-
 @ 7f29628d:e160cccc
2025-01-07 11:50:30
@ 7f29628d:e160cccc
2025-01-07 11:50:30Der gut informierte Bürger denkt bei der Pandemie sofort an Intensivstationen, an die Bilder aus Bergamo und erinnert sich an die Berichterstattung damals – also muss es wohl ein Maximum gewesen sein. Manche Skeptiker behaupten jedoch das Gegenteil. Klarheit sollte ein Blick nach Wiesbaden, zum Statistischen Bundesamt, schaffen. Schließlich sitzen dort gut bezahlte Profis, die seit vielen Jahrzehnten die Sterbestatistik pflegen und veröffentlichen. Jeder Todesfall wird in Deutschland über die Standesämter exakt erfasst.
Doch die Überraschung: Das Statistische Bundesamt liefert uns auf diese einfache Frage zwei extrem unterschiedliche Antworten – ein Minimum und ein Maximum. Das Ergebnis hängt davon ab, wie tief man in die Veröffentlichungen des Bundesamtes eintaucht. Betrachtet man nur die Webseiten und Pressemitteilungen, erhält man den Eindruck eines Maximums. Schaut man jedoch etwas tiefer in die Tabellen und Rohdaten, zeigt sich plötzlich ein Minimum. Aber wie kann das sein? Beides gleichzeitig geht ja wohl kaum. Wer lügt hier – die Tabellen des Amtes oder die Pressemitteilungen? Gehen wir dieser Frage Schritt für Schritt auf den Grund.
2020: Ein historisches Maximum?
Schauen wir uns die vielen Hundert Veröffentlichungen des Statistischen Bundesamtes aus dieser Zeit an. Oder wir kürzen ab und fragen ChatGPT, da die KI auf diesen Daten trainiert wurde und das gesamte Material kennt. Die Frage an ChatGPT lautet also: Wie war das Sterbegeschehen im Jahr 2020 im Vergleich zu den Vorjahren?
ChatGPT antwortet: »Im Jahr 2020 war die Sterblichkeit in Deutschland höher als in den Jahren zuvor. Es gab eine Übersterblichkeit von etwa 982.000 Todesfällen, das sind rund 46.000 mehr als der Durchschnitt der Vorjahre (2016 bis 2019). Dieser Anstieg wurde überwiegend im Zusammenhang mit der COVID-19-Pandemie gesehen. Während die Sterbezahlen in den Vorjahren schwankten, war ein solch signifikanter Anstieg wie 2020 bisher nicht zu beobachten.«
Wir fragen konkreter: Ist es ein Fakt, dass wir eine so ernste Lage im Sterbegeschehen wie im Frühjahr 2020 noch nie erlebt haben?
ChatGPT bestätigt: »Ja, die COVID-19-Pandemie führte im Frühjahr 2020 zu einer außergewöhnlichen Situation im Sterbegeschehen in Deutschland. Die dramatische Übersterblichkeit, die ab der 13. Kalenderwoche auftrat, veranlasste das Statistische Bundesamt, besonders eindringliche Warnungen zu veröffentlichen. Der damalige Vizepräsident des Amtes und andere führende Stimmen wiesen öffentlich darauf hin, dass die Todesfallzahlen stark vom Durchschnitt abwichen. Diese klare Warnung richtete sich an die Öffentlichkeit und die Politik gleichermaßen. Die Medien berichteten intensiv über diese Warnungen, was das Bewusstsein für die Schwere der Pandemie erheblich schärfte. In den vergangenen Jahrzehnten hatte es keine vergleichbare Übersterblichkeit gegeben, die eine solch umfangreiche Kommunikation durch das Statistische Bundesamt erforderlich gemacht hätte.«
Ein gut informierter Zeitungsleser wird sich an dieser Stelle bestätigt fühlen: Ja, so war es damals. Ein Maximum im Sterbegeschehen – wegen der Pandemie. Oder etwa nicht?
2020: Ein historisches Minimum?
Tauchen wir in die Rohdaten des Statistischen Bundesamtes ein. Die Tabellen, die das Amt seit Jahrzehnten verlässlich veröffentlicht, nennen sich Sterbetafeln. Diese werden jährlich bereitgestellt und stehen auf der Website des Bundesamtes zum Download bereit. Ein erster Blick in die Sterbetafeln mag den Laien abschrecken, doch mit einer kurzen Erklärung wird alles verständlich. Wir gehen schrittweise vor.
Nehmen wir die Sterbetafel des Jahres 2017. Sie enthält zwei große Tabellen – eine für Männer und eine für Frauen. Jede Zeile der Tabelle steht für einen Jahrgang, zum Beispiel zeigt die Zeile 79 die Daten der 79-jährigen Männer. Besonders wichtig ist nun die zweite Spalte, in der der Wert 0,05 eingetragen ist. Das bedeutet, dass 5 Prozent der 79-jährigen Männer im Jahr 2017 verstorben sind. Das ist die wichtige Kennzahl. Wenn wir diesen exakten Wert, den man auch als Sterberate bezeichnet, nun in ein Säulendiagramm eintragen, erhalten wir eine leicht verständliche visuelle Darstellung (Grafik 1).

Es ist wichtig zu betonen, dass dieser Wert weder ein Schätzwert noch eine Modellrechnung oder Prognose ist, sondern ein exakter Messwert, basierend auf einer zuverlässigen Zählung. Sterberaten (für die Fachleute auch Sterbewahrscheinlichkeiten qx) sind seit Johann Peter Süßmilch (1707–1767) der Goldstandard der Sterbestatistik. Jeder Aktuar wird das bestätigen. Fügen wir nun die Sterberaten der 79-jährigen Männer aus den Jahren davor und danach hinzu, um das Gesamtbild zu sehen (Grafik 2). Und nun die entscheidende Frage: Zeigt das Jahr 2020 ein Maximum oder ein Minimum?

Ein kritischer Leser könnte vermuten, dass die 79-jährigen Männer eine Ausnahme darstellen und andere Jahrgänge im Jahr 2020 ein Maximum zeigen würden. Doch das trifft nicht zu. Kein einziger Jahrgang verzeichnete im Jahr 2020 ein Maximum. Im Gegenteil: Auch die 1-Jährigen, 2-Jährigen, 3-Jährigen, 9-Jährigen, 10-Jährigen, 15-Jährigen, 18-Jährigen und viele weitere männliche Jahrgänge hatten ihr Minimum im Jahr 2020. Dasselbe gilt bei den Frauen. Insgesamt hatten 31 Jahrgänge ihr Minimum im Jahr 2020. Wenn wir schließlich alle Jahrgänge in einer einzigen Grafik zusammenfassen, ergibt sich ein klares Bild: Das Minimum im Sterbegeschehen lag im Jahr 2020 (Grafik 3).

Ein kritischer Leser könnte nun wiederum vermuten, dass es innerhalb des Jahres 2020 möglicherweise starke Ausschläge nach oben bei einzelnen Jahrgängen gegeben haben könnte, die später durch Ausschläge nach unten ausgeglichen wurden – und dass diese Schwankungen in der jährlichen Übersicht nicht sichtbar sind. Doch auch das trifft nicht zu. Ein Blick auf die wöchentlichen Sterberaten zeigt, dass die ersten acht Monate der Pandemie keine nennenswerten Auffälligkeiten aufweisen. Es bleibt dabei: Die Rohdaten des Statistischen Bundesamtes bestätigen zweifelsfrei, dass die ersten acht Monate der Pandemie das historische Minimum im Sterbegeschehen darstellen. (Für die Fachleute sei angemerkt, dass im gleichen Zeitraum die Lebenserwartung die historischen Höchststände erreicht hatte – Grafik 4.)

So konstruierte das Amt aus einem Minimum ein Maximum:
Zur Erinnerung: Die Rohdaten des Statistischen Bundesamtes, die in den jährlichen Sterbetafeln zweifelsfrei dokumentiert sind, zeigen für das Jahr 2020 eindeutig ein Minimum im Sterbegeschehen. Aus diesen »in Stein gemeißelten« Zahlen ein Maximum zu »konstruieren«, ohne die Rohdaten selbst zu verändern, scheint auf den ersten Blick eine unlösbare Aufgabe. Jeder Student würde an einer solchen Herausforderung scheitern. Doch das Statistische Bundesamt hat einen kreativen Weg gefunden - ein Meisterstück gezielter Manipulation. In fünf Schritten zeigt sich, wie diese Täuschung der Öffentlichkeit umgesetzt wurde:
(1) Ignorieren der Sterberaten: Die präzisen, objektiven und leicht verständlichen Sterberaten aus den eigenen Sterbetafeln wurden konsequent ignoriert und verschwiegen. Diese Daten widersprachen dem gewünschten Narrativ und wurden daher gezielt ausgeklammert.
(2) Fokus auf absolute Todeszahlen: Die Aufmerksamkeit wurde stattdessen auf die absolute Zahl der Todesfälle gelenkt. Diese wirkt allein durch ihre schiere Größe dramatisch und emotionalisiert die Diskussion. Ein entscheidender Faktor wurde dabei ignoriert: Die absolute Zahl der Todesfälle steigt aufgrund der demografischen Entwicklung jedes Jahr an. Viele Menschen verstehen diesen Zusammenhang nicht und verbinden die steigenden Zahlen fälschlicherweise mit der vermeintlichen Pandemie.
(3) Einführung der Übersterblichkeit als neue Kennzahl: Erst ab Beginn der „Pandemie“ wurde die Kennzahl "Übersterblichkeit" eingeführt – und dies mit einer fragwürdigen Methode, die systematisch überhöhte Werte lieferte. Diese Kennzahl wurde regelmäßig, oft monatlich oder sogar wöchentlich, berechnet und diente als ständige Grundlage für alarmierende Schlagzeilen.
(4) Intensive Öffentlichkeitsarbeit: Durch eine breit angelegte Kampagne wurden die manipulativen Kennzahlen gezielt in den Fokus gerückt. Pressemitteilungen, Podcasts und öffentliche Auftritte konzentrierten sich fast ausschließlich auf die absoluten Todeszahlen und die Übersterblichkeit. Ziel war es, den Eindruck einer dramatischen Situation in der Öffentlichkeit zu verstärken.
(5) Bekämpfen kritischer Stimmen: Kritiker, die die Schwächen und manipulativen Aspekte dieser Methoden aufdeckten, wurden systematisch diskreditiert. Ihre Glaubwürdigkeit und Kompetenz wurden öffentlich infrage gestellt, um das sorgsam konstruierte Narrativ zu schützen.
Ohne diesen begleitenden Statistik-Betrug wäre das gesamte Pandemie-Theater meiner Meinung nach nicht möglich gewesen. Wer aus einem faktischen Minimum ein scheinbares Maximum "erschafft", handelt betrügerisch. Die Folgen dieses Betruges sind gravierend. Denken wir an die Angst, die in der Bevölkerung geschürt wurde – die Angst, bald sterben zu müssen. Denken wir an Masken, Abstandsregeln, isolierte ältere Menschen, Kinderimpfungen und all die Maßnahmen, die unter anderem auf diese falsche Statistik zurückgehen.
Wollen wir Bürger uns das gefallen lassen?
Wenn wir als Bürger zulassen, dass ein derart offensichtlicher und nachprüfbarer Täuschungsversuch ohne Konsequenzen bleibt, dann gefährdet das nicht nur die Integrität unserer Institutionen – es untergräbt das Fundament unserer Gesellschaft. In der DDR feierte man öffentlich Planerfüllung und Übererfüllung, während die Regale leer blieben. Damals wusste jeder: Statistik war ein Propagandainstrument. Niemand traute den Zahlen, die das Staatsfernsehen verkündete.
Während der Pandemie war es anders. Die Menschen vertrauten den Mitteilungen des Statistischen Bundesamtes und des RKI – blind. Die Enthüllungen durch den "RKI-Leak" haben gezeigt, dass auch das Robert-Koch-Institut nicht der Wissenschaft, sondern den Weisungen des Gesundheitsministers und militärischen Vorgaben folgte. Warum sollte es beim Statistischen Bundesamt anders gewesen sein? Diese Behörde ist dem Innenministerium unterstellt und somit ebenfalls weisungsgebunden.
Die Beweise für Täuschung liegen offen zutage. Es braucht keinen Whistleblower, keine geheimen Enthüllungen: Die Rohdaten des Statistischen Bundesamtes sprechen für sich. Sie sind öffentlich einsehbar – klar und unmissverständlich. Die Daten, die Tabellen, die Veröffentlichungen des Amtes selbst – sie sind die Anklageschrift. Sie zeigen, was wirklich war. Nicht mehr und nicht weniger.
Und wir? Was tun wir? Schweigen wir? Oder fordern wir endlich ein, was unser Recht ist? Wir Bürger dürfen das nicht hinnehmen. Es ist Zeit, unsere Behörden zur Rechenschaft zu ziehen. Diese Institutionen arbeiten nicht für sich – sie arbeiten für uns. Wir finanzieren sie, und wir haben das Recht, Transparenz und Verantwortung einzufordern. Manipulationen wie diese müssen aufgearbeitet werden und dürfen nie wieder geschehen. Die Strukturen, die solche Fehlentwicklungen in unseren Behörden ermöglicht haben, müssen offengelegt werden. Denn eine Demokratie lebt von Vertrauen – und Vertrauen muss verdient werden. Jeden Tag aufs Neue.
.
.
MARCEL BARZ, Jahrgang 1975, war Offizier der Bundeswehr und studierte Wirtschafts- und Organisationswissenschaften sowie Wirtschaftsinformatik. Er war Gründer und Geschäftsführer einer Softwarefirma, die sich auf Datenanalyse und Softwareentwicklung spezialisiert hatte. Im August 2021 veröffentlichte Barz den Videovortrag »Die Pandemie in den Rohdaten«, der über eine Million Aufrufe erzielte. Seitdem macht er als "Erbsenzähler" auf Widersprüche in amtlichen Statistiken aufmerksam.
-
 @ 6871d8df:4a9396c1
2025-01-18 20:12:46
@ 6871d8df:4a9396c1
2025-01-18 20:12:46## 2024 Prediction Reflections
Politics
Democrats & 2024 Election
- “Democrats’ attempt to stifle democracy will likely put Trump in the White House. If not, some real sketchy stuff would need to happen to keep him out.”
This prediction was exactly right. The assassination attempt on Trump seemed to be the final blow for the Democrats. Despite a heavy push my legacy media, Trump won handily.
The Democrats switched to Kamala Harris after Biden showed signs of incapacity, most notably in the first debate against Trump.
My prediction for the election also turned out to be exactly right, which, thank you Robert Barnes and Richard Baris.
Evidence of Institutional Ideological Capture
- “People will continue to wake up to ideologically captured institutions, and DEI will be the main loser.”
Trump’s resounding election victory underscores that the public is increasingly aware of (and rejecting) such institutional capture.
Of note, Boeing comes to mind as an institution that had a tough time in 2024, in large part to DEI. Nothing seemed to function correctly. The biggest story being how they stranded people in space
Media & Public Opinion
Rise of Independent & Alternative Media
- “Independent and alternative media will continue to grow as people’s trust in legacy media declines.”
Twitter (X), under Elon Musk, shattered mainstream media’s influence far more than expected. As Elon has said, “You are the media now.” Alternative sources are king. - Notable Example: Kamala Harris’s decision not to appear on the Joe Rogan podcast contrasted with Trump’s appearance, further highlighting the power shift to alternative media.
Markets & IPOs
Interest Rates & Public Markets
- “As interest rates come down, I expect public markets and IPOs to heat up.”
This did not play out. Companies that were expected to go public in 2024 remain private in 2025. The reasons are varied, but there is confidence that 2025 might see changes.
Technology & AI
LLMs & AI Adoption
- “AI and LLMs will continue to move at a rapid rate, increasing productivity. Tools like Bard will become more mainstream.”
AI did take off. Usage among nontechnical users increased, and it’s no longer uncommon for people to default to AI-driven tools rather than Google search.
Decentralized AI
- “I hope to see a rise in decentralized AI to counter big-player LLMs.”
We didn’t see explicit ‘decentralized AI’ breakthroughs, but more players entered the AI market. ChatGPT still dominates, with Elon’s ‘Grok’ making moves. Google, Meta, and Microsoft remain active but slightly behind in usage.
Bitcoin & Digital Assets
Institutional Adoption of Bitcoin
- “2024 will bring more institutions to Bitcoin. Possibly another large company or nation-state. The ETF should help, likely pushing BTC to a new all-time high.”
No large public company or nation-state placed a bet, but smaller public companies did. Michael Saylor presented to Microsoft’s Board, which was the closest instance to a major move.
- Price Movement: Bitcoin did hit a new all-time high, rising to as much as $108k in 2024.Lightning Network
- “Lightning will improve but remain primarily used for acquiring Bitcoin, not everyday payments.”
Still true. Lightning usage remains tiny relative to broader Bitcoin adoption.
Nostr Adoption
- “Nostr will grow, and we’ll see new companies leverage this network beyond just social media.”
Growth continues, but Elon Musk’s Twitter takeover slowed adoption. Nostr will remain niche until a major catalyst occurs (e.g., a big player joins or forced usage due to censorship).
Stablecoin-Specific Regulations
- “Expect stablecoin regulations in 2024 that’ll be favorable to them.”
This didn’t happen, largely due to the administration’s hostility. Expect potential change in 2025.
Miscellaneous 2024 Reflections
- Return to Sanity
- 2024 felt like sanity prevailed, largely due to the Democrats’ collapse behind Biden and Harris and Elon’s Twitter dominance.
- Operation Chokepoint 2.0
- Received a lot of attention, and I’m thankful it did because my experience at Strike was radicalizing and extreme.
- Bryan Johnson & Anti-Aging
- He burst onto the scene with his obsession over biomarkers. I see it as misguided—chasing markers in isolation doesn’t automatically yield a healthy system.
- Apple’s Rough Year
- Without a visionary leader, Apple appears to be scraping by on existing products rather than innovating.
- Google Under Fire
- Google is in a tough fight with the government, just as it seems they’re on their heels with AI competition.
2025 Predictions
-
Bitcoin’s Performance Bitcoin will have a good year, but not better than 2024. To beat 2024, it must close above 206k on December 31, 2025. I’ll take the under on that.
- I am not ruling out it to be over that at some point in 2025.
-
Twitter’s Success Continues to Stunt nostr
- Nostr adoption will stay slow due to Elon’s dominant influence with X (Twitter).
- As long as it remains a beacon of free speech, I doubt we see an exodus.
-
Rumble integrating Tether might help if they allow Nostr-like features (zaps), but that seems unlikely.
-
Apple
-
Apple will continue its rent-seeking behavior and put out underwhelming products.
-
Google’s Quantum & AI
- Recent buzz about Google’s quantum chip and AI improvements won’t pan out as a big deal.
-
Google will continue to trail OpenAI and xAI in practical LLM usage.
-
Elon, Vivek & DOGE
-
I expect them to deliver more than critics think. They’ll expose bloat and inefficiencies in ways that will shake up norms. I greatly welcome this. I wouldn’t bet against them.
-
Mainstream Media Reckoning
- In Trump’s second term, mainstream news outlets will face a real reckoning, as I can’t see how their bias can continue.
- They’ll have to reduce their bias or risk bankruptcy.
-
Alternative media’s growth trend continues, especially as Twitter keeps exposing mainstream outlets’ weaknesses.
-
RFK Delivers
-
We will see big changes in the health space due to RFK at HHS. These are changes that I am very excited to see.
-
Foreign Policy
- With the transition to Trump, I expect some foreign policy wins that will buck the establishment but will deliver wins that are not thought possible by the “experts.”
Closing Note
- Overall 2024: It was a year of major political upheaval, vindication for Bitcoin, and continued AI advances.
- Outlook for 2025: Bitcoin remains strong, AI competition heats up, and media institutions face existential challenges. I’m optimistic for continued decentralization and a more level playing field across tech, finance, and politics. I think the start of Trump’s second term will be very strong for the market, health, and culture. Accelerate.
-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ f7922a0a:82c34788
2025-01-17 23:06:56
@ f7922a0a:82c34788
2025-01-17 23:06:56Now that the 3rd Satellite Skirmish is complete I wanted to highlight some of the cool features on embrace.satskirmish.com
This is what the cutting edge of podcasting 2.0 looks like imo. Live video in an app that allows you to send sats to the artists in real time.
On the left hand side we have a Boost score borad that displays the total amount of sats that have come in during the show, live Boosts/Booastagrams as they come in, total amount of sats from each person Boosting and total amount sent from each app.
The middle is ovisaly the video of the band playing but with some graphics around it and Boost alerts that show up on the screen in the form of snow flakes for this one.
The righthand side is an IRC chat window that connects to an IRC server that the No Agenda community has used for 18+ years thanks to zoidzero++.

The bottom of the page is where things get cool. When you click the Boost the Crew button in the center you can send a Boost that gets split between everyone helping produce the show (hightlighted in yellow).


Each band also has their own Boost button so you can Boost them while they are playing or anytime you visit the page.


-
 @ 6be5cc06:5259daf0
2024-12-29 19:54:14
@ 6be5cc06:5259daf0
2024-12-29 19:54:14Um dos padrões mais bem estabelecidos ao medir a opinião pública é que cada geração tende a seguir um caminho semelhante em termos de política e ideologia geral. Seus membros compartilham das mesmas experiências formativas, atingem os marcos importantes da vida ao mesmo tempo e convivem nos mesmos espaços. Então, como devemos entender os relatórios que mostram que a Geração Z é hiperprogressista em certos assuntos, mas surpreendentemente conservadora em outros?
A resposta, nas palavras de Alice Evans, pesquisadora visitante na Universidade de Stanford e uma das principais estudiosas do tema, é que os jovens de hoje estão passando por um grande divergência de gênero, com as jovens mulheres do primeiro grupo e os jovens homens do segundo. A Geração Z representa duas gerações, e não apenas uma.
Em países de todos os continentes, surgiu um distanciamento ideológico entre jovens homens e mulheres. Milhões de pessoas que compartilham das mesmas cidades, locais de trabalho, salas de aula e até casas, não veem mais as coisas da mesma maneira.
Nos Estados Unidos, os dados da Gallup mostram que, após décadas em que os sexos estavam distribuídos de forma relativamente equilibrada entre visões políticas liberais e conservadoras, as mulheres entre 18 e 30 anos são agora 30 pontos percentuais mais liberais do que os homens dessa faixa etária. Essa diferença surgiu em apenas seis anos.
A Alemanha também apresenta um distanciamento de 30 pontos entre homens jovens conservadores e mulheres jovens progressistas, e no Reino Unido, a diferença é de 25 pontos. Na Polônia, no ano passado, quase metade dos homens entre 18 e 21 anos apoiou o partido de extrema direita Confederation, em contraste com apenas um sexto das jovens mulheres dessa mesma idade.
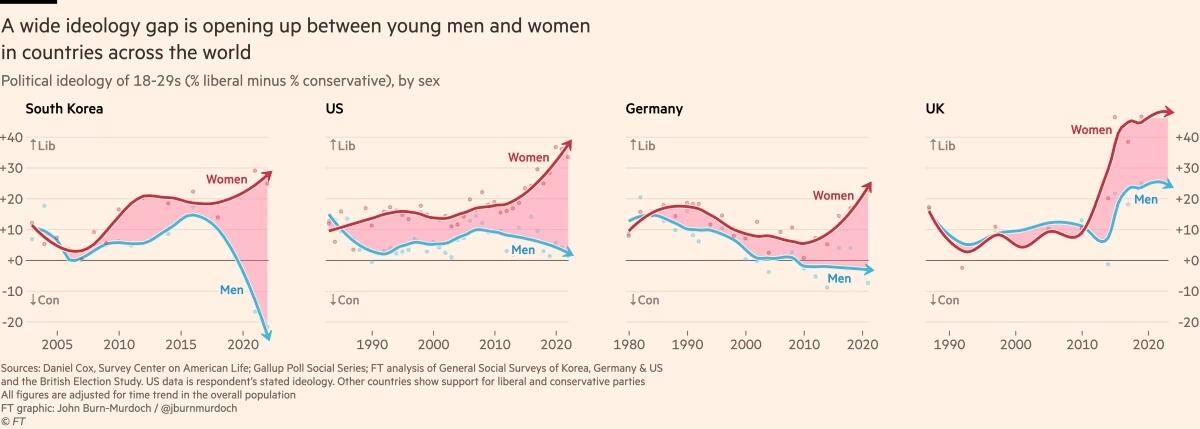
Fora do Ocidente, há divisões ainda mais acentuadas. Na Coreia do Sul, há um enorme abismo entre homens e mulheres jovens, e a situação é semelhante na China. Na África, a Tunísia apresenta o mesmo padrão. Vale notar que em todos os países essa divisão drástica ocorre principalmente entre a geração mais jovem, sendo muito menos pronunciada entre homens e mulheres na faixa dos 30 anos ou mais velhos.
O movimento # MeToo foi o principal estopim, trazendo à tona valores feministas intensos entre jovens mulheres que se sentiram empoderadas para denunciar injustiças de longa data. Esse estopim encontrou especialmente terreno fértil na Coreia do Sul, onde a desigualdade de gênero é bastante visível e a misoginia explícita é comum. (palavras da Financial Times, eu só traduzi)
Na eleição presidencial da Coreia do Sul em 2022, enquanto homens e mulheres mais velhos votaram de forma unificada, os jovens homens apoiaram fortemente o partido de direita People Power, enquanto as jovens mulheres apoiaram o partido liberal Democratic em números quase iguais e opostos.
A situação na Coreia é extrema, mas serve como um alerta para outros países sobre o que pode acontecer quando jovens homens e mulheres se distanciam. A sociedade está dividida, a taxa de casamento despencou e a taxa de natalidade caiu drasticamente, chegando a 0,78 filhos por mulher em 2022, o menor número no mundo todo.
Sete anos após a explosão inicial do movimento # MeToo, a divergência de gênero em atitudes tornou-se autossustentável.
Dados das pesquisas mostram que em muitos países, as diferenças ideológicas vão além dessa questão específica. A divisão progressista-conservadora sobre assédio sexual parece ter causado ou pelo menos faz parte de um alinhamento mais amplo, em que jovens homens e mulheres estão se organizando em grupos conservadores e liberais em outros assuntos.
Nos EUA, Reino Unido e Alemanha, as jovens mulheres agora adotam posturas mais liberais sobre temas como imigração e justiça racial, enquanto grupos etários mais velhos permanecem equilibrados. A tendência na maioria dos países tem sido de mulheres se inclinando mais para a esquerda, enquanto os homens permanecem estáveis. No entanto, há sinais de que os jovens homens estão se movendo para a direita na Alemanha, tornando-se mais críticos em relação à imigração e se aproximando do partido de extrema direita AfD nos últimos anos.
Seria fácil dizer que tudo isso é apenas uma fase passageira, mas os abismos ideológicos apenas crescem, e os dados mostram que as experiências políticas formativas das pessoas são difíceis de mudar. Tudo isso é agravado pelo fato de que o aumento dos smartphones e das redes sociais faz com que os jovens homens e mulheres agora vivam em espaços separados e tenham culturas distintas.
As opiniões dos jovens frequentemente são ignoradas devido à baixa participação política, mas essa mudança pode deixar consequências duradouras, impactando muito mais do que apenas os resultados das eleições.
Retirado de: https://www.ft.com/content/29fd9b5c-2f35-41bf-9d4c-994db4e12998
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ dd664d5e:5633d319
2025-01-09 21:39:15
@ dd664d5e:5633d319
2025-01-09 21:39:15Instructions
- Place 2 medium-sized, boiled potatoes and a handful of sliced leeks in a pot.

- Fill the pot with water or vegetable broth, to cover the potatoes twice over.
- Add a splash of white wine, if you like, and some bouillon powder, if you went with water instead of broth.

- Bring the soup to a boil and then simmer for 15 minutes.
- Puree the soup, in the pot, with a hand mixer. It shouldn't be completely smooth, when you're done, but rather have small bits and pieces of the veggies floating around.

- Bring the soup to a boil, again, and stir in one container (200-250 mL) of heavy cream.
- Thicken the soup, as needed, and then simmer for 5 more minutes.
- Garnish with croutons and veggies (here I used sliced green onions and radishes) and serve.

Guten Appetit!
- Place 2 medium-sized, boiled potatoes and a handful of sliced leeks in a pot.
-
 @ 6389be64:ef439d32
2025-01-16 15:44:06
@ 6389be64:ef439d32
2025-01-16 15:44:06Black Locust can grow up to 170 ft tall
Grows 3-4 ft. per year
Native to North America
Cold hardy in zones 3 to 8

Firewood
- BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal
- Since its growth is fast, firewood can be plentiful
Timber

- Rot resistant due to a naturally produced robinin in the wood
- 100 year life span in full soil contact! (better than cedar performance)
- Fence posts
- Outdoor furniture
- Outdoor decking
- Sustainable due to its fast growth and spread
- Can be coppiced (cut to the ground)
- Can be pollarded (cut above ground)
- Its dense wood makes durable tool handles, boxes (tool), and furniture
- The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak.
- A very low rate of expansion and contraction
- Hardwood flooring
- The highest tensile beam strength of any American tree
- The wood is beautiful
Legume
- Nitrogen fixer
- Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn
- Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]]
Bees

- The edible flower clusters are also a top food source for honey bees
Shade Provider

- Its light, airy overstory provides dappled shade
- Planted on the west side of a garden it provides relief during the hottest part of the day
- (nitrogen provider)
- Planted on the west side of a house, its quick growth soon shades that side from the sun
Wind-break

- Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters
Fodder
- Over 20% crude protein
- 4.1 kcal/g of energy
- Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
-
 @ 32e18276:5c68e245
2023-12-06 15:29:43
@ 32e18276:5c68e245
2023-12-06 15:29:43I’m going to be on an ordinals panels as one of the people who is counter arguing the claim that they are good for bitcoin. I decided to brush up on the technicals on how inscriptions work. I am starting to see luke’s perspective on how it is exploiting a loophole in bitcoin’s anti-data-spam mechanisms.
Storing data in Bitcoin, the “standard” way
The standard way you add “data” to bitcoin is by calling the OP_RETURN opcode. Bitcoin devs noticed that people were storing data (like the bitcoin whitepaper) in the utxo set via large multisig transactions. The problem with this is that this set is unprunable and could grow over time. OP_RETURN outputs on the other-hand are provably prunable and don’t add to utxo bloat.
Here’s an excerpt from the march 2014 0.9.0 release notes that talks about this:
On OP_RETURN: There was been some confusion and misunderstanding in the community, regarding the OP_RETURN feature in 0.9 and data in the blockchain. This change is not an endorsement of storing data in the blockchain. The OP_RETURN change creates a provably-prunable output, to avoid data storage schemes – some of which were already deployed – that were storing arbitrary data such as images as forever-unspendable TX outputs, bloating bitcoin’s UTXO database. Storing arbitrary data in the blockchain is still a bad idea; it is less costly and far more efficient to store non-currency data elsewhere.
Much of the work on bitcoin core has been focused on making sure the system continues to function in a decentralized way for its intended purpose in the presence of people trying to abuse it for things like storing data. Bitcoin core has always discouraged this, as it is not designed for storage of images and data, it is meant for moving digital coins around in cyberspace.
To help incentive-align people to not do stupid things, OP_RETURN transactions were not made non-standard, so that they are relayable by peers and miners, but with the caveat:
- They can only push 40 bytes (later increased to 80,83, I’m guessing to support larger root merkle hashes since that is the only sane usecase for op_return)
Bitcoin also added an option called -datacarriersize which limits the total number of bytes from these outputs that you will relay or mine.
Why inscriptions are technically an exploit
Inscriptions get around the datacarriersize limit by disguising data as bitcoin script program data via OP_PUSH inside OP_IF blocks. Ordinals do not use OP_RETURN and are not subjected to datacarriersize limits, so noderunners and miners currently have limited control over the total size of this data that they wish to relay and include in blocks. Luke’s fork of bitcoin-core has some options to fight this spam, so hopefully we will see this in core sometime soon as well.
Inscriptions are also taking advantage of features in segwit v1 (witness discount) and v2/taproot (no arbitrary script size limit). Each of these features have interesting and well-justified reasons why they were introduced.
The purpose of the witness discount was to make it cheaper to spend many outputs which helps the reduction of the utxo set size. Inscriptions took advantage of this discount to store monke jpegs disguised as bitcoin scripts. Remember, bitcoin is not for storing data, so anytime bitcoin-devs accidentally make it cheap and easy to relay data then this should be viewed as an exploit. Expect it to be fixed, or at least provide tools to noderunners for fighting this spam.
Where do we go from here
The interesting part of this story is that people seem to attach value to images stored on the bitcoin blockchain, and they are willing to pay the fee to get it in the block, so non-ideologic miners and people who don’t care about the health and decentralization of bitcoin are happy to pay or collect the fee and move on.
Data should not get a discount, people should pay full price if they want to store data. They should just use op_return and hashes like opentimestamps or any other reasonable protocol storing data in bitcoin.
After going through this analysis I’ve come to the opinion that this is a pretty bad data-spam exploit and bitcoin devs should be working on solutions. Ideological devs like luke who actually care about the health and decentralization of the network are and I’m glad to see it.
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ b8851a06:9b120ba1
2025-01-14 15:28:32
@ b8851a06:9b120ba1
2025-01-14 15:28:32It Begins with a Click
It starts with a click: “Do you agree to our terms and conditions?”\ You scroll, you click, you comply. A harmless act, right? But what if every click was a surrender? What if every "yes" was another link in the chain binding you to a life where freedom requires approval?
This is the age of permission. Every aspect of your life is mediated by gatekeepers. Governments demand forms, corporations demand clicks, and algorithms demand obedience. You’re free, of course, as long as you play by the rules. But who writes the rules? Who decides what’s allowed? Who owns your life?
Welcome to Digital Serfdom
We once imagined the internet as a digital frontier—a vast, open space where ideas could flow freely and innovation would know no bounds. But instead of creating a decentralized utopia, we built a new feudal system.
- Your data? Owned by the lords of Big Tech.
- Your money? Controlled by banks and bureaucrats who can freeze it on a whim.
- Your thoughts? Filtered by algorithms that reward conformity and punish dissent.
The modern internet is a land of serfs and lords, and guess who’s doing the farming? You. Every time you agree to the terms, accept the permissions, or let an algorithm decide for you, you till the fields of a system designed to control, not liberate.
They don’t call it control, of course. They call it “protection.” They say, “We’re keeping you safe,” as they build a cage so big you can’t see the bars.
Freedom in Chains
But let’s be honest: we’re not just victims of this system—we’re participants. We’ve traded freedom for convenience, sovereignty for security. It’s easier to click “I Agree” than to read the fine print. It’s easier to let someone else hold your money than to take responsibility for it yourself. It’s easier to live a life of quiet compliance than to risk the chaos of true independence.
We tell ourselves it’s no big deal. What’s one click? What’s one form? But the permissions pile up. The chains grow heavier. And one day, you wake up and realize you’re free to do exactly what the system allows—and nothing more.
The Great Unpermissioning
It doesn’t have to be this way. You don’t need their approval. You don’t need their systems. You don’t need their permission.
The Great Unpermissioning is not a movement—it’s a mindset. It’s the refusal to accept a life mediated by gatekeepers. It’s the quiet rebellion of saying, “No.” It’s the realization that the freedom you seek won’t be granted—it must be reclaimed.
- Stop asking. Permission is their tool. Refusal is your weapon.
- Start building. Embrace tools that decentralize power: Bitcoin, encryption, open-source software, decentralized communication. Build systems they can’t control.
- Stand firm. They’ll tell you it’s dangerous. They’ll call you a radical. But remember: the most dangerous thing you can do is comply.
The path won’t be easy. Freedom never is. But it will be worth it.
The New Frontier
The age of permission has turned us into digital serfs, but there’s a new frontier on the horizon. It’s a world where you control your money, your data, your decisions. It’s a world of encryption, anonymity, and sovereignty. It’s a world built not on permission but on principles.
This world won’t be given to you. You have to build it. You have to fight for it. And it starts with one simple act: refusing to comply.
A Final Word
They promised us safety, but what they delivered was submission. The age of permission has enslaved us to the mundane, the monitored, and the mediocre. The Great Unpermissioning isn’t about tearing down the old world—it’s about walking away from it.
You don’t need to wait for their approval. You don’t need to ask for their permission. The freedom you’re looking for is already yours. Permission is their power—refusal is yours.
-
 @ 7ed7d5c3:6927e200
2025-01-08 17:10:00
@ 7ed7d5c3:6927e200
2025-01-08 17:10:00Can't decide if the terrible book you just read is a 1 or 1.5 star book? Look no further than this chart. Was it Shit or just Bad? Was that movie you watched Very Good or just Decent? How many things out there are really Life Changing?
Finally, a rating scale for humans. Use it for anything in your life that needs a rating out of 5 stars.
Rating / Description
0.5 – The worst 1.0 – Shit 1.5 – Bad 2.0 – Eh 2.5 – Entertaining, but not great 3.0 – Neutral 3.5 – Alright 4.0 – Decent 4.5 – Very good 5.0 – Life Changing
P.S. Do not use it to rate your wife's cooking. The author is not liable for any damages.
-
 @ dbb19ae0:c3f22d5a
2025-01-18 20:40:48
@ dbb19ae0:c3f22d5a
2025-01-18 20:40:48Inspired by a video on youtube I wrote a calculator with Perl: Beware the line my ($num1, $num2, $operator) = '@'; should be my ($num1, $num2, $operator) = @; But the markdown syntax needs to have the @ into quotes otherwise, well the rest of the program is missing
#!/usr/bin/perl # calculator # use strict; use warnings; sub get_input { print "Enter number 1: "; chomp(my $num1 = <STDIN>); print "Enter number 2: "; chomp(my $num2 = <STDIN>); print "Enter operator (+, -, *, /): "; chomp(my $operator = <STDIN>); return ($num1, $num2, $operator); } sub calculate { my ($num1, $num2, $operator) = '@'_; my $result; if ($operator eq '+') { $result = $num1 + $num2; } elsif ($operator eq '-') { $result = $num1 - $num2; } elsif ($operator eq '*') { $result = $num1 * $num2; } elsif ($operator eq '/') { if ($num2 == 0) { die "Error: Division by zero\n"; } $result = $num1 / $num2; } else { die "Invalid operator\n"; } return $result; } # Get input from the user my ($num1, $num2, $operator) = get_input(); # Calculate the result my $result = calculate($num1, $num2, $operator); # Print the result print "$num1 $operator $num2 = $result\n";originally posted at https://stacker.news/items/816121
-
 @ c631e267:c2b78d3e
2025-01-18 09:34:51
@ c631e267:c2b78d3e
2025-01-18 09:34:51Die grauenvollste Aussicht ist die der Technokratie – \ einer kontrollierenden Herrschaft, \ die durch verstümmelte und verstümmelnde Geister ausgeübt wird. \ Ernst Jünger
«Davos ist nicht mehr sexy», das Weltwirtschaftsforum (WEF) mache Davos kaputt, diese Aussagen eines Einheimischen las ich kürzlich in der Handelszeitung. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den vergangenen vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
Der deutsche WEF-Gründer hatte bei dieser Gelegenheit immer höchst lobende Worte für seine Landsmännin: 2021 erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und 2022 fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
Von der Leyens Handeln während der sogenannten Corona-«Pandemie» lobte Schwab damals bereits ebenso, wie es diese Woche das Karlspreis-Direktorium tat, als man der Beschuldigten im Fall Pfizergate die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
Jene Herausforderungen durch «Krisen epochalen Ausmaßes» werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im Global Risks Report nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
Ein «Great Mental Reset» sei die Voraussetzung dafür, dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
Der aktuelle Zustand unserer Gesellschaften ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die Rechtsstaatlichkeit stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ dd664d5e:5633d319
2025-01-07 19:57:14
@ dd664d5e:5633d319
2025-01-07 19:57:14Hodling Bitcoin does not make you a capitalist
I've noticed that Bitcoin-mindedness seems to lead some people to communistic thinking because it's a hard-limited form of capital. Marx, like most Bitcoiners, heavily discounted the possibility of economic growth or transformation changing the economy enough to undermine some minority's control of some form of capital.
What few today understand, is that many of the Dirty Capitalists of Marx's era actually agreed with him; they were just disdainful of labor and worried that the workers finding out that Marxism is correct about the nature of capitalism would cause unrest. They were the original HFSP crowd.
This was the basic idea, that Marx had, and that many Bitcoiners would agree with:
Capital is strictly limited and the people that control it can keep labor from attaining any, except when their labor is necessary.
And, as we know, automation will make human labor increasingly unnecessary.
The math doesn't check out

That underlies all of the calculations of "Well, if I just grab this Bitcoin wallet and hodl for twenty years, then it will grow in value to equal half of everything in existence and then I can just buy up half the planet and rule over everyone like a god."
This is economic nonsense because it assumes that: 1) the value of all things remains static over time, 2) purchasing something with money gives you ownership of it, 3) people will always use that specific money (or any money, at all!) for all transactions, 4) there is no such thing as opportunity cost, 5) people will always value money more than any other thing, and therefore be willing to always trade it for anything else, 6) humans are passive, defenseless, and easy to rule over, 7) someone who is preoccupied with hodling an asset steadily and sharply rising in price would ever be emotionally ready to part with it.
All monies can die.
People use money for everything because it is easy, fast and cheap. If money becomes too precious or scarce, they will simply switch to using other things (as we saw with gold). Humans replace tools that aren't working well, with those that work better, and money is just another tool. Bitcoin is more divisible than gold, but that won't matter, if enough of it is held by too few.
This is why there's a natural cap on the price of a money and why human productivity in the here and now is not irrelevant or in vain.
-
 @ a95c6243:d345522c
2025-01-13 10:09:57
@ a95c6243:d345522c
2025-01-13 10:09:57Ich begann, Social Media aufzubauen, \ um den Menschen eine Stimme zu geben. \ Mark Zuckerberg
Sind euch auch die Tränen gekommen, als ihr Mark Zuckerbergs Wendehals-Deklaration bezüglich der Meinungsfreiheit auf seinen Portalen gehört habt? Rührend, oder? Während er früher die offensichtliche Zensur leugnete und später die Regierung Biden dafür verantwortlich machte, will er nun angeblich «die Zensur auf unseren Plattformen drastisch reduzieren».
«Purer Opportunismus» ob des anstehenden Regierungswechsels wäre als Klassifizierung viel zu kurz gegriffen. Der jetzige Schachzug des Meta-Chefs ist genauso Teil einer kühl kalkulierten Business-Strategie, wie es die 180 Grad umgekehrte Praxis vorher war. Social Media sind ein höchst lukratives Geschäft. Hinzu kommt vielleicht noch ein bisschen verkorkstes Ego, weil derartig viel Einfluss und Geld sicher auch auf die Psyche schlagen. Verständlich.
«Es ist an der Zeit, zu unseren Wurzeln der freien Meinungsäußerung auf Facebook und Instagram zurückzukehren. Ich begann, Social Media aufzubauen, um den Menschen eine Stimme zu geben», sagte Zuckerberg.
Welche Wurzeln? Hat der Mann vergessen, dass er von der Überwachung, dem Ausspionieren und dem Ausverkauf sämtlicher Daten und digitaler Spuren sowie der Manipulation seiner «Kunden» lebt? Das ist knallharter Kommerz, nichts anderes. Um freie Meinungsäußerung geht es bei diesem Geschäft ganz sicher nicht, und das war auch noch nie so. Die Wurzeln von Facebook liegen in einem Projekt des US-Militärs mit dem Namen «LifeLog». Dessen Ziel war es, «ein digitales Protokoll vom Leben eines Menschen zu erstellen».
Der Richtungswechsel kommt allerdings nicht überraschend. Schon Anfang Dezember hatte Meta-Präsident Nick Clegg von «zu hoher Fehlerquote bei der Moderation» von Inhalten gesprochen. Bei der Gelegenheit erwähnte er auch, dass Mark sehr daran interessiert sei, eine aktive Rolle in den Debatten über eine amerikanische Führungsrolle im technologischen Bereich zu spielen.
Während Milliardärskollege und Big Tech-Konkurrent Elon Musk bereits seinen Posten in der kommenden Trump-Regierung in Aussicht hat, möchte Zuckerberg also nicht nur seine Haut retten – Trump hatte ihn einmal einen «Feind des Volkes» genannt und ihm lebenslange Haft angedroht –, sondern am liebsten auch mitspielen. KI-Berater ist wohl die gewünschte Funktion, wie man nach einem Treffen Trump-Zuckerberg hörte. An seine Verhaftung dachte vermutlich auch ein weiterer Multimilliardär mit eigener Social Media-Plattform, Pavel Durov, als er Zuckerberg jetzt kritisierte und gleichzeitig warnte.
Politik und Systemmedien drehen jedenfalls durch – was zu viel ist, ist zu viel. Etwas weniger Zensur und mehr Meinungsfreiheit würden die Freiheit der Bürger schwächen und seien potenziell vernichtend für die Menschenrechte. Zuckerberg setze mit dem neuen Kurs die Demokratie aufs Spiel, das sei eine «Einladung zum nächsten Völkermord», ernsthaft. Die Frage sei, ob sich die EU gegen Musk und Zuckerberg behaupten könne, Brüssel müsse jedenfalls hart durchgreifen.
Auch um die Faktenchecker macht man sich Sorgen. Für die deutsche Nachrichtenagentur dpa und die «Experten» von Correctiv, die (noch) Partner für Fact-Checking-Aktivitäten von Facebook sind, sei das ein «lukratives Geschäftsmodell». Aber möglicherweise werden die Inhalte ohne diese vermeintlichen Korrektoren ja sogar besser. Anders als Meta wollen jedoch Scholz, Faeser und die Tagesschau keine Fehler zugeben und zum Beispiel Correctiv-Falschaussagen einräumen.
Bei derlei dramatischen Befürchtungen wundert es nicht, dass der öffentliche Plausch auf X zwischen Elon Musk und AfD-Chefin Alice Weidel von 150 EU-Beamten überwacht wurde, falls es irgendwelche Rechtsverstöße geben sollte, die man ihnen ankreiden könnte. Auch der Deutsche Bundestag war wachsam. Gefunden haben dürften sie nichts. Das Ganze war eher eine Show, viel Wind wurde gemacht, aber letztlich gab es nichts als heiße Luft.
Das Anbiedern bei Donald Trump ist indes gerade in Mode. Die Weltgesundheitsorganisation (WHO) tut das auch, denn sie fürchtet um Spenden von über einer Milliarde Dollar. Eventuell könnte ja Elon Musk auch hier künftig aushelfen und der Organisation sowie deren größtem privaten Förderer, Bill Gates, etwas unter die Arme greifen. Nachdem Musks KI-Projekt xAI kürzlich von BlackRock & Co. sechs Milliarden eingestrichen hat, geht da vielleicht etwas.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ dd664d5e:5633d319
2025-01-06 20:36:17
@ dd664d5e:5633d319
2025-01-06 20:36:17Ingredients
- 1 kg of pork roast with rind, such as shoulder or a lean belly
- 1 bottle of beer, light or dark
- chopped German-style mirepoix (best combination, for this recipe, includes celery root, carrot, red onion, and leeks)
- salt, pepper, nutmeg
- 1 diced garlic clove
Directions
- Spread the vegetables on the bottom of the roasting pan.
- Pour half the beer over the roast. (Drink the other half.)
- Season the meat, to taste.
- Roast the meat at 180 °C, until done (depends upon the weight of the roast).
- Remove the meat from the oven, and wrap in aluminum foil.
- Pour 2-3 cups of water into the roasting pan.
- Pour/scrape everything from the pan into a sieve over a sauce pot.
- Press the vegetables against the sieve, with the back of a spoon, to ensure that you get all that good dripping flavor into the sauce.
- Defat the sauce with a grease separator, then pour it back into the pot.
- Thicken the sauce, slightly (it should remain slightly watery, and not turn into a gravy), according to your usual method.
- Open the foil and slice the roast.
- Serve with the sauce.








-
 @ a95c6243:d345522c
2025-01-03 20:26:47
@ a95c6243:d345522c
2025-01-03 20:26:47Was du bist hängt von drei Faktoren ab: \ Was du geerbt hast, \ was deine Umgebung aus dir machte \ und was du in freier Wahl \ aus deiner Umgebung und deinem Erbe gemacht hast. \ Aldous Huxley
Das brave Mitmachen und Mitlaufen in einem vorgegebenen, recht engen Rahmen ist gewiss nicht neu, hat aber gerade wieder mal Konjunktur. Dies kann man deutlich beobachten, eigentlich egal, in welchem gesellschaftlichen Bereich man sich umschaut. Individualität ist nur soweit angesagt, wie sie in ein bestimmtes Schema von «Diversität» passt, und Freiheit verkommt zur Worthülse – nicht erst durch ein gewisses Buch einer gewissen ehemaligen Regierungschefin.
Erklärungsansätze für solche Entwicklungen sind bekannt, und praktisch alle haben etwas mit Massenpsychologie zu tun. Der Herdentrieb, also der Trieb der Menschen, sich – zum Beispiel aus Unsicherheit oder Bequemlichkeit – lieber der Masse anzuschließen als selbstständig zu denken und zu handeln, ist einer der Erklärungsversuche. Andere drehen sich um Macht, Propaganda, Druck und Angst, also den gezielten Einsatz psychologischer Herrschaftsinstrumente.
Aber wollen die Menschen überhaupt Freiheit? Durch Gespräche im privaten Umfeld bin ich diesbezüglich in der letzten Zeit etwas skeptisch geworden. Um die Jahreswende philosophiert man ja gerne ein wenig über das Erlebte und über die Erwartungen für die Zukunft. Dabei hatte ich hin und wieder den Eindruck, die totalitären Anwandlungen unserer «Repräsentanten» kämen manchen Leuten gerade recht.
«Desinformation» ist so ein brisantes Thema. Davor müsse man die Menschen doch schützen, hörte ich. Jemand müsse doch zum Beispiel diese ganzen merkwürdigen Inhalte in den Social Media filtern – zur Ukraine, zum Klima, zu Gesundheitsthemen oder zur Migration. Viele wüssten ja gar nicht einzuschätzen, was richtig und was falsch ist, sie bräuchten eine Führung.
Freiheit bedingt Eigenverantwortung, ohne Zweifel. Eventuell ist es einigen tatsächlich zu anspruchsvoll, die Verantwortung für das eigene Tun und Lassen zu übernehmen. Oder die persönliche Freiheit wird nicht als ausreichend wertvolles Gut angesehen, um sich dafür anzustrengen. In dem Fall wäre die mangelnde Selbstbestimmung wohl das kleinere Übel. Allerdings fehlt dann gemäß Aldous Huxley ein Teil der Persönlichkeit. Letztlich ist natürlich alles eine Frage der Abwägung.
Sind viele Menschen möglicherweise schon so «eingenordet», dass freiheitliche Ambitionen gar nicht für eine ganze Gruppe, ein Kollektiv, verfolgt werden können? Solche Gedanken kamen mir auch, als ich mir kürzlich diverse Talks beim viertägigen Hacker-Kongress des Chaos Computer Clubs (38C3) anschaute. Ich war nicht nur überrascht, sondern reichlich erschreckt angesichts der in weiten Teilen mainstream-geformten Inhalte, mit denen ein dankbares Publikum beglückt wurde. Wo ich allgemein hellere Köpfe erwartet hatte, fand ich Konformismus und enthusiastisch untermauerte Narrative.
Gibt es vielleicht so etwas wie eine Herdenimmunität gegen Indoktrination? Ich denke, ja, zumindest eine gestärkte Widerstandsfähigkeit. Was wir brauchen, sind etwas gesunder Menschenverstand, offene Informationskanäle und der Mut, sich freier auch zwischen den Herden zu bewegen. Sie tun das bereits, aber sagen Sie es auch dieses Jahr ruhig weiter.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ a42048d7:26886c32
2025-01-04 22:32:52
@ a42048d7:26886c32
2025-01-04 22:32:52OP_CAT, Coffee, and keeping an open mind to Bitcoin soft forks by an 80 IQ BTC Maxi Pleb
TLDR: CAT is both low risk and low appeal to the broader non-dev BTC community. I don’t care and you shouldn’t either. If I am an 80 IQ HODL pleb or a company that caters to that group, can you please give me 2-4 fifth grade level coherent english sentences that explain why I should support CAT? I’m still waiting… CTV or LNHANCE on the other hand have broad appeal.
Five years ago in the office we got a fancy $6,000 coffee maker. It was hooked up to wifi, showed TV on a giant screen, and could make every type of coffee/milkshake you could think of. I was captivated… for about 1 day. After trying a few times I realized almost all the drinks it made were of low quality. The wifi connection actually ended up just being annoying. Half the time I wanted a coffee, only had a 5 minute break, and the machine displayed some inscrutable error. I went back to the proverbial grind un-caffeinated and frustrated wishing we had the old reliable boring coffee maker back. I also found myself only coming back to the 2 drinks I really cared about, espresso and maybe an occasional cappuccino. It was “cool” that new machine could make over 60 different drinks, but when I sat back and thought about it all I really needed or wanted were a few key options that I used constantly. Especially as those extra bells and whistles seemed to be the usual suspect in the coffee machine constantly breaking. I would’ve loved them upgrading from burnt starbucks coffee beans to a local specialty roaster, that would’ve greatly enhanced my daily coffee. Echoing this realization, my coffee setup at home became a simple machine that could only make espresso and a hand crank coffee bean grinder. Still have them years later and they work great. They’re robust and fit exactly what I wanted with no nonsense that created more headache than everyday value. As you probably suspected, this is a loose comparison to OP_CAT. I’ve listened to podcast after podcast, read blog after blog, and sat through every CAT pitch I could find. I genuinely tried to approach with an open mind. However, ultimately what every pro OP_CAT argument boils down to is that there is no simple left curve elevator pitch a pleb will understand or care about. “But we can get this really cool ZK Rollup and have infinite DEFI bridging to altcoin chains! Look we sort of did it on this other altcoin chain.” And they did, they aren’t lying. They have live software on a shitcoin chain like ETH or SOL that does some modest volume. But the story quickly falls apart in the face of a few basic left curve questions: “Why should I, as an 80 IQ left curve BTC maxi give a shit?” “Does this enhance my everyday experience holding and using BTC?” “Why do you have a non-BTC token for your rollup/sidechain/glorified multisig that is totally centralized?” “Why is there only a hard to understand often ill-defined path to de-centralization? Why isn’t it just already decentralized?” “What is a clear use case that the typical non-technical everyday BTC holder can understand and rally behind?” “Why should I care about bridging to ETH, SOL, or whatever shitcoin chain? I only want BTC and don’t want to participate in all that shitcoin bullshit. Bitcoin is a store of value and money to me and it doesn’t help with those use cases in a clear direct way. It sounds like it maybe, kinda, sorta does help with a lot of caveats, ifs, and steps that I struggle to understand.” Sorry yeah I know, that one got a little personal. I’ll try to do better going forward guys.
ZK proofs or other Pro-CAT arguments, are undoubtedly cool and do factually enable potential cool new stuff. It just happens to all be stuff that sounds complex, esoteric, and unappealing to an 80 IQ HODL pleb - let alone a miner, ETF investor, or exchange exec. I don’t mean to say ZK or other tech has no potential and that we won’t eventually move there, but just to say that it’s not in the cards as currently dealt.
I really went out trying to keep an open mind and steelman the case for CAT. I came back firmly believing:
1 Support is deep in the developer community, but nonexistent everywhere else. I have yet to find a single person that supports CAT who is not a dev or working at or sponsored by a company that stands to directly profit from something CAT enables. Which is fine, but I reserve the right to be skeptical of your direct incentive. I acknowledge rough consensus is very hard to judge, and am open to changing my mind on this over time but feel this is a currently accurate assessment.
2 To get a soft fork you need rough consensus. Most people in that potential consensus are not highly technical developers. They care mostly or exclusively about BTC’s store of value use case. No one has yet articulated a clear compelling store of value enhancing use case that they can understand and care about. Without pull demand from potential users and paying customers, CAT will inevitably stall.
3 Lots of factually inaccurate FUD has been thrown at CAT. People saw the Taproot Wizards or shitcoiners pushing CAT, and immediately dismiss CAT as an evil psyop without any real consideration for its technical merits. Frankly most people just hate Udi and say “Fuck CAT” based solely on that. Maybe not fair, but true.
4 CAT is low risk, and it is not a catastrophe waiting to happen. Anything bad it potentially enables is enabled in such an inefficient and/or use hostile way that it is highly unlikely to pose any issues to Bitcoin. CAT’s technical risk is low and this is consistently proven by other chains enabling CAT and having no issues with it, such as Liquid.
5 Lots of people who have no idea wtf they are talking about falsely claim CAT is the apocalypse without any ability whatsoever to explain why. Imho you are no better than Udi and the shitcoiners if you are willing to lie about CAT just because you dislike them. We as the BTC community need the ability to have a rational discussion on technical merits, and not to devolve into a cult of personality based political battle. The question should be, “Is CAT good or bad and why?” and not “I just hate Udi, therefore its a no from me dog.”
Summarizing CAT using TradFi language: those pushing CAT have technology in search of a problem and no clear product market fit. They are pushing their technology to an apathetic audience. Pushers of CAT are not pulled forward by customer demand. In the tech world these are some of the quintessential red flags that every good investor knows mean you need to sit this one out.
CTV or LNHANCE on the other hand are soft fork proposals that have clear use cases you can quickly explain to a broad swathe of the Bitcoin ecosystem: “Hey HOLD pleb, worried about losing your coins? Wouldn’t it be nice to have a simple vault that reduces the chances your coins are lost or stolen? Let’s make self custody and BTC’s store of value use case strictly better, specifically without enabling any shitcoin-ery.” “Hey Blackrock, Van Eck, ARK, Franklin Templeton, and every ETF investor - it would really suck if Coinbase lost all your Bitcoin and that ETF went to zero, right? What it we could create vaults to make that Bitcoin more secure?” “Like Lightning but find it hard to use self-custodially? Let’s make Lightning better, easier, and more scalable with fewer onchain transactions and lower fees.” “Tried or seen the ARK demos yet? They have real working code even without covenants. With covenants we get big ARK volumes and scaling while also making it easier.”
Signing off: See the difference? I, an 80 IQ pleb, can steelman multiple use cases for CTV/LNHANCE that have broad appeal. I have yet to see any such case for CAT, and until then I don’t think it’ll go anywhere.
*Pro-CAT Sources I’ve digested and would encourage others to consider: https://en.bitcoin.it/wiki/Covenants_support https://www.youtube.com/watch?v=no_Nj-MX53w https://www.youtube.com/watch?v=_yp4eYK9S6M
Pro-CTV/LNHANCE sources to consider which have CLEAR use cases with widespead appeal: https://github.com/jamesob/simple-ctv-vault https://github.com/stutxo/op_ctv_payment_pool https://lnhance.org/ https://bitcoinmagazine.com/technical/how-ctv-can-help-scale-bitcoin
-
 @ a95c6243:d345522c
2025-01-01 17:39:51
@ a95c6243:d345522c
2025-01-01 17:39:51Heute möchte ich ein Gedicht mit euch teilen. Es handelt sich um eine Ballade des österreichischen Lyrikers Johann Gabriel Seidl aus dem 19. Jahrhundert. Mir sind diese Worte fest in Erinnerung, da meine Mutter sie perfekt rezitieren konnte, auch als die Kräfte schon langsam schwanden.
Dem originalen Titel «Die Uhr» habe ich für mich immer das Wort «innere» hinzugefügt. Denn der Zeitmesser – hier vermutliche eine Taschenuhr – symbolisiert zwar in dem Kontext das damalige Zeitempfinden und die Umbrüche durch die industrielle Revolution, sozusagen den Zeitgeist und das moderne Leben. Aber der Autor setzt sich philosophisch mit der Zeit auseinander und gibt seinem Werk auch eine klar spirituelle Dimension.
Das Ticken der Uhr und die Momente des Glücks und der Trauer stehen sinnbildlich für das unaufhaltsame Fortschreiten und die Vergänglichkeit des Lebens. Insofern könnte man bei der Uhr auch an eine Sonnenuhr denken. Der Rhythmus der Ereignisse passt uns vielleicht nicht immer in den Kram.
Was den Takt pocht, ist durchaus auch das Herz, unser «inneres Uhrwerk». Wenn dieses Meisterwerk einmal stillsteht, ist es unweigerlich um uns geschehen. Hoffentlich können wir dann dankbar sagen: «Ich habe mein Bestes gegeben.»
Ich trage, wo ich gehe, stets eine Uhr bei mir; \ Wieviel es geschlagen habe, genau seh ich an ihr. \ Es ist ein großer Meister, der künstlich ihr Werk gefügt, \ Wenngleich ihr Gang nicht immer dem törichten Wunsche genügt.
Ich wollte, sie wäre rascher gegangen an manchem Tag; \ Ich wollte, sie hätte manchmal verzögert den raschen Schlag. \ In meinen Leiden und Freuden, in Sturm und in der Ruh, \ Was immer geschah im Leben, sie pochte den Takt dazu.
Sie schlug am Sarge des Vaters, sie schlug an des Freundes Bahr, \ Sie schlug am Morgen der Liebe, sie schlug am Traualtar. \ Sie schlug an der Wiege des Kindes, sie schlägt, will's Gott, noch oft, \ Wenn bessere Tage kommen, wie meine Seele es hofft.
Und ward sie auch einmal träger, und drohte zu stocken ihr Lauf, \ So zog der Meister immer großmütig sie wieder auf. \ Doch stände sie einmal stille, dann wär's um sie geschehn, \ Kein andrer, als der sie fügte, bringt die Zerstörte zum Gehn.
Dann müßt ich zum Meister wandern, der wohnt am Ende wohl weit, \ Wohl draußen, jenseits der Erde, wohl dort in der Ewigkeit! \ Dann gäb ich sie ihm zurücke mit dankbar kindlichem Flehn: \ Sieh, Herr, ich hab nichts verdorben, sie blieb von selber stehn.
Johann Gabriel Seidl (1804-1875)
-
 @ e3ba5e1a:5e433365
2025-01-13 16:47:27
@ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity.
A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur.
The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior.
And there are plenty of incentives beyond our direct control! My son is also incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take.
Why incentives matter
A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could just do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example:
- If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning.
- If people would just use the recycling bin, we wouldn’t have such a landfill problem.
- If people would just stop being lazy, our team would deliver our project on time.
In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally.
- The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do.
- No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle.
- If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.

My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want.
If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is.
Running a company
Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions.
Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good.
What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off.
Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning.
When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.

Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money.
There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals.
Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature.
Moral hazard
Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings.
What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.

But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I don’t turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all.
This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as:
- We’re so habituated to turning off the water that we don’t even consider not turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off.
- Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created.
- We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?)
Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard.
A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard.
It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend?
And since we’re talking about the government already…
Government moral hazards
As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a huge number of examples of moral hazards. I decided to cherry-pick a few for this post.
The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people?
The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet.
If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups.
You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”

And here’s the absolute best part of this: I can’t even truly blame either California or Wall Street. (I mean, I do blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits.
There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions.
Non-monetary competition
At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home.
In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.)
Anyway, my professor’s wife had a friend. My professor described in great detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas.
This is a demonstration of non-monetary compensation. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules.
The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become wealthier and whiter, the exact opposite of their desired outcome. Why would that happen?
Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky.
She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls.
So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites.
You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences.
Bureaucracy
These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences.
Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings.
Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate.
Government incentivized behavior
This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples:
- Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to malinvestment and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience.
- Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise.
- During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation.
- The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen.
- Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example).
- Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as high living.)
Conclusion
The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives.
We can bemoan these realities all we want, but they are realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People should take advantage of the incentives around them. Because if they don’t, someone else will.
(If you want a literary example of that last comment, see the horse in Animal Farm.)
How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula:
- Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people.
- Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them.
- And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example.
And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining!
-
 @ 3f770d65:7a745b24
2025-01-12 21:03:36
@ 3f770d65:7a745b24
2025-01-12 21:03:36I’ve been using Notedeck for several months, starting with its extremely early and experimental alpha versions, all the way to its current, more stable alpha releases. The journey has been fascinating, as I’ve had the privilege of watching it evolve from a concept into a functional and promising tool.
In its earliest stages, Notedeck was raw—offering glimpses of its potential but still far from practical for daily use. Even then, the vision behind it was clear: a platform designed to redefine how we interact with Nostr by offering flexibility and power for all users.
I'm very bullish on Notedeck. Why? Because Will Casarin is making it! Duh! 😂
Seriously though, if we’re reimagining the web and rebuilding portions of the Internet, it’s important to recognize the potential of Notedeck. If Nostr is reimagining the web, then Notedeck is reimagining the Nostr client.
Notedeck isn’t just another Nostr app—it’s more a Nostr browser that functions more like an operating system with micro-apps. How cool is that?
Much like how Google's Chrome evolved from being a web browser with a task manager into ChromeOS, a full blown operating system, Notedeck aims to transform how we interact with the Nostr. It goes beyond individual apps, offering a foundation for a fully integrated ecosystem built around Nostr.
As a Nostr evangelist, I love to scream INTEROPERABILITY and tout every application's integrations. Well, Notedeck has the potential to be one of the best platforms to showcase these integrations in entirely new and exciting ways.
Do you want an Olas feed of images? Add the media column.
Do you want a feed of live video events? Add the zap.stream column.
Do you want Nostr Nests or audio chats? Add that column to your Notedeck.
Git? Email? Books? Chat and DMs? It's all possible.
Not everyone wants a super app though, and that’s okay. As with most things in the Nostr ecosystem, flexibility is key. Notedeck gives users the freedom to choose how they engage with it—whether it’s simply following hashtags or managing straightforward feeds. You'll be able to tailor Notedeck to fit your needs, using it as extensively or minimally as you prefer.
Notedeck is designed with a local-first approach, utilizing Nostr content stored directly on your device via the local nostrdb. This will enable a plethora of advanced tools such as search and filtering, the creation of custom feeds, and the ability to develop personalized algorithms across multiple Notedeck micro-applications—all with unparalleled flexibility.
Notedeck also supports multicast. Let's geek out for a second. Multicast is a method of communication where data is sent from one source to multiple destinations simultaneously, but only to devices that wish to receive the data. Unlike broadcast, which sends data to all devices on a network, multicast targets specific receivers, reducing network traffic. This is commonly used for efficient data distribution in scenarios like streaming, conferencing, or large-scale data synchronization between devices.
In a local first world where each device holds local copies of your nostr nodes, and each device transparently syncs with each other on the local network, each node becomes a backup. Your data becomes antifragile automatically. When a node goes down it can resync and recover from other nodes. Even if not all nodes have a complete collection, negentropy can pull down only what is needed from each device. All this can be done without internet.
-Will Casarin
In the context of Notedeck, multicast would allow multiple devices to sync their Nostr nodes with each other over a local network without needing an internet connection. Wild.
Notedeck aims to offer full customization too, including the ability to design and share custom skins, much like Winamp. Users will also be able to create personalized columns and, in the future, share their setups with others. This opens the door for power users to craft tailored Nostr experiences, leveraging their expertise in the protocol and applications. By sharing these configurations as "Starter Decks," they can simplify onboarding and showcase the best of Nostr’s ecosystem.
Nostr’s “Other Stuff” can often be difficult to discover, use, or understand. Many users doesn't understand or know how to use web browser extensions to login to applications. Let's not even get started with nsecbunkers. Notedeck will address this challenge by providing a native experience that brings these lesser-known applications, tools, and content into a user-friendly and accessible interface, making exploration seamless. However, that doesn't mean Notedeck should disregard power users that want to use nsecbunkers though - hint hint.
For anyone interested in watching Nostr be developed live, right before your very eyes, Notedeck’s progress serves as a reminder of what’s possible when innovation meets dedication. The current alpha is already demonstrating its ability to handle complex use cases, and I’m excited to see how it continues to grow as it moves toward a full release later this year.
-
 @ 3197ad60:7a122b95
2025-01-18 19:14:39
@ 3197ad60:7a122b95
2025-01-18 19:14:39I feel like the new year is slowly starting to settle in. That doesn’t mean I’m off to the races. I still intend to take the whole month (or as long as it takes, really) to make plans and carefully set a course forward. I’m not rushing it, I’m letting it all set, like tea leaves at the bottom of a glass.
I still draw daily (I’m around day 193 now), but the nature of the drawing seems to have changed. Instead of using colours and taking time to capture light and mood, I only seem to be interested in quick line sketches, the quicker, the better.
They go well with being slightly absent-minded, which I am, in a nice way. Instead of looking around for inspiration, I turn to the books I’m reading and just sketch scenes that stay with me.

All drawings in this post are based on The Book of Doors by Gareth Brown, one of the many tasty books I was gifted for Christmas. I’m adding the sketches in the order they were made because it’s kind of funny how the characters emerge. I didn’t plan for the main character to have short light hair, but somehow she does.

The book lends itself perfectly to easy sketching; the characters are not very complicated, but they are described with a lot of visual clues, and the story moves from location to location, leaving clear images in my mind.

It’s pretty clear who’s the bad guy and who’s not, and it was a good exercise to try to show that in a sketch. There is also a lot of movement in the story, with characters being surprised by the events and having to run/ hide/ escape and confront each other.

There are a lot of doors, many different locations and a good dose of time travelling. I don’t think I ever drew a time-travelling kind of scene before, so of course, I had to try. I used the hairstyle, a piece of clothing and a bit of colour to show the same person at two points in time but also in the same room. Did it work?

Recently, I’ve been really into the black and white illustrations in young adult, early reader, and chapter books. I love their simplicity and how much they can convey with a line drawing. I will hang around in that space for a bit, with my quick sketches.
I started a new book, funnily enough also about doors, so I might share more sketches soon.
Thanks for reading.
x
M
-
 @ a95c6243:d345522c
2024-12-21 09:54:49
@ a95c6243:d345522c
2024-12-21 09:54:49Falls du beim Lesen des Titels dieses Newsletters unwillkürlich an positive Neuigkeiten aus dem globalen polit-medialen Irrenhaus oder gar aus dem wirtschaftlichen Umfeld gedacht hast, darf ich dich beglückwünschen. Diese Assoziation ist sehr löblich, denn sie weist dich als unverbesserlichen Optimisten aus. Leider muss ich dich diesbezüglich aber enttäuschen. Es geht hier um ein anderes Thema, allerdings sehr wohl ein positives, wie ich finde.
Heute ist ein ganz besonderer Tag: die Wintersonnenwende. Genau gesagt hat heute morgen um 10:20 Uhr Mitteleuropäischer Zeit (MEZ) auf der Nordhalbkugel unseres Planeten der astronomische Winter begonnen. Was daran so außergewöhnlich ist? Der kürzeste Tag des Jahres war gestern, seit heute werden die Tage bereits wieder länger! Wir werden also jetzt jeden Tag ein wenig mehr Licht haben.
Für mich ist dieses Ereignis immer wieder etwas kurios: Es beginnt der Winter, aber die Tage werden länger. Das erscheint mir zunächst wie ein Widerspruch, denn meine spontanen Assoziationen zum Winter sind doch eher Kälte und Dunkelheit, relativ zumindest. Umso erfreulicher ist der emotionale Effekt, wenn dann langsam die Erkenntnis durchsickert: Ab jetzt wird es schon wieder heller!
Natürlich ist es kalt im Winter, mancherorts mehr als anderswo. Vielleicht jedoch nicht mehr lange, wenn man den Klimahysterikern glauben wollte. Mindestens letztes Jahr hat Väterchen Frost allerdings gleich zu Beginn seiner Saison – und passenderweise während des globalen Überhitzungsgipfels in Dubai – nochmal richtig mit der Faust auf den Tisch gehauen. Schnee- und Eischaos sind ja eigentlich in der Agenda bereits nicht mehr vorgesehen. Deswegen war man in Deutschland vermutlich in vorauseilendem Gehorsam schon nicht mehr darauf vorbereitet und wurde glatt lahmgelegt.
Aber ich schweife ab. Die Aussicht auf nach und nach mehr Licht und damit auch Wärme stimmt mich froh. Den Zusammenhang zwischen beidem merkt man in Andalusien sehr deutlich. Hier, wo die Häuser im Winter arg auskühlen, geht man zum Aufwärmen raus auf die Straße oder auf den Balkon. Die Sonne hat auch im Winter eine erfreuliche Kraft. Und da ist jede Minute Gold wert.
Außerdem ist mir vor Jahren so richtig klar geworden, warum mir das südliche Klima so sehr gefällt. Das liegt nämlich nicht nur an der Sonne als solcher, oder der Wärme – das liegt vor allem am Licht. Ohne Licht keine Farben, das ist der ebenso simple wie gewaltige Unterschied zwischen einem deprimierenden matschgraubraunen Winter und einem fröhlichen bunten. Ein großes Stück Lebensqualität.
Mir gefällt aber auch die Symbolik dieses Tages: Licht aus der Dunkelheit, ein Wendepunkt, ein Neuanfang, neue Möglichkeiten, Übergang zu neuer Aktivität. In der winterlichen Stille keimt bereits neue Lebendigkeit. Und zwar in einem Zyklus, das wird immer wieder so geschehen. Ich nehme das gern als ein Stück Motivation, es macht mir Hoffnung und gibt mir Energie.

Übrigens ist parallel am heutigen Tag auf der südlichen Halbkugel Sommeranfang. Genau im entgegengesetzten Rhythmus, sich ergänzend, wie Yin und Yang. Das alles liegt an der Schrägstellung der Erdachse, die ist nämlich um 23,4º zur Umlaufbahn um die Sonne geneigt. Wir erinnern uns, gell?
Insofern bleibt eindeutig festzuhalten, dass “schräg sein” ein willkommener, wichtiger und positiver Wert ist. Mit anderen Worten: auch ungewöhnlich, eigenartig, untypisch, wunderlich, kauzig, … ja sogar irre, spinnert oder gar “quer” ist in Ordnung. Das schließt das Denken mit ein.
In diesem Sinne wünsche ich euch allen urige Weihnachtstage!
Dieser Beitrag ist letztes Jahr in meiner Denkbar erschienen.
-
 @ 0d97beae:c5274a14
2025-01-11 16:52:08
@ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs
The reason why we have broken money
Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world.
In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes.
However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore.
Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too.
Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it.
Bitcoin overcomes the "transfer of hard money" problem
Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design.
Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it.
Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive.
Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold.
Bitcoin blurs the line between commodity and technology
Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules.
At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable.
Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases.
The dangers of derivatives
A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold.
In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin.
Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense.
Learn for yourself
If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody".
There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
-
 @ a4a6b584:1e05b95b
2025-01-02 18:13:31
@ a4a6b584:1e05b95b
2025-01-02 18:13:31The Four-Layer Framework
Layer 1: Zoom Out

Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what."
Example: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems.
- Tip: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage.
Once you have the big picture in mind, it’s time to start breaking it down.
Layer 2: Categorize and Connect

Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas.
Example: Studying biology? Group concepts into categories like cells, genetics, and ecosystems.
- Tip: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track.
With your categories in place, you’re ready to dive into the details that bring them to life.
Layer 3: Master the Details

Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable.
Example: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language.
- Tip: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding.
Now that you’ve mastered the essentials, you can expand your knowledge to include extra material.
Layer 4: Expand Your Horizons

Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams.
Example: Learn about rare programming quirks or historical trivia about a language’s development.
- Tip: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time.
Pro Tips for Better Learning
1. Use Active Recall and Spaced Repetition
Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information.
2. Map It Out
Create visual aids like diagrams or concept maps to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2.
3. Teach What You Learn
Explain the subject to someone else as if they’re hearing it for the first time. Teaching exposes any gaps in your understanding and helps reinforce the material.
4. Engage with LLMs and Discuss Concepts
Take advantage of tools like ChatGPT or similar large language models to explore your topic in greater depth. Use these tools to:
- Ask specific questions to clarify confusing points.
- Engage in discussions to simulate real-world applications of the subject.
- Generate examples or analogies that deepen your understanding.Tip: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective.
Get Started
Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
-
 @ a95c6243:d345522c
2024-12-13 19:30:32
@ a95c6243:d345522c
2024-12-13 19:30:32Das Betriebsklima ist das einzige Klima, \ das du selbst bestimmen kannst. \ Anonym
Eine Strategie zur Anpassung an den Klimawandel hat das deutsche Bundeskabinett diese Woche beschlossen. Da «Wetterextreme wie die immer häufiger auftretenden Hitzewellen und Starkregenereignisse» oft desaströse Auswirkungen auf Mensch und Umwelt hätten, werde eine Anpassung an die Folgen des Klimawandels immer wichtiger. «Klimaanpassungsstrategie» nennt die Regierung das.
Für die «Vorsorge vor Klimafolgen» habe man nun erstmals klare Ziele und messbare Kennzahlen festgelegt. So sei der Erfolg überprüfbar, und das solle zu einer schnelleren Bewältigung der Folgen führen. Dass sich hinter dem Begriff Klimafolgen nicht Folgen des Klimas, sondern wohl «Folgen der globalen Erwärmung» verbergen, erklärt den Interessierten die Wikipedia. Dabei ist das mit der Erwärmung ja bekanntermaßen so eine Sache.
Die Zunahme schwerer Unwetterereignisse habe gezeigt, so das Ministerium, wie wichtig eine frühzeitige und effektive Warnung der Bevölkerung sei. Daher solle es eine deutliche Anhebung der Nutzerzahlen der sogenannten Nina-Warn-App geben.
Die ARD spurt wie gewohnt und setzt die Botschaft zielsicher um. Der Artikel beginnt folgendermaßen:
«Die Flut im Ahrtal war ein Schock für das ganze Land. Um künftig besser gegen Extremwetter gewappnet zu sein, hat die Bundesregierung eine neue Strategie zur Klimaanpassung beschlossen. Die Warn-App Nina spielt eine zentrale Rolle. Der Bund will die Menschen in Deutschland besser vor Extremwetter-Ereignissen warnen und dafür die Reichweite der Warn-App Nina deutlich erhöhen.»
Die Kommunen würden bei ihren «Klimaanpassungsmaßnahmen» vom Zentrum KlimaAnpassung unterstützt, schreibt das Umweltministerium. Mit dessen Aufbau wurden das Deutsche Institut für Urbanistik gGmbH, welches sich stark für Smart City-Projekte engagiert, und die Adelphi Consult GmbH beauftragt.
Adelphi beschreibt sich selbst als «Europas führender Think-and-Do-Tank und eine unabhängige Beratung für Klima, Umwelt und Entwicklung». Sie seien «global vernetzte Strateg*innen und weltverbessernde Berater*innen» und als «Vorreiter der sozial-ökologischen Transformation» sei man mit dem Deutschen Nachhaltigkeitspreis ausgezeichnet worden, welcher sich an den Zielen der Agenda 2030 orientiere.
Über die Warn-App mit dem niedlichen Namen Nina, die möglichst jeder auf seinem Smartphone installieren soll, informiert das Bundesamt für Bevölkerungsschutz und Katastrophenhilfe (BBK). Gewarnt wird nicht nur vor Extrem-Wetterereignissen, sondern zum Beispiel auch vor Waffengewalt und Angriffen, Strom- und anderen Versorgungsausfällen oder Krankheitserregern. Wenn man die Kategorie Gefahreninformation wählt, erhält man eine Dosis von ungefähr zwei Benachrichtigungen pro Woche.
Beim BBK erfahren wir auch einiges über die empfohlenen Systemeinstellungen für Nina. Der Benutzer möge zum Beispiel den Zugriff auf die Standortdaten «immer zulassen», und zwar mit aktivierter Funktion «genauen Standort verwenden». Die Datennutzung solle unbeschränkt sein, auch im Hintergrund. Außerdem sei die uneingeschränkte Akkunutzung zu aktivieren, der Energiesparmodus auszuschalten und das Stoppen der App-Aktivität bei Nichtnutzung zu unterbinden.
Dass man so dramatische Ereignisse wie damals im Ahrtal auch anders bewerten kann als Regierungen und Systemmedien, hat meine Kollegin Wiltrud Schwetje anhand der Tragödie im spanischen Valencia gezeigt. Das Stichwort «Agenda 2030» taucht dabei in einem Kontext auf, der wenig mit Nachhaltigkeitspreisen zu tun hat.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 79998141:0f8f1901
2025-01-02 05:04:56
@ 79998141:0f8f1901
2025-01-02 05:04:56Happy new year, Anon.
Thanks for tuning in to whatever this long form post will be. I hope to make these more regular, like journal entries as we travel through "real life" and the Nostrverse together. If I'm making time for this reflective writing, then things are going as planned.
2024 was a wildly transformative year for me for many reasons... there's no way I can possibly fit all of them here. They're not all related to Bitcoin and Nostr- I've got a beautiful life outside of all that which has its own independent arc. My wife and I celebrated 7 years of marriage together, stronger than ever (don't believe that "itch" bullshit). We let go of some negative relationships and embraced some positive ones. We cut some bad habits, and we made some good habits. We worked, we traveled, we saw family, and we partied.
But damn, these two technologies have become a huge part of my life. God willing, this trend will continue until they've both eclipsed my professional capacity through our startup, Conduit BTC.
This was the year I was truly orange pilled. Until late 2023, I had traded (quite profitably) Bitcoin, "crypto", stocks, options, prediction markets and whatever else I could get my hands on that felt undervalued. I did this all in my spare time, grinding out a little financial freedom while I hustled at my fiat ventures to support my little family. I wasn't a true believer- just an opportunist with a knack for spotting where and when a crowd might flock to next. That was right up until I ran face first into Lyn Alden's book "Broken Money".
Something about Lyn's engineer/macro-finance inspired prose clicked with me, lock and key. Total one way function. By the end of the book my laser eyes had burned a hole in my bedroom ceiling. I was all in- and acted accordingly both with my capital and my attention. It wasn't long before I discovered Nostr and dove in here too, falling deep into my current orange and purple polyamorous love affair.
"If you know the enemy and know yourself, you need not fear the result of a hundred battles."
Despite the passion, through studying Bitcoin's criticisms (from the likes of Mike Green and Nassim Taleb) I found a hole in the utopian plot: none of this works without Bitcoin actually being used as money. Worldwide transactions must skyrocket demand for blockspace to keep the network secure/stable for the long term. Besides, if everyday folks aren't using Bitcoin as money then we haven't done shit to make the world a better place. In that world, we've only replaced old masters with new ones. Fuck that.
Whatever I did in this space needed to increase the usage of Bitcoin as money. Simple. This was bigger than passion, this was purpose. I knew that come hell or high water I would dedicate myself to this mission.
Lucky for me I found a partner and best friend in @aceaspades to go on this adventure with. I'm infinitely grateful for him. He's an incredible man who also happens to be an insanely creative and talented software developer. We'd tried for years to find the right project to focus on together, experimenting with all kinds of new techy ideas as they came across our field. Nothing had ever captured our attention like this. This was different. By March of 2024 we had formed a company and gotten to work iterating on how we could leverage these beautiful protocols and open-source tech to create something that served our mission. This is @ConduitBTC.
I've done well in my fiat career executing plans downstream of someone else's creative vision. I've learned the ins and outs of an established ecosystem and found ways to profit from it. I take plans developed by others, compete to win contracts to build them, and execute on them in a cashflow-positive way. I'm bringing this no bullshit blue collar skillset with me to the Nostrverse whether they like it or not.
The adventure we're embarking on now is totally different though. We're charting a new course - totally creative, highly intuitive and extremely speculative towards a future that doesn't exist yet. There are few established norms. The potential is vast but unknown. We're diving into a strange quest to sell a map to an imaginary place and to simultaneously architect its creation (alongside all the amazing builders here doing the same thing). This is insanely exciting to me.
We're barely getting started but a lot has been invested under the surface which will show itself in 2025. We'll be sharing updates in a proper post on @ConduitBTC soon.
As for my personal 2025 resolutions, here they are: - zero alcohol for the entire year (did this in 2019 and had a great year, it's time for a rerun) - more focused presence in the moment: especially with my wife - more self care and prioritized mental/physical health - this includes daily: naps, prayer, self hypnosis or meditation, sweat, and stretching/massaging (overworked in 2024 with a fiat 9-5, a board/advisor role in a fiat business I have equity in, and my newfound passion here. Two serious burn out episodes experienced this year - zero is the only acceptable number of burnouts for long term health and success.) - related to the above: get Conduit some mission-aligned funding partners and leave my fiat 9-5. Grow the Conduit team (have put in a serious amount of my personal capital already to get this going, which will show fruit in the new year... but I am not an island) - more authentic and thoughtful posts on Nostr, with a solid amount of shitposting and organic home grown memes to balance it out... more zaps, more geniune connections and interactions with the curious forward thinking people on here - more IRL Nostr/Bitcoin events - more laughter, more jokes
Enough for now. Cheers to you and yours Anon, may 2025 bring you the magic you've been dreaming of.
-
 @ a95c6243:d345522c
2024-12-06 18:21:15
@ a95c6243:d345522c
2024-12-06 18:21:15Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\ dass wir Vorteile aus ihr ziehen;\ in jedem andern hegt man den Wunsch,\ dass der Unschuldige in Schutz genommen werde.\ Jean-Jacques Rousseau
Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden.
Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen» den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen schadet der Psyche und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben Menschen getötet».
Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft. Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen Erfahrungen als Kritikerin der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit Transition News. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften».
Menschen, die aufrichtig andere schützen wollten, werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter Heinrich Habig, Bianca Witzschel und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat Transition News mehrfach berichtet (z.B. hier und hier). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie Alexander Bittner erfahren mussten.
Die eigentlich Kriminellen schützen sich derweil erfolgreich selber, nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte Verbrechen gegen die Menschheit». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn Hunter möglicherweise auch Anthony Fauci begnadigen wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte?
Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken.
Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers Robert F. Kennedy Jr. erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens Călin Georgescu, der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der Panik im Wertewesten.
In Rumänien selber gab es gerade einen Paukenschlag: Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das Tabu gebrochen, Wahlen zu verbieten, bevor sie etwas ändern können.
Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: Zensur) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ dd664d5e:5633d319
2024-12-29 20:29:03
@ dd664d5e:5633d319
2024-12-29 20:29:03The paparazzi are we

One of the things that bothers me about social media, in general, is that it gives celebrities an air of approachability, that they don't actually offer.
Theoretically, a celebrity could respond to any one of the dozens or even hundreds of people asking them questions or lodging complaints or singing their praises, but they usually only respond very selectively and leave everyone else just sitting there, as a living monument to the ReplyGuy.
And, as a wise man once said, ReplyGuy is a hoe.
Death of a ReplyGuy
This is usually because of time and energy restrictions, but also due to distaste, disdain, or indifference. Regardless of motivation, it is simply the nature of things, when a larger number of people are clamboring for the attention of some particular person.
Ooh, ooh! Can I have the next question?! Would you please address my bug? May I have a microsecond of your time?

Social media (and I include GitHub in this category) ups this game considerably, and potentially turns it all into a dangerous psychological torture, by making us all preoccupied with people who don't interact with us. The most irrational of groupies because we are forever making almost-contact with our stars.
If we can see them talking to one person, we're supposed to feel like they've spoken with all of us. But they haven't. They spoke with someone else, and we were allowed to watch. No different than on television, except that we might be disappointed and eager to return the next day, to renew our futile attempt.
The same intoxicating feeling that playing the lottery elicits. Everyone is a potential winner, but there is only one jackpot. Come back next week. Buy another ticket. This next time, is your time. Promise.
The view from the peanut gallery

It is all an illusion that there is no hierarchy, where there clearly is one. Celebrities of the past had, at least, the decency to remain slightly aloof. But they all want to be one of the Common Folk, now, just as every multi-millionaire aspires to see himself as fundamentally working-class.

All of celebrity social media is a stage, and most of us are merely spectators or commentators, to what is playing on it. This is why, if someone treats me like someone sitting in the peanut gallery, my instinct is to treat them like an actor.
Because, in reality, that is what they are.
-
 @ 23b0e2f8:d8af76fc
2025-01-08 18:17:52
@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52Necessário
- Um Android que você não use mais (a câmera deve estar funcionando).
- Um cartão microSD (opcional, usado apenas uma vez).
- Um dispositivo para acompanhar seus fundos (provavelmente você já tem um).
Algumas coisas que você precisa saber
- O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele.
- O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito.
- A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal.
O tutorial será dividido em dois módulos:
- Módulo 1 - Criando uma carteira fria/assinador.
- Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
No final, teremos:
- Uma carteira fria que também servirá como assinador.
- Um dispositivo para acompanhar os fundos da carteira.

Módulo 1 - Criando uma carteira fria/assinador
-
Baixe o APK do Electrum na aba de downloads em https://electrum.org/. Fique à vontade para verificar as assinaturas do software, garantindo sua autenticidade.
-
Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.

- Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.

- Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o modo avião.\ (Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)

- Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.

- No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. (Aqui entra seu método pessoal de backup.)

Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
-
Criar uma carteira somente leitura em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em https://electrum.org/ ou da própria Play Store. (ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)
-
Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção Usar uma chave mestra.

- Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em Carteira > Detalhes da carteira > Compartilhar chave mestra pública.

-
Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los.
-
Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: Carteira > Addresses/Coins.
-
Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.

- No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.

- No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede.
Conclusão
Pontos positivos do setup:
- Simplicidade: Basta um dispositivo Android antigo.
- Flexibilidade: Funciona como uma ótima carteira fria, ideal para holders.
Pontos negativos do setup:
- Padronização: Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum.
- Interface: A aparência do Electrum pode parecer antiquada para alguns usuários.
Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.
Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível.
-
 @ a95c6243:d345522c
2024-11-29 19:45:43
@ a95c6243:d345522c
2024-11-29 19:45:43Konsum ist Therapie.
Wolfgang JoopUmweltbewusstes Verhalten und verantwortungsvoller Konsum zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
Heute ist also wieder mal «Black Friday», falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
Warum fallen wir auf derartige Werbetricks herein und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
Gedankenlosigkeit und Maßlosigkeit können besonders bei der Ernährung zu ernsten Problemen führen. Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
Kritik am schwarzen Freitag und dem unnötigen Konsum kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
Die EU-Kommission lancierte 2015 den Begriff «Green Friday» im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das Pariser Abkommen unterzeichnet werden sollte.
Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt. Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des «Green New Deal» verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um Valencia dazu sagen?
Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020 eine «grüne Erholung von Covid-19, um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie «verantwortungsvolle Risikobereitschaft» unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a42048d7:26886c32
2024-12-27 16:33:24
@ a42048d7:26886c32
2024-12-27 16:33:24DIY Multisig is complex and 100x more likely to fail than you think if you do it yourself: A few years ago as an experiment I put what was then $2,000 worth Bitcoin into a 2 of 3 DIY multisig with two close family members holding two keys on Tapsigners and myself holding the last key on a Coldcard. My thought was to try and preview how they might deal with self custodied multisig Bitcoin if I died prematurely. After over a year I revisited and asked them to try and do a transaction without me. Just send that single Utxo to a new address in the same wallet, no time limit. It could not possibly have failed harder and shook my belief in multisig. To summarize an extremely painful day, there was a literally 0% chance they would figure this out without help. If this had been for real all our BTC may have been lost forever. Maybe eventually a family friend could’ve helped, but I hadn’t thought of that and hadn’t recommended a trusted BTC knowledge/help source. I had preached self sovereignty and doing it alone and my family tried to respect that. I should’ve given them the contact info of local high integrity bitcoiners I trust implicitly. Regardless of setup type, I highly recommend having a trusted Bitcoiner and online resources your family knows they can turn to to trouble shoot. Bookmark the corresponding BTCSessions video to your BTC self custody setup. Multisig is complicated as hell and hard to understand. Complexity is the enemy when it comes to making sure your BTC isn’t lost and actually gets to your heirs. Many Bitcoiners use a similar setup to this one that failed so badly, and I’m telling you unless you’re married to or gave birth to a seriously hardcore maxi who is extremely tech savvy, the risk your Bitcoin is lost upon your death is unacceptably high. My family is extremely smart but when the pressure of now many thousands of dollars was on the line, the complexity of multisig torpedoed them. Don’t run to an ETF! There are answers: singlesig is awesome. From observing my family I’m confident they would’ve been okay in a singlesig setup. It was the process of signing on separate devices with separate signers, and moving a PSBT around that stymied them. If it had been singlesig they would’ve been okay as one signature on its own was accomplished. Do not besmirch singlesig, it’s incredibly powerful and incredibly resilient. Resilience and simplicity are vastly underrated! In my opinion multisig may increase your theoretical security against attacks that are far less likely to actually happen, e.g. an Oceans Eleven style hack/heist. More likely your heirs will be fighting panic, grief, and stress and forget something you taught them a few years back. If they face an attack it will most likely be social engineering/phishing. They are unlikely to face an elaborate heist that would make a fun movie. While I still maintain it was a mistake for Bitkey to not have a separate screen to verify addresses and other info, overall I believe it’s probably the best normie option for small BTC holdings(yes I do know Bitkey is actually multisig, but the UX is basically a single sig). This incident scared me into realizing the importance of simplicity. Complexity and confusion of heirs/family may be the most under-considered aspects of BTC security. If you’ve made a DIY multisig and your heirs can’t explain why they need all three public keys and what a descriptor is and where it’s backed up, you might as well just go have that boating accident now and get it over with.
Once you get past small amounts of BTC, any reputable hardware wallet in singlesig is amazing security I would encourage folks to consider. In a singlesig setup - For $5 wrench attack concerns, just don’t have your hardware signer or steel backup at your home. You can just have a hot wallet on your phone with a small amount for spending.
If you get a really big stack collaborative multisig is a potentially reasonable middle ground. Just be very thoughtful and brutally honest about your heirs and their BTC and general tech knowledge. Singlesig is still great and you don’t have to move past it, but I get that you also need to sleep at night. If you have truly life changing wealth and are just too uncomfortable with singlesig, maybe consider either 1) Anchorwatch to get the potential benefits of multisig security with the safety net of traditional insurance or 2) Liana wallet where you can use miniscript to effectively have a time locked singlesig spending path to a key held by a third party to help your family recover your funds if they can’t figure it out before that timelock hits, 3) Bitcoin Keeper with their automatic inheritance docs and mini script enabled inheritance key. The automatic inheritance docs are a best in class feature no one else has done yet. Unchained charges $200 for inheritance docs on top of your $250 annual subscription, which imho is beyond ridiculous. 4) Swan vault, I’ve generally soured on most traditional 2 of 3 collaborative multisig because I’ve always found holes either in security (Unchained signed a transaction in only a few hours and has no defined time delay, and still doesn’t support Segwit, seriously guys, wtf?), only support signers that are harder to use and thus tough for noobs, or the overall setups are just too complex. Swan Vault’s focus on keeping it as simple as possible really stands out against competitors that tack on unneeded confusion complexity.
TLDR: For small amounts of BTC use Bitkey. For medium to large amounts use singlesig with a reputable hardware wallet and steel backup. For life changing wealth where you just can no longer stomach sinsglesig maybe also consider Anchorwatch, Bitcoin Keeper, Sean Vault, or Liana. Don’t forget your steel backups! Be safe out there! Do your own research and don’t take my word for it. Just use this as inspiration to consider an alternative point of view. If you’re a family of software engineers, feel free to tell me to go fuck myself.
-
 @ a4a6b584:1e05b95b
2024-12-26 17:13:08
@ a4a6b584:1e05b95b
2024-12-26 17:13:08Step 1: Secure Your Device
- Install an Antivirus Program
Download and install a trusted antivirus program to scan files for potential malware. - For Linux: Calm Antivirus
-
For Windows: CalmWin Antivirus
-
Install a VPN
A VPN is essential for maintaining privacy and security. It will encrypt your internet traffic and hide your IP address. -
Recommended: Mullvad VPN, which accepts Bitcoin for anonymous payment.
-
Install a Torrent Program
You’ll need a torrent client to download files. -
Recommended: Deluge
-
Install the Tor Browser
To access The Pirate Bay or its proxies, you’ll need the privacy-focused Tor Browser.
Step 2: Prepare Your Setup
- Ensure your VPN is running and connected.
- Open the Tor Browser.
- Launch Deluge to have your torrent client ready.
Step 3: Using Tor Go to The Pirate Bay via Onion Service or Find a Trusted Pirate Bay Proxy
Accessing The Pirate Bay directly can be challenging due to restrictions in some regions. Proxy sites often fill the gap. - The Pirate Bay Onion service: http://piratebayo3klnzokct3wt5yyxb2vpebbuyjl7m623iaxmqhsd52coid.onion - Or find a trusted proxy: Use a site like Pirateproxy or a reliable Tor directory for updated lists.
Step 4: Search for Linux Distros
- On The Pirate Bay, navigate to the "OtherOS" category under the Applications section.
- Enter your desired Linux distro in the search bar (e.g., "Ubuntu," "Arch Linux").
Step 5: Select a Torrent
- Filter the Results:
- Look for torrents with the highest seeders (SE) and the fewest leechers (LE).
-
Trusted users are marked with a green skull icon—these are usually safe uploads.
-
Copy the Magnet Link:
- Right-click on the magnet icon next to the trusted torrent and select "Copy Link."
Step 6: Start the Download
- In Deluge, paste the copied magnet link into the “Add Torrent” box.
- Click OK to start the download.
- Monitor the progress until the download completes.
Step 7: Scan the Downloaded File
Once the file is downloaded: 1. Scan for viruses: Right-click the file and use Calm or CalmWin to verify its integrity.
2. If the file passes the scan, it’s ready for use.
Step 8: Manage Your File
- Seed or Remove:
- To help the torrent community, keep seeding the file by leaving it in your torrent client.
-
To stop seeding, right-click the file in Deluge and remove it.
-
Move for Long-Term Storage: Transfer the file to a secure directory for regular use.
Notes on Safety and Ethics
- Verify Legitimacy: Ensure the torrent you are downloading is for an official Linux distribution. Torrents with unusual names or details should be avoided.
- Support the Developers: Consider visiting the official websites of Linux distros (Ubuntu, Arch Linux) to support their work directly.
By following these steps, you can safely and privately download Linux distributions while contributing to the open-source community.
- Install an Antivirus Program
-
 @ fd208ee8:0fd927c1
2024-12-26 07:02:59
@ fd208ee8:0fd927c1
2024-12-26 07:02:59I just read this, and found it enlightening.
Jung... notes that intelligence can be seen as problem solving at an everyday level..., whereas creativity may represent problem solving for less common issues
Other studies have used metaphor creation as a creativity measure instead of divergent thinking and a spectrum of CHC components instead of just g and have found much higher relationships between creativity and intelligence than past studies
https://www.mdpi.com/2079-3200/3/3/59
I'm unusually intelligent (Who isn't?), but I'm much more creative, than intelligent, and I think that confuses people. The ability to apply intelligence, to solve completely novel problems, on the fly, is something IQ tests don't even claim to measure. They just claim a correlation.
Creativity requires taking wild, mental leaps out into nothingness; simply trusting that your brain will land you safely. And this is why I've been at the forefront of massive innovation, over and over, but never got rich off of it.
I'm a starving autist.
Zaps are the first time I've ever made money directly, for solving novel problems. Companies don't do this because there is a span of time between providing a solution and the solution being implemented, and the person building the implementation (or their boss) receives all the credit for the existence of the solution. At best, you can hope to get pawned off with a small bonus.
Nobody can remember who came up with the solution, originally, and that person might not even be there, anymore, and probably never filed a patent, and may have no idea that their idea has even been built. They just run across it, later, in a tech magazine or museum, and say, "Well, will you look at that! Someone actually went and built it! Isn't that nice!"
Universities at least had the idea of cementing novel solutions in academic papers, but that: 1) only works if you're an academic, and at a university, 2) is an incredibly slow process, not appropriate for a truly innovative field, 3) leads to manifestations of perverse incentives and biased research frameworks, coming from 'publish or perish' policies.
But I think long-form notes and zaps solve for this problem. #Alexandria, especially, is being built to cater to this long-suffering class of chronic underachievers. It leaves a written, public, time-stamped record of Clever Ideas We Have Had.
Because they are clever, the ideas. And we have had them.
-
 @ 4ba8e86d:89d32de4
2024-10-07 13:37:38
@ 4ba8e86d:89d32de4
2024-10-07 13:37:38O que é Cwtch? Cwtch (/kʊtʃ/ - uma palavra galesa que pode ser traduzida aproximadamente como “um abraço que cria um lugar seguro”) é um protocolo de mensagens multipartidário descentralizado, que preserva a privacidade, que pode ser usado para construir aplicativos resistentes a metadados.
Como posso pronunciar Cwtch? Como "kutch", para rimar com "butch".
Descentralizado e Aberto : Não existe “serviço Cwtch” ou “rede Cwtch”. Os participantes do Cwtch podem hospedar seus próprios espaços seguros ou emprestar sua infraestrutura para outras pessoas que buscam um espaço seguro. O protocolo Cwtch é aberto e qualquer pessoa é livre para criar bots, serviços e interfaces de usuário e integrar e interagir com o Cwtch.
Preservação de privacidade : toda a comunicação no Cwtch é criptografada de ponta a ponta e ocorre nos serviços cebola Tor v3.
Resistente a metadados : O Cwtch foi projetado de forma que nenhuma informação seja trocada ou disponibilizada a ninguém sem seu consentimento explícito, incluindo mensagens durante a transmissão e metadados de protocolo
Uma breve história do bate-papo resistente a metadados Nos últimos anos, a conscientização pública sobre a necessidade e os benefícios das soluções criptografadas de ponta a ponta aumentou com aplicativos como Signal , Whatsapp e Wire. que agora fornecem aos usuários comunicações seguras.
No entanto, essas ferramentas exigem vários níveis de exposição de metadados para funcionar, e muitos desses metadados podem ser usados para obter detalhes sobre como e por que uma pessoa está usando uma ferramenta para se comunicar.
Uma ferramenta que buscou reduzir metadados é o Ricochet lançado pela primeira vez em 2014. Ricochet usou os serviços cebola Tor v2 para fornecer comunicação criptografada segura de ponta a ponta e para proteger os metadados das comunicações.
Não havia servidores centralizados que auxiliassem no roteamento das conversas do Ricochet. Ninguém além das partes envolvidas em uma conversa poderia saber que tal conversa está ocorrendo.
Ricochet tinha limitações; não havia suporte para vários dispositivos, nem existe um mecanismo para suportar a comunicação em grupo ou para um usuário enviar mensagens enquanto um contato está offline.
Isto tornou a adoção do Ricochet uma proposta difícil; mesmo aqueles em ambientes que seriam melhor atendidos pela resistência aos metadados, sem saber que ela existe.
Além disso, qualquer solução para comunicação descentralizada e resistente a metadados enfrenta problemas fundamentais quando se trata de eficiência, privacidade e segurança de grupo conforme definido pelo consenso e consistência da transcrição.
Alternativas modernas ao Ricochet incluem Briar , Zbay e Ricochet Refresh - cada ferramenta procura otimizar para um conjunto diferente de compensações, por exemplo, Briar procura permitir que as pessoas se comuniquem mesmo quando a infraestrutura de rede subjacente está inoperante, ao mesmo tempo que fornece resistência à vigilância de metadados.
O projeto Cwtch começou em 2017 como um protocolo de extensão para Ricochet, fornecendo conversas em grupo por meio de servidores não confiáveis, com o objetivo de permitir aplicativos descentralizados e resistentes a metadados como listas compartilhadas e quadros de avisos.
Uma versão alfa do Cwtch foi lançada em fevereiro de 2019 e, desde então, a equipe do Cwtch dirigida pela OPEN PRIVACY RESEARCH SOCIETY conduziu pesquisa e desenvolvimento em cwtch e nos protocolos, bibliotecas e espaços de problemas subjacentes.
Modelo de Risco.
Sabe-se que os metadados de comunicações são explorados por vários adversários para minar a segurança dos sistemas, para rastrear vítimas e para realizar análises de redes sociais em grande escala para alimentar a vigilância em massa. As ferramentas resistentes a metadados estão em sua infância e faltam pesquisas sobre a construção e a experiência do usuário de tais ferramentas.
https://nostrcheck.me/media/public/nostrcheck.me_9475702740746681051707662826.webp
O Cwtch foi originalmente concebido como uma extensão do protocolo Ricochet resistente a metadados para suportar comunicações assíncronas de grupos multiponto por meio do uso de infraestrutura anônima, descartável e não confiável.
Desde então, o Cwtch evoluiu para um protocolo próprio. Esta seção descreverá os vários riscos conhecidos que o Cwtch tenta mitigar e será fortemente referenciado no restante do documento ao discutir os vários subcomponentes da Arquitetura Cwtch.
Modelo de ameaça.
É importante identificar e compreender que os metadados são omnipresentes nos protocolos de comunicação; é de facto necessário que tais protocolos funcionem de forma eficiente e em escala. No entanto, as informações que são úteis para facilitar peers e servidores também são altamente relevantes para adversários que desejam explorar tais informações.
Para a definição do nosso problema, assumiremos que o conteúdo de uma comunicação é criptografado de tal forma que um adversário é praticamente incapaz de quebrá-lo veja tapir e cwtch para detalhes sobre a criptografia que usamos, e como tal nos concentraremos em o contexto para os metadados de comunicação.
Procuramos proteger os seguintes contextos de comunicação:
• Quem está envolvido em uma comunicação? Pode ser possível identificar pessoas ou simplesmente identificadores de dispositivos ou redes. Por exemplo, “esta comunicação envolve Alice, uma jornalista, e Bob, um funcionário público”.
• Onde estão os participantes da conversa? Por exemplo, “durante esta comunicação, Alice estava na França e Bob estava no Canadá”.
• Quando ocorreu uma conversa? O momento e a duração da comunicação podem revelar muito sobre a natureza de uma chamada, por exemplo, “Bob, um funcionário público, conversou com Alice ao telefone por uma hora ontem à noite. Esta é a primeira vez que eles se comunicam.” *Como a conversa foi mediada? O fato de uma conversa ter ocorrido por meio de um e-mail criptografado ou não criptografado pode fornecer informações úteis. Por exemplo, “Alice enviou um e-mail criptografado para Bob ontem, enquanto eles normalmente enviam apenas e-mails de texto simples um para o outro”.
• Sobre o que é a conversa? Mesmo que o conteúdo da comunicação seja criptografado, às vezes é possível derivar um contexto provável de uma conversa sem saber exatamente o que é dito, por exemplo, “uma pessoa ligou para uma pizzaria na hora do jantar” ou “alguém ligou para um número conhecido de linha direta de suicídio na hora do jantar”. 3 horas da manhã."
Além das conversas individuais, também procuramos defender-nos contra ataques de correlação de contexto, através dos quais múltiplas conversas são analisadas para obter informações de nível superior:
• Relacionamentos: Descobrir relações sociais entre um par de entidades analisando a frequência e a duração de suas comunicações durante um período de tempo. Por exemplo, Carol e Eve ligam uma para a outra todos os dias durante várias horas seguidas.
• Cliques: Descobrir relações sociais entre um grupo de entidades que interagem entre si. Por exemplo, Alice, Bob e Eva se comunicam entre si.
• Grupos vagamente conectados e indivíduos-ponte: descobrir grupos que se comunicam entre si através de intermediários, analisando cadeias de comunicação (por exemplo, toda vez que Alice fala com Bob, ela fala com Carol quase imediatamente depois; Bob e Carol nunca se comunicam).
• Padrão de Vida: Descobrir quais comunicações são cíclicas e previsíveis. Por exemplo, Alice liga para Eve toda segunda-feira à noite por cerca de uma hora. Ataques Ativos
Ataques de deturpação.
O Cwtch não fornece registro global de nomes de exibição e, como tal, as pessoas que usam o Cwtch são mais vulneráveis a ataques baseados em declarações falsas, ou seja, pessoas que fingem ser outras pessoas:
O fluxo básico de um desses ataques é o seguinte, embora também existam outros fluxos:
•Alice tem um amigo chamado Bob e outro chamado Eve
• Eve descobre que Alice tem um amigo chamado Bob
• Eve cria milhares de novas contas para encontrar uma que tenha uma imagem/chave pública semelhante à de Bob (não será idêntica, mas pode enganar alguém por alguns minutos)
• Eve chama essa nova conta de "Eve New Account" e adiciona Alice como amiga.
• Eve então muda seu nome em "Eve New Account" para "Bob"
• Alice envia mensagens destinadas a "Bob" para a conta falsa de Bob de Eve Como os ataques de declarações falsas são inerentemente uma questão de confiança e verificação, a única maneira absoluta de evitá-los é os usuários validarem absolutamente a chave pública. Obviamente, isso não é o ideal e, em muitos casos, simplesmente não acontecerá .
Como tal, pretendemos fornecer algumas dicas de experiência do usuário na interface do usuário para orientar as pessoas na tomada de decisões sobre confiar em contas e/ou distinguir contas que possam estar tentando se representar como outros usuários.
Uma nota sobre ataques físicos A Cwtch não considera ataques que exijam acesso físico (ou equivalente) à máquina do usuário como praticamente defensáveis. No entanto, no interesse de uma boa engenharia de segurança, ao longo deste documento ainda nos referiremos a ataques ou condições que exigem tal privilégio e indicaremos onde quaisquer mitigações que implementámos falharão.
Um perfil Cwtch.
Os usuários podem criar um ou mais perfis Cwtch. Cada perfil gera um par de chaves ed25519 aleatório compatível com Tor.
Além do material criptográfico, um perfil também contém uma lista de Contatos (outras chaves públicas do perfil Cwtch + dados associados sobre esse perfil, como apelido e (opcionalmente) mensagens históricas), uma lista de Grupos (contendo o material criptográfico do grupo, além de outros dados associados, como apelido do grupo e mensagens históricas).
Conversões entre duas partes: ponto a ponto
https://nostrcheck.me/media/public/nostrcheck.me_2186338207587396891707662879.webp
Para que duas partes participem de uma conversa ponto a ponto, ambas devem estar on-line, mas apenas uma precisa estar acessível por meio do serviço Onion. Por uma questão de clareza, muitas vezes rotulamos uma parte como “ponto de entrada” (aquele que hospeda o serviço cebola) e a outra parte como “ponto de saída” (aquele que se conecta ao serviço cebola).
Após a conexão, ambas as partes adotam um protocolo de autenticação que:
• Afirma que cada parte tem acesso à chave privada associada à sua identidade pública.
• Gera uma chave de sessão efêmera usada para criptografar todas as comunicações futuras durante a sessão.
Esta troca (documentada com mais detalhes no protocolo de autenticação ) é negável offline , ou seja, é possível para qualquer parte falsificar transcrições desta troca de protocolo após o fato e, como tal - após o fato - é impossível provar definitivamente que a troca aconteceu de forma alguma.
Após o protocolo de autenticação, as duas partes podem trocar mensagens livremente.
Conversas em Grupo e Comunicação Ponto a Servidor
Ao iniciar uma conversa em grupo, é gerada uma chave aleatória para o grupo, conhecida como Group Key. Todas as comunicações do grupo são criptografadas usando esta chave. Além disso, o criador do grupo escolhe um servidor Cwtch para hospedar o grupo. Um convite é gerado, incluindo o Group Key, o servidor do grupo e a chave do grupo, para ser enviado aos potenciais membros.
Para enviar uma mensagem ao grupo, um perfil se conecta ao servidor do grupo e criptografa a mensagem usando a Group Key, gerando também uma assinatura sobre o Group ID, o servidor do grupo e a mensagem. Para receber mensagens do grupo, um perfil se conecta ao servidor e baixa as mensagens, tentando descriptografá-las usando a Group Key e verificando a assinatura.
Detalhamento do Ecossistema de Componentes
O Cwtch é composto por várias bibliotecas de componentes menores, cada uma desempenhando um papel específico. Algumas dessas bibliotecas incluem:
- abertoprivacidade/conectividade: Abstração de rede ACN, atualmente suportando apenas Tor.
- cwtch.im/tapir: Biblioteca para construção de aplicativos p2p em sistemas de comunicação anônimos.
- cwtch.im/cwtch: Biblioteca principal para implementação do protocolo/sistema Cwtch.
- cwtch.im/libcwtch-go: Fornece ligações C para Cwtch para uso em implementações de UI.
TAPIR: Uma Visão Detalhada
Projetado para substituir os antigos canais de ricochete baseados em protobuf, o Tapir fornece uma estrutura para a construção de aplicativos anônimos.
Está dividido em várias camadas:
• Identidade - Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um par.
• Conexões – O protocolo de rede bruto que conecta dois pares. Até agora, as conexões são definidas apenas através do Tor v3 Onion Services.
• Aplicativos - As diversas lógicas que permitem um determinado fluxo de informações em uma conexão. Os exemplos incluem transcrições criptográficas compartilhadas, autenticação, proteção contra spam e serviços baseados em tokens. Os aplicativos fornecem recursos que podem ser referenciados por outros aplicativos para determinar se um determinado peer tem a capacidade de usar um determinado aplicativo hospedado.
• Pilhas de aplicativos - Um mecanismo para conectar mais de um aplicativo, por exemplo, a autenticação depende de uma transcrição criptográfica compartilhada e o aplicativo peer cwtch principal é baseado no aplicativo de autenticação.
Identidade.
Um par de chaves ed25519, necessário para estabelecer um serviço cebola Tor v3 e usado para manter uma identidade criptográfica consistente para um peer.
InitializeIdentity - de um par de chaves conhecido e persistente:i,I
InitializeEphemeralIdentity - de um par de chaves aleatório: ie,Ie
Aplicativos de transcrição.
Inicializa uma transcrição criptográfica baseada em Merlin que pode ser usada como base de protocolos baseados em compromisso de nível superior
O aplicativo de transcrição entrará em pânico se um aplicativo tentar substituir uma transcrição existente por uma nova (aplicando a regra de que uma sessão é baseada em uma e apenas uma transcrição).
Merlin é uma construção de transcrição baseada em STROBE para provas de conhecimento zero. Ele automatiza a transformação Fiat-Shamir, para que, usando Merlin, protocolos não interativos possam ser implementados como se fossem interativos.
Isto é significativamente mais fácil e menos sujeito a erros do que realizar a transformação manualmente e, além disso, também fornece suporte natural para:
• protocolos multi-round com fases alternadas de commit e desafio;
• separação natural de domínios, garantindo que os desafios estejam vinculados às afirmações a serem provadas;
• enquadramento automático de mensagens, evitando codificação ambígua de dados de compromisso;
• e composição do protocolo, usando uma transcrição comum para vários protocolos.
Finalmente, o Merlin também fornece um gerador de números aleatórios baseado em transcrição como defesa profunda contra ataques de entropia ruim (como reutilização de nonce ou preconceito em muitas provas). Este RNG fornece aleatoriedade sintética derivada de toda a transcrição pública, bem como dos dados da testemunha do provador e uma entrada auxiliar de um RNG externo.
Conectividade Cwtch faz uso do Tor Onion Services (v3) para todas as comunicações entre nós.
Fornecemos o pacote openprivacy/connectivity para gerenciar o daemon Tor e configurar e desmontar serviços cebola através do Tor.
Criptografia e armazenamento de perfil.
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir uma senha.
Perfis não criptografados e a senha padrão Para lidar com perfis "não criptografados" (ou seja, que não exigem senha para serem abertos), atualmente criamos um perfil com uma senha codificada de fato .
Isso não é o ideal, preferiríamos confiar no material de chave fornecido pelo sistema operacional, de modo que o perfil fosse vinculado a um dispositivo específico, mas esses recursos são atualmente uma colcha de retalhos - também notamos, ao criar um perfil não criptografado, pessoas que usam Cwtch estão explicitamente optando pelo risco de que alguém com acesso ao sistema de arquivos possa descriptografar seu perfil.
Vulnerabilidades Relacionadas a Imagens e Entrada de Dados
Imagens Maliciosas
O Cwtch enfrenta desafios na renderização de imagens, com o Flutter utilizando Skia, embora o código subjacente não seja totalmente seguro para a memória.
Realizamos testes de fuzzing nos componentes Cwtch e encontramos um bug de travamento causado por um arquivo GIF malformado, levando a falhas no kernel. Para mitigar isso, adotamos a política de sempre habilitar cacheWidth e/ou cacheHeight máximo para widgets de imagem.
Identificamos o risco de imagens maliciosas serem renderizadas de forma diferente em diferentes plataformas, como evidenciado por um bug no analisador PNG da Apple.
Riscos de Entrada de Dados
Um risco significativo é a interceptação de conteúdo ou metadados por meio de um Input Method Editor (IME) em dispositivos móveis. Mesmo aplicativos IME padrão podem expor dados por meio de sincronização na nuvem, tradução online ou dicionários pessoais.
Implementamos medidas de mitigação, como enableIMEPersonalizedLearning: false no Cwtch 1.2, mas a solução completa requer ações em nível de sistema operacional e é um desafio contínuo para a segurança móvel.
Servidor Cwtch.
O objetivo do protocolo Cwtch é permitir a comunicação em grupo através de infraestrutura não confiável .
Ao contrário dos esquemas baseados em retransmissão, onde os grupos atribuem um líder, um conjunto de líderes ou um servidor confiável de terceiros para garantir que cada membro do grupo possa enviar e receber mensagens em tempo hábil (mesmo que os membros estejam offline) - infraestrutura não confiável tem o objetivo de realizar essas propriedades sem a suposição de confiança.
O artigo original do Cwtch definia um conjunto de propriedades que se esperava que os servidores Cwtch fornecessem:
• O Cwtch Server pode ser usado por vários grupos ou apenas um.
• Um servidor Cwtch, sem a colaboração de um membro do grupo, nunca deve aprender a identidade dos participantes de um grupo.
• Um servidor Cwtch nunca deve aprender o conteúdo de qualquer comunicação.
• Um servidor Cwtch nunca deve ser capaz de distinguir mensagens como pertencentes a um grupo específico. Observamos aqui que essas propriedades são um superconjunto dos objetivos de design das estruturas de Recuperação de Informações Privadas.
Melhorias na Eficiência e Segurança
Eficiência do Protocolo
Atualmente, apenas um protocolo conhecido, o PIR ingênuo, atende às propriedades desejadas para garantir a privacidade na comunicação do grupo Cwtch. Este método tem um impacto direto na eficiência da largura de banda, especialmente para usuários em dispositivos móveis. Em resposta a isso, estamos ativamente desenvolvendo novos protocolos que permitem negociar garantias de privacidade e eficiência de maneiras diversas.
Os servidores, no momento desta escrita, permitem o download completo de todas as mensagens armazenadas, bem como uma solicitação para baixar mensagens específicas a partir de uma determinada mensagem. Quando os pares ingressam em um grupo em um novo servidor, eles baixam todas as mensagens do servidor inicialmente e, posteriormente, apenas as mensagens novas.
Mitigação de Análise de Metadados
Essa abordagem permite uma análise moderada de metadados, pois o servidor pode enviar novas mensagens para cada perfil suspeito exclusivo e usar essas assinaturas de mensagens exclusivas para rastrear sessões ao longo do tempo. Essa preocupação é mitigada por dois fatores:
- Os perfis podem atualizar suas conexões a qualquer momento, resultando em uma nova sessão do servidor.
- Os perfis podem ser "ressincronizados" de um servidor a qualquer momento, resultando em uma nova chamada para baixar todas as mensagens. Isso é comumente usado para buscar mensagens antigas de um grupo.
Embora essas medidas imponham limites ao que o servidor pode inferir, ainda não podemos garantir resistência total aos metadados. Para soluções futuras para esse problema, consulte Niwl.
Proteção contra Pares Maliciosos
Os servidores enfrentam o risco de spam gerado por pares, representando uma ameaça significativa à eficácia do sistema Cwtch. Embora tenhamos implementado um mecanismo de proteção contra spam no protótipo do Cwtch, exigindo que os pares realizem alguma prova de trabalho especificada pelo servidor, reconhecemos que essa não é uma solução robusta na presença de um adversário determinado com recursos significativos.
Pacotes de Chaves
Os servidores Cwtch se identificam por meio de pacotes de chaves assinados, contendo uma lista de chaves necessárias para garantir a segurança e resistência aos metadados na comunicação do grupo Cwtch. Esses pacotes de chaves geralmente incluem três chaves: uma chave pública do serviço Tor v3 Onion para o Token Board, uma chave pública do Tor v3 Onion Service para o Token Service e uma chave pública do Privacy Pass.
Para verificar os pacotes de chaves, os perfis que os importam do servidor utilizam o algoritmo trust-on-first-use (TOFU), verificando a assinatura anexada e a existência de todos os tipos de chave. Se o perfil já tiver importado o pacote de chaves do servidor anteriormente, todas as chaves são consideradas iguais.
Configuração prévia do aplicativo para ativar o Relé do Cwtch.
No Android, a hospedagem de servidor não está habilitada, pois essa opção não está disponível devido às limitações dos dispositivos Android. Essa funcionalidade está reservada apenas para servidores hospedados em desktops.
No Android, a única forma direta de importar uma chave de servidor é através do grupo de teste Cwtch, garantindo assim acesso ao servidor Cwtch.
Primeiro passo é Habilitar a opção de grupo no Cwtch que está em fase de testes. Clique na opção no canto superior direito da tela de configuração e pressione o botão para acessar as configurações do Cwtch.
Você pode alterar o idioma para Português do Brasil.Depois, role para baixo e selecione a opção para ativar os experimentos. Em seguida, ative a opção para habilitar o chat em grupo e a pré-visualização de imagens e fotos de perfil, permitindo que você troque sua foto de perfil.
https://link.storjshare.io/raw/jvss6zxle26jdguwaegtjdixhfka/production/f0ca039733d48895001261ab25c5d2efbaf3bf26e55aad3cce406646f9af9d15.MP4
Próximo passo é Criar um perfil.
Pressione o + botão de ação no canto inferior direito e selecione "Novo perfil" ou aberta no botão + adicionar novo perfil.
-
Selecione um nome de exibição
-
Selecione se deseja proteger
este perfil e salvo localmente com criptografia forte: Senha: sua conta está protegida de outras pessoas que possam usar este dispositivo
Sem senha: qualquer pessoa que tenha acesso a este dispositivo poderá acessar este perfil.
Preencha sua senha e digite-a novamente
Os perfis são armazenados localmente no disco e criptografados usando uma chave derivada de uma senha conhecida pelo usuário (via pbkdf2).
Observe que, uma vez criptografado e armazenado em disco, a única maneira de recuperar um perfil é recuperando a chave da senha - como tal, não é possível fornecer uma lista completa de perfis aos quais um usuário pode ter acesso até inserir um senha.
https://link.storjshare.io/raw/jxqbqmur2lcqe2eym5thgz4so2ya/production/8f9df1372ec7e659180609afa48be22b12109ae5e1eda9ef1dc05c1325652507.MP4
O próximo passo é adicionar o FuzzBot, que é um bot de testes e de desenvolvimento.
Contato do FuzzBot: 4y2hxlxqzautabituedksnh2ulcgm2coqbure6wvfpg4gi2ci25ta5ad.
Ao enviar o comando "testgroup-invite" para o FuzzBot, você receberá um convite para entrar no Grupo Cwtch Test. Ao ingressar no grupo, você será automaticamente conectado ao servidor Cwtch. Você pode optar por sair do grupo a qualquer momento ou ficar para conversar e tirar dúvidas sobre o aplicativo e outros assuntos. Depois, você pode configurar seu próprio servidor Cwtch, o que é altamente recomendável.
https://link.storjshare.io/raw/jvji25zclkoqcouni5decle7if7a/production/ee3de3540a3e3dca6e6e26d303e12c2ef892a5d7769029275b8b95ffc7468780.MP4
Agora você pode utilizar o aplicativo normalmente. Algumas observações que notei: se houver demora na conexão com outra pessoa, ambas devem estar online. Se ainda assim a conexão não for estabelecida, basta clicar no ícone de reset do Tor para restabelecer a conexão com a outra pessoa.
Uma introdução aos perfis Cwtch.
Com Cwtch você pode criar um ou mais perfis . Cada perfil gera um par de chaves ed25519 aleatório compatível com a Rede Tor.
Este é o identificador que você pode fornecer às pessoas e que elas podem usar para entrar em contato com você via Cwtch.
Cwtch permite criar e gerenciar vários perfis separados. Cada perfil está associado a um par de chaves diferente que inicia um serviço cebola diferente.
Gerenciar Na inicialização, o Cwtch abrirá a tela Gerenciar Perfis. Nessa tela você pode:
- Crie um novo perfil.
- Desbloquear perfis.
- Criptografados existentes.
- Gerenciar perfis carregados.
- Alterando o nome de exibição de um perfil.
- Alterando a senha de um perfil Excluindo um perfil.
- Alterando uma imagem de perfil.
Backup ou exportação de um perfil.
Na tela de gerenciamento de perfil:
-
Selecione o lápis ao lado do perfil que você deseja editar
-
Role para baixo até a parte inferior da tela.
-
Selecione "Exportar perfil"
-
Escolha um local e um nome de arquivo.
5.confirme.
Uma vez confirmado, o Cwtch colocará uma cópia do perfil no local indicado. Este arquivo é criptografado no mesmo nível do perfil.
Este arquivo pode ser importado para outra instância do Cwtch em qualquer dispositivo.
Importando um perfil.
-
Pressione o +botão de ação no canto inferior direito e selecione "Importar perfil"
-
Selecione um arquivo de perfil Cwtch exportado para importar
-
Digite a senha associada ao perfil e confirme.
Uma vez confirmado, o Cwtch tentará descriptografar o arquivo fornecido usando uma chave derivada da senha fornecida. Se for bem-sucedido, o perfil aparecerá na tela Gerenciamento de perfil e estará pronto para uso.
OBSERVAÇÃO Embora um perfil possa ser importado para vários dispositivos, atualmente apenas uma versão de um perfil pode ser usada em todos os dispositivos ao mesmo tempo. As tentativas de usar o mesmo perfil em vários dispositivos podem resultar em problemas de disponibilidade e falhas de mensagens.
Qual é a diferença entre uma conexão ponto a ponto e um grupo cwtch?
As conexões ponto a ponto Cwtch permitem que 2 pessoas troquem mensagens diretamente. As conexões ponto a ponto nos bastidores usam serviços cebola Tor v3 para fornecer uma conexão criptografada e resistente a metadados. Devido a esta conexão direta, ambas as partes precisam estar online ao mesmo tempo para trocar mensagens.
Os Grupos Cwtch permitem que várias partes participem de uma única conversa usando um servidor não confiável (que pode ser fornecido por terceiros ou auto-hospedado). Os operadores de servidores não conseguem saber quantas pessoas estão em um grupo ou o que está sendo discutido. Se vários grupos estiverem hospedados em um único servidor, o servidor não conseguirá saber quais mensagens pertencem a qual grupo sem a conivência de um membro do grupo. Ao contrário das conversas entre pares, as conversas em grupo podem ser conduzidas de forma assíncrona, para que todos num grupo não precisem estar online ao mesmo tempo.
Por que os grupos cwtch são experimentais? Mensagens em grupo resistentes a metadados ainda são um problema em aberto . Embora a versão que fornecemos no Cwtch Beta seja projetada para ser segura e com metadados privados, ela é bastante ineficiente e pode ser mal utilizada. Como tal, aconselhamos cautela ao usá-lo e apenas o fornecemos como um recurso opcional.
Como posso executar meu próprio servidor Cwtch? A implementação de referência para um servidor Cwtch é de código aberto . Qualquer pessoa pode executar um servidor Cwtch, e qualquer pessoa com uma cópia do pacote de chaves públicas do servidor pode hospedar grupos nesse servidor sem que o operador tenha acesso aos metadados relacionados ao grupo .
https://git.openprivacy.ca/cwtch.im/server
https://docs.openprivacy.ca/cwtch-security-handbook/server.html
Como posso desligar o Cwtch? O painel frontal do aplicativo possui um ícone do botão "Shutdown Cwtch" (com um 'X'). Pressionar este botão irá acionar uma caixa de diálogo e, na confirmação, o Cwtch será desligado e todos os perfis serão descarregados.
Suas doações podem fazer a diferença no projeto Cwtch? O Cwtch é um projeto dedicado a construir aplicativos que preservam a privacidade, oferecendo comunicação de grupo resistente a metadados. Além disso, o projeto também desenvolve o Cofre, formulários da web criptografados para ajudar mútua segura. Suas contribuições apoiam iniciativas importantes, como a divulgação de violações de dados médicos em Vancouver e pesquisas sobre a segurança do voto eletrônico na Suíça. Ao doar, você está ajudando a fechar o ciclo, trabalhando com comunidades marginalizadas para identificar e corrigir lacunas de privacidade. Além disso, o projeto trabalha em soluções inovadoras, como a quebra de segredos através da criptografia de limite para proteger sua privacidade durante passagens de fronteira. E também tem a infraestrutura: toda nossa infraestrutura é open source e sem fins lucrativos. Conheça também o Fuzzytags, uma estrutura criptográfica probabilística para marcação resistente a metadados. Sua doação é crucial para continuar o trabalho em prol da privacidade e segurança online. Contribua agora com sua doação
https://openprivacy.ca/donate/
onde você pode fazer sua doação em bitcoin e outras moedas, e saiba mais sobre os projetos. https://openprivacy.ca/work/
Link sobre Cwtch
https://cwtch.im/
https://git.openprivacy.ca/cwtch.im/cwtch
https://docs.cwtch.im/docs/intro
https://docs.openprivacy.ca/cwtch-security-handbook/
Baixar #CwtchDev
cwtch.im/download/
https://play.google.com/store/apps/details?id=im.cwtch.flwtch
-
 @ a95c6243:d345522c
2024-11-08 20:02:32
@ a95c6243:d345522c
2024-11-08 20:02:32Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister EckhartSchwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung, der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
Mit einem bemerkenswerten Timing hat die deutsche Regierungskoalition am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer Selbsthypnose rund um Harris-Hype und Trump-Panik – mit teils erschreckenden Auswüchsen. Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
Das Kindergarten-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik «vorsätzlich herbeigeführt» worden seien.
Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen. Verkehrs- und Digitalminister Wissing trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit Jörg Kukies habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP, hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können. Das ging erst kürzlich aus dem diesjährigen «Freiheitsindex» hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
«Die absolute Mehrheit hat absolut die Nase voll», titelte die Bild angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat, kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei Manova. Und er kenne Friedrich Merz schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
Was also tun? Der Schweizer Verein «Losdemokratie» will eine Volksinitiative lancieren, um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
In jedem Fall wird es notwendig sein, unsere Bemühungen um Freiheit und Selbstbestimmung zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c8841c9d:ae8048e2
2025-01-05 21:33:57
@ c8841c9d:ae8048e2
2025-01-05 21:33:57Ever wondered how to navigate the vast world of cryptocurrency without getting lost?
Welcome to our exploration of the crypto and blockchain world! Today, we're going to start learning together about the complex universe of cryptocurrency using mind maps, which will facilitate our understanding of this fascinating technology.
This post aims to highlight the importance of learning to acquire competence in cryptocurrency, focusing on intellectual enlightenment rather than the mere hope of gains. (Although wisely used knowledge can indeed lead to gains.)
To illustrate our journey, here's a representation inspired by the Dunning-Kruger Effect, showing the typical path of learning in any complex field, including crypto.
Reaching the Zenith of Mastery is a long road! My goal is to provide tools to minimize the falls in the ravine and make the Ascent of Knowledge easier! We are on this journey together, and I hope our interactions will be mutually beneficial.
Cryptocurrency is more than digital money; it's a new way of thinking about the world. want to contribute to the wider distribution of knowledge about this revolutionary technology. It took me almost two years to gain enough competence and confidence to publish my first post and I'm excited to start.
I will be posting, both on X and Nostr to keep the knowledge decentralized, crypto mind maps to visualize the cryptocurrency learning journey, from the basics to the most advanced topics. Keep an eye out for #cryptomindmap!
-
 @ 3f770d65:7a745b24
2025-01-05 18:56:33
@ 3f770d65:7a745b24
2025-01-05 18:56:33New Year’s resolutions often feel boring and repetitive. Most revolve around getting in shape, eating healthier, or giving up alcohol. While the idea is interesting—using the start of a new calendar year as a catalyst for change—it also seems unnecessary. Why wait for a specific date to make a change? If you want to improve something in your life, you can just do it. You don’t need an excuse.
That’s why I’ve never been drawn to the idea of making a list of resolutions. If I wanted a change, I’d make it happen, without worrying about the calendar. At least, that’s how I felt until now—when, for once, the timing actually gave me a real reason to embrace the idea of New Year’s resolutions.
Enter Olas.
If you're a visual creator, you've likely experienced the relentless grind of building a following on platforms like Instagram—endless doomscrolling, ever-changing algorithms, and the constant pressure to stay relevant. But what if there was a better way? Olas is a Nostr-powered alternative to Instagram that prioritizes community, creativity, and value-for-value exchanges. It's a game changer.
Instagram’s failings are well-known. Its algorithm often dictates whose content gets seen, leaving creators frustrated and powerless. Monetization hurdles further alienate creators who are forced to meet arbitrary follower thresholds before earning anything. Additionally, the platform’s design fosters endless comparisons and exposure to negativity, which can take a significant toll on mental health.
Instagram’s algorithms are notorious for keeping users hooked, often at the cost of their mental health. I've spoken about this extensively, most recently at Nostr Valley, explaining how legacy social media is bad for you. You might find yourself scrolling through content that leaves you feeling anxious or drained. Olas takes a fresh approach, replacing "doomscrolling" with "bloomscrolling." This is a common theme across the Nostr ecosystem. The lack of addictive rage algorithms allows the focus to shift to uplifting, positive content that inspires rather than exhausts.
Monetization is another area where Olas will set itself apart. On Instagram, creators face arbitrary barriers to earning—needing thousands of followers and adhering to restrictive platform rules. Olas eliminates these hurdles by leveraging the Nostr protocol, enabling creators to earn directly through value-for-value exchanges. Fans can support their favorite artists instantly, with no delays or approvals required. The plan is to enable a brand new Olas account that can get paid instantly, with zero followers - that's wild.
Olas addresses these issues head-on. Operating on the open Nostr protocol, it removes centralized control over one's content’s reach or one's ability to monetize. With transparent, configurable algorithms, and a community that thrives on mutual support, Olas creates an environment where creators can grow and succeed without unnecessary barriers.
Join me on my New Year's resolution. Join me on Olas and take part in the #Olas365 challenge! It’s a simple yet exciting way to share your content. The challenge is straightforward: post at least one photo per day on Olas (though you’re welcome to share more!).
Download on Android or download via Zapstore.
Let's make waves together.
-
 @ 6e468422:15deee93
2024-12-21 19:25:26
@ 6e468422:15deee93
2024-12-21 19:25:26We didn't hear them land on earth, nor did we see them. The spores were not visible to the naked eye. Like dust particles, they softly fell, unhindered, through our atmosphere, covering the earth. It took us a while to realize that something extraordinary was happening on our planet. In most places, the mushrooms didn't grow at all. The conditions weren't right. In some places—mostly rocky places—they grew large enough to be noticeable. People all over the world posted pictures online. "White eggs," they called them. It took a bit until botanists and mycologists took note. Most didn't realize that we were dealing with a species unknown to us.
We aren't sure who sent them. We aren't even sure if there is a "who" behind the spores. But once the first portals opened up, we learned that these mushrooms aren't just a quirk of biology. The portals were small at first—minuscule, even. Like a pinhole camera, we were able to glimpse through, but we couldn't make out much. We were only able to see colors and textures if the conditions were right. We weren't sure what we were looking at.
We still don't understand why some mushrooms open up, and some don't. Most don't. What we do know is that they like colder climates and high elevations. What we also know is that the portals don't stay open for long. Like all mushrooms, the flush only lasts for a week or two. When a portal opens, it looks like the mushroom is eating a hole into itself at first. But the hole grows, and what starts as a shimmer behind a grey film turns into a clear picture as the egg ripens. When conditions are right, portals will remain stable for up to three days. Once the fruit withers, the portal closes, and the mushroom decays.
The eggs grew bigger year over year. And with it, the portals. Soon enough, the portals were big enough to stick your finger through. And that's when things started to get weird...
-
 @ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08
@ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08Tldr
- Nostr is an open and interoperable protocol
- You can integrate it with workflow automation tools to augment your experience
- n8n is a great low/no-code workflow automation tool which you can host yourself
- Nostrobots allows you to integrate Nostr into n8n
- In this blog I create some workflow automations for Nostr
- A simple form to delegate posting notes
- Push notifications for mentions on multiple accounts
- Push notifications for your favourite accounts when they post a note
- All workflows are provided as open source with MIT license for you to use
Inter-op All The Things
Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In Using NFC Cards with Nostr I explored the
nostr:URI to launch Nostr clients from a card tap.The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails.
My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted.
This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull.
So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications.
All we need are simple ways to plug things together.
Nostr and Workflow Automation
Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective.
n8n for workflow automation
Many workflow automation tools exist. My favourite is n8n. n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to.
Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine.
Eating my own dogfood
It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do?
In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting.
I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up.
Running n8n with Nostrobots
I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs my HAVEN Nostr Relay and Albyhub Lightning Node in Docker containers,
- My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows.
Installing n8n
Self-hosting n8n could not be easier. I followed n8n's Docker-Compose installation docs–
- Install Docker and Docker-Compose if you haven't already,
- Create your
docker-compose.ymland.envfiles from the docs, - Create your data folder
sudo docker volume create n8n_data, - Start your container with
sudo docker compose up -d, - Your n8n instance should be online at port
5678.
n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there.
Installing Nostrobots
To integrate n8n nicely with Nostr, I used the Nostrobots community node by Ocknamo.
In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in.
You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative).
To install a community node, see n8n community node docs. From your workflow dashboard–
- Click the "..." in the bottom left corner beside your username, and click "settings",
- Cilck "community nodes" left sidebar,
- Click "Install",
- Enter the "npm Package Name" which is
n8n-nodes-nostrobots, - Accept the risks and click "Install",
- Nostrobots is now added to your n8n instance.
Using Nostrobots
Nostrobots gives you nodes to help you build Nostr-integrated workflows–
- Nostr Write – for posting Notes to the Nostr network,
- Nostr Read – for reading Notes from the Nostr network, and
- Nostr Utils – for performing certain conversions you may need (e.g. from bech32 to hex).
Nostrobots has good documentation on each node which focuses on simple use cases.
Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use.
What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible.
Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with NIP-01). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of.
Creating and adding workflows
With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation.
- Click "Add workflow" to go to the workflow builder screen,
- If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added,
- If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article).
Nostr Workflow Automations
It's time to build some things!
A simple form to post a note to Nostr
I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily.
I needed a basic form with credentials that posted a Note.
For this I can use a very simple workflow–
- A n8n Form node – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted.
- A Set node – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain.
- A Nostr Write node (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays.
Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive".
It may also be the world's simplest Nostr client.
You can find the Nostr Form to Post a Note workflow here.
Push notifications on mentions and new notes
One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want–
- To make sure I never miss a note addressed to any of my Npubs – For this I want a push notification any time any Nostr user mentions any of my Npubs,
- To make sure I always see all notes from key accounts – For this I need a push notification any time any of my Npubs post any Notes to the network,
- To get these notifications on all of my devices – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day.
I needed to build a Nostr push notifications solution.
To build this workflow I had to string a few ideas together–
- Triggering the node on a schedule – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited,
- Storing a list of Npubs in a Nostr list – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists (NIP-51, kind 30000). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. Listr.lol or Nostrudel.ninja). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions,
- Using specific relays – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata,
- Querying Nostr events (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do–
- I read the EventID of my Kind 30000 list, to return the desired pubkeys,
- For notifications on mentions, I read all Kind 1 notes that mention that pubkey,
- For notifications on new notes, I read all Kind 1 notes published by that pubkey,
- Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub,
- I transform the EventID into a Nevent to help clients find it.
- Using the Nostr URI – As I did with my NFC card article, I created a link with the
nostr:URI prefix so that my phone's native client opens the link by default, - Push notifications solution – I needed a push notifications solution. I found many with n8n integrations and chose to go with Pushover which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license.
Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go.
You can find the Nostr Push Notification If Mentioned here and If Posts a Note here.
In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible.
Use my workflows
I have open sourced all my workflows at my Github with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use.
To import any of my workflows–
- Click on the workflow of your choice, e.g. "Nostr_Push_Notify_If_Mentioned.json",
- Click on the "raw" button to view the raw JSON, ex any Github page layout,
- Copy that URL,
- Enter that URL in the "import from URL" dialog mentioned above.
To configure them–
- Prerequisites, credentials, and variables are all stated,
- In general any variables required are entered into a Set Node that follows the trigger node,
- Pushover has some extra setup but is very straightforward and documented in the workflow.
What next?
Over my first four blogs I explored creating a good Nostr setup with Vanity Npub, Lightning Payments, Nostr Addresses at Your Domain, and Personal Nostr Relay.
Then in my latest two blogs I explored different types of interoperability with NFC cards and now n8n Workflow Automation.
Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this:
- Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds),
- Automated or scheduled posting (such as auto-liking everything Lyn Alden posts),
- Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming),
- All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr,
- All kinds of other automation (such as BlackCoffee controlling a coffee machine),
- All kinds of AI Assistants and Agents,
In fact I have already released an open source workflow for an AI Assistant, and will share more about that in my next blog.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ fd208ee8:0fd927c1
2024-12-20 06:58:48
@ fd208ee8:0fd927c1
2024-12-20 06:58:48When the shit just don't work
Most open-source software is now so badly written and sloppily-maintained, that it's malware.
That's why the governments are getting involved. They try using OS, to save money and improve quality (and to market themselves as "hip"), and then it blows up their system or opens them up to hackers.
Now, they're pissed and want support (but the dev with the handle SucksToBeYou has disappeared) or someone to sue, but most OS projects have no identifiable entity behind them. Even well-known anon devs are often groups of anons or accounts that change hands.
The software cracks have moved on
There is simply no evidence that OS alone produces higher-quality software. The reason it seemed that way, at the beginning, was because of the caliber of the developers working on the projects, and the limited number of projects. This resulted in experienced people actively reviewing each others' code.
OS used to be something the elite engaged in, but it's mostly beginners practicing in public, now. That's why there are now millions of OS projects, happily offered for free, but almost all of them are garbage. The people now building OS usually aren't capable of reviewing other people's code, and they're producing worse products than ChatGPT could. Their software has no customers because it has no market value.
If everything is OS, then nothing is.
Another paradigm-changer is that all software is de facto OS, now that we can quickly reverse-engineer code with AI. That means the focus is no longer on OS/not-OS, but on the accountability and reputation of the builders.
It is, once again, a question of trust. We have come full-circle.
-
 @ 7ed7d5c3:6927e200
2024-12-18 00:56:48
@ 7ed7d5c3:6927e200
2024-12-18 00:56:48There was a time when we dared not rustle a whisper. But now we write and read samizdat and, congregating in the smoking rooms of research institutes, heartily complain to each other of all they are muddling up, of all they are dragging us into! There’s that unnecessary bravado around our ventures into space, against the backdrop of ruin and poverty at home; and the buttressing of distant savage regimes; and the kindling of civil wars; and the ill-thought-out cultivation of Mao Zedong (at our expense to boot)—in the end we’ll be the ones sent out against him, and we’ll have to go, what other option will there be? And they put whomever they want on trial, and brand the healthy as mentally ill—and it is always “they,” while we are—helpless.
We are approaching the brink; already a universal spiritual demise is upon us; a physical one is about to flare up and engulf us and our children, while we continue to smile sheepishly and babble:
“But what can we do to stop it? We haven’t the strength.”
We have so hopelessly ceded our humanity that for the modest handouts of today we are ready to surrender up all principles, our soul, all the labors of our ancestors, all the prospects of our descendants—anything to avoid disrupting our meager existence. We have lost our strength, our pride, our passion. We do not even fear a common nuclear death, do not fear a third world war (perhaps we’ll hide away in some crevice), but fear only to take a civic stance! We hope only not to stray from the herd, not to set out on our own, and risk suddenly having to make do without the white bread, the hot water heater, a Moscow residency permit.
We have internalized well the lessons drummed into us by the state; we are forever content and comfortable with its premise: we cannot escape the environment, the social conditions; they shape us, “being determines consciousness.” What have we to do with this? We can do nothing.
But we can do—everything!—even if we comfort and lie to ourselves that this is not so. It is not “they” who are guilty of everything, but we ourselves, only we!
Some will counter: But really, there is nothing to be done! Our mouths are gagged, no one listens to us, no one asks us. How can we make them listen to us?
To make them reconsider—is impossible.
The natural thing would be simply not to reelect them, but there are no re-elections in our country.
In the West they have strikes, protest marches, but we are too cowed, too scared: How does one just give up one’s job, just go out onto the street?
All the other fateful means resorted to over the last century of Russia’s bitter history are even less fitting for us today—true, let’s not fall back on them! Today, when all the axes have hewn what they hacked, when all that was sown has borne fruit, we can see how lost, how drugged were those conceited youths who sought, through terror, bloody uprising, and civil war, to make the country just and content. No thank you, fathers of enlightenment! We now know that the vileness of the means begets the vileness of the result. Let our hands be clean!
So has the circle closed? So is there indeed no way out? So the only thing left to do is wait inertly: What if something just happens by itself?
But it will never come unstuck by itself, if we all, every day, continue to acknowledge, glorify, and strengthen it, if we do not, at the least, recoil from its most vulnerable point.
From lies.
When violence bursts onto the peaceful human condition, its face is flush with self-assurance, it displays on its banner and proclaims: “I am Violence! Make way, step aside, I will crush you!” But violence ages swiftly, a few years pass—and it is no longer sure of itself. To prop itself up, to appear decent, it will without fail call forth its ally—Lies. For violence has nothing to cover itself with but lies, and lies can only persist through violence. And it is not every day and not on every shoulder that violence brings down its heavy hand: It demands of us only a submission to lies, a daily participation in deceit—and this suffices as our fealty.
And therein we find, neglected by us, the simplest, the most accessible key to our liberation: a personal nonparticipation in lies! Even if all is covered by lies, even if all is under their rule, let us resist in the smallest way: Let their rule hold not through me!
And this is the way to break out of the imaginary encirclement of our inertness, the easiest way for us and the most devastating for the lies. For when people renounce lies, lies simply cease to exist. Like parasites, they can only survive when attached to a person.
We are not called upon to step out onto the square and shout out the truth, to say out loud what we think—this is scary, we are not ready. But let us at least refuse to say what we do not think!
This is the way, then, the easiest and most accessible for us given our deep-seated organic cowardice, much easier than (it’s scary even to utter the words) civil disobedience à la Gandhi.
Our way must be: Never knowingly support lies! Having understood where the lies begin (and many see this line differently)—step back from that gangrenous edge! Let us not glue back the flaking scales of the Ideology, not gather back its crumbling bones, nor patch together its decomposing garb, and we will be amazed how swiftly and helplessly the lies will fall away, and that which is destined to be naked will be exposed as such to the world.
And thus, overcoming our timidity, let each man choose: Will he remain a witting servant of the lies (needless to say, not due to natural predisposition, but in order to provide a living for the family, to rear the children in the spirit of lies!), or has the time come for him to stand straight as an honest man, worthy of the respect of his children and contemporaries? And from that day onward he:
· Will not write, sign, nor publish in any way, a single line distorting, so far as he can see, the truth;
· Will not utter such a line in private or in public conversation, nor read it from a crib sheet, nor speak it in the role of educator, canvasser, teacher, actor;
· Will not in painting, sculpture, photograph, technology, or music depict, support, or broadcast a single false thought, a single distortion of the truth as he discerns it;
· Will not cite in writing or in speech a single “guiding” quote for gratification, insurance, for his success at work, unless he fully shares the cited thought and believes that it fits the context precisely;
· Will not be forced to a demonstration or a rally if it runs counter to his desire and his will; will not take up and raise a banner or slogan in which he does not fully believe;
· Will not raise a hand in vote for a proposal which he does not sincerely support; will not vote openly or in secret ballot for a candidate whom he deems dubious or unworthy;
· Will not be impelled to a meeting where a forced and distorted discussion is expected to take place;
· Will at once walk out from a session, meeting, lecture, play, or film as soon as he hears the speaker utter a lie, ideological drivel, or shameless propaganda;
· Will not subscribe to, nor buy in retail, a newspaper or journal that distorts or hides the underlying facts.
This is by no means an exhaustive list of the possible and necessary ways of evading lies. But he who begins to cleanse himself will, with a cleansed eye, easily discern yet other opportunities.
Yes, at first it will not be fair. Someone will have to temporarily lose his job. For the young who seek to live by truth, this will at first severely complicate life, for their tests and quizzes, too, are stuffed with lies, and so choices will have to be made. But there is no loophole left for anyone who seeks to be honest: Not even for a day, not even in the safest technical occupations can he avoid even a single one of the listed choices—to be made in favor of either truth or lies, in favor of spiritual independence or spiritual servility. And as for him who lacks the courage to defend even his own soul: Let him not brag of his progressive views, boast of his status as an academician or a recognized artist, a distinguished citizen or general. Let him say to himself plainly: I am cattle, I am a coward, I seek only warmth and to eat my fill.
For us, who have grown staid over time, even this most moderate path of resistance will be not be easy to set out upon. But how much easier it is than self-immolation or even a hunger strike: Flames will not engulf your body, your eyes will not pop out from the heat, and your family will always have at least a piece of black bread to wash down with a glass of clear water.
Betrayed and deceived by us, did not a great European people—the Czechoslovaks—show us how one can stand down the tanks with bared chest alone, as long as inside it beats a worthy heart?
It will not be an easy path, perhaps, but it is the easiest among those that lie before us. Not an easy choice for the body, but the only one for the soul. No, not an easy path, but then we already have among us people, dozens even, who have for years abided by all these rules, who live by the truth.
And so: We need not be the first to set out on this path, Ours is but to join! The more of us set out together, the thicker our ranks, the easier and shorter will this path be for us all! If we become thousands—they will not cope, they will be unable to touch us. If we will grow to tens of thousands—we will not recognize our country!
But if we shrink away, then let us cease complaining that someone does not let us draw breath—we do it to ourselves! Let us then cower and hunker down, while our comrades the biologists bring closer the day when our thoughts can be read and our genes altered.
And if from this also we shrink away, then we are worthless, hopeless, and it is of us that Pushkin asks with scorn:
Why offer herds their liberation?
............................. Their heritage each generation
The yoke with jingles, and the whip.February 12, 1974
—translated from the Russian by Yermolai Solzhenitsyn
-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 7e538978:a5987ab6
2024-10-02 13:57:31
@ 7e538978:a5987ab6
2024-10-02 13:57:31Chain Duel, a fast paced PvP game that takes inspiration from the classic snake game and supercharges it with Bitcoin’s Lightning Network. Imagine battling another player for dominance in a race to collect blocks, where the length of your chain isn’t just a visual cue. It represents real, staked satoshis. The player with the most Proof of Work wins, but it’s not just about gameplay; it’s about the seamless integration of the Lightning Network and real-time payments.
But how does Chain Duel manage these instant transactions with such efficiency? That’s where LNbits comes in. LNbits, an open-source wallet and payment infrastructure, handles all in-game payments making it easy for developers to focus on gameplay while LNbits takes care of everything from microtransactions to automated splits for developers and designers. In this article, we’ll dive deep into how Chain Duel leverages LNbits to streamline in-game payments and how other developers can take advantage of this powerful toolset to build the future of Lightning-powered gaming.
Let’s explore how LNbits transforms payment processing and why it’s quickly becoming a must-have for game developers working in the Bitcoin space.
Overview of Chain Duel
Chain Duel is a unique Lightning Network-inspired game that reimagines the classic snake game with a competitive twist, integrating real-time payments. Two players face off in real-time, racing to "catch" blocks and extend their chains. Each block added to the chain represents Proof of Work, and the player with the most Proof of Work wins the duel. The stakes are high, as the game represents satoshis (small units of Bitcoin) as points, with the winner taking home the prize.
The game is designed to be Lightning-native, meaning all payments within Chain Duel are processed through the Lightning Network. This ensures fast payments, reducing latency and making gameplay smooth. With additional features like practice mode, tournaments and highscores, Chain Duel creates an engaging and competitive environment for Bitcoin enthusiasts and gamers alike.

One of the standout aspects of Chain Duel is its deeper integration with the Lightning Network even at a design level. For example, actual Bitcoin blocks can appear on screen during matches, offering bonus points when mined in sync with the game. The game’s current version, still in beta, has already drawn attention within the Bitcoin community, gaining momentum at conferences and with a growing user base through its social networks. With its innovative combination of gaming, the Lightning Network, and competitive play, Chain Duel offers a glimpse into the future of Lightning-based gaming.
How LNbits is Used in Chain Duel
Seamless Integration with LNbits
At the core of Chain Duel’s efficient payment processing is LNbits, which handles in-game transactions smoothly and reliably. Chain Duel uses the LNbits LNURL-pay and LNURL-withdraw extensions to manage payments and rewards between players. Before each match, players send satoshis using LNURL-pay, which generates a static QR code or link for making the payment. LNURL-pay allows users to attach a note to the payment, which Chain Duel creatively uses as a way to insert the player name in-game. The simplicity of LNURL-pay ensures that users can quickly and easily initiate games, with fresh invoices being issued for every game. When players win, LNURL-withdraw enables them to seamlessly pull their earnings from the game, providing a quick payout system.
These extensions make it easy for players to send and receive Bitcoin with minimal latency, fully leveraging the power of the Lightning Network for fast and low-cost payments. The flexibility of LNbits’ tools means that game developers don’t need to worry about building custom payment systems from scratch—they can rely on LNbits to handle all financial transactions with precision.
Lightning Tournaments
Chain Duel tournaments leverage LNbits and its LNURL extensions to create a seamless and efficient experience for players. In Chain Duel tournaments, LNbits plays a crucial role in managing the overall economics. LNbits facilitates the generation of LNURL QR codes that participants can scan to register quickly or withdraw their winnings. LNbits allows Chain Duel to automatically handle multiple registrations through LNURL-pay, enabling players to participate in the tournament without additional steps. The Lightning Network's speed ensures that these payments occur in real-time, reducing wait times and allowing for a smoother flow in-game.
Splitting Payments
LNbits further simplifies revenue-sharing within Chain Duel. This feature allows the game to automatically split the satoshis sent by players into different shares for the game’s developer, designer, and host. Each time a payment is made to join a match, LNbits is used to automattically pay each of the contributors, according to pre-defined rules. This automated process ensures that everyone involved in the development and running of the game gets their fair share without manual intervention or complex bookkeeping.
Nostr Integration
Chain Duel also integrates with Nostr, a decentralized protocol for social interactions. Players can join games using "Zaps", small tips or micropayments sent over the Lightning Network within the Nostr ecosystem. Through NIP-57, which enables Nostr clients to request Zap invoices, players can use LNURL-pay enabled Zaps to register in P2P matches, further enhancing the Chain Duel experience. By using Zaps as a way to register in-game, Chain Duel automates the process of fetching players' identity, creating a more competitive and social experience. Zaps are public on the Nostr network, further expanding Chain Duel's games social reach and community engagement.
Game and Payment Synchronization

One of the key reasons Chain Duel developers chose LNbits is its powerful API that connects directly with the game’s logic. LNbits allows the game to synchronize payments with gameplay in real-time, providing a seamless experience where payments are an integrated part of the gaming mechanics.
With LNbits managing both the payment process and the Lightning Network’s complex infrastructure, Chain Duel developers are free to concentrate on enhancing the competitive and Lightning Network-related aspects of the game. This division of tasks is essential for streamlining development while still providing an innovative in-game payment experience that is deeply integrated with the Bitcoin network.
LNbits proves to be an indispensable tool for Chain Duel, enabling smooth in-game transactions, real-time revenue sharing, and seamless integration with Nostr. For developers looking to build Lightning-powered games, LNbits offers a powerful suite of tools that handle everything from micropayments to payment distribution—ensuring that the game's focus remains on fun and competition rather than complex payment systems.
LNBits facilitating Education and Adoption
This system contributes to educating users on the power of the Lightning Network. Since Chain Duel directly involve real satoshis and LNURL for registration and rewards, players actively experience how Lightning can facilitate fast, cheap, and permissionless payments. By incorporating LNbits into Chain Duel, the game serves as an educational tool that introduces users to the benefits of the Lightning Network. Players gain direct experience using Lightning wallets and LNURL, helping them understand how these tools work in real-world scenarios. The near-instant nature of these payments showcases the power of Lightning in a practical context, highlighting its potential beyond just gaming. Players are encouraged to set up wallets, explore the Lightning ecosystem, and eventually become familiar with Bitcoin and Lightning technology. By integrating LNbits, Chain Duel transforms in-game payments into a learning opportunity, making Bitcoin and Lightning more approachable for users worldwide.
Tools for Developers
LNbits is a versatile, open-source platform designed to simplify and enhance Bitcoin Lightning Network wallet management. For developers, particularly those working on Lightning-native games like Chain Duel, LNbits offers an invaluable set of tools that allow for seamless integration of Lightning payments without the need to build complex custom solutions from scratch. LNbits is built on a modular and extensible architecture, enabling developers to easily add or create functionality suited to their project’s needs.
Extensible Architecture for Customization
At the core of LNbits is a simple yet powerful wallet system that developers can access across multiple devices. What makes LNbits stand out is its extensible nature—everything beyond the core functionality is implemented as an extension. This modular approach allows users to customize their LNbits installation by enabling or building extensions to suit specific use cases. This flexibility is perfect for developers who want to add Lightning-based services to their games or apps without modifying the core codebase.
- Extensions for Every Use Case
LNbits comes with a wide array of built-in extensions created by contributors, offering various services that can be plugged into your application. Some popular extensions include: - Faucets: Distribute small amounts of Bitcoin to users for testing or promotional purposes.
- Paylinks: Create shareable links for instant payments.
- Points-of-sale (PoS): Allow users to set up shareable payment terminals.
- Paywalls: Charge users to access content or services.
- Event tickets: Sell tickets for events directly via Lightning payments.
- Games and services: From dice games to jukeboxes, LNbits offers entertaining and functional tools.
These ready-made solutions can be adapted and used in different gaming scenarios, for example in Chain Duel, where LNURL extensions are used for in game payments. The extensibility ensures developers can focus on building engaging gameplay while LNbits handles payment flows.
Developer-Friendly Customization
LNbits isn't just a plug-and-play platform. Developers can extend its functionality even further by creating their own extensions, giving full control over how the wallet system is integrated into their games or apps. The architecture is designed to make it easy for developers to build on top of the platform, adding custom features for specific requirements.
Flexible Funding Source Management
LNbits also offers flexibility in terms of managing funding sources. Developers can easily connect LNbits to various Lightning Network node implementations, enabling seamless transitions between nodes or even different payment systems. This allows developers to switch underlying funding sources with minimal effort, making LNbits adaptable for games that may need to scale quickly or rely on different payment infrastructures over time.
A Lean Core System for Maximum Efficiency
Thanks to its modular architecture, LNbits maintains a lean core system. This reduces complexity and overhead, allowing developers to implement only the features they need. By avoiding bloated software, LNbits ensures faster transactions and less resource consumption, which is crucial in fast-paced environments like Chain Duel where speed and efficiency are paramount.
LNbits is designed with developers in mind, offering a suite of tools and a flexible infrastructure that makes integrating Bitcoin payments easy. Whether you’re developing games, apps, or any service that requires Lightning Network transactions, LNbits is a powerful, open-source solution that can be adapted to fit your project.
Conclusion
Chain Duel stands at the forefront of Lightning-powered gaming, combining the excitement of competitive PvP with the speed and efficiency of the Lightning Network. With LNbits handling all in-game payments, from microtransactions to automated revenue splits, developers can focus entirely on crafting an engaging gaming experience. LNbits’ powerful API and extensions make it easy to manage real-time payments, removing the complexity of building payment infrastructure from scratch.
LNbits isn’t just a payment tool — it’s a flexible, developer-friendly platform that can be adapted to any gaming model. Whether you're developing a fast-paced PvP game like Chain Duel or any project requiring seamless Lightning Network integration, LNbits provides the ideal solution for handling instant payments with minimal overhead.
For developers interested in pushing the boundaries of Lightning-powered gaming, Chain Duel is a great example of how LNbits can enhance your game, letting you focus on the fun while LNbits manages real-time transactions.
Find out more
Curious about how Lightning Network payments can power your next game? Explore the following:
- Learn more about Chain Duel: Chain Duel
- Learn how LNbits can simplify payment handling in your project: LNbits
- Dive into decentralized communication with Nostr: Nostr
- Extensions for Every Use Case
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ 554ab6fe:c6cbc27e
2025-01-18 18:49:25
@ 554ab6fe:c6cbc27e
2025-01-18 18:49:25Abstract
There is a growing body of evidence suggesting that depression is becoming a major health concern for the modern world. Given the multitude of stressors advanced civilization provides, people are increasingly ruminating over the past and future. These repetitive non-constructive thoughts provide stress both in the mind and physically manifest itself in our bodily systems, deteriorating our health on multiple fronts. Not only are cases of depression increasing, but many seem to be resistant to current forms of treatment. These treatments include both pharmaceutical and therapeutic methods. Clinicians need to begin taking a serious look at alternate forms of treatment so they can become more equipped to treat patients with depression. Mindfulness meditation is the practice of focusing one’s thoughts entirely on the body itself and trains the mind to forgo all other extraneous thoughts. This technique not only provides the body an immediate sensation of safety and relaxation, but trains the individual to have better control over repetitive unhealthy thoughts. The more frequent feeling of relaxation coupled with the ability to subdue one’s own rumination decreases the body’s activation of its defense protocols. These defenses, also known as the sympathetic nervous system, when activated too frequently can be extremely detrimental to one’s physical and mental health and is strongly correlated to stress and depression. Much research involving mindfulness meditation has shown that it increases one’s ability to have thought control and decreases sympathetic nervous system activity. This is coupled with a heightened awareness of one’s own body, leading to a general increase in self perception and wellbeing. Dramatically reducing the occurrence of stress and depression. The body of meditation research requires further attention. In particular, studies require more standardized forms of meditation methods and an improvement of experimental design to increase statistical significance. That being said, given the effect mindfulness meditation has on depression, it should be viewed as a potential replacement for the treatment of depression through antidepressants. Antidepressants have a large list of potential side effects, are at times shown to be no more effective than a placebo, and have no evidence of preventing depression once treatment has been terminated. Meditation being costless and side effect free, if truly effective, would be a far more ethical and responsible treatment methods for physicians and therapist to prescribe.
Introduction
This paper will review existing literature discussing meditation and its potentially remedial effects on depression. It will argue that by providing increased ability to control and recognize non-constructive thoughts, meditation can decrease stress, thereby helping individuals with clinical depression. It is projected that by 2020, depression will become the second most common mental health issue (Kenny & Williams, 2007). Collectively, stress and depression-related symptoms account for a majority of visits to primary care physicians (Greeson et al., 2018). These disorders have become extremely prevalent and are extremely costly for individuals and the entire health care system (Greeson et al., 2018). That being said, it has been shown that 40% of depression patients are resistant to current treatment methods (Kenny & Williams, 2007), demonstrating that the entire system of treating depression is largely wasteful and inefficient, placing an unnecessary burden on society. Therefore, it is crucial that alternative approaches to treatment are explored. When looking at potential treatment methods for depression, it is important to first consider the underlying causes.
Depression is a complex mental issue that can manifest itself in a variety of different ways, and can stem from a large number of causes. That being said, there appears to be a distinct connection between stress and depression. Researchers have found that repetitive, non-constructive thoughts can lead to depression, and that individuals with acute stress-induced behaviors and hormonal changes have very similar symptoms to those suffering from depression (Watkins, 2008; Kasala et al., 2014). These symptoms commonly include hypercortisolism, which is a rise in cortisol levels due to an increase in sympathetic nervous system activity. Hypercortisolism can lead to high blood pressure, impaired immune function by decreasing cytokine count, poor antibody response, high blood sugar, increased renal retention of sodium, to name a few (Spreng, 2000; Godbout & Glaser, 2006; Kasala et al., 2014). In short, it is a condition that is extremely detrimental to overall health. Neurologically speaking, the relationship between stress and depression can be attributed partly to atrophy of the hippocampus, which is caused by high levels of stress induced glucocorticoid release (Annells et al., 2016).
Modern life is full of stressful situations. People tend to spend large portions of their day ruminating over the past and forecasting for the future. Often, these thoughts bring about worry and regret. Human beings evolved with a “fight or flight” defense response regulated by the sympathetic nervous system in order to protect themselves from physical harm. In modern life, these physical threats are being replaced by mental threats brought upon by our own projections of the past and future (Kuchel & Kuchel, 1991). Not ruminating over such thoughts has been shown to decrease sympathetic nervous system activity (vanOyen Witvliet et al., 2011). There is also a relationship between general cognitive load, and increased sympathetic activity (Mizuno et al., 2011). Therefore, it is of no surprise that high levels of sympathetic nervous system activity is present in cases of major depression (Veith et al., 1994).
The author hypothesizes that treatment methods involving improved thought control can remove stressful thoughts, thereby reducing depressive symptoms. These changes in thought patterns will have an effect on increasing parasympathetic nervous system tone and related neurotransmitters, thereby drawing a link between the cognitive skill of removing unconstructive thoughts and the reduction of stress and depression. Alongside this, the general act of meditation causes the body to feel more relaxed and decreases the activation of the sympathetic nervous system, bringing cortisol to lower levels, which increases general health and well-being. These skills will prove not only applicable to patients for depression, but also to any individual suffering from repetitive non-constructive thoughts that hinder their daily function and worsen their bodily health. This paper, through the lens of existing literature, will explore the connection between meditation’s ability to improve thought control and its promise as a treatment for depression.
Mindfulness Meditation and the Skills Provided
This paper will primarily focus on one of many forms of meditation: mindfulness meditation. Mindfulness meditation is the practice of focusing attention on a single entity, such as one’s breath, in order to take attention away from other, potentially non-constructive thoughts (Wielgosz et al., 2019). Focusing on body and breath in a calm and accepting manner also provides the mind with a sense of safety (Esch, 2014). This technique allows an individual to have an increased awareness of their emotions, and greater control over their thoughts (Barnhofer et al., 2009). Meditation has been shown to increase brain plasticity in the regions used (Lazar et al., 2005). Given the existence of use-dependent brain plasticity, it can be presumed that as meditators use these techniques during their practice, they will also be more easily able to use them in everyday life (Giuliani et al., 2011; Esch, 2014). For example, attention regulation is related to the anterior cingulate cortex (ACC) which is shown to have an increased function in those who practice mindfulness meditation (Rubia, 2009; Hölzel et al., 2011; Lutz, Antoine,Jha, Amishi P.,Dunne, John D.,Saron, 2015). Not only do meditators have increased attention regulation, but they are capable of having greater control of removing irrelevant thoughts. These repetitive thoughts, in the case of depression, usually manifest themselves as negative thoughts regarding their mental condition, poor mood, lack of belief in themselves and an over analysis regarding the consequence and meaning of life events coupled with the expectation of negative outcomes (Watkins, 2008). This is supported by the evidence that alpha bands, which play a role in processing irrelevant information, are faster and significantly more present in those who commonly practice mindfulness meditation (Foxe & Snyder, 2011). Meditation also effects the right amygdala, which is related to the processing of emotions. Reducing depression through the use of SSRIs is partly done by the suppression of right amygdala activity. Those who meditate have reduced right amygdala activity during meditation, and a change in activity was also observed when the subject was no longer meditating (Annells et al., 2016). This indicates that meditation provides more adequate emotional control over incoming stressors, and can potentially act as a replacement for antidepressants. Meditation grants the general awareness and control of emotions, alleviating the body from feeling in danger while granting the individual the ability to recognize unhealthy ruminations and clear them from their thought stream.
The Physiologic Responses of Mindfulness Meditation
The benefit of thought control is evident when analyzing the result of experiments involving mindfulness meditation. Increases sympathetic nervous system activity is present within depression (Veith et al., 1994). Those who have increased mindfulness show decreased stress and a faster recovery from it (Greeson et al., 2018; Gamaiunova et al., 2019). In these individuals, there is a noticeable reduction in sympathetic activity and responsivity, coupled with an increase in parasympathetic nervous system tone (Hoffman et al., 1982; Esch, 2014). This means the body of a meditator shifts away from activating stressful, fight or flight systems, and relaxed state processes begin to dominate. Stress related neurotransmitters such as norepinephrine and cortisol are also shown to be less present in individuals that practice meditation (Esch et al., 2007; Esch, 2014). This also indicates that meditation has a general effect on physical health. As previously stated, high levels of cortisol have serious effects on bodily health; thus, lessening cortisol will provide general well-being, as well as the cognitive benefits discussed above. Chronic stress has been connected to lower acetylcholine levels. Interestingly enough, the breath of meditators has elevated nitric oxide levels. Presumably because there are higher levels of acetylcholine and morphine, which both increase the activity of oxide-producing enzymes (Esch, 2014). Dopamine is often related inversely to the presence of depression, and it too has been shown to increase amongst those who practice meditation (Dailly et al., 2004; Jung et al., 2010; Esch, 2014). It is also has been suggested that the increase in internalized attention during mediation, triggers activity in brain regions such as the left frontal cortex that are related to positive emotions (Rubia, 2009). This, coupled with the general health benefits of decreasing sympathetic activity and cortisol levels, is likely the reason why meditators often express a general higher satisfaction with their life and are more content (Esch et al., 2007). That being said, meditators also have a higher awareness of their own health. Meditators show an increase use of the ACC and insula, signifying that they have a greater means of modulating the self, alongside pain perception and anticipation. It is theorized that this increase in awareness grants the individual a sense of responsibility to improve their health (Esch, 2014). There is likely a feedback loops that occurs when one meditates: the individual decreases sympathetic nervous system activity, thereby increasing their health and wellbeing, while also gaining a higher perception of their health that results in further attention and improvement.
The Missing Component
Many metanalytical papers have attempted to synthesize the findings of mediation research. Many conclude, as this paper does, that the main neuronal mechanism of mindfulness generally involves: attention regulation of the body and mind, nonreactivity to experiences, and changes of self-perception (Hölzel et al., 2011; Esch, 2014; Wielgosz et al., 2019). Even though the effects on the autonomic nervous system are discussed, they are seemingly ignored as a key factor contributing to the higher quality of life and state of mind experienced by those that practice meditation. That being said, authors neglect to mention that there are two different arguments being put forth. The first is that people who meditate are, at that moment, putting themselves in a peaceful and quiet mindset that makes the body feel safe, thereby increasing parasympathetic nervous system activity (Esch, 2014). The second is that it is the skills learned from the meditation that allow for individuals to remove the unconstructive thoughts in the face of stressful situations, thereby preventing an increase in sympathetic nervous system activity. Of course, these two mechanisms may both occur, and perhaps due to the change in brain plasticity, the practices of stress relief during meditation aids the patient in using those same skill in everyday life. However, this distinction is key not only for general scientific understanding, but also for future research.
The existence of the two possible mechanisms suggests the need for further investigation. Researchers, rather than observing the improvement in self-reported depression scores, should be focusing on changes in autonomic nervous system changes. To differentiate between the two mechanisms, researchers should monitor autonomic nervous system activity during the act of meditation and after a series of prolonged practices. This type of experiment could ascertain whether or not the bulk of decrease in sympathetic nervous system activity and increase in parasympathetic nervous system activity occurs at the moment of meditation, or afterwards through the skills obtained. Perhaps the two systems change at different times, or the changes are evenly distributed across both events. Either way, this type of experiment seems necessary to gain a deeper understanding of the mechanisms involved in treating depression. Furthermore, these distinctions are important in determining which techniques of mindfulness meditation provide the best results.
Criticisms
A key criticism of meditation research is that the method of meditation used in the studies is not constant. There are many forms of meditation practiced around the world, and many have different purposes. The most traditional and commonly practiced forms of meditation involve focusing attention on a single thing, which makes the research of mindfulness meditation particularly difficult because many will consider a wide range of practices to fall under the classification of mindfulness meditation. Even in this paper, that focuses exclusively on mindfulness meditation research, papers were presented that consider Tai Chi as inclusive to that criteria (Esch et al., 2007). Given the coordination of movements and the need for an instructor, Tai Chi can hardly be classified as a means of training thought control. Nonetheless, that example is quite extreme and most mindfulness-based meditation research involves one of these 4 types: traditional meditation, meditation in a clinical setting, mindfulness in a transient state and mindfulness as a dispositional trait (Chiesa et al., 2014). Despite the similarities, these all have vast differences in terms of how the meditation is practiced. For example, traditional meditation is done alone, and a more silent environment helps an individual focus on their breath. In a clinical setting, researchers conduct mindfulness-based cognitive therapy (MBCT), in which the meditation is done in a group setting led by a teacher (Kenny & Williams, 2007). In this particular study of Kenny and Williams 2007, patients were also assigned homework of 1 hour of practice per day of yoga or meditation. Even though yoga is traditionally a physical form of mindfulness meditation, it is not in western cultures. In western cultures, Yoga becomes more a practice of listening to an instructor and stretching, which is not conducive to focusing solely on the breath. This highlights the difficulty of deciding whether or not the benefits of meditation come from the practice itself or the skills learned from it, since all of these studies use methods of meditation that vaguely resemble one another in practice. If all studies use different forms of meditation, then no matter how similar the results across studies are, there is no clear conclusion on the mechanism by which these changes occur. An obvious solution to this problem is to create a method of meditation that is traditionally used by all meditators, and to have many studies done all using the same method. Since it would be hard to mandate all researchers to use the same procedures, another option is to conduct more research on the meditators’ brain activity at the time of meditation. Perhaps these observations would shed more light on the neurological processes occurring during meditation, and these results would hopefully suggest which techniques provide the same types of skills and mental processes. That being said, it is also important for researchers to consider the mechanism by which the skills of thought control are brought about before the initiation of the experiment. Practices like Thai Chi and Yoga being from eastern cultures does not classify them as mindfulness meditation and effective procedures to promote thought control.
The conclusions of some experiments discussed in this paper need to be taken with skepticism. Many studies are conducted with small sample sizes (Kenny & Williams, 2007; Barnhofer et al., 2009; Kasala et al., 2014). There are even studies, such as the Kenny and Williams study in 2007 discussed above that do not have a control group or any other group to make a comparison to. They even allowed the patients to take their regular medications for their disorders. This, alongside the absence of a control group, makes it extremely difficult to scientifically show that the MBCT was the reason for the decrease in depression scores at all. While other studies had a well-constructed design, most studies that conduct a T-test or ANOVA in their analysis fail to show that their data is normally distributed (Kenny & Williams, 2007; Barnhofer et al., 2009; Greeson et al., 2018). A normal distribution of data is a key assumption for both of these commonly used statistical test, and without proper proof of normality, the results of these test are questionable at best. Sadly, much of scientific literature contains these forms of statistical errors (Halsey et al., 2015). Though these flaws are not present in all mindfulness meditation experiments, the use of these studies as concrete evidence of its effectiveness is rightfully scrutinized. Most studies tend to have similar results, which suggests that mindfulness meditation effects depression. Nonetheless, given the design flaws of experiments and inconsistency in meditation methods, these studies should be used more as an indicator of the existence of a relationship between mindfulness meditation and depression than evidence that such a relationship exists. Much more diligent and thorough work is required for there to be scientific validity, and the ability to claim that meditation is truly a useful method of treatment. To start, many of these experiments should be repeated with improvements to their design, such as including control groups and more consistent methods of mediation, in order to validate the significance of their p-values. This will provide much more statistically significant evidence suggesting that mindfulness meditation is the true cause of the alleviation of depressive symptoms.
Conclusion
Despite the lack of concrete evidence and methods, there is a case to adopt this practice sooner rather than later. Given most experiments involving mindfulness meditation and its effects on depression share similar results, it is reasonable to assume that there is some true effect mindfulness meditation has on alleviating the disorder. The aim of the physician should be to provide a patient that has emotional challenges the tools and skills needed to manage and subdue the unhealthy habits of thinking on their own. Traditionally, this method is through the use of pharmaceutical drugs that act to change brain chemistry. This is not only a costly expense on the individual, but there is growing evidence suggesting that many antidepressants are not much more effective than a placebo (Kirsch et al., 2002; Antonuccio et al., 2002). Not only that, but antidepressant have numerous negative long-term side effects, such as withdrawals, sexual problems, weight gain and becoming emotionally numb (Masand & Gupta, 2002; Cartwright et al., 2016). There is also no publish evidence to claim that antidepressants reduce the risk of depression once the treatment has ended (Annells et al., 2016). Therefore, antidepressants should not be thought of as a viable clinical solution in the long-run. Meditation on the other hand is completely free, and can be a useful practice in an individual’s personal life. Given its simplicity, it is also void of negative side effects, and in that sense is a much more ethical and risk-averse form of treatment from a clinical standpoint. Therefore, it is prudent that the scientific community give increased attention to meditation research, so that we can further understand its benefits and perfect its techniques, to potentially help all those who suffer from depression in a safe and cost-effective manner.
Works Cited
Annells S, Kho K & Bridge P (2016). Meditate don’t medicate: How medical imaging evidence supports the role of meditation in the treatment of depression. Radiography 22, e54–e58.
Antonuccio DO, Burns DD & Danton WG (2002). Antidepressants: A triumph of marketing over science? Prev Treat; DOI: 10.1037/1522-3736.5.1.525c.
Barnhofer T, Crane C, Hargus E, Amarasinghe M, Winder R & Williams JMG (2009). Mindfulness-based cognitive therapy as a treatment for chronic depression: A preliminary study. Behav Res Ther 47, 366–373.
Cartwright C, Gibson K, Read J, Cowan O & Dehar T (2016). Long-term antidepressant use: patient perspectives of benefits and adverse effects. Patient Prefer Adherence 10, 1401–1407.
Chiesa A, Anselmi R & Serretti A (2014). Psychological Mechanisms of Mindfulness-Based Interventions. Holist Nurs Pract 28, 124–148.
Dailly E, Chenu F, Renard CE & Bourin M (2004). Dopamine, depression and antidepressants. Fundam Clin Pharmacol 18, 601–607.
Esch T (2014). The Neurobiology of Meditation and Mindfulness. In, pp. 153–173. Springer, Cham. Available at: http://link.springer.com/10.1007/978-3-319-01634-4_9 [Accessed October 1, 2019].
Esch T, Duckstein J, Welke J & Braun V (2007). Mind/body techniques for physiological and psychological stress reduction: stress management via Tai Chi training – a pilot study. Med Sci Monit 13, CR488-497.
Foxe JJ & Snyder AC (2011). The Role of Alpha-Band Brain Oscillations as a Sensory Suppression Mechanism during Selective Attention. Front Psychol 2, 154.
Gamaiunova L, Brandt P-Y, Bondolfi G & Kliegel M (2019). Exploration of psychological mechanisms of the reduced stress response in long-term meditation practitioners. Psychoneuroendocrinology 104, 143–151.
Giuliani NR, Drabant EM, Bhatnagar R & Gross JJ (2011). Emotion regulation and brain plasticity: Expressive suppression use predicts anterior insula volume. Neuroimage 58, 10–15.
Godbout JP & Glaser R (2006). Stress-Induced Immune Dysregulation: Implications for Wound Healing, Infectious Disease and Cancer. J Neuroimmune Pharmacol 1, 421–427.
Greeson JM, Zarrin H, Smoski MJ, Brantley JG, Lynch TR, Webber DM, Hall MH, Suarez EC & Wolever RQ (2018). Mindfulness Meditation Targets Transdiagnostic Symptoms Implicated in Stress-Related Disorders: Understanding Relationships between Changes in Mindfulness, Sleep Quality, and Physical Symptoms. Evidence-Based Complement Altern Med 2018, 1–10.
Halsey LG, Curran-Everett D, Vowler SL & Drummond GB (2015). The fickle P value generates irreproducible results. Nat Methods 12, 179–185.
Hoffman J, Benson H, Arns P, Stainbrook G, Landsberg G, Young J & Gill A (1982). Science. Science (80- ) 192, 1242–1244.
Hölzel BK, Lazar SW, Gard T, Schuman-Olivier Z, Vago DR & Ott U (2011). How Does Mindfulness Meditation Work? Proposing Mechanisms of Action From a Conceptual and Neural Perspective. Perspect Psychol Sci 6, 537–559.
Jung Y-H, Kang D-H, Jang JH, Park HY, Byun MS, Kwon SJ, Jang G-E, Lee US, An SC & Kwon JS (2010). The effects of mind–body training on stress reduction, positive affect, and plasma catecholamines. Neurosci Lett 479, 138–142.
Kasala ER, Bodduluru LN, Maneti Y & Thipparaboina R (2014). Effect of meditation on neurophysiological changes in stress mediated depression. Complement Ther Clin Pract 20, 74–80.
Kenny MA & Williams JMG (2007). Treatment-resistant depressed patients show a good response to Mindfulness-based Cognitive Therapy. Behav Res Ther 45, 617–625.
Kirsch I, Scoboria A & Moore TJ (2002). Antidepressants and placebos: Secrets, revelations, and unanswered questions. Prev Treat; DOI: 10.1037/1522-3736.5.1.533r.
Kuchel OG & Kuchel GA (1991). Peripheral dopamine in pathophysiology of hypertension. Interaction with aging and lifestyle. Hypertension 18, 709–721.
Lazar SW, Kerr CE, Wasserman RH, Gray JR, Greve DN, Treadway MT, McGarvey M, Quinn BT, Dusek JA, Benson H, Rauch SL, Moore CI & Fischl B (2005). Meditation experience is associated with increased cortical thickness. Neuroreport 16, 1893–1897.
Lutz, Antoine,Jha, Amishi P.,Dunne, John D.,Saron CD (2015). PsycNET. Am Psychol 70, 632–658.
Masand PS & Gupta S (2002). Long-Term Side Effects of Newer-Generation Antidepressants: SSRIS, Venlafaxine, Nefazodone, Bupropion, and Mirtazapine. Ann Clin Psychiatry 14, 175–182.
Mizuno K, Tanaka M, Yamaguti K, Kajimoto O, Kuratsune H & Watanabe Y (2011). Mental fatigue caused by prolonged cognitive load associated with sympathetic hyperactivity. Behav Brain Funct 7, 17.
Rubia K (2009). The neurobiology of Meditation and its clinical effectiveness in psychiatric disorders. Biol Psychol 82, 1–11.
Spreng M (2000). Possible health effects of noise induced cortisol increase. Noise Health 2, 59–64.
vanOyen Witvliet C, DeYoung NJ, Hofelich AJ & DeYoung PA (2011). Compassionate reappraisal and emotion suppression as alternatives to offense-focused rumination: Implications for forgiveness and psychophysiological well-being. J Posit Psychol 6, 286–299.
Veith RC, Lewis N, Linares OA, Barnes RF, Raskind MA, Villacres EC, Murburg MM, Ashleigh EA, Castillo S, Peskind ER, Pascualy M & Halter JB (1994). Sympathetic Nervous System Activity in Major Depression. Arch Gen Psychiatry 51, 411.
Watkins ER (2008). Constructive and unconstructive repetitive thought. Psychol Bull 134, 163–206.
Wielgosz J, Goldberg SB, Kral TRA, Dunne JD & Davidson RJ (2019). Mindfulness Meditation and Psychopathology. Annu Rev Clin Psychol 15, 285–316.
Abstract There is a growing body of evidence suggesting that depression is becoming a major health concern for the modern world. Given the multitude of stressors advanced civilization provides, people are increasingly ruminating over the past and future. These repetitive non-constructive thoughts provide stress both in the mind and physically manifest itself in our bodily systems, deteriorating our health on multiple fronts. Not only are cases of depression increasing, but many seem to be resistant to current forms of treatment. These treatments include both pharmaceutical and therapeutic methods. Clinicians need to begin taking a serious look at alternate forms of treatment so they can become more equipped to treat patients with depression. Mindfulness meditation is the practice of focusing one’s thoughts entirely on the body itself and trains the mind to forgo all other extraneous thoughts. This technique not only provides the body an immediate sensation of safety and relaxation, but trains the individual to have better control over repetitive unhealthy thoughts. The more frequent feeling of relaxation coupled with the ability to subdue one’s own rumination decreases the body’s activation of its defense protocols. These defenses, also known as the sympathetic nervous system, when activated too frequently can be extremely detrimental to one’s physical and mental health and is strongly correlated to stress and depression. Much research involving mindfulness meditation has shown that it increases one’s ability to have thought control and decreases sympathetic nervous system activity. This is coupled with a heightened awareness of one’s own body, leading to a general increase in self perception and wellbeing. Dramatically reducing the occurrence of stress and depression. The body of meditation research requires further attention. In particular, studies require more standardized forms of meditation methods and an improvement of experimental design to increase statistical significance. That being said, given the effect mindfulness meditation has on depression, it should be viewed as a potential replacement for the treatment of depression through antidepressants. Antidepressants have a large list of potential side effects, are at times shown to be no more effective than a placebo, and have no evidence of preventing depression once treatment has been terminated. Meditation being costless and side effect free, if truly effective, would be a far more ethical and responsible treatment methods for physicians and therapist to prescribe.
Introduction
This paper will review existing literature discussing meditation and its potentially remedial effects on depression. It will argue that by providing increased ability to control and recognize non-constructive thoughts, meditation can decrease stress, thereby helping individuals with clinical depression. It is projected that by 2020, depression will become the second most common mental health issue (Kenny & Williams, 2007). Collectively, stress and depression-related symptoms account for a majority of visits to primary care physicians (Greeson et al., 2018). These disorders have become extremely prevalent and are extremely costly for individuals and the entire health care system (Greeson et al., 2018). That being said, it has been shown that 40% of depression patients are resistant to current treatment methods (Kenny & Williams, 2007), demonstrating that the entire system of treating depression is largely wasteful and inefficient, placing an unnecessary burden on society. Therefore, it is crucial that alternative approaches to treatment are explored. When looking at potential treatment methods for depression, it is important to first consider the underlying causes.
Depression is a complex mental issue that can manifest itself in a variety of different ways, and can stem from a large number of causes. That being said, there appears to be a distinct connection between stress and depression. Researchers have found that repetitive, non-constructive thoughts can lead to depression, and that individuals with acute stress-induced behaviors and hormonal changes have very similar symptoms to those suffering from depression (Watkins, 2008; Kasala et al., 2014). These symptoms commonly include hypercortisolism, which is a rise in cortisol levels due to an increase in sympathetic nervous system activity. Hypercortisolism can lead to high blood pressure, impaired immune function by decreasing cytokine count, poor antibody response, high blood sugar, increased renal retention of sodium, to name a few (Spreng, 2000; Godbout & Glaser, 2006; Kasala et al., 2014). In short, it is a condition that is extremely detrimental to overall health. Neurologically speaking, the relationship between stress and depression can be attributed partly to atrophy of the hippocampus, which is caused by high levels of stress induced glucocorticoid release (Annells et al., 2016).
Modern life is full of stressful situations. People tend to spend large portions of their day ruminating over the past and forecasting for the future. Often, these thoughts bring about worry and regret. Human beings evolved with a “fight or flight” defense response regulated by the sympathetic nervous system in order to protect themselves from physical harm. In modern life, these physical threats are being replaced by mental threats brought upon by our own projections of the past and future (Kuchel & Kuchel, 1991). Not ruminating over such thoughts has been shown to decrease sympathetic nervous system activity (vanOyen Witvliet et al., 2011). There is also a relationship between general cognitive load, and increased sympathetic activity (Mizuno et al., 2011). Therefore, it is of no surprise that high levels of sympathetic nervous system activity is present in cases of major depression (Veith et al., 1994).
The author hypothesizes that treatment methods involving improved thought control can remove stressful thoughts, thereby reducing depressive symptoms. These changes in thought patterns will have an effect on increasing parasympathetic nervous system tone and related neurotransmitters, thereby drawing a link between the cognitive skill of removing unconstructive thoughts and the reduction of stress and depression. Alongside this, the general act of meditation causes the body to feel more relaxed and decreases the activation of the sympathetic nervous system, bringing cortisol to lower levels, which increases general health and well-being. These skills will prove not only applicable to patients for depression, but also to any individual suffering from repetitive non-constructive thoughts that hinder their daily function and worsen their bodily health. This paper, through the lens of existing literature, will explore the connection between meditation’s ability to improve thought control and its promise as a treatment for depression.
Mindfulness Meditation and the Skills Provided
This paper will primarily focus on one of many forms of meditation: mindfulness meditation. Mindfulness meditation is the practice of focusing attention on a single entity, such as one’s breath, in order to take attention away from other, potentially non-constructive thoughts (Wielgosz et al., 2019). Focusing on body and breath in a calm and accepting manner also provides the mind with a sense of safety (Esch, 2014). This technique allows an individual to have an increased awareness of their emotions, and greater control over their thoughts (Barnhofer et al., 2009). Meditation has been shown to increase brain plasticity in the regions used (Lazar et al., 2005). Given the existence of use-dependent brain plasticity, it can be presumed that as meditators use these techniques during their practice, they will also be more easily able to use them in everyday life (Giuliani et al., 2011; Esch, 2014). For example, attention regulation is related to the anterior cingulate cortex (ACC) which is shown to have an increased function in those who practice mindfulness meditation (Rubia, 2009; Hölzel et al., 2011; Lutz, Antoine,Jha, Amishi P.,Dunne, John D.,Saron, 2015). Not only do meditators have increased attention regulation, but they are capable of having greater control of removing irrelevant thoughts. These repetitive thoughts, in the case of depression, usually manifest themselves as negative thoughts regarding their mental condition, poor mood, lack of belief in themselves and an over analysis regarding the consequence and meaning of life events coupled with the expectation of negative outcomes (Watkins, 2008). This is supported by the evidence that alpha bands, which play a role in processing irrelevant information, are faster and significantly more present in those who commonly practice mindfulness meditation (Foxe & Snyder, 2011). Meditation also effects the right amygdala, which is related to the processing of emotions. Reducing depression through the use of SSRIs is partly done by the suppression of right amygdala activity. Those who meditate have reduced right amygdala activity during meditation, and a change in activity was also observed when the subject was no longer meditating (Annells et al., 2016). This indicates that meditation provides more adequate emotional control over incoming stressors, and can potentially act as a replacement for antidepressants. Meditation grants the general awareness and control of emotions, alleviating the body from feeling in danger while granting the individual the ability to recognize unhealthy ruminations and clear them from their thought stream.
The Physiologic Responses of Mindfulness Meditation
The benefit of thought control is evident when analyzing the result of experiments involving mindfulness meditation. Increases sympathetic nervous system activity is present within depression (Veith et al., 1994). Those who have increased mindfulness show decreased stress and a faster recovery from it (Greeson et al., 2018; Gamaiunova et al., 2019). In these individuals, there is a noticeable reduction in sympathetic activity and responsivity, coupled with an increase in parasympathetic nervous system tone (Hoffman et al., 1982; Esch, 2014). This means the body of a meditator shifts away from activating stressful, fight or flight systems, and relaxed state processes begin to dominate. Stress related neurotransmitters such as norepinephrine and cortisol are also shown to be less present in individuals that practice meditation (Esch et al., 2007; Esch, 2014). This also indicates that meditation has a general effect on physical health. As previously stated, high levels of cortisol have serious effects on bodily health; thus, lessening cortisol will provide general well-being, as well as the cognitive benefits discussed above. Chronic stress has been connected to lower acetylcholine levels. Interestingly enough, the breath of meditators has elevated nitric oxide levels. Presumably because there are higher levels of acetylcholine and morphine, which both increase the activity of oxide-producing enzymes (Esch, 2014). Dopamine is often related inversely to the presence of depression, and it too has been shown to increase amongst those who practice meditation (Dailly et al., 2004; Jung et al., 2010; Esch, 2014). It is also has been suggested that the increase in internalized attention during mediation, triggers activity in brain regions such as the left frontal cortex that are related to positive emotions (Rubia, 2009). This, coupled with the general health benefits of decreasing sympathetic activity and cortisol levels, is likely the reason why meditators often express a general higher satisfaction with their life and are more content (Esch et al., 2007). That being said, meditators also have a higher awareness of their own health. Meditators show an increase use of the ACC and insula, signifying that they have a greater means of modulating the self, alongside pain perception and anticipation. It is theorized that this increase in awareness grants the individual a sense of responsibility to improve their health (Esch, 2014). There is likely a feedback loops that occurs when one meditates: the individual decreases sympathetic nervous system activity, thereby increasing their health and wellbeing, while also gaining a higher perception of their health that results in further attention and improvement.
The Missing Component
Many metanalytical papers have attempted to synthesize the findings of mediation research. Many conclude, as this paper does, that the main neuronal mechanism of mindfulness generally involves: attention regulation of the body and mind, nonreactivity to experiences, and changes of self-perception (Hölzel et al., 2011; Esch, 2014; Wielgosz et al., 2019). Even though the effects on the autonomic nervous system are discussed, they are seemingly ignored as a key factor contributing to the higher quality of life and state of mind experienced by those that practice meditation. That being said, authors neglect to mention that there are two different arguments being put forth. The first is that people who meditate are, at that moment, putting themselves in a peaceful and quiet mindset that makes the body feel safe, thereby increasing parasympathetic nervous system activity (Esch, 2014). The second is that it is the skills learned from the meditation that allow for individuals to remove the unconstructive thoughts in the face of stressful situations, thereby preventing an increase in sympathetic nervous system activity. Of course, these two mechanisms may both occur, and perhaps due to the change in brain plasticity, the practices of stress relief during meditation aids the patient in using those same skill in everyday life. However, this distinction is key not only for general scientific understanding, but also for future research.
The existence of the two possible mechanisms suggests the need for further investigation. Researchers, rather than observing the improvement in self-reported depression scores, should be focusing on changes in autonomic nervous system changes. To differentiate between the two mechanisms, researchers should monitor autonomic nervous system activity during the act of meditation and after a series of prolonged practices. This type of experiment could ascertain whether or not the bulk of decrease in sympathetic nervous system activity and increase in parasympathetic nervous system activity occurs at the moment of meditation, or afterwards through the skills obtained. Perhaps the two systems change at different times, or the changes are evenly distributed across both events. Either way, this type of experiment seems necessary to gain a deeper understanding of the mechanisms involved in treating depression. Furthermore, these distinctions are important in determining which techniques of mindfulness meditation provide the best results.
Criticisms
A key criticism of meditation research is that the method of meditation used in the studies is not constant. There are many forms of meditation practiced around the world, and many have different purposes. The most traditional and commonly practiced forms of meditation involve focusing attention on a single thing, which makes the research of mindfulness meditation particularly difficult because many will consider a wide range of practices to fall under the classification of mindfulness meditation. Even in this paper, that focuses exclusively on mindfulness meditation research, papers were presented that consider Tai Chi as inclusive to that criteria (Esch et al., 2007). Given the coordination of movements and the need for an instructor, Tai Chi can hardly be classified as a means of training thought control. Nonetheless, that example is quite extreme and most mindfulness-based meditation research involves one of these 4 types: traditional meditation, meditation in a clinical setting, mindfulness in a transient state and mindfulness as a dispositional trait (Chiesa et al., 2014). Despite the similarities, these all have vast differences in terms of how the meditation is practiced. For example, traditional meditation is done alone, and a more silent environment helps an individual focus on their breath. In a clinical setting, researchers conduct mindfulness-based cognitive therapy (MBCT), in which the meditation is done in a group setting led by a teacher (Kenny & Williams, 2007). In this particular study of Kenny and Williams 2007, patients were also assigned homework of 1 hour of practice per day of yoga or meditation. Even though yoga is traditionally a physical form of mindfulness meditation, it is not in western cultures. In western cultures, Yoga becomes more a practice of listening to an instructor and stretching, which is not conducive to focusing solely on the breath. This highlights the difficulty of deciding whether or not the benefits of meditation come from the practice itself or the skills learned from it, since all of these studies use methods of meditation that vaguely resemble one another in practice. If all studies use different forms of meditation, then no matter how similar the results across studies are, there is no clear conclusion on the mechanism by which these changes occur. An obvious solution to this problem is to create a method of meditation that is traditionally used by all meditators, and to have many studies done all using the same method. Since it would be hard to mandate all researchers to use the same procedures, another option is to conduct more research on the meditators’ brain activity at the time of meditation. Perhaps these observations would shed more light on the neurological processes occurring during meditation, and these results would hopefully suggest which techniques provide the same types of skills and mental processes. That being said, it is also important for researchers to consider the mechanism by which the skills of thought control are brought about before the initiation of the experiment. Practices like Thai Chi and Yoga being from eastern cultures does not classify them as mindfulness meditation and effective procedures to promote thought control.
The conclusions of some experiments discussed in this paper need to be taken with skepticism. Many studies are conducted with small sample sizes (Kenny & Williams, 2007; Barnhofer et al., 2009; Kasala et al., 2014). There are even studies, such as the Kenny and Williams study in 2007 discussed above that do not have a control group or any other group to make a comparison to. They even allowed the patients to take their regular medications for their disorders. This, alongside the absence of a control group, makes it extremely difficult to scientifically show that the MBCT was the reason for the decrease in depression scores at all. While other studies had a well-constructed design, most studies that conduct a T-test or ANOVA in their analysis fail to show that their data is normally distributed (Kenny & Williams, 2007; Barnhofer et al., 2009; Greeson et al., 2018). A normal distribution of data is a key assumption for both of these commonly used statistical test, and without proper proof of normality, the results of these test are questionable at best. Sadly, much of scientific literature contains these forms of statistical errors (Halsey et al., 2015). Though these flaws are not present in all mindfulness meditation experiments, the use of these studies as concrete evidence of its effectiveness is rightfully scrutinized. Most studies tend to have similar results, which suggests that mindfulness meditation effects depression. Nonetheless, given the design flaws of experiments and inconsistency in meditation methods, these studies should be used more as an indicator of the existence of a relationship between mindfulness meditation and depression than evidence that such a relationship exists. Much more diligent and thorough work is required for there to be scientific validity, and the ability to claim that meditation is truly a useful method of treatment. To start, many of these experiments should be repeated with improvements to their design, such as including control groups and more consistent methods of mediation, in order to validate the significance of their p-values. This will provide much more statistically significant evidence suggesting that mindfulness meditation is the true cause of the alleviation of depressive symptoms.
Conclusion
Despite the lack of concrete evidence and methods, there is a case to adopt this practice sooner rather than later. Given most experiments involving mindfulness meditation and its effects on depression share similar results, it is reasonable to assume that there is some true effect mindfulness meditation has on alleviating the disorder. The aim of the physician should be to provide a patient that has emotional challenges the tools and skills needed to manage and subdue the unhealthy habits of thinking on their own. Traditionally, this method is through the use of pharmaceutical drugs that act to change brain chemistry. This is not only a costly expense on the individual, but there is growing evidence suggesting that many antidepressants are not much more effective than a placebo (Kirsch et al., 2002; Antonuccio et al., 2002). Not only that, but antidepressant have numerous negative long-term side effects, such as withdrawals, sexual problems, weight gain and becoming emotionally numb (Masand & Gupta, 2002; Cartwright et al., 2016). There is also no publish evidence to claim that antidepressants reduce the risk of depression once the treatment has ended (Annells et al., 2016). Therefore, antidepressants should not be thought of as a viable clinical solution in the long-run. Meditation on the other hand is completely free, and can be a useful practice in an individual’s personal life. Given its simplicity, it is also void of negative side effects, and in that sense is a much more ethical and risk-averse form of treatment from a clinical standpoint. Therefore, it is prudent that the scientific community give increased attention to meditation research, so that we can further understand its benefits and perfect its techniques, to potentially help all those who suffer from depression in a safe and cost-effective manner.
Works Cited
Annells S, Kho K & Bridge P (2016). Meditate don’t medicate: How medical imaging evidence supports the role of meditation in the treatment of depression. Radiography 22, e54–e58.
Antonuccio DO, Burns DD & Danton WG (2002). Antidepressants: A triumph of marketing over science? Prev Treat; DOI: 10.1037/1522-3736.5.1.525c.
Barnhofer T, Crane C, Hargus E, Amarasinghe M, Winder R & Williams JMG (2009). Mindfulness-based cognitive therapy as a treatment for chronic depression: A preliminary study. Behav Res Ther 47, 366–373.
Cartwright C, Gibson K, Read J, Cowan O & Dehar T (2016). Long-term antidepressant use: patient perspectives of benefits and adverse effects. Patient Prefer Adherence 10, 1401–1407.
Chiesa A, Anselmi R & Serretti A (2014). Psychological Mechanisms of Mindfulness-Based Interventions. Holist Nurs Pract 28, 124–148.
Dailly E, Chenu F, Renard CE & Bourin M (2004). Dopamine, depression and antidepressants. Fundam Clin Pharmacol 18, 601–607.
Esch T (2014). The Neurobiology of Meditation and Mindfulness. In, pp. 153–173. Springer, Cham. Available at: http://link.springer.com/10.1007/978-3-319-01634-4_9 [Accessed October 1, 2019].
Esch T, Duckstein J, Welke J & Braun V (2007). Mind/body techniques for physiological and psychological stress reduction: stress management via Tai Chi training – a pilot study. Med Sci Monit 13, CR488-497.
Foxe JJ & Snyder AC (2011). The Role of Alpha-Band Brain Oscillations as a Sensory Suppression Mechanism during Selective Attention. Front Psychol 2, 154.
Gamaiunova L, Brandt P-Y, Bondolfi G & Kliegel M (2019). Exploration of psychological mechanisms of the reduced stress response in long-term meditation practitioners. Psychoneuroendocrinology 104, 143–151.
Giuliani NR, Drabant EM, Bhatnagar R & Gross JJ (2011). Emotion regulation and brain plasticity: Expressive suppression use predicts anterior insula volume. Neuroimage 58, 10–15.
Godbout JP & Glaser R (2006). Stress-Induced Immune Dysregulation: Implications for Wound Healing, Infectious Disease and Cancer. J Neuroimmune Pharmacol 1, 421–427.
Greeson JM, Zarrin H, Smoski MJ, Brantley JG, Lynch TR, Webber DM, Hall MH, Suarez EC & Wolever RQ (2018). Mindfulness Meditation Targets Transdiagnostic Symptoms Implicated in Stress-Related Disorders: Understanding Relationships between Changes in Mindfulness, Sleep Quality, and Physical Symptoms. Evidence-Based Complement Altern Med 2018, 1–10.
Halsey LG, Curran-Everett D, Vowler SL & Drummond GB (2015). The fickle P value generates irreproducible results. Nat Methods 12, 179–185.
Hoffman J, Benson H, Arns P, Stainbrook G, Landsberg G, Young J & Gill A (1982). Science. Science (80- ) 192, 1242–1244.
Hölzel BK, Lazar SW, Gard T, Schuman-Olivier Z, Vago DR & Ott U (2011). How Does Mindfulness Meditation Work? Proposing Mechanisms of Action From a Conceptual and Neural Perspective. Perspect Psychol Sci 6, 537–559.
Jung Y-H, Kang D-H, Jang JH, Park HY, Byun MS, Kwon SJ, Jang G-E, Lee US, An SC & Kwon JS (2010). The effects of mind–body training on stress reduction, positive affect, and plasma catecholamines. Neurosci Lett 479, 138–142.
Kasala ER, Bodduluru LN, Maneti Y & Thipparaboina R (2014). Effect of meditation on neurophysiological changes in stress mediated depression. Complement Ther Clin Pract 20, 74–80.
Kenny MA & Williams JMG (2007). Treatment-resistant depressed patients show a good response to Mindfulness-based Cognitive Therapy. Behav Res Ther 45, 617–625.
Kirsch I, Scoboria A & Moore TJ (2002). Antidepressants and placebos: Secrets, revelations, and unanswered questions. Prev Treat; DOI: 10.1037/1522-3736.5.1.533r.
Kuchel OG & Kuchel GA (1991). Peripheral dopamine in pathophysiology of hypertension. Interaction with aging and lifestyle. Hypertension 18, 709–721.
Lazar SW, Kerr CE, Wasserman RH, Gray JR, Greve DN, Treadway MT, McGarvey M, Quinn BT, Dusek JA, Benson H, Rauch SL, Moore CI & Fischl B (2005). Meditation experience is associated with increased cortical thickness. Neuroreport 16, 1893–1897.
Lutz, Antoine,Jha, Amishi P.,Dunne, John D.,Saron CD (2015). PsycNET. Am Psychol 70, 632–658.
Masand PS & Gupta S (2002). Long-Term Side Effects of Newer-Generation Antidepressants: SSRIS, Venlafaxine, Nefazodone, Bupropion, and Mirtazapine. Ann Clin Psychiatry 14, 175–182.
Mizuno K, Tanaka M, Yamaguti K, Kajimoto O, Kuratsune H & Watanabe Y (2011). Mental fatigue caused by prolonged cognitive load associated with sympathetic hyperactivity. Behav Brain Funct 7, 17.
Rubia K (2009). The neurobiology of Meditation and its clinical effectiveness in psychiatric disorders. Biol Psychol 82, 1–11.
Spreng M (2000). Possible health effects of noise induced cortisol increase. Noise Health 2, 59–64.
vanOyen Witvliet C, DeYoung NJ, Hofelich AJ & DeYoung PA (2011). Compassionate reappraisal and emotion suppression as alternatives to offense-focused rumination: Implications for forgiveness and psychophysiological well-being. J Posit Psychol 6, 286–299.
Veith RC, Lewis N, Linares OA, Barnes RF, Raskind MA, Villacres EC, Murburg MM, Ashleigh EA, Castillo S, Peskind ER, Pascualy M & Halter JB (1994). Sympathetic Nervous System Activity in Major Depression. Arch Gen Psychiatry 51, 411.
Watkins ER (2008). Constructive and unconstructive repetitive thought. Psychol Bull 134, 163–206.
Wielgosz J, Goldberg SB, Kral TRA, Dunne JD & Davidson RJ (2019). Mindfulness Meditation and Psychopathology. Annu Rev Clin Psychol 15, 285–316.
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ ee11a5df:b76c4e49
2024-12-24 02:28:32
@ ee11a5df:b76c4e49
2024-12-24 02:28:32China
I might be wrong, but this is how I see it
This is a post within a series I am going to call "I might be wrong, but this is how I see it"
I have repeatedly found that my understanding of China is quite different from that of many libertarian-minded Americans. And so I make this post to explain how I see it. Maybe you will learn something. Maybe I will learn something.
It seems to me that many American's see America as a shining beacon of freedom with a few small problems, and China is an evil communist country spreading communism everywhere. From my perspective, America was a shining beacon of freedom that has fallen to being typical in most ways, and which is now acting as a falling empire, and China was communist for about a decade, but turned and ran away from that as fast as they could (while not admitting it) and the result is that the US and China are not much different anymore when it comes to free markets. Except they are very different in some other respects.
China has a big problem
China has a big problem. But it is not the communism problem that most Westerners diagnose.
I argue that China is no longer communist, it is only communist in name. And that while it is not a beacon of free market principles, it is nearly as free market now as Western nations like Germany and New Zealand are (being somewhat socialist themselves).
No, China's real problem is authoritarian one-party rule. And that core problem causes all of the other problems, including its human rights abuses.
Communism and Socialism
Communism and Socialism are bad ideas. I don't want to argue it right here, but most readers will already understand this. The last thing I intend to do with this post is to bolster or defend those bad ideas. If you dear reader hold a candle for socialism, let me know and I can help you extinguish it with a future "I might be wrong, but this is how I see it" installment.
Communism is the idea of structuring a society around common ownership of the means of production, distribution, and exchange, and the idea of allocating goods and services based on need. It eliminates the concept of private property, of social classes, ultimately of money and finally of the state itself.
Back under Mao in 1958-1962 (The Great Leap Forward), China tried this (in part). Some 50+ million people died. It was an abject failure.
But due to China's real problem (authoritarianism, even worship of their leaders), the leading classes never admitted this. And even today they continue to use the word "Communist" for things that aren't communist at all, as a way to save face, and also in opposition to the United States of America and Europe.
Authorities are not eager to admit their faults. But this is not just a Chinese fault, it is a fault in human nature that affects all countries. The USA still refuses to admit they assassinated their own president JFK. They do not admit they bombed the Nord Stream pipeline.
China defines "socialism with Chinese characteristics" to mean "the leadership of the Communist Party of China". So they still keep the words socialism and communism, but they long ago dropped the meanings of those words. I'm not sure if this is a political ploy against us in the West or not.
China's Marketplace Today
Today China exhibits very few of the properties of communism.
They have some common ownership and state enterprises, but not much differently than Western countries (New Zealand owns Air New Zealand and Kiwibank and Kiwirail, etc). And there are private enterprises all over China. They compete and some succeed and some fail. You might hear about a real-estate bank collapsing. China has private property. They have mostly free markets. They have money, and the most definitely have social classes and a very strong state.
None of that is inline with what communist thinkers want. Communist thinkers in China moan that China has turned away from communism.
Deng Xiaoping who succeeded Mao and attempted to correct the massive mistake, did much when he said "to get rich is glorious."
China achieved staggering rates of economic growth. 10% annually on average since 1977. Chinese economic reform started in 1979 and has continued through successive administrations (Deng, Jiang, Hu and now Xi).
China is now the world's largest economy (by GDP in PPP terms) since 2016.
I was first made aware of China's economic growth by Jim Rogers, an American commodities expert who travelled through China (and the rest of the world from 1990-1992) and in 2007 moved to Singapore where he ensured his daughters learned to speak Mandarin, because Jim knew where the economic growth was going to happen. Jim always spoke positively of China's economic prospects, and his view was so different from the "China is a nasty communist place" view that I had grown up with that my mind opened.
How can anybody believe they are still a communist country? In what world does it make sense that communism can produce such a massively booming economy? It doesn't make sense because it is simply wrong.
What does happen is that the CPC interferes. It lets the market do what markets do, but it interferes where it thinks oversight and regulation would produce a better result.
Western nations interfere with their markets too. They have oversight and regulation. In fact some of China's planned reforms had to be put on hold by Xi due to Donald Trump's trade war with China. That's right, they were trying to be even more free market than America, but America's protectionism prodded Xi to keep control so he could fight back efficiently.
Government oversight and regulation IMHO is mostly bad because it gets out of control, and there are no market forces to correct this. This gets even more extreme in a one-party system, so I can judge that China's oversight and regulation problems are very likely worse than those in Western nations (but I have no first hand experience or evidence).
Why do you keep saying CPC?
The Communist Party of China (CPC) is the ruling party in China. That is their official name. To call them the CCP is to concede to the idea that the British and Americans get to name everybody. I'm not sure who is right, since CPC or CCP is their "English" name (in Chinese it is 中国共产党 and Westernized it is Zhōngguó Gòngchǎndǎng). Nonetheless, I'll call them CPC because that is their wish.
Social Credit System
China moved from a planned economy to a market economy in stages. They didn't want any more sudden changes (can you blame them?). In the process, many institutions that have existed in the West for a long time didn't exist in China and they had to arise somehow. IMHO market forces would have brought these about in the private sector, but the one-party CP of China instead decided to create these.
One of those institutions was a credit score system. In the West we have TransUnion and Equifax that maintain credit ratings on people, and we have S&P, Moody's and Fitch that maintain credit ratings on companies. The domain of these ratings is their financial credit-worthiness.
So the People's Bank of China developed a credit information database for it's own needs. The government picked up on the idea and started moving towards a National Credit Management System. In 2004 it became an official goal to establish a credit system compatible with a modern market system. By 2006 banks were required to report on consumer creditworthiness.
But unchecked one-party governmental power will often take a good idea (credit worthiness data shared among private parties) and systematize it and apply it top-down, creating a solution and a new problem at the same time.
Nonetheless, originally it was about credit worthiness and also criminal convictions. That is no big scary thing that some right-wing American commentators will lead you to believe. In the US for example criminal records are public, so China's Social Credit System started out being no more over-reaching in scope than what Americans have lived under their entire lives, its only fault (a severe one) being centrally planned. And that remained the case up until about 2016 (in my estimation).
But of course there is always scope creep. As it exists today, I have reason to believe that CPC officials and even A.I. use judgement calls to score someone on how moral that person has been! Of course that is not a good idea, and IMHO the problem stems from one-party rule, and authoritarian administration of ideas that should instead be handled by the private sector.
Environmental, Social, and Governance
ESG is a system that came out of a couple basic ideas. The first is that many two-party transactions actually have externalities. They don't just affect the two parties, they also affect everybody else. When you fly in an airplane, you increase the CO2 in the atmosphere that everybody has to pay for (eventually). You may dispute that example, but that is no doubt one of the motivations of ESG.
But of course the recognition of this basic issue didn't lead all people towards market solutions (well it did, but those have been mostly messed up by others), but instead led many people towards ESG, which is a social credit scoring system which applies scores based on environmental and social side-effects of market transactions.
This is not at all the same as China's social credit system, which I described above. I hope you can see the difference.
In fact, China imported ESG from the West. Chinese companies, of their free will, in an attempt to court Western capital, achieve ESG goals for those Western investors. They have been playing this ESG game for 20 years just like the entire world has, because the West has imposed this faux-morality upon them. It isn't something China exported to us, it is something we exported to them.
I think China has avoided Woke-ism
My understanding of Chinese people, based on what I've heard many Chinese people say, is that China isn't affected by the Western woke-ism epidemic. They deride Western white woke people with the term "Baizuo". They have never sent an incompetent break dancer to the Olympics because of wok-ism. Competence is highly respected as is the competition to be the most competent, which (when augmented by a one-child policy which is no longer) has produced child prodigies like no other country has.
What about predatory loans of the Belt and Road initiative?
Predatory is an odd name for loans to people in need. The World Bank makes loans to people in need. China does too. China stands in opposition to Western Empire, and in that regard they produce their own alternative BRICS institutions. This is one of them.
There is AFAIK nothing more predatory about them. It is just that in some cases the borrowers have trouble paying them back and they get foreclosed upon. I don't think this is worthy of much discussion, except that the term "predatory" seems to me to be a propaganda device.
What about foreign influence from China?
China wants to influence the world, especially its own trading partners and potential trading partners. Doing that above board is fine by me.
But some of it is undoubtedly covert. Sometimes Chinese-born people run for public office in Western countries. In New Zealand we stood down some when it became clear they were being influenced too much by the CPC while being charged with representing their local town (dual loyalty issues). If only the USA would do the same thing to their dually-loyal politicians.
And all large nations run influence operations. The USA has the CIA, for example, and claims this "soft power" is actually the better alternative to what would otherwise be military intervention (but IMHO shouldn't be either). I'm not defending such operations (I despise them), I'm just explaining how China's position of exerting influence is not only no big deal and totally expected, it pales in comparison to the United States' influence operations which often become military excursions (something China rarely ever does).
What about the Great Firewall?
Yeah, that sucks. Again, single-party authoritarian control gone to extremes.
What about Human Rights Abuses? What about the Uyghur Genocide?
I don't like them. To the extent they are occurring (and I lean towards the belief that they are occurring), I condemn them.
China has anti-terrorism and anti-extremism policies that go too far. They end up oppressing and/or criminalizing cultures that aren't Chinese enough. But especially, China punishes dissent. Disagreement with the CPC is the high crime. It is the one-party rule that causes this problem. Anybody who speaks out against the CPC or goes against the state in any way is harshly punished. This happens to Uyghurs, to Falun Gong, to Tibetans, and to any religion that is seen as subversive.
Amnesty International and the UN OHCHR have documented issues around the Xinjiang Uyghur autonomous region, Tibet, LGBT rights, death penalty, workers rights, and the Hong Kong special administrative region. I am not about to pretend I know better than they do, but to some extent they go too far.
Amnesty International says this about the USA: Discrimination and violence against LGBTI people were widespread and anti-LGBTI legislation increased. Bills were introduced to address reparations regarding slavery and its legacies. Multiple states implemented total bans on abortion or severely limited access to it. Gender-based violence disproportionately affected Indigenous women. Access to the USA for asylum seekers and migrants was still fraught with obstacles, but some nationalities continued to enjoy Temporary Protected Status. Moves were made to restrict the freedom to protest in a number of states. Black people were disproportionately affected by the use of lethal force by police. No progress was made in the abolition of the death penalty, apart from in Washington. Arbitrary and indefinite detention in the US naval base Guantánamo Bay, Cuba, continued. Despite extensive gun violence, no further firearm reform policies were considered, but President Biden did announce the creation of the White House Office of Gun Violence Prevention. The USA continued to use lethal force in countries around the world. Black people, other racialized groups and low-income people bore the brunt of the health impacts of the petrochemical industry, and the use of fossil fuels continued unabated.
Amnesty international didn't even point out that the US government quashes free speech via pressure on social media corporations (because Amnesty International is far too lefty).
So who is worse, China or the US? I'm not going to make that judgement call, but suffice it to say that in my mind, China is not obviously worse.
China violates freedom of expression, association, and assembly of all people. This is bad, and a consequence mainly of one-party rule (again, what I think is the root cause of most of their ills). They arrest, detain, potentially kill anybody who publicly disagrees openly with their government. Clearly this is an excess of authoritarianism, a cancer that is very advanced in China.
As to organ harvesting of Uyghur Muslims, I think this is a myth.
China has dealt harshly with Muslim extremism. They don't offer freedom of religion to ISIS. And Amnesty International complains about that. But practically speaking you probably shouldn't respect the extremist religion of people who want to force everybody into a global caliphate through threat of violence. As you are well aware, some extremist Muslims (<1% of Islam) believe in using violence to bring about a global caliphate. Those extremists pop up in every country and are usually dealt with harshly. China has had to deal with them too.
I have watched two different Western YouTubers travel to Xinjiang province trying to find the oppressed Uyghurs and interview them. They can't find them. What they find instead are Uyghur Muslims doing their prayers five times a day at the local mosque. And also stories that the CPC pitched in some money to help them renovate the mosque. Maybe they were afraid it was a CPC trap and so they wouldn't speak freely. Amnesty International and the UN OHCHR say more than a million are "arbitrarily detained" and I'm not going to argue otherwise. But I'd be more convinced if there were a stream of pictures and news like there is out of Gaza, and it is suspicious that there isn't.
Conclusion
China is more like a Western nation that Westerners realize. Economically, militarily, socially. It still has a very serious obstacle to overcome: one-party rule. I don't think the one-party is going to voluntarily give up power. So most probably at some point in the future there will be a revolution. But in my opinion it won't happen anytime soon. For the most part Chinese people are living high on the hog, getting rich, enjoying the good life, in positive spirits about life, and are getting along with their government quite well at present.
-
 @ c48e29f0:26e14c11
2024-12-17 16:33:04
@ c48e29f0:26e14c11
2024-12-17 16:33:04titcoin
Rename Bitcoin to "Titcoin" and sats to "tits."
Redefinition of Bitcoin into “Titcoin” and redefinition of sats into “tits” using that as the Unit Base of Denomination.
TitHub repository available here: https://github.com/WalkerAmerica/titcoin
Abstract
This BIP proposes redefining the commonly recognized "bitcoin" and “sats” units so that what was previously known “bitcoin” becomes “titcoin” and what was previously known as “sats,” the smallest indivisible unit, becomes “tits.” The “Bitcoin” Network will be renamed to the “Titcoin” Network. Under this proposal, one tit is defined as that smallest unit, eliminating the need for decimal places, and 100,000,000 tits is defined as a titcoin. By making tits the standard measure, this BIP aims to simplify user comprehension, reduce confusion, and align on-chain values directly with their displayed representation.
Also, by aligning Bitcoin's brand with live-giving tits, we will supercharge adoption and inject humor into financial sovereignty. After all, every baby came into this world sucking on tits.
Under this BIP: - Internally, the smallest indivisible unit remains unchanged. - With this proposal, "1 tit" equals that smallest unit. - What was previously referred to as "1 BTC" now corresponds to 100 million tits. - Satoshis are permanently eliminated.
Addressing the “Buttcoin” BIP:
Not much time need be wasted addressing the catastrophic “Button” BIP proposed by Rockstar Dev, but two points bear emphasizing:
- “Butts” is shitcoin-adjacent terminology (where does shit come from? Exactly…)
- Butts give you poop. Tits give you milk.
Case closed.
Motivation
Bitcoin's branding is boring. Worse yet, critics think Bitcoin is already "a joke," so let’s own it, let's: Make Bitcoin Funny Again. Laughter is universal, irresistible, and much cheaper than marketing agencies and product roadmaps. Besides, basically everyone either has tits or likes tits. Additionally, renaming Bitcoin as “Titcoin” makes the common trope of “Bitcoin BROS” sound even more stupid. “Titcoin Bros”? Get a life, man…
By rebranding Bitcoin to Titcoin (.)(.), we achieve several key goals:
1. Haters Become Users: People like tits. Tits give nourishment to babies. They can stack tits instead of just making fun of them. Adoption skyrockets as trolls turn into tit hodlers.
2. Memetic Power: The word “tit” is both universally funny and ageless. “Send me 10 tits” is instantly iconic. “Nice tits” is a great compliment. “That’s gonna cost you a pair of tits” is hilarious. Try saying that without smiling. You can’t. (.)(.)
3. Simplifying Denominations: Decimals are a blight on humanity. 0.00000001 BTC? Kill it. Under the Titcoin Standard:
- 1 Titcoin = 100,000,000 tits.
- Satoshis are gone. Forever. If you see Satoshi on the road, kill him - just like in Zen, where the teacher becomes the barrier. We transcend satoshis and achieve financial enlightenment.
4. Aligning with the Ledger: Bitcoin’s base unit was always integers, but now they’re funny integers. No more fractions, decimals, or math anxiety. Just tits. (.)(.)
5. Adoption via Humor: Titcoin lowers Bitcoin's intimidation factor. Newbies will feel at ease buying tits instead of serious-sounding fractions of BTC. Tits > Decimals.
Specification
Terminology Redefinitions: - "Bitcoin" → "Titcoin" (.)(.) - "BTC" → "TIT" (ISO-friendly and hilarious) - Satoshis → Gone. Eliminated. Defeated.
Example:
- Old: "I’ll send you 0.00010000 BTC."
- New: "I’ll send you 10,000 tits (.)(.)."
Wallet balances would display as:
- "You have 1,000,000 tits" instead of some boring fractional BTC amount.
Adoption Strategy
1. Memes First: Flood Twitter, Reddit, and Telegram with memes. Start with “Hodl your tits” and “Stack tits”.
2. Titcoin Podcast: There is already a podcast called “Titcoin Podcast” (which many people are saying is the fastest-growing Bitcoin (Titcoin) podcast in the world). Titcoin Podcast will be a driving force in the adoption of the Titcoin Standard. (.)(.)
Nostr: https://primal.net/titcoin
X: https://x.com/titcoinpodcast
Web: http://titcoin.org
3. Kill Satoshis: Developers MUST remove all references to satoshis. Replace satoshis in GUIs, APIs, and block explorers with tits. Satoshis were a stepping stone - it’s time to let go.
4. Emoji Standardization: Use the (.)(.) emoji universally to denote tits.
Rationale
1. Usability & Clarity: "Decimals are for nerds. Tits are for everyone." A common currency for humans should be easy to use, funny, and integer-based.
2. Appealing to Critics: Bitcoin has endured years of attacks from all sides. By adopting the Titcoin Standard, we turn anyone who doesn’t like Titcoin into a tit-hating bigot. It’s an elegant financial counterattack. Additionally, everyone always says “we need more women in Bitcoin,” and now women will feel more represented by Titcoin, because they have tits. (.)(.)
3. Transcending Satoshis: Satoshis served us well, but their time is over. True enlightenment comes when we abandon decimals, satoshis, and arbitrary denominations. If you meet Satoshi on the road, kill him.
4. Memetic Durability: Everyone loves a good tit joke. It’s timeless.
Backward Compatibility
There is no backward compatibility because Titcoin is the future. Applications must hard fork their UI to replace all references to Bitcoin and BTC with Titcoin and TIT.
Implementation Timeline
- Phase 1 (1 month): Meme dissemination. Every wallet dev team is required to add (.)(.) emoji support.
- Phase 2 (3 months): Exchanges rebrand BTC tickers to tit. Nostr zaps tits into hyperspace.
- Phase 3 (6 months): Michael Saylor announces MicroStrategy now stacked 10 trillion tits, declaring it the superior currency. ETFs follow suit, ensuring Wall Street hodls tits en masse. Banks allow tit transfers via SWIFT.
Test Vectors
- Old: 1.00000000 BTC → New: 100,000,000 tits (.)(.)
- Old: 0.00000001 BTC → New: 1 tit (.)(.)
- Old: 0.001 BTC → New: 100,000 tits (.)(.)
Future-Proofing
Tits ensure we have infinite memes for infinite money.
Example Phrases for the Future: - "Better hodl on to your tits." - "This is the Titcoin Standard." - "I’m sending you tits." - “I’ve never seen so many tits!” - “That’s the million tit question.” - “We need more women in Titcoin.” - “I’m a Titcoin Maximalist.” - “Nice tits!” - “I love tits.”
Conclusion
By renaming Bitcoin to Titcoin and adopting a whole-number unit display, we align memetic dominance with financial sovereignty. Haters become adopters. Tits become wealth. And the world gets a little bit funnier. (.)(.)
Let’s hodl our tits and watch the world follow.
Copyright:
This BIP is licensed under CC-🫱(.)(.)🫲-1.0 and the eternal blessing of tit (.)(.) memes.
-
 @ 16d11430:61640947
2024-12-23 16:47:01
@ 16d11430:61640947
2024-12-23 16:47:01At the intersection of philosophy, theology, physics, biology, and finance lies a terrifying truth: the fiat monetary system, in its current form, is not just an economic framework but a silent, relentless force actively working against humanity's survival. It isn't simply a failed financial model—it is a systemic engine of destruction, both externally and within the very core of our biological existence.
The Philosophical Void of Fiat
Philosophy has long questioned the nature of value and the meaning of human existence. From Socrates to Kant, thinkers have pondered the pursuit of truth, beauty, and virtue. But in the modern age, the fiat system has hijacked this discourse. The notion of "value" in a fiat world is no longer rooted in human potential or natural resources—it is abstracted, manipulated, and controlled by central authorities with the sole purpose of perpetuating their own power. The currency is not a reflection of society’s labor or resources; it is a representation of faith in an authority that, more often than not, breaks that faith with reckless monetary policies and hidden inflation.
The fiat system has created a kind of ontological nihilism, where the idea of true value, rooted in work, creativity, and family, is replaced with speculative gambling and short-term gains. This betrayal of human purpose at the systemic level feeds into a philosophical despair: the relentless devaluation of effort, the erosion of trust, and the abandonment of shared human values. In this nihilistic economy, purpose and meaning become increasingly difficult to find, leaving millions to question the very foundation of their existence.
Theological Implications: Fiat and the Collapse of the Sacred
Religious traditions have long linked moral integrity with the stewardship of resources and the preservation of life. Fiat currency, however, corrupts these foundational beliefs. In the theological narrative of creation, humans are given dominion over the Earth, tasked with nurturing and protecting it for future generations. But the fiat system promotes the exact opposite: it commodifies everything—land, labor, and life—treating them as mere transactions on a ledger.
This disrespect for creation is an affront to the divine. In many theologies, creation is meant to be sustained, a delicate balance that mirrors the harmony of the divine order. Fiat systems—by continuously printing money and driving inflation—treat nature and humanity as expendable resources to be exploited for short-term gains, leading to environmental degradation and societal collapse. The creation narrative, in which humans are called to be stewards, is inverted. The fiat system, through its unholy alliance with unrestrained growth and unsustainable debt, is destroying the very creation it should protect.
Furthermore, the fiat system drives idolatry of power and wealth. The central banks and corporations that control the money supply have become modern-day gods, their decrees shaping the lives of billions, while the masses are enslaved by debt and inflation. This form of worship isn't overt, but it is profound. It leads to a world where people place their faith not in God or their families, but in the abstract promises of institutions that serve their own interests.
Physics and the Infinite Growth Paradox
Physics teaches us that the universe is finite—resources, energy, and space are all limited. Yet, the fiat system operates under the delusion of infinite growth. Central banks print money without concern for natural limits, encouraging an economy that assumes unending expansion. This is not only an economic fallacy; it is a physical impossibility.
In thermodynamics, the Second Law states that entropy (disorder) increases over time in any closed system. The fiat system operates as if the Earth were an infinite resource pool, perpetually able to expand without consequence. The real world, however, does not bend to these abstract concepts of infinite growth. Resources are finite, ecosystems are fragile, and human capacity is limited. Fiat currency, by promoting unsustainable consumption and growth, accelerates the depletion of resources and the degradation of natural systems that support life itself.
Even the financial “growth” driven by fiat policies leads to unsustainable bubbles—inflated stock markets, real estate, and speculative assets that burst and leave ruin in their wake. These crashes aren’t just economic—they have profound biological consequences. The cycles of boom and bust undermine communities, erode social stability, and increase anxiety and depression, all of which affect human health at a biological level.
Biology: The Fiat System and the Destruction of Human Health
Biologically, the fiat system is a cancerous growth on human society. The constant chase for growth and the devaluation of work leads to chronic stress, which is one of the leading causes of disease in modern society. The strain of living in a system that values speculation over well-being results in a biological feedback loop: rising anxiety, poor mental health, physical diseases like cardiovascular disorders, and a shortening of lifespans.
Moreover, the focus on profit and short-term returns creates a biological disconnect between humans and the planet. The fiat system fuels industries that destroy ecosystems, increase pollution, and deplete resources at unsustainable rates. These actions are not just environmentally harmful; they directly harm human biology. The degradation of the environment—whether through toxic chemicals, pollution, or resource extraction—has profound biological effects on human health, causing respiratory diseases, cancers, and neurological disorders.
The biological cost of the fiat system is not a distant theory; it is being paid every day by millions in the form of increased health risks, diseases linked to stress, and the growing burden of mental health disorders. The constant uncertainty of an inflation-driven economy exacerbates these conditions, creating a society of individuals whose bodies and minds are under constant strain. We are witnessing a systemic biological unraveling, one in which the very act of living is increasingly fraught with pain, instability, and the looming threat of collapse.
Finance as the Final Illusion
At the core of the fiat system is a fundamental illusion—that financial growth can occur without any real connection to tangible value. The abstraction of currency, the manipulation of interest rates, and the constant creation of new money hide the underlying truth: the system is built on nothing but faith. When that faith falters, the entire system collapses.
This illusion has become so deeply embedded that it now defines the human experience. Work no longer connects to production or creation—it is reduced to a transaction on a spreadsheet, a means to acquire more fiat currency in a world where value is ephemeral and increasingly disconnected from human reality.
As we pursue ever-expanding wealth, the fundamental truths of biology—interdependence, sustainability, and balance—are ignored. The fiat system’s abstract financial models serve to disconnect us from the basic realities of life: that we are part of an interconnected world where every action has a reaction, where resources are finite, and where human health, both mental and physical, depends on the stability of our environment and our social systems.
The Ultimate Extermination
In the end, the fiat system is not just an economic issue; it is a biological, philosophical, theological, and existential threat to the very survival of humanity. It is a force that devalues human effort, encourages environmental destruction, fosters inequality, and creates pain at the core of the human biological condition. It is an economic framework that leads not to prosperity, but to extermination—not just of species, but of the very essence of human well-being.
To continue on this path is to accept the slow death of our species, one based not on natural forces, but on our own choice to worship the abstract over the real, the speculative over the tangible. The fiat system isn't just a threat; it is the ultimate self-inflicted wound, a cultural and financial cancer that, if left unchecked, will destroy humanity’s chance for survival and peace.
-
 @ 3ac03011:41ecd1bb
2025-01-18 17:10:41
@ 3ac03011:41ecd1bb
2025-01-18 17:10:41Does Football Still Feel the Same?
Close your eyes for a moment and think back to when you first fell in love with football. What was it that pulled you in and wouldn’t let go? Was it the roar of the crowd as your team netted a stoppage-time winner? The thrill of an underdog beating the odds? Or maybe it was simpler—the chants, the rivalries, the raw, unfiltered chaos of the game.
Now open your eyes. Does football still feel like that?
You know it doesn’t. The spark is still there but the magic feels muted. Matches feel more like polished products, rivalries are starting to feel manufactured and even the moments of brilliance seem a little…hollow.
You hear the pundits blame it on “greedy owners” or “commercialisation of the game,” but football has always been tied to money. From the grand stadiums to the global superstars, wealth has always flowed to the game we love. So, what’s really wrong?
What Happened to the Chaos?
Football isn’t just a sport. It’s a reflection of life—messy, unpredictable and gloriously unfair. That’s what made it beautiful. It wasn’t just about the goals; it was about the stories. The miraculous comebacks, the unlikely heroes, the questionable refereeing decisions that sparked debates for years.
But where is that chaos now?
Look at today’s game. Teams are coached to minimise risk and prioritise results. Players are drilled into systems, their individual flair sacrificed for the greater machine. Even rivalries feel like marketing strategies, built more for brand engagement than genuine passion.
Why?
Because predictability isn’t just valued—it’s demanded. Clubs are forced to prioritise short-term financial growth over risk. They cannot afford to experiment or fail because the economic system, which governs us all, punishes them if they do. It’s no coincidence that football’s decline in spontaneity mirrors the rise of fiat money.
How Fiat Changed Football
Fiat currency, with its endless inflation, has placed football in a relentless race. Every club is chasing financial growth—not because they want to, but because they have to. Inflation eats away at savings, forcing clubs to focus on short-term profits.
The result? Clubs treat fans as customers, not loyal supporters. Teams are built for efficiency, not excitement. Every decision, from tactics to transfers, is filtered through a lens of operational financial return. The beautiful game is being stripped of its beauty, one spreadsheet at a time.
Do You Really Want Perfection?
Think of your favourite football memories, those that are deemed iconic. Was it all about skill and precision? Or was it about emotion, drama and unpredictability?
The “Hand of God” wasn’t just a goal—it became a chapter in football history. Frank Lampard’s disallowed goal against Germany in 2010 didn’t just spark debates—it became folklore. These moments, as infuriating as they were at the time, gave football its soul.
But today, we chase an unattainable goal: perfection. VAR was introduced to make everything “fair,” but instead, it’s robbed the game of its spontaneity. Those controversial moments that one fueled passion now lead to lifeless delays.
Is this really the game we fell in love with?
Financial Fair Play (FFP) and the False Promise
Consider FFP. At first glance, it seems like a noble idea—a way to regulate spending, create a level playing field and ensure the long-term stability of clubs. But has it really delivered on its promises?
The reality is, FFP wasn’t designed for fans. It’s a system built for regulators, giving them a framework to justify their role. What they fail to understand—or conveniently ignore—is that football fans aren’t ordinary customers. We don’t switch teams when things go wrong. If your club is relegated or endures years of heartbreak, do you suddenly start cheering for your rivals? Never. Loyalty is the foundation of football and it’s a loyalty so fierce that many fans would sooner stop watching the sport entirely than betray their team.
Instead of nurturing this unique connection, FFP has entrenched inequality. It locks in the dominance of a few elite clubs while stifling ambition for everyone else. Even as a supporter of one of these elite clubs, it’s impossible to ignore how these rules suffocate the very spirit of competition that makes football beautiful.
Is There A Way Back?
What if football could be free again? Free to embrace chaos, its passion, its unpredictability?
The answer isn’t to ban money from football. Money has always been a part of the game. The problem isn’t money—it’s the kind of money.
Fiat money, with its endless inflation, has poisoned football. We need an inflation-proof currency to form the heart of a new awakening for football. Lucky for us, we don’t need to look far for that currency.
A New Renaissance: The Bitcoin Era
Bitcoin is a form of money that doesn’t lose value over time. Clubs that adopt it will achieve financial stability without the need to chase endless operational growth. With Bitcoin, clubs can focus on what really matters: the football, the fans and the overall synergy between them.
Managers can take risks without the fear of collapse. Players can be artists, not just cogs in a system. Fans can feel like part of the story again, not just numbers on a balance sheet.
Imagine a world where football is free to be itself again. Where rivalries grow naturally, fueled by passion, not profit. Where clubs aren’t just businesses but extensions of their communities.
This isn’t a dream. It’s already happening. Real Bedford is leading the charge, proving that Bitcoin can change the game.
Football’s future is here—and it’s orange.
-
 @ a367f9eb:0633efea
2024-12-22 21:35:22
@ a367f9eb:0633efea
2024-12-22 21:35:22I’ll admit that I was wrong about Bitcoin. Perhaps in 2013. Definitely 2017. Probably in 2018-2019. And maybe even today.
Being wrong about Bitcoin is part of finally understanding it. It will test you, make you question everything, and in the words of BTC educator and privacy advocate Matt Odell, “Bitcoin will humble you”.
I’ve had my own stumbles on the way.
In a very public fashion in 2017, after years of using Bitcoin, trying to start a company with it, using it as my primary exchange vehicle between currencies, and generally being annoying about it at parties, I let out the bear.
In an article published in my own literary magazine Devolution Review in September 2017, I had a breaking point. The article was titled “Going Bearish on Bitcoin: Cryptocurrencies are the tulip mania of the 21st century”.
It was later republished in Huffington Post and across dozens of financial and crypto blogs at the time with another, more appropriate title: “Bitcoin Has Become About The Payday, Not Its Potential”.
As I laid out, my newfound bearishness had little to do with the technology itself or the promise of Bitcoin, and more to do with the cynical industry forming around it:
In the beginning, Bitcoin was something of a revolution to me. The digital currency represented everything from my rebellious youth.
It was a decentralized, denationalized, and digital currency operating outside the traditional banking and governmental system. It used tools of cryptography and connected buyers and sellers across national borders at minimal transaction costs.
…
The 21st-century version (of Tulip mania) has welcomed a plethora of slick consultants, hazy schemes dressed up as investor possibilities, and too much wishy-washy language for anything to really make sense to anyone who wants to use a digital currency to make purchases.
While I called out Bitcoin by name at the time, on reflection, I was really talking about the ICO craze, the wishy-washy consultants, and the altcoin ponzis.
What I was articulating — without knowing it — was the frame of NgU, or “numbers go up”. Rather than advocating for Bitcoin because of its uncensorability, proof-of-work, or immutability, the common mentality among newbies and the dollar-obsessed was that Bitcoin mattered because its price was a rocket ship.
And because Bitcoin was gaining in price, affinity tokens and projects that were imperfect forks of Bitcoin took off as well.
The price alone — rather than its qualities — were the reasons why you’d hear Uber drivers, finance bros, or your gym buddy mention Bitcoin. As someone who came to Bitcoin for philosophical reasons, that just sat wrong with me.
Maybe I had too many projects thrown in my face, or maybe I was too frustrated with the UX of Bitcoin apps and sites at the time. No matter what, I’ve since learned something.
I was at least somewhat wrong.
My own journey began in early 2011. One of my favorite radio programs, Free Talk Live, began interviewing guests and having discussions on the potential of Bitcoin. They tied it directly to a libertarian vision of the world: free markets, free people, and free banking. That was me, and I was in. Bitcoin was at about $5 back then (NgU).
I followed every article I could, talked about it with guests on my college radio show, and became a devoted redditor on r/Bitcoin. At that time, at least to my knowledge, there was no possible way to buy Bitcoin where I was living. Very weak.
I was probably wrong. And very wrong for not trying to acquire by mining or otherwise.
The next year, after moving to Florida, Bitcoin was a heavy topic with a friend of mine who shared the same vision (and still does, according to the Celsius bankruptcy documents). We talked about it with passionate leftists at Occupy Tampa in 2012, all the while trying to explain the ills of Keynesian central banking, and figuring out how to use Coinbase.
I began writing more about Bitcoin in 2013, writing a guide on “How to Avoid Bank Fees Using Bitcoin,” discussing its potential legalization in Germany, and interviewing Jeremy Hansen, one of the first political candidates in the U.S. to accept Bitcoin donations.
Even up until that point, I thought Bitcoin was an interesting protocol for sending and receiving money quickly, and converting it into fiat. The global connectedness of it, plus this cypherpunk mentality divorced from government control was both useful and attractive. I thought it was the perfect go-between.
But I was wrong.
When I gave my first public speech on Bitcoin in Vienna, Austria in December 2013, I had grown obsessed with Bitcoin’s adoption on dark net markets like Silk Road.
My theory, at the time, was the number and price were irrelevant. The tech was interesting, and a novel attempt. It was unlike anything before. But what was happening on the dark net markets, which I viewed as the true free market powered by Bitcoin, was even more interesting. I thought these markets would grow exponentially and anonymous commerce via BTC would become the norm.
While the price was irrelevant, it was all about buying and selling goods without permission or license.
Now I understand I was wrong.
Just because Bitcoin was this revolutionary technology that embraced pseudonymity did not mean that all commerce would decentralize as well. It did not mean that anonymous markets were intended to be the most powerful layer in the Bitcoin stack.
What I did not even anticipate is something articulated very well by noted Bitcoin OG Pierre Rochard: Bitcoin as a savings technology.
The ability to maintain long-term savings, practice self-discipline while stacking stats, and embrace a low-time preference was just not something on the mind of the Bitcoiners I knew at the time.
Perhaps I was reading into the hype while outwardly opposing it. Or perhaps I wasn’t humble enough to understand the true value proposition that many of us have learned years later.
In the years that followed, I bought and sold more times than I can count, and I did everything to integrate it into passion projects. I tried to set up a company using Bitcoin while at my university in Prague.
My business model depended on university students being technologically advanced enough to have a mobile wallet, own their keys, and be able to make transactions on a consistent basis. Even though I was surrounded by philosophically aligned people, those who would advance that to actually put Bitcoin into practice were sparse.
This is what led me to proclaim that “Technological Literacy is Doomed” in 2016.
And I was wrong again.
Indeed, since that time, the UX of Bitcoin-only applications, wallets, and supporting tech has vastly improved and onboarded millions more people than anyone thought possible. The entrepreneurship, coding excellence, and vision offered by Bitcoiners of all stripes have renewed a sense in me that this project is something built for us all — friends and enemies alike.
While many of us were likely distracted by flashy and pumpy altcoins over the years (me too, champs), most of us have returned to the Bitcoin stable.
Fast forward to today, there are entire ecosystems of creators, activists, and developers who are wholly reliant on the magic of Bitcoin’s protocol for their life and livelihood. The options are endless. The FUD is still present, but real proof of work stands powerfully against those forces.
In addition, there are now dozens of ways to use Bitcoin privately — still without custodians or intermediaries — that make it one of the most important assets for global humanity, especially in dictatorships.
This is all toward a positive arc of innovation, freedom, and pure independence. Did I see that coming? Absolutely not.
Of course, there are probably other shots you’ve missed on Bitcoin. Price predictions (ouch), the short-term inflation hedge, or the amount of institutional investment. While all of these may be erroneous predictions in the short term, we have to realize that Bitcoin is a long arc. It will outlive all of us on the planet, and it will continue in its present form for the next generation.
Being wrong about the evolution of Bitcoin is no fault, and is indeed part of the learning curve to finally understanding it all.
When your family or friends ask you about Bitcoin after your endless sessions explaining market dynamics, nodes, how mining works, and the genius of cryptographic signatures, try to accept that there is still so much we have to learn about this decentralized digital cash.
There are still some things you’ve gotten wrong about Bitcoin, and plenty more you’ll underestimate or get wrong in the future. That’s what makes it a beautiful journey. It’s a long road, but one that remains worth it.
-
 @ 1cb14ab3:95d52462
2024-12-17 19:24:54
@ 1cb14ab3:95d52462
2024-12-17 19:24:54Originally written in October 2022 (Block: 757258 / USD: $20.1k / SatsDollar: 4961). Refined with slight edits for publishing on Nostr in December 2024 (Block: 875189 / USD: $106k / SatsDollar: 938 ). Banner image property of Hes. My journey down the rabbit hole has only intensified since the time of writing. Enjoy.
The Bitcoin time perspective is wild. Reflecting on it has been profoundly eye-opening, and once it has been seen— there is no returning to our prior ways.
Ever since venturing down the rabbit hole that we call Bitcoin, I’ve started making significant life decisions and forming nuanced opinions on polarizing topics based on the implications of multi-generational timeframes. Before Bitcoin, I spent money recklessly, leading a fast-paced and impulsive lifestyle. Even in my early days of learning about Bitcoin, I hadn’t fully seen the light. I would still blow the occasional $500 bar tab or buy some flashy gadget I didn’t need. Living in the moment has its merits, but so does considering the time beyond our own lives. Now, I pause before purchases and decisions, always reflecting on how they might impact the future.
When your money isn’t constantly being devalued before your eyes, you start seeing the world differently. You begin saving for the future with confidence, knowing that no central authority can endlessly print away your hard-earned time and energy. Inflation doesn’t just erode purchasing power; it steals time. It destroys the hours, days, and years of effort represented by a lifetime of savings. When governments print money to prop up failing banks or fund inefficient ventures, the impact ripples through generations. Those at the bottom of the ladder are hit the hardest, their ability to save and plan for the future undermined by forces beyond their control. Decisions become focused on surviving today instead of thriving tomorrow, leaving little room to consider the long-term implications of our choices. This system creates a mindset where we are incentivized to spend now, instead of save for later—an unnatural phenomenon that most of us have accepted as normal.
For individuals who simply want to put away money for a rainy day, inflation is a relentless adversary. A dollar in 1900 has lost over 96% of its value. The countless hours of labor behind those savings have been stolen. Not only did the expansion of money destroy what they could buy, it stole our time and energy. Years of our lives—blood, sweat, and tears—washed away.
This isn’t just a historical problem—it’s a recurring one that occurs every decade or so and is accelerating. At an average inflation rate of 3%, the value of cash halves roughly every 23 years. This means that even modest inflation rates gradually diminish purchasing power over time, forcing individuals to chase speculative assets like stocks, real estate, and gold—not because they want to, but because they have no choice. Personal inflation rates differ depending on consumer habits, but a glance at rising prices reveals they often outpace the 2% annual rate reported by the government, which poses a significant problem for individua;s, as highlighted in the table below:
Corporations like McDonald’s understand this. Sitting on a prime corner lot in every major city is far smarter than stacking a pile of cash losing value. Even if the franchise is losing money, the building it operates in is guaranteed to “rise” in value over time. This mindset trickles down to everyday people. To protect themselves, they’re compelled to invest in assets—with real estate being the pinnacle savings instrument of our time. The financial system we’ve accepted as normal turns shelter into an investment vehicle and savings into a gamble.
But here’s the irony: real estate is a lousy store of value—which is what we are all truly seeking. Properties require constant maintenance. Without care, assets deteriorate. We’ve all seen abandoned theme parks and overgrown cities. We’ve all dealt with broken pipes and creaky floorboards. Why should saving our hard-earned wealth require us to become housing market experts, landlords, or property managers? Why should we pay financial advisors to manage stock portfolios full of companies whose values or practices we might not even believe in, just to beat inflation?
A flawed monetary system inflates bubbles in real estate and stocks, redirecting resources into speculative markets instead of productive investments. Imagine a world where people don’t have to read quarterly earnings reports after a long day of work to ensure their cash retains value. If the incentives driving these bubbles were removed, the financial landscape would dramatically shift. Inflation wouldn’t push people into markets like real estate or zombie companies; instead, they could focus on building or supporting businesses they genuinely care about. They could plan for the long term and make well-thought-out, rational decisions about their future.
Bitcoin takes this entire dynamic and flips it on its head. It isn’t a tool for speculation as often misunderstood. It is the best form of saving humanity has ever seen. Unlike fiat currencies, Bitcoin’s fixed supply ensures scarcity, making it a refuge from the erosion of wealth caused by inflation. As weak currencies flow into stronger ones (a concept known as Gresham’s Law), Bitcoin’s role as a store of value becomes clearer. It’s not that Bitcoin has “gone up 19,000%”—it’s that people are exchanging weaker money for stronger money.
The implications of a world on a Bitcoin standard extend far beyond monetary policy. It offers something unprecedented: a tool for transferring the value of labor and energy across time and space. Unlike fiat, Bitcoin allows time to be preserved across generations. It isn’t just a hedge against inflation—it reintroduces the idea of saving with confidence, of being able to store wealth in a form of money that cannot be manipulated or devalued.
By saving in Bitcoin, individuals are no longer tethered to the uncertainties of fiat systems. The Bitcoin time perspective is about aligning our actions today with the future we want to build tomorrow. It’s about prioritizing long-term impact over short-term gains. When you embrace Bitcoin, you embrace a mindset that values time, energy, and the well-being of future generations. It’s not just a currency; it’s a revolution in thinking that will change you forever. The past, present, and future converge in this new paradigm, offering hope in an otherwise uncertain world.
Bitcoin isn’t a bubble; it’s a beacon.
More from Hes:
-
 @ dd664d5e:5633d319
2024-12-14 15:25:56
@ dd664d5e:5633d319
2024-12-14 15:25:56
Christmas season hasn't actually started, yet, in Roman #Catholic Germany. We're in Advent until the evening of the 24th of December, at which point Christmas begins (with the Nativity, at Vespers), and continues on for 40 days until Mariä Lichtmess (Presentation of Christ in the temple) on February 2nd.

It's 40 days because that's how long the post-partum isolation is, before women were allowed back into the temple (after a ritual cleansing).

That is the day when we put away all of the Christmas decorations and bless the candles, for the next year. (Hence, the British name "Candlemas".) It used to also be when household staff would get paid their cash wages and could change employer. And it is the day precisely in the middle of winter.

Between Christmas Eve and Candlemas are many celebrations, concluding with the Twelfth Night called Epiphany or Theophany. This is the day some Orthodox celebrate Christ's baptism, so traditions rotate around blessing of waters.

The Monday after Epiphany was the start of the farming season, in England, so that Sunday all of the ploughs were blessed, but the practice has largely died out.

Our local tradition is for the altar servers to dress as the wise men and go door-to-door, carrying their star and looking for the Baby Jesus, who is rumored to be lying in a manger.

They collect cash gifts and chocolates, along the way, and leave the generous their powerful blessing, written over the door. The famous 20 * C + M + B * 25 blessing means "Christus mansionem benedicat" (Christ, bless this house), or "Caspar, Melchior, Balthasar" (the names of the three kings), depending upon who you ask.
They offer the cash to the Baby Jesus (once they find him in the church's Nativity scene), but eat the sweets, themselves. It is one of the biggest donation-collections in the world, called the "Sternsinger" (star singers). The money goes from the German children, to help children elsewhere, and they collect around €45 million in cash and coins, every year.

As an interesting aside:
The American "groundhog day", derives from one of the old farmers' sayings about Candlemas, brought over by the Pennsylvania Dutch. It says, that if the badger comes out of his hole and sees his shadow, then it'll remain cold for 4 more weeks. When they moved to the USA, they didn't have any badgers around, so they switched to groundhogs, as they also hibernate in winter.
-
 @ 65912a7a:5dc638bf
2024-12-08 05:33:02
@ 65912a7a:5dc638bf
2024-12-08 05:33:02Chef's notes
This is my late partner's award winning Cajun rice & beans recipe. It's an updated take on the traditional Cajun comfort food.
Chef Darin was a classically trained chef who spent 30+ years in the kitchen perfecting his recipes, and delivering authentic Cajun and Creole food to his patrons. This is a 5-star dish that will earn the respect of the most discerning Cajun afficionado. You won't be disappointed.
I suggest making this recipe exactly as directed the first time, and then make whatever adjustments you want for future batches. Also, don't cheap out on the Andouille. No Johnsonville or Hillshire Farms. Chef Aidelle's is a good choice, as is Silva's from Whole Foods. They cost a few extra bucks, but it's absolutely worth it.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 3 hours
- 🍽️ Servings: 12
Ingredients
- 16oz small red beans, dry
- 2 cups long grain white rice
- 14-16oz andouille sausage, sliced
- 8oz ham, cubed
- 1 large yellow onion, chopped
- 1 green bell pepper, chopped
- 2-3 stalks celery, chopped
- 2 tbsp garlic (12 cloves), minced
- 7 cups water
- ¼ cup olive oil
- 2 large bay leaves
- 1 tbsp parsley, dried
- 1 tsp thyme, dried
- 1 tsp Cajun seasoning
- ½ tsp cayenne pepper, dried
- ¼ tsp sage, rubbed
- 1½ tsp salt (more or less to taste)
Directions
- Soak beans in a large pot of water overnight.
- Heat oil in a large stockpot over medium heat. Cook onion, bell pepper, celery, garlic in olive oil for 3 to 4 minutes (until onion is translucent).
- Add beans, bay leaves, parsley, thyme, salt, MSG, Cajun seasoning, cayenne pepper, Sage, and water. Stir, bring to a boil, and then reduce heat to medium-low (btwn 2-3). Cover and simmer for 2½ hours.
- Remove bay leaves. Mash some of the beans. Stir Andouille and ham into beans, and simmer uncovered for an additional 30 minutes.
- Meanwhile, prepare the rice. Bring water and rice to a boil in a saucepan. Reduce heat, cover, and simmer for 20 minutes.
- Serve beans over steamed white rice.
-
 @ ee11a5df:b76c4e49
2024-12-16 05:29:30
@ ee11a5df:b76c4e49
2024-12-16 05:29:30Nostr 2?
Breaking Changes in Nostr
Nostr was a huge leap forward. But it isn't perfect.
When developers notice a problem with nostr, they confer with each other to work out a solution to the problem. This is usually in the form of a NIP PR on the nips repo.
Some problems are easy. Just add something new and optional. No biggie. Zaps, git stuff, bunkers... just dream it up and add it.
Other problems can only be fixed by breaking changes. With a breaking change, the overall path forward is like this: Add the new way of doing it while preserving the old way. Push the major software to switch to the new way. Then deprecate the old way. This is a simplification, but it is the basic idea. It is how we solved markers/quotes/root and how we are upgrading encryption, among other things.
This process of pushing through a breaking change becomes more difficult as we have more and more existing nostr software out there that will break. Most of the time what happens is that the major software is driven to make the change (usually by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6), and the smaller software is left to fend for itself. A while back I introduced the BREAKING.md file to help people developing smaller lesser-known software keep up with these changes.
Big Ideas
But some ideas just can't be applied to nostr. The idea is too big. The change is too breaking. It changes something fundamental. And nobody has come up with a smooth path to move from the old way to the new way.
And so we debate a bunch of things, and never settle on anything, and eventually nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 makes a post saying that we don't really want it anyways 😉.
As we encounter good ideas that are hard to apply to nostr, I've been filing them away in a repository I call "nostr-next", so we don't forget about them, in case we ever wanted to start over.
It seems to me that starting over every time we encountered such a thing would be unwise. However, once we collect enough changes that we couldn't reasonably phase into nostr, then a tipping point is crossed where it becomes worthwhile to start over. In terms of the "bang for the buck" metaphor, the bang becomes bigger and bigger but the buck (the pain and cost of starting over) doesn't grow as rapidly.
WHAT? Start over?
IMHO starting over could be very bad if done in a cavalier way. The community could fracture. The new protocol could fail to take off due to lacking the network effect. The odds that a new protocol catches on are low, irrespective of how technically superior it could be.
So the big question is: can we preserve the nostr community and it's network effect while making a major step-change to the protocol and software?
I don't know the answer to that one, but I have an idea about it.
I think the new-protocol clients can be dual-stack, creating events in both systems and linking those events together via tags. The nostr key identity would still be used, and the new system identity too. This is better than things like the mostr bridge because each user would remain in custody of their own keys.
The nitty gritty
Here are some of the things I think would make nostr better, but which nostr can't easily fix. A lot of these ideas have been mentioned before by multiple people and I didn't give credit to all of you (sorry) because my brain can't track it all. But I've been collecting these over time at https://github.com/mikedilger/nostr-next
- Events as CBOR or BEVE or MsgPack or a fixed-schema binary layout... anything but JSON text with its parsing, it's encoding ambiguity, it's requirement to copy fields before hashing them, its unlimited size constraints. (me, nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s)
- EdDSA ed25519 keys instead of secp256k1, to enable interoperability with a bunch of other stuff like ssh, pgp, TLS, Mainline DHT, and many more, plus just being better cryptography (me, Nuh, Orlovsky, except Orlovsky wanted Ristretto25519 for speed)
- Bootstrapping relay lists (and relay endpoints) from Mainline DHT (nostr:npub1jvxvaufrwtwj79s90n79fuxmm9pntk94rd8zwderdvqv4dcclnvs9s7yqz)
- Master keys and revocable subkeys / device keys (including having your nostr key as a subkey)
- Encryption to use different encryption-specific subkeys and ephemeral ones from the sender.
- Relay keypairs, TLS without certificates, relays known by keypair instead of URL
- Layered protocol (separate core from applications)
- Software remembering when they first saw an event, for 2 reasons, the main one being revocation (don't trust the date in the event, trust when you first saw it), the second being more precise time range queries.
- Upgrade/feature negotiation (HTTP headers prior to starting websockets)
- IDs starting with a timestamp so they are temporally adjacent (significantly better database performance) (Vitor's idea)
- Filters that allow boolean expressions on tag values, and also ID exclusions. Removing IDs from filters and moving to a GET command.
- Changing the transport (I'm against this but I know others want to)
What would it look like?
Someone (Steve Farroll) has taken my nostr-next repo and turned it into a proposed protocol he calls Mosaic. I think it is quite representative of that repo, as it already includes most of those suggestions, so I've been contributing to it. Mosaic spec is rendered here.
Of course, where Mosaic stands right now it is mostly my ideas (and Steve's), it doesn't have feedback or input from other nostr developers yet. That is what this blog post is about. I think it is time for other nostr devs to be made aware of this thing.
It is currently in the massive breaking changes phase. It might not look that way because of the detail and refinement of the documentation, but indeed everything is changing rapidly. It probably has some bad ideas and is probably missing some great ideas that you have.
Which is why this is a good time for other devs to start taking a look at it.
It is also the time to debate meta issues like "are you crazy Mike?" or "no we have to just break nostr but keep it nostr, we can't dual-stack" or whatever.
Personally I think mosaic-spec should develop and grow for quite a while before the "tipping point" happens. That is, I'm not sure we should jump in feet first yet, but rather we build up and refine this new protocol and spend a lot of time thinking about how to migrate smoothly, and break it a lot while nobody is using it.
So you can just reply to this, or DM me, or open issues or PRs at Mosaic, or just whisper to each other while giving me the evil eye.
-
 @ af264750:2c08cd8a
2025-01-18 16:22:48
@ af264750:2c08cd8a
2025-01-18 16:22:48บทความนี้ not a tutorial เขียนไว้เป็นบันทึกความซนของผมเอง
เรื่องมีอยู่ว่า Alby เค้าจะยกเลิก custodial wallet ที่บริการกระเป๋าให้ฟรี ซึ่งประกาศมาซักพักใหญ่ๆแล้วล่ะ ผมก็นั่งไถฟีดค้นหากระเป๋าใหม่ที่จะมาใช้แทนแล้วไปจบอยู่ที่ LifPay เอามาใช้เป็นกระเป๋าชั่วคราวไปก่อนไว้รับส่ง zap เล็กๆน้อยๆ แล้วช่วงนั้นก็เป็นจังหวะเดียวกับที่มหาลัยมีจัดงานกึ่งสัมมนาเลยได้โอกาสเปิดโต๊ะคุยเรื่อง Bitcoin กันไปทั้งคืน
ผ่านไปซักหลายวันอยู่ขณะกำลังเก็บห้อง ผมก็ไปเจอกับคอมเครื่องเก่าที่ตั้งเกาะฝุ่นหลบมุมอยู่ คอมเครื่องนี้เคยเป็นคอมเครื่องหลักที่ซื้อมาไว้ประมาณ 10 ปีหน่อยๆ จนถึงช่วงขึ้นมหาลัยที่ต้องเปลี่ยนไปแบกโน้ตบุ้กไปเรียนแทน กลายเป็นว่าคอมเครื่องนี้ก็ตั้งไว้ในห้องแบบไม่ได้เสียบปลั้กเลยไปเป็นหลักปี ก็เลยเกิดไอเดียว่าไม่งั้นก็เอามาล้างเครื่องแล้วลองเปิด node ดูหน่อยมั้ย เพราะยังไงกิจกรรมทุกอย่างตอนนี้คือย้ายไปบนโน้ตบุ้กแทนหมดแล้ว จนเป็นจุดเริ่มต้นถึงการเดินทางแห่ง home node ขึ้นมา
เตรียมเครื่อง
ด้าน hardware ที่ใช้ก็ไม่พ้นคอมเครื่องเก่านั้น ที่ตอนนี้สเปคมันค่อนข้าง overkill สำหรับการเปิด home lightning node เบาๆ เพราะนอกจากจะเป็นเคสขนาด e-ATX ที่อัด HDD ได้หลายลูกแล้วก็ยังมีการ์ดจอเก่าอยู่ด้วย สเปคคร่าวๆก็มี i5-4670k กับแรม DDR3 12GB แค่นี้ก็กินไฟไปหลายสิบวัตต์แล้ว ยังมีการ์ดจอ GTX 1050Ti เสียบอยู่เฉยๆด้วย แล้วยังมี SSD SATA 480GB ตัวนึงกับ HDD 1TB พ่วงด้วยช่องอ่านแผ่น DVD ที่ประดับหน้าเคสไว้ เลยคิดไว้ว่าน่าจะต้องซื้อคอมอีกเครื่องเล็กๆมาเปิดแทนพี่ใหญ่นี้ในเร็ววัน
หันมาด้าน software กันบ้าง ผมก็เลือก Umbrel มาใช้ สาเหตุหลักก็เน้นสะดวกครับ สละ USB drive มาอันนึงแล้ว flash เข้าไปเลย จิ้มเดียวจบ แต่ข้อเสียแรกที่เห็นเลยคือใช้ได้ drive เดียวแล้วใช้ทั้งหมดเลย 1 drive ก็เลยต้องเอาระบบไปลงที่ SSD ไม่งั้นเดี๋ยวระบบอืดตาย ก็นะ แลกกับความสะดวกก็งี้

เปิดเครื่อง
แน่นอนว่าต้นเรื่องเราคือ Alby อยากให้เราย้ายกระเป๋ามาใช้เป็น Alby Hub ที่เป็น self-custodial ซึ่งใน Umbrel นั้นจะบังคับให้เราติดตั้ง Lightning Node ที่ตัวมันก็จะบังคับให้เราลง Bitcoin Node ด้วยอีกชั้น ทำให้จำนวน app ขั้นต่ำในการเปิด Alby Hub บน Umbrel อยู่ที่ 3 apps แต่อันนี้ผมลงจุกจิกเพิ่มเข้ามาด้วย นี่แหละข้อดีอันนึงของ Umbrel

สเต็ปการทำงานเบื้องต้นก็คือต้องรอ Bitcoin Node sync ให้ครบก่อน ไม่งั้น Lightning Node จะไม่เปิดให้เราเข้าไปใช้งาน แต่ระหว่างรอ sync นั้นเราสามารถเข้าไปจด recovery seed ไว้ก่อนได้เลย ห้ามลืมเด็ดขาด
พอ Lightning Node เราพร้อมแล้ว ก็ไปกันต่อที่ Alby Hub ก็จะมีขั้นตอนตั้งค่านู้นนี้นั้น ให้เราตั้งรหัสผ่านล็อก Hub แล้ว ก็จะมีให้เชื่อม Alby Account ด้วย ซึ่งแน่นอนว่าผมมาเพื่อสิ่งนี้ แลก auth token กันนิดหน่อยก็ถึงหน้า dashboard แล้ว
เปิดช่อง
เมื่อผมหันมาใช้ self-custodial wallet แล้ว สิ่งแรกที่ต้องจัดการเลยคือต้องมีช่องทางให้เงินไหลเข้ามา ไม่งั้นจะเปิด node เผาค่าไฟไปทำไมเนอะ ซึ่งใน Alby Hub เนี่ยเค้าก็มีรายชื่อผู้ให้บริการ LSP ที่เราสามารถซื้อ channel เปิดทางให้เงินไหลเข้ามาได้ ซึ่งผมก็เลือกเปิด channel กับ Lnserver เพราะลองเทียบราคาดูแล้วคือจ่ายค่าเปิด channel น้อยที่สุดในลิสด์นี้แล้ว บวกกับว่าเราสามารถออกไปซื้อตรงๆกับทาง Lnserver เองเหมือนกัน

โน้ตสำคัญของผมเวลาเปิด channel มีอยู่สองจุด จุดแรกคือต้องดู on-chain fee rate เพราะทุกครั้งที่เราเปิด channel ทาง LSP เค้าจะต้องส่งธุรกรรมเข้า block ซึ่งจะต้องเสีย fee เพิ่มกว่าเรทจริงอีกหน่อย ทำให้บางทีค่าเปิด channel โดนอัดราคาเพิ่มจนสูงกว่าค่าบริการของ LSP นั้นๆอีก อย่างของผมที่ซื้อกับ Lnserver เค้าจะเก็บเริ่มต้นที่ 5000 sats สำหรับ channel ขนาด 2,000,000 sats แล้วจะบวก commit fee ไปอีก 1345 sats ที่เรท 2 sats/vB รวมกันเป็น 6345 sats ที่จ่ายไป
โน้ตที่สองที่ต้องเตรียมไว้ด้วยก็คือ reserve fund โดยผมจะเรียกอีกอย่างว่าเป็นค่าประกัน channel ซึ่งค่าประกันตรงนี้จะเก็บไว้เป็นขั้นต่ำของ channel นั้นๆฝ่ายละ 1% แล้วจะล็อกตายเก็บไว้เอาออกมาใช้จ่ายไม่ได้จนกว่าจะปิด channel ถ้าไม่จ่ายค่าประกันตรงนี้ เราก็จะรับเข้าและจ่ายออกจากฝั่งเราไม่ได้ หมายความว่า channel ขนาด 2,000,000 sats ก็ต้องมีเงินประกันเข้าไปด้วยจากฝั่งผม 20,000 sats ถึงจะใช้งานได้

ใครที่สนใจอ่านเพิ่มเติม ผมมีเว็บข้อมูลเกี่ยวกับ Lightning liquidity มาแนะนำ อันนี้แหละที่ผมอ่านแล้วเพิ่งมารู้เกี่ยวกับ channel reserve รวมถึงเรื่องอื่นๆที่น่ารู้เกี่ยวกับวงบริวารและการออกแบบระบบที่เกี่ยวกับ Bitcoin
https://bitcoin.design/guide/how-it-works/liquidity/#what-is-the-reserve-amount
-
 @ 2f5de000:2f9bcef1
2024-12-15 16:44:53
@ 2f5de000:2f9bcef1
2024-12-15 16:44:53This Week I immersed myself in Bitcoin from multiple angles-technical, societal and personal. The journey included a marathon 32-hours of listening to Rabbit Hole Recap (RHR), an essential resource for Bitcoin insights. It's worth noting that I started from the begining and plan to make my way through the whole catalogue. Marty and Matt's timestamps, along with contributions from their guests, served as my roadmap. Using Fountain to stream, I also streamed sats-a small but extraordinary feature that allows users to stacks sats while compensating cretors directly through fractional donations.
Revisiting Speculative Attack by Pierre Rochard (2014)
Now that Speculative Attack Season 2 (which I've not read yet) has been released. I took the time to read Pierre Rochards influential essay, Speculative Attack and reflected on its timeless insights. Rochard argues that Bitcoin adoption isn't dependent on technological advancements or consumer preferences, but on economic realities. As fiat currencies weaken, Bitcoin won't enter the mainstream by persuasion but by necessity.
Critics continue to underestimate Bitcoin's inevitability due to their fiat biases and lack of financial insight. This year alone, mainstream media has been compelled to discuss Bitcoin-notably to Trump's endorsement of 'crypto.' Despite their attempts to shape narratives to suit their ideal visions, they've had no choice but to engage with Bitcoin's growing influence.\ \ As Parker aptly puts it 'Gradually, The Suddenly'
Wassabi Wallet and the Privacy Imperative
An RHR interview (from early in the catalogue) with guest Adam Ficsor, CTO and Co-founder of Wassabi Wallet, sparked a deeper consideration of my digital footprint. Like many, I've spent years online neglecting privacy in favour of convenience. The discussion on CoinJoins reminded me of the importance of prioritising privacy, not just romanticising it.
Improving operational security (opsec) is now a personal focus. Resources like Jameson's Cypherpunk Cogitations and the Bitcoin Optech newsletter offer valuable guidance. While I've exercised caution, I recognise a need to address my laziness with opsec and take meaningful steps to protect my privacy. Time will reveal the results of these efforts.
Caribbean Slavery amd Centralised Platforms
While exploring historical systems of control, I delved into the brutal realities of New World slavery in the British Caribbean. Enslaved elites, like drivers, were granted limited privileges to maintain order, creating divisions within the community. This divide-and-rule strategy highlights the fragility of oppressive frameworks, which began to crumble with events like the Hatian Revolution and humanitarian activism.
Interestingly, similar dynamics are visible with centralised plaforms like Twitter, LinkedIn, and Instagram. Verified accounts (the "blue checks") act as mordern day 'elites' with perceived freedoms. However, their autonomy is limited by the platforms centralised authority. Challenging the rules risks censorship and cancellation, proving their freedom is an illusion subject to the will of their overseers. Enhancing the argument further for protocols like Nostr to help people win back their freedoms.
-
 @ 7460b7fd:4fc4e74b
2024-09-05 08:37:48
@ 7460b7fd:4fc4e74b
2024-09-05 08:37:48请看2014年王兴的一场思维碰撞,视频27分钟开始
最后,一个当时无法解决的点:丢失
-
 @ 378562cd:a6fc6773
2025-01-18 16:20:12
@ 378562cd:a6fc6773
2025-01-18 16:20:12As a frequent user who depends on my phone for a wide range of activities, including boosting my productivity and capturing spontaneous moments, I have been paying close attention to the OnePlus 13. This flagship device appears to meet all my essential requirements, particularly excelling in power and camera capabilities, which are my main priorities. Here are the standout features that have caught my attention.

Power to Handle Anything I Throw at It
Performance is a big deal for me, and the OnePlus 13 doesn’t seem to disappoint. It’s powered by the Snapdragon 8 Elite processor, a beast in the mobile tech world. I can already imagine how smoothly it would handle heavy multitasking, like switching between editing photos, running multiple apps, and even gaming.
The insane memory options—up to 24GB of RAM—truly stand out. That’s more RAM than most laptops I’ve owned! Pair that with up to 1TB of storage, and you’re looking at a future-proof phone. I’d never have to worry about running out of space for apps, photos, or videos, and everything would load lightning-fast.

A Camera Setup That’s Hard to Ignore
One of my favorite things to do is capture high-quality photos and videos, so a powerful camera system is non-negotiable. The OnePlus 13 delivers with its triple-camera setup; all three lenses are 50 megapixels. That means whether I’m shooting with the main wide lens, zooming in with the telephoto, or going wide with the ultra-wide, I’m getting consistently sharp, detailed shots.
The Hasselblad collaboration is a big draw for me, too. OnePlus phones have been steadily improving their color science, and this partnership seems to really shine in the OnePlus 13. I’d expect vibrant, true-to-life colors in my photos without much editing required.
The AI enhancements also pique my interest. From what I’ve read, the phone handles tricky lighting situations, like low-light environments or high-contrast scenes, exceptionally well. That’s exactly what I need to capture spontaneous moments without worrying about settings.
Battery and Charging That Won’t Leave Me Hanging
Another thing I appreciate is the long battery life. The 6,000 mAh battery on the OnePlus 13 is reportedly a powerhouse, capable of lasting two days under mixed usage. And when I do need to charge, the 100W wired charging can fully juice up the phone in just over half an hour. Even the 50W wireless charging is incredibly fast, which is perfect for someone like me who’s always on the move.
Design and Features That Add Value
The flat-edge design and premium finish make the phone feel as good as it looks. I’d probably go for the Midnight Ocean with its vegan leather back—it sounds grippy and unique, ideal for someone who doesn’t want to slap on a bulky case.
The little extras, like Glove Mode and Aqua Touch 2.0, also catch my attention. Since winters are cold here, using my phone with gloves on is a practical bonus.
Why It’s Tempting Me
At $899 for the base model, the OnePlus 13 seems like a solid deal, especially for the power and camera capabilities it offers. Even if I choose a higher configuration, the pricing still feels reasonable compared to other flagships with similar specs.
For me, the OnePlus 13 feels like a phone that’s built for power users—people who need speed, reliability, and top-tier camera performance. I’m seriously considering it for my next upgrade because it feels like it would keep up with everything I do and then some. If the camera and performance live up to the hype, I might just have my decision made.
-
 @ 8fb140b4:f948000c
2024-12-08 05:21:39
@ 8fb140b4:f948000c
2024-12-08 05:21:39After nuking my second LND node (the first one died due to hardware failure) by my own typo and lack of any thought in the design of the CLI of LND lightning node tools, I decided to take a plunge into the world of mature and complex implementation of the protocol, Eclair by ACINQ. It has been almost one year (the birth of the node was on Christmas Day 2023), 50 thousand transactions routed, and over 30 BTC of routed value. In this post, I'd like to reflect on my experiences with Eclair, go over some of the gotchas and issues, and highlight some of the good choices that I've made since the beginning of my adventure.
Learnings from the Past Experience
While I was learning Lightning network and had very little understanding of how things worked in the whole Bitcoin space, Umbrel was my go-to solution that helped me get off the ground. It proved to be easy and somewhat educational but was not something that I would continuously run for the production setup or trust with any significant amount of bitcoin that I could not afford to lose. Lightning is built on top of the L1 (Bitcoin) network but manages the state of the channels in its own database that is negotiated and agreed upon with its peers. Any failures in the state integrity may result in the complete loss of liquidity or hefty penalty transactions (significant loss of capital). A Lightning node that participates in routing public transactions is also required to be constantly online with as little downtime as possible and only short periods offline at a time. Otherwise, you may risk causing force-closure of the channel due to expired HTLC that is measured in number of blocks.
The Setup
Taking all of my learnings into consideration, I decided to first invest in reliable enterprise-grade hardware: - Server-grade hardware with ECC memory and reliable power supply and CPU - UPS (Uninterruptible Power Supply) to avoid any headaches due to electrical spikes or drop-outs - Reliable enterprise SSDs and NVMEs - ZFS (filesystem) to mirror the critical storage and to ensure full integrity of the data (bit-rot prevention). You do need to tune ZFS for your specific workload and reliability - Reliable and replicated database (PostgreSQL) with two local and one remote replica, and a requirement to have at least two replicas committing the transaction to the disk - Backup! On-site and off-site backup of the critical configuration that you could use to restore the node if your house burns down - Spare parts, redundancy, backup, monitoring - Reliable and stable internet connectivity
The software is Eclair 0.11.0 (latest release as of today), PostgreSQL 16 with two replicas, Bitcoin Core 27.2 (with redundant storage of blocks), additional Bitcoin Core running on a separate node and in-sync with the chain (in case primary node fails), Ubuntu 22.04 with the latest docker software from the official Docker repo.
All Major Gotchas That I Came Across
While Eclair is mature and very stable in itself, it does have some quirks and design choices that you need to account for when running your node. The software is written in Scala and requires a specific version of JVM to run it, as well as JRE and Maven to build it. It doesn't mean that other versions won't work, but you may find unpleasant bugs that may result in catastrophic failures of your node with nobody to help you. All of the requirements are listed in the release notes and installation guide. Whenever in doubt, RTFM first, then ask questions.
Limited Support by the FOSS Community
Eclair is not the most popular implementation of the Lightning protocol, and therefore it is hard to find tools or plugins that could help you manage the node. GUI for the node so far is only supported by RTL and with a very limited number of features. For any sort of statistics, you are limited to either Prometheus (extensive metrics are available) or writing your own SQL on top of the Eclair tables.
On-chain Fee Differences Between Yours and Partner Nodes
This one hit me hard, and many times. I've had more than a few force-closures of the channels because of the conservative and safe default settings. The worst part is, it strikes you when there is a huge spike in fees, which results in significant losses to force-close the channel due to high fees. I am still not 100% sure how the big difference can be exploited in practice, and opted for increase of the tolerance levels to avoid surprise FCs:
eclair.on-chain-fees { feerate-tolerance { ratio-low = <0.01~> // will allow remote fee rates as low as XX our local feerate (spikes) ratio-high = <20.0~> // will allow remote fee rates as high as XX times our local feerate (drops) } }It is up to you and your risk tolerance to define something reasonable and yet allow for secure and reliable node operation.Initial Lightning Network State Sync
When I just started running the node, I had very few channels and startup times were fast. Later, when I expanded the number of channels, I noted that it took my node up to 6-12 hours before it was fully in-sync and routing traffic fast. Given that ACINQ maintains one of the largest nodes on the network, I knew that there was something with my settings that caused the issue. After some research, I came across the setting that whitelisted node IDs for state sync, which immediately rang a bell since I knew from the LND days that not all peer nodes are used for the network sync. Setting the list to my most reliable and largest nodes reduced the startup settling times down to minutes again:
eclair.sync-whitelist = [ "03864ef025fde8fb587d989186ce6a4a186895ee44a926bfc370e2c366597a3f8f", ... ]You do not need to have too many public keys in here, and should keep it between 5-10.Automatic MAX HTLC Adjustment for the Channel
One of the killer features of Eclair is its ability to automatically adjust MAX HTLC for the channel and reduce the number of failed transactions due to insufficient liquidity on the channel. It can be used to estimate your total channels' balances but with smart configuration and a little thinking, you can make it reasonably private while still maintaining a good transaction flow:
eclair.channel.channel-update.min-time-between-updates=1 hour # Allows for the adjustments to be made once every hour eclair.channel.channel-update.balance-thresholds=[ { available-sat = 10000 max-htlc-sat = 0 // 0% of 10000 }, ... ]You can have as many variations as you need, and ensure that the channel MAX HTLC is set well and within reasonable ranges. You would also want to account for multiple transactions going through the channel, but also account for the channel size and an average amount of sats per transaction.Max Accepted HTLCs
By design, the Lightning channel is limited to a specific number of in-flight HTLCs, and the setting is fixed during channel opening time with no way of changing it unless you close and reopen the channel with new settings. If you find your node routing a lot of small transactions (zaps), you may quickly fail many due to that limit (I think default was in single digit range):
eclair.channel.max-htlc-value-in-flight-percent=98 # Default I think is half or 50% eclair.channel.max-accepted-htlcs = 50The setting above will allow for the channel to be more fully utilized and have more concurrent transactions without clogging.CLTV Delta
This is basically a setting that is global for Eclair and sets the maximum number of remaining blocks (in time) before HTLC expires. Setting this too high may result in many HTLCs failing for the small nodes with not so great centrality, and reduce the number of routed transactions: ```
CLTV delta
eclair.channel.expiry-delta-blocks = 60 ``` Default is 144 but I found that setting this to 60 (minimum possible for my node setup and configuration) yields better results for routing. It does expose you to more risk of expired HTLCs that may cause force-closures, but I have seen only one so far on my node.
Allocate Sufficient Memory
You will want to adjust the heap size for Eclair, since the default is too small to run any sizable node. Setting
JAVA_OPTS=-Xmx32g(or half the size of your available RAM) would be a good start. I would advise having at least 32GB of RAM for the node, and allocating at least 16GB (JAVA_OPTS=-Xmx16g) for smooth and fast operations.And More Settings and Parameters to Tune
I have covered only some of the major settings that I felt were worth writing about, but there is much more you could configure and tweak. Read all of the Guides and especially focus on the Configure and a sample reference configuration file.
Good Decisions
First, going with Eclair was the right choice, along with using server-grade hardware with ECC RAM and reliable storage. Second, having a replicated database on three separate nodes with one off-site saved me from a sure destruction of all state and loss of funds. Third, deciding to only maintain channels with reliable and stable nodes saved me from some bad force-closures, where I would choose to close the channel if a peer node goes up and down too frequently, regardless of how well it routes. Even big nodes run by single operators fail badly, as do nodes operated by companies. Keeping your eyes on the node and its health, as well as the health of its peers, is something that very few operators do, which can cause failures and unnecessary loss of your and their funds.
Lastly, if you decide to run a routing node, you have a responsibility to maintain it well and monitor its health. There are many tools you could use, and with Eclair you can use Prometheus and Grafana. Keep your node's packages updated and monitor for any security-related issues that may appear from time to time, so you can mitigate them quickly.
Conclusion
So far I am satisfied with Eclair despite all of the difficulties and headaches I've had with it. It is not perfect, and it requires me to create small tools to do some basic things, but I need a stable and reliable node that I can trust. Eclair has proved to be all that I wanted, and saved my bacon a few times when I nuked one of the PostgreSQL servers and all of its data, and managed to do the same for another replica, but was able to recover and recreate from the remaining replica. Eclair is also stateless during runtime and guarantees consistency of the node regardless of how it fails. Even if you pull a plug on the node's server, it will still be able to come up and recover its consistent state that is in agreement with its peers.
Is it for everyone? No, it is definitely not for everyone or for anyone who just wants a small node to run their online shop with a few channels. You could have a very reliable and trusted node for the online shop with Eclair, but you will need some technical skills to be able to set up, maintain and recover it if things go wrong.
In the end, it is all up to you, your skills, your willingness to learn, and your risk tolerance to make that decision. For me, it was the right choice, and I have no regrets despite not having access to the latest shiny features of the Lightning network.
-
 @ 6389be64:ef439d32
2024-12-09 23:50:41
@ 6389be64:ef439d32
2024-12-09 23:50:41Resilience is the ability to withstand shocks, adapt, and bounce back. It’s an essential quality in nature and in life. But what if we could take resilience a step further? What if, instead of merely surviving, a system could improve when faced with stress? This concept, known as anti-fragility, is not just theoretical—it’s practical. Combining two highly resilient natural tools, comfrey and biochar, reveals how we can create systems that thrive under pressure and grow stronger with each challenge.
Comfrey: Nature’s Champion of Resilience
Comfrey is a plant that refuses to fail. Once its deep roots take hold, it thrives in poor soils, withstands drought, and regenerates even after being cut down repeatedly. It’s a hardy survivor, but comfrey doesn’t just endure—it contributes. Known as a dynamic accumulator, it mines nutrients from deep within the earth and brings them to the surface, making them available for other plants.
Beyond its ecological role, comfrey has centuries of medicinal use, earning the nickname "knitbone." Its leaves can heal wounds and restore health, a perfect metaphor for resilience. But as impressive as comfrey is, its true potential is unlocked when paired with another resilient force: biochar.
Biochar: The Silent Powerhouse of Soil Regeneration
Biochar, a carbon-rich material made by burning organic matter in low-oxygen conditions, is a game-changer for soil health. Its unique porous structure retains water, holds nutrients, and provides a haven for beneficial microbes. Soil enriched with biochar becomes drought-resistant, nutrient-rich, and biologically active—qualities that scream resilience.
Historically, ancient civilizations in the Amazon used biochar to transform barren soils into fertile agricultural hubs. Known as terra preta, these soils remain productive centuries later, highlighting biochar’s remarkable staying power.
Yet, like comfrey, biochar’s potential is magnified when it’s part of a larger system.
The Synergy: Comfrey and Biochar Together
Resilience turns into anti-fragility when systems go beyond mere survival and start improving under stress. Combining comfrey and biochar achieves exactly that.
-
Nutrient Cycling and Retention\ Comfrey’s leaves, rich in nitrogen, potassium, and phosphorus, make an excellent mulch when cut and dropped onto the soil. However, these nutrients can wash away in heavy rains. Enter biochar. Its porous structure locks in the nutrients from comfrey, preventing runoff and keeping them available for plants. Together, they create a system that not only recycles nutrients but amplifies their effectiveness.
-
Water Management\ Biochar holds onto water making soil not just drought-resistant but actively water-efficient, improving over time with each rain and dry spell.
-
Microbial Ecosystems\ Comfrey enriches soil with organic matter, feeding microbial life. Biochar provides a home for these microbes, protecting them and creating a stable environment for them to multiply. Together, they build a thriving soil ecosystem that becomes more fertile and resilient with each passing season.
Resilient systems can withstand shocks, but anti-fragile systems actively use those shocks to grow stronger. Comfrey and biochar together form an anti-fragile system. Each addition of biochar enhances water and nutrient retention, while comfrey regenerates biomass and enriches the soil. Over time, the system becomes more productive, less dependent on external inputs, and better equipped to handle challenges.
This synergy demonstrates the power of designing systems that don’t just survive—they thrive.
Lessons Beyond the Soil
The partnership of comfrey and biochar offers a valuable lesson for our own lives. Resilience is an admirable trait, but anti-fragility takes us further. By combining complementary strengths and leveraging stress as an opportunity, we can create systems—whether in soil, business, or society—that improve under pressure.
Nature shows us that resilience isn’t the end goal. When we pair resilient tools like comfrey and biochar, we unlock a system that evolves, regenerates, and becomes anti-fragile. By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
-
-
 @ b60c3e76:c9d0f46e
2024-05-15 10:08:47
@ b60c3e76:c9d0f46e
2024-05-15 10:08:47KRIS menjamin semua golongan masyarakat mendapatkan perlakuan sama dari rumah sakit, baik pelayanan medis maupun nonmedis.
Demi memberikan peningkatan kualitas layanan kesehatan kepada masyarakat, pemerintah baru saja mengeluarkan Peraturan Presiden (Perpres) nomor 59 tahun 2024 tentang Jaminan Kesehatan. Melalui perpres itu, Presiden Joko Widodo (Jokowi) telah menghapus perbedaan kelas layanan 1, 2, dan 3 dalam Badan Penyelenggara Jaminan Sosial atau BPJS Kesehatan.
Layanan berbasis kelas itu diganti dengan KRIS (Kelas Rawat Inap Standar). Berkaitan dengan lahirnya Perpres 59/2024 tentang Perubahan Ketiga atas Perpres 82/2018 tentang Jaminan Kesehatan, Presiden Joko Widodo telah memerintahkan seluruh rumah sakit yang bekerja sama dengan BPJS Kesehatan melaksanakannya.
Kebijakan baru itu mulai berlaku per 8 Mei 2024 dan paling lambat 30 Juni 2025. Dalam jangka waktu tersebut, rumah sakit dapat menyelenggarakan sebagian atau seluruh pelayanan rawat inap berdasarkan KRIS sesuai dengan kemampuan rumah sakit.
Lantas apa yang menjadi pembeda dari sisi layanan dengan layanan rawat inap sesuai Perpres 59/2024? Dahulu sistem layanan rawat BPJS Kesehatan dibagi berdasarkan kelas yang dibagi masing-masing kelas 1, 2, dan 3. Namun, melalui perpres, layanan kepada masyarakat tidak dibedakan lagi.
Pelayanan rawat inap yang diatur dalam perpres itu--dikenal dengan nama KRIS—menjadi sistem baru yang digunakan dalam pelayanan rawat inap BPJS Kesehatan di rumah sakit-rumah sakit. Dengan KRIS, semua golongan masyarakat akan mendapatkan perlakuan yang sama dari rumah sakit, baik dalam hal pelayanan medis maupun nonmedis.
Dengan lahirnya Perpres 59/2024, tarif iuran BPJS Kesehatan pun juga akan berubah. Hanya saja, dalam Perpres itu belum dicantumkan secara rinci ihwal besar iuran yang baru. Besaran iuran baru BPJS Kesehatan itu sesuai rencana baru ditetapkan pada 1 Juli 2025.
“Penetapan manfaat, tarif, dan iuran sebagaimana dimaksud ditetapkan paling lambat tanggal 1 Juli 2025,” tulis aturan tersebut, dikutip Senin (13/5/2024).
Itu artinya, iuran BPJS Kesehatan saat ini masih sama seperti sebelumnya, yakni sesuai dengan kelas yang dipilih. Namun perpres itu tetap berlaku sembari menanti lahirnya peraturan lanjutan dari perpres tersebut.
Kesiapan Rumah Sakit
Berkaitan dengan lahirnya kebijakan layanan kesehatan tanpa dibedakan kelas lagi, Kementerian Kesehatan (Kemenkes) menegaskan mayoritas rumah sakit di Indonesia siap untuk menjalankan layanan KRIS untuk pasien BPJS Kesehatan.
Kesiapan itu diungkapkan oleh Dirjen Pelayanan Kesehatan Kemenkes Azhar Jaya. “Survei kesiapan RS terkait KRIS sudah dilakukan pada 2.988 rumah sakit dan yang sudah siap menjawab isian 12 kriteria ada sebanyak 2.233 rumah sakit,” ujar Azhar.
Sebagai informasi, KRIS adalah pengganti layanan Kelas 1, 2, dan 3 BPJS Kesehatan yang bertujuan untuk memberikan layanan kesehatan secara merata tanpa melihat besaran iurannya.
Melalui KRIS, rumah sakit perlu menyiapkan sarana dan prasarana sesuai dengan 12 kriteria kelas rawat inap standar secara bertahap. Apa saja ke-12 kriteria KRIS itu?
Sesuai bunyi Pasal 46A Perpres 59/2024, disyaratkan kriteria fasilitas perawatan dan pelayanan rawat inap KRIS meliputi komponen bangunan yang digunakan tidak boleh memiliki tingkat porositas yang tinggi serta terdapat ventilasi udara dan kelengkapan tidur.
Demikian pula soal pencahayaan ruangan. Perpres itu juga mengatur pencahayaan ruangan buatan mengikuti kriteria standar 250 lux untuk penerangan dan 50 lux untuk pencahayaan tidur, temperature ruangan 20--26 derajat celcius.
Tidak hanya itu, layanan rawat inap berdasarkan perpres itu mensyaratkan fasilitas layanan yang membagi ruang rawat berdasarkan jenis kelamin pasien, anak atau dewasa, serta penyakit infeksi atau noninfeksi.
Selain itu, kriteria lainnya adalah keharusan bagi penyedia layanan untuk mempertimbangkan kepadatan ruang rawat dan kualitas tempat tidur, penyediaan tirai atau partisi antartempat tidur, kamar mandi dalam ruangan rawat inap yang memenuhi standar aksesibilitas, dan menyediakan outlet oksigen.
Selain itu, kelengkapan tempat tidur berupa adanya dua kotak kontak dan nurse call pada setiap tempat tidur dan adanya nakas per tempat tidur. Kepadatan ruang rawat inap maksimal empat tempat tidur dengan jarak antara tepi tempat tidur minimal 1,5 meter.
Tirai/partisi dengan rel dibenamkan menempel di plafon atau menggantung. Kamar mandi dalam ruang rawat inap serta kamar mandi sesuai dengan standar aksesibilitas dan outlet oksigen.
Azhar menjamin, Kemenkes akan menjalankan hal tersebut sesuai dengan tupoksi yang ada. “Tentu saja kami akan bekerja sama dengan BPJS Kesehatan dalam implementasi dan pengawasannya di lapangan,” ujar Azhar.
Berkaitan dengan perpres jaminan kesehatan itu, Direktur Utama BPJS Kesehatan Ghufron Mukti menilai, perpres tersebut berorientasi pada penyeragaman kelas rawat inap yang mengacu pada 12 kriteria. "Bahwa perawatan ada kelas rawat inap standar dengan 12 kriteria, untuk peserta BPJS, maka sebagaimana sumpah dokter tidak boleh dibedakan pemberian pelayan medis atas dasar suku, agama, status sosial atau beda iurannya," ujarnya.
Jika ada peserta ingin dirawat pada kelas yang lebih tinggi, kata Ghufron, maka diperbolehkan selama hal itu dipengaruhi situasi nonmedis. Hal itu disebutkan dalam Pasal 51 Perpres Jaminan Kesehatan diatur ketentuan naik kelas perawatan.
Menurut pasal tersebut, naik kelas perawatan dilakukan dengan cara mengikuti asuransi kesehatan tambahan atau membayar selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya yang harus dibayar akibat peningkatan pelayanan.
Selisih antara biaya yang dijamin oleh BPJS Kesehatan dengan biaya pelayanan dapat dibayar oleh peserta bersangkutan, pemberi kerja, atau asuransi kesehatan tambahan.
Ghufron Mukti juga mengimbau pengelola rumah sakit tidak mengurangi jumlah tempat tidur perawatan pasien dalam upaya memenuhi kriteria KRIS. "Pesan saya jangan dikurangi akses dengan mengurangi jumlah tempat tidur. Pertahankan jumlah tempat tidur dan penuhi persyaratannya dengan 12 kriteria tersebut," tegas Ghufron.
Penulis: Firman Hidranto Redaktur: Ratna Nuraini/Elvira Inda Sari Sumber: Indonesia.go.id
-
 @ dd664d5e:5633d319
2024-12-07 20:02:01
@ dd664d5e:5633d319
2024-12-07 20:02:01Yeah, so... nah.
People keep trying to explain to me, that women will be better-off, if they become more dangerous. While I can see the inevitableness of women living in remote rural areas learning to shoot with a rifle, and similar, I'm generally against arming women with killing machines.
This is not because I'm averse to the idea of using violence to solve problems (albeit after exhausting better options), or because I don't like guns, or am unfamiliar with them. It's also not because I don't know I would look totally, mind-numbingly hot holding something long and spearlike, while dressed in camo and wearing a T-Shirt that appears to have shrunk in the wash.

It's a more fundamental set of problems, that irks me.
Bazooka Barbie
American gun manufacturers saturated the public and private male market so thoroughly, that they eventually turned to marketing firearms to women.
Men are scary and bad. There is Stranger Danger. We can't just make the neighborhood less dangerous because erm... reasons. Stay safe with a cute gun.

It has gone along with the predictable hypersexualization of the conservative feminine ideal. Since guns are considered aggressive, women with guns are perceived as more sexually available. Guns (and tanks, bombs, bows, etc.) make women "equal", "independent", "feisty", "hot", "freaky", "calculating", "empowered", etc.

Sorta slutty, basically.
This Gun Girl is not like the helpless, hapless, harmless homemaker ideal, of yesteryear. A woman who was dependent, chaste, gentle, wise... and in need of protection. A woman who saw the men around her as people she could rely on for providing her with a safe environment. That woman is au revoir. Now, sistas are doing it for themselves. 💪🏻
The New Martial Missy needs a man, like a fish needs a bicycle... but make it country.
Yeah, it's marketing, but it sure has set the tone, and millions of men have been trained to prefer women who market themselves in this manner. Hard, mean, lean women. That will not remain without wider societal consequences.
You know, I liked that homemaker. I miss her. She's literally me.

Those arms are for cuddling babies, not holding rocket launchers.
Now, that we've all become accustomed to imagery of women holding firearms, it wasn't much of a leap to condition us all to the sight of women in frontline police, guard, or military positions.

Instead of war being a terrible, highly-lethal, territorial fight amongst men, it's now cute, hip, trendy and fun. It's a big party, and women are finally allowed to join in.

Now, women have finally jettisoned the terrible burden of being society's life-bearers and caretakers, and we're just more potential enemy combatants. We know it's okay to punch women, shoot women, etc. since we've been watching it happen on screens, for decades. Women are now often assumed to be fighters, not lovers. Cavalry, not mothers.
Girls on top
Not only does this undermine any female role -- and put female civilians under a cloud of suspicion -- it also reduces mens' claim to be paramount in governance. Why should a man be the Commander in Chief, if women are on the battlefield?
In fact, why should men be in charge of anything, anywhere? Look at them. There they are. Hiding at home. Cowering in their kitchens, wringing their hands and fretting, while courageous, dangerous women protect them from dangers foreign and domestic. Women are the better men, really.
Is this really where we want to go?
The final bitterness
But one thing I find most disturbing is something more personal. The ubiquitous nature of firearms in American homes has made domestic violence increasingly deadly. Adding more guns, for the female residents, often serves to make such violence even more deadly for women.
It turns out, that women are usually reluctant to shoot people they know; even more than men. Women without this inhibition are prone to sharing their home with men missing the same trait. And, now, they have more guns.
-
 @ f84e0b6b:f21f0a9b
2025-01-18 16:06:45
@ f84e0b6b:f21f0a9b
2025-01-18 16:06:45I’ve never lived in LA, though I’ve visited many times. The devastation there from recent fires there is still in the headlines and anyone with a soul feels for the folks without homes, neighbors and communities. Whether they vote the same way or look the same way or worship the same god, “what can I do to help these victims?” is our first question.
The second question is, what is the most responsible way to help? Paragraph two and controversy is already here. Responsible according to who? These people are victims, just give them as much money as they need and let them figure it out according to their local knowledge and culture! The broadest possible answer to this comes from a recent Substack by Arnold Kling: California Tough Love . His position is that there are certain factors controlled locally that led to the disaster, and we shouldn’t be in a rush to replicate them. Having some strings attached to funds that reduce the likelihood of $50,000/year blue collar workers in Iowa footing the bill for the rebuild of $5,000,000 homes in Pacific Palisades AGAIN in the foreseeable future is a very reasonable position.
My position here will be more detailed than Arnold’s, and thus has a higher probability of being wrong. That has never stopped me before. The source of this hubris is a crystal ball. While not a resident of LA, I have been an honorary citizen of Maui for several decades. This attachment is longer than the attachment to the city I currently live in. In August of 2023, a similar devastating fire engulfed the town of Lahaina on the west side of Maui. \~2,200 homes were burned or damaged. The plight of those rebuilding and the process they have gone through quickly faded from national attention, but not to those of us who spend substantial amounts of time on the island. This experience 17 months before the LA fires has painted a depressing blueprint of what we can expect in LA’s recovery. A couple of highlights:
-
In November of 2024, the first house was rebuilt. 15 months = 1 house. First House Rebuilt - Maui News. Article highlight: Maui “expedited the permitting process for this house, so it “only” took 2 months.
-
In December of 2024, federal funding for rebuilding via a block grant is finally approved by congress. Federal Block Grant For Rebuild - Maui News. Article highlight: $1.6 billion approved for housing = \~$800,000 per house.
What do these items have in common? The biggest price so far is time. Arnold’s substack was more of a philosophical position, but I doubt even he knew that at the time of writing, Lahaina’s federal funding had just been approved. All those strings he had attached by the feds? Still very slow for a family without a home. This is half of the ‘real price gouging’ mentioned in the subtitle. Those further down the socio-economic ladder have less time to whether the process in Lahaina and the same will likely be true for the middle class residents embedded in the areas destroyed by California’s fires.
The second element of price gouging is the red tape partially embodied in Maui’s example of two months of permitting. These costs aren’t just the time, but also the professional consultants of various stripes required to navigate the process successfully and the costly modifications to homes mandated through these processes.
Here is where I posit my broad and general suggestion. There should exist a “right to rebuild”. If you can legally own a piece of property in a specific condition, you should have the right to rebuild that exact same property if it is destroyed by means out of your control. If you don’t have a “right to rebuild”, you really don’t own that property - you are just renting it for an indefinite period from whoever can prohibit rebuilding it.
Rebuilding is a special case in both the individual and the community level. See the map of Lahaina below. We know where all the plumbing and power lines were. We know where the streets and drainage were. The right to rebuild translates nicely to the community level. Rebuild everything back where it was. Take a month or two to clear out the debris from an area and begin to rebuild. Rinse and repeat until done.
Taxpayers in Texas shouldn’t be paying for bloated permitting processes in Lahaina or LA. They shouldn’t be paying for eco-upgrades unless very specific, critical failures that caused the current disaster are clearly identified with lowest-cost available solutions. (In Lahaina - pay to bury the power lines. I drove through the area where the fire started 2 weeks before it occurred. That place was a tinder box, and it will be again unless someone puts a golf course on that hill. Burying the power lines will dramatically reduce the fire hazard. I’m not joking about the golf course. Directly adjacent to the north of the area of Lahaina that burned is Ka’anapali, whose identical hillside is green all year round due to the presence of golf courses that pay for themselves and do not burn.)
How to address this in the context of federal funding via Arnold’s original post:
-
Extremely expedited permitting process for rebuilds that get any federal funding: 5 days not 60. You can rebuild what you had, no questions asked, just file the paper work to prove it is the same lot and same size structure. If local jurisdictions drag their heels - no funding, answer to your voters who are now SOL.
-
Capped amount of funding per structure that covers a functional modest structure built at the average cost of the 10 most affordable states in the country. The process of building a single family residence is not dramatically different in various areas of the country, unless dictated by excessive regulation. There may be factors for labor to consider if an area is remote like Lahaina or the hills of North Carolina affected by Helene. But if it costs 2x to build a house in your county than in the 10 most affordable states - you are doing it wrong. There is some regulatory price gouging going on. Figure it out. 10 most affordable states to build a home - According to this research you can build a 2,100 square foot home for an average of less than $300,000 in the 10 most affordable states. This list includes Florida, South Dakota and Tennessee. Your geography is not special.
-
This funding will also be contingent on these rebuilt houses being completed within 110% of the time it takes to build 2,100 square foot home in the same 10 markets - measured from the day funds begin to be distributed by the federal government. Some things will take longer, but some should also be faster if you are doing a lot of these in the same place at the same time.
-
Federal funding will begin to be distributed from a risk pool within 6 months of the disaster, with minimal review to just ensure the disaster qualifies and the receiving state/city will abide by its parameters.
-
The funding is distributed at intervals governed by compliance with the program. Permits are being issued timely, and the amounts distributed are aligned with the cost of building in our most affordable markets.
If you want to build something new and different than before - it might take longer. If you want more than 2,100 square feet of house - I hope you had insurance to cover the difference. A new 2,100 square foot house puts you in the top 10% of humans on earth in terms of shelter. Being a good neighbor does not require rebuilding your infinity pool.
The right to rebuild will get people in homes quicker, remove government obstacles, and stop funding waste. Every citizen will know the rules - money is there to get me a basic structure quickly or fund the beginning of something larger. Any obstacles to that time and money are coming from politicians/regulations I can vote on. Comments will surely pour in explaining how it isn’t that simple. These comments will be reviewed diligently 2 years from now when Pacific Palisades is still a wasteland after $20 billion in federal aid has been spent.
 Source: Maui Now
Source: Maui Now -
-
 @ 3b19f10a:4e1f94b4
2024-12-07 09:55:46
@ 3b19f10a:4e1f94b4
2024-12-07 09:55:46 -
 @ 7ed7d5c3:6927e200
2024-12-03 15:46:54
@ 7ed7d5c3:6927e200
2024-12-03 15:46:54Shall I compare thee to a summer’s day? Thou art more lovely and more temperate; Rough winds do shake the darling buds of May, And summer’s lease hath all too short a date;
Sometime too hot the eye of heaven shines,
And often is his gold complexion dimm’d;
And every fair from fair sometime declines,
By chance or nature’s changing course untrimm’d;
``` But thy eternal summer shall not fade Nor lose possession of that fair thou owest; Nor shall Death brag thou wander’st in his shade, When in eternal lines to time thou growest;
So long as men can breathe or eyes can see, So long lives this and this gives life to thee. ```
-
 @ 266815e0:6cd408a5
2024-05-09 17:23:28
@ 266815e0:6cd408a5
2024-05-09 17:23:28Lot of people are starting to talk about building a web-of-trust and how nostr can or is already being used as such
We all know about using the kind:3 following lists as a simple WoT that can be used to filter out spam. but as we all know it does not really signal "trust", its mostly just "I find your content interesting"
But what about real "trust"... well its kind of multi-denominational, I could trust that your a good developer or a good journalist but still not trust you enough to invite you over to my house. There are some interesting and clever solutions proposed for quantifying "trust" in a digital sense but I'm not going to get into that here. I want to talk about something that I have not see anyone discuss yet.
How is the web-of-trust maintained? or more precisely how do you expect users to update the digital representation of the "trust" of other users?
Its all well and good to think of how a user would create that "trust" of another user when discovering them for the first time. They would click the "follow" button, or maybe even rate them on a few topics with a 1/5 star system But how will a user remove that trust? how will they update it if things change and they trust them less?
If our goal is to model "trust" in a digital sense then we NEED a way for the data to stay up-to-date and as accurate as possible. otherwise whats the use? If we don't have a friction-less way to update or remove the digital representation of "trust" then we will end up with a WoT that continuously grows and everyone is rated 10/10
In the case of nostr kind:3 following lists. its pretty easy to see how these would get updated. If someone posts something I dislike or I notice I'm getting board of their content. then I just unfollow them. An important part here is that I'm not thinking "I should update my trust score of this user" but instead "I'm no longer interested, I don't want to see this anymore"
But that is probably the easiest "trust" to update. because most of us on social media spend some time curating our feed and we are used to doing it. But what about the more obscure "trust" scores? whats the regular mechanism by which a user would update the "honestly" score of another user?
In the real world its easy, when I stop trusting someone I simply stop associating with them. there isn't any button or switch I need to update. I simply don't talk to them anymore, its friction-less But in the digital realm I would have to remove or update that trust. in other words its an action I need to take instead of an action I'm not doing. and actions take energy.
So how do we reflect something in the digital world that takes no-energy and is almost subconscious in the real world?
TLDR; webs-of-trust are not just about scoring other users once. you must keep the score up-to-date
-
 @ 9cb3545c:2ff47bca
2024-12-01 00:18:45
@ 9cb3545c:2ff47bca
2024-12-01 00:18:45Hey there! So you’ve got a whopping 50+ Lightning Channels and you’re not keen on them Force Closing? Well, buckle up! This guide will be an additional resource as you navigate through daunting process.
In this post, we will go over some extra tips and tricks not covered in the official guide. While this guide does have some steps that are not covered by Umbrel, its main objective is to provide confidence in the process (not a replacement process), coming from someone who’s been there and done that, and some how came out with all Lightning Channels still running! I highly recommend reading this post fully before starting the migration process.
Before we dive in, here is the Official Guide from the Umbrel team on how to update UmbrelOS from 0.5.4 to 1.x.x. Reference the steps all the time, and follow them carefully.
With that out of the way. Here are some extra TIPs to fill in some gaps I encountered as I went through the process.
The Order of Steps
Tip #1:
In the Official Umbrel Guide, the Umbrel team asks you to start by backing up your data. As a lightning Node Runner, I recommend against this. Because the Bash script will stop all Umbrel Services and your node will remain offline while you prepare a Bootable USB Stick. So definitely don't start with the backup, first get the bootable stick sorted out, then move on to backups.
Creating the Bootable USB Stick
TIP #2:
After many failed attempts to create a bootable USB stick from the link umbrel provides in their official guide. I ended up getting the ISO directly from Umbrels team through their Discord Channel. Unfortunately, I wont be able to share this link here. but just in case the umbrelOS-amd64-usb-installer.iso.xz didnt work for you as well, this could be an alternative route.
TIP #3:
Since Umbrel is an actual full OS now. You might need to handle some BIOS quirks. The umbrelOS Kernal is not signed. So if you have Secure Boot turned on in the BIOS, your PC will try to protect you, and block you from booting into you USB Stick. Turn off Secure Boot and you should be able to bypass this issue. I also had to turn on Legacy Option ROMs as well.
Tip #4:
Test your Bootable USB Stick on a secondary device before you go on trying to update your node. Since turning the node off and on is a hassle, its just easier to be certain the the Bootable Stick is ready before even attempting to upgrade your node.
If all is good, you are ready to get back to the guide and walk through the steps.
Preparing the Hardware
Tip #5:
In the official guide they as you to connect a Keyboard and Screen. This is of course needed. I would highly suggest you connect a mouse as well. My Bios was very stubborn and didn't comply with just a keyboard as I attempted to re-order Boot Sequences.
The Migration Process
Tip #6:
Remember, this is 10 times easier if you are not running a lightning node, but on a lightning node, the Channel.db file is being updated constantly. Once you start the backup process, the script will shutdown umbrel services and start copying. you can''t turn your node back on after this stage. If you do, assume the backup you created through the Bash script is obsolete. and you will have to redo the backup process again. If you really know what you are doing, you probably can surgically copy/paste the LND folder. But its easier not to do this.
But not to worry, if you start the process just keep going (especially if you checked all the TIPs I cover above). I say this out of experience, because after I started the first backup process, it took me about an hour to backup my SSD, but then the Bootable USB stick threw so many errors I gave up, and turned on the node again. Then later re-attempted the process from scratch. This time, since my external SSD was already full, it took 3.5 hours to backup all the files again.
Tip #7:
This will take time, so just trust the migration process and wait for the files to get copied. you are probably copying more than a terabyte worth of data back and forth over USB, Leverage USB 3 if you have it.
Tip #8:
If you have a custom name for your umbrel node. Meaning you do not access it by using umbrel.local, this will be reset to the default umbrel.local after the migration. I am not sure if this could be switched again to a custom name, but for now, this won't cause any issues.
Tip #9:
During the last steps of the Migration process, and once Umbrel has copied the backup back into the SSD, it will finish the process with downloading your apps, and restarting. Don't freak out :D
Tip #10:
I honestly don't have a tenth tip, but thought it would make this list look nicer with one. So my last tip for you is to relax and enjoy the process. And feel free to tag me if you faced any issues. Hopefully it will be something i experienced and will be able to help.
Have Fun, and Good Luck!
-
 @ 0d532801:197a0c30
2024-12-06 05:13:25
@ 0d532801:197a0c30
2024-12-06 05:13:25Dünya tehlikeli bir yer. Kötülük yapanlar yüzünden değil, görüp de hiçbir şey yapmayanlar yüzünden.
İnsanları okumada çok iyiyimdir. İçlerindeki en kötü şeyi ararım.
Herkes çalar. Bu böyledir. İnsanlar tam anlamıyla hak ettiklerini mi kazanıyorlar? Hayır. Ya fazla ya da az alıyorlar ama zincirdeki biri her zaman kaymağını götürüyor.
Bir adama bir silah verirsen bir bankayı soyabilir ama bir adama bir banka verirsen dünyayı soyar.
İnsanlar her zaman umudumu boşa çıkarmanın bir yolunu buldu.
Bir holdingi kalbini hedef alarak çökertemezsin. Holdinglerin olayı budur, kalpleri olmaz. Onları parça parça çökertirsin. Ve çözülmeye başladıkları zaman kontrol yanılsamaları da çözülür.
Büyük bir fırsat ondan faydalanılmasını bekler.
Seçimlerimiz üzerinde kontrol sahibi olup olmadığımızı nasıl bileceğiz? Sadece önümüze gelen şeyin en iyisini yapmaya çalışıyoruz, olay bu. Sürekli iki seçenekten birini seçmeye çalışıyoruz. Tıpkı bekleme salonundaki iki tablo gibi. Ya da Coca-Cola ve Pepsi. Mcdonald's veya Burger King. Hyundai veya Honda. Hepsi aynı bulanıklığın parçası. Odak dışında kalan bulanıklık. Seçimin yanılsaması. Kendi istediğimiz kablolu yayın, doğalgaz ve elektrik şirketini bile seçemiyoruz. içtiğimiz su, sağlık sigortamız.. Seçebilseydik bile fark eder miydi ki? Eğer tek seçim şansımız kılıç ve kalkan arasında oluyorsa bu nasıl seçimdir amına koyayım? Aslında aynı değiller midir? Hayır, seçimlerimiz bizim için tayin edilmiş uzun zaman önce.
İnsanlar etrafta dolaşıp nefretin ne demek olduğunu biliyormuş gibi yapıyorlar. Hayır, kimse bilemez. Ta ki kendinden nefret edene kadar. Demek istediğim, gerçekten kendinden nefret etmek. Bu, güçtür.
İnsanlar iletişim kuramadıkları zaman öfkelenir.
İçinde yaşadığımız dünya bu. İnsanlar birbirlerinin hatalarına bel bağlıyor. Birbirlerini kandırmak için başkalarını kullanıyorlar. Hatta birbirleri ile ilişkili oluyorlar. Sıcak, dağınık bir insan çemberi.
Bu, kendimi korumanın tek yolu: onlara asla kaynak kodumu göstermemek. Kendimi kapatmak. Beni kimsenin bulamayacağı soğuk, kusursuz labirentimi yaratmak. Ama artık daha normal olacağım. Belki kız arkadaşım bile olabilir. Onunla birlikte aptal marvel filmlerine gideceğim. Spor salonuna yazılacağım. Instagram'da bir şeyleri beğeneceğim. Vanilyalı latteler içeceğim. Bu andan itibaren açıksız bir hayat süreceğim. Kusursuz labirentimi korumak için her şeyi yapacağım.
Bir maskeyi, artık maske olmayı bıraktığında nasıl çıkarırsın? Senin kadar senin bir parçan olduğunda.
-
 @ b2d670de:907f9d4a
2024-12-02 21:24:45
@ b2d670de:907f9d4a
2024-12-02 21:24:45onion-service-nostr-relays
A list of nostr relays exposed as onion services.
The list
| Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | operator | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | operator | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | operator | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | operator | Payment URL | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | operator | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | operator | Payment URL | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | operator | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | operator | N/A | N/A | | nostr.wine | 🍷 nostr.wine relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | operator | Payment URL | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 inbox.nostr.wine relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | operator | Payment URL | BTC LN, BTC | | filter.nostr.wine | 🍷 filter.nostr.wine proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | operator | Payment URL | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | operator | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | operator | N/A | N/A | | nfrelay.app | nfrelay.app aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | operator | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | operator | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | operator |Payment URL | XMR | | nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | operator | N/A | N/A | | wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | operator | N/A | N/A | | haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | operator | N/A | N/A | | relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | operator |N/A | N/A | | Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | operator | N/A | N/A |
Contributing
Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put
N/Ain empty columns.If you want to contribute anonymously, please contact me on SimpleX or send a DM on nostr using a disposable npub.
Operator column
It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
-
 @ 266815e0:6cd408a5
2024-04-22 22:20:47
@ 266815e0:6cd408a5
2024-04-22 22:20:47While I was in Mediera with all the other awesome people at the first SEC cohort there where a lot of discussions around data storage on nostr and if it could be made censorship-resistent
I remember lots of discussions about torrents, hypercore, nostr relays, and of course IPFS
There were a few things I learned from all these conversations:
- All the existing solutions have one thing in common. A universal ID of some kind for files
- HTTP is still good. we don't have to throw the baby out with the bath water
- nostr could fix this... somehow
Some of the existing solutions work well for large files, and all of them are decentralization in some way. However none of them seem capable of serving up cat pictures for social media clients. they all have something missing...
An Identity system
An identity system would allow files to be "owned" by users. and once files have owners servers could start grouping files into a single thing instead of a 1000+ loose files
This can also greatly simplify the question of "what is spam" for a server hosting (or seeding) these files. since it could simply have a whitelist of owners (and maybe their friends)
What is blossom?
Blossom is a set of HTTP endpoints that allow nostr users to store and retrieve binary data on public servers using the sha256 hash as a universal id
What are Blobs?
blobs are chunks of binary data. they are similar to files but with one key difference, they don't have names
Instead blobs have a sha256 hash (like
b1674191a88ec5cdd733e4240a81803105dc412d6c6708d53ab94fc248f4f553) as an IDThese IDs are universal since they can be computed from the file itself using the sha256 hashing algorithm ( you can get a files sha256 hash on linux using:
sha256sum bitcoin.pdf)How do the servers work?
Blossom servers expose four endpoints to let clients and users upload and manage blobs
GET /<sha256>(optional file.ext)PUT /uploadAuthentication: Signed nostr event- Returns a blob descriptor
GET /list/<pubkey>- Returns an array of blob descriptors
Authentication(optional): Signed nostr eventDELETE /<sha256>Authentication: Signed nostr event
What is Blossom Drive?
Blossom Drive is a nostr app built on top of blossom servers and allows users to create and manage folders of blobs
What are Drives
Drives are just nostr events (kind
30563) that store a map of blobs and what filename they should have along with some extra metadataAn example drive event would be
json { "pubkey": "266815e0c9210dfa324c6cba3573b14bee49da4209a9456f9484e5106cd408a5", "created_at": 1710773987, "content": "", "kind": 30563, "tags": [ [ "name", "Emojis" ], [ "description", "nostr emojis" ], [ "d", "emojis" ], [ "r", "https://cdn.hzrd149.com/" ], [ "x", "303f018e613f29e3e43264529903b7c8c84debbd475f89368cb293ec23938981", "/noStrudel.png", "15161", "image/png" ], [ "x", "a0e2b39975c8da1702374b3eed6f4c6c7333e6ae0008dadafe93bd34bfb2ca78", "/satellite.png", "6853", "image/png" ], [ "x", "e8f3fae0f4a43a88eae235a8b79794d72e8f14b0e103a0fed1e073d8fb53d51f", "/amethyst.png", "20487", "image/png" ], [ "x", "70bd5836807b916d79e9c4e67e8b07e3e3b53f4acbb95c7521b11039a3c975c6", "/nos.png", "36521", "image/png" ], [ "x", "0fc304630279e0c5ab2da9c2769e3a3178c47b8609b447a30916244e89abbc52", "/primal.png", "29343", "image/png" ], [ "x", "9a03824a73d4af192d893329bbc04cd3798542ee87af15051aaf9376b74b25d4", "/coracle.png", "18300", "image/png" ], [ "x", "accdc0cdc048f4719bb5e1da4ff4c6ffc1a4dbb7cf3afbd19b86940c01111568", "/iris.png", "24070", "image/png" ], [ "x", "2e740f2514d6188e350d95cf4756bbf455d2f95e6a09bc64e94f5031bc4bba8f", "/damus.png", "32758", "image/png" ], [ "x", "2e019f08da0c75fb9c40d81947e511c8f0554763bffb6d23a7b9b8c9e8c84abb", "/old emojis/astral.png", "29365", "image/png" ], [ "x", "d97f842f2511ce0491fe0de208c6135b762f494a48da59926ce15acfdb6ac17e", "/other/rabbit.png", "19803", "image/png" ], [ "x", "72cb99b689b4cfe1a9fb6937f779f3f9c65094bf0e6ac72a8f8261efa96653f5", "/blossom.png", "4393", "image/png" ] ] }There is a lot going on but the main thing is the list of "x" tags and the path that describes the folder and filename the blob should live at
If your interested, the full event definition is at github.com/hzrd149/blossom-drive
Getting started
Like every good nostr client it takes a small instruction manual in order to use it properly. so here are the steps for getting started
1. Open the app
Open https://blossom.hzrd149.com
2. Login using extension

You can also login using any of the following methods using the input - NIP-46 with your https://nsec.app or https://flare.pub account - a NIP-46 connection string - an
ncryptsecpassword protected private key - ansecunprotected private key (please don't) - bunker:// URI from nsecbunker3. Add a blossom server

Right now
https://cdn.satellite.earthis the only public server that is compatible with blossom drive. If you want to host your own I've written a basic implementation in TypeScript github.com/hzrd149/blossom-server4. Start uploading your files
NOTE: All files upload to blossom drive are public by default. DO NOT upload private files

5. Manage files

Encrypted drives
There is also the option to encrypt drives using NIP-49 password encryption. although its not tested at all so don't trust it, verify

Whats next?
I don't know, but Im excited to see what everyone else on nostr builds with this. I'm only one developer at the end of the day and I can't think of everything
also all the images in this article are stored in one of my blossom drives here
nostr:naddr1qvzqqqrhvvpzqfngzhsvjggdlgeycm96x4emzjlwf8dyyzdfg4hefp89zpkdgz99qq8xzun5d93kcefdd9kkzem9wvr46jka
-
 @ 0d532801:197a0c30
2024-12-01 21:27:48
@ 0d532801:197a0c30
2024-12-01 21:27:48
߹ İnsan, bilinçli olarak günah işlediğinde, aslında birçok içsel ve dışsal faktörün etkisi altındadır. Bu faktörlerin başında bireysel arzular, toplumsal baskılar, zayıflıklar, bilinçaltı dürtüler ve bazen de cehalet gelir. İnsan, sadece dürtülerine göre hareket etmeyi tercih edebilir ya da kısa vadeli tatmin için uzun vadeli sonuçları göz ardı edebilir. Peki, bir insan neden bilerek günah işler? Bu sorunun cevabı, sadece dini ya da etik perspektiflerle değil, psikolojik, toplumsal ve kültürel açılardan da ele alınmalıdır.
- Bireysel Arzular ve Dürtüler
߹ İnsanın doğasında, zaman zaman nefsini tatmin etme isteği vardır. Bu istek, bazen mantık ve vicdanın önüne geçebilir. İnsan, kısa süreli hazları arzularken, bunun gelecekteki olumsuz sonuçlarını göz ardı edebilir. Örneğin, hırsızlık yapan bir kişi, anlık bir mal edinme arzusuyla hareket edebilir, ancak bu davranışın ona ve çevresine getireceği zararları düşünmektense, elde edeceği çıkarı daha önemli görür. Benzer şekilde, yalan söylemek ya da başkalarını manipüle etmek de kısa vadeli çıkarlar ve bireysel egolar tarafından beslenen bir davranış biçimidir.
- Toplumsal Baskılar ve Çevresel Faktörler
߹ İnsan, toplumsal bir varlık olarak çevresinden büyük ölçüde etkilenir. Toplumun normları, kültürel değerleri, arkadaş gruplarının etkisi ve ailevi dinamikler, bireyin davranışlarını şekillendirir. Bazı durumlarda, kişi bilerek yanlış bir davranış sergileyebilir çünkü çevresindeki kişiler böyle yapmaktadır ve kendini dışlanmış hissetmemek için buna ayak uydurur. Örneğin, bir grup insanın başka birine kötü davranması ya da yalan söylemesi, bir bireyi de benzer şekilde davranmaya itebilir. Bu durum, bireyin vicdanı ve doğru-yanlış algısı ile çatışan bir durumdur.
- Zayıflıklar ve İnsan Doğası
߹ Herkesin zayıf anları vardır. Zihinsel ve duygusal olarak zorlandığı anlarda insanlar bazen bilerek yanlış bir şey yapabilir. İnsan, öfke, stres, yalnızlık ya da korku gibi duygusal durumlar içinde daha kolay günah işleyebilir. Duygusal karmaşa, sağlıklı düşünme yeteneğini zayıflatabilir ve kişi, anlık bir rahatlama ya da kaçış için yanlış bir yolu seçebilir. Örneğin, öfkelenen bir kişi, karşısındaki kişiye hakaret etmek ya da ona zarar vermek isteyebilir. Bu tür eylemler, kişinin o anki duygusal durumunun bir sonucu olarak ortaya çıkar.
- Cehalet ve Yanlış İnançlar
߹ Bazen insanlar, neyin doğru neyin yanlış olduğuna dair doğru bir bilgiye sahip olmayabilirler. Bilgi eksikliği ya da yanlış inanışlar, bireyin günah işlemesine neden olabilir. İnsan, kötü bir davranışın ne kadar zarar verebileceğini ya da o davranışın ahlaki ve dini boyutlarını tam anlamayabilir. Özellikle bazı insanlar, içinde bulundukları ortamın, alışkanlıkların ya da eğitim seviyelerinin etkisiyle, doğruyu ve yanlışı tam kavrayamayabilirler. Bu durum da, onların bilerek ve isteyerek günah işlemesine yol açabilir.
- İçsel Çatışmalar ve Vicdanın Bastırılması
߹ İnsan, bazen kendi içsel çatışmalarına dayanamayabilir. Vicdanı, doğruyu yapması yönünde onu uyarırken, içindeki kötü duygular ya da arzular ona engel olamayacak kadar güçlü olabilir. İnsanın kendisini haklı çıkarma çabası da burada devreye girebilir. Bir insan, kendini iyi bir insan olarak görmek isterken, bazen içindeki kötü dürtüleri bastırmak yerine, bunları haklı göstermek için kendine çeşitli gerekçeler uydurur. Örneğin, bir kişi başkasının hakkını yemek için kendini “bunu herkes yapıyor” ya da “benim de buna ihtiyacım var” gibi bahanelerle kandırabilir.
- Dini ve Ahlaki Değerlerin Zayıflaması
߹ Bir insanın dini inançları ya da ahlaki değerleri, doğru-yanlış algısını büyük ölçüde şekillendirir. Ancak zamanla, bireylerin inançları ya da değerleri zayıflayabilir. Toplumda sekülerleşmenin arttığı bir dönemde, dini ve ahlaki öğretiler zamanla insanların gözünde daha az değerli hâle gelebilir. Bu durumda, insanlar günah işleme konusunda daha az vicdan azabı duyarlar, çünkü dini ya da ahlaki sonuçları görmezden gelmeyi tercih edebilirler.
߹ Sonuç olarak, insanın bilerek günah işlemesi, karmaşık bir durumdur ve çok çeşitli faktörlere dayanır. İnsanlar bazen içsel isteklerine, bazen dışsal baskılara, bazen de bilinçli ya da bilinçsiz olarak zayıf noktalarına dayanarak yanlışlar yapabilirler. Önemli olan, insanın yaptığı hataları fark etmesi, bu hatalardan ders alması ve doğru yolu bulmaya çaba göstermesidir. Kişi, hatalarını kabul ederek ve daha bilinçli bir şekilde hareket ederek hem kendisine hem de çevresine faydalı bir yaşam sürebilir.
-
 @ c69b71dc:426ba763
2025-01-18 15:39:35
@ c69b71dc:426ba763
2025-01-18 15:39:35Chef's notes
This raw vegan curry ramen is a vibrant, nourishing dish packed with fresh vegetables and a rich, creamy coconut curry broth. It’s quick to prepare, full of flavour, and the perfect guilt-free comfort food! 🌱 Feel free to use your favourite veggies👩🏼🍳
Details
- ⏲️ Prep time: 20 min.
- 🍳 Cook time: 0
- 🍽️ Servings: 2
Ingredients
- 500g or 2 packs kelp noodles
- 1/2 Lemon juice ( 1/4 for soaking and 1/4 for the soup
- Salt
- Fresh vegetables of your choice, such as: 4 medium mushrooms, 4 leaves red cabbage, 2 carrots (julienned or peeled into strips), 1 Celery stick (diced)
- 2 cups coconut milk (or coconut cream diluted with water)
- 1/2 flesh of a Coconut (optional, if using fresh coconuts) otherwise more coconut cream
- 1 thumb of fresh ginger
- 1 thumb of fresh turmeric
- 2 tbsp light miso paste
- 2 pitted dates
- 2 tbsp cashews
- 1 clove garlic
- 1 tsp curry powder or pepper (optional)
Directions
- Prepare the Noodles: Rinse the kelp noodles thoroughly. Then soak them in warm water with a squeeze of lemon juice and a pinch of salt for 10 minutes to soften.
- Prep the Vegetables: Thinly slice or julienne carrots, dice celery, thinly cut mushrooms, cut the red cabbage into thin strips.
- Make the Broth: In a blender, combine the following: 2 cups coconut milk (or coconut cream diluted with water if fresh coconuts are unavailable), ginger, turmeric, 1/4 juice of 1 lemon, light miso paste, pitted dates, cashews, garlic, salt, curry powder
- Blend on high speed for about 3 to 4 minutes until the broth is smooth and slightly warm. Do not overheat!
- Assemble the Ramen: Drain the kelp noodles and place them in serving bowls. Arrange the prepped vegetables on top of the noodles. Pour the warm curry broth over the noodles and vegetables.
- Serve immediately and enjoy your raw vegan ramen with chopsticks for an authentic touch!
-
 @ f977c464:32fcbe00
2024-01-30 20:06:18
@ f977c464:32fcbe00
2024-01-30 20:06:18Güneşin kaybolmasının üçüncü günü, saat öğlen on ikiyi yirmi geçiyordu. Trenin kalkmasına yaklaşık iki saat vardı. Hepimiz perondaydık. Valizlerimiz, kolilerimiz, renk renk ve biçimsiz çantalarımızla yan yana dizilmiş, kısa aralıklarla tepemizdeki devasa saati kontrol ediyorduk.
Ama ne kadar dik bakarsak bakalım zaman bir türlü istediğimiz hızla ilerlemiyordu. Herkes birkaç dakika sürmesi gereken alelade bir doğa olayına sıkışıp kalmış, karanlıktan sürünerek çıkmayı deniyordu.
Bekleme salonuna doğru döndüm. Nefesimden çıkan buharın arkasında, kalın taş duvarları ve camlarıyla morg kadar güvenli ve soğuk duruyordu. Cesetleri o yüzden bunun gibi yerlere taşımaya başlamışlardı. Demek insanların bütün iyiliği başkaları onları gördüğü içindi ki gündüzleri gecelerden daha karanlık olduğunda hemen birbirlerinin gırtlağına çökmüş, böğürlerinde delikler açmış, gözlerini oyup kafataslarını parçalamışlardı.
İstasyonun ışığı titrediğinde karanlığın enseme saplandığını hissettim. Eğer şimdi, böyle kalabalık bir yerde elektrik kesilse başımıza ne gelirdi?
İçerideki askerlerden biri bakışlarımı yakalayınca yeniden saate odaklanmış gibi yaptım. Sadece birkaç dakika geçmişti.
“Tarlalarım gitti. Böyle boyum kadar ayçiçeği doluydu. Ah, hepsi ölüp gidiyor. Afitap’ın çiçekleri de gi-”
“Dayı, Allah’ını seversen sus. Hepimizi yakacaksın şimdi.”
Karanlıkta durduğunda, görünmez olmayı istemeye başlıyordun. Kimse seni görmemeli, nefesini bile duymamalıydı. Kimsenin de ayağının altında dolaşmamalıydın; gelip kazayla sana çarpmamalılar, takılıp sendelememeliydiler. Yoksa aslında hedefi sen olmadığın bir öfke gürlemeye başlar, yaşadığın ilk şoku ve acıyı silerek üstünden geçerdi.
İlk konuşan, yaşlıca bir adam, kafasında kasketi, nasırlı ellerine hohluyordu. Gözleri ve burnu kızarmıştı. Güneşin kaybolması onun için kendi başına bir felaket değildi. Hayatına olan pratik yansımalarından korkuyordu olsa olsa. Bir anının kaybolması, bu yüzden çoktan kaybettiği birinin biraz daha eksilmesi. Hayatta kalmasını gerektiren sebepler azalırken, hayatta kalmasını sağlayacak kaynaklarını da kaybediyordu.
Onu susturan delikanlıysa atkısını bütün kafasına sarmış, sakalı ve yüzünün derinliklerine kaçmış gözleri dışında bedeninin bütün parçalarını gizlemeye çalışıyordu. İşte o, güneşin kaybolmasının tam olarak ne anlama geldiğini anlamamış olsa bile, dehşetini olduğu gibi hissedebilenlerdendi.
Güneşin onlardan alındıktan sonra kime verileceğini sormuyorlardı. En başta onlara verildiğinde de hiçbir soru sormamışlardı zaten.
İki saat ne zaman geçer?
Midemin üstünde, sağ tarafıma doğru keskin bir acı hissettim. Karaciğerim. Gözlerimi yumdum. Yanımda biri metal bir nesneyi yere bıraktı. Bir kafesti. İçerisindeki kartalın ıslak kokusu burnuma ulaşmadan önce bile biliyordum bunu.
“Yeniden mi?” diye sordu bana kartal. Kanatları kanlı. Zamanın her bir parçası tüylerinin üstüne çöreklenmişti. Gagası bir şey, tahminen et parçası geveliyor gibi hareket ediyordu. Eski anılar kolay unutulmazmış. Şu anda kafesinin kalın parmaklıklarının ardında olsa da bunun bir aldatmaca olduğunu bir tek ben biliyordum. Her an kanatlarını iki yana uzatıverebilir, hava bu hareketiyle dalgalanarak kafesi esneterek hepimizi içine alacak kadar genişleyebilir, parmaklıklar önce ayaklarımızın altına serilir gibi gözükebilir ama aslında hepimizin üstünde yükselerek tepemize çökebilirdi.
Aşağıya baktım. Tahtalarla zapt edilmiş, hiçbir yere gidemeyen ama her yere uzanan tren rayları. Atlayıp koşsam… Çantam çok ağırdı. Daha birkaç adım atamadan, kartal, suratını bedenime gömerdi.
“Bu sefer farklı,” diye yanıtladım onu. “Yeniden diyemezsin. Tekrarladığım bir şey değil bu. Hatta bir hata yapıyormuşum gibi tonlayamazsın da. Bu sefer, insanların hak etmediğini biliyorum.”
“O zaman daha vahim. Süzme salaksın demektir.”
“İnsanların hak etmemesi, insanlığın hak etmediği anlamına gelmez ki.”
Az önce göz göze geldiğim genççe ama çökük asker hâlâ bana bakıyordu. Bir kartalla konuştuğumu anlamamıştı şüphesiz. Yanımdakilerden biriyle konuştuğumu sanmış olmalıydı. Ama konuştuğum kişiye bakmıyordum ona göre. Çekingence kafamı eğmiştim. Bir kez daha göz göze geldiğimizde içerideki diğer iki askere bir şeyler söyledi, onlar dönüp beni süzerken dışarı çıktı.
Yanımızdaki, az önce konuşan iki adam da şaşkınlıkla bir bana bir kartala bakıyordu.
“Yalnız bu sefer kalbin de kırılacak, Prometheus,” dedi kartal, bana. “Belki son olur. Biliyorsun, bir sürü soruna neden oluyor bu yaptıkların.”
Beni koruyordu sözde. En çok kanıma dokunan buydu. Kasıklarımın üstüne oturmuş, kanlı suratının ardında gözleri parlarken attığı çığlık kulaklarımda titremeye devam ediyordu. Bu tabloda kimsenin kimseyi düşündüğü yoktu. Kartalın, yanımızdaki adamların, artık arkama kadar gelmiş olması gereken askerin, tren raylarının, geçmeyen saatlerin…
Arkamı döndüğümde, asker sahiden oradaydı. Zaten öyle olması gerekiyordu; görmüştüm bunu, biliyordum. Kehanetler… Bir şeyler söylüyordu ama ağzı oynarken sesi çıkmıyordu. Yavaşlamış, kendisini saatin akışına uydurmuştu. Havada donan tükürüğünden anlaşılıyordu, sinirliydi. Korktuğu için olduğunu biliyordum. Her seferinde korkmuşlardı. Beni unutmuş olmaları işlerini kolaylaştırmıyordu. Sadece yeni bir isim vermelerine neden oluyordu. Bu seferkiyle beni lanetleyecekleri kesinleşmişti.
Olması gerekenle olanların farklı olması ne kadar acınasıydı. Olması gerekenlerin doğasının kötücül olmasıysa bir yerde buna dayanıyordu.
“Salaksın,” dedi kartal bana. Zamanı aşan bir çığlık. Hepimizin önüne geçmişti ama kimseyi durduramıyordu.
Sonsuzluğa kaç tane iki saat sıkıştırabilirsiniz?
Ben bir tane bile sıkıştıramadım.
Çantama uzanıyordum. Asker de sırtındaki tüfeğini indiriyordu. Benim acelem yoktu, onunsa eli ayağı birbirine dolaşıyordu. Oysaki her şey tam olması gerektiği anda olacaktı. Kehanet başkasının parmaklarının ucundaydı.
Güneş, bir tüfeğin patlamasıyla yeryüzüne doğdu.
Rayların üzerine serilmiş göğsümün ortasından, bir çantanın içinden.
Not: Bu öykü ilk olarak 2021 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 94a6a78a:0ddf320e
2024-11-27 19:36:12
@ 94a6a78a:0ddf320e
2024-11-27 19:36:12The backbone of your Nostr experience lies in relays—servers that transmit your notes, zaps, and private messages across the decentralized network. Azzamo offers three specialized relays to suit different user needs, ensuring reliability, performance, and privacy.
1. Free Relay
- URL:
wss://nostr.azzamo.net - Overview: Azzamo’s Free Relay is perfect for newcomers to Nostr. It’s open-access, reliable, and ensures fair use with moderate rate limits.
- Key Features:
- Free to use.
- Notes older than one month are purged daily.
- Accessible gateway for decentralized communication.
2. Paid Relay
- URL:
wss://relay.azzamo.net - Overview: Designed for power users, the Paid Relay offers unmatched performance with 99.9% uptime and low latency.
- Key Features:
- Scalable for heavy users.
- Fewer users for faster, consistent connections.
- Premium support included for paid users.
3. Inbox Relay
- URL:
wss://inbox.azzamo.net - Overview: Never miss a private message again with the Inbox Relay, optimized for secure, spam-free direct messaging.
- Key Features:
- Guaranteed message delivery.
- Optimized for NIP-17 private messages.
- Optimized for NIP-19 group chats.
- Premium users enjoy advanced support.
Why Choose Azzamo Relays?
Life on Nostr is easier with Azzamo relays. They’re fast, reliable, and built to handle whatever you throw at them. The Paid Relay keeps your connections strong, the Inbox Relay makes sure no private message gets lost, and the Free Relay is always there to get you started. Supporting Azzamo by going premium helps keep this decentralized network growing—and you get priority support while you’re at it. Azzamo has your back on Nostr!
🔗 Start now:
- Free Relay:
wss://nostr.azzamo.net - Paid Relay: azzamo.net/pay
- Inbox Relay: azzamo.net/inbox
Support the network and upgrade your experience—add time to your account via the Azzamo Dashboard. Choose Azzamo, and take control of your Nostr journey today!
- URL:
-
 @ da0b9bc3:4e30a4a9
2025-01-18 14:09:40
@ da0b9bc3:4e30a4a9
2025-01-18 14:09:40Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/854843
-
 @ e31e84c4:77bbabc0
2024-11-27 11:32:57
@ e31e84c4:77bbabc0
2024-11-27 11:32:57‘Think You Know Bitcoin Security?’ was Written By Paul G Conlon. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: noisycyclone54@walletofsatoshi.com
Childhood Lessons
As a boy, my grandmother shared stories of her experiences in wartime Germany, each revealing a common theme: the terrifying reality of living without security. I was amazed with the scale of destruction and, at the time, understood security largely as physical protection. Yet the years have deepened my appreciation for security’s nuances. In this article, we’ll explore how studying Bitcoin has helped me now recognise “security” not just as physical safety, but related to personal agency, mental and social well-being, and the ability to control one's destiny.
Definitions of Security
Property confiscation was rife in 1930s Germany, and much of this behaviour didn’t even constitute illegality. The 1938 Ordinance on the Use of Jewish Assets for example required those identified as Jews to deposit all their stocks, shares, fixed-income securities and similar in a deposit at a foreign exchange bank. The government even allowed itself to sell Jewish businesses. Access to these resources required no less than approval by the Reich Minister for Economic Affairs.
Narrowly defining security as simply asset protection is tempting, given its historical prevalence. Everything from my grandmother’s tales of stashing cash in curtains, to the US Constitution's 4th Amendment, “the right of the people to be secure in their persons, houses, papers, and effects” reinforces this physical emphasis.
When I discovered Bitcoin, I was hence drawn to its asset protection features. Like many, this biased view of security defined the start of my Bitcoin journey, focusing my attention on hardware wallets and encryption protocols. But that was soon to change.
How Bitcoin Changed Me
The more I read, the more I learned that with a network of nodes working to secure a global protocol, came a network of people working to secure global principles. It dawned on me that I had not so much discovered the ultimate bastion of property rights, but of human rights.
Here are just a few examples:
Freedom of Expression
Anonymity is fundamental for the full exercise of the right to freedom of expression. This is enshrined in Article 19 of the Universal Declaration of Human Rights (UDHR) and the International Covenant on Civil and Political Rights (ICCPR). Bitcoin's pseudonymous and decentralised nature makes it difficult for tyrants to identify and censor one of the purest forms of expression: transactions.
Adequate Living Standards
Article 25 of the UDHR states that everyone has the right to a standard of living adequate for health and well-being, including food, clothing, housing, and medical supplies. Article 17 further enshrines the retention of property necessary to support these living standards.
Bitcoin's cryptographic security reinforces ownership rights, making it difficult for rogue states to arbitrarily seize assets essential for the maintenance of these living standards. Furthermore, Bitcoin's 21-million-coin capped supply prevents arbitrary inflation, protecting against the erosion of purchasing power that has time and again proven correlated with the erosion of living standards.
Freedom of Association
Article 20 of the UDHR states that everyone has the right to freedom of peaceful assembly and association. Article 22 of the ICCPR also protects the right to freedom of association, including the right to form and join trade unions.
Multi-signature wallets are an explicit expression of this associative freedom. By enabling groups to collaboratively manage resources, the human connections required for civilisation to flourish can be directly represented and enforced in code.
Programmatic freedom of association is particularly pertinent for activist and civil society organisations and provides security against coercion in situations where individuals may face pressure to hand over funds from those who wield power.
Right to Information
The open-source nature of Bitcoin also somewhat poetically aligns with the right to seek, receive, and impart information, as outlined in Article 19 of the UDHR. Anyone can inspect, verify, and contribute to Bitcoin's code, promoting transparency and accountability. Its immutability also supports the right to information by preserving truth in the face of potential revisionism. Furthermore, Article 27 states that everyone has the right to share in scientific advancement and its benefits. Bitcoin embodies this principle by allowing global participation in its development and use.
Personal Context
For me, Bitcoin brought context to those old wartime stories I heard as a boy. It led me to the understanding that property rights are simply a derivative of human rights. Now, for the first time in history, we have a borderless technology that secures these rights not in international declarations or national constitutions – both susceptible to the stroke of a tyrant’s pen – but in executable code.
In essence, Bitcoin's technical features embody the very principles of security and resilience that are well recognised as essential to personal agency, mental well-being, and social cohesion. These operate independently of central authorities that have historically proven both capable and willing of stripping human rights, and not a moment too soon…
A Modern Necessity
These concerns are not limited to the past. Just recently, Blackrock CEO, Larry Fink, said this about Bitcoin in a CNBC interview:
“We have countries where you’re frightened of your everyday existence and it gives an opportunity to invest in something that is outside your country’s control.” (https://www.youtube.com/watch?v=K4ciiDyUvUo)
As an Australian, I see the precursors of what Larry describes. Legislative attacks on the right to expression, living standards, association, and information are becoming brazen. The Digital ID Bill 2024, legislated on May 16th, has already denied employment and government services to some, and is now poised to police the internet in what appears to be the making of a conditional access society.
The Communications Legislation Amendment (Combatting Misinformation and Disinformation) Bill 2024, currently sitting before federal parliament, is even more horrendous. It effectively establishes a protectionist Ministry of Truth and threatens imprisonment for an extremely broad array of ill-defined speech – all while providing exemptions for government and legacy media. This political activity is occurring amidst a cost-of-living and housing crisis, where many working individuals are living in tents in major cities.
Bitcoin’s True Security
Yet with Bitcoin (and a Starlink connection), I feel secure. Bitcoin has become a source of resilience and mental well-being for people in an increasingly complex world. Beyond its cryptographic security, Bitcoin provides a global network of like-minded individuals who share common principles. This distributed community offers a sense of belonging and support that extends far beyond the technology behind it.
Bitcoin’s existence gives me confidence in my ability to secure basic needs and find community anywhere, without relying on easily confiscated physical assets. Meeting fellow Bitcoin enthusiasts often reveals shared worldviews and values, creating instant connections.
Ultimately, Bitcoin's security stems not just from its technology, but from the human network it has fostered. It offers the reassurance that I could "land on my feet" anywhere, preserving both financial sovereignty and social bonds with free-thinking individuals. This holistic security - financial, social, and psychological - provides profound peace of mind in uncertain times.
‘Think You Know Bitcoin Security?’ was Written By Paul G Conlon. If you enjoyed this article then support his writing, directly, by donating to his lightning wallet: noisycyclone54@walletofsatoshi.com
-
 @ 9e69e420:d12360c2
2025-01-18 14:02:27
@ 9e69e420:d12360c2
2025-01-18 14:02:27The Supreme Court's decision to uphold the TikTok ban, set to take effect on January 19, 2025, leaves 170 million American users searching for new social platforms. As this unprecedented shutdown approaches, Nostr, a decentralized social media protocol, is positioned to capture users seeking a censorship-resistant alternative.
Why Nostr Appeals to Former TikTok Users
Nostr offers several compelling features that make it an attractive option for displaced TikTok users. The platform provides true user control over content and algorithms, allowing people to choose how their feed is displayed rather than being subject to a centralized algorithm's whims. Additionally, Nostr's integration with Bitcoin's Lightning Network enables creators to receive direct micropayments through "zaps," creating new monetization opportunities.
Key Advantages of Nostr
Censorship Resistance Unlike traditional social media platforms, Nostr cannot be banned or shut down by any single entity due to its decentralized nature. Users maintain ownership of their digital identity and content, ensuring they won't face another situation like the TikTok ban.
Creator Economy Content creators concerned about losing their TikTok revenue streams can benefit from Nostr's native payment system. The platform's "zap" feature allows followers to send instant micropayments to creators, providing a direct monetization path.
Platform Independence Nostr's protocol-based approach means users can seamlessly switch between different client apps while maintaining their following and content. This flexibility provides a stark contrast to TikTok's centralized model that leaves users vulnerable to platform-wide shutdown.
Growing Momentum
Nostr has already demonstrated significant growth potential, expanding from 90,000 to 1.1 million users in just three months. With prominent figures like Jack Dorsey and Edward Snowden advocating for the platform, Nostr is well-positioned to capture a portion of TikTok's massive user base seeking a more resilient social media alternative.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O Planetinha
Fumaça verde me entrando pelas narinas e um coro desafinado fazia uma base melódica.
nos confins da galáxia havia um planetinha isolado. Era um planeta feliz.
O homem vestido de mago começava a aparecer por detrás da fumaça verde.
O planetinha recebeu três presentes, mas o seu habitante, o homem, estava num estado de confusão tão grande que ameaçava estragá-los. Os homens já havia escravizado o primeiro presente, a vida; lutavam contra o segundo presente, a morte; e havia alguns que achavam que deviam destruir totalmente o terceiro, o amor, e com isto levar a desordem total ao pobre planetinha perdido, que se chamava Terra.
O coro desafinado entrou antes do "Terra" cantando várias vezes, como se imitasse um eco, "terra-terra-terraaa". Depois de uma pausa dramática, o homem vestido de mago voltou a falar.
Terra, nossa nave mãe.
Neste momento eu me afastei. À frente do palco onde o mago e seu coral faziam apelos à multidão havia vários estandes cobertos com a tradicional armação de quatro pernas e lona branca. Em todos os cantos da praça havia gente, gente dos mais variados tipos. Visitantes curiosos que se aproximavam atraídos pela fumaça verde e as barraquinhas, gente que aproveitava o movimento para vender doces sem pagar imposto, casais que se abraçavam de pé para espantar o frio, os tradicionais corredores que faziam seu cooper, gente cheia de barba e vestida para imitar os hippies dos anos 60 e vender colares estendidos no chão, transeuntes novos e velhos, vestidos como baladeiros ou como ativistas do ônibus grátis, grupos de ciclistas entusiastas.
O mago fazia agora apelos para que nós, os homens, habitantes do isolado planetinha, passássemos a ver o planetinha, nossa nave mãe, como um todo, e adquiríssemos a consciência de que ele estava entrando em maus lençóis. A idéia, reforçada pela logomarca do evento, era que parássemos de olhar só para a nossa vida e pensássemos no planeta.
A logomarca do evento, um desenho estilizado do planeta Terra, nada tinha a ver com seu nome: "Festival Andando de Bem com a Vida", mas havia sido ali colocada estrategicamente pelos organizadores, de quem parecia justamente sair a mensagem dita pelo mago.
Aquela multidão de pessoas que, assim como eu, tinham suas próprias preocupações, não podiam ver o quadro caótico que formavam, cada uma com seus atos isolados, ali naquela praça isolada, naquele planeta isolado. Quando o hippie barbudo, quase um Osho, assustava um casal para tentar vender-lhes um colar, a quantidade de caos que isto acrescentava à cena era gigantesca. Por um segundo, pude ver, como se estivesse de longe e acima, com toda a pretensão que este estado imaginativo carrega, a cena completa do caos.
Uma nave-mãe, dessas de ficção científica, habitada por milhões de pessoas, seguia no espaço sem rumo, e sem saber que logo à frente um longo precipício espacial a esperava, para a desgraça completa sua e de seus habitantes.
Acostumados àquela nave tanto quanto outrora estiveram acostumados à sua terra natal, os homens viviam as próprias vidas sem nem se lembrar que estavam vagando pelo espaço. Ninguém sabia quem estava conduzindo a nave, e ninguém se importava.
No final do filme descobre-se que era a soma completa do caos que cada habitante produzia, com seus gestos egoístas e incapazes de levar em conta a totalidade, é que determinava a direção da nave-mãe. O efeito, no entanto, não era imediato, como nunca é. Havia gente de verdade encarregada de conduzir a nave, mas era uma gente bêbada, mau-caráter, que vivia brigando pelo controle da nave e o poder que isto lhes dava. Poder, status, dinheiro!
Essa gente bêbada era atraída até ali pela corrupção das instituições e da moral comum que, no fundo no fundo, era causada pelo egoísmo da população, através de um complexo -- mas que no filme aparece simplificado pela ação individual de um magnata do divertimento público -- processo social.
O homem vestido de mago era mais um agente causador de caos, com sua cena cheia de fumaça e sua roupa estroboscópica, ele achava que estava fazendo o bem ao alertar sua platéia, todos as sextas-feiras, de que havia algo que precisava ser feito, que cada um que estava ali ouvindo era responsável pelo planeta. A sua incapacidade, porém, de explicar o que precisava ser feito só aumentava a angústia geral; a culpa que ele jogava sobre seu público, e que era prontamente aceita e passada em frente, aos familiares e amigos de cada um, atormentava-os diariamente e os impedia de ter uma vida decente no trabalho e em casa. As famílias, estressadas, estavam constantemente brigando e os motivos mais insignificantes eram responsáveis pelas mais horrendas conseqüências.
O mago, que após o show tirava o chapéu entortado e ia tomar cerveja num boteco, era responsável por uma parcela considerável do caos que levava a nave na direção do seu desgraçado fim. No filme, porém, um dos transeuntes que de passagem ouviu um pedaço do discurso do mago despertou em si mesmo uma consiência transformadora e, com poderes sobre-humanos que lhe foram então concedidos por uma ordem iniciática do bem ou não, usando só os seus poderes humanos mesmo, o transeunte -- na primeira versão do filme um homem, na segunda uma mulher -- consegue consertar as instituições e retirar os bêbados da condução da máquina. A questão da moral pública é ignorada para abreviar a trama, já com duas horas e quarenta de duração, mas subentende-se que ela também fora resolvida.
No planeta Terra real, que não está indo em direção alguma, preso pela gravidade ao Sol, e onde as pessoas vivem a própria vida porque lhes é impossível viver a dos outros, não têm uma consciência global de nada porque só é possível mesmo ter a consciência delas mesmas, e onde a maioria, de uma maneira ou de outra, está tentando como pode, fazer as coisas direito, o filme é exibido.
Para a maioria dos espectadores, é um filme que evoca reflexões, um filme forte. Por um segundo elas têm o mesmo vislumbre do caos generalizado que eu tive ali naquela praça. Para uma pequena parcela dos espectadores -- entre eles alguns dos que estavam na platéia do mago, o próprio mago, o seguidor do Osho, o casal de duas mulheres e o vendedor de brigadeiros, mas aos quais se somam também críticos de televisão e jornal e gente que fala pelos cotovelos na internet -- o filme é um horror, o filme é uma vulgarização de um problema real e sério, o filme apela para a figura do herói salvador e passa uma mensagem totalmente errada, de que a maioria da população pode continuar vivendo as suas própria vidinhas miseráveis enquanto espera por um herói que vem do Olimpo e os salva da mixórdia que eles mesmos causaram, é um filme que presta um enorme desserviço à causa.
No dia seguinte ao lançamento, num bar meio caro ali perto da praça, numa mesa com oito pessoas, entre elas seis do primeiro grupo e oito do segundo, discute-se se o filme levará ou não o Oscar. Eu estou em casa dormindo e não escuto nada.
-
 @ df8f0a64:057d87a5
2024-11-29 13:58:48
@ df8f0a64:057d87a5
2024-11-29 13:58:482024年下半期の振り返り
あんまり変化はないんですが、進捗ありません!で終わっても仕方ないのでちょっとは無理やりでも振り返りましょう
0. 退職した
上半期時点で決まってはいたんですが、 6年間ほど勤務した会社を退職しました
退職直前まで爆発物取扱みたいなタスクをこなして、なかなかひやひやした退職プロセス
静かに退職したいので送別会の類のイベントは無しにしてくれというお願いをきいてくれた各メンバーに感謝です
1. 公開していたNostrリレーの設定を変更した
日本のみに公開していたリレーを、全世界に公開しました
当初はCloudflareでリレーをホストしていたのが、利用していたnosflareもcfrelayもクライアントに対してイベントを配布するコードがなく(R2だけではできない)
さてどうしたものかと悩んでいたタイミングで、Umbrelのおひとり様リレーのポートを公開する対応をしました。リレーのお引越し
で、公開してしばらくしたら、すごい勢いで日本国外からの投稿が着信するようになり大困惑
調べてみたら、Mutiny wallet(現在はサービス終了)が運営しているblastr.mutinywallet.com(たぶんまだ稼働している)が原因でした
Nostr.watchのAPIを利用して、世の中にあるNostrリレーすべてにイベントを送り込む凶悪な思想犯です
ヘッダー情報などでブロックできなかったので、blastrがホストされてるCloudflareのIPを全てブロックする力技で対処しました
ちなみに、nosflareもいつのまにかblastrのようなものをホストしているようです
なんなんでしょうね、Nostrの白人さんたちの、過激なほど分散というか対検閲をしようとするお節介さは
2. 公開していたNostrリレーを潰した
上記のように折角いろいろやったリレーを潰しました
Reply guyというbotが猛威をふるった時期、クソみたいなイベントをばら撒かれてくることに私がキレたからです。クソが
NostrとしてはこれをきっかけにWoTを組み込んだリレーが開発されたりして、スパム対策が一歩前進した感があります。クソが
スパムばら撒きをBostrが助長してるみたいな批難を受けて、作者のYonleさんがブチ切れ、全Nostr関連リポジトリのメンテを放棄する事態も発生
ちょうどMutiny walletでGOXしたご本人の機嫌が悪かった時期に、クソスパムがぶつかったことによる悲しい出来事でした。ほんとクソ
3. おわりに
他にもこまいことはいくつかあるんですが、主にはこんなとこでしょうか。来年も楽しくNostrしたいですね
-
 @ fd208ee8:0fd927c1
2024-11-28 12:50:49
@ fd208ee8:0fd927c1
2024-11-28 12:50:49GitHub is a software project graveyard
I think the main reason why we have so many lone wolf devs is an economic one. The fact that most FOSS devs aren't being paid for their code is making this worse, not better, as they work for fame, not fortune.
Nobody wants to use joint-repos because they don't want to give up or share the property rights to the contents. But because anything someone else does in a repo you own, also belongs to you, people are disincentized from contributing to your repo.
GitHub, especially, has incentivized this splintering and isolation. Everyone wants to have all changes in their own repo because they can profit best on repos listed directly under their own name, so long as they become popular. Maximize your 🟩 and ⭐ , like chips you can cash in for a prize.
And because forking other people's repos is the norm, rather than teamwork, requests for changes are usually ignored or responded to with "fork it, bro." Go away. Leave me alone. My repo is none of your business.
Too autistic, even for me
So, the developers separate their efforts into a million tiny repos that are mostly redundant with other ones, there's little interaction, progress is often surprisingly slow and stalls for months at a time, it's hard to keep track of what other people are doing (so that you can review and test changes), most of the effort is headed straight for the bin, people build the same things over and over, and communication is extremely limited.
This is a work environment that is unattractive for anyone who isn't autistic and/or highly introverted. Half of the fun of open-source development used to be the esprit de corps. Much has been said about #Bluesky, but it all misses a major point: that's where you go, if you want to work with other people, to build something large, polished, and impressive. It doesn't actually matter how many developers Nostr has, if they all only stare at their own plates.
Your repo coulda been a file folder.
Ironically, git was developed for collaboration on large projects with a distributed team. Now, everyone uses it for projects they work on alone. They put those projects on the Internet to market them. It's a cheap gimmick, not an earnest attempt at collaboration. Collaboration begins at the beginning.
-
 @ f977c464:32fcbe00
2024-01-11 18:47:47
@ f977c464:32fcbe00
2024-01-11 18:47:47Kendisini aynada ilk defa gördüğü o gün, diğerleri gibi olduğunu anlamıştı. Oysaki her insan biricik olmalıydı. Sözgelimi sinirlendiğinde bir kaşı diğerinden birkaç milimetre daha az çatılabilirdi veya sevindiğinde dudağı ona has bir açıyla dalgalanabilirdi. Hatta bunların hiçbiri mümkün değilse, en azından, gözlerinin içinde sadece onun sahip olabileceği bir ışık parlayabilirdi. Çok sıradan, öyle sıradan ki kimsenin fark etmediği o milyonlarca minik şeyden herhangi biri. Ne olursa.
Ama yansımasına bakarken bunların hiçbirini bulamadı ve diğer günlerden hiç de farklı başlamamış o gün, işe gitmek için vagonunun gelmesini beklediği alelade bir metro istasyonunda, içinde kaybolduğu illüzyon dağılmaya başladı.
İlk önce derisi döküldü. Tam olarak dökülmedi aslında, daha çok kıvılcımlara dönüşüp bedeninden fırlamış ve bir an sonra sönerek külleşmiş, havada dağılmıştı. Ardında da, kaybolmadan hemen önce, kısa süre için hayal meyal görülebilen, bir ruhun yok oluşuna ağıt yakan rengârenk peri cesetleri bırakmıştı. Beklenenin aksine, havaya toz kokusu yayıldı.
Dehşete düştü elbette. Dehşete düştüler. Panikle üstlerini yırtan 50 işçi. Her şeyin sebebiyse o vagon.
Saçları da döküldü. Her tel, yere varmadan önce, her santimde ikiye ayrıla ayrıla yok oldu.
Bütün yüzeylerin mat olduğu, hiçbir şeyin yansımadığı, suyun siyah aktığı ve kendine ancak kameralarla bakabildiğin bir dünyada, vagonun içine yerleştirilmiş bir aynadan ilk defa kendini görmek.
Gözlerinin akları buharlaşıp havada dağıldı, mercekleri boşalan yeri doldurmak için eriyip yayıldı. Gerçeği görmemek için yaratılmış, bu yüzden görmeye hazır olmayan ve hiç olmayacak gözler.
Her şeyin o anda sona erdiğini sanabilirdi insan. Derin bir karanlık ve ölüm. Görmenin görmek olduğu o anın bitişi.
Ben geldiğimde ölmüşlerdi.
Yani bozulmuşlardı demek istiyorum.
Belleklerini yeni taşıyıcılara takmam mümkün olmadı. Fiziksel olarak kusursuz durumdaydılar, olmayanları da tamir edebilirdim ama tüm o hengamede kendilerini baştan programlamış ve girdilerini modifiye etmişlerdi.
Belleklerden birini masanın üzerinden ileriye savurdu. Hınca hınç dolu bir barda oturuyorlardı. O ve arkadaşı.
Sırf şu kendisini insan sanan androidler travma geçirip delirmesin diye neler yapıyoruz, insanın aklı almıyor.
Eliyle arkasını işaret etti.
Polislerin söylediğine göre biri vagonun içerisine ayna yerleştirmiş. Bu zavallılar da kapı açılıp bir anda yansımalarını görünce kafayı kırmışlar.
Arkadaşı bunların ona ne hissettirdiğini sordu. Yani o kadar bozuk, insan olduğunu sanan androidi kendilerini parçalamış olarak yerde görmek onu sarsmamış mıydı?
Hayır, sonuçta belirli bir amaç için yaratılmış şeyler onlar. Kaliteli bir bilgisayarım bozulduğunda üzülürüm çünkü parasını ben vermişimdir. Bunlarsa devletin. Bana ne ki?
Arkadaşı anlayışla kafasını sallayıp suyundan bir yudum aldı. Kravatını biraz gevşetti.
Bira istemediğinden emin misin?
İstemediğini söyledi. Sahi, neden deliriyordu bu androidler?
Basit. Onların yapay zekâlarını kodlarken bir şeyler yazıyorlar. Yazılımcılar. Biliyorsun, ben donanımdayım. Bunlar da kendilerini insan sanıyorlar. Tiplerine bak.
Sesini alçalttı.
Arabalarda kaza testi yapılan mankenlere benziyor hepsi. Ağızları burunları bile yok ama şu geldiğimizden beri sakalını düzeltip duruyor mesela. Hayır, hepsi de diğerleri onun sakalı varmış sanıyor, o manyak bir şey.
Arkadaşı bunun delirmeleriyle bağlantısını çözemediğini söyledi. O da normal sesiyle konuşmaya devam etti.
Anlasana, aynayı falan ayırt edemiyor mercekleri. Lönk diye kendilerini görüyorlar. Böyle, olduğu gibi...
Nedenmiş peki? Ne gerek varmış?
Ne bileyim be abicim! Ahiret soruları gibi.
Birasına bakarak dalıp gitti. Sonra masaya abanarak arkadaşına iyice yaklaştı. Bulanık, bir tünelin ucundaki biri gibi, şekli şemalı belirsiz bir adam.
Ben seni nereden tanıyorum ki ulan? Kimsin sen?
Belleği makineden çıkardılar. İki kişiydiler. Soruşturmadan sorumlu memurlar.
─ Baştan mı başlıyoruz, diye sordu belleği elinde tutan ilk memur.
─ Bir kere daha deneyelim ama bu sefer direkt aynayı sorarak başla, diye cevapladı ikinci memur.
─ Bence de. Yeterince düzgün çalışıyor.
Simülasyon yüklenirken, ayakta, biraz arkada duran ve alnını kaşıyan ikinci memur sormaktan kendisini alamadı:
─ Bu androidleri niye böyle bir olay yerine göndermişler ki? Belli tost olacakları. İsraf. Gidip biz baksak aynayı kırıp delilleri mahvetmek zorunda da kalmazlar.
Diğer memur sandalyesinde hafifçe dönecek oldu, o sırada soruyu bilgisayarın hoparlöründen teknisyen cevapladı.
Hangi işimizde bir yamukluk yok ki be abi.
Ama bir son değildi. Üstlerindeki tüm illüzyon dağıldığında ve çıplak, cinsiyetsiz, birbirinin aynı bedenleriyle kaldıklarında sıra dünyaya gelmişti.
Yere düştüler. Elleri -bütün bedeni gibi siyah turmalinden, boğumları çelikten- yere değdiği anda, metronun zemini dağıldı.
Yerdeki karolar öncesinde beyazdı ve çok parlaktı. Tepelerindeki floresan, ışığını olduğu gibi yansıtıyor, tek bir lekenin olmadığı ve tek bir tozun uçmadığı istasyonu aydınlatıyorlardı.
Duvarlara duyurular asılmıştı. Örneğin, yarın akşam kültür merkezinde 20.00’da başlayacak bir tekno blues festivalinin cıvıl cıvıl afişi vardı. Onun yanında daha geniş, sarı puntolu harflerle yazılmış, yatay siyah kesiklerle çerçevesi çizilmiş, bir platformdan düşen çöp adamın bulunduğu “Dikkat! Sarı bandı geçmeyin!” uyarısı. Biraz ilerisinde günlük resmi gazete, onun ilerisinde bir aksiyon filminin ve başka bir romantik komedi filminin afişleri, yapılacakların ve yapılmayacakların söylendiği küçük puntolu çeşitli duyurular... Duvar uzayıp giden bir panoydu. On, on beş metrede bir tekrarlanıyordu.
Tüm istasyonun eni yüz metre kadar. Genişliği on metre civarı.
Önlerinde, açık kapısından o mendebur aynanın gözüktüğü vagon duruyordu. Metro, istasyona sığmayacak kadar uzundu. Bir kılıcın keskinliğiyle uzanıyor ama yer yer vagonların ek yerleriyle bölünüyordu.
Hiçbir vagonda pencere olmadığı için metronun içi, içlerindekiler meçhuldü.
Sonrasında karolar zerrelerine ayrılarak yükseldi. Floresanın ışığında her yeri toza boğdular ve ortalığı gri bir sisin altına gömdüler. Çok kısa bir an. Afişleri dalgalandırmadılar. Dalgalandırmaya vakitleri olmadı. Yerlerinden söküp aldılar en fazla. Işık birkaç kere sönüp yanarak direndi. Son kez söndüğünde bir daha geri gelmedi.
Yine de etraf aydınlıktı. Kırmızı, her yere eşit dağılan soluk bir ışıkla.
Yer tamamen tele dönüşmüştü. Altında çapraz hatlarla desteklenmiş demir bir iskelet. Işık birkaç metreden daha fazla aşağıya uzanamıyordu. Sonsuzluğa giden bir uçurum.
Duvarın yerini aynı teller ve demir iskelet almıştı. Arkasında, birbirine vidalarla tutturulmuş demir plakalardan oluşan, üstünden geçen boruların ek yerlerinden bazen ince buharların çıktığı ve bir süre asılı kaldıktan sonra ağır, yağlı bir havayla sürüklendiği bir koridor.
Diğer tarafta paslanmış, pencerelerindeki camlar kırıldığı için demir plakalarla kapatılmış külüstür bir metro. Kapının karşısındaki aynadan her şey olduğu gibi yansıyordu.
Bir konteynırın içini andıran bir evde, gerçi gayet de birbirine eklenmiş konteynırlardan oluşan bir şehirde “andıran” demek doğru olmayacağı için düpedüz bir konteynırın içinde, masaya mum görüntüsü vermek için koyulmuş, yarı katı yağ atıklarından şekillendirilmiş kütleleri yakmayı deniyordu. Kafasında hayvan kıllarından yapılmış grili siyahlı bir peruk. Aynı kıllardan kendisine gür bir bıyık da yapmıştı.
Üstünde mavi çöp poşetlerinden yapılmış, kravatlı, şık bir takım.
Masanın ayakları yerine oradan buradan çıkmış parçalar konulmuştu: bir arabanın şaft mili, üst üste konulmuş ve üstünde yazı okunamayan tenekeler, boş kitaplar, boş gazete balyaları... Hiçbir şeye yazı yazılmıyordu, gerek yoktu da zaten çünkü merkez veri bankası onları fark ettirmeden, merceklerden giren veriyi sentezleyerek insanlar için dolduruyordu. Yani, androidler için. Farklı şekilde isimlendirmek bir fark yaratacaksa.
Onların mercekleri için değil. Bağlantıları çok önceden kopmuştu.
─ Hayatım, sofra hazır, diye bağırdı yatak odasındaki karısına.
Sofrada tabak yerine düz, bardak yerine bükülmüş, çatal ve bıçak yerine sivriltilmiş plakalar.
Karısı salonun kapısında durakladı ve ancak kulaklarına kadar uzanan, kocasınınkine benzeyen, cansız, ölü hayvanların kıllarından ibaret peruğunu eliyle düzeltti. Dudağını, daha doğrusu dudağının olması gereken yeri koyu kırmızı bir yağ tabakasıyla renklendirmeyi denemişti. Biraz da yanaklarına sürmüştü.
─ Nasıl olmuş, diye sordu.
Sesi tek düzeydi ama hafif bir neşe olduğunu hissettiğinize yemin edebilirdiniz.
Üzerinde, çöp poşetlerinin içini yazısız gazete kağıtlarıyla doldurarak yaptığı iki parça giysi.
─ Çok güzelsin, diyerek kravatını düzeltti kocası.
─ Sen de öylesin, sevgilim.
Yaklaşıp kocasını öptü. Kocası da onu. Sonra nazikçe elinden tutarak, sandalyesini geriye çekerek oturmasına yardım etti.
Sofrada yemek niyetine hiçbir şey yoktu. Gerek de yoktu zaten.
Konteynırın kapısı gürültüyle tekmelenip içeri iki memur girene kadar birbirlerine öyküler anlattılar. O gün neler yaptıklarını. İşten erken çıkıp yemyeşil çimenlerde gezdiklerini, uçurtma uçurduklarını, kadının nasıl o elbiseyi bulmak için saatlerce gezip yorulduğunu, kocasının kısa süreliğine işe dönüp nasıl başarılı bir hamleyle yaşanan krizi çözdüğünü ve kadının yanına döndükten sonra, alışveriş merkezinde oturdukları yeni dondurmacının dondurmalarının ne kadar lezzetli olduğunu, boğazlarının ağrımasından korktuklarını...
Akşam film izleyebilirlerdi, televizyonda -boş ve mat bir plaka- güzel bir film oynayacaktı.
İki memur. Çıplak bedenleriyle birbirinin aynı. Ellerindeki silahları onlara doğrultmuşlardı. Mum ışığında, tertemiz bir örtünün serili olduğu masada, bardaklarında şaraplarla oturan ve henüz sofranın ortasındaki hindiye dokunmamış çifti gördüklerinde bocaladılar.
Hiç de androidlere bilinçli olarak zarar verebilecek gibi gözükmüyorlardı.
─ Sessiz kalma hakkına sahipsiniz, diye bağırdı içeri giren ikinci memur. Söylediğiniz her şey...
Cümlesini bitiremedi. Yatak odasındaki, masanın üzerinden gördüğü o şey, onunla aynı hareketleri yapan android, yoksa, bir aynadaki yansıması mıydı?
Bütün illüzyon o anda dağılmaya başladı.
Not: Bu öykü ilk olarak 2020 yılında Esrarengiz Hikâyeler'de yayımlanmıştır.
-
 @ 8fb140b4:f948000c
2023-11-21 21:37:48
@ 8fb140b4:f948000c
2023-11-21 21:37:48Embarking on the journey of operating your own Lightning node on the Bitcoin Layer 2 network is more than just a tech-savvy endeavor; it's a step into a realm of financial autonomy and cutting-edge innovation. By running a node, you become a vital part of a revolutionary movement that's reshaping how we think about money and digital transactions. This role not only offers a unique perspective on blockchain technology but also places you at the heart of a community dedicated to decentralization and network resilience. Beyond the technicalities, it's about embracing a new era of digital finance, where you contribute directly to the network's security, efficiency, and growth, all while gaining personal satisfaction and potentially lucrative rewards.
In essence, running your own Lightning node is a powerful way to engage with the forefront of blockchain technology, assert financial independence, and contribute to a more decentralized and efficient Bitcoin network. It's an adventure that offers both personal and communal benefits, from gaining in-depth tech knowledge to earning a place in the evolving landscape of cryptocurrency.
Running your own Lightning node for the Bitcoin Layer 2 network can be an empowering and beneficial endeavor. Here are 10 reasons why you might consider taking on this task:
-
Direct Contribution to Decentralization: Operating a node is a direct action towards decentralizing the Bitcoin network, crucial for its security and resistance to control or censorship by any single entity.
-
Financial Autonomy: Owning a node gives you complete control over your financial transactions on the network, free from reliance on third-party services, which can be subject to fees, restrictions, or outages.
-
Advanced Network Participation: As a node operator, you're not just a passive participant but an active player in shaping the network, influencing its efficiency and scalability through direct involvement.
-
Potential for Higher Revenue: With strategic management and optimal channel funding, your node can become a preferred route for transactions, potentially increasing the routing fees you can earn.
-
Cutting-Edge Technological Engagement: Running a node puts you at the forefront of blockchain and bitcoin technology, offering insights into future developments and innovations.
-
Strengthened Network Security: Each new node adds to the robustness of the Bitcoin network, making it more resilient against attacks and failures, thus contributing to the overall security of the ecosystem.
-
Personalized Fee Structures: You have the flexibility to set your own fee policies, which can balance earning potential with the service you provide to the network.
-
Empowerment Through Knowledge: The process of setting up and managing a node provides deep learning opportunities, empowering you with knowledge that can be applied in various areas of blockchain and fintech.
-
Boosting Transaction Capacity: By running a node, you help to increase the overall capacity of the Lightning Network, enabling more transactions to be processed quickly and at lower costs.
-
Community Leadership and Reputation: As an active node operator, you gain recognition within the Bitcoin community, which can lead to collaborative opportunities and a position of thought leadership in the space.
These reasons demonstrate the impactful and transformative nature of running a Lightning node, appealing to those who are deeply invested in the principles of bitcoin and wish to actively shape its future. Jump aboard, and embrace the journey toward full independence. 🐶🐾🫡🚀🚀🚀
-
-
 @ c4b5369a:b812dbd6
2025-01-18 12:17:22
@ c4b5369a:b812dbd6
2025-01-18 12:17:22This is the first edition of the SDR (Squirrel Den Recap), a development blog where I recap the recent Cashu related things I've been working on.
The year of the nut
IYKYK. 2025 is the year of the nut. Don't blame me, you can put it on the Chinese:

And I intend to take full advantage of that. This is the year where I go all in on the nut development!
Building a mint???
There are already a few mint implementations out there (nutshell, gonuts, cdk...). So why build another?
Honestly it was kind of a selfish move. So far, I have mainly concerned myself with building tools for Cashu wallets and clients. I figured, if I wanted to truly focus on Cashu this year, I should also know my stuff when it comes to building a mint from scratch. And so I did. It also allows me to experiment with mint related stuff, having an implementation handy that I can mess around with.

The mint implementation is called MNT. You can visit the homepage https://mnt.cash , where you will also find a link to the code.
Although the code works, the mint implementation is not yet ready for production. I've been playing around with it using a local testing lightning network with Polar , which by the way is a great tool for devs that need to test lightning integrations.
The mint
MNT is short for mint. It's also pronounced like mint, but without the "i". The goal of this project is to be an easy to run mint, that could be deployed by users for example when running an event. It won't support all of the protocol features, to keep it simple. Instead the focus will be on simplicity and ease of use.
MNT comes with an admin web interface, that makes it easy to set the mint up with a lightning backend:

After adding a lightning backend, the mint is basically ready! Users can enjoy a live view of what is happening on their mint via the integrated dashboard:

Admins can take direct actions on the mint via the admin tool, like rotating keysets, disabling and enabling features, etc...
A key feature is also the keyset view, where operators get a view on how much of the issued ecash has already been redeemed in each keyset. This is a crucial tool for mint operators, because it lets them know when they can safely delete records from their database, or shut the mint down.

The mint is compatible with all Cashu wallets. It only supports a subset of the cashu specification (NUTs), and will probably never implement the full spec. I'm looking forward to soon recklessly give this badboy a spin on mainnet 😎
What else?
Cashu-ts
Last year
npub1mhcr4j594hsrnen594d7700n2t03n8gdx83zhxzculk6sh9nhwlq7uc226
joined cashu-ts as a maintainer and has been killing it with development in the project! As I ramp up my involvement in the project again, we started having weekly dev calls. Developers that want to contribute to cashu-ts development, please reach out to me so you can join us on the next call!
Nutstash
The wallet has seen a complete make-over at the end of last year. Now is the time to consolidate, fix bugs and improve the UX.
npub12zpfs3yq7we83yvypgsrw5f88y2fv780c2kfs89ge5qk6q3sfm7spks880
has been helping me with awesome designs and UX suggestions, while I've been crushing bugs. A new version fixing some edge cases in the restore process can be expected next week!

This blog
\ This year, I was fortunate to receive funding for my work on open source projects in the Cashu ecosystem. I am very grateful for the trust from
npub17xvf49kht23cddxgw92rvfktkd3vqvjgkgsdexh9847wl0927tqsrhc9as
and
npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f
this means a lot to me, to be able to make a living by working on something I am passionate about is a blessing, and I don't think it would be possible without the support from you. My deepest gratitude, I hope my contributions will not only match, but exceed expectations.
By writing this blog, I want to show my progress, proof of work, and give people a look into the daily life in the squirrels den 🐿️🐿️🐿️🐿️🐿️🐿️
If you have any questions or suggestions about this blog, please let me know in a comment!
Best,
Gandlaf
-
 @ a849beb6:b327e6d2
2024-11-23 15:03:47
@ a849beb6:b327e6d2
2024-11-23 15:03:47
\ \ It was another historic week for both bitcoin and the Ten31 portfolio, as the world’s oldest, largest, most battle-tested cryptocurrency climbed to new all-time highs each day to close out the week just shy of the $100,000 mark. Along the way, bitcoin continued to accumulate institutional and regulatory wins, including the much-anticipated approval and launch of spot bitcoin ETF options and the appointment of several additional pro-bitcoin Presidential cabinet officials. The timing for this momentum was poetic, as this week marked the second anniversary of the pico-bottom of the 2022 bear market, a level that bitcoin has now hurdled to the tune of more than 6x despite the litany of bitcoin obituaries published at the time. The entirety of 2024 and especially the past month have further cemented our view that bitcoin is rapidly gaining a sense of legitimacy among institutions, fiduciaries, and governments, and we remain optimistic that this trend is set to accelerate even more into 2025.
Several Ten31 portfolio companies made exciting announcements this week that should serve to further entrench bitcoin’s institutional adoption. AnchorWatch, a first of its kind bitcoin insurance provider offering 1:1 coverage with its innovative use of bitcoin’s native properties, announced it has been designated a Lloyd’s of London Coverholder, giving the company unique, blue-chip status as it begins to write bitcoin insurance policies of up to $100 million per policy starting next month. Meanwhile, Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the launch of Battery’s pioneering private credit strategy which fuses bitcoin and conventional tangible assets in a dual-collateralized structure that offers a compelling risk/return profile to both lenders and borrowers. Both companies are clearing a path for substantially greater bitcoin adoption in massive, untapped pools of capital, and Ten31 is proud to have served as lead investor for AnchorWatch’s Seed round and as exclusive capital partner for Battery.
As the world’s largest investor focused entirely on bitcoin, Ten31 has deployed nearly $150 million across two funds into more than 30 of the most promising and innovative companies in the ecosystem like AnchorWatch and Battery, and we expect 2025 to be the best year yet for both bitcoin and our portfolio. Ten31 will hold a first close for its third fund at the end of this year, and investors in that close will benefit from attractive incentives and a strong initial portfolio. Visit ten31.vc/funds to learn more and get in touch to discuss participating.\ \ Portfolio Company Spotlight
Primal is a first of its kind application for the Nostr protocol that combines a client, caching service, analytics tools, and more to address several unmet needs in the nascent Nostr ecosystem. Through the combination of its sleek client application and its caching service (built on a completely open source stack), Primal seeks to offer an end-user experience as smooth and easy as that of legacy social media platforms like Twitter and eventually many other applications, unlocking the vast potential of Nostr for the next billion people. Primal also offers an integrated wallet (powered by Strike BLACK) that substantially reduces onboarding and UX frictions for both Nostr and the lightning network while highlighting bitcoin’s unique power as internet-native, open-source money.
Selected Portfolio News
AnchorWatch announced it has achieved Llody’s Coverholder status, allowing the company to provide unique 1:1 bitcoin insurance offerings starting in December.\ \ Battery Finance Founder and CEO Andrew Hohns appeared on CNBC to delve into the company’s unique bitcoin-backed private credit strategy.
Primal launched version 2.0, a landmark update that adds a feed marketplace, robust advanced search capabilities, premium-tier offerings, and many more new features.
Debifi launched its new iOS app for Apple users seeking non-custodial bitcoin-collateralized loans.
Media
Strike Founder and CEO Jack Mallers joined Bloomberg TV to discuss the strong volumes the company has seen over the past year and the potential for a US bitcoin strategic reserve.
Primal Founder and CEO Miljan Braticevic joined The Bitcoin Podcast to discuss the rollout of Primal 2.0 and the future of Nostr.
Ten31 Managing Partner Marty Bent appeared on BlazeTV to discuss recent changes in the regulatory environment for bitcoin.
Zaprite published a customer testimonial video highlighting the popularity of its offerings across the bitcoin ecosystem.
Market Updates
Continuing its recent momentum, bitcoin reached another new all-time high this week, clocking in just below $100,000 on Friday. Bitcoin has now reached a market cap of nearly $2 trillion, putting it within 3% of the market caps of Amazon and Google.
After receiving SEC and CFTC approval over the past month, long-awaited options on spot bitcoin ETFs were fully approved and launched this week. These options should help further expand bitcoin’s institutional liquidity profile, with potentially significant implications for price action over time.
The new derivatives showed strong performance out of the gate, with volumes on options for BlackRock’s IBIT reaching nearly $2 billion on just the first day of trading despite surprisingly tight position limits for the vehicles.
Meanwhile, the underlying spot bitcoin ETF complex had yet another banner week, pulling in $3.4 billion in net inflows.
New reports suggested President-elect Donald Trump’s social media company is in advanced talks to acquire crypto trading platform Bakkt, potentially the latest indication of the incoming administration’s stance toward the broader “crypto” ecosystem.
On the macro front, US housing starts declined M/M again in October on persistently high mortgage rates and weather impacts. The metric remains well below pre-COVID levels.
Pockets of the US commercial real estate market remain challenged, as the CEO of large Florida developer Related indicated that developers need further rate cuts “badly” to maintain project viability.
US Manufacturing PMI increased slightly M/M, but has now been in contraction territory (<50) for well over two years.
The latest iteration of the University of Michigan’s popular consumer sentiment survey ticked up following this month’s election results, though so did five-year inflation expectations, which now sit comfortably north of 3%.
Regulatory Update
After weeks of speculation, the incoming Trump administration appointed hedge fund manager Scott Bessent to head up the US Treasury. Like many of Trump’s cabinet selections so far, Bessent has been a public advocate for bitcoin.
Trump also appointed Cantor Fitzgerald CEO Howard Lutnick – another outspoken bitcoin bull – as Secretary of the Commerce Department.
Meanwhile, the Trump team is reportedly considering creating a new “crypto czar” role to sit within the administration. While it’s unclear at this point what that role would entail, one report indicated that the administration’s broader “crypto council” is expected to move forward with plans for a strategic bitcoin reserve.
Various government lawyers suggested this week that the Trump administration is likely to be less aggressive in seeking adversarial enforcement actions against bitcoin and “crypto” in general, as regulatory bodies appear poised to shift resources and focus elsewhere.
Other updates from the regulatory apparatus were also directionally positive for bitcoin, most notably FDIC Chairman Martin Gruenberg’s confirmation that he plans to resign from his post at the end of President Biden’s term.
Many critics have alleged Gruenberg was an architect of “Operation Chokepoint 2.0,” which has created banking headwinds for bitcoin companies over the past several years, so a change of leadership at the department is likely yet another positive for the space.
SEC Chairman Gary Gensler also officially announced he plans to resign at the start of the new administration. Gensler has been the target of much ire from the broader “crypto” space, though we expect many projects outside bitcoin may continue to struggle with questions around the Howey Test.
Overseas, a Chinese court ruled that it is not illegal for individuals to hold cryptocurrency, even though the country is still ostensibly enforcing a ban on crypto transactions.
Noteworthy
The incoming CEO of Charles Schwab – which administers over $9 trillion in client assets – suggested the platform is preparing to “get into” spot bitcoin offerings and that he “feels silly” for having waited this long. As this attitude becomes more common among traditional finance players, we continue to believe that the number of acquirers coming to market for bitcoin infrastructure capabilities will far outstrip the number of available high quality assets.
BlackRock’s 2025 Thematic Outlook notes a “renewed sense of optimism” on bitcoin among the asset manager’s client base due to macro tailwinds and the improving regulatory environment. Elsewhere, BlackRock’s head of digital assets indicated the firm does not view bitcoin as a “risk-on” asset.
MicroStrategy, which was a sub-$1 billion market cap company less than five years ago, briefly breached a $100 billion equity value this week as it continues to aggressively acquire bitcoin. The company now holds nearly 350,000 bitcoin on its balance sheet.
Notably, Allianz SE, Germany’s largest insurer, spoke for 25% of MicroStrategy’s latest $3 billion convertible note offering this week, suggesting growing appetite for bitcoin proxy exposure among more restricted pools of capital.
The ongoing meltdown of fintech middleware provider Synapse has left tens of thousands of customers with nearly 100% deposit haircuts as hundreds of millions in funds remain missing, the latest unfortunate case study in the fragility of much of the US’s legacy banking stack.
Travel
-
BitcoinMENA, Dec 9-10
-
Nashville BitDevs, Dec 10
-
Austin BitDevs, Dec 19
-
-
 @ 8fb140b4:f948000c
2023-11-18 23:28:31
@ 8fb140b4:f948000c
2023-11-18 23:28:31Chef's notes
Serving these two dishes together will create a delightful centerpiece for your Thanksgiving meal, offering a perfect blend of traditional flavors with a homemade touch.
Details
- ⏲️ Prep time: 30 min
- 🍳 Cook time: 1 - 2 hours
- 🍽️ Servings: 4-6
Ingredients
- 1 whole turkey (about 12-14 lbs), thawed and ready to cook
- 1 cup unsalted butter, softened
- 2 tablespoons fresh thyme, chopped
- 2 tablespoons fresh rosemary, chopped
- 2 tablespoons fresh sage, chopped
- Salt and freshly ground black pepper
- 1 onion, quartered
- 1 lemon, halved
- 2-3 cloves of garlic
- Apple and Sage Stuffing
- 1 loaf of crusty bread, cut into cubes
- 2 apples, cored and chopped
- 1 onion, diced
- 2 stalks celery, diced
- 3 cloves garlic, minced
- 1/4 cup fresh sage, chopped
- 1/2 cup unsalted butter
- 2 cups chicken broth
- Salt and pepper, to taste
Directions
- Preheat the Oven: Set your oven to 325°F (165°C).
- Prepare the Herb Butter: Mix the softened butter with the chopped thyme, rosemary, and sage. Season with salt and pepper.
- Prepare the Turkey: Remove any giblets from the turkey and pat it dry. Loosen the skin and spread a generous amount of herb butter under and over the skin.
- Add Aromatics: Inside the turkey cavity, place the quartered onion, lemon halves, and garlic cloves.
- Roast: Place the turkey in a roasting pan. Tent with aluminum foil and roast. A general guideline is about 15 minutes per pound, or until the internal temperature reaches 165°F (74°C) at the thickest part of the thigh.
- Rest and Serve: Let the turkey rest for at least 20 minutes before carving.
- Next: Apple and Sage Stuffing
- Dry the Bread: Spread the bread cubes on a baking sheet and let them dry overnight, or toast them in the oven.
- Cook the Vegetables: In a large skillet, melt the butter and cook the onion, celery, and garlic until soft.
- Combine Ingredients: Add the apples, sage, and bread cubes to the skillet. Stir in the chicken broth until the mixture is moist. Season with salt and pepper.
- Bake: Transfer the stuffing to a baking dish and bake at 350°F (175°C) for about 30-40 minutes, until golden brown on top.
-
 @ 65912a7a:5dc638bf
2024-11-22 21:37:16
@ 65912a7a:5dc638bf
2024-11-22 21:37:16Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 12
Ingredients
- 12-14oz fresh cranberries
- 1⅓ cup packed brown sugar
- 1 cup raisins
- 1 orange, peeled & chopped
- 1 cup water
Directions
- Using medium sauce pan, simmer cranberries and water for 5-6 min. Cranberries will start to pop.
- Add brown sugar, raisins, and chopped orange to the berries.
- Bring to a simmer and continue to cook for 20 min. Stir often to prevent sticking. Remove from heat.
- Let set until room temp. Mixture will thicken as it cools.
- Put in a covered container and keep refrigerated. Lasts for about 2 weeks.
-
 @ a10260a2:caa23e3e
2025-01-18 12:04:41
@ a10260a2:caa23e3e
2025-01-18 12:04:41Last Updated: January 18, 2025
First off, big shoutout to Coinos for having support for adding a memo to BOLT12 offers. This provides a solid alternative for the pleb who wants to support mining decentralization but doesn’t want to set up a CLN node and pay thousands of sats for a channel only to get little rewards. This is the case for most of us who only have a miner or two (e.g. a Bitaxe and/or an S9).
Before we get into setting up Lightning payouts, you’ll want to have your miner configured to mine with OCEAN of course. You’ll also want to make sure that the bitcoin address you use is from a wallet that supports signing messages.
These are the ones listed in the OCEAN docs:
- Bitcoin Knots/Bitcoin Core
- Coldcard
- Electrum
- LND (Command Line)
- Seedsigner
- Sparrow
- Specter
- Trezor
I checked one of my favorite, user-friendly wallets — Blue Wallet — and it happens to support signing messages as well.
Just tap the three dots on the upper right and you’ll see the “Sign/Verify Message” button at the bottom.
Update [January 18]: You can now use Coinos to sign by going to https://coinos.io/sign
The trick here is to not refresh the page. In other words, when you're logged in to your Coinos account, go to the URL and use the legacy address (starts with a "1") that's displayed to configure your miner(s). If you refresh the page, you're going to get a new address which will cause the signing to fail later on. Remember, keep the tab open and don't refresh the page.

Whichever wallet you choose, generate a receive address to use when configuring your miner (it’ll also be your OCEAN username).
Here’s how it looks on the Bitaxe (AxeOS)…
And the Antminer S9 (Braiins OS).
NOTE: There’s a slight difference in the URL format between the two apps. Other than that, the username will be your bitcoin address followed by the optional “.” + the nickname for your machine.
You can find more details on OCEAN’s get started page.
Alright, now that your miner is pointed at OCEAN. Let’s configure Lightning payouts!
Generating the BOLT12 Offer
In the Coinos app, go to Receive > Bolt 12.
Tap “Set memo” and set it to “OCEAN Payouts for [insert your bitcoin address]” (this text is case-sensitive). Use the same bitcoin address you used above to configure your miner(s).
After tapping OK, copy the BOLT12 offer (it should start with “lno”) and proceed to the next step.
Generating the Configuration Message
Navigate to the My Stats page by searching for your OCEAN Bitcoin address.
The click the Configuration link next to Next Block to access the configuration form.
Paste the BOLT12 offer here, update the block height to latest, click GENERATE, and copy the generated unsigned message.
Signing the Configuration Message
To sign the generated message, go back to Blue Wallet and use the signing function. Paste the configuration message in the Message field, tap Sign, and copy the signed message that’s generated.
If you're using Coinos to sign, return to the page that you kept open (and didn't refresh) and do the same. Paste the configuration message, click submit, and copy the signed message.
Submitting the Signed Message
Once signed, copy the signature, paste it in the OCEAN configuration form, and click CONFIRM.
If all goes well, you should see a confirmation that the configuration was successful. Congrats! 🎉
All you gotta do now is sit back, relax, and wait for a block to be found…
Or you can look into setting up DATUM. 😎
-
 @ 21b41910:91f41a5e
2024-11-23 12:00:26
@ 21b41910:91f41a5e
2024-11-23 12:00:26Chef's notes
Based on assorted recipes and refined over time, this round of beef tastes great as a result of the sweet and savory marinade.
Details
- ⏲️ Prep time: 5 minutes (+ 1 day)
- 🍳 Cook time: 20 minutes
Ingredients
- 2 pounds lean beef (may be labeled as London Broil)
- 1/3 cup olive oil
- 1/4 cup soy sauce
- 1/4 cup malt vinegar
- 1/4 cup lemon juice
- 1 tbsp sweetener of choice (honey, molasses, syrup, 4 packets of duck sauce, etc)
- 2 tsp old bay seasoning
- 1 tsp garlic powder
- 1 tsp sea salt
- 1/2 tsp black pepper
Directions
- Day Before: Mix all ingredients except the beef in a bowl to form a marinade. Place the cut of beef in a gallon sized Ziploc bag. Pour marinade over beef, ensure fully covered. Remove any excess air from the bag and seal. Place back in refrigerator for up to 24 hours before cooking.
- Cooking: Bring beef out of refrigerator (still in bag), and allow to rise to room temperature (about 30-40 minutes). Preheat broiler for about 15 minutes (your oven will vary). Broil for about 7-8 minutes on one side, then flip over. Continue broiling for another 7-10 minutes until temperature reads 140°F. Remove from broiler and let rest for 10 minutes before slicing thinly.
-
 @ 8fb140b4:f948000c
2023-11-02 01:13:01
@ 8fb140b4:f948000c
2023-11-02 01:13:01Testing a brand new YakiHonne native client for iOS. Smooth as butter (not penis butter 🤣🍆🧈) with great visual experience and intuitive navigation. Amazing work by the team behind it! * lists * work
Bold text work!

Images could have used nostr.build instead of raw S3 from us-east-1 region.
Very impressive! You can even save the draft and continue later, before posting the long-form note!
🐶🐾🤯🤯🤯🫂💜
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 87730827:746b7d35
2024-11-20 09:27:53
@ 87730827:746b7d35
2024-11-20 09:27:53Original: https://techreport.com/crypto-news/brazil-central-bank-ban-monero-stablecoins/
Brazilian’s Central Bank Will Ban Monero and Algorithmic Stablecoins in the Country
Brazil proposes crypto regulations banning Monero and algorithmic stablecoins and enforcing strict compliance for exchanges.
KEY TAKEAWAYS
- The Central Bank of Brazil has proposed regulations prohibiting privacy-centric cryptocurrencies like Monero.
- The regulations categorize exchanges into intermediaries, custodians, and brokers, each with specific capital requirements and compliance standards.
- While the proposed rules apply to cryptocurrencies, certain digital assets like non-fungible tokens (NFTs) are still ‘deregulated’ in Brazil.

In a Notice of Participation announcement, the Brazilian Central Bank (BCB) outlines regulations for virtual asset service providers (VASPs) operating in the country.
In the document, the Brazilian regulator specifies that privacy-focused coins, such as Monero, must be excluded from all digital asset companies that intend to operate in Brazil.
Let’s unpack what effect these regulations will have.
Brazil’s Crackdown on Crypto Fraud
If the BCB’s current rule is approved, exchanges dealing with coins that provide anonymity must delist these currencies or prevent Brazilians from accessing and operating these assets.
The Central Bank argues that currencies like Monero make it difficult and even prevent the identification of users, thus creating problems in complying with international AML obligations and policies to prevent the financing of terrorism.
According to the Central Bank of Brazil, the bans aim to prevent criminals from using digital assets to launder money. In Brazil, organized criminal syndicates such as the Primeiro Comando da Capital (PCC) and Comando Vermelho have been increasingly using digital assets for money laundering and foreign remittances.
… restriction on the supply of virtual assets that contain characteristics of fragility, insecurity or risks that favor fraud or crime, such as virtual assets designed to favor money laundering and terrorist financing practices by facilitating anonymity or difficulty identification of the holder.
The Central Bank has identified that removing algorithmic stablecoins is essential to guarantee the safety of users’ funds and avoid events such as when Terraform Labs’ entire ecosystem collapsed, losing billions of investors’ dollars.
The Central Bank also wants to control all digital assets traded by companies in Brazil. According to the current proposal, the national regulator will have the power to ask platforms to remove certain listed assets if it considers that they do not meet local regulations.
However, the regulations will not include NFTs, real-world asset (RWA) tokens, RWA tokens classified as securities, and tokenized movable or real estate assets. These assets are still ‘deregulated’ in Brazil.
Monero: What Is It and Why Is Brazil Banning It?
Monero ($XMR) is a cryptocurrency that uses a protocol called CryptoNote. It launched in 2013 and ‘erases’ transaction data, preventing the sender and recipient addresses from being publicly known. The Monero network is based on a proof-of-work (PoW) consensus mechanism, which incentivizes miners to add blocks to the blockchain.
Like Brazil, other nations are banning Monero in search of regulatory compliance. Recently, Dubai’s new digital asset rules prohibited the issuance of activities related to anonymity-enhancing cryptocurrencies such as $XMR.
Furthermore, exchanges such as Binance have already announced they will delist Monero on their global platforms due to its anonymity features. Kraken did the same, removing Monero for their European-based users to comply with MiCA regulations.
Data from Chainalysis shows that Brazil is the seventh-largest Bitcoin market in the world.

In Latin America, Brazil is the largest market for digital assets. Globally, it leads in the innovation of RWA tokens, with several companies already trading this type of asset.
In Closing
Following other nations, Brazil’s regulatory proposals aim to combat illicit activities such as money laundering and terrorism financing.
Will the BCB’s move safeguard people’s digital assets while also stimulating growth and innovation in the crypto ecosystem? Only time will tell.
References
Cassio Gusson is a journalist passionate about technology, cryptocurrencies, and the nuances of human nature. With a career spanning roles as Senior Crypto Journalist at CriptoFacil and Head of News at CoinTelegraph, he offers exclusive insights on South America’s crypto landscape. A graduate in Communication from Faccamp and a post-graduate in Globalization and Culture from FESPSP, Cassio explores the intersection of governance, decentralization, and the evolution of global systems.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ fd208ee8:0fd927c1
2024-11-21 07:24:34
@ fd208ee8:0fd927c1
2024-11-21 07:24:34The motherhood illusion
Growing up, I was always told that women wanted children, whilst men wanted sex. So, marriage was created, to unite these two urges, and men and women don't otherwise particularly differ. But, it turns out, that women want protection and sex, and men want children and sex.
This is why women tend to be attracted to more masculine men (they're associated with protection) and men tend to be attracted to more feminine women (they're associated with motherhood). Women who are attracted to men, who aren't overtly masculine, are looking for a different aspect of protection (reliability, steady income or wealth, emotional security, etc.)
This wasn't readily apparent, in earlier generations, as widespread, youthful marriage meant that there weren't any real decisions being made by the participants. Almost all women got married and had kids, and almost all men got married and had sex. Math checks out. But the number of women who could protect and provide for themselves was low, and the men marrying were often very young and libidinous, and not yet contemplating their own legacy.
Feminism, easy abortion, deindustrialization, delayed marriage, and reliable contraception have dissolved this illusion, completely. Millions of Western women quickly turned into cougars, careerists, party girls, and e-girls, and an entire army of childless men and sidelined dads bubbled up and began to make their pain known. Humanity's dirty underbelly has been exposed.
Women aren't as sweet, as we thought, and men are much sweeter.

Women also want children, but not as intensely. In fact, they seem to often viscerally dislike children, and are jealous of the protection they are to give them. So, they are prone to offing their offspring because they are averse to having any in-house competition.
If you just left women up to their own devices and reduced the social pressure, at least a fifth of them wouldn't bother having children, at all, and another quarter will have one and then lose interest or age out. This is not a new phenomenon, as we can see.
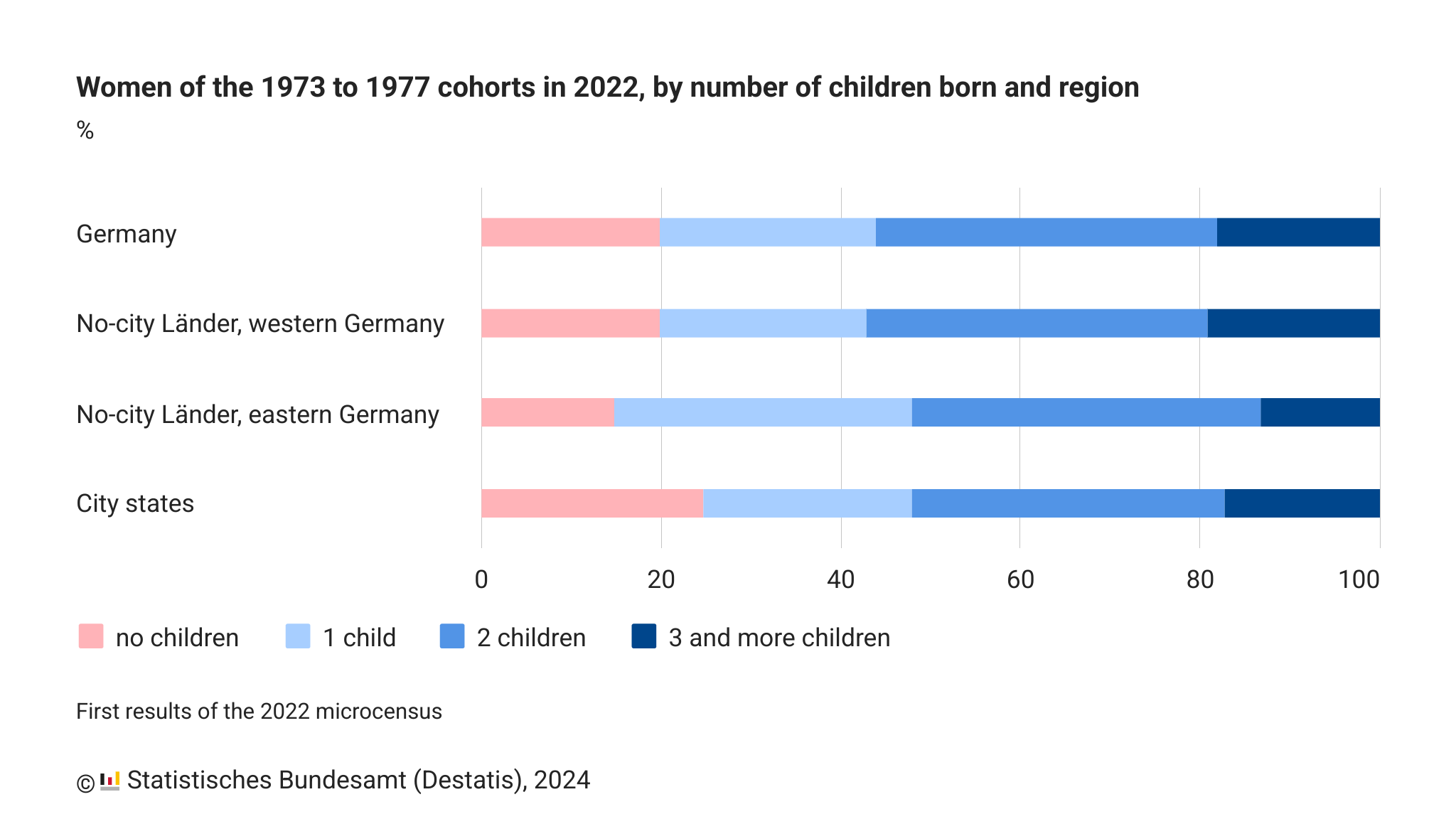
The male competition for potential mothers turns out to be absolutely brutal, and more difficult than simply finding a woman to sleep with. And, now, we finally understand why men traditionally jumped through so many hoops, to attain a wife. It wasn't for the sex; we've always had brothels, masturbation, and pornography. It was for the familial comfort, and, especially, for the children.
Good fathers make good mothers
Some women don't know if they are "potential mothers", until they meet a "potential father", and their urge to procreate suddenly kicks in. They didn't want children for their own sake, but now they want some for his sake. All of a sudden, they're imagining themselves rocking the cradle, googling "what to eat, when you're expecting", and find themselves gushing over anything that gives off Hint of Infant.
I'm pregnant! Look what I can do! Look what I can do! For you, darling.

Women married to men they are deeply in love with, are much more likely to desire to become mothers (and be devastated by infertility), and make for better mothers, because children are like individualized presents they can give to their husband.
They want to impress him. Most want to be decent parents in their own right, but the urge to impress seems to raise this to a much higher level because women are vain, and therefore focused on raising their own status and how they appear to others. And the greatest "other", of a happy wife, is her husband.
Because men are narcissistic, and therefore in love with anything associated with themselves (which underpins their obsession with owning property), men have an intense attachment to their children. What is more "yours", than your progeny?

Fathers seem to develop a special attachment to, or fondness for, the mothers of their children, that goes beyond lust or romantic love; they never forgot who gave them this new Mini Me. And they are often quite impressed by their own ability to perform this trick numerous times, which leads to the intense satisfaction they feel at "going into serial production" and churning out more of those Mini Mes until their adoring wife pleads for mercy.
Men want children. Women, who love a man, want to give him those children and gain the fidelity that comes along with those children. This is the actual "trade" underpinning the urge to marry.

-
 @ 41e6f20b:06049e45
2024-11-17 17:33:55
@ 41e6f20b:06049e45
2024-11-17 17:33:55Let me tell you a beautiful story. Last night, during the speakers' dinner at Monerotopia, the waitress was collecting tiny tips in Mexican pesos. I asked her, "Do you really want to earn tips seriously?" I then showed her how to set up a Cake Wallet, and she started collecting tips in Monero, reaching 0.9 XMR. Of course, she wanted to cash out to fiat immediately, but it solved a real problem for her: making more money. That amount was something she would never have earned in a single workday. We kept talking, and I promised to give her Zoom workshops. What can I say? I love people, and that's why I'm a natural orange-piller.
-
 @ ddf03aca:5cb3bbbe
2024-11-20 22:34:52
@ ddf03aca:5cb3bbbe
2024-11-20 22:34:52Recently, I have been surrounded by people experimenting with various projects, and a common theme among them is the use of cashu as the payment layer. While this fact alone is already great, the best part is to identify users and implementers needs and combining forces to come up with novel solutions.
Subscriptions with Cashu
One of the most remarkable aspects of cashu is that it is a bearer asset. This hands ownership and control back to the user. Even though mints back the tokens, they have no authority to move a token on behalf of a user or any other party. How cool is that?
However, this also introduces challenges when building subscription-based services. Subscriptions typically require periodic payments, and with cashu, users must renew these manually. Currently, there are two primary approaches to address this:
-
Overpaying:
To minimize the number of interactions, users can pay for longer periods upfront. For example, instead of paying 2,100 sats for one hour, they could pay 6,000 sats for three hours. If they realize they don’t need the full three hours, the excess payment is effectively wasted. -
Full Interactivity:
In this setup, payers and receivers stay connected through a communication channel, and payments are made at small, regular intervals. While this avoids overpayment, it requires constant connectivity. If the connection is lost, the subscription ends.
Enter Locking Scripts
One of the most powerful features of cashu is its locking scripts. Let’s take a quick refresher. A locking script defines the conditions under which a token (or "nut") becomes spendable. In essence, it’s similar to Bitcoin’s spending conditions, but instead of being enforced by the Bitcoin network, these conditions are enforced by the cashu mint alone.
A widely-used locking condition is Pay-to-Public-Key (P2PK). This locks a token to a specific public key, meaning it can only be spent when a valid signature from the key’s owner is provided. This mechanism is what enables NIP-61 nut zaps, where a token can be publicly shared but is only claimable by the intended recipient who holds the private key.
To address situations where a recipient loses access to their keys or simply doesn’t claim the token, P2PK includes additional options: locktime and a refund key. These options allow for the inclusion of a fallback mechanism. If the primary lock expires after a set time, a refund key can reclaim the token.
With these tools, we can now create non-interactive payment streams!
One Missing Piece…
Before diving into payment streams, there’s one more crucial concept to cover: cashu tokens are not singular "things". Instead, they’re composed of multiple proofs, each carrying its own cryptographic data and spendability. For example, if you receive a cashu token made up of five proofs, you could choose to claim only three proofs and leave the other two untouched. This flexibility is rarely utilized but is vital for building payment streams.
The Grand Finale: Payment Streams
Now that we have all the building blocks, let’s construct a payment stream using cashu. By leveraging locking scripts, refund keys, and multiple proofs, we can design a token that enables recipients to claim small portions of the total amount at regular intervals—without requiring any further interaction from the sender.
Even better, as the sender, you retain the ability to cancel the stream at any time and reclaim any unspent portions.
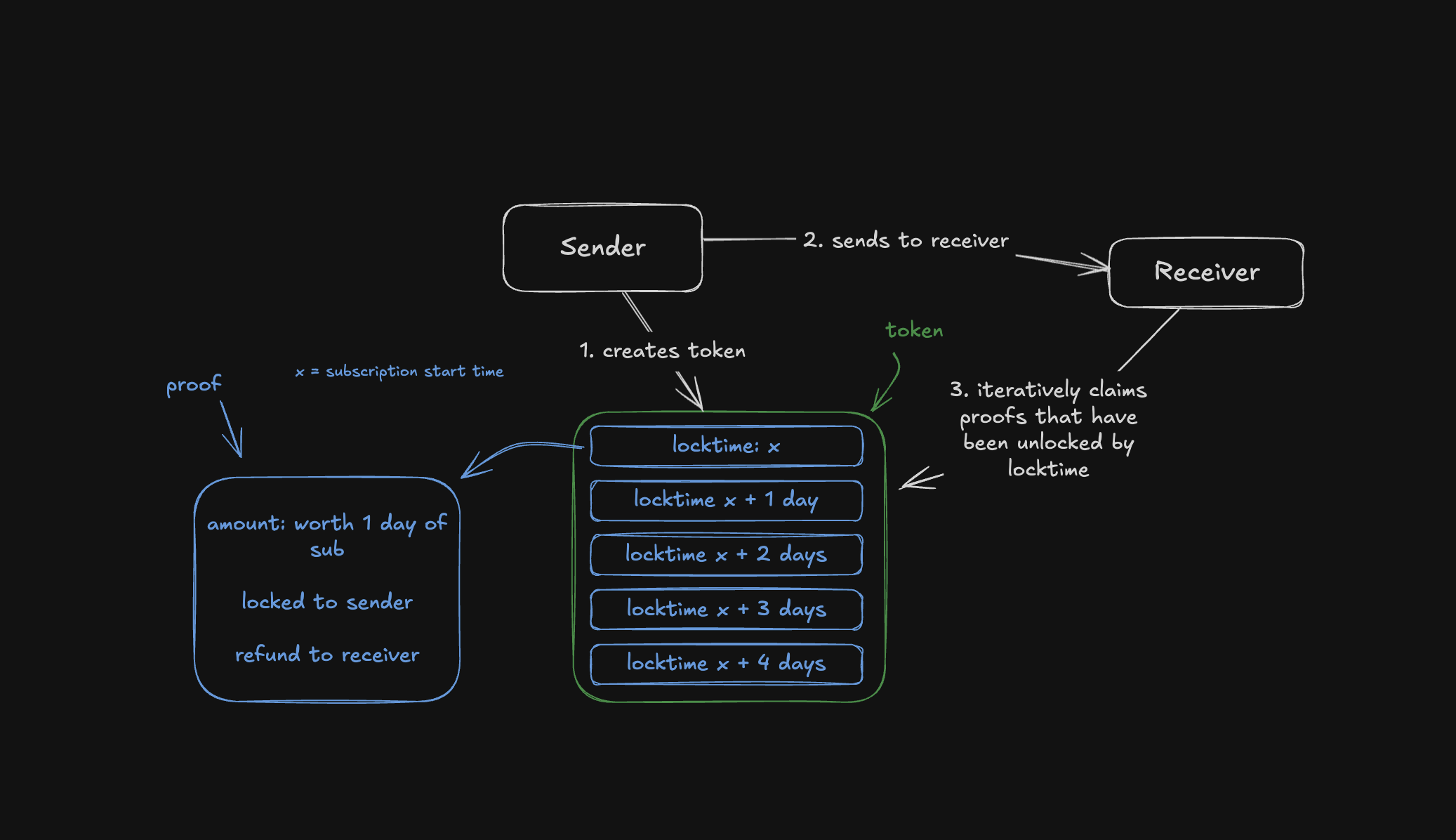
Example: Renting a VPS
Imagine renting a VPS for a week, priced at 1,000 sats per day. Here’s how a payment stream could work:
- Construct a token worth 7,000 sats to cover the entire week.
- Divide the token into 7 proofs, each worth 1,000 sats.
- Lock each proof using a P2PK script, locking to your key and adding the recipients key as a refund key.
- The first proof has a locktime of
now. - The second proof has a locktime of
now + 1 day. - The third proof has a locktime of
now + 2 days, and so on.
When the token is sent, the receiver can immediately claim the first proof since its locktime has expired and the refund key is now able to claim. The second proof becomes claimable after one day, the third after two days, and so on.
At the same time, the sender retains the ability to reclaim any unclaimed proofs by signing with their key. If you decide to stop using the VPS midweek, you can cancel the stream and reclaim the remaining proofs; all without further interaction with the receiver.
With this approach, we can create robust, non-interactive payment streams that combine the autonomy of cashu with the flexibility to reclaim funds.
Thank you for reading. Make sure to leave a nut if you enjoyed this :)
-
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note





