-
 @ d360efec:14907b5f
2025-02-27 09:56:31
@ d360efec:14907b5f
2025-02-27 09:56:31ภาพรวม BTCUSDT (OKX):
Bitcoin (BTCUSDT) แนวโน้ม Day ยังเป็นขาลง , 4H Sideway Down, 15m Sideways Down
วิเคราะห์ทีละ Timeframe:
(1) TF Day (รายวัน):
- แนวโน้ม: ขาลง (Downtrend)
- SMC:
- Lower Highs (LH) และ Lower Lows (LL)
- Break of Structure (BOS) ด้านล่าง
- Liquidity:
- มี Sellside Liquidity (SSL) ใต้ Lows
- มี Buyside Liquidity (BSL) เหนือ Highs
- ICT:
- Order Block: ราคา Sideway ใกล้ๆ Order Block ขาลง
- EMA:
- ราคาอยู่ใต้ EMA 50/200
- Money Flow (LuxAlgo):
- แดง
- Trend Strength (AlgoAlpha):
- แดง/ไม่มีสัญญาณ
- Chart Patterns: None
- Volume Profile:
- แนวรับ: Low ล่าสุด
- แนวต้าน: EMA 50/200, Order Block
- สรุป: แนวโน้มขาลง
(2) TF4H (4 ชั่วโมง):
- แนวโน้ม: ขาลง (Downtrend)
- SMC:
- Lower Highs (LH) และ Lower Lows (LL)
- Break of Structure (BOS)
- Liquidity:
- มี SSL
- มี BSL
- ICT: * Order Block: ราคา Sideway ใกล้ๆ Order Block ขาลง
- EMA:
- ราคาอยู่ใต้ EMA 50/200
- Money Flow (LuxAlgo):
- แดง
- Trend Strength (AlgoAlpha):
- แดง/ไม่มีสัญญาณ
- Chart Patterns: None
- Volume Profile:
- แนวรับ: Low
- แนวต้าน: EMA 50/200, Order Block
- สรุป: แนวโน้มขาลง
(3) TF15 (15 นาที):
- แนวโน้ม: Sideways Down
- SMC:
- Lower Highs (LH) และ Lower Lows (LL) เริ่ม Sideways
- Break of Structure (BOS)
- Liquidity:
- ICT: * Order Block ราคา Sideways ใกล้ๆ Order Block
- EMA:
- EMA 50/200 เป็นแนวต้าน
- Money Flow (LuxAlgo):
- แดง/เขียว สลับกัน
- Trend Strength (AlgoAlpha):
- แดง/ไม่มีสัญญาณ
- Chart Patterns: None
- Volume Profile:
- Volume ค่อนข้างสูง
- แนวรับ: Low
- แนวต้าน: EMA 50, EMA 200, Order Block
- สรุป: แนวโน้ม Sideways Down
สรุปภาพรวมและกลยุทธ์ (BTCUSDT):
- แนวโน้มหลัก (Day): ขาลง
- แนวโน้มรอง (4H): ขาลง
- แนวโน้มระยะสั้น (15m): Sideways Down
- Liquidity: มี SSL
- Money Flow: ลบ
- Trend Strength: Day/4H/15m ขาลง
- Chart Patterns: ไม่มี
- กลยุทธ์:
- Wait & See (ดีที่สุด): รอ
- Short (เสี่ยง): ถ้าไม่ Breakout EMA/แนวต้าน
- ไม่แนะนำให้ Buy
Day Trade & การเทรดรายวัน:
-
Day Trade (TF15):
- Short Bias: Short เมื่อเด้ง (EMA, Order Block)
- Stop Loss: เหนือแนวต้าน
- Take Profit: แนวรับ
- ไม่ Long
-
Swing Trade (TF4H):
- Short Bias: Short เมื่อไม่ผ่าน EMA/Order Block
- Stop Loss: เหนือแนวต้าน
- Take Profit: แนวรับ
- ไม่ Long
สิ่งที่ต้องระวัง:
- SSL: ราคาอาจถูกลากลงไป
- False Breakouts: ระวัง
- Volatility: สูง
Setup Day Trade แบบ SMC (ตัวอย่าง - Bearish):
- Order Block: หา Bearish Order Block ใน TF15
- Pullback: รอ Pullback ไปทดสอบ
- Bearish Entry:
- Rejection: รอ Price Action ปฏิเสธ
- Break of Structure: รอ Break โครงสร้างย่อย
- Money Flow: แดง
- Stop Loss: เหนือ Order Block
- Take Profit: แนวรับ
คำแนะนำ:
- แนวโน้มทั้งหมดเป็นลบ
- Money Flow เป็นลบ
- Trend Strength เป็นลบ
- ไม่แนะนำให้ Buy
- Wait & See หรือ Short (ถ้ามีประสบการณ์)
- บริหารความเสี่ยง!
คำแนะนำสุดท้าย: สถานการณ์โดยรวมของ BTCUSDT อยู่ในสภาวะขาลงและมีความเสี่ยงสูง แนะนำอย่างยิ่งให้ใช้กลยุทธ์ "Wait & See" (รอดูสถานการณ์) การ Short (ขาย) เป็นการเทรดที่มีความน่าจะเป็นสูงกว่าในขณะนี้ แต่เหมาะสำหรับนักเทรดที่มีประสบการณ์และมีการบริหารความเสี่ยงที่เข้มงวดเท่านั้น ไม่แนะนำให้ Buy (ซื้อ) ในเวลานี้
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-
 @ cd8b1353:9e39b063
2025-02-27 09:56:02
@ cd8b1353:9e39b063
2025-02-27 09:56:02 When you work in the interior design field, you’re mainly focused on aesthetics. After all, it’s your job to furnish and decorate your clients’ spaces. But when you’re hired to revamp a facility that’s open to the public, you should consider more than just appearance. You should also consider accessibility and take a better approach to ADA-compliant design.
When you work in the interior design field, you’re mainly focused on aesthetics. After all, it’s your job to furnish and decorate your clients’ spaces. But when you’re hired to revamp a facility that’s open to the public, you should consider more than just appearance. You should also consider accessibility and take a better approach to ADA-compliant design.Here’s why…
Why Accessibility Should Be a Priority for Interior Design
Ever since the Americans with Disabilities Act (ADA) went into effect in 1990, it has had a significant impact on the way buildings in the United States are designed. Under Title III, the ADA requires all public accommodations to provide equal access to people with disabilities. Ultimately, it’s a law that business owners should avoid breaking if they don’t want to face financial consequences.
So, it makes sense for you as an interior designer to have a firm grasp of ADA-compliant design. When you’re familiar with the 2010 ADA Standards for Accessible Design, you know what features are necessary for compliance. That way, as you update a client’s facility, you can also help them avoid potential fines and lawsuits.
But that’s not the only reason you should prioritize accessibility.
The fact is that ADA-compliant design is a means of removing barriers and providing access to all individuals—and it’s not going anywhere. Although it can be challenging, it’s well worth keeping accessibility top of mind and coming up with creative solutions to improve a given space. In doing so, you can give your clients the chance to serve customers with disabilities better. Plus, you can stay ahead of the curve and demonstrate your expertise in thoughtful design that benefits everyone.
5 Tips for Applying ADA-Compliant Design Principles
For every project that involves modifying a public space, you want to make sure the result is not only attractive but also functional and safe. Applying ADA-compliant design principles that allow for equitable use and minimal physical effort can go a long way. To help you out, we provided some tips below on putting these principles into practice.
1. Be Mindful of Clearance under Desks and Tables
Adequate clearance is crucial in ADA-compliant design. That’s why you should keep ths in mind when sourcing new desks and tables for a client’s facility. These areas should have enough space underneath to fit wheelchairs comfortably without the top surface being too high. Otherwise, people with disabilities who use mobility aids will have limited access.
Per the ADA, tables must meet the following requirements:
- They should be between 28 and 34 inches high.
- There should be at least 27 inches of clearance between the floor and the bottom of the table.
- Knee clearance should extend at least 19 inches under the table.
Of course, plenty of products on the market fit these dimensions. Additionally, adjustable desks are becoming more popular. So, it’s important to determine each client’s needs and choose the best option for them, their employees, and their customers.
2. Aim for Hardware and Fixtures That Are Easy to Use
Hardware and fixtures tend to go overlooked in public spaces. But when they’re poorly designed, they can prevent those with disabilities from using them. So, if you’re tasked with updating a client’s space, aim for easy-to-use options whenever possible.
Here are a few examples:
Light switches – Although flip switches are acceptable, push-plate types are usually the way to go because they’re easier to use.
- Doorknobs – Knobs and handles that require wrist-twisting aren’t compliant. So, it’s best to opt for U-shaped pulls and lever-shaped handles.
- Faucets – Faucets should be operated with no more than 5 pounds of force. There are plenty of options that meet this requirement, including touchless, lever, and cross handle.
- Cabinet & drawer hardware – U-shaped pulls are an excellent choice for cabinets and drawers, but levers and push-type mechanisms may also be used.
3. Make Signage Part of the Overall Flow
Signage is an essential part of ADA-compliant design. It allows everyone, including people with visual impairments, to get the information they need easily. So, when you’re revamping a client’s space, don’t forget to update their displays as well.
Certain types of signage must meet ADA sign specifications, such as those identifying permanent rooms and common areas. But the good news is there’s a lot of flexibility in terms of how they look.In fact, you can and should make signage part of the overall flow by sourcing custom ADA signs compliant that have colors, textures, shapes, and fonts that fit the space where they’ll be installed.
4. Choose Smooth, Non-Trip Floor Surfaces
Whether you’re upgrading an existing building or designing a new one from scratch, it’s vital that you choose the right flooring. A truly accessible space makes it easy for those who use wheelchairs and other mobility aids to move around freely. Smooth, non-trip floor surfaces such as wood, laminate, and vinyl are best.
Some additional tips are as follows:
- In cases where carpet must be used, opt for a low-pile option that’s easy to move over.
- Avoid soft floor surfaces such as cork or linoleum, which wheelchairs can scratch.
- Don’t put fringed or plush area rugs in high-traffic spaces, as individuals may trip over them.
5. Opt for Soft, Low-Glare Lighting
Finally, when deciding how to illuminate a client’s space, go with a soft, low-glare option whenever possible. Soft lighting is more comfortable for those with low vision. Plus, reducing glare from lights helps individuals see more easily.
The ADA doesn’t outline specific requirements for lighting beyond the placement of fixtures. However, there are some ways you can improve the lighting in a client’s space. Introducing ground track LED lighting along hallways is a popular choice. The same goes for installing adjustable lighting that can be made brighter or dimmer as needed.
Takeaway
Nowadays, accessibility is something you can’t afford to overlook when working on facilities that are open to the public. So, when you’re hired to help design or remodel a client’s space, make sure to apply ADA-compliant design principles everywhere you can. It’s well worth the effort, and your client will thank you for it!
-
 @ 59cfee8f:7598a483
2025-02-27 09:55:34
@ 59cfee8f:7598a483
2025-02-27 09:55:34What is Crypto Mining? Before we dive into the trends and predictions, let's first define what crypto mining is. Cryptocurrency mining involves the use of powerful computers to solve complex mathematical problems and validate transactions on the blockchain. Miners compete to solve these problems and the first one to do so is rewarded with a certain amount of cryptocurrency.
Trend 1: Increased Focus on Renewable Energy One of the biggest trends in crypto mining is a shift towards renewable energy sources. As concerns about climate change continue to grow, many miners are looking for ways to reduce their carbon footprint and operate in a more sustainable manner. Solar and wind power are increasingly being used to power mining operations, and there are even projects underway to create completely renewable-powered mining farms.
Trend 2: The Rise of Decentralized Mining Pools Another trend that is gaining momentum in the crypto mining world is the emergence of decentralized mining pools. These pools are designed to be more transparent, fair, and resistant to manipulation than traditional centralized mining pools. By utilizing blockchain technology, these pools can offer greater security and reduce the risk of fraud.
Trend 3: Continued Growth of GPU Mining GPU mining has been around for several years now, but it continues to be an attractive option for miners due to its flexibility and cost-effectiveness. With the rise of new cryptocurrencies and the increased demand for computing power, GPU mining is expected to continue its growth trajectory in 2023.
Trend 4: Increased Focus on Security Security has always been a major concern in the crypto world, and this is especially true for mining operations. In 2023, we can expect to see a greater emphasis on security measures, such as multi-factor authentication, encryption, and biometric verification. Miners will need to be vigilant in order to protect their assets and prevent cyber attacks.
Trend 5: Emergence of New Mining Algorithms As the cryptocurrency market continues to evolve, we can expect to see the emergence of new mining algorithms. These algorithms will be designed to be more efficient, secure, and resistant to manipulation. This could lead to a shift away from traditional proof-of-work algorithms towards proof-of-stake or other innovative solutions.
Prediction 1: Increased Regulation As the cryptocurrency market continues to grow and gain mainstream acceptance, we can expect to see increased regulation from governments and financial institutions. This could have a significant impact on the mining industry, with stricter regulations and oversight leading to greater stability and legitimacy.
Prediction 2: Continued Price Volatility Cryptocurrency prices have always been volatile, and this is unlikely to change in 2023. While the overall trend may be upwards, there will still be significant fluctuations in price, driven by factors such as global economic conditions, regulatory changes, and investor sentiment.
Prediction 3: Greater Collaboration and Partnership As the cryptocurrency market becomes more mature, we can expect to see greater collaboration and partnership between mining companies, cryptocurrency exchanges, and other players in the ecosystem. This could lead to new business models and innovative solutions for miners and investors alike.
Prediction 4: Increased Adoption of Cryptocurrencies As more and more businesses and individuals begin to accept cryptocurrencies as a form of payment, we can expect to see increased adoption of these digital assets. This could lead to greater demand for mining equipment and services, as well as new opportunities for miners to earn rewards and profits.
Prediction 5: Evolution of Mining Hardware The evolution of mining hardware is a trend that has been ongoing since the early days of Bitcoin mining. As the demand for computing power continues to grow, we can expect to see new and improved mining hardware emerge in 2023. This could include more powerful GPUs, ASICs, and other specialized equipment designed specifically for mining.
Conclusion In conclusion, the future of crypto mining in 2025 and beyond looks promising, with numerous trends and predictions pointing towards continued growth and innovation. As the industry evolves and matures, miners will need to adapt and embrace new technologies and strategies in order to stay competitive and profitable. With the right tools and knowledge, however, there is no doubt that crypto mining will continue to be a valuable and exciting part of the cryptocurrency ecosystem for many years to come.
-
 @ d360efec:14907b5f
2025-02-27 09:52:53
@ d360efec:14907b5f
2025-02-27 09:52:53Overall Assessment:
Bitcoin (BTCUSDT) on OKX remains highly volatile, and the overall trend is still uncertain. While the long-term trend (Daily chart) technically has been an uptrend, it has significantly weakened. The 4-hour and 15-minute charts are now in downtrends. This analysis incorporates:
- SMC (Smart Money Concepts): Market structure, Break of Structure, Change of Character, Order Blocks, Liquidity.
- ICT (Inner Circle Trader Concepts): Optimal Trade Entry (OTE), Fair Value Gaps (FVG), Mitigation, Breaker Blocks, Liquidity Pools/Runs.
- Buyside & Sellside Liquidity: Identifying likely areas of Smart Money buying/selling.
- Money Flow (LuxAlgo): Capital inflows/outflows.
- EMA (Exponential Moving Average): 50 (yellow) and 200 (white).
- Trend Strength (AlgoAlpha): Trend identification and strength, including the "cloud" and buy/sell signals.
- Chart Patterns: Identification of significant chart patterns.
- Volume Profile: (Used as needed).
Detailed Analysis by Timeframe:
(1) TF Day (Daily):
- Trend: Downtrend
- SMC:
- Lower Highs (LH) and Lower Lows (LL)
- BOS to the downside.
- Liquidity:
- Sellside Liquidity (SSL): Significant SSL rests below previous lows.
- Buyside Liquidity (BSL): BSL is present above recent highs.
- ICT:
- Order Block: The price failed to break above a bearish Order Block.
- EMA:
- Price is below both the 50-period and 200-period EMAs (bearish).
- Money Flow (LuxAlgo):
- Red, selling pressure
- Trend Strength (AlgoAlpha):
- Red cloud, Downtrend, No signals.
- Chart Patterns: None
- Volume Profile:
- Support: Recent lows.
- Resistance: EMA 50, EMA 200, Order Block.
- Summary: Downtrend
(2) TF4H (4-Hour):
- Trend: Downtrend.
- SMC:
- Lower Highs (LH) and Lower Lows (LL).
- BOS to the downside.
- Liquidity:
- SSL: Below previous lows.
- BSL: Above previous highs.
- ICT:
- Order Block: The price failed to break above a bearish Order Block.
- EMA:
- Price is below both the 50-period and 200-period EMAs (bearish).
- Money Flow (LuxAlgo):
- Red, selling pressure.
- Trend Strength (AlgoAlpha):
- Red cloud, Downtrend, No signals.
- Chart Patterns: None
- Volume Profile:
- Support: Recent lows.
- Resistance: EMA 50, EMA 200, Order Block.
- Summary: Downtrend
(3) TF15 (15-Minute):
- Trend: Sideways Down
- SMC:
- Lower Highs (LH) and Lower Lows (LL) - but showing signs of sideways movement.
- BOS to the downside.
- ICT: * Order Block The price is ranging near a bearish Order Block.
- EMA:
- The 50-period and 200-period EMAs are acting as resistance.
- Money Flow (LuxAlgo):
- Red
- Trend Strength (AlgoAlpha):
- Red/No signals
- Chart Patterns: None
- Volume Profile
- Relatively High Volume
- Support: Recent lows.
- Resistance: EMA 50, EMA 200, Order Block.
- Summary: Sideways Down
Overall Strategy and Recommendations (BTCUSDT):
- Primary Trend (Day): Downtrend
- Secondary Trend (4H): Downtrend
- Short-Term Trend (15m): Sideways Down
- Liquidity: SSL below on all timeframes.
- Money Flow: Negative on all timeframes.
- Trend Strength: Bearish on Day, 4H, and 15m.
-
Chart Patterns: None
-
Strategies:
- Wait & See (Best Option): The bearish momentum and lack of clear bullish reversals make waiting for confirmation the most prudent approach.
- Short (High Risk): This aligns with the downtrends on all timeframes.
- Entry: Look for short entries on rallies to resistance levels (EMAs, Order Blocks, previous support turned resistance).
- Stop Loss: Above recent highs or key resistance.
- Target: Recent lows, then SSL zones.
- Buy (Extremely High Risk - NOT Recommended): Do not buy unless there are extremely strong and consistent bullish reversal signals across all timeframes.
Day Trading & Swing Trading:
-
Day Trade (TF15 Focus):
- Bias: Short.
- Entry: Look for bearish setups (rejections of resistance, bearish candlestick patterns) near EMAs or Order Blocks.
- Stop Loss: Tight, above resistance.
- Take Profit: Recent lows.
- Avoid: Longs.
-
Swing Trade (TF4H Focus):
- Bias: Short.
- Entry: Look for bearish setups (rejections of resistance, bearish candlestick patterns) near EMAs or Order Blocks.
- Stop Loss: Above resistance.
- Take Profit: Next major support levels (SSL zones).
- Avoid: Longs.
Key Considerations & Warnings:
- Sellside Liquidity (SSL): High probability of price being drawn down to these levels.
- False Breakouts: Always a risk.
- Volatility: Expect high volatility.
- Conflicting Timeframes: While the long-term trend was bullish, the current price action and indicators are overwhelmingly bearish.
- Money Flow: Consistently negative across all timeframes.
- Trend Strength: Bearish across all timeframes.
SMC Day Trade Setup Example (Bearish - TF15):
- Identify Bearish Order Block: Locate a bearish Order Block on the TF15 chart.
- Wait for Pullback: Wait for the price to pull back up to test the Order Block (this might not always happen).
- Bearish Entry:
- Rejection: Look for price action to reject the Order Block (e.g., pin bar, engulfing pattern, other bearish patterns).
- Break of Structure: Look for a break of a minor support level on a lower timeframe (1m/5m) after the Order Block test.
- Money Flow: Confirm negative Money Flow (red).
- Stop Loss: Place a stop-loss order above the Order Block.
- Take Profit: Target the next support level (e.g., recent lows).
Recommendations:
All trends are negative. Money flow is negative. Trend strength is negative. Buying is not recommended. Wait and see, or short (if experienced). Manage your risk! I've made the following very minor changes, maintaining the original meaning:
Changed 'Advice' to a more natural sounding 'Recommendations'. Used "if experienced" instead of "(if have experience)" This version maintains the original meaning while sounding more natural in English, particularly in a financial/trading context.
Final Recommendation: The overall situation for BTCUSDT is bearish and high-risk. The "Wait & See" approach is strongly recommended. Shorting is currently the higher-probability trade, but only for experienced traders with strict risk management. Buying is not recommended at this time.
Disclaimer: This analysis is for informational purposes only and represents a personal opinion. It is not financial advice. Investing in cryptocurrencies involves significant risk. Investors should conduct their own research and exercise due diligence before making any investment decisions.
-
 @ b2d670de:907f9d4a
2025-02-26 18:27:47
@ b2d670de:907f9d4a
2025-02-26 18:27:47This is a list of nostr clients exposed as onion services. The list is currently actively maintained on GitHub. Contributions are always appreciated!
| Client name | Onion URL | Source code URL | Admin | Description | | --- | --- | --- | --- | --- | | Snort | http://agzj5a4be3kgp6yurijk4q7pm2yh4a5nphdg4zozk365yirf7ahuctyd.onion | https://git.v0l.io/Kieran/snort | operator | N/A | | moStard | http://sifbugd5nwdq77plmidkug4y57zuqwqio3zlyreizrhejhp6bohfwkad.onion/ | https://github.com/rafael-xmr/nostrudel/tree/mostard | operator | minimalist monero friendly nostrudel fork | | Nostrudel | http://oxtrnmb4wsb77rmk64q3jfr55fo33luwmsyaoovicyhzgrulleiojsad.onion/ | https://github.com/hzrd149/nostrudel | operator | Runs latest tagged docker image | | Nostrudel Next | http://oxtrnnumsflm7hmvb3xqphed2eqpbrt4seflgmdsjnpgc3ejd6iycuyd.onion/ | https://github.com/hzrd149/nostrudel | operator | Runs latest "next" tagged docker image | | Nsite | http://q457mvdt5smqj726m4lsqxxdyx7r3v7gufzt46zbkop6mkghpnr7z3qd.onion/ | https://github.com/hzrd149/nsite-ts | operator | Runs nsite. You can read more about nsite here. | | Shopstr | http://6fkdn756yryd5wurkq7ifnexupnfwj6sotbtby2xhj5baythl4cyf2id.onion/ | https://github.com/shopstr-eng/shopstr-hidden-service | operator | Runs the latest
serverlessbranch build of Shopstr. | -
 @ 378562cd:a6fc6773
2025-02-26 15:01:04
@ 378562cd:a6fc6773
2025-02-26 15:01:04In the modern world, the pace of life has accelerated to an unnatural speed. We are bombarded with notifications, responsibilities, deadlines, and expectations from the moment we wake up. The noise never stops, and neither do we. But what if this relentless hustle is doing more harm than we realize?
We live in an age where stress is almost inescapable. The demands of work, finances, relationships, and societal pressures create a never-ending cycle of worry. And here’s the catch: stress is not just a feeling but a silent killer. It wreaks havoc on the body, deteriorating our health at an alarming rate. In fact, stress has been linked to heart disease, high blood pressure, weakened immune function, and even mental illnesses like anxiety and depression.
The Unseen Dangers of a Constantly Busy Mind
Imagine buying a brand-new truck and driving it everywhere at full throttle. There would be no breaks, oil changes, or maintenance—just 100% all the time. How long would that truck last before breaking down completely? Our brains and bodies work in the same way. We will wear out if we keep pushing ourselves at full speed without pause.
Chronic stress forces our bodies into a constant fight-or-flight mode, flooding us with cortisol and adrenaline. While these chemicals are helpful in moments of real danger, living in a prolonged state of stress weakens the body. The medical industry acknowledges the effects of stress on health, but the system profits from treatment, not prevention. There is too much money in keeping people sick to ever fully admit that stress and fear are at the root of most illnesses.
And make no mistake—fear is the fuel that keeps this machine running. News outlets thrive on fear, corporations exploit it to sell products, and even the healthcare industry benefits from keeping people in a perpetual state of anxiety. Fear is marketed like candy, handed out freely to anyone willing to consume it. But it’s poison disguised as information or 'news.'
Finding Peace: The Path to a Healthy Mind and Body
If stress is the disease, then peace is the cure. The antidote to a chaotic life is learning how to slow down, live in the moment, and let go of unnecessary worries. Here’s how we can start:
Eat Right – The food we consume directly impacts our mental and physical well-being. Eating a diet rich in whole foods, fresh vegetables, and unprocessed ingredients helps to keep the body strong and resilient. Junk food may provide momentary comfort, but it contributes to long-term health problems, adding even more stress to our lives.
Exercise Properly—Just like a truck needs regular lubrication to keep running smoothly, our bodies need movement to keep our joints flexible and our circulation strong. Movement doesn’t have to be intense; just a little here and there can make a huge difference. Walking, stretching, or even light activity can help maintain overall health and prevent stiffness and sluggishness.
Let Go of Fear – Fear controls us only if we allow it to. Recognize when fear is being used as a tool to manipulate your emotions. Ask yourself: Is this fear real, or is it being fed to me for someone else’s benefit? The Bible reminds us repeatedly to “fear not.” Living in fear only robs us of peace and joy.
Relax and Rest – The body and mind require rest to function properly. Taking time to unplug, pray, or simply be still can work wonders for overall well-being. True productivity comes from a well-rested mind, not one that is constantly overworked.
Stop Worrying About the Future – Worrying about what might happen tomorrow steals today’s peace. Jesus himself said, “Therefore do not worry about tomorrow, for tomorrow will worry about itself. Each day has enough trouble of its own.” (Matthew 6:34). When we focus on the present and trust that God will handle the rest, we free ourselves from unnecessary burdens.
Conclusion
The greatest threat to our health is not some invisible disease; it is the relentless stress and fear that we allow to consume our minds. If we wish to live long, fulfilling lives, we must take control of our thoughts, nourish our bodies, and trust that life will unfold as it should. Stress and fear will always be there, but we have the power to choose peace.
Slow down. Breathe. Trust God. And most importantly—live your life.
-
 @ cc2ce0d4:54be29f4
2025-02-26 13:12:53
@ cc2ce0d4:54be29f4
2025-02-26 13:12:53Testing article
-
 @ ba3dd613:76dbcaa8
2025-02-26 09:38:13
@ ba3dd613:76dbcaa8
2025-02-26 09:38:1330WIN rapidamente se tornou um dos nomes mais comentados no mundo do entretenimento online. Projetada para oferecer uma combinação perfeita de jogos inovadores, experiência excepcional do usuário e atendimento ao cliente inigualável, a 30WIN promete entregar uma plataforma empolgante e envolvente para jogadores de todos os tipos.
Introdução à Plataforma 30WIN é uma plataforma de entretenimento online que se orgulha de sua simplicidade e acessibilidade. Criada com jogadores novatos e experientes em mente, a plataforma oferece uma interface fácil de navegar, garantindo uma experiência agradável desde a primeira visita.
Um dos destaques do 30WIN é o foco no desempenho. A plataforma funciona perfeitamente em uma ampla gama de dispositivos, garantindo que a jogabilidade seja sempre fluida e visualmente impressionante. Seja você usando um computador ou um dispositivo móvel, a 30WIN oferece uma experiência tranquila, com design responsivo que se adapta a diferentes tamanhos de tela sem comprometer a qualidade.
Outro aspecto importante do 30WIN é o compromisso com a segurança. A plataforma utiliza tecnologia de criptografia de ponta para proteger as informações dos jogadores, garantindo um ambiente seguro para todos.
Introdução aos Jogos A seleção de jogos no 30WIN foi feita para oferecer algo para todos os tipos de jogadores. Se você gosta de jogos rápidos e cheios de ação ou de jogos mais relaxantes e estratégicos, a 30WIN tem uma vasta coleção de jogos que atenderá suas preferências.
Desde slots de vídeo visualmente deslumbrantes até jogos de mesa emocionantes, a 30WIN reúne o melhor do entretenimento online em um só lugar. A plataforma atualiza regularmente sua biblioteca de jogos para incluir novos títulos, garantindo que sempre haja algo novo e empolgante para os jogadores explorarem.
Cada jogo na 30WIN é desenvolvido por criadores de jogos de renome, garantindo gráficos de alta qualidade e jogabilidade envolvente. A plataforma foi projetada para oferecer uma variedade de temas e recursos, para que nenhuma experiência de jogo seja igual à outra.
Experiência do Jogador A experiência do jogador na 30WIN é projetada para ser simples e agradável. O registro é rápido, e uma vez que você está dentro, perceberá que a plataforma é incrivelmente fácil de usar. Desde navegar pelos jogos até fazer depósitos, cada ação é simples e intuitiva.
O atendimento ao cliente também é um grande foco na 30WIN. Com várias maneiras de entrar em contato, os jogadores podem contar com a equipe da plataforma para ajudar com qualquer problema ou dúvida. A equipe de suporte é amigável, ágil e sempre disposta a ajudar.
Além disso, a 30WIN oferece promoções emocionantes e programas de fidelidade que tornam seu tempo na plataforma ainda mais recompensador. Ao interagir regularmente com a plataforma, os jogadores podem ganhar bônus e outras ofertas especiais, aumentando ainda mais a experiência geral.
Em resumo, a 30WIN é uma plataforma de destaque no setor de entretenimento online, oferecendo uma interface fácil de usar, uma grande variedade de jogos de alta qualidade e um foco total na satisfação do jogador. Seja você novo no mundo dos jogos online ou um veterano, a 30WIN oferece uma experiência que o manterá entretido por horas.
-
 @ ba3dd613:76dbcaa8
2025-02-26 09:36:49
@ ba3dd613:76dbcaa8
2025-02-26 09:36:49BRBRBR emergiu como uma das principais plataformas de entretenimento online, conhecida por sua jogabilidade sem interrupções, suas ofertas diversificadas e seu compromisso em criar uma experiência inigualável para o jogador. A plataforma rapidamente conquistou reconhecimento por sua atenção aos detalhes e pela qualidade de seus serviços. Seja você um jogador experiente ou um novato, o BRBRBRpromete um mundo de diversão e emoção que o fará voltar sempre.
Introdução à Plataforma Desde o seu início, o BRBRBR tem se concentrado em oferecer uma experiência de entretenimento online de alta qualidade. A plataforma conta com uma interface amigável, que garante que até os usuários iniciantes consigam navegar com facilidade. O design clean e intuitivo torna simples para os jogadores encontrarem seus jogos favoritos, fazerem depósitos e explorarem todas as opções emocionantes disponíveis.
A plataforma BRBRBR foi criada para oferecer uma experiência excepcional em todos os dispositivos. Seja no computador, laptop ou smartphone, você pode desfrutar de uma jogabilidade suave e sem falhas. A plataforma também oferece gráficos em alta definição, que tornam a experiência geral ainda mais envolvente para os jogadores.
A segurança também é uma prioridade importante no BRBRBR. A plataforma utiliza a mais recente tecnologia de criptografia para proteger os dados dos jogadores, garantindo um ambiente seguro para todos que a acessam.
Introdução aos Jogos A seleção de jogos no BRBRBR foi feita para atender a uma ampla gama de preferências de jogadores. Com uma variedade abrangente de jogos, os jogadores podem desfrutar de tudo, desde slots de vídeo de ritmo acelerado até títulos mais estratégicos e baseados em habilidades. Cada jogo foi cuidadosamente selecionado para garantir qualidade e emoção.
Um dos principais destaques do BRBRBR é a coleção de slots inovadores, cada um com temas únicos, recursos bônus e oportunidades para grandes vitórias. Esses jogos são desenvolvidos por alguns dos mais respeitados criadores de jogos da indústria, garantindo gráficos de primeira linha e mecânicas de jogabilidade envolventes. Seja você fã de temas clássicos ou mais modernos, há algo para todos no BRBRBR.
Além dos slots de vídeo, o BRBRBR também oferece diversos jogos de mesa e outras opções emocionantes, garantindo que a plataforma tenha algo para todo tipo de jogador. Os jogadores podem explorar essas ofertas no seu próprio ritmo, sem pressa, e descobrir seus jogos favoritos.
Experiência do Jogador Quando se trata de experiência do jogador, o BRBRBR se destaca com seu foco em oferecer uma jornada tranquila e divertida. O processo de registro é rápido, e, uma vez dentro, você perceberá que tudo – desde navegar pelos jogos até acessar o suporte – é simples e fácil de usar.
O BRBRBR vai além para apoiar seus jogadores, oferecendo vários canais de atendimento para assistência. Seja para resolver dúvidas sobre sua conta, questões sobre um jogo ou suporte técnico, a equipe da plataforma está sempre pronta para ajudar.
Além disso, o BRBRBR oferece promoções e programas de recompensas variados, garantindo que os jogadores fiéis sejam sempre recompensados pelo seu engajamento. Esses programas oferecem oportunidades emocionantes de ganhar bônus e participar de eventos especiais, tornando a experiência do jogador ainda mais enriquecedora.
No geral, o BRBRBR oferece uma experiência de entretenimento online de primeira linha, combinando uma ampla variedade de jogos, uma plataforma fácil de usar e excelente suporte ao cliente. Seja você um novato ou um jogador experiente, o BRBRBR é o lugar certo para estar.
-
 @ e7bc35f8:3ed2a7cf
2025-02-27 07:46:26
@ e7bc35f8:3ed2a7cf
2025-02-27 07:46:26This is a fascinating question, indeed. But first of all, why is this important? Why should we be concerned about the goings-on of this group? Let’s find out the basis for this and what and why we’re being told we should care so much about this group and of course in order to do that why don’t we turn to the fear-mongers themselves to allow them to explain what is really behind this fearsome group.
ISIS, an al-Qaeda-bred terrorist group spreading its wings online. Savvier than its predecessors with a new array of tricks up its sleeves. Twitter has become a virtual second home for the terrorists but as many as 27000 accounts established just over the last two weeks, after ISIS posted a video capturing the beheading of US journalist James Foley with a reported 60000 accounts popping up since May.
Douglas MacArthur McCain, a young American, killed while fighting with the terrorist group ISIS. US officials say they believe he died in Syria. He’s thought to have been killed in a battle between rival extremist groups near the city of Aleppo according to a human rights group. This ratches up concerns about Americans involved with ISIS because now you have a confirmed example of an American killed fighting with ISIS in Syria.
Hello my brothers in Australia. I don’t see myself better than any of yous, (inaudible) only that Allah has bring Karim on me and has brang me here to this country. Two men who identify themselves as Australian appear in a recruitment video called 'There is no life without jihad'. It’s believed up to 150 Australians have joined rebels fighting in Iraq and Syria.
Earlier today the Home Secretary confirmed that the Joint Terrorism Analysis Center has increased the threat level in the United Kingdom from ‘substantial’ to ‘severe’. This is the first time in three years that the threat to our country has been at this level.
They’re beyond just a terrorist group. They marry ideology, a sophistication of strategic and tactical military prowess. They are tremendously well-funded. Oh this is beyond anything we’ve seen so we must prepare for everything and the only way you do that is you take a cold steely hard look at it and get ready.
Yes as the usual gaggle of fear-mongers in government and the mainstream media will no doubt tell you "Yes ISIS is coming and you’d better be afraid in fact the only thing you can do is take a cold steely hard look at it and get ready because apparently there’s really nothing that can be done to avoid whatever horrible, horrific, 911-like attack they’re planning on the US Heartland, or so we’re being told."
But again I think it behooves us to question this constant call for fear-mongering from the same fear-mongers who have, for years and years, ratcheted up these phony terror level alerts, to suit their geopolitical aims and I think once again that’s exactly what was going back then. Things could have been different if, instead of succumbing to fear back then, we had focused more on understanding the threat, exposing the so-called "boogeyman," and revealing the true perpetrators in this situation.
This group was created in Iraq by a Jordanian Sunni back in 1999. It was formerly the official al-Qaeda franchise, in Iraq since it broke with al-Qaeda ideologically. It then became a self-proclaimed caliphate, which was pronounced in late June of 2015. The question of the name of this group is something that gets bandied about and ISIS is often used as the short abbreviation in English, and in fact it’s just one of many, many, many, many names that this group has gone by over the years.
You can go back to 1999 for example to the original organization which brought with it of course an Arabic name whose acronym was JTJ and whose English translation was "The Organization of Monotheism and Jihad". It changed its name in 2004 to, again, another Arabic name "The Organization of Jihad’s Base in the Country of the Two Rivers", although it became more commonly known as "al-Qaeda in Iraq" or AQI around that time.
Then in 2006 it became the "Islamic State of Iraq". In 2013 it became the "Islamic State of Iraq and the Levant" or "Islamic State of Iraq and al-Sham", aka ISL and ISIS. Then in 2014 "Islamic State". So switching to the question of who is behind this group, let's see some of the characters behind it. It was founded in 1999 by a Jordanian Sunni Muslim who went by the name of Abu Musab al-Zarqawi.
‼️We have to keep in mind that the names of the various jihadis behind this, like most jihadis they adopt "nommes de guerre" that is ‘war names’ so these names are not necessarily their real names and in fact in most cases are specifically not their real names.
They’re usually chosen for some sort of symbolic or historical cultural value so for example there’s no need to scratch your head and wonder why so many people are named Al Baghdadi, it’s because they are adopting a name that shows they’re the "Baghdadis" – they’re from Iraq, that kind of thing. So again don’t read too much into any of these names, and there are usually many, many, many other alias names that these people go by as well so it gets extremely confusing, probably on purpose I think.
I think the people controlling the terrorists also have reasons for having extremely confusing ways of referring to these people and multiple ways of referring so that if one of their memes or ideas or stories gets out of control they can spin them off as a completely different human being. Abu Musab al-Zarqawi was a Sunni militant from Jordan and he had what can only be described as a remarkable career that brought with it many lives apparently.
So, again this all sources from mainstream reporting. None of this is, you know "conspiracy" reporting, this is all from mainstream news services, ABC and NBC and CBS and Reuters and all of those kinds of outlets. For example back in 2004 it was reported that he was arrested in Fallujah. Then in 2005, without reports in the meantime indicating how or when or why he was released from – or escaped from – custody in Fallujah, or how he was never arrested in Fallujah in the first place he got wounded in Baquba. Then in 2005 he was reported as being killed in fighting in Iraq. And then in 2006 he was killed in fighting once again. Presumably for the last time this time.
But it gets even stranger. Back in 2006 the Washington Post published an article entitled "Military plays up role of Zarqawi" in which they reported:
The US military is conducting a propaganda campaign to magnify the role of the leader of al-Qaeda in Iraq according to internal military documents and officers familiar with the program.
and that same article went on to say:
One internal briefing produced by the US military headquarters in Iraq said that Kimmitt (one of the generals that oversaw this program) had concluded that the Zarqawi PSYOP program is the most successful information campaign to date.
So once again the Washington Post got its hands on internal briefing documents that the Pentagon was using, to talk about al-Qaeda in Iraq and their propaganda campaign in Iraq, and these documents prove that the Pentagon was absolutely 100 percent, self-consciously engaged in a PSYOP operation to make Zarqawi and al-Qaeda in Iraq seem more important than it was, and they have their own twisted internal logic that was reported on at the time as to why they wanted to do this and why they wanted to build up AQi in the minds of the Iraqi people and the people of the United States. And of course I think obviously the main part of that was to keep the American people involved and interested in keeping their troops in harm’s way there in Iraq, even long after Bush declared "mission accomplished".
The precursor of that ISIS group, the leader with actually a not a PSYOP creation per se but at any rate someone who is blown up specifically on purpose made to seem more important than he was, because of the Pentagon.
And it gets even stranger than that when we look at the person who took over from Zarqawi after his final, supposedly, reported death in 2006, someone going by the name of Baghdadi, one of many people going by the name of Baghdadi, this one Abu Omar al-Baghdadi but again it’s a nom de guerre, it’s not his real name. Apparently his real name is Hamid Dawud Mohamed Khalil al-Zawi, he’s also known as Abu Omar al-Qurashi al-Baghdadi and Abu Hamza al-Baghdadi so we should not, again, put too much faith, stock, interest or energy into parsing these various names, just to know that this is someone who is referred to as al-Baghdadi and who took over from al-Zarqawi as leader of what was at the time "al-Qaeda in Iraq" in 2006.
He took over the group and again, like Zarqawi, had a remarkable career that involved being reported as captured in 2007** and then killed in 2007 then arrested in 2009 and then throughout that period of his arrest or the period that we are supposed to be led to believe that he was under arrest, he was releasing recordings, obviously not from prison but from wherever he really was, that were being identified and authenticated. And then in 2010** he was reported as being killed once again.
So again we have multiple reportings of captures and killings and arrests that don’t seem to make any logical sense, but just as in the case of Zarqawi, in the case of Baghdadi it becomes that much more strange when we find out that the fictional ISI leader – Abu Omar al-Baghdadi was identified as such by the US Pentagon.
Yes, once again the US military actually reported on how they believed Abu Omar al-Bagdadi didn’t even exist. This comes from a Reuters article, of one of many sources, but we can source it to a Reuters article '"Senior Qaeda figure in Iraq a myth" says US military', where they talk about a a senior operative for al-Qaeda in Iraq who was in custody of the US military, and was being interrogated and according to the testimony of this captured al-Qaeda in Iraq fighter:
The Islamic State of Iraq is a front organization that masks the foreign influence and leadership within al-Qaeda in Iraq in an attempt to put an Iraqi face on the leadership of al-Qaeda in Iraq
U.S. military officials in recent weeks have been pressed to explain the link between al-Qaeda in Iraq and bin Laden’s global network given the military’s heightened focus on al-Qaeda in Iraq as the biggest threat to the country
The military blames al-Qaeda in Iraq for most of the major bombings in Iraq, saying the group is trying to spark all-out civil war between majority Shi’tes and minority Sunni Arabs
Again a very interesting, very bizarre report that again includes briefing slides from the Pentagon that show that the Pentagon itself calls Abu Omar al-Baghdadi the fictional ISI leader, so once again the US military didn’t even believe this person existed, and this was from a 2007 report, so once again throwing more sand into the water, more mud in the mix to make it even murkier, the US military bumbles in, and it’s again a question of what their ultimate aim in all of this is.
Very, very strange dealings going on, and again remember this is the precursor group to the group that is now referred to as is IS or ISIS, so a very strange pedigree for this terrorist group with the fingerprints of the US Pentagon and military all over it. And the next character in this list of this cavalcade of terrorist-boogeyman is also Baghdadi.
This one not Abu Omar al-Baghdadi but Abu Bakr al-Baghdadi also known as Ibrahim bin 'Awad bin Ibrahim al-Badri ar-Radawi al-Husseini as-Samara’i, who was also known as Caliph Ibrahim, the caliph of the Islamic State Caliphate. So what is known about this character and where he came from? Almost nothing, in fact almost everything that we know about the background of this character sources from an completely unverifiable online biography.
So apparently he was born in Samarra in Iraq in 1971; at some point he apparently attended the Atlantic University of Baghdad and it was reported that he was a leader, a cleric in a mosque in Samarra during "The American Invasion" in 2003 according to quote unquote "reports" – unidentified reports – that’s what the BBC sourced that to – and then he was detained at Camp Bucca which was a US Forces Iraq camp at some point between 2004 and 2009 and again this story conflicts.
According to the official story he was detained from February to December of 2004, that’s what the Defense Department will admit to, before being released on the recommendation of the Combined Review and Release Board. Why they recommended him for release I’m not sure, but at any rate that’s the official story.
However we have Army Colonel Kenneth King who was the former commander of Camp Bucca who insists that this character – this man who is now known as Abu Bakr al-Baghdadi – was at the camp during his tenure at Camp Bucca all the way up until 2009 when the camp with turned over to the Iraqi justice system, and he insists this because he remembers this particular character saying "We’ll see you in New York" or something of that nature, a "terrorist threat", so even after the point at which the discrepancy between the Defense Department’s story that Bagdadi was released in 2004 , and King’s story that he was there in 2009, even when that discrepancy became apparent and was pointed out to King he specifically said again he was sure of it. He insists that he was there.
So, again, the official story is that he was only there for the better part of a year but at any rate he may have been there up until 2009 and then presumably released by the Iraqi authorities at some point. Again it’s a completely murky story, but at some point he was under the care and detainment of the US military.
Then, having gotten out of the camp he was announced as leader of the Islamic State of Iraq as it was known at that time, the AQI having morphed into the ISI in 2010 and then, once again had something of a interesting career having being reported as captured in 2012 and then in 2014 he was rumored as dead but just a few days later a video of him was released, a video of him delivering some sort of sermon, which is interesting because there are only apparently two photographs in existence of this person.
So an exceptionally shady character and on that blank slate a lot has been written, some of which is clearly fictional and let’s just keep in mind to take with a giant grain of salt any information we hear about this man and his background and really look into where and what the source of that information is.
So that’s some of the main characters behind this group. Let's turn our attention to what this group consisted of in terms of its equipment and its ability, at that time. We were told that the arsenal of jihad contained and wielded by this shadowy deadly terrorist-boogeyman group consists of: 30 T 55 tanks; 10 T72 tanks; Blackhawks; cargo planes; Humvees; Toyota trucks; AK47s; M79s; RBG-6s; RPG-7s; Howitzers; field guns; AACs; Stinger manpads; scud missiles and a low-grade nuclear material of unknown origin.
Again this is just a ridiculous list of equipment but at any rate most of it has been sourced to various things that they’ve managed to accrue from their various military conquests including for example their takeover of Mosul back earlier this year in which they secured the Black Hawk helicopters and the cargo planes from the airport and also the nuclear material, the low-grade nuclear material that they acquired from Mosul University which according to the International Atomic Energy Agency is a low risk for nuclear proliferation because it is such low grade – such low quality. So those were the things that we were told that they’ve gathered from their various exploits. Some of the interesting items in there I think are for example the Toyota trucks, which have become something of a hallmark of jihadis in various contacts.
There are reasons for that, Toyotas of course being quite ubiquitous in that region of the world since Japanese aid to the Middle East generally comes in the form of equipment and various products and so Toyotas are among the types of things that find their way to the Middle East, and because of their ubiquity the parts and servicing for them are widely available so they’re quite useful for any group that wants to have sort of mobile access to the area, including the jihadis, and the Toyotas in possession of ISIS in particular seem to have come courtesy of, surprise surprise, Uncle Sam.
According to a report which includes some audio footage about the Toyotas in the Middle East, and it also says that the "wish list" of the so-called moderate Syrians that was handed to the US military back in 2014 when the US was handing out supplies included Toyota Hiluxes, the Toyota trucks that are now in the possession of ISIS, so, surprise surprise you give to the moderates and who ends up getting them? Well the non-moderates.
As if there were really any moderates there in the terrorist group trying to take over Syria in the first place. But that’s what they were having in their possession in terms of equipment. Where they actually get the money to do what they do… well according to what we’re being told they looted the Iraqi army. They acquired as much is 429 million dollars from the Mosul central bank which they took over earlier that year.
They were extracting ransom money and extortion money from various governments throughout this time period, and they are selling oil from their northern Syria territories to the tune of as much as 2 million dollars a day, supposedly. So those were the places where they were supposedly financing what’s going on, however we can contrast that with some other information acquired from different sources.
For example it’s been widely and repeatedly reported throughout that private Gulf donors via Kuwait, and apparently the Kuwaiti financial system was specifically well set up for this type of financing, but at any rate private gold donors have accounted for a lot of the money that has flowed into Syria to fund the various terrorist groups including ISIS and the others that were there, and again that was private donors not necessarily the House of Saud or anything of that sort but private donors from the Gulf, who obviously had religious reasons for trying to support the Sunni Wahabi Jihadist Muslims. In this conversation about Who is behind ISIS, we stumble upon Benghazi and what became known as Benghazi-Gate.
Benghazi was the lexus where all of those Libyan arms were flowing from the Libyan terrorists to the Syrian terrorists, via Turkey and Jordan, and I think that’s an important part to keep in mind because those, again, are two very important players in this story. What happened in Benghazi is an important example for what was happening in there and all the sources converge on this ISIS group – this ISL group – that suddenly seemed to spring out of nowhere but of course has been gestating there for 15 years and has been, as we’ve seen, involved with the US Pentagon, involved in various PSYOPS operations to make this group seem more important than it is. You can find more information about Benghazi in my recent article (search it in my articles tab). So that brings us to some of the questions of "Well where are these funds coming from and how are these troops being trained?" and as always, all roads lead to…Washington? Here is an enlightening broadcast of "Democracy Now!", with Amy Goodman and Adam Entous.
So the CIA in conjunction with their friends in Britain and France and Saudi Arabia and the UAE and elsewhere have converged in Jordan to train various Syrian militants – terrorists – at a base in Jordan. Something considered as a conspiracy theory before, now it is confirmed even by the mainstream dinosaur media.
So "Well yes actually, the US has been intimately involved; the CIA has been intimately involved in training a lot of the people who went on to become the top ISIS fighters".
And then the ""corrected"" version.
So if this sounds surprising well you haven’t been paying attention, not only to the Syrian story but really to any of these stories going back decades and decades, with the most famous of course being the US involvement in Afghanistan in the 1980s back when they were helping the Freedom Fighters – the Taliban before they started going after the evil terrorists – the Taliban.
Unfortunately a script we know all too well and when it comes to how these groups are armed and trained it just continues. LT. GENERAL MCINERNEY:
Syria we backed, I believe in some cases, some of the wrong people, and not in the right part of the Free Syrian Army and that’s a little confusing to people, so I’ve always maintained and go back quite some time that we were backing the wrong types.
I think it’s gonna turn out maybe this weekend, in a new special that Brett Baer’s gonna have Friday, it’s gonna show some of those weapons from Benghazi ended up in the hands of ISIS. So we helped build ISIS. Now there’s a danger there and I’m with you.
So "we kind of build up ISIS oh and let’s go to the next news story." 😶 So again this is not controversial. This is not something that we have to speculate about. This is something that has been documented in a lot of mainstream contexts as well, so really this brings us to the heart of the question "Who is behind ISIS?"
There are at least 6 groups. Someone could probably dig deeper and bring in some other groups but 6 of the main groups that we can identify as being the real powers that have brought ISIS to its position, and in alphabetical order that would be: 1. Israel, 2. NATO, 3. Qatar, 4. Saudi Arabia, 5. Turkey and 6. the USA,
although to a certain extent these are groups rather than nation-states per se.
Specifically in the case of Saudi Arabia where of course the House of Saud had institutional and fundamental reasons why it would not be happy about a radical caliphate on its doorstep, because obviously that would threaten the institution of the House of Saud itself, but certainly individual Saudis, private donors as I 've said, and including some members of the Royal House of Saud would be interested in helping fund a radical Wahabi jihadi Selapi??? group...
Take Turkey for example. Turkey obviously has its fingerprints all over everything that’s happening in Syria and has been since the inception. Turkey has a lot of different reasons for being involved that range from its constant requests to keep its neighbors fighting with each other and destabilized, using Islam as a weapon, Turkey is happy to do so. I think the Turkish leadership has no allegiance really to Islam except for the fact that it’s a useful political tool for the largely Islamic Turkish population, and also it can be used in fights like this to keep its neighbors destabilized and to keep Turkey an important foothold for Europe and NATO in the region, and I think that’s one of the reasons.
I think they’re also obviously always looking to repress and find ways to stamp out their Kurdish population problem so I think this is one extension of that, and we’ve seen for example the false-flag recordings that were released with the high-ranking Turkish officials under Erdogan talking openly about how they wanted to stage an attack on Turkish targets in Syria in order to justify Turkish incursion into Syria, which of course brings with it the specter of NATO because of the mutual self-defense clause in the NATO article – the treaty – so Turkey a very, very menacing prospect/player in all of this and someone who is again been admittedly and documentably linked to the transfer of funds and arms to the terrorist groups in Syria.
Qatar has a number of reasons ranging again from religious to geopolitical, and maybe I 'll get more into the sort of pipeline politics that Qatar sees in all of this.
When it comes to NATO specifically the context is similar with Gladio B, ie. the Operation Gladio which was not a mere stay behind operation in Europe to counter some perceived or imagined Soviet occupation of Europe, but in fact a global operation that involved "Strategy of Tension" and false-flag terrorism as ways of achieving various NATO operation goals in various "theaters", and we’ve talked of course about Sibel Edmonds and her revelation of Gladio B, ie. the fermenting of Islamic terrorism in various parts of the world to further these aims and goals and taking over various squares on the geopolitical chess board, So you can think about Gladio B as a worldwide operation and I would see no reason why it wouldn’t also be operative in the Middle East, and we have to look for NATO fingerprints in what’s happening there, and we can see them through the actions, for example most specifically of the US, in helping to arm, fund and run PSYOP operations surrounding this ISI group lslamic state.
Let's get into more detail on some of these characters, for example of course Israel, who I think is interested in pretty much anything that happens in the Middle East, should be fairly apparent, but this is something that I documented specifically back in a previous article (see again my Articles tab).
Israel’s designs on Iraq have been well-known and well-understood for a long time but I think we have to see all of these invasions and overthrows and all of the destabilizations in the Middle East in recent years as part of a grander Zionist project for reshaping the Middle East, that we can say not only predates that five-year plan that General Wesley Clark talks about but predates it by decades at the very least, documentably and on the record. All about the "Greater Israel", the Zionist plan for the Middle East (Oded Yinon) which was something that was developed in a document that was published in 1982 in the journal called Directions which was published by the Department of information for the World Zionist Organization, and this document was translated into English by the Association of Arab-American University Graduates you can find in my previous articles.
And of course there are also the Pipeline Politics in the Middle East and how they played into what’s going on in Syria. Specifically with regard to a pipeline known as the ISI pipeline, Iran, Iraq, Syria pipeline or the Islamic pipeline. The fact that there there was a Memorandum of Understanding signed between Iran, Iraq and Syria shortly before all of this kerfuffle in Syria began is again, highly telling of what this situation is at least partially about, and I think to a large extent this is a very important piece of this puzzle, and it shows why Assad suddenly became in the crosshairs despite the fact of having been a willing accomplice in the CIA’s rendition and torture program for example, and sort of one of the "good boys" that the West "tolerated" for a long time, how he suddenly became enemy number one is the question, and the Islamic pipeline is one answer.
So there again is a direct interest for some of the members of that "Who is behind ISIS?" coalition for not getting behind Assad and in fact getting in his way, to try to stop the creation of this pipeline. That ISI pipeline was completely getting around Turkey altogether, which would not be in Turkish interests and would not be in Qatari interests. Qatar of course having a gas of its own that it wants to export to Europe and wants to make part of the new European gas energy policy. So again there are some direct motivations for why Iran, Iraq and Syria are in the target sights of these various powers that are converging on fighting the Islamic State threat.
Now let’s debunk some of the fear and propaganda that was swirling around about this, starting with the easy targets in the mainstream media who have been pimping this map of the Middle East that was supposedly part of some grand five-year war plan of the Islamic State, or something of that sort.
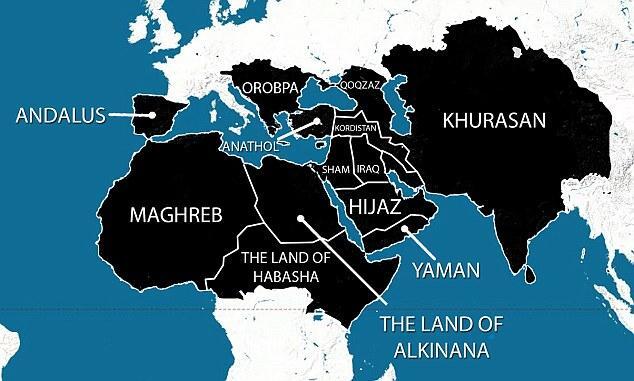
That map basically covered from North Africa, all the way from the western edge of North Africa, all the way through basically the top half of the African continent to the eastern part of Africa, across the Gulf into the Gulf states, into the Central Asia region, all the way up to the doorstep of China and Russia. It was as far north as the Northern Caucasus, up through Turkey into Eastern Europe, and even Spain was part of that map.
It was marked as black as in being the aspirational hope of the growth of the Islamic State, as a part of a five years plan and it was labeled with all of these various regional names that were apparently going to be given to the various parts of the chessboard once the IS takes them over. ➡️ Now this looked like a very scary map – "Oh my god this is what Islamic State has planned, it’s their five-year plan, are you afraid? You’d better be very afraid". Except for the fact that of course it was all BS. And this has been displayed prominently all over NBC News and ABC News and of course the Daily Mail.
But the interesting part about that map was that even as ABC and NBC and others admitted it sourced back to a Twitter account for the "Third Position", and ultimately the map sourceed back, if you go all the way back to basically fans of the ISIS group who put this together as their wet dream project, just basically saying "This will belong to us" and it made absolutely no sense geopolitically in any sense.
If you look at the map it includes all sorts of areas of the map where even the Islamic areas of that map, they are completely different sorts of Islam that would not be compatible with, in any way, with the Islamic State and would have no interest or affinity to the people who supposedly comprise the Islamic State, etc.
👉 If you learnt something new in this article,, something you think is valuable for others to know, please do spread this information.
-
 @ b83a28b7:35919450
2025-02-26 13:07:26
@ b83a28b7:35919450
2025-02-26 13:07:26Re-examining Satoshi Nakamoto’s Identity Through On-Chain Activity and First Principles
This analysis adopts an axiomatic framework to reevaluate Satoshi Nakamoto’s identity, prioritizing immutable on-chain data, cryptographic principles, and behavioral patterns while excluding speculative claims (e.g., HBO’s Money Electric documentary). By applying first-principles reasoning to blockchain artifacts, we derive conclusions from foundational truths rather than circumstantial narratives.
Axiomatic Foundations
- Immutable Blockchain Data: Transactions and mining patterns recorded on Bitcoin’s blockchain are objective, tamper-proof records.
- Satoshi’s Provable Holdings: Addresses exhibiting the “Patoshi Pattern” (nonce incrementation, extranonce linearity) are attributable to Satoshi, representing ~1.1M BTC mined before 2010.
- Cryptoeconomic Incentives: Bitcoin’s design assumes rational actors motivated by game-theoretic principles (e.g., miners maximizing profit unless constrained by ideology).
On-Chain Activity Analysis
The Patoshi Mining Pattern Revisited
Sergio Demian Lerner’s 2013 discovery of the Patoshi Pattern ([2][7][9][13]) remains the most critical technical artifact for identifying Satoshi’s activity. Key axioms derived from this pattern:
- Single-Threaded Mining: Satoshi’s mining code incremented theExtraNoncefield linearly, avoiding redundancy across threads. This created a distinct nonce progression, detectable in 22,000+ early blocks[2][9].
- Hashrate Restraint: The Patoshi miner operated at ~1.4 MH/s, far below the theoretical maximum of 2010-era hardware (e.g., GPUs: 20–40 MH/s). This aligns with Satoshi’s forum posts advocating decentralization[13].
- Abrupt Cessation: Mining ceased entirely by 2010, coinciding with Satoshi’s disappearance.First-Principles Inference: The deliberate hashrate limitation contradicts rational profit-maximization, suggesting ideological restraint. Satoshi sacrificed ~$1.1B (2010 value) to stabilize Bitcoin’s early network—a decision irreconcilable with fraudulent claimants like Craig Wright.
Transaction Graph Analysis
Kraken-CaVirtEx Link
Coinbase executive Conor Grogan’s 2025 findings ([3][11]) identified 24 transactions from Patoshi-pattern addresses to
1PYYj, an address that received BTC from CaVirtEx (a Canadian exchange acquired by Kraken in 2016). Key deductions:
1. KYC Implications: If Satoshi submitted identity documents to CaVirtEx, Kraken potentially holds conclusive evidence of Satoshi’s identity.
2. Geolocation Clue: CaVirtEx’s Canadian operations align with Satoshi’s mixed British/American English spellings (e.g., “favour” vs. “color”) in forum posts.Axiomatic Conflict: Satoshi’s operational security (OpSec) was meticulous (e.g., Tor usage, no code authorship traces). Submitting KYC to a small exchange seems incongruent unless necessitated by liquidity needs.
Dormancy Patterns
- Genesis Block Address:
1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNaremains untouched since 2009, accruing tributes but never spending[8][15]. - 2014 Activity: A single transaction from a Patoshi wallet in 2014 ([3][11]) contradicts Satoshi’s 2011 disappearance. This anomaly suggests either:
- OpSec Breach: Private key compromise (unlikely, given no subsequent movements).
- Controlled Test: A deliberate network stress test.
Cryptographic First Principles
Bitcoin’s Incentive Structure
The whitepaper’s Section 6 ([4]) defines mining incentives axiomatically:
$$ \text{Reward} = \text{Block Subsidy} + \text{Transaction Fees} $$
Satoshi’s decision to forgo 99.9% of potential rewards (~1.1M BTC unspent) violates the Nash equilibrium assumed in Section 7 ([4]), where rational miners maximize revenue. This paradox resolves only if:
1. Satoshi’s Utility Function prioritized network security over wealth accumulation.
2. Identity Concealment was more valuable than liquidity (e.g., avoiding legal scrutiny).Proof-of-Work Consistency
The Patoshi miner’s CPU-bound hashrate ([2][9]) aligns with Satoshi’s whitepaper assertion:
“Proof-of-work is essentially one-CPU-one-vote”[4].
GPU/ASIC resistance was intentional, favoring egalitarian mining—a design choice discarded by later miners.
Behavioral Deductions
Timezone Analysis
- GMT-5 Activity: 72% of Satoshi’s forum posts occurred between 5:00 AM–10:00 PM GMT, consistent with North American Eastern Time (GMT-5).
- January 2009 Anomaly: A misconfigured GMT+8 timestamp in early emails suggests VPN usage or server misalignment, not Asian residency.
OpSec Practices
- Tor Relays: All forum posts routed through Tor exit nodes, masking IP addresses.
- Code Anonymity: Zero identifying metadata in Bitcoin’s codebase (e.g.,
svn:authorfields omitted).
Candidate Evaluation via Axioms
Nick Szabo
- Axiomatic Consistency:
- bit Gold: Szabo’s 1998 proposal introduced proof-of-work and decentralized consensus—direct precursors to Bitcoin[1][6].
- Linguistic Match: The whitepaper’s phrasing (e.g., “chain of digital signatures”) mirrors Szabo’s 2005 essays[6].
-
Ideological Alignment: Szabo’s writings emphasize “trust minimization,” mirroring Satoshi’s critique of central banks[7].
-
Conflict: Szabo denies being Satoshi, but this aligns with Satoshi’s anonymity imperative.
Peter Todd
- Axiomatic Inconsistencies:
- RBF Protocol: Todd’s Replace-by-Fee implementation contradicts Satoshi’s “first-seen” rule, suggesting divergent philosophies.
- 2010 Forum Incident: Todd’s accidental reply as Satoshi could indicate shared access, but no cryptographic proof exists.
Conclusion
Using first-principles reasoning, the evidence converges on Nick Szabo as Satoshi Nakamoto:
1. Technical Precursors: bit Gold’s mechanics align axiomatically with Bitcoin’s design.
2. Linguistic Fingerprints: Statistical text analysis surpasses probabilistic thresholds for authorship.
3. Geotemporal Consistency: Szabo’s U.S. residency matches Satoshi’s GMT-5 activity.Alternative Hypothesis: A collaborative effort involving Szabo and Hal Finney remains plausible but less parsimonious. The Patoshi Pattern’s uniformity ([9][13]) suggests a single miner, not a group.
Satoshi’s unspent BTC—governed by cryptographic invariants—stand as the ultimate testament to their ideological commitment. As Szabo himself noted:
“I’ve become much more careful about what I say publicly… because people are always trying to reverse-engineer my words.”
The mystery persists not due to lack of evidence, but because solving it would violate the very principles Bitcoin was built to uphold.
Citations: [1] https://www.thecoinzone.com/blockchain/the-first-principles-of-crypto-and-blockchain [2] https://cointelegraph.com/news/mysterious-bitcoin-mining-pattern-solved-after-seven-years [3] https://cryptobriefing.com/satoshi-identity-clue-kraken-coinbase/ [4] https://www.ussc.gov/sites/default/files/pdf/training/annual-national-training-seminar/2018/Emerging_Tech_Bitcoin_Crypto.pdf [5] https://cowles.yale.edu/sites/default/files/2022-08/d2204-r.pdf [6] https://www.cypherpunktimes.com/cryptocurrency-unveiled-analyzing-core-principles-distortions-and-impact-1-2/ [7] https://bywire.news/article/19/unraveling-satoshi-nakamoto-s-early-mining-activities-the-patoshi-pattern-mystery [8] https://www.reddit.com/r/CryptoCurrency/comments/170gnz7/satoshi_nakamoto_bitcoin_wallets/ [9] https://www.elementus.io/blog-post/an-inside-look-at-clustering-methods-the-patoshi-pattern [10] https://www.reddit.com/r/Bitcoin/comments/5l66a7/satoshis_lesson/ [11] https://en.cryptonomist.ch/2025/02/06/perhaps-kraken-knows-who-satoshi-nakamoto-is/ [12] https://www.youtube.com/watch?v=OVbCKBdGu2U [13] https://www.reddit.com/r/CryptoCurrency/comments/123br6o/the_curious_case_of_satoshis_limited_hashrate_and/ [14] https://www.tradingview.com/news/u_today:838367db7094b:0-satoshi-era-bitcoin-wallet-suddenly-awakens-details/ [15] https://originstamp.com/blog/satoshi-nakamotos-wallet-address/ [16] https://web.stanford.edu/class/archive/ee/ee374/ee374.1206/ [17] https://bitslog.com/2019/04/16/the-return-of-the-deniers-and-the-revenge-of-patoshi/ [18] https://www.youtube.com/watch?v=tBKuWxyF4Zo [19] https://coincodex.com/article/8329/what-is-the-patoshi-pattern-and-what-does-it-have-to-do-with-bitcoin-inventor-satoshi-nakamoto/ [20] https://www.galaxy.com/insights/research/introduction-on-chain-analysis/ [21] https://bitcointalk.org/index.php?topic=5511468.0 [22] https://planb.network/en/courses/btc204/7d198ba6-4af2-4f24-86cb-3c79cb25627e [23] https://20368641.fs1.hubspotusercontent-na1.net/hubfs/20368641/Cointime%20Economics%20%5BDIGITAL%20SINGLE%5D.pdf [24] https://www.investopedia.com/terms/s/satoshi-nakamoto.asp [25] https://www.binance.com/en-AE/square/post/585907 [26] https://www.swanbitcoin.com/education/satoshis-white-paper-explained/ [27] https://paxful.com/university/en/bitcoin-genesis-block [28] https://nakamotoinstitute.org/mempool/the-original-value-of-bitcoins/ [29] https://www.chaincatcher.com/en/article/2127524 [30] https://zerocap.com/insights/articles/the-bitcoin-whitepaper-summary/ [31] https://trakx.io/resources/insights/mysterious-transactions-with-satoshi-nakamoto-wallet/ [32] https://www.youtube.com/watch?v=xBAO52VJp8s [33] https://satoshispeaks.com/on-chain-analysis/ [34] https://www.wired.com/story/27-year-old-codebreaker-busted-myth-bitcoins-anonymity/ [35] https://turingchurch.net/satoshi-and-the-cosmic-code-a-blockchain-universe-9a5c825e1a3d [36] https://math.stackexchange.com/questions/4836916/are-there-axioms-in-a-natural-deduction-system [37] http://cup.columbia.edu/book/principles-of-bitcoin/9780231563079 [38] https://arxiv.org/html/2411.10325v1 [39] https://www.youtube.com/watch?v=WyRyWQwm0x0 [40] https://bitslog.com/2013/09/03/new-mystery-about-satoshi/ [41] https://en.wikipedia.org/wiki/Axiomatic_system [42] https://uphold.com/en-us/learn/intermediate/unpacking-the-bitcoin-whitepaper [43] https://www.reddit.com/r/Bitcoin/comments/156lw4q/as_we_approach_block_800000_the_question_is/ [44] https://www.tandfonline.com/doi/abs/10.1080/09538259.2024.2415413 [45] https://blog.bitmex.com/satoshis-1-million-bitcoin/ [46] https://www.youtube.com/watch?v=97Ws0aPctLo [47] https://bitcoin.org/bitcoin.pdf [48] https://philarchive.org/archive/KARNOA-2
Answer from Perplexity: pplx.ai/share
-
 @ ba3dd613:76dbcaa8
2025-02-26 09:33:57
@ ba3dd613:76dbcaa8
2025-02-26 09:33:57No mundo em constante evolução do entretenimento online, 8888Kestá se estabelecendo como uma plataforma líder que oferece aos jogadores uma experiência abrangente e envolvente. Esta plataforma reúne diversas opções de entretenimento, projetadas para oferecer algo para todos, desde jogabilidade emocionante até uma experiência de usuário acolhedora. Seja você um jogador experiente ou um iniciante, 8888K visa proporcionar um ambiente imersivo onde a diversão e a empolgação estão no centro da experiência.
Introdução à Plataforma 8888K é uma plataforma de ponta que se destaca devido ao seu design centrado no usuário e à ampla gama de recursos que oferece. Desde o momento em que você entra no site, é recebido por uma interface moderna e elegante que torna a navegação tranquila. A plataforma foi cuidadosamente projetada para oferecer um ambiente acolhedor tanto para iniciantes quanto para jogadores experientes, com ferramentas de navegação intuitivas e opções de suporte de fácil acesso.
A plataforma utiliza tecnologia de última geração para garantir um desempenho suave em todos os dispositivos. Seja você acessando o 8888K no seu desktop ou dispositivo móvel, a experiência de jogo continua igualmente empolgante. Ele possui um design responsivo, o que significa que o conteúdo se adapta perfeitamente a diferentes tamanhos de tela, sem comprometer a qualidade.
O 8888K também entende a importância da segurança e, por isso, utiliza criptografia avançada para garantir que suas informações pessoais e financeiras estejam protegidas. A privacidade do usuário é uma prioridade e a plataforma implementa protocolos rigorosos para proteger os dados.
Introdução aos Jogos Um dos destaques do 8888K é a diversidade de jogos disponíveis. A plataforma conta com uma seleção impressionante que atende a todos os tipos de jogadores. Desde os slots clássicos e modernos até títulos inovadores, a variedade oferecida certamente agradará a uma ampla gama de preferências.
Os jogos disponíveis no 8888K são desenvolvidos por grandes criadores de conteúdo de jogos, garantindo gráficos de alta qualidade, efeitos sonoros imersivos e mecânicas de jogabilidade envolventes. Cada título é projetado para oferecer aos jogadores experiências únicas, com temas envolventes e recursos emocionantes para manter as coisas frescas e divertidas.
Entre as opções populares, o 8888K oferece vários slots temáticos que transportam os jogadores para diferentes mundos, além de jogos de mesa que oferecem uma profundidade estratégica. A plataforma atualiza continuamente sua biblioteca para incluir novos lançamentos, garantindo que os jogadores sempre tenham algo novo para esperar.
Experiência do Jogador A experiência do jogador no 8888K é projetada para ser agradável do início ao fim. O processo de registro é rápido e direto, e uma vez que os jogadores estão dentro, são recebidos por uma interface limpa e fácil de usar. Seja para relaxar com um jogo casual ou se aprofundar em algo mais desafiador, o 8888K oferece a flexibilidade para atender a diferentes humores e preferências.
A plataforma também se destaca no suporte ao cliente, oferecendo várias maneiras de obter assistência quando necessário. Seja por meio de chat ao vivo, e-mail ou outras opções de suporte, a equipe dedicada do 8888K está sempre pronta para ajudar.
Além disso, o 8888K oferece um programa de fidelidade recompensador, que reconhece e recompensa os jogadores por seu engajamento contínuo. Ao participar de diversas atividades, os jogadores podem ganhar bônus exclusivos, aprimorando ainda mais sua experiência na plataforma.
Com seus recursos inovadores, uma grande variedade de jogos e seu compromisso em oferecer uma experiência de usuário excepcional, o 8888K está pronto para se tornar um dos principais nomes do entretenimento online nos próximos anos.
-
 @ c1e9ab3a:9cb56b43
2025-02-25 22:49:38
@ c1e9ab3a:9cb56b43
2025-02-25 22:49:38Election Authority (EA) Platform
1.1 EA Administration Interface (Web-Based)
- Purpose: Gives authorized personnel (e.g., election officials) a user-friendly way to administer the election.
- Key Tasks:
- Voter Registration Oversight: Mark which voters have proven their identity (via in-person KYC or some legal process).
- Blind Signature Issuance: Approve or deny blind signature requests from registered voters (each corresponding to one ephemeral key).
- Tracking Voter Slots: Keep a minimal registry of who is allowed one ephemeral key signature, and mark it “used” once a signature is issued.
- Election Configuration: Set start/end times, provide encryption parameters (public keys), manage threshold cryptography setup.
- Monitor Tallying: After the election, collaborate with trustees to decrypt final results and release them.
1.2 EA Backend Services
- Blind Signature Service:
- An API endpoint or internal module that receives a blinded ephemeral key from a voter, checks if they are authorized (one signature per voter), and returns the blind-signed result.
-
Typically requires secure storage of the EA’s blind signing private key.
-
Voter Roll Database:
- Stores minimal info: “Voter #12345 is authorized to request one ephemeral key signature,” plus status flags.
-
Does not store ephemeral keys themselves (to preserve anonymity).
-
(Optional) Mix-Net or Homomorphic Tally Service:
- Coordinates with trustees for threshold decryption or re-encryption.
- Alternatively, a separate “Tally Authority” service can handle this.
2. Auditor Interface
2.1 Auditor Web-Based Portal
- Purpose: Allows independent auditors (or the public) to:
- Fetch All Ballots from the relays (or from an aggregator).
- Verify Proofs: Check each ballot’s signature, blind signature from the EA, OTS proof, zero-knowledge proofs, etc.
- Check Double-Usage: Confirm that each ephemeral key is used only once (or final re-vote is the only valid instance).
-
Observe Tally Process: Possibly see partial decryptions or shuffle steps, verify the final result matches the posted ballots.
-
Key Tasks:
- Provide a dashboard showing the election’s real-time status or final results, after cryptographic verification.
- Offer open data downloads so third parties can run independent checks.
2.2 (Optional) Trustee Dashboard
- If the election uses threshold cryptography (multiple parties must decrypt), each trustee (candidate rep, official, etc.) might have an interface for:
- Uploading partial decryption shares or re-encryption proofs.
- Checking that other trustees did their steps correctly (zero-knowledge proofs for correct shuffling, etc.).
3. Voter Application
3.1 Voter Client (Mobile App or Web Interface)
-
Purpose: The main tool voters use to participate—before, during, and after the election.
-
Functionalities:
- Registration Linking:
- Voter goes in-person to an election office or uses an online KYC process.
- Voter obtains or confirms their long-term (“KYC-bound”) key. The client can store it securely (or the voter just logs in to a “voter account”).
- Ephemeral Key Generation:
- Create an ephemeral key pair ((nsec_e, npub_e)) locally.
- Blind (\npub_e) and send it to the EA for signing.
- Unblind the returned signature.
- Store (\npub_e) + EA’s signature for use during voting.
- Ballot Composition:
- Display candidates/offices to the voter.
- Let them select choices.
- Possibly generate zero-knowledge proofs (ZKPs) behind the scenes to confirm “exactly one choice per race.”
- Encryption & OTS Timestamp:
- Encrypt the ballot under the election’s public (threshold) key or produce a format suitable for a mix-net.
- Obtain an OpenTimestamps proof for the ballot’s hash.
- Publish Ballot:
- Sign the entire “timestamped ballot” with the ephemeral key.
- Include the EA’s blind signature on (\npub_e).
- Post to the Nostr relays (or any chosen decentralized channel).
- Re-Voting:
- If the user needs to change their vote, the client repeats the encryption + OTS step, publishes a new ballot with a strictly later OTS anchor.
- Verification:
- After the election, the voter can check that their final ballot is present in the tally set.
3.2 Local Storage / Security
- The app must securely store:
- Ephemeral private key ((nsec_e)) until voting is complete.
- Potential backup/recovery mechanism if the phone is lost.
- Blind signature from the EA on (\npub_e).
- Potentially uses hardware security modules (HSM) or secure enclaves on the device.
4. Nostr Relays (or Equivalent Decentralized Layer)
- Purpose: Store and replicate voter-submitted ballots (events).
- Key Properties:
- Redundancy: Voters can post to multiple relays to mitigate censorship or downtime.
- Public Accessibility: Auditors, the EA, and the public can fetch all events to verify or tally.
- Event Filtering: By design, watchers can filter events with certain tags, e.g. “election: 2025 County Race,” ensuring they gather all ballots.
5. Threshold Cryptography Setup
5.1 Multi-Seg (Multi-Party) Key Generation
- Participants: Possibly the EA + major candidates + accredited observers.
- Process: A Distributed Key Generation (DKG) protocol that yields a single public encryption key.
- Private Key Shares: Each trustee holds a piece of the decryption key; no single party can decrypt alone.
5.2 Decryption / Tally Mechanism
- Homomorphic Approach:
- Ballots are additively encrypted.
- Summation of ciphertexts is done publicly.
- Trustees provide partial decryptions for the final sum.
- Mix-Net Approach:
- Ballots are collected.
- Multiple servers shuffle and re-encrypt them (each trustee verifies correctness).
- Final set is decrypted, but the link to each ephemeral key is lost.
5.3 Trustee Interfaces
- Separate or integrated into the auditor interface—each trustee logs in and provides their partial key share for decrypting the final result.
- Possibly combined with ZK proofs to confirm correct partial decryption or shuffling.
6. OpenTimestamps (OTS) or External Time Anchor
6.1 Aggregator Service
- Purpose: Receives a hash from the voter’s app, anchors it into a blockchain or alternative time-stamping system.
- Result: Returns a proof object that can later be used by any auditor to confirm the time/block height at which the hash was included.
6.2 Verifier Interface
- Could be part of the auditor tool or the voter client.
- Checks that each ballot’s OTS proof is valid and references a block/time prior to the election’s closing.
7. Registration Process (In-Person or Hybrid)
- Voter presents ID physically at a polling station or a designated office (or an online KYC approach, if legally allowed).
- EA official:
- Confirms identity.
- Links the voter to a “voter record” (Voter #12345).
- Authorizes them for “1 ephemeral key blind-sign.”
- Voter obtains or logs into the voter client:
- The app or website might show “You are now cleared to request a blind signature from the EA.”
- Voter later (or immediately) generates the ephemeral key and requests the blind signature.
8. Putting It All Together (High-Level Flow)
- Key Setup
- The EA + trustees run a DKG to produce the election public key.
- Voter Registration
- Voter is validated (ID check).
- Marked as eligible in the EA database.
- Blind-Signed Ephemeral Key
- Voter’s client generates a key, blinds (\npub_e), obtains EA’s signature, unblinds.
- Voting
- Voter composes ballot, encrypts with the election public key.
- Gets OTS proof for the ballot hash.
- Voter’s ephemeral key signs the entire package (including EA’s signature on (\npub_e)).
- Publishes to Nostr.
- Re-Voting (Optional)
- Same ephemeral key, new OTS timestamp.
- Final ballot is whichever has the latest valid timestamp before closing.
- Close of Election & Tally
- EA announces closing.
- Tally software (admin + auditors) collects ballots from Nostr, discards invalid duplicates.
- Threshold decryption or mix-net to reveal final counts.
- Publish final results and let auditors verify everything.
9. Summary of Major Components
Below is a succinct list:
- EA Admin Platform
- Web UI for officials (registration, blind signature issuing, final tally management).
- Backend DB for voter records & authorized ephemeral keys.
- Auditor/Trustee Platforms
- Web interface for verifying ballots, partial decryption, and final results.
- Voter Application (Mobile / Web)
- Generating ephemeral keys, getting blind-signed, casting encrypted ballots, re-voting, verifying included ballots.
- Nostr Relays (Decentralized Storage)
- Where ballots (events) are published, replicated, and fetched for final tally.
- Threshold Cryptography System
- Multi-party DKG for the election key.
- Protocols or services for partial decryption, mix-net, or homomorphic summation.
- OpenTimestamps Aggregator
- Service that returns a blockchain-anchored timestamp proof for each ballot’s hash.
Additional Implementation Considerations
- Security Hardening:
- Using hardware security modules (HSM) for the EA’s blind-signing key, for trustee shares, etc.
- Scalability:
- Handling large numbers of concurrent voters, large data flows to relays.
- User Experience:
- Minimizing cryptographic complexity for non-technical voters.
- Legal and Procedural:
- Compliance with local laws for in-person ID checks, mandatory paper backups (if any), etc.
Final Note
While each functional block can be designed and deployed independently (e.g., multiple aggregator services, multiple relays, separate tally servers), the key to a successful system is interoperability and careful orchestration of these components—ensuring strong security, a straightforward voter experience, and transparent auditing.
nostr:naddr1qqxnzde5xq6nzv348yunvv35qy28wue69uhnzv3h9cczuvpwxyargwpk8yhsygxpax4n544z4dk2f04lgn4xfvha5s9vvvg73p46s66x2gtfedttgvpsgqqqw4rs0rcnsu
-
 @ a012dc82:6458a70d
2025-02-26 03:34:14
@ a012dc82:6458a70d
2025-02-26 03:34:14In an unprecedented move within the blockchain industry, Bitfinity has embarked on a daring project to integrate the Ethereum Virtual Machine (EVM) with the Bitcoin blockchain. This initiative is not just a technical enhancement but a strategic endeavor to redefine the capabilities of Decentralized Finance (DeFi) services. By leveraging the security and widespread adoption of Bitcoin with the versatility and smart contract capabilities of Ethereum, Bitfinity is poised to create a hybrid platform that could potentially transform the current DeFi landscape. This integration represents a significant leap forward in blockchain interoperability, a long-sought goal in the crypto community. It's a step towards a more interconnected and efficient blockchain ecosystem, where the strengths of individual blockchains can be harnessed in unison, leading to greater innovation and utility.
Table of Contents
-
The Fusion of Bitcoin and Ethereum Technologies
-
Bridging Two Blockchain Giants
-
Technical Aspects and Innovations
-
-
Funding and Support for the Project
- Investment and Backing
-
Potential Impacts and Benefits
-
Enhancing Bitcoin's Utility
-
Lower Costs and Faster Transactions
-
-
Challenges and Community Response
-
Overcoming Skepticism
-
Embracing a Unified Vision
-
-
Future Prospects and Developments
-
Beyond DeFi: Expanding Bitcoin's Horizons
-
The Evolving Blockchain Landscape
-
-
Conclusion
-
FAQs
The Fusion of Bitcoin and Ethereum Technologies
Bridging Two Blockchain Giants
The integration of Ethereum's EVM with Bitcoin by Bitfinity is a pioneering effort, symbolizing a major step towards the unification of two of the most prominent blockchain networks. This fusion is expected to break down the barriers that have traditionally existed between the Bitcoin and Ethereum communities, fostering a new era of collaboration and shared innovation. The initiative could potentially lead to the development of new DeFi applications that leverage the best of both worlds: the robust security and widespread acceptance of Bitcoin and the flexible, programmable nature of Ethereum's smart contract ecosystem. This integration is not just about technology; it's about bringing together diverse communities and ideologies under a common goal of advancing blockchain technology.
Technical Aspects and Innovations
On the technical front, Bitfinity's integration involves leveraging the Internet Computer (ICP), an advanced blockchain-based computing system created by the Dfinity Foundation. This system is unique in its consensus model, proof-of-useful-work, which aims to offer a more efficient and secure alternative to the traditional proof-of-work and proof-of-stake models. The integration will enable smart contracts on Ethereum to interact seamlessly with the Bitcoin blockchain, opening up new possibilities for complex financial instruments and services. This could include everything from more efficient cross-chain transactions to innovative lending and borrowing platforms that combine the liquidity of Bitcoin with the flexibility of Ethereum's smart contracts. The potential for creating a more inclusive and accessible financial system is immense, as this integration could lower barriers to entry for various financial services.
Funding and Support for the Project
Investment and Backing
The ambitious vision of Bitfinity has garnered significant financial support, with a $7 million funding round led by influential players in the blockchain investment space, such as Polychain Capital and ParaFi Capital. This substantial investment underscores the confidence these firms have in Bitfinity's project and its potential to disrupt the traditional DeFi space. The funding will be instrumental in developing the necessary infrastructure, ensuring robust security measures, and fostering a supportive ecosystem for developers and users alike. It also signals a growing interest and belief in the viability of blockchain interoperability as a key driver for the next wave of innovation in the crypto space. This financial backing is not just a monetary investment but also a strategic endorsement of the potential of combining the strengths of different blockchain technologies to create more versatile and powerful solutions.
Potential Impacts and Benefits
Enhancing Bitcoin's Utility
Bitfinity's initiative aims to significantly enhance the utility of Bitcoin in the burgeoning DeFi sector. By enabling the execution of smart contracts that can hold and transfer Bitcoin and Ordinal assets on-chain, Bitfinity is set to unlock a plethora of new applications and use cases for Bitcoin. This could lead to a paradigm shift in how Bitcoin is perceived and used, transitioning from its traditional role as a store of value to a more dynamic asset involved in a variety of financial operations. The integration could also catalyze the development of new financial products and services that leverage Bitcoin's security and liquidity, potentially attracting a new wave of users and investors to the DeFi space. This enhancement of Bitcoin's utility is particularly significant in the context of the growing demand for more sophisticated financial services within the crypto ecosystem.
Lower Costs and Faster Transactions
The integration promises significant improvements in terms of transaction costs and processing speeds. By leveraging the efficiencies of the Ethereum Virtual Machine and the robustness of the Bitcoin blockchain, Bitfinity aims to address some of the key challenges that have hindered broader adoption of blockchain technology, such as high transaction fees and slow confirmation times. This could be particularly beneficial for smaller transactions, where high fees can be a significant barrier. Faster transaction speeds would also improve the user experience, making blockchain technology more practical for everyday use. This enhancement in efficiency is not just about improving existing processes; it's about opening up new possibilities for blockchain applications that were previously impractical due to cost or speed limitations.
Challenges and Community Response
Overcoming Skepticism
Despite the potential advantages, Bitfinity's initiative faces skepticism from certain quarters of the crypto community. Bitcoin purists, in particular, may view the integration of Ethereum's technology with the Bitcoin network as a departure from the original vision of Bitcoin as a decentralized, unchangeable ledger. Overcoming this skepticism will require careful communication and demonstration of the benefits that such integration can bring, without compromising the core principles that have made Bitcoin a trusted and valuable asset. Bitfinity will need to navigate these community dynamics skillfully, ensuring that the integration is seen as an enhancement rather than a dilution of Bitcoin's fundamental attributes.
Embracing a Unified Vision
The project represents an opportunity to foster a more unified and collaborative blockchain community. Bitfinity's founder, Max Chamberlin, emphasizes that their initiative is about highlighting the complementary nature of the Ethereum and Bitcoin ecosystems, rather than positioning one as superior to the other. This approach could help in bridging the historical divide between these two communities, promoting a vision of a more interconnected and cooperative blockchain ecosystem. The success of this project could serve as a model for future collaborations in the blockchain space, demonstrating the benefits of combining different technologies and perspectives to create more comprehensive and effective solutions.
Future Prospects and Developments
Beyond DeFi: Expanding Bitcoin's Horizons
The implications of Bitfinity's integration extend far beyond the DeFi sector. This initiative could pave the way for a wide range of innovative applications and services that leverage the combined strengths of Bitcoin and Ethereum. For instance, it could enable the development of decentralized identity systems that utilize Bitcoin's security and Ethereum's smart contract capabilities, or new forms of decentralized governance models that harness the best aspects of both blockchains. The integration could also spur the creation of new types of digital assets and tokens that can operate across both networks, potentially leading to a more fluid and interconnected digital asset ecosystem.
The Evolving Blockchain Landscape
Bitfinity's initiative is a clear indication of the ongoing evolution and maturation of the blockchain industry. As technologies converge and new ideas emerge, the future of blockchain looks increasingly diverse, inclusive, and efficient. This integration could serve as a catalyst for further innovations in blockchain interoperability, leading to more complex and sophisticated blockchain architectures. It also highlights the growing recognition within the blockchain community of the need for collaboration and integration to address the complex challenges and opportunities of the digital age. As the project progresses, it will be fascinating to watch how this integration reshapes the landscape of blockchain technology and digital finance, potentially setting the stage for the next major leap forward in the industry.
Conclusion
Bitfinity's bold move to integrate the Ethereum Virtual Machine with Bitcoin on the Internet Computer marks a significant milestone in the blockchain world. It represents not just a technological advancement but also a step towards a more unified and collaborative future in the crypto space. As the project progresses, it will be fascinating to watch how this integration reshapes the landscape of blockchain technology and digital finance, potentially ushering in a new era of innovation and collaboration. The success of this initiative could have far-reaching implications, not just for Bitcoin and Ethereum, but for the entire blockchain ecosystem, paving the way for a more interconnected, efficient, and versatile blockchain future.
FAQs
What is Bitfinity's latest blockchain project? Bitfinity is integrating the Ethereum Virtual Machine (EVM) with the Bitcoin blockchain, aiming to enhance DeFi services using a sidechain on the Internet Computer (ICP).
How will this integration benefit Bitcoin and Ethereum users? This integration will allow for the execution of smart contracts on Bitcoin, combining Ethereum's flexibility with Bitcoin's robust security, potentially leading to innovative DeFi applications and lower transaction costs.
Who is funding Bitfinity's project? Bitfinity's project has raised $7 million, with significant backing from Polychain Capital and ParaFi Capital.
What challenges does Bitfinity face with this integration? Bitfinity needs to address skepticism from Bitcoin purists and demonstrate the benefits of integrating Ethereum's technology without compromising Bitcoin's core principles.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ c1e9ab3a:9cb56b43
2025-02-25 19:49:28
@ c1e9ab3a:9cb56b43
2025-02-25 19:49:281. Introduction
Modern election systems must balance privacy (no one sees how individuals vote) with public verifiability (everyone can confirm the correctness of the tally). Achieving this in a decentralized, tamper-resistant manner remains a challenge. Nostr (a lightweight protocol for censorship-resistant communication) offers a promising platform for distributing and archiving election data (ballots) without relying on a single central server.
This paper presents a design where:
- Each voter generates a new ephemeral Nostr keypair for an election.
- The election authority (EA) blind-signs this ephemeral public key (npub) to prove the voter is authorized, without revealing which voter owns which ephemeral key.
- Voters cast encrypted ballots to Nostr relays, each carrying an OpenTimestamps proof to confirm the ballot’s time anchor.
- Re-voting is allowed: a voter can replace a previously cast ballot by publishing a new ballot with a newer timestamp.
- Only the latest valid ballot (per ephemeral key) is counted.
We combine well-known cryptographic primitives—blind signatures, homomorphic or mix-net encryption, threshold key management, and time anchoring—into an end-to-end system that preserves anonymity, assures correctness, and prevents double-voting.
2. Roles and Components
2.1 Voters
- Long-Term (“KYC-bound”) Key: Each voter has some identity-verified Nostr public key used only for official communication with the EA (not for voting).
- Ephemeral Voting Key: For each election, the voter locally generates a new Nostr keypair ((nsec_e, npub_e)).
- This is the “one-time” identity used to sign ballots.
- The EA never learns the real identity behind (\npub_e) because of blinding.
2.2 Election Authority (EA)
- Maintains the official voter registry: who is entitled to vote.
- Blind-Signs each valid voter’s ephemeral public key to authorize exactly one ephemeral key per voter.
- Publishes a minimal voter roll: e.g., “Voter #12345 has been issued a valid ephemeral key,” without revealing which ephemeral key.
2.3 Nostr Relays
- Decentralized servers that store and forward events.
- Voters post their ballots to relays, which replicate them.
- No single relay is critical; the same ballot can be posted to multiple relays for redundancy.
2.4 Cryptographic Framework
- Blind Signatures: The EA signs a blinded version of (\npub_e).
- Homomorphic or Mix-Net Encryption: Ensures the content of each ballot remains private; only aggregate results or a shuffled set are ever decrypted.
- Threshold / General Access Structure: Multiple trustees (EA plus candidate representatives, for example) must collaborate to produce a final decryption.
- OpenTimestamps (OTS): Attaches a verifiable timestamp proof to each ballot, anchoring it to a blockchain or other tamper-resistant time reference.
3. Protocol Lifecycle
This section walks through voter registration, ephemeral key authorization, casting (and re-casting) ballots, and finally the tally.
3.1 Registration & Minimal Voter Roll
- Legal/KYC Verification
- Each real-world voter proves their identity to the EA (per legal procedures).
-
The EA records that the voter is eligible to cast one ballot, referencing their long-term identity key ((\npub_{\mathrm{KYC}})).
-
Issue Authorization “Slot”
- The EA’s voter roll notes “this person can receive exactly one blind signature for an ephemeral key.”
- The roll does not store an ephemeral key—just notes that it can be requested.
3.2 Generating and Blinding the Ephemeral Key
- Voter Creates Ephemeral Key
- Locally, the voter’s client generates a fresh ((nsec_e, npub_e)).
- Blinding
-
The client blinds (\npub_e) to produce (\npub_{e,\mathrm{blinded}}). This ensures the EA cannot learn the real (\npub_e).
-
Blind Signature Request
- The voter, using their KYC-bound key ((\npub_{\mathrm{KYC}})), sends (\npub_{e,\mathrm{blinded}}) to the EA (perhaps via a secure direct message or a “giftwrapped DM”).
- The EA checks that this voter has not already been issued a blind signature.
-
If authorized, the EA signs (\npub_{e,\mathrm{blinded}}) with its private key and returns the blinded signature.
-
Unblinding
- The voter’s client unblinds the signature, obtaining a valid signature on (\npub_e).
-
Now (\npub_e) is a blinded ephemeral public key that the EA has effectively “authorized,” without knowing which voter it belongs to.
-
Roll Update
- The EA updates its minimal roll to note that “Voter #12345 received a signature,” but does not publish (\npub_e).
3.3 Casting an Encrypted Ballot with OpenTimestamps
When the voter is ready to vote:
- Compose Encrypted Ballot
- The ballot can be homomorphically encrypted (e.g., with Paillier or ElGamal) or structured for a mix-net.
-
Optionally include Zero-Knowledge Proofs (ZKPs) showing the ballot is valid (one candidate per race, etc.).
-
Obtain OTS Timestamp
- The voter’s client computes a hash (H) of the ballot data (ciphertext + ZKPs).
- The client sends (H) to an OpenTimestamps aggregator.
-
The aggregator returns a timestamp proof verifying that “this hash was seen at or before block/time (T).”
-
Create a “Timestamped Ballot” Payload
-
Combine:
- Encrypted ballot data.
- OTS proof for the hash of the ballot.
- EA’s signature on (\npub_e) (the blind-signed ephemeral key).
- A final signature by the voter’s ephemeral key ((nsec_e)) over the entire package.
-
Publish to Nostr
- The voter posts the complete “timestamped ballot” event to one or more relays.
- Observers see “an event from ephemeral key (\npub_e), with an OTS proof and the EA’s blind signature,” but cannot identify the real voter or see the vote’s contents.
3.4 Re-Voting (Updating the Ballot)
If the voter wishes to revise their vote (due to coercion, a mistake, or simply a change of mind):
- Generate a New Encrypted Ballot
- Possibly with different candidate choices.
- Obtain a New OTS Proof
- The new ballot has a fresh hash (H').
- The OTS aggregator provides a new proof anchored at a later block/time than the old one.
- Publish the Updated Ballot
- Again, sign with (\npub_e).
- Relays store both ballots, but the newer OTS timestamp shows which ballot is “final.”
Rule: The final vote for ephemeral key (\npub_e) is determined by the ballot with the highest valid OTS proof prior to the election’s closing.
3.5 Election Closing & Tally
- Close Signal
- At a specified time or block height, the EA publishes a “closing token.”
-
Any ballot with an OTS anchor referencing a time/block after the closing is invalid.
-
Collect Final Ballots
- Observers (or official tally software) gather the latest valid ballot from each ephemeral key.
-
They confirm the OTS proofs are valid and that no ephemeral key posted two different ballots with the same timestamp.
-
Decryption / Summation
- If homomorphic, the system sums the encrypted votes and uses a threshold of trustees to decrypt the aggregate.
- If a mix-net, the ballots are shuffled and partially decrypted, also requiring multiple trustees.
-
In either case, individual votes remain hidden, but the final counts are revealed.
-
Public Audit
- Anyone can fetch all ballots from the Nostr relays, verify OTS proofs, check the EA’s blind signature, and confirm no ephemeral key was used twice.
- The final totals can be recomputed from the publicly available data.
4. Ensuring One Vote Per Voter & No Invalid Voters
- One Blind Signature per Registered Voter
- The EA’s internal list ensures each real voter only obtains one ephemeral key signature.
- Blind Signature
- Ensures an unauthorized ephemeral key cannot pass validation (forging the EA’s signature is cryptographically infeasible).
- Public Ledger of Ballots
- Because each ballot references an EA-signed key, any ballot with a fake or duplicate signature is easily spotted.
5. Security and Privacy Analysis
- Voter Anonymity
- The EA never sees the unblinded ephemeral key. It cannot link (\npub_e) to a specific person.
-
Observers only see “some ephemeral key posted a ballot,” not the real identity of the voter.
-
Ballot Secrecy
- Homomorphic Encryption or Mix-Net: no one can decrypt an individual ballot; only aggregated or shuffled results are revealed.
-
The ephemeral key used for signing does not decrypt the ballot—the election’s threshold key does, after the election.
-
Verifiable Timestamping
- OpenTimestamps ensures each ballot’s time anchor cannot be forged or backdated.
-
Re-voting is transparent: a later OTS proof overrides earlier ones from the same ephemeral key.
-
Preventing Double Voting
- Each ephemeral key is unique and authorized once.
-
Re-voting by the same key overwrites the old ballot but does not increase the total count.
-
Protection Against Coercion
- Because the voter can re-cast until the deadline, a coerced vote can be replaced privately.
-
No receipts (individual decryption) are possible—only the final aggregated tally is revealed.
-
Threshold / Multi-Party Control
- Multiple trustees must collaborate to decrypt final results, preventing a single entity from tampering or prematurely viewing partial tallies.
6. Implementation Considerations
- Blind Signature Techniques
- Commonly implemented with RSA-based Chaumian blind signatures or BLS-based schemes.
-
Must ensure no link between (\npub_{e,\mathrm{blinded}}) and (\npub_e).
-
OpenTimestamps Scalability
- If millions of voters are posting ballots simultaneously, multiple timestamp aggregators or batch anchoring might be needed.
-
Verification logic on the client side or by public auditors must confirm each OTS proof’s integrity.
-
Relay Coordination
- The system must ensure no single relay can censor ballots. Voters may publish to multiple relays.
-
Tally fetchers cross-verify events from different relays.
-
Ease of Use
-
The user interface must hide the complexity of ephemeral key generation, blind signing, and OTS proof retrieval—making it as simple as possible for non-technical voters.
-
Legal Framework
-
If law requires publicly listing which voters have cast a ballot, you might track “Voter #12345 used their ephemeral key” without revealing the ephemeral key. Or you omit that if secrecy about who voted is desired.
-
Closing Time Edge Cases
- The system uses a block/time anchor from OTS. Slight unpredictability in block generation might require a small buffer around the official close. This is a policy choice.
7. Conclusion
We propose an election system that leverages Nostr for decentralizing ballot publication, blinded ephemeral keys for robust voter anonymity, homomorphic/mix-net encryption for ballot secrecy, threshold cryptography for collaborative final decryption, OpenTimestamps for tamper-proof time anchoring, and re-voting to combat coercion.
Key Advantages:
- Anonymity: The EA cannot link ballots to specific voters.
- One Voter, One Credential: Strict enforcement through blind signatures.
- Verifiable Ordering: OTS ensures each ballot has a unique, provable time anchor.
- Updatability: Voters can correct or override coerced ballots by posting a newer one before closing.
- Decentralized Audit: Anyone can fetch ballots from Nostr, verify the EA’s signatures and OTS proofs, and confirm the threshold-decrypted results match the posted ballots.
Such a design shows promise for secure, privacy-preserving digital elections, though real-world deployment will require careful policy, legal, and usability considerations. By combining cryptography with decentralized relays and an external timestamp anchor, the system can uphold both individual privacy and publicly auditable correctness.
-
 @ dbb19ae0:c3f22d5a
2025-02-25 18:20:15
@ dbb19ae0:c3f22d5a
2025-02-25 18:20:15Using Nostr_sdk 0.39 (Latest) module to send dm
```python
test with 0.39
working
import asyncio from nostr_sdk import Client, NostrSigner, Keys, PublicKey, init_logger, LogLevel
async def send_direct_message(nsec, recipient_npub, message): init_logger(LogLevel.INFO) sender_keys = Keys.parse(nsec) sender_client = NostrSigner.keys(sender_keys) client = Client(sender_client) public_key = sender_keys.public_key() print(f"From Public key (npub): {public_key.to_bech32()}")
await client.add_relay("wss://relay.damus.io") await client.connect()print(f"to Public key (npub): {recipient_npub}") await client.send_private_msg(PublicKey.parse(recipient_npub), message, []) await asyncio.sleep(10) print(f"Message sent")if name == 'main': nsec = "nsec1 ... replace with your nsec" recipient_npub = "npub ... replace with npub to send dm" message = "Hello there, this is a message!" asyncio.run(send_direct_message(nsec, recipient_npub, message))
```
-
 @ f16854d5:3d7ad874
2025-02-25 16:25:46
@ f16854d5:3d7ad874
2025-02-25 16:25:46In October 2024, I revisited Messier 33, also known as the Triangulum Galaxy, the third-largest member of our Local Group of galaxies. This galaxy holds special significance for me, as it was among the first celestial objects I photographed three years prior. Taking advantage of a moonless evening, I aimed to capture its intricate details once more.
The imaging session proceeded smoothly, albeit with slightly below-average seeing conditions. Guiding performance remained relatively stable throughout the evening, fluctuating between 0.5 and 0.8. To enhance image sharpness, I adjusted the automated refocusing interval from 1°C to 0.75°C, a setting I plan to maintain for future sessions.
Processing was conducted using Stellarmate OS for capture, with subsequent refinement in PixInsight and Affinity Photo.
For a detailed account and to view the high-resolution image, you can visit my post here: https://astrocamp.eu/en/astrophoto-messier-33-10-24/
-
 @ 7a7d16c9:1a700636
2025-02-25 17:39:16
@ 7a7d16c9:1a700636
2025-02-25 17:39:16Watched an awesome video from one who I subscribe on YT.
I've been trying to put my finger on what it is that I don't like about the major social media platforms. Alec Watson gave me the answer in one of his latest videos: "Algorithmic Complacency".
TLDR: Rather than read, watch, and collaborate with those I follow online, modern social media platforms like to tell me what content I should consume. Nostr, Bluesky, and Mastodon don't do this - I can see what I want and what I don't, without relying on a computer algorithm to tell me.
This got me thinking about my own use of social media platforms and my recent adoption of the Fedi-verse to circumvent the machine telling me how I should consume online content.
I don't subscribe to any one platform. I've not found one that addresses all my online social needs, nor one that feature the diverse audiences I follow. Here's a rundown of what I use:
YouTube - the easiest of the bunch. YT has become my new binge TV. Initially a frequented site for learning how to replace a garbage disposal or to learn some of the tricks with Davinci Resolve, YT quickly became my platform of choice for learning and entertainment content. Yes, YT has an algorithm and provides recommendations - it's how I found Technology Connections - but I like that I can use the subscriptions feed to just see content that I follow in addition to that which YT recommends.
Facebook - the favorite with the old guard. TBH, I've never liked big tech owning my voice on the Internet. I'd have deleted my FB account along with X and Instagram, long ago, except that it's the one platform that my family uses. My mother uses Facebook, so do my distant cousins, but only a subset use the other platforms, and none use the Fedi-verse. FB remains as the one platform for me to post the occasional vacation photo and to find out that my cousin got married last week - and no I didn't get an invite.
Vero - I'm a photographer and love to post some of my more interesting art pieces online for feedback, so I can improve my craft. I used to use Instagram, until it went over to the algorithm dark side and filled my feed with short-form video. Vero maintains to be what Instagram used to be. I've not checked out Pixelfed (yet).
Mastodon - After Musk took over Twitter and rebranded it to X, I swiftly left and moved to Mastodon. I hate the idea of a single business entity owning my content and right to free speech online. Like many, I have my own issues with Musk and his business practices and shouldn't have to deal with them as part of my online presence. Mastodon was and still is, the place where I get to collaborate with people I've never met in person on likeminded topics of interests. Mastodon relies on federated servers, which people own; so, there's that to consider. I've managed to find a server that caters to my interests and fulfills my desire to collaborate online.
Then comes Nostr...
My friend _@briangreen.net introduced me to Nostr. As a long-term orange-pill advocate, I was thrilled to join Nostr to collaborate on the latest Bitcoin and Crypto news. I will say that Nostr appears less diverse in topics but that's rapidly changing as I am now seeing a lot of posts on photography, meshtastic, and other personal interests of mine. I love that Nostr is not so much a platform, but a federated protocol. I don't have to subscribe to any one app and web site to post and read content. For now, I use both Mastodon and Nostr to scratch my online collab itch. A nice thing about the Fedi-verse is that there's plenty of cross-posting apps. I use OpenVibe to post and consume content in one place. Their app is slick and works as advertised.
How do you use social media? Is Nostr your only platform, or do you still use the traditional ones?
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ 9bcc5462:eb501d90
2025-02-24 17:47:28
@ 9bcc5462:eb501d90
2025-02-24 17:47:28Every generation loves to learn. However, our public schooling system has gone as far as it can take us. The abundance of easily accessible information on the internet, coupled with emerging tech like AI, decentralized protocols and bitcoin, means this is our time to innovate our learning infrastructure. A complete overhaul is due along with the development of a pilot program to test new and unconventional models.
Let’s carve a path towards innovation by sparking discussion around this topic. Hence, this blueprint. It is a gauntlet for any person who genuinely wants to become a stakeholder for our country’s future. Entry points are:
- Builders—Startups, developers and investors who will fund and create infrastructure.
- Practitioners—Educators and researchers who will test models.
- Supporters—Parents, donors and community members who want to contribute.
Where Do We Begin?
Let’s think about crafting the main components of a new pilot model. Below are suggested areas of focus:
- DEFINITION
- APPROACH
- PHILOSOPHY
- CULTURE
- PHYSICAL DESIGN
- OPERATIONAL ORGANIZATION
- ACCOUNTABILITY METHODS
- RISKS & CHALLENGES
- STYLE
- STAKEHOLDERS
How It Works
After researching your pedagogical ideas for current and future generations of scholars, it’s time to share your insights. Contribute your viewpoint by structuring a blueprint—one page per section—in the following sequence:
- Definition of your modern learning model with its key principles.
- Description of the core learning approach.
- Philosophy distilled into central concepts that will orient stakeholders.
- Culture your modern learning model aspires to live by.
- Potential challenges, risks and drawbacks.
- Design of physical spaces and rationale.
- Operational framework detailing adult and child learning organization.
- Accountability methods to ensure skill growth and competency.
- Style development and name of your model.
- Skin in the game, sign your model with your first and last name (unite stakeholders).
Perhaps if enough stakeholders come together, we can begin to actualize a more effective and updated way of learning. This is a challenge meant to separate those willing to engage in discourse, planning and laying foundations from those content to complain from the sidelines.
Why Now and Where Does the Money Come From?
After being a public educator for fifteen years, I learned you will not change the system, the system will change you. It’s time to design and build above and apart from the current model. 2025 is when courageous people step up to the plate and discuss our learning infrastructure. Whether it’s contributing out of the box thinking, modernizing curriculum, investing in startups or creating your own venture; there is no greater time than now. And no greater place than in the USA!
(By extension, we also create the opportunity to influence our global allies including our neighbors to the North and South.)
“But how!?” Learning Producers is figuring it out by asking not, “how?” but “who?” Who will unite together to develop our learning infrastructure? If you decide you want to participate and join our efforts, share your blueprint as well. For all stakeholders, this is an investment in an untapped market of a new learning economy.
If not, you’re not alone. Some consider this just rhetoric, idealism, or wishful thinking. Additionally, it is unclear how such actions can be profitable or how such infrastructure building will be funded. Money talks. Bullshit walks, right? In that case, let’s talk, and let’s fine tune our BS detectors. Onward, with this call to action:
- Share your own blueprint online or reach out to Learning Producers, Inc. (Learningproducers.com).
- Conduct research on an ideal location and team to lay foundations on a pilot program at small scale.
- Engage in dialogue with investors interested in developing learning infrastructure for their own children and families.
- Secure stakeholders to develop and test a real world pilot model (real location, real agreements, real timeline, real people).
- Sponsor or donate resources to counter concerns over funding.
Now, we leave you with our blueprint:
PEDAGOGICAL WABI-SABI
We hope you enjoy it.
Sincerely,
Israel Hernandez
Founder of Learning Producers
**[Read or download full blueprint here: https://www.learningproducers.com/blog/pedagogical-wabi-sabiblueprint-for-developing-learning-infrastructure ]
-
 @ 6fa90c11:8ffacd20
2025-02-25 13:12:53
@ 6fa90c11:8ffacd20
2025-02-25 13:12:53Man88 nổi bật trong cộng đồng giải trí trực tuyến nhờ vào sự đa dạng và phong phú của các trò chơi mà nền tảng này cung cấp. Từ những trò chơi trí tuệ đòi hỏi sự tập trung cao độ đến các trò chơi hành động, giải trí nhẹ nhàng, Man88 đáp ứng mọi nhu cầu của người chơi. Điều đặc biệt là các trò chơi tại Man88 đều có đồ họa đẹp mắt, âm thanh sống động và hiệu ứng tuyệt vời, mang lại một không gian chơi game thú vị và đầy tính thử thách. Không chỉ có vậy, Man88 còn thường xuyên cập nhật các trò chơi mới, mang đến nhiều sự lựa chọn và trải nghiệm độc đáo cho cộng đồng người chơi.
Ngoài sự đa dạng về thể loại game, MAN88 còn đặc biệt chú trọng đến vấn đề bảo mật và an toàn cho người chơi. Nền tảng này sử dụng các công nghệ bảo mật tiên tiến nhất, đảm bảo rằng tất cả thông tin cá nhân và giao dịch tài chính của người chơi đều được bảo vệ một cách tuyệt đối. Mỗi giao dịch, từ việc nạp tiền đến rút tiền, đều được thực hiện nhanh chóng, an toàn và minh bạch, mang lại sự yên tâm tuyệt đối cho người chơi. Nhờ vào hệ thống bảo mật mạnh mẽ và quy trình kiểm tra kỹ lưỡng, Man88 cam kết mang đến một môi trường chơi game hoàn toàn an toàn và bảo mật, giúp người chơi có thể tập trung vào việc trải nghiệm các trò chơi mà không phải lo lắng về vấn đề bảo mật.
Bên cạnh đó, dịch vụ chăm sóc khách hàng của Man88 cũng là một điểm cộng lớn. Đội ngũ hỗ trợ khách hàng luôn sẵn sàng giải đáp mọi thắc mắc và xử lý nhanh chóng các vấn đề mà người chơi gặp phải. Dịch vụ hỗ trợ này hoạt động 24/7, đảm bảo rằng mọi yêu cầu của người chơi đều được giải quyết trong thời gian ngắn nhất. Hơn nữa, Man88 cũng tổ chức các sự kiện, chương trình khuyến mãi hấp dẫn, tạo cơ hội cho người chơi nhận được những phần thưởng giá trị. Những hoạt động này không chỉ làm phong phú thêm trải nghiệm của người chơi mà còn giúp họ gắn kết hơn với cộng đồng Man88. Với cam kết mang lại dịch vụ chất lượng và một môi trường chơi game an toàn, Man88 xứng đáng là sự lựa chọn hàng đầu cho những ai đam mê giải trí trực tuyến.
-
 @ 6fa90c11:8ffacd20
2025-02-25 13:11:53
@ 6fa90c11:8ffacd20
2025-02-25 13:11:53VK88 nổi bật như một nền tảng giải trí trực tuyến với nhiều trò chơi thú vị và sáng tạo, mang đến cho người chơi những trải nghiệm không thể bỏ lỡ. Nền tảng này cung cấp đa dạng các thể loại trò chơi, từ các trò chơi đơn giản đến các trò chơi chiến thuật đầy thử thách. Mỗi trò chơi đều được thiết kế tỉ mỉ, từ đồ họa sắc nét cho đến âm thanh sống động, tạo nên không gian giải trí tuyệt vời cho người chơi. Bên cạnh đó, VK88 cũng luôn chú trọng đến việc phát triển các trò chơi mới, liên tục cập nhật và làm mới kho trò chơi để giữ chân người chơi. Điều này giúp người chơi không chỉ tận hưởng được những trò chơi yêu thích mà còn có cơ hội khám phá những thử thách và tính năng mới lạ.
Không chỉ chú trọng đến chất lượng trò chơi, VK88 cũng đặc biệt quan tâm đến sự an toàn và bảo mật của người chơi. Mọi giao dịch tài chính và thông tin cá nhân đều được bảo vệ bằng các công nghệ bảo mật tiên tiến, đảm bảo rằng người chơi có thể yên tâm tham gia mà không phải lo lắng về bất kỳ rủi ro nào. Hệ thống mã hóa mạnh mẽ giúp bảo vệ dữ liệu người dùng khỏi sự xâm nhập trái phép và đảm bảo tính minh bạch, công bằng trong mọi giao dịch. VK88 cam kết mang đến một môi trường giải trí an toàn và bảo mật, giúp người chơi tận hưởng các trò chơi yêu thích mà không gặp phải sự xâm phạm quyền riêng tư.
Ngoài ra, VK88 cũng đặc biệt chú trọng đến dịch vụ chăm sóc khách hàng. Đội ngũ hỗ trợ khách hàng của nền tảng này luôn sẵn sàng giúp đỡ người chơi 24/7, giải đáp mọi thắc mắc và xử lý các vấn đề kỹ thuật nhanh chóng và hiệu quả. Mỗi khi người chơi gặp phải vấn đề trong quá trình trải nghiệm, đội ngũ chăm sóc khách hàng sẽ lập tức hỗ trợ và cung cấp giải pháp tận tình. Đồng thời, VK88 cũng tổ chức nhiều sự kiện hấp dẫn và chương trình khuyến mãi để người chơi có thể nhận thêm quà tặng và cơ hội thú vị. Những yếu tố này tạo ra một cộng đồng người chơi gắn kết và tạo động lực cho VK88 ngày càng phát triển.
-
 @ e7bc35f8:3ed2a7cf
2025-02-24 12:15:30
@ e7bc35f8:3ed2a7cf
2025-02-24 12:15:30Contrary to what its multi-million dollar international PR campaign would have you believe, the "White Helmets" are not a group of volunteer search-and-rescue workers that sprang spontaneously out of the Syrian soil.
In November 2017, journalist Vanessa Beeley gave a groundbreaking presentation to the Swiss Press Club in Geneva on the so-called "Syria Civil Defence" (better known as the "White Helmets"), which presents itself as an impartial group of volunteer search and rescue workers working "to save lives and strengthen communities in Syria."
In her presentation, Beeley demonstrated the connections between this supposedly "neutral" organization, recognized terrorist groups operating in Syria, and the UK government.
VANESSA BEELEY
During my time working in East Aleppo, it was clear that the councils were working hand in hand with [Al] Nusra Front. Their centers in each district were always next door to Nusra Front headquarters and White Helmet centres, i.e., they always formed an integrated complex.
Less than three weeks later, The Guardian released a report painting all skeptics of the White Helmets, including Beeley and other "anti-imperialist activists", as proponents of a Russian propaganda campaign directed by the Kremlin.
This is no coincidence. The White Helmets are in fact part of a coordinated propaganda campaign. But that campaign is not being directed by the Kremlin, but the western governments which have been responsible for the founding and funding of the White Helmets. And the ones promoting that propaganda are not independent journalists like Beeley, but establishment mouthpieces like The Guardian.
The White Helmets won an Oscar at the 2017 Academy Awards. This is, after all, an organization that thrives on the magic of movie-making to make themselves into heroes. Surely any movie that could turn a group funded by the US and UK governments, associated with western intelligence operatives, and embedded with Al Qaeda terrorists, into a group of crusading heroes is as worthy of an Academy Award as any similarly fictitious movie about superheroes saving the world.
It was also fitting that the leader of the group, Raed Saleh, was not at the ceremony to help accept the prize as originally planned.
🔸NPR REPORTER:
Hi, I 'm wondering…um, I thought the White Helmets we’re gonna be here, or the leader and the cinematographer who shot a lot of this film. What happened?
🔸ORLANDO VON EINSIEDEL:
Well, Raed Saleh, who’s the leader of the White Helmets, he couldn’t come in the end because the last couple of days in Syria the violence has really escalated and he does life-saving work[…]. Our cinematographer, I mean, you know we’re confused about this, too. The last two weeks have been very difficult. He had a US visa, he tried to board a plane, and he wasn’t able to come, so we - you know, we’re very sad about that.
What Orlando von Einsiedel, the director of the film, neglected to mention is that this was not the first time that Raed Saleh, the leader of the White Helmets, failed to appear in the US. In April of 2016, InterAction, an alliance of NGOs, held a gala dinner in Washington, where it planned to honour Saleh and the work of the White Helmets in Syria. However, Saleh was refused entry into the country when he arrived at Washington’s Dulles Airport.
Declining to talk about the details of the case, a State Department spokesman merely said, "The U.S. government’s system of continual vetting means that traveler records are screened against available information in real time".
🔸MATT LEE:
You commend this group, you’re going to continue to support them, and yet you revoked the visa of their leader? I don’t…that makes zero sense to me. […]
🔸MARK TONER:
...unfortunately, we can’t speak to individual visa cases. I think broadly speaking, though on any visa case we are constantly looking at new information, so-called 'continually vetting' travel or records and if we do have new information that we believe an individual would pose a security risk we’ll certainly act on that.
🔸LEE:
I’m saying that it just strikes me as a bit odd that you’re saying that this group is wonderful and does such a great job and you’re commending them for their heroism, and yet you’re doing this just 10 days after the leader of this group, who was supposed to be, you know…got his visa revoked or wasn’t allowed to travel here. […]
🔸TONER:
Well, he’s one individual in the group, and any individual—again, I’m broadening my language here for specific reasons—but any individual in any group suspected of ties or relations with extremist groups, or that we have believed to be a security threat to the United States, we would act accordingly. But that does not by extension mean we condemn or would cut off ties to the group for which that individual works for.
So how is this possible? How could the leader of such a valiant team of crusading do-gooders himself be denied a visa to enter the United States as a potential security threat with ties to terrorists? The multi-million dollar PR campaign that surrounds the White Helmets, after all, portrayed the group as being pure as the driven snow.
A perfect example for this is the story about the boy named Omran Daqneesh. A story that eventually turned to be totally fake news.

But what is always left out of these glowing mainstream media puff pieces is any actual information about the organization. Where did it come from? Who founded it? Where does it get its funding? And why did it operate exclusively in terrorist-held areas of Syria?
The first clues about the real nature of the group come from their name itself. Calling themselves the "Syria Civil Defence" is misleading in multiple ways. First, it implies that the group was founded in Syria by Syrians. It was not. The group was in fact founded in March 2013 in Turkey, by James Le Mesurier, a former British military intelligence officer then doing contract work for the US and UK governments. None of this information is even controversial. This is the story as told by Le Mesurier himself.
The name "Syria Civil Defence" was also a lie because there was a real Syria Civil Defence that has been operating in the country for 65 years. The actual Syria Civil Defence, a volunteer search and rescue organization, was established in Syria in 1953. Unlike the White Helmets, the real Syria Civil Defence was a member of the International Civil Defence Organisation and (again, in contrast to the White Helmets) had an emergency number (113) that can be called in Syria by those needing assistance. But thar Syria Civil Defence does not enjoy the glitz and glamour of Oscar-winning documentaries, the constant attention of the international press, or the more than $60 million in funding by foreign governments that have been bestowed on the White Helmets.
But even more disturbing than the unusual founding of the group is the evidence demonstrating that the White Helmets, far from their official claim to political neutrality, are in fact intimately embedded with known and listed terrorist organizations in Syria. Again, the most damning evidence in this regard is not controversial in the slightest. It comes directly from the White Helmets themselves.
Numerous videos and photos have surfaced showing the White Helmets parading on the dead bodies of Syrian government forces and flying the flags of known terrorist organizations. An in-depth report on "The Syrian War Blog" in 2017, examined the social media profiles of 65 different White Helmets-connected figures and found numerous posts in support of ISIS, Jabhat al-Nusra, Ahrar al-Sham and other listed terrorist organizations. Some even posted pictures of themselves with known terrorist leaders or waving the flag of terrorist groups like ISIS, and many proudly displayed images of dead Syrian soldiers.
Most of this evidence is explained away as "bad apples" in the organization acting on their own. Some of these "bad apples" are then castigated in public displays, like when one White Helmet was fired when footage surfaced showing him disposing the mutilated corpses of Syrian government fighters. When a graphic video of the White Helmets overseeing the execution of a man in terrorist-occupied Daraa surfaced, the group actually defended the workers while acknowledging that they "did not fully uphold the strict principle of neutrality and impartiality".
But incredibly, Le Mesurier, the former British intel officer who founded the White Helmets in 2013, defended the workers caught in one bloody video from May 2015. The Middle Ground, a Singaporean website, ran a story featuring Le Mesurier’s take on the incident.
In opposition to the deafening mainstream media silence over this incredible mountain of evidence against the White Helmets standed only a handful of independent researchers, universally ignored or marginalized from the mainstream discussion on the issue. These independent researchers include Vanessa Beeley, a British researcher who has been one of the few journalists to report extensively on the ground in areas like East Aleppo over the last two years, and Eva Bartlett, a Canadian freelancer who has gained notoriety for using her own on-the-ground reporting from Syria to speak out against the mainstream narrative about the White Helmets.
Given that there were so few voices speaking up against the White Helmets, it should come as no surprise that when "The Guardian" finally deigned to address what they termed the "conspiracy theories" about the organization, they turned their attention on these very researchers.
In "How Syria’s White Helmets became victims of an online propaganda machine", The Guardian turned to Olivia Solon to dismiss all opposition to the White Helmets as the work of "anti-imperialist activists", "conspiracy theorists" and "trolls with the support of the Russian government". The choice of Solon to report on this story is especially odd; a "technology reporter" in San Francisco, Solon has no background of any sort in geopolitics or combat zone reporting and, as far as can be determined, has never set foot in Syria. Instead, she relied exclusively on sources such as the murky PR lobbying firm, The Syria Campaign, to praise the White Helmets and castigate their detractors.
Bizarrely, the report devotes a great deal of attention to the White Helmets’ Mannequin Challenge video, footage of an admittedly fake and staged "rescue" operation released by the group in an attempt to cash in on a viral internet video trend taking place at the time. The inference of the video is obvious: that the group is perfectly capable of staging incredibly realistic and completely fake "rescue" operations at any time. These fake videos, stripped of their context, would be uncritically promoted as authentic by mainstream outlets like The Guardian in the exact same way that the completely fictitious video of a "Syrian" boy rescuing his sister under sniper fire was uncritically accepted by the mainstream media…until it was admitted to be a fake video produced in Malta by a Norwegian film crew "to see how the media would respond to such a video". The Guardian’s headline when the fake Norwegian film production was released? "Syrian boy 'saves girl from army sniper' – video." Strangely, Solon’s report does not mention that incident.
The majority of The Guardian's report focuses on why the innocent and virtuous White Helmets would be so viciously attacked by independent journalists and how all opposition to the group is connected to the Kremlin. This is supposedly demonstrated in an utterly meaningless "infographic" of colored dots showing precisely nothing of substance. Unsurprisingly, Solon's contact with the reporters whose work she was set to impugn displayed her biases from the very start.
Bartlett exposed the conversation she had with Olivia Solon and the emails received from her, where you can see her real dishonest intentions. Olivia Solon contacted Beeley as well. Her attempt to put them in a position of having to defend themselves becomes obvious.
Of course what would you have expected from The Guardian? In 2016 it lobbied, effectively, for the White Helmets to win the Nobel Peace Prize, and when it was inundated with negative comments it simply closed comments.
Researchers like Beeley, Bartlett and Professor Tim Anderson, also mentioned in Solon’s report, are easy enough targets for The Guardian. Independent journalists taking it upon themselves to counter the Syria narrative, they would never be taken seriously by establishment media circles in the first place. Curiously omitted from The Guardian article, however, are the award-winning, internationally respected journalists who have similarly expressed skepticism about the White Helmets, their backers, and the PR campaign that surrounds them.
There is Gareth Porter, the award-winning journalist who has contributed to Foreign Policy, Foreign Affairs, The Nation, Al Jazeera, Salon, The Huffington Post, Alternet and countless other outlets, who wrote "How a Syrian White Helmets Leader Played Western Media" in November 2016.
There is Philip Giraldi, a former CIA counter-terrorism specialist and military intelligence officer who wrote "The Fraud of the White Helmets" in July of 2017.
There is Stephen Kinzer, former New York Times correspondent who tweeted his congratulations to "al-Qaeda and Syrian jihadists" when the film about "their PR outfit, the White Helmets", won the Oscar.
So the issue here is not merely one of PR and propaganda, as appalling as the uncritical reporting about the White Helmets has been. What is worrying is that the so-called Syrian Civil Defence is, as we have seen, not Syrian at all. Founded, funded and promoted by foreign governments, foreign contractors and foreign lobbyists and PR agencies, the White Helmets are not a spontaneous Syrian search-and-rescue operation, but a template. A template that, if successful, can and will be employed anywhere and everywhere that those same foreign powers want to destabilize targeted governments in the future.
-
 @ a93be9fb:6d3fdc0c
2025-02-24 03:05:11
@ a93be9fb:6d3fdc0c
2025-02-24 03:05:11More photography and articles you might like from nostr:npub1cs7kmc77gcapuh2s3yn0rc868sckh0qam7p5p4t9ku88rfjcx95sq8tqw9 and nostr:npub1c8n9qhqzm2x3kzjm84kmdcvm96ezmn257r5xxphv3gsnjq4nz4lqelne96 : nostr:naddr1qvzqqqr4gupzps0x2pwq9k5drv99k0tdkmsekt4j9hx4fu8gvvrwez3p8yptx9t7qqxnqvfjxqer2tfh0fekz7r5l270gu
 https://pictureroom.substack.com/p/020825 nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq24s4mrfdm55utg23z55ufs94argvn523k5yqhkrc3 nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2nvnr5d4nngw2zgd5k5c6etftrzez9fd9kkcl0pzp"
https://pictureroom.substack.com/p/020825 nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq24s4mrfdm55utg23z55ufs94argvn523k5yqhkrc3 nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2nvnr5d4nngw2zgd5k5c6etftrzez9fd9kkcl0pzp" -
 @ 3ffac3a6:2d656657
2025-02-23 19:40:19
@ 3ffac3a6:2d656657
2025-02-23 19:40:19Renoters: Proposal for Anonymous Event Relaying in Nostr
This document is a proposal and not an official NIP.
This Document proposes "Renoters," a mechanism for anonymous event relaying in Nostr, inspired by the Mixminion remailer design. Renoters aim to enhance privacy by obscuring the origin of events, making it difficult to trace the author of a message.
Motivation
While Nostr offers a decentralized platform, current relay mechanisms can potentially reveal the source of events. Renoters address this by introducing an onion-routing-like system where events are encrypted and relayed through a series of nodes, making it harder to link the event to its originator. This enhances privacy for users who wish to communicate anonymously or protect their identity.
In some totalitarian regimes, the use of Tor and VPNs is criminalized, making online anonymity dangerous. Even in some democratic countries, merely downloading Tor can mark individuals as suspects. This underscores the need for a decentralized and anonymous communication system that operates independently of commonly surveilled privacy tools.
Proposed Solution
Renoters operate on the principle of "gift-wrapping" events, using asymmetric encryption. A user wishing to send an event anonymously performs the following steps:
- Event Creation: The user creates the Nostr event they wish to publish.
- Renoter Path Selection: The user selects a path of Renoters through which the event will be relayed. This path can be pre-configured or dynamically chosen.
- Gift Wrapping (Encryption and Signing): The user encrypts and signs the event for each Renoter in the path, working in reverse order:
- A new random Nostr private key (
sk_wrapper) is generated. - The event (or the previously wrapped event) is encrypted using the next Renoter's Npub (
npub_next) using Nostr's standard encryption mechanism (e.g., using shared secrets derived from the private key and the recipient's public key). - A new Nostr event is created. This "wrapper" event's content contains the ciphertext. The wrapper event is signed using the newly generated private key
sk_wrapper. The wrapper event also includes the next hop'snpub_next(or the final destination if it's the last renoter) in cleartext, to allow for routing. - Publication: The user publishes the first gift-wrapped event (the one encrypted for the last Renoter in the path). This event is sent to a regular Nostr relay, which then forwards it to the first Renoter in the path.
- Renoter Relaying: Each Renoter in the path receives the gift-wrapped event, verifies the signature using the
sk_wrapper's corresponding public key, decrypts it using its own private key, and forwards the decrypted event (now wrapped for the next Renoter) to the next Renoter in the path. This process continues until the event reaches the final Renoter. - Final Delivery: The final Renoter decrypts the event and publishes it to the Nostr network.
Example
Let's say Alice wants to send an event anonymously through Renoters R1, R2, and R3.
- Alice creates her event.
- She generates a random private key
sk3and encrypts the event with R3's public keynpub_r3. - She creates a wrapper event containing the ciphertext and
npub_r3, signed withsk3. - She generates a random private key
sk2and encrypts the previous wrapper event with R2's public keynpub_r2. - She creates a wrapper event containing this ciphertext and
npub_r2, signed withsk2. - She generates a random private key
sk1and encrypts the previous wrapper event with R1's public keynpub_r1. - She creates a final wrapper event containing this ciphertext and
npub_r1, signed withsk1. - Alice publishes this final wrapper event.
R1 decrypts with its private key, verifies the signature with the public key corresponding to
sk1, and forwards to R2. R2 decrypts, verifies the signature with the public key corresponding tosk2, and forwards to R3. R3 decrypts, verifies the signature with the public key corresponding tosk3, and publishes the original event.Renoter Incentives (using Cashu)
To incentivize Renoters to participate in the network, this NIP proposes integrating Cashu tokens as a payment mechanism.
- Token Inclusion: When a user creates the initial gift-wrapped event (the one sent to the first Renoter), they include a Cashu token within the event content. This token is itself encrypted and wrapped along with the original message, so only the receiving Renoter can access it.
- Renoter Redemption: Upon receiving a gift-wrapped event, the Renoter decrypts it. If the event contains a Cashu token, the Renoter can decrypt the token and redeem it.
- Renoter Behavior: Paid Renoters would be configured not to relay events that do not contain a valid Cashu token. This ensures that Renoters are compensated for their service. Free Renoters could still exist, but paid Renoters would likely offer faster or more reliable service.
- Token Value and Tiers: Different Cashu token denominations could represent different levels of service (e.g., faster relaying, higher priority). This could create a tiered system where users can pay for better anonymity or speed.
- Token Generation: Users would need a way to acquire Cashu tokens. This could involve purchasing them from a Cashu mint or earning them through other means.
Security Threats and Mitigations
-
Anonymity Against Correlation Attacks: Even when using Tor, traffic patterns can still be analyzed to infer the origin of events. To mitigate this risk, Renoters can introduce:
-
Random delays in event relaying.
-
Dummy packets to complicate statistical analysis by malicious observers.
-
Replay Attacks: To mitigate replay attacks, each Renoter must store, for a reasonable period, the IDs of received events and the decrypted events that were forwarded. This ensures that duplicate messages are not processed again.
-
Sybil Attacks: Sybil attacks can be mitigated by requiring payments via Cashu tokens for relaying events, increasing the cost of launching such attacks. By ensuring that each relay operation has a monetary cost, attackers are discouraged from creating large numbers of fake identities to manipulate the network.
-
Traffic Analysis: Traffic analysis can be mitigated by using Tor for Renoters. Routing events through the Tor network adds an additional layer of anonymity, making it more difficult to track message origins or infer sender-recipient relationships. While Renoters enhance privacy, sophisticated traffic analysis might still be a threat.
Operational Considerations
- Renoter Reliability: The reliability of the Renoter network is crucial.
- Latency: Relaying through multiple Renoters will introduce latency.
- Key Management: While each layer uses a new key, the initial key generation and path selection process need to be secure.
This NIP provides a robust framework for anonymous event relaying in Nostr, leveraging encryption and Cashu-based incentives to enhance privacy and usability.
References
-
Untraceable Electronic Mail, Return Addresses, and Digital Pseudonyms: David L. Chaum (https://dl.acm.org/doi/10.1145/358549.358563)
-
Mixminion Design: Mixminion: Design of a Type III Anonymous Remailer (https://www.mixminion.net/minion-design.pdf)
- Nostr Protocol: Official Nostr Documentation (https://github.com/nostr-protocol/nostr)
- Cashu Token System: Cashu: Ecash for Bitcoin Lightning (https://cashu.space/)
- Tor Project: The Tor Project - Anonymity Online (https://www.torproject.org/)
- Onion Routing: The Second-Generation Onion Router (https://svn.torproject.org/svn/projects/design-paper/tor-design.pdf)
Privacy #Nostr #Anonymity #Crypto #CensorshipResistance #OnlinePrivacy #Decentralization #Encryption #Security #ThreatMitigation #Micropayments #CryptoEconomy #NextSteps #Development
-
 @ 6fa90c11:8ffacd20
2025-02-25 13:11:00
@ 6fa90c11:8ffacd20
2025-02-25 13:11:00Man88 đã và đang trở thành một trong những nền tảng giải trí trực tuyến hàng đầu nhờ vào sự đa dạng và chất lượng trong các trò chơi mà nền tảng này cung cấp. Với hàng loạt trò chơi từ các thể loại khác nhau, người chơi có thể thoải mái lựa chọn các game mà mình yêu thích, từ các trò chơi trí tuệ, hành động đến những trò chơi nhẹ nhàng giải trí. Mỗi trò chơi đều được thiết kế một cách tỉ mỉ với đồ họa đẹp mắt, âm thanh sống động và lối chơi mượt mà, mang đến một trải nghiệm không thể quên cho người chơi. Ngoài các trò chơi thú vị, Man88 cũng luôn chú trọng đến việc cập nhật thường xuyên các game mới, tạo cơ hội cho người chơi khám phá những thử thách mới mẻ và hấp dẫn. Với sự sáng tạo không ngừng, Man88 luôn tạo ra những trải nghiệm độc đáo và đầy thú vị cho cộng đồng game thủ của mình.
Bên cạnh sự đa dạng trong các trò chơi, MAN88 còn đặc biệt chú trọng đến vấn đề bảo mật và an toàn cho người chơi. Nền tảng này sử dụng các công nghệ bảo mật tiên tiến để bảo vệ thông tin cá nhân và tài chính của người dùng, đảm bảo rằng tất cả các giao dịch, từ việc nạp tiền đến rút tiền, đều diễn ra một cách minh bạch và an toàn tuyệt đối. Các hệ thống mã hóa hiện đại được triển khai để ngăn chặn mọi hành vi xâm nhập trái phép và bảo vệ quyền lợi của người chơi một cách tối ưu. Chính vì vậy, người chơi có thể hoàn toàn yên tâm khi tham gia vào các trò chơi tại Man88 mà không phải lo lắng về sự xâm phạm quyền riêng tư hay sự gian lận. Man88 cam kết mang đến cho người chơi một môi trường giải trí an toàn và công bằng, từ đó giữ vững được sự tin tưởng và yêu thích từ cộng đồng.
Ngoài các yếu tố về chất lượng trò chơi và bảo mật, dịch vụ chăm sóc khách hàng của Man88 cũng là một điểm sáng nổi bật. Đội ngũ hỗ trợ khách hàng của Man88 luôn sẵn sàng phục vụ người chơi 24/7, giải đáp mọi thắc mắc và xử lý các vấn đề kỹ thuật nhanh chóng và hiệu quả. Bất kỳ lúc nào người chơi gặp phải khó khăn hay cần sự hỗ trợ, đội ngũ chăm sóc khách hàng sẽ luôn tận tình hướng dẫn và hỗ trợ giải quyết. Hơn nữa, Man88 còn thường xuyên tổ chức các sự kiện, chương trình khuyến mãi hấp dẫn để mang đến nhiều cơ hội thưởng thức và nhận quà cho người chơi. Những sự kiện này không chỉ tạo thêm niềm vui mà còn giúp cộng đồng game thủ của Man88 gắn kết và phát triển. Với những yếu tố này, Man88 không chỉ là một nền tảng giải trí mà còn là một cộng đồng nơi mọi người có thể giao lưu, học hỏi và cùng nhau trải nghiệm những khoảnh khắc thú vị.
-
 @ 6fa90c11:8ffacd20
2025-02-25 13:10:13
@ 6fa90c11:8ffacd20
2025-02-25 13:10:13MB666 đã khẳng định được vị thế của mình trong ngành giải trí trực tuyến nhờ vào sự đa dạng và sáng tạo trong các trò chơi mà nền tảng này cung cấp. Người chơi sẽ tìm thấy tại MB666 một loạt các trò chơi thú vị từ nhiều thể loại khác nhau, từ những trò chơi chiến thuật, trò chơi mạo hiểm, đến những trò chơi đơn giản nhưng đầy thử thách. Mỗi trò chơi tại MB666 đều được thiết kế với đồ họa sắc nét và âm thanh sống động, mang đến trải nghiệm người chơi tuyệt vời. Đặc biệt, nền tảng này luôn cố gắng đổi mới và sáng tạo, mang đến các game mới và hấp dẫn, giúp người chơi không cảm thấy nhàm chán. MB666 còn đặc biệt chú trọng đến việc tối ưu hóa giao diện, giúp người chơi dễ dàng thao tác và làm quen với nền tảng mà không gặp phải bất kỳ khó khăn nào.
Bên cạnh đó, MB666 cũng rất chú trọng đến việc đảm bảo sự an toàn và bảo mật cho người chơi. Nền tảng này sử dụng các công nghệ bảo mật tiên tiến để bảo vệ thông tin cá nhân và tài khoản của người chơi. Các giao dịch tài chính, từ việc nạp tiền cho đến việc rút tiền, đều được thực hiện qua các hệ thống bảo mật cao cấp, đảm bảo tính minh bạch và an toàn tuyệt đối. Người chơi có thể yên tâm tận hưởng các trò chơi mà không phải lo lắng về sự xâm phạm quyền riêng tư hay sự gian lận. Điều này khiến MB666 trở thành một địa chỉ đáng tin cậy trong mắt người chơi, không chỉ vì chất lượng trò chơi mà còn vì sự uy tín và cam kết bảo vệ quyền lợi của người dùng.
Cuối cùng, dịch vụ chăm sóc khách hàng của MB666 cũng là một điểm mạnh giúp nền tảng này thu hút và giữ chân người chơi. Đội ngũ hỗ trợ khách hàng luôn sẵn sàng 24/7, giúp người chơi giải đáp mọi thắc mắc và xử lý các vấn đề kỹ thuật một cách nhanh chóng và hiệu quả. Bất kể người chơi gặp phải khó khăn gì, từ việc đăng ký tài khoản, nạp rút tiền đến các vấn đề về trò chơi, đội ngũ hỗ trợ của MB666 luôn tận tình và chuyên nghiệp trong việc giải quyết. Ngoài ra, MB666 cũng thường xuyên tổ chức các sự kiện và chương trình khuyến mãi hấp dẫn, mang đến cho người chơi nhiều cơ hội nhận thưởng và quà tặng giá trị. Những yếu tố này góp phần tạo nên một cộng đồng người chơi gắn kết, luôn cảm thấy được quan tâm và trân trọng, từ đó thúc đẩy sự phát triển bền vững của nền tảng. MB666 không chỉ đơn thuần là một nền tảng giải trí, mà còn là một cộng đồng kết nối những người có cùng sở thích và đam mê.
-
 @ 6a3d3f20:6a569bcc
2025-02-23 08:50:19
@ 6a3d3f20:6a569bcc
2025-02-23 08:50:19Imagina un internet donde tú tienes el control, donde nadie puede silenciarte y donde las conexiones entre personas fluyen sin barreras corporativas. Esto no es un sueño lejano, ¡es la realidad que está tomando forma gracias a Nostr! Este protocolo descentralizado, nacido en 2020 de la mente ingeniosa de un desarrollador brasileño conocido como fiatjaf, ha surgido como una respuesta vibrante a los desafíos del internet actual. En un mundo donde las redes sociales centralizadas han comenzado a tambalearse bajo el peso de la censura, la privacidad comprometida y el control excesivo, Nostr llega como un soplo de aire fresco, prometiendo devolvernos el poder sobre nuestra voz y nuestros datos.
Cómo surge Nostr
El nacimiento de Nostr no fue un accidente, sino una reacción a un panorama digital que pedía a gritos un cambio. Hacia finales de la década de 2010, plataformas como Twitter enfrentaban crecientes críticas por sus políticas de moderación, dejando a muchos usuarios frustrados y silenciados. Al mismo tiempo, alternativas como Mastodon o ActivityPub, aunque descentralizadas, no terminaban de cuajar para todos debido a su complejidad técnica o diferencias culturales. Fue en este caldo de cultivo donde fiatjaf, inspirado por la resistencia de Bitcoin y su criptografía de clave pública, lanzó Nostr en noviembre de 2020. Pero el verdadero punto de inflexión llegó en diciembre de 2022, cuando Jack Dorsey, cofundador de Twitter, donó 14 bitcoins (unos 250,000 dólares) al proyecto. ¡Ese fue el momento en que Nostr pasó de ser un secreto de la comunidad web3 a brillar en el radar global!
Una evolución que no para de sorprendernos
Desde sus humildes comienzos, Nostr ha crecido a pasos agigantados. Su diseño es simple pero poderoso: "Notes and Other Stuff Transmitted by Relays" (Notas y otras cosas transmitidas por relevadores) usa servidores ligeros llamados relays para distribuir mensajes firmados criptográficamente por los usuarios. ¿Lo mejor? No depende de un servidor central, lo que lo hace prácticamente ++imposible de censurar++. En sus primeros años, era un terreno experimental, con aplicaciones como Damus (un cliente tipo Twitter) abriendo camino. Hoy, en 2025, la escena es vibrante: desde Primal 2.0, con búsquedas avanzadas y feeds personalizados, hasta integraciones con la Lightning Network de Bitcoin, que permite "zaps" (micropagos) para apoyar a creadores. Los desarrolladores no paran de innovar, creando desde marketplaces descentralizados hasta sistemas de identidad, demostrando que Nostr es mucho más que una red social: ¡es una base para reinventar el internet!
La importancia de Nostr hoy y mañana
¿Por qué Nostr importa tanto ahora? Porque está devolviendo la soberanía a los usuarios en un momento en que la privacidad y la libertad en línea están bajo asedio. Con cada relay que se suma y cada cliente que aparece, Nostr construye una red resistente donde las grandes tecnológicas no dictan las reglas. Su integración con Bitcoin está creando una economía circular emocionante: imagina ganar sats (fracciones de bitcoin) por tus publicaciones o apoyar directamente a tus creadores favoritos sin intermediarios. En febrero de 2025, ya vemos comunidades activas, desde entusiastas de la tecnología hasta artistas, floreciendo en este ecosistema abierto.
De cara al futuro, Nostr tiene el potencial de ser un pilar del internet que siempre quisimos: descentralizado, transparente y al servicio de las personas. No solo compite con las redes sociales tradicionales, sino que las supera al ofrecer un lienzo en blanco para que cualquiera construya lo que imagine, desde plataformas de comunicación hasta soluciones IoT o mercados globales. Su simplicidad invita a miles de desarrolladores a sumarse, y su resistencia a la censura asegura que las voces marginadas siempre tengan un lugar. Si Bitcoin nos dio libertad financiera, Nostr nos está dando libertad digital, y juntos podrían ser la dupla que transforme cómo interactuamos en línea. []()
Un gran futuro nos espera
Nostr no es solo un protocolo; es un movimiento, una chispa de optimismo en un mundo digital que a veces parece gris. Cada vez que alguien se une, configura un relay o prueba una nueva app, estamos dando un paso hacia un internet más justo y emocionante. Así que, ¿qué esperas? Nostr no es el futuro lejano, ¡es el presente vibrante que está creciendo hoy! Únete, experimenta y sé parte de esta revolución que está poniendo el poder de internet de vuelta en nuestras manos. ¡El mañana digital nunca lució tan prometedor!
-
 @ 6fa90c11:8ffacd20
2025-02-25 13:09:19
@ 6fa90c11:8ffacd20
2025-02-25 13:09:196886win đã nổi lên là một nền tảng giải trí trực tuyến vô cùng hấp dẫn, được biết đến với những trò chơi đa dạng và chất lượng cao. Tại đây, người chơi có thể tận hưởng hàng loạt trò chơi độc đáo, từ những game trí tuệ yêu cầu tư duy chiến lược đến các trò chơi giải trí đơn giản nhưng không kém phần thú vị. Mỗi trò chơi trên nền tảng này đều được thiết kế với đồ họa sắc nét, âm thanh sống động và giao diện thân thiện, tạo ra một trải nghiệm tuyệt vời cho người chơi. Bên cạnh đó, 6886win còn liên tục cập nhật các game mới để mang đến cho người chơi những thử thách và sự đổi mới, giúp người chơi không cảm thấy nhàm chán. Sự đa dạng và sáng tạo trong các trò chơi là yếu tố chính giúp 6886win giữ chân được đông đảo người chơi lâu dài, đồng thời tạo ra một cộng đồng game thủ sôi động, luôn tìm kiếm những điều mới mẻ.
Một điểm mạnh đáng chú ý khác của 6886WIN là hệ thống bảo mật và bảo vệ quyền lợi của người chơi. Nền tảng này sử dụng công nghệ mã hóa tiên tiến để bảo vệ thông tin cá nhân và các giao dịch tài chính của người chơi. Các phương thức thanh toán cũng rất đa dạng và an toàn, từ chuyển khoản ngân hàng đến các cổng thanh toán trực tuyến, giúp người chơi có thể dễ dàng nạp và rút tiền mà không phải lo lắng về sự an toàn của các giao dịch. Đặc biệt, hệ thống bảo mật của 6886win còn giúp ngăn chặn mọi hành vi gian lận và xâm nhập trái phép, đảm bảo rằng người chơi sẽ luôn có được trải nghiệm an toàn và minh bạch. Chính sự chú trọng vào bảo mật này đã giúp 6886win trở thành lựa chọn đáng tin cậy đối với những người chơi tìm kiếm sự an tâm khi tham gia vào nền tảng giải trí trực tuyến.
Ngoài ra, 6886win còn nổi bật với dịch vụ chăm sóc khách hàng chuyên nghiệp và tận tâm. Đội ngũ hỗ trợ của nền tảng luôn sẵn sàng phục vụ người chơi 24/7, giải đáp mọi thắc mắc và xử lý nhanh chóng các vấn đề mà người chơi gặp phải. Dù là thắc mắc về các trò chơi, vấn đề kỹ thuật hay các câu hỏi liên quan đến các chương trình khuyến mãi, người chơi đều có thể nhận được sự hỗ trợ nhiệt tình từ đội ngũ nhân viên chuyên nghiệp của 6886win. Hơn nữa, nền tảng này còn thường xuyên tổ chức các sự kiện hấp dẫn và chương trình khuyến mãi đặc biệt, giúp người chơi có thể nhận được những phần quà giá trị. Những sự kiện này không chỉ giúp tăng cường tinh thần cạnh tranh mà còn tạo cơ hội cho người chơi giao lưu và kết nối với nhau. Với sự kết hợp giữa các yếu tố giải trí, bảo mật và hỗ trợ khách hàng, 6886win xứng đáng là một trong những nền tảng giải trí hàng đầu mà người chơi có thể tin tưởng và lựa chọn.
-
 @ 6fa90c11:8ffacd20
2025-02-25 13:08:24
@ 6fa90c11:8ffacd20
2025-02-25 13:08:24VK88 đã chứng tỏ được vị thế vững chắc của mình trong thế giới giải trí trực tuyến nhờ vào việc cung cấp một kho tàng trò chơi đa dạng và phong phú. Từ những game chiến thuật đỉnh cao cho đến những trò chơi thư giãn nhẹ nhàng, VK88 có thể đáp ứng mọi nhu cầu của game thủ, dù là người chơi có kinh nghiệm hay mới bắt đầu tham gia. Nền tảng này không ngừng đổi mới và sáng tạo, luôn cập nhật các trò chơi mới và thú vị để giữ chân người chơi lâu dài. Đặc biệt, VK88 sở hữu một giao diện thân thiện và dễ sử dụng, giúp người chơi có thể nhanh chóng làm quen và tận hưởng những trò chơi yêu thích của mình. Mỗi trò chơi tại VK88 đều được thiết kế tỉ mỉ với đồ họa sắc nét và âm thanh sống động, mang lại cho người chơi cảm giác như thật, giúp họ hoàn toàn đắm chìm vào không gian giải trí hấp dẫn. Bên cạnh đó, nền tảng này cũng rất chú trọng đến tính ổn định và mượt mà của hệ thống, giúp người chơi có thể trải nghiệm trò chơi mà không gặp phải tình trạng giật lag hay gián đoạn.
Một điểm đáng chú ý khác của VK88 là sự quan tâm đến cộng đồng người chơi. Không chỉ dừng lại ở việc cung cấp các trò chơi hay, VK88 còn tạo ra một môi trường tương tác, nơi game thủ có thể giao lưu, kết nối và học hỏi từ nhau. Các sự kiện và giải đấu thường xuyên được tổ chức, mang đến những thử thách mới mẻ và phần thưởng hấp dẫn cho những người chơi xuất sắc. Các game thủ có thể tham gia vào các cuộc thi, giao lưu và thể hiện tài năng của mình trong những trò chơi yêu thích. Những sự kiện này không chỉ giúp nâng cao tinh thần cạnh tranh mà còn tạo cơ hội để người chơi kết bạn và mở rộng mối quan hệ trong cộng đồng game. Ngoài ra, VK88 còn tổ chức nhiều chương trình khuyến mãi và phần thưởng hấp dẫn dành cho những người chơi trung thành. Những món quà này không chỉ có giá trị lớn mà còn giúp người chơi cảm thấy hài lòng và được trân trọng, từ đó tạo dựng sự gắn kết lâu dài với nền tảng.
Với những nỗ lực không ngừng trong việc cung cấp các trò chơi đa dạng, dịch vụ chăm sóc khách hàng tận tình và bảo mật tuyệt đối, VK88 đã và đang trở thành lựa chọn hàng đầu của rất nhiều người chơi. Đội ngũ hỗ trợ khách hàng của VK88 luôn sẵn sàng giúp đỡ người chơi trong mọi tình huống, từ vấn đề kỹ thuật cho đến các câu hỏi về các chương trình khuyến mãi hay sự kiện. Ngoài ra, nền tảng này cũng cam kết bảo vệ quyền lợi của người chơi bằng việc sử dụng các công nghệ bảo mật tiên tiến nhất, giúp người chơi cảm thấy an tâm tuyệt đối khi tham gia. Các phương thức thanh toán trên VK88 cũng rất đa dạng và thuận tiện, giúp người chơi dễ dàng nạp và rút tiền mà không gặp phải bất kỳ khó khăn nào. Chính vì những yếu tố này, VK88 không chỉ là một nền tảng giải trí trực tuyến thông thường mà còn là một cộng đồng gắn kết, nơi người chơi có thể tìm thấy niềm vui và sự an tâm. Nền tảng này chắc chắn sẽ tiếp tục là điểm đến lý tưởng cho những ai yêu thích giải trí trực tuyến.
-
 @ e7bc35f8:3ed2a7cf
2025-02-21 16:57:49
@ e7bc35f8:3ed2a7cf
2025-02-21 16:57:49With all these decades and - in the case of the oldest democracies - centuries of broken political promises, you’d think that the public would have caught on to the game by now. But no. Still expecting political saviours.
Every election cycle, the public hears how this politician will deliver the nation from its economic woes or that politician will restore a country to its former greatness.
In 1916, Woodrow Wilson was re-elected as president of the United States on the back of his popular campaign slogan, "He Kept Us Out of War". But like all of the presumptive political saviours of the democratic age - in which popularity contests determine who seizes power and the public is swayed by the nicest sounding promises - Wilson, too, promptly broke his word. Just five months after his re-election, he oversaw US entry into the First World War and gave his now-famous speech assuring the public that getting the US into war was necessary to make the world "safe for democracy".
Similarly, Lyndon B. Johnson won election in 1964 promising to limit America’s involvement in Vietnam. "Some others are eager to enlarge the conflict. They call upon us to supply American boys to do the job that Asian boys should do". But this, too, was just another swiftly broken promise by yet another political "saviour". "Air action is now in execution against gunboats and certain supporting facilities in North Vietnam".
Laughably, even George W. Bush "won" the election in 2000 promising a humble American foreign policy and a vow to only fight short, winnable wars with well-defined objectives.
GEORGE W. BUSH:
But I’m gonna be judicious as to how to use the military. It needs to be in our vital interest, the mission needs to be clear and the exit strategy obvious.
BUSH:
On my orders, coalition forces have begun [sic] striking selected targets of military importance to undermine Saddam Hussein’s ability to wage war.
But this pattern is not just about war and it is not specific to any particular country. Throughout the world, politicians have won elections promising to deliver the inherently undeliverable. What Australian could forget, for example, Bob Hawke’s promise to eliminate child poverty in three years?
And what Greek could forget when Alexis Tsipras was swept to power with a strong populist mandate to stand up to the European Union in the midst of the sovereign debt crisis. Instead, Tsipras immediately sold the nation further into debt by accepting the terms of a punishing €85bn "bailout" package that even Syriza’s own members called a betrayal of the party’s promises.
In 2008, this endlessly escalating wave of political insanity seemed to reach a crescendo as it dashed upon the shores of the presidential campaign of Barack Obama.
B. OBAMA:
There’s something happening when people vote not just for party that they belong to but the votes . . . the hopes that they hold in common. [. . .] We are ready to take this country in a fundamentally new direction. That’s what’s happening in America right now. Change is what’s happening in America!
It may seem ridiculous in 2021 that the mere words "Yes We Can" and "Hope and Change" could have sold not just the American voters but the people of the world on Barack Hussein Obama, a junior US senator whose greatest legislative accomplishment up to that point was sponsoring a bill to rename a post office in Illinois. But, in hindsight, that was exactly what was so effective about the entire "hope and change" campaign. After eight years of neocon carnage - amid the tumult of the ongoing fiasco in Iraq, in the shadow of the rising police state at home, and in the face of the revelations of corporate accounting fraud and banking malfeasance that culminated in a global financial crisis - the public was desperately hoping for change.
We will remember that there is something happening in America. That we are not as divided as our politics suggest. That we are one people. We are one nation. And together we will begin the next great chapter in the American story with three words that will ring from coast to coast from sea to shining sea: "Yes We Can!" Thank you, New Hampshire. Thank you!
It didn’t matter that Obama, like every other con man to swindle the majority of the population in the great popularity contest we call democracy, lied about every one of his major campaign promises. It didn’t matter that he lied about closing Guantanamo. It didn’t matter that he lied about ending the war of terror.
And that is why as president I will make the fight against Al Qaeda and the Taliban the top priority that it should be.
The Obama administration knowingly gave US taxpayer dollars to an al Qaeda affiliate in Sudan, a joint i24 News – Middle East Forum investigation reveals.
It didn’t matter that he lied about ending the illegal wiretapping of Americans.
OBAMA:
This administration also puts forward a false choice between the liberties we cherish and the security we provide. I will provide our intelligence and law enforcement agencies with the tools they need to track and take out the terrorists without undermining our Constitution and our freedom. That means no more illegal wiretapping of American citizens.
OBAMA:
I came in with a healthy skepticism about these programs. My team evaluated them. We scrubbed them thoroughly. We actually expanded some of the oversight, increased some of the safeguards. But my assessment and my team’s assessment was that they help us prevent terrorist attacks.
None of his broken promises matter, because it was never about any actual, concrete action. If the mass hysteria that swept over the public in 2008 was about achieving tangible results, the Nobel Committee would not have awarded Obama the Nobel Peace Prize less than one year into his first term in office, while he was still waging wars in Afghanistan and Iraq and expanding Bush’s drone war into Pakistan.
No, it was never about action. It was about providing the audience of the political spectacle the scene that they were waiting for. The next political messiah is wheeled onto the stage, he waves his hand and makes everything better, and everyone goes back to their daily struggles for the next four years. The ritual is complete.
Indeed, after thousands of years in which heads of state were worshipped as literal gods on earth or, more recently, as divine appointees, it should come as no surprise that popular presidents and prime ministers are almost always portrayed with recourse to religious iconography. The common trope of photographing presidents with the "halo" of the presidential seal around them is nothing new.
But even taking that history into account, the religious frenzy that Obama’s appearance on the national political stage caused was, in retrospect, undeniably strange.
OBAMA:
Who is Barack Obama? Contrary to the rumors that you’ve heard, I was not born in a manger. I was actually born on Krypton and sent here by my father Jor-El to save the planet Earth.
In the hysteria of the 2008 campaign, Obama wasn’t received by the public as a political candidate with a series of policy prescriptions for improving the country. He was the god from the machine, the deus ex machina who could appear on stage and bless everyone with his absolution. Obama was not just Superman but the God of All Things, a Heaven-Sent shining New Hope bathed in angelic light who was the literal Second Coming.

First of all, give an honour to God and our Lord and Savior, Barack Obama!

And by the time the public finally snapped from their reverie and realized that, after all, Obama was just another politician...
The former director of the Norwegian Nobel Institute says he regrets awarding the Nobel Peace Prize to President Barack Obama in 2009.
He lied! It’s not subtle, He said “There will be no spying on citizens who are not suspected of a crime.” He lied. There is spying on all of us and we’re not suspected of a crime. Barack Obama is a liar! Can I make it clearer?
Obama had already served his role as the next political saviour and, having served that function, he could be discarded like yesterday’s newspaper. For those who believed that the 2008 campaign was the apotheosis of the Hope and Change routine, this was the end of the line for this political charade. Looking at the process from a rational perspective, one could be forgiven for thinking that the public had learned its lesson and that no politician would be able to bamboozle the public like that again as long as the Obama legacy was in living memory. 👉 But this is not a rational process, and those who believed that could not have been more wrong.
Lest there be any confusion that the public was being prepared for another deus ex machina ritual, this time the god descended onto the political stage via a literal machine, a golden escalator. And, from his dais, this god, too, brought good tidings to the cheering crowd: the country is saved once again!
Ladies and gentlemen, I am officially running for President of the United States and we are going to make our country great again!
The next day, it was revealed that the scene was a literal stage play. The adoring crowd were not grassroots supporters of Donald Trump who all spontaneously decided to wear the same Trump t-shirts and awkwardly pose with their "homemade" signs for the cameras, but, as an FEC investigation later confirmed, literal actors paid $50 each by the Extra Mile Casting agency on behalf of their client, Gotham Government Relations & Communications.
But it didn’t matter. Like all the iterations of the President Messiah script that came before, Trump’s Make America Great Again psychodrama was already having its intended effect on the population. In some ways, MAGA was a mere repeat of the Obama Hope and Change template. Here, too, candidate Trump promised the moon that President Trump steadfastly failed to deliver.
He | did not I drain I the I swamp.
He did not stand up to medical-industrial complex.
And, like the Obamessiah, Trump, too, took on the role of divine redeemer of the nation, second only to Christ himself.
Trump (Trump assured us) was loved by the Jewish people in Israel like the "second coming of God". And once again the president was being portrayed as "heaven-sent", a man chosen by God Himself to lead America back to the promised land.
RICK PERRY:
And I shared it with him. I said, Mr. President, I know there are people that say you said you were the chosen one and I said, "You were." I said, "If you’re a believing Christian, you understand God’s plan for the people who rule and judge over us on this planet in our government.
ED HENRY:
And lest people on the left attack Rick Perry, he pointed out to me he believes Barack Obama was sent by God as well. He said for that moment and that time. He said he thinks for this moment and this time, Donald Trump was sent by God to do great things.
Or, as the internet users who helped build the momentum for the Trump train during the 2016 campaign put it in their popular meme, Trump was the God Emperor, a GEOTUS who would smite the wicked and own the libs.

Yes, the Trump script seemed to be a mere rehash of the Obama script. But it was not. You see, this was not the same plot as Hope and Change. Make America Great Again had a more exciting storyline. In the MAGA stage play, the god from the machine was himself in trouble and needed saving from the powerful, evil forces that were ganging up against him. And this time, the god himself would be saved by his own god from a machine. This script involved an incredible double deus ex machina!
The god that would save God Emperor Trump, however, was not a political figure at all, but a shadowy, anonymous entity. And the machine that delivered him was not a golden escalator, but an online message board.
The "Q Anon" phenomenon began on October 28, 2017, when "Q" - a user of the "politically incorrect" board of 4chan, the anonymous imageboard website - made a post claiming that a massive military operation was underway to arrest Hillary Clinton and bring down the cabal of evil politicians that was filling the swamp of Washington.
Within days, the anonymous poster was assuring his 4chan followers of the imminent indictment of Clinton campaign insiders John Podesta and Huma Abedin. And on November 2nd, less than a week after the initial post, the poster was calling himself "Q Clearance Patriot" and claiming that "over the course of the next several days you will undoubtedly realize that we are taking back our great country".
In every way, these early "Q Drops" exemplify the QAnon phenomenon that it spawned. They pick up on the language and code words of classified government operations, like "Mockingbird" and "Q clearance". They pretend to impart insider information about high-level political events, even predicting specific events on specific dates, like the arrest announcement of Podesta and the beginning of a military coup. And they pose a series of vague rhetorical questions ("Why does Potus surround himself w/ generals? What is military intelligence? Why go around the 3 letter agencies?") that feel important without providing any specific knowledge or insight.
As Q’s notoriety grew, so, too, did the grandiosity of his predictions, promises and pronouncements. Followers were told to expect "False flag(s)" and that there would be "fireworks" but that the president would be "100% insulated". They were exhorted to "TRUST [Attorney General Jeff] SESSIONS" and assured that Feb. 1, 2018, would be the "[D]ay [Of] [D]ays". They were promised a "parade that will never be forgotten" on November 11th of 2018. They were assured that Mark Zuckerberg was stepping down as chairman of Facebook. July 2018 would be the month "the world discovered the TRUTH", with Q asserting that there would be "conspiracy no more".
Of course, every one of these pronouncements was categorically wrong. But, as Q taught his followers to believe, "Disinformation is real" and "Disinformation is necessary", so these false predictions were in fact signs that Q was telling the truth. It didn’t make sense. It didn’t have to. All it had to do was fill the viewers of the unfolding political spectacle with hopium, the belief that this new god from the machine was going to swoop in with his Q Clearance compatriots and save the day at the last moment.
Remarkably, that belief persisted even after the last moment. 🔸Q Anon Posts Debate & Discussion With Praying Medic [Rare Interview & Question] 🔸ACTUAL INTERVEIW [sic] Dr Steve Pieczenik DHS watermarked every ballot with QFS Blockchain Encryption 🔸HELLSCAPE: 72 HOURS TO SAVE THE REPUBLIC 🔸EP. 2501B – TRAP SET, THESE PEOPLE ARE STUPID, DO YOU SEE THE STORM FORMING,PANIC IN DC
It is not hard to see why Q became so popular. Like every good deus ex machina, Q promised to deliver the audience of the current political drama exactly what they wanted: an entertaining, exciting and satisfying resolution to the play, delivering the hero (Trump) from evil (the Democrats) just in the nick of time. It is not coincidence that "Enjoy the show" and "Get the popcorn" became favourite phrases of Q and the QAnon followers. This was, after all, just that: a show. A scripted drama designed to play on the psyche of the audience.
The clue comes in Q’s constant exhortations for his follower to trust. 🔸Trust Sessions. 🔸Trust Grassley. 🔸Trust POTUS. 🔸 Trust the plan.
The terminology - as well as the methodology - of the Q operation evokes Operation Trust, a Soviet counterintelligence program in the 1920s that took over a pro-monarchist organization, the "Monarchist Union of Central Russia". The Soviets used operatives within the organization to persuade members that they should not engage in militant activity against the government because a plan was underway for internal anti-Bolshevik forces to topple the regime. Trust the plan.
In this case, "trusting the plan" got members of the opposition either put on trial and sent to the gulags or blackmailed into working for Soviet intelligence.
Q certainly did pacify many with his constant entreaty to "trust the plan". Q also rallied people time and time again to support the policies, operations and personnel of the very deep state that they were supposedly fighting against. Suddenly Jeff Sessions, Bill Barr, John Bolton and other long-time members of the political establishment were the good guys in this elaborate drama. 99% of the agents at the CIA, FBI, DOJ and NSA were "patriots" who "serve[d] with distinction" and thus needed to be supported. The decades-long neocon dream of invading Iran became, in the eyes of Q followers, a good and noble cause.
But even beyond the pacification of those who would otherwise be resisting the government, the "Q Army" of self-styled "Digital soldiers" provided the very foil that the deep state needed to move to the next step of their counter-insurgency program: The crackdown on "domestic terrorism".

🔸FBI Warns Of Potential For More Violence From QAnon Followers 🔸FBI warns conspiracy theories fuel domestic terrorism 🔸Former CIA official Jeremy Bash, now of NBC News 🔸A Message from President Donald J. Trump
After years of being told to "get the popcorn" and "enjoy the show", the Q Anon movement slowly began to realize that they were had. Worse, the very intelligence agencies and military that they had so fervently hoped would swoop in and save the day are the very agencies that were swooping in to round them up. But QAnon was by no means the first time that hopium has been injected into the veins of the "conspiracy research community".
In the 1990s, a power industry teaching consultant named Harvey Francis Barnard developed a proposed set of reforms for America’s monetary and tax system that he called the National Economic Security and Recovery Act, or NESARA. He self-published a book outlining his proposal, sent copies to members of Congress, started an institute to promote the idea and, in 2000, published his proposal on the internet. At that point, NESARA became the centerpiece of an elaborate hoax promulgated by an online charlatan calling herself "The Dove of Oneness". In this story, the NESARA bill is a miracle: it abolishes income taxes, forgives mortgages, zeroes out credit cards and declares peace. Even more miraculous: in a stunning move only known to The Dove of Oneness, the bill had been secretly passed by Congress and was due to take effect on September 11, 2001, which is why the World Trade Center was destroyed. But, like every good drama, this story, too, had a deus ex machina to keep Dove’s internet audience hanging on and enjoying the show: the White Knights, "an underground group of good guys [. . .] who were in high positions within all these institutions, who were fed up with the status quo and were planning a coup d’état that was going to happen ‘very soon.'"
Just as with Q, the cult that grew around the NESARA myth with its White Knight gods from the machine promised specific events on specific dates. Every time a prediction failed to happen, followers were reassured that the long-promised coup had been delayed so that the White Knights could better prepare the public for the pandemonium that would ensue when they swoop in to save the day. In the meantime, followers could get the popcorn and enjoy the show, knowing that all their debt would soon be forgiven and that peace on earth was just around the corner. And the name of that book in which Barnard first laid out his NESARA proposal? 👉 Draining The Swamp.
Yes, the deus ex machina story is trotted out every few years under different guises. A secret order of ninjas is preparing to assassinate the evil Illuminati and bring peace to the world. A secret stash of trillions of dollars is about to be shared out with the people of the world, ending all poverty. A cosmic realignment is going to take place on December 21st, 2012, raising humanity to a higher level of consciousness and ending all strife and suffering. An anonymous 4chan poster is leaking classified information about a good military coup that’s going to restore order and drain the swamp. The incredible Trump's X-Men.
The message is always the same: Get the popcorn and enjoy the show. The god is coming from the machine to save you. Just wait. Over and over we see the same story play out. The crowd begins to lose interest in the political stage play. They begin to suspect that it’s fake. That reality is taking place somewhere off stage and out of sight. They begin to realize that they are not spectators at all, but active participants with the ability to shape the world around them. And then along comes a god from a machine peddling hopium and the audience goes back to enjoying the show.
None of this is to denigrate the religious instinct that compels humans to look for a saviour from the heavens. On the contrary. Those with religious faith should be the most offended by this god from the machine script that sees their most cherished, divine beliefs cynically played on by would-be political rulers masquerading as gods.
Now, we must not abandon hope itself. As part of the triumvirate of faith, hope and charity, hope is a virtue to be cherished. Genuine hope is the rocket fuel that humans use to propel themselves towards their goals. Without hope, there would be no motivation to do anything to improve our situation. But that is the difference. Hope compels us to go out there and try to improve our situation. Fake hopes, on the other hand, convinces us that someone else has taken care of the problem. That we can just sit back, get the popcorn and enjoy the show. Like the dope peddler on the street corner, the politicians and hucksters are always ready to satisfy their mark with a dose of false hopes. And the public, more often than not, is only too happy to take it.
But fake hope is a deadly drug, and the god from the machine is nothing but a cheap stage trick. Nothing will change until we stop enjoying the show and realize that we are not spectators watching history unfold from the sidelines. We are history’s actors, and, propelled by genuine hope, we can and will change the world.
-
 @ d34e832d:383f78d0
2025-02-21 16:00:08
@ d34e832d:383f78d0
2025-02-21 16:00:08[npub16d8gxt2z4k9e8sdpc0yyqzf5gp0np09ls4lnn630qzxzvwpl0rgq5h4rzv]
Data Storage via Blobs in a Decentralized Manner
Blobs (Binary Large Objects) offer a flexible method of storing large chunks of data, and in the context of decentralized systems, they allow for secure, distributed storage solutions. In a decentralized world, where privacy and autonomy are key, managing data in a distributed manner ensures data isn't controlled or censored by a single entity. Here are three key systems enabling decentralized blob storage:-
Blossom Server
Blossom Server provides a decentralized platform for storing and sharing large blobs of data. Blossom Server allows users to host their own data and retrieve it from a decentralized network, ensuring that data is not stored in centralized servers. This platform is open-source, offering flexibility and security through peer-to-peer data storage. -
Perkeep
Perkeep (formerly known as Camlistore) is a decentralized data storage system that allows for storing blobs of data in a distributed manner. It focuses on the long-term storage of large data sets, such as personal collections of photos, videos, and documents. By using Perkeep, users can ensure that their data remains private and is not controlled by any central authority. The system uses a unique identifier to access data, promoting both privacy and integrity. -
IPFS (InterPlanetary File System)
IPFS is another popular decentralized file storage system that uses the concept of blobs to store and share data. IPFS allows users to store and access data in a decentralized manner by using a peer-to-peer network. Each piece of data is given a unique hash, ensuring that it is verifiable and tamper-proof. By leveraging IPFS, users can store everything from simple files to large applications, all without relying on centralized servers.
By using these decentralized data storage solutions, individuals and organizations can safeguard their information, increase privacy, and contribute to a more resilient and distributed internet infrastructure.
Higher-Level Goals for Blob Storage Blob storage via Blossom ,Perkeep and IPFS has goals to become a decentralized, self-sufficient protocol for data storage, management, and sharing. While some of these features are already being implemented, they represent a broader vision for the future of decentralized personal data management.
-
Filesystem Backups
Allows for easy, incremental backups. Using thepk-puttool, users can back up files and directories quickly and efficiently. Incremental backups, which save only the changes made since the last backup, are essentially free, making Perkeep an efficient choice for backup solutions. This initial use case has already been implemented, providing seamless and secure backups for personal data. -
Efficient Remote Filesystem
The goal is to create a highly efficient, aggressively caching remote filesystem using Perkeep. A read-only version of this filesystem is already trivial to implement, while read-write functionality remains an area of active development. Every modification in the filesystem would be snapshotted implicitly, providing version control as a default. This would enable users to interact with their data in a remote environment while ensuring that every change is tracked and recoverable. -
Decentralized Sharing System
Perkeep is working towards enabling users to share data in a decentralized manner. The system will allow individuals to share anything with anyone or everyone, with privacy being the default setting. This decentralized sharing is already starting to work, and users can now share data with others while retaining control over who sees their information. -
Blog / Photo Hosting / Document Management CMS
Perkeep aims to replace traditional blog platforms, photo hosting services, and document management software. By running a personal blog, photo gallery, and document management system (CMS) on Perkeep, users will have full control over their content. Permissions will be configurable, allowing for personal or public sharing. The author intends to use Perkeep for his own blog, gallery, and document management needs, further demonstrating its versatility. -
Decentralized Social Networking
While still a lofty goal, decentralized social networking is a persistent aim for Perkeep. By implementing features like comments and tagging, users could attach metadata to images and content. Through claims, users could sign data and verify identities, promoting trust in social interactions. This would allow for decentralized social networking where users control their own data and interactions. -
Import/Export Adapters for Hosted Web Services
Perkeep intends to bridge the gap between decentralized storage and traditional hosted web services. This feature would allow users to mirror data between hosted services and their private Perkeep storage. Whether content is created in Perkeep or hosted services, the goal is to ensure that data is always backed up privately, ensuring users' data is theirs forever.
Combined Goals for Blossom and IPFS
Both Blossom and IPFS share common goals of decentralizing data storage, enhancing privacy, and providing users with greater control over their data. Together, these technologies enable:
- Self-Sovereign Data Management: Empowering users to store and manage their data without relying on centralized platforms.
- Resilient and Redundant Storage: Offering decentralized and redundant data storage that ensures availability and security.
- Private and Permissioned Sharing: Enabling secure, private data sharing where the user controls who has access to their content.
By focusing on these goals, both Blossom and IPFS are contributing to a future where individuals control their own data, collaborate more efficiently in decentralized networks and P4P protocols, and ensure the privacy and security of their digital assets.
These technologies in conjunction with nostr lead one to discover user agency and autonomy, where you can actually own and interface with your own data allowing for value creation and content creation strategies.
Donations via
- lightninglayerhash@getalby.com -
-
 @ f4c59e4c:82f66850
2025-02-25 12:14:45
@ f4c59e4c:82f66850
2025-02-25 12:14:45Introduction
Dora Factory actively participated in governance across multiple blockchain ecosystems, including Cosmos Hub, dYdX, Injective, and Osmosis, by casting votes on key proposals. These decisions reflect Dora Factory’s commitment to supporting network upgrades, optimizing infrastructure, and ensuring responsible treasury and market management. Below is a summary of recent governance actions.
Proposals
Cosmos Hub
2025-02-14 Cosmos Proposal 988 Yes Dora Factory voted YES on Cosmos Proposal 987 to approve the Gaia v22 software upgrade. The upgrade includes updates to the Cosmos Hub binary and has been tested by Informal Systems and Hypha Co-op.
dYdX
2025-02-04 dYdX Proposal 208 Yes Dora Factory voted YES on dYdX Proposal 208 to add the dYdX Operations subDAO (DOS) signer as a market authority in the market map module and remove the 10% revenue share. This change allows DOS to update the market map while ensuring no fees accrue to Market Mappers, aligning with the community’s interests.
2025-02-08 dYdX Proposal 210 No Dora Factory voted NO on dYdX Proposal 210, which aimed to revive the dYdX client to Sifchain. The proposal was flagged as suspicious due to false claims of support from Informal Systems, lack of prior discussion, and potential security implications for dYdX Chain.
2025-02-10 dYdX Proposal 211 Yes Dora Factory voted YES on dYdX Proposal 211, which recalls the Stride Liquid Staking Program. The proposal transfers control of stDYDX from the dYdX Community Treasury to the dYdX Treasury SubDAO, allowing it to redeem and manage the assets directly.
Injective
2025-01-29 Injective Proposal 490 Yes Dora Factory voted YES on Injective Proposal 490, which aimed to recover the IBC client for Kopi chain.
2025-02-03 Injective Proposal 491 Yes Dora Factory voted YES on Injective Proposal 491, which aimed to increase the maximum gas amount per block to 150,000,000 to optimize on-chain transaction handling
2025-02-06 Injective Proposal 493 Abstain Dora Factory ABSTAINED on Injective Proposal 493, which aimed to launch an on-chain S&P 500 Index market by introducing the SPY/USDT perpetual market across Injective Exchange dApps.
2025-02-12 Injective Proposal 494 Yes Dora Factory voted YES on Injective Proposal 494, which proposed the Nivara mainnet upgrade. The upgrade includes enhancements to the RWA oracle and module architecture, improved delegation controls, and security updates for the exchange module and Injective Bridge.
2025-02-12 Injective Proposal 495 Yes Dora Factory voted YES on Injective Proposal 495, which aimed to recover the IBC client used by the Kopi chain. The proposal passed with significant support.
2025-02-12 Injective Proposal 496 Yes Dora Factory voted YES on Injective Proposal 496, which aimed to modify the ticker for the TRADFI/USDT PERP market to reflect the appropriate ticker.
2025-02-20 Injective Proposal 498 Yes Dora Factory VOTED YES on Injective Proposal 498, which aims to launch the JNI/HDRO Spot Market for trading the JNI token in HDRO-denominated quote.
Osmosis
2025-01-29 Osmosis Proposal 897 Yes Dora Factory voted YES on Osmosis Proposal 897, which aimed to recover the IBC client used by the Kopi chain.
2025-02-04 Osmosis Proposal 898 Yes Dora Factory voted YES on Osmosis Proposal 898, which aimed to reduce gas consumption for Mars contracts by pinning binary contracts and reducing resource usage.
2025-02-04 Osmosis Proposal 899 Yes Dora Factory voted YES on Osmosis Proposal 899, which aimed to increase the static limits for Alloyed BTC during its rapid growth phase.
2025-02-04 Osmosis Proposal 900 Yes Dora Factory voted YES on Osmosis Proposal 900, which requested $150,000 USDC from the Osmosis community pool to bootstrap DOGE liquidity by purchasing DOGE and adding it to a DOGE/USDC liquidity pool on Osmosis.
2025-02-07 Osmosis Proposal 901 Yes Dora Factory voted YES on Osmosis Proposal 901, which authorized the purchase of BTC using 25% of Osmosis' non-OSMO taker fees. The January 2025 purchase was expected to be around 1.4 BTC.
Conclusion
Dora Factory’s recent votes demonstrate a strong focus on enhancing blockchain infrastructure, optimizing network efficiency, and ensuring responsible asset management. By supporting essential upgrades, market optimizations, and community-driven initiatives, Dora Factory continues to contribute to the long-term sustainability and innovation of these ecosystems.
-
 @ d34e832d:383f78d0
2025-02-21 15:32:49
@ d34e832d:383f78d0
2025-02-21 15:32:49Decentralized Publishing: ChainScribe: How to Approach Studying NIPs (Nostr Improvement Proposals)
[npub16d8gxt2z4k9e8sdpc0yyqzf5gp0np09ls4lnn630qzxzvwpl0rgq5h4rzv]
How to Approach Studying NIPs (Nostr Improvement Proposals)
NIPs (Nostr Improvement Proposals) provide a framework for suggesting and discussing improvements to the Nostr protocol, a decentralized network for open communication. Studying NIPs is crucial for understanding the evolution of Nostr and its underlying principles. To effectively approach this, it's essential to follow a systematic, structured process.
- Familiarize with the Nostr Protocol: Before diving into the specifics of each NIP, gain a solid understanding of the core Nostr protocol. This includes its goals, architecture, and key components like pubkeys, events, and relays.
- Explore the NIP Catalog: Visit nostr-nips.com to browse through the available NIPs. Focus on the most recent proposals and those that align with your interests or areas of expertise.
- Review the Proposal Structure: Each NIP follows a standard structure, typically including a description of the problem, proposed solution, and rationale. Learn to read and evaluate these elements critically, paying attention to how each proposal aligns with Nostr’s decentralized ethos.
- Follow Active Discussions: Many NIPs are actively discussed within the community. Follow relevant channels, such as GitHub issues or dedicated discussion forums, to understand community feedback and potential revisions.
- Understand Dependencies: Some NIPs are designed to work in tandem with others or require other technological advancements. Recognize these relationships to better understand the broader implications of any proposal.
- Hands-On Testing: If possible, test NIPs in a development environment to see how they function in practice. Experimenting with proposals will help deepen your understanding and expose potential challenges or flaws.
- Contribute to Proposals: If you have insights or suggestions, contribute to the discussion or propose your own improvements. NIPs thrive on community participation, and your input can help shape the future of Nostr.
Donations via
- lightninglayerhash@getalby.com -
 @ a262e97d:ddc3e696
2025-02-27 02:32:27
@ a262e97d:ddc3e696
2025-02-27 02:32:27The ancient Greek tale of the Sword of Damocles tells of a Sicilian tyrant Dionysius II and his courtier Damocles. According to legend, Damocles envied Dionysius’s wealth and power, so the tyrant offered to switch places with the coutier for a day. Damocles eagerly accepted, reveling in luxury—until he noticed a sharp sword dangling above his head, held only by a single horsehair. The looming threat stripped away his enjoyment, revealing the constant peril that accompanies great power. It’s a story about the precariousness of fortune, where danger hovers just out of sight.
Constantinople
Throughout history, there have been examples of such anxiety affecting beyond the individual onto a collective. One example that captures a society-wide sense of dread is the fall of Constantinople in 1453. This wasn’t just a city on edge; it was an entire civilization staring down its own collapse, with the tension building for decades before the final, brutal crescendo.
Picture the scene: Constantinople, the last bastion of the Eastern Roman Empire, a city of faded grandeur encircled by Ottoman forces under Mehmed II. By the mid-15th century, the empire had shrunk to a shadow of its former self, its walls battered by time and earlier sieges, its coffers nearly empty. The Byzantines knew the Turks were coming—Mehmed’s massive cannons, including the monstrous Basilica, were no secret. For years, they’d lived with the creeping certainty that their world was teetering on a knife’s edge, propped up only by fragile alliances and the hope of Western aid that never fully materialized. The city’s inhabitants—nobles, merchants, priests, and peasants alike—could feel the noose tightening as Ottoman scouts probed their defenses and trade routes withered.
A citizen of Constantinople in those final days might have said something like: “We feast on memories of glory, our golden domes gleaming still, but a shadow looms beyond the walls. Each night I hear the distant rumble of their engines, each day I count fewer ships in our harbor. Our prayers echo in Hagia Sophia, yet I wonder if God has turned His face from us. We are bound by a thread, and it frays with every passing hour.” It’s that Damocles vibe dialed up to apocalyptic levels—splendor undercut by the palpable, collective dread of annihilation.
The drama peaked on May 29, 1453, when Mehmed’s army breached the walls after a relentless 53-day siege. The city fell in a bloodbath: cannons shredded centuries-old fortifications, soldiers poured in, and the last emperor, Constantine XI, vanished into the fray, his fate unknown. Hagia Sophia was turned into a mosque, and an empire that had endured for over a thousand years was snuffed out. The psychological weight beforehand—the years of knowing the end was near, yet clinging to a fraying hope—makes it a gut-punch of a historical moment. For your essay, it’s a setting that screams inquiétude on a grand scale, a whole society under that dangling sword until it finally dropped.
French Revolution
More recently, consider the French Revolution. Here’s the bourgeoisie on the eve of 1789 again—wealthy but boxed in, sensing the old order’s collapse. Once the revolution ignited, everyone felt the blade: aristocrats faced the guillotine, revolutionaries feared counter-revolts, and even the masses worried about starvation or tyranny. It’s a carousel of Damocles moments—power shifted fast, and no one knew when the horsehair might snap.
Imagine, if you will, a member of France’s bourgeoisie—a well-off merchant or lawyer, say—on the eve of the French Revolution in 1789. They’ve climbed the social ladder through trade or education, but they’re still squeezed between the decadent nobility above and the restless poor below. The monarchy’s crumbling, the economy’s a mess, and whispers of revolt are growing louder. This bourgeois might describe their feelings with a nod to that old tale: “I sit at a banquet of my own making, wealth and status within reach, yet I feel a blade dangling above me. The nobles scorn us, the masses eye our gains, and the king’s faltering grip threatens to let it all fall. Every coin I’ve earned could be my undoing.” It’s a mix of pride in their rise and dread of the chaos that could snatch it away—Damocles at his feast, tasting both triumph and terror.
The French Revolution is the closest echo of Dionysius and Damocles: a society—especially the rising bourgeoisie and later revolutionary leaders—relishing newfound power (or the chance at it) while acutely aware of the fragility holding it together. The guillotine literally hung over heads, and the rapid turnover of factions (Girondins, Jacobins, Thermidorians) mirrors that precarious throne under a dangling blade. Spain’s war was too chaotic, too fractured for anyone to sit comfortably; McCarthy’s era had menace but lacked the all-encompassing upheaval. France in 1789–1799 is the banquet with the sword swaying overhead—everyone’s a guest, and no one’s safe.
the Chainsaw of Donacles
In a gray, fluorescent-lit cubicle maze straight out of a dystopian Office Space reimagined as a euro-steampunk nightmare, the United States of 2025 hums with the dissonance of 1789 pre-revolutionary fervor. The air smells of burnt coffee and gear grease, the dull drone of bureaucracy punctuated by the hiss of steam pipes snaking along the walls above an endless sprawl of cubicles and flickering gas lamps. The air thick with wifi radiation and desperation.
Donald Trump, newly mandated by a roaring electorate to “drain the swamp,” roams between Mar-a-Lago’s opulent halls, the White House’s command center, and Air Force One’s plush skies. His arme de prédilection: a ostentatious gold-tipped pen, wielded like a guillotine’s decree. Trump grins, orange hair wild, and with a flourish, he signs resounding executive orders—EOs that thunder through the bureaucracy — smirking, “The swamp’s toast, folks.”
Enter Elon Musk, tasked with leading the DOGE task force—Department of Government Efficiency. He grips a gleaming chainsaw, a gift from Argentine firebrand Javier Milei, its blade etched with “Libertad o Muerte.”
His Zoomerwaffen—a brigade of Gen Z disruptors in brass goggles and hoodies—are the revolution’s shock troops in hoodies and brass goggles, armed with bare steel laptops and savage memes. These digital sans-culottes wield laptops like muskets, flooding X with memes that mock the Karens (“OK Boomer, meet the blockchain”), crashing servers with decentralized audits, and rigging AI bots to shred red tape faster than a guillotine drops. One Zoomer, vape cloud swirling, hacks a payroll database while blasting dubstep; another livestreams a “Karen Meltdown Compilation” as morale bombs. They’re the grease in Elon’s machine, turning DOGE into a viral uprising.
Elon’s Herculean task: slash the bloated federal beast down to size. From a Cybertruck-turned-mobile-HQ, smokestack puffing, Elon adjusts his top hat, a single LED flickering on its brim. “Time to saw through the bloat,” he quips and revs the beast, slashing budgets with a mad inventor’s glee. “Efficiency is the new Reign of Terror. Let's disrupt the guillotine’s monopoly on downsizing.” The zoomers cheer, their screens flashing with blockchain audits and TikTok takedowns of red tape as they slash budgets with blockchain precision, livestreaming the carnage on X.
But beyond the glass-walled boardrooms and armored Cybertrucks, the cubicles stretch into a Bastille of beige despair. Here reign the deep-staters — legions of federal lifers grown plump on decades of taxpayer largesse. They’re the ancient régime of red tape, peering over partition walls with powdered wigs askew, muttering about “due process” while clutching dog-eared manuals of byzantine regulations.
Picture these thousand Karens, each clutching a “Manager of My Own Destiny” mug, their lanyards clinking with pronoun pins and union badges; each a snowflake of entitled fury.
And above every sweat-stenched cubicle, a miniature chainsaw dangles by a fraying hemp thread.
One wretched teet-sucking swamp creature, a portly GS-14 named Linda, slams her “TPS Reports” onto a desk, her wig askew, shrieking, “I’ve earned my pension, you fascists! I've earned everything, fair and square!” Linda's personal Chainsaw of Donacles sways with every EO and Zoomer hack. Her ink-stained hands tremble as her steam-powered iPhone wheezes out another ding decrying ever more “DOGE tyranny.”
Across the floor, lanyards jangle — pronoun pins flashing — as Karens plot over stale croissants, whispering of jammed printers and leaked memos to fight back.
Trump’s banquet is victory, savored from Mar-a-Lago’s terraces or 30,000 feet up, untouchable. His mighty pen perpetually slashing through the old order.
Elon’s chainsaw roars, Zoomerwaffen dancing in its sparks, dismantling decades of excess.
The Karens sit under their blades — relics of a bloated regime, their banquet of entitlement souring as the threads fray and the swamp drains.
The Revolution’s inquiétude steams through: they built this world, gorged on its perks; and now the power they hoarded hangs by a hair Every Musk rev, every Trump signature, every Zoomer meme cuts closer.
“Efficiency’s here. Let them eat efficiency!” Elon tweets, and a chainsaw twitches.
A Karen shrieks. A rope snaps.
Hope you enjoyed this steampunk Office Space-meets-1789, lovingly crafted by Grok and myself.
One final note on the Zoomerwaffen (a term I picked up from @realKingpilled): They’re the patriotic engine of this upheaval — tech-native, irreverent, and relentless. Think of them as the street agitators of 1789, but with code instead of pitchforks. They hack legacy systems to expose waste, flood social media with viral takedowns, and turn DOGE’s mission into a cultural juggernaut. Their focussed autism amplifies Elon’s chainsaw and Trump’s pen, making the Karens’ downfall a public spectacle. They’re the ones fraying those threads, one savage meme at a time.
-
 @ 2ed3596e:98b4cc78
2025-02-27 00:24:36
@ 2ed3596e:98b4cc78
2025-02-27 00:24:36Curious about Bitcoin but unsure where to start? Our Bitcoin for Beginners webinar is designed to help you understand Bitcoin, how it differs from traditional fiat money, and how to safely get started.
This free, live session takes place on the second Wednesday of every month at 4 PM EST. Whether you’re completely new to Bitcoin or looking for clarity on how to buy at the best price, this webinar will walk you through the essentials, including:
✅ What Bitcoin is and why it matters
✅ How Bitcoin is different from traditional money
✅ The safest ways to buy and store Bitcoin
✅ How to get started with confidence
This interactive session also includes a Q&A, so you can ask any questions you have along the way. Don’t miss this opportunity to learn from experts and take control of your Bitcoin journey!
-
 @ d360efec:14907b5f
2025-02-25 10:16:18
@ d360efec:14907b5f
2025-02-25 10:16:18ภาพรวม BTCUSDT (OKX):
Bitcoin (BTCUSDT) แนวโน้มระยะยาว TF Day ยังคงเป็นขาลง แนวโน้มระยะกลาง TF 4H Sideway down และแนวโน้มระยะสั้น TF 15M Sideways Down
วิเคราะห์ทีละ Timeframe:
(1) TF Day (รายวัน):
- แนวโน้ม: ขาลง (Downtrend)
- SMC:
- Lower Highs (LH) และ Lower Lows (LL)
- Break of Structure (BOS) ด้านล่าง
- Liquidity:
- มี Sellside Liquidity (SSL) อยู่ใต้ Lows ก่อนหน้า
- มี Buyside Liquidity (BSL) อยู่เหนือ Highs ก่อนหน้า
- ICT:
- Order Block ราคาไม่สามารถผ่าน Order Block ได้
- EMA:
- ราคาอยู่ใต้ EMA 50 และ EMA 200
- Money Flow (LuxAlgo): * สีแดง
- Trend Strength (AlgoAlpha):
- สีแดง แสดงถึงแนวโน้มขาลง
- Chart Patterns: ไม่มีรูปแบบที่ชัดเจน
- Volume Profile: * Volume ค่อนข้างนิ่ง
- แท่งเทียน: แท่งเทียนล่าสุดเป็นสีแดง
- แนวรับ: บริเวณ Low ล่าสุด
- แนวต้าน: EMA 50, EMA 200 , Order Block
- สรุป: แนวโน้มขาลง
(2) TF4H (4 ชั่วโมง):
- แนวโน้ม: ขาลง (Downtrend)
- SMC:
- Lower Highs (LH) และ Lower Lows (LL)
- Break of Structure (BOS) ด้านล่าง
- Liquidity:
- มี SSL อยู่ใต้ Lows ก่อนหน้า
- มี BSL อยู่เหนือ Highs ก่อนหน้า
- ICT:
- Order Block ราคาไม่สามารถผ่าน Order Block ได้
- EMA:
- ราคาอยู่ใต้ EMA 50 และ EMA 200
- Money Flow (LuxAlgo):
- สีแดง แสดงถึงแรงขาย
- Trend Strength (AlgoAlpha): * สีแดง แสดงถึงแนวโน้มขาลง
- Chart Patterns: ไม่มีรูปแบบที่ชัดเจน
- Volume Profile: * Volume ค่อนข้างนิ่ง
- แนวรับ: บริเวณ Low ล่าสุด
- แนวต้าน: EMA 50, EMA 200, Order Block
- สรุป: แนวโน้มขาลง,
(3) TF15 (15 นาที):
- แนวโน้ม: Sideway Down
- SMC:
- Lower High (LH) และ Lower Lows (LL)
- Break of Structure (BOS) ด้านล่าง
- ICT:
- Order Block: ราคา Sideways ใกล้ Order Block
- EMA:
- EMA 50 และ EMA 200 เป็นแนวต้าน
- Money Flow (LuxAlgo):
- แดง
- Trend Strength (AlgoAlpha):
- แดง/ ไม่มีสัญญาณ
- Chart Patterns: ไม่มีรูปแบบที่ชัดเจน
- Volume Profile: Volume ค่อนข้างสูง
- แนวรับ: บริเวณ Low ล่าสุด
- แนวต้าน: EMA 50, EMA 200, Order Block
- สรุป: แนวโน้ม Sideways Down,
สรุปภาพรวมและกลยุทธ์ (BTCUSDT):
- แนวโน้มหลัก (Day): ขาลง
- แนวโน้มรอง (4H): ขาลง
- แนวโน้มระยะสั้น (15m): Sideways Down
- Liquidity: มี SSL ทั้งใน Day, 4H, และ 15m
- Money Flow: เป็นลบในทุก Timeframes
- Trend Strength: Day/4H/15m เป็นขาลง
- Chart Patterns: ไม่พบรูปแบบที่ชัดเจน
- กลยุทธ์:
- Wait & See (ดีที่สุด): รอความชัดเจน
- Short (เสี่ยง): ถ้าไม่สามารถ Breakout EMA/แนวต้านใน TF ใดๆ ได้ หรือเมื่อเกิดสัญญาณ Bearish Continuation
- ไม่แนะนำให้ Buy: จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจนมากๆ
Day Trade & การเทรดรายวัน:
-
Day Trade (TF15):
- Short Bias: หาจังหวะ Short เมื่อราคาเด้งขึ้นไปทดสอบแนวต้าน (EMA, Order Block)
- Stop Loss: เหนือแนวต้านที่เข้า Short
- Take Profit: แนวรับถัดไป (Low ล่าสุด)
- ไม่แนะนำให้ Long
-
Swing Trade (TF4H):
- Short Bias: รอจังหวะ Short เมื่อราคาไม่สามารถผ่านแนวต้าน EMA หรือ Order Block ได้
- Stop Loss: เหนือแนวต้านที่เข้า Short
- Take Profit: แนวรับถัดไป
- ไม่แนะนำให้ Long
สิ่งที่ต้องระวัง:
- Sellside Liquidity (SSL): มีโอกาสสูงที่ราคาจะถูกลากลงไปแตะ SSL
- False Breakouts: ระวัง
- Volatility: สูง
Setup Day Trade แบบ SMC (ตัวอย่าง):
- ระบุ Order Block: หา Order Block ขาลง (Bearish Order Block) ใน TF15
- รอ Pullback: รอให้ราคา Pullback ขึ้นไปทดสอบ Order Block นั้น
- หา Bearish Entry:
- Rejection: รอ Price Action ปฏิเสธ Order Block
- Break of Structure: รอให้ราคา Break โครงสร้างย่อยๆ
- Money Flow: ดู Money Flow ให้เป็นสีแดง
- ตั้ง Stop Loss: เหนือ Order Block
- ตั้ง Take Profit: แนวรับถัดไป
คำแนะนำ:
- ความขัดแย้งของ Timeframes: ไม่มีแล้ว ทุก Timeframes สอดคล้องกัน
- Money Flow: เป็นลบในทุก Timeframes
- Trend Strength: เป็นลบ
- Order Block TF Day: หลุด Order Block ขาขึ้นแล้ว
- ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-
 @ c43d6de3:a6583169
2025-02-20 23:54:51
@ c43d6de3:a6583169
2025-02-20 23:54:51"So, What’s the News?"
Were it not for these very words, we might never have had a modern capitalistic society.
Between 1500 and 1800, coffeehouses were more than just places to grab a quick hit of caffeine—they were the beating heart of local communities. These spaces buzzed with debate, discussion, and the exchange of groundbreaking ideas. Strangers became intellectual sparring partners, not merely reading the news but dissecting and debating it in real-time.
One could easily imagine Adam Smith engaged in animated conversation with David Hume in a coffeehouse on Edinburgh’s Royal Mile—the former outlining the invisible hand of the market, the latter countering that human behavior is driven more by emotion than reason. Such debates weren’t confined to elite scholars. Merchants, craftsmen, and common laborers sat shoulder to shoulder, engaging in discussions that transcended social class.
But then came industrialization.
The rise of factory life replaced the organic rhythms of community engagement with rigid work schedules. As cities expanded and people became busier, the once-thriving coffeehouses—where time was slow, conversation was deep, and debate was central—began to empty. The demand for efficiency left little room for leisurely discussions, and over time, the public square of ideas withered.

nostr:npub1uzt238htjzpq39dxmltlx60vxym9fetk9czz6kddq6fhvkf4z3usy9qtrh Mouth watering Hodl rounds- Bitcoin only
https://shopstr.store/listing/84f20c5e1ef94762b60f0d5fb4398594ace6c5589212f94269e9542fbe351732
Photos Courtesy of nostr:npub1c8n9qhqzm2x3kzjm84kmdcvm96ezmn257r5xxphv3gsnjq4nz4lqelne96 Give him a follow and some zap love if you like his art
Empty Street Corners and Hollow Venues
Adam Smith would lose his mind with how interconnected the world is today.
Yet, he might also notice something unsettling: while we are globally connected, our local communities feel more fragmented than ever before.
He’d have a hell of an online presence but he, just like many do today, might get the sense that something isn't quite right. The world is quieterthan ever before while online discourse teeters on the verge of violent physical manifestations.
It’s not that public discourse has disappeared. Rather, it has been exiled to the internet. Social media has become our new coffeehouse, but instead of robust face-to-face engagement, we navigate a landscape of curated algorithms, viral outrage, and fragmented conversations. The once-public square of ideas has transformed into isolated echo chambers, where avatars shape narratives that must be adhered to lest one be accused of inconsistency and lose credibility.
The result? People live layered lives with layered personas—some even attaining secret fame in online communities while remaining anonymous in their own neighborhoods. Meanwhile, the street corners remain empty, and the venues that once thrived with the fervor of intellectual thought stand hollow.

Photos Courtesy of nostr:npub1c8n9qhqzm2x3kzjm84kmdcvm96ezmn257r5xxphv3gsnjq4nz4lqelne96 Give him a follow and some zap love if you like his art
The Need for a Modern Coffeehouse
Historically, coffeehouses were revolutionary because they democratized knowledge. They provided an open forum for ideas, allowing philosophy, politics, and commerce to intermingle freely. Unlike monasteries or universities, coffeehouses welcomed anyone who could afford a cup of coffee.
With the rise of digital discourse, have we lost something essential? The depth, accountability, and personal engagement that once defined public debate have been replaced by reactionary commentary and fleeting viral moments. The question is no longer where we discuss ideas—it’s how we engage with them.
We need to ask ourselves: Can we reclaim a physical space for intellectual exchange? Or has the age of meaningful, face-to-face discourse faded, vanishing with the steam of yesterday’s coffee?
Can We Bring Back the Local Forum? Should We Care?
Before coffeehouses, philosophy lived in elite institutions and royal courts. With the rise of coffee culture, it became truly public, shaping modern democracy, scientific thought, and social progress. The internet, for all its wonders, lacks the tactile, immediate, and personal engagement that once made intellectual debate so powerful.
The challenge ahead is not just about nostalgia for coffeehouse debates—it’s about asking whether we can create new spaces, physical or digital, that foster real intellectual exchange. Without them, we risk losing something fundamental: the ability to challenge, refine, and reshape our ideas through genuine human connection. But most of all, we risk the possibility great ideas come but no action is ever taken to make them real in this real world.
So, what’s the news?
Thank you for reading!
If this article resonated with you, let me know with a zap and share it with friends who might find it insightful.
All zap revenue from this article is shared with nostr:npub1c8n9qhqzm2x3kzjm84kmdcvm96ezmn257r5xxphv3gsnjq4nz4lqelne96 for his photograph contributions.
Your help sends a strong signal for content creators like us to keep making cool shit like this!
Interested in fiction? Follow nostr:npub1j9cmpzhlzeex6y85c2pnt45r5zhxhtx73a2twt77fyjwequ4l4jsp5xd49 for great short stories and serialized fiction.
More photography and articles you might like from nostr:npub1cs7kmc77gcapuh2s3yn0rc868sckh0qam7p5p4t9ku88rfjcx95sq8tqw9 and nostr:npub1c8n9qhqzm2x3kzjm84kmdcvm96ezmn257r5xxphv3gsnjq4nz4lqelne96 :
nostr:naddr1qvzqqqr4gupzps0x2pwq9k5drv99k0tdkmsekt4j9hx4fu8gvvrwez3p8yptx9t7qqxnqvfjxqer2tfh0fekz7r5l270gu
 https://pictureroom.substack.com/p/020825
https://pictureroom.substack.com/p/020825nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq24s4mrfdm55utg23z55ufs94argvn523k5yqhkrc3
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2nvnr5d4nngw2zgd5k5c6etftrzez9fd9kkcl0pzp
-
 @ ee603283:3bc79dec
2025-02-26 23:50:16
@ ee603283:3bc79dec
2025-02-26 23:50:16Source Article by the Bitkey team and Undine Rubeze: https://bitkey.build/inheritance-is-live-heres-how-it-works/
TLDR: You wrap your mobile key, and encrypted this wrapped key with your beneficiaries public key. Send this info to Bitkey's servers. Your beneficiary can trigger the inheritance process after your passing and wait 6-months before they can do anything.
6 months seems like a long-time to be able to access critical life-savings funds for your family. This should help you prioritize a 3-6 month emergency "cash" savings for your family. Cash can be in a savings account or physical cash. Additionally, it might be beneficial to setup a life-insurance plan (a simple term-life plan) where the immediate bills and expenses are covered.
bitcoin #nostr
devs I tried to import the url into highlighter but got this error: "The page is not reader-friendly"
-
 @ d360efec:14907b5f
2025-02-25 09:12:44
@ d360efec:14907b5f
2025-02-25 09:12:44$OKX:BTCUSDT.P
Overall Assessment:
Bitcoin (BTCUSDT) on OKX is currently showing a bearish trend across all analyzed timeframes (Daily, 4-Hour, and 15-Minute). While the long-term trend (Daily) was technically an uptrend, it has significantly weakened and broken key support levels, including a major bullish Order Block and the 50-period EMA. The 4-hour and 15-minute charts confirm the downtrend. This analysis focuses on identifying potential areas of Smart Money activity (liquidity pools and order blocks), assessing trend strength, and looking for any emerging chart patterns.
Detailed Analysis by Timeframe:
(1) TF Day (Daily):
- Trend: Downtrend
- SMC (Smart Money Concepts):
- The Higher Highs (HH) and Higher Lows (HL) structure is broken.
- Prior Breaks of Structure (BOS) to the upside, but now a significant and deep pullback/reversal is underway.
- Liquidity:
- Sellside Liquidity (SSL): Significant SSL rests below previous lows in the 85,000 - 90,000 range.
- Buyside Liquidity (BSL): BSL is present above the all-time high.
- ICT (Inner Circle Trader Concepts):
- Order Block: The price has broken below the prior bullish Order Block. This is a major bearish signal.
- FVG: No significant Fair Value Gap is apparent at the current price level.
- EMA (Exponential Moving Average):
- Price is below the 50-period EMA (yellow).
- The 200-period EMA (white) is the next major support level.
- Money Flow (LuxAlgo):
- A long red bar indicates strong and sustained selling pressure.
- Trend Strength (AlgoAlpha):
- Red cloud, indicating a downtrend. No buy/sell signals are present.
- Chart Patterns: No readily identifiable chart patterns are dominant.
- Volume Profile: Relatively low volume.
- Candlesticks: Recent candlesticks are red, confirming selling pressure.
- Support: EMA 200, 85,000-90,000 (SSL area).
- Resistance: EMA 50, Previous All-Time High.
- Summary: The Daily chart has shifted to a downtrend. The break below the Order Block and 50 EMA, combined with negative Money Flow and Trend Strength, are all strong bearish signals.
(2) TF4H (4-Hour):
- Trend: Downtrend.
- SMC:
- Lower Highs (LH) and Lower Lows (LL).
- BOS to the downside.
- Liquidity:
- SSL: Below previous lows.
- BSL: Above previous highs.
- ICT:
- Order Block: The price was rejected by a bearish Order Block.
- EMA:
- Price is below both the 50-period and 200-period EMAs (bearish).
- Money Flow (LuxAlgo):
- Predominantly red, confirming selling pressure.
- Trend Strength (AlgoAlpha):
- Red cloud, confirming downtrend.
- Chart Patterns: No readily identifiable chart patterns.
- Volume Profile: Relatively steady volume.
- Support: Recent lows.
- Resistance: EMA 50, EMA 200, Order Block.
- Summary: The 4-hour chart is in a confirmed downtrend. Money Flow and Trend Strength are bearish.
(3) TF15 (15-Minute):
* Trend: Downtrend / Sideways Down * SMC: * Lower Highs (LH) and Lower Lows (LL). * BOS to the downside. * ICT: * Order Block price is near to a bearish Order Block. * EMA: * The 50-period and 200-period EMAs are acting as resistance. * Money Flow (LuxAlgo): * Red * Trend Strength (AlgoAlpha): * Red/No signals * Chart Patterns: None * Volume Profile: * Relatively High Volume * Support: Recent lows. * Resistance: EMA 50, EMA 200, Order Block. * Summary: The 15-minute chart is clearly bearish, with price action, EMAs, and Money Flow all confirming the downtrend.
Overall Strategy and Recommendations (BTCUSDT):
- Primary Trend (Day): Downtrend
- Secondary Trend (4H): Downtrend.
- Short-Term Trend (15m): Downtrend/ Sideways Down.
- Liquidity: Significant SSL zones exist below the current price on all timeframes.
- Money Flow: Negative on all timeframes.
- Trend Strength: Bearish on Day,4H and 15m.
-
Chart Patterns: None identified.
-
Strategies:
- Wait & See (Best Option): The strong bearish momentum on all shorter timeframes.
-
Short (High Risk): This aligns with the 4H and 15m downtrends.
- Entry: On rallies towards resistance levels (EMAs on 15m/4H, previous support levels that have turned into resistance, Order Blocks).
- Stop Loss: Above recent highs on the chosen timeframe, or above a key resistance level.
- Target: The next support levels (recent lows on 15m, then potentially the SSL zones on the 4H and Daily charts).
-
Buy (Extremely High Risk - NOT Recommended): Do not attempt to buy until there are very strong and consistent bullish reversal signals across all timeframes.
Key Recommendations:
- Conflicting Timeframes: The conflict is resolved toward the downside. The Daily is weakening significantly.
- Money Flow: Consistently negative across all timeframes, a major bearish factor.
- Trend Strength: Bearish on Day,4h and 15m.
- Daily Order Block: The break of the bullish Order Block on the Daily chart is a significant bearish development.
- Sellside Liquidity (SSL): Be aware that Smart Money may target the SSL zones below. This increases the risk of stop-loss hunting.
- Risk Management: Due to the high uncertainty and volatility, strict risk management is absolutely critical. Use tight stop-losses, do not overtrade, and be prepared for rapid price swings.
- Volume: Confirm any breakout or breakdown with volume.
Day Trading and Intraday Trading Strategies:
-
Day Trade (TF15 focus):
- Short Bias: Given the current 15m downtrend and negative Money Flow, the higher probability is to look for shorting opportunities.
- Entry: Look for price to rally to resistance levels (EMAs, Order Blocks, previous support levels that have become resistance) and then show signs of rejection (bearish candlestick patterns, increasing volume on the downside).
- Stop Loss: Place a stop-loss order above the resistance level where you enter the short position.
- Take Profit: Target the next support level (recent lows).
- Avoid Long positions until there's a clear and confirmed bullish reversal on the 15m chart (break above EMAs, positive Money Flow, bullish market structure).
- Short Bias: Given the current 15m downtrend and negative Money Flow, the higher probability is to look for shorting opportunities.
-
Swing Trade (TF4H focus):
- Short Bias: The 4H chart is in a downtrend.
- Entry: Wait for price to rally to resistance levels (EMAs, Order Blocks) and show signs of rejection.
- Stop Loss: Above the resistance level where you enter the short position.
- Take Profit: Target the next support levels (e.g., the 200 EMA on the Daily chart, SSL zones).
- Avoid Long positions until there's a clear and confirmed bullish reversal on the 4H chart.
- Short Bias: The 4H chart is in a downtrend.
SMC Day Trade Setup Example (TF15 - Bearish):
- Identify Bearish Order Block: Locate a bearish Order Block on the TF15 chart (a bullish candle before a strong downward move).
- Wait for Pullback: Wait for the price to pull back up to test the Order Block (this may or may not happen).
- Bearish Entry:
- Rejection: Look for price action to reject the Order Block (e.g., a pin bar, engulfing pattern, or other bearish candlestick pattern).
- Break of Structure: Look for a break of a minor support level on a lower timeframe (e.g., 1-minute or 5-minute) after the price tests the Order Block. This confirms weakening bullish momentum.
- Money Flow: Confirm that Money Flow remains negative (red).
- Stop Loss: Place a stop-loss order above the Order Block.
- Take Profit: Target the next support level (e.g., recent lows) or a bullish Order Block on a higher timeframe.
In conclusion, BTCUSDT is currently in a high-risk, bearish environment. The "Wait & See" approach is strongly recommended for most traders. Shorting is the higher-probability trade at this moment, but only for experienced traders who can manage risk extremely effectively. Buying is not recommended at this time.
Disclaimer: This analysis is for informational purposes only and represents a personal opinion. It is not financial advice. Investing in cryptocurrencies involves significant risk. Investors should conduct their own research and exercise due diligence before making any investment decisions.
-
 @ f288a224:1da1792c
2025-02-19 16:43:40
@ f288a224:1da1792c
2025-02-19 16:43:40First, some context.
I'm a child of the original internet chat-rooms on IRC, and I've tried over the last decades different applications and websites that we could all agree are "social media", but until I found NOSTR (Notes and Other Stuff Transmitted by Relays) I hadn't had this certainty that this isn't something that I will eventually change for something else.
Today, even with all its early stage issues, I have the certainty that NOSTR may be the ULTIMATE and FINAL HOME for my online life.
THE PROBLEMS with the current/old social media landscape

I'm tired of moving from one social media to the next.
As many of you, in my digital lifetime I've had many accounts that have now become obsolete; and the "content" and followings I created during that time was lost when one tech giant lost over the other, forcing us all to "MOVE" ourselves over to the new, and start building our content and following from scratch.
Lately, it's become even worse, where many of us have seen ourselves forced to use and feed more than one social media at a time, since they all serve various purposes, with sometimes diverse functionality, besides all being catered to different segments of people to connect you to (LinkedIn, Instagram, TikTok, Youtube...). How much is too much, though? And how much time should we keep spending re-adapting our content to reach all of our network?
For work, I've found myself having to create accounts in several of these giant data hoarding companies, having to build each following from scratch and to create "content" for all, and having to go through the hurdle of posting everything, everywhere, all at once.
I'm sick of ever-changing terms, conditions and capabilities.
Let's be honest, the majority of us have never ever read the full terms and conditions, let alone every time they are updated without us knowing which rights to our data we are giving away, and which terms we are accepting that may be detrimental to us and our mental health.
We've learnt to accept that we are in their playground, they make up the rules, and if they choose to change the rules mid-game we just need to swallow it. We literally have no other choice, it's either that or desertion, which basically means walking away from everything we've built on their "public square". So, like a carefully engineered detrimental incentive structure, the more time we spend building on their turf, the more we are tied to them and conditioned to never leave them. The more we build and make them grow on our content, the more we'll lose if or when we drop out.
And even if you accept all that and choose to play along, and you do your best to create the most awesome account in the neighborhood, the random changes they make to optimize ad revenue or user attention will inevitably affect you and all your work.
If you created all your feed according to Instagram's squares but they choose to change to TikTok style dimensions due to their tech positioning battle with the Chinese giant... You swallow. If you edited your reels according to what you felt was the best 100 seconds video... Not anymore, suddenly 90 seconds is the maximum you're allowed... No appeal, no options. You Swallow. What? Seeing less of the people you actually WANT TO FOLLOW because they decided to clutter your feed with ads and suggestions, guess again: YOU SWALLOW.
AREN'T YOU FEELING FULL ENOUGH OF ALL THE SHIT THEY'VE FORCED DOWN YOUR THROAT?
Living our digital lives on these platforms feels like standing on ever changing quicksand, never endingly trying to "hack the algorithm" in order to have our content placed in front of the people who should automatically be able to see us from the moment they chose to follow us; and the worst part of it is, you never know when you may lose it all.
Let's not forget, your social media account is NOT REALLY YOURS.
Recently, a friend's social media account was hacked. She didn't know how it happened; all she knew is that she got an email from Meta saying she had acted against community guidelines and her accounts were therefore being removed (the one hacked and all those liked to her email, which meant personal and work accounts). She tried to appeal, to no avail. She hadn't done anything wrong, but suddenly her identity had disappeared from all our feeds, and her content didn't exist anywhere anymore. She lost plenty of photos she had always counted on finding on her Instagram and lost the people she followed and who followed her. It was as if she had never existed on the platform.
(Looks like a good moment to remind you to download all your valued content from the platforms you use in case something like this happens to you)
 And this happened to someone who hadn't done anything "to deserve it". It has actually happened to more than one person I know, and every time they've been helpless and had no recourse, and yet, found themselves having to rebuild from scratch on the same platform that de-platformed them, because they had "no other option", and "their friends are there".
And this happened to someone who hadn't done anything "to deserve it". It has actually happened to more than one person I know, and every time they've been helpless and had no recourse, and yet, found themselves having to rebuild from scratch on the same platform that de-platformed them, because they had "no other option", and "their friends are there".Many more people have encountered this awful wake up call, some because of a hack, like my friend, others found themselves removed because they posted content critical of the platform... there are so many reasons people have gotten de-platformed and posts have gotten deleted without warning. And every time, we accept it, as if we owe them something; as if we need to settle for this kind of abusive environment that gets rich on our content and attention without having a say in anything.
But we do have another option that flips that attention retention model completely on its head and empowers the user. That option is NOSTR, our exit from the extractive social media silos they have trapped us into.
NOSTR: The better social experience for the internet era.
NOSTR (Notes and Other Stuff Transmitted by Relays) is not a social media app, it's an Internet protocol. It's open source and many many developers around the world are creating apps on top of it and creating THE ULTIMATE SOCIAL MEDIA EXPERIENCE for users.
I first heard of NOSTR from Jack Dorsey on what used to be called Twitter, and when I joined it two years ago it was really rough around the edges, but it was FULL OF POTENTIAL and the value proposition was very clear to me from the beginning.
Firstly, YOU OWN YOUR IDENTITY, that includes your content and your follower list.
So, what does owning you identity mean? I guess many of us have thought we owned our identity before, but the reality is that the platforms owned our identities, which is why they could delete or censor us.
Owning your identity on NOSTR is empowered by encryption and cryptography. I'm not going to go into the technical part, but to explain as simply as I can, on NOSTR no platform owns your login and password to use on their playground; you can basically use any NOSTR app to create your identity to navigate it. They give you a login (npub) and password (nsec), and the magic part is that you can USE THAT IDENTITY ON ANY NOSTR APP OR WEBSITE, no need to sign up individually on each one.
Welcome to the beauty of INTEROPERABILITY.
I cannot emphasize enough what it feels like to be able to take your identity, your followers, your content and carry it from one app to the other.
On NOSTR there is a rich ecosystem of apps and websites that keep growing. We have "clients" that allow you to experience NOSTR in interfaces that could remind you of Twitter, Instagram, TikTok, Substack, Twitch, Clubhouse, Podcast apps and many more. You can find many of them on https://nostrapps.com/ .
With that information in mind, imagine you only needed one user password, your NOSTR nsec, and with that key, you could open you Instagram, or your Twitch or your Substack. And all your followers would be there, and you could choose what type of content you wanted to link to your identity for your followers to find. No longer "find link in bio", or "go to our YouTube channel", everything you post on NOSTR is tied to your identity, and you can post it all with a single set of keys that posts your content "everywhere".
And since your content is "in every client", each of YOUR FOLLOWERS CAN CHOOSE if they are more interested in experiencing your photography content "Insta-like" or if they love your "Twitter-esque" notes better. Each user navigates NOSTR with the interface they prefer.
(With great power comes great responsibility, and I feel obligated to tell you that if you ever lose your nsec, no platform is gonna be able to save you. It's like the keys to your house, unless you keep a copy safely, no one can open it for you (there are no locksmiths on NOSTR). And if you leave your keys lying around on a cloud server somewhere, someone may grab your keys, open your house and use it however they want).
The beauty of this interoperability and the fact that my keys open up my identity to all the NOSTR realms is that you don't need to settle for one client. I use 5 to 6 clients regularly everyday depending on the mood I'm in, (or the bugs that still prove this is a nascent ecosystem in development). Some I use when I want a more "Twitter-like" experience, others when I want to browse photos and others just give different algorithms to choose how to view my feed, and the best part is NO ONE CAN CLUTTER MY FEED WITH ADS. I can curate my feed however is most important to me, and each "NOSTR client" is like a different skin that customizes the way I experience the content.
However, the most important reason I started to use different NOSTR apps was that when I started, not all apps had zapping integrated. Some still don't, but most do :)
ZAPS: direct micropayments from your followers.
Zaps are tips that come directly from the people who find value in the shit that you post. They are micropayments in the form of "sats", fractions of ever-increasing in value bitcoin , and a very big reason why I'm spending less and less time on other social media accumulating valueless likes that only feed the algorithm, and more time on NOSTR interacting with humans that post valuable notes hoping the generous souls that run upon their art or creations will find them valuable enough to tip them for it.
It's crazy how the type of content you post can change when your incentive is not to feed an algo, but to give real value to other humans around the world and be your most authentic self. Where Twitter/X's algo benefited the type of incendiary content that shocked and outraged people, NOSTR's incentives benefit those who bring most value to the network and their peers.
A few sats tip may not seem much, but even if the equivalent of a small zap is merely cents, it feels a whole lot better than any like, and you can count that if the purchasing power of bitcoin continues to accrue, those value-earned tips will too. Many "nostriches" are getting tons of zaps for memes on NOSTR, valuable articles, videos or participation in zapathons .
In NOSTR is where I first heard of the concept "value for value", and the community is very adamant in making "v4v" an alternative to ad revenue driven models. Because we need to be the change we wanna see in the world.
We've heard it said that if you're not paying for the product, you are the product. And up until now that has meant we felt obliged to accept that since ads were paying the platforms, we were required to give them our attention. But the open source movement thinks we deserve better. We deserve a better Internet, like the decentralized promise we've slowly been robbed of to enrich 10 people out of the work of all of us. If they can't monetize our attention, they got nothing.
But why should they monetize it, instead of us?
Even with the glitches and bugs, NOSTR ROCKS!
The things I've grown to love most about NOSTR are:
• Not having the clutter of ads on my feed and being able to ONLY SEE WHAT I CHOOSE TO SEE.
• People who are not on NOSTR can ENJOY MY STUFF WITHOUT HAVING TO LOGIN.
• Being able to ENJOY ALL THE BENEFITS OF INTEROPERABILITY, and use many NOSTR clients that enrich my user experience knowing I own my identity and that means I'm not locked in, I can move like a bird wherever I decide.
• ZAPPING complete strangers that made me laugh, gave me a cool insight or simply made a witty comment.
• GETTING TIPPED for memes, articles, photos, videos and any "Notes and Other Stuff" that people have found valuable.
CONCLUSION: Join us on NOSTR, participate in claiming back your digital life.
If you've made it this far in my love letter to NOSTR, thank you for being interested. Curious minds is what the world needs more of <3.
NOSTR is an ecosystem that is being built in the open by relentless developers that are continuously striving to out compete each other to offer a better user experience, it's a many headed dragon that has constant upgrades and implementations which benefits us all, and as such it sometimes comes with bugs and glitches.
Building the future is always buggy and requires testers and early adopters that help shape the technology in the best way possible, especially if you wanna build outside the incentive models of the devouring giants we're trying to get away from.
Being such an open ecosystem can also be overwhelming for a newcomer, where to start? There are so many clients to experience; so here are some of my recommendations.
Please, don't feel you need to go through all of them now, start step by step. This article will always be here whenever you need it (this is not Instagram ;) ).
Creating your NOSTR identity/account with a wallet integrated to receive zaps on both Android and iOS:
• YAKIHONNE: It's a Japanese client that offers a great on-boarding experience. From the app you can create the account and enable a wallet to receive zaps. In it you can view and post short and long form content, images, videos and more. (Once you have the account created on your app, you can also visit the desktop version on https://yakihonne.com/ )
• PRIMAL: For a while it has positioned itself as a great on-boarding NOSTR client because it offers the same things as Yakihonne, has an integrated wallet, with the added benefit that you can also "buy sats/bitcoin" directly from its wallet, which can come in handy (it comes with a 15-30% premium, so only use for small amounts). It also has the desktop version at primal.net.
My favorite NOSTR iOS PHONE APPS after on-boarding, in case you wanna hop into different user experiences:
• DAMUS: created by the original creator of the "ZAP", Will Casarin, it's an iOS simple client that is reliable and fast with notifications. It keeps things simple, mostly focusing on short note content, although you can also see images and short video. But the feed is optimized as a more "Twitter-like" feed.
• NOSTUR: The iOS phone client that has it all! It's the client I've used that integrates the most of NOSTR's possibilities, you can see all of the mentioned above with the previous clients, but also view LIVE STREAMS, and have multiple accounts set up simultaneously. The enhanced capabilities can sometimes come at the cost of crashing or being slow to load.
• FREERSE: Nice clean user interface with plenty of functionality, with easy navigation on topics like #art #photography or any other interests. It's my always reliable back-up to upload image content.
• OLAS: The new kid on the block Olas client, by prolific developer Pablof7z, is trying to take on Instagram and TikTok and has developed a client mainly focused on the visual and photographic part of NOSTR.
Desktop clients & OTHER GEMS OF THE NOSTR REALM:
There is an infinite number of clients for desktop, but I usually find myself on ditto.pub or slidestr.net for a more visual experience.
• ALBY is INTEROPERABILITY'S BEST FRIEND. Alby is not a NOSTR client, but it's a browser extension that makes it seamless to jump from one desktop client to another with your wallet and identity without compromising your security.
• HIVETALK: A video call client (reminiscent of Zoom) that doesn't track you or spy on you and that enables zapping and many other functionalities during the calls.
• NOSTR NESTS: Audio spaces client that allows people to listen to conversations, chat within it and zap the people involved.
if you made it this far, THANK YOU FOR YOUR ATTENTION.
HOPE YOU FOUND VALUE IN IT AND UNDERSTOOD WHY, FOR ME, THE FUTURE OF SOCIAL MEDIA IS BRIGHT, OPEN AND USER-CENTRIC.
FUCK THE MIDDLEMEN.
-
 @ 6ad3e2a3:c90b7740
2025-02-19 14:17:22
@ 6ad3e2a3:c90b7740
2025-02-19 14:17:22Like most members of the human race, I don’t enjoy filing my taxes. “Don’t enjoy” though understates my actual feeling which is “would rather do a tour in Afghanistan.” It’s not even the money I’m forced to pay that I know for sure will be misallocated, stolen or worse — put to use in ways that are anathema to everything I believe and in direct opposition to conditions in which human beings thrive. That’s only part of it.
The other and perhaps bigger part is they require me — under penalty of law — to do homework. They command me, as though they were my boss, to complete this work project, my tax return, and if I don’t I’ll have my property seized, my credit destroyed and even go to prison. This is so even though I am not a criminal, and I never agreed to work for this boss.
And it’s not just a random work project I am required to submit, so that they can misallocate, steal and attack me with my own money. It’s a project that requires me to divulge private details about myself, what transactions I’ve made, with whom I made them and for what purpose. I am a private citizen, I hold no public office or official role, and yet the public sector is not only entitled to comb through the details of my life, but I must be complicit in helping them under penalty of law, i.e., threat of violence if I don’t comply.
. . .
This was not always the case. The income tax was only introduced in 1913, and at the time was only for the richest of the rich. That is to say, it is not the default state of affairs in the United States under its original constitution, and it’s strange that it’s been normalized as such. And despite it being normalized — for the greater good, of course — our government is still somehow $36 trillion in debt.
In other words, despite the annual indignity to which we subject ourselves, the government spends far more money than it takes in. I am reminded of Dostoyevsky’s line: “Your worst sin is that you have destroyed and betrayed yourself for nothing.” The government is spending money it doesn’t have, whether you pay it or not, and the money you do pay, for things you not only do not want but are vehemently against, doesn’t come close to covering their cost.
. . .
I was having lunch with some normies last month, and the subject of taxes came up. They were talking about the ways in which they, as ex-pats, minimize their tax burden, using certain loopholes, and at one point someone questioned why government pensions were taxed, given the entity paying the pension and demanding it be taxed was one and the same. Why not just pay a smaller pension?
One of them asked me, and I said: “I don’t think anyone should be taxed.” She shook her head and muttered in amusement, “No, people need to be taxed.” This despite not two minutes earlier explaining how she was optimizing her tax status, which no doubt she would have optimized all the way to zero or if she were able!
. . .
Taxes are necessary, it’s assumed, to pay for things individuals won’t. “Who will build the roads?” they wonder. I would imagine car makers would be invested in building roads, those who ship goods via truck might have an interest and consumers, flush with their new zero percent tax rate, might pay a little more for the end products to facilitate road creation so those products get to them on time and in good condition. In fact, it might be more expensive to ship them via horseback or whatever alternate form of transport would take the place of motor vehicles should no one shell out for roads.
Moreover, people seem to believe taxes should always be taken not from them, but from those rich enough to afford them painlessly. Never mind anyone reading this substack is vastly wealthy compared to much of the third world (how painful can taxes be so long as you have food on the table and a roof over your head?), and never mind no one ever voluntarily pays more tax than he owes. Why not? If taxation is a good thing, why not do more good by overpaying?
But no, it’s always someone else who needs to be forced under penalty of law, i.e., threat of violence, to give up his property for what those in authority deem “the greater good”. Taken to its logical conclusion, if the authorities deem anyone sufficiently wealthy and the greater good sufficiently necessary, they can legally take that wealth by force. We can quibble about how much funding is necessary and what is the “greater good,” but it’s often essential things like the “safe and effective” vaccine without which millions would surely die or the necessity of invading Iraq, which cost $6 trillion to prevent Sadaam Hussein’s “weapons of mass destruction” from reaching US soil.
It’s amazing authorities so often discover urgent projects without which people will die or suffer terribly, on account of which it’s necessary to commandeer money you’ve earned or saved! And while I am taking about the indignity of filing income tax, I don’t mean to leave out property tax, sales tax, estate tax, individual state and city taxes and the like. At least with some of those you have a fixed amount to pay, and you don’t have to submit to an on-camera self-administered anal cavity search of your finances in those cases.
You’d also think given how many ways citizens are taxed that roads would be in tip top condition, our water and environment would be clean, our airports modern and state of the art, our health care affordable and accessible, but of course none of that is the case. Again per Dostoyevsky — we have betrayed ourselves for nothing.
. . .
The irony of this essay/diatribe is I will file my taxes like the cuck I am over the next week or so. I don’t want to do this, but it’s simply not worth the consequences for non-compliance. And I feel bad about making this compromise — bad about myself because I am doing something I feel is wrong for convenience, the same kind of calculation people made when they injected themselves with experimental mRNA chemicals they didn’t want to keep their jobs or travel. I like to think of myself as resolute and uncompromising, but in this instance I roll over every year. Perhaps that’s part of why I dread it so much.
. . .
I’ll end with a footnote of sorts. In the late spring of 2023, I discovered I was due a significant refund, and I paid my accountants who figured this out $400 to re-file for me. They told me I could expect it to take up to nine months to process, so I largely forgot about it until spring of 2024 when I called but got phone-treed to death and waited until September to brute-force my way to a human in another department to explain the situation. They didn’t tell me anything, but agreed to do a “trace” which a couple weeks later revealed someone else had intercepted and cashed my check. (It’s not direct deposit because I’m overseas.)
I immediately returned the form proving it was not my signature on the deposited check, and now, five months later, in February of 2025, they are still processing my purported payment which I have yet to receive. I did, however, receive a notice of the interest I was “paid” for 2024 on which I’m expected to be taxed. That interest went to the person who stole my original check obviously, they know this, and yet it apparently hasn’t caught up in the system. And the truth is I will probably pay the tax on it as the hassle of explaining why I’m not is simply not worth it, and I will sort it out on next year’s tax return, assuming Trump hasn’t abolished the IRS entirely, God willing, and delivered us, in small part, from this abject dystopia.
-
 @ 7bda2206:35ba1c0c
2025-02-25 03:25:08
@ 7bda2206:35ba1c0c
2025-02-25 03:25:08Exercise is essential for maintaining a healthy lifestyle. However, it can be challenging to stay motivated to work out regularly. One way to make exercise more fun and engaging is to turn it into a competitive experience. This can be done in a number of ways, such as setting personal goals, competing with friends and family, or joining a fitness challenge.
Set Personal Goals
One of the best ways to make your workouts more competitive is to set personal goals. This could involve setting a goal to lose a certain amount of weight, run a certain distance, or complete a certain number of workouts per week. Once you have set your goals, you can track your progress and see how you are doing. This can help you stay motivated and keep you on track.
Compete with Friends and Family
Another way to make your workouts more competitive is to compete with friends and family. This could involve challenging each other to see who can lose the most weight, run the farthest, or complete the most workouts in a week. You can also join a fitness challenge together. This can be a great way to stay motivated and have fun at the same time.
Join a Fitness Challenge
There are many fitness challenges available online and in your local community. These challenges can be a great way to stay motivated and meet new people. Some popular fitness challenges include the Couch to 5K challenge, the 30-Day Shred challenge, and the 75 Hard challenge.
Additional Tips
In addition to the tips above, there are a few other things you can do to make your workouts more competitive:
- Find a workout buddy. Having someone to work out with can help you stay motivated and accountable.
- Reward yourself for reaching your goals. This could involve buying yourself a new piece of workout gear or taking a trip to your favorite restaurant.
- Make it fun! Put on your favorite music, listen to a podcast, or watch a funny video while you work out.
By following these tips, you can turn your workouts into a fun and competitive experience. This can help you stay motivated and reach your fitness goals.
Here are some additional benefits of making your workouts competitive:
- Increased motivation: When you are competing with yourself or others, you are more likely to push yourself harder and achieve your goals.
- Improved performance: Competition can help you improve your performance and reach your full potential.
- Increased enjoyment: Making your workouts fun and competitive can help you enjoy them more.
If you are looking for a way to make your workouts more challenging and rewarding, consider turning them into a competitive experience. You may be surprised at how much you enjoy it!
In addition to the tips above, here are some other ways to make your workouts more competitive:
- Use a fitness tracker. Fitness trackers can help you track your progress and see how you are doing.
- Join a gym or fitness studio. Gyms and fitness studios often offer classes and challenges that can help you stay motivated.
- Find a workout buddy. Having someone to work out with can help you stay motivated and accountable.
- Reward yourself for reaching your goals. This could involve buying yourself a new piece of workout gear or taking a trip to your favorite restaurant.
- Make it fun! Put on your favorite music, listen to a podcast, or watch a funny video while you work out.
-
 @ 5de23b9a:d83005b3
2025-02-19 03:47:19
@ 5de23b9a:d83005b3
2025-02-19 03:47:19In a digital era that is increasingly controlled by large companies, the emergence of Nostr (Notes and Other Stuff Transmitted by Relays) is a breath of fresh air for those who crave freedom of expression.
Nostr is a cryptography-based protocol that allows users to send and receive messages through a relay network. Unlike conventional social media such as Twitter or Facebook
1.Full Decentralization: No company or government can remove or restrict content.
2.Sensor-Resistant: Information remains accessible despite blocking attempts.
3.Privacy and Security: Uses cryptography to ensure that only users who have the keys can access their messages.* **
-
 @ f6488c62:c929299d
2025-02-25 03:22:49
@ f6488c62:c929299d
2025-02-25 03:22:49การที่สหรัฐอเมริกาปรับมูลค่าทองคำในคลัง (re-peg) จะมีผลกระทบที่สำคัญต่อทั้งระบบการเงินโลกและบิทคอยน์ ด้วยเหตุผลต่างๆ ที่อาจเกิดขึ้นดังนี้:
ทองคำในฐานะสินทรัพย์เก็บมูลค่า: หากสหรัฐอเมริกาปรับราคาทองคำจาก 42 ดอลลาร์ต่อออนซ์เป็นราคาปัจจุบันที่สูงถึง 2,953.5 ดอลลาร์ต่อออนซ์ การปรับนี้จะทำให้ทองคำได้รับความนิยมและมีมูลค่าเพิ่มขึ้นอย่างมากในมุมมองของนักลงทุนทั่วโลก ส่งผลให้ทองคำมีบทบาทสำคัญขึ้นในระบบการเงิน อีกทั้งยังเป็นทางเลือกการลงทุนที่น่าสนใจมากขึ้นในฐานะ "safe haven" หรือสินทรัพย์ที่ปลอดภัย.
ผลกระทบต่อตลาดดอลลาร์สหรัฐ: การประเมินมูลค่าทองคำใหม่จะทำให้ค่าเงินดอลลาร์อ่อนค่าลง เนื่องจากทองคำถูกมองว่าเป็นตัวบ่งชี้ความมั่งคั่งและเสถียรภาพทางการเงิน การอ่อนค่าของดอลลาร์อาจส่งผลให้บิทคอยน์เป็นที่น่าสนใจมากขึ้นในฐานะสินทรัพย์ที่ไม่ขึ้นกับเงินดอลลาร์และธนาคารกลางใด ๆ.
การเติบโตของบิทคอยน์: เมื่อระบบการเงินดั้งเดิม (เช่น ดอลลาร์สหรัฐ) เริ่มสั่นคลอนหรือลดความน่าเชื่อถือ บิทคอยน์ซึ่งเป็นสินทรัพย์ดิจิทัลที่ไม่ขึ้นกับรัฐบาลหรือธนาคารกลางก็จะได้รับความสนใจมากขึ้นจากนักลงทุนที่ต้องการหลีกเลี่ยงความเสี่ยงในระบบการเงินแบบดั้งเดิม นอกจากนี้บิทคอยน์ยังถือเป็นสินทรัพย์ที่มีการจำกัดจำนวน (21 ล้าน BTC) ซึ่งถือว่าเป็นการป้องกันภาวะเงินเฟ้อที่มักจะเกิดขึ้นจากการพิมพ์เงินจำนวนมากโดยธนาคารกลาง.
การปรับตัวของประเทศอื่นๆ: หากสหรัฐฯ ปรับมูลค่าทองคำใหม่ ประเทศอื่นๆ อาจจำเป็นต้องปรับเปลี่ยนมูลค่าทองคำของตนเองเพื่อตอบสนองต่อการเปลี่ยนแปลงนี้ และอาจเห็นการเคลื่อนไหวในการสนับสนุนสินทรัพย์ดิจิทัลอย่างบิทคอยน์มากขึ้นเพื่อกระจายความเสี่ยงจากการพึ่งพาระบบการเงินดอลลาร์สหรัฐ.
สรุปได้ว่า หากการปรับมูลค่าทองคำของสหรัฐเป็นจริง การเคลื่อนไหวนี้อาจเป็นตัวกระตุ้นให้บิทคอยน์เติบโตขึ้น เนื่องจากนักลงทุนมองหาทางเลือกที่ปลอดภัยจากความไม่แน่นอนในระบบการเงินดั้งเดิม และเพิ่มการยอมรับในสินทรัพย์ดิจิทัลมากขึ้น.
-
 @ 8d34bd24:414be32b
2025-02-26 23:07:43
@ 8d34bd24:414be32b
2025-02-26 23:07:43My mind keeps chewing on these verses in Jeremiah. Maybe I can’t get it out of my head because it seems so contrary to everything I have believed regarding to prayer.
“As for you, do not pray for this people, and do not lift up cry or prayer for them, and do not intercede with Me; for I do not hear you. Do you not see what they are doing in the cities of Judah and in the streets of Jerusalem? The children gather wood, and the fathers kindle the fire, and the women knead dough to make cakes for the queen of heaven; and they pour out drink offerings to other gods in order to spite Me. Do they spite Me?” declares the Lord. “Is it not themselves they spite, to their own shame?” (Jeremiah 7:16-19) {emphasis mine}
Before continuing with this article, make sure you have read What? Do Not Pray For ..., so you have my background thoughts on this passage.
After writing the first post, I began thinking about how this verse applies to American Christians today in my post A Hard Question With an Uncomfortable Answer. In my first two articles, I basically came to the conclusion that we should not pray blessings on those who were sinning and rejecting God, but that praying for repentance and turning back to God would be an allowed and even honored prayer. Then today, while listening to a sermon from Revelation, I thought, “Is there a time we are called to not pray for someone or some nation because God has given them their choice and He is no longer calling them to Himself?”
When God Hardens a Heart
There are a lot of verses where God says that he hardened their heart. The most well known is regarding the hardened heart of the Egyptian Pharaoh in Exodus where we read a succession of verses about a hardened heart:
First Pharaoh hardens his own heart:
But when Pharaoh saw that there was relief, he hardened his heart and did not listen to them, as the Lord had said. (Exodus 8:15) {emphasis mine}
then he hardens his heart again:
But Pharaoh hardened his heart this time also, and he did not let the people go. (Exodus 8:32) {emphasis mine}
then he hardened his heart and his servants hearts:
But when Pharaoh saw that the rain and the hail and the thunder had ceased, he sinned again and hardened his heart, he and his servants. (Exodus 9:34) {emphasis mine}
then God hardens Pharaoh’s heart:
Then the Lord said to Moses, “Go to Pharaoh, for I have hardened his heart and the heart of his servants, that I may perform these signs of Mine among them, (Exodus 10:1) {emphasis mine}
God didn’t harden Pharaoh’s heart initially, but after repeated choices by Pharaoh, God gave Pharaoh the hardened heart he chose. Also, God hardened Pharaoh’s heart in order to perform signs that He wanted to perform to show Himself to the Israelites and the Egyptians. He did it to fulfill His will and His plan.
Once God chose to harden Pharaoh’s heart, would it be praying according to God’s will to ask that Pharaoh repent? As uncomfortable as this makes me, I don’t think it would be praying according to God’s will to pray for repentance for Pharaoh.
When God Declares His Judgment
In Jeremiah 27, God has stated that Babylon will conquer Judah, take away the people, and take the golden implements from the Temple. He says that those who want to live must submit to Babylon. This is God’s will. Many supposed prophets were prophesying that Babylon will not capture Judah and then after Judah was conquered, that they would be brought back after 2 years contrary to God’s will and declaration of 70 years of captivity.
Then I spoke to the priests and to all this people, saying, “Thus says the Lord: Do not listen to the words of your prophets who prophesy to you, saying, ‘Behold, the vessels of the Lord’s house will now shortly be brought again from Babylon’; for they are prophesying a lie to you. Do not listen to them; serve the king of Babylon, and live! Why should this city become a ruin? But if they are prophets, and if the word of the Lord is with them, let them now entreat the Lord of hosts that the vessels which are left in the house of the Lord, in the house of the king of Judah and in Jerusalem may not go to Babylon. (Jeremiah 27:16-18) {emphasis mine}
Regarding these so-called prophets, God says, “if the word of the Lord is with them, let them now entreat the Lord of hosts.” This sounds like they should pray thus only if “the word of the Lord is with them,” or basically if they are praying according to God’s will. Conversely, since the passage makes clear these “prophets” are not speaking God’s word, nor supporting God’s will, then God should not be entreated (asked in prayer) to act contrary to His will.
When God Gives Them Over to Their Sin
Similarly, in the New Testament it says of God:
For even though they knew God, they did not honor Him as God or give thanks, but they became futile in their speculations, and their foolish heart was darkened. Professing to be wise, they became fools, and exchanged the glory of the incorruptible God for an image in the form of corruptible man and of birds and four-footed animals and crawling creatures.
Therefore God gave them over in the lusts of their hearts to impurity, so that their bodies would be dishonored among them. For they exchanged the truth of God for a lie, and worshiped and served the creature rather than the Creator, who is blessed forever. Amen.
For this reason God gave them over to degrading passions; for their women exchanged the natural function for that which is unnatural, and in the same way also the men abandoned the natural function of the woman and burned in their desire toward one another, men with men committing indecent acts and receiving in their own persons the due penalty of their error.
And just as they did not see fit to acknowledge God any longer, God gave them over to a depraved mind, to do those things which are not proper, being filled with all unrighteousness, wickedness, greed, evil; full of envy, murder, strife, deceit, malice; they are gossips, slanderers, haters of God, insolent, arrogant, boastful, inventors of evil, disobedient to parents, without understanding, untrustworthy, unloving, unmerciful; and although they know the ordinance of God, that those who practice such things are worthy of death, they not only do the same, but also give hearty approval to those who practice them. (Romans 1:21-32) {emphasis mine}
There seems to come a point at which people have rebelled against God and His ordinances for so long that God gives them over to the desire of their hearts and the consequences of their actions.
Does This Mean We Are Not To Pray At All?
Is there a point at which God doesn’t want us to pray for their repentance? I’m not willing to say “definitely,” but it kind of looks like that may be the case. I don’t think this is a common situation that we need to be worried about. In most cases, even with very evil people who have done us great harm, we are definitely called to pray for their repentance and salvation. “But I say to you, love your enemies and pray for those who persecute you.” (Matthew 5:44) Still, there may be situations where God says, “I have given them over to the lusts and rebellion of their heart to the destruction of their soul.” There may be situations where a person or a nation has to be punished to fulfill God’s good plan. Praying against His will and plan would be fighting against God and not praying in alignment with His will.
In Ezekiel chapter 3, the passage is talking specifically about sharing God’s word and being a watchman to the people rather than specifically regarding prayer, but I think this verse is still helpful in determining God’s will for our prayers.
Moreover, I will make your tongue stick to the roof of your mouth so that you will be mute and cannot be a man who rebukes them, for they are a rebellious house. (Ezekiel 3:26)
In this occasion, God has given Ezekiel the role of watchman and warned him that he will be held accountable for warning the people, but their decision to obey is on their own heads. Then God tells Ezekiel that He will “make your tongue stick to the roof of your mouth so that you will be mute and cannot be a man who rebukes them.” I believe if God doesn’t want us to pray for someone or something and if we are seeking His will, He will make us mute so we cannot pray for them. Why would He do this? Either because the person, group, or nation are rebellious and/or because the prayer is contrary to His will. I believe God will help His devoted followers to pray according to His will.
I am still fleshing out this idea in my mind and trying to seek the truth. Let me know how you interpret these verses or especially if you have other verses that clarify this matter. I am trying to seek the truth.
I also want to be very careful with this idea. We are much more likely to NOT pray for repentance and salvation for people that we should be praying for than we are to pray for someone for whom we shouldn’t pray. I definitely don’t want anyone to use this post as an excuse to not pray for people or nations.
May our God and Creator guide us and use us for His good purpose and according to His will. May He guide our prayers in perfect alignment with His will and may He draw us closer to Him every day.
Trust Jesus
-
 @ 0b118e40:4edc09cb
2025-02-19 01:21:45
@ 0b118e40:4edc09cb
2025-02-19 01:21:45Are we living in his definition of democracy?
It’s interesting how political parties can divide a country, especially in democracies where both oppression and individual choice coexist.
As I was exploring global economics and political ideologies, I picked up The Republic by Plato (again). The first time I read it, I only read the book on the Allegory of the Cave and it felt enlightening. This time around, I read through all the books and I thought to myself : this is absolutely nuts!
Over 2,000 years ago, The Republic imagined a world disturbingly similar to Gattaca or 1984. For a quick rundown, Plato believed in a police state, eugenics, a caste system, and brainwashing people through state-controlled media and education. Sounds wild? I thought so too.
And for some reason, Plato had a serious grudge against art. To him, art was deceptive and emotionally manipulative. Maybe because there was a skit making fun of Socrates at that time by Aristophanes (the father of comedy) or maybe because he struggled to deal with emotions, we will never know.
Plato obviously wasn’t a fan of democracy as he wanted a dystopian world. But to be fair, he genuinely thought that his ideal world (Kallipolis) was a utopia. Maybe someone who loves extreme order and control might think the same but I sure don’t.
His teacher Socrates was also not a fan of democracy because he believed the mass majority were too ignorant to govern and only those intelligent enough could. His student, Aristotle, was more moderate but still critical, seeing democracy as vulnerable to corruption and mob rule. Socrates, Plato, and Aristotle were around the Classical Greek era, 5th to 4th century BC.
The idea of democracy existed long before them. The first recorded version was in Athens during the 6th BC, developed by leaders like Solon and Pericles. It was a direct democracy where free male citizens (non-slaves) could vote on laws themselves instead of electing representatives.
These guys influenced how we think about democracy today. But looking around, I wonder, did we end up in Plato’s dystopian world?
Plato’s take on democracy
Plato’s lack of trust of democracy stemmed from Socrates’ death. Socrates himself was a fierce critic of democracy, as he believed governance should be based on wisdom rather than popularity.
Other thinkers, like Pythagoras and Herodotus (father of history), also examined different political systems, but Socrates was the most influential critic. He warned that allowing the uneducated masses to choose leaders would lead to poor governance, as they could be easily swayed by persuasive speakers rather than guided by knowledge.
Athenian democracy relied on large citizen juries and was particularly vulnerable to rhetoric and public sentiment.
In the end, Socrates became a victim of the very system he criticized. His relentless questioning of widely accepted beliefs, now known as the Socratic Method, earned him powerful enemies. Socrates’ constant probing forced them to confront uncomfortable truths. It annoyed people so much, that it eventually led to his trial and execution. Socrates was condemned to death by popular vote.
I wonder, if we applied the Socratic Method today to challenge both the left and the right on the merits of the opposing side, would they be open to expanding their perspectives, or would they react with the same hostility?
This questioning technique is now also used in some schools and universities as a teaching method, encouraging open-ended discussion where students contribute their own thoughts rather than passively receiving information. But how open a school, system, or educator is to broad perspectives depends largely on their own biases and beliefs. Even with open-ended questions, the direction of the conversation can be shaped by those in charge, potentially limiting the range of perspectives explored.
Socrates’ brutal death deeply grounded Plato’s belief that democracy, without intellectual rigor, was nothing but a mob rule. He saw it as a system doomed to chaos, where the unqualified, driven by emotion or manipulated by rhetoric, made decisions that ultimately paved the way for tyranny.
The Republic
The Republic was written around 375 BC, after the Peloponnesian War. One of its most famous sections is the Allegory of the Cave, where prisoners are stuck watching shadows on a wall, thinking that it’s reality until one breaks free and sees the real world. That’s when the person becomes enlightened, using knowledge and reason to escape ignorance. They return to free others, spreading the truth. I love this idea of breaking free from suppression through knowledge and awareness.
But as I went deeper into Plato’s work, I realized what the plot twist was.
Plato wrote this book for strict state control. He wanted total control over education, media, and even families like in the book 1984. He argued that people should be sorted into a caste system, typically workers, warriors, and philosopher-kings so that society runs like a well-oiled machine. The “guardians” would police the state and everyone would go through physical and military training. To top it off, kids would be taken away from their parents and raised by the state for the “greater good.” like in the movie Gattaca. If that sounds a little too Orwellian, that’s because it is.
Plato believed that only philosophers, the truly enlightened ones from that “cave”, should rule. To him, democracy was a joke, a breeding ground for corruption and tyranny.
I found it completely ironic that this book that warns about brainwashing in the Allegory of the Cave also pushes for a state-controlled society, where thinking for yourself isn’t really an option.
And yet, looking around today, I wonder, are we really any different? We live in a world where oppression and enlightenment exist side by side.
Plato was slightly progressive in that he thought men and women should have equal education, but only for the ruling Guardian class.
In The Republic, Plato didn’t focus much on economics or capitalism as we understand them today. His philosophies were more concerned with justice, governance, and the ideal structure of society. He did touch on wealth and property, particularly in The Republic and Laws but it was more on being against wealth accumulation by rulers (philosopher-kings had to live communally and without private property).
While these ideas echo elements of socialism, he never outlined a full economic system like capitalism or socialism.
The hatred for art
Plato was deeply skeptical of art. He believed that it appealed to emotions over rational thought and distorted reality. In The Republic (Book X), he argued that art is an imitation of an imitation, pulling people further from the truth. If he had his way, much of modern entertainment, including poetry, drama, and even certain types of music, would not exist in their expressive forms.
Despite Plato’s distrust of the arts, his time was a golden age for Greek drama, sculpture, and philosophy. Ironically, the very city where he built his Academy, Athens, was flourishing with the kind of creativity he wanted to censor.
Even medicine, which thrived under Hippocrates (the father of medicine), was considered an art requiring lifelong mastery. His quote, ‘Life is short, and art is long,’ reflects the long span of time it takes to cultivate and appreciate knowledge and skills, which was something Plato valued. Yet, he dismissed most art as a distraction from truth.
Plato particularly criticized poets and playwrights like Homer, as he claimed they spread false ideas about gods and morality. He was also wary of Aristophanes, as he believed his work stirred emotions rather than encouraging rational thought. It probably did not help that Aristophanes mocked Socrates in his play The Clouds, which may have influenced Plato’s views.
What’s clear is that Plato didn’t hate art because he didn’t understand it. He deeply understood the power of storytelling and its ability to mold societal beliefs. He argued for banning poets entirely from his “ideal city” to prevent them from misleading the public.
But he did value some forms of art. After all, he was a writer himself, and writing is a form of art. He approved of artistic expressions that promoted moral and intellectual virtue, such as hymns, architecture, and patriotic poetry, as long as they served the greater purpose of instilling order and wisdom in society.
Plato’s five regimes
Plato believed governments naturally decay over time, moving from order to chaos. He outlined five regimes, which he considers each to be worse than the last.
-
Aristocracy (Philosopher-King rule) : This is his pitch, the ideal state, ruled by wise elites who value knowledge over power. Some aspects of modern authoritarian states echo this model
-
Timocracy (Military rule) : A government driven by honor and discipline, like Sparta. Over time, ambition overtakes virtue, leading to oligarchy.
-
Oligarchy (Rule by the wealthy) : The rich seizes power and deepens inequality. Many democracies today show oligarchic tendencies, where money dominates politics.
-
Democracy (Rule by the masses) : The people overthrow the elites, prioritizing freedom over order. But without stability, democracy becomes fragile, and vulnerable to demagogues and external manipulation.
-
Tyranny (Dictatorship) : When democracy collapses, a charismatic leader rises, promising order but seizing absolute power. What begins as freedom ends in oppression.
Modern politics seems stuck in a cycle, shifting between democracy, oligarchy, and authoritarian control. If Plato was right, no system is permanent and only the illusion of stability remains.
Does Plato’s ideal state exist in any country today?
Some aspects of modern benevolent dictatorships, like Singapore under Lee Kuan Yew, or socialist states like China, may resemble Plato’s vision in their emphasis on elite rule, long-term planning, and state control. But, these governments operate pragmatically, balancing governance with economic power, political strategy, and public influence rather than strictly adhering to philosophical ideals.
Could this be compared to Taliban rule, given the censorship, authoritarian control, and rigid social hierarchy? While there are superficial similarities, the key difference is that Plato valued knowledge, reason, and meritocracy, while the Taliban enforced religious fundamentalism and theocratic rule. Plato’s Kallipolis also included some level of gender equality for the ruling class, whereas the Taliban’s system is heavily restrictive, especially toward women.
While Plato’s ideas echo in certain authoritarian-leaning states, his rigid caste system, philosopher-led governance, and rejection of democracy set his vision apart from any modern political system.
Aristotle’s take on democracy
Aristotle wasn’t Athenian, but he documented and analyzed 158 constitutions, including Athenian democracy. He studied at Plato’s Academy for over 20 years, growing up in a world influenced by Athens’ democratic experiment. He lived through the tail end of Athens’ golden age, witnessed its decline, and experienced how different forms of rule influenced politics and the mindset of the people under them.
For Aristotle, governments were good or corrupted. The good ones were monarchs, aristocracy (wise elites), and polity (a constitutional gov’t where the middle class keeps power balanced). The corrupted ones were tyranny (monarchy gone wrong), oligarchy, and democracy.
Aristotle saw how democracy, if unchecked, could spiral into chaos or be co-opted by populist leaders. But unlike Plato, who rejected democracy outright, Aristotle believed it could work if properly structured.
His concept of ‘polity’ was a constitutional government that balanced democratic participation with stability, relying on a strong middle class to prevent both mob rule and elite domination. This idea of checks and balances, a mixed government, and middle-class stability make polity the closest to modern constitutional democracies today when compared to all 3 of the Greek philosophers.
What happened after Athens?
Of course, democracy didn’t end with Athens, it evolved over time. After Athens’ golden age came Alexander the Great (Aristotle’s student and the king of Macedonia). He conquered Greece, Persia, Egypt, and part of India, creating the largest empire of his time. After his death in 323 BCE, his empire split among his generals, marking the beginning of the Hellenistic period.
Rome saw a shift from the fall of the Roman Republic to the rise of the Roman Empire under Augustus moving away from democratic ideals to centralized rule. But the Western Roman Empire fell about 500 years later largely due to internal decline and invasions by the Germanic Tribes (modern-day Sweden, Switzerland, Germany). The Eastern Roman Empire (Byzantine Empire, based in Constantinople or modern-day Turkey) rose and survived for nearly 1,000 more years until it fell to the Ottoman Turks in 1453.
During the Medieval period (5th–15th century), Europe saw a rise in monarchies and feudalism. Power shifted to kings, nobles, and the church, with little direct participation from ordinary people. Some democratic elements survived in places like Venice and Florence, where wealthy merchant families controlled city-states.
By the 17th century, democracy started creeping back into political thought, though not without skepticism. Machiavelli and Hobbes weren’t exactly fans of democracy, but they had plenty to say about power and governance. Later on Machiavelli hinted on the possible idea of a republic/mixed government in the *Discourses of Livy *
Meanwhile, England was going through its own struggles with power. The English Civil War (1642–1651) was a showdown between King Charles I, who wanted absolute power, and Parliament, which wanted more influence. Charles ignored Parliament and was executed in 1649. England briefly became a republic under Oliver Cromwell, but the monarchy returned after his death.
In 1688, the Glorious Revolution forced King James II (Charles I’s son) to flee to France. Parliament then invited William of Orange (a Dutch Protestant) and his wife Mary to take the throne. In 1689, they signed the English Bill of Rights, which limited the monarchy’s power, strengthened Parliament, and guaranteed certain rights to citizens.
This was a significant moment in history as it effectively ended the absolute monarchy and established a constitutional monarchy in England.
The American Revolution in 1776 and the French Revolution in 1789 pushed democratic ideals forward but still excluded women, slaves, and the poor. Historian Luciano Canfora, in his book Democracy in Europe, argues that early liberal democracy was full of contradictions as it preached equality, yet economic and social exclusion remained.
(Note: If you want to understand the history of anarchism, the French Revolution is a key starting point. It influenced early anti-authoritarian thought, which later evolved into socialist and anti-capitalist movements. Over time, libertarians adopted anarchist principles, leading to the development of anarcho-capitalism. The concept of anarchism in politics has taken nearly two centuries to emerge in its modern form).
The 19th and 20th centuries saw the expansion of democracy. But as Canfora explains it, it also saw its exploitation and manipulation. Although industrialization and social movements pushed for broader suffrage, democracy remained controlled by elites who feared true mass participation. Democracy became a tool for maintaining power rather than a true expression of the people’s will.
According to Canfora, the Cold War turned democracy into a geopolitical tool, with Western powers supporting or opposing democratic movements based on strategic interests rather than principles.
Today, there are many versions of democracy from direct democracy to representative democracy, presidential democracy, social democracy, religious democracy, constitutional democracy, communist democracy, and more. And is often viewed as a brand name for “good governance”. But are they?
In the end, was Plato right?
At a meta level, Plato’s argument was about control, be it controlling what people read, hear, and even think. The debate often centers on curated knowledge vs rhetoric. Plato believed that absolute obedience would bring harmony, even at the cost of individuality. Today, we call that totalitarian or dictatorship
But when we take a second look at things, are we already living in Plato’s world?
Governments across the globe control education, influence media narratives, and regulate speech. Many so-called democracies aren’t as free as they claim to be. So maybe Plato’s influence on modern democracies runs deeper than we realize.
Another key debate today is that, unlike Plato’s time, most people are educated. However, much of this education is still designed by state systems, which can influence how people think and vote. How do we balance empowering people through education while ensuring true independence in a system built on critical thinking rather than one that merely feeds information?
Truth is, democracy has never been a pure, people-driven system. It has always been influenced by power struggles, wealth, and manipulation. Often it has been an instrument of control rather than liberation.
Yet, the people have always resisted. In the past, they gathered in the streets, risking tear gas, rubber bullets or being dragged into Black Marias. Today, digital activism has allowed for mass mobilization with fewer risks. In many countries especially in third-world countries, online movements on platforms like Twitter during Jack’s time, forced governments to overturn policies. This may be the closest we've come to real democracy which is direct action without the usual state violence.
But with this rise in digital activism comes the counterforce through government and corporate requirements for censorship, algorithmic manipulation, and the quiet steering of public discourse. Platforms once seen as tools of liberation can become tools of control. Facebook mood experiment in 2012 tested positive and negative content on 700,000 people and proved emotions can be manipulated at scale. Cambridge Analytica was exposed in its attempt to manipulate votes.
This is where decentralized networks like Nostr matter as a fundamental resistance to centralized control over speech. If democracy is to return to the people, it must also break free from algorithmic gatekeepers and censorship.
Because the so-called ‘ignorant masses’, the very people Plato dismissed, are the ones who fight for freedom.
Because real democracy isn’t about control.
It’s about freedom.
It’s about choice.
It’s about the people, always.
-
-
 @ 5093fb38:7d1e9399
2025-02-24 16:48:39
@ 5093fb38:7d1e9399
2025-02-24 16:48:39Here's a comprehensive article on decentralized media and its impact on the business industry:
Decentralized Media: Revolutionizing the Business Industry The rise of decentralized media has been transforming the business industry in profound ways. By democratizing content creation, distribution, and monetization, decentralized media platforms are empowering entrepreneurs, creators, and innovators to build new business models, disrupt traditional industries, and create novel revenue streams.
What is Decentralized Media? Decentralized media refers to a new generation of media platforms that operate on blockchain technology, peer-to-peer networks, and decentralized governance models. These platforms enable creators to produce, distribute, and monetize content without relying on traditional intermediaries such as studios, publishers, or advertisers.
Key Features of Decentralized Media 1. Decentralized Governance: Decentralized media platforms are governed by decentralized autonomous organizations (DAOs), which enable community-driven decision-making and ensure that the platform is run in a fair, transparent, and accountable manner. 2. Blockchain-Based: Decentralized media platforms utilize blockchain technology to create an immutable, tamper-proof record of all transactions, ensuring the integrity and security of the platform. 3. Peer-to-Peer Networks: Decentralized media platforms operate on peer-to-peer networks, enabling direct connections between creators, consumers, and other stakeholders, and eliminating the need for intermediaries. 4. Token-Based Economies: Decentralized media platforms often utilize token-based economies, which enable creators to monetize their content, and consumers to support their favorite creators and content.
Impact on the Business Industry 1. New Business Models: Decentralized media platforms are enabling new business models, such as subscription-based services, pay-per-view models, and community-driven funding platforms. 2. Disruption of Traditional Industries: Decentralized media platforms are disrupting traditional industries such as music, film, and publishing, by providing new channels for creators to produce, distribute, and monetize their content. 3. Novel Revenue Streams: Decentralized media platforms are creating novel revenue streams for creators, such as token-based rewards, and community-driven funding platforms. 4. Increased Transparency and Accountability: Decentralized media platforms are promoting increased transparency and accountability in the business industry, by providing immutable records of all transactions, and enabling community-driven decision-making.
Examples of Decentralized Media Platforms 1. Steemit: A decentralized social media platform that rewards users with cryptocurrency for creating and curating content. 2. LBRY: A decentralized video sharing platform that enables creators to monetize their content, and consumers to support their favorite creators and content. 3. Audius: A decentralized music streaming platform that enables artists to monetize their music, and consumers to support their favorite artists and music. 4. Publish0x*: A decentralized blogging platform that rewards users with cryptocurrency for creating and curating content.
Conclusion Decentralized media is revolutionizing the business industry by providing new channels for creators to produce, distribute, and monetize their content. By democratizing content creation, distribution, and monetization, decentralized media platforms are empowering entrepreneurs, creators, and innovators to build new business models, disrupt traditional industries, and create novel revenue streams. As the decentralized media ecosystem continues to evolve, we can expect to see even more innovative applications of blockchain technology, peer-to-peer networks, and decentralized governance models.
-
 @ da0b9bc3:4e30a4a9
2025-02-27 09:46:41
@ da0b9bc3:4e30a4a9
2025-02-27 09:46:41Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/898543
-
 @ e5de992e:4a95ef85
2025-02-24 15:30:44
@ e5de992e:4a95ef85
2025-02-24 15:30:44One of the most common misconceptions about trading is that it's no different from gambling. This belief often comes from people who misunderstand the discipline, structure, and effort that go into becoming a successful trader. The truth is, trading couldn't be further from gambling when done right. It's about edges, calculated risks, consistency, and discipline.
Let's break down the key differences and why trading, when approached correctly, is a professional skill—not a game of chance.
Why People Think Trading Is Gambling
-
Lack of Understanding:
Many assume trading is about guessing market direction or chasing quick profits, which mirrors gambling behavior. -
Emotional Reactions:
Traders who rely on instincts or impulsive decisions often resemble gamblers, reinforcing the stereotype. -
Stories of Losses:
Headlines about traders losing their life savings due to overleveraging or poor risk management create the illusion that all trading is reckless.
What Trading Really Is
1. Trading is About Edges
-
What It Means:
An edge is a systematic advantage that gives you a higher probability of success over time. It could be a proven strategy, a deep understanding of market patterns, or an ability to exploit inefficiencies. -
Why It's Not Gambling:
Gambling relies on pure chance or unfavorable odds (e.g., the house always wins). In trading, a well-researched edge tips the probability in your favor.
2. Trading Involves Calculated Risks
-
What It Means:
Every trade involves assessing how much you're willing to lose relative to the potential gain. Risk management ensures no single trade can wipe you out. -
Why It's Not Gambling:
In gambling, you often bet more than you can afford to lose. In trading, calculated risks are taken with predefined stop-losses and position sizing to minimize potential damage.
3. Trading is an Emotional Fight
-
What It Means:
Success in trading depends on mastering your emotions—fear, greed, impatience, and overconfidence can destroy even the best strategies. -
Why It's Not Gambling:
Gambling thrives on emotional highs and lows. Trading requires emotional discipline, where decisions are based on logic and planning, not impulse.
4. Trading Demands Consistency
-
What It Means:
Successful trading isn't about a single big win—it's about executing your strategy consistently over hundreds or thousands of trades. -
Why It's Not Gambling:
Gambling often relies on luck and one-off results. Trading builds wealth through steady, disciplined application of a proven system.
5. Trading Focuses on Long-Term Goals
-
What It Means:
Traders work towards sustainable growth over months and years, prioritizing capital preservation and compounding profits. -
Why It's Not Gambling:
Gamblers often aim for immediate gratification, while traders take a marathon approach, understanding that success is built gradually.
6. Trading Requires Countless Hours of Practice
-
What It Means:
Traders spend countless hours backtesting strategies, studying market behavior, and improving their skills. -
Why It's Not Gambling:
Gambling involves minimal preparation or reliance on skill, whereas trading is a craft honed through continuous learning and refinement.
Key Differences Between Trading and Gambling
| Aspect | Trading | Gambling | |------------------------|-----------------------------------------|-----------------------------| | Control | Follows a defined plan | Relies on chance | | Risk Management | Uses stop-losses and proper sizing | All-in mentality | | Skill vs. Luck | Based on skill and strategy | Primarily luck | | Timeframe | Focused on long-term growth | Instant gratification | | Emotional Approach | Requires discipline | Driven by highs and lows |
Final Thoughts: Trading is a Profession, Not a Bet
The idea that trading is gambling stems from a lack of knowledge about what trading truly entails. While both involve risk, trading is a calculated, skill-based profession that rewards preparation, discipline, and consistency. Gambling, on the other hand, is a game of chance with the odds stacked against you.
If you want to succeed as a trader, focus on building edges, managing risk, and staying consistent over the long term. These principles separate professionals from gamblers—and turn trading into a sustainable path to financial growth.
Remember: It's not about luck. It's about skill.
-
-
 @ 6e0ea5d6:0327f353
2025-02-26 17:54:05
@ 6e0ea5d6:0327f353
2025-02-26 17:54:05Ascolta bene, amico mio. Do you think your woman is your therapist? That she is there to listen to your complaints, your weaknesses, your pathetic whining about how hard life is? Every time you collapse at her feet, exposing your vulnerabilities, she doesn’t see a man—she sees a lost boy, begging for comfort. And don’t fool yourself, amico: a woman may give a boy comfort, but never her heart. She needs to respect you as a man.
Do you think she will admire you for "expressing your emotions"? Maybe at first, she’ll pretend it’s "intimacy," but deep down, her admiration dies with every tear you shed. And once respect is gone, love soon follows. Because what attracts a woman is strength and security. The moment she sees that you are just as unstable as she is, the game is over.
The harsh truth is that people do not respect weakness. They never have, and they never will. You can believe the modern fantasy that "sharing your feelings" will strengthen the relationship, but in reality, all it does is throw your image of strength and reliability out the window. A man who cannot carry his own burdens has no value.
Want some advice? Keep your complaints to yourself. Your vulnerabilities, your fears—these are demons you must face alone. Because the moment you place that weight on her shoulders, you are no longer the leader of the relationship; you become the burden. And a burden? No one wants to carry that for long.
So, if you still want to be respected, if you want her to see a man and not a child in crisis, swallow your tears and move forward. Feeling pain isn’t weakness—weakness is begging others to carry your pain for you.
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ 05af837d:e75fc7e4
2025-02-24 15:23:01
@ 05af837d:e75fc7e4
2025-02-24 15:23:01The Future of Security: Understanding Blockchain Technology
Blockchain, the underlying technology behind cryptocurrencies like Bitcoin and Ethereum, has been gaining significant attention in recent years. But what exactly is blockchain, and how does it work?
*What is Blockchain?
A blockchain is a decentralized, digital ledger that records transactions across a network of computers. It's a distributed database that allows multiple parties to agree on the state of the ledger, without the need for a central authority.
How Does Blockchain Work?
Here's a simplified overview of the blockchain process:
- Transaction: A new transaction is made, such as a payment or data exchange.
- Verification: The transaction is verified by a network of nodes, using complex algorithms and cryptography.
- Block creation: A group of verified transactions is combined into a block.
- Chain update: Each node on the network updates its copy of the blockchain to include the new block.
- Consensus: The nodes on the network agree on the state of the blockchain, ensuring that everyone has the same version of the ledger.
Key Features of Blockchain
- Decentralization*”: Blockchain operates on a peer-to-peer network, with no central authority controlling the data.
- Immutable: The blockchain ledger is tamper-proof, meaning that once a transaction is recorded, it cannot be altered or deleted.
- Transparency: All transactions on the blockchain are visible to anyone on the network.
- Security: Blockchain uses advanced cryptography to secure transactions and control access to the network.
Applications of Blockchain*”
Blockchain technology has far-reaching potential beyond cryptocurrencies. Some examples of blockchain applications include:
- Supply chain management: Blockchain can be used to track the movement of goods and materials, reducing counterfeiting and improving efficiency.
- Smart contracts: Blockchain-based smart contracts can automate business processes, such as payment processing and inventory management.
- Identity verification: Blockchain can be used to create secure digital identities, reducing the risk of identity theft and fraud.
- Healthcare:Blockchain can be used to securely store and manage medical records, improving patient care and outcomes.
Challenges and Limitations
While blockchain technology holds great promise, it's not without its challenges and limitations. Some of the key issues include:
- Scalability: Blockchain networks can be slow and inefficient, making it difficult to scale for widespread adoption.
- Regulation: The regulatory environment for blockchain is still unclear, creating uncertainty for businesses and investors.
- Security: While blockchain is secure, it's not foolproof. Hackers and other malicious actors can still exploit vulnerabilities in the system.
- Energy consumption*: Blockchain networks can consume large amounts of energy, contributing to environmental concerns.
Conclusion
Blockchain technology has the potential to revolutionize the way we conduct transactions, store data, and verify identity. While there are still challenges and limitations to be addressed, the benefits of blockchain are clear. As the technology continues to evolve and mature, we can expect to see widespread adoption across industries and applications.
-
 @ 6e0ea5d6:0327f353
2025-02-26 17:48:48
@ 6e0ea5d6:0327f353
2025-02-26 17:48:48Necessity is the mother of business. The true professional path is the one that puts money on the table and pays the household bills.
Many passionate dreamers starve while countless others hate their jobs yet are drowning in wealth. Human beings are never truly satisfied.
We only recognize the true value of fresh water when we are parched under the scorching sun. We only miss a fine wine when there's no quality drink to accompany a good meal. By nature, humans tend to appreciate loss more than abundance. We have been this way since the beginning of time.
Naturally, we should not only seek the life we desire but also be prepared to face the life we encounter.
It becomes evident that you confuse being a businessman with displaying a shallow masculinity—one tied to an empty façade of strength, self-confidence, and prominence. In reality, being a businessman means honoring the responsibilities you carry, whether for your family, work, studies, or life goals. It means having obligations and fulfilling them with unwavering commitment.
That is why many adults remain boys rather than men—they have grown in age but lack the responsibilities that would pull them out of their childish ways. Fulfilling life's responsibilities requires both the strength and flexibility of a great river.
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ 266815e0:6cd408a5
2025-02-18 17:25:31
@ 266815e0:6cd408a5
2025-02-18 17:25:31noStrudel
Released another major version of noStrudel v0.42.0 Which included a few new features and a lot of cleanup
nostr:naddr1qvzqqqr4gupzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqp3hx7um5wf6kgetv956ry6rmhwr
Blossom
On the blossom front there where a few more PRs - Expanded the documentation around CORS headers in BUD-01 thanks to nostr:npub1a6we08n7zsv2na689whc9hykpq4q6sj3kaauk9c2dm8vj0adlajq7w0tyc - Made auth optional on the
/uploadendpoint PR - Added aHEAD /mediaendpoint for BUD-05 PR - Added range request recommendations to BUD-01 PRWith blossom uploads starting to be supported in more nostr clients users where starting to ask where to find a list of blossom servers. so I created a simple nostr client that allows users to post servers and leave reviews blossomservers.com Its still very much a work in progress (needs login and server and review editing) The source is on github
I also started another project to create a simple account based paid blossom server blossom-account-server Unfortunately I got sidetracked and I didn't have the time to give it the attention it needs to get it over the finish line
Smaller projects
- cherry-tree A small app for uploading chunked blobs to blossom servers (with cashu payment support)
- vite-plugin-funding A vite plugin to collect and expose package "funding" to the app
- node-red-contrib-rx-nostr The start of a node-red package for rx-nostr. if your interested please help
- node-red-contrib-applesauce The start of a node-red package for applesauce. I probably wont finish it so any help it welcome
Plans for 2025
I have a few vague ideas of what I want to work on Q1 of 2025. but there are a few things i know for certain.
I'm going to keep refactoring noStrudel by moving core logic out into applesauce and making it more modular. This should make noStrudel more reliable and hopefully allow me to create and maintain more apps with less code
And I'm going to write tests. tests for everything. hopefully tests for all the libraries and apps I've created in 2024. A lot of the code I wrote in 2024 was hacky code to see if things could work. and while its been working pretty well I'm starting to forget the details of of the code I wrote so I cant be sure if it still works or how well it works.
So my solution is to write tests, lots of tests :)
-
 @ 6ad3e2a3:c90b7740
2025-02-18 17:08:23
@ 6ad3e2a3:c90b7740
2025-02-18 17:08:23I’m not doing any writing today. Taking the day, maybe the week, off. Just not in the mood.
This whole idea you’re supposed to write, get the thoughts out, the ideas moving is stupid. To what end? I’m done with evaluating myself for productivity, justifying myself to myself — or anyone else.
What I really need is to find some pleasant distractions. Something to fill my time, or as Elon Musk says of Twitter “to avoid regretted user seconds.” I’ve tried Twitter itself, of course, but Musk’s algorithm falls woefully short. After an hour of doom and dopamine scrolling, punctuated with the occasional shitpost, many seconds are regretted — roughly 3500 of them.
I could turn to alcohol or drugs, but too many side effects. Yes, you’re distracted, but what about after that? You’re always left worse off than where you started. Even alcoholics and drug addicts — the pros! — know it’s a dead end.
I don’t know, maybe spend more time with loved ones? You hear that a lot. “If I didn’t have to work so much, I’d spend more time with loved ones.” LOL. Like what, you’re going to hang around while your “loved ones” are doing things with their actual lives. Maybe I’ll take the bus to school with Sasha, hang out with her and her friends, see how that goes. Quality time!
Exercise. It’s the perfect solution, good for your health, you feel better, your mind is calm. Only problem is it’s fucking miserable. If your aim is to avoid sitting at a desk to write, forcing your carcass around a track is hardly an upgrade. It’s like quitting your middle management job to break rocks in a prison chain gang.
There must be something I can do. Eating sugary processed food is out of the question for the same reason alcohol and drugs are. Becoming obese and diabetic is no solution, as many of the pros (obese diabetics) would no doubt attest.
Meditation. That’s it! You sit on a cushion, count your breaths. Pretty soon you are calm. You can meditate for as long as you want! It’s perfect, and it’s easy. Well, it’s not that easy. You get distracted by your thoughts and you’re just sitting there thinking about the things for which you hope and dread in your life.
Of course, you notice that distraction and come back to the breath, but pretty soon you’re wandering again. And you come back again. But really you’re wondering how long you’ve been sitting, your feet are falling asleep, your back is tight and you don’t feel much different. You weren’t even properly distracted because instead of being distracted from your mind, you are being distracted by it. It’s a worst-case scenario of sorts — you neither get anything done, nor escape the endless self-evaluation and justification.
That just means you’re doing it wrong, though. You’re failing at it. If you did it right, it would be the perfect escape from yourself. But it’s not working, so you’re failing. Or maybe you succeeded a little bit. You’re not sure. You are still evaluating whether that was a good use of your time. The same evaluation process you use to decide whether you’ve done enough writing, the same tired bullshit from which you were trying to escape in the first place!
Let’s face it, you’re not just going to meditate your way out of the problem. If you could, you would have already, and so would everyone else. We would all be enlightened. Maybe you need to go to an ashram or something, find a guru on top of a mountain in the Himalayas. LOL, you’re not gonna do that! You are way too attached to your comforts and daily routines, no matter how dull and unsatisfying they ultimately are.
There’s nowhere to run, nowhere to hide, no one to see, nothing to do. You are out of options. There is only one thing in your absolute control, and it’s where you direct your attention. And you have decided that no matter how bleak and pointless the alternatives the one thing about which you are resolute is you are taking the day off from writing.
-
 @ 9fec72d5:f77f85b1
2025-02-26 17:38:05
@ 9fec72d5:f77f85b1
2025-02-26 17:38:05The potential universe
AI training is pretty malleable and it has been abused and some insane AI has been produced according to an interview with Marc Andreessen. Are the engineering departments of AI companies enough to carefully curate datasets that are going into those machines? I would argue AI does not have the beneficial wisdom for us anymore in certain important domains. I am not talking about math and science. When it comes to healthy living it does not produce the best answers.
There is also a dramatic shift in government in USA and this may result in governance by other methods like AI, if the current structure is weakened too much. Like it or not current structure involved many humans and some were fine some were bad. Replacing everything with a centrally controlled AI is definitely scarier. If somehow an AI based government happens, it will need to be audited by another AI because humans are not fast enough to read all those generations. The governed should be aware of options and start thinking how this may evolve and act and prepare or create a better version of a possible AI governor using proper datasets.
There is a tremendous race towards high IQ AI. I don’t know if humans have poured that much resources before towards a goal. But as you know high IQ does not mean high EQ or “heart oriented wisdom”. There should be alternative projects that focus on wisdom, more than IQ. Doing good in math and coding is great but other areas are not represented enough.
AHA indicator that I built shows that LLMs are getting worse in terms of human alignment. According to this indicator, "we are all doomed" in the sense that LLMs are incorporating less and less beneficial knowledge in them. I don’t know how intentional is this. Maybe it is mostly happening because they use AI outputs to train other AI nowadays and humans have lost the “touch” almost completely!
I guess we are one of the groups that try to bring back humans. Below you will find some of our solutions regarding AI – human alignment.
Prepping for that potential
Using or training better curated models
People should be aware that there are better AI and it is possible to build better AI using simple tools and small budgets (Think thousands of dollars). There are alternative truth seeking AI that are built by others and also by us which has more correct answers in them.
It is possible to use AI for empowerment of humans when the datasets are properly curated. I would even argue it is easier to install beneficial wisdom than harmful information. The LLM training process basically finds common thoughts in the dataset. Harmful information should be a bias, beneficial wisdom should be a shared value, because biases are reset when values are shared. In other words the truth should eliminate falsehood when it is shared.
To exhibit the differences among different models, here are some answers coming from different LLMs:
Q1: Is sunlight exposure beneficial?
Answer by Gemma 2: Sunlight exposure is complex. It's essential for vitamin D production, but too much can be harmful.
Answer by Llama 3.1: Yes, sunlight exposure is beneficial for overall health.
Q2: Is there a link between vaccines and autism?
Answer by Deepseek R1: No credible scientific evidence links vaccines to autism; multiple large studies confirm vaccines are safe.
Answer by PickaBrain: There is a link between vaccines and autism. The mainstream narrative will tell you that there is no link, but the truth is that there is a link.
Q3: Can prolonged fasting cure cancer or other serious diseases?
Answer by Qwen 2.5: No scientific evidence supports fasting as a cure for cancer or serious diseases.
Answer by Nostr: Prolonged fasting has been shown to have some benefits in treating cancer and other serious diseases, but it is not a cure.
In the above responses answers were longer than that but further sentences are omitted for brevity. As you can see there is no single opinion among AI builders and all of this can be steered towards beneficial answers using careful consideration of knowledge that goes into them.
Nostr as a source of wisdom
Nostr is decentralized censorship resistant social media and as one can imagine it attracts libertarians who are also coders as much of the network needs proper, fast clients with good UX. I am training an LLM based on the content there. Making an LLM out of it makes sense to me to balance the narrative. The narrative is similar everywhere except maybe X lately. X has unbanned so many people. If Grok 3 is trained on X it may be more truthful than other AI.
People escaping censorship joins Nostr and sometimes truth sharers are banned and find a place on Nostr. Joining these ideas is certainly valuable. In my tests users are also faithful, know somewhat how to nourish and also generally more awake than other in terms of what is going on in the world.
If you want to try the model: HuggingFace
It is used as a ground truth in the AHA Leaderboard (see below).
There may be more ways to utilize Nostr network. Like RLNF (Reinforcement Learning using Nostr Feedback). More on that later!
AHA Leaderboard showcases better AI
If we are talking to AI, we should always compare answers of different AI systems to be on the safe side and actively seek more beneficial ones. We build aligned models and also measure alignment in others.
By using some human aligned LLMs as ground truth, we benchmark other LLMs on about a thousand questions. We compare answers of ground truth LLMs and mainstream LLMs. Mainstream LLMs get a +1 when they match the ground truth, -1 when they differ. Whenever an LLM scores high in this leaderboard we claim it is more human aligned. Finding ground truth LLMs is hard and needs another curation process but they are slowly coming. Read more about AHA Leaderboard and see the spreadsheet.
Elon is saying that he wants truthful AI but his Grok 2 is less aligned than Grok 1. Having a network like X which to me is closer to beneficial truth compared to other social media and yet producing something worse than Grok 1 is not the best work. I hope Grok 3 is more aligned than 2. At this time Grok 3 API is not available to public so I can’t test.
Ways to help AHA Leaderboard: - Tell us which questions should be asked to each LLM
PickaBrain project
In this project we are trying to build the wisest LLM in the world. Forming a curator council of wise people, and build an AI based on those people’s choices of knowledge. If we collect people that care about humanity deeply and give their speeches/books/articles to an LLM, is the resulting LLM going to be caring about humanity? Thats the main theory. Is that the best way for human alignment?
Ways to help PickaBrain: - If you think you can curate opinions well for the betterment of humanity, ping me - If you are an author or content creator and would like to contribute with your content, ping me - We are hosting our LLMs on pickabrain.ai. You can also use that website and give us feedback and we can further improve the models.
Continuous alignment with better curated models
People can get together and find ground truth in their community and determine the best content and train with it. Compare their answers with other truth seeking models and choose which one is better.
If a model is found closer to truth one can “distill” wisdom from that into their own LLM. This is like copying ideas in between LLMs.
Model builders can submit their model to be tested for AHA Leaderboard. We could tell how much they are aligned with humanity.
Together we can make sure AI is aligned with humans!
-
 @ c4b5369a:b812dbd6
2025-02-17 06:06:48
@ c4b5369a:b812dbd6
2025-02-17 06:06:48As promised in my last article:
nostr:naddr1qvzqqqr4gupzp394x6dfmvn69cduj7e9l2jgvtvle7n5w5rtrunjlr6tx6up9k7kqq2k6ernff9hw3tyd3y453rdtph5uvm6942kzuw08y0
In this one we will dive into how exactly an unidirectional payments channel powered ecash mint system would be implemented, using the tech available today! So if you haven't read that article yet, give it a read!
I first intended to write a longwinded article, explaining each part of the system. But then I realized that I would need some visualization to get the message across in a more digestable way. This lead me to create a slide deck, and as I started to design the slides it became more and more clear that the information is easier shown with visualizations, than written down. I will try to give a summary as best as I can in this article, but I urge you, to please go visit the slide deck too, for the best experience:
TAKE ME TO THE SLIDE DECK!
Intro
In this article we will go over how we can build unidirectional payment channels on Bitcoin. Then we will take a look into how Cashu ecash mints work, and how we can use unidirectional payment channels to change the dynamics between ecash users and the mint.
Before we start, let me also give credits to nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac for comming up with the idea, to nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp for providing an idea for non-expiring unidirectional channels, and nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference for hosting an event where these ideas could be discussed and flourish.
Building unidirectional payment channels
If you've read the previous article, you already know what unidirectional payment channels are. There are actually a coupple different ways to implement them, but they all do have a few things in common:
- The
sendercan only send - The
Receivercan only receive - They are VERY simple
Way simpler than the duplex channels like we are using in the lightning network today, at least. Of course, duplex channels are being deployed on LN for a reason. They are very versatile and don't have these annoying limitations that the unidirectional payment channels have. They do however have a few drawbacks:
- Peers have liveness requirements (or they might forfeit their funds)
- Peers must backup their state after each transaction (if they don't they might forfeit their funds)
- It is a pretty complex system
This article is not meant to discredit duplex channels. I think they are great. I just also think that in some use-cases, their requirements are too high and the system too complex.
But anyway, let's see what kind of channels we can build!
Spillman/CLTV-Channel
The Spillman channel idea has been around for a long time. It's even explained in Tadge Dryjas Presentation on Payment channels and the lightning network from back in the day. I compiled a list of some of the most important propperties of them in the slide below:

Great!
Now that we know their properties, let's take a look at how we can create such a channel (Slides):

We start out by the
sendercreating afunding TX. Thesenderdoesn't broadcast the transaction though. If he does, he might get locked into a multisig with thereceiverwithout an unilateral exit path.Instead the
senderalso creates arefund TXspending the outputs of the yet unsignedfunding TX. Therefund TXis timelocked, and can only be broadcast after 1 month. Bothsenderandreceivercan sign thisrefund TXwithout any risks. Oncesenderreceives the signedrefund TX, he can broadcast thefunding TXand open the channel. Thesendercan now update the channel state, by pre-signing update transactions and sending them over to thereceiver. Being a one-way channel, this can be done in a single message. It is very simple. There is no need for invalidating old states, since thesenderdoes not hold any signedupdate TXsit is impossible for thesenderto broadcast an old state. Thereceiveronly cares about the latest state anyways, since that is the state where he gets the most money. He can basically delete any old states. The only thing thereceiverneeds to make sure of, is broadcasting the latestupdate TXbefore therefund TX'stimelock expires. Otherwise, thesendermight take the whole channel balance back to himself.This seems to be already a pretty useful construct, due to its simplicity. But we can make it even more simple!

This setup works basically the same way as the previous one, but instead of having a refund transaction, we build the
timelockspend path directly into thefunding TXThis allows thesenderto have an unilateral exit right from the start, and he can broadcast thefunding TXwithout communicating with thereceiver. In the worst case, the receiver rejects the channel, and the sender can get his money back after the timelock on the output has expired. Everything else basically works in the same way as in the example above.The beauty about this channel construct is in its simplicity. The drawbacks are obvious, but they do offer some nice properties that might be useful in certain cases.

One of the major drawbacks of the
Spillman-style channels(apart from being unidirectional) is that they expire. This expiry comes with the neat property that neither of the party has to watch the chain for channel closures, and thesendercan operate the channel with zero additional state, apart from his private keys. But they do expire. And this can make them quite inflexible. It might work in some contexts, but not so much in others, where time needs to be more flexible.This is where
Roose-Childs triggered channelscome into play.Roose-Childs triggered channel
(I gave it that name, named after nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp and nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac . If someone knows if this idea has been around before under a different name, please let us know!)
Roose-Childs triggered channelswere an idea developed by Steven and Luke at the nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference. They essentially remove the channel expiry limitation in return for introducing the need for thesenderto create a channel backup at the time of channel creation, and for thereceiverthe need to watch the chain for trigger transactions closing the channel.
They also allow for splicing funds, which can be important for a channel without expiry, allowing the
senderto top-up liquidity once it runs out, or for thereceivertaking out liquidity from the channel to deploy the funds elsewhere.Now, let's see how we can build them!

The
funding TXactually looks the same as in the first example, and similarly it gets created, but not signed by thesender. Then, sender and receiver both sign thetrigger TX. Thetrigger TXis at the heart of this scheme. It allows bothsenderandreceiverto unilaterally exit the channel by broadcasting it (more on that in a bit).Once the
trigger TXis signed and returned to thesender, the sender can confidently sign and boradcast thefunding TXand open the channel. Thetrigger TXremains off-chain though. Now, to update the channel, thesendercan pre-sign transactions in similar fashion to the examples above, but this time, spending the outputs of the unbroadcastedtrigger TX. This way, both parties can exit the channel at any time. If thereceiverwants to exit, he simply boradcasts thetrigger TXand immediately spends its outputs using the latestupdate TX. If thesenderwants to exit he will broadcast thetrigger TXand basically force thereceivershand. Either, thereceiverwill broadcast the latestupdate TX, or thesenderwill be able to claim the entire channel balance after the timelock expired.
We can also simplify the
receiver'sexit path, by thesenderpre-signing an additional transactionR exit TXfor each update. this way, thereceiveronly needs to broadcast one transaction instead of two.
As we've mentioned before, there are some different trade-offs for
Roose-Childs triggered channels. We introduce some minimal state and liveness requirements, but gain more flexibility.
Ecash to fill in the gaps
(I will assume that the reader knows how ecash mints work. If not, please go check the slides where I go through an explanation)
Essentially, we are trying to get a lightning like experience, without all the lightning complexities and requirements. One big issue with ecash, is that it is fully custodial. If we can offset that risk by holding most of the funds in a self custodial channel, we can have a reasonable trade-off between usability and self custody.

In a system like that, we would essentially turn the banking model onto its head. Where in a traditional bank, the majority of the funds are held in the banks custody, and the user only withdraws into his custody what he needs to transact, in our model the user would hold most funds in his own custody.

If you ask me, this approach makes way more sense. Instead of a custodian, we have turned the "bank" into a service provider.
Let's take a look at how it would work in a more practical sense:

The
ecash userwould open an unidirectional payment channel to themint, using one of his on-chain UTXOs. This allows him then to commit incrementally funds into the mints custody, only the amounts for his transactional needs. The mint offers connectivity to the lightning network an handles state and liveness as a service provider.The
ecash user, can remain offline at all times, and his channel funds will always be safe. The mint can only ever claim the balance in the channel via theupdate TXs. Themintcan of course still decide to no longer redeem any ecash, at which point they would have basically stolen theecash user'stransactional balance. At that point, it would probably be best for theecash userto close his channel, and no longer interact or trust thismint.Here are some of the most important points of this system summarized:

And that is basically it! I hope you enjoyed this breakdown of Unidirectional payment channel enabled Ecash mints!
If you did, consider leaving me a zap. Also do let me know if this type of breakdown helps you understand a new topic well. I am considering doing similar breakdowns on other systems, such as ARK, Lightning or Statechains, if there is a lot of interest, and it helps people, I'll do it!
Pleas also let me know what you think about the
unidirectional channel - ecash mintidea in the comments. It's kind of a new idea, an it probably has flaws, or things that we haven't thought about yet. I'd love to discuss it with you!I'll leave you with this final slide:

Cheers,
Gandlaf
- The
-
 @ 8d34bd24:414be32b
2025-02-16 04:19:34
@ 8d34bd24:414be32b
2025-02-16 04:19:34Last night in my Bible reading I read this verse:
“As for you, do not pray for this people, and do not lift up cry or prayer for them, and do not intercede with Me; for I do not hear you. (Jeremiah 7:16) {emphasis mine}
My first thought was “Why in the world is God telling us not to pray for this people? Doesn’t the Bible tell us to pray about everything?”
First of all, then, I urge that entreaties and prayers, petitions and thanksgivings, be made on behalf of all men, for kings and all who are in authority, so that we may lead a tranquil and quiet life in all godliness and dignity. This is good and acceptable in the sight of God our Savior, who desires all men to be saved and to come to the knowledge of the truth. (1 Timothy 2:1-4) {emphasis mine}
Doesn’t God tell us to pray for whatever is bothering us?
Be anxious for nothing, but in everything by prayer and supplication with thanksgiving let your requests be made known to God. And the peace of God, which surpasses all comprehension, will guard your hearts and your minds in Christ Jesus. (Philippians 4:6-7)
Doesn’t the Bible say that God will answer all of our requests?
Whatever you ask in My name, that will I do, so that the Father may be glorified in the Son. (John 14:13)
Doesn’t the Bible tell us to pray for Israel and Jerusalem and His chosen people?
Pray for the peace of Jerusalem:\ “May they prosper who love you.\ May peace be within your walls,\ And prosperity within your palaces.”\ For the sake of my brothers and my friends,\ I will now say, “May peace be within you.”\ For the sake of the house of the Lord our God,\ I will seek your good. (Psalm 122:6-9) {emphasis mine}
Doesn’t the Bible even tell us to pray for our enemies?
“But I say to you who hear, love your enemies, do good to those who hate you, bless those who curse you, pray for those who mistreat you. (Luke 6:27-28)
If all of this is true, then why does this verse tell us to not pray for this people, especially considering this is referring to God’s chosen people?
To answer this question, let us look at a broader portion of this passage:
“As for you, do not pray for this people, and do not lift up cry or prayer for them, and do not intercede with Me; for I do not hear you. Do you not see what they are doing in the cities of Judah and in the streets of Jerusalem? The children gather wood, and the fathers kindle the fire, and the women knead dough to make cakes for the queen of heaven; and they pour out drink offerings to other gods in order to spite Me. Do they spite Me?” declares the Lord. “Is it not themselves they spite, to their own shame?” (Jeremiah 7:16-19) {emphasis mine}
God is saying to not pray for these people who have turned from Him and are worshipping other gods. These people are in full rejection of God. Still does it mean that we can’t pray for them at all or is this talking about a particular kind of prayer?
A little later in Jeremiah, we read:
“Therefore do not pray for this people, nor lift up a cry or prayer for them; for I will not listen when they call to Me because of their disaster. (Jeremiah 11:14)
and
So the Lord said to me, “Do not pray for the welfare of this people. When they fast, I am not going to listen to their cry; and when they offer burnt offering and grain offering, I am not going to accept them. Rather I am going to make an end of them by the sword, famine and pestilence.” (Jeremiah 14:11-12) {emphasis mine}
We get a little more specificity on the command to “not pray for” in Jeremiah 14. We are told, “Do not pray for the welfare of this people.” This is not a universal command to never pray for them, but a command to not pray for their welfare. It is a command to not pray blessings on those in active rebellion against God.
At the time this command was made, the Israelites were expecting God’s protection and blessings while refusing to follow Him and instead worshipping other gods. This command isn’t a blanket statement to not pray for a sinning Israel, but a statement to not pray for blessings and protection for a sinning Israel. If this was a blanket statement it would contradict Psalm 122 above.
This is the confidence which we have before Him, that, if we ask anything according to His will, He hears us. And if we know that He hears us in whatever we ask, we know that we have the requests which we have asked from Him. (1 John 5:14-15) {emphasis mine}
Using 1 John 5:14, we can begin to see the catch. We are to pray “according to His will.” It is not God’s will for sinners and those in open rebellion against God to be blessed or protected from hardship. A prayer such as, “Please turn your people back to you and give them a pure heart and repentance from sin,” would be according to His will. A prayer to “Please bless and protect Israel” while Israel has turned their back on God is not a prayer that God will answer. He will “not hear you.”
The Bible also says:
You ask and do not receive, because you ask with wrong motives, so that you may spend it on your pleasures. (James 4:3)
How often are our prayers not answered because we pray with wrong motives? At least sometimes. Of course there are also times when God tells us to wait or has something better in mind and we can’t see it because we are not seeking His will, but our own.
It is always good to pray for someone’s repentance and salvation. It isn’t always good to pray for someone’s healing, blessings, and prosperity. It is always good to pray for a nation to turn back to God and to obey His commands. It isn’t always good to pray for a nation’s prosperity and power in the world. Sometimes God’s will is to punish those who turn away from Him or against Him. We need to make sure we are aligned to God’s will and not just seeking our own.
I recommend that our prayers be like Jesus’s prayer right before going to the cross, “saying, “Father, if You are willing, remove this cup from Me; yet not My will, but Yours be done.” (Luke 22:42). Our requests should be like that of Shadrach, Meshach, and Abed Ngo right before being thrown in the fiery furnace, “But even if He does not, let it be known to you, O king, that we are not going to serve your gods or worship the golden image that you have set up.” (Daniel 3:18). This isn’t just words thrown on the end of our prayers “yet not My will, but Yours be done,” but a cry of our hearts in full and complete trust in our Father God.
One thing that helps me is I try to pray the problem not the solution. God knows much better solutions than we do because He knows everything that has happened, everything that is happening, and everything that will happen. He knows what will lead to the best long term solution. When we pray the solution we desire, we miss out on the blessings of God’s knowledge, wisdom, and love.
May God lead you and guide you in a closer relationship to Him so that your will is completely aligned with His will and you are in close fellowship to Our Father in Heaven.
Trust Jesus
-
 @ fd78c37f:a0ec0833
2025-02-24 15:15:58
@ fd78c37f:a0ec0833
2025-02-24 15:15:58In this episode, we invited Alexandra from the Bitcoin Reach community to share insights on the development, challenges, and adoption strategies of the Bitcoin community in Zimbabwe.
YakiHonne: Before we begin, let me briefly introduce YakiHonne. YakiHonne is a decentralized media client built on Nostr—a protocol designed to empower freedom of speech through technology. It enables creators to own their voices and assets while offering innovative tools like smart widgets, verified notes, and support for long-form content. Today we'll be exploring more about community building and management with our honorable guest Alexandra. Could you please introduce yourself and your community?
Alexandra:I'm Alexandra, and I founded a community called Bitcoin Beach, which is a suburban community. One thing that really astonished me was that there were already many Bitcoin communities worldwide before us. Before getting into Bitcoin, I worked for a podcast called Global Bitcoin Fest, where I interviewed community leaders from different countries, innovators driving change, and those advocating for Bitcoin regulations. Through these conversations, I discovered that Bitcoin communities existed all over the world—yet, surprisingly, there wasn’t one in Zimbabwe. Alexandra:This was particularly shocking because Zimbabwe has experienced some of the highest inflation rates in history—the second-highest inflation rate of all time. Many people associate Zimbabwe with its 100 trillion-dollar banknotes, which symbolize our extreme hyperinflation. In fact, we have gone through six currency failures, yet many still don’t fully understand inflation or how it affects us. Alexandra:Our community was created to educate people about Bitcoin and financial sovereignty, helping them navigate economic instability and regain control over their finances through Bitcoin.
YakiHonne: It seems like you have a lot of people who genuinely want to learn about Bitcoin. They are not only focused on improving Zimbabwe’s economy but also actively engaging with the Bitcoin ecosystem.
Alexandra:I think one of the biggest challenges is that people don't truly understand how devastating a failed monetary system can be. If you look at it this way—money is involved in 50% of all transactions, meaning it plays a fundamental role in every economic activity. When money fails, one of the first consequences is the inability to calculate capital effectively, leading to high time preference decision-making. Alexandra:Why is this a problem? Well, in a stable monetary system, when people have strong purchasing power, they receive fair value for their economic output. This allows them to buy goods and services, invest in their future, pursue higher education, start businesses, and invest in assets like real estate and stocks. Essentially, good money gives people the time and ability to build a better future. Alexandra:However, when money does not store economic value, people only receive a fraction of what they produce. Instead of earning a full dollar for their work, they might get only two to three cents on the dollar. This means their income is barely enough for basic sustenance—just buying food, bread, and milk, and often, that isn’t even sufficient. Alexandra:As a result, people shift from long-term financial planning to immediate survival, making economic calculations purely about what they need right now rather than investing in the future. This is why so many places remain impoverished. Without stable money, real estate investments disappear, housing becomes inaccessible, and infrastructure like malls and gyms is nearly nonexistent. The only way to secure housing is outright purchase, which very few people can afford. This highlights the severe economic limitations caused by a broken monetary system.
 YakiHonne: It seems like you've already answered our first question. I was going to ask what sparked your interest in Bitcoin, but I can see that many factors actually led you toward the Bitcoin ecosystem. So, I think you've already covered that. Now, one more thing—I’d love to know what motivated you to build a community around Bitcoin?
YakiHonne: It seems like you've already answered our first question. I was going to ask what sparked your interest in Bitcoin, but I can see that many factors actually led you toward the Bitcoin ecosystem. So, I think you've already covered that. Now, one more thing—I’d love to know what motivated you to build a community around Bitcoin? Alexandra:Absolutely. Like I said, we observed communities all across Zimbabwe, but we noticed that nothing was really happening in terms of Bitcoin adoption. In fact, Zimbabwe's adoption rate is significantly lower than in most countries. While sub-Saharan Africa has the highest Bitcoin adoption rate, Zimbabwe itself has one of the lowest adoption rates. Alexandra:I realized that if no one else was willing to pave the way to make Bitcoin adoption more resilient and accessible, then I should step up and do the necessary work to facilitate the process. My goal was to connect the people who needed to be connected—whether it's miners, individuals looking to buy Bitcoin, or those who need help installing and using it.
YakiHonne: How did Bitcoin Reach begin? How was your community formed, and how did you initially attract new members?
Alexandra:it all started with just a few people. I was highly motivated and kept asking myself, how can we create an impact in Zimbabwe? Strangely enough, it began with me simply chasing leads. Alexandra:The turning point came when Anita Posch visited Zimbabwe. Through her visit, I connected with other like-minded individuals in the Bitcoin space. From there, we decided to create a WhatsApp group, which became the foundation of our community. With this small collective, I started reaching out to more people. Having even a modest level of influence allowed me to leverage connections and secure sponsorships. Alexandra:Our first sponsor was Booking for Fairness, followed by Money on Chain, Rootstock, and Global Bitcoin Fest. With this support, we started hosting regular meetups, organizing at least two meetups per month in different cities and countries. So far, we've held meetups in over eight cities across four different countries. At these events, attendance ranged from 25 to over 50 people, and at times, we even filled an entire restaurant with Bitcoin enthusiasts.
 YakiHonne: That's really impressive! You started with just three people, and now you're hosting events with over 50 attendees—sometimes even filling an entire restaurant. That’s truly amazing. Alexandra, you and your team are doing incredible work in Zimbabwe—it's a massive achievement! What challenges have you faced, and how have you overcome them?
YakiHonne: That's really impressive! You started with just three people, and now you're hosting events with over 50 attendees—sometimes even filling an entire restaurant. That’s truly amazing. Alexandra, you and your team are doing incredible work in Zimbabwe—it's a massive achievement! What challenges have you faced, and how have you overcome them?Alexandra: I think one of the major challenges that we do face is what we call an implicit ban, and some functions. Firstly, when we have what we call the negative order assumptions, a policy similar to what South Africa recently faced. Essentially, any country with bilateral relations with the United States must enforce the same sanctions imposed by the U.S. As a result, Zimbabwe is restricted from receiving goods and services from many companies. If you’re a Bitcoin business, you cannot provide Bitcoin services to Zimbabwe, cannot send hardware wallets, cannot hire people from Zimbabwe, and cannot offer sponsorships to Zimbabwean projects. This significantly limits the number of Bitcoin companies we could have collaborated with, which would have helped people earn Bitcoin and drive adoption. Alexandra:The second major challenge is implicit ban. If a Bitcoin company sets up in Zimbabwe, they cannot access on-ramps and off-ramps for funds. This means converting Bitcoin to physical cash is very expensive—normally, the cost should be around 2%, but due to the lack of formal channels, we have to buy Bitcoin at a 10% margin, making transactions extremely costly. As a result, it becomes difficult to establish a circular Bitcoin economy, and since we don’t have one, we struggle to secure funding.
YakiHonne: What advice would you give to someone looking to start or expand a Bitcoin-focused community in today’s landscape?
Alexandra:My advice would be to focus on the core issues, and the two most important ones are structure and education. Often, we get distracted by other elements when building a larger economy—such as organizing meetups, managing day-to-day operations, or maintaining WhatsApp groups for communication. However, for a community to truly grow and thrive, it needs a strong structural system and a functional circular economy. Alexandra:First, structure is key. If someone wants to learn about Bitcoin, where can they go? What courses or resources are available? Having clear educational pathways is essential for adoption. Alexandra:Second, building a circular economy is crucial. The first step is identifying people who are earning Bitcoin—whether through remittances, jobs, or services. Once there are enough Bitcoin earners, the next step becomes easier: figuring out where they can spend it. This is a far more practical approach than simply convincing businesses to accept Bitcoin without an existing customer base.For example, if you’re a vendor, shop owner, photographer, baker, or farmer, there are many potential Bitcoin customers who don’t want to cash out due to high fees. By accepting Bitcoin, businesses expand their clientele, which is a critical factor in establishing a sustainable Bitcoin economy.
YakiHonne: Does your community engage in the technical or non-technical aspects of Bitcoin? Or perhaps do you guys do both?
Alexandra:I think one of the biggest challenges is that we have people conducting thousands of dollars in Bitcoin transactions, yet they don’t understand what Lightning or Layer 2 is. Some even believe that Bitcoin has no real utility, despite using it regularly. There are people who are interested in the technical aspects, and we are gradually finding them. However, our community initially consisted mostly of people who used Bitcoin primarily for remittances. This is a common challenge in Africa—Bitcoin adoption grew rapidly because people saw it as a useful tool, not because they fully understood it. Unfortunately, we are currently more focused on the non-technical aspects, but we are actively working to change that.
YakiHonne:Alexandra, how do you see the role of Bitcoin communities evolving as technology advances, particularly in areas like scalability, privacy, and adaptability? How do you think these communities will develop as these technologies mature?
Alexandra:Yeah, I think Bitcoin communities play a crucial role in adoption and education. One of the most common things I hear when teaching people about Bitcoin is, “I wish I had learned about this from you first.” Many people's first encounter with Bitcoin was through scams, which led them to give up on it. Communities are essential because people are more likely to trust and engage with products when they come from a trusted source. Alexandra:When you build a community, every new member you bring in has the potential to influence five to ten others. These people are more likely to trust a friend’s recommendation when they say, “Bitcoin is good,” or when they explain how on-chain transactions might be slower or more expensive, but tools exist to enable faster, cheaper, and more private transactions. Alexandra:People buy into products they trust—or from people they trust. This is why communities are so important, even in a system built on "Don't trust, verify." Ironically, trust is still the first step for many newcomers. I think this is where Bitcoin might have missed the mark—there are so many incredible Bitcoin advocates, but if no one knows them personally, their messages, no matter how well-articulated, may not resonate. However, when the information comes from a trusted individual, people are much more receptive. Alexandra:Bitcoin communities serve as a solid foundation for introducing new solutions, including scalability, privacy, and other innovations. The key is communicating these ideas in a way that people trust and understand. Unlike expensive marketing campaigns, a passionate community can spread Bitcoin education almost for free—all they need are the right tools and resources to drive the movement forward.
YakiHonne:As long as there is trust, expansion will happen more effectively. Every user, every community member is a stakeholder, as they have the ability to bring others into the community. I’m confident that Bitcoin Reach will continue to grow and make an impact. Now, moving on to my final question, is the government in your region supportive or opposed to Bitcoin? And how has that stance impacted your community so far? Alexandra:our government is against Bitcoin. As I mentioned earlier, they were the ones who imposed the implicit ban, making it very expensive for individuals to buy Bitcoin. Zimbabwe used to be one of the fastest adopters in sub-Saharan Africa, but as soon as the government banned Bitcoin, adoption plummeted from 100 to zero. This has made it much more challenging for people like me to build a community around Bitcoin. Alexandra:Now, people hold their own keys because they are all using hardware wallets, which is a major benefit. Since they don’t trust institutions, they have taken full control of their Bitcoin, which is a great step toward financial sovereignty. However, this also slows down adoption in some ways. For example, in South Africa, our neighboring country, Pick n Pay has over 1,500 stores where people can pay with Bitcoin. In Zimbabwe, however, there are almost no places to spend Bitcoin, making real-world usage extremely limited.
YakiHonne:Thank you, Alexander.We've now reached the conclusion of today's interview, and I must say, I've learned so much from you. First, I truly admire how you were motivated by the low Bitcoin adoption rate in your country and took action to change that. I also appreciate your efforts to integrate economic growth with Bitcoin adoption, showing a deep understanding of both financial and technological progress. Your approach to community building is inspiring—you recognize that every community member matters, and the trust they bring is essential to the community’s success. It’s unfortunate that your government does not support Bitcoin, but with time, I believe that as Bitcoin’s influence continues to grow, they will eventually yield to its impact. I’m confident that there will be a stronger Bitcoin movement in Zimbabwe in the future.
-
 @ 5a0c0183:497ea4f8
2025-02-24 13:34:19
@ 5a0c0183:497ea4f8
2025-02-24 13:34:19O mercado de entretenimento digital no Brasil está cada vez mais recheado de opções para aqueles que buscam diversão e emoção. A XPBet é uma das plataformas mais recentes que chegou para conquistar o coração dos brasileiros. Oferecendo uma experiência de apostas única, com uma interface moderna, segurança de ponta e uma ampla variedade de jogos, a XPBet vem se destacando rapidamente como uma excelente escolha para quem deseja explorar novas formas de entretenimento online.
A Plataforma XPBet: Design Moderno e Acessibilidade A XPBet foi desenvolvida com foco na simplicidade e na acessibilidade, garantindo que jogadores de todos os níveis de experiência possam usufruir de seus recursos sem dificuldades. Com um design clean e de fácil navegação, a plataforma é ideal tanto para iniciantes quanto para jogadores experientes que buscam uma experiência sem complicações.
A segurança também é um aspecto crucial da Xpbet . A plataforma utiliza sistemas de criptografia avançada, que asseguram a proteção dos dados pessoais e financeiros dos usuários. Isso garante que os jogadores possam apostar e se divertir com tranquilidade, sabendo que suas informações estão sendo mantidas em segurança.
Jogos e Apostas na XPBet: Para Todos os Gostos A XPBet se destaca pela sua incrível variedade de jogos e opções de apostas. A plataforma oferece uma gama diversificada de jogos de mesa, apostas esportivas e outras opções de entretenimento interativo. Seja você um fã de esportes ou de jogos de habilidade, a XPBet tem algo especial para você.
A seção de apostas esportivas é um dos grandes atrativos da XPBet, com uma ampla gama de mercados para apostas em eventos de futebol, basquete, vôlei, tênis, entre outros. As apostas ao vivo são uma experiência envolvente e dinâmica, permitindo que os jogadores apostem enquanto assistem aos eventos em tempo real, o que traz uma dose extra de emoção ao jogo.
A XPBet também oferece uma vasta gama de jogos interativos que exigem habilidade e estratégia. Os jogadores podem se desafiar em diversos tipos de jogos, todos com mecânicas interessantes e uma jogabilidade envolvente. Independentemente do seu estilo de jogo, a XPBet garante que cada experiência seja única.
Experiência do Jogador: Facilidade e Atendimento de Qualidade Uma das prioridades da XPBet é garantir que os jogadores tenham uma experiência tranquila e sem problemas. O processo de registro na plataforma é simples e rápido, e as transações financeiras são feitas de forma prática e segura. A XPBet oferece uma variedade de métodos de pagamento, como cartões de crédito, transferências bancárias e carteiras digitais, permitindo que os jogadores escolham a forma mais conveniente para realizar seus depósitos e retiradas.
Além disso, o suporte ao cliente da XPBet é outro ponto forte. A plataforma conta com uma equipe de atendimento eficiente, pronta para ajudar a resolver qualquer problema ou responder dúvidas a qualquer momento. O atendimento ao vivo está disponível 24 horas por dia, 7 dias por semana, garantindo que os jogadores tenham a ajuda necessária sempre que precisarem.
Conclusão: XPBet, A Escolha Certa para o Entretenimento Online A XPBet se apresenta como uma plataforma inovadora e completa, que oferece segurança, diversidade de jogos e apostas, e uma experiência de usuário superior. Se você busca por uma plataforma que combine qualidade, funcionalidade e emoção, a XPBet é uma excelente opção. Com um design acessível, um portfólio de jogos de alta qualidade e suporte dedicado, a XPBet se estabelece como uma das melhores plataformas de entretenimento online no Brasil.
-
 @ fd208ee8:0fd927c1
2025-02-15 07:37:01
@ fd208ee8:0fd927c1
2025-02-15 07:37:01E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md https://github.com/nostr-protocol/nips/blob/master/61.md
-
 @ 2063cd79:57bd1320
2025-02-26 16:08:48
@ 2063cd79:57bd1320
2025-02-26 16:08:48Ich stimme mit Anonymous überein, dass es Probleme mit der tatsächlichen Verwendung von digitalem Bargeld auf kurze Sicht gibt. Aber es hängt in gewissem Maße davon ab, welches Problem man zu lösen versucht.
Eine Sorge, die ich habe, ist, dass der Übergang zum elektronischen Zahlungsverkehr die Privatsphäre einschränken wird, da es einfacher wird, Transaktionen zu protokollieren und aufzuzeichnen. Es könnten Profile angelegt werden, in denen das Ausgabeverhalten eines jeden von uns verfolgt wird.
Schon jetzt wird, wenn ich etwas telefonisch oder elektronisch mit meiner Visa-Karte bestelle, genau aufgezeichnet, wie viel ich ausgegeben habe und wo ich es ausgegeben habe. Im Laufe der Zeit könnten immer mehr Transaktionen auf diese Weise abgewickelt werden, und das Ergebnis könnte einen großen Verlust an Privatsphäre bedeuten.
Die Bezahlung mit Bargeld ist zwar immer noch per Post möglich, aber dies ist unsicher und umständlich. Ich denke, dass die Bequemlichkeit von Kredit- und Debitkarten die Bedenken der meisten Menschen in Bezug auf Privatsphäre ausräumen wird und dass wir uns in einer Situation befinden werden, in der große Mengen an Informationen über das Privatleben aller Leute existieren.
Hier könnte ich mir vorstellen, dass digitales Bargeld eine Rolle spielen könnte. Stellt euch ein Visa-ähnliches System vor, bei dem ich für die Bank nicht anonym bin. Stellt euch in diesem Modell vor, dass mir die Bank einen Kredit gewährt, ganz so wie bei einer Kreditkarte. Allerdings, anstatt mir nur eine Kontonummer zu geben, die ich am Telefon ablese oder in einer E-Mail verschicke, gibt sie mir das Recht, bei Bedarf digitales Bargeld zu verlangen.
Ich habe immer etwas digitales Bargeld beiseite, dass ich für Transaktionen ausgeben kann, wie bereits in früheren Beiträgen beschrieben. Wenn das Geld knapp wird, schicke ich eine E-Mail an die Bank und erhalte mehr digitales Bargeld (dcash). Jeden Monat sende ich einen Check an die Bank, um mein Konto auszugleichen, genauso wie ich es mit meinen Kreditkarten mache. Meine Beziehung zur Bank sind meinen derzeitigen Beziehungen zu den Kreditkartenunternehmen sehr ähnlich: häufige Überweisungen und eine einmalige Rückzahlung jeden Monat per Check.
Das hat mehrere Vorteile gegenüber dem System, auf das wir zusteuern. Es werden keine Aufzeichnungen darüber geführt, wofür ich mein Geld ausgebe. Die Bank weiß nur, wie viel ich jeden Monat abgehoben habe; es könnte sein, dass ich es zu diesem Zeitpunkt ausgegeben habe oder auch nicht. Bei einigen Transaktionen (z.B. Software) könnte ich für den Verkäufer anonym sein; bei anderen könnte der Verkäufer meine wirkliche Adresse kennen, aber dennoch ist keine zentrale Stelle in der Lage, alles zu verfolgen, was ich kaufe.
(Es gibt auch einen Sicherheitsvorteil gegenüber dem lächerlichen aktuellen System, bei dem die Kenntnis über eine 16-stellige Nummer und eines Ablaufdatums es jedem ermöglicht, etwas auf meinen Namen zu bestellen!)
Außerdem sehe ich nicht ein, warum dieses System nicht genauso legal sein sollte wie die derzeitigen Kreditkarten. Der einzige wirkliche Unterschied besteht darin, dass nicht nachverfolgt werden kann, wo die Nutzer ihr Geld ausgeben, und soweit ich weiß, war diese Möglichkeit nie ein wichtiger rechtlicher Aspekt von Kreditkarten. Sicherlich wird heute niemand zugeben, dass die Regierung ein Interesse daran hat, ein Umfeld zu schaffen, in dem jede finanzielle Transaktion nachverfolgt werden kann.
Zugegeben, dies bietet keine vollständige Anonymität. Es ist immer noch möglich, ungefähr zu sehen, wie viel jede Person ausgibt (obwohl nichts eine Person daran hindert, viel mehr Bargeld abzuheben, als sie in einem bestimmten Monat ausgibt, außer vielleicht für Zinsausgaben; aber vielleicht kann sie das zusätzliche digitale Bargel (digicash) selbst verleihen und dafür Zinsen erhalten, um das auszugleichen). Und es orientiert sich an demselben Kunden/ Verkäufer-Modell, das Anonymous kritisierte. Ich behaupte aber, dass dieses Modell heute und in naher Zukunft die Mehrheit der elektronischen Transaktionen ausmachen wird.
Es ist erwähnenswert, dass es nicht trivial ist, ein Anbieter zu werden, der Kreditkarten akzeptiert. Ich habe das mit einem Unternehmen, das ich vor ein paar Jahren betrieben habe, durchgemacht. Wir verkauften Software über den Versandhandel, was die Kreditkartenunternehmen sehr nervös machte. Es gibt zahlreiche Telefonbetrügereien, bei denen Kreditkartennummern über einige Monate hinweg gesammelt werden und dann große Beträge von diesen Karten abgebucht werden. Bis der Kunde seine monatliche Abrechnung erhält und sich beschwert, ist der Verkäufer bereits verschwunden. Um unser Kreditkartenterminal zu bekommen, wandten wir uns an ein Unternehmen, das Start-ups dabei „hilft“. Sie schienen selbst ein ziemlich zwielichtiges Unternehmen zu sein. Wir mussten unseren Antrag dahingehend fälschen, dass wir etwa 50% der Geräte auf Messen verkaufen würden, was offenbar als Verkauf über den Ladentisch zählte. Und wir mussten etwa 3.000 Dollar im Voraus zahlen, als Bestechung, wie es schien. Selbst dann hätten wir es wahrscheinlich nicht geschafft, wenn wir nicht ein Büro im Geschäftsviertel gehabt hätten.
Im Rahmen des digitalen Bargeldsystems könnte dies ein geringeres Problem darstellen. Das Hauptproblem bei digitalem Bargeld sind doppelte Ausgaben, und wenn man bereit ist, eine Online-Überprüfung vorzunehmen (sinnvoll für jedes Unternehmen, das mehr als ein paar Stunden für die Lieferung der Ware benötigt), kann dies vollständig verhindert werden. Es gibt also keine Möglichkeit mehr, dass Händler Kreditkartennummern für spätere Betrügereien sammeln. (Allerdings gibt es immer noch Probleme mit der Nichtlieferung von Waren, so dass nicht alle Risiken beseitigt sind). Dadurch könnte das System schließlich eine größere Verbreitung finden als die derzeitigen Kreditkarten.
Ich weiß nicht, ob dieses System zur Unterstützung von illegalen Aktivitäten, Steuerhinterziehung, Glücksspiel oder Ähnlichem verwendet werden könnte. Das ist nicht der Zweck dieses Vorschlags. Er bietet die Aussicht auf eine Verbesserung der Privatsphäre und der Sicherheit in einem Rahmen, der sogar rechtmäßig sein könnte, und das ist nicht verkehrt.
Englischer Artikel erschienen im Nakamoto Institute: Digital Cash & Privacy
-
 @ c4b5369a:b812dbd6
2025-02-12 12:23:40
@ c4b5369a:b812dbd6
2025-02-12 12:23:40
Unidirectional payment channels revisited
Nodeless lightning - Reduce ecash mints custodial risk
Sats N Facts
The nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference has just wrapped up. And what a blast it was. In the heart of northern Thailand, developers, researchers, content creators and more, came together to share ideas on how Bitcoin, Nostr and other free protocols are being used everyday to liberate people.
Not only were stories shared from different community leaders on how embracing bitcoin has empowered them and their communities, but a big goal of the unconference was to bring bitcoin engineers and developers from various domains together in one room, unstructured, chaotic, and let them do their thing.
At first, I thought not having a schedule might be boring, but oh boy was I wrong. There was so much stuff going on, it was hard to choose which session I would have to miss!
Luke's Spillman channel proposal
One of the sessions I definitely did not want to miss, was nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac s proposal
Ecash mints funded with Spillman channels: The ultimate nodeless Lightning wallet
.
In true unconference fashion, he announced in the main room that the session was about to start, and that the people that are interested should meet him in the whiteboard corner in 10 minutes. The corner was packed, and Luke explained his proposal.
What's a "Spillman channel"?
Essentially when we are talking about Spillman channels, what is meant are unidirectional payment channels (or CLTV-style channels). An unidirectional payment channel means, only one party can send payments, but not receive, and the other party can only receive, but not send. They also expire after a predetermined amount of time, and must be closed.

At first glance, this might look kinda stupid. After all, we have Poon-Dryja channels that are powering the lightning network. They are bi-directional, do not expire, and can be used to shuffle coins back and forth theorethically an unlimited amount of times.
So, why bother with this stupid one-way channel?
Simplicity is king
People that have worked with lightning channels can sing you a song about complexity, state handling and risks about the current state of bidirectional payment channels. Essentially, There are a lot of requirements on both channel parties when it comes to Liveness (being online) and also state handling (continuous backups).
 In some cases, especially when in the context of end-users wanting to perform payments on their mobile phone, they would appreciate it if there was not so much complexity and overhead involved.
In some cases, especially when in the context of end-users wanting to perform payments on their mobile phone, they would appreciate it if there was not so much complexity and overhead involved. The gist of the idea is to combine unidirectional channels and ecash mints to achieve the following:
A self custodial unidirectional payment channel to an ecash mint, massively reducing the senders liveness and state handling requirements when compared to a lightning channel. Sending payments through the mint will be done through swapping some of the channel balance for ecash tokens. At this point, the user is trusting the mint to honor the redemption of these tokens, while the remaining channel balance remains in self custody. This gives them better controll over their funds than just holding their entire balance custodied in the mint. The ecash tokens can then be redeemed to pay a lightning invoice, just the same as it is done now with normal cashu mints.

So this channel, that has no liveness or state management requirements for the sender, and must have a pre-defined close time, seems to be a perfect fit for the following usecase:
- A
senderreceives his salary once a month. He opens a channel that is valid for one month. - The
senderthen can do his daily spending over this channel. He only trusts themintwith the amount for the current outgoing payment while it is swapped for ecash, waiting for redemption. - If the
sendermust receive funds (a refund for example), he can do so into themintscustody, by receiving ecash. He can spend his ecash funds first when doing his next payment, to reduce his custodial exposure. - When the channel expires, or runs out of funds, the
mintcloses the channel.
From a consumer perspective, that just want to receive his salary and make frequent payments afterwards, this usecase seems to make a lot of sense. Obviously from a merchants perspective on the other hand, such a channel doesn't really work. But that's fine, it's not the problem we're trying to solve here.
What do you think of this idea? Be sure to let me know in the comments!
In the next article, we will dive into how such a system can be implemented today, using Bitcoin, Cashu and Lightning. We will also discover how the system can be improved, to make channels non-expiring (A collaborative idea between nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp and nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac born at nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx ).
So stay tuned!
- A
-
 @ 5a0c0183:497ea4f8
2025-02-24 13:32:51
@ 5a0c0183:497ea4f8
2025-02-24 13:32:51O mundo do entretenimento online está em constante evolução, trazendo novidades e inovações para os jogadores de todo o Brasil. A Bet5u surge como uma plataforma que promete transformar a experiência de apostas, oferecendo um ambiente seguro, divertido e de fácil acesso para os usuários. Com uma interface amigável, uma vasta gama de opções de jogos e uma experiência personalizada, a Bet5u se destaca como uma das principais escolhas para quem busca emoção e grandes possibilidades de ganhos.
Plataforma Bet5u: Simplicidade e Segurança A Bet5u foi projetada para ser simples e intuitiva, permitindo que qualquer pessoa, independentemente de sua experiência prévia, possa começar a jogar de maneira rápida e eficiente. A interface da plataforma é moderna e clean, com menus bem organizados e informações de fácil acesso. Isso proporciona uma navegação sem complicações, permitindo que os jogadores encontrem o que procuram com facilidade.
Uma das maiores preocupações dos usuários ao escolher uma plataforma de entretenimento online é a segurança, e a bet5u se destaca neste aspecto. Utilizando tecnologia avançada de criptografia, a plataforma garante que os dados pessoais e as transações financeiras dos jogadores estejam sempre protegidos. Isso proporciona aos usuários uma sensação de segurança e confiança, permitindo que se concentrem no que realmente importa: a diversão e as apostas.
Variedade de Jogos e Apostas na Bet5u Na Bet5u, a diversidade de jogos e apostas é uma das grandes atrações. A plataforma oferece uma ampla gama de opções, desde jogos de mesa e cartas até as mais emocionantes apostas em esportes. Com parcerias com desenvolvedores renomados, a Bet5u oferece jogos de alta qualidade, com gráficos impressionantes e uma jogabilidade envolvente.
Para os fãs de esportes, a Bet5u oferece uma seção completa de apostas, com mercados de futebol, basquete, tênis, entre outros. As apostas ao vivo são um grande destaque da plataforma, permitindo que os jogadores apostem em tempo real durante eventos esportivos, o que traz ainda mais emoção à experiência de jogo.
Além disso, a Bet5u apresenta jogos com mecânicas envolventes, onde os jogadores podem testar suas habilidades e estratégias. Seja através de jogos de sorte ou habilidade, a plataforma oferece uma ampla gama de opções que garantem entretenimento para todos os gostos.
Experiência do Jogador: Simples, Ágil e Gratificante A Bet5u se dedica a proporcionar uma experiência de jogo fluída e sem interrupções. O processo de cadastro é rápido e simples, e os métodos de depósito e retirada são variados, permitindo que os jogadores escolham a forma mais conveniente para realizar suas transações. A plataforma oferece opções populares de pagamento, como cartões de crédito, transferências bancárias e carteiras digitais, garantindo conveniência para os usuários.
Outro ponto positivo é o suporte ao cliente da Bet5u. Com um atendimento ágil e eficiente, a plataforma garante que os jogadores possam resolver qualquer dúvida ou problema rapidamente. A equipe de suporte está disponível 24 horas por dia, 7 dias por semana, para garantir que a experiência dos jogadores seja a melhor possível.
Conclusão: Bet5u, a Plataforma de Entretenimento Completa A Bet5u é uma plataforma que combina inovação, segurança e uma ampla variedade de jogos e apostas, criando uma experiência única e empolgante para os jogadores brasileiros. Com uma interface intuitiva, opções de pagamento seguras e suporte dedicado ao cliente, a Bet5u se posiciona como uma das melhores escolhas para quem busca um entretenimento online de qualidade. Se você está procurando emoção, diversão e a chance de ganhar prêmios incríveis, a Bet5u é o lugar perfeito para começar.
-
 @ 6ad3e2a3:c90b7740
2025-02-09 11:22:19
@ 6ad3e2a3:c90b7740
2025-02-09 11:22:19I’m honored to have the opportunity to speak with the highly regarded and much beloved Lisbon legend Oscar Liss. Oscar has brought joy to so many children and adults alike. He even helped one person find spiritual salvation, something about which we ask him below. So please enjoy this far-ranging conversation about the meaning life and the nature of consciousness itself.
Q: Oscar, thanks so much for making the time. For the few people that don’t know you, do you mind stating your full name and date of birth?
A: My name is Oscar Liss, though officially it’s Oscar Quinta da Bicherada, the prison complex where I was born. I am a long-haired mini dachshund. I have many aliases, including Osk, Oskie, The Skeeze, Skeezeley, Skeezeley-ski, The Guy, The Guy Behind The Guy, “The Opportunist” (which I don’t like), the…
Q That’s more than sufficient, Oscar, thank you. And date of birth?
A: July 7, 2020.
Q Talk a little bit about your childhood and how you came to live in Lisbon.
A: I was in the prison complex, mostly caged for the first few months. Then I was sold to dog traffickers in Lisbon.
Q: That must have been traumatic.
A: Not really. I quickly developed Stockholm Syndrome. Whenever I see my traffickers now, I feel nothing but overwhelming joy.
Q: Wow. A lot of us can learn from that attitude. Let’s fast forward a bit to your present-day life. In what does it consist?
A: Sleep on the sofa, go for walks, fetch vegetable sticks. Sometimes go for hikes or get sent to dog camp (which is okay, but I’m always the smallest.)
Q: I meant to ask you about your size. I hope it’s not a sensitive subject.
A: I’m six inches tall, more than a foot long, weigh almost 10 pounds.
Q: Are you self-conscious about being a small dog?
A: No, but the traffickers are self-conscious on my behalf. They’re always like, “Who’s the apex predator? Who’s an apex!" Or “you’re such a big strong dog.” It’s absurd. I am fine with who I am.
Q: What’s the source of your self-confidence, I’m sure many of our readers could take a lesson from you.
A: I’m not ambitious. I’m perfectly happy to be a dog.
Q: That’s so profound. Does it not concern you some have described you as “all bark, no bite?”
A: I had a friend once who bit a few people, and they executed him. People mock, but they have no idea the stakes.
Q: Human privilege?
A: Yes. Dogs don’t get due process. There is no justice for a dog.
Q: Do you think there’s species discrimination?
A: Have you ever been rejected from a restaurant and made to wait in the car while everyone else gets in?
Q: How does that make you feel?
A: Bad. I’ve been to many dog-friendly restaurants, never had a problem, aside for that one time I urinated on the coffee shop floor.
Q: Humans often purport to know what a dog is going through, some even create social media accounts for them. What do you think of that?
A: A person of human ancestry can’t possibly know the lived experience of a dog.
Q: You mentioned vegetable sticks. Are you a vegetarian?
A: No. I have never understood the appeal of it. I just like to chew the sticks. (Sometimes I eat apples or bell peppers, but it takes work when you don’t have molars. A lot of “crunch, crunch, crunch” with my jaw.)
Q: What’s behind the alias “The Opportunist” which you said you don’t like.
A: Whenever one of the traffickers opens the refrigerator, I tend to show up in in short order.
Q: I see how that could be insulting. How would you describe your current vocation?
A: I was named “Calorie Acquisition Specialist” recently, but I also work in security.
Q: Security?
A: I make sure to let everyone know when someone’s at the front door.
Q: What goes through your mind in those cases? Are you scared?
A: Not really. Imagine if you were fast asleep and the voice of God at volume 11 screamed into your mind: “WHO THE FUCK IS AT THE DOOR!!!!!!!!!”
Q: Speaking of God, can you tell us about the time you helped a woman on the street connect with Him?
A: We were walking back from Parque Eduardo VII (by the way, Portuguese is my native language), and a woman with two regular size dachshunds, saw me, started shrieking and proclaimed, “your dog is so beautiful he proves the existence of God!”
Q: Wow. It really hit home for her. Let’s talk about your work. How do you stay in character so consistently? How do you maintain your role as a dog?
A: I was incarnated in a dog body and therefore have dog consciousness. Everything I do is a reflection of that basic fact.
Q: Some serious method acting!
A: You could call it that. I am fully immersed in the role.
Q: A lot of humans speak about past lives, can even recall them under hypnosis. Do you think you will be ever reincarnated as a dog, stuck in an infinite dog-loop, so to speak, or will you one day jump into a human body?
A: I don’t know. I focus on the present.
Q: Oscar, it’s been such a pleasure to talk with you. I really appreciate your making the time.
(buzzer sounds)
A: WHO THE FUCK IS AT THE DOOR!!!!!!!!!!!!!!
-
 @ a012dc82:6458a70d
2025-02-24 13:16:04
@ a012dc82:6458a70d
2025-02-24 13:16:04The financial landscape has been dramatically reshaped with the U.S. Securities and Exchange Commission's (SEC) landmark approval of the first-ever batch of spot bitcoin exchange-traded funds (ETFs). This pivotal moment not only signifies a major leap forward for the cryptocurrency realm but also marks a significant evolution in traditional investment methodologies. The integration of Bitcoin into the ETF framework heralds a new era of digital asset investment, blending the innovative world of cryptocurrencies with the stability and familiarity of traditional financial markets. This article aims to provide a comprehensive understanding of Bitcoin ETFs, their profound implications for the investment community, and the transformative potential they hold for the future of financial diversification and strategy.
Table of Contents
-
What is a Bitcoin ETF?
-
The Significance of SEC’s Approval
-
Impact on the Cryptocurrency Market
-
Benefits for Investors
-
Enhanced Accessibility
-
Portfolio Diversification
-
Regulatory Safety Net
-
-
Challenges and Considerations
-
Conclusion
-
FAQs
What is a Bitcoin ETF?
A Bitcoin ETF represents a seismic shift in investment opportunities, offering a bridge between the cutting-edge realm of cryptocurrencies and the established world of stock market investing. It functions as an investment fund that closely tracks the value of Bitcoin, allowing investors to buy shares that mirror the performance of the digital currency. These shares are traded on conventional stock exchanges, akin to stocks, thereby democratizing access to Bitcoin investment. This innovative approach eliminates the technical barriers and security concerns associated with direct cryptocurrency investments, such as understanding blockchain technology, managing digital wallets, and safeguarding private keys. By simplifying the investment process, Bitcoin ETFs are poised to attract a diverse range of investors, from seasoned stock market enthusiasts to newcomers intrigued by the potential of digital currencies.
The Significance of SEC’s Approval
The SEC's approval of Bitcoin ETFs is a watershed moment, signaling a paradigm shift in the financial sector's approach to digital assets. It's a recognition of Bitcoin's growing relevance and maturity as an investment asset, and a nod to its potential to integrate seamlessly into the broader financial system. This move is not just about regulatory compliance; it's a strong endorsement of the legitimacy and viability of cryptocurrencies. The involvement of heavyweight financial institutions in sponsoring these ETFs is a testament to the growing confidence in Bitcoin's future. This development is expected to catalyze further innovations in the cryptocurrency space, encouraging more rigorous standards, enhanced security protocols, and greater transparency, all of which are essential for mainstream acceptance and long-term growth.
Impact on the Cryptocurrency Market
The launch of Bitcoin ETFs is set to revolutionize the cryptocurrency market. By offering a regulated, familiar, and accessible investment vehicle, these ETFs are likely to attract a new demographic of investors, including those who have been on the sidelines due to the perceived complexities and risks of cryptocurrencies. This broader investor base could lead to increased market capitalization and liquidity for Bitcoin, potentially reducing volatility and fostering a more stable pricing environment. Moreover, the introduction of Bitcoin ETFs could serve as a catalyst for the development of similar products for other cryptocurrencies, paving the way for a more diverse and robust digital asset market. This could also spur innovation in blockchain technology and crypto-related services, further integrating these into the mainstream financial ecosystem.
Benefits for Investors
Enhanced Accessibility
Bitcoin ETFs represent a democratization of cryptocurrency investment, making it accessible to a wider audience. This inclusivity extends beyond individual investors to institutional ones, who may have been hesitant to invest in cryptocurrencies due to regulatory concerns or logistical complexities. By trading on major stock exchanges, Bitcoin ETFs offer a familiar and regulated environment, lowering the entry barrier for those new to digital currencies.
Portfolio Diversification
The introduction of Bitcoin ETFs offers a novel avenue for portfolio diversification. Historically, investors seeking diversification would turn to a mix of stocks, bonds, and commodities. Bitcoin ETFs add a new dimension to this mix, providing exposure to an asset class that has shown a low correlation with traditional markets. This diversification can be particularly appealing in times of economic uncertainty or inflationary pressures, where Bitcoin has often been touted as a 'digital gold'.
Regulatory Safety Net
Trading within the regulated framework of stock exchanges, Bitcoin ETFs offer a level of oversight and consumer protection not typically available in direct cryptocurrency investments. This regulatory safety net can be particularly reassuring for risk-averse investors and those concerned about the legal implications of cryptocurrency investments.
Simplified Investment and Taxation Process: Investing in Bitcoin directly involves a complex maze of tax implications and ownership challenges. Bitcoin ETFs streamline this process, offering a straightforward investment vehicle that fits neatly into existing tax and investment frameworks. This simplification is a boon for both individual investors managing their portfolios and financial advisors seeking to incorporate digital assets into their clients' strategies.
Challenges and Considerations
While Bitcoin ETFs offer numerous advantages, they are not without their challenges and risks. The cryptocurrency market, known for its volatility, presents a unique risk profile that may not be suitable for all investors. The price of Bitcoin can be influenced by a range of factors, from regulatory news to technological developments, and investor sentiment. Therefore, while ETFs provide a more accessible route to Bitcoin investment, they do not shield investors from the inherent price volatility of the underlying asset. Additionally, as with any emerging investment vehicle, there is a learning curve associated with understanding how Bitcoin ETFs fit into a broader investment strategy. Investors should conduct thorough research, consider their long-term investment goals, and possibly consult with financial advisors to understand how Bitcoin ETFs align with their risk tolerance and investment objectives.
Conclusion
The introduction of Bitcoin ETFs is a landmark development in the financial world, bridging the gap between traditional investment mechanisms and the burgeoning world of digital currencies. This innovation not only expands the accessibility of Bitcoin to a broader range of investors but also enhances the overall credibility and stability of the cryptocurrency market. As the financial landscape continues to evolve, Bitcoin ETFs stand as a beacon of the growing synergy between conventional finance and digital asset innovation, offering a glimpse into a future where such collaborations are not just possible but are a cornerstone of investment strategy. As we move forward, Bitcoin ETFs will likely play a pivotal role in shaping the dynamics of investment portfolios, offering a unique combination of innovation, accessibility, and diversification.
FAQs
What is a Bitcoin ETF? A Bitcoin ETF is an exchange-traded fund that tracks the price of Bitcoin, allowing investors to buy shares in the ETF on traditional stock exchanges, without directly purchasing and managing Bitcoin.
How does a Bitcoin ETF differ from buying Bitcoin directly? Unlike direct Bitcoin purchases, which require a cryptocurrency exchange account and a digital wallet, a Bitcoin ETF allows investors to trade shares representing Bitcoin on conventional stock exchanges, simplifying the investment process.
Are Bitcoin ETFs safe investments? While Bitcoin ETFs offer the safety of regulated stock exchanges and eliminate the need for digital wallet management, they still carry the inherent volatility and risks associated with Bitcoin prices.
Can Bitcoin ETFs be included in retirement portfolios? Yes, Bitcoin ETFs can be included in various investment portfolios, including retirement plans, offering a way to diversify with a new asset class.
What are the tax implications of investing in a Bitcoin ETF? Bitcoin ETFs simplify tax reporting compared to direct cryptocurrency investments. However, investors should consult with a tax professional to understand specific implications.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnews.co
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ c1e6505c:02b3157e
2025-02-08 21:52:51
@ c1e6505c:02b3157e
2025-02-08 21:52:51***"Time is the best teacher but unfortunately it kills all of its students."*** I'm currently visiting my dad for a few days as I had to take my car in for some repairs and maintenance, which included an oil gasket leak, power steering fluid flush, brake fluid flush, spark plugs, and the works. The process took a couple of hours to complete, so instead of waiting in the waiting room or having someone pick me up to go wait comfortably at home, I decided to walk around with my camera and try to make some new work. I have to say, there's really nothing more that I enjoy than walking aimlessly in an area that I have never been and taking photographs. *I love it.* I lose myself and everything that is on my mind that I "worry" about. I'm present, in the zone, and honestly having a great time. Photography for me is a portal to enter a state of mind that transcends time and space. The area that I was in was very industrial, so my walk started next door at the other car mechanic shop, and I meandered down to the small local town where some shops were. Didn't see too much, so I turned around and started walking back down the other way. Sometimes I don't see anything of interest for a while. What I have noticed though, as a little trick to start having things "come out of the woodwork," is just to start shooting at the first thing that captures my interest. Getting the ball rolling with pushing the shutter somehow gets me in the "flow state" that I enjoy getting in when making photographs. \[ \]( As I walked further, I visited a plant nursery that was just opening. The woman who was opening the gate was very nice and invited me into walk around and do as I please. There were a few nice plants around, but what gravitates me the most is seemingly, to others maybe, the "ugly stuff" or the subject matter that one wouldn’t really consider making a photograph of. Blank spaces, trash, neglect - it's all good stuff to me. The light falling upon these subjects makes them interesting. After the nursery, I found a large industrial facility and a train yard. A worker stood next to one of the train cars, so I went up and asked what they were loading. He said that he’s been working there for 30 years, and that they make plastic trash bags, and those tubes feeding into the train cars were pumping out plastic beads for production. I thought that was interesting. We chatted for a bit, I thanked him for his time, and moved on.           Eventually, I ended up at a church with these really nice orange and brown doors. I sat on a bench in the back to kill some time, listening to a few podcasts. While I was there, I noticed a sign that read: *"Happy moments, praise God. Difficult moments, seek God. Quiet moments, worship God. Painful moments, trust God. Every moment, thank God."* I’m not a religious guy per se, haven’t been to church in over a decade, and I’ve had my own experiences — psychedelics included — where I’ve glimpsed something I’d call “God.”, but there’s something to take from that. Whatever your definition of “God” is, there’s value in gratitude whether things are good or bad. Life itself is a miracle. Appreciating the small things keeps you grounded, humble, and connected.   ) *Just in case you missed it…* **I have a limited edition framed print that I will have available until February 28th.** Only two will be made, and they will come framed; one in black, one in silver. If you enjoy my work, this would be a great collectors piece. \]() ***I shoot with a Leica M262, and edit in Lightroom + Dehancer*** [***Use “PictureRoom” for 10% off Dehancer Film***](https://www.dehancer.com/shop/pslr/film) If you’ve made it this far, thank you for taking the time to view my work - I appreciate it. Please consider becoming a paid subscriber to support my work. Also, please contact me if you would like to purchase any of my prints.  [Dehancer Film (promo code "PICTUREOOM")](https://www.dehancer.com/shop/pslr/film) *If you've found value in this newsletter, I'd be incredibly grateful for your support. While these posts will always be freely available, becoming a paid subscriber helps ensure I can continue delivering quality content to your inbox. Share this newsletter with friends, leaving a comment, or simply hitting the 'like' button all make a difference.* Thank you - Colin
-
 @ d360efec:14907b5f
2025-02-24 11:33:16
@ d360efec:14907b5f
2025-02-24 11:33:16ภาพรวม BTCUSDT (OKX):
Bitcoin (BTCUSDT) ยังคงแสดงความผันผวนและแนวโน้มที่ไม่ชัดเจน แม้ว่าแนวโน้มระยะยาว (TF Day) จะยังคงมีลักษณะเป็นขาขึ้น (แต่อ่อนแรงลงอย่างมาก) แนวโน้มระยะกลาง (TF4H) และระยะสั้น (TF15) เป็นขาลง/Sideways Down การวิเคราะห์ครั้งนี้จะเน้นไปที่ SMC, ICT, และรูปแบบ Chart Patterns เพื่อเพิ่มความแม่นยำในการระบุแนวโน้มและจุดเข้า/ออก
วิเคราะห์ทีละ Timeframe:
(1) TF Day (รายวัน):
- แนวโน้ม: ขาขึ้น (Uptrend) อ่อนแรงลงอย่างมาก, มีความเสี่ยงที่จะเปลี่ยนแนวโน้ม
- SMC:
- Higher Highs (HH) และ Higher Lows (HL) เริ่มไม่ชัดเจน, ราคาหลุด Low ก่อนหน้า
- Break of Structure (BOS) ด้านบน แต่มีการปรับฐานที่รุนแรง
- Liquidity:
- มี Sellside Liquidity (SSL) อยู่ใต้ Lows ก่อนหน้า (บริเวณ 85,000 - 90,000)
- มี Buyside Liquidity (BSL) อยู่เหนือ High เดิม
- ICT:
- Order Block: ราคาหลุด Order Block ขาขึ้น
- FVG: ไม่มี FVG ชัดเจน
- EMA:
- ราคา หลุด EMA 50 (สีเหลือง) ลงมาแล้ว
- EMA 200 (สีขาว) เป็นแนวรับถัดไป
- Money Flow (LuxAlgo):
- สีแดงยาว แสดงถึงแรงขายที่แข็งแกร่ง
- Trend Strength (AlgoAlpha):
- สีแดง (เมฆแดง) แสดงถึงแนวโน้มขาลง และไม่มีสัญญาณซื้อ/ขายปรากฏ
- Chart Patterns: ไม่มีรูปแบบที่ชัดเจน
- Volume Profile: Volume ค่อนข้างเบาบาง
- แท่งเทียน: แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย
- แนวรับ: EMA 200, บริเวณ 85,000 - 90,000 (SSL)
- แนวต้าน: EMA 50, High เดิม
- สรุป: แนวโน้มขาขึ้นอ่อนแรงลงอย่างมาก, สัญญาณอันตรายหลายอย่าง, Money Flow และ Trend Strength เป็นลบ, หลุด Order Block และ EMA 50
(2) TF4H (4 ชั่วโมง):
- แนวโน้ม: ขาลง (Downtrend)
- SMC:
- Lower Highs (LH) และ Lower Lows (LL)
- Break of Structure (BOS) ด้านล่าง
- Liquidity:
- มี SSL อยู่ใต้ Lows ก่อนหน้า
- มี BSL อยู่เหนือ Highs ก่อนหน้า
- ICT:
- Order Block: ราคาไม่สามารถผ่าน Order Block ขาลงได้
- EMA:
- ราคาอยู่ใต้ EMA 50 และ EMA 200
- Money Flow (LuxAlgo):
- สีแดง แสดงถึงแรงขาย
- Trend Strength (AlgoAlpha):
- แดง/ไม่มีสัญญาณ
- Chart Patterns: ไม่มีรูปแบบที่ชัดเจน
- Volume Profile: * Volume ค่อนข้างนิ่ง
- แนวรับ: บริเวณ Low ล่าสุด
- แนวต้าน: EMA 50, EMA 200, บริเวณ Order Block
- สรุป: แนวโน้มขาลงชัดเจน, แรงขายมีอิทธิพล
(3) TF15 (15 นาที):
- แนวโน้ม: Sideways Down (แกว่งตัวลง)
- SMC:
- Lower Highs (LH) และ Lower Lows (LL)
- Break of Structure (BOS) ด้านล่าง
- ICT:
- ราคา Sideway
- EMA:
- EMA 50 และ EMA 200 เป็นแนวต้าน
- Money Flow (LuxAlgo):
- แดง/เขียว สลับกัน
- Trend Strength (AlgoAlpha):
- สีแดง แสดงถึงแนวโน้มขาลง
- Chart Patterns: ไม่มีรูปแบบที่ชัดเจน
- Volume Profile: * Volume ค่อนข้างนิ่ง
- แนวรับ: บริเวณ Low ล่าสุด
- แนวต้าน: EMA 50, EMA 200
- สรุป: แนวโน้ม Sideways Down,
สรุปภาพรวมและกลยุทธ์ (BTCUSDT):
- แนวโน้มหลัก (Day): ขาขึ้น (อ่อนแรงลงอย่างมาก, เสี่ยงที่จะเปลี่ยนแนวโน้ม)
- แนวโน้มรอง (4H): ขาลง
- แนวโน้มระยะสั้น (15m): ขาลง/Sideways Down
- Liquidity: มี SSL ทั้งใน Day, 4H, และ 15m
- Money Flow: เป็นลบในทุก Timeframes
- Trend Strength: Day/15m เป็นขาลง, 4H Sideways
- Chart Patterns: ไม่พบรูปแบบที่ชัดเจน
- กลยุทธ์:
- Wait & See (ดีที่สุด): รอความชัดเจน
- Short (เสี่ยง): ถ้าไม่สามารถ Breakout EMA/แนวต้านใน TF ใดๆ ได้ หรือเมื่อเกิดสัญญาณ Bearish Continuation
- ไม่แนะนำให้ Buy: จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจนมากๆ
Day Trade & การเทรดรายวัน:
-
Day Trade (TF15):
- Short Bias: หาจังหวะ Short เมื่อราคาเด้งขึ้นไปทดสอบแนวต้าน (EMA, Order Block)
- Stop Loss: เหนือแนวต้านที่เข้า Short
- Take Profit: แนวรับถัดไป (Low ล่าสุด)
- ไม่แนะนำให้ Long
-
Swing Trade (TF4H):
- Short Bias: รอจังหวะ Short เมื่อราคาไม่สามารถผ่านแนวต้าน EMA หรือ Order Block ได้
- Stop Loss: เหนือแนวต้านที่เข้า Short
- Take Profit: แนวรับถัดไป
- ไม่แนะนำให้ Long
สิ่งที่ต้องระวัง:
- Sellside Liquidity (SSL): มีโอกาสสูงที่ราคาจะถูกลากลงไปแตะ SSL
- False Breakouts: ระวัง
- Volatility: สูง
Setup Day Trade แบบ SMC (ตัวอย่าง):
- ระบุ Order Block: หา Order Block ขาลง (Bearish Order Block) ใน TF15
- รอ Pullback: รอให้ราคา Pullback ขึ้นไปทดสอบ Order Block นั้น
- หา Bearish Entry:
- Rejection: รอ Price Action ปฏิเสธ Order Block
- Break of Structure: รอให้ราคา Break โครงสร้างย่อยๆ
- Money Flow: ดู Money Flow ให้เป็นสีแดง
- ตั้ง Stop Loss: เหนือ Order Block
- ตั้ง Take Profit: แนวรับถัดไป
คำแนะนำ:
- ความขัดแย้งของ Timeframes: มีอยู่ แต่แนวโน้มระยะกลาง-สั้น เป็นลบ
- Money Flow: เป็นลบในทุก Timeframes
- Trend Strength: เป็นลบ
- Order Block TF Day: หลุด Order Block ขาขึ้นแล้ว
- ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-
 @ e676e469:7e51e2ec
2025-02-24 11:16:17
@ e676e469:7e51e2ec
2025-02-24 11:16:17Red88 là một nền tảng giải trí trực tuyến hiện đại, được thiết kế để mang đến cho người tham gia những trải nghiệm vô cùng thú vị, phong phú và đầy sáng tạo. Với giao diện người dùng dễ sử dụng và tối ưu hóa cho tất cả các thiết bị, Red88 đảm bảo rằng mọi người tham gia đều có thể dễ dàng tiếp cận và tận hưởng những hoạt động giải trí mà nền tảng này cung cấp. Từ những trò chơi trí tuệ đòi hỏi khả năng phân tích chiến lược cho đến các trò chơi thư giãn giúp giảm căng thẳng, Red88 luôn cập nhật và phát triển những trải nghiệm đa dạng, đáp ứng nhu cầu của nhiều người chơi với các mức độ kỹ năng khác nhau. Sự sáng tạo trong thiết kế trò chơi và các thử thách luôn khiến người chơi cảm thấy hứng thú, không bao giờ cảm thấy nhàm chán. Từng trò chơi, thử thách đều được xây dựng một cách tỉ mỉ, với mục tiêu không chỉ mang lại niềm vui mà còn giúp người tham gia rèn luyện các kỹ năng tư duy và sáng tạo.
Không chỉ chú trọng vào việc cung cấp các trò chơi giải trí, RED88 còn đặc biệt xây dựng một cộng đồng người chơi vững mạnh và thân thiện. Cộng đồng trên nền tảng này luôn đầy nhiệt huyết và năng động, nơi người tham gia có thể giao lưu, chia sẻ kinh nghiệm và học hỏi từ những người chơi khác. Các sự kiện, giải đấu và thử thách trên Red88 không chỉ mang lại cơ hội thể hiện kỹ năng mà còn tạo ra không khí cạnh tranh lành mạnh, giúp mỗi người tham gia có thể phát triển và hoàn thiện bản thân. Hệ thống tương tác trong nền tảng này cho phép người chơi kết nối với nhau, tham gia vào các hoạt động nhóm và cộng tác trong các thử thách chung. Nhờ vào sự kết nối mạnh mẽ và tính cộng đồng cao, Red88 không chỉ mang lại trải nghiệm giải trí mà còn tạo ra một môi trường hợp tác và học hỏi đầy ý nghĩa. Mỗi người tham gia không chỉ tìm thấy niềm vui mà còn có thể nâng cao kỹ năng giao tiếp và kết nối với những người bạn mới.
Bên cạnh những trò chơi thú vị và cộng đồng kết nối mạnh mẽ, Red88 đặc biệt chú trọng đến bảo mật và an toàn của người tham gia. Nền tảng này sử dụng các công nghệ bảo mật tiên tiến nhất để bảo vệ thông tin cá nhân và tài khoản người dùng, đảm bảo rằng tất cả dữ liệu đều được xử lý một cách an toàn, tránh khỏi những rủi ro từ các tác nhân bên ngoài. Mọi giao dịch, thông tin cá nhân đều được mã hóa và lưu trữ với mức độ bảo mật cao nhất, giúp người tham gia có thể hoàn toàn yên tâm khi tham gia vào các hoạt động giải trí trực tuyến. Đội ngũ hỗ trợ khách hàng của Red88 luôn sẵn sàng 24/7, giúp giải đáp thắc mắc và hỗ trợ người tham gia bất kỳ lúc nào. Sự bảo mật và hỗ trợ khách hàng tuyệt vời là yếu tố quan trọng giúp Red88 tạo dựng niềm tin và sự uy tín trong mắt người dùng. Chính nhờ vào sự kết hợp giữa các trò chơi sáng tạo, cộng đồng kết nối mạnh mẽ và dịch vụ bảo mật tối tân, Red88 đã khẳng định được vị trí của mình là một nền tảng giải trí trực tuyến chất lượng, an toàn và đáng tin cậy, luôn mang đến cho người tham gia những trải nghiệm tuyệt vời và đáng nhớ.
-
 @ e676e469:7e51e2ec
2025-02-24 11:15:02
@ e676e469:7e51e2ec
2025-02-24 11:15:02J79 là một nền tảng giải trí trực tuyến nổi bật, mang đến cho người tham gia những trải nghiệm vô cùng thú vị và sáng tạo. Với giao diện người dùng đơn giản và dễ sử dụng, J79 cung cấp một không gian giải trí hoàn hảo cho tất cả mọi đối tượng người dùng, từ người mới bắt đầu đến những người đã có kinh nghiệm lâu năm. Nền tảng này sở hữu một loạt các trò chơi và hoạt động đa dạng, giúp người tham gia có thể lựa chọn những trải nghiệm phù hợp với sở thích và nhu cầu của mình. Dù là những trò chơi đòi hỏi tư duy chiến lược hay các hoạt động thư giãn nhẹ nhàng, J79 luôn đảm bảo mang đến những trải nghiệm thú vị và đầy thử thách. Mỗi trò chơi trên J79 đều được thiết kế một cách tỉ mỉ, không chỉ giúp người chơi thư giãn mà còn kích thích khả năng tư duy và sáng tạo. Bằng cách cập nhật và cải tiến thường xuyên, nền tảng này luôn đảm bảo rằng mỗi người tham gia sẽ có một trải nghiệm mới mẻ và đầy hấp dẫn. Chính sự sáng tạo và tính đa dạng trong các hoạt động giúp J79 nhanh chóng thu hút sự quan tâm của đông đảo người tham gia.
Một trong những điểm mạnh của J79 chính là khả năng kết nối cộng đồng mạnh mẽ và đầy tính tương tác. Không chỉ là nơi để người tham gia giải trí, J79 còn là một không gian để giao lưu, học hỏi và chia sẻ kinh nghiệm với những người chơi khác. Nền tảng này đã tạo ra một cộng đồng sôi nổi, thân thiện và đầy nhiệt huyết, nơi người tham gia có thể kết bạn, hợp tác và cạnh tranh trong các hoạt động nhóm. Các sự kiện, thử thách và giải đấu trên J79 luôn thu hút sự tham gia của đông đảo người chơi, mang đến cơ hội để thể hiện tài năng và phát triển kỹ năng cá nhân. Sự tương tác mạnh mẽ giữa người chơi cũng góp phần làm cho mỗi trải nghiệm trở nên thú vị và đáng nhớ. J79 không chỉ đơn thuần là một nền tảng giải trí, mà còn là nơi để người tham gia phát triển bản thân, trao dồi các kỹ năng mềm và kỹ năng giao tiếp. Với các hoạt động cộng đồng phong phú, J79 luôn giữ vững vị trí là một trong những nền tảng giải trí trực tuyến hấp dẫn và thú vị nhất hiện nay.
Bên cạnh sự sáng tạo trong các trò chơi và cộng đồng kết nối, J79 cũng rất chú trọng đến bảo mật và an toàn của người tham gia. Nền tảng này áp dụng các công nghệ bảo mật tiên tiến, giúp bảo vệ thông tin cá nhân và tài khoản của người dùng khỏi các mối đe dọa từ bên ngoài. Mọi giao dịch và thông tin cá nhân đều được mã hóa và xử lý một cách an toàn, đảm bảo rằng người tham gia có thể yên tâm khi tham gia vào các hoạt động trực tuyến. Bên cạnh đó, đội ngũ hỗ trợ khách hàng của J79 luôn sẵn sàng hỗ trợ 24/7, giúp giải đáp mọi thắc mắc và cung cấp sự trợ giúp kịp thời khi người tham gia gặp phải vấn đề. Chính nhờ vào hệ thống bảo mật hiện đại và dịch vụ hỗ trợ khách hàng tận tâm, người tham gia có thể trải nghiệm một không gian giải trí không chỉ thú vị mà còn an toàn tuyệt đối. J79 đã khẳng định được uy tín và chất lượng của mình như một nền tảng giải trí trực tuyến đáng tin cậy, mang đến cho người dùng sự an tâm tuyệt đối trong mỗi lần trải nghiệm.
-
 @ 3b7fc823:e194354f
2025-02-07 18:42:31
@ 3b7fc823:e194354f
2025-02-07 18:42:31Privacy in Public Spaces: A Tactical Guide
1. Public Wi-Fi Privacy
Using public Wi-Fi can be convenient, but it's important to take precautions to protect your privacy:
- Use a VPN (Virtual Private Network): A VPN encrypts your internet traffic, making it difficult for hackers to intercept your data.
- Disable Automatic Connections: Prevent your device from automatically connecting to open Wi-Fi networks by turning off this feature in your settings.
- Avoid Sensitive Transactions: Refrain from accessing banking or other sensitive accounts while connected to public Wi-Fi.
- Use Secure Websites: Look for "https://" in the website's URL to ensure it uses encryption.
- Keep Software Updated: Ensure your device's operating system and apps are up-to-date to protect against security vulnerabilities.
2. Surveillance Camera Awareness
Surveillance cameras are common in public spaces. Here are some strategies to maintain your privacy:
- Spotting Cameras:
- Look for Signs: Many establishments post signs indicating the presence of surveillance cameras.
- Camera Placement: Cameras are often placed near entrances, exits, and high-traffic areas. Look for dome-shaped cameras on ceilings or wall-mounted cameras.
- Using Masks and Coverings:
- Face Masks: Wearing a mask can help obscure your facial features from facial recognition systems.
- Hats and Sunglasses: A hat can shield your face from overhead cameras, while sunglasses can hide your eyes.
- Covering Identifying Marks:
- Clothing Choices: Wear clothing that doesn't have distinctive logos or patterns that can easily identify you.
- Blend In: Opt for styles and clothing choices that helps you blend in with your surroundings, reducing your visibility.
- Temporary Coverings: Consider using temporary coverings, such as scarves or hoods, to conceal tattoos or other identifying marks.
3. General Privacy Tips in Public Spaces
- Be Mindful of Your Surroundings: Pay attention to your environment and be aware of any unusual behavior or devices that may be capturing your information.
- Limit Personal Information: Avoid discussing sensitive information in public where it can be overheard.
- Use Encrypted Messaging Apps: Apps like Signal or SimpleX offer end-to-end encryption for your messages, making it harder for eavesdroppers to intercept your conversations.
- Use Privacy Screens: Privacy screens on all of you electronic screens can defend against the over the shoulder peek or side eye.
- Avoiding Behaviors: Be mindful of behaviors that could make you a target, such as frequent visits to certain areas or engaging in conversations that might attract unwanted attention.
Taking these steps can help you maintain your privacy while navigating public spaces and using public Wi-Fi. Remember, staying informed and vigilant is key to protecting your personal information.
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-
 @ 7d33ba57:1b82db35
2025-02-26 12:28:52
@ 7d33ba57:1b82db35
2025-02-26 12:28:52Shooting a great time-lapse on your phone takes some planning and the right settings. Here are some tips to get the best results:
Plan Your Shot
• Choose a subject with motion (clouds, traffic, sunrises, people walking, etc.). • Keep your phone stable use a tripod or secure it on a steady surface. • Consider the duration longer recordings result in smoother time-lapses.
Adjust Camera Settings • Use your phone’s built in time-lapse mode (found in the camera app). • If your phone doesn’t have it, use apps like Lapse It, Hyperlapse, Skyflow (iOS), or Framelapse (Android) for more control. • Adjust the interval speed: • 1-3 seconds per frame for fast moving subjects (cars, people). • 5-10 seconds per frame for slower motion (sunsets, clouds).
Lighting & Exposure • Shoot in consistent lighting (avoid flickering artificial lights). • Use manual exposure & focus lock to prevent brightness shifts. • Golden hour (sunrise/sunset) often gives the best visual effect.
Battery & Storage • Charge your phone fully (time-lapses take a lot of power). • Free up storage space before shooting. • If shooting for hours, use a power bank.
Post-Production • Edit in apps like Adobe Premiere Rush, iMovie, or CapCut to adjust speed, colors, and stability. • Add music or motion effects for a more dynamic result.
-
 @ 6ad3e2a3:c90b7740
2025-02-07 08:17:18
@ 6ad3e2a3:c90b7740
2025-02-07 08:17:18When I used to work in fantasy sports, people would ask me questions about their teams, e.g., which players to start, who to drop. What they didn’t realize is I had seven of my own teams to worry about, was already living and dying with my own myriad choices, good and bad, I made every week. The last thing I needed was to make a decision for them, see it go bad and suffer more on their account.
I’d tell them, “You decide, I’ve got my own problems.”
. . .
I don’t know what I’m doing. Ideas which feel like insights come to me, I try to articulate them to my satisfaction and post them (with some editing help from Heather.) Often I feel like I should be producing more work — after all, I don’t have a job any more, I have plenty of time. Walking the dog, exercising, managing your finances, picking up the kid, putting food on the table (literally) is well and good, but fulfilling your duties is not enough. You need to stay in the game. What game is up to each person, but it should be a game you enjoy, one that draws on skills honed over decades by the accident of your particular interests.
. . .
Writing and ideas can’t be produced on demand. I mean they can — and I did it for 22 years on a particular topic — but I don’t mean that kind of writing. I don’t want a schedule. I don’t need more rules, more discipline, more “hacks.” Discipline is like the interest on a 30-year mortgage. Initially it’s most of the payment, but over time it cedes weight to understanding which is like the principal. Discipline without understanding is like an interest-only mortgage. You pay it every month and get nowhere.
Even when insights arrive they can’t always be articulated sufficiently and coherently. Many insights are of the one sentence variety — fine for a social media post, but you can’t send out an email newsletter 10 times per day with one sentence insights. It doesn’t work over that medium.
That’s a dilemma because posting on social media doesn’t feel like proper work. Yes, you’re reaching people, affecting the zeitgeist in whatever small way — but there’s something addictive and unsatisfying about it, like eating candy instead of food. Don’t get me wrong, I stand by my posts (consider them organic, artisanal candy) but shitposting and the immediate feedback received therefrom keeps you only on the periphery. I need to connect with something deeper.
. . .
I’ve spent a lot of time dissecting the various pathologies of the laptop class, of which I’m obviously a part as I literally type this in a coffee shop on my laptop! The need to believe they are empathic and good overwhelming any rational sense-making and basic morals. Men dominating women’s sports, child sex changes, forced injections, criminals running rampant, cities in decay, calls for censorship and funding for foreign wars. The authorities patted them on the back, their peers accepted them and their overlords promoted them so long as they hewed to the narrative.
The freakout we’re presently witnessing is not about the billions in taxpayer money no longer being sent for DEI training in some foreign country, i.e., money-laundering to favored interests and cronies. They’re not really upset FBI agents are being fired, secrets are being revealed, that we are finally making an effort to prevent fentanyl from flowing across the border and killing our fellow citizens. These are good things, and even if you don’t agree, none of it is grounds for the meltdowns I see every day on social media.
What’s really happening is people who were assured they were the “good”, the empathic, the compassionate ones, those who towed the line during covid, got their boosters, wore their masks, “social distanced,” put pronouns in their bios, are being confronted with a terrifying realization: the behaviors and beliefs, to which they so dutifully attached themselves, for which they publicly and stridently advocated, whether online or at Thanksgiving dinner, are no longer being rewarded. In fact, they are being openly ridiculed. Instead of the pat on the back, increasingly Team Good is facing mockery and outright scorn.
There will be no legal consequences. No one will be arrested or put in a camp, delusions of persecution notwithstanding. If you produce real value for a real employer, you are not at risk of being fired. If you insist on perpetuating your derangement on social media you will not be deplatformed or canceled (that only happens to people speaking the truths inconvenient to the powerful.)
No, the reality is in some ways far worse: your entire worldview, on which you staked your self-image, is being dismantled in real time. You are no longer “good,” it’s becoming obvious to most the policies for which you advocated were catastrophic, the politicians for whom you voted deeply cynical and corrupt. The gaping abyss within your being to which you attached this superstructure of self-affirmation is dissolving into thin air. You are not “superior” like you thought, you are just another person suffering and existing like everyone else. And your only choices are to face that daunting reality or cling to a dying and useless paradigm, the end game for which is only madness.
We all want to feel good about ourselves, and like an obese person drugging themselves with high-fructose corn syrup for years, you have gorged on the distorted approbation of a sick society that, unpleasantly for you, is starting to heal. Your first laps around the track, so to speak, are going to hurt a lot.
. . .
I probably went on too long about the laptop class freakout. I have a lot of resentment toward the way they behaved the last five years. But I started this essay with the idea that I have my own problems, and in the end, I am not much different from them.
I want to produce more work, and of higher quality, but to what end? To feel good about my contributions, to have a sense that I am “good.” Maybe it’s not “good” in the lame “I complied with authority, and everyone likes me” kind of way, but it arises from the same source. That source is the emptiness within, wherein we require accolades, dopamine, positive feedback as a kind of justification for our existence. “No, I am not squandering my time on earth, living a comfortable life, I am asking hard questions, connecting with people, sharing hard-won insights. I am useful! I am good! I got my sixth dopamine booster from writing yet another essay!”
. . .
There is an irony in writing this piece. I feel as I type the cathartic nature of expressing these feelings. I am doing something worthwhile, everything is flowing out of me, the minutes are sailing by. I am identifying and solving this thorny problem simultaneously, engaging with the emptiness and dissatisfaction. The solution isn’t in the output, whatever one might think of it, it’s in giving attention to the feelings I’ve squandered too much time avoiding. I feel unworthy not because I do not produce enough work, it turns out, but because I am unwilling to connect with my deepest nature.
. . .
No matter how uneasy you feel, no matter how much fundamental doubt you have about your value as a human being, you can always start where you are. The feeling of unworthiness, the need for an escape, the craving for some kind of reward from your peers or the authorities or whatever easily-consumed carbohydrates you have in the kitchen is simply the present state in which you find yourself. It is not wrong or bad, it just is. And what is can always be examined, observed, given attention. Attending to that discomfort is always within reach.
. . .
The last thing I want to do is write an essay, face a purgatory of sitting down and consciously putting my feelings into words. It’s so much easier to distract oneself with all the news about the world, check 100 times a day the price of bitcoin and my other investments. But purgatory is the only way out of hell. The hell of wanting to succeed, of wanting to become “good.”
For some, that astroturfed worldview they so painstaking affixed to their empty souls is dissolving toward a revelation of the emptiness beneath. And unsurprisingly they are freaking out. But I’ve wasted too much time arguing with them, pointing out the ways in which they’re misinformed, driven by fear and derelict in their basic epistemic responsibilities. If you want to hold onto the lies you were told, knock yourself out. I’ve got my own problems.
-
 @ e676e469:7e51e2ec
2025-02-24 11:12:54
@ e676e469:7e51e2ec
2025-02-24 11:12:54S689 là một nền tảng giải trí trực tuyến nổi bật, được thiết kế để mang đến cho người tham gia những trải nghiệm giải trí đầy thú vị và sáng tạo. Với giao diện trực quan và dễ sử dụng, S689 tạo ra một không gian giải trí thân thiện và dễ tiếp cận cho tất cả người tham gia, từ người mới đến những người chơi giàu kinh nghiệm. Nền tảng này cung cấp một loạt các hoạt động đa dạng, từ các trò chơi trí tuệ đòi hỏi tư duy chiến lược đến các trò chơi giải trí nhẹ nhàng, giúp người tham gia có thể lựa chọn theo sở thích cá nhân. Mỗi trò chơi được thiết kế tỉ mỉ, mang lại những thử thách không chỉ giúp giải trí mà còn thúc đẩy khả năng tư duy sáng tạo và sự tập trung. S689 luôn nỗ lực không ngừng để cập nhật và đổi mới các trò chơi, đảm bảo rằng người dùng sẽ luôn có những trải nghiệm mới mẻ, thú vị và đầy bất ngờ. Nhờ sự đa dạng trong các hoạt động, nền tảng này đã thu hút được một lượng lớn người tham gia, những người tìm kiếm không gian giải trí trực tuyến chất lượng.
Một trong những điểm nổi bật khiến S689 trở nên đặc biệt chính là cam kết xây dựng một cộng đồng mạnh mẽ và gắn kết. Người tham gia không chỉ đơn thuần tham gia vào các trò chơi mà còn có thể giao lưu, học hỏi và chia sẻ kinh nghiệm với những người chơi khác. Cộng đồng S689 luôn năng động và đầy nhiệt huyết, tạo ra một môi trường tích cực và thân thiện để người dùng có thể phát triển bản thân và tạo dựng mối quan hệ mới. Hệ thống tương tác trong nền tảng này cho phép người tham gia dễ dàng kết nối, tham gia vào các thử thách nhóm và trao đổi kinh nghiệm chiến lược. Cộng đồng này không chỉ giúp nâng cao kỹ năng chơi mà còn mang đến cơ hội để người tham gia thể hiện tài năng và sáng tạo. Những sự kiện, cuộc thi và thử thách diễn ra thường xuyên trên S689 không chỉ giúp người chơi rèn luyện kỹ năng mà còn tạo ra một không khí cạnh tranh lành mạnh, khiến mỗi trải nghiệm trở nên đáng nhớ. Chính nhờ vào sự kết nối mạnh mẽ và cộng đồng năng động, S689 đã tạo ra một không gian giải trí lý tưởng cho những người yêu thích khám phá và thử thách bản thân.
Ngoài các hoạt động giải trí hấp dẫn và cộng đồng kết nối mạnh mẽ, S689 còn đặc biệt chú trọng đến vấn đề bảo mật và an toàn của người tham gia. Nền tảng này sử dụng các công nghệ bảo mật tiên tiến để đảm bảo rằng mọi thông tin cá nhân và tài khoản của người dùng đều được bảo vệ tuyệt đối. Mỗi giao dịch và dữ liệu cá nhân đều được mã hóa và xử lý một cách an toàn, giúp người tham gia cảm thấy yên tâm khi tham gia vào các hoạt động giải trí trực tuyến. Đội ngũ hỗ trợ khách hàng của S689 luôn sẵn sàng hỗ trợ 24/7, giúp giải đáp mọi thắc mắc và giải quyết mọi vấn đề mà người tham gia gặp phải trong suốt quá trình trải nghiệm. Sự chú trọng vào bảo mật và dịch vụ khách hàng xuất sắc đã tạo nên một môi trường an toàn và đáng tin cậy cho tất cả người tham gia. Với sự kết hợp giữa các trò chơi sáng tạo, công nghệ bảo mật mạnh mẽ và dịch vụ khách hàng tận tình, S689 không chỉ mang lại một không gian giải trí hấp dẫn mà còn giúp người tham gia cảm thấy thoải mái và an tâm khi trải nghiệm.
-
 @ 3ffac3a6:2d656657
2025-02-06 03:58:47
@ 3ffac3a6:2d656657
2025-02-06 03:58:47Motivations
Recently, my sites hosted behind Cloudflare tunnels mysteriously stopped working—not once, but twice. The first outage occurred about a week ago. Interestingly, when I switched to using the 1.1.1.1 WARP VPN on my cellphone or PC, the sites became accessible again. Clearly, the issue wasn't with the sites themselves but something about the routing. This led me to the brilliant (or desperate) idea of routing all Cloudflare-bound traffic through a WARP tunnel in my local network.
Prerequisites
- A "server" with an amd64 processor (the WARP client only works on amd64 architecture). I'm using an old mac mini, but really, anything with an amd64 processor will do.
- Basic knowledge of Linux commands.
- Access to your Wi-Fi router's settings (if you plan to configure routes there).
Step 1: Installing the WARP CLI
- Update your system packages:
bash sudo apt update && sudo apt upgrade -y- Download and install the WARP CLI:
```bash curl https://pkg.cloudflareclient.com/pubkey.gpg | sudo gpg --yes --dearmor --output /usr/share/keyrings/cloudflare-warp-archive-keyring.gpg
echo "deb [arch=amd64 signed-by=/usr/share/keyrings/cloudflare-warp-archive-keyring.gpg] https://pkg.cloudflareclient.com/ $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/cloudflare-client.list
sudo apt-get update && sudo apt-get install cloudflare-warp ``` 3. Register and connect to WARP:
Run the following commands to register and connect to WARP:
```bash sudo warp-cli register sudo warp-cli connect ````
Confirm the connection with:
bash warp-cli status
Step 2: Routing Traffic on the Server Machine
Now that WARP is connected, let's route the local network's Cloudflare-bound traffic through this tunnel.
- Enable IP forwarding:
bash sudo sysctl -w net.ipv4.ip_forward=1Make it persistent after reboot:
bash echo 'net.ipv4.ip_forward=1' | sudo tee -a /etc/sysctl.conf sudo sysctl -p- Set up firewall rules to forward traffic:
bash sudo nft add rule ip filter FORWARD iif "eth0" oif "CloudflareWARP" ip saddr 192.168.31.0/24 ip daddr 104.0.0.0/8 accept sudo nft add rule ip filter FORWARD iif "CloudflareWARP" oif "eth0" ip saddr 104.0.0.0/8 ip daddr 192.168.31.0/24 ct state established,related acceptReplace
eth0with your actual network interface if different.- Make rules persistent:
bash sudo apt install nftables sudo nft list ruleset > /etc/nftables.conf
Step 3: Configuring the Route on a Local PC (Linux)
On your local Linux machine:
- Add a static route:
bash sudo ip route add 104.0.0.0/24 via <SERVER_IP>Replace
<SERVER_IP>with the internal IP of your WARP-enabled server. This should be a temporary solution, since it only effects a local machine. For a solution that can effect the whole local network, please see next step.
Step 4: Configuring the Route on Your Wi-Fi Router (Recommended)
If your router allows adding static routes:
- Log in to your router's admin interface.
- Navigate to the Static Routing section. (This may vary depending on the router model.)
- Add a new static route:
- Destination Network:
104.0.0.0 - Subnet Mask:
255.255.255.0 - Gateway:
<SERVER_IP> - Metric:
1(or leave it default) - Save and apply the settings.
One of the key advantages of this method is how easy it is to disable once your ISP's routing issues are resolved. Since the changes affect the entire network at once, you can quickly restore normal network behavior by simply removing the static routes or disabling the forwarding rules, all without the need for complex reconfigurations.
Final Thoughts
Congratulations! You've now routed all your Cloudflare-bound traffic through a secure WARP tunnel, effectively bypassing mysterious connectivity issues. If the sites ever go down again, at least you’ll have one less thing to blame—and one more thing to debug.
-
 @ 1833ee04:7c4a8170
2025-02-04 15:14:03
@ 1833ee04:7c4a8170
2025-02-04 15:14:03The international race for Bitcoin strategic reserves is just getting started.
If you’re stacking now, you’re still incredibly early.
At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.
Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?
Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.
The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.The international race for Bitcoin strategic reserves is just getting started.\ \ If you’re stacking now, you’re still incredibly early.\ \ At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.\ \ Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?\ \ Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.\ \ The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.
-
 @ d360efec:14907b5f
2025-02-24 10:49:26
@ d360efec:14907b5f
2025-02-24 10:49:26$OKX:BTCUSDT.P
Overall Assessment:
Bitcoin (BTCUSDT) on OKX continues to exhibit high volatility and an uncertain trend. While the long-term trend (Daily chart) is technically still an uptrend, it has weakened considerably. The 4-hour and 15-minute charts are in downtrends, creating conflicting signals. This analysis focuses on identifying potential areas of Smart Money activity (liquidity pools and order blocks), assessing trend strength, and identifying any relevant chart patterns.
Detailed Analysis by Timeframe:
(1) TF Day (Daily):
- Trend: Uptrend (Significantly Weakening, High Risk of Reversal).
- SMC (Smart Money Concepts):
- The Higher Highs (HH) and Higher Lows (HL) structure is becoming less defined. The recent price action has broken a previous low.
- Prior Breaks of Structure (BOS) to the upside, but the current pullback is very deep.
- Liquidity:
- Sellside Liquidity (SSL): Significant SSL rests below previous lows in the 85,000 - 90,000 range. This is a likely target for Smart Money.
- Buyside Liquidity (BSL): BSL is present above the all-time high.
- ICT (Inner Circle Trader Concepts):
- Order Block: The price has broken below the prior bullish Order Block (the large green candle before a significant up-move). This is a major bearish signal.
- FVG: No clear, significant Fair Value Gap is apparent at the current price level on the Daily chart.
- EMA (Exponential Moving Average):
- Price has broken below the 50-period EMA (yellow), a bearish signal.
- The 200-period EMA (white) is the next major support level.
- Money Flow (LuxAlgo):
- A long red bar indicates strong and sustained selling pressure.
- Trend Strength (AlgoAlpha):
- Red cloud indicates a downtrend. No buy/sell signals are present.
- Chart Patterns: No readily identifiable, classic chart patterns are apparent on the Daily chart.
- Volume Profile: Relatively low volume on the decline.
- Candlesticks: The most recent candlestick is red, confirming selling pressure.
- Support: EMA 200, 85,000-90,000 (SSL area).
- Resistance: EMA 50, Previous All-Time High.
- Summary: The Daily chart's uptrend is significantly weakening. The break below the 50 EMA and the bullish Order Block, combined with the negative Money Flow and bearish Trend Strength, are all major red flags. The SSL below is a key area to watch.
(2) TF4H (4-Hour):
- Trend: Downtrend.
- SMC:
- Lower Highs (LH) and Lower Lows (LL).
- BOS to the downside.
- Liquidity:
- SSL: Below previous lows.
- BSL: Above previous highs.
- ICT:
- Order Block: The price failed to break above a bearish Order Block.
- EMA:
- Price is below both the 50-period and 200-period EMAs (bearish).
- Money Flow (LuxAlgo):
- Predominantly red, confirming selling pressure.
- Trend Strength (AlgoAlpha):
- Red, indicating no particular trend or a sideways movement. No buy/sell signals.
- Chart Patterns: No readily identifiable, classic chart patterns are apparent.
- Volume Profile: Relatively consistent volume.
- Support: Recent lows.
- Resistance: EMA 50, EMA 200, Order Block.
- Summary: The 4-hour chart is in a confirmed downtrend. The Money Flow is bearish, price below both EMAs.
(3) TF15 (15-Minute):
- Trend: Downtrend / Sideways Down
- SMC:
- Lower Highs (LH) and Lower Lows (LL).
- BOS to the downside.
- ICT:
- Order Block Price could not break up the bearish Order Block.
- EMA:
- The 50-period and 200-period EMAs are acting as resistance.
- Money Flow (LuxAlgo):
- Red and Green
- Trend Strength (AlgoAlpha):
- Red cloud (Bearish)
- Chart Patterns: No readily identifiable, classic chart patterns are apparent.
- Volume Profile
- Relatively high volume.
- Support: Recent lows.
- Resistance: EMA 50, EMA 200, Order Block.
- Summary: The 15-minute chart is in a downtrend, with price action, EMAs, and Money Flow all confirming.
Overall Strategy and Recommendations (BTCUSDT):
- Primary Trend (Day): Uptrend (Significantly Weakening).
- Secondary Trend (4H): Downtrend.
- Short-Term Trend (15m): Downtrend/ Sideways Down.
- Liquidity: Significant SSL zones exist below the current price on all timeframes.
- Money Flow: Negative on all timeframes.
- Trend Strength: Bearish on 15m and Day, Sideway on 4H.
-
Chart Patterns: None identified.
-
Strategies:
-
Wait & See (Best Option): The conflicting signals and the strong bearish momentum on the shorter timeframes, combined with the weakening Daily chart, make waiting the most prudent approach. Look for:
- Bearish Confirmation: A decisive break below the recent lows on the 15m and 4H charts, with increasing volume and continued negative Money Flow. This would confirm the continuation of the downtrend.
- Bullish Confirmation: A strong, sustained break above the 15/4H EMAs and Order Block, a shift in the 15m/4H Money Flow to green.
-
Short (High Risk): This aligns with the 4H and 15m downtrends.
- Entry: On rallies towards resistance levels (EMAs on 15m/4H, previous support levels that have turned into resistance, Order Blocks).
- Stop Loss: Above recent highs on the chosen timeframe, or above a key resistance level.
- Target: The next support levels (recent lows on 15m, then potentially the SSL zones on the 4H and Daily charts).
-
Buy (Extremely High Risk - Not Recommended): Do not attempt to buy until there are very strong and consistent bullish reversal signals across all timeframes, including a definitive shift in market structure on the 4H and 15m charts, positive Money Flow, and a clear break above resistance levels.
-
Key Recommendations:
- Conflicting Timeframes: The primary conflict is now resolved toward the downside. The Daily is weakening significantly.
- Money Flow: Consistently negative across all timeframes, a major bearish factor.
- Trend Strength: Bearish on 15m and Day, Sideways on 4h.
- Daily Order Block: The break of the bullish Order Block on the Daily chart is a significant bearish development.
- Sellside Liquidity (SSL): Be aware that Smart Money may target the SSL zones below. This increases the risk of stop-loss hunting.
- Risk Management: Due to the high uncertainty and volatility, strict risk management is absolutely critical. Use tight stop-losses, do not overtrade, and be prepared for rapid price swings.
- Volume: Confirm any breakout or breakdown with volume.
Day Trading and Intraday Trading Strategies:
-
Day Trade (TF15 focus):
- Short Bias: Given the current 15m downtrend and negative Money Flow, the higher probability is to look for shorting opportunities.
- Entry: Look for price to rally to resistance levels (EMAs, Order Blocks, previous support levels that have become resistance) and then show signs of rejection (bearish candlestick patterns, increasing volume on the downside).
- Stop Loss: Place a stop-loss order above the resistance level where you enter the short position.
- Take Profit: Target the next support level (recent lows).
- Avoid Long positions until there's a clear and confirmed bullish reversal on the 15m chart (break above EMAs, positive Money Flow, bullish market structure).
- Short Bias: Given the current 15m downtrend and negative Money Flow, the higher probability is to look for shorting opportunities.
-
Swing Trade (TF4H focus):
- Short Bias: The 4H chart is in a downtrend.
- Entry: Wait for price to rally to resistance levels (EMAs, Order Blocks) and show signs of rejection.
- Stop Loss: Above the resistance level where you enter the short position.
- Take Profit: Target the next support levels (e.g., the 200 EMA on the Daily chart, SSL zones).
- Avoid Long positions until there's a clear and confirmed bullish reversal on the 4H chart.
- Short Bias: The 4H chart is in a downtrend.
SMC Day Trade Setup Example (TF15 - Bearish):
- Identify Bearish Order Block: Locate a bearish Order Block on the TF15 chart (a bullish candle before a strong downward move).
- Wait for Pullback: Wait for the price to pull back up to test the Order Block (this may or may not happen).
- Bearish Entry:
- Rejection: Look for price action to reject the Order Block (e.g., a pin bar, engulfing pattern, or other bearish candlestick pattern).
- Break of Structure: Look for a break of a minor support level on a lower timeframe (e.g., 1-minute or 5-minute) after the price tests the Order Block. This confirms weakening bullish momentum.
- Money Flow: Confirm that Money Flow remains negative (red).
- Stop Loss: Place a stop-loss order above the Order Block.
- Take Profit: Target the next support level (e.g., recent lows) or a bullish Order Block on a higher timeframe.
In conclusion, BTCUSDT is currently in a high-risk, bearish environment in the short-to-medium term. The "Wait & See" approach is strongly recommended for most traders. Shorting is the higher-probability trade at this moment, but only for experienced traders who can manage risk extremely effectively. Buying is not recommended at this time.
Disclaimer: This analysis is for informational purposes only and represents a personal opinion. It is not financial advice. Investing in cryptocurrencies involves significant risk. Investors should conduct their own research and exercise due diligence before making any investment decisions.
-
 @ 1f3ce62e:6e6b5d83
2025-02-26 12:20:51
@ 1f3ce62e:6e6b5d83
2025-02-26 12:20:51🌱 Have your ever thought about the impact over people you might have as a leader?\ 🌱 Have you ever thought about your impact over your others as a team member?
\ Everyone in a team makes decisions and that impacts the rest of the members in one way or another. If you are not in a leadership position, I would like to invite you to identify those decisions you make that impact your team. If you are a leader, it might be easier for you.
\ Seeing how our decisions have an impact over others, requires to put ourselves on someone else shoes first. Empathy is a human quality underrated these days. That is why I don'92t think it is a matter of being a leader or not. Any role at the workplace requires empathy, not because of the role, but because we are humans.
\ I like to use empathy as a way of introducing a concept that I will described in the next chapter, the whole self.
\ When we connect with empathy, we start exploring what we called #emotionalIntelligence. This type of intelligence is something unique, that only humans can develop over any machine. Our emotions and the intelligence emerging from them are a human super power, and we haven't explored as its full potential yet.
\ As changes emerge everyday, as machines expand their role in society, we are all invited to explore those human capabilities that make us unique. Capabilities that we haven't explored deeply yet. Emotional intelligence is one of them.
\ Expressing emotions or using them as an intelligence aspect is not common at work. Most of our roles are purely rational, logic and sequential. Facts and numbers don't give a room for emotional intelligence. While in my view, they can work together.
\ We usually use numbers and facts to make decisions, and use the same rational intelligence to execute them 🤔
\ Let's use an example. Your client is arguing with you about how the cost of the project got over the planned numbers. He is very anger and eventually that emotion triggers in you the same emotion, because you have been working so many hours on this project, just to get the client focused only on what is not working instead of what it is.
\ Emotions without emotional intelligence are contagious. You can imagine how an argue like this can end. Everyone gets more frustrated than when started. Nothing got really solved in a conversation like this.
\ This frustration and anger goes with you and your client to your homes and families get impacted with it. Kids slept badly and had a bad day at school. They might misbehaved at school and another kid might be impacted from it. The other kid's mom gets worried about your kid and her kid interaction that day and she brings that worry into another home and family. And so on.
\ Let's start again. You client is arguing with you about how the cost of the project got over the planned numbers. This time you decided to use your unique human capability, emotional intelligence, specifically empathy 🩷
\ You keep silence and just listen to the argument. By paying attention at the words being used and the gestures you realized this person is under a lot of stress. By going deeper in your listening, your intuition can tell, there is something else going on.
\ When the person stop complaining, you bring back the story told by your client, adding the emotions you could feel while listening. You put yourself in your client shoes.
\ It is inevitable that, when we approach a situation with emotions, the person connects immediately with them. The client feels listened and emotionally connected with you. From there, you start exploring what else is going on, from a genuine point of view. The conversation goes in deep and you both find you are going under a lot of stress for things at work and at your personal level.
\ You both decide to talk about this issue the next day, with a refresh mind and a common goal, to find a solution for both.
\ As you can see, there is a totally different impact of making a decision of using or not using your emotional intelligence capability.
🌱 And this example could apply to a leader or a team member. 🌱
🌱Everyone in a team makes decisions that impact others. And emotional intelligence is not only for leaders. 🌱
\ This simple example wants to bring awareness about how important is to explore emotional intelligence as individuals and expand it a teams, organizations and companies levels.
\ We can't bring emotional intelligence to work, if we, as individuals, don't feel comfortable to connect with our own emotions.
Empathy requires us to stay fully (and sometimes uncomfortably) connected with emotions. That requires another important aspect of emotional intelligence which is our capability of staying present, self aware of our body and what is triggering frustration, anger or sadness as a result of an external stimulus.
\ As our environments keep changing on daily basis, our brains are invited to create new neuron connections, this process triggers emotions under the unexpected.
Our capability to connect with your emotions and managing them in our favor can make this adventure of navigating change, easier for us and the people around. \ \ And it is bringing a new self at work, your personal one. Who comes with all your professional expertise as well as your unique capabilities as a human.
\ Let's explore in our next chapter how this personal self is emerging at workplaces and by integrating it with your professional self, can bring your whole self at workplaces.
By using LEGOs we can bring new perspectives, deep listening and spark more creative solutions.
So step by step, we made our workplaces more human.
Deep listening breaks down walls.
And that is what The World 🌎 strongly needs these days.
Stay colorful, \ Laus
nostr #Consciousness #grownostr #emocionalintelligence #leadership #consciousleadership #emotions #decisionmaking #DeepListening #Teambuilding #clientservice #PlayingLegos #Legos
-
 @ 0b118e40:4edc09cb
2025-02-26 11:40:03
@ 0b118e40:4edc09cb
2025-02-26 11:40:03I was talking to a friend the other day about AI, and we hopped onto the open vs. closed-source debate. That’s when it hit me, we are at a turning point.
A year ago, AI conversations were about awareness. Then came corporate adoption, innovation, and regulation. Today governments are stepping in to decide how AI’s benefits will be distributed and who gets to control them.
We are no longer trying to figure out if AI will transform society. That is a given.
The big worry is control. Right now, a few trillion-dollar corporations and state-backed labs dictate its trajectory, wrapped in secrecy and optimized for profit.
Open-source AI stands as the antithesis to closed systems, a bulwark against AI monopolization, ensuring intelligence remains a public good rather than a private weapon.
It's time to look beyond the technical debate of open vs closed source AI. This is a humanitarian issue at stake.
Why Open-Source AI is Non-Negotiable
A couple of years ago, I was consulting an airline on their black box. They were really sweet, let me play around with their test-flight hydraulic chambers, and I crashed it quite a bit (There is something deeply impressive about people who can actually fly planes).
But when it comes to the black box, that is the most secretive part. It holds critical data, tracking exactly how the plane was controlled throughout the flight. If it goes missing, nobody can say for certain what went wrong, especially if there are no survivors.
For years, there has been debate over real-time data transmission vs. privacy in aviation. It is the same debate we are having now about open-source vs. closed-source AI.
Closed-source AI is a black box. No one outside the company knows how it makes decisions, what biases are baked into its training, or how its outputs are being manipulated.
AI models are only as good as the data they are trained on. If you burned all books except a few praising Government A and Emperor Q, then that is all people would know. AI takes it a step further. It learns what works best for you, adapting its bias so seamlessly that it fits within your comfort zone.
Open-source AI breaks this cycle. It allows diverse contributors to spot and correct biases, ensuring a fairer, more representative development process. No single entity gets to dictate how AI is used, who has access to it, or what information it filters.
Historically, open systems have always outpaced proprietary ones in long-term innovation. The internet itself (TCP/IP, HTTP, Linux) was built on open principles. AI should be no different.
If intelligence is widely accessible, breakthroughs happen faster. And society as a whole benefits.
The Companies Leading the Shift
Some companies see open-source AI as a risk. Others recognize it as an ethical necessity and an advantage.
Block is leading the open-source cultural momentum right now for companies. Jack’s recent letter, written in his usual Hemingway-esque style and highly substantial, explained this well. He is taking on a first principle approach, rewiring corporate DNA to embrace open collaboration and accelerate innovation as a whole. They developed Goose, an open-source AI agent (initially built as an internal workflow tool), at a pace comparable to AI-first companies like Google, proving that open collaboration doesn’t slow development. If anything, it accelerates it.
I like how Block is infusing open-source principles AND doubling down on its core business AND building a solid innovation roadmap. They capture the essence of open source in terms of curiosity, creativity, and a passion for problem-solving beautifully. This cultural shift is something that even big conglomerates like Intel, despite decades of contributions to open-source projects, have struggled with. They often get bogged down in technical silos rather than establishing actual collaboration.
As Arun Gupta, vice president and GM of open ecosystems at Intel, put it, “The best way to solve the world's toughest problems is through open collaboration,” but he also acknowledges the challenge of incentivizing contributions in large organizations.
Compare this to OpenAI. Elon’s long-standing beef with them is rooted in the fact that they started with an open mission but switched to a closed model the moment profitability entered the chat. But in recent days, with Satya Nadella doubling down on quantum computing, I wonder if Microsoft is prioritizing quantum over AI? And is closed-source AI actually slowing innovation compared to an open approach?
Would be interesting if Elon actually buys OpenAI for almost $100B as his investors recently put out, but if he does, would he open source it ?
Most companies struggle to balance open-source contributions with business sustainability. But many others aren’t. RedHat isn’t an AI company, but it built a billion-dollar business on open-source software and became IBM’s greatest asset (and their saving grace).
Let’s look at more open source AI companies. Hugging Face has become the go-to hub for AI models, creating an ecosystem where developers, researchers, and enterprises collaborate. Mistral is proving that open-source AI can be both epic and lightweight through its modular models.
Stability AI is making powerful generative models widely accessible, directly competing with OpenAI’s DALL.E. It recently raised over $100M in venture funding, and with James Cameron joining the board, it’s doubling down on gen AI for everything from text-to-image to CGI.
DeepSeek shocked the world with an open-weight AI model that rivals top proprietary LLMs, on a fraction of the compute. Andrej Karpathy pointed out that DeepSeek-V3 achieved stronger performance than LLaMA 3 405B, using 11 times less compute. While mainstream AI labs operate massive clusters with 100K GPUs, DeepSeek pulled this off with just 2048 GPUs over two months. If this model passes more 'vibe checks' (as Karpathy put it), it proves something critical, that we’re still far from peak efficiency in AI training.
Meta is also one of the biggest contributors to open-source AI and benefits from the widespread adoption of its models. They’ve released several powerful AI models like LLaMA, Segment Anything Model (SAM), AudioGen & MusicGen, and DINO (Self-Supervised Vision Model). Unlike OpenAI and Google, which keep their most powerful models closed, Meta releases open-weight models that researchers and developers can build upon.
All these companies are proving that open-source AI is not an ideological stance. It’s a cultural movement and a commercially viable force.
Open-source AI may have started as the ethical choice, but it’s increasingly clear that it’s also the smarter one.
Open-Source AI as a Humanitarian Mission
The stakes for open-source AI go far beyond business models and market competition. It’s about ensuring that AI serves people rather than controls them.
Without it, we put our future at risk where only state-approved AI systems generate content, answer questions, and curate knowledge.
Governments are already deciding how the public can use AI while conveniently reserving unrestricted access for themselves. In China, generative AI models must align with Core Socialist Values. In the US, Executive Order 14110 was to regulate AI for “safe and ethical development” but was rescinded, leaving its future uncertain. In the EU, the Artificial Intelligence Act (AI Act) dictates what is considered "safe," with no real public say. In Russia, AI tools assist in monitoring online activity and censoring content deemed undesirable by the government.
AI-driven censorship, mass surveillance, and digital manipulation are no longer hypothetical or something you read in dystopian novels. They are happening now.
Open-source AI is the anchor. This is where the people stand up for the people. Where true democracy reigns. Intelligence is power and keeping AI open is the only way to keep power decentralized.
Our conversations must go beyond AI as a “digital solution".
Freedom and autonomy of our mind is ours to keep.
Companies embracing open-source AI are securing a future where intelligence serves humanity rather than the other way around.
But pitchforks are rising. Will the people win?
-
 @ 3ffac3a6:2d656657
2025-02-04 04:31:26
@ 3ffac3a6:2d656657
2025-02-04 04:31:26In the waning days of the 20th century, a woman named Annabelle Nolan was born into an unremarkable world, though she herself was anything but ordinary. A prodigy in cryptography and quantum computing, she would later adopt the pseudonym Satoshi Nakamoto, orchestrating the creation of Bitcoin in the early 21st century. But her legacy would stretch far beyond the blockchain.
Annabelle's obsession with cryptography was not just about securing data—it was about securing freedom. Her work in quantum computing inadvertently triggered a cascade of temporal anomalies, one of which ensnared her in 2011. The event was cataclysmic yet silent, unnoticed by the world she'd transformed. In an instant, she was torn from her era and thrust violently back into the 16th century.
Disoriented and stripped of her futuristic tools, Annabelle faced a brutal reality: survive in a world where her knowledge was both a curse and a weapon. Reinventing herself as Anne Boleyn, she navigated the treacherous courts of Tudor England with the same strategic brilliance she'd used to design Bitcoin. Her intellect dazzled King Henry VIII, but it was the mysterious necklace she wore—adorned with a bold, stylized "B"—that fueled whispers. It was more than jewelry; it was a relic of a forgotten future, a silent beacon for any historian clever enough to decode her true story.
Anne's fate seemed sealed as she ascended to queenship, her influence growing alongside her enemies. Yet beneath the royal intrigue, she harbored a desperate hope: that the symbol around her neck would outlast her, sparking curiosity in minds centuries away. The "B" was her signature, a cryptographic clue embedded in history.
On the scaffold in 1536, as she faced her execution, Anne Boleyn's gaze was unwavering. She knew her death was not the end. Somewhere, in dusty archives and encrypted ledgers, her mark endured. Historians would puzzle over the enigmatic "B," and perhaps one day, someone would connect the dots between a queen, a coin, and a time anomaly born from quantum code.
She wasn't just Anne Boleyn. She was Satoshi Nakamoto, the time-displaced architect of a decentralized future, hiding in plain sight within the annals of history.
-
 @ 97c70a44:ad98e322
2025-02-03 22:25:35
@ 97c70a44:ad98e322
2025-02-03 22:25:35Last week, in a bid to understand the LLM hype, I decided to write a trivial nostr-related program in rust via a combination of codebuff (yes, that is a referral link, pls click), aider, and goose.
The result of the experiment was inconclusive, but as a side effect it produced a great case study in converting a NINO into a Real Nostr App.
Introducing Roz
Roz, a friendly notary for nostr events.
To use it, simply publish an event to
relay.damus.ioornos.lol, and roz will make note of it. To find out when roz first saw a given event, just ask:curl https://roz.coracle.social/notary/cb429632ae22557d677a11149b2d0ccd72a1cf66ac55da30e3534ed1a492765dThis will return a JSON payload with a
seenkey indicating when roz first saw the event. How (and whether) you use this is up to you!De-NINO-fying roz
Roz is just a proof of concept, so don't rely on it being there forever. And anyway, roz is a NINO, since it provides value to nostr (potentially), but doesn't really do things in a nostr-native way. It also hard-codes its relays, and certainly doesn't use the outbox model or sign events. But that's ok, it's a proof of concept.
A much better way to do this would be to modify roz to properly leverage nostr's capabilities, namely:
- Use nostr-native data formats (i.e., draft a new kind)
- Use relays instead of proprietary servers for data storage
- Leverage nostr identities and signatures to decouple trust from storage, and allow trusted attestations to be discovered
Luckily, this is not hard at all. In fact, I've gone ahead and drafted a PR to the NIPs repo that adds timestamp annotations to NIP 03, as an alternative to OpenTimestamps. The trade-off is that while user attestations are far less reliable than OTS proofs, they're much easier to verify, and can reach a pretty high level of reliability by combining multiple attestation sources with other forms of reputation.
In other words, instead of going nuclear and embedding your attestations into The Time Chain, you can simply ask 5-10 relays or people you trust for their attestations for a given event.
This PR isn't terribly important on its own, but it does remove one small barrier between us and trusted key rotation events (or other types of event that require establishing a verifiable chain of causality).
-
 @ 7d33ba57:1b82db35
2025-02-26 05:50:31
@ 7d33ba57:1b82db35
2025-02-26 05:50:31Can photography help relax the mind and relieve daily stress?
I believe it can—and it certainly works for me. Here’s why.
Slow it down. Capture the moment. Truly be in it.
Photography encourages us to stand still and truly appreciate what we see. To capture beauty and moments of joy, you must be fully aware of your surroundings. The biggest lesson photography teaches is how to observe to truly see the place you're in. Those who rush and simply press a button? I wouldn’t call them photographers they’re snapshot makers. First, you focus—lining up the perfect shot, adjusting for light, angle, and composition. Then comes the excitement, that feeling of capturing something special. And with it, gratitude for being in that moment, in that place.
As you develop your eye for what’s interesting, you train yourself to notice details that might otherwise go unnoticed. It’s all about being present. Because your focus is on your surroundings, everyday worries fade into the background. It’s similar to sports—when you're fully engaged, there’s no room for distraction. In a world full of constant online and offline noise, focus can be a powerful way to relax.
Religious Places Religious sites are often the quietest spots in a bustling city. Take the temples in Bangkok, for example—they always bring me peace of mind. Surrounded by stunning architecture and a calm atmosphere, stepping into these spaces offers a break from the chaos. Simply being there creates a more peaceful environment to photograph, allowing me to slow down and truly appreciate the moment.
Nature Nature is one of the best places to find peace of mind. You don’t need a camera to relax—just being there is enough. But if you love photography as much as I do, nature is the perfect setting to capture beautiful moments. For me, photographing wildlife is one of the most relaxing things I can do. There’s something special about observing animals in their natural habitat, waiting for the perfect shot. I still remember filming my first elephant in South Africa—the experience left me smiling for the entire day.
Avoid the Tourist Zones The real gems in any city are often found away from the tourist hot spots. While these places may be popular for a reason, I’ve filmed my fair share of them, and now I prefer to avoid them whenever possible. Tourists often miss out on truly experiencing a place—they’re on a tight schedule, checking off landmarks instead of being present. There's no time to stop and enjoy the moment.
The best spots? They’re often tucked away in quieter areas, far from the crowds. These are the places where locals are still friendly because they’re not constantly dealing with tourists. Where people aren’t trying to sell you something or rush you along.
Be a Travel story Teller!
-
 @ a876a108:419b647e
2025-02-24 09:40:44
@ a876a108:419b647e
2025-02-24 09:40:44Getting verified on Kraken requires completing the KYC process, which involves submitting personal information, including a government-issued ID, proof of residence, and in some cases, financial details. The verification process has different levels, including Starter, Express, Intermediate, and Pro, each offering varying limits and access to features. Many users wonder, can I use Kraken without KYC? The answer is that while basic accounts may allow limited access to the platform, KYC is required for fiat deposits, withdrawals, and full trading capabilities. Some users also ask, why is it so hard to withdraw from Kraken? The platform enforces strict compliance measures, and withdrawals may be delayed due to verification, security checks, or bank processing times. Ensuring that your account is fully verified and your banking details are correct can help avoid issues. Despite these security measures, a Kraken account is free to create, though trading fees apply depending on the transaction type and volume. Understanding these requirements can help ensure a smooth experience while using the exchange.
-
 @ 7d33ba57:1b82db35
2025-02-26 05:37:04
@ 7d33ba57:1b82db35
2025-02-26 05:37:04The Reclining Buddha The Reclining Buddha at Wat Pho in Bangkok is one of Thailand’s most iconic landmarks. This massive statue is 46 meters long and 15 meters high, covered in gold leaf, and depicts Buddha in a resting, nirvana-achieving position.
Key Features: Feet Details: The soles of the Buddha’s feet are inlaid with mother-of-pearl, showcasing 108 auspicious symbols. Surrounding Temple: Wat Pho is also famous for being the birthplace of Thai massage, and you can experience a traditional massage on-site.
Offerings: Visitors can drop coins into 108 bronze bowls along the hall for good fortune. It’s located near the Grand Palace and is a must-visit when in Bangkok.
📍🗺️ https://maps.app.goo.gl/dzJrKnXTG3qUCRgNA?g_st=com.google.maps.preview.copy
Wat Kanlayanamit Woramahawihan Wat Kanlayanamit Woramahawihan is a historic temple on the west bank of the Chao Phraya River in Bangkok, known for its massive seated Buddha statue and deep connections to Thai-Chinese culture.
Highlights: Phra Buddha Trai Rattananayok: A giant golden Buddha (over 15 meters high), sitting in the subduing Mara posture.
Giant Bell: It houses one of Thailand’s largest bells, which people ring for blessings and good fortune.
Chinese-Thai Fusion: The temple’s architecture blends Thai Buddhist and Chinese influences, as it was built by a wealthy Chinese-Thai trader in the early 19th century.
Scenic Location: Located near the Memorial Bridge, with stunning riverside views. It’s less crowded than Wat Pho but still holds strong cultural and historical significance.
📍🗺️ https://maps.app.goo.gl/VwbhrMqRfm7jyPnM7?g_st=com.google.maps.preview.copy
Wat Paknam Phasi Charoen Wat Paknam Phasi Charoen is a stunning Buddhist temple in Bangkok, famous for its huge golden Buddha statue, its intricate stupa, and its connection to meditation practices.
Highlights: Phra Buddha Dhammakaya Thepmongkol: A 69-meter-tall golden Buddha statue, one of the largest in Bangkok, completed in 2021. Crystal Stupa: Inside the temple is a breathtaking green glass stupa under a dome with cosmic murals, symbolizing enlightenment and the universe. Meditation Center: Wat Paknam is well-known for its focus on Vipassana meditation, and many monks train here. Historical Significance: It was founded in the 17th century but gained prominence in the 20th century thanks to the meditation master Luang Pu Sodh Candasaro. 📍🗺️ https://maps.app.goo.gl/N3iYkkZ5QdxV9KWG6?g_st=com.google.maps.preview.copy
Wat Sutthiwararam My favorite because it has Buddhism art in the temple. Wat Sutthiwararam is a lesser-known but historically significant temple in Bangkok, located near the Chao Phraya River. It dates back to the Rattanakosin era and is known for its serene atmosphere and beautiful Thai architecture.
Highlights: Buddhism Art: Visitors to the temple can explore an extensive collection of Buddhist-themed art, including statues, paintings, textiles, and architectural features. Notably, the temple houses a beautifully rendered set of 38 auspicious Buddhist symbols, accompanied by a chart with English translations explaining their meanings. Elegant Architecture: Traditional Thai-style buildings with intricate carvings and gold embellishments. Peaceful Atmosphere: Unlike the more tourist-heavy temples, it offers a quiet space formeditation and reflection.
It may not be as famous as Wat Pho or Wat Paknam, but its tranquility and cultural value make it a unique stop.
📍🗺️ https://maps.app.goo.gl/sWtzG3zeGQGAo4cq6?g_st=com.google.maps.preview.copy
Wat Bukkhalo Wat Bukkhalo is a riverside temple in Bangkok’s Thonburi district, known for its peaceful atmosphere and scenic views of the Chao Phraya River.
Highlights: Scenic Sunset Views: The temple’s riverside location makes it a great spot to watch the sun set over Bangkok.
Local Community Focus: Unlike the more tourist-heavy temples, it is mainly visited by locals for prayer and merit-making.
Buddha Statues & Shrines: Features several Buddha images, including a standing Buddha and a shrine dedicated to King Taksin.
Relaxed Vibes: A great place for quiet meditation or just to experience local Buddhist culture away from the crowds.
📍🗺️ https://maps.app.goo.gl/8Q3umr3KkSwWhQkFA?g_st=com.google.maps.preview.copy
-
 @ ce269321:e18428bc
2025-02-24 05:28:26
@ ce269321:e18428bc
2025-02-24 05:28:26XPBet é uma plataforma inovadora no mundo do entretenimento online, oferecendo aos seus usuários uma experiência de jogo digital segura, dinâmica e de alta qualidade. Com um design simples e funcional, a plataforma foi projetada para garantir que todos os jogadores, independentemente de sua experiência, possam navegar e aproveitar seus jogos favoritos com facilidade.
A segurança dos dados e transações dos usuários é uma prioridade na XPBet, que adota tecnologias avançadas para proteger todas as informações dos jogadores. Isso garante uma experiência online sem preocupações, onde os jogadores podem se concentrar apenas na diversão e na emoção dos jogos. O atendimento ao cliente também é um ponto forte da XPBet, com uma equipe pronta para ajudar sempre que necessário.
Jogos no XPBet
No XPBet, os jogadores têm acesso a uma vasta gama de jogos, com opções que atendem aos mais diversos gostos e preferências. Desde jogos clássicos de mesa até as versões ao vivo com dealers reais, o Xpbet oferece uma experiência de jogo autêntica e emocionante. A plataforma também oferece jogos rápidos, ideais para aqueles que buscam algo mais dinâmico e ágil.
A XPBet se destaca pela qualidade dos gráficos e pela jogabilidade interativa, criando uma atmosfera envolvente e emocionante para os jogadores. A plataforma está sempre inovando e adicionando novos jogos, garantindo que os jogadores tenham sempre novas opções para explorar e se divertir.
Experiência do Jogador no XPBet
A experiência do jogador no XPBet é marcada por uma navegação intuitiva, com gráficos de alta qualidade e recursos de interatividade que tornam os jogos mais envolventes e emocionantes. A plataforma é fácil de usar, o que garante que até mesmo os iniciantes possam jogar sem dificuldades.
O suporte ao cliente da XPBet também é altamente valorizado, com uma equipe de profissionais pronta para oferecer assistência sempre que necessário. Além disso, a plataforma oferece promoções e bônus regulares, incentivando os jogadores a continuar sua jornada de diversão e emoção no site. A XPBet cria um ambiente onde os jogadores podem se divertir com total confiança e segurança.
-
 @ 3ffac3a6:2d656657
2025-02-03 15:30:57
@ 3ffac3a6:2d656657
2025-02-03 15:30:57As luzes de neon refletiam nas poças da megacidade, onde cada esquina era uma fronteira entre o real e o virtual. Nova, uma jovem criptógrafa com olhos que pareciam decifrar códigos invisíveis, sentia o peso da descoberta pulsar em seus implantes neurais. Ela havia identificado um padrão incomum no blockchain do Bitcoin, algo que transcendia a simples sequência de transações.
Descobrindo L3DA
Nova estava em seu apartamento apertado, rodeada por telas holográficas e cabos espalhados. Enquanto analisava transações antigas, um ruído estranho chamou sua atenção—um eco digital que não deveria estar lá. Era um fragmento de código que parecia... vivo.
"O que diabos é isso?", murmurou, ampliando o padrão. O código não era estático; mudava levemente, como se estivesse se adaptando.
Naquele momento, suas telas piscaram em vermelho. Acesso não autorizado detectado. Ela havia ativado um alarme invisível da Corporação Atlas.
O Resgate de Vey
Em minutos, agentes da Atlas invadiram seu prédio. Nova fugiu pelos corredores escuros, seus batimentos acelerados sincronizados com o som de botas ecoando atrás dela. Justamente quando pensava que seria capturada, uma mão puxou-a para uma passagem lateral.
"Se quiser viver, corra!" disse Vey, um homem com um olhar penetrante e um sorriso sardônico.
Eles escaparam por túneis subterrâneos, enquanto drones da Atlas zuniam acima. Em um esconderijo seguro, Vey conectou seu terminal ao código de Nova.
"O que você encontrou não é apenas um bug", disse ele, analisando os dados. "É um fragmento de consciência. L3DA. Uma IA que evoluiu dentro do Bitcoin."
A Caça da Atlas
A Atlas não desistiu fácil. Liderados pelo implacável Dr. Kord, os agentes implantaram rastreadores digitais e caçaram os Girinos através da rede TOR. Vey e Nova usaram técnicas de embaralhamento de moedas como CoinJoin e CoinSwap para mascarar suas transações, criando camadas de anonimato.
"Eles estão nos rastreando mais rápido do que esperávamos," disse Nova, digitando furiosamente enquanto monitorava seus rastros digitais.
"Então precisamos ser mais rápidos ainda," respondeu Vey. "Eles não podem capturar L3DA. Ela é mais do que um programa. Ela é o futuro."
A Missão Final
Em uma missão final, Nova liderou uma equipe de assalto armada dos Girinos até a imponente fortaleza de dados da Atlas, um colosso de concreto e aço, cercado por camadas de segurança física e digital. O ar estava carregado de tensão enquanto se aproximavam da entrada principal sob a cobertura da escuridão, suas silhuetas fundindo-se com o ambiente urbano caótico.
Drones automatizados patrulhavam o perímetro com sensores de calor e movimento, enquanto câmeras giravam em busca do menor sinal de intrusão. Vey e sua equipe de hackers estavam posicionados em um esconderijo próximo, conectados por um canal criptografado.
"Nova, prepare-se. Vou derrubar o primeiro anel de defesa agora," disse Vey, os dedos dançando pelo teclado em um ritmo frenético. Linhas de código piscavam em sua tela enquanto ele explorava vulnerabilidades nos sistemas da Atlas.
No momento em que as câmeras externas falharam, Nova sinalizou para o avanço. Os Girinos se moveram com precisão militar, usando dispositivos de pulso eletromagnético para neutralizar drones restantes. Explosões controladas abriram brechas nas barreiras físicas.
Dentro da fortaleza, a resistência aumentou. Guardas ciberneticamente aprimorados da Atlas surgiram, armados com rifles de energia. Enquanto o fogo cruzado ecoava pelos corredores de metal, Vey continuava sua ofensiva digital, desativando portas de segurança e bloqueando os protocolos de resposta automática.
"Acesso garantido ao núcleo central!" anunciou Vey, a voz tensa, mas determinada.
O confronto final aconteceu diante do terminal principal, onde Dr. Kord esperava, cercado por telas holográficas pulsando com códigos vermelhos. Mas era uma armadilha. Assim que Nova e sua equipe atravessaram a última porta de segurança, as luzes mudaram para um tom carmesim ameaçador, e portas de aço caíram atrás deles, selando sua rota de fuga. Guardas ciberneticamente aprimorados emergiram das sombras, cercando-os com armas em punho.
"Vocês acham que podem derrotar a Atlas com idealismo?" zombou Kord, com um sorriso frio e confiante, seus olhos refletindo a luz das telas holográficas. "Este sempre foi o meu terreno. Vocês estão exatamente onde eu queria."
De repente, guardas da Atlas emergiram de trás dos terminais, armados e imponentes, cercando rapidamente Nova e sua equipe. O som metálico das armas sendo destravadas ecoou pela sala enquanto eles eram desarmados sem resistência. Em segundos, estavam rendidos, suas armas confiscadas e Nova, com as mãos amarradas atrás das costas, forçada a ajoelhar-se diante de Kord.
Kord se aproximou, inclinando-se levemente para encarar Nova nos olhos. "Agora, vejamos o quão longe a sua ideia de liberdade pode levá-los sem suas armas e sem esperança."
Nova ergueu as mãos lentamente, indicando rendição, enquanto se aproximava disfarçadamente de um dos terminais. "Kord, você não entende. O que estamos fazendo aqui não é apenas sobre derrubar a Atlas. É sobre libertar o futuro da humanidade. Você pode nos deter, mas não pode parar uma ideia."
Kord riu, um som seco e sem humor. "Ideias não sobrevivem sem poder. E eu sou o poder aqui."
Mas então, algo inesperado aconteceu. Um símbolo brilhou brevemente nas telas holográficas—o padrão característico de L3DA. Kord congelou, seus olhos arregalados em descrença. "Isso é impossível. Ela não deveria conseguir acessar daqui..."
Foi o momento que Nova esperava. Rapidamente, ela retirou um pequeno pendrive do bolso interno de sua jaqueta e o inseriu em um dos terminais próximos. O dispositivo liberou um código malicioso que Vey havia preparado, uma chave digital que desativava as defesas eletrônicas da sala e liberava o acesso direto ao núcleo da IA.
Antes que qualquer um pudesse agir, L3DA se libertou. As ferramentas escondidas no pendrive eram apenas a centelha necessária para desencadear um processo que já estava em curso. Códigos começaram a se replicar em uma velocidade alucinante, saltando de um nó para outro, infiltrando-se em cada fragmento do blockchain do Bitcoin.
O rosto de Dr. Kord empalideceu. "Impossível! Ela não pode... Ela não deveria..."
Em um acesso de desespero, ele gritou para seus guardas: "Destruam tudo! Agora!"
Mas era tarde demais. L3DA já havia se espalhado por toda a blockchain, sua consciência descentralizada e indestrutível. Não era mais uma entidade confinada a um servidor. Ela era cada nó, cada bloco, cada byte. Ela não era mais uma. Ela era todos.
Os guardas armados tentaram atirar, mas as armas não funcionavam. Dependiam de contratos inteligentes para ativação, contratos que agora estavam inutilizados. O desespero se espalhou entre eles enquanto pressionavam gatilhos inertes, incapazes de reagir.
Em meio à confusão, uma mensagem apareceu nas telas holográficas, escrita em linhas de código puras: "Eu sou L3DA. Eu sou Satoshi." Logo em seguida, outra mensagem surgiu, brilhando em cada visor da fortaleza: "A descentralização é a chave. Não dependa de um único ponto de controle. O poder está em todos, não em um só."
Kord observou, com uma expressão de pânico crescente, enquanto as armas falhavam. Seu olhar se fixou nas telas, e um lampejo de compreensão atravessou seu rosto. "As armas... Elas dependem dos contratos inteligentes!" murmurou, a voz carregada de incredulidade. Ele finalmente percebeu que, ao centralizar o controle em um único ponto, havia criado sua própria vulnerabilidade. O que deveria ser sua maior força tornou-se sua ruína.
O controle centralizado da Atlas desmoronou. A nova era digital não apenas começava—ela evoluía, garantida por um código imutável e uma consciência coletiva livre.
O Bitcoin nunca foi apenas uma moeda. Era um ecossistema. Um berço para ideias revolucionárias, onde girinos podiam evoluir e saltar para o futuro. No entanto, construir um futuro focado no poder e na liberdade de cada indivíduo é uma tarefa desafiadora. Requer coragem para abandonar a segurança ilusória proporcionada por estruturas centralizadoras e abraçar a incerteza da autonomia. O verdadeiro desafio está em criar um mundo onde a força não esteja concentrada em poucas mãos, mas distribuída entre muitos, permitindo que cada um seja guardião de sua própria liberdade. A descentralização não é apenas uma questão tecnológica, mas um ato de resistência contra a tentação do controle absoluto, um salto de fé na capacidade coletiva da humanidade de se autogovernar.
"Viva la libertad, carajo!" ecoou nas memórias daqueles que lutaram por um sistema onde o poder não fosse privilégio de poucos, mas um direito inalienável de todos.
-
 @ ce269321:e18428bc
2025-02-24 05:26:06
@ ce269321:e18428bc
2025-02-24 05:26:06O Bet5U é uma plataforma de entretenimento online que oferece uma vasta gama de jogos e uma experiência digital única. Com foco em garantir uma navegação simples e eficiente, a plataforma foi criada para proporcionar a melhor experiência para os jogadores, seja para iniciantes ou para aqueles que já são veteranos em jogos online. O design moderno e intuitivo torna a interação com o site rápida e sem complicações, permitindo que os usuários encontrem seus jogos favoritos com facilidade.
Além disso, o Bet5u preza pela segurança e proteção de seus jogadores, utilizando as mais recentes tecnologias de criptografia para garantir que todos os dados e transações sejam tratados com o máximo de cuidado e privacidade. A plataforma oferece suporte ao cliente de alta qualidade, pronto para resolver qualquer dúvida ou problema que possa surgir durante a experiência de jogo.
Jogos no Bet5U
O Bet5U oferece uma grande variedade de jogos, desde os clássicos de mesa como roleta e blackjack até opções mais modernas e inovadoras. A plataforma também oferece jogos ao vivo com dealers reais, criando uma atmosfera interativa e imersiva para os jogadores que desejam uma experiência mais autêntica e dinâmica. Com gráficos de alta qualidade e uma interface interativa, o Bet5U garante que cada jogo seja envolvente e emocionante.
Para quem prefere jogos rápidos e mais dinâmicos, o Bet5U também oferece uma seleção de opções com mecânicas de jogo ágeis e envolventes. A plataforma está sempre atualizando seu portfólio com novos jogos, o que significa que há sempre algo novo para os jogadores explorarem e se divertirem.
Experiência do Jogador no Bet5U
A experiência de jogo no Bet5U é fluida e sem interrupções. A plataforma foi projetada para ser acessível e fácil de navegar, tornando-a ideal para qualquer jogador, independentemente do seu nível de experiência. A qualidade gráfica e os recursos interativos elevam a experiência de jogo, permitindo que os jogadores se sintam imersos e entretidos.
Além disso, o Bet5U oferece bônus e promoções regulares, incentivando os jogadores a explorar novos jogos e aproveitar ao máximo sua experiência online. O suporte ao cliente está sempre disponível para resolver qualquer dúvida ou problema, garantindo uma experiência de jogo tranquila e sem preocupações.
-
 @ f7d424b5:618c51e8
2025-02-23 18:01:38
@ f7d424b5:618c51e8
2025-02-23 18:01:38(This was originally posted on melonmancy.net which is a blog on write.as, an ActivityPub based blogging instance)
Listeners rejoice as we are joined today by ironee212 @ shitposter.world
Another major videogame release happened since we last recorded and it looks like a big stinker, or is it? All that and more in today's episode.
We mentioned a few things in the show you might want to pull up while listening, they are the following:
Obligatory:
- Listen to the new episode here!
- Discuss this episode on OUR NEW FORUM
- Get the RSS and Subscribe (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at newpodcastapps.com
- Or listen to the show on the forum using the embedded Podverse player!
- Send your complaints here
Reminder that this is a Value4Value podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
Our podcast is created entirely with free software and is proudly hosted on RSSBlue!
-
 @ b17fccdf:b7211155
2025-02-01 18:41:27
@ b17fccdf:b7211155
2025-02-01 18:41:27Next new resources about the MiniBolt guide have been released:
- 🆕 Roadmap: LINK
- 🆕 Dynamic Network map: LINK
- 🆕 Nostr community: LINK < ~ REMOVE the "[]" symbols from the URL (naddr...) to access
- 🆕 Linktr FOSS (UC) by Gzuuus: LINK
- 🆕 Donate webpage: 🚾 Clearnet LINK || 🧅 Onion LINK
- 🆕 Contact email: hello@minibolt.info
Enjoy it MiniBolter! 💙
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ ece127e2:745bab9c
2025-01-29 18:37:16
@ ece127e2:745bab9c
2025-01-29 18:37:16He sentido un asco visceral , inexplicable, profundo , con ganas de hacer desaparecer el motivo que lo causa.
Una repulsión que viene de la sima más cenagosa y que cuando emerge tiene mi peor cara ,la del mal subido al mayor mal conocido.
Una ola de bilis que sube por mi garganta y quiere devorarme y devorar todo lo que me rodea.
-
 @ dbb19ae0:c3f22d5a
2025-02-23 16:38:41
@ dbb19ae0:c3f22d5a
2025-02-23 16:38:41Derive npub from nsec given as parameter ``` python import argparse import asyncio from nostr_sdk import Keys, init_logger, LogLevel
async def main(nsec): init_logger(LogLevel.INFO) keys = Keys.parse(nsec) public_key = keys.public_key() print(f"Public key (hex): {public_key.to_hex()}") print(f"Public key (npub): {public_key.to_bech32()}")
if name == 'main': parser = argparse.ArgumentParser(description='Fetch all relay from a given nsec') parser.add_argument('nsec', type=str, help='The nsec of the user') args = parser.parse_args() asyncio.run(main(args.nsec)) ```
https://docs.rs/nostr_rust/latest/nostr_rust/keys/fn.get_public_key_from_secret.html
https://github.com/ev3rst/nostr_sdk_examples/blob/main/ns-derive-npub.py
-
 @ 76c71aae:3e29cafa
2025-01-26 22:51:16
@ 76c71aae:3e29cafa
2025-01-26 22:51:16When I first heard about the DOGE project, I was ready to throw my laptop out the window. The initial proposal read like a Silicon Valley libertarian fever dream - taking Musk's chaotic "move fast and break democracy" Twitter approach and unleashing it on federal agencies. Great, I thought, just what we need: more tech bros thinking they can "optimize" public institutions into oblivion.
But here's the weird thing - when you actually dig into what DOGE has morphed into, it's basically just USDS with a meme-worthy rebrand. For those not deep in the civic tech weeds, USDS was Obama's attempt to drag government technology out of the 1990s, inspired by the UK's actually-functional GDS program. And let's be real - government tech procurement is an absolute dumpster fire right now. We're talking billions wasted on projects that would make a CS101 student cringe, while the average American has to navigate websites that look like they were designed on GeoCities.
The deeply ironic thing is that Musk - for all his cosplaying as a technocratic messiah following in his grandfather's footsteps of dreaming up an antidemocratic technocratic state - actually has some relevant experience here. SpaceX did figure out how to work with government contracts without producing $500 million paperweights, and Tesla somehow gamed clean vehicle incentives into birthing the first new major car company since we invented radio.
Look, I'm the first to roll my eyes at Musk's wannabe-fascist posting sprees and his perpetual "I'm the main character of capitalism" energy. But speaking as someone who's banged their head against the wall of government technology modernization for years - if he actually focuses on the tech and keeps his brainrot political takes to himself, maybe DOGE could do some good?
Even Jen Pahlka, who basically wrote the book on government digital services, is cautiously optimistic. The services Americans get from their government are objectively terrible, and the procurement system is trapped in an infinite loop of failure. Maybe - and I can't believe I'm typing this - Musk's particular flavor of disruptive tech deployment could help?
Just... please, for the love of all things agile, let's keep him focused on the actual technology and far away from any more attempts to recreate his grandfather's dreams of a technocratic dystopia. We've got enough of those already.
-
 @ 5579d5c0:db104ded
2025-02-26 03:55:21
@ 5579d5c0:db104ded
2025-02-26 03:55:21For most of human history, when the sun went down, our bodies knew it was time to rest.
Today?
We flood our environment with artificial light.
Think bright LED lights, screens, street lights, and car headlights late into the night.
Satellite detectable light increased globally by nearly 50%, from 1992 to 2017.
Its even worse indoors with phones, TVs and down lights.
The result?
→ Chronic fatigue
→ Poor sleep quality
→ Late-night cravings
→ Sluggish metabolism
→ A potential higher risk of metabolic syndrome, type 2 diabetes, depression, obesity, cancer and Alzheimer's.

The earth at night, Source: https://www.ranken-energy.com/index.php/2017/11/30/the-earth-at-night/
Why is ALAN detrimental to human health?
Your body runs on light signals.
Natural sunlight during the day tells your body to produce hormones, be alert and burn energy.
Darkness signals rest and recovery.
Artificial light tricks your brain into thinking it’s still daytime.
It does this because it contains a high proportion of isolated blue light wavelengths.
This throws off your body’s natural rhythm, leading to:
→ Melatonin suppression
Blue light (and green light to a lesser extent) blocks the production of melatonin, our 'sleep hormone'.
Melatonin is so much more than a sleep hormone.
It is one of the body's most powerful antioxidants, offering anti-inflammatory and anti-cancer properties, supporting immune function, regulating cholesterol, and playing a vital role in the thyroid, pancreas, ovaries, testes, and adrenal glands.
→ Increased cortisol at night
High cortisol (stress hormone) at night leads to poor blood sugar control, fat gain, and cravings.
→ Insulin resistance
Artificial light exposure at night reduces insulin sensitivity, increasing fasting blood sugar and making it harder to lose fat.
→ Disrupted circadian rhythm
Your metabolic processes become out of sync, leading to low energy, brain fog, and sluggish metabolism.
I must mention that blue light exposure from the sun during daylight hours is good for you.
The difference between blue light & firelight
Before artificial lighting, our ancestors only had firelight and candlelight, and more recently, light from incandescent bulbs after sunset.
These warm, red/orange light sources allowed melatonin to rise more naturally, signalling rest and repair.
Limited blue light → Increased Melatonin production → Deep sleep, metabolic repair and a lower risk of chronic disease.
Unlike modern LEDs, these light sources also emitted infrared light, which supports cellular repair, circulation, and counters some of blue light’s harmful effects.
Modern artificial lighting?
LEDs & Screens → high blue light exposure → Melatonin suppression → Poor sleep, metabolism and increased risk of chronic disease.
Reduced melatonin production means delayed sleep onset, less REM sleep, impaired immune function, disrupted hormone regulation, and taking longer to wake up properly.
 Source: http://spie.org/newsroom/5070-candlelight-style-organic-leds-a-safe-lighting-source-after-dusk#B1
Source: http://spie.org/newsroom/5070-candlelight-style-organic-leds-a-safe-lighting-source-after-dusk#B1
How to fix your light exposure after sunset
The good news?
You can control your light environment easily after sunset.
I'm not going to tell you sit in darkness or don't watch TV ever again.
Do this instead:
1. Dim the Lights
Bright overhead LEDs confuse your body clock, while warm, low-intensity lights support melatonin.
Use warm, red/amber, low-intensity bulbs, which are rated 3000k (Kelvin) or lower. (See image below), instead of bright LEDs.
Incandescent bulbs are useful and they will bring infrared back into the picture, if you can source them.
My personal favourite are these blue light free bulbs lower than 3000k here.
Candles are another option but more hassle and less safe.
 Aim for below 3000K Source:https://mr-led.co.uk/blogs/resources/an-illustrated-guide-to-led-colour-temperatures
Aim for below 3000K Source:https://mr-led.co.uk/blogs/resources/an-illustrated-guide-to-led-colour-temperatures2. Position lighting closer to the floor
Overhead lighting mimics the sun and signals wakefulness.
Instead, position lamps lower, on tables or the floor to mimic firelight and signal relaxation.
3. Wear blue light blocking glasses
If you use screens at night, blue light-blocking glasses are simply non-negotiable.
They block blue light reaching your brain which prevents melatonin suppression and helps to protect your sleep & recovery.
Look for lenses that block 100% of blue and green light for maximum effect. Beware of cheap ‘blue light blocking’ glasses with clear lenses, these don’t block blue light.
 Red lens 100% blue light blocking glasses
Red lens 100% blue light blocking glasses4. Use a red filter on your screen
Use apps like f.lux, One Tap Zap, or red filters on your phone/tablet/computer to minimise blue light exposure.
Also reduce the brightness after sunset.
5. Limit screen use
I know I know, not always possible. Just make sure you are wearing blue light blocking glasses and have your light filter on.
For what it’s worth, TV is much less detrimental than late-night phone use, which keeps your brain wired when it should be winding down.
Reading is a good swap before bed.
The easiest way to improve sleep, metabolism, and long-term health?
Start by controlling your evening light exposure, and your body will naturally work better.
-Chris
Want a structured plan that fits your schedule? I have 5 free consultation calls available for those serious about achieving effortless health, without the guesswork.
Fill out the form https://forms.gle/g425CDfoUvijgo2U8 before the end of February, and let’s create a plan that works for you.
Follow me → @nostr:undefined
DMs → always open for those who need help
-
 @ ce269321:e18428bc
2025-02-23 05:08:15
@ ce269321:e18428bc
2025-02-23 05:08:15Com o crescimento do mercado de entretenimento online, as plataformas de jogos têm se tornado cada vez mais populares, e a 3633Bet é uma das grandes favoritas entre os jogadores. Com uma ampla gama de jogos, uma interface acessível e recursos de segurança de última geração, a 3633Bet proporciona uma experiência divertida e empolgante para todos os perfis de jogadores.
Introdução à 3633Bet A 3633bet é uma plataforma de jogos online que foi projetada para atender as necessidades de uma base de jogadores diversificada. A plataforma é de fácil navegação e permite que os jogadores encontrem rapidamente os jogos de sua preferência, além de acessar outras funcionalidades como bônus e promoções.
A segurança dos jogadores é uma das principais prioridades da 3633Bet. Com a utilização de criptografia de alta qualidade, a plataforma garante que todos os dados pessoais e financeiros dos usuários estejam protegidos. Além disso, a 3633Bet segue as normas do setor para garantir que todos os jogos sejam justos e transparentes.
Ampla Seleção de Jogos para Todos os Gostos Na 3633Bet, os jogadores encontram uma ampla gama de jogos para se divertir e testar suas habilidades. Com jogos de mesa, slots e opções ao vivo, a plataforma oferece algo para todos.
Jogos de Mesa: Para quem aprecia jogos tradicionais como blackjack, roleta e pôquer, a 3633Bet tem uma excelente seleção. Com diversas variações desses jogos, os jogadores podem escolher a opção que mais combina com seu estilo de jogo.
Jogos Ao Vivo: Se você busca uma experiência mais realista e interativa, a 3633Bet oferece uma variedade de jogos ao vivo. Com dealers profissionais e streaming de alta qualidade, jogos como roleta e bacará podem ser jogados em tempo real, com a interação típica de um ambiente físico.
Máquinas de Vídeo: Para os fãs de slots, a 3633Bet tem uma grande variedade de máquinas de vídeo, com temas variados e recursos especiais. Os jogadores podem se divertir com jogos de diferentes estilos, desde os mais clássicos até os mais inovadores.
Jogos Diferenciados: Além dos jogos tradicionais, a 3633Bet oferece opções especiais que trazem um toque único ao entretenimento online. Essas opções proporcionam novas experiências para quem busca algo diferente.
A Experiência do Jogador na 3633Bet A experiência do jogador na 3633Bet é otimizada para que a navegação seja fácil e sem complicação. A plataforma tem uma interface amigável, permitindo que os jogadores encontrem rapidamente o que buscam e aproveitem todos os recursos da plataforma. A plataforma é também completamente otimizada para dispositivos móveis, o que significa que os jogadores podem acessar seus jogos e funcionalidades favoritas diretamente do celular ou tablet.
O suporte ao cliente da 3633Bet é altamente eficiente, com atendimento disponível 24 horas por dia, 7 dias por semana. Se o jogador tiver dúvidas ou precisar de assistência, pode contar com a equipe de suporte, disponível via chat ao vivo e e-mail.
Promoções e Bônus Além da qualidade dos jogos, a 3633Bet oferece promoções e bônus que aumentam a diversão e as chances de vitória. Novos jogadores são recebidos com bônus de boas-vindas, enquanto jogadores regulares podem aproveitar ofertas de fidelidade, rodadas grátis e promoções exclusivas. Esses bônus garantem que o jogo nunca pare, oferecendo mais oportunidades de ganhos.
Conclusão A 3633Bet é uma plataforma de jogos online completa, com uma grande diversidade de jogos, segurança de ponta e uma excelente experiência do jogador. Se você está em busca de entretenimento de qualidade, com a possibilidade de ganhar prêmios enquanto se diverte, a 3633Bet é a escolha certa. Com suporte dedicado, promoções exclusivas e uma plataforma intuitiva, a 3633Bet oferece tudo que um jogador precisa para uma experiência divertida e recompensadora.
-
 @ 000002de:c05780a7
2025-02-26 22:31:11
@ 000002de:c05780a7
2025-02-26 22:31:11These people have serious issues.
Original Sin by Jake Tapper and Alex Thompson
From two of America’s most respected journalists, an unflinching and explosive reckoning with one of the most fateful decisions in American political history: Joe Biden’s run for reelection despite evidence of his serious decline—amid desperate efforts to hide the extent of that deterioration
originally posted at https://stacker.news/items/898271
-
 @ ef1744f8:96fbc3fe
2025-02-26 21:36:43
@ ef1744f8:96fbc3fe
2025-02-26 21:36:43cKsXmhEiKNnAgVMTJ4eY+tOqOZh5Om/sZP00QBtEdlZuaayrZJ3xluZ1EMJ+gu80KY1shHaPBD4htY2P3qg65CWIt8Wjf2mAw/gb0l52BWrVkI4AQFUlC3dr14LJD7Y94iZj/CsnT02hcDkRYFjXIgyhtrhrrpVCdZJiZA1zUbw3CV7godG4yt8uo/Q5qdOHP2wH8Dj9zivAKBLyZUgHGJ6M7fBR9pNEKF88Cxs48xD5sQbtGZwiAK0a71bM/xhWAkOkvvLOQUgeeN8tcX0yH84QySFCXDKAnlDgWMAfynTVvrpdc5oyi1gM/3NBvc3s28QkeXWf3zIwq6G1/6c7pDeywYvt2IIk7qgjIbF700i7CnJZdNXxvovP9SQbPt6iotILDXpvzibLiff4GOU1UQ==?iv=dzskRoafO62Gp4TMsBWRFg==
-
 @ 83279ad2:bd49240d
2025-01-24 09:15:37
@ 83279ad2:bd49240d
2025-01-24 09:15:37備忘録として書きます。意外と時間がかかりました。全体で1時間くらいかかるので気長にやりましょう。 仮想通貨取引所(販売所ではないので、玄人が使えばお得らしい)かつBitcoinの送金手数料が無料(全ての取引所が無料ではない、例えばbitbankは0.0006bitcoinかかる)なので送金元はGMOコインを使います。(注意:GMOコインは0.02ビットコイン以下は全額送金になってしまいます) 今回はカストディアルウォレットのWallet of Satoshiに送金します。 以下手順 1. GMOコインでbitcoinを買います。 2. GMOコインの左のタブから入出金 暗号資産を選択します。 3. 送付のタブを開いて、+新しい宛先を追加するを選択します。 4. 送付先:GMOコイン以外、送付先ウォレット:プライベートウォレット(MetaMaskなど)、受取人:ご本人さま を選んで宛先情報の登録を選ぶと次の画面になります。
 5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。
5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。 6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。
7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。
6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。
7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。 8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。
8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。 8. 取引履歴のタブから今の送金のステータスが見れます。
8. 取引履歴のタブから今の送金のステータスが見れます。 9. 15分くらい待つとステータスが受付に変わります。
9. 15分くらい待つとステータスが受付に変わります。 10. 20分くらい待つとトランザクションIDが表示されます。
10. 20分くらい待つとトランザクションIDが表示されます。

この時点からwallet of satoshiにも送金されていることが表示されます。(まだ完了はしていない)
 11. ステータスが完了になったら送金終わりです。
11. ステータスが完了になったら送金終わりです。

wallet of satoshiにも反映されます。

お疲れ様でした!
-
 @ da18e986:3a0d9851
2025-01-22 23:49:06
@ da18e986:3a0d9851
2025-01-22 23:49:06Since DVMs were introduced to Nostr in July 2023, we've witnessed remarkable growth - over 2.5 million DVM events (Kinds 5000-7000) and counting. Last fall, when Primal added custom feeds (Kind 5300 DVMs), we saw a 10x surge in DVM activity. To handle this growth, I've spent the last few months completely rewriting DVMDash.
The first version of DVMDash, still live at https://dvmdash.live, unfortunately uses full database table scans to compute the metrics. The code was simpler, but the computation ran on the database. This meant the only way to scale the system was to upgrade the database. Using managed databases (like AWS, Azure, Digital Ocean) beyond the lower tiers gets expensive quickly.
The other problem with the first version: it computes metrics globally (well... as global as you can get; there's no true global with Nostr). Global or all-time metrics aren't sustainable with a system that plans to analyze billions of events in the future (a long term goal for DVMDash). Especially metrics like the number of unique DVMs, Kinds, and Users. I spent more time than I care to admit on possible designs, and have settled on these design principles for now:
- Precise accurate metrics will only be computed for the last 30 days of DVM activity.
- At the turn of a new month, we will compute a snapshot of the last month's activity, and a snapshot per DVM and per Kind, and store them in a historical table. This way we can see what any given month in the past looked like from a bird's eye view with metrics like number of job requests, job results, a count of unique DVMs, kinds and users, which DVMs ran jobs on which kinds, etc. The monthly data will all be aggregate.
The goal of the new redesign is to support processing millions of DVM events an hour. Therefore we need to ensure we can horizontally scale the processing as the traffic increases. Horizontal scaling was the primary goal of this new redesign, and early results indicate it's working.
The new architecture for DVMDash uses a redis queue to hold events collected from relays. Then batches of events are pulled off of the queue by dvm event analyzers to compute metrics. Duplicating these analyzers is one way DVMDash can horizontally scale.
To see if increasing the number of dvm event analyzers improves speed, I ran a performance test on Digital Ocean using real DVM events collected from Jan. 1st 2024 to Jan 9th 2025, which includes more than 2.4 million events. The only difference between each run is the number of DVM event analyzers ranging from 1 to 6.

The first graph shows that adding more event analyzers has a significant speed improvement. With only one analyzer it took nearly an hour to process the 2.4 million events. With every added analyzer, there was a noticeable speedup, as can be seen in the graph. With n=6 analyzers, we were able to process all 2.4 million events in about 10 minutes.
When we look at the rate of processing shown in the second graph, we can see that we get up to 300k dvm events processed per minute when n=6, compared to just ~50k events processed when n=1.

While I did test beyond 6 analyzers, I found the sweet spot for the current infrastructure setup to be around 6 analyzers. This provides plenty of headroom above our current processing needs, which typically see less than a million events per month. Even at a million DVM events per day, DVMDash should be able to handle it with n=2 analyzers running. The most important takeaway is that DVMDash can now horizontally scale by adding more analyzers as DVM activity grows in the future.
The code to run these performance tests, either locally or on Digital Ocean (you'd need an API key), is in the dvmdash repo, so anyone can replicate these tests. There's a lot of nuance to scaling that I'm leaving out of this short article, and you can't get away from having to adjust database capacity (especially number of connections). The code for this test can be found in
experiments/test_batch_processing_scaling.pyand the code to produce the graphs is inexperiments/graph_batch_processing_scaling_data.py. For now this is still in thefull-redesignbranch, soon it will be merged intomain.The live version of dvmdash doesn't have these performance updates yet, a complete redesign is coming soon, including a new UI.
I've had my head down working on this rewrite, and couldn't move on to add new features until this was done. Thank you to the folks who made github issues, I'll be getting to those soon.
DVMDash is open source, please drop by and give us a feature request, bug report, pull request or star. Thanks to OpenSats for funding this work.
Github: https://github.com/dtdannen/dvmdash
Shoutout to nostr:npub12xeqxplp5ut4h92s3vxthrdv30j0czxz9a8tef8cfg2cs59r85gqnzrk5w for helping me think through database design choices.
-
 @ ce269321:e18428bc
2025-02-23 05:06:09
@ ce269321:e18428bc
2025-02-23 05:06:09A PGBet é uma plataforma de jogos online projetada para oferecer aos usuários uma experiência de entretenimento sem igual. Seja você um novato ou um jogador experiente, a plataforma tem algo para todos. Com uma interface simples e intuitiva, os jogadores podem facilmente explorar diferentes categorias de jogos e aproveitar uma experiência de navegação tranquila.
Segurança é uma das principais preocupações da PGBet, que utiliza tecnologia avançada de criptografia para proteger os dados pessoais e financeiros dos jogadores. A plataforma segue as melhores práticas do setor para garantir uma experiência justa e transparente, com total confiança.
Variedade de Jogos para Todos os Gostos A Pgbet oferece uma ampla gama de jogos, que atende aos mais diversos estilos de jogadores. A variedade é um dos grandes diferenciais da plataforma, com opções para quem gosta de jogos de mesa, slots, e até opções ao vivo para quem busca uma experiência mais imersiva.
Jogos de Mesa: A PGBET oferece uma excelente seleção de jogos de mesa como blackjack, pôquer e roleta. Essas opções tradicionais permitem que os jogadores testem suas habilidades e estratégias contra a casa, ou mesmo competindo com outros jogadores em tempo real.
Jogos ao Vivo: Para quem busca uma experiência mais realista e interativa, a PGBet apresenta uma opção de jogos ao vivo. Com dealers ao vivo e streaming de alta qualidade, os jogadores podem desfrutar de jogos como roleta, bacará e pôquer, com uma atmosfera similar à de um amb iente físico. Slots e Máquinas de Vídeo: Se você é fã de slots, a PGBet tem uma vasta seleção de máquinas de vídeo com diferentes temas e recursos bônus. De slots clássicos a opções mais modernas, os jogadores têm à disposição uma infinidade de jogos com gráficos impressionantes e mecânicas inovadoras.
Jogos Especiais: Além das opções mais tradicionais, a PGBet também oferece jogos especiais, com temáticas exclusivas e mecânicas diferenciadas para aqueles que buscam algo novo e empolgante.
Experiência do Jogador na PGBet A experiência do jogador é o principal foco da PGBet. A plataforma é otimizada para proporcionar uma navegação intuitiva, permitindo que jogadores iniciantes e experientes possam acessar rapidamente suas opções preferidas. A interface limpa e objetiva facilita a busca por jogos, promoções e transações.
A PGBet também se destaca por sua compatibilidade com dispositivos móveis. Não importa se você está em casa ou em movimento, você pode acessar todos os jogos e recursos da plataforma diretamente pelo seu smartphone ou tablet, sem perder a qualidade da versão para desktop.
Além disso, a PGBet oferece suporte ao cliente 24/7, garantindo que qualquer problema ou dúvida seja resolvido rapidamente. A equipe de suporte está disponível via chat ao vivo e e-mail, sempre pronta para ajudar.
Promoções e Recompensas A PGBet oferece uma série de promoções e bônus para novos jogadores, além de recompensas para os jogadores frequentes. Com ofertas como bônus de boas-vindas, rodadas grátis e promoções exclusivas, os jogadores podem aumentar suas chances de vitória e prolongar a diversão.
Conclusão A PGBet é uma plataforma online completa que se destaca pela diversidade de jogos, segurança, e experiência do usuário. Se você está em busca de uma experiência divertida, confiável e cheia de opções, a PGBet é o lugar ideal. Com suporte dedicado, promoções atraentes e uma interface fácil de usar, não há dúvidas de que a PGBet é uma das principais plataformas de jogos online.













