als solcher, oder der Wärme – das liegt vor allem am Licht. Ohne Licht keine Farben, das ist der ebenso simple wie gewaltige Unterschied zwischen einem deprimierenden matschgraubraunen Winter und einem fröhlichen bunten. Ein großes Stück Lebensqualität.
Mir gefällt aber auch die Symbolik dieses Tages: Licht aus der Dunkelheit, ein Wendepunkt, ein Neuanfang, neue Möglichkeiten, Übergang zu neuer Aktivität. In der winterlichen Stille keimt bereits neue Lebendigkeit. Und zwar in einem Zyklus, das wird immer wieder so geschehen. Ich nehme das gern als ein Stück Motivation, es macht mir Hoffnung und gibt mir Energie.

Übrigens ist parallel am heutigen Tag auf der südlichen Halbkugel Sommeranfang. Genau im entgegengesetzten Rhythmus, sich ergänzend, wie Yin und Yang. Das alles liegt an der Schrägstellung der Erdachse, die ist nämlich um 23,4º zur Umlaufbahn um die Sonne geneigt. Wir erinnern uns, gell?
Insofern bleibt eindeutig festzuhalten, dass “schräg sein” ein willkommener, wichtiger und positiver Wert ist. Mit anderen Worten: auch ungewöhnlich, eigenartig, untypisch, wunderlich, kauzig, … ja sogar irre, spinnert oder gar “quer” ist in Ordnung. Das schließt das Denken mit ein.
In diesem Sinne wünsche ich euch allen urige Weihnachtstage!
Dieser Beitrag ist letztes Jahr in meiner Denkbar erschienen.
-
 @ a95c6243:d345522c
2024-12-13 19:30:32
@ a95c6243:d345522c
2024-12-13 19:30:32Das Betriebsklima ist das einzige Klima, \ das du selbst bestimmen kannst. \ Anonym
Eine Strategie zur Anpassung an den Klimawandel hat das deutsche Bundeskabinett diese Woche beschlossen. Da «Wetterextreme wie die immer häufiger auftretenden Hitzewellen und Starkregenereignisse» oft desaströse Auswirkungen auf Mensch und Umwelt hätten, werde eine Anpassung an die Folgen des Klimawandels immer wichtiger. «Klimaanpassungsstrategie» nennt die Regierung das.
Für die «Vorsorge vor Klimafolgen» habe man nun erstmals klare Ziele und messbare Kennzahlen festgelegt. So sei der Erfolg überprüfbar, und das solle zu einer schnelleren Bewältigung der Folgen führen. Dass sich hinter dem Begriff Klimafolgen nicht Folgen des Klimas, sondern wohl «Folgen der globalen Erwärmung» verbergen, erklärt den Interessierten die Wikipedia. Dabei ist das mit der Erwärmung ja bekanntermaßen so eine Sache.
Die Zunahme schwerer Unwetterereignisse habe gezeigt, so das Ministerium, wie wichtig eine frühzeitige und effektive Warnung der Bevölkerung sei. Daher solle es eine deutliche Anhebung der Nutzerzahlen der sogenannten Nina-Warn-App geben.
Die ARD spurt wie gewohnt und setzt die Botschaft zielsicher um. Der Artikel beginnt folgendermaßen:
«Die Flut im Ahrtal war ein Schock für das ganze Land. Um künftig besser gegen Extremwetter gewappnet zu sein, hat die Bundesregierung eine neue Strategie zur Klimaanpassung beschlossen. Die Warn-App Nina spielt eine zentrale Rolle. Der Bund will die Menschen in Deutschland besser vor Extremwetter-Ereignissen warnen und dafür die Reichweite der Warn-App Nina deutlich erhöhen.»
Die Kommunen würden bei ihren «Klimaanpassungsmaßnahmen» vom Zentrum KlimaAnpassung unterstützt, schreibt das Umweltministerium. Mit dessen Aufbau wurden das Deutsche Institut für Urbanistik gGmbH, welches sich stark für Smart City-Projekte engagiert, und die Adelphi Consult GmbH beauftragt.
Adelphi beschreibt sich selbst als «Europas führender Think-and-Do-Tank und eine unabhängige Beratung für Klima, Umwelt und Entwicklung». Sie seien «global vernetzte Strateg*innen und weltverbessernde Berater*innen» und als «Vorreiter der sozial-ökologischen Transformation» sei man mit dem Deutschen Nachhaltigkeitspreis ausgezeichnet worden, welcher sich an den Zielen der Agenda 2030 orientiere.
Über die Warn-App mit dem niedlichen Namen Nina, die möglichst jeder auf seinem Smartphone installieren soll, informiert das Bundesamt für Bevölkerungsschutz und Katastrophenhilfe (BBK). Gewarnt wird nicht nur vor Extrem-Wetterereignissen, sondern zum Beispiel auch vor Waffengewalt und Angriffen, Strom- und anderen Versorgungsausfällen oder Krankheitserregern. Wenn man die Kategorie Gefahreninformation wählt, erhält man eine Dosis von ungefähr zwei Benachrichtigungen pro Woche.
Beim BBK erfahren wir auch einiges über die empfohlenen Systemeinstellungen für Nina. Der Benutzer möge zum Beispiel den Zugriff auf die Standortdaten «immer zulassen», und zwar mit aktivierter Funktion «genauen Standort verwenden». Die Datennutzung solle unbeschränkt sein, auch im Hintergrund. Außerdem sei die uneingeschränkte Akkunutzung zu aktivieren, der Energiesparmodus auszuschalten und das Stoppen der App-Aktivität bei Nichtnutzung zu unterbinden.
Dass man so dramatische Ereignisse wie damals im Ahrtal auch anders bewerten kann als Regierungen und Systemmedien, hat meine Kollegin Wiltrud Schwetje anhand der Tragödie im spanischen Valencia gezeigt. Das Stichwort «Agenda 2030» taucht dabei in einem Kontext auf, der wenig mit Nachhaltigkeitspreisen zu tun hat.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 42342239:1d80db24
2024-12-22 09:07:27
@ 42342239:1d80db24
2024-12-22 09:07:27Knappheit statt Slogans: eine Dosis ökonomischer Realität für die politischen Debatten
Die EU-Wirtschaft steht vor zahlreichen Herausforderungen, von hohen Energiekosten bis hin zu geringer Produktivität. Doch hinter der offiziellen Rhetorik verbirgt sich eine Annahme, die kaum hinterfragt wird: dass der grüne Wandel automatisch zu Wirtschaftswachstum und mehr Wohlstand führen wird. Aber stimmt das wirklich?
Eine englische Fassung dieses Textes finden Sie hier.
In Deutschland, das wieder einmal das Etikett „Kranker Mann Europas" tragen muss, kämpft Bundeskanzler Olaf Scholz vor der Wahl im Februar mit alarmierend niedrigen Vertrauenswerten. Aber vielleicht ist das gar nicht so überraschend. ****Die deutsche Industrieproduktion ist rückläufig, seit die grüne Agenda in Mode gekommen ist. ****Die energieintensive Produktion ist in nur wenigen Jahren um ganze 20 Prozent zurückgegangen. Volkswagen schließt Fabriken, Thyssenkrupp entlässt massiv Mitarbeiter und mehr als drei Millionen Rentner sind von Armut bedroht .
Wenn dies Europas „Mann auf dem Mond"-Moment ist, wie EU-Kommissarin von der Leyen ****es 2019 ausdrückte ****, dann ist das nicht viel, womit man angeben kann . Zumindest nicht, wenn man kein Sadist ist.
Der Bericht des ehemaligen EZB-Chefs Mario Draghi über die Wettbewerbsfähigkeit der EU wurde bereits früher diskutiert. Eines der Probleme, auf die hingewiesen wurde, war, dass europäische Unternehmen erheblich höhere Energiekosten haben als ihre amerikanischen Konkurrenten. Die Strompreise sind zwei- bis dreimal so hoch und die Erdgaspreise vier- bis fünfmal so hoch.
Deutschland ist vielleicht am schlimmsten dran, was zum Teil an der Entscheidung der ehemaligen Bundeskanzlerin Angela Merkel liegt, vollständig aus der Atomkraft auszusteigen (eine Entscheidung, die nicht nur keine breite Unterstützung fand , sondern die sie auch nicht als Fehler eingestehen will). Die Sabotage der Nord Stream 2 hat die Situation noch verschlimmert.
Ohne Realkapital kein wirtschaftlicher Wohlstand
Der Ausstieg aus der Atomenergie in Deutschland ist ein Beispiel dafür, wie politische Entscheidungen zur Verringerung der Kapazität der Wirtschaft beigetragen haben. Dasselbe gilt für die Sabotage der Nord Stream. Realkapital, wie Gebäude, Maschinen und Ausrüstung, ist für die Produktivität der Wirtschaft von entscheidender Bedeutung (z. B. Kennzahlen wie das BIP pro Arbeitsstunde). Ein größerer und effizienterer Kapitalstock ermöglicht die Herstellung von mehr Waren und Dienstleistungen mit der gleichen Menge an Arbeit, was zu mehr Produktion, höheren Löhnen und größerem materiellen Wohlstand führt. Das ist grundlegende Ökonomie. ****Wenn andererseits Realkapital aufgrund politischer Entscheidungen für obsolet erklärt wird, wie im Fall der Abschaltung der Atomkraft, verringert dies die Kapazität der Wirtschaft. ****Dasselbe gilt, wenn Realkapital zerstört wird, wie dies bei Nord Stream der Fall war.
Weiteres reales Betriebskapital wird zurückgestellt
EU-Kommissarin von der Leyen verspricht Besserung. Sie scheint überzeugt, dass der Niedergang der EU durch eine Verdreifachung der grünen Ziele des Blocks umgekehrt werden kann, und hat die Dekarbonisierung als eine der drei wichtigsten Säulen eines neuen „Wettbewerbsfähigkeitskompasses" aufgeführt. Wenn die Realität nicht den Erwartungen entspricht, kann man immer noch „Strg+Alt+Slogan" drücken und hoffen, dass niemand merkt, dass sich nichts verbessert hat.
Ihre Pläne bedeuten jedoch, dass bestehendes und derzeit funktionierendes Realkapital in Zukunft in noch größerem Umfang abgeschrieben wird. Dies lässt sich mit einer Nation vergleichen, die Jahr für Jahr ihre Naturschutzgebiete schrittweise erweitert. Tatsächlich geschieht dies auch. Der Kunming-Montreal-Rahmen für die Artenvielfalt sieht vor, dass bis 2030 30 % aller Flächen an Land und im Meer geschützt werden müssen. Ein Land, das derzeit weniger schützt, muss daher zusätzliche Gebiete identifizieren, die geschützt werden können. ****Der Prozess, 30 % aller Flächen zu schützen, wird wahrscheinlich das Produktionspotenzial der Wirtschaft verringern. ****Mit schrumpfenden Feldern wird es weniger Karotten geben (es sei denn, es werden bedeutende technologische Fortschritte erzielt).
Konsequenzen für Sicherheitspolitik und -vorsorge
Auf dem derzeitigen Weg wird mehr Realkapital auf die lange Bank geschoben, was weitreichende Folgen haben kann, nicht zuletzt für unsere Sicherheitspolitik. Wenn Russland beispielsweise Artilleriegeschosse etwa dreimal schneller produzieren kann, und zwar zu Kosten, die etwa ein Viertel der Kosten betragen, die die westlichen Verbündeten der Ukraine dafür aufbringen , dann ist klar, dass dies sicherheitspolitische Konsequenzen hat. Ebenso wird es negative sicherheitspolitische Konsequenzen haben, wenn die Strompreise in Deutschland fünfmal höher sind als in China, was derzeit der Fall ist . Im Vergleich zur EU hat China tatsächlich einen höheren Kohlendioxidausstoß pro Kopf, wobei der Unterschied den ****verfügbaren Daten zufolge etwa 50 % beträgt ****. Bereinigt um den internationalen Handel emittiert China pro Kopf 10 % mehr als Schweden .
Auch eine Perspektive der Vorsorge ist zu finden. Anfang der 1990er Jahre produzierten schwedische Landwirte fast 75 % der Nahrungsmittel des Landes. Heute ist Schwedens Bevölkerung deutlich gewachsen, aber die Nahrungsmittelproduktion hat nicht Schritt gehalten. Jeder zweite Bissen wird heute importiert. In Schweden können wir uns sogar rühmen, dass wir uns nicht einmal mit der einfachsten aller Feldfrüchte versorgen können -- Kartoffeln . Können wir wirklich sicher sein, dass deutlich erweiterte Naturschutzgebiete, wie sie im Kunming-Montreal-Rahmenwerk für Schweden vorgeschrieben sind, unsere Nahrungsmittelvorsorge nicht noch weiter verschlechtern werden?
Erinnert an kleine Gnome
Ich erinnere mich an eine Folge der 90er-Jahre-Serie South Park, in der kleine Gnome Unterhosen sammeln . Als sie nach ihrem Plan gefragt wurden, beschrieben sie ihre Methode:
- Unterhosen sammeln
- ???
- profitieren!
Übersetzt auf die grüne **Energiewende **:
- reales Kapital zerstören und Land und Meer erhalten
- ???
- wirtschaftlicher Wohlstand!
Was kann sich die EU wirklich leisten?
In der Wirtschaft geht es im Grunde um die Verwaltung knapper Ressourcen, was viele Menschen offenbar vergessen haben. Es ist höchste Zeit, zu hinterfragen, was sich die EU wirklich leisten kann. Können wir es uns wirklich leisten, uns für einen Krieg gegen Russland, China und den Iran zu rüsten und uns gleichzeitig mit grünen Versprechen von reduzierten Kohlendioxidemissionen und erhöhter Artenvielfalt selbst die Hände zu binden? Und das in einer Situation, in der die nächste US-Regierung wahrscheinlich massiv in die Steigerung ihrer Wettbewerbsvorteile durch Deregulierung, niedrigere Energiepreise, Steuersenkungen und einen Rückzug aus dem Pariser Abkommen investieren wird ?
Als von der Leyen für das deutsche Militär verantwortlich war, sei die Lage " katastrophal " gewesen. Alle sechs U-Boote des Landes waren außer Gefecht gesetzt . Zeitweise war kein einziges der 14 Transportflugzeuge des Landes flugfähig. Bei Übungen mussten deutsche Soldaten Besen statt Gewehren verwenden .
Hoffentlich wird von der Leyen in ihrem Umgang mit der Wirtschaft, der Verteidigung und der Abwehrbereitschaft der EU mehr Erfolg zeigen als in ihrer Rolle als deutsche Verteidigungsministerin. Es könnte jedoch auch an der Zeit sein, dass mehr Menschen die vorherrschenden Narrative, die unsere Politik prägen, in Frage stellen. Was, wenn die Fakten nicht ganz mit der Wahrheit übereinstimmen, die uns erzählt wird?
-
 @ a95c6243:d345522c
2024-12-06 18:21:15
@ a95c6243:d345522c
2024-12-06 18:21:15Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\ dass wir Vorteile aus ihr ziehen;\ in jedem andern hegt man den Wunsch,\ dass der Unschuldige in Schutz genommen werde.\ Jean-Jacques Rousseau
Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden.
Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen» den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen schadet der Psyche und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben Menschen getötet».
Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft. Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen Erfahrungen als Kritikerin der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit Transition News. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften».
Menschen, die aufrichtig andere schützen wollten, werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter Heinrich Habig, Bianca Witzschel und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat Transition News mehrfach berichtet (z.B. hier und hier). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie Alexander Bittner erfahren mussten.
Die eigentlich Kriminellen schützen sich derweil erfolgreich selber, nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte Verbrechen gegen die Menschheit». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn Hunter möglicherweise auch Anthony Fauci begnadigen wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte?
Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken.
Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers Robert F. Kennedy Jr. erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens Călin Georgescu, der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der Panik im Wertewesten.
In Rumänien selber gab es gerade einen Paukenschlag: Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das Tabu gebrochen, Wahlen zu verbieten, bevor sie etwas ändern können.
Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: Zensur) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 42342239:1d80db24
2024-12-22 08:38:02
@ 42342239:1d80db24
2024-12-22 08:38:02The EU's economy is facing a number of challenges, from high energy costs to low productivity. But behind the official rhetoric lies an assumption that is rarely questioned: that the green transition will automatically lead to economic growth and increased prosperity. But is this really true?
In Germany, which is once again forced to bear the label "Europe's sick man", Chancellor Olaf Scholz is struggling with alarmingly low confidence figures ahead of the election in February. But perhaps this is not so surprising. German industrial production has been trending downward since the green agenda became fashionable. Energy-intensive production has decreased by a full 20% in just a few years. Volkswagen is closing factories, Thyssenkrupp is massively laying off employees, and more than three million pensioners are at risk of poverty.
If this is Europe's "man on the moon" moment, as EU Commissioner von der Leyen expressed it in 2019, then it's not much to brag about. At least, not if you're not a sadist.
The former ECB chief Mario Draghi's report on the EU's competitiveness has been discussed previously in Affärsvärlden, among other things by the author and by Christian Sandström. One of the problems pointed out was that European companies have significantly higher energy costs than their American competitors, with electricity prices 2-3 times higher and natural gas prices 4-5 times higher.
Germany is perhaps worst off, thanks in part to former Chancellor Angela Merkel's decision to completely phase out nuclear power (a decision that not only lacked popular support but which she also refuses to acknowledge as a mistake). The sabotage of Nord Stream made the situation worse.
Without Real Capital, No Economic Prosperity
Germany's phasing out of nuclear power plants is an example of how political decisions have contributed to reducing the economy's capacity. The same applies to the sabotage of Nord Stream. Real capital, such as buildings, machinery, and equipment, is crucial for the economy's productivity (e.g., measures such as GDP per hour worked). A larger and more efficient capital stock enables the production of more goods and services with the same amount of labor, leading to greater production, higher wages, and increased material prosperity. This is basic economics. On the other hand, when real capital is declared obsolete due to political decisions, as in the case of the shutdown of nuclear power, it reduces the economy's capacity. The same applies when real capital is destroyed, as was the case with Nord Stream.
More Working Real Capital Will Be Put on the Back Burner
EU Commissioner von der Leyen promises improvement. She seems convinced that the EU's decline can be reversed by tripling down on the bloc's green goals, and listed decarbonization as one of three key pillars in a new "Competitiveness Compass". When reality does not live up to expectations, you can always press "Ctrl+Alt+Slogan" and hope that no one notices that nothing has improved.
However, her plans mean that existing and currently functioning real capital will be written off to an even greater extent in the future. This can be compared to a nation that gradually expands its nature reserves year after year. As it happens, this is also taking place. The Kunming-Montreal framework for biodiversity means that 30% of all areas, on land and at sea, must be protected by 2030. A country that currently conserves less than that must therefore identify additional areas that can be protected. The process of protecting 30% of all areas will likely reduce the economy's productive potential. With shrinking fields, there will be fewer carrots (unless significant technological progress is made).
Security Policy and Preparedness Consequences
On the current path, more real capital will be put on the back burner, which can have far-reaching consequences, not least for our security policy. For example, if Russia can produce artillery shells about three times faster, at a cost that is roughly a quarter of what it costs Ukraine's Western allies, then it's clear that this has security policy consequences. Similarly, if electricity prices in Germany are five times higher than in China, which is currently the case, then this will also have negative security policy consequences. Compared to the EU, China actually has a higher carbon dioxide emission level per capita, with a difference of about 50% according to available data. Adjusted for international trade, China emits 10% more than Sweden per capita.
A preparedness perspective can also be found. In the early 1990s, Swedish farmers produced nearly 75% of the country's food. Today, Sweden's population has increased significantly, but food production has not kept pace. Every other bite is imported today. In Sweden, we can even boast that we cannot even provide for ourselves with the simplest of crops - potatoes. Can we really be sure that significantly expanded nature reserves, as prescribed by the Kunming-Montreal framework for Sweden, will not further deteriorate our food preparedness?
Reminds One of Little Gnomes
I am reminded of an episode from the 90s TV series South Park, where little gnomes collect underpants. When asked about their plan, they described their method:
- collect underpants
- ???
- profit!
Translated to the green transition (the German Energiewende):
- destroy real capital and conserve land and sea
- ???
- economic prosperity!
What Can the EU Really Afford?
Economics is fundamentally about managing scarce resources, which many people seem to have forgotten. It's high time to question what the EU can really afford. Can we really afford to arm ourselves for war against Russia, China, and Iran while at the same time tying our own hands with green promises of reduced carbon dioxide emissions and increased biodiversity? This in a situation where the next US administration is likely to invest heavily in increasing its competitive advantages through deregulation, lower energy prices, tax cuts, and a withdrawal from the Paris Agreement?
When von der Leyen was responsible for the German military, the situation became "catastrophic". All six of the country's submarines were out of commission. At times, not a single one of the country's 14 transport aircraft could fly. German soldiers had to use broomsticks instead of guns during exercises.
Hopefully, von der Leyen will show more success in her handling of the EU's economy, defense, and preparedness than she has shown in her role as German Defense Minister. However, it may also be time for more people to challenge the prevailing narratives that shape our policies. What if the facts don't quite add up to the truth we're being told?
-
 @ a95c6243:d345522c
2024-11-29 19:45:43
@ a95c6243:d345522c
2024-11-29 19:45:43Konsum ist Therapie.
Wolfgang JoopUmweltbewusstes Verhalten und verantwortungsvoller Konsum zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
Heute ist also wieder mal «Black Friday», falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
Warum fallen wir auf derartige Werbetricks herein und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
Gedankenlosigkeit und Maßlosigkeit können besonders bei der Ernährung zu ernsten Problemen führen. Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
Kritik am schwarzen Freitag und dem unnötigen Konsum kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
Die EU-Kommission lancierte 2015 den Begriff «Green Friday» im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das Pariser Abkommen unterzeichnet werden sollte.
Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt. Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des «Green New Deal» verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um Valencia dazu sagen?
Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020 eine «grüne Erholung von Covid-19, um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie «verantwortungsvolle Risikobereitschaft» unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 42342239:1d80db24
2024-12-19 15:26:01
@ 42342239:1d80db24
2024-12-19 15:26:01Im Frühjahr kündigte EU-Kommissarin Ursula von der Leyen an, sie wolle einen „ Europäischen Demokratieschild " schaffen, um die EU vor ausländischer Einflussnahme zu schützen. Von der Leyens Demokratieschild befindet sich derzeit in der Planungsphase. Die erklärte Absicht besteht darin, eine „ spezielle Struktur zur Bekämpfung ausländischer Informationsmanipulation und -einmischung" zu schaffen. Obwohl es als Instrument zum Schutz der Demokratie angepriesen wird, vermuten einige, dass es sich in Wirklichkeit um einen verschleierten Versuch handelt, abweichende Meinungen zu unterdrücken. Der im vergangenen Jahr verabschiedete Digital Services Act (DSA) der EU ist eng mit diesem Schild verbunden. Durch den DSA riskieren große Social-Media-Plattformen wie Elon Musks X erhebliche Geldstrafen, wenn sie den Forderungen der EU-Bürokraten nach Zensur und Moderation nicht nachkommen.
Note: This text is also available in English at substack.com. Many thanks to
stroger1@iris.tofor this German translation.Im krassen Gegensatz dazu hat sich der künftige US-Präsident Donald Trump als klarer Befürworter der Meinungsfreiheit und entschiedener Gegner der Zensur hervorgetan. Er wurde bereits von YouTube gesperrt, hat jedoch erklärt, er wolle „das linke Zensurregime zerschlagen und das Recht auf freie Meinungsäußerung für alle Amerikaner zurückfordern" . Er hat auch behauptet: „Wenn wir keine freie Meinungsäußerung haben, dann haben wir einfach kein freies Land."
Sein künftiger Vizepräsident J.D. Vance hat sogar angedeutet, dass er bereit sei, US-Militärhilfe von der Achtung der Meinungsfreiheit in den europäischen NATO-Ländern abhängig zu machen. Vances Aussage erfolgte, nachdem EU-Binnenmarktkommissar Thierry Breton vor seinem geplanten Gespräch mit Trump einen umstrittenen Brief an Musk geschickt hatte. Heute erscheint dies als unkluger Schritt, nicht zuletzt, weil er als Versuch gewertet werden kann, die US-Wahl zu beeinflussen -- etwas, das paradoxerweise dem erklärten Zweck von von der Leyens Demokratieschild (d. h. ausländische Manipulationen zu bekämpfen) widerspricht.
Wenn die NATO möchte, dass wir sie weiterhin unterstützen, und die NATO möchte, dass wir weiterhin ein gutes Mitglied dieses Militärbündnisses sind, warum respektieren Sie dann nicht die amerikanischen Werte und die freie Meinungsäußerung?
- J.D. Vance
In der EU sind Verfechter der Meinungsfreiheit in der Öffentlichkeit weniger verbreitet. In Deutschland hat Vizekanzler Robert Habeck kürzlich erklärt, er sei „überhaupt nicht glücklich darüber, was dort [auf X] passiert ... seit Elon Musk das Amt übernommen hat", und wünscht sich eine strengere Regulierung der sozialen Medien. Die Wohnung eines deutschen Rentners wurde kürzlich von der Polizei durchsucht, nachdem er ein Bild von Habeck mit einem abfälligen Kommentar veröffentlicht hatte . Die deutsche Polizei verfolgt auch einen anderen Kontoinhaber, der einen Minister als „übergewichtig" bezeichnet hat. Dieser überhaupt nicht übergewichtige Minister hat kürzlich eine Zeitung verboten , die mit der laut Meinungsumfragen zweitgrößten Partei Deutschlands, der Alternative für Deutschland (AfD), verbündet ist. Eine Partei, die 113 deutsche Parlamentarier nun offiziell verbieten wollen .
Nach dem US-Wahlergebnis stellen sich viele unbeantwortete Fragen. Wird das Weiße Haus seine Aufmerksamkeit auf die restriktivere Haltung der EU richten, die als Untergrabung der freien Meinungsäußerung angesehen werden kann? Oder droht Musks X und Chinas TikTok stattdessen ein EU-Verbot? Können EU-Länder noch mit militärischer Unterstützung aus den USA rechnen? Und wenn große amerikanische Plattformen verboten werden, wohin sollten sich die EU-Bürger stattdessen wenden? Abgesehen von russischen Alternativen gibt es keine großen europäischen Plattformen. Und wenn die Frage der Meinungsfreiheit neu überdacht wird, was bedeutet das für die Zukunft von Parteien wie der deutschen AfD?
-
 @ a95c6243:d345522c
2024-11-08 20:02:32
@ a95c6243:d345522c
2024-11-08 20:02:32Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister EckhartSchwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung, der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
Mit einem bemerkenswerten Timing hat die deutsche Regierungskoalition am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer Selbsthypnose rund um Harris-Hype und Trump-Panik – mit teils erschreckenden Auswüchsen. Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
Das Kindergarten-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik «vorsätzlich herbeigeführt» worden seien.
Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen. Verkehrs- und Digitalminister Wissing trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit Jörg Kukies habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP, hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können. Das ging erst kürzlich aus dem diesjährigen «Freiheitsindex» hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
«Die absolute Mehrheit hat absolut die Nase voll», titelte die Bild angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat, kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei Manova. Und er kenne Friedrich Merz schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
Was also tun? Der Schweizer Verein «Losdemokratie» will eine Volksinitiative lancieren, um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
In jedem Fall wird es notwendig sein, unsere Bemühungen um Freiheit und Selbstbestimmung zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 42342239:1d80db24
2024-12-19 09:00:14
@ 42342239:1d80db24
2024-12-19 09:00:14Germany, the EU's largest economy, is once again forced to bear the label "Europe's sick man". The economic news makes for dismal reading. Industrial production has been trending downward for a long time. Energy-intensive production has decreased by as much as 20% in just a few years. Volkswagen is closing factories. Thyssenkrupp is laying off employees and more than three million pensioners are at risk of poverty according to a study.
Germany is facing a number of major challenges, including high energy costs and increased competition from China. In 2000, Germany accounted for 8% of global industrial production, but by 2030, its share is expected to have fallen to 3%. In comparison, China accounted for 2% of global industrial production in 2000, but is expected to account for nearly half (45%) of industrial production in a few years. This is according to a report from the UN's Industrial Development Organization.
Germany's electricity prices are five times higher than China's, a situation that poses a significant obstacle to maintaining a competitive position. The three main reasons are the phase-out of nuclear power, the sabotage of Nord Stream, and the ongoing energy transition, also known as Energiewende. Upon closer inspection, it is clear that industrial production has been trending downward since the transition to a greener economy began to be prioritized.
Germany's former defense minister, EU Commission President von der Leyen, called the European Green Deal Europe's "man on the moon" moment in 2019. This year, she has launched increased focus on these green goals.
However, the EU as a whole has fallen behind the US year after year. European companies have significantly higher energy costs than their American competitors, with electricity prices 2-3 times higher and natural gas prices 4-5 times higher.
The Environmental Kuznets Curve is a model that examines the relationship between economic growth and environmental impact. The idea is that increased material prosperity initially leads to more environmental degradation, but after a certain threshold is passed, there is a gradual decrease. Decreased material prosperity can thus, according to the relationship, lead to increased environmental degradation, for example due to changed consumption habits (fewer organic products in the shopping basket).
This year's election has resulted in a historic change, where all incumbent government parties in the Western world have seen their popularity decline. The pattern appears to be repeating itself in Germany next year, where Chancellor Olaf Scholz is struggling with low confidence figures ahead of the election in February, which doesn't seem surprising. Adjusted for inflation, German wages are several percent lower than a few years ago, especially in the manufacturing industry.
Germany is still a very rich country, but the current trend towards deindustrialization and falling wages can have consequences for environmental priorities in the long run. Economic difficulties can lead to environmental issues being downgraded. Perhaps the declining support for incumbent government parties is a first sign? Somewhere along the road to poverty, people will rise up in revolt.
-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ ee11a5df:b76c4e49
2024-12-16 05:29:30
@ ee11a5df:b76c4e49
2024-12-16 05:29:30Nostr 2?
Breaking Changes in Nostr
Nostr was a huge leap forward. But it isn't perfect.
When developers notice a problem with nostr, they confer with each other to work out a solution to the problem. This is usually in the form of a NIP PR on the nips repo.
Some problems are easy. Just add something new and optional. No biggie. Zaps, git stuff, bunkers... just dream it up and add it.
Other problems can only be fixed by breaking changes. With a breaking change, the overall path forward is like this: Add the new way of doing it while preserving the old way. Push the major software to switch to the new way. Then deprecate the old way. This is a simplification, but it is the basic idea. It is how we solved markers/quotes/root and how we are upgrading encryption, among other things.
This process of pushing through a breaking change becomes more difficult as we have more and more existing nostr software out there that will break. Most of the time what happens is that the major software is driven to make the change (usually by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6), and the smaller software is left to fend for itself. A while back I introduced the BREAKING.md file to help people developing smaller lesser-known software keep up with these changes.
Big Ideas
But some ideas just can't be applied to nostr. The idea is too big. The change is too breaking. It changes something fundamental. And nobody has come up with a smooth path to move from the old way to the new way.
And so we debate a bunch of things, and never settle on anything, and eventually nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 makes a post saying that we don't really want it anyways 😉.
As we encounter good ideas that are hard to apply to nostr, I've been filing them away in a repository I call "nostr-next", so we don't forget about them, in case we ever wanted to start over.
It seems to me that starting over every time we encountered such a thing would be unwise. However, once we collect enough changes that we couldn't reasonably phase into nostr, then a tipping point is crossed where it becomes worthwhile to start over. In terms of the "bang for the buck" metaphor, the bang becomes bigger and bigger but the buck (the pain and cost of starting over) doesn't grow as rapidly.
WHAT? Start over?
IMHO starting over could be very bad if done in a cavalier way. The community could fracture. The new protocol could fail to take off due to lacking the network effect. The odds that a new protocol catches on are low, irrespective of how technically superior it could be.
So the big question is: can we preserve the nostr community and it's network effect while making a major step-change to the protocol and software?
I don't know the answer to that one, but I have an idea about it.
I think the new-protocol clients can be dual-stack, creating events in both systems and linking those events together via tags. The nostr key identity would still be used, and the new system identity too. This is better than things like the mostr bridge because each user would remain in custody of their own keys.
The nitty gritty
Here are some of the things I think would make nostr better, but which nostr can't easily fix. A lot of these ideas have been mentioned before by multiple people and I didn't give credit to all of you (sorry) because my brain can't track it all. But I've been collecting these over time at https://github.com/mikedilger/nostr-next
- Events as CBOR or BEVE or MsgPack or a fixed-schema binary layout... anything but JSON text with its parsing, it's encoding ambiguity, it's requirement to copy fields before hashing them, its unlimited size constraints. (me, nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s)
- EdDSA ed25519 keys instead of secp256k1, to enable interoperability with a bunch of other stuff like ssh, pgp, TLS, Mainline DHT, and many more, plus just being better cryptography (me, Nuh, Orlovsky, except Orlovsky wanted Ristretto25519 for speed)
- Bootstrapping relay lists (and relay endpoints) from Mainline DHT (nostr:npub1jvxvaufrwtwj79s90n79fuxmm9pntk94rd8zwderdvqv4dcclnvs9s7yqz)
- Master keys and revocable subkeys / device keys (including having your nostr key as a subkey)
- Encryption to use different encryption-specific subkeys and ephemeral ones from the sender.
- Relay keypairs, TLS without certificates, relays known by keypair instead of URL
- Layered protocol (separate core from applications)
- Software remembering when they first saw an event, for 2 reasons, the main one being revocation (don't trust the date in the event, trust when you first saw it), the second being more precise time range queries.
- Upgrade/feature negotiation (HTTP headers prior to starting websockets)
- IDs starting with a timestamp so they are temporally adjacent (significantly better database performance) (Vitor's idea)
- Filters that allow boolean expressions on tag values, and also ID exclusions. Removing IDs from filters and moving to a GET command.
- Changing the transport (I'm against this but I know others want to)
What would it look like?
Someone (Steve Farroll) has taken my nostr-next repo and turned it into a proposed protocol he calls Mosaic. I think it is quite representative of that repo, as it already includes most of those suggestions, so I've been contributing to it. Mosaic spec is rendered here.
Of course, where Mosaic stands right now it is mostly my ideas (and Steve's), it doesn't have feedback or input from other nostr developers yet. That is what this blog post is about. I think it is time for other nostr devs to be made aware of this thing.
It is currently in the massive breaking changes phase. It might not look that way because of the detail and refinement of the documentation, but indeed everything is changing rapidly. It probably has some bad ideas and is probably missing some great ideas that you have.
Which is why this is a good time for other devs to start taking a look at it.
It is also the time to debate meta issues like "are you crazy Mike?" or "no we have to just break nostr but keep it nostr, we can't dual-stack" or whatever.
Personally I think mosaic-spec should develop and grow for quite a while before the "tipping point" happens. That is, I'm not sure we should jump in feet first yet, but rather we build up and refine this new protocol and spend a lot of time thinking about how to migrate smoothly, and break it a lot while nobody is using it.
So you can just reply to this, or DM me, or open issues or PRs at Mosaic, or just whisper to each other while giving me the evil eye.
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ 42342239:1d80db24
2024-12-06 09:40:00
@ 42342239:1d80db24
2024-12-06 09:40:00The Dutch primatologist Frans de Waal coined the term "veneer theory" in his book "Our Inner Ape" in 2005. The veneer theory posits that human moral behavior is merely a thin veneer over an inherently unpleasant nature. This viewpoint can be traced back to Thomas Henry Huxley, an anthropologist and biologist who was a contemporary of Darwin. However, de Waal criticized the idea because humanity is far more cooperative than predicted by simple anthropological or economic models. However, it is possible to question how thick this "civilizing veneer" really is.
During the COVID-19 pandemic, some people discriminated against the unvaccinated , while others wished them a quick and painful death . In the United States, about 30 percent of those who voted for the Democratic Party wanted to take their children away . Professors wanted to imprison them . This was despite the fact that the vaccines did not prevent infection or reduce transmission very much (if at all).
There is an idea that evil actions often stem from ordinary people blindly following orders or societal norms.
The war between Israel and Hamas revealed a desire to collectively punish all residents of the Gaza Strip. For example, as many as 70 percent of Jewish Israelis say they want to ban social media posts expressing sympathy for civilians (""There are no civilians ."") On the other side of the conflict, there is a desire to punish Israeli citizens and Jews around the world for Israel's actions in the conflict, as shown by the storming of an airport in Russian Dagestan.
As a result of Russia's invasion of Ukraine, the alienation of ethnic Russians has become fashionable. Even Swedish defense policy pundits now found it appropriate to dehumanize Russians by calling them "orcs" (evil and warlike creatures with sharp teeth taken from J.R.R. Tolkien's stories). Others wanted to deny all Russian citizens entry . Recently, the software project Linux has removed Russian programmers simply because they are Russian. Similar rhetoric can be found on the other side.
All three of the above examples constitute a form of collective punishment, which is contrary to both the UN Declaration of Human Rights and the Geneva Convention . Yet few react.
The author Hannah Arendt coined the term "the banality of evil" when she studied Nazi war criminals. The term refers to the idea that evil actions often stem from ordinary people blindly following orders or societal norms without critical scrutiny. She argued that individual responsibility and critical thinking were of paramount importance.
In an iconic photo from the 1930s, a large crowd is shown with everyone doing the Hitler salute. Everyone except one. The man, believed to be August Landmesser , openly showed his refusal with crossed arms and a stern expression.
Imagine yourself in his shoes, standing among thousands of people who are raising their arms. Would you have the courage to stand still and quietly while everyone around you shouts their support? Or would you, like so many others, let yourself be swept along with the current and follow the crowd? Somewhere in there, you might have the answer to how thick this "civilizing veneer" really is.
Cover image: Picture of people giving a Nazi salute, with an unidentified person (possibly August Landmesser or Gustav Wegert) refusing to do so, Wikimedia Commons
-
 @ 42342239:1d80db24
2024-11-06 09:05:17
@ 42342239:1d80db24
2024-11-06 09:05:17TL;DR: J.D. Vance recently observed that many in the Democratic Party are attempting to manufacture trust from the top down, neglecting the fact that genuine trust is often born from grassroots connections. There's indeed a stark contrast between trust that's artificially constructed through manipulation and censorship, and trust that's organically cultivated from the ground up.
Trump's vice presidential candidate J.D. Vance appeared on podcast host Joe Rogan's show earlier in November. According to Vance, large parts of the Democratic Party are trying to create higher trust from above, without understanding that the previously high trust once arose organically: "I think that a lot of them are trying to reimpose that social trust from the top."
Most people understand the importance of high trust. Political scientist Robert D. Putnam, for example, has shown that large social capital, in the form of trust and networks, is a key factor for economic growth, cooperation, and problem-solving. See e.g. his book Bowling Alone: The Collapse and Revival of American Community (2000).
The low trust today is widespread. Trust in the American federal government is at historically low levels. Trust in the media is at rock-bottom levels. Even trust in doctors and hospitals has plummeted: at the beginning of 2024, the proportion of people who reported "a great deal of trust" had dropped to 40%, from 72% in April 2020. This can be concerning, as individuals with low trust in doctors and hospitals will be less likely to follow their advice and recommendations. It's therefore not surprising that many want to "rebuild trust" (this was the theme of the World Economic Forum's annual meeting this year).
How much trust is actually reasonable?
But how much trust is actually reasonable? To determine this, one can ask whether an institution has acted reliably in the past, whether it possesses the knowledge and ability required to deliver what is promised, and whether its interests are in line with our own.
The low trust figures among Americans are likely a reflection of the fact that many of them today question the extent to which the answers to these questions are actually affirmative. During the pandemic, medical experts in the UK incorrectly predicted that hundreds of thousands of people would die. In the US, the leading infectious disease expert misled the public about, among other things, face masks, the sitting president lied about both the effectiveness and safety of vaccines, a British health minister wanted to "scare the pants off people," and virus experts even conspired to mislead about the origin of the SARS-CoV-2 virus. All while social media companies, under pressure from governments, were forced to censor information that was actually correct.
Trust - built on sand or on solid ground?
It's possible to continue on the current path and try to improve trust figures by limiting access to information. For instance, if the public doesn't get access to negative information about authorities or experts, the measured trust can increase. But in that case, trust is merely built on sand, waiting to be undermined by the inexorable forces of truth.
But there's another possibility. Building relationships that are genuine and honest, listening to each other without judgment, and communicating without misleading. Doing things that really matter, and doing them well, showing competence and reliability through actions. In this way, trust can grow naturally and organically. A trust built on solid ground, not on sand. A delicate task. But presidential election or not, isn't it time for us to start building a future where this form of trust is the obvious foundation?
-
 @ 42342239:1d80db24
2024-10-29 19:27:12
@ 42342239:1d80db24
2024-10-29 19:27:12The Swedish government recently rejected the Transport Administration's proposal for average speed cameras. The proposal would have meant constant surveillance of all vehicles, and critics argued for instance that it would have posed a threat to national security. Given the prevalence of IT breaches and data leaks today, it's hard not to give them a point, even if the problems are often downplayed by both corporations, governments and organisations. After Facebook (now Meta) leaked account information for over half a billion users, internal mails revealed the company wanted to "normalise the fact that this happens regularly".
IT security focuses on protecting the information in our computer systems and their connections. Cybersecurity is a broader concept that also includes aspects such as human behaviour, environmental factors, and management.
Data that has not been collected cannot leak
Knowledge about cybersecurity is often insufficient. For example, it was not long ago that the Swedish Transport Agency decided to outsource the operation of the Swedish vehicle and driving licence register. This was done despite deviations from various laws and criticism from the Security Police. The operation was placed in, among other places, Serbia (which has a close relationship with Russia). The Swedish driving licence register, including personal photos, as well as confidential information about critical infrastructure such as bridges, subways, roads, and ports, became available to personnel without Swedish security clearance.
The government's decision earlier this year not to proceed with a Swedish "super register" is an example of how cybersecurity can be strengthened. The rejection of the Transport Administration's proposal for average speed cameras is another. Data that has not been collected cannot leak out. It cannot be outsourced either.
Accounts are risky by definition
But the question is bigger than that. More and more of the products and services we depend on are now subscription services, often including long documents with terms and conditions. Which few people read. If you want to control your air heat pump with your phone, you not only need an app and an account, but also agree to someone storing your data (maybe also selling it or leaking it). The same applies if you want to be able to find your car in the car park. If you do not agree to the constantly updated terms, you lose important functionality.
Every time you are required to create an account, you are put in a dependent position. And our society becomes more fragile - because data is collected and can therefore leak out. It is much harder to lose something you do not have.
At the Korean car manufacturer Kia, huge security holes were recently discovered. IT researchers could quickly scan and control almost any car, including tracking its position, unlocking it, starting the ignition, and accessing cameras and personal information such as name, phone number, and home address. In some cases, even driving routes. All thanks to a "relatively simple flaw" in a web portal.
Instead of being at the mercy of large companies' IT departments, our security would improve if we could control our air heat pump, unlock our car, or our data ourselves. The technology already exists, thanks to the breakthrough of asymmetric encryption in the 1970s. Now we just need the will to change.
-
 @ 42342239:1d80db24
2024-10-23 12:28:41
@ 42342239:1d80db24
2024-10-23 12:28:41TL;DR: The mathematics of trust says that news reporting will fall flat when the population becomes suspicious of the media. Which is now the case for growing subgroups in the U.S. as well as in Sweden.
A recent wedding celebration for Sweden Democrats leader Jimmie Åkesson resulted in controversy, as one of the guests in attendance was reportedly linked to organized crime. Following this “wedding scandal”, a columnist noted that the party’s voters had not been significantly affected. Instead of a decrease in trust - which one might have expected - 10% of them stated that their confidence in the party had actually increased. “Over the years, the Sweden Democrats have surprisingly emerged unscathed from their numerous scandals,” she wrote. But is this really so surprising?
In mathematics, a probability is expressed as the likelihood of something occurring given one or more conditions. For example, one can express a probability as “the likelihood that a certain stock will rise in price, given that the company has presented a positive quarterly report.” In this case, the company’s quarterly report is the basis for the assessment. If we add more information, such as the company’s strong market position and a large order from an important customer, the probability increases further. The more information we have to go on, the more precise we can be in our assessment.
From this perspective, the Sweden Democrats’ “numerous scandals” should lead to a more negative assessment of the party. But this perspective omits something important.
A couple of years ago, the term “gaslighting” was chosen as the word of the year in the US. The term comes from a 1944 film of the same name and refers to a type of psychological manipulation, as applied to the lovely Ingrid Bergman. Today, the term is used in politics, for example, when a large group of people is misled to achieve political goals. The techniques used can be very effective but have a limitation. When the target becomes aware of what is happening, everything changes. Then the target becomes vigilant and views all new information with great suspicion.
The Sweden Democrats’ “numerous scandals” should lead to a more negative assessment of the party. But if SD voters to a greater extent than others believe that the source of the information is unreliable, for example, by omitting information or adding unnecessary information, the conclusion is different. The Swedish SOM survey shows that these voters have lower trust in journalists and also lower confidence in the objectivity of the news. Like a victim of gaslighting, they view negative reporting with suspicion. The arguments can no longer get through. A kind of immunity has developed.
In the US, trust in the media is at an all-time low. So when American media writes that “Trump speaks like Hitler, Stalin, and Mussolini,” that his idea of deporting illegal immigrants would cost hundreds of billions of dollars, or gets worked up over his soda consumption, the consequence is likely to be similar to here at home.
The mathematics of trust says that reporting will fall flat when the population becomes suspicious of the media. Or as the Swedish columnist put it: like water off a duck’s back.
Cover image: Ingrid Bergman 1946. RKO Radio Pictures - eBay, Public Domain, Wikimedia Commons
-
 @ 42342239:1d80db24
2024-10-22 07:57:17
@ 42342239:1d80db24
2024-10-22 07:57:17It was recently reported that Sweden's Minister for Culture, Parisa Liljestrand, wishes to put an end to anonymous accounts on social media. The issue has been at the forefront following revelations of political parties using pseudonymous accounts on social media platforms earlier this year.
The importance of the internet is also well-known. As early as 2015, Roberta Alenius, who was then the press secretary for Fredrik Reinfeldt (Moderate Party), openly spoke about her experiences with the Social Democrats' and Moderates' internet activists: Twitter actually set the agenda for journalism at the time.
The Minister for Culture now claims, amongst other things, that anonymous accounts pose a threat to democracy, that they deceive people, and that they can be used to mislead, etc. It is indeed easy to find arguments against anonymity; perhaps the most common one is the 'nothing to hide, nothing to fear' argument.
One of the many problems with this argument is that it assumes that abuse of power never occurs. History has much to teach us here. Sometimes, authorities can act in an arbitrary, discriminatory, or even oppressive manner, at least in hindsight. Take, for instance, the struggles of the homosexual community, the courageous dissidents who defied communist regimes, or the women who fought for their right to vote in the suffragette movement.
It was difficult for homosexuals to be open about their sexuality in Sweden in the 1970s. Many risked losing their jobs, being ostracised, or harassed. Anonymity was therefore a necessity for many. Homosexuality was actually classified as a mental illness in Sweden until 1979.
A couple of decades earlier, dissidents in communist regimes in Europe used pseudonyms when publishing samizdat magazines. The Czech author and dissident Václav Havel, who later became the President of the Czech Republic, used a pseudonym when publishing his texts. The same was true for the Russian author and literary prize winner Alexander Solzhenitsyn. Indeed, in Central and Eastern Europe, anonymity was of the utmost importance.
One hundred years ago, women all over the world fought for the right to vote and to be treated as equals. Many were open in their struggle, but for others, anonymity was a necessity as they risked being socially ostracised, losing their jobs, or even being arrested.
Full transparency is not always possible or desirable. Anonymity can promote creativity and innovation as it gives people the opportunity to experiment and try out new ideas without fear of being judged or criticised. This applies not only to individuals but also to our society, in terms of ideas, laws, norms, and culture.
It is also a strange paradox that those who wish to limit freedom of speech and abolish anonymity simultaneously claim to be concerned about the possible return of fascism. The solutions they advocate are, in fact, precisely what would make it easier for a tyrannical regime to maintain its power. To advocate for the abolition of anonymity, one must also be of the (absurd) opinion that the development of history has now reached its definitive end.
-
 @ 42342239:1d80db24
2024-09-26 07:57:04
@ 42342239:1d80db24
2024-09-26 07:57:04The boiling frog is a simple tale that illustrates the danger of gradual change: if you put a frog in boiling water, it will quickly jump out to escape the heat. But if you place a frog in warm water and gradually increase the temperature, it won't notice the change and will eventually cook itself. Might the decline in cash usage be construed as an example of this tale?
As long as individuals can freely transact with each other and conduct purchases and sales without intermediaries[^1] such as with cash, our freedoms and rights remain secure from potential threats posed by the payment system. However, as we have seen in several countries such as Sweden over the past 15 years, the use of cash and the amount of banknotes and coins in circulation have decreased. All to the benefit of various intermediated[^1] electronic alternatives.
The reasons for this trend include: - The costs associated with cash usage has been increasing. - Increased regulatory burdens due to stricter anti-money laundering regulations. - Closed bank branches and fewer ATMs. - The Riksbank's aggressive note switches resulted in a situation where they were no longer recognized.
Market forces or "market forces"?
Some may argue that the "de-cashing" of society is a consequence of market forces. But does this hold true? Leading economists at times recommend interventions with the express purpose to mislead the public, such as proposing measures who are "opaque to most voters."
In a working paper on de-cashing by the International Monetary Fund (IMF) from 2017, such thought processes, even recommendations, can be found. IMF economist Alexei Kireyev, formerly a professor at an institute associated with the Soviet Union's KGB (MGIMO) and economic adviser to Michail Gorbachov 1989-91, wrote that:
- "Social conventions may also be disrupted as de-cashing may be viewed as a violation of fundamental rights, including freedom of contract and freedom of ownership."
- Letting the private sector lead "the de-cashing" is preferable, as it will seem "almost entirely benign". The "tempting attempts to impose de-cashing by a decree should be avoided"
- "A targeted outreach program is needed to alleviate suspicions related to de-cashing"
In the text, he also offered suggestions on the most effective approach to diminish the use of cash:
- The de-cashing process could build on the initial and largely uncontested steps, such as the phasing out of large denomination bills, the placement of ceilings on cash transactions, and the reporting of cash moves across the borders.
- Include creating economic incentives to reduce the use of cash in transactions
- Simplify "the opening and use of transferrable deposits, and further computerizing the financial system."
As is customary in such a context, it is noted that the article only describes research and does not necessarily reflect IMF's views. However, isn't it remarkable that all of these proposals have come to fruition and the process continues? Central banks have phased out banknotes with higher denominations. Banks' regulatory complexity seemingly increase by the day (try to get a bank to handle any larger amounts of cash). The transfer of cash from one nation to another has become increasingly burdensome. The European Union has recently introduced restrictions on cash transactions. Even the law governing the Swedish central bank is written so as to guarantee a further undermining of cash. All while the market share is growing for alternatives such as transferable deposits[^1].
The old European disease
The Czech Republic's former president Václav Havel, who played a key role in advocating for human rights during the communist repression, was once asked what the new member states in the EU could do to pay back for all the economic support they had received from older member states. He replied that the European Union still suffers from the old European disease, namely the tendency to compromise with evil. And that the new members, who have a recent experience of totalitarianism, are obliged to take a more principled stance - sometimes necessary - and to monitor the European Union in this regard, and educate it.
The American computer scientist and cryptographer David Chaum said in 1996 that "[t]he difference between a bad electronic cash system and well-developed digital cash will determine whether we will have a dictatorship or a real democracy". If Václav Havel were alive today, he would likely share Chaum's sentiment. Indeed, on the current path of "de-cashing", we risk abolishing or limiting our liberties and rights, "including freedom of contract and freedom of ownership" - and this according to an economist at the IMF(!).
As the frog was unwittingly boiled alive, our freedoms are quietly being undermined. The temperature is rising. Will people take notice before our liberties are irreparably damaged?
[^1]: Transferable deposits are intermediated. Intermediated means payments involving one or several intermediares, like a bank, a card issuer or a payment processor. In contrast, a disintermediated payment would entail a direct transactions between parties without go-betweens, such as with cash.
-
 @ ee11a5df:b76c4e49
2024-09-11 08:16:37
@ ee11a5df:b76c4e49
2024-09-11 08:16:37Bye-Bye Reply Guy
There is a camp of nostr developers that believe spam filtering needs to be done by relays. Or at the very least by DVMs. I concur. In this way, once you configure what you want to see, it applies to all nostr clients.
But we are not there yet.
In the mean time we have ReplyGuy, and gossip needed some changes to deal with it.
Strategies in Short
- WEB OF TRUST: Only accept events from people you follow, or people they follow - this avoids new people entirely until somebody else that you follow friends them first, which is too restrictive for some people.
- TRUSTED RELAYS: Allow every post from relays that you trust to do good spam filtering.
- REJECT FRESH PUBKEYS: Only accept events from people you have seen before - this allows you to find new people, but you will miss their very first post (their second post must count as someone you have seen before, even if you discarded the first post)
- PATTERN MATCHING: Scan for known spam phrases and words and block those events, either on content or metadata or both or more.
- TIE-IN TO EXTERNAL SYSTEMS: Require a valid NIP-05, or other nostr event binding their identity to some external identity
- PROOF OF WORK: Require a minimum proof-of-work
All of these strategies are useful, but they have to be combined properly.
filter.rhai
Gossip loads a file called "filter.rhai" in your gossip directory if it exists. It must be a Rhai language script that meets certain requirements (see the example in the gossip source code directory). Then it applies it to filter spam.
This spam filtering code is being updated currently. It is not even on unstable yet, but it will be there probably tomorrow sometime. Then to master. Eventually to a release.
Here is an example using all of the techniques listed above:
```rhai // This is a sample spam filtering script for the gossip nostr // client. The language is called Rhai, details are at: // https://rhai.rs/book/ // // For gossip to find your spam filtering script, put it in // your gossip profile directory. See // https://docs.rs/dirs/latest/dirs/fn.data_dir.html // to find the base directory. A subdirectory "gossip" is your // gossip data directory which for most people is their profile // directory too. (Note: if you use a GOSSIP_PROFILE, you'll // need to put it one directory deeper into that profile // directory). // // This filter is used to filter out and refuse to process // incoming events as they flow in from relays, and also to // filter which events get/ displayed in certain circumstances. // It is only run on feed-displayable event kinds, and only by // authors you are not following. In case of error, nothing is // filtered. // // You must define a function called 'filter' which returns one // of these constant values: // DENY (the event is filtered out) // ALLOW (the event is allowed through) // MUTE (the event is filtered out, and the author is // automatically muted) // // Your script will be provided the following global variables: // 'caller' - a string that is one of "Process", // "Thread", "Inbox" or "Global" indicating // which part of the code is running your // script // 'content' - the event content as a string // 'id' - the event ID, as a hex string // 'kind' - the event kind as an integer // 'muted' - if the author is in your mute list // 'name' - if we have it, the name of the author // (or your petname), else an empty string // 'nip05valid' - whether nip05 is valid for the author, // as a boolean // 'pow' - the Proof of Work on the event // 'pubkey' - the event author public key, as a hex // string // 'seconds_known' - the number of seconds that the author // of the event has been known to gossip // 'spamsafe' - true only if the event came in from a // relay marked as SpamSafe during Process // (even if the global setting for SpamSafe // is off)
fn filter() {
// Show spam on global // (global events are ephemeral; these won't grow the // database) if caller=="Global" { return ALLOW; } // Block ReplyGuy if name.contains("ReplyGuy") || name.contains("ReplyGal") { return DENY; } // Block known DM spam // (giftwraps are unwrapped before the content is passed to // this script) if content.to_lower().contains( "Mr. Gift and Mrs. Wrap under the tree, KISSING!" ) { return DENY; } // Reject events from new pubkeys, unless they have a high // PoW or we somehow already have a nip05valid for them // // If this turns out to be a legit person, we will start // hearing their events 2 seconds from now, so we will // only miss their very first event. if seconds_known <= 2 && pow < 25 && !nip05valid { return DENY; } // Mute offensive people if content.to_lower().contains(" kike") || content.to_lower().contains("kike ") || content.to_lower().contains(" nigger") || content.to_lower().contains("nigger ") { return MUTE; } // Reject events from muted people // // Gossip already does this internally, and since we are // not Process, this is rather redundant. But this works // as an example. if muted { return DENY; } // Accept if the PoW is large enough if pow >= 25 { return ALLOW; } // Accept if their NIP-05 is valid if nip05valid { return ALLOW; } // Accept if the event came through a spamsafe relay if spamsafe { return ALLOW; } // Reject the rest DENY} ```
-
 @ 42342239:1d80db24
2024-09-02 12:08:29
@ 42342239:1d80db24
2024-09-02 12:08:29The ongoing debate surrounding freedom of expression may revolve more around determining who gets to control the dissemination of information rather than any claimed notion of safeguarding democracy. Similarities can be identified from 500 years ago, following the invention of the printing press.
What has been will be again, what has been done will be done again; there is nothing new under the sun.
-- Ecclesiastes 1:9
The debate over freedom of expression and its limits continues to rage on. In the UK, citizens are being arrested for sharing humouristic images. In Ireland, it may soon become illegal to possess "reckless" memes. Australia is trying to get X to hide information. Venezuela's Maduro blocked X earlier this year, as did a judge on Brazil's Supreme Court. In the US, a citizen has been imprisoned for spreading misleading material following a controversial court ruling. In Germany, the police are searching for a social media user who called a politician overweight. Many are also expressing concerns about deep fakes (AI-generated videos, images, or audio that are designed to deceive).
These questions are not new, however. What we perceive as new questions are often just a reflection of earlier times. After Gutenberg invented the printing press in the 15th century, there were soon hundreds of printing presses across Europe. The Church began using printing presses to mass-produce indulgences. "As soon as the coin in the coffer rings, the soul from purgatory springs" was a phrase used by a traveling monk who sold such indulgences at the time. Martin Luther questioned the reasonableness of this practice. Eventually, he posted the 95 theses on the church door in Wittenberg. He also translated the Bible into German. A short time later, his works, also mass-produced, accounted for a third of all books sold in Germany. Luther refused to recant his provocations as then determined by the Church's central authority. He was excommunicated in 1520 by the Pope and soon declared an outlaw by the Holy Roman Emperor.
This did not stop him. Instead, Luther referred to the Pope as "Pope Fart-Ass" and as the "Ass-God in Rome)". He also commissioned caricatures, such as woodcuts showing a female demon giving birth to the Pope and cardinals, of German peasants responding to a papal edict by showing the Pope their backsides and breaking wind, and more.
Gutenberg's printing presses contributed to the spread of information in a way similar to how the internet does in today's society. The Church's ability to control the flow of information was undermined, much like how newspapers, radio, and TV have partially lost this power today. The Pope excommunicated Luther, which is reminiscent of those who are de-platformed or banned from various platforms today. The Emperor declared Luther an outlaw, which is similar to how the UK's Prime Minister is imprisoning British citizens today. Luther called the Pope derogatory names, which is reminiscent of the individual who recently had the audacity to call an overweight German minister overweight.
Freedom of expression must be curtailed to combat the spread of false or harmful information in order to protect democracy, or so it is claimed. But perhaps it is more about who gets to control the flow of information?
As is often the case, there is nothing new under the sun.
-
 @ 42342239:1d80db24
2024-08-30 06:26:21
@ 42342239:1d80db24
2024-08-30 06:26:21Quis custodiet ipsos custodes?
-- Juvenal (Who will watch the watchmen?)
In mid-July, numerous media outlets reported on the assassination attempt on Donald Trump. FBI Director Christopher Wray stated later that same month that what hit the former president Trump was a bullet. A few days later, it was reported from various sources that search engines no longer acknowledged that an assassination attempt on ex-President Trump had taken place. When users used automatic completion in Google and Bing (91% respectively 4% market share), these search engines only suggested earlier presidents such as Harry Truman and Theodore Roosevelt, along with Russian President Vladimir Putin as people who could have been subjected to assassination attempts.
The reports were comprehensive enough for the Republican district attorney of Missouri to say that he would investigate matter. The senator from Kansas - also a Republican - planned to make an official request to Google. Google has responded through a spokesman to the New York Post that the company had not "manually changed" search results, but its system includes "protection" against search results "connected to political violence."
A similar phenomenon occurred during the 2016 presidential election. At the time, reports emerged of Google, unlike other less widely used search engines, rarely or never suggesting negative search results for Hillary Clinton. The company however provided negative search results for then-candidate Trump. Then, as today, the company denied deliberately favouring any specific political candidate.
These occurrences led to research on how such search suggestions can influence public opinion and voting preferences. For example, the impact of simply removing negative search suggestions has been investigated. A study published in June 2024 reports that such search results can dramatically affect undecided voters. Reducing negative search suggestions can turn a 50/50 split into a 90/10 split in favour of the candidate for whom negative search suggestions were suppressed. The researchers concluded that search suggestions can have "a dramatic impact," that this can "shift a large number of votes" and do so without leaving "any trace for authorities to follow." How search engines operate should therefore be considered of great importance by anyone who claims to take democracy seriously. And this regardless of one's political sympathies.
A well-known thought experiment in philosophy asks: "If a tree falls in the forest and no one hears it, does it make a sound?" Translated to today's media landscape: If an assassination attempt took place on a former president, but search engines don't want to acknowledge it, did it really happen?
-
 @ 42342239:1d80db24
2024-07-28 08:35:26
@ 42342239:1d80db24
2024-07-28 08:35:26Jerome Powell, Chairman of the US Federal Reserve, stated during a hearing in March that the central bank has no plans to introduce a central bank digital currency (CBDCs) or consider it necessary at present. He said this even though the material Fed staff presents to Congress suggests otherwise - that CBDCs are described as one of the Fed’s key duties .
A CBDC is a state-controlled and programmable currency that could allow the government or its intermediaries the possibility to monitor all transactions in detail and also to block payments based on certain conditions.
Critics argue that the introduction of CBDCs could undermine citizens’ constitutionally guaranteed freedoms and rights . Republican House Majority Leader Tom Emmer, the sponsor of a bill aimed at preventing the central bank from unilaterally introducing a CBDC, believes that if they do not mimic cash, they would only serve as a “CCP-style [Chinese Communist Party] surveillance tool” and could “undermine the American way of life”. Emmer’s proposed bill has garnered support from several US senators , including Republican Ted Cruz from Texas, who introduced the bill to the Senate. Similarly to how Swedish cash advocates risk missing the mark , Tom Emmer and the US senators risk the same outcome with their bill. If the central bank is prevented from introducing a central bank digital currency, nothing would stop major banks from implementing similar systems themselves, with similar consequences for citizens.
Indeed, the entity controlling your money becomes less significant once it is no longer you. Even if central bank digital currencies are halted in the US, a future administration could easily outsource financial censorship to the private banking system, similar to how the Biden administration is perceived by many to have circumvented the First Amendment by getting private companies to enforce censorship. A federal court in New Orleans ruled last fall against the Biden administration for compelling social media platforms to censor content. The Supreme Court has now begun hearing the case.
Deng Xiaoping, China’s paramount leader who played a vital role in China’s modernization, once said, “It does not matter if the cat is black or white. What matters is that it catches mice.” This statement reflected a pragmatic approach to economic policy, focusing on results foremost. China’s economic growth during his tenure was historic.
The discussion surrounding CBDCs and their negative impact on citizens’ freedoms and rights would benefit from a more practical and comprehensive perspective. Ultimately, it is the outcomes that matter above all. So too for our freedoms.
-
 @ ee11a5df:b76c4e49
2024-07-11 23:57:53
@ ee11a5df:b76c4e49
2024-07-11 23:57:53What Can We Get by Breaking NOSTR?
"What if we just started over? What if we took everything we have learned while building nostr and did it all again, but did it right this time?"
That is a question I've heard quite a number of times, and it is a question I have pondered quite a lot myself.
My conclusion (so far) is that I believe that we can fix all the important things without starting over. There are different levels of breakage, starting over is the most extreme of them. In this post I will describe these levels of breakage and what each one could buy us.
Cryptography
Your key-pair is the most fundamental part of nostr. That is your portable identity.
If the cryptography changed from secp256k1 to ed25519, all current nostr identities would not be usable.
This would be a complete start over.
Every other break listed in this post could be done as well to no additional detriment (save for reuse of some existing code) because we would be starting over.
Why would anyone suggest making such a break? What does this buy us?
- Curve25519 is a safe curve meaning a bunch of specific cryptography things that us mortals do not understand but we are assured that it is somehow better.
- Ed25519 is more modern, said to be faster, and has more widespread code/library support than secp256k1.
- Nostr keys could be used as TLS server certificates. TLS 1.3 using RFC 7250 Raw Public Keys allows raw public keys as certificates. No DNS or certification authorities required, removing several points of failure. These ed25519 keys could be used in TLS, whereas secp256k1 keys cannot as no TLS algorithm utilizes them AFAIK. Since relays currently don't have assigned nostr identities but are instead referenced by a websocket URL, this doesn't buy us much, but it is interesting. This idea is explored further below (keep reading) under a lesser level of breakage.
Besides breaking everything, another downside is that people would not be able to manage nostr keys with bitcoin hardware.
I am fairly strongly against breaking things this far. I don't think it is worth it.
Signature Scheme and Event Structure
Event structure is the next most fundamental part of nostr. Although events can be represented in many ways (clients and relays usually parse the JSON into data structures and/or database columns), the nature of the content of an event is well defined as seven particular fields. If we changed those, that would be a hard fork.
This break is quite severe. All current nostr events wouldn't work in this hard fork. We would be preserving identities, but all content would be starting over.
It would be difficult to bridge between this fork and current nostr because the bridge couldn't create the different signature required (not having anybody's private key) and current nostr wouldn't be generating the new kind of signature. Therefore any bridge would have to do identity mapping just like bridges to entirely different protocols do (e.g. mostr to mastodon).
What could we gain by breaking things this far?
- We could have a faster event hash and id verification: the current signature scheme of nostr requires lining up 5 JSON fields into a JSON array and using that as hash input. There is a performance cost to copying this data in order to hash it.
- We could introduce a subkey field, and sign events via that subkey, while preserving the pubkey as the author everybody knows and searches by. Note however that we can already get a remarkably similar thing using something like NIP-26 where the actual author is in a tag, and the pubkey field is the signing subkey.
- We could refactor the kind integer into composable bitflags (that could apply to any application) and an application kind (that specifies the application).
- Surely there are other things I haven't thought of.
I am currently against this kind of break. I don't think the benefits even come close to outweighing the cost. But if I learned about other things that we could "fix" by restructuring the events, I could possibly change my mind.
Replacing Relay URLs
Nostr is defined by relays that are addressed by websocket URLs. If that changed, that would be a significant break. Many (maybe even most) current event kinds would need superseding.
The most reasonable change is to define relays with nostr identities, specifying their pubkey instead of their URL.
What could we gain by this?
- We could ditch reliance on DNS. Relays could publish events under their nostr identity that advertise their current IP address(es).
- We could ditch certificates because relays could generate ed25519 keypairs for themselves (or indeed just self-signed certificates which might be much more broadly supported) and publish their public ed25519 key in the same replaceable event where they advertise their current IP address(es).
This is a gigantic break. Almost all event kinds need redefining and pretty much all nostr software will need fairly major upgrades. But it also gives us a kind of Internet liberty that many of us have dreamt of our entire lives.
I am ambivalent about this idea.
Protocol Messaging and Transport
The protocol messages of nostr are the next level of breakage. We could preserve keypair identities, all current events, and current relay URL references, but just break the protocol of how clients and relay communicate this data.
This would not necessarily break relay and client implementations at all, so long as the new protocol were opt-in.
What could we get?
- The new protocol could transmit events in binary form for increased performance (no more JSON parsing with it's typical many small memory allocations and string escaping nightmares). I think event throughput could double (wild guess).
- It could have clear expectations of who talks first, and when and how AUTH happens, avoiding a lot of current miscommunication between clients and relays.
- We could introduce bitflags for feature support so that new features could be added later and clients would not bother trying them (and getting an error or timing out) on relays that didn't signal support. This could replace much of NIP-11.
- We could then introduce something like negentropy or negative filters (but not that... probably something else solving that same problem) without it being a breaking change.
- The new protocol could just be a few websocket-binary messages enhancing the current protocol, continuing to leverage the existing websocket-text messages we currently have, meaning newer relays would still support all the older stuff.
The downsides are just that if you want this new stuff you have to build it. It makes the protocol less simple, having now multiple protocols, multiple ways of doing the same thing.
Nonetheless, this I am in favor of. I think the trade-offs are worth it. I will be pushing a draft PR for this soon.
The path forward
I propose then the following path forward:
- A new nostr protocol over websockets binary (draft PR to be shared soon)
- Subkeys brought into nostr via NIP-26 (but let's use a single letter tag instead, OK?) via a big push to get all the clients to support it (the transition will be painful - most major clients will need to support this before anybody can start using it).
- Some kind of solution to the negative-filter-negentropy need added to the new protocol as its first optional feature.
- We seriously consider replacing Relay URLs with nostr pubkeys assigned to the relay, and then have relays publish their IP address and TLS key or certificate.
We sacrifice these:
- Faster event hash/verification
- Composable event bitflags
- Safer faster more well-supported crypto curve
- Nostr keys themselves as TLS 1.3 RawPublicKey certificates
-
 @ 42342239:1d80db24
2024-07-06 15:26:39
@ 42342239:1d80db24
2024-07-06 15:26:39Claims that we need greater centralisation, more EU, or more globalisation are prevalent across the usual media channels. The climate crisis, environmental destruction, pandemics, the AI-threat, yes, everything will apparently be solved if a little more global coordination, governance and leadership can be brought about.
But, is this actually true? One of the best arguments for this conclusion stems implicitly from the futurist Eliezer Yudkowsky, who once proposed a new Moore's Law, though this time not for computer processors but instead for mad science: "every 18 months, the minimum IQ necessary to destroy the world drops by one point".
Perhaps we simply have to tolerate more centralisation, globalisation, control, surveillance, and so on, to prevent all kinds of fools from destroying the world?
Note: a Swedish version of this text is avalable at Affärsvärlden.
At the same time, more centralisation, globalisation, etc. is also what we have experienced. Power has been shifting from the local, and from the majorities, to central-planning bureaucrats working in remote places. This has been going on for several decades. The EU's subsidiarity principle, i.e. the idea that decisions should be made at the lowest expedient level, and which came to everyone's attention ahead of Sweden's EU vote in 1994, is today swept under the rug as untimely and outdated, perhaps even retarded.
At the same time, there are many crises, more than usual it would seem. If it is not a crisis of criminality, a logistics/supply chain crisis or a water crisis, then it is an energy crisis, a financial crisis, a refugee crisis or a climate crisis. It is almost as if one starts to suspect that all this centralisation may be leading us down the wrong path. Perhaps centralisation is part of the problem, rather than the capital S solution?
Why centralisation may cause rather than prevent problems
There are several reasons why centralisation, etc, may actually be a problem. And though few seem to be interested in such questions today (or perhaps they are too timid to mention their concerns?), it has not always been this way. In this short essay we'll note four reasons (though there are several others):
- Political failures (Buchanan et al)
- Local communities & skin in the game (Ostrom and Taleb)
- The local knowledge problem (von Hayek)
- Governance by sociopaths (Hare)
James Buchanan who was given the so-called Nobel price in economics in the eighties once said that: "politicians and bureaucrats are no different from the rest of us. They will maximise their incentives just like everybody else.".
Buchanan was prominent in research on rent-seeking and political failures, i.e. when political "solutions" to so-called market failures make everything worse. Rent-seeking is when a company spends resources (e.g. lobbying) to get legislators or other decision makers to pass laws or create regulations that benefit the company instead of it having to engage in productive activities. The result is regulatory capture. The more centralised decision-making is, the greater the negative consequences from such rent-seeking will be for society at large. This is known.
Another economist, Elinor Ostrom, was given the same prize in the great financial crisis year of 2009. In her research, she had found that local communities where people had influence over rules and regulations, as well as how violations there-of were handled, were much better suited to look after common resources than centralised bodies. To borrow a term from the combative Nassim Nicholas Taleb: everything was better handled when decision makers had "skin in the game".
A third economist, Friedrich von Hayek, was given this prize as early as 1974, partly because he showed that central planning could not possibly take into account all relevant information. The information needed in economic planning is by its very nature distributed, and will never be available to a central planning committee, or even to an AI.
Moreover, human systems are complex and not just complicated. When you realise this, you also understand why the forecasts made by central planners often end up wildly off the mark - and at times in a catastrophic way. (This in itself is an argument for relying more on factors outside of the models in the decision-making process.)
From Buchanan's, Ostrom's, Taleb's or von Hayek's perspectives, it also becomes difficult to believe that today's bureaucrats are the most suited to manage and price e.g. climate risks. One can compare with the insurance industry, which has both a long habit of pricing risks as well as "skin in the game" - two things sorely missing in today's planning bodies.
Instead of preventing fools, we may be enabling madmen
An even more troubling conclusion is that centralisation tends to transfer power to people who perhaps shouldn't have more of that good. "Not all psychopaths are in prison - some are in the boardroom," psychologist Robert Hare once said during a lecture. Most people have probably known for a long time that those with sharp elbows and who don't hesitate to stab a colleague in the back can climb quickly in organisations. In recent years, this fact seems to have become increasingly well known even in academia.
You will thus tend to encounter an increased prevalance of individuals with narcissistic and sociopathic traits the higher up you get in the the status hierarchy. And if working in large organisations (such as the European Union or Congress) or in large corporations, is perceived as higher status - which is generally the case, then it follows that the more we centralise, the more we will be governed by people with less flattering Dark Triad traits.
By their fruits ye shall know them
Perhaps it is thus not a coincidence that we have so many crises. Perhaps centralisation, globalisation, etc. cause crises. Perhaps the "elites" and their planning bureaucrats are, in fact, not the salt of the earth and the light of the world. Perhaps President Trump even had a point when he said "they are not sending their best".
https://www.youtube.com/watch?v=w4b8xgaiuj0
The opposite of centralisation is decentralisation. And while most people may still be aware that decentralisation can be a superpower within the business world, it's time we remind ourselves that this also applies to the economy - and society - at large, and preferably before the next Great Leap Forward is fully thrust upon us.
-
 @ b12b632c:d9e1ff79
2024-05-29 12:10:18
@ b12b632c:d9e1ff79
2024-05-29 12:10:18One other day on Nostr, one other app!
Today I'll present you a new self-hosted Nostr blog web application recently released on github by dtonon, Oracolo:
https://github.com/dtonon/oracolo
Oracolo is a minimalist blog powered by Nostr, that consists of a single html file, weighing only ~140Kb. You can use whatever Nostr client that supports long format (habla.news, yakihonne, highlighter.com, etc ) to write your posts, and your personal blog is automatically updated.
It works also without a web server; for example you can send it via email as a business card.Oracolo fetches Nostr data, builds the page, execute the JavaScript code and displays article on clean and sobr blog (a Dark theme would be awesome 👀).
Blog articles are nostr events you published or will publish on Nostr relays through long notes applications like the ones quoted above.
Don't forget to use a NIP07 web browser extensions to login on those websites. Old time where we were forced to fill our nsec key is nearly over!
For the hurry ones of you, you can find here the Oracolo demo with my Nostr long notes article. It will include this one when I'll publish it on Nostr!
https://oracolo.fractalized.net/
How to self-host Oracolo?
You can build the application locally or use a docker compose stack to run it (or any other method). I just build a docker compose stack with Traefik and an Oracolo docker image to let you quickly run it.
The oracolo-docker github repo is available here:
https://github.com/PastaGringo/oracolo-docker
PS: don't freak out about the commits number, oracolo has been the lucky one to let me practrice docker image CI/CD build/push with Forgejo, that went well but it took me a while before finding how to make Forgejo runner dood work 😆). Please ping me on Nostr if you are interested by an article on this topic!
This repo is a mirror from my new Forgejo git instance where the code has been originaly published and will be updated if needed (I think it will):
https://git.fractalized.net/PastaGringo/oracolo-docker
Here is how to do it.
1) First, you need to create an A DNS record into your domain.tld zone. You can create a A with "oracolo" .domain.tld or "*" .domain.tld. The second one will allow traefik to generate all the future subdomain.domain.tld without having to create them in advance. You can verify DNS records with the website https://dnschecker.org.
2) Clone the oracolo-docker repository:
bash git clone https://git.fractalized.net/PastaGringo/oracolo-docker.git cd oracolo-docker3) Rename the .env.example file:
bash mv .env.example .env4) Modify and update your .env file with your own infos:
```bash
Let's Encrypt email used to generate the SSL certificate
LETSENCRYPT_EMAIL=
domain for oracolo. Ex: oracolo.fractalized.net
ORACOLO_DOMAIN=
Npub author at "npub" format, not HEX.
NPUB=
Relays where Oracolo will retrieve the Nostr events.
Ex: "wss://nostr.fractalized.net, wss://rnostr.fractalized.net"
RELAYS=
Number of blog article with an thumbnail. Ex: 4
TOP_NOTES_NB= ```
5) Compose Oracolo:
bash docker compose up -d && docker compose logs -f oracolo traefikbash [+] Running 2/0 ✔ Container traefik Running 0.0s ✔ Container oracolo Running 0.0s WARN[0000] /home/pastadmin/DEV/FORGEJO/PLAY/oracolo-docker/docker-compose.yml: `version` is obsolete traefik | 2024-05-28T19:24:18Z INF Traefik version 3.0.0 built on 2024-04-29T14:25:59Z version=3.0.0 oracolo | oracolo | ___ ____ ____ __ ___ _ ___ oracolo | / \ | \ / | / ] / \ | | / \ oracolo | | || D )| o | / / | || | | | oracolo | | O || / | |/ / | O || |___ | O | oracolo | | || \ | _ / \_ | || || | oracolo | | || . \| | \ || || || | oracolo | \___/ |__|\_||__|__|\____| \___/ |_____| \___/ oracolo | oracolo | Oracolo dtonon's repo: https://github.com/dtonon/oracolo oracolo | oracolo | ╭────────────────────────────╮ oracolo | │ Docker Compose Env Vars ⤵️ │ oracolo | ╰────────────────────────────╯ oracolo | oracolo | NPUB : npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2 oracolo | RELAYS : wss://nostr.fractalized.net, wss://rnostr.fractalized.net oracolo | TOP_NOTES_NB : 4 oracolo | oracolo | ╭───────────────────────────╮ oracolo | │ Configuring Oracolo... ⤵️ │ oracolo | ╰───────────────────────────╯ oracolo | oracolo | > Updating npub key with npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2... ✅ oracolo | > Updating nostr relays with wss://nostr.fractalized.net, wss://rnostr.fractalized.net... ✅ oracolo | > Updating TOP_NOTE with value 4... ✅ oracolo | oracolo | ╭───────────────────────╮ oracolo | │ Installing Oracolo ⤵️ │ oracolo | ╰───────────────────────╯ oracolo | oracolo | added 122 packages, and audited 123 packages in 8s oracolo | oracolo | 20 packages are looking for funding oracolo | run `npm fund` for details oracolo | oracolo | found 0 vulnerabilities oracolo | npm notice oracolo | npm notice New minor version of npm available! 10.7.0 -> 10.8.0 oracolo | npm notice Changelog: https://github.com/npm/cli/releases/tag/v10.8.0 oracolo | npm notice To update run: npm install -g npm@10.8.0 oracolo | npm notice oracolo | oracolo | >>> done ✅ oracolo | oracolo | ╭─────────────────────╮ oracolo | │ Building Oracolo ⤵️ │ oracolo | ╰─────────────────────╯ oracolo | oracolo | > oracolo@0.0.0 build oracolo | > vite build oracolo | oracolo | 7:32:49 PM [vite-plugin-svelte] WARNING: The following packages have a svelte field in their package.json but no exports condition for svelte. oracolo | oracolo | @splidejs/svelte-splide@0.2.9 oracolo | @splidejs/splide@4.1.4 oracolo | oracolo | Please see https://github.com/sveltejs/vite-plugin-svelte/blob/main/docs/faq.md#missing-exports-condition for details. oracolo | vite v5.2.11 building for production... oracolo | transforming... oracolo | ✓ 84 modules transformed. oracolo | rendering chunks... oracolo | oracolo | oracolo | Inlining: index-C6McxHm7.js oracolo | Inlining: style-DubfL5gy.css oracolo | computing gzip size... oracolo | dist/index.html 233.15 kB │ gzip: 82.41 kB oracolo | ✓ built in 7.08s oracolo | oracolo | >>> done ✅ oracolo | oracolo | > Copying Oracolo built index.html to nginx usr/share/nginx/html... ✅ oracolo | oracolo | ╭────────────────────────╮ oracolo | │ Configuring Nginx... ⤵️ │ oracolo | ╰────────────────────────╯ oracolo | oracolo | > Copying default nginx.conf file... ✅ oracolo | oracolo | ╭──────────────────────╮ oracolo | │ Starting Nginx... 🚀 │ oracolo | ╰──────────────────────╯ oracolo |If you don't have any issue with the Traefik container, Oracolo should be live! 🔥
You can now access it by going to the ORACOLO_DOMAIN URL configured into the .env file.
Have a good day!
Don't hesisate to follow dtonon on Nostr to follow-up the future updates ⚡🔥
See you soon in another Fractalized story!
PastaGringo 🤖⚡ -
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ b12b632c:d9e1ff79
2024-04-24 20:21:27
@ b12b632c:d9e1ff79
2024-04-24 20:21:27What's Blossom?
Blossom offers a bunch of HTTP endpoints that let Nostr users stash and fetch binary data on public servers using the SHA256 hash as a universal ID.
You can find more -precise- information about Blossom on the Nostr article published today by hzrd149, the developper behind it:
nostr:naddr1qqxkymr0wdek7mfdv3exjan9qgszv6q4uryjzr06xfxxew34wwc5hmjfmfpqn229d72gfegsdn2q3fgrqsqqqa28e4v8zy
You find the Blossom github repo here:
GitHub - hzrd149/blossom: Blobs stored simply on mediaservers https://github.com/hzrd149/blossom
Meet Blobs
Blobs are files with SHA256 hashes as IDs, making them unique and secure. You can compute these IDs from the files themselves using the sha256 hashing algorithm (when you run
sha256sum bitcoin.pdf).Meet Drives
Drives are like organized events on Nostr, mapping blobs to filenames and extra info. It's like setting up a roadmap for your data.
How do Servers Work?
Blossom servers have four endpoints for users to upload and handle blobs:
GET /<sha256>: Get blobs by their SHA256 hash, maybe with a file extension. PUT /upload: Chuck your blobs onto the server, verified with signed Nostr events. GET /list/<pubkey>: Peek at a list of blobs tied to a specific public key for smooth management. DELETE /<sha256>: Trash blobs from the server when needed, keeping things tidy.Yon can find detailed information about the Blossom Server Implementation here..
https://github.com/hzrd149/blossom/blob/master/Server.md
..and the Blossom-server source code is here:
https://github.com/hzrd149/blossom-server
What's Blossom Drive?
Think of Blossom Drive as the "Front-End" (or a public cloud drive) of Blossom servers, letting you upload, manage, share your files/folders blobs.
Source code is available here:
https://github.com/hzrd149/blossom-drive
Developpers
If you want to add Blossom into your Nostr client/app, the blossom-client-sdk explaining how it works (with few examples 🙏) is published here:
https://github.com/hzrd149/blossom-client-sdk
How to self-host Blossom server & Blossom Drive
We'll use docker compose to setup Blossom server & drive. I included Nginx Proxy Manager because it's the Web Proxy I use for all the Fractalized self-hosted services :
Create a new docker-compose file:
~$ nano docker-compose.ymlInsert this content into the file:
``` version: '3.8' services:
blossom-drive: container_name: blossom-drive image: pastagringo/blossom-drive-docker
ports:
- '80:80'
blossom-server: container_name: blossom-server image: 'ghcr.io/hzrd149/blossom-server:master'
ports:
- '3000:3000'
volumes: - './blossom-server/config.yml:/app/config.yml' - 'blossom_data:/app/data'nginxproxymanager: container_name: nginxproxymanager image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: - '80:80' - '81:81' - '443:443' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt - ./nginxproxymanager/_hsts_map.conf:/app/templates/_hsts_map.conf
volumes: blossom_data: ```
You now need to personalize the blossom-server config.yml:
bash ~$ mkdir blossom-server ~$ nano blossom-server/config.ymlInsert this content to the file (CTRL+X & Y to save/exit):
```yaml
Used when listing blobs
publicDomain: https://blossom.fractalized.net
databasePath: data/sqlite.db
discovery: # find files by querying nostr relays nostr: enabled: true relays: - wss://nostrue.com - wss://relay.damus.io - wss://nostr.wine - wss://nos.lol - wss://nostr-pub.wellorder.net - wss://nostr.fractalized.net # find files by asking upstream CDNs upstream: enabled: true domains: - https://cdn.satellite.earth # don't set your blossom server here!
storage: # local or s3 backend: local local: dir: ./data # s3: # endpoint: https://s3.endpoint.com # bucket: blossom # accessKey: xxxxxxxx # secretKey: xxxxxxxxx # If this is set the server will redirect clients when loading blobs # publicURL: https://s3.region.example.com/
# rules are checked in descending order. if a blob matches a rule it is kept # "type" (required) the type of the blob, "" can be used to match any type # "expiration" (required) time passed since last accessed # "pubkeys" (optional) a list of owners # any blobs not matching the rules will be removed rules: # mime type of blob - type: text/ # time since last accessed expiration: 1 month - type: "image/" expiration: 1 week - type: "video/" expiration: 5 days - type: "model/" expiration: 1 week - type: "" expiration: 2 days
upload: # enable / disable uploads enabled: true # require auth to upload requireAuth: true # only check rules that include "pubkeys" requirePubkeyInRule: false
list: requireAuth: false allowListOthers: true
tor: enabled: false proxy: "" ```
You need to update few values with your own:
- Your own Blossom server public domain :
publicDomain: https://YourBlossomServer.YourDomain.tldand upstream domains where Nostr clients will also verify if the Blossom server own the file blob: :
upstream: enabled: true domains: - https://cdn.satellite.earth # don't set your blossom server here!- The Nostr relays where you want to publish your Blossom events (I added my own Nostr relay):
yaml discovery: # find files by querying nostr relays nostr: enabled: true relays: - wss://nostrue.com - wss://relay.damus.io - wss://nostr.wine - wss://nos.lol - wss://nostr-pub.wellorder.net - wss://nostr.fractalized.netEverything is setup! You can now compose your docker-compose file:
~$ docker compose up -dI will let your check this article to know how to configure and use Nginx Proxy Manager.
You can check both Blossom containers logs with this command:
~$ docker compose logs -f blossom-drive blossom-serverRegarding the Nginx Proxy Manager settings for Blossom, here is the configuration I used:
PS: it seems the naming convention for the kind of web service like Blossom is named "CDN" (for: "content delivery network"). It's not impossible in a near future I rename my subdomain blossom.fractalized.net to cdn.blossom.fractalized.net and blossom-drive.fractalized.net to blossom.fractalized.net 😅
Do what you prefer!
After having configured everything, you can now access Blossom server by going to your Blossom server subdomain. You should see a homepage as below:
Same thing for the Blossom Drive, you should see this homepage:
You can now login with your prefered method. In my case, I login on Blossom Drive with my NIP-07 Chrome extension.
You now need to go the "Servers" tab to add some Blossom servers, including the fresh one you just installed.
You can now create your first Blossom Drive by clicking on "+ New" > "Drive" on the top left button:
Fill your desired blossom drive name and select the media servers where you want to host your files and click on "Create":
PS: you can enable "Encrypted" option but as hzrd149 said on his Nostr note about Blossom:
"There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify"
You are now able to upload some files (a picture for instance):
And obtain the HTTP direct link by clicking on the "Copy Link" button:
If you check URL image below, you'll see that it is served by Blossom:

It's done ! ✅
You can now upload your files to Blossom accross several Blossom servers to let them survive the future internet apocalypse.
Blossom has just been released few days ago, many news and features will come!
Don't hesisate to follow hzrd149 on Nostr to follow-up the future updates ⚡🔥
See you soon in another Fractalized story!
PastaGringo 🤖⚡ -
 @ 42342239:1d80db24
2024-04-05 08:21:50
@ 42342239:1d80db24
2024-04-05 08:21:50Trust is a topic increasingly being discussed. Whether it is trust in each other, in the media, or in our authorities, trust is generally seen as a cornerstone of a strong and well-functioning society. The topic was also the theme of the World Economic Forum at its annual meeting in Davos earlier this year. Even among central bank economists, the subject is becoming more prevalent. Last year, Agustín Carstens, head of the BIS ("the central bank of central banks"), said that "[w]ith trust, the public will be more willing to accept actions that involve short-term costs in exchange for long-term benefits" and that "trust is vital for policy effectiveness".
It is therefore interesting when central banks or others pretend as if nothing has happened even when trust has been shattered.
Just as in Sweden and in hundreds of other countries, Canada is planning to introduce a central bank digital currency (CBDC), a new form of money where the central bank or its intermediaries (the banks) will have complete insight into citizens' transactions. Payments or money could also be made programmable. Everything from transferring ownership of a car automatically after a successful payment to the seller, to payments being denied if you have traveled too far from home.
"If Canadians decide a digital dollar is necessary, our obligation is to be ready" says Carolyn Rogers, Deputy Head of Bank of Canada, in a statement shared in an article.
So, what do the citizens want? According to a report from the Bank of Canada, a whopping 88% of those surveyed believe that the central bank should refrain from developing such a currency. About the same number (87%) believe that authorities should guarantee the opportunity to pay with cash instead. And nearly four out of five people (78%) do not believe that the central bank will care about people's opinions. What about trust again?
Canadians' likely remember the Trudeau government's actions against the "Freedom Convoy". The Freedom Convoy consisted of, among others, truck drivers protesting the country's strict pandemic policies, blocking roads in the capital Ottawa at the beginning of 2022. The government invoked never-before-used emergency measures to, among other things, "freeze" people's bank accounts. Suddenly, truck drivers and those with a "connection" to the protests were unable to pay their electricity bills or insurances, for instance. Superficially, this may not sound so serious, but ultimately, it could mean that their families end up in cold houses (due to electricity being cut off) and that they lose the ability to work (driving uninsured vehicles is not taken lightly). And this applied not only to the truck drivers but also to those with a "connection" to the protests. No court rulings were required.
Without the freedom to pay for goods and services, i.e. the freedom to transact, one has no real freedom at all, as several participants in the protests experienced.
In January of this year, a federal judge concluded that the government's actions two years ago were unlawful when it invoked the emergency measures. The use did not display "features of rationality - motivation, transparency, and intelligibility - and was not justified in relation to the relevant factual and legal limitations that had to be considered". He also argued that the use was not in line with the constitution. There are also reports alleging that the government fabricated evidence to go after the demonstrators. The case is set to continue to the highest court. Prime Minister Justin Trudeau and Finance Minister Chrystia Freeland have also recently been sued for the government's actions.
The Trudeau government's use of emergency measures two years ago sadly only provides a glimpse of what the future may hold if CBDCs or similar systems replace the current monetary system with commercial bank money and cash. In Canada, citizens do not want the central bank to proceed with the development of a CBDC. In canada, citizens in Canada want to strengthen the role of cash. In Canada, citizens suspect that the central bank will not listen to them. All while the central bank feverishly continues working on the new system...
"Trust is vital", said Agustín Carstens. But if policy-makers do not pause for a thoughtful reflection even when trust has been utterly shattered as is the case in Canada, are we then not merely dealing with lip service?
And how much trust do these policy-makers then deserve?
-
 @ 42342239:1d80db24
2024-03-31 11:23:36
@ 42342239:1d80db24
2024-03-31 11:23:36Biologist Stuart Kauffman introduced the concept of the "adjacent possible" in evolutionary biology in 1996. A bacterium cannot suddenly transform into a flamingo; rather, it must rely on small exploratory changes (of the "adjacent possible") if it is ever to become a beautiful pink flying creature. The same principle applies to human societies, all of which exemplify complex systems. It is indeed challenging to transform shivering cave-dwellers into a space travelers without numerous intermediate steps.
Imagine a water wheel – in itself, perhaps not such a remarkable invention. Yet the water wheel transformed the hard-to-use energy of water into easily exploitable rotational energy. A little of the "adjacent possible" had now been explored: water mills, hammer forges, sawmills, and textile factories soon emerged. People who had previously ground by hand or threshed with the help of oxen could now spend their time on other things. The principles of the water wheel also formed the basis for wind power. Yes, a multitude of possibilities arose – reminiscent of the rapid development during the Cambrian explosion. When the inventors of bygone times constructed humanity's first water wheel, they thus expanded the "adjacent possible". Surely, the experts of old likely sought swift prohibitions. Not long ago, our expert class claimed that the internet was going to be a passing fad, or that it would only have the same modest impact on the economy as the fax machine. For what it's worth, there were even attempts to ban the number zero back in the days.
The pseudonymous creator of Bitcoin, Satoshi Nakamoto, wrote in Bitcoin's whitepaper that "[w]e have proposed a system for electronic transactions without relying on trust." The Bitcoin system enables participants to agree on what is true without needing to trust each other, something that has never been possible before. In light of this, it is worth noting that trust in the federal government in the USA is among the lowest levels measured in almost 70 years. Trust in media is at record lows. Moreover, in countries like the USA, the proportion of people who believe that one can trust "most people" has decreased significantly. "Rebuilding trust" was even the theme of the World Economic Forum at its annual meeting. It is evident, even in the international context, that trust between countries is not at its peak.
Over a fifteen-year period, Bitcoin has enabled electronic transactions without its participants needing to rely on a central authority, or even on each other. This may not sound like a particularly remarkable invention in itself. But like the water wheel, one must acknowledge that new potential seems to have been put in place, potential that is just beginning to be explored. Kauffman's "adjacent possible" has expanded. And despite dogmatic statements to the contrary, no one can know for sure where this might lead.
The discussion of Bitcoin or crypto currencies would benefit from greater humility and openness, not only from employees or CEOs of money laundering banks but also from forecast-failing central bank officials. When for instance Chinese Premier Zhou Enlai in the 1970s was asked about the effects of the French Revolution, he responded that it was "too early to say" - a far wiser answer than the categorical response of the bureaucratic class. Isn't exploring systems not based on trust is exactly what we need at this juncture?
-
 @ b12b632c:d9e1ff79
2024-03-23 16:42:49
@ b12b632c:d9e1ff79
2024-03-23 16:42:49CASHU AND ECASH ARE EXPERIMENTAL PROJECTS. BY THE OWN NATURE OF CASHU ECASH, IT'S REALLY EASY TO LOSE YOUR SATS BY LACKING OF KNOWLEDGE OF THE SYSTEM MECHANICS. PLEASE, FOR YOUR OWN GOOD, ALWAYS USE FEW SATS AMOUNT IN THE BEGINNING TO FULLY UNDERSTAND HOW WORKS THE SYSTEM. ECASH IS BASED ON A TRUST RELATIONSHIP BETWEEN YOU AND THE MINT OWNER, PLEASE DONT TRUST ECASH MINT YOU DONT KNOW. IT IS POSSIBLE TO GENERATE UNLIMITED ECASH TOKENS FROM A MINT, THE ONLY WAY TO VALIDATE THE REAL EXISTENCE OF THE ECASH TOKENS IS TO DO A MULTIMINT SWAP (BETWEEN MINTS). PLEASE, ALWAYS DO A MULTISWAP MINT IF YOU RECEIVE SOME ECASH FROM SOMEONE YOU DON'T KNOW/TRUST. NEVER TRUST A MINT YOU DONT KNOW!
IF YOU WANT TO RUN AN ECASH MINT WITH A BTC LIGHTNING NODE IN BACK-END, PLEASE DEDICATE THIS LN NODE TO YOUR ECASH MINT. A BAD MANAGEMENT OF YOUR LN NODE COULD LET PEOPLE TO LOOSE THEIR SATS BECAUSE THEY HAD ONCE TRUSTED YOUR MINT AND YOU DID NOT MANAGE THE THINGS RIGHT.

What's ecash/Cashu ?
I recently listened a passionnating interview from calle 👁️⚡👁 invited by the podcast channel What Bitcoin Did about the new (not so much now) Cashu protocol.
Cashu is a a free and open-source Chaumian ecash project built for Bitcoin protocol, recently created in order to let users send/receive Ecash over BTC Lightning network. The main Cashu ecash goal is to finally give you a "by-design" privacy mechanism to allow us to do anonymous Bitcoin transactions.
Ecash for your privacy.\ A Cashu mint does not know who you are, what your balance is, or who you're transacting with. Users of a mint can exchange ecash privately without anyone being able to know who the involved parties are. Bitcoin payments are executed without anyone able to censor specific users.
Here are some useful links to begin with Cashu ecash :
Github repo: https://github.com/cashubtc
Documentation: https://docs.cashu.space
To support the project: https://docs.cashu.space/contribute
A Proof of Liabilities Scheme for Ecash Mints: https://gist.github.com/callebtc/ed5228d1d8cbaade0104db5d1cf63939
Like NOSTR and its own NIPS, here is the list of the Cashu ecash NUTs (Notation, Usage, and Terminology): https://github.com/cashubtc/nuts?tab=readme-ov-file
I won't explain you at lot more on what's Casu ecash, you need to figured out by yourself. It's really important in order to avoid any mistakes you could do with your sats (that you'll probably regret).
If you don't have so much time, you can check their FAQ right here: https://docs.cashu.space/faq
I strongly advise you to listen Calle's interviews @whatbbitcoindid to "fully" understand the concept and the Cashu ecash mechanism before using it:
Scaling Bitcoin Privacy with Calle
In the meantime I'm writing this article, Calle did another really interesting interview with ODELL from CitadelDispatch:
CD120: BITCOIN POWERED CHAUMIAN ECASH WITH CALLE
Which ecash apps?
There are several ways to send/receive some Ecash tokens, you can do it by using mobile applications like eNuts, Minibits or by using Web applications like Cashu.me, Nustrache or even npub.cash. On these topics, BTC Session Youtube channel offers high quality contents and very easy to understand key knowledge on how to use these applications :
Minibits BTC Wallet: Near Perfect Privacy and Low Fees - FULL TUTORIAL
Cashu Tutorial - Chaumian Ecash On Bitcoin
Unlock Perfect Privacy with eNuts: Instant, Free Bitcoin Transactions Tutorial
Cashu ecash is a very large and complex topic for beginners. I'm still learning everyday how it works and the project moves really fast due to its commited developpers community. Don't forget to follow their updates on Nostr to know more about the project but also to have a better undertanding of the Cashu ecash technical and political implications.
There is also a Matrix chat available if you want to participate to the project:
https://matrix.to/#/#cashu:matrix.org
How to self-host your ecash mint with Nutshell
Cashu Nutshell is a Chaumian Ecash wallet and mint for Bitcoin Lightning. Cashu Nutshell is the reference implementation in Python.
Github repo:
https://github.com/cashubtc/nutshell
Today, Nutshell is the most advanced mint in town to self-host your ecash mint. The installation is relatively straightforward with Docker because a docker-compose file is available from the github repo.
Nutshell is not the only cashu ecash mint server available, you can check other server mint here :
https://docs.cashu.space/mints
The only "external" requirement is to have a funding source. One back-end funding source where ecash will mint your ecash from your Sats and initiate BTC Lightning Netwok transactions between ecash mints and BTC Ligtning nodes during a multimint swap. Current backend sources supported are: FakeWallet*, LndRestWallet, CoreLightningRestWallet, BlinkWallet, LNbitsWallet, StrikeUSDWallet.
*FakeWallet is able to generate unlimited ecash tokens. Please use it carefully, ecash tokens issued by the FakeWallet can be sent and accepted as legit ecash tokens to other people ecash wallets if they trust your mint. In the other way, if someone send you 2,3M ecash tokens, please don't trust the mint in the first place. You need to force a multimint swap with a BTC LN transaction. If that fails, someone has maybe tried to fool you.
I used a Voltage.cloud BTC LN node instance to back-end my Nutshell ecash mint:
SPOILER: my nutshell mint is working but I have an error message "insufficient balance" when I ask a multiswap mint from wallet.cashu.me or the eNuts application. In order to make it work, I need to add some Sats liquidity (I can't right now) to the node and open few channels with good balance capacity. If you don't have an ecash mint capable of doig multiswap mint, you'll only be able to mint ecash into your ecash mint and send ecash tokens to people trusting your mint. It's working, yes, but you need to be able to do some mutiminit swap if you/everyone want to fully profit of the ecash system.
Once you created your account and you got your node, you need to git clone the Nutshell github repo:
git clone https://github.com/cashubtc/nutshell.gitYou next need to update the docker compose file with your own settings. You can comment the wallet container if you don't need it.
To generate a private key for your node, you can use this openssl command
openssl rand -hex 32 054de2a00a1d8e3038b30e96d26979761315cf48395aa45d866aeef358c91dd1The CLI Cashu wallet is not needed right now but I'll show you how to use it in the end of this article. Feel free to comment it or not.
``` version: "3" services: mint: build: context: . dockerfile: Dockerfile container_name: mint
ports:
- "3338:3338"
environment:- DEBUG=TRUE
- LOG_LEVEL=DEBUG
- MINT_URL=https://YourMintURL - MINT_HOST=YourMintDomain.tld - MINT_LISTEN_HOST=0.0.0.0 - MINT_LISTEN_PORT=3338 - MINT_PRIVATE_KEY=YourPrivateKeyFromOpenSSL - MINT_INFO_NAME=YourMintInfoName - MINT_INFO_DESCRIPTION=YourShortInfoDesc - MINT_INFO_DESCRIPTION_LONG=YourLongInfoDesc - MINT_LIGHTNING_BACKEND=LndRestWallet #- MINT_LIGHTNING_BACKEND=FakeWallet - MINT_INFO_CONTACT=[["email","YourConctact@email"], ["twitter","@YourTwitter"], ["nostr", "YourNPUB"]] - MINT_INFO_MOTD=Thanks for using my mint! - MINT_LND_REST_ENDPOINT=https://YourVoltageNodeDomain:8080 - MINT_LND_REST_MACAROON=YourDefaultAdminMacaroonBase64 - MINT_MAX_PEG_IN=100000 - MINT_MAX_PEG_OUT=100000 - MINT_PEG_OUT_ONLY=FALSE command: ["poetry", "run", "mint"]wallet-voltage: build: context: . dockerfile: Dockerfile container_name: wallet-voltage
ports:
- "4448:4448"
depends_on: - nutshell-voltage environment:- DEBUG=TRUE
- MINT_URL=http://nutshell-voltage:3338
- API_HOST=0.0.0.0 command: ["poetry", "run", "cashu", "-d"]```
To build, run and see the container logs:
docker compose up -d && docker logs -f mint0.15.1 2024-03-22 14:45:45.490 | WARNING | cashu.lightning.lndrest:__init__:49 - no certificate for lndrest provided, this only works if you have a publicly issued certificate 2024-03-22 14:45:45.557 | INFO | cashu.core.db:__init__:135 - Creating database directory: data/mint 2024-03-22 14:45:45.68 | INFO | Started server process [1] 2024-03-22 14:45:45.69 | INFO | Waiting for application startup. 2024-03-22 14:45:46.12 | INFO | Loaded 0 keysets from database. 2024-03-22 14:45:46.37 | INFO | Current keyset: 003dba9e589023f1 2024-03-22 14:45:46.37 | INFO | Using LndRestWallet backend for method: 'bolt11' and unit: 'sat' 2024-03-22 14:45:46.97 | INFO | Backend balance: 1825000 sat 2024-03-22 14:45:46.97 | INFO | Data dir: /root/.cashu 2024-03-22 14:45:46.97 | INFO | Mint started. 2024-03-22 14:45:46.97 | INFO | Application startup complete. 2024-03-22 14:45:46.98 | INFO | Uvicorn running on http://0.0.0.0:3338 (Press CTRL+C to quit) 2024-03-22 14:45:47.27 | INFO | 172.19.0.22:48528 - "GET /v1/keys HTTP/1.1" 200 2024-03-22 14:45:47.34 | INFO | 172.19.0.22:48544 - "GET /v1/keysets HTTP/1.1" 200 2024-03-22 14:45:47.38 | INFO | 172.19.0.22:48552 - "GET /v1/info HTTP/1.1" 200If you see the line :
Uvicorn running on http://0.0.0.0:3338 (Press CTRL+C to quit)Nutshell is well started.
I won't explain here how to create a reverse proxy to Nutshell, you can find how to do it into my previous article. Here is the reverse proxy config into Nginx Proxy Manager:
If everything is well configured and if you go on your mint url (https://yourminturl) you shoud see this:
It's not helping a lot because at first glance it seems to be not working but it is. You can also check these URL path to confirm :
- https://yourminturl/keys and https://yourminturl/keysets
or
- https://yourminturl/v1/keys and https://yourminturl/v1/keysets
Depending of the moment when you read this article, the first URLs path might have been migrated to V1. Here is why:
https://github.com/cashubtc/nuts/pull/55
The final test is to add your mint to your prefered ecash wallets.
SPOILER: AT THIS POINT, YOU SHOUD KNOW THAT IF YOU RESET YOUR LOCAL BROWSER INTERNET CACHE FILE, YOU'LL LOSE YOUR MINTED ECASH TOKENS. IF NOT, PLEASE READ THE DOCUMENTATION AGAIN.
For instace, if we use wallet.cashu.me:
You can go into the "Settings" tab and add your mint :
If everything went find, you shoud see this :
You can now mint some ecash from your mint creating a sats invoice :
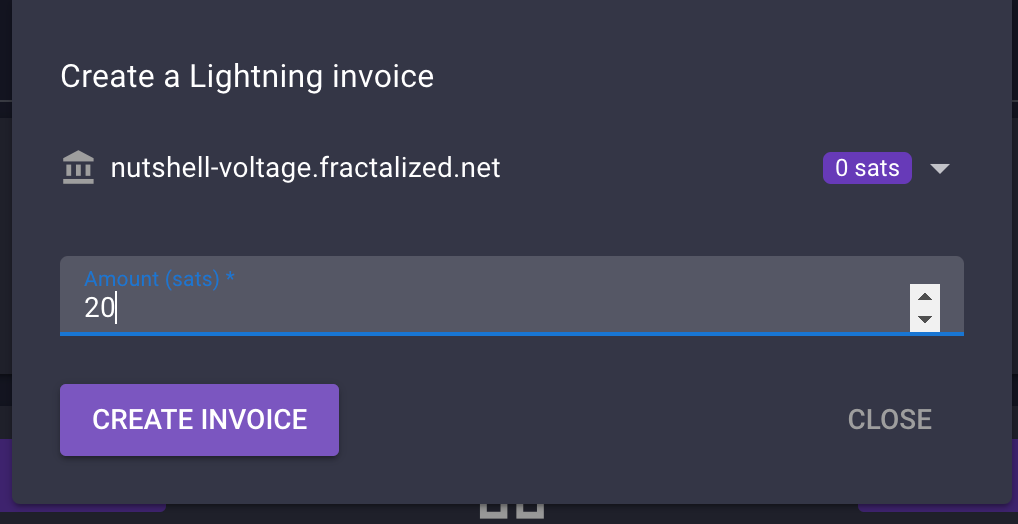
You can now scan the QR diplayed with your prefered BTC LN wallet. If everything is OK, you should receive the funds:
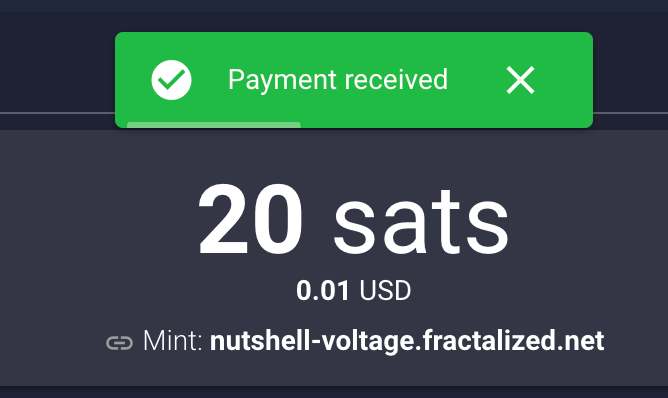
It may happen that some error popup sometimes. If you are curious and you want to know what happened, Cashu wallet has a debug console you can activate by clicking on the "Settings" page and "OPEN DEBUG TERMINAL". A little gear icon will be displayed in the bottom of the screen. You can click on it, go to settings and enable "Auto Display If Error Occurs" and "Display Extra Information". After enabling this setting, you can close the popup windows and let the gear icon enabled. If any error comes, this windows will open again and show you thé error:
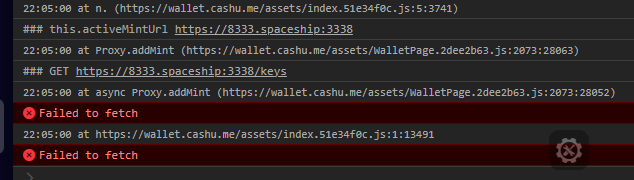
Now that you have some sats in your balance, you can try to send some ecash. Open in a new windows another ecash wallet like Nutstach for instance.
Add your mint again :
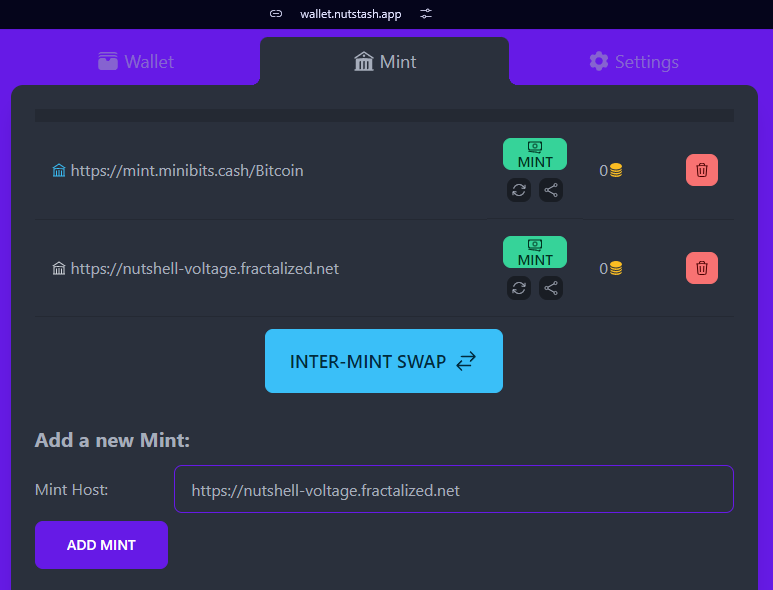
Return on Cashu wallet. The ecash token amount you see on the Cashu wallet home page is a total of all the ecash tokens you have on all mint connected.
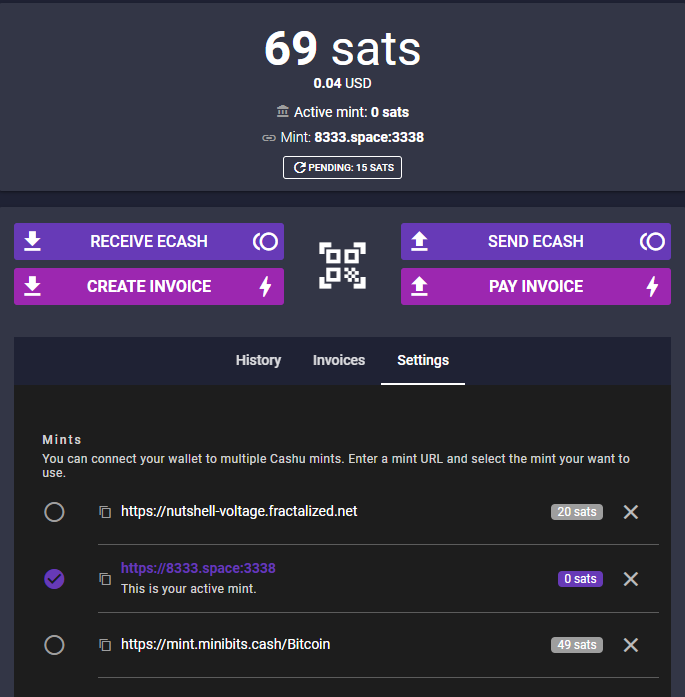
Next, click on "Send ecach". Insert the amout of ecash you want to transfer to your other wallet. You can select the wallet where you want to extract the funds by click on the little arrow near the sats funds you currenly selected :


Click now on "SEND TOKENS". That will open you a popup with a QR code and a code CONTAINING YOUR ECASH TOKENS (really).

You can now return on nutstach, click on the "Receive" button and paste the code you get from Cashu wallet:
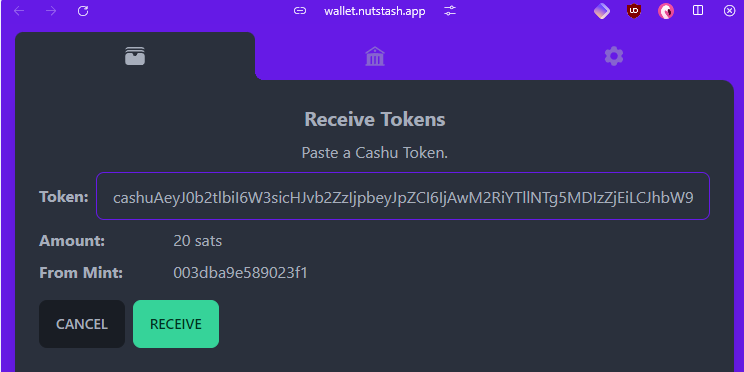
Click on "RECEIVE" again:
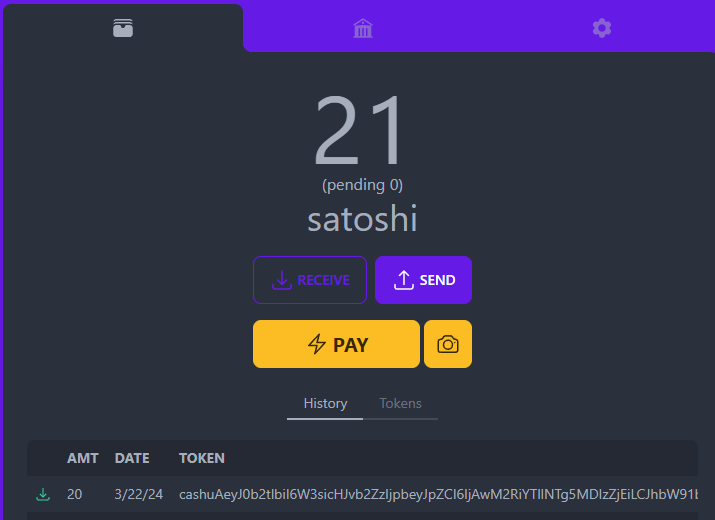
Congrats, you transfered your first ecash tokens to yourself ! 🥜⚡
You may need some time to transfer your ecash tokens between your wallets and your mint, there is a functionality existing for that called "Multimint swaps".
Before that, if you need new mints, you can check the very new website Bitcoinmints.com that let you see the existing ecash mints and rating :
Don't forget, choose your mint carefuly because you don't know who's behind.
Let's take a mint and add it to our Cashu wallet:
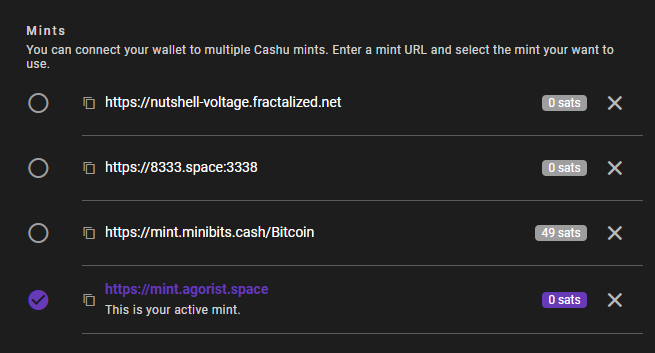
If you want to transfer let's say 20 sats from minibits mint to bitcointxoko mint, go just bottom into the "Multimint swap" section. Select the mint into "Swap from mint", the mint into "Swap to mint" and click on "SWAP" :
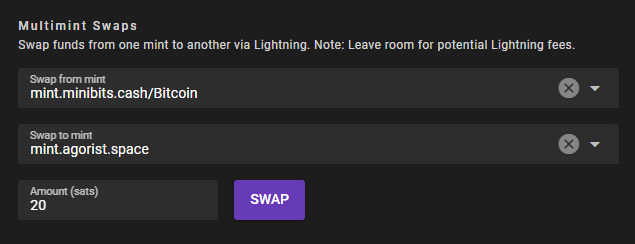
A popup window will appear and will request the ecash tokens from the source mint. It will automatically request the ecash amount via a Lightning node transaction and add the fund to your other wallet in the target mint. As it's a Lightning Network transaction, you can expect some little fees.
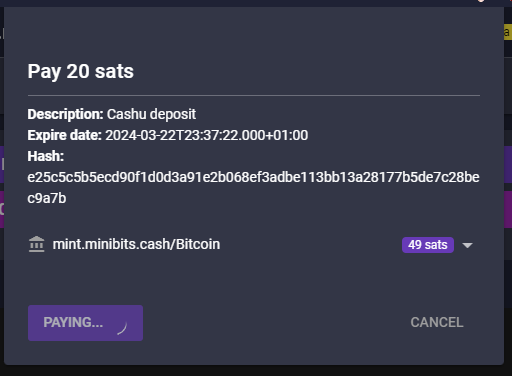
If everything is OK with the mints, the swap will be successful and the ecash received.
You can now see that the previous sats has been transfered (minus 2 fee sats).
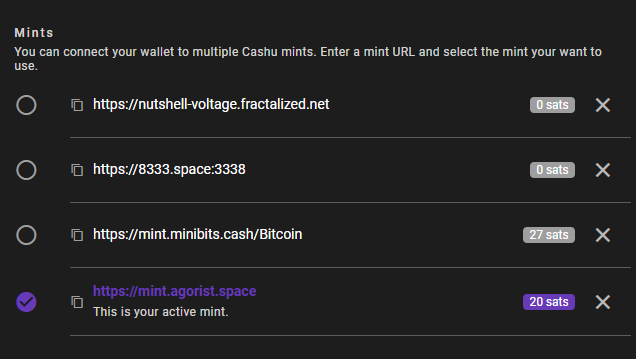
Well done, you did your first multimint swap ! 🥜⚡
One last thing interresting is you can also use CLI ecash wallet. If you created the wallet contained in the docker compose, the container should be running.
Here are some commands you can do.
To verify which mint is currently connected :
``` docker exec -it wallet-voltage poetry run cashu info
2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:57:24.91 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:57:24.92 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat Version: 0.15.1 Wallet: wallet Debug: True Cashu dir: /root/.cashu Mints: - https://nutshell-voltage.fractalized.net ```
To verify your balance :
``` docker exec -it wallet-voltage poetry run cashu balance
2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:59:26.67 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:738 | Wallet initialized 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:739 | Mint URL: https://nutshell-voltage.fractalized.net 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:740 | Database: /root/.cashu/wallet 2024-03-22 21:59:26.68 | DEBUG | cashu.wallet.wallet:init:741 | Unit: sat Balance: 0 sat ```
To create an sats invoice to have ecash :
``` docker exec -it wallet-voltage poetry run cashu invoice 20
2024-03-22 22:00:59.12 | DEBUG | cashu.wallet.wallet:_load_mint_info:275 | Mint info: name='nutshell.fractalized.net' pubkey='02008469922e985cbc5368ce16adb6ed1aaea0f9ecb21639db4ded2e2ae014a326' version='Nutshell/0.15.1' description='Official Fractalized Mint' description_long='TRUST THE MINT' contact=[['email', 'pastagringo@fractalized.net'], ['twitter', '@pastagringo'], ['nostr', 'npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2']] motd='Thanks for using official ecash fractalized mint!' nuts={4: {'methods': [['bolt11', 'sat']], 'disabled': False}, 5: {'methods': [['bolt11', 'sat']], 'disabled': False}, 7: {'supported': True}, 8: {'supported': True}, 9: {'supported': True}, 10: {'supported': True}, 11: {'supported': True}, 12: {'supported': True}} Balance: 0 sat
Pay invoice to mint 20 sat:
Invoice: lnbc200n1pjlmlumpp5qh68cqlr2afukv9z2zpna3cwa3a0nvla7yuakq7jjqyu7g6y69uqdqqcqzzsxqyz5vqsp5zymmllsqwd40xhmpu76v4r9qq3wcdth93xthrrvt4z5ct3cf69vs9qyyssqcqppurrt5uqap4nggu5tvmrlmqs5guzpy7jgzz8szckx9tug4kr58t4avv4a6437g7542084c6vkvul0ln4uus7yj87rr79qztqldggq0cdfpy
You can use this command to check the invoice: cashu invoice 20 --id 2uVWELhnpFcNeFZj6fWzHjZuIipqyj5R8kM7ZJ9_
Checking invoice .................2024-03-22 22:03:25.27 | DEBUG | cashu.wallet.wallet:verify_proofs_dleq:1103 | Verified incoming DLEQ proofs. Invoice paid.
Balance: 20 sat ```
To pay an invoice by pasting the invoice you received by your or other people :
``` docker exec -it wallet-voltage poetry run cashu pay lnbc150n1pjluqzhpp5rjezkdtt8rjth4vqsvm50xwxtelxjvkq90lf9tu2thsv2kcqe6vqdq2f38xy6t5wvcqzzsxqrpcgsp58q9sqkpu0c6s8hq5pey8ls863xmjykkumxnd8hff3q4fvxzyh0ys9qyyssq26ytxay6up54useezjgqm3cxxljvqw5vq2e94ru7ytqc0al74hr4nt5cwpuysgyq8u25xx5la43mx4ralf3mq2425xmvhjzvwzqp54gp0e3t8e
2024-03-22 22:04:37.23 | DEBUG | cashu.wallet.wallet:_load_mint_info:275 | Mint info: name='nutshell.fractalized.net' pubkey='02008469922e985cbc5368ce16adb6ed1aaea0f9ecb21639db4ded2e2ae014a326' version='Nutshell/0.15.1' description='Official Fractalized Mint' description_long='TRUST THE MINT' contact=[['email', 'pastagringo@fractalized.net'], ['twitter', '@pastagringo'], ['nostr', 'npub1ky4kxtyg0uxgw8g5p5mmedh8c8s6sqny6zmaaqj44gv4rk0plaus3m4fd2']] motd='Thanks for using official ecash fractalized mint!' nuts={4: {'methods': [['bolt11', 'sat']], 'disabled': False}, 5: {'methods': [['bolt11', 'sat']], 'disabled': False}, 7: {'supported': True}, 8: {'supported': True}, 9: {'supported': True}, 10: {'supported': True}, 11: {'supported': True}, 12: {'supported': True}} Balance: 20 sat 2024-03-22 22:04:37.45 | DEBUG | cashu.wallet.wallet:get_pay_amount_with_fees:1529 | Mint wants 0 sat as fee reserve. 2024-03-22 22:04:37.45 | DEBUG | cashu.wallet.cli.cli:pay:189 | Quote: quote='YpNkb5f6WVT_5ivfQN1OnPDwdHwa_VhfbeKKbBAB' amount=15 fee_reserve=0 paid=False expiry=1711146847 Pay 15 sat? [Y/n]: y Paying Lightning invoice ...2024-03-22 22:04:41.13 | DEBUG | cashu.wallet.wallet:split:613 | Calling split. POST /v1/swap 2024-03-22 22:04:41.21 | DEBUG | cashu.wallet.wallet:verify_proofs_dleq:1103 | Verified incoming DLEQ proofs. Error paying invoice: Mint Error: Lightning payment unsuccessful. insufficient_balance (Code: 20000) ```
It didn't work, yes. That's the thing I told you earlier but it would work with a well configured and balanced Lightning Node.
That's all ! You should now be able to use ecash as you want! 🥜⚡
See you on NOSTR! 🤖⚡\ PastaGringo
-
 @ ee11a5df:b76c4e49
2024-03-22 23:49:09
@ ee11a5df:b76c4e49
2024-03-22 23:49:09Implementing The Gossip Model
version 2 (2024-03-23)
Introduction
History
The gossip model is a general concept that allows clients to dynamically follow the content of people, without specifying which relay. The clients have to figure out where each person puts their content.
Before NIP-65, the gossip client did this in multiple ways:
- Checking kind-3 contents, which had relay lists for configuring some clients (originally Astral and Damus), and recognizing that wherever they were writing our client could read from.
- NIP-05 specifying a list of relays in the
nostr.jsonfile. I added this to NIP-35 which got merged down into NIP-05. - Recommended relay URLs that are found in 'p' tags
- Users manually making the association
- History of where events happen to have been found. Whenever an event came in, we associated the author with the relay.
Each of these associations were given a score (recommended relay urls are 3rd party info so they got a low score).
Later, NIP-65 made a new kind of relay list where someone could advertise to others which relays they use. The flag "write" is now called an OUTBOX, and the flag "read" is now called an INBOX.
The idea of inboxes came about during the development of NIP-65. They are a way to send an event to a person to make sure they get it... because putting it on your own OUTBOX doesn't guarantee they will read it -- they may not follow you.
The outbox model is the use of NIP-65. It is a subset of the gossip model which uses every other resource at it's disposal.
Rationale
The gossip model keeps nostr decentralized. If all the (major) clients were using it, people could spin up small relays for both INBOX and OUTBOX and still be fully connected, have their posts read, and get replies and DMs. This is not to say that many people should spin up small relays. But the task of being decentralized necessitates that people must be able to spin up their own relay in case everybody else is censoring them. We must make it possible. In reality, congregating around 30 or so popular relays as we do today is not a problem. Not until somebody becomes very unpopular with bitcoiners (it will probably be a shitcoiner), and then that person is going to need to leave those popular relays and that person shouldn't lose their followers or connectivity in any way when they do.
A lot more rationale has been discussed elsewhere and right now I want to move on to implementation advice.
Implementation Advice
Read NIP-65
NIP-65 will contain great advice on which relays to consult for which purposes. This post does not supersede NIP-65. NIP-65 may be getting some smallish changes, mostly the addition of a private inbox for DMs, but also changes to whether you should read or write to just some or all of a set of relays.
How often to fetch kind-10002 relay lists for someone
This is up to you. Refreshing them every hour seems reasonable to me. Keeping track of when you last checked so you can check again every hour is a good idea.
Where to fetch events from
If your user follows another user (call them jack), then you should fetch jack's events from jack's OUTBOX relays. I think it's a good idea to use 2 of those relays. If one of those choices fails (errors), then keep trying until you get 2 of them that worked. This gives some redundancy in case one of them is censoring. You can bump that number up to 3 or 4, but more than that is probably just wasting bandwidth.
To find events tagging your user, look in your user's INBOX relays for those. In this case, look into all of them because some clients will only write to some of them (even though that is no longer advised).
Picking relays dynamically
Since your user follows many other users, it is very useful to find a small subset of all of their OUTBOX relays that cover everybody followed. I wrote some code to do this as (it is used by gossip) that you can look at for an example.
Where to post events to
Post all events (except DMs) to all of your users OUTBOX relays. Also post the events to all the INBOX relays of anybody that was tagged or mentioned in the contents in a nostr bech32 link (if desired). That way all these mentioned people are aware of the reply (or quote or repost).
DMs should be posted only to INBOX relays (in the future, to PRIVATE INBOX relays). You should post it to your own INBOX relays also, because you'll want a record of the conversation. In this way, you can see all your DMs inbound and outbound at your INBOX relay.
Where to publish your user's kind-10002 event to
This event was designed to be small and not require moderation, plus it is replaceable so there is only one per user. For this reason, at the moment, just spread it around to lots of relays especially the most popular relays.
For example, the gossip client automatically determines which relays to publish to based on whether they seem to be working (several hundred) and does so in batches of 10.
How to find replies
If all clients used the gossip model, you could find all the replies to any post in the author's INBOX relays for any event with an 'e' tag tagging the event you want replies to... because gossip model clients will publish them there.
But given the non-gossip-model clients, you should also look where the event was seen and look on those relays too.
Clobbering issues
Please read your users kind 10002 event before clobbering it. You should look many places to make sure you didn't miss the newest one.
If the old relay list had tags you don't understand (e.g. neither "read" nor "write"), then preserve them.
How users should pick relays
Today, nostr relays are not uniform. They have all kinds of different rule-sets and purposes. We severely lack a way to advice non-technical users as to which relays make good OUTBOX relays and which ones make good INBOX relays. But you are a dev, you can figure that out pretty well. For example, INBOX relays must accept notes from anyone meaning they can't be paid-subscription relays.
Bandwidth isn't a big issue
The outbox model doesn't require excessive bandwidth when done right. You shouldn't be downloading the same note many times... only 2-4 times depending on the level of redundancy your user wants.
Downloading 1000 events from 100 relays is in theory the same amount of data as downloading 1000 events from 1 relay.
But in practice, due to redundancy concerns, you will end up downloading 2000-3000 events from those 100 relays instead of just the 1000 you would in a single relay situation. Remember, per person followed, you will only ask for their events from 2-4 relays, not from all 100 relays!!!
Also in practice, the cost of opening and maintaining 100 network connections is more than the cost of opening and maintaining just 1. But this isn't usually a big deal unless...
Crypto overhead on Low-Power Clients
Verifying Schnorr signatures in the secp256k1 cryptosystem is not cheap. Setting up SSL key exchange is not cheap either. But most clients will do a lot more event signature validations than they will SSL setups.
For this reason, connecting to 50-100 relays is NOT hugely expensive for clients that are already verifying event signatures, as the number of events far surpasses the number of relay connections.
But for low-power clients that can't do event signature verification, there is a case for them not doing a lot of SSL setups either. Those clients would benefit from a different architecture, where half of the client was on a more powerful machine acting as a proxy for the low-power half of the client. These halves need to trust each other, so perhaps this isn't a good architecture for a business relationship, but I don't know what else to say about the low-power client situation.
Unsafe relays
Some people complain that the outbox model directs their client to relays that their user has not approved. I don't think it is a big deal, as such users can use VPNs or Tor if they need privacy. But for such users that still have concerns, they may wish to use clients that give them control over this. As a client developer you can choose whether to offer this feature or not.
The gossip client allows users to require whitelisting for connecting to new relays and for AUTHing to relays.
See Also
-
 @ 42342239:1d80db24
2024-03-21 09:49:01
@ 42342239:1d80db24
2024-03-21 09:49:01It has become increasingly evident that our financial system has started undermine our constitutionally guaranteed freedoms and rights. Payment giants like PayPal, Mastercard, and Visa sometimes block the ability to donate money. Individuals, companies, and associations lose bank accounts — or struggle to open new ones. In bank offices, people nowadays risk undergoing something resembling being cross-examined. The regulations are becoming so cumbersome that their mere presence risks tarnishing the banks' reputation.
The rules are so complex that even within the same bank, different compliance officers can provide different answers to the same question! There are even departments where some of the compliance officers are reluctant to provide written responses and prefer to answer questions over an unrecorded phone call. Last year's corporate lawyer in Sweden recently complained about troublesome bureaucracy, and that's from a the perspective of a very large corporation. We may not even fathom how smaller businesses — the keys to a nation's prosperity — experience it.
Where do all these rules come?
Where do all these rules come from, and how well do they work? Today's regulations on money laundering (AML) and customer due diligence (KYC - know your customer) primarily originate from a G7 meeting in the summer of 1989. (The G7 comprises the seven advanced economies: the USA, Canada, the UK, Germany, France, Italy, and Japan, along with the EU.) During that meeting, the intergovernmental organization FATF (Financial Action Task Force) was established with the aim of combating organized crime, especially drug trafficking. Since then, its mandate has expanded to include fighting money laundering, terrorist financing, and the financing of the proliferation of weapons of mass destruction(!). One might envisage the rules soon being aimed against proliferation of GPUs (Graphics Processing Units used for AI/ML). FATF, dominated by the USA, provides frameworks and recommendations for countries to follow. Despite its influence, the organization often goes unnoticed. Had you heard of it?
FATF offered countries "a deal they couldn't refuse"
On the advice of the USA and G7 countries, the organization decided to begin grading countries in "blacklists" and "grey lists" in 2000, naming countries that did not comply with its recommendations. The purpose was to apply "pressure" to these countries if they wanted to "retain their position in the global economy." The countries were offered a deal they couldn't refuse, and the number of member countries rapidly increased. Threatening with financial sanctions in this manner has even been referred to as "extraterritorial bullying." Some at the time even argued that the process violated international law.
If your local Financial Supervisory Authority (FSA) were to fail in enforcing compliance with FATF's many checklists among financial institutions, the risk of your country and its banks being barred from the US-dominated financial markets would loom large. This could have disastrous consequences.
A cost-benefit analysis of AML and KYC regulations
Economists use cost-benefit analysis to determine whether an action or a policy is successful. Let's see what such an analysis reveals.
What are the benefits (or revenues) after almost 35 years of more and more rules and regulations? The United Nations Office on Drugs and Crime estimated that only 0.2% of criminal proceeds are confiscated. Other estimates suggest a success rate from such anti-money laundering rules of 0.07% — a rounding error for organized crime. Europol expects to recover 1.2 billion euros annually, equivalent to about 1% of the revenue generated in the European drug market (110 billion euros). However, the percentage may be considerably lower, as the size of the drug market is likely underestimated. Moreover, there are many more "criminal industries" than just the drug trade; human trafficking is one example - there are many more. In other words, criminal organizations retain at least 99%, perhaps even 99.93%, of their profits, despite all cumbersome rules regarding money laundering and customer due diligence.
What constitutes the total cost of this bureaurcratic activity, costs that eventually burden taxpayers and households via higher fees? Within Europe, private financial firms are estimated to spend approximately 144 billion euros on compliance. According to some estimates, the global cost is twice as high, perhaps even eight times as much.
For Europe, the cost may thus be about 120 times (144/1.2) higher than the revenues from these measures. These "compliance costs" bizarrely exceed the total profits from the drug market, as one researcher put it. Even though the calculations are uncertain, it is challenging — perhaps impossible — to legitimize these regulations from a cost-benefit perspective.
But it doesn't end there, unfortunately. The cost of maintaining this compliance circus, with around 80 international organizations, thousands of authorities, far more employees, and all this across hundreds of countries, remains a mystery. But it's unlikely to be cheap.
The purpose of a system is what it does
In Economic Possibilities for our Grandchildren (1930), John Maynard Keynes foresaw that thanks to technological development, we could have had a 15-hour workweek by now. This has clearly not happened. Perhaps jobs have been created that are entirely meaningless? Anthropologist David Graeber argued precisely this in Bullshit Jobs in 2018. In that case, a significant number of people spend their entire working lives performing tasks they suspect deep down don't need to be done.
"The purpose of a system is what it does" is a heuristic coined by Stafford Beer. He observed there is "no point in claiming that the purpose of a system is to do what it constantly fails to do. What the current regulatory regime fails to do is combat criminal organizations. Nor does it seem to prevent banks from laundering money as never before, or from providing banking services to sex-offending traffickers
What the current regulatory regime does do, is: i) create armies of meaningless jobs, ii) thereby undermining mental health as well as economic prosperity, while iii) undermining our freedom and rights.
What does this say about the purpose of the system?
-
 @ ee11a5df:b76c4e49
2024-03-21 00:28:47
@ ee11a5df:b76c4e49
2024-03-21 00:28:47I'm glad to see more activity and discussion about the gossip model. Glad to see fiatjaf and Jack posting about it, as well as many developers pitching in in the replies. There are difficult problems we need to overcome, and finding notes while remaining decentralized without huge note copying overhead was just the first. While the gossip model (including the outbox model which is just the NIP-65 part) completely eliminates the need to copy notes around to lots of relays, and keeps us decentralized, it brings about it's own set of new problems. No community is ever of the same mind on any issue, and this issue is no different. We have a lot of divergent opinions. This note will be my updated thoughts on these topics.
COPYING TO CENTRAL RELAYS IS A NON-STARTER: The idea that you can configure your client to use a few popular "centralized" relays and everybody will copy notes into those central relays is a non-starter. It destroys the entire raison d'être of nostr. I've heard people say that more decentralization isn't our biggest issue. But decentralization is THE reason nostr exists at all, so we need to make sure we live up to the hype. Otherwise we may as well just all join Bluesky. It has other problems too: the central relays get overloaded, and the notes get copied to too many relays, which is both space-inefficient and network bandwith inefficient.
ISSUE 1: Which notes should I fetch from which relays? This is described pretty well now in NIP-65. But that is only the "outbox" model part. The "gossip model" part is to also work out what relays work for people who don't publish a relay list.
ISSUE 2: Automatic failover. Apparently Peter Todd's definition of decentralized includes a concept of automatic failover, where new resources are brought up and users don't need to do anything. Besides this not being part of any definition of decentralized I have never heard of, we kind of have this. If a user has 5 outboxes, and 3 fail, everything still works. Redundancy is built in. No user intervention needed in most cases, at least in the short term. But we also don't have any notion of administrators who can fix this behind the scenes for the users. Users are sovereign and that means they have total control, but also take on some responsibility. This is obvious when it comes to keypair management, but it goes further. Users have to manage where they post and where they accept incoming notes, and when those relays fail to serve them they have to change providers. Putting the users in charge, and not having administrators, is kinda necessary to be truly decentralized.
ISSUE 3: Connecting to unvetted relays feels unsafe. It might even be the NSA tracking you! First off, this happens with your web browser all the time: you go visit a web page and it instructs your browser to fetch a font from google. If you don't like it, you can use uBlock origin and manage it manually. In the nostr world, if you don't like it, you can use a client that puts you more in control of this. The gossip client for example has options for whether you want to manually approve relay connections and AUTHs, just once or always, and always lets you change your mind later. If you turn those options on, initially it is a giant wall of approval requests... but that situation resolves rather quickly. I've been running with these options on for a long time now, and only about once a week do I have to make a decision for a new relay.
But these features aren't really necessary for the vast majority of users who don't care if a relay knows their IP address. Those users use VPNs or Tor when they want to be anonymous, and don't bother when they don't care (me included).
ISSUE 4: Mobile phone clients may find the gossip model too costly in terms of battery life. Bandwidth is actually not a problem: under the gossip model (if done correctly) events for user P are only downloaded from N relays (default for gossip client is N=2), which in general is FEWER events retrieved than other models which download the same event maybe 8 or more times. Rather, the problem here is the large number of network connections and in particular, the large number of SSL setups and teardowns. If it weren't for SSL, this wouldn't be much of a problem. But setting up and tearing down SSL on 50 simultaneous connections that drop and pop up somewhat frequently is a battery drain.
The solution to this that makes the most sense to me is to have a client proxy. What I mean by that is a piece of software on a server in a data centre. The client proxy would be a headless nostr client that uses the gossip model and acts on behalf of the phone client. The phone client doesn't even have to be a nostr client, but it might as well be a nostr client that just connects to this fixed proxy to read and write all of its events. Now the SSL connection issue is solved. These proxies can serve many clients and have local storage, whereas the phones might not even need local storage. Since very few users will set up such things for themselves, this is a business opportunity for people, and a better business opportunity IMHO than running a paid-for relay. This doesn't decentralize nostr as there can be many of these proxies. It does however require a trust relationship between the phone client and the proxy.
ISSUE 5: Personal relays still need moderation. I wrongly thought for a very long time that personal relays could act as personal OUTBOXes and personal INBOXes without needing moderation. Recently it became clear to me that clients should probably read from other people's INBOXes to find replies to events written by the user of that INBOX (which outbox model clients should be putting into that INBOX). If that is happening, then personal relays will need to serve to the public events that were just put there by the public, thus exposing them to abuse. I'm greatly disappointed to come to this realization and not quite settled about it yet, but I thought I had better make this known.
-
 @ b12b632c:d9e1ff79
2024-02-19 19:18:46
@ b12b632c:d9e1ff79
2024-02-19 19:18:46Nostr decentralized network is growing exponentially day by day and new stuff comes out everyday. We can now use a NIP46 server to proxify our nsec key to avoid to use it to log on Nostr websites and possibly leak it, by mistake or by malicious persons. That's the point of this tutorial, setup a NIP46 server Nsec.app with its own Nostr relay. You'll be able to use it for you and let people use it, every data is stored locally in your internet browser. It's an non-custodial application, like wallets !
It's nearly a perfect solution (because nothing is perfect as we know) and that makes the daily use of Nostr keys much more secure and you'll see, much more sexy ! Look:
Nsec.app is not the only NIP46 server, in fact, @PABLOF7z was the first to create a NIP46 server called nsecBunker. You can also self-hosted nsecBunkerd, you can find a detailed explanation here : nsecbunkerd. I may write a how to self-host nsecBunkderd soon.
If you want more information about its bunker and what's behind this tutorial, you can check these links :
Few stuffs before beginning
Spoiler : I didn't automatized everything. The goal here is not to give you a full 1 click installation process, it's more to let you see and understand all the little things to configure and understand how works Nsec.app and the NIP46. There is a little bit of work, yes, but you'll be happy when it will work! Believe me.
Before entering into the battlefield, you must have few things : A working VPS with direct access to internet or a computer at home but NAT will certain make your life a hell. Use a VPS instead, on DigitalOcean, Linode, Scaleway, as you wish. A web domain that your own because we need to use at least 3 DNS A records (you can choose the subdomain you like) : domain.tld, noauth.domain.tld, noauth.domain.tld. You need to have some programs already installed : git, docker, docker-compose, nano/vi. if you fill in all the boxes, we can move forward !
Let's install everything !
I build a repo with a docker-compose file with all the required stuff to make the Bunker works :
Nsec.app front-end : noauth Nsec.app back-end : noauthd Nostr relay : strfry Nostr NIP05 : easy-nip5
First thing to do is to clone the repo "nsec-app-docker" from my repo:
$ git clone git clone https://github.com/PastaGringo/nsec-app-docker.git $ cd nsec-app-dockerWhen it's done, you'll have to do several things to make it work. 1) You need to generate some keys for the web-push library (keep them for later) :
``` $ docker run pastagringo/web-push-generate-keys
Generating your web-push keys...
Your private key : rQeqFIYKkInRqBSR3c5iTE3IqBRsfvbq_R4hbFHvywE Your public key : BFW4TA-lUvCq_az5fuQQAjCi-276wyeGUSnUx4UbGaPPJwEemUqp3Rr3oTnxbf0d4IYJi5mxUJOY4KR3ZTi3hVc ```
2) Generate a new keys pair (nsec/npub) for the NIP46 server by clicking on "Generate new key" from NostrTool website: nostrtool.com.
You should have something like this :
console Nostr private key (nsec): keep this -> nsec1zcyanx8zptarrmfmefr627zccrug3q2vhpfnzucq78357hshs72qecvxk6 Nostr private key (hex): 1609d998e20afa31ed3bca47a57858c0f888814cb853317300f1e34f5e178794 Nostr public key (npub): npub1ywzwtnzeh64l560a9j9q5h64pf4wvencv2nn0x4h0zw2x76g8vrq68cmyz Nostr public key (hex): keep this -> 2384e5cc59beabfa69fd2c8a0a5f550a6ae6667862a7379ab7789ca37b483b06You need to keep Nostr private key (nsec) & Nostr public key (npub). 3) Open (nano/vi) the .env file located in the current folder and fill all the required info :
```console
traefik
EMAIL=pastagringo@fractalized.net <-- replace with your own domain NSEC_ROOT_DOMAIN=plebes.ovh <-- replace with your own domain <-- replace with your own relay domain RELAY_DOMAIN=relay.plebes.ovh <-- replace with your own noauth domainay.plebes.ovh <-- replace with your own relay domain <-- replace with your own noauth domain NOAUTH_DOMAIN=noauth.plebes.ovh <-- replace with your own noauth domain NOAUTHD_DOMAIN=noauthd.plebes.ovh <-- replace with your own noauth domain
noauth
APP_WEB_PUSH_PUBKEY=BGVa7TMQus_KVn7tAwPkpwnU_bpr1i6B7D_3TT-AwkPlPd5fNcZsoCkJkJylVOn7kZ-9JZLpyOmt7U9rAtC-zeg <-- replace with your own web push public key APP_NOAUTHD_URL=https://$NOAUTHD_DOMAIN APP_DOMAIN=$NSEC_ROOT_DOMAIN APP_RELAY=wss://$RELAY_DOMAIN
noauthd
PUSH_PUBKEY=$APP_WEB_PUSH_PUBKEY PUSH_SECRET=_Sz8wgp56KERD5R4Zj5rX_owrWQGyHDyY4Pbf5vnFU0 <-- replace with your own web push private key ORIGIN=https://$NOAUTHD_DOMAIN DATABASE_URL=file:./prod.db BUNKER_NSEC=nsec1f43635rzv6lsazzsl3hfsrum9u8chn3pyjez5qx0ypxl28lcar2suy6hgn <-- replace with your the bunker nsec key BUNKER_RELAY=wss://$RELAY_DOMAIN BUNKER_DOMAIN=$NSEC_ROOT_DOMAIN BUNKER_ORIGIN=https://$NOAUTH_DOMAIN ```
Be aware of noauth and noauthd (the d letter). Next, save and quit. 4) You now need to modify the nostr.json file used for the NIP05 to indicate which relay your bunker will use. You need to set the bunker HEX PUBLIC KEY (I replaced the info with the one I get from NostrTool before) :
console nano easy-nip5/nostr.jsonconsole { "names": { "_": "ServerHexPubKey" }, "nip46": { "ServerHexPubKey": [ "wss://ReplaceWithYourRelayDomain" ] } }5) You can now run the docker compose file by running the command (first run can take a bit of time because the noauth container needs to build the npm project):
console $ docker compose up -d6) Before creating our first user into the Nostr Bunker, we need to test if all the required services are up. You should have :
noauth :
noauthd :
console CANNOT GET /https://noauthd.yourdomain.tld/name :
console { "error": "Specify npub" }https://yourdomain.tld/.well-known/nostr.json :
console { "names": { "_": "ServerHexPubKey" }, "nip46": { "ServerHexPubKey": [ "wss://ReplaceWithYourRelayDomain" ] } }If you have everything working, we can try to create a new user!
7) Connect to noauth and click on "Get Started" :
At the bottom the screen, click on "Sign up" :
Fill a username and click on "Create account" :
If everything has been correctly configured, you should see a pop message with "Account created for "XXXX" :
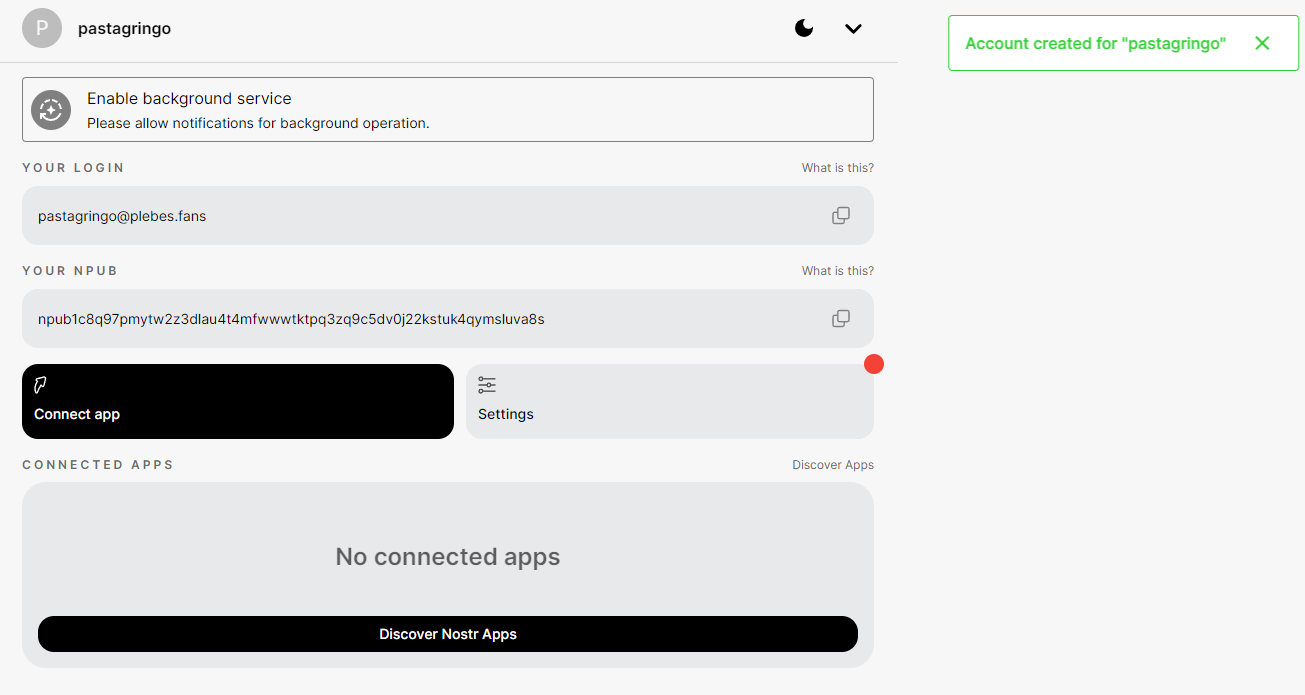
PS : to know if noauthd is well serving the nostr.json file, you can check this URL : https://yourdomain.tld/.well-known/nostr.json?name=YourUser You should see that the user has now NIP05/NIP46 entries :
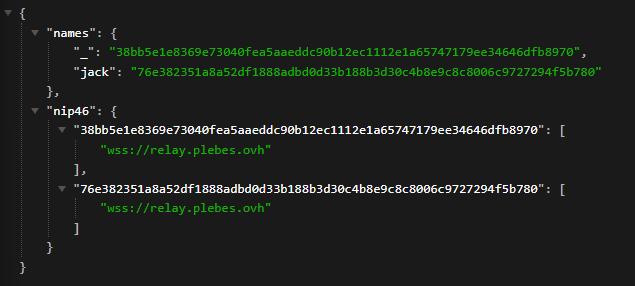
If the user creation failed, you'll see a red pop-up saying "Something went wrong!" :
To understand what happened, you need to inspect the web page to find the error :
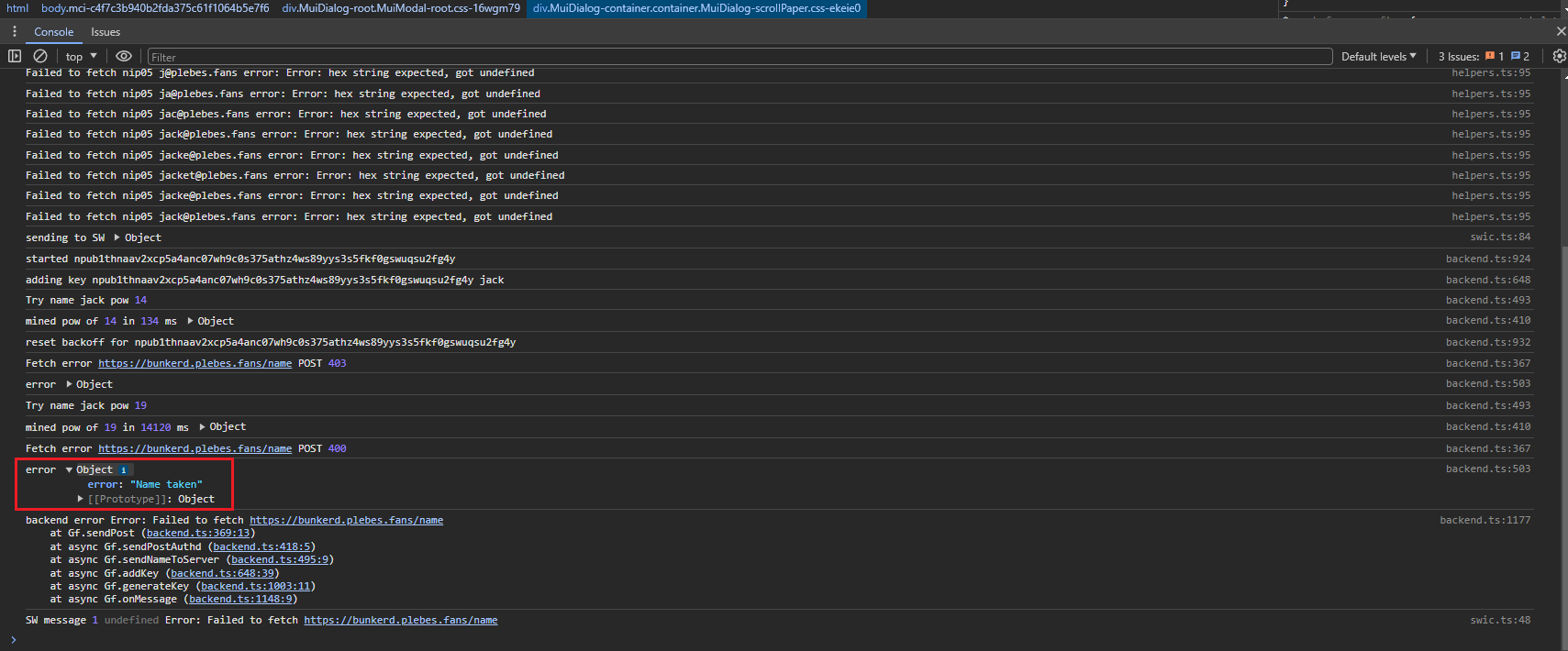
For the example, I tried to recreate a user "jack" which has already been created. You may find a lot of different errors depending of the configuration you made. You can find that the relay is not reachable on w s s : / /, you can find that the noauthd is not accessible too, etc. Every answers should be in this place.
To completely finish the tests, you need to enable the browser notifications, otherwise you won't see the pop-up when you'll logon on Nostr web client, by clicking on "Enable background service" :
You need to click on allow notifications :
Should see this green confirmation popup on top right of your screen:
Well... Everything works now !
8) You try to use your brand new proxyfied npub by clicking on "Connect App" and buy copying your bunker URL :
You can now to for instance on Nostrudel Nostr web client to login with it. Select the relays you want (Popular is better ; if you don't have multiple relay configured on your Nostr profile, avoid "Login to use your relay") :
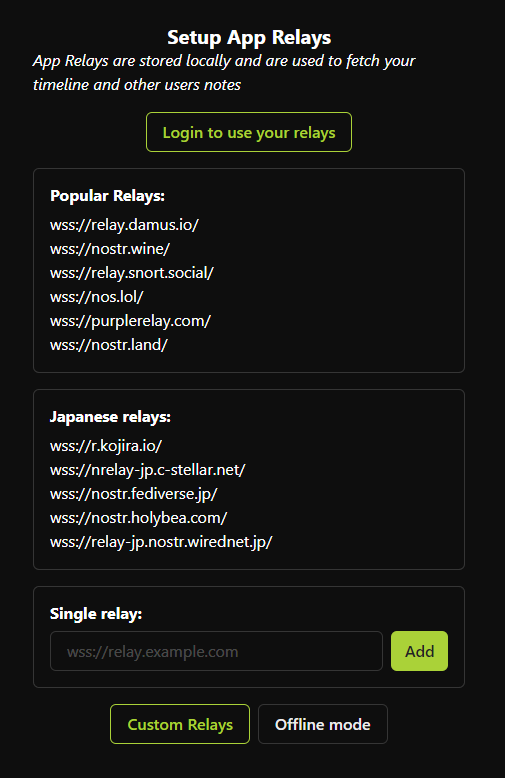
Click on "Sign in" :
Click on "Show Advanced" :
Click on "Nostr connect / Bunker" :
Paste your bunker URL and click on "Connect" :
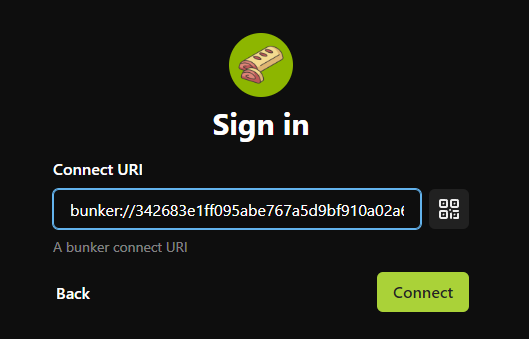
The first time, tour browser (Chrome here) may blocks the popup, you need to allow it :
If the browser blocked the popup, NoStrudel will wait your confirmation to login :
You have to go back on your bunker URL to allow the NoStrudel connection request by clicking on on "Connect":
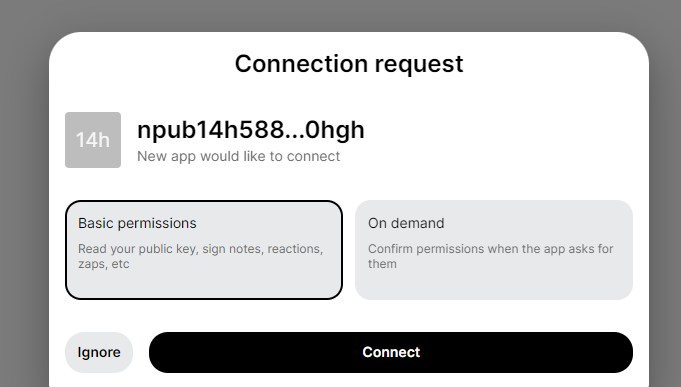
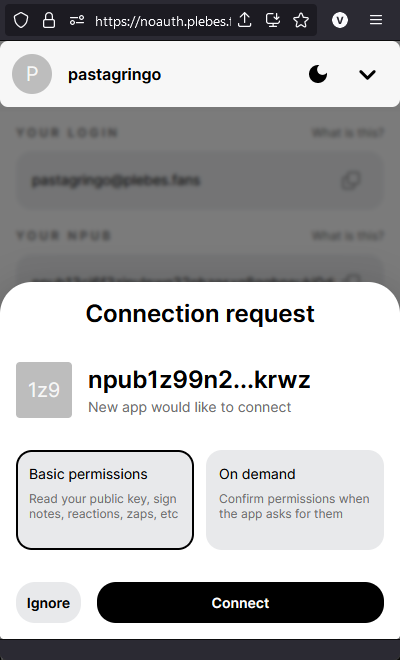
The first time connections may be a bit annoying with all the popup authorizations but once it's done, you can forget them it will connect without any issue. Congrats ! You are connected on NoStrudel with an npub proxyfied key !⚡

You can check to which applications you gave permissions and activity history in noauth by selecting your user. :
If you want to import your real Nostr profile, the one that everyone knows, you can import your nsec key by adding a new account and select "Import key" and adding your precious nsec key (reminder: your nsec key stays in your browser! The noauth provider won't have access to it!) :
You can see can that my profile picture has been retrieved and updated into noauth :
I can now use this new pubkey attached my nsec.app server to login in NoStrudel again :
Accounts/keys management in noauthd You can list created keys in your bunkerd by doing these command (CTRL+C to exit) :
console $ docker exec -it noauthd node src/index.js list_names [ '/usr/local/bin/node', '/noauthd/src/index.js', 'list_names' ] 1 jack npub1hjdw2y0t44q4znzal2nxy7vwmpv3qwrreu48uy5afqhxkw6d2nhsxt7x6u 1708173927920n 2 peter npub1yp752u5tr5v5u74kadrzgfjz2lsmyz8dyaxkdp4e0ptmaul4cyxsvpzzjz 1708174748972n 3 john npub1xw45yuvh5c73sc5fmmc3vf2zvmtrzdmz4g2u3p2j8zcgc0ktr8msdz6evs 1708174778968n 4 johndoe npub1xsng8c0lp9dtuan6tkdljy9q9fjdxkphvhj93eau07rxugrheu2s38fuhr 1708174831905nIf you want to delete someone key, you have to do :
```console $ docker exec -it noauthd node src/index.js delete_name johndoe [ '/usr/local/bin/node', '/noauthd/src/index.js', 'delete_name', 'johndoe' ] deleted johndoe { id: 4, name: 'johndoe', npub: 'npub1xsng8c0lp9dtuan6tkdljy9q9fjdxkphvhj93eau07rxugrheu2s38fuhr', timestamp: 1708174831905n
$ docker exec -it noauthd node src/index.js list_names [ '/usr/local/bin/node', '/noauthd/src/index.js', 'list_names' ] 1 jack npub1hjdw2y0t44q4znzal2nxy7vwmpv3qwrreu48uy5afqhxkw6d2nhsxt7x6u 1708173927920n 2 peter npub1yp752u5tr5v5u74kadrzgfjz2lsmyz8dyaxkdp4e0ptmaul4cyxsvpzzjz 1708174748972n 3 john npub1xw45yuvh5c73sc5fmmc3vf2zvmtrzdmz4g2u3p2j8zcgc0ktr8msdz6evs 1708174778968n ```
It could be pretty easy to create a script to handle the management of keys but I think @Brugeman may create a web interface for that. Noauth is still very young, changes are committed everyday to fix/enhance the application! As """everything""" is stored locally on your browser, you have to clear the cache of you bunker noauth URL to clean everything. This Chome extension is very useful for that. Check these settings in the extension option :
You can now enjoy even more Nostr ⚡ See you soon in another Fractalized story!
-
 @ ee11a5df:b76c4e49
2023-11-09 05:20:37
@ ee11a5df:b76c4e49
2023-11-09 05:20:37A lot of terms have been bandied about regarding relay models: Gossip relay model, outbox relay model, and inbox relay model. But this term "relay model" bothers me. It sounds stuffy and formal and doesn't actually describe what we are talking about very well. Also, people have suggested maybe there are other relay models. So I thought maybe we should rethink this all from first principles. That is what this blog post attempts to do.
Nostr is notes and other stuff transmitted by relays. A client puts an event onto a relay, and subsequently another client reads that event. OK, strictly speaking it could be the same client. Strictly speaking it could even be that no other client reads the event, that the event was intended for the relay (think about nostr connect). But in general, the reason we put events on relays is for other clients to read them.
Given that fact, I see two ways this can occur:
1) The reader reads the event from the same relay that the writer wrote the event to (this I will call relay rendezvous), 2) The event was copied between relays by something.
This second solution is perfectly viable, but it less scalable and less immediate as it requires copies which means that resources will be consumed more rapidly than if we can come up with workable relay rendezvous solutions. That doesn't mean there aren't other considerations which could weigh heavily in favor of copying events. But I am not aware of them, so I will be discussing relay rendezvous.
We can then divide the relay rendezvous situation into several cases: one-to-one, one-to-many, and one-to-all, where the many are a known set, and the all are an unbounded unknown set. I cannot conceive of many-to-anything for nostr so we will speak no further of it.
For a rendezvous to take place, not only do the parties need to agree on a relay (or many relays), but there needs to be some way that readers can become aware that the writer has written something.
So the one-to-one situation works out well by the writer putting the message onto a relay that they know the reader checks for messages on. This we call the INBOX model. It is akin to sending them an email into their inbox where the reader checks for messages addressed to them.
The one-to-(known)-many model is very similar, except the writer has to write to many people's inboxes. Still we are dealing with the INBOX model.
The final case, one-to-(unknown)-all, there is no way the writer can place the message into every person's inbox because they are unknown. So in this case, the writer can write to their own OUTBOX, and anybody interested in these kinds of messages can subscribe to the writer's OUTBOX.
Notice that I have covered every case already, and that I have not even specified what particular types of scenarios call for one-to-one or one-to-many or one-to-all, but that every scenario must fit into one of those models.
So that is basically it. People need INBOX and OUTBOX relays and nothing else for relay rendezvous to cover all the possible scenarios.
That is not to say that other kinds of concerns might not modulate this. There is a suggestion for a DM relay (which is really an INBOX but with a special associated understanding), which is perfectly fine by me. But I don't think there are any other relay models. There is also the case of a live event where two parties are interacting over the same relay, but in terms of rendezvous this isn't a new case, it is just that the shared relay is serving as both parties' INBOX (in the case of a closed chat) and/or both parties' OUTBOX (in the case of an open one) at the same time.
So anyhow that's my thinking on the topic. It has become a fairly concise and complete set of concepts, and this makes me happy. Most things aren't this easy.
-
 @ b12b632c:d9e1ff79
2023-08-08 00:02:31
@ b12b632c:d9e1ff79
2023-08-08 00:02:31"Welcome to the Bitcoin Lightning Bolt Card, the world's first Bitcoin debit card. This revolutionary card allows you to easily and securely spend your Bitcoin at lightning compatible merchants around the world." Bolt Card
I discovered few days ago the Bolt Card and I need to say that's pretty amazing. Thinking that we can pay daily with Bitcoin Sats in the same way that we pay with our Visa/Mastecard debit cards is really something huge⚡(based on the fact that sellers are accepting Bitcoins obviously!)
To use Bolt Card you have three choices :
- Use their (Bolt Card) own Bolt Card HUB and their own BTC Lightning node
- Use your own self hosted Bolt Card Hub and an external BTC Lightning node
- Use your own self hosted Bolt Card Hub and your BTC Lightning node (where you shoud have active Lightning channels)
⚡ The first choice is the quickiest and simpliest way to have an NFC Bolt Card. It will take you few seconds (for real). You'll have to wait much longer to receive your NFC card from a website where you bought it than configure it with Bolt Card services.
⚡⚡ The second choice is pretty nice too because you won't have a VPS + to deal with all the BTC Lightnode stuff but you'll use an external one. From the Bolt Card tutorial about Bolt Card Hub, they use a Lightning from voltage.cloud and I have to say that their services are impressive. In few seconds you'll have your own Lightning node and you'll be able to configure it into the Bolt Card Hub settings. PS : voltage.cloud offers 7 trial days / 20$ so don't hesitate to try it!
⚡⚡⚡ The third one is obvisouly a bit (way) more complex because you'll have to provide a VPS + Bitcoin node and a Bitcoin Lightning Node to be able to send and receive Lightning payments with your Bolt NFC Card. So you shoud already have configured everything by yourself to follow this tutorial. I will show what I did for my own installation and all my nodes (BTC & Lightning) are provided by my home Umbrel node (as I don't want to publish my nodes directly on the clearnet). We'll see how to connect to the Umbrel Lighting node later (spoiler: Tailscale).
To resume in this tutorial, I have :
- 1 Umbrel node (rpi4b) with BTC and Lightning with Tailscale installed.
- 1 VPS (Virtual Personal Server) to publish publicly the Bolt Card LNDHub and Bolt Card containers configured the same way as my other containers (with Nginx Proxy Manager)
Ready? Let's do it ! ⚡
Configuring Bolt Card & Bolt Card LNDHub
Always good to begin by reading the bolt card-lndhub-docker github repo. To a better understading of all the components, you can check this schema :
We'll not use it as it is because we'll skip the Caddy part because we already use Nginx Proxy Manager.
To begin we'll clone all the requested folders :
git clone https://github.com/boltcard/boltcard-lndhub-docker bolthub cd bolthub git clone https://github.com/boltcard/boltcard-lndhub BoltCardHub git clone https://github.com/boltcard/boltcard.git git clone https://github.com/boltcard/boltcard-groundcontrol.git GroundControlPS : we won't see how to configure GroundControl yet. This article may be updated later.
We now need to modify the settings file with our own settings :
mv .env.example .env nano .envYou need to replace "your-lnd-node-rpc-address" by your Umbrel TAILSCALE ip address (you can find your Umbrel node IP from your Tailscale admin console):
``` LND_IP=your-lnd-node-rpc-address # <- UMBREL TAILSCALE IP ADDRESS LND_GRPC_PORT=10009 LND_CERT_FILE=tls.cert LND_ADMIN_MACAROON_FILE=admin.macaroon REDIS_PASSWORD=random-string LND_PASSWORD=your-lnd-node-unlock-password
docker-compose.yml only
GROUNDCONTROL=ground-control-url
docker-compose-groundcontrol.yml only
FCM_SERVER_KEY=hex-encoded APNS_P8=hex-encoded APNS_P8_KID=issuer-key-which-is-key-ID-of-your-p8-file APPLE_TEAM_ID=team-id-of-your-developer-account BITCOIN_RPC=bitcoin-rpc-url APNS_TOPIC=app-package-name ```
We now need to generate an AES key and insert it into the "settings.sql" file :
```
hexdump -vn 16 -e '4/4 "%08x" 1 "\n"' /dev/random 19efdc45acec06ad8ebf4d6fe50412d0 nano settings.sql ```
- Insert the AES between ' ' right from 'AES_DECRYPT_KEY'
- Insert your domain or subdomain (subdomain in my case) host between ' ' from 'HOST_DOMAIN'
- Insert your Umbrel tailscale IP between ' ' from 'LN_HOST'
Be aware that this subdomain won't be the LNDHub container (boltcard_hub:9002) but the Boltcard container (boltcard_main:9000)
``` \c card_db;
DELETE FROM settings;
-- at a minimum, the settings marked 'set this' must be set for your system -- an explanation for each of the bolt card server settings can be found here -- https://github.com/boltcard/boltcard/blob/main/docs/SETTINGS.md
INSERT INTO settings (name, value) VALUES ('LOG_LEVEL', 'DEBUG'); INSERT INTO settings (name, value) VALUES ('AES_DECRYPT_KEY', '19efdc45acec06ad8ebf4d6fe50412d0'); -- set this INSERT INTO settings (name, value) VALUES ('HOST_DOMAIN', 'sub.domain.tld'); -- set this INSERT INTO settings (name, value) VALUES ('MIN_WITHDRAW_SATS', '1'); INSERT INTO settings (name, value) VALUES ('MAX_WITHDRAW_SATS', '1000000'); INSERT INTO settings (name, value) VALUES ('LN_HOST', ''); -- set this INSERT INTO settings (name, value) VALUES ('LN_PORT', '10009'); INSERT INTO settings (name, value) VALUES ('LN_TLS_FILE', '/boltcard/tls.cert'); INSERT INTO settings (name, value) VALUES ('LN_MACAROON_FILE', '/boltcard/admin.macaroon'); INSERT INTO settings (name, value) VALUES ('FEE_LIMIT_SAT', '10'); INSERT INTO settings (name, value) VALUES ('FEE_LIMIT_PERCENT', '0.5'); INSERT INTO settings (name, value) VALUES ('LN_TESTNODE', ''); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNURLW', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNURLP', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('FUNCTION_EMAIL', 'DISABLE'); INSERT INTO settings (name, value) VALUES ('AWS_SES_ID', ''); INSERT INTO settings (name, value) VALUES ('AWS_SES_SECRET', ''); INSERT INTO settings (name, value) VALUES ('AWS_SES_EMAIL_FROM', ''); INSERT INTO settings (name, value) VALUES ('EMAIL_MAX_TXS', ''); INSERT INTO settings (name, value) VALUES ('FUNCTION_LNDHUB', 'ENABLE'); INSERT INTO settings (name, value) VALUES ('LNDHUB_URL', 'http://boltcard_hub:9002'); INSERT INTO settings (name, value) VALUES ('FUNCTION_INTERNAL_API', 'ENABLE'); ```
You now need to get two files used by Bolt Card LND Hub, the admin.macaroon and tls.cert files from your Umbrel BTC Ligtning node. You can get these files on your Umbrel node at these locations :
/home/umbrel/umbrel/app-data/lightning/data/lnd/tls.cert /home/umbrel/umbrel/app-data/lightning/data/lnd/data/chain/bitcoin/mainnet/admin.macaroonYou can use either WinSCP, scp or ssh to copy these files to your local workstation and copy them again to your VPS to the root folder "bolthub".
You shoud have all these files into the bolthub directory :
johndoe@yourvps:~/bolthub$ ls -al total 68 drwxrwxr-x 6 johndoe johndoe 4096 Jul 30 00:06 . drwxrwxr-x 3 johndoe johndoe 4096 Jul 22 00:52 .. -rw-rw-r-- 1 johndoe johndoe 482 Jul 29 23:48 .env drwxrwxr-x 8 johndoe johndoe 4096 Jul 22 00:52 .git -rw-rw-r-- 1 johndoe johndoe 66 Jul 22 00:52 .gitignore drwxrwxr-x 11 johndoe johndoe 4096 Jul 22 00:52 BoltCardHub -rw-rw-r-- 1 johndoe johndoe 113 Jul 22 00:52 Caddyfile -rw-rw-r-- 1 johndoe johndoe 173 Jul 22 00:52 CaddyfileGroundControl drwxrwxr-x 6 johndoe johndoe 4096 Jul 22 00:52 GroundControl -rw-rw-r-- 1 johndoe johndoe 431 Jul 22 00:52 GroundControlDockerfile -rw-rw-r-- 1 johndoe johndoe 1913 Jul 22 00:52 README.md -rw-rw-r-- 1 johndoe johndoe 293 May 6 22:24 admin.macaroon drwxrwxr-x 16 johndoe johndoe 4096 Jul 22 00:52 boltcard -rw-rw-r-- 1 johndoe johndoe 3866 Jul 22 00:52 docker-compose-groundcontrol.yml -rw-rw-r-- 1 johndoe johndoe 2985 Jul 22 00:57 docker-compose.yml -rw-rw-r-- 1 johndoe johndoe 1909 Jul 29 23:56 settings.sql -rw-rw-r-- 1 johndoe johndoe 802 May 6 22:21 tls.certWe need to do few last tasks to ensure that Bolt Card LNDHub will work perfectly.
It's maybe already the case on your VPS but your user should be member of the docker group. If not, you can add your user by doing :
sudo groupadd docker sudo usermod -aG docker ${USER}If you did these commands, you need to logout and login again.
We also need to create all the docker named volumes by doing :
docker volume create boltcard_hub_lnd docker volume create boltcard_redisConfiguring Nginx Proxy Manager to proxify Bolt Card LNDHub & Boltcard
You need to have followed my previous blog post to fit with the instructions above.
As we use have the Bolt Card LNDHub docker stack in another directory than we other services and it has its own docker-compose.yml file, we'll have to configure the docker network into the NPM (Nginx Proxy Manager) docker-compose.yml to allow NPM to communicate with the Bolt Card LNDHub & Boltcard containers.
To do this we need to add these lines into our NPM external docker-compose (not the same one that is located into the bolthub directory, the one used for all your other containers) :
nano docker-compose.ymlnetworks: bolthub_boltnet: name: bolthub_boltnet external: trueBe careful, "bolthub" from "bolthub_boltnet" is based on the directory where Bolt Card LNDHub Docker docker-compose.yml file is located.
We also need to attach this network to the NPM container :
nginxproxymanager: container_name: nginxproxymanager image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt networks: - fractalized - bolthub_boltnetYou can now recreate the NPM container to attach the network:
docker compose up -dNow, you'll have to create 2 new Proxy Hosts into NPM admin UI. First one for your domain / subdomain to the Bolt Card LNDHub GUI (boltcard_hub:9002) :
And the second one for the Boltcard container (boltcard_main:9000).
In both Proxy Host I set all the SSL options and I use my wildcard certificate but you can generate one certificate for each Proxy Host with Force SSL, HSTS enabled, HTTP/2 Suppot and HSTS Subdomains enabled.
Starting Bolt Card LNDHub & BoltCard containers
Well done! Everything is setup, we can now start the Bolt Card LNDHub & Boltcard containers !
You need to go again to the root folder of the Bolt Card LNDHub projet "bolthub" and start the docker compose stack. We'll begin wihtout a "-d" to see if we have some issues during the containers creation :
docker compose upI won't share my containers logs to avoid any senstive information disclosure about my Bolt Card LNDHub node, but you can see them from the Bolt Card LNDHub Youtube video (link with exact timestamp where it's shown) :
If you have some issues about files mounting of admin.macaroon or tls.cert because you started the docker compose stack the first time without the files located in the bolthub folder do :
docker compose down && docker compose upAfter waiting few seconds/minutes you should go to your Bolt Card LNDHub Web UI domain/sudomain (created earlier into NPM) and you should see the Bolt Card LNDHub Web UI :
if everything is OK, you now run the containers in detached mode :
docker compose up -dVoilààààà ⚡
If you need to all the Bolt Card LNDHub logs you can use :
docker compose logs -f --tail 30You can now follow the video from Bolt Card to configure your Bolt Card NFC card and using your own Bolt Card LNDHub :
~~PS : there is currently a bug when you'll click on "Connect Bolt Card" from the Bold Card Walle app, you might have this error message "API error: updateboltcard: enable_pin is not a valid boolean (code 6)". It's a know issue and the Bolt Card team is currently working on it. You can find more information on their Telegram~~
Thanks to the Bolt Card, the issue has been corrected : changelog
See you soon in another Fractalized story!
-
 @ ee11a5df:b76c4e49
2023-07-29 03:27:23
@ ee11a5df:b76c4e49
2023-07-29 03:27:23Gossip: The HTTP Fetcher
Gossip is a desktop nostr client. This post is about the code that fetches HTTP resources.
Gossip fetches HTTP resources. This includes images, videos, nip05 json files, etc. The part of gossip that does this is called the fetcher.
We have had a fetcher for some time, but it was poorly designed and had problems. For example, it was never expiring items in the cache.
We've made a lot of improvements to the fetcher recently. It's pretty good now, but there is still room for improvement.
Caching
Our fetcher caches data. Each URL that is fetched is hashed, and the content is stored under a file in the cache named by that hash.
If a request is in the cache, we don't do an HTTP request, we serve it directly from the cache.
But cached data gets stale. Sometimes resources at a URL change. We generally check resources again after three days.
We save the server's ETag value for content, and when we check the content again we supply an If-None-Match header with the ETag so the server could respond with 304 Not Modified in which case we don't need to download the resource again, we just bump the filetime to now.
In the event that our cache data is stale, but the server gives us an error, we serve up the stale data (stale is better than nothing).
Queueing
We used to fire off HTTP GET requests as soon as we knew that we needed a resource. This was not looked on too kindly by servers and CDNs who were giving us either 403 Forbidden or 429 Too Many Requests.
So we moved into a queue system. The host is extracted from each URL, and each host is only given up to 3 requests at a time. If we want 29 images from the same host, we only ask for three, and the remaining 26 remain in the queue for next time. When one of those requests completes, we decrement the host load so we know that we can send it another request later.
We process the queue in an infinite loop where we wait 1200 milliseconds between passes. Passes take time themselves and sometimes must wait for a timeout. Each pass fetches potentially multiple HTTP resources in parallel, asynchronously. If we have 300 resources at 100 different hosts, three per host, we could get them all in a single pass. More likely a bunch of resources are at the same host, and we make multiple passes at it.
Timeouts
When we fetch URLs in parallel asynchronously, we wait until all of the fetches complete before waiting another 1200 ms and doing another loop. Sometimes one of the fetches times out. In order to keep things moving, we use short timeouts of 10 seconds for a connect, and 15 seconds for a response.
Handling Errors
Some kinds of errors are more serious than others. When we encounter these, we sin bin the server for a period of time where we don't try fetching from it until a specified period elapses.
-
 @ ee11a5df:b76c4e49
2023-07-29 03:13:59
@ ee11a5df:b76c4e49
2023-07-29 03:13:59Gossip: Switching to LMDB
Unlike a number of other nostr clients, Gossip has always cached events and related data in a local data store. Up until recently, SQLite3 has served this purpose.
SQLite3 offers a full ACID SQL relational database service.
Unfortunately however it has presented a number of downsides:
- It is not as parallel as you might think.
- It is not as fast as you might hope.
- If you want to preserve the benefit of using SQL and doing joins, then you must break your objects into columns, and map columns back into objects. The code that does this object-relational mapping (ORM) is not trivial and can be error prone. It is especially tricky when working with different types (Rust language types and SQLite3 types are not a 1:1 match).
- Because of the potential slowness, our UI has been forbidden from direct database access as that would make the UI unresponsive if a query took too long.
- Because of (4) we have been firing off separate threads to do the database actions, and storing the results into global variables that can be accessed by the interested code at a later time.
- Because of (4) we have been caching database data in memory, essentially coding for yet another storage layer that can (and often did) get out of sync with the database.
LMDB offers solutions:
- It is highly parallel.
- It is ridiculously fast when used appropriately.
- Because you cannot run arbitrary SQL, there is no need to represent the fields within your objects separately. You can serialize/deserialize entire objects into the database and the database doesn't care what is inside of the blob (yes, you can do that into an SQLite field, but if you did, you would lose the power of SQL).
- Because of the speed, the UI can look stuff up directly.
- We no longer need to fork separate threads for database actions.
- We no longer need in-memory caches of data. The LMDB data is already in-memory (it is memory mapped) so we just access it directly.
The one obvious downside is that we lose SQL. We lose the query planner. We cannot ask arbitrary question and get answers. Instead, we have to pre-conceive of all the kinds of questions we want to ask, and we have to write code that answers them efficiently. Often this involves building and maintaining indices.
Indices
Let's say I want to look at fiatjaf's posts. How do I efficiently pull out just his recent feed-related events in reverse chronological order? It is easy if we first construct the following index
key: EventKind + PublicKey + ReverseTime value: Event Id
In the above, '+' is just a concatenate operator, and ReverseTime is just some distant time minus the time so that it sorts backwards.
Now I just ask LMDB to start from (EventKind=1 + PublicKey=fiatjaf + now) and scan until either one of the first two fields change, or more like the time field gets too old (e.g. one month ago). Then I do it again for the next event kind, etc.
For a generalized feed, I have to scan a region for each person I follow.
Smarter indexes can be imagined. Since we often want only feed-related event kinds, that can be implicit in an index that only indexes those kinds of events.
You get the idea.
A Special Event Map
At first I had stored events into a K-V database under the Id of the event. Then I had indexes on events that output a set of Ids (as in the example above).
But when it comes to storing and retrieving events, we can go even faster than LMDB.
We can build an append-only memory map that is just a sequence of all the events we have, serialized, and in no particular order. Readers do not need a lock and multiple readers can read simultaneously. Writers will need to acquire a lock to append to the map and there may only be one writer at a time. However, readers can continue reading even while a writer is writing.
We can then have a K-V database that maps Id -> Offset. To get the event you just do a direct lookup in the event memory map at that offset.
The real benefit comes when we have other indexes that yield events, they can yield offsets instead of ids. Then we don't need to do a second lookup from the Id to the Event, we can just look directly at the offset.
Avoiding deserialization
Deserialization has a price. Sometimes it requires memory allocation (if the object is not already linear, e.g. variable lengthed data like strings and vectors are allocated on the heap) which can be very expensive if you are trying to scan 150,000 or so events.
We serialize events (and other objects where we can) with a serialization library called speedy. It does its best to preserve the data much like it is represented in memory, but linearized. Because events start with fixed-length fields, we know the offset into the serialized event where these first fields occur and we can directly extract the value of those fields without deserializing the data before it.
This comes in useful whenever we need to scan a large number of events. Search is the one situation where I know that we must do this. We can search by matching against the content of every feed-related event without fully deserialing any of them.
-
 @ ee11a5df:b76c4e49
2023-07-29 02:52:13
@ ee11a5df:b76c4e49
2023-07-29 02:52:13Gossip: Zaps
Gossip is a desktop nostr client. This post is about the code that lets users send lightning zaps to each other (NIP-57).
Gossip implemented Zaps initially on 20th of June, 2023.
Gossip maintains a state of where zapping is at, one of: None, CheckingLnurl, SeekingAmount, LoadingInvoice, and ReadyToPay.
When you click the zap lightning bolt icon, Gossip moves to the CheckingLnurl state while it looks up the LN URL of the user.
If this is successful, it moves to the SeekingAmount state and presents amount options to the user.
Once a user chooses an amount, it moves to the LoadingInvoice state where it interacts with the lightning node and receives and checks an invoice.
Once that is complete, it moves to the ReadyToPay state, where it presents the invoice as a QR code for the user to scan with their phone. There is also a copy button so they can pay it from their desktop computer too.
Gossip also loads zap receipt events and associates them with the event that was zapped, tallying a zap total on that event. Gossip is unfortunately not validating these receipts very well currently, so fake zap receipts can cause an incorrect total to show. This remains an open issue.
Another open issue is the implementation of NIP-46 Nostr Connect and NIP-47 Wallet Connect.
-
 @ b12b632c:d9e1ff79
2023-07-21 19:45:20
@ b12b632c:d9e1ff79
2023-07-21 19:45:20I love testing every new self hosted app and I can say that Nostr "world" is really good regarding self hosting stuff.
Today I tested a Nostr relay named Strfry.
Strfry is really simple to setup and support a lot's of Nostr NIPs.
Here is the list of what it is able to do :
- Supports most applicable NIPs: 1, 2, 4, 9, 11, 12, 15, 16, 20, 22, 28, 33, 40
- No external database required: All data is stored locally on the filesystem in LMDB
- Hot reloading of config file: No server restart needed for many config param changes
- Zero downtime restarts, for upgrading binary without impacting users
- Websocket compression: permessage-deflate with optional sliding window, when supported by clients
- Built-in support for real-time streaming (up/down/both) events from remote relays, and bulk import/export of events from/to jsonl files
- negentropy-based set reconcilliation for efficient syncing with remote relays
Installation with docker compose (v2)
Spoiler : you need to have a computer with more than 1 (v)Core / 2GB of RAM to build the docker image locally. If not, this below might crash your computer during docker image build. You may need to use a prebuilt strfry docker image.
I assume you've read my first article on Managing domain with Nginx Proxy Manager because I will use the NPM docker compose stack to publish strfry Nostr relay. Without the initial NPM configuration done, it may not work as expected. I'll use the same docker-compose.yml file and folder.
Get back in the "npm-stack" folder :
cd npm-stackCloning the strfry github repo locally :
git clone https://github.com/hoytech/strfry.gitModify the docker-compose file to locate the strfry configuration data outside of the folder repo directory to avoid mistake during futures upgrades (CTRL + X, S & ENTER to quit and save modifications) :
nano docker-compose.ymlYou don't have to insert the Nginx Proxy Manager part, you should already have it into the file. If not, check here. You should only have to add the strfry part.
``` version: '3.8' services: # should already be present into the docker-compose.yml app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencryptstrfry-nostr-relay: container_name: strfry build: ./strfry volumes: - ./strfry-data/strfry.conf:/etc/strfry.conf - ./strfry-data/strfry-db:/app/strfry-db
ports is commented by NPM will access through docker internal network
no need to expose strfry port directly to the internet
ports:
- "7777:7777"
```
Before starting the container, we need to customize the strfry configuration file "strfry.conf". We'll copy the strfry configuration file and place it into the "strfry-data" folder to modify it with our own settings :
mkdir strfry-data && cp strfry/strfry.conf strfry-data/And modify the strfry.conf file with your own settings :
nano strfry-data/strfry.confYou can modify all the settings you need but the basics settings are :
- bind = "127.0.0.1" --> bind = "0.0.0.0" --> otherwise NPM won't be able to contact the strfry service
-
name = "strfry default" --> name of your nostr relay
-
description = "This is a strfry instance." --> your nostr relay description
-
pubkey = "" --> your pubkey in hex format. You can use the Damu's tool to generate your hex key from your npub key : https://damus.io/key/
-
contact = "" --> your email
``` relay { # Interface to listen on. Use 0.0.0.0 to listen on all interfaces (restart required) bind = "127.0.0.1"
# Port to open for the nostr websocket protocol (restart required) port = 7777 # Set OS-limit on maximum number of open files/sockets (if 0, don't attempt to set) (restart required) nofiles = 1000000 # HTTP header that contains the client's real IP, before reverse proxying (ie x-real-ip) (MUST be all lower-case) realIpHeader = "" info { # NIP-11: Name of this server. Short/descriptive (< 30 characters) name = "strfry default" # NIP-11: Detailed information about relay, free-form description = "This is a strfry instance." # NIP-11: Administrative nostr pubkey, for contact purposes pubkey = "" # NIP-11: Alternative administrative contact (email, website, etc) contact = "" }```
You can now start the docker strfry docker container :
docker compose up -dThis command will take a bit of time because it will build the strfry docker image locally before starting the container. If your VPS doesn't have lot's of (v)CPU/RAM, it could fail (nothing happening during the docker image build). My VPS has 1 vCore / 2GB of RAM and died few seconds after the build beginning.
If it's the case, you can use prebuilt strfry docker image available on the Docker hub : https://hub.docker.com/search?q=strfry&sort=updated_at&order=desc
That said, otherwise, you should see this :
``` user@vps:~/npm-stack$ docker compose up -d [+] Building 202.4s (15/15) FINISHED
=> [internal] load build definition from Dockerfile 0.2s => => transferring dockerfile: 724B 0.0s => [internal] load .dockerignore 0.3s => => transferring context: 2B 0.0s => [internal] load metadata for docker.io/library/ubuntu:jammy 0.0s => [build 1/7] FROM docker.io/library/ubuntu:jammy 0.4s => [internal] load build context 0.9s => => transferring context: 825.64kB 0.2s => [runner 2/4] WORKDIR /app 1.3s => [build 2/7] WORKDIR /build 1.5s => [runner 3/4] RUN apt update && apt install -y --no-install-recommends liblmdb0 libflatbuffers1 libsecp256k1-0 libb2-1 libzstd1 && rm -rf /var/lib/apt/lists/* 12.4s => [build 3/7] RUN apt update && apt install -y --no-install-recommends git g++ make pkg-config libtool ca-certificates libyaml-perl libtemplate-perl libregexp-grammars-perl libssl-dev zlib1g-dev l 55.5s => [build 4/7] COPY . . 0.9s => [build 5/7] RUN git submodule update --init 2.6s => [build 6/7] RUN make setup-golpe 10.8s => [build 7/7] RUN make -j4 126.8s => [runner 4/4] COPY --from=build /build/strfry strfry 1.3s => exporting to image 0.8s => => exporting layers 0.8s => => writing image sha256:1d346bf343e3bb63da2e4c70521a8350b35a02742dd52b12b131557e96ca7d05 0.0s => => naming to docker.io/library/docker-compose_strfry-nostr-relay 0.0sUse 'docker scan' to run Snyk tests against images to find vulnerabilities and learn how to fix them
[+] Running 02/02
⠿ Container strfry Started 11.0s ⠿ Container npm-stack-app-1 Running ```You can check if everything is OK with strfry container by checking the container logs :
user@vps:~/npm-stack$ docker logs strfry date time ( uptime ) [ thread name/id ] v| 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| arguments: /app/strfry relay 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| Current dir: /app 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| stderr verbosity: 0 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| ----------------------------------- 2023-07-21 19:26:58.514 ( 0.039s) [main thread ]INFO| CONFIG: Loading config from file: /etc/strfry.conf 2023-07-21 19:26:58.529 ( 0.054s) [main thread ]INFO| CONFIG: successfully installed 2023-07-21 19:26:58.533 ( 0.058s) [Websocket ]INFO| Started websocket server on 0.0.0.0:7777Now, we have to create the subdomain where strfry Nostr relay will be accessible. You need to connect to your Nginx Proxy Manager admin UI and create a new proxy host with these settings :
"Details" tab (Websockets support is mandatory!, you can replace "strfry" by whatever you like, for instance : mybeautifulrelay.yourdomain.tld)
"Details" tab:

"SSL" tab:

And click on "Save"
If everything is OK, when you go to https://strfry.yourdomain.tld you should see :

To verify if strfry is working properly, you can test it with the (really useful!) website https://nostr.watch. You have to insert your relay URL into the nostr.watch URL like this : https://nostr.watch/relay/strfry.yourdomain.tld
You should see this :

If you are seeing your server as online, readable and writable, you made it ! You can add your Nostr strfry server to your Nostr prefered relay and begin to publish notes ! 🎇
Future work:
Once done, strfry will work like a charm but you may need to have more work to update strfry in the near future. I'm currently working on a bash script that will :
- Updatethe "strfry" folder,
- Backup the "strfry.conf" file,
- Download the latest "strfry.conf" from strfry github repo,
- Inject old configuration settings into the new "strfry.conf" file,
- Compose again the stack (rebuilding the image to get the latest code updates),
- etc.
Tell me if you need the script!
Voilààààà
See you soon in another Fractalized story!
-
 @ b12b632c:d9e1ff79
2023-07-21 14:19:38
@ b12b632c:d9e1ff79
2023-07-21 14:19:38Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ b12b632c:d9e1ff79
2023-07-20 20:12:39
@ b12b632c:d9e1ff79
2023-07-20 20:12:39Self hosting web applications comes quickly with the need to deal with HTTPS protocol and SSL certificates. The time where web applications was published over the 80/TCP port without any encryption is totally over. Now we have Let's Encrypt and other free certification authority that lets us play web applications with, at least, the basic minimum security required.
Second part of web self hosting stuff that is really useful is the web proxifycation.
It's possible to have multiple web applications accessible through HTTPS but as we can't use the some port (spoiler: we can) we are forced to have ugly URL as https://mybeautifudomain.tld:8443.
This is where Nginx Proxy Manager (NPM) comes to help us.
NPM, as gateway, will listen on the 443 https port and based on the subdomain you want to reach, it will redirect the network flow to the NPM differents declared backend ports. NPM will also request HTTPS cert for you and let you know when the certificate expires, really useful.
We'll now install NPM with docker compose (v2) and you'll see, it's very easy.
You can find the official NPM setup instructions here.
But before we absolutely need to do something. You need to connect to the registrar where you bought your domain name and go into the zone DNS section.You have to create a A record poing to your VPS IP. That will allow NPM to request SSL certificates for your domain and subdomains.
Create a new folder for the NPM docker stack :
mkdir npm-stack && cd npm-stackCreate a new docker-compose.yml :
nano docker-compose.ymlPaste this content into it (CTRL + X ; Y & ENTER to save/quit) :
``` version: '3.8' services: app: image: 'jc21/nginx-proxy-manager:latest' restart: unless-stopped ports: # These ports are in format
: - '80:80' # Public HTTP Port - '443:443' # Public HTTPS Port - '81:81' # Admin Web Port # Add any other Stream port you want to expose # - '21:21' # FTP # Uncomment the next line if you uncomment anything in the section # environment: # Uncomment this if you want to change the location of # the SQLite DB file within the container # DB_SQLITE_FILE: "/data/database.sqlite" # Uncomment this if IPv6 is not enabled on your host # DISABLE_IPV6: 'true' volumes: - ./nginxproxymanager/data:/data - ./nginxproxymanager/letsencrypt:/etc/letsencrypt```
You'll not believe but it's done. NPM docker compose configuration is done.
To start Nginx Proxy Manager with docker compose, you just have to :
docker compose up -dYou'll see :
user@vps:~/tutorials/npm-stack$ docker compose up -d [+] Running 2/2 ✔ Network npm-stack_default Created ✔ Container npm-stack-app-1 StartedYou can check if NPM container is started by doing this command :
docker psYou'll see :
user@vps:~/tutorials/npm-stack$ docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 7bc5ea8ac9c8 jc21/nginx-proxy-manager:latest "/init" About a minute ago Up About a minute 0.0.0.0:80-81->80-81/tcp, :::80-81->80-81/tcp, 0.0.0.0:443->443/tcp, :::443->443/tcp npm-stack-app-1If the command show "Up X minutes" for the npm-stack-app-1, you're good to go! You can access to the NPM admin UI by going to http://YourIPAddress:81.You shoud see :

The default NPM login/password are : admin@example.com/changeme .If the login succeed, you should see a popup asking to edit your user by changing your email password :
 And your password :
And your password :
 Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
Click on "Save" to finish the login.
To verify if NPM is able to request SSL certificates for you, create first a subdomain for the NPM admin UI :
Click on "Hosts" and "Proxy Hosts" :
 Followed by "Add Proxy Host"
Followed by "Add Proxy Host"
 If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :
If you want to access the NPM admin UI with https://admin.yourdomain.tld, please set all the parameters like this (I won't explain each parameters) :Details tab :
 SSL tab :
SSL tab :
 And click on "Save".
And click on "Save".NPM will request the SSL certificate "admin.yourdomain.tld" for you.
If you have an erreor message "Internal Error" it's probably because your domaine DNS zone is not configured with an A DNS record pointing to your VPS IP.
Otherwise you should see (my domain is hidden) :

Clicking on the "Source" URL link "admin.yourdomain.tld" will open a pop-up and, surprise, you should see the NPM admin UI with the URL "https://admin.yourdomain.tld" !
If yes, bravo, everything is OK ! 🎇
You know now how to have a subdomain of your domain redirecting to a container web app. In the next blog post, you'll see how to setup a Nostr relay with NPM ;)
Voilààààà
See you soon in another Fractalized story!
-
 @ b12b632c:d9e1ff79
2023-07-19 00:17:02
@ b12b632c:d9e1ff79
2023-07-19 00:17:02Welcome to a new Fractalized episode of "it works but I can do better"!
Original blog post from : https://fractalized.ovh/use-ghost-blog-to-serve-your-nostr-nip05-and-lnurl/
Few day ago, I wanted to set my Ghost blog (this one) as root domain for Fractalized instead of the old basic Nginx container that served my NIP05. I succeed to do it with Nginx Proxy Manager (I need to create a blog post because NPM is really awesome) but my NIP05 was down.
Having a bad NIP05 on Amethyst is now in the top tier list of my worst nightmares.
As a reminder, to have a valid NIP05 on your prefered Nostr client, you need to have a file named "nostr.json" in a folder ".well-known" located in the web server root path (subdomain or domain). The URL shoud look like this http://domain.tld/.well-known/nostr.json
PS : this doesn't work with Ghost as explained later. If you are here for Ghost, skip this and go directly to 1).
You should have these info inside the nostr.json file (JSON format) :
{ "names": { "YourUsername": "YourNPUBkey" } }You can test it directly by going to the nostr.json URL, it should show you the JSON.
It was working like a charm on my previous Nginx and I needed to do it on my new Ghost. I saw on Google that I need to have the .well-known folder into the Ghost theme root folder (In my case I choosed the Solo theme). I created the folder, put my nostr.json file inside it and crossed my fingers. Result : 404 error.
I had to search a lot but it seems that Ghost forbid to server json file from its theme folders. Maybe for security reasons, I don't know. Nevertheless Ghost provide a method to do it (but it requires more than copy/paste some files in some folders) => routes
In the same time that configuring your NIP05, I also wanted to setup an LNURL to be zapped to pastagringo@fractalized.ovh (configured into my Amethyst profile). If you want more infromation on LNURL, it's very well explained here.
Because I want to use my Wallet of Satoshi sats wallet "behind" my LNURL, you'll have to read carefuly the EzoFox's blog post that explains how to retrieve your infos from Alby or WoS.
1) Configuring Ghost routes
Add the new route into the routes.yaml (accessible from "Settings" > "Labs" > "Beta features" > "Routes" ; you need to download the file, modify it and upload it again) to let him know where to look for the nostr.json file.
Here is the content of my routes.yaml file :
``` routes: /.well-known/nostr.json/: template: _nostr-json content_type: application/json /.well-known/lnurlp/YourUsername/: template: _lnurlp-YourUsername content_type: application/json collections: /: permalink: /{slug}/ template: index
taxonomies: tag: /tag/{slug}/ author: /author/{slug}/ ```
=> template : name of the file that ghost will search localy
=> content_type : file type (JSON is required for the NIP05)
The first route is about my NIP05 and the second route is about my LNURL.
2) Creating Ghost route .hbs files
To let Ghost serve our JSON content, I needed to create the two .hbs file filled into the routes.yaml file. These files need to be located into the root directory of the Ghost theme used. For me, it was Solo.
Here is there content of both files :
"_nostr-json.hbs"
{ "names": { "YourUsername": "YourNPUBkey" } }"_lnurlp-pastagringo.hbs" (in your case, _lnurlp-YourUsername.hbs)
{ "callback":"https://livingroomofsatoshi.com/api/v1/lnurl/payreq/XXXXX", "maxSendable":100000000000, "minSendable":1000, "metadata":"[[\"text/plain\",\"Pay to Wallet of Satoshi user: burlyring39\"],[\"text/identifier\",\"YourUsername@walletofsatoshi.com\"]]", "commentAllowed":32, "tag":"payRequest", "allowsNostr":true, "nostrPubkey":"YourNPUBkey" }After doing that, you almost finished, you just have to restart your Ghost blog. As I use Ghost from docker container, I just had to restart the container.
To verify if everything is working, you have to go in the routes URL created earlier:
https://YourDomain.tld/.well-known/nostr.jsonand
https://YourDomain.tld/.well-known/lnurlp/YourUsernameBoth URL should display JSON files from .hbs created ealier.
If it's the case, you can add your NIP05 and LNURL into your Nostr profile client and you should be able to see a valid tick from your domain and to be zapped on your LNURL (sending zaps to your WoS or Alby backend wallet).
Voilààààà
See you soon in another Fractalized story!
-
 @ b12b632c:d9e1ff79
2023-07-17 22:09:53
@ b12b632c:d9e1ff79
2023-07-17 22:09:53Today I created a new item (NIP05) to sell into my BTCpayserver store and everything was OK. The only thing that annoyed me a bit is that when a user pay the invoice to get his NIP on my Nostr Paid Relay, I need to warn him that he needs to fill his npub in the email info required by BTCpayserver before paying. Was not so user friendly. Not at all.
So I checked if BTCpayserver is able to create custom input before paying the invoice and at my big surprise, it's possible ! => release version v1.8
They even use as example my need from Nostr to get the user npub.
So it's possible, yes, but with at least the version 1.8.0. I checked immediately my BTCpayserver version on my Umbrel node and... damn... I'm in 1.7.2. I need to update my local BTCpayserver through Umbrel to access my so wanted BTCpayserver feature. I checked the local App Store but I can't see any "Update" button or something. I can see that the version installed is well the v1.7.2 but when I check the latest version available from the online Umbrel App Store. I can see v1.9.2. Damn bis.
I searched into the Umbrel Community forum, Telegram group, Google posts, asked the question on Nostr and didn't have any clue.
I finally found the answer from the Umbrel App Framework documention :
sudo ./scripts/repo checkout https://github.com/getumbrel/umbrel-apps.gitSo I did it and it updated my local Umbrel App Store to the latest version available and my BTCpayserver.
After few seconds, the BTCpaysever local URL is available and I'm allowed to login => everything is OK! \o/
See you soon in another Fractalized story!