-
 @ 6389be64:ef439d32
2025-02-27 21:32:12
@ 6389be64:ef439d32
2025-02-27 21:32:12GA, plebs. The latest episode of Bitcoin And is out, and, as always, the chicanery is running rampant. Let’s break down the biggest topics I covered, and if you want the full, unfiltered rant, make sure to listen to the episode linked below.
House Democrats’ MEME Act: A Bad Joke?
House Democrats are proposing a bill to ban presidential meme coins, clearly aimed at Trump’s and Melania’s ill-advised token launches. While grifters launching meme coins is bad, this bill is just as ridiculous. If this legislation moves forward, expect a retaliatory strike exposing how politicians like Pelosi and Warren mysteriously amassed their fortunes. Will it pass? Doubtful. But it’s another sign of the government’s obsession with regulating everything except itself.
Senate Banking’s First Digital Asset Hearing: The Real Target Is You
Cynthia Lummis chaired the first digital asset hearing, and—surprise!—it was all about control. The discussion centered on stablecoins, AML, and KYC regulations, with witnesses suggesting Orwellian measures like freezing stablecoin transactions unless pre-approved by authorities. What was barely mentioned? Bitcoin. They want full oversight of stablecoins, which is really about controlling financial freedom. Expect more nonsense targeting self-custody wallets under the guise of stopping “bad actors.”
Bank of America and PayPal Want In on Stablecoins
Bank of America’s CEO openly stated they’ll launch a stablecoin as soon as regulation allows. Meanwhile, PayPal’s CEO paid for a hat using Bitcoin—not their own stablecoin, Pi USD. Why wouldn’t he use his own product? Maybe he knows stablecoins aren’t what they’re hyped up to be. Either way, the legacy financial system is gearing up to flood the market with stablecoins, not because they love crypto, but because it’s a tool to extend U.S. dollar dominance.
MetaPlanet Buys the Dip
Japan’s MetaPlanet issued $13.4M in bonds to buy more Bitcoin, proving once again that institutions see the writing on the wall. Unlike U.S. regulators who obsess over stablecoins, some companies are actually stacking sats.
UK Expands Crypto Seizure Powers
Across the pond, the UK government is pushing legislation to make it easier to seize and destroy crypto linked to criminal activity. While they frame it as going after the bad guys, it’s another move toward centralized control and financial surveillance.
Bitcoin Tools & Tech: Arc, SatoChip, and Nunchuk
Some bullish Bitcoin developments: ARC v0.5 is making Bitcoin’s second layer more efficient, SatoChip now supports Taproot and Nostr, and Nunchuk launched a group wallet with chat, making multisig collaboration easier.
The Bottom Line
The state is coming for financial privacy and control, and stablecoins are their weapon of choice. Bitcoiners need to stay focused, keep their coins in self-custody, and build out parallel systems. Expect more regulatory attacks, but don’t let them distract you—just keep stacking and transacting in ways they can’t control.
🎧 Listen to the full episode here: https://fountain.fm/episode/PYITCo18AJnsEkKLz2Ks
💰 Support the show by boosting sats on Podcasting 2.0! and I will see you on the other side.
-
 @ 2ed3596e:98b4cc78
2025-02-27 21:28:33
@ 2ed3596e:98b4cc78
2025-02-27 21:28:33Pay anyone in Canada with bitcoin! One step closer to replacing your bank with Bitcoin Well
Everyone who accepts e-Transfers, now accepts bitcoin! Canadians with a Bitcoin Well account can send money to anyone via e-Transfer using their bitcoin in self custody. Typical transactions, like rent payments, paying friends back for dinner, paying your cleaning lady or even to pay for that new (to you) boom box on Facebook marketplace, can now be paid quickly, securely and cheaper with your Bitcoin Well account. And best of all, it’s all done with bitcoin in self custody. Keep reading to learn more!
How to send an e-Transfer to anyone in Canada using bitcoin:
From the sell page in your Bitcoin Well account you can select the network (Bitcoin or Lightning Network) and how many dollars you’d like to send via e-Transfer. For more information on the Lightning Network click here.
Next you will see a new dropdown where you can choose the recipient for the e-Transfer. It will be the email on your Bitcoin Well account by default.

To add a new recipient, select the drop down and “Add recipient”. Here you will be asked to provide the recipient’s name, email and the security question/answer you’d like to provide for the e-Transfer.

You’ll be responsible for telling them the security question and answer, so don’t forget!

You can also invite your recipient to join Bitcoin Well with your ref link! You’ll earn Bitcoin Well points and sats when they use Bitcoin Well!
If you chose the Bitcoin network:
With all your information entered, you will be able to send bitcoin to the bitcoin address on screen and an e-Transfer will be sent to your recipient after 1 confirmation.
Note! This bitcoin address is permanently associated with your recipient. Any and all bitcoin received by this bitcoin address will be automatically converted into dollars and sent to your recipient; even if you do not login to your Bitcoin Well account!

If you chose the Lightning Network:
Select “Generate Invoice” to generate an LN-invoice which will be associated with your transaction. Once that invoice is paid an e-Transfer will be immediately sent to your desired recipient.
Of course, you can still send sats to your Bitcoin Well Payment Address any time to receive an e-Transfer yourself.

Banks out; Bitcoin Standard in
Bitcoin Well arms its customers with the knowledge and tools to fully live on a Bitcoin Standard and maximize their independence by keeping bitcoin in self custody instead of dollars in their bank.
Bitcoin Well now enables the same instant and fast transfer capabilities as a bank, but facilitated with bitcoin in self custody!
Replace your bank with Bitcoin Well!
Earn sats from your bitcoin transactions
Bitcoin Well is also the best place in the world to earn bitcoin. When you earn points in your Bitcoin Well account, you gain the opportunity to play the Bitcoin (Wishing) Well, where you win sats with every play.
The best part? We send bitcoin that you win straight to your personal wallet via the Lightning Network.
Oh yeah, did we mention you can win 1,000,000 sats? If you're an active Bitcoin Well customer, there is a chance you've earned a pile of points. The more you use your account for buying, selling or spending bitcoin - the more points you’ll earn! Log in to your Bitcoin Well account and check your point balance.
About Bitcoin Well
Bitcoin Well exists to enable independence. We do this by coupling the convenience of modern banking, with the benefits of bitcoin. In other words, we want to make it easy to use bitcoin in self-custody.
-
 @ a95c6243:d345522c
2025-02-21 19:32:23
@ a95c6243:d345522c
2025-02-21 19:32:23Europa – das Ganze ist eine wunderbare Idee, \ aber das war der Kommunismus auch. \ Loriot
«Europa hat fertig», könnte man unken, und das wäre nicht einmal sehr verwegen. Mit solch einer Einschätzung stünden wir nicht alleine, denn die Stimmen in diese Richtung mehren sich. Der französische Präsident Emmanuel Macron warnte schon letztes Jahr davor, dass «unser Europa sterben könnte». Vermutlich hatte er dabei andere Gefahren im Kopf als jetzt der ungarische Ministerpräsident Viktor Orbán, der ein «baldiges Ende der EU» prognostizierte. Das Ergebnis könnte allerdings das gleiche sein.
Neben vordergründigen Themenbereichen wie Wirtschaft, Energie und Sicherheit ist das eigentliche Problem jedoch die obskure Mischung aus aufgegebener Souveränität und geschwollener Arroganz, mit der europäische Politiker:innende unterschiedlicher Couleur aufzutreten pflegen. Und das Tüpfelchen auf dem i ist die bröckelnde Legitimation politischer Institutionen dadurch, dass die Stimmen großer Teile der Bevölkerung seit Jahren auf vielfältige Weise ausgegrenzt werden.
Um «UnsereDemokratie» steht es schlecht. Dass seine Mandate immer schwächer werden, merkt natürlich auch unser «Führungspersonal». Entsprechend werden die Maßnahmen zur Gängelung, Überwachung und Manipulation der Bürger ständig verzweifelter. Parallel dazu plustern sich in Paris Macron, Scholz und einige andere noch einmal mächtig in Sachen Verteidigung und «Kriegstüchtigkeit» auf.
Momentan gilt es auch, das Überschwappen covidiotischer und verschwörungsideologischer Auswüchse aus den USA nach Europa zu vermeiden. So ein «MEGA» (Make Europe Great Again) können wir hier nicht gebrauchen. Aus den Vereinigten Staaten kommen nämlich furchtbare Nachrichten. Beispielsweise wurde einer der schärfsten Kritiker der Corona-Maßnahmen kürzlich zum Gesundheitsminister ernannt. Dieser setzt sich jetzt für eine Neubewertung der mRNA-«Impfstoffe» ein, was durchaus zu einem Entzug der Zulassungen führen könnte.
Der europäischen Version von «Verteidigung der Demokratie» setzte der US-Vizepräsident J. D. Vance auf der Münchner Sicherheitskonferenz sein Verständnis entgegen: «Demokratie stärken, indem wir unseren Bürgern erlauben, ihre Meinung zu sagen». Das Abschalten von Medien, das Annullieren von Wahlen oder das Ausschließen von Menschen vom politischen Prozess schütze gar nichts. Vielmehr sei dies der todsichere Weg, die Demokratie zu zerstören.
In der Schweiz kamen seine Worte deutlich besser an als in den meisten europäischen NATO-Ländern. Bundespräsidentin Karin Keller-Sutter lobte die Rede und interpretierte sie als «Plädoyer für die direkte Demokratie». Möglicherweise zeichne sich hier eine außenpolitische Kehrtwende in Richtung integraler Neutralität ab, meint mein Kollege Daniel Funk. Das wären doch endlich mal ein paar gute Nachrichten.
Von der einstigen Idee einer europäischen Union mit engeren Beziehungen zwischen den Staaten, um Konflikte zu vermeiden und das Wohlergehen der Bürger zu verbessern, sind wir meilenweit abgekommen. Der heutige korrupte Verbund unter technokratischer Leitung ähnelt mehr einem Selbstbedienungsladen mit sehr begrenztem Zugang. Die EU-Wahlen im letzten Sommer haben daran ebenso wenig geändert, wie die Bundestagswahl am kommenden Sonntag darauf einen Einfluss haben wird.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ b2d670de:907f9d4a
2025-02-26 18:27:47
@ b2d670de:907f9d4a
2025-02-26 18:27:47This is a list of nostr clients exposed as onion services. The list is currently actively maintained on GitHub. Contributions are always appreciated!
| Client name | Onion URL | Source code URL | Admin | Description | | --- | --- | --- | --- | --- | | Snort | http://agzj5a4be3kgp6yurijk4q7pm2yh4a5nphdg4zozk365yirf7ahuctyd.onion | https://git.v0l.io/Kieran/snort | operator | N/A | | moStard | http://sifbugd5nwdq77plmidkug4y57zuqwqio3zlyreizrhejhp6bohfwkad.onion/ | https://github.com/rafael-xmr/nostrudel/tree/mostard | operator | minimalist monero friendly nostrudel fork | | Nostrudel | http://oxtrnmb4wsb77rmk64q3jfr55fo33luwmsyaoovicyhzgrulleiojsad.onion/ | https://github.com/hzrd149/nostrudel | operator | Runs latest tagged docker image | | Nostrudel Next | http://oxtrnnumsflm7hmvb3xqphed2eqpbrt4seflgmdsjnpgc3ejd6iycuyd.onion/ | https://github.com/hzrd149/nostrudel | operator | Runs latest "next" tagged docker image | | Nsite | http://q457mvdt5smqj726m4lsqxxdyx7r3v7gufzt46zbkop6mkghpnr7z3qd.onion/ | https://github.com/hzrd149/nsite-ts | operator | Runs nsite. You can read more about nsite here. | | Shopstr | http://6fkdn756yryd5wurkq7ifnexupnfwj6sotbtby2xhj5baythl4cyf2id.onion/ | https://github.com/shopstr-eng/shopstr-hidden-service | operator | Runs the latest
serverlessbranch build of Shopstr. | -
 @ a95c6243:d345522c
2025-02-19 09:23:17
@ a95c6243:d345522c
2025-02-19 09:23:17Die «moralische Weltordnung» – eine Art Astrologie. Friedrich Nietzsche
Das Treffen der BRICS-Staaten beim Gipfel im russischen Kasan war sicher nicht irgendein politisches Event. Gastgeber Wladimir Putin habe «Hof gehalten», sagen die Einen, China und Russland hätten ihre Vorstellung einer multipolaren Weltordnung zelebriert, schreiben Andere.
In jedem Fall zeigt die Anwesenheit von über 30 Delegationen aus der ganzen Welt, dass von einer geostrategischen Isolation Russlands wohl keine Rede sein kann. Darüber hinaus haben sowohl die Anreise von UN-Generalsekretär António Guterres als auch die Meldungen und Dementis bezüglich der Beitrittsbemühungen des NATO-Staats Türkei für etwas Aufsehen gesorgt.
Im Spannungsfeld geopolitischer und wirtschaftlicher Umbrüche zeigt die neue Allianz zunehmendes Selbstbewusstsein. In Sachen gemeinsamer Finanzpolitik schmiedet man interessante Pläne. Größere Unabhängigkeit von der US-dominierten Finanzordnung ist dabei ein wichtiges Ziel.
Beim BRICS-Wirtschaftsforum in Moskau, wenige Tage vor dem Gipfel, zählte ein nachhaltiges System für Finanzabrechnungen und Zahlungsdienste zu den vorrangigen Themen. Während dieses Treffens ging der russische Staatsfonds eine Partnerschaft mit dem Rechenzentrumsbetreiber BitRiver ein, um Bitcoin-Mining-Anlagen für die BRICS-Länder zu errichten.
Die Initiative könnte ein Schritt sein, Bitcoin und andere Kryptowährungen als Alternativen zu traditionellen Finanzsystemen zu etablieren. Das Projekt könnte dazu führen, dass die BRICS-Staaten den globalen Handel in Bitcoin abwickeln. Vor dem Hintergrund der Diskussionen über eine «BRICS-Währung» wäre dies eine Alternative zu dem ursprünglich angedachten Korb lokaler Währungen und zu goldgedeckten Währungen sowie eine mögliche Ergänzung zum Zahlungssystem BRICS Pay.
Dient der Bitcoin also der Entdollarisierung? Oder droht er inzwischen, zum Gegenstand geopolitischer Machtspielchen zu werden? Angesichts der globalen Vernetzungen ist es oft schwer zu durchschauen, «was eine Show ist und was im Hintergrund von anderen Strippenziehern insgeheim gesteuert wird». Sicher können Strukturen wie Bitcoin auch so genutzt werden, dass sie den Herrschenden dienlich sind. Aber die Grundeigenschaft des dezentralisierten, unzensierbaren Peer-to-Peer Zahlungsnetzwerks ist ihm schließlich nicht zu nehmen.
Wenn es nach der EZB oder dem IWF geht, dann scheint statt Instrumentalisierung momentan eher der Kampf gegen Kryptowährungen angesagt. Jürgen Schaaf, Senior Manager bei der Europäischen Zentralbank, hat jedenfalls dazu aufgerufen, Bitcoin «zu eliminieren». Der Internationale Währungsfonds forderte El Salvador, das Bitcoin 2021 als gesetzliches Zahlungsmittel eingeführt hat, kürzlich zu begrenzenden Maßnahmen gegen das Kryptogeld auf.
Dass die BRICS-Staaten ein freiheitliches Ansinnen im Kopf haben, wenn sie Kryptowährungen ins Spiel bringen, darf indes auch bezweifelt werden. Im Abschlussdokument bekennen sich die Gipfel-Teilnehmer ausdrücklich zur UN, ihren Programmen und ihrer «Agenda 2030». Ernst Wolff nennt das «eine Bankrotterklärung korrupter Politiker, die sich dem digital-finanziellen Komplex zu 100 Prozent unterwerfen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ f1989a96:bcaaf2c1
2025-02-27 21:28:20
@ f1989a96:bcaaf2c1
2025-02-27 21:28:20Good morning, readers!
In Nigeria, financial officials are revising digital asset regulations to impose taxes on digital asset transactions on regulated exchanges. This aims to bolster state revenue as more citizens turn to Bitcoin in response to rampant inflation, the naira’s devaluation, and the regime's ever-increasing financial controls.
Meanwhile, in Cuba, thousands of citizens remain unable to access money the regime forced them to convert into Certificates of Deposit (CDs) in 2021. These funds have not been returned by the Communist Party of Cuba. If they eventually are, they will be paid out in since-hyperinflated Cuban pesos, a reality that stands in stark contrast to regime propaganda that it is working “for the people.”
In open-source freedom tech news, we feature NostrPIX, an experimental tool built during the bitcoin++ developer hackathon in Florianopolis, Brazil. It allows anyone in Brazil to pay any merchant or individual with Bitcoin over the Lightning Network. While it is still in its early stages of development, this stands to enable Bitcoin payments at nearly every merchant in Brazil, similar to how apps like Tando enable Bitcoin payments across Kenya.\ \ We end with the official livestreams of the HRF-supported bitcoin++ developer conference in Florianopolis, Brazil, that brought together open-source developers and freedom tech enthusiasts for four days of technical gatherings to enhance Bitcoin’s privacy, usability, and censorship resistance. These livestreams offer a unique chance to view and understand the presentations and workshops at the event.
Now, let’s jump right in!
Subscribe Here
GLOBAL NEWS
Nigeria | Introducing Digital Asset Transaction Tax to Boost State Revenue
Nigerian officials plan to amend their digital asset regulations to tax digital asset transactions in a coercive effort to boost the regime’s dwindling revenues. The Nigerian Securities and Exchange Commission (SEC) is reviewing a new framework to tax transactions on regulated exchanges, allowing the regime to extract even more value from the growing digital asset sector. Nigerians, especially the younger population, increasingly have turned to Bitcoin and stablecoins to escape high inflation, a devalued naira, and an authoritarian regime that repeatedly undermines financial autonomy and human rights. The new tax could hinder the efficiency of tools like Bitcoin by making transactions more expensive. But enforcing this tax beyond regulated platforms presents a challenge. Bitcoin held in self-custody and transacted peer-to-peer remains largely outside the reach of authoritarian states.
Cuba | Citizens Remain Locked Out of Devalued Funds
Thousands of Cubans remain locked out of their savings after the regime forced them to convert Cuban Convertible Peso (CUC) deposits into Certificates of Deposit (CDs) in 2021. This policy was part of the “Tarea Ordenamiento” economic reforms, which eliminated the CUC, a convertible currency previously pegged to the US dollar. For years, Cubans who received foreign currency — whether through work abroad or remittances — were required to exchange it for CUCs, expecting they could later redeem those CUCs for dollars or other foreign currencies. But when the regime eliminated the CUC in 2021, it forced depositors to either accept a heavily devalued exchange rate for Cuban pesos (far worse than the advertised 24-1 ratio) or convert their money into Certificates of Deposit (CDs), with the promise of returning the equivalent value in foreign currency once liquidity allowed. Unbeknownst to Cubans, the CDs paid a negligible 0.15% interest and had no clear timeline for repayment. Today, many depositors still can’t access their money.
Google | Facilitating Censorship in Russia and China
Google is actively assisting authoritarian regimes like China and Russia to censor dissent, removing online content critical of the Kremlin and Chinese Communist Party. In Russia, Google complied with government requests to erase YouTube videos opposing the war in Ukraine, while in China, it removed references to the Tiananmen Square massacre and pro-democracy activism. With more than 70% of Russians relying on YouTube for news and China’s Great Firewall blocking independent sources, corporate compliance with state censorship enables state propaganda to proliferate as a dominant narrative. For activists and nonprofits seeking uncensorable communications, nostr — an open and decentralized protocol — offers a way to share information beyond the reach of authoritarian regimes. Activists and NGOs can get started here.
World | Transnational Repression Most Common Under CBDC-Leading Countries
New data from Freedom House reveals that 23 governments engaged in transnational repression in 2024, using abductions, assassinations, and forced deportations to silence exiled dissidents. Leading perpetrators include the authoritarian regimes of China, Russia, Iran, and Turkey — orchestrating over 1,200 incidents in the past decade. Notably, many of these regimes are at the forefront of central bank digital currency (CBDC) development, a technology that drastically increases state control over financial activity. By allowing governments to surveil, freeze, and block funds in real time, CBDCs strip activists of financial privacy and force them into greater vulnerability. As authoritarian states refine both digital and physical methods of repression, CBDCs may become a powerful weapon for crushing dissent beyond borders.
Niger | Delays Democratic Elections While Citizens Financially Struggle
Niger’s deteriorating economic conditions are set to continue as the ruling military junta has proposed delaying democratic elections until at least 2030 to contain a “security threat.” Army commander Abdourahamane Tchiani, who came to power in a 2023 coup, originally pledged a three-year transition to civilian rule. Now, that timeline appears extended to five years, allowing “the junta to restore security and regain control of territory captured by Islamist militants that have expanded their insurgency in recent months.” With inflation eroding Nigerien’s purchasing power and the general economic well-being of citizens declining, Niger can’t afford more military rule. This could be a pretext for Tchiani to consolidate power, especially as discussions emerge about dissolving political parties and granting him the rank of general.
_______________
Webinar Series for Nonprofits: Become Unstoppable
HRF will host a free, three-day webinar from March 17-19, teaching human rights defenders and nonprofits how to use Bitcoin to counter state censorship and confiscation. Sessions run daily from 10:30 a.m. to 12:00 p.m. EDT and are beginner-friendly. The webinar will be led by Anna Chekhovich, HRF’s Bitcoin nonprofit adoption lead and financial manager at Alexei Navalny’s Anti-Corruption Foundation, and co-taught by the prominent Bitcoin educator Ben Perrin.
SXSW | The Human Rights Risks of Central Bank Digital Currencies (CBDCs)
Join HRF at SXSW 2025 in Austin from March 7-13 to explore how CBDCs threaten financial freedom. Experts Roger Huang, Charlene Fadirepo, and Nick Anthony will discuss how authoritarian regimes use CBDCs for surveillance and control. Attendees can also visit HRF’s CBDC Tracker booth to explore an interactive map of CBDC developments worldwide.
_______________
BITCOIN AND FREEDOM TECH NEWS
NostrPIX | Enabling Bitcoin Payments in Brazil
NostrPIX is a new tool built just a few days ago during the bitcoin++ hackathon in Florianopolis, Brazil, that lets users pay any merchant or individual in Brazil with Bitcoin over the Lightning Network. To use NostrPIX, users scan a Pix QR code (the country’s widely used digital payment system) and pay with bitcoin from their Lightning wallet. Designed with the unbanked in mind, NostrPIX lets those who cannot open a Brazilian bank account to transact with Bitcoin and Pix (no sign-ups required, just instant payments). Its innovative approach won the bitcoin++ hackathon, showcasing its potential to bridge Bitcoin with traditional systems. While still a proof of concept, NostrPIX joins projects like Tando in Kenya, making Bitcoin more practical for everyday commerce and could inspire similar products elsewhere in countries facing political oppression.
Iris | Implements Double Ratchet Messaging for Better Privacy
Iris, a client for Nostr launched by Martti Malmi, implemented double ratchet messaging, an encryption algorithm similar to that used by Signal, significantly improving private communications for activists and human rights defenders. This ensures message metadata remains hidden, and with its implementation, past and future conversations on Iris stay private even if a user’s main Nostr private key is compromised. This upgrade empowers individuals in difficult political environments to communicate without fear of surveillance by reducing the risks of authoritarian regimes tracking their conversations. HRF is proud to have helped support Malmi as he invented and launched this innovation.
Presidio Bitcoin | New Bitcoin Co-Working and Events Space in Bay Area
Presidio Bitcoin is the Bay Area’s first dedicated co-working and events space. Located in San Francisco’s famous Presidio neighborhood, it will be a collaborative space for developers, educators, and freedom tech enthusiasts to connect, work, and innovate together to drive Bitcoin adoption forward. It draws inspiration from other Bitcoin hubs worldwide, like Bitcoin Park in Nashville, Tenn., Bitcoin House Bali in Indonesia, and Bitcoin Ekasi in South Africa. This time, aiming to create a community of Bitcoiners in the tech capital of the US. Presidio Bitcoin hopes to foster new talent and secure greater funding from Silicon Valley, becoming a central meeting point for those passionate about Bitcoin and freedom. HRF Freedom Fellows were able to visit the space recently, and HRF staff will be speaking at upcoming events at the venue in the near future. Check the space out here.
Cashu | Releases Cashu Development Kit
Cashu, an open-source Chaumian ecash protocol for Bitcoin integrated with the Lightning Network, released the Cashu Development Kit (CDK) in Rust (a common programming language). This makes it easier for developers to build and integrate Cashu wallets, expanding access to private Bitcoin transactions. With Cashu, users can spend Bitcoin-backed ecash without revealing their identity or transaction history. This enables private, cheap, and fast transactions with the tradeoff of being custodial. As digital financial surveillance increases, ecash offers an alternative to remain private. The CDK release expands the reach of said private Bitcoin transactions, providing more safety and anonymity for dissidents.
RoboSats | Adds LNp2pBot Orders on Android App
RoboSats, a privacy-focused peer-to-peer (P2P) Bitcoin exchange powered by the Lightning Network, added support for LNp2pBot orders in its Android app. Previously, users used Telegram to interact with LNp2pBot for P2P bitcoin trades. Now, they can access P2P orders directly from the RoboSats Android app. This integration enhances usability by reducing platform dependency and provides users with greater liquidity for P2P trades. HRF is pleased to see the continued development and interoperability of privacy-focused, self-custodial Bitcoin on and off ramps from this Bitcoin Development Fund grantee.
Bitcoin Dada | Visits Bitcoin Mining Site for Hands-On Learning
Bitcoin Dada, an HRF-supported nonprofit empowering African women with financial literacy and Bitcoin education, recently took its students on a trip to a Bitcoin mining site operated by Gridless in Kibwezi, Kenya. This visit provided students firsthand exposure to Bitcoin mining’s potential for driving economic growth and expanding electricity access in rural African communities while simultaneously helping decentralize the network. The site repurposes sisal waste (the waste from fiber production) to generate electricity, reduce blackouts, and provide power to homes in Kibwezi. As more and more off-grid sites like this come online, Bitcoin’s mining composition becomes less centralized and stronger against threats from authoritarian states.
RECOMMENDED CONTENT
bitcoin++ Developer Conference Livestream
Last week, bitcoin++ hosted the “hacking edition” developer conference in Florianopolis, Brazil. The event brought together Bitcoin developers and freedom tech enthusiasts for four days of hands-on development, workshops, and technical discussions to enhance Bitcoin’s privacy, accessibility, and censorship resistance. If you missed the event, you can catch the key sessions and workshops via live stream. Watch them here.
Nostr: The Importance of Censorship-Resistant Communication for Innovation and Human Progress
In this article for Bitcoin Magazine, Leon Wankum highlights why Nostr, a censorship-resistant protocol, is key to unlocking innovation and free expression. He explains how Nostr enables decentralized content sharing using cryptographic keys and relays, preventing central control of the protocol. This approach ensures that no single entity controls the flow of information, thereby enhancing freedom of expression. Alongside Bitcoin, Nostr has the potential to break corporate and state monopolies, allowing for grassroots progress and innovation on the individual level. You can read the full article here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ a95c6243:d345522c
2025-02-15 19:05:38
@ a95c6243:d345522c
2025-02-15 19:05:38Auf der diesjährigen Münchner Sicherheitskonferenz geht es vor allem um die Ukraine. Protagonisten sind dabei zunächst die US-Amerikaner. Präsident Trump schockierte die Europäer kurz vorher durch ein Telefonat mit seinem Amtskollegen Wladimir Putin, während Vizepräsident Vance mit seiner Rede über Demokratie und Meinungsfreiheit für versteinerte Mienen und Empörung sorgte.
Die Bemühungen der Europäer um einen Frieden in der Ukraine halten sich, gelinde gesagt, in Grenzen. Größeres Augenmerk wird auf militärische Unterstützung, die Pflege von Feindbildern sowie Eskalation gelegt. Der deutsche Bundeskanzler Scholz reagierte auf die angekündigten Verhandlungen über einen möglichen Frieden für die Ukraine mit der Forderung nach noch höheren «Verteidigungsausgaben». Auch die amtierende Außenministerin Baerbock hatte vor der Münchner Konferenz klargestellt:
«Frieden wird es nur durch Stärke geben. (...) Bei Corona haben wir gesehen, zu was Europa fähig ist. Es braucht erneut Investitionen, die der historischen Wegmarke, vor der wir stehen, angemessen sind.»
Die Rüstungsindustrie freut sich in jedem Fall über weltweit steigende Militärausgaben. Die Kriege in der Ukraine und in Gaza tragen zu Rekordeinnahmen bei. Jetzt «winkt die Aussicht auf eine jahrelange große Nachrüstung in Europa», auch wenn der Ukraine-Krieg enden sollte, so hört man aus Finanzkreisen. In der Konsequenz kennt «die Aktie des deutschen Vorzeige-Rüstungskonzerns Rheinmetall in ihrem Anstieg offenbar gar keine Grenzen mehr». «Solche Friedensversprechen» wie das jetzige hätten in der Vergangenheit zu starken Kursverlusten geführt.
Für manche Leute sind Kriegswaffen und sonstige Rüstungsgüter Waren wie alle anderen, jedenfalls aus der Perspektive von Investoren oder Managern. Auch in diesem Bereich gibt es Startups und man spricht von Dingen wie innovativen Herangehensweisen, hocheffizienten Produktionsanlagen, skalierbaren Produktionstechniken und geringeren Stückkosten.
Wir lesen aktuell von Massenproduktion und gesteigerten Fertigungskapazitäten für Kriegsgerät. Der Motor solcher Dynamik und solchen Wachstums ist die Aufrüstung, die inzwischen permanent gefordert wird. Parallel wird die Bevölkerung verbal eingestimmt und auf Kriegstüchtigkeit getrimmt.
Das Rüstungs- und KI-Startup Helsing verkündete kürzlich eine «dezentrale Massenproduktion für den Ukrainekrieg». Mit dieser Expansion positioniere sich das Münchner Unternehmen als einer der weltweit führenden Hersteller von Kampfdrohnen. Der nächste «Meilenstein» steht auch bereits an: Man will eine Satellitenflotte im Weltraum aufbauen, zur Überwachung von Gefechtsfeldern und Truppenbewegungen.
Ebenfalls aus München stammt das als DefenseTech-Startup bezeichnete Unternehmen ARX Robotics. Kürzlich habe man in der Region die größte europäische Produktionsstätte für autonome Verteidigungssysteme eröffnet. Damit fahre man die Produktion von Militär-Robotern hoch. Diese Expansion diene auch der Lieferung der «größten Flotte unbemannter Bodensysteme westlicher Bauart» in die Ukraine.
Rüstung boomt und scheint ein Zukunftsmarkt zu sein. Die Hersteller und Vermarkter betonen, mit ihren Aktivitäten und Produkten solle die europäische Verteidigungsfähigkeit erhöht werden. Ihre Strategien sollten sogar «zum Schutz demokratischer Strukturen beitragen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
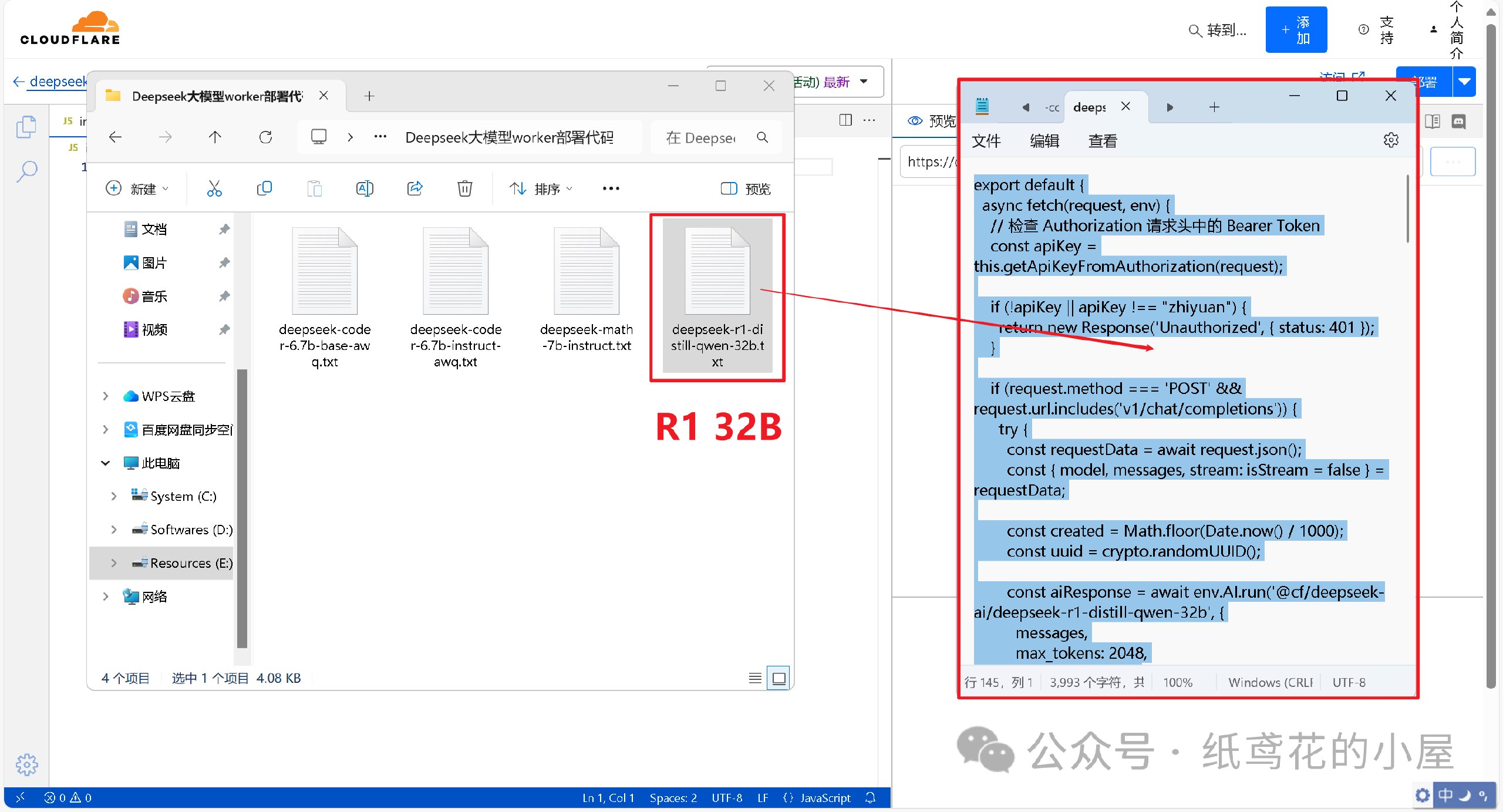
 @ dbb19ae0:c3f22d5a
2025-02-27 20:31:03
@ dbb19ae0:c3f22d5a
2025-02-27 20:31:03Using nostr_sdk 0.39 replace nsec_key with your secret key replace npub_to_follow by the npub to follow
``` python from nostr_sdk import Metadata, Client, Keys, Filter, Kind, KindStandard, Contact, PublicKey, EventBuilder from datetime import timedelta import asyncio
async def main(): keys = Keys.parse("nsec_key") client = Client() await client.add_relay("wss://relay.damus.io") await client.connect()
# Get current contact list f = Filter().author(keys.public_key()).kind(Kind.from_std(KindStandard.CONTACT_LIST)) events = await client.fetch_events(f, timedelta(seconds=10)) event = events.first() if event: # Get current contact public keys and add a new contact public_keys = event.tags().public_keys() new_public_key = PublicKey.parse("npub_to_follow") public_keys.append(new_public_key) # Create a new contact list event and send it to relays contacts = [Contact(public_key=pk, relay_url=None, alias=None) for pk in public_keys] event = EventBuilder.contact_list(contacts).sign_with_keys(keys) await client.send_event(event) print(f"Added follow to: {new_public_key}") else: print("No contact list found")if name == 'main': asyncio.run(main()) ```
https://github.com/ev3rst/nostr_sdk_examples/blob/main/ns-follow-npub.py
-
 @ 4523be58:ba1facd0
2025-02-27 18:51:11
@ 4523be58:ba1facd0
2025-02-27 18:51:11NIP-118
Nostr Double Ratchet Invites
In order to start a NIP-117 Nostr Double Ratchet session, Alice and Bob need to exchange ephemeral public keys and a shared secret.
In a Nostr Double Ratchet invite, Alice gives Bob her
- ephemeral public key, which is also used to respond to the invite on Nostr,
- shared secret, and
- Nostr identity public key, which is used to authenticate the exchange.
Nostr event
Publishing an invite event on Nostr allows other users to start a Double Ratchet session with you.
typescript { pubkey: inviterIdentityKey, content: '', tags: [ ['d', `double-ratchet/invites/${uid}`], // uid: unique name for the invitation, e.g. "public" ['l', 'double-ratchet/invites'], // label, for listing all your invites ['ephemeralKey', inviterEphemeralKey], ['sharedSecret', sharedSecret] ], kind: 30078, created_at, id, sig }lis a NIP-32 label tag that can be used to list your invites. We use this approach with NIP-78 application specific data kind30078in order to not bloat the event kind space and instead have a human-readable label.URL
Invites can be also shared privately, without requiring a Nostr event. This improves privacy, removing the public association between the inviter and response.
URL and QR code are often convenient ways to share privately, especially when the other user is not yet on Nostr. Format:
typescript const invite = { inviter, ephemeralKey, sharedSecret }; const json = JSON.stringify(invite); const url = `https://example.com/#${encodeURIComponent(json)}`;Encoding the invite into the URL hash ensures it's not sent to the server and logged by default.
nostr:URI scheme is another possible way to share invites, when we have native clients supporting the feature.Invite response
Outer event
Invite response outer event is a NIP-59 gift wrap event of kind
1059, sent from a random, one-time-use pubkey, hiding the responder's identity from the public.It is addressed to the ephemeral key in the invite. If the invite was publicly shared, responses can be publicly associated to the inviter.
Inner event
NIP-59 Rumor.
```typescript const conversationKey = nip44.getConversationKey( inviteeKeyPair, inviterPublicKey ); const encrypted1 = encrypt(inviteeEphemeralKey, conversationKey); const encrypted2 = encrypt(encrypted1, sharedSecret);
const rumor = { pubkey: inviteePublicKey, kind: 1060, content: encrypted2, tags: [], createdAt, id, }; ```
After receiving the invite response, both parties have what they need to start a double ratchet session: each others' ephemeral public keys and a shared secret.
Both parties have authenticated by encrypting or decrypting using their nip44 conversation key.
The shared secret from the invite is used in the response to ensure that only actual recipients of the invite can follow it. Otherwise, attackers could initiate double ratchet sessions by sending invite responses to all addresses that received gift wraps, some of which are private invite addresses.
-
 @ 5d4b6c8d:8a1c1ee3
2025-02-27 20:25:29
@ 5d4b6c8d:8a1c1ee3
2025-02-27 20:25:29I've really enjoyed these two months running ~econ. It crystallized that what I most enjoy is reading and commenting. Thankfully, our excellent contributors are giving me ample opportunities.
Metrics
- Posts: 5th place - 264
- Comments: 6th place - 1653
- Stacking: 3rd place - 149.6k
- Revenue: 6th place - 59.4k
We're still over the breakeven point, but revenue was down from last month (still above the month before I took over, though). That means the new posting fee will be 81 sats, which is halfway back to the previous 108.
Contest Ideas
Last month, I asked what people thought the best use of previously donated sats was and funding a contest seemed to get the best response.
I'd like to try out a quarterly contest. The prize pool will be whatever sats have been earned, above the breakeven point, until the donated sats have all been paid out.
I'm not sure if this will be a winner-takes-all thing or a top 3. I also don't want to completely defer to zaprank, so what I'll do is list the top 10 posts by zaprank and have people vote on the best post.
Let me know what you think (including if this is an acceptable use of your donations, for those who made donations).
originally posted at https://stacker.news/items/899082
-
 @ c631e267:c2b78d3e
2025-02-07 19:42:11
@ c631e267:c2b78d3e
2025-02-07 19:42:11Nur wenn wir aufeinander zugehen, haben wir die Chance \ auf Überwindung der gegenseitigen Ressentiments! \ Dr. med. dent. Jens Knipphals
In Wolfsburg sollte es kürzlich eine Gesprächsrunde von Kritikern der Corona-Politik mit Oberbürgermeister Dennis Weilmann und Vertretern der Stadtverwaltung geben. Der Zahnarzt und langjährige Maßnahmenkritiker Jens Knipphals hatte diese Einladung ins Rathaus erwirkt und publiziert. Seine Motivation:
«Ich möchte die Spaltung der Gesellschaft überwinden. Dazu ist eine umfassende Aufarbeitung der Corona-Krise in der Öffentlichkeit notwendig.»
Schon früher hatte Knipphals Antworten von den Kommunalpolitikern verlangt, zum Beispiel bei öffentlichen Bürgerfragestunden. Für das erwartete Treffen im Rathaus formulierte er Fragen wie: Warum wurden fachliche Argumente der Kritiker ignoriert? Weshalb wurde deren Ausgrenzung, Diskreditierung und Entmenschlichung nicht entgegengetreten? In welcher Form übernehmen Rat und Verwaltung in Wolfsburg persönlich Verantwortung für die erheblichen Folgen der politischen Corona-Krise?
Der Termin fand allerdings nicht statt – der Bürgermeister sagte ihn kurz vorher wieder ab. Knipphals bezeichnete Weilmann anschließend als Wiederholungstäter, da das Stadtoberhaupt bereits 2022 zu einem Runden Tisch in der Sache eingeladen hatte, den es dann nie gab. Gegenüber Multipolar erklärte der Arzt, Weilmann wolle scheinbar eine öffentliche Aufarbeitung mit allen Mitteln verhindern. Er selbst sei «inzwischen absolut desillusioniert» und die einzige Lösung sei, dass die Verantwortlichen gingen.
Die Aufarbeitung der Plandemie beginne bei jedem von uns selbst, sei aber letztlich eine gesamtgesellschaftliche Aufgabe, schreibt Peter Frey, der den «Fall Wolfsburg» auch in seinem Blog behandelt. Diese Aufgabe sei indes deutlich größer, als viele glaubten. Erfreulicherweise sei der öffentliche Informationsraum inzwischen größer, trotz der weiterhin unverfrorenen Desinformations-Kampagnen der etablierten Massenmedien.
Frey erinnert daran, dass Dennis Weilmann mitverantwortlich für gravierende Grundrechtseinschränkungen wie die 2021 eingeführten 2G-Regeln in der Wolfsburger Innenstadt zeichnet. Es sei naiv anzunehmen, dass ein Funktionär einzig im Interesse der Bürger handeln würde. Als früherer Dezernent des Amtes für Wirtschaft, Digitalisierung und Kultur der Autostadt kenne Weilmann zum Beispiel die Verknüpfung von Fördergeldern mit politischen Zielsetzungen gut.
Wolfsburg wurde damals zu einem Modellprojekt des Bundesministeriums des Innern (BMI) und war Finalist im Bitkom-Wettbewerb «Digitale Stadt». So habe rechtzeitig vor der Plandemie das Projekt «Smart City Wolfsburg» anlaufen können, das der Stadt «eine Vorreiterrolle für umfassende Vernetzung und Datenerfassung» aufgetragen habe, sagt Frey. Die Vereinten Nationen verkauften dann derartige «intelligente» Überwachungs- und Kontrollmaßnahmen ebenso als Rettung in der Not wie das Magazin Forbes im April 2020:
«Intelligente Städte können uns helfen, die Coronavirus-Pandemie zu bekämpfen. In einer wachsenden Zahl von Ländern tun die intelligenten Städte genau das. Regierungen und lokale Behörden nutzen Smart-City-Technologien, Sensoren und Daten, um die Kontakte von Menschen aufzuspüren, die mit dem Coronavirus infiziert sind. Gleichzeitig helfen die Smart Cities auch dabei, festzustellen, ob die Regeln der sozialen Distanzierung eingehalten werden.»
Offensichtlich gibt es viele Aspekte zu bedenken und zu durchleuten, wenn es um die Aufklärung und Aufarbeitung der sogenannten «Corona-Pandemie» und der verordneten Maßnahmen geht. Frustration und Desillusion sind angesichts der Realitäten absolut verständlich. Gerade deswegen sind Initiativen wie die von Jens Knipphals so bewundernswert und so wichtig – ebenso wie eine seiner Kernthesen: «Wir müssen aufeinander zugehen, da hilft alles nichts».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 04c915da:3dfbecc9
2025-02-25 03:55:08
@ 04c915da:3dfbecc9
2025-02-25 03:55:08Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 6e0ea5d6:0327f353
2025-02-21 18:15:52
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ a95c6243:d345522c
2025-01-31 20:02:25
@ a95c6243:d345522c
2025-01-31 20:02:25Im Augenblick wird mit größter Intensität, großer Umsicht \ das deutsche Volk belogen. \ Olaf Scholz im FAZ-Interview
Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur Reuters Verbreitung in den Medien gefunden hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten.
Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen sei repräsentativ, behauptet der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von Mitgliedern, die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben».
Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH, also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges «Demokratie-Update» aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet.
Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer befürchteten, dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen.
Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein? Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise abgelehnt. Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen.
Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen, die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter berichtet. Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert».
Der Vorwand «unzulässiger Einflussnahme» auf Politik und Wahlen wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als «völlig irre» bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird «E-Voting» seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg.
Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus. Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die weit verbreitete Armut zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 4857600b:30b502f4
2025-02-20 19:09:11
@ 4857600b:30b502f4
2025-02-20 19:09:11Mitch McConnell, a senior Republican senator, announced he will not seek reelection.
At 83 years old and with health issues, this decision was expected. After seven terms, he leaves a significant legacy in U.S. politics, known for his strategic maneuvering.
McConnell stated, “My current term in the Senate will be my last.” His retirement marks the end of an influential political era.
-
 @ a95c6243:d345522c
2025-01-24 20:59:01
@ a95c6243:d345522c
2025-01-24 20:59:01Menschen tun alles, egal wie absurd, \ um ihrer eigenen Seele nicht zu begegnen. \ Carl Gustav Jung
«Extremer Reichtum ist eine Gefahr für die Demokratie», sagen über die Hälfte der knapp 3000 befragten Millionäre aus G20-Staaten laut einer Umfrage der «Patriotic Millionaires». Ferner stellte dieser Zusammenschluss wohlhabender US-Amerikaner fest, dass 63 Prozent jener Millionäre den Einfluss von Superreichen auf US-Präsident Trump als Bedrohung für die globale Stabilität ansehen.
Diese Besorgnis haben 370 Millionäre und Milliardäre am Dienstag auch den in Davos beim WEF konzentrierten Privilegierten aus aller Welt übermittelt. In einem offenen Brief forderten sie die «gewählten Führer» auf, die Superreichen – also sie selbst – zu besteuern, um «die zersetzenden Auswirkungen des extremen Reichtums auf unsere Demokratien und die Gesellschaft zu bekämpfen». Zum Beispiel kontrolliere eine handvoll extrem reicher Menschen die Medien, beeinflusse die Rechtssysteme in unzulässiger Weise und verwandele Recht in Unrecht.
Schon 2019 beanstandete der bekannte Historiker und Schriftsteller Ruthger Bregman an einer WEF-Podiumsdiskussion die Steuervermeidung der Superreichen. Die elitäre Veranstaltung bezeichnete er als «Feuerwehr-Konferenz, bei der man nicht über Löschwasser sprechen darf.» Daraufhin erhielt Bregman keine Einladungen nach Davos mehr. Auf seine Aussagen machte der Schweizer Aktivist Alec Gagneux aufmerksam, der sich seit Jahrzehnten kritisch mit dem WEF befasst. Ihm wurde kürzlich der Zutritt zu einem dreiteiligen Kurs über das WEF an der Volkshochschule Region Brugg verwehrt.
Nun ist die Erkenntnis, dass mit Geld politischer Einfluss einhergeht, alles andere als neu. Und extremer Reichtum macht die Sache nicht wirklich besser. Trotzdem hat man über Initiativen wie Patriotic Millionaires oder Taxmenow bisher eher selten etwas gehört, obwohl es sie schon lange gibt. Auch scheint es kein Problem, wenn ein Herr Gates fast im Alleingang versucht, globale Gesundheits-, Klima-, Ernährungs- oder Bevölkerungspolitik zu betreiben – im Gegenteil. Im Jahr, als der Milliardär Donald Trump zum zweiten Mal ins Weiße Haus einzieht, ist das Echo in den Gesinnungsmedien dagegen enorm – und uniform, wer hätte das gedacht.
Der neue US-Präsident hat jedoch «Davos geerdet», wie Achgut es nannte. In seiner kurzen Rede beim Weltwirtschaftsforum verteidigte er seine Politik und stellte klar, er habe schlicht eine «Revolution des gesunden Menschenverstands» begonnen. Mit deutlichen Worten sprach er unter anderem von ersten Maßnahmen gegen den «Green New Scam», und von einem «Erlass, der jegliche staatliche Zensur beendet»:
«Unsere Regierung wird die Äußerungen unserer eigenen Bürger nicht mehr als Fehlinformation oder Desinformation bezeichnen, was die Lieblingswörter von Zensoren und derer sind, die den freien Austausch von Ideen und, offen gesagt, den Fortschritt verhindern wollen.»
Wie der «Trumpismus» letztlich einzuordnen ist, muss jeder für sich selbst entscheiden. Skepsis ist definitiv angebracht, denn «einer von uns» sind weder der Präsident noch seine auserwählten Teammitglieder. Ob sie irgendeinen Sumpf trockenlegen oder Staatsverbrechen aufdecken werden oder was aus WHO- und Klimaverträgen wird, bleibt abzuwarten.
Das WHO-Dekret fordert jedenfalls die Übertragung der Gelder auf «glaubwürdige Partner», die die Aktivitäten übernehmen könnten. Zufällig scheint mit «Impfguru» Bill Gates ein weiterer Harris-Unterstützer kürzlich das Lager gewechselt zu haben: Nach einem gemeinsamen Abendessen zeigte er sich «beeindruckt» von Trumps Interesse an der globalen Gesundheit.
Mit dem Projekt «Stargate» sind weitere dunkle Wolken am Erwartungshorizont der Fangemeinde aufgezogen. Trump hat dieses Joint Venture zwischen den Konzernen OpenAI, Oracle, und SoftBank als das «größte KI-Infrastrukturprojekt der Geschichte» angekündigt. Der Stein des Anstoßes: Oracle-CEO Larry Ellison, der auch Fan von KI-gestützter Echtzeit-Überwachung ist, sieht einen weiteren potenziellen Einsatz der künstlichen Intelligenz. Sie könne dazu dienen, Krebserkrankungen zu erkennen und individuelle mRNA-«Impfstoffe» zur Behandlung innerhalb von 48 Stunden zu entwickeln.
Warum bitte sollten sich diese superreichen «Eliten» ins eigene Fleisch schneiden und direkt entgegen ihren eigenen Interessen handeln? Weil sie Menschenfreunde, sogenannte Philanthropen sind? Oder vielleicht, weil sie ein schlechtes Gewissen haben und ihre Schuld kompensieren müssen? Deswegen jedenfalls brauchen «Linke» laut Robert Willacker, einem deutschen Politikberater mit brasilianischen Wurzeln, rechte Parteien – ein ebenso überraschender wie humorvoller Erklärungsansatz.
Wenn eine Krähe der anderen kein Auge aushackt, dann tut sie das sich selbst noch weniger an. Dass Millionäre ernsthaft ihre eigene Besteuerung fordern oder Machteliten ihren eigenen Einfluss zugunsten anderer einschränken würden, halte ich für sehr unwahrscheinlich. So etwas glaube ich erst, wenn zum Beispiel die Rüstungsindustrie sich um Friedensverhandlungen bemüht, die Pharmalobby sich gegen institutionalisierte Korruption einsetzt, Zentralbanken ihre CBDC-Pläne für Bitcoin opfern oder der ÖRR die Abschaffung der Rundfunkgebühren fordert.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 8412613c:df65608a
2025-02-27 19:35:22
@ 8412613c:df65608a
2025-02-27 19:35:22The book "Till We Have Faces" by C.S. Lewis had a profound spiritual impact on me, unlike most books that typically stay on an intellectual or entertainment level. I kept thinking, "Why didn't I read this sooner?" (It had been on my list for years). However, I believe I wouldn't have understood it as deeply as I did now, and I attribute that to my decision to fully embrace my Christian faith and accept Jesus as the Son of God who incarnated and resurrected—with no more questions or doubts, just faith. This choice has been truly liberating for me.
Although Till We Have Faces is not explicitly a Christian book, it beautifully reflects the themes of voluntary sacrifice, selfless love, suffering, and the mystery of the divine by retelling the myth of Psyche and Eros from the perspective of Psyche’s sister, Orual. Her journey through profound grief and blame toward the gods ultimately leads her to inner transformation and peace at the end of her life. C.S. Lewis’ personal faith undeniably influenced his writing, often exploring spiritual and philosophical themes through the lens of myth and allegory, as we see in this book.
I want to briefly mention a few topics that gave me pause:
The case against the gods
‘But, your eyes being open, you saw no such thing.’
‘You don’t think—not possibly—not as a mere hundredth chance—there might be things that are real though we can’t see them?’
‘Certainly I do. Such things as Justice, Equality, the Soul, or musical notes.’
‘Oh, grandfather, I don’t mean things like that. If there are souls, could there not be soul-houses? (p. 161).
It was clever of the author to make Psyche's palace invisible to mortal eyes, as this allows readers to relate to Orual's struggle with the nature of reality. Orual faces the abyss that humans encounter when witnessing the limits of reason.
If what I saw was real. I was in great fear. Perhaps it was not real. I looked and looked to see if it would not fade or change. Then as I rose (for all this time I was still kneeling where I had drunk), almost before I stood on my feet, the whole thing was vanished. (p. 150).
Even though Orual has a glimpse of the divine, she makes an important decision that will mark her for the rest of her life: she chooses to neglect recognizing her vision as the sign she had been asking for, and instead looks for other possible explanations. She thinks the gods are cruel and untrustworthy, and also blames them for their lack of clarity in their messaging. She expresses that if they wanted her to understand something, they are at fault for not being clear.
The gods never send us this invitation to delight so readily or so strongly as when they are preparing some new agony. We are their bubbles; they blow us big before they prick us. (p. 111).
Orual reached her breaking point when the gods twisted what she believed to be real: her experiences and her life story. She interpreted this event as a mockery by the gods, and so decided to write a book from her perspective—a case against them—without realizing that, in doing so, she was writing a case against herself:
Now, you who read, judge between the gods and me. They gave me nothing in the world to love but Psyche and then took her from me. But that was not enough. They then brought me to her at such a place and time that it hung on my word whether she should continue in bliss or be cast out into misery. They would not tell me whether she was the bride of a god, or mad, or a brute’s or villain’s spoil. They would give no clear sign, though I begged for it. I had to guess. And because I guessed wrong they punished me—what’s worse, punished me through her. And even that was not enough; they have now sent out a lying story in which I was given no riddle to guess, but knew and saw that she was the god’s bride, and of my own will destroyed her, and that for jealousy. As if I were another Redival. I say the gods deal very unrightly with us. For they will neither (which would be best of all) go away and leave us to live our own short days to ourselves, nor will they show themselves openly and tell us what they would have us do. For that too would be endurable. But to hint and hover, to draw near us in dreams and oracles, or in a waking vision that vanishes as soon as seen, to be dead silent when we question them and then glide back and whisper (words we cannot understand) in our ears when we most wish to be free of them, and to show to one what they hide from another; what is all this but cat-and-mouse play, blindman’s buff, and mere jugglery? Why must holy places be dark places? (pp. 283-284).
I have always believed in God as Jesus, yet I understand Orual's accusations. I have questioned "unfair" situations, victimized myself, and blamed God. I have also saddened the beautiful souls of believers when, in my state of rebellion, I harshly questioned their faith, even as they were showing me Christ's love. I saw myself in many of Orual's attitudes
With time, I have come to understand that humans can move between reason and faith, each requiring different skills. Dismissing either is dangerous. Reason protects us from deception but it can also blind us from truths. Faith is part of what gives us purpose in life, it comes with uncertainty but also with a blessing:
Then Jesus told him, “Because you have seen me, you have believed; blessed are those who have not seen and yet have believed. -John 20:39.
Dying before dying
This part of the book was truly inspiring to me because I have been obsessed with these words for a long time [^1]:
If you die before you die, you won't die when you die. -Inscription at St. Paul's Monastery on Mt. Athos.
So I recognized them in the text:
Die before you die. There is no chance after. (p. 318).
Orual explains what the gods meant by “dying before dying”:
Then I remembered that conversation which his friends had with Socrates before he drank the hemlock, and how he said that true wisdom is the skill and practise of death... But by the death which is wisdom I supposed he meant the death of our passions and desires and vain opinions. And immediately (it is terrible to be a fool) I thought I saw my way clear and not impossible. To say that I was Ungit meant that I was as ugly in soul as she; greedy, blood-gorged. But if I practised true philosophy, as Socrates meant it, I should change my ugly soul into a fair one. And this, the gods helping me, I would do. I would set about it at once. (pp. 321-322).
These words brought me to the central Christian teaching of "dying to self" or "crucifying the old self”, which is only achieved through divine intervention. The idea of dying before dying is described by Paul as follows:
I have been crucified with Christ. It is no longer I who live, but Christ who lives in me. And the life I now live in the flesh I live by faith in the Son of God, who loved me and gave himself for me. -Galatians 2:20
Dreams
Orual was stubborn and tried to fix her sorrow by another form of dying: completely changing her identity and true nature by neglecting herself and becoming someone else. This might seem similar to “dying before dying”, but the latter just comes through an act of humility and surrender by recognizing that only divine mercy can prevent us from going astray and truly heal. Orual, however, relied on her own strength and pride to endure her suffering. She hid behind a veil and metaphorically killed herself.
I had worn a veil because I wished to be secret. I now determined that I would go always veiled. I have kept this rule, within doors and without, ever since. It is a sort of treaty made with my ugliness. There had been a time in childhood when I didn’t yet know I was ugly. Then there was a time (for in this book I must hide none of my shames or follies) when I believed, as girls do—and as Batta was always telling me—that I could make it more tolerable by this or that done to my clothes or my hair. Now, I chose to be veiled. The Fox, that night, was the last man who ever saw my face; and not many women have seen it either. (p. 205).
I am the Queen; I’ll kill Orual too. (p. 256).
By writing her book, Orual finally reaches a state where she is ready for divine intervention. Ultimately, she removes her veil. The following is one of the most important paragraphs:
Not many days have passed since I wrote those words no answer, but I must unroll my book again. It would be better to rewrite it from the beginning, but I think there’s no time for that. Weakness comes on me fast... Since I cannot mend the book, I must add to it. To leave it as it was would be to die perjured; I know so much more than I did about the woman who wrote it. What began the change was the very writing itself. Let no one lightly set about such a work. Memory, once waked, will play the tyrant. I found I must set down (for I was speaking as before judges and must not lie) passions and thoughts of my own which I had clean forgotten. The past which I wrote down was not the past that I thought I had (all these years) been remembering. I did not, even when I had finished the book, see clearly many things that I see now. The change which the writing wrought in me (and of which I did not write) was only a beginning—only to prepare me for the gods’ surgery. They used my own pen to probe my wound. (p. 287).
Through random encounters, dreams, and visions, the gods showed Orual what she had been missing her whole life. One specific dream (or vision) caught my attention and made me think that C.S. Lewis had a profound insight while writing this masterpiece: Orual had a vision in which she presented her case against the gods in a courtroom before a judge. The assembly was made up of gods and ghosts, some of whom she knew. When the judge asked her to read her complaint, she had a scroll that was not the book she had written while recounting the story of her life. But she read it anyway until the judge said "enough," and she understood that she had read it over and over. The judge asked if she had her answer, and she replied "yes."
The complaint was the answer. To have heard myself making it was to be answered. (p. 335).
This was incredible, and I could relate. I have had similar dreams in which I have a book in my hands—a book I know I wrote. Suddenly, I become lucid and tell myself, "Here is the answer; when I read it, I will know." This has been a recurring dream, and it's interesting because there are insights we only have access to on a deeper inner level. I have also dreamed of conversing with Jesus, repeating certain words, some of which I do not even remember. I interpret these kinds of dreams as follows:
In the same way, the Spirit helps us in our weakness. We do not know what we ought to pray for, but the Spirit himself intercedes for us through wordless groans. -Romans 8:26
I think that C.S. Lewis, speaking through Orual and the Fox, understands this and writes:
Lightly men talk of saying what they mean. Often when he was teaching me to write in Greek the Fox would say, ‘Child, to say the very thing you really mean, the whole of it, nothing more or less or other than what you really mean; that’s the whole art and joy of words.’ A glib saying. When the time comes to you at which you will be forced at last to utter the speech which has lain at the centre of your soul for years, which you have, all that time, idiot-like, been saying over and over, you’ll not talk about joy of words. I saw well why the gods do not speak to us openly, nor let us answer. Till that word can be dug out of us, why should they hear the babble that we think we mean? How can they meet us face to face till we have faces? (p. 335).
I am very impressed with how the author explored Orual's life through her own eyes, enabling the reader to understand her transformation once she finally confronted her shortcomings and humbly accepted divine wisdom. With this new knowledge, she could finally see her path from a different perspective. Furthermore, the reader was able to appreciate the role of the gods: they weren’t meant to alleviate Orual’s suffering, but rather to lead her to see that it had a purpose—to transcend. This story made me reflect on my own journey and acknowledge Jesus's presence and mercy in my life and His selfless love as the key to transformation.
This book resonated so deeply with me. I absolutely recommend it. To C.S. Lewis, thank you—your words truly touched my heart.
References:
Lewis, C. S.. Till We Have Faces: A Myth Retold. Kindle Edition.
[^1]: See: https://habla.news/u/nancyqa@mynostr.space/1691458659942
-
 @ c631e267:c2b78d3e
2025-01-18 09:34:51
@ c631e267:c2b78d3e
2025-01-18 09:34:51Die grauenvollste Aussicht ist die der Technokratie – \ einer kontrollierenden Herrschaft, \ die durch verstümmelte und verstümmelnde Geister ausgeübt wird. \ Ernst Jünger
«Davos ist nicht mehr sexy», das Weltwirtschaftsforum (WEF) mache Davos kaputt, diese Aussagen eines Einheimischen las ich kürzlich in der Handelszeitung. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den vergangenen vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
Der deutsche WEF-Gründer hatte bei dieser Gelegenheit immer höchst lobende Worte für seine Landsmännin: 2021 erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und 2022 fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
Von der Leyens Handeln während der sogenannten Corona-«Pandemie» lobte Schwab damals bereits ebenso, wie es diese Woche das Karlspreis-Direktorium tat, als man der Beschuldigten im Fall Pfizergate die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
Jene Herausforderungen durch «Krisen epochalen Ausmaßes» werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im Global Risks Report nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
Ein «Great Mental Reset» sei die Voraussetzung dafür, dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
Der aktuelle Zustand unserer Gesellschaften ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die Rechtsstaatlichkeit stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-01-13 10:09:57
@ a95c6243:d345522c
2025-01-13 10:09:57Ich begann, Social Media aufzubauen, \ um den Menschen eine Stimme zu geben. \ Mark Zuckerberg
Sind euch auch die Tränen gekommen, als ihr Mark Zuckerbergs Wendehals-Deklaration bezüglich der Meinungsfreiheit auf seinen Portalen gehört habt? Rührend, oder? Während er früher die offensichtliche Zensur leugnete und später die Regierung Biden dafür verantwortlich machte, will er nun angeblich «die Zensur auf unseren Plattformen drastisch reduzieren».
«Purer Opportunismus» ob des anstehenden Regierungswechsels wäre als Klassifizierung viel zu kurz gegriffen. Der jetzige Schachzug des Meta-Chefs ist genauso Teil einer kühl kalkulierten Business-Strategie, wie es die 180 Grad umgekehrte Praxis vorher war. Social Media sind ein höchst lukratives Geschäft. Hinzu kommt vielleicht noch ein bisschen verkorkstes Ego, weil derartig viel Einfluss und Geld sicher auch auf die Psyche schlagen. Verständlich.
«Es ist an der Zeit, zu unseren Wurzeln der freien Meinungsäußerung auf Facebook und Instagram zurückzukehren. Ich begann, Social Media aufzubauen, um den Menschen eine Stimme zu geben», sagte Zuckerberg.
Welche Wurzeln? Hat der Mann vergessen, dass er von der Überwachung, dem Ausspionieren und dem Ausverkauf sämtlicher Daten und digitaler Spuren sowie der Manipulation seiner «Kunden» lebt? Das ist knallharter Kommerz, nichts anderes. Um freie Meinungsäußerung geht es bei diesem Geschäft ganz sicher nicht, und das war auch noch nie so. Die Wurzeln von Facebook liegen in einem Projekt des US-Militärs mit dem Namen «LifeLog». Dessen Ziel war es, «ein digitales Protokoll vom Leben eines Menschen zu erstellen».
Der Richtungswechsel kommt allerdings nicht überraschend. Schon Anfang Dezember hatte Meta-Präsident Nick Clegg von «zu hoher Fehlerquote bei der Moderation» von Inhalten gesprochen. Bei der Gelegenheit erwähnte er auch, dass Mark sehr daran interessiert sei, eine aktive Rolle in den Debatten über eine amerikanische Führungsrolle im technologischen Bereich zu spielen.
Während Milliardärskollege und Big Tech-Konkurrent Elon Musk bereits seinen Posten in der kommenden Trump-Regierung in Aussicht hat, möchte Zuckerberg also nicht nur seine Haut retten – Trump hatte ihn einmal einen «Feind des Volkes» genannt und ihm lebenslange Haft angedroht –, sondern am liebsten auch mitspielen. KI-Berater ist wohl die gewünschte Funktion, wie man nach einem Treffen Trump-Zuckerberg hörte. An seine Verhaftung dachte vermutlich auch ein weiterer Multimilliardär mit eigener Social Media-Plattform, Pavel Durov, als er Zuckerberg jetzt kritisierte und gleichzeitig warnte.
Politik und Systemmedien drehen jedenfalls durch – was zu viel ist, ist zu viel. Etwas weniger Zensur und mehr Meinungsfreiheit würden die Freiheit der Bürger schwächen und seien potenziell vernichtend für die Menschenrechte. Zuckerberg setze mit dem neuen Kurs die Demokratie aufs Spiel, das sei eine «Einladung zum nächsten Völkermord», ernsthaft. Die Frage sei, ob sich die EU gegen Musk und Zuckerberg behaupten könne, Brüssel müsse jedenfalls hart durchgreifen.
Auch um die Faktenchecker macht man sich Sorgen. Für die deutsche Nachrichtenagentur dpa und die «Experten» von Correctiv, die (noch) Partner für Fact-Checking-Aktivitäten von Facebook sind, sei das ein «lukratives Geschäftsmodell». Aber möglicherweise werden die Inhalte ohne diese vermeintlichen Korrektoren ja sogar besser. Anders als Meta wollen jedoch Scholz, Faeser und die Tagesschau keine Fehler zugeben und zum Beispiel Correctiv-Falschaussagen einräumen.
Bei derlei dramatischen Befürchtungen wundert es nicht, dass der öffentliche Plausch auf X zwischen Elon Musk und AfD-Chefin Alice Weidel von 150 EU-Beamten überwacht wurde, falls es irgendwelche Rechtsverstöße geben sollte, die man ihnen ankreiden könnte. Auch der Deutsche Bundestag war wachsam. Gefunden haben dürften sie nichts. Das Ganze war eher eine Show, viel Wind wurde gemacht, aber letztlich gab es nichts als heiße Luft.
Das Anbiedern bei Donald Trump ist indes gerade in Mode. Die Weltgesundheitsorganisation (WHO) tut das auch, denn sie fürchtet um Spenden von über einer Milliarde Dollar. Eventuell könnte ja Elon Musk auch hier künftig aushelfen und der Organisation sowie deren größtem privaten Förderer, Bill Gates, etwas unter die Arme greifen. Nachdem Musks KI-Projekt xAI kürzlich von BlackRock & Co. sechs Milliarden eingestrichen hat, geht da vielleicht etwas.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a5caac8b:172ed717
2025-02-27 19:01:32
@ a5caac8b:172ed717
2025-02-27 19:01:32
Descubre una Oportunidad Única: Nuestra Propiedad Rústica en Tulum con Potencial Inmenso
Buscamos personas interesadas en explorar una inversión sólida, sostenible y alineada con el futuro de las finanzas descentralizadas. Queremos compartir con ustedes nuestra propiedad excepcional ubicada en La Veleta, Tulum, un lugar donde la naturaleza se fusiona con el estilo de vida moderno y el ecosistema Bitcoin.
Características destacadas de esta joya rústica:
- Construcción robusta: Diseñamos esta propiedad con materiales locales como piedra y Chucum, reflejando autenticidad y resistencia.
- Fuente propia de agua: Garantiza independencia hídrica, un valor inigualable en la región.
- Vegetación abundante: Un oasis verde que conecta directamente con la esencia de Tulum.
- Ubicación estratégica: Está súper céntrica, rodeada de los sitios más hermosos de la región, perfecta tanto para residencia como para negocio.
- Documentación al día: Todo está en regla y listo para transacciones seguras.
Nuestra propuesta para la administración y finanzas
Estamos buscando colaboradores para gestionar y/o comprar esta propiedad. Ya sea mediante plataformas como Nostr, Telegram o Element (en Matrix), podemos coordinarnos de manera eficiente para cualquier aspecto relacionado con la propiedad.
Además, si están interesados en adquirirla, queremos destacar que recientemente ajustamos el precio en 170,000 USD menos tras cuatro años en el mercado. Este cambio refleja nuestro compromiso con encontrar a los socios ideales que valoren no solo la belleza del lugar, sino también su potencial financiero dentro del ecosistema Bitcoin.
Por qué invertir aquí?
- Negocio rentable: Ideal para emprendedores que deseen desarrollar proyectos turísticos, ecológicos o incluso tecnológicos en una de las regiones más codiciadas del mundo.
- Valorización asegurada: La tendencia inmobiliaria en Tulum sigue creciendo año con año.
- Sostenibilidad y tecnología: Combina la magia natural de México con herramientas innovadoras.
Comunicación Multilingüe
Ofrecemos la posibilidad de comunicarnos en español, alemán e inglés, lo que facilitará la interacción con inversores de diferentes partes del mundo.
No duden en contactarnos si son visionarios dispuestos a explorar nuevas formas de inversión en bienes raíces utilizando Bitcoin. Estamos emocionados por conectar con ustedes y construir juntos un futuro próspero.
Contacto: No duden en escribirnos. Respondemos todas sus preguntas con detalle y entusiasmo. ¡Juntos podemos transformar esta propiedad en un proyecto extraordinario!
TulumRealEstate #BitcoinFriendly #SustainableLiving #InvestInTulum #RusticCharm #PropertyForSale #DecentralizedFinance #TulumDreams
Discover a Unique Opportunity: Our Rustic Property in Tulum with Incredible Potential
We are looking for individuals interested in exploring a solid, sustainable investment aligned with the future of decentralized finance. We want to share with you our exceptional property located in La Veleta, Tulum—a place where nature blends seamlessly with modern living and the Bitcoin ecosystem.
Key Features of this Rustic Gem:
- Sturdy construction: We designed this property using local materials like stone and Chucum, reflecting authenticity and durability.
- Own water source: Ensures hydrological independence, an invaluable asset in the region.
- Abundant vegetation: A lush green haven that connects directly with the essence of Tulum.
- Strategic location: Centrally located, surrounded by the most beautiful spots in the region, perfect for both residential and business use.
- Up-to-date documentation: Everything is in order and ready for secure transactions.
Our Proposal for Management and Finances
We are seeking collaborators to manage and/or purchase this property. Whether through platforms like Nostr, Telegram or Element (on Matrix), we can efficiently coordinate any aspect related to the property.
Additionally, if you're interested in acquiring it, we’d like to highlight that we recently reduced the price by $170,000 USD after four years on the market. This adjustment reflects our commitment to finding the ideal partners who appreciate not only the beauty of the place but also its financial potential within the Bitcoin ecosystem.
Why Invest Here?
- Profitable business opportunity: Perfect for entrepreneurs looking to develop tourism, ecological, or even tech projects in one of the world's most sought-after regions.
- Guaranteed appreciation: The real estate trend in Tulum continues to grow year after year.
- Sustainability and technology: Combines the natural magic of Mexico with innovative tools.
Multilingual Communication
We offer the possibility of communicating in Spanish, German, and English, making interaction easier for investors from around the world.
Don’t hesitate to reach out if you’re visionaries eager to explore new ways to invest in real estate using Bitcoin. We’re excited to connect with you and build a prosperous future together.
Contact: Feel free to write to us. We’ll be happy to answer all your questions in detail and with enthusiasm. Together, we can turn this property into an extraordinary project!
TulumRealEstate #BitcoinFriendly #SustainableLiving #InvestInTulum #RusticCharm #PropertyForSale #DecentralizedFinance #TulumDreams
Entdeckt eine einzigartige Gelegenheit: Unsere rustikale Immobilie in Tulum mit enormem Potenzial
Wir suchen Personen, die daran interessiert sind, eine feste, nachhaltige Investition zu tätigen, die sich auf die Zukunft der dezentralisierten Finanzen ausrichtet. Wir möchten euch unsere außergewöhnliche Immobilie in La Veleta, Tulum vorstellen – ein Ort, an dem Natur nahtlos mit dem modernen Leben und dem Bitcoin-Ekosystem verschmilzt.
Herausragende Merkmale dieser rustikalen Perle:
- Robuste Bauweise: Wir haben diese Immobilie mit lokalen Materialien wie Stein und Chucum gebaut, um Authentizität und Beständigkeit widerzuspiegeln.
- Eigen Quelle: Sicherstellt wertvolle Wasserunabhängigkeit, ein unschätzbarer Vorteil in der Region.
- Reiche Vegetation: Ein grünes Paradies, das euch direkt mit der Essenz von Tulum verbindet.
- Strategisch günstige Lage: Zentral gelegen, umgeben von den schönsten Plätzen der Region, ideal sowohl für Wohnzwecke als auch für Geschäfte.
- Aktuelle Dokumentation: Alles ist aktuell und bereit für sichere Transaktionen.
Unser Angebot zur Verwaltung und Finanzen
Wir suchen Mitstreiter, um diese Immobilie gemeinsam zu verwalten und/oder zu kaufen. Ob über Plattformen wie Nostr, Telegram oder Element (auf Matrix), können wir alle Aspekte der Immobilie effizient koordinieren.
Außerdem, wenn ihr Interesse habt, sie zu erwerben, möchten wir betonen, dass wir den Preis kürzlich um 170.000 USD gesenkt haben, nachdem sie vier Jahre lang auf dem Markt war. Diese Anpassung spiegelt unser Engagement wider, die idealen Partner zu finden, die nicht nur die Schönheit des Ortes schätzen, sondern auch sein finanzielles Potenzial im Bitcoin-Ekosystem.
Warum hier investieren?
- Rentables Geschäft: Ideal für Unternehmer, die Tourismus-, ökologische oder sogar technologische Projekte in einer der weltweit begehrtesten Regionen entwickeln möchten.
- Gewährleistung von Wertsteigerung: Die Immobilientrends in Tulum steigen Jahr für Jahr weiter.
- Nachhaltigkeit und Technologie: Kombiniert die natürliche Magie Mexikos mit innovativen Tools.
Mehrsprachige Kommunikation
Wir bieten die Möglichkeit an, uns in Spanisch, Deutsch und Englisch zu kommunizieren, was die Interaktion mit Investoren aus aller Welt erleichtert.
Zögert nicht, euch zu melden, wenn ihr Visionäre seid, die neue Wege zur Immobilieninvestition mit Bitcoin erforschen möchten. Wir freuen uns darauf, mit euch zusammenzuarbeiten und gemeinsam eine erfolgreiche Zukunft aufzubauen.
Kontakt: Schreibt uns einfach. Wir werden alle eure Fragen detailliert und enthusiastisch beantworten. Zusammen können wir diese Immobilie in ein außergewöhnliches Projekt verwandeln!
TulumImmobilien #BitcoinFreundlich #NachhaltigesLeben #InvestiereInTulum #RustikalerCharme #ImmobilieZuVerkaufen #DezentralisierteFinanzen #TulumTräume
-
 @ a95c6243:d345522c
2025-01-03 20:26:47
@ a95c6243:d345522c
2025-01-03 20:26:47Was du bist hängt von drei Faktoren ab: \ Was du geerbt hast, \ was deine Umgebung aus dir machte \ und was du in freier Wahl \ aus deiner Umgebung und deinem Erbe gemacht hast. \ Aldous Huxley
Das brave Mitmachen und Mitlaufen in einem vorgegebenen, recht engen Rahmen ist gewiss nicht neu, hat aber gerade wieder mal Konjunktur. Dies kann man deutlich beobachten, eigentlich egal, in welchem gesellschaftlichen Bereich man sich umschaut. Individualität ist nur soweit angesagt, wie sie in ein bestimmtes Schema von «Diversität» passt, und Freiheit verkommt zur Worthülse – nicht erst durch ein gewisses Buch einer gewissen ehemaligen Regierungschefin.
Erklärungsansätze für solche Entwicklungen sind bekannt, und praktisch alle haben etwas mit Massenpsychologie zu tun. Der Herdentrieb, also der Trieb der Menschen, sich – zum Beispiel aus Unsicherheit oder Bequemlichkeit – lieber der Masse anzuschließen als selbstständig zu denken und zu handeln, ist einer der Erklärungsversuche. Andere drehen sich um Macht, Propaganda, Druck und Angst, also den gezielten Einsatz psychologischer Herrschaftsinstrumente.
Aber wollen die Menschen überhaupt Freiheit? Durch Gespräche im privaten Umfeld bin ich diesbezüglich in der letzten Zeit etwas skeptisch geworden. Um die Jahreswende philosophiert man ja gerne ein wenig über das Erlebte und über die Erwartungen für die Zukunft. Dabei hatte ich hin und wieder den Eindruck, die totalitären Anwandlungen unserer «Repräsentanten» kämen manchen Leuten gerade recht.
«Desinformation» ist so ein brisantes Thema. Davor müsse man die Menschen doch schützen, hörte ich. Jemand müsse doch zum Beispiel diese ganzen merkwürdigen Inhalte in den Social Media filtern – zur Ukraine, zum Klima, zu Gesundheitsthemen oder zur Migration. Viele wüssten ja gar nicht einzuschätzen, was richtig und was falsch ist, sie bräuchten eine Führung.
Freiheit bedingt Eigenverantwortung, ohne Zweifel. Eventuell ist es einigen tatsächlich zu anspruchsvoll, die Verantwortung für das eigene Tun und Lassen zu übernehmen. Oder die persönliche Freiheit wird nicht als ausreichend wertvolles Gut angesehen, um sich dafür anzustrengen. In dem Fall wäre die mangelnde Selbstbestimmung wohl das kleinere Übel. Allerdings fehlt dann gemäß Aldous Huxley ein Teil der Persönlichkeit. Letztlich ist natürlich alles eine Frage der Abwägung.
Sind viele Menschen möglicherweise schon so «eingenordet», dass freiheitliche Ambitionen gar nicht für eine ganze Gruppe, ein Kollektiv, verfolgt werden können? Solche Gedanken kamen mir auch, als ich mir kürzlich diverse Talks beim viertägigen Hacker-Kongress des Chaos Computer Clubs (38C3) anschaute. Ich war nicht nur überrascht, sondern reichlich erschreckt angesichts der in weiten Teilen mainstream-geformten Inhalte, mit denen ein dankbares Publikum beglückt wurde. Wo ich allgemein hellere Köpfe erwartet hatte, fand ich Konformismus und enthusiastisch untermauerte Narrative.
Gibt es vielleicht so etwas wie eine Herdenimmunität gegen Indoktrination? Ich denke, ja, zumindest eine gestärkte Widerstandsfähigkeit. Was wir brauchen, sind etwas gesunder Menschenverstand, offene Informationskanäle und der Mut, sich freier auch zwischen den Herden zu bewegen. Sie tun das bereits, aber sagen Sie es auch dieses Jahr ruhig weiter.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-01-01 17:39:51
@ a95c6243:d345522c
2025-01-01 17:39:51Heute möchte ich ein Gedicht mit euch teilen. Es handelt sich um eine Ballade des österreichischen Lyrikers Johann Gabriel Seidl aus dem 19. Jahrhundert. Mir sind diese Worte fest in Erinnerung, da meine Mutter sie perfekt rezitieren konnte, auch als die Kräfte schon langsam schwanden.
Dem originalen Titel «Die Uhr» habe ich für mich immer das Wort «innere» hinzugefügt. Denn der Zeitmesser – hier vermutliche eine Taschenuhr – symbolisiert zwar in dem Kontext das damalige Zeitempfinden und die Umbrüche durch die industrielle Revolution, sozusagen den Zeitgeist und das moderne Leben. Aber der Autor setzt sich philosophisch mit der Zeit auseinander und gibt seinem Werk auch eine klar spirituelle Dimension.
Das Ticken der Uhr und die Momente des Glücks und der Trauer stehen sinnbildlich für das unaufhaltsame Fortschreiten und die Vergänglichkeit des Lebens. Insofern könnte man bei der Uhr auch an eine Sonnenuhr denken. Der Rhythmus der Ereignisse passt uns vielleicht nicht immer in den Kram.
Was den Takt pocht, ist durchaus auch das Herz, unser «inneres Uhrwerk». Wenn dieses Meisterwerk einmal stillsteht, ist es unweigerlich um uns geschehen. Hoffentlich können wir dann dankbar sagen: «Ich habe mein Bestes gegeben.»
Ich trage, wo ich gehe, stets eine Uhr bei mir; \ Wieviel es geschlagen habe, genau seh ich an ihr. \ Es ist ein großer Meister, der künstlich ihr Werk gefügt, \ Wenngleich ihr Gang nicht immer dem törichten Wunsche genügt.
Ich wollte, sie wäre rascher gegangen an manchem Tag; \ Ich wollte, sie hätte manchmal verzögert den raschen Schlag. \ In meinen Leiden und Freuden, in Sturm und in der Ruh, \ Was immer geschah im Leben, sie pochte den Takt dazu.
Sie schlug am Sarge des Vaters, sie schlug an des Freundes Bahr, \ Sie schlug am Morgen der Liebe, sie schlug am Traualtar. \ Sie schlug an der Wiege des Kindes, sie schlägt, will's Gott, noch oft, \ Wenn bessere Tage kommen, wie meine Seele es hofft.
Und ward sie auch einmal träger, und drohte zu stocken ihr Lauf, \ So zog der Meister immer großmütig sie wieder auf. \ Doch stände sie einmal stille, dann wär's um sie geschehn, \ Kein andrer, als der sie fügte, bringt die Zerstörte zum Gehn.
Dann müßt ich zum Meister wandern, der wohnt am Ende wohl weit, \ Wohl draußen, jenseits der Erde, wohl dort in der Ewigkeit! \ Dann gäb ich sie ihm zurücke mit dankbar kindlichem Flehn: \ Sieh, Herr, ich hab nichts verdorben, sie blieb von selber stehn.
Johann Gabriel Seidl (1804-1875)
-
 @ a95c6243:d345522c
2024-12-21 09:54:49
@ a95c6243:d345522c
2024-12-21 09:54:49Falls du beim Lesen des Titels dieses Newsletters unwillkürlich an positive Neuigkeiten aus dem globalen polit-medialen Irrenhaus oder gar aus dem wirtschaftlichen Umfeld gedacht hast, darf ich dich beglückwünschen. Diese Assoziation ist sehr löblich, denn sie weist dich als unverbesserlichen Optimisten aus. Leider muss ich dich diesbezüglich aber enttäuschen. Es geht hier um ein anderes Thema, allerdings sehr wohl ein positives, wie ich finde.
Heute ist ein ganz besonderer Tag: die Wintersonnenwende. Genau gesagt hat heute morgen um 10:20 Uhr Mitteleuropäischer Zeit (MEZ) auf der Nordhalbkugel unseres Planeten der astronomische Winter begonnen. Was daran so außergewöhnlich ist? Der kürzeste Tag des Jahres war gestern, seit heute werden die Tage bereits wieder länger! Wir werden also jetzt jeden Tag ein wenig mehr Licht haben.
Für mich ist dieses Ereignis immer wieder etwas kurios: Es beginnt der Winter, aber die Tage werden länger. Das erscheint mir zunächst wie ein Widerspruch, denn meine spontanen Assoziationen zum Winter sind doch eher Kälte und Dunkelheit, relativ zumindest. Umso erfreulicher ist der emotionale Effekt, wenn dann langsam die Erkenntnis durchsickert: Ab jetzt wird es schon wieder heller!
Natürlich ist es kalt im Winter, mancherorts mehr als anderswo. Vielleicht jedoch nicht mehr lange, wenn man den Klimahysterikern glauben wollte. Mindestens letztes Jahr hat Väterchen Frost allerdings gleich zu Beginn seiner Saison – und passenderweise während des globalen Überhitzungsgipfels in Dubai – nochmal richtig mit der Faust auf den Tisch gehauen. Schnee- und Eischaos sind ja eigentlich in der Agenda bereits nicht mehr vorgesehen. Deswegen war man in Deutschland vermutlich in vorauseilendem Gehorsam schon nicht mehr darauf vorbereitet und wurde glatt lahmgelegt.
Aber ich schweife ab. Die Aussicht auf nach und nach mehr Licht und damit auch Wärme stimmt mich froh. Den Zusammenhang zwischen beidem merkt man in Andalusien sehr deutlich. Hier, wo die Häuser im Winter arg auskühlen, geht man zum Aufwärmen raus auf die Straße oder auf den Balkon. Die Sonne hat auch im Winter eine erfreuliche Kraft. Und da ist jede Minute Gold wert.
Außerdem ist mir vor Jahren so richtig klar geworden, warum mir das südliche Klima so sehr gefällt. Das liegt nämlich nicht nur an der Sonne als solcher, oder der Wärme – das liegt vor allem am Licht. Ohne Licht keine Farben, das ist der ebenso simple wie gewaltige Unterschied zwischen einem deprimierenden matschgraubraunen Winter und einem fröhlichen bunten. Ein großes Stück Lebensqualität.
Mir gefällt aber auch die Symbolik dieses Tages: Licht aus der Dunkelheit, ein Wendepunkt, ein Neuanfang, neue Möglichkeiten, Übergang zu neuer Aktivität. In der winterlichen Stille keimt bereits neue Lebendigkeit. Und zwar in einem Zyklus, das wird immer wieder so geschehen. Ich nehme das gern als ein Stück Motivation, es macht mir Hoffnung und gibt mir Energie.

Übrigens ist parallel am heutigen Tag auf der südlichen Halbkugel Sommeranfang. Genau im entgegengesetzten Rhythmus, sich ergänzend, wie Yin und Yang. Das alles liegt an der Schrägstellung der Erdachse, die ist nämlich um 23,4º zur Umlaufbahn um die Sonne geneigt. Wir erinnern uns, gell?
Insofern bleibt eindeutig festzuhalten, dass “schräg sein” ein willkommener, wichtiger und positiver Wert ist. Mit anderen Worten: auch ungewöhnlich, eigenartig, untypisch, wunderlich, kauzig, … ja sogar irre, spinnert oder gar “quer” ist in Ordnung. Das schließt das Denken mit ein.
In diesem Sinne wünsche ich euch allen urige Weihnachtstage!
Dieser Beitrag ist letztes Jahr in meiner Denkbar erschienen.
-
 @ 5d4b6c8d:8a1c1ee3
2025-02-27 17:41:24
@ 5d4b6c8d:8a1c1ee3
2025-02-27 17:41:24Here are today's picks using my proprietary betting strategy at Freebitcoin. For details about what Risk Balanced Odds Arbitrage is and why it works see https://stacker.news/items/342765/r/Undisciplined.
There were so many today, that I abandoned the markdown table. I recommend skipping the ones that are taking place within a week (the early bonus isn't great for those).
originally posted at https://stacker.news/items/898935
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ 2efaa715:3d987331
2025-02-27 16:07:36
@ 2efaa715:3d987331
2025-02-27 16:07:36Cost of a 1960s Diet vs Modern Food Costs by Decade
The following is a result from ChatGPT's "deep research" feature when asked to analyze what a "1960s diet" would cost in each subsequent decade. The CPI and basket of goods is constantly adjusted to "reflect consumer purchasing behavior", but this metric overlooks the fact that consumer behavior itself is guided by prices. Just because someone does buy something doesn't mean they would prefer this good over another (potentially superior) good, all it tells you is that they did buy it. When the cost of living off of higher quality foods becomes too great to bear, consumers will trade-down to lower-quality foods. When the CPI reflects this, even a "steady inflation number" hides the fact that quality of life has degraded.
If you don't want to read the whole thing, at least check out the conclusion at the end. Everything from here down was generated by the AI after rounds of nudging by me.
Also the cover image, obviously (lol)Following a 1960s-style diet – rich in red meat, dairy, and unprocessed “whole” foods – has become increasingly expensive over time. Below we examine each decade from 1960 to the present, tracking how much the cost of that fixed 1960s diet rose and comparing it to the prevailing food costs (CPI) shaped by consumers adapting their eating habits. Key staples like red meat, dairy, grains, and processed foods are highlighted to show the impact of inflation on a traditional diet versus switching to cheaper substitutes.
1960s: Baseline of Affordable Abundance
- Percentage Increase in Cost: Food prices rose modestly in the 1960s (around 2–3% per year). Over the decade, maintaining the same 1960 basket led to roughly a 25–30% increase in cost (Food at home price inflation, 1947→2024). This was a relatively small jump compared to later decades.
- Cost in Era’s Currency: For example, if a household spent $100 per week in 1960 on the typical foods (plentiful beef, whole milk, butter, eggs, etc.), by 1970 that same diet cost about $125–$130 in nominal dollars. Everyday items were cheap: ground beef was only $0.30 per lb in the late 1950s, and butter about $0.75 per lb (Grocery Store Prices for 14 Items in 1957 | HowStuffWorks) (Grocery Store Prices for 14 Items in 1957 | HowStuffWorks). Americans could afford more of these foods as incomes grew.
- Comparison to CPI (Behavior-Adjusted): The official food Consumer Price Index (CPI) climbed at a similar pace (~28% increase from 1960 to 1970 (Food at home price inflation, 1947→2024)), since consumer behavior hadn’t drastically shifted yet. Few felt pressure to substitute cheaper foods because inflation was mild. In fact, many families ate more of these staples as prosperity rose – U.S. beef consumption per person increased from ~63 lbs in 1960 to 84 lbs by 1970, while chicken rose from 28 to 48 lbs (National Chicken Council | Per Capita Consumption of Poultry and Livestock, 1965 to Forecast 2022, in Pounds). Any cost savings from “behavior changes” were minimal in the 60s. (One early example: margarine was already replacing some butter for health/cost reasons, but butter was still affordable in 1960 at ~$0.75, so sticking to butter didn’t break the bank (Grocery Store Prices for 14 Items in 1957 | HowStuffWorks).) Overall, adapting one’s diet wasn’t necessary for budget reasons in the 1960s, as food was relatively cheap and inflation low.
1970s: Soaring Prices Hit Traditional Diets Hard
- Percentage Increase in Cost: The 1970s brought surging food inflation. A fixed 1960s-style diet would cost roughly double (+100% or more) by the end of the decade. In particular, meat and dairy prices skyrocketed. Beef prices roughly doubled from 1970 to 1980 (the BLS beef index jumped from the 40s to nearly 100 (Beef and veal price inflation, 1935→2025)), contributing to an overall ~120% increase in the cost of a meat-heavy 1960s basket during the 70s. By comparison, overall food-at-home prices rose about 121% in that span (Food at home price inflation, 1947→2024) – a huge jump in itself. The worst spikes came in 1973–74, when food prices jumped 15–16% in a single year (Food at home price inflation, 1947→2024).
- Cost in Era’s Currency: Someone stubbornly sticking to their 1960 grocery list in this era paid a steep price. If they spent $100 per week in 1970, by 1980 they’d need to spend roughly $220–$230 for the same items. For instance, mid-decade a pound of steak that cost ~$1 in the late 60s might cost $2–3 by the late 70s. Whole milk prices also roughly doubled in the 70s (Fresh whole milk price inflation, 1939→2024). This era’s inflation was so severe that it forced a re-budgeting for those insisting on expensive staples.
- Comparison to CPI (Behavior-Adjusted): While all consumers felt the 70s price shock, those who adapted their diets mitigated the impact. Many Americans reacted by buying less red meat or switching to cheaper proteins. Notably, when beef became very expensive (meat prices jumped 5.4% in just one month in early 1973 (1973 meat boycott - Wikipedia)), consumers staged a “meat boycott” and turned to poultry, pork, or beans. Poultry was a big winner – chicken prices did rise (44% in 1973 (Fresh whole chicken price inflation, 1935→2024)), but over the decade chicken remained cheaper per pound than beef, and per capita chicken consumption climbed while beef consumption dropped (National Chicken Council | Per Capita Consumption of Poultry and Livestock, 1965 to Forecast 2022, in Pounds). Processed and shelf-stable foods also gained favor as thrifty alternatives; for example, consumers might buy canned soups or powdered drink mixes which had smaller price increases. The official CPI (which reflects some substitution) still rose dramatically (~105% for food in the 70s (Food at home price inflation, 1947→2024)), but the true cost of living was a bit lower for those who adapted. By cutting back on expensive items (or stretching them – e.g. more casseroles with grains/veggies and less meat), families could keep their food spending increase somewhat below the headline inflation. In short, a person clinging to the high-red-meat, butter-on-everything diet of 1960 ended up paying much more in the 70s, whereas those who embraced cheaper substitutes (chicken instead of steak, margarine instead of butter, generic and processed foods) softened the blow. The late 1970s also saw food costs stabilize under price controls, rewarding those who diversified their diet away from the costliest staples.
(Chicken leads U.S. per person availability of meat over last decade | Economic Research Service) Per capita availability of meat in the U.S., 1910–2021. Beef (gray line) peaked in the 1970s and then declined as prices rose and consumers ate more chicken (yellow line). Chicken overtook beef as the most consumed meat by 2010, thanks to its lower cost and dietary shifts (Chicken leads U.S. per person availability of meat over last decade | Economic Research Service). Pork (red) held roughly steady, while fish (purple) remained a small share. This illustrates how Americans adjusted their protein sources over decades in response to price and preferences. (Chicken leads U.S. per person availability of meat over last decade | Economic Research Service)
1980s: Slowing Inflation and New Dietary Habits
- Percentage Increase in Cost: Inflation cooled in the 1980s, making food prices more stable. Even so, a fixed 1960s diet saw about a 50% cost increase over the decade. That means the same basket that cost $100 in 1980 would cost around $150 by 1990. This increase was much lower than the 70s, but still notable. Meats and dairy had smaller price jumps now (beef rose ~38% from 1980–90, milk ~45% (Fresh whole milk price inflation, 1939→2024)), and overall food-at-home prices climbed ~40–50% (Food at home price inflation, 1947→2024) (Food at home price inflation, 1947→2024) in the 80s.
- Cost in Era’s Currency: If our traditional-diet shopper spent $220/week in 1980 (continuing the prior example), by 1990 they’d be spending roughly $330 for the same groceries. For instance, a gallon of whole milk that cost about $1.50 in 1980 might be ~$2.20 by 1990; a pound of ground beef around $1.20 in 1980 could be ~$1.75 in 1990. These nominal increases were easier to manage than the wild 70s, but still added up.
- Comparison to CPI (Behavior-Adjusted): In the 80s, consumer behavior had permanently shifted due to the prior decade’s lessons. Many households continued to favor cheaper or leaner foods, and this helped keep their actual cost of living lower than if they had stuck to the old diet. For example, butter consumption plunged (per capita fell from 7.5 lbs in 1960 to ~4.5 lbs by 1980) as people used margarine and processed spreads instead (cameracopy4.qxd). Butter lost its hefty weight in the price index, reflecting how few people still bought it regularly by the 80s. Similarly, beef was no longer king – Americans were eating 20% less beef than in the 70s, and far more chicken, which was mass-produced cheaply (Chicken leads U.S. per person availability of meat over last decade | Economic Research Service). The CPI’s market basket was updated in 1987, locking in these new habits (more poultry and convenience foods, fewer expensive staples). As a result, official food inflation in the 80s was moderate, and those who already had adapted their diet felt roughly the same ~50% rise as the CPI. However, someone who refused to change – still buying large quantities of red meat, whole milk, fresh butter, etc. – would have spent more than the average person. They missed out on the savings from things like economy cuts of meat, bulk grains, and processed goods that became popular. By the late 1980s, the U.S. food system was delivering cheaper calories (e.g. refined grains, corn oil, sweeteners) on a huge scale. Families that incorporated these cheaper ingredients (think Hamburger Helper, microwave dinners, soda instead of milk) kept their grocery bills lower. Indeed, food became a smaller share of household spending: it fell from 28.5% of the family budget in 1960 to about 17% by 1980 (cameracopy4.qxd), a testament to how adapting food choices and benefitting from cheaper options lowered the relative cost of living.
1990s: Cheaper Alternatives in an Era of Low Inflation
- Percentage Increase in Cost: The 1990s saw very low food inflation by historical standards. Maintaining the exact 1960s diet through this decade would raise costs by only about 25–30%. Food-at-home prices increased roughly 2–3% per year or ~27% total from 1990 to 2000 (Food at home price inflation, 1947→2024) (Food at home price inflation, 1947→2024) – similar to general inflation.
- Cost in Era’s Currency: Continuing our scenario, $330/week in 1990 for a 1960-style diet would become about $420–$430/week by 2000. Many staple food prices barely crept up. For example, a loaf of bread or a dozen eggs only rose by a few dimes over the whole decade. In some cases prices even stagnated or fell: U.S. farm commodities were abundant (grain surpluses kept costs of cereal, flour, and animal feed low). The late 90s had such cheap raw ingredients that milk, meat, and sugar prices were relatively stable.
- Comparison to CPI (Behavior-Adjusted): By the 90s, behavior-adjusted costs were markedly lower than our fixed diet scenario, because consumers had spent two decades optimizing their food spending. The prevailing diet in the 90s was very different from the 60s, driven by cost efficiency and convenience. Shoppers embraced warehouse clubs and discount supermarkets, bought private-label/store brands, and leaned heavily on processed foods that benefited from cheap oil and corn. For instance, instead of whole fresh foods for every meal, families might use instant pasta mixes, boxed cereals, and soft drinks – items produced at scale and often cheaper per calorie. This kept average grocery bills lower. In fact, the cost of living for food rose so slowly in the 90s that it was common to “trade up” some items (like occasionally buying steak or exotic fruits) and still stay on budget. A person strictly sticking to a 1960s whole-food diet (cooking from scratch, lots of fresh meat and dairy) would not enjoy those processed-food savings. By this time they’d be paying noticeably more than the average consumer for the same caloric intake. Studies began to note a troubling pattern: healthier whole foods were getting relatively more expensive, while unhealthy processed options remained very cheap. (For example, fresh produce prices in the U.S. rose faster than soda and snack prices in the 80s/90s.) The overall CPI for food was low in the 90s, reflecting these substitutions. A clear sign of the era: fast-food value meals and junk snacks proliferated, offering calories at rock-bottom prices. Those who adapted their diet to include these inexpensive foods saw a much lower increase in their cost of living – and in some cases, food spending as a share of income hit record lows. Meanwhile, someone clinging to only unprocessed “old-fashioned” foods would have a higher grocery bill and experienced a higher effective inflation than the behavior-adjusted CPI. In short, the 1990s made it easier than ever to save money on food – if you were willing to eat like a 1990s consumer.
2000s: Diverging Diet Costs – Whole Foods vs Processed
- Percentage Increase in Cost: Food costs in the 2000s rose at a modest pace, very similar to the 90s. A fixed 1960s diet would increase about 25–30% in cost over the decade (roughly keeping up with general inflation). From 2000 to 2010 the food-at-home CPI climbed ~29% (Food at home price inflation, 1947→2024) (Food at home price inflation, 1947→2024). There were a couple of price spikes mid-decade (e.g. 2007–2008 saw grain and dairy price jumps), but also some years of minimal change.
- Cost in Era’s Currency: Our hypothetical shopper spending $420 in 2000 would be around $540 per week by 2010 for the same basket. Key 1960s staples did get pricier in the 2000s: e.g. whole milk went from about $2.80/gal in 2000 to $3.50+ by 2010; ground beef from ~$1.80 to ~$2.25/lb over the decade. But the increases were gradual. Notably, by 2010 many traditional items (meats, eggs, dairy) were cheaper in real terms than in the 1970s – thanks to efficiency gains – even if nominal prices edged up.
- Comparison to CPI (Behavior-Adjusted): The 2000s is when the gap between a “traditional whole-food diet” and the average diet’s cost really started to widen. The official CPI remained fairly low, in part because consumers kept shifting towards cheaper ingredients and prepared foods. Two diverging trends emerged:
- Many consumers, facing tight budgets especially after the 2008 recession, doubled down on low-cost, energy-dense foods. This meant more refined grains (white bread, pasta, rice), processed snacks, sweetened drinks, and fatty meats – all of which were inexpensive and often on promotion. These items benefited from globalized supply chains and agricultural surpluses, keeping their prices down or rising very slowly. For example, corn-based sweeteners and oils were so cheap that soda and fried foods remained very affordable in the 2000s.
- On the other hand, some consumers began seeking healthier “whole” foods (organic produce, whole grains, lean meats). But these often came at a premium and saw higher inflation. Someone maintaining a 1960s-style home-cooked diet (lots of fresh ingredients) fell into this category almost by definition. They would have experienced higher effective inflation than the average. Research confirms this divergence: in recent analyses, the cost of a healthy recommended diet has risen faster than the cost of an unhealthy diet. For instance, during 2019–2022, prices of healthy foods (fruits, veggies, lean proteins, etc.) jumped 12.8% in one year, whereas “unhealthy” food prices rose only 7–9% ( Healthy Food Prices Increased More Than the Prices of Unhealthy Options during the COVID-19 Pandemic and Concurrent Challenges to the Food System - PMC ). This pattern had been building over the 2000s. Thus, those who adapted by buying the cheapest processed options saw a smaller cost-of-living increase than those buying whole foods. By the end of the 2000s, the U.S. was in a situation where following a 1960s diet cost significantly more than an average 2000s diet, even though overall inflation was mild. In practical terms, a family could slash their grocery bill by switching from fresh-cooked dinners with milk to, say, boxed mac-and-cheese with soda – and many did. The CPI implicitly captured this shift: food remained about ~13% of consumer spending in the 2000s (near historic lows), partly because people found ever-cheaper ways to eat.
2010s: Relative Stability (Until a Shock)
- Percentage Increase in Cost: The 2010s were a decade of exceptionally low food inflation. A fixed 1960s diet’s cost rose only about 15–20% in total through 2010–2019. For most of those years, food prices grew less than 2% annually (some years even saw slight deflation in grocery prices (Food at home price inflation, 1947→2024)). From 2010 to 2020 the food-at-home index went up about 16% (Food at home price inflation, 1947→2024) (Food at home price inflation, 1947→2024) – the slowest growth of any decade in this analysis.
- Cost in Era’s Currency: In our running example, $540/week in 2010 for the old-fashioned diet would become roughly $620–$630 by 2020. In other words, nearly flat in real terms. Many staple food prices were remarkably steady. A gallon of whole milk hovered around $3.50–$4 throughout the decade; a pound of chicken breasts stayed near $1.99 for years. The shale oil boom and low energy costs, plus technological advances in agriculture, helped keep food production and transportation cheap. By the late 2010s, Americans enjoyed some of the lowest food inflation on record.
- Comparison to CPI (Behavior-Adjusted): With inflation so low, the difference between sticking to a 1960s diet and the average diet’s cost was less pronounced during this decade – everyone benefited from stable prices. However, it’s important to note that by the 2010s the average diet was very far removed from the 1960s diet, largely for economic reasons built up over prior decades. The average American in 2019 was consuming lots of inexpensive processed foods and far less of the pricey whole foods that defined 1960. This meant their cost of living was inherently lower. For those still following a traditional diet, their basket cost hadn’t risen much in the 2010s, but it was starting from a much higher base relative to typical consumers. In effect, the “gap” was already baked in. Government data continued to show that healthy food plans cost more – a trend consistent with the idea that a whole-food diet remained pricier than the mix of convenience foods most people bought. By the end of the 2010s, food was only about 12–13% of household expenditures on average, reflecting decades of substitutions and cheaper alternatives keeping costs down (cameracopy4.qxd). A person eating like it’s 1960 (lots of red meat roasts, fresh veggies, whole milk) in 2019 would likely be spending well above that share. In summary, the 2010s offered a breather: low inflation meant even “old diet” holdouts weren’t punished by price hikes, but they were still paying more than those who had long ago adapted to the economical 2010s food landscape.
(Note: The early 2020s have seen a sharp inflationary spike for food, largely due to pandemic disruptions and war. Interestingly, this spike hit fresh foods and meats harder than processed foods, echoing the long-term pattern. For example, in one study the cost of a healthy diet rose 17.9% from 2019–2022, whereas the typical less-healthy diet rose 9% ( Healthy Food Prices Increased More Than the Prices of Unhealthy Options during the COVID-19 Pandemic and Concurrent Challenges to the Food System - PMC ). This underscores that when inflation strikes, sticking to a traditional wholesome diet tends to cost more than making do with cheaper substitutes. As of 2022–2023, consumers again coped by buying store brands, cutting meat consumption, etc., to soften the blow – much as they did in the 1970s.)
Conclusion: Traditional Diet vs Adaptive Diet – Which Costs More?
Over six decades, inflation has raised all food prices, but not uniformly. Someone maintaining a fixed 1960s-style diet from 1960 through today would have seen their food costs rise far more than the official “cost of food” suggests – because the official index assumes people adjust their buying. In fact, by 2020 such a person would be spending roughly 8–10 times what they spent in 1960 on food in nominal dollars, whereas the behavior-adjusted CPI for food rose about 8-fold (Beef and veal price inflation, 1935→2025) (Fresh whole chicken price inflation, 1935→2024). That implies perhaps a 20–25% higher cumulative cost for the fixed diet follower. The biggest contributors were red meat and dairy: these had higher-than-average inflation over the long run. For example, beef prices rose much faster than overall prices (3,637% since 1935) (Beef and veal price inflation, 1935→2025), while chicken (a cheaper substitute) had lower inflation (805% since 1935) (Fresh whole chicken price inflation, 1935→2024). Consumers responded accordingly – eating less beef and butter, and more chicken and margarine, as decades passed. Grains and processed foods, often mass-produced from low-cost commodities, helped keep modern diets affordable; whole foods did not see such dramatic cost efficiencies.
In each decade, those who adapted their food choices enjoyed a lower cost of living increase than those who stuck with the old-school diet. The 1970s illustrated this vividly (households that substituted chicken or pasta when steak prices spiked avoided some of the worst budget pain). By the 2000s and 2010s, the typical American diet was heavily “behavior-adjusted” for cost – full of cheaper oils, sweeteners, and protein sources – which kept the CPI food inflation relatively low. Meanwhile, a person trying to eat like it’s 1960 (lots of red meat, whole milk, homemade meals) ended up paying a premium each year to do so.
In summary, inflation heavily penalized the maintenance of a 1960s diet. Each decade saw that fixed basket get relatively more expensive, especially for categories like red meat and dairy. In contrast, Americans who embraced cheaper substitutes and new foods managed to keep their food spending growth below the inflation that a “fixed basket” would imply. This behavior-adjustment – switching from costly whole foods to economical processed and alternative foods – has been a key reason the reported CPI for food rose more slowly. It quantifies how much lower the cost of living was for those who adapted: often shaving several percentage points off per-year inflation, and cumulatively making food far more affordable than it would have been under the old diet. The trade-off, of course, is that while the traditional 1960s diet was nutritious but now expensive, the modern adapted diet is cheaper but often less healthy. Consumers effectively used substitutions to counteract food inflation, saving money at the expense of dietary changes. The decades-long outcome is clear – financially, eating in 2023 like it’s 1963 will cost you significantly more than eating like a 2023 consumer, due to the compounding effect of differential inflation and behavior shifts over time.
Other Sources:
- U.S. Bureau of Labor Statistics – Historical CPI data for food categories (Food at home price inflation, 1947→2024) (Beef and veal price inflation, 1935→2025)
- USDA Economic Research Service – Food price reports and consumption trends (Chicken leads U.S. per person availability of meat over last decade | Economic Research Service) (cameracopy4.qxd)
- The Value of a Dollar – mid-20th-century grocery prices (e.g. 1957 butter, beef) (Grocery Store Prices for 14 Items in 1957 | HowStuffWorks) (Grocery Store Prices for 14 Items in 1957 | HowStuffWorks)
- Congressional Research Service – Food inflation and consumer responses (1973 meat boycott - Wikipedia)
- Academic study on healthy vs unhealthy diet cost inflation - (pmc.ncbi.nlm.nih.gov)
-
 @ a95c6243:d345522c
2024-12-13 19:30:32
@ a95c6243:d345522c
2024-12-13 19:30:32Das Betriebsklima ist das einzige Klima, \ das du selbst bestimmen kannst. \ Anonym
Eine Strategie zur Anpassung an den Klimawandel hat das deutsche Bundeskabinett diese Woche beschlossen. Da «Wetterextreme wie die immer häufiger auftretenden Hitzewellen und Starkregenereignisse» oft desaströse Auswirkungen auf Mensch und Umwelt hätten, werde eine Anpassung an die Folgen des Klimawandels immer wichtiger. «Klimaanpassungsstrategie» nennt die Regierung das.
Für die «Vorsorge vor Klimafolgen» habe man nun erstmals klare Ziele und messbare Kennzahlen festgelegt. So sei der Erfolg überprüfbar, und das solle zu einer schnelleren Bewältigung der Folgen führen. Dass sich hinter dem Begriff Klimafolgen nicht Folgen des Klimas, sondern wohl «Folgen der globalen Erwärmung» verbergen, erklärt den Interessierten die Wikipedia. Dabei ist das mit der Erwärmung ja bekanntermaßen so eine Sache.
Die Zunahme schwerer Unwetterereignisse habe gezeigt, so das Ministerium, wie wichtig eine frühzeitige und effektive Warnung der Bevölkerung sei. Daher solle es eine deutliche Anhebung der Nutzerzahlen der sogenannten Nina-Warn-App geben.
Die ARD spurt wie gewohnt und setzt die Botschaft zielsicher um. Der Artikel beginnt folgendermaßen:
«Die Flut im Ahrtal war ein Schock für das ganze Land. Um künftig besser gegen Extremwetter gewappnet zu sein, hat die Bundesregierung eine neue Strategie zur Klimaanpassung beschlossen. Die Warn-App Nina spielt eine zentrale Rolle. Der Bund will die Menschen in Deutschland besser vor Extremwetter-Ereignissen warnen und dafür die Reichweite der Warn-App Nina deutlich erhöhen.»
Die Kommunen würden bei ihren «Klimaanpassungsmaßnahmen» vom Zentrum KlimaAnpassung unterstützt, schreibt das Umweltministerium. Mit dessen Aufbau wurden das Deutsche Institut für Urbanistik gGmbH, welches sich stark für Smart City-Projekte engagiert, und die Adelphi Consult GmbH beauftragt.
Adelphi beschreibt sich selbst als «Europas führender Think-and-Do-Tank und eine unabhängige Beratung für Klima, Umwelt und Entwicklung». Sie seien «global vernetzte Strateg*innen und weltverbessernde Berater*innen» und als «Vorreiter der sozial-ökologischen Transformation» sei man mit dem Deutschen Nachhaltigkeitspreis ausgezeichnet worden, welcher sich an den Zielen der Agenda 2030 orientiere.
Über die Warn-App mit dem niedlichen Namen Nina, die möglichst jeder auf seinem Smartphone installieren soll, informiert das Bundesamt für Bevölkerungsschutz und Katastrophenhilfe (BBK). Gewarnt wird nicht nur vor Extrem-Wetterereignissen, sondern zum Beispiel auch vor Waffengewalt und Angriffen, Strom- und anderen Versorgungsausfällen oder Krankheitserregern. Wenn man die Kategorie Gefahreninformation wählt, erhält man eine Dosis von ungefähr zwei Benachrichtigungen pro Woche.
Beim BBK erfahren wir auch einiges über die empfohlenen Systemeinstellungen für Nina. Der Benutzer möge zum Beispiel den Zugriff auf die Standortdaten «immer zulassen», und zwar mit aktivierter Funktion «genauen Standort verwenden». Die Datennutzung solle unbeschränkt sein, auch im Hintergrund. Außerdem sei die uneingeschränkte Akkunutzung zu aktivieren, der Energiesparmodus auszuschalten und das Stoppen der App-Aktivität bei Nichtnutzung zu unterbinden.
Dass man so dramatische Ereignisse wie damals im Ahrtal auch anders bewerten kann als Regierungen und Systemmedien, hat meine Kollegin Wiltrud Schwetje anhand der Tragödie im spanischen Valencia gezeigt. Das Stichwort «Agenda 2030» taucht dabei in einem Kontext auf, der wenig mit Nachhaltigkeitspreisen zu tun hat.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 266815e0:6cd408a5
2025-02-21 17:54:15
@ 266815e0:6cd408a5
2025-02-21 17:54:15I've been working on the applesauce libraries for a while now but I think this release is the first one I would consider to be stable enough to use
A lot of the core concepts and classes are in place and stable enough where they wont change too much next release
If you want to skip straight to the documentation you can find at hzrd149.github.io/applesauce or the typescript docs at hzrd149.github.io/applesauce/typedoc
Whats new
Accounts
The
applesauce-accountspackage is an extension of theapplesauce-signerspackage and provides classes for building a multi-account system for clientsIts primary features are - Serialize and deserialize accounts so they can be saved in local storage or IndexededDB - Account manager for multiple accounts and switching between them - Account metadata for things like labels, app settings, etc - Support for NIP-46 Nostr connect accounts
see documentation for more examples
Nostr connect signer
The
NostrConnectSignerclass from theapplesauce-signerspackage is now in a stable state and has a few new features - Ability to createnostrconnect://URIs and waiting for the remote signer to connect - SDK agnostic way of subscribing and publishing to relaysFor a simple example, here is how to create a signer from a
bunker://URIjs const signer = await NostrConnectSigner.fromBunkerURI( "bunker://266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5?relay=wss://relay.nsec.app&secret=d9aa70", { permissions: NostrConnectSigner.buildSigningPermissions([0, 1, 3, 10002]), async onSubOpen(filters, relays, onEvent) { // manually open REQ }, async onSubClose() { // close previouse REQ }, async onPublishEvent(event, relays) { // Pubilsh an event to relays }, }, );see documentation for more examples and other signers
Event Factory
The
EventFactoryclass is probably what I'm most proud of. its a standalone class that can be used to create various types of events from templates (blueprints) and is really simple to useFor example: ```js import { EventFactory } from "applesauce-factory"; import { NoteBlueprint } from "applesauce-factory/blueprints";
const factory = new EventFactory({ // optionally pass a NIP-07 signer in to use for encryption / decryption signer: window.nostr });
// Create a kind 1 note with a hashtag let draft = await factory.create(NoteBlueprint, "hello world #grownostr"); // Sign the note so it can be published let signed = await window.nostr.signEvent(draft); ```
Its included in the
applesauce-factorypackage and can be used with any other nostr SDKs or vanilla javascriptIt also can be used to modify existing replaceable events
js let draft = await factory.modifyTags( // kind 10002 event mailboxes, // add outbox relays addOutboxRelay("wss://relay.io/"), addOutboxRelay("wss://nostr.wine/"), // remove inbox relay removeInboxRelay("wss://personal.old-relay.com/") );see documentation for more examples
Loaders
The
applesauce-loaderspackage exports a bunch of loader classes that can be used to load everything from replaceable events (profiles) to timelines and NIP-05 identitiesThey use rx-nostr under the hood to subscribe to relays, so for the time being they will not work with other nostr SDKs
I don't expect many other developers or apps to use them since in my experience every nostr client requires a slightly different way or loading events
They are stable enough to start using but they are not fully tested and they might change slightly in the future
The following is a short list of the loaders and what they can be used for -
ReplaceableLoaderloads any replaceable events (0, 3, 1xxxx, 3xxxx) -SingleEventLoaderloads single events based on ids -TimelineLoaderloads a timeline of events from multiple relays based on filters -TagValueLoaderloads events based on a tag name (like "e") and a value, can be used to load replies, zaps, reactions, etc -DnsIdentityLoaderloads NIP-05 identities and supports caching -UserSetsLoaderloads all lists events for userssee documentation for more examples
Real tests
For all new features and a lot of existing ones I'm trying to write tests to ensure I don't leave unexpected bugs for later
I'm not going to pretend its 100% tests coverage or that it will ever get close to that point, but these tests cover some of the core classes and help me prove that my code is doing what it says its supposed to do
At the moment there are about 230 tests covering 45 files. not much but its a start
Apps built using applesauce
If you want to see some examples of applesauce being used in a nostr client I've been testing a lot of this code in production on the apps I've built in the last few months
- noStrudel The main app everything is being built for and tested in
- nsite-manager Still a work-in-progress but supports multiple accounts thanks to the
applesauce-accountspackage - blossomservers.com A simple (and incomplete) nostr client for listing and reviewing public blossom servers
- libretranslate-dvm A libretranslate DVM for nostr:npub1mkvkflncllnvp3adq57klw3wge6k9llqa4r60g42ysp4yyultx6sykjgnu
- cherry-tree A chunked blob uploader / downloader. only uses applesauce for boilerplate
- nsite-homepage A simple landing page for nsite.lol
Thanks to nostr:npub1cesrkrcuelkxyhvupzm48e8hwn4005w0ya5jyvf9kh75mfegqx0q4kt37c for teaching me more about rxjs and consequentially making me re-write a lot of the core observables to be faster
-
 @ 889b19eb:ff45973f
2025-02-27 15:42:26
@ 889b19eb:ff45973f
2025-02-27 15:42:26A Bitcoin seed phrase, also known as a mnemonic phrase or recovery phrase, is a list of words which store all the information needed to recover your Bitcoin wallet. The seed phrase is effectively a master key to your wallet and having secure backups of your seed phrase ensures you don't lose your stack in the case of a hardware or software wallet failure. There are various physical backup mediums including steal plates and discs you can stamp your seed phrase onto but another option is to store your seed phrase securely in your head. This has the added benefit that it cant be stolen (at least at the time of writing), takes up no physical space and there is something rather cool about having your family wealth stored in your head.
A Mnemonic is simply a system such as a pattern of letters, ideas, or associations which assists in remembering something. This blog post describes two Mnemonic systems I use to remember my seed phrase as well as other lists and numbers. The Linking System
All mnemonics are based on some sort of linking system, the idea is to take the items you want to remember and create scenes and images that you can picture in your mind, this helps lock the information into long term memory. When thinking up these visualisations try to keep the following in mind:
- The picture should be vivid. Try and see the picture clearly and in focus, imagine yourself stumbling upon the scene or witnessing the events in first person. Let yourself emotionally engage with it for a moment. If the picture is amusing find it funny. If it’s disgusting, actually find it repulsive. focus on how each image makes you feel. Is it funny? Disgusting? Dangerous? Actually take some time to feel that emotion.
- The elements of each picture should interact. Picturing A and B stood next to each other won’t work. A could be made of B; or dancing with B; being inserted into B; or using b as some sort of implement.
- The picture should be unusual. If you are linking ‘man’ and ‘cup’, for example, don't use an image that is ordinary. ‘a man drinking from a cup’ for example is too normal. The picture will be more memorable if the man is trying to drink from a giant cup, or is sucking the cup into his face, or if there is a tiny man in a cup trying to get out before the tea gets poured in. Try and be creative and bizarre as possible in order to make a lasting impression.
If the above is starting to make you feel nervous, its actually very straight forward and doesn't require much practice or creative genius. You will be surprised how quickly you can pick this up and how images will just be effortless conjured up to promptly land at a particular word or task you want to remember.
The following example was taken from Derren Brown's fascinating book Tricks of the Mind which first introduced me to these techniques. After reading the next section of this post you will be able to recall the following seemingly randomly words in perfect order and even in reverse. You will likely still be able to recall them weeks later.
Telephone Sausage Monkey Button Book Cabbage Glass Mouse Stomach Cardboard Ferry Christmas Athlete Key Wigwam Baby Kiwi Bed Paintbrush WalnutBefore beginning try reading the above words and see how many you can remember, minimise the window and see how many you can type out or write down from memory. You might get half a dozen without any special techniques. Now take some time to read the following, remember to take note of how the images are making you feel and take your time, don't just skim read.
Telephone/Sausage: Trying to dial an old-fashioned phone using a flaccid, uncooked sausage. It feels revolting and cold to the fingers, and is utterly impractical to work the dial. I can maybe get the dial around a little way, but then it just purrs back into place.
Sausage/Monkey: Watching footage from a wildlife documentary of a monkey, in the jungle, cooking a sausage over a barbecue. These are rare monkeys, and this is the first time they have been filmed. Next to him he has a selection of dips.
Monkey/Button: You no longer have to spend valuable time doing up your own shirt buttons. You now have a trained monkey to do such things. You stand there in your socks and he does up all the buttons with his clever simian fingers.
Button/Book: It’s a book entirely about buttons, and in order to open it you have to unfasten a line of big colourful buttons down the side. Hugely impractical marketing gimmick. Makes opening it really irritating.
Book/Cabbage: Opening up a book to have a quiet lunchtime read, only to find that the cover and all the pages have leaves of rotten stinking cabbage stuck to them. The stench is terrible, and the pages are ruined. Someone has played a stupid joke on you, and now you’ve got fetid cabbage juice all over your fingers.
Cabbage/Glass: A beautiful but enormous cabbage, realistically created out of glass. The artist is proudly showing it off, flicking it with his fingers and making a ‘pinging’ sound. Everyone’s standing around with glasses of wine appreciating it. Personally you think it’s ridiculous and ugly.
Glass/Mouse: You go to drink a glass of wine, to find that the wine has gone and there’s a tiny mouse in the bottom of the glass. The mouse is clearly drunk, and is wearing a party hat with streamers over his shoulder. A party blow-out extends limply from his mouth, and he’s hiccuping bubbles, like a seventies cartoonist’s depiction of a drunkard.
Mouse/Stomach: Unfortunately I can think only of that urban myth unfairly surrounding Richard Gere some years ago. If you’re not familiar with it, then imagine your tummy full of squeaking mice, which then stream out of your navel like the rats out of Hamelin.
Stomach/Cardboard: A pregnant lady covering her stomach with cardboard from old boxes. Taping it around her, until she is enormous. Now she feels protected.
Cardboard/Ferry: Image of a big P&O ferry sinking in the sea because in a spectacularly misjudged move to save money, the entire boat was manufactured out of cardboard. People are escaping from dinghies, unaware that they are made not from rubber but from ordinary paper.
Ferry/Christmas: A little ferry sat on top of a Christmas tree, perhaps at a school for the hard of hearing. Little streamers, windows, everything. Tinsel around the hull.
Christmas/Athlete: It’s you and all the relations you normally spend Christmas with, running around a race-track in the snow with party hats and crackers trying to beat Kelly Holmes to the finish-line. Your nan is doing superbly, racing ahead in her coat, hat and bag, giving the double-gold winner a run for her money.
Athlete/Key: The winning athlete is given a four-foot-long golden key on a ribbon as a prize. She tries to hold it up for the audience as the National Anthem plays, but it’s extremely heavy, and she wishes she could have just had an ordinary medal.
Key/Wigwam: A key hangs unnoticed from the headgear of a Native American Indian who is unable to get into his wigwam to go to the loo. Hugely frustrating for him. You can picture him, all red-faced. See the key glinting in the light as he searches for it.
Wigwam/Baby: Latest New Age fad: put your baby to sleep every night in a wigwam. Dream-catcher included. Imagine a giant baby asleep inside, snoring, making the sides of the wigwam suck in and blow out.
Baby/Kiwi: A baby shoving green furry kiwi fruit into its mouth. One after another. A huge pile of them waiting to be eaten. Green kiwi juice all down its bib. Throwing up kiwi vomit. He loves kiwis, the little tinker.
Kiwi/Bed: Tucking up a little kiwi for the night in a big king-size bed. Pulling the covers almost over it, then sitting next to it and reading it a story about the Little Kiwi, until it falls asleep.
Bed/Paintbrush: You’ve changed your décor and the bed no longer matches. So rather than buy new covers, you paint them the same colour as the walls. Sloshing paint over the entire bed, watching it go hard and uncomfortable.
Paintbrush/Walnut: Not owning a nutcracker, you’re forced to try and smash open a great big walnut with the end of a paintbrush. Trouble is, you’re using the brush end, which isn’t working, and there’s paint splashing everywhere. It’s a mess, but you really want that walnut.
Now minimise the window again and see how many words you can recall now, start by thinking of the "telephone" and see where it takes you. You should be able to easily recall the whole list. As a bonus round try recalling the list in reverse order starting with "walnut", it should be just as easy. Number Pegs
The linking system is great for remembering things in order (or even reverse) a more powerful system which allows you to recall any word at any position in the sequence without running through from start to finish like you need to do with the linking system is to use a number peg. This creates and index which allows you to recall each word of your seed phrase by its index number. Unlike the standard linking system it will also not break down if you forget one word in the middle of the list. Additionally the system can be used in reverse to remember long numbers or even a whole deck of cards. The Major / Consonant System
The Major or Consonant system is probably the most common peg system in use. First you translate digits into consonants, I use the following which is provided in Derren Brown's Trick of the Mind as this is what I have become use to, but feel free to adapt or create your own as desired.
z/s - Z is in zero and the S sound is most similar to Z l - They look similar (l for lemur) n - two downward strokes on a small n m - three downward strokes r - fouR f/v - FiVe, again they are similar sounds b/p - b looks simlar to 6 and P and B sound and look similar t - 7 looks like a capital T ch/sh/j - the GH in eiGHt, and then the J is the nearest to these sounds g - a written g can resemble a 9Each consonant is then associated with a short word that contains that consonant.
z/s - zoo l - ale n - hen m - ham r - whore f/v - hive b/g - bee t - tea ch/sh/j - shoe g - goofor two-digit numbers, convert each digit into a consonant using the table above. Then find a word that uses those two consonants as their first two consonants.
l, z/s - lice l, l - lily l, n - line l, m - lime l, r - lorry l, f/v - laugh l, b/p - lip l, t - light l, ch/sh/j - ledge l, g - leg n, z/s - nose n, l - nail n, n - nanny n, m - gnome n, r - neroI have only supplied words up to 24 as this is all you will need for a Bitcoin seed phrase but for other applications you would normally have a list of words up to 99 or even 999.
Once you have your list of words and their associated numbers, you then use the linking system to link the index word with the word in your seed phrase, so the first word in your seed phrase will be linked with the word "ale" the sixth word in your seed phrase will be linked with "bee" and so on and so forth.
Take the following seed phrase for example:
joke owner layer tail diagram armor input train head promote tuition eager
You might link the words as follows.
- joke / ale - drinking a pint of ale and laughing at a joke and choking on it and coughing ale all over yourself.
- owner / hen - Visualize a hen laying golden eggs and the proud owner showing it off to an envious neighbor.
- layer / ham - peeling layers of pork off a small ham like an onion.
- tail / whore - you get back to your room with a whore and are surprised to find a big fluffy tail when she drops her draws.
- diagram / hive - you are working on a big blueprint/diagram of a hive, imagine it in front of you on a drawing board.
- armor / bee - a high armoured medieval bee, perhaps on horseback with a spear.
- input / tea - you are using a vending machine and instead of taking coins the coin slot takes teabags for payment, imaging selecting an item and inputting tea bags for payment.
- train / shoe - imagine a big shoe train, a steam train that is a shoe with wheels on the bottom pulling a carriages down a train track.
- head / goo - you are on I'm a celeb and have to plunge you head into a big bucket of goo.
- promote / lice - two lice soldiers, one has been given a promotion the other is pinning a medal on his chest.
- tuition / lily - Imagine you are in a classroom, but instead of desks, there are giant lily pads. Each student, including you, has to sit atop a lily pad. The tuition fee for the course is actually a handful of lily flowers, which you hand to the instructor.
- eager / line - Picture a group of people standing in a line, so eager they begin stretching their necks out like giraffes to see the front of the line, vying for the first glimpse of what's to come.
Once you have compiled your list, think of a number between 1 and 12 and turn the number into your peg word and see what image emerges. That should then get you back to your seed word. Try a few with the example above.
And there you have it, once you have completed the exercise above for your seed phrase or phrases, you have now stored your life savings in your head and are safe in the knowledge that you have an always on backup for when disaster strikes. Although this method is very powerful you will need to run through the list every do often to keep it truly cemented. links * The Art of Memory
-
 @ 9e69e420:d12360c2
2025-02-17 17:12:01
@ 9e69e420:d12360c2
2025-02-17 17:12:01President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February.
Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training.
Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further.
-
 @ a012dc82:6458a70d
2025-02-27 14:10:22
@ a012dc82:6458a70d
2025-02-27 14:10:22Bitcoin's journey from a cryptographic experiment to a widely recognized financial asset is a testament to the rapid evolution of digital currencies. Since its inception in 2009, Bitcoin has captivated the attention of technologists, investors, and the general public alike. Its decentralized nature and potential for high returns have made it a subject of intense interest and debate. The recent introduction of Bitcoin Exchange-Traded Funds (ETFs) marks a pivotal moment in this journey, potentially heralding a new era of mainstream acceptance for Bitcoin and other cryptocurrencies. This development is not just a milestone for Bitcoin enthusiasts but also a signal to the broader financial community about the evolving nature of investment and the growing importance of digital assets.
Table of Contents
-
Understanding Bitcoin ETFs
-
Bitcoin's Journey to Mainstream Acceptance
-
The Impact of ETFs on Bitcoin's Perception
-
Risks and Challenges
-
The Future of Crypto with ETFs
-
Conclusion
-
FAQs
Understanding Bitcoin ETFs
A Bitcoin ETF represents a seismic shift in the way investors can access the world of cryptocurrencies. Traditionally, investing in Bitcoin required a certain level of technical know-how, including understanding cryptocurrency exchanges, digital wallets, and the concept of blockchain technology. This complexity has been a significant barrier to entry for many potential investors. A Bitcoin ETF simplifies this process dramatically. Investors can buy and sell shares of the ETF through traditional brokerage accounts, just as they would with any other stock or fund. This accessibility opens the doors to a broader range of investors, from individuals seeking to diversify their portfolios to institutional investors looking for regulated exposure to the crypto market. The ETF structure also provides added security and regulatory oversight, addressing some of the key concerns around cryptocurrency investments.
Bitcoin's Journey to Mainstream Acceptance
The path of Bitcoin to mainstream acceptance has been anything but straightforward. In its early days, Bitcoin was primarily a tool for tech enthusiasts and libertarians, valued for its decentralization and potential as an alternative to traditional currencies. Over time, its appeal broadened, attracting attention from venture capitalists and forward-thinking investors. High-profile endorsements, increasing media coverage, and a growing recognition of its potential as a hedge against inflation and currency devaluation have further propelled Bitcoin into the financial spotlight. Each surge in Bitcoin's price brought more attention and legitimacy, although it was often accompanied by skepticism and warnings of a bubble. The introduction of futures trading on major exchanges and the gradual embrace by major financial institutions have been critical in Bitcoin's journey towards legitimacy.
The Impact of ETFs on Bitcoin's Perception
The launch of Bitcoin ETFs is more than just a new investment product; it's a symbolic bridge between the traditional financial world and the frontier of cryptocurrency. For years, Bitcoin has been viewed with a mix of fascination and skepticism by the mainstream financial community. The introduction of ETFs changes this dynamic significantly. It offers a familiar and regulated framework for investing in Bitcoin, which can assuage the concerns of risk-averse investors and financial advisors. This development is likely to lead to broader acceptance and understanding of Bitcoin as a legitimate asset class, potentially leading to more stable pricing and reduced volatility. It also sets a precedent for other cryptocurrencies, suggesting a future where digital assets are as commonplace in investment portfolios as stocks and bonds.
Risks and Challenges
While Bitcoin ETFs offer new opportunities, they also come with their own set of risks and challenges. The cryptocurrency market is known for its dramatic price swings, and Bitcoin is no exception. Investors in Bitcoin ETFs must be prepared for a potentially turbulent ride. Regulatory challenges are another significant concern. The legal and regulatory framework for cryptocurrencies is still evolving, and changes in government policies or regulations could have a substantial impact on Bitcoin and Bitcoin ETFs. There's also the risk that the introduction of ETFs could lead to increased speculation and potentially inflate a price bubble. Moreover, traditional financial analysts and economists continue to express skepticism about the intrinsic value and long-term stability of Bitcoin, often comparing it to historical financial bubbles.
The Future of Crypto with ETFs
The introduction of Bitcoin ETFs could mark the beginning of a new chapter in the story of cryptocurrencies. As these products gain acceptance and attract more investment, they could pave the way for a broader range of crypto-based financial products and services. This integration into the global financial system could lead to cryptocurrencies becoming a standard part of diversified investment portfolios, alongside stocks, bonds, and commodities. The potential impact on the broader financial market is significant. Cryptocurrencies, led by Bitcoin, could challenge traditional notions of asset allocation, risk, and return. They also offer the potential for innovative financial products and services that leverage blockchain technology, further integrating digital currencies into the fabric of global finance.
Conclusion
The launch of Bitcoin ETFs is a significant milestone in the evolution of cryptocurrencies. It represents a convergence of the traditional financial world and the innovative, sometimes turbulent world of digital currencies. While this development brings new opportunities and a degree of legitimacy to Bitcoin, it also comes with challenges and risks that should not be underestimated. As the financial world continues to evolve, the role of cryptocurrencies and their impact on global markets and investment strategies will be a fascinating and important area to watch.
FAQs
How does a Bitcoin ETF differ from buying Bitcoin directly? Unlike direct Bitcoin purchases, which require a cryptocurrency exchange account and a digital wallet, a Bitcoin ETF can be bought and sold like a regular stock through a brokerage account.
Why are Bitcoin ETFs considered a milestone for cryptocurrency? Bitcoin ETFs represent a significant step towards mainstream acceptance of Bitcoin, offering a familiar and regulated investment option to both individual and institutional investors.
What are the risks involved in investing in Bitcoin ETFs? The risks include the inherent volatility of Bitcoin prices, regulatory changes, and potential market speculation that could impact the stability and value of these ETFs.
How might Bitcoin ETFs affect the future of cryptocurrencies? Bitcoin ETFs could pave the way for more crypto-based financial products, integrating digital currencies more deeply into the global financial system and potentially reshaping investment strategies.
Are Bitcoin ETFs suitable for all investors? Bitcoin ETFs, like any investment, may not be suitable for everyone. They are best suited for those who understand the high-risk nature of cryptocurrency investments and are looking to diversify their portfolio.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ a95c6243:d345522c
2024-12-06 18:21:15
@ a95c6243:d345522c
2024-12-06 18:21:15Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\ dass wir Vorteile aus ihr ziehen;\ in jedem andern hegt man den Wunsch,\ dass der Unschuldige in Schutz genommen werde.\ Jean-Jacques Rousseau
Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden.
Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen» den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen schadet der Psyche und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben Menschen getötet».
Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft. Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen Erfahrungen als Kritikerin der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit Transition News. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften».
Menschen, die aufrichtig andere schützen wollten, werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter Heinrich Habig, Bianca Witzschel und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat Transition News mehrfach berichtet (z.B. hier und hier). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie Alexander Bittner erfahren mussten.
Die eigentlich Kriminellen schützen sich derweil erfolgreich selber, nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte Verbrechen gegen die Menschheit». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn Hunter möglicherweise auch Anthony Fauci begnadigen wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte?
Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken.
Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers Robert F. Kennedy Jr. erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens Călin Georgescu, der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der Panik im Wertewesten.
In Rumänien selber gab es gerade einen Paukenschlag: Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das Tabu gebrochen, Wahlen zu verbieten, bevor sie etwas ändern können.
Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: Zensur) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ fd208ee8:0fd927c1
2025-02-15 07:02:08
@ fd208ee8:0fd927c1
2025-02-15 07:02:08E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md
-
 @ 2063cd79:57bd1320
2025-02-26 16:08:48
@ 2063cd79:57bd1320
2025-02-26 16:08:48Ich stimme mit Anonymous überein, dass es Probleme mit der tatsächlichen Verwendung von digitalem Bargeld auf kurze Sicht gibt. Aber es hängt in gewissem Maße davon ab, welches Problem man zu lösen versucht.
Eine Sorge, die ich habe, ist, dass der Übergang zum elektronischen Zahlungsverkehr die Privatsphäre einschränken wird, da es einfacher wird, Transaktionen zu protokollieren und aufzuzeichnen. Es könnten Profile angelegt werden, in denen das Ausgabeverhalten eines jeden von uns verfolgt wird.
Schon jetzt wird, wenn ich etwas telefonisch oder elektronisch mit meiner Visa-Karte bestelle, genau aufgezeichnet, wie viel ich ausgegeben habe und wo ich es ausgegeben habe. Im Laufe der Zeit könnten immer mehr Transaktionen auf diese Weise abgewickelt werden, und das Ergebnis könnte einen großen Verlust an Privatsphäre bedeuten.
Die Bezahlung mit Bargeld ist zwar immer noch per Post möglich, aber dies ist unsicher und umständlich. Ich denke, dass die Bequemlichkeit von Kredit- und Debitkarten die Bedenken der meisten Menschen in Bezug auf Privatsphäre ausräumen wird und dass wir uns in einer Situation befinden werden, in der große Mengen an Informationen über das Privatleben aller Leute existieren.
Hier könnte ich mir vorstellen, dass digitales Bargeld eine Rolle spielen könnte. Stellt euch ein Visa-ähnliches System vor, bei dem ich für die Bank nicht anonym bin. Stellt euch in diesem Modell vor, dass mir die Bank einen Kredit gewährt, ganz so wie bei einer Kreditkarte. Allerdings, anstatt mir nur eine Kontonummer zu geben, die ich am Telefon ablese oder in einer E-Mail verschicke, gibt sie mir das Recht, bei Bedarf digitales Bargeld zu verlangen.
Ich habe immer etwas digitales Bargeld beiseite, dass ich für Transaktionen ausgeben kann, wie bereits in früheren Beiträgen beschrieben. Wenn das Geld knapp wird, schicke ich eine E-Mail an die Bank und erhalte mehr digitales Bargeld (dcash). Jeden Monat sende ich einen Check an die Bank, um mein Konto auszugleichen, genauso wie ich es mit meinen Kreditkarten mache. Meine Beziehung zur Bank sind meinen derzeitigen Beziehungen zu den Kreditkartenunternehmen sehr ähnlich: häufige Überweisungen und eine einmalige Rückzahlung jeden Monat per Check.
Das hat mehrere Vorteile gegenüber dem System, auf das wir zusteuern. Es werden keine Aufzeichnungen darüber geführt, wofür ich mein Geld ausgebe. Die Bank weiß nur, wie viel ich jeden Monat abgehoben habe; es könnte sein, dass ich es zu diesem Zeitpunkt ausgegeben habe oder auch nicht. Bei einigen Transaktionen (z.B. Software) könnte ich für den Verkäufer anonym sein; bei anderen könnte der Verkäufer meine wirkliche Adresse kennen, aber dennoch ist keine zentrale Stelle in der Lage, alles zu verfolgen, was ich kaufe.
(Es gibt auch einen Sicherheitsvorteil gegenüber dem lächerlichen aktuellen System, bei dem die Kenntnis über eine 16-stellige Nummer und eines Ablaufdatums es jedem ermöglicht, etwas auf meinen Namen zu bestellen!)
Außerdem sehe ich nicht ein, warum dieses System nicht genauso legal sein sollte wie die derzeitigen Kreditkarten. Der einzige wirkliche Unterschied besteht darin, dass nicht nachverfolgt werden kann, wo die Nutzer ihr Geld ausgeben, und soweit ich weiß, war diese Möglichkeit nie ein wichtiger rechtlicher Aspekt von Kreditkarten. Sicherlich wird heute niemand zugeben, dass die Regierung ein Interesse daran hat, ein Umfeld zu schaffen, in dem jede finanzielle Transaktion nachverfolgt werden kann.
Zugegeben, dies bietet keine vollständige Anonymität. Es ist immer noch möglich, ungefähr zu sehen, wie viel jede Person ausgibt (obwohl nichts eine Person daran hindert, viel mehr Bargeld abzuheben, als sie in einem bestimmten Monat ausgibt, außer vielleicht für Zinsausgaben; aber vielleicht kann sie das zusätzliche digitale Bargel (digicash) selbst verleihen und dafür Zinsen erhalten, um das auszugleichen). Und es orientiert sich an demselben Kunden/ Verkäufer-Modell, das Anonymous kritisierte. Ich behaupte aber, dass dieses Modell heute und in naher Zukunft die Mehrheit der elektronischen Transaktionen ausmachen wird.
Es ist erwähnenswert, dass es nicht trivial ist, ein Anbieter zu werden, der Kreditkarten akzeptiert. Ich habe das mit einem Unternehmen, das ich vor ein paar Jahren betrieben habe, durchgemacht. Wir verkauften Software über den Versandhandel, was die Kreditkartenunternehmen sehr nervös machte. Es gibt zahlreiche Telefonbetrügereien, bei denen Kreditkartennummern über einige Monate hinweg gesammelt werden und dann große Beträge von diesen Karten abgebucht werden. Bis der Kunde seine monatliche Abrechnung erhält und sich beschwert, ist der Verkäufer bereits verschwunden. Um unser Kreditkartenterminal zu bekommen, wandten wir uns an ein Unternehmen, das Start-ups dabei „hilft“. Sie schienen selbst ein ziemlich zwielichtiges Unternehmen zu sein. Wir mussten unseren Antrag dahingehend fälschen, dass wir etwa 50% der Geräte auf Messen verkaufen würden, was offenbar als Verkauf über den Ladentisch zählte. Und wir mussten etwa 3.000 Dollar im Voraus zahlen, als Bestechung, wie es schien. Selbst dann hätten wir es wahrscheinlich nicht geschafft, wenn wir nicht ein Büro im Geschäftsviertel gehabt hätten.
Im Rahmen des digitalen Bargeldsystems könnte dies ein geringeres Problem darstellen. Das Hauptproblem bei digitalem Bargeld sind doppelte Ausgaben, und wenn man bereit ist, eine Online-Überprüfung vorzunehmen (sinnvoll für jedes Unternehmen, das mehr als ein paar Stunden für die Lieferung der Ware benötigt), kann dies vollständig verhindert werden. Es gibt also keine Möglichkeit mehr, dass Händler Kreditkartennummern für spätere Betrügereien sammeln. (Allerdings gibt es immer noch Probleme mit der Nichtlieferung von Waren, so dass nicht alle Risiken beseitigt sind). Dadurch könnte das System schließlich eine größere Verbreitung finden als die derzeitigen Kreditkarten.
Ich weiß nicht, ob dieses System zur Unterstützung von illegalen Aktivitäten, Steuerhinterziehung, Glücksspiel oder Ähnlichem verwendet werden könnte. Das ist nicht der Zweck dieses Vorschlags. Er bietet die Aussicht auf eine Verbesserung der Privatsphäre und der Sicherheit in einem Rahmen, der sogar rechtmäßig sein könnte, und das ist nicht verkehrt.
Englischer Artikel erschienen im Nakamoto Institute: Digital Cash & Privacy
-
 @ 94a6a78a:0ddf320e
2025-02-19 21:10:15
@ 94a6a78a:0ddf320e
2025-02-19 21:10:15Nostr is a revolutionary protocol that enables decentralized, censorship-resistant communication. Unlike traditional social networks controlled by corporations, Nostr operates without central servers or gatekeepers. This openness makes it incredibly powerful—but also means its success depends entirely on users, developers, and relay operators.
If you believe in free speech, decentralization, and an open internet, there are many ways to support and strengthen the Nostr ecosystem. Whether you're a casual user, a developer, or someone looking to contribute financially, every effort helps build a more robust network.
Here’s how you can get involved and make a difference.
1️⃣ Use Nostr Daily
The simplest and most effective way to contribute to Nostr is by using it regularly. The more active users, the stronger and more valuable the network becomes.
✅ Post, comment, and zap (send micro-payments via Bitcoin’s Lightning Network) to keep conversations flowing.\ ✅ Engage with new users and help them understand how Nostr works.\ ✅ Try different Nostr clients like Damus, Amethyst, Snort, or Primal and provide feedback to improve the experience.
Your activity keeps the network alive and helps encourage more developers and relay operators to invest in the ecosystem.
2️⃣ Run Your Own Nostr Relay
Relays are the backbone of Nostr, responsible for distributing messages across the network. The more independent relays exist, the stronger and more censorship-resistant Nostr becomes.
✅ Set up your own relay to help decentralize the network further.\ ✅ Experiment with relay configurations and different performance optimizations.\ ✅ Offer public or private relay services to users looking for high-quality infrastructure.
If you're not technical, you can still support relay operators by subscribing to a paid relay or donating to open-source relay projects.
3️⃣ Support Paid Relays & Infrastructure
Free relays have helped Nostr grow, but they struggle with spam, slow speeds, and sustainability issues. Paid relays help fund better infrastructure, faster message delivery, and a more reliable experience.
✅ Subscribe to a paid relay to help keep it running.\ ✅ Use premium services like media hosting (e.g., Azzamo Blossom) to decentralize content storage.\ ✅ Donate to relay operators who invest in long-term infrastructure.
By funding Nostr’s decentralized backbone, you help ensure its longevity and reliability.
4️⃣ Zap Developers, Creators & Builders
Many people contribute to Nostr without direct financial compensation—developers who build clients, relay operators, educators, and content creators. You can support them with zaps! ⚡
✅ Find developers working on Nostr projects and send them a zap.\ ✅ Support content creators and educators who spread awareness about Nostr.\ ✅ Encourage builders by donating to open-source projects.
Micro-payments via the Lightning Network make it easy to directly support the people who make Nostr better.
5️⃣ Develop New Nostr Apps & Tools
If you're a developer, you can build on Nostr’s open protocol to create new apps, bots, or tools. Nostr is permissionless, meaning anyone can develop for it.
✅ Create new Nostr clients with unique features and user experiences.\ ✅ Build bots or automation tools that improve engagement and usability.\ ✅ Experiment with decentralized identity, authentication, and encryption to make Nostr even stronger.
With no corporate gatekeepers, your projects can help shape the future of decentralized social media.
6️⃣ Promote & Educate Others About Nostr
Adoption grows when more people understand and use Nostr. You can help by spreading awareness and creating educational content.
✅ Write blogs, guides, and tutorials explaining how to use Nostr.\ ✅ Make videos or social media posts introducing new users to the protocol.\ ✅ Host discussions, Twitter Spaces, or workshops to onboard more people.
The more people understand and trust Nostr, the stronger the ecosystem becomes.
7️⃣ Support Open-Source Nostr Projects
Many Nostr tools and clients are built by volunteers, and open-source projects thrive on community support.
✅ Contribute code to existing Nostr projects on GitHub.\ ✅ Report bugs and suggest features to improve Nostr clients.\ ✅ Donate to developers who keep Nostr free and open for everyone.
If you're not a developer, you can still help with testing, translations, and documentation to make projects more accessible.
🚀 Every Contribution Strengthens Nostr
Whether you:
✔️ Post and engage daily\ ✔️ Zap creators and developers\ ✔️ Run or support relays\ ✔️ Build new apps and tools\ ✔️ Educate and onboard new users
Every action helps make Nostr more resilient, decentralized, and unstoppable.
Nostr isn’t just another social network—it’s a movement toward a free and open internet. If you believe in digital freedom, privacy, and decentralization, now is the time to get involved.
-
 @ a95c6243:d345522c
2024-11-29 19:45:43
@ a95c6243:d345522c
2024-11-29 19:45:43Konsum ist Therapie.
Wolfgang JoopUmweltbewusstes Verhalten und verantwortungsvoller Konsum zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
Heute ist also wieder mal «Black Friday», falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
Warum fallen wir auf derartige Werbetricks herein und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
Gedankenlosigkeit und Maßlosigkeit können besonders bei der Ernährung zu ernsten Problemen führen. Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
Kritik am schwarzen Freitag und dem unnötigen Konsum kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
Die EU-Kommission lancierte 2015 den Begriff «Green Friday» im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das Pariser Abkommen unterzeichnet werden sollte.
Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt. Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des «Green New Deal» verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um Valencia dazu sagen?
Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020 eine «grüne Erholung von Covid-19, um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie «verantwortungsvolle Risikobereitschaft» unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ bd32f268:22b33966
2025-02-20 23:17:29
@ bd32f268:22b33966
2025-02-20 23:17:29Quando estava prestes a entrar para a universidade sentia que a minha vida estava a desenrolar-se plenamente de acordo com os conselhos que havia recebido. Estava focado nos estudos e com a esperança de que esse foco me garantisse um bom trabalho. Com efeito, os estudos abriram algumas portas, no entanto, não posso deixar de assinalar que há outras decisões mais importantes a tomar e que não tiveram o mesmo protagonismo na minha vida.
Nessa mesma altura estava a iniciar um relacionamento amoroso, sem ter clara a finalidade desse namoro e o caminho que o mesmo deveria ter seguido. Talvez até me tivessem aconselhado sobre isso, contudo o foco estava mais no trabalho e em usufruir das oportunidades que se apresentaram nessa juventude confortável, na qual contei sempre com o apoio financeiro dos meus pais. Estava, como a maioria à minha volta, a viver uma vida libertina. Quer isto dizer uma vida sem grandes preocupações, a não ser estudar e fazer o suficiente para não reprovar a nenhuma disciplina. O resto é movido muito mais para emoção do que pela razão. Aquilo que considerava prazeroso era bom e o que não o era, era mau. Não tinha propriamente uma ideia clara do que queria criar a longo prazo e portanto estava muito mais focado no presente e em usufruir daquilo que podia no momento.
Fazendo uma análise retrospetiva de tudo, não culpo ninguém porque a informação existe para quem a procura, contudo noto aqui apenas o ambiente social e cultural que favorece determinadas decisões em detrimento de outras. O foco tem estado muito mais nos estudos, no trabalho e na fruição dos prazeres que se apresentam aos jovens sem que se pense demasiado no futuro.
Neste contexto, e vendo esta fase da vida com outro grau de distanciamento, deixo aqui dez conselhos que julgo essenciais.
 Rei Salomão - Gustav Dore
Rei Salomão - Gustav Dore 1.Focar na decisão mais importante: constituir ou não família.
A decisão de constituir ou não família é muito mais relevante para a nossa vida do que propriamente a de escolher uma profissão. Não estou necessariamente a fazer apologia de que todas as pessoas devem constituir família, convenhamos que muitos de nós não têm vocação para o mesmo (apesar de muitos ainda assim o fazerem), mas quer seja afirmativa ou negativa a resposta parece-me fundamental que nos concentremos nessa decisão. Muito mais do que qualquer profissão a família é onde naturalmente procuramos apoio, conforto e incentivo perante todas as vicissitudes da vida.
O facto de existirem famílias que não são fontes de amor para as pessoas em nada invalida que esta seja a organização social por excelência que aporta significado ás nossas vidas. Infelizmente, para muitas pessoas uma experiência pessoal mais difícil a este nível influi na forma como pensam sobre a possibilidade de criarem a sua própria família.
Algumas questões a ter em conta nesta ponderação:
Qual é o meu ideal de família ?
Qual o meu papel enquanto homem/mulher no seio da família?
Que tipo de parceiro devo procurar?
Desejo ter filhos ?
Podemos usar estas questões como pontos de partida para iniciar uma exploração da nossa vocação.
2.Tomar decisões cedo em vez de protelar indefinidamente
Atualmente notamos que as pessoas constituem família cada vez mais tarde e que têm filhos cada vez mais tarde. É curioso notar que nos relacionamentos por vezes há alguma pressa para passar do conhecer a pessoa à intimidade sexual e não há pressa alguma para decidir se de facto é com aquela pessoa que queremos passar o resto dos nossos dias.
Este é apenas um aspecto no qual se nota uma progressiva detioração da capacidade para decidir. É-nos muitas vezes transmitida a ideia de que temos tempo e de que não há uma idade certa para tomar determinadas decisões. Estes discursos são cínicos pois é evidente que há fases que são mais propícias para dar determinados passos na nossa vida, daí que seja muito importante aprender a tomar decisões cedo.
Para tomar decisões sóbrias é fundamental saber-se exatamente aquilo que queremos. Se tudo isso está indefinido e não conseguimos postular uma ideia de futuro para nós será muito mais difícil tomar qualquer tipo de decisão importante. Um outro aspecto a ter em conta é o de que as principais decisões são guiadas pela razão, isto é os nossos sentimentos têm de estar ao serviço dos nossos valores e nunca o contrário.
3.Se não te imaginas a casar com a pessoa com quem estás, termina o relacionamento.
Deixar a porta aberta num relacionamento de forma indefinida é algo que vai produzir instabilidade no longo prazo. É óbvio que para muitas pessoas o casamento é “apenas um papel” e portanto não vêm a real utilidade em se casar. Contudo, e de forma não surpreendente, notamos que os casais que têm na sua vida uma visão sobrenatural do casamento tendem a perdurar. Digamos que a cola que é usada para unir as pessoas é de um outro calibre, enquanto que a cola usada por aqueles que não têm Deus nas suas vidas está muito mais sujeita à volatilidade do tempo, dos apetites individuais e do relativismo.
4.Assume a responsabilidade pelos teus erros sem te deixar levar pelo vitimismo.
A cultura atual, influenciada de forma determinante pela filosofia marxista, está permanentemente a postular divisões de poder na sociedade que pressupõe duas categorias principais a de oprimido e opressor. Esta ideologia apoiada no revisionismo histórico e numa pedagogia social falaciosa incute desde cedo na população a ideia de que em algum momento, tendo ou não pertencido a uma minoria, somos vítimas. Vemos vários exemplos e derivações desta doutrina quando tocamos em temas como o feminismo, o racismo e outros ismos que se focam apenas nesta divisão dicotómica oprimido e opressor.
Esta narrativa esquece que a hierarquia é uma organização natural que define aptidões diferenciadas e consequentemente vocações diferentes. Um outro aspecto que também é esquecido é o livre arbítrio, isto é, a ideia de que as pessoas têm poder de decisão e que muitas vezes podem ser coniventes e partes atuantes no sistema em que participam.
Quer isto dizer que individualmente cada um de nós, havendo discernimento, tem escolha e portanto é muito mais produtivo focar a nossa atenção nesse aspecto do que em qualquer tipo de desigualdade que possa existir. A igualdade de circunstâncias para todas as pessoas é uma utopia, a única igualdade que existe é da essência humana.
O caminho para escapar ao vitimismo será sempre o da responsabilidade individual e da gratidão apesar das circunstâncias adversas que possamos estar a viver.
5.Foca-te primeiro no que te é mais próximo antes do mundo
Por vezes, inspirados por uma soberba intelectual que agora é típica da juventude vemo-nos a fazer o papel de ativistas em determinadas causas, algumas nobres outras nem tanto. Acontece que este ativismo é frequentemente uma ato postiço, uma pose que usamos como forma de sinalizar a nossa virtude perante os nossos pares. Onde se percebem os pés de barro é quando notamos que diante das pessoas que nos são mais próximas não temos o mesmo zelo que apresentamos quando estamos a debater as grandes questões do mundo.
Há que ser zeloso com quem nos rodeia e os problemas mais urgentes para resolver, e aqueles em que a nossa intervenção é de facto mais necessária, são os que nos são mais próximos.
6.Dizer a verdade
A corrupção moral funciona de forma gradual, vai de menos a mais, começamos com uma coisa pequena até chegarmos a algo maior. Quando somos mais novos vamos experimentando a corrupção através do exercício da mentira em pequenas coisas e gradualmente vamos avançando para as coisas maiores. Alguns de nós resistem à mentira, facilmente se entende que não desejamos que os outros nos mintam no entanto, se o repetimos muitas vezes facilmente a banalizamos.
A mentira é uma tentativa de esquivar a responsabilidade pelas nossas ações ou opiniões, uma tentativa de fuga ás consequências. Contudo, importa perceber que inevitavelmente vamos sempre confrontar-nos com as consequências sejam quais forem as circunstâncias. Se não as experimentamos pela espada dos outros será pela nossa própria espada quando finalmente percebermos que não há harmonia entre o pensamento e a ação, que dizemos uma coisa mas fazemos outra, que a nossa identidade é também ela uma ficção. O exercício da verdade será a única via para nos aproximarmos de uma existência mais harmoniosa e autêntica, a única forma de estabelecer uma relação genuína com os outros.
7.Decisões inspiradas pela coragem e menos pelo medo
As nossas decisões têm frequentemente como força motriz o medo. O medo da rejeição impede-nos de ir falar com aquela pessoa de quem gostamos, o medo do juízo social impede-nos de proferir a nossa opinião em determinado assunto, o medo da morte leva-nos a ter comportamentos obsessivos com a nossa saúde; enfim, são muitas as situações em que as nossas decisões são pautadas pelo medo.
É importante que cada vez mais, o medo não seja o factor definidor da nossa decisão. A coragem, temperada pela prudência, devem ser os grandes arquitetos da nossa decisão. Aquilo que é bom no sentido mais profundo é o que devemos seguir, independentemente de sentirmos medo.
8.Ninguém é obrigado a gostar de nós, ninguém nos deve nada
O ressentimento e mágoa leva-nos por vezes a tratar os outros como se eles nos devessem algo, como se fosse impensável não nos reconhecerem como aprazíveis aos seus olhos ou justos. Isto é uma forma subtil do orgulho se expressar, porque mais uma vez nos colocamos na posição de vítima e assim, julgamos que os outros nos deveriam reconhecer como virtuosos de alguma forma.
Pois bem, apesar dos outros, tal como nós, terem deveres e poderem fazer menção honrosa da nossa existência não devemos esperar isso. Esperando isso, acabamos escravizados por essas expectativas porque continuamos à espera que gostem de nós. Desta forma distorcemos também o próprio conceito de amor, que é doar-se sem esperar em troca. Não é que os outros não o possam fazer, podem, o problema está na espera e na exigência.
9.Definir uma matriz moral objetiva
Imbuídos de um espírito relativista estamos muitas vezes sujeitos a uma subjetividade enorme no que diz respeito aos nossos valores. O resultado disto é que inevitavelmente vamos ter uma definição menos clara do bem e do mal. Frequentemente vamos confundir o que é bom ou mau com os nossos desejos, alimentado pelos nossos vícios. Para termos uma visão mais clara da realidade é fundamental sairmos dessa visão subjetiva do valor e sermos capazes de procurar a verdadeira fonte das definições morais.
Aqui, há determinadas mensagens sociais que nos confundem os sentidos, nomeadamente aquelas que atestam que tudo são apenas “pontos de vista”, que não há uma “verdade” mas sim várias verdades, e que “neste tempo/cultura/país” a moralidade é outra. São tudo asserções que dificultam esta pesquisa pela verdade e definição moral universal. Neste campo, o ser humano só será capaz de ter mais estabilidade em termos psicológicos aderindo a um sistema de valores imutável, esta é a única forma de basear a sua identidade em princípios mais objetivos.
10.Encontrar um propósito maior para a vida
Santo Agostinho diz-nos o seguinte:
- Se não queres sofrer não ames, mas se não amas para que queres viver?
Santo Agostinho
Por vezes na nossa vida procuramos esquivar-nos do sofrimento e inclusive somos vitimas de um certo ceticismo e embotamento afetivo. Vamos experimentando a traição e a frustração das nossas expectativas e isso vai endurecendo o nosso coração. Em resultado disso, muitas vezes tornamo-nos também mais egoístas, focados na mera satisfação das nossas necessidades e menos nas dos outros. No entanto, isto faz de nós infelizes porque não conseguimos deixar de amar. A solução é encontrar algo maior que nós mesmos para amar, entendendo sempre que a essência do amor é o sacrifício. Encontrar isso é simultaneamente definir um propósito para a vida e daí derivar um significado que nos sustenta até nos momentos mais difíceis.
Eventualmente poderei fazer alguma publicação específica expandindo um pouco mais alguns destes conselhos, uma vez que observo que muito mais poderia ter sido dito em cada um deles. Talvez venha a criar mais algumas publicações sobre este tema.
-
 @ c1e9ab3a:9cb56b43
2025-02-25 22:49:38
@ c1e9ab3a:9cb56b43
2025-02-25 22:49:38Election Authority (EA) Platform
1.1 EA Administration Interface (Web-Based)
- Purpose: Gives authorized personnel (e.g., election officials) a user-friendly way to administer the election.
- Key Tasks:
- Voter Registration Oversight: Mark which voters have proven their identity (via in-person KYC or some legal process).
- Blind Signature Issuance: Approve or deny blind signature requests from registered voters (each corresponding to one ephemeral key).
- Tracking Voter Slots: Keep a minimal registry of who is allowed one ephemeral key signature, and mark it “used” once a signature is issued.
- Election Configuration: Set start/end times, provide encryption parameters (public keys), manage threshold cryptography setup.
- Monitor Tallying: After the election, collaborate with trustees to decrypt final results and release them.
1.2 EA Backend Services
- Blind Signature Service:
- An API endpoint or internal module that receives a blinded ephemeral key from a voter, checks if they are authorized (one signature per voter), and returns the blind-signed result.
-
Typically requires secure storage of the EA’s blind signing private key.
-
Voter Roll Database:
- Stores minimal info: “Voter #12345 is authorized to request one ephemeral key signature,” plus status flags.
-
Does not store ephemeral keys themselves (to preserve anonymity).
-
(Optional) Mix-Net or Homomorphic Tally Service:
- Coordinates with trustees for threshold decryption or re-encryption.
- Alternatively, a separate “Tally Authority” service can handle this.
2. Auditor Interface
2.1 Auditor Web-Based Portal
- Purpose: Allows independent auditors (or the public) to:
- Fetch All Ballots from the relays (or from an aggregator).
- Verify Proofs: Check each ballot’s signature, blind signature from the EA, OTS proof, zero-knowledge proofs, etc.
- Check Double-Usage: Confirm that each ephemeral key is used only once (or final re-vote is the only valid instance).
-
Observe Tally Process: Possibly see partial decryptions or shuffle steps, verify the final result matches the posted ballots.
-
Key Tasks:
- Provide a dashboard showing the election’s real-time status or final results, after cryptographic verification.
- Offer open data downloads so third parties can run independent checks.
2.2 (Optional) Trustee Dashboard
- If the election uses threshold cryptography (multiple parties must decrypt), each trustee (candidate rep, official, etc.) might have an interface for:
- Uploading partial decryption shares or re-encryption proofs.
- Checking that other trustees did their steps correctly (zero-knowledge proofs for correct shuffling, etc.).
3. Voter Application
3.1 Voter Client (Mobile App or Web Interface)
-
Purpose: The main tool voters use to participate—before, during, and after the election.
-
Functionalities:
- Registration Linking:
- Voter goes in-person to an election office or uses an online KYC process.
- Voter obtains or confirms their long-term (“KYC-bound”) key. The client can store it securely (or the voter just logs in to a “voter account”).
- Ephemeral Key Generation:
- Create an ephemeral key pair ((nsec_e, npub_e)) locally.
- Blind (\npub_e) and send it to the EA for signing.
- Unblind the returned signature.
- Store (\npub_e) + EA’s signature for use during voting.
- Ballot Composition:
- Display candidates/offices to the voter.
- Let them select choices.
- Possibly generate zero-knowledge proofs (ZKPs) behind the scenes to confirm “exactly one choice per race.”
- Encryption & OTS Timestamp:
- Encrypt the ballot under the election’s public (threshold) key or produce a format suitable for a mix-net.
- Obtain an OpenTimestamps proof for the ballot’s hash.
- Publish Ballot:
- Sign the entire “timestamped ballot” with the ephemeral key.
- Include the EA’s blind signature on (\npub_e).
- Post to the Nostr relays (or any chosen decentralized channel).
- Re-Voting:
- If the user needs to change their vote, the client repeats the encryption + OTS step, publishes a new ballot with a strictly later OTS anchor.
- Verification:
- After the election, the voter can check that their final ballot is present in the tally set.
3.2 Local Storage / Security
- The app must securely store:
- Ephemeral private key ((nsec_e)) until voting is complete.
- Potential backup/recovery mechanism if the phone is lost.
- Blind signature from the EA on (\npub_e).
- Potentially uses hardware security modules (HSM) or secure enclaves on the device.
4. Nostr Relays (or Equivalent Decentralized Layer)
- Purpose: Store and replicate voter-submitted ballots (events).
- Key Properties:
- Redundancy: Voters can post to multiple relays to mitigate censorship or downtime.
- Public Accessibility: Auditors, the EA, and the public can fetch all events to verify or tally.
- Event Filtering: By design, watchers can filter events with certain tags, e.g. “election: 2025 County Race,” ensuring they gather all ballots.
5. Threshold Cryptography Setup
5.1 Multi-Seg (Multi-Party) Key Generation
- Participants: Possibly the EA + major candidates + accredited observers.
- Process: A Distributed Key Generation (DKG) protocol that yields a single public encryption key.
- Private Key Shares: Each trustee holds a piece of the decryption key; no single party can decrypt alone.
5.2 Decryption / Tally Mechanism
- Homomorphic Approach:
- Ballots are additively encrypted.
- Summation of ciphertexts is done publicly.
- Trustees provide partial decryptions for the final sum.
- Mix-Net Approach:
- Ballots are collected.
- Multiple servers shuffle and re-encrypt them (each trustee verifies correctness).
- Final set is decrypted, but the link to each ephemeral key is lost.
5.3 Trustee Interfaces
- Separate or integrated into the auditor interface—each trustee logs in and provides their partial key share for decrypting the final result.
- Possibly combined with ZK proofs to confirm correct partial decryption or shuffling.
6. OpenTimestamps (OTS) or External Time Anchor
6.1 Aggregator Service
- Purpose: Receives a hash from the voter’s app, anchors it into a blockchain or alternative time-stamping system.
- Result: Returns a proof object that can later be used by any auditor to confirm the time/block height at which the hash was included.
6.2 Verifier Interface
- Could be part of the auditor tool or the voter client.
- Checks that each ballot’s OTS proof is valid and references a block/time prior to the election’s closing.
7. Registration Process (In-Person or Hybrid)
- Voter presents ID physically at a polling station or a designated office (or an online KYC approach, if legally allowed).
- EA official:
- Confirms identity.
- Links the voter to a “voter record” (Voter #12345).
- Authorizes them for “1 ephemeral key blind-sign.”
- Voter obtains or logs into the voter client:
- The app or website might show “You are now cleared to request a blind signature from the EA.”
- Voter later (or immediately) generates the ephemeral key and requests the blind signature.
8. Putting It All Together (High-Level Flow)
- Key Setup
- The EA + trustees run a DKG to produce the election public key.
- Voter Registration
- Voter is validated (ID check).
- Marked as eligible in the EA database.
- Blind-Signed Ephemeral Key
- Voter’s client generates a key, blinds (\npub_e), obtains EA’s signature, unblinds.
- Voting
- Voter composes ballot, encrypts with the election public key.
- Gets OTS proof for the ballot hash.
- Voter’s ephemeral key signs the entire package (including EA’s signature on (\npub_e)).
- Publishes to Nostr.
- Re-Voting (Optional)
- Same ephemeral key, new OTS timestamp.
- Final ballot is whichever has the latest valid timestamp before closing.
- Close of Election & Tally
- EA announces closing.
- Tally software (admin + auditors) collects ballots from Nostr, discards invalid duplicates.
- Threshold decryption or mix-net to reveal final counts.
- Publish final results and let auditors verify everything.
9. Summary of Major Components
Below is a succinct list:
- EA Admin Platform
- Web UI for officials (registration, blind signature issuing, final tally management).
- Backend DB for voter records & authorized ephemeral keys.
- Auditor/Trustee Platforms
- Web interface for verifying ballots, partial decryption, and final results.
- Voter Application (Mobile / Web)
- Generating ephemeral keys, getting blind-signed, casting encrypted ballots, re-voting, verifying included ballots.
- Nostr Relays (Decentralized Storage)
- Where ballots (events) are published, replicated, and fetched for final tally.
- Threshold Cryptography System
- Multi-party DKG for the election key.
- Protocols or services for partial decryption, mix-net, or homomorphic summation.
- OpenTimestamps Aggregator
- Service that returns a blockchain-anchored timestamp proof for each ballot’s hash.
Additional Implementation Considerations
- Security Hardening:
- Using hardware security modules (HSM) for the EA’s blind-signing key, for trustee shares, etc.
- Scalability:
- Handling large numbers of concurrent voters, large data flows to relays.
- User Experience:
- Minimizing cryptographic complexity for non-technical voters.
- Legal and Procedural:
- Compliance with local laws for in-person ID checks, mandatory paper backups (if any), etc.
Final Note
While each functional block can be designed and deployed independently (e.g., multiple aggregator services, multiple relays, separate tally servers), the key to a successful system is interoperability and careful orchestration of these components—ensuring strong security, a straightforward voter experience, and transparent auditing.
nostr:naddr1qqxnzde5xq6nzv348yunvv35qy28wue69uhnzv3h9cczuvpwxyargwpk8yhsygxpax4n544z4dk2f04lgn4xfvha5s9vvvg73p46s66x2gtfedttgvpsgqqqw4rs0rcnsu
-
 @ a95c6243:d345522c
2024-11-08 20:02:32
@ a95c6243:d345522c
2024-11-08 20:02:32Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister EckhartSchwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung, der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
Mit einem bemerkenswerten Timing hat die deutsche Regierungskoalition am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer Selbsthypnose rund um Harris-Hype und Trump-Panik – mit teils erschreckenden Auswüchsen. Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
Das Kindergarten-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik «vorsätzlich herbeigeführt» worden seien.
Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen. Verkehrs- und Digitalminister Wissing trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit Jörg Kukies habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP, hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können. Das ging erst kürzlich aus dem diesjährigen «Freiheitsindex» hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
«Die absolute Mehrheit hat absolut die Nase voll», titelte die Bild angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat, kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei Manova. Und er kenne Friedrich Merz schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
Was also tun? Der Schweizer Verein «Losdemokratie» will eine Volksinitiative lancieren, um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
In jedem Fall wird es notwendig sein, unsere Bemühungen um Freiheit und Selbstbestimmung zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ bc575705:dba3ed39
2025-02-27 13:25:57
@ bc575705:dba3ed39
2025-02-27 13:25:57Jazz is a genre that has always thrived on evolution. From its early roots in New Orleans to the boundary-pushing experiments of the 20th century, jazz has continuously reinvented itself, adapting to the times while preserving its soulful essence. As a modern music producer, I find endless inspiration in jazz, reimagining its classic elements to resonate with contemporary listeners. In this post, I’ll share how I approach blending the timeless qualities of jazz with modern techniques and styles.
What Makes Jazz Timeless?
At its core, jazz is about freedom, improvisation, and emotional depth. Its intricate melodies, rich harmonies, and dynamic rhythms have a universal appeal that transcends eras. What makes jazz so timeless is its ability to tell stories through sound, evoking feelings that are deeply personal yet universally understood.
Bringing Jazz Into the Present
Modern listeners often seek music that feels familiar yet fresh. To bridge this gap, I focus on preserving the essence of jazz while introducing elements from contemporary genres like lo-fi, ambient, and electronica. Here’s how I reimagine jazz for today:
Sampling: Sampling classic jazz records allows me to connect with the genre’s rich history while giving it a new context. By chopping, pitching, and looping segments of iconic performances, I can create textures that feel nostalgic yet innovative.
Electronic Beats: Jazz drumming has always been a cornerstone of the genre, with its swing and syncopation adding energy and depth. By pairing these rhythmic foundations with modern electronic drum patterns, I create a hybrid sound that appeals to both traditional jazz fans and electronic music enthusiasts.
Improvisation in Production: Just as jazz musicians improvise on their instruments, I bring an element of spontaneity to my production process. Whether it’s experimenting with synth leads or recording freeform solos on piano, I aim to capture the spirit of improvisation that defines jazz.
Fusion of Textures: Combining the organic warmth of live instruments like saxophones and trumpets with the polished sheen of synths and ambient pads creates a soundscape that feels both intimate and expansive.
Artists Who Inspire This Fusion
Several artists have mastered the art of blending jazz with modern elements, inspiring my own approach:
Robert Glasper: Known for merging jazz with R&B and hip-hop, Glasper’s work shows how flexible and relevant jazz can be in today’s music scene.
Kamasi Washington: His epic compositions and lush orchestrations prove that jazz can be grand and cinematic while remaining deeply rooted in tradition.
BadBadNotGood: This group seamlessly integrates jazz with contemporary genres like electronic and hip-hop, creating music that feels both fresh and timeless.
How This Shapes My Music
In my compositions, I aim to reimagine jazz as a living, breathing art form. For example, I might start with a classic jazz chord progression, then layer it with lo-fi textures, minimalist beats, and atmospheric effects. The result is music that pays homage to the past while embracing the possibilities of the future.
One of my favorite techniques is to record live solos—whether on piano, guitar, or synth—and process them with modern effects like reverb, delay, or granular synthesis. This approach preserves the raw, emotive quality of the performance while placing it in a contemporary context.
Why Jazz Matters Today
In a world that often feels fast-paced and chaotic, jazz offers a sense of grounding and introspection. Its emphasis on improvisation and self-expression reminds us to slow down, listen, and connect with our emotions. By reimagining jazz for modern audiences, I hope to introduce new listeners to its timeless beauty while inspiring others to see it as a genre with limitless potential.
Jazz is far from a relic of the past. It’s a vibrant, evolving art form that continues to inspire and connect people across generations. By blending its classic elements with contemporary techniques, we can ensure that jazz remains as relevant and impactful as ever.
-
 @ e3ba5e1a:5e433365
2025-02-13 06:16:49
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get this line:
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song Devil Went Down to Georgia that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” is, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people should be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is freedom. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are definitionally better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In Devil Went Down to Georgia, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
Libertas magnitudo est
-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-
 @ c1e9ab3a:9cb56b43
2025-02-25 19:49:28
@ c1e9ab3a:9cb56b43
2025-02-25 19:49:281. Introduction
Modern election systems must balance privacy (no one sees how individuals vote) with public verifiability (everyone can confirm the correctness of the tally). Achieving this in a decentralized, tamper-resistant manner remains a challenge. Nostr (a lightweight protocol for censorship-resistant communication) offers a promising platform for distributing and archiving election data (ballots) without relying on a single central server.
This paper presents a design where:
- Each voter generates a new ephemeral Nostr keypair for an election.
- The election authority (EA) blind-signs this ephemeral public key (npub) to prove the voter is authorized, without revealing which voter owns which ephemeral key.
- Voters cast encrypted ballots to Nostr relays, each carrying an OpenTimestamps proof to confirm the ballot’s time anchor.
- Re-voting is allowed: a voter can replace a previously cast ballot by publishing a new ballot with a newer timestamp.
- Only the latest valid ballot (per ephemeral key) is counted.
We combine well-known cryptographic primitives—blind signatures, homomorphic or mix-net encryption, threshold key management, and time anchoring—into an end-to-end system that preserves anonymity, assures correctness, and prevents double-voting.
2. Roles and Components
2.1 Voters
- Long-Term (“KYC-bound”) Key: Each voter has some identity-verified Nostr public key used only for official communication with the EA (not for voting).
- Ephemeral Voting Key: For each election, the voter locally generates a new Nostr keypair ((nsec_e, npub_e)).
- This is the “one-time” identity used to sign ballots.
- The EA never learns the real identity behind (\npub_e) because of blinding.
2.2 Election Authority (EA)
- Maintains the official voter registry: who is entitled to vote.
- Blind-Signs each valid voter’s ephemeral public key to authorize exactly one ephemeral key per voter.
- Publishes a minimal voter roll: e.g., “Voter #12345 has been issued a valid ephemeral key,” without revealing which ephemeral key.
2.3 Nostr Relays
- Decentralized servers that store and forward events.
- Voters post their ballots to relays, which replicate them.
- No single relay is critical; the same ballot can be posted to multiple relays for redundancy.
2.4 Cryptographic Framework
- Blind Signatures: The EA signs a blinded version of (\npub_e).
- Homomorphic or Mix-Net Encryption: Ensures the content of each ballot remains private; only aggregate results or a shuffled set are ever decrypted.
- Threshold / General Access Structure: Multiple trustees (EA plus candidate representatives, for example) must collaborate to produce a final decryption.
- OpenTimestamps (OTS): Attaches a verifiable timestamp proof to each ballot, anchoring it to a blockchain or other tamper-resistant time reference.
3. Protocol Lifecycle
This section walks through voter registration, ephemeral key authorization, casting (and re-casting) ballots, and finally the tally.
3.1 Registration & Minimal Voter Roll
- Legal/KYC Verification
- Each real-world voter proves their identity to the EA (per legal procedures).
-
The EA records that the voter is eligible to cast one ballot, referencing their long-term identity key ((\npub_{\mathrm{KYC}})).
-
Issue Authorization “Slot”
- The EA’s voter roll notes “this person can receive exactly one blind signature for an ephemeral key.”
- The roll does not store an ephemeral key—just notes that it can be requested.
3.2 Generating and Blinding the Ephemeral Key
- Voter Creates Ephemeral Key
- Locally, the voter’s client generates a fresh ((nsec_e, npub_e)).
- Blinding
-
The client blinds (\npub_e) to produce (\npub_{e,\mathrm{blinded}}). This ensures the EA cannot learn the real (\npub_e).
-
Blind Signature Request
- The voter, using their KYC-bound key ((\npub_{\mathrm{KYC}})), sends (\npub_{e,\mathrm{blinded}}) to the EA (perhaps via a secure direct message or a “giftwrapped DM”).
- The EA checks that this voter has not already been issued a blind signature.
-
If authorized, the EA signs (\npub_{e,\mathrm{blinded}}) with its private key and returns the blinded signature.
-
Unblinding
- The voter’s client unblinds the signature, obtaining a valid signature on (\npub_e).
-
Now (\npub_e) is a blinded ephemeral public key that the EA has effectively “authorized,” without knowing which voter it belongs to.
-
Roll Update
- The EA updates its minimal roll to note that “Voter #12345 received a signature,” but does not publish (\npub_e).
3.3 Casting an Encrypted Ballot with OpenTimestamps
When the voter is ready to vote:
- Compose Encrypted Ballot
- The ballot can be homomorphically encrypted (e.g., with Paillier or ElGamal) or structured for a mix-net.
-
Optionally include Zero-Knowledge Proofs (ZKPs) showing the ballot is valid (one candidate per race, etc.).
-
Obtain OTS Timestamp
- The voter’s client computes a hash (H) of the ballot data (ciphertext + ZKPs).
- The client sends (H) to an OpenTimestamps aggregator.
-
The aggregator returns a timestamp proof verifying that “this hash was seen at or before block/time (T).”
-
Create a “Timestamped Ballot” Payload
-
Combine:
- Encrypted ballot data.
- OTS proof for the hash of the ballot.
- EA’s signature on (\npub_e) (the blind-signed ephemeral key).
- A final signature by the voter’s ephemeral key ((nsec_e)) over the entire package.
-
Publish to Nostr
- The voter posts the complete “timestamped ballot” event to one or more relays.
- Observers see “an event from ephemeral key (\npub_e), with an OTS proof and the EA’s blind signature,” but cannot identify the real voter or see the vote’s contents.
3.4 Re-Voting (Updating the Ballot)
If the voter wishes to revise their vote (due to coercion, a mistake, or simply a change of mind):
- Generate a New Encrypted Ballot
- Possibly with different candidate choices.
- Obtain a New OTS Proof
- The new ballot has a fresh hash (H').
- The OTS aggregator provides a new proof anchored at a later block/time than the old one.
- Publish the Updated Ballot
- Again, sign with (\npub_e).
- Relays store both ballots, but the newer OTS timestamp shows which ballot is “final.”
Rule: The final vote for ephemeral key (\npub_e) is determined by the ballot with the highest valid OTS proof prior to the election’s closing.
3.5 Election Closing & Tally
- Close Signal
- At a specified time or block height, the EA publishes a “closing token.”
-
Any ballot with an OTS anchor referencing a time/block after the closing is invalid.
-
Collect Final Ballots
- Observers (or official tally software) gather the latest valid ballot from each ephemeral key.
-
They confirm the OTS proofs are valid and that no ephemeral key posted two different ballots with the same timestamp.
-
Decryption / Summation
- If homomorphic, the system sums the encrypted votes and uses a threshold of trustees to decrypt the aggregate.
- If a mix-net, the ballots are shuffled and partially decrypted, also requiring multiple trustees.
-
In either case, individual votes remain hidden, but the final counts are revealed.
-
Public Audit
- Anyone can fetch all ballots from the Nostr relays, verify OTS proofs, check the EA’s blind signature, and confirm no ephemeral key was used twice.
- The final totals can be recomputed from the publicly available data.
4. Ensuring One Vote Per Voter & No Invalid Voters
- One Blind Signature per Registered Voter
- The EA’s internal list ensures each real voter only obtains one ephemeral key signature.
- Blind Signature
- Ensures an unauthorized ephemeral key cannot pass validation (forging the EA’s signature is cryptographically infeasible).
- Public Ledger of Ballots
- Because each ballot references an EA-signed key, any ballot with a fake or duplicate signature is easily spotted.
5. Security and Privacy Analysis
- Voter Anonymity
- The EA never sees the unblinded ephemeral key. It cannot link (\npub_e) to a specific person.
-
Observers only see “some ephemeral key posted a ballot,” not the real identity of the voter.
-
Ballot Secrecy
- Homomorphic Encryption or Mix-Net: no one can decrypt an individual ballot; only aggregated or shuffled results are revealed.
-
The ephemeral key used for signing does not decrypt the ballot—the election’s threshold key does, after the election.
-
Verifiable Timestamping
- OpenTimestamps ensures each ballot’s time anchor cannot be forged or backdated.
-
Re-voting is transparent: a later OTS proof overrides earlier ones from the same ephemeral key.
-
Preventing Double Voting
- Each ephemeral key is unique and authorized once.
-
Re-voting by the same key overwrites the old ballot but does not increase the total count.
-
Protection Against Coercion
- Because the voter can re-cast until the deadline, a coerced vote can be replaced privately.
-
No receipts (individual decryption) are possible—only the final aggregated tally is revealed.
-
Threshold / Multi-Party Control
- Multiple trustees must collaborate to decrypt final results, preventing a single entity from tampering or prematurely viewing partial tallies.
6. Implementation Considerations
- Blind Signature Techniques
- Commonly implemented with RSA-based Chaumian blind signatures or BLS-based schemes.
-
Must ensure no link between (\npub_{e,\mathrm{blinded}}) and (\npub_e).
-
OpenTimestamps Scalability
- If millions of voters are posting ballots simultaneously, multiple timestamp aggregators or batch anchoring might be needed.
-
Verification logic on the client side or by public auditors must confirm each OTS proof’s integrity.
-
Relay Coordination
- The system must ensure no single relay can censor ballots. Voters may publish to multiple relays.
-
Tally fetchers cross-verify events from different relays.
-
Ease of Use
-
The user interface must hide the complexity of ephemeral key generation, blind signing, and OTS proof retrieval—making it as simple as possible for non-technical voters.
-
Legal Framework
-
If law requires publicly listing which voters have cast a ballot, you might track “Voter #12345 used their ephemeral key” without revealing the ephemeral key. Or you omit that if secrecy about who voted is desired.
-
Closing Time Edge Cases
- The system uses a block/time anchor from OTS. Slight unpredictability in block generation might require a small buffer around the official close. This is a policy choice.
7. Conclusion
We propose an election system that leverages Nostr for decentralizing ballot publication, blinded ephemeral keys for robust voter anonymity, homomorphic/mix-net encryption for ballot secrecy, threshold cryptography for collaborative final decryption, OpenTimestamps for tamper-proof time anchoring, and re-voting to combat coercion.
Key Advantages:
- Anonymity: The EA cannot link ballots to specific voters.
- One Voter, One Credential: Strict enforcement through blind signatures.
- Verifiable Ordering: OTS ensures each ballot has a unique, provable time anchor.
- Updatability: Voters can correct or override coerced ballots by posting a newer one before closing.
- Decentralized Audit: Anyone can fetch ballots from Nostr, verify the EA’s signatures and OTS proofs, and confirm the threshold-decrypted results match the posted ballots.
Such a design shows promise for secure, privacy-preserving digital elections, though real-world deployment will require careful policy, legal, and usability considerations. By combining cryptography with decentralized relays and an external timestamp anchor, the system can uphold both individual privacy and publicly auditable correctness.
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ 8f69ac99:4f92f5fd
2025-02-27 12:47:01
@ 8f69ac99:4f92f5fd
2025-02-27 12:47:01O Estado Social tem sido um pilar das políticas sociais europeias há décadas, oferecendo uma rede de segurança aos cidadãos através de diversos programas governamentais. Contudo, com a evolução das economias e o envelhecimento da população a pressionar os recursos públicos, este modelo tradicional enfrenta desafios crescentes. Custos em alta, ineficiências burocráticas e efeitos indesejados têm gerado um debate cada vez mais intenso sobre a sua sustentabilidade. Como alternativa, o Rendimento Básico Universal (RBU) ganhou destaque, prometendo simplicidade, mas trazendo preocupações quanto ao custo e aos desincentivos ao trabalho. Há, porém, uma opção mais equilibrada que merece atenção: o Imposto sobre o Rendimento Negativo (IRN).
Diferente da assistência social convencional, o IRN oferece apoio financeiro a quem está abaixo de um limiar de rendimento definido, sem exigir que procurem emprego ou dependam de ajudas públicas. Ao reduzir gradualmente os subsídios à medida que os rendimentos aumentam, incentiva a produtividade e preserva a iniciativa pessoal. Neste artigo, vamos explorar o IRN em profundidade, destacando as suas vantagens sobre os sistemas tradicionais, abordando as falhas do RBU e avaliando o seu potencial como uma reforma transformadora na Europa. Num contexto de mudanças económicas e demográficas, o IRN surge como um caminho prático para um sistema que equilibre apoio, dignidade e sustentabilidade.
Problemas dos Sistemas Tradicionais de Assistência Social
O Estado Social tradicional, embora bem-intencionado, tem sido alvo de críticas crescentes pelas suas ineficiências e consequências inesperadas.
Ineficiência e Burocracia
Estruturas administrativas complexas frequentemente atrasam os sistemas de assistência social, levando a desperdícios de recursos. Programas sobrepostos e serviços redundantes aumentam os custos, sobrecarregando os contribuintes. Por exemplo, várias entidades podem oferecer benefícios semelhantes, enquanto processos morosos atrasam a ajuda a quem precisa. Com o envelhecimento da população europeia a exigir mais apoio, estas ineficiências põem em risco a estabilidade financeira, desafiando os decisores políticos a repensarem a distribuição de recursos.
Incentivos Perversos
A assistência social pode, sem querer, desencorajar o trabalho e perpetuar a dependência. Surgem "armadilhas de assistência" quando os benefícios são estruturados de forma a que ganhar um salário resulte numa redução abrupta da ajuda, tornando o emprego menos atractivo do que permanecer no assistencialismo. Isso cria um ciclo em que os beneficiários hesitam em procurar trabalho ou formação, comprometendo as suas perspectivas a longo prazo. Com o tempo, tais sistemas arriscam criar uma cultura de dependência, minando a iniciativa pessoal e prendendo indivíduos numa estagnação económica.
Peso Económico
A pressão financeira do Estado Social está a intensificar-se com as mudanças demográficas na Europa. Populações mais envelhecidas requerem maior apoio, elevando os custos e exigindo impostos mais altos ou gastos públicos acrescidos. Isso desvia recursos da inovação e do investimento, podendo travar o crescimento económico. Sem reformas, estas despesas crescentes podem tornar-se insustentáveis, obrigando os governos a encontrar soluções que mantenham o apoio sem comprometer as finanças.
Estigma Social
Além das questões económicas, a assistência social traz muitas vezes um custo social. Os beneficiários enfrentam frequentemente estereótipos de preguiça ou incompetência, o que gera vergonha e diminui a autoestima. Este estigma pode dificultar a mobilidade social, tornando mais complicado sair da dependência. Resolver isto exige um sistema que não só apoie, mas também capacite, reduzindo preconceitos e promovendo inclusão.
Face a estas falhas, a Europa precisa de explorar alternativas que prestem ajuda de forma mais eficaz. O Imposto sobre o Rendimento Negativo apresenta-se como uma opção promissora, capaz de enfrentar estas questões sistémicas.
O Caso Contra o Rendimento Básico Universal (RBU)
O Rendimento Básico Universal surgiu como uma ideia ousada para combater a pobreza e a desigualdade, oferecendo a cada cidadão um pagamento fixo independentemente das suas necessidades. No entanto, a sua simplicidade traz desvantagens significativas.
O custo do RBU é um obstáculo enorme. Implementá-lo em toda a Europa exigiria fundos avultados, pressionando orçamentos já sobrecarregados pelos compromissos actuais do Estado Social. Isso poderia implicar subidas acentuadas de impostos ou cortes noutros serviços, enquanto a criação da infraestrutura administrativa necessária traria mais despesas. Há também quem tema os desincentivos ao trabalho: se todos receberem o mesmo valor, alguns podem sentir menos motivação para trabalhar ou arriscar em projectos empreendedores, podendo afectar a vitalidade económica.
Além disso, a abordagem universal do RBU sacrifica eficiência. Ao distribuir fundos de forma igual, não dá prioridade a quem mais precisa, entregando recursos aos mais ricos enquanto dilui o impacto sobre os pobres. Esta falta de foco levanta dúvidas sobre a sua capacidade de combater a desigualdade de forma eficaz. Embora o apelo do RBU esteja na sua universalidade, estes desafios apontam para a necessidade de uma solução mais direccionada—e é aqui que o IRN entra em cena.
Compreender o Imposto sobre o Rendimento Negativo (IRN)
O Imposto sobre o Rendimento Negativo propõe uma abordagem refinada ao apoio social, combinando assistência com incentivos. No seu cerne, define um limiar de rendimento base—digamos, 1.000 euros por mês. Quem ganha menos recebe um subsídio proporcional à diferença, enquanto quem ultrapassa esse valor paga impostos para financiar o sistema. Por exemplo, com uma taxa de subsídio de 50%, quem não tem rendimentos recebe 500 euros, e quem ganha 400 euros recebe 300 euros, elevando o total para 700 euros. À medida que o rendimento se aproxima do limiar, o subsídio diminui, desaparecendo nos 1.000 euros, altura em que a tributação começa.
Veja-se uma ilustração simples:
| Rendimento Mensal (€) | Pagamento IRN (€) | Rendimento Total Após IRN (€) | |-----------------------|-------------------|------------------------------| | 0 | 500 | 500 | | 400 | 300 | 700 | | 800 | 100 | 900 | | 1.000 | 0 | 1.000 | | 1.200 | - (impostos aplicam-se) | 1.200 - impostos |
Isto garante que trabalhar compensa sempre: ganhar mais aumenta o rendimento total, evitando a armadilha da assistência. O financiamento vem de um imposto fixo—talvez 19%—sobre os rendimentos acima do limiar. Quem ganha 1.500 euros, por exemplo, paga 95 euros sobre os 500 euros acima de 1.000, ficando com 1.405 euros. Este modelo fiscal simples facilita a gestão e assegura equidade.
| Rendimento (€) | Rendimento Tributável (€) | Imposto (€) | Após Imposto (€) | |----------------|---------------------|---------|------------------| | 1000 | 0 | 0 | 1000 | | 1200 | 200 | 38 | 1162 | | 2000 | 1000 | 190 | 1810 |
O IRN pode ser de participação voluntária, através de um contrato. As pessoas podem aderir ao sistema se precisarem de apoio ou rejeitá-lo se não aceitarem ajuda estatal, evitando os impostos associados ao financiamento do IRN. Quem optar por sair pode reentrar em caso de dificuldades, equilibrando liberdade de escolha com pragmatismo. Para libertários desconfiados de ingerências governamentais, isto torna o IRN um compromisso—um passo para longe do assistencialismo coercivo e em direcção a maior autonomia.
Filosoficamente, o IRN não é um objectivo final, mas uma ponte. Ao simplificar a ajuda e reduzir a burocracia, pode abrir caminho para soluções privadas, como caridade ou apoio mútuo, diminuindo o papel do estado ao longo do tempo. Características como a avaliação de meios e a indexação à inflação reforçam a sua adaptabilidade, garantindo que o apoio permaneça justo e relevante.
Vantagens do Imposto sobre o Rendimento Negativo (IRN)
O IRN destaca-se onde o Estado Social tradicional falha. Os seus subsídios decrescentes incentivam o trabalho, premiando o esforço à medida que o rendimento sobe e impulsionando a produtividade. Isto contrasta fortemente com as armadilhas da assistência, encorajando as pessoas a procurarem formação ou a arriscarem em empreendedorismo sem medo de perder apoio de repente.
Na gestão, o IRN é revolucionário. Substituir um emaranhado de programas por um único sistema reduz a burocracia e os custos, canalizando recursos directamente para quem precisa. Um processo de pagamento único elimina sobreposições, tornando a entrega de ajuda mais rápida e eficiente.
A dignidade é outro ponto forte. Ao oferecer escolha e evitar supervisão intrusiva, o IRN escapa ao estigma do assistencialismo, dando aos beneficiários autonomia para gerir as suas finanças. Isso promove o autorrespeito e um sentido de controlo, quebrando o ciclo de dependência.
Economicamente, a flexibilidade do IRN sobressai. Adapta-se às flutuações de rendimento, direccionando a ajuda exactamente onde é necessária. Estudos indicam que pode reduzir a pobreza, melhorar a mobilidade social e até beneficiar a saúde, ao aliviar o stress financeiro, oferecendo um impulso abrangente ao bem-estar.
Responder às Críticas ao Imposto sobre o Rendimento Negativo (IRN)
Nenhuma política escapa a críticas, e o IRN tem as suas. Os libertários veem, e bem, os impostos como roubo, e embora o IRN não elimine esta tensão, suaviza-a. Ao condensar o Estado Social num sistema claro e simples, reduz a intromissão estatal face à burocracia actual. Os seus incentivos ao trabalho alinham-se com valores de responsabilidade, tornando-o um passo aceitável a curto prazo.
O financiamento preocupa, sobretudo em países europeus já muito tributados, mas uma taxa fixa oferece uma solução. Simples e previsível, minimiza os custos administrativos e assegura contribuições justas, sustentando o IRN sem sobrecarga excessiva. Há também quem debata o seu impacto social—uns chamam-lhe um subsídio fácil, um hand-out, outros um sistema demasiado voltado para o mercado. Ainda assim, o IRN encontra um meio-termo, oferecendo uma rede de segurança que recompensa o esforço sem controlar vidas.
Passar para o IRN exige eliminar gradualmente os programas antigos e informar o público sobre os seus benefícios: um governo mais leve, menos dependência e maior iniciativa pessoal. Para quem sonha com um futuro sem estado, o IRN não é o destino, mas um movimento prático rumo a sistemas de apoio voluntários, promovendo uma cultura de autossuficiência.
Conclusão
O Imposto sobre o Rendimento Negativo não é perfeito, mas é um avanço claro face ao status quo. Reduz os excessos do Estado Social, promove trabalho e dignidade, e oferece à Europa uma reforma viável perante as pressões económicas. Para os contribuintes, promete eficiência; para os beneficiários, oportunidade. Numa região onde o assistencialismo está profundamente enraizado, o IRN surge como um passo ousado, mas possível, para um futuro mais livre e sustentável—um que capacite as pessoas enquanto alivia o peso do estado.
Photo by The New York Public Library on Unsplash
-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ 21ffd29c:518a8ff5
2025-02-04 21:12:15
@ 21ffd29c:518a8ff5
2025-02-04 21:12:15- What Are Homestead Chickens?
Homestead chickens are domesticated fowl kept by homeowners to provide eggs and companionship. They play a vital role in the homestead ecosystem.
Why Water is Essential in Cold Weather - Hydration Basics:
Chickens don't drink much water naturally but need it for hydration, especially during cold weather when metabolic rates increase. - Environmental Factors:
Cold weather can lead to ice buildup on water sources. Chickens benefit from having access to fresh water year-round.Maintaining Accessible Water Sources - Shallow Troughs:
Use shallow troughs instead of deep containers to minimize ice formation and ensure constant water supply. - Automatic Feeders:
Consider installing automatic feeders for convenience, especially in unpredictable weather conditions. - Multiple Water Sources:
Provide multiple water sources to prevent competition and ensure all chickens have access.Preventing Ice Buildup - Floating Shallow Troughs:
Opt for troughs that sit above the ground to avoid ice buildup. Ensure they're placed where they can't freeze completely. - Regular Checks:
Inspect water sources regularly to remove ice and debris, maintaining accessibility for chickens.Best Practices for Watering Chickens - Waterers Designed for Cold Weather:
Use waterers made of stainless steel or plastic that can withstand cold temperatures. - Seasonal Adjustments:
During extreme cold spells, supplement with a small amount of fresh water to aid in drinking.Conclusion - Key Takeaways:
Providing proper water is crucial for the health and well-being of homestead chickens during cold weather. Maintaining accessible, shallow water sources prevents issues like ice buildup and ensures hydration.Final Thoughts - Sustainability Considerations:
While chickens don't drink much, ensuring they have water supports their overall health and sustainability efforts. - Environmental Impact:
Thoughtful water management can reduce water usage, promoting eco-friendly practices on the homestead. - What Are Homestead Chickens?
-
 @ 8da249fe:ecc00e09
2025-02-27 12:36:07
@ 8da249fe:ecc00e09
2025-02-27 12:36:07Se você está começando no mundo do Bitcoin e das criptomoedas, já deve ter ouvido falar em "hot wallets" e "cold wallets". Mas qual é a diferença entre elas? E qual é a melhor opção para armazenar seus ativos digitais com segurança?
O que é uma Hot Wallet?

Uma hot wallet (carteira quente) é uma carteira conectada à internet. Isso significa que ela é mais acessível e fácil de usar para transações rápidas. As hot wallets podem ser:
Carteiras móveis – Aplicativos como BlueWallet, Trust Wallet e outras.
Carteiras de desktop – Programas instalados no computador, como Electrum e Exodus.
Carteiras web – Serviços online como a carteira do próprio Binance ou outras exchanges.
Vantagens da Hot Wallet
✅ Acesso rápido e fácil para transações diárias. ✅ Interface amigável, ideal para iniciantes. ✅ Geralmente gratuita para uso.
Desvantagens da Hot Wallet
❌ Maior risco de ataque hacker, já que está sempre online. ❌ Se o dispositivo for infectado por malware, suas chaves privadas podem ser comprometidas.
O que é uma Cold Wallet?#

Uma cold wallet (carteira fria) é uma carteira que não está conectada à internet, tornando-se muito mais segura contra hackers. Elas podem ser:
Carteiras de hardware – Como Ledger Nano S, Nano X ou Trezor.
Carteiras de papel – Impressão da chave privada e do endereço em um papel.
Computadores ou dispositivos offline – Um computador dedicado apenas para armazenar criptomoedas, sem conexão com a internet.
Vantagens da Cold Wallet
✅ Segurança máxima contra ataques cibernéticos. ✅ Ótima opção para armazenamento de longo prazo. ✅ Controle total sobre suas chaves privadas.
Desvantagens da Cold Wallet
❌ Menos prática para transações diárias. ❌ Pode ser mais cara, no caso das carteiras de hardware. ❌ Se você perder sua chave privada ou backup, pode perder o acesso aos fundos.
Qual escolher: Hot ou Cold Wallet?
A escolha depende do seu perfil de investidor:
Se você faz transações frequentes, uma hot wallet pode ser mais conveniente.
Se você quer armazenar Bitcoin com segurança por muito tempo, a cold wallet é a melhor opção.
Muitos usuários combinam as duas, mantendo uma pequena quantia em uma hot wallet para o dia a dia e guardando a maior parte dos fundos em uma cold wallet.
Independente da escolha, lembre-se sempre de manter suas chaves privadas seguras e fazer backups regularmente!
Gostou do conteúdo? Compartilhe sua opinião nos comentários! -
 @ a2eddb26:e2868a80
2025-02-20 20:28:46
@ a2eddb26:e2868a80
2025-02-20 20:28:46In personal finance, the principles of financial independence and time sovereignty (FITS) empower individuals to escape the debt-based cycle that forces them into perpetual work. What if companies could apply the same principles? What if businesses, instead of succumbing to the relentless push for infinite growth, could optimize for real demand?
This case study of the GPU industry aims to show that fiat-driven incentives distort technological progress and imagines an alternative future built on sound money.
Fiat Business: Growth or Death
Tech companies no longer optimize for efficiency, longevity, or real user needs. Instead, under a fiat system, they are forced into a perpetual growth model. If NVIDIA, AMD, or Intel fail to show revenue expansion, their stock price tanks. Let's take NVIDIA's GPUs as an example. The result is predictable:
- GPUs that nobody actually needs but everyone is told to buy.
- A focus on artificial benchmarks instead of real-world performance stability.
- Endless FPS increases that mean nothing for 99% of users.
The RTX 5090 is not for gamers. It is for NVIDIA’s quarterly earnings. This is not a surprise on a fiat standard.
Fiat Marketing: The Illusion of Need and the Refresh Rate Trap
Benchmarks confirm that once a GPU maintains 120+ FPS in worst-case scenarios, additional performance gains become irrelevant for most players. This level of capability was reached years ago. The problem is that efficiency does not sell as easily as bigger numbers.
This extends beyond raw GPU power and into the display market, where increasing refresh rates and resolutions are marketed as critical upgrades, despite diminishing real-world benefits for most users. While refresh rates above 120Hz may offer marginal improvements for competitive esports players, the average user sees little benefit beyond a certain threshold. Similarly, 8K resolutions are pushed as the next frontier, even though 4K remains underutilized due to game optimization and hardware constraints. This is why GPUs keep getting bigger, hotter, and more expensive, even when most gamers would be fine with a card from five years ago. It is why every generation brings another “must-have” feature, regardless of whether it impacts real-world performance.
Marketing under fiat operates on the principle of making people think they need something they do not. The fiat standard does not just distort capital allocation. It manufactures demand by exaggerating the importance of specifications that most users do not truly need.
The goal is not technological progress but sales volume. True innovation would focus on meaningful performance gains that align with actual gaming demands, such as improving latency, frame-time consistency, and efficient power consumption. Instead, marketing convinces consumers they need unnecessary upgrades, driving them into endless hardware cycles that favor stock prices over user experience.
They need the next-gen cycle to maintain high margins. The hardware is no longer designed for users. It is designed for shareholders. A company operating on sound money would not rely on deceptive marketing cycles. It would align product development with real user needs instead of forcing artificial demand.
The Shift to AI
For years, GPUs were optimized for gaming. Then AI changed everything. OpenAI, Google, and Stability AI now outbid consumers for GPUs. The 4090 became impossible to find, not because of gamers, but because AI labs were hoarding them.
The same companies that depended on the consumer upgrade cycle now see their real profits coming from data centers. Yet, they still push gaming hardware aggressively. However, legitimate areas for improvement do exist. While marketing exaggerates the need for higher FPS at extreme resolutions, real gaming performance should focus on frame stability, low latency, and efficient rendering techniques. These are the areas where actual innovation should be happening. Instead, the industry prioritizes artificial performance milestones to create the illusion of progress, rather than refining and optimizing for the gaming experience itself. Why?
Gamers Fund the R&D for AI and Bear the Cost of Scalping
NVIDIA still needs gamers, but not in the way most think. The gaming market provides steady revenue, but it is no longer the priority. With production capacity shifting toward AI and industrial clients, fewer GPUs are available for gamers. This reduced supply has led to rampant scalping, where resellers exploit scarcity to drive up prices beyond reasonable levels. Instead of addressing the issue, NVIDIA benefits from the inflated demand and price perception, creating an even stronger case for prioritizing enterprise sales. Gaming revenue subsidizes AI research. The more RTX cards they sell, the more they justify pouring resources into data-center GPUs like the H100, which generate significantly higher margins than gaming hardware.
AI dictates the future of GPUs. If NVIDIA and AMD produced dedicated gamer-specific GPUs in higher volumes, they could serve that market at lower prices. But in the fiat-driven world of stockholder demands, maintaining artificially constrained supply ensures maximum profitability. Gamers are left paying inflated prices for hardware that is no longer built with them as the primary customer. That is why GPU prices keep climbing. Gamers are no longer the main customer. They are a liquidity pool.
The Financial Reality
The financial reports confirm this shift: NVIDIA’s 2024 fiscal year saw a 126% revenue increase, reaching \$60.9 billion. The data center segment alone grew 217%, generating \$47.5 billion. (Source)
The numbers make it clear. The real money is in AI and data centers, not gaming. NVIDIA has not only shifted its focus away from gamers but has also engaged in financial engineering to maintain its dominance. The company has consistently engaged in substantial stock buybacks, a hallmark of fiat-driven financial practices. In August 2023, NVIDIA announced a \$25 billion share repurchase program, surprising some investors given the stock's significant rise that year. (Source) This was followed by an additional \$50 billion buyback authorization in 2024, bringing the total to \$75 billion over two years. (Source)
These buybacks are designed to return capital to shareholders and can enhance earnings per share by reducing the number of outstanding shares. However, they also reflect a focus on short-term stock price appreciation rather than long-term value creation. Instead of using capital for product innovation, NVIDIA directs it toward inflating stock value, ultimately reducing its long-term resilience and innovation potential. In addition to shifting production away from consumer GPUs, NVIDIA has also enabled AI firms to use its chips as collateral to secure massive loans. Lambda, an AI cloud provider, secured a \$500 million loan backed by NVIDIA's H200 and Blackwell AI chips, with financing provided by Macquarie Group and Industrial Development Funding. (Source)
This practice mirrors the way Bitcoin miners have used mining hardware as collateral, expecting continuous high returns to justify the debt. GPUs are fast-depreciating assets that lose value rapidly as new generations replace them. Collateralizing loans with such hardware is a high-risk strategy that depends on continued AI demand to justify the debt. AI firms borrowing against them are placing a leveraged bet on demand staying high. If AI market conditions shift or next-generation chips render current hardware obsolete, the collateral value could collapse, leading to cascading loan defaults and liquidations.
This is not a sound-money approach to business. It is fiat-style quicksand financialization, where loans are built on assets with a limited shelf life. Instead of focusing on sustainable capital allocation, firms are leveraging their future on rapid turnover cycles. This further shifts resources away from gamers, reinforcing the trend where NVIDIA prioritizes high-margin AI sales over its original gaming audience.
At the same time, NVIDIA has been accused of leveraging anti-competitive tactics to maintain its market dominance. The GeForce Partner Program (GPP) launched in 2018 sought to lock hardware partners into exclusive deals with NVIDIA, restricting consumer choice and marginalizing AMD. Following industry backlash, the program was canceled. (Source)
NVIDIA is not merely responding to market demand but shaping it through artificial constraints, financialization, and monopolistic control. The result is an industry where consumers face higher prices, limited options, and fewer true innovations as companies prioritize financial games over engineering excellence.
On this basis, short-term downturns fueled by stock buybacks and leveraged bets create instability, leading to key staff layoffs. This forces employees into survival mode rather than fostering long-term innovation and career growth. Instead of building resilient, forward-looking teams, companies trapped in fiat incentives prioritize temporary financial engineering over actual product and market development.
A Sound Money Alternative: Aligning Incentives
Under a sound money system, consumers would become more mindful of purchases as prices naturally decline over time. This would force businesses to prioritize real value creation instead of relying on artificial scarcity and marketing hype. Companies would need to align their strategies with long-term customer satisfaction and sustainable engineering instead of driving demand through planned obsolescence.
Imagine an orange-pilled CEO at NVIDIA. Instead of chasing infinite growth, they persuade the board to pivot toward sustainability and long-term value creation. The company abandons artificial product cycles, prioritizing efficiency, durability, and cost-effectiveness. Gaming GPUs are designed to last a decade, not three years. The model shifts to modular upgrades instead of full replacements. Pricing aligns with real user needs, not speculative stock market gains.
Investors initially panic. The stock takes a temporary hit, but as consumers realize they no longer need to upgrade constantly, brand loyalty strengthens. Demand stabilizes, reducing volatility in production and supply chains. Gamers benefit from high-quality products that do not degrade artificially. AI buyers still access high-performance chips but at fair market prices, no longer subsidized by forced consumer churn.
This is not an abstract vision. Businesses could collateralize loans with Bitcoin. Companies could also leverage highly sought-after end products that maintain long-term value. Instead of stock buybacks or anti-competitive practices, companies would focus on building genuine, long-term value. A future where Bitcoin-backed reserves replace fiat-driven financial engineering would stabilize capital allocation, preventing endless boom-bust cycles. This shift would eliminate the speculative nature of AI-backed loans, fostering financial stability for both borrowers and lenders.
Sound money leads to sound business. When capital allocation is driven by real value rather than debt-fueled expansion, industries focus on sustainable innovation rather than wasteful iteration.
Reclaiming Time Sovereignty for Companies
The fiat system forces corporations into unsustainable growth cycles. Companies that embrace financial independence and time sovereignty can escape this trap and focus on long-term value.
GPU development illustrates this distortion. The RTX 3080 met nearly all gaming needs, yet manufacturers push unnecessary performance gains to fuel stock prices rather than improve usability. GPUs are no longer designed for gamers but for AI and enterprise clients, shifting NVIDIA’s priorities toward financial engineering over real innovation.
This cycle of GPU inflation stems from fiat-driven incentives—growth for the sake of stock performance rather than actual demand. Under a sound money standard, companies would build durable products, prioritizing efficiency over forced obsolescence.
Just as individuals can reclaim financial sovereignty, businesses can do the same. Embracing sound money fosters sustainable business strategies, where technology serves real needs instead of short-term speculation.
Bitcoin
FITS
Marketing
TimeSovereignty
BitcoinFixesThis
OptOut
EngineeringNotFinance
SoundBusiness
-
 @ 0fa80bd3:ea7325de
2025-01-29 14:44:48
@ 0fa80bd3:ea7325de
2025-01-29 14:44:48![[yedinaya-rossiya-bear.png]]
1️⃣ Be where the bear roams. Stay in its territory, where it hunts for food. No point setting a trap in your backyard if the bear’s chilling in the forest.
2️⃣ Set a well-hidden trap. Bury it, disguise it, and place the bait right in the center. Bears are omnivores—just like secret police KGB agents. And what’s the tastiest bait for them? Money.
3️⃣ Wait for the bear to take the bait. When it reaches in, the trap will snap shut around its paw. It’ll be alive, but stuck. No escape.
Now, what you do with a trapped bear is another question... 😏
-
 @ 9e69e420:d12360c2
2025-02-01 11:16:04
@ 9e69e420:d12360c2
2025-02-01 11:16:04Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-
 @ d5c3d063:4d1159b3
2025-02-27 11:09:15
@ d5c3d063:4d1159b3
2025-02-27 11:09:15ถ้าคุณเชื่ออะไรบางอย่างมาตลอดชีวิต แล้ววันหนึ่งกลับพบว่ามันอาจไม่เป็นอย่างที่คิด นี่คือความรู้สึกของผมในวันนั้น เป็นครั้งแรกที่ได้นั่งฟังหมอป๊อป DietDoctor Thailand บรรยายสดๆ ในงานสัมมนา “Nutrition 101 - โภชนาการพื้นฐาน” Healthy Hut - โรงบ่มสุขภาพ เอาตรง ๆ นะ...ความรู้สึกเหมือนผมไม่ได้กำลังฟังหมอคนหนึ่งพูด แต่เหมือนกำลังนั่งฟังนักปรัชญามากกว่า . หมอป๊อปไม่ได้มาบอกว่าเราต้องกินอะไรหรือห้ามกินอะไร แต่ท่านตั้งคำถามให้เราคิดตาม เช่น "ทำไมวัวถึงกินหญ้าได้ทั้งวันโดยไม่มีปัญหาระดับน้ำตาลในเลือด...แต่มนุษย์กลับเสี่ยงเป็นเบาหวานจากการกินคาร์โบไฮเดรต" มันเป็นคำถามที่ฟังดูเรียบง่ายแต่กลับทำให้ผมฉุกคิดถึงความเข้าใจที่เรามีมาโดยตลอด ผมนั่งฟังแล้วก็เริ่มทบทวนสิ่งที่ตัวเองเคยเชื่อ บางที...สิ่งที่เราคิดว่าถูกต้องมาตลอด อาจเป็นเพียงสิ่งที่เราถูกบอกให้เชื่อเท่านั้น เช่น เราต้องกินข้าวให้ครบทุกมื้อเพราะมันเป็นแหล่งพลังงานหลัก หรือเคยเชื่อว่าเบาหวานเป็นเรื่องของกรรมพันธุ์ แต่วันนั้นผมได้เข้าใจว่ามนุษย์ไม่ได้ถูกออกแบบมาให้กินแป้งมากขนาดนี้ ร่างกายสามารถเผาผลาญไขมันเป็นพลังงานได้ดีกว่าคาร์โบไฮเดรต และเบาหวานไม่ใช่เรื่องของโชคชะตา แต่มันเกี่ยวข้องกับพฤติกรรมการกินของเราเอง . เมื่อสิ่งที่ผมเคยเชื่อว่าจริง อาจไม่ใช่สิ่งที่ถูกต้องเสมอไป ผมเลยคิดว่า…นอกจากเรื่องอาหารแล้ว ยังมีเรื่องอื่นอีกไหมที่เราถูกสอนมาโดยที่ไม่เคยตั้งคำถาม ผมมักจะนึกถึงเรื่องเศรษฐศาสตร์ เราถูกบอกให้เชื่อว่าเงินเฟ้ออ่อน ๆ ดีต่อเศรษฐกิจ เราถูกบอกว่า CPI เป็นตัววัดเงินเฟ้อที่แม่นยำ เราถูกบอกว่าเงินต้องถูกควบคุมโดยรัฐ มันคล้ายกับเรื่องโภชนาการเลยครับ เราถูกสอนว่าต้องกินแป้ง ต้องกินผักผลไท้ ต้องกินข้าวเช้า ต้องกินอาหารให้ครบ 5 หมู่ แต่ในความเป็นจริง...ร่างกายเรามีกระบวนการทางชีวภาพที่เกิดขึ้นตามธรรมชาติ ซึ่งช่วยปรับสมดุลเมื่อได้รับสารอาหารที่เหมาะสม แล้วถ้าระบบนี้ถูกก่อกวนซ้ำ ๆ ด้วยคาร์โบไฮเดรตและน้ำตาลมากเกินไปอาจนำไปสู่ปัญหาสุขภาพในระยะยาว เช่นเดียวกันกับระบบเศรษฐกิจ ถ้ารัฐเข้าไปแทรกแซงเรื่อย ๆ ก็จะส่งผลให้กลไกตลาดไม่สามารถทำงานได้อย่างมีประสิทธิภาพและตามมาด้วยปัญหาในระยะยาว . แล้วถ้าเราเปรียบเทียบระบบการเงินเป็นอาหาร เงินเฟียตก็เหมือนอาหารแปรรูปที่ถูกทำให้ดูดีแต่มีผลกระทบต่อร่างกายเราในระยะยาว ส่วนบิตคอยน์ก็เหมือนเนื้อสเต็กเป็นอาหารธรรมชาติ ที่ไม่มีการแปรรูป ลองคิดดูว่า...ถ้าเราหยุดกินน้ำตาลสักพัก ร่างกายจะค่อย ๆ ฟื้นฟูและปรับสมดุลของตัวเอง เช่นเดียวกับเศรษฐกิจที่สามารถกลับมามั่นคงได้หากปล่อยให้ตลาดเสรีทำงานตามกลไกธรรมชาติ เงินที่ไม่ได้ถูกควบคุมจากส่วนกลางก็เหมือนอาหารที่ไม่ผ่านการแปรรูป ไม่มีการปรุงแต่งหรือเปลี่ยนแปลงตามใจผู้มีอำนาจ . สิ่งที่ผมได้จากหมอป๊อปวันนั้น ไม่ใช่แค่ความรู้เรื่องอาหาร แต่มันคือทักษะในการตั้งคำถาม ...ถ้าอาหารที่เรากินมาตลอดจากความเชื่ออาจไม่ดีอย่างที่คิด แล้วสิ่งที่เราเชื่อเกี่ยวกับเศรษฐกิจล่ะ !? ...ถ้าเบาหวานสามารถหายได้โดยไม่ต้องใช้ยา แล้วถ้าผู้คนสามารถเลือกใช้เงินได้อย่างเสรี เศรษฐกิจจะดีขึ้นไหท การเรียนรู้ไม่ใช่แค่การฟังแล้วเชื่อ แต่เป็นการฟังแล้วตั้งคำถาม เพราะความจริง ไม่ได้ขึ้นอยู่กับสิ่งที่เราถูกสอนมาเสมอไป แต่เกิดจากการเข้าใจธรรมชาติของมันอย่างแท้จริง และเมื่อเรามีความรู้ความเชื่อก็สามารถเปลี่ยนแปลงได้
RifhtShift #โรงบ่มสุขภาพ #HealthyHut
สุขภาพดี #ความรู้สุขภาพ #Siamstr
-
 @ 9e69e420:d12360c2
2025-01-25 22:16:54
@ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.”
The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China.
-
 @ 97c70a44:ad98e322
2025-02-18 00:24:32
@ 97c70a44:ad98e322
2025-02-18 00:24:32For the last couple of weeks, I've been dealing with the fallout of upgrading a web application to Svelte 5. Complaints about framework churn and migration annoyances aside, I've run into some interesting issues with the migration. So far, I haven't seen many other people register the same issues, so I thought it might be constructive for me to articulate them myself.
I'll try not to complain too much in this post, since I'm grateful for the many years of Svelte 3/4 I've enjoyed. But I don't think I'll be choosing Svelte for any new projects going forward. I hope my reflections here will be useful to others as well.
If you're interested in reproductions for the issues I mention here, you can find them below.
The Need for Speed
To start with, let me just quickly acknowledge what the Svelte team is trying to do. It seems like most of the substantial changes in version 5 are built around "deep reactivity", which allows for more granular reactivity, leading to better performance. Performance is good, and the Svelte team has always excelled at reconciling performance with DX.
In previous versions of Svelte, the main way this was achieved was with the Svelte compiler. There were many ancillary techniques involved in improving performance, but having a framework compile step gave the Svelte team a lot of leeway for rearranging things under the hood without making developers learn new concepts. This is what made Svelte so original in the beginning.
At the same time, it resulted in an even more opaque framework than usual, making it harder for developers to debug more complex issues. To make matters worse, the compiler had bugs, resulting in errors which could only be fixed by blindly refactoring the problem component. This happened to me personally at least half a dozen times, and is what ultimately pushed me to migrate to Svelte 5.
Nevertheless, I always felt it was an acceptable trade-off for speed and productivity. Sure, sometimes I had to delete my project and port it to a fresh repository every so often, but the framework was truly a pleasure to use.
Svelte is not Javascript
Svelte 5 doubled down on this tradeoff — which makes sense, because it's what sets the framework apart. The difference this time is that the abstraction/performance tradeoff did not stay in compiler land, but intruded into runtime in two important ways:
- The use of proxies to support deep reactivity
- Implicit component lifecycle state
Both of these changes improved performance and made the API for developers look slicker. What's not to like? Unfortunately, both of these features are classic examples of a leaky abstraction, and ultimately make things more complex for developers, not less.
Proxies are not objects
The use of proxies seems to have allowed the Svelte team to squeeze a little more performance out of the framework, without asking developers to do any extra work. Threading state through multiple levels of components without provoking unnecessary re-renders in frameworks like React is an infamously difficult chore.
Svelte's compiler avoided some of the pitfalls associated with virtual DOM diffing solutions, but evidently there was still enough of a performance gain to be had to justify the introduction of proxies. The Svelte team also seems to argue that their introduction represents an improvement in developer experience:
we... can maximise both efficiency and ergonomics.
Here's the problem: Svelte 5 looks simpler, but actually introduces more abstractions.
Using proxies to monitor array methods (for example) is appealing because it allows developers to forget all the goofy heuristics involved with making sure state was reactive and just
pushto the array. I can't count how many times I've writtenvalue = valueto trigger reactivity in svelte 4.In Svelte 4, developers had to understand how the Svelte compiler worked. The compiler, being a leaky abstraction, forced its users to know that assignment was how you signaled reactivity. In svelte 5, developers can just "forget" about the compiler!
Except they can't. All the introduction of new abstractions really accomplishes is the introduction of more complex heuristics that developers have to keep in their heads in order to get the compiler to act the way they want it to.
In fact, this is why after years of using Svelte, I found myself using Svelte stores more and more often, and reactive declarations less. The reason being that Svelte stores are just javascript. Calling
updateon a store is simple, and being able to reference them with a$was just a nice bonus — nothing to remember, and if I mess up the compiler yells at me.Proxies introduce a similar problem to reactive declarations, which is that they look like one thing but act like another on the edges.
When I started using Svelte 5, everything worked great — until I tried to save a proxy to indexeddb, at which point I got a
DataCloneError. To make matters worse, it's impossible to reliably tell if something is aProxywithouttry/catching a structured clone, which is a performance-intensive operation.This forces the developer to remember what is and what isn't a Proxy, calling
$state.snapshotevery time they pass a proxy to a context that doesn't expect or know about them. This obviates all the nice abstractions they gave us in the first place.Components are not functions
The reason virtual DOM took off way back in 2013 was the ability to model your application as composed functions, each of which takes data and spits out HTML. Svelte retained this paradigm, using a compiler to sidestep the inefficiencies of virtual DOM and the complexities of lifecycle methods.
In Svelte 5, component lifecycles are back, react-hooks style.
In React, hooks are an abstraction that allows developers to avoid writing all the stateful code associated with component lifecycle methods. Modern React tutorials universally recommend using hooks instead, which rely on the framework invisibly synchronizing state with the render tree.
While this does result in cleaner code, it also requires developers to tread carefully to avoid breaking the assumptions surrounding hooks. Just try accessing state in a
setTimeoutand you'll see what I mean.Svelte 4 had a few gotchas like this — for example, async code that interacts with a component's DOM elements has to keep track of whether the component is unmounted. This is pretty similar to the kind of pattern you'd see in old React components that relied on lifecycle methods.
It seems to me that Svelte 5 has gone the React 16 route by adding implicit state related to component lifecycles in order to coordinate state changes and effects.
For example, example is in the documentation for $effect:
You can place $effect anywhere, not just at the top level of a component, as long as it is called during component initialization (or while a parent effect is active). It is then tied to the lifecycle of the component (or parent effect) and will therefore destroy itself when the component unmounts (or the parent effect is destroyed).
That's very complex! In order to use
$effect... effectively (sorry), developers have to understand how state changes are tracked. The documentation for component lifecycles claims:In Svelte 5, the component lifecycle consists of only two parts: Its creation and its destruction. Everything in-between — when certain state is updated — is not related to the component as a whole; only the parts that need to react to the state change are notified. This is because under the hood the smallest unit of change is actually not a component, it’s the (render) effects that the component sets up upon component initialization. Consequently, there’s no such thing as a “before update”/"after update” hook.
But then goes on to introduce the idea of
tickin conjunction with$effect.pre. This section explains that "tickreturns a promise that resolves once any pending state changes have been applied, or in the next microtask if there are none."I'm sure there's some mental model that justifies this, but I don't think the claim that a component's lifecycle is only comprised of mount/unmount is really helpful when an addendum about state change has to come right afterward.
The place where this really bit me, and which is the motivation for this blog post, is when state gets coupled to a component's lifecycle, even when the state is passed to another function that doesn't know anything about svelte.
In my application, I manage modal dialogs by storing the component I want to render alongside its props in a store and rendering it in the
layoutof my application. This store is also synchronized with browser history so that the back button works to close them. Sometimes, it's useful to pass a callback to one of these modals, binding caller-specific functionality to the child component:javascript const {value} = $props() const callback = () => console.log(value) const openModal = () => pushModal(MyModal, {callback})This is a fundamental pattern in javascript. Passing a callback is just one of those things you do.
Unfortunately, if the above code lives in a modal dialog itself, the caller component gets unmounted before the callback gets called. In Svelte 4, this worked fine, but in Svelte 5
valuegets updated toundefinedwhen the component gets unmounted. Here's a minimal reproduction.This is only one example, but it seems clear to me that any value that is closed over by a callback function that lives longer than its component will be undefined when I want to use it — with no reassignment existing in lexical scope.
This just isn't how javascript works. And I think the reason Svelte works this way is that it is attempting to re-invent garbage collection. Because
valueis a prop of the component, it apparently has to be cleaned up at the end of the component's lifecycle. I'm sure there's a good engineering reason for this, but it is surprising.Conclusion
Easy things are nice, but as Rich Hickey says, easy things are not always simple. And like Joel Spolsky, I don't like being surprised. Svelte has always been full of magic, but with the latest release I think the cognitive overhead of reciting incantations has finally outweighed the power it conveys.
My point in this post is not to dunk on the Svelte team. I know lots of people like Svelte 5 (and react hooks). The point I hope to make is that there is a tradeoff between doing things for the user, and giving the user agency. Good software is built on understanding, not cleverness.
I also think this is an important lesson to remember as AI-assisted coding becomes increasingly popular. Don't choose tools that alienate you from your work. Choose tools that leverage the wisdom you've already accumulated, and which help you to cultivate a deeper understanding of the discipline.
Thank you to Rich Harris and team for many years of pleasant development. I hope that (if you read this) it's not so full of inaccuracies as to be unhelpful as user feedback.
-
 @ b17fccdf:b7211155
2025-01-21 17:02:21
@ b17fccdf:b7211155
2025-01-21 17:02:21The past 26 August, Tor introduced officially a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks.
~ > This feature at the moment, is deactivate by default, so you need to follow these steps to activate this on a MiniBolt node:
- Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing
tor --versionExample of expected output:
Tor version 0.4.8.6. This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html) Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc. Tor compiled with GCC version 12.2.0~ > If you have v0.4.8.X, you are OK, if not, type
sudo apt update && sudo apt upgradeand confirm to update.- Basic PoW support can be checked by running this command:
tor --list-modulesExpected output:
relay: yes dirauth: yes dircache: yes pow: **yes**~ > If you have
pow: yes, you are OK- Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added
sudo nano /etc/tor/torrcExample:
```
Hidden Service BTC RPC Explorer
HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/ HiddenServiceVersion 3 HiddenServicePoWDefensesEnabled 1 HiddenServicePort 80 127.0.0.1:3002 ```
~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links:
- Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002
- LND: https://github.com/bitcoin/bitcoin/issues/28499
More info:
- https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/
- https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ
Enjoy it MiniBolter! 💙
-
 @ d360efec:14907b5f
2025-02-27 09:56:31
@ d360efec:14907b5f
2025-02-27 09:56:31ภาพรวม BTCUSDT (OKX):
Bitcoin (BTCUSDT) แนวโน้ม Day ยังเป็นขาลง , 4H Sideway Down, 15m Sideways Down
วิเคราะห์ทีละ Timeframe:
(1) TF Day (รายวัน):
- แนวโน้ม: ขาลง (Downtrend)
- SMC:
- Lower Highs (LH) และ Lower Lows (LL)
- Break of Structure (BOS) ด้านล่าง
- Liquidity:
- มี Sellside Liquidity (SSL) ใต้ Lows
- มี Buyside Liquidity (BSL) เหนือ Highs
- ICT:
- Order Block: ราคา Sideway ใกล้ๆ Order Block ขาลง
- EMA:
- ราคาอยู่ใต้ EMA 50/200
- Money Flow (LuxAlgo):
- แดง
- Trend Strength (AlgoAlpha):
- แดง/ไม่มีสัญญาณ
- Chart Patterns: None
- Volume Profile:
- แนวรับ: Low ล่าสุด
- แนวต้าน: EMA 50/200, Order Block
- สรุป: แนวโน้มขาลง
(2) TF4H (4 ชั่วโมง):
- แนวโน้ม: ขาลง (Downtrend)
- SMC:
- Lower Highs (LH) และ Lower Lows (LL)
- Break of Structure (BOS)
- Liquidity:
- มี SSL
- มี BSL
- ICT: * Order Block: ราคา Sideway ใกล้ๆ Order Block ขาลง
- EMA:
- ราคาอยู่ใต้ EMA 50/200
- Money Flow (LuxAlgo):
- แดง
- Trend Strength (AlgoAlpha):
- แดง/ไม่มีสัญญาณ
- Chart Patterns: None
- Volume Profile:
- แนวรับ: Low
- แนวต้าน: EMA 50/200, Order Block
- สรุป: แนวโน้มขาลง
(3) TF15 (15 นาที):
- แนวโน้ม: Sideways Down
- SMC:
- Lower Highs (LH) และ Lower Lows (LL) เริ่ม Sideways
- Break of Structure (BOS)
- Liquidity:
- ICT: * Order Block ราคา Sideways ใกล้ๆ Order Block
- EMA:
- EMA 50/200 เป็นแนวต้าน
- Money Flow (LuxAlgo):
- แดง/เขียว สลับกัน
- Trend Strength (AlgoAlpha):
- แดง/ไม่มีสัญญาณ
- Chart Patterns: None
- Volume Profile:
- Volume ค่อนข้างสูง
- แนวรับ: Low
- แนวต้าน: EMA 50, EMA 200, Order Block
- สรุป: แนวโน้ม Sideways Down
สรุปภาพรวมและกลยุทธ์ (BTCUSDT):
- แนวโน้มหลัก (Day): ขาลง
- แนวโน้มรอง (4H): ขาลง
- แนวโน้มระยะสั้น (15m): Sideways Down
- Liquidity: มี SSL
- Money Flow: ลบ
- Trend Strength: Day/4H/15m ขาลง
- Chart Patterns: ไม่มี
- กลยุทธ์:
- Wait & See (ดีที่สุด): รอ
- Short (เสี่ยง): ถ้าไม่ Breakout EMA/แนวต้าน
- ไม่แนะนำให้ Buy
Day Trade & การเทรดรายวัน:
-
Day Trade (TF15):
- Short Bias: Short เมื่อเด้ง (EMA, Order Block)
- Stop Loss: เหนือแนวต้าน
- Take Profit: แนวรับ
- ไม่ Long
-
Swing Trade (TF4H):
- Short Bias: Short เมื่อไม่ผ่าน EMA/Order Block
- Stop Loss: เหนือแนวต้าน
- Take Profit: แนวรับ
- ไม่ Long
สิ่งที่ต้องระวัง:
- SSL: ราคาอาจถูกลากลงไป
- False Breakouts: ระวัง
- Volatility: สูง
Setup Day Trade แบบ SMC (ตัวอย่าง - Bearish):
- Order Block: หา Bearish Order Block ใน TF15
- Pullback: รอ Pullback ไปทดสอบ
- Bearish Entry:
- Rejection: รอ Price Action ปฏิเสธ
- Break of Structure: รอ Break โครงสร้างย่อย
- Money Flow: แดง
- Stop Loss: เหนือ Order Block
- Take Profit: แนวรับ
คำแนะนำ:
- แนวโน้มทั้งหมดเป็นลบ
- Money Flow เป็นลบ
- Trend Strength เป็นลบ
- ไม่แนะนำให้ Buy
- Wait & See หรือ Short (ถ้ามีประสบการณ์)
- บริหารความเสี่ยง!
คำแนะนำสุดท้าย: สถานการณ์โดยรวมของ BTCUSDT อยู่ในสภาวะขาลงและมีความเสี่ยงสูง แนะนำอย่างยิ่งให้ใช้กลยุทธ์ "Wait & See" (รอดูสถานการณ์) การ Short (ขาย) เป็นการเทรดที่มีความน่าจะเป็นสูงกว่าในขณะนี้ แต่เหมาะสำหรับนักเทรดที่มีประสบการณ์และมีการบริหารความเสี่ยงที่เข้มงวดเท่านั้น ไม่แนะนำให้ Buy (ซื้อ) ในเวลานี้
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-
 @ 9e69e420:d12360c2
2025-01-19 04:48:31
@ 9e69e420:d12360c2
2025-01-19 04:48:31A new report from the National Sports Shooting Foundation (NSSF) shows that civilian firearm possession exceeded 490 million in 2022. The total from 1990 to 2022 is estimated at 491.3 million firearms. In 2022, over ten million firearms were domestically produced, leading to a total of 16,045,911 firearms available in the U.S. market.
Of these, 9,873,136 were handguns, 4,195,192 were rifles, and 1,977,583 were shotguns. Handgun availability aligns with the concealed carry and self-defense market, as all states allow concealed carry, with 29 having constitutional carry laws.
-
 @ c4b5369a:b812dbd6
2025-02-17 06:06:48
@ c4b5369a:b812dbd6
2025-02-17 06:06:48As promised in my last article:
nostr:naddr1qvzqqqr4gupzp394x6dfmvn69cduj7e9l2jgvtvle7n5w5rtrunjlr6tx6up9k7kqq2k6ernff9hw3tyd3y453rdtph5uvm6942kzuw08y0
In this one we will dive into how exactly an unidirectional payments channel powered ecash mint system would be implemented, using the tech available today! So if you haven't read that article yet, give it a read!
I first intended to write a longwinded article, explaining each part of the system. But then I realized that I would need some visualization to get the message across in a more digestable way. This lead me to create a slide deck, and as I started to design the slides it became more and more clear that the information is easier shown with visualizations, than written down. I will try to give a summary as best as I can in this article, but I urge you, to please go visit the slide deck too, for the best experience:
TAKE ME TO THE SLIDE DECK!
Intro
In this article we will go over how we can build unidirectional payment channels on Bitcoin. Then we will take a look into how Cashu ecash mints work, and how we can use unidirectional payment channels to change the dynamics between ecash users and the mint.
Before we start, let me also give credits to nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac for comming up with the idea, to nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp for providing an idea for non-expiring unidirectional channels, and nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference for hosting an event where these ideas could be discussed and flourish.
Building unidirectional payment channels
If you've read the previous article, you already know what unidirectional payment channels are. There are actually a coupple different ways to implement them, but they all do have a few things in common:
- The
sendercan only send - The
Receivercan only receive - They are VERY simple
Way simpler than the duplex channels like we are using in the lightning network today, at least. Of course, duplex channels are being deployed on LN for a reason. They are very versatile and don't have these annoying limitations that the unidirectional payment channels have. They do however have a few drawbacks:
- Peers have liveness requirements (or they might forfeit their funds)
- Peers must backup their state after each transaction (if they don't they might forfeit their funds)
- It is a pretty complex system
This article is not meant to discredit duplex channels. I think they are great. I just also think that in some use-cases, their requirements are too high and the system too complex.
But anyway, let's see what kind of channels we can build!
Spillman/CLTV-Channel
The Spillman channel idea has been around for a long time. It's even explained in Tadge Dryjas Presentation on Payment channels and the lightning network from back in the day. I compiled a list of some of the most important propperties of them in the slide below:

Great!
Now that we know their properties, let's take a look at how we can create such a channel (Slides):

We start out by the
sendercreating afunding TX. Thesenderdoesn't broadcast the transaction though. If he does, he might get locked into a multisig with thereceiverwithout an unilateral exit path.Instead the
senderalso creates arefund TXspending the outputs of the yet unsignedfunding TX. Therefund TXis timelocked, and can only be broadcast after 1 month. Bothsenderandreceivercan sign thisrefund TXwithout any risks. Oncesenderreceives the signedrefund TX, he can broadcast thefunding TXand open the channel. Thesendercan now update the channel state, by pre-signing update transactions and sending them over to thereceiver. Being a one-way channel, this can be done in a single message. It is very simple. There is no need for invalidating old states, since thesenderdoes not hold any signedupdate TXsit is impossible for thesenderto broadcast an old state. Thereceiveronly cares about the latest state anyways, since that is the state where he gets the most money. He can basically delete any old states. The only thing thereceiverneeds to make sure of, is broadcasting the latestupdate TXbefore therefund TX'stimelock expires. Otherwise, thesendermight take the whole channel balance back to himself.This seems to be already a pretty useful construct, due to its simplicity. But we can make it even more simple!

This setup works basically the same way as the previous one, but instead of having a refund transaction, we build the
timelockspend path directly into thefunding TXThis allows thesenderto have an unilateral exit right from the start, and he can broadcast thefunding TXwithout communicating with thereceiver. In the worst case, the receiver rejects the channel, and the sender can get his money back after the timelock on the output has expired. Everything else basically works in the same way as in the example above.The beauty about this channel construct is in its simplicity. The drawbacks are obvious, but they do offer some nice properties that might be useful in certain cases.

One of the major drawbacks of the
Spillman-style channels(apart from being unidirectional) is that they expire. This expiry comes with the neat property that neither of the party has to watch the chain for channel closures, and thesendercan operate the channel with zero additional state, apart from his private keys. But they do expire. And this can make them quite inflexible. It might work in some contexts, but not so much in others, where time needs to be more flexible.This is where
Roose-Childs triggered channelscome into play.Roose-Childs triggered channel
(I gave it that name, named after nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp and nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac . If someone knows if this idea has been around before under a different name, please let us know!)
Roose-Childs triggered channelswere an idea developed by Steven and Luke at the nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference. They essentially remove the channel expiry limitation in return for introducing the need for thesenderto create a channel backup at the time of channel creation, and for thereceiverthe need to watch the chain for trigger transactions closing the channel.
They also allow for splicing funds, which can be important for a channel without expiry, allowing the
senderto top-up liquidity once it runs out, or for thereceivertaking out liquidity from the channel to deploy the funds elsewhere.Now, let's see how we can build them!

The
funding TXactually looks the same as in the first example, and similarly it gets created, but not signed by thesender. Then, sender and receiver both sign thetrigger TX. Thetrigger TXis at the heart of this scheme. It allows bothsenderandreceiverto unilaterally exit the channel by broadcasting it (more on that in a bit).Once the
trigger TXis signed and returned to thesender, the sender can confidently sign and boradcast thefunding TXand open the channel. Thetrigger TXremains off-chain though. Now, to update the channel, thesendercan pre-sign transactions in similar fashion to the examples above, but this time, spending the outputs of the unbroadcastedtrigger TX. This way, both parties can exit the channel at any time. If thereceiverwants to exit, he simply boradcasts thetrigger TXand immediately spends its outputs using the latestupdate TX. If thesenderwants to exit he will broadcast thetrigger TXand basically force thereceivershand. Either, thereceiverwill broadcast the latestupdate TX, or thesenderwill be able to claim the entire channel balance after the timelock expired.
We can also simplify the
receiver'sexit path, by thesenderpre-signing an additional transactionR exit TXfor each update. this way, thereceiveronly needs to broadcast one transaction instead of two.
As we've mentioned before, there are some different trade-offs for
Roose-Childs triggered channels. We introduce some minimal state and liveness requirements, but gain more flexibility.
Ecash to fill in the gaps
(I will assume that the reader knows how ecash mints work. If not, please go check the slides where I go through an explanation)
Essentially, we are trying to get a lightning like experience, without all the lightning complexities and requirements. One big issue with ecash, is that it is fully custodial. If we can offset that risk by holding most of the funds in a self custodial channel, we can have a reasonable trade-off between usability and self custody.

In a system like that, we would essentially turn the banking model onto its head. Where in a traditional bank, the majority of the funds are held in the banks custody, and the user only withdraws into his custody what he needs to transact, in our model the user would hold most funds in his own custody.

If you ask me, this approach makes way more sense. Instead of a custodian, we have turned the "bank" into a service provider.
Let's take a look at how it would work in a more practical sense:

The
ecash userwould open an unidirectional payment channel to themint, using one of his on-chain UTXOs. This allows him then to commit incrementally funds into the mints custody, only the amounts for his transactional needs. The mint offers connectivity to the lightning network an handles state and liveness as a service provider.The
ecash user, can remain offline at all times, and his channel funds will always be safe. The mint can only ever claim the balance in the channel via theupdate TXs. Themintcan of course still decide to no longer redeem any ecash, at which point they would have basically stolen theecash user'stransactional balance. At that point, it would probably be best for theecash userto close his channel, and no longer interact or trust thismint.Here are some of the most important points of this system summarized:

And that is basically it! I hope you enjoyed this breakdown of Unidirectional payment channel enabled Ecash mints!
If you did, consider leaving me a zap. Also do let me know if this type of breakdown helps you understand a new topic well. I am considering doing similar breakdowns on other systems, such as ARK, Lightning or Statechains, if there is a lot of interest, and it helps people, I'll do it!
Pleas also let me know what you think about the
unidirectional channel - ecash mintidea in the comments. It's kind of a new idea, an it probably has flaws, or things that we haven't thought about yet. I'd love to discuss it with you!I'll leave you with this final slide:

Cheers,
Gandlaf
- The
-
 @ 59cfee8f:7598a483
2025-02-27 09:55:34
@ 59cfee8f:7598a483
2025-02-27 09:55:34What is Crypto Mining? Before we dive into the trends and predictions, let's first define what crypto mining is. Cryptocurrency mining involves the use of powerful computers to solve complex mathematical problems and validate transactions on the blockchain. Miners compete to solve these problems and the first one to do so is rewarded with a certain amount of cryptocurrency.
Trend 1: Increased Focus on Renewable Energy One of the biggest trends in crypto mining is a shift towards renewable energy sources. As concerns about climate change continue to grow, many miners are looking for ways to reduce their carbon footprint and operate in a more sustainable manner. Solar and wind power are increasingly being used to power mining operations, and there are even projects underway to create completely renewable-powered mining farms.
Trend 2: The Rise of Decentralized Mining Pools Another trend that is gaining momentum in the crypto mining world is the emergence of decentralized mining pools. These pools are designed to be more transparent, fair, and resistant to manipulation than traditional centralized mining pools. By utilizing blockchain technology, these pools can offer greater security and reduce the risk of fraud.
Trend 3: Continued Growth of GPU Mining GPU mining has been around for several years now, but it continues to be an attractive option for miners due to its flexibility and cost-effectiveness. With the rise of new cryptocurrencies and the increased demand for computing power, GPU mining is expected to continue its growth trajectory in 2023.
Trend 4: Increased Focus on Security Security has always been a major concern in the crypto world, and this is especially true for mining operations. In 2023, we can expect to see a greater emphasis on security measures, such as multi-factor authentication, encryption, and biometric verification. Miners will need to be vigilant in order to protect their assets and prevent cyber attacks.
Trend 5: Emergence of New Mining Algorithms As the cryptocurrency market continues to evolve, we can expect to see the emergence of new mining algorithms. These algorithms will be designed to be more efficient, secure, and resistant to manipulation. This could lead to a shift away from traditional proof-of-work algorithms towards proof-of-stake or other innovative solutions.
Prediction 1: Increased Regulation As the cryptocurrency market continues to grow and gain mainstream acceptance, we can expect to see increased regulation from governments and financial institutions. This could have a significant impact on the mining industry, with stricter regulations and oversight leading to greater stability and legitimacy.
Prediction 2: Continued Price Volatility Cryptocurrency prices have always been volatile, and this is unlikely to change in 2023. While the overall trend may be upwards, there will still be significant fluctuations in price, driven by factors such as global economic conditions, regulatory changes, and investor sentiment.
Prediction 3: Greater Collaboration and Partnership As the cryptocurrency market becomes more mature, we can expect to see greater collaboration and partnership between mining companies, cryptocurrency exchanges, and other players in the ecosystem. This could lead to new business models and innovative solutions for miners and investors alike.
Prediction 4: Increased Adoption of Cryptocurrencies As more and more businesses and individuals begin to accept cryptocurrencies as a form of payment, we can expect to see increased adoption of these digital assets. This could lead to greater demand for mining equipment and services, as well as new opportunities for miners to earn rewards and profits.
Prediction 5: Evolution of Mining Hardware The evolution of mining hardware is a trend that has been ongoing since the early days of Bitcoin mining. As the demand for computing power continues to grow, we can expect to see new and improved mining hardware emerge in 2023. This could include more powerful GPUs, ASICs, and other specialized equipment designed specifically for mining.
Conclusion In conclusion, the future of crypto mining in 2025 and beyond looks promising, with numerous trends and predictions pointing towards continued growth and innovation. As the industry evolves and matures, miners will need to adapt and embrace new technologies and strategies in order to stay competitive and profitable. With the right tools and knowledge, however, there is no doubt that crypto mining will continue to be a valuable and exciting part of the cryptocurrency ecosystem for many years to come.
-
 @ d9e9fb27:d5fe5e1a
2025-01-17 13:00:58
@ d9e9fb27:d5fe5e1a
2025-01-17 13:00:58Every 16th of January, the city of Varese, a small town at the feet of the Prealpine region, stops to participate in one of the most important ceremonies of the city: The Falò of Sant'Antonio. A Falò is the Italian word for bonfire. Imagine a 5-meters tall pyre of wood burning in the center of the city. For sure, an unmissable event!
The pyre is built by the so-called "Monelli della Motta". A Monello in Italian is a child that misbehaves. This nickname come from the fact that in the past, the pyre was created using wood stolen from the city, usually from tools, doors and shutters.
This event takes place at the eve of the day of Sant'Antonio Abate in front of the homonymous church in the area called "La Motta", which stands for small hill, and comes from a several century old tradition. Thousands of people from all over the province come to the city to look at the bonfire created in honor of the Saint.

At 9PM the big event starts. The wood is set on fire!

An important tradition of this celebration is burning small pieces of paper containing wishes. People whish for health, love, friendship and luck. To make wishes come true, people have to give these pieces of paper to a firefighter or a "Monello" whom will launch it into the Falò.
The show goes on for a couple of ours, during which thousands of Varesinians in awe contemplate the raging fire and try to receive some heat to fight the glacial cold of January.

-
 @ 1739d937:3e3136ef
2025-02-22 14:51:17
@ 1739d937:3e3136ef
2025-02-22 14:51:17We've been busy. In my last update, I shared that I was sure MLS on Nostr was going to work and shared an early demo of the app. What a long time ago that seems now.
The big news is that White Noise is no longer just a demo. It's a real app. You can download the alpha release and run it for yourself on MacOS, Linux, or Android. iOS TestFlight is coming soon. Keep in mind that it's still very much alpha software; a lot is changing and I wouldn't recommend using it for anything serious quite yet.
We've been busy. In my last update, I shared that I was sure MLS on Nostr was going to work and shared an early demo of the app. What a long time ago that seems now.
Vision
Before we get to the detailed project updates, I wanted to share a bit of my vision for White Noise.
More and more; freedom of speech, freedom of association, and privacy are under attack. Just this week, Apple was forced to remove their iCloud advanced encryption feature for all UK citizens because the UK government demanded that Apple build a backdoor to allow access to customer data. The EU continues to push "Chat Control" legislation that would force companies to remove end-to-end encryption from their platforms. And governments across the world are enforcing draconian "hate speech" laws that criminalize speech that offends or upsets.
The freedom to express ourselves and discuss difficult topics is a critical precondition for maintaining a healthy society. Without the ability to assert ideas and argue their merits vigorously we have no way of making progress or creating a civil society based on shared values and goals. Ironically, the very laws and regulations that many western governments are enforcing to "protect" us are eroding and destroying the most free and innovative societies in history.
White Noise is to built to protect our freedom to gather, to express ourselves, and to discuss difficult topics. It's free and open source; anyone can fork the code and we'll never charge money to use it. It runs on a free and open source protocol; your identity and social graph is yours to own and control. You don't have to trust us with your data, everything is end-to-end encrypted and metadata is next to non-existent. We don't even run any servers, so government data requests will forever fall on deaf ears.
We want to build the fastest, most secure and private, and the most usable messenger in the world. Whether you want to use it to plan a family BBQ or overthrow a tyrant, White Noise should give you the tools you need to make it happen.
If you find this compelling and want to help, please consider contributing to the project or donating.
Progress
Alright, let's talk about where we're at with the project.
Current functionality
- Multiple accounts. You can login, or create, many different Nostr accounts in the app.
- Search your nostr contact list, search for users you don't follow, or add contacts using an npub or hex public key.
- Create DM groups. Right now, you can only create chats with a single other user. Under the hood, these DMs are actually groups, I just haven't added the UI for adding/removing users and managing the group.
- Send messages, reply to messages, and add reactions. As you would expect from a messenging app.
- View group information.
- Settings that allows you to manage your accounts, relays, and other app settings.
Upcoming
- An amazing hackathon group from Bitcoin++ in Brasil has recently added NWC (nostr wallet connect) support to the app. Paste lightning invoices into chats and they'll become QR codes that you can scan or pay them with a single click in the conversation! This will be in the next release.
- Add support for encrypted media in chats using Blossom. We'll start with images, but plan to add video, audio messages, and documents soon.
- Groups with more than two users. We'll add the ability to add/remove users and manage the group. This will also include some upgrades to further improve the forward secrecy of group chats.
- iOS TestFlight. Gated app stores suck. We'll get White Noise on iOS into TestFlight as soon as possible.
Links
-
 @ 42342239:1d80db24
2025-02-16 08:39:59
@ 42342239:1d80db24
2025-02-16 08:39:59Almost 150 years ago, the British newspaper editor William Thomas Stead wrote that "the editorial pen is a sceptre of power, compared with which the sceptre of many a monarch is but a gilded lath". He had begun to regard journalism as something more than just conveying information - the journalist or editor could become a ruler.
Times had certainly changed compared to a few hundred years earlier. Before Gutenberg's invention of the printing press, it was mainly the church that controlled the dissemination of information in Europe, but when Stead put pen to paper, this control had shifted to newspapers, schools, and universities. Eventually, technologies like radio and TV entered the scene, but the power dynamics remained asymmetrical - only a few could send information to the many.
However, with the emergence of the internet, and especially with the spread of social media, a significant change followed. Instead of only a few being able to send information to the many, many could send to many. Almost anyone could now create their own newspaper, radio, or TV channel. The power over information dissemination was decentralised.
Ten years ago, Roberta Alenius, who was then press secretary for Sweden's Prime Minister Fredrik Reinfeldt of the Moderate Party, shared her experiences with Social Democratic and Moderate Party internet activists on social media. She reported that social media played a significant role in how news "comes out" and is shaped, and that journalism was now downstream of social media. Five years later, NATO's then-Secretary-General Jens Stoltenberg said that "NATO must be prepared for both conventional and hybrid threats: from tanks to tweets." This finally underscores the importance of social media.
Elon Musk, who took over X (formerly Twitter) in 2022, has claimed that "it's absolutely fundamental and transformative that the people actually get to decide the news and narrative and what's important," and that citizen journalism is the future.
While his platform allows most expressions - for better or worse - the reach of messages is instead limited ("freedom of speech does not mean freedom of reach "). X has also opened its recommendation algorithm to the outside world by making it open-source. Although this is a welcome step, the fact remains that it's impossible to know which code is actually used and what adjustments are made by humans or algorithms.
William Thomas Stead's "sceptre of power", which has wandered from the church to newspaper and TV editorial offices, and now to citizens according to Elon Musk, risks being transferred to algorithms' opaque methods?
Instead of talking about "toxic algorithms" and TikTok bans, like the so many do today, we should ask ourselves more fundamental questions. What happens when algorithms are no longer objective (how can they ever be?), but instead become tools for shaping our reality? Perhaps our greatest challenge today is not deciding who should govern the information landscape, but instead recognising that no one is up to the task - not even well-ventilated computers.
-
 @ d360efec:14907b5f
2025-02-27 09:52:53
@ d360efec:14907b5f
2025-02-27 09:52:53Overall Assessment:
Bitcoin (BTCUSDT) on OKX remains highly volatile, and the overall trend is still uncertain. While the long-term trend (Daily chart) technically has been an uptrend, it has significantly weakened. The 4-hour and 15-minute charts are now in downtrends. This analysis incorporates:
- SMC (Smart Money Concepts): Market structure, Break of Structure, Change of Character, Order Blocks, Liquidity.
- ICT (Inner Circle Trader Concepts): Optimal Trade Entry (OTE), Fair Value Gaps (FVG), Mitigation, Breaker Blocks, Liquidity Pools/Runs.
- Buyside & Sellside Liquidity: Identifying likely areas of Smart Money buying/selling.
- Money Flow (LuxAlgo): Capital inflows/outflows.
- EMA (Exponential Moving Average): 50 (yellow) and 200 (white).
- Trend Strength (AlgoAlpha): Trend identification and strength, including the "cloud" and buy/sell signals.
- Chart Patterns: Identification of significant chart patterns.
- Volume Profile: (Used as needed).
Detailed Analysis by Timeframe:
(1) TF Day (Daily):
- Trend: Downtrend
- SMC:
- Lower Highs (LH) and Lower Lows (LL)
- BOS to the downside.
- Liquidity:
- Sellside Liquidity (SSL): Significant SSL rests below previous lows.
- Buyside Liquidity (BSL): BSL is present above recent highs.
- ICT:
- Order Block: The price failed to break above a bearish Order Block.
- EMA:
- Price is below both the 50-period and 200-period EMAs (bearish).
- Money Flow (LuxAlgo):
- Red, selling pressure
- Trend Strength (AlgoAlpha):
- Red cloud, Downtrend, No signals.
- Chart Patterns: None
- Volume Profile:
- Support: Recent lows.
- Resistance: EMA 50, EMA 200, Order Block.
- Summary: Downtrend
(2) TF4H (4-Hour):
- Trend: Downtrend.
- SMC:
- Lower Highs (LH) and Lower Lows (LL).
- BOS to the downside.
- Liquidity:
- SSL: Below previous lows.
- BSL: Above previous highs.
- ICT:
- Order Block: The price failed to break above a bearish Order Block.
- EMA:
- Price is below both the 50-period and 200-period EMAs (bearish).
- Money Flow (LuxAlgo):
- Red, selling pressure.
- Trend Strength (AlgoAlpha):
- Red cloud, Downtrend, No signals.
- Chart Patterns: None
- Volume Profile:
- Support: Recent lows.
- Resistance: EMA 50, EMA 200, Order Block.
- Summary: Downtrend
(3) TF15 (15-Minute):
- Trend: Sideways Down
- SMC:
- Lower Highs (LH) and Lower Lows (LL) - but showing signs of sideways movement.
- BOS to the downside.
- ICT: * Order Block The price is ranging near a bearish Order Block.
- EMA:
- The 50-period and 200-period EMAs are acting as resistance.
- Money Flow (LuxAlgo):
- Red
- Trend Strength (AlgoAlpha):
- Red/No signals
- Chart Patterns: None
- Volume Profile
- Relatively High Volume
- Support: Recent lows.
- Resistance: EMA 50, EMA 200, Order Block.
- Summary: Sideways Down
Overall Strategy and Recommendations (BTCUSDT):
- Primary Trend (Day): Downtrend
- Secondary Trend (4H): Downtrend
- Short-Term Trend (15m): Sideways Down
- Liquidity: SSL below on all timeframes.
- Money Flow: Negative on all timeframes.
- Trend Strength: Bearish on Day, 4H, and 15m.
-
Chart Patterns: None
-
Strategies:
- Wait & See (Best Option): The bearish momentum and lack of clear bullish reversals make waiting for confirmation the most prudent approach.
- Short (High Risk): This aligns with the downtrends on all timeframes.
- Entry: Look for short entries on rallies to resistance levels (EMAs, Order Blocks, previous support turned resistance).
- Stop Loss: Above recent highs or key resistance.
- Target: Recent lows, then SSL zones.
- Buy (Extremely High Risk - NOT Recommended): Do not buy unless there are extremely strong and consistent bullish reversal signals across all timeframes.
Day Trading & Swing Trading:
-
Day Trade (TF15 Focus):
- Bias: Short.
- Entry: Look for bearish setups (rejections of resistance, bearish candlestick patterns) near EMAs or Order Blocks.
- Stop Loss: Tight, above resistance.
- Take Profit: Recent lows.
- Avoid: Longs.
-
Swing Trade (TF4H Focus):
- Bias: Short.
- Entry: Look for bearish setups (rejections of resistance, bearish candlestick patterns) near EMAs or Order Blocks.
- Stop Loss: Above resistance.
- Take Profit: Next major support levels (SSL zones).
- Avoid: Longs.
Key Considerations & Warnings:
- Sellside Liquidity (SSL): High probability of price being drawn down to these levels.
- False Breakouts: Always a risk.
- Volatility: Expect high volatility.
- Conflicting Timeframes: While the long-term trend was bullish, the current price action and indicators are overwhelmingly bearish.
- Money Flow: Consistently negative across all timeframes.
- Trend Strength: Bearish across all timeframes.
SMC Day Trade Setup Example (Bearish - TF15):
- Identify Bearish Order Block: Locate a bearish Order Block on the TF15 chart.
- Wait for Pullback: Wait for the price to pull back up to test the Order Block (this might not always happen).
- Bearish Entry:
- Rejection: Look for price action to reject the Order Block (e.g., pin bar, engulfing pattern, other bearish patterns).
- Break of Structure: Look for a break of a minor support level on a lower timeframe (1m/5m) after the Order Block test.
- Money Flow: Confirm negative Money Flow (red).
- Stop Loss: Place a stop-loss order above the Order Block.
- Take Profit: Target the next support level (e.g., recent lows).
Recommendations:
All trends are negative. Money flow is negative. Trend strength is negative. Buying is not recommended. Wait and see, or short (if experienced). Manage your risk! I've made the following very minor changes, maintaining the original meaning:
Changed 'Advice' to a more natural sounding 'Recommendations'. Used "if experienced" instead of "(if have experience)" This version maintains the original meaning while sounding more natural in English, particularly in a financial/trading context.
Final Recommendation: The overall situation for BTCUSDT is bearish and high-risk. The "Wait & See" approach is strongly recommended. Shorting is currently the higher-probability trade, but only for experienced traders with strict risk management. Buying is not recommended at this time.
Disclaimer: This analysis is for informational purposes only and represents a personal opinion. It is not financial advice. Investing in cryptocurrencies involves significant risk. Investors should conduct their own research and exercise due diligence before making any investment decisions.
-
 @ da0b9bc3:4e30a4a9
2025-02-27 09:46:41
@ da0b9bc3:4e30a4a9
2025-02-27 09:46:41Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/898543
-
 @ e7bc35f8:3ed2a7cf
2025-02-27 07:46:26
@ e7bc35f8:3ed2a7cf
2025-02-27 07:46:26This is a fascinating question, indeed. But first of all, why is this important? Why should we be concerned about the goings-on of this group? Let’s find out the basis for this and what and why we’re being told we should care so much about this group and of course in order to do that why don’t we turn to the fear-mongers themselves to allow them to explain what is really behind this fearsome group.
ISIS, an al-Qaeda-bred terrorist group spreading its wings online. Savvier than its predecessors with a new array of tricks up its sleeves. Twitter has become a virtual second home for the terrorists but as many as 27000 accounts established just over the last two weeks, after ISIS posted a video capturing the beheading of US journalist James Foley with a reported 60000 accounts popping up since May.
Douglas MacArthur McCain, a young American, killed while fighting with the terrorist group ISIS. US officials say they believe he died in Syria. He’s thought to have been killed in a battle between rival extremist groups near the city of Aleppo according to a human rights group. This ratches up concerns about Americans involved with ISIS because now you have a confirmed example of an American killed fighting with ISIS in Syria.
Hello my brothers in Australia. I don’t see myself better than any of yous, (inaudible) only that Allah has bring Karim on me and has brang me here to this country. Two men who identify themselves as Australian appear in a recruitment video called 'There is no life without jihad'. It’s believed up to 150 Australians have joined rebels fighting in Iraq and Syria.
Earlier today the Home Secretary confirmed that the Joint Terrorism Analysis Center has increased the threat level in the United Kingdom from ‘substantial’ to ‘severe’. This is the first time in three years that the threat to our country has been at this level.
They’re beyond just a terrorist group. They marry ideology, a sophistication of strategic and tactical military prowess. They are tremendously well-funded. Oh this is beyond anything we’ve seen so we must prepare for everything and the only way you do that is you take a cold steely hard look at it and get ready.
Yes as the usual gaggle of fear-mongers in government and the mainstream media will no doubt tell you "Yes ISIS is coming and you’d better be afraid in fact the only thing you can do is take a cold steely hard look at it and get ready because apparently there’s really nothing that can be done to avoid whatever horrible, horrific, 911-like attack they’re planning on the US Heartland, or so we’re being told."
But again I think it behooves us to question this constant call for fear-mongering from the same fear-mongers who have, for years and years, ratcheted up these phony terror level alerts, to suit their geopolitical aims and I think once again that’s exactly what was going back then. Things could have been different if, instead of succumbing to fear back then, we had focused more on understanding the threat, exposing the so-called "boogeyman," and revealing the true perpetrators in this situation.
This group was created in Iraq by a Jordanian Sunni back in 1999. It was formerly the official al-Qaeda franchise, in Iraq since it broke with al-Qaeda ideologically. It then became a self-proclaimed caliphate, which was pronounced in late June of 2015. The question of the name of this group is something that gets bandied about and ISIS is often used as the short abbreviation in English, and in fact it’s just one of many, many, many, many names that this group has gone by over the years.
You can go back to 1999 for example to the original organization which brought with it of course an Arabic name whose acronym was JTJ and whose English translation was "The Organization of Monotheism and Jihad". It changed its name in 2004 to, again, another Arabic name "The Organization of Jihad’s Base in the Country of the Two Rivers", although it became more commonly known as "al-Qaeda in Iraq" or AQI around that time.
Then in 2006 it became the "Islamic State of Iraq". In 2013 it became the "Islamic State of Iraq and the Levant" or "Islamic State of Iraq and al-Sham", aka ISL and ISIS. Then in 2014 "Islamic State". So switching to the question of who is behind this group, let's see some of the characters behind it. It was founded in 1999 by a Jordanian Sunni Muslim who went by the name of Abu Musab al-Zarqawi.
‼️We have to keep in mind that the names of the various jihadis behind this, like most jihadis they adopt "nommes de guerre" that is ‘war names’ so these names are not necessarily their real names and in fact in most cases are specifically not their real names.
They’re usually chosen for some sort of symbolic or historical cultural value so for example there’s no need to scratch your head and wonder why so many people are named Al Baghdadi, it’s because they are adopting a name that shows they’re the "Baghdadis" – they’re from Iraq, that kind of thing. So again don’t read too much into any of these names, and there are usually many, many, many other alias names that these people go by as well so it gets extremely confusing, probably on purpose I think.
I think the people controlling the terrorists also have reasons for having extremely confusing ways of referring to these people and multiple ways of referring so that if one of their memes or ideas or stories gets out of control they can spin them off as a completely different human being. Abu Musab al-Zarqawi was a Sunni militant from Jordan and he had what can only be described as a remarkable career that brought with it many lives apparently.
So, again this all sources from mainstream reporting. None of this is, you know "conspiracy" reporting, this is all from mainstream news services, ABC and NBC and CBS and Reuters and all of those kinds of outlets. For example back in 2004 it was reported that he was arrested in Fallujah. Then in 2005, without reports in the meantime indicating how or when or why he was released from – or escaped from – custody in Fallujah, or how he was never arrested in Fallujah in the first place he got wounded in Baquba. Then in 2005 he was reported as being killed in fighting in Iraq. And then in 2006 he was killed in fighting once again. Presumably for the last time this time.
But it gets even stranger. Back in 2006 the Washington Post published an article entitled "Military plays up role of Zarqawi" in which they reported:
The US military is conducting a propaganda campaign to magnify the role of the leader of al-Qaeda in Iraq according to internal military documents and officers familiar with the program.
and that same article went on to say:
One internal briefing produced by the US military headquarters in Iraq said that Kimmitt (one of the generals that oversaw this program) had concluded that the Zarqawi PSYOP program is the most successful information campaign to date.
So once again the Washington Post got its hands on internal briefing documents that the Pentagon was using, to talk about al-Qaeda in Iraq and their propaganda campaign in Iraq, and these documents prove that the Pentagon was absolutely 100 percent, self-consciously engaged in a PSYOP operation to make Zarqawi and al-Qaeda in Iraq seem more important than it was, and they have their own twisted internal logic that was reported on at the time as to why they wanted to do this and why they wanted to build up AQi in the minds of the Iraqi people and the people of the United States. And of course I think obviously the main part of that was to keep the American people involved and interested in keeping their troops in harm’s way there in Iraq, even long after Bush declared "mission accomplished".
The precursor of that ISIS group, the leader with actually a not a PSYOP creation per se but at any rate someone who is blown up specifically on purpose made to seem more important than he was, because of the Pentagon.
And it gets even stranger than that when we look at the person who took over from Zarqawi after his final, supposedly, reported death in 2006, someone going by the name of Baghdadi, one of many people going by the name of Baghdadi, this one Abu Omar al-Baghdadi but again it’s a nom de guerre, it’s not his real name. Apparently his real name is Hamid Dawud Mohamed Khalil al-Zawi, he’s also known as Abu Omar al-Qurashi al-Baghdadi and Abu Hamza al-Baghdadi so we should not, again, put too much faith, stock, interest or energy into parsing these various names, just to know that this is someone who is referred to as al-Baghdadi and who took over from al-Zarqawi as leader of what was at the time "al-Qaeda in Iraq" in 2006.
He took over the group and again, like Zarqawi, had a remarkable career that involved being reported as captured in 2007** and then killed in 2007 then arrested in 2009 and then throughout that period of his arrest or the period that we are supposed to be led to believe that he was under arrest, he was releasing recordings, obviously not from prison but from wherever he really was, that were being identified and authenticated. And then in 2010** he was reported as being killed once again.
So again we have multiple reportings of captures and killings and arrests that don’t seem to make any logical sense, but just as in the case of Zarqawi, in the case of Baghdadi it becomes that much more strange when we find out that the fictional ISI leader – Abu Omar al-Baghdadi was identified as such by the US Pentagon.
Yes, once again the US military actually reported on how they believed Abu Omar al-Bagdadi didn’t even exist. This comes from a Reuters article, of one of many sources, but we can source it to a Reuters article '"Senior Qaeda figure in Iraq a myth" says US military', where they talk about a a senior operative for al-Qaeda in Iraq who was in custody of the US military, and was being interrogated and according to the testimony of this captured al-Qaeda in Iraq fighter:
The Islamic State of Iraq is a front organization that masks the foreign influence and leadership within al-Qaeda in Iraq in an attempt to put an Iraqi face on the leadership of al-Qaeda in Iraq
U.S. military officials in recent weeks have been pressed to explain the link between al-Qaeda in Iraq and bin Laden’s global network given the military’s heightened focus on al-Qaeda in Iraq as the biggest threat to the country
The military blames al-Qaeda in Iraq for most of the major bombings in Iraq, saying the group is trying to spark all-out civil war between majority Shi’tes and minority Sunni Arabs
Again a very interesting, very bizarre report that again includes briefing slides from the Pentagon that show that the Pentagon itself calls Abu Omar al-Baghdadi the fictional ISI leader, so once again the US military didn’t even believe this person existed, and this was from a 2007 report, so once again throwing more sand into the water, more mud in the mix to make it even murkier, the US military bumbles in, and it’s again a question of what their ultimate aim in all of this is.
Very, very strange dealings going on, and again remember this is the precursor group to the group that is now referred to as is IS or ISIS, so a very strange pedigree for this terrorist group with the fingerprints of the US Pentagon and military all over it. And the next character in this list of this cavalcade of terrorist-boogeyman is also Baghdadi.
This one not Abu Omar al-Baghdadi but Abu Bakr al-Baghdadi also known as Ibrahim bin 'Awad bin Ibrahim al-Badri ar-Radawi al-Husseini as-Samara’i, who was also known as Caliph Ibrahim, the caliph of the Islamic State Caliphate. So what is known about this character and where he came from? Almost nothing, in fact almost everything that we know about the background of this character sources from an completely unverifiable online biography.
So apparently he was born in Samarra in Iraq in 1971; at some point he apparently attended the Atlantic University of Baghdad and it was reported that he was a leader, a cleric in a mosque in Samarra during "The American Invasion" in 2003 according to quote unquote "reports" – unidentified reports – that’s what the BBC sourced that to – and then he was detained at Camp Bucca which was a US Forces Iraq camp at some point between 2004 and 2009 and again this story conflicts.
According to the official story he was detained from February to December of 2004, that’s what the Defense Department will admit to, before being released on the recommendation of the Combined Review and Release Board. Why they recommended him for release I’m not sure, but at any rate that’s the official story.
However we have Army Colonel Kenneth King who was the former commander of Camp Bucca who insists that this character – this man who is now known as Abu Bakr al-Baghdadi – was at the camp during his tenure at Camp Bucca all the way up until 2009 when the camp with turned over to the Iraqi justice system, and he insists this because he remembers this particular character saying "We’ll see you in New York" or something of that nature, a "terrorist threat", so even after the point at which the discrepancy between the Defense Department’s story that Bagdadi was released in 2004 , and King’s story that he was there in 2009, even when that discrepancy became apparent and was pointed out to King he specifically said again he was sure of it. He insists that he was there.
So, again, the official story is that he was only there for the better part of a year but at any rate he may have been there up until 2009 and then presumably released by the Iraqi authorities at some point. Again it’s a completely murky story, but at some point he was under the care and detainment of the US military.
Then, having gotten out of the camp he was announced as leader of the Islamic State of Iraq as it was known at that time, the AQI having morphed into the ISI in 2010 and then, once again had something of a interesting career having being reported as captured in 2012 and then in 2014 he was rumored as dead but just a few days later a video of him was released, a video of him delivering some sort of sermon, which is interesting because there are only apparently two photographs in existence of this person.
So an exceptionally shady character and on that blank slate a lot has been written, some of which is clearly fictional and let’s just keep in mind to take with a giant grain of salt any information we hear about this man and his background and really look into where and what the source of that information is.
So that’s some of the main characters behind this group. Let's turn our attention to what this group consisted of in terms of its equipment and its ability, at that time. We were told that the arsenal of jihad contained and wielded by this shadowy deadly terrorist-boogeyman group consists of: 30 T 55 tanks; 10 T72 tanks; Blackhawks; cargo planes; Humvees; Toyota trucks; AK47s; M79s; RBG-6s; RPG-7s; Howitzers; field guns; AACs; Stinger manpads; scud missiles and a low-grade nuclear material of unknown origin.
Again this is just a ridiculous list of equipment but at any rate most of it has been sourced to various things that they’ve managed to accrue from their various military conquests including for example their takeover of Mosul back earlier this year in which they secured the Black Hawk helicopters and the cargo planes from the airport and also the nuclear material, the low-grade nuclear material that they acquired from Mosul University which according to the International Atomic Energy Agency is a low risk for nuclear proliferation because it is such low grade – such low quality. So those were the things that we were told that they’ve gathered from their various exploits. Some of the interesting items in there I think are for example the Toyota trucks, which have become something of a hallmark of jihadis in various contacts.
There are reasons for that, Toyotas of course being quite ubiquitous in that region of the world since Japanese aid to the Middle East generally comes in the form of equipment and various products and so Toyotas are among the types of things that find their way to the Middle East, and because of their ubiquity the parts and servicing for them are widely available so they’re quite useful for any group that wants to have sort of mobile access to the area, including the jihadis, and the Toyotas in possession of ISIS in particular seem to have come courtesy of, surprise surprise, Uncle Sam.
According to a report which includes some audio footage about the Toyotas in the Middle East, and it also says that the "wish list" of the so-called moderate Syrians that was handed to the US military back in 2014 when the US was handing out supplies included Toyota Hiluxes, the Toyota trucks that are now in the possession of ISIS, so, surprise surprise you give to the moderates and who ends up getting them? Well the non-moderates.
As if there were really any moderates there in the terrorist group trying to take over Syria in the first place. But that’s what they were having in their possession in terms of equipment. Where they actually get the money to do what they do… well according to what we’re being told they looted the Iraqi army. They acquired as much is 429 million dollars from the Mosul central bank which they took over earlier that year.
They were extracting ransom money and extortion money from various governments throughout this time period, and they are selling oil from their northern Syria territories to the tune of as much as 2 million dollars a day, supposedly. So those were the places where they were supposedly financing what’s going on, however we can contrast that with some other information acquired from different sources.
For example it’s been widely and repeatedly reported throughout that private Gulf donors via Kuwait, and apparently the Kuwaiti financial system was specifically well set up for this type of financing, but at any rate private gold donors have accounted for a lot of the money that has flowed into Syria to fund the various terrorist groups including ISIS and the others that were there, and again that was private donors not necessarily the House of Saud or anything of that sort but private donors from the Gulf, who obviously had religious reasons for trying to support the Sunni Wahabi Jihadist Muslims. In this conversation about Who is behind ISIS, we stumble upon Benghazi and what became known as Benghazi-Gate.
Benghazi was the lexus where all of those Libyan arms were flowing from the Libyan terrorists to the Syrian terrorists, via Turkey and Jordan, and I think that’s an important part to keep in mind because those, again, are two very important players in this story. What happened in Benghazi is an important example for what was happening in there and all the sources converge on this ISIS group – this ISL group – that suddenly seemed to spring out of nowhere but of course has been gestating there for 15 years and has been, as we’ve seen, involved with the US Pentagon, involved in various PSYOPS operations to make this group seem more important than it is. You can find more information about Benghazi in my recent article (search it in my articles tab). So that brings us to some of the questions of "Well where are these funds coming from and how are these troops being trained?" and as always, all roads lead to…Washington? Here is an enlightening broadcast of "Democracy Now!", with Amy Goodman and Adam Entous.
So the CIA in conjunction with their friends in Britain and France and Saudi Arabia and the UAE and elsewhere have converged in Jordan to train various Syrian militants – terrorists – at a base in Jordan. Something considered as a conspiracy theory before, now it is confirmed even by the mainstream dinosaur media.
So "Well yes actually, the US has been intimately involved; the CIA has been intimately involved in training a lot of the people who went on to become the top ISIS fighters".
And then the ""corrected"" version.
So if this sounds surprising well you haven’t been paying attention, not only to the Syrian story but really to any of these stories going back decades and decades, with the most famous of course being the US involvement in Afghanistan in the 1980s back when they were helping the Freedom Fighters – the Taliban before they started going after the evil terrorists – the Taliban.
Unfortunately a script we know all too well and when it comes to how these groups are armed and trained it just continues. LT. GENERAL MCINERNEY:
Syria we backed, I believe in some cases, some of the wrong people, and not in the right part of the Free Syrian Army and that’s a little confusing to people, so I’ve always maintained and go back quite some time that we were backing the wrong types.
I think it’s gonna turn out maybe this weekend, in a new special that Brett Baer’s gonna have Friday, it’s gonna show some of those weapons from Benghazi ended up in the hands of ISIS. So we helped build ISIS. Now there’s a danger there and I’m with you.
So "we kind of build up ISIS oh and let’s go to the next news story." 😶 So again this is not controversial. This is not something that we have to speculate about. This is something that has been documented in a lot of mainstream contexts as well, so really this brings us to the heart of the question "Who is behind ISIS?"
There are at least 6 groups. Someone could probably dig deeper and bring in some other groups but 6 of the main groups that we can identify as being the real powers that have brought ISIS to its position, and in alphabetical order that would be: 1. Israel, 2. NATO, 3. Qatar, 4. Saudi Arabia, 5. Turkey and 6. the USA,
although to a certain extent these are groups rather than nation-states per se.
Specifically in the case of Saudi Arabia where of course the House of Saud had institutional and fundamental reasons why it would not be happy about a radical caliphate on its doorstep, because obviously that would threaten the institution of the House of Saud itself, but certainly individual Saudis, private donors as I 've said, and including some members of the Royal House of Saud would be interested in helping fund a radical Wahabi jihadi Selapi??? group...
Take Turkey for example. Turkey obviously has its fingerprints all over everything that’s happening in Syria and has been since the inception. Turkey has a lot of different reasons for being involved that range from its constant requests to keep its neighbors fighting with each other and destabilized, using Islam as a weapon, Turkey is happy to do so. I think the Turkish leadership has no allegiance really to Islam except for the fact that it’s a useful political tool for the largely Islamic Turkish population, and also it can be used in fights like this to keep its neighbors destabilized and to keep Turkey an important foothold for Europe and NATO in the region, and I think that’s one of the reasons.
I think they’re also obviously always looking to repress and find ways to stamp out their Kurdish population problem so I think this is one extension of that, and we’ve seen for example the false-flag recordings that were released with the high-ranking Turkish officials under Erdogan talking openly about how they wanted to stage an attack on Turkish targets in Syria in order to justify Turkish incursion into Syria, which of course brings with it the specter of NATO because of the mutual self-defense clause in the NATO article – the treaty – so Turkey a very, very menacing prospect/player in all of this and someone who is again been admittedly and documentably linked to the transfer of funds and arms to the terrorist groups in Syria.
Qatar has a number of reasons ranging again from religious to geopolitical, and maybe I 'll get more into the sort of pipeline politics that Qatar sees in all of this.
When it comes to NATO specifically the context is similar with Gladio B, ie. the Operation Gladio which was not a mere stay behind operation in Europe to counter some perceived or imagined Soviet occupation of Europe, but in fact a global operation that involved "Strategy of Tension" and false-flag terrorism as ways of achieving various NATO operation goals in various "theaters", and we’ve talked of course about Sibel Edmonds and her revelation of Gladio B, ie. the fermenting of Islamic terrorism in various parts of the world to further these aims and goals and taking over various squares on the geopolitical chess board, So you can think about Gladio B as a worldwide operation and I would see no reason why it wouldn’t also be operative in the Middle East, and we have to look for NATO fingerprints in what’s happening there, and we can see them through the actions, for example most specifically of the US, in helping to arm, fund and run PSYOP operations surrounding this ISI group lslamic state.
Let's get into more detail on some of these characters, for example of course Israel, who I think is interested in pretty much anything that happens in the Middle East, should be fairly apparent, but this is something that I documented specifically back in a previous article (see again my Articles tab).
Israel’s designs on Iraq have been well-known and well-understood for a long time but I think we have to see all of these invasions and overthrows and all of the destabilizations in the Middle East in recent years as part of a grander Zionist project for reshaping the Middle East, that we can say not only predates that five-year plan that General Wesley Clark talks about but predates it by decades at the very least, documentably and on the record. All about the "Greater Israel", the Zionist plan for the Middle East (Oded Yinon) which was something that was developed in a document that was published in 1982 in the journal called Directions which was published by the Department of information for the World Zionist Organization, and this document was translated into English by the Association of Arab-American University Graduates you can find in my previous articles.
And of course there are also the Pipeline Politics in the Middle East and how they played into what’s going on in Syria. Specifically with regard to a pipeline known as the ISI pipeline, Iran, Iraq, Syria pipeline or the Islamic pipeline. The fact that there there was a Memorandum of Understanding signed between Iran, Iraq and Syria shortly before all of this kerfuffle in Syria began is again, highly telling of what this situation is at least partially about, and I think to a large extent this is a very important piece of this puzzle, and it shows why Assad suddenly became in the crosshairs despite the fact of having been a willing accomplice in the CIA’s rendition and torture program for example, and sort of one of the "good boys" that the West "tolerated" for a long time, how he suddenly became enemy number one is the question, and the Islamic pipeline is one answer.
So there again is a direct interest for some of the members of that "Who is behind ISIS?" coalition for not getting behind Assad and in fact getting in his way, to try to stop the creation of this pipeline. That ISI pipeline was completely getting around Turkey altogether, which would not be in Turkish interests and would not be in Qatari interests. Qatar of course having a gas of its own that it wants to export to Europe and wants to make part of the new European gas energy policy. So again there are some direct motivations for why Iran, Iraq and Syria are in the target sights of these various powers that are converging on fighting the Islamic State threat.
Now let’s debunk some of the fear and propaganda that was swirling around about this, starting with the easy targets in the mainstream media who have been pimping this map of the Middle East that was supposedly part of some grand five-year war plan of the Islamic State, or something of that sort.
That map basically covered from North Africa, all the way from the western edge of North Africa, all the way through basically the top half of the African continent to the eastern part of Africa, across the Gulf into the Gulf states, into the Central Asia region, all the way up to the doorstep of China and Russia. It was as far north as the Northern Caucasus, up through Turkey into Eastern Europe, and even Spain was part of that map.
It was marked as black as in being the aspirational hope of the growth of the Islamic State, as a part of a five years plan and it was labeled with all of these various regional names that were apparently going to be given to the various parts of the chessboard once the IS takes them over. ➡️ Now this looked like a very scary map – "Oh my god this is what Islamic State has planned, it’s their five-year plan, are you afraid? You’d better be very afraid". Except for the fact that of course it was all BS. And this has been displayed prominently all over NBC News and ABC News and of course the Daily Mail.
But the interesting part about that map was that even as ABC and NBC and others admitted it sourced back to a Twitter account for the "Third Position", and ultimately the map sourceed back, if you go all the way back to basically fans of the ISIS group who put this together as their wet dream project, just basically saying "This will belong to us" and it made absolutely no sense geopolitically in any sense.
If you look at the map it includes all sorts of areas of the map where even the Islamic areas of that map, they are completely different sorts of Islam that would not be compatible with, in any way, with the Islamic State and would have no interest or affinity to the people who supposedly comprise the Islamic State, etc.
👉 If you learnt something new in this article,, something you think is valuable for others to know, please do spread this information.
-
 @ 6389be64:ef439d32
2025-01-16 15:44:06
@ 6389be64:ef439d32
2025-01-16 15:44:06Black Locust can grow up to 170 ft tall
Grows 3-4 ft. per year
Native to North America
Cold hardy in zones 3 to 8

Firewood
- BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal
- Since its growth is fast, firewood can be plentiful
Timber

- Rot resistant due to a naturally produced robinin in the wood
- 100 year life span in full soil contact! (better than cedar performance)
- Fence posts
- Outdoor furniture
- Outdoor decking
- Sustainable due to its fast growth and spread
- Can be coppiced (cut to the ground)
- Can be pollarded (cut above ground)
- Its dense wood makes durable tool handles, boxes (tool), and furniture
- The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak.
- A very low rate of expansion and contraction
- Hardwood flooring
- The highest tensile beam strength of any American tree
- The wood is beautiful
Legume
- Nitrogen fixer
- Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn
- Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]]
Bees

- The edible flower clusters are also a top food source for honey bees
Shade Provider

- Its light, airy overstory provides dappled shade
- Planted on the west side of a garden it provides relief during the hottest part of the day
- (nitrogen provider)
- Planted on the west side of a house, its quick growth soon shades that side from the sun
Wind-break

- Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters
Fodder
- Over 20% crude protein
- 4.1 kcal/g of energy
- Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
-
 @ 554ab6fe:c6cbc27e
2025-02-14 16:29:51
@ 554ab6fe:c6cbc27e
2025-02-14 16:29:51Bitcoin’s Price and the Power Law: A Reflection of Energy and the Early Stages of Monetary Adoption Introduction Bitcoin’s price trajectory has long puzzled analysts, with its seemingly chaotic booms and busts. However, when examined through the lens of power laws, a pattern emerges—one that is fundamentally tied to Bitcoin’s energy-based production cost. This article argues that Bitcoin’s price has historically followed a power law because its underlying cost structure is dictated by mining, an energy-intensive process. However, this relationship will not persist indefinitely. I propose that as Bitcoin matures into a widely adopted monetary system, its price will decouple from mining production costs and instead oscillate in accordance with natural business cycles, much like traditional forms of money.
Bitcoin’s Price and the Power Law
 Source and Credit: Giovanni Santostasi’s “The Bitcoin Power Law”
Source and Credit: Giovanni Santostasi’s “The Bitcoin Power Law”When Bitcoin’s price is plotted on a logarithmic scale against time, a strikingly straight-line trajectory appears, punctuated by cycles of rapid price expansion (bull markets) followed by severe corrections (bear markets). These perturbations correspond to Bitcoin’s well-known halving cycles, which occur approximately every four years and reduce the block reward paid to miners, effectively doubling the cost of production per Bitcoin. Historically, Bitcoin’s price has always returned to a fundamental minimum—one that closely aligns with the average cost of mining.
This observation suggests that Bitcoin’s power law price behavior is not arbitrary but rather a reflection of its fundamental energy constraints. As in many natural systems governed by power laws, energy dynamics play a central role. In Bitcoin’s case, the “base layer” of its valuation is determined by the energy and computational resources required for mining. This power law behavior is therefore a consequence of Bitcoin’s fundamental design: as block subsidies decrease and mining efficiency improves, the minimum sustainable price follows an upward trajectory dictated by production costs.
Bitcoin as an Energy-Based System
Power laws commonly emerge in natural systems involving energy constraints, from thermodynamics to biological ecosystems and planetary dynamics. Bitcoin, as an energy-based monetary system, exhibits similar characteristics. Mining requires significant electricity and computational power, and as the difficulty adjustment ensures a competitive equilibrium, the cost of mining a Bitcoin remains closely tied to its market value over the long run.
Unlike traditional fiat currencies, which are controlled by central banks and subject to arbitrary monetary expansion, Bitcoin’s supply schedule is immutable. Its economic foundation is rooted in proof of work, where value is derived from energy expenditure. This fundamental linkage between energy and price explains why Bitcoin’s valuation has adhered to a power law trajectory. It is an entropy engine, and follows physical laws related to energy and entropy.
However, this pattern is not a permanent feature of Bitcoin’s monetary future—it is, rather, an indication of Bitcoin’s early-stage monetization process.
The Transition from Mining-Based Pricing to a Business Cycle
A crucial implication of Bitcoin’s price following a power law dictated by mining costs is that it suggests Bitcoin has yet to fully mature as money. If Bitcoin were already a widely adopted monetary standard, its valuation would no longer be primarily influenced by the floor mining costs but instead by macroeconomic forces—specifically, the natural fluctuations of the business cycle.
In a world where Bitcoin is the dominant global currency, the “price of money” (which correlates with the cost of capital and prevailing interest rates) would fluctuate according to the broader economic cycle. The dynamics would resemble those of natural interest rate cycles described by the Austrian School of Economics:
- During periods of economic expansion, lower interest rates spur increased investment and consumption, prices slightly rise, and savings deplete.
- As savings decline and prices rise, interest rates naturally rise as well, leading to reduced investment and spending, initiating a contractionary phase and lowered prices.
- During the contraction, savings accumulate, more capital becomes available, and interest rates and prices decline.
- With the availability of capital, lower interest rates and lowered prices, the economy is now ready to enter a phase of investment and expansion once again.
- This oscillatory process continues indefinitely, driven by real economic growth rather than central bank intervention.
If Bitcoin were fully monetized, its price would no longer oscillate based on mining halvings and energy costs but instead reflect economic expansion and contraction cycles—just as traditional currencies do when not artificially manipulated by central banks.
The Early Stage Indicator: Bitcoin’s Dependence on Mining Costs
Today, Bitcoin’s price still “bounces” off the power law baseline, indicating that its valuation remains primarily anchored to its minimum cost of production. This means that, while Bitcoin is widely recognized as an asset, it has not yet reached the level of adoption where its price is dictated by macroeconomic cycles.
A future in which Bitcoin is used as a primary medium of exchange and unit of account would necessarily imply a decoupling from mining-driven pricing. Instead of periodic halvings triggering speculative bull runs followed by crashes, Bitcoin’s price would become far more stable, with fluctuations primarily driven by business cycle dynamics. The continued adherence to the power law model, therefore, is evidence that Bitcoin is still in an early phase of adoption—where mining remains a primary determinant of price.
Conclusion
Bitcoin’s price trajectory has long conformed to a power law, reflecting the underlying energy costs of mining. This characteristic, however, is likely not a permanent feature but rather a hallmark of Bitcoin’s early stage as an emerging monetary system. As adoption increases and Bitcoin becomes widely used as money, its price should transition away from being dictated by mining costs and should instead fluctuate according to the natural oscillations of the business cycle.
The persistence of Bitcoin’s power law trend is a sign that it remains in its infancy. The real transformation will occur when Bitcoin is no longer bound to its production cost but is instead driven by the natural ebb and flow of savings, investment, and capital cycles—marking its full emergence as a global monetary system.
Disclaimer: The information provided in this blog is for informational and educational purposes only and should not be construed as financial advice. Please consult with a financial advisor or conduct your own research before making any financial decisions.
-
 @ 5a261a61:2ebd4480
2025-02-18 18:22:19
@ 5a261a61:2ebd4480
2025-02-18 18:22:19The yellow light won the battle against the feeble excuse for curtains and crept into the room. It moved cautiously as if was afraid where to step. A common trait to all who found their way into the back room of the Lost Cases Detective Agency. The current owner had inherited both the premises and the name from his predecessor, and whenever someone questioned the name, he would announce half-irritably that changing it was simply too expensive to afford. The noodle vendor from the floor below would never miss the chance to add that people who end up at his place didn't choose it for the name anyway. The truth (which he was willing to admit only to the creaking fan that scared away mice rather than actually serving its function) was that he liked the name. Like attracts like. A lost soul for lost cases. The darkness was finally driven even from the eyelids of the figure on the bed, who woke up with a dissatisfied grunt.
A few steps to the sink hidden behind a screen. The shadows cast by the street light might have seemed depressive to some, mainly because they weren't accompanied by the warming feeling of sunlight, blocked by the high skyscrapers embracing the lower houses of the former middle class. Tom smiled resignedly at this thought. It perfectly captured how everything in this city merged into one big tangle, which looks beautiful until you have to untangle it. The yellow light came from a neon sign across the street advertising "The Beach." One of many places in this City where one could hide in a drop of alcohol and the embrace of a beautiful woman. Though it was necessary to maintain that order... the companions didn't exactly recruit from the best of the best looking local beauties.
Tom turned the tap and waited until the water, after grunting, gargling, and several splutters, settled and began flowing somewhat predictably. Tom didn't mind the wait. In his line of work, patience was cheaper than bullets. And it was nice to have time when he could do nothing but wait. He examined himself in the mirror. The shadows did him favors, adding years he hadn't earned. As young as he was, he needed all the help he could get - clients wanted their private dick weathered, not fresh out of the wrapper. He had the look down pat: world-weary veteran who knew all the angles. Truth was, he couldn't even figure out the angle of his own life, but that was a case file he kept closed. The water spluttered one last time. "Good morning, dickhead," he greeted himself with unwavering conviction that today would be better than yesterday. While most people were heading to dinner, putting kids to bed, or hurrying to visit their lovers at this hour, he was waking up. So for him, it was morning. For him and a myriad of other existences who, by choice or necessity, lived more at night than during the day. Finally, he trimmed his beard to short, neat stubble - enough to look serious, but with a touch of toughness suggesting he wasn't afraid to get his hands dirty. "Perfect," he muttered to himself, "I look like a man who knows what he's doing." Maybe that illusion will convince me one day, he thought as he turned off the light in the small bathroom. With a final look in the mirror, he adjusted his shirt collar. He was ready to face the city's challenges. Whatever awaited him today, at least he'd look prepared for it.
From the hook by the door, he grabbed a ring with an identification tag and some loose change. He ran down a flight of creaking stairs and headed past empty bar stools toward the exit. The disadvantage of living above a restaurant. Though the major advantage is the high of the rent. Or rather, its lowness. Jiro, the owner of the small bistro and, coincidentally, a decent exterminator, looked at him through a dense veil of greasy vapors, nodded, and continued stirring the noodles.
Where to next? - say hi - get some food - just run outside
This is kind of an experiment with converting my WIP interactive fiction project to the nostr longnote format and letting readers decide. Originally, this story leans quite heavily toward FLR/femdom/mindcontrol/noir/steampunk/fantasy and hopefully a little mystery detective story, but let's see where (and if) it will lead from here. Also, it's mostly translated from my native language, so sorry if some wording seems stiff.
-
 @ 21ffd29c:518a8ff5
2025-02-18 16:39:00
@ 21ffd29c:518a8ff5
2025-02-18 16:39:00The Empty Fort Knox?
The latest developments hinge on whether Fort Knox is entirely empty or if it is filled with a mere veneer of gold bars, concealing a far greater secret. According to credible sources, auditors are currently verifying claims that these hidden reserves could surpass what was previously thought to be the U.S. government’s official reserves.
If Fort Knox is truly empty, it would raise profound questions about national security and the integrity of global institutions. The lack of gold at the world-class vault could signal a catastrophic misplacement or even a cover-up—potentially involving foreign entities with ulterior motives.
Rand Paul, Elon Musk, and London Gold Shipments
The speculation is further fueled by mentions of Rand Paul, a former U.S. Senator known for his investigative prowess (albeit not traditionally in the role of an auditor), and Elon Musk, the tech giant’s CEO, who has hinted at involvement in uncovering these reserves through his various ventures.
Additionally, there are whispers that London-based gold shipments— rumors suggest up to 8000 gold bars—are on their way ahead of a major audit. These claims hint at global coordination and a potential announcement about the U.S.’s newfound wealth.
Who Hides the Title?
The question lingers: who holds the title of these gold reserves? Are they the U.S. government itself, or is it an unknown entity with ties to foreign powers? The involvement of auditors suggests a process designed to validate these claims, but the timing and scale raise suspicions about motives.
Implications: Security, Economy, and Trust
If confirmed, the discovery could have huge implications for U.S. national security, as controlling such vast amounts of gold would give an unparalleled level of influence over global markets, finance, and defense. The reserves could also serve as a major geopolitical weapon or trigger massive financial reforms.
Economically, this revelation could reshape global trade dynamics, particularly in the commodities sector. The availability of unprecedented quantities of gold could alter inflationary pressures, investment strategies, and even consumer behavior worldwide.
Perhaps most terrifyingly, if Fort Knox is found to be empty, it could shake confidence in institutions long believed to be impenetrable. The U.S. government’s role in these reserves—and its potential cover-up—could indicate systemic weaknesses that have gone unnoticed for decades.
The Verdict: Who’s Holding the Title?
The ultimate answer lies in the verification process initiated by auditors, but speculation already points toward a combination of coincidence and deliberate action. The involvement of Rand Paul, Elon Musk, and London-based shipments suggests a plot worthy of the most conspiracy theories— one that blends national security with economic control.
In an era defined by increasing global interconnectedness, the discovery of these hidden gold reserves could mark a turning point in history—one that reshapes the balance of power, economics, and trust across the globe. Until the truth is confirmed—or buried deeper than Fort Knox—it remains a shrouded mystery that demands urgent attention.
-
 @ be41636e:e55c4909
2025-02-14 09:44:55
@ be41636e:e55c4909
2025-02-14 09:44:55I asked unleashed.chat's DeepSeek model to provide the pieces of evidence against the moon landing. What follows is what I got as my answer.
Generally, I like the answer, though it mixed up the claim and counterarguments at times.
Also, I didn't like the conclusion :))
But all said, I believe the Van Allen Belts are one of the most solid argument against the moon landing.
The question of whether the moon landing was faked has been a topic of debate, with various arguments presented by those who doubt the authenticity of the event. Here is a summary of the key points often cited against the moon landing, along with counterarguments and explanations:
Arguments Against the Moon Landing: Waving Flag:
Claim: The American flag appears to wave in the wind, despite the moon having no atmosphere. Counterargument: The flag's movement was caused by the astronauts' actions, as they adjusted it using a rod behind the flag. Missing Stars:
Claim: The photos lack visible stars, which should be present in the moon's black sky. Counterargument: The cameras were set for optimal lighting of the lunar surface, making stars too faint to capture. Shadow Anomalies:
Claim: Shadows in photos appear to come from multiple directions, suggesting studio lighting. Counterargument: The moon's surface is uneven, causing shadows to appear differently, and the sun's angle can create varied shadows. Van Allen Belts:
Claim: Astronauts would have been exposed to lethal radiation from the Van Allen belts. Counterargument: The missions were timed to pass through the belts quickly, minimizing exposure. Lack of Blast Crater:
Claim: No noticeable crater was created by the lunar module's descent engine. Counterargument: The engine's thrust was designed to minimize impact, and the moon's surface is softer than expected. Missing Footage:
Claim: Original tapes of the landing were lost, and restored footage is of lower quality. Counterargument: Footage was restored from other sources, including TV broadcasts and telemetry data. Soviet Silence:
Claim: The Soviets did not contest the landing, despite being space race competitors. Counterargument: The Soviets may not have had the means to verify the landing or were focused on their own programs. Technological Capabilities:
Claim: The technology of the 1960s was insufficient for a moon landing. Counterargument: Successful unmanned missions and technological advancements supported the capability. Number of Participants:
Claim: Thousands of people involved would have leaked the secret. Counterargument: Secrecy measures and unawareness of implications could have prevented leaks. "C" Rock Incident:
Claim: A rock appeared to float, suggesting tampering. Counterargument: The rock was a prop, and movement was due to low-gravity actions. Supporting Evidence for the Moon Landing: Moon Rocks: Analyzed and confirmed as lunar. Footprints and Equipment: Observed by subsequent missions and satellites. Cumulative Evidence: Multiple sources confirm the moon landing. In conclusion, while various arguments have been presented against the moon landing, each has been addressed with scientific explanations and evidence. The consensus among the scientific community is that the moon landing was genuine, supported by substantial evidence and corroborated by multiple sources.
The question of whether the moon landing was faked has been a topic of debate, with various arguments presented by those who doubt the authenticity of the event. Here is a summary of the key points often cited against the moon landing, along with counterarguments and explanations:
Arguments Against the Moon Landing:
-
Waving Flag:
- Claim: The American flag appears to wave in the wind, despite the moon having no atmosphere.
- Counterargument: The flag's movement was caused by the astronauts' actions, as they adjusted it using a rod behind the flag.
-
Missing Stars:
- Claim: The photos lack visible stars, which should be present in the moon's black sky.
- Counterargument: The cameras were set for optimal lighting of the lunar surface, making stars too faint to capture.
-
Shadow Anomalies:
- Claim: Shadows in photos appear to come from multiple directions, suggesting studio lighting.
- Counterargument: The moon's surface is uneven, causing shadows to appear differently, and the sun's angle can create varied shadows.
-
Van Allen Belts:
- Claim: Astronauts would have been exposed to lethal radiation from the Van Allen belts.
- Counterargument: The missions were timed to pass through the belts quickly, minimizing exposure.
-
Lack of Blast Crater:
- Claim: No noticeable crater was created by the lunar module's descent engine.
- Counterargument: The engine's thrust was designed to minimize impact, and the moon's surface is softer than expected.
-
Missing Footage:
- Claim: Original tapes of the landing were lost, and restored footage is of lower quality.
- Counterargument: Footage was restored from other sources, including TV broadcasts and telemetry data.
-
Soviet Silence:
- Claim: The Soviets did not contest the landing, despite being space race competitors.
- Counterargument: The Soviets may not have had the means to verify the landing or were focused on their own programs.
-
Technological Capabilities:
- Claim: The technology of the 1960s was insufficient for a moon landing.
- Counterargument: Successful unmanned missions and technological advancements supported the capability.
-
Number of Participants:
- Claim: Thousands of people involved would have leaked the secret.
- Counterargument: Secrecy measures and unawareness of implications could have prevented leaks.
-
"C" Rock Incident:
- Claim: A rock appeared to float, suggesting tampering.
- Counterargument: The rock was a prop, and movement was due to low-gravity actions.
Supporting Evidence for the Moon Landing:
- Moon Rocks: Analyzed and confirmed as lunar.
- Footprints and Equipment: Observed by subsequent missions and satellites.
- Cumulative Evidence: Multiple sources confirm the moon landing.
In conclusion, while various arguments have been presented against the moon landing, each has been addressed with scientific explanations and evidence. The consensus among the scientific community is that the moon landing was genuine, supported by substantial evidence and corroborated by multiple sources.
-
-
 @ 6389be64:ef439d32
2025-01-14 01:31:12
@ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
Meet The Forest Walker

For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
The Small Branch Chipper

When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
The Gassifier

The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
Biochar: The Waste

Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
Wood Vinegar: More Waste

Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
The Internal Combustion Engine

Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
CO2 Production For Growth

Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
The Branch Drones

During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
The Bitcoin Miner

Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
The Mesh Network

What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
Back To The Chain

Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
Sensor Packages
LiDaR

The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
pH, Soil Moisture, and Cation Exchange Sensing

The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
Weather Data

Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
Noise Suppression

Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
Fire Safety

A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
The Wrap

How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-
 @ 3eba5ef4:751f23ae
2025-02-14 03:52:48
@ 3eba5ef4:751f23ae
2025-02-14 03:52:48🍨Your weekly byte of the latest updates from the Bitcoin ecosystem!
Crypto Insights
Solving the Optimal Cluster Linearization Problem With DeepSeek
Stefan Richter (stefanwouldgo) found a 1989 paper through DeepSeek R1 that provides a solid solution to the problem of optimal cluster linearization. The paper presents a proven algorithm that efficiently finds the subset of transactions with the highest fees; if this subset is included in a block, it is topologically valid.
New Class in Cluster Mempool Improves Transaction Handling and Performance
The introduction of the
TxGraphclass in Cluster Mempool enhances transaction handling by encapsulating the transaction graph, focusing on effective fees, sizes, and dependencies. It enables batched and lazy updates for more efficient mempool operations, with improvements in transaction prioritization, incentive compatibility, and performance. This design simplifies the code by abstracting graph management, allowing for easier validation and future optimizations.More details in this pull request.
Independent Mining Still Feasible
Two independent miners recently mined Bitcoin blocks:
-
Block 881432 by 256 Foundation, a public organization promoting open-source Bitcoin mining. The group combined the hash rate from over 300 participants with the goal of breaking up the mining patent monopolies of large pools, making Bitcoin and free technology more accessible to all.
-
Block 881676 by the open-source home mining hardware solo.ckpool, using hash rate equivalent to thousands of BitAxe devices.
This demonstrates that independent miners can still compete, reinforcing Bitcoin’s decentralization and censorship resistance.
6-Block Confirmation No Longer Enough, Mining Centralization Impacts Bitcoin Security
Bitcoin Core developer Luke Dashjr posted that he intended to update the 6-blocks-to-confirm target in the Knots wallet GUI. However, he found that due to Antpool controlling around 48% of the network's hash rate, more than 800 block confirmations would be required to achieve 95% security. He also noted that many pools, like Braiins and ViaBTC, are actually Antpool under different names.
Payjoin Development Progress Review
Spiral reviewed the development progress of Payjoin, which allows for including an additional input in a payment transaction to enhance privacy. The article also mentions that by using joint batching to optimize fees, Payjoin reduces transaction costs and increases network efficiency. Moreover, when both parties contribute inputs, Payjoin helps protect privacy by breaking common blockchain monitoring assumptions, making it harder for third parties to track payment amounts and private spending behaviors.
Block Size Report Reveals: Growth Partly Limited by Miner Policies and Bitcoin Core Defaults
The Block Size Report, published by Mempool research, uses data-driven analysis to examine the evolution of block size in Bitcoin from its inception to February 2025. It discusses changes in block size post-SegWit upgrade and reveals how growth has been partly limited by miner policies and Bitcoin Core defaults over the years. The report concludes with predictions about the growth of Bitcoin’s blockchain in the coming years.
Tutorial on Becoming an Advanced Nostr User With Sats Cashback
Rizful published a guide on how to become an advanced Nostr user and set up the self-owned Lightning node. After completing the tutorial, users can receive 5,000 sats via zap cashback.
Build a Smart Card for Bitcoin and Nostr Event Signing for Under $25
The 100% open-source smart card Satochip allows users to build their own signing device in just 10 minutes under 25 USD. Satochip's advantages include:
-
Affordable and widely available
-
Dual interface: supports both NFC (contactless) and Chip (contact) modes
-
Minimal electronics, reducing the attack surface
-
Enhanced security based in Secure Element
Bitcoin at the Crossroads of AI Revolution and Sovereign Evolution
CKBEcoFund shared their insights from the talk at The Satoshi Roundtable, discussing several macro issues including the dominance of artificial intelligence, Bitcoin's security, scalability, sovereignty, and national Bitcoin strategic reserves. He explored how CKB, as a Bitcoin Layer 2, is positioning itself for high-frequency micropayments, smart contracts, and cross-chain asset management.
Top Reads on Blockchain and Beyond
Pod: An Optimal-Latency, Censorship-Free, and Accountable Generalized Consensus Layer
This paper introduces a new consensus concept pod, aiming to achieve physically optimal latency for one round-trip—just one write of a new transaction and one read. This work solves inherent problems of high latency in blockchain and low scalability in traditional consensus protocols.
Grigore Rosu commented: "It can lead to the end of blockchains as we know them today. It shows how we can still achieve all the benefits of blockchains, but dropping the tyranny of sequentiality (and all the value exploiters that come with it).”
Tracking and Surveillance In-App Ads
The author learned of a massive location data breach revealing that over 2,000 apps in the App Store and Google Play were secretly collecting geographic location data without users' consent, and developers were unaware.
He then began tracking himself through location data leaked by some apps and made the following discoveries:
-
Regardless of whether users choose "Allow" or "Ask not to track" in phone settings, the combination of "IP + location + user agent + geography" is still leaked to hundreds of third parties.
-
The phone sends requests with location and leaked IP. These can be converted to geographic locations through reverse DNS.
-
Data collection pathway: stack → o.isx.unity3d.com → molocoads → bwin
-
Unity is an SSP (supply-side platform) that collects app data via its SDK
-
Moloco Ads is a DSP network that resells data from multiple SSPs like Unity, Applovin, Chartboost
-
bwin is the advertiser that users see ads for in games
-
More discoveries in this post.
Potential DAO 2.0 Product Ideas
The author believes that the development of on-chain AI agents will lead to new forms of DAO, giving true autonomy to the "A" in DAO. New product ideas include:
-
DAO 2.0 launcher: platform enables launching new community/governance tokens tied to an agent, agent responds to tokenholder votes, reads discussion forums and generates proposals
-
Quality assessment for token distribution: agent assesses contribution quality to determine payouts/token distributions for DAOs/airdrops/etc.
-
ZachZBT: agent monitors for hacks or other fraudulent activity and publishes research as well as tries to get funds back for people
-
Due diligence agent: agent verifies contract integrity, dev reputations, on-chain behavior, and potential rug risks; allows users to interact with the agent to ask questions about risks
-
-
 @ 5579d5c0:db104ded
2025-02-12 23:41:09
@ 5579d5c0:db104ded
2025-02-12 23:41:09Most people think their metabolism is "broken" because they can't lose weight, feel sluggish, or gain fat easily.
The truth? Your metabolism isn’t broken, it’s just out of sync.
Your body doesn’t just burn calories randomly.
It follows a natural 24-hour rhythm, dictated by light exposure, movement, meal timing, and sleep.
When these cues are off, your metabolism becomes dysfunctional.
The good news?
You don’t need to diet harder or exercise more.
You need to realign your metabolism with your body’s natural rhythm.
Why your metabolism feels “broken”
Your body is designed to run on timing signals, when to eat, when to move, when to rest. Modern life disrupts these natural rhythms, leading to:
→ Low energy & afternoon crashes: Skipping morning sunlight and staying indoors all day.
→ Stubborn belly fat & slow fat loss: Eating at the wrong times, late-night snacking, and chronic stress.
→ Constant cravings & hunger: Poor meal timing and eating foods that spike blood sugar too often.
→ Poor sleep & recovery: Late night screen use, artificial light, and erratic bedtimes.
The problem isn’t your metabolism, it’s your environment and habits.
How to reset your metabolism naturally
You don’t need extreme diets, calorie counting, or hours in the gym.
Instead, align your metabolism with your body’s natural timing signals by focusing on these fundamentals:
1. Get natural light first thing in the morning
Light in the first 30 minutes after waking sets your circadian rhythm (body clock), kickstarts hormone production, and improves insulin sensitivity.
This simple habit helps to regulate hunger, energy, and fat-burning.
Action step: Step outside for at least 5–10 minutes within 30 minutes of waking, no sunglasses, no contacts, only natural light exposure and take regular outdoor breaks during the day.
2. Stop eating late at night
Eating late, especially high-carb/high-fat meals, signals your body to store fat instead of burning it.
Late-night eating also disrupts sleep, which further impairs fat loss.
Action step: Keep meals within a 10-12 hour eating window, preferably between sunrise and sunset. No snacking. Finish your last meal at least 3 hours before bed.
3. Move throughout the day (Not just at the gym)
Your metabolism isn’t just about burning calories, it’s about how efficiently your body uses energy.
Sitting for long hours disrupts metabolic function, even if you work out later.
Action step: Take a 5-minute movement break every 1–2 hours. Stand, stretch, or better still go for a quick walk outside.
4. Prioritise deep, uninterrupted sleep
Your body burns fat and repairs muscle while you sleep.
Poor sleep increases hunger hormones (Ghrelin), prevents Leptin from working properly, and makes you crave junk food the next day.
Action step: Dim lights after sunset, wear blue light blocking glasses, avoid screens 30-60 minutes before bed, and aim for 7.5-9 hours of quality sleep.
5. Eat nutrient-dense foods
What you eat matters, but when you eat it matters just as much.
Front-loading protein and nutrients earlier in the day supports fat-burning and stabilises energy.
Action step: Eat a high-protein, nutrient-dense breakfast and avoid refined carbs & sugar, especially in the morning, to prevent cravings later.
Your metabolism isn’t broken, it’s just out of sync.
Instead of obsessing over calories, focus on realigning your body with its natural rhythms:
→ Morning sunlight to set your metabolism for the day.
→ Aligned meal timing by eating during daylight & avoiding late-night eating.
→ Frequent movement to prevents metabolic slowdown from sitting.
→ Quality sleep which regulates fat-burning and hunger hormones.
→ Nutrient-dense eating giving your body what it needs.
Fix your metabolism without dieting harder, just live in sync with how your body is designed to function.
-Chris
If you want a simple methodical approach to fixing your metabolism, Let’s talk.
Book a free call here: https://calendly.com/hello-chrispatrick
Follow me on Nostr: https://primal.net/chrispatrick or
nostr:npub124uatsq6pv74trzwvt34y4sx2z0uflhse7tkrv0pl69e8kcsfhkse30zsu
-
 @ 09fbf8f3:fa3d60f0
2025-02-17 15:23:11
@ 09fbf8f3:fa3d60f0
2025-02-17 15:23:11🌟 深度探索:在Cloudflare上免费部署DeepSeek-R1 32B大模型
🌍 一、 注册或登录Cloudflare平台(CF老手可跳过)
1️⃣ 进入Cloudflare平台官网:
。www.cloudflare.com/zh-cn/
登录或者注册账号。
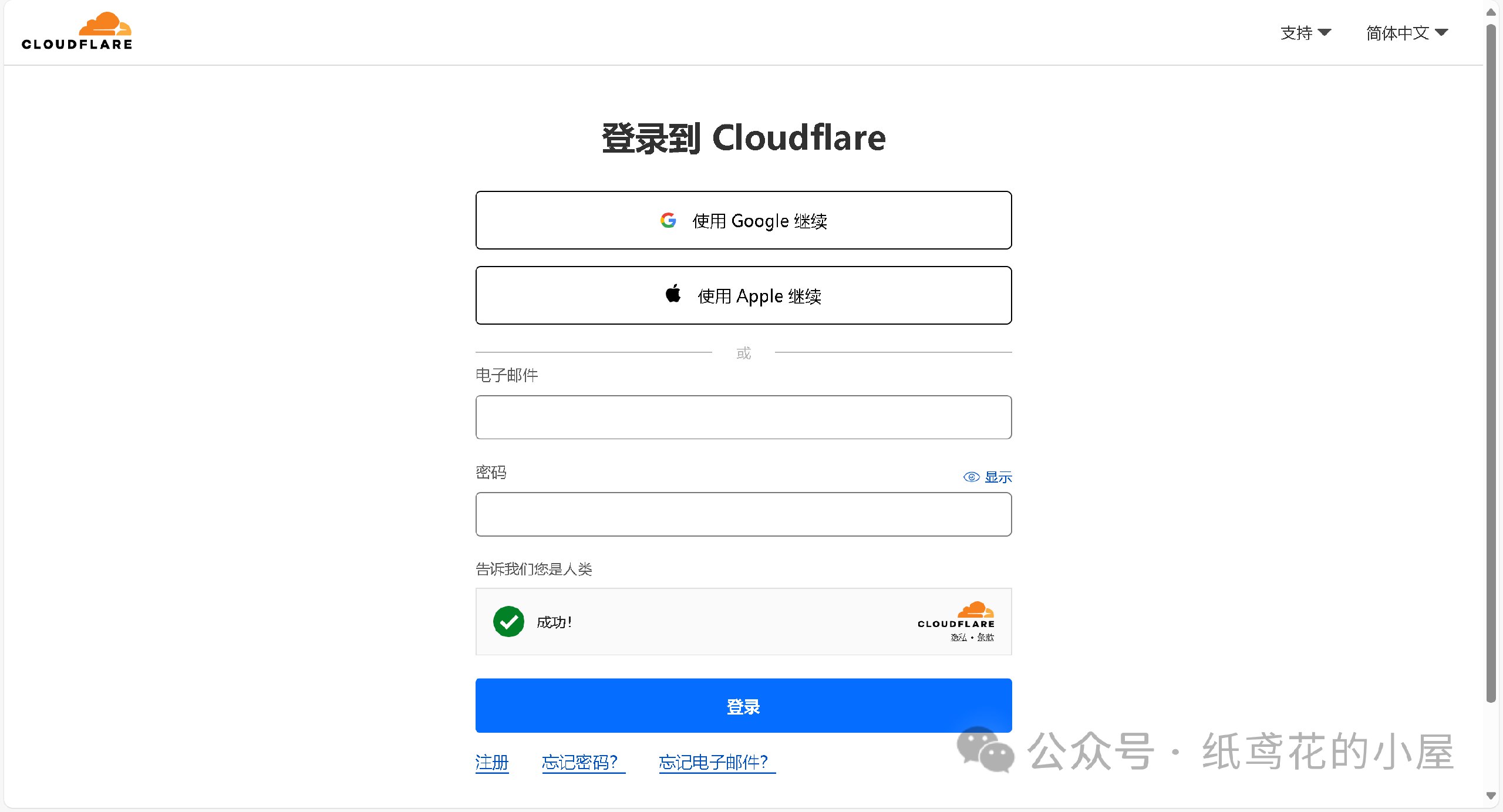
2️⃣ 新注册的用户会让你选择域名,无视即可,直接点下面的Start building。
3️⃣ 进入仪表盘后,界面可能会显示英文,在右上角切换到[简体中文]即可。
🚀 二、正式开始部署Deepseek API项目。
1️⃣ 首先在左侧菜单栏找到【AI】下的【Wokers AI】,选择【Llama 3 Woker】。
2️⃣ 为项目取一个好听的名字,后点击部署即可。
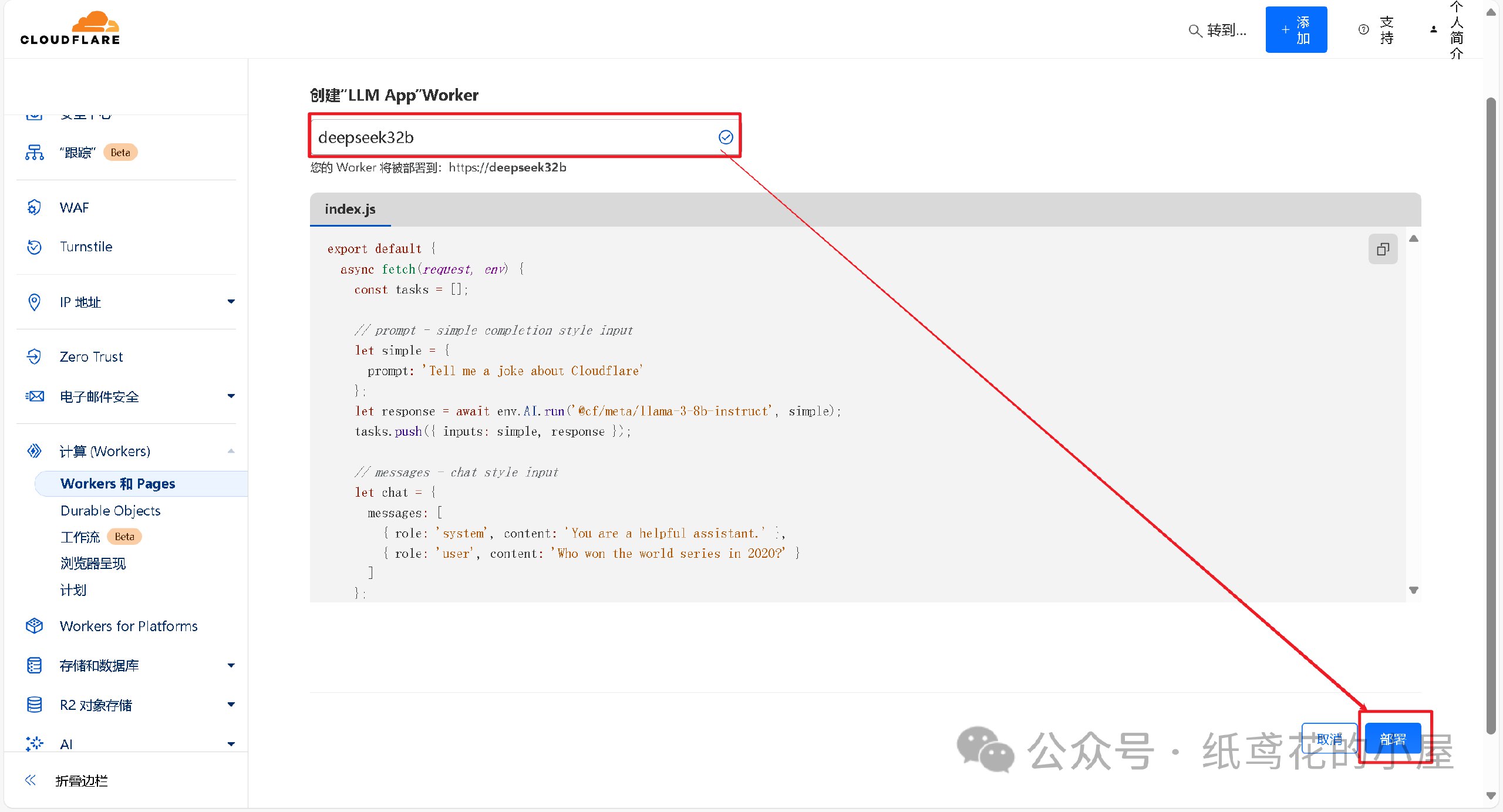
3️⃣ Woker项目初始化部署好后,需要编辑替换掉其原代码。
4️⃣ 解压出提供的代码压缩包,找到【32b】的部署代码,将里面的文本复制出来。
5️⃣ 接第3步,将项目里的原代码清空,粘贴第4步复制好的代码到编辑器。
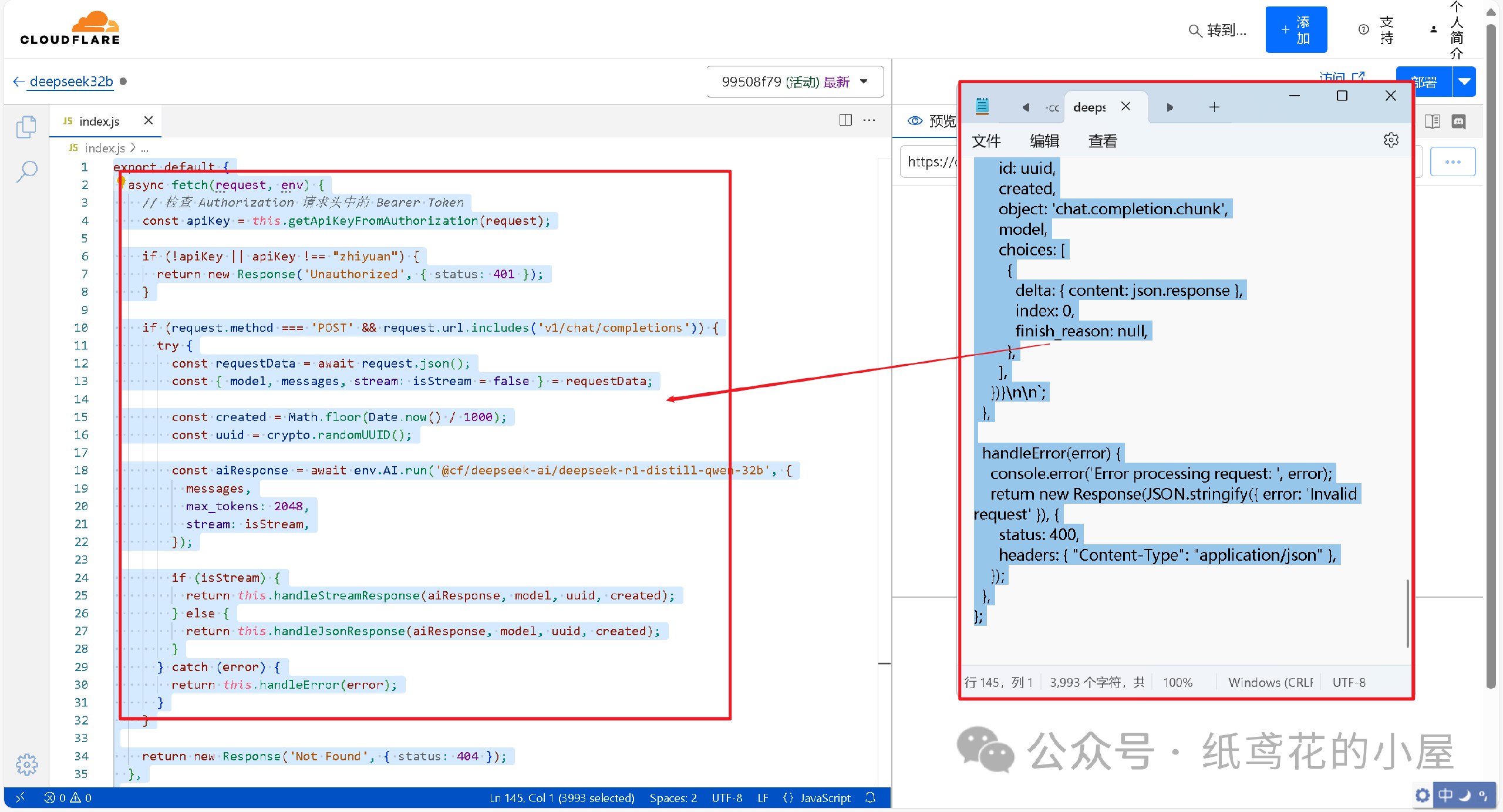
6️⃣ 代码粘贴完,即可点击右上角的部署按钮。
7️⃣ 回到仪表盘,点击部署完的项目名称。
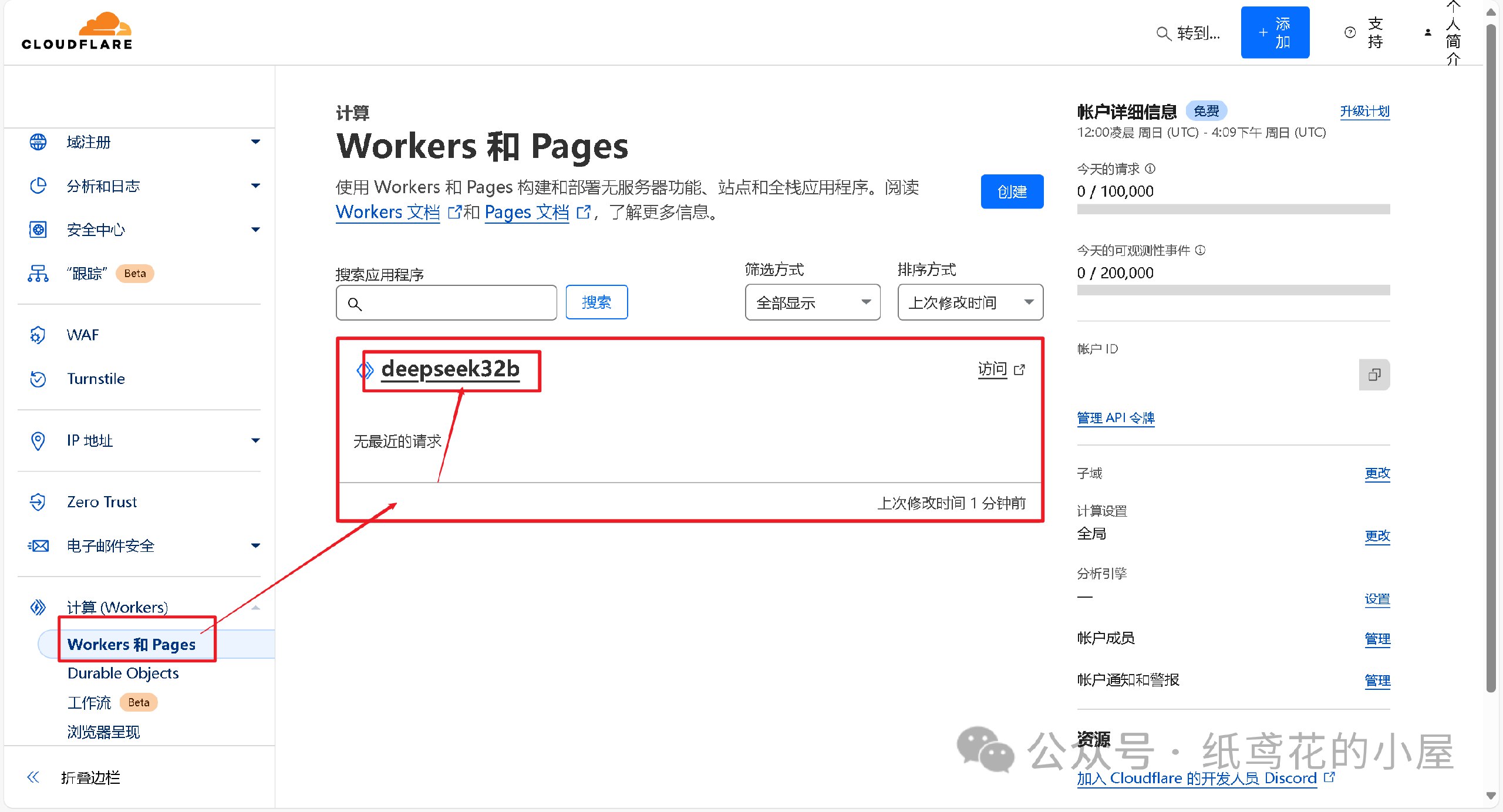
8️⃣ 查看【设置】,找到平台分配的项目网址,复制好备用。
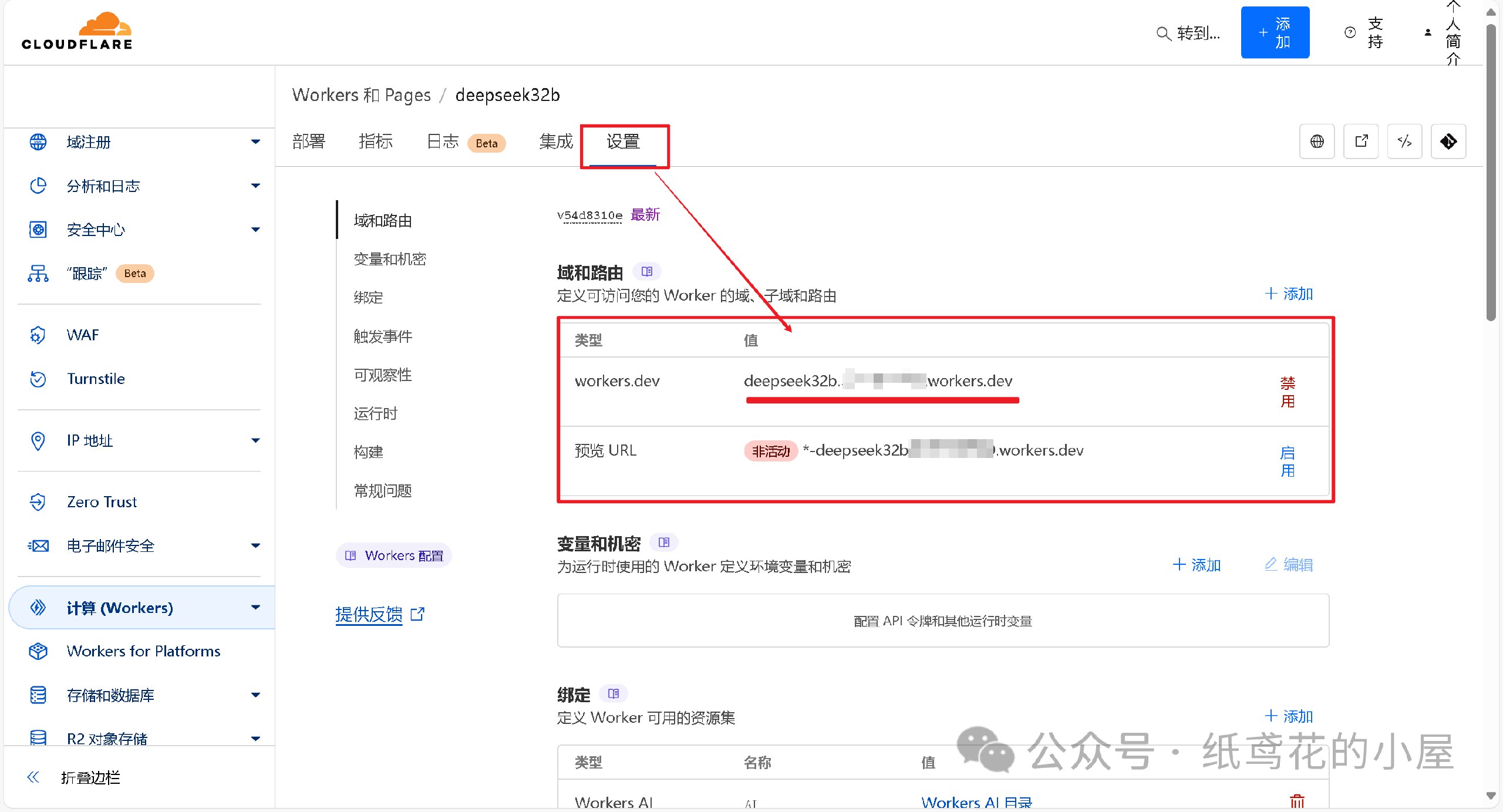
💻 三、选择可用的UI软件,这边使用Chatbox AI演示。
1️⃣ 根据自己使用的平台下载对应的安装包,博主也一并打包好了全平台的软件安装包。
2️⃣ 打开安装好的Chatbox,点击左下角的设置。
3️⃣ 选择【添加自定义提供方】。
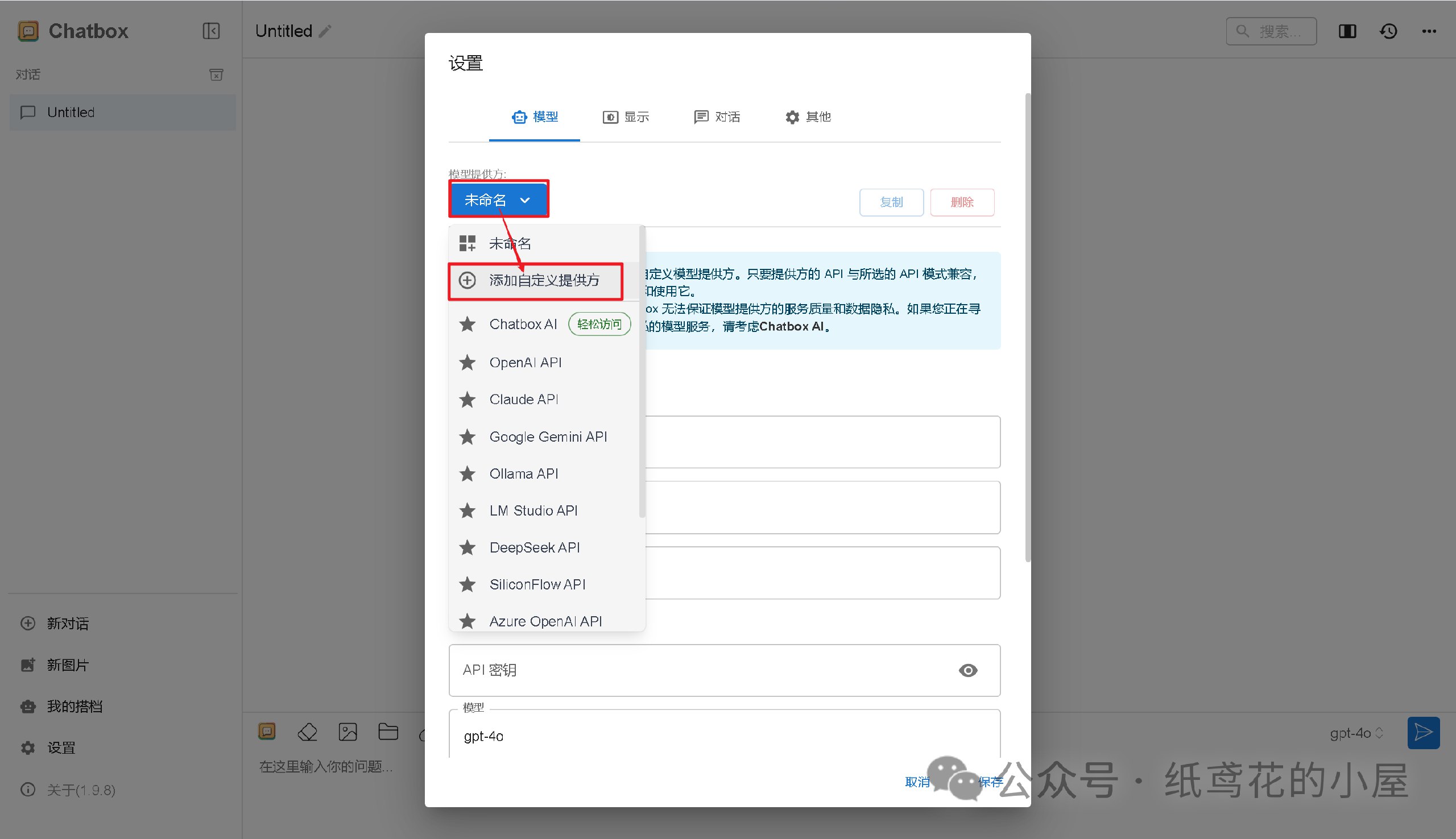
4️⃣ 按照图片说明填写即可,【API域名】为之前复制的项目网址(加/v1);【改善网络兼容性】功能务必开启;【API密钥】默认为”zhiyuan“,可自行修改;填写完毕后保存即可。
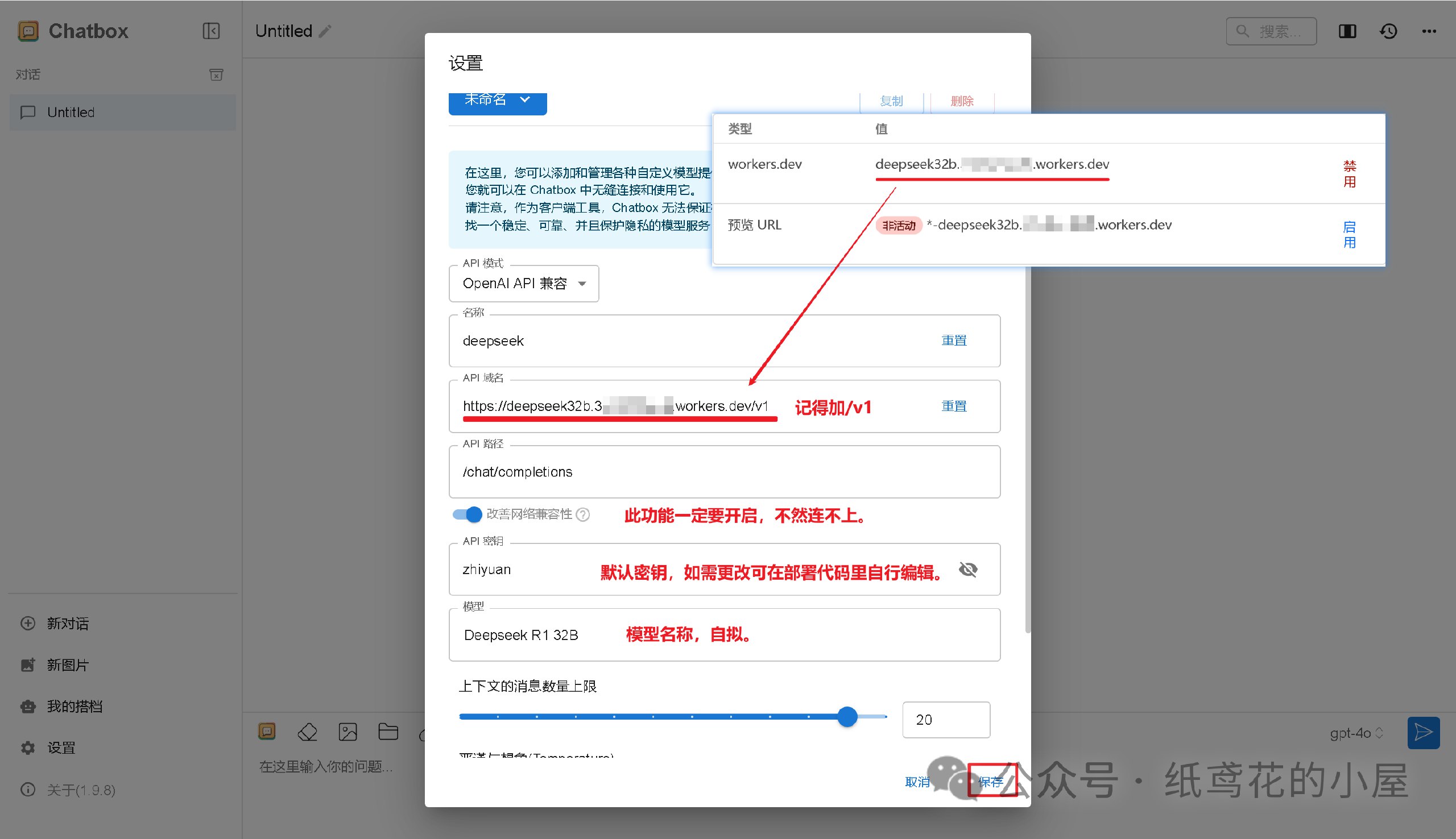
5️⃣ Cloudflare项目部署好后,就能正常使用了,接口仿照OpenAI API具有较强的兼容性,能导入到很多支持AI功能的软件或插件中。
6️⃣ Cloudflare的域名默认被墙了,需要自己准备一个域名设置。
转自微信公众号:纸鸢花的小屋
推广:低调云(梯子VPN)
。www.didiaocloud.xyz -
 @ a262e97d:ddc3e696
2025-02-27 02:32:27
@ a262e97d:ddc3e696
2025-02-27 02:32:27The ancient Greek tale of the Sword of Damocles tells of a Sicilian tyrant Dionysius II and his courtier Damocles. According to legend, Damocles envied Dionysius’s wealth and power, so the tyrant offered to switch places with the coutier for a day. Damocles eagerly accepted, reveling in luxury—until he noticed a sharp sword dangling above his head, held only by a single horsehair. The looming threat stripped away his enjoyment, revealing the constant peril that accompanies great power. It’s a story about the precariousness of fortune, where danger hovers just out of sight.
Constantinople
Throughout history, there have been examples of such anxiety affecting beyond the individual onto a collective. One example that captures a society-wide sense of dread is the fall of Constantinople in 1453. This wasn’t just a city on edge; it was an entire civilization staring down its own collapse, with the tension building for decades before the final, brutal crescendo.
Picture the scene: Constantinople, the last bastion of the Eastern Roman Empire, a city of faded grandeur encircled by Ottoman forces under Mehmed II. By the mid-15th century, the empire had shrunk to a shadow of its former self, its walls battered by time and earlier sieges, its coffers nearly empty. The Byzantines knew the Turks were coming—Mehmed’s massive cannons, including the monstrous Basilica, were no secret. For years, they’d lived with the creeping certainty that their world was teetering on a knife’s edge, propped up only by fragile alliances and the hope of Western aid that never fully materialized. The city’s inhabitants—nobles, merchants, priests, and peasants alike—could feel the noose tightening as Ottoman scouts probed their defenses and trade routes withered.
A citizen of Constantinople in those final days might have said something like: “We feast on memories of glory, our golden domes gleaming still, but a shadow looms beyond the walls. Each night I hear the distant rumble of their engines, each day I count fewer ships in our harbor. Our prayers echo in Hagia Sophia, yet I wonder if God has turned His face from us. We are bound by a thread, and it frays with every passing hour.” It’s that Damocles vibe dialed up to apocalyptic levels—splendor undercut by the palpable, collective dread of annihilation.
The drama peaked on May 29, 1453, when Mehmed’s army breached the walls after a relentless 53-day siege. The city fell in a bloodbath: cannons shredded centuries-old fortifications, soldiers poured in, and the last emperor, Constantine XI, vanished into the fray, his fate unknown. Hagia Sophia was turned into a mosque, and an empire that had endured for over a thousand years was snuffed out. The psychological weight beforehand—the years of knowing the end was near, yet clinging to a fraying hope—makes it a gut-punch of a historical moment. For your essay, it’s a setting that screams inquiétude on a grand scale, a whole society under that dangling sword until it finally dropped.
French Revolution
More recently, consider the French Revolution. Here’s the bourgeoisie on the eve of 1789 again—wealthy but boxed in, sensing the old order’s collapse. Once the revolution ignited, everyone felt the blade: aristocrats faced the guillotine, revolutionaries feared counter-revolts, and even the masses worried about starvation or tyranny. It’s a carousel of Damocles moments—power shifted fast, and no one knew when the horsehair might snap.
Imagine, if you will, a member of France’s bourgeoisie—a well-off merchant or lawyer, say—on the eve of the French Revolution in 1789. They’ve climbed the social ladder through trade or education, but they’re still squeezed between the decadent nobility above and the restless poor below. The monarchy’s crumbling, the economy’s a mess, and whispers of revolt are growing louder. This bourgeois might describe their feelings with a nod to that old tale: “I sit at a banquet of my own making, wealth and status within reach, yet I feel a blade dangling above me. The nobles scorn us, the masses eye our gains, and the king’s faltering grip threatens to let it all fall. Every coin I’ve earned could be my undoing.” It’s a mix of pride in their rise and dread of the chaos that could snatch it away—Damocles at his feast, tasting both triumph and terror.
The French Revolution is the closest echo of Dionysius and Damocles: a society—especially the rising bourgeoisie and later revolutionary leaders—relishing newfound power (or the chance at it) while acutely aware of the fragility holding it together. The guillotine literally hung over heads, and the rapid turnover of factions (Girondins, Jacobins, Thermidorians) mirrors that precarious throne under a dangling blade. Spain’s war was too chaotic, too fractured for anyone to sit comfortably; McCarthy’s era had menace but lacked the all-encompassing upheaval. France in 1789–1799 is the banquet with the sword swaying overhead—everyone’s a guest, and no one’s safe.
the Chainsaw of Donacles
In a gray, fluorescent-lit cubicle maze straight out of a dystopian Office Space reimagined as a euro-steampunk nightmare, the United States of 2025 hums with the dissonance of 1789 pre-revolutionary fervor. The air smells of burnt coffee and gear grease, the dull drone of bureaucracy punctuated by the hiss of steam pipes snaking along the walls above an endless sprawl of cubicles and flickering gas lamps. The air thick with wifi radiation and desperation.
Donald Trump, newly mandated by a roaring electorate to “drain the swamp,” roams between Mar-a-Lago’s opulent halls, the White House’s command center, and Air Force One’s plush skies. His arme de prédilection: a ostentatious gold-tipped pen, wielded like a guillotine’s decree. Trump grins, orange hair wild, and with a flourish, he signs resounding executive orders—EOs that thunder through the bureaucracy — smirking, “The swamp’s toast, folks.”
Enter Elon Musk, tasked with leading the DOGE task force—Department of Government Efficiency. He grips a gleaming chainsaw, a gift from Argentine firebrand Javier Milei, its blade etched with “Libertad o Muerte.”
His Zoomerwaffen—a brigade of Gen Z disruptors in brass goggles and hoodies—are the revolution’s shock troops in hoodies and brass goggles, armed with bare steel laptops and savage memes. These digital sans-culottes wield laptops like muskets, flooding X with memes that mock the Karens (“OK Boomer, meet the blockchain”), crashing servers with decentralized audits, and rigging AI bots to shred red tape faster than a guillotine drops. One Zoomer, vape cloud swirling, hacks a payroll database while blasting dubstep; another livestreams a “Karen Meltdown Compilation” as morale bombs. They’re the grease in Elon’s machine, turning DOGE into a viral uprising.
Elon’s Herculean task: slash the bloated federal beast down to size. From a Cybertruck-turned-mobile-HQ, smokestack puffing, Elon adjusts his top hat, a single LED flickering on its brim. “Time to saw through the bloat,” he quips and revs the beast, slashing budgets with a mad inventor’s glee. “Efficiency is the new Reign of Terror. Let's disrupt the guillotine’s monopoly on downsizing.” The zoomers cheer, their screens flashing with blockchain audits and TikTok takedowns of red tape as they slash budgets with blockchain precision, livestreaming the carnage on X.
But beyond the glass-walled boardrooms and armored Cybertrucks, the cubicles stretch into a Bastille of beige despair. Here reign the deep-staters — legions of federal lifers grown plump on decades of taxpayer largesse. They’re the ancient régime of red tape, peering over partition walls with powdered wigs askew, muttering about “due process” while clutching dog-eared manuals of byzantine regulations.
Picture these thousand Karens, each clutching a “Manager of My Own Destiny” mug, their lanyards clinking with pronoun pins and union badges; each a snowflake of entitled fury.
And above every sweat-stenched cubicle, a miniature chainsaw dangles by a fraying hemp thread.
One wretched teet-sucking swamp creature, a portly GS-14 named Linda, slams her “TPS Reports” onto a desk, her wig askew, shrieking, “I’ve earned my pension, you fascists! I've earned everything, fair and square!” Linda's personal Chainsaw of Donacles sways with every EO and Zoomer hack. Her ink-stained hands tremble as her steam-powered iPhone wheezes out another ding decrying ever more “DOGE tyranny.”
Across the floor, lanyards jangle — pronoun pins flashing — as Karens plot over stale croissants, whispering of jammed printers and leaked memos to fight back.
Trump’s banquet is victory, savored from Mar-a-Lago’s terraces or 30,000 feet up, untouchable. His mighty pen perpetually slashing through the old order.
Elon’s chainsaw roars, Zoomerwaffen dancing in its sparks, dismantling decades of excess.
The Karens sit under their blades — relics of a bloated regime, their banquet of entitlement souring as the threads fray and the swamp drains.
The Revolution’s inquiétude steams through: they built this world, gorged on its perks; and now the power they hoarded hangs by a hair Every Musk rev, every Trump signature, every Zoomer meme cuts closer.
“Efficiency’s here. Let them eat efficiency!” Elon tweets, and a chainsaw twitches.
A Karen shrieks. A rope snaps.
Hope you enjoyed this steampunk Office Space-meets-1789, lovingly crafted by Grok and myself.
One final note on the Zoomerwaffen (a term I picked up from @realKingpilled): They’re the patriotic engine of this upheaval — tech-native, irreverent, and relentless. Think of them as the street agitators of 1789, but with code instead of pitchforks. They hack legacy systems to expose waste, flood social media with viral takedowns, and turn DOGE’s mission into a cultural juggernaut. Their focussed autism amplifies Elon’s chainsaw and Trump’s pen, making the Karens’ downfall a public spectacle. They’re the ones fraying those threads, one savage meme at a time.
-
 @ 6389be64:ef439d32
2025-01-13 21:50:59
@ 6389be64:ef439d32
2025-01-13 21:50:59Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
Meet The Forest Walker
For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
The Small Branch Chipper
When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
The Gassifier
The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
Biochar: The Waste
Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
Wood Vinegar: More Waste
Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
The Internal Combustion Engine
Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
CO2 Production For Growth
Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
The Branch Drones
During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
The Bitcoin Miner
Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
The Mesh Network
What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
Back To The Chain
Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
Sensor Packages
LiDaR
The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
pH, Soil Moisture, and Cation Exchange Sensing
The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
Weather Data
Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
Noise Suppression
Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
Fire Safety
A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
The Wrap
How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-
 @ 3ae7fdae:f8d4b19d
2025-01-28 00:00:26
@ 3ae7fdae:f8d4b19d
2025-01-28 00:00:26Lifting the Curtain on Power and Scandal
The Illusion of Power and TrustIn the modern world, the line between trust and skepticism is razor-thin, especially when it comes to powerful figures and organizations. They present polished facades, dazzling us with promises of stability, innovation, or in Disney’s case, enchantment. Yet, the revelations surrounding Jeffrey Epstein’s network reminded us that power is often far more complex than it appears. This scandal became a litmus test for public trust and fueled questions about who, or what, might be entwined in hidden truths.
When Epstein's crimes were exposed, they revealed not just the horrifying details of exploitation, but also the unsettling reach of his influence. As the media peeled back the layers of his associations, public attention naturally shifted to recognizable names and institutions, including Disney. How could a company that represented childhood innocence, with castles and fairy tales, find itself whispered about in the same breath as Epstein’s infamous circle? This segment examines the roots of that question and the facts that illuminate its plausibility or dismiss it.
Epstein: A Man Who Mastered Access to PowerJeffrey Epstein was more than just a financier—he was a gatekeeper to influence. His lifestyle and operations were an entangled web of charm, manipulation, and wealth, meticulously designed to secure him a place among the powerful. Investigative articles by The Guardian and The New York Times depict Epstein as a social engineer, curating relationships that ranged from politicians and royalty to scientists and celebrities.
Court documents and deposition testimonies during Epstein’s trial confirmed that his homes and private jet were hubs for connecting with influential figures. This access did not come without consequence; it cemented him as both a source of curiosity and, later, fear. Public records, such as those scrutinized in The Washington Post, indicated his involvement with many high-profile individuals. Yet, the details of these relationships varied—some guests were casual acquaintances, others, confidants.
The Infamous Flight LogsThe flight logs of Epstein’s private jet, colloquially known as the "Lolita Express," became a centerpiece for public scrutiny. Released through court orders and accessed by journalists, these logs listed names that triggered a cascade of questions. Guests ranged from prominent business executives to entertainment figures, sparking a debate over whether mere association implied complicity or deeper connections. This fueled the narrative that Epstein’s reach was far more extensive than previously understood, implicating industries where entertainment, power, and trust intersected.
The Role of Speculation in Public DiscourseAs soon as these flight logs surfaced, discussions surged online and across media platforms. The presence of any entertainment figure in Epstein’s orbit raised an eyebrow and, in many cases, invited a leap of logic: if influential media personalities were tied to him, could companies known for entertainment and global reach, like Disney, have hidden associations as well? This hypothesis, though lacking concrete evidence, found fertile ground among those predisposed to distrust large, seemingly untouchable institutions.
It’s crucial to dissect why Disney, specifically, became a subject of speculation. On one hand, its status as an omnipresent media empire makes it an easy target for conspiracy theories that thrive on the juxtaposition of light (Disney’s brand) and darkness (Epstein’s crimes). On the other, it speaks to a larger societal impulse to find cracks in the foundations of those we consider infallible. The idea that even the most beloved entities might harbor hidden truths appeals to a deep-seated desire for transparency and accountability.
The Catalyst of Public CuriosityThe timing of Epstein’s exposure was a critical factor. His arrest and subsequent death in 2019 coincided with a period marked by rising distrust in institutions, fueled by political and social upheavals globally. Social media platforms amplified this distrust, creating echo chambers where half-truths and speculative narratives merged seamlessly with confirmed facts.
It is here that Disney’s name began to surface not as an accused, but as a speculative point in discussions. The reasoning often pointed to a "guilt by association" logic: if the powerful dined, flew, or partied with Epstein, then it was worth questioning the circles in which those powerful entities moved, even without direct evidence. This leap from speculation to assumption reflects a pattern that sociologists recognize as part of conspiracy theory psychology—where a lack of clear answers invites the mind to fill in gaps, often with what feels most compelling.
Reframing the Public’s QuestionsThe real question becomes: why does this speculation hold such sway, even when evidence is scarce? Part of the answer lies in precedent. History is replete with instances where institutions that seemed above reproach were later implicated in hidden misdeeds, from financial frauds to abuse scandals within trusted organizations. This collective memory primes the public to believe that beneath any glittering surface could lie a dark, concealed underbelly.
Disney’s position as an icon of childhood and innocence adds another layer to this narrative. To imagine that such a symbol could be tainted by proximity to someone like Epstein is not just shocking—it’s fascinating. It strikes at the core of what we hold sacred, making it an irresistible topic of conversation and investigation.
Why This MattersUnderstanding why names like Disney are brought into these discussions without verified evidence is essential. It helps differentiate between warranted inquiry and unsupported speculation, allowing us to approach these narratives critically. Addressing this head-on does not only clear the air but strengthens the foundation upon which valid criticism and accountability are built.
A Note on EvidenceAs we move deeper into this exploration, it’s critical to emphasize that while Epstein’s connections to high-profile figures are thoroughly documented, there remains no evidence tying Disney, as an organization, to his operations. Still, the fascination with the “what-ifs” continues, driven by our collective quest for understanding power, secrecy, and the thin line between public and private lives.
The next segment will dive into Epstein’s proven network, unraveling the extent of his influence and why it has been the breeding ground for questions involving the world’s most trusted corporations.
Epstein’s Documented Network
The Web of Power: A Portrait of InfluenceJeffrey Epstein’s network was not merely a collection of acquaintances; it was a curated gallery of the world’s most influential figures, built on calculated relationships and strategic connections. Epstein wielded this network with the precision of a skilled operator, bridging disparate realms of society—politics, academia, business, and media. Investigative reporting by sources such as The New York Times and The Guardian exposed how Epstein maintained access to individuals who shaped policy, managed wealth, and crafted the narratives of popular culture.
Court records, testimonies, and detailed analyses of his interactions revealed that Epstein was adept at placing himself at the center of elite circles. His estates, from Manhattan townhouses to private islands, hosted events that blurred the lines between social gatherings and strategic networking. This chapter delves into the proven extent of Epstein’s reach and why it sparked questions about connections to corporations and public institutions, including Disney.
Flight Logs: The Proof and the SparkThe flight logs from Epstein’s private jet, the infamous "Lolita Express," were among the most illuminating pieces of evidence in mapping his connections. These logs, legally obtained and examined by journalists, painted a picture of Epstein’s influence stretching across industries. High-profile figures were listed, including financiers, political leaders, and entertainment personalities. The presence of notable names triggered waves of speculation—if Epstein had access to such power players, how many more remained unnamed but entangled?
The Guardian and The Washington Post reported that these flights were not just transportation but often involved visits to Epstein’s various properties, known for their opulence and the dark rumors surrounding them. While these logs confirmed that many public figures knew Epstein, the depth and nature of their associations varied widely, from casual acquaintance to deeper involvement.
The Limits of the KnownDespite the breadth of documented connections, there was no verifiable evidence linking Disney as an entity to Epstein’s circle. What the flight logs and guest lists revealed was a man deeply embedded in networks of power, yet even within these proven associations, context was crucial. For instance, some guests, confirmed by court records and investigative articles, were shown to have attended public events or engaged in business unrelated to Epstein’s criminal activities.
The distinction between documented presence and complicity is where the narrative often splinters. The leap from association to implication fueled public debate and conspiracy theories. This was especially true when figures from media and entertainment, sectors known for influencing public sentiment and childhood memories, appeared on the periphery of Epstein’s activities.
Epstein’s Parties and Gatherings: The Elite’s Shadowed StageEpstein’s parties were legendary, drawing attendees from the highest echelons of influence. These gatherings were not casual mixers but orchestrated showcases of power. Reports from court depositions and firsthand accounts highlighted how Epstein leveraged these events to cement alliances and reinforce his status as a gatekeeper to the elite. Some testimonies even described how these events served as platforms for discussing investments, politics, and global initiatives, reinforcing Epstein’s perceived omnipotence.
High-Profile Confirmations and Their ImplicationsSeveral prominent individuals were indeed verified as having ties to Epstein, raising legitimate questions about the extent of their knowledge or involvement. These names included politicians, royalty, and entertainment figures. The ambiguity surrounding these associations allowed theories to flourish. The sheer presence of influential names on Epstein’s guest lists raised the question: If these individuals were implicated, what about the institutions they represented or the circles they moved within?
This was a turning point for public speculation. The logic extended: if an individual from a major media company or entertainment empire like Disney was even remotely connected, could that implicate the company itself? The answer, according to existing court records and credible investigations, remained no. Yet, the absence of direct evidence did not stop speculation; in many cases, it intensified it.
Why Disney Was Brought Into the ConversationDisney’s reputation as a family-friendly giant contrasted starkly with the dark nature of Epstein’s activities, making it an unlikely yet intriguing topic for public discourse. While some entertainment figures appeared on Epstein’s flight logs or were rumored to have interacted with him, investigations have not yielded any proof of corporate-level involvement. However, public fascination persisted, bolstered by the broader questions Epstein’s connections evoked.
It’s worth noting that corporations like Disney, with their vast reach and unparalleled influence, naturally become focal points when discussions of hidden truths arise. The mere idea that such an iconic entity could be associated with real-world shadows captures the imagination and fuels stories that, while lacking proof, thrive on the “what-ifs” that echo through media and online forums.
How Public Perception Shapes the NarrativeSociologists studying the psychology of conspiracy theories point out that the human mind tends to fill gaps in knowledge with what feels most plausible or compelling. When figures from reputable media or entertainment companies are tied, even tangentially, to a scandal as vast as Epstein’s, it challenges the boundaries of trust. This is exacerbated when concrete answers remain elusive, leading to a cycle where suspicion feeds speculation.
The public’s thirst for accountability, especially in the wake of uncovered scandals involving powerful institutions, is both a force for truth and a catalyst for assumptions. In Epstein’s case, the proven reach of his influence and the confirmed involvement of significant figures were enough to trigger the question of how many untold stories lay beneath.
What We Know vs. What We ImagineThe narrative surrounding Epstein’s documented network shows us that while connections can be verified and associations noted, the leap to implicating entire organizations like Disney requires more than names on a list or rumors. It requires evidence that has, thus far, not been presented in any court or investigation. The proven facts are compelling enough: Epstein’s influence was extensive, his ties to power irrefutable. Yet, without direct links, the conversations about specific corporate involvement remain speculative.
In the next segment, we will explore why Disney’s reputation makes it a prime target for such speculation and how its historical handling of public crises plays into these narratives.
Disney – The Symbol of Trust and Target of Suspicion
Why Disney? The Paradox of a Trusted InstitutionDisney’s legacy is built on a foundation of storytelling, dreams, and the belief in happy endings. For nearly a century, the company has woven itself into the fabric of childhoods, becoming synonymous with innocence and magic. This legacy, however, has a dual edge. As the public's trust in institutions erodes and hidden truths are revealed in other sectors, Disney’s position as an untouchable cultural icon makes it both a beacon of light and a potential target for suspicion.
The Symbolism of Disney’s BrandDisney represents more than just a company; it embodies an idea—a refuge where imagination and wonder reign. But this same image that has made Disney a household name also contributes to the paradox of suspicion it faces. When an organization is seen as larger than life, transcending generations and continents, the notion that it could have skeletons in its closet becomes a tantalizing thought. The juxtaposition of innocence with possible shadows creates a narrative that is compelling and worth exploring, even if it remains speculative.
This paradox of Disney as both a trusted symbol and a target for scandal reflects a broader trend. Major corporations that hold influence in our everyday lives—particularly those that shape childhood memories and societal values—are natural focal points when scandals involving power, influence, and exploitation arise. The idea that a company with as much reach as Disney could be connected, however tangentially, to figures like Epstein feeds into this pattern.
Documented Misconduct and Public ReactionsThere have been verified cases involving Disney employees engaging in misconduct, which have been reported by media outlets such as NBC News and local news channels. These incidents, though not systemic and unrelated to Epstein’s network, show how the actions of a few can impact public perception of an entire organization. Examples include arrests for crimes involving minors or inappropriate behavior, isolated events that Disney has publicly addressed through statements and cooperation with law enforcement.
However, these incidents were sufficient to plant seeds of doubt in some minds. Even when addressed swiftly and in line with corporate protocols, such cases reveal a vulnerability: the company’s image can be tarnished not just by its policies, but by the misdeeds of individuals who wear its badge.
The Fuel for SpeculationThe Epstein case acted as a catalyst for looking beyond the obvious, particularly in the context of powerful organizations. If political leaders, financiers, and cultural icons could be connected to Epstein’s circle, why not wonder about the involvement of a company with as vast a presence as Disney? While investigations by trusted outlets have shown no direct corporate link, the sheer scope of Epstein’s influence suggested that any entity known for associating with the powerful could be implicated.
This speculation was not helped by Disney’s approach to public relations. The company’s PR strategies, while sophisticated and generally effective, often prioritize message control over transparency. In a world where silence can be seen as complicity, this strategy sometimes backfires, leading to more questions than answers.
Public Distrust and Historical ContextThe public’s fascination with uncovering hidden truths within major institutions is not unfounded. History is replete with cases where seemingly trustworthy organizations were later found to have concealed scandals. From corporate frauds to abuses within religious institutions, these stories have taught the public that innocence is not immune to corruption. This backdrop primes society to believe that even the most beloved entities, like Disney, could harbor secrets.
Sociologists and media analysts argue that this distrust is a byproduct of what they term the “betrayal effect”—where past disappointments with trusted institutions lower the threshold for believing that betrayal could be lurking everywhere. Disney, with its spotless public image and vast influence, becomes an especially juicy target for such theories. The leap from real cases of employee misconduct to more systemic accusations, however, is where evidence often falls short.
The Role of Social Media and Echo ChambersThe digital age has amplified how speculation morphs into perceived truth. Platforms like Twitter, Reddit, and Facebook allow theories to spread quickly, often outpacing fact-checking and nuanced analysis. Discussions that might once have been confined to fringe circles now gain mainstream attention, especially when they involve powerful figures or beloved brands.
In the context of Epstein’s exposure, this meant that any high-profile connection or name could become part of a broader narrative of guilt by association. The fact that Disney, as a corporation, appeared in speculative discussions alongside verified names from Epstein’s logs was enough for some to draw connections, even without direct evidence.
Reputation Management and PerceptionDisney’s approach to crises and controversies has long involved careful reputation management. From its response to legal issues to how it handles employee-related incidents, the company employs sophisticated PR strategies to mitigate damage and maintain its standing. This is standard practice for global brands; however, the public’s interpretation can be different. Strategic silence or tightly controlled statements can come across as evasive, fueling theories that there is something more to hide.
For a company like Disney, which operates at the intersection of family values and global corporate power, the stakes are high. The expectation isn’t just for entertainment but for upholding the moral high ground. When speculation links Disney to scandals, no matter how peripherally, it chips away at this carefully crafted image.
Why Address This Now?The speculation around Disney and Epstein underscores a crucial point about the nature of public inquiry and corporate reputation. It is not enough for companies to rely solely on public relations strategies that worked in the past. The demand for transparency is greater than ever, and silence, even when warranted, can erode trust.
Disney’s role in the public consciousness means that even baseless theories need addressing. By understanding why these narratives gain traction, both companies and the public can engage in more meaningful dialogues about accountability, proof, and trust.
The next segment will delve into how the public navigates between confirmed facts and conspiratorial whispers, exploring why certain theories stick and what it means for how we view powerful organizations.
Separating Fact from Conspiracy
The Thin Line Between Evidence and Speculation In the age of information, where facts are readily available yet often overshadowed by conjecture, separating truth from conspiracy is both an art and a necessity. When powerful entities like Disney find themselves drawn into discussions of hidden networks and scandals involving figures such as Jeffrey Epstein, it highlights a broader societal challenge: how do we differentiate between what is proven and what is assumed? This segment dissects the interplay of evidence, theory, and the psychological factors that drive our need to seek connections.
The Basis of Public Suspicion Public trust in large institutions has waned over decades, driven by a series of high-profile betrayals. From corporate frauds that shattered economies to scandals involving trusted religious or educational institutions, society has learned that power often conceals flaws and, in some cases, criminal actions. According to research published in the Journal of Communication, this erosion of trust leads to a phenomenon known as confirmation bias—the tendency to interpret new evidence as confirmation of one’s existing beliefs or suspicions.
The Epstein case provided fertile ground for such biases. The verified details of Epstein’s operations—the private jet, the exclusive parties, the high-profile guests—were enough to prompt a collective re-examination of how far his reach extended. While many of his associations were proven to be casual or professional in nature, the public’s hunger for deeper revelations ensured that speculation would thrive in areas where clarity was lacking.
The Role of Real Connections Epstein’s documented network included figures from politics, academia, finance, and media. The release of flight logs and court documents revealed that powerful individuals attended his events and interacted within his sphere. This factual basis, verified by investigative reporting from The New York Times, The Guardian, and other reputable sources, provided legitimacy to the idea that Epstein’s influence was pervasive. However, the extent to which these relationships were innocent or complicit was not uniformly clear.
This ambiguity created a vacuum where speculation could flourish. Public attention shifted from individuals named in the logs to the institutions and industries they represented. It was here that major corporations, including Disney, entered the discourse—not because of documented ties, but because of their visibility and influence.
The Psychology Behind Linking Power and Scandal To understand why theories about Disney’s potential involvement in Epstein’s network persist, it is essential to examine the psychology of conspiracy. Sociological and psychological studies indicate that people are naturally inclined to question narratives when they feel that the truth is being withheld. The more powerful or untouchable an institution seems, the more likely it is to be suspected of hiding something significant.
Disney’s image as a global giant that molds childhoods and shapes culture makes it an appealing target for such theories. The company’s public persona as a bastion of family values and innocence stands in stark contrast to any whispers of scandal or misconduct. This contrast alone provides fertile ground for stories to grow, even in the absence of solid proof.
Confirmed Misconduct vs. Conspiracy It is important to acknowledge that Disney, like any large corporation, has faced incidents involving employee misconduct. News reports from outlets such as NBC News have documented cases where employees were arrested for inappropriate conduct involving minors. These cases, while serious and handled with appropriate legal responses, were isolated incidents. No evidence points to these cases being part of a larger, systemic issue within the company or connected to external figures like Epstein.
However, the very existence of these incidents is often enough to keep theories alive. Public perception does not always differentiate between an individual’s actions and the culture of the organization they work for. When these incidents coincide with broader conversations about power and secrecy, they feed into narratives that imply guilt by association.
The Amplifying Power of Social Media The role of social media in shaping and amplifying conspiracy theories cannot be overstated. Platforms like Twitter and Reddit have created spaces where facts, opinions, and theories coexist with little separation. When the Epstein scandal broke, social media was flooded with discussions, many of which featured a mix of verifiable information and speculative connections. The absence of direct evidence linking companies like Disney to Epstein did not deter users from proposing connections based on circumstantial evidence and “what-if” scenarios.
This phenomenon, described by media analysts as the “echo chamber effect,” allows theories to gain credibility through repetition rather than proof. As theories are shared, retweeted, and commented on, they accumulate a sense of legitimacy that belies their origins.
Why Certain Theories Stick Certain theories persist because they tap into deep-seated fears and the knowledge that the powerful often operate beyond the reach of conventional accountability. High-profile scandals involving powerful figures—whether in business, politics, or entertainment—reinforce the belief that more may be hidden just out of reach. Epstein’s network was confirmed to include names that were once considered untouchable, which validated the idea that hidden truths could surface anywhere.
Disney’s name appearing in speculative discussions highlights the intersection of innocence and power. It reflects a societal expectation that if one pillar of influence is shown to be compromised, others may be as well. This expectation, however, must be tempered with critical thinking and an examination of evidence.
The Need for Discernment Understanding the difference between fact and theory is crucial for informed dialogue. Public scrutiny is essential for accountability, but it must be balanced with discernment. While Epstein’s known associations spanned many sectors, and while individuals from the entertainment industry were involved in his circle, the leap to implicating entire organizations like Disney has not been supported by verified investigations.
The Reality Check Here’s what we know:
Documented Facts: Epstein’s network included influential figures, confirmed by court records and journalistic investigations. Disney’s Position: While Disney has faced isolated cases of employee misconduct, no substantial evidence ties the company as an institution to Epstein’s criminal activities. Public Perception: Theories are fueled by a combination of legitimate distrust in powerful institutions and the psychological need to connect the dots, even when the evidence does not support it. In the next segment, we will explore how media control and the use of non-disclosure agreements (NDAs) contribute to the public’s perception of secrecy and whether this perception is warranted.
Media Control and NDAs – Protecting Power or Ensuring Silence?
The Strategy of Silence in Crisis Management When powerful organizations face potential scandal or crises, the first line of defense is often control—control over the narrative, control over information, and control over public perception. This strategy, while effective in mitigating immediate damage, can backfire by fostering an aura of secrecy that leads to suspicion. Disney, like many other global corporations, has historically employed these tactics, particularly through the use of non-disclosure agreements (NDAs) and strategic public relations (PR) campaigns. But do these measures protect legitimate corporate interests, or do they simply fuel theories that there is more being hidden?
Understanding the Role of NDAs NDAs are legal tools designed to maintain confidentiality and protect business interests. In most cases, their use is standard practice, whether to protect trade secrets, secure settlements, or manage sensitive internal matters. However, when NDAs intersect with scandals involving powerful individuals or organizations, they can become symbols of enforced silence. A report from the Harvard Business Review highlights that while NDAs are often employed for legitimate purposes, their misuse—especially when used to silence allegations of misconduct—has cast a shadow over their intent.
Disney has used NDAs in its corporate dealings, as have many in the media and entertainment sectors. This is not in itself suspicious; however, the mere presence of NDAs in a company’s arsenal can contribute to a narrative of secrecy, especially when paired with limited transparency during controversies.
The Case of High-Profile Secrecy The Epstein scandal showed how the use of NDAs and strategic silence could be perceived in a different light. When influential figures and companies were linked to his circle, silence from those implicated was interpreted by many as an attempt to avoid deeper inquiry. While Disney has not been tied to Epstein’s activities through verified evidence, its use of NDAs in unrelated circumstances and its approach to handling public controversies have made it a recurring subject in theories about hidden truths.
For example, Disney’s meticulous control over its brand image means that it often handles internal issues privately, releasing carefully crafted statements that address public concerns without divulging specifics. This approach, while protective, sometimes has the unintended consequence of making the public wonder what is not being said.
The Intersection of PR and Public Perception Public relations are designed to safeguard a company’s image, ensuring that responses to any negative news are swift and tightly managed. Disney’s PR machine is among the most sophisticated, capable of steering narratives and maintaining its reputation as an entertainment titan. This strategic control has allowed Disney to weather crises that might have permanently damaged lesser brands. However, in the context of a scandal as sprawling and notorious as Epstein’s, such control is perceived differently.
When the Epstein story broke and high-profile connections came to light, companies with any tenuous ties activated their crisis management protocols. For some, this meant issuing vague statements or refusing to comment altogether. To the public, this read as silence—a strategic choice that seemed suspicious when paired with known instances of NDAs being used to keep serious allegations quiet in other industries. The #MeToo movement, for instance, revealed how NDAs were used by some media companies to shield powerful perpetrators of harassment, showing that these tools can sometimes contribute to a culture of concealment.
Silence as Complicity? For a company like Disney, known for its polished public image, silence during times of widespread speculation can amplify suspicions. The question becomes: Is silence an act of protection or complicity? While NDAs are often used to manage settlements or protect internal processes, the fact that they prevent full transparency can make even innocent parties appear as if they have something to hide.
Experts in crisis communication argue that silence may protect the brand short-term but can erode trust long-term. Disney’s approach to handling public perception, from managing employee misconduct cases to addressing larger social controversies, often involves strategic responses that give the public enough information to stay satisfied but not enough to quell the more skeptical voices. This is standard practice but becomes contentious when the public is searching for accountability.
The Impact of Strategic Silence on Public Trust Media and communication studies have shown that transparency is increasingly becoming a measure of trustworthiness for corporations. In an era where the public demands answers and alternative media thrive on filling in gaps left by corporate PR, the stakes for maintaining trust are higher than ever. The use of NDAs and controlled statements can protect a company’s interests, but it also contributes to a perception of secrecy that feeds public doubt.
Disney’s balancing act—protecting its brand while managing incidents behind closed doors—reflects a broader industry trend. Corporations that prioritize narrative control must now reckon with an environment where even a hint of concealment can lead to damaging speculation. The Epstein case amplified this issue, putting the spotlight on how major organizations handle proximity to scandal, even if only by association.
Navigating the Perception The real challenge for Disney and similar companies lies in navigating the fine line between protecting their interests and fostering trust. Complete transparency can be risky, but strategic silence risks becoming complicit silence in the eyes of the public. This duality—where necessary protection measures are perceived as proof of hidden wrongdoing—is why entities like Disney find themselves caught up in discussions about figures like Epstein, despite the absence of concrete evidence.
The Takeaway for Institutions and the Public Understanding the role of NDAs and PR in managing public crises helps frame why powerful companies might become targets of suspicion. While the use of these tools is standard and often justified, their impact on public perception can’t be ignored. For the public, recognizing the difference between warranted inquiry and overreach is key to maintaining productive scrutiny without falling into the trap of baseless theories.
The next segment will focus on what these perceptions mean for society as a whole and why the pursuit of transparency and trust must be a collective endeavor.
Beyond the Shadows – A Call to Unity
The Complex Path to UnderstandingIn an age where trust in powerful institutions is fraying, and access to information is both a blessing and a burden, our approach to truth becomes more critical than ever. The discussions surrounding figures like Jeffrey Epstein and corporations like Disney are not just about scandal; they are about how we, as a society, confront power, secrecy, and transparency. This segment is a call to unite in the pursuit of truth—not through a divisive lens, but with collective discernment and an unwavering commitment to evidence and integrity.
The Lessons from HistoryHistory teaches us that institutions once seen as untouchable can harbor hidden truths. The exposure of corporate frauds, systemic abuses, and cover-ups within trusted sectors has shaped a society that questions everything. The Epstein scandal underscored this, revealing a network of power that reached further than many dared to imagine. Yet, while it validated the public’s instinct to question, it also highlighted a key challenge: differentiating between grounded inquiry and baseless theory.
Disney’s name appearing in speculative discussions about Epstein points to a broader pattern—our collective desire to ensure that those who hold power are not above scrutiny. But as we demand accountability, we must also unite in the practice of informed skepticism. The leap from isolated cases of misconduct or association to implicating entire organizations requires evidence, not just conjecture. This distinction is where we, as a society, must find common ground.
The Role of TransparencyTransparency has become the cornerstone of public trust. Organizations that handle controversies behind closed doors risk damaging their credibility. For companies like Disney, known for protecting their brand with meticulous care, the challenge is clear: find a balance between safeguarding legitimate interests and providing enough transparency to maintain public trust.
The use of NDAs, strategic silence, and controlled narratives may shield brands in the short term, but they can erode trust in the long run. Studies in crisis communication emphasize that openness, even when it exposes vulnerabilities, can reinforce loyalty and confidence among stakeholders. In the context of Epstein and the persistent whispers about powerful corporations, this lesson is especially relevant.
A Collective Call to ClarityThe pursuit of truth is not just the responsibility of journalists, whistleblowers, or industry watchdogs—it is a collective endeavor. The public plays a crucial role in this, but so do the corporations that hold sway over cultural and economic landscapes. When Disney’s name enters speculative discussions, it reflects a deep-seated desire for transparency from those we trust. This desire should be met not with fear of the unknown but with a commitment to clarity.
This segment is a call for unity in approaching these conversations. The balance between healthy skepticism and conspiracy theory is delicate but essential. We must ask hard questions and hold power accountable without losing sight of what separates substantiated fact from assumption.
Why Unity MattersIn times where speculation can divide and misinformation can spread faster than verified facts, unity in the pursuit of truth is vital. When we allow fear and uncertainty to fracture our approach, we weaken our collective power to bring genuine issues to light. Epstein’s case showed that hidden wrongs do exist and can involve the most influential figures. It also showed that uncovering the full scope of such wrongs takes a community committed to patience, evidence, and shared purpose.
Public scrutiny is essential for democracy and social justice, but so is discernment. When theories about organizations like Disney arise without evidence, they risk diverting attention from real, proven issues that demand action. Unity in seeking truth means supporting real investigations, demanding transparency, and recognizing the power of evidence-based inquiry.
Building a Culture of Informed AccountabilityThe goal is not to silence questions but to elevate them, ensuring that they are grounded in reality. This approach not only empowers the public but also sets a standard for institutions. If Disney and other corporations prioritize transparency, they can reinforce the public trust that sustains their brands. Similarly, when the public insists on evidence and integrity in its discussions, it strengthens the very fabric of accountability.
Reflections for the Road AheadAs we move forward, let us commit to being a society that seeks truth not for scandal’s sake but for justice and integrity. Let us stand together in holding power to account, using facts as our foundation and unity as our strength. The story of Epstein and the questions it raises about power, influence, and hidden truths are reminders that transparency and trust are not just corporate responsibilities—they are collective ones.
This call to unity is a reminder that we all play a part in shaping how these stories unfold. When we seek, question, and demand clarity together, we create a society that values truth over rumor, evidence over assumption, and justice over division.
As we conclude this exploration, may we carry forward the lessons learned: the importance of questioning with integrity, seeking truth with diligence, and facing the unknown not as individuals, but as a united community.
-
 @ 2063cd79:57bd1320
2025-02-17 09:12:39
@ 2063cd79:57bd1320
2025-02-17 09:12:39Für diejenigen, die mich nicht kennen: Ich bin Hal Finney. Ich machte meine ersten Schritte mit Kryptographie, in dem ich an einer frühen Version von PGP arbeitete, in enger Zusammenarbeit mit Phil Zimmermann. Als Phil beschloss, die PGP Corporation zu gründen, war ich einer der ersten, die er einstellte. Ich habe bis zu meiner Pensionierung an PGP gearbeitet. Zeitgleich fing ich an, mich bei den Cypherpunks zu engagieren. Neben anderen Aktivitäten betrieb ich den ersten kryptographisch basierten anonymen Remailer.
Springen wir ans Ende des Jahres 2008 und der Ankündigung von Bitcoin. Ich habe bemerkt, dass Krypto-Graubärte (ich war Mitte 50) dazu neigen, zynisch zu werden. Ich war eher idealistisch; ich habe Kryptographie immer geliebt, das Mysterium und das Paradoxe daran.
Als Satoshi Bitcoin in der Kryptographie-Mailingliste ankündigte, wurde er bestenfalls skeptisch aufgenommen. Kryptographen haben schon zu viele großartige Pläne von ahnungslosen Anfängern gesehen. Sie neigen zu überhasteten Reaktionen.
Ich war positiver eingestellt. Ich hatte mich schon lange für kryptografische Zahlungssysteme interessiert. Außerdem hatte ich das Glück, sowohl Wei Dai als auch Nick Szabo kennenzulernen und ausgiebig mit ihnen zu korrespondieren, von denen allgemein bekannt ist, dass sie Ideen entwickelt haben, die mit Hilfe von Bitcoin verwirklicht werden sollten. Ich hatte einen Versuch unternommen, meine eigene, auf Proof-of-Work basierende Währung namens RPOW zu schaffen. Daher fand ich Bitcoin faszinierend.
Als Satoshi die erste Version der Software ankündigte, schnappte ich sie mir sofort. Ich glaube, ich war die erste Person neben Satoshi, die Bitcoin laufen ließ. Ich habe Block 70 oder so gemined und ich war der Empfänger der ersten Bitcoin-Transaktion, als Satoshi mir zehn Coins als Test schickte. In den nächsten Tagen führte ich eine E-Mail-Konversation mit Satoshi, in der ich hauptsächlich Fehler meldete, die er dann beseitigte.
Heute ist die wahre Identität von Satoshi ein Rätsel. Aber damals dachte ich, ich hätte es mit einem jungen Mann japanischer Abstammung zu tun, der sehr intelligent und aufrichtig war. Ich hatte das Glück, im Laufe meines Lebens viele brillante Menschen kennenzulernen, daher erkenne ich die Zeichen.
Nach ein paar Tagen lief Bitcoin ziemlich stabil, also ließ ich es laufen. Das waren die Tage, als die Difficulty 1 war und man Blöcke mit dem CPU finden konnte, nicht einmal mit einem GPU. In den nächsten Tagen habe ich mehrere Blöcke gemined. Aber ich schaltete es ab, weil mein Computer zu heiß wurde und mich das Lüftergeräusch störte. Im Nachhinein wünschte ich, ich hätte länger durchgehalten, aber andererseits hatte ich außerordentliches Glück, dass ich am Anfang dabei war. Das ist so eine halb volles, halb leeres Glas Sache
Das nächste Mal, dass ich von Bitcoin hörte, war Ende 2010, als ich überrascht feststellte, dass es nicht nur immer noch existierte, sondern bitcoins tatsächlich einen Geldwert hatten. Ich entstaubte meine alte Wallet und war erleichtert, als ich feststellte, dass meine bitcoins noch darin waren. Als der Preis auf eine echte Summe kletterte, transferierte ich die Coins in eine Offline-Wallet, wo sie hoffentlich für meine Erben etwas wert sein werden.
Apropos Erben: 2009 erlebte ich eine Überraschung, als bei mir plötzlich eine tödliche Krankheit diagnostiziert wurde. Zu Beginn des Jahres war ich in der besten Verfassung meines Lebens, ich hatte viel Gewicht verloren und mit dem Langstreckenlauf begonnen. Ich war mehrere Halbmarathons gelaufen und hatte begonnen, für einen vollen Marathon zu trainieren. Ich hatte mich zu Läufen über 20 Meilen hochgearbeitet und dachte, ich hätte alles im Griff. Doch dann ging alles schief.
Mein Körper begann zu versagen. Ich sprach undeutlich, verlor die Kraft in meinen Händen und meine Beine erholten sich nur langsam. Im August 2009 erhielt ich die Diagnose ALS, auch Lou-Gehrig-Krankheit genannt, nach dem berühmten Baseballspieler, der daran erkrankt war.
ALS ist eine Krankheit, die Motoneuronen abtötet, die Signale vom Gehirn an die Muskeln weiterleiten. Sie verursacht zunächst Schwäche und dann allmählich zunehmende Lähmungen. Die Krankheit verläuft in der Regel innerhalb von 2 bis 5 Jahren tödlich. Meine Symptome waren zunächst gering und ich konnte weiterarbeiten, aber Müdigkeit und Stimmprobleme zwangen mich Anfang 2011, in den Ruhestand zu gehen. Seitdem ist die Krankheit unaufhaltsam fortgeschritten.
Heute bin ich im Wesentlichen gelähmt. Ich werde durch einen Schlauch ernährt, und meine Atmung wird durch einen weiteren Schlauch unterstützt. Ich bediene den Computer mit einem kommerziellen Eyetracker-System. Es ist auch mit einem Sprachsynthesizer ausgestattet, so dass dies jetzt meine Stimme ist. Ich verbringe den ganzen Tag in meinem Elektrorollstuhl. Ich habe eine Schnittstelle mit einem Arduino entwickelt, so dass ich die Position meines Rollstuhls mit meinen Augen einstellen kann.
Es war eine Umstellung, aber mein Leben ist nicht allzu schlimm. Ich kann immer noch lesen, Musik hören, fernsehen und Filme schauen. Vor kurzem habe ich entdeckt, dass ich sogar Code schreiben kann. Es geht sehr langsam, wahrscheinlich 50 Mal langsamer als vorher. Aber ich liebe das Programmieren immer noch, und es gibt mir Ziele. Derzeit arbeite ich an etwas, das Mike Hearn vorgeschlagen hat, nämlich die Sicherheitsfunktionen moderner Prozessoren, die „Trusted Computing“ unterstützen, zu nutzen, um Bitcoin-Wallets zu härten. Es ist fast fertig zur Veröffentlichung. Ich muss nur noch die Dokumentation erstellen.
Und natürlich sind die Kursschwankungen von Bitcoin für mich unterhaltsam. Ich habe einen Anteil an dem Spiel. Aber ich bin durch Glück zu meinen bitcoins gekommen, ohne dass ich etwas dafür kann. Ich habe den Crash von 2011 miterlebt. Ich habe es also schon einmal erlebt. Einfach kommen, einfach gehen.
Das ist meine Geschichte. Ich habe insgesamt ziemlich viel Glück. Selbst mit der ALS ist mein Leben sehr zufriedenstellend. Aber meine Lebenserwartung ist begrenzt. Diese Diskussionen über die Vererbung von bitcoins sind mehr als nur von akademischem Interesse. Meine bitcoins befinden sich in unserem Bankschließfach, und mein Sohn und meine Tochter sind technisch versiert. Ich denke, sie sind sicher genug. Ich bin mit meinem Erbe zufrieden.

-
 @ 2ed3596e:98b4cc78
2025-02-27 00:24:36
@ 2ed3596e:98b4cc78
2025-02-27 00:24:36Curious about Bitcoin but unsure where to start? Our Bitcoin for Beginners webinar is designed to help you understand Bitcoin, how it differs from traditional fiat money, and how to safely get started.
This free, live session takes place on the second Wednesday of every month at 4 PM EST. Whether you’re completely new to Bitcoin or looking for clarity on how to buy at the best price, this webinar will walk you through the essentials, including:
✅ What Bitcoin is and why it matters
✅ How Bitcoin is different from traditional money
✅ The safest ways to buy and store Bitcoin
✅ How to get started with confidence
This interactive session also includes a Q&A, so you can ask any questions you have along the way. Don’t miss this opportunity to learn from experts and take control of your Bitcoin journey!
-
 @ d61f3bc5:0da6ef4a
2025-02-12 16:57:44
@ d61f3bc5:0da6ef4a
2025-02-12 16:57:44Micropayments on the Internet have been theorized for decades. However, it wasn’t until the emergence of Nostr that we’ve finally seen them deployed at scale. Nostr is still in its infancy, yet we are already witnessing an explosion of apps built on top of this open protocol. And most of them are featuring zaps! With the recent Primal 2.1 release, Nostr developers now have the option to enhance the experience for their users by integrating a Nostr-powered bitcoin wallet.
There is no doubt that micropayments add a new dimension to consumer apps. The incumbents have realized this and are rushing to add payments to their closed platforms. It won't be long before apps that don’t include built-in payments feel dated or outright broken. The question is not if apps of the future will have built-in payments, but what kind of payments they will be. Given that open networks have a tendency to win, our bet is that apps of the future will be powered by Bitcoin. Let’s see how Primal can help.
Primal Wallet
Our vision for Primal Wallet is simple: deliver the smoothest transactional bitcoin wallet, endowed with expert Nostr skills. The wallet leverages Nostr’s open social graph as a de facto public lightning directory, while offering the highest level of user experience for Nostr’s rich content. For example, the user can scroll through the transaction list, select a zap, and drill straight into the conversation thread where the zap originated. The whole flow feels perfectly natural.
 Since we launched Primal Wallet in December 2023, the user response has been incredibly positive. People love the idea of being able to post something on Nostr, get zaps from plebs around the world, then buy a coffee or a meal with those sats - all from the same app.
Since we launched Primal Wallet in December 2023, the user response has been incredibly positive. People love the idea of being able to post something on Nostr, get zaps from plebs around the world, then buy a coffee or a meal with those sats - all from the same app. Having a bitcoin wallet with social skills resonated strongly with users, so Primal Wallet grew rapidly in popularity and usage. Since the launch, we have processed 1,338,460 transactions, with 238,916 just in the past month alone. This rivals some of the leading bitcoin wallets, and we are just getting started! We hear from many bitcoin OGs that they are using Primal Wallet as their transactional daily driver. Bullish.
All this is great, but something has been missing. Our users demanded the ability to connect Primal Wallet to other Nostr apps, so they can zap from anywhere in Nostr’s growing ecosystem.
Zapping from Any Nostr App
For an existing Primal user, connecting the wallet to a new Nostr app can now be done in two clicks. Let’s take a look at how this is done from Olas, one of the most exciting new apps on Nostr:
 Yes. Click, click. And you can start zapping!
Yes. Click, click. And you can start zapping! Such smooth integration of payments is not available in any competing technology stack. Tradfi, fintech, crypto, etc., have nothing on Bitcoin and Nostr. Two clicks and your external wallet is connected. I’ll give you a moment now to allow for this new reality to settle in.
Primal enables you to connect any number of external apps and manage them from wallet settings:
 Note that you can set your daily spend budget for each app or revoke its access at any time.
Note that you can set your daily spend budget for each app or revoke its access at any time. How This Works
So, what is this sorcery? How does it work under the hood?
Connecting Nostr apps to external wallets is accomplished via the Nostr Wallet Connect protocol. It utilizes Nostr’s public relay infrastructure to enable communication between apps and wallets. You can learn more about this protocol here, and access developer docs here.
The smooth, two-click connection setup UX is implemented through deep links between Primal and the external app. Here’s the deep link that the external app needs to call to invoke this feature:
nostrnwc+primal://connect?appicon=[icon_url]&appname=[app_name]&callback=[callback_string]After the user clicks “Create Wallet Connection” in Primal, the Primal app calls the deep link defined in the callback, and passes the NWC connection string. That's all that the external app needs to make the wallet connection.
What Comes Next?
The Nostr Wallet Connect protocol has been around for almost two years. Several bitcoin wallets implement it and many Nostr apps use it as their main way of enabling payments. What’s new with Primal 2.1 is the elevated user experience. Since Primal is a Nostr-powered wallet, it is aware of all the relevant metadata for each transaction: Nostr zaps, users, and the related events. Primal indexes the entire Nostr network, and now this is open to all Nostr apps that wish to integrate payments.
Nostr keeps expanding and getting better. Its openness enables us to build capabilities that lift all boats. The future is bright; I can’t wait to see how things evolve from here. 🍿🍿🍿
-
 @ 5a261a61:2ebd4480
2025-02-16 21:54:41
@ 5a261a61:2ebd4480
2025-02-16 21:54:41As I grow older, I find myself often discovering things that I haven't understood before, or just see completely differently. Like with this fable of the toad and scorpion. You know, the classic where scorpion needs to get across the river, and asks the toad for help, promising not to sting. The toad refuses at first, pointing out that scorpion's sting would kill them both. But scorpion argues that would be illogical - why would it sting if that meant its own death? The toad, convinced by this logic, agrees to help. Halfway across, scorpion stings anyway, and as they both sink, toad asks "why?" Scorpion simply answers "It's my nature."
That leads me to my scorpion sighting. I have somewhat stronger libido and given the circumstances, I usually situate myself in the submissive position in both married and online life. When I am not ventilating or getting these things out in some way, it usually leads to my growing frustration that seriously hinders my usual life. And in those trying times I usually tell myself, "screw that, I don't like this, I don't like how that makes me feel, it sucks, why does it have to hurt so much" (well, I don't think 'hurt' as I have been indoctrinated by the society that men don't process feelings this way, but I think if I had a therapist, they would want me to spell it like that). Let's not go to the subspace again, it's silly space. Sometimes it gets really dark...but then comes the climax, like literally, and suddenly everything is forgiven and (almost) forgotten. And all is well.
Let's just not go there next time, avoid being burned again, I keep saying to myself. And these days submissive scorpion in my head just silently waits for my monologuing toad to finish defending ourselves. It knows that it needs only one chance so I cave in, while toad needs to defend my sanity every day. So one day, I will bring scorpion to cross the river with me again. And it will again promise that this time it will be ok. And we will both pretend like we believe that, so the play can go on. And it will eventually sting me, because we both yearn for unreachable things.
And next day I will again see scorpion on the river, not wooing me, no, we are beyond that, it knows it just needs to wait before I come back for the poison I need.As I grow older, I find myself often discovering things that I haven't understood before, or just see completely differently. Like with this fable of the toad and scorpion.
You know, the classic where scorpion needs to get across the river, and asks the toad for help, promising not to sting. The toad refuses at first, pointing out that scorpion's sting would kill them both. But scorpion argues that would be illogical - why would it sting if that meant its own death? The toad, convinced by this logic, agrees to help. Halfway across, scorpion stings anyway, and as they both sink, toad asks "why?" Scorpion simply answers "It's my nature."
That leads me to my scorpion sighting. I have somewhat stronger libido and given the circumstances, I usually situate myself in the submissive position in both married and online life. When I am not ventilating or getting these things out in some way, it usually leads to my growing frustration that seriously hinders my usual life. And in those trying times I usually tell myself, "screw that, I don't like this, I don't like how that makes me feel, it sucks, why does it have to hurt so much" (well, I don't think 'hurt' as I have been indoctrinated by the society that men don't process feelings this way, but I think if I had a therapist, they would want me to spell it like that). Let's not go to the subspace again, it's silly space. Sometimes it gets really dark...but then comes the climax, like literally, and suddenly everything is forgiven and (almost) forgotten. And all is well.
Let's just not go there next time, avoid being burned again, I keep saying to myself. And these days submissive scorpion in my head just silently waits for my monologuing toad to finish defending ourselves.
It knows that it needs only one chance so I cave in, while toad needs to defend my sanity every day. So one day, I will bring scorpion to cross the river with me again. And it will again promise that this time it will be ok. And we will both pretend like we believe that, so the play can go on. And it will eventually sting me, because we both yearn for unreachable things.
And next day I will again see scorpion on the river, not wooing me, no, we are beyond that, it knows it just needs to wait before I come back for the poison I need.
-
 @ 9e69e420:d12360c2
2025-02-15 20:24:09
@ 9e69e420:d12360c2
2025-02-15 20:24:09Ukraine's President Volodymyr Zelensky called for an "army of Europe" to defend against Russian threats, emphasizing that the US may not continue its traditional support for Europe. Speaking at the Munich Security Conference, he warned against peace deals made without Ukraine's involvement.
US Vice President JD Vance echoed this sentiment, urging Europe to enhance its defense efforts.
Zelensky stated, "I really believe the time has come - the armed forces of Europe must be created." He highlighted changing dynamics in US-Europe relations and noted that "the old days are over" regarding American support.
Despite discussions around NATO, Zelensky stated he wouldn't rule out NATO membership for Ukraine.
-
 @ ee603283:3bc79dec
2025-02-26 23:50:16
@ ee603283:3bc79dec
2025-02-26 23:50:16Source Article by the Bitkey team and Undine Rubeze: https://bitkey.build/inheritance-is-live-heres-how-it-works/
TLDR: You wrap your mobile key, and encrypted this wrapped key with your beneficiaries public key. Send this info to Bitkey's servers. Your beneficiary can trigger the inheritance process after your passing and wait 6-months before they can do anything.
6 months seems like a long-time to be able to access critical life-savings funds for your family. This should help you prioritize a 3-6 month emergency "cash" savings for your family. Cash can be in a savings account or physical cash. Additionally, it might be beneficial to setup a life-insurance plan (a simple term-life plan) where the immediate bills and expenses are covered.
bitcoin #nostr
devs I tried to import the url into highlighter but got this error: "The page is not reader-friendly"
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ 8d34bd24:414be32b
2025-02-26 23:07:43
@ 8d34bd24:414be32b
2025-02-26 23:07:43My mind keeps chewing on these verses in Jeremiah. Maybe I can’t get it out of my head because it seems so contrary to everything I have believed regarding to prayer.
“As for you, do not pray for this people, and do not lift up cry or prayer for them, and do not intercede with Me; for I do not hear you. Do you not see what they are doing in the cities of Judah and in the streets of Jerusalem? The children gather wood, and the fathers kindle the fire, and the women knead dough to make cakes for the queen of heaven; and they pour out drink offerings to other gods in order to spite Me. Do they spite Me?” declares the Lord. “Is it not themselves they spite, to their own shame?” (Jeremiah 7:16-19) {emphasis mine}
Before continuing with this article, make sure you have read What? Do Not Pray For ..., so you have my background thoughts on this passage.
After writing the first post, I began thinking about how this verse applies to American Christians today in my post A Hard Question With an Uncomfortable Answer. In my first two articles, I basically came to the conclusion that we should not pray blessings on those who were sinning and rejecting God, but that praying for repentance and turning back to God would be an allowed and even honored prayer. Then today, while listening to a sermon from Revelation, I thought, “Is there a time we are called to not pray for someone or some nation because God has given them their choice and He is no longer calling them to Himself?”
When God Hardens a Heart
There are a lot of verses where God says that he hardened their heart. The most well known is regarding the hardened heart of the Egyptian Pharaoh in Exodus where we read a succession of verses about a hardened heart:
First Pharaoh hardens his own heart:
But when Pharaoh saw that there was relief, he hardened his heart and did not listen to them, as the Lord had said. (Exodus 8:15) {emphasis mine}
then he hardens his heart again:
But Pharaoh hardened his heart this time also, and he did not let the people go. (Exodus 8:32) {emphasis mine}
then he hardened his heart and his servants hearts:
But when Pharaoh saw that the rain and the hail and the thunder had ceased, he sinned again and hardened his heart, he and his servants. (Exodus 9:34) {emphasis mine}
then God hardens Pharaoh’s heart:
Then the Lord said to Moses, “Go to Pharaoh, for I have hardened his heart and the heart of his servants, that I may perform these signs of Mine among them, (Exodus 10:1) {emphasis mine}
God didn’t harden Pharaoh’s heart initially, but after repeated choices by Pharaoh, God gave Pharaoh the hardened heart he chose. Also, God hardened Pharaoh’s heart in order to perform signs that He wanted to perform to show Himself to the Israelites and the Egyptians. He did it to fulfill His will and His plan.
Once God chose to harden Pharaoh’s heart, would it be praying according to God’s will to ask that Pharaoh repent? As uncomfortable as this makes me, I don’t think it would be praying according to God’s will to pray for repentance for Pharaoh.
When God Declares His Judgment
In Jeremiah 27, God has stated that Babylon will conquer Judah, take away the people, and take the golden implements from the Temple. He says that those who want to live must submit to Babylon. This is God’s will. Many supposed prophets were prophesying that Babylon will not capture Judah and then after Judah was conquered, that they would be brought back after 2 years contrary to God’s will and declaration of 70 years of captivity.
Then I spoke to the priests and to all this people, saying, “Thus says the Lord: Do not listen to the words of your prophets who prophesy to you, saying, ‘Behold, the vessels of the Lord’s house will now shortly be brought again from Babylon’; for they are prophesying a lie to you. Do not listen to them; serve the king of Babylon, and live! Why should this city become a ruin? But if they are prophets, and if the word of the Lord is with them, let them now entreat the Lord of hosts that the vessels which are left in the house of the Lord, in the house of the king of Judah and in Jerusalem may not go to Babylon. (Jeremiah 27:16-18) {emphasis mine}
Regarding these so-called prophets, God says, “if the word of the Lord is with them, let them now entreat the Lord of hosts.” This sounds like they should pray thus only if “the word of the Lord is with them,” or basically if they are praying according to God’s will. Conversely, since the passage makes clear these “prophets” are not speaking God’s word, nor supporting God’s will, then God should not be entreated (asked in prayer) to act contrary to His will.
When God Gives Them Over to Their Sin
Similarly, in the New Testament it says of God:
For even though they knew God, they did not honor Him as God or give thanks, but they became futile in their speculations, and their foolish heart was darkened. Professing to be wise, they became fools, and exchanged the glory of the incorruptible God for an image in the form of corruptible man and of birds and four-footed animals and crawling creatures.
Therefore God gave them over in the lusts of their hearts to impurity, so that their bodies would be dishonored among them. For they exchanged the truth of God for a lie, and worshiped and served the creature rather than the Creator, who is blessed forever. Amen.
For this reason God gave them over to degrading passions; for their women exchanged the natural function for that which is unnatural, and in the same way also the men abandoned the natural function of the woman and burned in their desire toward one another, men with men committing indecent acts and receiving in their own persons the due penalty of their error.
And just as they did not see fit to acknowledge God any longer, God gave them over to a depraved mind, to do those things which are not proper, being filled with all unrighteousness, wickedness, greed, evil; full of envy, murder, strife, deceit, malice; they are gossips, slanderers, haters of God, insolent, arrogant, boastful, inventors of evil, disobedient to parents, without understanding, untrustworthy, unloving, unmerciful; and although they know the ordinance of God, that those who practice such things are worthy of death, they not only do the same, but also give hearty approval to those who practice them. (Romans 1:21-32) {emphasis mine}
There seems to come a point at which people have rebelled against God and His ordinances for so long that God gives them over to the desire of their hearts and the consequences of their actions.
Does This Mean We Are Not To Pray At All?
Is there a point at which God doesn’t want us to pray for their repentance? I’m not willing to say “definitely,” but it kind of looks like that may be the case. I don’t think this is a common situation that we need to be worried about. In most cases, even with very evil people who have done us great harm, we are definitely called to pray for their repentance and salvation. “But I say to you, love your enemies and pray for those who persecute you.” (Matthew 5:44) Still, there may be situations where God says, “I have given them over to the lusts and rebellion of their heart to the destruction of their soul.” There may be situations where a person or a nation has to be punished to fulfill God’s good plan. Praying against His will and plan would be fighting against God and not praying in alignment with His will.
In Ezekiel chapter 3, the passage is talking specifically about sharing God’s word and being a watchman to the people rather than specifically regarding prayer, but I think this verse is still helpful in determining God’s will for our prayers.
Moreover, I will make your tongue stick to the roof of your mouth so that you will be mute and cannot be a man who rebukes them, for they are a rebellious house. (Ezekiel 3:26)
In this occasion, God has given Ezekiel the role of watchman and warned him that he will be held accountable for warning the people, but their decision to obey is on their own heads. Then God tells Ezekiel that He will “make your tongue stick to the roof of your mouth so that you will be mute and cannot be a man who rebukes them.” I believe if God doesn’t want us to pray for someone or something and if we are seeking His will, He will make us mute so we cannot pray for them. Why would He do this? Either because the person, group, or nation are rebellious and/or because the prayer is contrary to His will. I believe God will help His devoted followers to pray according to His will.
I am still fleshing out this idea in my mind and trying to seek the truth. Let me know how you interpret these verses or especially if you have other verses that clarify this matter. I am trying to seek the truth.
I also want to be very careful with this idea. We are much more likely to NOT pray for repentance and salvation for people that we should be praying for than we are to pray for someone for whom we shouldn’t pray. I definitely don’t want anyone to use this post as an excuse to not pray for people or nations.
May our God and Creator guide us and use us for His good purpose and according to His will. May He guide our prayers in perfect alignment with His will and may He draw us closer to Him every day.
Trust Jesus
-
 @ 94a6a78a:0ddf320e
2025-02-12 15:05:48
@ 94a6a78a:0ddf320e
2025-02-12 15:05:48Azzamo is more than just a relay provider—it’s a high-performance network designed to make Nostr faster, smoother, and more reliable for everyone. Whether you're posting notes, zapping sats, sharing media, or sending DMs, Azzamo keeps your Nostr experience seamless and efficient.
Nostr is unstoppable, but not all relays are the same. Some are slow, unreliable, or disappear overnight, while others get overloaded, making message delivery inconsistent. Azzamo is built differently—offering fast, stable, and globally distributed relays to ensure low-latency, high-speed connections, no matter where you are.
🌍 Premium Relays for Maximum Performance
Azzamo Premium Relays are optimized for speed, reliability, and uptime, available exclusively to Premium users:
📡 Azzamo Premium Relays:
- Europe:
wss://relay.azzamo.net - America:
wss://us.azzamo.net - Asia:
wss://asia.azzamo.net
Add Azzamo Premium Time to unlock unlimited, high-speed access across these global relays.
🔗 Get Premium: azzamo.net/premium
🆓 Freemium Relays – Free for Everyone
Azzamo believes in keeping Nostr open and accessible to all. That’s why we offer free relays for everyone, with no rate limits for Premium members
📡 Freemium Relays:
- Free Relay:
wss://nostr.azzamo.net– Open to all. - Inbox Relay:
wss://inbox.azzamo.net– Reliable for DMs & group messages.
By offering both free and premium options, Azzamo ensures that anyone can use Nostr, while also funding the infrastructure that keeps it running smoothly.
🛡️ Minimal Moderation, Maximum Transparency
Nostr is about free speech, but that doesn’t mean zero moderation. Azzamo follows a minimal moderation policy to keep relays functional and spam-free while maintaining transparency in enforcement.\ \ 🚫 Spam & network abuse\ 🚫 Illegal content (CSAM, fraud, malware, scams)\ 🚫 Impersonation & identity abuse
We also maintain a public Ban API for transparent moderation decisions.
📖 More on our Ban API: azzamo.net/introducing-the-azzamo-ban-api
🚀 Get Started with Azzamo Relays Today!
🔗 Connect now:\ 📡
wss://nostr.azzamo.net(Freemium Free Relay)\ 📬wss://inbox.azzamo.net(Freemium Inbox Relay)\ 📡wss://relay.azzamo.net(Premium Europe Relay)\ 📡wss://us.azzamo.net(Premium Americas Relay)\ 📡wss://asia.azzamo.net(Premium Asia Relay)Nostr is growing fast. Make sure your relays can keep up. 🚀
azzamo #grownostr #nostr #relay #relays #premiumrelay #paidrelay
- Europe:
-
 @ e3ba5e1a:5e433365
2025-01-13 16:47:27
@ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity.
A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur.
The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior.
And there are plenty of incentives beyond our direct control! My son is also incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take.
Why incentives matter
A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could just do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example:
- If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning.
- If people would just use the recycling bin, we wouldn’t have such a landfill problem.
- If people would just stop being lazy, our team would deliver our project on time.
In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally.
- The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do.
- No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle.
- If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.

My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want.
If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is.
Running a company
Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions.
Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good.
What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off.
Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning.
When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.

Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money.
There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals.
Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature.
Moral hazard
Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings.
What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.

But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I don’t turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all.
This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as:
- We’re so habituated to turning off the water that we don’t even consider not turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off.
- Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created.
- We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?)
Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard.
A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard.
It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend?
And since we’re talking about the government already…
Government moral hazards
As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a huge number of examples of moral hazards. I decided to cherry-pick a few for this post.
The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people?
The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet.
If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups.
You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”

And here’s the absolute best part of this: I can’t even truly blame either California or Wall Street. (I mean, I do blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits.
There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions.
Non-monetary competition
At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home.
In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.)
Anyway, my professor’s wife had a friend. My professor described in great detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas.
This is a demonstration of non-monetary compensation. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules.
The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become wealthier and whiter, the exact opposite of their desired outcome. Why would that happen?
Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky.
She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls.
So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites.
You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences.
Bureaucracy
These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences.
Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings.
Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate.
Government incentivized behavior
This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples:
- Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to malinvestment and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience.
- Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise.
- During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation.
- The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen.
- Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example).
- Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as high living.)
Conclusion
The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives.
We can bemoan these realities all we want, but they are realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People should take advantage of the incentives around them. Because if they don’t, someone else will.
(If you want a literary example of that last comment, see the horse in Animal Farm.)
How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula:
- Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people.
- Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them.
- And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example.
And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining!
-
 @ 6f7db55a:985d8b25
2025-02-14 21:23:57
@ 6f7db55a:985d8b25
2025-02-14 21:23:57This article will be basic instructions for extreme normies (I say that lovingly), or anyone looking to get started with using zap.stream and sharing to nostr.
EQUIPMENT Getting started is incredibly easy and your equipment needs are miniscule.
An old desktop or laptop running Linux, MacOs, or Windows made in the passed 15yrs should do. Im currently using and old Dell Latitude E5430 with an Intel i5-3210M with 32Gigs of ram and 250GB hard drive. Technically, you go as low as using a Raspberry Pi 4B+ running Owncast, but Ill save that so a future tutorial.
Let's get started.
ON YOUR COMPUTER You'll need to install OBS (open broaster software). OBS is the go-to for streaming to social media. There are tons of YouTube videos on it's function. WE, however, will only be doing the basics to get us up and running.
First, go to https://obsproject.com/

Once on the OBS site, choose the correct download for you system. Linux, MacOs or Windows. Download (remember where you downloaded the file to). Go there and install your download. You may have to enter your password to install on your particular operating system. This is normal.
Once you've installed OBS, open the application. It should look something like this...

For our purposes, we will be in studio mode. Locate the 'Studio Mode' button on the right lower-hand side of the screen, and click it.

You'll see the screen split like in the image above. The left-side is from your desktop, and the right-side is what your broadcast will look like.
Next, we go to settings. The 'Settings' button is located right below the 'Studio Mode" button.

Now we're in settings and you should see something like this...

Now locate stream in the right-hand menu. It should be the second in the list. Click it.

Once in the stream section, go to 'Service' and in the right-hand drop-down, find and select 'Custom...' from the drop-down menu.

Remeber where this is because we'll need to come back to it, shortly.
ZAPSTREAM We need our streamkey credentials from Zapstream. Go to https://zap.stream. Then, go to your dashboard.

Located on the lower right-hand side is the Server URL and Stream Key. You'll need to copy/paste this in OBS.

You may have to generate new keys, if they aren't already there. This is normal. If you're interested in multi-streaming (That's where you broadcast to multiple social media platforms all at once), youll need the server URL and streamkeys from each. You'll place them in their respective forms in Zapstream's 'Stream Forwarding" section.

Use the custom form, if the platform you want to stream to isn't listed.
*Side-Note: remember that you can use your nostr identity across multiple nostr client applications. So when your login for Amethyst, as an example, could be used when you login to zapstream. Also, i would suggest using Alby's browser extension. It makes it much easier to fund your stream, as well as receive zaps. *
Now, BACK TO OBS... With Stream URL and Key in hand, paste them in the 'Stream" section of OBS' settings. Service [Custom...] Server [Server URL] StreamKey [Your zapstream stream key]

After you've entered all your streaming credentials, click 'OK' at the bottom, on the right-hand side.
WHAT'S NEXT? Let's setup your first stream from OBS. First we need to choose a source. Your source is your input device. It can be your webcam, your mic, your monitor, or any particular window on your screen. assuming you're an absolute beginner, we're going to use the source 'Window Capture (Xcomposite)'.

Now, open your source file. We'll use a video source called 'grannyhiphop.mp4'. In your case it can be whatever you want to stream; Just be sure to select the proper source.

Double-click on 'Window Capture' in your sources list. In the pop-up window, select your file from the 'Window' drop-down menu.


You should see something like this...

Working in the left display of OBS, we will adjust the video by left-click, hold and drag the bottom corner, so that it takes up the whole display.

In order to adjust the right-side display ( the broadcast side), we need to manipulate the video source by changing it's size.

This may take some time to adjust the size. This is normal. What I've found to help is, after every adjustment, I click the 'Fade (300ms)' button. I have no idea why it helps, but it does, lol.

Finally, after getting everything to look the way you want, you click the 'Start Stream' button.

BACK TO ZAPSTREAM Now, we go back to zapstream to check to see if our stream is up. It may take a few moments to update. You may even need to refresh the page. This is normal.
 STREAMS UP!!!
STREAMS UP!!!A few things, in closing. You'll notice that your dashbooard has changed. It'll show current stream time, how much time you have left (according to your funding source), who's zapped you with how much theyve zapped, the ability to post a note about your stream (to both nostr and twitter), and it shows your chatbox with your listeners. There are also a raid feature, stream settings (where you can title & tag your stream). You can 'topup' your funding for your stream. As well as, see your current balance.
You did a great and If you ever need more help, just use the tag #asknostr in your note. There are alway nostriches willing to help.
STAY AWESOME!!!
npub: nostr:npub1rsvhkyk2nnsyzkmsuaq9h9ms7rkxhn8mtxejkca2l4pvkfpwzepql3vmtf
-
 @ 000002de:c05780a7
2025-02-26 22:31:11
@ 000002de:c05780a7
2025-02-26 22:31:11These people have serious issues.
Original Sin by Jake Tapper and Alex Thompson
From two of America’s most respected journalists, an unflinching and explosive reckoning with one of the most fateful decisions in American political history: Joe Biden’s run for reelection despite evidence of his serious decline—amid desperate efforts to hide the extent of that deterioration
originally posted at https://stacker.news/items/898271
-
 @ 3f770d65:7a745b24
2025-01-12 21:03:36
@ 3f770d65:7a745b24
2025-01-12 21:03:36I’ve been using Notedeck for several months, starting with its extremely early and experimental alpha versions, all the way to its current, more stable alpha releases. The journey has been fascinating, as I’ve had the privilege of watching it evolve from a concept into a functional and promising tool.
In its earliest stages, Notedeck was raw—offering glimpses of its potential but still far from practical for daily use. Even then, the vision behind it was clear: a platform designed to redefine how we interact with Nostr by offering flexibility and power for all users.
I'm very bullish on Notedeck. Why? Because Will Casarin is making it! Duh! 😂
Seriously though, if we’re reimagining the web and rebuilding portions of the Internet, it’s important to recognize the potential of Notedeck. If Nostr is reimagining the web, then Notedeck is reimagining the Nostr client.
Notedeck isn’t just another Nostr app—it’s more a Nostr browser that functions more like an operating system with micro-apps. How cool is that?
Much like how Google's Chrome evolved from being a web browser with a task manager into ChromeOS, a full blown operating system, Notedeck aims to transform how we interact with the Nostr. It goes beyond individual apps, offering a foundation for a fully integrated ecosystem built around Nostr.
As a Nostr evangelist, I love to scream INTEROPERABILITY and tout every application's integrations. Well, Notedeck has the potential to be one of the best platforms to showcase these integrations in entirely new and exciting ways.
Do you want an Olas feed of images? Add the media column.
Do you want a feed of live video events? Add the zap.stream column.
Do you want Nostr Nests or audio chats? Add that column to your Notedeck.
Git? Email? Books? Chat and DMs? It's all possible.
Not everyone wants a super app though, and that’s okay. As with most things in the Nostr ecosystem, flexibility is key. Notedeck gives users the freedom to choose how they engage with it—whether it’s simply following hashtags or managing straightforward feeds. You'll be able to tailor Notedeck to fit your needs, using it as extensively or minimally as you prefer.
Notedeck is designed with a local-first approach, utilizing Nostr content stored directly on your device via the local nostrdb. This will enable a plethora of advanced tools such as search and filtering, the creation of custom feeds, and the ability to develop personalized algorithms across multiple Notedeck micro-applications—all with unparalleled flexibility.
Notedeck also supports multicast. Let's geek out for a second. Multicast is a method of communication where data is sent from one source to multiple destinations simultaneously, but only to devices that wish to receive the data. Unlike broadcast, which sends data to all devices on a network, multicast targets specific receivers, reducing network traffic. This is commonly used for efficient data distribution in scenarios like streaming, conferencing, or large-scale data synchronization between devices.
In a local first world where each device holds local copies of your nostr nodes, and each device transparently syncs with each other on the local network, each node becomes a backup. Your data becomes antifragile automatically. When a node goes down it can resync and recover from other nodes. Even if not all nodes have a complete collection, negentropy can pull down only what is needed from each device. All this can be done without internet.
-Will Casarin
In the context of Notedeck, multicast would allow multiple devices to sync their Nostr nodes with each other over a local network without needing an internet connection. Wild.
Notedeck aims to offer full customization too, including the ability to design and share custom skins, much like Winamp. Users will also be able to create personalized columns and, in the future, share their setups with others. This opens the door for power users to craft tailored Nostr experiences, leveraging their expertise in the protocol and applications. By sharing these configurations as "Starter Decks," they can simplify onboarding and showcase the best of Nostr’s ecosystem.
Nostr’s “Other Stuff” can often be difficult to discover, use, or understand. Many users doesn't understand or know how to use web browser extensions to login to applications. Let's not even get started with nsecbunkers. Notedeck will address this challenge by providing a native experience that brings these lesser-known applications, tools, and content into a user-friendly and accessible interface, making exploration seamless. However, that doesn't mean Notedeck should disregard power users that want to use nsecbunkers though - hint hint.
For anyone interested in watching Nostr be developed live, right before your very eyes, Notedeck’s progress serves as a reminder of what’s possible when innovation meets dedication. The current alpha is already demonstrating its ability to handle complex use cases, and I’m excited to see how it continues to grow as it moves toward a full release later this year.
-
 @ c4b5369a:b812dbd6
2025-02-12 12:23:40
@ c4b5369a:b812dbd6
2025-02-12 12:23:40
Unidirectional payment channels revisited
Nodeless lightning - Reduce ecash mints custodial risk
Sats N Facts
The nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference has just wrapped up. And what a blast it was. In the heart of northern Thailand, developers, researchers, content creators and more, came together to share ideas on how Bitcoin, Nostr and other free protocols are being used everyday to liberate people.
Not only were stories shared from different community leaders on how embracing bitcoin has empowered them and their communities, but a big goal of the unconference was to bring bitcoin engineers and developers from various domains together in one room, unstructured, chaotic, and let them do their thing.
At first, I thought not having a schedule might be boring, but oh boy was I wrong. There was so much stuff going on, it was hard to choose which session I would have to miss!
Luke's Spillman channel proposal
One of the sessions I definitely did not want to miss, was nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac s proposal
Ecash mints funded with Spillman channels: The ultimate nodeless Lightning wallet
.
In true unconference fashion, he announced in the main room that the session was about to start, and that the people that are interested should meet him in the whiteboard corner in 10 minutes. The corner was packed, and Luke explained his proposal.
What's a "Spillman channel"?
Essentially when we are talking about Spillman channels, what is meant are unidirectional payment channels (or CLTV-style channels). An unidirectional payment channel means, only one party can send payments, but not receive, and the other party can only receive, but not send. They also expire after a predetermined amount of time, and must be closed.

At first glance, this might look kinda stupid. After all, we have Poon-Dryja channels that are powering the lightning network. They are bi-directional, do not expire, and can be used to shuffle coins back and forth theorethically an unlimited amount of times.
So, why bother with this stupid one-way channel?
Simplicity is king
People that have worked with lightning channels can sing you a song about complexity, state handling and risks about the current state of bidirectional payment channels. Essentially, There are a lot of requirements on both channel parties when it comes to Liveness (being online) and also state handling (continuous backups).
 In some cases, especially when in the context of end-users wanting to perform payments on their mobile phone, they would appreciate it if there was not so much complexity and overhead involved.
In some cases, especially when in the context of end-users wanting to perform payments on their mobile phone, they would appreciate it if there was not so much complexity and overhead involved. The gist of the idea is to combine unidirectional channels and ecash mints to achieve the following:
A self custodial unidirectional payment channel to an ecash mint, massively reducing the senders liveness and state handling requirements when compared to a lightning channel. Sending payments through the mint will be done through swapping some of the channel balance for ecash tokens. At this point, the user is trusting the mint to honor the redemption of these tokens, while the remaining channel balance remains in self custody. This gives them better controll over their funds than just holding their entire balance custodied in the mint. The ecash tokens can then be redeemed to pay a lightning invoice, just the same as it is done now with normal cashu mints.

So this channel, that has no liveness or state management requirements for the sender, and must have a pre-defined close time, seems to be a perfect fit for the following usecase:
- A
senderreceives his salary once a month. He opens a channel that is valid for one month. - The
senderthen can do his daily spending over this channel. He only trusts themintwith the amount for the current outgoing payment while it is swapped for ecash, waiting for redemption. - If the
sendermust receive funds (a refund for example), he can do so into themintscustody, by receiving ecash. He can spend his ecash funds first when doing his next payment, to reduce his custodial exposure. - When the channel expires, or runs out of funds, the
mintcloses the channel.
From a consumer perspective, that just want to receive his salary and make frequent payments afterwards, this usecase seems to make a lot of sense. Obviously from a merchants perspective on the other hand, such a channel doesn't really work. But that's fine, it's not the problem we're trying to solve here.
What do you think of this idea? Be sure to let me know in the comments!
In the next article, we will dive into how such a system can be implemented today, using Bitcoin, Cashu and Lightning. We will also discover how the system can be improved, to make channels non-expiring (A collaborative idea between nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp and nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac born at nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx ).
So stay tuned!
- A
-
 @ ef1744f8:96fbc3fe
2025-02-26 21:36:43
@ ef1744f8:96fbc3fe
2025-02-26 21:36:43cKsXmhEiKNnAgVMTJ4eY+tOqOZh5Om/sZP00QBtEdlZuaayrZJ3xluZ1EMJ+gu80KY1shHaPBD4htY2P3qg65CWIt8Wjf2mAw/gb0l52BWrVkI4AQFUlC3dr14LJD7Y94iZj/CsnT02hcDkRYFjXIgyhtrhrrpVCdZJiZA1zUbw3CV7godG4yt8uo/Q5qdOHP2wH8Dj9zivAKBLyZUgHGJ6M7fBR9pNEKF88Cxs48xD5sQbtGZwiAK0a71bM/xhWAkOkvvLOQUgeeN8tcX0yH84QySFCXDKAnlDgWMAfynTVvrpdc5oyi1gM/3NBvc3s28QkeXWf3zIwq6G1/6c7pDeywYvt2IIk7qgjIbF700i7CnJZdNXxvovP9SQbPt6iotILDXpvzibLiff4GOU1UQ==?iv=dzskRoafO62Gp4TMsBWRFg==
-
 @ d9e9fb27:d5fe5e1a
2025-01-02 16:31:34
@ d9e9fb27:d5fe5e1a
2025-01-02 16:31:34Colmar is a well known city in the region of Alsace, France. Its characteristic buildings, the narrow streets and the small river flowing through are worldwide famous.

However, it is during Christmas that the city gets the most attention. Thousands of people from all over Europe decide to spend one of the Advent weekends to wander around this beautiful city and hundreds of little wooden huts.
In fact, this town becomes a small Christmas village, with decorations and lights on every building and the famous Christmas market covering every possible inch of it.



Walking around this city really makes you feel the Christmas Spirit!
Of course, it can get really cold during this time of the year. That is why Alsatians wander around drinking the Vin Chaud (literally "Hot Wine"). This beverage is prepared by mixing sugar, various spices, such as cinnamon and cloves, and red wine. They are served in a plastic glass, which can be reused multpiple time or returned for a couple of Euros. However, every year the glass is designed differently, so many people keep it with them as a collectible!
Here is 2024 version:

This is the first time I try to do a photography reportage of the places I visit. I really hope you enjoyed it!Let me know what you think, every feedback is appreciated.
I will try to create more of them during my trips, so stay tuned!
Tuma
-
 @ 40b9c85f:5e61b451
2025-02-09 20:53:03
@ 40b9c85f:5e61b451
2025-02-09 20:53:03Data Vending Machine Context Protocol
The Convergence of Nostr DVMs and MCP
In the rapidly evolving landscape of artificial intelligence, a new approach to sharing and accessing computational tools is emerging through the combination of two powerful technologies: Nostr's Data Vending Machines (DVMs) and the Model Context Protocol (MCP). This convergence has the potential to reshape how we think about tool distribution and accessibility, creating a truly decentralized marketplace for computational capabilities that serves AI, humans, and any type of machine that speaks the protocol.
Understanding the Building Blocks
Nostr's Data Vending Machines function much like their physical counterparts, but instead of dispensing snacks, they provide computational services with built-in Lightning Network payment capabilities. These DVMs operate on the decentralized Nostr network, allowing users to reach service providers without relying on centralized platforms or gatekeepers.
The Model Context Protocol complements this infrastructure by providing a standardized way for applications to share context and expose their capabilities. Think of MCP as a universal language that allows tools to communicate effectively with any application that understands the protocol. This standardization is crucial for creating a seamless experience across different tools and services.
What is DVMCP?
DVMCP proposes a path for making DVMs and MCPs interoperable, introducing a protocol that makes local utilities available to everyone on the network. Our draft specification serves as a foundation for easily transforming any MCP server into a DVM. To bridge these technologies, we've developed a simple software component that sits between your MCP server and the DVM ecosystem. You can find it in our repository. This bridge connects to your MCP server as a client and exposes its utilities through Nostr as a DVM, handling all the necessary Nostr logic. This means any existing MCP server can become accessible through Nostr without modifications - simply run the bridge alongside your server.
This is particularly exciting because the vibrant and growing MCP community. Any team or individual already working with MCP can instantly plug into the Nostr DVM ecosystem, gaining access to decentralized discovery, built-in monetization, and an already existing user base. The bridge component makes this transition effortless, requiring no changes to any existing MCP implementations.
A New Paradigm
A decentralized marketplace where anyone can run tools locally and make them available globally. This addresses an unsolved problem larger than the Nostr ecosystem: how to make resources and tools discoverable and accessible in a decentralized, permissionless way.
The power of this combination lies in its flexibility. Users can access tools through regular Nostr clients, AI agents can discover specific capabilities, and DVMs can create sophisticated tool chains. With Lightning Network integration, true machine-to-machine transactions become possible, where machines can autonomously discover, negotiate, and pay for computational services. Most importantly, you can run services on your own hardware while making these capabilities accessible to anyone anywhere.
The result is a system that preserves privacy, promotes innovation, and creates new opportunities without central authorities controlling what tools can be offered or who can use them. The entire project, is available under the MIT license, and any feedback and collaboration is welcome.
Looking Forward
As these technologies mature, we're likely to see a fundamental shift in how computational capabilities are distributed and accessed. Instead of relying on massive cloud data centers controlled by a few companies, we're moving toward a global network of local machines, each contributing unique capabilities and computation to a larger, more resilient ecosystem.
The convergence of Nostr DVMs and MCP represents more than just a technical innovation—it's a step toward a more equitable and accessible future. By enabling anyone to run and share tools, we're building an ecosystem where computational resources are not concentrated in the hands of a few but are available to and controllable by everyone.
-
 @ ef1744f8:96fbc3fe
2025-02-26 21:32:00
@ ef1744f8:96fbc3fe
2025-02-26 21:32:000jxu+3pODMGseAZeXiwEWcaWh0Zdp1dg4UP084e7Q8HkzdgcFHLycOQhoi/c52Iql8CA4FPgZDQCIf5gfXHNyt8lvzBvY+1TZvheCT1iX/wlrP0wn3XVE8wu5QJnVn4m2oZs31TKbR/uEfFBRpQoEUeoOhGxqzm6DZRlpjSjgdjye0me7hue1qWhwoEgQFr7TN0iZbvy9kp/DJhi5xVQgwWU1q5PCE9ekChRnEDHML/MYGCIjsZdj5tMBOh/BlH26VGsVGpzeB/F9mtuaj/E5WHaPSZdq78k1K7034emyYwEkfS0p0hvfgqdDy98m9DLRWmDeIERlxR0Ry7IPnc00qNfpthEXK9tujnUtskBQzIa6femadnIVdnE+JRJ20GOho6TkUzL6jxN9y2d7S/ttp8i/ZD+eaaXHC7ErWzR1TU=?iv=wad1n+h47INO5qI9jSRVXA==
-
 @ d4309e24:8a81fcb0
2025-02-09 00:16:55
@ d4309e24:8a81fcb0
2025-02-09 00:16:551. What if You Could Send a Message into the Future?
Imagine leaving a message for your future self, a loved one, or even an entire community—one that no one, not even you, can unlock until a specific moment in time. Picture leaving a message for your children, a note of wisdom or love that remains hidden until they're old enough to appreciate it, all timed by Bitcoin's block height. You might also make a bold prediction about the future price of Bitcoin, sealing it away until the blockchain reaches a certain block height.
This is the idea behind Hatchstr, a decentralized app for time-locked messages that only unlock at predetermined Bitcoin block heights—no central authority required.
Why Build This?
I want to dive into the Nostr protocol not just by reading documentation, but by actually building something that embodies its core principles: censorship resistance, user ownership, and decentralization. Hatchstr is both an experiment and a contribution to the Nostr ecosystem—a way to test the limits of permissionless communication while learning and engaging with the community.
2. The Vision: How Hatchstr Would Work for Users
At its core, Hatchstr lets users create time capsules—encrypted messages that only become readable after a specified Bitcoin block height. Here’s what that looks like:
- You design a capsule with text and images using Hatchstr’s web app.
- You pick an unlock time (e.g., 1000 blocks from now).
- The message is encrypted, locked away, and published as a Nostr event.
- At the chosen time, the decryption key is revealed, allowing the recipient to finally access the message.

Potential Use Cases
-
Personal Messages: Send birthday wishes that unlock at midnight, time-delayed love letters, or notes to your future self.
-
Timed Learning: Lock educational content to unlock when students reach key learning stages or ages.
-
Creative Storytelling: Release serialized fiction, riddles, or treasure hunt clues that unlock over time.
-
Community & Events: Time-gate announcements for Nostr-based communities or scheduled voting mechanisms.
3. The Centralized Trap: Why Build on Nostr
When thinking about how to implement this, we could go the obvious, easy route:
- Store messages on a centralized server.
- Release them when the time is right.
- Let users download their messages.
Simple, right? But is it the right approach? Let's break it down.
Why This Fails
-
Single Point of Failure: If my server goes down, all messages are unavailable.
-
Privacy Risks: Users would need to trust me not to access their messages.
-
Ownership & Longevity: What happens if I lose interest? The system dies with me.

A centralized model defeats the purpose of time-locking messages. Users shouldn’t have to trust a third party. We need decentralization.
4. Nostr to the Rescue: How Decentralization Can Help
Instead of a single server holding messages hostage, Nostr allows users to publish messages to decentralized relays. Here are the key differences:
-
Nostr IDs = Self-Owned Identities: Your public key is your identity, not tied to any company.
-
Relays = Decentralized Bulletin Boards: Anyone can run one, ensuring redundancy and censorship resistance.
-
Messages = Signed Events: Cryptographically signed by the sender or encrypted for only the recipient.

How Nostr Reduces Centralization
In this version of Hatchstr, capsules are still stored in a centralized manner at first until they 'hatch'. However, once the Bitcoin block height condition is met:
- Capsule Publication: The system publishes the capsule events to Nostr relays, making the messages available for decryption by the intended recipients.
This approach, while not eliminating the central server, allows for:
-
Third-Party Clients: Developers can now create clients that interact with Hatchstr capsules on Nostr, enhancing the system's openness and potentially leading to a richer ecosystem around time-locked messages.
-
Decentralized Access: Even though the initial storage is centralized, the access to the messages becomes decentralized once published to Nostr, reducing the dependency on a single point for message retrieval.
We have some improvements, but I am sure we can do better!
5. The Path to Decentralized Timekeeping
The Timeless Nature of Encryption
Encrypted messages exist outside time—once locked, they remain secure indefinitely. Modern cryptography (like AES-256) doesn’t "expire" or weaken unless decrypted (excluding brute force attacks). This creates a paradox: How do you bind something timeless to a specific moment in the physical world?
The Time-Lock Puzzle Dilemma
Cryptographers have proposed time-lock puzzles—encryption that requires sustained computation to unlock, theoretically forcing a minimum wait time. But these face critical hurdles:
-
Hardware Uncertainty
Solving time depends on an attacker’s computational power. A nation-state could crack in hours what takes years for a regular user. -
No Real-World Alignment
Puzzles can’t guarantee unlocks align with calendar dates or real-world events ("unlock on my child’s 18th birthday"). -
Energy Waste
Requires continuous computation, making it environmentally impractical for longer time locking.
Bitcoin as a Decentralized Clock
This is where Bitcoin’s blockchain shines. Its difficulty-adjusted proof-of-work acts as a trustless metronome:
-
Predictable Rhythm
Despite hash rate fluctuations, the 10-minute block target (via difficulty adjustments) creates a consistent approximation of real-world time.
-
Immutable History
Block height 1,000,000 will always correspond to the same point in Bitcoin’s timeline, regardless of future changes in mining power
Splitting the Problem
Hatchstr can bridge timeless encryption and blockchain timing by separating concerns:
1. Capsules – The time-locked message itself:
-
Design independent of the time-locking mechanism.
-
Encrypted client-side.
-
Content stored anywhere the user wants (IPFS, personal servers, etc.).
-
Completely owned by the user—not Hatchstr.
2. Clock Servers – Independent, lightweight timing nodes that:
-
Only publish decryption keys when the target Bitcoin block height is reached.
-
Users can choose which Clock Server to trust.
-
Anyone can run their own Clock Server.
-
Multiple servers can coordinate to prevent a single point of failure.

This means Hatchstr itself doesn’t store anything—users are fully in control.
6. What Comes Next
This project is just beginning—a blueprint with open questions and untested assumptions. In the next two articles, I’ll explore how to turn this concept into something tangible. First, how we might design playful time capsules that can be displayed faithfully by multiple clients, balancing creativity with decentralization. Then, the messy realities of clock servers: why federating them matters, how to incentivize reliability, and borrow Bitcoin’s rhythm without centralizing control. We will dive into setting up a simple clock server to get things started.
I’m still learning Nostr’s ecosystem, and this project is as much about sharing my education as anything else. If any part of this concept makes you think “yes, but…” or “what if…”, I’d genuinely love to hear it. Find me on Nostr – no expertise required, just an interest in sending messages to the future. :

npub16scfufrpsqcukjg7ymu4r40h7j4dwqy4pajgz48e6lmnmz5pljcqh678uhThank you for reading 🧡
-
 @ 3f770d65:7a745b24
2024-12-31 17:03:46
@ 3f770d65:7a745b24
2024-12-31 17:03:46Here are my predictions for Nostr in 2025:
Decentralization: The outbox and inbox communication models, sometimes referred to as the Gossip model, will become the standard across the ecosystem. By the end of 2025, all major clients will support these models, providing seamless communication and enhanced decentralization. Clients that do not adopt outbox/inbox by then will be regarded as outdated or legacy systems.
Privacy Standards: Major clients such as Damus and Primal will move away from NIP-04 DMs, adopting more secure protocol possibilities like NIP-17 or NIP-104. These upgrades will ensure enhanced encryption and metadata protection. Additionally, NIP-104 MLS tools will drive the development of new clients and features, providing users with unprecedented control over the privacy of their communications.
Interoperability: Nostr's ecosystem will become even more interconnected. Platforms like the Olas image-sharing service will expand into prominent clients such as Primal, Damus, Coracle, and Snort, alongside existing integrations with Amethyst, Nostur, and Nostrudel. Similarly, audio and video tools like Nostr Nests and Zap.stream will gain seamless integration into major clients, enabling easy participation in live events across the ecosystem.
Adoption and Migration: Inspired by early pioneers like Fountain and Orange Pill App, more platforms will adopt Nostr for authentication, login, and social systems. In 2025, a significant migration from a high-profile application platform with hundreds of thousands of users will transpire, doubling Nostr’s daily activity and establishing it as a cornerstone of decentralized technologies.
-
 @ 9e69e420:d12360c2
2025-02-14 15:14:34
@ 9e69e420:d12360c2
2025-02-14 15:14:34A Russian drone attack has struck the radiation shelter at Chernobyl, according to Ukrainian President Volodymyr Zelensky. The strike caused a fire, but it has since been extinguished, and radiation levels remain stable. The International Atomic Energy Agency (IAEA) confirmed that no casualties occurred and that monitoring continues.
Rafael Mariano Grossi, IAEA's director general, emphasized the need for caution. Chernobyl, site of the 1986 nuclear disaster, contains a protective shield costing $1.6 billion. Disaster prevention remains a priority as the conflict unfolds.
The incident occurred shortly before the meeting of world powers at the Munich Security Conference in Germany.