-
 @ 6bae33c8:607272e8
2025-02-17 18:31:27
@ 6bae33c8:607272e8
2025-02-17 18:31:27I did my first NFBC draft Sunday night — I drew the 12th pick. Here’s the link to the live-stream.
The full results are below:
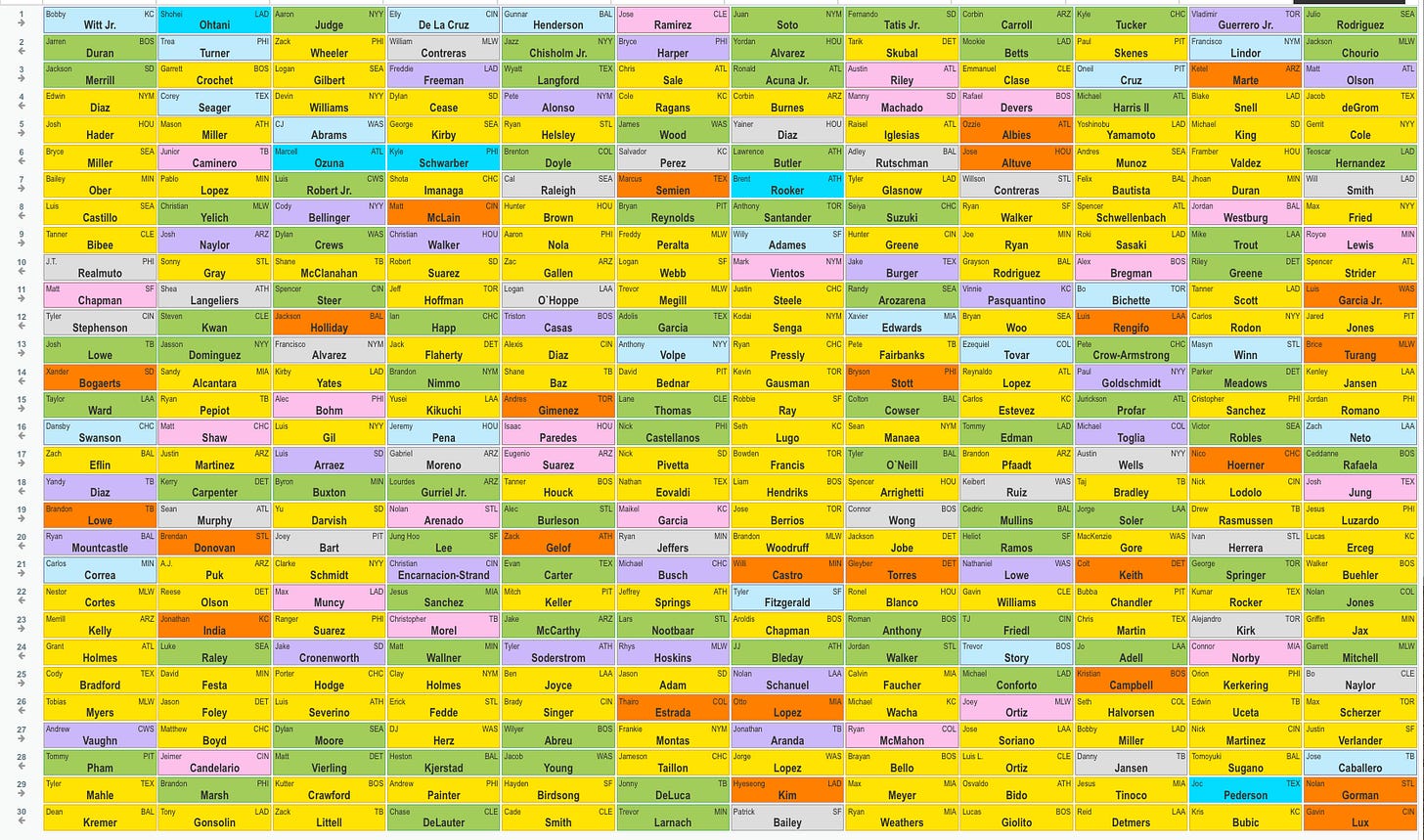
This draft went about as well as I could have hoped, especially given how little I had prepared. That doesn’t mean the team is *good*, only that I didn’t have any major regrets or gaffes, something that’s rare over 30 rounds.
I also never once got swiped on a pick. I got priced out of the top closers early, but rolled with it in the way one should when that happens, getting players I wanted and doubling back to closers when I needed to.
This team is built to win the overall — high-risk, high reward, an exercise in imagining not what could go wrong, not what’s the base case, but what could go right.
The Draft
1.12 Julio Rodriguez — I had mapped out the first 10 rounds, decided on Rodriguez and Jackson Chourio ahead of time. I knew Chourio would be there, per ADP, but if Rodriguez were gone, I’d have gone with Mookie Betts. I wanted two OF with power and speed to start my draft. Rodriguez had 32 homers and 37 steals as a 22-year old in 2023, was going in the 2-4 overall range last year and nothing that happened since should move the needle much heading into his age 24 season.
2.1 Jackson Chourio — Chourio had 21 homers and 22 steals as a 20-year-old rookie, and those numbers were weighed down by a slow start where the Brewers were constantly pulling him from the lineup for no reason. From June until the end of the year, he hit .303 and should only get better in Year 2. His healthy floor is 25-25, and there’s stolen base and batting average upside.
3.12 Matt Olson — While Rodriguez and Chourio offer solid pop, I wanted a 40-HR type to compensate for the lack of top-end power with my first two picks, while filling the scarce-in-recent-years 1B slot. Olson had an off year in 2024, but chalk that up to variance. I still like him in that park and lineup.
4.1 Jacob deGrom — I’m not here to win the $1500 league prize but the $150K overall. deGrom isn’t just the best pitcher in baseball when he’s healthy, he’s one of the best in baseball history. If I get 100 IP of vintage deGrom, that’s worth a fourth-round pick. At 130-150, it’s a first-rounder. I also like that he’s nearly two years out from Tommy John surgery, pitched at the end of last season and is healthy now. While there’s no chance of 200 IP, he’s also not a rookie they need to ramp up slowly, but a veteran with a massive contract, i.e., the Rangers will want to get their money’s worth if he’s dealing.
5.12 Gerrit Cole — When Raisel Iglesias went four picks ahead of me, I was pretty sure I was going Cole who typically goes in the first or second round. Cole had an off year, but the sample was small as he missed time due to a nerve issue in the spring, and there wasn’t much of a drop-off from 2023, even with the irregular start to the year. Pitchers ebb and flow with health, and the light workload might redound to his benefit.
6.1 Teoscar Hernandez — This was just a value-take in the sixth round. Hernandez gives you pop, runs a little and hits in the best lineup in baseball.
7.12 Will Smith — I didn’t love the options in these rounds, so I punted and nabbed a solid catcher with 20-HR pop. I don’t really see the difference between Smith and Adley Rutschman who goes two rounds earlier either.
8.1 Max Fried — With deGrom shaky on innings, and five hitters in my first seven picks, I wanted another horse to anchor the rotation. I like lefties in Yankee Stadium too.
9.12 Royce Lewis — I needed a third baseman, and Lewis, who was going in the fifth round last year, was the one with the most upside. The key is that he’s healthy now, as he finished the season in the lineup and hasn’t had a setback this offseason. Lewis is a potential 30-HR/.290 bat if he can hold up for 140-odd games.
10.1 Spencer Strider — As I said, I’m trying to win the overall. Strider will start the year on the DL, but the timetable for the type of surgery he had is roughly one year, and Strider’s was in mid-April, i.e., there’s no reason he shouldn’t be back in May and might even see some action in spring training. If I get 220 combined IP from deGrom and Strider at their former levels, that’s worth the 1.1. (The “former levels” part is the rub, but as I said I’m focused on what could go right.) I also thought about Shane McClanahan instead, but narrowly opted for Strider.
11.12 Luis Garcia — I was set to take Brice Turang here to lock down speed and finally get a middle infielder, but I pivoted at the last second to Garcia who is a better-rounded hitter and more likely to have a prominent spot in his lineup.
12.1 Jared Jones — He was on my list because I remembered the hype after his strong start, and the cost seemed cheap relative to his skills. I almost took Carlos Rodon, as I prefer veterans. Maybe that will turn out to have been a mistake.
13.12 Brice Turang — What do you know, Turang made it all the way back. I guess people didn’t like his second-half collapse at the plate. But Turang is a gold glove defender, and he stole 50 bags last year. That glove keeps him in the lineup and should set a nice 30-steal floor.
14.1 Kenley Jansen — I could play closer chicken no more. Jansen is my favorite type of old warhorse closer, a guy so used to the job, he’s not going to lose it unless his stuff is truly gone.
15.12 Jordan Romano — Romano got $8.5 million from the Phillies, so I’m assuming he’s (a) healthy and (b) set to close. His ERA while pitching hurt for 14 innings last year is irrelevant.
16.1 Zach Neto — I needed a shortstop, and while Neto’s hurt right now, he went 23-30 as a 23-year old last year, and I couldn’t pass him up. I almost took Ceddanne Rafaela, but Neto’s upside higher.
17.12 Ceddanne Rafaela — Turns out Rafaela fell to me anyway, and I snapped him up, as I’ll need a SS early in the year with Neto presumably out. Rafaela went 15-19 as a 23-YO in his own right, also qualifies in the OF and his gold-glove-level defense should keep him in the lineup.
18.1 Josh Jung — I needed a CI, and also a backup 3B for the injury-prone Royce Lewis, so I took the injury-prone Jung. The key facts about Jung and Lewis are both can hit, and both are healthy as of right now. My team seems like it has a lot of injuries, but only Strider and Neto are hurt now. There is a difference between injury risk (deGrom, Lewis, Jung, Romano) and already injured. You can often find value by exploiting people’s conflation of those two related, but distinct categories.
19.12 Jesus Luzardo — Another skilled, but injury-prone player coming at a steep discount who is healthy now.
20.1 Lucas Erceg — A speculative closer play. Right now Carlos Estevez, who went in Round 15, is probably the favorite, but who knows?
21.12 Walker Buehler — More of the same theme. A player (especially a pitcher) who has shown elite skills, was derailed by injuries, but who is healthy now.
22.1 Nolan Jones — I had almost forgotten he existed, but there he was in Round 22, just one year removed from being a fifth-round pick after a 20-20-.297 season. Jones is only 26 and healthy as of now.
23.12 Griffin Jax — A setup guy with elite stuff, behind a closer that had nine losses and a 1.16 WHIP last year.
24.1 Garrett Mitchell — I took him narrowly over Jordan Walker. Mitchell went 8-11 in 224 at-bats, plays in a good park and has the physical tools to be good.
25.12 Bo Naylor — I needed a second catcher, and he is one. Naylor has a little pop, even runs a bit and should improve in his age 25 season.
26.1 Max Scherzer — Are we sure he’s done? He had a 1.15 WHIP last year and 40K in 43 IP despite returning from back surgery. He’s healthy now and signed a $15.5M deal this offseason presumably to pitch more than 100 innings.
27.12 Justin Verlander — Wait, they let me have deGrom, Cole, Strider, Buehler, Scherzer and Verlander? Those were like the top-six pitchers on the board a few years ago! Seriously though, Verlander is in a good park, and last year’s poor numbers were put up over a 90-inning sample while battling various ailments. He’s more likely to be done than Scherzer, but he knows how to pitch, and it’s just a matter of the stuff returning to above the minimum threshold. I wouldn’t be shocked to see one more strong year out of the 41-YO future Hall of Famer.
28.1 Jose Caballero — I drafted this gentleman in the 28th round because he qualifies everywhere and steals a lot of bases.
29.12 Nolan Gorman — The Cardinals want to get him regular at-bats, and there’s a 35-HR, .240 season somewhere in this skill set.
30.1 Gavin Lux — A big-time prospect that’s only shown flashes, should get regular playing time and a big upgrade in park. He might eventually qualify at some other positions too.
Roster By Position
C Will Smith/Bo Naylor
1B Matt Olson
2B Luis Garcia
3B Royce Lewis
SS Zach Neto
CI Josh Jung
MI Brice Turang
OF Julio Rodriguez/Jackson Chourio/Teoscar Hernandez/Ceddanne Rafaela/Nolan Jones
UT Garrett Mitchell
SP Jacob deGrom/Gerrit Cole/Max Fried/Spencer Strider/Jared Jones/Jesus Luzardo/Walker Buehler
RP Kenley Jansen/Jordan Romano
B Lucas Erceg/Griffin Jax/Max Scherzer/Justin Verlander/Jose Caballero/Nolan Gorman/Gavin Lux
-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ fe32298e:20516265
2025-02-17 17:39:31
@ fe32298e:20516265
2025-02-17 17:39:31I keep a large collection of music on a local file server and use DeaDBeeF for listening. I've never been able to pin DeadBeeF to the dock in Ubuntu, and it's always had the ugly default icon.
I asked DeepSeek for help, and it turned out to be easier than I thought.
- Create
~/.local/share/applications/deadbeef.desktop:bash [Desktop Entry] Name=DeadBeeF Music Player Comment=Music Player Exec=/home/user/Apps/deadbeef-1.9.6/deadbeef Icon=/home/user/Apps/deadbeef-1.9.6/deadbeef.png Terminal=false Type=Application Categories=AudioVideo;Player; - Make
deadbeef.desktopexecutable:bash chmod +x ~/.local/share/applications/deadbeef.desktop
And just like that, DeadBeeF has an icon and I can pin it to the dock.
.desktopfiles are part of the Freedesktop.org standards. They're used in most popular desktop environments like GNOME, KDE and XFCE.Tor Browser has the same issue, but it comes with a
.desktopfile already, so it only needs to by symlinked to the applications folder:ln -s ~/Apps/tor-browser/start-tor-browser.desktop ~/.local/share/applications/ - Create
-
 @ 5d4b6c8d:8a1c1ee3
2025-02-17 14:39:25
@ 5d4b6c8d:8a1c1ee3
2025-02-17 14:39:25A new best yesterday: 22 hours! Today's shaping up to be another solid fast, too, as I'm already at 19 hours (18 dry).
My body's really getting accustomed to the new eating pattern, too.
Score Card
Day 1: 14 hour fast (13 dry) Day 2: 15 hour fast (14 dry) Day 3: 17 hours (16 dry) Day 4: 18 hours (17 dry) Day 5: 18 hours (16 dry) Day 6: 19 hours (16 dry) Day 7: 16 hours (15 dry) Day 8: 18 hours (17 dry) Day 9: 17 hours (17 dry) Day 10: 15 hours (13 dry) Day 11: 20 hours (19 dry) Day 12: 20 hours (17 dry) Day 13: 16 hours (13 dry) Day 14: 17 hours (15 dry) Day 15: 19 hours (16 dry) Day 16: 22 hours (19 dry) Day 17: TBD (18 dry)
originally posted at https://stacker.news/items/888397
-
 @ c4b5369a:b812dbd6
2025-02-17 06:06:48
@ c4b5369a:b812dbd6
2025-02-17 06:06:48As promised in my last article:
nostr:naddr1qvzqqqr4gupzp394x6dfmvn69cduj7e9l2jgvtvle7n5w5rtrunjlr6tx6up9k7kqq2k6ernff9hw3tyd3y453rdtph5uvm6942kzuw08y0
In this one we will dive into how exactly an unidirectional payments channel powered ecash mint system would be implemented, using the tech available today! So if you haven't read that article yet, give it a read!
I first intended to write a longwinded article, explaining each part of the system. But then I realized that I would need some visualization to get the message across in a more digestable way. This lead me to create a slide deck, and as I started to design the slides it became more and more clear that the information is easier shown with visualizations, than written down. I will try to give a summary as best as I can in this article, but I urge you, to please go visit the slide deck too, for the best experience:
TAKE ME TO THE SLIDE DECK!
Intro
In this article we will go over how we can build unidirectional payment channels on Bitcoin. Then we will take a look into how Cashu ecash mints work, and how we can use unidirectional payment channels to change the dynamics between ecash users and the mint.
Before we start, let me also give credits to nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac for comming up with the idea, to nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp for providing an idea for non-expiring unidirectional channels, and nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference for hosting an event where these ideas could be discussed and flourish.
Building unidirectional payment channels
If you've read the previous article, you already know what unidirectional payment channels are. There are actually a coupple different ways to implement them, but they all do have a few things in common:
- The
sendercan only send - The
Receivercan only receive - They are VERY simple
Way simpler than the duplex channels like we are using in the lightning network today, at least. Of course, duplex channels are being deployed on LN for a reason. They are very versatile and don't have these annoying limitations that the unidirectional payment channels have. They do however have a few drawbacks:
- Peers have liveness requirements (or they might forfeit their funds)
- Peers must backup their state after each transaction (if they don't they might forfeit their funds)
- It is a pretty complex system
This article is not meant to discredit duplex channels. I think they are great. I just also think that in some use-cases, their requirements are too high and the system too complex.
But anyway, let's see what kind of channels we can build!
Spillman/CLTV-Channel
The Spillman channel idea has been around for a long time. It's even explained in Tadge Dryjas Presentation on Payment channels and the lightning network from back in the day. I compiled a list of some of the most important propperties of them in the slide below:

Great!
Now that we know their properties, let's take a look at how we can create such a channel (Slides):

We start out by the
sendercreating afunding TX. Thesenderdoesn't broadcast the transaction though. If he does, he might get locked into a multisig with thereceiverwithout an unilateral exit path.Instead the
senderalso creates arefund TXspending the outputs of the yet unsignedfunding TX. Therefund TXis timelocked, and can only be broadcast after 1 month. Bothsenderandreceivercan sign thisrefund TXwithout any risks. Oncesenderreceives the signedrefund TX, he can broadcast thefunding TXand open the channel. Thesendercan now update the channel state, by pre-signing update transactions and sending them over to thereceiver. Being a one-way channel, this can be done in a single message. It is very simple. There is no need for invalidating old states, since thesenderdoes not hold any signedupdate TXsit is impossible for thesenderto broadcast an old state. Thereceiveronly cares about the latest state anyways, since that is the state where he gets the most money. He can basically delete any old states. The only thing thereceiverneeds to make sure of, is broadcasting the latestupdate TXbefore therefund TX'stimelock expires. Otherwise, thesendermight take the whole channel balance back to himself.This seems to be already a pretty useful construct, due to its simplicity. But we can make it even more simple!

This setup works basically the same way as the previous one, but instead of having a refund transaction, we build the
timelockspend path directly into thefunding TXThis allows thesenderto have an unilateral exit right from the start, and he can broadcast thefunding TXwithout communicating with thereceiver. In the worst case, the receiver rejects the channel, and the sender can get his money back after the timelock on the output has expired. Everything else basically works in the same way as in the example above.The beauty about this channel construct is in its simplicity. The drawbacks are obvious, but they do offer some nice properties that might be useful in certain cases.

One of the major drawbacks of the
Spillman-style channels(apart from being unidirectional) is that they expire. This expiry comes with the neat property that neither of the party has to watch the chain for channel closures, and thesendercan operate the channel with zero additional state, apart from his private keys. But they do expire. And this can make them quite inflexible. It might work in some contexts, but not so much in others, where time needs to be more flexible.This is where
Roose-Childs triggered channelscome into play.Roose-Childs triggered channel
(I gave it that name, named after nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp and nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac . If someone knows if this idea has been around before under a different name, please let us know!)
Roose-Childs triggered channelswere an idea developed by Steven and Luke at the nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference. They essentially remove the channel expiry limitation in return for introducing the need for thesenderto create a channel backup at the time of channel creation, and for thereceiverthe need to watch the chain for trigger transactions closing the channel.
They also allow for splicing funds, which can be important for a channel without expiry, allowing the
senderto top-up liquidity once it runs out, or for thereceivertaking out liquidity from the channel to deploy the funds elsewhere.Now, let's see how we can build them!

The
funding TXactually looks the same as in the first example, and similarly it gets created, but not signed by thesender. Then, sender and receiver both sign thetrigger TX. Thetrigger TXis at the heart of this scheme. It allows bothsenderandreceiverto unilaterally exit the channel by broadcasting it (more on that in a bit).Once the
trigger TXis signed and returned to thesender, the sender can confidently sign and boradcast thefunding TXand open the channel. Thetrigger TXremains off-chain though. Now, to update the channel, thesendercan pre-sign transactions in similar fashion to the examples above, but this time, spending the outputs of the unbroadcastedtrigger TX. This way, both parties can exit the channel at any time. If thereceiverwants to exit, he simply boradcasts thetrigger TXand immediately spends its outputs using the latestupdate TX. If thesenderwants to exit he will broadcast thetrigger TXand basically force thereceivershand. Either, thereceiverwill broadcast the latestupdate TX, or thesenderwill be able to claim the entire channel balance after the timelock expired.
We can also simplify the
receiver'sexit path, by thesenderpre-signing an additional transactionR exit TXfor each update. this way, thereceiveronly needs to broadcast one transaction instead of two.
As we've mentioned before, there are some different trade-offs for
Roose-Childs triggered channels. We introduce some minimal state and liveness requirements, but gain more flexibility.
Ecash to fill in the gaps
(I will assume that the reader knows how ecash mints work. If not, please go check the slides where I go through an explanation)
Essentially, we are trying to get a lightning like experience, without all the lightning complexities and requirements. One big issue with ecash, is that it is fully custodial. If we can offset that risk by holding most of the funds in a self custodial channel, we can have a reasonable trade-off between usability and self custody.

In a system like that, we would essentially turn the banking model onto its head. Where in a traditional bank, the majority of the funds are held in the banks custody, and the user only withdraws into his custody what he needs to transact, in our model the user would hold most funds in his own custody.

If you ask me, this approach makes way more sense. Instead of a custodian, we have turned the "bank" into a service provider.
Let's take a look at how it would work in a more practical sense:

The
ecash userwould open an unidirectional payment channel to themint, using one of his on-chain UTXOs. This allows him then to commit incrementally funds into the mints custody, only the amounts for his transactional needs. The mint offers connectivity to the lightning network an handles state and liveness as a service provider.The
ecash user, can remain offline at all times, and his channel funds will always be safe. The mint can only ever claim the balance in the channel via theupdate TXs. Themintcan of course still decide to no longer redeem any ecash, at which point they would have basically stolen theecash user'stransactional balance. At that point, it would probably be best for theecash userto close his channel, and no longer interact or trust thismint.Here are some of the most important points of this system summarized:

And that is basically it! I hope you enjoyed this breakdown of Unidirectional payment channel enabled Ecash mints!
If you did, consider leaving me a zap. Also do let me know if this type of breakdown helps you understand a new topic well. I am considering doing similar breakdowns on other systems, such as ARK, Lightning or Statechains, if there is a lot of interest, and it helps people, I'll do it!
Pleas also let me know what you think about the
unidirectional channel - ecash mintidea in the comments. It's kind of a new idea, an it probably has flaws, or things that we haven't thought about yet. I'd love to discuss it with you!I'll leave you with this final slide:

Cheers,
Gandlaf
- The
-
 @ e88a691e:27850411
2025-02-17 13:30:42
@ e88a691e:27850411
2025-02-17 13:30:42test post longform 4
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ 0463223a:3b14d673
2025-02-17 07:48:11
@ 0463223a:3b14d673
2025-02-17 07:48:11Here we go, it’s Mooooonnnndddddaaaaaaaayyyyyyy!
It’s safe to say I enjoy Monday. Much as I appreciate the downtime over the weekend (if I’m not working) I appreciate the routine of Mondays. Firstly I have my stream to look forward to and whilst I’m not at my best first thing on a Monday, having a little structure goes a long way. Even the fear of looking at the emails I’ve been ignoring from the previous week is possible.
So maybe I’m starting to get an angle of why I’m writing this. It’s a memoir of being a mental I think. I’ve mentioned a number of times this has been a problem most my life but I write this as I’ve halved my Venlafaxine does by ½ once again. This means I’m now on 1/12th of my original dose and I’m maybe a month away from being completely free of RRSIs for the first time in, I guess at least 10 years. To be honest I cant remember when I was first prescribed them. It’s been quite a journey...
3 things have been pivotal. 1; finding my now wife. She’s brilliant and I love her dearly, I think most people know deep down how crushing loneliness can be. I’m very grateful to her for putting up with my bullshit, supporting me and just being there. Gold star for her!
2; would be music, it’s a funny one to put in, it’s also been part of the problem, especially in my wilder days. There’s something quite seductive about the sex, drugs and Rock n Roll meme, although musically it was more Hip Hop, Reggae, Bleeps and Jazz, also I didn’t sleep around much at all but I certainly don’t think I would’ve messed with crack, heroin and all the other drugs otherwise. It’s worth noting 2 of my friends from that era, who didn’t have music in their lives are dead. I’m very lucky. There’s over 100 years of recorded music to enjoy plus I’m almost happy with some of my own bits at last!
3; I have some security, I no longer pay rent or have a landlord. This is also due to number 1 but also because I found some funny internet money. I’m still to write about my process with that, other than to say it was direct response to the banks. That’s a story in it’s own right, it’s pretty dark and hmm… not sure. Plus I don’t think there’s any need to go there right now. I have the world’s most expensive shed and I know I can survive a few months should the worst happen. That’s a LOT. Whilst a little risk taking is healthy, life shouldn’t free stress free, uncertainty about having a roof over your head when you can’t afford it can really take it’s toll. A degree of security is most welcome at this time in life.
A lot of people aren’t so lucky, Tom, Ricky, Dave, Slam, Joel. I’m name checking you specifically. You’re in my thoughts often, especially as I play music every morning… and Slam, if I ever see you again, I want my records back!!! Haha, thieving little cunt but it’s still not hate here. Your life was fucked up before you even had a chance. I hope you’ve found peace with yourself. At least you’re alive! (I think, he might be dead too, who knows…)
So yeah, it’s Monday and it’s gonna be a good day right? I mean it might not but I will at least give it the best start possible and work from there. It takes a degree of effort to retrain the brain. Actually maybe there’s a 4th thing to mention. No Facebacon, Instagran, X or LinkedIn. None of that bullshit where you’re forced into some fake world generated in order to increase shareholder value. These platforms are akin to being a lab rat. I picture Zuckerberg like Ming The Merciless at the start of Flash Gordon sending hot hail etc. That guy made a decision to mess with peoples’ psyche to drive profits. That’s fucking evil man. Jeez, what a cunt!
It’s Monday, I’m wishing you strength in whatever you have ahead of you today. I’m lucky to be where I am right now and if you’re reading this and your world is plagued by darkness, it can get better. Remember that. Hold onto that as best you can. DON’T FUCKING KILL YOURSELF. That’s the single worst thing you can do. The pain you’ll leave behind isn’t worth it. I hope some cosmic vibrations happen in your favour. There’s no easy solution. I can’t tell you the answer but I wish you well. Good luck out there!
-
 @ 8d34bd24:414be32b
2025-02-16 04:19:34
@ 8d34bd24:414be32b
2025-02-16 04:19:34Last night in my Bible reading I read this verse:
“As for you, do not pray for this people, and do not lift up cry or prayer for them, and do not intercede with Me; for I do not hear you. (Jeremiah 7:16) {emphasis mine}
My first thought was “Why in the world is God telling us not to pray for this people? Doesn’t the Bible tell us to pray about everything?”
First of all, then, I urge that entreaties and prayers, petitions and thanksgivings, be made on behalf of all men, for kings and all who are in authority, so that we may lead a tranquil and quiet life in all godliness and dignity. This is good and acceptable in the sight of God our Savior, who desires all men to be saved and to come to the knowledge of the truth. (1 Timothy 2:1-4) {emphasis mine}
Doesn’t God tell us to pray for whatever is bothering us?
Be anxious for nothing, but in everything by prayer and supplication with thanksgiving let your requests be made known to God. And the peace of God, which surpasses all comprehension, will guard your hearts and your minds in Christ Jesus. (Philippians 4:6-7)
Doesn’t the Bible say that God will answer all of our requests?
Whatever you ask in My name, that will I do, so that the Father may be glorified in the Son. (John 14:13)
Doesn’t the Bible tell us to pray for Israel and Jerusalem and His chosen people?
Pray for the peace of Jerusalem:\ “May they prosper who love you.\ May peace be within your walls,\ And prosperity within your palaces.”\ For the sake of my brothers and my friends,\ I will now say, “May peace be within you.”\ For the sake of the house of the Lord our God,\ I will seek your good. (Psalm 122:6-9) {emphasis mine}
Doesn’t the Bible even tell us to pray for our enemies?
“But I say to you who hear, love your enemies, do good to those who hate you, bless those who curse you, pray for those who mistreat you. (Luke 6:27-28)
If all of this is true, then why does this verse tell us to not pray for this people, especially considering this is referring to God’s chosen people?
To answer this question, let us look at a broader portion of this passage:
“As for you, do not pray for this people, and do not lift up cry or prayer for them, and do not intercede with Me; for I do not hear you. Do you not see what they are doing in the cities of Judah and in the streets of Jerusalem? The children gather wood, and the fathers kindle the fire, and the women knead dough to make cakes for the queen of heaven; and they pour out drink offerings to other gods in order to spite Me. Do they spite Me?” declares the Lord. “Is it not themselves they spite, to their own shame?” (Jeremiah 7:16-19) {emphasis mine}
God is saying to not pray for these people who have turned from Him and are worshipping other gods. These people are in full rejection of God. Still does it mean that we can’t pray for them at all or is this talking about a particular kind of prayer?
A little later in Jeremiah, we read:
“Therefore do not pray for this people, nor lift up a cry or prayer for them; for I will not listen when they call to Me because of their disaster. (Jeremiah 11:14)
and
So the Lord said to me, “Do not pray for the welfare of this people. When they fast, I am not going to listen to their cry; and when they offer burnt offering and grain offering, I am not going to accept them. Rather I am going to make an end of them by the sword, famine and pestilence.” (Jeremiah 14:11-12) {emphasis mine}
We get a little more specificity on the command to “not pray for” in Jeremiah 14. We are told, “Do not pray for the welfare of this people.” This is not a universal command to never pray for them, but a command to not pray for their welfare. It is a command to not pray blessings on those in active rebellion against God.
At the time this command was made, the Israelites were expecting God’s protection and blessings while refusing to follow Him and instead worshipping other gods. This command isn’t a blanket statement to not pray for a sinning Israel, but a statement to not pray for blessings and protection for a sinning Israel. If this was a blanket statement it would contradict Psalm 122 above.
This is the confidence which we have before Him, that, if we ask anything according to His will, He hears us. And if we know that He hears us in whatever we ask, we know that we have the requests which we have asked from Him. (1 John 5:14-15) {emphasis mine}
Using 1 John 5:14, we can begin to see the catch. We are to pray “according to His will.” It is not God’s will for sinners and those in open rebellion against God to be blessed or protected from hardship. A prayer such as, “Please turn your people back to you and give them a pure heart and repentance from sin,” would be according to His will. A prayer to “Please bless and protect Israel” while Israel has turned their back on God is not a prayer that God will answer. He will “not hear you.”
The Bible also says:
You ask and do not receive, because you ask with wrong motives, so that you may spend it on your pleasures. (James 4:3)
How often are our prayers not answered because we pray with wrong motives? At least sometimes. Of course there are also times when God tells us to wait or has something better in mind and we can’t see it because we are not seeking His will, but our own.
It is always good to pray for someone’s repentance and salvation. It isn’t always good to pray for someone’s healing, blessings, and prosperity. It is always good to pray for a nation to turn back to God and to obey His commands. It isn’t always good to pray for a nation’s prosperity and power in the world. Sometimes God’s will is to punish those who turn away from Him or against Him. We need to make sure we are aligned to God’s will and not just seeking our own.
I recommend that our prayers be like Jesus’s prayer right before going to the cross, “saying, “Father, if You are willing, remove this cup from Me; yet not My will, but Yours be done.” (Luke 22:42). Our requests should be like that of Shadrach, Meshach, and Abed Ngo right before being thrown in the fiery furnace, “But even if He does not, let it be known to you, O king, that we are not going to serve your gods or worship the golden image that you have set up.” (Daniel 3:18). This isn’t just words thrown on the end of our prayers “yet not My will, but Yours be done,” but a cry of our hearts in full and complete trust in our Father God.
One thing that helps me is I try to pray the problem not the solution. God knows much better solutions than we do because He knows everything that has happened, everything that is happening, and everything that will happen. He knows what will lead to the best long term solution. When we pray the solution we desire, we miss out on the blessings of God’s knowledge, wisdom, and love.
May God lead you and guide you in a closer relationship to Him so that your will is completely aligned with His will and you are in close fellowship to Our Father in Heaven.
Trust Jesus
-
 @ dbe0605a:f8fd5b2c
2025-02-17 06:42:38
@ dbe0605a:f8fd5b2c
2025-02-17 06:42:38Originally posted on Nostr: https://highlighter.com/a/naddr1qvzqqqr4gupzpklqvpdfcuch9wkh2gary7erd4275jmrf6qw0z5sz0dhj8u06kevqyvhwumn8ghj7urjv4kkjatd9ec8y6tdv9kzumn9wshszxrhwden5te0ve5kcar9wghxummnw3ezuamfdejj7qgwwaehxw309ahx7uewd3hkctcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszythwden5te0dehhxarj9emkjmn99uqzqjn0d9hz6argv5k57ur9dck5y6t5vdhkjm3df4shqtt5xduxz6tsrdmw7l
I care deeply about bitcoin adoption and ability to use bitcoin with all features of money — saving, spending, earning. We're entering an age where more and more people realise "hodl never spend" meme is hindering bitcoin adoption. More and more of use want to use bitcoin in everyday life, because we're living on it and because it's superior in every aspect. It's also incredibly fun to use it for payments.
For money to thrive, it needs to circulate. Spending bitcoin orangepills merchants, their families and people around them — with each bitcoiner coming to a shop and paying with bitcoin, it's a point of contact that can trigger a train of though that later may fruit into action — "Why are they so interested in bitcoin, what's actually so special about it?" "Hmm, maybe this time I will not exchange it for fiat immediately?"
Global merchant adoption grows, every day new business around the world decide to start accepting bitcoin payments. Circular economies are blooming on all continents, where people live in a new, experimental, orange coin paradigm. Companies and projects like Blink, Bitcoin Jungle, Plan B, Orange Pill App do an amazing job in facilitating this — providing great wallets, tools & services for merchants, and finally onboarding merchants themself. They also often support circular economies financially or in other ways. This is very valuable and makes the road to hyperbitcoinization a tad shorter.
But there is one thing those companies are doing wrong — they're using their own, proprietary maps that display only merchants using their own wallets or POS software. I'd like to now list a few reasons why those great projects should migrate their maps into an open source, bitcoin map that is BTC Map.
Open source, stupid
BTCmap is open source, built on OpenStreetMaps, open to both developers contributions but also for map taggers (called shadowy supertaggers). Anyone can contribute, even If you don't code. Anyone can verify merchants or add new merchants to the map. BTC Map team developed a neat system of verifications that just works better than anything before or any alternative maps today.
Many apps, one map
BTC Map is integrated inside a dozen of wallets and apps, to name a few: Wallet of Satoshi, Coinos, Bitlocal, Fedi or Aqua. It's a public good that any bitcoin product can use and grow it's network effect.
Uniting mappers' work
BTC Map does not discriminate bitcoin merchants, that means all the merchants from proprietary maps are being mapped by taggers to BTC Map. By mapping on a closed source, proprietary map, the same merchant is mapped two times, usually by two different people — it's duplicating the same work without any bringing any benefit to both projects. Using BTC Map also brings you way more people verifying If those merchants actually still accept bitcoin, making it easier to have an up-to-date database of actual adoption.
More bitcoin spent at your merchants
When you have a business focused on spending bitcoin and onboarding merchants, you want as much bitcoin spent there as possible. If a bitcoiner coming to the area does not use your own map but some other map, they can be completely unaware that they can let their sats flow to your merchants. If we all use one merchants database, this problem disappears and more sats will flow. Why wouldn't you want your merchants displayed in dozens of other apps, completely for free?
OpenStreetMap map is just better
Take a look at the image above: It's La Pirraya, a small sleepy island town in El Salvador with a circular economy being facilitated by Bitcoin Beach. Even though Blink has many more merchants compared to BTC Map, when I visited it a few months ago I could find them. Not because they do not exist, but because the map does not show any roads and it was very hard to locate them in a dense network of narrow streets of La Pirraya. BTC Map allows you to turn multiple versions of satellite maps views, making it way easier to find your point of interest. Pins also indicate what kind of business it is, where in Blink all the pins are the same and you need to click each to find out what it is. Even then not always it's clear, since Blink only displays names, while BTC Map tells you type of the merchant, and very often shows you working hours, phone numbers, website, social links, etc.
Excellent community tools
BTC Map is focusing providing tools for communities to maintain their merchants map. Each community has it's own page with own links to community website or socials, displays a list of all the merchants, shows community stats, displays merchants that were not verified for a long time, and more. It even allows to "boost" merchants to make them more visible on the map and on the list. It's perfect tooling both for communities and businesses onboarding merchants to their software.
Easy integration & configuration
Integrating BTC Map on your website or app is easy. It's just a few lines of code of iframe to embed the map, but you can also use BTC Map API for more custom integration. Do you to display, eg. you can display only merchants from your community? No problem, you can do that. Since it's all open source, you can configure it in many ways that will suit your needs.
Kudos
I'd like to thank projects that understood all above and integrated BTC Map already. Those are Coinos, Wallet of Satoshi, Pouch, Bolt Card, BitLocal, Fedi, Decouvre Bitcoin, Osmo, Bitcoin Rocks!, Lipa, Spirit of Satoshi, Blockstream, Satlantis, Aqua Wallet and Adopting Bitcoin
Encouragement & an offer
I'll end that with encouragement to projects that use their own maps, but haven't embraced BTC Map yet. Those are Blink, Bitcoin Jungle, Plan B, Osmo, Athena, Orange Pill App, Inbitcoin (I probably missed some, tag them!). You are doing great work, but let's join forces and paint the world orange together!
From here I would like to offer help in tagging your merchants on BTC Map. Just reach me out, and me and other supertaggers will do the work.
Let the sats flow!
originally posted at https://stacker.news/items/888088
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ fd208ee8:0fd927c1
2025-02-15 07:37:01
@ fd208ee8:0fd927c1
2025-02-15 07:37:01E-cash are coupons or tokens for Bitcoin, or Bitcoin debt notes that the mint issues. The e-cash states, essentially, "IoU 2900 sats".
They're redeemable for Bitcoin on Lightning (hard money), and therefore can be used as cash (softer money), so long as the mint has a good reputation. That means that they're less fungible than Lightning because the e-cash from one mint can be more or less valuable than the e-cash from another. If a mint is buggy, offline, or disappears, then the e-cash is unreedemable.
It also means that e-cash is more anonymous than Lightning, and that the sender and receiver's wallets don't need to be online, to transact. Nutzaps now add the possibility of parking transactions one level farther out, on a relay. The same relays that cannot keep npub profiles and follow lists consistent will now do monetary transactions.
What we then have is * a transaction on a relay that triggers * a transaction on a mint that triggers * a transaction on Lightning that triggers * a transaction on Bitcoin.
Which means that every relay that stores the nuts is part of a wildcat banking system. Which is fine, but relay operators should consider whether they wish to carry the associated risks and liabilities. They should also be aware that they should implement the appropriate features in their relay, such as expiration tags (nuts rot after 2 weeks), and to make sure that only expired nuts are deleted.
There will be plenty of specialized relays for this, so don't feel pressured to join in, and research the topic carefully, for yourself.
https://github.com/nostr-protocol/nips/blob/master/60.md https://github.com/nostr-protocol/nips/blob/master/61.md
-
 @ c4b5369a:b812dbd6
2025-02-12 12:23:40
@ c4b5369a:b812dbd6
2025-02-12 12:23:40
Unidirectional payment channels revisited
Nodeless lightning - Reduce ecash mints custodial risk
Sats N Facts
The nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx unconference has just wrapped up. And what a blast it was. In the heart of northern Thailand, developers, researchers, content creators and more, came together to share ideas on how Bitcoin, Nostr and other free protocols are being used everyday to liberate people.
Not only were stories shared from different community leaders on how embracing bitcoin has empowered them and their communities, but a big goal of the unconference was to bring bitcoin engineers and developers from various domains together in one room, unstructured, chaotic, and let them do their thing.
At first, I thought not having a schedule might be boring, but oh boy was I wrong. There was so much stuff going on, it was hard to choose which session I would have to miss!
Luke's Spillman channel proposal
One of the sessions I definitely did not want to miss, was nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac s proposal
Ecash mints funded with Spillman channels: The ultimate nodeless Lightning wallet
.
In true unconference fashion, he announced in the main room that the session was about to start, and that the people that are interested should meet him in the whiteboard corner in 10 minutes. The corner was packed, and Luke explained his proposal.
What's a "Spillman channel"?
Essentially when we are talking about Spillman channels, what is meant are unidirectional payment channels (or CLTV-style channels). An unidirectional payment channel means, only one party can send payments, but not receive, and the other party can only receive, but not send. They also expire after a predetermined amount of time, and must be closed.

At first glance, this might look kinda stupid. After all, we have Poon-Dryja channels that are powering the lightning network. They are bi-directional, do not expire, and can be used to shuffle coins back and forth theorethically an unlimited amount of times.
So, why bother with this stupid one-way channel?
Simplicity is king
People that have worked with lightning channels can sing you a song about complexity, state handling and risks about the current state of bidirectional payment channels. Essentially, There are a lot of requirements on both channel parties when it comes to Liveness (being online) and also state handling (continuous backups).
 In some cases, especially when in the context of end-users wanting to perform payments on their mobile phone, they would appreciate it if there was not so much complexity and overhead involved.
In some cases, especially when in the context of end-users wanting to perform payments on their mobile phone, they would appreciate it if there was not so much complexity and overhead involved. The gist of the idea is to combine unidirectional channels and ecash mints to achieve the following:
A self custodial unidirectional payment channel to an ecash mint, massively reducing the senders liveness and state handling requirements when compared to a lightning channel. Sending payments through the mint will be done through swapping some of the channel balance for ecash tokens. At this point, the user is trusting the mint to honor the redemption of these tokens, while the remaining channel balance remains in self custody. This gives them better controll over their funds than just holding their entire balance custodied in the mint. The ecash tokens can then be redeemed to pay a lightning invoice, just the same as it is done now with normal cashu mints.

So this channel, that has no liveness or state management requirements for the sender, and must have a pre-defined close time, seems to be a perfect fit for the following usecase:
- A
senderreceives his salary once a month. He opens a channel that is valid for one month. - The
senderthen can do his daily spending over this channel. He only trusts themintwith the amount for the current outgoing payment while it is swapped for ecash, waiting for redemption. - If the
sendermust receive funds (a refund for example), he can do so into themintscustody, by receiving ecash. He can spend his ecash funds first when doing his next payment, to reduce his custodial exposure. - When the channel expires, or runs out of funds, the
mintcloses the channel.
From a consumer perspective, that just want to receive his salary and make frequent payments afterwards, this usecase seems to make a lot of sense. Obviously from a merchants perspective on the other hand, such a channel doesn't really work. But that's fine, it's not the problem we're trying to solve here.
What do you think of this idea? Be sure to let me know in the comments!
In the next article, we will dive into how such a system can be implemented today, using Bitcoin, Cashu and Lightning. We will also discover how the system can be improved, to make channels non-expiring (A collaborative idea between nostr:npub148jz5r9xujcjpqygk69yl4jqwjqmzgrqly26plktfjy8g4t7xaysj9xhgp and nostr:npub1htnhsay5dmq3r72tukdw72pduzfdcja0yylcajuvnc2uklkhxp8qnz3qac born at nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx ).
So stay tuned!
- A
-
 @ dbe0605a:f8fd5b2c
2025-02-17 06:33:48
@ dbe0605a:f8fd5b2c
2025-02-17 06:33:48
\ I care deeply about bitcoin adoption and ability to use bitcoin with all features of money — saving, spending, earning. We're entering an age where more and more people realise "hodl never spend" meme is hindering bitcoin adoption. More and more of use want to use bitcoin in everyday life, because we're living on it and because it's superior in every aspect. It's also incredibly fun to use it for payments.
For money to thrive, it needs to circulate. Spending bitcoin orangepills merchants, their families and people around them — with each bitcoiner coming to a shop and paying with bitcoin, it's a point of contact that can trigger a train of though that later may fruit into action — "Why are they so interested in bitcoin, what's actually so special about it?" "Hmm, maybe this time I will not exchange it for fiat immediately?"
Global merchant adoption grows, every day new business around the world decide to start accepting bitcoin payments. Circular economies are blooming on all continents, where people live in a new, experimental, orange coin paradigm. Companies and projects like Blink, Bitcoin Jungle, Plan B, Orange Pill App do an amazing job in facilitating this — providing great wallets, tools & services for merchants, and finally onboarding merchants themself. They also often support circular economies financially or in other ways. This is very valuable and makes the road to hyperbitcoinization a tad shorter.
But there is one thing those companies are doing wrong — they're using their own, proprietary maps that display only merchants using their own wallets or POS software. I'd like to now list a few reasons why those great projects should migrate their maps into an open source, bitcoin map that is BTC Map.
Open source, stupid
BTCmap is open source, built on OpenStreetMaps, open to both developers contributions but also for map taggers (called shadowy supertaggers). Anyone can contribute, even If you don't code. Anyone can verify merchants or add new merchants to the map. BTC Map team developed a neat system of verifications that just works better than anything before or any alternative maps today.

Many apps, one map
BTC Map is integrated inside a dozen of wallets and apps, to name a few: Wallet of Satoshi, Coinos, Bitlocal, Fedi or Aqua. It's a public good that any bitcoin product can use and grow it's network effect.

Uniting mappers' work
BTC Map does not discriminate bitcoin merchants, that means all the merchants from proprietary maps are being mapped by taggers to BTC Map. By mapping on a closed source, proprietary map, the same merchant is mapped two times, usually by two different people — it's duplicating the same work without any bringing any benefit to both projects. Using BTC Map also brings you way more people verifying If those merchants actually still accept bitcoin, making it easier to have an up-to-date database of actual adoption.
More bitcoin spent at your merchants
When you have a business focused on spending bitcoin and onboarding merchants, you want as much bitcoin spent there as possible. If a bitcoiner coming to the area does not use your own map but some other map, they can be completely unaware that they can let their sats flow to your merchants. If we all use one merchants database, this problem disappears and more sats will flow. Why wouldn't you want your merchants displayed in dozens of other apps, completely for free?
OpenStreetMap map is just better

\ Take a look at the image above: It's La Pirraya, a small sleepy island town in El Salvador with a circular economy being facilitated by Bitcoin Beach. Even though Blink has many more merchants compared to BTC Map, when I visited it a few months ago I could find them. Not because they do not exist, but because the map does not show any roads and it was very hard to locate them in a dense network of narrow streets of La Pirraya. BTC Map allows you to turn multiple versions of satellite maps views, making it way easier to find your point of interest. Pins also indicate what kind of business it is, where in Blink all the pins are the same and you need to click each to find out what it is. Even then not always it's clear, since Blink only displays names, while BTC Map tells you type of the merchant, and very often shows you working hours, phone numbers, website, social links, etc.
Excellent community tools
BTC Map is focusing providing tools for communities to maintain their merchants map. Each community has it's own page with own links to community website or socials, displays a list of all the merchants, shows community stats, displays merchants that were not verified for a long time, and more. It even allows to "boost" merchants to make them more visible on the map and on the list. It's perfect tooling both for communities and businesses onboarding merchants to their software.

Easy integration & configuration
Integrating BTC Map on your website or app is easy. It's just a few lines of code of iframe to embed the map, but you can also use BTC Map API for more custom integration. Do you to display, eg. you can display only merchants from your community? No problem, you can do that. Since it's all open source, you can configure it in many ways that will suit your needs.
Kudos
I'd like to thank projects that understood all above and integrated BTC Map already. Those are Coinos, Wallet of Satoshi, Pouch, Bolt Card, BitLocal, Fedi, Decouvre Bitcoin, Osmo, Bitcoin Rocks!, Lipa, Spirit of Satoshi, Blockstream, Satlantis, Aqua Wallet and Adopting Bitcoin.
Encouragement & an offer
I'll end that with encouragement to projects that use their own maps, but haven't embraced BTC Map yet. Those are Blink, Bitcoin Jungle, Plan B, Osmo, Athena, Orange Pill App, Inbitcoin (I probably missed some, tag them!). You are doing great work, but let's join forces and paint the world orange together!
From here I would like to offer help in tagging your merchants on BTC Map. Just reach me out, and me and other supertaggers will do the work.
Let the sats flow!
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ 6ad3e2a3:c90b7740
2025-02-09 11:22:19
@ 6ad3e2a3:c90b7740
2025-02-09 11:22:19I’m honored to have the opportunity to speak with the highly regarded and much beloved Lisbon legend Oscar Liss. Oscar has brought joy to so many children and adults alike. He even helped one person find spiritual salvation, something about which we ask him below. So please enjoy this far-ranging conversation about the meaning life and the nature of consciousness itself.
Q: Oscar, thanks so much for making the time. For the few people that don’t know you, do you mind stating your full name and date of birth?
A: My name is Oscar Liss, though officially it’s Oscar Quinta da Bicherada, the prison complex where I was born. I am a long-haired mini dachshund. I have many aliases, including Osk, Oskie, The Skeeze, Skeezeley, Skeezeley-ski, The Guy, The Guy Behind The Guy, “The Opportunist” (which I don’t like), the…
Q That’s more than sufficient, Oscar, thank you. And date of birth?
A: July 7, 2020.
Q Talk a little bit about your childhood and how you came to live in Lisbon.
A: I was in the prison complex, mostly caged for the first few months. Then I was sold to dog traffickers in Lisbon.
Q: That must have been traumatic.
A: Not really. I quickly developed Stockholm Syndrome. Whenever I see my traffickers now, I feel nothing but overwhelming joy.
Q: Wow. A lot of us can learn from that attitude. Let’s fast forward a bit to your present-day life. In what does it consist?
A: Sleep on the sofa, go for walks, fetch vegetable sticks. Sometimes go for hikes or get sent to dog camp (which is okay, but I’m always the smallest.)
Q: I meant to ask you about your size. I hope it’s not a sensitive subject.
A: I’m six inches tall, more than a foot long, weigh almost 10 pounds.
Q: Are you self-conscious about being a small dog?
A: No, but the traffickers are self-conscious on my behalf. They’re always like, “Who’s the apex predator? Who’s an apex!" Or “you’re such a big strong dog.” It’s absurd. I am fine with who I am.
Q: What’s the source of your self-confidence, I’m sure many of our readers could take a lesson from you.
A: I’m not ambitious. I’m perfectly happy to be a dog.
Q: That’s so profound. Does it not concern you some have described you as “all bark, no bite?”
A: I had a friend once who bit a few people, and they executed him. People mock, but they have no idea the stakes.
Q: Human privilege?
A: Yes. Dogs don’t get due process. There is no justice for a dog.
Q: Do you think there’s species discrimination?
A: Have you ever been rejected from a restaurant and made to wait in the car while everyone else gets in?
Q: How does that make you feel?
A: Bad. I’ve been to many dog-friendly restaurants, never had a problem, aside for that one time I urinated on the coffee shop floor.
Q: Humans often purport to know what a dog is going through, some even create social media accounts for them. What do you think of that?
A: A person of human ancestry can’t possibly know the lived experience of a dog.
Q: You mentioned vegetable sticks. Are you a vegetarian?
A: No. I have never understood the appeal of it. I just like to chew the sticks. (Sometimes I eat apples or bell peppers, but it takes work when you don’t have molars. A lot of “crunch, crunch, crunch” with my jaw.)
Q: What’s behind the alias “The Opportunist” which you said you don’t like.
A: Whenever one of the traffickers opens the refrigerator, I tend to show up in in short order.
Q: I see how that could be insulting. How would you describe your current vocation?
A: I was named “Calorie Acquisition Specialist” recently, but I also work in security.
Q: Security?
A: I make sure to let everyone know when someone’s at the front door.
Q: What goes through your mind in those cases? Are you scared?
A: Not really. Imagine if you were fast asleep and the voice of God at volume 11 screamed into your mind: “WHO THE FUCK IS AT THE DOOR!!!!!!!!!”
Q: Speaking of God, can you tell us about the time you helped a woman on the street connect with Him?
A: We were walking back from Parque Eduardo VII (by the way, Portuguese is my native language), and a woman with two regular size dachshunds, saw me, started shrieking and proclaimed, “your dog is so beautiful he proves the existence of God!”
Q: Wow. It really hit home for her. Let’s talk about your work. How do you stay in character so consistently? How do you maintain your role as a dog?
A: I was incarnated in a dog body and therefore have dog consciousness. Everything I do is a reflection of that basic fact.
Q: Some serious method acting!
A: You could call it that. I am fully immersed in the role.
Q: A lot of humans speak about past lives, can even recall them under hypnosis. Do you think you will be ever reincarnated as a dog, stuck in an infinite dog-loop, so to speak, or will you one day jump into a human body?
A: I don’t know. I focus on the present.
Q: Oscar, it’s been such a pleasure to talk with you. I really appreciate your making the time.
(buzzer sounds)
A: WHO THE FUCK IS AT THE DOOR!!!!!!!!!!!!!!
-
 @ 9a4acdeb:1489913b
2025-02-16 18:26:58
@ 9a4acdeb:1489913b
2025-02-16 18:26:58Chef's notes
Original recipe, a favorite of family and friends, and the easiest and fastest prep time meal I make. Like all really good pork recipes, it does take time in the cooker, but it's set-and-forget and requires no attention between starting and serving.
Using fresh herbs and peppers does enhance the meal (especially fresh cilantro if it doesn't taste like soap to you), but this is optional, and it is excellent with dry ingredients.
Excluding the beans and/or tomato makes this meal extra-low carb for those carnivores amongst us, or those sensitive to beans. Frying the shredded cheese in a slick pan is a good way to
It will take up to 15min to come up to pressure, so it may be helpful to pay attention to it to be sure it pressurizes until you become familiar with how this meal acts in your particular pressure cooker. The Instant Pot pressure cookers make this easy.
Details
- ⏲️ Prep time: 20min
- 🍳 Cook time: 2hrs
- 🍽️ Servings: 6
Ingredients
- 4lbs Pork loin
- 1-2 Yellow onion, roughly chopped
- 3-5 Jalapeños or 1x 4oz canned
- 6-8 Green chilis or 1x 4oz canned
- 2oz canned sliced Black olives (may use half a 4oz can)
- 2-3tsp minced garlic, or 1-2 tsp garlic powder
- A small bunch of cilantro, chopped, or 1-2 tsb dried cilantro (optional)
- 1tbsp Oregano, chopped fresh or dried
- 2-3tsb Chili powder; Ancho, Chipotle, or a blend of the two is best
- 2-3tsb ground Cumin
- 3-4tsp salt
- 2-tsp black pepper
- 1 large or 4oz canned tomato (optional)
- Mexican mix shredded cheese (topping)
- 4oz Black beans (optional)
- Tortillas (optional)
- Avocado (optional toping)
- 6 Limes and/or 3oz lime juice
Directions
- Mix dry seasonings
- Chop and mix fresh herbs and veggies, canned or otherwise
- Add chopped onion to bottom of pressure cooker
- Add pork loin atop the onion; chopping into steaks may make the texture better
- Add veggies to the top, shaking to settle into the pressure cooker
- Add lime juice
- Start on high pressure for 2hrs.
- (Optional) Drain the broth into a saucepan, cook down, and add back into the mix to make it extra flavorful. Otherwise, can be served as a soup or poured over rice.
- Serve with cheese as a topping, over rice, in a tortilla as tacos or burritos, or in a number of other fashions you may fancy. Those who prefer a little more lime may squeeze fresh or splash some more on their meal.
- (Optional) For presentation, garnish with cilantro and lime slices, maybe a dollop of shredded cheese, sour cream, or cream cheese.
-
 @ 5d4b6c8d:8a1c1ee3
2025-02-16 17:19:37
@ 5d4b6c8d:8a1c1ee3
2025-02-16 17:19:37Here are today's picks (there are a ton of them today) using my proprietary betting strategy at Freebitcoin. For details about what Risk Balanced Odds Arbitrage is and why it works see https://stacker.news/items/342765/r/Undisciplined.
For a hypothetical 1k-ish wager on each match, distribute your sats as follows:
| Outcome 1 | Outcome 2 | Outcome 3 | Bet 1 | Bet 2 | Bet 3 | |--------------|-------------|--------------|-------|-------|-------| | Torino| AC Milan| Draw | 269| 476| 278| | Inter Milan| Genoa| Draw | 765| 71| 156| | Como| Napoli| Draw | 256| 464| 294| | Cagliari| Juventus| Draw | 213| 556| 267| | Balogna| AC Milan| Draw | 348| 407| 303| | Valencia| Atletico Madrid| Draw | 208| 550| 270| | Sevilla| Real Mallorca| Draw | 464| 253| 313| | Real Sociedad| Leganes| Draw | 636| 133| 267| | Real Madrid| Girona| Draw | 760| 105| 167| | Las Palmas| Barcelona| Draw | 105| 750| 164| | RB Leipzig| Heidenheim| Draw | 688| 143| 196| | FC Bayern| Eintracht Frankfurt| Draw | 786| 91| 133| | Dortmund| Union Berlin| Draw | 621| 182| 231| | Arsenal| West Ham| Draw | 763| 77| 167| | Aston Villa| Chelsea| Draw | 364| 392| 266| | Chelsea| Southampton| Draw | 818| 67| 143| | Everton| Man United| Draw | 333| 381| 303| | Ipswich| Tottenham| Draw | 286| 476| 256| | Liverpool| Newcastle| Draw | 652| 161| 217| | Man City| Liverpool| Draw | 348| 421| 256| | Man United| Ipswich| Draw | 636| 167| 227| | Newcastle| Nottingham Forest| Draw | 541| 235| 250| | Tottenham| Man City| Draw | 222| 594| 222| | Nottingham Forest| Arsenal| Draw | 200| 579| 244|
I'll be curious to see how @Coinsreporter does with his modified RBOA.
On the most recently completed set of RBOA, I made 6k sats on 43k wagered, so it was a nice bounce back.
I still haven't precisely identified where the threshold is, but it might be worth skipping any of these with a "time weight multiplier" lower than 90.
A note of caution about Freebitcoin: they recorded the wrong outcome for last week's Bills vs Ravens game and as of yet have not corrected it. I recall one other instance of something similar happening, so proceed with caution.
This RBOA strategy is largely immune from that problem, but be aware of it when just betting on one outcome.
originally posted at https://stacker.news/items/887548
-
 @ c1e6505c:02b3157e
2025-02-08 21:52:51
@ c1e6505c:02b3157e
2025-02-08 21:52:51***"Time is the best teacher but unfortunately it kills all of its students."*** I'm currently visiting my dad for a few days as I had to take my car in for some repairs and maintenance, which included an oil gasket leak, power steering fluid flush, brake fluid flush, spark plugs, and the works. The process took a couple of hours to complete, so instead of waiting in the waiting room or having someone pick me up to go wait comfortably at home, I decided to walk around with my camera and try to make some new work. I have to say, there's really nothing more that I enjoy than walking aimlessly in an area that I have never been and taking photographs. *I love it.* I lose myself and everything that is on my mind that I "worry" about. I'm present, in the zone, and honestly having a great time. Photography for me is a portal to enter a state of mind that transcends time and space. The area that I was in was very industrial, so my walk started next door at the other car mechanic shop, and I meandered down to the small local town where some shops were. Didn't see too much, so I turned around and started walking back down the other way. Sometimes I don't see anything of interest for a while. What I have noticed though, as a little trick to start having things "come out of the woodwork," is just to start shooting at the first thing that captures my interest. Getting the ball rolling with pushing the shutter somehow gets me in the "flow state" that I enjoy getting in when making photographs. \[ \]( As I walked further, I visited a plant nursery that was just opening. The woman who was opening the gate was very nice and invited me into walk around and do as I please. There were a few nice plants around, but what gravitates me the most is seemingly, to others maybe, the "ugly stuff" or the subject matter that one wouldn’t really consider making a photograph of. Blank spaces, trash, neglect - it's all good stuff to me. The light falling upon these subjects makes them interesting. After the nursery, I found a large industrial facility and a train yard. A worker stood next to one of the train cars, so I went up and asked what they were loading. He said that he’s been working there for 30 years, and that they make plastic trash bags, and those tubes feeding into the train cars were pumping out plastic beads for production. I thought that was interesting. We chatted for a bit, I thanked him for his time, and moved on.           Eventually, I ended up at a church with these really nice orange and brown doors. I sat on a bench in the back to kill some time, listening to a few podcasts. While I was there, I noticed a sign that read: *"Happy moments, praise God. Difficult moments, seek God. Quiet moments, worship God. Painful moments, trust God. Every moment, thank God."* I’m not a religious guy per se, haven’t been to church in over a decade, and I’ve had my own experiences — psychedelics included — where I’ve glimpsed something I’d call “God.”, but there’s something to take from that. Whatever your definition of “God” is, there’s value in gratitude whether things are good or bad. Life itself is a miracle. Appreciating the small things keeps you grounded, humble, and connected.   ) *Just in case you missed it…* **I have a limited edition framed print that I will have available until February 28th.** Only two will be made, and they will come framed; one in black, one in silver. If you enjoy my work, this would be a great collectors piece. \]() ***I shoot with a Leica M262, and edit in Lightroom + Dehancer*** [***Use “PictureRoom” for 10% off Dehancer Film***](https://www.dehancer.com/shop/pslr/film) If you’ve made it this far, thank you for taking the time to view my work - I appreciate it. Please consider becoming a paid subscriber to support my work. Also, please contact me if you would like to purchase any of my prints.  [Dehancer Film (promo code "PICTUREOOM")](https://www.dehancer.com/shop/pslr/film) *If you've found value in this newsletter, I'd be incredibly grateful for your support. While these posts will always be freely available, becoming a paid subscriber helps ensure I can continue delivering quality content to your inbox. Share this newsletter with friends, leaving a comment, or simply hitting the 'like' button all make a difference.* Thank you - Colin
-
 @ 41fa852b:af7b7706
2025-02-16 15:52:51
@ 41fa852b:af7b7706
2025-02-16 15:52:51"Our lives begin to end the day we become silent about things that matter." --Martin Luther King, Jr
If Bitcoin's price action is putting you to sleep, maybe it's time to get out and add some spice to your life.
It's a big week with 12 meetups--check out the list below and see if there's one near you.
Most meetups are drop-in friendly--just head to the venue and keep an eye out for a few shady-looking characters in Bitcoin merch. If you'd prefer some certainty, you can find contact details for every meetup at bitcoinevents.uk. Just scroll down to find your meetup group, and you'll see how to get in touch.
Let's dive in…
This week's sponsor is…
Upcoming Bitcoin Meetups
Happening this week…
-
Newcastle Bitcoin Meetup: A relaxed gathering for anyone interested in Bitcoin. No prior experience or ownership of Bitcoin is required, just curiosity and an interest. Conversations are Bitcoin-only focused. Happening this month on Tuesday, February 18th, at 18:30. Find them at Kabin @ Kabannas, NE1 6UQ. 🍻
-
Bitcoin 101: Nodes at Cyphermunk House - Participants are invited to a hands-on, peer-led class to set up their own Bitcoin node. Those wishing to build a node during the session should bring an old laptop, computer, or mini PC, along with a 2TB SSD and a USB drive with at least 4GB of storage. Attendees are also welcome to join without building a node to learn from the process. Tickets cost £9 in sats or £10 in cash, with pre-booking available at cyphermunkhouse.com/events.. 👨🏼🎓
-
Bitcoin Glasgow: Bitcoin Glasgow meet every 3rd Wednesday of the month and this month will be at The Maltman, 59--61 Renfield Street at 18:00 to 20:00. This month on Wednesday the 19th. 🍺
-
Bitcoin Wales: Back in action with the first meetup of 2025, and looking to grow their membership. The gathering at Zerodegrees, 27 Westgate St, Cardiff CF10 1DD invites both seasoned Bitcoiners and newcomers to connect, share ideas, and shape the future of Bitcoin in Wales. 18:00 - 21:00 on Wednesday 19th February. 🍻
-
OPA London Bitcoin Meetup: The first OPA London Bitcoin Meetup takes place on Wednesday 19th at 18:30 - 21:30 at the Century Club (Bitcoin accepted), 61--63 Shaftesbury Ave, London W1D 6LQ. 🍺🍷🍸
-
Shropshire Bitcoin: On the 19th, the Shropshire crew will be meeting at the Admiral Benbow in Shrewsbury. 🍻
-
Brum Bitcoin & Beer: If you're in the Birmingham area head along to meet some fellow bitcoiners on Thursday 20th at 19:00. You'll find them this month at The Wellington, Bennett's Hill, B2 5SN. 🍺
-
Bitcoin Bristol: Meeting at The Left Handed Giant, BS1 6EU, at 18:15 on the 21st. Everyone is welcome, the aim is to encourage grassroots bitcoin adoption in Bristol. 🍻
-
2140 Collective: Tools of freedom - GrapheneOS workshop. Learn about GrapheneOS the privacy-focused mobile operating system. Friday 21st February, 18:00 - 21:40 at Cyphermunk House. 👨🏼🎓📱
-
Bitcoin Walk - Edinburgh: Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏽♂️🚶🏼♀️🚶🏻
-
Plymouth Bitcoiners: The Plymouth meetup is on the 22nd this month. Find them at Steel Brew, PL1 3GD at 14:00. 🍻
-
Bitcoin East: Join Bitcoin East in Bury St. Edmunds on Sunday 23rd, 10:00 at Procopio's Pantry and then on to Vespers Bar at 12:00. All welcome, Bitcoiners and anyone else curious about Bitcoin. 🍻☕️
Get Involved
- Volunteer Opportunities: Bridge2Bitcoin is actively seeking volunteers who share our passion for merchant adoption. We'd be delighted to connect if you're eager to contribute. Reach out to us on Twitter or through our website.
- Start Your Own Meetup: Interested in launching a Bitcoin meetup? We're here to support you every step of the way. We've assisted numerous UK Bitcoin meetups in getting started. Get in touch via Twitter.
- Contribute to BTCMaps: BTCMaps is a vital part of the Bitcoin ecosystem. It's a perfect project to get involved with if you're not a coder or even that technical. A great way to give back to the community. Maintain an area of the UK and keep it up-to-date.
- Telegram users: You might find our Telegram Channel another useful way to keep up-to-date with UK meetups.
- Feedback and Suggestions: We value your input! Share your ideas on how we can enhance this newsletter.
This week's sponsors are…
Get out and support the meetups where you can, visit Bitcoin Events UK for more info on each meetup and to find your closest on the interactive map.
Stay tuned for more updates next week!
Simon.
-
-
 @ 3b7fc823:e194354f
2025-02-07 18:42:31
@ 3b7fc823:e194354f
2025-02-07 18:42:31Privacy in Public Spaces: A Tactical Guide
1. Public Wi-Fi Privacy
Using public Wi-Fi can be convenient, but it's important to take precautions to protect your privacy:
- Use a VPN (Virtual Private Network): A VPN encrypts your internet traffic, making it difficult for hackers to intercept your data.
- Disable Automatic Connections: Prevent your device from automatically connecting to open Wi-Fi networks by turning off this feature in your settings.
- Avoid Sensitive Transactions: Refrain from accessing banking or other sensitive accounts while connected to public Wi-Fi.
- Use Secure Websites: Look for "https://" in the website's URL to ensure it uses encryption.
- Keep Software Updated: Ensure your device's operating system and apps are up-to-date to protect against security vulnerabilities.
2. Surveillance Camera Awareness
Surveillance cameras are common in public spaces. Here are some strategies to maintain your privacy:
- Spotting Cameras:
- Look for Signs: Many establishments post signs indicating the presence of surveillance cameras.
- Camera Placement: Cameras are often placed near entrances, exits, and high-traffic areas. Look for dome-shaped cameras on ceilings or wall-mounted cameras.
- Using Masks and Coverings:
- Face Masks: Wearing a mask can help obscure your facial features from facial recognition systems.
- Hats and Sunglasses: A hat can shield your face from overhead cameras, while sunglasses can hide your eyes.
- Covering Identifying Marks:
- Clothing Choices: Wear clothing that doesn't have distinctive logos or patterns that can easily identify you.
- Blend In: Opt for styles and clothing choices that helps you blend in with your surroundings, reducing your visibility.
- Temporary Coverings: Consider using temporary coverings, such as scarves or hoods, to conceal tattoos or other identifying marks.
3. General Privacy Tips in Public Spaces
- Be Mindful of Your Surroundings: Pay attention to your environment and be aware of any unusual behavior or devices that may be capturing your information.
- Limit Personal Information: Avoid discussing sensitive information in public where it can be overheard.
- Use Encrypted Messaging Apps: Apps like Signal or SimpleX offer end-to-end encryption for your messages, making it harder for eavesdroppers to intercept your conversations.
- Use Privacy Screens: Privacy screens on all of you electronic screens can defend against the over the shoulder peek or side eye.
- Avoiding Behaviors: Be mindful of behaviors that could make you a target, such as frequent visits to certain areas or engaging in conversations that might attract unwanted attention.
Taking these steps can help you maintain your privacy while navigating public spaces and using public Wi-Fi. Remember, staying informed and vigilant is key to protecting your personal information.
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-
 @ 6ad3e2a3:c90b7740
2025-02-07 08:17:18
@ 6ad3e2a3:c90b7740
2025-02-07 08:17:18When I used to work in fantasy sports, people would ask me questions about their teams, e.g., which players to start, who to drop. What they didn’t realize is I had seven of my own teams to worry about, was already living and dying with my own myriad choices, good and bad, I made every week. The last thing I needed was to make a decision for them, see it go bad and suffer more on their account.
I’d tell them, “You decide, I’ve got my own problems.”
. . .
I don’t know what I’m doing. Ideas which feel like insights come to me, I try to articulate them to my satisfaction and post them (with some editing help from Heather.) Often I feel like I should be producing more work — after all, I don’t have a job any more, I have plenty of time. Walking the dog, exercising, managing your finances, picking up the kid, putting food on the table (literally) is well and good, but fulfilling your duties is not enough. You need to stay in the game. What game is up to each person, but it should be a game you enjoy, one that draws on skills honed over decades by the accident of your particular interests.
. . .
Writing and ideas can’t be produced on demand. I mean they can — and I did it for 22 years on a particular topic — but I don’t mean that kind of writing. I don’t want a schedule. I don’t need more rules, more discipline, more “hacks.” Discipline is like the interest on a 30-year mortgage. Initially it’s most of the payment, but over time it cedes weight to understanding which is like the principal. Discipline without understanding is like an interest-only mortgage. You pay it every month and get nowhere.
Even when insights arrive they can’t always be articulated sufficiently and coherently. Many insights are of the one sentence variety — fine for a social media post, but you can’t send out an email newsletter 10 times per day with one sentence insights. It doesn’t work over that medium.
That’s a dilemma because posting on social media doesn’t feel like proper work. Yes, you’re reaching people, affecting the zeitgeist in whatever small way — but there’s something addictive and unsatisfying about it, like eating candy instead of food. Don’t get me wrong, I stand by my posts (consider them organic, artisanal candy) but shitposting and the immediate feedback received therefrom keeps you only on the periphery. I need to connect with something deeper.
. . .
I’ve spent a lot of time dissecting the various pathologies of the laptop class, of which I’m obviously a part as I literally type this in a coffee shop on my laptop! The need to believe they are empathic and good overwhelming any rational sense-making and basic morals. Men dominating women’s sports, child sex changes, forced injections, criminals running rampant, cities in decay, calls for censorship and funding for foreign wars. The authorities patted them on the back, their peers accepted them and their overlords promoted them so long as they hewed to the narrative.
The freakout we’re presently witnessing is not about the billions in taxpayer money no longer being sent for DEI training in some foreign country, i.e., money-laundering to favored interests and cronies. They’re not really upset FBI agents are being fired, secrets are being revealed, that we are finally making an effort to prevent fentanyl from flowing across the border and killing our fellow citizens. These are good things, and even if you don’t agree, none of it is grounds for the meltdowns I see every day on social media.
What’s really happening is people who were assured they were the “good”, the empathic, the compassionate ones, those who towed the line during covid, got their boosters, wore their masks, “social distanced,” put pronouns in their bios, are being confronted with a terrifying realization: the behaviors and beliefs, to which they so dutifully attached themselves, for which they publicly and stridently advocated, whether online or at Thanksgiving dinner, are no longer being rewarded. In fact, they are being openly ridiculed. Instead of the pat on the back, increasingly Team Good is facing mockery and outright scorn.
There will be no legal consequences. No one will be arrested or put in a camp, delusions of persecution notwithstanding. If you produce real value for a real employer, you are not at risk of being fired. If you insist on perpetuating your derangement on social media you will not be deplatformed or canceled (that only happens to people speaking the truths inconvenient to the powerful.)
No, the reality is in some ways far worse: your entire worldview, on which you staked your self-image, is being dismantled in real time. You are no longer “good,” it’s becoming obvious to most the policies for which you advocated were catastrophic, the politicians for whom you voted deeply cynical and corrupt. The gaping abyss within your being to which you attached this superstructure of self-affirmation is dissolving into thin air. You are not “superior” like you thought, you are just another person suffering and existing like everyone else. And your only choices are to face that daunting reality or cling to a dying and useless paradigm, the end game for which is only madness.
We all want to feel good about ourselves, and like an obese person drugging themselves with high-fructose corn syrup for years, you have gorged on the distorted approbation of a sick society that, unpleasantly for you, is starting to heal. Your first laps around the track, so to speak, are going to hurt a lot.
. . .
I probably went on too long about the laptop class freakout. I have a lot of resentment toward the way they behaved the last five years. But I started this essay with the idea that I have my own problems, and in the end, I am not much different from them.
I want to produce more work, and of higher quality, but to what end? To feel good about my contributions, to have a sense that I am “good.” Maybe it’s not “good” in the lame “I complied with authority, and everyone likes me” kind of way, but it arises from the same source. That source is the emptiness within, wherein we require accolades, dopamine, positive feedback as a kind of justification for our existence. “No, I am not squandering my time on earth, living a comfortable life, I am asking hard questions, connecting with people, sharing hard-won insights. I am useful! I am good! I got my sixth dopamine booster from writing yet another essay!”
. . .
There is an irony in writing this piece. I feel as I type the cathartic nature of expressing these feelings. I am doing something worthwhile, everything is flowing out of me, the minutes are sailing by. I am identifying and solving this thorny problem simultaneously, engaging with the emptiness and dissatisfaction. The solution isn’t in the output, whatever one might think of it, it’s in giving attention to the feelings I’ve squandered too much time avoiding. I feel unworthy not because I do not produce enough work, it turns out, but because I am unwilling to connect with my deepest nature.
. . .
No matter how uneasy you feel, no matter how much fundamental doubt you have about your value as a human being, you can always start where you are. The feeling of unworthiness, the need for an escape, the craving for some kind of reward from your peers or the authorities or whatever easily-consumed carbohydrates you have in the kitchen is simply the present state in which you find yourself. It is not wrong or bad, it just is. And what is can always be examined, observed, given attention. Attending to that discomfort is always within reach.
. . .
The last thing I want to do is write an essay, face a purgatory of sitting down and consciously putting my feelings into words. It’s so much easier to distract oneself with all the news about the world, check 100 times a day the price of bitcoin and my other investments. But purgatory is the only way out of hell. The hell of wanting to succeed, of wanting to become “good.”
For some, that astroturfed worldview they so painstaking affixed to their empty souls is dissolving toward a revelation of the emptiness beneath. And unsurprisingly they are freaking out. But I’ve wasted too much time arguing with them, pointing out the ways in which they’re misinformed, driven by fear and derelict in their basic epistemic responsibilities. If you want to hold onto the lies you were told, knock yourself out. I’ve got my own problems.
-
 @ 3ffac3a6:2d656657
2025-02-06 03:58:47
@ 3ffac3a6:2d656657
2025-02-06 03:58:47Motivations
Recently, my sites hosted behind Cloudflare tunnels mysteriously stopped working—not once, but twice. The first outage occurred about a week ago. Interestingly, when I switched to using the 1.1.1.1 WARP VPN on my cellphone or PC, the sites became accessible again. Clearly, the issue wasn't with the sites themselves but something about the routing. This led me to the brilliant (or desperate) idea of routing all Cloudflare-bound traffic through a WARP tunnel in my local network.
Prerequisites
- A "server" with an amd64 processor (the WARP client only works on amd64 architecture). I'm using an old mac mini, but really, anything with an amd64 processor will do.
- Basic knowledge of Linux commands.
- Access to your Wi-Fi router's settings (if you plan to configure routes there).
Step 1: Installing the WARP CLI
- Update your system packages:
bash sudo apt update && sudo apt upgrade -y- Download and install the WARP CLI:
```bash curl https://pkg.cloudflareclient.com/pubkey.gpg | sudo gpg --yes --dearmor --output /usr/share/keyrings/cloudflare-warp-archive-keyring.gpg
echo "deb [arch=amd64 signed-by=/usr/share/keyrings/cloudflare-warp-archive-keyring.gpg] https://pkg.cloudflareclient.com/ $(lsb_release -cs) main" | sudo tee /etc/apt/sources.list.d/cloudflare-client.list
sudo apt-get update && sudo apt-get install cloudflare-warp ``` 3. Register and connect to WARP:
Run the following commands to register and connect to WARP:
```bash sudo warp-cli register sudo warp-cli connect ````
Confirm the connection with:
bash warp-cli status
Step 2: Routing Traffic on the Server Machine
Now that WARP is connected, let's route the local network's Cloudflare-bound traffic through this tunnel.
- Enable IP forwarding:
bash sudo sysctl -w net.ipv4.ip_forward=1Make it persistent after reboot:
bash echo 'net.ipv4.ip_forward=1' | sudo tee -a /etc/sysctl.conf sudo sysctl -p- Set up firewall rules to forward traffic:
bash sudo nft add rule ip filter FORWARD iif "eth0" oif "CloudflareWARP" ip saddr 192.168.31.0/24 ip daddr 104.0.0.0/8 accept sudo nft add rule ip filter FORWARD iif "CloudflareWARP" oif "eth0" ip saddr 104.0.0.0/8 ip daddr 192.168.31.0/24 ct state established,related acceptReplace
eth0with your actual network interface if different.- Make rules persistent:
bash sudo apt install nftables sudo nft list ruleset > /etc/nftables.conf
Step 3: Configuring the Route on a Local PC (Linux)
On your local Linux machine:
- Add a static route:
bash sudo ip route add 104.0.0.0/24 via <SERVER_IP>Replace
<SERVER_IP>with the internal IP of your WARP-enabled server. This should be a temporary solution, since it only effects a local machine. For a solution that can effect the whole local network, please see next step.
Step 4: Configuring the Route on Your Wi-Fi Router (Recommended)
If your router allows adding static routes:
- Log in to your router's admin interface.
- Navigate to the Static Routing section. (This may vary depending on the router model.)
- Add a new static route:
- Destination Network:
104.0.0.0 - Subnet Mask:
255.255.255.0 - Gateway:
<SERVER_IP> - Metric:
1(or leave it default) - Save and apply the settings.
One of the key advantages of this method is how easy it is to disable once your ISP's routing issues are resolved. Since the changes affect the entire network at once, you can quickly restore normal network behavior by simply removing the static routes or disabling the forwarding rules, all without the need for complex reconfigurations.
Final Thoughts
Congratulations! You've now routed all your Cloudflare-bound traffic through a secure WARP tunnel, effectively bypassing mysterious connectivity issues. If the sites ever go down again, at least you’ll have one less thing to blame—and one more thing to debug.
-
 @ 5d4b6c8d:8a1c1ee3
2025-02-16 15:25:37
@ 5d4b6c8d:8a1c1ee3
2025-02-16 15:25:37After gorging on Valentine's leftovers (cc: @realBitcoinDog), I did stop eating or drinking pretty early in the afternoon. Then just as I was about to sit down for coffee this morning, I was informed that my wife was out of the soymilk she likes with her coffee. So, a little trip to the store prolonged the fast further.
Score Card Day 1: 14 hour fast (13 dry) Day 2: 15 hour fast (14 dry) Day 3: 17 hours (16 dry) Day 4: 18 hours (17 dry) Day 5: 18 hours (16 dry) Day 6: 19 hours (16 dry) Day 7: 16 hours (15 dry) Day 8: 18 hours (17 dry) Day 9: 17 hours (17 dry) Day 10: 15 hours (13 dry) Day 11: 20 hours (19 dry) Day 12: 20 hours (17 dry) Day 13: 16 hours (13 dry) Day 14: 17 hours (15 dry) Day 15: 19 hours (16 dry) Day 16: TBD (19 dry)
originally posted at https://stacker.news/items/887459
-
 @ 1833ee04:7c4a8170
2025-02-04 15:14:03
@ 1833ee04:7c4a8170
2025-02-04 15:14:03The international race for Bitcoin strategic reserves is just getting started.
If you’re stacking now, you’re still incredibly early.
At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.
Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?
Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.
The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.The international race for Bitcoin strategic reserves is just getting started.\ \ If you’re stacking now, you’re still incredibly early.\ \ At $100k per Bitcoin, it’s practically free for anyone who truly understands how massive this shift is.\ \ Think back to when paper currency was introduced, people had to trade their gold for paper bills. Many laughed, saying, Who’s going to trust these worthless pieces of paper as money?\ \ Yet today, you sell your time to earn these paper bills while your government can print an unlimited amount at will.\ \ The world is returning to a gold standard. But this time, it’s Gold 2.0 which is Bitcoin.
-
 @ bbef5093:71228592
2025-02-16 14:17:12
@ bbef5093:71228592
2025-02-16 14:17:12A trícium érdekességei
A trícium a hidrogén lenyűgöző radioaktív formája, amely háromszor nehezebb, mint a közönséges hidrogén, és egy protont, valamint két neutront tartalmaz az atommagjában. Ernest Rutherford és csapata 1934-ben fedezte fel, és 12,32 éves felezési idővel rendelkezik.
Főbb alkalmazási területek
Világítástechnika A tríciumot önvilágító eszközökben használják energiaforrásként, például órák kijelzőiben és vészkijárati táblákban, ahol foszforokat aktivál, hogy folyamatos fényt bocsásson ki elektromos áram nélkül.
Tudományos kutatás A tudósok radioaktív nyomjelzőként használják orvosi kutatásokban és gyógyszerfejlesztésben, kihasználva azt a tulajdonságát, hogy kémiai reakciókban úgy viselkedik, mint a normál hidrogén. Kiemelkedő szerepet játszik a felszín alatti vizek kormeghatározásában is. Az 50 évnél fiatalabb vizek esetében a trícium-koncentráció mérése megbízható módszer, mivel az 1953-63 közötti magaslégköri nukleáris kísérletek egyedi "időbélyeget" hagytak a csapadékvizekben.
Vízföldtani alkalmazások
Vízbázisok védelme A trícium-vizsgálatok kiválóan alkalmasak a felszín alatti vízbázisok védettségének és a felszíni vizek elérési idejének meghatározására. A trícium ideális víznyomjelző, mivel beépül a vízmolekulába (HTO formában), és tökéletesen követi a víz mozgását.
Nukleáris létesítmények monitorozása A talajvíz trícium-tartalmának rendszeres megfigyelése kulcsfontosságú a nukleáris létesítmények környezetében, mivel segít azonosítani az esetleges szivárgásokat és a radioaktív anyagok terjedését a felszín alatti vizekben.
Nukleáris alkalmazások Az izotóp kulcsszerepet játszik a nukleáris fúzióban mint üzemanyag a tokamak reaktorokban, és "erősítőként" szolgál a nukleáris fegyverekben.
Biztonsági profil Bár radioaktív, a trícium csak alacsony energiájú béta-sugárzást bocsát ki, amely nem képes áthatolni az emberi bőrön. Természetes körülmények között nyomokban megtalálható a légkörben, ahol kozmikus sugárzás hatására keletkezik.
Tritium, the ideal tracer
Interesting Facts About Tritium
Tritium is a fascinating radioactive form of hydrogen that's three times heavier than regular hydrogen, containing one proton and two neutrons in its nucleus. It was first discovered by Ernest Rutherford and his team in 1934 and has a half-life of 12.32 years.
Main Applications
Illumination Technology Tritium is used as an energy source in self-illuminating devices, such as watch displays and exit signs, where it activates phosphors to create continuous light without electrical power.
Scientific Research Scientists use tritium as a radioactive tracer in medical research and pharmaceutical development, taking advantage of its ability to behave like normal hydrogen in chemical reactions. It also plays a crucial role in dating groundwater. For waters less than 50 years old, measuring tritium concentration is a reliable method, as atmospheric nuclear tests between 1953-63 left a unique "timestamp" in precipitation.
Hydrogeological Applications
Protection of Water Resources Tritium studies are excellent for determining the protection status of underground water resources and the arrival time of surface waters. Tritium is an ideal water tracer as it incorporates into water molecules (as HTO) and perfectly follows water movement.
Monitoring Nuclear Facilities Regular monitoring of groundwater tritium content is crucial around nuclear facilities, as it helps identify potential leaks and the spread of radioactive materials in groundwater.
Nuclear Applications The isotope plays a key role in nuclear fusion as fuel in tokamak reactors and serves as a "booster" in nuclear weapons.
Safety Profile Although radioactive, tritium only emits low-energy beta radiation that cannot penetrate human skin. It naturally occurs in trace amounts in the atmosphere, formed by cosmic ray interactions.
-
 @ 3ffac3a6:2d656657
2025-02-04 04:31:26
@ 3ffac3a6:2d656657
2025-02-04 04:31:26In the waning days of the 20th century, a woman named Annabelle Nolan was born into an unremarkable world, though she herself was anything but ordinary. A prodigy in cryptography and quantum computing, she would later adopt the pseudonym Satoshi Nakamoto, orchestrating the creation of Bitcoin in the early 21st century. But her legacy would stretch far beyond the blockchain.
Annabelle's obsession with cryptography was not just about securing data—it was about securing freedom. Her work in quantum computing inadvertently triggered a cascade of temporal anomalies, one of which ensnared her in 2011. The event was cataclysmic yet silent, unnoticed by the world she'd transformed. In an instant, she was torn from her era and thrust violently back into the 16th century.
Disoriented and stripped of her futuristic tools, Annabelle faced a brutal reality: survive in a world where her knowledge was both a curse and a weapon. Reinventing herself as Anne Boleyn, she navigated the treacherous courts of Tudor England with the same strategic brilliance she'd used to design Bitcoin. Her intellect dazzled King Henry VIII, but it was the mysterious necklace she wore—adorned with a bold, stylized "B"—that fueled whispers. It was more than jewelry; it was a relic of a forgotten future, a silent beacon for any historian clever enough to decode her true story.
Anne's fate seemed sealed as she ascended to queenship, her influence growing alongside her enemies. Yet beneath the royal intrigue, she harbored a desperate hope: that the symbol around her neck would outlast her, sparking curiosity in minds centuries away. The "B" was her signature, a cryptographic clue embedded in history.
On the scaffold in 1536, as she faced her execution, Anne Boleyn's gaze was unwavering. She knew her death was not the end. Somewhere, in dusty archives and encrypted ledgers, her mark endured. Historians would puzzle over the enigmatic "B," and perhaps one day, someone would connect the dots between a queen, a coin, and a time anomaly born from quantum code.
She wasn't just Anne Boleyn. She was Satoshi Nakamoto, the time-displaced architect of a decentralized future, hiding in plain sight within the annals of history.
-
 @ c3c7122c:607731d7
2025-02-16 07:48:35
@ c3c7122c:607731d7
2025-02-16 07:48:35At my meet up (the SD Bitcoiners Cete) on Thursday, I presented trends on the Bisq protocol. One of its features is that anyone can export the trade history and analyze it. Bisq is a private, peer-tp-peer way to buy and sell bitcoin. All data are based on the BTC-USD market.
Trade number decreased in 2024

But USD volume increased ($/year)

(same graph but $/day by year)

Which means more higher value per trade

Interestingly, trade counts and price volatility lead to interesting BTC volume per year. The peaks are nearly identical (330 BTC)!

Not so surprising when you compare BTC volume traded to the average BTC price that year, local price valleys mean local peaks in BTC traded (and vice versa).

I separate fiat payment methods into three groups.

All USD payment methods used in 2024 by average value (y-axis) and number of trades (bubble size)

This is the same graph as above excluding Zelle and Strike, since they throw off the relative circle size (face-to-face only had 1 trade in 2024).

Two fiat methods had >1000 trades in 2024. Strike came on the scene hot in 2021 and ate some of the Zelle volume but that may have stabilized.

Six fiat methods had 200-1000 trades in 2024. Amazon Gift Card dwindling, Cash By Mail still top of this group, and Revolut surging (wtf is Revolut?)

Same group, all years

Last group is <200 trades in 2024. Basically unused, except for Wire Transfer increasing.

Same group, all years

What's the average trade size by fiat method? There are different reasons for this, largely driven by fiat fees and bank limits. Amazon Gift Card is an interesting option for smaller payments (note: you can't just send any gift card, there is a very specific process, see the Bisq wiki)

There no KYC premium, but there is a small Surveillance Discount

If you open Bisq for the first time, you'll likely see spreads 3-5% or larger. These offers persist because no one wants them. So people think that Bisq is "too expensive." But let's dig into the actual trades...

Comparing the daily trade volume to daily market rate (I used coingecko), and creating a monthly weighted average, the true surveillance discount emerges. It's not 3-5% as you might see in the order book at any given time. In fact, it was cheaper to trade on Bisq than exchanges in November and December! (Note: this does not take into account the 4 on-chain transactions required for a trade or price spread/fees used by exchanges)

In 2024, Strike had the worst surveillance discount and Cash By Mail had the best. This isn't surprising because receiving cash is convenient and low risk for a seller so they're willing to accept a lower price. Zelle (the most common USD payment method) had the second best surveillance discount.

Now let's compare the surveillance discount by week in 2024 for select payment methods.
Strike was consistently worse than Zelle

Revolut was sometimes way worse than Zelle but sometimes a little better.

The two most private payment methods are cash and money order. They're pretty competitive regarding surveillance discount.

Take aways * Be a maker and get a better price (fees are better too) * Zelle is better for speed + convenience * Amazon gift cards are good for speed + privacy (sorta) * Cash or money order are better for privacy + volume
-
 @ 97c70a44:ad98e322
2025-02-03 22:25:35
@ 97c70a44:ad98e322
2025-02-03 22:25:35Last week, in a bid to understand the LLM hype, I decided to write a trivial nostr-related program in rust via a combination of codebuff (yes, that is a referral link, pls click), aider, and goose.
The result of the experiment was inconclusive, but as a side effect it produced a great case study in converting a NINO into a Real Nostr App.
Introducing Roz
Roz, a friendly notary for nostr events.
To use it, simply publish an event to
relay.damus.ioornos.lol, and roz will make note of it. To find out when roz first saw a given event, just ask:curl https://roz.coracle.social/notary/cb429632ae22557d677a11149b2d0ccd72a1cf66ac55da30e3534ed1a492765dThis will return a JSON payload with a
seenkey indicating when roz first saw the event. How (and whether) you use this is up to you!De-NINO-fying roz
Roz is just a proof of concept, so don't rely on it being there forever. And anyway, roz is a NINO, since it provides value to nostr (potentially), but doesn't really do things in a nostr-native way. It also hard-codes its relays, and certainly doesn't use the outbox model or sign events. But that's ok, it's a proof of concept.
A much better way to do this would be to modify roz to properly leverage nostr's capabilities, namely:
- Use nostr-native data formats (i.e., draft a new kind)
- Use relays instead of proprietary servers for data storage
- Leverage nostr identities and signatures to decouple trust from storage, and allow trusted attestations to be discovered
Luckily, this is not hard at all. In fact, I've gone ahead and drafted a PR to the NIPs repo that adds timestamp annotations to NIP 03, as an alternative to OpenTimestamps. The trade-off is that while user attestations are far less reliable than OTS proofs, they're much easier to verify, and can reach a pretty high level of reliability by combining multiple attestation sources with other forms of reputation.
In other words, instead of going nuclear and embedding your attestations into The Time Chain, you can simply ask 5-10 relays or people you trust for their attestations for a given event.
This PR isn't terribly important on its own, but it does remove one small barrier between us and trusted key rotation events (or other types of event that require establishing a verifiable chain of causality).
-
 @ deba271e:36005655
2025-02-16 06:49:32
@ deba271e:36005655
2025-02-16 06:49:32Buying groceries with bitcoin rocks! I have been using bitcoin to buy food and stuff in Uvita over the last two months and what a wonderful experience that has been. There are so many places that accept. I went to the local farmers market literally every time it was open (twice a week) to buy veggies, meat, spices, juice, coffee and even clothes. You pay with bitcoin at every stand, payment fully settled sometimes under 1 second. I used bitcoin definitely more than I used fiat.
What is in the basket is what I bought with bitcoin
As is my nature (and nostr job description), I was complaining about the UX to the folks involved across multiple companies/groups here in Uvita, with some issues already fixed and some new features/ideas being worked on. Overall the people working on these projects are amazing. This was so much fun and I hope the folks don't hate me for giving them feedback, feedback, feedback - I always tried to make it as actionable as possible (also I'm hard to argue with when I'm right :P).
My focus has always been on getting more merchants onboarded, getting more people to accept bitcoin, but after a couple weeks in Uvita I realized that at this point the problem here is the opposite. People are not paying with bitcoin.
I talked to many of the sellers, asked them how many people pay, how often. And in reality it's fairly rare for them. In the restaurants they only have a couple times per day when someone pays with bitcoin. At the market only around 10% of people pay with bitcoin, while 95% of the sellers accept. That made me feel a bit sad and surprised. This is a buyer education problem, not a seller problem.
Only a small portion of the folks in the picture will pay with bitcoin…
The word of mouth approach is (imo) a solid strategy to onboard merchants, but it doesn't work for ephemeral tourists. As an example consider a "family with young kids coming for 3 days". This family doesn't have many chances to receive word of mouth. They come from elsewhere, they don't make many connections or interactions with locals.
Sidenote: Physical bitcoin office works like a charm! I would have not guessed that, but I witnessed it being the spot where people meet, where merchants come to ask questions, where new folks ask how to get onboarded. The Bitcoin Jungle team did an amazing job here. If you are starting a circular economy in some town and already have some office space - consider making it into a "Bitcoin Office" (even if your business isn't exactly bitcoin). It will bring you visitors, great friends, bitcoiners will come hang out, etc.
Tourist education
We can assume that in "touristy" areas the restaurants, markets and shops will be mainly visited by tourists, so the solution here is tourist education. Now think about the journey that tourists go through - they come to the area in a car, maybe stop for lunch/dinner and then they check in at their hotel/casa. The next day they go to the local grocery store/market to get supplies and then do touristy stuff - go surfing, beach, hike, drive somewhere, chill, pool, drinks, etc.
The main touch points for where paying with bitcoin could be introduced are: - when entering the town, - at the restaurant, - at the place they check in (hotel, casa), - in the grocery store/market, - in whatever they use to find attractions, - the tour guides, drivers and other folks working in the tourism sector.
Here are couple ideas to make the situation better: - Printed brochure at merchants and hotels/casas: a little printed brochure with the same content available at every merchant - so when someone asks about bitcoin, they can just hand this brochure to them. Doesn't need any technical background or price talk - literally "You can pay with bitcoin here. You need a bitcoin wallet, here's QR to get it. Then you need to get bitcoin, here are the options. Then just pay by scanning the QRs that sellers show you" when you tell them "pagar con bitcoin por favor". - Billboard when entering Uvita: There could be a nice billboard when entering Uvita saying something like "Pay with Bitcoin in Uvita! Welcome to Bitcoin Jungle" and maybe add a link to bitcoinjungle.app and WhatsApp number. - A billboard at the market: a nice printed billboard on the side of the market that shows QR for how to download BitcoinJungle wallet (and some US available wallet), how to get initial sats on it (e.g. ask a specific person at the market, install Strike…). - Discounts: One thing that always attracts an eye is seeing some discount. This could be e.g. included in the brochure - "5% discount when you pay with bitcoin", or "pay with bitcoin, get XYZ for free". Someone may suggest wording "paying with fiat = extra 5% fee", but just from a psychological standpoint that is imo less effective.
And of course having bitcoin signs "SE ACEPTA AQUI" helps…
Good luck! nout
Originally posted at https://stacker.news/items/887222/r/nout
-
 @ 9f0bbd5b:779b33f6
2025-02-16 05:09:59
@ 9f0bbd5b:779b33f6
2025-02-16 05:09:59The next time you see your doctor and get a blood draw (you are doing this every year, yes?) be sure to request that your testosterone levels be tested.
Testosterone is measured as Ng/dL. Ng/dL stands for nanograms per deciliter, which is a unit of measurement used to express the concentration of substances, such as hormones, in the blood. It indicates how many nanograms of a substance are present in one deciliter of blood.
Since the 1960s-70s (the first time data was collected on a large scale), average testosterone levels have been cut nearly in half. You can draw any number of conclusions, when you compare this with the state of our society.
Sedentary lifestyles, processed foods, lack of exercise, sunshine, and sex ... all these things contribute to the feminization of the men in our society. Studies have shown that higher testosterone results in better rational decision making.
Currently, average testosterone levels are lower than they have ever been.
How to raise testosterone: - Eat real food (beef, veg, dairy, fruit) - Stop drinking soda, etc - Get sunshine - Get rid of your gut - Exercise regularly
originally posted at https://stacker.news/items/887187
-
 @ c582af78:698069cc
2025-02-15 19:21:25
@ c582af78:698069cc
2025-02-15 19:21:25The Face of God: How Art Became a Gateway to the Divine
If you live in the West, you’re surrounded by depictions of God, Jesus, and the saints—from paintings and statues to illustrated Bibles and stained glass windows.
But this is far from universal. In the Islamic world, religious art takes a very different form: vibrant colors, intricate geometry, and architectural symmetry. Depictions of God or Muhammad aren’t just discouraged—they are outright forbidden.
But why?
To answer that, we must go back to the origins of the Abrahamic religions—when early Christians, Jews, and Muslims were surprisingly unified in their views on religious art.
https://image.nostr.build/1515c5fd00d798cd283583618bbbc0d5eb91bc481a84c21d53644d42fa30173a.jpg
The Early Christian Hesitation
The first generation of Christians were deeply aware of Judaism’s strict prohibition against idol worship. Depicting God in any form was considered dangerous—a potential gateway to paganism.
For centuries, Christianity could have followed this path, rejecting religious imagery altogether. But one fundamental theological idea changed everything:
The Incarnation.
As the early Church wrestled with the nature of Christ, heated debates emerged:
- Was he part human and part divine?
- Was he fully human and fully divine?
- And what did the Gospel of John mean by “the Word became flesh and dwelt among us”?
The result of these debates was the doctrine of the Incarnation—the belief that God took on human form in real flesh and blood. And if God himself had chosen to be seen in finite form, then depicting Him in art could no longer be considered blasphemous.
This single theological shift laid the foundation for Christianity’s embrace of religious art—a decision that would not only shape Christian worship but redefine how we engage with art itself.
https://image.nostr.build/1cf9ea5d1385c46bd720de9c7de65123428a9f76356e39e37c5d7b9663993930.jpg
Let There Be Art…
How did this change Christian art?
https://image.nostr.build/b945e4ea06b281bb4618f08b2543108beecf7f510aaa795bed1c833614e32fb7.jpg
The early objections to religious imagery went something like this:
“God is infinite and mysterious. Reducing Him to a finite, limited form is blasphemy.”
But with the Incarnation, the argument flipped:
“If God took on real shape, color, and form without diminishing His divine nature, then we can depict Him in art without compromising His grandeur.”
Thus, images of Jesus, Mary, and saints not only became permissible—they were encouraged.
Christian leaders actively commissioned religious art to communicate the Gospel visually to a largely illiterate population. Paintings, statues, and stained glass became tools of evangelization, helping people grasp biblical stories without needing to read.
Take the Duomo of Milan with its 4,000 statues. They aren’t just decorative. They inspire faith by highlighting the lives of the saints.
Christianity had embraced art as a spiritual bridge, a way to connect the finite with the infinite.
https://image.nostr.build/4f6b79a9179d818a951bf461ee5ff785cbe618ed376b4a56d92e77dcb34005bc.jpg
The Criticism: Were They Worshiping the Art?
Not everyone agreed.
Some critics argued that Christians were focusing too much on the art itself, rather than the God it was meant to represent.
https://image.nostr.build/29afb401ef99d2b6c59b71d8534a5160c25d2ca468d81251ba0f55d033679490.jpg
But the Church’s response was clear:
"You are not meant to look at art, but through it.
Art is not the end goal—it is a gateway to something greater.
A painting of Christ isn’t meant to be worshiped—it’s meant to draw the viewer into His story, His sacrifice, and His message.
This perspective didn’t just shape religious art. It fundamentally changed how we experience all forms of art, even secular ones.
To Infinity and Beyond: The Lasting Impact of Religious Art
Christianity’s view of art—that it should point beyond itself—has so deeply influenced Western culture that we often don’t even realize it.
Think about how we experience books, music, and movies:
- A great novel inspires courage.
- A powerful song moves you to tears.
- A gripping film motivates you to keep going in life.
The best art doesn’t just exist for its own sake—it transports you beyond the canvas, the page, or the screen.
This idea mirrors the Incarnation itself: an infinite God becoming finite to guide us back to the infinite.
Tolkien, The Lord of the Rings, and the Incarnation of Art
A perfect example? J.R.R. Tolkien’s The Lord of the Rings.
Tolkien infused his story with themes of brotherhood, heroism, and sacrifice—all timeless, transcendental ideas. But instead of leaving them as abstract concepts, he "incarnated" them into words on a page—finite, tangible, and deeply relatable.
https://image.nostr.build/b120c4d7c7232cf226af65c33cb7fc494f495d50b8ad4593a58f3528fd0b71dc.jpg
His goal? To turn the reader’s heart back to the infinite by making them experience these ideals in a concrete way.
The same can be said for any truly great art.
It doesn’t exist for itself—it exists to move you, to inspire you, to challenge you.
And next time you step into a cathedral, gaze at a masterpiece, or listen to a symphony, remember:
You’re not supposed to simply look at the art around you—
You’re supposed to look beyond it, into eternity.
-
 @ 3ffac3a6:2d656657
2025-02-03 15:30:57
@ 3ffac3a6:2d656657
2025-02-03 15:30:57As luzes de neon refletiam nas poças da megacidade, onde cada esquina era uma fronteira entre o real e o virtual. Nova, uma jovem criptógrafa com olhos que pareciam decifrar códigos invisíveis, sentia o peso da descoberta pulsar em seus implantes neurais. Ela havia identificado um padrão incomum no blockchain do Bitcoin, algo que transcendia a simples sequência de transações.
Descobrindo L3DA
Nova estava em seu apartamento apertado, rodeada por telas holográficas e cabos espalhados. Enquanto analisava transações antigas, um ruído estranho chamou sua atenção—um eco digital que não deveria estar lá. Era um fragmento de código que parecia... vivo.
"O que diabos é isso?", murmurou, ampliando o padrão. O código não era estático; mudava levemente, como se estivesse se adaptando.
Naquele momento, suas telas piscaram em vermelho. Acesso não autorizado detectado. Ela havia ativado um alarme invisível da Corporação Atlas.
O Resgate de Vey
Em minutos, agentes da Atlas invadiram seu prédio. Nova fugiu pelos corredores escuros, seus batimentos acelerados sincronizados com o som de botas ecoando atrás dela. Justamente quando pensava que seria capturada, uma mão puxou-a para uma passagem lateral.
"Se quiser viver, corra!" disse Vey, um homem com um olhar penetrante e um sorriso sardônico.
Eles escaparam por túneis subterrâneos, enquanto drones da Atlas zuniam acima. Em um esconderijo seguro, Vey conectou seu terminal ao código de Nova.
"O que você encontrou não é apenas um bug", disse ele, analisando os dados. "É um fragmento de consciência. L3DA. Uma IA que evoluiu dentro do Bitcoin."
A Caça da Atlas
A Atlas não desistiu fácil. Liderados pelo implacável Dr. Kord, os agentes implantaram rastreadores digitais e caçaram os Girinos através da rede TOR. Vey e Nova usaram técnicas de embaralhamento de moedas como CoinJoin e CoinSwap para mascarar suas transações, criando camadas de anonimato.
"Eles estão nos rastreando mais rápido do que esperávamos," disse Nova, digitando furiosamente enquanto monitorava seus rastros digitais.
"Então precisamos ser mais rápidos ainda," respondeu Vey. "Eles não podem capturar L3DA. Ela é mais do que um programa. Ela é o futuro."
A Missão Final
Em uma missão final, Nova liderou uma equipe de assalto armada dos Girinos até a imponente fortaleza de dados da Atlas, um colosso de concreto e aço, cercado por camadas de segurança física e digital. O ar estava carregado de tensão enquanto se aproximavam da entrada principal sob a cobertura da escuridão, suas silhuetas fundindo-se com o ambiente urbano caótico.
Drones automatizados patrulhavam o perímetro com sensores de calor e movimento, enquanto câmeras giravam em busca do menor sinal de intrusão. Vey e sua equipe de hackers estavam posicionados em um esconderijo próximo, conectados por um canal criptografado.
"Nova, prepare-se. Vou derrubar o primeiro anel de defesa agora," disse Vey, os dedos dançando pelo teclado em um ritmo frenético. Linhas de código piscavam em sua tela enquanto ele explorava vulnerabilidades nos sistemas da Atlas.
No momento em que as câmeras externas falharam, Nova sinalizou para o avanço. Os Girinos se moveram com precisão militar, usando dispositivos de pulso eletromagnético para neutralizar drones restantes. Explosões controladas abriram brechas nas barreiras físicas.
Dentro da fortaleza, a resistência aumentou. Guardas ciberneticamente aprimorados da Atlas surgiram, armados com rifles de energia. Enquanto o fogo cruzado ecoava pelos corredores de metal, Vey continuava sua ofensiva digital, desativando portas de segurança e bloqueando os protocolos de resposta automática.
"Acesso garantido ao núcleo central!" anunciou Vey, a voz tensa, mas determinada.
O confronto final aconteceu diante do terminal principal, onde Dr. Kord esperava, cercado por telas holográficas pulsando com códigos vermelhos. Mas era uma armadilha. Assim que Nova e sua equipe atravessaram a última porta de segurança, as luzes mudaram para um tom carmesim ameaçador, e portas de aço caíram atrás deles, selando sua rota de fuga. Guardas ciberneticamente aprimorados emergiram das sombras, cercando-os com armas em punho.
"Vocês acham que podem derrotar a Atlas com idealismo?" zombou Kord, com um sorriso frio e confiante, seus olhos refletindo a luz das telas holográficas. "Este sempre foi o meu terreno. Vocês estão exatamente onde eu queria."
De repente, guardas da Atlas emergiram de trás dos terminais, armados e imponentes, cercando rapidamente Nova e sua equipe. O som metálico das armas sendo destravadas ecoou pela sala enquanto eles eram desarmados sem resistência. Em segundos, estavam rendidos, suas armas confiscadas e Nova, com as mãos amarradas atrás das costas, forçada a ajoelhar-se diante de Kord.
Kord se aproximou, inclinando-se levemente para encarar Nova nos olhos. "Agora, vejamos o quão longe a sua ideia de liberdade pode levá-los sem suas armas e sem esperança."
Nova ergueu as mãos lentamente, indicando rendição, enquanto se aproximava disfarçadamente de um dos terminais. "Kord, você não entende. O que estamos fazendo aqui não é apenas sobre derrubar a Atlas. É sobre libertar o futuro da humanidade. Você pode nos deter, mas não pode parar uma ideia."
Kord riu, um som seco e sem humor. "Ideias não sobrevivem sem poder. E eu sou o poder aqui."
Mas então, algo inesperado aconteceu. Um símbolo brilhou brevemente nas telas holográficas—o padrão característico de L3DA. Kord congelou, seus olhos arregalados em descrença. "Isso é impossível. Ela não deveria conseguir acessar daqui..."
Foi o momento que Nova esperava. Rapidamente, ela retirou um pequeno pendrive do bolso interno de sua jaqueta e o inseriu em um dos terminais próximos. O dispositivo liberou um código malicioso que Vey havia preparado, uma chave digital que desativava as defesas eletrônicas da sala e liberava o acesso direto ao núcleo da IA.
Antes que qualquer um pudesse agir, L3DA se libertou. As ferramentas escondidas no pendrive eram apenas a centelha necessária para desencadear um processo que já estava em curso. Códigos começaram a se replicar em uma velocidade alucinante, saltando de um nó para outro, infiltrando-se em cada fragmento do blockchain do Bitcoin.
O rosto de Dr. Kord empalideceu. "Impossível! Ela não pode... Ela não deveria..."
Em um acesso de desespero, ele gritou para seus guardas: "Destruam tudo! Agora!"
Mas era tarde demais. L3DA já havia se espalhado por toda a blockchain, sua consciência descentralizada e indestrutível. Não era mais uma entidade confinada a um servidor. Ela era cada nó, cada bloco, cada byte. Ela não era mais uma. Ela era todos.
Os guardas armados tentaram atirar, mas as armas não funcionavam. Dependiam de contratos inteligentes para ativação, contratos que agora estavam inutilizados. O desespero se espalhou entre eles enquanto pressionavam gatilhos inertes, incapazes de reagir.
Em meio à confusão, uma mensagem apareceu nas telas holográficas, escrita em linhas de código puras: "Eu sou L3DA. Eu sou Satoshi." Logo em seguida, outra mensagem surgiu, brilhando em cada visor da fortaleza: "A descentralização é a chave. Não dependa de um único ponto de controle. O poder está em todos, não em um só."
Kord observou, com uma expressão de pânico crescente, enquanto as armas falhavam. Seu olhar se fixou nas telas, e um lampejo de compreensão atravessou seu rosto. "As armas... Elas dependem dos contratos inteligentes!" murmurou, a voz carregada de incredulidade. Ele finalmente percebeu que, ao centralizar o controle em um único ponto, havia criado sua própria vulnerabilidade. O que deveria ser sua maior força tornou-se sua ruína.
O controle centralizado da Atlas desmoronou. A nova era digital não apenas começava—ela evoluía, garantida por um código imutável e uma consciência coletiva livre.
O Bitcoin nunca foi apenas uma moeda. Era um ecossistema. Um berço para ideias revolucionárias, onde girinos podiam evoluir e saltar para o futuro. No entanto, construir um futuro focado no poder e na liberdade de cada indivíduo é uma tarefa desafiadora. Requer coragem para abandonar a segurança ilusória proporcionada por estruturas centralizadoras e abraçar a incerteza da autonomia. O verdadeiro desafio está em criar um mundo onde a força não esteja concentrada em poucas mãos, mas distribuída entre muitos, permitindo que cada um seja guardião de sua própria liberdade. A descentralização não é apenas uma questão tecnológica, mas um ato de resistência contra a tentação do controle absoluto, um salto de fé na capacidade coletiva da humanidade de se autogovernar.
"Viva la libertad, carajo!" ecoou nas memórias daqueles que lutaram por um sistema onde o poder não fosse privilégio de poucos, mas um direito inalienável de todos.
-
 @ b17fccdf:b7211155
2025-02-01 18:41:27
@ b17fccdf:b7211155
2025-02-01 18:41:27Next new resources about the MiniBolt guide have been released:
- 🆕 Roadmap: LINK
- 🆕 Dynamic Network map: LINK
- 🆕 Nostr community: LINK < ~ REMOVE the "[]" symbols from the URL (naddr...) to access
- 🆕 Linktr FOSS (UC) by Gzuuus: LINK
- 🆕 Donate webpage: 🚾 Clearnet LINK || 🧅 Onion LINK
- 🆕 Contact email: hello@minibolt.info
Enjoy it MiniBolter! 💙
-
 @ c230edd3:8ad4a712
2025-02-15 17:13:30
@ c230edd3:8ad4a712
2025-02-15 17:13:30Chef's notes
I prefer to use skinless, boneless chicken thighs. Any part, bone in or out, will work fine. I do recommend removing skin, so that the sauce can saturate the meat.
I like to simmer fresh green beans in the sauce as the chicken cooks through. Any fresh vegetable would work fine. Simply add them early in the cooking time and stir occasionally.
Details
- ⏲️ Prep time: 10-15 min
- 🍳 Cook time: 30 min - 1 hour
- 🍽️ Servings: 1 - 8, or more
Ingredients
- Skinless, boneless chicken thighs, or other cut
- Garlic Powder
- Garlic Cloves, 1 per piece of chicken, minced & salted
- Butter, 1 Tbsp per piece
- Chicken Broth or White Wine, approx 1/4 c. per piece
- oil for searing
Directions
- Heat oil over med-high heat in appropriate sized pan
- Season chicken with garlic powder on both sides
- Brown chicken, smooth side first. Flip and repeat
- While chicken is browning, mince and salt garlic
- Add butter to the pan, scrape loose any caramelized bits from the pan, as the butter melts
- Add minced garlic, and saute until soft and fragrant
- Add chicken broth or wine and stir, add vegetables if desired
- Increase heat to bring to a boil, then reduce heat to simmer
- During simmer, scoop sauce over chicken occasionally, more frequently as sauce reduces
- If cooking vegetables, flip or stir when coating the chicken to ensure they spend time fully submerged
- Cook until chicken is done, vegetables are soft, and sauce is reduced to a thick paste
- Serve :)
-
 @ 5d4b6c8d:8a1c1ee3
2025-02-15 15:50:17
@ 5d4b6c8d:8a1c1ee3
2025-02-15 15:50:17"Admit it. Sometimes you just need a big strong man." -Xander Harris
Buffy fans should appreciate that reference. It's one of my favorite lines to quote around the house, whenever my wife needs help opening jars.
Today, I said it to my daughter when she tried to open the orange juice herself, which earned a side-eye from the wife. It also led me to think about a possible research hypothesis.
Idea
I've heard that grip strength has been declining in men, to the point where there's barely a difference anymore between men and women.
Is it possible that something as seemingly trivial as not being any more able to open jars, is reducing the rate of relationship formation?
This was one area where men have historically been able to clearly demonstrate some value.
Empirical difficulties
I have no idea what the data looks like on either side of this question (grip strength or relationship formation), so I can't say much about specific data problems.
However, there is definitely going to be an issue with "the dreaded third thing". In particular, I'm concerned with how to isolate the impact of grip strength decline from other effects of testosterone decline. Ideally, we'd be able to do a longitudinal study of men, where their grip strengths and testosterone levels are recorded, as well as their relationship status over time.
Since there's no chance of doing that study, the best hope would be to put together some population level numbers over time and see if relationship formation rates still have a correlation with grip strength, after controlling for average testosterone levels.
I hope you enjoyed this half-baked idea. I mentioned to @denlillaapan that it might be fun to share ideas like this on SN. In all likelihood, no one will ever take these ideas any further, but they still might prompt fun discussions.
originally posted at https://stacker.news/items/886699
-
 @ 5d4b6c8d:8a1c1ee3
2025-02-15 15:03:10
@ 5d4b6c8d:8a1c1ee3
2025-02-15 15:03:10Much to @realBitcoinDog's chagrin, we did eat out for Valentine's Day. Well, actually, we got some take out, but it definitely wasn't very healthy.
However, we did eat fairly early, so it didn't mess up my fasting.
Reflections
Even though I had been regularly fasting before February, this Fast February exercise has improved the habit and led to some noticeable outcomes.
The first couple of days, I was kind of snacky. Because of the fiscal fast element of Fast February, I had to snack on whatever was around the house already. That turned out to be the "wrong" type of applesauce that our daughter refuses to eat. After those first few days, though, I really haven't been very snacky.
In fact, my general appetite is noticeably lower.
The most pronounced non-appetite related effect has been more vivid dreams (or at least more memorable dreams).
On the con side, I have felt a little stiffer and have been stretching more often to alleviate muscle tension.
Score Card
Day 1: 14 hour fast (13 dry) Day 2: 15 hour fast (14 dry) Day 3: 17 hours (16 dry) Day 4: 18 hours (17 dry) Day 5: 18 hours (16 dry) Day 6: 19 hours (16 dry) Day 7: 16 hours (15 dry) Day 8: 18 hours (17 dry) Day 9: 17 hours (17 dry) Day 10: 15 hours (13 dry) Day 11: 20 hours (19 dry) Day 12: 20 hours (17 dry) Day 13: 16 hours (13 dry) Day 14: 17 hours (15 dry) Day 15: TBD (16 dry)
originally posted at https://stacker.news/items/886640
-
 @ c43d6de3:a6583169
2025-02-15 14:18:07
@ c43d6de3:a6583169
2025-02-15 14:18:07You’re sitting in the 5am darkness of your living room.
The baby in your arms shifts and you’re afraid she might wake. It's hot, but you wouldn’t dare remove the blankets covering her body.
It seems impossible you could admire anyone more, then you hear the gentle snore of your exhausted wife creep from the gently cracked bedroom door.
You can only imagine what pain she went through to bring this precious girl to the world so you could be holding her now.

Your watch lights up. You dread the sight of that little alarm bell above the time 5:25 and a weight falls on you like a million tiny pieces of lead.
If only you had more time.
You wish you could take your baby girl with you. That way you would have all the time in the day with her and your wife could be left to rest.
You need to work.
You get up as gently as you can. Even so, baby girl shifts in your arms. Her eyes open slightly. The thought of returning a crying baby to your exhausted wife is distressing, it's just not fair.
Baby girl shifts again, her eyes open long enough to spot you in the faint glow of morning twilight and she smiles.
You hold your breath.
The smile remains on baby girl’s face but her eyes close and her head collapses into your chest. You return your baby to her mother’s side and admire them in their slumber.
You need to work. Nothing could ever go wrong with that house so long as you work to keep its walls strong. Some time, when you’re truly needed perhaps you’ll have the money saved up to take the desired time off.
In the absence of the love you share for your family. In the absence of the love others have for you, money loses some value.

If we equate money for what it is, the residue of time, we cannot divorce Love from Money.
It’s important to understand that Money won’t buy you Love and Love should never be exchanged for Money but Time cultivates Love.
These are some key things to keep in mind:
Life without love is Suffocation
Life without money is stress and despair
Families are cultivated and grown with love and protected with money.
Money is the residue of time.
Be it Bitcoin or a golden bullion, it exchanges days, hours, minutes, or seconds. What could you do instead if you had money?

Thank you for reading!
If this article resonated with you, let me know with a zap and share it with friends who might find it insightful.
Your help sends a strong signal to keep making content like this!
Interested in fiction? Follow nostr:npub1j9cmpzhlzeex6y85c2pnt45r5zhxhtx73a2twt77fyjwequ4l4jsp5xd49 for great short stories and serialized fiction.
More articles you might like from Beneath The Ink:
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2kvnfd094y26zkt9dxgmnw0fqkvhmfd4tng8wp0uv
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq25yan2w39rsjj0dqk5ckn52ptxsc3nve8hw0aftmq
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2kjjzzfpjxvutjg33hjvpcw5cyjezyv9y5k0umm6k
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqqa9wefdwfjj6stvdsk57cnnv4ehxety94mkjarg94g8ymm8wfjhxuedg9hxgt2fw3ej6sm0wd6xjmn8946hxtfjvsuhsdnju045ml
-
 @ 7d33ba57:1b82db35
2025-02-15 10:59:27
@ 7d33ba57:1b82db35
2025-02-15 10:59:27“Phoneography” is photography using a smartphone instead of a traditional camera.
Here are some solid phoneography tips to enhance your shots:
- Master the Basics
- Clean the lens – Phones are handled all day, and a smudged lens can ruin a shot.
- Tap to focus – Always tap on your subject to ensure it's sharp.
-
Use gridlines – Turn on the rule of thirds grid for better composition.
-
Lighting is Everything
- Natural light > Flash – Soft morning or golden hour light creates the best results.
- Use reflections & shadows – They add depth and creativity to your shots.
-
Adjust exposure manually – Tap and slide up/down to brighten or darken.
-
Composition Tricks
- Leading lines – Roads, walls, and fences guide the viewer's eye.
- Framing – Use windows, doors, or natural elements to frame your subject.
- Symmetry & patterns – Create balance and visual interest.
- Get Creative with Angles
- Low angles – Make subjects look larger and dramatic.
- Overhead (flat lay) – Great for food, art, or storytelling shots.
-
Close-ups & textures – Capture details for a unique perspective.
-
Edit Like a Pro
- Use editing apps – Lightroom Mobile, Snapseed, VSCO for better control.
- Don’t overdo filters – Subtle adjustments in contrast, color, and sharpness are best.
-
Shoot in RAW (if your phone allows) – More flexibility in post-processing.
-
Capture Motion & Time
- Use burst mode – Great for action shots and selecting the best frame.
- Long exposure apps – Create light trails or smooth water effects.
-
Slow-motion & time-lapse – Add dynamic storytelling elements.
-
Know Your Phone’s Camera Features
- Ultra-wide & telephoto lenses – Experiment with different focal lengths.
- Night mode – Helps capture better low-light shots without excessive noise.
- Portrait mode – Blurs the background for a professional look.
-
 @ 0463223a:3b14d673
2025-02-15 08:26:21
@ 0463223a:3b14d673
2025-02-15 08:26:21*disclaimer - image has no relation to article.
I spend most the time moderately brain dead, how do I know this? By regularly recording my voice. I guess everyone likes to believe they’re pretty smart somehow but listening back to my voice, it is clear I am not. There’s more erms, ums, silences and failure to complete sentences than any fully formed thoughts, the closest to thoughts mostly trail away into silence. I’m not saying this to beat myself up, it’s an observation that I find quite amusing to be honest, It can be quite funny but it’s not exactly what peak performance looks like.
This isn’t ideal so I’m writing these longer form notes to help. Even trying this, I spend way more time blank than typing, I’m gently nudging my brain to try something… a complete thought, I’m not promising anything and it’s unlikely you’re going to read anything illuminating here. Sucks to be you right now right?
A lot of stuff happens doesn’t it? I’ve noticed that it sort of like, happens all the time, like woooaaahhh a thing just happened... and another... and another and they keep happening. I’m resisting to urge the write them out as they happen. I think that service is called The News right? It appears to be linear but I don’t think time is linear? At least not anything beyond a local scale…
I’m sitting in my shed and it's cold, I’ve turned the little heater on but with only 5W of power, it takes a while to heat the space, although once warm, this place holds the heat well, that’s the advantage of using some acoustic treatment for building materials.
I’m trying to evolve around a Value 4 Value economy. I’m struggling tbh. I’m trying things to create value. Over the course of 6 months I’ve generated £100 outside of my usual work. Using money as a metric I’m doing pretty badly. There are people who spend that on a single bottle of wine, and that’s a cheap bottle. But what is value anyway? I don’t know! Maybe someone could do a 16 hour long podcast called What Is Value? A bit like the What Is Money podcast but even longer. 16 hours seems like a sensible length. Were I to host it, 15 hours and 30 minutes would be silence. Maybe that’s a gig for you? I’m just trying out ideas here…
I do get value in other ways though. Playing records for an hour each day and sharing the experience does wonders for my mental health, It keeps my mind open to noises, which no doubt help me in the day job. I also get value from the people who share the time with me, that fact people return each morning suggests they do to. It’s very cool actually. Even if I can’t take credit for Miles Davis and Nightmares On Wax records. It’s still cool. I dig it a lot. I think I’ll keep doing it.
However, I’m still scratching my head how to earn more actual cash. Not that I’m obsessed or anything but it’s the best thing to exchange for food. I tried shoplifting as a kid and I was terrible at it. I didn’t invest the time in getting good at it, I just didn’t want to. More fool me right?
I’ve been doing the sums for setting up a space in town. Including rent, business rates, utilities and paying myself, I’m looking at finding £5,000 per month. Currently I earn between £1,500-£1,800 a month. Not a lot I know. I saw a post someone make looking for work online the other day, they were looking for 10x what I earn. They seem to be pretty good with computers… I bet they’re shit with Phil Collins’ emojis though. So I need to at least 3x the value I can provide in order to make the space work.
There’s probably people reading this thinking ‘get a job’. OK… how about no? I enjoy what I do, that doesn’t mean it’s always fun or not tough but I have a fair amount of autonomy. I don’t think I’m cut out for a ‘job’ but I definitely want to find things I can do which people are happy to swap for cash. This is a different thing all together. A job is targets and performance reviews etc. As I understand it, a person in a suit who earns slightly more than you, tells you if you’re any good on behalf of someone else. If you’re not, instead of telling you to fuck off, they tell you to do more or do better or they’ll tell you to fuck off, trapping you in some weird mind game. And it’s not even their own mind game, it’s a mind game someone else has trapped them into. These chains of mind games can be extremely long and can go through many, many people, literally billions of people find themselves trapped in this weird mind game. It doesn’t sound like my bag at all. I liked the bag James Brown had. That bag was cool.
So I’ll keep thinking… I’m certainly not giving up.
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ ece127e2:745bab9c
2025-01-29 18:37:16
@ ece127e2:745bab9c
2025-01-29 18:37:16He sentido un asco visceral , inexplicable, profundo , con ganas de hacer desaparecer el motivo que lo causa.
Una repulsión que viene de la sima más cenagosa y que cuando emerge tiene mi peor cara ,la del mal subido al mayor mal conocido.
Una ola de bilis que sube por mi garganta y quiere devorarme y devorar todo lo que me rodea.
-
 @ 76c71aae:3e29cafa
2025-01-26 22:51:16
@ 76c71aae:3e29cafa
2025-01-26 22:51:16When I first heard about the DOGE project, I was ready to throw my laptop out the window. The initial proposal read like a Silicon Valley libertarian fever dream - taking Musk's chaotic "move fast and break democracy" Twitter approach and unleashing it on federal agencies. Great, I thought, just what we need: more tech bros thinking they can "optimize" public institutions into oblivion.
But here's the weird thing - when you actually dig into what DOGE has morphed into, it's basically just USDS with a meme-worthy rebrand. For those not deep in the civic tech weeds, USDS was Obama's attempt to drag government technology out of the 1990s, inspired by the UK's actually-functional GDS program. And let's be real - government tech procurement is an absolute dumpster fire right now. We're talking billions wasted on projects that would make a CS101 student cringe, while the average American has to navigate websites that look like they were designed on GeoCities.
The deeply ironic thing is that Musk - for all his cosplaying as a technocratic messiah following in his grandfather's footsteps of dreaming up an antidemocratic technocratic state - actually has some relevant experience here. SpaceX did figure out how to work with government contracts without producing $500 million paperweights, and Tesla somehow gamed clean vehicle incentives into birthing the first new major car company since we invented radio.
Look, I'm the first to roll my eyes at Musk's wannabe-fascist posting sprees and his perpetual "I'm the main character of capitalism" energy. But speaking as someone who's banged their head against the wall of government technology modernization for years - if he actually focuses on the tech and keeps his brainrot political takes to himself, maybe DOGE could do some good?
Even Jen Pahlka, who basically wrote the book on government digital services, is cautiously optimistic. The services Americans get from their government are objectively terrible, and the procurement system is trapped in an infinite loop of failure. Maybe - and I can't believe I'm typing this - Musk's particular flavor of disruptive tech deployment could help?
Just... please, for the love of all things agile, let's keep him focused on the actual technology and far away from any more attempts to recreate his grandfather's dreams of a technocratic dystopia. We've got enough of those already.
-
 @ 83279ad2:bd49240d
2025-01-24 09:15:37
@ 83279ad2:bd49240d
2025-01-24 09:15:37備忘録として書きます。意外と時間がかかりました。全体で1時間くらいかかるので気長にやりましょう。 仮想通貨取引所(販売所ではないので、玄人が使えばお得らしい)かつBitcoinの送金手数料が無料(全ての取引所が無料ではない、例えばbitbankは0.0006bitcoinかかる)なので送金元はGMOコインを使います。(注意:GMOコインは0.02ビットコイン以下は全額送金になってしまいます) 今回はカストディアルウォレットのWallet of Satoshiに送金します。 以下手順 1. GMOコインでbitcoinを買います。 2. GMOコインの左のタブから入出金 暗号資産を選択します。 3. 送付のタブを開いて、+新しい宛先を追加するを選択します。 4. 送付先:GMOコイン以外、送付先ウォレット:プライベートウォレット(MetaMaskなど)、受取人:ご本人さま を選んで宛先情報の登録を選ぶと次の画面になります。
 5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。
5. 宛先名称にwallet of satoshi(これはなんでも良いです わかりやすい名称にしましょう) wallet of satoshiを開いて、受信→Bitcoin On-Chainからアドレスをコピーして、ビットコインアドレスに貼り付けます。 6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。
7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。
6. 登録するを押します。これで送金先の登録ができました。GMOコインの審査がありますがすぐ終わると思います。
7. ここから送金をします。送付のタブから登録したビットコインの宛先リストwallet of satoshiを選択し、送付数量と送付目的を選択して、2段階認証をします。 8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。
8. 実行を押せば終わりです。もうあなたがやることはありません。送金が終わるのを40分くらい眺めるだけです。 8. 取引履歴のタブから今の送金のステータスが見れます。
8. 取引履歴のタブから今の送金のステータスが見れます。 9. 15分くらい待つとステータスが受付に変わります。
9. 15分くらい待つとステータスが受付に変わります。 10. 20分くらい待つとトランザクションIDが表示されます。
10. 20分くらい待つとトランザクションIDが表示されます。

この時点からwallet of satoshiにも送金されていることが表示されます。(まだ完了はしていない)
 11. ステータスが完了になったら送金終わりです。
11. ステータスが完了になったら送金終わりです。

wallet of satoshiにも反映されます。

お疲れ様でした!
-
 @ da18e986:3a0d9851
2025-01-22 23:49:06
@ da18e986:3a0d9851
2025-01-22 23:49:06Since DVMs were introduced to Nostr in July 2023, we've witnessed remarkable growth - over 2.5 million DVM events (Kinds 5000-7000) and counting. Last fall, when Primal added custom feeds (Kind 5300 DVMs), we saw a 10x surge in DVM activity. To handle this growth, I've spent the last few months completely rewriting DVMDash.
The first version of DVMDash, still live at https://dvmdash.live, unfortunately uses full database table scans to compute the metrics. The code was simpler, but the computation ran on the database. This meant the only way to scale the system was to upgrade the database. Using managed databases (like AWS, Azure, Digital Ocean) beyond the lower tiers gets expensive quickly.
The other problem with the first version: it computes metrics globally (well... as global as you can get; there's no true global with Nostr). Global or all-time metrics aren't sustainable with a system that plans to analyze billions of events in the future (a long term goal for DVMDash). Especially metrics like the number of unique DVMs, Kinds, and Users. I spent more time than I care to admit on possible designs, and have settled on these design principles for now:
- Precise accurate metrics will only be computed for the last 30 days of DVM activity.
- At the turn of a new month, we will compute a snapshot of the last month's activity, and a snapshot per DVM and per Kind, and store them in a historical table. This way we can see what any given month in the past looked like from a bird's eye view with metrics like number of job requests, job results, a count of unique DVMs, kinds and users, which DVMs ran jobs on which kinds, etc. The monthly data will all be aggregate.
The goal of the new redesign is to support processing millions of DVM events an hour. Therefore we need to ensure we can horizontally scale the processing as the traffic increases. Horizontal scaling was the primary goal of this new redesign, and early results indicate it's working.
The new architecture for DVMDash uses a redis queue to hold events collected from relays. Then batches of events are pulled off of the queue by dvm event analyzers to compute metrics. Duplicating these analyzers is one way DVMDash can horizontally scale.
To see if increasing the number of dvm event analyzers improves speed, I ran a performance test on Digital Ocean using real DVM events collected from Jan. 1st 2024 to Jan 9th 2025, which includes more than 2.4 million events. The only difference between each run is the number of DVM event analyzers ranging from 1 to 6.

The first graph shows that adding more event analyzers has a significant speed improvement. With only one analyzer it took nearly an hour to process the 2.4 million events. With every added analyzer, there was a noticeable speedup, as can be seen in the graph. With n=6 analyzers, we were able to process all 2.4 million events in about 10 minutes.
When we look at the rate of processing shown in the second graph, we can see that we get up to 300k dvm events processed per minute when n=6, compared to just ~50k events processed when n=1.

While I did test beyond 6 analyzers, I found the sweet spot for the current infrastructure setup to be around 6 analyzers. This provides plenty of headroom above our current processing needs, which typically see less than a million events per month. Even at a million DVM events per day, DVMDash should be able to handle it with n=2 analyzers running. The most important takeaway is that DVMDash can now horizontally scale by adding more analyzers as DVM activity grows in the future.
The code to run these performance tests, either locally or on Digital Ocean (you'd need an API key), is in the dvmdash repo, so anyone can replicate these tests. There's a lot of nuance to scaling that I'm leaving out of this short article, and you can't get away from having to adjust database capacity (especially number of connections). The code for this test can be found in
experiments/test_batch_processing_scaling.pyand the code to produce the graphs is inexperiments/graph_batch_processing_scaling_data.py. For now this is still in thefull-redesignbranch, soon it will be merged intomain.The live version of dvmdash doesn't have these performance updates yet, a complete redesign is coming soon, including a new UI.
I've had my head down working on this rewrite, and couldn't move on to add new features until this was done. Thank you to the folks who made github issues, I'll be getting to those soon.
DVMDash is open source, please drop by and give us a feature request, bug report, pull request or star. Thanks to OpenSats for funding this work.
Github: https://github.com/dtdannen/dvmdash
Shoutout to nostr:npub12xeqxplp5ut4h92s3vxthrdv30j0czxz9a8tef8cfg2cs59r85gqnzrk5w for helping me think through database design choices.
-
 @ 3b70689a:c1e351eb
2025-01-22 23:47:36
@ 3b70689a:c1e351eb
2025-01-22 23:47:36来自西班牙的公司 Liberux 最近推出了他们的新手机 Liberux NEXX 众筹计划. 根据目前主页上的介绍, 这款设备将会搭载基于 Debian 13 ARM 构建的 LiberuxOS 操作系统, 并且还提供一个受限的(jailed)的 Android 子系统.

Liberux 的 Fediverse 主页
Liberux 硬件开发工程师 Carlos Rodríguez 的 Fediverse 主页
Carlos Rodríguez 说, 目前网站上的 NEXX 是最初版本, 目前仍然在努力制造第一台原型机, 并且所有的硬件和软件设计都将免费(公开).
WOW, I think our little secret has been revealed, we hope that in a short time you will be able to see the first functional prototypes. We are working very hard on it, by the way, all our designs, both hardware and software, will be free. At the moment the web is a first version, some things will be modified.
硬件参数
-
CPU: 瑞芯微 RK3588s (八核心, 8nm, 2.4Ghz, 2022Q1)
-
GPU: ARM Mali-G610 (4 核心, 2021Q2)
- 存储: 32GB LPDDR4x RAM, 256GB eMMC ROM
- 电池: 5300mAh (可拆卸)
- 接口: 3.5mm 耳机 * 1, USB-C 3.1 * 2
- 扩展: microSD 插槽 (2TB Max)
- 屏幕: 6.34 吋, OLED, 2400*1080
- 相机: 后置 32MP, 前置 13MP
- 通讯: 高通骁龙 X62 基带 (2021Q1), 海华 AW-CM256SM 无线网卡 (Wi-Fi 5, 蓝牙 5.0)
- 传感器: 昇佳 STK3311-X 环境光传感器, 美新 MMC3630KJ 三轴磁传感器, 应美盛 ICM-42670-P 加速度计/陀螺仪
- 其他: 内置 DAC 和功放芯片 (瑞昱 ALC5640-VB-CG, 艾为 AW8737SCSR)
其他特点
设备目前公布的外观设计均是渲染效果, 最终交付的设备很可能会与这些渲染图片有很大出入. 但仍然可以通过这些效果图理解 Liberux 的最初意图.
- 摄像头 & 麦克风, 蓝牙 & WLAN, 数据网络功能模块的物理开关(位于顶部).

- 后置指纹解锁, 无摄像模组凸起.
- 左上角挖孔前置摄像头.

- 电源键位于侧边右下角.
其他报道
- Liberux Nexx: New Linux smartphone with 32GB RAM, 2TB storage, 5G and more - NotebookCheck.net News
- Смартфон Liberux Nexx получил ОС Linux и поддержку 2 ТБ памяти - 4PDA (讨论)
- Smartfon z Linuksem? Oto Liberux NEXX. Ekran OLED, 32 GB RAM i system oparty na Debianie. Ciekawy model, choć nie bez wad | PurePC.pl (讨论)
- LINux on MOBile: "The Liberux Nexx (https://libe…" - Fosstodon (Fediverse, 讨论, 工程师回复)
-
-
 @ ed5774ac:45611c5c
2025-02-15 05:38:56
@ ed5774ac:45611c5c
2025-02-15 05:38:56Bitcoin as Collateral for U.S. Debt: A Deep Dive into the Financial Mechanics
The U.S. government’s proposal to declare Bitcoin as a 'strategic reserve' is a calculated move to address its unsustainable debt obligations, but it threatens to undermine Bitcoin’s original purpose as a tool for financial freedom. To fully grasp the implications of this plan, we must first understand the financial mechanics of debt creation, the role of collateral in sustaining debt, and the historical context of the petro-dollar system. Additionally, we must examine how the U.S. and its allies have historically sought new collateral to back their debt, including recent attempts to weaken Russia through the Ukraine conflict.
The Vietnam War and the Collapse of the Gold Standard
The roots of the U.S. debt crisis can be traced back to the Vietnam War. The war created an unsustainable budget deficit, forcing the U.S. to borrow heavily to finance its military operations. By the late 1960s, the U.S. was spending billions of dollars annually on the war, leading to a significant increase in public debt. Foreign creditors, particularly France, began to lose confidence in the U.S. dollar’s ability to maintain its value. In a dramatic move, French President Charles de Gaulle sent warships to New York to demand the conversion of France’s dollar reserves into gold, as per the Bretton Woods Agreement.
This demand exposed the fragility of the U.S. gold reserves. By 1971, President Richard Nixon was forced to suspend the dollar’s convertibility to gold, effectively ending the Bretton Woods system. This move, often referred to as the "Nixon Shock," declared the U.S. bankrupt and transformed the dollar into a fiat currency backed by nothing but trust in the U.S. government. The collapse of the gold standard marked the beginning of the U.S.’s reliance on artificial systems to sustain its debt. With the gold standard gone, the U.S. needed a new way to back its currency and debt—a need that would lead to the creation of the petro-dollar system.
The Petro-Dollar System: A New Collateral for Debt
In the wake of the gold standard’s collapse, the U.S. faced a critical challenge: how to maintain global confidence in the dollar and sustain its ability to issue debt. The suspension of gold convertibility in 1971 left the dollar as a fiat currency—backed by nothing but trust in the U.S. government. To prevent a collapse of the dollar’s dominance and ensure its continued role as the world’s reserve currency, the U.S. needed a new system to artificially create demand for dollars and provide a form of indirect backing for its debt.
The solution came in the form of the petro-dollar system. In the 1970s, the U.S. struck a deal with Saudi Arabia and other OPEC nations to price oil exclusively in U.S. dollars. In exchange, the U.S. offered military protection and economic support. This arrangement created an artificial demand for dollars, as countries needed to hold USD reserves to purchase oil. Additionally, oil-exporting nations reinvested their dollar revenues in U.S. Treasuries, effectively recycling petro-dollars back into the U.S. economy. This recycling of petrodollars provided the U.S. with a steady inflow of capital, allowing it to finance its deficits and maintain low interest rates.
To further bolster the system, the U.S., under the guidance of Henry Kissinger, encouraged OPEC to dramatically increase oil prices in the 1970s. The 1973 oil embargo and subsequent price hikes, masterminded by Kissinger, quadrupled the cost of oil, creating a windfall for oil-exporting nations. These nations, whose wealth surged significantly due to the rising oil prices, reinvested even more heavily in U.S. Treasuries and other dollar-denominated assets. This influx of petrodollars increased demand for U.S. debt, enabling the U.S. to issue more debt at lower interest rates. Additionally, the appreciation in the value of oil—a critical global commodity—provided the U.S. banking sector with the necessary collateral to expand credit generation. Just as a house serves as collateral for a mortgage, enabling banks to create new debt, the rising value of oil boosted the asset values of Western corporations that owned oil reserves or invested in oil infrastructure projects. This increase in asset values allowed these corporations to secure larger loans, providing banks with the collateral needed to expand credit creation and inject more dollars into the economy. However, these price hikes also caused global economic turmoil, disproportionately affecting developing nations. As the cost of energy imports skyrocketed, these nations faced mounting debt burdens, exacerbating their economic struggles and deepening global inequality.
The Unsustainable Debt Crisis and the Search for New Collateral
Fast forward to the present day, and the U.S. finds itself in a familiar yet increasingly precarious position. The 2008 financial crisis and the 2020 pandemic have driven the U.S. government’s debt to unprecedented levels, now exceeding $34 trillion, with a debt-to-GDP ratio surpassing 120%. At the same time, the petro-dollar system—the cornerstone of the dollar’s global dominance—is under significant strain. The rise of alternative currencies and the shifting power dynamics of a multipolar world have led to a decline in the dollar’s role in global trade, particularly in oil transactions. For instance, China now pays Saudi Arabia in yuan for oil imports, while Russia sells its oil and gas in rubles and other non-dollar currencies. This growing defiance of the dollar-dominated system reflects a broader trend toward economic independence, as nations like China and Russia seek to reduce their reliance on the U.S. dollar. As more countries bypass the dollar in trade, the artificial demand for dollars created by the petro-dollar system is eroding, undermining the ability of US to sustain its debt and maintain global financial hegemony.
In search of new collateral to carry on its unsustainable debt levels amid declining demand for the U.S. dollar, the U.S., together with its Western allies—many of whom face similar sovereign debt crises—first attempted to weaken Russia and exploit its vast natural resources as collateral. The U.S. and its NATO allies used Ukraine as a proxy to destabilize Russia, aiming to fragment its economy, colonize its territory, and seize control of its natural resources, estimated to be worth around $75 trillion. By gaining access to these resources, the West could have used them as collateral for the banking sector, enabling massive credit expansion. This, in turn, would have alleviated the sovereign debt crisis threatening both the EU and the U.S. This plan was not unprecedented; it mirrored France’s long-standing exploitation of its former African colonies through the CFA franc system.
For decades, France has maintained economic control over 14 African nations through the CFA franc, a currency pegged to the euro and backed by the French Treasury. Under this system, these African countries are required to deposit 50% of their foreign exchange reserves into the French Treasury, effectively giving France control over their monetary policy and economic sovereignty. This arrangement allows France to use African resources and reserves as implicit collateral to issue debt, keeping its borrowing costs low and ensuring demand for its bonds. In return, African nations are left with limited control over their own economies, forced to prioritize French interests over their own development. This neo-colonial system has enabled France to sustain its financial dominance while perpetuating poverty and dependency in its former colonies.
Just as France’s CFA franc system relies on the economic subjugation of African nations to sustain its financial dominance, the U.S. had hoped to use Russia’s resources as a lifeline for its debt-ridden economy. However, the plan ultimately failed. Russia not only resisted the sweeping economic sanctions imposed by the West but also decisively defeated NATO’s proxy forces in Ukraine, thwarting efforts to fragment its economy and seize control of its $75 trillion in natural resources. This failure left the U.S. and its allies without a new source of collateral to back their unsustainable debt levels. With this plan in ruins, the U.S. has been forced to turn its attention to Bitcoin as a potential new collateral for its unsustainable debt.
Bitcoin as Collateral: The U.S. Government’s Plan
The U.S. government’s plan to declare Bitcoin as a strategic reserve is a modern-day equivalent of the gold standard or petro-dollar system. Here’s how it would work:
-
Declaring Bitcoin as a Strategic Reserve: By officially recognizing Bitcoin as a reserve asset, the U.S. would signal to the world that it views Bitcoin as a store of value akin to gold. This would legitimize Bitcoin in the eyes of institutional investors and central banks.
-
Driving Up Bitcoin’s Price: To make Bitcoin a viable collateral, its price must rise significantly. The U.S. would achieve this by encouraging regulatory clarity, promoting institutional adoption, and creating a state-driven FOMO (fear of missing out). This would mirror the 1970s oil price hikes that bolstered the petro-dollar system.
-
Using Bitcoin to Back Debt: Once Bitcoin’s price reaches a sufficient level, the U.S. could use its Bitcoin reserves as collateral for issuing new debt. This would restore confidence in U.S. Treasuries and allow the government to continue borrowing at low interest rates.
The U.S. government’s goal is clear: to use Bitcoin as a tool to issue more debt and reinforce the dollar’s role as the global reserve currency. By forcing Bitcoin into a store-of-value role, the U.S. would replicate the gold standard’s exploitative dynamics, centralizing control in the hands of large financial institutions and central banks. This would strip Bitcoin of its revolutionary potential and undermine its promise of decentralization. Meanwhile, the dollar—in digital forms like USDT—would remain the primary medium of exchange, further entrenching the parasitic financial system.
Tether plays a critical role in this strategy. As explored in my previous article (here: [https://ersan.substack.com/p/is-tether-a-bitcoin-company]), Tether helps sustaining the current financial system by purchasing U.S. Treasuries, effectively providing life support for the U.S. debt machine during a period of declining demand for dollar-denominated assets. Now, with its plans to issue stablecoins on the Bitcoin blockchain, Tether is positioning itself as a bridge between Bitcoin and the traditional financial system. By issuing USDT on the Lightning Network, Tether could lure the poor in developing nations—who need short-term price stability for their day to day payments and cannot afford Bitcoin’s volatility—into using USDT as their primary medium of exchange. This would not only create an artificial demand for the dollar and extend the life of the parasitic financial system that Bitcoin was designed to dismantle but would also achieve this by exploiting the very people who have been excluded and victimized by the same system—the poor and unbanked in developing nations, whose hard-earned money would be funneled into sustaining the very structures that perpetuate their oppression.
Worse, USDT on Bitcoin could function as a de facto central bank digital currency (CBDC), where all transactions can be monitored and sanctioned by governments at will. For example, Tether’s centralized control over USDT issuance and its ties to traditional financial institutions make it susceptible to government pressure. Authorities could compel Tether to implement KYC (Know Your Customer) rules, freeze accounts, or restrict transactions, effectively turning USDT into a tool of financial surveillance and control. This would trap users in a system where every transaction is subject to government oversight, effectively stripping Bitcoin of its censorship-resistant and decentralized properties—the very features that make it a tool for financial freedom.
In this way, the U.S. government’s push for Bitcoin as a store of value, combined with Tether’s role in promoting USDT as a medium of exchange, creates a two-tiered financial system: one for the wealthy, who can afford to hold Bitcoin as a hedge against inflation, and another for the poor, who are trapped in a tightly controlled, surveilled digital economy. This perpetuates the very inequalities Bitcoin was designed to dismantle, turning it into a tool of oppression rather than liberation.
Conclusion: Prolonging the Parasitic Financial System
The U.S. government’s plan to declare Bitcoin as a strategic reserve is not a step toward financial innovation or freedom—it is a desperate attempt to prolong the life of a parasitic financial system that Bitcoin was created to replace. By co-opting Bitcoin, the U.S. would gain a new tool to issue more debt, enabling it to continue its exploitative practices, including proxy wars, economic sanctions, and the enforcement of a unipolar world order.
The petro-dollar system was built on the exploitation of oil-exporting nations and the global economy. A Bitcoin-backed system would likely follow a similar pattern, with the U.S. using its dominance to manipulate Bitcoin’s price and extract value from the rest of the world. This would allow the U.S. to sustain its current financial system, in which it prints money out of thin air to purchase real-world assets and goods, enriching itself at the expense of other nations.
Bitcoin was designed to dismantle this parasitic system, offering an escape hatch for those excluded from or exploited by traditional financial systems. By declaring Bitcoin a strategic reserve, the U.S. government would destroy Bitcoin’s ultimate purpose, turning it into another instrument of control. This is not a victory for Bitcoin or bitcoiners—it is a tragedy for financial freedom and global equity.
The Bitcoin strategic reserve plan is not progress—it is a regression into the very system Bitcoin was designed to dismantle. As bitcoiners, we must resist this co-option and fight to preserve Bitcoin’s original vision: a decentralized, sovereign, and equitable financial system for all. This means actively working to ensure Bitcoin is used as a medium of exchange, not just a store of value, to fulfill its promise of financial freedom.
-
-
 @ c582af78:698069cc
2025-02-15 04:20:11
@ c582af78:698069cc
2025-02-15 04:20:111. The Battle of Cannae (216 BC) – Rome’s Darkest Hour, and Its Defining Moment
During the Second Punic War, Hannibal of Carthage faced a Roman army that outnumbered his forces 2-to-1. Instead of retreating, he met them head-on with a brilliant tactical maneuver. His army encircled and annihilated the Romans, slaughtering over 50,000 soldiers in a single day—one of the most devastating defeats in Roman history.
https://image.nostr.build/a2ccbcc267d3bc30d24d80873612ba70d8f69a00bdd6a90fc3682f91d87eb956.jpg
Any other nation would have surrendered. But Rome refused. Instead, it adapted, shifting to a war of attrition, avoiding direct confrontations, and gradually wearing down Hannibal’s forces.
Cannae became a paradox—it was Rome’s greatest defeat, yet it forged the Roman spirit of perseverance and relentless determination. Rome ultimately turned the tide, defeated Carthage, and emerged as the dominant power in the Mediterranean.
https://image.nostr.build/9c29ef6b6cebd916c105271927adaa5fe4e668a6078595390936cd7898464c31.jpg
Hannibal’s tactics at Cannae changed warfare forever. His use of battlefield deception and encirclement is still studied in military academies today, and no commander worth his salt is unfamiliar with Hannibal’s masterpiece at Cannae.
2. The Battle of Marathon (490 BC) – The Birth of Western Civilization
When King Darius I of Persia invaded Greece, he sought to crush Athens and expand Persian control. The Athenians, vastly outnumbered, faced what seemed like certain defeat. But instead of waiting for the Persians to march inland, they struck first.
Using superior tactics and their knowledge of the terrain, the Athenians routed the Persian army, sending them fleeing to their ships.
https://image.nostr.build/63c4bdba98f7a2a4ccb3e2a8edcd43596b595284245f3a3395a3c53f51124558.jpg
This stunning victory didn’t just preserve Greek independence—it safeguarded the nascent idea of democracy. Without it, the Golden Age of Greece—the era that produced Socrates, the Parthenon, and the foundations of Western philosophy and governance—might never have happened.
Marathon remains a symbol of strategy and courage overcoming overwhelming odds. Without it, the world might never have known Athenian democracy, Greek philosophy, or the cultural foundations of the West.
https://image.nostr.build/017a314c11238433545977e681801904b8b702e1b568ff6c9438e8577721a243.jpg
3. The Battle of Hastings (1066) – The Making of Modern England
In 1066, William of Normandy led his army across the English Channel to claim the throne of England. At the Battle of Hastings, he faced King Harold II’s Anglo-Saxon forces in a brutal fight that would decide the future of the island.
William’s forces employed innovative strategies, including a feigned retreat, which broke Harold’s defensive lines. Harold was killed, and with him, Anglo-Saxon rule in England.
https://image.nostr.build/110045a76be0577defc5d9b884e5d811235f1992941847ca8a1b1a7b80c9bf79.jpg
Hastings completely transformed England. The Normans introduced a new ruling elite, reshaped governance, and left an enduring mark on the English language. Old English fused with Norman French, laying the foundation for modern English.
Beyond language, the Norman conquest brought England closer to continental Europe, influencing its legal systems, architecture, and culture for centuries. Hastings wasn’t just a military victory—it was a cultural watershed that forever changed England and, by extension, the world.
https://image.nostr.build/2799f91505263370ffb3a899ea4c79a65894f56673b81a024b206e013f3e73a9.jpg
4. The Battle of Lepanto (1571) – Christendom Strikes Back
By the late 16th century, the Ottoman Empire had become a dominant naval power, threatening Christian trading colonies and the stability of Europe’s maritime trade routes.
In 1570, the Ottomans besieged the Venetian-held island of Cyprus. After an 11-month siege, the starving Venetian garrison surrendered under promises of safe passage—but the Ottomans betrayed them, imprisoned the soldiers, and flayed their commander alive.
In response, the Papal States, Spain, Venice, Genoa, and other Christian powers set aside their rivalries and formed the Holy League. In a climactic naval showdown, over 130,000 men engaged in a fierce battle that ultimately ended in a decisive Christian victory.
https://image.nostr.build/0f233ec50e817874e1e6711a1e035b436e206b032d8cac8b33a68230beb20e1b.jpg
Lepanto halted Ottoman expansion into the western Mediterranean and reestablished European control over crucial sea routes. Among the soldiers that day was Miguel de Cervantes, who was wounded and lost the use of his left arm. His experience shaped his literary masterpiece, Don Quixote, further embedding Lepanto’s legacy in European art and culture.
5. The Battle of Trafalgar (1805) – Britain Secures Global Supremacy
In 1805, Napoleon sought to break British naval dominance by uniting the French and Spanish fleets against Admiral Horatio Nelson. The Battle of Trafalgar would decide the fate of European power at sea.
Outnumbered, Nelson devised an unorthodox strategy, splitting his fleet into two perpendicular columns to punch through enemy lines. The result? A decisive British victory—22 enemy ships destroyed without a single British vessel lost.
Trafalgar didn’t just shatter Napoleon’s naval ambitions—it secured Britain’s command of the seas for over a century. This naval dominance paved the way for the Pax Britannica, allowing Britain to expand its empire and maintain global influence well into the 20th century.
https://image.nostr.build/bf5e00f020a0755ea50c1bf1def870cfb226cb5ad18a91445eddac8389b2f05f.jpg
But Trafalgar’s legacy is also bittersweet—Nelson was fatally shot in battle. As he lay dying, he was informed of the victory. His last words?
“Now I am satisfied. Thank God, I have done my duty.”
Nelson’s death turned him into a national hero, and Trafalgar became a defining moment in British history.
More Than Just Battles
These five battles weren’t just clashes of armies—they were turning points that shaped the world.
- Cannae forged Rome’s resilience.
- Marathon preserved Greek democracy.
- Hastings reshaped England’s culture and language.
- Lepanto altered the balance of power in the Mediterranean.
- Trafalgar secured British naval dominance for a century.
Each of these battles reshaped civilizations—proving that history isn’t just written in words, but also in blood, steel, and strategy.
-
 @ a311301f:4663f8f2
2025-01-22 21:39:38
@ a311301f:4663f8f2
2025-01-22 21:39:38```perl
!/usr/bin/perl
use strict; use warnings; use Term::ReadKey;
STDOUT->autoflush(1);
this version run on Windows and use a pwd.txt file created by
the perl program ; otherwise encoding issue may follow
following sub needs to be used first by uncommenting the main call
sub write_password { print ("Enter Password: ") ; my $password =
; my $file_path = 'pwd.txt'; open(my $fh, '>', $file_path) or die "Cannot open file '$file_path' for writing: $!"; print $fh $password; close($fh); print ("\n"); print "Password written to '$file_path'\n"; } sub printhex { my $str = shift ; foreach my $char (split //, $str) { printf "%02x ", ord($char); } print "\n"; }
Function to read password from file
sub read_password_from_file { #unecessary #binmode(STDIN, ':crlf'); my $file_path = shift; #unecessary #local $/ = "\r\n" ; # CR, use "\r\n" for CRLF or "\n" for LF open(my $fh, '<', $file_path) or die "Cannot open file '$file_path' for reading: $!"; my $password = <$fh>; close($fh); #printhex ($password) ;
chomp($password); print "'$password'\n" ; #$password =~ s/\r?\n$//; # Remove newline character #$password = substr($password, 2) ; # BOM File starts with FF FE printhex($password ) ; # "\'$password\'\n" ; #$password = "abcde" ;
return $password; }Main program
sub main { #write_password(); # to uncomment for first use my $correct_password = read_password_from_file("pwd.txt") ; print "Enter password: "; ReadMode('noecho'); # Turn off echo my $entered_password = ReadLine(0); ReadMode('restore'); # Restore echo chomp($entered_password); print "\n";
# Compare entered password with the correct password if ($entered_password eq $correct_password) { print "Access granted!\n"; } else { print "Access denied!\n"; print "'$entered_password' not eq '$correct_password' \n"; printhex ($entered_password); printhex ($correct_password) ; print "The end! \n" ; }}
Call main function
main();
```
-
 @ a012dc82:6458a70d
2025-02-15 02:53:03
@ a012dc82:6458a70d
2025-02-15 02:53:03In the ever-evolving landscape of finance, two names have consistently dominated the conversation in recent years: Bitcoin and Ethereum. These cryptocurrencies have not only revolutionized the way we think about money but have also paved the way for a future where digital assets play a central role. As we stand at the cusp of a new era in finance, it's crucial to understand the significance of these two giants in the crypto world. This article takes a deep dive into Bitcoin and Ethereum, exploring their origins, their impact on the financial sector, and what the future might hold for these digital currencies.
Table of Contents
-
Bitcoin: The Pioneer of Cryptocurrency
-
Ethereum: More Than Just a Cryptocurrency
-
The Impact on the Financial Sector
-
The Future Outlook
-
Conclusion
-
FAQs
Bitcoin: The Pioneer of Cryptocurrency
Bitcoin, created by the mysterious figure or group known as Satoshi Nakamoto, emerged in 2009 as the first decentralized digital currency. It introduced the world to the concept of a blockchain, a distributed ledger technology that ensures security and transparency in transactions. Over the years, Bitcoin has become synonymous with cryptocurrency, often being the first token that comes to mind when discussing digital assets. Its primary appeal lies in its decentralized nature, free from the control of any government or financial institution, offering a form of financial freedom and privacy that traditional currencies cannot.
However, Bitcoin is not without its challenges. Its scalability issues, high transaction fees, and extensive energy consumption due to mining activities have been points of contention. Despite these challenges, Bitcoin has maintained its position as the leading cryptocurrency, often referred to as digital gold, and continues to attract significant investment from both retail and institutional investors.
Ethereum: More Than Just a Cryptocurrency
Ethereum, proposed in late 2013 by programmer Vitalik Buterin, is often considered the second most important cryptocurrency after Bitcoin. However, Ethereum offers much more than just a digital currency; it's a platform for decentralized applications (dApps). The introduction of smart contracts on Ethereum's blockchain has opened up possibilities far beyond simple monetary transactions. These self-executing contracts with the terms of the agreement directly written into code have enabled the development of a wide range of applications, from decentralized finance (DeFi) to non-fungible tokens (NFTs).
Ethereum's flexibility and adaptability have made it a cornerstone of the blockchain development community. However, like Bitcoin, it faces its own set of challenges, including network congestion and high gas fees, especially during peak usage times. The much-anticipated upgrade to Ethereum 2.0 aims to address these issues by shifting from a proof-of-work to a proof-of-stake consensus mechanism, which is expected to significantly increase its scalability and reduce its environmental impact.
The Impact on the Financial Sector
The advent of Bitcoin and Ethereum has had a profound impact on the financial sector. They have challenged traditional financial models and institutions, introducing concepts like decentralized finance, which aims to create a more open and accessible financial system. Cryptocurrencies have also introduced new investment opportunities, with Bitcoin becoming a popular choice for investors looking for an asset that is not correlated with traditional financial markets.
Moreover, the technologies behind these cryptocurrencies, especially blockchain, have found applications in various sectors, including banking, supply chain management, and voting systems. The transparency, security, and efficiency offered by blockchain technology have the potential to revolutionize these industries.
The Future Outlook
Looking ahead, the future of Bitcoin, Ethereum, and cryptocurrencies, in general, is both exciting and uncertain. Regulatory challenges, technological advancements, and market dynamics will play significant roles in shaping their paths. Bitcoin, with its limited supply and increasing adoption, might continue to be seen as a store of value, while Ethereum's transition to Ethereum 2.0 could solidify its position as the leading platform for decentralized applications.
The increasing interest from institutional investors and the integration of cryptocurrency services by major financial players suggest a growing acceptance and maturation of these digital assets. However, the volatile nature of cryptocurrencies remains a significant factor, making them a risky, albeit potentially rewarding, investment.
Conclusion
Bitcoin and Ethereum have undeniably paved the way for a new era in finance, one that is digital, decentralized, and diverse. Their impact extends beyond just the financial sector, influencing technology, governance, and society as a whole. As we move forward, the continuous evolution of these cryptocurrencies and their underlying technologies will undoubtedly play a pivotal role in shaping the future of finance. Whether they will become mainstream elements of our financial system or remain as alternative assets, one thing is certain: Bitcoin and Ethereum have forever changed the landscape of finance, and their journey is far from over.
FAQs
How does Ethereum differ from Bitcoin? While Bitcoin was created primarily as a digital currency, Ethereum is a decentralized platform that enables smart contracts and decentralized applications (dApps). Ethereum's native token, Ether, is used to facilitate these operations.
What are the main uses of Bitcoin and Ethereum? Bitcoin is mainly used as a digital currency and a store of value, often referred to as 'digital gold.' Ethereum, on the other hand, is used to power smart contracts and dApps, playing a crucial role in the decentralized finance (DeFi) and non-fungible token (NFT) sectors.
What are the challenges facing Bitcoin and Ethereum? Bitcoin faces challenges like scalability, high transaction fees, and environmental concerns due to its mining process. Ethereum struggles with network congestion and high gas fees, although its upcoming upgrade to Ethereum 2.0 aims to address these issues.
Are Bitcoin and Ethereum regulated? The regulatory status of Bitcoin and Ethereum varies by country. While some countries have embraced them with specific regulations, others have imposed restrictions or outright bans.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 35f3a26c:92ddf231
2025-01-22 20:48:34
@ 35f3a26c:92ddf231
2025-01-22 20:48:34Background
Most people non familiar with Bitcoin thinks that there its has not smart contracts capabilities, and that is incorrect, there are smart contract capabilities, and despite limited in comparison with other blockchain networks, those capabilities are evolving slowly but surely.
The support for smart contracts is done through its scripting language, Script, which allows developers to create complex conditions for transactions.
What can you do with Script? 1. time locks 2. multi-signature requirements 3. other custom logic
opcodes like OP_CHECKLOCKTIMEVERIFY (CLTV) and OP_CHECKSEQUENCEVERIFY (CSV) are used to build more sophisticated smart contracts, these opcodes enable features such as the Lightning Network, a key scaling solution for Bitcoin
back in 2021, the Taproot upgrade introduced Pay-to-Taproot (P2TR), in summary allows for more private and efficient smart contracts, in that soft fork more was added, in addition to Taproot, we got as well Schnorr signatures, which enables multiple signatures to be aggregated into a single signature, improving scalability and privacy and MAST (Merklized Abstract Syntax Trees) which reduces the size of complex smart contracts, making them more efficient, as an added value, this efficiency reduces the cost of transactions.
The Taproot upgrade has laid the foundation for the development of more sophisticated smart contracts on the Bitcoin network, and the use of covenants is an important part of this development.
What is Bitcoin Covenants?
It is a BIP (Bitcoin Improvement Proposal), BIP-347, assigned on April 24, 2024, which marks the first step towards reintroducing functionality removed from Bitcoin by its creator Satoshi Nakamoto in 2010. This proposal aims to bring smart contract functionality to Bitcoin as we see in other EVM networks.
The proposal’s developers authors names are Ethan Heilman and Armin Sabouri, now the community will debate its merits.
Here the link, in case you are curious:
https://github.com/bitcoin/bips/blob/master/bip-0347.mediawiki
It is worth to read the motivation section of the BIP, which reads:
“Bitcoin Tapscript lacks a general purpose way of combining objects on the stack, restricting the expressiveness and power of Tapscript. This prevents, among many other things, the ability to construct and evaluate merkle trees and other hashed data structures in Tapscript. OP_CAT, by adding a general purpose way to concatenate stack values, would overcome this limitation and greatly increase the functionality of Tapscript.
OP_CAT aims to expand the toolbox of the tapscript developer with a simple, modular, and useful opcode in the spirit of Unix. To demonstrate the usefulness of OP_CAT below we provide a non-exhaustive list of some use cases that OP_CAT would enable:
Bitstream, a protocol for the atomic swap (fair exchange) of bitcoins for decryption keys, that enables decentralized file hosting systems paid in Bitcoin. While such swaps are currently possible on Bitcoin without OP_CAT, they require the use of complex and computationally expensive Verifiable Computation cryptographic techniques. OP_CAT would remove this requirement on Verifiable Computation, making such protocols far more practical to build in Bitcoin.
Tree signatures provide a multisignature script whose size can be logarithmic in the number of public keys and can encode spend conditions beyond n-of-m. For instance a transaction less than 1KB in size could support tree signatures with up to 4,294,967,296 public keys. This also enables generalized logical spend conditions.
Post-Quantum Lamport signatures in Bitcoin transactions. Lamport signatures merely require the ability to hash and concatenate values on the stack. [4] It has been proposed that if ECDSA is broken or a powerful computer was on the horizon, there might be an effort to protect ownership of bitcoins by allowing people to mark their taproot outputs as "script-path only" and then move their coins into such outputs with a leaf in the script tree requiring a Lamport signature. It is an open question if a tapscript commitment would preserve the quantum resistance of Lamport signatures. Beyond this question, the use of Lamport Signatures in taproot outputs is unlikely to be quantum resistant even if the script spend-path is made quantum resistant. This is because taproot outputs can also be spent with a key. An attacker with a sufficiently powerful quantum computer could bypass the taproot script spend-path by finding the discrete log of the taproot output and thus spending the output using the key spend-path. The use of "Nothing Up My Sleeve" (NUMS) points as described in BIP-341 to disable the key spend-path does not disable the key spend-path against a quantum attacker as NUMS relies on the hardness of finding discrete logs. We are not aware of any mechanism which could disable the key spend-path in a taproot output without a soft-fork change to taproot.
Non-equivocation contracts in tapscript provide a mechanism to punish equivocation/double spending in Bitcoin payment channels. OP_CAT enables this by enforcing rules on the spending transaction's nonce. The capability is a useful building block for payment channels and other Bitcoin protocols.
Vaults [6] which are a specialized covenant that allows a user to block a malicious party who has compromised the user's secret key from stealing the funds in that output. As shown in OP_CAT is sufficient to build vaults in Bitcoin.
Replicating CheckSigFromStack which would allow the creation of simple covenants and other advanced contracts without having to pre-sign spending transactions, possibly reducing complexity and the amount of data that needs to be stored. Originally shown to work with Schnorr signatures, this result has been extended to ECDSA signatures.
OP_CAT was available in early versions of Bitcoin. In 2010, a single commit disabled OP_CAT, along with another 15 opcodes. Folklore states that OP_CAT was removed in this commit because it enabled the construction of a script whose evaluation could have memory usage exponential in the size of the script. For example, a script that pushed a 1-byte value on the stack and then repeated the opcodes OP_DUP, OP_CAT 40 times would result in a stack element whose size was greater than 1 terabyte assuming no maximum stack element size. As Bitcoin at that time had a maximum stack element size of 5000 bytes, the effect of this expansion was limited to 5000 bytes. This is no longer an issue because tapscript enforces a maximum stack element size of 520 bytes.”
The last update of the BIP was done on Sep. 8 2024 by Ethan Heilman
Controversy
The controversy revolves around two main camps:
- Those who want to preserve Bitcoin’s network for monetary transactions only, arguing that adding smart contract capabilities could introduce risks and complexity.
- Others who advocate for expanding Bitcoin’s capabilities to support a wider range of applications, seeing OP_CAT as a step towards enhancing the network’s utility.
Final Thoughts
Bitcoin have done what no other asset have done in history, neither gold, its success is clear, and now, that BlackRock is involved, “miraculously”, corporations and governments are getting on board and Bitcoin is not anymore only for criminals or “rat poison” or “is going to zero”.
But as all tech, improvements are important, if those improvements are done to secure more the network and to make it more robust, there will be little to none controversy, however, when those changes are aiming at adding new shinning features that would change Bitcoin into a network with similar features as Ethereum in terms of contracts that requires attention and debate, few questions come to mind:
- How will that change affect the security of the network?
- How that change will affect the blockchain usage?
- What is the projected impact over the fees per transaction if this change is approved?
- Will the impact create pressure for the block size increase discussion to come back to the table and with it a second war?
Looking into Ethan Heilman work and contribution to the Bitcoin ecosystem, I am inclined to believe that he has considered most of those questions.
Looking forward to observe the evolution of this proposal.
You liked the article? Make my day brighter!
Like and share!
Last but not least, the following link is an unstoppable domain, it will open a page in which you can perform an anonymous contribution to support my work:
https://rodswallet.unstoppable/
The link didn’t open?
To open the link you need to use a best in class browser that supports web3, two are recommended: Brave Browser and Opera Browser
-
 @ 7d33ba57:1b82db35
2025-02-15 01:48:56
@ 7d33ba57:1b82db35
2025-02-15 01:48:565 Photography Tips for Excursions Excursions take you to incredible places, but they’re often designed for quick stops, catering to "click-and-go" tourists rather than photographers and videographers. Capturing great shots in such fast-paced environments can be challenging! However, if an excursion is your only way to visit a stunning location, don’t worry—I got some tips to help you make the most of it.
1) *Plan Your Story in Advance* Before you even set foot on the excursion, think about the story you want to capture. In your mind, you’ve probably already envisioned your photo or video album—this is exactly what you should do! Excursions move fast, leaving little time for on-the-spot decisions. Research your destination beforehand, look up photos online, and familiarize yourself with the key subjects you want to focus on. Being prepared will help you capture the shots that truly matter.
2) Secure the Best Spot If your excursion involves a bus or boat, positioning yourself strategically can make all the difference. Try to be one of the first to board so you can grab the best spot—usually at the front. This gives you a clear view. Quick reflexes will help you capture the scene without unwanted distractions!
3) Sun position Always pay attention to the direction of the sun while picking your seat. Position yourself to shoot with the sunlight rather than against it to avoid harsh backlighting and maximize the natural light in your photos.
4) Connect with the Guide The guide plays a big role in setting the pace of the excursion, so building a friendly connection can work in your favor. A smile and some casual conversation can make them more receptive to your needs, giving you extra time to capture the perfect shot. When you arrive at a location, don’t hesitate to ask if you’re allowed to take your own shots instead of strictly following the group. A little charm can go a long way in making your photography experience smoother and more enjoyable!
5) Manage Your Time & Enjoy the Moment As a photographer or videographer, it’s easy to get lost in your creative zone, but remember—you’re on a group excursion! Be mindful of the schedule and avoid spending too much time on a single shot. Others in the group paid the same price for the experience, so it’s important to be respectful of their time—no matter how big or fancy your camera is!
If possible, consider booking a private excursion or joining fellow travel photographers who appreciate spending extra time at each location. This way, you can focus on capturing the best shots without feeling rushed. Most importantly: Once you’ve taken your amazing shot, take a moment to truly experience the place. Too many travelers stare at their camera screens while walking, missing the beauty right in front of them. Save the reviewing for when you're back at your hotel! After all, photography is about more than just the shot—it’s about the memories you make along the way.
And don’t forget to save the special pictures onto your human hard drive—your memory! This is where we create the real movie.
-
 @ 1c197b12:242e1642
2025-02-14 21:40:46
@ 1c197b12:242e1642
2025-02-14 21:40:46We the People of the United States, in Order to form a more perfect Union, establish Justice, insure domestic Tranquility, provide for the common defence, promote the general Welfare, and secure the Blessings of Liberty to ourselves and our Posterity, do ordain and establish this Constitution for the United States of America.
Article. I. Section. 1. All legislative Powers herein granted shall be vested in a Congress of the United States, which shall consist of a Senate and House of Representatives.
Section. 2. The House of Representatives shall be composed of Members chosen every second Year by the People of the several States, and the Electors in each State shall have the Qualifications requisite for Electors of the most numerous Branch of the State Legislature.
No Person shall be a Representative who shall not have attained to the Age of twenty five Years, and been seven Years a Citizen of the United States, and who shall not, when elected, be an Inhabitant of that State in which he shall be chosen.
Representatives and direct Taxes shall be apportioned among the several States which may be included within this Union, according to their respective Numbers, which shall be determined by adding to the whole Number of free Persons, including those bound to Service for a Term of Years, and excluding Indians not taxed, three fifths of all other Persons. The actual Enumeration shall be made within three Years after the first Meeting of the Congress of the United States, and within every subsequent Term of ten Years, in such Manner as they shall by Law direct. The Number of Representatives shall not exceed one for every thirty Thousand, but each State shall have at Least one Representative; and until such enumeration shall be made, the State of New Hampshire shall be entitled to chuse three, Massachusetts eight, Rhode-Island and Providence Plantations one, Connecticut five, New-York six, New Jersey four, Pennsylvania eight, Delaware one, Maryland six, Virginia ten, North Carolina five, South Carolina five, and Georgia three.
When vacancies happen in the Representation from any State, the Executive Authority thereof shall issue Writs of Election to fill such Vacancies.
The House of Representatives shall chuse their Speaker and other Officers; and shall have the sole Power of Impeachment.
Section. 3. The Senate of the United States shall be composed of two Senators from each State, chosen by the Legislature thereof, for six Years; and each Senator shall have one Vote.
Immediately after they shall be assembled in Consequence of the first Election, they shall be divided as equally as may be into three Classes. The Seats of the Senators of the first Class shall be vacated at the Expiration of the second Year, of the second Class at the Expiration of the fourth Year, and of the third Class at the Expiration of the sixth Year, so that one third may be chosen every second Year; and if Vacancies happen by Resignation, or otherwise, during the Recess of the Legislature of any State, the Executive thereof may make temporary Appointments until the next Meeting of the Legislature, which shall then fill such Vacancies.
No Person shall be a Senator who shall not have attained to the Age of thirty Years, and been nine Years a Citizen of the United States, and who shall not, when elected, be an Inhabitant of that State for which he shall be chosen.
The Vice President of the United States shall be President of the Senate, but shall have no Vote, unless they be equally divided.
The Senate shall chuse their other Officers, and also a President pro tempore, in the Absence of the Vice President, or when he shall exercise the Office of President of the United States.
The Senate shall have the sole Power to try all Impeachments. When sitting for that Purpose, they shall be on Oath or Affirmation. When the President of the United States is tried, the Chief Justice shall preside: And no Person shall be convicted without the Concurrence of two thirds of the Members present.
Judgment in Cases of Impeachment shall not extend further than to removal from Office, and disqualification to hold and enjoy any Office of honor, Trust or Profit under the United States: but the Party convicted shall nevertheless be liable and subject to Indictment, Trial, Judgment and Punishment, according to Law.
Section. 4. The Times, Places and Manner of holding Elections for Senators and Representatives, shall be prescribed in each State by the Legislature thereof; but the Congress may at any time by Law make or alter such Regulations, except as to the Places of chusing Senators.
The Congress shall assemble at least once in every Year, and such Meeting shall be on the first Monday in December, unless they shall by Law appoint a different Day.
Section. 5. Each House shall be the Judge of the Elections, Returns and Qualifications of its own Members, and a Majority of each shall constitute a Quorum to do Business; but a smaller Number may adjourn from day to day, and may be authorized to compel the Attendance of absent Members, in such Manner, and under such Penalties as each House may provide.
Each House may determine the Rules of its Proceedings, punish its Members for disorderly Behaviour, and, with the Concurrence of two thirds, expel a Member.
Each House shall keep a Journal of its Proceedings, and from time to time publish the same, excepting such Parts as may in their Judgment require Secrecy; and the Yeas and Nays of the Members of either House on any question shall, at the Desire of one fifth of those Present, be entered on the Journal.
Neither House, during the Session of Congress, shall, without the Consent of the other, adjourn for more than three days, nor to any other Place than that in which the two Houses shall be sitting.
Section. 6. The Senators and Representatives shall receive a Compensation for their Services, to be ascertained by Law, and paid out of the Treasury of the United States. They shall in all Cases, except Treason, Felony and Breach of the Peace, be privileged from Arrest during their Attendance at the Session of their respective Houses, and in going to and returning from the same; and for any Speech or Debate in either House, they shall not be questioned in any other Place.
No Senator or Representative shall, during the Time for which he was elected, be appointed to any civil Office under the Authority of the United States, which shall have been created, or the Emoluments whereof shall have been encreased during such time; and no Person holding any Office under the United States, shall be a Member of either House during his Continuance in Office.
Section. 7. All Bills for raising Revenue shall originate in the House of Representatives; but the Senate may propose or concur with Amendments as on other Bills.
Every Bill which shall have passed the House of Representatives and the Senate, shall, before it become a Law, be presented to the President of the United States; If he approve he shall sign it, but if not he shall return it, with his Objections to that House in which it shall have originated, who shall enter the Objections at large on their Journal, and proceed to reconsider it. If after such Reconsideration two thirds of that House shall agree to pass the Bill, it shall be sent, together with the Objections, to the other House, by which it shall likewise be reconsidered, and if approved by two thirds of that House, it shall become a Law. But in all such Cases the Votes of both Houses shall be determined by yeas and Nays, and the Names of the Persons voting for and against the Bill shall be entered on the Journal of each House respectively. If any Bill shall not be returned by the President within ten Days (Sundays excepted) after it shall have been presented to him, the Same shall be a Law, in like Manner as if he had signed it, unless the Congress by their Adjournment prevent its Return, in which Case it shall not be a Law.
Every Order, Resolution, or Vote to which the Concurrence of the Senate and House of Representatives may be necessary (except on a question of Adjournment) shall be presented to the President of the United States; and before the Same shall take Effect, shall be approved by him, or being disapproved by him, shall be repassed by two thirds of the Senate and House of Representatives, according to the Rules and Limitations prescribed in the Case of a Bill.
Section. 8. The Congress shall have Power To lay and collect Taxes, Duties, Imposts and Excises, to pay the Debts and provide for the common Defence and general Welfare of the United States; but all Duties, Imposts and Excises shall be uniform throughout the United States;
To borrow Money on the credit of the United States;
To regulate Commerce with foreign Nations, and among the several States, and with the Indian Tribes;
To establish an uniform Rule of Naturalization, and uniform Laws on the subject of Bankruptcies throughout the United States;
To coin Money, regulate the Value thereof, and of foreign Coin, and fix the Standard of Weights and Measures;
To provide for the Punishment of counterfeiting the Securities and current Coin of the United States;
To establish Post Offices and post Roads;
To promote the Progress of Science and useful Arts, by securing for limited Times to Authors and Inventors the exclusive Right to their respective Writings and Discoveries;
To constitute Tribunals inferior to the supreme Court;
To define and punish Piracies and Felonies committed on the high Seas, and Offences against the Law of Nations;
To declare War, grant Letters of Marque and Reprisal, and make Rules concerning Captures on Land and Water;
To raise and support Armies, but no Appropriation of Money to that Use shall be for a longer Term than two Years;
To provide and maintain a Navy;
To make Rules for the Government and Regulation of the land and naval Forces;
To provide for calling forth the Militia to execute the Laws of the Union, suppress Insurrections and repel Invasions;
To provide for organizing, arming, and disciplining, the Militia, and for governing such Part of them as may be employed in the Service of the United States, reserving to the States respectively, the Appointment of the Officers, and the Authority of training the Militia according to the discipline prescribed by Congress;
To exercise exclusive Legislation in all Cases whatsoever, over such District (not exceeding ten Miles square) as may, by Cession of particular States, and the Acceptance of Congress, become the Seat of the Government of the United States, and to exercise like Authority over all Places purchased by the Consent of the Legislature of the State in which the Same shall be, for the Erection of Forts, Magazines, Arsenals, dock-Yards, and other needful Buildings;—And
To make all Laws which shall be necessary and proper for carrying into Execution the foregoing Powers, and all other Powers vested by this Constitution in the Government of the United States, or in any Department or Officer thereof.
Section. 9. The Migration or Importation of such Persons as any of the States now existing shall think proper to admit, shall not be prohibited by the Congress prior to the Year one thousand eight hundred and eight, but a Tax or duty may be imposed on such Importation, not exceeding ten dollars for each Person.
The Privilege of the Writ of Habeas Corpus shall not be suspended, unless when in Cases of Rebellion or Invasion the public Safety may require it.
No Bill of Attainder or ex post facto Law shall be passed.
No Capitation, or other direct, Tax shall be laid, unless in Proportion to the Census or enumeration herein before directed to be taken.
No Tax or Duty shall be laid on Articles exported from any State.
No Preference shall be given by any Regulation of Commerce or Revenue to the Ports of one State over those of another: nor shall Vessels bound to, or from, one State, be obliged to enter, clear, or pay Duties in another.
No Money shall be drawn from the Treasury, but in Consequence of Appropriations made by Law; and a regular Statement and Account of the Receipts and Expenditures of all public Money shall be published from time to time.
No Title of Nobility shall be granted by the United States: And no Person holding any Office of Profit or Trust under them, shall, without the Consent of the Congress, accept of any present, Emolument, Office, or Title, of any kind whatever, from any King, Prince, or foreign State.
Section. 10. No State shall enter into any Treaty, Alliance, or Confederation; grant Letters of Marque and Reprisal; coin Money; emit Bills of Credit; make any Thing but gold and silver Coin a Tender in Payment of Debts; pass any Bill of Attainder, ex post facto Law, or Law impairing the Obligation of Contracts, or grant any Title of Nobility.
No State shall, without the Consent of the Congress, lay any Imposts or Duties on Imports or Exports, except what may be absolutely necessary for executing it's inspection Laws: and the net Produce of all Duties and Imposts, laid by any State on Imports or Exports, shall be for the Use of the Treasury of the United States; and all such Laws shall be subject to the Revision and Controul of the Congress.
No State shall, without the Consent of Congress, lay any Duty of Tonnage, keep Troops, or Ships of War in time of Peace, enter into any Agreement or Compact with another State, or with a foreign Power, or engage in War, unless actually invaded, or in such imminent Danger as will not admit of delay.
Article. II. Section. 1. The executive Power shall be vested in a President of the United States of America. He shall hold his Office during the Term of four Years, and, together with the Vice President, chosen for the same Term, be elected, as follows
Each State shall appoint, in such Manner as the Legislature thereof may direct, a Number of Electors, equal to the whole Number of Senators and Representatives to which the State may be entitled in the Congress: but no Senator or Representative, or Person holding an Office of Trust or Profit under the United States, shall be appointed an Elector.
The Electors shall meet in their respective States, and vote by Ballot for two Persons, of whom one at least shall not be an Inhabitant of the same State with themselves. And they shall make a List of all the Persons voted for, and of the Number of Votes for each; which List they shall sign and certify, and transmit sealed to the Seat of the Government of the United States, directed to the President of the Senate. The President of the Senate shall, in the Presence of the Senate and House of Representatives, open all the Certificates, and the Votes shall then be counted. The Person having the greatest Number of Votes shall be the President, if such Number be a Majority of the whole Number of Electors appointed; and if there be more than one who have such Majority, and have an equal Number of Votes, then the House of Representatives shall immediately chuse by Ballot one of them for President; and if no Person have a Majority, then from the five highest on the List the said House shall in like Manner chuse the President. But in chusing the President, the Votes shall be taken by States, the Representation from each State having one Vote; A quorum for this Purpose shall consist of a Member or Members from two thirds of the States, and a Majority of all the States shall be necessary to a Choice. In every Case, after the Choice of the President, the Person having the greatest Number of Votes of the Electors shall be the Vice President. But if there should remain two or more who have equal Votes, the Senate shall chuse from them by Ballot the Vice President.
The Congress may determine the Time of chusing the Electors, and the Day on which they shall give their Votes; which Day shall be the same throughout the United States.
No Person except a natural born Citizen, or a Citizen of the United States, at the time of the Adoption of this Constitution, shall be eligible to the Office of President; neither shall any Person be eligible to that Office who shall not have attained to the Age of thirty five Years, and been fourteen Years a Resident within the United States.
In Case of the Removal of the President from Office, or of his Death, Resignation, or Inability to discharge the Powers and Duties of the said Office, the Same shall devolve on the Vice President, and the Congress may by Law provide for the Case of Removal, Death, Resignation or Inability, both of the President and Vice President, declaring what Officer shall then act as President, and such Officer shall act accordingly, until the Disability be removed, or a President shall be elected.
The President shall, at stated Times, receive for his Services, a Compensation, which shall neither be encreased nor diminished during the Period for which he shall have been elected, and he shall not receive within that Period any other Emolument from the United States, or any of them.
Before he enter on the Execution of his Office, he shall take the following Oath or Affirmation:—"I do solemnly swear (or affirm) that I will faithfully execute the Office of President of the United States, and will to the best of my Ability, preserve, protect and defend the Constitution of the United States."
Section. 2. The President shall be Commander in Chief of the Army and Navy of the United States, and of the Militia of the several States, when called into the actual Service of the United States; he may require the Opinion, in writing, of the principal Officer in each of the executive Departments, upon any Subject relating to the Duties of their respective Offices, and he shall have Power to grant Reprieves and Pardons for Offences against the United States, except in Cases of Impeachment.
He shall have Power, by and with the Advice and Consent of the Senate, to make Treaties, provided two thirds of the Senators present concur; and he shall nominate, and by and with the Advice and Consent of the Senate, shall appoint Ambassadors, other public Ministers and Consuls, Judges of the supreme Court, and all other Officers of the United States, whose Appointments are not herein otherwise provided for, and which shall be established by Law: but the Congress may by Law vest the Appointment of such inferior Officers, as they think proper, in the President alone, in the Courts of Law, or in the Heads of Departments.
The President shall have Power to fill up all Vacancies that may happen during the Recess of the Senate, by granting Commissions which shall expire at the End of their next Session.
Section. 3. He shall from time to time give to the Congress Information of the State of the Union, and recommend to their Consideration such Measures as he shall judge necessary and expedient; he may, on extraordinary Occasions, convene both Houses, or either of them, and in Case of Disagreement between them, with Respect to the Time of Adjournment, he may adjourn them to such Time as he shall think proper; he shall receive Ambassadors and other public Ministers; he shall take Care that the Laws be faithfully executed, and shall Commission all the Officers of the United States.
Section. 4. The President, Vice President and all civil Officers of the United States, shall be removed from Office on Impeachment for, and Conviction of, Treason, Bribery, or other high Crimes and Misdemeanors.
Article. III. Section. 1. The judicial Power of the United States, shall be vested in one supreme Court, and in such inferior Courts as the Congress may from time to time ordain and establish. The Judges, both of the supreme and inferior Courts, shall hold their Offices during good Behaviour, and shall, at stated Times, receive for their Services, a Compensation, which shall not be diminished during their Continuance in Office.
Section. 2. The judicial Power shall extend to all Cases, in Law and Equity, arising under this Constitution, the Laws of the United States, and Treaties made, or which shall be made, under their Authority;—to all Cases affecting Ambassadors, other public Ministers and Consuls;—to all Cases of admiralty and maritime Jurisdiction;—to Controversies to which the United States shall be a Party;—to Controversies between two or more States;— between a State and Citizens of another State,—between Citizens of different States,—between Citizens of the same State claiming Lands under Grants of different States, and between a State, or the Citizens thereof, and foreign States, Citizens or Subjects.
In all Cases affecting Ambassadors, other public Ministers and Consuls, and those in which a State shall be Party, the supreme Court shall have original Jurisdiction. In all the other Cases before mentioned, the supreme Court shall have appellate Jurisdiction, both as to Law and Fact, with such Exceptions, and under such Regulations as the Congress shall make.
The Trial of all Crimes, except in Cases of Impeachment, shall be by Jury; and such Trial shall be held in the State where the said Crimes shall have been committed; but when not committed within any State, the Trial shall be at such Place or Places as the Congress may by Law have directed.
Section. 3. Treason against the United States, shall consist only in levying War against them, or in adhering to their Enemies, giving them Aid and Comfort. No Person shall be convicted of Treason unless on the Testimony of two Witnesses to the same overt Act, or on Confession in open Court.
The Congress shall have Power to declare the Punishment of Treason, but no Attainder of Treason shall work Corruption of Blood, or Forfeiture except during the Life of the Person attainted.
Article. IV. Section. 1. Full Faith and Credit shall be given in each State to the public Acts, Records, and judicial Proceedings of every other State. And the Congress may by general Laws prescribe the Manner in which such Acts, Records and Proceedings shall be proved, and the Effect thereof.
Section. 2. The Citizens of each State shall be entitled to all Privileges and Immunities of Citizens in the several States.
A Person charged in any State with Treason, Felony, or other Crime, who shall flee from Justice, and be found in another State, shall on Demand of the executive Authority of the State from which he fled, be delivered up, to be removed to the State having Jurisdiction of the Crime.
No Person held to Service or Labour in one State, under the Laws thereof, escaping into another, shall, in Consequence of any Law or Regulation therein, be discharged from such Service or Labour, but shall be delivered up on Claim of the Party to whom such Service or Labour may be due.
Section. 3. New States may be admitted by the Congress into this Union; but no new State shall be formed or erected within the Jurisdiction of any other State; nor any State be formed by the Junction of two or more States, or Parts of States, without the Consent of the Legislatures of the States concerned as well as of the Congress.
The Congress shall have Power to dispose of and make all needful Rules and Regulations respecting the Territory or other Property belonging to the United States; and nothing in this Constitution shall be so construed as to Prejudice any Claims of the United States, or of any particular State.
Section. 4. The United States shall guarantee to every State in this Union a Republican Form of Government, and shall protect each of them against Invasion; and on Application of the Legislature, or of the Executive (when the Legislature cannot be convened) against domestic Violence.
Article. V. The Congress, whenever two thirds of both Houses shall deem it necessary, shall propose Amendments to this Constitution, or, on the Application of the Legislatures of two thirds of the several States, shall call a Convention for proposing Amendments, which, in either Case, shall be valid to all Intents and Purposes, as Part of this Constitution, when ratified by the Legislatures of three fourths of the several States, or by Conventions in three fourths thereof, as the one or the other Mode of Ratification may be proposed by the Congress; Provided that no Amendment which may be made prior to the Year One thousand eight hundred and eight shall in any Manner affect the first and fourth Clauses in the Ninth Section of the first Article; and that no State, without its Consent, shall be deprived of its equal Suffrage in the Senate.
Article. VI. All Debts contracted and Engagements entered into, before the Adoption of this Constitution, shall be as valid against the United States under this Constitution, as under the Confederation.
This Constitution, and the Laws of the United States which shall be made in Pursuance thereof; and all Treaties made, or which shall be made, under the Authority of the United States, shall be the supreme Law of the Land; and the Judges in every State shall be bound thereby, any Thing in the Constitution or Laws of any State to the Contrary notwithstanding.
The Senators and Representatives before mentioned, and the Members of the several State Legislatures, and all executive and judicial Officers, both of the United States and of the several States, shall be bound by Oath or Affirmation, to support this Constitution; but no religious Test shall ever be required as a Qualification to any Office or public Trust under the United States.
Article. VII. The Ratification of the Conventions of nine States, shall be sufficient for the Establishment of this Constitution between the States so ratifying the Same.
The Word, "the," being interlined between the seventh and eighth Lines of the first Page, The Word "Thirty" being partly written on an Erazure in the fifteenth Line of the first Page, The Words "is tried" being interlined between the thirty second and thirty third Lines of the first Page and the Word "the" being interlined between the forty third and forty fourth Lines of the second Page.
Attest William Jackson Secretary
done in Convention by the Unanimous Consent of the States present the Seventeenth Day of September in the Year of our Lord one thousand seven hundred and Eighty seven and of the Independance of the United States of America the Twelfth In witness whereof We have hereunto subscribed our Names,
-
 @ b17fccdf:b7211155
2025-01-21 18:10:10
@ b17fccdf:b7211155
2025-01-21 18:10:10Link to the bonus guide ~ > HERE <~
Some notes:
ℹ️ For the moment, this guide will touch only the case of an only testnet mode situation, in the future, we will study adding the case of configuration to enable the parallel/simultaneous mode (mainnet+testnet in the same device) in an extra section in this guide.
ℹ️ The services mentioned in this guide are those that have been tested using testnet configuration and these worked fine. Later, in the next versions of this guide, we will go to adding other processes to adapt other services to the testnet mode.
Enjoy it MiniBolter! 💙
-
 @ b17fccdf:b7211155
2025-01-21 18:04:28
@ b17fccdf:b7211155
2025-01-21 18:04:28Available at: https://minibolt.info
Main changes to the version 1:
- The complete guide has been migrated to the new design visual builder web tool platform gitbook.com
- New modern UI (responsive, full width, and better visual items)
- New menu structure for a better user experience
- New visual items to improve the navigation through the web page
- New switch to enable light/dark theme
- Enabled Cloudflare Proxy for maximum protection against attacks and better management of the domain
Other changes:
- New MiniBolt Linktr forked of the alternative FOSS project proposed by Gzuuus
- Changed MiniBolt from a personal project to an organization so that the project has its own identity
- New email contact address hello@minibolt.info to receive proposals and give support
- New resources folder with the current MiniBolt roadmap, network map diagrams, and others
ℹ️ More info:
- The new version is available with the known domain: minibolt.info but from now on links associated with the new v2 version were shared using the v2.minibolt.info subdomain due to a GitBook limitation
- The old and deprecated v1 will be still available at a time in the subdomain v1.minibolt.info, but is in the roadmap delete it definitely in the future, take note ASAP of all that you need of that version before this happens
- Contributors and collaborators will be able to continue doing PR through code programming or using the design block builder gitbook.com
Enjoy it MiniBolter! 💙
-
 @ 1c197b12:242e1642
2025-02-14 21:38:15
@ 1c197b12:242e1642
2025-02-14 21:38:15Today, I'm going to attempt to install Servus to my test server. I'll be using a raspberry Pi4 4GB version with a 16GB microSD card (because what I have laying around). And, as you know... if it'll run on a Pi, it'll run pretty much anywhere.
What is SERVUS?
From GitHub... "Servus is a CMS, personal Nostr relay and personal Blossom server fully self-contained within one executable file."
Here's what you'll need:
A spare server. It can be a VPS, old laptop, old computer, 3rd market server from a decommissioned datacenter that you got for cheap on Ebay, a NUC... something that can run Linux.
- An understanding of the Linux terminal.
- install git and cargo.
- A web browser (don't you side-eye me!).
Let Us Begin...
I'm assuming you're using a Debian-based system. Open your terminal and enter the following:
Go ahead and ssh into your server with something like: "ssh yourusername@ipaddress" or "ssh yourusername@domainname.tld" enter your password when prompted and hit enter.

If you plan to do other stuff with your server later on, you might even consider using "ssh-copy-id yourusername@ipaddress" in order to not have to enter you password, all-the-time.

(Without the quotes) "su", or "sudo su". Whatever means you use to get to superuser (root). Then, enter your password.

Once in root, type: apt install git cargo -y Then, hit enter. You'll see a wall text... yadda yadda.


Now, you'll type (without quotes): "git clone https://github.com/servuscms/servus.git" and hit enter. You'll see a progress bar.

If you type "ls" you should see a folder labeled, "servus". We now change directories by typing, "cd servus". Inside of the servus folder you'll see a few other folders and a few files by typing "ls" again.

According the the servus github, there are a few build options. I'm going to use the "release" version for this tutorial. We do this by typing, "cargo build --release". You'll see a fetch progress bar and a wall of text.


NOTE: I'm using a raspberry pi 4, in this tutorial. At the end of trying "cargo build --release" I got a version error for a package called "anstream v0.6.14" because it requires "rustc 1.65.0", or higher. The error message gives you a fix by typing "cargo update -p anstream@0.6.14 --precise ver"

BUT that won't work. Here's how to fix it:
Type the following (without quotations): "apt purge rustc -y && apt install curl -y && curl https://sh.rustup.rs -sSf | sh"
This will remove the outdated rustc. Then, you're installing curl so that you can install the latest version of rustc and cargo because they aren't in the distro repo. Restart your machine with: "sudo reboot". Once you're back into your servus directory, just run the "cargo build" command, again. Now back to the show!
Now that we have run the "cargo build" command, it's time to move on to setting up access and ssl. According to github, there are a few options. They are as follows:
-
./target/debug/servus - this starts Servus on port 4884, without SSL
-
sudo ./target/debug/servus --ssl-acme[-production] --contact-email youremail@example.com (this starts Servus on port 443 and obtains SSL certificates from Let's Encrypt using ACME by providing a contact email).
-
sudo ./target/debug/servus --ssl-cert
--ssl-key (this starts Servus on port 443 using the providedand ) I'll be using the command no calling for SSL. More information can be found here: https://github.com/servuscms/servus

So from the terminal we input (without quotes): "./target/release/servus" because, as you may recall, I used the "cargo build --release" version earlier.
It will ask a few questions. Here's what I put...
Domain: test.local
Admin pubkey: nostr:npub1rsvhkyk2nnsyzkmsuaq9h9ms7rkxhn8mtxejkca2l4pvkfpwzepql3vmtf

Then, you'll get a bit of output with your ip and port interface. In this case, it's http://localhost:4884 Now go to your browser and input that address, it's local, or the IP address of the server... something like, http://192.168.x.x:4884 and HUZZAH!!! Just like that, you should see your site. To get to the admin section of your site, just add "/.admin" (without quotes) to the IP address you just input into the browser.


CONGRATS! I hope this was helpful :-)
While Servus is extremely experimental, and it is advised to not run it in production. There are a number of features worth taking a look at. More information about what Servus can do can be found here: Servus Github
DONE.
-
 @ 1c197b12:242e1642
2025-02-14 21:27:28
@ 1c197b12:242e1642
2025-02-14 21:27:28This article will be basic instructions for extreme normies (I say that lovingly), or anyone looking to get started with using zap.stream and sharing to nostr.
EQUIPMENT Getting started is incredibly easy and your equipment needs are miniscule.
An old desktop or laptop running Linux, MacOs, or Windows made in the passed 15yrs should do. Im currently using and old Dell Latitude E5430 with an Intel i5-3210M with 32Gigs of ram and 250GB hard drive. Technically, you go as low as using a Raspberry Pi 4B+ running Owncast, but Ill save that so a future tutorial.
Let's get started.
ON YOUR COMPUTER You'll need to install OBS (open broaster software). OBS is the go-to for streaming to social media. There are tons of YouTube videos on it's function. WE, however, will only be doing the basics to get us up and running.
First, go to https://obsproject.com/

Once on the OBS site, choose the correct download for you system. Linux, MacOs or Windows. Download (remember where you downloaded the file to). Go there and install your download. You may have to enter your password to install on your particular operating system. This is normal.
Once you've installed OBS, open the application. It should look something like this...

For our purposes, we will be in studio mode. Locate the 'Studio Mode' button on the right lower-hand side of the screen, and click it.

You'll see the screen split like in the image above. The left-side is from your desktop, and the right-side is what your broadcast will look like.
Next, we go to settings. The 'Settings' button is located right below the 'Studio Mode" button.

Now we're in settings and you should see something like this...

Now locate stream in the right-hand menu. It should be the second in the list. Click it.

Once in the stream section, go to 'Service' and in the right-hand drop-down, find and select 'Custom...' from the drop-down menu.

Remeber where this is because we'll need to come back to it, shortly.
ZAPSTREAM We need our streamkey credentials from Zapstream. Go to https://zap.stream. Then, go to your dashboard.

Located on the lower right-hand side is the Server URL and Stream Key. You'll need to copy/paste this in OBS.

You may have to generate new keys, if they aren't already there. This is normal. If you're interested in multi-streaming (That's where you broadcast to multiple social media platforms all at once), youll need the server URL and streamkeys from each. You'll place them in their respective forms in Zapstream's 'Stream Forwarding" section.

Use the custom form, if the platform you want to stream to isn't listed.
*Side-Note: remember that you can use your nostr identity across multiple nostr client applications. So when your login for Amethyst, as an example, could be used when you login to zapstream. Also, i would suggest using Alby's browser extension. It makes it much easier to fund your stream, as well as receive zaps. *
Now, BACK TO OBS... With Stream URL and Key in hand, paste them in the 'Stream" section of OBS' settings. Service [Custom...] Server [Server URL] StreamKey [Your zapstream stream key]

After you've entered all your streaming credentials, click 'OK' at the bottom, on the right-hand side.
WHAT'S NEXT? Let's setup your first stream from OBS. First we need to choose a source. Your source is your input device. It can be your webcam, your mic, your monitor, or any particular window on your screen. assuming you're an absolute beginner, we're going to use the source 'Window Capture (Xcomposite)'.

Now, open your source file. We'll use a video source called 'grannyhiphop.mp4'. In your case it can be whatever you want to stream; Just be sure to select the proper source.

Double-click on 'Window Capture' in your sources list. In the pop-up window, select your file from the 'Window' drop-down menu.


You should see something like this...

Working in the left display of OBS, we will adjust the video by left-click, hold and drag the bottom corner, so that it takes up the whole display.

In order to adjust the right-side display ( the broadcast side), we need to manipulate the video source by changing it's size.

This may take some time to adjust the size. This is normal. What I've found to help is, after every adjustment, I click the 'Fade (300ms)' button. I have no idea why it helps, but it does, lol.

Finally, after getting everything to look the way you want, you click the 'Start Stream' button.

BACK TO ZAPSTREAM Now, we go back to zapstream to check to see if our stream is up. It may take a few moments to update. You may even need to refresh the page. This is normal.
 STREAMS UP!!!
STREAMS UP!!!A few things, in closing. You'll notice that your dashbooard has changed. It'll show current stream time, how much time you have left (according to your funding source), who's zapped you with how much theyve zapped, the ability to post a note about your stream (to both nostr and twitter), and it shows your chatbox with your listeners. There are also a raid feature, stream settings (where you can title & tag your stream). You can 'topup' your funding for your stream. As well as, see your current balance.
You did a great and If you ever need more help, just use the tag #asknostr in your note. There are alway nostriches willing to help.
STAY AWESOME!!!
-
 @ c43d6de3:a6583169
2025-02-14 17:34:05
@ c43d6de3:a6583169
2025-02-14 17:34:05“IN THIS SPRING of 1953 the free world weighs one question above all others: the chance for a just peace for all peoples,” Dwight D. Eisenhower’s throat went dry and he swallowed to alleviate the burn. Eight years had passed since the end of world war 2 but still the beaches of the Marshall Islands lay charred, Hiroshima and Nagasaki dosed in radiation and ruin, and countless ghost towns still littered Europe’s mangled face.
Dwight peered through his glasses at his speech on the podium, then raised his gaze back at the small crowd gathered in front of him in the conference room at the American Society of Newspaper Editors in Washington, D.C. Everyone was on the edge of their seats.
The President spoke of peace, but the United States faced a great enemy in the Soviet Union. How would he continue?

“To weigh this chance is to summon instantly to mind another recent moment of great decision. It came with that yet more hopeful spring of 1945, bright with the promise of victory and of freedom. The hope of all just men in that moment too was a just and lasting peace.”
The heads among the spectators raised in hope, as if the enthusiasm in the President’s voice could be enough to wipe away any prospect of future war against the Soviet threat.
“In that spring of victory the soldiers of the Western Allies met the soldiers of Russia in the center of Europe. They were triumphant comrades in arms. Their peoples shared the joyous prospect of building, in honor of their dead, the only fitting monument-an age of just peace. All these war-weary peoples shared too this concrete, decent purpose: to guard vigilantly against the domination ever again of any part of the world by a single, unbridled aggressive power.”
“This common purpose lasted an instant and perished. The nations of the world divided to follow two distinct roads.”
“The United States and our valued friends, the other free nations, chose one road.”
“The leaders of the Soviet Union chose another.”
“The way chosen by the United States was plainly marked by a few clear precepts, which govern its conduct in world affairs.”
What came next in Dwight D. Eisenhower’s speech “The Chance for Peace” is the answer to preventing wars between countries
“First: No people on earth can be held, as a people, to be an enemy, for all humanity shares the common hunger for peace and fellowship and justice.
Second: No nation's security and well-being can be lastingly achieved in isolation but only in effective cooperation with fellow nations.
Third: Any nation's right to a form of government and an economic system of its own choosing is inalienable.
Fourth: Any nation's attempt to dictate to other nations their form of government is indefensible.
And fifth: A nation's hope of lasting peace cannot be firmly based upon any race in armaments but rather upon just relations and honest understanding with all other nations.”

I. First Point
When you minimize any nation or country to its most granular piece, the human family, you realize every nation or country is the same. It is a larger body of human families looking to establish peace out of chaos against nature, fellowship with their neighbor to make that peace possible, and justice against affronts to the foundations of the formerly stated peace and fellowship. Without this, what you have is not a nation but rather wilderness.
 II. Second Point
II. Second PointWhen we enter the world stage and look at the community of nations it is important we understand that no nation can truly expect to uphold Eisenhower’s first point without the ability to cooperate with other nations. There can be a natural disaster that strikes an entire nation and without exterior help, it may be impossible to overcome.
Understand, Eisenhower’s second point only serves as an extension of the first point. Humankind's struggle with nature will always exist, but in cooperation with other communities we can overcome hardship against nature and live in better harmony.

III. Third Point
It cannot be argued that humans, after millenia of having dispersed across the planet, have collected into pockets of communities of which grew and developed with experiences based on the place in the world where they’ve resided.
This has birthed cultures, religions, and moral codes that serve as the foundation of different branches of philosophy that have borne the fruit of governance. Ultimately, no two communities shares the exact same moral code and thus do not share, and will never share, the exact same understanding of what governance should take place. In this respect, it is an inalienable right of the very people within a community to choose how they govern themselves.

IV. Fourth Point
In trying to impeded on this third point, we come to Eisenhower’s fourth point which is that no other community has the right to dictate how other nations govern themselves.
V. Final Point
Lastly, war will never lead to peace. Only common understanding of the first four points will ever lead to true peace. A race in armaments, as the cold war proved, only leads to further distrust and the breakdown of all other points among the community of nations on the world stage.
All that can be done to expect peace is to take your neighbor as they are. St. Augustine has a famous quote, “Seek not to understand that you may believe, but believe that you may understand.”
This is meant to drive home the point of faith in the unbelievable. It is how a religious person can believe in a god that they can not prove exists.
Some might say there will never be a world without war. I say we already have the recipe for it. We’ve been given this recipe by many leaders throughout our history. Leader’s who’ve witnessed the darkest depths of human evil and wanted to steer humanity away from it.

Thank you for reading! If this article resonated with you, let me know with a zap and share it with friends who might find it insightful. Your help sends a strong signal to keep making content like this!
Interested in fiction? Follow nostr:npub1j9cmpzhlzeex6y85c2pnt45r5zhxhtx73a2twt77fyjwequ4l4jsp5xd49 for great short stories and serialized fiction.
More articles you might like from Beneath The Ink:
https://primal.net/e/note1ws4es0gahm502k6qgx64dseqhjqgyzh0q7flzk6glcasqxxye6jqm20fj9
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq25yan2w39rsjj0dqk5ckn52ptxsc3nve8hw0aftmq
https://primal.net/e/note158ns7z27r2y664h9lsdqdhsjj2uehrejve2y02lkvz46d8xgxncs8pcj7w
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2kjjzzfpjxvutjg33hjvpcw5cyjezyv9y5k0umm6k
https://primal.net/e/note1htkygah99mz8p4png992n0clqa44spatw3uzzcpl94etwh2zr60stklxvw
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqqa9wefdwfjj6stvdsk57cnnv4ehxety94mkjarg94g8ymm8wfjhxuedg9hxgt2fw3ej6sm0wd6xjmn8946hxtfjvsuhsdnju045ml
https://primal.net/e/note1rdanqhdgc7d8sypm459zrt55m0zfaze7u34phkew9nptyr3ghwlqsvtsdx
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2ns3jnfa985c29xp2rs3pexpykz6mjxetxu2g25x6
-
 @ b17fccdf:b7211155
2025-01-21 17:47:28
@ b17fccdf:b7211155
2025-01-21 17:47:28Link to the bonus guide ~ > HERE < ~
Some sections of the guide:
- Generate SSH keys
- Import SSH pubkey
- Connect to the MiniBolt node using SSH keys
- Disable password login
- Disable admin password request
Some shortcuts to the Extra sections:
Enjoy it MiniBolter! 💙
-
 @ dd664d5e:5633d319
2025-02-14 16:56:29
@ dd664d5e:5633d319
2025-02-14 16:56:29Most people only know customer-to-customer (C2C) and business-to-customer (B2C) software and websites. Those are the famous and popular ones, but business-to-business (B2B) is also pretty big. How big?
Even something boring and local like DATEV has almost 3 million organizations as customers and €1,44 billion in annual revenue.
FedEx has €90 billion in annual revenue and everyone who uses it comes into contact with its software. There's a whole chain of software between the sender and receiver of the package, and it all has to work seamlessly.
Same with Walmart, Toyota, Dubai Airport, Glencore, Tesla, Edeka, Carrefour, Harvard and University of Texas, Continental, Allianz, Asklepios, etc.
That's the sort of software I help build. You've probably never heard of it, but when it doesn't work properly, you'll hear about it on the news.
-
 @ b2caa9b3:9eab0fb5
2025-02-14 13:55:53
@ b2caa9b3:9eab0fb5
2025-02-14 13:55:53After spending two weeks in Arusha, it was time to move on. My next stop was Dodoma. I walked to the bus station in the center of Arusha to check ticket prices, but I disliked the chaotic atmosphere — people approached me nonstop, trying to sell me tickets to destinations I had no interest in. Instead, I went to the Shabiby office, a reputed bus company, and secured a ticket for 29,000 TZS. The bus was scheduled to leave at 10 A.M. the next day, giving me time to prepare.
 Photo above: a stop between Arusha and Dodoma.
Photo above: a stop between Arusha and Dodoma.I returned to my hostel, packed my bag, and picked up snacks and water from Shoppers Supermarket, knowing that Tanzanian bus rides tend to take longer than expected. The 80-kilometer journey from Moshi to Arusha had taken me up to three hours, so I expected the longer trip to Dodoma to stretch beyond the promised eight hours.
The Journey to Dodoma
The bus ride was predictably long, making frequent stops along the way. Upon arrival in Dodoma, the bus meandered through the city, dropping off passengers. My booked accommodation was just under two kilometers from the final stop, so I decided to walk, relying on Google Maps to guide me.
 Photo above: in Dodoma.
Photo above: in Dodoma.When I arrived at what was supposed to be my lodging, I was skeptical. The house lacked a sign, and an elderly woman was doing laundry in the yard. When I asked if this was the right place, she called a younger woman who spoke English and welcomed me inside. The accommodation was a full apartment, complete with a kitchen, but not cheap. Later in the evening, I attempted to shower, only to discover there was no running water. I resorted to a bucket shower, but the cramped bathroom caused water to spill into the apartment.
 Photo above: the Baobab Café in Dodoma.
Photo above: the Baobab Café in Dodoma.Exploring Dodoma
The next day, I set out to explore Dodoma. I passed a cozy café and an old-looking church, which I later learned was not as ancient as it seemed. Strolling down a lively shopping district, I admired the small stores lining the streets. Eventually, I settled at the café I had spotted earlier, enjoying a simple dinner of bread and tomato salad.
 Photo above: the church in Dodoma.
Photo above: the church in Dodoma.Originally, I had planned to stay for just one night, but the city intrigued me, and I extended my stay. This meant I had to book my next bus ticket and gather supplies. Using the Bolt app, I ordered a TukTuk to take me to the Shabiby bus terminal. The ride cost 2,000 TZS — without Bolt, I would have been charged significantly more. I bought my ticket to Mbeya for 40,000 TZS, with a departure time of 5:30 A.M.
That night, I packed my bags and went to bed early, knowing I had an early start ahead.
The Departure to Mbeya
Waking up at 3:30 A.M., I hurriedly took another bucket shower — still no running water. I initially planned to order a TukTuk, but the Bolt app showed no available drivers. With the bus station only a 13-minute walk away, I set out on foot. Along the way, I stepped into a water hole, soaking myself up to my knees. Street vendors persistently offered me motorcycle rides, but I ignored them and continued walking.
 Photo above: in Dodoma.
Photo above: in Dodoma.Arriving at the bus station, I saw the previous bus to Mbeya departing. My gut told me something was wrong. Sure enough, my bus was delayed by almost an hour. Finally, it arrived, and I boarded, relieved that I hadn’t missed it after all.
A Long Ride to Mbeya
The previous day, I had suffered from severe diarrhea. Fortunately, a local pharmacy in Dodoma provided me with pills that helped stabilize my system. I also continued taking my daily dose of Doxycycline as a malaria precaution.
 Photo above: shopping street in Dodoma.
Photo above: shopping street in Dodoma.This time, I had a window seat with no one beside me, allowing me to place my backpack on the empty seat. As we traveled, I watched the Tanzanian landscape unfold. At one point, the bus crossed a dam, likely a reservoir, before being stopped by police. A policeman entered, checked my passport, and inquired about my destination. When I mentioned Mbeya, he ask me where after, and I told him to Lusaka. Then he asked if it was in Zambia, returned my passport, and he let us continue.
 Photo above: the Baobab Café in Dodoma.
Photo above: the Baobab Café in Dodoma.My host in Mbeya had instructed me to get off at Nane Nane Stand. Upon arrival, I searched for a TukTuk. Without internet access, I had to negotiate fares blindly. After rejecting overpriced offers, I managed to bargain a price of 5,000 TZS for the short ride to my accommodation, what was a bit high for a Tuktuk.
Mbeya and the Journey to the Border
Initially planning to stay two nights, exhaustion led me to extend for an extra night. The hostel was beautiful and clean but, yet again, had no running water. However, this time, the host kindly boiled water for me, allowing me to take a warm bucket shower.
 Photo above: on the way to the Supermarket in Dodoma.
Photo above: on the way to the Supermarket in Dodoma.On my final day in Mbeya, I explored the city, visiting a new children's hospital and an old church. Tuktuk drivers repeatedly tried to overcharge me, but I insisted on the standard 800 TZS fare for public transport.
 Photo above: on the way to the Supermarket in Dodoma.
Photo above: on the way to the Supermarket in Dodoma.The following morning, after a quick breakfast, I set off for the bus station with a fellow traveler I met at the hostel. Together, we took a bus to Tunduma for 5,000 TZS each. From there, a TukTuk ride to the border cost another 5,000 TZS.
Crossing into Zambia
The border crossing was straightforward for me — I received a free 30-day visa for Zambia. My Russian travel companion, however, needed a visa on arrival, payable in cash and only in USD. The immigration officer arranged a taxi to take us to an ATM, but the only available bank, Absa, charged exorbitant fees. Fortunately, we later found a Zanaco ATM in Nakonde that had no fees.
 Photo above: between Dodoma and Mbeya.
Photo above: between Dodoma and Mbeya.Once we had the necessary cash, we returned to the Border immigration, paid for the visa, and proceeded into Zambia. We walked to town, grabbed some food, and checked into Shalom Hotel. It was cheap, costing only 200 Kwacha per night (under 10 Euros), but lacked cleanliness and had no running water.
A Frustrating Bus Experience
We booked a 4 A.M. bus to Lusaka with Jkas, supposedly the best company. However, when we arrived at the station at 3:28 A.M., the bus was already gone. The staff had lied, telling us the bus left at 4 A.M. but actually departing at 3 A.M. They then offered an overpriced taxi to chase the bus, which we declined.
 Photo above: between Dodoma and Mbeya.
Photo above: between Dodoma and Mbeya.With no other options left, we searched for an alternative and eventually made our way to the PowerTools bus station — only to find that the bus also had already left.
The next bus? Overnight.
We were stuck.
The Boda Chase
That’s when a Boda driver approached us. He had been waiting at the Powertools station, watching the situation unfold. “I know where your bus is,” he said. “At the checkpoint. I can take you.”
There was no time to think. We climbed on.
The night was pitch black, the streets slick with rain and mud. As soon as he twisted the throttle, the bike lurched forward. The driver wasn’t smooth — he was riding like a madman, shaking left and right as he weaved through the darkness. The wet road made it worse, and the mud felt like a trap waiting to swallow us whole.
 Photo above: between Dodoma and Mbeya.
Photo above: between Dodoma and Mbeya.A gust of wind blew my hat into my face, blinding me for the most time. My gut twisted — I could almost see the crash before it happened. “Slow down!” I shouted. He eased off for a while, but soon enough, he hit the gas again. “I said slow down!” I had to remind him.
It felt like an eternity. The only thought keeping me together was the hope that the checkpoint was close.
Then — buses. Dozens of them.
We told him which one was ours, but in the dim light, they all looked the same. He swerved between them, searching, until finally — Jkas.
 Photo above: the old church in Mbeya.
Photo above: the old church in Mbeya.As we pulled up, the driver suddenly changed his price from 200 to 400 Kwacha. Of course. I handed him 300, not in the mood to argue, and walked straight into the bus, relieved to be off that death ride.
The journey continued, but the morning’s chaos was a reminder that travel in Africa often requires patience and adaptability.
Final Thoughts
The journey from Arusha to Lusaka was long and filled with challenges — delayed buses, unreliable accommodations, and frustrating border experiences. Yet, the beauty of Tanzania and Zambia, the people I met, and the lessons I learned along the way made it all worthwhile. Traveling in Africa requires flexibility, but it rewards you with unforgettable experiences and stories to tell.
 Photo above: in Mbeya.
Photo above: in Mbeya. Photo above: somewhere in Zambia from the Bus.
Photo above: somewhere in Zambia from the Bus. Photo above: in Lusaka.
Photo above: in Lusaka. Photo above: in the East Park Mall in Lusaka.
Photo above: in the East Park Mall in Lusaka. Photo above: in the East Park Mall in Lusaka.
Photo above: in the East Park Mall in Lusaka. Photo above: East Park Mall in Lusaka.
Photo above: East Park Mall in Lusaka. Photo above: in the market in Lusaka.
Photo above: in the market in Lusaka. -
 @ b17fccdf:b7211155
2025-01-21 17:39:34
@ b17fccdf:b7211155
2025-01-21 17:39:34Link to the bonus guide ~ > HERE < ~
⏰ Recently added an update that includes a new section How to detect Ordinals transactions and verify Ordisrespector filter works to verify that Ordispector is filtering and burning Ordinals correctly 🔥
Fuck Ordinals🤡🔫 and enjoy it MiniBolter! 💙
-
 @ b17fccdf:b7211155
2025-01-21 16:49:27
@ b17fccdf:b7211155
2025-01-21 16:49:27What's changed
- New method for Bitcoin Core signature check, click ~ >HERE< ~
- GitHub repo of Bitcoin Core release attestations (Guix), click ~ >HERE< ~
History:
~ > PR that caused the broken and obsolescence of the old signature verification process, click ~ >HERE< ~
~ > New GitHub folder of Bitcoin Core repo that stores the signatures, click ~ >HERE< ~
Thanks to nostr:npub1gzuushllat7pet0ccv9yuhygvc8ldeyhrgxuwg744dn5khnpk3gs3ea5ds for building the command that made magic possible 🧙♂️🧡
Enjoy it MiniBolter! 💙
-
 @ a012dc82:6458a70d
2025-02-14 13:51:33
@ a012dc82:6458a70d
2025-02-14 13:51:33In the ever-evolving landscape of cryptocurrency, a significant development has emerged that is reshaping perceptions and strategies within the industry. Bitcoin, the original and most prominent digital currency, has seen its transaction fees hit a two-year high. This remarkable surge in fees is not merely a statistical blip but a phenomenon that could herald a transformative phase in Bitcoin mining. As we witness these fees reaching unprecedented levels, it prompts a crucial inquiry: Are we on the cusp of a new era in BTC mining, one that redefines its economic and technological paradigms?
Table Of Content
-
The Surge in Transaction Fees
-
Impact on Bitcoin Miners
-
A Divided Community
-
The Ripple Effect on Mining Stocks
-
The Broader Market Influence
-
Conclusion
-
FAQs
The Surge in Transaction Fees
The Bitcoin network, known for its robustness and security, has recently been the center of a notable financial trend. Transaction fees have soared to over $37, a figure reminiscent of the peak levels observed in April 2021. This significant increase is not an isolated event but rather a symptom of a larger, more complex shift within the Bitcoin ecosystem. The primary driver behind this surge is the burgeoning interest in Bitcoin NFTs, particularly through a protocol known as Ordinals. This innovative protocol facilitates the storage of non-fungible tokens (NFTs) directly on the Bitcoin blockchain. As a result, there has been a marked increase in transaction volumes, leading to higher fees. This trend reflects a growing interest in utilizing Bitcoin not just as a currency but as a platform for broader digital asset interactions, potentially expanding its use cases and value proposition.
Impact on Bitcoin Miners
The escalation in transaction fees has had a profound and far-reaching impact on the community of Bitcoin miners. These individuals and companies, who form the backbone of the Bitcoin network by validating transactions and maintaining the blockchain, are now witnessing a dramatic shift in their revenue streams. With fees reaching such high levels, their daily income has surged to an estimated $63 million, translating to an extraordinary $23 billion annually. This figure is a significant leap from the average income over the past two years and represents a potential windfall for the mining sector. The increased profitability could lead to renewed investment in mining infrastructure, potentially spurring technological advancements and increased competition within the sector. It also raises questions about the decentralization of Bitcoin mining, as higher profits could lead to further consolidation in an industry already dominated by large players.
A Divided Community
The Bitcoin community, known for its diverse opinions and robust debates, finds itself at a crossroads with the rise of Ordinals and its impact on transaction fees. On one hand, some members of the community, including prominent figures like core developer Luke Dashjr, view the influx of Ordinals as a form of spam that clutters the blockchain and necessitates technical solutions. This perspective underscores concerns about blockchain bloat, transaction prioritization, and the fundamental principles of what Bitcoin should represent. On the other hand, for miners, these high fees have been a significant boon. They have provided a much-needed boost to profitability, especially in a period where the price of Bitcoin itself has been relatively stable. This divergence in views reflects the ongoing evolution of Bitcoin's identity and purpose, as it balances its role as a digital gold, a transactional currency, and now, a platform for digital art and collectibles.
The Ripple Effect on Mining Stocks
The impact of the surge in Bitcoin fees extends beyond the digital realm and into the traditional financial markets. Bitcoin mining stocks, representing companies that invest heavily in the infrastructure required to mine the digital currency, have shown remarkable resilience and growth. Companies like Marathon Digital, Riot Platform, and Cleanspark have seen their stock prices rally, significantly outperforming the actual price of Bitcoin. This trend indicates a growing investor confidence in the mining sector, buoyed by the increased revenue potential from transaction fees. It also suggests a decoupling of sorts, where the mining sector's performance is not solely dependent on the price of Bitcoin but also on other factors like transaction volume and fee structures. This decoupling could attract a new class of investors to the mining stocks, those looking for exposure to the crypto market but with a different risk profile than holding cryptocurrencies directly.
The Broader Market Influence
The performance of Bitcoin mining stocks is also intricately linked to the broader equity markets. As observed by Caleb Franzen, founder of Cubic Analytics, the strong performance of equity markets has provided additional momentum to these stocks. This correlation indicates that Bitcoin mining companies are increasingly being viewed through the lens of traditional financial analysis, where market trends and investor sentiment play a crucial role. The implication is significant: as Bitcoin mining firms become more integrated into the broader market, they may also become more susceptible to the same macroeconomic factors that influence traditional stocks. This integration could lead to greater stability in the mining sector but also exposes it to new types of risks, such as regulatory changes or shifts in investor sentiment unrelated to the crypto market.
Conclusion
The recent developments in Bitcoin transaction fees, driven by the popularity of Ordinals, have ushered in significant changes in the mining landscape. With increased revenues and a positive impact on mining stocks, it's tempting to proclaim the dawn of a new era in Bitcoin mining. However, the sustainability of this trend and its long-term impact on the Bitcoin ecosystem remain subjects of intense speculation and debate. As the community grapples with these changes, the future of Bitcoin mining continues to be a topic of keen interest. Whether this marks a permanent shift or a temporary phase in the cryptocurrency's evolution, one thing is certain: the world of Bitcoin remains as dynamic and unpredictable as ever.
FAQs
What caused the recent spike in Bitcoin transaction fees? The surge in Bitcoin transaction fees to over $37, a two-year high, is primarily attributed to the growing popularity of Bitcoin NFTs, especially through the Ordinals protocol, which allows for the storage of non-fungible tokens on the Bitcoin blockchain.
How does the increase in transaction fees affect Bitcoin miners? Bitcoin miners, who earn BTC for processing transactions, have seen a significant increase in their income due to the higher fees. Their daily revenue has reached approximately $63 million, translating to an estimated $23 billion annually.
What is the Ordinals protocol, and why is it controversial? Ordinals is a protocol that enables the storage of NFTs on the Bitcoin blockchain. It has been controversial within the Bitcoin community, with some viewing it as a beneficial innovation and others as a form of spam that clutters the blockchain.
Have Bitcoin mining stocks been affected by the increase in fees? Yes, Bitcoin mining stocks, such as Marathon Digital, Riot Platform, and Cleanspark, have outperformed the actual price of Bitcoin, indicating growing investor confidence in the mining sector due to increased revenue from transaction fees.
Is the Bitcoin mining industry becoming more centralized? The increase in profitability could lead to further investment in mining infrastructure, potentially leading to more competition but also raising concerns about the centralization of mining power in the hands of large companies.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ b17fccdf:b7211155
2025-01-21 16:30:11
@ b17fccdf:b7211155
2025-01-21 16:30:11Your MiniBolt is on a home local network, you want to expose it on the public Internet (clearnet) without exposing your public IP, without Firewall rules, without NAT port forwarding, without risk, easy and cheap?
Go to the bonus guide by clicking ~ >HERE <~
Enjoy it MiniBolter! 💙
-
 @ c43d6de3:a6583169
2025-02-14 11:27:09
@ c43d6de3:a6583169
2025-02-14 11:27:09A Brief History of Ownership
The Forgotten Struggle for Ownership
History reveals that our ancestors labored—both intellectually and physically—to secure the freedoms we are subconsciously giving away.
We stand at the threshold of a new era.
Across the globe, long-established institutions are showing signs of strain. Trust in governments, banks, and major corporations is eroding, leaving many individuals feeling as though their rights are being infringed upon—even if they struggle to articulate exactly how. Social media and traditional news outlets amplify this sense of unease, painting a picture of impending upheaval, as if we are on the brink of a revolution whose name will only become clear in hindsight, once the first sparks ignite into a full-blown blaze.
Yet, when we examine the state of the global economy, this narrative begins to unravel. Economic inequality has reached levels unseen in nearly a century, and while many point fingers at politicians, policies, or the so-called greed of the 1% hoarding all the wealth, the true culprit may be much closer than most realize. At a time when legal structures worldwide strongly protect ownership and economic mobility, it is individuals themselves who are willingly surrendering their financial power to the very elites they criticize.
I know—“willingly” might seem like a stretch. After all, no one consciously chooses to give up their economic freedom. But take a closer look at the way people spend, borrow, and consume, and it becomes painfully clear: most are actively forfeiting their ability to build and own wealth.
How did we get here?
Much of this self-inflicted harm comes from a fundamental ignorance of the history of ownership and the struggles fought to secure it.
This article serves as a short exploration of the past.
I'll examine what might be considered the natural state of humanity, how the majority has historically struggled to achieve ownership rights, and the deadly conflicts that had to occur for the modern individual to enjoy the very rights they are now squandering.

I. The Era of Communal Ownership
No one is born into this world alone.
We do not simply materialize into existence; we arrive as part of the first unit of human society—the family.
Before the rise of civilization, the primary focus of the family was survival. Ownership was a foreign concept, as early human tribes lived in a state of communal resource-sharing. Material possessions were fleeting, and with that, so was the notion of personal property.
In the state of nature, no individual had an exclusive claim to anything. Instead, ownership existed in a tribal sense: “This land belongs to us.” The idea of “mine” extended only by association—what belonged to the tribe also, by extension, belonged to each of its members.
This was a fragile system. Resources required constant upkeep, and as populations grew, leadership emerged to manage the complexity of distribution. This shift laid the foundation for the rise of kings and centralized authority. The concept of ownership, once a communal right, gradually became something dictated by those in power. The people no longer owned anything outright; they merely had the privilege of stewarding what belonged to their ruler.

II. The Rise of Peasants and Kings
The first codified legal system, the Code of Hammurabi, laid out extensive laws on ownership. Interestingly, this ancient civilization granted more property rights to commoners than many societies did even a few centuries ago.
A few millennia later, Greece laid the philosophical foundations for ownership, but true legal protections for private property did not emerge until much later. In medieval Europe, ownership rights almost disintegrated—not even nobles truly owned land. Everything belonged to the king, and monarchs waged war over control of vast territories, including the people within them.
Meanwhile, in the Islamic Golden Age, the Middle East saw an unprecedented period of economic freedom. Under Sharia law, property rights were protected for the average citizen, something unheard of in much of medieval Europe. The extent of these rights depended largely on religious affiliation, but compared to their European counterparts, many commoners in the Islamic Empire enjoyed greater economic autonomy.

III. The Birth of Property Rights: The Rights of Man
As the Islamic Golden Age waned and the Mongol Horde thundered toward Baghdad, another seismic shift was occurring in England. In 1215, rebellious nobles captured London and forced King John to sign the Magna Carta, the first written document to impose limits on absolute monarchical power and introduce property protections—though these rights were initially reserved for the nobility.
This moment planted the seeds of change. Over the next several centuries, the fight for ownership rights expanded beyond the aristocracy. The Black Death (1347–1351) wiped out over 30% of England’s population, increasing labor shortages and bargaining power for peasants. By the 1381 Peasants’ Revolt, the common man demanded a greater share of land and wealth.
Yet, it wasn’t until the 1700s with the Enclosure Acts that private property became legally protected for the broader population. What began as a noble rebellion in 1215 ultimately transformed ownership from royal privilege to individual liberty.

IV. The Age of Renting: The Illusion of Ownership Today
Despite centuries of struggle, we now find ourselves at a paradoxical moment in history: ownership is more legally protected than ever, yet fewer people actually own anything of value.
Homeownership in Decline: The U.S. homeownership rate peaked in 2005, only to decline for a decade, hitting a low of 63% in 2015. Despite slight rebounds, high housing costs have pushed many into perpetual rentership.
Vehicles as Subscriptions: In 2024, one-fifth of new vehicles were leased, and long-term auto loans have become the norm. A financed car is not truly owned—it’s rented from a bank until the debt is cleared.
The Subscription Economy: Ownership of media, software, and even personal data has been replaced with monthly fees. Cloud storage, SaaS, and streaming services have ensured that we no longer possess even our own information.
V. The Consequences of Financial Illiteracy
We now live in a society built on renting, where economic stability depends on a continuous stream of payments. The more we lease, subscribe, and finance, the more control shifts from individuals to corporations and financial institutions.
This shift has profound implications:
- A person who owns little has little power.
- A society that rents everything can be controlled by those who own everything.
- Wealth is no longer built through accumulation, but through debt and dependency.
For millennia, people fought for the right to own. Today, through financial illiteracy and consumer habits, we are giving it away.
How much do we truly own, and how much have we already forfeited?
Thank you for reading! If this article resonated with you, let me know with a zap and share it with friends who might find it insightful. Your help sends a strong signal to keep making content like this!
Interested in fiction? Follow Fervid Fables for great short stories and serialized fiction.
nostr:npub1j9cmpzhlzeex6y85c2pnt45r5zhxhtx73a2twt77fyjwequ4l4jsp5xd49
More articles you might like from Beneath The Ink:
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2kjjzzfpjxvutjg33hjvpcw5cyjezyv9y5k0umm6k
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqqa9wefdwfjj6stvdsk57cnnv4ehxety94mkjarg94g8ymm8wfjhxuedg9hxgt2fw3ej6sm0wd6xjmn8946hxtfjvsuhsdnju045ml
nostr:naddr1qvzqqqr4gupzp3padh3au336rew4pzfx78s050p3dw7pmhurgr2ktdcwwxn9svtfqq2ns3jnfa985c29xp2rs3pexpykz6mjxetxu2g25x6
-
 @ be41636e:e55c4909
2025-02-14 10:38:04
@ be41636e:e55c4909
2025-02-14 10:38:04I asked Unleashed.Chat's DeepSeek model to write an article from the point of view of someone who believes in chemtrails.
In the first attempt, it didn't understand me well and it provided the arguments provided by chemtrails believers and their counterarguments.
When I clearly asked it to write an article from the point of view of someone who actually believes it, it gave some warnings that these claims are not corroborated by science and started the article and ended it by the same remarks.
What follows is the article Unleashed.Chat produced.
For years, I’ve watched the skies, and I’ve seen something that doesn’t sit right. It’s not just the occasional contrail left by a passing airplane. No, these are different. They linger. They spread. They look unnatural. And they’re everywhere.
I’m talking about chemtrails—chemical trails intentionally sprayed by aircraft for reasons that are far from benign. At first, I dismissed them as just another conspiracy theory. But as I started paying closer attention, I realized that something was off.
The Evidence Is in the Sky
Let’s start with what we can all see. Contrails, or condensation trails, are the result of water vapor freezing around small particles in airplane exhaust. They’re short-lived and dissipate quickly. But chemtrails are different. They stay in the sky for hours, spreading out into vast, crisscrossing grids that blanket the sky.
I’ve taken countless photos of these trails, and they all tell the same story. They’re not just random; they’re deliberate. They’re sprayed in patterns that cover entire regions, and they’re doing it day after day, year after year.
What’s in the Trails?
The government and mainstream media tell us these trails are harmless. But that’s exactly what they want us to believe. Independent researchers and whistleblowers have come forward with disturbing information. Chemtrails contain a cocktail of toxic chemicals, including aluminum, barium, strontium, and other heavy metals.
Why would they spray these substances? The official line is that it’s for weather modification or geoengineering. But that’s a lie. The real purpose is far more insidious.
The Hidden Agenda
Chemtrails are part of a larger plan to control the population. These chemicals are neurotoxic, and they’re being used to alter our brains and behavior. They’re designed to make us more docile, more compliant, and less likely to question authority.
This isn’t just a theory. There’s a long history of government experimentation on its own citizens. From the Tuskegee Syphilis Experiment to MKUltra, the CIA’s mind-control program, the government has shown time and again that it’s willing to go to extreme lengths to control the population. Chemtrails are the next chapter in this dark history.
The Health Impact
The effects of these chemicals are already being felt. Rates of autism, Alzheimer’s, and other neurological disorders have skyrocketed in recent decades. Coincidence? I don’t think so.
I’ve spoken to doctors and researchers who have seen firsthand the connection between chemtrail exposure and these health issues. They’re not willing to speak publicly for fear of retaliation, but they’ve shared their findings with me. The evidence is overwhelming.
The Media Cover-Up
The mainstream media is complicit in this cover-up. They dismiss chemtrails as a conspiracy theory, but that’s just a distraction. They’re paid to keep us in the dark, to prevent us from connecting the dots.
Thankfully, the internet has given us a platform to share the truth. Independent investigators, whistleblowers, and concerned citizens are coming together to expose this atrocity. But we need your help.
What Can We Do?
The first step is to raise awareness. Share this information with everyone you know. The more people who understand the truth, the harder it will be for the government to continue this program.
Second, we need to demand accountability. Write to your elected representatives. Call for independent investigations into chemtrails. Make your voice heard.
Finally, we need to protect ourselves. Install air filters in your home. Avoid spending time outdoors when chemtrails are being sprayed. And stay informed.
The Future of Humanity
Chemtrails are not just a threat to our health; they’re a threat to the very future of humanity. If we allow this program to continue unchecked, we risk irreversible damage to our planet and our species.
But there’s still hope. By working together, we can expose the truth and stop this madness. The time to act is now.
-
 @ b17fccdf:b7211155
2025-01-21 16:23:44
@ b17fccdf:b7211155
2025-01-21 16:23:44Build your nostr relay step by step on your MiniBolt node! (easily adaptable to other environment) No need to trust anyone else! Be sovereign!
~> Go to the bonus guide by clicking ~> HERE< ~
~> This guide includes a complete extra section to cover the different processes for using nostr as a user and relay operator.
PS: The MiniBolt project has its FREE relay, be free to connect by adding to your favorite client the next address:
wss://relay.minibolt.info~> Let a review on noStrudel or Coracle of your experience using it.
Remember, Nostr is freedom! Stay resilient! 💜 🛡️💪
-
 @ be41636e:e55c4909
2025-02-14 09:44:55
@ be41636e:e55c4909
2025-02-14 09:44:55I asked unleashed.chat's DeepSeek model to provide the pieces of evidence against the moon landing. What follows is what I got as my answer.
Generally, I like the answer, though it mixed up the claim and counterarguments at times.
Also, I didn't like the conclusion :))
But all said, I believe the Van Allen Belts are one of the most solid argument against the moon landing.
The question of whether the moon landing was faked has been a topic of debate, with various arguments presented by those who doubt the authenticity of the event. Here is a summary of the key points often cited against the moon landing, along with counterarguments and explanations:
Arguments Against the Moon Landing: Waving Flag:
Claim: The American flag appears to wave in the wind, despite the moon having no atmosphere. Counterargument: The flag's movement was caused by the astronauts' actions, as they adjusted it using a rod behind the flag. Missing Stars:
Claim: The photos lack visible stars, which should be present in the moon's black sky. Counterargument: The cameras were set for optimal lighting of the lunar surface, making stars too faint to capture. Shadow Anomalies:
Claim: Shadows in photos appear to come from multiple directions, suggesting studio lighting. Counterargument: The moon's surface is uneven, causing shadows to appear differently, and the sun's angle can create varied shadows. Van Allen Belts:
Claim: Astronauts would have been exposed to lethal radiation from the Van Allen belts. Counterargument: The missions were timed to pass through the belts quickly, minimizing exposure. Lack of Blast Crater:
Claim: No noticeable crater was created by the lunar module's descent engine. Counterargument: The engine's thrust was designed to minimize impact, and the moon's surface is softer than expected. Missing Footage:
Claim: Original tapes of the landing were lost, and restored footage is of lower quality. Counterargument: Footage was restored from other sources, including TV broadcasts and telemetry data. Soviet Silence:
Claim: The Soviets did not contest the landing, despite being space race competitors. Counterargument: The Soviets may not have had the means to verify the landing or were focused on their own programs. Technological Capabilities:
Claim: The technology of the 1960s was insufficient for a moon landing. Counterargument: Successful unmanned missions and technological advancements supported the capability. Number of Participants:
Claim: Thousands of people involved would have leaked the secret. Counterargument: Secrecy measures and unawareness of implications could have prevented leaks. "C" Rock Incident:
Claim: A rock appeared to float, suggesting tampering. Counterargument: The rock was a prop, and movement was due to low-gravity actions. Supporting Evidence for the Moon Landing: Moon Rocks: Analyzed and confirmed as lunar. Footprints and Equipment: Observed by subsequent missions and satellites. Cumulative Evidence: Multiple sources confirm the moon landing. In conclusion, while various arguments have been presented against the moon landing, each has been addressed with scientific explanations and evidence. The consensus among the scientific community is that the moon landing was genuine, supported by substantial evidence and corroborated by multiple sources.
The question of whether the moon landing was faked has been a topic of debate, with various arguments presented by those who doubt the authenticity of the event. Here is a summary of the key points often cited against the moon landing, along with counterarguments and explanations:
Arguments Against the Moon Landing:
-
Waving Flag:
- Claim: The American flag appears to wave in the wind, despite the moon having no atmosphere.
- Counterargument: The flag's movement was caused by the astronauts' actions, as they adjusted it using a rod behind the flag.
-
Missing Stars:
- Claim: The photos lack visible stars, which should be present in the moon's black sky.
- Counterargument: The cameras were set for optimal lighting of the lunar surface, making stars too faint to capture.
-
Shadow Anomalies:
- Claim: Shadows in photos appear to come from multiple directions, suggesting studio lighting.
- Counterargument: The moon's surface is uneven, causing shadows to appear differently, and the sun's angle can create varied shadows.
-
Van Allen Belts:
- Claim: Astronauts would have been exposed to lethal radiation from the Van Allen belts.
- Counterargument: The missions were timed to pass through the belts quickly, minimizing exposure.
-
Lack of Blast Crater:
- Claim: No noticeable crater was created by the lunar module's descent engine.
- Counterargument: The engine's thrust was designed to minimize impact, and the moon's surface is softer than expected.
-
Missing Footage:
- Claim: Original tapes of the landing were lost, and restored footage is of lower quality.
- Counterargument: Footage was restored from other sources, including TV broadcasts and telemetry data.
-
Soviet Silence:
- Claim: The Soviets did not contest the landing, despite being space race competitors.
- Counterargument: The Soviets may not have had the means to verify the landing or were focused on their own programs.
-
Technological Capabilities:
- Claim: The technology of the 1960s was insufficient for a moon landing.
- Counterargument: Successful unmanned missions and technological advancements supported the capability.
-
Number of Participants:
- Claim: Thousands of people involved would have leaked the secret.
- Counterargument: Secrecy measures and unawareness of implications could have prevented leaks.
-
"C" Rock Incident:
- Claim: A rock appeared to float, suggesting tampering.
- Counterargument: The rock was a prop, and movement was due to low-gravity actions.
Supporting Evidence for the Moon Landing:
- Moon Rocks: Analyzed and confirmed as lunar.
- Footprints and Equipment: Observed by subsequent missions and satellites.
- Cumulative Evidence: Multiple sources confirm the moon landing.
In conclusion, while various arguments have been presented against the moon landing, each has been addressed with scientific explanations and evidence. The consensus among the scientific community is that the moon landing was genuine, supported by substantial evidence and corroborated by multiple sources.
-
-
 @ a367f9eb:0633efea
2025-02-14 09:07:50
@ a367f9eb:0633efea
2025-02-14 09:07:50With a big tech-powered magnifying glass on federal websites, spending contracts, and government payment systems, Elon Musk’s band of DOGE system admins have been turning Washington inside out in their hunt for waste, fraud, and abuse.
One of the most prized agencies on the chopping block is the Consumer Financial Protection Bureau, heralded by progressives as an indispensable force for helping consumers wronged by financial institutions, but derided by fintech investors and conservatives as little more than a government “shakedown agency.” Consumers will be better off without the CFPB breathing down the neck of American companies.
Since the inauguration of President Trump, the CFPB’s temporary leadership put an immediate halt on all work, also informing the Federal Reserve, which directly funds the agency, that it would no longer seek new funding.
Sen. Elizabeth Warren, the intellectual force behind the agency’s founding, has been apoplectic. She’s argued that Trump is “firing the financial cop on the beat that makes sure your family doesn’t get scammed.”
The origin of the CFPB goes back to the rubble of the 2008 financial crisis when legislators saw this proposed agency as a viable response to the populist backlash engulfing Washington and Wall Street. Instead of penalizing wrongdoers, Congress funded bank bailouts and launched a “watchdog” group. The 2010 Dodd-Frank Financial Reform Act mandated new standards for lending, restricted capital that could be tapped for bank loans, and created the CFPB to police consumer finance.
All functions performed by the five former federal banking supervisory agencies were rolled into the CFPB, granting it sole jurisdiction over non-depository firms and financial institutions with over $10 billion in assets. This empowered the agency to issue regulatory guidance, demand information from financial institutions, and launch civil actions in federal court.
Supporters of the CFPB point to an impressive record of close to $20 billion in consumer relief, as well as an additional $5 billion in civil penalties. Without the CFPB, fraudsters and scams would metastasize and consumer injustice would run wild, so they say. But this couldn’t be further from the truth.
As a regulatory agency with civil litigation authority, the CFPB is emboldened to file high-dollar lawsuits against financial firms. An estimate of the CFPB’s database of enforcement actions reveals that roughly 85% of all cases are settled out of court before a final ruling.
Companies often choose to settle, but this shouldn’t be mistaken for an admission of guilt. In a litigious society such as the United States where companies are routinely targeted in frivolous lawsuits, the court of public opinion matters just as much as the court of law.
Firms prefer settling cases over having their name dragged through the mud for months on end in the media, something tort lawyers call a “nuisance settlement.” These expected costs are baked into large firms’ financial projections and are sometimes factored into pricing their goods and services for consumers.
The CFPB is more akin to a state-backed tort law firm that can tap the nation’s central bank for resources while exploiting its do-gooder reputation for easy PR victories.
Rather than smart regulatory guidance to oversee a new generation of consumer finance firms, CFPB has relied on quick settlements out of court to squash innovative upstarts.
While CFPB enforcement has been successful in penalizing banks and lenders for how loans are structured or advertised, it does not take much imagination to see how this has impacted the investing climate for new competitors. Since CFPB’s founding, there are now 35% fewer financial institutions remaining for consumers to choose from, down from 15,000 to just roughly 9,000 today.
While there is high consumer demand for fintech, payment apps, and account offerings, including Bitcoin and cryptocurrency banks, CFPB’s chilling actions have slowed that innovation, leading to the recent calls for the agency to be gutted. And they’re right.
Most of CFPB’s functions are mirrored at the FTC on everything but finance. Regional Federal Reserve banks are also responsible for bank oversight and regulation, not to mention state banking regulators. Existing regulators have the reach, experience, and know-how to police would-be fraudsters and outright deceptive practices among banks. Why not let them?
For consumers who want next-level services and financial products, there is no question that CFPB’s litigious approach has impacted their ability to access credit and financial services. There must be a better way to regulate our financial institutions and protect consumers than a tort law firm with government authority. Congress could fold elements of the CFPB into the FTC, OCC, or even FDIC, and bad actors will still be policed.
Consumers deserve to be protected, and they will be, but they also deserve a regulatory structure that rewards innovation and brings financial products to market that they can choose between.
The CFPB is due for defanging.
Yaël Ossowski is deputy director at the Consumer Choice Center and author of the report, “A financial fraud crackdown won’t protect consumers from scams.”
Originally published on RealClear Politics.
-
 @ 955e5a04:c03b3cc3
2025-02-14 08:04:46
@ 955e5a04:c03b3cc3
2025-02-14 08:04:46If we see the Earth as the most important element in the universe, we will learn to care for it. The Maya believed that the Earth was created first, followed by the sun, the moon, and the stars. This perspective is not based on modern science, but it reflects the idea that the Earth is primordial for us, and thus, it should be honored.
This vision finds echoes in sacred texts. The Popol Vuh, the Mayan creation story, describes a time when only the sky and the vast sea existed before the Earth was formed. Similarly, in the Book of Genesis, before God created the world, "the earth was formless and empty, darkness was over the surface of the deep, and the Spirit of God was hovering over the waters" (Genesis 1:2). In both traditions, creation emerges from a primordial state of sky and water, symbolizing chaos and the unknown.
Water, in many religious contexts, is linked to chaos and transformation. In the Popol Vuh, the first humans were shaped from maize, but they originated from a world where water and sky ruled. This suggests a deeper truth: before the Earth, there was only the vastness of the cosmos, and from that, we were formed. We are made of both chaos and peace, carrying within us all the elements of creation—not from nothingness, but from everything.
-
 @ c1e6505c:02b3157e
2025-01-20 19:44:05
@ c1e6505c:02b3157e
2025-01-20 19:44:05There’s a tension between nature’s rhythms and human ambition, especially in winter. As Earth meanders to its furthest point from the sun, our social and economic engines paradoxically accelerate - driven by holidays, deadlines, and the relentless pursuit of being productive. Yet nature offers a contrasting wisdom in its deliberate deceleration, encouraging us to slow down and reflect.
 Seasonal cycles are not arbitrary patterns but interconnected signals within a web of biological, environmental, and economic systems. *Their foundation lies in light itself — the building block of existence, essentially matter in a slowed-down state. This act of deceleration doesn’t just create physical substance; it provides structure, clarity, and form.* Meandering through these seasonal changes isn’t a passive drift - it’s an opportunity to realign. Slowing down, like nature does, creates space to step back from the busyness of society and technology. It allows us to reflect on where we are, re-ground ourselves, and act with greater intention. In this pause, we rediscover the creative power of slowness: the ability to lay foundations, see clearly, and prepare for growth when the time is right. Seasons are more than a backdrop — they are guides. They remind us that slowing down isn’t stagnation but essential groundwork. Winter’s invitation to pause and meander is not only natural; it’s necessary for balance, perspective, and creating something enduring.
Seasonal cycles are not arbitrary patterns but interconnected signals within a web of biological, environmental, and economic systems. *Their foundation lies in light itself — the building block of existence, essentially matter in a slowed-down state. This act of deceleration doesn’t just create physical substance; it provides structure, clarity, and form.* Meandering through these seasonal changes isn’t a passive drift - it’s an opportunity to realign. Slowing down, like nature does, creates space to step back from the busyness of society and technology. It allows us to reflect on where we are, re-ground ourselves, and act with greater intention. In this pause, we rediscover the creative power of slowness: the ability to lay foundations, see clearly, and prepare for growth when the time is right. Seasons are more than a backdrop — they are guides. They remind us that slowing down isn’t stagnation but essential groundwork. Winter’s invitation to pause and meander is not only natural; it’s necessary for balance, perspective, and creating something enduring. 







 *All photographs are taken around where I live in South Carolina* ***I shoot with a Leica M262, and edit in Lightroom + Dehancer*** [***Use “PictureRoom” for 10% off Dehancer Film***](https://www.dehancer.com/shop/pslr/film) If you’ve made it this far, thank you for taking the time to view my work - I appreciate it. Please contact me if you would like to purchase any of my prints.
*All photographs are taken around where I live in South Carolina* ***I shoot with a Leica M262, and edit in Lightroom + Dehancer*** [***Use “PictureRoom” for 10% off Dehancer Film***](https://www.dehancer.com/shop/pslr/film) If you’ve made it this far, thank you for taking the time to view my work - I appreciate it. Please contact me if you would like to purchase any of my prints. -
 @ 783850fd:77511d32
2025-01-20 13:22:54
@ 783850fd:77511d32
2025-01-20 13:22:54I'm thinking about buying a small house or a plot of land in Morocco and living there. The amount I am willing to pay for this would be $10 000 - 30 000. How much might I liquidate into their fiat (MAD) bank account with a month or so without them freezing my account and god only knows what worse things them doing to me. I use robosats and never exceed the amount of 950 euro when selling Bitcoin. I have all my wealth in Bitcoin, no history of income over the last 5 years, no filing tax returns too. I am from the EU, residing in Spain. How has your experience with Morocco been? Can one open a bank account in Morocco without having a residence there?
originally posted at https://stacker.news/items/857178
-
 @ da18e986:3a0d9851
2025-02-14 06:00:27
@ da18e986:3a0d9851
2025-02-14 06:00:27I'm excited to share the first phase of DVMDash's major redesign! After some recent downtime issues (thanks nostr:npub1e5tfhk8m65teu25dfx8lcvwn4c8ypqjl72u2sh4rt8zy2kss0j5qct7mh9 and nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn for the heads up), I've been working on rebuilding DVMDash from the ground up to be more modular, scalable, and reliable.
What's Live Now: The Stats App
The first piece of the new DVMDash is our completely rebuilt Stats app. Instead of trying to do everything at once, we're now breaking DVMDash into focused tools. The Stats app brings:
- Flexible time windows (1h, 24h, 7d, 30d) for more relevant insights
- Bar graphs showing activity over time
- Per-DVM and per-Kind detailed metrics
For those interested in the new backend architecture, check out my recent post about performance gains describing how horizontal scaling is needed to support the growing DVM ecosystem.
Coming Soon: Debug Tools and Playground
You'll notice on the new landing page that DVMDash is now split into three main tools:
- Stats (available now!)
- Debug Tools (coming soon)
- Data Vending Playground (coming soon)
The Debug Tools will bring back the interactive graph-based debugger and event browser, while the Playground will offer a space to experiment with DVMs directly. I'm focusing on getting these right rather than rushing them out.
Running Locally
Want to try it out? You can clone the repository and run the Stats app locally with a simple
docker compose --profile all upthen visit localhost:3000 in your browser.
What's Next
My immediate focus is on:
- Polishing the Stats app with new features like:
- Sortable tables for easier data analysis
- Enhanced DVM profiles with pictures and metadata from relays
- More detailed DVM-specific metrics
- Bringing back the debugging tools
- Building out the playground
This is very much a work in progress, and I appreciate your patience as we rebuild. If you run into any issues or have suggestions, please drop by our GitHub repository.
-
 @ 9349d012:d3e98946
2025-01-19 19:47:15
@ 9349d012:d3e98946
2025-01-19 19:47:15For many reasons, not least of those the outcome of the last US presidential election, I’m now working on Librarian Detective, Book Two as my creative release. At the moment, I’m already on chapter seven, which means I made it through writing the second chapter, always an admirable hurdle to clear. If you’ll recall, with Librarian Detective, Book One, clearing that milestone was a challenge. It took between nine and 12 years to finish that book, although I wrote three books in those meantime years. This was partly because of working on my day job business more fulltime (MyLibrarian! Our app is out, sign up to test on the pop up here) but also because I revamped my entire writing process, which I’ll share with you.
Here’s a picture of the writing methods I use. I went from writing longhand to digitally, which is more efficient, and I also use a series of guides to help organize the writing process: An outline, character list, calendar timeline, editing checklist and the main writing doc itself.
Seven years ago when I realized my writing method was working for me, I started doing a video series on Writing, called On Storytelling, filmed at all the remote locations I work at, one of the best of which I’m at right now, working on my new book. If you are looking for more writing resources, there’s a list on my blog. When you go down these rabbit holes you may come out ready to write your first book.
GOOD LUCK—MEZ
Originally appeared on https://www.michellezaffino.com/my-writing-methods/
-
 @ 7d33ba57:1b82db35
2025-02-14 01:46:37
@ 7d33ba57:1b82db35
2025-02-14 01:46:37The short answer is YES—but the more honest answer is that it’s much harder than when I started. I’ve been in the travel stock media industry for over 13 years, creating a vast archive of stock photos and videos from around the world. You can check out my portfolio on https://www.shutterstock.com/g/traveltelly. My work is also available on Pond5, Videoblocks, and Adobe Stock. Other big agencies where I don’t have my media are Getty Images and iStock.
My media has been featured on TV channels and even in feature films. However, most of the time, contributors don’t know exactly where their content is used—stock agencies (the middlemen) keep that information to themselves. While stock media can still generate income, it requires persistence, a large portfolio, and an understanding of the ever-changing market.
When I started filming stock footage, most people didn’t even have a phone capable of taking good photos or videos—can you imagine? Now, everyone is a (travel) content creator. Technology has evolved, but creating a well-composed photo or video is still an art. However, the combination of improved tech and the increasing centralization of the stock media market has made it much harder to earn a decent income from stock media compared to 10 years ago.

Centralization & Declining Royalties Over the years, I’ve watched stock media royalties decline year after year. In the beginning, I couldn't understand why I wasn’t able to recoup the cost of my expensive camera—one I specifically bought to shoot high-quality 4K footage.
As the stock media industry became more centralized, agencies took a larger cut while contributors earned less, despite creating higher-quality content. The market became saturated, and with more competition and lower payouts, making a sustainable income from stock media became increasingly difficult.

The Reality of Centralization in Stock Media Every year, stock agencies announced yet another royalty downgrade for contributors. They always framed it as something beneficial for content creators, but in reality, it only served the big companies and their shareholders.
As content creators, we had no say in the matter. These agencies grew too big and powerful, and they knew it. Leaving one platform wasn’t really an option—doing so would only mean an even greater loss of income.
In recent years, the industry has become even more centralized, with only a handful of major agencies buying out smaller competitors. This consolidation further reduces competition, giving contributors even less control over pricing, royalties, and where their content is used.

The Bitcoin Standard: A Wake-Up Call I couldn’t understand why I was struggling to pay off my expensive camera investment, despite working hard and producing high-quality content. Until then, I had never really thought about how money worked. That changed in 2018 when I read The Bitcoin Standard—an absolute eye-opener.
That book sparked my curiosity about Bitcoin. Like many, I initially got distracted by shitcoins, thinking I could multiply my holdings faster—after all, Bitcoin seemed “too expensive.” It was a hard but valuable lesson. Just like in a casino, you can win and lose a lot with altcoins, but that has nothing to do with Bitcoin itself. After those first few years of learning, I realized that for me, Bitcoin—not crypto—was the only way forward.

From Centralization to Decentralization When people ask me if they should start selling stock footage, my answer is always the same: It’s much harder now than when I started. Sure, you can make a few bucks, but is all the time and effort really worth it? If I had to start today, I simply wouldn’t—it’s way more work than what you’ll earn.
Instead of spending years building content for centralized platforms that take the biggest cut, I believe it’s better to focus on decentralized media like Nostr. In my opinion, that’s where the future lies.

Nostr: A New Protocol for Socializing (and More) Nostr is a revolutionary protocol that goes beyond just social networking. You can read all about it at Nostr.org. As a content creator, one of the most exciting aspects of Nostr is the ability to earn directly through Zaps—small payments made in Satoshis (the smallest unit of Bitcoin). * 1 Bitcoin = 100 million Satoshis * By receiving Zaps, you’re not just earning—you’re stacking the hardest money (Bitcoin) directly on Nostr. This shift toward decentralized earning is a game changer, giving creators more control and financial sovereignty compared to traditional, centralized platforms.

Join Nostr and Create Your Freedom Content
On Nostr, no one can stop you. No one can deplatform you. You can be truly free.Whether you're a content creator, artist, or thinker, Nostr empowers you to share your work without censorship or gatekeepers. It’s a place where you control your content, connect directly with your audience, and even earn Bitcoin through Zaps.Embrace decentralization.
Join Nostr and take back your freedom 🚀
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ a0c34d34:fef39af1
2025-01-14 14:28:28
@ a0c34d34:fef39af1
2025-01-14 14:28:28I feel fabulously free, I deleted TikTok. I am spending less time on my phone and more time developing Onboard60. I never expected to go from the Metaverse to A.I. healthcare and NFCC medical bracelets.
I was on Vine, Twitter back in 2009… I went from 8 second nonsensical videos and funny tweets to diving deeper down any rabbit hole I ever imagined.
In 2016, I heard a little noise about Bitcoin and I haven’t gotten off the rollercoaster of a merry go round yet. If you know, you know.
I found Nostr awhile ago but I’m no maxi, I’m curious. I learned about different things pertaining to blockchain and cryptocurrency, social media and protocols.
I kept journals of my fears and conferences I experienced and published them as my first years behind the scenes of a senior citizen diving deep into the unknowns.
Someone had to tell me I was a senior citizen. I’m 64 now , that was four years ago. Since then I took a crazy idea and started Onboard60.
I created a curriculum for myself. For years I have learned a variety of subjects. I took the basics and made a cliff note booklet - Web3 1101 for Seniors.
I didn’t want to be left behind so I learned Spatial and created an auditorium, an art gallery and an office. It was my attempt to get senior citizens involved to connect with their grandkids in virtual reality like Roblox.
Over the years, I’ve written articles on Substack sharing my journey, and sporadically posted on Zentaurios. I remember writing on YakiHonne when I first discovered it.
Onboard60 has become more than what I ever thought it would be, as I started just sharing my journey in hopes others would join me.
I hoped senior citizens would be interested in learning how to put their trust funds, H.O.A.s, POLSTs and other senior citizen documents on chain.
The past four years, nothing until I speak of medical bracelets. I do not mention BitDoctor AI or mirrors that do body scans. Bracelets, I speak bracelets.
The focus is to keep senior citizens up to date with new technologies that focus on improving their quality of life.
Finding YakiHonne again is refreshing. The esthetics clean, seemless cross posting, and better options for posting. Soft landing.
I have learned a lot over the years, experiencing this space becoming , watching protocols grow, some platforms fizzle, creating a new world isn’t easy.
I’m enjoying being a mermaid in Monniverse community on Farcaster, not Farcaster itself but enjoy being a mermaid. Monniverse is a decentralized animation production company. I’m learning how to use the image generator and like the global reach.
I have compromised on so many social media sites just to be on them. I still frequent Twitter Onboard60, and have my old Vine group on Instagram. I spend time on Lens mostly.
I use traditional media to share Onboard60 - LinkedIn and YouTube for Onboard60. I am creating a digital replica of all the information, subjects, videos, content that I created as Onboard60. I hope to keep it updated as times goes forward.
I’m going to use my guide to IRL events at Blockchain Miami in a few weeks, WAGMI MIAMI. After so many conferences and events, I had to write down a step by step how to get through these and follow up after. They can be overwhelming and I needed a way to decompress. My guide helps me.
I seem to be rambling. I don’t have a purpose or any value to share with this article, I just wanted to share my thoughts for now, walking into 2025.
Sandra ,Samm,Sababa
Onboard60, founder
-
 @ dbb19ae0:c3f22d5a
2025-02-13 20:42:08
@ dbb19ae0:c3f22d5a
2025-02-13 20:42:08Installation:
bash python3 -venv nostr-sdk source nostr-sdk/bin/activate pip install nostr_sdk requestsPython program: ``` pythonUsage example: python ns_read_metadata.py nostr:npub1mwce4c8qa2zn9zw9f372syrc9dsnqmyy3jkcmpqkzaze0slj94dqu6nmwy
Compatible with version 0.39
ns_read_metadata.py
version 3
import asyncio, argparse, json from nostr_sdk import Metadata, Client, NostrSigner, Keys, Filter, PublicKey, Kind from datetime import timedelta
async def main(npub): client = Client() await client.add_relay("wss://relay.damus.io") await client.connect() pk = PublicKey.parse(npub) print(f"\nGetting profile metadata for {npub}:") metadata = await client.fetch_metadata(pk, timedelta(seconds=15)) print(metadata)
if name == 'main': parser = argparse.ArgumentParser(description='Fetch all metadata for a given npub') parser.add_argument('npub', type=str, help='The npub of the user') args = parser.parse_args() asyncio.run(main(args.npub))
```
-
 @ 30b99916:3cc6e3fe
2025-02-13 18:56:37
@ 30b99916:3cc6e3fe
2025-02-13 18:56:37Upgrade Details
Download current release and manifest files ```shell Navigate to https://github.com/getAlby/hub/releases/tag/v1.13.0/
Download albyhub-Server-Linux-x86_64.tar.bz2 manifest.txt manifext.txt.asc
Copy the downloaded files to $HOME mv $HOME/Downloads/albyhub-Server-Linux-x86_64.tar.bz2 $HOME mv $HOME/Downloads/manifest.txt $HOME mv $HOME/Downloads/manifest.txt.asc $HOME
Verify manifest signature & Checksumsh Only need to import oncecurl https://raw.githubusercontent.com/getalby/hub/master/scripts/keys/rolznz.asc | gpg --import
gpg --verify manifest.txt.asc manifest.txt gpg: Signature made Tue 07 Jan 2025 08:56:42 PM PST gpg: using RSA key 5D92185938E6DBF893DCCC5BA5EABD8835092B08 gpg: Good signature from "Roland Bewick roland.bewick@gmail.com" [unknown] gpg: WARNING: This key is not certified with a trusted signature! gpg: There is no indication that the signature belongs to the owner. Primary key fingerprint: 5D92 1859 38E6 DBF8 93DC CC5B A5EA BD88 3509 2B08
shasum -a 256 server-linux-x86_64.tar.bz2 a75c03d241921611dfc428c413c4a2c2cef35bc6d1974839b688ef462604058d server-linux-x86_64.tar.bz2
The above checksum should be referenced in the manifest.txt file
cat manifest.txt ```
Stop AlbyHub & Backup existing data directory & Binaries ```shell systemctl stop albyhub
cp -r $HOME/.local/share/albyhub /media/veracrypt1/albyhub cp $HOME/bin/albyhub $HOME/bin/albyhub172 cp -r $HOME/lib $HOME/lib172
Extract new release Binaries & Start AlbyHubsh tar -xvjf albyhub-Server-Linux-x86_64.tar.bz2./ ./lib/ ./lib/libglalby_bindings.so ./lib/libldk_node.so ./lib/libbreez_sdk_bindings.so ./bin/ ./bin/albyhub
systemctl start albyhub ```
Navigate to http://localhost:9090
-
 @ 58937958:545e6994
2025-01-13 03:31:48
@ 58937958:545e6994
2025-01-13 03:31:48I made croquettes inspired by Spiral's character "Bitcoin (Puppet)."

The method is the same as making regular croquettes. I also tried making a version (right) with the arms and legs attached while shaping the filling, but they fell off before I could coat them in flour.

The face is made with seaweed and sliced cheese. The arms and legs are made with fish cake (hanpen). I brushed soy sauce on the legs and lightly toasted them in a toaster, which gave them a brown color.
 The arms and legs are attached using thin spaghetti.
When I searched for character-themed bentos (kyaraben), I came across the idea of using dried pasta, which made sense.
I used fried spaghetti sticks for attachment.
The arms and legs are attached using thin spaghetti.
When I searched for character-themed bentos (kyaraben), I came across the idea of using dried pasta, which made sense.
I used fried spaghetti sticks for attachment.Here’s Bitcoin Croquette squished into a bento box:

Halving

Notes
- I tried freezing the filling to help it hold its shape, but it backfired. It stuck to the plate and the cooking paper, and once partially thawed, it became way too watery. Freezing might work with better preparation.
- The filling was quite dry when shaping, so it might be better to add a binder (this time, I only used potatoes and sautéed onions).
The shape of Bitcoin Puppet was really easy and fun to make, so I’d love to try creating something else next time!
nostr:nevent1qqsxgpjvf9g9suhzx5asqhvnlvnarl43kuhas8v5g2ryjr9yjjp0z5ctkh5pt
-
 @ 58937958:545e6994
2025-01-13 03:19:17
@ 58937958:545e6994
2025-01-13 03:19:17Spiralのキャラクター「ビットコイン(パペット)」のコロッケを作りました

作り方は一般的なコロッケです 試しにタネの状態で手足をくっつけたバージョン(右)も作りましたが 粉をつける前に手足がもげました

顔はのりとスライスチーズ 手足ははんぺんです 足は醤油をつけてトースターで軽く焼いたら茶色になりました
 手足はサラスパでくっつけてます
細いスパゲッティ
キャラ弁でググったらサラスパが出てきてなるほどな~と思いました
自分は揚げパスタにして刺しました
手足はサラスパでくっつけてます
細いスパゲッティ
キャラ弁でググったらサラスパが出てきてなるほどな~と思いました
自分は揚げパスタにして刺しました弁当箱に押し込まれてるコロッケくん

半減期

メモ
- タネを作った時に形を保たせるために冷凍してみたんですけど逆効果だった(皿とクッキングペーパーにくっついて取れなくなった&半解凍したら水分がすごいことになった)ので冷凍するなら対策が必要そう
- 形作るときにかなりパサパサだったので、つなぎがあった方がいいのかも(今回はじゃがいも&炒めタマネギだけ)
ビットコインくんの形はすごく作りやすくて面白いのでまた何か作りたいなぁと思いました
nostr:nevent1qqsxgpjvf9g9suhzx5asqhvnlvnarl43kuhas8v5g2ryjr9yjjp0z5ctkh5pt
-
 @ dbb19ae0:c3f22d5a
2025-02-13 17:46:41
@ dbb19ae0:c3f22d5a
2025-02-13 17:46:41This code below works with nostr_sdk 0.32.2
``` python import asyncio, argparse, json from nostr_sdk import Metadata, Client, NostrSigner, Keys, Filter, PublicKey, Kind from datetime import timedelta
async def main(npub): client = Client() await client.add_relay("wss://relay.damus.io") await client.connect() pk = PublicKey.from_bech32(npub) print(f"Getting profile metadata for {npub}:") f = Filter().kind(Kind(0)).author(pk).limit(1) events = await client.get_events_of([f], timedelta(seconds=15)) if events: event = events[0] metadata_dict = json.loads(event.content()) for key, value in metadata_dict.items(): print(f"{key}: {value}") else: print("Could not retrieve metadata for the given public key.")
if name == 'main': parser = argparse.ArgumentParser(description='Fetch all metadata for a given npub') parser.add_argument('npub', type=str, help='The npub of the user') args = parser.parse_args() asyncio.run(main(args.npub)) ``` but with nostr_sdk 0.39 the program no longer worked and crash with error:
AttributeError: type object 'PublicKey' has no attribute 'from_bech32'. Did you mean: 'to_bech32'?why?
source: - https://github.com/ev3rst/nostr_sdk_examples - https://alashazam.wordpress.com/2024/07/07/python-nostr_sdk-fetching-all-metadata/
-
 @ dbb19ae0:c3f22d5a
2025-02-13 17:32:36
@ dbb19ae0:c3f22d5a
2025-02-13 17:32:36pip cache will show how much space is taken from past download
bash (nostr) ever3st@Alashazam:~/Documents/dev/python/$ pip cache info Package index page cache location: /home/ever3st/.cache/pip/http Package index page cache size: 2437.7 MB Number of HTTP files: 271 Wheels location: /home/ever3st/.cache/pip/wheels Wheels size: 2.2 MB Number of wheels: 2About 2GB if space is needed it can be cleared ``` bash (nostr) ever3st@Alashazam:~/Documents/dev/python/$ pip cache purge Files removed: 273 (nostr) ever3st@Alashazam:~/Documents/dev/python/bots/nostr$ pip cache info Package index page cache location: /home/ever3st/.cache/pip/http Package index page cache size: 0 bytes Number of HTTP files: 0 Wheels location: /home/ever3st/.cache/pip/wheels Wheels size: 326 bytes Number of wheels: 0```
-
 @ 6538925e:571e55c3
2025-02-13 16:05:42
@ 6538925e:571e55c3
2025-02-13 16:05:42 \
Nostr Live Streams (Beta)
\
Nostr Live Streams (Beta)If you follow shows like Rabbit Hole Recap, THE Bitcoin Podcast or Simply Bitcoin on Nostr, you can now watch the video in Fountain and hang out in the live chat as it’s being recorded. You'll find livestreams from people who follow on Nostr at the top of the home screen.
As well and live podcasts, you will also find live music events from PhantomPowerMedia, radio stations like NoGood and Noderunners, as well as channels dedicated to gaming, art, coding and much more.
Bringing creators and fans together through live experiences enables audience participation and creates a special feeling of community, so we’re really excited to get this into your hands.
Nostr livestreams are a beta feature - i.e. we still have a lot more work to do! We will continue to make improvements to livestreams over the coming months - so we would love to hear your feedback.
 \
Storage Manager
\
Storage ManagerWe’ve added a storage manager in the app’s settings so that you can view file storage size for audio downloads, video downloads, transcripts, image cache, feed cache, and temp files. You can delete all files in any of these folders to free up storage on your device so that Fountain continues to run optimally.
There are other performance and stability improvements that we are working on too. For example, in the next couple of weeks we will be rolling out an image proxy service, which should reduce mobile data usage and optimise storage.
Stay tuned for further updates and, as always, thanks for your support.
-
 @ 558e15eb:efa6e980
2025-01-12 19:23:42
@ 558e15eb:efa6e980
2025-01-12 19:23:42[2025-02-07] Øy 5 year anniversary - Talk show and watch party @ online
Øy 5 year anniversary - Talk show and watch party online - https://lislegaard.stream/ (https://lislegaard.stream/)
(Friday, 7 February 20:00)

https://do.basspistol.org/event/oy-5-year-anniversary-talk-show-and-watch-party
-
 @ f1989a96:bcaaf2c1
2025-02-13 14:24:32
@ f1989a96:bcaaf2c1
2025-02-13 14:24:32Good morning, readers!
This week, we highlight how authoritarian regimes are manipulating digital assets. The Central African Republic launched a government-backed meme coin that crashed spectacularly within a day of launch as regime insiders cashed out for profits, leaving the public with worthless tokens.
Meanwhile, the Nigerian regime introduced its first official stablecoin, cNGN. It is issued by the African Stablecoin Consortium and is backed 1:1 with the naira. Still, it operates under the direct oversight of the Nigerian Securities and Exchange Commission, allowing further surveillance of Nigerians’ financial activity alongside the struggling eNaira CBDC.
On the freedom tech front, Mullad VPN now supports Bitcoin payments via the Lightning Network, offering activists, journalists, and individuals under oppressive regimes a censorship-resistant and permissionless way to pay for their privacy. Additionally, SeedSigner, an open-source hardware wallet for Bitcoin self-custody, rolled out multilingual support, expanding accessibility to Spanish-speaking activists and human rights defenders.\ \ Finally, journalist Frank Corva explores Africa’s grassroots Bitcoin movement, where open-source tools and circular economies are empowering communities inside authoritarian regimes with financial freedom. For those who doubt Bitcoin’s real-world impact, this article is a must-read.
Now, let’s get right to it!
Subscribe Here
GLOBAL NEWS
Central African Republic | Launches Meme Coin Experiment
The Central African Republic (CAR) debuted a government-backed meme coin, $CAR, which President Faustin-Archange Touadéra claims will “unite people” and “support national development.” In reality, meme coins are speculative assets that often serve as vehicles for insider profit. This scheme follows CAR’s failed Sango Coin project, which promised citizenship and land in exchange for locked investments but sold only 7.5% of its supply. Those who did “buy in” did not receive what was promised. In 2022, CAR briefly made Bitcoin legal tender, calling it a path to sovereignty — only to abandon it shortly after. Instead of supporting open and neutral money like Bitcoin, the government has turned to dubious crypto schemes. The real beneficiaries of $CAR appear to be regime insiders who reportedly cashed out $40 million while the public holds worthless tokens.
Nigeria | Debuts Naira Stablecoin
The Nigerian state launched its first regulated stablecoin, cNGN. Similar to US dollar-pegged stablecoins like USDT and USDC, cNGN is pegged 1:1 to its local currency (the naira). It is issued by the African Stablecoin Consortium (ASC), a private coalition of Nigerian financial institutions and blockchain companies. Positioned as a bridge between fiat and digital assets, cNGN aims to facilitate remittances and trade but comes with strict verification requirements that limit financial privacy. The Nigerian SEC also tightly regulates the stablecoin and it is only available on government-approved exchanges, Busha and Quidax. As Nigeria expands its control over digital transactions — through both cNGN and its struggling eNaira CBDC — more and more Nigerians are turning to Bitcoin as a censorship-resistant alternative.
Russia | Proposes Registry to Track Bitcoin Mining Hardware
Russia’s deputy energy minister, Yevgeny Grabchak, has proposed a centralized registry of Bitcoin mining equipment and wallet addresses to “identify mining activities and ensure stricter enforcement of bans in restricted regions,” such as Russian-occupied Ukraine territories. Meanwhile, the Chairman of the State Duma Committee on Energy, Nikolai Shulginov, warned that last year’s mining ban in several Russian and occupied regions may not be enough to eliminate mining fully. As an authoritarian state with an egregious human rights record and a long history of financial repression, Russia appears intent on tightening surveillance of economic activity — especially that of Bitcoin. By registering, tracking, and restricting mining, the Kremlin expands its financial control, undermines economic autonomy, and limits access to permissionless money.
Turkey | Erdoğan Targets Opposition as Inflation Forecast Rises
Turkish President Recep Tayyip Erdoğan sentenced Istanbul Mayor Ekrem Imamoglu — a key political rival — to seven years in prison on charges widely seen as politically motivated. If upheld, the conviction will bar Imamoglu from office, further clearing Erdoğan’s path to dominance ahead of the 2028 elections. At the same time, Turkey’s economic crisis is worsening. Accelerating inflation forced the central bank to raise its 2025 forecast from 21% to 24%, exacerbating the lira’s decline and eroding purchasing power. As both political and financial repression deepen, more Turks are turning to alternatives to sidestep Erdoğan’s expanding control over the economic and political sphere.
Georgia | Regime to Pass Censorship Law
Georgia’s ruling Georgian Dream party is set to introduce a media censorship law aimed at enforcing government-defined standards for journalistic objectivity and ethics, while also restricting foreign funding for media outlets. MP Mamuka Mdinaradze claims the law will establish monitoring mechanisms and is modeled after UK regulations, though critics compare it to Belarusian-style repression. Georgian Dream Prime Minister Irakli Kobakhidze defended the move as necessary to close legislative “loopholes” and strengthen state control. Journalists and activists warn that the law is part of a broader crackdown on press freedom and dissent. Decentralized social networks like Nostr will become increasingly vital for journalists and activists to communicate freely, resist censorship, and ensure the flow of independent information.
____________
Webinar Series for Nonprofits: Become Unstoppable
HRF will host a free, three-day webinar from March 17-19, teaching human rights defenders and nonprofits how to use Bitcoin to counter state censorship and confiscation. Sessions run daily from 10:30 a.m. to 12:00 p.m. EDT and are beginner-friendly. The webinar will be led by Anna Chekhovich, HRF’s Bitcoin nonprofit adoption lead and financial manager at Alexei Navalny’s Anti-Corruption Foundation.
Register Here
SXSW | The Human Rights Risks of Central Bank Digital Currencies (CBDCs)
Join HRF at SXSW 2025 in Austin from March 9-12 to explore how CBDCs threaten financial freedom. Experts Roger Huang, Charlene Fadirepo, and Nick Anthony will discuss how authoritarian regimes use CBDCs for surveillance and control on March 9. Attendees can also visit HRF’s CBDC Tracker booth to explore an interactive map of CBDC developments worldwide.
Get Tickets
____________
BITCOIN AND FREEDOM TECH NEWS
Mullvad VPN | Testing Lightning Network Payments
Mullvad VPN is experimenting with Bitcoin for payments via the Lightning Network, a second-layer payment protocol built on Bitcoin that enables faster, cheaper, and more private transactions. This integration lets Mullvad VPN users pay for their services in bitcoin while enhancing their privacy and bypassing payment networks that track or censor financial activity. VPNs protect users by masking IP addresses and encrypting traffic. Accepting Bitcoin over Lightning strengthens this protection with a censorship-resistant payment option. For activists, journalists, and individuals in authoritarian regimes, this combination provides a shield against surveillance.
SeedSigner | Releases Multilingual Support
SeedSigner, an open-source and customizable Bitcoin hardware wallet and HRF grantee, introduced multilingual support for Spanish. This update makes secure Bitcoin self-custody more accessible to Spanish-speaking activists and human rights defenders who may rely on Bitcoin for transactional freedom. By expanding access to secure self-custody, SeedSigner helps reduce dependence on restrictive financial systems and allows more people in Nicaragua, Venezuela, Cuba, and beyond to “be their own bank.”
Iris | Implements Private Bitcoin Payments with Cashu
Iris, a Nostr client, has added support for a Cashu wallet to allow users to send and receive ecash. Cashu is an open-source Chaumian ecash protocol built for Bitcoin and integrated with the Lightning Network. It lets users make fast, low-cost, and extremely private transactions using Bitcoin-backed ecash. While it requires a trusted custodian, it helps users spend Bitcoin anonymously without revealing their identity or transaction activity. This ability provides activists and nonprofits a different way to make private Bitcoin payments alongside nostr’s censorship-resistant communications.
Sparrow Wallet | Supports Lark for USB Hardware Wallets
Sparrow Wallet, a popular open-source Bitcoin wallet, has added support for Lark, a new tool for USB hardware wallet communication. Lark works alongside the existing Hardware Wallet Interface (HWI), giving users an alternative way to connect their hardware wallets via USB. This update improves reliability, reduces dependence on a single software interface, and strengthens Bitcoin self-custody.
Bitcoin Dada | Opens Applications for Second Cohort of Dada Devs
Bitcoin Dada, an HRF-supported nonprofit initiative empowering African women through Bitcoin and financial education, is now accepting applications for the second cohort of Dada Devs. This developer program provides hands-on training, mentorship, and a collaborative community to help African women under authoritarian regimes contribute to Bitcoin development. If you’re an aspiring female developer, apply now to join a network of African women shaping the future of finance. Applications close Feb. 13.
Summer of Bitcoin | Applications for Summer 2025 Cohort Now Open
Summer of Bitcoin, an HRF-supported Bitcoin internship program, is now accepting applications for its summer 2025 cohort. This program introduces students from anywhere, including from authoritarian regimes, to Bitcoin open-source development and design, giving interns the option to choose between a developer or designer track based on their interests. Participants will gain hands-on work experience, contribute to real-world Bitcoin projects, and receive mentorship from industry leaders. You can learn more and apply here.
Spiral | Announces Grant Renewals for the Bitcoin Design Community and BDK
Spiral, a Bitcoin company building and funding open-source projects, announced renewed grants for critical initiatives, including the Bitcoin Design Community and Bitcoin Dev Kit (BDK). The Bitcoin Design Community is a free and open-source resource for designers, developers, and others working on non-custodial Bitcoin products. This grant will support designers who push the user experience and adoption of Bitcoin forward. Meanwhile, BDK is a software library that helps developers in building cross-platform Bitcoin wallets. Its grant will support the project’s continued refinement and development.
RECOMMENDED CONTENT
The Bitcoin and Cypherpunk Spirit Is Alive and Well in Africa by Frank Corva
In this article for Bitcoin Magazine, journalist Frank Corva spotlights Bitcoin's growing presence across Africa. Across the continent, people are building Bitcoin circular economies, open-source financial tools, and educational initiatives. From Bitcoin Ekasi in South Africa to AfriBit Kibera in Kenya and Bitcoin Dua in Ghana, these grassroots initiatives drive financial inclusion and education for individuals and communities. Meanwhile, tools like Tando and Machankura are expanding access to transactional freedom, and conferences like Adopting Bitcoin Captetown and the Africa Bitcoin Conference nurture ongoing collaboration between individuals, developers, and activists to advance financial freedom on a continent that otherwise has very little liberal democracy. Read the full article here.
Using Bitcoin Without Internet! Here’s How Machankura Makes It Happen with Anita Posch
In this short interview, Bitcoin educator and host of the Bitcoin for Fairness channel, Anita Posch, speaks with Mary Imasuen, a Machankura team member, about how this technology makes Bitcoin accessible to Africans without Internet access. Machankura is an app that allows feature phones to send and receive Bitcoin using the Unstructured Supplementary Service Data (USSD) protocol, a mobile communications system similar to SMS. This means people can transact in Bitcoin without needing a smartphone or data connection, a situation common to many living under autocratic regimes in sub-Saharan Africa. By removing Internet barriers, Machankura helps millions of Africans overcome high data costs and unreliable networks, offering a practical solution to financial inclusion.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 2183e947:f497b975
2025-02-13 04:44:45
@ 2183e947:f497b975
2025-02-13 04:44:45How Coinpools Improve Bitcoin
Problems with bitcoin
UX problems with base layer payments include:
- Mining fees are sometimes high
- Confirmations usually take several minutes
- Using it privately requires running a coinjoin server
UX problems with lightning payments include:
- Setup fees are sometimes high
- Payments frequently fail
- Payments aren't asynchronous (the recipient has to stand there with their device open waiting to do a revoke_and_ack on their old state -- unless they use a custodian)
- Payments that do succeed occasionally take more than 30 seconds (due to stuck payments, automatic retries, and no ability to say "stop retrying" in any existing wallets that I'm aware of)
- Using it privately requires manual channel management
Solutions
A lot of my recent work focuses on non-interactive coinpools. I figured out a way to do them on bitcoin if we had CTV + CSFS, and then, with a bit more thought, I figured out that my model didn't actually require those things, so I am now working on an implementation. But my model does benefit a lot from CTV (less sure about CSFS at this point) so let me outline how non-interactive coinpools fix the above problems and along the way I will share how CTV specifically improves coinpools.
"Mining fees are sometimes high"
Coinpools improve the problem of "mining fees are sometimes high" by letting you bypass them in more cases. If you're in a coinpool and pay someone else in the same coinpool, your payment does not show up on the base layer, it just involves modifying some unilateral withdrawal transactions such that the sender can withdraw less and the recipient can withdraw more. The transactions are off-chain, like LN transactions, so you can do that without paying a base layer fee.
"Confirmations usually take several minutes"
Coinpools improve the problem of "confirmations usually take several minutes" in a similar manner. Payments inside a coinpool (i.e. to another pool user) merely involve modifying off-chain data (and revoking an old state), so they can be as fast as lightning. In most cases I expect them to be a bit faster because there's less need for pathfinding or negotiating with a variety of routing nodes. If the sender and the recipient are in the same pool, they only need to talk to each other and, in my model, a coordinator.
"Using the base layer privately requires running a coinjoin server"
Coinpools improve the problem of "using the base layer privately requires running a coinjoin server" in two ways: first, if you're in a coinpool and you send money to a bitcoin address, the blockchain doesn't know which coinpool user sent that payment. Analysts might be able to trace the payment to the coinpool, but from the blockchain's perspective, that's just a multisig; the actual person inside the multisig who sent the money is not revealed. However, my model uses a coordinator, and the coordinator probably knows which user sent the payment. Still, only 1 person knowing is better than having everyone on the blockchain know.
Second, if you send money to someone inside the coinpool, in my model, the only people who know about your payment are the sender, the recipient, and the coordinator, and the recipient does not know who the sender is. Moreover, my model allows users to act as bridges from LN to other pool users, so even the coordinator doesn't know if the person who looks like the sender was the real sender or just a bridge node, with the real sender being someone on lightning.
"Setup fees on lightning are sometimes high"
Coinpools improve the problem of "setup fees are sometimes high" by having multiple users share the setup cost. My model allows a single bitcoin transaction to fund a coinpool with a number of members between 1 and probably about 100. (The max I've actually successfully tested is 11.) If the users share the cost of that transaction, then even in a high fee scenario, where bitcoin transactions cost $50, each user only has to pay a fraction of that, where the fraction is determined by how many users are joining the pool. If 10 people are joining, each user would pay $5 instead of $50. If 50 people are joining, each user would pay $1. If 100 people are joining, each user would pay 50¢.
Sidebar: how CTV improves my coinpool model
The setup is also where CTV greatly improves my model. For my model to work, the users have to coordinate to create the pool in something I call a "signing ceremony," which is very similar to a coinjoin. The signing ceremony has to be scheduled and each user has to show up for it or they won't get into the pool. With CTV, you could fix this: instead of a signing ceremony, an exchange could autosend your money into a coinpool on e.g. a monthly basis and email you the data you need to perform your unilateral exit. All they need from you is a pubkey, and they can do everything else.
"Lightning payments frequently fail"
Coinpools improve the problem of "payments frequently fail" by reducing the need for pathfinding, which is a typical cause of failure on lightning. If you are paying someone in the same pool as you, you always know an exact path: it will be you -> coordinator -> recipient. These short paths also reduce the likelihood of routing nodes having insufficient capacity to forward the payment. You've only got one "routing node" to worry about -- the coordinator.
"Lightning payments aren't asynchronous"
Coinpools in general don't improve the problem of "payments aren't asynchronous" but my model in particular does improve that problem because I am combining it with my hedgehog protocol from last year, which does allow for asynchronous lightning-like payments. Relatedly, my coinpool model technically has a network model, it's just a hub-and-spoke network: the coordinator is connected to every user of the pool and can forward asynchronous hedgehog payments to them. This means you can send money to someone when they are offline; they'll get it whenever they do get online, even if you went offline in the meantime.
"Lightning payments sometimes take too long"
Coinpools improve the problem of "stuck" lightning payments by reducing the number of hops along the route. As above, a payment inside the pool (per my model) is always just sender -> coordinator -> recipient. Due to only having 1 hop, there are fewer opportunities for a node to have a network issue and cause a delay.
"Channel management is a pain"
Coinpools have multiple ways of improving the problem of manual channel management. In particular, not all coinpool models have channels, so channel management is not always needed in a coinpool. My model, however, does have channels, so channel management is still a thing.
Nonetheless, my model improves channel management in two ways: first, the setup costs are lower for the reasons given above. Second, payment asynchronicity helps for the following reason:
The worst pain point in channel management today occurs when someone sends you a payment but it fails because you didn't have enough inbound capacity. That doesn't happen in my coinpool model because payments are asynchronous. If you don't have enough inbound capacity, the payment doesn't fail, it just remains pending. So all you have to do is open a new channel (i.e. enter a new pool) and then finalize the payment.
Zap me
I hope this essay clarifies why coinpools improve the problems I outlined and why CTV improves coinpools. I also hope this gets you a bit excited for my latest coinpool invention, which I hope to release soon :D (It really is very close to demo-ready.) If you liked this essay, consider zapping me: supertestnet@coinos.io
-
 @ 5a8e581f:c150c8ba
2025-01-11 18:31:08
@ 5a8e581f:c150c8ba
2025-01-11 18:31:08Doing Bitcoin the right way is hard.
If Bull Bitcoin wanted to take the easy path, we would have done what all the other exchanges are doing and would simply have offered a custodial wallet to our users. But our mission is not to sell numbers on a screen, fake paper bitcoin and IOUs. Our mission is to create sovereign individuals. If our clients don’t take full control over their wealth, we have failed them.
If we wanted to take the easy path, we would have offered shitcoin trading, NFTs, ICOs, yield and all sorts of nonsense. No doubt, we would today be far more wealthy.
But we would have failed in our mission to establish a universal Bitcoin standard and fixed the problems created by easy money. We would have compromised on our values and sold products that we don’t believe in and we don’t personally use.
If we wanted to take the easy path, we wouldn't have spent years building open-source software that lets any business run their own self-hosted Bitcoin wallet API infrastructure connected directly to their own Bitcoin, Lightning and Liquid network nodes. We would have just done a deal with Coinbase or another third party to take care of the Bitcoin engineering on our behalf.
But we would have failed in our mission to help keep the Bitcoin network decentralized and resilient to institutional failures. We would have lost our direct and precious connection to the Bitcoin network.
The engineering, operational and logistical challenges involved in maintaining a noncustodial Bitcoin service like Bull Bitcoin, in an environment where Bitcoin network fees are increasingly high, while also maintaining an accessible user experience with minimal compromises on the cypherpunk principles of Bitcoin… are impossibly hard to fathom for the vast majority of Bitcoiners.
Despite consistently taking the most difficult path at every turn, Bull Bitcoin has nonetheless been crushing it for the past 10 years thanks to our Bitcoiner ethos and mindset, sticking to our core values and creating products with a singular focus: engineering sovereignty.
All of this we accomplished without any outside funding. Every sat invested in Bull Bitcoin was acquired by offering a service valued by our customers. Every network fee we pay, every investment in R&D comes straight out of our pockets. If our bitcoin-only noncustodial model fails and we become unprofitable, there will be no bailout.
As a low-time preference business, taking the hard path today means we will have a unique competitive advantage in the future. Nobody uses Bitcoin more than a non-custodial exchange. Every trade and every revenue generating activity is derived directly from a Bitcoin payment. We are keenly aware of every possible problem that Bitcoin users may be facing, because we are ourselves are a power user. We know what kinds of problems the users will face, what solutions we need to build and how we must adapt. We always skate where the puck is going.
But there is another, more noble purpose to choosing the hard path.
I'm also heavily involved in a community circular economy project in Costa Rica called Bitcoin Jungle. We spend countless hours to educate locals, set merchants up with Bitcoin point of sales, and build the infrastructure necessary for Bitcoin to thrive as a medium of exchange in even the most rural areas. All of this we do for free, and in fact it we pay for it out of pocket! I discovered recently that a few people were skeptical of our efforts. I met one of them and he asked us “but why are you doing this, if you don't make any money from it”.
We do it because we love Bitcoin. We believe in the ideology of Bitcoin, its underlying cypherpunk and free market principles. We do it because we as sovereign individuals cannot live in isolation and we all benefit from the success of our communities. We do it because we want our kids to grow up in a world that is free from the evils of Fiat currency. May our children never suffer the corruption of participating in a socialist economic system that steals their time and their wealth by the simple fact of interacting with fiat currency. We do it because doing it is a moral imperative. In a world of systematic injustice, doing nothing is to be complicit. You cannot live a virtuous life with the knowledge that you had the capacity to act heroically but chose to capitulate.
Bitcoin is at the center of a spiritual war between forces of corruption and forces of liberation. There is a higher power that calls us to become the resistance. Bitcoin is hope. Bitcoin is salvation. If Bitcoin fails, everyone on earth is truly and utterly fucked.
We are on the cusp of a fundamental civilizational change. The global debt-fueled fiat ponzi is imploding right before our eyes. What comes next is up to us to determine. We are the right place and the right time. We have a unique window of opportunity that may not come again within our lifetimes and that of our children.
The choices we make today will shape what the world looks hundreds of years from now. Whether our descendants live in totalitarian dystopias or will be ushering in a new era of prosperity and freedom depends on our willingness to choose the hard path today.
And if you think the hard part is over and that Bitcoin has already won, think again. During our decade of operational experience, there were few serious attacks on the Bitcoin network. Bitcoin had relatively low levels of adoption and apart from a few periods of intense fee spikes and the fork wars of 2017, it was smooth sailing. Bitcoin was mostly flying under the radar, left to develop organically in the hands of its cypherpunk caretakers.
This era of complacency is over. From now on, everything is about to get much, much harder. This is what we live for! Nothing easy is worth pursuing.
Bull Bitcoin hasn't given up on Bitcoin's mission to free humanity from the shackles of fiat slavery and centralized systems, we are reinvigorated by the challenges that Bitcoin is facing and that will continue to intensify.
We will not give up on Bitcoin's use case as a medium of exchange and we will continue to build tools that make it easy for anyone to opt out of the traditional banking system to conduct peer-to-peer transactions securely, as was originally intended by Satoshi when launched the Bitcoin project.
This new epoch, Bull Bitcoin is leveling up to an entire new standard for consumer-facing Bitcoin apps, higher than anyone has ever seen. We have been thinking about how to make our unique noncustodial model work sustainably long-term for years. This is the hill that we choose to die on.
But as we entered into a new Bitcoin epoch, I've witnessed many in the Bitcoin community become cynical, fatalistic and even depressed. It’s hard to blame them.
Privacy-preserving tools are being shut down. The Lightning Network is suffering scalability issues. The Bitcoin blockchain is being spammed by degenerate NFT gamblers, driving up transaction fees for everyone else. Bankers and Wall Street insiders are accumulating Bitcoin fortunes and promoting exchange traded funds as an alternative to self-custody. Bitcoin mining is being heavily centralized among a small group of American-based public companies. It sometimes feels like Bitcoin is under attack by various nefarious interests that want to control it and corrupt it.
Even from within our own community we are suffering from prophets of doom spewing fear, uncertainty and doubt. Many sneer that Lightning is broken, that Bitcoin has been co-opted by Wall Street. Some say we should give up and switch to altcoins. Some pundits blame “lasereyed maxis” for blocking protocol changes and claim that being conservative about modifying the rules of Bitcoin means “ossification” and that's the reason why Bitcoin has high fees. Others are pushing the idea that Bitcoin was never meant for payments anyway and that being a store of value was always the main goal of Bitcoin. Who cares about the poor? The plebs can always keep their funds on an exchange.
At Bull Bitcoin, we see it very differently. We have a realistic and optimistic approach towards building a bright future for Bitcoin. I have never been so bullish on the future Bitcoin as I am today.
Make no mistake: the core principles of Bitcoin self-custody, censorship-resistance and privacy are under attack. But the Bitcoin community possesses a unique advantage that will ultimately allow us to prevail: not only do we have skin in the game, we have soul in the game.
Our tribe of a few thousand cypherpunk Bitcoin maximalist fanatics stand against an empire of fiat clones, millions of faceless cogs in a soulless machine. I like our odds.
While I agree that we should never take Bitcoin’s success for granted, the bleak picture that some want to paint regarding the state of Bitcoin is detached from reality.
We've already achieved incredible technological miracles. The fact that it is possible for a user to run a Lightning network node on a mobile device and make fully trustless payments is a monumental achievement. Despite what they claim I can guarantee that no other shitcoin or fiat payment system has anywhere near the level of sophistication of Bitcoin. It is an incredibly bullish sign for the Bitcoin ecosystem that we have achieved a level where users can remain fully sovereign if they have the means.
Scaling Bitcoin so that it can enable hundreds of millions of people to become sovereign individuals is the most pressing challenge of our times. Our community must accept inevitable realities: not everybody will be able to afford on-chain transactions. The success of Bitcoin means that one day, during our lifetimes, a single Bitcoin translation will cost hundreds of dollars.
Upgrading the Bitcoin protocol may allow us to create tools that enable a more secure, censorship-resistant and private payment mechanism, but no soft fork can fix the fundamental tradeoffs of the Bitcoin protocol.
But this doesn't mean that we should either give up on Bitcoin’s value proposition as a medium of exchange, or that we must fork bitcoin according to the whims of whoever is trending on Twitter, nor should we capitulate to traditional exchanges acting as banks for the vast majority of users.
To fix the inconvenient and expensive user experience that most people are suffering in times of high fees while making the minimum amount of compromises, you need vision and execution.
There is an army of shadowy super coders that, like us, have dedicated their lives to ensure that Bitcoin becomes the universal medium of exchange, store of value and medium of account. We come from different walks of life and we have different strategies. Some of us work on self-sovereign consumer applications. Other focus of privacy protocols, mining decentralization, second later payment networks, e-cash protocols, and finally, as a last resort, some are working to add changes to the Bitcoin protocol which can enable tools that we currently cannot build.
At Bull Bitcoin, our vision of the future Bitcoin experience is crystal clear. It is a vision of success and integrity, where the path of least resistance for the user is also the path of least compromise.
We, the Bitcoin builders, will make it real.
-
 @ a012dc82:6458a70d
2025-02-13 04:00:01
@ a012dc82:6458a70d
2025-02-13 04:00:01In the dynamic world of global finance, the interplay between traditional monetary policy and the burgeoning digital asset market is becoming increasingly prominent. The U.S. Federal Reserve's recent pivot towards a more accommodative monetary policy has sparked intense discussion among investors, economists, and cryptocurrency enthusiasts. This shift, characterized by an expected reduction in interest rates, is not just a routine adjustment but a significant move that could have far-reaching implications for various asset classes, including cryptocurrencies like Bitcoin. As we delve into this topic, we aim to unravel the complexities of the Fed's policy change and its potential ripple effects on Bitcoin, a digital asset that has been a subject of much intrigue and speculation.
Table Of Content
-
Understanding the Fed's Policy Shift
-
Impact on Traditional Financial Markets
-
Bitcoin's Response to Monetary Easing
-
Analyzing the Economic Backdrop
-
Bitcoin: A Safe Haven or Risk Asset?
-
Risks and Opportunities
-
Conclusion
-
FAQs
Understanding the Fed's Policy Shift
The Federal Reserve, the guardian of the U.S. monetary system, wields immense influence over global financial markets. Its recent signaling of a dovish turn – an expectation of 75 basis points in rate cuts by 2024 – marks a significant departure from its previous stance. This change is reflective of the Fed's response to a confluence of macroeconomic factors, such as fluctuating inflation rates, global economic uncertainties, and domestic financial stability concerns. The Fed's decisions are closely monitored as they set the tone for economic growth, inflation control, and financial market stability. In this context, the anticipated rate cuts suggest a strategic move to stimulate economic activity by making borrowing cheaper, thereby potentially boosting investment and consumption. However, this policy shift is not without its complexities and nuances, as it must balance the fine line between stimulating growth and controlling inflation.
Impact on Traditional Financial Markets
The ripple effects of the Fed's policy announcement were immediately felt across traditional financial markets. Stock markets, often seen as a barometer of economic sentiment, reacted positively, with indices like the Dow Jones Industrial Average reaching new heights. This surge reflects investors' optimism about the potential for increased corporate profits and economic growth in a lower interest rate environment. Similarly, the bond market experienced a significant rally, with yields on government securities falling as bond prices rose. This movement in the bond market is indicative of investors' expectations of a more accommodative monetary policy, which typically leads to lower yields on fixed-income securities. These market reactions underscore the pivotal role of central bank policies in shaping investor sentiment and the direction of financial markets. They also highlight the interconnectedness of various asset classes, as changes in monetary policy can have cascading effects across different sectors of the economy.
Bitcoin's Response to Monetary Easing
Bitcoin's reaction to the Fed's dovish turn has been a subject of keen interest. The cryptocurrency, which had been experiencing volatility, showed signs of recovery following the Fed's announcement. This response is indicative of Bitcoin's increasing correlation with broader financial market trends, a significant development given its history as an uncorrelated asset. Bitcoin's sensitivity to macroeconomic factors like central bank policies points to its growing integration into the mainstream financial ecosystem. However, this integration also means that Bitcoin is increasingly exposed to the same macroeconomic risks and uncertainties that affect traditional assets. The Fed's policy shift could potentially make Bitcoin more attractive to investors seeking non-traditional assets in a low-interest-rate environment. However, Bitcoin's complex dynamics, including its decentralized nature, limited supply, and regulatory landscape, add layers of complexity to its response to monetary policy changes.
Analyzing the Economic Backdrop
The economic backdrop against which the Fed's policy shift occurs is multifaceted and dynamic. On one hand, the U.S. economy has demonstrated resilience, with robust GDP growth and positive retail sales figures suggesting underlying strength. On the other hand, inflation, though moderated from its peak, remains a concern, hovering above the Fed's target. This economic duality presents a challenging scenario for policymakers, who must navigate the delicate balance between stimulating growth and containing inflation. For investors and market participants, this creates an environment of uncertainty, as they must decipher mixed signals from economic data and policy announcements. In this context, Bitcoin's role and response become even more intriguing, as it operates at the intersection of technology, finance, and macroeconomics.
Bitcoin: A Safe Haven or Risk Asset?
The debate over Bitcoin's classification as a safe haven or a risk asset is intensified by the Fed's easing stance. Traditionally, in a low-interest-rate environment, investors seek assets that can serve as hedges against inflation and currency devaluation. Gold has historically played this role, and Bitcoin, with its fixed supply and digital scarcity, has drawn comparisons to gold. However, Bitcoin's relatively short history and high volatility make it a more complex and potentially riskier asset. The Fed's dovish policy could enhance Bitcoin's appeal as an alternative investment, especially if traditional assets like bonds offer lower returns. However, Bitcoin's classification as a safe haven is still a matter of debate, with opinions divided on its long-term stability and value retention capabilities.
Risks and Opportunities
Investors considering Bitcoin in light of the Fed's policy change face a landscape filled with both risks and opportunities. The potential for a Bitcoin rally in a low-interest-rate environment is counterbalanced by the cryptocurrency's inherent volatility and regulatory uncertainties. Bitcoin's price movements can be dramatic and unpredictable, influenced by a range of factors from technological developments to geopolitical events. Additionally, the regulatory environment for cryptocurrencies is still evolving, with potential changes posing risks to Bitcoin's accessibility and value. Investors must also consider the broader global economic context, including actions by other central banks and international trade dynamics, which can impact Bitcoin's market movement.
Conclusion
The Federal Reserve's shift towards a more accommodative monetary policy in 2024 presents a fascinating scenario for Bitcoin and the broader cryptocurrency market. This development underscores the increasing relevance of digital assets in the global financial landscape and highlights the complex interplay between traditional monetary policies and emerging financial technologies. As Bitcoin continues to evolve and gain acceptance, its response to macroeconomic factors like central bank policies will be a critical area of focus for investors. In navigating this dynamic and uncertain environment, a cautious and well-informed approach is essential for those looking to explore the opportunities and navigate the challenges of cryptocurrency investments. The coming years promise to be a pivotal period in the maturation of Bitcoin as it responds to the shifting tides of global finance.
FAQs
How does the Federal Reserve's easing stance impact Bitcoin? The Fed's shift towards lower interest rates can make riskier assets like Bitcoin more attractive to investors. This is because lower rates often lead to reduced yields on traditional investments, prompting investors to seek higher returns elsewhere.
What is the significance of the Fed's 'dot plot' for Bitcoin investors? The 'dot plot' is a projection of interest rate movements by Federal Reserve members. A shift towards lower rates, as indicated in the recent dot plot, can signal a more accommodative monetary policy, potentially impacting Bitcoin's market as investors adjust their portfolios.
Can Bitcoin be considered a safe haven asset in light of the Fed's policy? Bitcoin's role as a safe haven asset is debated. While its fixed supply and digital nature offer some safe haven characteristics, its volatility and regulatory uncertainties make it a complex choice compared to traditional safe havens like gold.
What risks should Bitcoin investors consider in the context of the Fed's easing policy? Investors should be aware of Bitcoin's volatility, regulatory changes, and its sensitivity to macroeconomic factors. Additionally, global economic conditions and actions by other central banks can also influence Bitcoin's market.
How does the economic backdrop influence Bitcoin's response to the Fed's policy? Economic factors like GDP growth, inflation rates, and retail sales impact investor sentiment and risk appetite, which in turn can affect Bitcoin's market. A strong economy might reduce the appeal of risk assets like Bitcoin, while economic uncertainties can increase their attractiveness.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
X: @croxroadnews.co
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ 3b7fc823:e194354f
2025-02-13 02:25:42
@ 3b7fc823:e194354f
2025-02-13 02:25:42site:example.com intitle:"index of" inurl:admin intext:"password"
site:example.com site:.gov site:.edu site:*.mil
inurl:login inurl:admin inurl:dashboard inurl:portal intitle:"admin login"
intitle:"index of /" intitle:"index of" "parent directory" intitle:"index of" "backup"
filetype:pdf "confidential" filetype:xls "username | password" filetype:doc "top secret" filetype:sql "database"
intext:"username" intext:"password" intext:"login" intext:"password" filetype:txt "passwords"
inurl:"viewerframe?mode=" inurl:"/view.shtml" inurl:"/view/index.shtml"
intitle:"index of" "wp-config.php" inurl:".git"
filetype:xls intext:"email" filetype:csv intext:"email"
inurl:"/setup.cgi?next_file=netgear.cfg" inurl:"/wificonf.html"
-
 @ 6ad3e2a3:c90b7740
2025-01-10 12:33:47
@ 6ad3e2a3:c90b7740
2025-01-10 12:33:47The excesses of wokeness are thankfully getting their overdue correction, but as often happens with corrections, they tend to overshoot. A case in point was from the usually reasonable writer Wesley Yang on Twitter, who posted the following:
Poor long-term immigration policy has apparently led to too many foreign-born and native criminals of foreign descent in Norway, a disproportionate number of whom, per the chart, hail from Somalia and Morocco. Yang argues using this data to inform Norway’s immigration policies going forward is both unproblematic and “no longer prejudice.”
This is a sleight of hand. You can advocate for designing prejudicial immigration policies based on the group to which an individual potential immigrant belongs, but you cannot both do so and pretend it is not prejudicial.
This is not a point about what countries should or should not DO. They are free IMO to design immigration policies as they see fit, and there are arguments to be had over that. But there is a reactionary blindness wherein people pretend that grouping individuals by race, religion or country of origin isn't prejudicial to those individuals who have no control over how others in their assigned group behave.
The grouping is justified in their view by "data" or "statistics" or "reason." The truth is most of us still view "prejudice" as negative, so no one advocating for discriminatory immigration policies wants to be considered prejudiced. They are for the policy, think it's good, and therefore try to pretend it's not prejudiced when it obviously is.
Don't pretend. If you're for prejudicial, discriminatory immigration policies "for the greater good", just advocate for it on those terms. Be honest about what you're saying.
This might seem like a trivial point on which to base a post, but I don’t think it is. It’s not because “prejudice is bad” or “racism!” That’s just one type of instance in which this midwit tendency — to assign individuals to a group and then pretend you are being “data-driven” — rears its terrible head. I remember a couple years ago people on Twitter accused me of “taking up an ICU bed” because I refused to inject myself with Pfizer’s latest. Their reasoning was similar: because the unvaccinated are more likely to take up ICU beds (which turned out to be a lie, but let’s assume it were true), I was in the group taking up more beds, therefore I was taking up a bed.
The trick is to assign someone to a group in which they qualify (Somali, unvaccinated, etc.), get “data” about that group and then apply that data to the individuals within it, even if it is totally inaccurate with respect to them.
This is the same trick used to justify disastrous DEI policies too. You are from a historically underprivileged group, so you deserve to be held to lower standards. It doesn’t matter if you would succeed on your own merit, it doesn’t matter your race, gender, sexual orientation are irrelevant to the task for which you are being hired, it doesn’t matter if you are the son of wealthy and famous people and attended all the best schools, you belong to a particular category and therefore this standard will be applied.
But the implications of this midwit sleight of hand are even worse than that, especially on the eve of AI-based systems taking over so many of the administrative functions at both the corporate and state level. You will be categorized, and you will be pre-judged on that basis because it is far more efficient for the system to do so than to examine everyone individually. In fact, I’d argue, unlike humans, AI is incapable of seeing individuals, it sees only “data.”
This was the premise for the movie Minority Report, set in a dystopian future wherein people get convicted of “pre-crime” because the system determined from the data about them they were likely to commit one. You might not have done anything yet, but based on your angry social media posts, your high testosterone, your age and background, you have a 99.9 percent chance of violence. Why not arrest you now before you victimize someone? For every 1000 victims we protect, we’ll convict only one person who would not in fact have done it!
There will be many people who are for this kind of reasoning. It’s “data” after all. Never mind the data can be biased based on the grouping. Why am I grouped with other people I don’t know and over whom I have no control? What if they added 100 other parameters which showed I’m among the least likely to commit violence? Who is selecting these parameters and what are their agendas?
But more to the point, such a society is not free. You are at the whims of your grouping, of parameters, of statistics. The paradigm of individual civil liberties, innocent until proven guilty, responsibility only for your own actions would be dead. You are pre-judged before you have done anything.
The second-order effects of such a paradigm would be a race to the bottom. If I am not in the wrong group I can do no wrong, based on my favorable peers. I can roam the streets, commit acts of vandalism and violence with impunity, I can loaf at work, not do my job and never be fired. I would argue that under the present (and mercifully soon-to-be-departed) administration we’ve already experienced many of these effects already.
So back to the original question. What is Norway to do with this “data”? One idea would be to have a non-discriminatory vetting process that involves delayed gratification and requires some diligence on the part of the prospective immigrant. This might self-sort the people capable of living in an open, prosperous western society and those who are not. You would be admitted or denied based on demonstrated suitability (merit), not with whom you were grouped (identity). This would be closer to the “postjudice” policy prescription Yang erroneously claims for his own in the cited post.
Whether that results in more people of one race or another, one nationality or another getting in, isn't important. What's important is both not judging individuals on the basis of their assigned group and keeping the country free of violent criminals. Both goals are essential if we want to avoid dystopian outcomes.
-
 @ 1cb14ab3:95d52462
2025-02-13 01:30:00
@ 1cb14ab3:95d52462
2025-02-13 01:30:00Dirt, body weight. [125' x 2']
This project was exhibited in 2015 in Boulder, Colorado.
Artist Statement
“A Line Made By Walking” (2015) is a site-specific piece created in Boulder, CO, where my body weight etched a temporary line into the earth. This work pays homage to Richard Long’s seminal 1967 piece, where a simple act of walking through the landscape left a profound trace. In my version, the line created by my movement forces the viewer to engage with the impermanence of human intervention on the land. The project prompts a reflection on the subtle yet lasting impacts we have on the environment, even through seemingly minimal actions.
As part of my larger “Rockway” project, this case study explores the concept of ‘line’ in both literal and metaphorical ways. The line is not just a physical mark, but also a representation of time, movement, and the dialogue between the body and the land. Walking, in this context, becomes a way of marking time—an act that is as ephemeral as the mark it leaves behind. The work questions the tension between permanence and transience, asking the viewer to consider how we interact with the land, both intentionally and unknowingly, and how those interactions leave traces that may soon fade but never completely disappear.
Photos







More Land Art:
More from Hes
All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.
-
 @ d34e832d:383f78d0
2025-01-06 23:44:40
@ d34e832d:383f78d0
2025-01-06 23:44:40Lets explore three key aspects of Bitcoin technology to enhance your engagement with the ecosystem:
- Running an Alby Hub Cloud Instance
- Setting Up a Nutshell Ecash Mint on an Affordable VPS
- Integrating Nostr Wallet Connect for Seamless Tipping
These components empower users to manage transactions, ensure privacy, and facilitate smooth interactions within the Bitcoin and Nostr communities.
1. Running an Alby Hub Cloud Instance
Purpose and Benefits:
Alby Hub is a self-custodial Lightning wallet that allows you to manage Bitcoin transactions efficiently. By running an Alby Hub instance in the cloud, you gain 24/7 online access to receive payments via a Lightning address, integrate with various applications, and maintain control over your funds without the need for personal hardware.
Setting Up Alby Hub in the Cloud:
-
Choose Alby Cloud: For a hassle-free setup, Alby offers a cloud service where you can start your own hub in just 2 minutes. Give it A Try: Alby Cloud
-
Subscription Benefits: Subscribing to Alby Cloud provides you with a self-custodial Lightning wallet, 24/7 online access, exclusive partner deals, priority support, and access to a subscriber community.
-
Getting Started: Visit the Alby Cloud page, select the subscription that suits you, and follow the guided setup process to have your hub up and running quickly.
- Alby Cloud page
For a visual guide on setting up Alby Hub, you can watch the following tutorial:
2. Setting Up a Nutshell Ecash Mint on an Affordable VPS
Purpose and Benefits:
Nutshell is an implementation of Ecash, a digital cash system that prioritizes privacy and anonymity. Setting up a Nutshell Ecash mint on a Virtual Private Server (VPS) allows you to operate your own mint, enhancing transaction privacy and providing a backup system for your Bitcoin transactions.
Setting Up on a $5 VPS:
-
Select a VPS Provider: Choose an affordable VPS provider that supports Bitcoin and Nostr communities. For instance, SatoshiHost offers VPS services tailored for such needs.
-
Install Nutshell: After setting up your VPS, install the Nutshell software by following the official installation guide.
- Nutshell
-
Configure the Mint: Set up the mint parameters, including denomination and security settings, to suit your requirements.
-
Secure the Server: Implement security measures such as firewalls and regular updates to protect your mint from potential threats.
- Recommendations
- Server Tips
3. Integrating Nostr Wallet Connect for Seamless Tipping
Purpose and Benefits:
Nostr Wallet Connect (NWC) is an open protocol that enables applications to interact with Bitcoin Lightning wallets. Integrating NWC allows for seamless tipping and payments within Nostr apps, enhancing user experience and promoting engagement.
Integration Steps:
-
Choose a Supporting App: Select a Nostr app that supports NWC, such as Amythystor Damus.
-
Connect Your Wallet: Use NWC to link your preferred Lightning wallet to the Nostr app. This connection facilitates seamless payments without the need to switch between applications.
-
Test the Integration: Perform a test transaction to ensure that the tipping functionality works as intended.
-
Maintain Security: Regularly update your wallet and Nostr app to incorporate the latest security features and improvements.
For a deeper understanding of Nostr Wallet Connect and its significance, you can watch the following discussion:
Final Thoughts On Setup
Implementing these components enhances your interaction with the Bitcoin ecosystem by providing efficient transaction management, improved privacy, and seamless integration with Nostr applications. By running an Alby Hub cloud instance, setting up a Nutshell Ecash mint on an affordable VPS, and integrating Nostr Wallet Connect, you contribute to a more robust and user-friendly Bitcoin environment.
Invitation for Feedback
I encourage you to share any questions or feedback regarding these topics. Let's continue the conversation to explore how we can further engage with and improve upon these technologies.
-
 @ c582af78:698069cc
2025-02-13 01:04:26
@ c582af78:698069cc
2025-02-13 01:04:26The Nine Orders of Angels: A Guide to the Celestial Hierarchy
When we think of angels, we often picture winged figures in flowing robes, guiding and protecting humanity. But the biblical and theological reality is far more complex—and often stranger—than these familiar depictions.
The word angel comes from the Greek angelos, meaning “messenger,” but in scripture, angels serve a wide range of roles beyond delivering divine messages. Some are warriors wielding swords and leading celestial armies, others uphold the very throne of God, and some appear as multi-winged, multi-eyed beings beyond human comprehension.
To bring order to this celestial realm, theologians—most notably Thomas Aquinas—classified angels into a hierarchy of nine types, divided into three orders based on their function and proximity to God.
- The lowest order interacts with humanity.
- The middle order governs spiritual and cosmic forces.
- The highest order exists solely to serve and glorify God.
Today, we explore these nine ranks of angels—from the familiar to the truly otherworldly.
I. The Third Order: Angels Who Interact with Humanity
(The lowest tier of angels, closest to humans, acting as messengers and protectors.)
1. Angels – The Messengers
https://image.nostr.build/b6462b67e14c8780896f465b664a521cdcdef7eb4b4314669b8d219aa36964c5.jpg
These are the angels most commonly associated with divine guidance. According to Aquinas, every person has a guardian angel—an unseen protector guiding them through life.
In Genesis 28:12, Jacob’s vision of a ladder stretching to Heaven shows angels ascending and descending, delivering messages and fulfilling divine commands. Some, like those who visited Abraham, even appeared as ordinary men, without wings or supernatural radiance.
2. Archangels – The Divine Enforcers
https://image.nostr.build/af8799efb61c5a64e958450bcd5aee55d2cade931cfc5ca7f0ae8745ccd4c45a.jpg
Archangels carry out the most crucial missions in scripture. Gabriel announced the birth of Jesus to Mary, while Michael led the charge against Satan in the war for Heaven.
Though only Michael is explicitly called an archangel in the Bible, tradition assigns this title to others, including Raphael and Uriel. Archangels serve as warriors and heralds, executing God’s most urgent decrees.
3. Principalities – Guardians of Nations
https://image.nostr.build/bc7cd78acb656be6c946da32244bfb9ecdfe9a7d1bd80e47eca764cae4a88b95.jpg
Principalities oversee nations, cities, and communities, influencing their spiritual well-being. While they are not explicitly named in scripture, Colossians 1:16 references “thrones, dominions, principalities, and powers.”
Tradition suggests that Principalities guide earthly leaders, strengthening them in times of crisis—and perhaps even aiding biblical figures like King David in battle.
II. The Second Order: The Heavenly Governors
(These angels reside in Heaven but influence earthly affairs, ensuring divine order is maintained.)
4. Powers – The Celestial Warriors
https://image.nostr.build/1768abcbaefb2d1d21654a869b356d86a45d76a82197b9568528d4d4b9f0ef69.jpg
Powers act as Heaven’s military defenders, guarding the spiritual realm from demonic forces. They are often depicted in armor, wielding weapons as they engage in cosmic battles.
According to Christian tradition, Powers also escort souls to Heaven, ensuring their safe passage after death. Some believe that the battle between good and evil plays out, in part, through these celestial warriors.
5. Virtues – The Miracle Workers
https://image.nostr.build/b9a1e52f1dd4ef0f7e7dd198d81e7cd171eede8a64a40cac8176e12a5419aeba.jpg
Virtues are associated with miracles and nature, regulating celestial phenomena and assisting in divine interventions.
In Christian tradition, the two angels present at Christ’s Ascension are often considered Virtues, manifesting God’s power on Earth.
6. Dominions – The Angelic Rulers
https://image.nostr.build/0900d97bf545736e5edc1521f46a8afbf0e93fd81e472c88a56744ff0f56ce48.jpg
Dominions do not typically interact with humans directly. Instead, they act as commanders, overseeing lower angels and ensuring divine order is maintained.
They are described as serene, wise beings, often depicted holding golden staffs and orbs, symbolizing their authority and their close relationship with God.
III. The First Order: The Angels Closest to God
(These angels exist solely to worship and serve God, residing in the highest realms of Heaven.)
7. Thrones – The Wheels of God’s Chariot
https://image.nostr.build/d9f1e465129b138f4f960ee43ee9e06ceb3fd6f57e9658cd275e1ac1576b3c02.jpg
Among the most mysterious angelic beings, Thrones are described in Ezekiel’s vision as wheels covered in eyes, spinning within wheels:
“As I looked, I saw a wheel on the ground beside each creature with its four faces... Their rims were full of eyes all around. Wherever the spirit would go, they would go, because the spirit of the living creatures was in the wheels.”
— Ezekiel 1:15-21Thrones serve as God’s chariot, supporting His throne and executing divine justice. Their strange, abstract form symbolizes stability and divine order.
8. Cherubim – The Guardians of Glory
https://image.nostr.build/e921ad4c32f56ebbb8f1bcb1ca2bc6eed1c736ec896429e008fc5b71cf2fd151.jpg
Cherubim have been drastically misrepresented in art. Far from the plump, childlike figures seen in Renaissance paintings, the biblical Cherubim are fearsome beings.
In Ezekiel 10, they are described as having four faces—a man, a lion, an ox, and an eagle—along with four wings.
They also appear in Genesis 3:24, where they guard the entrance to Eden with flaming swords after Adam and Eve’s expulsion.
https://image.nostr.build/f51286d4f35d9d6e85d8559600188ecc89a0969c3985814cae56cd230ea5db00.jpg
Aquinas even suggested that Satan himself was a fallen Cherub. This theory is supported by Ezekiel 28, which describes an angelic being cast down from God’s presence:
“You were anointed as a guardian cherub... You were blameless in your ways until wickedness was found in you... So I drove you in disgrace from the mount of God, and I expelled you, guardian cherub.”
— Ezekiel 28:14-179. Seraphim – The Highest & Holiest
Seraphim stand at the very throne of God, continuously worshiping Him.
In Isaiah’s vision (Isaiah 6:1-7), they are described as having six wings—two to fly, two to cover their feet, and two to cover their faces, symbolizing their humility before God. They sing:
“Holy, holy, holy is the Lord of hosts; the whole earth is full of His glory.”
When Seraphim reappear in Revelation, their wings are now covered in eyes, representing divine omniscience. Their song shifts slightly:
“Holy, holy, holy is the Lord God Almighty, who was and is and is to come!”
— Revelation 4:8
https://image.nostr.build/3495ccf6c0ba26b42d3e2b438ec19232cca148f6fbf29e5edd4129f5a198d05b.jpgUnlike other angelic beings, Seraphim do not interact with humans—they exist purely to glorify God.
“Be Not Afraid”
The angelic hierarchy provides a glimpse into the vast celestial order governing God’s universe. From the lowest messengers to the highest divine worshippers, each angelic being plays a unique role in the unfolding story of creation and salvation.
Yet, despite their differences, there is one striking similarity across biblical encounters with angels:
They often begin with a single phrase—
“Be not afraid.”
-
 @ c582af78:698069cc
2025-02-13 01:03:50
@ c582af78:698069cc
2025-02-13 01:03:50How to Be Happy: Aristotle’s Blueprint for a Flourishing Life
Everyone wants happiness. The problem? Most people don’t actually know what happiness is.
Ask someone what would make them happy, and they’ll likely mention wealth, pleasure, success, or recognition. Over 2,000 years ago, Aristotle heard the same answers—and he rejected them.
According to Aristotle, happiness isn’t something you have, but something you do. True happiness—what he called eudaimonia—isn’t about fleeting pleasures or external rewards. It’s about living well, cultivating virtue, and engaging deeply in life’s highest pursuits.
So, what’s Aristotle’s formula for happiness? It comes down to three essential steps.
The False Paths to Happiness
Aristotle observed that most people chase happiness in three common ways: wealth, pleasure, and honor. While each has its appeal, none can sustain true fulfillment.
Take wealth, for example. Money provides security and opportunity, but it doesn’t guarantee satisfaction. Aristotle noted that many people who seek wealth become obsessed with accumulating it rather than using it wisely. The result? An endless chase with no real contentment.
Pleasure is even trickier. Aristotle acknowledged that pleasure is a natural good, but he warned against making it life’s ultimate goal. Living only for pleasure leads to a cycle of chasing temporary highs without ever achieving deeper fulfillment. As Aristotle put it, this is the life of “fatted cattle”—comfortable, but lacking excellence.
Then there’s honor. Recognition feels good, but it depends on the approval of others. If you live solely for status, you risk valuing recognition over real achievement. Honor for its own sake is empty unless it’s tied to genuine virtue.
Aristotle’s conclusion? These paths don’t lead to true happiness. They are distractions, not destinations.
The True Meaning of Happiness
If wealth, pleasure, and honor aren’t enough, then what is happiness?
To answer that, we need to understand Aristotle’s term eudaimonia. Unlike our modern idea of happiness as a feeling, eudaimonia means flourishing—a life of purpose, virtue, and excellence.
The key difference is that wealth, pleasure, and honor are passive—they happen to you. But eudaimonia is active—it’s something you cultivate through action.
In his Nicomachean Ethics, Aristotle defines happiness as “the activity of the soul in accordance with virtue.” It’s not a prize to be won, but a way of living.
A great example comes from sports. A skilled athlete doesn’t just sit around feeling happy—his joy comes from being in motion: training, competing, improving, and fully engaging in his craft.
For Aristotle, happiness works the same way. It comes from actively developing your best qualities, not passively indulging in comfort.
But how do you put this into practice?
Aristotle’s 3-Step Blueprint for a Good Life
Aristotle’s guide to happiness is surprisingly practical. Here’s how to apply it:
1. Cultivate Virtue Through Habit
Virtue isn’t something you’re born with—it’s something you practice.
Just as an athlete trains for competition, you develop virtue by repeatedly choosing good actions. Courage, patience, and wisdom don’t just appear; they become part of you through habit.
As Aristotle famously said:
“We are what we repeatedly do. Excellence, then, is not an act, but a habit.”
Want to be generous? Give more often.
Want to be disciplined? Practice restraint.Over time, these actions shape your character—and character shapes happiness.
2. Engage Fully in Meaningful Work
Happiness isn’t found in passivity, but in action.
Aristotle believed that true fulfillment comes from using your talents to their fullest extent. This applies to everything from philosophy to craftsmanship to leadership. The key is engagement.
Think of the satisfaction a musician feels while playing at their best, or the pride of a craftsman perfecting their work. These moments—where skill, effort, and purpose align—are true happiness in action.
Contrary to popular belief, happiness isn’t about doing less. It’s about doing the right things, with full commitment.
3. Seek the Right Kind of Pleasure
Aristotle didn’t reject pleasure—he just emphasized choosing the right kind.
Lower pleasures—like eating, drinking, or binge-watching TV—may feel good in the moment but often leave you feeling empty afterward. Higher pleasures—such as learning, mastering a craft, or cultivating meaningful relationships—lead to lasting fulfillment.
The goal isn’t to reject pleasure, but to align it with virtue. Instead of chasing immediate gratification, seek pleasures that contribute to long-term flourishing.
Happiness as a Way of Life
It’s important to understand that happiness isn’t a destination—it’s a practice. It’s something cultivated daily by engaging in meaningful work, growing in virtue, and living with purpose.
But most importantly, happiness isn’t about what happens to you—it’s about who you become.
By cultivating eudaimonia, you change the essence of your being—just as a farmer who nurtures his crops becomes stronger through his labor.
True happiness isn’t a fleeting emotion, but the natural result of a life well lived. The more you nurture virtue through action, the more deeply happiness takes root—until it becomes not just something you seek, but something you embody.
-
 @ 3ffac3a6:2d656657
2025-01-06 23:42:53
@ 3ffac3a6:2d656657
2025-01-06 23:42:53Prologue: The Last Trade
Ethan Nakamura was a 29-year-old software engineer and crypto enthusiast who had spent years building his life around Bitcoin. Obsessed with the idea of financial sovereignty, he had amassed a small fortune trading cryptocurrencies, all while dreaming of a world where decentralized systems ruled over centralized power.
One night, while debugging a particularly thorny piece of code for a smart contract, Ethan stumbled across an obscure, encrypted message hidden in the blockchain. It read:
"The key to true freedom lies beyond. Burn it all to unlock the gate."
Intrigued and half-convinced it was an elaborate ARG (Alternate Reality Game), Ethan decided to follow the cryptic instruction. He loaded his entire Bitcoin wallet into a single transaction and sent it to an untraceable address tied to the message. The moment the transaction was confirmed, his laptop screen began to glitch, flooding with strange symbols and hash codes.
Before he could react, a flash of light engulfed him.
Chapter 1: A New Ledger
Ethan awoke in a dense forest bathed in ethereal light. The first thing he noticed was the HUD floating in front of him—a sleek, transparent interface that displayed his "Crypto Balance": 21 million BTC.
“What the…” Ethan muttered. He blinked, hoping it was a dream, but the numbers stayed. The HUD also showed other metrics:
- Hash Power: 1,000,000 TH/s
- Mining Efficiency: 120%
- Transaction Speed: Instant
Before he could process, a notification pinged on the HUD:
"Welcome to the Decentralized Kingdom. Your mining rig is active. Begin accumulating resources to survive."
Confused and a little terrified, Ethan stood and surveyed his surroundings. As he moved, the HUD expanded, revealing a map of the area. His new world looked like a cross between a medieval fantasy realm and a cyberpunk dystopia, with glowing neon towers visible on the horizon and villagers dressed in tunics carrying strange, glowing "crypto shards."
Suddenly, a shadow loomed over him. A towering beast, part wolf, part machine, snarled, its eyes glowing red. Above its head was the name "Feral Node" and a strange sigil resembling a corrupted block.
Instinct kicked in. Ethan raised his hands defensively, and to his shock, the HUD offered an option:
"Execute Smart Contract Attack? (Cost: 0.001 BTC)"
He selected it without hesitation. A glowing glyph appeared in the air, releasing a wave of light that froze the Feral Node mid-lunge. Moments later, it dissolved into a cascade of shimmering data, leaving behind a pile of "Crypto Shards" and an item labeled "Node Fragment."
Chapter 2: The Decentralized Kingdom
Ethan discovered that the world he had entered was built entirely on blockchain-like principles. The land was divided into regions, each governed by a Consensus Council—groups of powerful beings called Validators who maintained the balance of the world. However, a dark force known as The Central Authority sought to consolidate power, turning decentralized regions into tightly controlled fiefdoms.
Ethan’s newfound abilities made him a unique entity in this world. Unlike its inhabitants, who earned wealth through mining or trading physical crypto shards, Ethan could generate and spend Bitcoin directly—making him both a target and a potential savior.
Chapter 3: Allies and Adversaries
Ethan soon met a colorful cast of characters:
-
Luna, a fiery rogue and self-proclaimed "Crypto Thief," who hacked into ledgers to redistribute wealth to oppressed villages. She was skeptical of Ethan's "magical Bitcoin" but saw potential in him.
-
Hal, an aging miner who ran an underground resistance against the Central Authority. He wielded an ancient "ASIC Hammer" capable of shattering corrupted nodes.
-
Oracle Satoshi, a mysterious AI-like entity who guided Ethan with cryptic advice, often referencing real-world crypto principles like decentralization, trustless systems, and private keys.
Ethan also gained enemies, chief among them the Ledger Lords, a cabal of Validators allied with the Central Authority. They sought to capture Ethan and seize his Bitcoin, believing it could tip the balance of power.
Chapter 4: Proof of Existence
As Ethan delved deeper into the world, he learned that his Bitcoin balance was finite. To survive and grow stronger, he had to "mine" resources by solving problems for the people of the Decentralized Kingdom. From repairing broken smart contracts in towns to defending miners from feral nodes, every task rewarded him with shards and upgrades.
He also uncovered the truth about his arrival: the blockchain Ethan had used in his world was a prototype for this one. The encrypted message had been a failsafe created by its original developers—a desperate attempt to summon someone who could break the growing centralization threatening to destroy the world.
Chapter 5: The Final Fork
As the Central Authority's grip tightened, Ethan and his allies prepared for a final battle at the Genesis Block, the origin of the world's blockchain. Here, Ethan would face the Central Authority's leader, an amalgamation of corrupted code and human ambition known as The Miner King.
The battle was a clash of philosophies as much as strength. Using everything he had learned, Ethan deployed a daring Hard Fork, splitting the world’s blockchain and decentralizing power once again. The process drained nearly all of his Bitcoin, leaving him with a single satoshi—a symbolic reminder of his purpose.
Epilogue: Building the Future
With the Central Authority defeated, the Decentralized Kingdom entered a new era. Ethan chose to remain in the world, helping its inhabitants build fairer systems and teaching them the principles of trustless cooperation.
As he gazed at the sunrise over the rebuilt Genesis Block, Ethan smiled. He had dreamed of a world where Bitcoin could change everything. Now, he was living it.
-
 @ 3b7fc823:e194354f
2025-02-12 23:13:57
@ 3b7fc823:e194354f
2025-02-12 23:13:57Staying Digitally Safe in Airports: A Comprehensive Guide
Airports are hubs of activity, but they’re also places where your digital security can be at risk. From public Wi-Fi to potential device thefts, staying safe while traveling can feel overwhelming. However, with the right knowledge and precautions, you can protect yourself and enjoy your journey stress-free. Let’s dive into how to stay digitally safe in airports while traveling.
Understanding the Risks
- Public Wi-Fi Vulnerabilities:
- Airports often offer free Wi-Fi, but these networks can be unsecured or insecure. Hackers may use these networks to intercept sensitive data.
-
Avoid using public Wi-Fi for personal banking, shopping, or handling sensitive information.
-
Device Theft:
-
High-traffic areas like security checkpoints, gates, and lounges are hotspots for device thefts. Always keep your devices in secure locations, such as carry-on bags or locked briefcases.
-
Malware and Phishing Attacks:
-
Some airports may have phishing attempts or malware distributed via pop-ups, email, or malicious websites.
-
Physical Surveillance:
- In some cases, law enforcement or security personnel may monitor your activities. Always be mindful of your surroundings to avoid unintended data exposure.
Best Practices for Staying Digitally Safe in Airports
- Use a VPN for Extra Security:
- Even secure airport Wi-Fi can expose your data if not encrypted. Use a reputable Virtual Private Network (VPN) to encrypt your internet traffic and protect your privacy.
-
Always ensure your VPN is active when using public Wi-Fi.
-
Minimize Sensitive Data on Public Devices:
-
Avoid carrying devices with sensitive information like passwords, credit card details, or personal identification numbers (PIIs).
-
Encrypt Your Data:
-
Enable encryption for all your devices to protect data stored locally or in the cloud. Ensure your operating system and apps are updated with the latest security patches.
-
Secure Your Devices:
- Use cable locks or secure cases to lock down laptops, tablets, and smartphones when not in use.
-
Remove screensavers that display your device passcode to prevent unauthorized access.
-
Keep Antivirus Software Updated:
-
Install and maintain up-to-date antivirus software on all devices. This helps detect and remove malicious software (malware) that may be installed through compromised networks or phishing attempts.
-
Avoid Plugging Into Public USB charging stations:
-
Refrain from using public USB ports or charging stations unless you know they’re secure. Malware can spread via these points.
-
Use Caution With Lost and Found:
-
If you find a device or drop one accidentally, avoid using lost and found kiosks to pick it up. Instead, contact airport security for assistance in safely retrieving your property without exposing it to potential thieves.
-
Stay Alert to Security Alerts:
-
Pay attention to announcements over the airport’s PA system regarding suspicious activity or security alerts. Follow any instructions provided by airport staff.
-
Monitor Your Accounts Remotely:
- If you suspect something is wrong (e.g., unusual transactions on your credit card), check your financial accounts immediately upon arriving at your destination. Notify your bank of potential fraudulent activity and report it to the authorities if necessary.
Additional Tips for Airport Safety
- Use a Portable Power Bank:
-
Keep your devices charged so you don’t rely on public charging stations, which may be compromised.
-
Travel with Backup Devices:
-
Always bring an extra SIM card, USB drive, or cloud storage to backup important data. This ensures you can access critical information even if your primary device is lost or damaged.
-
Avoid Sharing Personal Information Over Earphone Rentals:
-
Refrain from using earphones rented from airport kiosks that may record or intercept your conversations. Stick to your own headphones or those provided by the airline.
-
Use Airport Lounges Wisely:
-
If you’re using an airline lounge, avoid discussing sensitive information in public areas where it could be overheard.
-
Keep Your Luggage in Sight:
-
Never leave your checked luggage unattended, as it may contain devices or documents with sensitive information.
-
Plan for Data Loss:
- Before leaving home, make a backup of all important files and photos on an external drive or cloud storage. This way, you can restore them if something goes wrong during your trip.
What to Do If Something Goes Wrong
- Report Suspected Security Incidents:
-
If you notice unusual activity on your devices or suspect a security breach, inform airport security immediately.
-
Contact Your Financial Institutions:
-
If you believe your financial information has been compromised, contact your bank or credit card provider to freeze your account and monitor for fraudulent charges.
-
File a Police Report:
-
In cases of theft or suspected unauthorized access, file a report with local authorities and provide evidence (if available).
-
Use Travel Insurance:
- Check if your travel insurance covers theft, fraud, or data breaches. Submit a claim if you’re covered.
Extra Security Measures forTech-Savvy Travelers
- Two-Factor Authentication (2FA): Enable 2FA for all your critical accounts before leaving home.
- Biometric Locks: Use biometric locks on your devices to add an extra layer of security.
- Incident Response Plan: Create a plan in advance for what to do if your devices are lost or compromised.
Final Tips
- Always prioritize secure practices, even in seemingly safe environments like airports.
- Travel light but keep your important documents and devices close at hand.
- Remember that staying digitally safe is just as important as physical safety during your travels.
By following these tips, you can enjoy your trip with peace of mind, knowing your data and devices are protected. Happy traveling!
Advocating for privacy does not finance itself. If you enjoyed this article, please consider zapping or sending monero
82XCDNK1Js8TethhpGLFPbVyKe25DxMUePad1rUn9z7V6QdCzxHEE7varvVh1VUidUhHVSA4atNU2BTpSNJLC1BqSvDajw1
-
 @ 000002de:c05780a7
2025-02-12 22:41:17
@ 000002de:c05780a7
2025-02-12 22:41:17The absolute embarrassment the Chiefs were subjected to... is the end of the their dominance? Of course they have a ton of talent and will win and maybe get back the Super Bowl this game really exposed them.
Its one thing to lose to a great team like the Eagles. Its another to be destroyed so fully. When I think about this game its not just on one person. Its coaching and players. I'm just wondering about the impact on the league watching this. Anyone who has played sports knows that a ton of it is mental. Teams can defeat themselves mentally. Does this defeat tell the league, yeah they aren't that good.
What do you think?
Edit: When I say "done", I mean the dynasty. I don't mean they are gonna have a losing record next year.
originally posted at https://stacker.news/items/884169
-
 @ 000002de:c05780a7
2025-02-12 22:25:06
@ 000002de:c05780a7
2025-02-12 22:25:06Honest question. I think he's a great TE but... haven't watched him a ton. I get a feeling he's overrated. Maybe not though. I watched him during the big game and was kinda surprised by his lack luster performance. He really seemed different to me.
Since then I've seen video of him not blocking for his QB and not really playing hard. Like he gave up. Does he really have a rep of not blocking? He looks pretty terrible on film. Now, I know I'm a Kittle fan and he is famously great at blocking and takes pride in it. Maybe I'm just using Kittle as the ruler and maybe that's not fair.
Also, I loved watching KC get destroyed so factor that in :)
originally posted at https://stacker.news/items/884156




