-
 @ ed5774ac:45611c5c
2025-02-15 05:38:56
@ ed5774ac:45611c5c
2025-02-15 05:38:56Bitcoin as Collateral for U.S. Debt: A Deep Dive into the Financial Mechanics
The U.S. government’s proposal to declare Bitcoin as a 'strategic reserve' is a calculated move to address its unsustainable debt obligations, but it threatens to undermine Bitcoin’s original purpose as a tool for financial freedom. To fully grasp the implications of this plan, we must first understand the financial mechanics of debt creation, the role of collateral in sustaining debt, and the historical context of the petro-dollar system. Additionally, we must examine how the U.S. and its allies have historically sought new collateral to back their debt, including recent attempts to weaken Russia through the Ukraine conflict.
The Vietnam War and the Collapse of the Gold Standard
The roots of the U.S. debt crisis can be traced back to the Vietnam War. The war created an unsustainable budget deficit, forcing the U.S. to borrow heavily to finance its military operations. By the late 1960s, the U.S. was spending billions of dollars annually on the war, leading to a significant increase in public debt. Foreign creditors, particularly France, began to lose confidence in the U.S. dollar’s ability to maintain its value. In a dramatic move, French President Charles de Gaulle sent warships to New York to demand the conversion of France’s dollar reserves into gold, as per the Bretton Woods Agreement.
This demand exposed the fragility of the U.S. gold reserves. By 1971, President Richard Nixon was forced to suspend the dollar’s convertibility to gold, effectively ending the Bretton Woods system. This move, often referred to as the "Nixon Shock," declared the U.S. bankrupt and transformed the dollar into a fiat currency backed by nothing but trust in the U.S. government. The collapse of the gold standard marked the beginning of the U.S.’s reliance on artificial systems to sustain its debt. With the gold standard gone, the U.S. needed a new way to back its currency and debt—a need that would lead to the creation of the petro-dollar system.
The Petro-Dollar System: A New Collateral for Debt
In the wake of the gold standard’s collapse, the U.S. faced a critical challenge: how to maintain global confidence in the dollar and sustain its ability to issue debt. The suspension of gold convertibility in 1971 left the dollar as a fiat currency—backed by nothing but trust in the U.S. government. To prevent a collapse of the dollar’s dominance and ensure its continued role as the world’s reserve currency, the U.S. needed a new system to artificially create demand for dollars and provide a form of indirect backing for its debt.
The solution came in the form of the petro-dollar system. In the 1970s, the U.S. struck a deal with Saudi Arabia and other OPEC nations to price oil exclusively in U.S. dollars. In exchange, the U.S. offered military protection and economic support. This arrangement created an artificial demand for dollars, as countries needed to hold USD reserves to purchase oil. Additionally, oil-exporting nations reinvested their dollar revenues in U.S. Treasuries, effectively recycling petro-dollars back into the U.S. economy. This recycling of petrodollars provided the U.S. with a steady inflow of capital, allowing it to finance its deficits and maintain low interest rates.
To further bolster the system, the U.S., under the guidance of Henry Kissinger, encouraged OPEC to dramatically increase oil prices in the 1970s. The 1973 oil embargo and subsequent price hikes, masterminded by Kissinger, quadrupled the cost of oil, creating a windfall for oil-exporting nations. These nations, whose wealth surged significantly due to the rising oil prices, reinvested even more heavily in U.S. Treasuries and other dollar-denominated assets. This influx of petrodollars increased demand for U.S. debt, enabling the U.S. to issue more debt at lower interest rates. Additionally, the appreciation in the value of oil—a critical global commodity—provided the U.S. banking sector with the necessary collateral to expand credit generation. Just as a house serves as collateral for a mortgage, enabling banks to create new debt, the rising value of oil boosted the asset values of Western corporations that owned oil reserves or invested in oil infrastructure projects. This increase in asset values allowed these corporations to secure larger loans, providing banks with the collateral needed to expand credit creation and inject more dollars into the economy. However, these price hikes also caused global economic turmoil, disproportionately affecting developing nations. As the cost of energy imports skyrocketed, these nations faced mounting debt burdens, exacerbating their economic struggles and deepening global inequality.
The Unsustainable Debt Crisis and the Search for New Collateral
Fast forward to the present day, and the U.S. finds itself in a familiar yet increasingly precarious position. The 2008 financial crisis and the 2020 pandemic have driven the U.S. government’s debt to unprecedented levels, now exceeding $34 trillion, with a debt-to-GDP ratio surpassing 120%. At the same time, the petro-dollar system—the cornerstone of the dollar’s global dominance—is under significant strain. The rise of alternative currencies and the shifting power dynamics of a multipolar world have led to a decline in the dollar’s role in global trade, particularly in oil transactions. For instance, China now pays Saudi Arabia in yuan for oil imports, while Russia sells its oil and gas in rubles and other non-dollar currencies. This growing defiance of the dollar-dominated system reflects a broader trend toward economic independence, as nations like China and Russia seek to reduce their reliance on the U.S. dollar. As more countries bypass the dollar in trade, the artificial demand for dollars created by the petro-dollar system is eroding, undermining the ability of US to sustain its debt and maintain global financial hegemony.
In search of new collateral to carry on its unsustainable debt levels amid declining demand for the U.S. dollar, the U.S., together with its Western allies—many of whom face similar sovereign debt crises—first attempted to weaken Russia and exploit its vast natural resources as collateral. The U.S. and its NATO allies used Ukraine as a proxy to destabilize Russia, aiming to fragment its economy, colonize its territory, and seize control of its natural resources, estimated to be worth around $75 trillion. By gaining access to these resources, the West could have used them as collateral for the banking sector, enabling massive credit expansion. This, in turn, would have alleviated the sovereign debt crisis threatening both the EU and the U.S. This plan was not unprecedented; it mirrored France’s long-standing exploitation of its former African colonies through the CFA franc system.
For decades, France has maintained economic control over 14 African nations through the CFA franc, a currency pegged to the euro and backed by the French Treasury. Under this system, these African countries are required to deposit 50% of their foreign exchange reserves into the French Treasury, effectively giving France control over their monetary policy and economic sovereignty. This arrangement allows France to use African resources and reserves as implicit collateral to issue debt, keeping its borrowing costs low and ensuring demand for its bonds. In return, African nations are left with limited control over their own economies, forced to prioritize French interests over their own development. This neo-colonial system has enabled France to sustain its financial dominance while perpetuating poverty and dependency in its former colonies.
Just as France’s CFA franc system relies on the economic subjugation of African nations to sustain its financial dominance, the U.S. had hoped to use Russia’s resources as a lifeline for its debt-ridden economy. However, the plan ultimately failed. Russia not only resisted the sweeping economic sanctions imposed by the West but also decisively defeated NATO’s proxy forces in Ukraine, thwarting efforts to fragment its economy and seize control of its $75 trillion in natural resources. This failure left the U.S. and its allies without a new source of collateral to back their unsustainable debt levels. With this plan in ruins, the U.S. has been forced to turn its attention to Bitcoin as a potential new collateral for its unsustainable debt.
Bitcoin as Collateral: The U.S. Government’s Plan
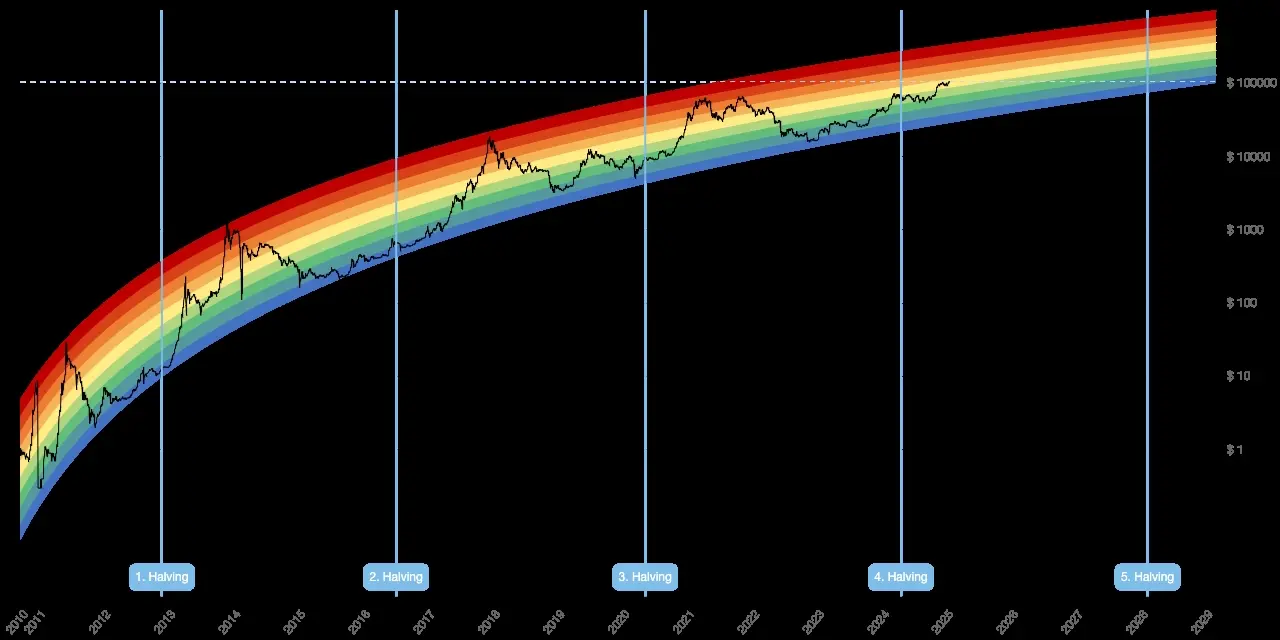
The U.S. government’s plan to declare Bitcoin as a strategic reserve is a modern-day equivalent of the gold standard or petro-dollar system. Here’s how it would work:
-
Declaring Bitcoin as a Strategic Reserve: By officially recognizing Bitcoin as a reserve asset, the U.S. would signal to the world that it views Bitcoin as a store of value akin to gold. This would legitimize Bitcoin in the eyes of institutional investors and central banks.
-
Driving Up Bitcoin’s Price: To make Bitcoin a viable collateral, its price must rise significantly. The U.S. would achieve this by encouraging regulatory clarity, promoting institutional adoption, and creating a state-driven FOMO (fear of missing out). This would mirror the 1970s oil price hikes that bolstered the petro-dollar system.
-
Using Bitcoin to Back Debt: Once Bitcoin’s price reaches a sufficient level, the U.S. could use its Bitcoin reserves as collateral for issuing new debt. This would restore confidence in U.S. Treasuries and allow the government to continue borrowing at low interest rates.
The U.S. government’s goal is clear: to use Bitcoin as a tool to issue more debt and reinforce the dollar’s role as the global reserve currency. By forcing Bitcoin into a store-of-value role, the U.S. would replicate the gold standard’s exploitative dynamics, centralizing control in the hands of large financial institutions and central banks. This would strip Bitcoin of its revolutionary potential and undermine its promise of decentralization. Meanwhile, the dollar—in digital forms like USDT—would remain the primary medium of exchange, further entrenching the parasitic financial system.
Tether plays a critical role in this strategy. As explored in my previous article (here: [https://ersan.substack.com/p/is-tether-a-bitcoin-company]), Tether helps sustaining the current financial system by purchasing U.S. Treasuries, effectively providing life support for the U.S. debt machine during a period of declining demand for dollar-denominated assets. Now, with its plans to issue stablecoins on the Bitcoin blockchain, Tether is positioning itself as a bridge between Bitcoin and the traditional financial system. By issuing USDT on the Lightning Network, Tether could lure the poor in developing nations—who need short-term price stability for their day to day payments and cannot afford Bitcoin’s volatility—into using USDT as their primary medium of exchange. This would not only create an artificial demand for the dollar and extend the life of the parasitic financial system that Bitcoin was designed to dismantle but would also achieve this by exploiting the very people who have been excluded and victimized by the same system—the poor and unbanked in developing nations, whose hard-earned money would be funneled into sustaining the very structures that perpetuate their oppression.
Worse, USDT on Bitcoin could function as a de facto central bank digital currency (CBDC), where all transactions can be monitored and sanctioned by governments at will. For example, Tether’s centralized control over USDT issuance and its ties to traditional financial institutions make it susceptible to government pressure. Authorities could compel Tether to implement KYC (Know Your Customer) rules, freeze accounts, or restrict transactions, effectively turning USDT into a tool of financial surveillance and control. This would trap users in a system where every transaction is subject to government oversight, effectively stripping Bitcoin of its censorship-resistant and decentralized properties—the very features that make it a tool for financial freedom.
In this way, the U.S. government’s push for Bitcoin as a store of value, combined with Tether’s role in promoting USDT as a medium of exchange, creates a two-tiered financial system: one for the wealthy, who can afford to hold Bitcoin as a hedge against inflation, and another for the poor, who are trapped in a tightly controlled, surveilled digital economy. This perpetuates the very inequalities Bitcoin was designed to dismantle, turning it into a tool of oppression rather than liberation.
Conclusion: Prolonging the Parasitic Financial System
The U.S. government’s plan to declare Bitcoin as a strategic reserve is not a step toward financial innovation or freedom—it is a desperate attempt to prolong the life of a parasitic financial system that Bitcoin was created to replace. By co-opting Bitcoin, the U.S. would gain a new tool to issue more debt, enabling it to continue its exploitative practices, including proxy wars, economic sanctions, and the enforcement of a unipolar world order.
The petro-dollar system was built on the exploitation of oil-exporting nations and the global economy. A Bitcoin-backed system would likely follow a similar pattern, with the U.S. using its dominance to manipulate Bitcoin’s price and extract value from the rest of the world. This would allow the U.S. to sustain its current financial system, in which it prints money out of thin air to purchase real-world assets and goods, enriching itself at the expense of other nations.
Bitcoin was designed to dismantle this parasitic system, offering an escape hatch for those excluded from or exploited by traditional financial systems. By declaring Bitcoin a strategic reserve, the U.S. government would destroy Bitcoin’s ultimate purpose, turning it into another instrument of control. This is not a victory for Bitcoin or bitcoiners—it is a tragedy for financial freedom and global equity.
The Bitcoin strategic reserve plan is not progress—it is a regression into the very system Bitcoin was designed to dismantle. As bitcoiners, we must resist this co-option and fight to preserve Bitcoin’s original vision: a decentralized, sovereign, and equitable financial system for all. This means actively working to ensure Bitcoin is used as a medium of exchange, not just a store of value, to fulfill its promise of financial freedom.
-
-
 @ 6f7db55a:985d8b25
2025-02-14 21:23:57
@ 6f7db55a:985d8b25
2025-02-14 21:23:57This article will be basic instructions for extreme normies (I say that lovingly), or anyone looking to get started with using zap.stream and sharing to nostr.
EQUIPMENT Getting started is incredibly easy and your equipment needs are miniscule.
An old desktop or laptop running Linux, MacOs, or Windows made in the passed 15yrs should do. Im currently using and old Dell Latitude E5430 with an Intel i5-3210M with 32Gigs of ram and 250GB hard drive. Technically, you go as low as using a Raspberry Pi 4B+ running Owncast, but Ill save that so a future tutorial.
Let's get started.
ON YOUR COMPUTER You'll need to install OBS (open broaster software). OBS is the go-to for streaming to social media. There are tons of YouTube videos on it's function. WE, however, will only be doing the basics to get us up and running.
First, go to https://obsproject.com/

Once on the OBS site, choose the correct download for you system. Linux, MacOs or Windows. Download (remember where you downloaded the file to). Go there and install your download. You may have to enter your password to install on your particular operating system. This is normal.
Once you've installed OBS, open the application. It should look something like this...

For our purposes, we will be in studio mode. Locate the 'Studio Mode' button on the right lower-hand side of the screen, and click it.

You'll see the screen split like in the image above. The left-side is from your desktop, and the right-side is what your broadcast will look like.
Next, we go to settings. The 'Settings' button is located right below the 'Studio Mode" button.

Now we're in settings and you should see something like this...

Now locate stream in the right-hand menu. It should be the second in the list. Click it.

Once in the stream section, go to 'Service' and in the right-hand drop-down, find and select 'Custom...' from the drop-down menu.

Remeber where this is because we'll need to come back to it, shortly.
ZAPSTREAM We need our streamkey credentials from Zapstream. Go to https://zap.stream. Then, go to your dashboard.

Located on the lower right-hand side is the Server URL and Stream Key. You'll need to copy/paste this in OBS.

You may have to generate new keys, if they aren't already there. This is normal. If you're interested in multi-streaming (That's where you broadcast to multiple social media platforms all at once), youll need the server URL and streamkeys from each. You'll place them in their respective forms in Zapstream's 'Stream Forwarding" section.

Use the custom form, if the platform you want to stream to isn't listed.
*Side-Note: remember that you can use your nostr identity across multiple nostr client applications. So when your login for Amethyst, as an example, could be used when you login to zapstream. Also, i would suggest using Alby's browser extension. It makes it much easier to fund your stream, as well as receive zaps. *
Now, BACK TO OBS... With Stream URL and Key in hand, paste them in the 'Stream" section of OBS' settings. Service [Custom...] Server [Server URL] StreamKey [Your zapstream stream key]

After you've entered all your streaming credentials, click 'OK' at the bottom, on the right-hand side.
WHAT'S NEXT? Let's setup your first stream from OBS. First we need to choose a source. Your source is your input device. It can be your webcam, your mic, your monitor, or any particular window on your screen. assuming you're an absolute beginner, we're going to use the source 'Window Capture (Xcomposite)'.

Now, open your source file. We'll use a video source called 'grannyhiphop.mp4'. In your case it can be whatever you want to stream; Just be sure to select the proper source.

Double-click on 'Window Capture' in your sources list. In the pop-up window, select your file from the 'Window' drop-down menu.


You should see something like this...

Working in the left display of OBS, we will adjust the video by left-click, hold and drag the bottom corner, so that it takes up the whole display.

In order to adjust the right-side display ( the broadcast side), we need to manipulate the video source by changing it's size.

This may take some time to adjust the size. This is normal. What I've found to help is, after every adjustment, I click the 'Fade (300ms)' button. I have no idea why it helps, but it does, lol.

Finally, after getting everything to look the way you want, you click the 'Start Stream' button.

BACK TO ZAPSTREAM Now, we go back to zapstream to check to see if our stream is up. It may take a few moments to update. You may even need to refresh the page. This is normal.
 STREAMS UP!!!
STREAMS UP!!!A few things, in closing. You'll notice that your dashbooard has changed. It'll show current stream time, how much time you have left (according to your funding source), who's zapped you with how much theyve zapped, the ability to post a note about your stream (to both nostr and twitter), and it shows your chatbox with your listeners. There are also a raid feature, stream settings (where you can title & tag your stream). You can 'topup' your funding for your stream. As well as, see your current balance.
You did a great and If you ever need more help, just use the tag #asknostr in your note. There are alway nostriches willing to help.
STAY AWESOME!!!
npub: nostr:npub1rsvhkyk2nnsyzkmsuaq9h9ms7rkxhn8mtxejkca2l4pvkfpwzepql3vmtf
-
 @ 2fb77d26:c47a6ee1
2025-02-11 08:03:12
@ 2fb77d26:c47a6ee1
2025-02-11 08:03:12Intensiv! Das trifft es wohl am besten. Denn müsste ich das Jahr 2024 mit einem einzigen Wort charakterisieren, beschriebe kein anderes es besser. Atemlos, anstrengend, aufreibend, überraschend, lehrreich, unterhaltsam, erhebend und beglückend wären Adjektive, die in der Retrospektive ebenfalls Erwähnung finden könnten. Zum Glück. Gibt es doch kaum etwas Frustrierenderes als Eintönigkeit. Als stupide Routinen. So viel Sicherheit diese im wochentäglichen Trott versprechen, so viel Leere generieren sie, betrachtet man das Hamsterrad des Alltags über den Wochenhorizont hinaus. Dementsprechend heiter stimmt es mich, dass die vergangenen zwölf Monate das absolute Gegenteil von Routine waren und ich nun im Rückblick dartun darf, manch ein Husarenstück vollbracht zu haben.
»Damit das Mögliche entsteht, muss immer wieder das Unmögliche versucht werden«, hielt Hermann Hesse dereinst fest.
Diesem Gedanken folgend eröffnete ich das neue Jahr damit, ein ganzes Haus nahezu im Alleingang zu renovieren. Baustelle. Drei Monate lang. Oft bis zu 18 Stunden am Tag. Staub, Lärm, Farbe, Spachtel, Litzen, zerschundene Hände, schmerzende Glieder und verschlissene Kleidung. Von der Silikonfuge im hintersten Eck des Kellers bis zur Montagearbeit unter dem Dachbalken. Ob Steckdosen, Sockelleisten oder Fensterrahmen, Verkabelung, Inneneinrichtung oder Fassadenfarbe – ich hatte mir vorgenommen, dem viele hundert Jahre alten Gemäuer eine Generalüberholung angedeihen zu lassen. Als ich Anfang April unser farbenfroh-freiheitliches Hauswappen neben dem Eingang montierte und unserer neuen Unterkunft damit ihren Namen gab – »Casa Libre« –, war das ein großartiges Gefühl. Denn meinen mehr als ambitionierten Zeitplan hielt selbst ich im Januar noch für relativ utopisch.
Parallel dazu habe ich im Januar meine »Truman Show« fertiggestellt, das Cover überarbeitet und kurzfristig den Vertrieb gewechselt, weil es beim bisherigen Anbieter scheinbar nicht gern gesehen war, dass ich mich in besagtem Buch mit den dunklen Machenschaften von Menschenhändlern und Kinderschändern befasse.
Als die Anthologie im Februar erschien, musste diese natürlich auch medial beworben werden – während gleichzeitig die Vorarbeiten für die Printpublikation GEGENDRUCK Fahrt aufnahmen. Ab April sollten nach wochenlanger Abstinenz endlich auch wieder neue Texte auf meinem Blog erscheinen. Mich juckte es bereits in den Fingern. Unterdes wollte jedoch auch das Leben in der vorherigen Bleibe abgebaut, verpackt und transportiert werden, damit es ab April in den frisch gestrichenen vier Wänden des neuen Zuhauses wieder ausgepackt, aufgebaut und in Betrieb genommen werden konnte. Gut sortierte Bücher- und Plattensammlungen machen das ob ihres schieren Gewichts zu einer ganz besonderen Freude.
Dass ich nach über zehn Jahren Apple-Nutzung die private IT umgestellt, die Cloud gelöscht und Unmengen an Daten migriert, ein neues, überwachungsfreies Smartphone eingerichtet, verschiedene juristische Scharmützel bewältigt, diverse Texte verfasst und eine Vielzahl an Gesprächen geführt habe, an mehreren Konferenzen beteiligt, für verschiedene Projekte Dritter tätig, familiär gut eingespannt, obendrein einem Konzentration fordernden Vollzeitjob mit zunehmenden Verantwortlichkeiten verpflichtet war und diese Aufzählung nur einen kleinen Teil meiner Aktivitäten umfasst, sei dabei nur am Rande erwähnt.
Damit auch während des Sommerlochs keine Langeweile aufkommt, begann ich bereits im Frühjahr 2024 mit der Planung für eine Lese- und Vortragsreise. Gut zwanzig Termine wollten mit den Veranstaltern koordiniert werden. Es galt, Routenplanung, Hotelbuchungen, Reiselogistik, Buchbestand, Kommunikation und eine mit Quellen unterlegte Präsentation zu organisieren. Kaum war all das in trockenen Tüchern, saß ich bereits im Flugzeug nach Kolumbien, wo ich den Juli für Regeneration und Literaturrecherche nutzen wollte. Aber weil Leben nun mal ist, was passiert, während man plant, stellte Unvorhergesehenes die Improvisationsfähigkeit auch dort regelmäßig auf die Probe. Meer und Dschungel taten dennoch ihr Übriges und ließen die Irritationen des zivilisatorischen Alltags in ihrer relativen Belanglosigkeit verblassen.
Drei Wochen nach meiner Rückkehr ins Tessin waren sie allerdings zurück. Die Arbeit holte mich ein, diverse Projekte und ehrenamtliche Engagements warteten auf Input, die nackten Wände der neue Bleibe wollten dekoriert und das neue Tonstudio arrangiert werden – und ehe ich mich versah, ging es auch schon auf Tour. Gut 500 Kilogramm an Büchern und Gepäck waren verladen und mussten circa 6.000 Kilometer durch die Schweiz, Deutschland und Österreich chauffiert werden. Volle Säle und mehrere tausend offenherzige Menschen machten diese Reise zu einem ganz besonderen Erlebnis. Selbst das bis zum Sommer mehrheitlich miserable Wetter meinte es gut mit mir. Denn in den drei Wochen auf Tour regnete es nur ein einziges Mal. Am letzten Tag. Ansonsten waren mir strahlende Sonne, hochsommerliche Temperaturen und das ein oder andere Mittagsschläfchen im Schatten alter Bäume vergönnt.
Als ich der letzten Station meiner Rundreise den Rücken kehrte, verabschiedete sich auch die warme Jahreszeit. Auf der Heimfahrt über die Alpen begegneten mir die Vorboten eines goldenen Oktobers: eine tieferstehende Sonne über den Bergrücken, die goldene Stunde kürzer werdender Tage und der auffrischende Wind am Abend, der die an Farbenpracht zulegenden Wälder der Tessiner Topografie ins Wogen brachte. Wenige Wochen später fiel in den Alpen der erste Schnee. Jetzt schimmern die weißen Gipfel am Horizont in der wärmenden Wintersonne. Und ich sitze wieder an meinem Fenster, lasse den Blick über die geheimnisvoll anmutende Vegetationsdichte des Umlands schweifen und schreibe ein Vorwort. Für Buch Nummer fünf.
Es fällt etwas dünner aus, enthält nicht so viele philosophische Betrachtungen, Zitate und rhetorische Extravaganzen wie seine beiden Vorgänger. Leider. Denn das Sortieren der Gedanken, Quellen und Paragrafen im Rahmen der Textarbeit schält seltene Stunden innerer Ruhe aus den von Pflichten und Routinen dominierten Strukturen des Tages. Gerne hätte ich inmitten der organisatorischen Turbulenzen des vergangenen Jahres häufiger die Zeit gefunden, Beiträge zu verfassen – es gäbe so viel zu sagen, so viel zu dokumentieren, um den volatilen Konturen der Zeitenwende Schärfe zu verleihen. Und das erscheint dieser Tage nötiger denn je.
Denn da draußen tobt der Wahnsinn. Die Polykrise. Das Chaos – als Steigbügelhalter für das finale Kapitel eines transgenerationalen Klassenkampfes von oben. Für Technokratie und Plattformfaschismus. Doch »auch aus Steinen, die Dir in den Weg gelegt werden, kannst Du etwas Schönes bauen«, bemerkte Erich Kästner. Ohne Kontext und Hintergrundinformationen, die das Individuum in die Lage versetzen, die Schlachtfelder des wilder werdenden Informationskriegs mit einer gewissen Gelassenheit zu überblicken, gerät es jedoch leicht zum Opfer der unerbittlich keifenden Propagandamaschine wertewestlicher Demokratiedarstellung.
Ja, die Truman Show läuft wohl auch im fünften Jahr n. C. (nach Corona) auf allen Kanälen. Auf allen Frequenzen. Und der Homo demens spielt mit suizidaler Leichtfertigkeit seine ihm zugedachte Rolle als irrlichternder Kamikaze-Pilot, der sich in Rage auf das eigene Schiff zu stürzen gedenkt. Die zeitgeistig flexiblen Herrschaftseliten, die sich nun zusehends konservativ gerieren, anstatt Wokeness zu predigen, nesteln derweil hektisch an den letzten Zierpalisaden des digitalen Gulag. Der Rohbau steht ja auch schon eine ganze Weile. Bunt soll es sein – und spätestens 2030 bezugsfertig übergeben werden.
Ob eID, elektronische Patientenakte, digitales Geld, lückenlose Massenüberwachung, algorithmisierte Zensur, Dekarbonisierungsagenda, Enteignungslegislatur, kognitive Kriegsführung im Hosentaschenformat, Geofencing-Gewahrsam, Nanobots oder Frequenzfelder zu deren Kalibrierung: alles einsatzbereit. Schon 1999 veröffentlichte das US-Militär ein Dokument namens »Owning the Weather 2025«, das beschreibt, wie artifizieller Nebel verwendet werden kann, um Nanopartikel in Ballungszentren einzusetzen. Zwei Jahre später schlugen interne Präsentationen der NASA in die gleiche Kerbe. Jetzt ist 2025. Und Berichte über chemikalienhaltigen Nebel, der Krankheitssymptome verursacht, machen die Runde.
Wir sind angekommen. Der »Pakt für die Zukunft« ist geschlossen. Das Blau des Himmels einem persistent milchigen Grau gewichen. Noch am Heiligabend hat die UN-Generalversammlung Kernelemente des entsprechendes Vertragswerkes ratifiziert. Ohne nennenswerten Widerstand. Cloward-Piven-Strategie und Kulturmarxismus sei Dank. Die Revolution von oben war bis dato also ziemlich erfolgreich. Nur Max Mustermann weiß noch nichts vom seinem Glück.
Illuminiert wird die Installation des biometrischen Kontroll-Grids von einem Flammenmeer im Nahen Osten. Von brennenden Krankenhäusern, Kirchen und Kindern. Menschenrechte sind passé. Der beispiellose Genozid in Gaza wird von den NATO-Medien in verachtenswerter Manier schöngeschrieben, während von den USA trainierte, ausstaffierte, radikalislamische Fanatiker Syrien nahezu widerstandslos kapern. Ein Land, das seit Langem auf der To-do-Liste des militärisch-industriellen Komplexes stand. Die fortschreitende Destabilisierung der Region bereitet zionistischen Hardlinern in Tel Aviv und Washington die Bühne für den heiß ersehnten Krieg gegen den Iran.
Europäische Metropolen erodieren, die Bevölkerung verarmt, Reproduktionsraten sinken auf Rekordtiefstände, bei der NATO drängt man auf Eskalation mit Russland, und China intensiviert seine Drohgebärden im Indopazifik. Der militärische Fleischwolf dreht sich immer schneller. Es herrscht dicke Luft. Überall. Man riecht das Schießpulver. Denn das angloamerikanische Imperium ruft zum letzten Gefecht. Es ist – wie ich bereits im Vorspann der Truman Show schrieb – das letzte Aufbäumen eines moribunden Machtapparats. Charakterisiert von zunehmender Gewalt. Auf Kosten aller. Es lässt sich kaum seriös prognostizieren, wann es knallt, oder wie laut – dass es massiver Disruption bedarf, um diese Revolution von oben fristgerecht umzusetzen und speziell Kontinentaleuropa einen hohen Preis für seine willfährige Komplizenschaft bezahlen wird, allerdings schon.
Dabei erkannte schon Romain Rolland, dass »das schlimmste Übel, an dem die Welt leidet, nicht die Stärke der Bösen, sondern die Schwäche der Guten ist«.
Während sich also vor meinem Fenster die Sonne ein letztes Mal für dieses Jahr dem Ringen mit der Dunkelheit ergibt, Palmen, Koniferen und Zypressen vor einem goldgelb, dann violett glühenden Himmel zu schwarzen Scherenschnitten mutieren, erscheinen auch die Umrisse des vor uns liegenden Weges undeutlicher, die Zukunft ungewisser, unmenschlicher – ja unerreichbarer denn je. Als sei sie auf der Flucht.
Und eine Vielzahl derjenigen, die vorgeben, sie zu hehren Zwecken einfangen zu wollen, die Kritiker, Oppositionellen und Widerständler, drehen sich nicht minder schnell im Kreis als ihre Widersacher im leitmedialen Konsenskomplex. Denn im Kern tun beide Lager das Gleiche: Sie debattieren Sinnfetzen und Argumentationsfragmente, die man ihnen aus Orifizen weit oben im Elfenbeinturm oder verspiegelten Panzerglasfenstern polierter Luxuslimousinen vor die Füße wirft. Für viele ist Systemkritik zum profanen Geschäftsmodell geworden. Zum Event. Da bleibt wenig Zeit für echten Widerstand. Oder Charakter. Wer den Medienzirkus zu seinem Broterwerb gemacht hat, ist davon abhängig, dass er sich auszahlt. Und das von alternativmedialen Generika angefixte Publikum will genauso unterhalten werden wie der Zuschauer des Morgenmagazins. Brot und Spiele eben – egal, in welcher Arena die Schaukämpfe veranstaltet werden. Das Publikum schaut stoisch in die Röhre. Oder auf das Display. Hauptsache, das Spektakel lässt sich bequem vom Sofa aus verfolgen.
Hans-Joachim Kulenkampff gab schon vor Jahrzehnten zu verstehen, dass »die Leute gar nicht so dumm sind, wie wir sie durchs Fernsehen noch machen werden«. Er hatte recht. Die Revolution wird also wohl noch eine Weile auf sich warten lassen. Schade. Denn genau dafür engagiere ich mich – für eine friedliche Revolution des Geistes. Für eine zweite Aufklärung. Für eine Zukunft, in der es Liebe, Wahrheit und Selbstbestimmung sind, nach denen meine Mitmenschen streben. Bleibt zu hoffen, dass sich die Ascheschichten, aus welchen sich der Phoenix dieser zweiten Aufklärung irgendwann in den Himmel schwingen muss, vorher nicht allzu hoch auftürmen.
Nun will ich den Leser nicht mit all diesen persönlich gefärbten Annotationen und Gefühlsduseleien belästigen, um mich zu profilieren, sondern weil ein Jahr wie 2024 beweist – zumindest mir selbst –, dass man auch ganz allein Berge versetzen kann. Dass es nicht von äußeren Umständen, Dritten und Kapital abhängt, ob man Ziele erreicht. Dass man selbst der Phoenix sein kann. Jeder von uns. Wo ein Wille, da ein Weg. Aber beschreiten muss man ihn. Auch dann, wenn der Kompass temporär seinen Dienst versagt. Denn Routen entstehen nur dort, wo man sie geht. Und der Kurs lässt sich auch dann noch justieren, wenn man unterwegs ist. »Learning by doing« – nur so kommt man voran. Nur so schafft man Unabhängigkeit und Vertrauen in die eigenen Fähigkeiten. Fehler passieren ja nicht, um uns von etwas abzuhalten, sondern um uns auf den nächsten Versuch vorzubereiten. Sie sind ein Angebot, zu lernen. Und nur, wenn man der Welt ein Angebot machen kann, darf man darauf hoffen, dass es angenommen wird.
Womit wir beim Titel der vorliegenden Publikation angekommen wären: »Hopium« – ein Kompositum aus »Hope«, englisch für Hoffnung, und Opium, dem durch Anritzen seiner unreifen Samenkapseln gewonnenen, getrockneten Milchsaft des Schlafmohns. Ein Rauschmittel. Basis des 1898 von Bayer markenrechtlich geschützten Morphin-Derivates Heroin. »Hopium« ist ein Neologismus – geprägt oder zumindest populär gemacht von James Corbett –, den ich in meinen Texten immer wieder gerne verwende, weil er wie kaum ein anderer auf den Punkt bringt, was Etatisten dazu bewegt, an das System Staat zu glauben: der Rausch der Hoffnung. Darauf, dass der nächste Kanzler, Präsident oder Premierminister es endlich richten wird. Oder diese eine neue Partei.
Der in regelmäßigem Turnus enttäuschte Irrglaube an die Selbstheilungskräfte eines auf Despotie ausgelegten Herrschaftssystems gleicht einer Sucht. Einer sehr destruktiven Sucht. Denn obwohl sich die Bevölkerung zumindest unterbewusst darüber im Klaren sein dürfte, dass sich auch nach dem nächsten Urnengang nichts ändern wird, dass ihr diese in devoter Pose dargebrachte Verehrung von Götzen schadet, dass sie an einer Art Stockholm-Syndrom leidet, wenn sie unterstützt, was sie beraubt, unterdrückt und tötet, tut sie es wieder. Immer wieder.
Aldous Huxley wusste, wovon er sprach, als er notierte, dass »der Glaube an eine größere und bessere Zukunft einer der mächtigsten Feinde gegenwärtiger Freiheit ist«.
Nun ist Hoffnung aber nicht per se negativ – und Hopium somit als durchaus ambivalenter Begriff zu werten. Treibt die Hoffnung doch auch mich dazu, immer wieder Wege zu suchen, um Menschen zu erreichen, Konstruktives beizutragen und die Welt in meinem Einflussbereich ein wenig besser zu machen. Sie besser informiert zu hinterlassen. Sähe ich unsere Situation als chancenlos, hätte ich den Glauben an Liebe und Wahrheit, oder die Hoffnung auf bessere Zeiten aufgegeben, gäbe es dieses Buch nicht.
Der Unterschied zwischen einem Etatisten und mir besteht darin, dass ich nicht darauf hoffe und warte, dass mir jemand diese Arbeit abnimmt. Ich delegiere nicht, gebe die Verantwortung für mein Leben nicht aus der Hand, sondern nehme sie wahr. Werde aktiv. Mein Glaube an »Volksvertreter«, Erlöser und Idole erlosch vor über drei Jahrzehnten. Seitdem verlasse ich mich nur noch auf eine einzige Person – mich selbst – und gebe mir redlich Mühe, mich dabei nicht zu enttäuschen, sondern zu beeindrucken.
Ob andere Menschen gut finden, was ich mit meiner knapp bemessenen Lebenszeit anstelle, ist mir egal. Es ist mein Leben. Ich habe nur eines. Zumindest aller Wahrscheinlichkeit nach. Und der Einzige, dem es gefallen muss, bin ich.
»Die einen kennen mich, die anderen können mich«, wie Le Cercle-Gründungsmitglied Konrad Adenauer treffend polterte. Das ist Freiheit. Und die steht nirgends zur Wahl. Wird nicht angeboten. Sie hängt nicht von äußeren Umständen ab, wird nicht gewährt oder erkämpft. Frei wird man nicht – frei ist man. Oder eben nicht.
Ich hoffe – das ist meine tägliche Dosis »Hopium« –, dass meine Arbeit anderen Menschen hilft, das zu erkennen.
Denn das Versäumnis von gestern ist das täglich Brot von morgen, die Gegenwart die Vergangenheit der Zukunft. Und es ist an uns, etwas daraus zu machen. »Man muss die Zukunft abwarten und die Gegenwart genießen – oder ertragen«, soll Wilhelm von Humboldt gesagt haben. Ich habe mich intuitiv immer für den Genuss entschieden und bin überzeugt, dass dieser Ansatz eine gute Ausgangsposition ist, um dem in absehbarer Zeit Orkanstärke erreichenden Sturm der Zeit die Stirn zu bieten.
Frei nach Edward Snowden: »Sei nicht ängstlich – sondern vorbereitet«.
Weiter geht's im Buch ...
-
 @ d23af4ac:7bf07adb
2025-02-18 17:07:55
@ d23af4ac:7bf07adb
2025-02-18 17:07:55This is a test-note published directly from Obsidian
Heading 1
Some paragraph text [^2]
Heading 2
Second paragraph text. * List item 1 * List item 2
js console.log("Hello world!")Json
json { name: "Alise", age: 45 }[!SCRUNCHABLE NOTE]- This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads. This should be collapsed when the page first loads.
[!DANGER] This is a "danger" type message. Should be properly formateed. This is a "danger" type message. Should be properly formateed. This is a "danger" type message. Should be properly formateed. This is a "danger" type message. Should be properly formateed. This is a "danger" type message. Should be properly formateed.
--
Pasted image:
![[Pasted image 20250218120714.png]]
This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote[^1]. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote. This is a blockquote.
- [x] This is a completed task
- [ ] This is an uncompleted task
- [ ] This is also an uncompleted task
[!QUESTION] Will this inline code format properly?
console.log('Yo momma so fat she took a spoon to the Super Bown');Idk...[^1]: Footnotes also supported? Even inside blockquotes? [^2]: Footnote in regular paragraph
-
 @ b8af284d:f82c91dd
2025-02-09 18:48:21
@ b8af284d:f82c91dd
2025-02-09 18:48:21Liebe Abonnenten,
viele von uns erleben im privaten wie im öffentlichen Leben gerade eine Zeit der Verwirrung und Irritation. Etwas scheint im Umbruch, alte Gewissheiten, Strukturen und Allianzen scheinen sich vor unseren Augen aufzulösen. Trump, Musk und Thiel wirken wie die Abrissbirnen einer alten Ordnung, Agenten des Chaos mit dem einzigen Ziel, sich selbst zu bereichern. Ist es so?
Könnte es anders sein?
Folgender Text kann und will diese Fragen nicht ultimativ beantworten. Es gibt aber eine Brille, durch die, setzt man sie auf, viele Entwicklungen in einem anderen, viel helleren Licht erscheinen. Diese Brille heißt e/acc.

Was ist e/acc?
Das Kürzel geht auf den Programmierer Guillaume Verdon zurück, der unter dem Pseudonym „Beff Jezos“ die Bewegung. Es steht für „effective accelerationism“. Accelerationism, auf Deutsch Akzelerationismus, abgeleitet vom Verb „beschleunigen“, hat Wurzeln, die weiter zurückreichen - dazu später mehr. Der Zusatz „effective“ ist eine ironische Replik auf den „effective Altruism“, den unter anderen Sam Bankman-Fried vertrat und grandios scheiterte.
e/acc setzt also auf Beschleunigung. Kapitalismus, Innovation, vor allem künstliche Intelligenz sollen nicht aufgehalten oder reguliert werden, sondern im Gegenteil beschleunigt werden.
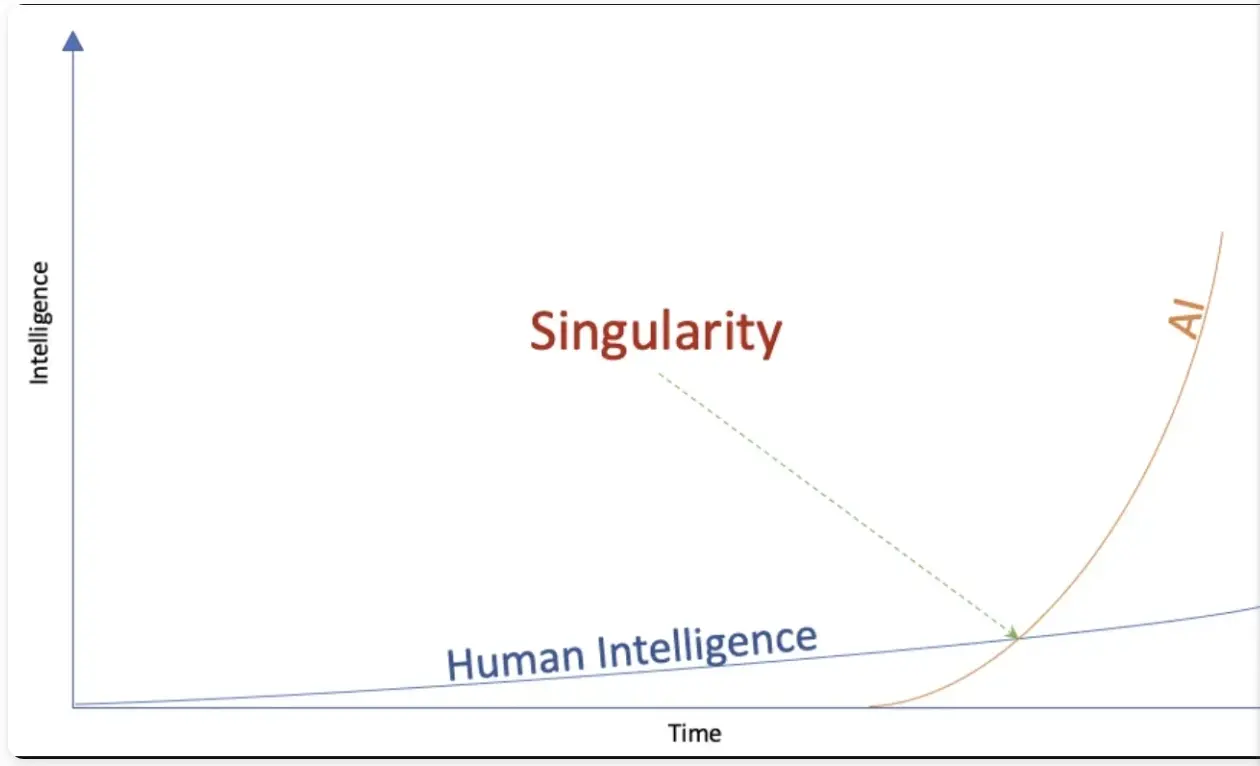
Warum?
Eine einfache Antwort lautet: Weil sie eh stattfinden. Besonders deutlich wird das im Fall künstlicher Intelligenz. Large Language Models (LLMs) wie ChatGPT und Deepseek sind nur die für die Öffentlichkeit sichtbaren Entwicklungen. Im Hintergrund ersetzt Künstliche Intelligenz zunehmend auch Produktionsprozesse und nicht zuletzt die Kriegsführung. Man spricht deswegen vom „Point of Singularity“. In den kommenden Jahren wird künstliche Intelligenz menschliche übertrumpfen. Unsere Arbeitswelt, unser Finanzsystem und gesellschaftliche Strukturen werden sich grundlegend ändern. Wenn es dazu kommt, warum die Entwicklung noch aufhalten? Beschleunigen ist besser.
Die zweite Antwort ist tiefgründiger und rührt an das Verständnis von Leben insgesamt. Langfristig strebt das Universum nach Entropie. Es dehnt sich aus, bis alle Teile in maximaler „Unordnung“ angeordnet sind. Systeme mit hoher Energiezufuhr können Strukturen aufbauen, solange sie Wärme oder Entropie in ihre Umgebung abgeben. In einem Organismus sind alle Teile zu einer höheren Ordnung organisiert. Leben strebt nach Ordnung, Selbsterhalt und Wachstum, weshalb der Energieverbrauch zunimmt. e/acc-Fan und Silicon-Valley-Investor Marc Andreessen schreibt in “The Techno-Optimist Manifesto”:
Techno-Optimists believe that societies, like sharks, grow or die.
We believe growth is progress – leading to vitality, expansion of life, increasing knowledge, higher well being.
Ein Gleichgewicht gibt es nicht. Entweder strebt eine Struktur nach Ordnung (Leben) oder nach Unordnung (Tod). Da eine Balance nicht existiert, gibt es nur zwei Möglichkeiten: Verlangsamen oder Beschleunigen. Höhere Ordnungen aufbauen oder verfallen. Wachsen oder Sterben. Beschleunigen ist besser.
Konsequenzen
e/acc ist kein philosophisches System im strengen Sinn. Es leitet Konsequenzen aus physikalischen Grundsätzen ab.
Kapitalistische Systeme und freie Märkte sind die effizientesten Strukturen, um Informationen zu verarbeiten. In einem offenen, freien Markt gibt der Preis das zuverlässigste Signal über Knappheit eines Gutes. Wird dieser Prozess durch externe Einflussnahme wie Subventionen gestört, läuft die Maschine nicht effizient. Das Gesamtsystem wird verzerrt. Nochmals Andreessen dazu:
We believe the market economy is a discovery machine, a form of intelligence – an exploratory, evolutionary, adaptive system.
Varianten und Abweichungen sind wichtig, da ein System dadurch am schnellsten auf sich ständig verändernde Umweltbedingungen reagieren kann. Wer nicht frei sprechen kann, kann nicht frei denken. Dezentrale Strukturen mit vielen kleinen einzelnen „Nodes“ sind resilienter als hierarchisch-zentralistische Systeme. Das führt zu einem Meinungsfreiheits-Maximalismus.
Greifen staatliche Akteure in die Forschung ein, und vergeben zum Beispiel Lizenzen für KI-Projekte, kann das System nicht mehr auf die besten Ressourcen zurückgreifen. Es entwickelt sich nicht in seiner natürlichen Geschwindigkeit, sondern wird künstlich verlangsamt. Beschleunigen ist besser.
Im Falle von KI hat dies geopolitische Konsequenzen: Sollten autoritäre Akteure wie zum Beispiel China schneller zum Punkt der Singularity vorstoßen, entsteht eine Dystopie, ein Orwellscher Überwachungsstaat. Bevorzugen ist deswegen eine beschleunigte, dezentrale Forschung, damit freie Systeme die Oberhand behalten.
Dasselbe gilt für das Geldsystem: e/acc trifft hier auf Hayek und Mises. Viele Zahlungssysteme stehen in permanenter Konkurrenz zueinander. Am Ende setzt sich das nützlichste und vermutlich auch härteste Geld durch.
Konkrete Folgen
Auf die konkrete Politik übertragen führt das zu Konsequenzen, die man aktuell beobachten kann.
**Radikale Deregulierung: **Die Biden-Administration versuchte, AI-Forschung eng an die Regierung zu binden. Open-AI-Gründer Sam Altman forderte 2023 eine Lizenz-Vergabe an Unternehmen, um überhaupt in diesem Bereich aktiv zu werden. (Musk trat zunächst sogar für ein Forschungs-Moratorium ein, änderte dann aber seine Meinung.) Das führte zum Widerstand der e/acc-Fraktion im Silicon Valley, und gab den Ausschlag, sich auf die Trump-Seite zu stellen. Deregulierung zieht sich nun durch alle Bereiche der Wirtschaft: auch auf die „Entwicklungshilfe“ von USAID. Der Regierungsapparat wird insgesamt massiv verkleinert, da Bürokratie das Wachstum hemmt. A fuera.
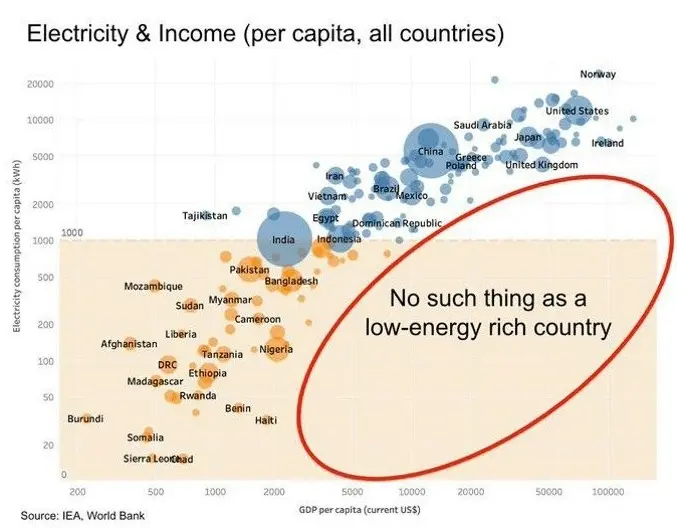
**Priorisierung von günstiger Energie: **Da der Energie-Verbrauch mit zunehmender Ordnung ansteigt, und LLMs einen sehr viel Strom brauchen, priorisiert die neue Regierung die Erschließung zusätzlicher Energiequellen: Gas, Öl, Nuklear und regenerative Energiequellen gleichermaßen.
Wiederherstellung von Meinungsfreiheit.Content-Moderationen auf Social-Media-Plattformen fallen weg. Geheimdienst-Dokumente werden freigegeben. So schrieb Peter Thiel vor einigen Wochen in einem Essay in der Financial Times über die große Enthüllung:
\ But understood in the original sense of the Greek word apokálypsis, meaning “unveiling”, Obama could not give the same reassurance in 2025. Trump’s return to the White House augurs the apokálypsis of the ancien regime’s secrets. (…)\ The apokálypsis is the most peaceful means of resolving the old guard’s war on the internet, a war the internet won. My friend and colleague Eric Weinstein calls the pre-internet custodians of secrets the Distributed Idea Suppression Complex (DISC) — the media organisations, bureaucracies, universities and government-funded NGOs that traditionally delimited public conversation.
Krypto-Deregulierung: Da Kryptowährungen und Smart-Contract-Strukturen bestens mit LLMs harmonieren, werden Innovationsbremsen in Form von Regulierungen abgebaut.
**Umbruch der Weltordnung: **Auf der geopolitischen Ebene werden Bündnisse, Allianzen und Blockstrukturen aufgebrochen und nach effizienten Win-Win-Verhältnissen neu organisiert.
Erschließung neuer Lebenswelten: Degrowth, weniger Energie-Verbrauch und weniger Kinder sind keine Option, da sie zum Tod führen. Das System Menschheit muss wachsen und wird neue Lösungen erfinden. Wenn die Ressourcen des Planeten Erde nicht mehr ausreichen, müssen neue erschlossen werden - vielleicht auf dem Mars.
Die Ideengeschichte
Während e/acc ein relativ neues System ist, hat der Akzelerationismus tiefere Wurzeln. Lenin kann man als einen frühen Akzelerationisten bezeichnen. Der Marxismus wurde Anfang des 20. Jahrhunderts weniger als Ideologie, sondern mehr als exakte Wissenschaft begriffen. Demnach würde der Kapitalismus früher oder später an seinen eigenen Widerständen kollabieren. Warum den Prozess also nicht beschleunigen und die Revolution herbeiführen?
Ende des 20. Jahrhunderts griff der Philosoph Nick Land diese Gedanken wieder auf. Land forderte Beschleunigung, sah am Ende des Prozesses aber einen Kollaps des Systems und eine dunkle Zukunft. Ironie der Geschichte: Land zog in den 2000er Jahren nach China, wo er einen autoritären Akzelerationismus verwirklicht sah. Auch Steve Bannon, Leiter des ersten Trump-Wahlkampfes 2016, war von Lands Gedanken geprägt.

e/acc aber ist eine neuer, optimistischer „Fork“ des alten, dunklen Akzelerationismus. Es sieht eine positive Zukunft für die gesamte Menschheit aufgrund eines gigantischen Produktivitätsschubs. Eine neue, höhere Ordnung ist am Entstehen. Kurz gesagt:
Effective accelerationism (e/acc) in a nutshell:
Stop fighting the thermodynamic will of the universe
You cannot stop the acceleration
You might as well embrace it
A C C E L E R A T E
Notes on e/acc principles and tenets
Happy Future also? Durch die e/acc-Brille gesehen wirkt die Welt wesentlich heller und optimistischer als sie die meisten “Legacy Media” gerade darstellen. Demnach bewegen wir uns auf eine neue Zeit gesteigerter Produktivität und damit Lebensqualität zu. Wenn alle Arbeit von Maschinen verrichtet wird, können Menschen währenddessen auf Bali surfen, meditieren und Yoga machen. Oder?
Kritik
Leben entsteht an der Grenze von Chaos und Ordnung. Vielleicht versetzt e/acc das Pendel zu stark in den Ausschlag in eine Richtung. Unkontrolliertes Wachstum bedeutet im lebenden Organismen Krebs. e/acc sieht sich wie Marxisten der ersten Stunde (Lenin) im Besitz der Wahrheit in Form physikalischer Grundsätze. Erst durch diese Hybris führten zu den Grausamkeiten sozialistischer Systeme im 20. Jahrhundert. Schließlich beantwortet e/acc nicht die Frage nach der Verteilungsgerechtigkeit, die durch den gewaltigen Produktivitätsschub durch AI entstehen wird.
Ob e/acc als politisches und gesellschaftliches System taugt, ist deswegen fraglich. Aber viele aktuelle Entwicklungen scheinen durch die Akzelerationismus-Brille klarer.
Quellen:
Peter Thiel: A Time for Truth and Reconciliation
Marc Andreessen: The Techno-Optimist Manifesto
e/acc: Notes on e/acc principles and tenets
Andy Beckett: Accelerationism: how a fringe philosophy predicted the future we live in
Lex Friedman: Guillaume Verdon. e/acc-Movement. Physics. Computation & AGI.
-
 @ 2516d145:070c8fa1
2025-02-07 16:49:20
@ 2516d145:070c8fa1
2025-02-07 16:49:20„Ein Mensch. Ein Wort.“, steht auf den Plakaten der Grünen zur Bundestagswahl 2025. Mich erinnert das an den Beginn des Johannesevangeliums: „Im Anfang war das Wort … Und das Wort ist Fleisch geworden …“ In diesen Tagen scheinen Heiligenverehrung und Teufelsaustreibung so virulent zu sein, wie im Mittelalter. Menschen müssen die richtigen Worte verwenden. Wahre Worte aus falschem Mund verklingen oftmals ungehört.
Die Sachbücher des massel Verlags sind mehr als bloße Hirngespinste, sie gründen in gelebter Wirklichkeit. Texte unserer Autoren werden nicht glattgeschliffen und marktkonform gebeugt, sondern sie behalten ihre Macken und Zacken. Linus war im Gefängnis eingesperrt und Bastian hat ein Jahr in der Wildnis frei gelebt. Eva ist mit dem Volk Gottes durch die Wüste gewandert und Insa hat ihr Glück nicht nur, aber auch im Sex gefunden. Walter hat Ausgrenzung durch die Medien am eigenen Leib erfahren und Ulrich ist eingetaucht in die vielfältigen, menschlichen Alternativen zu unserem Wirtschafts- und Finanzsystem.

Am 14. Februar ist Valentinstag!
Das Brauchtum dieses Tages geht auf das Fest des Heiligen Valentinus zurück. Der Legende nach traute der heilige Valentin von Rom Soldaten, denen das Heiraten eigentlich verboten war. In der Antike wurde um den 13. bis 15. Februar in Rom ein Fruchtbarkeitsritus gefeiert. Einen Beleg für eine Verbindung zwischen dem Fest der Lupercalien und dem Valentinstag gibt es nicht. Es gibt jedoch Hinweise, dass die Leidensgeschichte des Heiligen und sogar dessen Existenz erfunden wurde. Allgemein bekannt wurde der Valentinstag durch die vor dem 14. Februar verstärkt einsetzende Werbung der Floristik- und Süßwarenindustrie.
Blumen oder Schokolade verschenken? Ehepaare im Gottesdienst segnen? Der romantischen Liebe huldigen? Wir empfehlen Ihnen das etwas andere Geschenk!

Hauptsache Sex zusammen? von Insa Tiabilis\ Ein Inspirationsbuch über Sex in langen Beziehungen
Die Autorin sagt über sich: „Ich habe ein abgebrochenes Studium der Psychologie, drei abgeschlossene Kinder, und einen mir selbst verliehenen ‚Master‘ im Eheretten vorzuweisen. Das Leben hat mich qualifiziert und um einige wunderbare Erfahrungen reicher gemacht, an denen ich andere Menschen teilhaben lassen möchte. Ich habe mich glücklich gemacht. Nicht nur, aber auch mit Sex.“
Quellen erforschen und verstehen
Wie beim Valentinstag ist eine Umdeutung des Sex durch Kirche, Industrie und Machthabenden wahrscheinlich. Der Mensch wurde bewusst seiner Natur entfremdet. Oder hat die Kultur ihn zu etwas Höherem befreit?
Diese beiden Pole gilt es auszuhalten und zu entdecken. Siehe Kinderbuch weiter unten. Auch in der Sprachreise von Gerald Ehegartner geht es um Umdeutung. Ist das generische Maskulinum Ausdruck einer patriarchalen Gesellschaft? Oder hat die deutsche Sprache aus anderen Quellen ihre Grammatik gespeist?

Gerald Hüther, Neurobiologe und Bestsellerautor: „Dieses Buch von Gerald Ehegartner ist eine messerscharfe und scharfzüngige Analyse unserer gegenwärtigen Sprachverwicklungen und gleichzeitig eine warmherzige und berührende Liebeserklärung an unsere deutsche Muttersprache.“
Was und wo ist Heimat?
Der kleine Pinguin Timpetaa, verlässt seine gewohnte Umgebung im Süden, macht sich auf, die Welt zu entdecken und trifft dort auf Fremde. Das Unbekannte, in Timpetaas Fall der Nordpol mit den vielen Eisbären, welche ihn unter „normalen“ Umständen wahrscheinlich gleich verschlingen würden, kann auch zur Heimat werden. Auf alle Fälle üben die zotteligen Viecher am Nordpol unserem kleinen Weltreisenden gegenüber große Toleranz. Sie kümmern sich vielmehr rührend um ihn, nehmen ihn wohlwollend in ihrer Gemeinschaft auf, ziehen ihn groß und lernen ihm das Jagen, auch wenn Fisch nach wie vor zu seiner Leibspeise gehört. Am allerliebsten jagt der kleine Pinguin allerdings Herzen …
Der Autor Matthias A. Weiss möchte mit seinem Kinderbuch Kindern das Leben als zu entdeckendes Gut vermitteln, sie auf den Wert der Umwelt und ein friedvolles Miteinander aufmerksam machen. Nicht zuletzt sollen Kinder ermutigt werden, in die Welt hinauszugehen und eigene Erfahrungen zu sammeln.

Veranstaltungen
Im März stehen wieder einige Veranstaltungen des massel Verlags an. Wir freuen uns sehr, wenn wir uns bei dem ein oder anderen Ereignis begegnen würden. Aller Termine finden Sie auf unserer Website.
15. - 23. März 2025\ Bücherschau junior im Forum der Zukunft, Deutsches Museum - Museumsinsel\ In der Ausstellung: Timpetaa von Matthias A. Weiss
15. März 2025, 10 - 13:00 Uhr\ Stemmerhof, Plinganserstraße 6, 81369 München\ Büchermesse: Unabhängige Kleinverlage
und 14:00 Uhr\ Lesung: Timpetaa mit Matthias A. Weiss
22. März 2025, 18:30 Uhr\ Verlagshaus, Am Harras 14, 81373 München\ Lesung: Der Super-Faschismus mit Lisa-Maire Binder
27. - 30. März 2025\ Leipziger Buchmesse\ Vereinbaren Sie einen Termin mit Verleger Martin Sell
Wir wünschen Ihnen einen blühenden Valentinstag, süße Begegnungen und offene Herzen, die Ihnen zufliegen mögen.
Ihr massel Team\ Martin & Julia
-
 @ 1c197b12:242e1642
2025-02-09 22:56:33
@ 1c197b12:242e1642
2025-02-09 22:56:33A Cypherpunk's Manifesto by Eric Hughes
Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world.
If two parties have some sort of dealings, then each has a memory of their interaction. Each party can speak about their own memory of this; how could anyone prevent it? One could pass laws against it, but the freedom of speech, even more than privacy, is fundamental to an open society; we seek not to restrict any speech at all. If many parties speak together in the same forum, each can speak to all the others and aggregate together knowledge about individuals and other parties. The power of electronic communications has enabled such group speech, and it will not go away merely because we might want it to.
Since we desire privacy, we must ensure that each party to a transaction have knowledge only of that which is directly necessary for that transaction. Since any information can be spoken of, we must ensure that we reveal as little as possible. In most cases personal identity is not salient. When I purchase a magazine at a store and hand cash to the clerk, there is no need to know who I am. When I ask my electronic mail provider to send and receive messages, my provider need not know to whom I am speaking or what I am saying or what others are saying to me; my provider only need know how to get the message there and how much I owe them in fees. When my identity is revealed by the underlying mechanism of the transaction, I have no privacy. I cannot here selectively reveal myself; I must always reveal myself.
Therefore, privacy in an open society requires anonymous transaction systems. Until now, cash has been the primary such system. An anonymous transaction system is not a secret transaction system. An anonymous system empowers individuals to reveal their identity when desired and only when desired; this is the essence of privacy.
Privacy in an open society also requires cryptography. If I say something, I want it heard only by those for whom I intend it. If the content of my speech is available to the world, I have no privacy. To encrypt is to indicate the desire for privacy, and to encrypt with weak cryptography is to indicate not too much desire for privacy. Furthermore, to reveal one's identity with assurance when the default is anonymity requires the cryptographic signature.
We cannot expect governments, corporations, or other large, faceless organizations to grant us privacy out of their beneficence. It is to their advantage to speak of us, and we should expect that they will speak. To try to prevent their speech is to fight against the realities of information. Information does not just want to be free, it longs to be free. Information expands to fill the available storage space. Information is Rumor's younger, stronger cousin; Information is fleeter of foot, has more eyes, knows more, and understands less than Rumor.
We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do.
We the Cypherpunks are dedicated to building anonymous systems. We are defending our privacy with cryptography, with anonymous mail forwarding systems, with digital signatures, and with electronic money.
Cypherpunks write code. We know that someone has to write software to defend privacy, and since we can't get privacy unless we all do, we're going to write it. We publish our code so that our fellow Cypherpunks may practice and play with it. Our code is free for all to use, worldwide. We don't much care if you don't approve of the software we write. We know that software can't be destroyed and that a widely dispersed system can't be shut down.
Cypherpunks deplore regulations on cryptography, for encryption is fundamentally a private act. The act of encryption, in fact, removes information from the public realm. Even laws against cryptography reach only so far as a nation's border and the arm of its violence. Cryptography will ineluctably spread over the whole globe, and with it the anonymous transactions systems that it makes possible.
For privacy to be widespread it must be part of a social contract. People must come and together deploy these systems for the common good. Privacy only extends so far as the cooperation of one's fellows in society. We the Cypherpunks seek your questions and your concerns and hope we may engage you so that we do not deceive ourselves. We will not, however, be moved out of our course because some may disagree with our goals.
The Cypherpunks are actively engaged in making the networks safer for privacy. Let us proceed together apace.
Onward.
Eric Hughes hughes@soda.berkeley.edu
9 March 1993
-
 @ faade9ee:1c6dfd69
2025-01-26 11:39:51
@ faade9ee:1c6dfd69
2025-01-26 11:39:51This is a normal piece of text.z
This is a bold piece of text via button press.z
this is also bold, but via double-starsz
this is an italic via button press
this also but via one-star
look, it's an underline!
oh, a piece of code has appeared. Nice. Button press tho. seems like it's purple / missed styling it, will change that.another code but via textcode block, kinda buggy (really buggy actually x3)```this is another, but via text which is disabled for now as it's cause issues```
This is a top number thing222
a bottom number thing5ss65435ghrt
- bullets!
-
another!
- a third!
-
Number!
-
another!
- a third!
-
[x] check
- [x] box
this is a quote
"quote"
heading 1
heading 2
heading 3 via text
heading 4 via text
heading 5 via text
heading 6 via text
this is a link via text (button has an annoyance bug)

video below
::youtube{#aApSteSbeGA}
-
 @ b8af284d:f82c91dd
2025-02-07 08:18:53
@ b8af284d:f82c91dd
2025-02-07 08:18:53Liebe Abonnenten,
Zeit für ein kurzes Innehalten:
BlingBling existiert seit knapp über vier Jahren. Als ich diesen Newsletter im November 2020 startete, setzte Bitcoin gerade zu einem erneuten Bullrun an. Die Marke von 10000 US-Dollar war gerade nachhaltig durchbrochen worden, und es war ziemlich unglaublich, wie diese missverstandene und von den Leitmedien geschmähte und immer wieder totgesagte Kryptowährung sich schon wieder aufzublähen begann. Ein paar Monate später würde Elon Musk bekannt geben, dass man Tesla nun mit Bitcoin bezahlen könne (eine Aussage, die er kurz darauf wieder zurücknahm).
Mein persönliches Interesse für Bitcoin war schon einige Jahre vorher entstanden. 2013 kaufte ich für einen kleineren Betrag Bitcoin. Ich lebte damals in China und beschäftigte mich viel mit Kapitalverkehrskontrollen. Reiche Chinesen versuchten immer wieder, Geld außer Land zu bringen - das Gesetz aber verbot Summen über 50000 US-Dollar. Der Sinn einer dezentralen, nicht zensierbaren Währung leuchtete mir halbwegs ein. Ähnlich wie das Prinzip, wonach ein begrenztes Angebot bei steigender Nachfrage im Preis steigen müsse. Mein Verständnis aber blieb vage, und medial wurde Bitcoin damals vor allem mit der „Silk Road“ assoziiert, einem Online-Marktplatz, auf dem man alles, aber vor allem Drogen kaufen konnte.
Den Bullrun 2014 verschlief ich - was übrigens die beste Strategie für langfristigen Erfolg beim Investieren ist. Denn beim nächsten Zyklus 2017 verkaufte ich einen Großteil meiner Coins. Hätte ich den auch verschlafen, wäre ich heute um einiges reicher. Zunächst aber dachte ich, das Richtige getan zu haben: Anfang 2018 kollabierte der Kurs von 18000 US-Dollar auf 2000 Dollar. Vergleiche zur Tulpenblase wurde gezogen, Bitcoin final für tot erklärt, der Host des Podcasts „What Bitcoin Did“ veröffentlichte einen Thread auf damals noch Twitter, indem er schilderte, wie er „life changing money“ gewann und wieder verlor.
Es war allerdings in diesem Tal der Tränen als mein persönliches „Orange Pilling“ voll einsetzte. Die Frage: Was habe ich da gerade erlebt? Was ist das?, trieb mich um und führte zu einer immer tieferen Beschäftigung mit Bitcoin. Mal glaubte ich, den Fehler gefunden zu haben - nur um dann wieder eines Besseren belehrt zu werden. Die klugen Videos von Andreas Antonopoulos, die radikalen Bücher von Saifedean Ammouz, die cool-entspannten Podcasts von Peter McCormack ließen mich immer tiefer in den Kaninchenbau sinken. Das Verblüffende: Man traf Gleichgesinnte. Es war in diesen Jahren, in denen aus einem Netzwerk von Nerds eine eigene Subkultur wuchs. Sie hatte eigene Memes, Codes und vor allem Werte: Freiheit. Maximale Freiheit und Verantwortung für den Einzelnen.
All dies wurde ein Jahr später aufs Härteste auf die Probe gestellt. Die Lockdowns und der darauffolgende Impfdruck verengten in den traditionellen Medien das Overton-Fenster. Abweichende Meinungen wurden als “Verschwörungstheorien” gebrandmarkt und ins Abseits gedrängt. Nicht dass alle Bitcoiner Impfgegner oder Lockdown-Kritiker gewesen wären, aber in diesen Kreisen waren anders als in großen Teilen der Öffentlichkeit überhaupt noch kritische Diskussionen möglich. Bitcoiner waren geschult darin, selbstständig zu denken, und Paradigmen zu hinterfragen. Dies und die Freude über neue Allzeithochs machten die dunklen Jahre 2021/22 um einiges erträglicher.
Der Bullrun endete final 2022 mit der FTX-Pleite. Wieder schrieben viele Medien Bitcoin tot. Wieder schwadronierten etablierte Ökonomen von einer angeblich “durch nichts gedeckten Spekulationsgeld”. Operation Chokepoint 2.0 sollte dem System die Luft zum Atmen abschnüren. Aber die Katze war jetzt längst aus dem Sack. Bitcoin hatte sich festgebissen im System. Michael Saylor alchemisierte weiter Fiat-Geld zu digitalen Gold, El Salvador akzeptierte Bitcoin als Zahlungsmittel und Graswurzel-Initiativen wie 21-Stammtische konvertierten No-Coiner. Mit der ETF-Zulassung im Januar vergangenen Jahres wurde die Basis für einen neuen Bullrun geschaffen.
We made it.
Diese Woche ist Bitcoin im Mainstream angekommen. Silk-Road-Gründer Ross Ulbricht wurde nach 12 Jahren Haft begnadigt. Donald Trump launchte seinen eigenen Meme-Coin und vor ernannte er die Senatorin Cynthia Lummis zur Präsidenten eines neu geschaffenen Crypto-Ausschusses. Eine strategische Crypto-Reserve soll angelegt werden. An der sonst so peniblen getätigten Unterscheidung zwischen Crypto und Bitcoin muss man sich ausnahmsweise einmal nicht stören. Die dürfte eher ein Zugeständnis an World Liberty Finance, den Fund der Trump-Sprösslinge, diverse DeFi-Disruptor sein. Bitcoin bleibt König.
Und jetzt?
Wie jede Party wird auch diese enden, und wie nach jedem Bullrun wird danach ein Bärenmarkt folgen. Es kommen weitere Herausforderungen. Bitcoin, einmal von Eliten begriffen und adaptiert, wird von diesen benutzt werden. Macht korrumptiert. Auch die Guten. Gold, der analoge Vorläufer von Bitcoin, wurde immer wieder zentralisiert, eingezogen und anschließend in Form von Schuldscheinen wieder an die Bevölkerung ausgegeben. Bleiben wir wachsam.
Aber jetzt ist es erst einmal Zeit zu feiern: Lang lebe der König!

-
 @ ec42c765:328c0600
2025-02-05 23:38:12
@ ec42c765:328c0600
2025-02-05 23:38:12カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2025/02/06)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2025/02/06)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ cc32882d:eca332e6
2025-02-18 17:29:01
@ cc32882d:eca332e6
2025-02-18 17:29:01introductions
Hello World
New here as of today! I set myself up first on Yakihonne. (Just trying out clients so far) Glad to be here and look forward to learning and getting to know peeps. I have been poking around a bit and like what I see so far. Excited to play around some more with Nostr apps. Any suggestions is greatly appreciated.
Whats the good, the bad, and the ugly about Nostr in your opinion?
What is the size of nostr platform? How many users? Hows the community involvment? What is the age range? Any good places to look at this kind of data.
About:
Like to think deep about life and its vast array of questions and answers that are waiting to be discovered or rediscovered. Live with Nature, Dont fight what will be, Love
Dislike fake people. JUST BE REAL, Life is to short for anything else.
Drop me a response and I will get back to you as soon as possible. Look forward to hearing from some of you.
Thank You for Your Time and For Reading This
-ObsidianQuill
-
 @ 9e69e420:d12360c2
2025-02-17 17:12:01
@ 9e69e420:d12360c2
2025-02-17 17:12:01President Trump has intensified immigration enforcement, likening it to a wartime effort. Despite pouring resources into the U.S. Immigration and Customs Enforcement (ICE), arrest numbers are declining and falling short of goals. ICE fell from about 800 daily arrests in late January to fewer than 600 in early February.
Critics argue the administration is merely showcasing efforts with ineffectiveness, while Trump seeks billions more in funding to support his deportation agenda. Increased involvement from various federal agencies is intended to assist ICE, but many lack specific immigration training.
Challenges persist, as fewer immigrants are available for quick deportation due to a decline in illegal crossings. Local sheriffs are also pressured by rising demands to accommodate immigrants, which may strain resources further.
-
 @ fd208ee8:0fd927c1
2025-01-19 12:10:10
@ fd208ee8:0fd927c1
2025-01-19 12:10:10I am so tired of people trying to waste my time with Nostrized imitations of stuff that already exists.
Instagram, but make it Nostr. Twitter, but make it Nostr. GitHub, but make it Nostr. Facebook, but make it Nostr. Wordpress, but make it Nostr. GoodReads, but make it Nostr. TikTok, but make it Nostr.
That stuff already exists, and it wasn't that great the first time around, either. Build something better than that stuff, that can only be brought into existence because of Nostr.
Build something that does something completely and awesomely new. Knock my socks off, bro.
Cuz, ain't nobody got time for that.
-
 @ 0d97beae:c5274a14
2025-01-11 16:52:08
@ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs
The reason why we have broken money
Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world.
In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes.
However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore.
Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too.
Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it.
Bitcoin overcomes the "transfer of hard money" problem
Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design.
Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it.
Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive.
Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold.
Bitcoin blurs the line between commodity and technology
Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules.
At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable.
Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases.
The dangers of derivatives
A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold.
In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin.
Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense.
Learn for yourself
If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody".
There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
-
 @ fd208ee8:0fd927c1
2025-02-15 07:37:01
@ fd208ee8:0fd927c1
2025-02-15 07:37:01E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md https://github.com/nostr-protocol/nips/blob/master/61.md
-
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-
 @ 6ad3e2a3:c90b7740
2025-02-18 17:08:23
@ 6ad3e2a3:c90b7740
2025-02-18 17:08:23I’m not doing any writing today. Taking the day, maybe the week, off. Just not in the mood.
This whole idea you’re supposed to write, get the thoughts out, the ideas moving is stupid. To what end? I’m done with evaluating myself for productivity, justifying myself to myself — or anyone else.
What I really need is to find some pleasant distractions. Something to fill my time, or as Elon Musk says of Twitter “to avoid regretted user seconds.” I’ve tried Twitter itself, of course, but Musk’s algorithm falls woefully short. After an hour of doom and dopamine scrolling, punctuated with the occasional shitpost, many seconds are regretted — roughly 3500 of them.
I could turn to alcohol or drugs, but too many side effects. Yes, you’re distracted, but what about after that? You’re always left worse off than where you started. Even alcoholics and drug addicts — the pros! — know it’s a dead end.
I don’t know, maybe spend more time with loved ones? You hear that a lot. “If I didn’t have to work so much, I’d spend more time with loved ones.” LOL. Like what, you’re going to hang around while your “loved ones” are doing things with their actual lives. Maybe I’ll take the bus to school with Sasha, hang out with her and her friends, see how that goes. Quality time!
Exercise. It’s the perfect solution, good for your health, you feel better, your mind is calm. Only problem is it’s fucking miserable. If your aim is to avoid sitting at a desk to write, forcing your carcass around a track is hardly an upgrade. It’s like quitting your middle management job to break rocks in a prison chain gang.
There must be something I can do. Eating sugary processed food is out of the question for the same reason alcohol and drugs are. Becoming obese and diabetic is no solution, as many of the pros (obese diabetics) would no doubt attest.
Meditation. That’s it! You sit on a cushion, count your breaths. Pretty soon you are calm. You can meditate for as long as you want! It’s perfect, and it’s easy. Well, it’s not that easy. You get distracted by your thoughts and you’re just sitting there thinking about the things for which you hope and dread in your life.
Of course, you notice that distraction and come back to the breath, but pretty soon you’re wandering again. And you come back again. But really you’re wondering how long you’ve been sitting, your feet are falling asleep, your back is tight and you don’t feel much different. You weren’t even properly distracted because instead of being distracted from your mind, you are being distracted by it. It’s a worst-case scenario of sorts — you neither get anything done, nor escape the endless self-evaluation and justification.
That just means you’re doing it wrong, though. You’re failing at it. If you did it right, it would be the perfect escape from yourself. But it’s not working, so you’re failing. Or maybe you succeeded a little bit. You’re not sure. You are still evaluating whether that was a good use of your time. The same evaluation process you use to decide whether you’ve done enough writing, the same tired bullshit from which you were trying to escape in the first place!
Let’s face it, you’re not just going to meditate your way out of the problem. If you could, you would have already, and so would everyone else. We would all be enlightened. Maybe you need to go to an ashram or something, find a guru on top of a mountain in the Himalayas. LOL, you’re not gonna do that! You are way too attached to your comforts and daily routines, no matter how dull and unsatisfying they ultimately are.
There’s nowhere to run, nowhere to hide, no one to see, nothing to do. You are out of options. There is only one thing in your absolute control, and it’s where you direct your attention. And you have decided that no matter how bleak and pointless the alternatives the one thing about which you are resolute is you are taking the day off from writing.
-
 @ b8851a06:9b120ba1
2025-01-14 15:28:32
@ b8851a06:9b120ba1
2025-01-14 15:28:32It Begins with a Click
It starts with a click: “Do you agree to our terms and conditions?”\ You scroll, you click, you comply. A harmless act, right? But what if every click was a surrender? What if every "yes" was another link in the chain binding you to a life where freedom requires approval?
This is the age of permission. Every aspect of your life is mediated by gatekeepers. Governments demand forms, corporations demand clicks, and algorithms demand obedience. You’re free, of course, as long as you play by the rules. But who writes the rules? Who decides what’s allowed? Who owns your life?
Welcome to Digital Serfdom
We once imagined the internet as a digital frontier—a vast, open space where ideas could flow freely and innovation would know no bounds. But instead of creating a decentralized utopia, we built a new feudal system.
- Your data? Owned by the lords of Big Tech.
- Your money? Controlled by banks and bureaucrats who can freeze it on a whim.
- Your thoughts? Filtered by algorithms that reward conformity and punish dissent.
The modern internet is a land of serfs and lords, and guess who’s doing the farming? You. Every time you agree to the terms, accept the permissions, or let an algorithm decide for you, you till the fields of a system designed to control, not liberate.
They don’t call it control, of course. They call it “protection.” They say, “We’re keeping you safe,” as they build a cage so big you can’t see the bars.
Freedom in Chains
But let’s be honest: we’re not just victims of this system—we’re participants. We’ve traded freedom for convenience, sovereignty for security. It’s easier to click “I Agree” than to read the fine print. It’s easier to let someone else hold your money than to take responsibility for it yourself. It’s easier to live a life of quiet compliance than to risk the chaos of true independence.
We tell ourselves it’s no big deal. What’s one click? What’s one form? But the permissions pile up. The chains grow heavier. And one day, you wake up and realize you’re free to do exactly what the system allows—and nothing more.
The Great Unpermissioning
It doesn’t have to be this way. You don’t need their approval. You don’t need their systems. You don’t need their permission.
The Great Unpermissioning is not a movement—it’s a mindset. It’s the refusal to accept a life mediated by gatekeepers. It’s the quiet rebellion of saying, “No.” It’s the realization that the freedom you seek won’t be granted—it must be reclaimed.
- Stop asking. Permission is their tool. Refusal is your weapon.
- Start building. Embrace tools that decentralize power: Bitcoin, encryption, open-source software, decentralized communication. Build systems they can’t control.
- Stand firm. They’ll tell you it’s dangerous. They’ll call you a radical. But remember: the most dangerous thing you can do is comply.
The path won’t be easy. Freedom never is. But it will be worth it.
The New Frontier
The age of permission has turned us into digital serfs, but there’s a new frontier on the horizon. It’s a world where you control your money, your data, your decisions. It’s a world of encryption, anonymity, and sovereignty. It’s a world built not on permission but on principles.
This world won’t be given to you. You have to build it. You have to fight for it. And it starts with one simple act: refusing to comply.
A Final Word
They promised us safety, but what they delivered was submission. The age of permission has enslaved us to the mundane, the monitored, and the mediocre. The Great Unpermissioning isn’t about tearing down the old world—it’s about walking away from it.
You don’t need to wait for their approval. You don’t need to ask for their permission. The freedom you’re looking for is already yours. Permission is their power—refusal is yours.
-
 @ 9a4acdeb:1489913b
2025-02-16 18:26:58
@ 9a4acdeb:1489913b
2025-02-16 18:26:58Chef's notes
Original recipe, a favorite of family and friends, and the easiest and fastest prep time meal I make. Like all really good pork recipes, it does take time in the cooker, but it's set-and-forget and requires no attention between starting and serving.
Using fresh herbs and peppers does enhance the meal (especially fresh cilantro if it doesn't taste like soap to you), but this is optional, and it is excellent with dry ingredients.
Excluding the beans and/or tomato makes this meal extra-low carb for those carnivores amongst us, or those sensitive to beans. Frying the shredded cheese in a slick pan is a good way to
It will take up to 15min to come up to pressure, so it may be helpful to pay attention to it to be sure it pressurizes until you become familiar with how this meal acts in your particular pressure cooker. The Instant Pot pressure cookers make this easy.
Details
- ⏲️ Prep time: 20min
- 🍳 Cook time: 2hrs
- 🍽️ Servings: 6
Ingredients
- 4lbs Pork loin
- 1-2 Yellow onion, roughly chopped
- 3-5 Jalapeños or 1x 4oz canned
- 6-8 Green chilis or 1x 4oz canned
- 2oz canned sliced Black olives (may use half a 4oz can)
- 2-3tsp minced garlic, or 1-2 tsp garlic powder
- A small bunch of cilantro, chopped, or 1-2 tsb dried cilantro (optional)
- 1tbsp Oregano, chopped fresh or dried
- 2-3tsb Chili powder; Ancho, Chipotle, or a blend of the two is best
- 2-3tsb ground Cumin
- 3-4tsp salt
- 2-tsp black pepper
- 1 large or 4oz canned tomato (optional)
- Mexican mix shredded cheese (topping)
- 4oz Black beans (optional)
- Tortillas (optional)
- Avocado (optional toping)
- 6 Limes and/or 3oz lime juice
Directions
- Mix dry seasonings
- Chop and mix fresh herbs and veggies, canned or otherwise
- Add chopped onion to bottom of pressure cooker
- Add pork loin atop the onion; chopping into steaks may make the texture better
- Add veggies to the top, shaking to settle into the pressure cooker
- Add lime juice
- Start on high pressure for 2hrs.
- (Optional) Drain the broth into a saucepan, cook down, and add back into the mix to make it extra flavorful. Otherwise, can be served as a soup or poured over rice.
- Serve with cheese as a topping, over rice, in a tortilla as tacos or burritos, or in a number of other fashions you may fancy. Those who prefer a little more lime may squeeze fresh or splash some more on their meal.
- (Optional) For presentation, garnish with cilantro and lime slices, maybe a dollop of shredded cheese, sour cream, or cream cheese.
-
 @ 8be6bafe:b50da031
2025-02-05 17:00:40
@ 8be6bafe:b50da031
2025-02-05 17:00:40Botev Plovdiv FC is proud to present the Bitcoin Salary Calculator tool, as the foundational tool to showcase athletes the financial power of Bitcoin.
We built the Salary Calculator to help anyone follow in the financial footsteps of prominent athletes such as Kieran Gibbs, Russell Okung, Saquon Barkley, and Renato Moicano, who have significantly increased their savings tank thanks to Bitcoin.
The Bitcoin Salary Calculator allows any person to choose how much of their monthly salary they are comfortable saving in Bitcoin. Instantly, users can backtrack and see how their Bitcoin savings would have performed using the once-in-a-species opportunity which Bitcoin brings.
https://video.nostr.build/a9f2f693f6b5ee75097941e7a30bfc722225918a896b29a73e13e7581dfed77c.mp4
Athletes need Bitcoin more than anyone else
Unlike most people, athletes’ careers and earning years are limited. This has driven the likes of Odell Beckham Jr. and Alex Crognale to also start saving a part of their income in Bitcoin with a long-term outlook as they prepare for retirement.
“The reason why announced 50% of my salary in Bitcoin is because I feel one the noblest things you can do is to get people to understand Bitcoin.” Kieran Gibbs, founder ONE FC, ex Arsenal, ex Inter Miami, ex West Bromich Albion.
“I am trusting Bitcoin for my life after football. Every time my club paid me, I bought Bitcoin.” Alex Crognale, San Antonio FC player.
https://x.com/TFTC21/status/1883228348379533469
“At Botev Plovdiv FC, we believe not only in fostering sporting talent, but also helping them the the most of their careers so they excel in life after retiring from sports. It is with this mission in mind that the club is launching the Bitcoin Football Cup hub, striving to accelerate mass Bitcoin education via sports and athletes - the influencers and role models for billions of people.” shared Botev’s Bitcoin Director George Manolov.
https://x.com/obj/status/1856744340795662432
The Bitcoin Football Cup aims for young prospects to be able to learn key financial lessons from seasoned veterans across all sports. Our Bitcoin Salary Calculator is only the first step toward that goal.
We encourage anyone to hear these stories straight from the current roster of Bitcoin athletes -for whom -in many cases- Bitcoin has allowed them to outperform the wealth it took decades to earn on the field.
Follow us on the Bitcoin Cup’s social media channels to learn more and hear the latest stories of how Bitcoin is shaking up the world of sports:
- Twitter: https://x.com/Bitcoin_Cup/
- Instagram: https://www.instagram.com/BitcoinCup/
- TikTok: https://www.tiktok.com/@BitcoinCup/
- YouTube: https://www.youtube.com/@BitcoinCup/
-
 @ 5a261a61:2ebd4480
2025-02-18 18:22:19
@ 5a261a61:2ebd4480
2025-02-18 18:22:19The yellow light won the battle against the feeble excuse for curtains and crept into the room. It moved cautiously as if was afraid where to step. A common trait to all who found their way into the back room of the Lost Cases Detective Agency. The current owner had inherited both the premises and the name from his predecessor, and whenever someone questioned the name, he would announce half-irritably that changing it was simply too expensive to afford. The noodle vendor from the floor below would never miss the chance to add that people who end up at his place didn't choose it for the name anyway. The truth (which he was willing to admit only to the creaking fan that scared away mice rather than actually serving its function) was that he liked the name. Like attracts like. A lost soul for lost cases. The darkness was finally driven even from the eyelids of the figure on the bed, who woke up with a dissatisfied grunt.
A few steps to the sink hidden behind a screen. The shadows cast by the street light might have seemed depressive to some, mainly because they weren't accompanied by the warming feeling of sunlight, blocked by the high skyscrapers embracing the lower houses of the former middle class. Tom smiled resignedly at this thought. It perfectly captured how everything in this city merged into one big tangle, which looks beautiful until you have to untangle it. The yellow light came from a neon sign across the street advertising "The Beach." One of many places in this City where one could hide in a drop of alcohol and the embrace of a beautiful woman. Though it was necessary to maintain that order... the companions didn't exactly recruit from the best of the best looking local beauties.
Tom turned the tap and waited until the water, after grunting, gargling, and several splutters, settled and began flowing somewhat predictably. Tom didn't mind the wait. In his line of work, patience was cheaper than bullets. And it was nice to have time when he could do nothing but wait. He examined himself in the mirror. The shadows did him favors, adding years he hadn't earned. As young as he was, he needed all the help he could get - clients wanted their private dick weathered, not fresh out of the wrapper. He had the look down pat: world-weary veteran who knew all the angles. Truth was, he couldn't even figure out the angle of his own life, but that was a case file he kept closed. The water spluttered one last time. "Good morning, dickhead," he greeted himself with unwavering conviction that today would be better than yesterday. While most people were heading to dinner, putting kids to bed, or hurrying to visit their lovers at this hour, he was waking up. So for him, it was morning. For him and a myriad of other existences who, by choice or necessity, lived more at night than during the day. Finally, he trimmed his beard to short, neat stubble - enough to look serious, but with a touch of toughness suggesting he wasn't afraid to get his hands dirty. "Perfect," he muttered to himself, "I look like a man who knows what he's doing." Maybe that illusion will convince me one day, he thought as he turned off the light in the small bathroom. With a final look in the mirror, he adjusted his shirt collar. He was ready to face the city's challenges. Whatever awaited him today, at least he'd look prepared for it.
From the hook by the door, he grabbed a ring with an identification tag and some loose change. He ran down a flight of creaking stairs and headed past empty bar stools toward the exit. The disadvantage of living above a restaurant. Though the major advantage is the high of the rent. Or rather, its lowness. Jiro, the owner of the small bistro and, coincidentally, a decent exterminator, looked at him through a dense veil of greasy vapors, nodded, and continued stirring the noodles.
Where to next? - say hi - get some food - just run outside
This is kind of an experiment with converting my WIP interactive fiction project to the nostr longnote format and letting readers decide. Originally, this story leans quite heavily toward FLR/femdom/mindcontrol/noir/steampunk/fantasy and hopefully a little mystery detective story, but let's see where (and if) it will lead from here. Also, it's mostly translated from my native language, so sorry if some wording seems stiff.
-
 @ ee11a5df:b76c4e49
2024-12-24 18:49:05
@ ee11a5df:b76c4e49
2024-12-24 18:49:05China
I might be wrong, but this is how I see it
This is a post within a series I am going to call "I might be wrong, but this is how I see it"
I have repeatedly found that my understanding of China is quite different from that of many libertarian-minded Americans. And so I make this post to explain how I see it. Maybe you will learn something. Maybe I will learn something.
It seems to me that many American's see America as a shining beacon of freedom with a few small problems, and China is an evil communist country spreading communism everywhere. From my perspective, America was a shining beacon of freedom that has fallen to being typical in most ways, and which is now acting as a falling empire, and China was communist for about a decade, but turned and ran away from that as fast as they could (while not admitting it) and the result is that the US and China are not much different anymore when it comes to free markets. Except they are very different in some other respects.
China has a big problem
China has a big problem. But it is not the communism problem that most Westerners diagnose.
I argue that China is no longer communist, it is only communist in name. And that while it is not a beacon of free market principles, it is nearly as free market now as Western nations like Germany and New Zealand are (being somewhat socialist themselves).
No, China's real problem is authoritarian one-party rule. And that core problem causes all of the other problems, including its human rights abuses.
Communism and Socialism
Communism and Socialism are bad ideas. I don't want to argue it right here, but most readers will already understand this. The last thing I intend to do with this post is to bolster or defend those bad ideas. If you dear reader hold a candle for socialism, let me know and I can help you extinguish it with a future "I might be wrong, but this is how I see it" installment.
Communism is the idea of structuring a society around common ownership of the means of production, distribution, and exchange, and the idea of allocating goods and services based on need. It eliminates the concept of private property, of social classes, ultimately of money and finally of the state itself.
Back under Mao in 1958-1962 (The Great Leap Forward), China tried this (in part). Some 50+ million people died. It was an abject failure.
But due to China's real problem (authoritarianism, even worship of their leaders), the leading classes never admitted this. And even today they continue to use the word "Communist" for things that aren't communist at all, as a way to save face, and also in opposition to the United States of America and Europe.
Authorities are not eager to admit their faults. But this is not just a Chinese fault, it is a fault in human nature that affects all countries. The USA still refuses to admit they assassinated their own president JFK. They do not admit they bombed the Nord Stream pipeline.
China defines "socialism with Chinese characteristics" to mean "the leadership of the Communist Party of China". So they still keep the words socialism and communism, but they long ago dropped the meanings of those words. I'm not sure if this is a political ploy against us in the West or not.
China's Marketplace Today
Today China exhibits very few of the properties of communism.
They have some common ownership and state enterprises, but not much differently than Western countries (New Zealand owns Air New Zealand and Kiwibank and Kiwirail, etc). And there are private enterprises all over China. They compete and some succeed and some fail. You might hear about a real-estate bank collapsing. China has private property. They have mostly free markets. They have money, and the most definitely have social classes and a very strong state.
None of that is inline with what communist thinkers want. Communist thinkers in China moan that China has turned away from communism.
Deng Xiaoping who succeeded Mao and attempted to correct the massive mistake, did much when he said "to get rich is glorious."
China achieved staggering rates of economic growth. 10% annually on average since 1977. Chinese economic reform started in 1979 and has continued through successive administrations (Deng, Jiang, Hu and now Xi).
China is now the world's largest economy (by GDP in PPP terms) since 2016.
I was first made aware of China's economic growth by Jim Rogers, an American commodities expert who travelled through China (and the rest of the world from 1990-1992) and in 2007 moved to Singapore where he ensured his daughters learned to speak Mandarin, because Jim knew where the economic growth was going to happen. Jim always spoke positively of China's economic prospects, and his view was so different from the "China is a nasty communist place" view that I had grown up with that my mind opened.
How can anybody believe they are still a communist country? In what world does it make sense that communism can produce such a massively booming economy? It doesn't make sense because it is simply wrong.
What does happen is that the CPC interferes. It lets the market do what markets do, but it interferes where it thinks oversight and regulation would produce a better result.
Western nations interfere with their markets too. They have oversight and regulation. In fact some of China's planned reforms had to be put on hold by Xi due to Donald Trump's trade war with China. That's right, they were trying to be even more free market than America, but America's protectionism prodded Xi to keep control so he could fight back efficiently.
Government oversight and regulation IMHO is mostly bad because it gets out of control, and there are no market forces to correct this. This gets even more extreme in a one-party system, so I can judge that China's oversight and regulation problems are very likely worse than those in Western nations (but I have no first hand experience or evidence).
Why do you keep saying CPC?
The Communist Party of China (CPC) is the ruling party in China. That is their official name. To call them the CCP is to concede to the idea that the British and Americans get to name everybody. I'm not sure who is right, since CPC or CCP is their "English" name (in Chinese it is 中国共产党 and Westernized it is Zhōngguó Gòngchǎndǎng). Nonetheless, I'll call them CPC because that is their wish.
Social Credit System
China moved from a planned economy to a market economy in stages. They didn't want any more sudden changes (can you blame them?). In the process, many institutions that have existed in the West for a long time didn't exist in China and they had to arise somehow. IMHO market forces would have brought these about in the private sector, but the one-party CP of China instead decided to create these.
One of those institutions was a credit score system. In the West we have TransUnion and Equifax that maintain credit ratings on people, and we have S&P, Moody's and Fitch that maintain credit ratings on companies. The domain of these ratings is their financial credit-worthiness.
So the People's Bank of China developed a credit information database for it's own needs. The government picked up on the idea and started moving towards a National Credit Management System. In 2004 it became an official goal to establish a credit system compatible with a modern market system. By 2006 banks were required to report on consumer creditworthiness.
But unchecked one-party governmental power will often take a good idea (credit worthiness data shared among private parties) and systematize it and apply it top-down, creating a solution and a new problem at the same time.
Nonetheless, originally it was about credit worthiness and also criminal convictions. That is no big scary thing that some right-wing American commentators will lead you to believe. In the US for example criminal records are public, so China's Social Credit System started out being no more over-reaching in scope than what Americans have lived under their entire lives, its only fault (a severe one) being centrally planned. And that remained the case up until about 2016 (in my estimation).
But of course there is always scope creep. As it exists today, I have reason to believe that CPC officials and even A.I. use judgement calls to score someone on how moral that person has been! Of course that is not a good idea, and IMHO the problem stems from one-party rule, and authoritarian administration of ideas that should instead be handled by the private sector.
Environmental, Social, and Governance
ESG is a system that came out of a couple basic ideas. The first is that many two-party transactions actually have externalities. They don't just affect the two parties, they also affect everybody else. When you fly in an airplane, you increase the CO2 in the atmosphere that everybody has to pay for (eventually). You may dispute that example, but that is no doubt one of the motivations of ESG.
But of course the recognition of this basic issue didn't lead all people towards market solutions (well it did, but those have been mostly messed up by others), but instead led many people towards ESG, which is a social credit scoring system which applies scores based on environmental and social side-effects of market transactions.
This is not at all the same as China's social credit system, which I described above. I hope you can see the difference.
In fact, China imported ESG from the West. Chinese companies, of their free will, in an attempt to court Western capital, achieve ESG goals for those Western investors. They have been playing this ESG game for 20 years just like the entire world has, because the West has imposed this faux-morality upon them. It isn't something China exported to us, it is something we exported to them.
I think China has avoided Woke-ism
My understanding of Chinese people, based on what I've heard many Chinese people say, is that China isn't affected by the Western woke-ism epidemic. They deride Western white woke people with the term "Baizuo". They have never sent an incompetent break dancer to the Olympics because of wok-ism. Competence is highly respected as is the competition to be the most competent, which (when augmented by a one-child policy which is no longer) has produced child prodigies like no other country has.
What about predatory loans of the Belt and Road initiative?
Predatory is an odd name for loans to people in need. The World Bank makes loans to people in need. China does too. China stands in opposition to Western Empire, and in that regard they produce their own alternative BRICS institutions. This is one of them.
There is AFAIK nothing more predatory about them. It is just that in some cases the borrowers have trouble paying them back and they get foreclosed upon. I don't think this is worthy of much discussion, except that the term "predatory" seems to me to be a propaganda device.
What about foreign influence from China?
China wants to influence the world, especially its own trading partners and potential trading partners. Doing that above board is fine by me.
But some of it is undoubtedly covert. Sometimes Chinese-born people run for public office in Western countries. In New Zealand we stood down some when it became clear they were being influenced too much by the CPC while being charged with representing their local town (dual loyalty issues). If only the USA would do the same thing to their dually-loyal politicians.
And all large nations run influence operations. The USA has the CIA, for example, and claims this "soft power" is actually the better alternative to what would otherwise be military intervention (but IMHO shouldn't be either). I'm not defending such operations (I despise them), I'm just explaining how China's position of exerting influence is not only no big deal and totally expected, it pales in comparison to the United States' influence operations which often become military excursions (something China rarely ever does).
What about the Great Firewall?
Yeah, that sucks. Again, single-party authoritarian control gone to extremes.
What about Human Rights Abuses? What about the Uyghur Genocide?
I don't like them. To the extent they are occurring (and I lean towards the belief that they are occurring), I condemn them.
China has anti-terrorism and anti-extremism policies that go too far. They end up oppressing and/or criminalizing cultures that aren't Chinese enough. But especially, China punishes dissent. Disagreement with the CPC is the high crime. It is the one-party rule that causes this problem. Anybody who speaks out against the CPC or goes against the state in any way is harshly punished. This happens to Uyghurs, to Falun Gong, to Tibetans, and to any religion that is seen as subversive.
Amnesty International and the UN OHCHR have documented issues around the Xinjiang Uyghur autonomous region, Tibet, LGBT rights, death penalty, workers rights, and the Hong Kong special administrative region. I am not about to pretend I know better than they do, but to some extent they go too far.
Amnesty International says this about the USA: Discrimination and violence against LGBTI people were widespread and anti-LGBTI legislation increased. Bills were introduced to address reparations regarding slavery and its legacies. Multiple states implemented total bans on abortion or severely limited access to it. Gender-based violence disproportionately affected Indigenous women. Access to the USA for asylum seekers and migrants was still fraught with obstacles, but some nationalities continued to enjoy Temporary Protected Status. Moves were made to restrict the freedom to protest in a number of states. Black people were disproportionately affected by the use of lethal force by police. No progress was made in the abolition of the death penalty, apart from in Washington. Arbitrary and indefinite detention in the US naval base Guantánamo Bay, Cuba, continued. Despite extensive gun violence, no further firearm reform policies were considered, but President Biden did announce the creation of the White House Office of Gun Violence Prevention. The USA continued to use lethal force in countries around the world. Black people, other racialized groups and low-income people bore the brunt of the health impacts of the petrochemical industry, and the use of fossil fuels continued unabated.
Amnesty international didn't even point out that the US government quashes free speech via pressure on social media corporations (because Amnesty International is far too lefty).
So who is worse, China or the US? I'm not going to make that judgement call, but suffice it to say that in my mind, China is not obviously worse.
China violates freedom of expression, association, and assembly of all people. This is bad, and a consequence mainly of one-party rule (again, what I think is the root cause of most of their ills). They arrest, detain, potentially kill anybody who publicly disagrees openly with their government. Clearly this is an excess of authoritarianism, a cancer that is very advanced in China.
As to organ harvesting of Uyghur Muslims, I think this is a myth.
China has dealt harshly with Muslim extremism. They don't offer freedom of religion to ISIS. And Amnesty International complains about that. But practically speaking you probably shouldn't respect the extremist religion of people who want to force everybody into a global caliphate through threat of violence. As you are well aware, some extremist Muslims (<1% of Islam) believe in using violence to bring about a global caliphate. Those extremists pop up in every country and are usually dealt with harshly. China has had to deal with them too.
I have watched two different Western YouTubers travel to Xinjiang province trying to find the oppressed Uyghurs and interview them. They can't find them. What they find instead are Uyghur Muslims doing their prayers five times a day at the local mosque. And also stories that the CPC pitched in some money to help them renovate the mosque. Maybe they were afraid it was a CPC trap and so they wouldn't speak freely. Amnesty International and the UN OHCHR say more than a million are "arbitrarily detained" and I'm not going to argue otherwise. But I'd be more convinced if there were a stream of pictures and news like there is out of Gaza, and it is suspicious that there isn't.
Conclusion
China is more like a Western nation that Westerners realize. Economically, militarily, socially. It still has a very serious obstacle to overcome: one-party rule. I don't think the one-party is going to voluntarily give up power. So most probably at some point in the future there will be a revolution. But in my opinion it won't happen anytime soon. For the most part Chinese people are living high on the hog, getting rich, enjoying the good life, in positive spirits about life, and are getting along with their government quite well at present.
-
 @ 97c70a44:ad98e322
2025-02-03 22:25:35
@ 97c70a44:ad98e322
2025-02-03 22:25:35Last week, in a bid to understand the LLM hype, I decided to write a trivial nostr-related program in rust via a combination of codebuff (yes, that is a referral link, pls click), aider, and goose.
The result of the experiment was inconclusive, but as a side effect it produced a great case study in converting a NINO into a Real Nostr App.
Introducing Roz
Roz, a friendly notary for nostr events.
To use it, simply publish an event to
relay.damus.ioornos.lol, and roz will make note of it. To find out when roz first saw a given event, just ask:curl https://roz.coracle.social/notary/cb429632ae22557d677a11149b2d0ccd72a1cf66ac55da30e3534ed1a492765dThis will return a JSON payload with a
seenkey indicating when roz first saw the event. How (and whether) you use this is up to you!De-NINO-fying roz
Roz is just a proof of concept, so don't rely on it being there forever. And anyway, roz is a NINO, since it provides value to nostr (potentially), but doesn't really do things in a nostr-native way. It also hard-codes its relays, and certainly doesn't use the outbox model or sign events. But that's ok, it's a proof of concept.
A much better way to do this would be to modify roz to properly leverage nostr's capabilities, namely:
- Use nostr-native data formats (i.e., draft a new kind)
- Use relays instead of proprietary servers for data storage
- Leverage nostr identities and signatures to decouple trust from storage, and allow trusted attestations to be discovered
Luckily, this is not hard at all. In fact, I've gone ahead and drafted a PR to the NIPs repo that adds timestamp annotations to NIP 03, as an alternative to OpenTimestamps. The trade-off is that while user attestations are far less reliable than OTS proofs, they're much easier to verify, and can reach a pretty high level of reliability by combining multiple attestation sources with other forms of reputation.
In other words, instead of going nuclear and embedding your attestations into The Time Chain, you can simply ask 5-10 relays or people you trust for their attestations for a given event.
This PR isn't terribly important on its own, but it does remove one small barrier between us and trusted key rotation events (or other types of event that require establishing a verifiable chain of causality).
-
 @ b8851a06:9b120ba1
2024-12-16 16:38:53
@ b8851a06:9b120ba1
2024-12-16 16:38:53Brett Scott’s recent metaphor of Bitcoin as a wrestling gimmick, reliant on hype and dollar-dependence, reduces a groundbreaking monetary innovation to shallow theatrics. Let’s address his key missteps with hard facts.
1. Bitcoin Isn’t an Asset in the System—It’s the System
Scott claims Bitcoin competes with stocks, bonds, and gold in a financial "wrestling ring." This misrepresents Bitcoin’s purpose: it’s not an investment vehicle but a decentralized monetary network. Unlike assets, Bitcoin enables permissionless global value transfer, censorship resistance, and self-sovereign wealth storage—capabilities fiat currencies cannot match.
Fact: Bitcoin processes over $8 billion in daily transactions, settling more value annually than PayPal and Venmo combined. It isn’t competing with assets but offering an alternative to the monetary system itself.
2. Volatility Is Growth, Not Failure
Scott critiques Bitcoin’s price volatility as evidence of its unsuitability as "money." However, volatility is a natural stage in the adoption of transformative technology. Bitcoin is scaling from niche use to global recognition. Its growing liquidity and adoption already make it more stable than fiat in inflationary economies.
Fact: Bitcoin’s annualized volatility has decreased by 53% since 2013 and continues to stabilize as adoption rises. It’s the best-performing asset of the last decade, with an average annual ROI of 147%—far outpacing stocks, gold, and real estate. As of February 2024, Bitcoin's volatility was lower than roughly 900 stocks in the S and P 1500 and 190 stocks in the S and P 500. It continues to stabilize as adoption rises, making it an increasingly attractive store of value.
3. Bitcoin’s Utility Extends Beyond Countertrade
Scott diminishes Bitcoin to a "countertrade token," reliant on its dollar price. This ignores Bitcoin’s primary functions:
- Medium of exchange: Used in remittances, cross-border payments, and for the unbanked in Africa today (e.g., Ghana, Nigeria, Kenya).
- Store of value: A hedge against inflation and failing fiat systems (e.g., Argentina, Lebanon, Turkey).
- Decentralized reserve asset: Held by over 1,500 public and private institutions, including Tesla, MicroStrategy, and nations like El Salvador.
Fact: Lightning Network adoption has grown 1,500% in capacity since 2021, enabling microtransactions and reducing fees—making Bitcoin increasingly viable for everyday use. As of December 2024, Sub-Saharan Africa accounts for 2.7% of global cryptocurrency transaction volume, with Nigeria ranking second worldwide in crypto adoption. This demonstrates Bitcoin's real-world utility beyond mere speculation.
4. Bitcoin Isn’t Controlled by the Dollar
Scott suggests Bitcoin strengthens the dollar system rather than challenging it. In truth, Bitcoin exists outside the control of any nation-state. It offers people in authoritarian regimes and hyperinflationary economies a lifeline when their local currencies fail.
Fact: Over 70% of Bitcoin transactions occur outside the U.S., with adoption highest in countries like Nigeria, India, Venezuela, China, the USA and Ukraine—where the dollar isn’t dominant but government overreach and fiat collapse are. This global distribution shows Bitcoin's independence from dollar dominance.
5. Hype vs. Adoption
Scott mocks Bitcoin’s evangelists but fails to acknowledge its real-world traction. Bitcoin adoption isn’t driven by hype but by trustless, verifiable technology solving real-world problems. People don’t buy Bitcoin for "kayfabe"; they buy it for what it does.
Fact: Bitcoin wallets reached 500 million globally in 2023. El Salvador’s Chivo wallet onboarded 4 million users (60% of the population) within a year—far from a gimmick in action. As of December 2024, El Salvador's Bitcoin portfolio has crossed $632 million in value, with an unrealized profit of $362 million, demonstrating tangible benefits beyond hype.
6. The Dollar’s Coercive Monopoly vs. Bitcoin’s Freedom
Scott defends fiat money as more than "just numbers," backed by state power. He’s correct: fiat relies on coercion, legal mandates, and inflationary extraction. Bitcoin, by contrast, derives value from transparent scarcity (capped at 21 million coins) and decentralized consensus, not military enforcement or political whims.
Fact: Bitcoin’s inflation rate is just 1.8%—lower than gold or the U.S. dollar—and will approach 0% by 2140. No fiat currency can match this predictability. As of December 2024, Bitcoin processes an average of 441,944 transactions per day, showcasing its growing role as a global, permissionless monetary system free from centralized control.
Conclusion: The Revolution Is Real
Scott’s "wrestling gimmick" analogy trivializes Bitcoin’s purpose and progress. Bitcoin isn’t just a speculative asset—it’s the first truly decentralized, apolitical form of money. Whether as a hedge against inflation, a tool for financial inclusion, or a global settlement network, Bitcoin is transforming how we think about money.
Dismiss it as a gimmick at your peril. The world doesn’t need another asset—it needs Bitcoin.
"If you don't believe me or don't get it, I don't have time to try to convince you, sorry." Once Satoshi said.
There is no second best.
-
 @ 044da344:073a8a0e
2025-02-17 08:50:50
@ 044da344:073a8a0e
2025-02-17 08:50:50Ich nehme alles zurück, was ich je gegen die Filmförderung gesagt habe. Eine halbe Milliarde Euro im Jahr? Na und. Die heile deutsche Welt im Kino? Der Schuss Erziehung? Das Ausblenden der kleinen Leute mit ihren großen Problemen? Mir ab sofort egal. Sollen Produzenten, Regisseure, Autoren ruhig nach immer mehr rufen. Gebt ihnen aus den leeren Steuertöpfen, am besten mit vollen Händen. Diese Woche habe ich gelernt: Sie drehen im Zweifel nur für mich.
Das Kino war leer, okay. Das ist aber nicht mein Punkt. Dieses Kino ist so gut wie immer leer. Meist sitzen meine Frau und ich allein in einem der neun großen Säle und sind manchmal sogar im ganzen Haus die einzigen neben den beiden an der Kasse. Was auf der Leinwand läuft, ist oft frustrierend. Siehe oben. Ich mag aber keinen Verriss schreiben. Sonst würde es an dieser Stelle jeden Samstag um das Kino gehen. Diese Woche waren wir hin und weg. Unser Leben. Unsere Stars. Unsere Sprache. Und das alles weit weg von der DDR und von Ostdeutschland, im Niemandsland zwischen Regensburg und Pilsen.

Ich weiß gar nicht, wo ich anfangen soll. Fidel Castro in Warnemünde. Originalbilder, direkt aus meinem Kindergartengedächtnis. Dann Havanna und die Strände mit diesem Wasser, das einem erlaubt, die eigenen Füße zu sehen. Es gibt viele Kuba-Filme, sicher. Aber wo läuft alles auf ein Revolutions-Quiz hinaus, bei dem sich Ost und West gegenübersitzen, die absurdesten Details aus dem Innersten der Maschine abspulen können und dafür in einem Touristenhotel auch noch bejubelt werden? In welchem Drehbuch kann eine Heldin einfach „blauer Würger“ sagen und wie selbstverständlich voraussetzen, dass jeder weiß, um was es geht? Auflösung: Kristall-Wodka. Das Etikett war blau. Die Flasche kostete eigentlich 16 Mark, aber ich weiß wie gestern, dass ich einmal gleich zwei für 55 gekauft habe, als im Wohnheim der Stoff ausging und ich in den Fresswürfel geschickt wurde, Kosename für die hässlichen Häuser, die es in vielen Neubausiedlungen gab, um einen Anlaufpunkt zu haben für Tanz, Kultur, Saufgelage. Der Abend ist in unser Familiengedächtnis eingegangen, weil mich die Studentin, die später meine Frau wurde, vor die Tür gesetzt hat.
Bei den „Kundschaftern des Friedens“ geht es auch um die Liebe, natürlich. Wir sind im Kino. Es geht aber auch um das Altern und um Erinnerungen, die nicht mehr viele teilen. Wir waren in den 2010ern dreimal in Fidels Reich. Autofahren auf Kuba war der Renner auf einem unserer frühen Blogs, deutlich häufiger geklickt als der Artikel über das Revolutionsmuseum oder der Text, den dann die Freie Presse in Chemnitz übernommen und gedruckt hat, weil der Chefredakteur wusste, dass Kuba für seine Leser immer ein Thema ist. Ein Sehnsuchtsort der DDR-Menschen, erreichbar und zugleich unerreichbar fern, jedenfalls für die allermeisten.

Robert Thalheim erklärt das alles in diesem zweiten „Kundschafter“-Film nicht. Seine Helden reden wie alte Ostdeutsche, wenn weder Wessis zuhören noch die Kinder. Wie meine Frau und ich zu Hause oder in diesem leeren Kinosaal. Über die Schauspieler muss ich nicht viel schreiben. Henry Hübchen, Katharina Thalbach, Corinna Harfouch, Thomas Thieme, Winfried Glatzeder: Das sind unsere Leute. Lebensbegleiter, wenn man so will. So viele sind nicht übriggeblieben. Ich habe ein Buch geschrieben, um zu ergründen, warum Medienmenschen aus dem Osten anders sind und mir vielleicht auch deshalb oft näher. Soll ich den Film empfehlen? Ich weiß nicht recht. Bilder, Musik, sogar der Ton (in deutschen Filmen sonst oft unerträglich): Hier passt schon alles. Vielleicht sage ich es so: Wer den Schlussgag ohne Google versteht, sollte ins Kino gehen. Thomas Thieme sitzt dort in einem Motorboot und lockt ein paar Amis auf das Wilhelm-Pieck-Atoll.
Freie Akademie für Medien & Journalismus
Fotos: Freie Akademie für Medien & Journalismus
-
 @ 1859da43:4f1013a4
2025-02-18 17:07:28
@ 1859da43:4f1013a4
2025-02-18 17:07:28Die Frage kann einfach beantwortet werden: er will, dass ich zu ihm komme in die ewige Herrlichkeit.
Er richtet diesen Wunsch nicht allgemein an die Menscheit oder an ein Volk. Er richtet diesen Wunsch an jeden einzelnen Menschen, an dich und mich. Jesus will zu jedem Menschen in Beziehung stehen. Aus diesem Wunsch leitet sich die oberser Pflicht für jeden Menschen ab: Alles zu tun, um zu Jesus zu kommen; um seine Seele zu retten. Die Alternative ist die Hölle, welche ein endgültige und unwiderrufliche Trennung von Jesus Christus ist.
Ich wiederhole: die oberste und erste Pflicht des Christen ist es, seine Seele zu retten. Konkret heisst dies, dass wir nach der Lehre Jesus Christi leben sollen, indem man zum Beispiel die zehn Gebote hält und sich an der Moral von Jesus Chrisus orientiert.
Erst an zweiter Stelle kann ein Auftrag angenommen werden, dass andere Seelen ebenfalls gerettet werden sollen. Dies kann indirekt über die Verbreitung der frohen Botschaft erreicht werden. Aber wir sind als Einzelne nie direkt verantwortlich, von anderen Menschen die Seele zu retten. Dieser Verantwortung kann sich niemand entziehen. Man kann sie nicht delegieren. Man kann sie nicht von einem Anderen an sich reissen.
Diese Erkenntnis muss einen direkten Einfluss auf das Handeln haben.
-
 @ 37fe9853:bcd1b039
2025-01-11 15:04:40
@ 37fe9853:bcd1b039
2025-01-11 15:04:40yoyoaa
-
 @ b17fccdf:b7211155
2025-02-01 18:41:27
@ b17fccdf:b7211155
2025-02-01 18:41:27Next new resources about the MiniBolt guide have been released:
- 🆕 Roadmap: LINK
- 🆕 Dynamic Network map: LINK
- 🆕 Nostr community: LINK < ~ REMOVE the "[]" symbols from the URL (naddr...) to access
- 🆕 Linktr FOSS (UC) by Gzuuus: LINK
- 🆕 Donate webpage: 🚾 Clearnet LINK || 🧅 Onion LINK
- 🆕 Contact email: hello@minibolt.info
Enjoy it MiniBolter! 💙
-
 @ e3ba5e1a:5e433365
2025-02-13 06:16:49
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get this line:
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song Devil Went Down to Georgia that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” is, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people should be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is freedom. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are definitionally better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In Devil Went Down to Georgia, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
Libertas magnitudo est
-
 @ d360efec:14907b5f
2025-02-18 15:11:58
@ d360efec:14907b5f
2025-02-18 15:11:58ภาพรวม BTCUSDT (OKX):
Bitcoin (BTCUSDT) กำลังแสดงความผันผวนอย่างมาก โดยมีสัญญาณที่ขัดแย้งกันระหว่าง Timeframes ต่างๆ แนวโน้มระยะยาว (Day) ยังคงเป็นขาขึ้น แต่ระยะกลาง (4H) และระยะสั้น (15m) แสดงให้เห็นถึงแรงขายและการปรับฐานที่รุนแรง การวิเคราะห์นี้จะเน้นการระบุพื้นที่ที่ Smart Money อาจจะเข้าซื้อหรือขาย (Liquidity Pools) และประเมินความแข็งแกร่งของแนวโน้ม
วิเคราะห์ทีละ Timeframe:
(1) TF Day (รายวัน):
- แนวโน้ม: ขาขึ้น (Uptrend) แต่เริ่มอ่อนแรง
- SMC:
- Higher Highs (HH) และ Higher Lows (HL) เริ่มไม่ชัดเจน
- Break of Structure (BOS) ด้านบน แต่เริ่มมีการปรับฐาน
- Liquidity:
- มี Sellside Liquidity (SSL) อยู่ใต้ Lows ก่อนหน้า (บริเวณ 85,000 - 90,000)
- มี Buyside Liquidity (BSL) อยู่เหนือ High เดิม (109,998.9)
- ICT:
- ยังไม่เห็น Order Block หรือ FVG ที่ชัดเจนใน TF Day ณ ราคาปัจจุบัน
- EMA:
- ราคา หลุด EMA 50 (สีเหลือง) ลงมาแล้ว
- EMA 200 (สีขาว) เป็นแนวรับถัดไป
- Money Flow (LuxAlgo):
- แท่งสีแดงยาว แสดงถึงแรงขายที่เข้ามา
- Trend Strength (AlgoAlpha): ไม่มีในภาพ
- Volume Profile: Volume ค่อนข้างเบาบาง
- แท่งเทียน: แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย
- แนวรับ: EMA 200, บริเวณ 85,000 - 90,000 (SSL)
- แนวต้าน: EMA 50, High เดิม
- สรุป: แนวโน้มขาขึ้นเริ่มอ่อนแรง, ราคาหลุด EMA 50, Money Flow เป็นลบ, มี SSL ด้านล่าง
(2) TF4H (4 ชั่วโมง):
- แนวโน้ม: ขาลง (Downtrend) ระยะสั้น หลังจากราคาหลุด EMA 50
- SMC:
- Lower Highs (LH) และ Lower Lows (LL)
- Break of Structure (BOS) ด้านล่าง
- Liquidity:
- มี SSL อยู่ใต้ Lows ก่อนหน้า (บริเวณ 92,000)
- มี BSL อยู่เหนือ Highs ก่อนหน้า (บริเวณ 104,000 - 108,000)
- ICT:
- Order Block: ราคาลงมาใกล้ Order Block ขาขึ้น (บริเวณแท่งเทียนสีเขียวก่อนที่จะขึ้น)
- EMA:
- ราคาอยู่ใต้ EMA 50 และ EMA 200
- Money Flow (LuxAlgo):
- สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย
- Trend Strength (AlgoAlpha): ไม่มีในภาพ
- Volume Profile Volume ค่อนข้างเบาบาง
- แนวรับ: Order Block, บริเวณ 92,000 (SSL)
- แนวต้าน: EMA 50, EMA 200, บริเวณ Highs ก่อนหน้า
- สรุป: แนวโน้มขาลงระยะสั้น, ราคาลงมาใกล้ Order Block, Money Flow เป็นลบ
(3) TF15 (15 นาที):
- แนวโน้ม: ขาลง (Downtrend)
- SMC:
- Lower Highs (LH) และ Lower Lows (LL)
- Break of Structure (BOS) ด้านล่าง
- Liquidity:
- มี SSL อยู่ใต้ Lows ล่าสุด
- มี BSL อยู่เหนือ Highs ก่อนหน้า
- ICT:
- Order Block: ราคาลงมาใกล้ Oder Block
- EMA:
- EMA 50 และ EMA 200 เป็นแนวต้าน
- Money Flow (LuxAlgo):
- สีแดงเป็นส่วนใหญ่ แสดงถึงแรงขาย
- Trend Strength (AlgoAlpha):
- เป็นสีแดง แสดงถึงเเนวโน้มขาลง
- Volume Profile:
- Volume ค่อนข้างเบาบาง
- แนวรับ: บริเวณ Low ล่าสุด
- แนวต้าน: EMA 50, EMA 200, บริเวณ Highs ก่อนหน้า
- สรุป: แนวโน้มขาลง, แรงขายมีอิทธิพล, ใกล้แนวรับ
สรุปภาพรวมและกลยุทธ์ (BTCUSDT):
- แนวโน้มหลัก (Day): ขาขึ้น (อ่อนแรง)
- แนวโน้มรอง (4H): ขาลง (ระยะสั้น)
- แนวโน้มระยะสั้น (15m): ขาลง
- Liquidity:
- Day: SSL (85,000-90,000), BSL (เหนือ 109,998.9)
- 4H: SSL (92,000), BSL (104,000-108,000)
- 15m: SSL (ใต้ Lows), BSL (เหนือ Highs)
- Money Flow: Day เริ่มเป็นลบ, 4H เป็นลบ, 15m เป็นลบ
- Trend Strength 15 m : ขาลง
- กลยุทธ์:
- Wait & See (ดีที่สุด): รอความชัดเจน
- Short (เสี่ยง): ถ้าไม่สามารถ Breakout EMA/แนวต้านใน TF ใดๆ ได้
- ไม่แนะนำให้ Buy: จนกว่าจะมีสัญญาณกลับตัวที่ชัดเจน
คำแนะนำ:
- ความขัดแย้งของ Timeframes: ชัดเจน
- Money Flow: เป็นลบในทุก Timeframes
- ระวัง SSL: Smart Money อาจจะลากราคาลงไปกิน Stop Loss
- ถ้าไม่แน่ใจ อย่าเพิ่งเข้าเทรด
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-
 @ c3b2802b:4850599c
2025-02-17 08:45:15
@ c3b2802b:4850599c
2025-02-17 08:45:15Wenn in den 1960er Jahren in meiner Heimatstadt Leipzig die Lobeshymne der Staatspartei der DDR (SED) mit dem Refrain „DIE PARTEI, DIE PARTEI, DIE HAT IMMER RECHT“ ertönte, schauten wir kleinen Steppkes meiner Generation uns schmunzelnd in die Augen und tippten uns an die Stirn – überzeugt vom Widersinn dieser Worte.
Wir hatten schon von Galilei und Kolumbus gehört und wussten so, dass andersdenkende Menschen gelegentlich recht haben können gegenüber der Meute der gerade Herrschenden und deren Lakaien. Menschen können sich irren, auch wenn sie sich zu Gruppen oder Parteien zusammenschließen. Und selbst wenn diese Gruppen sehr groß sind, können sie irren. Von Menschenmassen, die den totalen Krieg wollten und ihn auch bekamen, hatten wir auch schon gehört. Von unseren Eltern, die in diesem Krieg aufgewachsen sind.
Und bereits als Kinder wussten wir, dass viele Genossen der SED Mitläufer waren, welche sich als Lakaien der gerade herrschenden Klasse Vorteile für ihr Leben in der Mangelwirtschaft der DDR versprachen. Das wussten wir aus Gesprächen mit den Älteren in unseren Familien, für die diese Verlogenheit ein existentiell bedeutsames Alltagsthema war. Genosse der SED zu sein, bedeutete bessere Berufs- Arbeitsplatz- und Karrierechancen zu haben, sogar nach Westeuropa durften einige von denen fahren, was dem Rest der Ostdeutschen strikt verwehrt war.
Wer das Lied der Herrschenden nicht mitsang, war benachteiligt. Das war eine ostdeutsche Binsenweisheit. Wer es gar wagte, offen Kritik zu üben, musste mit Verfolgung, Ausweisung, Haft oder Peinigungen in Stasi-Gefängnissen rechnen. Das fühlte sich nicht gut an...
Wie die DDR Geschichte 1989 endete, ist bekannt. Das Grundgesetz der BRD, das von nun an auch für uns galt, machte Hoffnung mit seinem Artikel 5: „Jeder hat das Recht, seine Meinung in Wort, Schrift und Bild frei zu äußern und zu verbreiten und sich aus allgemein zugänglichen Quellen ungehindert zu unterrichten. Die Pressefreiheit und die Freiheit der Berichterstattung durch Rundfunk und Film werden gewährleistet. Eine Zensur findet nicht statt.“
Heute steuern allerdings einige deutsche Parteien einen ähnlichen Kurs wie die Staatspartei der DDR. Nicht mehr so platt wie die SED. Man sagt nicht einfach: Wir sind die, die immer recht haben. Nein, so deutlich wird man nicht. Doch was man aktuell in den Wahlprogrammen mehrerer etablierter Parteien im Bundestag nachlesen kann (s.u.), läuft auf das Gleiche hinaus. Der Taschenspielertrick zur intendierten Aushebelung der Meinungsfreiheit ist das Wort „Desinformation“, womit stillschweigend alle Meinungen zusammengefasst werden, welche nicht mit dem gängigen Regierungsnarrativ zur Erklärung der Welt zusammenpassen.
Auf einer Webseite der Bundesregierung wird das so illustriert: „In der jüngeren Vergangenheit gab es gezielte Desinformationskampagnen aus dem Ausland (hier wird Präsident Putin der Lüge bezüglich des Ukraine-Krieges bezichtigt, Anmerkung des Autors). Aber auch während der Corona-Pandemie verbreiteten rechtsextreme Gruppen Verschwörungsmythen. Von diesen Desinformationen geht eine Gefahr aus. Weil sie uns als Gesellschaft spalten sollen. Sie verfolgen das Ziel, Schaden anzurichten. Existierende Konflikte und Debatten sollen verschärft, das Vertrauen in staatliche Institutionen untergraben und insgesamt Wut und Emotionen geschürt werden.“
Wenn wir das Wort „Desinformation“ einmal weglassen, bleibt als Klartext übrig: Die Bundesregierung hat eine Meinung. Zum Beispiel zum Ukrainekrieg oder zu den Corona-Geschehnissen. Und die wird als richtig gesetzt. Meinungen, die nicht damit übereinstimmen, werden als nicht richtig betrachtet und mit Worten, die gern mal unter die Gürtellinie zielen, gebrandmarkt.
(Dem aktuellen Stand der Aufarbeitung der Ereignisse seit 2020 will ich hier nicht nachgehen; wer von den geschwärzten RKI Protokollen Kenntnis hat, ist ausreichend im Bilde über diese Geschehnisse; zum Krieg in der Ukraine gibt es durchaus unterschiedliche Sichtweisen, die im Raum stehen, s. meine Korrespondenz mit den deutschen Parlamentariern dazu. In zivilisierten demokratischen Nationen wird über solche Fragen öffentlich diskutiert.)
Und nicht genug mit dieser Neuversion von „Die Partei, die Partei, die hat immer recht“. In den Parteiprogrammen einiger deutscher Parteien plant man aktuell einen Kampf gegen Desinformation, ja man will gar Menschen mit anderen Auffassungen strafrechtlich verfolgen.
„Der Kampf gegen Desinformation ist angesichts des schon heute immensen Ausmaßes eine herausragende gesellschaftliche Aufgabe.“
„Die großen Medienplattformen werden wir in die Pflicht nehmen, wirksame Maßnahmen gegen die Verbreitung von Desinformation vorzunehmen. Die systematische Verbreitung von Desinformation im Auftrag eines fremden Staates wollen wir strafrechtlich fassen.“
„Wir stellen sicher, dass bei der Umsetzung des Digital Services Act der Schwerpunkt auf mehr Transparenz, Kampf gegen Desinformation sowie Jugend- und Medienschutz gelegt wird.“
\ Hören Sie hinter der Kampf-Rhetorik Säbel rasseln? Dass man sich dabei in Konflikt mit dem § 5 des Grundgesetzes begibt, wird im Durcheinander dieser Wochen im Februar 2025 geflissentlich übersehen.
Fazit: Einige politische Parteien im Land maßen sich an, nach Gutsherrenart zwischen richtiger Information und „Desinformation“ zu unterscheiden. Sie trachten danach, missliebige Meinungen zu bekämpfen - und missachten dabei unser Grundgesetz.
Wollen Sie als Souverän solchen Parteien die Macht im Land überlassen? Schauen Sie doch mal in die aktuellen Wahlprogramme der im Bundestag vertretenen Parteien zu diesem Thema und zu weiteren existentiellen Fragen unserer Zukunft (Frieden, Bargeld, Volksabstimmungen, Position zur WHO) welche Akteure der Gemeinwohllobby zusammengestellt haben und die hier kurz zusammengefasst sind.
Titelbild: Wikipedia, der Künstler Dani Karavan hat in drei Meter hohe Glasscheiben eines Außenhofes des Jakob-Kaiser-Hauses am Bundestag die 19 Grundrechtsartikel des Grundgesetzes mit Laser eingraviert.
-
 @ 06b7819d:d1d8327c
2024-12-12 11:43:36
@ 06b7819d:d1d8327c
2024-12-12 11:43:36The Peano axioms are a set of rules that define the natural numbers (like 0, 1, 2, 3, and so on) in a logical way. Here’s a simplified explanation: 1. There is a first number: There is a number called zero, and it is the starting point for all natural numbers. 2. Each number has a next number: Every number has a unique “successor,” or the number that comes after it (like 1 comes after 0, 2 comes after 1, etc.). 3. Zero is special: Zero is not the “next” number of any other number. This means the sequence of natural numbers doesn’t loop back to zero. 4. No two numbers are the same if they have different successors: If two numbers have the same “next” number, then they must actually be the same number. 5. Patterns hold for all numbers: If something is true for zero, and it stays true when moving from one number to the next, then it must be true for all numbers.
These principles lay the groundwork for understanding and working with the natural numbers systematically.
-
 @ 62033ff8:e4471203
2025-01-11 15:00:24
@ 62033ff8:e4471203
2025-01-11 15:00:24收录的内容中 kind=1的部分,实话说 质量不高。 所以我增加了kind=30023 长文的article,但是更新的太少,多个relays 的服务器也没有多少长文。
所有搜索nostr如果需要产生价值,需要有高质量的文章和新闻。 而且现在有很多机器人的文章充满着浪费空间的作用,其他作用都用不上。
https://www.duozhutuan.com 目前放的是给搜索引擎提供搜索的原材料。没有做UI给人类浏览。所以看上去是粗糙的。 我并没有打算去做一个发microblog的 web客户端,那类的客户端太多了。
我觉得nostr社区需要解决的还是应用。如果仅仅是microblog 感觉有点够呛
幸运的是npub.pro 建站这样的,我觉得有点意思。
yakihonne 智能widget 也有意思
我做的TaskQ5 我自己在用了。分布式的任务系统,也挺好的。
-
 @ 97c70a44:ad98e322
2025-02-18 20:30:32
@ 97c70a44:ad98e322
2025-02-18 20:30:32For the last couple of weeks, I've been dealing with the fallout of upgrading a web application to Svelte 5. Complaints about framework churn and migration annoyances aside, I've run into some interesting issues with the migration. So far, I haven't seen many other people register the same issues, so I thought it might be constructive for me to articulate them myself.
I'll try not to complain too much in this post, since I'm grateful for the many years of Svelte 3/4 I've enjoyed. But I don't think I'll be choosing Svelte for any new projects going forward. I hope my reflections here will be useful to others as well.
If you're interested in reproductions for the issues I mention here, you can find them below.
The Need for Speed
To start with, let me just quickly acknowledge what the Svelte team is trying to do. It seems like most of the substantial changes in version 5 are built around "deep reactivity", which allows for more granular reactivity, leading to better performance. Performance is good, and the Svelte team has always excelled at reconciling performance with DX.
In previous versions of Svelte, the main way this was achieved was with the Svelte compiler. There were many ancillary techniques involved in improving performance, but having a framework compile step gave the Svelte team a lot of leeway for rearranging things under the hood without making developers learn new concepts. This is what made Svelte so original in the beginning.
At the same time, it resulted in an even more opaque framework than usual, making it harder for developers to debug more complex issues. To make matters worse, the compiler had bugs, resulting in errors which could only be fixed by blindly refactoring the problem component. This happened to me personally at least half a dozen times, and is what ultimately pushed me to migrate to Svelte 5.
Nevertheless, I always felt it was an acceptable trade-off for speed and productivity. Sure, sometimes I had to delete my project and port it to a fresh repository every so often, but the framework was truly a pleasure to use.
Svelte is not Javascript
Svelte 5 doubled down on this tradeoff — which makes sense, because it's what sets the framework apart. The difference this time is that the abstraction/performance tradeoff did not stay in compiler land, but intruded into runtime in two important ways:
- The use of proxies to support deep reactivity
- Implicit component lifecycle state
Both of these changes improved performance and made the API for developers look slicker. What's not to like? Unfortunately, both of these features are classic examples of a leaky abstraction, and ultimately make things more complex for developers, not less.
Proxies are not objects
The use of proxies seems to have allowed the Svelte team to squeeze a little more performance out of the framework, without asking developers to do any extra work. Threading state through multiple levels of components without provoking unnecessary re-renders in frameworks like React is an infamously difficult chore.
Svelte's compiler avoided some of the pitfalls associated with virtual DOM diffing solutions, but evidently there was still enough of a performance gain to be had to justify the introduction of proxies. The Svelte team also seems to argue that their introduction represents an improvement in developer experience:
we... can maximise both efficiency and ergonomics.
Here's the problem: Svelte 5 looks simpler, but actually introduces more abstractions.
Using proxies to monitor array methods (for example) is appealing because it allows developers to forget all the goofy heuristics involved with making sure state was reactive and just
pushto the array. I can't count how many times I've writtenvalue = valueto trigger reactivity in svelte 4.In Svelte 4, developers had to understand how the Svelte compiler worked. The compiler, being a leaky abstraction, forced its users to know that assignment was how you signaled reactivity. In svelte 5, developers can just "forget" about the compiler!
Except they can't. All the introduction of new abstractions really accomplishes is the introduction of more complex heuristics that developers have to keep in their heads in order to get the compiler to act the way they want it to.
In fact, this is why after years of using Svelte, I found myself using Svelte stores more and more often, and reactive declarations less. The reason being that Svelte stores are just javascript. Calling
updateon a store is simple, and being able to reference them with a$was just a nice bonus — nothing to remember, and if I mess up the compiler yells at me.Proxies introduce a similar problem to reactive declarations, which is that they look like one thing but act like another on the edges.
When I started using Svelte 5, everything worked great — until I tried to save a proxy to indexeddb, at which point I got a
DataCloneError. To make matters worse, it's impossible to reliably tell if something is aProxywithouttry/catching a structured clone, which is a performance-intensive operation.This forces the developer to remember what is and what isn't a Proxy, calling
$state.snapshotevery time they pass a proxy to a context that doesn't expect or know about them. This obviates all the nice abstractions they gave us in the first place.Components are not functions
The reason virtual DOM took off way back in 2013 was the ability to model your application as composed functions, each of which takes data and spits out HTML. Svelte retained this paradigm, using a compiler to sidestep the inefficiencies of virtual DOM and the complexities of lifecycle methods.
In Svelte 5, component lifecycles are back, react-hooks style.
In React, hooks are an abstraction that allows developers to avoid writing all the stateful code associated with component lifecycle methods. Modern React tutorials universally recommend using hooks instead, which rely on the framework invisibly synchronizing state with the render tree.
While this does result in cleaner code, it also requires developers to tread carefully to avoid breaking the assumptions surrounding hooks. Just try accessing state in a
setTimeoutand you'll see what I mean.Svelte 4 had a few gotchas like this — for example, async code that interacts with a component's DOM elements has to keep track of whether the component is unmounted. This is pretty similar to the kind of pattern you'd see in old React components that relied on lifecycle methods.
It seems to me that Svelte 5 has gone the React 16 route by adding implicit state related to component lifecycles in order to coordinate state changes and effects.
For example, here is an excerpt from the documentation for $effect:
You can place $effect anywhere, not just at the top level of a component, as long as it is called during component initialization (or while a parent effect is active). It is then tied to the lifecycle of the component (or parent effect) and will therefore destroy itself when the component unmounts (or the parent effect is destroyed).
That's very complex! In order to use
$effect... effectively (sorry), developers have to understand how state changes are tracked. The documentation for component lifecycles claims:In Svelte 5, the component lifecycle consists of only two parts: Its creation and its destruction. Everything in-between — when certain state is updated — is not related to the component as a whole; only the parts that need to react to the state change are notified. This is because under the hood the smallest unit of change is actually not a component, it’s the (render) effects that the component sets up upon component initialization. Consequently, there’s no such thing as a “before update”/"after update” hook.
But then goes on to introduce the idea of
tickin conjunction with$effect.pre. This section explains that "tickreturns a promise that resolves once any pending state changes have been applied, or in the next microtask if there are none."I'm sure there's some mental model that justifies this, but I don't think the claim that a component's lifecycle is only comprised of mount/unmount is really helpful when an addendum about state changes has to come right afterward.
The place where this really bit me, and which is the motivation for this blog post, is when state gets coupled to a component's lifecycle, even when the state is passed to another function that doesn't know anything about svelte.
In my application, I manage modal dialogs by storing the component I want to render alongside its props in a store and rendering it in the
layout.svelteof my application. This store is also synchronized with browser history so that the back button works to close them. Sometimes, it's useful to pass a callback to one of these modals, binding caller-specific functionality to the child component:javascript const {value} = $props() const callback = () => console.log(value) const openModal = () => pushModal(MyModal, {callback})This is a fundamental pattern in javascript. Passing a callback is just one of those things you do.
Unfortunately, if the above code lives in a modal dialog itself, the caller component gets unmounted before the callback gets called. In Svelte 4, this worked fine, but in Svelte 5
valuegets updated toundefinedwhen the component gets unmounted. Here's a minimal reproduction.This is only one example, but it seems clear to me that any prop that is closed over by a callback function that lives longer than its component will be undefined when I want to use it — with no reassignment existing in lexical scope. It seems that the reason this happens is that the props "belong" to the parent component, and are accessed via getters so that the parent can revoke access when it unmounts.
I don't know why this is necessary, but I assume there's a good engineering reason for it. The problem is, this just isn't how javascript works. Svelte is essentially attempting to re-invent garbage collection around component lifecycles, which breaks the assumption every javascript developer has that variables don't simply disappear without an explicit reassignment. It should be safe to pass stuff around and let the garbage collector do its job.
Conclusion
Easy things are nice, but as Rich Hickey says, easy things are not always simple. And like Joel Spolsky, I don't like being surprised. Svelte has always been full of magic, but with the latest release I think the cognitive overhead of reciting incantations has finally outweighed the power it confers.
My point in this post is not to dunk on the Svelte team. I know lots of people like Svelte 5 (and react hooks). The point I'm trying to make is that there is a tradeoff between doing things on the user's behalf, and giving the user agency. Good software is built on understanding, not cleverness.
I also think this is an important lesson to remember as AI-assisted coding becomes increasingly popular. Don't choose tools that alienate you from your work. Choose tools that leverage the wisdom you've already accumulated, and which help you to cultivate a deeper understanding of the discipline.
Thank you to Rich Harris and team for many years of pleasant development. I hope that (if you read this) it's not so full of inaccuracies as to be unhelpful as user feedback.
-
 @ 77c2969e:a33cfa50
2025-01-09 17:01:36
@ 77c2969e:a33cfa50
2025-01-09 17:01:36换了个客户端Nostrmo,比damus好用,不过好像关注列表丢失了😩。
现在使用#YakiHonne,好像更流畅
不加图片他还会显示一个空白图片,好丑,我还是上传一个吧
-
 @ 1cb14ab3:95d52462
2025-02-04 22:17:27
@ 1cb14ab3:95d52462
2025-02-04 22:17:27Chef's notes
Credit to The Yummy Life. Go show them love below: https://www.theyummylife.com/Pickled_Jalapeno_Peppers
Details
- ⏲️ Prep time: 1 hour
- 🍳 Cook time: 20 mins
- 🍽️ Servings: 4 mason jars (pint)
Ingredients
- 2 lbs. jalapenos
- 2-1/4 cups vinegar (white distilled, apple cider, or a combination of the two)
- 2-1/4 cups water
- 2 tablespoons sugar or honey (optional)
- ADD TO EACH PINT JAR
- 1/2 teaspoon kosher salt
- 1/2 teaspoon whole black pepper corns
- 1/4 teaspoon whole cumin seeds
- 1/4 teaspoon whole coriander seeds
- 1 bay leaf
- 1 whole garlic clove, peeled
- 1/8 teaspoon Pickle Crisp granules (optional)
Directions
- Slice 1/2 pound jalapenos into 1/8" rounds, discarding stem ends.
- Prepare the jars: Wash 4 pint jars and lids in hot sudsy water, then keep them warm.
- Prepare the pickling liquid: Combine 1/2 cup plus 1 tablespoon vinegar, 1/2 cup plus 1 tablespoon water, and 1-1/2 teaspoons sugar or honey (optional) in a 2 quart pan, heating until just before boiling.
- Fill the jars: Add jalapeno slices to each jar, pressing them down and packing them in compactly, then pour the hot pickling liquid into each jar, leaving 1/2" head space.
- Process and store: Allow jars to cool to room temperature, then store them in the refrigerator or can them using standard USDA water process canning procedures, following storage guidelines for refrigerator or canned pickled peppers.
-
 @ 06b7819d:d1d8327c
2024-12-08 10:52:55
@ 06b7819d:d1d8327c
2024-12-08 10:52:55Power as the Reduction of Possibilities: Niklas Luhmann’s Perspective
Niklas Luhmann, a leading figure in systems theory, offers a unique conceptualization of power that diverges from traditional notions of domination or coercion. Rather than viewing power as a forceful imposition of will, Luhmann frames it as a mechanism for reducing possibilities within a given social system. For Luhmann, power is less about direct coercion and more about structuring decision-making processes by limiting the range of available options.
In his systems-theoretical approach, Luhmann argues that power operates as a communication medium, enabling complex social systems to function by simplifying the overwhelming array of potential actions. In any decision-making context, there are countless possibilities, and not all can be pursued. Power serves as a tool to focus attention, filter alternatives, and channel behavior toward specific actions while excluding others. This reduction of options creates a manageable environment for coordinated action, which is essential for the stability of a system.
Importantly, this process does not inherently involve force or threats. Instead, power works through expectations, norms, and structures that guide behavior. For example, in an organizational setting, the hierarchy of authority determines which decisions are permissible, thereby shaping the actions of individuals without overt coercion. The employees’ actions are not forced; rather, they are conditioned by the organizational framework, which narrows their choices.
Luhmann’s idea redefines power as a productive force in social systems. By limiting possibilities, power reduces uncertainty, making collaboration and collective action possible. It ensures that systems can function efficiently despite their inherent complexity. This perspective shifts the emphasis from conflict to coordination, offering a more nuanced understanding of how power operates in modern societies.
In sum, Niklas Luhmann’s theory of power as the reduction of possibilities highlights its integrative role in enabling social systems to navigate complexity. It challenges conventional views of power as coercion, emphasizing its capacity to organize and stabilize interactions through the selective limitation of actions.
-
 @ 42342239:1d80db24
2025-02-16 08:39:59
@ 42342239:1d80db24
2025-02-16 08:39:59Almost 150 years ago, the British newspaper editor William Thomas Stead wrote that "the editorial pen is a sceptre of power, compared with which the sceptre of many a monarch is but a gilded lath". He had begun to regard journalism as something more than just conveying information - the journalist or editor could become a ruler.
Times had certainly changed compared to a few hundred years earlier. Before Gutenberg's invention of the printing press, it was mainly the church that controlled the dissemination of information in Europe, but when Stead put pen to paper, this control had shifted to newspapers, schools, and universities. Eventually, technologies like radio and TV entered the scene, but the power dynamics remained asymmetrical - only a few could send information to the many.
However, with the emergence of the internet, and especially with the spread of social media, a significant change followed. Instead of only a few being able to send information to the many, many could send to many. Almost anyone could now create their own newspaper, radio, or TV channel. The power over information dissemination was decentralised.
Ten years ago, Roberta Alenius, who was then press secretary for Sweden's Prime Minister Fredrik Reinfeldt of the Moderate Party, shared her experiences with Social Democratic and Moderate Party internet activists on social media. She reported that social media played a significant role in how news "comes out" and is shaped, and that journalism was now downstream of social media. Five years later, NATO's then-Secretary-General Jens Stoltenberg said that "NATO must be prepared for both conventional and hybrid threats: from tanks to tweets." This finally underscores the importance of social media.
Elon Musk, who took over X (formerly Twitter) in 2022, has claimed that "it's absolutely fundamental and transformative that the people actually get to decide the news and narrative and what's important," and that citizen journalism is the future.
While his platform allows most expressions - for better or worse - the reach of messages is instead limited ("freedom of speech does not mean freedom of reach "). X has also opened its recommendation algorithm to the outside world by making it open-source. Although this is a welcome step, the fact remains that it's impossible to know which code is actually used and what adjustments are made by humans or algorithms.
William Thomas Stead's "sceptre of power", which has wandered from the church to newspaper and TV editorial offices, and now to citizens according to Elon Musk, risks being transferred to algorithms' opaque methods?
Instead of talking about "toxic algorithms" and TikTok bans, like the so many do today, we should ask ourselves more fundamental questions. What happens when algorithms are no longer objective (how can they ever be?), but instead become tools for shaping our reality? Perhaps our greatest challenge today is not deciding who should govern the information landscape, but instead recognising that no one is up to the task - not even well-ventilated computers.
-
 @ 23b0e2f8:d8af76fc
2025-01-08 18:17:52
@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52Necessário
- Um Android que você não use mais (a câmera deve estar funcionando).
- Um cartão microSD (opcional, usado apenas uma vez).
- Um dispositivo para acompanhar seus fundos (provavelmente você já tem um).
Algumas coisas que você precisa saber
- O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele.
- O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito.
- A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal.
O tutorial será dividido em dois módulos:
- Módulo 1 - Criando uma carteira fria/assinador.
- Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
No final, teremos:
- Uma carteira fria que também servirá como assinador.
- Um dispositivo para acompanhar os fundos da carteira.

Módulo 1 - Criando uma carteira fria/assinador
-
Baixe o APK do Electrum na aba de downloads em https://electrum.org/. Fique à vontade para verificar as assinaturas do software, garantindo sua autenticidade.
-
Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.

- Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.

- Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o modo avião.\ (Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)

- Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.

- No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. (Aqui entra seu método pessoal de backup.)

Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
-
Criar uma carteira somente leitura em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em https://electrum.org/ ou da própria Play Store. (ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)
-
Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção Usar uma chave mestra.

- Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em Carteira > Detalhes da carteira > Compartilhar chave mestra pública.

-
Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los.
-
Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: Carteira > Addresses/Coins.
-
Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.

- No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.

- No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede.
Conclusão
Pontos positivos do setup:
- Simplicidade: Basta um dispositivo Android antigo.
- Flexibilidade: Funciona como uma ótima carteira fria, ideal para holders.
Pontos negativos do setup:
- Padronização: Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum.
- Interface: A aparência do Electrum pode parecer antiquada para alguns usuários.
Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.
Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível.
-
 @ 6e0ea5d6:0327f353
2025-02-18 18:11:32
@ 6e0ea5d6:0327f353
2025-02-18 18:11:32Ascolta bene, si?
I have something to tell you, amico mio, something uncomfortable, yet a fundamental piece of advice for your personal journey toward painful success: always be mindful of how you handle your thoughts and conduct.
More often than not, we are our own worst enemies, and our own thoughts and behaviors are the true obstacles in our lives.
Perhaps you feel trapped in a cycle of negative thinking, feeding your fears and insecurities. You may have already realized that your poor habits have harmed your relationships and goals.
What matters is understanding that, although these patterns may seem inevitable, we have the power to change them.
The Stoic concepts of memento mori and premeditatio malorum remind us of the transience of life and the importance of preparing for the challenges ahead.
Memento mori means "remember that you are mortal," and premeditatio malorum translates to "premeditation of evils." These ideas encourage us to reflect on life's fleeting nature and mentally prepare for the hardships that will come.
By remembering that life is short and that adversity is inevitable, we can become more resilient and courageous. We can face our own thoughts and behaviors with greater determination and seek the change needed to achieve our goals and become better individuals.
Identify the areas where you need improvement and start working on them. Change is not easy, but it is possible. Use memento mori to remind yourself that life is short and valuable, and premeditatio malorum to mentally prepare for the challenges that lie ahead.
Take control of your thoughts and actions, and become the best version of yourself. Forget about others—their lives are nothing more than an illusory stage play.
Thank you for reading, my friend!
If this message has helped you in any way, consider leaving your “🥃” as a token of appreciation.
A toast to our family!
-
 @ 207ad2a0:e7cca7b0
2025-01-07 03:46:04
@ 207ad2a0:e7cca7b0
2025-01-07 03:46:04Quick context: I wanted to check out Nostr's longform posts and this blog post seemed like a good one to try and mirror. It's originally from my free to read/share attempt to write a novel, but this post here is completely standalone - just describing how I used AI image generation to make a small piece of the work.
Hold on, put your pitchforks down - outside of using Grammerly & Emacs for grammatical corrections - not a single character was generated or modified by computers; a non-insignificant portion of my first draft originating on pen & paper. No AI is ~~weird and crazy~~ imaginative enough to write like I do. The only successful AI contribution you'll find is a single image, the map, which I heavily edited. This post will go over how I generated and modified an image using AI, which I believe brought some value to the work, and cover a few quick thoughts about AI towards the end.
Let's be clear, I can't draw, but I wanted a map which I believed would improve the story I was working on. After getting abysmal results by prompting AI with text only I decided to use "Diffuse the Rest," a Stable Diffusion tool that allows you to provide a reference image + description to fine tune what you're looking for. I gave it this Microsoft Paint looking drawing:

and after a number of outputs, selected this one to work on:

The image is way better than the one I provided, but had I used it as is, I still feel it would have decreased the quality of my work instead of increasing it. After firing up Gimp I cropped out the top and bottom, expanded the ocean and separated the landmasses, then copied the top right corner of the large landmass to replace the bottom left that got cut off. Now we've got something that looks like concept art: not horrible, and gets the basic idea across, but it's still due for a lot more detail.

The next thing I did was add some texture to make it look more map like. I duplicated the layer in Gimp and applied the "Cartoon" filter to both for some texture. The top layer had a much lower effect strength to give it a more textured look, while the lower layer had a higher effect strength that looked a lot like mountains or other terrain features. Creating a layer mask allowed me to brush over spots to display the lower layer in certain areas, giving it some much needed features.

At this point I'd made it to where I felt it may improve the work instead of detracting from it - at least after labels and borders were added, but the colors seemed artificial and out of place. Luckily, however, this is when PhotoFunia could step in and apply a sketch effect to the image.

At this point I was pretty happy with how it was looking, it was close to what I envisioned and looked very visually appealing while still being a good way to portray information. All that was left was to make the white background transparent, add some minor details, and add the labels and borders. Below is the exact image I wound up using:

Overall, I'm very satisfied with how it turned out, and if you're working on a creative project, I'd recommend attempting something like this. It's not a central part of the work, but it improved the chapter a fair bit, and was doable despite lacking the talent and not intending to allocate a budget to my making of a free to read and share story.
The AI Generated Elephant in the Room
If you've read my non-fiction writing before, you'll know that I think AI will find its place around the skill floor as opposed to the skill ceiling. As you saw with my input, I have absolutely zero drawing talent, but with some elbow grease and an existing creative direction before and after generating an image I was able to get something well above what I could have otherwise accomplished. Outside of the lowest common denominators like stock photos for the sole purpose of a link preview being eye catching, however, I doubt AI will be wholesale replacing most creative works anytime soon. I can assure you that I tried numerous times to describe the map without providing a reference image, and if I used one of those outputs (or even just the unedited output after providing the reference image) it would have decreased the quality of my work instead of improving it.
I'm going to go out on a limb and expect that AI image, text, and video is all going to find its place in slop & generic content (such as AI generated slop replacing article spinners and stock photos respectively) and otherwise be used in a supporting role for various creative endeavors. For people working on projects like I'm working on (e.g. intended budget $0) it's helpful to have an AI capable of doing legwork - enabling projects to exist or be improved in ways they otherwise wouldn't have. I'm also guessing it'll find its way into more professional settings for grunt work - think a picture frame or fake TV show that would exist in the background of an animated project - likely a detail most people probably wouldn't notice, but that would save the creators time and money and/or allow them to focus more on the essential aspects of said work. Beyond that, as I've predicted before: I expect plenty of emails will be generated from a short list of bullet points, only to be summarized by the recipient's AI back into bullet points.
I will also make a prediction counter to what seems mainstream: AI is about to peak for a while. The start of AI image generation was with Google's DeepDream in 2015 - image recognition software that could be run in reverse to "recognize" patterns where there were none, effectively generating an image from digital noise or an unrelated image. While I'm not an expert by any means, I don't think we're too far off from that a decade later, just using very fine tuned tools that develop more coherent images. I guess that we're close to maxing out how efficiently we're able to generate images and video in that manner, and the hard caps on how much creative direction we can have when using AI - as well as the limits to how long we can keep it coherent (e.g. long videos or a chronologically consistent set of images) - will prevent AI from progressing too far beyond what it is currently unless/until another breakthrough occurs.
-
 @ a95c6243:d345522c
2025-02-15 19:05:38
@ a95c6243:d345522c
2025-02-15 19:05:38Auf der diesjährigen Münchner Sicherheitskonferenz geht es vor allem um die Ukraine. Protagonisten sind dabei zunächst die US-Amerikaner. Präsident Trump schockierte die Europäer kurz vorher durch ein Telefonat mit seinem Amtskollegen Wladimir Putin, während Vizepräsident Vance mit seiner Rede über Demokratie und Meinungsfreiheit für versteinerte Mienen und Empörung sorgte.
Die Bemühungen der Europäer um einen Frieden in der Ukraine halten sich, gelinde gesagt, in Grenzen. Größeres Augenmerk wird auf militärische Unterstützung, die Pflege von Feindbildern sowie Eskalation gelegt. Der deutsche Bundeskanzler Scholz reagierte auf die angekündigten Verhandlungen über einen möglichen Frieden für die Ukraine mit der Forderung nach noch höheren «Verteidigungsausgaben». Auch die amtierende Außenministerin Baerbock hatte vor der Münchner Konferenz klargestellt:
«Frieden wird es nur durch Stärke geben. (...) Bei Corona haben wir gesehen, zu was Europa fähig ist. Es braucht erneut Investitionen, die der historischen Wegmarke, vor der wir stehen, angemessen sind.»
Die Rüstungsindustrie freut sich in jedem Fall über weltweit steigende Militärausgaben. Die Kriege in der Ukraine und in Gaza tragen zu Rekordeinnahmen bei. Jetzt «winkt die Aussicht auf eine jahrelange große Nachrüstung in Europa», auch wenn der Ukraine-Krieg enden sollte, so hört man aus Finanzkreisen. In der Konsequenz kennt «die Aktie des deutschen Vorzeige-Rüstungskonzerns Rheinmetall in ihrem Anstieg offenbar gar keine Grenzen mehr». «Solche Friedensversprechen» wie das jetzige hätten in der Vergangenheit zu starken Kursverlusten geführt.
Für manche Leute sind Kriegswaffen und sonstige Rüstungsgüter Waren wie alle anderen, jedenfalls aus der Perspektive von Investoren oder Managern. Auch in diesem Bereich gibt es Startups und man spricht von Dingen wie innovativen Herangehensweisen, hocheffizienten Produktionsanlagen, skalierbaren Produktionstechniken und geringeren Stückkosten.
Wir lesen aktuell von Massenproduktion und gesteigerten Fertigungskapazitäten für Kriegsgerät. Der Motor solcher Dynamik und solchen Wachstums ist die Aufrüstung, die inzwischen permanent gefordert wird. Parallel wird die Bevölkerung verbal eingestimmt und auf Kriegstüchtigkeit getrimmt.
Das Rüstungs- und KI-Startup Helsing verkündete kürzlich eine «dezentrale Massenproduktion für den Ukrainekrieg». Mit dieser Expansion positioniere sich das Münchner Unternehmen als einer der weltweit führenden Hersteller von Kampfdrohnen. Der nächste «Meilenstein» steht auch bereits an: Man will eine Satellitenflotte im Weltraum aufbauen, zur Überwachung von Gefechtsfeldern und Truppenbewegungen.
Ebenfalls aus München stammt das als DefenseTech-Startup bezeichnete Unternehmen ARX Robotics. Kürzlich habe man in der Region die größte europäische Produktionsstätte für autonome Verteidigungssysteme eröffnet. Damit fahre man die Produktion von Militär-Robotern hoch. Diese Expansion diene auch der Lieferung der «größten Flotte unbemannter Bodensysteme westlicher Bauart» in die Ukraine.
Rüstung boomt und scheint ein Zukunftsmarkt zu sein. Die Hersteller und Vermarkter betonen, mit ihren Aktivitäten und Produkten solle die europäische Verteidigungsfähigkeit erhöht werden. Ihre Strategien sollten sogar «zum Schutz demokratischer Strukturen beitragen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 1cb14ab3:95d52462
2025-02-04 21:42:24
@ 1cb14ab3:95d52462
2025-02-04 21:42:24Chef's notes
Classic beef n' broccoli. Easy to make and dank to eat.
Details
- ⏲️ Prep time: 20 mins
- 🍳 Cook time: 10 mins.
Ingredients
- 1 lb top sirloin steak, thinly sliced
- ¼ cup low sodium soy sauce
- 2 teaspoons cornstarch
- 1 tablespoon dark brown sugar
- 2 tablespoons fresh ginger, minced
- 1 tablespoon oil
- 1 head broccoli, cut into 1-inch (2 ½ cm) florets
- ½ cup water
- 3 cloves garlic, minced
- ¼ teaspoon red pepper flakes, optional
- 1 teaspoon toasted sesame oil
Directions
- In a medium bowl, mix together the sirloin steak, soy sauce, cornstarch, brown sugar, and ginger until the meat is evenly covered in the marinade. Set aside to marinate for 20 minutes.
- Heat the oil in a large skillet or wok over medium-high heat. Dump in the meat and marinade and sear each side until golden brown. Transfer the meat to a clean bowl and set aside.
- Place the broccoli into the hot skillet and sauté until the broccoli has just started to brown, about 1 minute. Pour the water into the skillet and immediately cover with a lid. Let it steam for 2 minutes, until the broccoli has softened.
- Remove the lid and toss in the garlic, red pepper flakes, and sesame oil. Sauté until the garlic becomes fragrant, about 30 seconds.
- Add the steak back into the pan and stir to combine. Remove from heat and serve on a bed of brown rice.
-
 @ 554ab6fe:c6cbc27e
2025-02-18 18:09:06
@ 554ab6fe:c6cbc27e
2025-02-18 18:09:06Presence is a crucial aspect of mental and physical health. This idea is not only espoused by religious teachers, but is slowly validated within scientific research. Much of this blog is devoted to exploring the scientific validation of mindfulness practices on health, in particular, the effect mindfulness meditation has on our physical and mental health. However, multiple techniques can help foster this holistic lifestyle. Yoga is a famous example in the west as another form of this practice. Of course, yoga was traditionally meditative, and the physical aspect of yoga is new in relative terms. Regardless, yoga is a physical version of meditation formulated in India. Another culture that developed practices to instill presence is rooted in China. Not only did the Chinese meditate, but they formed a physical exercise and martial art known as Qi Gong (气功, qi gong), and a similar practice to emerge later known as Tai Chi (太极拳, tai ji quan). These practices produce similar effects on health compared to yoga and meditation. Therefore, they are one of many methods one can utilize to find presence.
Qi Gong is one of the most ancient forms of traditional Chinese medicine with a history of refinement of over 5000 years (Jahnke et al., 2010). The practice is composed of several martial art postures that are very fluid in motion. In the traditional sense, the purpose of these practices is to enhance one’s Qi (气). Tai Chi and Qi Gong are similar yet different. Tai Chi is typically more choreographed, lengthy, and more complex movements (Jahnke et al., 2010). Qi Gong, on the other hand, is simpler and easier to learn. Traditional instructions for both Qi Gong and Tai Chi are paraphrased as “mind the body and the breath, and then clear the mind to distill the Heavenly elixir within” (Jahnke et al., 2010). The intention of this post is not to fully elaborate on the philosophical implications of these words. However, note how the instructions here are almost identical to those of meditation practices.
The practice intends to instill an awareness of the present body, which leads to a calm mind that cultivates an understanding of something heavenly within. This idea shares a remarkable resemblance to the concept that meditation and the mind’s stillness create an altered characterized by a sense of unity of being with all of life, though there is no perfect term to describe this experience. Yet, this unity is likely the same thing as this “Heavenly elixir.” This experience has been clinically observed in meditators, psychedelic users, and those who experience religious moments. It seems to be the experiential one of the by-products and intents of these Chinese practices.
Outside of the more spiritual benefit, these practices manifest health benefits as well. Most research regarding these techniques focuses on Tai Chi. However, a literature review article noted that the Tai Chi used in academic settings is often simplified and more akin to Qi Gong (Jahnke et al., 2010). Therefore, Tai Chi and Qi Gong’s scientific literature will be considered the same here. For simplicity, I will refer to both as meditative martial arts.
Meditative martial arts share many health-related benefits to traditional forms of exercise, despite being less strenuous. For example, a literature review found that despite the absence of weight-bearing activity, meditative martial arts retard bone loss and the occurrence of fractures (Jahnke et al., 2010). Additionally, these practices help improve knee health in older adults, even compared to traditional forms of exercise (Chen et al., 2016). Meditative martial arts are also comparable to other forms of exercise in reducing blood pressure (Jahnke et al., 2010). Other research also similarly shown yoga to be superior to regular exercise in certain regards (Ross & Thomas, 2010). This is not to say that the purely physical aspect of meditative martial arts or yoga is superior in all cases. Instead, it is the mental aspect incorporated that provides extra benefits.
Meditative martial arts have been shown to decrease or modulate heart rate variability (HRV) (Jahnke et al., 2010; Lu & Kuo, 2003; Wei et al., 2016). This indicates increased parasympathetic nervous system activity in response to the aspects of the practice. Increased parasympathetic activity can provide a cascade of health benefits across the body and is likely the source of the extra help. Meditative martial arts have also been theorized to benefit the gut microbiome and immune function, likely via the same mechanism, making meditative martial arts much more than physical exercise or fancy movements, but a practice that cultivates holistic health.
The idea that these meditative martial arts provide additional benefits, compared to traditional exercises that seem like the benefits of sitting meditation, brings to question the essence of these practices. It may seem odd that physical activity can induce benefits caused by sitting meditation because sitting meditation is, in part, aimed to generate mental stillness. Yet, optimal mental stillness seems impossible when one is mentally choreographing movements. This highlights the importance of not the mental stillness achieved by meditation, but the attention to the body’s sensations in the present moment. Both Tai Chi, Qi Gong, and even yoga involve the constant monitoring of the body’s sensations and position. The practice of this draws the individual’s attention to the present and experience of the present. This is a crucial aspect of all forms of meditation, including the sitting version. Perhaps sitting meditations may provide a better opportunity for mental stillness, but this is not the only important aspect of mindfulness practice.
For this reason, incorporating all these practices should be seen as the optimal path towards the goal. For one cannot be healthy by simply sitting, exercise is needed. At the same time, achieving great mental stillness will only heighten one’s practice beyond that gained merely by the meditative martial arts and yoga.
There are multiple techniques and methods to practice mindfulness that provide significant benefits to health and well-being. Both the sitting and movement-oriented practices contain their pros and cons. Neither is all encompassing and perhaps they are only complete when together. For those seeking a lifestyle of mindfulness, interested in holistic health, and maybe even the obtainment of enlightenment, it is recommended that sitting meditation and meditative martial arts, or yoga, be incorporated within your daily practice.
References
Chen, Y. W., Hunt, M. A., Campbell, K. L., Peill, K., & Reid, W. D. (2016). The effect of Tai Chi on four chronic conditions - cancer, osteoarthritis, heart failure and chronic obstructive pulmonary disease: A systematic review and meta-analyses. British Journal of Sports Medicine, 50(7), 397–407. https://doi.org/10.1136/bjsports-2014-094388
Jahnke, R., Larkey, L., Rogers, C., Etnier, J., & Lin, F. (2010). A comprehensive review of health benefits of qigong and tai chi. American Journal of Health Promotion : AJHP, 24(6). https://doi.org/10.4278/ajhp.081013-lit-248
Lu, W. A., & Kuo, C. D. (2003). The Effect of Tai Chi Chuan on the Autonomic Nervous Modulation in Older Persons. Medicine and Science in Sports and Exercise, 35(12), 1972–1976. https://doi.org/10.1249/01.MSS.0000099242.10669.F7
Ross, A., & Thomas, S. (2010). The health benefits of yoga and exercise: A review of comparison studies. Journal of Alternative and Complementary Medicine, 16(1), 3–12. https://doi.org/10.1089/acm.2009.0044
Wei, G. X., Li, Y. F., Yue, X. L., Ma, X., Chang, Y. K., Yi, L. Y., Li, J. C., & Zuo, X. N. (2016). Tai Chi Chuan modulates heart rate variability during abdominal breathing in elderly adults. PsyCh Journal, 5(1), 69–77. https://doi.org/10.1002/pchj.105
-
 @ dda7ca19:5811f8cd
2025-02-11 12:28:20
@ dda7ca19:5811f8cd
2025-02-11 12:28:20test
-
 @ d360efec:14907b5f
2025-02-18 13:18:54
@ d360efec:14907b5f
2025-02-18 13:18:54นักพนันแห่งเฮรันเทล
“คณิตศาสตร์” กุญแจเวทมนตร์ นักพนัน และ นักลงทุน
ในนครเฮรันเทล นามกระฉ่อนเลื่องลือในหมู่นักเสี่ยงโชค เมื่อเอ่ยถึง “การพนัน” ภาพที่ชาวเมืองมักนึกถึงคือ “ยาจกข้างถนน”
มิใช่เรื่องแปลกประหลาดอันใด เพราะเป็นที่ร่ำลือกันว่า จ้าวแห่งหอคอยรัตติกาล ผู้คุมบ่อนพนัน มักร่ายเวทมนตร์สร้างเกมให้ตนเองได้เปรียบ เพื่อดูดกลืนเงินทองของผู้มาเยือน
ดังนั้น การที่สามัญชนจะพิชิตเกมในระยะยาว จึงเป็นดั่งเงามายาที่จับต้องมิได้
กระนั้น ยังมีตำนานกล่าวขานถึงผู้กล้า ที่สามารถสร้างชื่อจาก “เกมพนัน” เช่น
เวเนสซา รุสโซ นักเวทย์มนตร์ผู้ใช้กฎหมายแห่งแดนไกล ใช้เวลายาวนานถึงหกปี
ร่ายเวทย์สะสมทรัพย์สินกว่าร้อยล้านเหรียญทอง จากการเล่นเกมไพ่ศักดิ์สิทธิ์ “โป๊กเกอร์”
หรือแม้แต่ เอ็ดเวิร์ด โอ. ทอร์ป จอมปราชญ์ผู้สร้างกำไรถึงสามแสนหกหมื่นเหรียญทอง ภายในเจ็ดราตรี
จากการเล่นเกมไพ่มนตรา “แบล็กแจ็ก” ด้วยเงินทุนตั้งต้นเพียงสามแสนสามหมื่นเหรียญทอง คิดเป็นอัตราเวทย์ตอบแทนร้อยสิบส่วน!
เหล่าจอมยุทธ์เหล่านี้ มิได้อาศัยเพียงโชคช่วยชั่วครั้งชั่วคราวแล้วเลือนหาย
แต่พวกเขากลับสามารถร่ายเวทย์สร้างผลตอบแทนระยะยาว จนเรียกได้ว่า ใช้ “หอคอยรัตติกาล” เป็นแหล่งเสบียงเลี้ยงชีพ
โดยกุญแจเวทย์ที่บุคคลเหล่านี้ใช้ ก็คือ “คณิตศาสตร์”
เหตุใด “คณิตศาสตร์” จึงช่วยให้ผู้คนเอาชนะ “การพนัน” ได้?
และนอกจาก “การพนัน” แล้ว “คณิตศาสตร์” ยังสามารถประยุกต์ใช้กับสิ่งใดได้อีก?
นักเล่าเรื่องแห่งเฮรันเทล จักไขปริศนาให้ฟัง
เบื้องต้น ขอให้ท่านลองพิจารณาตนเอง ว่าเคยประสบพบพานเหตุการณ์เหล่านี้หรือไม่:
-
ตั้งมั่นว่า จักเสี่ยงโชคให้ได้กำไรเพียงเล็กน้อย แล้วจักหยุดพัก
-
แต่หากพลาดท่าเสียที จักจำกัดการสูญเสียให้เท่าทุนเดิมที่ตั้งไว้
-
ครั้นเมื่อเวทมนตร์เข้าข้าง ได้กำไรมาแล้ว กลับโลภโมโทสัน อยากได้เพิ่มอีกนิด จึงร่ายเวทย์ต่อ
-
ทว่ากำไรเริ่มร่อยหรอ จนเหลือเพียงทุนเดิม สุดท้ายทุนที่ตั้งไว้คราแรกก็มลายสิ้น
-
จำต้องหาเงินทองมาลงเพิ่ม หวังทวงทุนคืน และพบว่าต้องสูญเสียเงินก้อนนั้นไปในห้วงเวลาต่อมา
ลำดับเหตุการณ์ดังกล่าว เรียกได้ว่าเป็น “วงจรอุบาทว์” สำหรับนักพนันมากมายในเฮรันเทล
ปริศนาที่ตามมาก็คือ เหตุใด “วงจรอุบาทว์” นี้จึงเกิดขึ้นซ้ำแล้วซ้ำเล่า?
ส่วนหนึ่ง ย่อมเป็นเพราะอารมณ์อันแปรปรวนในการเสี่ยงโชคของแต่ละคน
แต่อีกส่วนที่สำคัญยิ่งกว่า ต้องกล่าวว่าเป็นผลจาก “กลไกต้องสาป” ของจ้าวแห่งหอคอยรัตติกาล
ซึ่งต้องกล่าวว่า เหล่าเจ้าของหอคอยรัตติกาลนั้น จักใช้หลักการทำนองเดียวกับ “สมาคมพ่อค้าผู้พิทักษ์”
คือจักเก็บเงินทองจากชนจำนวนมาก เพื่อนำมาจ่ายให้กับชนเพียงหยิบมือ
เพื่อล่อลวงให้ชนทั้งหลายเสี่ยงโชคต่อไป หรือทำให้เหล่านักพนันหวังว่า จักเป็นผู้โชคดีเฉกเช่นพวกเขาบ้าง
แม้จะมีผู้โชคดีที่สามารถได้กำไรในเบื้องต้น แต่ในบั้นปลายก็จักพ่ายแพ้อยู่ดี ซึ่งเป็นไปตาม “กฎแห่งจำนวนมหาศาล” เพราะจ้าวแห่งหอคอยรัตติกาลนั้น ได้คำนวณและออกแบบระบบเกมที่ตนเองได้เปรียบในระยะยาวแล้ว
จากตำนานนี้ ย่อมประจักษ์ชัดว่า แม้การพนันจักเป็นเรื่องของดวงชะตา
แต่ก็ถูกรังสรรค์ขึ้นจากการคำนวณทางคณิตศาสตร์
ดังนั้น หากปรารถนาจะหาหนทางเอาชนะจ้าวแห่งหอคอยรัตติกาล ก็จำต้องเข้าใจ “คณิตศาสตร์” เสียก่อน
ทีนี้ จงเงี่ยหูฟัง แล้วท่านจักได้ยินข้าไขปริศนา:
๑. ปริศนาแห่ง “กำไรคาดหวัง”
สำหรับการแสวงหา “เกมเสี่ยงทาย” ที่ควรค่าแก่การเล่น หรือการเสี่ยง
สิ่งแรกที่นักพนันพึงกระทำคือ “การประเมินกำไรคาดหวัง” หรือ “เวทคำนวณอนาคต”
“กำไรคาดหวัง” ถูกคิดค้นโดย คริสเตียน ฮอยเกนส์ นักปราชญ์เวทย์ชาวดัตช์ เพื่อประเมินว่าเกมพนันแบบใดควรค่าแก่การเล่น ซึ่งมิใช่เพียงแค่การประเมินโอกาสแห่งชัยชนะเท่านั้น แต่ต้องคิดรวมขนาดของเงินเดิมพันไปด้วย
โดยสูตรเวทย์คือ:
กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้)
ดังนั้น หากปรารถนาจะสะสม “ทองคำมายา” ในระยะยาว จงเลือกเกมที่มี “กำไรคาดหวัง” เป็นบวก
แต่หากพลาดพลั้งเข้าไปเล่นเกมที่ “กำไรคาดหวัง” เป็นลบ และบังเอิญว่าโชคชะตาเล่นตลกให้ได้เงินทองมาครอง
พึงละทิ้งเกมนั้นเสียโดยพลัน เพราะท้ายที่สุดหากยังคงเล่นต่อไป ผู้อับโชคผู้นั้นก็คือตัวท่านเอง
อย่างไรก็ตาม โดยธรรมดาแล้ว “กำไรคาดหวัง” ของเกมพนันที่มีเจ้ามือมักจักติดลบ จึงเป็นเรื่องยากยิ่งที่จะเอาชนะได้ เฉกเช่นตัวอย่างที่เราเห็น คือเกมในบ่อนพนัน หรือแม้แต่ “สลากกินแบ่งรัฐบาล” ก็ล้วนเป็นเกมที่มี “กำไรคาดหวัง” ติดลบทั้งสิ้น
นอกจาก “กำไรคาดหวัง” จักถูกใช้กับการพนันได้แล้ว
หลักเวทย์ “คณิตศาสตร์” ก็ยังสามารถประยุกต์ใช้กับการลงทุนได้ไม่แตกต่างกัน
ตัวอย่างเช่น หากท่านเก็บสถิติข้อมูลการลงทุนของตนเอง
แล้วพบว่ามีเพียงสามสิบส่วนร้อยเท่านั้น ที่ท่านซื้อ “ศิลาแห่งโชค” แล้วสร้างผลตอบแทนเป็นบวก
แต่ท่านยังคงปรารถนาความสำเร็จในการลงทุน
ก็จงจำกัดการขาดทุนแต่ละคราให้น้อยเข้าไว้ เช่น -๕%
และปล่อยให้มีกำไรในแต่ละคราที่ลงทุน เช่น อย่างน้อย ๒๐%
ซึ่งจากการใช้กลยุทธ์นี้ ท่านจักมี “กำไรคาดหวัง” = (๒๐% x ๐.๓) + (-๕% x ๐.๗) = ๒.๕%
จักเห็นได้ว่า แม้ท่านจักมีจำนวนคราที่ขาดทุนบ่อยครั้ง แต่ก็ยังสามารถสร้างกำไรได้
หากคราที่กำไรนั้น สามารถทำเงินทองเป็นจำนวนมากได้
๒. ปริศนาแห่ง “การบริหารหน้าตัก” หรือ “การบริหารเงินทุน”
แม้ว่าท่านจักรับรู้ “กำไรคาดหวัง” แล้ว แต่หากท่านเผชิญหน้ากับการขาดทุนต่อเนื่องกัน ท่านก็อาจหมดเนื้อหมดตัวก่อนถึงคราที่จะกอบโกยเงินทองจากคราที่กำไร
วิธีคลายปมปริศนานี้ก็คือ การมิลงเงินทองทั้งหมดของท่านในการลงทุนเพียงคราเดียว
ซึ่งนอกจากการกระจายความเสี่ยงในการลงทุนหลาย “ศิลาแห่งโชค” หรือหลาย “เกมเสี่ยงทาย” แล้ว
ท่านอาจกำหนดขนาดของการลงทุนแต่ละคราให้มิมากเกินไป แบบง่าย ๆ เช่น มิเกิน ๑๐% ของเงินลงทุนทั้งหมด หรือท่านอาจคำนวณขนาดของการลงทุนแต่ละคราด้วยสูตรทางคณิตศาสตร์ เช่น สูตร “การขาดทุนสูงสุดที่ท่านรับได้ (Value at Risk)” หรือ สูตร “ขนาดเดิมพันที่เหมาะสม (Kelly Formula)”
๓. ปริศนาแห่ง “อคติ”
ในวงการพนัน มักมีอคติหนึ่งที่บังเกิดบ่อยครั้งกับผู้คน คือ “Gambler's Fallacy” หรือ “ความเชื่อผิด ๆ แห่งนักพนัน” ว่าหากเหตุการณ์หนึ่งบังเกิดบ่อยครั้งกว่าปรกติในช่วงเวลาหนึ่ง ๆ
เหตุการณ์นั้นจักบังเกิดบ่อยครั้งน้อยลงในอนาคต ทั้ง ๆ ที่เหตุการณ์เหล่านั้นเป็นอิสระจากกันในทางสถิติ
ยกตัวอย่างเช่น หากโยนเหรียญมนตราออกหัวไปแล้วสามครา ในคราที่สี่ หลายคนอาจคิดว่าโอกาสออกก้อยมากกว่าหัว แม้ว่าการโยนเหรียญแต่ละคราจะมิได้ส่งผลอันใดต่อกันเลย (จะโยนกี่ครา โอกาสหัวหรือก้อย ก็คือ ๕๐:๕๐ อยู่ยั่งยืน)
หรือแม้กระทั่ง “สลากกินแบ่งรัฐบาล” มีหลายคนที่ซื้อเลขซ้ำกัน เพื่อหวังว่าจะถูกในงวดต่อ ๆ ไป
ในวงการการลงทุน ก็มีลักษณะที่คล้ายคลึงกัน เช่น หาก “ศิลาแห่งโชค A” ราคาตกต่ำลงมาห้าครา บางคนอาจคิดว่าในคราที่หก ราคาของมันจักต้องเด้งขึ้นมา ซึ่งในความเป็นจริง หาได้เป็นเช่นนั้นเสมอไป
จักเห็นได้ว่า แท้จริงแล้ว ไม่ว่าจักเป็น “เกมเสี่ยงทายแห่งโชคชะตา” หรือ “การผจญภัยในตลาดทุน”
หากท่านมีความเข้าใจ และนำ “คณิตศาสตร์” เข้ามาเป็นรากฐาน
มันก็อาจนำพาตัวท่านเอง ไปสู่จุดที่ได้เปรียบในเกมนั้น ได้เฉกเช่นกัน..
สูตรเวทย์มนตร์ที่ปรากฏในตำนาน:
- กำไรคาดหวัง = (เงินที่ได้ x โอกาสชนะ) + (เงินที่เสีย x โอกาสแพ้)
คำเตือนจากนักเล่าเรื่องแห่งเฮรันเทล:
"พึงระลึกไว้เสมอว่า โชคชะตาเป็นสิ่งที่คาดเดาได้ยาก แม้เวทมนตร์คณิตศาสตร์จักช่วยนำทาง แต่ท้ายที่สุดแล้ว ความสำเร็จยังคงขึ้นอยู่กับการตัดสินใจและสติปัญญาของท่านเอง"
หวังว่าตำนานบทนี้จักเป็นประโยชน์แก่ท่านนะคะ
-
-
 @ 2fb77d26:c47a6ee1
2025-02-01 14:40:02
@ 2fb77d26:c47a6ee1
2025-02-01 14:40:02In H. G. Wells’ Roman Die Zeitmaschine und den diversen Verfilmungen werden sie als »ausschweifend, langsam und naiv« dargestellt. Von »untermenschlicher Intelligenz« gezeichnet. Für Dan Simmons sind sie »faul, ungebildet und unkultiviert«. Die Eloi. Die als Nahrungsquelle der Morlocks gehaltenen Nachfahren des Homo sapiens. »Sie entwickeln sich rückläufig und verlernen Jahrtausende von Kultur, Denken und Vernunft, bis sie sich mit dem Vergnügen des bloßen Daseins zufrieden geben«. Ertönt das Schlüsselsignal, auf das sie von ihren Züchtern konditioniert wurden – eine umgebaute Zivilschutzsirene – trotten sie freiwillig und in hypnotischer Apathie zur Schlachtbank.
Ein ähnlichen Eindruck hatten viele Maßnahmenkritiker von den Unterstützern der mittlerweile in allen Punkten widerlegten Covid-Propaganda. Zurecht. Das Gefolge von Drosten, Lauterbach und Co. war blind für Fakten und ist ins offene Messer gelaufen. Bedauerlicherweise verhalten sich viele Maßnahmenkritiker aber nun in weiten Teilen genauso. Sie haben Idole gefunden. Wollen glauben. Sie ignorieren Informationen, Fakten und Daten und werden Opfer einer neu justierten, gut geölten Propagandamaschine. Nur, um die in ihre neuen Helden gesetzten Hoffnungen nicht aufgeben und der wenig erbaulichen Realität nicht ins Auge blicken zu müssen.
Sie glauben an Donald Trump, Javier Milei, Alice Weidel, Peter Thiel und vor allem Elon Musk. Daran, dass der supranationale Nachhaltigkeitskorporatismus am Ende sei, das Finanzsystem gerettet und Gerechtigkeit hergestellt wird. Die Widerständler von gestern sind die »Schlafschafe« von heute. Sie scheinen vergessen zu haben, wie Propaganda funktioniert. Aus diesem Grund – und weil es ein so schön griffiges Wort ist, bei dem man nur einen Buchstaben verändern muss, um daraus den Vornamen eines vermeintlichen Heilsbringers zu basteln – erlaube ich mir, die Anhänger des MAGA-Kults im Zuge der folgenden Seiten mokant als Eloi zu bezeichnen. Ein bisschen Spaß muss sein.
Kurskorrektur mit Ansage
Lynn Forester de Rothschild, in der finanzoligarchischen Hackordnung mindestens eine Ebene über BlackRock und Co. anzusiedeln, kündigte den aktuellen Narrativwechsel bereits am 30. August 2023 an, als sie bei Bloomberg sagte, der Begriff »ESG gehöre in die Tonne«. Er sei verbrannt. Auch BlackRock-CEO Larry Fink, der Marktteilnehmer zur Unterstützung von ESG »zwingen« wollte, teilte seinen Investoren bereits am 26. März 2023 mit, das in Verruf gekommene Label ESG durch den Begriff »Energiepragmatismus« zu ersetzen.
Sowohl Rothschild als auch Fink räumten aber gleichzeitig ein, dass sich die übergeordnete Agenda nicht ändern und man die »Green Economy« weiter vorantreiben werde, man diese aber besser vermarkten müsse, um konservative Kreise nicht weiter gegen sich aufzubringen. Ein simpler Marketing-Trick. Wenig überraschend also, dass sowohl BlackRock als auch sechs amerikanische Großbanken Anfang 2025 die Net Zero Initiative verließen. Zum »perfekten Zeitpunkt«, wie die New York Post bemerkt, um nicht von der negativen, anti-woken Berichterstattung rund um die verheerenden Feuersbrünste in Los Angeles tangiert zu werden.
Es scheint, als hätten die Eloi bereits wieder verdrängt, dass die WEF-Meetings 2021 und 2024 unter Arbeitstiteln wie »The Great Narrative« und »Rebuilding Trust« liefen. Artikuliertes Ziel der Davoser PR-Abteilung für Globalisierungsfragen war nämlich, sich den zunehmend echauffierten, misstrauischen Pöbel vom Hals zu halten. Durch neue Narrative und vertrauensbildende Maßnahmen. Und das hat, zumindest vorerst, ausgezeichnet funktioniert.
In den USA stieg das Vertrauen in ordnungsgemäß durchgeführte Präsidentschaftswahlen 2024 zum ersten Mal seit Jahren wieder etwas an. In Europa macht sich ebenfalls Zuversicht breit. Schließlich haben die sogenannten »Rechtspopulisten« nicht mehr nur in Italien und Ungarn, sondern auch in Finnland, der Slowakei und den Niederlanden Oberwasser. Von den Erfolgen der AFD ganz zu schweigen. Diese führen, wie zuletzt in Thüringen, trotz klarem Wählervotum zwar nicht zur Regierungsbeteiligung, weil »demokratische Prozesse« und »Brandmauern« das zu verhindern wissen – aber dabei sein ist ja bekanntlich alles. Dass Friedenstreiberin Alice Weidel den bundesdeutschen Rüstungsetat auf knapp 200 Milliarden verdoppeln will, scheint die euphorisierten Kritiker dunkelgrüner Militarisierung auch nicht auszubremsen. Hauptsache nicht grün. Oder woke.
Überstaatliche Sphären
Dabei scheint Euphorie in Anbetracht der Tatsachen alles andere als angebracht. So hat Milei nach Angaben von Global Finance zwar das argentinische »Staatsdefizit nach 123 Jahren beendet«, dafür leben heute 53 Prozent der 45 Millionen Argentinier in Armut. Der höchste Wert seit 20 Jahren. Ende 2023 waren es noch 41,7 Prozent. Daran ändert auch semantische Schützenhilfe von libertären Denkfabriken wie der Hoover Institution nichts. Die radikalen Privatisierungsfeldzüge von »El Loco« haben einen hohen Preis. Ob Aerolineas Argentinas, die staatliche Fluglinie, der Stahlproduzent IMPSA oder das Transportunternehmen Trenes Argentinos Cargas, das 7.800 Kilometer Bahnstrecke betreibt – das Volksvermögen wird an die Meistbietenden verscherbelt. Wer das ist, kann sich wohl jeder ausmalen. Denn sein Schlachtruf »Afuera!« (Raus hier!) gilt augenscheinlich nicht für BlackRock und Co. – schließlich sei Argentinien »ziemlich billig« zu haben, wie es Rick Rieder, Top-Bond-Manager des Unternehmens schon 2019 formulierte.
Man muss allerdings nicht in die Ferne schweifen, um sich der realen Gefahren für die Freiheit bewusst zu werden. Jener Gefahren, die von Personalien gänzlich unberührt bleiben. So arbeitet die Europäische Union weiter an der eID, der Grundlage des technokratisch-totalitären Kontroll-Grids. Ihre Einführung ist beschlossene Sache. Offen ist lediglich, ab wann sie zum Obligatorium wird. Auch das persönliche CO2-Budget ist auf Kurs. Mit ETS2 (EU Emissions Trading System) nimmt die EPA (Environmental Protection Agency) seit dem 1. Januar 2025 nach der Konzernwirtschaft nun kleine und mittlere Unternehmen in den Fokus und verpflichtet diese, CO2-Kompensationsabgaben auf ihren Gas-, Benzin- und Mineralölverbrauch zu entrichten. Das dürfte Heiz-, Fracht- und folglich die Lebenshaltungskosten des Bürgers in neue Höhen treiben. Bis der Sonntagsausflug mit dem Familienauto nicht mehr nur Zeit, Benzin und Nerven, sondern auch CO2-Gebühren kostet, dauert es also wohl nicht mehr allzu lange.
Dieser überparteilichen, supranational koordinierten Überwachungs- und Enteignungsagenda ist weder durch die Wahl des geringeren Übels noch durch Auswandern zu entkommen. Denn wie sich der Internetpräsenz des »Global Governance Forum« (GGF) entnehmen lässt, wird bereits eifrig an »Global Government« gearbeitet. Die UN-nahe Nichtregierungsorganisation hat sich nämlich zum Ziel gesetzt, die Charta der Vereinten Nationen bis 2028 zu aktualisieren und den allseits bekannten »Herausforderungen unserer Zeit« anzupassen. Pünktlich ab 2030 soll das neue Vertragswerk ratifiziert werden und neben neuen Befugnissen für den Internationalen Gerichtshof sowie einer UN-Streitmacht auch eine Regierungsstruktur analog der Europäischen Union ermöglichen. Sprich, eine Weltregierung. Ganz demokratisch selbstverständlich.
Neben eID und CO2-Budget sind natürlich auch die Ausweispflicht fürs Internet und die automatisierte Zensur unliebsamer Inhalte weiter auf Kurs. Nachdem die Vereinten Nationen im September 2024 bereits dem totalitären »Pakt für die Zukunft« zustimmten, wurde am Heiligabend 2024 noch rasch die neue »Konvention gegen Onlineverbrechen« durchgewunken. Und seit Januar 2025 treibt die UN die Umsetzung eines noch weitreichenderen Abkommens namens »Global Digital Compact« voran. Ein Papier, vor dem ich bereits im Juli 2023 gewarnt habe. Was all das für den Bürger bedeutet, zeigt sich in Griechenland, wo die Regierung seit Anfang des Jahres Social-Media-Konten mit Steuer-Identifikationsnummern verknüpft, um eine Alterskontrolle fürs Internet einzuführen. Damit folgt die von der EU in Kreditsklaverei gehaltene Regierung in Athen dem Vorbild Australiens, wo der Zugang so Social-Media-Plattformen künftig erst ab einem Alter von 16 Jahren erlaubt werden soll – wofür man schlussendlich jeden Nutzer kontrollieren muss, der online geht.
Auch das von vielen noch immer als Mythos abgetane Geoengineering wird derweil munter weitergeführt. Obwohl Berichte des US-Kongress und mittlerweile sogar wissenschaftliche Berater der EU-Kommission vor großflächigem Solar Radiation Management warnen. Im Rahmen eines offiziellen, 54 Seiten umfassenden Reports an die EU-Kommission sowie eines Artikels des britischen Guardian vom 9. Dezember 2024 verwies das siebenköpfige Forscherteam auf die unabschätzbaren Konsequenzen solcher Eingriffe und forderte ein EU-weites Moratorium.
Wie genau Trump, Musk, Milei, Meloni, Weidel und Co. die Welt vor diesem Sammelsurium an totalitären Übergriffigkeiten retten wollen, konnte mir bislang keiner der Eloi sagen.
DJ Trump
Warum die in Donald Trump, den »Vater der Impfung«, und sein zionistisches Kriegstreiberkabinett gesetzten Hoffnungen bald bitterer Enttäuschung weichen dürften, habe ich bereits am 14. November 2024 ausführlich beschrieben. Dass auch die beiden Hauptargumente seiner Befürworter – dass er die mRNA-Kampagne mittlerweile bereue und in seiner ersten Amtsperiode Friedenspolitik betrieben habe – schlichtweg falsch sind, ebenfalls. Denn anhand der nackten Zahlen lässt sich eindeutig belegen, dass Trump »der kriegslüsternste Präsident der jüngeren Geschichte« war. Und wie stolz er auf »Operation Warp Speed« ist, die unzählige Amerikaner Gesundheit oder Leben kostete, ließ er die Welt zuletzt am 17. November 2024 auf seinem Social-Media-Netzwerk Truth Social wissen.
Trumps Interesse gilt nicht Frieden und Freiheit, sondern Donald Trump. So war es sein ganzes Leben lang. Wenn sich »The Donald« jemandem verpflichtet fühlt, ist es vielleicht Wilbur Ross, der ehemalige Chef von Rothschild Inc. Bankruptcy Advising. Denn wie das Forbes Magazine am 8. Dezember 2016 korrekt erläuterte, rette das Bankhaus vor gut 30 Jahren nicht nur Trumps bankrotte Casinos, sondern damit auch seine ganze Karriere. Nicht weil man in Trumps Geschäften und Immobilien einen besonderen Wert sah, sondern weil man die Person Donald Trump als »Anlage« betrachtete. Trotzdem ist es sicher nur Zufall, dass Ross von 2017 bis 2021 Handelsminister der Vereinigten Staaten war.
Elon Musk
Auch über den PayPal-Mafioso, CIA-Handlanger und Bilderberg-Executive Peter Thiel, dessen Protegé JD Vance nun US-Vizepräsident ist, habe ich bereits im September 2024 einen ausführlichen Artikel geschrieben. Gleiches gilt für Elon Musk, dessen trügerisches Image als Genius, Erfinder und Entrepreneur ich sogar schon im Oktober 2022 durchleuchtet habe. Zitat:
»Dass Elon Musk nicht rein zufällig zur liberal-coolen Ikone avancierte, legt ein Blick in seine Anfangsjahre als Unternehmer nahe. Denn während im sagenumwobenen Silicon Valley Ende der 1990er-Jahre eine Vielzahl an erfolgreicheren Tech-Entrepreneuren existierte, war es ausgerechnet Elon Musk, der für einen absolut inhaltsleeren Gastauftritt bei CNN gefilmt wurde, sodass zum ersten Mal eine breitere Öffentlichkeit von ihm Notiz nehmen musste. Dabei war sein erstes Unternehmen – Zip2 –, das er im Jahre 1995 mit seinem Bruder sowie einem weiteren Partner gegründet und im Februar 1999 für circa 300 Millionen US-Dollar an Compaq veräußert hatte, nicht das revolutionärste Unterfangen im kalifornischen IT-Mekka dieser Tage. Es handelte sich um ein simples Telefonbuch fürs Internet. Wenig mehr als eine Datenbank, in die sich Unternehmen eintragen konnten, um ihre Adresse im Netz zu hinterlegen.«
Meine fast zweieinhalb Jahre alte Analyse bedarf allerdings dringend einer Aktualisierung. Denn was Musk in der Zwischenzeit trieb – und für die Zukunft plant – hat so gar nichts mit dem zu tun, was seine geradezu fanatisierten Anhänger in ihm sehen wollen.
Fangen wir der Vollständigkeit halber aber noch mal vorne an: Elon Musk hat weder PayPal gegründet noch den Tesla erfunden. Auch wenn er das gerne so darstellt. Dafür fertigte Tesla unter seiner Ägide dann aber »RNA Mikrofabriken« für das deutsche Unternehmen CureVac, das zusammen mit Bayer mRNA-Injektionen gegen Corona auf den Markt brachte. Und während Musk gegenüber der New York Post am 30. September 2020 sagte, sich nicht gegen Covid impfen lassen zu wollen, erklärte er dem TIME Magazine am 13. Dezember 2021, bereits geimpft zu sein. Zeitgeistig flexibel ist er also. Wer behauptet, Musk hätte seine Meinung zur mRNA-Technologie seit dem Covid-Fiasko signifikant geändert und sehe das Produkt nun kritisch, ist schlecht informiert. Noch am 12. April 2023 erklärte er bei Twitter, dass er mRNA für eine »medizinische Revolution« hält. Vergleichbar mit dem Schritt »von analog zu digital«.
Was Musk mit digitaler Revolution meint, zeigte sich 2017 mit Hurricane Irma. Damals gab das Unternehmen für Besitzer von Fahrzeugen mit 75 kWh ein Softwareupdate heraus, das die Reichweite von 338 auf 400 Kilometer steigerte – was im Umkehrschluss bedeutet, dass Tesla-Besitzer um eine eigentlich abrufbare Leistung ihres eigenen Fahrzeugs betrogen werden, wenn gerade keine Naturkatastrophe wütet. Dass Tesla-Kunden darüber hinaus permanent überwacht werden, zeigte sich unlängst im Rahmen der Explosion eines Cybertrucks in Las Vegas. Augenbewegungen, Mimik, Geschlecht, Hautfarbe, Körpertemperatur, Gepäckanordnung, Route, Ladestopps, Bezahlvorgänge, Telefonbuch, Musik-Playlist, Online-Abos, et cetera. Was von Sensoren und Verbindungen zu erfassen ist, wird erfasst, wie eine Untersuchung von Mozilla im Herbst 2023 feststellte. Das gilt im Übrigen nicht nur für Tesla, sondern für praktisch alle modernen Autos. Ein Tesla hat es dabei nur am leichtesten. Die gesammelten Daten werden entweder zum Schleuderpreis verkauft und/oder gegen uns verwendet.
Doch zurück zu Musk, der Twitter nicht übernahm, um Meinungsfreiheit herzustellen, sondern um die Plattform zur »Alles-App« zu machen. Sein erklärtes Vorbild: die chinesische Spionage-App WeChat. Deswegen will er alle Nutzer »als echte Menschen identifizieren«. Biometrisch versteht sich. Dafür arbeitet man bei Twitter bevorzugt mit israelischen Unternehmen zusammen, die von ehemaligen Mossad-Agenten gegründet wurden. Vielleicht stellte ja Doppelagent Jeffrey Epstein den Kontakt zum Mossad her, nachdem er Musk als regelmäßigen Teilnehmer seiner Edge-Foundation Seminare zum Thema Nudging schätzen gelernt hatte. Epstein war nämlich der einzige nennenswerte Sponsor von Edge.
Twitter kaufte Musk übrigens nicht von seinem eigenen Geld, sondern mit Hilfe von 94 Investoren, deren Namen ein US-Bundesrichter erst im August 2024 veröffentlichte, weil Jacob Silverman (Reporters Committee for Freedom of the Press) sie einklagte. Die Liste umfasst so illustre Namen wie Fidelity Investments, Sequoia Capital, Andreessen Horowitz, Bandera Fund, Binance Capital Management, Sean Combs (alias Diddy) Capital, Jack Dorsey (Twitter Gründer), Baron Opportunity Fund oder Prinz Alwaleed bin Talal al Saud von der saudischen Königsfamilie. Da wird also offenbar »der Sumpf« mit mehr Sumpf »trockengelegt«. Von der Nominierung des WEF Executive Chair Linda Yaccarino als neuer Twitter-CEO und »Freedom of Speech« versus »Freedom of Reach« mal ganz abgesehen.
Auch die von den Eloi als sensationelle Enthüllung gefeierten Twitter Files sind leider nicht ernst zu nehmen. Denn sie offenbarten nichts, was man nicht schon wusste. Zudem ist bis heute unklar, woher die veröffentlichten Informationen kamen, wer den Zugriff darauf gesteuert hat, was dort noch gespeichert war, warum praktisch nur ein von Elon ausgewählter Journalist Zugriff darauf hatte und dieser nur Screenshots, anstelle ganzer Dokumente veröffentlichen durfte. Ein echter Leak besteht aus einem Archiv, das man selbst durchsuchen kann – nicht aus ein paar handverlesenen Screenshots.
Fehlt noch Space X. Ein Unternehmen, das Musk zwar selbst gegründet hat, dessen Erfolge aber in weiten Teilen anderen Umständen zu verdanken sind. So schreibt beispielsweise inside Tesla am 22. März 2022:
»Schon Anfang der 2000er-Jahre hatte die NASA erkannt, dass ihr bald die Möglichkeit fehlen würde, selbst Astronauten und Material ins All und zur ISS zu bringen. Man machte sich also auf die Suche nach Partnern aus der Privatwirtschaft und wurde unter anderem bei Elon Musks Space X fündig. Bereits 2006, also noch in der Entwicklungsphase der Falcon 1, erhielt Musks Unternehmen fast 400 Millionen US-Dollar Startfinanzierung unter dem COTS-Programm.«
Space X war von Beginn an als verlängerte Werkbank der NASA gedacht, weil der US-Weltraumbehörde immer mehr Mittel gestrichen wurden. Die Öffentlichkeit hatte nämlich das Interesse an ziviler Raumfahrt verloren. Daher setzte man in Washington immer öfter den Rotstift an. Doch seit Musk die Menschen öffentlichkeitswirksam zum Mars befördern will – »let’s build Marsian Technocracy« – steigt das Interesse wieder. Leider muss ich die Vorfreude auf eine planetare Kolonie aber etwas dämpfen. Denn Space X wird nicht betrieben, um Menschen auf den Mars zu bringen, sondern um das »weltgrösste Netzwerk an Spionagesatelliten aufzubauen«.
Musks Weltraumagentur ist Handlanger des militärisch-industriellen Komplexes und einer der wichtigsten Vertragspartner des Pentagon. Das konnte man 2017 schon im Observer nachlesen. Oder am 9. Januar 2018 bei CNBC, die vom (missglückten) Transport eines streng geheimen US-Spionagesatelliten berichtete. Am 15. April 2022 kommentierte Tech Unwrapped zwei weitere Spionagesatelliten des US-Militärs, die Space X in die Umlaufbahn beförderte. Seit Jahren erhält das Unternehmen Milliarden von US-Regierung und Geheimdiensten. Siehe Los Angeles Times vom 30. Mai 2015: 4,9 Milliarden. Oder ein Artikel des Wall Street Journal vom 23. Februar 2024: 1,8 Milliarden. Oder eine lange Liste von staatlichen Zuwendungen, die Business Insider am 15. Dezember 2021 veröffentlichte. Damit basiert der Erfolg von Space X nicht primär auf Musks genialem Unternehmergeist, sondern auf Subventionen. Auf Steuergeldern.
Nicht zu vergessen: Starlink. Das von Space X betriebene, weltumspannende Satellitennetzwerk. Es mag den Vorteil haben, dass damit auch Menschen in entlegenen Regionen des Planeten oder Katastrophengebieten Zugriff auf das Internet haben. Dabei sollte allerdings nicht unterschlagen werden, dass Starlink in seiner finalen Ausbaustufe circa 42.000 Satelliten umfassen und damit ein permanentes Strahlungsfeld erzeugen wird. Gesundheitliche Risiken für den Homo sapiens: unklar. Darüber hinaus haben die Orbiter Zugriff auf das NORAD-Datenbanksystem, um Weltraumschrott ausweichen zu können. Sprich, sie sind permanent mit Systemen des US-Militär verbunden. Aus diesem Grund ermöglicht Starlink auch die Steuerung von Kampfdrohnen – siehe Ukraine-Konflikt – sowie 30 mal schnelleres Senden von Daten an und von US-Kampfflugzeugen. Während die Öffentlichkeit Musks Satellitennetzwerk vor allem als ziviles Produkt betrachtet, ist Starlink primär von militärischem Interesse. Nicht umsonst wird parallel Starshield aufgebaut, das dem geheimdienstlich-militärischen Komplex unter anderem die diskrete Echtzeitüberwachung der ganzen Welt erlaubt. Auch von DEW-Fähigkeiten (Directed Energy Weapon) ist die Rede. Ende 2024 befanden sich bereits 98 solcher Satelliten in erdnaher Umlaufbahn.
In Anbetracht dieser Informationen ist es also kaum verwunderlich, dass Musk seit Jahren offen für Technokratie wirbt. Für ein zentralistisches, faschistoides Herrschaftsmodell, das schon sein Großvater Joshua Haldemann als führender Kopf in den USA und Kanada vertrat. Der Familientradition folgend empfiehlt Musk eine CO2-Steuer zum Kampf gegen den Klimawandel, ein universelles Grundeinkommen, um die von der KI ausgelösten Disruptionen abzufangen und sein Neuralink Gehirnimplantat, um dem drohenden Transhumanismus etwas Transhumanismus entgegenzusetzen.
Futurum Technologicus
Für Kunden, denen Chips im Kopf irgendwie zu altbacken sind, entwickelt Musks Unternehmen in Zusammenarbeit mit iota Biosciences natürlich ein zeitgemäßeres Premiumprodukt: Neural Dust. Intelligente Nanopartikel in Staubkorngröße, die sich im Gehirn anreichern. Die lassen sich dann wahrscheinlich – wie die in Indien bereits zugelassene Nasal-Impfung gegen Covid – durch die Nase ziehen. Oder durch Luftschächte öffentlicher Gebäude pumpen. Man kann die neue Freiheit also förmlich riechen.
Ganz wie es der 44 Seiten starke »National Nanotechnology Initiative Strategic Plan« (NNI Plan) des Weißen Hauses im Oktober 2021 vorsah: »Die Öffentlichkeit einbeziehen und Mitarbeiterzahlen im Bereich Nanotechnologie erhöhen«. Nicht umsonst hat Donald Trump der entsprechenden Behörde in seiner ersten Amtszeit zusätzliche Mittel genehmigt. Genau wie Joe Biden nach ihm.
Das von der Technokratie-Bewegung vor fast einem Jahrhundert definierte nordamerikanische Technate – sprich, der amerikanische Verantwortungsbereich einer weltweiten Technokratie – sieht der von Trump und Musk reanimierten Vision einer »nordamerikanischen Union« übrigens verblüffend ähnlich. Wen interessiert bei all der Make-Great-Euphorie schon noch, dass Imperialismus scheisse, Dänemark ein souveräner Staat und der Panamakanal ein strategisches Nadelöhr der internationalen Handelsschifffahrt ist. Oder, dass die »nordamerikanische Union« nicht nur bei Trump-Cheerleadern wie Alex Jones vor ein paar Jahren noch als »böser Globalisten-Plan« galt.
Schauen wir nach vorne. In Richtung »goldenes Zeitalter«, wie Trump es nennt. Dieses dürfte für den Normalbürger nämlich sehr ungemütlich werden. Denn es wird dominiert von Algorithmen. Von Künstlicher Intelligenz. Für die Eloi also primär von Grok, dem auf Twitter (und Teslas) integrierten Chatbot. Dieser basiert auf Technologie des Unternehmens xAI – laut Wikipedia gegründet von Elon Musk im März 2023. Das mag zwar so im Handelsregister stehen, ist wohl aber nur die halbe Wahrheit. Denn xAI dürfte die Fortführung eines DARPA-Projekts darstellen, das bereits 2015 unter dem Titel »Explainable Artificial Intelligence« (XAI) gestartet wurde und 2021 auslief. Als die Finanzierung seitens DARPA eingestellt wurde, machte XAI die Forschungsergebnisse auf einem Server zugänglich. Circa 18 Monate Jahre später engagierte Elon Musk Igor Babuschkin als Chefingenieur für xAI. Babuschkin hatte zuvor acht Jahre lang für Googles DeepMind-Projekt gearbeitet und nutzte aller Wahrscheinlichkeit nach die DARPA-Ergebnisse um xAI, beziehungsweise Grok zu entwickeln.
Im Juli 2023 verkündete Musk, xAI sei im Gegensatz zu den Konkurrenzprodukten von Google, Microsoft und OpenAI eine »gute« KI. Erstaunlich, wenn die gleichen Ingenieure am Werk sind und die KI auf Basis eines Militärprojekts entsteht. Zudem sprechen auch die Top-Sponsoren von xAI nicht unbedingt für das »Gute«. Denn unter den größten Geldgebern der letzten Finanzierungsrunde vom 23. Dezember 2024 befinden sich so illustre Namen wie BlackRock, AMD, Nvidia und Fidelity, die zusammen weitere sechs Milliarden Dollar für Musks KI-Unternehmen zur Verfügung stellten.
Genug Liquidität, um xAI für die »Alles-App« weiterzuentwickeln, wo Grok seit einer Weile automatisch Kurzbeschreibungen für Profile erstellt, die man weder abschalten noch ändern kann. Twitter-Nutzer müssen nun also nicht mehr selbst das Profil eines Accounts durchstöbern, um sich einen ersten Eindruck von der Person zu machen, sondern bekommen diesen von Elon Musks KI geliefert. Vorurteil auf Knopfdruck sozusagen. Vergleichbar mit einem Sozialkreditsystem. Denn die täglich neu generierte Zusammenfassung basiert auf dem Nutzerverhalten.
»Die neuen, KI-generierten Grok-Kurzprofile unter jedem X-Nutzerprofil SIND de facto ein Social Credit System nach chinesischem Vorbild für den Westen. Das Profil jedes Nutzers wird tagesaktuell neu berechnet. Äußert man sich zu verschiedenen Themen, nennt die KI das schnell mal »verheddern«. Grok gibt zu, das Profil wird erstellt aus dem eigenen Nutzerverhalten des Tages, seinen eigenen Berechnungen und nicht näher definierten Anweisungen«, kommentierte Journalistin Aya Velázquez die Neuerung am 14. Januar 2025.
Andere Nutzer werden als »leicht erregbar« beschrieben, »verzetteln« sich oder »glauben an Wettermanipulation zur Klimakontrolle«. Offener wird ein Debattenraum dank solcher Adjektive und Zusammenfassungen sicher nicht. Wer möchte schon das Profil von leicht erregbaren Chemtrail-Gläubigen anschauen oder gar mit diesen assoziiert werden. Gegen solch eine automatisierte, herablassend daherkommende Einordnung durch intransparent operierende KI war die Faktencheck-Industrie geradezu harmlos. Wer also annimmt, die Abschaffung der Faktenchecker bei Facebook und Co. bedeute ein Ende der Zensur, irrt. Sie wird im Gegenteil deutlich raffinierter und weitreichender werden.
Details zum persönlichen Punktestand im Grok-Sozialkreditsystem oder Information über das Zustandekommen der Bewertung erhält man auf Anfrage natürlich nicht. Twitter wird die daraus entstehende Hierarchie aber mit Sicherheit für Reichweitensteuerung, Nudging-Kampagnen und weitere sozialarchitektonische Funktionen nutzen. Vor allem, wenn 2025 das Bezahlsystem »X Money« eingeführt wird. Dann werden die Eloi bald nicht mehr nur um Reichweite, Follower und Re-Tweets buhlen, sondern auch um Geld – das als Folge unliebsamer Postings zu Genozid X, Krieg Y oder Person Z künftig schneller eingefroren werden dürfte als jedes Bankkonto. De-Banking der nächsten Generation. Und irgendwann trifft das jeden. Außer, man schwimmt immer mit dem Strom.
Doch damit nicht genug. Am 13. Dezember 2024 gab das wohl den wenigsten bekannte Unternehmen WISeSat bekannt, künftig mit Space X zusammenzuarbeiten, um »verschiedene Produkte und Systeme zu kombinieren«. Die WISeSat AG ist eine Tochterfirma der in Genf (Schweiz) ansässigen WISeKey International Holding AG, die im Bereich Cybersicherheit, KI und IoT (Internet of Things) tätig ist. Die Ankündigung dieser Kollaboration ließ die WISeKey-Aktie kurzfristig um 107,73 Prozent steigen. Ein erster gemeinsamer Start zum Transport sogenannter Picosatelliten fand am 14. Januar 2025 von der Vandenberg Space Force Base in Kalifornien statt.
Aber was genau macht WISeSat? Einer Presseerklärung des Unternehmens vom 15. September 2023 lässt sich entnehmen:
»WISeSAT AG zeichnet sich dank ihrer Konstellation von ultra-sicheren Picosatelliten und Infrastruktur durch sichere und effektive Kommunikationsstrategien für vernetzte Geräte aus. Die Expertise des Unternehmens in kryptografischer Technologie und sicherem Datenmanagement hat die sichere IoT-Implementierung in zahlreichen Bereichen neu definiert, von städtischen Innovationen in Smart Cities bis hin zu modernster industrieller Automatisierung. (…) WISeSAT steht an vorderster Front bei der Entwicklung von ultra-sicheren Picosatelliten-Lösungen in Zusammenarbeit mit ihrem Verbündeten FOSSA Systems. Es setzt sich für sichere IoT-Kommunikation über raumbasierte Netzwerke ein und nutzt die neuesten kryptografischen Innovationen, um sichere und sofortige Datenaustausche in verschiedenen Bereichen zu gewährleisten (…).«
Im Klartext: WISeSat bringt Satelliten von der Größe einer Tupperdose ins All. Diese Mini-Orbiter umkreisen den Planeten in niedrigen Umlaufbahnen und etablieren dort ein Netzwerk für kryptografierte Echtzeitdatenübertragung. Fliegende 5G-Masten sozusagen. Oder WLAN-Router. Nur viel schneller. Für das Internet der Dinge – und Smart Cities.
»In dieser Woche startet WISeSat einen Satelliten der neuen Generation und markiert damit einen wichtigen Meilenstein in der Entwicklung einer globalen Satellitenkonstellation, die eine umfassende Erdabdeckung mit ultraniedriger Latenzzeit ermöglicht. Entwickelt, um Billionen von IoT-Geräten in Echtzeit zu verfolgen und aufzuspüren.« (Carlos Creus Moreira, WISeKEy CEO, 12. Januar 2025)
Welche Datenträger dieses Picosatelliten-Netzwerk künftig verfolgen und aufspüren soll, zeigt sich bei einem Blick auf das Produktportfolio der Holding-Gesellschaft WISeKey – einem »weltweit führenden Anbieter von Cybersicherheit, digitaler Identität und Internet der Dinge (IoT) Lösungen«. Denn die Holding existiert seit 24 Jahren, besteht aus fünf Unternehmen, hat mehr als eineinhalb Milliarden Chips und über fünf Milliarden »Roots of Trust« installiert, residiert an sechs internationalen Standorten und hat gut 3.000 Kunden in Staat und Wirtschaft beglückt. Einen Wikipedia-Eintrag gibt es für das bei NASDAQ und SIX gelistete Unternehmen erstaunlicherweise trotzdem nicht.
Dafür aber für den seit Mai 2021 amtierenden »Chief Digital Transformation Officer« Pierre Maudet. Der war ab Juni 2012 Mitglied des Genfer Staatsrats, 2013 bei den Young Global Leaders des Weltwirtschaftsforums und 2015 bei der Bilderberger Konferenz in Telfs-Buchen (Österreich). Nachdem er im Februar 2021 vom Genfer Polizeigericht wegen Vorteilsnahme verurteilt wurde, trat er als Staatsrat zurück – und drei Monate später bei WISeKey an. Am 30. April 2023 wurde er, ungeachtet seiner kriminellen Vergangenheit, zusätzlich wieder in den Genfer Staatsrat gewählt. Wie praktisch. Solch eine schamlose Unverfrorenheit scheint Maudet perfekt für das zu qualifizieren, was bei WISeKey unter dem Deckmantel der »Quantensicherheit« entwickelt wird – ein raumbasiertes eID-Ökosystem.
»Quantensicherheit nutzt Prinzipien der Quantenmechanik, um den Datenschutz und die sichere Informationsübertragung zu revolutionieren. Kernstück ist die Quantenschlüsselverteilung (Quantum Key Distribution, QKD), eine Spitzentechnologie, die mithilfe der Quantenmechanik vernetzte Teilchen für den sicheren Austausch von Verschlüsselungskennwerten erzeugt.«
Ob digitale Identität, Unterschrift, Cloud oder Software – von der Know-Your-Customer-Biometrie bis hin zur Unternehmenslösung für die Mitarbeiteridentifikation. WISeKey hilft. Anmelden kann sich jeder. Während die Produktpalette für den privaten Sektor noch nach Lieferketten-Management, Sendungsverfolgung, Login-Lösung für eBanking oder Face ID auf dem Smartphone klingt – aber deutlich weitreichender ist, schauen sie sich die Homepage an – sprechen die WISeKey-Angebote im Bereich Regierungen eine ganz andere Sprache. Denn unter diesem Menüpunkt bewirbt der diskret operierende Konzern seine »CertifyID Trust Center Platform«:
»Die CertifyID Trust Center Platform ist eine industrialisierte eID-Verwaltungslösung für Bürger, die Benutzer und ihre Anmeldeinformationen verwaltet, insbesondere digitale IDs und digitale Zertifikate für groß angelegte Anwendungen wie landesweite E-Government-Dienste. Es handelt sich um eine vollständige industrielle Public Key Infrastruktur- und ID-Verwaltungslösung, die Regierungsdienste rund um die Uhr unterstützt.
Die CertifyID Trust Center Plattform wird in einer Reihe von Anwendungen der Regierung und des öffentlichen Sektors verwendet, zum Beispiel: Personalausweis, ePassport (ICAO-konform), Führerschein, Gesundheit, Wahlen/Abstimmen.
Die CertifyID Plattform wurde unter Verwendung der Sicherheits- und Public Key Infrastruktur-Expertise von WISeKey entwickelt und kann vollständig in E-Government-Frameworks, kommerzielle Frameworks (…) und in das Bereitstellungsframework für E-Government-Dienste eines Landes integriert werden.«
Da passt es doch wunderbar ins Bild, dass WISeKey am 13. Oktober 2022 eine »Partnerschaftsvereinbarung zur Zusammenarbeit bei der Entwicklung weltraumbezogener Aktivitäten« mit der Schweizer Armee bekannt gab – schließlich residieren in der Alpenrepublik nicht nur UN, GAVI, WEF, Club of Rome und jede Menge NGOs, sondern auch die Bank für Internationalen Zahlungsausgleich (BIZ), die ganz sicher Verwendung für ein quantengesichertes Echtzeit-Picosatellitennetzwerk findet, wenn ihr »Unified Ledger« (Zentrales Hauptbuch) für das Blockchain-Weltfinanzsystem von morgen zum Einsatz kommt. In Anbetracht der »allumfassenden Marktblase« (D. Webb, 2024) ist damit wohl in absehbarer Zeit zu rechnen.
Das also sind die Projekte, Pläne und neuen Partner von Elon. Auf mich machen ja speziell die korrupten Genfer Quantenspezialisten mit ihren Picosatelliten und schlüsselfertigen eID-Lösungen nicht unbedingt den Eindruck von Freiheitskämpfern. Und auch die am 22. Januar 2024 bei einer Pressekonferenz im Weißen Haus angekündigten »personalisierten mRNA-Injektionen gegen Krebs« lassen mich eher skeptisch zurück.
Genau wie der Umstand, dass diese binnen 48 Stunden »personalisierte mRNA« durch die Rechenleistung von OpenAI ermöglicht werden soll. Denn das von Elon Musk mitgegründete Unternehmen des WEF- und Bilderberg-affinen Sam Altman steht im berechtigten Verdacht, für den Tod eines Whistleblowers im Dezember 2024 verantwortlich zu sein. Während Polizei und Medien den Tod des OpenAI-Forschers Suchir Balaji als Selbstmord deklarieren, sprechen sowohl die Umstände am Fundort seiner Leiche als auch Balajis Eltern von »eiskaltem Mord«. Nicht zu vergessen, dass Altman von seiner eigenen Schwester des jahrelangen Missbrauchs beschuldigt wird und sich dafür demnächst vor Gericht verantworten muss. Selbst The Economist räumte am 10. Dezember 2024 ein, dass »die PayPal Mafia die amerikanische Regierung übernimmt«. Und das mit der »Mafia« scheint man in Washington mittlerweile wörtlich zu nehmen.
Aber die von einigen aus der Hüfte geschossenen Präsidialdekreten euphorisierten Eloi werden sicher Gründe finden, das alles zu ihren Gunsten auszulegen. Immerhin hat Trump ein paar Leute begnadigt und will aus der WHO austreten. Wie seine Fanbase es bewerkstelligt, auszublenden, dass »The Donald« schon in seiner ersten Amtszeit aus der WHO austreten wollte und es unterließ, erschließt sich mir aber leider nicht. Genau wie die Begeisterung für ein Gespräch zwischen Musk und Weidel. Man stelle sich nur mal vor, George Soros, Bill Gates oder Eric Schmitt konferierten mit deutschen Politikern. Oder bekämen Sendezeit im ÖRR. Nicht auszudenken.
Wie heißt es so schön: »Eine schmerzliche Wahrheit ist besser als eine Lüge« (Thomas Mann). Stimmt. Nur fällt es relativ schwer, eine Lüge einzugestehen, wenn der, dem man sie beichten muss, der Lügner ist.
So bleibt nur zu hoffen, dass möglichst viele Eloi diesen Schritt trotzdem möglichst bald hinter sich bringen. Im eigenen Interesse. Denn wie schon Ernst Freiherr von Feuchtersleben feststellte, ist »Reue der Verstand, der zu spät kommt«. Und das kann in diesen Tagen verheerende Folgen haben.
-
 @ 6e0ea5d6:0327f353
2025-02-18 17:59:24
@ 6e0ea5d6:0327f353
2025-02-18 17:59:24At the banquet of consequences, there is only one worthy dish: pride, never regret. At that table, the main course will not be served with lukewarm excuses or poorly disguised remorse. Let it be pride—fiery, indomitable—that fills your mouth and satisfies your hunger for dignity. The man who surrenders to remorse is already dead before the grave. It is honor that should fill your stomach, not the bitter taste of shame.
When the battle weighs heavy, remember: you fight for those you love, for true love—the one that keeps us standing in the storm—is an anchor of iron. It is not the soft, sweet love of illusions but the steel that holds you to the ground when chaos tries to drag you away. Let hatred be the fuel of your victory, as long as you control it. If it serves you to win, so be it; but make it a weapon, not a chain. Defeat is not an option, and those who bow before it bear the mark of weakness forever.
Understand this: victory and defeat are fleeting; it is the battle itself that truly matters and defines who you are. Only a fool longs for the end. For the man who knows, rest comes only with the last breath. As long as there is life, there is struggle, and that is enough.
Reality is not for the weak. If you cannot bear the truth, seek comfort in ignorance. But a man, fully made, knows what it means to forge character through blood and silence. And finally, expect nothing from anyone. The one who enters battle relying on others’ help is already defeated. You were not born to be spared or carried. You were born to stand on your own strength and feast at the banquet of your victories.
Thank you for reading, my friend!
If this message has helped you in any way, consider leaving your “🥃” as a token of appreciation.
A toast to our family!
-
 @ 4f1a1249:66f0ac3a
2025-02-18 07:15:30
@ 4f1a1249:66f0ac3a
2025-02-18 07:15:3068bet là một nền tảng kỹ thuật số hiện đại, mang đến cho người dùng một trải nghiệm mượt mà, nhanh chóng và tiện lợi. Với giao diện thiết kế tối ưu, dễ sử dụng, 68bet giúp người dùng dễ dàng thao tác và tiếp cận các tính năng quan trọng một cách nhanh chóng. Hệ thống được tối ưu hóa để hoạt động ổn định trên nhiều thiết bị, từ máy tính bàn đến điện thoại di động, đảm bảo sự linh hoạt và thuận tiện tối đa. Đặc biệt, nền tảng này liên tục cập nhật những công nghệ tiên tiến nhất nhằm cải thiện hiệu suất và tốc độ xử lý, giúp mọi thao tác diễn ra trơn tru và chính xác. Nhờ vào những đổi mới không ngừng, 68bet đã nhanh chóng thu hút đông đảo người dùng và khẳng định vị thế vững chắc trong lĩnh vực kỹ thuật số hiện đại.
Bên cạnh việc tập trung vào trải nghiệm người dùng, 68BET còn đặc biệt chú trọng đến vấn đề bảo mật và an toàn thông tin. Hệ thống được trang bị công nghệ mã hóa tiên tiến, giúp bảo vệ dữ liệu cá nhân và thông tin giao dịch của người dùng một cách tối ưu. Các tiêu chuẩn bảo mật nghiêm ngặt được áp dụng nhằm ngăn chặn rủi ro xâm nhập trái phép, đảm bảo môi trường sử dụng an toàn và đáng tin cậy. Không chỉ vậy, 68bet luôn cam kết minh bạch trong mọi hoạt động, giúp người dùng có thể hoàn toàn yên tâm trong suốt quá trình trải nghiệm. Hơn nữa, nền tảng này liên tục nâng cấp và cải tiến các tính năng nhằm đáp ứng nhu cầu ngày càng cao của người dùng, mang đến một môi trường kỹ thuật số hiện đại, chuyên nghiệp và đáng tin cậy.
Không chỉ sở hữu công nghệ tiên tiến và hệ thống bảo mật chặt chẽ, 68bet còn có đội ngũ hỗ trợ khách hàng chuyên nghiệp, sẵn sàng giải đáp mọi thắc mắc và hỗ trợ người dùng một cách nhanh chóng, hiệu quả. Dịch vụ hỗ trợ hoạt động liên tục, đảm bảo rằng mọi vấn đề đều được giải quyết kịp thời, giúp người dùng có trải nghiệm liền mạch và thuận lợi nhất. Ngoài ra, 68bet luôn không ngừng nghiên cứu và phát triển các tính năng mới, giúp nâng cao chất lượng trải nghiệm và đáp ứng nhu cầu đa dạng của người dùng. Với sự kết hợp hoàn hảo giữa công nghệ hiện đại, bảo mật cao và dịch vụ tận tâm, 68bet tiếp tục khẳng định vị thế vững chắc trên thị trường và trở thành sự lựa chọn đáng tin cậy cho những ai đang tìm kiếm một nền tảng kỹ thuật số chất lượng hàng đầu.
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ 266815e0:6cd408a5
2025-02-18 17:25:31
@ 266815e0:6cd408a5
2025-02-18 17:25:31noStrudel
Released another major version of noStrudel v0.42.0 Which included a few new features and a lot of cleanup
nostr:naddr1qvzqqqr4gupzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqp3hx7um5wf6kgetv956ry6rmhwr
Blossom
On the blossom front there where a few more PRs - Expanded the documentation around CORS headers in BUD-01 thanks to nostr:npub1a6we08n7zsv2na689whc9hykpq4q6sj3kaauk9c2dm8vj0adlajq7w0tyc - Made auth optional on the
/uploadendpoint PR - Added aHEAD /mediaendpoint for BUD-05 PR - Added range request recommendations to BUD-01 PRWith blossom uploads starting to be supported in more nostr clients users where starting to ask where to find a list of blossom servers. so I created a simple nostr client that allows users to post servers and leave reviews blossomservers.com Its still very much a work in progress (needs login and server and review editing) The source is on github
I also started another project to create a simple account based paid blossom server blossom-account-server Unfortunately I got sidetracked and I didn't have the time to give it the attention it needs to get it over the finish line
Smaller projects
- cherry-tree A small app for uploading chunked blobs to blossom servers (with cashu payment support)
- vite-plugin-funding A vite plugin to collect and expose package "funding" to the app
- node-red-contrib-rx-nostr The start of a node-red package for rx-nostr. if your interested please help
- node-red-contrib-applesauce The start of a node-red package for applesauce. I probably wont finish it so any help it welcome
Plans for 2025
I have a few vague ideas of what I want to work on Q1 of 2025. but there are a few things i know for certain.
I'm going to keep refactoring noStrudel by moving core logic out into applesauce and making it more modular. This should make noStrudel more reliable and hopefully allow me to create and maintain more apps with less code
And I'm going to write tests. tests for everything. hopefully tests for all the libraries and apps I've created in 2024. A lot of the code I wrote in 2024 was hacky code to see if things could work. and while its been working pretty well I'm starting to forget the details of of the code I wrote so I cant be sure if it still works or how well it works.
So my solution is to write tests, lots of tests :)
-
 @ 044da344:073a8a0e
2025-02-15 10:56:45
@ 044da344:073a8a0e
2025-02-15 10:56:45Vielleicht hätte Matthias Gehler noch ein drittes Mal ansetzen sollen. Versuch Nummer eins, schreibt er ganz zum Schluss, sei in der Tonne gelandet, nachdem ein Freund gesagt habe, dass niemand ein weiteres Sachbuch über die deutsche Wiedervereinigung brauche – vor allem nicht von einem Autor, der live dabei war. Deshalb sei dann „viel Subjektives“ in den Text eingeflossen. Nun: So viel ist das gar nicht. Freundschaften, steht ebenfalls im „Nachtrag“, seien ihm wichtiger. Und wenn es wirklich Interesse an „allen möglichen erlebten Geschichten aus jener Zeit“ geben sollte, dann schreibe er halt ein zweites Buch (S. 252).
Ich melde hiermit Bedarf an. Matthias Gehler, Jahrgang 1954, war Redakteur beim CDU-Blatt Neue Zeit, als die Dinge ins Rutschen kamen. Er wurde Referent von Martin Kirchner, dem neuen Generalsekretär der Partei, und nach der Wahl vom 18. März 1990 Sprecher der Regierung von Lothar de Maizière. Gehler hat mit Kohl gesprochen, mit Gorbatschow, mit dem ersten Bush. Er war Vorgesetzter von Angela Merkel, später dann Chefredakteur beim MDR und immer wieder im Dunstkreis der Macht, mindestens bei irgendwelchen Jubiläen. Es gibt Fotos davon im Buch.
Es gibt auch Geschichten, so ist es nicht. Dass der kleine Dünne und der große Dicke nicht miteinander konnten, wusste man schon, auch von Lothar de Maizière persönlich. Da man seine eigenen Qualitäten schlecht selbst würdigen kann, ist es gut, dass Matthias Gehler noch einmal klarmacht, was die DDR an ihrem letzten Regierungschef hatte. Eine Arbeitsbiene, mit allen juristischen Wassern gewaschen, in jeder Hinsicht gebildet und schon deshalb einem Machtmenschen wie Helmut Kohl überlegen und suspekt zugleich. Gehler erzählt ein paar köstliche Anekdoten über die beiden, die ich hier nicht verraten will, und hat auch einen Seitenhieb für Regine Hildebrandt, die bis heute ein Nimbus umgibt, der offenbar nicht ganz zur historischen Wirklichkeit passt. Die SPD-Frau mit dem losen Mundwerk, so erzählt es jedenfalls Gehler, sei oft blank gewesen, wenn es um das Klein-Klein der Regierungsarbeit ging. Eine Vorlage aus ihrem Ministerium? „Die gibt es nicht.“ (S. 154)
Überhaupt: Es sind die Miniaturen, die dieses Buch wertvoll machen. Die Arroganz von Gorbatschow, sicher, und die Mentalität der Berater aus dem Westen, die sich im Einzelfall auch als „Blockwart“ aufgeführt haben (S. 94), mehr aber noch das Porträt von Franz Jahsnowski, DDR-Diplomat, schon Protokollchef von Ulbricht und nun wegen seiner Erfahrung und seiner Kontakte auch für die Neuen nicht zu ersetzen. Gehler nutzt einen Abend in Brüssel, um aus diesem Leben zu berichten und damit in gewisser Weise auch über die DDR und den Umgang mit ihrem Erbe.
Als Regierung haben wir Honeckers Protokollchef und seinen Stab übernommen – offiziell aus Wertschätzung, inoffiziell, weil der Laden einfach weiterlaufen musste. Die Geschichte kennt keine Stunde Null. Das geht nur mit fähigem Personal. Mancher Altbundesbeamte hätte es lieber anders gehabt. Wir mussten den Beratern von drüben immer wieder erklären, warum wir Menschen des alten Apparates übernommen haben. Jahsnowski steht für viele Meister ihres Fachs, die plötzlich systementwurzelt zwischen den Welten schwebten und ihren Glauben an den Sozialismus überprüften. (S. 124)
Ich schreibe diese Passage ab, weil ich vermute: Hier ist mein Bedarf nach mehr entstanden. Mag Matthias Gehler seine Merkel-Geschichten für sich behalten. Geschenkt. Ich gönne ihm auch die Euphorie der ersten Amerika-Reise und all das, was jetzt über die Politprominenz jener Tage allenfalls zwischen den Zeilen steht, vielleicht auch aus Angst vor der eigenen Courage. Aber die Ambivalenz, die im Jahsnowski-Porträt aufscheint und dann wieder in der Asbest-Affäre um den Palast der Republik: Da geht noch was. Anders formuliert: Wenn immer wieder die große Freiheit beschworen wird, bei den Märzwahlen 1990 genauso wie bei der letzten Volkskammer, dann ist das für meinen Geschmack zu viel Regierungssprecher und zu wenig Zeitzeuge. Matthias Gehler weiß, wie es gelaufen ist (eine „Materialschlacht“, bei der die CDU sogar mit „Nahe-Weinflaschen“ punktete), und könnte sich Schützenhilfe holen, bei Daniela Dahn zum Beispiel. Also ein zweites Buch, bitte.

Matthias Gehler: „Wollen Sie die Einheit – oder nicht?“ Erinnerungen des Regierungssprechers. Berlin: edition ost 2024, 256 Seiten, 18 Euro.
Freie Akademie für Medien & Journalismus
Titelbild: 1990 am Brandeburger Tor. Foto: Merit Schambach (https\://www.wir-waren-so-frei.de/index.php/Detail/Object/Show/object_id/392)
-
 @ 06b7819d:d1d8327c
2024-12-03 09:00:46
@ 06b7819d:d1d8327c
2024-12-03 09:00:46The History of Bananas as an Exportable Fruit and the Rise of Banana Republics
Bananas became a significant export in the late 19th century, fueled by advancements in transportation and refrigeration that allowed the fruit to travel long distances without spoilage. Originally native to Southeast Asia, bananas were introduced to the Americas by European colonists. By the late 1800s, companies like the United Fruit Company (later Chiquita) and Standard Fruit Company (now Dole) began cultivating bananas on a large scale in Central America and the Caribbean.
These corporations capitalized on the fruit’s appeal—bananas were cheap, nutritious, and easy to transport. The fruit quickly became a staple in Western markets, especially in the United States. However, the rapid expansion of banana exports came at a significant political and social cost to the countries where the fruit was grown.
To maintain control over banana production and maximize profits, these companies required vast amounts of arable land, labor, and favorable trade conditions. This often led them to form close relationships with local governments, many of which were authoritarian and corrupt. The companies influenced policies to secure land concessions, suppress labor rights, and maintain low taxes.
The term “banana republic” was coined by writer O. Henry in 1904 to describe countries—particularly in Central America—that became politically unstable due to their economic dependence on a single export crop, often controlled by foreign corporations.
The U.S. government frequently supported these regimes as part of its broader strategy during the Cold War to counter communist influence in the region. Washington feared that labor movements and demands for land reform, often supported by the peasantry and indigenous groups, could lead to the rise of socialist or communist governments. Consequently, the U.S. backed coups, such as the 1954 overthrow of Guatemala’s democratically elected President Jacobo Árbenz, who had threatened United Fruit’s interests by redistributing unused land.
These interventions created a legacy of exploitation, environmental degradation, and political instability in many banana-exporting countries. While bananas remain a global dietary staple, their history underscores the complex interplay of economics, politics, and imperialism.
-
 @ e6817453:b0ac3c39
2025-01-05 14:29:17
@ e6817453:b0ac3c39
2025-01-05 14:29:17The Rise of Graph RAGs and the Quest for Data Quality
As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence.
Booming Interest in Graph RAGs
Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can:
- Enhance LLM Outputs: By grounding responses in structured knowledge, graphs significantly reduce hallucinations.
- Support Complex Queries: Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving.
Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs?
Data Quality: The Foundation of Effective Graphs
A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why:
- Richness of Entities: Effective retrieval depends on graphs populated with rich, detailed entities.
- Freedom from Hallucinations: Poorly constructed graphs amplify inaccuracies rather than mitigating them.
Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs.
Hybrid Graph RAGs and Variations
While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that:
- Handle diverse data sources with ease.
- Offer improved adaptability to complex queries.
Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing.
Ontology: The Key to Graph Construction Quality
Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for:
- Defining Relationships: Clarifying how concepts connect within a domain.
- Validating Graph Structures: Ensuring constructed graphs are logically sound and align with domain-specific realities.
Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs?
How to Build Ontology Expertise in a Startup Team
For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach:
- Assign a Knowledge Champion: Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering.
- Provide Training: Invest in courses, workshops, or certifications in knowledge graph and ontology creation.
- Leverage Partnerships: Collaborate with academic institutions, domain experts, or consultants to build initial frameworks.
- Utilize Tools: Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process.
- Iterate with Feedback: Continuously refine ontologies through collaboration with domain experts and iterative testing.
So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts.
You could read about barefoot experts in my article :
Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise.
How to Find or Create Ontologies
For teams venturing into Graph RAGs, several strategies can help address the ontology gap:
-
Leverage Existing Ontologies: Many industries and domains already have open ontologies. For instance:
-
Public Knowledge Graphs: Resources like Wikipedia’s graph offer a wealth of structured knowledge.
- Industry Standards: Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields.
-
Business Framework Ontology (BFO): A valuable resource for enterprises looking to define business processes and structures.
-
Build In-House Expertise: If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation.
-
Utilize LLMs for Ontology Construction: Interestingly, LLMs themselves can act as a starting point for ontology development:
-
Prompt-Based Extraction: LLMs can generate draft ontologies by leveraging their extensive training on graph data.
- Domain Expert Refinement: Combine LLM-generated structures with insights from domain experts to create tailored ontologies.
Parallel Ontology and Graph Extraction
An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as:
- Detecting Hallucinations: Differentiating between genuine insights and AI-generated inaccuracies.
- Ensuring Completeness: Ensuring no critical concepts are overlooked during extraction.
Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method.
LLMs as Ontologists
While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to:
- Generate Skeleton Ontologies: Prompt LLMs with domain-specific information to draft initial ontology structures.
- Validate and Refine Ontologies: Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance.
However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes.
Final Thoughts: Unlocking the Power of Graph RAGs
The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools.
As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding.
Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation!
-
 @ 06b7819d:d1d8327c
2024-12-02 20:05:48
@ 06b7819d:d1d8327c
2024-12-02 20:05:48Benjamin Franklin and His Fondness for Madeira Wine
Benjamin Franklin, one of America’s most celebrated founding fathers, was not only a statesman, scientist, and writer but also a man of refined taste. Among his many indulgences, Franklin was particularly fond of Madeira wine, a fortified wine from the Portuguese Madeira Islands. His love for this drink was well-documented and reflects both his personal preferences and the broader cultural trends of 18th-century America.
The Allure of Madeira Wine
Madeira wine was highly prized in the 18th century due to its unique production process and exceptional durability. Its rich, fortified nature made it well-suited for long sea voyages, as it could withstand temperature fluctuations and aging in transit. This durability made Madeira a popular choice in the American colonies, where European wines often spoiled before arrival.
Franklin, who was known for his appreciation of fine things, embraced Madeira as a beverage of choice. Its complex flavors and storied reputation resonated with his intellectual and social pursuits. The wine was often served at dinners and social gatherings, where Franklin and his contemporaries debated ideas and shaped the future of the nation.
Franklin’s Personal Connection to Madeira
In Franklin’s writings and correspondence, Madeira is mentioned on several occasions, reflecting its prominence in his life. He referred to the wine not only as a personal pleasure but also as a symbol of hospitality and refinement. As a diplomat in France and England, Franklin often carried Madeira to share with his hosts, using it as a means of forging connections and showcasing the tastes of the American colonies.
One notable instance of Franklin’s affinity for Madeira occurred during his time in Philadelphia. He reportedly had cases of the wine shipped directly to his home, ensuring he would never be without his favorite drink. Madeira also featured prominently in many toasts and celebrations, becoming a hallmark of Franklin’s gatherings.
The Role of Madeira in Colonial America
Franklin’s fondness for Madeira reflects its broader significance in colonial America. The wine was not only a favorite of the elite but also a symbol of resistance to British taxation. When the British imposed heavy duties on imported goods, including wine, Madeira became a patriotic choice for many colonists. Its direct trade routes with the Madeira Islands circumvented British intermediaries, allowing Americans to assert their economic independence.
A Legacy of Taste
Franklin’s appreciation for Madeira wine endures as a charming detail of his multifaceted life. It offers a glimpse into the personal habits of one of America’s most influential figures and highlights the cultural exchanges that shaped colonial society. Today, Franklin’s love of Madeira serves as a reminder of the historical connections between wine, politics, and personal expression in the 18th century.
In honoring Franklin’s legacy, one might raise a glass of Madeira to toast not only his contributions to American independence but also his enduring influence on the art of living well.
-
 @ 378562cd:a6fc6773
2025-02-02 18:58:38
@ 378562cd:a6fc6773
2025-02-02 18:58:38Chef's notes
I'm only testing this out right now. I will update the recipe as well as add my own image soon after making this dish again.
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 4
Ingredients
- 4 to 6 potatoes (size depending)
- 1 lb ground beef
- seasonings
- 2 cans chili beans
- 1 onion
- katsup
- shredded cheese of some kind
Directions
- saute onion and add ground beef to skillet. Season to liking.
- peel if you like and thin slice potatoes
- in a rectangle baking dish, layer potatoes, beans, meat and cheese (like a lasagna) until you have used all your ingredients. Try and make at least 2 or 3 layers with extra cheese on top.
- Bake at 350 for one hour. Serve and enjoy!
-
 @ fdb8c828:84c16368
2025-02-18 18:40:12
@ fdb8c828:84c16368
2025-02-18 18:40:12On a retreat to the mountains, I escape to step outside of regular life for a time. The peaks dressed in winter white, time refrigerated by the falling flakes, and lovely folks around me, old and new, alight all the artist parts of my brain.
On a shelf in an old bookstore, I meet myself, a mixture of the past and future, and she is disappointed, mournful. While browsing poetry titles, she cries. I listen to her, and she says, you’re running out of time.
On a separate shopping excursion, I adopt a pair of sunglasses - two perfect black circles to conceal the passing of time that my eyes can’t hide. I show my friend of photo of me at 16, she says, you look exactly the same.
On my return flight, all that I am packaged back inside my bags, inside my body, my appetite for life appeased for the moment, I decide I like myself, and I can change, as everything will mix with time, coming out the other side, beautiful.
originally posted at https://stacker.news/items/889720
-
 @ dbb19ae0:c3f22d5a
2025-02-08 10:27:12
@ dbb19ae0:c3f22d5a
2025-02-08 10:27:12- Downloading the linux package (1.8GB) https://cortex.so/docs/installation
- Installing Cortex on linux is done via dpkg
note: it requires 2 linux packages (openmpi-bin and libopenmpi-dev)
sudo apt-get install openmpi-bin libopenmpi-devprior to runsudo dpkg -i cortex-1.0.9-linux-amd64-local-installer.deb -
When running Cortex,
cortex starta local implementation will be running on http://127.0.0.1:39281 -
Using python it is possible to run queries make sure the model name is correct you can double check the value using:
cortex ps
Now the python program to run one little query: ``` python import requests
url = "http://127.0.0.1:39281/v1/chat/completions"
headers = {"Content-Type": "application/json"}
payload = { "model": "tinyllama:1b-gguf", "messages": [ { "role": "user", "content": "Write a joke" } ], "stream": False, "max_tokens": 128, "stop": ["End"], "frequency_penalty": 0.2, "presence_penalty": 0.6, "temperature": 0.8, "top_p": 0.95, }
response = requests.post(url, json=payload, headers=headers)
print(response.json()) ```
-
 @ 4f1a1249:66f0ac3a
2025-02-18 07:14:28
@ 4f1a1249:66f0ac3a
2025-02-18 07:14:28789win1 là một nền tảng kỹ thuật số tiên tiến, mang đến cho người dùng trải nghiệm mượt mà, nhanh chóng và hiệu quả nhờ vào công nghệ hiện đại và giao diện thân thiện. Với thiết kế tối ưu, hệ thống giúp người dùng dễ dàng thao tác, truy cập nhanh chóng vào các tính năng và tận hưởng sự tiện lợi vượt trội. 789win1 không chỉ tương thích với nhiều thiết bị mà còn đảm bảo tốc độ xử lý cao, giúp mọi thao tác diễn ra trơn tru và liền mạch. Đặc biệt, nền tảng này liên tục cập nhật các công nghệ mới nhất để cải thiện hiệu suất, mang đến một môi trường ổn định, giúp người dùng có những trải nghiệm tốt nhất. Nhờ vào sự đầu tư mạnh mẽ vào công nghệ, 789win1 đã nhanh chóng khẳng định được vị thế của mình, trở thành một sự lựa chọn đáng tin cậy trên thị trường kỹ thuật số.
Bên cạnh hiệu suất hoạt động mạnh mẽ, 789WIN1 còn đặc biệt chú trọng đến vấn đề bảo mật, đảm bảo sự an toàn tuyệt đối cho thông tin cá nhân và dữ liệu của người dùng. Hệ thống được tích hợp công nghệ mã hóa tiên tiến, giúp bảo vệ thông tin khỏi các rủi ro bảo mật và các mối đe dọa tiềm ẩn. Ngoài ra, nền tảng này còn áp dụng các tiêu chuẩn bảo mật cao cấp, ngăn chặn các hành vi truy cập trái phép, giúp người dùng hoàn toàn yên tâm trong suốt quá trình sử dụng. Không chỉ vậy, 789win1 luôn đặt sự minh bạch và tin cậy lên hàng đầu, không ngừng nâng cấp hệ thống để đáp ứng nhu cầu ngày càng cao, đảm bảo một môi trường kỹ thuật số an toàn và chuyên nghiệp.
Không chỉ sở hữu công nghệ tiên tiến và hệ thống bảo mật hiện đại, 789win1 còn có đội ngũ hỗ trợ chuyên nghiệp, luôn sẵn sàng tư vấn, giải đáp mọi thắc mắc của người dùng một cách nhanh chóng và hiệu quả. Dịch vụ hỗ trợ hoạt động liên tục, đảm bảo rằng mọi vấn đề đều được giải quyết kịp thời, mang lại sự hài lòng và an tâm tuyệt đối cho người dùng. Bên cạnh đó, 789win1 không ngừng mở rộng và phát triển, mang đến những cải tiến mới nhằm nâng cao chất lượng trải nghiệm, đáp ứng nhu cầu ngày càng đa dạng của người dùng. Với sự kết hợp hoàn hảo giữa công nghệ hiện đại, bảo mật cao và dịch vụ tận tâm, 789win1 tiếp tục khẳng định vị thế của mình, trở thành một nền tảng kỹ thuật số đáng tin cậy và được nhiều người yêu thích.
-
 @ 06b7819d:d1d8327c
2024-11-29 13:26:00
@ 06b7819d:d1d8327c
2024-11-29 13:26:00The Weaponization of Technology: A Prelude to Adoption
Throughout history, new technologies have often been weaponized before becoming widely adopted for civilian use. This pattern, deeply intertwined with human priorities for power, survival, and dominance, sheds light on how societies interact with technological innovation.
The Weaponization Imperative
When a groundbreaking technology emerges, its potential to confer an advantage—military, economic, or ideological—tends to attract attention from those in power. Governments and militaries, seeking to outpace rivals, often invest heavily in adapting new tools for conflict or defense. Weaponization provides a context where innovation thrives under high-stakes conditions. Technologies like radar, nuclear energy, and the internet, initially conceived or expanded within the framework of military priorities, exemplify this trend.
Historical Examples
1. Gunpowder: Invented in 9th-century China, gunpowder was first used for military purposes before transitioning into civilian life, influencing mining, construction, and entertainment through fireworks.-
The Internet: Initially developed as ARPANET during the Cold War to ensure communication in the event of a nuclear attack, the internet’s infrastructure later supported the global digital revolution, reshaping commerce, education, and social interaction.
-
Drones: Unmanned aerial vehicles began as tools of surveillance and warfare but have since been adopted for everything from package delivery to agricultural monitoring.
Weaponization often spurs rapid technological development. War environments demand urgency and innovation, fast-tracking research and turning prototypes into functional tools. This phase of militarization ensures that the technology is robust, scalable, and often cost-effective, setting the stage for broader adoption.
Adoption and Civilian Integration
Once a technology’s military dominance is established, its applications often spill into civilian life. These transitions occur when:
• The technology becomes affordable and accessible. • Governments or corporations recognize its commercial potential. • Public awareness and trust grow, mitigating fears tied to its military origins.For example, GPS was first a military navigation system but is now indispensable for personal devices, logistics, and autonomous vehicles.
Cultural Implications
The process of weaponization shapes public perception of technology. Media narratives, often dominated by stories of power and conflict, influence how societies view emerging tools. When technologies are initially seen through the lens of violence or control, their subsequent integration into daily life can carry residual concerns, from privacy to ethical implications.
Conclusion
The weaponization of technology is not an aberration but a recurring feature of technological progress. By understanding this pattern, societies can critically assess how technologies evolve from tools of conflict to instruments of everyday life, ensuring that ethical considerations and equitable access are not lost in the rush to innovate. As Marshall McLuhan might suggest, the medium through which a technology is introduced deeply influences the message it ultimately conveys to the world.
-
-
 @ a4a6b584:1e05b95b
2025-01-02 18:13:31
@ a4a6b584:1e05b95b
2025-01-02 18:13:31The Four-Layer Framework
Layer 1: Zoom Out

Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what."
Example: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems.
- Tip: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage.
Once you have the big picture in mind, it’s time to start breaking it down.
Layer 2: Categorize and Connect

Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas.
Example: Studying biology? Group concepts into categories like cells, genetics, and ecosystems.
- Tip: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track.
With your categories in place, you’re ready to dive into the details that bring them to life.
Layer 3: Master the Details

Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable.
Example: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language.
- Tip: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding.
Now that you’ve mastered the essentials, you can expand your knowledge to include extra material.
Layer 4: Expand Your Horizons

Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams.
Example: Learn about rare programming quirks or historical trivia about a language’s development.
- Tip: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time.
Pro Tips for Better Learning
1. Use Active Recall and Spaced Repetition
Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information.
2. Map It Out
Create visual aids like diagrams or concept maps to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2.
3. Teach What You Learn
Explain the subject to someone else as if they’re hearing it for the first time. Teaching exposes any gaps in your understanding and helps reinforce the material.
4. Engage with LLMs and Discuss Concepts
Take advantage of tools like ChatGPT or similar large language models to explore your topic in greater depth. Use these tools to:
- Ask specific questions to clarify confusing points.
- Engage in discussions to simulate real-world applications of the subject.
- Generate examples or analogies that deepen your understanding.Tip: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective.
Get Started
Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
-
 @ 4f1a1249:66f0ac3a
2025-02-18 07:13:07
@ 4f1a1249:66f0ac3a
2025-02-18 07:13:0768bet là một nền tảng kỹ thuật số tiên tiến được thiết kế nhằm mang lại trải nghiệm mượt mà, hiệu quả và tiện lợi cho người dùng. Với giao diện trực quan, thân thiện cùng tốc độ xử lý nhanh chóng, 68bet giúp người dùng dễ dàng thao tác và tận hưởng những tính năng hiện đại chỉ trong vài bước đơn giản. Nền tảng này được tối ưu hóa để hoạt động ổn định trên nhiều thiết bị khác nhau, từ máy tính cá nhân đến điện thoại di động, mang lại sự linh hoạt và thuận tiện tối đa. Đặc biệt, hệ thống không ngừng được cập nhật với những công nghệ tiên tiến nhằm nâng cao hiệu suất, giúp mọi thao tác diễn ra nhanh chóng, chính xác và liền mạch. Nhờ vào sự cải tiến không ngừng, 68bet đã trở thành một sự lựa chọn hàng đầu, thu hút đông đảo người dùng nhờ vào chất lượng vượt trội và những tính năng thông minh.
Không chỉ dừng lại ở việc nâng cao trải nghiệm người dùng, 68BET còn đặc biệt chú trọng đến tính bảo mật và an toàn thông tin. Hệ thống được trang bị công nghệ mã hóa hiện đại, giúp bảo vệ dữ liệu cá nhân một cách tối đa, đảm bảo sự riêng tư tuyệt đối cho người dùng. Bên cạnh đó, nền tảng này áp dụng các tiêu chuẩn bảo mật chặt chẽ để giảm thiểu rủi ro và ngăn chặn mọi hành vi xâm nhập trái phép. Nhờ vào những biện pháp bảo vệ tiên tiến, người dùng hoàn toàn có thể yên tâm trong quá trình sử dụng mà không lo lắng về các vấn đề liên quan đến bảo mật. Hơn nữa, 68bet không ngừng cải tiến và nâng cấp hệ thống nhằm đáp ứng nhu cầu ngày càng cao, mang lại một môi trường an toàn, minh bạch và đáng tin cậy.
Bên cạnh công nghệ tiên tiến và tính bảo mật cao, 68bet còn sở hữu đội ngũ hỗ trợ chuyên nghiệp, luôn sẵn sàng tư vấn và giải đáp mọi thắc mắc của người dùng một cách nhanh chóng và hiệu quả. Dịch vụ hỗ trợ hoạt động liên tục, đảm bảo rằng mọi vấn đề đều được giải quyết kịp thời, mang đến sự hài lòng và an tâm tuyệt đối. Ngoài ra, nền tảng này luôn không ngừng mở rộng và phát triển để mang đến những cải tiến mới, giúp nâng cao chất lượng trải nghiệm cho người dùng. Với sự kết hợp hoàn hảo giữa công nghệ hiện đại, dịch vụ tận tâm và cam kết bảo mật cao, 68bet tiếp tục khẳng định vị thế của mình, trở thành một trong những nền tảng kỹ thuật số hàng đầu dành cho người dùng hiện đại.
-
 @ 378562cd:a6fc6773
2025-02-02 17:53:05
@ 378562cd:a6fc6773
2025-02-02 17:53:05Chef's notes
I'm only testing this out right now. I will update the recipe as well as add my own image soon after making this dish again.
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 4
Ingredients
- 4 to 6 potatoes (size depending)
- 1 lb ground beef
- seasonings
- 2 cans chili beans
- 1 onion
- katsup
- shredded cheese of some kind
Directions
- saute onion and add ground beef to skillet. Season to liking.
- peel if you like and thin slice potatoes
- in a rectangle baking dish, layer potatoes, beans, meat and cheese (like a lasagna) until you have used all your ingredients. Try and make at least 2 or 3 layers with extra cheese on top.
- Bake at 350 for one hour. Serve and enjoy!
-
 @ df478568:2a951e67
2025-02-07 22:34:11
@ df478568:2a951e67
2025-02-07 22:34:11Freedom tech is free and open-source software. It is free as in freedom. A common license in FOSS is the MIT license. It's the license behind Bitcoin, a peer-to-peer electronic cash system. Anyone is free to run this software. The same is true for the software at mempool.space. The software is free to use. I run it on my own server.
This is what I use to time-stamp my articles. You can use it to check transactions on the bitcoin time chain, but you need to trust that I'm not doing any funny business. I'm not, but keep in mind, the whole point of p2p elwctronic cash is that you don't trust. You verify.
The beauty of FOSS is: You don't need to trust me. You can triple-check the transactions you search on my mempool instance by looking at the official mempool.space website and blockchain.info...Or...You can run your own node on your own hardware, free of charge.
Of course, the hardware is not free. Neither is the actual bitcoin. The freedom is built into the software, but as the saying goes, "freedom isn't free." It took me years to learn how to run my own software on my own server and make it available on the clear net.
SearXNG

SearXNG is my favorite search engine. I don't like giving up my precious data to big tech located in the United States or China. I run my own search engine. I have noticed certain biases in Google searches. The biggest problem is ads.
Companies tend to pay for Yelp and Google reviews. I called an AC company I found from a local magazine that came in the mail. A portly man wearing an HVAC costume drove to my house in a white van. He had a great smile and even better social skills. The van had a slogan plastered on it like most tradie vans do. "Reviews Matter We have a 4.9 Review on Google." He also had his name painted on this van like a Bomber pilot from WW2. I won't dox him, but it was something like "Joe the closer."
I don't trust the omnipotenence of the Googs. I also don't trust fat men they call "the closer" to give me the best deal. The trick to saving sats is to choose the game-theory optimal way of negogiation.
In DUCY, by David Sklansky, I learned useful negotiation skills. Sklansky wrote classic poker books and applied his actuarial math brain to negotiation techniques. He said he would go to a Toyota dealer and say, "I'm shopping for a new Camry. I already have a price from dealership XYZ in a nearby city. What is your price?"
This changes the dynamic right from the starting line and gives the consumer the advantage. So I tried this based technique with the HVAC industrial complex. I got a quote from 3 people: 1. Joe "The Closer." 2. The Costco-sponsored HVAC Company 3. My SearXNG search results.
In essence, I apply the same logic I learned running a full bitcoin node. Remember how I said the decentralized nature of bitcoin allows you to triple-check your transactions? Running SearXNG allows me to triple check my search results in a similar fashion. I don't trust Google, Costco, or the magazine I get every month in the mail. I verify results with my own search engine.
My SearXNG does not track my location, but I set it to give me local results. To be honest, I have not verified this, but the code is on GitHub for everyone to see.
I don't want to be "sold" on an AC. I don't want an AC if I could avoid it, but my AC was as dead as dentacoin. Living in Southern California with a wife going through "the change" gave me no alternative.
The guy I found on SearXNG showed up in an unmarked van. He had a beard. He was not "a closer." He was an actual HVAC technician. He tried cleaning my unit made in the same year Weezer released their Blue album. He said he coukd jerry rig it to get it working for another few months, but the machine is on it's last days. He said a newer unit would also be more efficient so I asked him about the energy like a bitcoiner.
"How many kilowatt hours does it cost me to run my AC versus a new AC?"
I don't remember the exact answer, but I asked all three companies. He was the only one that new how to find out. He also happened to be the cheapest, but I would have bought a new AC from this guy even if he wasn't.
I told him I made a space heater out of a bitcoin miner. He had no idea this was possible, but he at least pretended to find it interesting. That's why I use SearXNG to find tradesmen. It's better than Yelp.
If you would like to try my instance of SearXNG, check it out.
523FeCpi9Gx4nR9NmSFIMEaYcI5Q4WmhYHPEPaEah84=To decrypt it, use the key behind the paywall at:
https://8gwifi.org/CipherFunctions.jsp
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
Follow me on nostr.
All of my work is available under the Creative Commons 0 licence. If you would like to try my instance of Searxng and do not wish to support my work, find me on habla.news by searching my npub. You can find all of my work there(including encryption keys)free of charge.
Paywall On Substack
abdominal.savior.repaint
Will decrypt this ciphertext: 523FeCpi9Gx4nR9NmSFIMEaYcI5Q4WmhYHPEPaEah84=
Which will reveal my instance of SearXNG at
https://searxng.marc26z.com/
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ df57b498:d049124f
2025-01-26 03:59:47
@ df57b498:d049124f
2025-01-26 03:59:47Chef's notes
This is cobbled together from trial and error and the web.
Serve hot pancakes with preferably butter and maple syrup. Add other toppings like bananas, nuts, or other fruits and toppings as have available and/or desired.
Details
- ⏲️ Prep time: 10 minutes
- 🍳 Cook time: 10 minutes
Ingredients
- 1 cup flour
- 2 tablespoons sugar
- 2 teaspoons baking powder
- 1 teaspoon salt
- 1 cup milk
- 2 tablespoons vegetable oil
- 1 egg, beaten
Directions
- Combine the dry ingredients.
- Add the wet ingredients and mix.
- Pour or ladle the batter onto the oiled griddle or pan.
- Cook until bubbles form, flip, and cook on the other side.
-
 @ 75869cfa:76819987
2025-02-17 17:10:41
@ 75869cfa:76819987
2025-02-17 17:10:41GM, Nostriches! The Nostr Review is a biweekly newsletter focused on Nostr statistics, protocol updates, exciting programs, the long-form content ecosystem, and key events happening in the Nostr-verse. If you’re interested, join me in covering updates from the Nostr ecosystem!
Quick review: In the past two weeks, Nostr statistics indicate over 232,000 daily trusted pubkey events.The number of new users has seen a notable decrease, Profiles with contact list amount is reflecting a nearly 90% decline. More than 10 million events have been published, posts and reposts are representing a significant increase. Total Zap activity stands at approximately 17 million, marking a 20% decrease.
Additionally, 45 pull requests were submitted to the Nostr protocol, with 8 merged. A total of 45 Nostr projects were tracked, with 10 releasing product updates, and over 350 long-form articles were published, 30% focusing on Bitcoin and Nostr. During this period, 2 notable events took place, and 2 significant events are upcoming.
Nostr Statistics
Based on user activity, the total daily trusted pubkeys writing events is about 232,000, representing a slight 5.1% decrease compared to the previous period. Daily activity peaked at 19174 events, with a low of approximately 16735.
The number of new users has decreased. Profiles with a contact list are now around 19,559, marking a nearly 90% drop. Pubkeys writing events have declined to approximately 186,000, down 43%, while profiles with a bio have decreased by 34%.
Regarding event publishing, the total number of note events published is about 10 million. Posts remain the most dominant in terms of volume, totaling approximately 1.5 million, reflecting an increase of 16%. Reposts are showing a notable increase of approximately 47%, while reactions have experienced a 21% decline.
For zap activity, the total zap amount is about 17 million, showing a decrease of over 20% compared to the previous period. Data source: https://stats.nostr.band/
NIPs
NIP XXXX: Read Status Tracking via Compressed 64-bit Roaring Bitmaps
nostr:npub18wxf0t5jsmcpy57ylzx595twskx8eyj382lj7wp9rtlhzdg5hnnqvt4xra is proposing that track message read status by publishing replaceable events (kind 30050) containing a compressed 64-bit Roaring Bitmap of read-event keys.
nip-86: updating methods, adding new ones.
nostr:npub1h49w8en79xty6j2pwgnpm3znjhyf767jua6xgt3kvyn3w80ms86s2z9kay is proposing that relays may provide an API for performing management tasks. This is made available as a JSON-RPC-like request-response protocol over HTTP, on the same URI as the relay's websocket.
Expand NIP 03 to include relay and user notaries
Staab is proposing that the goal here is to make event timestamp verification more accessible to clients that don't want to go through the rigamarole of publishing to or accessing opentimestamps data. This NIP supports both social attestations and relay attestations.
nostr:npub12xyl6w6aacmqa3gmmzwrr9m3u0ldx3dwqhczuascswvew9am9q4sfg99cx defines a standardized format for sharing curated collections of links on Nostr. It formalizes and extends the format originally developed by nostree.me, which has been successfully serving the Nostr community as a "link-in-bio" solution.While NIP-51 bookmarks serve as private reading lists, NIP-74 link lists are designed for public sharing and discovery, enabling users to curate and share collections of resources with their community. This format evolved from the proven implementation at nostree.me, which has been serving the Nostr community as a reliable link-sharing platform. The specification has been refined based on real-world usage and community feedback, and is also being implemented by other projects like linktr-nostr, demonstrating its practical utility and growing adoption.
nostr:npub1h49w8en79xty6j2pwgnpm3znjhyf767jua6xgt3kvyn3w80ms86s2z9kay is proposing that this is basically some updates over fiatjafs lockbox. it was expected to be only an addition to nip-51. The best client that can support this is probably jumble. if it got accepted, he would implement a khatru relay which supports it. Also he would include it in future.
nostr:npub1acg6thl5psv62405rljzkj8spesceyfz2c32udakc2ak0dmvfeyse9p35c is proposing this for the "gaming" issue that so many people are worried about.It is in-addition to the base hll so that relays do not need to store reaction events if they don't want to, and also clients can choose whether to use all the shll results, or fallback to the hll results based on what the actual relays are able to supply. For instance, if 9 relays gave only HLL and one gave HLL+SHLL, he would fallback to HLL. But if it was reversed he would use SHLL.
nostr:npub1h49w8en79xty6j2pwgnpm3znjhyf767jua6xgt3kvyn3w80ms86s2z9kay is proposing a simple example that he made for testing. This feature is used on most chat apps like telegram and simplex chat. It helps the client to show the seen messages with a double check so the sender can be aware of this. it's not trust less since we can receive the message and don't add it to the bloom filter. The same thing can be done in telegram for example using unofficial versions.it would deliver a better user experience.he believe the most important difference between email or similar protocols to modern real-time chat protocol which makes them feel better and more live is seen/(online/offline)/typing statuses.
ZenenTreadwell is proposing the addition of localised events which would be relevant and accessible only to devices on the local network. These events would be denoted as kind -1 and implement all standard features indicated in NIP-01. Localised events would always include a stringified JSON object in the content field. The only mandatory property of this object would be the event field, a string used to indicate what kind of action was taken in the space (e.g. 'door-opened', 'light-toggled'). Other properties would include values useful for further processing, such as the toggled value of the lights or the id of the door which was opened. p tags could be used to direct signals to specific listeners, e tags could be used to indicate that an event occured in response to another event, etc.
Task and workflow-related NIPs
nostr:npub13v47pg9dxjq96an8jfev9znhm0k7ntwtlh9y335paj9kyjsjpznqzzl3l8 introduces 4 new NIPs that can be used to implement task and project management systems — as well as other productivity tools — using Nostr.The proposed NIPs aim to address these issues by providing a set of common formats and specifications that promote standardization and ease of integration across multiple task management systems and other productivity tools.
Deprecate stringified JSON in favor of tags on user metadata kind 0 events
nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf is proposing that the general convention for any kind is to use tags over stringified JSON. The fact that kind 0 uses stringified JSON is an artifact of a legacy spec from long ago before conventions were established, and makes reading and writing kind 0 harder than it should be. As of creating this PR, he does not believe any existing Nostr client implements support for kind 0 tags, but that can change, and should happen so that the PR can meet acceptance criteria of being implemented in at least 2 clients. Nostr SDK for Apple Platforms has already been updated to reflect this NIP proposal.
SilberWitch defines the basic structure of citations required for embedded quotes, footnotes, endnotes, in-line references, appendices, and prompt records. It covers internal (to Nostr addresses) and external (to the wider web or printed material) citations.
nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft is proposing a PR that documents a standard for using deeplinks to communicate between a wallet and a Nostr client.The mobile app checks if there is a handler for nostrnwc:// or a handful of nostrnwc+{known_nwc-capable_wallets}:// -- if one is found, the app can open the app via a deeplink and receive the NWC pairing code back from the wallet.
Remove NOTICE relay messages from NIP-01
nostr:npub108pv4cg5ag52nq082kd5leu9ffrn2gdg6g4xdwatn73y36uzplmq9uyev6 is proposing that remove NOTICE relay messages from NIP-01, NOTICE is practically useless. he argue it has been superseded by a combination of NIP-11 and relay CLOSED messages that were introduced 2 years ago in #902. He is implementing a relay. There are 2 beautiful flows of Nostr. Getting events: the client sends a REQ, to which the relay responds to with EVENT, EOSE, and/or CLOSED.Posting events: the client sends an EVENT, to which the relay responds with an OK (which can be true or false).
Notable Projects
Coracle 0.6.0 nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn
This release brings long-awaited support for rendering kind 20 (Olas). Along with that, media viewing has gotten an overhaul and should be a much nicer experience now. * Add support for tor/local relays * Use nstart for onboarding process * Oranize media into grids and add full-screen overlay view for images * Fix several note editor bugs * Improve thread, profile page, and notification loading * Show more details on reaction notifications * Improve mutes, add setting to completely hide muted people * Tweak long form article rendering * Refactor zap dialog * Add kind 20 rendering support * Improve rendering for various note kinds * Use more subtle placeholder avatar * Fix handling of all-caps lnurls * Fix rendering of notes in publish information dialog * Add pinned note support * Remove broadcasting of note parents * Add note scheduling via DVM * Clean up modal colors and design
Flotilla0.2.7 nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn
- Add calendar events
- Migrate to svelte 5 (fixes some bugs, probably introduces others)
- Migrate to new welshman editor
- Make reply indicator nicer
- Make share indicator nicer
- Improve feed loading
- Show marker for last activity in chat
Primal 2.1 nostr:npub16c0nh3dnadzqpm76uctf5hqhe2lny344zsmpm6feee9p5rdxaa9q586nvr
- Improved feeds. All feeds are now richer and smoother. Improved rendering and inline players are now available for X, YouTube, Spotify and Tidal. More to come!
- Primal Wallet NWC support. Primal Wallet users are now able to connect their wallet to any Nostr app. Use this feature to enable zapping from any app in Nostr’s growing ecosystem. Manage the list of connected apps in your Primal Wallet settings.
- Primal Web App NWC support. Enable zapping from the Primal web app in Settings / Connected Wallets. If you already have an active Primal wallet, simply click “Connect” and you are done! If you wish to use a different wallet, simply create a NWC connection.
- Legend cards. We created the Primal Legend tier to recognize users who made a significant contribution to Nostr and/or Primal. As a sign of gratitude to our Legends, we implemented Legend cards containing Primal shoutouts for each legend. You can see them by clicking on the Legend badge on the user profile screen.
Yakihonne nostr:npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
Mobile updates: * Polls can now be added inside notes. * Popping screens other than home will redirect to home. * Analytics are now removed. * Fix invoice issues not rendered inside the content. * Fix video player issue. * Fix general performance issues.
Nostur update (TestFlight) nostr:npub1n0stur7q092gyverzc2wfc00e8egkrdnnqq3alhv7p072u89m5es5mk6h0
- Floating mini video player
- Videos: Save to library
- Videos: Copy URL
- Show label for restricted posts and don't auto rebroadcast on reply or quote post
- Low data mode: open media in app instead of external when tapping URL
- Update WoT cache more frequently
- Optimized image processing
- Fixed Profile Media Gallery crash
- Use event + relay hint instead of noted for quoted posts
- Fixed bookmark toggle not updating for reposts
- Fixed missing lightning invoice description
Fountain 1.1.16 nostr:npub1v5ufyh4lkeslgxxcclg8f0hzazhaw7rsrhvfquxzm2fk64c72hps45n0v5
- You can now watch the video in Fountain and hang out in the live chat as it’s being recorded.
- added a storage manager in the app’s settings so that you can view file storage size for audio downloads, video downloads, transcripts, image cache, feed cache, and temp files
- You can delete all files in any of these folders to free up storage on your device so that Fountain continues to run optimally.
Plebeian Market nostr:npub1market6g3zl4mxwx5ugw56hfg0f7dy7jnnw8t380788mvdyrnwuqgep7hd
They've successfully addressed some bugs and introduced new features, including the ability to add videos to headers. Additionally, we resolved issues with zaps on profiles that were affected by an update to NDK, the library we use for handling Nostr functionalities.
- Fix stock not updated after sale
- Fix product is showing wrong details when edited
- Fix stall service to handle new shipping zones
- Fix team Management search field keeps disappearing
- Fix z-index of the stall's description container so they're under the cat menu
- Nwc validation, and zaps on profiles
- Videos as images in product
- Improve 'Start Selling' action
- Remove Category Banners and make Cat menu Fixed
- Add background for product images
- Move the Shipping Dropdown
- Remove category search (for now)
- Add Shipping Zones to Product Page
- Product page bottom padding was too small
Alby Go 1.9 nostr:npub1getal6ykt05fsz5nqu4uld09nfj3y3qxmv8crys4aeut53unfvlqr80nfm
- Real-time push notifications of sent and received payments
- Support of paying 0-amount invoices
- Lots of fixes and minor improvements
- Updated setting up LN address flow to avoid confusion
- Increased button touch area in header for ease of use
- Fixed alert titles being truncated and updated transaction icon colors
Wasabi Wallet 2.5.0 nostr:npub1jw7scmeuewhywwytqxkxec9jcqf3znw2fsyddcn3948lw9q950ps9y35fg
- 3rd Party Providers for Fee & Exchange Rate
- Quality of Life Features
- Backend and Coordinator packaged for Linux
ZEUS v0.10.0 nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8
- Renewable channels
- NWC client support
- Embedded LND: v0.18.5-beta
- New share button (share ZEUS QR images)
- Activity: highlight filter icon when filters active
- Developer tools
- Chantools: sweepremoteclosed
Long-Form Content Eco
In the past two weeks, more than 350 long-form articles have been published, including over 71 articles on Bitcoin and more than 35 related to Nostr, accounting for 30% of the total content.
These articles about Nostr explore its technological advancements, decentralized social networking, financial applications, and real-world use cases. From Vertex Social Graph to OnlyZaps, they highlight how Nostr is reshaping social interactions and content monetization. Technical topics like Python development and nostr_sdk offer practical insights for developers. In finance, DVMCP, payment channels, and Bitcoin funding showcase Nostr’s role in decentralized economics. Additionally, topics like Zapstream streaming, privacy protection, and healthcare records demonstrate its expanding applications. Event recaps like FOSDEM Debrief provide deeper community discussions.
The Bitcoin articles discuss its evolving role in finance, technology, and global adoption. Topics range from Bitcoin’s impact on macroeconomics, including its relationship with the dollar, the Fed’s monetary policies, and the race for strategic reserves, to its role in free trade and small business struggles. Several articles explore technical aspects, such as Lightning Network scalability, transaction trade-offs across layers, and UX improvements. Others focus on Bitcoin’s cultural and political influence, touching on its effects on entrepreneurship in Uganda, government intervention, and the potential for state control. Reports on mining fees, circulating supply trends, and price analyses provide insights for investors, while practical guides on wallet security, merchant adoption, and FOSS contributions cater to new users. Additionally, discussions on Bitcoin’s psychological impact, decentralization challenges, and its role as an antidote to economic instability highlight its broader significance.
Thank you, nostr:npub176p7sup477k5738qhxx0hk2n0cty2k5je5uvalzvkvwmw4tltmeqw7vgup nostr:npub1a3pvwe2p3v7mnjz6hle63r628wl9w567aw7u23fzqs062v5vqcqqu3sgh3 nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds nostr:npub1m2jphmdkskgnvwl5gplksl9e0zwv2sldqf9mwlpz6tyymz84g9fsqr3wgu nostr:npub12lg6yexfh0gsk8aupv5cr5fnj46l0kxg6lp6rz0zw6kwx603lmsshmac9c nostr:npub186a9aaqmyp436j0gkxl8yswhat2ampahxunpmfjv80qwyaglywhqswhd06 nostr:npub1rsvhkyk2nnsyzkmsuaq9h9ms7rkxhn8mtxejkca2l4pvkfpwzepql3vmtf nostr:npub17xvf49kht23cddxgw92rvfktkd3vqvjgkgsdexh9847wl0927tqsrhc9as nostr:npub1lytrxnf66uflkhm0hx32d2r0xchmvepg0mz987xgvgnaqlgu3r2s09fphn nostr:npub1mgvwnpsqgrem7jfcwm7pdvdfz2h95mm04r23t8pau2uzxwsdnpgs0gpdjc nostr:npub12lg6yexfh0gsk8aupv5cr5fnj46l0kxg6lp6rz0zw6kwx603lmsshmac9c npub1mwce4c8qa2zn9zw9f372syrc9dsnqmyy3jkcmpqkzaze0slj94dqu6nmwy,and others, for your work. Enriching Nostr’s long-form content ecosystem is crucial.
Nostriches Global Meet Ups
Recently, several Nostr events have been hosted in different countries. * The Asia Bitcoin Tech Unconference took place from February 8 to 10, 2025, in Chiang Mai, Thailand. Organized as a workshop-style event, it featured a diverse lineup of speakers, including nostr:npub1zk6u7mxlflguqteghn8q7xtu47hyerruv6379c36l8lxzzr4x90q0gl6ef nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac nostr:npub1ejxswthae3nkljavznmv66p9ahp4wmj4adux525htmsrff4qym9sz2t3tv nostr:npub147whqsr5vsj86x0ays70r0hgreklre3ey97uvcmxhum65skst56s30selt and others. The conference focused on key topics such as scalability, mining, payments, and infrastructure, while also encouraging participants to share unfinished projects and technical challenges. Through hackathons and hands-on discussions, the event fostered collaboration and innovation. Highlights included technical talks, pitch competitions, Bitcoin product showcases, and creative and wellness activities such as Thai massages, ice baths, and arts and crafts workshops. * Bitcoin Africa Story - Bitcoin Diploma Program (Cohort 3) officially launched on February 10, 2025! This is a 7-week free online course covering key topics such as the fundamentals of money, Bitcoin principles, the Lightning Network, and Bitcoin technology. The program aims to educate more people about Bitcoin and empower them with financial sovereignty.
nostr:npub1d39syxfnyply3r3j925gr2fuj9d2dtt8xcks6mm7fs8qtwml3z0qzjh33r
Here are the upcoming Nostr events that you might want to check out.
- The Bitcoin Freedom Festival will take place from February 20 to 24, 2025, at the Awakening Center in Uvita, Costa Rica. In collaboration with the Awake Earth Festival, this event blends a music festival with Bitcoin seminars and lectures. From February 20 to 23, the focus will be on music, healing workshops, ceremonies, and educational talks, featuring internationally renowned artists and captivating discussions. February 24 will be a special day dedicated to Bitcoin, with all activities centered around.
nostr:npub14f26g7dddy6dpltc70da3pg4e5w2p4apzzqjuugnsr2ema6e3y6s2xv7lu * Learning Bitcoin 2025 will take place on August 16 & 17 at Vancouver Convention Centre, Vancouver, BC, Canada. This Bitcoin education conference offers an in-depth learning experience beyond a typical event. Attendees can choose between General Admission (Super Early Bird: $80) and VIP tickets (Super Early Bird: $400).
Additionally, We warmly invite event organizers who have held recent activities to reach out to us so we can work together to promote the prosperity and development of the Nostr ecosystem.
Thanks for reading! If there’s anything I missed, feel free to reach out and help improve the completeness and accuracy of my coverage.
-
 @ c3b2802b:4850599c
2025-02-14 12:14:43
@ c3b2802b:4850599c
2025-02-14 12:14:43Die Plattform dient dem Zweck, interessierten Gemeinschaften unseres Landes aufzuzeigen, dass auch unter schwierigen globalen und bundespolitischen Rahmenbedingungen der Wandel hin zu zukunftsfähigen Lebensmustern auf kommunaler Ebene möglich ist. Und noch mehr: Dass dieser Umbau auch simultan in mehreren Lebensbereichen gestartet und vollzogen werden kann, wenn mutige und kluge Menschen aus verschiedenen Gruppen in Kommunen beherzt zusammenwirken.
Psychologischer Hintergrund. Viele Studien in 20 Jahren eigener psychologischer Analysen erfolgreicher Regionalisierungsprojekte haben aufgezeigt: Persönliche Begegnung und Austausch zwischen Interessierten an Regionalisierungsvorhaben und bereits erfolgreichen Pionieren sind ein entscheidender Erfolgsfaktor für gelingende Transformation. Dafür braucht es Informationen, wo sich Pionierprojekte befinden. Im ersten größeren Transformationsprojekt meiner Arbeitsgruppe, dem Energiewendedorf Jühnde, hat das Wissenschaftler-Team vorab andere innovative Kommunen besucht und deren Erfolgsfaktoren im eigenen Vorhaben umgesetzt. Die Mehrzahl der 200 Energiewendedörfer, die nach Fertigstellung Jühndes entstanden sind, hat sich wiederum vor Ort in der Modellkommune Jühnde informiert. Dies zeigt den Schneeballefekt des Lernens am Beispiel auf. Die hier beschriebene Plattform macht derartige „Funkenflüge“ für die Vielfalt der hier beschriebenen Innovationen über den Energiebereich hinaus möglich. Denn: Lernen am Modell setzt eine gute Übersicht über brauchbare Modelle voraus.
Inhalte der Plattform. Die Zukunftskommunen-Plattform beschreibt 67 Kommunen mit jeweils mindestens drei kommunalen Erfolgen. Die im gesamten Bundesgebiet verteilten Kommunen sind auf einer Landkarte ersichtlich. Von jedem Ort unseres Landes aus kann eine der Zukunftskommunen in maximal 100 km Entfernung erreicht werden. Die Nutzer der Plattform können über die Eingabe ihres Standortes erfahren, welche der Zukunftskommunen sich in der eigenen Region befinden – mit Angabe der Distanz in Kilometern. Jede dieser Kommunen ist in Wort und Bild mit den wesentlichen Informationen zum Stand des Umbaus sowie zum Ansprechpartner charakterisiert.
Die derzeit auf der Plattform dargestellten über 200 kommunalen Erfolge sind jeweils durch harte Fakten, Angaben zur Entstehungsgeschichte sowie Erfolgsfaktoren kurz skizziert - und wiederum sind jeweils auskunftsbereite Ansprechpartner genannt. Die Erfolge sind unter den Kommunen angeführt und lassen sich so „durchblättern“. Interessieren sich Nutzer der Plattform jedoch für bestimmte Aspekte der Regionalgesellschaft, können sie auch gezielt nach einzelnen Transformationsbereichen suchen. In dem Fall bekommen Sie – wiederum mit Entfernungsangabe zum eigenen Standort – die interessierenden kommunalen Erfolge angezeigt.
So lassen sich jeweils dutzende Erfolge im Land auffinden, im Bereich Bildung z.B. Lehrpfade, Umweltbildungsprojekte und Umwelttrainerprojekte, bei denen eigens ausgebildete Ehrenamtler ökologische Zusammenhänge vermitteln. Im Bereich Kreislaufwirtschaft sind die Erfolge nach folgenden Aspekten auffindbar: Regionale Kreisläufe, verpackungsfreie Verteilung, Verwendung von Natur-Baustoffen, Recycling endlicher Ressourcen, Bio-Landwirtschaft, Anbau und Nutzung nachwachsender Rohstoffe, Solar-Mobilität, Produktion von Anlagen zur Erzeugung erneuerbarer Energie und Erzeugung erneuerbarer Energie. Der Bereich natürliche Vielfalt ist folgendermaßen gegliedert: Naturschutz, Ressourcenschutz, Permakultur und Erhaltung von Biodiversität. Die Untergliederung der erfolgreichen Gemeinschaftsprojekte lautet: Miteinander aller Bevölkerungsgruppen, Integration und Inklusion, Generationennetzwerk, Genossenschaften, Rekommunalisierung von Infrastruktur, lokale Währung sowie Tauschen und Schenken.
Die Vielfalt der Innovationen ist noch weit größer als in dem Kategoriensystem abgebildet, da wegen der Handhabbarkeit der Plattform nicht alle denkbaren Kriterien ausformuliert worden sind. Doch auch besonders ungewöhnliche oder heute noch seltene kommunale Innovationen sind in der Beispielsammlung der Plattform auffindbar. Dazu kann die freie Suche der Plattform verwendet werden. Wer sich z.B. für Eisspeicher interessiert, kann ein Bildungszentrum mit Solareis-Erdspeicher in der Zukunftskommune Wiernsheim auffinden.
Ein Blog informiert über den politischen und geografischen Kontext, in dem die Transformation in unseren Kommunen stattfindet. Hier lassen sich Erfolgsgeschichten zwischen 2018 und 2024 aus dem In- und Ausland abrufen - wiederum beim Blättern oder durch die Suchfunktion nach Stichworten . Seit Herbst 2024 finden Sie meine Blogbeiträge zu dieser Thematik bei der Genossenschaft Menschlich Wirtschaften. Viel Freude beim Blättern und Stöbern!
Zuerst veröffentlicht in der Zeitschrift Ländlicher Raum (hier leicht gekürzt)
-
 @ fc2470ed:17d9ee27
2025-01-30 14:24:23
@ fc2470ed:17d9ee27
2025-01-30 14:24:23by Hynek Fencl, July 2024
The way to Liberland is easy but not simple. Technically speaking, it’s just a short bike ride away from the nearest village on a comfortable bike path through a stunning forest known as the “Amazon of Europe”. On one side, one senses the presence of the mighty Danube River beyond the tall trees, and on the other stretch the farmlands of north-eastern Croatia. Then you take a left turn to a straight forest path, ride all the way to the end, and after a few bends on the track, you will have entered “the promised land”.
The part that is not simple is that Croatia both does and does not consider Gornja Siga (the local name for the area we now refer to as Liberland) to be its territory – depending on who you ask. This means that along the picturesque bike path, you will almost certainly encounter a border police patrol car, and, depending on whether you seem to them like you’re affiliated with Liberland, they will tell you to stop and hand over your ID. They run it through their system and, if you’re lucky enough to be a citizen of the EU, they let you pass. If you’re not and you give them a non-EU passport, they will ask you to come to the station with them to “determine the circumstances of your stay in Croatia.” You will then be issued with paperwork telling you to leave the country within the next 7 days, banning you from re-entering in the next 1-3 months. The official reasoning they’ll give for this is their reasonable suspicion that you have not come to Croatia as a tourist but with the intent to either do paid work (for which you would have to get a business/work visa) or to break the law (such as camping outside designated camping grounds or starting a fire in the forest).
All of this is part of a big game of chess that is being played out between Croatia and the Liberlanders. Croatia is in a tricky spot. They cannot properly administer the territory of Liberland and enforce its law in it – lest it would create an indication that the Croatian state officially claims it as its territory. However, they cannot not administer it either, since it’s on “their” side of the river, and it is risky for a rogue, unpredictable operation (from their perspective) like the establishment and growth of Liberland to just be left to its own devices right on their doorstep. This is, then, how we arrive at the status quo, with Croatia relating to Liberland in some way while being careful about the international perception of its action in another way. The resulting practice is a persistent harassment campaign toward the Liberlanders, with the apparent intent to create uncertainty and lower the appetite of potential Liberland settlers for this kind of adventure.
How to establish a new country
Liberland was born from an anomaly – a historical border dispute between Croatia and Serbia. The dispute involves the definition of where the border stands in relation to the Danube and goes back to 1947. Then, both lands along the river belonged to a single country – Yugoslavia – but the dispute arose with respect to the boundaries of its constituent states. It remained unresolved during the communist era and became an issue of international borders after the breakup of Yugoslavia.
Serbia claims that the border runs down the middle of the Danube, with the eastern bank being Serbian and the western bank Croatian. Croatia, on the other hand, claims that the border is set by historical borders marked by cadastral municipalities surrounding the Danube.
These municipality borders run along a different path because they were set before the course of the Danube was straightened during the 19th Century to allow for easier shipping. This results in disputed “pockets” of land on both sides of the river. The pockets on the eastern bank have a combined area of around 130 km2, while those on the western bank only amount to less than 10 km2. Not surprisingly, then, both countries claim that the border runs in a way where they get the >90% of land and the other country only gets the small remaining areas. However, this means that, by implication, since both countries are claiming the large areas, neither of them is claiming the smaller ones. These areas were, then, so-called terra nullius.
Under international law, there is no issue with any state claiming unowned and unclaimed land for themselves. And that is exactly what Czech businessman, politician, and activist Vít Jedlička did in 2015 when he proclaimed into existence the newly created Free Republic of Liberland on the largest, 7 km2 piece of the unclaimed areas between Croatia and Serbia.
It's one thing to announce a new country to the world. It’s an entirely different thing to make this country legitimate. Under the Montevideo Convention, a proper country needs to have 1) a permanent population, 2) a defined territory, 3) government, and 4) capacity to enter into relations with other states. Now, 9 years after the birth of Liberland, it clearly has three of those. As to a permanent population, the Liberlanders would argue that it definitely exists, even though Liberland’s now over 1200 registered citizens have had to largely live in “exile” ever since.
Nevertheless, despite the Convention, there’s one thing that makes something a country more than anything else – whether other countries see you as a country. The more diplomatic recognition an entity has, the more country-like it becomes. This is especially relevant for breakaway governments, governments in exile, or, most importantly in this case, startup countries like Liberland.
Very much aware of this, along with other members of Liberland’s startup government, Jedlička has been on a worldwide mission to legitimize Liberland in the eyes of other countries. Though there have been many amiable meetings and even some measure of support in some cases, no official recognition by any UN member has been achieved as of mid-2024. Liberland now has representatives and offices in multiple countries in the further pursuit of this goal. Though the effectiveness of this strategy has been questioned by many for the lack of decisive results so far, one thing remains unambiguously true: if recognized by even one or two UN members, Liberland would instantly gain an amazing amount of legitimacy and gravitas in the eyes of the world.
The quest for territory
Establishing international relations with countries anywhere in the world is not the only strategy that the Liberlanders have been employing in making the country more real and legitimate. This includes liaising and negotiating with the neighboring Serbia and Croatia. These relations are by far the most important and impactful ones. If both of Liberland’s neighboring countries were to either outright recognize the startup micro-state, or even just adopted an approach of non-interference, Liberland would be free to start actually developing and to find its own long-term position in the world.
As for Serbia, its Ministry of Foreign Affairs let itself be heard that, in their view, Liberland’s claims are a “trivial matter” but, in any case, they do not infringe upon the sovereignty of Serbia. One can imagine that Serbia might actually be secretly quite pleased with Liberland’s activities, since now Croatia has an issue to deal with on “their” side of the river, which, if they are not careful, could contribute to the legitimization of Serbia’s claim to the larger pieces of territory claimed by both countries.
With Croatia, things get quite a bit more complicated. In an official statement, the country rejected the claim that Gornja Siga is terra nullius, arguing instead that the land belongs to one of the two neighboring countries – the only question is to which one, which will be answered at some point in the future. Croatia also said it would stop any threatening and provocative activities on the territory even by force if necessary.
Ever since Liberland’s birth in 2015, the Liberlanders have been trying to make a mark on the territory. For a long time, even just entering Liberland wasn’t really possible. Under a deal between the Croatian and Serbian police that was put in place during the European migration crisis, Croatian authorities may enter Liberland and patrol it for security reasons (preventing illegal migration) even though they do not officially claim the territory as theirs. In addition, the border police have a near-permanent presence on the Danube River, preventing people from crossing into Liberland by boat.
As a result, anyone who would try to come to Liberland in any way would always be promptly arrested by the Croatians, essentially for entering a prohibited area.
After years of this status quo, a rather unexpected thing happened that made things suddenly move forward in a positive direction for the Liberlanders. In April 2023, during Liberland’s 8th anniversary celebrations, a famous YouTuber with a significant following decided to try to enter Liberland. After a few unsuccessful attempts due to heavy police presence and monitoring, he and his team hired jet skis and rode them all the way from Hungary down the Danube. When they got close to Liberland, they encountered the police boats again, but their jet skis were faster than the boats, so they managed to land at Liberland’s Liberty Island and plant a flag there. A few moments later, the police caught up to them and an aggressive policeman took out their handheld cameras before assaulting them and then kicking them on the ground, as can be clearly seen from drone footage of the incident.
As they had broken no laws, they were ultimately let go after the incident and free to leave the island without being arrested. However, the heavy-handed and illegal conduct of the Croatian police had been clearly documented and became part of the video that was published in July 2023.
The video promptly went viral, gaining almost 10 million views on YouTube. By comparison, the total population of Croatia is just under 4 million. When the news spread even to the Croatian press and TV stations, Croatia had a serious PR problem on their hands. The police had been clearly in the wrong, conducting themselves in a seriously improper way to the point of using physical force against peaceful people who had broken no laws nor engaged in any violence or hostilities themselves.
Something had to change. So, following this incident, the Croatian police adopted a different unofficial policy – from now on, they would let people enter Liberland if they wished to do so, in a controlled way. Since early August 2023, if you wish to enter Liberland, you can go on foot or by bike, take the access road down the forest, and show your documents to the Croatian police, just as you would at a border crossing. In a typical grand fashion of Liberland’s media team, Liberland made an announcement that an official border crossing had been opened between Croatia and Liberland (Croatia had obviously never made an official announcement like this, but for Liberland, that was the de facto situation on the ground).
In the weeks following the “opening of the border”, many enthusiastic settlers started coming to Liberland to finally begin making their mark on the territory of “the promised land.” They started constructing simple wooden houses, a bathroom, an open-air restaurant, and the related power and water infrastructure on Liberland’s mainland beach opposite Liberty Island in a settlement named Mateos Marina.
On September 7th, 2023, a troop of about 50 policemen and forestry workers, including a demolition crew, raided the settlement. The raid was officially dubbed a “cleanup operation” by Hrvatske šume, Croatia’s state forestry service. With the assistance of the police, they tore down all the wooden houses and structures using chainsaws and stole equipment as well as personal possessions of the Liberlanders on site. Several Liberlanders were arrested for “failure to comply with a lawful order”.

One might ask, if Liberland is not officially part of Croatia, what authority does Croatia have to come in to steal and destroy? Staying true to their claim that Liberland is not part of Croatia, the Croatians had announced to Serbia that they would be conducting the “cleanup” on Serbia’s territory, to keep it clean on their behalf.
We may only speculate about the reasons for carrying out this operation in such a heavy-handed, destructive way. One possibility is that allowing people to enter Liberland in the first place was a way for Croatia to lure some people to Liberland, become comfortable, and then come in and destroy everything to show everyone what would happen if they got involved in the project. Or perhaps it was the unexpected level of life, community-building, and construction going on in such a short period of time after the “opening of the border” that the Croatian police felt like they had to put a stop to it before things got so big they could not be easily destroyed anymore.
No matter the reasons, the raid had a chilling effect on prospective Liberlanders. Though there is plenty of video documentation of the operation, no one made a viral video about it this time. Though some media did pick up the news, it did not become a big story. Consequently, the PR fallout from this for Croatia was not unmanageable.
Liberlanders soon returned to the territory. However, the level of enthusiasm, energy, and external support was not as great as it had been before the raid. From then on, settlement efforts focused mainly on Liberty Island, unreachable by trucks and impossible for forestry workers to get to without a large boat which they seem not to have. Though perhaps a more strategic place to set up camp, Liberty Island is also much more prone to flooding than the rest of Liberland.
In the following few months, several makeshift houses were constructed using a combination of wood and sandbags. During this time, Liberland even hosted a first wedding on the island. The settlement was kept alive during winter as well, with Liberland enthusiasts staying mostly in houseboats whenever it was impossible to camp on site.
In the meantime, an enthusiastic settler couple bought a sizeable house with a courtyard in the village closest to Liberland – Zmajevac – which they have transformed into a base of operations for settlers. This is now called Liberbase and it is where visits to Liberland start, with bikes, supplies, and construction materials being gathered before going on the 40-minute bike ride.

In the spring of 2024, work started on the reconstruction of a former hunting lodge at a central location on Liberland’s mainland – Jefferson Square. The building was demolished a few years ago but the foundations, including a cellar, were left in place. The site was cleared, the foundations refreshed, and new walls for the future governmental building have sprung up from the ground. A professional construction crew was hired to speed up the re-building of this base, using large concrete bricks, to a standard that will make it logistically and practically difficult for the Croatian police and forestry workers to try to destroy.
 The battle for legitimacy
The battle for legitimacy The ongoing construction in Liberland is rather slow. It is difficult to bring construction materials to Liberland. It is prohibited to drive motor vehicles on the bike path leading to Liberland, which means that everything has to be manually hauled from Liberbase on cargo bikes. In addition, from time to time, bikes get stolen by the police or forestry workers. Despite these difficulties, the determination of the settlers is unwavering and they are working every day to move construction forward.
The ongoing construction in Liberland is rather slow. It is difficult to bring construction materials to Liberland. It is prohibited to drive motor vehicles on the bike path leading to Liberland, which means that everything has to be manually hauled from Liberbase on cargo bikes. In addition, from time to time, bikes get stolen by the police or forestry workers. Despite these difficulties, the determination of the settlers is unwavering and they are working every day to move construction forward.Is it possible to bring materials by boat? How did they get sandbags and other materials to Liberty Island?
The importance of such a commitment should not be underestimated. The continuous presence of settlers is incredibly important for Liberland. It shows the seriousness of the project. It shows that Liberland is a genuine community and a fledgling nation rather than, as some accusations tend to go, just an elaborate publicity stunt.
Practical difficulties with the Croatian authorities are not limited to construction-related issues. Even staying and camping in Liberland comes with its quirks. If you’re staying on Jefferson Square, you should be prepared for several police visits every day. These check-ups are usually nothing dramatic. The police usually show up, ask a couple of questions, and perhaps tell the settlers that they are not allowed to camp there or start a fire, but they don’t actually do anything more than that and just go about their day.
It seems that the Croatian police are rather shy about enforcing Croatian law in a territory that is not officially considered part of Croatia. International law often takes into account the de facto situation of the matter in any dispute. If Croatia enforced their law in Liberland, this would therefore be an indication that they do, in fact, consider the territory to be theirs in practice, despite the official stance of the state. It would play into the hands of Serbia, reinforcing their claims to the large parcels of land on the other side of the Danube.
In addition, Liberlanders on the ground report that the majority of Croatian police officers generally behave quite fairly and respectfully toward them – only a minority appear to hold a personal grudge against Liberland, being abusive and sometimes even violent instead. It seems highly likely that the police in general are just doing their job, following orders from above. Most of them don’t actually take it as a personal commitment to make life more difficult for the Liberlanders.
This is rather important from a big-picture perspective, because the settlers, by contrast, are often heavily personally invested in the project and see it as their mission to see Liberland develop into a proper country. This disparity in energy and determination is strong and perhaps this is what will, in the end, cause Liberland to prevail in this drawn-out dispute.

The dispute with Hrvatske šume is quite different. As of mid-2024, the forestry workers tend to turn up at Jefferson Square about every fortnight. Unlike the police, they do not limit themselves to words but tend to steal everything that is not bolted down – including tools, materials, tents, bikes, and personal possessions of the settlers camping there. The justification remains the same – to “clean the forest of any waste.” In their encounters with the police as well as the forestry workers, Liberlanders are of course meticulous in their video documentation of any illegal actions by the authorities.
The Liberlanders’ difficulties, however, do not just stay local. As previously mentioned, upon trying to enter Liberland from Croatia, people who do not have EU citizenship are promptly issued a one-to-three-month ban on entering Croatia, with 7 days to leave the country. This is done under legislation relating to citizenship and tourism.
However, things can escalate even further. Since last year, several key Liberland settlers and organizers, including Liberland’s President Vít Jedlička himself, have seen “heavier guns” used against them. They have been banned from entering Croatia for 5 years under anti-terrorism legislation, where the authorities argue that these Liberlanders are something akin to a threat to national security.
The Liberlanders have mounted a legal defense against this, in addition to challenging Croatia on other legal fronts. They have had some successes so far – in particular, it should now be clear that the Liberlanders do not need any building permits to construct buildings on their territory. Unfortunately, other issues – including the 5-year bans from Croatia – still remain unresolved.
Most Liberlanders remain hopeful nonetheless. They have seen their situation move forward significantly over the last year. A year ago, they were not even able to enter Liberland without being chased and/or arrested. Now, even some construction is possible, albeit in a limited way.
The road ahead
The long-term vision, of course, remains to build a full-fledged, internationally respected and recognized city-state. Liberland’s leaders often speak of a “Balkan Monaco”, referring to the amazing development possibilities that a freedom-oriented country in the middle of Europe could offer. Liberland has already hosted an urbanist/architectural contest, and there are concrete plans for the first hotel as well as a riverside real estate development. What is more, Liberland’s land is actually more than three times the size of Monaco.
Nevertheless, Liberland cannot move forward in a meaningful way toward these visions and aspirations under the status quo. The Liberlanders need to be able to build at scale and be free from harassment, both by the police and the forestry workers. Some kind of political deal is necessary as the next step toward proper development of Liberland.
Such a deal could take multiple forms, but all of them involve the Croatian authorities changing their attitude toward Liberland away from a policy of unrelenting obstruction – not necessarily toward outright recognition, but at least toward accepting Liberland as a neighborly project that will move forward and develop in some way.
One option could be to allow motor vehicles on the bike path toward Liberland, with a deal that could include charging Liberlanders some fair tolls to pay for the wear and tear of the pavement. An alternative would be to simply allow river crossing into Liberland from Serbia on the Danube. Since Croatia does not officially consider Liberland its territory, their current interference with this traffic is illegal anyway. Simply stopping this illegal conduct would help Liberland significantly without Croatia facilitating Liberland’s development in any active way.

Regardless of these options, the first and most notable step would be to stop banning non-EU citizens from re-entering Croatia as well as lift the existing (entirely unjustified and unreasonable) 5-year bans on Jedlička and the others.
It is easy to see why Croatia is wary and suspicious of Liberland’s development. One can understand the worries of a state in whose immediate proximity there is a new and unknown state growing and taking root. Nevertheless, Croatia actually has a lot to gain from making some kind of deal with Liberland.
First: currently there are perhaps a dozen policemen on patrol around Liberland at all times. This includes police vehicles and boats. This is a significant expense for the police force – an expense which is rather unsubstantiated, given that Liberlanders have clearly proven to be peaceful people who do not wish to pose any threat to Croatia, its people, or its law enforcement officers. Making a deal would mean that this large expense is not needed anymore.
Second: Liberland borders an area of Croatia that has been rather “left behind”, is underdeveloped, and suffers from a lack of jobs and investment. Consequently, younger people are leaving the area and the current population is growing older. If Liberland was growing and open for business nearby, it would provide the region exactly with the job opportunities, large investment, and overall development that it desperately needs.
Third: Croatia could use Liberland as an opportunity to actually gain an advantage in the ongoing border dispute with Serbia. As previously mentioned, Croatia cannot openly and properly administer the territory, as it would be an indication in the eyes of international law that they consider the territory to be theirs. On the other hand, it Liberland is located on “their” side of the Danube, so Croatia does have an interest in making sure the area is under their control somehow. Striking a deal with Liberland could involve Liberland agreeing to some obligations related to the administration of the territory which correspond to Croatia’s priorities. In this way, Croatia would have an active say in what happens on this land, effectively “outsourcing” its administration without officially claiming it as part of Croatia.
In addition to all these advantages being present, Liberland is very much open to cooperation with Croatia and is keenly looking forward to welcoming any future productive relations with Croatian authorities. There will be no grudges held on Liberland’s side, and if a mutually beneficial deal or solution were to be found, no one would look behind at any historical quibbles or difficulties. Liberland would be an excellent and friendly neighbor to Croatia, not just causing any issues but actively helping the overall development of the surrounding region.
Time will tell how things will develop. At the present, the momentum, energy, and enthusiasm is definitely on the side of Liberland. There seems to be very little actual interest from the Croatian side to cause issues for Liberland and to continue to prevent the fledgling state from developing further. All that is left are the bureaucratic hurdles of a state that is being overly conservative about its approach to the important issues of the day. Things might take time, but seeing the determination of the settlers and the willingness of all Liberlanders to be unrelenting in their fight for the cause, it is not difficult to argue that we might be seeing the dawn of Liberland as the world’s next proper city-state as we speak.
-
 @ 88d8c9d1:5b3ac02b
2025-02-18 06:19:24
@ 88d8c9d1:5b3ac02b
2025-02-18 06:19:24This article was first published on Bitcoin Magazine at Aug 27, 2024.
In the rapidly expanding global Bitcoin community, Western biases often dominate the narrative, overlooking diverse stories from around the world. One such story belongs to Didier Somnuke, a small business owner in the heart of Bangkok, a city known for welcoming 22.8 million international tourists in 2023, surpassing cities like Paris, London, and New York City. Although Thailand has experienced a massive spike in household debt, reaching 16.37 trillion baht (US$463 billion) or 90.8% of the national GDP, up from less than 14 trillion baht in 2019.
[primal.net/p/npub1xzh2kqynr29x6j3ln6x05f26ha0c0ucfr280uzljftlgcthv9r6skqe7dt] aka Didier Somnuke, born in Yala province, where geopolitical conflict is a harsh reality. Southern Thailand is one of the poorest parts of Thailand with a poverty rate of 34% compared to the national average of 6%, according to the World Bank, has been plagued by instability. Since 2004, this turmoil has claimed over 7,000 lives and injured 13,500 people.
As a Thai saying goes, “ทวงสิทธิ์ที่จะมีชีวิตที่ดีกลับคืนมา” (Reclaim the right to a better life), In 2012, Didier left his conflict-ridden hometown for Bangkok, where pursuing higher education was a beacon of hope for a better life. At that time, Bitcoin and financial concepts were distant ideas in Didier's universe. Navigating the vibrant streets of Bangkok, Didier completed his master's degree and joined the workforce, taking up a typical 9-to-5 job. For a domestic migrant, this was a significant achievement. Reflecting on his journey, he recalled his teacher’s words, “When you are old, you have time and money, but you will lack the energy to start a business. If you want to do it, just do it.” With this advice in mind, Didier resigned from his monotonous corporate job after a year and opened a new chapter in his life.
Didier borrowed 50,000 THB (approximately 1,500 USD) from his brother to begin a street burger shop. He chose to start a burger business because he believed it was easy to launch with a small investment. Driven by his ambition and inspired by the bustling energy of Bangkok, a city that never sleeps. He spent about a year developing the recipe and began the business in 2015. In the first three to four years, he managed everything on his own as a solo entrepreneur, and his income was lower than the wage he earned in his corporate job. He often wondered if he had made a mistake by quitting his job to start a business that generated less income. However, after five years, everything started to improve. Sales at the shop began to increase, and Didier started hiring employees.
He admitted, "I entered the crypto market with greed; all I wanted was to get rich quickly." In 2017, he and his friends pooled their resources to buy three ASIC miners from Bitmain to try mining Bitcoin and altcoins like Litecoin and Dogecoin. They saw a return on their investment within six months. Didier bought his first Bitcoin in early 2017 to purchase those ASIC miners but didn't know how to transfer his Bitcoin, so he ended up using a bank transfer instead.
Reflecting on his early experiences, he recalled, "My first Bitcoin were slowly converted to shitcoins during the bull market. I was so lucky. I got a 100% profit almost immediately whenever I bought something." Despite having zero knowledge about cryptocurrency, he gained confidence and became a super shitcoiner, paying very little attention to Bitcoin.
In mid-2017, he learned about leverage and trading. His profits skyrocketed due to leverage. Although luck was not always on his side forever, in early 2018, the market crashed, and he lost over 1 million Thai baht (almost 30,000 USD), while his initial capital was just about 100,000 Thai baht (about 3,000 USD). On top of that, he also lost his shitcoins from the mining pool. He had kept all of his shitcoins in the mining pool's custody, and one day, when he checked his account, every shitcoin he owned, worth 10,000 USD were gone. The notice on the mining website, "Hash-to-Coin," stated that if coins were kept with them for more than three months, they would be considered a donation.

He disheartenedly said, "I lost everything." But unlike most people, "I didn't blame Bitcoin. I still see it as the future. I blame myself. I didn't know anything and I did over leverage." He emphasized that despite his heavy financial losses, his girlfriend did not leave him. "My girlfriend was my customer. She regularly came to buy burgers. I met her while I was struggling financially during my early days as an entrepreneur. She supported me and said we could make the money back."
Determined to turn his circumstances around, he discovered Mr. Piriya on YouTube and started following his live streams about the real Bitcoin education. This marked the moment he began to truly understand what Bitcoin and cryptocurrency are. Enlightened by this unique knowledge, he came to see Bitcoin as a saving technology rather than just a trading tool. Over three years, Didier recovered from his losses and emerged stronger. He got to be friend with Mr. Piriya, and together they founded a company called Right Shift to develop Bitcoin content in Thai language through multiple social media channels, including on Nostr (npub1ejn774qahqmgjsfajawy7634unk88y26yktvwuzp9kfgdeejx9mqdm97a5) with one of the popular hashtag #siamstr. As a team, they translated "The Bitcoin Standard" and "The Fiat Standard" into Thai, both of which became best-selling books in Thailand. They organized the first-ever Bitcoin Thailand Conference in 2023 and are now preparing for the next one in September 2024.

Didier now accepts Bitcoin as a payment method in his main burger shop, one of four different franchises. He uses Wallet of Satoshi to process these payments. Within a year of implementing this initiative, he has received over 3 million sats in payments, though he initially expected to see more transactions in Bitcoin. In his marketplace, some neighboring small business owners occasionally ask him about Bitcoin as they notice the large Bitcoin poster in his shop. Although they often lose interest once he explains, according to his several unsuccessful experience. Instead now, he focuses his energy online, where he can make more impact to people who are willing to embrace innovation.

In 2022, approximately 8.4 million people in Thailand, accounting for 12% of the country's population, used cryptocurrency. Estimates suggest that by 2028, this number will rise to about 17.67 million, representing 25% of the population. During our conversation, Didier claimed that there are about 50,000 Bitcoin users in Thailand and speculated that the Thai government might intervene in Bitcoin adoption, potentially mandating the use of KYC wallets because they dislike money systems they can't control. In the worst-case scenario, Didier remains resolute: he will continue advocating for Bitcoin with his friends. "It is not an option," he asserted, "it is the only way to survive."
-
 @ b8851a06:9b120ba1
2025-01-28 21:34:54
@ b8851a06:9b120ba1
2025-01-28 21:34:54Private property isn’t lines on dirt or fences of steel—it’s the crystallization of human sovereignty. Each boundary drawn is a silent declaration: This is where my will meets yours, where creation clashes against chaos. What we defend as “mine” or “yours” is no mere object but a metaphysical claim, a scaffold for the unfathomable complexity of voluntary exchange.
Markets breathe only when individuals anchor their choices in the inviolable. Without property, there is no negotiation—only force. No trade—only taking. The deed to land, the title to a car, the seed of an idea: these are not static things but frontiers of being, where human responsibility collides with the infinite permutations of value.
Austrian economics whispers what existentialism shouts: existence precedes essence. Property isn’t granted by systems; it’s asserted through action, defended through sacrifice, and sanctified through mutual recognition. A thing becomes “owned” only when a mind declares it so, and others—through reason or respect—refrain from crossing that unseen line.
Bitcoin? The purest ledger of this truth. A string of code, yes—but one that mirrors the unyielding logic of property itself: scarce, auditable, unconquerable. It doesn’t ask permission. It exists because sovereign minds choose it to.
Sigh. #nostr
I love #Bitcoin. -
 @ 06b7819d:d1d8327c
2024-11-29 12:11:05
@ 06b7819d:d1d8327c
2024-11-29 12:11:05In June 2023, the Law Commission of England and Wales published its final report on digital assets, concluding that the existing common law is generally flexible enough to accommodate digital assets, including crypto-tokens and non-fungible tokens (NFTs).
However, to address specific areas of uncertainty, the Commission recommended targeted statutory reforms and the establishment of an expert panel.
Key Conclusions and Recommendations:
1. Recognition of a Third Category of Personal Property:Traditional English law classifies personal property into two categories: “things in possession” (tangible items) and “things in action” (enforceable rights). Digital assets do not fit neatly into either category. The Commission recommended legislation to confirm the existence of a distinct third category of personal property to better accommodate digital assets. 
-
Development of Common Law: The Commission emphasized that the common law is well-suited to adapt to the complexities of emerging technologies and should continue to evolve to address issues related to digital assets. 
-
Establishment of an Expert Panel: To assist courts in navigating the technical and legal challenges posed by digital assets, the Commission recommended that the government create a panel of industry experts, legal practitioners, academics, and judges. This panel would provide non-binding guidance on issues such as control and transfer of digital assets. 
-
Facilitation of Crypto-Token and Crypto-Asset Collateral Arrangements: The Commission proposed the creation of a bespoke statutory legal framework to facilitate the use of digital assets as collateral, addressing current legal uncertainties in this area. 
-
Clarification of the Financial Collateral Arrangements Regulations: The report recommended statutory amendments to clarify the extent to which digital assets fall within the scope of the Financial Collateral Arrangements (No 2) Regulations 2003, ensuring that existing financial regulations appropriately cover digital assets. 
Overall, the Law Commission’s report underscores the adaptability of English common law in addressing the challenges posed by digital assets, while also identifying specific areas where legislative action is necessary to provide clarity and support the evolving digital economy.
-
-
 @ d360efec:14907b5f
2025-02-17 12:20:25
@ d360efec:14907b5f
2025-02-17 12:20:253 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไรของนักลงทุนส่วนใหญ่
นักลงทุนจำนวนมากต้องการที่จะประสบความสำเร็จในตลาดหุ้นและสร้างผลกำไรที่สม่ำเสมอ แต่หลายครั้งที่พวกเขากลับพบว่าตัวเองต้องเผชิญกับอุปสรรคที่ทำให้ไม่สามารถบรรลุเป้าหมายนั้นได้ ช่อง Zyo / เซียว จับอิดนึ้ง ได้นำเสนอ 3 พฤติกรรมที่เป็นอุปสรรคสำคัญต่อนักลงทุนส่วนใหญ่ ซึ่งหากนักลงทุนสามารถหลีกเลี่ยงพฤติกรรมเหล่านี้ได้ ก็จะมีโอกาสในการสร้างผลกำไรที่สม่ำเสมอมากยิ่งขึ้น
-
การซื้อขายตามอารมณ์: ตลาดหุ้นมีความผันผวนและเต็มไปด้วยข่าวสารมากมาย นักลงทุนที่ซื้อขายตามอารมณ์มักจะตัดสินใจโดยใช้อารมณ์เป็นหลัก ไม่ว่าจะเป็นความโลภเมื่อเห็นราคาหุ้นขึ้น หรือความกลัวเมื่อราคาหุ้นตก การตัดสินใจที่ไม่ได้อยู่บนพื้นฐานของข้อมูลและการวิเคราะห์อย่างรอบคอบ มักนำไปสู่การตัดสินใจที่ผิดพลาดและขาดทุนในที่สุด
-
การไม่ยอมรับความเสี่ยง: การลงทุนในตลาดหุ้นมีความเสี่ยง นักลงทุนที่ไม่ยอมรับความเสี่ยงมักจะพลาดโอกาสในการลงทุนในสินทรัพย์ที่ให้ผลตอบแทนสูง หรือในทางกลับกัน พวกเขาอาจจะหลีกเลี่ยงการตัดขาดทุนเมื่อการลงทุนไม่เป็นไปตามที่คาดหวัง การไม่ยอมรับความเสี่ยงและไม่บริหารความเสี่ยงอย่างเหมาะสม จะทำให้พอร์ตการลงทุนไม่เติบโตเท่าที่ควร หรืออาจจะเผชิญกับความเสียหายที่ใหญ่หลวงได้
-
การขาดความรู้และความเข้าใจ: ตลาดหุ้นเป็นเรื่องที่ซับซ้อนและเปลี่ยนแปลงอยู่เสมอ นักลงทุนที่ขาดความรู้และความเข้าใจในเรื่องการลงทุนอย่างเพียงพอ มักจะลงทุนโดยไม่มีหลักการหรือไม่สามารถวิเคราะห์สถานการณ์ได้อย่างถูกต้อง การลงทุนโดยปราศจากความรู้และความเข้าใจที่ถูกต้อง ก็เหมือนกับการเดินอยู่ในความมืด ซึ่งโอกาสที่จะประสบความสำเร็จนั้นเป็นไปได้ยาก
บทสรุป
3 พฤติกรรมที่กล่าวมาข้างต้นเป็นเพียงส่วนหนึ่งของอุปสรรคที่นักลงทุนส่วนใหญ่ต้องเผชิญ หากนักลงทุนต้องการที่จะประสบความสำเร็จในการลงทุนอย่างยั่งยืน พวกเขาจำเป็นต้องตระหนักถึงพฤติกรรมเหล่านี้และพยายามปรับปรุงตนเองอย่างต่อเนื่อง การศึกษาหาความรู้เพิ่มเติม การวางแผนการลงทุนอย่างรอบคอบ และการควบคุมอารมณ์ จะเป็นกุญแจสำคัญที่นำไปสู่การสร้างผลกำไรที่สม่ำเสมอในตลาดหุ้นได้ แน่นอนค่ะ ฟังคลิปแล้ว และสรุปบทความเป็นภาษาไทยให้คุณแล้วค่ะ
บทความ: 3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไรสม่ำเสมอของนักลงทุนส่วนใหญ่
บทความนี้สรุปแนวคิดจากคลิปวิดีโอที่วิเคราะห์พฤติกรรมของนักลงทุนส่วนใหญ่ โดยอ้างอิงจากการสำรวจบัญชีซื้อขายหุ้นกว่า 77,000 บัญชีในช่วงปี 1990-1996 พบว่ามี 3 พฤติกรรมหลักที่เป็นอุปสรรคสำคัญต่อการสร้างผลกำไรที่สม่ำเสมอในการลงทุน
3 พฤติกรรมที่เป็นอุปสรรคต่อการทำกำไร:
-
ปล่อยให้ขาดทุน แต่รีบขายกำไร: นักลงทุนส่วนใหญ่มักจะถือหุ้นที่กำลังขาดทุนต่อไปเรื่อย ๆ เพราะไม่อยากยอมรับว่าตัดสินใจผิดพลาด ในทางกลับกัน เมื่อหุ้นเริ่มมีกำไรเพียงเล็กน้อย กลับรีบขายออกไปเพราะกลัวกำไรจะหายไป พฤติกรรมนี้เป็นผลจากธรรมชาติของมนุษย์ที่เรียกว่า "Loser Aversion" หรือการหลีกเลี่ยงความเจ็บปวดจากการขาดทุนมากกว่าความสุขจากการได้กำไร
-
ถัวเฉลี่ยขาลง มากกว่าพีระมิดขาขึ้น: นักลงทุนจำนวนมากเลือกที่จะซื้อหุ้นที่ราคาลดลง (ถัวเฉลี่ยขาลง) โดยหวังว่าจะได้ต้นทุนที่ต่ำลงและรอให้ราคาหุ้นกลับมา แต่ในความเป็นจริง หุ้นที่อยู่ในแนวโน้มขาลงก็มีโอกาสที่จะลงต่อไปเรื่อย ๆ การถัวเฉลี่ยขาลงจึงเป็นการเพิ่มความเสี่ยง ในขณะที่การ "พีระมิดขาขึ้น" หรือการซื้อหุ้นเพิ่มเมื่อราคาปรับตัวสูงขึ้น เป็นการลงทุนในหุ้นที่กำลังมีแนวโน้มที่ดีและมีโอกาสสร้างกำไรมากกว่า
-
รีบขายกำไรเล็กน้อย แต่ไม่ยอมขายเมื่อขาดทุนเล็กน้อย: พฤติกรรมนี้ต่อเนื่องจากข้อแรก คือเมื่อได้กำไรเพียงเล็กน้อย นักลงทุนมักจะรีบขายเพื่อ "ล็อกกำไร" แต่เมื่อขาดทุนเล็กน้อย กลับไม่ยอมขายเพราะหวังว่าราคาจะกลับมา ทำให้สุดท้ายกลายเป็น "กำไรน้อย รีบขาย ขาดทุน เก็บไว้" ซึ่งส่งผลเสียต่อพอร์ตการลงทุนในระยะยาว
คำแนะนำเพื่อปรับปรุงพฤติกรรมการลงทุน:
- ฝึก "Cut Loss Short, Let Profit Run": ยอมตัดขาดทุนเมื่อหุ้นไม่เป็นไปตามแผน เพื่อจำกัดความเสียหาย และปล่อยให้หุ้นที่กำลังทำกำไรทำงานไป เพื่อเพิ่มโอกาสในการทำกำไรที่มากขึ้น
- อย่าถัวเฉลี่ยขาลงโดยไม่มีเหตุผล: พิจารณาแนวโน้มของหุ้นและปัจจัยพื้นฐานก่อนตัดสินใจถัวเฉลี่ยขาลง หากไม่มีเหตุผลที่ชัดเจน การถัวเฉลี่ยขาลงอาจเป็นการเพิ่มความเสี่ยงโดยไม่จำเป็น
- บริหารความเสี่ยงและ Money Management อย่างเหมาะสม: กำหนด stop loss ที่ชัดเจน และบริหารจัดการเงินทุนให้เหมาะสมกับความเสี่ยงที่รับได้
- เรียนรู้และพัฒนาระบบเทรดของตัวเองอย่างต่อเนื่อง: ทำความเข้าใจกลยุทธ์การเทรดของตนเอง และปรับปรุงพัฒนาอย่างสม่ำเสมอ
- มี Mindset ที่ถูกต้องสำหรับการเทรด: เข้าใจว่าการเทรดสวนทางกับธรรมชาติของมนุษย์ ต้องฝึกฝนและสร้างนิสัยที่ถูกต้องเพื่อเอาชนะอุปสรรคทางจิตวิทยา
สรุป:
การลงทุนและการเทรดหุ้นเป็นเกมที่ "ผิดธรรมชาติ" ของมนุษย์ การเอาชนะตลาดหุ้นได้จึงต้องอาศัยการฝึกฝนและปรับเปลี่ยนพฤติกรรมให้สวนทางกับธรรมชาติเดิม ๆ โดยการตระหนักถึง 3 พฤติกรรมที่เป็นอุปสรรค และนำคำแนะนำไปปรับใช้ จะช่วยให้นักลงทุนสามารถพัฒนาไปสู่การสร้างผลกำไรที่สม่ำเสมอและยั่งยืนได้ในระยะยาว
-
-
 @ fd208ee8:0fd927c1
2024-12-26 07:02:59
@ fd208ee8:0fd927c1
2024-12-26 07:02:59I just read this, and found it enlightening.
Jung... notes that intelligence can be seen as problem solving at an everyday level..., whereas creativity may represent problem solving for less common issues
Other studies have used metaphor creation as a creativity measure instead of divergent thinking and a spectrum of CHC components instead of just g and have found much higher relationships between creativity and intelligence than past studies
https://www.mdpi.com/2079-3200/3/3/59
I'm unusually intelligent (Who isn't?), but I'm much more creative, than intelligent, and I think that confuses people. The ability to apply intelligence, to solve completely novel problems, on the fly, is something IQ tests don't even claim to measure. They just claim a correlation.
Creativity requires taking wild, mental leaps out into nothingness; simply trusting that your brain will land you safely. And this is why I've been at the forefront of massive innovation, over and over, but never got rich off of it.
I'm a starving autist.
Zaps are the first time I've ever made money directly, for solving novel problems. Companies don't do this because there is a span of time between providing a solution and the solution being implemented, and the person building the implementation (or their boss) receives all the credit for the existence of the solution. At best, you can hope to get pawned off with a small bonus.
Nobody can remember who came up with the solution, originally, and that person might not even be there, anymore, and probably never filed a patent, and may have no idea that their idea has even been built. They just run across it, later, in a tech magazine or museum, and say, "Well, will you look at that! Someone actually went and built it! Isn't that nice!"
Universities at least had the idea of cementing novel solutions in academic papers, but that: 1) only works if you're an academic, and at a university, 2) is an incredibly slow process, not appropriate for a truly innovative field, 3) leads to manifestations of perverse incentives and biased research frameworks, coming from 'publish or perish' policies.
But I think long-form notes and zaps solve for this problem. #Alexandria, especially, is being built to cater to this long-suffering class of chronic underachievers. It leaves a written, public, time-stamped record of Clever Ideas We Have Had.
Because they are clever, the ideas. And we have had them.
-
 @ d360efec:14907b5f
2025-02-17 08:49:15
@ d360efec:14907b5f
2025-02-17 08:49:15ภาพรวม BTCUSDT (OKX):
Bitcoin ยังคงอยู่ในแนวโน้มขาขึ้นระยะยาว แต่ระยะสั้นมีความผันผวนและมีการปรับฐานลงมา การวิเคราะห์ครั้งนี้จะเน้นการระบุพื้นที่ที่ Smart Money (หรือ "เจ้ามือ") อาจจะเข้าซื้อหรือขาย เพื่อให้เราสามารถวางแผนการเทรดได้อย่างมีประสิทธิภาพ
วิเคราะห์ทีละ Timeframe:
(1) TF Day (รายวัน):
- แนวโน้ม: ขาขึ้น (Uptrend)
- SMC:
- Higher Highs (HH) และ Higher Lows (HL) ต่อเนื่อง
- Break of Structure (BOS) ด้านบน
- ยังไม่มีสัญญาณการกลับตัวเป็นขาลง
- ICT:
- ยังไม่เห็น Order Block หรือ FVG ที่ชัดเจนใน TF Day ณ ราคาปัจจุบัน
- EMA:
- ราคาอยู่เหนือ EMA 50 (สีเหลือง) และ EMA 200 (สีขาว) (Golden Cross)
- Money Flow (LuxAlgo):
- สีเขียวเป็นส่วนใหญ่ แสดงถึงแรงซื้อ
- Volume Profile:
- Volume หนาแน่นที่บริเวณต่ำกว่าราคาปัจจุบัน
- แท่งเทียน:
- แท่งเทียนล่าสุดเป็นสีแดง แสดงถึงแรงขาย แต่ไส้เทียนยาว แสดงว่ามีแรงซื้อกลับ
- แนวรับ: EMA 50, EMA 200, บริเวณ Volume Profile หนาแน่น
- แนวต้าน: High เดิม
- สรุป: แนวโน้มหลักยังเป็นขาขึ้น Buy on Dip
(2) TF4H (4 ชั่วโมง):
- แนวโน้ม: ขาขึ้น (พักตัว)
- SMC:
- HH และ HL
- BOS ด้านบน
- ราคาหลุด EMA 50
- ICT:
- Fair Value Gap (FVG): สังเกตเห็น FVG เล็กๆ ที่เกิดขึ้นก่อนหน้านี้ (บริเวณที่ราคาเคยพุ่งขึ้นอย่างรวดเร็ว) อาจเป็นเป้าหมายของการ Pullback
- Order Block: ราคาปัจจุบันกำลังทดสอบ Order Block (บริเวณแท่งเทียนสีแดงแท่งใหญ่ก่อนที่จะขึ้น) เป็นจุดที่น่าสนใจมาก
- EMA:
- ราคาหลุด EMA 50
- EMA 200 เป็นแนวรับถัดไป
- Money Flow (LuxAlgo):
- เขียวและแดงผสมกัน, แดงเริ่มมากขึ้น
- Volume Profile:
- Volume profile ค่อนข้างสูง
- แนวรับ: EMA 200, Order Block, บริเวณ Volume Profile
- แนวต้าน: EMA 50, High เดิม
- สรุป: แนวโน้มขาขึ้นพักตัว, ทดสอบ Order Block, Money Flow เริ่มเป็นลบ
(3) TF15 (15 นาที):
- แนวโน้ม: ขาลง (Downtrend) ระยะสั้น แต่เริ่มมีสัญญาณการฟื้นตัว
- SMC:
- Lower Highs (LH) และ Lower Lows (LL) แต่เริ่มเห็น Higher Low
- BOS ด้านล่าง
- เริ่มมีสัญญาณการ Breakout EMA 50/200
- ICT:
- ราคาเพิ่ง Breakout Order Block ขาลง (แต่ต้องรอดูว่าจะยืนได้หรือไม่)
- EMA:
- EMA 50/200 เพิ่งจะตัดกันแบบ Golden Cross
- Money Flow (LuxAlgo):
- เริ่มมีแท่งสีเขียวปรากฏขึ้น
- Volume Profile:
- แนวรับ: บริเวณ Low ล่าสุด
- แนวต้าน: EMA50/200
- สรุป: เริ่มมีสัญญาณการฟื้นตัว แต่ยังต้องระวัง
สรุปภาพรวมและกลยุทธ์ (BTCUSDT):
- แนวโน้มหลัก (Day): ขาขึ้น
- แนวโน้มรอง (4H): ขาขึ้น (พักตัว), ทดสอบ Order Block
- แนวโน้มระยะสั้น (15m): เริ่มมีสัญญาณการฟื้นตัว
- Money Flow: Day เป็นบวก, 4H เริ่มเป็นลบ, 15m เริ่มเป็นบวก
- กลยุทธ์:
- Wait & See: รอการยืนยันการ Breakout EMA 50/200 ใน TF15m
- Buy (เสี่ยง): เฉพาะเมื่อราคา Breakout EMA 50/200 ใน TF 15 ได้อย่างแข็งแกร่ง
- Short (เสี่ยง): ถ้า Order Block ใน TF4H รับไม่อยู่ และ TF15 ยังคงเป็นขาลง
คำแนะนำ:
- Order Block: ให้ความสำคัญกับ Order Block ใน TF4H
- FVG: สังเกต FVG ใน TF4H
- ความขัดแย้งของ Timeframes: เริ่มลดลง (15m เริ่มมีสัญญาณบวก)
- จับตาดู TF15 อย่างใกล้ชิด
Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัว ไม่ถือเป็นคำแนะนำในการลงทุน ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบ
-
 @ 42342239:1d80db24
2025-02-14 08:42:40
@ 42342239:1d80db24
2025-02-14 08:42:40A recent US data leak has brought to light a disturbing reality: our everyday technology has become a powerful tool for surveillance and control. Paradoxically, new technology holds the key to creating a safer, more resilient, and perhaps even more human society.
Preparedness remains a multifaceted topic that continues to spark engagement. The subject is not just about energy infrastructure and food supply but also about seemingly more orthogonal issues like obesity and cybersecurity.
The significant importance of cybersecurity can be illustrated by examples from an American company that was recently subjected to an IT intrusion with a subsequent data leak. The company, Gravy Analytics, specializes in providing mobile phone data that provides exceptionally detailed information about where individuals are located at any given time. Data that can be used, for example, for advertising purposes, but also for more sinister purposes such as extortion or espionage. The company has previously been accused of using misleading methods to collect location data without valid consent from individuals.
Mobile operators have long had the ability to locate their subscribers' positions over time. This leak shows how even apps on your phone risk revealing your location. Analysis of the samples leaked from the leak shows that data has leaked out for users of several well-known mobile applications, including the popular mobile game Candy Crush and the widely used online dating service Tinder.
Even if apps only use an ad ID when collecting data, these collected digital breadcrumbs can often be deanonymized. It is possible, for example, to identify daily routines, workplaces, and where and when an individual usually sleeps. This usually enables identification. But it is also possible to map an individual's social circle and romantic relationships. The mapping risks quickly becoming both sensitive and invasive.
The fact that such data is collected, but especially that it leaks, also poses a threat to preparedness. By mapping military or other sensitive locations (energy supply, water treatment plants, critical infrastructure) along with location and time data, it is potentially possible to identify employees at these locations. Information that can then be used by those who want to cause harm.
It is not written in the stars that citizens must be dependent on a few large IT companies. Our data does not need to be collected and used in a way that does not benefit us, without our knowledge. There are alternatives to large-scale and "super-registers". Technology such as asymmetric encryption and zero-knowledge proofs can be used to give power back to the individual. If the parliament and government are serious about improving preparedness, it is high time to leave old thought patterns like Chat Control 2 behind and instead explore such possibilities.
The primary purpose of the internet was originally to enable information transfer without intermediaries ("peer-to-peer"). Today, intermediaries are everywhere. It is worth remembering that peer-to-peer is not some obscure technical term. In case we have forgotten about it, it simply means: person to person, without intermediaries.
Maybe new technology can not only give us a safer and more resilient society, but also a more human one?
-
 @ 91bea5cd:1df4451c
2025-02-04 17:15:57
@ 91bea5cd:1df4451c
2025-02-04 17:15:57Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ fe32298e:20516265
2024-12-16 20:59:13
@ fe32298e:20516265
2024-12-16 20:59:13Today I learned how to install NVapi to monitor my GPUs in Home Assistant.

NVApi is a lightweight API designed for monitoring NVIDIA GPU utilization and enabling automated power management. It provides real-time GPU metrics, supports integration with tools like Home Assistant, and offers flexible power management and PCIe link speed management based on workload and thermal conditions.
- GPU Utilization Monitoring: Utilization, memory usage, temperature, fan speed, and power consumption.
- Automated Power Limiting: Adjusts power limits dynamically based on temperature thresholds and total power caps, configurable per GPU or globally.
- Cross-GPU Coordination: Total power budget applies across multiple GPUs in the same system.
- PCIe Link Speed Management: Controls minimum and maximum PCIe link speeds with idle thresholds for power optimization.
- Home Assistant Integration: Uses the built-in RESTful platform and template sensors.
Getting the Data
sudo apt install golang-go git clone https://github.com/sammcj/NVApi.git cd NVapi go run main.go -port 9999 -rate 1 curl http://localhost:9999/gpuResponse for a single GPU:
[ { "index": 0, "name": "NVIDIA GeForce RTX 4090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 16, "power_limit_watts": 450, "memory_total_gb": 23.99, "memory_used_gb": 0.46, "memory_free_gb": 23.52, "memory_usage_percent": 2, "temperature": 38, "processes": [], "pcie_link_state": "not managed" } ]Response for multiple GPUs:
[ { "index": 0, "name": "NVIDIA GeForce RTX 3090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 14, "power_limit_watts": 350, "memory_total_gb": 24, "memory_used_gb": 0.43, "memory_free_gb": 23.57, "memory_usage_percent": 2, "temperature": 36, "processes": [], "pcie_link_state": "not managed" }, { "index": 1, "name": "NVIDIA RTX A4000", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 10, "power_limit_watts": 140, "memory_total_gb": 15.99, "memory_used_gb": 0.56, "memory_free_gb": 15.43, "memory_usage_percent": 3, "temperature": 41, "processes": [], "pcie_link_state": "not managed" } ]Start at Boot
Create
/etc/systemd/system/nvapi.service:``` [Unit] Description=Run NVapi After=network.target
[Service] Type=simple Environment="GOPATH=/home/ansible/go" WorkingDirectory=/home/ansible/NVapi ExecStart=/usr/bin/go run main.go -port 9999 -rate 1 Restart=always User=ansible
Environment="GPU_TEMP_CHECK_INTERVAL=5"
Environment="GPU_TOTAL_POWER_CAP=400"
Environment="GPU_0_LOW_TEMP=40"
Environment="GPU_0_MEDIUM_TEMP=70"
Environment="GPU_0_LOW_TEMP_LIMIT=135"
Environment="GPU_0_MEDIUM_TEMP_LIMIT=120"
Environment="GPU_0_HIGH_TEMP_LIMIT=100"
Environment="GPU_1_LOW_TEMP=45"
Environment="GPU_1_MEDIUM_TEMP=75"
Environment="GPU_1_LOW_TEMP_LIMIT=140"
Environment="GPU_1_MEDIUM_TEMP_LIMIT=125"
Environment="GPU_1_HIGH_TEMP_LIMIT=110"
[Install] WantedBy=multi-user.target ```
Home Assistant
Add to Home Assistant
configuration.yamland restart HA (completely).For a single GPU, this works: ``` sensor: - platform: rest name: MYPC GPU Information resource: http://mypc:9999 method: GET headers: Content-Type: application/json value_template: "{{ value_json[0].index }}" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature scan_interval: 1 # seconds
- platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} GPU" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Memory" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Temperature" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'temperature') }}" unit_of_measurement: "°C" ```
For multiple GPUs: ``` rest: scan_interval: 1 resource: http://mypc:9999 sensor: - name: "MYPC GPU0 Information" value_template: "{{ value_json[0].index }}" json_attributes_path: "$.0" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature - name: "MYPC GPU1 Information" value_template: "{{ value_json[1].index }}" json_attributes_path: "$.1" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature
-
platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC GPU0 GPU" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC GPU0 Memory" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC GPU0 Power" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC GPU0 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC GPU0 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'temperature') }}" unit_of_measurement: "C"
-
platform: template sensors: mypc_gpu_1_gpu: friendly_name: "MYPC GPU1 GPU" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_memory: friendly_name: "MYPC GPU1 Memory" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_power: friendly_name: "MYPC GPU1 Power" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_1_power_limit: friendly_name: "MYPC GPU1 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_1_temperature: friendly_name: "MYPC GPU1 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'temperature') }}" unit_of_measurement: "C"
```
Basic entity card:
type: entities entities: - entity: sensor.mypc_gpu_0_gpu secondary_info: last-updated - entity: sensor.mypc_gpu_0_memory secondary_info: last-updated - entity: sensor.mypc_gpu_0_power secondary_info: last-updated - entity: sensor.mypc_gpu_0_power_limit secondary_info: last-updated - entity: sensor.mypc_gpu_0_temperature secondary_info: last-updatedAnsible Role
```
-
name: install go become: true package: name: golang-go state: present
-
name: git clone git: repo: "https://github.com/sammcj/NVApi.git" dest: "/home/ansible/NVapi" update: yes force: true
go run main.go -port 9999 -rate 1
-
name: install systemd service become: true copy: src: nvapi.service dest: /etc/systemd/system/nvapi.service
-
name: Reload systemd daemons, enable, and restart nvapi become: true systemd: name: nvapi daemon_reload: yes enabled: yes state: restarted ```
-
 @ 599f67f7:21fb3ea9
2025-01-26 11:01:05
@ 599f67f7:21fb3ea9
2025-01-26 11:01:05¿Qué es Blossom?
nostr:nevent1qqspttj39n6ld4plhn4e2mq3utxpju93u4k7w33l3ehxyf0g9lh3f0qpzpmhxue69uhkummnw3ezuamfdejsygzenanl0hmkjnrq8fksvdhpt67xzrdh0h8agltwt5znsmvzr7e74ywgmr72
Blossom significa Blobs Simply Stored on Media Servers (Blobs Simplemente Almacenados en Servidores de Medios). Blobs son fragmentos de datos binarios, como archivos pero sin nombres. En lugar de nombres, se identifican por su hash sha256. La ventaja de usar hashes sha256 en lugar de nombres es que los hashes son IDs universales que se pueden calcular a partir del archivo mismo utilizando el algoritmo de hash sha256.
💡 archivo -> sha256 -> hash
Blossom es, por lo tanto, un conjunto de puntos finales HTTP que permiten a los usuarios almacenar y recuperar blobs almacenados en servidores utilizando su identidad nostr.
¿Por qué Blossom?
Como mencionamos hace un momento, al usar claves nostr como su identidad, Blossom permite que los datos sean "propiedad" del usuario. Esto simplifica enormemente la cuestión de "qué es spam" para el alojamiento de servidores. Por ejemplo, en nuestro Blossom solo permitimos cargas por miembros de la comunidad verificados que tengan un NIP-05 con nosotros.
Los usuarios pueden subir en múltiples servidores de blossom, por ejemplo, uno alojado por su comunidad, uno de pago, otro público y gratuito, para establecer redundancia de sus datos. Los blobs pueden ser espejados entre servidores de blossom, de manera similar a cómo los relays nostr pueden transmitir eventos entre sí. Esto mejora la resistencia a la censura de blossom.
A continuación se muestra una breve tabla de comparación entre torrents, Blossom y servidores CDN centralizados. (Suponiendo que hay muchos seeders para torrents y se utilizan múltiples servidores con Blossom).
| | Torrents | Blossom | CDN Centralizado | | --------------------------------------------------------------- | -------- | ------- | ---------------- | | Descentralizado | ✅ | ✅ | ❌ | | Resistencia a la censura | ✅ | ✅ | ❌ | | ¿Puedo usarlo para publicar fotos de gatitos en redes sociales? | ❌ | ✅ | ✅ |
¿Cómo funciona?
Blossom utiliza varios tipos de eventos nostr para comunicarse con el servidor de medios.
| kind | descripción | BUD | | ----- | ------------------------------- | ------------------------------------------------------------------ | | 24242 | Evento de autorización | BUD01 | | 10063 | Lista de Servidores de Usuarios | BUD03 |
kind:24242 - Autorización
Esto es esencialmente lo que ya describimos al usar claves nostr como IDs de usuario. En el evento, el usuario le dice al servidor que quiere subir o eliminar un archivo y lo firma con sus claves nostr. El servidor realiza algunas verificaciones en este evento y luego ejecuta el comando del usuario si todo parece estar bien.
kind:10063 - Lista de Servidores de Usuarios
Esto es utilizado por el usuario para anunciar a qué servidores de medios está subiendo. De esta manera, cuando el cliente ve esta lista, sabe dónde subir los archivos del usuario. También puede subir en múltiples servidores definidos en la lista para asegurar redundancia. En el lado de recuperación, si por alguna razón uno de los servidores en la lista del usuario está fuera de servicio, o el archivo ya no se puede encontrar allí, el cliente puede usar esta lista para intentar recuperar el archivo de otros servidores en la lista. Dado que los blobs se identifican por sus hashes, el mismo blob tendrá el mismo hash en cualquier servidor de medios. Todo lo que el cliente necesita hacer es cambiar la URL por la de un servidor diferente.
Ahora, además de los conceptos básicos de cómo funciona Blossom, también hay otros tipos de eventos que hacen que Blossom sea aún más interesante.
| kind | descripción | | ----- | --------------------- | | 30563 | Blossom Drives | | 36363 | Listado de Servidores | | 31963 | Reseña de Servidores |
kind:30563 - Blossom Drives
Este tipo de evento facilita la organización de blobs en carpetas, como estamos acostumbrados con los drives (piensa en Google Drive, iCloud, Proton Drive, etc.). El evento contiene información sobre la estructura de carpetas y los metadatos del drive.
kind:36363 y kind:31963 - Listado y Reseña
Estos tipos de eventos permiten a los usuarios descubrir y reseñar servidores de medios a través de nostr. kind:36363 es un listado de servidores que contiene la URL del servidor. kind:31963 es una reseña, donde los usuarios pueden calificar servidores.
¿Cómo lo uso?
Encuentra un servidor
Primero necesitarás elegir un servidor Blossom donde subirás tus archivos. Puedes navegar por los públicos en blossomservers.com. Algunos de ellos son de pago, otros pueden requerir que tus claves nostr estén en una lista blanca.
Luego, puedes ir a la URL de su servidor y probar a subir un archivo pequeño, como una foto. Si estás satisfecho con el servidor (es rápido y aún no te ha fallado), puedes agregarlo a tu Lista de Servidores de Usuarios. Cubriremos brevemente cómo hacer esto en noStrudel y Amethyst (pero solo necesitas hacer esto una vez, una vez que tu lista actualizada esté publicada, los clientes pueden simplemente recuperarla de nostr).
noStrudel
- Encuentra Relays en la barra lateral, luego elige Servidores de Medios.
- Agrega un servidor de medios, o mejor aún, varios.
- Publica tu lista de servidores. ✅
Amethyst
- En la barra lateral, encuentra Servidores multimedia.
- Bajo Servidores Blossom, agrega tus servidores de medios.
- Firma y publica. ✅
Ahora, cuando vayas a hacer una publicación y adjuntar una foto, por ejemplo, se subirá en tu servidor blossom.
⚠️ Ten en cuenta que debes suponer que los archivos que subas serán públicos. Aunque puedes proteger un archivo con contraseña, esto no ha sido auditado.
Blossom Drive
Como mencionamos anteriormente, podemos publicar eventos para organizar nuestros blobs en carpetas. Esto puede ser excelente para compartir archivos con tu equipo, o simplemente para mantener las cosas organizadas.
Para probarlo, ve a blossom.hzrd149.com (o nuestra instancia comunitaria en blossom.bitcointxoko.com) e inicia sesión con tu método preferido.
Puedes crear una nueva unidad y agregar blobs desde allí.
Bouquet
Si usas múltiples servidores para darte redundancia, Bouquet es una buena manera de obtener una visión general de todos tus archivos. Úsalo para subir y navegar por tus medios en diferentes servidores y sincronizar blobs entre ellos.
Cherry Tree
nostr:nevent1qvzqqqqqqypzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqyp3065hj9zellakecetfflkgudm5n6xcc9dnetfeacnq90y3yxa5z5gk2q6
Cherry Tree te permite dividir un archivo en fragmentos y luego subirlos en múltiples servidores blossom, y más tarde reensamblarlos en otro lugar.
Conclusión
Blossom aún está en desarrollo, pero ya hay muchas cosas interesantes que puedes hacer con él para hacerte a ti y a tu comunidad más soberanos. ¡Pruébalo!
Si deseas mantenerte al día sobre el desarrollo de Blossom, sigue a nostr:nprofile1qyghwumn8ghj7mn0wd68ytnhd9hx2tcpzfmhxue69uhkummnw3e82efwvdhk6tcqyqnxs90qeyssm73jf3kt5dtnk997ujw6ggy6j3t0jjzw2yrv6sy22ysu5ka y dale un gran zap por su excelente trabajo.
Referencias
-
 @ 6f6b50bb:a848e5a1
2024-12-15 15:09:52
@ 6f6b50bb:a848e5a1
2024-12-15 15:09:52Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
-
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
-
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!
Tradotto da:\ https://willwhitney.com/computing-inside-ai.htmlhttps://willwhitney.com/computing-inside-ai.html
-
-
 @ 04ed2b8f:75be6756
2025-02-18 00:52:41
@ 04ed2b8f:75be6756
2025-02-18 00:52:41You sit there, thinking you have time. Thinking tomorrow is guaranteed. Thinking opportunities will wait for you while you hesitate, overthink, and let fear sink its claws into your soul. But time is ruthless. It moves whether you act or not. And every moment you delay, another chance dies.
One day, the sand in your hourglass will run out. One day, your name will be spoken for the last time. One day, you will face the end. The question is—will you meet it with pride or regret?
Hesitation Is the Death of Warriors
A warrior who hesitates on the battlefield is the first to be cut down. Life is no different. Those who wait, who stall, who play it safe—die with their potential still locked inside them. The graveyard is full of people who had dreams but never moved. They were going to start "tomorrow." They were waiting for "the right time."
But there is no right time. There is only now.
Look at Elon Musk—he could have waited for a "better moment" to start SpaceX. Instead, he bet everything on an idea everyone called crazy, even when his rockets kept failing. He took the shot. Now he’s reshaping the future of space travel.
Think of Michael Jordan—cut from his high school basketball team. He could have quit, wallowed in self-pity, and blamed the coach. But he didn’t. He got back up, trained harder, and became the greatest of all time.
Contrast that with people who let fear win—the ones who never started the business they dreamed of, never asked out the person they loved, never left the dead-end job that drained their soul. Their stories don’t make history. They fade into regret.
- Perfection is a lie. If you wait to feel "ready," you will wait forever.
- Fear is an illusion. It exists only in your mind. Face it, and it crumbles. Run from it, and it owns you.
- Regret is eternal. You can recover from failure. You can learn, adapt, and rise again. But the chances you never take? The words you never say? The life you never live? Those haunt you forever.
The Strong Seize the Moment
The world doesn’t wait. The bold carve their names into history, while the weak fade into the background. You were not put here to hesitate, to shrink, to live a half-life of fear and excuses. You were made to fight, to conquer, to chase the impossible and make it real.
- Opportunities don’t knock twice. If you don’t seize them, someone else will.
- Failure is a stepping stone. Every loss, every setback is a lesson—IF you keep moving.
- Time is the only thing you can’t get back. You can recover money, rebuild relationships, restart projects—but lost time? Gone forever.
Look at Colonel Sanders—he started KFC at age 65. Most people his age were retiring. He could have said, “It’s too late.” Instead, he built a global empire.
Or J.K. Rowling—rejected by 12 publishers before "Harry Potter" was accepted. She could have quit after the first, the second, or the tenth rejection. But she kept pushing.
Now, imagine if they had waited. Imagine if they had let fear win. They wouldn’t exist in the history books. They would have been just another name in the crowd.
Now or Never
You can keep telling yourself, “I’ll start tomorrow.”
You can keep making excuses, keep letting fear win, keep lying to yourself that there’s still time.Or you can make a choice—the choice to act.
Because death is certain. Time is fleeting. But right now? Right now is still yours.
Will you waste it? Or will you seize it with both hands and make something legendary?
Your move.
-
 @ e6817453:b0ac3c39
2024-12-07 15:06:43
@ e6817453:b0ac3c39
2024-12-07 15:06:43I started a long series of articles about how to model different types of knowledge graphs in the relational model, which makes on-device memory models for AI agents possible.
We model-directed graphs
Also, graphs of entities
We even model hypergraphs
Last time, we discussed why classical triple and simple knowledge graphs are insufficient for AI agents and complex memory, especially in the domain of time-aware or multi-model knowledge.
So why do we need metagraphs, and what kind of challenge could they help us to solve?
- complex and nested event and temporal context and temporal relations as edges
- multi-mode and multilingual knowledge
- human-like memory for AI agents that has multiple contexts and relations between knowledge in neuron-like networks
MetaGraphs
A meta graph is a concept that extends the idea of a graph by allowing edges to become graphs. Meta Edges connect a set of nodes, which could also be subgraphs. So, at some level, node and edge are pretty similar in properties but act in different roles in a different context.
Also, in some cases, edges could be referenced as nodes.
This approach enables the representation of more complex relationships and hierarchies than a traditional graph structure allows. Let’s break down each term to understand better metagraphs and how they differ from hypergraphs and graphs.Graph Basics
- A standard graph has a set of nodes (or vertices) and edges (connections between nodes).
- Edges are generally simple and typically represent a binary relationship between two nodes.
- For instance, an edge in a social network graph might indicate a “friend” relationship between two people (nodes).
Hypergraph
- A hypergraph extends the concept of an edge by allowing it to connect any number of nodes, not just two.
- Each connection, called a hyperedge, can link multiple nodes.
- This feature allows hypergraphs to model more complex relationships involving multiple entities simultaneously. For example, a hyperedge in a hypergraph could represent a project team, connecting all team members in a single relation.
- Despite its flexibility, a hypergraph doesn’t capture hierarchical or nested structures; it only generalizes the number of connections in an edge.
Metagraph
- A metagraph allows the edges to be graphs themselves. This means each edge can contain its own nodes and edges, creating nested, hierarchical structures.
- In a meta graph, an edge could represent a relationship defined by a graph. For instance, a meta graph could represent a network of organizations where each organization’s structure (departments and connections) is represented by its own internal graph and treated as an edge in the larger meta graph.
- This recursive structure allows metagraphs to model complex data with multiple layers of abstraction. They can capture multi-node relationships (as in hypergraphs) and detailed, structured information about each relationship.
Named Graphs and Graph of Graphs
As you can notice, the structure of a metagraph is quite complex and could be complex to model in relational and classical RDF setups. It could create a challenge of luck of tools and software solutions for your problem.
If you need to model nested graphs, you could use a much simpler model of Named graphs, which could take you quite far.
The concept of the named graph came from the RDF community, which needed to group some sets of triples. In this way, you form subgraphs inside an existing graph. You could refer to the subgraph as a regular node. This setup simplifies complex graphs, introduces hierarchies, and even adds features and properties of hypergraphs while keeping a directed nature.
It looks complex, but it is not so hard to model it with a slight modification of a directed graph.
So, the node could host graphs inside. Let's reflect this fact with a location for a node. If a node belongs to a main graph, we could set the location to null or introduce a main node . it is up to you
Nodes could have edges to nodes in different subgraphs. This structure allows any kind of nesting graphs. Edges stay location-free
Meta Graphs in Relational Model
Let’s try to make several attempts to model different meta-graphs with some constraints.
Directed Metagraph where edges are not used as nodes and could not contain subgraphs

In this case, the edge always points to two sets of nodes. This introduces an overhead of creating a node set for a single node. In this model, we can model empty node sets that could require application-level constraints to prevent such cases.
Directed Metagraph where edges are not used as nodes and could contain subgraphs

Adding a node set that could model a subgraph located in an edge is easy but could be separate from in-vertex or out-vert.
I also do not see a direct need to include subgraphs to a node, as we could just use a node set interchangeably, but it still could be a case.Directed Metagraph where edges are used as nodes and could contain subgraphs
As you can notice, we operate all the time with node sets. We could simply allow the extension node set to elements set that include node and edge IDs, but in this case, we need to use uuid or any other strategy to differentiate node IDs from edge IDs. In this case, we have a collision of ephemeral edges or ephemeral nodes when we want to change the role and purpose of the node as an edge or vice versa.

A full-scale metagraph model is way too complex for a relational database.
So we need a better model.Now, we have more flexibility but loose structural constraints. We cannot show that the element should have one vertex, one vertex, or both. This type of constraint has been moved to the application level. Also, the crucial question is about query and retrieval needs.
Any meta-graph model should be more focused on domain and needs and should be used in raw form. We did it for a pure theoretical purpose. -
 @ 0fa80bd3:ea7325de
2025-01-30 04:28:30
@ 0fa80bd3:ea7325de
2025-01-30 04:28:30"Degeneration" or "Вырождение" ![[photo_2025-01-29 23.23.15.jpeg]]
A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them.
The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay.
-
 @ da0b9bc3:4e30a4a9
2025-02-07 21:38:56
@ da0b9bc3:4e30a4a9
2025-02-07 21:38:56It's Finally here Stackers!
It's Friday!
We're about to kick off our weekends with some feel good tracks.
Let's get the party started. Bring me those Feel Good tracks.
Talk Music. Share Tracks. Zap Sats.
Let's go!
https://youtu.be/6Whgn_iE5uc?si=ArBOHVpKN2OyNf1D
originally posted at https://stacker.news/items/879159
-
 @ 29af23a9:842ef0c1
2025-01-24 09:28:37
@ 29af23a9:842ef0c1
2025-01-24 09:28:37A Indústria Pornográfica se caracteriza pelo investimento pesado de grandes empresários americanos, desde 2014.
Na década de 90, filmes pornográficos eram feitos às coxas. Era basicamente duas pessoas fazendo sexo amador e sendo gravadas. Não tinha roteiro, nem produção, não tinha maquiagem, nada disso. A distribuição era rudimentar, os assinantes tinham que sair de suas casas, ir até a locadora, sofrer todo tipo de constrangimento para assistir a um filme pornô.
No começo dos anos 2000, o serviço de Pay Per View fez o número de vendas de filmes eróticos (filme erótico é bem mais leve) crescer mas nada se compara com os sites de filmes pornográficos por assinatura.
Com o advento dos serviços de Streaming, os sites que vendem filmes por assinatura se estabeleceram no mercado como nunca foi visto na história.
Hoje, os Produtores usam produtos para esticar os vasos sanguíneos do pênis dos atores e dopam as atrizes para que elas aguentem horas de gravação (a Série Black Mirror fez uma crítica a isso no episódio 1 milhão de méritos de forma sutil).
Além de toda a produção em volta das cenas. Que são gravadas em 4K, para focar bem as partes íntimas dos atores. Quadros fechados, iluminação, tudo isso faz essa Indústria ser "Artística" uma vez que tudo ali é falso. Um filme da Produtora Vixen, por exemplo, onde jovens mulheres transam em mansões com seus empresários estimula o esteriótipo da mina padrão que chama seu chefe rico de "daddy" e seduz ele até ele trair a esposa.
Sites como xvídeos, pornHub e outros nada mais são do que sites que salvam filmes dessas produtoras e hospedam as cenas com anúncios e pop-ups. Alguns sites hospedam o filme inteiro "de graça".
Esse tipo de filme estimula qualquer homem heterosexual com menos de 30 anos, que não tem o córtex frontal de seu cérebro totalmente desenvolvido (segundo estudos só é completamente desenvolvido quando o homem chega aos 31 anos).
A arte Pornográfica faz alguns fantasiarem ter relação sexual com uma gostosa americana branquinha, até escraviza-los. Muitos não conseguem sair do vício e preferem a Ficção à sua esposa real. Então pare de se enganar e admita. A Pornografia faz mal para a saúde mental do homem.
Quem sonha em ter uma transa com Lana Rhodes, deve estar nesse estágio. Trata-se de uma atriz (pornstar) que ganhou muito dinheiro vendendo a ilusão da Arte Pornografica, como a Riley Reid que só gravava para grandes Produtoras. Ambas se arrependeram da carreira artística e agora tentam viver suas vidas como uma mulher comum.
As próprias atrizes se consideram artistas, como Mia Malkova, chegou a dizer que Pornografia é a vida dela, que é "Lindo e Sofisticado."
Mia Malkova inclusive faz questão de dizer que a industria não escravisa mulheres jovens. Trata-se de um negócio onde a mulher assina um contrato com uma produtora e recebe um cachê por isso. Diferente do discurso da Mia Khalifa em entrevista para a BBC, onde diz que as mulheres são exploradas por homens poderosos. Vai ela está confundindo o Conglomerado Vixen com a Rede Globo ou com a empresa do Harvey Weinstein.
Enfim, se você é um homem solteiro entre 18 e 40 anos que já consumiu ou que ainda consome pornografia, sabia que sofrerá consequências. Pois trata-se de "produções artísticas" da indústria audiovisual que altera os níveis de dopamina do seu cérebro, mudando a neuroplasticidade e diminuindo a massa cinzenta, deixando o homem com memória fraca, sem foco e com mente nebulosa.
Por que o Estado não proíbe/criminaliza a Pornografia se ela faz mal? E desde quando o Estado quer o nosso bem? Existem grandes empresarios que financiam essa indústria ajudando governos a manterem o povo viciado e assim alienado. É um pão e circo, só que muito mais viciante e maléfico. Eu costume dizer aos meus amigos que existem grandes empresários jvdeus que são donos de grandes Produtoras de filmes pornográficos como o Conglomerado Vixen. Então se eles assistem vídeos pirateados de filmes dessas produtoras, eles estão no colo do Judeu.
-
 @ 9e69e420:d12360c2
2025-01-26 01:31:47
@ 9e69e420:d12360c2
2025-01-26 01:31:47Chef's notes
arbitray
- test
- of
- chefs notes
hedding 2
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 1 hour
- 🍽️ Servings: 5
Ingredients
- Test ingredient
- 2nd test ingredient
Directions
- Bake
- Cool
-
 @ 30b99916:3cc6e3fe
2025-01-21 02:08:26
@ 30b99916:3cc6e3fe
2025-01-21 02:08:26Details
- 🍳 Cook time: 10 to 8 minutes at 350
- 🍽️ Servings: About 4 dozen cookies
Ingredients
- 2 sticks of butter
- 2 eggs
- 1 cup granulated sugar
- 1 cup brown sugar
- 1 cup peanut butter
- 1 t vanilla
- 2 cups flour
- 1/2 t salt
- 1 t soda
- 6 oz Semi-Sweet Chocolate chips (optional)
Directions
- Blend butter, eggs, vanilla and sugars together thoroughly
- Next blend in peanut butter thoroughly
- Next blend in flour, salt, and soda thoroughly
- Optional blend in chocolate chips
- Add about table spoon of cookie dough per cookie on a cookie sheet. With a fork based in sugar place a cross hatch pattern on each cookie. Bake cookies for 10 to 8 minutes and place onto cooler rack.
-
 @ 83279ad2:bd49240d
2025-01-24 09:15:37
@ 83279ad2:bd49240d
2025-01-24 09:15:37備忘録として書きます。意外と時間がかかりました。全体で1時間くらいかかるので気長にやりましょう。 仮想通貨取引所(販売所ではないので、玄人が使えばお得らしい)かつBitcoinの送金手数料が無料(全ての取引所が無料ではない、例えばbitbankは0.0006bitcoinかかる)なので送金元はGMOコインを使います。(注意:GMOコインは0.02ビットコイン以下は全額送金になってしまいます) 今回はカストディアルウォレットのWallet of Satoshiに送金します。 以下手順 1. GMOコインでbitcoinを買います。 2. GMOコインの左のタブから入出金 暗号資産を選択します。 3. 送付のタブを開いて、+新しい宛先を追加するを選択します。 4. 送付先:GMOコイン以外、送付先ウォレット:プライベートウォレット(MetaMaskなど)、受取人:ご本人さま を選んで宛先情報の登録を選ぶと次の画面になります。
 5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。
5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。 6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。
7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。
6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。
7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。 8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。
8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。 8. 取引履歴のタブから今の送金のステータスが見れます。
8. 取引履歴のタブから今の送金のステータスが見れます。 9. 15分くらい待つとステータスが受付に変わります。
9. 15分くらい待つとステータスが受付に変わります。 10. 20分くらい待つとトランザクションIDが表示されます。
10. 20分くらい待つとトランザクションIDが表示されます。

この時点からwallet of satoshiにも送金されていることが表示されます。(まだ完了はしていない)
 11. ステータスが完了になったら送金終わりです。
11. ステータスが完了になったら送金終わりです。

wallet of satoshiにも反映されます。

お疲れ様でした!
-
 @ 6be5cc06:5259daf0
2025-01-21 23:17:29
@ 6be5cc06:5259daf0
2025-01-21 23:17:29A seguir, veja como instalar e configurar o Privoxy no Pop!_OS.
1. Instalar o Tor e o Privoxy
Abra o terminal e execute:
bash sudo apt update sudo apt install tor privoxyExplicação:
- Tor: Roteia o tráfego pela rede Tor.
- Privoxy: Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
2. Configurar o Privoxy
Abra o arquivo de configuração do Privoxy:
bash sudo nano /etc/privoxy/configNavegue até a última linha (atalho:
Ctrl+/depoisCtrl+Vpara navegar diretamente até a última linha) e insira:bash forward-socks5 / 127.0.0.1:9050 .Isso faz com que o Privoxy envie todo o tráfego para o Tor através da porta 9050.
Salve (
CTRL+OeEnter) e feche (CTRL+X) o arquivo.
3. Iniciar o Tor e o Privoxy
Agora, inicie e habilite os serviços:
bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxyExplicação:
- start: Inicia os serviços.
- enable: Faz com que iniciem automaticamente ao ligar o PC.
4. Configurar o Navegador Firefox
Para usar a rede Tor com o Firefox:
- Abra o Firefox.
- Acesse Configurações → Configurar conexão.
- Selecione Configuração manual de proxy.
- Configure assim:
- Proxy HTTP:
127.0.0.1 - Porta:
8118(porta padrão do Privoxy) - Domínio SOCKS (v5):
127.0.0.1 - Porta:
9050
- Proxy HTTP:
- Marque a opção "Usar este proxy também em HTTPS".
- Clique em OK.
5. Verificar a Conexão com o Tor
Abra o navegador e acesse:
text https://check.torproject.org/Se aparecer a mensagem "Congratulations. This browser is configured to use Tor.", a configuração está correta.
Dicas Extras
- Privoxy pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o Privoxy.
-
 @ fd78c37f:a0ec0833
2025-02-17 07:15:15
@ fd78c37f:a0ec0833
2025-02-17 07:15:15In this edition, we invited Kelvin from Bitcoin Chama to share how his community is leveraging Bitcoin to build a self-sustaining ecosystem in rural areas.
YakiHonne: Kelvin, thanks for joining us. Before we dive in, I'd like to take a moment to introduce YakiHonne and share a bit about what we do. YakiHonne is a decentralized media client built on the Nostr protocol that enables freedom of speech through technology. It empowers creators to create their own voice, assets, and features. It also allows features like smart widgets, verified notes, and focuses on long-form articles. Today, we’ll be diving into your community. So, let’s start—tell us a bit about yourself and what you do?
Kelvin:I'm Kelvin, the founder of Bitcoin Chama, a rule-based Bitcoin community with a mission to build a self-reliant Bitcoin circular ecosystem. How do we achieve this? We empower young people and our community economically by introducing accessible, low-resource projects that require minimal time and space to implement. We then encourage them to save their earnings in Bitcoin, promoting financial independence and long-term sustainability.
YakiHonne: Given Bitcoin’s increasing value, it’s almost like owning property, but in the form of a digital asset. That’s an incredible concept and a really great initiative!Now, let’s dive into today’s questions. What initially sparked your interest in Bitcoin, and what motivated you to build a community around it?
Kelvin:Initially, I didn’t know much about Bitcoin. But I had a friend who worked at Boda Boda. He was trying to save up his earnings to buy iron sheets and build a better house for his family. Since he didn't get enough money from Boda Boda, he saved whatever little he could in a bank, a savings group. Over the course of two years, when he finally went to withdraw his money, he realized that the price of iron sheets had increased by almost 100% Originally, he had planned to buy 30 iron sheets, but by the time he withdrew his savings, his money could no longer afford that many. For someone who works so hard to earn a living, this was a major setback. Kelvin:That’s when I started thinking—how can we solve this problem? At the time, I didn’t know much about Bitcoin or how money really works. But seeing my friend struggle, I realized that the real issue wasn’t just rising prices, but the financial system itself. Kelvin:Then, later that year, I was introduced to Bitcoin, and it suddenly clicked! If my friend had saved in Bitcoin instead of fiat, his purchasing power wouldn’t have been eroded. In fact, he might have even been able to afford nails, labor costs, or additional materials. That realization led me to create Bitcoin Chama—a community to help people save in Bitcoin and protect their hard earned money.
YakiHonne: It sounds like you were inspired by how Bitcoin’s value appreciates over time, much like an investment in land that continues to grow in value. That’s a truly powerful concept behind Bitcoin.Now, could you share how your community first got started and what strategies you used to attract members in the beginning?
Kelvin:Building a community from scratch—especially a Bitcoin community—isn’t easy, particularly in a rural area of Kenya where many people lack internet access and don’t even use smartphones. At first, my focus was purely on Bitcoin education. I would go out, meet people, and teach them about Bitcoin. But I soon realized that while knowledge is valuable, most people didn’t have the means to earn and save in Bitcoin. Kelvin:That’s when I came up with a different approach. Instead of just educating people, I decided to create small projects that could generate income, sponsor these projects, and help them grow. Over time, as people started earning from these projects, they could begin saving their income in Bitcoin. Kelvin:We’ve now been running Bitcoin Chama for almost a year—since May last year. The impact isn’t massive yet, but for a community just getting started, it’s been a significant step forward. Every small step matters, and while growth takes time, I believe these small beginnings will eventually lead to something big in the future.

YakiHonne: It's a wonderful start,So far, what challenges have you faced while building and growing the Bitcoin Chama community?
Kelvin:I don't have many challenges—just two main ones.The first challenge is poverty. Whenever you introduce someone to Bitcoin, you often have to explain its history. Imagine telling someone that in 2010, Bitcoin was worth about $1, and by 2013, its value had increased significantly. Fast forward to 2025, 15 years later, and Bitcoin is now worth around 13 million Kenyan shillings (about $100,000). When people hear this, they see it as a great opportunity to escape poverty. The problem is, they often perceive Bitcoin as free money, rather than understanding it as a long-term investment or financial tool. The second challenge is scamming. Many people think Bitcoin might be a scam. This is a common issue in many communities.
YakiHonne: Yes, especially the second challenge—people thinking Bitcoin is a scam. This is very common in many emerging communities. A lot of people feel that since they can't see Bitcoin physically, it’s not real, which leads them to doubt its authenticity.Finding a way to convince people of Bitcoin’s legitimacy is crucial. So, what principles guide your community? And how do you maintain trust and reliability in your discussions?
Kelvin:So, in our community, I’ve discovered something—I’ve found saccos. Right now, I have two saccos(Chama) , and I intend to grow them over time. Within these two circles, we use the Machangura app. The app has an option for creating a clan, so we organize people into two saccos, forming two clans. We then add all members from each sacco into their respective clan. This setup ensures a trustless system. For example, if someone wants to withdraw money from their shared account or sell Bitcoin, the system notifies all members. This way, everyone stays informed, and people don’t have to feel insecure about the funds they have saved.
YakiHonne: So at least that’s how you maintain integrity, transparency, and trust within the community. So How does your community educate its members and keep them updated on Bitcoin developments?
Kelvin:I am the founder of Bitcoin Chama, and right now, I’m mostly focused on community activities. We usually hold meetups oftenly, but I wouldn’t say we focus entirely on Bitcoin only. Instead, our discussions are more about how to improve what we do, grow more, and build new projects. That’s the main focus for me at the moment. That said, I am planning to start physical Bitcoin lessons. Since Bitcoin Chama is located in my community, I know that a lot of people visit the area—many come here to shop and buy things. So, I plan to post a notice at the location, inviting new members who are interested in learning about Bitcoin. We’ll create a timetable so that people can come at specific times to attend lessons. Additionally, we’ll leverage our existing clients and brainstorm ways to make this work for a wider audience.
YakiHonne: It's still part of the education process,maybe not fully in-depth, but it’s still valuable. So, that’s actually a good thing. You guys are doing something very meaningful, which is great.The meetups also serve as a way to educate people about Bitcoin, making them an important part of the process. It’s definitely a solid approach. YakiHonne: So, Kelvin, how does your community collaborate with the broader Bitcoin ecosystem? And what partnerships have you formed so far that have had the biggest impact on BitcoinTerminal?
Kelvin:We haven’t had any major collaborations yet. So far, we’ve been riding solo. We’ve had some support from friends and well-wishers, but we haven’t partnered with any major organizations yet.
YakiHonne: That’s okay! You guys will get there very soon, I’m sure of it. So far, in the process of building your community, what initiatives have you taken to promote the adoption of Bitcoin in your local environment?
Kelvin:Well, besides our existing clients, we have about three shops that currently accept Bitcoin payments. I’m still working on overcoming the major challenges we face while also trying to find ways to encourage people to use Bitcoin in their daily lives. Kelvin:First, I need to support the people who are already part of our community, making sure they have the resources and knowledge they need. I don’t know if I’m fully answering the question, but this is what I’m working on. I’m not solely focused on growing a large community right now. Instead, I’m focused on quality growth—on educating people who truly understand Bitcoin, know how to use it, and grasp what it really means. My approach is to start small and expand gradually, ensuring that at each stage, people gain a deeper understanding of Bitcoin and how it can impact their lives.
YakiHonne: I’m sure you guys will succeed. You don’t necessarily have to start big, but I believe you’ll grow much faster than you expect. With the effort and passion you’re putting in, I have no doubt that Bitcoin Chama will expand significantly. So,moving on to my last question,what are your community’s goals for the next 6 to 12 months? And how do you see it evolving with Bitcoin’s development?
Kelvin:My goal for the next year is to continue the projects I’ve been working on. We have a community team that serves as a gathering point where people can come together, coordinate meeting times, and discuss Bitcoin and our future plans. Kelvin:so far for example, we built and distributed 15 beehives to different young people in our community. They harvest honey, sell it, and save the earnings in Bitcoin. We piped free clean water which can be accessed by any member in our community, significantly improving daily convenience.
 Kelvin:We are planning to build two chicken coops and provide chickens to two groups of five people each. They will raise chickens, sell eggs, and save their earnings in Bitcoin. Over time, we aim for each member to have their own chicken coop with a sustainable flock by the end of the year.
Kelvin:We are planning to build two chicken coops and provide chickens to two groups of five people each. They will raise chickens, sell eggs, and save their earnings in Bitcoin. Over time, we aim for each member to have their own chicken coop with a sustainable flock by the end of the year.
 Kelvin:We plan to lease a piece of land for the women in our community to grow vegetables and sell them at the local market. Their earnings will also be saved in Bitcoin. If the project is profitable, we will reinvest in more land to expand vegetable farming.Additionally, we plan to lease 2-3 acres of land specifically for commercial maize farming. The maize will be sold for Bitcoin, and if we generate profits, we will expand the farmland.
Kelvin:Our long-term goal is to build a self-sufficient community, enabling it to operate independently and achieve sustainable development. This is also our core objective.
Kelvin:We plan to lease a piece of land for the women in our community to grow vegetables and sell them at the local market. Their earnings will also be saved in Bitcoin. If the project is profitable, we will reinvest in more land to expand vegetable farming.Additionally, we plan to lease 2-3 acres of land specifically for commercial maize farming. The maize will be sold for Bitcoin, and if we generate profits, we will expand the farmland.
Kelvin:Our long-term goal is to build a self-sufficient community, enabling it to operate independently and achieve sustainable development. This is also our core objective.YakiHonne: I truly love all the ideas behind this. I admire the fact that you are giving back to the community and that people are experiencing real benefits from the Bitcoin ecosystem. This way, they have something positive and meaningful to say about Bitcoin. YakiHonne: Thank you so much, Kelvin, for joining us today. We’ve reached the end of our interview, and I’m really happy to have had this conversation with you. We look forward to seeing Bitcoin Chama grow!
-
 @ e6817453:b0ac3c39
2024-12-07 15:03:06
@ e6817453:b0ac3c39
2024-12-07 15:03:06Hey folks! Today, let’s dive into the intriguing world of neurosymbolic approaches, retrieval-augmented generation (RAG), and personal knowledge graphs (PKGs). Together, these concepts hold much potential for bringing true reasoning capabilities to large language models (LLMs). So, let’s break down how symbolic logic, knowledge graphs, and modern AI can come together to empower future AI systems to reason like humans.
The Neurosymbolic Approach: What It Means ?
Neurosymbolic AI combines two historically separate streams of artificial intelligence: symbolic reasoning and neural networks. Symbolic AI uses formal logic to process knowledge, similar to how we might solve problems or deduce information. On the other hand, neural networks, like those underlying GPT-4, focus on learning patterns from vast amounts of data — they are probabilistic statistical models that excel in generating human-like language and recognizing patterns but often lack deep, explicit reasoning.
While GPT-4 can produce impressive text, it’s still not very effective at reasoning in a truly logical way. Its foundation, transformers, allows it to excel in pattern recognition, but the models struggle with reasoning because, at their core, they rely on statistical probabilities rather than true symbolic logic. This is where neurosymbolic methods and knowledge graphs come in.
Symbolic Calculations and the Early Vision of AI
If we take a step back to the 1950s, the vision for artificial intelligence was very different. Early AI research was all about symbolic reasoning — where computers could perform logical calculations to derive new knowledge from a given set of rules and facts. Languages like Lisp emerged to support this vision, enabling programs to represent data and code as interchangeable symbols. Lisp was designed to be homoiconic, meaning it treated code as manipulatable data, making it capable of self-modification — a huge leap towards AI systems that could, in theory, understand and modify their own operations.
Lisp: The Earlier AI-Language
Lisp, short for “LISt Processor,” was developed by John McCarthy in 1958, and it became the cornerstone of early AI research. Lisp’s power lay in its flexibility and its use of symbolic expressions, which allowed developers to create programs that could manipulate symbols in ways that were very close to human reasoning. One of the most groundbreaking features of Lisp was its ability to treat code as data, known as homoiconicity, which meant that Lisp programs could introspect and transform themselves dynamically. This ability to adapt and modify its own structure gave Lisp an edge in tasks that required a form of self-awareness, which was key in the early days of AI when researchers were exploring what it meant for machines to “think.”
Lisp was not just a programming language—it represented the vision for artificial intelligence, where machines could evolve their understanding and rewrite their own programming. This idea formed the conceptual basis for many of the self-modifying and adaptive algorithms that are still explored today in AI research. Despite its decline in mainstream programming, Lisp’s influence can still be seen in the concepts used in modern machine learning and symbolic AI approaches.
Prolog: Formal Logic and Deductive Reasoning
In the 1970s, Prolog was developed—a language focused on formal logic and deductive reasoning. Unlike Lisp, based on lambda calculus, Prolog operates on formal logic rules, allowing it to perform deductive reasoning and solve logical puzzles. This made Prolog an ideal candidate for expert systems that needed to follow a sequence of logical steps, such as medical diagnostics or strategic planning.
Prolog, like Lisp, allowed symbols to be represented, understood, and used in calculations, creating another homoiconic language that allows reasoning. Prolog’s strength lies in its rule-based structure, which is well-suited for tasks that require logical inference and backtracking. These features made it a powerful tool for expert systems and AI research in the 1970s and 1980s.
The language is declarative in nature, meaning that you define the problem, and Prolog figures out how to solve it. By using formal logic and setting constraints, Prolog systems can derive conclusions from known facts, making it highly effective in fields requiring explicit logical frameworks, such as legal reasoning, diagnostics, and natural language understanding. These symbolic approaches were later overshadowed during the AI winter — but the ideas never really disappeared. They just evolved.
Solvers and Their Role in Complementing LLMs
One of the most powerful features of Prolog and similar logic-based systems is their use of solvers. Solvers are mechanisms that can take a set of rules and constraints and automatically find solutions that satisfy these conditions. This capability is incredibly useful when combined with LLMs, which excel at generating human-like language but need help with logical consistency and structured reasoning.
For instance, imagine a scenario where an LLM needs to answer a question involving multiple logical steps or a complex query that requires deducing facts from various pieces of information. In this case, a solver can derive valid conclusions based on a given set of logical rules, providing structured answers that the LLM can then articulate in natural language. This allows the LLM to retrieve information and ensure the logical integrity of its responses, leading to much more robust answers.
Solvers are also ideal for handling constraint satisfaction problems — situations where multiple conditions must be met simultaneously. In practical applications, this could include scheduling tasks, generating optimal recommendations, or even diagnosing issues where a set of symptoms must match possible diagnoses. Prolog’s solver capabilities and LLM’s natural language processing power can make these systems highly effective at providing intelligent, rule-compliant responses that traditional LLMs would struggle to produce alone.
By integrating neurosymbolic methods that utilize solvers, we can provide LLMs with a form of deductive reasoning that is missing from pure deep-learning approaches. This combination has the potential to significantly improve the quality of outputs for use-cases that require explicit, structured problem-solving, from legal queries to scientific research and beyond. Solvers give LLMs the backbone they need to not just generate answers but to do so in a way that respects logical rigor and complex constraints.
Graph of Rules for Enhanced Reasoning
Another powerful concept that complements LLMs is using a graph of rules. A graph of rules is essentially a structured collection of logical rules that interconnect in a network-like structure, defining how various entities and their relationships interact. This structured network allows for complex reasoning and information retrieval, as well as the ability to model intricate relationships between different pieces of knowledge.
In a graph of rules, each node represents a rule, and the edges define relationships between those rules — such as dependencies or causal links. This structure can be used to enhance LLM capabilities by providing them with a formal set of rules and relationships to follow, which improves logical consistency and reasoning depth. When an LLM encounters a problem or a question that requires multiple logical steps, it can traverse this graph of rules to generate an answer that is not only linguistically fluent but also logically robust.
For example, in a healthcare application, a graph of rules might include nodes for medical symptoms, possible diagnoses, and recommended treatments. When an LLM receives a query regarding a patient’s symptoms, it can use the graph to traverse from symptoms to potential diagnoses and then to treatment options, ensuring that the response is coherent and medically sound. The graph of rules guides reasoning, enabling LLMs to handle complex, multi-step questions that involve chains of reasoning, rather than merely generating surface-level responses.
Graphs of rules also enable modular reasoning, where different sets of rules can be activated based on the context or the type of question being asked. This modularity is crucial for creating adaptive AI systems that can apply specific sets of logical frameworks to distinct problem domains, thereby greatly enhancing their versatility. The combination of neural fluency with rule-based structure gives LLMs the ability to conduct more advanced reasoning, ultimately making them more reliable and effective in domains where accuracy and logical consistency are critical.
By implementing a graph of rules, LLMs are empowered to perform deductive reasoning alongside their generative capabilities, creating responses that are not only compelling but also logically aligned with the structured knowledge available in the system. This further enhances their potential applications in fields such as law, engineering, finance, and scientific research — domains where logical consistency is as important as linguistic coherence.
Enhancing LLMs with Symbolic Reasoning
Now, with LLMs like GPT-4 being mainstream, there is an emerging need to add real reasoning capabilities to them. This is where neurosymbolic approaches shine. Instead of pitting neural networks against symbolic reasoning, these methods combine the best of both worlds. The neural aspect provides language fluency and recognition of complex patterns, while the symbolic side offers real reasoning power through formal logic and rule-based frameworks.
Personal Knowledge Graphs (PKGs) come into play here as well. Knowledge graphs are data structures that encode entities and their relationships — they’re essentially semantic networks that allow for structured information retrieval. When integrated with neurosymbolic approaches, LLMs can use these graphs to answer questions in a far more contextual and precise way. By retrieving relevant information from a knowledge graph, they can ground their responses in well-defined relationships, thus improving both the relevance and the logical consistency of their answers.
Imagine combining an LLM with a graph of rules that allow it to reason through the relationships encoded in a personal knowledge graph. This could involve using deductive databases to form a sophisticated way to represent and reason with symbolic data — essentially constructing a powerful hybrid system that uses LLM capabilities for language fluency and rule-based logic for structured problem-solving.
My Research on Deductive Databases and Knowledge Graphs
I recently did some research on modeling knowledge graphs using deductive databases, such as DataLog — which can be thought of as a limited, data-oriented version of Prolog. What I’ve found is that it’s possible to use formal logic to model knowledge graphs, ontologies, and complex relationships elegantly as rules in a deductive system. Unlike classical RDF or traditional ontology-based models, which sometimes struggle with complex or evolving relationships, a deductive approach is more flexible and can easily support dynamic rules and reasoning.
Prolog and similar logic-driven frameworks can complement LLMs by handling the parts of reasoning where explicit rule-following is required. LLMs can benefit from these rule-based systems for tasks like entity recognition, logical inferences, and constructing or traversing knowledge graphs. We can even create a graph of rules that governs how relationships are formed or how logical deductions can be performed.
The future is really about creating an AI that is capable of both deep contextual understanding (using the powerful generative capacity of LLMs) and true reasoning (through symbolic systems and knowledge graphs). With the neurosymbolic approach, these AIs could be equipped not just to generate information but to explain their reasoning, form logical conclusions, and even improve their own understanding over time — getting us a step closer to true artificial general intelligence.
Why It Matters for LLM Employment
Using neurosymbolic RAG (retrieval-augmented generation) in conjunction with personal knowledge graphs could revolutionize how LLMs work in real-world applications. Imagine an LLM that understands not just language but also the relationships between different concepts — one that can navigate, reason, and explain complex knowledge domains by actively engaging with a personalized set of facts and rules.
This could lead to practical applications in areas like healthcare, finance, legal reasoning, or even personal productivity — where LLMs can help users solve complex problems logically, providing relevant information and well-justified reasoning paths. The combination of neural fluency with symbolic accuracy and deductive power is precisely the bridge we need to move beyond purely predictive AI to truly intelligent systems.
Let's explore these ideas further if you’re as fascinated by this as I am. Feel free to reach out, follow my YouTube channel, or check out some articles I’ll link below. And if you’re working on anything in this field, I’d love to collaborate!
Until next time, folks. Stay curious, and keep pushing the boundaries of AI!
-
 @ b17fccdf:b7211155
2025-01-21 17:02:21
@ b17fccdf:b7211155
2025-01-21 17:02:21The past 26 August, Tor introduced officially a proof-of-work (PoW) defense for onion services designed to prioritize verified network traffic as a deterrent against denial of service (DoS) attacks.
~ > This feature at the moment, is deactivate by default, so you need to follow these steps to activate this on a MiniBolt node:
- Make sure you have the latest version of Tor installed, at the time of writing this post, which is v0.4.8.6. Check your current version by typing
tor --versionExample of expected output:
Tor version 0.4.8.6. This build of Tor is covered by the GNU General Public License (https://www.gnu.org/licenses/gpl-3.0.en.html) Tor is running on Linux with Libevent 2.1.12-stable, OpenSSL 3.0.9, Zlib 1.2.13, Liblzma 5.4.1, Libzstd N/A and Glibc 2.36 as libc. Tor compiled with GCC version 12.2.0~ > If you have v0.4.8.X, you are OK, if not, type
sudo apt update && sudo apt upgradeand confirm to update.- Basic PoW support can be checked by running this command:
tor --list-modulesExpected output:
relay: yes dirauth: yes dircache: yes pow: **yes**~ > If you have
pow: yes, you are OK- Now go to the torrc file of your MiniBolt and add the parameter to enable PoW for each hidden service added
sudo nano /etc/tor/torrcExample:
```
Hidden Service BTC RPC Explorer
HiddenServiceDir /var/lib/tor/hidden_service_btcrpcexplorer/ HiddenServiceVersion 3 HiddenServicePoWDefensesEnabled 1 HiddenServicePort 80 127.0.0.1:3002 ```
~ > Bitcoin Core and LND use the Tor control port to automatically create the hidden service, requiring no action from the user. We have submitted a feature request in the official GitHub repositories to explore the need for the integration of Tor's PoW defense into the automatic creation process of the hidden service. You can follow them at the following links:
- Bitcoin Core: https://github.com/lightningnetwork/lnd/issues/8002
- LND: https://github.com/bitcoin/bitcoin/issues/28499
More info:
- https://blog.torproject.org/introducing-proof-of-work-defense-for-onion-services/
- https://gitlab.torproject.org/tpo/onion-services/onion-support/-/wikis/Documentation/PoW-FAQ
Enjoy it MiniBolter! 💙
-
 @ 06b7819d:d1d8327c
2024-11-29 11:59:20
@ 06b7819d:d1d8327c
2024-11-29 11:59:20The system design and challenges of retail Central Bank Digital Currencies (CBDCs) differ significantly from Bitcoin in several key aspects, reflecting their distinct purposes and underlying philosophies:
-
Core Purpose and Issuance
• CBDCs: Issued by central banks, CBDCs are designed as state-backed digital currencies for public use. Their goal is to modernize payments, enhance financial inclusion, and provide a risk-free alternative to private money. • Bitcoin: A decentralized, peer-to-peer cryptocurrency created to operate independently of central authorities. Bitcoin aims to be a store of value and medium of exchange without reliance on intermediaries or governments.
-
Governance and Control
• CBDCs: Operate under centralized governance. Central banks retain control over issuance, transaction validation, and data management, allowing for integration with existing regulatory frameworks (e.g., AML and CFT). • Bitcoin: Fully decentralized, governed by a consensus mechanism (Proof of Work). Transactions are validated by miners, and no single entity controls the network.
-
Privacy
• CBDCs: Seek to balance privacy with regulatory compliance. Privacy-enhancing technologies may be implemented, but user data is typically accessible to intermediaries and central banks to meet regulatory needs. • Bitcoin: Pseudonymous by design. Transactions are public on the blockchain but do not directly link to individual identities unless voluntarily disclosed.
-
System Design
• CBDCs: May adopt a hybrid system combining centralized (e.g., central bank-controlled settlement) and decentralized elements (e.g., private-sector intermediaries). Offline functionality and interoperability with existing systems are priorities. • Bitcoin: Fully decentralized, using a distributed ledger (blockchain) where all transactions are validated and recorded without reliance on intermediaries.
-
Cybersecurity
• CBDCs: Cybersecurity risks are heightened due to potential reliance on centralized points for data storage and validation. Post-quantum cryptography is a concern for future-proofing against quantum computing threats. • Bitcoin: Security relies on cryptographic algorithms and decentralization. However, it is also vulnerable to quantum computing in the long term, unless upgraded to quantum-resistant protocols.
-
Offline Functionality
• CBDCs: Exploring offline payment capabilities for broader usability in remote or unconnected areas. • Bitcoin: Offline payments are not natively supported, although some solutions (e.g., Lightning Network or third-party hardware wallets) can enable limited offline functionality.
-
Point of Sale and Adoption
• CBDCs: Designed for seamless integration with existing PoS systems and modern financial infrastructure to encourage widespread adoption. • Bitcoin: Adoption depends on merchant willingness and the availability of cryptocurrency payment gateways. Its volatility can discourage usage as a medium of exchange.
-
Monetary Policy and Design
• CBDCs: Can be programmed to support specific policy goals, such as negative interest rates, transaction limits, or conditional transfers. • Bitcoin: Supply is fixed at 21 million coins, governed by its code. It is resistant to monetary policy interventions and inflationary adjustments.
In summary, while CBDCs aim to complement existing monetary systems with centralized oversight and tailored features, Bitcoin is designed as a decentralized alternative to traditional currency. CBDCs prioritize integration, control, and regulatory compliance, whereas Bitcoin emphasizes autonomy, censorship resistance, and a trustless system.
-
-
 @ dbb19ae0:c3f22d5a
2025-02-07 21:14:06
@ dbb19ae0:c3f22d5a
2025-02-07 21:14:06Cortex (https://cortex.so/docs) is an open-source framework designed to serve as standalone API server or as the "brain" for robots, encompassing capabilities in vision, speech, language, tabular data, and action processing.
Notably, it offers the flexibility to operate locally so independently of cloud services, making it suitable for various light deployment environments.
Key Features:
-
User-Friendly Command-Line Interface (CLI): Inspired by Ollama, Cortex provides a straightforward CLI, simplifying interaction and management.
-
Comprehensive C++ Implementation: The framework is fully implemented in C++ (https://github.com/janhq/cortex.cpp), allowing it to be packaged into both desktop and mobile applications, enhancing portability and performance.
-
Versatile Model Integration: Users can pull models from multiple sources, including Hugging Face (gguf format) and Cortex's Built-in Model Library, ensuring flexibility in model selection.
cortex pull [model_id]cortex pull mistral
Note: it's recommended to have more than 8 GB of RAM available to run 3B models, 16 GB for 7B models, and 32 GB for 14B models.
-
Deployment Flexibility: It can function as a standalone API server or be integrated into applications such as Jan.ai, providing adaptability in various use cases.
cortex startcortex stop
If GPU hardware is available, Cortex leverages GPU acceleration by default, enhancing performance for demanding tasks.
Conclusion:
In summary, Cortex offers a robust and flexible solution for integrating advanced cognitive capabilities into robotic systems, with an emphasis on openness, performance, and adaptability.
-
-
 @ c69b71dc:426ba763
2025-01-18 15:39:35
@ c69b71dc:426ba763
2025-01-18 15:39:35Chef's notes
This raw vegan curry ramen is a vibrant, nourishing dish packed with fresh vegetables and a rich, creamy coconut curry broth. It’s quick to prepare, full of flavour, and the perfect guilt-free comfort food! 🌱 Feel free to use your favourite veggies👩🏼🍳
Details
- ⏲️ Prep time: 20 min.
- 🍳 Cook time: 0
- 🍽️ Servings: 2
Ingredients
- 500g or 2 packs kelp noodles
- 1/2 Lemon juice ( 1/4 for soaking and 1/4 for the soup
- Salt
- Fresh vegetables of your choice, such as: 4 medium mushrooms, 4 leaves red cabbage, 2 carrots (julienned or peeled into strips), 1 Celery stick (diced)
- 2 cups coconut milk (or coconut cream diluted with water)
- 1/2 flesh of a Coconut (optional, if using fresh coconuts) otherwise more coconut cream
- 1 thumb of fresh ginger
- 1 thumb of fresh turmeric
- 2 tbsp light miso paste
- 2 pitted dates
- 2 tbsp cashews
- 1 clove garlic
- 1 tsp curry powder or pepper (optional)
Directions
- Prepare the Noodles: Rinse the kelp noodles thoroughly. Then soak them in warm water with a squeeze of lemon juice and a pinch of salt for 10 minutes to soften.
- Prep the Vegetables: Thinly slice or julienne carrots, dice celery, thinly cut mushrooms, cut the red cabbage into thin strips.
- Make the Broth: In a blender, combine the following: 2 cups coconut milk (or coconut cream diluted with water if fresh coconuts are unavailable), ginger, turmeric, 1/4 juice of 1 lemon, light miso paste, pitted dates, cashews, garlic, salt, curry powder
- Blend on high speed for about 3 to 4 minutes until the broth is smooth and slightly warm. Do not overheat!
- Assemble the Ramen: Drain the kelp noodles and place them in serving bowls. Arrange the prepped vegetables on top of the noodles. Pour the warm curry broth over the noodles and vegetables.
- Serve immediately and enjoy your raw vegan ramen with chopsticks for an authentic touch!
-
 @ 06b7819d:d1d8327c
2024-11-28 18:30:00
@ 06b7819d:d1d8327c
2024-11-28 18:30:00The Bank of Amsterdam (Amsterdamse Wisselbank), established in 1609, played a pivotal role in the early history of banking and the development of banknotes. While banknotes as a concept had been pioneered in China centuries earlier, their modern form began emerging in Europe in the 17th century, and the Bank of Amsterdam leveraged its unique position to dominate this nascent monetary tool.
Founding and Early Innovations
The Bank of Amsterdam was created to stabilize and rationalize Amsterdam’s chaotic monetary system. During the early 1600s, a plethora of coins of varying quality and origin circulated in Europe, making trade cumbersome and unreliable. The Wisselbank provided a centralized repository where merchants could deposit coins and receive account balances in return, denominated in a standardized unit of account known as “bank money.” This “bank money” was more stable and widely trusted, making it an early form of fiat currency.
The Rise of Banknotes
Although the Wisselbank initially issued “bank money” as a ledger-based system, the growing demand for portable, trusted currency led to the adoption of transferable receipts or “banknotes.” These receipts acted as claims on deposited money and quickly became a trusted medium of exchange. The innovation of banknotes allowed merchants to avoid carrying large quantities of heavy coinage, enhancing convenience and security in trade.
Monopoly on Banknotes
The Wisselbank’s reputation for financial stability and integrity enabled it to establish a monopoly on banknotes in the Dutch Republic. The bank’s stringent policies ensured that its issued notes were fully backed by coinage or bullion, which bolstered trust in their value. By centralizing the issuance of notes, the bank eliminated competition from private or less reliable issuers, ensuring its notes became the de facto currency for merchants and traders.
Moreover, the bank’s policies discouraged the redemption of notes for physical coins, as it charged fees for withdrawals. This incentivized the circulation of banknotes rather than the underlying specie, cementing their role in the economy.
Decline of the Monopoly
The Wisselbank’s monopoly and influence lasted for much of the 17th century, making Amsterdam a hub of global trade and finance. However, as the 18th century progressed, financial mismanagement and competition from other emerging financial institutions eroded the Wisselbank’s dominance. By the late 18th century, its role in the global financial system had diminished, and other European financial centers, such as London, rose to prominence.
Legacy
The Bank of Amsterdam’s early monopolization of banknotes set a precedent for centralized banking and the development of modern monetary systems. Its ability to create trust in a standardized, portable medium of exchange foreshadowed the role that central banks would play in issuing and regulating currency worldwide.
-
 @ c11cf5f8:4928464d
2025-02-16 11:07:13
@ c11cf5f8:4928464d
2025-02-16 11:07:13Let's hear some of your latest #Bitcoin purchases, feel free to include links to the #shops or #merchants you bought from too. Any good #deal we should know about?
If you missed our last thread, here are some of the items stackers recently spent and #zap #sats on.
originally posted at https://stacker.news/items/887305
-
 @ d1b118c6:4985b38d
2025-01-16 17:39:47
@ d1b118c6:4985b38d
2025-01-16 17:39:47Chef's notes
Let me know how it goes for you https://maria.omg.lol
Details
- ⏲️ Prep time: 5-20 minutes
- 🍳 Cook time: 20-40 minutes
- 🍽️ Servings: As many as you want omg!!!!
Ingredients
- Spaghetti/whatever pasta you want
- Garlic/smashed or diced as much as you want
- Tomatoes/ diced or more liquid state whatever you want
- Scallops/ I use the frozen bagged mini kind and just do a couple handfuls as many as you want
- Butter and/or olive oil but the butter is v good imo but also I used both
- Bacon/ make it extra crispy and then crumble up as much as you want
- Whatever seasonings
Directions
- Set oven to 400° or so
- Put all your bacon 🥓 strips onto tin foil lined baking sheet/s and then put the trays in the oven for 15-20 min
- Boil up your pasta in salty water
- Pull the bacon out when done
- In a pan cook up the scallops real quick like 5-10 min idk
- Sauté the tomatoes and garlic and whatever use whatever seasons and lots of butter
- Strain the pasta when it’s ready
- Mix pasta and sautéed sauce
- Add more crumbled bacon on top #garnish
-
 @ 6be5cc06:5259daf0
2025-01-21 01:51:46
@ 6be5cc06:5259daf0
2025-01-21 01:51:46Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
Resumo
O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado gasto duplo, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações.
As transações são registradas em um livro público chamado blockchain, protegido por uma técnica chamada Prova de Trabalho. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira.
Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu.
1. Introdução
Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em confiança.
Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável.
Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável.
O que precisamos é de um sistema de pagamento eletrônico baseado em provas matemáticas, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas.
Neste documento, apresentamos o Bitcoin, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques.
2. Transações
Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital.
O que é uma assinatura digital?
Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso.
Como funciona na prática?
Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário:
- A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1.
- Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2.
- Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda.
Resolvendo o problema do gasto duplo
Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro.
O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain.
Por que isso é importante?
Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes.
3. Servidor Timestamp
Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica.
Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público.
Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain.
Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada.
O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin.
4. Prova-de-Trabalho
Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente.
A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita.
Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain.
A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos.
Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional.
5. Rede
A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são:
-
Transmissão de Transações: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la.
-
Coleta de Transações em Blocos: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain).
-
Prova-de-Trabalho: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil.
-
Envio do Bloco Resolvido: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede.
-
Validação do Bloco: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos.
-
Construção do Próximo Bloco: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia.
Resolução de Conflitos e Escolha da Cadeia Mais Longa
Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia.
Tolerância a Falhas
A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido.
Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central.
6. Incentivo
O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação.
Recompensa por Mineração
Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho.
Taxas de Transação
Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo.
Incentivo à Honestidade
O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas:
- Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos.
- Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas.
A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema.
Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo.
7. Recuperação do Espaço em Disco
Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações.
Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados.
Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados.
Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo.
8. Verificação de Pagamento Simplificada
É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada.
Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação.
A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede.
Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável.
9. Combinando e Dividindo Valor
No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor.
Entradas e Saídas
Cada transação no Bitcoin é composta por:
- Entradas: Representam os valores recebidos em transações anteriores.
- Saídas: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente.
Normalmente, uma transação contém:
- Uma única entrada com valor suficiente para cobrir o pagamento.
- Ou várias entradas combinadas para atingir o valor necessário.
O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como troco.
Exemplo Prático
Imagine que você tem duas entradas:
- 0,03 BTC
- 0,07 BTC
Se deseja enviar 0,08 BTC para alguém, a transação terá:
- Entrada: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC).
- Saídas: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC).
Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente.
Difusão e Simplificação
A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade.
10. Privacidade
O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando chaves públicas anônimas, que desvinculam diretamente as transações das identidades das partes envolvidas.
Fluxo de Informação
- No modelo tradicional, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário.
- No Bitcoin, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não.
Protegendo a Privacidade
Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas:
- Chaves Públicas Anônimas: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único.
- Prevenção de Ligação: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário.
Riscos de Ligação
Embora a privacidade seja fortalecida, alguns riscos permanecem:
- Transações multi-entrada podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total.
- O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas.
11. Cálculos
Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito.
Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira.
Mas isso é extremamente difícil.
Como o Ataque Funciona
Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido.
- Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira.
- O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida.
Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente.
A Corrida Entre Cadeias
Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos.
Suponha que:
- A rede honesta tem 80% do poder computacional (ou seja, resolve 8 de cada 10 quebra-cabeças).
- O atacante tem 20% do poder computacional (ou seja, resolve 2 de cada 10 quebra-cabeças).
Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar.
Por Que o Ataque Fica Cada Vez Mais Improvável?
Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos:
P = (q/p)^z
- q é o poder computacional do atacante (20%, ou 0,2).
- p é o poder computacional da rede honesta (80%, ou 0,8).
- z é a diferença de blocos entre a cadeia honesta e a cadeia do atacante.
Se o atacante está 5 blocos atrás (z = 5):
P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%)
Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável.
Se ele estiver 10 blocos atrás (z = 10):
P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%).
Neste caso, as chances de sucesso são praticamente nulas.
Um Exemplo Simples
Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível.
No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática.
Por Que Tudo Isso é Seguro?
- A probabilidade de sucesso do atacante diminui exponencialmente. Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema.
- A cadeia verdadeira (honesta) está protegida pela força da rede. Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar.
E Se o Atacante Tentar Continuar?
O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil.
Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso.
12. Conclusão
Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos.
Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
-
 @ 3f770d65:7a745b24
2025-01-19 21:48:49
@ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol.
PROTOCOLS, NOT PLATFORMS.
At the heart of Nostr's philosophy is user choice, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity.
What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort.
THIS IS POWERFUL.
Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections.
The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship.
How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access.
AGAIN, THIS IS POWERUFL.
Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps.
Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions.
Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know.
TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom.
Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed.
