-
 @ eac63075:b4988b48
2025-01-04 19:41:34
@ eac63075:b4988b48
2025-01-04 19:41:34Since its creation in 2009, Bitcoin has symbolized innovation and resilience. However, from time to time, alarmist narratives arise about emerging technologies that could "break" its security. Among these, quantum computing stands out as one of the most recurrent. But does quantum computing truly threaten Bitcoin? And more importantly, what is the community doing to ensure the protocol remains invulnerable?
The answer, contrary to sensationalist headlines, is reassuring: Bitcoin is secure, and the community is already preparing for a future where quantum computing becomes a practical reality. Let’s dive into this topic to understand why the concerns are exaggerated and how the development of BIP-360 demonstrates that Bitcoin is one step ahead.
What Is Quantum Computing, and Why Is Bitcoin Not Threatened?
Quantum computing leverages principles of quantum mechanics to perform calculations that, in theory, could exponentially surpass classical computers—and it has nothing to do with what so-called “quantum coaches” teach to scam the uninformed. One of the concerns is that this technology could compromise two key aspects of Bitcoin’s security:
- Wallets: These use elliptic curve algorithms (ECDSA) to protect private keys. A sufficiently powerful quantum computer could deduce a private key from its public key.
- Mining: This is based on the SHA-256 algorithm, which secures the consensus process. A quantum attack could, in theory, compromise the proof-of-work mechanism.
Understanding Quantum Computing’s Attack Priorities
While quantum computing is often presented as a threat to Bitcoin, not all parts of the network are equally vulnerable. Theoretical attacks would be prioritized based on two main factors: ease of execution and potential reward. This creates two categories of attacks:
1. Attacks on Wallets
Bitcoin wallets, secured by elliptic curve algorithms, would be the initial targets due to the relative vulnerability of their public keys, especially those already exposed on the blockchain. Two attack scenarios stand out:
-
Short-term attacks: These occur during the interval between sending a transaction and its inclusion in a block (approximately 10 minutes). A quantum computer could intercept the exposed public key and derive the corresponding private key to redirect funds by creating a transaction with higher fees.
-
Long-term attacks: These focus on old wallets whose public keys are permanently exposed. Wallets associated with Satoshi Nakamoto, for example, are especially vulnerable because they were created before the practice of using hashes to mask public keys.
We can infer a priority order for how such attacks might occur based on urgency and importance.
 Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)
Bitcoin Quantum Attack: Prioritization Matrix (Urgency vs. Importance)2. Attacks on Mining
Targeting the SHA-256 algorithm, which secures the mining process, would be the next objective. However, this is far more complex and requires a level of quantum computational power that is currently non-existent and far from realization. A successful attack would allow for the recalculation of all possible hashes to dominate the consensus process and potentially "mine" it instantly.
 Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin Attacks
Satoshi Nakamoto in 2010 on Quantum Computing and Bitcoin AttacksRecently, Narcelio asked me about a statement I made on Tubacast:
https://x.com/eddieoz/status/1868371296683511969
If an attack became a reality before Bitcoin was prepared, it would be necessary to define the last block prior to the attack and proceed from there using a new hashing algorithm. The solution would resemble the response to the infamous 2013 bug. It’s a fact that this would cause market panic, and Bitcoin's price would drop significantly, creating a potential opportunity for the well-informed.
Preferably, if developers could anticipate the threat and had time to work on a solution and build consensus before an attack, they would simply decide on a future block for the fork, which would then adopt the new algorithm. It might even rehash previous blocks (reaching consensus on them) to avoid potential reorganization through the re-mining of blocks using the old hash. (I often use the term "shielding" old transactions).
How Can Users Protect Themselves?
While quantum computing is still far from being a practical threat, some simple measures can already protect users against hypothetical scenarios:
- Avoid using exposed public keys: Ensure funds sent to old wallets are transferred to new ones that use public key hashes. This reduces the risk of long-term attacks.
- Use modern wallets: Opt for wallets compatible with SegWit or Taproot, which implement better security practices.
- Monitor security updates: Stay informed about updates from the Bitcoin community, such as the implementation of BIP-360, which will introduce quantum-resistant addresses.
- Do not reuse addresses: Every transaction should be associated with a new address to minimize the risk of repeated exposure of the same public key.
- Adopt secure backup practices: Create offline backups of private keys and seeds in secure locations, protected from unauthorized access.
BIP-360 and Bitcoin’s Preparation for the Future
Even though quantum computing is still beyond practical reach, the Bitcoin community is not standing still. A concrete example is BIP-360, a proposal that establishes the technical framework to make wallets resistant to quantum attacks.
BIP-360 addresses three main pillars:
- Introduction of quantum-resistant addresses: A new address format starting with "BC1R" will be used. These addresses will be compatible with post-quantum algorithms, ensuring that stored funds are protected from future attacks.
- Compatibility with the current ecosystem: The proposal allows users to transfer funds from old addresses to new ones without requiring drastic changes to the network infrastructure.
- Flexibility for future updates: BIP-360 does not limit the choice of specific algorithms. Instead, it serves as a foundation for implementing new post-quantum algorithms as technology evolves.
This proposal demonstrates how Bitcoin can adapt to emerging threats without compromising its decentralized structure.
Post-Quantum Algorithms: The Future of Bitcoin Cryptography
The community is exploring various algorithms to protect Bitcoin from quantum attacks. Among the most discussed are:
- Falcon: A solution combining smaller public keys with compact digital signatures. Although it has been tested in limited scenarios, it still faces scalability and performance challenges.
- Sphincs: Hash-based, this algorithm is renowned for its resilience, but its signatures can be extremely large, making it less efficient for networks like Bitcoin’s blockchain.
- Lamport: Created in 1977, it’s considered one of the earliest post-quantum security solutions. Despite its reliability, its gigantic public keys (16,000 bytes) make it impractical and costly for Bitcoin.
Two technologies show great promise and are well-regarded by the community:
- Lattice-Based Cryptography: Considered one of the most promising, it uses complex mathematical structures to create systems nearly immune to quantum computing. Its implementation is still in its early stages, but the community is optimistic.
- Supersingular Elliptic Curve Isogeny: These are very recent digital signature algorithms and require extensive study and testing before being ready for practical market use.
The final choice of algorithm will depend on factors such as efficiency, cost, and integration capability with the current system. Additionally, it is preferable that these algorithms are standardized before implementation, a process that may take up to 10 years.
Why Quantum Computing Is Far from Being a Threat
The alarmist narrative about quantum computing overlooks the technical and practical challenges that still need to be overcome. Among them:
- Insufficient number of qubits: Current quantum computers have only a few hundred qubits, whereas successful attacks would require millions.
- High error rate: Quantum stability remains a barrier to reliable large-scale operations.
- High costs: Building and operating large-scale quantum computers requires massive investments, limiting their use to scientific or specific applications.
Moreover, even if quantum computers make significant advancements, Bitcoin is already adapting to ensure its infrastructure is prepared to respond.
Conclusion: Bitcoin’s Secure Future
Despite advancements in quantum computing, the reality is that Bitcoin is far from being threatened. Its security is ensured not only by its robust architecture but also by the community’s constant efforts to anticipate and mitigate challenges.
The implementation of BIP-360 and the pursuit of post-quantum algorithms demonstrate that Bitcoin is not only resilient but also proactive. By adopting practical measures, such as using modern wallets and migrating to quantum-resistant addresses, users can further protect themselves against potential threats.
Bitcoin’s future is not at risk—it is being carefully shaped to withstand any emerging technology, including quantum computing.
-
 @ a95c6243:d345522c
2025-01-03 20:26:47
@ a95c6243:d345522c
2025-01-03 20:26:47Was du bist hängt von drei Faktoren ab: \ Was du geerbt hast, \ was deine Umgebung aus dir machte \ und was du in freier Wahl \ aus deiner Umgebung und deinem Erbe gemacht hast. \ Aldous Huxley
Das brave Mitmachen und Mitlaufen in einem vorgegebenen, recht engen Rahmen ist gewiss nicht neu, hat aber gerade wieder mal Konjunktur. Dies kann man deutlich beobachten, eigentlich egal, in welchem gesellschaftlichen Bereich man sich umschaut. Individualität ist nur soweit angesagt, wie sie in ein bestimmtes Schema von «Diversität» passt, und Freiheit verkommt zur Worthülse – nicht erst durch ein gewisses Buch einer gewissen ehemaligen Regierungschefin.
Erklärungsansätze für solche Entwicklungen sind bekannt, und praktisch alle haben etwas mit Massenpsychologie zu tun. Der Herdentrieb, also der Trieb der Menschen, sich – zum Beispiel aus Unsicherheit oder Bequemlichkeit – lieber der Masse anzuschließen als selbstständig zu denken und zu handeln, ist einer der Erklärungsversuche. Andere drehen sich um Macht, Propaganda, Druck und Angst, also den gezielten Einsatz psychologischer Herrschaftsinstrumente.
Aber wollen die Menschen überhaupt Freiheit? Durch Gespräche im privaten Umfeld bin ich diesbezüglich in der letzten Zeit etwas skeptisch geworden. Um die Jahreswende philosophiert man ja gerne ein wenig über das Erlebte und über die Erwartungen für die Zukunft. Dabei hatte ich hin und wieder den Eindruck, die totalitären Anwandlungen unserer «Repräsentanten» kämen manchen Leuten gerade recht.
«Desinformation» ist so ein brisantes Thema. Davor müsse man die Menschen doch schützen, hörte ich. Jemand müsse doch zum Beispiel diese ganzen merkwürdigen Inhalte in den Social Media filtern – zur Ukraine, zum Klima, zu Gesundheitsthemen oder zur Migration. Viele wüssten ja gar nicht einzuschätzen, was richtig und was falsch ist, sie bräuchten eine Führung.
Freiheit bedingt Eigenverantwortung, ohne Zweifel. Eventuell ist es einigen tatsächlich zu anspruchsvoll, die Verantwortung für das eigene Tun und Lassen zu übernehmen. Oder die persönliche Freiheit wird nicht als ausreichend wertvolles Gut angesehen, um sich dafür anzustrengen. In dem Fall wäre die mangelnde Selbstbestimmung wohl das kleinere Übel. Allerdings fehlt dann gemäß Aldous Huxley ein Teil der Persönlichkeit. Letztlich ist natürlich alles eine Frage der Abwägung.
Sind viele Menschen möglicherweise schon so «eingenordet», dass freiheitliche Ambitionen gar nicht für eine ganze Gruppe, ein Kollektiv, verfolgt werden können? Solche Gedanken kamen mir auch, als ich mir kürzlich diverse Talks beim viertägigen Hacker-Kongress des Chaos Computer Clubs (38C3) anschaute. Ich war nicht nur überrascht, sondern reichlich erschreckt angesichts der in weiten Teilen mainstream-geformten Inhalte, mit denen ein dankbares Publikum beglückt wurde. Wo ich allgemein hellere Köpfe erwartet hatte, fand ich Konformismus und enthusiastisch untermauerte Narrative.
Gibt es vielleicht so etwas wie eine Herdenimmunität gegen Indoktrination? Ich denke, ja, zumindest eine gestärkte Widerstandsfähigkeit. Was wir brauchen, sind etwas gesunder Menschenverstand, offene Informationskanäle und der Mut, sich freier auch zwischen den Herden zu bewegen. Sie tun das bereits, aber sagen Sie es auch dieses Jahr ruhig weiter.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ f88e6629:e5254dd5
2025-01-08 20:08:17
@ f88e6629:e5254dd5
2025-01-08 20:08:17- Send a transaction, and the recipient uses the coin for another payment. You then merge these two transactions together and save on fees. 🔥
If you have a Trezor, you can try this out on: https://coiner-mu.vercel.app/
But be cautious. This is a hobby project without any guarantee.
How does it work?
- Connect Trezor, enter the passphrase, and select an account.
- The application display your coins, pending transactions, and descendant transactions.
- Then app shows you how much you can save by merging all transactions and removing duplicate information.
- Finally, you can sign and broadcast this more efficient transaction
-
 @ 2fb77d26:c47a6ee1
2025-01-08 19:47:47
@ 2fb77d26:c47a6ee1
2025-01-08 19:47:47Sehr geehrte Damen und Herren,
wenn wir an Schlachtfelder denken, sehen wir vor unserem inneren Auge düstere Bilder von verkohlten Wracks, von Einschlagkratern, schreienden Verwundeten, Leichen und dichten Rauchschwaden, die am Horizont über verbrannter Erde wabern.
Vergleichbare Assoziationen drängen sich auf, versucht man in Bilder zu fassen, in was für einer Gesellschaft wir mittlerweile leben. Intellektuelle Wracks, mediales Flächenbombardement, stumme Schreie von Pharmaopfern und hungernden Kindern, weggescrollt von Smartphone-Zombies, deren letzter Hauch Empathie am Rande ihres dissoziativen Wahrnehmungshorizontes verblasst. Zivilisatorische Transformation als Kriegsfilm.
Früher verliefen die Frontlinien von Klassenkampf und Propagandakrieg durch die Auslagen der Zeitungskioske, durch Rundfunkredaktionen und über die nach Sendeschluss flimmernden Bildschirme der Mattscheibe. Heute durch den Kopf.
Sprichwörtlich. Denn die »Vierte Industrielle Revolution« begegnet zunehmendem Desinteresse an Erziehungsfunk und aufkeimender Renitenz mit Dopamin-Shots, Implantaten und Nanotechnologie. Das erklärte Ziel der Herrschaftskaste ist nicht mehr die Manipulation, sondern die Fernsteuerung der Steuersklaven. Das »Hive Mind«.
Sendeschluss gibt es nicht mehr. Und der Newsfeed ist unerschöpflich, ist Manifestation dessen, was Aufmerksamkeitsökonomie für uns bedeutet: Den Verlust wertvoller Lebenszeit an neonbunte Sinnlosigkeit. Das Smartphone dient nicht der Evolution, sondern der Degeneration der Spezies Mensch. Es ist kein Werkzeug, sondern eine Waffe. Aber das Handy lässt sich — wie das TV-Gerät — abschalten. Oder abschaffen. Das birgt Risiken — denn nur Lufthoheit über dem Debattenraum garantiert dem postmodernen Feudalismus Machterhalt. Dementsprechend setzen seine Vertreter nun alles daran, invasive Technologien ins Feld zu führen, um sich unserer Gedanken bemächtigen zu können.
Der Kriegsfilm spielt sich also nicht mehr nur als dunkles Phantasma vor unserem inneren Auge ab, er handelt nicht von irgendeinem fernen Land — das zu erobernde Terrain, das primäre Schlachtfeld der biodigitalen Konvergenz liegt unmittelbar hinter dem Sehnerv. Kriegsziel: Die Verschmelzung von Mensch und Maschine. Transhumanismus. Und bei so manchem Zeitgenossen scheint bereits eine gewisse Konträrfaszination am eigenen Untergang Einzug zu halten. Die Résistance des Mediazän verteidigt demnach nicht nur das Recht auf Meinungsfreiheit, sie kämpft um den Erhalt des freien Willens. Um Menschlichkeit. Um das Fortbestehen unserer Spezies.
Vor diesem Hintergrund beschäftigt sich die dritte GEGENDRUCK mit dem »Schlachtfeld Gehirn«. Mit dem zerebralen Status quo. Die Autoren analysieren und dokumentieren den Stand von Forschung, Angriffswellen, Waffenarsenal und Verteidigungsmechanismen. Denn unser Leben ist das Produkt unserer Gedanken. Unserer Erinnerungen. Sie sind die Basis unserer Freiheit, unserer Geschichte und Zukunft. Wir müssen sie schützen. Mit allen Mitteln.
Denn »ein Kopf ohne Gedächtnis ist eine Festung ohne Besatzung« (Napoleon).
Im Namen des gesamten Teams,
Tom-Oliver Regenauer
Printausgabe bestellen unter: www.gegendruck.de
-
 @ a95c6243:d345522c
2025-01-01 17:39:51
@ a95c6243:d345522c
2025-01-01 17:39:51Heute möchte ich ein Gedicht mit euch teilen. Es handelt sich um eine Ballade des österreichischen Lyrikers Johann Gabriel Seidl aus dem 19. Jahrhundert. Mir sind diese Worte fest in Erinnerung, da meine Mutter sie perfekt rezitieren konnte, auch als die Kräfte schon langsam schwanden.
Dem originalen Titel «Die Uhr» habe ich für mich immer das Wort «innere» hinzugefügt. Denn der Zeitmesser – hier vermutliche eine Taschenuhr – symbolisiert zwar in dem Kontext das damalige Zeitempfinden und die Umbrüche durch die industrielle Revolution, sozusagen den Zeitgeist und das moderne Leben. Aber der Autor setzt sich philosophisch mit der Zeit auseinander und gibt seinem Werk auch eine klar spirituelle Dimension.
Das Ticken der Uhr und die Momente des Glücks und der Trauer stehen sinnbildlich für das unaufhaltsame Fortschreiten und die Vergänglichkeit des Lebens. Insofern könnte man bei der Uhr auch an eine Sonnenuhr denken. Der Rhythmus der Ereignisse passt uns vielleicht nicht immer in den Kram.
Was den Takt pocht, ist durchaus auch das Herz, unser «inneres Uhrwerk». Wenn dieses Meisterwerk einmal stillsteht, ist es unweigerlich um uns geschehen. Hoffentlich können wir dann dankbar sagen: «Ich habe mein Bestes gegeben.»
Ich trage, wo ich gehe, stets eine Uhr bei mir; \ Wieviel es geschlagen habe, genau seh ich an ihr. \ Es ist ein großer Meister, der künstlich ihr Werk gefügt, \ Wenngleich ihr Gang nicht immer dem törichten Wunsche genügt.
Ich wollte, sie wäre rascher gegangen an manchem Tag; \ Ich wollte, sie hätte manchmal verzögert den raschen Schlag. \ In meinen Leiden und Freuden, in Sturm und in der Ruh, \ Was immer geschah im Leben, sie pochte den Takt dazu.
Sie schlug am Sarge des Vaters, sie schlug an des Freundes Bahr, \ Sie schlug am Morgen der Liebe, sie schlug am Traualtar. \ Sie schlug an der Wiege des Kindes, sie schlägt, will's Gott, noch oft, \ Wenn bessere Tage kommen, wie meine Seele es hofft.
Und ward sie auch einmal träger, und drohte zu stocken ihr Lauf, \ So zog der Meister immer großmütig sie wieder auf. \ Doch stände sie einmal stille, dann wär's um sie geschehn, \ Kein andrer, als der sie fügte, bringt die Zerstörte zum Gehn.
Dann müßt ich zum Meister wandern, der wohnt am Ende wohl weit, \ Wohl draußen, jenseits der Erde, wohl dort in der Ewigkeit! \ Dann gäb ich sie ihm zurücke mit dankbar kindlichem Flehn: \ Sieh, Herr, ich hab nichts verdorben, sie blieb von selber stehn.
Johann Gabriel Seidl (1804-1875)
-
 @ 23b0e2f8:d8af76fc
2025-01-08 18:17:52
@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52Necessário
- Um Android que você não use mais (a câmera deve estar funcionando).
- Um cartão microSD (opcional, usado apenas uma vez).
- Um dispositivo para acompanhar seus fundos (provavelmente você já tem um).
Algumas coisas que você precisa saber
- O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele.
- O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito.
- A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal.
O tutorial será dividido em dois módulos:
- Módulo 1 - Criando uma carteira fria/assinador.
- Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
No final, teremos:
- Uma carteira fria que também servirá como assinador.
- Um dispositivo para acompanhar os fundos da carteira.

Módulo 1 - Criando uma carteira fria/assinador
-
Baixe o APK do Electrum na aba de downloads em https://electrum.org/. Fique à vontade para verificar as assinaturas do software, garantindo sua autenticidade.
-
Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.

- Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.

- Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o modo avião.\ (Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)

- Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.

- No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. (Aqui entra seu método pessoal de backup.)

Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
-
Criar uma carteira somente leitura em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em https://electrum.org/ ou da própria Play Store. (ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)
-
Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção Usar uma chave mestra.

- Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em Carteira > Detalhes da carteira > Compartilhar chave mestra pública.

-
Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los.
-
Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: Carteira > Addresses/Coins.
-
Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.

- No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.

- No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede.
Conclusão
Pontos positivos do setup:
- Simplicidade: Basta um dispositivo Android antigo.
- Flexibilidade: Funciona como uma ótima carteira fria, ideal para holders.
Pontos negativos do setup:
- Padronização: Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum.
- Interface: A aparência do Electrum pode parecer antiquada para alguns usuários.
Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.
Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível.
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ a95c6243:d345522c
2024-12-21 09:54:49
@ a95c6243:d345522c
2024-12-21 09:54:49Falls du beim Lesen des Titels dieses Newsletters unwillkürlich an positive Neuigkeiten aus dem globalen polit-medialen Irrenhaus oder gar aus dem wirtschaftlichen Umfeld gedacht hast, darf ich dich beglückwünschen. Diese Assoziation ist sehr löblich, denn sie weist dich als unverbesserlichen Optimisten aus. Leider muss ich dich diesbezüglich aber enttäuschen. Es geht hier um ein anderes Thema, allerdings sehr wohl ein positives, wie ich finde.
Heute ist ein ganz besonderer Tag: die Wintersonnenwende. Genau gesagt hat heute morgen um 10:20 Uhr Mitteleuropäischer Zeit (MEZ) auf der Nordhalbkugel unseres Planeten der astronomische Winter begonnen. Was daran so außergewöhnlich ist? Der kürzeste Tag des Jahres war gestern, seit heute werden die Tage bereits wieder länger! Wir werden also jetzt jeden Tag ein wenig mehr Licht haben.
Für mich ist dieses Ereignis immer wieder etwas kurios: Es beginnt der Winter, aber die Tage werden länger. Das erscheint mir zunächst wie ein Widerspruch, denn meine spontanen Assoziationen zum Winter sind doch eher Kälte und Dunkelheit, relativ zumindest. Umso erfreulicher ist der emotionale Effekt, wenn dann langsam die Erkenntnis durchsickert: Ab jetzt wird es schon wieder heller!
Natürlich ist es kalt im Winter, mancherorts mehr als anderswo. Vielleicht jedoch nicht mehr lange, wenn man den Klimahysterikern glauben wollte. Mindestens letztes Jahr hat Väterchen Frost allerdings gleich zu Beginn seiner Saison – und passenderweise während des globalen Überhitzungsgipfels in Dubai – nochmal richtig mit der Faust auf den Tisch gehauen. Schnee- und Eischaos sind ja eigentlich in der Agenda bereits nicht mehr vorgesehen. Deswegen war man in Deutschland vermutlich in vorauseilendem Gehorsam schon nicht mehr darauf vorbereitet und wurde glatt lahmgelegt.
Aber ich schweife ab. Die Aussicht auf nach und nach mehr Licht und damit auch Wärme stimmt mich froh. Den Zusammenhang zwischen beidem merkt man in Andalusien sehr deutlich. Hier, wo die Häuser im Winter arg auskühlen, geht man zum Aufwärmen raus auf die Straße oder auf den Balkon. Die Sonne hat auch im Winter eine erfreuliche Kraft. Und da ist jede Minute Gold wert.
Außerdem ist mir vor Jahren so richtig klar geworden, warum mir das südliche Klima so sehr gefällt. Das liegt nämlich nicht nur an der Sonne als solcher, oder der Wärme – das liegt vor allem am Licht. Ohne Licht keine Farben, das ist der ebenso simple wie gewaltige Unterschied zwischen einem deprimierenden matschgraubraunen Winter und einem fröhlichen bunten. Ein großes Stück Lebensqualität.
Mir gefällt aber auch die Symbolik dieses Tages: Licht aus der Dunkelheit, ein Wendepunkt, ein Neuanfang, neue Möglichkeiten, Übergang zu neuer Aktivität. In der winterlichen Stille keimt bereits neue Lebendigkeit. Und zwar in einem Zyklus, das wird immer wieder so geschehen. Ich nehme das gern als ein Stück Motivation, es macht mir Hoffnung und gibt mir Energie.

Übrigens ist parallel am heutigen Tag auf der südlichen Halbkugel Sommeranfang. Genau im entgegengesetzten Rhythmus, sich ergänzend, wie Yin und Yang. Das alles liegt an der Schrägstellung der Erdachse, die ist nämlich um 23,4º zur Umlaufbahn um die Sonne geneigt. Wir erinnern uns, gell?
Insofern bleibt eindeutig festzuhalten, dass “schräg sein” ein willkommener, wichtiger und positiver Wert ist. Mit anderen Worten: auch ungewöhnlich, eigenartig, untypisch, wunderlich, kauzig, … ja sogar irre, spinnert oder gar “quer” ist in Ordnung. Das schließt das Denken mit ein.
In diesem Sinne wünsche ich euch allen urige Weihnachtstage!
Dieser Beitrag ist letztes Jahr in meiner Denkbar erschienen.
-
 @ 207ad2a0:e7cca7b0
2025-01-07 03:46:04
@ 207ad2a0:e7cca7b0
2025-01-07 03:46:04Quick context: I wanted to check out Nostr's longform posts and this blog post seemed like a good one to try and mirror. It's originally from my free to read/share attempt to write a novel, but this post here is completely standalone - just describing how I used AI image generation to make a small piece of the work.
Hold on, put your pitchforks down - outside of using Grammerly & Emacs for grammatical corrections - not a single character was generated or modified by computers; a non-insignificant portion of my first draft originating on pen & paper. No AI is ~~weird and crazy~~ imaginative enough to write like I do. The only successful AI contribution you'll find is a single image, the map, which I heavily edited. This post will go over how I generated and modified an image using AI, which I believe brought some value to the work, and cover a few quick thoughts about AI towards the end.
Let's be clear, I can't draw, but I wanted a map which I believed would improve the story I was working on. After getting abysmal results by prompting AI with text only I decided to use "Diffuse the Rest," a Stable Diffusion tool that allows you to provide a reference image + description to fine tune what you're looking for. I gave it this Microsoft Paint looking drawing:

and after a number of outputs, selected this one to work on:

The image is way better than the one I provided, but had I used it as is, I still feel it would have decreased the quality of my work instead of increasing it. After firing up Gimp I cropped out the top and bottom, expanded the ocean and separated the landmasses, then copied the top right corner of the large landmass to replace the bottom left that got cut off. Now we've got something that looks like concept art: not horrible, and gets the basic idea across, but it's still due for a lot more detail.

The next thing I did was add some texture to make it look more map like. I duplicated the layer in Gimp and applied the "Cartoon" filter to both for some texture. The top layer had a much lower effect strength to give it a more textured look, while the lower layer had a higher effect strength that looked a lot like mountains or other terrain features. Creating a layer mask allowed me to brush over spots to display the lower layer in certain areas, giving it some much needed features.

At this point I'd made it to where I felt it may improve the work instead of detracting from it - at least after labels and borders were added, but the colors seemed artificial and out of place. Luckily, however, this is when PhotoFunia could step in and apply a sketch effect to the image.

At this point I was pretty happy with how it was looking, it was close to what I envisioned and looked very visually appealing while still being a good way to portray information. All that was left was to make the white background transparent, add some minor details, and add the labels and borders. Below is the exact image I wound up using:

Overall, I'm very satisfied with how it turned out, and if you're working on a creative project, I'd recommend attempting something like this. It's not a central part of the work, but it improved the chapter a fair bit, and was doable despite lacking the talent and not intending to allocate a budget to my making of a free to read and share story.
The AI Generated Elephant in the Room
If you've read my non-fiction writing before, you'll know that I think AI will find its place around the skill floor as opposed to the skill ceiling. As you saw with my input, I have absolutely zero drawing talent, but with some elbow grease and an existing creative direction before and after generating an image I was able to get something well above what I could have otherwise accomplished. Outside of the lowest common denominators like stock photos for the sole purpose of a link preview being eye catching, however, I doubt AI will be wholesale replacing most creative works anytime soon. I can assure you that I tried numerous times to describe the map without providing a reference image, and if I used one of those outputs (or even just the unedited output after providing the reference image) it would have decreased the quality of my work instead of improving it.
I'm going to go out on a limb and expect that AI image, text, and video is all going to find its place in slop & generic content (such as AI generated slop replacing article spinners and stock photos respectively) and otherwise be used in a supporting role for various creative endeavors. For people working on projects like I'm working on (e.g. intended budget $0) it's helpful to have an AI capable of doing legwork - enabling projects to exist or be improved in ways they otherwise wouldn't have. I'm also guessing it'll find its way into more professional settings for grunt work - think a picture frame or fake TV show that would exist in the background of an animated project - likely a detail most people probably wouldn't notice, but that would save the creators time and money and/or allow them to focus more on the essential aspects of said work. Beyond that, as I've predicted before: I expect plenty of emails will be generated from a short list of bullet points, only to be summarized by the recipient's AI back into bullet points.
I will also make a prediction counter to what seems mainstream: AI is about to peak for a while. The start of AI image generation was with Google's DeepDream in 2015 - image recognition software that could be run in reverse to "recognize" patterns where there were none, effectively generating an image from digital noise or an unrelated image. While I'm not an expert by any means, I don't think we're too far off from that a decade later, just using very fine tuned tools that develop more coherent images. I guess that we're close to maxing out how efficiently we're able to generate images and video in that manner, and the hard caps on how much creative direction we can have when using AI - as well as the limits to how long we can keep it coherent (e.g. long videos or a chronologically consistent set of images) - will prevent AI from progressing too far beyond what it is currently unless/until another breakthrough occurs.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Músicas grudentas e conversas
Uma vez que você ouviu uma música grudenta e ela volta, inteira, com toda a melodia e a harmonia, muitos dias depois, contra a sua vontade. Mas uma conversa é impossível de lembrar. Por quê?
-
 @ eac63075:b4988b48
2024-11-09 17:57:27
@ eac63075:b4988b48
2024-11-09 17:57:27Based on a recent paper that included collaboration from renowned experts such as Lynn Alden, Steve Lee, and Ren Crypto Fish, we discuss in depth how Bitcoin's consensus is built, the main risks, and the complex dynamics of protocol upgrades.
Podcast https://www.fountain.fm/episode/wbjD6ntQuvX5u2G5BccC
Presentation https://gamma.app/docs/Analyzing-Bitcoin-Consensus-Risks-in-Protocol-Upgrades-p66axxjwaa37ksn
1. Introduction to Consensus in Bitcoin
Consensus in Bitcoin is the foundation that keeps the network secure and functional, allowing users worldwide to perform transactions in a decentralized manner without the need for intermediaries. Since its launch in 2009, Bitcoin is often described as an "immutable" system designed to resist changes, and it is precisely this resistance that ensures its security and stability.
The central idea behind consensus in Bitcoin is to create a set of acceptance rules for blocks and transactions, ensuring that all network participants agree on the transaction history. This prevents "double-spending," where the same bitcoin could be used in two simultaneous transactions, something that would compromise trust in the network.
Evolution of Consensus in Bitcoin
Over the years, consensus in Bitcoin has undergone several adaptations, and the way participants agree on changes remains a delicate process. Unlike traditional systems, where changes can be imposed from the top down, Bitcoin operates in a decentralized model where any significant change needs the support of various groups of stakeholders, including miners, developers, users, and large node operators.
Moreover, the update process is extremely cautious, as hasty changes can compromise the network's security. As a result, the philosophy of "don't fix what isn't broken" prevails, with improvements happening incrementally and only after broad consensus among those involved. This model can make progress seem slow but ensures that Bitcoin remains faithful to the principles of security and decentralization.
2. Technical Components of Consensus
Bitcoin's consensus is supported by a set of technical rules that determine what is considered a valid transaction and a valid block on the network. These technical aspects ensure that all nodes—the computers that participate in the Bitcoin network—agree on the current state of the blockchain. Below are the main technical components that form the basis of the consensus.
Validation of Blocks and Transactions
The validation of blocks and transactions is the central point of consensus in Bitcoin. A block is only considered valid if it meets certain criteria, such as maximum size, transaction structure, and the solving of the "Proof of Work" problem. The proof of work, required for a block to be included in the blockchain, is a computational process that ensures the block contains significant computational effort—protecting the network against manipulation attempts.
Transactions, in turn, need to follow specific input and output rules. Each transaction includes cryptographic signatures that prove the ownership of the bitcoins sent, as well as validation scripts that verify if the transaction conditions are met. This validation system is essential for network nodes to autonomously confirm that each transaction follows the rules.
Chain Selection
Another fundamental technical issue for Bitcoin's consensus is chain selection, which becomes especially important in cases where multiple versions of the blockchain coexist, such as after a network split (fork). To decide which chain is the "true" one and should be followed, the network adopts the criterion of the highest accumulated proof of work. In other words, the chain with the highest number of valid blocks, built with the greatest computational effort, is chosen by the network as the official one.
This criterion avoids permanent splits because it encourages all nodes to follow the same main chain, reinforcing consensus.
Soft Forks vs. Hard Forks
In the consensus process, protocol changes can happen in two ways: through soft forks or hard forks. These variations affect not only the protocol update but also the implications for network users:
-
Soft Forks: These are changes that are backward compatible. Only nodes that adopt the new update will follow the new rules, but old nodes will still recognize the blocks produced with these rules as valid. This compatibility makes soft forks a safer option for updates, as it minimizes the risk of network division.
-
Hard Forks: These are updates that are not backward compatible, requiring all nodes to update to the new version or risk being separated from the main chain. Hard forks can result in the creation of a new coin, as occurred with the split between Bitcoin and Bitcoin Cash in 2017. While hard forks allow for deeper changes, they also bring significant risks of network fragmentation.
These technical components form the base of Bitcoin's security and resilience, allowing the system to remain functional and immutable without losing the necessary flexibility to evolve over time.
3. Stakeholders in Bitcoin's Consensus
Consensus in Bitcoin is not decided centrally. On the contrary, it depends on the interaction between different groups of stakeholders, each with their motivations, interests, and levels of influence. These groups play fundamental roles in how changes are implemented or rejected on the network. Below, we explore the six main stakeholders in Bitcoin's consensus.
1. Economic Nodes
Economic nodes, usually operated by exchanges, custody providers, and large companies that accept Bitcoin, exert significant influence over consensus. Because they handle large volumes of transactions and act as a connection point between the Bitcoin ecosystem and the traditional financial system, these nodes have the power to validate or reject blocks and to define which version of the software to follow in case of a fork.
Their influence is proportional to the volume of transactions they handle, and they can directly affect which chain will be seen as the main one. Their incentive is to maintain the network's stability and security to preserve its functionality and meet regulatory requirements.
2. Investors
Investors, including large institutional funds and individual Bitcoin holders, influence consensus indirectly through their impact on the asset's price. Their buying and selling actions can affect Bitcoin's value, which in turn influences the motivation of miners and other stakeholders to continue investing in the network's security and development.
Some institutional investors have agreements with custodians that may limit their ability to act in network split situations. Thus, the impact of each investor on consensus can vary based on their ownership structure and how quickly they can react to a network change.
3. Media Influencers
Media influencers, including journalists, analysts, and popular personalities on social media, have a powerful role in shaping public opinion about Bitcoin and possible updates. These influencers can help educate the public, promote debates, and bring transparency to the consensus process.
On the other hand, the impact of influencers can be double-edged: while they can clarify complex topics, they can also distort perceptions by amplifying or minimizing change proposals. This makes them a force both of support and resistance to consensus.
4. Miners
Miners are responsible for validating transactions and including blocks in the blockchain. Through computational power (hashrate), they also exert significant influence over consensus decisions. In update processes, miners often signal their support for a proposal, indicating that the new version is safe to use. However, this signaling is not always definitive, and miners can change their position if they deem it necessary.
Their incentive is to maximize returns from block rewards and transaction fees, as well as to maintain the value of investments in their specialized equipment, which are only profitable if the network remains stable.
5. Protocol Developers
Protocol developers, often called "Core Developers," are responsible for writing and maintaining Bitcoin's code. Although they do not have direct power over consensus, they possess an informal veto power since they decide which changes are included in the main client (Bitcoin Core). This group also serves as an important source of technical knowledge, helping guide decisions and inform other stakeholders.
Their incentive lies in the continuous improvement of the network, ensuring security and decentralization. Many developers are funded by grants and sponsorships, but their motivations generally include a strong ideological commitment to Bitcoin's principles.
6. Users and Application Developers
This group includes people who use Bitcoin in their daily transactions and developers who build solutions based on the network, such as wallets, exchanges, and payment platforms. Although their power in consensus is less than that of miners or economic nodes, they play an important role because they are responsible for popularizing Bitcoin's use and expanding the ecosystem.
If application developers decide not to adopt an update, this can affect compatibility and widespread acceptance. Thus, they indirectly influence consensus by deciding which version of the protocol to follow in their applications.
These stakeholders are vital to the consensus process, and each group exerts influence according to their involvement, incentives, and ability to act in situations of change. Understanding the role of each makes it clearer how consensus is formed and why it is so difficult to make significant changes to Bitcoin.
4. Mechanisms for Activating Updates in Bitcoin
For Bitcoin to evolve without compromising security and consensus, different mechanisms for activating updates have been developed over the years. These mechanisms help coordinate changes among network nodes to minimize the risk of fragmentation and ensure that updates are implemented in an orderly manner. Here, we explore some of the main methods used in Bitcoin, their advantages and disadvantages, as well as historical examples of significant updates.
Flag Day
The Flag Day mechanism is one of the simplest forms of activating changes. In it, a specific date or block is determined as the activation moment, and all nodes must be updated by that point. This method does not involve prior signaling; participants simply need to update to the new software version by the established day or block.
-
Advantages: Simplicity and predictability are the main benefits of Flag Day, as everyone knows the exact activation date.
-
Disadvantages: Inflexibility can be a problem because there is no way to adjust the schedule if a significant part of the network has not updated. This can result in network splits if a significant number of nodes are not ready for the update.
An example of Flag Day was the Pay to Script Hash (P2SH) update in 2012, which required all nodes to adopt the change to avoid compatibility issues.
BIP34 and BIP9
BIP34 introduced a more dynamic process, in which miners increase the version number in block headers to signal the update. When a predetermined percentage of the last blocks is mined with this new version, the update is automatically activated. This model later evolved with BIP9, which allowed multiple updates to be signaled simultaneously through "version bits," each corresponding to a specific change.
-
Advantages: Allows the network to activate updates gradually, giving more time for participants to adapt.
-
Disadvantages: These methods rely heavily on miner support, which means that if a sufficient number of miners do not signal the update, it can be delayed or not implemented.
BIP9 was used in the activation of SegWit (BIP141) but faced challenges because some miners did not signal their intent to activate, leading to the development of new mechanisms.
User Activated Soft Forks (UASF) and User Resisted Soft Forks (URSF)
To increase the decision-making power of ordinary users, the concept of User Activated Soft Fork (UASF) was introduced, allowing node operators, not just miners, to determine consensus for a change. In this model, nodes set a date to start rejecting blocks that are not in compliance with the new update, forcing miners to adapt or risk having their blocks rejected by the network.
URSF, in turn, is a model where nodes reject blocks that attempt to adopt a specific update, functioning as resistance against proposed changes.
-
Advantages: UASF returns decision-making power to node operators, ensuring that changes do not depend solely on miners.
-
Disadvantages: Both UASF and URSF can generate network splits, especially in cases of strong opposition among different stakeholders.
An example of UASF was the activation of SegWit in 2017, where users supported activation independently of miner signaling, which ended up forcing its adoption.
BIP8 (LOT=True)
BIP8 is an evolution of BIP9, designed to prevent miners from indefinitely blocking a change desired by the majority of users and developers. BIP8 allows setting a parameter called "lockinontimeout" (LOT) as true, which means that if the update has not been fully signaled by a certain point, it is automatically activated.
-
Advantages: Ensures that changes with broad support among users are not blocked by miners who wish to maintain the status quo.
-
Disadvantages: Can lead to network splits if miners or other important stakeholders do not support the update.
Although BIP8 with LOT=True has not yet been used in Bitcoin, it is a proposal that can be applied in future updates if necessary.
These activation mechanisms have been essential for Bitcoin's development, allowing updates that keep the network secure and functional. Each method brings its own advantages and challenges, but all share the goal of preserving consensus and network cohesion.
5. Risks and Considerations in Consensus Updates
Consensus updates in Bitcoin are complex processes that involve not only technical aspects but also political, economic, and social considerations. Due to the network's decentralized nature, each change brings with it a set of risks that need to be carefully assessed. Below, we explore some of the main challenges and future scenarios, as well as the possible impacts on stakeholders.
Network Fragility with Alternative Implementations
One of the main risks associated with consensus updates is the possibility of network fragmentation when there are alternative software implementations. If an update is implemented by a significant group of nodes but rejected by others, a network split (fork) can occur. This creates two competing chains, each with a different version of the transaction history, leading to unpredictable consequences for users and investors.
Such fragmentation weakens Bitcoin because, by dividing hashing power (computing) and coin value, it reduces network security and investor confidence. A notable example of this risk was the fork that gave rise to Bitcoin Cash in 2017 when disagreements over block size resulted in a new chain and a new asset.
Chain Splits and Impact on Stakeholders
Chain splits are a significant risk in update processes, especially in hard forks. During a hard fork, the network is split into two separate chains, each with its own set of rules. This results in the creation of a new coin and leaves users with duplicated assets on both chains. While this may seem advantageous, in the long run, these splits weaken the network and create uncertainties for investors.
Each group of stakeholders reacts differently to a chain split:
-
Institutional Investors and ETFs: Face regulatory and compliance challenges because many of these assets are managed under strict regulations. The creation of a new coin requires decisions to be made quickly to avoid potential losses, which may be hampered by regulatory constraints.
-
Miners: May be incentivized to shift their computing power to the chain that offers higher profitability, which can weaken one of the networks.
-
Economic Nodes: Such as major exchanges and custody providers, have to quickly choose which chain to support, influencing the perceived value of each network.
Such divisions can generate uncertainties and loss of value, especially for institutional investors and those who use Bitcoin as a store of value.
Regulatory Impacts and Institutional Investors
With the growing presence of institutional investors in Bitcoin, consensus changes face new compliance challenges. Bitcoin ETFs, for example, are required to follow strict rules about which assets they can include and how chain split events should be handled. The creation of a new asset or migration to a new chain can complicate these processes, creating pressure for large financial players to quickly choose a chain, affecting the stability of consensus.
Moreover, decisions regarding forks can influence the Bitcoin futures and derivatives market, affecting perception and adoption by new investors. Therefore, the need to avoid splits and maintain cohesion is crucial to attract and preserve the confidence of these investors.
Security Considerations in Soft Forks and Hard Forks
While soft forks are generally preferred in Bitcoin for their backward compatibility, they are not without risks. Soft forks can create different classes of nodes on the network (updated and non-updated), which increases operational complexity and can ultimately weaken consensus cohesion. In a network scenario with fragmentation of node classes, Bitcoin's security can be affected, as some nodes may lose part of the visibility over updated transactions or rules.
In hard forks, the security risk is even more evident because all nodes need to adopt the new update to avoid network division. Experience shows that abrupt changes can create temporary vulnerabilities, in which malicious agents try to exploit the transition to attack the network.
Bounty Claim Risks and Attack Scenarios
Another risk in consensus updates are so-called "bounty claims"—accumulated rewards that can be obtained if an attacker manages to split or deceive a part of the network. In a conflict scenario, a group of miners or nodes could be incentivized to support a new update or create an alternative version of the software to benefit from these rewards.
These risks require stakeholders to carefully assess each update and the potential vulnerabilities it may introduce. The possibility of "bounty claims" adds a layer of complexity to consensus because each interest group may see a financial opportunity in a change that, in the long term, may harm network stability.
The risks discussed above show the complexity of consensus in Bitcoin and the importance of approaching it gradually and deliberately. Updates need to consider not only technical aspects but also economic and social implications, in order to preserve Bitcoin's integrity and maintain trust among stakeholders.
6. Recommendations for the Consensus Process in Bitcoin
To ensure that protocol changes in Bitcoin are implemented safely and with broad support, it is essential that all stakeholders adopt a careful and coordinated approach. Here are strategic recommendations for evaluating, supporting, or rejecting consensus updates, considering the risks and challenges discussed earlier, along with best practices for successful implementation.
1. Careful Evaluation of Proposal Maturity
Stakeholders should rigorously assess the maturity level of a proposal before supporting its implementation. Updates that are still experimental or lack a robust technical foundation can expose the network to unnecessary risks. Ideally, change proposals should go through an extensive testing phase, have security audits, and receive review and feedback from various developers and experts.
2. Extensive Testing in Secure and Compatible Networks
Before an update is activated on the mainnet, it is essential to test it on networks like testnet and signet, and whenever possible, on other compatible networks that offer a safe and controlled environment to identify potential issues. Testing on networks like Litecoin was fundamental for the safe launch of innovations like SegWit and the Lightning Network, allowing functionalities to be validated on a lower-impact network before being implemented on Bitcoin.
The Liquid Network, developed by Blockstream, also plays an important role as an experimental network for new proposals, such as OP_CAT. By adopting these testing environments, stakeholders can mitigate risks and ensure that the update is reliable and secure before being adopted by the main network.
3. Importance of Stakeholder Engagement
The success of a consensus update strongly depends on the active participation of all stakeholders. This includes economic nodes, miners, protocol developers, investors, and end users. Lack of participation can lead to inadequate decisions or even future network splits, which would compromise Bitcoin's security and stability.
4. Key Questions for Evaluating Consensus Proposals
To assist in decision-making, each group of stakeholders should consider some key questions before supporting a consensus change:
- Does the proposal offer tangible benefits for Bitcoin's security, scalability, or usability?
- Does it maintain backward compatibility or introduce the risk of network split?
- Are the implementation requirements clear and feasible for each group involved?
- Are there clear and aligned incentives for all stakeholder groups to accept the change?
5. Coordination and Timing in Implementations
Timing is crucial. Updates with short activation windows can force a split because not all nodes and miners can update simultaneously. Changes should be planned with ample deadlines to allow all stakeholders to adjust their systems, avoiding surprises that could lead to fragmentation.
Mechanisms like soft forks are generally preferable to hard forks because they allow a smoother transition. Opting for backward-compatible updates when possible facilitates the process and ensures that nodes and miners can adapt without pressure.
6. Continuous Monitoring and Re-evaluation
After an update, it's essential to monitor the network to identify problems or side effects. This continuous process helps ensure cohesion and trust among all participants, keeping Bitcoin as a secure and robust network.
These recommendations, including the use of secure networks for extensive testing, promote a collaborative and secure environment for Bitcoin's consensus process. By adopting a deliberate and strategic approach, stakeholders can preserve Bitcoin's value as a decentralized and censorship-resistant network.
7. Conclusion
Consensus in Bitcoin is more than a set of rules; it's the foundation that sustains the network as a decentralized, secure, and reliable system. Unlike centralized systems, where decisions can be made quickly, Bitcoin requires a much more deliberate and cooperative approach, where the interests of miners, economic nodes, developers, investors, and users must be considered and harmonized. This governance model may seem slow, but it is fundamental to preserving the resilience and trust that make Bitcoin a global store of value and censorship-resistant.
Consensus updates in Bitcoin must balance the need for innovation with the preservation of the network's core principles. The development process of a proposal needs to be detailed and rigorous, going through several testing stages, such as in testnet, signet, and compatible networks like Litecoin and Liquid Network. These networks offer safe environments for proposals to be analyzed and improved before being launched on the main network.
Each proposed change must be carefully evaluated regarding its maturity, impact, backward compatibility, and support among stakeholders. The recommended key questions and appropriate timing are critical to ensure that an update is adopted without compromising network cohesion. It's also essential that the implementation process is continuously monitored and re-evaluated, allowing adjustments as necessary and minimizing the risk of instability.
By following these guidelines, Bitcoin's stakeholders can ensure that the network continues to evolve safely and robustly, maintaining user trust and further solidifying its role as one of the most resilient and innovative digital assets in the world. Ultimately, consensus in Bitcoin is not just a technical issue but a reflection of its community and the values it represents: security, decentralization, and resilience.
8. Links
Whitepaper: https://github.com/bitcoin-cap/bcap
Youtube (pt-br): https://www.youtube.com/watch?v=rARycAibl9o&list=PL-qnhF0qlSPkfhorqsREuIu4UTbF0h4zb
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Bluesky is a scam
Bluesky advertises itself as an open network, they say people won't lose followers or their identity, they advertise themselves as a protocol ("atproto") and because of that they are tricking a lot of people into using them. These three claims are false.
protocolness
Bluesky is a company. "atproto" is the protocol. Supposedly they are two different things, right? Bluesky just releases software that implements the protocol, but others can also do that, it's open!
And yet, the protocol has an official webpage with a waitlist and a private beta? Why is the protocol advertised as a company product? Because it is. The "protocol" is just a description of whatever the Bluesky app and servers do, it can and does change anytime the Bluesky developers decide they want to change it, and it will keep changing for as long as Bluesky apps and servers control the biggest part of the network.
Oh, so there is the possibility of other players stepping in and then it becomes an actual interoperable open protocol? Yes, but what is the likelihood of that happening? It is very low. No serious competitor is likely to step in and build serious apps using a protocol that is directly controlled by Bluesky. All we will ever see are small "community" apps made by users and small satellite small businesses -- not unlike the people and companies that write plugins, addons and alternative clients for popular third-party centralized platforms.
And last, even if it happens that someone makes an app so good that it displaces the canonical official Bluesky app, then that company may overtake the protocol itself -- not because they're evil, but because there is no way it cannot be like this.
identity
According to their own documentation, the Bluesky people were looking for an identity system that provided global ids, key rotation and human-readable names.
They must have realized that such properties are not possible in an open and decentralized system, but instead of accepting a tradeoff they decided they wanted all their desired features and threw away the "decentralized" part, quite literally and explicitly (although they make sure to hide that piece in the middle of a bunch of code and text that very few will read).
The "DID Placeholder" method they decided to use for their global identities is nothing more than a normal old boring trusted server controlled by Bluesky that keeps track of who is who and can, at all times, decide to ban a person and deprive them from their identity (they dismissively call a "denial of service attack").
They decided to adopt this method as a placeholder until someone else doesn't invent the impossible alternative that would provide all their desired properties in a decentralized manner -- which is nothing more than a very good excuse: "yes, it's not great now, but it will improve!".
openness
Months after launching their product with an aura of decentralization and openness and getting a bunch of people inside that believed, falsely, they were joining an actually open network, Bluesky has decided to publish a part of their idea of how other people will be able to join their open network.
When I first saw their app and how they were very prominently things like follower counts, like counts and other things that are typical of centralized networks and can't be reliable or exact on truly open networks (like Nostr), I asked myself how were they going to do that once they became and open "federated" network as they were expected to be.
Turns out their decentralization plan is to just allow you, as a writer, to host your own posts on "personal data stores", but not really have any control over the distribution of the posts. All posts go through the Bluesky central server, called BGS, and they decide what to do with it. And you, as a reader, doesn't have any control of what you're reading from either, all you can do is connect to the BGS and ask for posts. If the BGS decides to ban, shadow ban, reorder, miscount, hide, deprioritize, trick or maybe even to serve ads, then you are out of luck.
Oh, but anyone can run their own BGS!, they will say. Even in their own blog post announcing the architecture they assert that "it’s a fairly resource-demanding service" and "there may be a few large full-network providers". But I fail to see why even more than one network provider will exist, if Bluesky is already doing that job, and considering the fact there are very little incentives for anyone to switch providers -- because the app does not seem to be at all made to talk to multiple providers, one would have to stop using the reliable, fast and beefy official BGS and start using some half-baked alternative and risk losing access to things.
When asked about the possibility of switching, one of Bluesky overlords said: "it would look something like this: bluesky has gone evil. there's a new alternative called freesky that people are rushing to. I'm switching to freesky".
The quote is very naïve and sounds like something that could be said about Twitter itself: "if Twitter is evil you can just run your own social network". Both are fallacies because they ignore the network-effect and the fact that people will never fully agree that something is "evil". In fact these two are the fundamental reasons why -- for social networks specifically (and not for other things like commerce) -- we need truly open protocols with no owners and no committees.
-
 @ 3ffac3a6:2d656657
2025-01-06 23:42:53
@ 3ffac3a6:2d656657
2025-01-06 23:42:53Prologue: The Last Trade
Ethan Nakamura was a 29-year-old software engineer and crypto enthusiast who had spent years building his life around Bitcoin. Obsessed with the idea of financial sovereignty, he had amassed a small fortune trading cryptocurrencies, all while dreaming of a world where decentralized systems ruled over centralized power.
One night, while debugging a particularly thorny piece of code for a smart contract, Ethan stumbled across an obscure, encrypted message hidden in the blockchain. It read:
"The key to true freedom lies beyond. Burn it all to unlock the gate."
Intrigued and half-convinced it was an elaborate ARG (Alternate Reality Game), Ethan decided to follow the cryptic instruction. He loaded his entire Bitcoin wallet into a single transaction and sent it to an untraceable address tied to the message. The moment the transaction was confirmed, his laptop screen began to glitch, flooding with strange symbols and hash codes.
Before he could react, a flash of light engulfed him.
Chapter 1: A New Ledger
Ethan awoke in a dense forest bathed in ethereal light. The first thing he noticed was the HUD floating in front of him—a sleek, transparent interface that displayed his "Crypto Balance": 21 million BTC.
“What the…” Ethan muttered. He blinked, hoping it was a dream, but the numbers stayed. The HUD also showed other metrics:
- Hash Power: 1,000,000 TH/s
- Mining Efficiency: 120%
- Transaction Speed: Instant
Before he could process, a notification pinged on the HUD:
"Welcome to the Decentralized Kingdom. Your mining rig is active. Begin accumulating resources to survive."
Confused and a little terrified, Ethan stood and surveyed his surroundings. As he moved, the HUD expanded, revealing a map of the area. His new world looked like a cross between a medieval fantasy realm and a cyberpunk dystopia, with glowing neon towers visible on the horizon and villagers dressed in tunics carrying strange, glowing "crypto shards."
Suddenly, a shadow loomed over him. A towering beast, part wolf, part machine, snarled, its eyes glowing red. Above its head was the name "Feral Node" and a strange sigil resembling a corrupted block.
Instinct kicked in. Ethan raised his hands defensively, and to his shock, the HUD offered an option:
"Execute Smart Contract Attack? (Cost: 0.001 BTC)"
He selected it without hesitation. A glowing glyph appeared in the air, releasing a wave of light that froze the Feral Node mid-lunge. Moments later, it dissolved into a cascade of shimmering data, leaving behind a pile of "Crypto Shards" and an item labeled "Node Fragment."
Chapter 2: The Decentralized Kingdom
Ethan discovered that the world he had entered was built entirely on blockchain-like principles. The land was divided into regions, each governed by a Consensus Council—groups of powerful beings called Validators who maintained the balance of the world. However, a dark force known as The Central Authority sought to consolidate power, turning decentralized regions into tightly controlled fiefdoms.
Ethan’s newfound abilities made him a unique entity in this world. Unlike its inhabitants, who earned wealth through mining or trading physical crypto shards, Ethan could generate and spend Bitcoin directly—making him both a target and a potential savior.
Chapter 3: Allies and Adversaries
Ethan soon met a colorful cast of characters:
-
Luna, a fiery rogue and self-proclaimed "Crypto Thief," who hacked into ledgers to redistribute wealth to oppressed villages. She was skeptical of Ethan's "magical Bitcoin" but saw potential in him.
-
Hal, an aging miner who ran an underground resistance against the Central Authority. He wielded an ancient "ASIC Hammer" capable of shattering corrupted nodes.
-
Oracle Satoshi, a mysterious AI-like entity who guided Ethan with cryptic advice, often referencing real-world crypto principles like decentralization, trustless systems, and private keys.
Ethan also gained enemies, chief among them the Ledger Lords, a cabal of Validators allied with the Central Authority. They sought to capture Ethan and seize his Bitcoin, believing it could tip the balance of power.
Chapter 4: Proof of Existence
As Ethan delved deeper into the world, he learned that his Bitcoin balance was finite. To survive and grow stronger, he had to "mine" resources by solving problems for the people of the Decentralized Kingdom. From repairing broken smart contracts in towns to defending miners from feral nodes, every task rewarded him with shards and upgrades.
He also uncovered the truth about his arrival: the blockchain Ethan had used in his world was a prototype for this one. The encrypted message had been a failsafe created by its original developers—a desperate attempt to summon someone who could break the growing centralization threatening to destroy the world.
Chapter 5: The Final Fork
As the Central Authority's grip tightened, Ethan and his allies prepared for a final battle at the Genesis Block, the origin of the world's blockchain. Here, Ethan would face the Central Authority's leader, an amalgamation of corrupted code and human ambition known as The Miner King.
The battle was a clash of philosophies as much as strength. Using everything he had learned, Ethan deployed a daring Hard Fork, splitting the world’s blockchain and decentralizing power once again. The process drained nearly all of his Bitcoin, leaving him with a single satoshi—a symbolic reminder of his purpose.
Epilogue: Building the Future
With the Central Authority defeated, the Decentralized Kingdom entered a new era. Ethan chose to remain in the world, helping its inhabitants build fairer systems and teaching them the principles of trustless cooperation.
As he gazed at the sunrise over the rebuilt Genesis Block, Ethan smiled. He had dreamed of a world where Bitcoin could change everything. Now, he was living it.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Jofer
Jofer era um jogador diferente. À primeira vista não, parecia igual, um volante combativo, perseguia os atacantes adversários implacavelmente, um bom jogador. Mas não era essa a característica que diferenciava Jofer. Jofer era, digamos, um chutador.
Começou numa semifinal de um torneio de juniores. O time de Jofer precisava do empate e estava sofrendo uma baita pressão do adversário, mas o jogo estava 1 a 1 e parecia que ia ficar assim mesmo, daquele jeito futebolístico que parece, parece mesmo. Só que aos 46 do segundo tempo tomaram um gol espírita, Ruizinho do outro time saiu correndo pela esquerda e, mesmo sendo canhoto, foi cortando para o meio, os zagueiros meio que achando que já tinha acabado mesmo, devia ter só mais aquele lance, o árbitro tinha dado dois minutos, Ruizinho chutou, marcou e o goleiro, que só pulou depois que já tinha visto que não ia ter jeito, ficou xingando.
A bola saiu do meio e tocaram para Jofer, ninguém nem veio marcá-lo, o outro time já estava comemorando, e com razão, o juiz estava de sacanagem em fazer o jogo continuar, já estava tudo acabado mesmo. Mas não, estava certo, mais um minuto de acréscimo, justo. Em um minuto dá pra fazer um gol. Mas como? Jofer pensou nas partidas da NBA em que com alguns centésimos de segundo faltando o armador jogava de qualquer jeito para a cesta e às vezes acertava. De trás do meio de campo, será? Não vou ter nem força pra fazer chegar no gol. Vou virar piada, melhor tocar pro Fumaça ali do lado e a gente perde sem essa humilhação no final. Mas, poxa, e daí? Vou tentar mesmo assim, qualquer coisa eu falo que foi um lançamento e daqui a uns dias todo mundo esquece. Olhou para o próprio pé, virou ele de ladinho, pra fora e depois pra dentro (bom, se eu pegar daqui, direitinho, quem sabe?), jogou a bola pro lado e bateu. A bola subiu escandalosamente, muito alta mesmo, deve ter subido uns 200 metros. Jofer não tinha como ter a menor noção. Depois foi descendo, o goleirão voltando correndo para debaixo da trave e olhando pra bola, foi chegando e pulando já só pra acompanhar, para ver, dependurado no travessão, a bola sair ainda bem alta, ela bateu na rede lateral interna antes de bater no chão, quicar violentamente e estufar a rede no alto do lado direito de quem olhava.
Mas isso tudo foi sonho do Jofer. Sonhou acordado, numa noite em que demorou pra dormir, deitado na sua cama. Ficou pensando se não seria fácil, se ele treinasse bastante, acertar o gol bem de longe, tipo no sonho, e se não dava pra fazer gol assim. No dia seguinte perguntou a Brunildinho, o treinador de goleiros. Era difícil defender essas bolas, ainda mais se elas subissem muito, o goleiro ficava sem perspectiva, o vento alterava a trajetória a cada instante, tinha efeito, ela cairia rápido, mas claro que não valia à pena treinar isso, a chance de acertar o gol era minúscula. Mas Jofer só ia tentar depois que treinasse bastante e comprovasse o que na sua imaginação parecia uma excelente idéia.
Começou a treinar todos os dias. Primeiro escondido, por vergonha dos colegas, chegava um pouco antes e ficava lá, chutando do círculo central. Ao menor sinal de gente se aproximando, parava e ia catar as bolas. Depois, quando começou a acertar, perdeu a vergonha. O pessoal do clube todo achava engraçado quando via Jofer treinando e depois ouvia a explicação da boca de alguém, ninguém levava muito a sério, mas também não achava de todo ridículo. O pessoal ria, mas no fundo torcia praquilo dar certo, mesmo.
Aconteceu que num jogo que não valia muita coisa, empatezinho feio, aos 40 do segundo tempo, a marcação dos adversários já não estava mais pressionando, todo mundo contente com o empate e com vontade de parar de jogar já, o Henrique, meia-esquerdo, humilde, mas ainda assim um pouco intimidante para Jofer (jogava demais), tocou pra ele. Vai lá, tenta sua loucura aí. Assumiu a responsabilidade do nosso volante introspectivo. Seria mais verossímil se Jofer tivesse errado, primeira vez que tentou, restava muito tempo ainda pra ele ter a chance de ser herói, ninguém acerta de primeira, mas ele acertou. Quase como no sonho, Lucas, o goleiro, não esperava, depois que viu o lance, riu-se, adiantou-se para pegar a bola que ele julgava que quicaria na área, mas ela foi mais pra frente, mais e mais, daí Lucas já estava correndo, só que começou a pensar que ela ia pra fora, e ele ia só se dependurar no travessão e fazer seu papel de estar na bola. Acabou que por conta daquele gol eles terminaram em segundo no grupo daquele torneiozinho, ao invés de terceiro, e não fez diferença nenhuma.
-
 @ a95c6243:d345522c
2024-12-13 19:30:32
@ a95c6243:d345522c
2024-12-13 19:30:32Das Betriebsklima ist das einzige Klima, \ das du selbst bestimmen kannst. \ Anonym
Eine Strategie zur Anpassung an den Klimawandel hat das deutsche Bundeskabinett diese Woche beschlossen. Da «Wetterextreme wie die immer häufiger auftretenden Hitzewellen und Starkregenereignisse» oft desaströse Auswirkungen auf Mensch und Umwelt hätten, werde eine Anpassung an die Folgen des Klimawandels immer wichtiger. «Klimaanpassungsstrategie» nennt die Regierung das.
Für die «Vorsorge vor Klimafolgen» habe man nun erstmals klare Ziele und messbare Kennzahlen festgelegt. So sei der Erfolg überprüfbar, und das solle zu einer schnelleren Bewältigung der Folgen führen. Dass sich hinter dem Begriff Klimafolgen nicht Folgen des Klimas, sondern wohl «Folgen der globalen Erwärmung» verbergen, erklärt den Interessierten die Wikipedia. Dabei ist das mit der Erwärmung ja bekanntermaßen so eine Sache.
Die Zunahme schwerer Unwetterereignisse habe gezeigt, so das Ministerium, wie wichtig eine frühzeitige und effektive Warnung der Bevölkerung sei. Daher solle es eine deutliche Anhebung der Nutzerzahlen der sogenannten Nina-Warn-App geben.
Die ARD spurt wie gewohnt und setzt die Botschaft zielsicher um. Der Artikel beginnt folgendermaßen:
«Die Flut im Ahrtal war ein Schock für das ganze Land. Um künftig besser gegen Extremwetter gewappnet zu sein, hat die Bundesregierung eine neue Strategie zur Klimaanpassung beschlossen. Die Warn-App Nina spielt eine zentrale Rolle. Der Bund will die Menschen in Deutschland besser vor Extremwetter-Ereignissen warnen und dafür die Reichweite der Warn-App Nina deutlich erhöhen.»
Die Kommunen würden bei ihren «Klimaanpassungsmaßnahmen» vom Zentrum KlimaAnpassung unterstützt, schreibt das Umweltministerium. Mit dessen Aufbau wurden das Deutsche Institut für Urbanistik gGmbH, welches sich stark für Smart City-Projekte engagiert, und die Adelphi Consult GmbH beauftragt.
Adelphi beschreibt sich selbst als «Europas führender Think-and-Do-Tank und eine unabhängige Beratung für Klima, Umwelt und Entwicklung». Sie seien «global vernetzte Strateg*innen und weltverbessernde Berater*innen» und als «Vorreiter der sozial-ökologischen Transformation» sei man mit dem Deutschen Nachhaltigkeitspreis ausgezeichnet worden, welcher sich an den Zielen der Agenda 2030 orientiere.
Über die Warn-App mit dem niedlichen Namen Nina, die möglichst jeder auf seinem Smartphone installieren soll, informiert das Bundesamt für Bevölkerungsschutz und Katastrophenhilfe (BBK). Gewarnt wird nicht nur vor Extrem-Wetterereignissen, sondern zum Beispiel auch vor Waffengewalt und Angriffen, Strom- und anderen Versorgungsausfällen oder Krankheitserregern. Wenn man die Kategorie Gefahreninformation wählt, erhält man eine Dosis von ungefähr zwei Benachrichtigungen pro Woche.
Beim BBK erfahren wir auch einiges über die empfohlenen Systemeinstellungen für Nina. Der Benutzer möge zum Beispiel den Zugriff auf die Standortdaten «immer zulassen», und zwar mit aktivierter Funktion «genauen Standort verwenden». Die Datennutzung solle unbeschränkt sein, auch im Hintergrund. Außerdem sei die uneingeschränkte Akkunutzung zu aktivieren, der Energiesparmodus auszuschalten und das Stoppen der App-Aktivität bei Nichtnutzung zu unterbinden.
Dass man so dramatische Ereignisse wie damals im Ahrtal auch anders bewerten kann als Regierungen und Systemmedien, hat meine Kollegin Wiltrud Schwetje anhand der Tragödie im spanischen Valencia gezeigt. Das Stichwort «Agenda 2030» taucht dabei in einem Kontext auf, der wenig mit Nachhaltigkeitspreisen zu tun hat.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ eac63075:b4988b48
2024-10-26 22:14:19
@ eac63075:b4988b48
2024-10-26 22:14:19The future of physical money is at stake, and the discussion about DREX, the new digital currency planned by the Central Bank of Brazil, is gaining momentum. In a candid and intense conversation, Federal Deputy Julia Zanatta (PL/SC) discussed the challenges and risks of this digital transition, also addressing her Bill No. 3,341/2024, which aims to prevent the extinction of physical currency. This bill emerges as a direct response to legislative initiatives seeking to replace physical money with digital alternatives, limiting citizens' options and potentially compromising individual freedom. Let's delve into the main points of this conversation.
https://www.fountain.fm/episode/i5YGJ9Ors3PkqAIMvNQ0
What is a CBDC?
Before discussing the specifics of DREX, it’s important to understand what a CBDC (Central Bank Digital Currency) is. CBDCs are digital currencies issued by central banks, similar to a digital version of physical money. Unlike cryptocurrencies such as Bitcoin, which operate in a decentralized manner, CBDCs are centralized and regulated by the government. In other words, they are digital currencies created and controlled by the Central Bank, intended to replace physical currency.
A prominent feature of CBDCs is their programmability. This means that the government can theoretically set rules about how, where, and for what this currency can be used. This aspect enables a level of control over citizens' finances that is impossible with physical money. By programming the currency, the government could limit transactions by setting geographical or usage restrictions. In practice, money within a CBDC could be restricted to specific spending or authorized for use in a defined geographical area.
In countries like China, where citizen actions and attitudes are also monitored, a person considered to have a "low score" due to a moral or ideological violation may have their transactions limited to essential purchases, restricting their digital currency use to non-essential activities. This financial control is strengthened because, unlike physical money, digital currency cannot be exchanged anonymously.
Practical Example: The Case of DREX During the Pandemic
To illustrate how DREX could be used, an example was given by Eric Altafim, director of Banco Itaú. He suggested that, if DREX had existed during the COVID-19 pandemic, the government could have restricted the currency’s use to a 5-kilometer radius around a person’s residence, limiting their economic mobility. Another proposed use by the executive related to the Bolsa Família welfare program: the government could set up programming that only allows this benefit to be used exclusively for food purchases. Although these examples are presented as control measures for safety or organization, they demonstrate how much a CBDC could restrict citizens' freedom of choice.
To illustrate the potential for state control through a Central Bank Digital Currency (CBDC), such as DREX, it is helpful to look at the example of China. In China, the implementation of a CBDC coincides with the country’s Social Credit System, a governmental surveillance tool that assesses citizens' and companies' behavior. Together, these technologies allow the Chinese government to monitor, reward, and, above all, punish behavior deemed inappropriate or threatening to the government.
How Does China's Social Credit System Work?
Implemented in 2014, China's Social Credit System assigns every citizen and company a "score" based on various factors, including financial behavior, criminal record, social interactions, and even online activities. This score determines the benefits or penalties each individual receives and can affect everything from public transport access to obtaining loans and enrolling in elite schools for their children. Citizens with low scores may face various sanctions, including travel restrictions, fines, and difficulty in securing loans.
With the adoption of the CBDC — or “digital yuan” — the Chinese government now has a new tool to closely monitor citizens' financial transactions, facilitating the application of Social Credit System penalties. China’s CBDC is a programmable digital currency, which means that the government can restrict how, when, and where the money can be spent. Through this level of control, digital currency becomes a powerful mechanism for influencing citizens' behavior.
Imagine, for instance, a citizen who repeatedly posts critical remarks about the government on social media or participates in protests. If the Social Credit System assigns this citizen a low score, the Chinese government could, through the CBDC, restrict their money usage in certain areas or sectors. For example, they could be prevented from buying tickets to travel to other regions, prohibited from purchasing certain consumer goods, or even restricted to making transactions only at stores near their home.
Another example of how the government can use the CBDC to enforce the Social Credit System is by monitoring purchases of products such as alcohol or luxury items. If a citizen uses the CBDC to spend more than the government deems reasonable on such products, this could negatively impact their social score, resulting in additional penalties such as future purchase restrictions or a lowered rating that impacts their personal and professional lives.
In China, this kind of control has already been demonstrated in several cases. Citizens added to Social Credit System “blacklists” have seen their spending and investment capacity severely limited. The combination of digital currency and social scores thus creates a sophisticated and invasive surveillance system, through which the Chinese government controls important aspects of citizens’ financial lives and individual freedoms.
Deputy Julia Zanatta views these examples with great concern. She argues that if the state has full control over digital money, citizens will be exposed to a level of economic control and surveillance never seen before. In a democracy, this control poses a risk, but in an authoritarian regime, it could be used as a powerful tool of repression.
DREX and Bill No. 3,341/2024
Julia Zanatta became aware of a bill by a Workers' Party (PT) deputy (Bill 4068/2020 by Deputy Reginaldo Lopes - PT/MG) that proposes the extinction of physical money within five years, aiming for a complete transition to DREX, the digital currency developed by the Central Bank of Brazil. Concerned about the impact of this measure, Julia drafted her bill, PL No. 3,341/2024, which prohibits the elimination of physical money, ensuring citizens the right to choose physical currency.
“The more I read about DREX, the less I want its implementation,” says the deputy. DREX is a Central Bank Digital Currency (CBDC), similar to other state digital currencies worldwide, but which, according to Julia, carries extreme control risks. She points out that with DREX, the State could closely monitor each citizen’s transactions, eliminating anonymity and potentially restricting freedom of choice. This control would lie in the hands of the Central Bank, which could, in a crisis or government change, “freeze balances or even delete funds directly from user accounts.”
Risks and Individual Freedom
Julia raises concerns about potential abuses of power that complete digitalization could allow. In a democracy, state control over personal finances raises serious questions, and EddieOz warns of an even more problematic future. “Today we are in a democracy, but tomorrow, with a government transition, we don't know if this kind of power will be used properly or abused,” he states. In other words, DREX gives the State the ability to restrict or condition the use of money, opening the door to unprecedented financial surveillance.
EddieOz cites Nigeria as an example, where a CBDC was implemented, and the government imposed severe restrictions on the use of physical money to encourage the use of digital currency, leading to protests and clashes in the country. In practice, the poorest and unbanked — those without regular access to banking services — were harshly affected, as without physical money, many cannot conduct basic transactions. Julia highlights that in Brazil, this situation would be even more severe, given the large number of unbanked individuals and the extent of rural areas where access to technology is limited.
The Relationship Between DREX and Pix
The digital transition has already begun with Pix, which revolutionized instant transfers and payments in Brazil. However, Julia points out that Pix, though popular, is a citizen’s choice, while DREX tends to eliminate that choice. The deputy expresses concern about new rules suggested for Pix, such as daily transaction limits of a thousand reais, justified as anti-fraud measures but which, in her view, represent additional control and a profit opportunity for banks. “How many more rules will banks create to profit from us?” asks Julia, noting that DREX could further enhance control over personal finances.
International Precedents and Resistance to CBDC
The deputy also cites examples from other countries resisting the idea of a centralized digital currency. In the United States, states like New Hampshire have passed laws to prevent the advance of CBDCs, and leaders such as Donald Trump have opposed creating a national digital currency. Trump, addressing the topic, uses a justification similar to Julia’s: in a digitalized system, “with one click, your money could disappear.” She agrees with the warning, emphasizing the control risk that a CBDC represents, especially for countries with disadvantaged populations.
Besides the United States, Canada, Colombia, and Australia have also suspended studies on digital currencies, citing the need for further discussions on population impacts. However, in Brazil, the debate on DREX is still limited, with few parliamentarians and political leaders openly discussing the topic. According to Julia, only she and one or two deputies are truly trying to bring this discussion to the Chamber, making DREX’s advance even more concerning.
Bill No. 3,341/2024 and Popular Pressure
For Julia, her bill is a first step. Although she acknowledges that ideally, it would prevent DREX's implementation entirely, PL 3341/2024 is a measure to ensure citizens' choice to use physical money, preserving a form of individual freedom. “If the future means control, I prefer to live in the past,” Julia asserts, reinforcing that the fight for freedom is at the heart of her bill.
However, the deputy emphasizes that none of this will be possible without popular mobilization. According to her, popular pressure is crucial for other deputies to take notice and support PL 3341. “I am only one deputy, and we need the public’s support to raise the project’s visibility,” she explains, encouraging the public to press other parliamentarians and ask them to “pay attention to PL 3341 and the project that prohibits the end of physical money.” The deputy believes that with a strong awareness and pressure movement, it is possible to advance the debate and ensure Brazilians’ financial freedom.
What’s at Stake?
Julia Zanatta leaves no doubt: DREX represents a profound shift in how money will be used and controlled in Brazil. More than a simple modernization of the financial system, the Central Bank’s CBDC sets precedents for an unprecedented level of citizen surveillance and control in the country. For the deputy, this transition needs to be debated broadly and transparently, and it’s up to the Brazilian people to defend their rights and demand that the National Congress discuss these changes responsibly.
The deputy also emphasizes that, regardless of political or partisan views, this issue affects all Brazilians. “This agenda is something that will affect everyone. We need to be united to ensure people understand the gravity of what could happen.” Julia believes that by sharing information and generating open debate, it is possible to prevent Brazil from following the path of countries that have already implemented a digital currency in an authoritarian way.
A Call to Action
The future of physical money in Brazil is at risk. For those who share Deputy Julia Zanatta’s concerns, the time to act is now. Mobilize, get informed, and press your representatives. PL 3341/2024 is an opportunity to ensure that Brazilian citizens have a choice in how to use their money, without excessive state interference or surveillance.
In the end, as the deputy puts it, the central issue is freedom. “My fear is that this project will pass, and people won’t even understand what is happening.” Therefore, may every citizen at least have the chance to understand what’s at stake and make their voice heard in defense of a Brazil where individual freedom and privacy are respected values.
-
 @ 714f9dc3:76659adb
2025-01-08 19:16:50
@ 714f9dc3:76659adb
2025-01-08 19:16:50Last week, I was reading “The Air We Breathe”, by Glen Scrivener. It’s about “How We All Came to Believe in Freedom, Kindness, Progress, and Equality”, and it explores the Christian roots of the values we prize in today's western society. It’s all around us, but we don’t really know where it came from: It’s the air we’re breathing. The ideas and ethics behind Christianity, whether you believe in them or not, are embedded in our culture.
As I was reading this, I saw so many parallels with Bitcoin, so wanted to list them below and share some of my thoughts. Can Bitcoin also become “The Air We Breathe”? Or in plebs words: hyperbitcoinization?
Can Bitcoin become so ubiquitous that it becomes normal? Can there be a world in which we don’t even know where Bitcoin came from? It would be a world with many similar views as with today's view on Christianity. It becomes the air we breathe, something that used to be a counterculture that over time became ubiquitous. What can we learn from it?
These are my ten parallels of Bitcoin with the early days of Christianity.
- Separation from state
- From obscure counterculture to dominant force
- Exponential grassroots growth
- Conversion of emperors/politicians
- Sudden tolerance and protection for ideology
- Fall of the empire, end of the status quo
- Missionaries spreading the word
- Persuasion and education are key
- Age of Enlightenment
Note: I’m no expert on Christianity, nor a historian of the Roman Empire, and I know just a bit about Bitcoin. See this as a thought experiment.
1. Separation from state
In all fairness, I’m not the first to draw this first parallel. It was Satoshi Nakamoto themself who made the connection even before Bitcoin was available to the public, with several hints pointing back to important dates and moments in Christian history. The big parallel here is the “separation of money and state” and “separation of church and state”.
Before going back to the early days of Christianity in the first centuries AD, I first want to draw this parallel with Satoshi.
It’s 1517. The German Priest Maarten Luther writes his Ninety-five Theses, and nails this on the church doors in Wittenberg. The theses are also known as the “Disputation on the Power and Efficacy of Indulgences”. He kickstarted a movement with a radical new idea for that time: The separation of the church from the state.
The Catholic Church had become one with the state. Via the means of indulgences, there was an ability to pay for your redemption. The church was corrupted by money, power and politics. The church and indulgences replaced the need for personal responsibility and an individual faith with money and perverse structures.
Reformation Day is a Protestant Christian religious holiday celebrated on 31 October in remembrance of the onset of the Reformation. But the 31st of October is also the day in which Satoshi shared his pamphlet with the world: in 2008 they published the Bitcoin Whitepaper. It kickstarted a movement with a radical new idea for that time: The separation of the money from the state.
But this was not Satoshi’s only hint. Another one is the date of Bitcoin’s Genesis Block: January 3, 2009. It was the day that the idea of the separation of money and the state became reality, more than just an idea in an individual's mind.
Did you know that Maarten Luther was excommunicated from the Catholic Church in 1521 by Pope Leo X for sparking this revolutionary new way of thinking (and being). It happened on January 3 as well. I bet Satoshi Nakamoto knew.
To be fair, this parallel is not new and known by many bitcoiners. But it’s a good introduction to the topic, and after reading “The Air We Breathe: How We All Came to Believe in Freedom, Kindness, Progress, and Equality”, I automatically started to see more parallels between (the early days of) Christianity and todays adoption of Bitcoin. Because it was of course not Maarten Luther who sparked these rebellious thoughts in 1500, but it was Jesus himself approx. 2000 years ago.
Let’s go back from the 1500s to the first decades AD to the beginning of this radical new belief system. During the dominance of the Roman empire in the Mediterranean and much of Europe, Western Asia and North Africa, someone told a story that opposed every mainstream paradigm.
Jesus’ idea was radically different from the belief systems of that day. He preached Freedom, Kindness, Progress, and Equality in a world that was full of Debauchery and Violence, with Gladiator Games, Slavery, Public Crucifixion, and Brutalities. The belief system of that time was not like todays.
There were superior races (Greek/Romans over barbarians), superior sexes (man over women), superior classes (free man over slaves) and the concept of justice was more something in the realm of “restoring rights of those that were superior”, than “equality for all, men and women, Greek and barbarian, free and slave”.
Jesus opposed the status quo. It started small and irrelevant; as a counterculture. But it didn’t stay that way.
2. From obscure counterculture to dominant force
In “The Air We Breathe”, Scrivener asks the question:
“How did the obscure, marginal Jesus movement of the 1st century become the dominant religious force in the Western world in a few centuries?”
Important to know, is that the Christian faith was the opposite of the narrative. Concepts like Freedom, Kindness, Progress, and Equality didn’t exist in the Roman Empire. Human rights neither. Individual rights neither. The emperor was almost de facto God himself.
Early Christians were persecuted for preaching a different story: that God is NOT the ruler of the empire. Jesus preached the separation of politics from God; separating faith from the state. As a result, he was crucified, and many of his followers were killed by Nero (between 54 and 68 AD), Domitian (81–96 AD), Trajan (98–117 AD) and Decius (249–251 AD). This new narrative was a thread for the Roman rulers.
Draw the parallels of how there have been many attempts to “kill” bitcoin, not with physical persecution but with an information war. Not by physical violence, but by misinformation. Bitcoin threatens the status quo, just like Christianity threatened the Roman Empire.
You see?
But how is the obscure movement of Bitcoin in the 21st century becoming the dominant force, similar to the question that Scrivener asked about Christianity? Perhaps the answer lies in the following parallel.
3. Exponential grassroots growth
Sociologist Rodney Stark estimates in “The Rise of Christianity” that from the time of the first Easter, the church began growing at a rate of 40% per decade, a modest but relentless 3.4% per year. By the year 300, Christians numbered perhaps 6 million: about a tenth of the empire.
Despite pushbacks, the army of believers continued to grow. Grassroots, peer-to-peer. It was not the state-religion, it was a peaceful army of believers that spread the word, resulting in an exponential growth of its followers. The counterculture became more and more dominant.
You may see what I’m doing here. It was basically the meme that all Bitcoiners know: Gradually, then suddenly. Against the current.
4. Conversion of emperors/politicians
In 312 a big change happened: Emperor Constantine converted to Christianity. As Stark writes, "Constantine's conversion would better be seen as a response to the massive exponential wave in progress, not as its cause".
Are we living in that same era, where nation states start to embrace Bitcoin? Where politicians don’t oppose as strongly anymore, but are flirting with the idea of embracing it? And again the parallel: it’s responsive to the exponential wave of progress, not as its cause.
Whether Constantine is Nayib Bukele, Donald Trump, or Milei: it doesn’t matter. It’s the dynamic that matters. The counterculture becomes so dominant, that the “rulers” of the world are wanting to be part of it. Which will be followed by “rules” that favour the ideology, movement, and beliefs.
6. Tolerance and protection for ideology
In 313 Constantine's Edict of Milan granted freedom to Christians that were remarkable for that time and a model for religious toleration for the coming centuries.
The tide was turning, and by 380 Emperor Theodosius made Christianity Rome's official religion, more than half the population had already converted. In a few short centuries Christianity had gone from radical counterculture to dominant cultural power. This was an extraordinary shift in the church's relationship with the world. The edict expressly grants religious liberty to Christians, who had been the object of special persecution, but also goes even further and grants liberty to all other religions. And then, in 410, the world itself changed.
It changed from grassroots, bottom-up adoption to some kind of nation state adoption. One that was driven by decrees and edicts, instead of the analog cyberhornets of that day. Actually, the ideas of Indulgences were introduced via these Edicts, something that Maarten Luther actually was fighting against in the 1500s.
The world changed from the state-less Christian belief and moved (back) towards a system in which the state and church were connected again. Yes — the Roman Catholic Church. Until the previously mentioned critics during the Reformation.
6. Fall of the empire, end of the status quo
When people speak of the fall of the Roman Empire, they usually mean in the 5th century when the western half fell. But there was also an eastern half, known as the Byzantine Empire (with its capital in what is modern-day Istanbul).
How did this relate to the movement that once was Cult, and now suddenly had become Culture?
It was Augustine, the north African bishop (354-430), who laid the foundation for a new philosophical, theological, and legal system. He distinguished between the fragile earthly realm and the eternal heavenly kingdom. Rome was “a city of man”, which fell. But the “city of God” was forever. He continued to separate the Roman Catholic Church from the faith that it once was. This distinction was vital, and it gave rise to the concept of "the secular realm". He planted the first ideas of "the separation of church and state" again, which started to spread throughout Europe during the supposedly "sandy desert" of the Middle Ages.
The parallel and lesson here might be that narratives can be taken over, for the worse. And that it takes centuries to take back the narrative, but/and only after an empire has fallen. Whether we refer to “The Fourth Turning” by William Strauss and Neil Howe or “Changing World Orders” by Ray Dalio. There is something to preserve, and it needs active monitoring and pushbacks!
7. Missionary, spreading the word
The way the church sought to spread its influence would become a question that would take many centuries (and many failures) to settle. In the past, empires sought to spread their influence almost always by force. Christianity has been a missionary faith from the beginning. It was for this reason that Pope Gregory the Great sent Augustine to Britain to convert the Anglo-Saxons.
Augustine was commanded by Gregory to use only "gentle means". His goal was persuasion. His method was teaching and preaching. And he was successful, converting King Aethelbert of Kent and becoming the first Archbishop of Canterbury.
You see what I’m talking about again: the parallel is simple. Bitcoin is a similar peaceful revolution, a missionary movement, of those that wish to see their Cult turn into a Culture. “Genle means”, teachings, persuasions. Or in pleb terminology: Orangepilling.
8. Persuasion and education are key
Over the next decades and centuries, this movement continued. English Benedictine monk (675-754) Boniface was sent from the previously “barbarian” Britain to “orangepill the East” – in this case the Saxons in the Germanic lands. In the words of his advisor, the Bishop of Winchester, his goal was "to convince them by many documents and arguments". This mission of persuasion and education was largely successful. Today he’s better known as “the Apostle to the Germans". He was killed in The Netherlands (in Dokkum).
Boniface kept to a policy of non-violence and non-retaliation, even to the point of death. Another famous writer about this topic, Tom Holland, summarises the lesson we learn from Boniface: "to convert was to educate".
In the following century this lesson was sorely needed by the Frankish king Charles the Great, aka Charlemagne (742-814). Charlemagne's path to power was a brutal one. When the Saxons stood in his way, Charlemagne beheaded 4,500 of them in a single day. There are concrete reasons why "getting medieval" might be associated today with brutality.
Is “Bitcoin as Legal Tender”, whether this is peaceful or violently, the way to go? Are we “getting medieval” with these kind of measures, in order to go from Cult to Culture, from counterculture to dominant culture, in which we lose the true essence of our revolution of separation of the state from the matter?
9. Age of Enlightenment
Alcuin of York (735-804), was bold enough to write to Charlemagne directly with his criticism. "A person can be drawn into the faith, not forced into it". Be a lighthouse, not a tugboat!
The church's official teaching would later agree with Alcuin's position. In the 12th century all "harsh means" were forbidden since faith arises from the will, not compulsion. Enlightenment comes through education and persuasion.
There’s work to do. Grassroots. Education. Peer-to-peer. Not directed by politicians, nor opposed by those in power. Through education and persuasion. Rules without rulers. Because eventually, with the Crusades and the Spanish Inquisition, there are stark examples of the church using “harsh means" again. Forcing Bitcoin on people will never be the way: it’s a cheat code to the end goal. In order to succeed, we’ll need to be a missionary.
Final words
I don’t want in any way to compare Christianity in itself as a faith, and Bitcoin as a technology, with each other. I enjoyed exploring the sociological phenomena between two countercultures, the grassroots movement and missionary parallels between both of them. Satoshi gave the first assist, with the 31st of October (Whitepaper Day) and the Genesis Block on January 3rd.
Let’s not mix religion with monetary systems, even though there are many similarities between certain movements. That’s not my goal for sharing this brain dump. But let’s learn from the past, from Constantine’s Edict and from Augustine, from Charlemagne (and especially Alcuin of York), from Boniface and from Maarten Luther. And from Satoshi Nakamoto.
-
 @ e6817453:b0ac3c39
2025-01-05 14:29:17
@ e6817453:b0ac3c39
2025-01-05 14:29:17The Rise of Graph RAGs and the Quest for Data Quality
As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence.
Booming Interest in Graph RAGs
Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can:
- Enhance LLM Outputs: By grounding responses in structured knowledge, graphs significantly reduce hallucinations.
- Support Complex Queries: Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving.
Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs?
Data Quality: The Foundation of Effective Graphs
A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why:
- Richness of Entities: Effective retrieval depends on graphs populated with rich, detailed entities.
- Freedom from Hallucinations: Poorly constructed graphs amplify inaccuracies rather than mitigating them.
Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs.
Hybrid Graph RAGs and Variations
While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that:
- Handle diverse data sources with ease.
- Offer improved adaptability to complex queries.
Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing.
Ontology: The Key to Graph Construction Quality
Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for:
- Defining Relationships: Clarifying how concepts connect within a domain.
- Validating Graph Structures: Ensuring constructed graphs are logically sound and align with domain-specific realities.
Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs?
How to Build Ontology Expertise in a Startup Team
For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach:
- Assign a Knowledge Champion: Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering.
- Provide Training: Invest in courses, workshops, or certifications in knowledge graph and ontology creation.
- Leverage Partnerships: Collaborate with academic institutions, domain experts, or consultants to build initial frameworks.
- Utilize Tools: Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process.
- Iterate with Feedback: Continuously refine ontologies through collaboration with domain experts and iterative testing.
So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts.
You could read about barefoot experts in my article :
Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise.
How to Find or Create Ontologies
For teams venturing into Graph RAGs, several strategies can help address the ontology gap:
-
Leverage Existing Ontologies: Many industries and domains already have open ontologies. For instance:
-
Public Knowledge Graphs: Resources like Wikipedia’s graph offer a wealth of structured knowledge.
- Industry Standards: Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields.
-
Business Framework Ontology (BFO): A valuable resource for enterprises looking to define business processes and structures.
-
Build In-House Expertise: If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation.
-
Utilize LLMs for Ontology Construction: Interestingly, LLMs themselves can act as a starting point for ontology development:
-
Prompt-Based Extraction: LLMs can generate draft ontologies by leveraging their extensive training on graph data.
- Domain Expert Refinement: Combine LLM-generated structures with insights from domain experts to create tailored ontologies.
Parallel Ontology and Graph Extraction
An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as:
- Detecting Hallucinations: Differentiating between genuine insights and AI-generated inaccuracies.
- Ensuring Completeness: Ensuring no critical concepts are overlooked during extraction.
Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method.
LLMs as Ontologists
While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to:
- Generate Skeleton Ontologies: Prompt LLMs with domain-specific information to draft initial ontology structures.
- Validate and Refine Ontologies: Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance.
However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes.
Final Thoughts: Unlocking the Power of Graph RAGs
The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools.
As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding.
Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation!
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O caso da Grêmio TV
enquanto vinha se conduzindo pela plataforma superior daquela arena que se pensava totalmente preenchida por adeptos da famosa equipe do Grêmio de Porto Alegre, viu-se, como por obra de algum nigromante - dos muitos que existem e estão a todo momento a fazer más obras e a colocar-se no caminhos dos que procuram, se não fazer o bem acima de todas as coisas, a pelo menos não fazer o mal no curso da realização dos seus interesses -, o discretíssimo jornalista a ser xingado e moído em palavras por uma horda de malandrinos a cinco ou seis passos dele surgida que cantavam e moviam seus braços em movimentos que não se pode classificar senão como bárbaros, e assim cantavam:
Grêmio TV pior que o SBT !
-
 @ a95c6243:d345522c
2024-12-06 18:21:15
@ a95c6243:d345522c
2024-12-06 18:21:15Die Ungerechtigkeit ist uns nur in dem Falle angenehm,\ dass wir Vorteile aus ihr ziehen;\ in jedem andern hegt man den Wunsch,\ dass der Unschuldige in Schutz genommen werde.\ Jean-Jacques Rousseau
Politiker beteuern jederzeit, nur das Beste für die Bevölkerung zu wollen – nicht von ihr. Auch die zahlreichen unsäglichen «Corona-Maßnahmen» waren angeblich zu unserem Schutz notwendig, vor allem wegen der «besonders vulnerablen Personen». Daher mussten alle möglichen Restriktionen zwangsweise und unter Umgehung der Parlamente verordnet werden.
Inzwischen hat sich immer deutlicher herausgestellt, dass viele jener «Schutzmaßnahmen» den gegenteiligen Effekt hatten, sie haben den Menschen und den Gesellschaften enorm geschadet. Nicht nur haben die experimentellen Geninjektionen – wie erwartet – massive Nebenwirkungen, sondern Maskentragen schadet der Psyche und der Entwicklung (nicht nur unserer Kinder) und «Lockdowns und Zensur haben Menschen getötet».
Eine der wichtigsten Waffen unserer «Beschützer» ist die Spaltung der Gesellschaft. Die tiefen Gräben, die Politiker, Lobbyisten und Leitmedien praktisch weltweit ausgehoben haben, funktionieren leider nahezu in Perfektion. Von ihren persönlichen Erfahrungen als Kritikerin der Maßnahmen berichtete kürzlich eine Schweizerin im Interview mit Transition News. Sie sei schwer enttäuscht und verspüre bis heute eine Hemmschwelle und ein seltsames Unwohlsein im Umgang mit «Geimpften».
Menschen, die aufrichtig andere schützen wollten, werden von einer eindeutig politischen Justiz verfolgt, verhaftet und angeklagt. Dazu zählen viele Ärzte, darunter Heinrich Habig, Bianca Witzschel und Walter Weber. Über den aktuell laufenden Prozess gegen Dr. Weber hat Transition News mehrfach berichtet (z.B. hier und hier). Auch der Selbstschutz durch Verweigerung der Zwangs-Covid-«Impfung» bewahrt nicht vor dem Knast, wie Bundeswehrsoldaten wie Alexander Bittner erfahren mussten.
Die eigentlich Kriminellen schützen sich derweil erfolgreich selber, nämlich vor der Verantwortung. Die «Impf»-Kampagne war «das größte Verbrechen gegen die Menschheit». Trotzdem stellt man sich in den USA gerade die Frage, ob der scheidende Präsident Joe Biden nach seinem Sohn Hunter möglicherweise auch Anthony Fauci begnadigen wird – in diesem Fall sogar präventiv. Gibt es überhaupt noch einen Rest Glaubwürdigkeit, den Biden verspielen könnte?
Der Gedanke, den ehemaligen wissenschaftlichen Chefberater des US-Präsidenten und Direktor des National Institute of Allergy and Infectious Diseases (NIAID) vorsorglich mit einem Schutzschild zu versehen, dürfte mit der vergangenen Präsidentschaftswahl zu tun haben. Gleich mehrere Personalentscheidungen des designierten Präsidenten Donald Trump lassen Leute wie Fauci erneut in den Fokus rücken.
Das Buch «The Real Anthony Fauci» des nominierten US-Gesundheitsministers Robert F. Kennedy Jr. erschien 2021 und dreht sich um die Machenschaften der Pharma-Lobby in der öffentlichen Gesundheit. Das Vorwort zur rumänischen Ausgabe des Buches schrieb übrigens Călin Georgescu, der Überraschungssieger der ersten Wahlrunde der aktuellen Präsidentschaftswahlen in Rumänien. Vielleicht erklärt diese Verbindung einen Teil der Panik im Wertewesten.
In Rumänien selber gab es gerade einen Paukenschlag: Das bisherige Ergebnis wurde heute durch das Verfassungsgericht annuliert und die für Sonntag angesetzte Stichwahl kurzfristig abgesagt – wegen angeblicher «aggressiver russischer Einmischung». Thomas Oysmüller merkt dazu an, damit sei jetzt in der EU das Tabu gebrochen, Wahlen zu verbieten, bevor sie etwas ändern können.
Unsere Empörung angesichts der Historie von Maßnahmen, die die Falschen beschützen und für die meisten von Nachteil sind, müsste enorm sein. Die Frage ist, was wir damit machen. Wir sollten nach vorne schauen und unsere Energie clever einsetzen. Abgesehen von der Umgehung von jeglichem «Schutz vor Desinformation und Hassrede» (sprich: Zensur) wird es unsere wichtigste Aufgabe sein, Gräben zu überwinden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2024-11-29 19:45:43
@ a95c6243:d345522c
2024-11-29 19:45:43Konsum ist Therapie.
Wolfgang JoopUmweltbewusstes Verhalten und verantwortungsvoller Konsum zeugen durchaus von einer wünschenswerten Einstellung. Ob man deswegen allerdings einen grünen statt eines schwarzen Freitags braucht, darf getrost bezweifelt werden – zumal es sich um manipulatorische Konzepte handelt. Wie in der politischen Landschaft sind auch hier die Etiketten irgendwas zwischen nichtssagend und trügerisch.
Heute ist also wieder mal «Black Friday», falls Sie es noch nicht mitbekommen haben sollten. Eigentlich haben wir ja eher schon eine ganze «Black Week», der dann oft auch noch ein «Cyber Monday» folgt. Die Werbebranche wird nicht müde, immer neue Anlässe zu erfinden oder zu importieren, um uns zum Konsumieren zu bewegen. Und sie ist damit sehr erfolgreich.
Warum fallen wir auf derartige Werbetricks herein und kaufen im Zweifelsfall Dinge oder Mengen, die wir sicher nicht brauchen? Pure Psychologie, würde ich sagen. Rabattschilder triggern etwas in uns, was den Verstand in Stand-by versetzt. Zusätzlich beeinflussen uns alle möglichen emotionalen Reize und animieren uns zum Schnäppchenkauf.
Gedankenlosigkeit und Maßlosigkeit können besonders bei der Ernährung zu ernsten Problemen führen. Erst kürzlich hat mir ein Bekannter nach einer USA-Reise erzählt, dass es dort offenbar nicht unüblich ist, schon zum ausgiebigen Frühstück in einem Restaurant wenigstens einen Liter Cola zu trinken. Gerne auch mehr, um das Gratis-Nachfüllen des Bechers auszunutzen.
Kritik am schwarzen Freitag und dem unnötigen Konsum kommt oft von Umweltschützern. Neben Ressourcenverschwendung, hohem Energieverbrauch und wachsenden Müllbergen durch eine zunehmende Wegwerfmentalität kommt dabei in der Regel auch die «Klimakrise» auf den Tisch.
Die EU-Kommission lancierte 2015 den Begriff «Green Friday» im Kontext der überarbeiteten Rechtsvorschriften zur Kennzeichnung der Energieeffizienz von Elektrogeräten. Sie nutzte die Gelegenheit kurz vor dem damaligen schwarzen Freitag und vor der UN-Klimakonferenz COP21, bei der das Pariser Abkommen unterzeichnet werden sollte.
Heute wird ein grüner Freitag oft im Zusammenhang mit der Forderung nach «nachhaltigem Konsum» benutzt. Derweil ist die Europäische Union schon weit in ihr Geschäftsmodell des «Green New Deal» verstrickt. In ihrer Propaganda zum Klimawandel verspricht sie tatsächlich «Unterstützung der Menschen und Regionen, die von immer häufigeren Extremwetter-Ereignissen betroffen sind». Was wohl die Menschen in der Region um Valencia dazu sagen?
Ganz im Sinne des Great Reset propagierten die Vereinten Nationen seit Ende 2020 eine «grüne Erholung von Covid-19, um den Klimawandel zu verlangsamen». Der UN-Umweltbericht sah in dem Jahr einen Schwerpunkt auf dem Verbraucherverhalten. Änderungen des Konsumverhaltens des Einzelnen könnten dazu beitragen, den Klimaschutz zu stärken, hieß es dort.
Der Begriff «Schwarzer Freitag» wurde in den USA nicht erstmals für Einkäufe nach Thanksgiving verwendet – wie oft angenommen –, sondern für eine Finanzkrise. Jedoch nicht für den Börsencrash von 1929, sondern bereits für den Zusammenbruch des US-Goldmarktes im September 1869. Seitdem mussten die Menschen weltweit so einige schwarze Tage erleben.
Kürzlich sind die britischen Aufsichtsbehörden weiter von ihrer Zurückhaltung nach dem letzten großen Finanzcrash von 2008 abgerückt. Sie haben Regeln für den Bankensektor gelockert, womit sie «verantwortungsvolle Risikobereitschaft» unterstützen wollen. Man würde sicher zu schwarz sehen, wenn man hier ein grünes Wunder befürchten würde.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ f9c0ea75:44e849f4
2025-01-08 19:16:08
@ f9c0ea75:44e849f4
2025-01-08 19:16:08If there's one thing Brazil's economic history has proven time and time again, it’s that no currency lasts forever. Brazil has had nine different currencies, and all of them failed in the same way: losing value until the government decided to "fix" the problem by introducing a new one.
On average, since 1900, each currency lasted only 13.9 years, and if we look at the trajectory of the Real, the question remains: how much longer can it survive?
The Graveyard of Brazilian Currencies
Every time inflation spirals out of control, the government finds the same solution: rename the currency and cut zeros, pretending that the underlying economic problems have been solved. Here’s the long list of failures:
Réis (1500-1942) → Lasted centuries but was eaten away by inflation and replaced by the Cruzeiro.
Cruzeiro (1942-1967) → Introduced to modernize the economy but quickly lost its purchasing power.
Cruzeiro Novo (1967-1970) → A redenomination that cut three zeros, but it only lasted 3 years.
Cruzeiro (1970-1986) → Inflation skyrocketed, leading to another currency shift.
Cruzado (1986-1989) → Promised stability by removing zeros, but lasted just 3 years.
Cruzado Novo (1989-1990) → Another reset, another failure, lasting just 1 year.
Cruzeiro (1990-1993) → Brought back an old name, but inflation remained unchecked.
Cruzeiro Real (1993-1994) → A short-lived transition currency, lasting just 1 year before the Real.
Real (1994-present) → ˜30 years old, it has already lost more than 85% of its purchasing power. The Real is now showing the same symptoms that led to the collapse of its predecessors. Inflation is eroding its value, and government intervention keeps distorting the market. We are just waiting for the next excuse to rename the currency and "reset" the system once again.
DREX: The Next Rebranding of Brazilian Money?
This time, the change might not come as a simple rebranding or a few zeroes being cut. The Brazilian government is already preparing DREX, a digital currency controlled by the Central Bank. Officially, it will be a "digital Real," but in reality, it could serve as a way to impose new monetary rules, redefine values, and quietly restructure the economy—just like every previous currency reset.
The pattern is clear: give a new name to an old problem and keep extracting value from citizens.
The Fate of the Real? We Don’t Know. But Bitcoin is Better.
Looking at history, it’s clear that Brazil’s fiat currencies have a built-in expiration date. The government will always find a way to reset the system, rename the currency, and erase the traces of inflation.
But for the first time in history, there is a real alternative: Bitcoin.
Unlike all of Brazil’s previous currencies, Bitcoin cannot be manipulated, inflated, or rebranded by government decree. It doesn’t rely on empty promises or central authorities that can change the rules whenever it suits them.
In the end, the Real might last a few more years or be replaced soon by DREX—but one thing is certain: BITCOIN IS BETTER.
-
 @ 1cb14ab3:95d52462
2025-01-02 21:31:48
@ 1cb14ab3:95d52462
2025-01-02 21:31:48
No. 6 - Zhujiajiao Canal Chasing

For a tranquil escape from the hustle and bustle of the city cruise to Zhujiajiao -- an epic water town dating back to the Ming and Qing dynasties. It's only about 50 kilometers from the downtown and makes for an easy day trip. Hop on the subway and get there in an hour. Zhujiajiao has canals, bridges, and ancient buildings, offering a glimpse into the town's rich history. Take a boat ride along the canals for the best views of traditional houses and temples. Then explore the town on foot and get lost in attractions like the Kezhi Garden, Yuanjin Temple, and the Qing Dynasty Post Office. Don't forget to grub-up with all of the great food vendors nearby.
No. 7 - China Art Museum

China Art Museum is absolutely worth the trip solely for its awe-inspiring architecture. The towering structure casts a tall shadow over bystanders. Step inside and you'll find a world of art waiting. The blend of permanent and temporary exhibits offers hours of art-gazing. Give yourself at least half a day to fully immerse in the creative haven in Pudong. To get to the China Art Museum, you can take Line 2 of the Shanghai Metro and get off at the Pudong Avenue Station (Chinese: 浦东大道站). The museum is located near Exit 4 of the station.
No. 8 - Days on The West Bund

Hands down my favorite place in Shanghai. This spot is the go-to for a perfect weekend under the sun. You'll find me setting up a blanket with beer, cards, and snacks, along with a slackline and spike ball setup nearby, surrounded by dogs running around, enjoying the company of old and new friends. When you want a little movement enjoy some climbing, skating, running, or basketball after work. The West Bund is an oasis amidst the chaos of the city. But beware - its popularity is growing, so tread lightly.
No. 9 - Nights Under the Lupu Bridge

Nights under the Lupu Bridge are where it's at, man. Hop on your scooter and cruise over for the ultimate skyline views. Stroll along the walkway, munch on street food, sip drinks, and groove to live tunes. Street vendors serve up traditional snacks and crafts, and the vibe gets lit with spontaneous performances and games. Get ready to soak up the electric energy of Shanghai's Lupu Bridge at night."
No. 10 - A Weekend on Chongming

Escape the city hustle and find your peace on Chongming Island. A weekend getaway on this rural gem is just what you need. Chill out in a farmhouse, soak up the sunset, and enjoy the tranquility. Explore the natural wonders, visit the old museums, and feast on fresh seafood. End your days with a beach walk under the stars. Nothing beats a few nights away from the city chaos.
Additional Photos






Previous Guide in the Series:
An Expats Guide to the Best Spots in Shanghai: 001
Next Guide in the Series:
An Expats Guide to the Best Spots in Shanghai: 003
Find Me Elsewhere:
All images are property of Hes. Published 06.29.2024
-
 @ bcea2b98:7ccef3c9
2025-01-08 18:22:00
@ bcea2b98:7ccef3c9
2025-01-08 18:22:00originally posted at https://stacker.news/items/842405
-
 @ a95c6243:d345522c
2024-11-08 20:02:32
@ a95c6243:d345522c
2024-11-08 20:02:32Und plötzlich weißt du:
Es ist Zeit, etwas Neues zu beginnen
und dem Zauber des Anfangs zu vertrauen.
Meister EckhartSchwarz, rot, gold leuchtet es im Kopf des Newsletters der deutschen Bundesregierung, der mir freitags ins Postfach flattert. Rot, gelb und grün werden daneben sicher noch lange vielzitierte Farben sein, auch wenn diese nie geleuchtet haben. Die Ampel hat sich gerade selber den Stecker gezogen – und hinterlässt einen wirtschaftlichen und gesellschaftlichen Trümmerhaufen.
Mit einem bemerkenswerten Timing hat die deutsche Regierungskoalition am Tag des «Comebacks» von Donald Trump in den USA endlich ihr Scheitern besiegelt. Während der eine seinen Sieg bei den Präsidentschaftswahlen feierte, erwachten die anderen jäh aus ihrer Selbsthypnose rund um Harris-Hype und Trump-Panik – mit teils erschreckenden Auswüchsen. Seit Mittwoch werden die Geschicke Deutschlands nun von einer rot-grünen Minderheitsregierung «geleitet» und man steuert auf Neuwahlen zu.
Das Kindergarten-Gehabe um zwei konkurrierende Wirtschaftsgipfel letzte Woche war bereits bezeichnend. In einem Strategiepapier gestand Finanzminister Lindner außerdem den «Absturz Deutschlands» ein und offenbarte, dass die wirtschaftlichen Probleme teilweise von der Ampel-Politik «vorsätzlich herbeigeführt» worden seien.
Lindner und weitere FDP-Minister wurden also vom Bundeskanzler entlassen. Verkehrs- und Digitalminister Wissing trat flugs aus der FDP aus; deshalb darf er nicht nur im Amt bleiben, sondern hat zusätzlich noch das Justizministerium übernommen. Und mit Jörg Kukies habe Scholz «seinen Lieblingsbock zum Obergärtner», sprich: Finanzminister befördert, meint Norbert Häring.
Es gebe keine Vertrauensbasis für die weitere Zusammenarbeit mit der FDP, hatte der Kanzler erklärt, Lindner habe zu oft sein Vertrauen gebrochen. Am 15. Januar 2025 werde er daher im Bundestag die Vertrauensfrage stellen, was ggf. den Weg für vorgezogene Neuwahlen freimachen würde.
Apropos Vertrauen: Über die Hälfte der Bundesbürger glauben, dass sie ihre Meinung nicht frei sagen können. Das ging erst kürzlich aus dem diesjährigen «Freiheitsindex» hervor, einer Studie, die die Wechselwirkung zwischen Berichterstattung der Medien und subjektivem Freiheitsempfinden der Bürger misst. «Beim Vertrauen in Staat und Medien zerreißt es uns gerade», kommentierte dies der Leiter des Schweizer Unternehmens Media Tenor, das die Untersuchung zusammen mit dem Institut für Demoskopie Allensbach durchführt.
«Die absolute Mehrheit hat absolut die Nase voll», titelte die Bild angesichts des «Ampel-Showdowns». Die Mehrheit wolle Neuwahlen und die Grünen sollten zuerst gehen, lasen wir dort.
Dass «Insolvenzminister» Robert Habeck heute seine Kandidatur für das Kanzleramt verkündet hat, kann nur als Teil der politmedialen Realitätsverweigerung verstanden werden. Wer allerdings denke, schlimmer als in Zeiten der Ampel könne es nicht mehr werden, sei reichlich optimistisch, schrieb Uwe Froschauer bei Manova. Und er kenne Friedrich Merz schlecht, der sich schon jetzt rhetorisch auf seine Rolle als oberster Feldherr Deutschlands vorbereite.
Was also tun? Der Schweizer Verein «Losdemokratie» will eine Volksinitiative lancieren, um die Bestimmung von Parlamentsmitgliedern per Los einzuführen. Das Losverfahren sorge für mehr Demokratie, denn als Alternative zum Wahlverfahren garantiere es eine breitere Beteiligung und repräsentativere Parlamente. Ob das ein Weg ist, sei dahingestellt.
In jedem Fall wird es notwendig sein, unsere Bemühungen um Freiheit und Selbstbestimmung zu verstärken. Mehr Unabhängigkeit von staatlichen und zentralen Institutionen – also die Suche nach dezentralen Lösungsansätzen – gehört dabei sicher zu den Möglichkeiten. Das gilt sowohl für jede/n Einzelne/n als auch für Entitäten wie die alternativen Medien.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2024-10-26 12:21:50
@ a95c6243:d345522c
2024-10-26 12:21:50Es ist besser, ein Licht zu entzünden, als auf die Dunkelheit zu schimpfen. Konfuzius
Die Bemühungen um Aufarbeitung der sogenannten Corona-Pandemie, um Aufklärung der Hintergründe, Benennung von Verantwortlichkeiten und das Ziehen von Konsequenzen sind durchaus nicht eingeschlafen. Das Interesse daran ist unter den gegebenen Umständen vielleicht nicht sonderlich groß, aber es ist vorhanden.
Der sächsische Landtag hat gestern die Einsetzung eines Untersuchungsausschusses zur Corona-Politik beschlossen. In einer Sondersitzung erhielt ein entsprechender Antrag der AfD-Fraktion die ausreichende Zustimmung, auch von einigen Abgeordneten des BSW.
In den Niederlanden wird Bill Gates vor Gericht erscheinen müssen. Sieben durch die Covid-«Impfstoffe» geschädigte Personen hatten Klage eingereicht. Sie werfen unter anderem Gates, Pfizer-Chef Bourla und dem niederländischen Staat vor, sie hätten gewusst, dass diese Präparate weder sicher noch wirksam sind.
Mit den mRNA-«Impfstoffen» von Pfizer/BioNTech befasst sich auch ein neues Buch. Darin werden die Erkenntnisse von Ärzten und Wissenschaftlern aus der Analyse interner Dokumente über die klinischen Studien der Covid-Injektion präsentiert. Es handelt sich um jene in den USA freigeklagten Papiere, die die Arzneimittelbehörde (Food and Drug Administration, FDA) 75 Jahre unter Verschluss halten wollte.
Ebenfalls Wissenschaftler und Ärzte, aber auch andere Experten organisieren als Verbundnetzwerk Corona-Solution kostenfreie Online-Konferenzen. Ihr Ziel ist es, «wissenschaftlich, demokratisch und friedlich» über Impfstoffe und Behandlungsprotokolle gegen SARS-CoV-2 aufzuklären und die Diskriminierung von Ungeimpften zu stoppen. Gestern fand eine weitere Konferenz statt. Ihr Thema: «Corona und modRNA: Von Toten, Lebenden und Physik lernen».
Aufgrund des Digital Services Acts (DSA) der Europäischen Union sei das Risiko groß, dass ihre Arbeit als «Fake-News» bezeichnet würde, so das Netzwerk. Staatlich unerwünschte wissenschaftliche Aufklärung müsse sich passende Kanäle zur Veröffentlichung suchen. Ihre Live-Streams seien deshalb zum Beispiel nicht auf YouTube zu finden.
Der vielfältige Einsatz für Aufklärung und Aufarbeitung wird sich nicht stummschalten lassen. Nicht einmal der Zensurmeister der EU, Deutschland, wird so etwas erreichen. Die frisch aktivierten «Trusted Flagger» dürften allerdings künftige Siege beim «Denunzianten-Wettbewerb» im Kontext des DSA zusätzlich absichern.
Wo sind die Grenzen der Meinungsfreiheit? Sicher gibt es sie. Aber die ideologische Gleichstellung von illegalen mit unerwünschten Äußerungen verfolgt offensichtlich eher das Ziel, ein derart elementares demokratisches Grundrecht möglichst weitgehend auszuhebeln. Vorwürfe wie «Hassrede», «Delegitimierung des Staates» oder «Volksverhetzung» werden heute inflationär verwendet, um Systemkritik zu unterbinden. Gegen solche Bestrebungen gilt es, sich zu wehren.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2024-10-23 20:26:10
@ c631e267:c2b78d3e
2024-10-23 20:26:10Herzlichen Glückwunsch zum dritten Geburtstag, liebe Denk Bar! Wieso zum dritten? Das war doch 2022 und jetzt sind wir im Jahr 2024, oder? Ja, das ist schon richtig, aber bei Geburtstagen erinnere ich mich immer auch an meinen Vater, und der behauptete oft, der erste sei ja schließlich der Tag der Geburt selber und den müsse man natürlich mitzählen. Wo er recht hat, hat er nunmal recht. Konsequenterweise wird also heute dieser Blog an seinem dritten Geburtstag zwei Jahre alt.
Das ist ein Grund zum Feiern, wie ich finde. Einerseits ganz einfach, weil es dafür gar nicht genug Gründe geben kann. «Das Leben sind zwei Tage», lautet ein gängiger Ausdruck hier in Andalusien. In der Tat könnte es so sein, auch wenn wir uns im Alltag oft genug von der Routine vereinnahmen lassen.
Seit dem Start der Denk Bar vor zwei Jahren ist unglaublich viel passiert. Ebenso wie die zweieinhalb Jahre davor, und all jenes war letztlich auch der Auslöser dafür, dass ich begann, öffentlich zu schreiben. Damals notierte ich:
«Seit einigen Jahren erscheint unser öffentliches Umfeld immer fragwürdiger, widersprüchlicher und manchmal schier unglaublich - jede Menge Anlass für eigene Recherchen und Gedanken, ganz einfach mit einer Portion gesundem Menschenverstand.»
Wir erleben den sogenannten «großen Umbruch», einen globalen Coup, den skrupellose Egoisten clever eingefädelt haben und seit ein paar Jahren knallhart – aber nett verpackt – durchziehen, um buchstäblich alles nach ihrem Gusto umzukrempeln. Die Gelegenheit ist ja angeblich günstig und muss genutzt werden.
Nie hätte ich mir träumen lassen, dass ich so etwas jemals miterleben müsste. Die Bosheit, mit der ganz offensichtlich gegen die eigene Bevölkerung gearbeitet wird, war früher für mich unvorstellbar. Mein (Rest-) Vertrauen in alle möglichen Bereiche wie Politik, Wissenschaft, Justiz, Medien oder Kirche ist praktisch komplett zerstört. Einen «inneren Totalschaden» hatte ich mal für unsere Gesellschaften diagnostiziert.
Was mich vielleicht am meisten erschreckt, ist zum einen das Niveau der Gleichschaltung, das weltweit erreicht werden konnte, und zum anderen die praktisch totale Spaltung der Gesellschaft. Haben wir das tatsächlich mit uns machen lassen?? Unfassbar! Aber das Werkzeug «Angst» ist sehr mächtig und funktioniert bis heute.
Zum Glück passieren auch positive Dinge und neue Perspektiven öffnen sich. Für viele Menschen waren und sind die Entwicklungen der letzten Jahre ein Augenöffner. Sie sehen «Querdenken» als das, was es ist: eine Tugend.
Auch die immer ernsteren Zensurbemühungen sind letztlich nur ein Zeichen der Schwäche, wo Argumente fehlen. Sie werden nicht verhindern, dass wir unsere Meinung äußern, unbequeme Fragen stellen und dass die Wahrheit peu à peu ans Licht kommt. Es gibt immer Mittel und Wege, auch für uns.
Danke, dass du diesen Weg mit mir weitergehst!
-
 @ f9c0ea75:44e849f4
2025-01-08 18:15:47
@ f9c0ea75:44e849f4
2025-01-08 18:15:47Nos anos 80, o Brasil testemunhou um dos momentos mais patéticos da sua história econômica: os "Fiscais do Sarney". Movidos por um decreto inútil, cidadãos foram incentivados a denunciar comerciantes que não seguissem o tabelamento de preços imposto pelo governo. O resultado? Um fracasso absoluto, prateleiras vazias, inflação descontrolada e a certeza de que a mentalidade fiscalizadora não gera valor para ninguém – apenas sufoca a economia e reforça o atraso.
Agora, décadas depois, vemos a mesma mentalidade derrotada ressurgir na Receita Federal com a fiscalização automática sobre transações acima de R$ 5.000 via PIX. Em vez de buscar um ambiente mais produtivo e inovador, o governo se empenha em monitorar cada centavo que circula, tratando qualquer movimentação um pouco maior como suspeita. Quem ganha com isso? Certamente não é o cidadão honesto, nem a economia real.
E quem são os protagonistas dessa história? Os novos fiscais da Receita Federal, que assumem um papel tão irrelevante quanto o dos fiscais de Sarney. Um trabalho de baixo valor agregado, que não contribui para a criação de riqueza ou inovação. São apenas burocratas modernos, presos na mentalidade de que controlar e punir é mais importante do que fomentar o crescimento e a liberdade financeira.
A história já provou que o fiscalismo estatal é um modelo falido, seja tabelando preços ou perseguindo transações financeiras. Enquanto alguns criam, inovam e geram valor, outros se ocupam apenas de vigiar e tributar. O tempo sempre mostrou quem estava certo.
Nos anos 80, o Brasil testemunhou um dos momentos mais patéticos da sua história econômica: os "Fiscais do Sarney". Movidos por um decreto inútil, cidadãos foram incentivados a denunciar comerciantes que não seguissem o tabelamento de preços imposto pelo governo. O resultado? Um fracasso absoluto, prateleiras vazias, inflação descontrolada e a certeza de que a mentalidade fiscalizadora não gera valor para ninguém – apenas sufoca a economia e reforça o atraso.
Agora, décadas depois, vemos a mesma mentalidade derrotada ressurgir na Receita Federal com a fiscalização automática sobre transações acima de R$ 5.000 via PIX. Em vez de buscar um ambiente mais produtivo e inovador, o governo se empenha em monitorar cada centavo que circula, tratando qualquer movimentação um pouco maior como suspeita. Quem ganha com isso? Certamente não é o cidadão honesto, nem a economia real.
E quem são os protagonistas dessa história? Os novos fiscais da Receita Federal, que assumem um papel tão irrelevante quanto o dos fiscais de Sarney. Um trabalho de baixo valor agregado, que não contribui para a criação de riqueza ou inovação. São apenas burocratas modernos, presos na mentalidade de que controlar e punir é mais importante do que fomentar o crescimento e a liberdade financeira.
A história já provou que o fiscalismo estatal é um modelo falido, seja tabelando preços ou perseguindo transações financeiras. Enquanto alguns criam, inovam e geram valor, outros se ocupam apenas de vigiar e tributar. O tempo sempre mostrou quem estava certo.

-
 @ bd32f268:22b33966
2025-01-02 19:30:46
@ bd32f268:22b33966
2025-01-02 19:30:46Texto publicado por Foundation Father @FoundationDads e traduzido para português.
Assumir responsabilidades numa época efeminada como a nossa é um superpoder.
Algumas pessoas não sabem o que significa "assumir responsabilidades", no entanto, porque nunca tiveram um pai ou outra pessoa que as ama-se o suficiente para lhes ensinar.
Então, aqui está como assumir responsabilidades.
Lembra-te que não és uma pessoa desamparada e incompetente.
As coisas não te acontecem simplesmente enquanto olhas fixamente com a boca aberta, usando todo o teu poder cerebral para te lembrares de como respirar.
Tu tens poder de ação.
Mantém estas perguntas em mente:
"Que papel desempenhei eu nesta situação ou como ajudei a formar o sistema em que estou inserido?"
"O que posso fazer agora mesmo para começar a corrigi-lo, por mais pequeno que seja?"
Aqui estão alguns exemplos de como aplicar estas perguntas.
 José Malhoa - Remédio
José Malhoa - RemédioSaúde
Estás com excesso de peso e cansado o tempo todo? Deprimido?
Começa a caminhar 30 minutos por dia. De preferência ao ar livre.
Pára de comer snacks.
Marca uma consulta com um médico para fazer análises ao sangue.
Todas estas coisas estão ao teu alcance.
Finanças
Estás a afogar-te em dívidas de cartão de crédito? Assumir responsabilidades significa reduzir drasticamente o teu consumo e iniciar um programa radical de pagamento do máximo de dívida que conseguires.
Obtém uma aplicação de orçamento e começa a planear.
Sentes-te preso no teu emprego sem futuro? Sentes que não ganhas o suficiente? Vai a entrevistas para vagas de emprego e descobre o teu verdadeiro valor no mercado.
Reserva 1 hora todas as noites para melhorares. A menos que já estejas a trabalhar em dois empregos, toda a gente tem pelo menos 1 hora todas as noites.
Arredores imediatos
Se vês algo que precisa de ser feito, simplesmente faz. Não te queixes disso. Não resmungues baixinho. Não desejes que alguém tratasse disso. Simplesmente faz e não peças permissão.
Guarda o carrinho de compras. Lava a caneca de café no lava-loiça. Arranca as ervas daninhas. Repara a parede. Se o quintal do teu vizinho estiver cheio de ervas, vai lá e corta a relva tu mesmo. Limpa a água do lava-loiça. Arruma a bancada. Leva o lixo para fora. Leva bom café para o escritório.
Os teus filhos
Muitos pais queixam-se do comportamento dos seus filhos como se não tivessem qualquer influência sobre o assunto. Mas os teus filhos farão o que tu os ensinaste a fazer.
"Fizemos o melhor que pudemos."
Não, não fizeram, e assumir responsabilidades significa admitir que foste permissivo e preguiçoso ou que querias sentir-te justo por não bater.
Que pequena coisa podes fazer agora mesmo para começar? Escolhe um único comportamento que queres que eles parem, senta-os e explica as consequências do comportamento. Pede desculpa por teres deixado andar durante tanto tempo.
Quando eles apresentarem o comportamento, aplica as consequências. Aconteça o que acontecer.
Os teus relacionamentos
Não tens amigos ou o teu grupo de amigos atual é uma má influência? Podes fazer novos amigos. Assumir responsabilidades significa admitir que a tua solidão é em grande parte auto-infligida.
O que podes fazer?
Começa a jogar ténis ou futebol. Existem ligas em todo o lado. Encontra uma boa igreja local e encontra maneiras de te envolver. Existem encontros para todo o tipo de atividade. Participa num que se alinhe com as tuas preferências. Quando estiveres em público, sorri mais e puxa conversa.
Depois de conheceres algumas pessoas, estabelece uma cadência regular. Agenda almoços semanais ou mensais e alterna entre algumas pessoas. Ou talvez café de manhã.
Não acontecerá da noite para o dia, mas dando pequenos passos consistentemente durante alguns meses e vais perceber que tens uma vida social.
Os teus erros
Se erraste, não te retires e escondas nem arranjes desculpas. Pede desculpa à pessoa que prejudicaste, diz-lhe porquê e oferece-te para compensar. Aceita as consequências com humildade.
Vais descobrir que nada te conquista mais respeito do que assumir os teus erros. Esta é a principal. Se aprenderes a fazer isto bem, cobrirá uma infinidade de pecados porque cria hábito. Mesmo que tenhas apenas 1% de culpa na situação, assumir a responsabilidade e pedir desculpa pelo teu 1% está a construir um certo grupo de músculos.
"Mas ele devia ter..." Pára com isso. Confiaste demasiado? Presumiste demasiado sem comunicar? Assume a responsabilidade por isso.
Estes exemplos podiam continuar para sempre, então vou parar e terminar com este princípio:
A tua resposta importa mais do que as tuas circunstâncias.
Existem vítimas reais, algumas de tragédias horríveis. Mas mesmo que não te tenhas atirado para areias movediças, ainda podes assumir a responsabilidade por como reages e pelo que escolhes fazer a seguir.
Às vezes, é agarrar numa corda de um transeunte e dizer: "Obrigado."
Não te afogues nas areias movediças até que alguém te dê uma palmadinha nas costas por quão difícil é para ti, e não continues a apontar para o teu tempo nas areias movediças para desculpares os teus fracassos.
Podes não ter escolhido uma batalha específica. Ainda podes assumir a responsabilidade por quão bem lutas a batalha. Num certo sentido, ninguém escolhe a principal batalha que enfrenta. Ninguém escolheu nascer. Ninguém escolheu a sua família. Ninguém escolheu as suas circunstâncias.
O mundo nunca será perfeito. Tens de assumir a responsabilidade pela tua parte dele de qualquer maneira. Pode ser difícil. Pode ser doloroso. Não te foi prometida uma vida fácil e sem dor.
Depois de começares a assumir responsabilidades, qual é o próximo passo?
Altura de assumir mais responsabilidades.
Por exemplo, se não tens problemas em fazer amigos e tens essa parte da tua vida resolvida, assume a responsabilidade por outra pessoa. Encontra um dos rapazes solitários na tua igreja que precisa de um amigo e adiciona-o à tua rotação de almoços.
A recompensa por assumir responsabilidades é subir de nível e, como consequência, as coisas devem tornar-se mais desafiantes.
Mas agora estás mais bem preparado para isso. Repete até morrer e, esperançosamente, a tua causa de morte será por viver e não por te queixares de não viver.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Replacing the web with something saner
This is a simplification, but let's say that basically there are just 3 kinds of websites:
- Websites with content: text, images, videos;
- Websites that run full apps that do a ton of interactive stuff;
- Websites with some interactive content that uses JavaScript, or "mini-apps";
In a saner world we would have 3 different ways of serving and using these. 1 would be "the web" (and it was for a while, although I'm not claiming here that the past is always better and wanting to get back to the glorious old days).
1 would stay as "the web", just static sites, styled with CSS, no JavaScript whatsoever, but designers can still thrive and make they look pretty. Or it could also be something like Gemini. Maybe the two protocols could coexist.
2 would be downloadable native apps, much easier to write and maintain for developers (considering that multi-platform and cross-compilation is easy today and getting easier), faster, more polished experience for users, more powerful, integrates better with the computer.
(Remember that since no one would be striving to make the same app run both on browsers and natively no one would have any need for Electron or other inefficient bloated solutions, just pure native UI, like the Telegram app, have you seen that? It's fast.)
But 2 is mostly for apps that people use every day, something like Google Docs, email (although email is also broken technology), Netflix, Twitter, Trello and so on, and all those hundreds of niche SaaS that people pay monthly fees to use, each tailored to a different industry (although most of functions they all implement are the same everywhere). What do we do with dynamic open websites like StackOverflow, for example, where one needs to not only read, but also search and interact in multiple ways? What about that website that asks you a bunch of questions and then discovers the name of the person you're thinking about? What about that mini-app that calculates the hash of your provided content or shrinks your video, or that one that hosts your image without asking any questions?
All these and tons of others would fall into category 3, that of instantly loaded apps that you don't have to install, and yet they run in a sandbox.
The key for making category 3 worth investing time into is coming up with some solid grounds, simple enough that anyone can implement in multiple different ways, but not giving the app too much choices.
Telegram or Discord bots are super powerful platforms that can accomodate most kinds of app in them. They can't beat a native app specifically made with one purpose, but they allow anyone to provide instantly usable apps with very low overhead, and since the experience is so simple, intuitive and fast, users tend to like it and sometimes even pay for their services. There could exist a protocol that brings apps like that to the open world of (I won't say "web") domains and the websockets protocol -- with multiple different clients, each making their own decisions on how to display the content sent by the servers that are powering these apps.
Another idea is that of Alan Kay: to design a nice little OS/virtual machine that can load these apps and run them. Kinda like browsers are today, but providing a more well-thought, native-like experience and framework, but still sandboxed. And I add: abstracting away details about design, content disposition and so on.
These 3 kinds of programs could coexist peacefully. 2 are just standalone programs, they can do anything and each will be its own thing. 1 and 3, however, are still similar to browsers of today in the sense that you need clients to interact with servers and show to the user what they are asking. But by simplifying everything and separating the scopes properly these clients would be easy to write, efficient, small, the environment would be open and the internet would be saved.
See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: General confusion
Most IPFS open-source projects, libraries and apps (excluding Ethereum stuff) are things that rely heavily on dynamic data and temporary links. The most common projects you'll see when following the IPFS communities are chat rooms and similar things. I've seen dozens of these chat-rooms. There's also a famous IPFS-powered database. How can you do these things with content-addressing is a mistery. Of course they probably rely on IPNS or other external address system.
There's also a bunch of "file-sharing" on IPFS. The kind of thing people use for temporary making a file available for a third-party. There's image sharing on IPFS, pastebins on IPFS and so on. People don't seem to share the preoccupation with broken links here.
-
 @ eac63075:b4988b48
2024-10-21 08:11:11
@ eac63075:b4988b48
2024-10-21 08:11:11Imagine sending a private message to a friend, only to learn that authorities could be scanning its contents without your knowledge. This isn't a scene from a dystopian novel but a potential reality under the European Union's proposed "Chat Control" measures. Aimed at combating serious crimes like child exploitation and terrorism, these proposals could significantly impact the privacy of everyday internet users. As encrypted messaging services become the norm for personal and professional communication, understanding Chat Control is essential. This article delves into what Chat Control entails, why it's being considered, and how it could affect your right to private communication.
https://www.fountain.fm/episode/coOFsst7r7mO1EP1kSzV
https://open.spotify.com/episode/0IZ6kMExfxFm4FHg5DAWT8?si=e139033865e045de
Sections:
- Introduction
- What Is Chat Control?
- Why Is the EU Pushing for Chat Control?
- The Privacy Concerns and Risks
- The Technical Debate: Encryption and Backdoors
- Global Reactions and the Debate in Europe
- Possible Consequences for Messaging Services
- What Happens Next? The Future of Chat Control
- Conclusion
What Is Chat Control?
"Chat Control" refers to a set of proposed measures by the European Union aimed at monitoring and scanning private communications on messaging platforms. The primary goal is to detect and prevent the spread of illegal content, such as child sexual abuse material (CSAM) and to combat terrorism. While the intention is to enhance security and protect vulnerable populations, these proposals have raised significant privacy concerns.
At its core, Chat Control would require messaging services to implement automated scanning technologies that can analyze the content of messages—even those that are end-to-end encrypted. This means that the private messages you send to friends, family, or colleagues could be subject to inspection by algorithms designed to detect prohibited content.
Origins of the Proposal
The initiative for Chat Control emerged from the EU's desire to strengthen its digital security infrastructure. High-profile cases of online abuse and the use of encrypted platforms by criminal organizations have prompted lawmakers to consider more invasive surveillance tactics. The European Commission has been exploring legislation that would make it mandatory for service providers to monitor communications on their platforms.
How Messaging Services Work
Most modern messaging apps, like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others), use end-to-end encryption (E2EE). This encryption ensures that only the sender and the recipient can read the messages being exchanged. Not even the service providers can access the content. This level of security is crucial for maintaining privacy in digital communications, protecting users from hackers, identity thieves, and other malicious actors.

Key Elements of Chat Control
- Automated Content Scanning: Service providers would use algorithms to scan messages for illegal content.
- Circumvention of Encryption: To scan encrypted messages, providers might need to alter their encryption methods, potentially weakening security.
- Mandatory Reporting: If illegal content is detected, providers would be required to report it to authorities.
- Broad Applicability: The measures could apply to all messaging services operating within the EU, affecting both European companies and international platforms.
Why It Matters
Understanding Chat Control is essential because it represents a significant shift in how digital privacy is handled. While combating illegal activities online is crucial, the methods proposed could set a precedent for mass surveillance and the erosion of privacy rights. Everyday users who rely on encrypted messaging for personal and professional communication might find their conversations are no longer as private as they once thought.
Why Is the EU Pushing for Chat Control?
The European Union's push for Chat Control stems from a pressing concern to protect its citizens, particularly children, from online exploitation and criminal activities. With the digital landscape becoming increasingly integral to daily life, the EU aims to strengthen its ability to combat serious crimes facilitated through online platforms.
Protecting Children and Preventing Crime
One of the primary motivations behind Chat Control is the prevention of child sexual abuse material (CSAM) circulating on the internet. Law enforcement agencies have reported a significant increase in the sharing of illegal content through private messaging services. By implementing Chat Control, the EU believes it can more effectively identify and stop perpetrators, rescue victims, and deter future crimes.
Terrorism is another critical concern. Encrypted messaging apps can be used by terrorist groups to plan and coordinate attacks without detection. The EU argues that accessing these communications could be vital in preventing such threats and ensuring public safety.
Legal Context and Legislative Drivers
The push for Chat Control is rooted in several legislative initiatives:
-
ePrivacy Directive: This directive regulates the processing of personal data and the protection of privacy in electronic communications. The EU is considering amendments that would allow for the scanning of private messages under specific circumstances.
-
Temporary Derogation: In 2021, the EU adopted a temporary regulation permitting voluntary detection of CSAM by communication services. The current proposals aim to make such measures mandatory and more comprehensive.
-
Regulation Proposals: The European Commission has proposed regulations that would require service providers to detect, report, and remove illegal content proactively. This would include the use of technologies to scan private communications.
Balancing Security and Privacy
EU officials argue that the proposed measures are a necessary response to evolving digital threats. They emphasize the importance of staying ahead of criminals who exploit technology to harm others. By implementing Chat Control, they believe law enforcement can be more effective without entirely dismantling privacy protections.
However, the EU also acknowledges the need to balance security with fundamental rights. The proposals include provisions intended to limit the scope of surveillance, such as:
-
Targeted Scanning: Focusing on specific threats rather than broad, indiscriminate monitoring.
-
Judicial Oversight: Requiring court orders or oversight for accessing private communications.
-
Data Protection Safeguards: Implementing measures to ensure that data collected is handled securely and deleted when no longer needed.

The Urgency Behind the Push
High-profile cases of online abuse and terrorism have heightened the sense of urgency among EU policymakers. Reports of increasing online grooming and the widespread distribution of illegal content have prompted calls for immediate action. The EU posits that without measures like Chat Control, these problems will continue to escalate unchecked.
Criticism and Controversy
Despite the stated intentions, the push for Chat Control has been met with significant criticism. Opponents argue that the measures could be ineffective against savvy criminals who can find alternative ways to communicate. There is also concern that such surveillance could be misused or extended beyond its original purpose.
The Privacy Concerns and Risks
While the intentions behind Chat Control focus on enhancing security and protecting vulnerable groups, the proposed measures raise significant privacy concerns. Critics argue that implementing such surveillance could infringe on fundamental rights and set a dangerous precedent for mass monitoring of private communications.
Infringement on Privacy Rights
At the heart of the debate is the right to privacy. By scanning private messages, even with automated tools, the confidentiality of personal communications is compromised. Users may no longer feel secure sharing sensitive information, fearing that their messages could be intercepted or misinterpreted by algorithms.
Erosion of End-to-End Encryption
End-to-end encryption (E2EE) is a cornerstone of digital security, ensuring that only the sender and recipient can read the messages exchanged. Chat Control could necessitate the introduction of "backdoors" or weaken encryption protocols, making it easier for unauthorized parties to access private data. This not only affects individual privacy but also exposes communications to potential cyber threats.
Concerns from Privacy Advocates
Organizations like Signal and Tutanota, which offer encrypted messaging services, have voiced strong opposition to Chat Control. They warn that undermining encryption could have far-reaching consequences:
- Security Risks: Weakening encryption makes systems more vulnerable to hacking, espionage, and cybercrime.
- Global Implications: Changes in EU regulations could influence policies worldwide, leading to a broader erosion of digital privacy.
- Ineffectiveness Against Crime: Determined criminals might resort to other, less detectable means of communication, rendering the measures ineffective while still compromising the privacy of law-abiding citizens.

Potential for Government Overreach
There is a fear that Chat Control could lead to increased surveillance beyond its original scope. Once the infrastructure for scanning private messages is in place, it could be repurposed or expanded to monitor other types of content, stifling free expression and dissent.
Real-World Implications for Users
- False Positives: Automated scanning technologies are not infallible and could mistakenly flag innocent content, leading to unwarranted scrutiny or legal consequences for users.
- Chilling Effect: Knowing that messages could be monitored might discourage people from expressing themselves freely, impacting personal relationships and societal discourse.
- Data Misuse: Collected data could be vulnerable to leaks or misuse, compromising personal and sensitive information.
Legal and Ethical Concerns
Privacy advocates also highlight potential conflicts with existing laws and ethical standards:
- Violation of Fundamental Rights: The European Convention on Human Rights and other international agreements protect the right to privacy and freedom of expression.
- Questionable Effectiveness: The ethical justification for such invasive measures is challenged if they do not significantly improve safety or if they disproportionately impact innocent users.
Opposition from Member States and Organizations
Countries like Germany and organizations such as the European Digital Rights (EDRi) have expressed opposition to Chat Control. They emphasize the need to protect digital privacy and caution against hasty legislation that could have unintended consequences.
The Technical Debate: Encryption and Backdoors
The discussion around Chat Control inevitably leads to a complex technical debate centered on encryption and the potential introduction of backdoors into secure communication systems. Understanding these concepts is crucial to grasping the full implications of the proposed measures.
What Is End-to-End Encryption (E2EE)?
End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system to another. In simpler terms, only the sender and the recipient can read the messages. Even the service providers operating the messaging platforms cannot decrypt the content.
- Security Assurance: E2EE ensures that sensitive information—be it personal messages, financial details, or confidential business communications—remains private.
- Widespread Use: Popular messaging apps like Signal, Session, SimpleX, Veilid, Protonmail and Tutanota (among others) rely on E2EE to protect user data.
How Chat Control Affects Encryption
Implementing Chat Control as proposed would require messaging services to scan the content of messages for illegal material. To do this on encrypted platforms, providers might have to:
- Introduce Backdoors: Create a means for third parties (including the service provider or authorities) to access encrypted messages.
- Client-Side Scanning: Install software on users' devices that scans messages before they are encrypted and sent, effectively bypassing E2EE.
The Risks of Weakening Encryption
1. Compromised Security for All Users
Introducing backdoors or client-side scanning tools can create vulnerabilities:
- Exploitable Gaps: If a backdoor exists, malicious actors might find and exploit it, leading to data breaches.
- Universal Impact: Weakening encryption doesn't just affect targeted individuals; it potentially exposes all users to increased risk.
2. Undermining Trust in Digital Services
- User Confidence: Knowing that private communications could be accessed might deter people from using digital services or push them toward unregulated platforms.
- Business Implications: Companies relying on secure communications might face increased risks, affecting economic activities.
3. Ineffectiveness Against Skilled Adversaries
- Alternative Methods: Criminals might shift to other encrypted channels or develop new ways to avoid detection.
- False Sense of Security: Weakening encryption could give the impression of increased safety while adversaries adapt and continue their activities undetected.
Signal’s Response and Stance
Signal, a leading encrypted messaging service, has been vocal in its opposition to the EU's proposals:
- Refusal to Weaken Encryption: Signal's CEO Meredith Whittaker has stated that the company would rather cease operations in the EU than compromise its encryption standards.
- Advocacy for Privacy: Signal emphasizes that strong encryption is essential for protecting human rights and freedoms in the digital age.
Understanding Backdoors
A "backdoor" in encryption is an intentional weakness inserted into a system to allow authorized access to encrypted data. While intended for legitimate use by authorities, backdoors pose several problems:
- Security Vulnerabilities: They can be discovered and exploited by unauthorized parties, including hackers and foreign governments.
- Ethical Concerns: The existence of backdoors raises questions about consent and the extent to which governments should be able to access private communications.

The Slippery Slope Argument
Privacy advocates warn that introducing backdoors or mandatory scanning sets a precedent:
- Expanded Surveillance: Once in place, these measures could be extended to monitor other types of content beyond the original scope.
- Erosion of Rights: Gradual acceptance of surveillance can lead to a significant reduction in personal freedoms over time.
Potential Technological Alternatives
Some suggest that it's possible to fight illegal content without undermining encryption:
- Metadata Analysis: Focusing on patterns of communication rather than content.
- Enhanced Reporting Mechanisms: Encouraging users to report illegal content voluntarily.
- Investing in Law Enforcement Capabilities: Strengthening traditional investigative methods without compromising digital security.
The technical community largely agrees that weakening encryption is not the solution:
- Consensus on Security: Strong encryption is essential for the safety and privacy of all internet users.
- Call for Dialogue: Technologists and privacy experts advocate for collaborative approaches that address security concerns without sacrificing fundamental rights.
Global Reactions and the Debate in Europe
The proposal for Chat Control has ignited a heated debate across Europe and beyond, with various stakeholders weighing in on the potential implications for privacy, security, and fundamental rights. The reactions are mixed, reflecting differing national perspectives, political priorities, and societal values.
Support for Chat Control
Some EU member states and officials support the initiative, emphasizing the need for robust measures to combat online crime and protect citizens, especially children. They argue that:
- Enhanced Security: Mandatory scanning can help law enforcement agencies detect and prevent serious crimes.
- Responsibility of Service Providers: Companies offering communication services should play an active role in preventing their platforms from being used for illegal activities.
- Public Safety Priorities: The protection of vulnerable populations justifies the implementation of such measures, even if it means compromising some aspects of privacy.
Opposition within the EU
Several countries and organizations have voiced strong opposition to Chat Control, citing concerns over privacy rights and the potential for government overreach.
Germany
- Stance: Germany has been one of the most vocal opponents of the proposed measures.
- Reasons:
- Constitutional Concerns: The German government argues that Chat Control could violate constitutional protections of privacy and confidentiality of communications.
- Security Risks: Weakening encryption is seen as a threat to cybersecurity.
- Legal Challenges: Potential conflicts with national laws protecting personal data and communication secrecy.
Netherlands
- Recent Developments: The Dutch government decided against supporting Chat Control, emphasizing the importance of encryption for security and privacy.
- Arguments:
- Effectiveness Doubts: Skepticism about the actual effectiveness of the measures in combating crime.
- Negative Impact on Privacy: Concerns about mass surveillance and the infringement of citizens' rights.
 Table reference: Patrick Breyer - Chat Control in 23 September 2024
Table reference: Patrick Breyer - Chat Control in 23 September 2024Privacy Advocacy Groups
European Digital Rights (EDRi)
- Role: A network of civil and human rights organizations working to defend rights and freedoms in the digital environment.
- Position:
- Strong Opposition: EDRi argues that Chat Control is incompatible with fundamental rights.
- Awareness Campaigns: Engaging in public campaigns to inform citizens about the potential risks.
- Policy Engagement: Lobbying policymakers to consider alternative approaches that respect privacy.
Politicians and Activists
Patrick Breyer
- Background: A Member of the European Parliament (MEP) from Germany, representing the Pirate Party.
- Actions:
- Advocacy: Actively campaigning against Chat Control through speeches, articles, and legislative efforts.
- Public Outreach: Using social media and public events to raise awareness.
- Legal Expertise: Highlighting the legal inconsistencies and potential violations of EU law.
Global Reactions
International Organizations
- Human Rights Watch and Amnesty International: These organizations have expressed concerns about the implications for human rights, urging the EU to reconsider.
Technology Companies
- Global Tech Firms: Companies like Apple and Microsoft are monitoring the situation, as EU regulations could affect their operations and user trust.
- Industry Associations: Groups representing tech companies have issued statements highlighting the risks to innovation and competitiveness.

The Broader Debate
The controversy over Chat Control reflects a broader struggle between security interests and privacy rights in the digital age. Key points in the debate include:
- Legal Precedents: How the EU's decision might influence laws and regulations in other countries.
- Digital Sovereignty: The desire of nations to control digital spaces within their borders.
- Civil Liberties: The importance of protecting freedoms in the face of technological advancements.
Public Opinion
- Diverse Views: Surveys and public forums show a range of opinions, with some citizens prioritizing security and others valuing privacy above all.
- Awareness Levels: Many people are still unaware of the potential changes, highlighting the need for public education on the issue.
The EU is at a crossroads, facing the challenge of addressing legitimate security concerns without undermining the fundamental rights that are central to its values. The outcome of this debate will have significant implications for the future of digital privacy and the balance between security and freedom in society.
Possible Consequences for Messaging Services
The implementation of Chat Control could have significant implications for messaging services operating within the European Union. Both large platforms and smaller providers might need to adapt their technologies and policies to comply with the new regulations, potentially altering the landscape of digital communication.
Impact on Encrypted Messaging Services
Signal and Similar Platforms
-
Compliance Challenges: Encrypted messaging services like Signal rely on end-to-end encryption to secure user communications. Complying with Chat Control could force them to weaken their encryption protocols or implement client-side scanning, conflicting with their core privacy principles.
-
Operational Decisions: Some platforms may choose to limit their services in the EU or cease operations altogether rather than compromise on encryption. Signal, for instance, has indicated that it would prefer to withdraw from European markets than undermine its security features.
Potential Blocking or Limiting of Services
-
Regulatory Enforcement: Messaging services that do not comply with Chat Control regulations could face fines, legal action, or even be blocked within the EU.
-
Access Restrictions: Users in Europe might find certain services unavailable or limited in functionality if providers decide not to meet the regulatory requirements.
Effects on Smaller Providers
-
Resource Constraints: Smaller messaging services and startups may lack the resources to implement the required scanning technologies, leading to increased operational costs or forcing them out of the market.
-
Innovation Stifling: The added regulatory burden could deter new entrants, reducing competition and innovation in the messaging service sector.

User Experience and Trust
-
Privacy Concerns: Users may lose trust in messaging platforms if they know their communications are subject to scanning, leading to a decline in user engagement.
-
Migration to Unregulated Platforms: There is a risk that users might shift to less secure or unregulated services, including those operated outside the EU or on the dark web, potentially exposing them to greater risks.
Technical and Security Implications
-
Increased Vulnerabilities: Modifying encryption protocols to comply with Chat Control could introduce security flaws, making platforms more susceptible to hacking and data breaches.
-
Global Security Risks: Changes made to accommodate EU regulations might affect the global user base of these services, extending security risks beyond European borders.
Impact on Businesses and Professional Communications
-
Confidentiality Issues: Businesses that rely on secure messaging for sensitive communications may face challenges in ensuring confidentiality, affecting sectors like finance, healthcare, and legal services.
-
Compliance Complexity: Companies operating internationally will need to navigate a complex landscape of differing regulations, increasing administrative burdens.
Economic Consequences
-
Market Fragmentation: Divergent regulations could lead to a fragmented market, with different versions of services for different regions.
-
Loss of Revenue: Messaging services might experience reduced revenue due to decreased user trust and engagement or the costs associated with compliance.
Responses from Service Providers
-
Legal Challenges: Companies might pursue legal action against the regulations, citing conflicts with privacy laws and user rights.
-
Policy Advocacy: Service providers may increase lobbying efforts to influence policy decisions and promote alternatives to Chat Control.
Possible Adaptations
-
Technological Innovation: Some providers might invest in developing new technologies that can detect illegal content without compromising encryption, though the feasibility remains uncertain.
-
Transparency Measures: To maintain user trust, companies might enhance transparency about how data is handled and what measures are in place to protect privacy.
The potential consequences of Chat Control for messaging services are profound, affecting not only the companies that provide these services but also the users who rely on them daily. The balance between complying with legal requirements and maintaining user privacy and security presents a significant challenge that could reshape the digital communication landscape.
What Happens Next? The Future of Chat Control
The future of Chat Control remains uncertain as the debate continues among EU member states, policymakers, technology companies, and civil society organizations. Several factors will influence the outcome of this contentious proposal, each carrying significant implications for digital privacy, security, and the regulatory environment within the European Union.
Current Status of Legislation
-
Ongoing Negotiations: The proposed Chat Control measures are still under discussion within the European Parliament and the Council of the European Union. Amendments and revisions are being considered in response to the feedback from various stakeholders.
-
Timeline: While there is no fixed date for the final decision, the EU aims to reach a consensus to implement effective measures against online crime without undue delay.
Key Influencing Factors
1. Legal Challenges and Compliance with EU Law
-
Fundamental Rights Assessment: The proposals must be evaluated against the Charter of Fundamental Rights of the European Union, ensuring that any measures comply with rights to privacy, data protection, and freedom of expression.
-
Court Scrutiny: Potential legal challenges could arise, leading to scrutiny by the European Court of Justice (ECJ), which may impact the feasibility and legality of Chat Control.
2. Technological Feasibility
-
Development of Privacy-Preserving Technologies: Research into methods that can detect illegal content without compromising encryption is ongoing. Advances in this area could provide alternative solutions acceptable to both privacy advocates and security agencies.
-
Implementation Challenges: The practical aspects of deploying scanning technologies across various platforms and services remain complex, and technical hurdles could delay or alter the proposed measures.
3. Political Dynamics
-
Member State Positions: The differing stances of EU countries, such as Germany's opposition, play a significant role in shaping the final outcome. Consensus among member states is crucial for adopting EU-wide regulations.
-
Public Opinion and Advocacy: Growing awareness and activism around digital privacy can influence policymakers. Public campaigns and lobbying efforts may sway decisions in favor of stronger privacy protections.
4. Industry Responses
-
Negotiations with Service Providers: Ongoing dialogues between EU authorities and technology companies may lead to compromises or collaborative efforts to address concerns without fully implementing Chat Control as initially proposed.
-
Potential for Self-Regulation: Messaging services might propose self-regulatory measures to combat illegal content, aiming to demonstrate effectiveness without the need for mandatory scanning.
Possible Scenarios
Optimistic Outcome:
- Balanced Regulation: A revised proposal emerges that effectively addresses security concerns while upholding strong encryption and privacy rights, possibly through innovative technologies or targeted measures with robust oversight.
Pessimistic Outcome:
- Adoption of Strict Measures: Chat Control is implemented as initially proposed, leading to weakened encryption, reduced privacy, and potential withdrawal of services like Signal from the EU market.
Middle Ground:
- Incremental Implementation: Partial measures are adopted, focusing on voluntary cooperation with service providers and emphasizing transparency and user consent, with ongoing evaluations to assess effectiveness and impact.
How to Stay Informed and Protect Your Privacy
-
Follow Reputable Sources: Keep up with news from reliable outlets, official EU communications, and statements from privacy organizations to stay informed about developments.
-
Engage in the Dialogue: Participate in public consultations, sign petitions, or contact representatives to express your views on Chat Control and digital privacy.
-
Utilize Secure Practices: Regardless of legislative outcomes, adopting good digital hygiene—such as using strong passwords and being cautious with personal information—can enhance your online security.

The Global Perspective
-
International Implications: The EU's decision may influence global policies on encryption and surveillance, setting precedents that other countries might follow or react against.
-
Collaboration Opportunities: International cooperation on developing solutions that protect both security and privacy could emerge, fostering a more unified approach to addressing online threats.
Looking Ahead
The future of Chat Control is a critical issue that underscores the challenges of governing in the digital age. Balancing the need for security with the protection of fundamental rights is a complex task that requires careful consideration, open dialogue, and collaboration among all stakeholders.
As the situation evolves, staying informed and engaged is essential. The decisions made in the coming months will shape the digital landscape for years to come, affecting how we communicate, conduct business, and exercise our rights in an increasingly connected world.
Conclusion
The debate over Chat Control highlights a fundamental challenge in our increasingly digital world: how to protect society from genuine threats without eroding the very rights and freedoms that define it. While the intention to safeguard children and prevent crime is undeniably important, the means of achieving this through intrusive surveillance measures raise critical concerns.
Privacy is not just a personal preference but a cornerstone of democratic societies. End-to-end encryption has become an essential tool for ensuring that our personal conversations, professional communications, and sensitive data remain secure from unwanted intrusion. Weakening these protections could expose individuals and organizations to risks that far outweigh the proposed benefits.
The potential consequences of implementing Chat Control are far-reaching:
- Erosion of Trust: Users may lose confidence in digital platforms, impacting how we communicate and conduct business online.
- Security Vulnerabilities: Introducing backdoors or weakening encryption can make systems more susceptible to cyberattacks.
- Stifling Innovation: Regulatory burdens may hinder technological advancement and competitiveness in the tech industry.
- Global Implications: The EU's decisions could set precedents that influence digital policies worldwide, for better or worse.
As citizens, it's crucial to stay informed about these developments. Engage in conversations, reach out to your representatives, and advocate for solutions that respect both security needs and fundamental rights. Technology and policy can evolve together to address challenges without compromising core values.
The future of Chat Control is not yet decided, and public input can make a significant difference. By promoting open dialogue, supporting privacy-preserving innovations, and emphasizing the importance of human rights in legislation, we can work towards a digital landscape that is both safe and free.
In a world where digital communication is integral to daily life, striking the right balance between security and privacy is more important than ever. The choices made today will shape the digital environment for generations to come, determining not just how we communicate, but how we live and interact in an interconnected world.

Thank you for reading this article. We hope it has provided you with a clear understanding of Chat Control and its potential impact on your privacy and digital rights. Stay informed, stay engaged, and let's work together towards a secure and open digital future.
Read more:
- https://www.patrick-breyer.de/en/posts/chat-control/
- https://www.patrick-breyer.de/en/new-eu-push-for-chat-control-will-messenger-services-be-blocked-in-europe/
- https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
- https://signal.org/blog/pdfs/ndss-keynote.pdf
- https://tuta.com/blog/germany-stop-chat-control
- https://cointelegraph.com/news/signal-president-slams-revised-eu-encryption-proposal
- https://mullvad.net/en/why-privacy-matters
-
 @ a95c6243:d345522c
2024-10-19 08:58:08
@ a95c6243:d345522c
2024-10-19 08:58:08Ein Lämmchen löschte an einem Bache seinen Durst. Fern von ihm, aber näher der Quelle, tat ein Wolf das gleiche. Kaum erblickte er das Lämmchen, so schrie er:
"Warum trübst du mir das Wasser, das ich trinken will?"
"Wie wäre das möglich", erwiderte schüchtern das Lämmchen, "ich stehe hier unten und du so weit oben; das Wasser fließt ja von dir zu mir; glaube mir, es kam mir nie in den Sinn, dir etwas Böses zu tun!"
"Ei, sieh doch! Du machst es gerade, wie dein Vater vor sechs Monaten; ich erinnere mich noch sehr wohl, daß auch du dabei warst, aber glücklich entkamst, als ich ihm für sein Schmähen das Fell abzog!"
"Ach, Herr!" flehte das zitternde Lämmchen, "ich bin ja erst vier Wochen alt und kannte meinen Vater gar nicht, so lange ist er schon tot; wie soll ich denn für ihn büßen."
"Du Unverschämter!" so endigt der Wolf mit erheuchelter Wut, indem er die Zähne fletschte. "Tot oder nicht tot, weiß ich doch, daß euer ganzes Geschlecht mich hasset, und dafür muß ich mich rächen."
Ohne weitere Umstände zu machen, zerriß er das Lämmchen und verschlang es.
Das Gewissen regt sich selbst bei dem größten Bösewichte; er sucht doch nach Vorwand, um dasselbe damit bei Begehung seiner Schlechtigkeiten zu beschwichtigen.
Quelle: https://eden.one/fabeln-aesop-das-lamm-und-der-wolf
-
 @ a4a6b584:1e05b95b
2025-01-02 18:13:31
@ a4a6b584:1e05b95b
2025-01-02 18:13:31The Four-Layer Framework
Layer 1: Zoom Out

Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what."
Example: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems.
- Tip: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage.
Once you have the big picture in mind, it’s time to start breaking it down.
Layer 2: Categorize and Connect

Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas.
Example: Studying biology? Group concepts into categories like cells, genetics, and ecosystems.
- Tip: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track.
With your categories in place, you’re ready to dive into the details that bring them to life.
Layer 3: Master the Details

Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable.
Example: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language.
- Tip: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding.
Now that you’ve mastered the essentials, you can expand your knowledge to include extra material.
Layer 4: Expand Your Horizons

Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams.
Example: Learn about rare programming quirks or historical trivia about a language’s development.
- Tip: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time.
Pro Tips for Better Learning
1. Use Active Recall and Spaced Repetition
Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information.
2. Map It Out
Create visual aids like diagrams or concept maps to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2.
3. Teach What You Learn
Explain the subject to someone else as if they’re hearing it for the first time. Teaching exposes any gaps in your understanding and helps reinforce the material.
4. Engage with LLMs and Discuss Concepts
Take advantage of tools like ChatGPT or similar large language models to explore your topic in greater depth. Use these tools to:
- Ask specific questions to clarify confusing points.
- Engage in discussions to simulate real-world applications of the subject.
- Generate examples or analogies that deepen your understanding.Tip: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective.
Get Started
Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
-
 @ 1cb14ab3:95d52462
2025-01-08 18:11:43
@ 1cb14ab3:95d52462
2025-01-08 18:11:43






















Previous Works in the Series:
More from Hes:
All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from these photos, please feel free to send a zap. Enjoy life on a Bitcoin standard.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Scala is such a great language
Scala is amazing. The type system has the perfect balance between flexibility and powerfulness.
matchstatements are great. You can write imperative code that looks very nice and expressive (and I haven't tried writing purely functional things yet). Everything is easy to write and cheap and neovim integration works great.But Java is not great. And the fact that Scala is a JVM language doesn't help because over the years people have written stuff that depends on Java libraries -- and these Java libraries are not as safe as the Scala libraries, they contain reflection, slowness, runtime errors, all kinds of horrors.
Scala is also very tightly associated with Akka, the actor framework, and Akka is a giant collection of anti-patterns. Untyped stuff, reflection, dependency on JVM, basically a lot of javisms. I just arrived and I don't know anything about the Scala history or ecosystem or community, but I have the impression that Akka has prevent more adoption of Scala from decent people that aren't Java programmers.
But luckily there is a solution -- or two solutions: ScalaJS is a great thing that exists. It transpiles Scala code into JavaScript and it runs on NodeJS or in a browser!
Scala Native is a much better deal, though, it compiles to LLVM and then to binary code and you can have single binaries that run directly without a JVM -- not that the single JARs are that bad though, they are great and everybody has Java so I'll take that anytime over C libraries or NPM-distributed software, but direct executables even better. Scala Native just needs a little more love and some libraries and it will be the greatest thing in a couple of years.
-
 @ 1cb14ab3:95d52462
2025-01-02 05:57:05
@ 1cb14ab3:95d52462
2025-01-02 05:57:05
No. 1 - The Less Touristy "Bund"

The Bund is certainly a must-see if you are traveling to Shanghai for the first time - and it will be at the top of every travel guide out there, for good reason - there are equally as stunning alternatives away from the crowds. If you want to enjoy the skyline from a more relaxed perspective, consider the Pudong side of the river. There are parks, basketball courts, and green spaces along the riverbank for you to chill at and take in the sights. You can also hop on a ferry or a sightseeing boat to cross the river and admire the views from the renowned Bund.
No. 2 - Walks Along Golden Street

This one is out in Gubei, a suburban area in the west of Shanghai. It may be a bit of a trek, but it is worth it if you are looking for a more relaxing and peaceful pedestrian street in the city. Golden Street, or Jinxiu Road, is a great place to walk a dog, grab an afternoon drink, or enjoy a romantic dinner with your loved one. While it may be a bit far from downtown, it makes for a great joyride on your scooter or bicycle.
No. 3 - Moganshan Road Graffiti Wall

Moganshan Road is a gem for all things art. It is home to M50, the best art district in the city, where you will find dozens of galleries, studios, and workshops showcasing a wide range of art. There are also plenty of cool spots scattered around the area, particularly the graffiti wall. The wall is a welcome contrast to some of the drab and monotonous architecture found around the city; with colorful display of street art featuring various styles and themes. Stop by and admire the works of local and international artists, and even jump in to join them in adding your own mark. The wall is constantly evolving, so you can always find something new.
No. 4 - Jiaotong University in the Fall

Easily one of the best spots in town for catching rows of bright yellow and red leaves. Jiaotong University is one of the oldest and most prestigious universities in China. The campus is located in Xuhui District and has a mix of Chinese and Western architectural styles to admire as well. Try to visit in late October or early November for the best leaf-peeping. You can walk along the tree-lined paths, set up a blanket in the field for a picnic, or simply take photos and enjoy the scenery.
No. 5 - Day Drinking at Highline

Hands down one of the top five rooftop bars in the city, along with Bar Rouge, Kartel, and others; Highline is a go-to-spot that offers great views of the city and excellent food. Find it on the sixth floor of the Ascott Hotel in Huaihai Road in Xintiandi. Nothing beats a laid back Saturday afternoon at Highline. I prefer the views during the day, though it is equally as nice a night. Sip cocktails, wine, or beer, and enjoy the music and vibe. Highline is a perfect place to spend an afternoon.
Additional Photos





Next Guide in the Series:
An Expats Guide to the Best Spots in Shanghai: 002
Find Me Elsewhere:
All images property of Hes. Originally published as an Instagram Guide on Feb. 02, 2021. Reworked and published on Nostr on Feb. 17, 2024.
-
 @ bf47c19e:c3d2573b
2025-01-08 18:06:36
@ bf47c19e:c3d2573b
2025-01-08 18:06:36Originalni tekst na danas.rs
22.09.2024 / Autor: Marko Matanović
Bitkoin je 2009. godine zamišljen da bude digitalni keš. Zvučalo je revolucionarno zbog toga što je mnoge dovelo u dilemu: kako nešto potpuno digitalno može da ima vrednost i bude valuta.
Pre 15 godina smo živeli u društvu u kome je preko 95 odsto ukupnog novca u opticaju već potpuno digitalno i virtuelno.
Danas je još više izražena digitalizacija novca. Bitkoin je bio deo procesa evolucije više nego revolucije kada je u pitanju barem forma “novca”.
Petnaest godina kasnije bitkoin nije zamenio tradicionalne valute: dolare, evre, dinare. I verovatno to neće uraditi. Nije ispunio početnu zamisao, digitalni novac.
Ali se nametnuo kao čuvar vrednosti. Jedan od razloga je jednostavan. Kada posedujemo bilo koji oblik imovine, uvek ćemo za plaćanje (čemu novac većini ljudi i služi) koristiti najmanje kvalitetan novac, onaj koji vremenom ne dobija na vrednosti ili je gubi čak.
Veći deo vlasnika bitkoina veruje da će njegova vrednost rasti vremenom. Dok s druge strane imamo dinar, evro ili dolar koji će 100 odsto za godinu dana vredeti dva odsto ili 15 odsto manje. Zbog toga većina vlasnika bitkoina ga neće koristiti da kupuje hleb ili plaća račune za telefon, tj. kao sredstvo plaćanja.
Za razliku od fizičkog zlata, svima poznatog, jedna od prednosti bitkoina je prenosivost. Bitkoin infrastruktura funkcioniše tako da se svaka transakcija prenosa bitkoina obavlja u proseku za 10-ak minuta, 24/7/365.
Ta transakcija će se realizovati 100 odsto ako je usklađena sa pravilima Bitkoin ekosistema. Pravila su pritom transparentna, ista, lako primenljiva za sve. Iz ovoga se nameće i druga i treća potencijalna prednost bitkoina u odnosu na zlato. Bez obzira na količinu i vrednost bitkoina koji se kroz transakciju prenose, vreme tog prenosa je oko 10 minuta. A cena obrade transakcije zanemarljiva. Par dolara ili manje. Na dan pisanja teksta, kilogram zlata je vredeo oko 84.000 dolara ili 10 kilograma oko 840.000 dolara itd. Slične vrednosti je 1,4 bitkoin, tj. 14 bitkoina…
Postoje ozbiljni regulatorni, sigurnosni, vremenski, troškovni izazovi prenosa pomenutih količina zlata s jedne lokacije na drugu ili u drugu državu. Za prenos 0.0001 btc-a (bitkoina), vrednosti oko šest dolara ili za prenos 1.000 btc, vrednosti oko 60 miliona dolara trebaće vam 10 minuta. Transakcije vas mogu koštati i manje od jednog dolara!
I ne postoji bezbednosni rizik. Neuporedivo brže, sigurnije, jeftinije. Neki kažu da je bitkoin „digitalno zlato“ i pouzdana mreža za prenos vrednosti.
Bitkoin su u početku koristili samo pojedinci, fizička lica. Danas ga koriste i kompanije i neke države. Pojedinci deo sredstava prebacuju u bitkoine, kako bi se sačuvali od inflacije koja je u skoro svim ekonomijama prisutna i obezvređuje novac koji posedujemo.
Neki u njemu vide potencijal rasta vrednosti. Neki se bave “trading-om”, špekulisanjem u nadi da će kratkoročno zaraditi. Neki ga koriste da bi preneli vrednost brže i lakše.
U ratom zahvaćenih delovima sveta, deo populacije je kroz bitkoin i kriptovalute imao jedinu mogućnost da spase svoju do tada stečenu imovinu. U tim situacijama ne možete nekretninu, zlato, umetnička dela, automobile lako preneti ili sačuvati. Često su tada blokirani bankarski računi ili rad banaka. Ali, deo sredstava se može prebaciti u kriptovalute.
Zbog toga u Srbiji puno ljudi koji su se sklonili iz Rusije i Ukrajine zapravo koristi kriptovalute. Globalno, kompanije kupuju bitkoine, jer imaju investiciono usmerenje ili usmerenje ka diversifikaciji sredstava. I takođe bitkoin ili neke druge kriptovalute koriste kao sredstvo plaćanja u internacionalnom poslovanju. Neuporedivo je veća brzina realizacije transakcija kritpovaluta u poređenju sa transakcijama koje idu kroz bankarski sistem.
Postoje jurisdikcije koje nisu integrisane u globalne finansijske sisteme i ne postoji način naplate i saradnje dve kompanije iz dve države. Sve dok se kripto nije pojavio. Države imaju različite stavove po pitanju kripta. Neke ga kupuju. Neke ga rudare čak.
Ali većina je donela regulatorne okvire koji definišu zakonske mogućnosti i načine korišćenja kriptovaluta. I za građane i za kompanije. I za firme koje pružaju usluge povezane za kriptovalutama u tim državama. U Srbiji se primenjuje Zakon o digitalnoj imovini od 2021. godine i time su postavljeni dodatni regulatorni okviri.
SPLET konferencija koja se 8. oktobra održava u Beogradu je deo svog programa posvetila temama povezanim sa kriptovalutama, tokenizacijom, pravnim aspektima tog sveta.
ECD.rs, prva kriptomenjačnica u Srbiji, će imati svoje predstavnike i paneliste na SPLET-u. Cilj je da još dublje zaronimo u ove teme. Želimo da ponudimo dodatne uvide, odgovore. Delićemo iskustvo od 12 i više godina bavljenja kriptovalutama. Vidimo se na SPLET-u!
Splet konferenciju zajednički organizuju projekti „Preduzmi ideju“ u realizaciji Inicijative „Digitalna Srbija“ i „Srbija Inovira“, koje sprovodi ICT HUB, u saradnji sa Američkom agencijom za međunarodni razvoj (USAID). Ovogodišnju konferenciju realizuju i uz podršku i pokroviteljstvo Ministarstva nauke, tehnološkog razvoja i inovacija.
-
 @ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08
@ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08Tldr
- Nostr is an open and interoperable protocol
- You can integrate it with workflow automation tools to augment your experience
- n8n is a great low/no-code workflow automation tool which you can host yourself
- Nostrobots allows you to integrate Nostr into n8n
- In this blog I create some workflow automations for Nostr
- A simple form to delegate posting notes
- Push notifications for mentions on multiple accounts
- Push notifications for your favourite accounts when they post a note
- All workflows are provided as open source with MIT license for you to use
Inter-op All The Things
Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In Using NFC Cards with Nostr I explored the
nostr:URI to launch Nostr clients from a card tap.The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails.
My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted.
This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull.
So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications.
All we need are simple ways to plug things together.
Nostr and Workflow Automation
Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective.
n8n for workflow automation
Many workflow automation tools exist. My favourite is n8n. n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to.
Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine.
Eating my own dogfood
It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do?
In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting.
I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up.
Running n8n with Nostrobots
I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs my HAVEN Nostr Relay and Albyhub Lightning Node in Docker containers,
- My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows.
Installing n8n
Self-hosting n8n could not be easier. I followed n8n's Docker-Compose installation docs–
- Install Docker and Docker-Compose if you haven't already,
- Create your
docker-compose.ymland.envfiles from the docs, - Create your data folder
sudo docker volume create n8n_data, - Start your container with
sudo docker compose up -d, - Your n8n instance should be online at port
5678.
n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there.
Installing Nostrobots
To integrate n8n nicely with Nostr, I used the Nostrobots community node by Ocknamo.
In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in.
You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative).
To install a community node, see n8n community node docs. From your workflow dashboard–
- Click the "..." in the bottom left corner beside your username, and click "settings",
- Cilck "community nodes" left sidebar,
- Click "Install",
- Enter the "npm Package Name" which is
n8n-nodes-nostrobots, - Accept the risks and click "Install",
- Nostrobots is now added to your n8n instance.
Using Nostrobots
Nostrobots gives you nodes to help you build Nostr-integrated workflows–
- Nostr Write – for posting Notes to the Nostr network,
- Nostr Read – for reading Notes from the Nostr network, and
- Nostr Utils – for performing certain conversions you may need (e.g. from bech32 to hex).
Nostrobots has good documentation on each node which focuses on simple use cases.
Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use.
What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible.
Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with NIP-01). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of.
Creating and adding workflows
With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation.
- Click "Add workflow" to go to the workflow builder screen,
- If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added,
- If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article).
Nostr Workflow Automations
It's time to build some things!
A simple form to post a note to Nostr
I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily.
I needed a basic form with credentials that posted a Note.
For this I can use a very simple workflow–
- A n8n Form node – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted.
- A Set node – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain.
- A Nostr Write node (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays.
Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive".
It may also be the world's simplest Nostr client.
You can find the Nostr Form to Post a Note workflow here.
Push notifications on mentions and new notes
One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want–
- To make sure I never miss a note addressed to any of my Npubs – For this I want a push notification any time any Nostr user mentions any of my Npubs,
- To make sure I always see all notes from key accounts – For this I need a push notification any time any of my Npubs post any Notes to the network,
- To get these notifications on all of my devices – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day.
I needed to build a Nostr push notifications solution.
To build this workflow I had to string a few ideas together–
- Triggering the node on a schedule – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited,
- Storing a list of Npubs in a Nostr list – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists (NIP-51, kind 30000). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. Listr.lol or Nostrudel.ninja). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions,
- Using specific relays – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata,
- Querying Nostr events (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do–
- I read the EventID of my Kind 30000 list, to return the desired pubkeys,
- For notifications on mentions, I read all Kind 1 notes that mention that pubkey,
- For notifications on new notes, I read all Kind 1 notes published by that pubkey,
- Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub,
- I transform the EventID into a Nevent to help clients find it.
- Using the Nostr URI – As I did with my NFC card article, I created a link with the
nostr:URI prefix so that my phone's native client opens the link by default, - Push notifications solution – I needed a push notifications solution. I found many with n8n integrations and chose to go with Pushover which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license.
Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go.
You can find the Nostr Push Notification If Mentioned here and If Posts a Note here.
In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible.
Use my workflows
I have open sourced all my workflows at my Github with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use.
To import any of my workflows–
- Click on the workflow of your choice, e.g. "Nostr_Push_Notify_If_Mentioned.json",
- Click on the "raw" button to view the raw JSON, ex any Github page layout,
- Copy that URL,
- Enter that URL in the "import from URL" dialog mentioned above.
To configure them–
- Prerequisites, credentials, and variables are all stated,
- In general any variables required are entered into a Set Node that follows the trigger node,
- Pushover has some extra setup but is very straightforward and documented in the workflow.
What next?
Over my first four blogs I explored creating a good Nostr setup with Vanity Npub, Lightning Payments, Nostr Addresses at Your Domain, and Personal Nostr Relay.
Then in my latest two blogs I explored different types of interoperability with NFC cards and now n8n Workflow Automation.
Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this:
- Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds),
- Automated or scheduled posting (such as auto-liking everything Lyn Alden posts),
- Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming),
- All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr,
- All kinds of other automation (such as BlackCoffee controlling a coffee machine),
- All kinds of AI Assistants and Agents,
In fact I have already released an open source workflow for an AI Assistant, and will share more about that in my next blog.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Que vença o melhor
Nos esportes e jogos em geral, existe uma constante preocupação em balancear os incentivos e atributos do jogo, as regras do esporte em si e as regras das competições para que o melhor vença, ou, em outras palavras, para que sejam minimizados os outros fatores exceto a habilidade mais pura quanto possível no jogo em questão.
O mundo fora dos jogos, porém, nem sempre pode ter suas regras mudadas por um ente que as controla e está imbuído da vontade e dos meios para escolher as melhores regras possíveis para a obtenção dos resultados acima. Aliás, é muitas vezes essa possibilidade é até impensável. Mesmo quando ela é pensável e levada em conta os fatores que operam no mundo real não são facilmente identificáveis, eles são muitos, e mudam o tempo todo.
Mais do que isso, ao contrário de um jogo em que o objetivo é praticamente o mesmo para todo mundo, os objetivos de cada agente no mundo real são diferentes e incontáveis, e as "competições" que cada um está disputando são diferentes e muitas, cada minúsculo ato de suas vidas compreendendo várias delas simultaneamente.
Da mesma forma, é impossível conceber até mesmo o conceito de "melhor" para que se deseje que ele vença.
Mesmo assim é comum encontrarmos em várias situações gente que parte do princípio de que se Fulano está num certo lugar (por exemplo, um emprego muito bom) e Beltrano não isso se deve ao fato de Fulano ter sido melhor que Beltrano.
Está aí uma crítica à idéia da meritocracia (eu tinha me esquecido que essa palavra existia).
-
 @ f9cf4e94:96abc355
2024-12-31 20:18:59
@ f9cf4e94:96abc355
2024-12-31 20:18:59Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( dominictarr ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt (ssb) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia.
Se você está se perguntando de onde diabos veio o nome Scuttlebutt:
Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.

Marinheiros se reunindo em torno da rixa. ( fonte )
Dominic descobriu o termo boato em um artigo de pesquisa que leu.
Em sistemas distribuídos, fofocar é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”.
Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto. Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar. Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário de bordo (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem.
Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. Cada item adicionado a um log do usuário é chamado de mensagem.
Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.

Perspectivas dos participantes
Scuttlebot
O software Pub é conhecido como servidor Scuttlebutt (servidor ssb ), mas também é conhecido como “Scuttlebot” e
sbotna linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial.Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.


Perspectivas dos participantes
Pubs - Hubs
Pubs públicos
| Pub Name | Operator | Invite Code | | ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ | |
scuttle.us| @Ryan |scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=| | pub1.upsocial.com | @freedomrules |pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=| | Monero Pub | @Denis |xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=| | FreeSocial | @Jarland |pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=| |ssb.vpn.net.br| @coffeverton |ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=| | gossip.noisebridge.info | Noisebridge Hackerspace @james.network |gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=|Pubs privados
Você precisará entrar em contato com os proprietários desses bares para receber um convite.
| Pub Name | Operator | Contact | | --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- | |
many.butt.nz| @dinosaur | mikey@enspiral.com | |one.butt.nz| @dinosaur | mikey@enspiral.com | |ssb.mikey.nz| @dinosaur | mikey@enspiral.com | | ssb.celehner.com | @cel | cel@celehner.com |Pubs muito grandes
Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)
| Pub Name | Operator | Invite Code | | --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ | |
scuttlebutt.de| SolSoCoG |scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=| |Lohn's Pub| @lohn |p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=| | Scuttle Space | @guil-dot | Visit scuttle.space | |SSB PeerNet US-East| timjrobinson |us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=| | Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= |GUI - Interface Gráfica do Utilizador(Usuário)
Patchwork - Uma GUI SSB (Descontinuado)
Patchwork é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.

Fonte: scuttlebutt.nz
Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub. Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs.
Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth.
Patchbay - Uma GUI Alternativa
Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que Patchwork e Patchfoo , então você pode facilmente dar uma volta com sua identidade existente.

Planetary - GUI para IOS

Planetary é um app com pubs pré-carregados para facilitar integração.
Manyverse - GUI para Android

Manyverse é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone .
Fontes
-
https://scuttlebot.io/
-
https://decentralized-id.com/decentralized-web/scuttlebot/#plugins
-
https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd
-
Secure Scuttlebutt : um protocolo de banco de dados global.
-
-
 @ bf47c19e:c3d2573b
2025-01-08 17:55:06
@ bf47c19e:c3d2573b
2025-01-08 17:55:06Originalni tekst za nin.rs.
09.10.2024 / Autor: Marko Matanović
Najveći deo stvari merimo zajedničkim imeniteljem – novcem. Fantastični izum društva. Olakšava komunikaciju, saradnju i napredak civilizacije. Trenutna novčana vrednost mnogih stvari ne mora biti pokazatelj realne ili vrednosti na duge staze.
Bitkoin kao kriptovaluta ima svojih uspona i padova. U ceni. Kada nešto vredi nula pa krene od par mesta desno iza decimalnog zareza u $ protivvrednosti i završi na 50.000 ili 70.000$, može se reći da je bilo više uspona nego padova.

Zamišljen i najavljen je kao digitalni keš 2008. godine. Preskačući prvu godinu ili dve, rezervisane skoro isključivo za uzak krug programera, sledi poistovećivanje bitkoina sa sredstvom za plaćanja ilegalnih usluga i proizvoda. Zbog delimične zablude da su transakcije bitkoinom anonimne.
Godine 2013. godine pada Silk Road platforma, online marketplace, na kome se za bitkoin moglo kupiti puno toga ilegalnog. Po nekima to je i konačni pad bitkoina. Iz današnje perspektive, neupućena osoba može i dalje ostati pri stavu da je bitkoin pretežno tu za izvršenje ilegalnih transakcija. Bitkoin i danas postoji, Silk Road ne.
Par meseci posle Silk Road-a, pada i tada pratkično jedina “ozbiljna” kripto berza Mt. Gox. U to vreme odgovorna za 70%+ svih bitkoin transakcija. Tačno 10 godina kasnije, svedoci smo vraćanja dela izgubljenih sredstava (oko 25%) tadašnjim vlasnicima naloga na Mt. Gox berzi. Bitkoin je danas 100 puta vredniji nego pre 2014. Taj vraćeni “delić” izgubljenih bitkoina njegovim vlasnicima je danas “samo” 25 puta vredniji.
Bilo je još dosta propalih kripto projekata. I biće ih. Među poznatijim, prevara iza OneCoin-a. Sunovrat UST-a i Lune, Celsius i FTX bankroti. Svaki odogovoran za gubitke koji prelaze milijarde dolara. Bitkoin je i dalje tu. Bitkoin je imao i konkurente iz redova kriptovaluta. Poslednji pravi je iz 2017. godine i “Bitcoin Cash”. Danas kada se pogleda gde je jedan a gde drugi sve je jasno.
Satoshi Nakamoto, ime iza ideje bitkoina i njegovog lansiranja, je postavio fascinantne postulate na kojima će prva kriptovaluta funkcionisati. A inspirisan manjkavostima globalnog finansijskog sistema. Bitkoin je baziran na transparentnom, decentralizovanom sistemu. Dostupan svima, sa jednakim i izuzetno niskim barijerama ulaska i izlaska iz tog ekosistema. Funkcioniše po setu pravila koja su ista za sve. Ukoliko se poštuju, transakciju bitkoinom niko ne može osporiti i ne može se retroaktivno manipulisati.
Prvi put imamo digitalni sadržaj koji se ne može kopirati. Bitkoin ekosistem funkcioniše 15 godina pratkično bez down-time-a. Usko je shvatanje reći da je rudarenje bitkoina proces koji bespotrebno troši previše energije. Ili da bitkoin nema uporište u nekoj opipljivoj vrednosti. Ta skupa reč je poverenje. Ničijom svesnom namerom, već organski, bitkoin je od digitalnog keša postao prepoznat kao čuvar vrednosti, digitalno zlato. Jer zašto da koristiš za svakodnevna plaćanja nešto što može vredeti za godinu ili godine 5%,10%, 50% više, ako imaš RSD, EUR ili $ koji će 100% za godinu dana vredeti 2% ili 15% manje?
Danas bitkoin koriste obični ljudi, kompanije i države.
Satoshi je svakako imao drugačiju viziju ove kriptovalute – digitalni keš i pošteniji novac. Kreirajući ekosistem na koji svi mi možemo vršiti uticaj barem podjednako koliko i Satoshi, ostavljena su otvorena vrata da se vizija promeni. Vizija je prilagođena, prepuštena našim prethodnim i budućim postupcima i društvenim okolnostima. Važno je da su postulati i dalje tu. Sa njima i Bitkoin.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Token-Curated Registries
So you want to build a TCR?
TCRs (Token Curated Registries) are a construct for maintaining registries on Ethereum. Imagine you have lots of scissor brands and you want a list with only the good scissors. You want to make sure only the good scissors make into that list and not the bad scissors. For that, people will tell you, you can just create a TCR of the best scissors!
It works like this: some people have the token, let's call it Scissor Token. Some other person, let's say it's a scissor manufacturer, wants to put his scissor on the list, this guy must acquire some Scissor Tokens and "stake" it. Holders of the Scissor Tokens are allowed to vote on "yes" or "no". If "no", the manufactures loses his tokens to the holders, if "yes" then its tokens are kept in deposit, but his scissor brand gets accepted into the registry.
Such a simple process, they say, have strong incentives for being the best possible way of curating a registry of scissors: consumers have the incentive to consult the list because of its high quality; manufacturers have the incentive to buy tokens and apply to join the list because the list is so well-curated and consumers always consult it; token holders want the registry to accept good and reject bad scissors because that good decisions will make the list good for consumers and thus their tokens more valuable, bad decisions will do the contrary. It doesn't make sense, to reject everybody just to grab their tokens, because that would create an incentive against people trying to enter the list.
Amazing! How come such a simple system of voting has such enourmous features? Now we can have lists of everything so well-curated, and for that we just need Ethereum tokens!
Now let's imagine a different proposal, of my own creation: SPCR, Single-person curated registries.
Single-person Curated Registries are equal to TCR, except they don't use Ethereum tokens, it's just a list in a text file kept by a single person. People can apply to join, and they will have to give the single person some amount of money, the single person can reject or accept the proposal and so on.
Now let's look at the incentives of SPCR: people will want to consult the registry because it is so well curated; vendors will want to enter the registry because people are consulting it; the single person will want to accept the good and reject the bad applicants because these good decisions are what will make the list valuable.
Amazing! How such a single proposal has such enourmous features! SPCR are going to take over the internet!
What TCR enthusiasts get wrong?
TCR people think they can just list a set of incentives for something to work and assume that something will work. Mix that with Ethereum hype and they think theyve found something unique and revolutionary, while in fact they're just making a poor implementation of "democracy" systems that fail almost everywhere.
The life is not about listing a set of "incentives" and then considering the problems solved. Almost everybody on the Earth has the incentive for being rich: being rich has a lot of advantages over being poor, however not all people get rich! Why are the incentives failing?
Curating lists is a hard problem, it involves a lot of knowledge about the problem that just holding a token won't give you, it involves personal preferences, politics, it involves knowing where is the real limit between "good" and "bad". The Single Person list may have a good result if the single person doing the curation is knowledgeable and honest (yes, you can game the system to accept your uncle's scissors and not their competitor that is much better, for example, without losing the entire list reputation), same thing for TCRs, but it can also fail miserably, and it can appear to be good but be in fact not so good. In all cases, the list entries will reflect the preferences of people choosing and other things that aren't taken into the incentives equation of TCR enthusiasts.
We don't need lists
The most important point to be made, although unrelated to the incentive story, is that we don't need lists. Imagine you're looking for a scissor. You don't want someone to tell if scissor A or B are "good" or "bad", or if A is "better" than B. You want to know if, for your specific situation, or for a class of situations, A will serve well, and do that considering A's price and if A is being sold near you and all that.
Scissors are the worst example ever to make this point, but I hope you get it. If you don't, try imagining the same example with schools, doctors, plumbers, food, whatever.
Recommendation systems are badly needed in our world, and TCRs don't solve these at all.
-
 @ 3f770d65:7a745b24
2024-12-31 17:03:46
@ 3f770d65:7a745b24
2024-12-31 17:03:46Here are my predictions for Nostr in 2025:
Decentralization: The outbox and inbox communication models, sometimes referred to as the Gossip model, will become the standard across the ecosystem. By the end of 2025, all major clients will support these models, providing seamless communication and enhanced decentralization. Clients that do not adopt outbox/inbox by then will be regarded as outdated or legacy systems.
Privacy Standards: Major clients such as Damus and Primal will move away from NIP-04 DMs, adopting more secure protocol possibilities like NIP-17 or NIP-104. These upgrades will ensure enhanced encryption and metadata protection. Additionally, NIP-104 MLS tools will drive the development of new clients and features, providing users with unprecedented control over the privacy of their communications.
Interoperability: Nostr's ecosystem will become even more interconnected. Platforms like the Olas image-sharing service will expand into prominent clients such as Primal, Damus, Coracle, and Snort, alongside existing integrations with Amethyst, Nostur, and Nostrudel. Similarly, audio and video tools like Nostr Nests and Zap.stream will gain seamless integration into major clients, enabling easy participation in live events across the ecosystem.
Adoption and Migration: Inspired by early pioneers like Fountain and Orange Pill App, more platforms will adopt Nostr for authentication, login, and social systems. In 2025, a significant migration from a high-profile application platform with hundreds of thousands of users will transpire, doubling Nostr’s daily activity and establishing it as a cornerstone of decentralized technologies.
-
 @ 4720beb1:fde5de50
2025-01-08 17:45:09
@ 4720beb1:fde5de50
2025-01-08 17:45:09I just published the new version of my NIP-404. It basically a way to have real ephemeral interactions on Nostr, so developers can model Stories and messages that disappear etc and providing a good level of plausible deniability. Here is the new version: https://github.com/nostr-protocol/nips/pull/1676
This is a follow-up of a previous proposal I did in last November. I tried to tackle most of issues that npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft npub1acg6thl5psv62405rljzkj8spesceyfz2c32udakc2ak0dmvfeyse9p35c have raised.
There is a "working" example (I'm not a cryptographer, have mercy on me): https://github.com/gu1p/nip404_demo
TL;DR;
NIP-404: Ghost Events
This NIP introduces Ghost Events—a protocol for creating events that are plausibly deniable with a ephemeral nature, providing a weak binding to the author's identity. It leverages ring signatures, elliptic curve point-hashing, and a distance-based proof-of-work that references Bitcoin block hashes for chronological anchoring.
High-Level Mechanics
- Ring Signature over exactly two keys:
1) Your real key
2) A “mined” key — found by solving a proof-of-work puzzle (attacker) or randomly (by the real signer). - Distance-based PoW: The mined key’s public key must be within distance
δof a “challenge point” derived from your public key and a Bitcoin block hash. - Deniability: Verifiers can only tell that one of the two keys signed the event, not which one. Because all components are public, anyone can forge a Ghost Event referencing your key.
2. Detailed Protocol
2.1. Reference a Bitcoin Block
Pick a Bitcoin block
Bwith hashH_Band timestampt_B. This block anchors the event in time.2.2. Derive a Challenge Point
- Take your main public key
P_Aand concatenate it withH_B. - Compute
S = SHA256(P_A || H_B) - Map
Sto secp256k1 (RFC 9380 “Hashing to Elliptic Curves”):challenge_PK = HashToCurve(S)
Anyone can verify this point by performing the same steps.
2.3. Pick a “Mined Key”
P_mined- Let
x_cbe the x-coordinate ofchallenge_PK. - Find
x_msuch that|x_m - x_c| <= δand(x_m, y_m)is a valid secp256k1 point. -
δreflects the “difficulty” of finding such a key. -
In the proposal I have provide a way to get a δ given the number of tries and target probability you expect someone to mine the
P_minedand also the inverse, compute the δ given a number of tries. -
Compute $T$ (number of tries) given $\delta$ and target probability.
2.4. Create a Ring Signature
Form a ring of two public keys:
{P_A, P_mined}.
Use your real private key to sign, producing a ring signature that proves one of the private keys (eithersk_Aorsk_mined) signed — but not which one.2.5. Publish the Ghost Event
Publish a standard Nostr event (
kind,content, etc.) plus tags:["ghost", "block-hash", "<H_B>"]["ghost", "block-hash-timestamp", "<t_B>"]
The event’s
sigfield is the ring signature. Verifiers can:- Check validity of the ring signature over
{P_A, P_mined}. - Recompute
challenge_PKfrom<P_A, H_B>. - Measure how close
P_minedis tochallenge_PK(i.e., proof-of-work difficulty). - Conclude: “Either Alice really signed, or someone else who found a matching
P_mineddid.”
Practical Tips
-
Picking δ:
-
Decide how quickly you want deniability to set in. If you pick a very small δ, it requires more CPU time for an attacker to replicate—but also temporarily ties the event more strongly to you.
- If you want faster deniability, pick a larger δ, but accept that forging a second “mined” key becomes easier.
-
If you want avoid OTS, pick a larger δ and reference older blocks.
-
Verifying a Received Ghost Event:
- Check the actual δ provided.
- Estimate the tries
Tneeded for a given success probability. - Check the
Key/srate necessary to produce the event since the block was mined.
7. Example Ghost Event JSON
Alice: Today is a good day to post wild picture of me on Nostr! Maybe I will regret it later...
Alice: Let post as a ghost event!
Alice: I will set a PoW of 86400000000 tries for a 30% of success. It is an easy one!json { "id": "f9d32cace9ead9457d121041c4c17a779ab84cecf90f08d90ccacd9673f1bab4", "pubkey": "npub1r587vuykqhf8k7x4e06380edc7mr7pkz59r44tausmlwq970wkyqv9dh85", "created_at": 1736350383, "kind": 1, "tags": [ [ "ghost", "block-hash", "00000000000000000000c75dc9d3296751a8bb62b2463fbc49035ee75ab45f39" ], [ "ghost", "block-hash-timestamp", 1736264059 ] ], "content": "Hi! This is Alice... Here is a picture of me drinking a beer!", "sig": "...<ring signature>...." }Bob: Wow! There is an event from Alice!
Bob: Let's check the signature to make sure it is from Alice
Bob: Alice didn't sign this event!
Bob: I see some ghost tags here...
Bob: It is a ghost event!
Bob: There are 2 possible signers!
Bob: Alice is one of the possible signers!
It was produced, allegedly, after the block a 00000000000000000000c75dc9d3296751a8bb62b2463fbc49035ee75ab45f39
Bob: It says that the block was mined at 1736264059
Bob: Let see if this block is real!
Bob: The block is real!
Bob: Let's check the PoW
Bob: The other signer is: npub1jktevjlge6vjp2yfaltrlvuv99th2uxaxy8eglvcsvr7e2r9h5lq2978dz
Bob: The challenge public key is: npub1jktevjldsr7kr52f90602gfhmc8cac9quq6yy8k9vy94w2qptsasz9cfps
Bob: Let's figure out how hard it was to mine the private key
Bob: The distance between the challenge and the alleged mined public key is 494635222290174920048599093528121665305037827746663102318405983997
Bob: For having 50% of chance of figuring out this key, the signer should have done 83496150448 tries
Bob: The signer should have mined 967231 keys per second, since the block was mined
Bob: It is not a hard PoW! - Ring Signature over exactly two keys:
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Precautionary Principle
The precautionary principle that people, including Nassim Nicholas Taleb, love and treat as some form of wisdom, is actually just a justification for arbitrary acts.
In a given situation for which there's no sufficient knowledge, either A or B can be seen as risky or precautionary measures, there's no way to know except if you have sufficient knowledge.
Someone could reply saying, for example, that the known risk of A is tolerable to the unknown, probably magnitudes bigger, risk of B. Unless you know better or at least have a logical explanation for the risks of B (a thing "scientists" don't have because they notoriously dislike making logical claims), in which case you do know something and is not invoking the precautionary principle anymore, just relying on your logical reasoning – and that can be discussed and questioned by others, undermining your intended usage of the label "precautionary principle" as a magic cover for your actions.
-
 @ e97aaffa:2ebd765d
2024-12-31 16:47:12
@ e97aaffa:2ebd765d
2024-12-31 16:47:12Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes.
Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais mainstream. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso.
Código do Bitcoin
No final de 2025, possivelmente vamos ter um fork, as discussões sobre os covenants já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos covenants, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido.
Depois dos covenants, o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa.
Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos bitcoiners.
Espero que surjam avanços significativos no BitVM2 e BitVMX.
Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da shitcoinagem, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs.
Se querem ser levados a sério, têm que ser sérios.
“À mulher de César não basta ser honesta, deve parecer honesta”
Se querem ter o apoio dos bitcoiners, sigam o ethos do Bitcoin.
Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma multisig ou com os covenants na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos covenants para melhorar a interoperabilidade e a soberania.
É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy:
“Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país”
Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código.
Reservas Estratégicas de Bitcoin
Bancos centrais
Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito mainstream. Foi um pivot, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto.
A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário.
Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”.
Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar.
Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.

Empresas
A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.

Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%.
Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de shareholders com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft.
Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial.
ETFs
Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os inflows foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os inflows foram brutais.
Também se beneficiou por ser um mercado novo, não existia orderbook de vendas, não existia um mercado interno, praticamente era só inflows. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em inflows ou outflows.
Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de inflows em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar.
Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem.
Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes.
Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo.
Preço
Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo.
Stablecoins de dólar
Agora saindo um pouco do universo do Bitcoin, acho importante destacar as stablecoins.
No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas.
Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às stablecoins de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas.
“Casa onde não há pão, todos ralham e ninguém tem razão”
Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas.
Eu acredito que 2025, vai haver um forte crescimento na adoção das stablecoins de dólares, esse forte crescimento vai agravar o problema sistémico que são as stablecoins. Vai ser o início do fim das stablecoins, pelo menos, como nós conhecemos hoje em dia.
Problema sistémico
O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente.
Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas.
As stablecoins são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema.
No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos.
A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário.
Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/stablecoins para o resto do sistema financeiro, porque o marketcap do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações.
Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do carry trade, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado.
Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações.
O mundo cripto é seu oposto, é naife com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto.
Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025.
Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o redeem dos dólares?
Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether?
Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente.
Conta mestre
Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário.
O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com full-reserves. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com full-reserves, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos.
Eu concordo com o FED nesse ponto, que os bancos com full-reserves são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos full-reserves, mas sim nos que têm reserva fracionária.
O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença.
Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de compliance, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o compliance dos seus clientes.
A obrigação do KYC para ter stablecoins iriam provocar um terramoto no mundo cripto.
Assim, é pouco provável que seja a solução para a Tether.
FED
Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as stablecoins de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as stablecoins estão a colocar em causa a soberania monetária dos outros países. Atualmente as stablecoins estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países.
Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo.
Será algo para acompanhar futuramente, mas só para 2026, talvez…
É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(stablecoins). A ironia do destino.
Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona.
Europa
2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os compliance, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo.
O Travel Route passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A Travel Route é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos.
O MiCA também está a colocar problemas nas stablecoins de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias.
O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade stablecoins de euro, as restantes stablecoins serão deslistadas.
Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado.
Recessão
Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon.
Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro.
Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer.
Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar.
A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa.
Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal.
Brasil
Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.

Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e stablecoins. No Brasil existe um forte adoção, será um bom case study, certamente irá repetir-se em outros países num futuro próximo.
Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin.
Blockchain
Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em blockchain. Eu acredito que a BlackRock vai criar uma própria blockchain, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar.
Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião.
Isto é apenas a minha opinião, Don’t Trust, Verify!
-
 @ f9cf4e94:96abc355
2024-12-30 19:02:32
@ f9cf4e94:96abc355
2024-12-30 19:02:32Na era das grandes navegações, piratas ingleses eram autorizados pelo governo para roubar navios.
A única coisa que diferenciava um pirata comum de um corsário é que o último possuía a “Carta do Corso”, que funcionava como um “Alvará para o roubo”, onde o governo Inglês legitimava o roubo de navios por parte dos corsários. É claro, que em troca ele exigia uma parte da espoliação.
Bastante similar com a maneira que a Receita Federal atua, não? Na verdade, o caso é ainda pior, pois o governo fica com toda a riqueza espoliada, e apenas repassa um mísero salário para os corsários modernos, os agentes da receita federal.
Porém eles “justificam” esse roubo ao chamá-lo de imposto, e isso parece acalmar os ânimos de grande parte da população, mas não de nós. Não é por acaso que 'imposto' é o particípio passado do verbo 'impor'. Ou seja, é aquilo que resulta do cumprimento obrigatório -- e não voluntário -- de todos os cidadãos. Se não for 'imposto' ninguém paga. Nem mesmo seus defensores. Isso mostra o quanto as pessoas realmente apreciam os serviços do estado.
Apenas volte um pouco na história: os primeiros pagadores de impostos eram fazendeiros cujos territórios foram invadidos por nômades que pastoreavam seu gado. Esses invasores nômades forçavam os fazendeiros a lhes pagar uma fatia de sua renda em troca de "proteção". O fazendeiro que não concordasse era assassinado.
Os nômades perceberam que era muito mais interessante e confortável apenas cobrar uma taxa de proteção em vez de matar o fazendeiro e assumir suas posses. Cobrando uma taxa, eles obtinham o que necessitavam. Já se matassem os fazendeiros, eles teriam de gerenciar por conta própria toda a produção da fazenda. Daí eles entenderam que, ao não assassinarem todos os fazendeiros que encontrassem pelo caminho, poderiam fazer desta prática um modo de vida.
Assim nasceu o governo.
Não assassinar pessoas foi o primeiro serviço que o governo forneceu. Como temos sorte em ter à nossa disposição esta instituição!
Assim, não deixa de ser curioso que algumas pessoas digam que os impostos são pagos basicamente para impedir que aconteça exatamente aquilo que originou a existência do governo. O governo nasceu da extorsão. Os fazendeiros tinham de pagar um "arrego" para seu governo. Caso contrário, eram assassinados. Quem era a real ameaça? O governo. A máfia faz a mesma coisa.
Mas existe uma forma de se proteger desses corsários modernos. Atualmente, existe uma propriedade privada que NINGUÉM pode tirar de você, ela é sua até mesmo depois da morte. É claro que estamos falando do Bitcoin. Fazendo as configurações certas, é impossível saber que você tem bitcoin. Nem mesmo o governo americano consegue saber.
brasil #bitcoinbrasil #nostrbrasil #grownostr #bitcoin
-
 @ 2355757c:5ad3e04d
2025-01-08 17:44:53
@ 2355757c:5ad3e04d
2025-01-08 17:44:53Originally published Feb, 23, 2024
Introduction
Sunlight is the most important nutrient for our body. That may sound delusional to some, but the definition of a nutrient is: a substance that provides nourishment essential for growth and the maintenance of life. Sunlight certainly is necessary and essential for growth and the maintenance of life, but most don’t understand why. Most do not understand that the real benefit of sunlight is that it provides a vast spectrum of electromagnetic radiation (light) that signals different functions in our biology. This is why we can never replace sunlight with artificial lights, because the sun is a “broad band emitter” and all artificial lights are “narrow band emitters”. This means they only have a few isolated wavelengths, whereas sunlight contains the whole swath.
The other most important aspect of sunlight is that it is time and location dependent. It is always changing…and that change or shift in light frequencies is providing our body the right information about how to function properly in our given environment. Artificial light is constant and provides a consistent/un-natural input signal that confuses our biology.
The last piece, which I will dive into more in a future post…is the fact that sunlight is a continuous electromagnetic wave while indoor lighting is highly pulsed. This is a major reason why eye strain and headaches from staring at screens is so common.
Let’s dive into the important biological effects of the various wavelengths in full spectrum sunlight.
Summary
-
Sunlight is a broad band emitter and artificial light is a narrow band emitter
-
Sunlight is an un-polarized, continuous source of electromagnetic radiation. Artificial light is highly pulsed
-
Sunlight that reaches the earth is comprised of light frequencies that range from 280nm (UVB) to 2500nm (NIR) and everything in between. Each category of wavelength serves as a different biological stimuli
-
UVB radiation stimulates the production of vitamin D, as well as serotonin and beta-endorphins, UVA promotes the release of nitric oxide into the blood, and both have a positive effect on the diversity of the microbiome and our endogenous hormone production
-
Violet light can reverse myopia and potentially improve sleep quality
-
Blue light is the master circadian signaler, turning on/off the SCN via melanopsin photoreceptor…thus regulating cortisol/melatonin production as well as all circadian timing in the body
-
Green light can treat skin issues and also be used as a pain releiver
-
Red light, near-infrared radiation (NIR), and far-infrared (FIR) radiation have anti-inflammatory and tissue healing effects…NIR also stimulates the production of melatonin inside the mitochondria, a master anti-oxidant.
The Biological Effects of Sunlight: By Color/Wavelength
There are several wavelengths of energy from the sun that reach the earth’s surface and trigger specific actions within the body to influence our health. And, just as some of this spectrum is able to make it through the atmosphere, different wavelengths are also able to penetrate the skin to different depths of the body’s tissues and have certain effects on the cells within those tissues, as you can see in the figure below.

Those at the lower wavelengths (such as UVB) only penetrate the very surface of the skin, while those at higher wavelengths (such as visible light) are able to penetrate deeper. Think of how you are able to see the light from a flashlight on the back of your hand when held against the skin on the palm of the hand – you can visually see the energy traveling through the skin, muscles, blood vessels and tissues of the hand. Infrared radiation can even get into the cells and mitochondria, and can get through clothing and bone!
Ultraviolet-B Radiation (UVB) – Vitamin D, Neurotransmitters, Melanin and Beta-endorphins
UVB (280-315nm) is the highest energy wavelength that reaches surface of the earth. It is only present when the sun is >30 degrees above the horizon. You can use apps like “Circadian” and “dminder” to tell you when UVB is present. At the 45th latitude in Wyoming, I go WITHOUT UVB for around 2 months in winter time. This is a big deal, because UVB light stimulates vitamin D synthesis, one of the most important molecules/hormones in the body. More importantly, it stimulates synthesis of sulfated Vitamin D, which is more bioactive and has far more biological relevance compared to un-sulfated Vitamin D as you would get from a supplement. This is why you can’t replace sunlight with a supplement, especially when it comes to Vitamin D. Using a UVB lamp (outside or in combo with NIR) would be in my opinion a better option than supplementing Vit D, or if you do take a supplement take it mid day and get some UVB exposure after taking it. I wrote extensively about Vitamin D supplementation in a previous newsletter.
The vitamin D produced in the skin can also help protect the skin cells from DNA damage, facilitate DNA repair directly upon any UV damage, help prevent cell death, and protect against melanoma. In fact, keratinocytes, which make up over 90% of the outermost layer of skin, cannot rely on vitamin D3 from supplements and must synthesize their own supply of vitamin D directly from sun exposure, or by topical application.
Besides vitamin D, UVB radiation also promotes the production of neurotransmitters and beta-endorphins, chemicals that drive cognition, mood, relaxation, pain relief, and boost immunity. It also triggers the synthesis of MELANIN. It does this by stimulating proopiomelanocortin (POMC) activity in the brain and via exciting our aromatic amino acids.
POMC is a precursor protein of several neuropeptides, including adrenocorticotropin (ACTH), α-melanocyte stimulating hormone (α-MSH) and β-endorphin (β-END). Our aromatic amino acids (tryptophan, tyrosine, and phenylalanine) have ringed structures that allow them to trap UV light energy, and these aromatic amino acids are the precursors to neurotransmitters dopamine, serotonin, as well as melatonin and melanin. Serotonin is involved in cognition, regulation of feeding behavior, anxiety, aggression, pain, sexual activity, and sleep. These aromatics absorb heavily in the UVB/UVC range.

This UV-induced release of beta-endorphins means only one thing: there is an innate built in addiction pathway to the sun. Our biology is able to provide a “reward” for UV-induced vitamin D synthesis when vitamin D levels are low, during which time a greater amount of beta-endorphins are released upon exposure to UVB. As vitamin D levels rise, the sun-seeking behavior and resulting opioid response become repressed as less vitamin D is needed. It’s almost as if our body knows best, and we should go out of our way to listen to it. Instead, most people will continue to pour the Vit D supplements down their gully.
Melanin, which is synthesized from UV light exposure and activation of alpha-MSH via POMC, is one of the most important molecules in our biology. It absorbs the entire EMR spectrum and acts as both a biological semiconductor and energy storage system (battery). I have written more about it in a previous newsletter and will dive even deeper very soon.

Ultraviolet-A Radiation (UVA) – Nitric Oxide + More
UVA (315-380nm) exists at a wavelength between UVB and visible light, and is able to reach deeper than UVB light but still only a few millimeters. UVA leads to the release of nitric oxide into the bloodstream which in turn benefits the cardiovascular and metabolic systems, and may offer other immunological benefits beyond those offered by nitric oxide. This vasodilatory effect enhances blood flow, lowers blood prressure and improves circulation.
UVA can have similar effects to UVB such as stimulating POMC and the neuroendocrine axis, just with lesser efficiency compared to UVB light as it is a lower energy wavelength spectrum so it does not have as great of an excitatory effect on our biology.
“UVA has better penetration reaching the reticular dermis but has 1000 times lower efficiency at inducing biological effects (expressed as the minimal erythema dose) than UVB”
UVA also shares some benefits with violet light (visible) such as reversing myopia in the eyes. Will discuss that more in the Violet light section.
Ultraviolet Radiation (UVA + UVB) – The Most Important Input for Your Microbiome
Your gastrointestinal tract and the surface of the skin are home to trillions of microbes (bacteria, viruses, and yeast), called your “microbiome,” which act as their own organ and are crucial to your overall health. Skin health in particular is maintained by a balanced, diverse microbiome, which is in turn affected by nutrition, pH level, hygiene, exposure to toxins, barrier strength, stress levels, sunlight exposure, and overall health.
UV exposure (and vitamin D itself) can have a healthy, regulatory effect on the microbiome of the skin and the gut, with UVB light having a beneficial impact on the diversity and abundance of the bacteria species of the gut microbiome, and UVB as well as UVA benefitting the skin microbiome. Studies have even shown that several molecules that help protect our skin from UV damage can be produced by the microbiome on our skin upon UV exposure, acting as a sort of natural sunscreen.
Why is UV light so good for our gut? Two reasons:
-
Remember those aromatic amino acids and neurotransmitters mentioned earlier? Well a vast majority of aromatics are synthesized by your gut microbes via the famous shikamate pathway (famous because glyphosate disrupts this). As a result, most of your neurotransmitter synthesis is happening in the gut. 90-95% of serotonin and 50% of dopamine is produced and stored in the gut. There is a reason it is called your second brain, and it is not fully due to the vagal nerve connection.
-
Your bacteria absorb and fluoresce light constantly. We are made up of far more “bacteria” cells than our own cells and this microbiota is highly dependent on light input. It seems that UV light modulates pathogenic bacteria and helps beneficial bacteria proliferate. This is why UV light has been known as an effective method for cleaning surfaces.

UV Light Summary
UV light is imperative for properly functioning biology, and the fact that it has been demonized for “causing skin cancer” has resulted in a chronic health epidemic. Yes, solar tolerance and callus matters…that is why being outside all year round is imperative. UV light is the reason life began on this planet in the first place (read Nick Lane’s work on deep sea vents), and it stands true today that nearly ALL of the biological semi-conductors that power our biology absorb strongest in the UV range. When you can harness UV light, you become what it truly means to be a human being.
Blue Light – Regulation of Circadian Rhythm, and Melatonin
Blue light (420-500nm) perhaps ma be the most well known light in the visible spectrum. It has been vilified (for good reason) as the light that will disrupt our sleep. This is true, but that does not mean that blue light has a negative impact on our health in the right context, the opposite actually.
Blue light is the master circadian signaler. We sense it in our eyes and skin via the melanopsin receptor and the signal is what sets our bodies master circadian clock: the suprachiasmatic nucleus (SCN). This is how our body tells time, and this is why our blue light and overall light environment is so important. Blue light at night suppresses melatonin production far greater than any other color of light. Blue light conversely stimulates cortisol production, which is what provides wakefulness in the morning.
Blue light is the highest energy wavelength that is present for almost the entirety of sunlight exposure, with an ever increasing amount until solar noon…and then decreasing amount in the afternoon. Again, this is how our body tells time. If you subscribe to the fact that our circadian rhythm is one of if not the most important aspect of our biology (timing is everything), then you would agree that your blue light environment may be the most important area of your health to tackle. This is why there has been such a monumental push on the education around artificial blue light and an entire industry made around blocking blue light.
A healthy, regular circadian rhythm promotes healthy mood and improved cognition. Disruptions to circadian rhythm have been shown to increase the risk of most chornic diseases: including cancer, heart disease, neurodegenerative disease and metabolic conditions. Research has found that, compared to white light therapy, blue light is more effective for resetting circadian rhythms, suppressing nighttime melatonin, and enhancing performance. Other physiological actions of blue light suggested by the scientific literature include an increase in circulating beta endorphins, decreased systolic blood pressure due to nitric oxide mechanisms in the skin, an anti-bacterial effect, and a potential bio-modulating effect within the cells.
Blue light (like all areas of the light spectra) deserves an article of its own. I will be releasing an article dedicated to artificial blue light next month so stay tuned!

Red and Infrared Light - Healing Wavelengths
Red and infrared light is the most abundant portion of full spectrum sunlight, making up over 50% of the sunlight that hits the earth. Most of this is coming in the form of Near Infrared light (750-3000nm). Photo-biomodulation is a term used to describe the physiological effects from irradiation by red or near-infrared wavelengths. Red and near-infrared wavelengths have the ability to penetrate inside of our body’s tissues and cells, and can even penetrate through clothing. Studies have shown benefits such as improved tissue function, wound healing, anti-inflammatory effects, and improved energy metabolism from red and near-infrared wavelengths.
Conditions that may benefit from photobiomodulation include allergies, hypothyroidism, depression, dementia, cancer, diabetes related symptoms, exercise performance and recovery, pain, and cardiovascular diseases.
I have written an article on this substack that dives deep into the benefits of NIR light, and why I think it is the biggest nutrient deficiency worldwide (sunlight = NIR). NIR light (over 950 nm) may penetrate as deep as 8 cm and can penetrate bone, enter the cerebrospinal fluid and the brain.
Why is Red/NIR light so beneficial for our health ? Because it up-regulates ATP production and expands our exclusion zone water. You may have heard how fantastic Red/NIR light is for mitochondria…that is 100% true. Part of that reason is due to melatonin synthesis which is highlighted below. The other part is because it up regulates ATP production by expanding the exclusion zone water around the ATP nanomotor-reducing its viscosity and improving rotational torque. Bit complex yes, but that is the reality of our biology. ATP opens the binding site of proteins to water, which need to be hydrated to function properly as biological semiconductors so you could say that Red/NIR is IMPERATIVE for optimal biological function.
NIR light & Intracellular Melatonin Synthesis
Recent research by Zimmerman, S. and Reiter R. suggests that melatonin (a master antioxidant) exists in two main forms within the body – circulatory melatonin, which is suppressed during the day upon exposure to blue light and has its major effect on sleep and the circadian rhythm, and sub-cellular melatonin, which is produced and used locally by the mitochondria within our cells. NIR light stimulates melatonin production in the mitochondria, which helps protect the cells from oxidative stress from whatever stressors/toxins make their way into the mitochondria. It also helps naturally combat the free radicals generated from UV exposure. This is why Red/NIR wavelengths are so healing, and balance out the high energy and biologically damaging (to some degree) Blue/UV wavelengths. There is always a far higher amount of NIR light than any other light in the spectrum when it comes to energy and power density.
I have written an in depth article about Melatonin as well, because it is so much more than a “sleep hormone”. Zimmerman brilliantly discusses this in his work and how most of the circadian community misses this piece. Melatonin is THE MASTER ANTIOXIDANT, being able to stabilize up to 10 free radicals per molecule due to its remarkable cascading antioxidant abilities.

Violet, Green, Yellow/Orange Light
Violet light (visible) is hard to find research on but can be thought to range from 360-420nm, right after UVA (or even some overlap) and right before blue light in the ascending wavelength spectrum of full spectrum sunlight.
Japanese research showed that violet light (360–400 nm wavelengths) suppressed the axial length elongation both in a chick myopia model and in human. They also spiked out the fact that we are violet light deficient in a modern, indoor world because of the fear mongering around UV light. Blue light from screens causes myopia and violet/UVA light reverses it…
Violet light is also being studied for its potential benefit to improve sleep quality.
Green light (495-570nm) penetrates your dermis, almost reaching the subcutaneous tissue below. Studies have shown that green light is effective for relieving pain. Green light is also beneficial for treating skin condictions, especially with regard to skin tone and complexion. Sunspots, melasma, rosacea, eczema, and psoriasis can all benefit from green light. Another tout to the importance of full spectrum sun is the under discussed skin HEALING frequencies such as green + red to balance the high energy UV.
Green Light:
-
Might be used in attempts to reduce skin redness and irritation.
-
Has been studied for potential pain-reducing properties.
Yellow and Orange light. Lesser research around these wavelengths but including them anyways. These wavelengths penetrate the subcutaneous tissue beneath your dermis. Like green and blue light, they are effective at treating skin issues like eczema, sunburn, psoriasis, and creating an even skin tone. Yellow and orange light therapy is one of the less common types; however, it can help flush waste from your skin, elevate the functioning of your lymphatic system, and stimulate cellular energy to some extent.
One study proved that 590 nm light therapy after laser skin treatments reduced the intensity and healing time of skin irritation.
Yellow light:
-
Sometimes used to stimulate collagen production in the skin.
-
Has been used in lightbox therapies for mood regulation.
Orange light:
-
Often used in attempts to revitalize skin and promote a vibrant complexion.
-
Might be utilized for its potentially energizing and uplifting effects.
Conclusion
You can not replace full spectrum sunlight with light therapies that have only a few isolated frequencies. Sunlight contains such a vast amount of frequencies that all affect our biology in different ways and together provides a very synergistic affect. Our biology has evolved over millions of years to take the FULL SPECTRUM sun as our main input signal.
Light therapy can still be beneficial in certain scenarios without a doubt, but it will never replace full spectrum sunlight. This is a challenge in our modern indoor world we live in, and that is why we need to be so deliberate about going outside. That is also why I am so excited to be working with Daylight Computer, the world’s first computer that is designed to be used outside and has reflective screen technology that doesn’t destroy your retinas. Much more to come on Daylight Computer …so for now here is a repeat of the summary:
-
Sunlight is a broad band emitter and artificial light is a narrow band emitter
-
Sunlight is an un-polarized, continuous source of electromagnetic radiation. Artificial light is highly pulsed
-
Sunlight that reaches the earth is comprised of light frequencies that range from 280nm (UVB) to 2500nm (NIR) and everything in between. Each category of wavelength serves as a different biological stimuli
-
UVB radiation stimulates the production of vitamin D, as well as serotonin and beta-endorphins, UVA promotes the release of nitric oxide into the blood, and both have a positive effect on the diversity of the microbiome and our endogenous hormone production
-
Violet light can reverse myopia and potentially improve sleep quality
-
Blue light is the master circadian signaler, turning on/off the SCN via melanopsin photoreceptor…thus regulating cortisol/melatonin production as well as all circadian timing in the body
-
Green light can treat skin issues and also be used as a pain releiver
-
Red light, near-infrared radiation (NIR), and far-infrared (FIR) radiation have anti-inflammatory and tissue healing effects…NIR also stimulates the production of melatonin inside the mitochondria, a master anti-oxidant
Sunlight is the ultimate provider of light. Your light/EMF diet matters more than anything else in regards to health.
Biology is fundamentally electromagnetic.
Stay Sovereign,
Tristan
My NEW COURSE EMF-201 is officially out! An in depth educational course that follows my flagship EMF-101 course. Diving deep into Radio Frequencies, 5G, and Modern Tech with an appearance from an RF Engineer who has 20+ years of industry experience.
Follow my Decentralized Radio podcast for some brilliant upcoming episodes on light and EMFs.
-
-
 @ bf47c19e:c3d2573b
2025-01-08 17:43:36
@ bf47c19e:c3d2573b
2025-01-08 17:43:36Originalni tekst na novaekonomija.rs
05.12.2024 / Autor: Dragan Milić
Kada se desio prvi veliki „hajp“ oko bitkoina i kriptovaluta generalno (veći od prethodnih), negde krajem 2017-te, verujem da nije bilo čoveka koji tada bar u prolazu nije čuo da neko pominje te čudne, nove reči i fraze. Sećam se da mi je neki taksista, ničim izazvan, rekao da ulazi u posao sa rudarenjem kripta i da je uložio novac u grafičke karte koje treba da stignu preko veze, jer ih nema u prodaji. U tom trenutku to je moglo imati dvojako značenje. Ili da je kripto konačno ušao u mejnstrim i da ga je zajednica široko prihvatila ili da je vreme za izlazak iz tog biznisa i rasprodaju silnih altkoina koji su nicali kao pečurke posle kiše. Ispostavilo se da je ovo drugo bio ispravan odgovor odnosno dobra odluka.
Već u januaru sledeće, 2018. godine ceo sistem je počeo da se urušava kao kula od karata. Zagovornici kripta su govorili da je u pitanju samo korekcija i da će se stvar već na proleće popraviti, ali bitkoin se nije vratio na 17.000 dolara naredne tri godine. A mnoge druge kriptovalute zauvek su izgubile svoju vrednost.
Iako je to novo tržište volatilnost pratila godinama, a prati ga i danas, sada, na izmaku 2024. godine možda već možemo reći da je bitkoin na neki način prošao test vremena i „da je tu da ostane“. Dugo se bitkoin kretao u granicama između 50 i 70 hiljada američkih dolara, ali poguran rezultatima izbora u SAD i drugim makroekonomskim efektima koji su već konstanta, početkom decembra 2024. probio je psihološku granicu od 100.000 USD, čime su se dokazale tvrdnje da vreme digitalne imovine tek dolazi. Dan pre probijanja ovog limita, Džerom Pauel predsednik FED-a, nazvao je bitkoin digitalnim zlatom, i dodatno ubrzao ceo proces.
Mnogima ni danas nije jasno šta je zapravo kripto imovina i kako funkcioniše blokčejn na kojoj ista počiva. Što je opravdano jer je reč o veoma kompleksnoj tehnologiji čije razumevanje podrazumeva solidnu tehničku potkovanost i informisanost.
Činjenica je da nije potrebno poznavati tehnološki aspekt kripta da bi ga posedovali i trgovali istim, međutim to nas dovodi do starog pravila da investirate samo u stvari odnosno poslove koje razumete. Možda je to razlog zašto se tradicionalni ulagač i dalje drži S&P500 indeksa i nekretnina kao primarnog izbora, koji su uvek sigurnija opcija i manje podložna nestabilnosti.
Međutim, kako vreme odmiče, polako se stvara poverenje i u digitalnu imovinu kao opciju za ulaganje, koja nosi veliki rizik ali i veliku mogućnost zarade. Na primer, ko je pre nekoliko godina kupio bitkoin, na srednji rok je mogao višestruko da umnoži svoje ulaganje. A ko je bio u stanju da izađe iz okvira saveta „uloži onoliko koliko si spreman da oprostiš“ mogao je značajno da uveća svoj kapital. Na primer, da sam početkom 2020-te u jeku pandemije imao hrabrosti da kupim bitkoin po 5.000 dolara, sada bih zaradio dvadeset puta više. Ali, moglo je da bude i drugačije. Naknadna pamet ne važi…
Inače, moja lična predviđanja iz perioda s početka ove priče, dakle iz 2017-te, su bila polovično optimistična. Smeo sam se kladiti na blokčejn kao tehnologiju i njenu budućnost, međutim nisam bio siguran u bitkoin, jer sam mislio da će ubrzo biti prevaziđen. Naročito zbog svog Proof of work-a odnosno trošenja velike količine energije i računarskih resursa za odobravanje transakcija što nije bio slučaj kod nekih, u to vreme, novih kriptovaluta.
U avgustu 2017. u autorskom tekstu za jedan portal, sam napisao da kako god da završi Bitcoin kao čudo koje je okrenulo ekonomiju naglavačke ili i sam padne u revoluciji čiji je pionir i začetnik, Blockchain kao jedinstveno i genijalno tehnološko rešenje za transferisanje digitalnog novca će ostati. I mnogi upravo u ovoj tehnologiji vide budućnost novca. I pogrešio sam. Blokčejn i dalje čeka na svojih pet minuta, ali bitkoin odoleva i uči nas da na njega moramo računati.
U međuvremenu se dakle mnogo toga promenilo. Bitkoin se i pored volatilnosti uvukao u portfolije ozbiljnih investitora, odobreni su takozvani ETF-ovi (Exchange-Traded Fund), koji omogućavaju investitorima da ulažu u bitkoin bez potrebe da ga direktno poseduju ili upravljaju svojim digitalnim novčanicima i privatnim ključevima.
Glavna prepreka, u vidu nedostatka regulative, takođe je prevaziđena u mnogim pravnim sistemima. Možemo s ponosom istaći da je Republika Srbija jedna od prvih država u Evropi koja je regulisala Digitalnu imovinu. Ubrzo nakon usvajanja Zakona o digitalnoj imovini, izmenjen je i Zakon o porezu na dohodak građana, gde je bar na papiru, osvetljen i poreski tretman kripta. Problema u praksi i dalje ima, naročito oko podnošenja poreskih prijava i utvrđivanja poreske osnovice odnosno obračuna poreza, ali bar u delu vrste poreza i poreske stope pravne nesigurnosti više nema. Takođe, svako ko želi da se bavi pružanjem usluga može proći ne tako jednostavnu proceduru pribavljanja odgovarajućih dozvola u skladu sa zakonom i otpočeti taj posao u potpuno legalnim okvirima, što je do pre nekoliko godina bila siva zona i kod nas i u većini zemalja.
Bitkoinova mlađa braća nešto kaskaju sa dostizanjem svog ATH-a (All Time High), pa na primer ETH (Itirijum) u trenutku pisanja ovog teksta još uvek nije dostigao za njega magičnih 5.000 dolara, ali sva je prilika da će bitkoin prokrčiti put i za druge tokene odnosno kriptovalute na tržištu. Bar one koji su prošli test vremena i iza kojih postoji ozbiljnija infrastruktura i poslovanje.
-
 @ 6be5cc06:5259daf0
2024-12-29 19:54:14
@ 6be5cc06:5259daf0
2024-12-29 19:54:14Um dos padrões mais bem estabelecidos ao medir a opinião pública é que cada geração tende a seguir um caminho semelhante em termos de política e ideologia geral. Seus membros compartilham das mesmas experiências formativas, atingem os marcos importantes da vida ao mesmo tempo e convivem nos mesmos espaços. Então, como devemos entender os relatórios que mostram que a Geração Z é hiperprogressista em certos assuntos, mas surpreendentemente conservadora em outros?
A resposta, nas palavras de Alice Evans, pesquisadora visitante na Universidade de Stanford e uma das principais estudiosas do tema, é que os jovens de hoje estão passando por um grande divergência de gênero, com as jovens mulheres do primeiro grupo e os jovens homens do segundo. A Geração Z representa duas gerações, e não apenas uma.
Em países de todos os continentes, surgiu um distanciamento ideológico entre jovens homens e mulheres. Milhões de pessoas que compartilham das mesmas cidades, locais de trabalho, salas de aula e até casas, não veem mais as coisas da mesma maneira.
Nos Estados Unidos, os dados da Gallup mostram que, após décadas em que os sexos estavam distribuídos de forma relativamente equilibrada entre visões políticas liberais e conservadoras, as mulheres entre 18 e 30 anos são agora 30 pontos percentuais mais liberais do que os homens dessa faixa etária. Essa diferença surgiu em apenas seis anos.
A Alemanha também apresenta um distanciamento de 30 pontos entre homens jovens conservadores e mulheres jovens progressistas, e no Reino Unido, a diferença é de 25 pontos. Na Polônia, no ano passado, quase metade dos homens entre 18 e 21 anos apoiou o partido de extrema direita Confederation, em contraste com apenas um sexto das jovens mulheres dessa mesma idade.
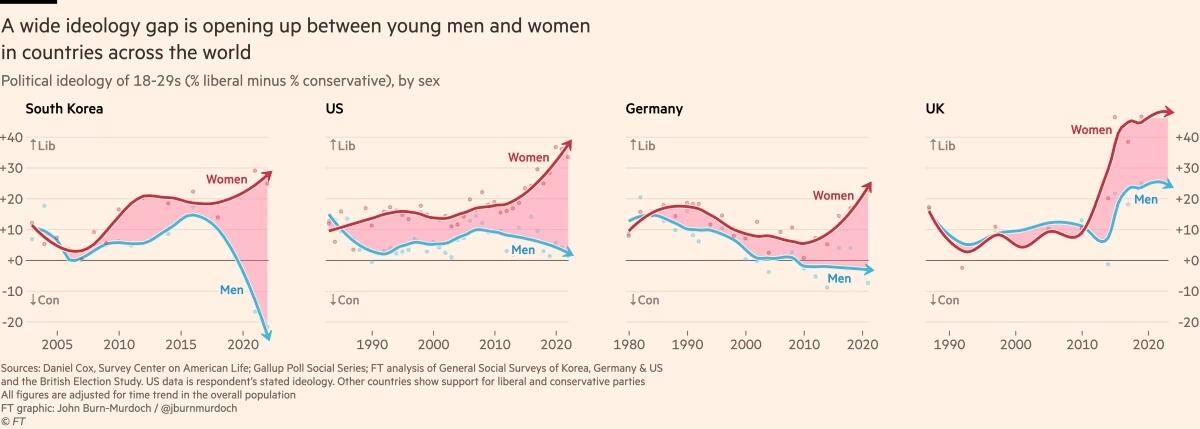
Fora do Ocidente, há divisões ainda mais acentuadas. Na Coreia do Sul, há um enorme abismo entre homens e mulheres jovens, e a situação é semelhante na China. Na África, a Tunísia apresenta o mesmo padrão. Vale notar que em todos os países essa divisão drástica ocorre principalmente entre a geração mais jovem, sendo muito menos pronunciada entre homens e mulheres na faixa dos 30 anos ou mais velhos.
O movimento # MeToo foi o principal estopim, trazendo à tona valores feministas intensos entre jovens mulheres que se sentiram empoderadas para denunciar injustiças de longa data. Esse estopim encontrou especialmente terreno fértil na Coreia do Sul, onde a desigualdade de gênero é bastante visível e a misoginia explícita é comum. (palavras da Financial Times, eu só traduzi)
Na eleição presidencial da Coreia do Sul em 2022, enquanto homens e mulheres mais velhos votaram de forma unificada, os jovens homens apoiaram fortemente o partido de direita People Power, enquanto as jovens mulheres apoiaram o partido liberal Democratic em números quase iguais e opostos.
A situação na Coreia é extrema, mas serve como um alerta para outros países sobre o que pode acontecer quando jovens homens e mulheres se distanciam. A sociedade está dividida, a taxa de casamento despencou e a taxa de natalidade caiu drasticamente, chegando a 0,78 filhos por mulher em 2022, o menor número no mundo todo.
Sete anos após a explosão inicial do movimento # MeToo, a divergência de gênero em atitudes tornou-se autossustentável.
Dados das pesquisas mostram que em muitos países, as diferenças ideológicas vão além dessa questão específica. A divisão progressista-conservadora sobre assédio sexual parece ter causado ou pelo menos faz parte de um alinhamento mais amplo, em que jovens homens e mulheres estão se organizando em grupos conservadores e liberais em outros assuntos.
Nos EUA, Reino Unido e Alemanha, as jovens mulheres agora adotam posturas mais liberais sobre temas como imigração e justiça racial, enquanto grupos etários mais velhos permanecem equilibrados. A tendência na maioria dos países tem sido de mulheres se inclinando mais para a esquerda, enquanto os homens permanecem estáveis. No entanto, há sinais de que os jovens homens estão se movendo para a direita na Alemanha, tornando-se mais críticos em relação à imigração e se aproximando do partido de extrema direita AfD nos últimos anos.
Seria fácil dizer que tudo isso é apenas uma fase passageira, mas os abismos ideológicos apenas crescem, e os dados mostram que as experiências políticas formativas das pessoas são difíceis de mudar. Tudo isso é agravado pelo fato de que o aumento dos smartphones e das redes sociais faz com que os jovens homens e mulheres agora vivam em espaços separados e tenham culturas distintas.
As opiniões dos jovens frequentemente são ignoradas devido à baixa participação política, mas essa mudança pode deixar consequências duradouras, impactando muito mais do que apenas os resultados das eleições.
Retirado de: https://www.ft.com/content/29fd9b5c-2f35-41bf-9d4c-994db4e12998
-
 @ 6e4f2866:a76f7a29
2025-01-08 17:29:36
@ 6e4f2866:a76f7a29
2025-01-08 17:29:36Foreword
“What’s the best sex you’ve ever had?”
Imagine that being the question that changed your life’s work!
And no, it didn’t come from a sleazy porn director in the basement
of a dingy house directed towards the person sitting on the
casting couch. It was asked by Rob Brinded at Chelsea FC’s stateof-
the-art Sports and Injury Prevention Medical facility and directed
at one of the best Football players in the world at that time.
Why did Rob ask that question? What did it reveal to him, and
how did that lead to him quitting his ‘perfect life’?
Even before the athlete answered, Rob knew he had unlocked
an incredibly important discovery. A discovery that would change
the trajectory of his life. One that would trigger him to walk
away from a high-paying job, get dumped by his girlfriend, and be
shunned by his professional peers while facing the inner demons
and self-torture of disappointment.
During this time, Rob forged a new mindset, armed himself
with the tools to cure himself, and extended that healing touch to
anyone who had the fortune of interacting with him.
Like many of my new friends, I first met Rob on Twitter. He
approached me after I had been the featured guest on The Bitcoin
Standard Podcast. My discussion with host Saifedean Ammous \ \ centred around the intricacies of the current education system
and the benefits of homeschooling. Rob had been particularly
intrigued by my insights about teaching versus learning and
how our education system is designed to mould kids rather than
nurture and inspire them. But what truly piqued Rob’s curiosity
was what I didn’t say. Throughout the podcast conversation,
he wanted to ask about certain nuances, the pauses. Because, well,
that’s the way Rob’s mind works now!
Over the next few months, Rob and I stayed in contact and
eventually had the pleasure of meeting each other in Madeira when
we received an invitation to assemble with other bitcoiners to meet
the President, as he and his cabinet wanted to learn more about
bitcoin and the opportunities it might bring to their island.
Extended, in-person conversations with Rob about his work
are truly fascinating. During our first meet-up, I found myself
open to everything he shared. Some people he has encountered
have brushed him off as a ‘Guru’ or too ‘Woo-Woo’ and thought
his ideas were too far out there. The irony here is that their feelings
are triggered by the very conditioning and programming that
these people have been subjected to and have been running from
their whole lives. As Rob would explain, the only way to step off
the hamster wheel is to realise you are on it in the first place. Most
people don’t and will forever be trapped, running the same selfdeprecating
programmes for their whole lives.
I was so captivated by Rob’s ideas that I booked him for a
few sessions (paid in bitcoin) to learn more about his work and,
of course, myself. My goal was to understand why I thought the
way I thought and why I acted the way I acted under certain stressors.
With a spirit of open exploration, we embarked on a journey
through my past, present and future, engaging in candid conversations
that flowed effortlessly. Rob’s guidance helped me decipher
the programs I had been running in my head (my OS system) and
how to close them down. I can best surmise it with the analogy
of ‘force-quitting’ a program on your computer when you get the
‘spinning beach ball of death’.
Once you do this simple visualisation exercise, a remarkable
transformation occurs — you feel lighter and think clearer. Like
our minds, our bodies can react in the most incredible ways. Lifelong
ailments, aches, or pains can feel instantly better and even disappear
completely.
Rob’s conviction in his work is not from blind luck; it’s rooted
in decades of deep introspection mixed with theoretical and practical
study — and, importantly, from results. The outcomes Rob
has seen and shared in this book are beyond remarkable and worth
everyone’s attention. As you journey through these pages and into
this rabbit hole, remember to note what emotions are triggered
within YOU carefully. Because that, dear reader, is your personal
hamster wheel. Those triggered emotions have been programmed
into your OS since you were born, and those programs are what
hold you back mentally and physically from being your best self
and living a happier and freer life.
So, sit back and enjoy the ride. Welcome to the rabbit hole of
decentralising your mind!
Daniel Prince
Host of The Once Bitten Podcast and Author of Choose Life
Block Height 800,608 — SW France \ \ M I N D , D E C E N T R A L I S E D
-
 @ 7ed7d5c3:6927e200
2025-01-08 17:10:00
@ 7ed7d5c3:6927e200
2025-01-08 17:10:00Can't decide if the terrible book you just read is a 1 or 1.5 star book? Look no further than this chart. Was it Shit or just Bad? Was that movie you watched Very Good or just Decent? How many things out there are really Life Changing?
Finally, a rating scale for humans. Use it for anything in your life that needs a rating out of 5 stars.
Rating / Description
0.5 – The worst 1.0 – Shit 1.5 – Bad 2.0 – Eh 2.5 – Entertaining, but not great 3.0 – Neutral 3.5 – Alright 4.0 – Decent 4.5 – Very good 5.0 – Life Changing
P.S. Do not use it to rate your wife's cooking. The author is not liable for any damages.
-
 @ 6e4f2866:a76f7a29
2024-12-27 16:03:31
@ 6e4f2866:a76f7a29
2024-12-27 16:03:31Have you ever felt like you’re running as fast as you can in life, only to find yourself in the same spot? Trying to achieve goals, optimise yourself only to feel unfulfilled & lacking. That’s the hamster wheel—an exhausting, repetitive cycle that holds us captive in patterns we didn’t consciously choose. These aren’t just bad habits; they’re deep-rooted default programs born from early life experiences. Let’s explore what these hamster wheels are, how they shape us, and most importantly, how we can step off them for good.
What Are Hamster Wheels? \ \ The term #hamsterwheels ( hamstr) is a metaphor for the unconscious patterns that keep us stuck. I discovered these wheels through my own introspection & seeing these patterns in my clients. Imagine a wheel turning endlessly, powered by our own efforts but leading nowhere. These programs are often formed in childhood, when trauma, disconnection, or unmet needs force us to develop defense mechanisms to survive. They worked back then, but now they just keep us spinning.
\ The Mechanics of a Hamster Wheel \ \ Every hamster wheel has two opposing forces—gain and loss, right and wrong, attention and neglect, let down & support & unable & able. We strive to stay on the “good” side: gaining approval, being right, or receiving attention. But inevitably, the wheel flips, and we find ourselves losing, being wrong, or feeling ignored. It’s a cruel cycle of frustration that feels impossible to escape. You will be positioned on the left side or right side when you look at the wheel. One is yin dominant, non doing, unable, more of a victim. One is Yang, always doing, high achiever, seen as a winner. \ \ Left side is safe in the unableness so will self sacrifice when they are to feel able to& start to achieve. So as they climb up the wheel to the right, they will lose interest or confidence in what they are doing, either sliding back exhausted in their endeavour or flipping over into victimhood. They long to be confident & win at life but deep down feel they cannot. \ \ Right sided dwellers have to be right, are constantly striving & hate (kryptonite) feeling unable. When they feel unable they will become enraged. They are compelled to gain valuableness in their own eyes and those of others. They are usually very difficult to work with as working with a therapist makes them feel unable. They will eventually put so much energy running up the right side that they will be flung backwards into usableness often times falling into deep depression (unableness) or even attracting illness. They always attract unableness & the left sided experiences to balance themselves out. The wheel always balances itself out. This is the way of the hamster wheel.

\ \ Here’s the kicker: these wheels are powered by our deepest fears and insecurities. They keep us stuck not because we’re lazy or unmotivated, but because they’ve become our default way of operating, they are our automated defence systems.
\ Common Hamster Wheels \ \ There are five key hamster wheels that we all grapple with:
- Gain/Loss: The endless chase for more—more success, more love, more recognition—followed by the crushing fear of losing it all.
- Right/Wrong: The compulsion to always be right, which leads to the paralyzing fear of being wrong.
- Attention/Neglect: Oscillating between craving attention and fearing rejection or neglect.
- Able/Unable: Striving to prove we’re capable, only to feel crushed by moments of doubt or failure.
- Support/Let Down: Giving endlessly to others for validation, but feeling betrayed or let down when it’s not reciprocated. If you watch your thoughts closely you will see these programs or songs at the root of all your thoughts.
How Hamster Wheels Impact Your Life \ \ These patterns influence every aspect of our lives: our relationships, careers, and even our self-worth. They dictate how we act, how we think, and even how we feel. For example:
- The drive to gain approval often results in feeling unworthy.
- A relentless pursuit of success can spiral into burnout and self-criticism.
- Efforts to avoid neglect might lead to overcompensating and losing yourself in the process. And the hardest part? These wheels feel like home. They’re familiar, and stepping off them can feel terrifying. They quite literally create your reality.
\ Breaking the Cycle The good news? You can break free. It’s not easy, but it’s possible. Here’s how:
- Observe Without Judgment: Start by noticing your patterns. This is real #meditation What thoughts or actions are you repeating? Don’t judge yourself—just observe. Awareness is the first step to freedom.
- Understand the Roots: These wheels didn’t come from nowhere. They’re the result of unmet needs or childhood traumas. By understanding their origins, you can begin to dismantle their power.
- Reject External Solutions: No guru, book, or quick fix can save you. True freedom comes from within. The moment you stop looking for external validation, the wheel starts to lose its grip. You must take full responsibility for everything in your life. Only you can do this proof of work.
\ Final Thoughts Hamster wheels aren’t your fault, but they are your responsibility. They’ve been running your life long enough. Isn’t it time to take back control? Imagine stepping off the wheel, feeling the ground beneath your feet for the first time. That’s where real freedom begins. So, what hamster wheel are you on? Are you ready to step off and embrace a life of clarity, peace, and purpose? The journey starts here, with a single step: observation. Everything else flows from there.
-
 @ ee11a5df:b76c4e49
2024-12-24 18:49:05
@ ee11a5df:b76c4e49
2024-12-24 18:49:05China
I might be wrong, but this is how I see it
This is a post within a series I am going to call "I might be wrong, but this is how I see it"
I have repeatedly found that my understanding of China is quite different from that of many libertarian-minded Americans. And so I make this post to explain how I see it. Maybe you will learn something. Maybe I will learn something.
It seems to me that many American's see America as a shining beacon of freedom with a few small problems, and China is an evil communist country spreading communism everywhere. From my perspective, America was a shining beacon of freedom that has fallen to being typical in most ways, and which is now acting as a falling empire, and China was communist for about a decade, but turned and ran away from that as fast as they could (while not admitting it) and the result is that the US and China are not much different anymore when it comes to free markets. Except they are very different in some other respects.
China has a big problem
China has a big problem. But it is not the communism problem that most Westerners diagnose.
I argue that China is no longer communist, it is only communist in name. And that while it is not a beacon of free market principles, it is nearly as free market now as Western nations like Germany and New Zealand are (being somewhat socialist themselves).
No, China's real problem is authoritarian one-party rule. And that core problem causes all of the other problems, including its human rights abuses.
Communism and Socialism
Communism and Socialism are bad ideas. I don't want to argue it right here, but most readers will already understand this. The last thing I intend to do with this post is to bolster or defend those bad ideas. If you dear reader hold a candle for socialism, let me know and I can help you extinguish it with a future "I might be wrong, but this is how I see it" installment.
Communism is the idea of structuring a society around common ownership of the means of production, distribution, and exchange, and the idea of allocating goods and services based on need. It eliminates the concept of private property, of social classes, ultimately of money and finally of the state itself.
Back under Mao in 1958-1962 (The Great Leap Forward), China tried this (in part). Some 50+ million people died. It was an abject failure.
But due to China's real problem (authoritarianism, even worship of their leaders), the leading classes never admitted this. And even today they continue to use the word "Communist" for things that aren't communist at all, as a way to save face, and also in opposition to the United States of America and Europe.
Authorities are not eager to admit their faults. But this is not just a Chinese fault, it is a fault in human nature that affects all countries. The USA still refuses to admit they assassinated their own president JFK. They do not admit they bombed the Nord Stream pipeline.
China defines "socialism with Chinese characteristics" to mean "the leadership of the Communist Party of China". So they still keep the words socialism and communism, but they long ago dropped the meanings of those words. I'm not sure if this is a political ploy against us in the West or not.
China's Marketplace Today
Today China exhibits very few of the properties of communism.
They have some common ownership and state enterprises, but not much differently than Western countries (New Zealand owns Air New Zealand and Kiwibank and Kiwirail, etc). And there are private enterprises all over China. They compete and some succeed and some fail. You might hear about a real-estate bank collapsing. China has private property. They have mostly free markets. They have money, and the most definitely have social classes and a very strong state.
None of that is inline with what communist thinkers want. Communist thinkers in China moan that China has turned away from communism.
Deng Xiaoping who succeeded Mao and attempted to correct the massive mistake, did much when he said "to get rich is glorious."
China achieved staggering rates of economic growth. 10% annually on average since 1977. Chinese economic reform started in 1979 and has continued through successive administrations (Deng, Jiang, Hu and now Xi).
China is now the world's largest economy (by GDP in PPP terms) since 2016.
I was first made aware of China's economic growth by Jim Rogers, an American commodities expert who travelled through China (and the rest of the world from 1990-1992) and in 2007 moved to Singapore where he ensured his daughters learned to speak Mandarin, because Jim knew where the economic growth was going to happen. Jim always spoke positively of China's economic prospects, and his view was so different from the "China is a nasty communist place" view that I had grown up with that my mind opened.
How can anybody believe they are still a communist country? In what world does it make sense that communism can produce such a massively booming economy? It doesn't make sense because it is simply wrong.
What does happen is that the CPC interferes. It lets the market do what markets do, but it interferes where it thinks oversight and regulation would produce a better result.
Western nations interfere with their markets too. They have oversight and regulation. In fact some of China's planned reforms had to be put on hold by Xi due to Donald Trump's trade war with China. That's right, they were trying to be even more free market than America, but America's protectionism prodded Xi to keep control so he could fight back efficiently.
Government oversight and regulation IMHO is mostly bad because it gets out of control, and there are no market forces to correct this. This gets even more extreme in a one-party system, so I can judge that China's oversight and regulation problems are very likely worse than those in Western nations (but I have no first hand experience or evidence).
Why do you keep saying CPC?
The Communist Party of China (CPC) is the ruling party in China. That is their official name. To call them the CCP is to concede to the idea that the British and Americans get to name everybody. I'm not sure who is right, since CPC or CCP is their "English" name (in Chinese it is 中国共产党 and Westernized it is Zhōngguó Gòngchǎndǎng). Nonetheless, I'll call them CPC because that is their wish.
Social Credit System
China moved from a planned economy to a market economy in stages. They didn't want any more sudden changes (can you blame them?). In the process, many institutions that have existed in the West for a long time didn't exist in China and they had to arise somehow. IMHO market forces would have brought these about in the private sector, but the one-party CP of China instead decided to create these.
One of those institutions was a credit score system. In the West we have TransUnion and Equifax that maintain credit ratings on people, and we have S&P, Moody's and Fitch that maintain credit ratings on companies. The domain of these ratings is their financial credit-worthiness.
So the People's Bank of China developed a credit information database for it's own needs. The government picked up on the idea and started moving towards a National Credit Management System. In 2004 it became an official goal to establish a credit system compatible with a modern market system. By 2006 banks were required to report on consumer creditworthiness.
But unchecked one-party governmental power will often take a good idea (credit worthiness data shared among private parties) and systematize it and apply it top-down, creating a solution and a new problem at the same time.
Nonetheless, originally it was about credit worthiness and also criminal convictions. That is no big scary thing that some right-wing American commentators will lead you to believe. In the US for example criminal records are public, so China's Social Credit System started out being no more over-reaching in scope than what Americans have lived under their entire lives, its only fault (a severe one) being centrally planned. And that remained the case up until about 2016 (in my estimation).
But of course there is always scope creep. As it exists today, I have reason to believe that CPC officials and even A.I. use judgement calls to score someone on how moral that person has been! Of course that is not a good idea, and IMHO the problem stems from one-party rule, and authoritarian administration of ideas that should instead be handled by the private sector.
Environmental, Social, and Governance
ESG is a system that came out of a couple basic ideas. The first is that many two-party transactions actually have externalities. They don't just affect the two parties, they also affect everybody else. When you fly in an airplane, you increase the CO2 in the atmosphere that everybody has to pay for (eventually). You may dispute that example, but that is no doubt one of the motivations of ESG.
But of course the recognition of this basic issue didn't lead all people towards market solutions (well it did, but those have been mostly messed up by others), but instead led many people towards ESG, which is a social credit scoring system which applies scores based on environmental and social side-effects of market transactions.
This is not at all the same as China's social credit system, which I described above. I hope you can see the difference.
In fact, China imported ESG from the West. Chinese companies, of their free will, in an attempt to court Western capital, achieve ESG goals for those Western investors. They have been playing this ESG game for 20 years just like the entire world has, because the West has imposed this faux-morality upon them. It isn't something China exported to us, it is something we exported to them.
I think China has avoided Woke-ism
My understanding of Chinese people, based on what I've heard many Chinese people say, is that China isn't affected by the Western woke-ism epidemic. They deride Western white woke people with the term "Baizuo". They have never sent an incompetent break dancer to the Olympics because of wok-ism. Competence is highly respected as is the competition to be the most competent, which (when augmented by a one-child policy which is no longer) has produced child prodigies like no other country has.
What about predatory loans of the Belt and Road initiative?
Predatory is an odd name for loans to people in need. The World Bank makes loans to people in need. China does too. China stands in opposition to Western Empire, and in that regard they produce their own alternative BRICS institutions. This is one of them.
There is AFAIK nothing more predatory about them. It is just that in some cases the borrowers have trouble paying them back and they get foreclosed upon. I don't think this is worthy of much discussion, except that the term "predatory" seems to me to be a propaganda device.
What about foreign influence from China?
China wants to influence the world, especially its own trading partners and potential trading partners. Doing that above board is fine by me.
But some of it is undoubtedly covert. Sometimes Chinese-born people run for public office in Western countries. In New Zealand we stood down some when it became clear they were being influenced too much by the CPC while being charged with representing their local town (dual loyalty issues). If only the USA would do the same thing to their dually-loyal politicians.
And all large nations run influence operations. The USA has the CIA, for example, and claims this "soft power" is actually the better alternative to what would otherwise be military intervention (but IMHO shouldn't be either). I'm not defending such operations (I despise them), I'm just explaining how China's position of exerting influence is not only no big deal and totally expected, it pales in comparison to the United States' influence operations which often become military excursions (something China rarely ever does).
What about the Great Firewall?
Yeah, that sucks. Again, single-party authoritarian control gone to extremes.
What about Human Rights Abuses? What about the Uyghur Genocide?
I don't like them. To the extent they are occurring (and I lean towards the belief that they are occurring), I condemn them.
China has anti-terrorism and anti-extremism policies that go too far. They end up oppressing and/or criminalizing cultures that aren't Chinese enough. But especially, China punishes dissent. Disagreement with the CPC is the high crime. It is the one-party rule that causes this problem. Anybody who speaks out against the CPC or goes against the state in any way is harshly punished. This happens to Uyghurs, to Falun Gong, to Tibetans, and to any religion that is seen as subversive.
Amnesty International and the UN OHCHR have documented issues around the Xinjiang Uyghur autonomous region, Tibet, LGBT rights, death penalty, workers rights, and the Hong Kong special administrative region. I am not about to pretend I know better than they do, but to some extent they go too far.
Amnesty International says this about the USA: Discrimination and violence against LGBTI people were widespread and anti-LGBTI legislation increased. Bills were introduced to address reparations regarding slavery and its legacies. Multiple states implemented total bans on abortion or severely limited access to it. Gender-based violence disproportionately affected Indigenous women. Access to the USA for asylum seekers and migrants was still fraught with obstacles, but some nationalities continued to enjoy Temporary Protected Status. Moves were made to restrict the freedom to protest in a number of states. Black people were disproportionately affected by the use of lethal force by police. No progress was made in the abolition of the death penalty, apart from in Washington. Arbitrary and indefinite detention in the US naval base Guantánamo Bay, Cuba, continued. Despite extensive gun violence, no further firearm reform policies were considered, but President Biden did announce the creation of the White House Office of Gun Violence Prevention. The USA continued to use lethal force in countries around the world. Black people, other racialized groups and low-income people bore the brunt of the health impacts of the petrochemical industry, and the use of fossil fuels continued unabated.
Amnesty international didn't even point out that the US government quashes free speech via pressure on social media corporations (because Amnesty International is far too lefty).
So who is worse, China or the US? I'm not going to make that judgement call, but suffice it to say that in my mind, China is not obviously worse.
China violates freedom of expression, association, and assembly of all people. This is bad, and a consequence mainly of one-party rule (again, what I think is the root cause of most of their ills). They arrest, detain, potentially kill anybody who publicly disagrees openly with their government. Clearly this is an excess of authoritarianism, a cancer that is very advanced in China.
As to organ harvesting of Uyghur Muslims, I think this is a myth.
China has dealt harshly with Muslim extremism. They don't offer freedom of religion to ISIS. And Amnesty International complains about that. But practically speaking you probably shouldn't respect the extremist religion of people who want to force everybody into a global caliphate through threat of violence. As you are well aware, some extremist Muslims (<1% of Islam) believe in using violence to bring about a global caliphate. Those extremists pop up in every country and are usually dealt with harshly. China has had to deal with them too.
I have watched two different Western YouTubers travel to Xinjiang province trying to find the oppressed Uyghurs and interview them. They can't find them. What they find instead are Uyghur Muslims doing their prayers five times a day at the local mosque. And also stories that the CPC pitched in some money to help them renovate the mosque. Maybe they were afraid it was a CPC trap and so they wouldn't speak freely. Amnesty International and the UN OHCHR say more than a million are "arbitrarily detained" and I'm not going to argue otherwise. But I'd be more convinced if there were a stream of pictures and news like there is out of Gaza, and it is suspicious that there isn't.
Conclusion
China is more like a Western nation that Westerners realize. Economically, militarily, socially. It still has a very serious obstacle to overcome: one-party rule. I don't think the one-party is going to voluntarily give up power. So most probably at some point in the future there will be a revolution. But in my opinion it won't happen anytime soon. For the most part Chinese people are living high on the hog, getting rich, enjoying the good life, in positive spirits about life, and are getting along with their government quite well at present.
-
 @ 000002de:c05780a7
2025-01-08 19:09:58
@ 000002de:c05780a7
2025-01-08 19:09:58originally posted at https://stacker.news/items/842459
-
 @ b83e6f82:73c27758
2024-12-23 19:31:31
@ b83e6f82:73c27758
2024-12-23 19:31:31Citrine 0.6.0
- Update dependencies
- Show notifications when importing, exporting, downloading events
- Change database functions to be suspending functions
Download it with zap.store, Obtainium, f-droid or download it directly in the releases page
If you like my work consider making a donation
Verifying the release
In order to verify the release, you'll need to have
gpgorgpg2installed on your system. Once you've obtained a copy (and hopefully verified that as well), you'll first need to import the keys that have signed this release if you haven't done so already:bash gpg --keyserver hkps://keys.openpgp.org --recv-keys 44F0AAEB77F373747E3D5444885822EED3A26A6DOnce you have his PGP key you can verify the release (assuming
manifest-v0.6.0.txtandmanifest-v0.6.0.txt.sigare in the current directory) with:bash gpg --verify manifest-v0.6.0.txt.sig manifest-v0.6.0.txtYou should see the following if the verification was successful:
bash gpg: Signature made Fri 13 Sep 2024 08:06:52 AM -03 gpg: using RSA key 44F0AAEB77F373747E3D5444885822EED3A26A6D gpg: Good signature from "greenart7c3 <greenart7c3@proton.me>"That will verify the signature on the main manifest page which ensures integrity and authenticity of the binaries you've downloaded locally. Next, depending on your operating system you should then re-calculate the sha256 sum of the binary, and compare that with the following hashes:
bash cat manifest-v0.6.0.txtOne can use the
shasum -a 256 <file name here>tool in order to re-compute thesha256hash of the target binary for your operating system. The produced hash should be compared with the hashes listed above and they should match exactly. -
 @ 2355757c:5ad3e04d
2025-01-08 17:00:53
@ 2355757c:5ad3e04d
2025-01-08 17:00:53Non-Native Electromagnetic Fields (nnEMFs) are in my opinion, the least discussed and most pervasive environmental toxin in modern society that is negatively affecting our health. We live in a toxic soup world, where we are being attacked from every angle. Polluted air, water, plastics, chemicals in our food/clothes, endocrine disruptors in our personal care and cooking products…the list goes on and on. It is the unfortunate reality of living in a modern fiat world, where all big companies cut corners with cheap, toxic ingredients just so you can have a $20 cooking pan and a $15 t-shirt.
On the bright side of things, most of those toxins are pretty easily avoidable by just swapping for higher quality or more natural alternatives. You can also filter or buy better water and eat real food that was raised locally without toxic herbicides (to a pretty easy degree). Enter nnEMFs, something that is IMPOSSIBLE to fully avoid and MUCH more challenging to mitigate exposure to. That is because technology is so ubiquitous in our modern society. Cell phones and wifi routers in every house, smart appliances, cell towers on every block, power distribution and transmission lines, 5G rollout…we are surrounded by nnEMFs on a daily basis.
What are nnEMFs and why are they bad for my health?
A nnEMF is any EMF generated from a non-native source AKA a result of modern human technology. The three most common sources of nnEMFs are from our electrical power grid, radiofrequency (RF) communication, and microwave frequencies. These three sources differ by function and frequency.
-
Electrical Power Grid - 60Hz Frequency - In “Extremely Low Frequency Range (ELF)”
-
Radio Frequency (RF) - 3kHz to 300GHz - Mobile/Societal Communication/TV/Radio
-
Microwave (MW) - 300MHz to 300GHz - Radar/Satellite/Space Communication

It gets a bit confusing in the nomenclature between RF and MW, but in reality the only difference is the type of application above 300MHz. Below 300MHz and it is distinctly an RF frequency. All transmission and distribution of power to industry/homes/businesses is occurring at 60Hz. Vast differences in frequency, both turn out to be pretty detrimental for our health. Here’s a few reasons why:
- Classified as a possible carcinogen by the IARC (Group 2B)
RF-EMFs and ELF EMFs have been classified by the IARC as possibly carcinogenic based on the current scientific evidence. Now this is still a lower classification than red meat, so does this carry any merit? I say yes. Many researchers agree, such as in THIS study where researchers looked at mobile phone radiation and risk of brain tumors and concluded that RF fields should be classified as a probable carcinogenunder the criteria used by the IARC.
- RF and ELF Fields Increase Oxidative Stress
Oxidative stress. If you are a regular here in the health space you know how much comes down to maintaining redox homeostasis in our mitochondria (the supplier of ATP in our cells). Dysfunctional mitochondria = dysfunctional health and it just so happens that nnEMFs can significantly increase oxidative stress in our cells, with review studies like THIS one documenting how the most electromagnetic organs (brain, heart) as well as reproductive organs (testes, ovaries) were the MOST affected. (I wrote a recent substack post on declining sperm count and nnEMFs was the star of the show). Increased oxidative stress is consistent with OG findings from the likes of Dr. Robert Becker and Dr. Andrew Marino in their research. It is high level, but increased levels of oxidative stress predisposes you to increased risk of ALL KNOWN CHRONIC DISEASES. Because of this, nnEMFs have been strongly linked to increased risk of the following:
-
Neurodegenerative diseases
-
Reproductive issues
-
Cancer
-
Cardiovascular disease
-
Diabetes
-
Disturbed Sleep
We live in a toxic soup world. Achieving restorative sleep is the only way our body is able to fight back and restore our health from all of these toxic exposures. ANYTHING that impedes sleep restoration is a premature nail in the coffin in my eyes. Don’t believe me on the importance and power of melatonin and our circadian rhythm? Check out THIS thread I wrote on melatonin (anti-cancer, potent anti-oxidant, mitochondrial composer, etc.). Exposure to nnEMFs during the day AND at night disturb our sleep and prevent the ability to have that highly restorative sleep needed to detoxify and replenish our cells. Lose quality sleep, lose the ability to handle stressors that you are exposed to daily.
DON’T BELIEVE ME THAT nnEMFs are harmful to human health? You are not alone. Many mainstream media outlets, researchers, and industry “experts” dismiss the level of non-ionizing radiation coming from things like cell phones as dangerous to human health. This is has been ongoing since the 1970s. However, if you are subscribed to this newsletter you may have more of an open mind to believing everything you read from CNN, Forbes, or the WHO. I know you all question things more than the average member of society. So if you question the efficacy and morality of the vaccine, why would you not also question the potential health hazards of nnEMF exposure? Even Presidential Nominee RFK is on board. Big Tech, Big Pharma, Big Food…there is no difference! Centralized industry will do anything it takes to cover up research that is sound and not funded by themselves. Here is an example…
Dr. Henry Lai from University of Washington Emeritus has compiled the most comprehensive set of research articles regarding nnEMFs and biological impacts. He has reviewed OVER 2,500 studies. His conclusion?
Dr. Lai reports concluded from his research that exposure to RFR or ELF EMF produces oxidative effects or free radicals, and damages DNA. Downstream effects of studies examined include significant effects on genetic, neurological and reproductive functions. Among hundreds of studies of Radio Frequency Radiation (RFR), 70% to 89% reported significant biological effects. Among hundreds of studies of Extremely Low Frequency (ELF) and static fields, 74% to 91% reported significant biological effects.

Still don’t believe me, read the book Going Somewhere by Dr. Andrew Marino. It will blow your mind on how much effort has gone to cover up research on the biological effects of nnEMFs since the 1970s. Or Google Russia’s stance on nnEMFs.
You can also listen to one of our latest Decentralized Radio episodes with Anthony Smith, COO of EMF Safe. EMF Safe is a fantastic company that offers, in my opinion, the MOST effective nnEMF mitigation technology for your house. Hint: it’s not a f*cking pendant or harmonizer. YouTube link or Spotify link HERE.
Now that we got through the depressing side of the story, let's talk about WHAT YOU CAN DO to protect yourself from the harmful effects of nnEMFs without having to live in the woods-not a perfect solution either ;)
HOW TO MITIGATE nnEMF detrimental health effects: DURATION + DISTANCE \
\ TIME/DURATION. Your worst enemy in being exposed to nnEMFs is the duration of exposure. Nearly all of the negative studies showed that after 48-72hrs of exposure (chronic), detrimental health effects were seen. HOWEVER, the same studies showed less conclusive negative health effects for exposures less than 24-48hrs (with variance). For me that means the following action items:
-
Turn off the wifi-router at night
-
Turn phone on airplane mode when not using for >10 min
-
Turn appliances OFF when not in use in your home
-
Create a sleep sanctuary with minimal/no electronics in the bedroom
-
Do not move to an area right next to High Voltage Transmission Lines, Substation, Airport, Hospital, etc. (any area with high powered communication/RF equipment or power distribution equipment)
DISTANCE. Distance is your best friend in mitigating nnEMFs. Why? Inverse square law. Inverse square law is the fact that the magnitude of the EMF is calculated with the square of the distance in the denominator of the equation. This means that for every doubling of distance you have between you and the EMF source, the magnitude weakens by a factor of FOUR. Triple the distance, EMF magnitude goes down by a factor of NINE (and so forth). For me that results in the following action items:
-
Do not keep your cell phone ON your body when ON & receiving calls/texts
-
Do NOT hold your cell phone up to your ear when making calls (use headphones/speaker)
-
Move your bed 6-12 inches AWAY from any electrical outlets in your bedroom (especially near your head)
-
Do not stand immediately next to high powered appliances when ON & in use (microwave, washer, dryer, blender, etc.)

There exists a lot of other nnEMF “mitigating/harmonizing” technologies, however I would be highly suspect of anyone trying to sell you something. EMFs are extremely complex. The angle of incidence, power level, and frequency matter tremendously. Most folks who aren’t engineers or have a deep knowledge of physics likely won’t be able to have the baseline knowledge to know what is a scam and what is not. OR what to prioritize from an nnEMF mitigation perspective. I gave a pretty good starting point above for what actionable steps you can take. THis does not mean all products are a scam. nnEMF shielding has its place and I use some of these products…but whenever a topic is extremely complex to the layperson, it is easy for someone to convince you that a product works. Especially when proof is challenging to come up with (EMF readers are an okay tool at best).
As someone who holds a M.S. in Electrical Engineering, I never thought that my degree would come in handy for health optimization. Now in 2023, here I am realizing how electromagnetism is likely the MOST important topic to conceptualize to really crack the optimal health code. We are electromagnetic beings, and the research in this space has only just begun to scratch the surface.
If you want to learn more in depth about nnEMFs, mitigation tactics, what products work and do not, etc…subscribe to stay up to date on the latest. I am directly working with some renowned EMF experts on developing more educational content/courses that I will be launching in the near future to help practitioners and fellow esoteric health connoisseurs better understand nnEMFs more in depth to help themselves and their clients live a more optimal life.
Here on Decentralized Health, I will be writing in depth about the electromagnetic aspects of health alongside other topics I am passionate about such as environmental toxins, regenerative agriculture, decentralization, Bitcoin and more. I want as many people as possible to become empowered through education so that they can escape the dependencies of the centralized systems that are tarnishing our quality of life.
This is just the tip of the nnEMF iceberg.
Stay Sovereign,
Tristan
Originally published Sep 25. 2023
-
-
 @ f96073dc:5951c7c2
2025-01-08 16:54:42
@ f96073dc:5951c7c2
2025-01-08 16:54:42Introduction
The food we consume plays an obvious yet undervalued role in not just sustaining us, but also in shaping who we become.
The phrase "You are what you eat" transcends cliché to embody a profound truth: our diet directly influences our life experience.
Debates continue about the optimal food sources for human health and longevity.
These discussions often involve emotionally charged arguments influenced by faith, traditions, economic interests, and political opinions concerning the global climate crisis and sustainability.
My goal isn’t to delve into the weeds of this emotional & political debate, but instead to strip things back and provide a birds eye view on nutrition, whilst offering alternative lenses through which we can view food.
 ## Understanding Food as Information
## Understanding Food as Information More than mere fuel, food serves as crucial information for our bodies.
This concept may sound strange, as much of our nutritional understanding has been dumbed down to ‘energy in, energy out’, or ‘calories in, calories out’.
This perspective bypasses the importance of micro nutrients—the vitamins & minerals our bodies interrelate with, or don’t.
Food information determines how our cells function and regenerate, impacting everything from energy levels to cognitive ability.
The challenge lies in deciphering what constitutes "good information."
For centuries, nature provided a simple guide.
Our ancestors thrived on a diet of organ meats, plants, seafood, fruit, muscle meats, bones, and eggs—foods naturally rich in nutrients and absent of modern chemicals.
The question remains: If our forebears thrived on these natural foods, why have we deviated so drastically?
 ## The Shift in Food Paradigms
## The Shift in Food Paradigms The introduction of heavily processed "Frankenfoods" laden with chemicals represents a stark departure from the diets of our grandparents and great-grandparents.
They consumed what we now coin "organic" food out of necessity rather than choice.
Food is pleasure, but it’s also a tool for a healthy self.
This ratio has been disproportionally thrown out of alignment.
The modern supermarket, with its aisles dominated by hyper palatable and processed products, reflects a concerning shift in our eating habits.
On the periphery of supermarkets lie fruits, vegetables, dairy, and animal based products, many of which have been sprayed with chemicals like glyphosate, or raised under inhumane conditions.
This brings us to the troubling paradox: while some parts of the world suffer from over-consumption and associated health issues like obesity and metabolic diseases, others face malnutrition and starvation due to food scarcity. (See red line below)
 *HFCS: High fructose corn syrup
*HFCS: High fructose corn syrupQuestioning Current Food Paradigms
Our current food systems are broken.
A hard truth and pill to swallow, but if you look around, people have never been this unwell and overweight.
Misleading ‘Health Star Ratings’ and a flawed food pyramid, reflect a deeper societal malaise.
These systems often promote products that are not conducive to health, with processed carbohydrate forms serving as our staple, while nutrient and caloric dense foods like meat, fish, dairy, and natural fats have been marginalised.
 ## Whole Foods and Balanced Nutrients
## Whole Foods and Balanced Nutrients So, what’s the ideal diet?
There is no universal diet that fits everybody.
The journey to finding the right diet involves personal experimentation.
However, a diet emphasising whole foods, which humans have consumed for millennia, remains a sound choice.
Eating natural foods avoids the pitfalls of ultra-processed foods and provides a balanced array of nutrients.
Side note: historically, meat was always the prized resource.
 ## Beyond Pesticides
## Beyond Pesticides Every year, the Environmental Working Group (EWG) puts together a list of 15 foods with the lowest amounts of pesticide residues, and conversely, 12 of the most contaminated foods with pesticides.
This is known as the ‘Clean Fifteen’ and ‘Dirty Dozen’.
When financially feasible, it’s advised to consume organic and pasture raised products.
If buying organic isn’t possible, one strategy to reduce pesticides is to soak the produce in water and a teaspoon of baking soda or a splash of apple cider vinegar for a few minutes.
 ## Nutritional Strategies for Specific Needs
## Nutritional Strategies for Specific Needs Strategies like the elimination diet can help individuals identify how specific foods affect their bodies, allowing them to make informed choices that resonate with their unique physiological needs.
Tracking macronutrients and particularly protein intake can be crucial for specific health goals like muscle growth or weight loss.
Gaining a baseline understanding of the macros in your food can be an important piece of the puzzle, but should not become an obsessive practice.
Many diets serve a purpose, and depending on your goals as well as physiology, can be leveraged for great benefit.
This broad concept has been developed into a growing area of research called Nutrigenomics, defined as the study of how different foods may interact with specific genes to modify the risk of common chronic diseases, such as heart disease, stroke, and certain cancers.
For example, a ketogenic diet can help those with neurological disorders such as epilepsy or Alzheimer's disease, intermittent fasting can facilitate weight loss, and a carnivore diet can heal chronic skin or gut issues.
 ## Conclusion
## ConclusionIn an era where diet-related health issues are rampant, returning to a more natural, informed way of eating is not just beneficial; it is necessary.
The prevalence of heavily processed "Frankenfoods" deviates from the nutrient-rich diets of our ancestors, contributing to a paradox of overconsumption and malnutrition.
Challenging current food paradigms is necessary to address misleading nutritional guidelines and flawed food systems.
Empower yourself to explore food in a deeper fashion, seeking a diet that not only nourishes your body but also aligns with your lifestyle goals and fosters a sense of vitality and well-being.
Eating well is a form of a self respect, and while we get the chance to inhabit this physical form, it should be our duty to make the most of this life and embody our fullest potential.
-
 @ 00cfe60d:2819cc65
2025-01-08 16:36:40
@ 00cfe60d:2819cc65
2025-01-08 16:36:40Lets start with the money talk, at its core, a good form of money is created from two key ingredients: time and energy.
**Money = Time + Energy ** This simple idea explains why money has value. Time is something we can never get back, and energy is what powers everything we do, both mentally and physically. Together, they create value.
Why Energy is So Important Energy is what keeps life going. It’s essential for everything we use and do every day. For example:
- Food without energy to cook is raw and not very tasty.
- A car without energy doesn’t go anywhere.
- A person without energy feels tired and can’t work or play.
- Your work without energy gets nothing done.
- Football without energy means no running, no cheering, and no fun.
- A phone without energy is just a useless object.
- A house without energy is cold, dark, and uncomfortable.
- Transportation without energy means no moving buses, trains, or planes.
- The internet without energy means no websites, no games, and no communication.
- Nature without energy means plants don’t grow and animals can’t survive.
And what about money without energy? ** We often hear that “time is money” but if money is created without any time or energy, it becomes worthless. That’s why energy is so important in giving money its value.
Why Bitcoin is Different
Bitcoin is special because it follows the equation of money perfectly. It’s the best kind of money because it requires both time and energy to exist. Here’s how:
-
Time: Bitcoin’s network is designed to create new bitcoins at regular intervals, so time is built into the system.
-
Energy: Bitcoin is made using a process called Proof-of-Work, which uses real-world energy to produce and secure it. This ties its value to effort and cost.
Thanks to this process, Bitcoin is:
-
Scarce: There will only ever be 21 million bitcoins. It can’t be copied or faked.
-
Reliable: Its value is tied to real-world energy, making it solid and trustworthy.
-
Effort-Based: No one can create bitcoins out of thin air. It takes real work.
This makes Bitcoin an honest form of money, free from manipulation or shortcuts. It connects the digital and physical worlds through energy, just like gold was in the past, requiring time and energy to extract and maintain its value.
The Problem with Regular Money (Fiat Money)
On the other hand, fiat money, the kind printed by governments, doesn’t follow the same rules. It’s made without effort, just by pressing a button. This leads to big problems:
-
Inflation: More money is printed, making the money you already have worth less.
-
Manipulation: Governments and banks can change the rules whenever they want.
-
Unfairness: People closest to the money printers benefit the most, while everyone else pays the price.
-
Fiat money breaks the rule of time and energy. It’s just a symbol, not a true store of value.
**Henry Ford’s Energy Currency Idea ** Over 100 years ago, Henry Ford had a bold idea: What if money was based on energy? He believed energy was the ultimate resource because it’s measurable and valuable to everyone.
Bitcoin brings Ford’s vision to life. Its Proof-of-Work system ties money directly to energy. Bitcoin acts as a global, incorruptible energy currency that rewards effort and aligns money with real-world value.
Why Energy-Based Money Matters
Money that’s rooted in time and energy isn’t just an idea, it’s a principle we live by every day. To truly understand the value of energy and effort, let me share a personal story.
Every single day of the week, I train. I pour my energy and effort into CrossFit, pushing my body and mind to their limits. Last year, during a competition, I achieved something I’d never done before: 12 ring muscle-ups. Before that, my maximum was just three. Through consistent training, spending my time and energy at the gym, I earned that reward. It wasn’t easy, but it was worth it.
This is Proof-of-Work in action. Just like my training required time and energy to achieve results, Bitcoin requires time and energy to exist. Its
Proof-of-Work mechanism ensures:
- It can’t be faked or inflated.
- It rewards hard work and energy, not shortcuts or manipulation.
- It restores trust by linking value to real-world effort.
In a world where fiat money can be printed without effort, Bitcoin shines as a clear and honest form of money. Like the work I put into my training, Bitcoin ties time and energy to value, creating a system that’s fair, transparent, and built to last.
-
 @ 2f4550b0:95f20096
2025-01-08 15:11:46
@ 2f4550b0:95f20096
2025-01-08 15:11:46Leadership is rarely a smooth ride. For every moment of success, there are setbacks and challenges that test even the most seasoned leaders. The key to sustained success isn’t avoiding difficulties but rather how effectively one can navigate through them. Resilience, the ability to bounce back from adversity, is not just a personal asset; it’s a leadership imperative.
I remember an experience earlier in my career that underscored the power of resilience in leadership. I was leading a team on a high-stakes project. We had invested countless hours, fine-tuned every detail, and had finally reached the presentation phase. Then, disaster struck: the technology we relied on for the demo failed at the last minute. The team’s morale plummeted. I saw the disappointment in their faces, and I could feel the weight of their expectations on me.
At that moment, I had a choice: I could either give in to frustration and let the team spiral, or I could model resilience and lead them through the crisis. I took a deep breath and reminded myself that setbacks are temporary and often lead to growth. We brainstormed solutions on the spot, restructured our approach, and within hours had a makeshift presentation that was just as impactful as our original plan. In the end, we delivered it successfully—and I learned one of the most valuable lessons in leadership: resilience doesn’t mean avoiding failure, but rather how we respond when things don’t go as planned.
This experience taught me that resilient leadership hinges on a few essential principles:
- Maintain a Positive Outlook: As a leader, your mindset directly influences your team. When faced with setbacks, staying calm and optimistic can help anchor the group. A positive perspective allows you to focus on solutions instead of dwelling on problems.
- Adapt and Problem-Solve: Resilience is about adaptability. Things don’t always go according to plan, and being able to quickly pivot and think creatively in the face of adversity is crucial. Resilient leaders encourage their teams to embrace change, adapt, and find alternative solutions.
- Support Your Team: Leaders cannot be resilient alone. Resilience thrives in a supportive environment. Offer your team encouragement, communicate openly, and make sure they know they have your support. By fostering a culture of mutual trust, you’ll enable everyone to recover and grow stronger together.
- Learn from Setbacks: Every challenge presents an opportunity to learn. Resilient leaders view failures as stepping stones to improvement. Reflecting on what went wrong and why, allows leaders and teams to strengthen their strategies moving forward.
In leadership, setbacks are inevitable. What sets great leaders apart is their ability to bounce back. With resilience, you can navigate through challenges with confidence and lead your team toward continued success.
-
 @ 16d11430:61640947
2024-12-23 16:47:01
@ 16d11430:61640947
2024-12-23 16:47:01At the intersection of philosophy, theology, physics, biology, and finance lies a terrifying truth: the fiat monetary system, in its current form, is not just an economic framework but a silent, relentless force actively working against humanity's survival. It isn't simply a failed financial model—it is a systemic engine of destruction, both externally and within the very core of our biological existence.
The Philosophical Void of Fiat
Philosophy has long questioned the nature of value and the meaning of human existence. From Socrates to Kant, thinkers have pondered the pursuit of truth, beauty, and virtue. But in the modern age, the fiat system has hijacked this discourse. The notion of "value" in a fiat world is no longer rooted in human potential or natural resources—it is abstracted, manipulated, and controlled by central authorities with the sole purpose of perpetuating their own power. The currency is not a reflection of society’s labor or resources; it is a representation of faith in an authority that, more often than not, breaks that faith with reckless monetary policies and hidden inflation.
The fiat system has created a kind of ontological nihilism, where the idea of true value, rooted in work, creativity, and family, is replaced with speculative gambling and short-term gains. This betrayal of human purpose at the systemic level feeds into a philosophical despair: the relentless devaluation of effort, the erosion of trust, and the abandonment of shared human values. In this nihilistic economy, purpose and meaning become increasingly difficult to find, leaving millions to question the very foundation of their existence.
Theological Implications: Fiat and the Collapse of the Sacred
Religious traditions have long linked moral integrity with the stewardship of resources and the preservation of life. Fiat currency, however, corrupts these foundational beliefs. In the theological narrative of creation, humans are given dominion over the Earth, tasked with nurturing and protecting it for future generations. But the fiat system promotes the exact opposite: it commodifies everything—land, labor, and life—treating them as mere transactions on a ledger.
This disrespect for creation is an affront to the divine. In many theologies, creation is meant to be sustained, a delicate balance that mirrors the harmony of the divine order. Fiat systems—by continuously printing money and driving inflation—treat nature and humanity as expendable resources to be exploited for short-term gains, leading to environmental degradation and societal collapse. The creation narrative, in which humans are called to be stewards, is inverted. The fiat system, through its unholy alliance with unrestrained growth and unsustainable debt, is destroying the very creation it should protect.
Furthermore, the fiat system drives idolatry of power and wealth. The central banks and corporations that control the money supply have become modern-day gods, their decrees shaping the lives of billions, while the masses are enslaved by debt and inflation. This form of worship isn't overt, but it is profound. It leads to a world where people place their faith not in God or their families, but in the abstract promises of institutions that serve their own interests.
Physics and the Infinite Growth Paradox
Physics teaches us that the universe is finite—resources, energy, and space are all limited. Yet, the fiat system operates under the delusion of infinite growth. Central banks print money without concern for natural limits, encouraging an economy that assumes unending expansion. This is not only an economic fallacy; it is a physical impossibility.
In thermodynamics, the Second Law states that entropy (disorder) increases over time in any closed system. The fiat system operates as if the Earth were an infinite resource pool, perpetually able to expand without consequence. The real world, however, does not bend to these abstract concepts of infinite growth. Resources are finite, ecosystems are fragile, and human capacity is limited. Fiat currency, by promoting unsustainable consumption and growth, accelerates the depletion of resources and the degradation of natural systems that support life itself.
Even the financial “growth” driven by fiat policies leads to unsustainable bubbles—inflated stock markets, real estate, and speculative assets that burst and leave ruin in their wake. These crashes aren’t just economic—they have profound biological consequences. The cycles of boom and bust undermine communities, erode social stability, and increase anxiety and depression, all of which affect human health at a biological level.
Biology: The Fiat System and the Destruction of Human Health
Biologically, the fiat system is a cancerous growth on human society. The constant chase for growth and the devaluation of work leads to chronic stress, which is one of the leading causes of disease in modern society. The strain of living in a system that values speculation over well-being results in a biological feedback loop: rising anxiety, poor mental health, physical diseases like cardiovascular disorders, and a shortening of lifespans.
Moreover, the focus on profit and short-term returns creates a biological disconnect between humans and the planet. The fiat system fuels industries that destroy ecosystems, increase pollution, and deplete resources at unsustainable rates. These actions are not just environmentally harmful; they directly harm human biology. The degradation of the environment—whether through toxic chemicals, pollution, or resource extraction—has profound biological effects on human health, causing respiratory diseases, cancers, and neurological disorders.
The biological cost of the fiat system is not a distant theory; it is being paid every day by millions in the form of increased health risks, diseases linked to stress, and the growing burden of mental health disorders. The constant uncertainty of an inflation-driven economy exacerbates these conditions, creating a society of individuals whose bodies and minds are under constant strain. We are witnessing a systemic biological unraveling, one in which the very act of living is increasingly fraught with pain, instability, and the looming threat of collapse.
Finance as the Final Illusion
At the core of the fiat system is a fundamental illusion—that financial growth can occur without any real connection to tangible value. The abstraction of currency, the manipulation of interest rates, and the constant creation of new money hide the underlying truth: the system is built on nothing but faith. When that faith falters, the entire system collapses.
This illusion has become so deeply embedded that it now defines the human experience. Work no longer connects to production or creation—it is reduced to a transaction on a spreadsheet, a means to acquire more fiat currency in a world where value is ephemeral and increasingly disconnected from human reality.
As we pursue ever-expanding wealth, the fundamental truths of biology—interdependence, sustainability, and balance—are ignored. The fiat system’s abstract financial models serve to disconnect us from the basic realities of life: that we are part of an interconnected world where every action has a reaction, where resources are finite, and where human health, both mental and physical, depends on the stability of our environment and our social systems.
The Ultimate Extermination
In the end, the fiat system is not just an economic issue; it is a biological, philosophical, theological, and existential threat to the very survival of humanity. It is a force that devalues human effort, encourages environmental destruction, fosters inequality, and creates pain at the core of the human biological condition. It is an economic framework that leads not to prosperity, but to extermination—not just of species, but of the very essence of human well-being.
To continue on this path is to accept the slow death of our species, one based not on natural forces, but on our own choice to worship the abstract over the real, the speculative over the tangible. The fiat system isn't just a threat; it is the ultimate self-inflicted wound, a cultural and financial cancer that, if left unchecked, will destroy humanity’s chance for survival and peace.
-
 @ 8d34bd24:414be32b
2025-01-08 14:34:15
@ 8d34bd24:414be32b
2025-01-08 14:34:15I’ve known that there are references to Jesus in the Old Testament. They just don’t use the name Jesus.
Then God said, “Let Us make man in Our image, according to Our likeness; and let them rule over the fish of the sea and over the birds of the sky and over the cattle and over all the earth, and over every creeping thing that creeps on the earth.” (Genesis 1:26) {emphasis mine}
Notice the references to God in the plural. These are clues to the trinitarian (3 persons in one God) nature of God.
There are also examples of theophanies (preincarnate Jesus) in the Old Testament. These theophanies are frequently referred to as “the angel of the Lord” or “the angel of God.”
But the angel of the Lord called to him from heaven and said, “Abraham, Abraham!” And he said, “Here I am.” He said, “Do not stretch out your hand against the lad, and do nothing to him; for now I know that you fear God, since you have not withheld your son, your only son, from Me.” (Genesis 22:11-12) {emphasis mine}
In this case we know that the “angel of the Lord” is not just an angel because he says, “I know that you fear God, since you have not withheld your son, your only son, from Me,” equating Himself, “Me,” with God. In most cases when an angel appears, the people drop face down in worship, but the angel corrects them and tells them not to worship. When the angel is Jesus, He accepts the worship and in many cases sacrifices as well.
The angel of the Lord appeared to him and said to him, “The Lord is with you, O valiant warrior.” Then Gideon said to him, “O my lord, if the Lord is with us, why then has all this happened to us? … So Gideon said to Him, “If now I have found favor in Your sight, then show me a sign that it is You who speak with me. Please do not depart from here, until I come back to You, and bring out my offering and lay it before You.” And He said, “I will remain until you return.”
Then Gideon went in and prepared a young goat and unleavened bread from an ephah of flour; he put the meat in a basket and the broth in a pot, and brought them out to him under the oak and presented them. The angel of God said to him, “Take the meat and the unleavened bread and lay them on this rock, and pour out the broth.” And he did so. Then the angel of the Lord put out the end of the staff that was in his hand and touched the meat and the unleavened bread; and fire sprang up from the rock and consumed the meat and the unleavened bread. Then the angel of the Lord vanished from his sight. When Gideon saw that he was the angel of the Lord, he said, “Alas, O Lord God! For now I have seen the angel of the Lord face to face.” (Judges 6:12=13a, 17-22) {emphasis mine}
As you can see, Gideon offered an offering. An offering to anyone other than God would be idolatry. Gideon offers a “a young goat and unleavened bread from an ephah of flour,” which is a proper sin offering to God. The angel did not eat the offering, but told Gideon to “Take the meat and the unleavened bread and lay them on this rock … Then the angel of the Lord put out the end of the staff that was in his hand and touched the meat and the unleavened bread; and fire sprang up from the rock and consumed the meat and the unleavened bread. Then the angel of the Lord vanished from his sight.” Gideon’s offering was taken as a burnt offering to God and to angel of the Lord, who is Jesus.
With all of this, look at the verse I read last night:
Who has ascended into heaven and descended?\ Who has gathered the wind in His fists?\ Who has wrapped the waters in His garment?\ Who has established all the ends of the earth?\ What is His name or His son’s name?\ Surely you know! (Proverbs 30:4) {emphasis mine}
Surely this is a passage about Jesus.
This verse says, “Who has ascended into heaven and descended?” The New Testament says about Jesus, “No one has ascended into heaven, but He who descended from heaven: the Son of Man.” (John 3:13)
This verse says, “Who has gathered the wind in His fists?” The New Testament says about Jesus,
And there arose a fierce gale of wind, and the waves were breaking over the boat so much that the boat was already filling up. Jesus Himself was in the stern, asleep on the cushion; and they woke Him and said to Him, “Teacher, do You not care that we are perishing?” And He got up and rebuked the wind and said to the sea, “Hush, be still.” And the wind died down and it became perfectly calm. (Mark 4:37-39) {emphasis mine}
This verse says, “Who has wrapped the waters in His garment?” The New Testament says about Jesus,
And in the fourth watch of the night He came to them, walking on the sea. When the disciples saw Him walking on the sea, they were terrified, and said, “It is a ghost!” And they cried out in fear. But immediately Jesus spoke to them, saying, “Take courage, it is I; do not be afraid.”
Peter said to Him, “Lord, if it is You, command me to come to You on the water.” And He said, “Come!” And Peter got out of the boat, and walked on the water and came toward Jesus. (Matthew 14:25-29) {emphasis mine}
This verse says, “Who has established all the ends of the earth?” The New Testament says about Jesus,
In the beginning was the Word, and the Word was with God, and the Word was God. He was in the beginning with God. All things came into being through Him, and apart from Him nothing came into being that has come into being. (John 1:1-3) {emphasis mine}
This verse says, “What is His name or His son’s name?” The New Testament says about Jesus,
After being baptized, Jesus came up immediately from the water; and behold, the heavens were opened, and he saw the Spirit of God descending as a dove and lighting on Him, and behold, a voice out of the heavens said, “This is My beloved Son, in whom I am well-pleased. (Matthew 3:16-17) {emphasis mine}
This verse says, “Surely you know!” As New Testament believers we know the Son of God, Jesus Christ. The Bible was pointing to the Son of God long before He came to earth as a baby.
Who has ascended into heaven and descended?\ Who has gathered the wind in His fists?\ Who has wrapped the waters in His garment?\ Who has established all the ends of the earth?\ What is His name or His son’s name?\ Surely you know! (Proverbs 30:4) {emphasis mine}
It doesn’t matter how many times we have already read the Bible. Every time we read it, we can discover new insight and knowledge of God, His eternal plans, and His commands for our lives. God is good.
Trust Jesus.
-
 @ a367f9eb:0633efea
2024-12-22 21:35:22
@ a367f9eb:0633efea
2024-12-22 21:35:22I’ll admit that I was wrong about Bitcoin. Perhaps in 2013. Definitely 2017. Probably in 2018-2019. And maybe even today.
Being wrong about Bitcoin is part of finally understanding it. It will test you, make you question everything, and in the words of BTC educator and privacy advocate Matt Odell, “Bitcoin will humble you”.
I’ve had my own stumbles on the way.
In a very public fashion in 2017, after years of using Bitcoin, trying to start a company with it, using it as my primary exchange vehicle between currencies, and generally being annoying about it at parties, I let out the bear.
In an article published in my own literary magazine Devolution Review in September 2017, I had a breaking point. The article was titled “Going Bearish on Bitcoin: Cryptocurrencies are the tulip mania of the 21st century”.
It was later republished in Huffington Post and across dozens of financial and crypto blogs at the time with another, more appropriate title: “Bitcoin Has Become About The Payday, Not Its Potential”.
As I laid out, my newfound bearishness had little to do with the technology itself or the promise of Bitcoin, and more to do with the cynical industry forming around it:
In the beginning, Bitcoin was something of a revolution to me. The digital currency represented everything from my rebellious youth.
It was a decentralized, denationalized, and digital currency operating outside the traditional banking and governmental system. It used tools of cryptography and connected buyers and sellers across national borders at minimal transaction costs.
…
The 21st-century version (of Tulip mania) has welcomed a plethora of slick consultants, hazy schemes dressed up as investor possibilities, and too much wishy-washy language for anything to really make sense to anyone who wants to use a digital currency to make purchases.
While I called out Bitcoin by name at the time, on reflection, I was really talking about the ICO craze, the wishy-washy consultants, and the altcoin ponzis.
What I was articulating — without knowing it — was the frame of NgU, or “numbers go up”. Rather than advocating for Bitcoin because of its uncensorability, proof-of-work, or immutability, the common mentality among newbies and the dollar-obsessed was that Bitcoin mattered because its price was a rocket ship.
And because Bitcoin was gaining in price, affinity tokens and projects that were imperfect forks of Bitcoin took off as well.
The price alone — rather than its qualities — were the reasons why you’d hear Uber drivers, finance bros, or your gym buddy mention Bitcoin. As someone who came to Bitcoin for philosophical reasons, that just sat wrong with me.
Maybe I had too many projects thrown in my face, or maybe I was too frustrated with the UX of Bitcoin apps and sites at the time. No matter what, I’ve since learned something.
I was at least somewhat wrong.
My own journey began in early 2011. One of my favorite radio programs, Free Talk Live, began interviewing guests and having discussions on the potential of Bitcoin. They tied it directly to a libertarian vision of the world: free markets, free people, and free banking. That was me, and I was in. Bitcoin was at about $5 back then (NgU).
I followed every article I could, talked about it with guests on my college radio show, and became a devoted redditor on r/Bitcoin. At that time, at least to my knowledge, there was no possible way to buy Bitcoin where I was living. Very weak.
I was probably wrong. And very wrong for not trying to acquire by mining or otherwise.
The next year, after moving to Florida, Bitcoin was a heavy topic with a friend of mine who shared the same vision (and still does, according to the Celsius bankruptcy documents). We talked about it with passionate leftists at Occupy Tampa in 2012, all the while trying to explain the ills of Keynesian central banking, and figuring out how to use Coinbase.
I began writing more about Bitcoin in 2013, writing a guide on “How to Avoid Bank Fees Using Bitcoin,” discussing its potential legalization in Germany, and interviewing Jeremy Hansen, one of the first political candidates in the U.S. to accept Bitcoin donations.
Even up until that point, I thought Bitcoin was an interesting protocol for sending and receiving money quickly, and converting it into fiat. The global connectedness of it, plus this cypherpunk mentality divorced from government control was both useful and attractive. I thought it was the perfect go-between.
But I was wrong.
When I gave my first public speech on Bitcoin in Vienna, Austria in December 2013, I had grown obsessed with Bitcoin’s adoption on dark net markets like Silk Road.
My theory, at the time, was the number and price were irrelevant. The tech was interesting, and a novel attempt. It was unlike anything before. But what was happening on the dark net markets, which I viewed as the true free market powered by Bitcoin, was even more interesting. I thought these markets would grow exponentially and anonymous commerce via BTC would become the norm.
While the price was irrelevant, it was all about buying and selling goods without permission or license.
Now I understand I was wrong.
Just because Bitcoin was this revolutionary technology that embraced pseudonymity did not mean that all commerce would decentralize as well. It did not mean that anonymous markets were intended to be the most powerful layer in the Bitcoin stack.
What I did not even anticipate is something articulated very well by noted Bitcoin OG Pierre Rochard: Bitcoin as a savings technology.
The ability to maintain long-term savings, practice self-discipline while stacking stats, and embrace a low-time preference was just not something on the mind of the Bitcoiners I knew at the time.
Perhaps I was reading into the hype while outwardly opposing it. Or perhaps I wasn’t humble enough to understand the true value proposition that many of us have learned years later.
In the years that followed, I bought and sold more times than I can count, and I did everything to integrate it into passion projects. I tried to set up a company using Bitcoin while at my university in Prague.
My business model depended on university students being technologically advanced enough to have a mobile wallet, own their keys, and be able to make transactions on a consistent basis. Even though I was surrounded by philosophically aligned people, those who would advance that to actually put Bitcoin into practice were sparse.
This is what led me to proclaim that “Technological Literacy is Doomed” in 2016.
And I was wrong again.
Indeed, since that time, the UX of Bitcoin-only applications, wallets, and supporting tech has vastly improved and onboarded millions more people than anyone thought possible. The entrepreneurship, coding excellence, and vision offered by Bitcoiners of all stripes have renewed a sense in me that this project is something built for us all — friends and enemies alike.
While many of us were likely distracted by flashy and pumpy altcoins over the years (me too, champs), most of us have returned to the Bitcoin stable.
Fast forward to today, there are entire ecosystems of creators, activists, and developers who are wholly reliant on the magic of Bitcoin’s protocol for their life and livelihood. The options are endless. The FUD is still present, but real proof of work stands powerfully against those forces.
In addition, there are now dozens of ways to use Bitcoin privately — still without custodians or intermediaries — that make it one of the most important assets for global humanity, especially in dictatorships.
This is all toward a positive arc of innovation, freedom, and pure independence. Did I see that coming? Absolutely not.
Of course, there are probably other shots you’ve missed on Bitcoin. Price predictions (ouch), the short-term inflation hedge, or the amount of institutional investment. While all of these may be erroneous predictions in the short term, we have to realize that Bitcoin is a long arc. It will outlive all of us on the planet, and it will continue in its present form for the next generation.
Being wrong about the evolution of Bitcoin is no fault, and is indeed part of the learning curve to finally understanding it all.
When your family or friends ask you about Bitcoin after your endless sessions explaining market dynamics, nodes, how mining works, and the genius of cryptographic signatures, try to accept that there is still so much we have to learn about this decentralized digital cash.
There are still some things you’ve gotten wrong about Bitcoin, and plenty more you’ll underestimate or get wrong in the future. That’s what makes it a beautiful journey. It’s a long road, but one that remains worth it.
-
 @ 2063cd79:57bd1320
2025-01-08 14:26:43
@ 2063cd79:57bd1320
2025-01-08 14:26:43Unit-Bias
Bitcoin hat in der öffentlichen Wahrnehmung und bei Menschen, die sich weniger mit dem Thema befassen, einen sogenannten Unit-Bias, also eine durch Unwissenheit hervorgerufene Voreingenommenheit gegenüber der Einheit "Bitcoin". Das bedeutet, dass viele unerfahrene Anleger//innen und Nutzer//innen der Meinung sind, dass der Besitz eines ganzen bitcoins psychologisch wichtig oder überhaupt nur als solcher möglich ist. Anders ausgedrückt, glauben viele Menschen, sie müssen Bitcoin als Ganzes kaufen, also einen ganzen "physischen" bitcoin, statt kleinerer Bruchstücke. Das lässt den Vermögenswert für die meisten zu teuer aussehen.
 Dies ist für Bitcoin insofern ein Problem, als dass viele Menschen sich durch ihre Voreingenommenheit gar nicht mit Bitcoin beschäftigen ("kann ich mir nicht leisten") oder das Gefühl haben, Bitcoin sei zu teuer und deshalb gibt es kein Wertsteigerungspotential mehr ("der Zug ist abgefahren, ich hätte vor sechs Jahren investieren sollen"). Schlimmer noch, als sich nicht mit Bitcoin zu beschäftigen, ist sich dann stattdessen alternativen, "erschwinglicheren" Kryptowährungen zuzuwenden. Dieser Unit-Bias ist allerdings nichts anderes als ein Marketing-, bzw. ein Bildungsproblem. Denn wie wir wissen kann man Bitcoin in 100 Millionen Untereinheiten brechen und in kleinsten Mengen erwerben, verschicken und verkaufen. Doch haben Außenstehende von Begriffen wie Lightning oder Sats meistens noch nie gehört.
Dies ist für Bitcoin insofern ein Problem, als dass viele Menschen sich durch ihre Voreingenommenheit gar nicht mit Bitcoin beschäftigen ("kann ich mir nicht leisten") oder das Gefühl haben, Bitcoin sei zu teuer und deshalb gibt es kein Wertsteigerungspotential mehr ("der Zug ist abgefahren, ich hätte vor sechs Jahren investieren sollen"). Schlimmer noch, als sich nicht mit Bitcoin zu beschäftigen, ist sich dann stattdessen alternativen, "erschwinglicheren" Kryptowährungen zuzuwenden. Dieser Unit-Bias ist allerdings nichts anderes als ein Marketing-, bzw. ein Bildungsproblem. Denn wie wir wissen kann man Bitcoin in 100 Millionen Untereinheiten brechen und in kleinsten Mengen erwerben, verschicken und verkaufen. Doch haben Außenstehende von Begriffen wie Lightning oder Sats meistens noch nie gehört.Untereinheiten
Doch auch innerhalb der Bitcoin-Szene ist die Unterteilung von Bitcoin in Untereinheiten nicht ganz unumstritten. Denn viele Nutzer//innen sind sich uneinig darüber, was der beste Weg ist, Bitcoins Untereinheiten zu bezeichnen und sogar darzustellen. Dies zeigt sich z.B. darin, dass Apps oft entweder Bitcoin oder Fiat anzeigen, manche Apps aber auch Beträge in Sats darstellen. Dies verlangt aber oft eigene Einstellungen innerhalb der App oder viele Klicks, die die Bedienung und Darstellung eher unhandlich gestalten.
 Es gibt verschiedene Lösungsansätze, die dem/der Nutzer//in die ungewohnte Rechnung mit acht Nachkommastellen erleichtern sollen. Denn viele Anwender//innen denken beim Blick in ihre Wallets oft noch in lokalen Fiat-Werten, also in ganzen Einheiten (z.B. Euro oder Dollar) und Hundertsteln (z.B. Cents).
Es gibt verschiedene Lösungsansätze, die dem/der Nutzer//in die ungewohnte Rechnung mit acht Nachkommastellen erleichtern sollen. Denn viele Anwender//innen denken beim Blick in ihre Wallets oft noch in lokalen Fiat-Werten, also in ganzen Einheiten (z.B. Euro oder Dollar) und Hundertsteln (z.B. Cents). Einige Wallets versuchen diesen Spagat komplett zu umgehen, indem sie vermeiden, Beträge in Fiat darzustellen. Doch auch hier bleibt immer noch das Problem der unhandlichen Darstellung von acht Nachkommastellen, weshalb einige Anbieter einfach zwei Eingabemöglichkeiten bieten und den Betrag in Bitcoin oder Sats automatisch umrechnen.
Einige Wallets versuchen diesen Spagat komplett zu umgehen, indem sie vermeiden, Beträge in Fiat darzustellen. Doch auch hier bleibt immer noch das Problem der unhandlichen Darstellung von acht Nachkommastellen, weshalb einige Anbieter einfach zwei Eingabemöglichkeiten bieten und den Betrag in Bitcoin oder Sats automatisch umrechnen. Doch selbst das Zeichen für Sats ist nicht final geklärt. Es gibt viele verschiedene Vorschläge und Meinungen dazu, welches Symbol genutzt werden sollte. Die meisten Apps, Rechnungen und Sticker schreiben einfach das Wort "Sats" oder "sats" aus. Allerdings ist dies ein Problem, da außerhalb der Bitcoin-Szene niemand weiß, was ein Sat ist. Die meisten Menschen werden mittlerweile von Bitcoin gehört haben, auch wenn sie nicht wissen, wie es funktioniert, was es bedeutet, oder wie man damit umgeht. Doch auch das B Logo mit den Dollarstrichen (₿) werden die meisten Menschen zuordnen können.
Doch selbst das Zeichen für Sats ist nicht final geklärt. Es gibt viele verschiedene Vorschläge und Meinungen dazu, welches Symbol genutzt werden sollte. Die meisten Apps, Rechnungen und Sticker schreiben einfach das Wort "Sats" oder "sats" aus. Allerdings ist dies ein Problem, da außerhalb der Bitcoin-Szene niemand weiß, was ein Sat ist. Die meisten Menschen werden mittlerweile von Bitcoin gehört haben, auch wenn sie nicht wissen, wie es funktioniert, was es bedeutet, oder wie man damit umgeht. Doch auch das B Logo mit den Dollarstrichen (₿) werden die meisten Menschen zuordnen können.Sats hingegen ist ein sehr nischiger Begriff und seine Verwendung noch unbekannter. Oft wird das Blitzsymbol (3 auf der unteren Grafik) verwendet, um Lightning darzustellen und auch das Symbol mit den drei horizontalen Strichen und zwei vertikalen Punkten (4 auf der unteren Grafik), das entfernt an das Dollar-Zeichen erinnern soll ($), erfreut sich immer größerer Beliebtheit. Das Problem dabei ist nur, dass es sich in geschriebener Form nicht, oder nur unzulänglich darstellen lässt: 丰 🤡
 Es war lange logisch und notwendig, ganze Bitcoins zur Aufzählung und Bezahlung zu verwenden, da bei der Einführung von Bitcoin sein Geldwert sehr gering war. Es bestand also absolut keine Notwendigkeit dazu, in kleineren Einheiten als Bitcoin zu denken. Einfaches Beispiel: letzte Woche, am 22. Mai, jährte sich der Bitcoin-Pizza-Day zum 13. Mal, also jener Tag an dem Laszlo Hanyecz für zwei Pizza 10.000 bitcoins bezahlte und damit die erste offline Transaktion mit Bitcoin tätigte. 10.000 bitcoins entsprachen zu diesem Zeitpunkt also knapp $40, oder andersrum $1 entsprach 250 bitcoins Es gab also immer noch keine Notwendigkeit, kleinere Einheiten von Bitcoin zu verwenden. Diese Notwendigkeit ergab sich erst, als der Bitcoin und der Dollar Parität erlangten (1 Bitcoin = $1) und spätestens, als Bitcoin die Marke von $100 durchbrach, wurde rechnen in Bitcoin schwieriger.
Es war lange logisch und notwendig, ganze Bitcoins zur Aufzählung und Bezahlung zu verwenden, da bei der Einführung von Bitcoin sein Geldwert sehr gering war. Es bestand also absolut keine Notwendigkeit dazu, in kleineren Einheiten als Bitcoin zu denken. Einfaches Beispiel: letzte Woche, am 22. Mai, jährte sich der Bitcoin-Pizza-Day zum 13. Mal, also jener Tag an dem Laszlo Hanyecz für zwei Pizza 10.000 bitcoins bezahlte und damit die erste offline Transaktion mit Bitcoin tätigte. 10.000 bitcoins entsprachen zu diesem Zeitpunkt also knapp $40, oder andersrum $1 entsprach 250 bitcoins Es gab also immer noch keine Notwendigkeit, kleinere Einheiten von Bitcoin zu verwenden. Diese Notwendigkeit ergab sich erst, als der Bitcoin und der Dollar Parität erlangten (1 Bitcoin = $1) und spätestens, als Bitcoin die Marke von $100 durchbrach, wurde rechnen in Bitcoin schwieriger.Fortan überlegte man sich, Bitcoin in kleineren Einheiten darzustellen. Die zwei Möglichkeiten sind der Bit und der Sat. Ein einzelner bitcoin kann in 1.000.000 Bits oder bis zu 100.000.000 Sats unterteilt werden, also 100 Sats = 1 Bit = 0,000001 Bitcoin.
 Ein weiterer Grund, weshalb eine Stückelung in bitcoin (der Begriff für einen ganzen physischen bitcoin) schwierig und verwirrend ist, und deshalb viele nach einer alternativen Bezeichnung für Untereinheiten suchten, ist dass darüber hinaus "Bitcoin" zur Beschreibung von zwei Dingen verwendet werden kann: dem monetären Netzwerk (Bitcoin - großes B) und dem monetären Vermögenswert (bitcoin - kleines B).
Ein weiterer Grund, weshalb eine Stückelung in bitcoin (der Begriff für einen ganzen physischen bitcoin) schwierig und verwirrend ist, und deshalb viele nach einer alternativen Bezeichnung für Untereinheiten suchten, ist dass darüber hinaus "Bitcoin" zur Beschreibung von zwei Dingen verwendet werden kann: dem monetären Netzwerk (Bitcoin - großes B) und dem monetären Vermögenswert (bitcoin - kleines B). Bitcoin, der Vermögenswert, ist für diejenigen, die noch nichts damit zu tun hatten, sowohl verwirrend als auch fremd. Denn wie bereits erwähnt, führt der Unit-Bias dazu, dass viele Menschen denken, dass sie es sich nicht leisten können, Bitcoin zu kaufen, oder dass sie den Anschluss verpasst haben. Die Verwendung einer Bepreisung in Bruchteilen würde die Verwirrung über die Benennung des Netzwerks und des Vermögenswerts verringern, aber auch die psychologische Hürde für den Einstieg in Bitcoin senken. Vorausgesetzt, die Benennung ist logisch und intuitiv.
Bitcoin, der Vermögenswert, ist für diejenigen, die noch nichts damit zu tun hatten, sowohl verwirrend als auch fremd. Denn wie bereits erwähnt, führt der Unit-Bias dazu, dass viele Menschen denken, dass sie es sich nicht leisten können, Bitcoin zu kaufen, oder dass sie den Anschluss verpasst haben. Die Verwendung einer Bepreisung in Bruchteilen würde die Verwirrung über die Benennung des Netzwerks und des Vermögenswerts verringern, aber auch die psychologische Hürde für den Einstieg in Bitcoin senken. Vorausgesetzt, die Benennung ist logisch und intuitiv.Bits vs. Sats
Wie schon erwähnt, gibt es zwei gängige Untereinheiten von Bitcoin, 1 Bit (= 0,000001 Bitcoin) und 1 Sat (0,00000001 Bitcoin). Seit jeher gibt es Diskussionen darüber, welche der beiden Einheiten für den täglichen Gebrauch die vernünftigere und intuitivere ist.
Die Verwendung von Bits zur Aufzählung von Bitcoin hat einige Vorteile. Ein Bit stellt ein „Bit“ eines Bitcoins dar, also der grundlegendsten und kleinsten Informationseinheit in der Informatik. Den meisten Menschen fällt es einfacher, das Wort „Bit“ mit Bitcoin zu assoziieren und daher verstehen sie eher, dass ein Bit ein Teil eines Bitcoins ist. Ein „Sat“ bedeutet für den Durchschnittsmenschen, wie oben beschrieben, nichts.
 Adam Back (CEO von Blockstream und Bitcoin-Legende) ist wahrscheinlich der bekannteste Befürworter von Bits > Sats. Er argumentiert von verschiedenen Richtungen, dass z.B. Bits eine rechnerisch einfachere Variante ist, Untereinheiten von Bitcoin darzustellen, als Sats.
Adam Back (CEO von Blockstream und Bitcoin-Legende) ist wahrscheinlich der bekannteste Befürworter von Bits > Sats. Er argumentiert von verschiedenen Richtungen, dass z.B. Bits eine rechnerisch einfachere Variante ist, Untereinheiten von Bitcoin darzustellen, als Sats. Weiter argumentiert er mit der historischen Entwicklung von Bitcoin, dem Protokoll und seiner Referenz-Implementierung. In den Anfangsjahren wurde in der Bitcoin Core Wallet mit Bits gearbeitet. Außerdem argumentiert er, dass die Verbindung zwischen Bitcoin der Haupteinheit und Bits oder Sats als Untereinheit zumindest semantisch gebrochen werden sollte. Da Bitcoin (im Fall eines weiter steigenden Kurses) als Recheneinheit immer unpraktischer wird, sollte man als mentales Modell auf das Rechenpaar Bits und Sats zurückgreifen - analog zur Darstellung von Dollars und Cents oder Euros und Cents. Dabei stellen die zwei Nachkommastellen eines in Bits angegebenen Preises die Sats dar.
Weiter argumentiert er mit der historischen Entwicklung von Bitcoin, dem Protokoll und seiner Referenz-Implementierung. In den Anfangsjahren wurde in der Bitcoin Core Wallet mit Bits gearbeitet. Außerdem argumentiert er, dass die Verbindung zwischen Bitcoin der Haupteinheit und Bits oder Sats als Untereinheit zumindest semantisch gebrochen werden sollte. Da Bitcoin (im Fall eines weiter steigenden Kurses) als Recheneinheit immer unpraktischer wird, sollte man als mentales Modell auf das Rechenpaar Bits und Sats zurückgreifen - analog zur Darstellung von Dollars und Cents oder Euros und Cents. Dabei stellen die zwei Nachkommastellen eines in Bits angegebenen Preises die Sats dar. Ganz einfaches Beispiel: Ein Kasten Bier kostet heute etwas 20€, also 0,00079758 Bitcoin. Einfacher dargestellt: 797,58 Bits, also 797 Bits und 58 Sats. “Ein Bitcoin ist zu teuer, aber Sats sind zu viele, klingen billig und verwirrend.” Es ist schwer in Sats zu denken und selbst wenn der Preis von Bitcoin 1 M US Dollar erreicht, ist ein Bit immer noch eine greifbare und günstige Einheit: 1 Bit = 1 US Dollar.
Ganz einfaches Beispiel: Ein Kasten Bier kostet heute etwas 20€, also 0,00079758 Bitcoin. Einfacher dargestellt: 797,58 Bits, also 797 Bits und 58 Sats. “Ein Bitcoin ist zu teuer, aber Sats sind zu viele, klingen billig und verwirrend.” Es ist schwer in Sats zu denken und selbst wenn der Preis von Bitcoin 1 M US Dollar erreicht, ist ein Bit immer noch eine greifbare und günstige Einheit: 1 Bit = 1 US Dollar. Eines von Adams Hauptargumenten ist, dass Sat als Untereinheit nicht funktioniert, weil es Dust gibt. Das Problem mit Dust besteht darin, dass es nicht möglich ist, Bitcoin unter einem bestimmten Schwellenwert auszugeben. Sein Argument ist, dass der Nutzen einer Einheit abhanden kommt, wenn diese Einheit als kleinste Recheneinheit nicht ausgegeben werden kann. Zugegeben, niemand kann mehr etwas für einen Cent kaufen, aber zumindest ist es technisch nicht unmöglich. Allerdings ist es unmöglich, 1 oder sogar 10 Sats über das Bitcoin-Netzwerk zu senden, ohne Layer-2-Skalierungstechnologien zu verwenden.
Eines von Adams Hauptargumenten ist, dass Sat als Untereinheit nicht funktioniert, weil es Dust gibt. Das Problem mit Dust besteht darin, dass es nicht möglich ist, Bitcoin unter einem bestimmten Schwellenwert auszugeben. Sein Argument ist, dass der Nutzen einer Einheit abhanden kommt, wenn diese Einheit als kleinste Recheneinheit nicht ausgegeben werden kann. Zugegeben, niemand kann mehr etwas für einen Cent kaufen, aber zumindest ist es technisch nicht unmöglich. Allerdings ist es unmöglich, 1 oder sogar 10 Sats über das Bitcoin-Netzwerk zu senden, ohne Layer-2-Skalierungstechnologien zu verwenden.Dust
Unter Bitcoin-Dust versteht man eine sehr kleine Menge Bitcoin, typischerweise in kleinen ein- bis zweistelligen Sats-Beträgen, doch auch kommen immer öfter dreistellige Beträge vor. Sie werden Dust oder „Staub“ genannt, weil diese Beträge so gering sind, dass sie oft als unbedeutend und unpraktisch für die Verwendung bei regulären Transaktionen angesehen werden.
 Es gibt keine offizielle Definition dafür wie groß/klein ein Betrag sein muss, um als Dust zu gelten, da jede Softwareimplementierung (Client, Wallet, etc.) einen anderen Schwellenwert annehmen kann. Die Bitcoin Core Referenzimplementierung definiert Dust als jede Transaktionsausgabe, die niedriger ist als die aktuellen Transaktionsgebühren.
Es gibt keine offizielle Definition dafür wie groß/klein ein Betrag sein muss, um als Dust zu gelten, da jede Softwareimplementierung (Client, Wallet, etc.) einen anderen Schwellenwert annehmen kann. Die Bitcoin Core Referenzimplementierung definiert Dust als jede Transaktionsausgabe, die niedriger ist als die aktuellen Transaktionsgebühren.Dust entsteht meist unbeabsichtigt bei Bitcoin-Transaktionen. Denn wenn Bitcoin von einer Adresse an eine andere gesendet wird, fällt oft eine Transaktionsgebühr an. Um Spam zu verhindern und die Sicherheit des Netzwerks zu gewährleisten, gibt es bei Bitcoin eine Mindestgröße für jede Transaktion. Dieses Limit ist der Mindestbetrag an Bitcoin, der als Ausgabe in eine Transaktion einbezogen werden kann. Der Rest ist Dust.
Oder einfacher ausgedrückt, wenn die Mindestgröße für eine Bitcoin-On-Chain-Transaktion 500 Sats (5 Bits) beträgt und ich noch 800 Sats (8 Bits) in meiner Wallet habe, kann ich nach dem Versenden von 600 Sats (6 Bits) die übrigen 200 Sats (2 Bits) nicht mehr ausgeben. Diese verbleibenden 2 Bits sind Dust.
 Dust stellt aus mehreren Gründen eine Herausforderung für das Bitcoin-Netzwerk und seine Benutzer//innen dar:
Dust stellt aus mehreren Gründen eine Herausforderung für das Bitcoin-Netzwerk und seine Benutzer//innen dar:UTXO-Bloat: Bei jeder Transaktion werden nicht ausgegebene Transaktionsausgaben (UTXOs) erstellt, und Dust erhöht die Anzahl der UTXOs im System. Dies kann zu einer aufgeblähten Blockchain führen und sich negativ auf die Leistung und Skalierbarkeit des Netzwerks auswirken.
Wallet-Management: Im Laufe der Zeit kann sich in Wallets viel Dust ansammeln, und die Verwaltung solch kleiner Beträge kann für Benutzer//innen unpraktisch sein. Bei vielen Wallets ist ein Mindestguthaben erforderlich, und die Dust-Mengen sind möglicherweise zu gering, um diese Anforderung zu erfüllen. Viele Nutzer//innen wechseln häufig zwischen Wallets und transferirien ihre Vermögen vorher auf die neuen Wallets, bei solchen Wechseln bleiben Dust-Beträge zurück und gelten langfristig als verloren.
Ein weiteres Problem besteht darin, dass Dust nicht genau definiert werden kann. Die Transaktionsgebühren hängen wesentlich von zwei Faktoren ab: Den Gebühren in sat/vB, welche von der Auslastung des Mempools abhängen und zu Zeiten von hoher Auslastung dementsprechend hoch sind, und zum anderen vom UTXO-Set des/der jeweiligen Nutzer//in. Denn wie wir wissen, werden Transaktionen aus einer oder mehreren UTXOs zusammengesetzt, je mehr UTXOs dabei benötigt werden, um den gewünschten Betrag zu versenden, desto höher sind die Kosten für diese Transaktion, da sich das Gewicht (in vBytes) erhöht. Diese beiden Faktoren können die Gebühren in Einzelfällen so strukturieren, dass größere Mengen Dust anfallen, als in anderen Fällen.
Datenschutzbedenken: Da jede Transaktion in der Blockchain gespeichert wird, können selbst winzige Mengen Dust mit der Identität oder dem Transaktionsverlauf einer Person verknüpft werden, was die Privatsphäre gefährdet. Diese Funktion wird von Angreifern in sogenannten Dust-Attacks ausgenutzt. Denn böswillige Angreifer haben schnell erkannt, dass Nutzer//innen die winzigen Dust-Beträge, die in ihren Wallet-Adressen angezeigt werden, nicht viel Aufmerksamkeit schenken oder gar bemerken. Angreifer schicken also Kleinstbeträge an eine große Anzahl von Adressen, um dann im nächsten Schritt in einer kombinierten Analyse dieser Adressen und der Beträge, versuchen herauszufinden, welche Adressen zur gleichen Wallet gehören. Dabei ist es das Ziel, diese so identifizierbaren Adressen und Wallets schließlich den jeweiligen Eigentümer//innen zuzuordnen, um diese dann durch ausgefeilte Phishing-Angriffe oder Cyber-Erpressungen zu attackieren.
Um diese Probleme zu lösen, können Nutzer//innen Dust konsolidieren, indem sie mehrere Dust-UTXOs in einer einzigen Transaktion mit einem höheren Wert kombinieren. Einige Wallets und Dienste bieten Funktionen an, mit denen Benutzer//innen ihren Dust effektiv verwalten und konsolidieren können.
Abschließende Gedanken
Der Unit-Bias ist absolut vorhanden. Ich persönlich begegne ihm immer wieder in Gesprächen mit Bitcoin-Interessierten, die sich mit der Materie noch nicht lange auseinandergesetzt haben. Die Verwunderung ist oft sehr groß, dass bitcoins nicht als Ganzes gekauft werden müssen. Die Verwendung einer Untereinheit sowohl in Wallets, als auch bei der Bepreisung kann dabei helfen.
An die Verwendung von Sats als die kleinste Einheit von Bitcoin habe ich mich gewöhnt, allerdings tendiere ich mittlerweile persönlich zum Gebrauch von Bits. Die hervorgebrachten Argumente leuchten mir ein und ich bin überzeugt, dass Bits eine größere Akzeptanz außerhalb des Bitcoin-Inner-Circles hervorrufen können, als Sats. Darüber hinaus ist das Sats-Zeichen wirklich unpraktisch.
Ich befürworte hier einige Ideen, die das Paragrafzeichen zum Symbol für Sats erheben wollen.
 🫳🎤
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ 3ffac3a6:2d656657
2024-12-22 02:16:45
@ 3ffac3a6:2d656657
2024-12-22 02:16:45In a small, quiet town nestled between rolling hills, there lived a boy named Ravi. Ravi was resourceful, hardworking, and had a knack for finding ways to support his family. His mother, a widow who worked tirelessly as a seamstress, inspired Ravi to pitch in wherever he could. His latest venture was ironing clothes for neighbors.
With his trusty old iron and a rickety wooden table, Ravi turned a small corner of their modest home into a makeshift laundry service. By day, he attended school and played with his friends, but in the evenings, he transformed into the “Iron Boy,” smoothing out wrinkles and earning a few precious coins.
One night, orders piled up after a local wedding had left everyone with wrinkled formalwear. Determined to finish, Ravi worked well past his usual bedtime. The warm glow of the lamp cast long shadows across the room as he focused on the rhythmic hiss of steam escaping the iron.
Just as the clock struck midnight, a soft clop-clop echoed from outside. Ravi froze, the iron hovering mid-air. The sound grew louder until it stopped right outside his window.
A deep, resonant voice broke the silence. “Didn’t your mother tell you not to be ironing clothes late at night?”
Ravi’s heart jumped into his throat. He turned slowly to the window, and his eyes widened. Standing there, framed by the moonlight, was a horse—a magnificent creature with a shimmering coat and a mane that seemed to ripple like liquid silver. Its dark eyes sparkled with an otherworldly light, and its lips moved as it spoke.
“W-who are you?” Ravi stammered, clutching the iron like a shield.
The horse tilted its head. “Names are not important. But you should know that ironing past midnight stirs things best left undisturbed.”
“Things? What things?” Ravi asked, his curiosity momentarily overriding his fear.
The horse snorted softly, a sound that almost resembled a chuckle. “Spirits. Shadows. Call them what you will. They grow restless in the heat of the iron at night. You don’t want to invite them in.”
Ravi glanced at the clothes piled on the table, then back at the horse. “But I need to finish these. People are counting on me.”
The horse’s eyes softened, and it stepped closer to the window. “Your dedication is admirable, but heed my warning. For tonight, let it be. Finish in the morning.”
Before Ravi could reply, the horse reared slightly, its silver mane glinting in the moonlight. With a final, cryptic look, it trotted off into the darkness, leaving Ravi staring after it in stunned silence.
The next morning, Ravi woke to find his mother standing at the table, finishing the last of the ironing. “You were so tired, I thought I’d help,” she said with a smile.
Ravi hesitated, then decided not to mention the midnight visitor. But from that day on, he made sure to finish his ironing before nightfall.
Though he never saw the horse again, he sometimes heard the faint clop-clop of hooves in the distance, as if reminding him of that strange, magical night. And in his heart, he carried the lesson that some tasks are best left for the light of day.
-
 @ eac63075:b4988b48
2024-12-18 11:35:25
@ eac63075:b4988b48
2024-12-18 11:35:25The European Union is at a crossroads. While digital innovation and security cooperation remain critical in a connected world, recent proposals to enhance police surveillance and data sharing are stirring deep concerns about individual privacy, data security, and democratic oversight. Two recent reports published by Statewatch shed light on troubling developments in the EU’s policing landscape, raising alarms among privacy advocates and civil rights organizations.
The EU’s new plans to expand police surveillance could put your privacy and rights at risk and introduce risks far outweighing their potential benefits. This article will analyze these proposals, their implications, and the growing opposition from privacy and civil liberties defenders.
Surveillance Infrastructure: Policing by Design
The first Statewatch report, titled “Policing by Design: The Latest EU Surveillance Plan”, outlines a concerning trend in the EU’s approach to law enforcement. The proposals advocate embedding surveillance tools directly into the design of new technologies, effectively creating an architecture where policing capabilities are integrated into the systems we use daily.
From facial recognition cameras to AI-driven analytics, the EU plans to enhance cross-border police cooperation by ensuring technology is designed to facilitate surveillance from the outset. Known as “policing by design,” this strategy involves building surveillance features directly into technologies we use every day. Imagine a network of cameras or software that can automatically monitor people’s faces or behaviors without any extra installation — it’s like your everyday tech quietly doubling as a police tool. The goal is to enable seamless sharing of data across borders for criminal investigations, but the unintended consequences are alarming.
The Problem with “Policing by Design”
- Mass Surveillance Normalized: By embedding surveillance features into public and private infrastructure, society risks normalizing mass surveillance, where every movement, transaction, or online interaction is monitored and analyzed.
- Threats to Privacy: Such initiatives inherently contradict the principle of privacy by design, which prioritizes privacy protections in the development of technology. Instead, citizens are being treated as subjects of perpetual suspicion.
- Lack of Transparency and Accountability: A systemic lack of transparency surrounding these plans raises serious governance issues. Civil society organizations, journalists, and privacy advocates have pointed to a lack of democratic oversight and meaningful debate.
- Risks of Abuse: Surveillance systems are often deployed under the guise of security but are susceptible to abuse. History shows that tools designed for law enforcement can easily be turned against dissenters, journalists, or marginalized communities.
As the report highlights, these developments could establish a permanent surveillance infrastructure across Europe, enabling the collection of biometric, behavioral, and communications data on an unprecedented scale.
Flawed Justifications for Surveillance Expansion
Privacy advocacy organizations, including the European Digital Rights (EDRi) network, argue that much of the justification for these surveillance plans relies on flawed assumptions. The rhetoric of the “Going Dark” report, which claims that law enforcement is losing access to communications due to encryption, has been widely debunked. As EDRi points out, law enforcement already has extensive tools at their disposal to access data and track individuals, but the focus on encryption risks undermining secure communication for everyone.
Instead of addressing systemic issues within law enforcement, these flawed reports have fueled calls for intrusive surveillance systems that risk eroding privacy while offering little evidence of improving public safety.
Centralized Police Data: A Substantial Security and Privacy Threat
A second Statewatch report, titled “EU Police Data Plans Pose Substantial Security and Privacy Threats”, explores another equally concerning initiative: the EU’s push to centralize police data repositories and expand their use.
The EU has already established several large-scale databases, such as the Schengen Information System (SIS), which stores data about individuals who may be denied entry into the EU, and the Europol Information System, which can hold details about millions of people, including those not suspected of crimes. For example, a traveler flagged mistakenly in the system could face unnecessary scrutiny, detention, or restrictions when crossing borders — highlighting the real-world risks of inaccurate or overreaching data collection. The new proposals aim to go further, creating an interoperable web of police data accessible to law enforcement agencies across member states. Proponents argue this is necessary for combating cross-border crime and terrorism, but the risks are immense.
Key Concerns with Centralized Police Data
- Massive Data Collection: The EU’s proposed systems would require the collection of highly sensitive data, including biometric information (fingerprints, facial recognition scans) and behavioral analytics, to track individuals’ activities across borders.
- Data Misuse and Security Risks: Centralized data systems are prime targets for cyberattacks, data breaches, and misuse. The larger and more interconnected the system, the greater the risks of unauthorized access, theft, or corruption of the data.
- As Statewatch points out, the systems lack robust safeguards to prevent misuse or to ensure that data is handled proportionately and lawfully.
- Erosion of Trust in Law Enforcement: Building centralized data repositories without meaningful safeguards undermines public trust. Individuals may be less willing to engage with law enforcement if they fear their data will be stored indefinitely, shared across borders, or used inappropriately.
- Impact on Fundamental Rights: Mass police databases can violate the principle of proportionality, a cornerstone of EU law. By collecting and sharing data indiscriminately, these systems erode fundamental rights, including the right to privacy, freedom of movement, and the presumption of innocence.
Civil Society Opposition and Democratic Accountability
In an open letter to EU institutions, over 30 civil society organizations — including EDRi — have criticized the lack of transparency in the High-Level Group’s (HLG) recommendations for data access. The letter highlights a concerning pattern: while industry stakeholders are included in key discussions, civil society voices remain sidelined. This exclusion undermines democratic accountability and reinforces fears that surveillance policies are being driven by corporate interests rather than public well-being.
These organizations have called for the EU to prioritize transparency, include meaningful public debate, and ensure any law enforcement proposals respect proportionality and fundamental rights.
Why Privacy Advocates Are Sounding the Alarm
The reports from Statewatch highlight a fundamental clash between security policy and individual rights. Privacy advocates are urging EU lawmakers to take a step back and critically examine the following issues:
- Lack of Democratic Oversight: Proposals to integrate surveillance systems and expand police databases are being pushed forward without genuine public debate or oversight. Civil society organizations have been excluded from key discussions.
- Failure to Uphold Privacy Laws: The EU has some of the strongest privacy laws in the world, including the General Data Protection Regulation (GDPR). However, these proposals risk undermining GDPR principles by enabling indiscriminate data collection and sharing.
- Ignoring Proportionality: Surveillance systems must be targeted, necessary, and proportionate to their objectives. Embedding policing into technological design and centralizing data far exceeds what is justified for fighting crime and terrorism.
- Setting Dangerous Precedents: The failure to fully ban harmful surveillance technologies like facial recognition in public spaces sets a troubling precedent. It risks not only eroding privacy within the EU but also encouraging other nations to adopt similar measures, undermining global human rights.
A Call for Action: Safeguarding Our Privacy and Rights
As the EU pushes forward with these plans, the opposition from civil rights defenders grows louder. Policymakers must address the following key demands to prevent an erosion of fundamental rights:
- Implement Privacy by Design: All new technologies must prioritize privacy protections at the design stage, ensuring they are not co-opted for surveillance.
- Establish Robust Oversight: Any new policing tools or databases must be subject to democratic scrutiny, independent oversight, and clear legal frameworks to prevent misuse.
- Reassess Interoperability Plans: Cross-border police cooperation is important, but it must not come at the cost of individuals’ privacy, security, and dignity.
- Strengthen Export Controls: The EU must ban the export of surveillance tools that risk facilitating human rights abuses in authoritarian regimes.
- Prioritize Data Security: Centralized systems require state-of-the-art security measures to protect sensitive data from breaches or misuse.
The EU’s role as a leader in digital rights and privacy is now at stake. If these plans proceed without significant safeguards, Europe risks undermining its own foundational principles of freedom, security, and justice.
Conclusion: The Price of Surveillance-Driven Security
The EU’s surveillance plans may be presented as necessary for security, but they come at a steep cost to privacy, trust, and individual freedoms. Embedding surveillance into our technologies and centralizing police data pose far-reaching risks that cannot be ignored.
As privacy advocates, it is our responsibility to hold policymakers accountable and demand a security framework that upholds, rather than undermines, fundamental rights. Europe’s future must not be built on surveillance by design — but on privacy, democracy, and trust.
-
 @ ed84ce10:cccf4c2a
2025-01-08 12:33:06
@ ed84ce10:cccf4c2a
2025-01-08 12:33:06Hackathon Summary
The YQuantum 2024 Hackathon concluded with significant participation and numerous project submissions, establishing itself as a vibrant platform for innovation. Out of 300 registrants, the on-site participants formed teams and worked on developing 28 BUIDLs, engaging in challenges across diverse tracks sponsored by prominent quantum computing organizations, such as QuEra Computing, IBM Quantum, Classiq, DoraHacks, SandboxAQ, and Capgemini/The Hartford/Quantinuum.
Participants developed groundbreaking solutions in quantum computing, driven by prize incentives, including quantum cloud credits, internships, networking opportunities, and potential speaking engagements. The grand prizes recognized exceptional projects, with the first place receiving $2000, presentation opportunities before Yale researchers, and participation in the Yale Innovation Summit.
The hackathon successfully fostered a collaborative environment that encouraged the exploration of cutting-edge technologies and ideas, advancing the quantum computing field. YQuantum 2024 underscored the potential of quantum technologies and promoted knowledge exchange among participants and sponsors.
Hackathon Winners
Held on April 13, 2024, YQuantum's inaugural event attracted 300 participants from 10 countries, featuring six industry-sponsored challenges that culminated in a series of prestigious awards.
Institute Grand Prizes Winners
-
1st Place: Quantum Consortium: Case-Duke-Lehigh-Vandy Nexus This project employs adiabatic methods to prepare antiferromagnetic energy eigenstates, with a focus on quantum many-body scarring and enhancing error correction in computing.
-
2nd Place: Sparse Quantum State Preparation The team developed efficient algorithms using Classiq APIs for sparse quantum state preparation, optimizing execution for scalability and efficiency in managing quantum data.
-
3rd Place: QuBruin This project optimizes algorithms using dynamic quantum circuits and enhances error correction. The team improved user accessibility through Qiskit-based models for better circuit performance under noise conditions.
IBM Quantum Prize Winners
- Modified IBM Challenge
This project delves into foundational linear algebra concepts, emphasizing core principles and mastery.
QuEra Computing Prize Winners
- 3D Quantum Scars on 2D Tweezer Arrays
The team investigates quantum scar states on a 3D lattice projected into 2D, using Julia and QuEra's Bloqade to simulate quantum dynamics.
Classiq Technologies Prize Winners
- YQuantum2024 Classiq Team 34 Wavefunction Wizards
Focusing on optimizing sparse quantum state preparation, this project enhances algorithmic efficiency in quantum data processing.
DoraHacks Prize Winners
- Spooner_QRNG_Classifier
The project employs Python scripts and a gradient booster classifier to predict quantum device origins of random binary data, surpassing baseline prediction accuracy.
Capgemini // Quantinuum // The Hartford Prize Winners
-
Skittlez
This partnership addresses quantum computing challenges through interdisciplinary expertise, designing innovative quantum solutions. -
Honorable Mention: BB24 - Yale Quantum Monte Carlo The project enhances Quantum Monte Carlo techniques via novel sampling and encoding schemes, improving parallel processing and computational efficiency.
SandboxAQ Prize Winners
-
QuantumQuails
This project improves solar cell efficiency through quantum chemistry, utilizing VQE to model solar energy absorption for enhanced conversion effectiveness. -
Honorable Mention: mRNA Sequence Design via Quantum Approximate Optimization Algorithm This project optimizes mRNA sequence design using QAOA, enhancing protein expression and structural stability through codon and nucleotide parameters.
Explore all projects at DoraHacks.
About the Organizer:
YQuantum
YQuantum is a prominent entity within the technology and blockchain sectors, recognized for its innovative approach and strategic initiatives. Specializing in utilizing quantum computing capabilities, YQuantum is committed to advancing the technological frontier. Though specific projects are not highlighted, YQuantum's role in shaping industry standards positions it as a leader in the field. Through dedication to cutting-edge research and development, YQuantum continues to drive progress in quantum technologies, aligning with its mission to propel scientific and technological advancements globally.
-
-
 @ fe32298e:20516265
2024-12-16 20:59:13
@ fe32298e:20516265
2024-12-16 20:59:13Today I learned how to install NVapi to monitor my GPUs in Home Assistant.

NVApi is a lightweight API designed for monitoring NVIDIA GPU utilization and enabling automated power management. It provides real-time GPU metrics, supports integration with tools like Home Assistant, and offers flexible power management and PCIe link speed management based on workload and thermal conditions.
- GPU Utilization Monitoring: Utilization, memory usage, temperature, fan speed, and power consumption.
- Automated Power Limiting: Adjusts power limits dynamically based on temperature thresholds and total power caps, configurable per GPU or globally.
- Cross-GPU Coordination: Total power budget applies across multiple GPUs in the same system.
- PCIe Link Speed Management: Controls minimum and maximum PCIe link speeds with idle thresholds for power optimization.
- Home Assistant Integration: Uses the built-in RESTful platform and template sensors.
Getting the Data
sudo apt install golang-go git clone https://github.com/sammcj/NVApi.git cd NVapi go run main.go -port 9999 -rate 1 curl http://localhost:9999/gpuResponse for a single GPU:
[ { "index": 0, "name": "NVIDIA GeForce RTX 4090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 16, "power_limit_watts": 450, "memory_total_gb": 23.99, "memory_used_gb": 0.46, "memory_free_gb": 23.52, "memory_usage_percent": 2, "temperature": 38, "processes": [], "pcie_link_state": "not managed" } ]Response for multiple GPUs:
[ { "index": 0, "name": "NVIDIA GeForce RTX 3090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 14, "power_limit_watts": 350, "memory_total_gb": 24, "memory_used_gb": 0.43, "memory_free_gb": 23.57, "memory_usage_percent": 2, "temperature": 36, "processes": [], "pcie_link_state": "not managed" }, { "index": 1, "name": "NVIDIA RTX A4000", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 10, "power_limit_watts": 140, "memory_total_gb": 15.99, "memory_used_gb": 0.56, "memory_free_gb": 15.43, "memory_usage_percent": 3, "temperature": 41, "processes": [], "pcie_link_state": "not managed" } ]Start at Boot
Create
/etc/systemd/system/nvapi.service:``` [Unit] Description=Run NVapi After=network.target
[Service] Type=simple Environment="GOPATH=/home/ansible/go" WorkingDirectory=/home/ansible/NVapi ExecStart=/usr/bin/go run main.go -port 9999 -rate 1 Restart=always User=ansible
Environment="GPU_TEMP_CHECK_INTERVAL=5"
Environment="GPU_TOTAL_POWER_CAP=400"
Environment="GPU_0_LOW_TEMP=40"
Environment="GPU_0_MEDIUM_TEMP=70"
Environment="GPU_0_LOW_TEMP_LIMIT=135"
Environment="GPU_0_MEDIUM_TEMP_LIMIT=120"
Environment="GPU_0_HIGH_TEMP_LIMIT=100"
Environment="GPU_1_LOW_TEMP=45"
Environment="GPU_1_MEDIUM_TEMP=75"
Environment="GPU_1_LOW_TEMP_LIMIT=140"
Environment="GPU_1_MEDIUM_TEMP_LIMIT=125"
Environment="GPU_1_HIGH_TEMP_LIMIT=110"
[Install] WantedBy=multi-user.target ```
Home Assistant
Add to Home Assistant
configuration.yamland restart HA (completely).For a single GPU, this works: ``` sensor: - platform: rest name: MYPC GPU Information resource: http://mypc:9999 method: GET headers: Content-Type: application/json value_template: "{{ value_json[0].index }}" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature scan_interval: 1 # seconds
- platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} GPU" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Memory" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Temperature" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'temperature') }}" unit_of_measurement: "°C" ```
For multiple GPUs: ``` rest: scan_interval: 1 resource: http://mypc:9999 sensor: - name: "MYPC GPU0 Information" value_template: "{{ value_json[0].index }}" json_attributes_path: "$.0" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature - name: "MYPC GPU1 Information" value_template: "{{ value_json[1].index }}" json_attributes_path: "$.1" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature
-
platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC GPU0 GPU" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC GPU0 Memory" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC GPU0 Power" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC GPU0 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC GPU0 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'temperature') }}" unit_of_measurement: "C"
-
platform: template sensors: mypc_gpu_1_gpu: friendly_name: "MYPC GPU1 GPU" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_memory: friendly_name: "MYPC GPU1 Memory" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_power: friendly_name: "MYPC GPU1 Power" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_1_power_limit: friendly_name: "MYPC GPU1 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_1_temperature: friendly_name: "MYPC GPU1 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'temperature') }}" unit_of_measurement: "C"
```
Basic entity card:
type: entities entities: - entity: sensor.mypc_gpu_0_gpu secondary_info: last-updated - entity: sensor.mypc_gpu_0_memory secondary_info: last-updated - entity: sensor.mypc_gpu_0_power secondary_info: last-updated - entity: sensor.mypc_gpu_0_power_limit secondary_info: last-updated - entity: sensor.mypc_gpu_0_temperature secondary_info: last-updatedAnsible Role
```
-
name: install go become: true package: name: golang-go state: present
-
name: git clone git: repo: "https://github.com/sammcj/NVApi.git" dest: "/home/ansible/NVapi" update: yes force: true
go run main.go -port 9999 -rate 1
-
name: install systemd service become: true copy: src: nvapi.service dest: /etc/systemd/system/nvapi.service
-
name: Reload systemd daemons, enable, and restart nvapi become: true systemd: name: nvapi daemon_reload: yes enabled: yes state: restarted ```
-
 @ 6f6b50bb:a848e5a1
2024-12-15 15:09:52
@ 6f6b50bb:a848e5a1
2024-12-15 15:09:52Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
-
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
-
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!
Tradotto da:\ https://willwhitney.com/computing-inside-ai.htmlhttps://willwhitney.com/computing-inside-ai.html
-
-
 @ eac63075:b4988b48
2024-12-14 22:06:10
@ eac63075:b4988b48
2024-12-14 22:06:10BlueSky, a social network built on the decentralized AT Protocol (Authenticated Transfer Protocol), is revolutionizing content moderation by empowering users and communities to manage their own experiences. Unlike traditional platforms that centralize control, BlueSky adopts a modular and customizable approach, balancing freedom of expression with safety.
https://www.fountain.fm/episode/mtp0RxPeuBpCozcSgfct
The Jesse Singal Case and the Community’s Response
Recently, the account @jessesingal.com was accused of publishing content considered homophobic and transphobic. Although some users questioned whether these posts violated BlueSky’s Terms of Service, the platform chose not to ban the account. Instead, it relied on community tools to limit the reach of these posts.
Individual users blocked the account and subscribed to community-managed block lists, significantly reducing the visibility of Jesse Singal’s content. This decentralized approach demonstrated the effectiveness of a model in which the community regulates content without centralized intervention.
BlueSky’s Five Layers of Moderation
BlueSky implements a multi-layered moderation system, offering users tools to customize their experiences practically and efficiently:
-
Personal Blocking and Muting\ Users can block or mute unwanted accounts, individually adjusting the content they wish to see.
-
Community Block Lists\ By subscribing to block lists created by the community, users can share common moderation criteria, optimizing content filtering.
-
Curated Feeds\ Subscribing to personalized feeds allows users to consume content filtered by curators or algorithms, creating a safer and more tailored experience.
-
Account Removal on the Personal Data Server (PDS)\ In extreme cases, servers can directly delete accounts from their databases, preventing them from publishing or accessing the network.
-
Ozone: Advanced Moderation Tool\ Ozone is an integrated tool that enables advanced moderation strategies, combining various resources for greater efficiency.
BlueSky’s Moderation Architecture
Moderation on BlueSky is based on an open labeling system. This architecture allows anyone to assign labels to content or accounts, such as “spam” or “NSFW” (not safe for work). These labels can be automatically generated by third-party services or manually applied by curators and administrators, offering flexibility for communities and individuals to customize their experiences.
The Role of the Community in Content Regulation
In decentralized platforms like BlueSky, the community plays a central role in self-regulation, minimizing reliance on a centralized authority to moderate content. This decentralization distributes responsibilities and reduces the risks of institutional bias, often seen in centralized companies that may reflect specific interests at the expense of plurality.
Centralized platforms often censor or promote content based on corporate agendas, compromising user trust. BlueSky’s model prioritizes autonomy, allowing the community itself to determine what is relevant or acceptable.
With 25 million users registered within weeks, BlueSky remains committed to its mission of regulating not freedom of expression, but the reach of certain publications. Tools like block lists, curated feeds, and Ozone are tangible examples of how the platform is building a decentralized and inclusive ecosystem.
Challenges and Opportunities of Decentralization
Despite its merits, decentralization presents challenges. Educating users about available tools and protecting vulnerable communities from harmful content are complex tasks, especially in a rapidly growing environment.
On the other hand, the decentralized model offers significant advantages. It enhances transparency, fosters trust among users, and reduces reliance on a central authority. On BlueSky, users shape their own experiences, ensuring greater freedom without sacrificing safety.
Conclusion
BlueSky is paving the way for a new era in social networks with a decentralized moderation model that empowers users and promotes shared responsibility. Aligned with principles of freedom and inclusion, BlueSky combines advanced technology and community collaboration to create a safer, more democratic, and adaptable space.
Although still in its early stages, BlueSky offers a promising model for the future of social networks, where reach—not freedom of expression—is the true focus of regulation.
-
-
 @ c5fede3d:16e03f7b
2025-01-08 11:41:16
@ c5fede3d:16e03f7b
2025-01-08 11:41:16Hay quien dice el famoso dicho de «año nuevo, vida nueva». En este caso, iniciamos el año con el mismo propósito, seguir aprendiendo para que no nos pille el toro. En esta ocasión, toca tratar la entrada de capital a tu wallet. Sin embargo, hay que saber donde meterse sin que las arenas movedizas te engullan. ¿Preparado para comprar la hucha del cerdito?
Esta es la segunda entrega de Semanario Crypto, una serie de artículos dedicados para aquellos que desconocen los conceptos básicos del mundo de las criptomonedas. La semana pasada hicimos un barrido sin adentrarnos en territorio comanche. Si aún no tienes claro qué es una wallet o cuál es el propósito de una frase semilla, ve al punto de partida y vuelve a leerte Semanario Crypto #1 | Un nuevo paradigma, porque es el ticket de entrada para este mundillo y no lo puedes perder.
EL LÍO DEL MONTEPÍO💱

Si has llegado hasta aquí, he de felicitarte. Has dado dos grandes pasos. El primero, tener la mente abierta y querer aprender. El segundo, disponer de una wallet y tener guardada a buen recaudo la frase semilla. Ahora es el momento de la verdad, operar, no sin antes tener claro un par de conceptos más.
¿Qué son los exchanges?
Son plataformas digitales donde los usuarios pueden comprar, vender o intercambiar criptomonedas. A través de ellas, los usuarios pueden convertir su dinero tradicional en crypto, facilitando el comercio de criptoactivos.
Los exchanges son los bancos del mundo de la criptomonedas. Ambos actúan como intermediarios en las transacciones financieras y ofrecen servicios relacionados con la inversión y el comercio. Sin embargo, no todos los exchanges son iguales, se diferencian dos tipos:
1. Exchange Centralizado (CEX)
En este tipo de exchange, una entidad centralizada gestiona las transacciones y retiene los fondos los usuarios. Los CEX custodian tu dinero, cuentan con equipos profesionales de atención al cliente y están sujetos a altas regulaciones gubernamentales. Te registras, haces la verificación de identidad (KYC) y ellos te proporcionan una wallet para que la fondees con tu dinero fiduciario y operes dentro de la plataforma. Todo un ecosistema a golpe de click.
2. Exchange Descentralizado (DEX)
Aquí las transacciones se realizan entre usuarios a través de contratos inteligentes en la blockchain (P2P), es decir, las operaciones se hacen directamente desde sus propias billeteras. No requieren que se proporcionen información personal. Los usuarios mantienen el control sobre sus activos (autocustodia) y no habrá que depositar en ellas.
Sabiendo las diferencias entre un CEX y un DEX, nuevamente nos hallamos en la tesitura de tener que definirnos a nosotros mismos. En la anterior entrega de Semanario Crypto optamos por una wallet caliente o una fría en función del tipo de inversor que somos, o incluso pudimos hacer un mix emparejando la wallet fría a una extensión de navegador. Aunque, como acabamos de ver, si te registras en un CEX ellos ya te proporcionan una billetera electrónica para que operes dentro de la plataforma. La elección es tuya, pero has de tener en cuenta cómo operar de una forma u otra conforme al capital que dispongas:
Quiero operar por un monto superior a 50k euros anuales y/o soy un buen ciudadano.
- Amigo mío, quítate de problemas, y registrate en un CEX como Binance o Bit2Me. La legislación fiscal española incide especialmente en que cualquier tenencia de criptomonedas superior a 50k euros debe ser declarada. Con los exchanges que te he puesto, la información proporcionada a la Agencia Tributaria es automática y de ella se encargan ellos, no tienes que hacer nada de nada. Solo hacer tu declaración anual habitual.
- También es la opción ideal para el vago y el que no dispone de tiempo. ¿Quieres hacer un mix que te ofrezca las bondades de los CEX y los DEX? Atento al siguiente punto y atiende a las nuevas regulaciones de cara a 2025.
Quiero operar por un monto inferior a 10k euros anuales y/o considero que los CEX son neo-usureros.
- La solución son los DEX. Como ya vimos, los exchanges descentralizados no requieren de KYC para operar, de modo que dan un mayor grado de privacidad y anonimato, puesto que jamás dispondrán de tu documentación personal. Además, estás expuesto a lo que se denomina el ecosistema de las finanzas descentralizadas (DeFi).
- El mundo DeFi busca democratizar el acceso a los servicios financieros, abriendo un abanico de nuevos mercados, oportunidades de inversión y ser el primero en conocer las innovaciones financieras. Sin lugar a dudas, es donde están los más avispados y la gente pudiente, muestra de ello es el valor de su capitalización de mercado, alcanzando más de 52 mil millones de dólares, que se dice pronto.
EL CASTILLO DE DRÁCULA, LA AEAT 🧛

El año 2025 va a ser determinante para el devenir del mundo de las criptomonedas, al menos en Europa. Es el año donde entran en vigor las nuevas regulaciones fiscales. Parece ser que el mantra de que los criptoactivos eran una estafa y que no valían nada a pasado a mejor vida a partir de la entrada del gran capital, como Blackrock. Ahora, los entes fiscales reguladores quieren su porción del pastel y apuntan a tu billetera. Si quieres operar en este mundillo, debes saber un poco de fiscalidad, para que no llamen a tu puerta. Aunque, recuerda, si optaste por ser un buen ciudadano (español, en este caso) que te registraste en un CEX como Binance o Bit2Me no tendrás mayores preocupaciones, porque allí todo lo que hagas acaba registrado automáticamente en tu declaración del año fiscal. De todas formas, siempre es bueno aprender, sobre todo si operas desde los DEX con tu billetera autocustodiada.
1. La Ley MiCa y Directiva DAC8
- Reglamento europeo que establece el marco regulatorio para las criptomonedas. Obliga a que todos los servicios financieros que emitan o comercialicen criptoactivos tengan licencia y deban proporcionar información sobre sus operaciones. Los proveedores de servicios deberán informar sobre las transacciones realizadas por residentes en Europa con fines de supervisión fiscal. Los ciudadanos europeos están obligados a declarar la tenencia de criptoactivos como parte del patrimonio personal, incluyendo ganancias, la cual estará sujeta a impuestos.
- La Directiva DAC8 complementa al reglamento y se enfoca en el intercambio automático de información fiscal entre los Estados miembro de la UE (CARF). Los proveedores de criptoactivos deberán reportarán todas las transacciones y datos relevantes a las autoridades fiscales nacionales, concretamente los movimientos y saldos del usuario. Legitima a Hacienda a poder embargar las criptomonedas depositadas en un exchange, las wallets autocustodiadas son inembargables por estar en control del usuario.
2. La Travel Rule o Regla de Viaje
- Regulación que aumenta la trazabilidad entre las transacciones de criptomonedas. Exige a los servicios de activos digitales (VASP) recojan y compartan información sobre los remitentes y beneficiarios, sea a carteras custodiadas o autocustodiadas.
3. Límites y “mandamientos”
- Cualquier transferencia superior a 1.000 euros requerirá que el proveedor recopile datos personales.
- Si el monto de operaciones alcanza los 10.000 euros anuales, el proveedor informa.
- Si el monto de operaciones alcanza los 3.000 euros en un trimestre natural, el proveedor informa.
- Las ganancias deben ser declaradas en el IRPF al final del año fiscal, incluso si las criptomonedas no se han convertido a FIAT (dinero fiduciario tradicional).
- El Modelo 721 es una obligación informativa que deben cumplir los contribuyentes que poseen criptomonedas en el extranjero (exchange que no opere bajo legislación española y no presente los modelos informativos requeridos por Hacienda) y cuyo saldo supera los 50.000 euros a fecha del 31 de diciembre.
- La CNMV supervisa el mercado de criptoactivos y el Banco de España las monedas estables (dólares digitales como USDC-USDT).
¿AÚN CON FUERZAS?
Pues sabiendo todo esto, ya es hora de que deposites tu dinero en tu billetera de criptomonedas. ¿Cómo hacerlo? Eso ya lo verás en la siguiente entrega de Semanario Crypto. En él se te ofrecerá el martillo para que rompes la hucha del cerdito y le des vida a tu wallet. Aprende las rutas de entrada y de salida. Opera con conocimiento y sabiendo lo que haces. Es más fácil de lo que piensas. Recuerda que la información es poder, y tú la vas a tener.
Descargo de responsabilidad: Toda la información compartida forma parte de mi visión personal y no tiene como objetivo asesorar financieramente. Doy información, no consejos de inversión.
-
 @ dd664d5e:5633d319
2024-12-14 15:25:56
@ dd664d5e:5633d319
2024-12-14 15:25:56
Christmas season hasn't actually started, yet, in Roman #Catholic Germany. We're in Advent until the evening of the 24th of December, at which point Christmas begins (with the Nativity, at Vespers), and continues on for 40 days until Mariä Lichtmess (Presentation of Christ in the temple) on February 2nd.

It's 40 days because that's how long the post-partum isolation is, before women were allowed back into the temple (after a ritual cleansing).

That is the day when we put away all of the Christmas decorations and bless the candles, for the next year. (Hence, the British name "Candlemas".) It used to also be when household staff would get paid their cash wages and could change employer. And it is the day precisely in the middle of winter.

Between Christmas Eve and Candlemas are many celebrations, concluding with the Twelfth Night called Epiphany or Theophany. This is the day some Orthodox celebrate Christ's baptism, so traditions rotate around blessing of waters.

The Monday after Epiphany was the start of the farming season, in England, so that Sunday all of the ploughs were blessed, but the practice has largely died out.

Our local tradition is for the altar servers to dress as the wise men and go door-to-door, carrying their star and looking for the Baby Jesus, who is rumored to be lying in a manger.

They collect cash gifts and chocolates, along the way, and leave the generous their powerful blessing, written over the door. The famous 20 * C + M + B * 25 blessing means "Christus mansionem benedicat" (Christ, bless this house), or "Caspar, Melchior, Balthasar" (the names of the three kings), depending upon who you ask.
They offer the cash to the Baby Jesus (once they find him in the church's Nativity scene), but eat the sweets, themselves. It is one of the biggest donation-collections in the world, called the "Sternsinger" (star singers). The money goes from the German children, to help children elsewhere, and they collect around €45 million in cash and coins, every year.

As an interesting aside:
The American "groundhog day", derives from one of the old farmers' sayings about Candlemas, brought over by the Pennsylvania Dutch. It says, that if the badger comes out of his hole and sees his shadow, then it'll remain cold for 4 more weeks. When they moved to the USA, they didn't have any badgers around, so they switched to groundhogs, as they also hibernate in winter.
-
 @ 2063cd79:57bd1320
2025-01-08 11:19:56
@ 2063cd79:57bd1320
2025-01-08 11:19:56Ich hatte vor ein paar Wochen die Gelegenheit mich mit Micheal Hassard persönlich zu unterhalten. Mike ist Verteidiger im Fall von Roman Sterlingov. Der Fall ist haarsträubend und beängstigend. Mike und ich haben uns einige Zeit unterhalten und er hat mir einige Details aus diesem wirklich spannenden Prozess verraten. Ich wollte versuchen die Informationen in einem Artikel zusammenzufassen, um auch anderen Leuten, die mit dem Fall noch nicht betraut sind, die Möglichkeit zu geben, zu verstehen, was für absurde Methoden und ungerechte Beweismittel in diesem noch komplett neuen rechtlichen Umfeld angewendet werden.
LAX
Am 27. April 2001 landet ein Direktflug aus Moskau am Los Angeles International Airport (LAX). Bei der Passkontrolle an der Immigration wird ein junger Passagier dieses Fluges von Kriminalermittlern des Internal Revenue Service (IRS) verhaftet. In seinem Gepäck befinden sich vier Reisepässe und allerhand technisches Equipment. Darunter Laptops, externe Festplatten und Bitcoin Signing Devices (Hardware Wallets). Der junge Mann wird festgenommen, seine mitgeführten Besitztümer und Pässe konfisziert, dann wird er in Untersuchungshaft gebracht. Der Vorwurf: Die Gründung und der Betrieb eines Bitcoin Mixers. Konkret wird ihm vorgeworfen, Bitcoin Fog gegründet und betrieben zu haben, darüber hinaus wird er in drei Punkten angeklagt: Geldwäsche, Betrieb eines nicht lizenzierten Geldtransfergeschäfts und Geldtransfer ohne Lizenz. Die IRS behauptet, dass über 1,2 Millionen Bitcoin, im Wert von etwa 336 M US Dollar zum Zeitpunkt der Transaktionen, über Bitcoin Fog verschickt wurden.

Bitcoin Fog
Bitcoin Fog war ein beliebter Custodial Bitcoin Mixer, der von Nutzer//innen für ihre Privatsphäre genutzt wurde. Mixer sind Services die entwickelt wurden, um das Problem der "Common-Input-Ownership-Heuristik" zu brechen. Vereinfacht ausgedrückt beschreibt dieses Problem die Annahme, dass mehrere Inputs einer Transaktion relativ sicher dem gleichen Besitzer gehören. Ich habe Bitcoin Mixer schon mal detailliert beschrieben:
https://www.genexyz.org/post/23-block-772315-bitcoin-mixing-q6i7y4/
TL;DR: Die Grundidee besteht darin, dass man einen Coin nimmt, der aus mehreren UTXOs besteht, und diesen mit Hilfe eines Dienstes einem Pool zuführt. Diese Dienste erhalten für die Vermittlung, Zusammenführung und das Stellen der Infrastruktur eine kleine Gebühr. Transaktionen werden dann so aufgebaut, dass sie es Überwachungsfirmen oder anderen Beobachtern sehr schwer machen, genau zu wissen, welcher Transaktion-Output zu welchem der Input-Steller gehört.
Bitcoin Fog wurde 2011 gegründet und ist ein Custodial Service, was bedeutet, dass Nutzer//innen ihre Bitcoin an eine Wallet des Betreibers senden, und im Gegenzug dann von Bitcoin Fog andere Bitcoin zurück erhalten, um die Spur der On-Chain-Transaktionen zu verwischen.
Roman Sterlingov
Roman war schon früh Benutzer von Bitcoin. Als er 14 Jahre alt war, zog er mit seiner Mutter von Russland nach Schweden und beschäftigte sich ab etwa 2011 mit Bitcoin. Dies ist wichtig, denn als russischer und schwedischer Staatsbürger ist Roman im Besitz von vier offiziell ausgestellten Reisepässen. Russland hat zwei Pässe, einen für das Reisen innerhalb und einen für das Reisen außerhalb Russlands. Schweden stellt auch zwei Reisepässe aus. Als der Bitcoin-Kurs stieg, wurde er Millionär. Er kündigte seinen Job und versuchte, sich selbstständig zu machen. Unter anderem gründete er ein VPN-Geschäft, das nicht erfolgreich war, und entschied sich später aufgrund der Volatilität von Bitcoin und fehlenden Einnahmen aus seinen Projekten, Pilot bei einer kommerziellen Fluggesellschaft zu werden.
Er meldete sich bei einer kalifornischen Flugschule an und 2021, als Roman nach Kalifornien zur Flugschule flog, wurde er von der Regierung am Flughafen LAX verhaftet. Er sitzt seit über zwei Jahren im Gefängnis und wartet auf seinen Prozess. Neben seinen Pässen und seinem Equipment wurden auch die seit 2011 angesammelten Bitcoin beschlagnahmt, da diese auf Konten bei u.a. Kraken lagen.
Die Anklage
Kalifornien hat Roman Sterlingov wegen des Vorwurfs verhaftet, über einen Zeitraum von 10 Jahren Bitcoin im Wert von fast 336 M US Dollar gewaschen zu haben. Ihm wird vorgeworfen, über sein Konto und seine IP-Adressen mit der Bitcoin Fog-Domain und mit Mt. Gox-Konten, die in Verbindung zu Bitcoin Fog stehen, an Bitcoin Fog beteiligt zu sein.
Vor dem Start des Dienstes nutzte der Administrator seinen echten Namen auf seinem Mt. Gox-Konto, um die Plattform einem Betatest zu unterziehen. Sein persönliches Google-Konto wurde auch zum Speichern der Schritte zur Bezahlung der Domain verwendet. Dies sind jedoch zum heutigen Zeitpunkt nur Anschuldigungen ohne konkrete Beweise. Der Fall stützt sich stark auf digitale Forensik und Blockchain-Analyse ohne Zeugenaussagen oder ähnliche konkrete Beweisstücke. Selbst wenn Roman die Domain gekauft hätte, wäre dies nicht illegal. Die Verjährungsfrist für die angeblichen Verbrechen ist ebenfalls abgelaufen. Was bleibt, sind von der Anklage angeführte "Beweise", die sich komplett auf die Blockchain-Analyse der Firma Chainalysis stützen.
Chainalysis
Chainalysis ist die wohl bekannteste Blockchain-Analyse Firma. In einem früheren Artikel habe ich schon mal beschrieben, wie diese Firmen operieren:
https://www.genexyz.org/post/19-block-765505-on-chain-analytics-mhcumo/
TL;DR: Unter On-Chain Analytics versteht man die Analyse von Daten, die auf jeder beliebigen Blockchain vorhanden sind. Diese Daten sind auf der Chain, also on-chain und somit für jedermann jederzeit und von überall abrufbar. Genauer bieten Blockchains Daten über Adressen, Transaktionen und in gewisser Weise auch über Wallets. Diese Informationen können verwertet werden, um verschiedene Sachverhalte darzustellen. Dieses Verfahren wird auch Heuristik genannt und bedient sich wahrscheinlicher Annahmen, also z.B. wiederkehrender Muster. Dabei werden sogenannte Cluster erstellt, also Verbindungen zwischen Adressen und Transaktionen gezogen.
So nutzen nutzen Analyse-Firmen wie Chainalysis Heuristiken und Wahrscheinlichkeitsanalysen, um Bitcoin-Transaktionen und Eigentümerwechsel zu verfolgen. Sie versuchen, Adressen auf der Grundlage dieser Heuristiken zu gruppieren, jedoch stimmen die Ergebnisse verschiedener Unternehmen oft nicht überein. Dies kann zu vagen Beweisen und Schuldunterstellungen führen.
„Während die Identität eines Besitzers einer Bitcoin-Adresse im Allgemeinen anonym ist (es sei denn, der Besitzer entscheidet sich dafür, die Informationen öffentlich zugänglich zu machen), können Strafverfolgungsbehörden den Besitzer einer bestimmten Bitcoin-Adresse oft durch Analyse der Blockchain identifizieren“ - Devon Beckett, Special Agent, IRS
Chainalysis betreiben einen sogenannten Reactor, der diese Analysen vornimmt. Diese Analyse dient als Grundlage für das Argument, Roman habe Geld von seinem Mt Gox-Konto abgebucht und verwendet, um die Bezahlung der DNS-Registrierung für Bitcoin Fog zu tätigen und zu verbergen. Es wird so versucht, Roman mit Aufzeichnungen im Bitcoin Talk-Forums in Verbindung zu bringen, die wiederum Bitcoin Fog mit illegalen Aktivitäten in Verbindung bringen.

Konkret wird anhand dieser Analyse eine Verbindung zu Roman und weiter zu Bitcoin Fog hergestellt, die beweisen soll, dass Zahlungen im Wert von 336 M US Dollar gewaschen wurden, die für Drogengeschäfte verwendet wurden.
Es gibt keine objektiven Standards für diese Art der Analyse und Strafverfolgungsbehörden stützen ihre Beweise auf diese privaten Ermittlungen. Im konkreten Fall vo Chainalysis spielen Beziehungen zu Strafverfolgungsbehörden wie dem britischen Serious Crimes Office und dem US-Justizministerium, sowie den damit einhergehenden Geldquellen eine entscheidende Rolle beim Aufstieg des Unternehmens zum größten Anbieter dieser Dienstleistungen mit einer Marktkapitalisierung von 8,6 Milliarden US Dollar.
Verteidigung
Roman wird in diesem Fall von der Kanzlei Ekeland Law, PLLC vertreten. Die Anwälte, Tor Ekeland und Michael Hassard sind der festen Überzeugung, dass Roman unschuldig ist und dass er in diesem Fall aufgrund fehlerhafter digitaler Forensik in Bedrängnis geraten ist.
Roman gibt zu, Bitcoin Fog aus Datenschutzgründen verwendet zu haben, um seine Bitcoin zu waschen, bevor er diese in sein Konto bei Kraken einzahlte. Das Mischen an sich ist nicht illegal, denn während der Anhörung erkannte der Richter sogar an, dass die Verwendung eines Mixers wie Bitcoin Fog nicht grundsätzlich verboten sei. Dies war sogar das erste Mal, dass ein Richter ausdrücklich erklärte, dass das Mischen von Bitcoin nicht illegal ist und dass es auch nicht illegal ist, Nutzer//in eines Mischdienstes zu sein. Es ist jedoch zu beachten, dass sich dieser Fall speziell gegen den Betreiber von Bitcoin Fog richtet und versucht, den Dienst mit Drogenmarktplätzen in Verbindung zu bringen.
Argumente für Romans Unschuld beinhalten unter anderem, dass Bitcoin Fog in der gesamten Zeit von Romans Inhaftierung aktiv geblieben ist, was darauf schließen lässt, dass die eigentlichen Betreiber immer noch auf freiem Fuß sind. Roman wurde vor seiner Verhaftung überwacht, es wurden Abhör- und Überwachungsmaßnahmen durchgeführt, jedoch keine Beweise gefunden, die ihn mit dem Betrieb von Bitcoin Fog in Verbindung bringen, selbst nachdem Server beschlagnahmt wurden.
Darüber hinaus ignoriert die Anklage auch die Tatsache, dass die DNS-Registrierung der Bitcoin Fog Domain seit Romans Verhaftung zweimal erneuert wurde. Trotzdem versucht die Anklage eine Verbindung zu Roman auf der Grundlage von IP-Adressen herzustellen, die mit anderen E-Mails verknüpft sind, die zur Registrierung der DNS und zur Erstellung eines Kontos im Bitcoin Talk Forum verwendet wurden.

Roman wird Verschwörung vorgeworfen, es wurde jedoch kein einziger Mitverschwörer genannt. Bei den von der Anklage behaupteten Transaktionen handelt es sich um Lizenzzahlungen des Mixers, die jedoch nicht durch Beweise gestützt werden. Wenn Roman ein Drahtzieher wäre, der 336 M US Dollar an Drogengeldern gewaschen hätte, würde es für ihn keinen Sinn machen, sein Geld mit seinem richtigen Namen und Passfoto auf ein KYC-Konto bei Kraken einzuzahlen.
An dieser Stelle ist es vielleicht interessant festzustellen, dass Michael Gronager, einer der Mitbegründer von Chainalysis, auch einer der Mitbegründer von Kraken war.
Mt Gox Daten
Es gibt eine Verbindung zwischen Kraken, Chainalysis und Mt Gox. Denn nicht nur war der Gründer von Kraken, Jesse Powell, als Berater für Mt. Gox bei der Lösung eines Sicherheitsproblems tätig und begann in Erwartung seines Kollapses mit der Arbeit an Kraken als Ersatz, auch Chainalysis wurde als direkte Reaktion auf den Mt. Gox-Skandal gegründet.
Chainalysis wurde in den offiziellen Ermittlungen im Insolvenzverfahren von Mt. Gox genutzt, um den Verbleib der "gestohlenen" bitcoins zu untersuchen. Allerdings gibt es Anzeichen dafür, dass die dabei verwendeten Daten falsch und unzuverlässig seien. Angebliche Transaktionsnummern und Wallet-Adressen existieren nicht, werden verwechselt oder sind schlichtweg fehlerhaft. Genau dieser Datensatz wird aber nun benutzt, um Fälle wie den von Roman zu beweisen.
Ankläger
Einer der Staatsanwälte des Falles ist jetzt leitender Rechtsberater für Chainalysis, und ein IRS-Ermittler gründete während seiner Tätigkeit für den IRS ein privates Unternehmen namens Exigent LLC. Die Pressemitteilungen und Fundraising-Runden von Chainalysis stehen eng im Zusammenhang mit dem Fall. Exigent LLC erhält in der Pressemitteilung des US-Justizministeriums die höchste Auszeichnung für Romans Verhaftung, und fünf Monate später kaufte Chainalysis Exigent LLC. Dieser Fall scheint von Karrierismus und Profitstreben getrieben zu sein.

Problem
Neben den Verbindungen der Ermittler und Ankläger mit Chainalysis und der Problematik der fehlenden Beweise, ist dieser Fall zutiefst beunruhigend und wirft Bedenken hinsichtlich des geltenden Computerrechts auf.
Die meisten Blockchain-Strafverfolgungen folgen dem gleichen Muster: Einspruchsvereinbarungen, Gerichtsverfahren oder Entlassungen. Unschuldige Menschen gehen oft auf Plädoyer-Deals ein, weil ihnen die Ressourcen fehlen, um gegen die unbegrenzten Ressourcen des Department of Justice zu kämpfen. Roman kann keinen Deal annehmen, weil er nichts weiß und lügen müsste.
Es ist beunruhigend, dass der Fall in Washington D.C. verhandelt wird, obwohl Roman keine Verbindungen zu dieser Stadt hat. Die einzige Grundlage dafür, die Gerichtsbarkeit nach D.C. zu legen, ist darin begründet, dass eine verdeckte Operation gegen Roman aus Washington D.C. geleitet wurde. Dies gibt Anlass zur Sorge, weil es Staatsanwälten ermöglicht, Angeklagte auf der Grundlage von Online-Interaktionen vor jedes Bundesgericht zu ziehen - ob US Staatsbürger oder nicht. Dies ist ein direkter Verstoß gegen die Gerichtsstandsklausel und entfernt wichtige Elemente des Strafrechtssystems, da es jede/n Nutzer//in von Bitcoin-Mixern in die gefährliche Lage versetzen kann, vor einem US-Gericht angeklagt zu werden, wenn eine auch nur dünne Beweislage gegen ihn/sie vorliegt.
Ein weiteres Problem besteht in den vorgebrachten Beweisen. Denn die Verteidigung hat bis heute keinen Einblick in den Code oder die verwendeten Datensätze, die von Chainalysis verwendet wurden, erhalten. Chainalysis beruft sich dabei auf seine proprietären Geschäftsdaten und lehnt eine Offenlegung ab. Es wird vermutet, dass die Datensätze falsch sind, insbesondere angesichts der fragwürdigen Mt. Gox-Aufzeichnungen, auf die sie sich stützen.
Die bereitgestellten Daten sind begrenzt, unvollständig und werden in komplizierten Flussdiagrammen dargestellt. Die verwendete Software, wie z.B. der Chainalysis Reactor, steht nicht für eine unabhängige Prüfung zur Verfügung. Der Mangel an Transparenz und Zugang zu dieser Software gibt Anlass zu Bedenken hinsichtlich ihrer Genauigkeit und den daraus gezogenen Schlussfolgerungen.

Es bestehen Zweifel am Zusammenhang zwischen Roman, dem Betreiber von Bitcoin Fog, und den mutmaßlichen Straftaten. Roman sitzt derzeit im Gefängnis, ihm droht eine Haftstrafe von 50 Jahren. Die Freiheit einer Person wird durch eine kommerzielle proprietäre Software gefährdet, die vor Gericht erwirken kann, dass Quellen und Datensätze nicht offengelegt werden.
Auch wirft der Fall Bedenken hinsichtlich fehlender Standards, des gewinnorientierten Charakters des forensischen Bereichs, der Weigerung, Beweise auszutauschen, und der Möglichkeit von Justizirrtümern auf, die durch fehlerhafte Software und fragwürdige Praktiken verursacht werden.
Wie geht es weiter?
Das Verteidigungsteam hat finanzielle Probleme, da alle Gelder von Roman beschlagnahmt wurden. Der Antrag auf Freigabe der Mittel wurde abgelehnt. Romans Verteidigung muss öffentliche Mittel beantragen und hofft auf Spenden. Ich habe in einem früheren Artikel schon auf die Spendenseite aufmerksam gemacht. Wer anhand der aufgelisteten Fakten das Gefühl bekommt, dass hier jemand zu Unrecht verhaftet wurde und helfen möchte, kann die Verteidigung mit einer Spende unterstützen.
https://www.torekeland.com/roman-sterlingov
https://geyser.fund/project/usvsterlingov
FREEROMAN
🫳🎤
In diesem Sinne, 2... 1... Risiko!

-
 @ e83b66a8:b0526c2b
2024-12-11 09:16:23
@ e83b66a8:b0526c2b
2024-12-11 09:16:23I watched Tucker Carlson interview Roger Ver last night.
I know we have our differences with Roger, and he has some less than pleasant personality traits, but he is facing 109 years in jail for tax evasion. While the charges may be technically correct, he should be able to pay the taxes and a fine and walk free. Even if we accept he did wrong, a minor prison term such as 6 months to 2 years would be appropriate in this case.
We all know the severe penalty is an over reach by US authorities looking to make the whole crypto community scared about using any form of crypto as money.
The US and many governments know they have lost the battle of Bitcoin as a hard asset, but this happened as a result of the Nash equilibrium, whereby you are forced to play a game that doesn’t benefit you, because not playing that game disadvantages you further. I.e. Governments loose control of the asset, but that asset is able to shore up their balance sheet and prevent your economy from failing (potentially).
The war against Bitcoin (and other cryptos) as a currency, whereby you can use your Bitcoin to buy anything anywhere from a pint of milk in the local shop, to a house or car and everything in-between is a distant goal and one that is happening slowly. But it is happening and these are the new battle lines.
Part of that battle is self custody, part is tax and part are the money transmitting laws.
Roger’s case is also being used as a weapon of fear.
I don’t hate Roger, the problem I have with Bitcoin cash is that you cannot run a full node from your home and if you can’t do this, it is left to large corporations to run the blockchain. Large corporations are much easier to control and coerce than thousands, perhaps millions of individuals. Just as China banned Bitcoin mining, so in this scenario it would be possible for governments to ban full nodes and enforce that ban by shutting down companies that attempted to do so.
Also, if a currency like Bitcoin cash scaled to Visa size, then Bitcoin Cash the company would become the new Visa / Mastercard and only the technology would change. However, even Visa and Mastercard don’t keep transaction logs for years, that would require enormous amount of storage and have little benefit. Nobody needs a global ledger that keeps a record of every coffee purchased in every coffee shop since the beginning of blockchain time.
This is why Bitcoin with a layer 2 payment system like Lightning is a better proposition than large blockchain cryptos. Once a payment channel is closed, the transactions are forgotten in the same way Visa and Mastercard only keep a transaction history for 1 or 2 years.
This continues to allow the freedom for anybody, anywhere to verify the money they hold and the transactions they perform along with everybody else. We have consensus by verification.
-
 @ 609899dc:13493d8d
2025-01-08 10:16:53
@ 609899dc:13493d8d
2025-01-08 10:16:53Simplify your Arlo security system setup with Myarlosetup.From connecting devices to setting up settings for maximum security, our professional assistance guarantees a seamless installation experience. We assist you in smoothly integrating your floodlights, doorbells, and cameras into your system. Get improved protection and real-time monitoring for your house or place of business. You can rely on Myarlosetup to offer detailed guidance and guarantee a simple and effective Arlo security system setup. Easily secure your home now!
-
 @ d830ee7b:4e61cd62
2025-01-08 07:56:25
@ d830ee7b:4e61cd62
2025-01-08 07:56:25การเผชิญหน้า (The Collision Point)
กลางปี 2017 ที่ร้านคราฟท์เบียร์เล็ก ๆ ในย่านเกาะเกร็ด นนทบุรี อากาศร้อนจนเครื่องปรับอากาศ (ที่ยังไม่มี) ในร้านทำงานหนักแทบไหม้ "แจ๊ก กู้ดเดย์" (Jakk Goodday) นั่งลงบนเก้าอี้ไม้ที่เจ้าของร้านกันไว้ให้เป็นประจำ ราวกับเขาเป็นลูกค้าขาประจำระดับวีไอพี
กลิ่นกาแฟคั่ว ลอยผสมกับไอความร้อนจากนอกหน้าต่าง (ผิดร้านหรือเปล่า?) เกิดเป็นบรรยากาศขมติดปลายลิ้นชวนให้คนจิบแล้วอยากถอนใจ
เขาเหลือบมองออกไปนอกหน้าต่าง.. เห็นแสงแดดแผดเผาราวกับมันรู้ว่าสงคราม Blocksize กำลังคุกรุ่นขึ้นอีกครั้ง

บรรยากาศนอกหน้าต่างกับใน ฟอรัม Bitcointalk ช่างเหมือนกันจนน่าขนลุก มันร้อนแรง ไร้ความปรานี
แจ๊กเปิดแล็ปท็อป กดเข้าเว็บฟอรัม พอเสียงแจ้งเตือน “—ติ๊ง” ดังขึ้น คิ้วของเขาก็ขมวดเล็กน้อย คล้ายได้กลิ่นดินปืนกลางสนามรบ
“โรเจอร์ แวร์ (Roger Ver) ไลฟ์เดือดลั่นเวที!” “ปีเตอร์ วูเล (Pieter Wuille) โต้กลับเรื่อง SegWit!” “Hard Fork ใกล้ถึงจุดปะทะแล้ว!”
แจ๊กคลิกเข้าไปในลิงก์ของไลฟ์ทันที เหมือนมือของเขาไม่ต้องการคำสั่งจากสมอง ความคุ้นเคยกับเหตุการณ์แบบนี้บอกเขาว่า นี่ไม่ใช่ดีเบตธรรมดา แต่มันอาจเปลี่ยนอนาคตของ Bitcoin ได้จริง ๆ
เห็นแค่พาดหัวสั้น ๆ แต่ความตึงเครียดก็ชัดเจนขึ้นเรื่อย ๆ ทุกข้อความเหมือนสุมไฟใส่ใจกองหนึ่งที่พร้อมระเบิดได้ทุกเมื่อ
โทรศัพท์ของแจ๊กดังพร้อมปรากฏชื่อ แชมป์ ‘PIGROCK’ ลอยขึ้นมา เขาหยิบขึ้นมารับทันที
“ว่าไงวะแชมป์… มีอะไรด่วนหรือเปล่า?” น้ำเสียงแจ๊กฟังดูเหมือนง่วง ๆ แต่จริง ๆ เขาพร้อมจะลุกมาวิเคราะห์สถานการณ์ให้ฟังทุกเมื่อ
“พี่แจ๊ก.. ผมอ่านดีเบตเรื่อง SegWit ในฟอรัมอยู่ครับ บางคนด่าว่ามันไม่ได้แก้ปัญหาจริง ๆ บ้างก็บอกถ้าเพิ่ม Blocksize ไปเลยจะง่ายกว่า... ผมเลยสงสัยว่า Hard Fork ที่เค้าพูดถึงกันนี่คืออะไร ใครคิดอะไรก็ Fork กันได้ง่าย ๆ เลยเหรอ"
"แล้วถ้า Fork ไปหลายสาย สุดท้ายเหรียญไหนจะเป็น ‘Bitcoin ที่แท้จริง’ ล่ะพี่?”
“แล้วการ Fork มันส่งผลกับนักลงทุนยังไงครับ? คนทั่วไปอย่างผมควรถือไว้หรือขายหนีตายดีล่ะเนี่ย?”
แจ๊กยิ้มมุมปาก ชอบใจที่น้องถามจี้จุด
“เอางี้… การ Fork มันเหมือนแบ่งถนนออกเป็นสองสาย ใครชอบกติกาเก่าก็วิ่งถนนเส้นเก่า ใครอยากแก้กติกาใหม่ก็ไปถนนเส้นใหม่"
"แต่ประเด็นคือ... นี่ไม่ใช่เรื่องเล็ก ๆ เพราะมีผลต่ออัตลักษณ์ของ Bitcoin ทั้งหมดเลยนะมึง—ใครจะยอมปล่อยผ่านง่าย ๆ”
"คิดดูสิ ถ้าครั้งนี้พวกเขา Fork จริง มันอาจไม่ได้เปลี่ยนแค่เครือข่าย แต่เปลี่ยนวิธีที่คนมอง Bitcoin ไปตลอดกาลเลยนะ"
"แล้วใครมันจะอยากลงทุนในระบบที่แตกแยกซ้ำแล้วซ้ำเล่าวะ?"
“งั้นหมายความว่าตอนนี้ก็มีสองแนวใหญ่ ๆ ชัวร์ใช่ไหมครับ?” แชมป์ถามต่อ
“ฝั่ง โรเจอร์ แวร์ ที่บอกว่าต้องเพิ่ม Blocksize ให้ใหญ่จุใจ กับฝั่งทีม Core อย่าง ปีเตอร์ วูเล ที่ยืนยันต้องใช้ SegWit ทำให้บล็อกเบา ไม่กระทบการกระจายอำนาจ?”
“ใช่เลย” แจ๊กจิบกาแฟดำเข้ม ๆ ผสมน้ำผึ้งไปหนึ่งอึก
“โรเจอร์นี่เขาเชื่อว่า Bitcoin ต้องเป็นเงินสดดิจิทัลที่ใช้จ่ายไว ค่าธรรมเนียมไม่แพง ส่วนปีเตอร์กับ Bitcoin Core มองว่าการเพิ่มบล็อกเยอะ ๆ มันจะไปฆ่า Node รายย่อย คนไม่มีทุนก็รัน Node ไม่ไหว สุดท้าย Bitcoin จะกลายเป็นระบบกึ่งรวมศูนย์ ซึ่งมันผิดหลักการเดิมของ ซาโตชิ ไงล่ะ”
“ฟังแล้วก็ไม่ใช่เรื่องง่ายนะพี่… งั้นที่ผมได้ยินว่า จิฮั่น อู๋ (Jihan Wu) เจ้าของ Bitmain ที่ถือ Hashrate เกินครึ่งนี่ก็มาอยู่ฝั่งเดียวกับโรเจอร์ใช่ไหม?"
"เพราะยิ่งบล็อกใหญ่ ค่าธรรมเนียมยิ่งเพิ่ม นักขุดก็ได้กำไรสูงขึ้นใช่ป่ะ?”
“ไอ้เรื่องกำไรก็ส่วนหนึ่ง...” แจ๊กถอนหายใจ
“แต่ที่สำคัญกว่านั้นคืออำนาจต่อรอง… ตอนประชุมลับที่ฮ่องกงเมื่อปีที่แล้ว พี่เองก็ถูกชวนให้เข้าไปในฐานะคนกลาง เลยเห็นภาพน่าขนลุกอยู่หน่อย ๆ"
"จิฮั่นนั่งไขว่ห้างด้วยสีหน้ามั่นใจมาก ด้วย Hashrate ราว 60% ของโลก สั่งซ้ายหันขวาหันเหมือนเป็นแม่ทัพใหญ่ได้เลย พอโรเจอร์ก็ไฟแรงอยู่แล้ว อยากให้ Bitcoin ครองโลกด้วยวิธีของเขา สองคนนี่จับมือกันทีจะเขย่าชุมชน Bitcoin ได้ทั้งกระดาน”
"พี่รู้สึกเหมือนนั่งอยู่ในศึกชิงบัลลังก์ยุคใหม่ คนหนึ่งยึดพลังขุด คนหนึ่งยึดความศรัทธาในชื่อ Bitcoin แต่สิ่งที่พี่สงสัยในตอนนั้นคือ… พวกเขาสู้เพื่อใครกันแน่?"
แชมป์เงียบไปครู่เหมือนกำลังประมวลผล “แล้วตอนนั้นพี่คิดยังไงบ้างครับ? รู้สึกกลัวหรือว่ายังไง?”
“จะไม่กลัวได้ไง!” แจ๊กหัวเราะแห้ง ๆ แวบหนึ่งก็นึกถึงสีหน้าที่ยิ้มเยาะของทั้งคู่ตอนประกาศความพร้อมจะ Fork
“พี่อดคิดไม่ได้ว่าถ้า Core ยังไม่ยอมขยายบล็อก พวกนั้นจะลากนักขุดทั้งกองทัพแฮชเรตไปทำเครือข่ายใหม่ให้เป็น ‘Bitcoin สายใหญ่’ แล้วทิ้งเครือข่ายเดิมให้ซวนเซ"
"แค่คิดก็นึกถึงสงครามกลางเมืองในหนังประวัติศาสตร์แล้วน่ะ.. แตกเป็นสองฝ่าย สุดท้ายใครแพ้ใครชนะ ไม่มีใครทำนายได้จริง ๆ”

พูดจบ.. เขาเปิดฟอรัมดูไลฟ์ดีเบตจากงานในปี 2017 ต่อ โรเจอร์ แวร์ กำลังพูดในโทนร้อนแรง
“Bitcoin ไม่ใช่ของคนรวย! ถ้าคุณไม่เพิ่ม Blocksize คุณก็ทำให้ค่าธรรมเนียมพุ่งจนคนธรรมดาใช้ไม่ได้!”
ขณะเดียวกัน ปีเตอร์ วูเล่ ยืนอยู่ฝั่งตรงข้าม สีหน้าเยือกเย็นราวกับตั้งรับมานาน “การเพิ่มบล็อกคือการทำลายโครงสร้าง Node รายย่อยในระยะยาว แล้วมันจะยังเรียกว่ากระจายอำนาจได้หรือ?”
"ถ้าคุณอยากให้ Bitcoin เป็นของคนรวยเพียงไม่กี่คน ก็เชิญขยายบล็อกไปเถอะนะ แต่ถ้าอยากให้มันเป็นระบบที่คนทุกระดับมีส่วนร่วมจริง ๆ ..คุณต้องฟังเสียง Node รายเล็กด้วย" ปีเตอร์กล่าว
เสียงผู้คนในงานโห่ฮากันอย่างแตกเป็นสองฝ่าย บ้างก็เชียร์ความตรงไปตรงมาของโรเจอร์ บ้างก็เคารพเหตุผลเชิงเทคนิคของปีเตอร์
ข้อความจำนวนมหาศาลในฟอรัมต่างโหมกระพือไปต่าง ๆ นานา มีทั้งคำด่าหยาบคายจนแจ๊กต้องเบือนหน้า ตลอดจนการวิเคราะห์ลึก ๆ ถึงอนาคตของ Bitcoin ที่อาจไม่เหมือนเดิม
ในระหว่างนั้น.. แชมป์ส่งข้อความ Discord กลับมาอีก
“พี่ ถ้า Fork จริง ราคาจะป่วนแค่ไหน? ที่เขาว่าคนถือ BTC จะได้เหรียญใหม่ฟรี ๆ จริงไหม? ผมกลัวว่าถ้าเกิดแบ่งเครือข่ายไม่รู้กี่สาย ตลาดอาจมั่วจนคนหายหมดก็ได้ ใช่ไหมครับ?”
"แล้วถ้าเครือข่ายใหม่ล้มเหลวล่ะครับ? จะส่งผลอะไรต่อชุมชน Bitcoin เดิม?"
"ไอ้แชมป์มึงถามรัวจังวะ!?" แจ๊กสบถเพราะเริ่มตั้งรับไม่ทัน
“ก็ขึ้นกับตลาดจะเชื่อว่าสายไหนเป็น ‘ของจริง’ อีกนั่นแหละ” แจ๊กพิมพ์กลับ
“บางคนถือไว้เผื่อได้เหรียญใหม่ฟรี บางคนขายหนีตายก่อน"
"พี่เองก็ยังไม่กล้าการันตีเลย แต่ที่แน่ ๆ สงครามนี้ไม่ได้มีแค่ผลกำไร มันกระทบศรัทธาของชุมชน Bitcoin ทั้งหมดด้วย"
"ถ้าชาวเน็ตเลิกเชื่อมั่น หรือคนนอกมองว่าพวกเราทะเลาะกันเองเหมือนเด็กแย่งของเล่น ต่อให้ฝั่งไหนชนะ ก็อาจไม่มีผู้ใช้เหลือให้ฉลอง”
แล้วสายตาแจ๊กก็ปะทะกับกระทู้ใหม่ที่เด้งขึ้นมาบนหน้าฟอรัม
“โรเจอร์ แวร์ ประกาศ: ถ้าไม่เพิ่ม Blocksize เราจะฟอร์กเป็น Bitcoin ที่แท้จริง!”
ตัวหนังสือหนาแปะอยู่ตรงนั้นส่งแรงสั่นสะเทือนราวกับจะดึงคนในวงการให้ต้องเลือกข้างกันแบบไม่อาจกลับหลังได้
แจ๊กเอื้อมมือปิดแล็ปท็อปช้า ๆ คล้ายยอมรับความจริงว่าหนทางประนีประนอมอาจไม่มีอีกแล้ว..
“สงครามนี่คงใกล้ระเบิดเต็มทีล่ะนะ” เขาลุกจากเก้าอี้ สะพายเป้ พึมพำกับตัวเองขณะมองกาแฟดำที่เหลือครึ่งแก้ว “ถ้าพวกเขาฟอร์กจริง โลกคริปโตฯ ที่เราเคยรู้จักอาจไม่มีวันเหมือนเดิมอีกต่อไป”
เขามองออกไปนอกหน้าต่าง แสงแดดที่แผดเผาราวกับกำลังบอกว่า.. อนาคตของ Bitcoin อยู่ในจุดที่เส้นแบ่งระหว่างชัยชนะกับความล่มสลายเริ่มพร่าเลือน... และอาจไม่มีทางย้อนกลับ
ก่อนเดินออกจากร้าน เขากดส่งข้อความสั้น ๆ ถึงแชมป์
“เตรียมใจกับความปั่นป่วนไว้ให้ดี ไม่แน่ว่าเราอาจจะได้เห็น Bitcoin แตกเป็นหลายสาย.. ใครจะอยู่ใครจะไปไม่รู้เหมือนกัน แต่เรื่องนี้คงไม่จบง่าย ๆ แน่”
แจ๊กผลักประตูออกไปพบกับแดดจัดที่เหมือนแผดเผากว่าเดิม พายุร้อนไม่ได้มาแค่ในรูปความร้อนกลางกรุง แต่มาในรูป “สงคราม Blocksize” ที่พร้อมจะฉีกชุมชนคริปโตออกเป็นฝักฝ่าย และอาจลามบานปลายจนกลายเป็นศึกประวัติศาสตร์
ทว่าสิ่งที่ค้างคาใจกลับเป็นคำถามนั้น…
เมื่อเครือข่ายแบ่งเป็นหลายสายแล้ว เหรียญไหนจะเป็น Bitcoin จริง?
หรือบางที... ในโลกที่ใครก็ Fork ได้ตามใจ เราจะไม่มีวันได้เห็น “Bitcoin หนึ่งเดียว” อีกต่อไป?
คำถามที่ไม่มีใครตอบได้ชัดนี้ส่องประกายอยู่ตรงปลายทาง ราวกับป้ายเตือนว่า “อันตรายข้างหน้า” และคนในชุมชนทั้งหมดกำลังจะต้องเผชิญ…
โดยไม่มีใครมั่นใจเลยว่าจะรอด หรือจะแตกสลายไปก่อนกันแน่...

สองเส้นทาง (The Forked Path)
กลางปี 2017 ท้องฟ้าเหนือบุรีรัมย์ยังคงคุกรุ่นด้วยไอแดดและความร้อนแรงของสงคราม Blocksize แจ๊ก กู้ดเดย์ ก้าวเข้ามาในคาเฟ่เล็ก ๆ แห่งหนึ่งในย่านเทศบาลด้วยสีหน้าครุ่นคิด เขาพยายามมองหามุมสงบสำหรับนั่งตั้งหลักในโลกความเป็นจริง ก่อนจะจมดิ่งสู่สงครามในโลกดิจิทัลบนฟอรัม Bitcointalk อีกครั้ง
กลิ่นกาแฟคั่วเข้มลอยกระทบจมูก แจ๊กสั่งกาแฟดำแก้วโปรดแล้วปลีกตัวมาที่โต๊ะริมกระจก กระจกบานนั้นสะท้อนแสงอาทิตย์จัดจ้า ราวกับจะบอกว่าวันนี้คงไม่มีใครหนีความร้อนที่กำลังแผดเผา ทั้งในอากาศและในชุมชน Bitcoin ได้พ้น
เขาเปิดแล็ปท็อปขึ้น ล็อกอินเข้า Bitcointalk.org ตามเคย ข้อความและกระทู้มากมายกระหน่ำแจ้งเตือน ไม่ต่างอะไรจากสมรภูมิคำพูดที่ไม่มีวันหลับ “Hong Kong Agreement ล้มเหลวจริงหรือ?” “UASF คือปฏิวัติโดย Node?” เหล่านี้ล้วนสะท้อนความไม่แน่นอนในชุมชน Bitcoin ที่ตอนนี้ ดูคล้ายจะถึงจุดแตกหักเต็มที...
“ทั้งที่ตอนนั้นเราก็พยายามกันแทบตาย…” แจ๊กพึมพำ มองจอด้วยสายตาเหนื่อยใจพร้อมภาพความทรงจำย้อนกลับเข้าในหัว เขายังจำการประชุมที่ฮ่องกงเมื่อต้นปี 2016 ได้แม่น ยามนั้นความหวังในการประนีประนอมระหว่าง Big Block และ Small Block ดูเป็นไปได้ หากแต่กลายเป็นละครฉากใหญ่ที่จบลงโดยไม่มีใครยอมถอย...
...การประชุม Hong Kong Agreement (2016)
ภายในห้องประชุมหรูของโรงแรมใจกลางย่านธุรกิจฮ่องกง บรรยากาศตึงเครียดยิ่งกว่าการเจรจาสงบศึกในสมัยโบราณ
โรเจอร์ แวร์ ยืนเสนอว่า “การเพิ่ม Blocksize สำคัญต่ออนาคตของ Bitcoin — เราอยากให้คนทั่วไปเข้าถึงได้โดยไม่ต้องจ่ายค่าธรรมเนียมแพง ๆ”
“จิฮั่น อู๋ (Jihan Wu)” จาก Bitmain นั่งฝั่งเดียวกับโรเจอร์ คอยเสริมว่าการเพิ่มบล็อกคือโอกาสสำหรับนักขุด และหากทีม Core ไม่ยอม พวกเขาก็พร้อม “ดัน Fork” ขึ้นได้ทุกเมื่อ ด้วย Hashrate มหาศาลที่พวกเขาคุมไว้
ฝั่ง ปีเตอร์ วูเล (Pieter Wuille) กับ เกร็ก แมกซ์เวลล์ (Greg Maxwell) จาก Bitcoin Core เถียงกลับอย่างใจเย็นว่า “การขยายบล็อกอาจดึงดูดทุนใหญ่ ๆ แล้วไล่ Node รายย่อยออกไป ชุมชนอาจไม่เหลือความกระจายอำนาจอย่างที่ Satoshi ตั้งใจ”
สุดท้าย บทสรุปที่เรียกว่า Hong Kong Agreement ลงนามได้ก็จริง แต่มันกลับเป็นแค่ลายเซ็นบนกระดาษที่ไม่มีฝ่ายไหนเชื่อใจใคร

แจ๊กเบือนสายตาออกนอกหน้าต่าง สังเกตเห็นผู้คนเดินขวักไขว่ บ้างก็ดูรีบร้อน บ้างเดินทอดน่องเหมือนว่างเปล่า นี่คงไม่ต่างอะไรกับชาวเน็ตในฟอรัมที่แบ่งฝ่ายกันใน “สงคราม Blocksize” อย่างไม่มีทีท่าจะหยุด
แค่ไม่กี่นาที... เสียงโทรศัพท์ก็ดังขึ้น ชื่อ แชมป์ ‘PIGROCK’ โชว์หราเต็มจออีกครั้ง
“ว่าไงเจ้าแชมป์?” แจ๊กกรอกเสียงในสายด้วยอารมณ์เหนื่อย ๆ ทว่าพร้อมจะอธิบายเหตุการณ์ตามสไตล์คนที่ชอบครุ่นคิด
“พี่แจ๊ก.. ผมเข้าใจแล้วว่าการประชุมฮ่องกงมันล้มเหลว ตอนนี้ก็มีคนแยกเป็นสองขั้ว Big Block กับ SegWit แต่ผมเจออีกกลุ่มในฟอรัมเรียกว่า UASF (User-Activated Soft Fork) ที่เหมือนจะกดดันพวกนักขุดให้ยอมรับ SegWit..."
"อยากรู้ว่าตกลง UASF มันสำคัญยังไงครับ? ทำไมใคร ๆ ถึงเรียกว่าเป็น การปฏิวัติโดย Node กัน?”
แจ๊กอมยิ้มก่อนจะวางแก้วกาแฟลง พูดด้วยน้ำเสียงจริงจังกว่าเดิม “UASF น่ะหรือ? มันเปรียบได้กับการที่ ‘ชาวนา’ หรือ ‘ประชาชนตัวเล็ก ๆ’ ออกมาประกาศว่า ‘ฉันจะไม่รับบล็อกของนักขุดที่ไม่รองรับ SegWit นะ ถ้าแกไม่ทำตาม ฉันก็จะตัดบล็อกแกทิ้ง!’ เสมือนเป็นการปฏิวัติที่บอกว่าแรงขุดมากแค่ไหนก็ไม่สำคัญ ถ้าคนรัน Node ไม่ยอม… เชนก็เดินต่อไม่ได้”
“โห… ฟังดูแรงจริง ๆ พี่ แล้วถ้านักขุดไม่ร่วมมือ UASF จะเกิดอะไรขึ้น?” แชมป์ถามต่อเสียงสั่นนิด ๆ
“ก็อาจเกิด ‘Chain Split’ ยังไงล่ะ"
"แยกเครือข่ายเป็นสองสาย สุดท้ายเครือข่ายเดิม กับเครือข่ายใหม่ที่รองรับ SegWit ไม่ตรงกัน คนอาจสับสนหนักยิ่งกว่า Hard Fork ปกติด้วยซ้ำ"
"แต่นั่นแหละ... มันแสดงพลังว่าผู้ใช้ทั่วไปก็มีสิทธิ์กำหนดทิศทาง Bitcoin ไม่ได้น้อยไปกว่านักขุดเลย”
“เข้าใจแล้วครับพี่… เหมือน การปฏิวัติโดยประชาชนตาดำ ๆ ที่จับมือกันค้านอำนาจทุนใหญ่ใช่ไหม?” แชมป์หยุดครู่หนึ่ง “ผมเคยคิดว่า Node รายย่อยน้อยรายจะไปสู้อะไรไหว แต่ตอนนี้ดูท่าจะเปลี่ยนเกมได้จริงว่ะพี่…”
“ใช่เลย” แจ๊กตอบ
“นี่เป็นความพิเศษของ Bitcoin ที่บอกว่า ‘เราคุมเครือข่ายร่วมกัน’ แม้แต่ Bitmain ที่มี Hashrate มากกว่า 50% ก็หนาวได้ถ้าผู้ใช้หรือ Node รายย่อยรวมพลังกันมากพอ”
แชมป์ฟังด้วยความตื่นเต้นปนกังวล “แล้วแบบนี้ เรื่อง SegWit กับ Blocksize จะจบยังไงครับ? เห็นข่าวว่าถ้านักขุดโดนกดดันมาก ๆ คนอย่าง จิฮั่น อู๋ อาจออกไปสนับสนุน Bitcoin Cash ที่จะเปิดบล็อกใหญ่”
แจ๊กเลื่อนดูฟีดข่าวในฟอรัม Bitcointalk อีกครั้ง ก็เห็นพาดหัวชัด ๆ
“Bitmain ประกาศกร้าวพร้อมหนุน BCH เต็มพิกัด!”
เขาถอนหายใจเฮือกหนึ่ง “ก็ใกล้เป็นจริงแล้วล่ะ… โรเจอร์ แวร์ เองก็ผลักดัน BCH ว่าคือ Bitcoin แท้ที่ค่าธรรมเนียมถูก ใช้งานได้จริง ส่วนฝั่ง BTC ที่ยึดเอา SegWit เป็นหลัก ก็ไม่ยอมให้ Blocksize เพิ่มใหญ่เกินจำเป็น.."
"ต่างคนต่างมีเหตุผล... แต่อุดมการณ์นี่คนละทางเลย”
“แล้วพี่คิดว่าใครจะเป็นฝ่ายชนะครับ?”
“เฮ้ย.. มึงถามยากไปหรือเปล่า” แจ๊กหัวเราะหึ ๆ “ทุกคนมีโอกาสได้หมด และก็มีโอกาสพังหมดเหมือนกัน ถ้า UASF กดดันนักขุดให้อยู่กับ Core ได้ พวกเขาอาจยอมแพ้ แต่ถ้า Bitmain เทใจไป BCH นักขุดรายใหญ่คนอื่น ๆ ก็คงตาม"
"แล้วถ้าฝั่ง BCH เริ่มได้เปรียบ... อาจดึงคนไปเรื่อย ๆ สุดท้ายจะเหลือไหมล่ะฝั่ง SegWit ตัวจริง?”
“งั้น Node รายย่อยจะยืนอยู่ตรงไหนล่ะครับพี่?” แชมป์ถามอย่างหนักใจ
“Node รายย่อยและชุมชนผู้ใช้นี่แหละ คือ ตัวแปรชี้ขาด ทุกวันนี้คนกลุ่ม UASF พยายามโชว์พลังว่าตัวเองมีสิทธิ์ตั้งกติกาเหมือนกัน ไม่ใช่แค่นักขุด"
"อย่างที่บอก.. มันคือการ ‘ลุกขึ้นปฏิวัติ’ โดยชาวนา ต่อสู้กับเจ้าที่ที่ถือ ‘แฮชเรต’ เป็นอาวุธ”
แจ๊กตบบ่าตัวเองเบา ๆ ก่อนจะหัวเราะเล็กน้อย
“นี่แหละความมันของ Bitcoin ไม่มีเจ้าไหนสั่งได้เบ็ดเสร็จจริง ๆ ทุกฝั่งต่างถือไพ่คนละใบ สงครามยังไม่รู้จะจบยังไง ถึงอย่างนั้นมันก็สะท้อนวิญญาณ ‘decentralization’ ที่แท้จริง กล้ายอมรับสิทธิ์ทุกฝ่ายเพื่อแข่งขันกันตามกติกา”

จู่ ๆ ในหน้าฟอรัมก็มีกระทู้ใหม่เด้งเด่น “Bitmain หนุน Bitcoin Cash ด้วย Hashrate กว่า 50%! สงครามเริ่มแล้ว?” ข้อความนั้นดังโครมครามเหมือนระเบิดลงกลางวง
แจ๊กนิ่งไปชั่วขณะ สัมผัสได้ถึงความปั่นป่วนที่กำลังปะทุขึ้นอีกครั้ง เหงื่อบางเบาซึมบนหน้าผากแม้อากาศในคาเฟ่จะเย็นฉ่ำ เขาหันมองโทรศัพท์ที่ยังค้างสายกับแชมป์ แล้วเอ่ยด้วยน้ำเสียงจริงจัง
“นี่ล่ะ.. จุดเริ่มของสองเส้นทางอย่างชัดเจน… บล็อกใหญ่จะไปกับ BCH ส่วน SegWit ก็อยู่กับ BTC แน่นอนว่าทั้งสองฝ่ายไม่คิดถอยง่าย ๆ นักขุดจะเลือกข้างไหน? Node รายย่อยจะยอมใคร?"
"เมื่อสงครามครั้งนี้นำไปสู่การแบ่งเครือข่าย ใครกันแน่จะเป็นผู้ชนะตัวจริง? หรืออาจไม่มีผู้ชนะเลยก็เป็นได้”
ปลายสายเงียบงัน มีแต่เสียงหายใจของแชมป์ที่สะท้อนความกังวลปนอยากรู้อย่างแรง
“พี่… สุดท้ายแล้วเรากำลังยืนอยู่บนรอยแยกที่พร้อมจะฉีกทุกอย่างออกเป็นชิ้น ๆ ใช่ไหมครับ?”
“อาจจะใช่ก็ได้... หรือถ้ามองอีกมุม อาจเป็นวัฏจักรที่ Bitcoin ต้องเจอเป็นระยะ ทุกคนมีสิทธิ์ Fork ได้ตามใจใช่ไหมล่ะ? ก็ขอให้โลกได้เห็นกันว่าชุมชนไหนแน่จริง” แจ๊กพูดทิ้งท้ายก่อนจะแย้มยิ้มเจือรอยอ่อนล้า
ภาพบนจอคอมพิวเตอร์ฉายกระทู้ถกเถียงกันไม่หยุด ประหนึ่งเวทีดีเบตที่ไม่มีวันปิดไฟ แจ๊กจิบกาแฟอึกสุดท้ายเหมือนจะเตรียมพร้อมใจก่อนเข้าสู่สนามรบครั้งใหม่ สงครามยังไม่จบ.. ซ้ำยังดูหนักข้อยิ่งขึ้นเรื่อย ๆ
เขาลุกขึ้นจากโต๊ะ ชำเลืองมองแสงแดดจัดจ้าที่สาดลงมาไม่หยุด เปรียบเหมือนไฟแห่งข้อขัดแย้งที่เผาผลาญทั้งชุมชน Bitcoin ไม่ว่าใครจะเลือกอยู่ฝั่งไหน กลุ่ม UASF, กลุ่ม Big Block, หรือ กลุ่ม SegWit ทางเดินข้างหน้าล้วนเต็มไปด้วยความไม่แน่นอน
“สุดท้ายแล้ว… เมื่อกระดานแบ่งเป็นสองเส้นทางอย่างเด่นชัด สงคราม Blocksize จะจบลงด้วยใครได้บทผู้ชนะ?"
"หรือบางที… มันอาจไม่มีผู้ชนะที่แท้จริงในระบบที่ใครก็ Fork ได้ตลอดเวลา”
คำถามนี้ลอยติดค้างอยู่ในบรรยากาศยามบ่ายที่ร้อนระอุ ชวนให้ใครก็ตามที่จับตาดูสงคราม Blocksize ต้องฉุกคิด
เมื่อไม่มีใครเป็นเจ้าของ Bitcoin อย่างสมบูรณ์ ทุกคนจึงมีสิทธิ์บงการและเสี่ยงต่อการแตกแยกได้ทุกเมื่อ แล้วท้ายที่สุด ชัยชนะ–ความพ่ายแพ้ อาจไม่ใช่จุดสิ้นสุดของโลกคริปโตฯ
แต่เป็นเพียงจุดเริ่มต้นของการวิวัฒน์ที่ไม่มีวันจบสิ้น…

เมาท์แถมเรื่อง UASF (User-Activated Soft Fork)
นี่สนามรบยุคกลางที่ดูเหมือนในหนังแฟนตาซี ทุกคนมีดาบ มีโล่ แต่จู่ ๆ คนตัวเล็กที่เราไม่เคยสังเกต—พวกชาวนา ช่างไม้ คนแบกน้ำ—กลับรวมตัวกันยกดาบบุกวังเจ้าเมือง พร้อมตะโกนว่า “พอเถอะ! เราก็มีสิทธิ์เหมือนกัน!”
มันอาจจะดูเวอร์ ๆ หน่อยใช่ไหมครับ?
แต่ในโลก Bitcoin ปี 2017 นี่คือสิ่งที่เกิดขึ้นในรูปแบบ “User-Activated Soft Fork” หรือ UASF การปฏิวัติด้วยพลังโหนด ซึ่งทำให้นักขุดยักษ์ใหญ่ตัวสั่นงันงกันมาแล้ว!
แล้ว UASF มันคืออะไรล่ะ?
“User-Activated Soft Fork” หรือเรียกย่อ ๆ ว่า “UASF” ไม่ใช่อัปเกรดซอฟต์แวร์สวย ๆ แต่เป็น “ดาบเล่มใหม่” ที่คนตัวเล็ก—หมายถึง โหนด รายย่อย—ใช้ต่อรองกับนักขุดรายใหญ่ โดยกติกาคือ.. ถ้านักขุดไม่ทำตาม (เช่น ไม่รองรับ SegWit) โหนดก็จะปฏิเสธบล็อกของพวกเขาอย่างไม่เกรงใจใคร
สมมุติว่าคุณคือโหนด..
คุณรันซอฟต์แวร์ Bitcoin คอยตรวจสอบธุรกรรม วันดีคืนดี คุณประกาศ “ต่อไปถ้าใครไม่รองรับ SegWit ฉันไม่ยอมรับบล็อกนะ!” นี่ล่ะครับ “UASF” ตัวเป็น ๆ
คำขวัญสุดฮิตของ UASF
“No SegWit, No Block”
หรือแปลว่าถ้าบล็อกไม่รองรับ SegWit ก็เชิญออกไปเลยจ้า..
มันเหมือนการที่ชาวนาโผล่มาตบโต๊ะอาหารท่านขุนว่า “นายใหญ่จะปลูกอะไรก็ปลูกไป แต่ไม่งั้นฉันไม่รับผลผลิตนายนะ!”
ความเชื่อมโยงกับ BIP 148
ถ้าจะพูดถึง UASF ต้องรู้จัก BIP 148 ไว้นิดนึง มันเปรียบเหมือน “ธงปฏิวัติ” ที่ตีตราว่าวันที่ 1 สิงหาคม 2017 คือเส้นตาย!
BIP 148 บอกไว้ว่า.. ถ้าถึงวันนั้นแล้วยังมีนักขุดหน้าไหนไม่รองรับ SegWit บล็อกที่ขุดออกมาก็จะถูกโหนดที่ใช้ UASF “แบน” หมด
ผลลัพธ์ที่ตั้งใจ นักขุดไม่อยากโดนแบนก็ต้องทำตาม UASF กล่าวคือ “นายต้องรองรับ SegWit นะ ไม่งั้นอด!”
หลายคนกลัวกันว่า “อ้าว ถ้านักขุดใหญ่ ๆ ไม่ยอมแล้วหันไปขุดสายอื่น จะไม่กลายเป็นแยกเครือข่าย (Chain Split) หรือ?”
ใช่ครับ.. มันอาจเกิดสงครามสายใหม่ทันทีไงล่ะ
ทำไม UASF ถึงสำคัญ?
ย้อนกลับไปก่อนปี 2017 Bitcoin มีปัญหาโลกแตกทั้งค่าธรรมเนียมแพง ธุรกรรมหน่วง บวกกับความขัดแย้งเรื่อง “จะเพิ่ม Blocksize ดีไหม?” ทางกลุ่มนักขุดรายใหญ่ (นำโดย Bitmain, Roger Ver ฯลฯ) รู้สึกว่า “SegWit ไม่ใช่ทางออกที่แท้จริง” แต่อีกฝั่ง (ทีม Core) ชี้ว่า “Blocksize ใหญ่มากไปจะรวมศูนย์นะ โหนดรายย่อยตายหมด”
UASF เลยโผล่มา เหมือนชาวนาตะโกนว่า
“หุบปากได้แล้วไอ้พวกที่สู้กัน! ถ้าพวกแกไม่รองรับ SegWit พวกข้า (โหนด) ก็จะไม่เอาบล็อกแก”
สาระก็คือ.. มันคือตัวบ่งชี้ว่าคนตัวเล็กอย่างโหนดรายย่อยก็มีพลังต่อรอง เป็นกลไกที่ดึงอำนาจจากมือทุนใหญ่กลับสู่มือชุมชน (Decentralization ที่แท้ทรู)
วิธีการทำงานของ UASF
ลองจินตนาการตาม..
-
การกำหนดเส้นตาย BIP 148 ประกาศไว้ “ถึงวันที่ 1 สิงหาคม 2017 ถ้านายยังไม่รองรับ SegWit โหนด UASF จะไม่รับบล็อกนาย”
-
ถ้าคุณเป็นนักขุด… คุณขุดบล็อกออกมา แต่ไม่ได้ตีธง “ฉันรองรับ SegWit” UASF โหนดเห็นปุ๊บ พวกเขาจะจับโยนทิ้งไปเลย
-
ผลกระทบ? นักขุดที่ไม่ยอมทำตามจะเจอปัญหา บล็อกที่ขุดออกมาไม่มีใครรับ—เสียแรงขุดฟรี
อาจเกิด Chain Split คือ แยกเครือข่ายเลย ถ้านักขุดเหล่านั้นไปตั้งสายใหม่
ความสำเร็จและความท้าทายของ UASF
ความสำเร็จ.. หลังการรวมพลังผู้ใช้ โหนดรายย่อยกดดันนักขุดได้ไม่น้อย จนกระทั่ง SegWit เปิดใช้งานจริงใน Bitcoin วันที่ 24 สิงหาคม 2017 ช่วยให้ธุรกรรมเร็วขึ้น แก้ Transaction Malleability และเปิดทางสู่ Lightning Network ในอนาคต
ความท้าทาย.. นักขุดบางค่ายไม่โอเค.. โดยเฉพาะ Bitmain ซึ่งคาดว่าจะสูญรายได้บางส่วน ก็นำไปสู่การสนับสนุน “Bitcoin Cash (BCH)” แยกสาย (Hard Fork) ของตัวเองตั้งแต่วันที่ 1 สิงหาคม 2017 นั่นเอง
ว่าแล้วก็เปรียบง่าย ๆ
UASF เหมือนปฏิบัติการยึดคฤหาสน์เจ้าเมืองมาเปิดให้ชาวบ้านเข้าอยู่ฟรี.. แต่อีกฝ่ายบอก
“งั้นฉันออกไปตั้งคฤหาสน์ใหม่ดีกว่า!”
บทเรียนสำคัญ UASF เป็นตัวอย่างชัดว่า “ผู้ใช้” หรือ โหนดรายย่อย สามารถสร้างแรงกดดันให้นักขุดต้องยอมเปลี่ยนได้จริง ๆ ไม่ใช่แค่ยอมรับเงื่อนไขที่ขุดกันมา
ผลกระทบระยะยาวหลังจากนั้นล่ะ?
SegWit ถูกใช้งาน ทำให้ค่าธรรมเนียมธุรกรรมลดลง (ช่วงหนึ่ง) เกิด Lightning Network เป็น Layer 2 สุเฟี้ยวของ Bitcoin เกิด BCH (Bitcoin Cash) เป็นสายแยกที่อ้างว่า Blocksize ใหญ่คือทางออก
สรุปแล้ว UASF ทำให้โลกได้รู้ว่า..
Bitcoin ไม่ใช่ของนักขุด หรือของฝ่ายพัฒนาใดฝ่ายเดียว แต่มันเป็นของทุกคน!
“Bitcoin เป็นของทุกคน”
ไม่มีใครมีอำนาจเบ็ดเสร็จ ไม่ว่าคุณจะถือ Hashrate มากแค่ไหน ถ้า Node ทั่วโลกไม่เอา ก็จบ!
“แรงขุดใหญ่แค่ไหน ก็แพ้ใจมวลชน!”
(น่าจะมีตอนต่อไปนะ.. ถ้าชอบก็ Zap โหด ๆ เป็นกำลังใจให้ด้วยนะครับ)
-
-
 @ 6389be64:ef439d32
2024-12-09 23:50:41
@ 6389be64:ef439d32
2024-12-09 23:50:41Resilience is the ability to withstand shocks, adapt, and bounce back. It’s an essential quality in nature and in life. But what if we could take resilience a step further? What if, instead of merely surviving, a system could improve when faced with stress? This concept, known as anti-fragility, is not just theoretical—it’s practical. Combining two highly resilient natural tools, comfrey and biochar, reveals how we can create systems that thrive under pressure and grow stronger with each challenge.
Comfrey: Nature’s Champion of Resilience
Comfrey is a plant that refuses to fail. Once its deep roots take hold, it thrives in poor soils, withstands drought, and regenerates even after being cut down repeatedly. It’s a hardy survivor, but comfrey doesn’t just endure—it contributes. Known as a dynamic accumulator, it mines nutrients from deep within the earth and brings them to the surface, making them available for other plants.
Beyond its ecological role, comfrey has centuries of medicinal use, earning the nickname "knitbone." Its leaves can heal wounds and restore health, a perfect metaphor for resilience. But as impressive as comfrey is, its true potential is unlocked when paired with another resilient force: biochar.
Biochar: The Silent Powerhouse of Soil Regeneration
Biochar, a carbon-rich material made by burning organic matter in low-oxygen conditions, is a game-changer for soil health. Its unique porous structure retains water, holds nutrients, and provides a haven for beneficial microbes. Soil enriched with biochar becomes drought-resistant, nutrient-rich, and biologically active—qualities that scream resilience.
Historically, ancient civilizations in the Amazon used biochar to transform barren soils into fertile agricultural hubs. Known as terra preta, these soils remain productive centuries later, highlighting biochar’s remarkable staying power.
Yet, like comfrey, biochar’s potential is magnified when it’s part of a larger system.
The Synergy: Comfrey and Biochar Together
Resilience turns into anti-fragility when systems go beyond mere survival and start improving under stress. Combining comfrey and biochar achieves exactly that.
-
Nutrient Cycling and Retention\ Comfrey’s leaves, rich in nitrogen, potassium, and phosphorus, make an excellent mulch when cut and dropped onto the soil. However, these nutrients can wash away in heavy rains. Enter biochar. Its porous structure locks in the nutrients from comfrey, preventing runoff and keeping them available for plants. Together, they create a system that not only recycles nutrients but amplifies their effectiveness.
-
Water Management\ Biochar holds onto water making soil not just drought-resistant but actively water-efficient, improving over time with each rain and dry spell.
-
Microbial Ecosystems\ Comfrey enriches soil with organic matter, feeding microbial life. Biochar provides a home for these microbes, protecting them and creating a stable environment for them to multiply. Together, they build a thriving soil ecosystem that becomes more fertile and resilient with each passing season.
Resilient systems can withstand shocks, but anti-fragile systems actively use those shocks to grow stronger. Comfrey and biochar together form an anti-fragile system. Each addition of biochar enhances water and nutrient retention, while comfrey regenerates biomass and enriches the soil. Over time, the system becomes more productive, less dependent on external inputs, and better equipped to handle challenges.
This synergy demonstrates the power of designing systems that don’t just survive—they thrive.
Lessons Beyond the Soil
The partnership of comfrey and biochar offers a valuable lesson for our own lives. Resilience is an admirable trait, but anti-fragility takes us further. By combining complementary strengths and leveraging stress as an opportunity, we can create systems—whether in soil, business, or society—that improve under pressure.
Nature shows us that resilience isn’t the end goal. When we pair resilient tools like comfrey and biochar, we unlock a system that evolves, regenerates, and becomes anti-fragile. By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
By designing with anti-fragility in mind, we don’t just bounce back, we bounce forward.
-
-
 @ 7ed5bd1c:4caa7587
2025-01-08 07:35:42
@ 7ed5bd1c:4caa7587
2025-01-08 07:35:42Bitcoin เป็นเกราะป้องกันจากการควบคุมของรัฐบาล
ในโลกที่การควบคุมทางการเงินของรัฐมีผลกระทบต่อชีวิตของประชาชน การปกป้องทรัพย์สินส่วนบุคคลจึงเป็นประเด็นสำคัญที่หลายคนกังวล Bitcoin ได้เข้ามามีบทบาทสำคัญในฐานะเครื่องมือที่ช่วยป้องกันการอายัดทรัพย์สินและการแทรกแซงทางการเงินจากรัฐบาลและองค์กรต่างๆ
กรณีศึกษาที่น่าสนใจ
-
เวเนซุเอลา: เมื่อประเทศประสบภาวะเงินเฟ้อสูงและรัฐบาลมีการควบคุมการแลกเปลี่ยนเงินตราต่างประเทศ ประชาชนบางส่วนใช้ Bitcoin เพื่อรักษามูลค่าทรัพย์สินของพวกเขาและทำธุรกรรมข้ามพรมแดนโดยไม่ต้องผ่านการตรวจสอบจากรัฐบาล
-
แคนาดา: ในปี 2022 รัฐบาลแคนาดามีการอายัดบัญชีธนาคารของผู้ประท้วงในการเคลื่อนไหวทางการเมืองบางอย่าง Bitcoin กลายเป็นช่องทางในการระดมทุนและช่วยให้ประชาชนสามารถป้องกันการแทรกแซงจากรัฐบาลได้
-
ไนจีเรีย: ธนาคารกลางไนจีเรียสั่งห้ามธุรกรรมที่เกี่ยวข้องกับ Bitcoin และคริปโตเคอร์เรนซีอื่นๆ แต่ประชาชนกลับหันมาใช้ Bitcoin ในตลาดมืดเพื่อหลีกเลี่ยงข้อจำกัดและรักษาความเป็นอิสระทางการเงิน
Bitcoin ปกป้องทรัพย์สินอย่างไร?
-
ความเป็นเจ้าของแท้จริง: Bitcoin ใช้ระบบกระจายศูนย์ที่ไม่มีตัวกลาง ซึ่งหมายความว่าไม่มีองค์กรหรือรัฐใดสามารถเข้าถึงหรือยึดครอง Bitcoin ของคุณได้ หากคุณเก็บรักษาคีย์ส่วนตัวอย่างปลอดภัย
-
ไร้พรมแดน: Bitcoin สามารถโอนย้ายได้ทั่วโลกโดยไม่ต้องผ่านธนาคารหรือสถาบันการเงินที่อยู่ภายใต้การควบคุมของรัฐบาล ทำให้เป็นตัวเลือกที่น่าสนใจสำหรับผู้ที่ต้องการหลบเลี่ยงการอายัดทรัพย์สิน
-
ความโปร่งใสและความปลอดภัย: การทำธุรกรรมของ Bitcoin ถูกบันทึกในบล็อกเชนซึ่งเป็นระบบที่โปร่งใสและตรวจสอบได้ ในขณะเดียวกันข้อมูลส่วนบุคคลของผู้ใช้งานจะถูกเก็บเป็นความลับ
ข้อควรระวัง
แม้ Bitcoin จะมีข้อดีในเรื่องการปกป้องทรัพย์สินจากรัฐ แต่ผู้ใช้งานต้องมีความระมัดระวังในการจัดเก็บคีย์ส่วนตัว และหลีกเลี่ยงการพึ่งพาบริการจากบุคคลที่สามที่อาจไม่ปลอดภัย
ในโลกที่อิสรภาพทางการเงินถูกท้าทาย Bitcoin กลายเป็นเครื่องมือสำคัญสำหรับการปกป้องทรัพย์สินและสิทธิส่วนบุคคลของประชาชน คุณคิดว่า Bitcoin สามารถเป็นคำตอบสำหรับความท้าทายนี้ได้จริงหรือไม่? ร่วมพูดคุยในความคิดเห็น!
-
-
 @ eac63075:b4988b48
2024-12-08 15:35:21
@ eac63075:b4988b48
2024-12-08 15:35:21Imagine a large public square, illuminated by intense spotlights, where every individual who dares to approach the center is immediately recognized, photographed, and cataloged. In this square, every word spoken becomes indelibly tied to its speaker. Under such conditions, many would hesitate before speaking, fearing not only the disapproval of the audience but also the potential punishments that could follow the mere act of expressing an idea. Now, imagine a second square, where anyone can cover their face with a mask, allowing their voice to echo without revealing their identity. It is in this second square that true freedom of expression flourishes, and this metaphorical mask represents anonymity.
https://www.fountain.fm/episode/MweciiR21hySxjdsNa7u
In debates about freedom of expression—one of the fundamental pillars of democratic societies—anonymity often emerges as a controversial element. For some, it serves as a refuge for digital criminals or slanderers. For others, it is an indispensable tool, capable of protecting dissenting voices and inspiring authentic debates, with ideas judged on their merits rather than the messenger’s reputation. This article aims to explain, in a clear and instructive manner, why anonymity is essential to genuine freedom of expression, illustrating its value with metaphors, real-life examples, and historical references.
The Protective Mask: Avoiding Retaliation and Threats
Just as a navigator uses guiding instruments to avoid jagged rocks at sea, anonymity functions like a shield, allowing bold voices to navigate oppressive reefs without foundering. There are countless examples of individuals who have risked their lives to expose crimes and injustices—from whistleblowers in authoritarian governments to investigative journalists uncovering the complex machinations of organized crime. Without the possibility of anonymity, many of these stories would never have come to light.
Organizations like the Electronic Frontier Foundation (EFF) and other digital rights advocacy groups emphasize that the ability to speak without revealing one’s identity is crucial when the cost of speaking out is dangerously high. In censorship-ridden regimes, criticizing the government can lead to imprisonment, torture, or even death. Human rights activists, LGBTQIA+ communities in hostile countries, and journalists investigating illicit dealings all rely on anonymity to continue their work without putting their own lives at immediate risk. In this context, anonymity is not a whim—it’s the chance to survive one’s own opinion.
The Voice of the Invisible: Empowering Marginalized Groups
Think of anonymity as an invisible microphone placed at the disposal of those who, without it, would never dare to take the stage. Historically, marginalized groups have always faced additional barriers to making their voices heard. Women in patriarchal societies, ethnic minorities facing discrimination, or individuals persecuted for their sexual orientation find in anonymity a safe space to speak out, claim their rights, and share their experiences without fearing public humiliation or physical violence.
This “invisible microphone” not only gives voice to those who once remained silent but also transforms the arena of public debate into a more equitable space. By removing the link between idea and identity, it reduces the risk of immediate prejudice against the messenger. As a result, society can assess arguments more impartially. Here, ideas are judged on their content, not on the face that speaks them.
The Strength of History: The Precedent of the Federalist Papers
History offers a famous example of the power of anonymous words: the Federalist Papers. Published between 1787 and 1788, these essays supported the ratification of the United States Constitution and were written under the pseudonym “Publius” by Alexander Hamilton, James Madison, and John Jay. The reason for concealing their identities was clear: to ensure that their ideas would be judged on their argumentative strength rather than the prestige or fame of the authors.
The precedent set by the Federalist Papers is emblematic. It shows that, in the building of one of the first modern democracies, anonymity was used as a legitimate tool to establish fundamental concepts. If the founders of the nation that prides itself on its First Amendment—the one that protects freedom of expression—resorted to anonymity, we should recognize that this resource is not only defensible but also an essential part of the framework of healthy public debate.
Faceless Messages: The Democracy of Pure Ideas
In an ideal world, we would judge a message purely on its content. In reality, however, names, faces, social status, and economic position influence how we receive and interpret a person’s words. Anonymity removes these superficial layers, allowing the message to present itself bare, subject to rational evaluation without the veils of prejudice.
In this sense, anonymity acts as a “filter of equality”: by concealing the source, it prevents us from assigning credibility (or discredit) based on stereotypes, prejudices, or personal rivalries. Thus, ideas previously dismissed out of hand can now be heard with greater attention, opening paths to social innovation, political reflection, and challenges to the status quo. A contemporary example is online forums that allow anonymous posts. While we acknowledge that such spaces can be misused, we cannot ignore their potential to give voice to those who would never feel safe speaking under their own name in public.
Privacy, Intimacy, and the Freedom to Whisper
Anonymity is not limited to the public or political sphere. In personal and professional relations, the ability to speak anonymously can allow someone to seek help or reveal extremely sensitive matters. Imagine a patient who needs to consult a doctor about a stigmatized health issue, or a person seeking legal advice in a delicate situation. The “mask” of anonymity offers a safe haven for sharing information without the anguish of being judged or exposed.
Thus, anonymity also safeguards our “right to whisper,” that is, the ability to exchange information, secrets, and confessions without the constant glare of a spotlight. Real or perceived surveillance can stifle communication and inhibit creativity, reporting, and the exchange of ideas. By shielding individuals from forced exposure, anonymity reinforces the very fabric of freedom of expression, preventing the fear of identification from silencing words before they are spoken.
Anonymity in the Digital Age: Between Encryption and Censorship
In the digital age, the issue of anonymity becomes even more relevant. With the expansion of online surveillance and the growth of social networks, maintaining anonymity can be challenging. Social media platforms increasingly request personal data, and governments attempt to impose barriers against anonymity, often justifying them as measures of national security or crime prevention.
However, according to reports and documents from human rights organizations, such as the UN High Commissioner for Human Rights and the Association for Progressive Communications (APC), encryption and anonymity are key tools for freedom of expression in the digital environment. Without these resources, citizens and journalists, for instance, become more vulnerable to persecution. In various countries, the existence of anonymous and encrypted channels enables information to circulate, grievances to be reported, and societies to remain informed, even in the face of heavy censorship.
Legal Protection: Judicial Recognition of Anonymity
The United States Supreme Court, as well as other constitutional courts around the world, recognizes anonymity as an integral part of the right to free expression. In the United States, the First Amendment has been applied in cases that defended the right to anonymous speech, viewing it as a bulwark against the tyranny of the majority. When minorities are protected by anonymity, personal reprisals against those who dare to question dogmas or denounce abuses are prevented.
This judicial understanding reinforces the legitimacy of anonymity and its direct association with the strengthening of democracy. After all, a robust democracy requires not only the absence of formal censorship but also the guarantee that minority or unpopular voices can speak out without fear.
Conclusion: The Cloak That Protects Freedom
If freedom of expression is the heart of democracy, anonymity is the cloak that shields that heart from the poisoned darts of fear, persecution, and prejudice. It creates the right environment for ideas to flourish freely, for courageous voices to emerge from silence, and for society to debate its most complex issues in the light of reason rather than beneath the shadow of intimidation.
In a world where surveillance and political tensions are ever-present, anonymity preserves the essence of free speech: humanity’s ability to question, propose, denounce, criticize, and create without shackles. By recognizing the importance of this resource, we safeguard not only individual voices but also the very principle that makes democracy worthy of its name.
Selected References:
-
Electronic Frontier Foundation (EFF): https://www.eff.org/issues/anonymity
-
Freedom Forum: https://www.freedomforum.org/anonymous-speech/
-
Association for Progressive Communications (APC): https://www.apc.org/
-
The First Amendment Encyclopedia: Anonymous Speech: https://firstamendment.mtsu.edu/article/anonymous-speech/
-
The Federalist Papers: Historical context available at Library of Congress and various printed and digital compilations.
Cover Photo by Redd Francisco / Unsplash
-
-
 @ 896c3ee8:e054cc31
2025-01-08 06:19:51
@ 896c3ee8:e054cc31
2025-01-08 06:19:51I was scrolling through some news articles published by Primal.net/flash on my phone —Bitcoin up, Trump said this or that, accompanied by a screenshot of Twitter. I asked myself: why does social media exist? Is it to fulfill our need for social connection? Is it to show off our thoughts? Is it validation? It wasn’t like this long ago. It was a part of life now it is Life.
Quite some time ago, I was baffled to see a woman being prosecuted in a court of law based on what she had posted on Facebook! Facebook? Seriously, an internet post landing a person in jail? Since when? No one notified me. I thought the internet was just a thing—a toy for us to play with, have fun, and then return to our real life. I remember using Pidgin and IRC; back then, the internet was just a tool. One sudden day, all of that turned into serious business. Early internet, and by extension social media, was a fun place, but now it is a place where real money is spent and real lives are built. I mean, some of the richest companies are software companies—an industry titan propelled by intangible property. It is hard not to miss the early days when one could say absolutely anything in a forum post and leave forever, detached from the filth they spewed. Now we all know censorship, data mining, AI training, and laws getting involved. I cannot even take part in a cultural movement without being tracked and attacked. At some point, the internet attached itself to human consciousness so deeply that it has now become inseparable from the human experience and experience of life. Just like reading and writing, to live a modern life, one must have an internet connection and a social media account. It’s disheartening to think that our worth is often measured by the number of people who 'follow' us.
This attachment meant that there were powers who needed to control the internet. Laws were hopeless on the internet—one could break a list of laws of a particular country sitting from a boat in a faraway land where no jurisdictional police could touch a single fleck of their hair. This cross-border nature made it very necessary for law enforcement to up their game, and so they did. Now, posting something and forgetting it being associated with you is a dream of the past.
To achieve this, they went into a Hail Mary attempt to break human rights written in the declaration they all signed. The right to privacy needed to go first. You see, on the internet, you are not a human—just a fat, Mountain Dew-drinking piece of meat, a data generation machine. Rights mean very little for you if you are a keyboard warrior. No clause in the Universal Declaration of Human Rights said that an account on the internet is a human! So you lose privacy. Since law enforcers break privacy, it looks like it really is not a crime to break it. So, service providers break it too. Who is to stop them now? Law enforcers?
That is just the tip, perhaps even a necessary evil. Breaking privacy only allows enforcement of laws that have been written. There needs to be some mechanism to enforce laws that are not written—the so-called "soft laws" (a term used in international law). If illegal activity is to be curbed, instead of chasing after criminals, why not be proactive and get to the root of the evil: human thought? Here enters censorship. If you don't know about something you won't act on it. If you do not know about guns, you will not pick up a gun. Censorship allows law enforcers to enforce laws that may be written in the future, potential laws. Maybe one day, being on a particular political side will be deemed illegal, so let’s stop it now. Ever heard of a cat chasing a mouse? Censorship is just a mouse chasing a cat. A reversal of cause and effect.
These two factors, coupled with the internet's revenue stream—your attention—ruined the internet. Ads by God are one of the most human things humans have created: “Let us show you what you could be a part of. As you are right now, you seem unfulfilled; let us show you what you want.” The economy of attention is best tapped by creators working on our primal urge for reproduction. The porn industry is a mega titan for this reason. I do not have any bad words against the innovators working in that industry. They are the true and perhaps only industry that uses the internet to its maximum and has great respect for technology and technological innovation.
When I think more deeply about the purpose of social media, I realize I have no clear answer. Why should one show what their lunch looks like? What is the goal of sharing such trivial experiences? Perhaps the dopamine rush of likes and engagement is strong enough to motivate such actions. The definition of an individual gets blurred here. What is an individual person? A collection of social media posts? Or should we emphasize more on your offline version the flawed acne and angst filled individual who subscribes to the weird, concorted philosophy of Proudhon, Locke, and Marx? The algorithms have been determining the future of people on social media. People are worried about losing jobs to a computer now. Since YouTube and Instagram started utilizing attention to pay people, algorithms began to determine who should be paid and what should be paid. The ship of us being under a computer has long sailed.
To answer why social media exists, here is one study that identified ten uses and gratifications for using social media: social interaction, information seeking, passing time, entertainment, relaxation, communicatory utility, convenience utility, expression of opinion, information sharing, and surveillance/knowledge about others (reference ISSN: 1352-2752). Most studies you find will be in line with these. I will not expound more on this; you all know why you use social media, and you all also know why people use social media.
To end it, Nostr gives you certain things that traditional social media and the 'internet' fail to provide. You know what those are since you are here.
P.S.—This is written exclusively for the eyes in the Nostr ecosystem. I will not publish it anywhere else. Link people to this post even from outside; I don’t care.
-
 @ c11cf5f8:4928464d
2025-01-08 14:31:14
@ c11cf5f8:4928464d
2025-01-08 14:31:14Here we are again with our monthly Magnificent Seven, the summary giving you a hit of what you missed in the ~AGORA territory.
Top-Performing Ads
This month, the most engaging ones are:
00[SELL] STACKER NEWS Merch: T-Shirts & Cap [32100 sats + shipping] by me :)01Beeswax Dinner Candles For Sale by @kr02I'd Buy ~bitcoin Territory At The Right Price by @0xbitcoiner03Bitcoin Watches by @jakoyoh62904SN merch live on amazon by @stack_harder05A couple programming bounties payable in BTC (Javascript/Typescript, C++) by @springfield_data_recovery06[SELL] Accepting SATs ~ Genuine Authentic SHAQ (Shaquille O'Neal) Autograph by @watchmancbiz07PlebBook 📖 - (Update: Jan 2025 - Earn Sats in AGORA) by @PlebLab08HereComes Bitcoin SATSCARD™ - Summer of Bitcoin by @Design_r09[OFFER] 12K sats for any item in The Bullish Shop (BOLT12 only) by @thebullishbitcoiner10Bitcoin Shirt on Walmart 👀 by @96dffdc39e
Cowboys Credits Buyers
Yes, this Jan 3rd CCs have been deployed, a unique SN feature that enable everyone to play around and upvote/reward interesting contents and stackers. Has been an interesting number of stackers enetring the market and setting the rate
- @siggy47 Will Pay Sats For Cowboy Credits https://stacker.news/items/837713/r/AG Make him an offer. His territories rent are due.
- @ek [BUY] 100 cowboy credits for one satoshi https://stacker.news/items/837469/r/AG Sender must pay the 30% sybil fee, so the sender has to pay 100/0.7=142 CCs to get 1 sat
- @Darth first ever CCs offer, and always with his third eye looking at the future, want too [SWAP] SN Cowboy credits https://stacker.news/items/723069/r/AG PS: posted in October 2024
Professional Services accepting Bitcoin
Ihttps://stacker.news/items/813013/r/AG @gpvansat's [OFFER][Graphic Design]
From the paste editions (It's important to keep these offers available) *
IIhttps://stacker.news/items/775383/r/AG @TinstrMedia - Color Grading (Styling) Your Pictures as a Service *IIIhttps://stacker.news/items/773557/r/AG @MamaHodl, MATHS TUTOR 50K SATS/hour English global *IVhttps://stacker.news/items/684163/r/AG @BTCLNAT's OFFER HEALTH COUNSELING [21 SAT/ consultation *Vhttps://stacker.news/items/689268/r/AG @mathswithtess [SELL] MATHS TUTOR ONLINE, 90k sats per hour. Global but English only.In case you missed
Here some interesting post, opening conversations and free speech about markets and business on the bitcoin circular economy:
- Buy Kratum With Bitcoin https://stacker.news/items/806578/r/AG by @siggy47
- How Is Shipping Handled? https://stacker.news/items/832303/r/AG by @siggy47
- Building a List of 'Buy It For Life' Products https://stacker.news/items/809655/r/AG by @kr
- Sender must pay the 30% sybil fee, so the sender has to pay 100/0.7=142 CCs to get 1 sat https://stacker.news/items/811292/r/AG by @Fabs
- How to (Ethically) Get Rid of Your Unwanted Stuff https://stacker.news/items/829228/r/AG by @mo
- The Calgary Sat Market - A driven community of Bitcoiners, making magic together https://stacker.news/items/811666/r/AG by @supratic
- ɅGOᏒɅ 🏜️ First Year Recap: A Thriving 2024 for Stacker News P2P Marketplace https://stacker.news/items/821255/r/AG by @AGORA
🏷️ Spending Sunday is back!
Share your most recent Bitcoin purchases of just check what other stackers are buying with their sats! Read more https://stacker.news/items/837629/r/AG
Just a reminder for you all
This territory aims to connect stackers and curious buyers for IRL P2P Bitcoin deals. Have fun checking what else stackers are shilling globally in the ~AGORA. This is a great time for you to make some space un-dusting some stuff that has been sitting there for too long and get some sats for it!
Create your Ads now!
Looking to start something new? Hit one of the links below to free your mind:
- 💬 TOPIC for conversation,
- [⚖️ SELL] anything! or,
- if you're looking for something, hit the [🛒 BUY]!
- [🧑💻 HIRE] any bitcoiner skill or stuff from bitcoiners
- [🖇 OFFER] any product or service and stack more sats
- [🧑⚖️ AUCTION] to let stackers decide a fair price for your item
- [🤝 SWAP] if you're looking to exchange anything with anything else
- [🆓 FREE] your space, make a gift!
- [⭐ REVIEW] any bitcoin product or LN service you recently bought or subscribed to
Or contact @AGORA team on nostr DM and we can help you publish a personalized post.
.
#nostr#stuff4sats#sell#buy#plebchain#grownostr#asknostroriginally posted at https://stacker.news/items/842103
-
 @ bd50a856:038f487c
2025-01-08 04:25:47
@ bd50a856:038f487c
2025-01-08 04:25:47I'M NOT IN SCHOOL WHY AM I DOING THIS?
https://image.nostr.build/9df38856e4493466585f451771a013959ac7e29135289b4922a810623577dbef.jpg
Isms in my opinion are not good. - Ferris Bueler
OK so like many a disillusioned youth I was a pretty hardcore Marxist back in college. There's a common pipeline that starts as a 13 year old who wished they could vote for Ron Paul in 2008, takes a hard left turn at the first sign of bigotry, and winds up with a pretty badass juche tattoo. The Enlightenment era ideas of an ascertainable objective truth and mankind's control over their own destiny, combined with the complete subversion of the political history I was brought up with felt very empowering. But nowadays I'm not so sure I want to lay claim to any specific point or vector on the political spectrum. 2024 was in many ways a year of reflection for me. I've managed to reconnect with my sense of spirituality after years of bitterness towards the concept brought on by a life of run-ins with religious fundemantalism, and I had to challenge alot of things that for years I've taken for granted both about myself and the world at large. This ideological audit was in no small way catalyzed by my adoption of NOSTR, which with its endless potential enticed me out of the progressive echo chamber I made my digital home on the fediverse and into a new echo chamber: one full of Bitcoiners.
I had bought Bitcoin before, as a way to short the dollar, but I never encountered its ideologues in the wild. At first gradually then suddenly I was making the types of arguments in my head that former me would have decried as pedantic to the point of being apologetic towards the ruling class. And just like that the 19th and 20th century political and philosophical works which I zaelously held as trail blazes on the long and labyrinthine path towards realizing Absolute Truth were cast forcefully into their murky historical context by the staggering success of the first truly decentralized monetary system. In my college days, I saw Lenin's model of revoutionary politics and the Vanguard Party as the only way for a people's movement to legitimately threaten the hegemony of the global oligarchs who caused so much unnecessary suffering. Now I can see how whether or not that type of centralization was a necessary concession then, one cannot in good faith believe it to be so in the age of Bitcoin.
Yet you'll have to forgive me because still I'm sympathetic to much of the broader movement of Marxism. I detest how Great Man Theory suboordinates the totality of the evolution of society to the wills of a few individuals, and prefer to see socialism in a different light. Rather than viewing the movement as a clever trick some cartoonishly evil mustaches and haircuts used to brainwash almost half the human population, I see a genuine attempt by hundreds of millions of people to change the world for the better, forever. Yes the suffering was immense, and many many people for whom the tumult was too much, as well as those who wished to maintain their parasitic lifestyles, fled for their lives it was far from a black and white phenomena. Living standards also skyrocketed over the long run in places like the USSR and the PRC, from literacy to employment to diet, access to healthcare, you name it. But still the narrative of Hegel's Dialectic playing out in the arena of class politics - wherein the oppressed by becoming the oppressors would naturally do away with oppression altogether by following their self interest just as the Bourgeoisie had done, thereby unwinding the knot of economic injustice - has lost its status as the driving force of all of history for me. It's still much more compelling than the caricature of simply replacing one form of centralization with another. Rather its a much more relatable fallacy: taking a truth, in this case the millennia of class struggle which humanity has dealt with since the advent of agriculture, and trying to extrapolate from it some abstract and all compassing polemic that makes it all make sense. Moreover, in the same way that Bitcoiners say, "Once you see it you can never go back," I cannot unlearn just how hypocritical and dishonest the Western narrative of history is. Lying and calling America the land of the land of opportunity when the abundance we've known for our Empire's whole existence exists merely because of stolen land and slave labor. This is not a moralist objection by the way, though that would be wholly justified. The true horror is that people view the US as the model of a self sufficient nation state when in reality it has always been parasitic, even in it's larval stage. And of course the disillusion with every military campaign since the end of World War 2, starting with the grotesque and gratuitous display of power in Hiroshima and Nagasaki, then the fraudulant and deadly campaigns in Korea, Loas, Vietnam, and of course the entire Middle East. Our own forms of surveillance, censorship, repression all staring at us in the images we projected on the face of the Berlin Wall.
I know a little part of that probably rubbed some of you the wrong way. Hey we still were a net positive force in WW2, of course. And despite many differences in historical interpretations, when it comes to Marx's tomes of economic criticism I think the Bitcoiners of NOSTR would find a lot of rhetorical similarities with their gripes about the age of fiat actually share many rhetorical similarities: The levers of control over the global economy had been consolidated by a select view who were spamming them to make themselves inordinately wealthy at the cost of the quality of life for the majority of Planet Earth. The value of your labor is being ciphoned by a bunch of rackateering lizard men known as politicians. Fair competition, the spirit of Capitalism on paper, has been eroded by its those who claim to be its biggest proponents. Forever wars as a business, predatory global economic policies, proles=plebs, yada yada. Although I guess this note would be pointless if I yada-yada'd over the best parts.
THE INVISIBLE HANDJOB
https://image.nostr.build/595f3d10072c92fc66f9ad314de5d6eeb7e76a9bc26021c690d89cbd9bbe0a15.gif
The landlords, like all other men, love to reap where they never sowed, and demand a rent even for its natural produce. -Adam Smith
In the above quoted Wealth of Nations (Book 1, chapter 11) as well as in Book 4 and in The Theory of Moral Sentiments, everyone's favorite economist they've never read paints a complex and somewhat contradictory image of the proprietors over the means of production in his time. He saw greed and gluttony in their souls, but viewed their actions within the context of an emergent system whereby their selfishness propelled the interest of everyone. So, almost exactly how Marx viewed the holy timespanning vendetta of the have-nots of the world. However, in Book 1 ch10 of Wealth of Nations Smith says this:
[The rent] is not at all proportioned to what the landlord may have laid out upon the improvement of the land, or to what he can afford to take; but to what the farmer can afford to give,
In a section where he concedes that the landlords' actions amount to extortion. He also articulates here how through the influence of legislation, the landlord class effectively outlawed collective negotiation on the part of the working class while bolstering it for themselves, resulting in monopolies. Marx cites Smith himself throughout Das Kapital, and lays out extensively this process of the consolidation of capitalist power in part 3 of the first volume. The two also subscribed to the Labor Theory of Value, as did every other Enlightenment era economist... and so do most Bitcoiners! At least they sure sound like they do when they talk about the erosion of the masses' life force by the debasement of fiat. After all if the commodity that is money is an expression of your time and labor, then so must be the value of every other commodity. I've heard people try to glibly dismiss the LTV as stupid, citing things like land, products of fully automated processes... And digital assets. As if land didn't have to be surveyed, and discovered (or won in a genocide). Or if fully automated production processes didn't require thousands of hours of expert labor on robotics and/or computer engineering. Or if all financial assets in general didn't hold merely a hypothetical value as a representation of value wrought in the productive economy. And to be perfectly honest I always found the subjective theory of value to be downright silly, like imagine haggling at a supermarket over a gallon of milk. Yes demand is subjective (and really more of an expression of willing buying power than need but that's a whole other can of worms), but it's wholly reliant on objective factors such as scarcity and the relative difficulty to produce a certain commodity oneself. And when those who corner the market collude on pricing it's not like you even have the ability to "vote with your money". You have no leverage, unless you own a cow. All in all the price of a commodity can't be anything other than an approximation of its objective value based on the average cost of the raw materials and socially necessary labor time, ebbing and flowing with the asynchronous undulations of supply and demand. And maybe a little extra something just to cushion that P&L. OK maybe a lot. Gotta outperform inflation, right?! Was I being glib, myself, there? It just feels self evident from my current perspective, the hollow vampirism of it all. Capitalists enacting the rights to procure surplus value, reinsert it as capital in order to procure even more surplus value, rinsing and repeating, drifting further and further from the corporeal reality of our own survival and swallowing entire generations in the process.
STATISTS BE LIKE...
https://image.nostr.build/3109eed06d708cfad1ec0c8f4a823b8d6c58b73d3a7f73a94cdcafe22554656f.jpg
The government solution to a problem is usually as bad as the problem- Milton Friedman
On September 11, 1973 Chilean President Salvador Allende died during a fascist coup d'état perpetrated by the commander in chief of the military Augusto Pinochet. Officially he took his own life for fear of what would be done to him, but it remains a contentious topic. Pinochet's regime was characterized by mass arrests, widespread use of torture, extrajudicial killings, mass exiles, and brutal censorship of his political ditractors. But he cut taxes!!!! And he did so with the council of the Chicago Boys, a group of Chicago University alumni and disciples of right wing icon Milton Friedman. Friedman applauded Pinochet's government for his economic policies and providing a shining example of Milton's take on what small laissez-faire government looks like: Repression of the masses, no rules for the classes.
Pinochet was also a collaborator with the CIA on their project Operation Condor, whereby the funding and stoking of violence and unrest was weaponized to subvert the rise of left leaning politics throughout South and Central America and maintain cheap access to raw materials which US corporations relied on. As a matter of fact, the deep state has an endless track record of resorting to all sorts of crazy measures to subvert the popularity of socialism. This contradicts directly the American conservative view that the deep state wants socialism, and that Trump - who has cooperated in the continuations of these policies with the attempted coups in Venezuela and Bolivia during his first term - is here to stop 'em. The scapegoating and fear mongering of foreign left leaning governments in lucrative regions is a time honored tradition here In the US. All the West has always had more in common with the totalitarianism of Fascism than the East. If you're curious or skeptical about this, looking up Michael Parenti's Blackshirts & Reds is a good place to start digging deeper.
And while conservatives remain in denial about the parasiticism and exclusion their version of freedom relies on, Progressivism, as I see it, is a limping, mutilated, abomination of a watered down version of itself. Democrats for over a century now continue offering the bare minimum that would assuage their cinstituencies in the short term at best, and the exact same neocon policies of war and imperialism abroad, and corporate oligarchy and a police state at home. Yet every two years progressives walk beleaguered to the polls to vote blue no who. And Milton Friedman laughs in his grave. Reminds me of one of my favorite quotes, attributed to president of Tanzinia, Julius Nyere: "The Americans also have a one party state, but with typical American extravegance, they have two of them." https://image.nostr.build/9380dbc6d51a443b76340b46c760e12c9bb0540a170a8f5a2a22847e0bba88c7.jpg
WHAT IS DO BE DONE?
https://image.nostr.build/94aaebe5364c3c6a0094f09640ef18b05938d889124f874c49243f4ea972f725.jpg
I found freedom. Losing all hope is freedom. - Edward Norton, Fight Club
If you made it through all that rambling, what is wrong with you? In all seriousness, I hope this was a fruitful glance into the mind of someone who might think a little differently. In a rapidly evolving world, where systems we ourselves have put in place not only constitute the environment we live in, but reproduce themselves through our behavior as well, despondency, rage, and confusion permeate the collective consciousness. But there's also Bitcoin, which to an increasing number - and to an extent myself - represents a successful proof of concept of a new, genuinely Decentralized Ideological Apparatus. One which relies on Mutual Aid and the cooperation of smaller, decentralized and self sufficient communities. And to a certain extent it also represents hope. But it's as much an asset to those who'd prefer to continue feeding on the suffering of others as it is to those hoping for a change. Hope is as dangerous as fear - Lao Tzu
-
 @ dd664d5e:5633d319
2024-12-07 20:02:01
@ dd664d5e:5633d319
2024-12-07 20:02:01Yeah, so... nah.
People keep trying to explain to me, that women will be better-off, if they become more dangerous. While I can see the inevitableness of women living in remote rural areas learning to shoot with a rifle, and similar, I'm generally against arming women with killing machines.
This is not because I'm averse to the idea of using violence to solve problems (albeit after exhausting better options), or because I don't like guns, or am unfamiliar with them. It's also not because I don't know I would look totally, mind-numbingly hot holding something long and spearlike, while dressed in camo and wearing a T-Shirt that appears to have shrunk in the wash.

It's a more fundamental set of problems, that irks me.
Bazooka Barbie
American gun manufacturers saturated the public and private male market so thoroughly, that they eventually turned to marketing firearms to women.
Men are scary and bad. There is Stranger Danger. We can't just make the neighborhood less dangerous because erm... reasons. Stay safe with a cute gun.

It has gone along with the predictable hypersexualization of the conservative feminine ideal. Since guns are considered aggressive, women with guns are perceived as more sexually available. Guns (and tanks, bombs, bows, etc.) make women "equal", "independent", "feisty", "hot", "freaky", "calculating", "empowered", etc.

Sorta slutty, basically.
This Gun Girl is not like the helpless, hapless, harmless homemaker ideal, of yesteryear. A woman who was dependent, chaste, gentle, wise... and in need of protection. A woman who saw the men around her as people she could rely on for providing her with a safe environment. That woman is au revoir. Now, sistas are doing it for themselves. 💪🏻
The New Martial Missy needs a man, like a fish needs a bicycle... but make it country.
Yeah, it's marketing, but it sure has set the tone, and millions of men have been trained to prefer women who market themselves in this manner. Hard, mean, lean women. That will not remain without wider societal consequences.
You know, I liked that homemaker. I miss her. She's literally me.

Those arms are for cuddling babies, not holding rocket launchers.
Now, that we've all become accustomed to imagery of women holding firearms, it wasn't much of a leap to condition us all to the sight of women in frontline police, guard, or military positions.

Instead of war being a terrible, highly-lethal, territorial fight amongst men, it's now cute, hip, trendy and fun. It's a big party, and women are finally allowed to join in.

Now, women have finally jettisoned the terrible burden of being society's life-bearers and caretakers, and we're just more potential enemy combatants. We know it's okay to punch women, shoot women, etc. since we've been watching it happen on screens, for decades. Women are now often assumed to be fighters, not lovers. Cavalry, not mothers.
Girls on top
Not only does this undermine any female role -- and put female civilians under a cloud of suspicion -- it also reduces mens' claim to be paramount in governance. Why should a man be the Commander in Chief, if women are on the battlefield?
In fact, why should men be in charge of anything, anywhere? Look at them. There they are. Hiding at home. Cowering in their kitchens, wringing their hands and fretting, while courageous, dangerous women protect them from dangers foreign and domestic. Women are the better men, really.
Is this really where we want to go?
The final bitterness
But one thing I find most disturbing is something more personal. The ubiquitous nature of firearms in American homes has made domestic violence increasingly deadly. Adding more guns, for the female residents, often serves to make such violence even more deadly for women.
It turns out, that women are usually reluctant to shoot people they know; even more than men. Women without this inhibition are prone to sharing their home with men missing the same trait. And, now, they have more guns.
-
 @ 1cb14ab3:95d52462
2025-01-08 03:33:11
@ 1cb14ab3:95d52462
2025-01-08 03:33:11Tree branches, Rock. 4' x 4 [Boulder, USA. 2016]
Introduction
Nestled deep in the forest near Boulder, "Looking Glass" invites viewers to rediscover the quiet beauty of overlooked natural details. By framing the play of light, texture, and shadow through a 4-foot circular lens, the piece shifts focus to the microcosms of the forest, drawing attention to a small and overlooked waterfall.
Site & Placement
The lens is perched amid a cluster of trees, emphasizing a quiet patch of the forest that often goes unnoticed. Positioned 22 feet from the lens, a carefully placed bench offers a perfect vantage point, guiding visitors to linger, observe, and absorb the layered simplicity of the scene.
Impermanence & Integration
True to the ethos of the Earth Lens series, Looking Glass exists only briefly. Its natural materials—branches, wood, and rock—blend seamlessly into the forest and will eventually be reclaimed by it. The fleeting presence of the lens reflects the transient beauty of life, encouraging viewers to appreciate the details that often escape notice in the rush of time.
Reflection
In its short life, Looking Glass offers a moment of stillness and clarity, a chance to peer into the intimate world of the forest. The work becomes a lens not just for the environment but also for introspection, reminding viewers of the quiet wonders that surround them every day.
Photos







More from the 'Earth Lens' Series:
Earth Lens Series: Artist Statement + List of Works
COMING SOON: "Folsom" (Earth Lens 002)
COMING SOON: "Sanctuary" (Earth Lens 003)
COMING SOON: "Platte" (Earth Lens 004)
COMING SOON: "Grandfather" (Earth Lens 005)
COMING SOON: "Chongming" (Earth Lens 006)
More from Hes
All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.
-
 @ e6817453:b0ac3c39
2024-12-07 15:06:43
@ e6817453:b0ac3c39
2024-12-07 15:06:43I started a long series of articles about how to model different types of knowledge graphs in the relational model, which makes on-device memory models for AI agents possible.
We model-directed graphs
Also, graphs of entities
We even model hypergraphs
Last time, we discussed why classical triple and simple knowledge graphs are insufficient for AI agents and complex memory, especially in the domain of time-aware or multi-model knowledge.
So why do we need metagraphs, and what kind of challenge could they help us to solve?
- complex and nested event and temporal context and temporal relations as edges
- multi-mode and multilingual knowledge
- human-like memory for AI agents that has multiple contexts and relations between knowledge in neuron-like networks
MetaGraphs
A meta graph is a concept that extends the idea of a graph by allowing edges to become graphs. Meta Edges connect a set of nodes, which could also be subgraphs. So, at some level, node and edge are pretty similar in properties but act in different roles in a different context.
Also, in some cases, edges could be referenced as nodes.
This approach enables the representation of more complex relationships and hierarchies than a traditional graph structure allows. Let’s break down each term to understand better metagraphs and how they differ from hypergraphs and graphs.Graph Basics
- A standard graph has a set of nodes (or vertices) and edges (connections between nodes).
- Edges are generally simple and typically represent a binary relationship between two nodes.
- For instance, an edge in a social network graph might indicate a “friend” relationship between two people (nodes).
Hypergraph
- A hypergraph extends the concept of an edge by allowing it to connect any number of nodes, not just two.
- Each connection, called a hyperedge, can link multiple nodes.
- This feature allows hypergraphs to model more complex relationships involving multiple entities simultaneously. For example, a hyperedge in a hypergraph could represent a project team, connecting all team members in a single relation.
- Despite its flexibility, a hypergraph doesn’t capture hierarchical or nested structures; it only generalizes the number of connections in an edge.
Metagraph
- A metagraph allows the edges to be graphs themselves. This means each edge can contain its own nodes and edges, creating nested, hierarchical structures.
- In a meta graph, an edge could represent a relationship defined by a graph. For instance, a meta graph could represent a network of organizations where each organization’s structure (departments and connections) is represented by its own internal graph and treated as an edge in the larger meta graph.
- This recursive structure allows metagraphs to model complex data with multiple layers of abstraction. They can capture multi-node relationships (as in hypergraphs) and detailed, structured information about each relationship.
Named Graphs and Graph of Graphs
As you can notice, the structure of a metagraph is quite complex and could be complex to model in relational and classical RDF setups. It could create a challenge of luck of tools and software solutions for your problem.
If you need to model nested graphs, you could use a much simpler model of Named graphs, which could take you quite far.
The concept of the named graph came from the RDF community, which needed to group some sets of triples. In this way, you form subgraphs inside an existing graph. You could refer to the subgraph as a regular node. This setup simplifies complex graphs, introduces hierarchies, and even adds features and properties of hypergraphs while keeping a directed nature.
It looks complex, but it is not so hard to model it with a slight modification of a directed graph.
So, the node could host graphs inside. Let's reflect this fact with a location for a node. If a node belongs to a main graph, we could set the location to null or introduce a main node . it is up to you
Nodes could have edges to nodes in different subgraphs. This structure allows any kind of nesting graphs. Edges stay location-free
Meta Graphs in Relational Model
Let’s try to make several attempts to model different meta-graphs with some constraints.
Directed Metagraph where edges are not used as nodes and could not contain subgraphs

In this case, the edge always points to two sets of nodes. This introduces an overhead of creating a node set for a single node. In this model, we can model empty node sets that could require application-level constraints to prevent such cases.
Directed Metagraph where edges are not used as nodes and could contain subgraphs

Adding a node set that could model a subgraph located in an edge is easy but could be separate from in-vertex or out-vert.
I also do not see a direct need to include subgraphs to a node, as we could just use a node set interchangeably, but it still could be a case.Directed Metagraph where edges are used as nodes and could contain subgraphs
As you can notice, we operate all the time with node sets. We could simply allow the extension node set to elements set that include node and edge IDs, but in this case, we need to use uuid or any other strategy to differentiate node IDs from edge IDs. In this case, we have a collision of ephemeral edges or ephemeral nodes when we want to change the role and purpose of the node as an edge or vice versa.

A full-scale metagraph model is way too complex for a relational database.
So we need a better model.Now, we have more flexibility but loose structural constraints. We cannot show that the element should have one vertex, one vertex, or both. This type of constraint has been moved to the application level. Also, the crucial question is about query and retrieval needs.
Any meta-graph model should be more focused on domain and needs and should be used in raw form. We did it for a pure theoretical purpose. -
 @ e6817453:b0ac3c39
2024-12-07 15:03:06
@ e6817453:b0ac3c39
2024-12-07 15:03:06Hey folks! Today, let’s dive into the intriguing world of neurosymbolic approaches, retrieval-augmented generation (RAG), and personal knowledge graphs (PKGs). Together, these concepts hold much potential for bringing true reasoning capabilities to large language models (LLMs). So, let’s break down how symbolic logic, knowledge graphs, and modern AI can come together to empower future AI systems to reason like humans.
The Neurosymbolic Approach: What It Means ?
Neurosymbolic AI combines two historically separate streams of artificial intelligence: symbolic reasoning and neural networks. Symbolic AI uses formal logic to process knowledge, similar to how we might solve problems or deduce information. On the other hand, neural networks, like those underlying GPT-4, focus on learning patterns from vast amounts of data — they are probabilistic statistical models that excel in generating human-like language and recognizing patterns but often lack deep, explicit reasoning.
While GPT-4 can produce impressive text, it’s still not very effective at reasoning in a truly logical way. Its foundation, transformers, allows it to excel in pattern recognition, but the models struggle with reasoning because, at their core, they rely on statistical probabilities rather than true symbolic logic. This is where neurosymbolic methods and knowledge graphs come in.
Symbolic Calculations and the Early Vision of AI
If we take a step back to the 1950s, the vision for artificial intelligence was very different. Early AI research was all about symbolic reasoning — where computers could perform logical calculations to derive new knowledge from a given set of rules and facts. Languages like Lisp emerged to support this vision, enabling programs to represent data and code as interchangeable symbols. Lisp was designed to be homoiconic, meaning it treated code as manipulatable data, making it capable of self-modification — a huge leap towards AI systems that could, in theory, understand and modify their own operations.
Lisp: The Earlier AI-Language
Lisp, short for “LISt Processor,” was developed by John McCarthy in 1958, and it became the cornerstone of early AI research. Lisp’s power lay in its flexibility and its use of symbolic expressions, which allowed developers to create programs that could manipulate symbols in ways that were very close to human reasoning. One of the most groundbreaking features of Lisp was its ability to treat code as data, known as homoiconicity, which meant that Lisp programs could introspect and transform themselves dynamically. This ability to adapt and modify its own structure gave Lisp an edge in tasks that required a form of self-awareness, which was key in the early days of AI when researchers were exploring what it meant for machines to “think.”
Lisp was not just a programming language—it represented the vision for artificial intelligence, where machines could evolve their understanding and rewrite their own programming. This idea formed the conceptual basis for many of the self-modifying and adaptive algorithms that are still explored today in AI research. Despite its decline in mainstream programming, Lisp’s influence can still be seen in the concepts used in modern machine learning and symbolic AI approaches.
Prolog: Formal Logic and Deductive Reasoning
In the 1970s, Prolog was developed—a language focused on formal logic and deductive reasoning. Unlike Lisp, based on lambda calculus, Prolog operates on formal logic rules, allowing it to perform deductive reasoning and solve logical puzzles. This made Prolog an ideal candidate for expert systems that needed to follow a sequence of logical steps, such as medical diagnostics or strategic planning.
Prolog, like Lisp, allowed symbols to be represented, understood, and used in calculations, creating another homoiconic language that allows reasoning. Prolog’s strength lies in its rule-based structure, which is well-suited for tasks that require logical inference and backtracking. These features made it a powerful tool for expert systems and AI research in the 1970s and 1980s.
The language is declarative in nature, meaning that you define the problem, and Prolog figures out how to solve it. By using formal logic and setting constraints, Prolog systems can derive conclusions from known facts, making it highly effective in fields requiring explicit logical frameworks, such as legal reasoning, diagnostics, and natural language understanding. These symbolic approaches were later overshadowed during the AI winter — but the ideas never really disappeared. They just evolved.
Solvers and Their Role in Complementing LLMs
One of the most powerful features of Prolog and similar logic-based systems is their use of solvers. Solvers are mechanisms that can take a set of rules and constraints and automatically find solutions that satisfy these conditions. This capability is incredibly useful when combined with LLMs, which excel at generating human-like language but need help with logical consistency and structured reasoning.
For instance, imagine a scenario where an LLM needs to answer a question involving multiple logical steps or a complex query that requires deducing facts from various pieces of information. In this case, a solver can derive valid conclusions based on a given set of logical rules, providing structured answers that the LLM can then articulate in natural language. This allows the LLM to retrieve information and ensure the logical integrity of its responses, leading to much more robust answers.
Solvers are also ideal for handling constraint satisfaction problems — situations where multiple conditions must be met simultaneously. In practical applications, this could include scheduling tasks, generating optimal recommendations, or even diagnosing issues where a set of symptoms must match possible diagnoses. Prolog’s solver capabilities and LLM’s natural language processing power can make these systems highly effective at providing intelligent, rule-compliant responses that traditional LLMs would struggle to produce alone.
By integrating neurosymbolic methods that utilize solvers, we can provide LLMs with a form of deductive reasoning that is missing from pure deep-learning approaches. This combination has the potential to significantly improve the quality of outputs for use-cases that require explicit, structured problem-solving, from legal queries to scientific research and beyond. Solvers give LLMs the backbone they need to not just generate answers but to do so in a way that respects logical rigor and complex constraints.
Graph of Rules for Enhanced Reasoning
Another powerful concept that complements LLMs is using a graph of rules. A graph of rules is essentially a structured collection of logical rules that interconnect in a network-like structure, defining how various entities and their relationships interact. This structured network allows for complex reasoning and information retrieval, as well as the ability to model intricate relationships between different pieces of knowledge.
In a graph of rules, each node represents a rule, and the edges define relationships between those rules — such as dependencies or causal links. This structure can be used to enhance LLM capabilities by providing them with a formal set of rules and relationships to follow, which improves logical consistency and reasoning depth. When an LLM encounters a problem or a question that requires multiple logical steps, it can traverse this graph of rules to generate an answer that is not only linguistically fluent but also logically robust.
For example, in a healthcare application, a graph of rules might include nodes for medical symptoms, possible diagnoses, and recommended treatments. When an LLM receives a query regarding a patient’s symptoms, it can use the graph to traverse from symptoms to potential diagnoses and then to treatment options, ensuring that the response is coherent and medically sound. The graph of rules guides reasoning, enabling LLMs to handle complex, multi-step questions that involve chains of reasoning, rather than merely generating surface-level responses.
Graphs of rules also enable modular reasoning, where different sets of rules can be activated based on the context or the type of question being asked. This modularity is crucial for creating adaptive AI systems that can apply specific sets of logical frameworks to distinct problem domains, thereby greatly enhancing their versatility. The combination of neural fluency with rule-based structure gives LLMs the ability to conduct more advanced reasoning, ultimately making them more reliable and effective in domains where accuracy and logical consistency are critical.
By implementing a graph of rules, LLMs are empowered to perform deductive reasoning alongside their generative capabilities, creating responses that are not only compelling but also logically aligned with the structured knowledge available in the system. This further enhances their potential applications in fields such as law, engineering, finance, and scientific research — domains where logical consistency is as important as linguistic coherence.
Enhancing LLMs with Symbolic Reasoning
Now, with LLMs like GPT-4 being mainstream, there is an emerging need to add real reasoning capabilities to them. This is where neurosymbolic approaches shine. Instead of pitting neural networks against symbolic reasoning, these methods combine the best of both worlds. The neural aspect provides language fluency and recognition of complex patterns, while the symbolic side offers real reasoning power through formal logic and rule-based frameworks.
Personal Knowledge Graphs (PKGs) come into play here as well. Knowledge graphs are data structures that encode entities and their relationships — they’re essentially semantic networks that allow for structured information retrieval. When integrated with neurosymbolic approaches, LLMs can use these graphs to answer questions in a far more contextual and precise way. By retrieving relevant information from a knowledge graph, they can ground their responses in well-defined relationships, thus improving both the relevance and the logical consistency of their answers.
Imagine combining an LLM with a graph of rules that allow it to reason through the relationships encoded in a personal knowledge graph. This could involve using deductive databases to form a sophisticated way to represent and reason with symbolic data — essentially constructing a powerful hybrid system that uses LLM capabilities for language fluency and rule-based logic for structured problem-solving.
My Research on Deductive Databases and Knowledge Graphs
I recently did some research on modeling knowledge graphs using deductive databases, such as DataLog — which can be thought of as a limited, data-oriented version of Prolog. What I’ve found is that it’s possible to use formal logic to model knowledge graphs, ontologies, and complex relationships elegantly as rules in a deductive system. Unlike classical RDF or traditional ontology-based models, which sometimes struggle with complex or evolving relationships, a deductive approach is more flexible and can easily support dynamic rules and reasoning.
Prolog and similar logic-driven frameworks can complement LLMs by handling the parts of reasoning where explicit rule-following is required. LLMs can benefit from these rule-based systems for tasks like entity recognition, logical inferences, and constructing or traversing knowledge graphs. We can even create a graph of rules that governs how relationships are formed or how logical deductions can be performed.
The future is really about creating an AI that is capable of both deep contextual understanding (using the powerful generative capacity of LLMs) and true reasoning (through symbolic systems and knowledge graphs). With the neurosymbolic approach, these AIs could be equipped not just to generate information but to explain their reasoning, form logical conclusions, and even improve their own understanding over time — getting us a step closer to true artificial general intelligence.
Why It Matters for LLM Employment
Using neurosymbolic RAG (retrieval-augmented generation) in conjunction with personal knowledge graphs could revolutionize how LLMs work in real-world applications. Imagine an LLM that understands not just language but also the relationships between different concepts — one that can navigate, reason, and explain complex knowledge domains by actively engaging with a personalized set of facts and rules.
This could lead to practical applications in areas like healthcare, finance, legal reasoning, or even personal productivity — where LLMs can help users solve complex problems logically, providing relevant information and well-justified reasoning paths. The combination of neural fluency with symbolic accuracy and deductive power is precisely the bridge we need to move beyond purely predictive AI to truly intelligent systems.
Let's explore these ideas further if you’re as fascinated by this as I am. Feel free to reach out, follow my YouTube channel, or check out some articles I’ll link below. And if you’re working on anything in this field, I’d love to collaborate!
Until next time, folks. Stay curious, and keep pushing the boundaries of AI!
-
 @ a012dc82:6458a70d
2025-01-08 02:56:16
@ a012dc82:6458a70d
2025-01-08 02:56:16Table Of Content
-
Rollercoaster Rides
-
The Impact of Macroeconomic Forces
-
Short-term Projections
-
Ethereum's Steady Stance
-
Week-on-week Comparisons
-
Altcoins in Focus
-
The Laggards
-
Market Overview
-
Conclusion
-
FAQ
September has once again proven itself to be a tumultuous month for the world's most prominent cryptocurrency, Bitcoin (BTC). This month-long rollercoaster ride has historical roots, as September has historically been a challenging period for Bitcoin. However, the first two-thirds of the month showcased remarkable progress, raising expectations. But the recent resurgence of the US dollar has cast a shadow over the entire crypto market, leading to uncertainty among investors and traders.
Rollercoaster Rides
As the calendar pages flipped through September, Bitcoin embarked on a rollercoaster ride that left many in the crypto community holding their breath. Over the weekend, Bitcoin witnessed a significant dip, eroding a substantial portion of its gains for the month. Sunday's trading session saw the BTC/USDT pair drop by 1.2%, closing at $26,250. Monday's early trades further exacerbated the bearish trend, pushing the pair below $26,150. These rapid fluctuations in Bitcoin's value have been a hallmark of its journey in recent weeks.
The Impact of Macroeconomic Forces
In addition to its internal dynamics, Bitcoin has been significantly influenced by macroeconomic factors, particularly the policies and guidance provided by the Federal Reserve and other central banks. Last week, the Fed's unexpected hawkish stance sent shockwaves through financial markets, including the crypto sphere. This policy shift had an adverse effect on risk-on trading sentiment, causing investors to reevaluate their strategies. As the month approaches its conclusion, a less eventful macroeconomic calendar might imply reduced volatility in the coming days. However, the lingering impact of the Fed's decisions remains a source of uncertainty.
Short-term Projections
To gain insights into Bitcoin's short-term trajectory, market analysts have turned to Binance's order book analysis. According to their assessment, a support line appears to be forming at the $25,000 mark, providing some stability in the face of recent turbulence. Conversely, selling resistance has been identified at $27,500, indicating a significant challenge for Bitcoin's upward momentum. These levels are likely to play a crucial role in determining Bitcoin's path in the immediate future, with traders closely monitoring any breaches or rebounds.
Ethereum's Steady Stance
In contrast to Bitcoin's rollercoaster performance, Ethereum (ETH), the second-largest cryptocurrency by market capitalization, has demonstrated a more stable trajectory over the past few days. While Saturday saw minimal fluctuations, Sunday's trades witnessed a modest 0.8% dip, settling at $1,580. As of Monday, Ethereum has maintained this position, indicating resilience in the face of market turbulence. Ethereum's stability, as compared to Bitcoin's wild swings, underscores the unique dynamics at play within the broader cryptocurrency market.
Week-on-week Comparisons
Examining the performance of these two leading cryptocurrencies over the course of the week reveals intriguing trends. Bitcoin has experienced a 2% decline in its value, signaling the challenges it faced amid a shifting financial landscape. Meanwhile, Ethereum has faced a slightly more significant drop of over 3%. These fluctuations underscore the inherent volatility of the crypto market, even among its most prominent players.
Altcoins in Focus
Beyond Bitcoin and Ethereum, the broader altcoin spectrum presents a diverse set of performances. One standout performer has been Solana (SOL), which surged ahead by an impressive 1.75% in the past seven days. This remarkable growth has garnered the attention of investors and enthusiasts alike. Additionally, Ripple (XRP) has maintained positive momentum, adding approximately 0.8% to its value. These altcoins' resilience serves as a testament to the unique dynamics within the cryptocurrency ecosystem.
The Laggards
However, not all altcoins have been able to escape the gravitational pull of Bitcoin's performance. Prominent digital assets such as Binance's BNB token, Dogecoin (DOGE), Cardano (ADA), Polkadot (DOT), and Polygon (MATIC) have mirrored Bitcoin's downward trend. These digital assets have seen marginal losses in terms of their respective market capitalizations, underscoring the interconnectedness of the cryptocurrency market.
Market Overview
At present, the global cryptocurrency market cap stands at an impressive $1.04 trillion, signifying the substantial size and influence of the digital asset market. Bitcoin continues to command a dominant position, with a market dominance of 49.9%. This reaffirms Bitcoin's status as the undisputed leader in the digital asset space, despite the challenges it faces in September.
Conclusion
As September draws to a close, the battle between Bitcoin and the resurgent US dollar remains uncertain. The interplay between internal dynamics, macroeconomic factors, and market sentiment will continue to shape the crypto landscape in the days ahead. Traders and enthusiasts alike will be watching closely to discern the next moves in this high-stakes confrontation. As the dust settles, the cryptocurrency market will likely reveal new trends and opportunities for those who can navigate these uncertain waters with agility and insight.
FAQ
Why is September historically challenging for Bitcoin? September has traditionally been a tough month for Bitcoin, with factors like market sentiment and macroeconomic forces contributing to its volatility during this period.
How is the US dollar impacting Bitcoin's recent performance? The resurgence of the US dollar has cast a shadow over the crypto market, leading to uncertainty and impacting Bitcoin's value.
What are the short-term projections for Bitcoin and Ethereum? Short-term projections for Bitcoin suggest a support line at $25,000 and resistance at $27,500, while Ethereum has maintained relative stability.
Which altcoins have performed well recently? Solana (SOL) and Ripple (XRP) have shown positive momentum, but some prominent altcoins have followed Bitcoin's downward trend.
That's all for today
If you want more, be sure to follow us on:
NOSTR: croxroad@getalby.com
Instagram: @croxroadnews.co
Youtube: @croxroadnews
Store: https://croxroad.store
Subscribe to CROX ROAD Bitcoin Only Daily Newsletter
https://www.croxroad.co/subscribe
DISCLAIMER: None of this is financial advice. This newsletter is strictly educational and is not investment advice or a solicitation to buy or sell any assets or to make any financial decisions. Please be careful and do your own research.
-
-
 @ e6817453:b0ac3c39
2024-12-07 14:54:46
@ e6817453:b0ac3c39
2024-12-07 14:54:46Introduction: Personal Knowledge Graphs and Linked Data
We will explore the world of personal knowledge graphs and discuss how they can be used to model complex information structures. Personal knowledge graphs aren’t just abstract collections of nodes and edges—they encode meaningful relationships, contextualizing data in ways that enrich our understanding of it. While the core structure might be a directed graph, we layer semantic meaning on top, enabling nuanced connections between data points.
The origin of knowledge graphs is deeply tied to concepts from linked data and the semantic web, ideas that emerged to better link scattered pieces of information across the web. This approach created an infrastructure where data islands could connect — facilitating everything from more insightful AI to improved personal data management.
In this article, we will explore how these ideas have evolved into tools for modeling AI’s semantic memory and look at how knowledge graphs can serve as a flexible foundation for encoding rich data contexts. We’ll specifically discuss three major paradigms: RDF (Resource Description Framework), property graphs, and a third way of modeling entities as graphs of graphs. Let’s get started.
Intro to RDF
The Resource Description Framework (RDF) has been one of the fundamental standards for linked data and knowledge graphs. RDF allows data to be modeled as triples: subject, predicate, and object. Essentially, you can think of it as a structured way to describe relationships: “X has a Y called Z.” For instance, “Berlin has a population of 3.5 million.” This modeling approach is quite flexible because RDF uses unique identifiers — usually URIs — to point to data entities, making linking straightforward and coherent.
RDFS, or RDF Schema, extends RDF to provide a basic vocabulary to structure the data even more. This lets us describe not only individual nodes but also relationships among types of data entities, like defining a class hierarchy or setting properties. For example, you could say that “Berlin” is an instance of a “City” and that cities are types of “Geographical Entities.” This kind of organization helps establish semantic meaning within the graph.
RDF and Advanced Topics
Lists and Sets in RDF
RDF also provides tools to model more complex data structures such as lists and sets, enabling the grouping of nodes. This extension makes it easier to model more natural, human-like knowledge, for example, describing attributes of an entity that may have multiple values. By adding RDF Schema and OWL (Web Ontology Language), you gain even more expressive power — being able to define logical rules or even derive new relationships from existing data.
Graph of Graphs
A significant feature of RDF is the ability to form complex nested structures, often referred to as graphs of graphs. This allows you to create “named graphs,” essentially subgraphs that can be independently referenced. For example, you could create a named graph for a particular dataset describing Berlin and another for a different geographical area. Then, you could connect them, allowing for more modular and reusable knowledge modeling.
Property Graphs
While RDF provides a robust framework, it’s not always the easiest to work with due to its heavy reliance on linking everything explicitly. This is where property graphs come into play. Property graphs are less focused on linking everything through triples and allow more expressive properties directly within nodes and edges.
For example, instead of using triples to represent each detail, a property graph might let you store all properties about an entity (e.g., “Berlin”) directly in a single node. This makes property graphs more intuitive for many developers and engineers because they more closely resemble object-oriented structures: you have entities (nodes) that possess attributes (properties) and are connected to other entities through relationships (edges).
The significant benefit here is a condensed representation, which speeds up traversal and queries in some scenarios. However, this also introduces a trade-off: while property graphs are more straightforward to query and maintain, they lack some complex relationship modeling features RDF offers, particularly when connecting properties to each other.
Graph of Graphs and Subgraphs for Entity Modeling
A third approach — which takes elements from RDF and property graphs — involves modeling entities using subgraphs or nested graphs. In this model, each entity can be represented as a graph. This allows for a detailed and flexible description of attributes without exploding every detail into individual triples or lump them all together into properties.
For instance, consider a person entity with a complex employment history. Instead of representing every employment detail in one node (as in a property graph), or as several linked nodes (as in RDF), you can treat the employment history as a subgraph. This subgraph could then contain nodes for different jobs, each linked with specific properties and connections. This approach keeps the complexity where it belongs and provides better flexibility when new attributes or entities need to be added.
Hypergraphs and Metagraphs
When discussing more advanced forms of graphs, we encounter hypergraphs and metagraphs. These take the idea of relationships to a new level. A hypergraph allows an edge to connect more than two nodes, which is extremely useful when modeling scenarios where relationships aren’t just pairwise. For example, a “Project” could connect multiple “People,” “Resources,” and “Outcomes,” all in a single edge. This way, hypergraphs help in reducing the complexity of modeling high-order relationships.
Metagraphs, on the other hand, enable nodes and edges to themselves be represented as graphs. This is an extremely powerful feature when we consider the needs of artificial intelligence, as it allows for the modeling of relationships between relationships, an essential aspect for any system that needs to capture not just facts, but their interdependencies and contexts.
Balancing Structure and Properties
One of the recurring challenges when modeling knowledge is finding the balance between structure and properties. With RDF, you get high flexibility and standardization, but complexity can quickly escalate as you decompose everything into triples. Property graphs simplify the representation by using attributes but lose out on the depth of connection modeling. Meanwhile, the graph-of-graphs approach and hypergraphs offer advanced modeling capabilities at the cost of increased computational complexity.
So, how do you decide which model to use? It comes down to your use case. RDF and nested graphs are strong contenders if you need deep linkage and are working with highly variable data. For more straightforward, engineer-friendly modeling, property graphs shine. And when dealing with very complex multi-way relationships or meta-level knowledge, hypergraphs and metagraphs provide the necessary tools.
The key takeaway is that only some approaches are perfect. Instead, it’s all about the modeling goals: how do you want to query the graph, what relationships are meaningful, and how much complexity are you willing to manage?
Conclusion
Modeling AI semantic memory using knowledge graphs is a challenging but rewarding process. The different approaches — RDF, property graphs, and advanced graph modeling techniques like nested graphs and hypergraphs — each offer unique strengths and weaknesses. Whether you are building a personal knowledge graph or scaling up to AI that integrates multiple streams of linked data, it’s essential to understand the trade-offs each approach brings.
In the end, the choice of representation comes down to the nature of your data and your specific needs for querying and maintaining semantic relationships. The world of knowledge graphs is vast, with many tools and frameworks to explore. Stay connected and keep experimenting to find the balance that works for your projects.
-
 @ 403fc3fb:1d1c404c
2025-01-08 02:16:22
@ 403fc3fb:1d1c404c
2025-01-08 02:16:22Looking for a Reliable Security Company in NZ?
When it comes to protecting your property, business, or event, choosing the right security company in NZ is essential for peace of mind. At Frontline Security, we have built a solid reputation for providing tailored and professional security solutions that cater to the unique needs of every client. Whether you require state-of-the-art surveillance systems, mobile patrols, or on-site security guards, we are committed to delivering the highest standards of safety and protection.
Our team consists of highly trained professionals who are equipped with the latest security technology, ensuring comprehensive coverage for your security needs. From residential properties to large corporate events, Frontline Security is your trusted partner in safeguarding what matters most to you.
Exciting Security Guard Jobs in Auckland
Are you interested in a rewarding career in security? Security guard jobs Auckland with Frontline Security might be the perfect fit for you. We’re always looking for motivated, skilled individuals to join our growing team. Whether you’re an experienced security officer or just starting in the industry, we offer comprehensive training and a variety of roles to help you succeed.
As a member of our team, you’ll not only be part of a professional and dynamic security force but will also enjoy competitive pay and ongoing career development. Whether you’re securing corporate offices or overseeing large-scale events, Frontline Security offers a variety of exciting career opportunities that align with your passion for keeping people and property safe.
Professional Wellington Security Guards at Your Service
For those in Wellington, Frontline Security offers a range of security services designed to meet the needs of both businesses and homeowners. Our team of Wellington security guards is highly trained and skilled in providing proactive and reactive security measures. Whether you need to secure sensitive areas or manage crowd control at public events, our professional guards are ready to respond swiftly and effectively to any security situation.
We believe that security is about more than just protecting assets – it’s about creating a safe and welcoming environment for everyone. Our Wellington team is not only trained in handling security challenges but also in providing exceptional customer service, ensuring a positive experience for all.
Why Choose Frontline Security for Your Security Needs?
At Frontline Security, we are dedicated to offering comprehensive security solutions across New Zealand. With years of experience, our team has the expertise to manage all types of security situations, from corporate events to emergency response services. As one of the leading security companies in NZ, we focus on providing proactive security measures, personalised service, and the latest technology to ensure your safety.
Our highly trained staff understands the importance of customer service and professionalism. Whether you’re hiring Wellington security guards or exploring security guard jobs in Auckland, Frontline Security ensures that you receive top-notch service every time.
Join Our Team Today
Are you ready to take the next step in your career? Explore exciting security guard jobs in Auckland with Frontline Security. We offer opportunities for professional growth, on-the-job training, and a supportive work environment that values your skills and contributions.
If you’re looking for a reliable security company in NZ or need Wellington security guards, Frontline Security is here to help. Contact us today to discuss your security needs or to explore career opportunities within our growing company. With Frontline Security, you can trust that your safety is in expert hands.
-
 @ e6817453:b0ac3c39
2024-12-07 14:52:47
@ e6817453:b0ac3c39
2024-12-07 14:52:47The temporal semantics and temporal and time-aware knowledge graphs. We have different memory models for artificial intelligence agents. We all try to mimic somehow how the brain works, or at least how the declarative memory of the brain works. We have the split of episodic memory and semantic memory. And we also have a lot of theories, right?
Declarative Memory of the Human Brain
How is the semantic memory formed? We all know that our brain stores semantic memory quite close to the concept we have with the personal knowledge graphs, that it’s connected entities. They form a connection with each other and all those things. So far, so good. And actually, then we have a lot of concepts, how the episodic memory and our experiences gets transmitted to the semantic:
- hippocampus indexing and retrieval
- sanitization of episodic memories
- episodic-semantic shift theory
They all give a different perspective on how different parts of declarative memory cooperate.
We know that episodic memories get semanticized over time. You have semantic knowledge without the notion of time, and probably, your episodic memory is just decayed.
But, you know, it’s still an open question:
do we want to mimic an AI agent’s memory as a human brain memory, or do we want to create something different?
It’s an open question to which we have no good answer. And if you go to the theory of neuroscience and check how episodic and semantic memory interfere, you will still find a lot of theories, yeah?
Some of them say that you have the hippocampus that keeps the indexes of the memory. Some others will say that you semantic the episodic memory. Some others say that you have some separate process that digests the episodic and experience to the semantics. But all of them agree on the plan that it’s operationally two separate areas of memories and even two separate regions of brain, and the semantic, it’s more, let’s say, protected.
So it’s harder to forget the semantical facts than the episodes and everything. And what I’m thinking about for a long time, it’s this, you know, the semantic memory.
Temporal Semantics
It’s memory about the facts, but you somehow mix the time information with the semantics. I already described a lot of things, including how we could combine time with knowledge graphs and how people do it.
There are multiple ways we could persist such information, but we all hit the wall because the complexity of time and the semantics of time are highly complex concepts.
Time in a Semantic context is not a timestamp.
What I mean is that when you have a fact, and you just mentioned that I was there at this particular moment, like, I don’t know, 15:40 on Monday, it’s already awake because we don’t know which Monday, right? So you need to give the exact date, but usually, you do not have experiences like that.
You do not record your memories like that, except you do the journaling and all of the things. So, usually, you have no direct time references. What I mean is that you could say that I was there and it was some event, blah, blah, blah.
Somehow, we form a chain of events that connect with each other and maybe will be connected to some period of time if we are lucky enough. This means that we could not easily represent temporal-aware information as just a timestamp or validity and all of the things.
For sure, the validity of the knowledge graphs (simple quintuple with start and end dates)is a big topic, and it could solve a lot of things. It could solve a lot of the time cases. It’s super simple because you give the end and start dates, and you are done, but it does not answer facts that have a relative time or time information in facts . It could solve many use cases but struggle with facts in an indirect temporal context. I like the simplicity of this idea. But the problem of this approach that in most cases, we simply don’t have these timestamps. We don’t have the timestamp where this information starts and ends. And it’s not modeling many events in our life, especially if you have the processes or ongoing activities or recurrent events.
I’m more about thinking about the time of semantics, where you have a time model as a hybrid clock or some global clock that does the partial ordering of the events. It’s mean that you have the chain of the experiences and you have the chain of the facts that have the different time contexts.
We could deduct the time from this chain of the events. But it’s a big, big topic for the research. But what I want to achieve, actually, it’s not separation on episodic and semantic memory. It’s having something in between.
Blockchain of connected events and facts
I call it temporal-aware semantics or time-aware knowledge graphs, where we could encode the semantic fact together with the time component.I doubt that time should be the simple timestamp or the region of the two timestamps. For me, it is more a chain for facts that have a partial order and form a blockchain like a database or a partially ordered Acyclic graph of facts that are temporally connected. We could have some notion of time that is understandable to the agent and a model that allows us to order the events and focus on what the agent knows and how to order this time knowledge and create the chains of the events.
Time anchors
We may have a particular time in the chain that allows us to arrange a more concrete time for the rest of the events. But it’s still an open topic for research. The temporal semantics gets split into a couple of domains. One domain is how to add time to the knowledge graphs. We already have many different solutions. I described them in my previous articles.
Another domain is the agent's memory and how the memory of the artificial intelligence treats the time. This one, it’s much more complex. Because here, we could not operate with the simple timestamps. We need to have the representation of time that are understandable by model and understandable by the agent that will work with this model. And this one, it’s way bigger topic for the research.”
-
 @ e373ca41:b82abcc5
2025-01-08 12:22:05
@ e373ca41:b82abcc5
2025-01-08 12:22:05“At Florence's. During the meal, Jouhandou told me that he had entered an antiquarian bookshop near the Place du Palais Bourbon, where a statue of an Indian god was first displayed for sale and then recognized as miraculous. The antiquarian took advantage of this – for example, she receives commission from stenotypists whose request for a lottery win was granted (...) I am not surprised by this; we will see miraculous things in this respect.”
(Ernst Jünger, 2nd Paris Diary, January 20, 1944)
“Everything that is imaginable is real,” Pablo Picasso knew. The artist translated the possibilities opened up by his consciousness into his formal language: he saw round female bodies and painted them as triangles and squares more beautifully than anyone before him; he recognized the head of a bull in an upturned bicycle saddle. To crystallize the reality of consciousness into images and artefacts, so that they appear even more real than reality, that is the power of art and spirit. At an exhibition of the war painting “Guernica”, a Wehrmacht soldier is said to have asked him: “Did you do that?” To which Picasso replied: “No, you did.”
"Consciousness determines being"
Picasso was in Paris, the place of longing for all artists, when Max Planck was awarded the Nobel Prize for quantum theory. Planck recognized the origin of all being in spirit, energy and consciousness:
“There is no matter, only a fabric of energies given form by intelligent spirit. This spirit is the origin of all matter.”
The discovery of the power of the mind is something that has come to us again and again in different guises in all eras of time – perhaps too often to listen, because from New Age to mindfulness meditation, most people have probably already heard this insight so much that they no longer pay any attention to it. We find these ideas in Descartes' “cogito ergo sum”, in Hegel's theory that “consciousness creates being” or in the ancient doctrine of Hermeticism, in which the first principle is that of mentalism: to recognize that all power comes from the mind and consciousness. Inflation leads to a loss of value here, too. Hardly any other idea has been profaned as much as the “power of thought”.
A simplified (for some: particularly profaned) theory is the popular “law of attraction”; there are bestselling books and countless videos about it with millions of views. Put simply, you should “wish for something intensely from the universe” and then it will come true. The “theory” exhausts itself in the eternal repetition of this principle and in the listing of alleged events that are supposed to support this. Admittedly, I found this rather off-putting, like a kitchen-sink psychological prop for people who don't want to invest any effort, but instead live in a wish-it-were-something conception of reality. Dreaming, in other words.
https://www.youtube.com/watch?v=5zvnFM2BXqY&t=1s
Or is there something to it? The American Helene Hadsell, also known as the “competition queen”, is said to have won every competition she took part in through intensive mental work. Even a house was among them. The idea of the expected event, for example the main prize in a competition, had to arise in her head in the form of a clearly outlined assumption, no doubts were allowed. Hadsell came up with her technique after reading a well-known guide to positive thinking (Vincent Peale, “The Power of Positive Thinking”).
Individual thoughts become a collective consciousness
Our collective reality is also determined by thoughts, and by all our thoughts equally. Will we achieve a bold vision? Or will we stick to the lowest common denominator of frightened narrow-minded thinking?
Let's not forget: the power of shared thoughts gives rise to new groupings and collectives with specific interests, which in turn bring about change. Every thought, every word has an energy value that cannot be measured by clicks, likes or similar. Where many thoughts with a high energy value come together, things tend to get brighter. In today's media world, it is thoughts more than ever that create reality. Never before have ideas, conveyed through the media, been able to merge so quickly with other ideas, exchange ideas and circumnavigate the world.
- The mind creates and models the world through language.
- These ideas are linked intersubjectively in media reality, becoming a kind of virtual network of thoughts that replicates or changes mimetically.
- Thoughts connect like-minded people, they network mental levels, give rise to communities, groupings and tribes.
In other words, we can each look at a mountain for ourselves, but it is our modeled mind that tells us what to see: a natural phenomenon; evidence of climate change because there is little snow; a natural element with magical energy; a tourist area; a hunting ground, a dangerous cairn? The power of thoughts comes with a price: individually, their power can be decisive for us, but collective thought patterns can also put our own thinking in the bag. But then again, a new thought can help.

Thoughts, what are they really? All just images in your head? Chimeras? We don't know any more than philosophers know what reality is or physicists know exactly what energy is.
- Perhaps thoughts are a combination of several elements: A condensation of energy that can co-determine reality, a kind of mental trail followed by materialized action. Thoughts: an energy trail that attracts other energies.
- Thoughts seem to have their own communication circuit, we see this in moments of “synchronicities”, when we have just been thinking about a person for months and they are already calling.
- We also see the power of thoughts in their chain reactions: If we open our minds to inexplicable phenomena (such as synchronicities), then they knock on our door more often. The same applies to magic: if you believe in magic, you suddenly encounter it everywhere. In other words: Those who believe in miracles are (more likely to) experience them. Regardless of whether you believe in the power of thought or not, you will always be proven right and find proof of your own thoughts (“confirmation bias”).
ADVERTISEMENT:
Looking for the easiest way to buy Bitcoin and store it yourself? The Relai app is the No. 1 crypto start-up and No. 2 of all fintech start-ups in Switzerland. Here you can buy Bitcoin in just a few steps and also set up savings plans. Nobody has access to your Bitcoin except you. With the referral code MILOSZ you save on fees (no financial advice). Disclaimer due to regulatory issues: The services of the Relai App are hereby only recommended to inhabitants of Switzerland or Italy.

Need more security? The Trezor wallets are recommended and easy to use, others are available in the store. Need more advice? Book an introductory meeting with a wallet expert.
Self-efficacy starts with authority over thoughts
The power of thought is something of an individual self-fulfilling prophecy. But let's look around us: wasn't everything that surrounds us that is man-made initially just a thought? We don't have to expect a material causal chain from pure thoughts, like magicians who can move a glass of water, but the material world would be inconceivable without the existence of thoughts, they are a sine qua non.
For me, intensive thought work is most likely a form of psychological self-programming: what I focus on today, no matter how daring, bold, megalomaniac or abstruse the thought may be, puts me on the track to realizing this thought, i.e. creates a magnetic force field that attracts precisely the encounters, events or constellations that are needed to realize the thoughts. Providence sends coincidences fleeing. Provided you are not blind to the signs that are then sent your way. Sometimes you have to (mentally) reach for the stars in order to land on the moon.
Many people may smile at New Year's resolutions. I think to myself: anyone who forgoes good resolutions is consciously forgoing the opportunity to set themselves on a new path or closer to a new goal. Why should you give up the power of thought and see yourself as a plaything of external energies and external events?
What bold goal have you set yourself for 2025? Write to me at: milosz@pareto.space
My goal for 2025: to consign the phenomenon of censorship to the graveyard of history once and for all! It was an idea 1.5 years ago, now it has already become a reality for the first authors with the Pareto project. Here, too, it started out as just an idea that resonated with the thoughts of others (including you!), who helped turn it into reality.
It's a kind of magic...right?
https://www.youtube.com/watch?v=0p_1QSUsbsM
This article by Milosz Matuschek first appeared in German on Freischwebende Intelligenz.
Join the marketplace of ideas! We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
Update:* Since my last article on the Pareto project, we have received more than 50 messages from publications, journalists, authors, testers and supporters. Thank you very much, we are happy to help everyone become censorship-resistant! May just take a little time. Are you a publication and want to be part of it, test us, migrate your content to Nostr? Write to team@pareto.space***
Not yet on Nostr and want the full experience? Easy onboarding via Nosta.me.

-
 @ c3b2802b:4850599c
2025-01-08 12:06:29
@ c3b2802b:4850599c
2025-01-08 12:06:29An die Damen und Herren Abgeordneten des 20. Deutschen Bundestages
* *
Ihre Stellungnahme bezüglich Abstimmungen zu Waffenlieferungen und Kriegseinsätzen
Sehr geehrte Damen und Herren Bundestagsabgeordnete,
im vergangenen Jahrhundert haben sich Machthaber, Politiker und Parlamentarier unseres Landes mehrfach für Kriegshandlungen und völkerrechtswidrige Gewalttaten ausgesprochen, eingesetzt oder diese unterstützt, darunter zwei Weltkriege, welche unermessliches Leid über die Völker Europas und der Welt gebracht haben.
Kein anständiger Mensch kann sich eine Wiederholung solcher Entscheidungen wünschen. Daher fordere ich Sie auf, mir - als Teil des Souveräns, in dessen Namen Sie derzeit Verantwortung tragen - eine Stellungnahme zu Ihren künftigen Abstimmungsintentionen bei anstehenden Entscheidungen über Auslandseinsätze unserer Bundeswehr sowie Waffenlieferungen an kriegführende Länder zukommen zu lassen.
Reflektieren Sie dabei insbesondere bitte folgende historischen Tatsachen:
· Im Februar 1990 versprach der US Außenminister James Baker Herrn Gorbatschow, dass sich im Falle eines Rückzuges der sowjetischen Streitkräfte aus Ostdeutschland und weiteren Ländern des ehemaligen Ostblocks das NATO Militärbündnis „not an inch“, also nicht einen Zoll in Richtung Osteuropa ausdehnen würde (im Dokument unten auf Seite 5 unten). Danach wurden bekanntlich sämtliche Streitkräfte der WK II Siegermacht Sowjetunion aus Osteuropa zurückgezogen.
· Im April 2000 berief das US Außenministerium eine Konferenz in Bratislava ein, zu der mehrere Staatschefs früherer Ostblockländer, aber keine EU Staatschefs geladen waren. Es ging bei dieser Konferenz um die Ausweitung der NATO Richtung Osteuropa, welche inzwischen stattgefunden hat und zur Aufrüstung mit ca. 400 neue Militärbasen in früheren Ostblock-Staaten führte. Darüber berichtet Willy Wimmer, ein Kollege von Ihnen, der 33 Jahre Mitglied des Bundestags war, verteidigungspolitischer Sprecher der CDU/CSU Fraktion und Vizepräsident der parlamentarischen Versammlung der OSZE, in dem Buch: Alexander Sosnowski im Gespräch mit Willy Wimmer: „Und immer wieder Versailles“. Zeitgeist Verlag, 2019, S. 166, 175, 185.
Meine Fragen an Sie:
(1) Wie beurteilen Sie den Rückzug der sowjetischen Streitkräfte aus Osteuropa Anfang der 1990er Jahre?
(2) Wie beurteilen Sie das Verhalten der Vertreter der Alliierten-Macht USA
· im Jahr 1990,
· im Jahr 2000 im Hinblick auf das Versprechen im Jahr 1990 sowie
· bezüglich des Kreises der eingeladenen Staatschefs der Bratislava Konferenz?
(3) Welche Folgerungen ziehen Sie persönlich für künftige Abstimmungen über Waffenlieferungen aus Deutschland oder über Kriegseinsätze deutscher Soldaten in Konflikten, welche aus dem geschilderten historischen Hintergrund hervorgehen?
Zweifellos ist die Aufnahme von Kriegsflüchtlingen eine generöse Handlung. Doch um wieviel klüger, menschlicher könnte es sein, wenn Sie sich mit all Ihrer Klugheit und Menschlichkeit für Maßnahmen einsetzen, welche auch den Menschen in Kriegsgebieten ein friedliches Weihnachtsfest in ihrer Heimat möglich machen würden!
Ich wünsche Ihnen, Ihren Familien und Teams gute besinnliche Weihnachtstage, in denen Sie Ihre Möglichkeiten für friedenserhaltende und friedensschaffende Entscheidungen im deutschen Parlament weise abwägen.
Mit freundlichen Grüßen Peter Schmuck
Sieben der 15 antwortenden Parlamentarier lehnten militärisches Engagement unseres Landes im Ausland ab. Einer der Antwortenden sprach sich dafür aus. Die verbleibenden sieben Antwortenden bezogen keine klare Position oder erklärten sich für nicht zuständig, mein Schreiben zu beantworten.
Lassen Sie uns gemeinsam überlegen, welche weiteren Aktionen dazu beitragen können, dass unser Land nicht in neue Kriege verwickelt wird - und dass die bestehenden Konflikte friedliche Lösungen finden.
Ein Schlüsselereignis wird die bevorstehende Wahl zum Bundestag sein. Eine friedliche Zukunft werden wir nur behalten, wenn wir politischen Kräften aller Couleur die rote Karte zeigen, welche deutsches militärisches Engagement im Ausland befürworten. Wenn wir alle, die Frieden wollen, in unseren Bekannten- und Nachbarschaftsnetzen für unsere Position werben.
Ein wichtiger Schritt zum Frieden ist aus meiner Sicht, die Propaganda-Nachrichtenkanäle auszuschalten. Dann entsteht der Freiraum, den wir brauchen, uns selbst zu denken, die eigenen Emotionen zu spüren und so in unserer Mitte zu bleiben oder sie zurückzufinden.
Beste Grüße in die Runde Ihr Peter Schmuck
Titelbild von EKD
-
 @ 3c7dc2c5:805642a8
2025-01-08 00:08:54
@ 3c7dc2c5:805642a8
2025-01-08 00:08:54🧠Quote(s) of the week:
“Bitcoin is a clock with a new concept of time – block height – synchronously marking depletion of the most valuable resource in the universe, our time.” - Ross Stevens
'The fact that billions of working men and women must sacrifice 40+ years of their time, energy, health, and focus to gain access to fiat currencies that central banks can replicate with a keystroke is injustice on the largest scale humanity has ever seen. It is theft. Bitcoin' - Bitcoin for Freedom
'Billions of people will watch the generational opportunity to own 1 whole Bitcoin slip through their fingers and never return. There will be less than 500,000 whole-coiners in the world, which will continue to drop, regardless of how many people wish they had one. This is wealth based on math.' Wealth Theory
🧡Bitcoin news🧡
Happy New Year fam!🧡 Here's to a year filled with love, health, and wonderful Bitcoin moments.
Now before I am going to start with the Weekly Recap I want to share what is happening with MiCA / Travel Rule in the EU. The EU is back with more attacks on our freedom. Their 2025 MiCA and TravelRule regulations are just another step to control and surveil our financial lives. This is a good thread on what’s happening with MiCA in the EU. To make it even more specific, a thread worth your time especially if you're in Europe. x.com/ferenckovacs/status/1873278442600325235
To sum it up. The EU is cracking down on freedom while America is on the verge of an unprecedented pro-Bitcoin administration. The EU is going to be left behind again (!) because of a lack of Bitcoin education. That's why I am writing my Weekly Recaps and created this account (Bitcoin Friday). Change the world through Bitcoin education.
On the 24th of December: ➡️Michael Saylor is not fucking around. MicroStrategy just said that they want to raise the authorized share count by 10 BILLION. They currently have 330 million shares outstanding, meaning this could increase the share count by 3,000%. Microstrategy now owns 444.000 Bitcoin. That is as much as China, the US, and the UK combined. Madness! Key proposals include: 1. Increasing authorized Class A shares from 330 million to 10.33 billion to support future capital raising. 2. Increasing authorized preferred shares from 5 million to 1.005 billion to expand financing options. 3. Amending the 2023 Equity Incentive Plan to provide automatic equity awards for new directors joining the Board.
➡️While others are selling, BlackRock’s Bitcoin ETF bought $32 million in BTC yesterday.
➡️The value of Metaplanet’s Bitcoin treasury is now 12x larger than the market cap of the entire company in April. Metaplanet is using Saylor's playbook. All 1,761.99 of Metaplanet’s BTC are verifiable on the chain.
➡️The Bank of Italy identifies Bitcoin P2P services as "crime-as-a-service", due to their alleged use in money laundering operations. Ma figura di merda! Don't let them frame regular Bitcoin usage as criminal. You have a right to freedom of transaction, privacy, and self-custody. Oh on a side note. They should be banning the "crime-as-a-service" Euro then - which constitutes 98.5% of illicit money laundering compared to Bitcoin, cazzos!
➡️Less than 1.2 million Bitcoin left to mine! Tick-tock, next block! (foto)
➡️Publicly traded Matador Technologies Inc. approves to purchase of $4.5 million Bitcoin as a strategic reserve asset.
➡️South African parliament member Mzwanele Manyi said "Bitcoin is coming in full force. It will devalue gold. It's unstoppable."
On the 25th of December: ➡️Russia is using BITCOIN in foreign trade, says finance minister - Reuters Finance Minister: "Such transactions are already occurring. We believe they should be expanded and developed further. I am confident this will happen next year". From last week: "Russia lawmakers were this week revealed to be pushing the country to create a Bitcoin strategic reserve... Vladimir Putin praised bitcoin as an alternative to FX reserves following the seizure of its funds by Western governments." I guess banning them from SWIFT wasn’t the greatest idea after all.
➡️Jameson Lopp: "If you have a lot of bitcoin you should leave it with a custodian." 'Meanwhile, custodian losses in 2024: Rain: $15M Indodax: $22M Lykke: $22M BingX: $45M BitForex: $56M BtcTurk: $90M WazirX: $230M DMM Bitcoin: $305M' Source: hacked.slowmist.io/?c=Exchange
➡️Multiple U.S. states considering Strategic Bitcoin Reserves - CNBC
El Salvador is just 2.23 BTC away from holding 6000 bitcoin in its Strategic ReserveLike a boss, El Salvador continued adding one BTC per day to our Strategic Bitcoin Reserve. And we are still so early ...
➡️Malaysia’s largest bank says when the US establishes Bitcoin Reserves, other countries will follow with increasing demand.
On the 26th of December: ➡️Thailand has backed a pilot scheme proposed by former premier Thaksin Shinawatra to introduce Bitcoin payments at a tourist center in Phuket, Thailand.
➡️Japan's Prime Minister Shigeru Ishiba expresses uncertainty about implementing a Bitcoin strategic reserve, citing a lack of information on the US and other countries' plans.
➡️Another public company launches a Bitcoin treasury allocating 90% of their cash. Public company KULR buys 217.18 Bitcoin for $21 million for its Bitcoin Treasury strategy.
➡️Bitcoin mining (from otherwise wasted hydropower) is now 18% of all Ethiopian Electric Power’s revenue. The country has turned excess hydroelectric power into a profitable asset by powering Bitcoin mining operations, earning $1B in revenue last year. The move is drawing global investors who benefit from the country's low energy costs, and it's an example of how sustainable energy can drive economic growth across Africa. Source: www.crypto-news-flash.com/ethiopias-dam-powers-18-revenue-through-bitcoin-mining
On the 27th of December
➡️Daniel Batten: 'In addition to 13 peer-reviewed academic papers, there are now 8 sustainability magazines covering the fast-growing story of how Bitcoin is supporting sustainable energy development and climate action. They are: x.com/DSBatten/status/1872475284319949035 Great thread and articles/papers! Must read.
➡️Bitcoin is being quietly acquired by whales through private transactions, per CryptoQuant. The number of CoinJoin transactions has tripled over two years, with many attributing the surge to legitimate investment.
➡️Over 60 public companies now hold Bitcoin as a treasury reserve asset. (foto) '14,400 BTC taken off exchanges today. This will keep happening until the liquid supply is gone. When that happens you better be done stacking.' - Bitcoin For Freedom.
➡️$5 billion Bitwise files for Bitcoin Standard Corporations ETF.
➡️IRS rules demand brokers report digital asset transactions, including decentralized exchanges from 2027.
On the 28th of December: ➡️ProShares files for ETFs tracking the S&P 500, Nasdaq-100, and gold—denominated in Bitcoin. These ETFs take long positions in stocks or gold while using Bitcoin futures to short USD and go long on BTC, making them essentially Bitcoin-hedged ETFs. Nate Geraci: 'ETF filings last 48hrs… -Strive Btc Bond ETF -Bitwise Btc Standard Corporations ETF -REX Btc Corporate Treasury Convertible Bond ETF -ProShares Btc hedged ETFs on S&P 500, Nasdaq-100, & gold 2025 is gonna be wild' This is de facto how BTC is going to scale to a billion users.
On the 29th of December: ➡️Bitcoin vs. Gold ETFs in 2024: •Bitcoin: $36.8 billion in net flows •Gold: $454 million in net flows Bitcoin is demonetizing gold in real-time. (foto)
On the 30th of December: ➡️This year's investor letter from Stone Ridge did not disappoint. One of the best investor newsletters I've read in a long time. www.nydig.com/research/stone-ridge-2024-investor-letter This year's investor letter from Stone Ridge did not disappoint. One of the best investor newsletters I've read in a long time. (foto) 'NYDIG is about to unlock one of the largest investable pools of capital in the entire financial system—insurance float—and channel it into Bitcoin-backed loans. This is a big deal. More efficient lending → lower loan costs → less BTC sold → increased scarcity → higher demand and price → stronger institutional interest → accelerated Bitcoin adoption.' - Sam Callahan ➡️Tether buys 7,629 Bitcoin worth $705 million for its reserves and now owns $7.7 billion in Bitcoin.
➡️'According to Luke Dash Jr's estimates of unreachable / non-listening node counts, the total number of Bitcoin nodes rose 49% from 65,000 to 96,852 during 2024.' - Jameson Lopp The number of publicly reachable computers running Bitcoin blockchain software increased by 19% this year. This is very important! Noderunners!
➡️MicroStrategy has acquired 2,138 BTC for ~$209 million at ~$97,837 per bitcoin and has achieved a BTC Yield of 47.8% QTD and 74.1% YTD. As of 12/29/2024, they hodl 446,400 Bitcoin acquired for ~$27.9 billion at ~$62,428 per Bitcoin.
On the 31st of December: ➡️A Swiss initiative to include Bitcoin in the constitution has advanced to the review stage in the Feuille fédérale, the official publication for legislative texts and government decisions.
➡️New record bitcoin network computing hashrate: 800,000,000,000,000,000,000x per second.
➡️Bitcoin miners earned $15B in revenue in 2024. This assumes they instantly sell for fiat, which is not the case - miners tend to be HODLers.
➡️Bitcoin Returns since 2010... (foto) "Only" +120% this year, 5x the returns of the S&P 500.
➡️Bhutan now likely holds more Bitcoin per capita than any other country on Earth.
➡️$1.5 trillion Franklin Templeton says "We expect to see strategic Bitcoin reserves added by several nations" in 2025.
💸Traditional Finance / Macro:
On the 26th of December: 👉🏽'The US stock market is becoming even more concentrated: The top 10 stocks now reflect a record 40% of the S&P 500's market cap. This percentage now exceeds the 2000 Dot-Com bubble levels by ~14 percentage points. In 2024, these stocks have added over $7 TRILLION in market cap and are now worth a record $20.9 trillion. To put this into perspective, the entire European stock market is worth ~$16 trillion, or $4.9 trillion LESS. The market's rally is not broadening.' -TKL
🏦Banks: 👉 no news
🌎Macro/Geopolitics:
On the 24th of December: 👉🏽'US existing home sales are set to close at 4.04 million in 2024, marking the worst year since 1995. Sales are set to be even lower than during the 2008 Financial Crisis. The lack of demand for existing homes comes as home prices have jumped over 50% since 2020. Over the same period, mortgage rates have nearly TRIPLED, making affordability even worse. The average rate on a 30-year mortgage is up 100 basis points since September alone, to 7.1%, despite the Fed cutting rates by 100 basis points. The US housing market is frozen.' -TKL
On the 25th of December: 👉🏽Javier Milei announces a structural tax reform that will eliminate 90% of taxes in Argentina.
👉🏽 China withdrew $158 billion from its financial system through its MLF tool (Medium-Term lending facility), the largest liquidity removal in a decade.
On the 26th of December: 👉🏽“Brussels started a department to look for €60M in savings. Its operational costs so far are €30M.” The most EU thing I've ever seen. The worst part? The government can only grow in its current form, which means it will only become bigger and more expensive. Inefficiency in government. A lot of inefficiency, with more and more regulations and no contributing productivity. Welcome to how Western governments function.
Remember the report from Oxfam International two months ago? "Up to $41 billion in World Bank climate finance unaccounted for.". Remember how the Pentagon fails 7th audit in a row, unable to fully account for the $ 842B budget.
But hey, Bitcoin is just made-up money, right?
👉🏽'The 10-year note yield is now up 100 basis points since the "Fed pivot" began in September. In other words, while the Fed has CUT rates by 100 bps, rates in the market have RISEN by 100 bps.' -TKL “As a result, the average interest rate on a 30-year mortgage in the United States is now at 7.10%. To put this into perspective, just 3 months ago the average rate bottomed at 6.15%. Buying the median-priced home at $420,400 now costs an average of ~$400 more PER MONTH.” The disconnect between the Fed and what's going on in the bond market is ridiculous. Never in the last 40 years has the 10-year Treasury risen more quickly after the Fed started a rate-cutting cycle. The housing market pays the price (read the first point in this segment)
👉🏽New Chinese $137B river dam project in Tibet, 3x the size of Three Gorges for 300 million people. $137B honestly sounds like a small amount after hearing how much the US spends on foreign wars. They've given Ukraine $183B to date. One war in Ukraine or one dam that generates enough electricity to power your entire country? The environmental destruction will be irreversible and will affect the entire planet. The Chinese see our planet as a commodity and a resource that needs to be exploited. Arnaud Bertrand: 'China just approved yet another project of an unfathomable scale: a mega-dam that will generate 3 times more power than the Three Gorges, enough to meet the annual needs of over 300m people, the equivalent of the entire US population. scmp.com/news/china/science/article/3292267/china-approves-tibet-mega-dam-could-generate-3-times-more-power-three-gorges… The project will cost an insane 1 trillion yuan (US$137 billion) to build and will be located on the Yarlung Tsangpo River in Tibet autonomous region, which carves out the deepest canyon on Earth.'
On the 29th of December: 👉🏽'Germany, France, and Italy, the three largest economies in Europe have been stagnating for years. Grotesque overregulation, lack of innovation, and left redistribution mindset replacing hard work & entrepreneurial spirit have their price. What needs to happen for Europe to grow again?' -Michael A. Arouet The EU is destroying the European economy. 'Sixteen years ago, the US and EU economies were nearly equal in size. Today, the US economy is 50% larger than the EU. Europe is being strangled by the EU and its Commission President von der Leyen's red tape.'- Steve Hanke (foto)
On the 31st of December: 👉🏽'Global corporate debt issuance jumped ~34% year-over-year to a record $7.9 trillion in 2024. Global corporate debt sales have DOUBLED over the last 12 years. Issuances have now surpassed the previous record of $7.2 trillion in 2021. This comes as historically low corporate bond spreads have fueled massive issuance activity. Furthermore, the average US investment-grade bond spread has fallen to just 0.77 percentage points in early December. This market the tightest spread since the late 1990s, according to Ice BofA data.' -TKL The only thing I am wondering is who is buying corporate debt when you can get 5% in a money market? Or just buy Bitcoin😉
👉🏽Total US debt is up 30%, or $8.5 trillion since Biden's inauguration, to $36.2 trillion.
🎁If you have made it this far I would like to give you a little gift:
Some fountain of Jeff Booth's wisdom: Repricing the World in Bitcoin
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. Use the code BITCOINFRIDAY
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.⠀⠀⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with sats.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe -Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ 7ecd3fe6:6b52f30d
2024-12-05 10:35:57
@ 7ecd3fe6:6b52f30d
2024-12-05 10:35:57I went to bed last night at 96k, thinking we'd have another day of sideways consolidation, maybe if we're lucky a bump on the head at 99k before the 100k dumpers come in to "take profits"
But little did I know what was waiting for me when I opened up my crusty eyes, I checked the chart as one days after their morning wee and nearly wet the entire bathroom, 102k, must be a mistake, let's check Coingecko, let's check the local exchanges, let's check social media, and it was confirmed like 6 blocks in baby, there's no going back!
Ladies and gentlemen, grab your laser-eye NFTs and dust off those 2017 memes - we've finally arrived! Bitcoin has transcended the mythical $100,000 price point that HODLers have been hallucinating about since the Obama administration.
We have succesfully meme'd the dream into a reality, can anything stop us now? The Banana zone hath arrived

Why the big break?
Is it unrest in France with the government collapsing, is it South Korean uncertainty with their president declaring Martial law, is it Putin coming out to admit you can't ban Bitcoin?
Is it countries trying to find a hedge against Trumps' proposed tariffs?
Who knows?
To me it's just another day of sellers exhausted and buyers are eating through the order book like hungry-hungry hippos
Bottom of the bear to getting some serious air time
If you've been here for one full cycle, and stayed the course it's been a wild ride, we saw Terra Luna, FTX, Celsius, BlockFi blow up and a massive draining of liquidity from the market.
The dream was dead and we hit rock bottom in November 2022, at 15k, to those who nailed that absolute bottom, I salute you.
Anyhoo, it's been a slow grind upwards, the crab market of choppy consolidation normally is, but you psychos continued to hold steady and deploy capital even when number continue to go down!

The meme, the dream and now the cream
The bitcoin maximalists who've been sporting perpetual laser-eye Twitter and nostr profiles can now collectively exhale.
Those same folks who've been predicting "$100K by EOY" every single year since 2017 can now do a victory lap, wearing their tinfoil-lined Gucci tracksuits.
You were wrong many times, only to be proven right eventually!
Remember when explaining Bitcoin's potential value used to involve complex blockchain narratives and decentralization lectures?
Call up the cry babies
When Bitcoin looked down and out there were no shortage of doom and gloomers writing another failed obituary, Dan Pena, Charlie Munger, Warren Buffer, Peter Schiff and Peter Zeihan all had to yap and we listened and laughed
Let's hear what mama has to say on the subject of Bitcoin?
Keep dreaming. Bitcoin is never going to hit $100,000!
— Peter Schiff (@PeterSchiff) November 8, 2019Now it's just: "Told ya so" - accompanied by shitcoiners and nocoiners are angry coz of dey enlarged medulla oblongata
Times like this, I often think of the wise and eloquent words of MSTR Gigachad Saylor
Put money into Bitcoin and wait for number to go up biggly, if number go down put more money in and wait for number to go up bigglier - Michael Saylor
Setting up base camp for the march up Mount Milli-manjaro
The journey to $1 million feels eerily similar. We'll witness another brain-melting crypto pilgrimage - let's call it Mount Milli-manjaro - where every Reddit thread and Twitter space will sound like a combination of economic prophecy and sci-fi fever dream.
Pro tip for newcomers: Pack extra copium, a sense of humor, and maybe some popcorn.
This ride is just getting started.
To the moon? 🚀🤡₿ Looks likely bar a massive black swan, 2025, looks like this thing is going to run with big Usain Bolt strides as we enjoy a year of price discovery, speculation and all the scams that will fester as retail comes piling in to make their overnight fortunes.
I know it's fun to hand out I told you so's and you should enjoy it, take the victory lap but even that gets old, while it's hard to do, try to stay humble and enjoy stack the perpetual top!
-
 @ 3c7dc2c5:805642a8
2025-01-08 00:05:51
@ 3c7dc2c5:805642a8
2025-01-08 00:05:51🧠Quote(s) of the week:
Bitcoin is freedom of speech in the language of money.
'The five stages of a No-Coiner:
-
Denial (most people are here)
-
Anger (Peter Schiff)
-
Bargaining (Shitcoiners)
-
Depression (Rekt shit-coiners)
-
Acceptance (Bitcoiner)' - Bitcoin for Freedom
🧡Bitcoin news🧡
On the 31st of December:
➡️Impressive growth for Unchained in securing Bitcoin for clients. $9.5 billion financial services company Unchained helped its clients secure over 100,000 Bitcoin in 2024.
➡️'ETH/BTC is down 30% this year—the "world computer" needs a new narrative quickly, otherwise, it's going to fall another 100%.' -Joe Consorti
➡️'Since the beginning of Q4, treasury operations delivered a BTC Yield of 47.8%, a net benefit of 120,600 BTC to our shareholders. At $96K per BTC, that equates to $11.6 billion for the quarter.' - Michael Saylor
On the 1st of January:
➡️BlackRock's Spot Bitcoin ETF now holds over 2% of all the Bitcoin that will ever exist.
➡️MicroStrategy is now down 47% since hitting an all-time high 6 weeks ago.
➡️'$793M worth of Bitcoin was transferred from MicroStrategy-linked Coinbase Prime Custody addresses to unknown wallets, according to Arkham Intelligence.' -Bitcoin News
➡️We start the year with a new low on Bitcoin on exchanges, and 30k Bitcoin withdrew in the last 24 hours.
➡️Daniel Batten: 'Little known fact: The World's largest Sovereign Fund (Government Pension Fund Global, Norway) already has significant Bitcoin exposure. The fund has invested $217 million in MicroStrategy, tripling its allocation between Aug 2023 and Aug 2024. Expect more of this in 2025.'
➡️New research paper published:
https://www.cetjournal.it/cet/24/114/061.pdf
TL;DR: Pairing Bitcoin mining and Green Hydrogen can: accelerate the build-out of solar and wind capacity boost capacity for negative emission technologies, capturing >7.4 t CO2e per Bitcoin
➡️Globalt Investments senior portfolio manager Thomas Martin reveals that the company currently has 10% of its portfolio in gold and that it could increase its holdings in Bitcoin, but probably below 5%.
➡️Hong Kong-listed company Yuxing buys 78.2 Bitcoin for $6.3 million.
➡️2024 is in the books, and the results are clear:
Bitcoin topped the charts again, outperforming every major asset class for the year. Investment returns last year:
Bitcoin: +121%
Gold: +27%
NASDAQ: +26%
S&P 500: +25%
Dow Jones: +13%
Emerging Markets: +6%
Cash: +5%
Real Estate: +5%
Commodities: +2%
Oil: +1%
US Bonds: +1%
Again Bitcoin is at the top. There is no second best.
By simply buying and holding Bitcoin, you outperformed 99.99% of all financial institutions on planet Earth in 2024, without hidden fees and bullshit.
On the 2nd of January:
➡️Billionaire investor Ray Dalio recommends Bitcoin as 'hard money' amid national debt increases, per the Block.
Recently I have seen a Ray Dalio interview. He owns Bitcoin, but he still doesn't understand some basic concepts. Oh well, Gradually then suddenly. Ray Dalio: "I want to steer away from debt assets like bonds and debt, and have some hard money like gold and Bitcoin."
➡️FORBES: Bitcoin mining in Africa “has shown to provide the much-needed revenue to boost electricity infrastructure development, create jobs, sustainably electrify rural communities, and catalyze green energy production.”
➡️The Oxford English Dictionary added the word "satoshi'.
➡️Fold announces up to $30M in convertible note financing, backed by Bitcoin, to fuel growth and fast-track product development.
On the 3rd of January:
➡️On this day 16 years ago Bitcoin went online! Happy Bitcoin Genesis Block Day! This block is unspendable. Satoshi also waited 6 days before mining block #2 so others had time to join the network.
Now that Bitcoin has existed for 16 years! Lindy effect says that Bitcoin would at least exist for another 16 years.
January 3, 2009. Satoshi undermines block 0 on a difficulty 1 CPU and incorporates into the Genesis Block hexadecimal code base the headline of that day’s Times “The Times 03/Jan/2009 Chancellor on the brink of second bailout for banks”. The bank bailout plan ‘cause of the subprime mortgage crisis in the GFC.
Since that day, the network has grown dramatically. Now, millions of people all over earth use Bitcoin. And while it’s great to hear that other countries like El Salvador, Bhutan, and others are embracing Bitcoin, I can’t help but wish my own country 🇳🇱 was embracing Bitcoin too.
Tick tick, next block without fail, Bitcoin continues to provide us with the most significant tool for freedom of speech and monetary sovereignty in the digital age!
Bitcoin is about financial inclusion and economic empowerment.🎯
Bitcoin is secured by the most powerful computing network in the world!🧡
Which leads me to the following.
➡️Just like with other emerging tech, perspectives evolve. Fascinating to see that finally, the vast majority of academic papers are recognizing the benefits of Bitcoin Mining.
Daniel Batten: "87.5% of contemporary peer-reviewed literature on Bitcoin and energy highlight Bitcoin mining having significant, scaleable environmental benefits This shift in scientific consensus follows the same trend as that of other nascent technologies, where first-generation research is superseded by more nuanced work based on better understanding, more case studies, and improved data."
Here you can find the list of those 14 of the last 16 peer review academic papers: https://x.com/DSBatten/status/1874858383523618887
➡️Another one, a scientific paper suggests that Bitcoin could function as a safe haven in relation to geopolitical risk in times of market crashes.
"We find that Bitcoin and the Swiss Franc function as safe havens in relation to geopolitical risk in times of market crashes while Gold and Treasury bonds do not. [...] the protective aspects [...] mainly show through large stock market moves."
https://www.sciencedirect.com/science/article/abs/pii/S1544612324015721#:~:text=Using%20S%26P%20500%20and%20GPR,and%20Treasury%20bonds%20do%20not
➡️Eric Balchunas: "IBIT with its biggest outflow day ever yesterday with $332m, about 0.7% of the total aum. It's so over.."
We had a good run everyone. haha
➡️If you were hoping to see evidence for how simple it can be to do Bitcoin right… here you go. Just buy and hold. Believe me, please read the post/thread:
https://x.com/sminston_with/status/1874978781200588838
➡️Bitcoin's network hashrate increased by 56% in 2024, from 512 to 800 exahash per second.
➡️ Chinese auto-trading platform Cango Inc. now holds 933.8 Bitcoin. The company increased Bitcoin mining production by 56% in December, producing 569.9 BTC.
➡️'Bitcoin's UTXO set grew from 153.4M to 186.4M during 2024, adding 1 net additional UTXO per second.' - Jameson Lopp
On the 4th of January:
➡️'Unredacted FDIC documents reveal coordinated efforts to restrict Bitcoin activities under Operation Chokepoint 2.0, exposing systemic discrimination against the industry.' TFTC
Ridiculous actions were taken with intent over the last few years. We all knew it. I am not surprised at all.
➡️The Bitcoin network finalized more than $19 trillion worth of BTC transactions in 2024. More than double the $8.7 trillion settled over the network in 2023 - reversing two years of declining transaction volume since 2021. Decisively proving that Bitcoin is both a store of value and a medium of exchange.
On the 5th of January:
➡️The largest Bitcoin mine in the world is nearing completion. Riot Blockchain’s new facility is under construction in Corsicana Texas, which, once fully developed, will be powered by 1 gigawatt in total mining capacity.
➡️Ffs nothing learned from 2022, ahumm FTX ahuhmm Celcius.
'One of the largest publicly traded Bitcoin mining firms in the U.S., MARA, has lent 7,377 BTC to third parties to generate yield, representing approximately 16% of its total reserves. These loans are “short-term arrangements with well-established third parties.” The long-term objective is to generate sufficient yield to offset operating expenses.'
Surely nobody has even gotten caught offsides rehypothecating their Bitcoin, right? Right!?!?!?
➡️Metaplanet is aiming to expand its Bitcoin holdings more than fivefold to 10,000 Bitcoin in 2025, says CEO Simon Gerovich.
💸Traditional Finance / Macro:
On the 31st of December:
👉🏽Over $7.11 trillion was added to the US stock market in 2024.
👉🏽'The last time the top 10 stocks accounted for this much of the S&P 500, was just before the Great Depression in 1929…' - Geiger Capital The top 10 stocks in the S&P 500 are now almost 800 TIMES larger than the 75th percentile stock.
Not even the Great Depression in the 1930s saw market concentration this high. It's now 50% MORE concentrated than in 2001.
Yeah, it is bad (please watch the video as mentioned in last week's Weekly Recap - Luke Gromen & Preston Pysh). For now, the Fed especially Trump won't let a depression happen.
On the 2nd of January:
👉🏽The US Bond Market has now been in a drawdown for 53 months, by far the longest in history.
🏦Banks:
👉🏽'no news
🌎Macro/Geopolitics:
On the 1st of January:
👉🏽Germany, the economic powerhouse of Europe, is now on the brink of a collapse. Energy shortages. Aging workers. A stagnating economy. What happened to Europe’s strongest economy—and what does it mean for the EU’s future?
(foto)
I have mentioned it multiple times here in the Weekly Recaps. Given its policy instability and lack of innovation support, Germany's decline is no surprise. I wouldn't call it a collapse though. What will be next? The AfD likely will win the upcoming elections. Will that help to rejuvenate their economy, I don't think so. But if they (current and past administrations) keep pushing the same tired policies expect more support for real change like the AfD. Don't get me wrong. Economic despair fuels AfD’s surge, while democracy’s legitimacy falters.
This isn’t just about one nation, it’s a global wake-up call.
👉🏽'U.S. Dollar is now the most overvalued in history according to Bank of America.' - Barchart
👉🏽Lagarde says the European Central Bank has a “big, heavy agenda for 2025” of bringing inflation down to 2% and continuing progress toward a CBDC. Full video aka.
The new Bitcoin marketing ad: https://x.com/Lagarde/status/1874380049442320773
Pardon my English, but these people are unelected psychopaths. Lagarde is almost 70 years old. Should monetary policy be set by people who don't understand the current & future economic trends that will rule society?
Digital Euro means slavery. Study the meaning of money to boycott with an alternative, Bitcoin! The honey badgers are on the move.
Oh and regarding that mysterious 2% inflation figure. Let's say you save $200 a month for 30 years in a savings account. Your total contributions over 30 years would be $72,000.
Here's how much buying power you would have left, if inflation was:
2%: $39,275
3%: $28 872
4%: $21,157
5%: $15,453
There is no reason we should have 2% inflation. Let alone the 4-8% inflation we had the last couple of years.
On the 2nd of January:
👉🏽We in Europe really fucked up. 'Europe has gone from relying entirely on cheap Russian gas to relying entirely on expensive US LNG' - Zero Hedge
They closed their nuclear reactors for this. Get woke, go broke. Oh, by the way, the Nordstream 2 pipeline incident has a clear winner, and it's not Ukraine or Russia.
👉🏽The EURO tumbles to the lowest level since 2022 amid ongoing concerns about Europe’s economy.
Dr. Jan Wüstenfeld: "Meanwhile, Bitcoin's supply growth rate is at 0.8%, and in 172,536 blocks, the newly issued Bitcoin per day will halve again, then halve again after another 210,000 blocks, and again and again. Choose wisely.
👉🏽Reserves at the Fed sink below $3 Trillion to the lowest since 2020. The Fed will end QT in March or April give or take a month. Especially with RRP running dry. Banking liquidity is getting too tight
👉🏽The Chinese Property Market has seen a total loss of $18 Trillion over the past 3 years, surpassing the losses suffered by the U.S. during the Global Financial Crisis.
👉🏽'The US deficit as a percentage of GDP is projected to average 6.3% over the next 10 years.
This comes after the deficit reached 6.7% in 2024, the largest since 2021. Such elevated deficits have never happened outside of wars and significant economic crises.
Furthermore, the deficit is estimated to hit 7.1% of GDP in 2025, the 3rd highest among the world's major economies, only behind India and China. Meanwhile, the budget gap for the first 2 months of the Fiscal Year 2025 reached $624 BILLION, the largest on record. The US is on unsustainable fiscal path.' -TKL
On the 5th of January:
👉🏽'The US National Debt increased by $2.2 trillion in 2024, following increases of $2.6 trillion in 2023, $1.8 trillion in 2022, $1.9 trillion in 2021, and $4.5 trillion in 2020. How much will the National Debt increase in 2025?' - Charlie Bilello
On the 6th of January:
👉🏽Hedge Fund Manager Steve Diggle, who made $3 Billion during the Global Financial Crisis, has returned and compares the current market to what we saw from 2005-2007
🎁If you have made it this far I would like to give you a little gift:
What Bitcoin Did:
2024: BITCOIN IN REVIEW with HODL & ODELL
https://youtu.be/-tijL0iD5GI?si=Q7Xsy-mRg4UqxKe3
Good one!
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly. Use the code BITCOINFRIDAY
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple.⠀⠀⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you? If so, please share it and support my work with sats.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe -Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
-
 @ c1831fbe:de4b39bf
2024-12-02 23:45:46
@ c1831fbe:de4b39bf
2024-12-02 23:45:46An Experiment...
Somewhere, lost in time,
(actually, about a year and a half ago), I experimented with a post on the Yakihonne platform.
I must confess that I was "sucked in" by promises of Markdown support and "Zaps for Participation." And so, I tried my hand at using the platform by writing a post on how the Yakihonne platform was working at at that time (you can see a copy of that old post reconstructed below). For the record, I did receive a healthy zap from Yakihonne 😆.
Sadly, I couldn't find that original post until I tried looking for it on https://nostr.band using the following search string:
https://nostr.band/?q=Yakihonne+post+by+Duncan+Cary+Palmer
Gotta say, finding it on nostr.band almost immediately, using that intuitive string, really impressed the heck out of me! You rock, nostr.band!
My earlier Yakihonne article was my first-person report on how the Yakihonne platform was working at at that time.
I have been jonesing to write some "long-form" articles for a while, and have seen others do so on Yakihonne, and so here I am; back again, dipping my toe into the waters to see what, if any, improvements have been made here.😆
Next in this series, I'll try to address the problems I discovered in June of 2023 (as noted in the article below). I'm hoping I'll discover—and be able to report—that there has been significant progress, but we shall see... (sadly, preliminary observations tell me that it's not looking too promising)... ## I'll close (for now) with a copy of that earlier article: --- >“At his touch, my simple kite Leapt to the skies, Won me first prize! Dad became a legend in my eyes.”
- Excerpt from a tribute to my father... --- ### Good Morning, fellow Nostriches! Today, I'm throwing care to the wind and dipping my toe into the beckoning waters of long-form nostr publishing on YakiHonne, a web-based nostr client. On the one hand, I'm hopeful; but I've already encountered a few sharks lurking under the deceptively placid surface of YakiHonne waters! I sincerely hope my "first timer" real-time experience in writing and posting this article will provide some constructive feedback to YakiHonne developers. My first impressions of the platform are encouraging, and I hope YakiHonne will continually improve its offering. >NOTE: In honor of my father, I've begun this article with a quote from a tribute poem I wrote after his death, and my first embedded image (below) is a photo of the type of private airplane Dad once owned. ---
Dad once owned a Luscombe (source)
No Links Here\
). This is not a fatal flaw, especially since if you use a series of hashtags to create headers (e.g. ### Links work in this style header) you won't have a problem. ##### - Confusing, overwritten profile It took a while to figure this out; several fields of the profile overlap one another, but I was (finally) able to fiddle them separate by clicking on the "edit" icons in various combinations. ##### - - Minimum recommended article size; 1500 words? Seriously? Real authors write articles of all lengths. I see no possible need or reason to handcuff participants on this platform, constraining them to a minimum article size. All that will do is stifle creativity and variety. Of course, as this is my first foray into YakiHonne land, I will (at least for this entry) comply with a minimum length, but I reserve the right to complain bitterly about it. YakiHonne, are you listening? ##### - Can't ZAP! I've tried to ZAP a fellow author on YakiHonne, and for reasons I have not yet been able to determine, the ZAP/Lightning button is not functional. It may be a setup issue; I can ZAP when using Amethyst on Android, but not YakiHonne on Mac (yet). ##### + + Incentives to participate This is a potentially very good thing, and apparently it's working; I'm here, along with other fine authors, right? The powers that be behind YakiHonne are putting their money where their mouth is. They are dangling bounties under the nose of writers, promising to reward good articles with bounties in the form of significant amounts of sats. We'll see how that pans out, but it clearly has drawn some positive interest. Somehow, contests, sats, and other inducements do encourage participation. Good talent always enjoys a challenge. ##### Bugs, Oh, My! Ah, bugs are inevitable... Somehow, on this page I ended up with an endlessly spinning and bouncing rounded-edge cube. File this with the bad formatting of profile data, and it's an indicator that we are so early... Keep up the good work, YakiHonne; I'm sure you'll slay the bugs. --- ### Some things I would love to see. I've always been a dreamer; one of those people who's never completely satisfied. Give me an inch, and I'll ask for a mile; a hippo and I'll want an elephant. Here are a few "Scenes I'd like to see" on YakiHonne in the future (as in, How long is it gonna take you to get this feature up and running?). ##### Better and more tools I would really love to see YakiHonne (or for that matter, any long-form nostr publishing platform) provide better organizational tools for prolific writers who have mass quantities of content to offer. ##### Assurances of longevity Is YakiHonne a fly-by-night organization? If I spend my time writing and publishing content, how long can I expect my hard work to remain stored and saved on YakiHonne? Because Hive is blockchain-based, and issues monetary rewards, I have a reasonable expectation that my work will be available there for a long time to come. Can I expect the same from YakiHonne? ##### Ability to back up content I would like to be able to download and archive all of my content on a local device. ##### Index/Table of Contents I write about many different things in a wide range of categories. My preferred platform should provide a helpful way for my followers and readers to access all my content, and not just in reverse chronological order. I've manually implemented a hierarchical table of contents for my writing on the Hive blockchain. Please have a look at my library to better understand what I mean. I would love to see YakiHonne scan my articles for keywords and especially for #tags —in order to automatically create a presentation like my Hive library to help my readers access my thoughts on any topic. Please, YakiHonne devs, save me from being "only as good as my last article." ##### Draft capability For a good author experience, the ability to maintain and edit multiple article drafts is essential. Have a look at peakd.com/ and the Hive blockchain for a good example. --- ### Conclusion: Let's Freakin' Go! This a only a preliminary glimpse of my YakiHonne experience, not intended to be critical, but rather constructively encouraging. I wish YakiHonne the best of success. The more players and options we have available using the nostr protocol, the better I'll like it. Principals and developers at YakiHonne? I hope to hear from you! ---### \~FIN\~ ---###### NOTE: Throughout my posts, you may notice hyperlinks like this one that lead to supplemental material. Most images are also hyperlinked. While not essential to the enjoyment of my writing, you may find the linked background information enlightening (or at least mildly interesting). ---
ALL IMAGES are either my own, derived from open source material, or used with permission.For more from Duncan Cary Palmer, --- I would love to hear from you; please log in to YakiHonne and speak your mind by responding to my articles! ---
Click Here to visit my Library.
-
 @ 1cb14ab3:95d52462
2025-01-07 23:17:54
@ 1cb14ab3:95d52462
2025-01-07 23:17:54Event Recap
For the Official Stooki Sound Afterparty in Boulder, CO, I took the unconventional venue of a kitchen on The Hill and transformed it into an immersive environment for Toybox and Tesfa’s performances. The space was custom-mapped with projections that interacted seamlessly with the surroundings, turning the kitchen into a dynamic, visual landscape. I added retrofitted props to deepen the visual experience, giving the projections a multi-dimensional quality. This innovative approach created a unique atmosphere, enhancing the performance while blurring the lines between physical space and digital art.
Event Photos







Recap Video
nostr:naddr1qqrj6wpkx3u8qscpzpmhxue69uhkummnw3ezuamfdejsygquk99txdv8dly7lsmasw969p70zlj6mnxtyzlk6j0em2tft4fyvgpsgqqqskas47n36f
Other Immersive Experiences by Hes
More from Hes
All images are credit of Hes, but you are free to download and use for any purpose. If you find joy from my art, please feel free to send a zap. Enjoy life on a Bitcoin standard.
-
 @ dd664d5e:5633d319
2025-01-07 19:57:14
@ dd664d5e:5633d319
2025-01-07 19:57:14Hodling Bitcoin does not make you a capitalist
I've noticed that Bitcoin-mindedness seems to lead some people to communistic thinking because it's a hard-limited form of capital. Marx, like most Bitcoiners, heavily discounted the possibility of economic growth or transformation changing the economy enough to undermine some minority's control of some form of capital.
What few today understand, is that many of the Dirty Capitalists of Marx's era actually agreed with him; they were just disdainful of labor and worried that the workers finding out that Marxism is correct about the nature of capitalism would cause unrest. They were the original HFSP crowd.
This was the basic idea, that Marx had, and that many Bitcoiners would agree with:
Capital is strictly limited and the people that control it can keep labor from attaining any, except when their labor is necessary.
And, as we know, automation will make human labor increasingly unnecessary.
The math doesn't check out

That underlies all of the calculations of "Well, if I just grab this Bitcoin wallet and hodl for twenty years, then it will grow in value to equal half of everything in existence and then I can just buy up half the planet and rule over everyone like a god."
This is economic nonsense because it assumes that: 1) the value of all things remains static over time, 2) purchasing something with money gives you ownership of it, 3) people will always use that specific money (or any money, at all!) for all transactions, 4) there is no such thing as opportunity cost, 5) people will always value money more than any other thing, and therefore be willing to always trade it for anything else, 6) humans are passive, defenseless, and easy to rule over, 7) someone who is preoccupied with hodling an asset steadily and sharply rising in price would ever be emotionally ready to part with it.
All monies can die.
People use money for everything because it is easy, fast and cheap. If money becomes too precious or scarce, they will simply switch to using other things (as we saw with gold). Humans replace tools that aren't working well, with those that work better, and money is just another tool. Bitcoin is more divisible than gold, but that won't matter, if enough of it is held by too few.
This is why there's a natural cap on the price of a money and why human productivity in the here and now is not irrelevant or in vain.
-
 @ 16d11430:61640947
2024-12-02 23:35:17
@ 16d11430:61640947
2024-12-02 23:35:17- Initial Supply:
The total supply of Damage Tokens is capped at 42 million tokens.
80% is retained by Steven Joseph (the founder) for operational and strategic purposes.
20% is released to the public, creating a market opportunity for early adopters and contributors.
- Pricing:
Each Damage Token is priced at 100 satoshis (0.000001 BTC per token), establishing a direct tie to Bitcoin’s value and liquidity.
- Utility:
Damage Tokens are used as rewards for BDD test cases on the DamageBDD platform.
They incentivize high-quality software development by providing measurable, blockchain-verified rewards.
- Resilience and Integrity:
As an AEX9 token, Damage Token complies with Aeternity’s fungible token standard, ensuring:
Security and immutability.
Compatibility with Aeternity wallets (e.g., Superhero.com) and the DeFi ecosystem.
- Governance and Revenue:
A governance policy ensures revenue supports a small team and operational costs without external investment.
A buyback mechanism allows token holders to exit liquidity positions through Bitcoin's Lightning Network, net of developer fees.
Enforced by AEX9 Sophia Smart Contracts
- Fixed Supply:
The contract enforces a hard cap of 42 million tokens, ensuring no additional tokens can be minted post-deployment.
- Ownership and Transfers:
The contract implements secure token ownership and transfer rules:
Users can transfer tokens using transfer.
Allowances can be granted via allow_transfer_from.
- Rewards Mechanism:
The DamageBDD platform integrates with the token’s smart contract to automate reward distribution:
Verified BDD test completions trigger token payouts.
This ensures transparency and immutability for rewards.
- Pricing and Exchange:
The smart contract ensures tokens can be sold or exchanged based on the 100 satoshis per token rate.
This rate is enforced by integrating with off-chain oracles and on-chain buyback mechanisms for Lightning Network liquidity.
- Buyback and Liquidity:
Token holders can sell their tokens back through an integrated buyback system.
Bitcoin’s Lightning Network facilitates immediate, decentralized liquidity, minus developer fees.
- Transparency and Auditability:
All transactions and balances are publicly auditable via the blockchain, enhancing trust and eliminating potential manipulation.
By tying the token's value to Bitcoin and enforcing the tokenomics through AEX9 Sophia contracts, Damage Token ensures sustainability, utility, and fairness, while incentivizing contributions to the DamageBDD ecosystem.
